Patents
Literature
1861 results about "Industrial control system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
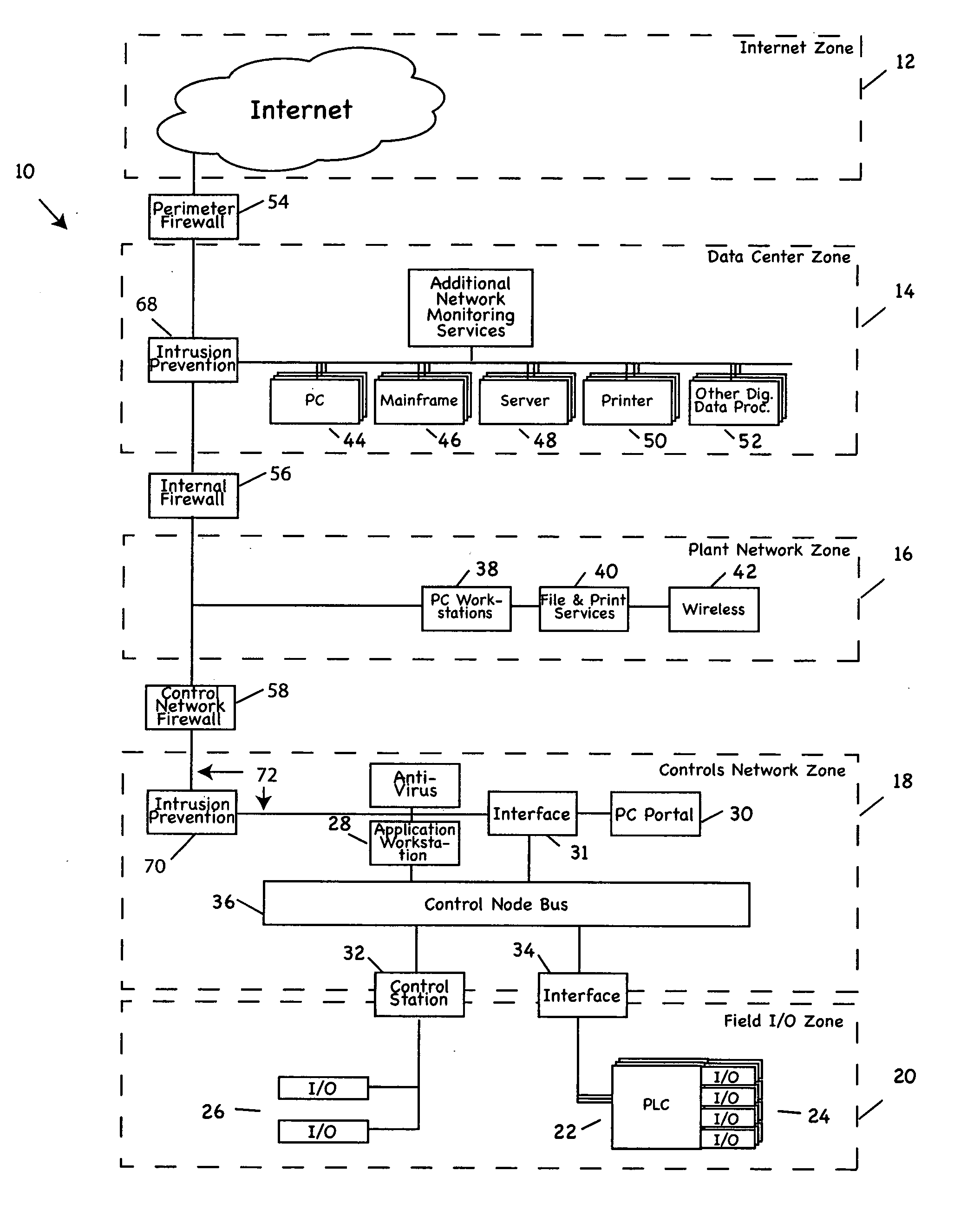
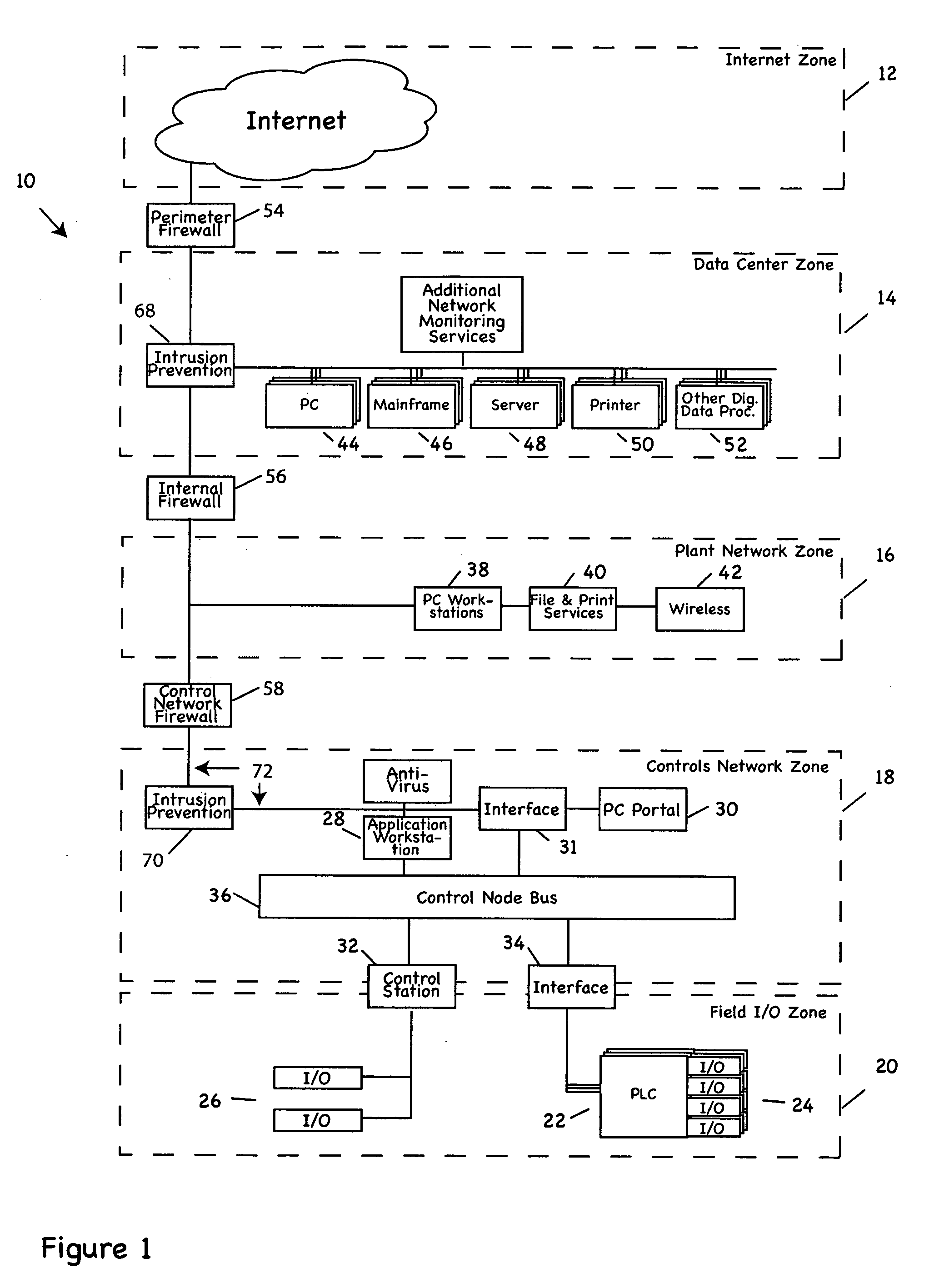
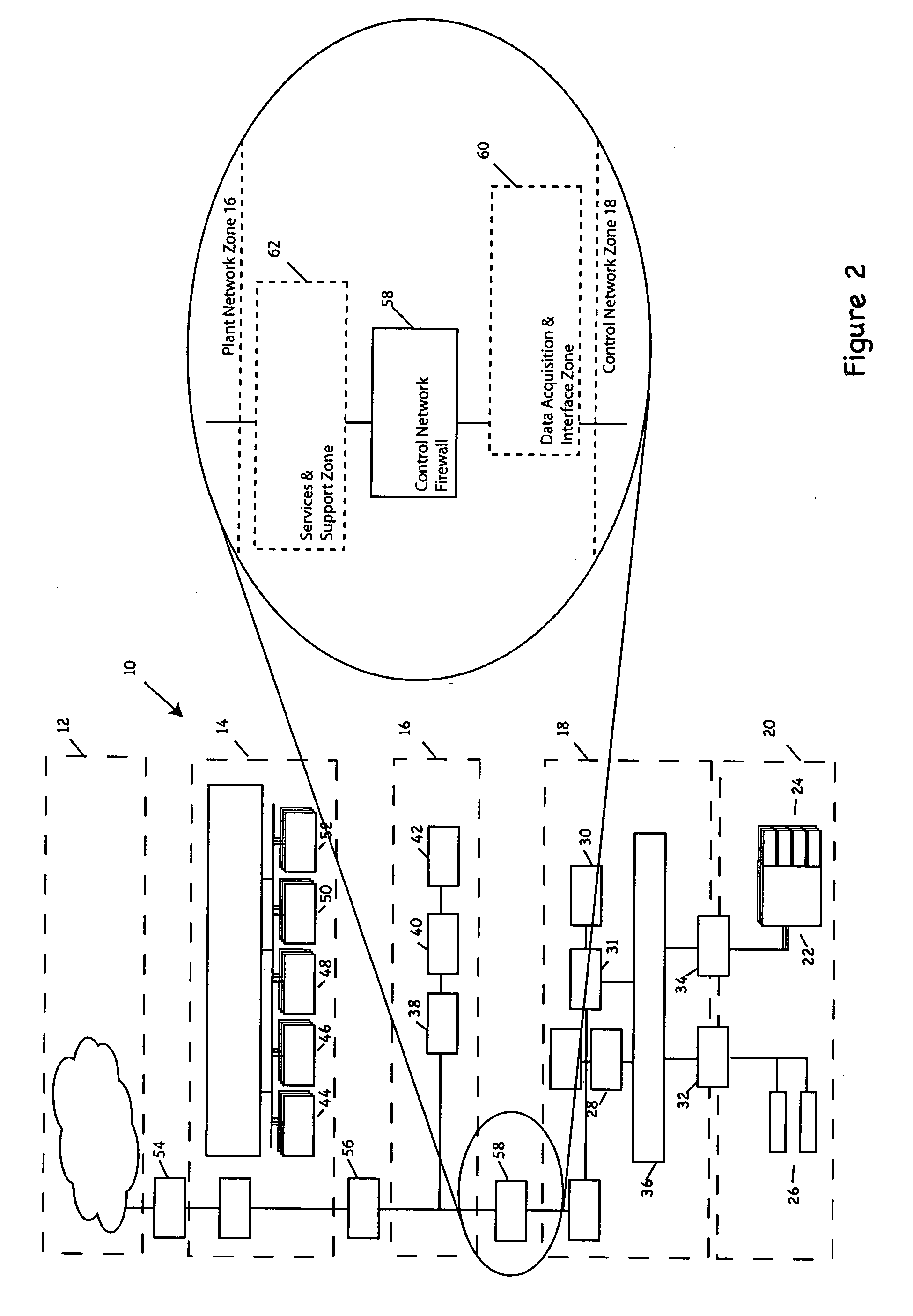
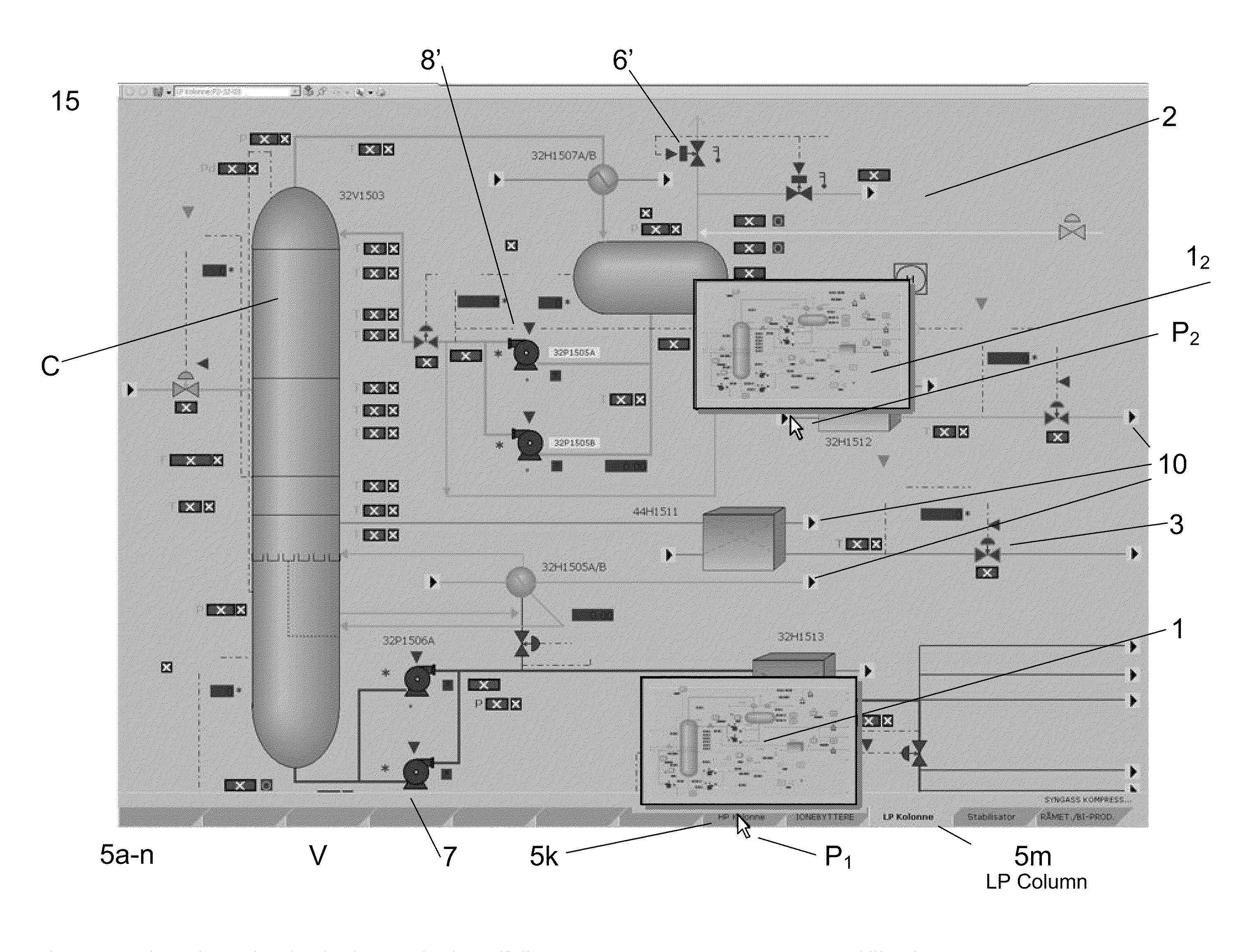
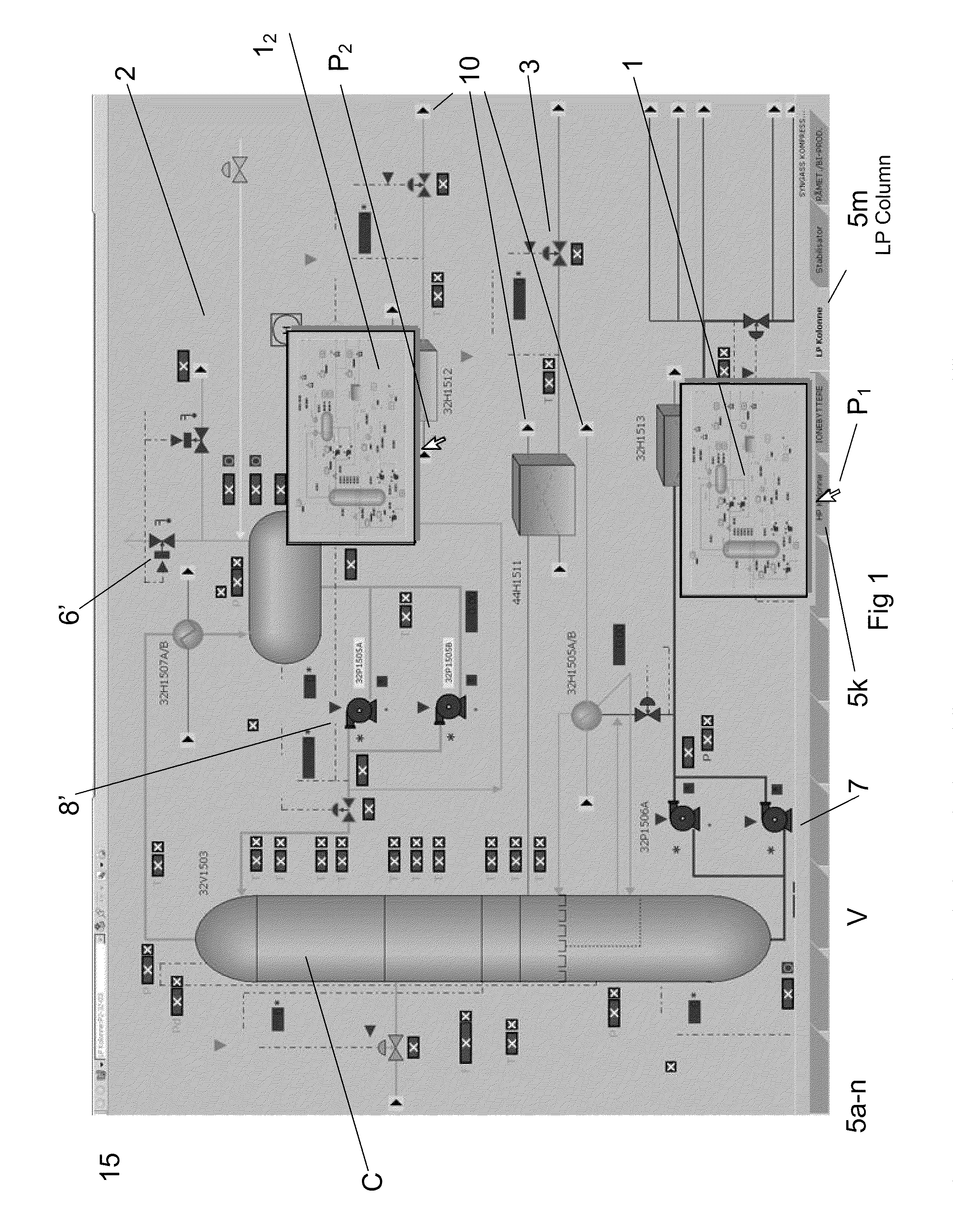
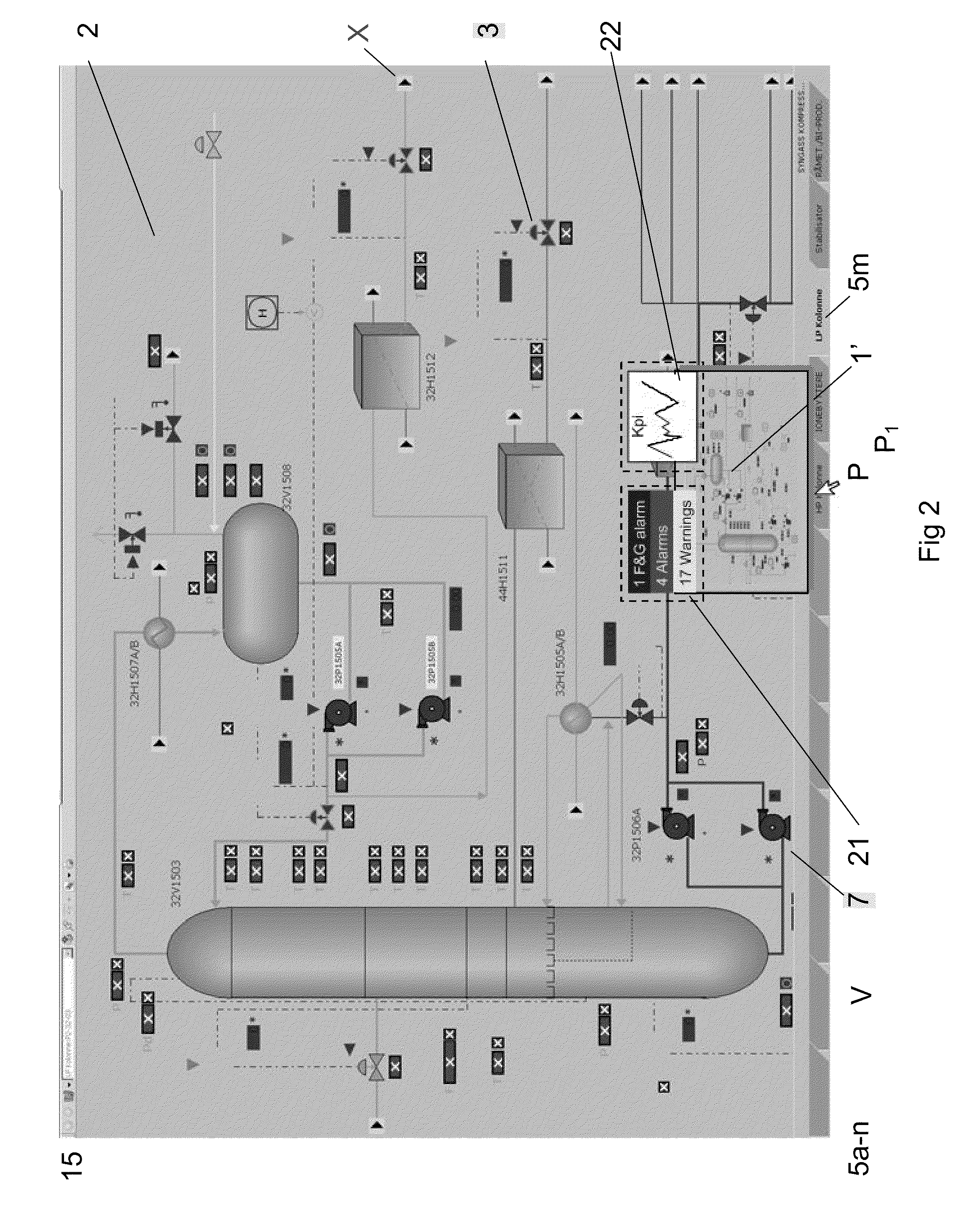
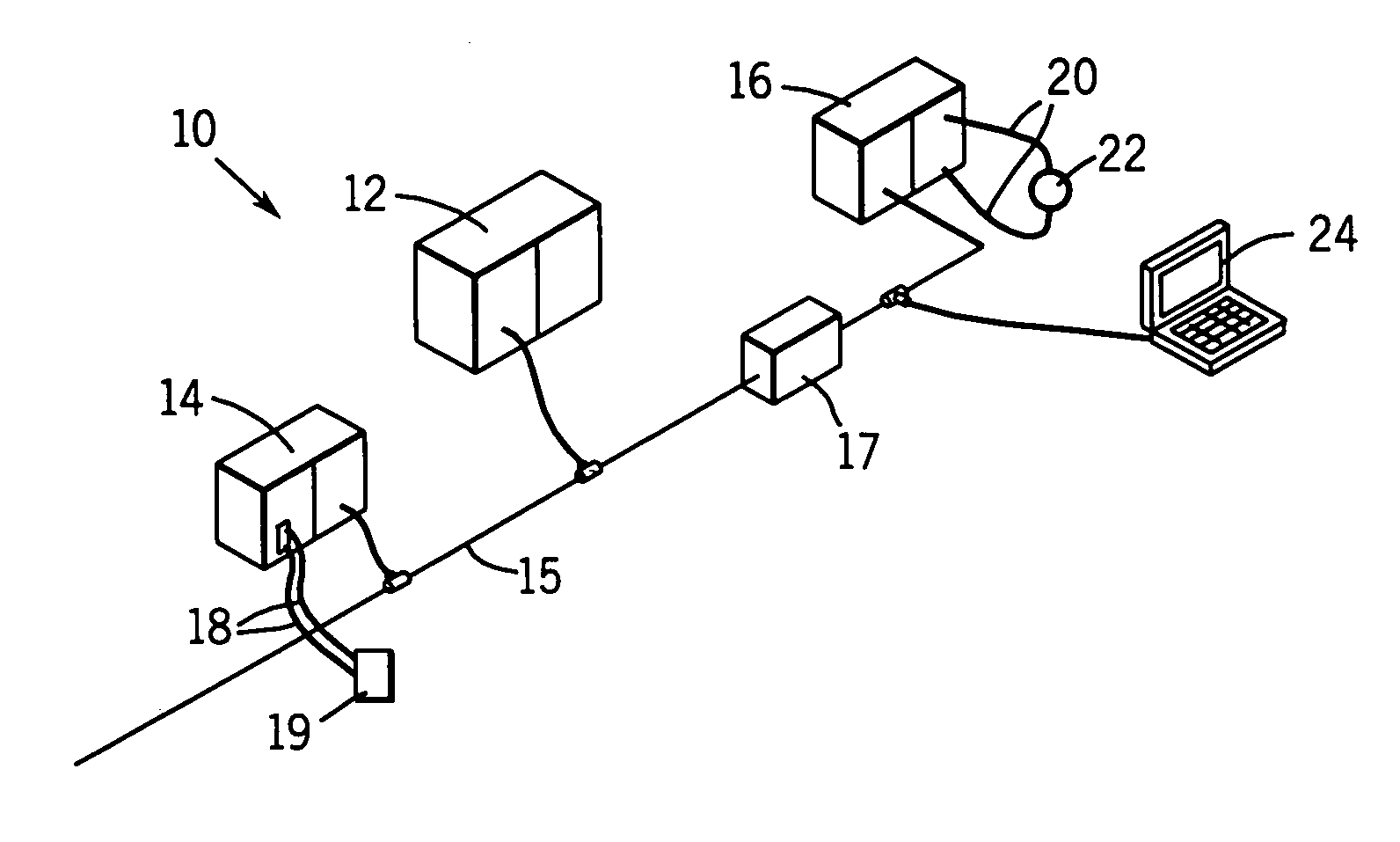
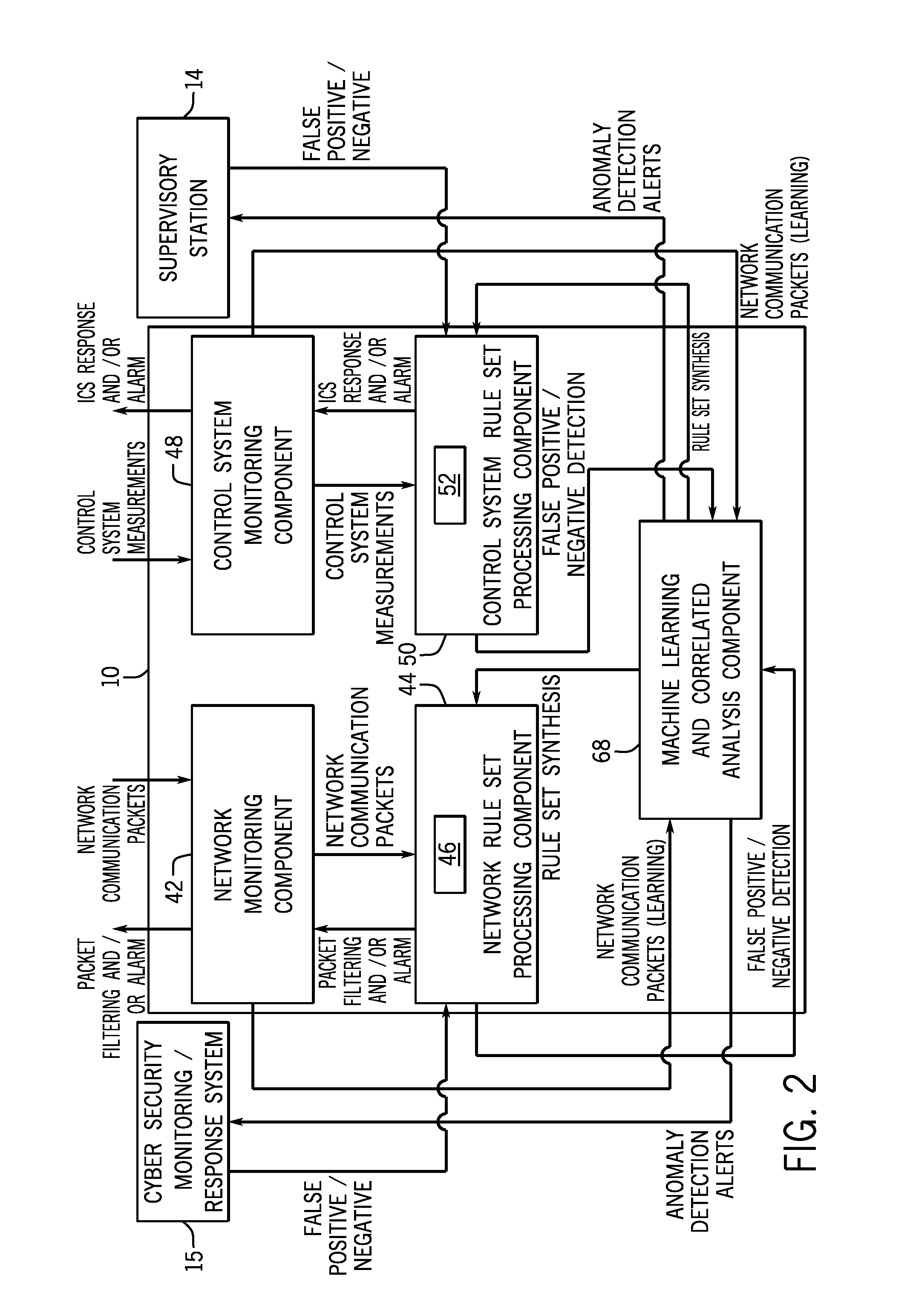
Industrial control system (ICS) is a general term that encompasses several types of control systems and associated instrumentation used for industrial process control. Such systems can range from a few modular panel-mounted controllers to large interconnected and interactive distributed control systems with many thousands of field connections. All systems receive data received from remote sensors measuring process variables (PVs), compare these with desired set points (SPs) and derive command functions which are used to control a process through the final control elements (FCEs), such as control valves.
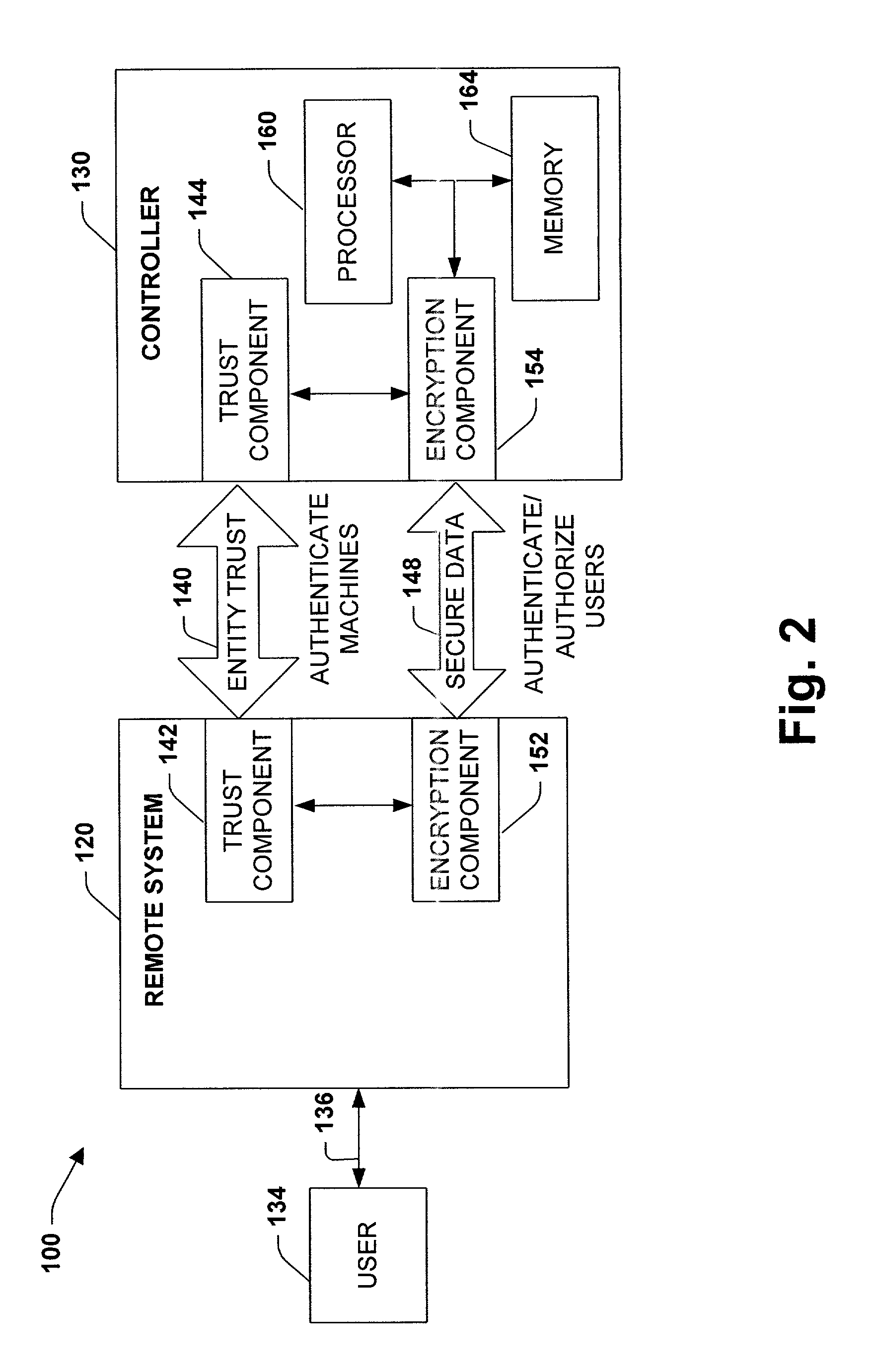
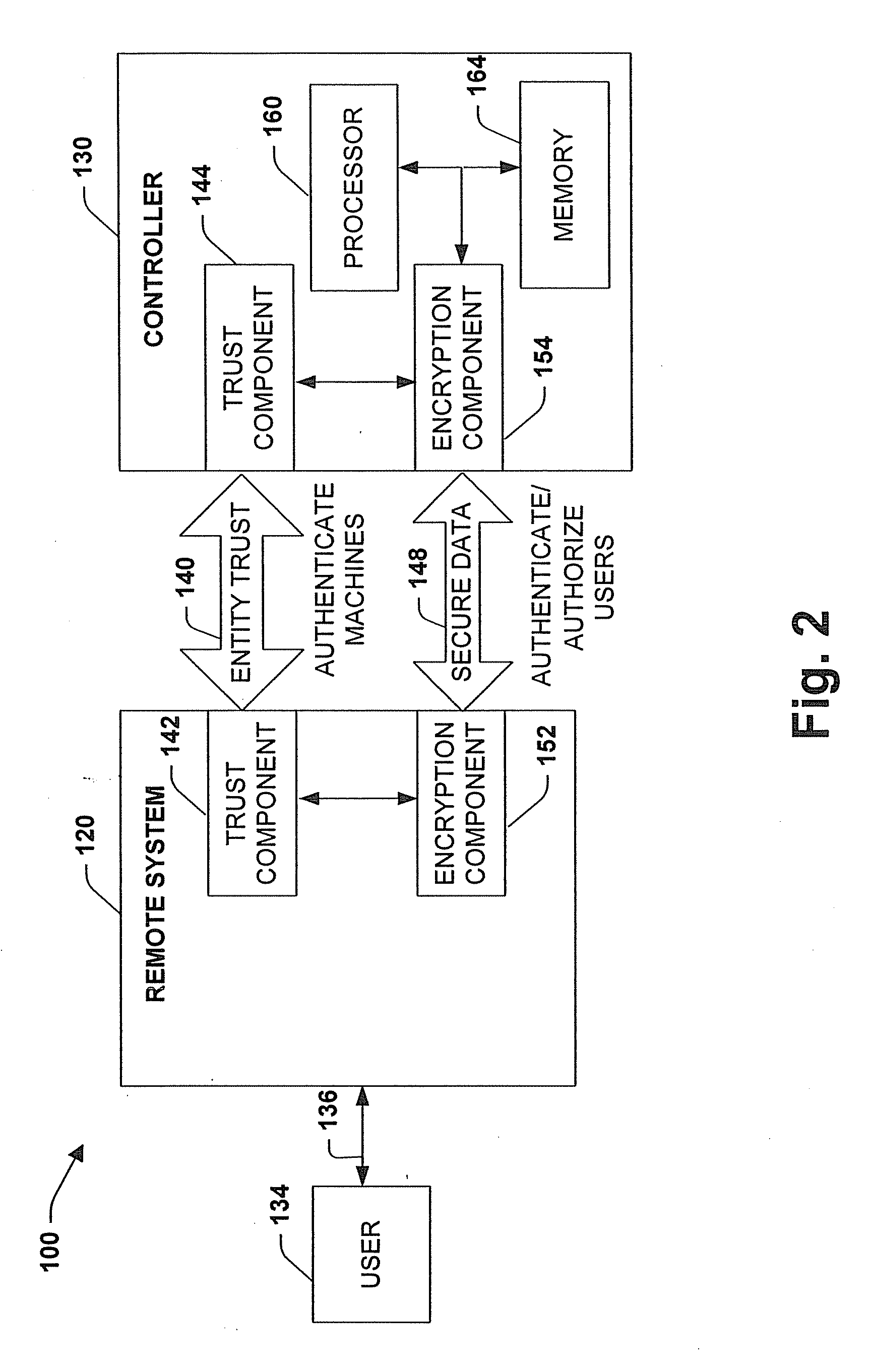
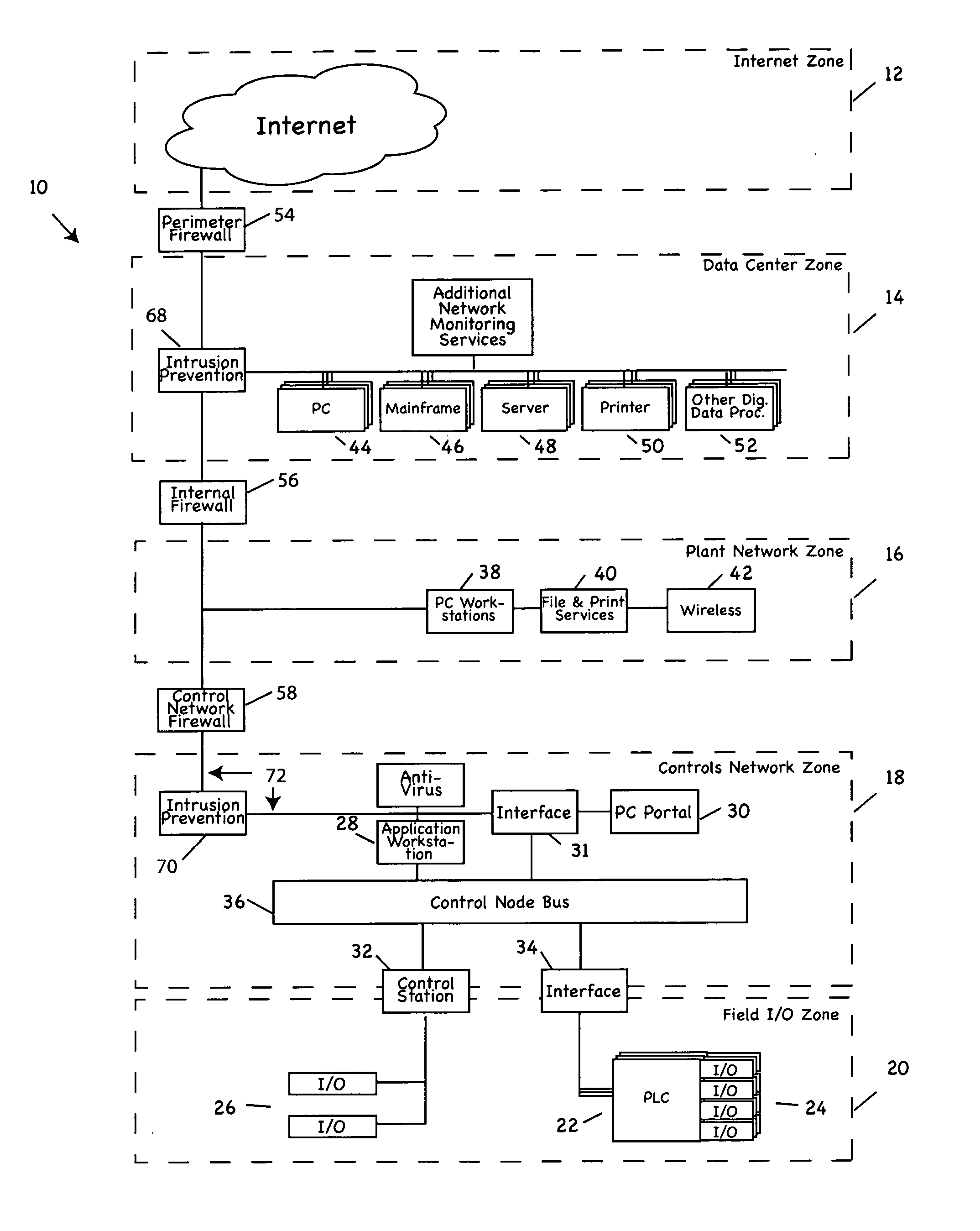
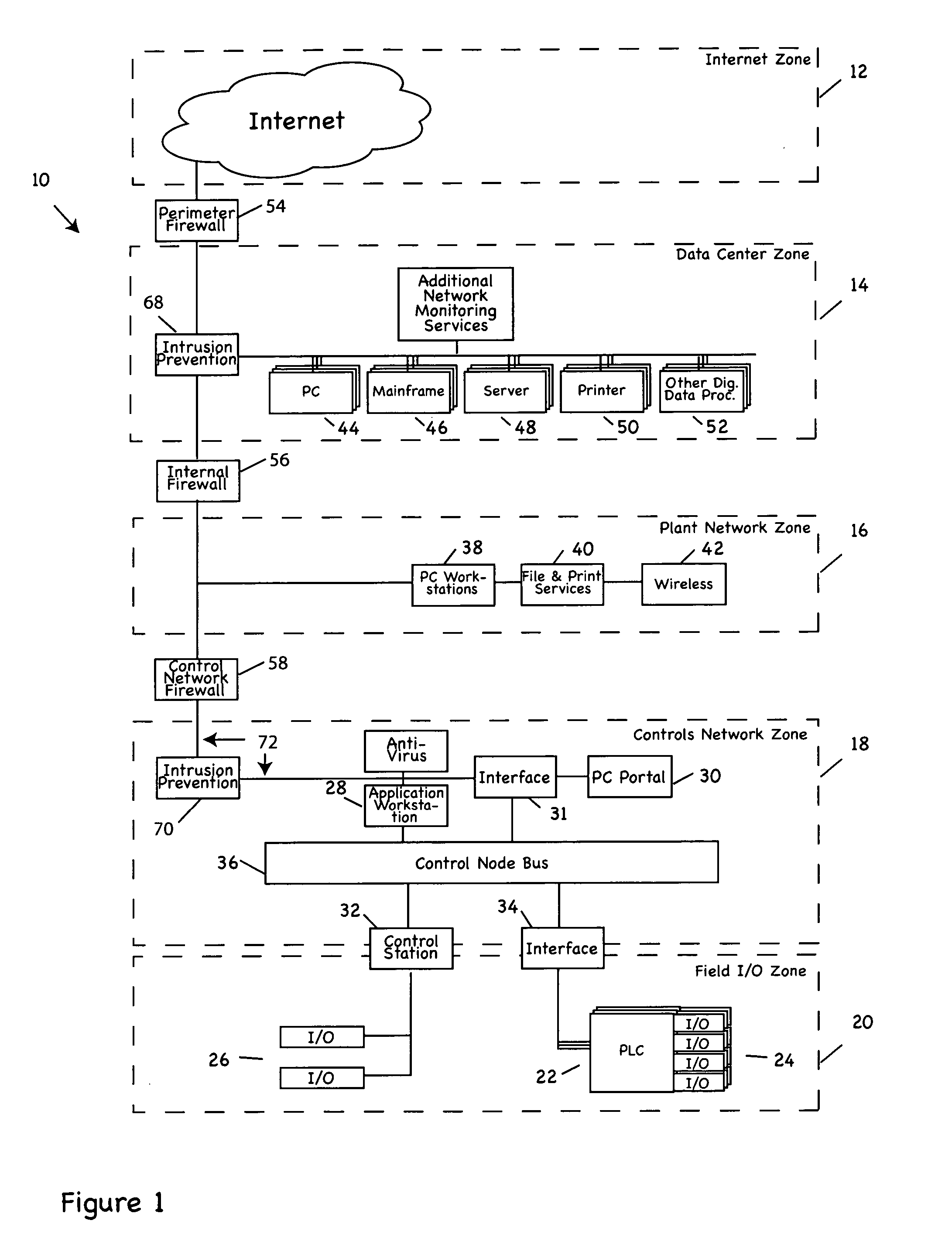
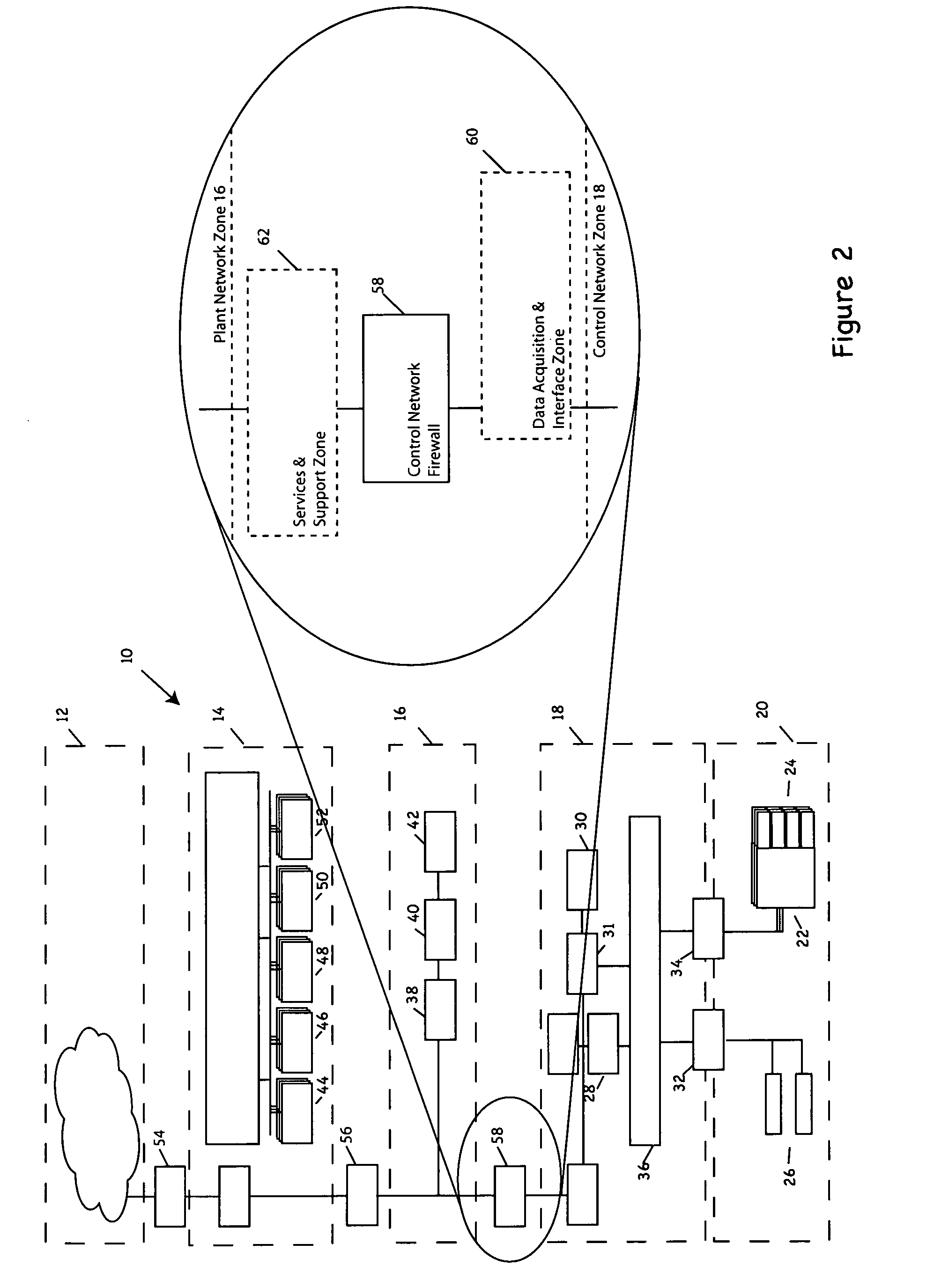
Process control methods and apparatus for intrusion detection, protection and network hardening
ActiveUS20060053491A1Memory loss protectionError detection/correctionEnvironmental control systemIntrusion prevention system
The invention provides an improved network and methods of operation thereof for use in or with process control systems, computer-based manufacturing or production control systems, environmental control systems, industrial control system, and the like (collectively, “control systems”). Those networks utilize a unique combination of firewalls, intrusion detection systems, intrusion protection devices and / or other devices for hardening (e.g., security against hacking, intrusion or other mischievous conduct) and / or intrusion detection. The networks and methods have application, by way of example, in plants, sites and other facilities in which networks that support control systems interface with corporate, business or other networks.
Owner:SCHNEIDER ELECTRIC SYST USA INC
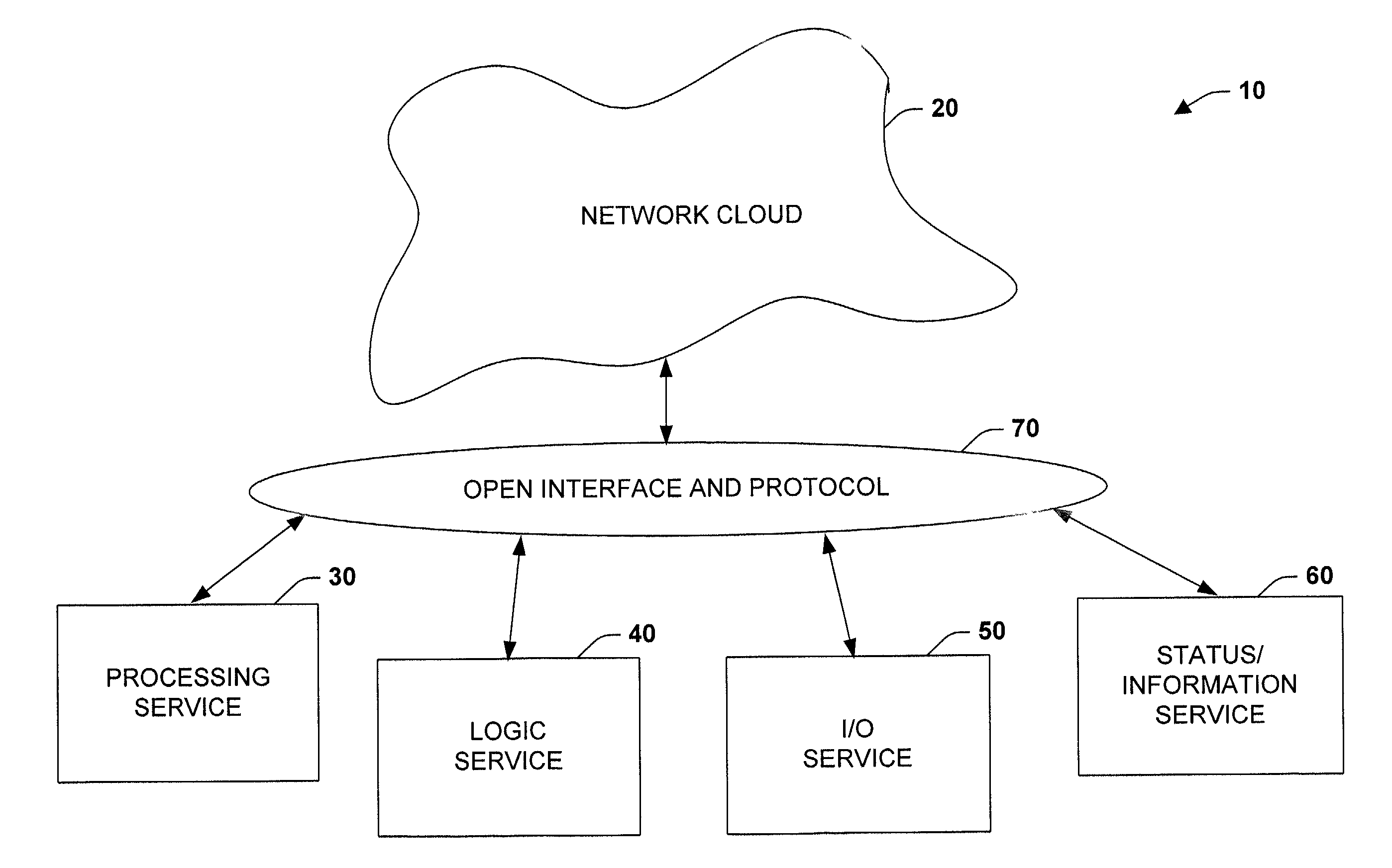
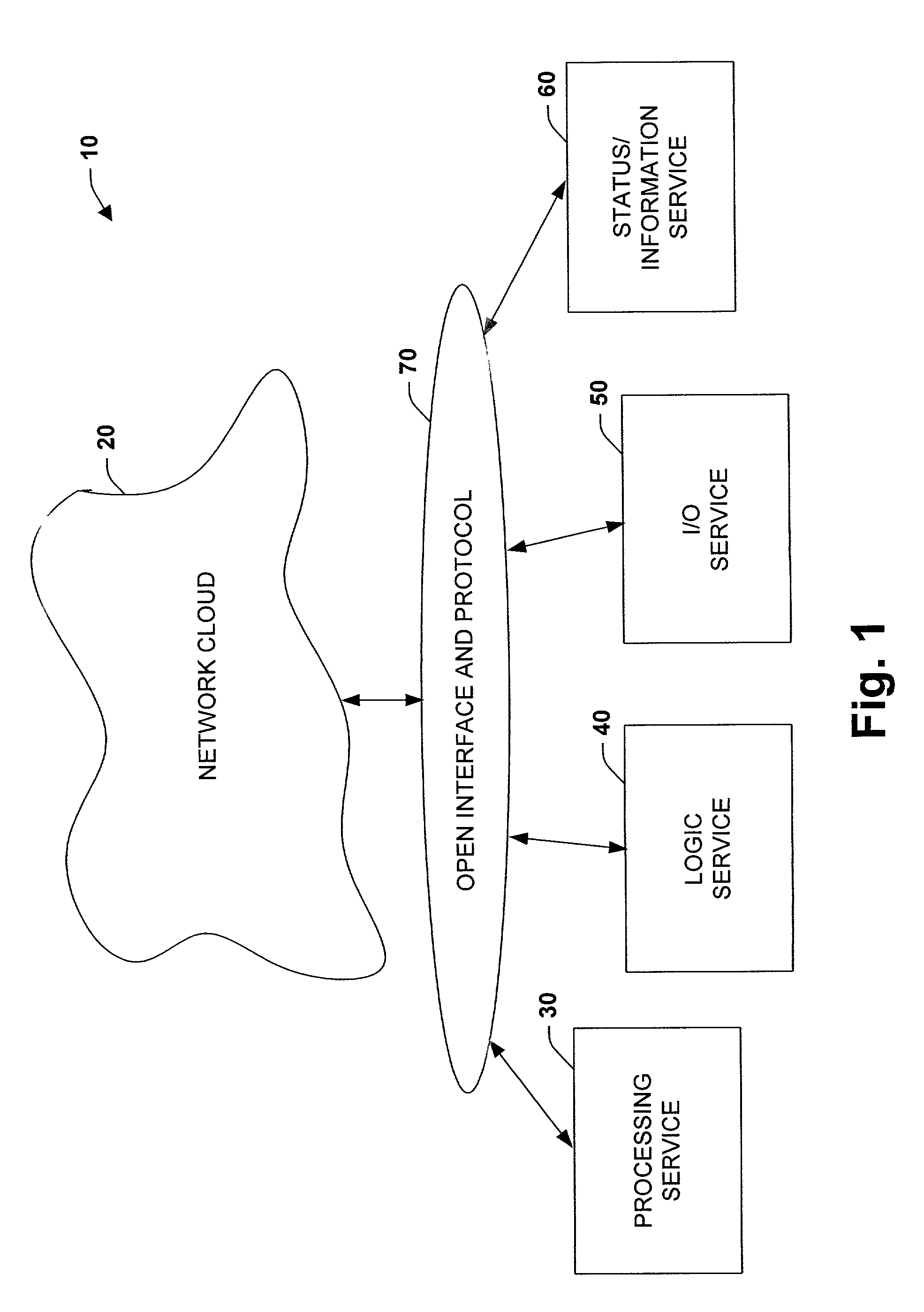
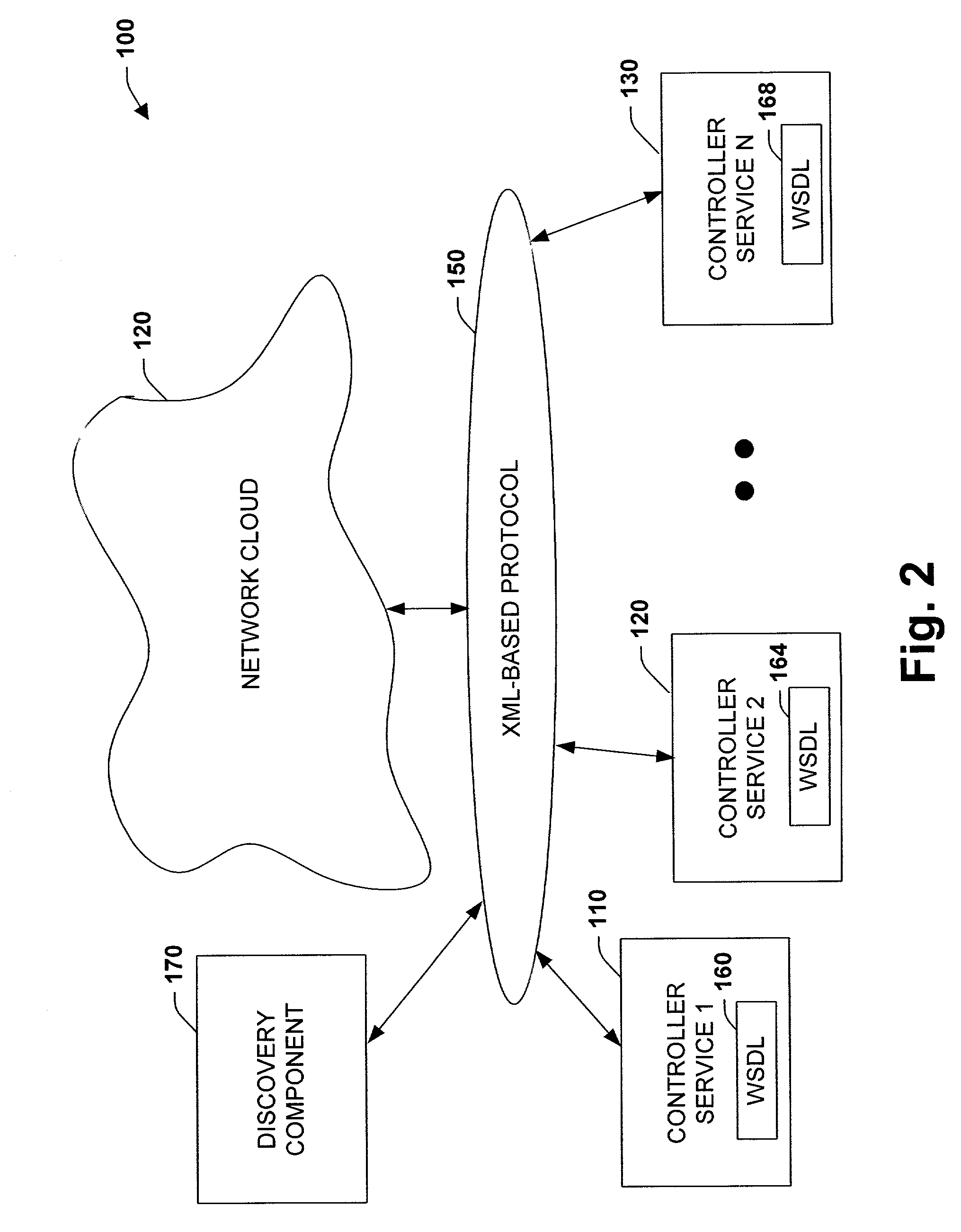
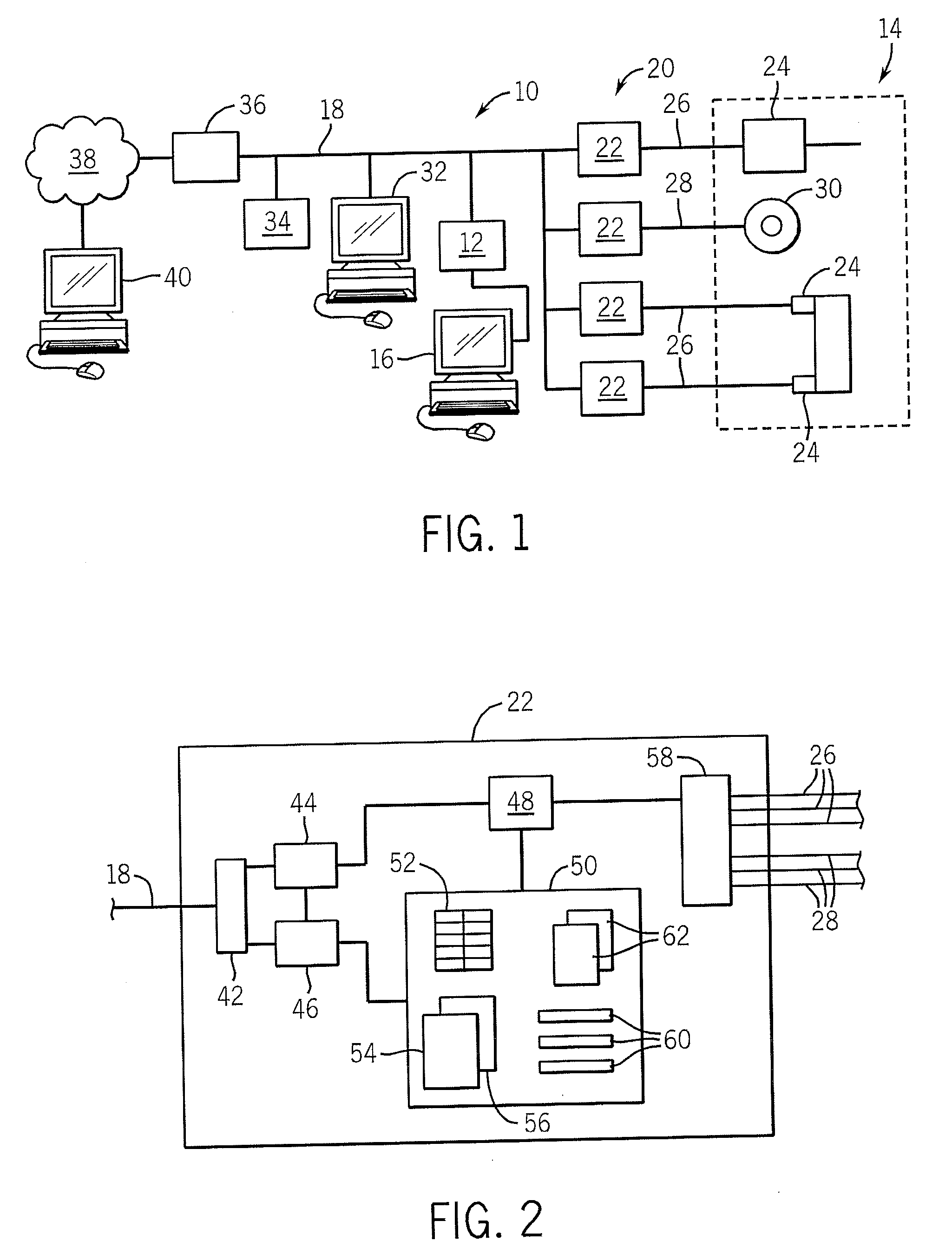
System and methodology providing open interface and distributed processing in an industrial controller environment
ActiveUS7151966B1Facilitate communicationPromote collaborationProgramme controlElectric controllersNetworking protocolApplication software
The present invention relates to a system and methodology providing virtual and remote component interactions in a networked industrial control environment. One or more components of an industrial control system are defined as a web service, wherein the components cooperate to support distributed controller functionality in all or portions of a virtual operating framework. For example, the components can include processing, logic, I / O and status components of an industrial control system. Standard and commonly available interfaces describe controller functionality in terms of the services, whereby controller applications are constructed via the components and associated interfaces. This can include discovery of other related services and employment of common web protocols to communicate between the services.
Owner:ROCKWELL AUTOMATION TECH
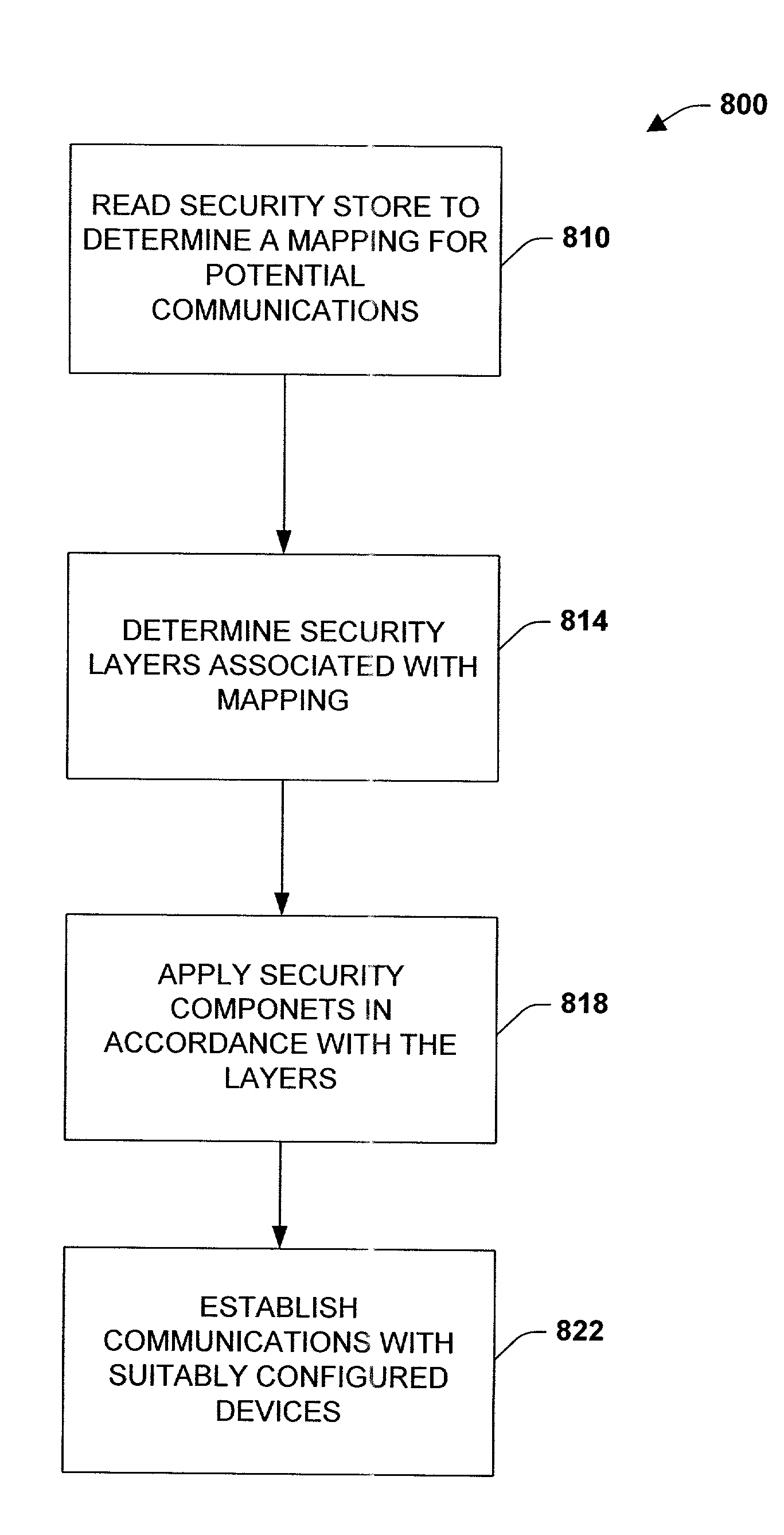
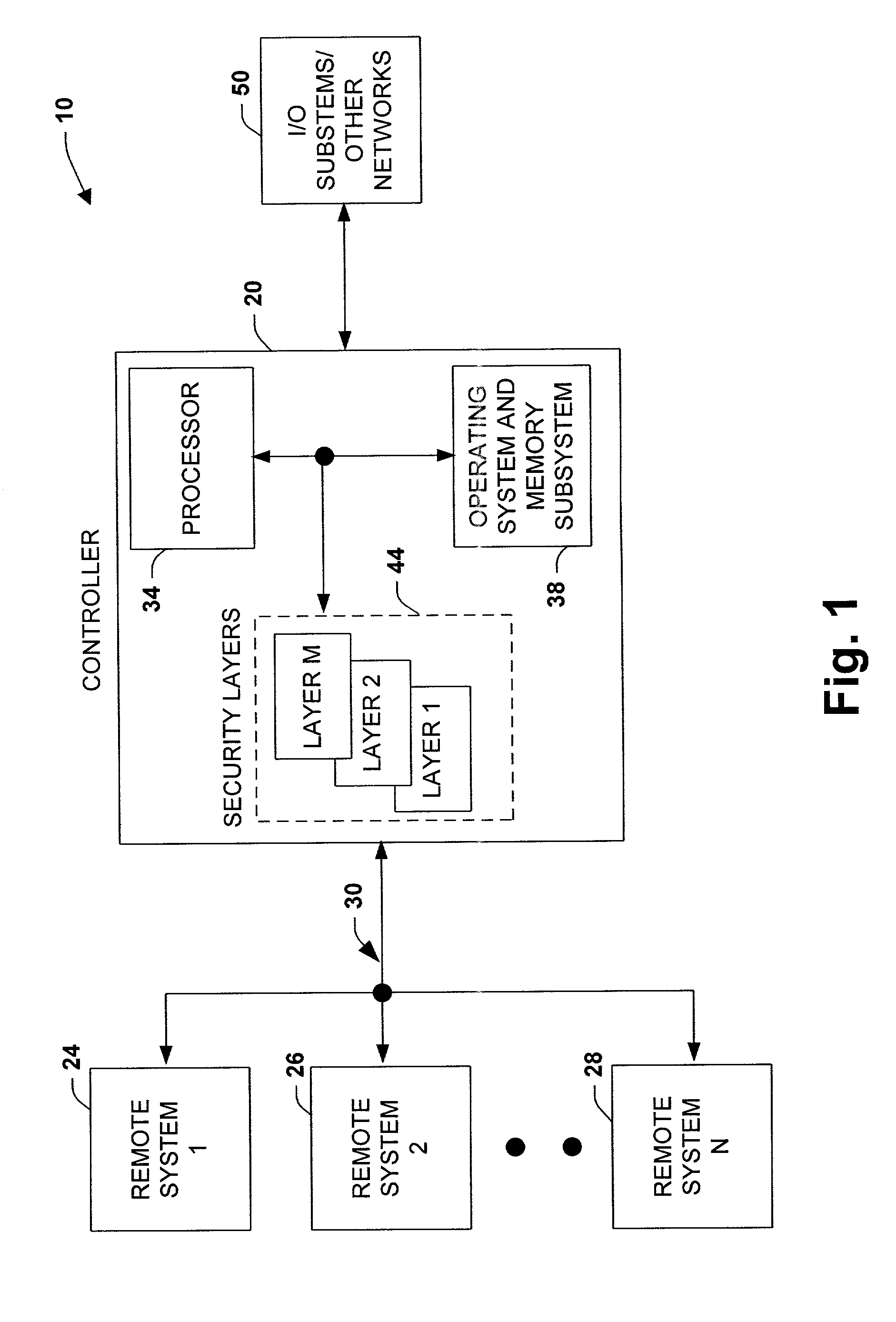
System and methodology providing multi-tier-security for network data exchange with industrial control components
ActiveUS7536548B1Well formedMitigates unauthorized data accessDigital data processing detailsUser identity/authority verificationOperational systemData access
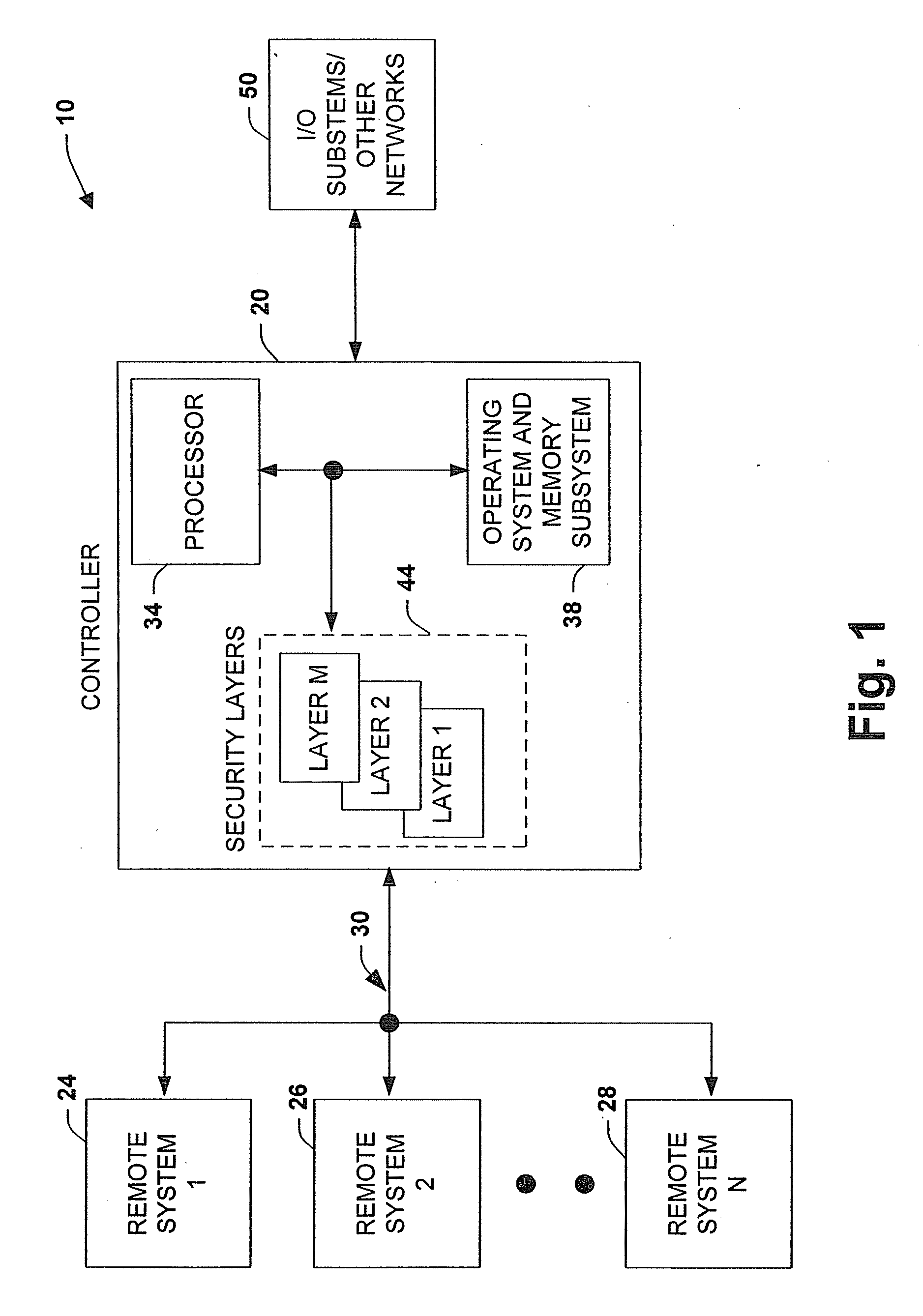
The present invention relates to a system and methodology facilitating network security and data access in an industrial control environment. An industrial control system is provided that includes an industrial controller to communicate with a network. At least one security layer can be configured in the industrial controller, wherein the security layer can be associated with one or more security components to control and / or restrict data access to the controller. An operating system manages the security layer in accordance with a processor to limit or mitigate communications from the network based upon the configured security layer or layers.
Owner:ROCKWELL AUTOMATION TECH
Method and system for cyber security management of industrial control systems
ActiveUS20110039237A1Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
Method and System for Providing a User Interface
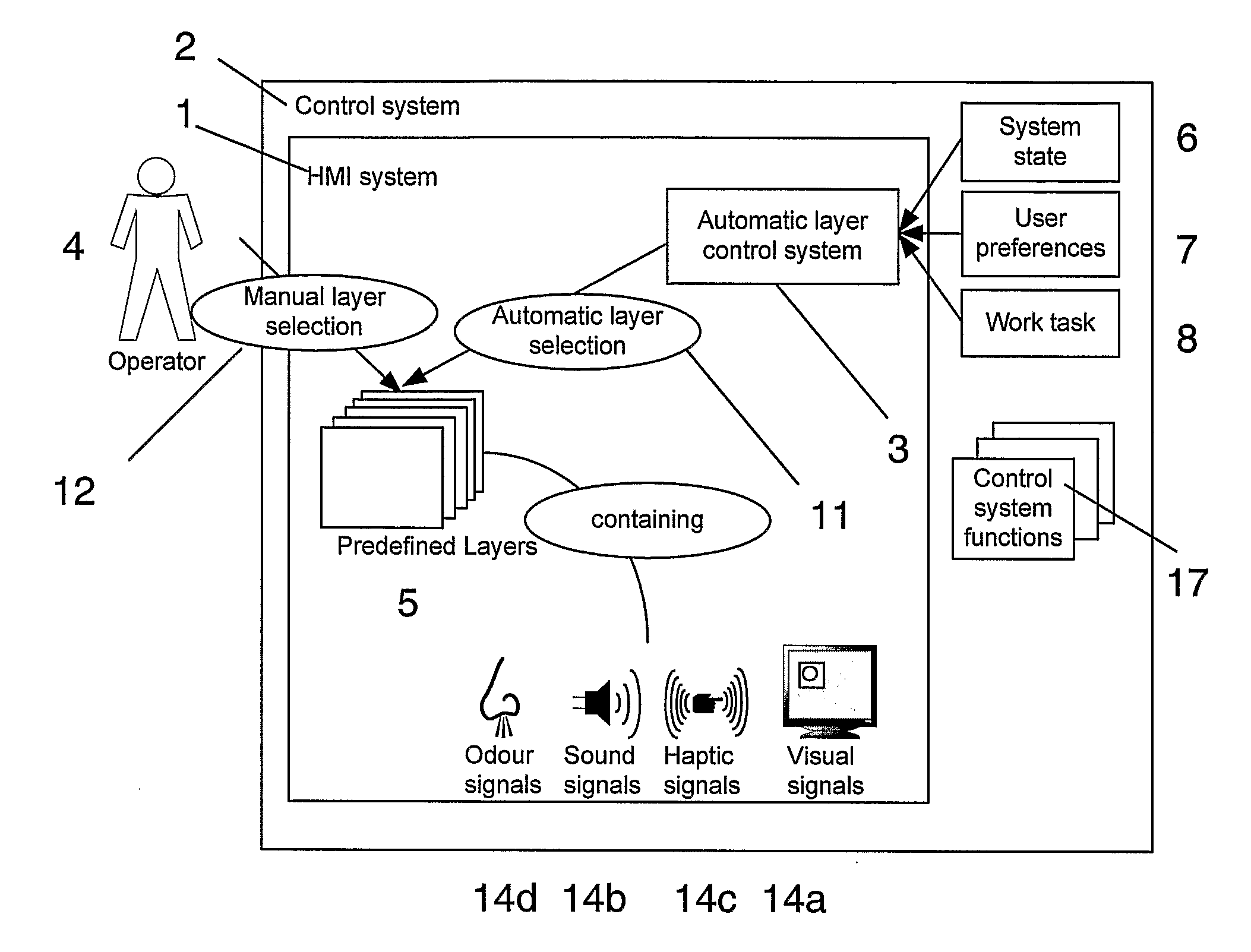
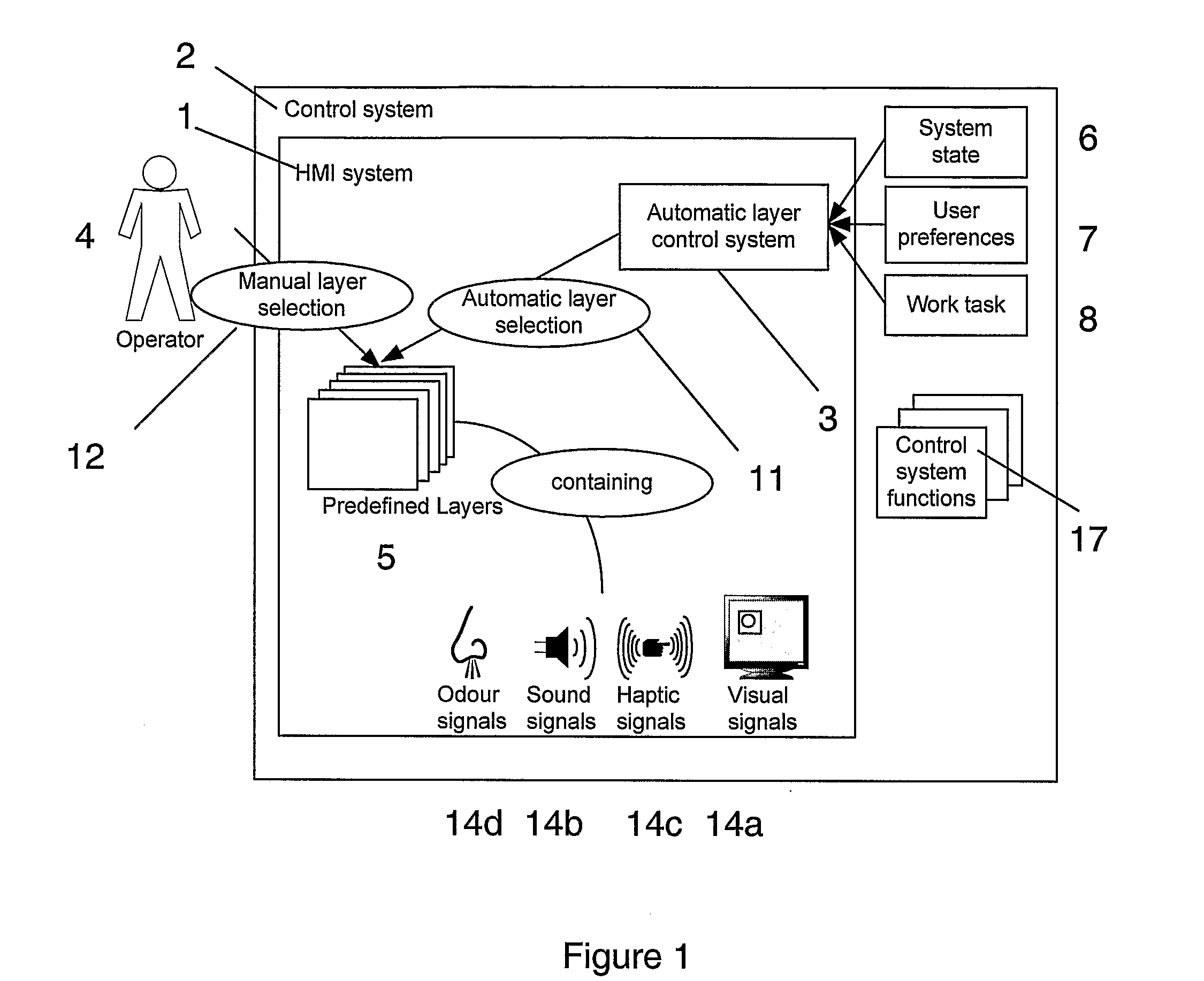
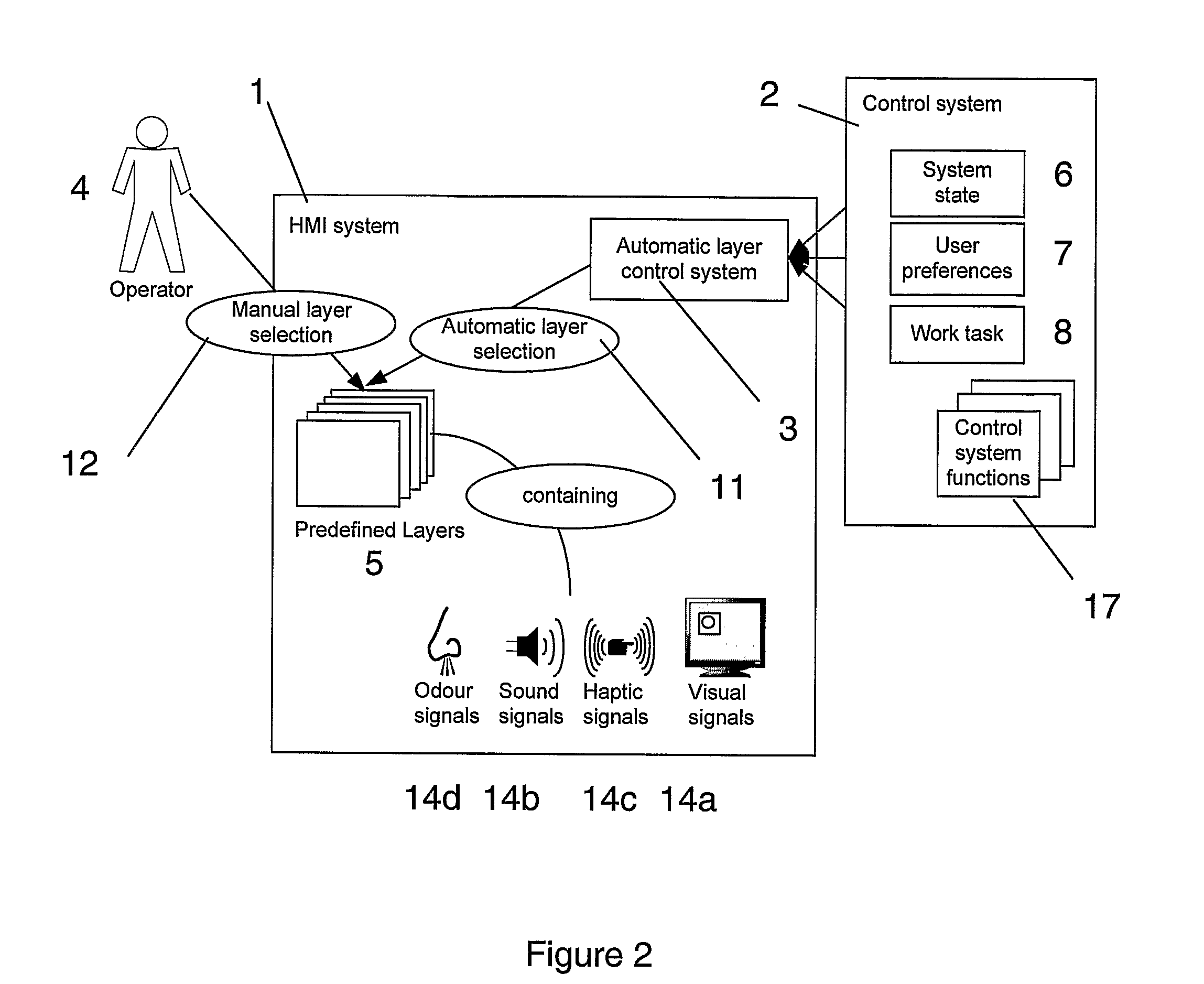
ActiveUS20090216341A1Improve loading timeFast informationProgramme controlComputer controlHuman–computer interactionIndustrial control system
A method for providing a user interface for an industrial control system. Information is presented at least in part displayed in layers or filters on one or more display screens of a control system. The control system may include other media for presenting or displaying information. The content for the one or more layers, which also provide an interface to a process state or function, is determined based on information available from the control system, dependent on which of the available items of the information shall be visually displayed or otherwise presented prominently, or displayed less prominently, or hidden. An interface, computer programs and a control system are also provided.
Owner:ABB (SCHWEIZ) AG
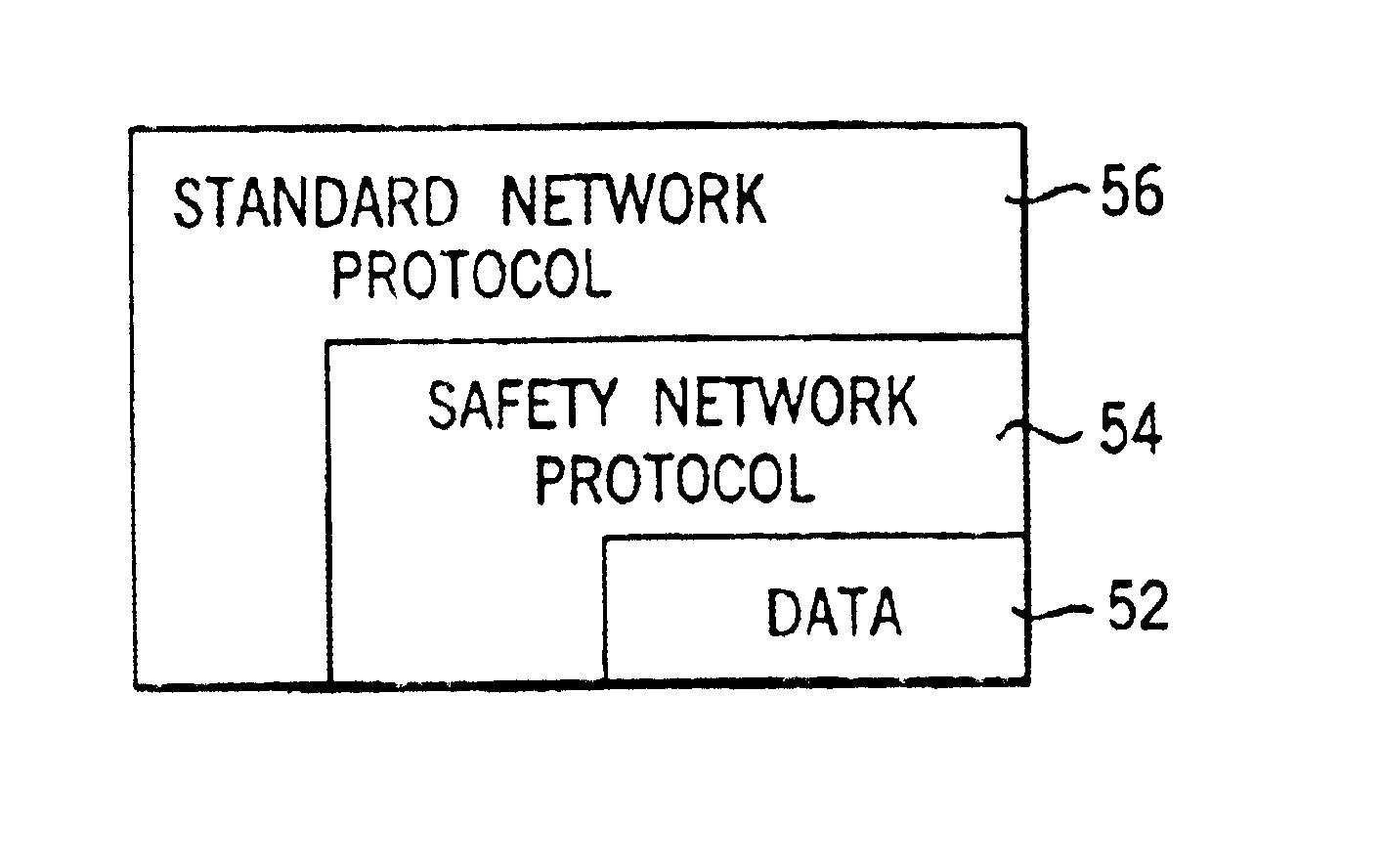
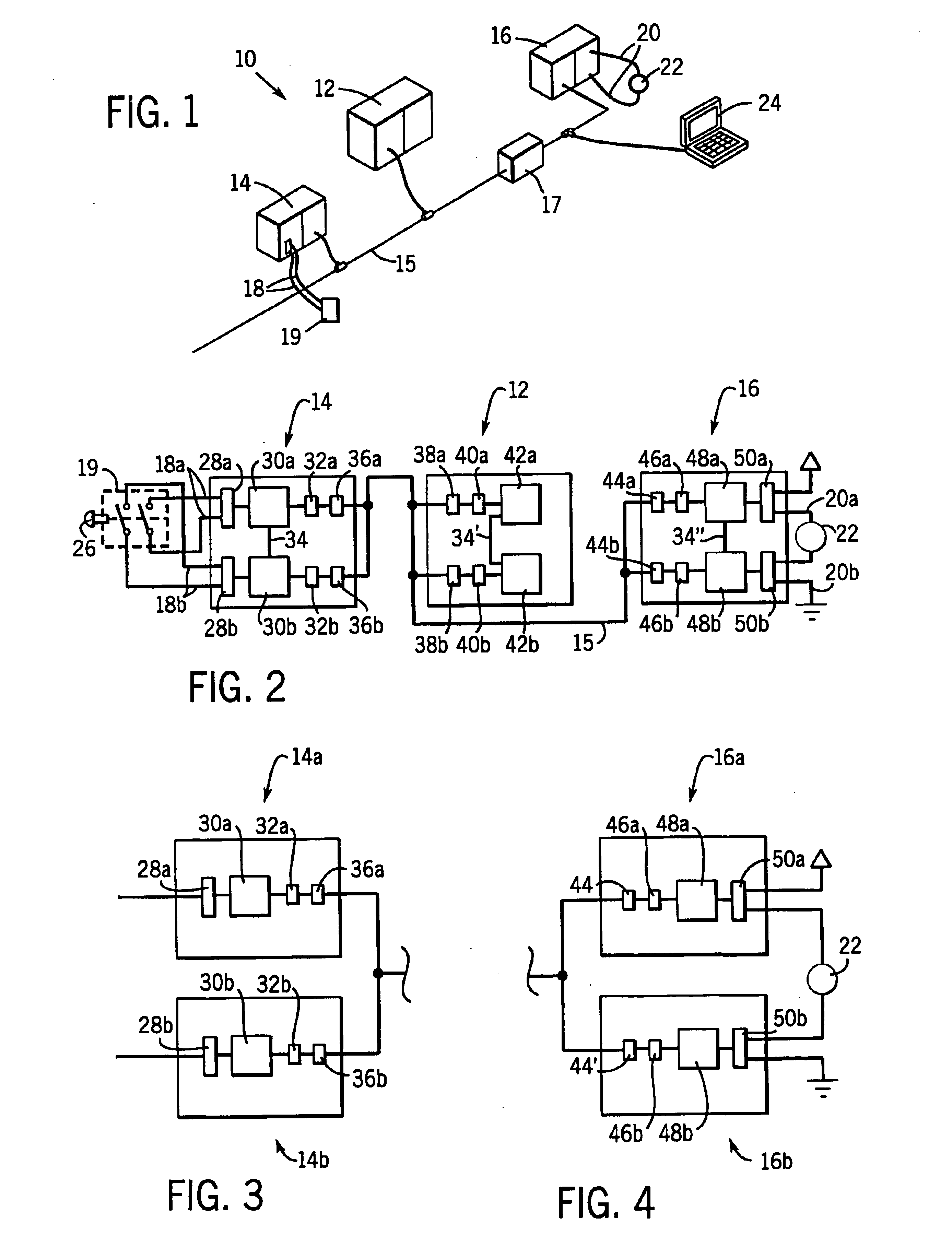
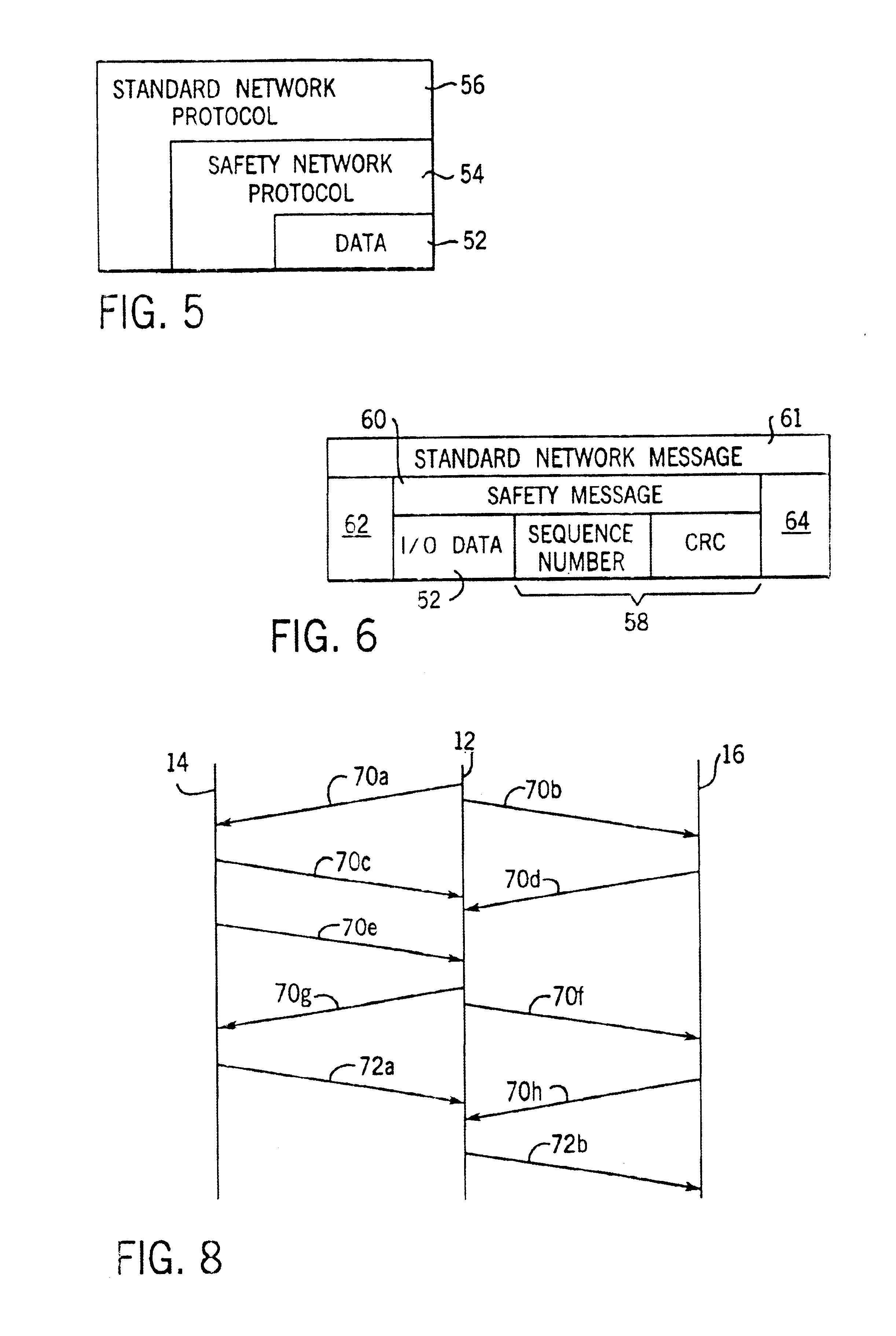
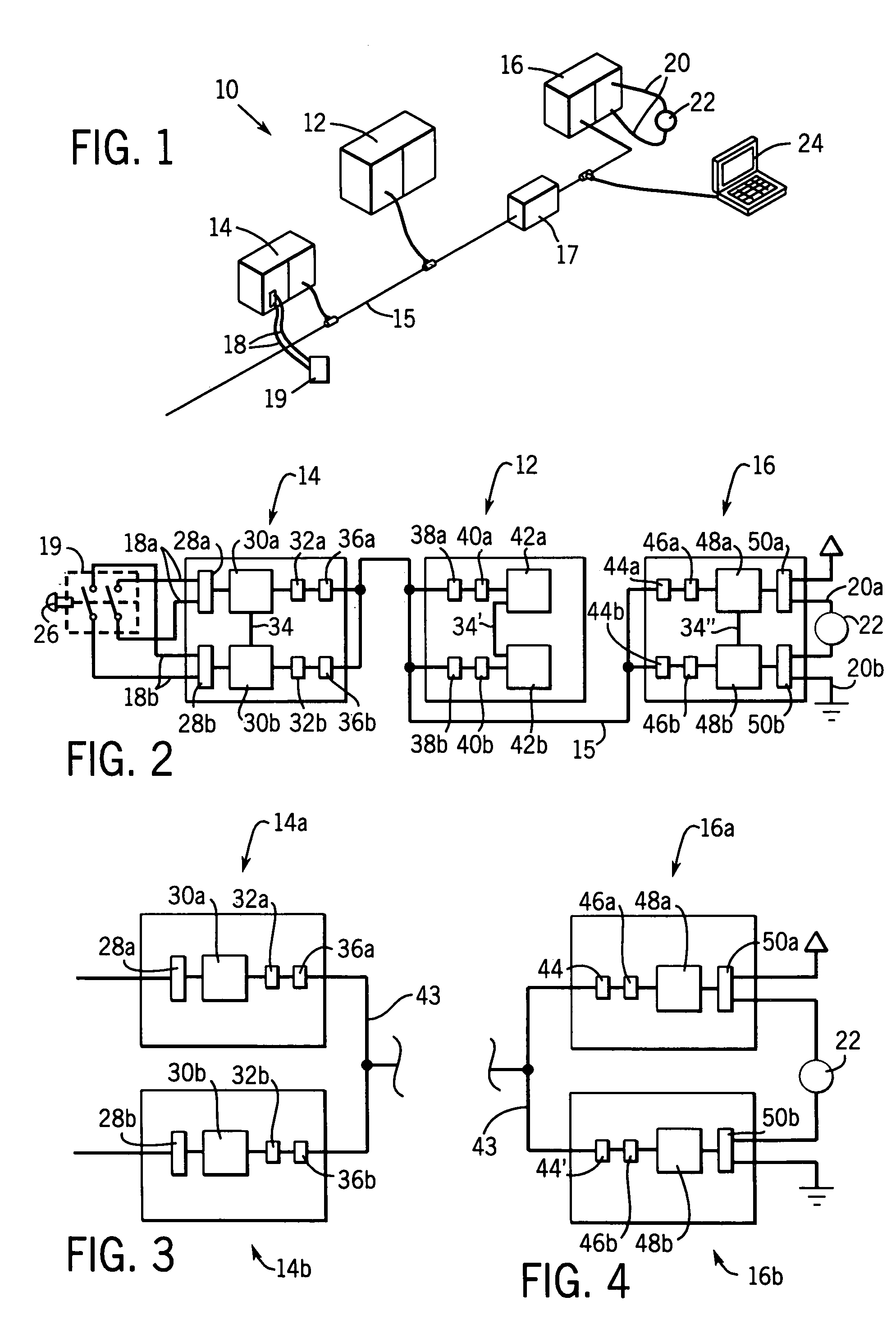
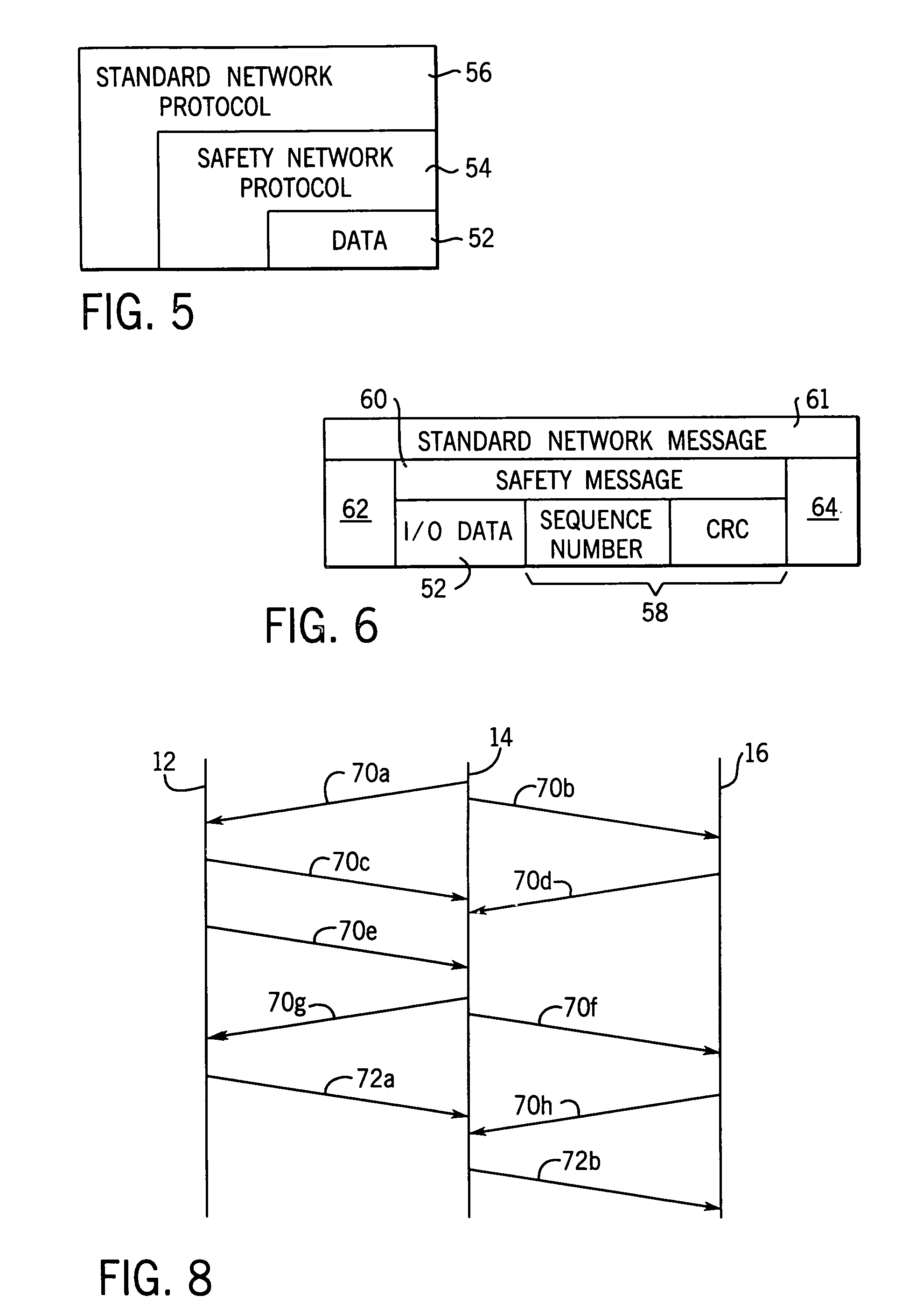
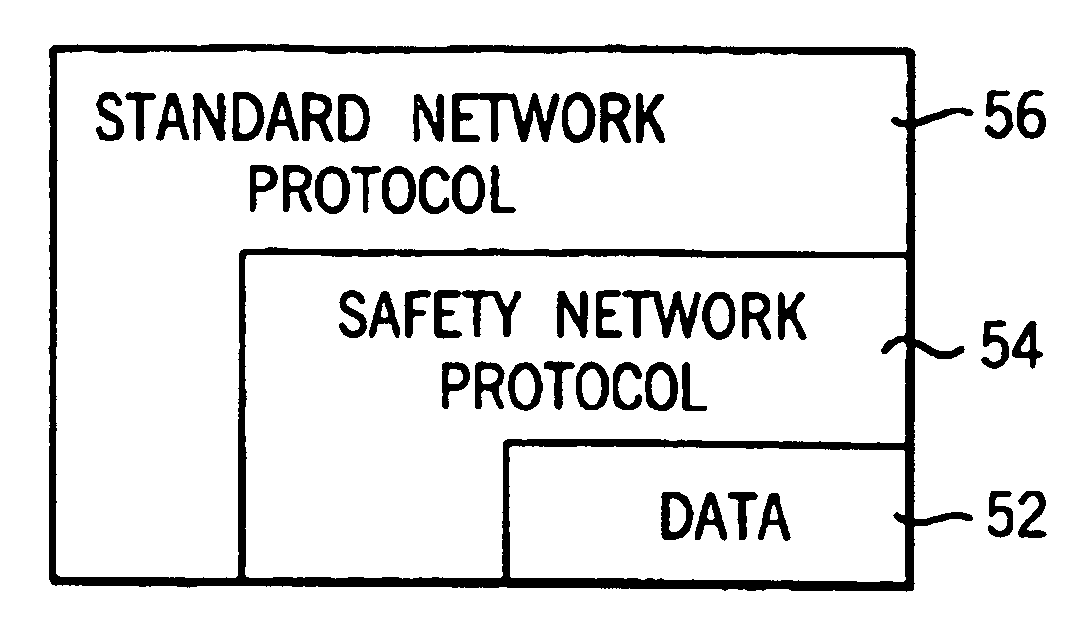
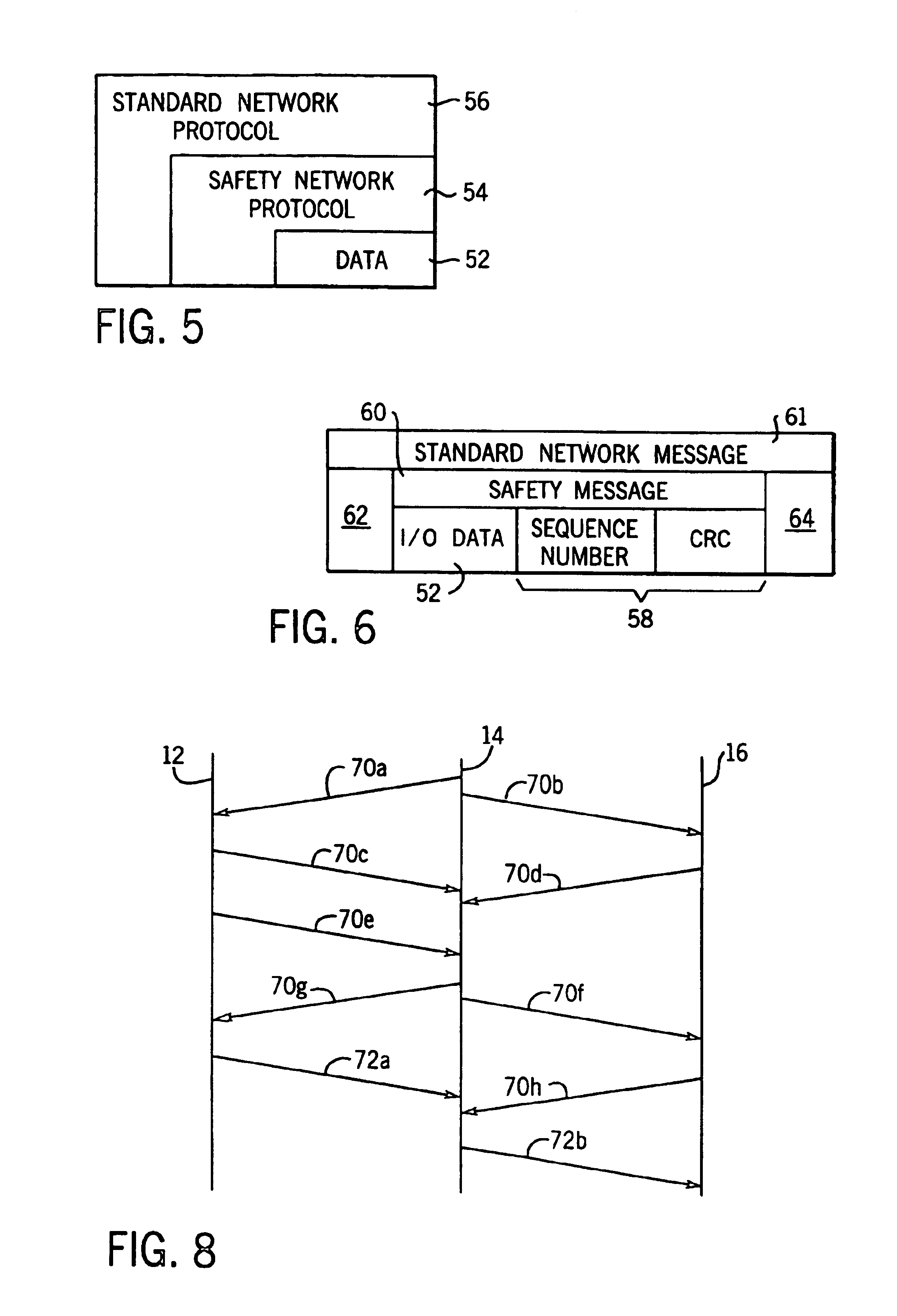
Network independent safety protocol for industrial controller
InactiveUS6891850B1Reduce errorsComputer controlSimulator controlNetworking protocolNetwork generation
A highly reliable industrial control system is produced using a network running a standard serial protocol. A safety protocol is embedded within the standard serial protocol by adding to special error detecting data redundant with the protocol of the standard serial network. In addition an overarching protocol involving timing of messages is imposed to provide the necessary level of reliability in the standard serial network. This approach allows the safety protocol to be used with a wide variety of commercially available serial communication standards without modification of the media or the specialized integrated circuits used for that communication. Safety protocol may be implemented in an additional level for integrated circuits or through firmware changes in programmable aspects of the industrial controller components.
Owner:ROCKWELL TECH
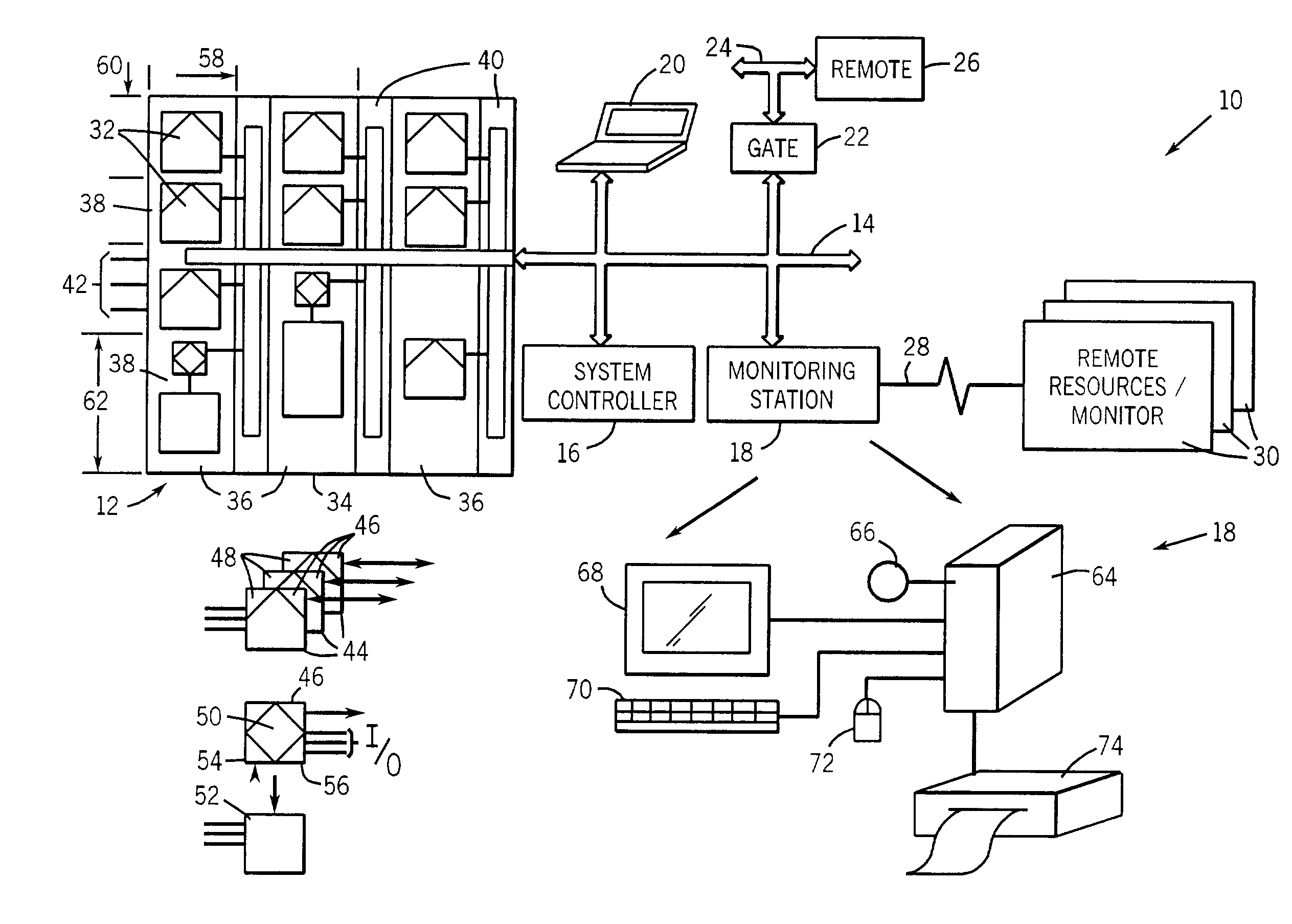
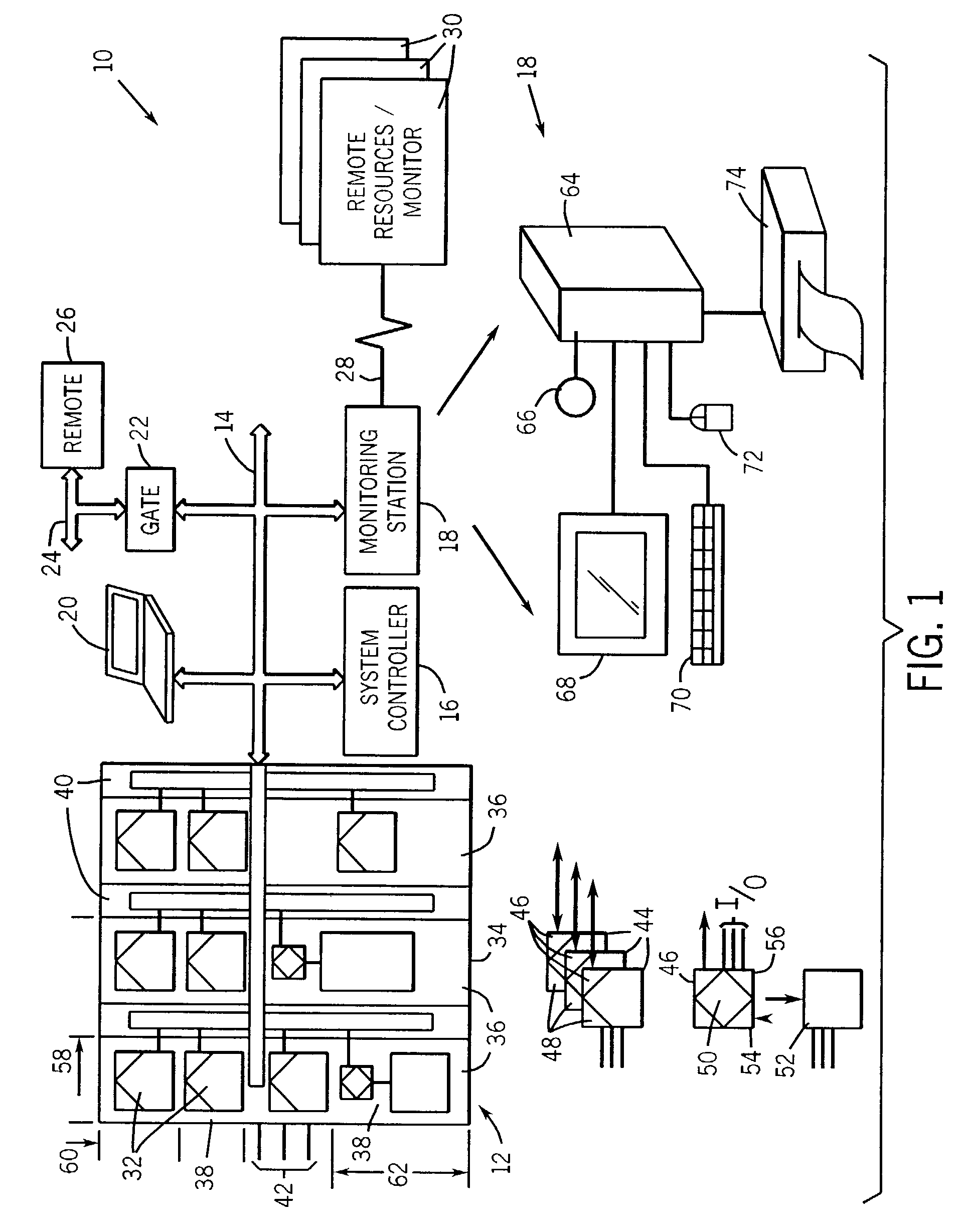
Industrial control and monitoring method and system
ActiveUS7092771B2Minimal programming effortGuaranteed uptimeComputer controlError detection/correctionMonitoring systemMotor control
A technique is provided for integrating human machine interfaces with control and monitoring systems. Control and monitoring systems may be integrated into a human machine interface to enable access to various systems including networked and programmable electrical components, such as components of motor control centers, and databases that including component, system designation data, configuration information, settings, and so forth. The database and components are accessed by execution of a program embedded in the human machine interface to provide desired information in response to selection of a particular physical component of the system. The information serves as the basis for an operator display through the human machine interface.
Owner:ROCKWELL AUTOMATION TECH
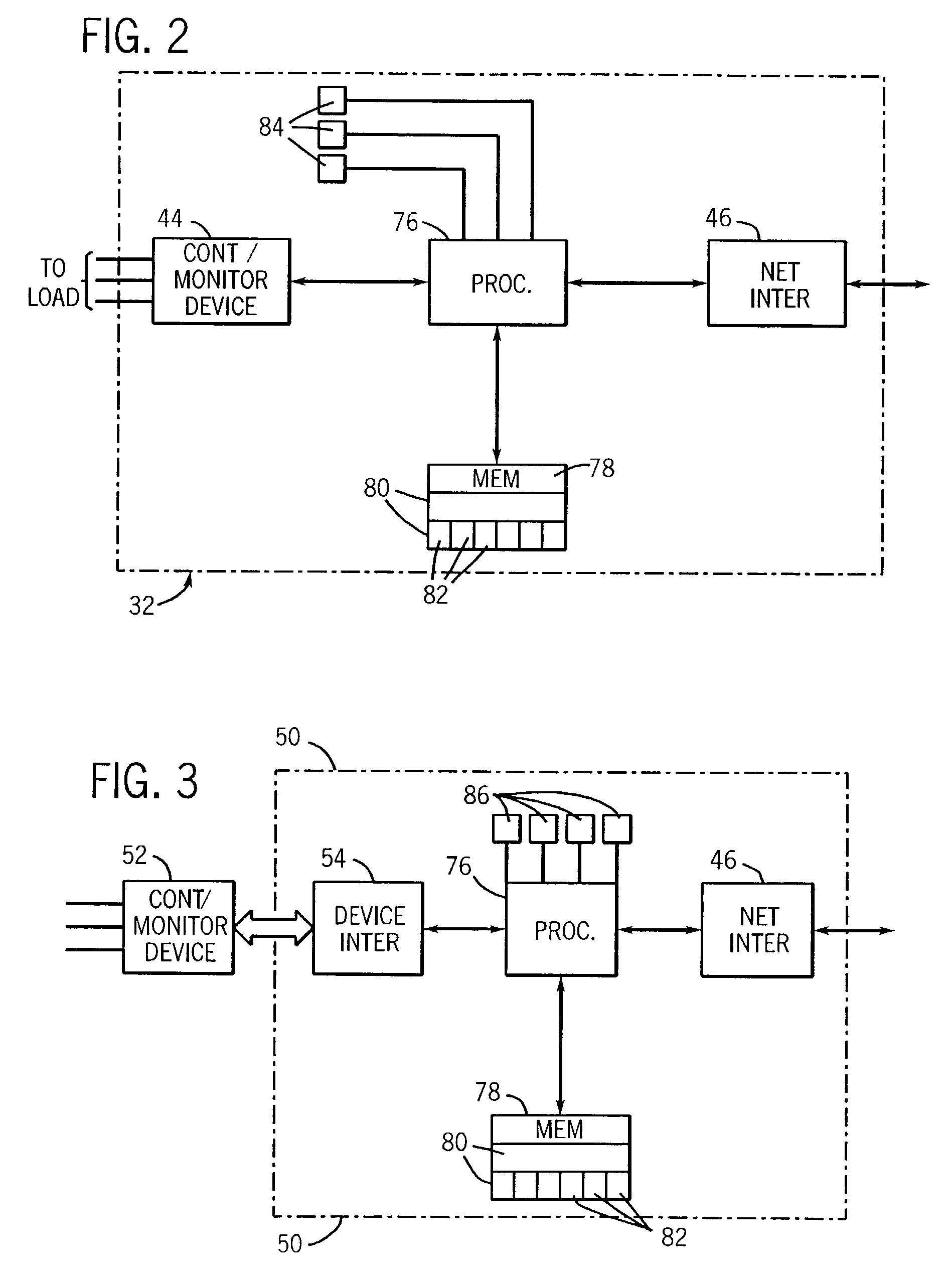
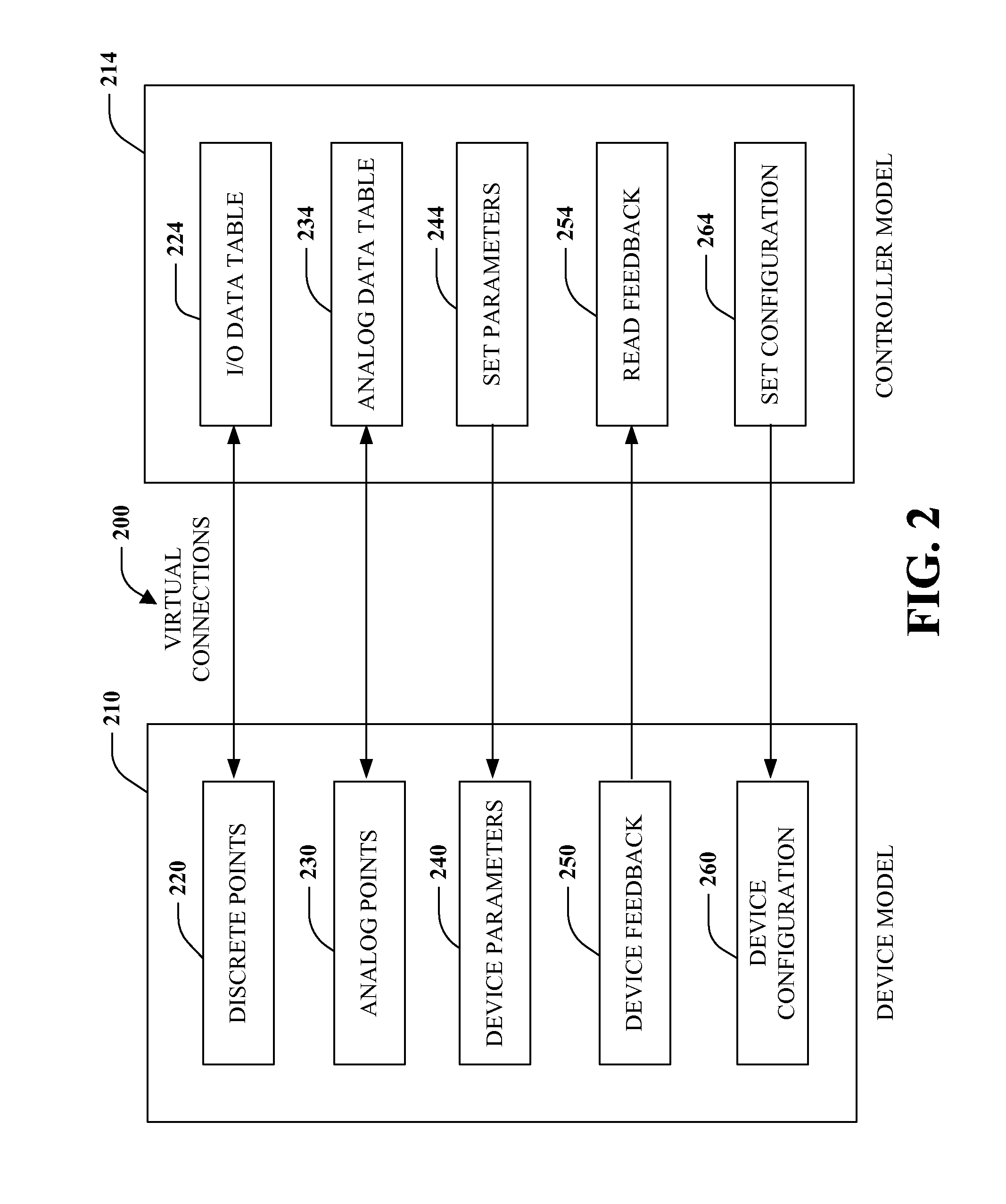
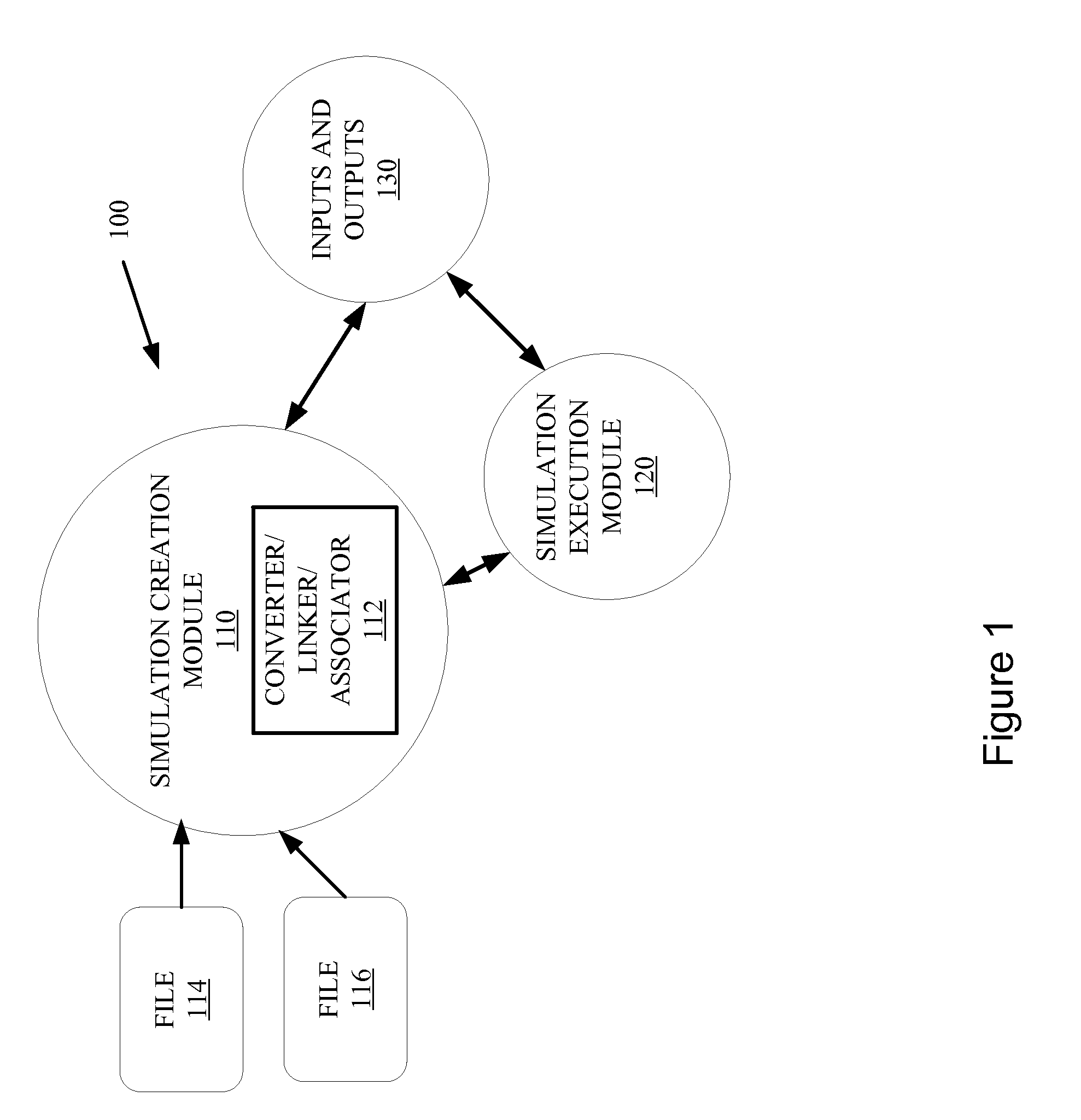
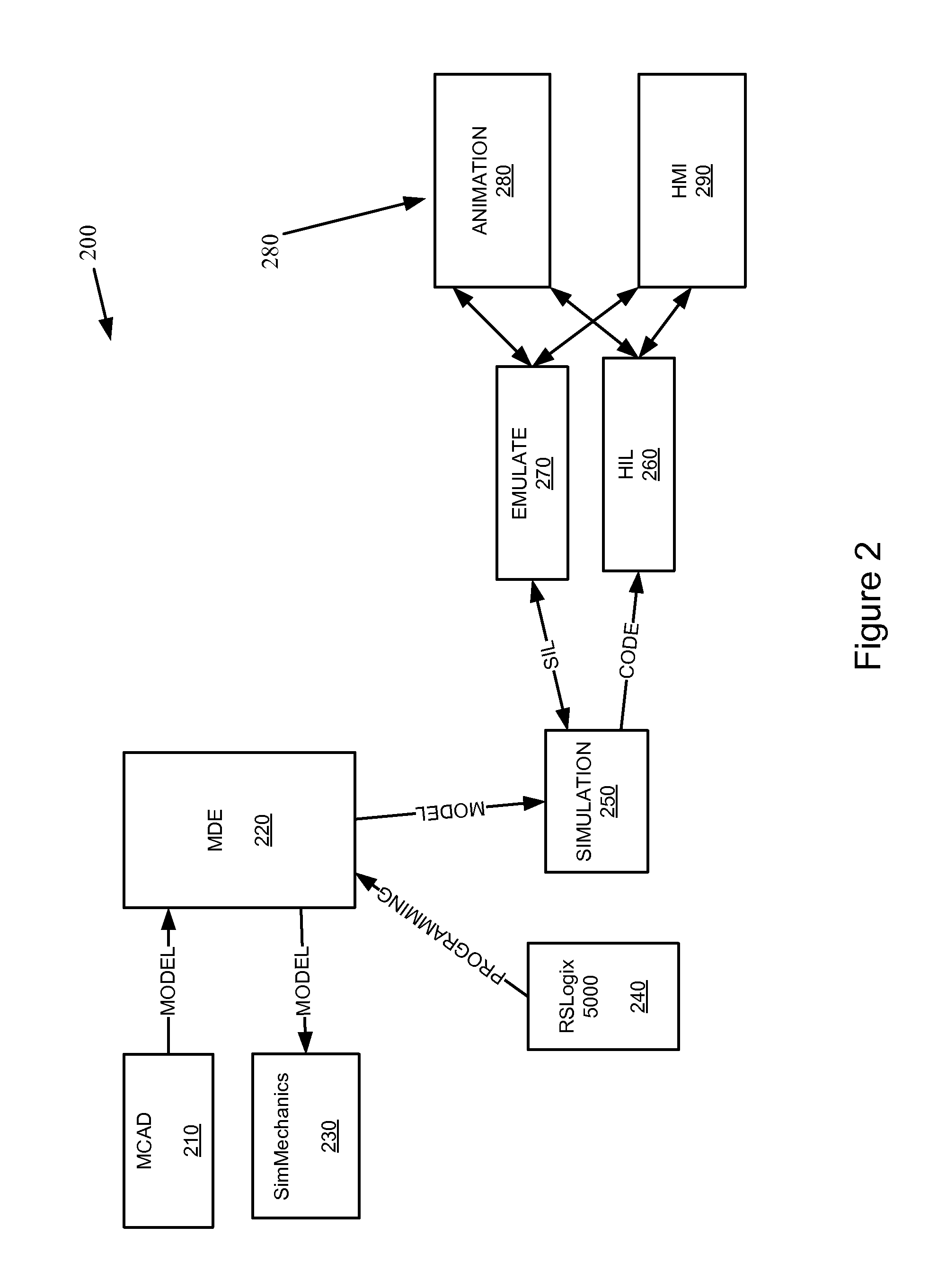
Integrated simulation of controllers and devices
InactiveUS20090089031A1Well formedSimulator controlAnalogue computers for control systemsSimulationIndustrial control system
A tool for simulating an industrial control system is provided. The tool includes a simulation component to emulate a controller according to a simulated execution environment and one or more simulation models for simulating devices associated with the controller, where the controller and the devices are integrated in a common simulation platform.
Owner:ROCKWELL AUTOMATION TECH
Method for adapting a computer-to-computer communication protocol for use in an industrial control system
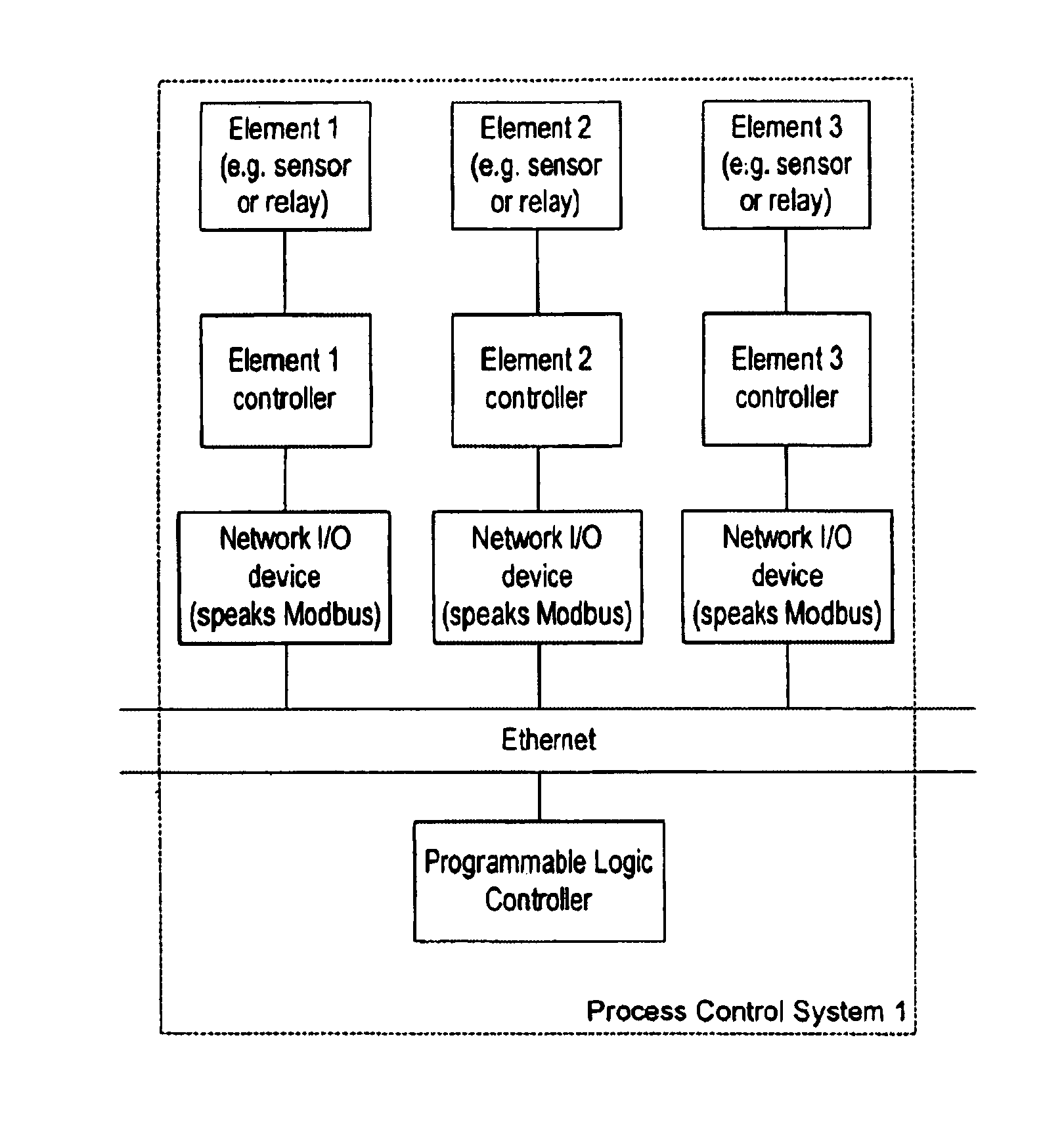
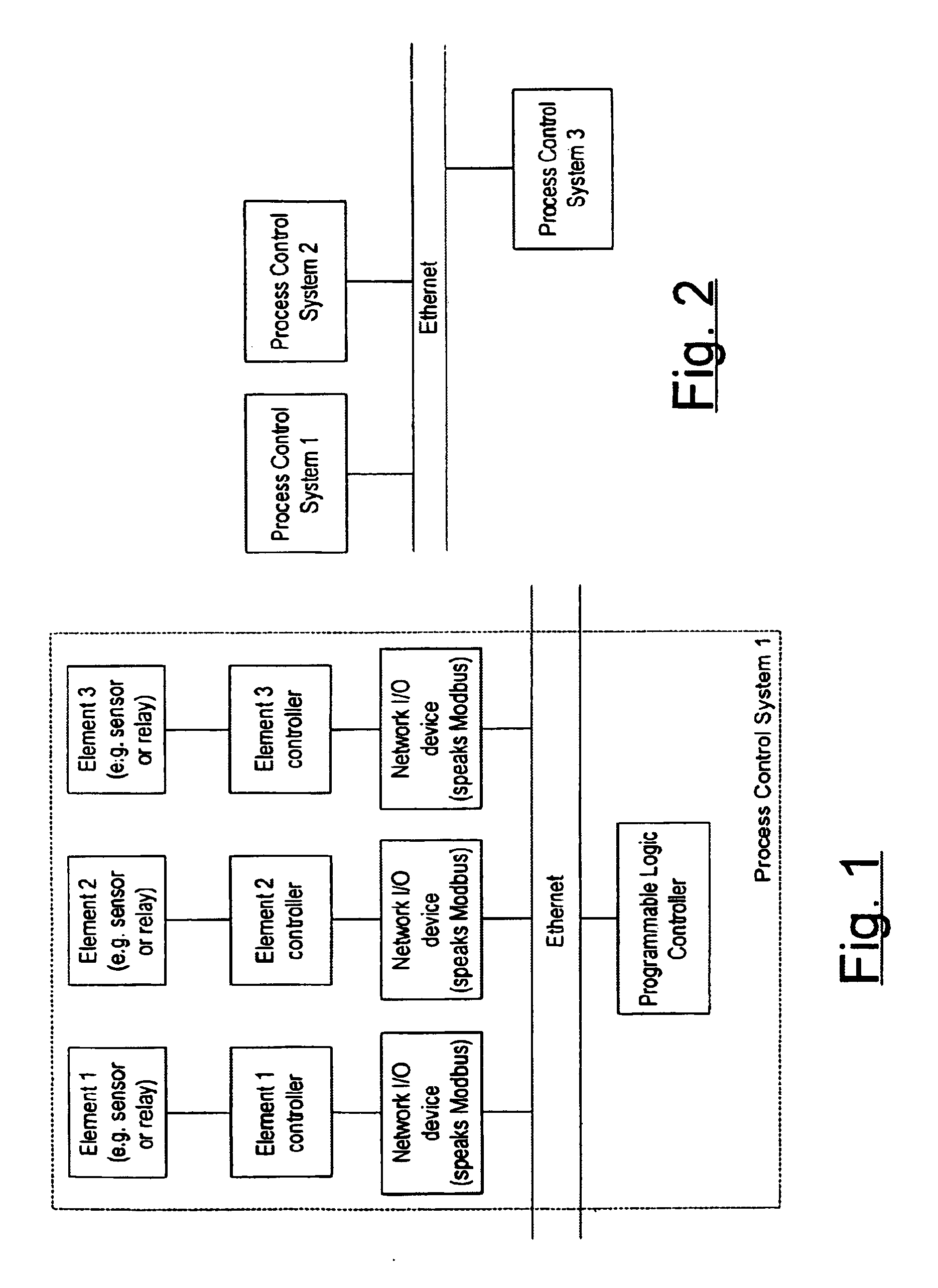
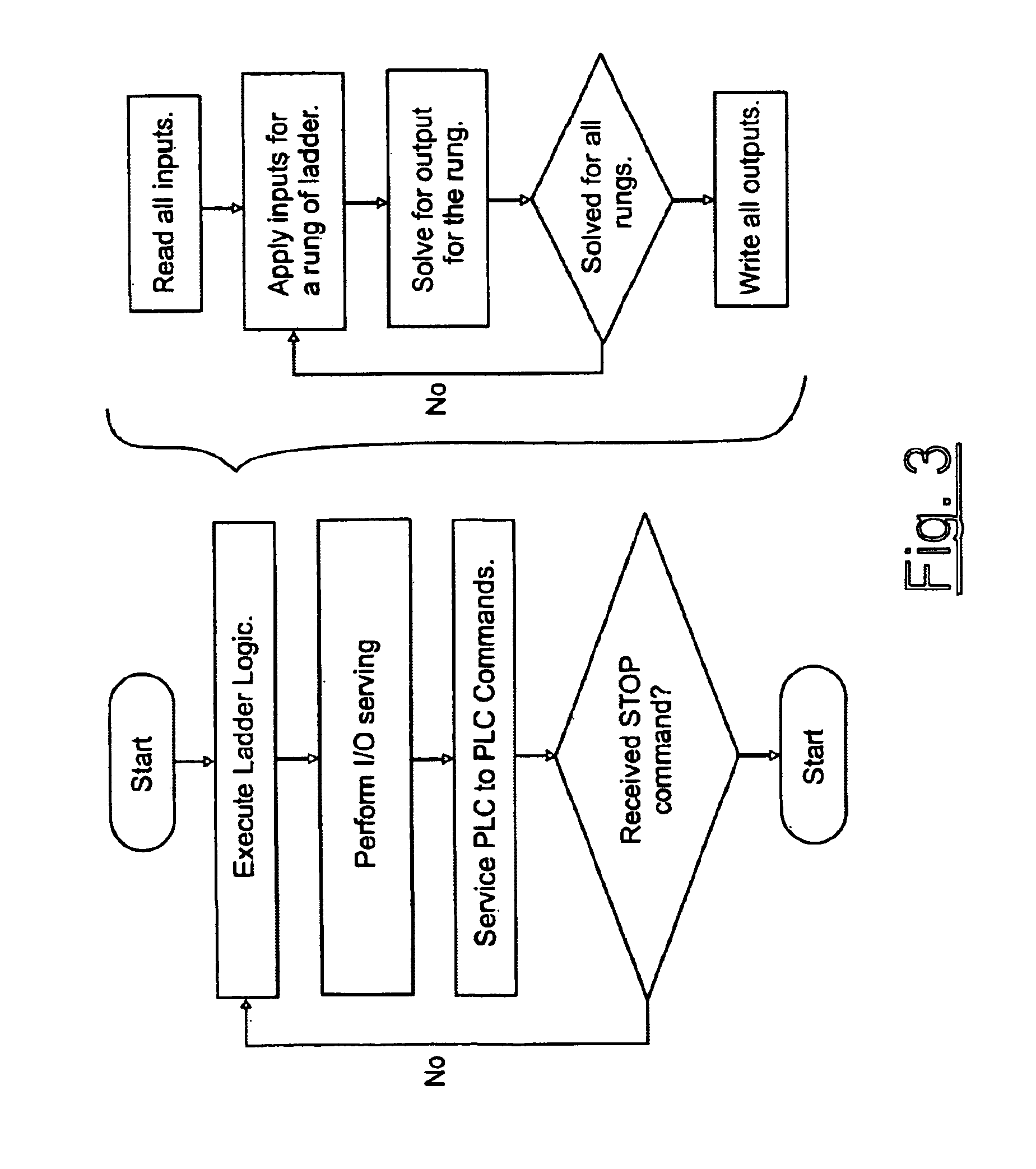
A method for adapting a computer-to-computer communication protocol, and especially TCP / IP, or any protocol implemented in a general purpose off-the-shelf network like Ethernet, for use in providing communication needed in an industrial control system, and especially an industrial control system using a programmable logic controller (PLC), where there is frequent communication between the PLC and control or monitoring elements, the method aimed at allowing the PLC to perform scanning of its ladder logic at a rate adequate for effective industrial control. The method includes making permanent-type TCP connections between the PLC and a control element or a monitoring element, use of a protocol for communication with a control or monitoring element in which both a read register and a write register instruction is included in a single communication transaction, such as a MODBUS command, and tuning communication between the PLC and a control element or a monitoring element.
Owner:SCHNEIDER AUTOMATION INC
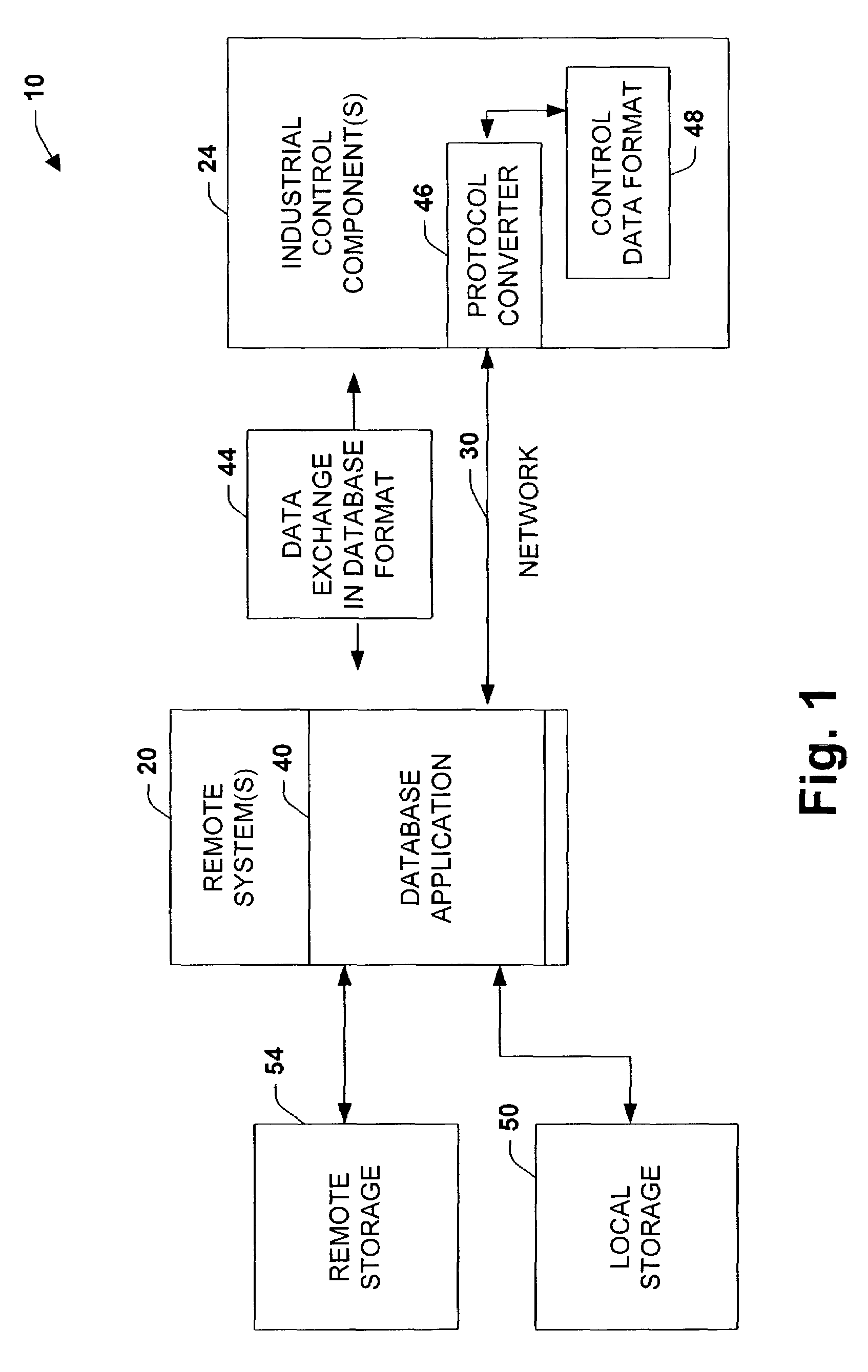
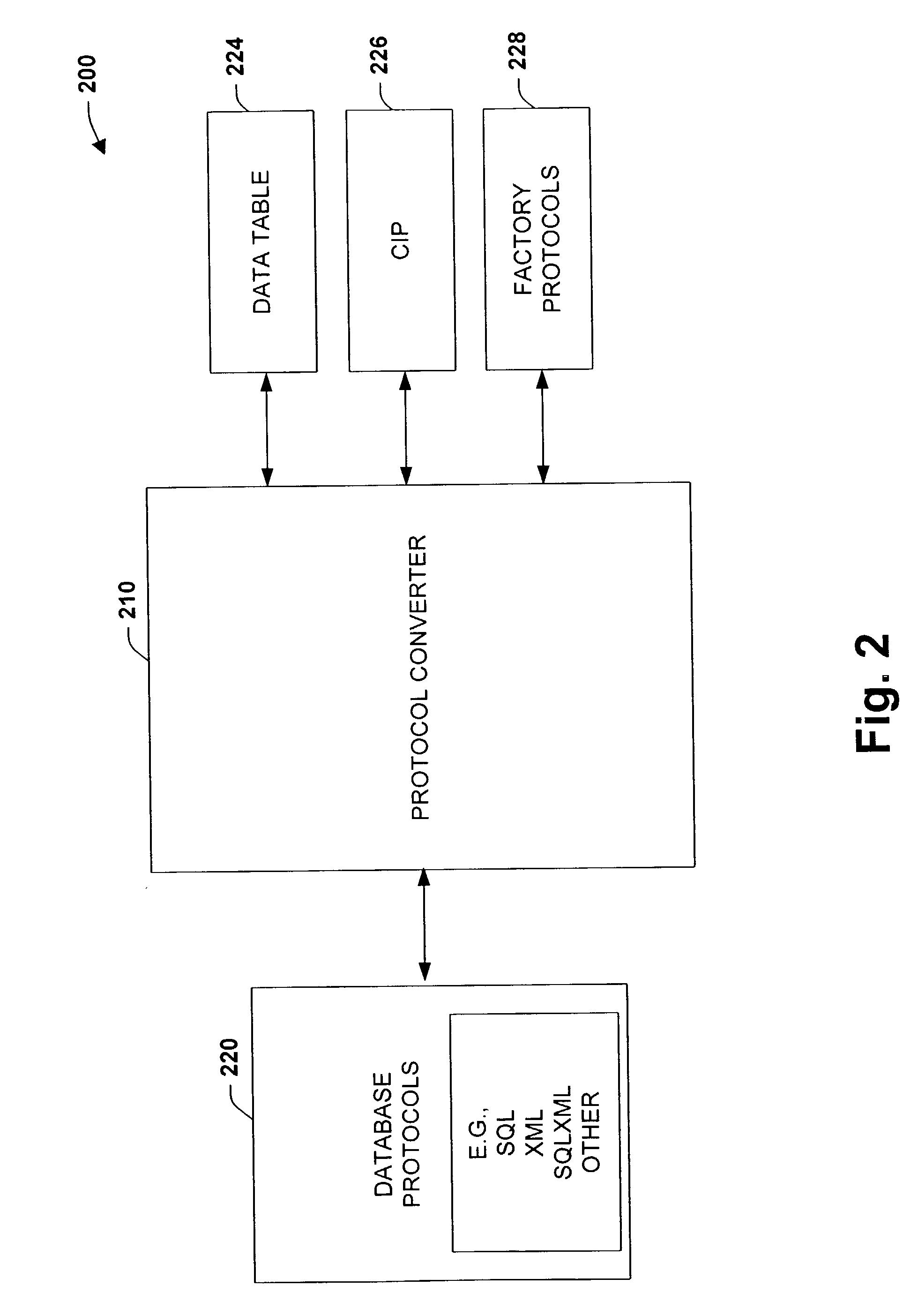
Embedded database systems and methods in an industrial controller environment
ActiveUS7467018B1More seamless integrationComputer controlSemi-structured data mapping/conversionEmbedded databaseNetwork data
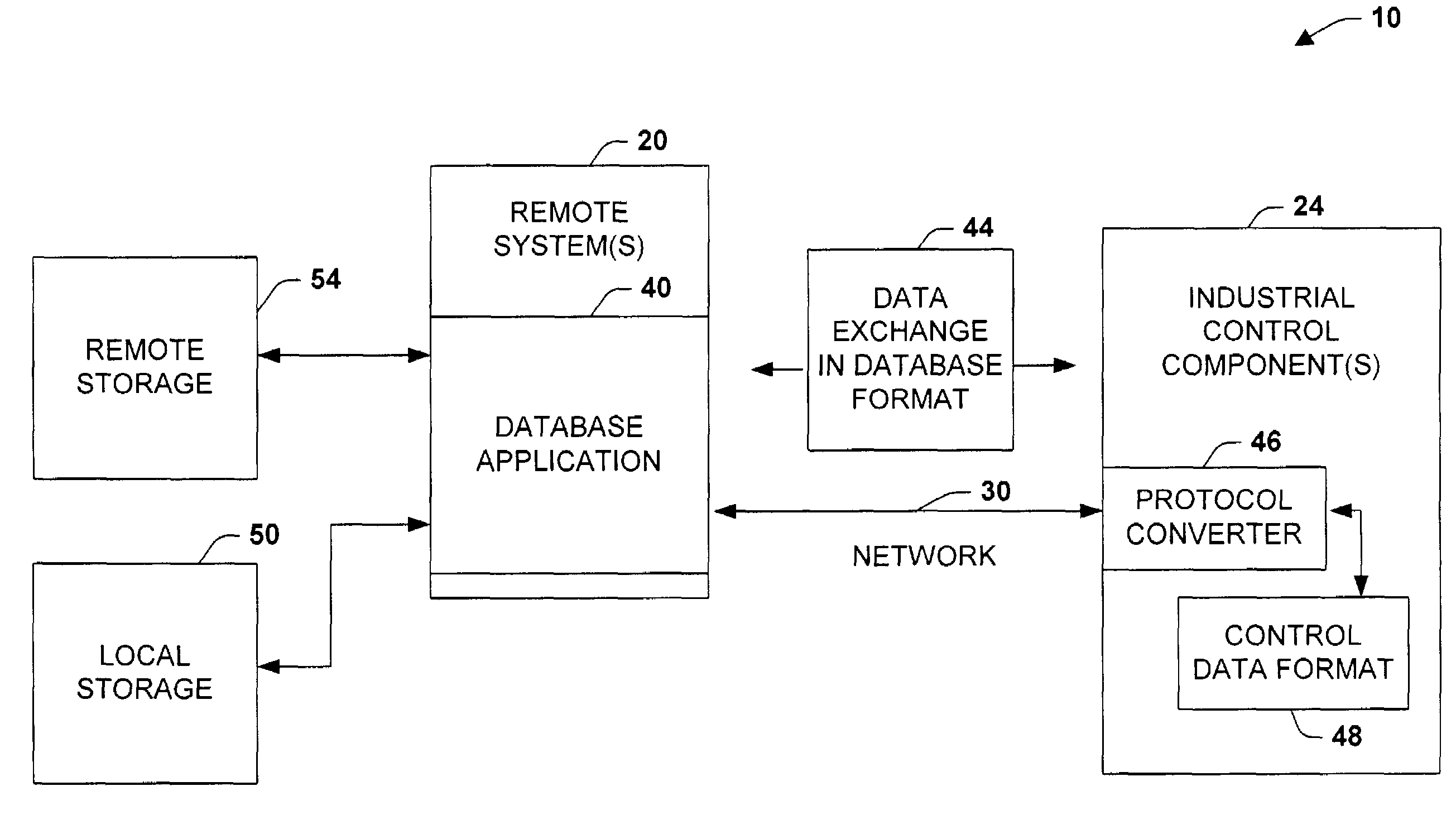
The present invention relates to systems and processes that provide network database interactions in an industrial controller environment. A database protocol component operating in a control environment is provided to convert control or factory protocols to a native language format associated with a network database. Such databases may be accessed in a structured format, wherein one or more control components may be adapted in a client and / or server configuration to freely exchange data in the structured format associated with the database. The database protocol component sends commands and / or data in the structured format when exchanging data with the database while converting the structured format to one or more protocols associated with an industrial control system when receiving commands and / or data therefrom.
Owner:ROCKWELL AUTOMATION TECH
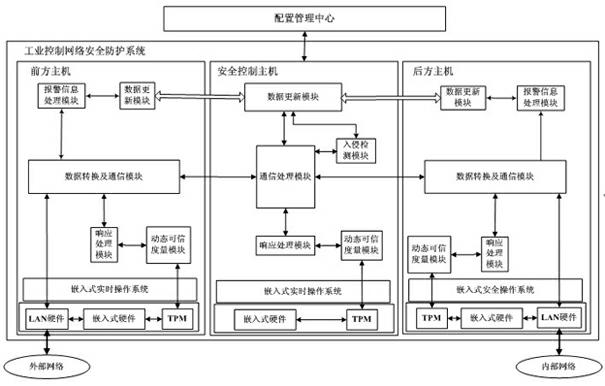
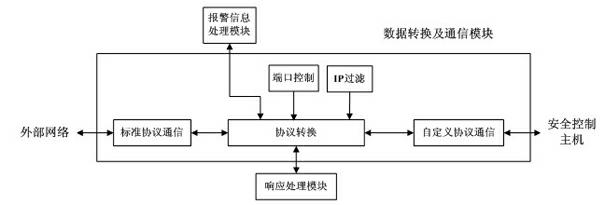
Industrial control network security protection method and system
InactiveCN102438026AImprove resistance to attackImprove securityUser identity/authority verificationData switching networksSystem transformationNetwork attack
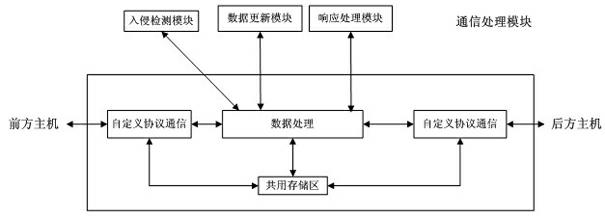
The invention discloses an industrial control network security protection method and an industrial control network security protection system. The method comprises the following steps that: aiming at an external network attack, a front host performs first layer data filter and access control on external network data; a security control host caches data through a common storage region, performs intrusion detection on the data, timely alarms illegal data and informs hosts on two sides; a rear host performs deep filter and access control on the data and causes the legal data to enter an internal network; aiming at an internal network attack, the rear host performs the first data filter and access control on internal network data; the security control host caches the data through the common storage region, performs the intrusion detection on the data, timely alarms the illegal data and informs the hosts on the two sides; and the front host performs the deep filter and access control on the data and causes the legal data to enter an external network. By the method and the system, the network security level of an industrial control system is increased, and the cost on investment, system transformation and management is reduced.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
Controller redundancy and switching method
ActiveCN103455005AIncrease flexibilityReduce distractionsTotal factory controlProgramme total factory controlControl lineIndustrial control system
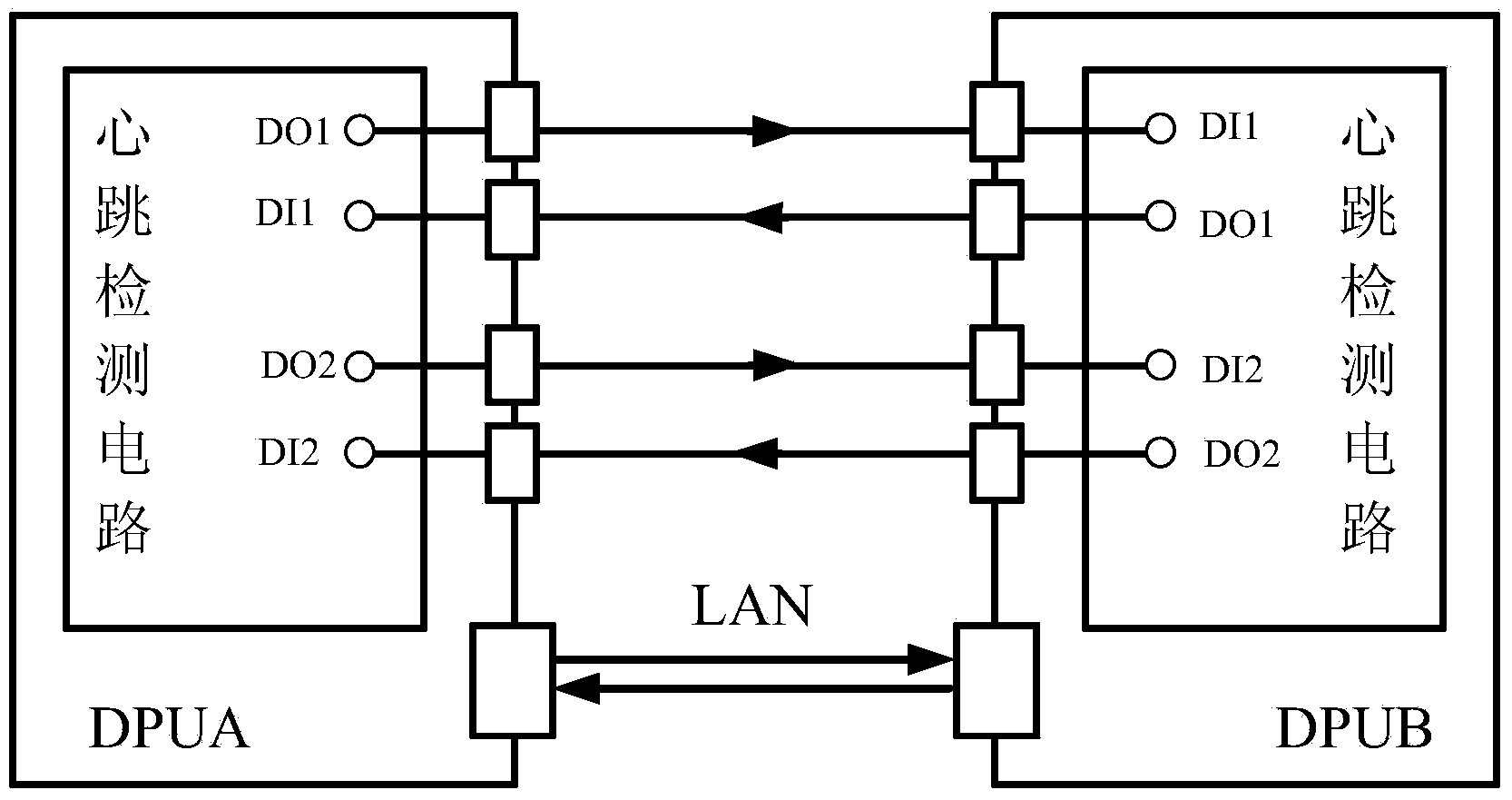
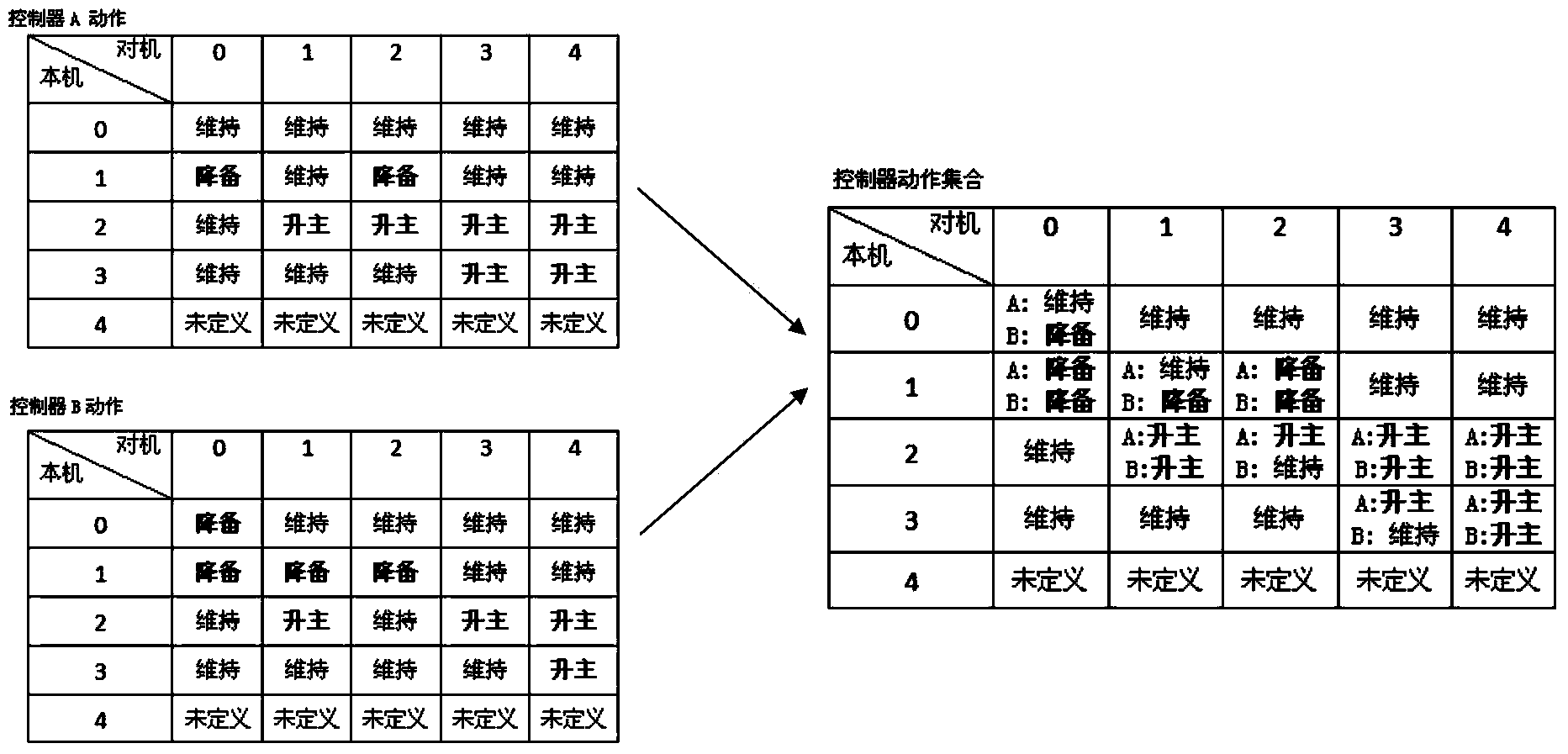
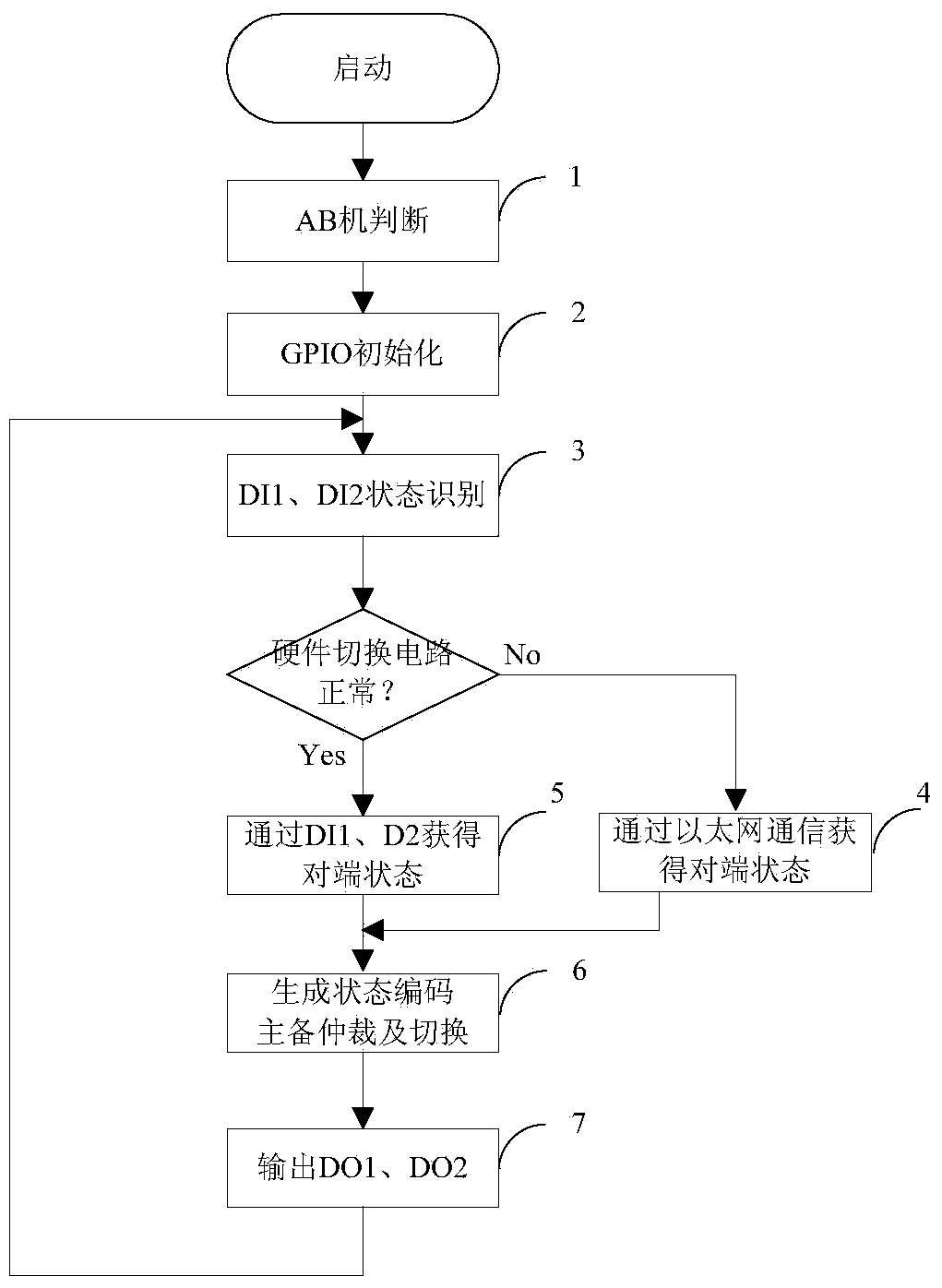
The invention discloses controller redundancy and a switching method. The method is used for the redundancy switching logic between an industrial controller main machine and a spare machine. Calculation and output synchronization between the main machine and the spare machine is guaranteed, and rapid undisturbed switching is achieved when the main machine fails. A switching circuit is composed of two pairs of GPIO control lines and a 100M Ethernet. Through recognition of low level states, pulse signal states and high level states of IOs, the normal state or the failure state of the opposite end controller main machine or the spare machine is obtained, and the normal state or the failure state of the main machine or the spare machine of an opposite end controller can be obtained in a communication mode when the hardware switching circuit fails, so that arbitration and switching of the main machine and the spare machine are achieved. The design method of state machines is adopted, the operation states of the controller are summarized to be five states that the main machine is normal, the main machine fails, the spare machine is normal, the spare machine fails, and opposite ends are powered off, and the arbitration treatment of the main machine and the spare machine is achieved through matrixes of the state machines. The hardware switching circuit and redundant communication serve as connecting signals between redundancy devices, reliability of redundancy switching control is greatly enhanced, and stable operation of an industrial control system can be effectively guaranteed.
Owner:BEIJING SIFANG JIBAO AUTOMATION +1
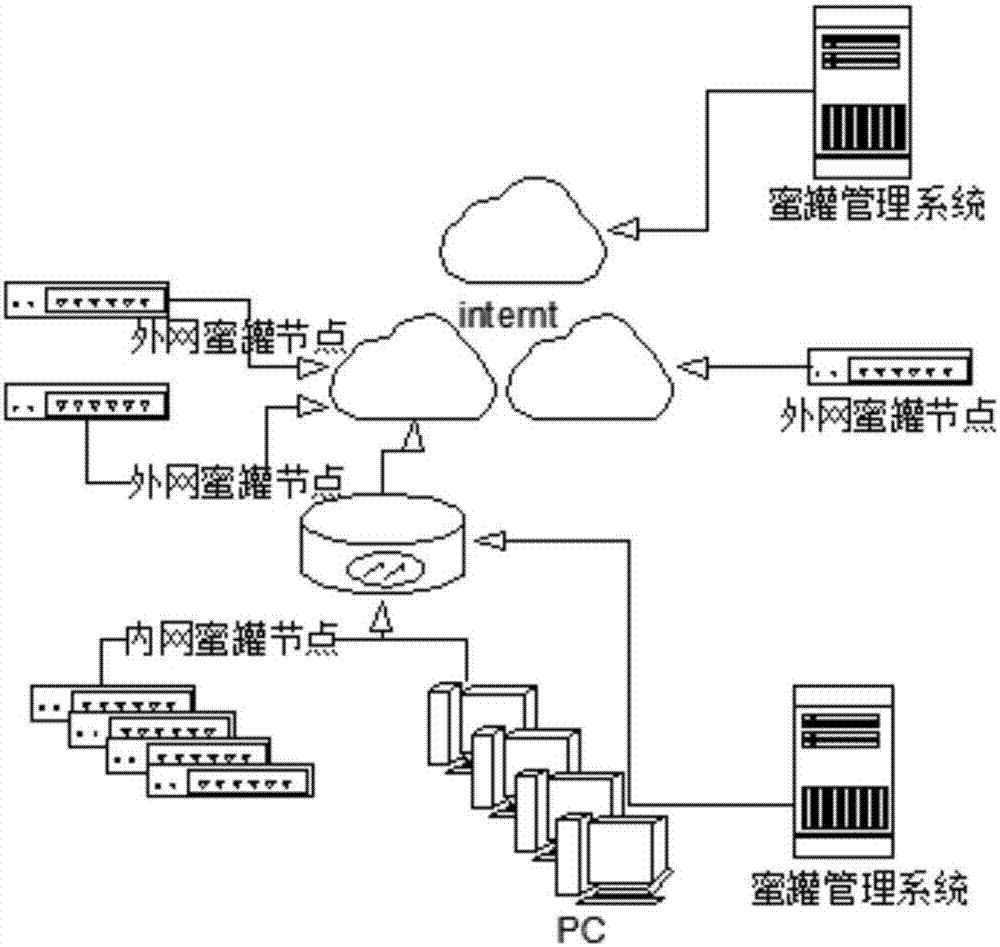
Industrial control network honeypot system
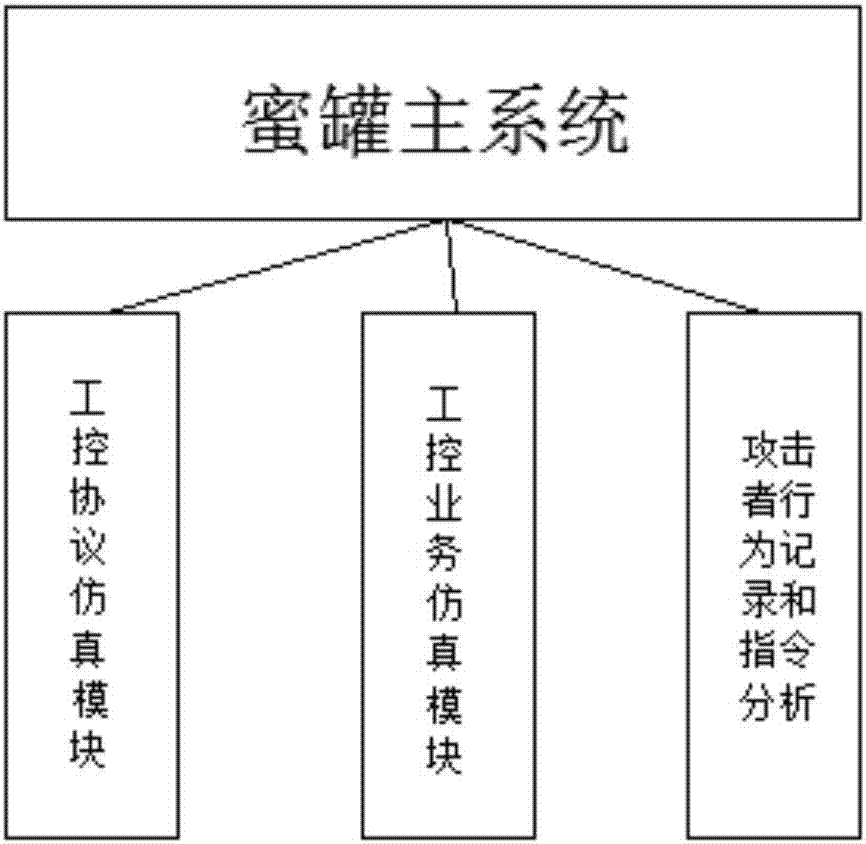
The invention discloses an industrial control network honeypot system, which comprises an external network honeypot node, an internal network honeypot node, a honeypot management system, Internt and a PC. The beneficial effects of the present invention are: the external network honeypot node can help users set up a disguised "business system" around the IP address of the core server, and induce attackers by constructing a real industry business SCADA template, thereby protecting the real business system, honeypot The management system can simulate SCADA and PLC system services, and can switch to different business types according to the multi-service templates preset in the system, making it impossible for attackers to distinguish the real attack target. The industrial control protocol simulation module creates a real industrial control system for attackers. The operating environment of the service, any operation and scanning attack behavior of the attacker will be recorded by the data analysis function of the honeypot system.
Owner:CHINA ELECTRONICS STANDARDIZATION INST +1
System and methodology providing multi-tier security for network data with industrial control components
The present invention relates to a system and methodology facilitating network security and data access in an industrial control environment. An industrial control system is provided that includes an industrial controller to communicate with a network. At least one security layer can be configured in the industrial controller, wherein the security layer can be associated with one or more security components to control and / or restrict data access to the controller. An operating system manages the security layer in accordance with a processor to limit or mitigate communications from the network based upon the configured security layer or layers.
Owner:ROCKWELL AUTOMATION TECH
Process control methods and apparatus for intrusion detection, protection and network hardening
ActiveUS20060294579A1Digital data processing detailsUser identity/authority verificationEnvironmental control systemProduction control system
The invention provides an improved network and methods of operation thereof for use in or with process control systems, computer-based manufacturing or production control systems, environmental control systems, industrial control system, and the like (collectively, “control systems”). Those networks utilize a unique combination of firewalls, intrusion detection systems, intrusion protection devices and / or other devices for hardening (e.g., security against hacking, intrusion or other mischievous conduct) and / or intrusion detection. The networks and methods have application, by way of example, in plants, sites and other facilities in which networks that support control systems interface with corporate, business or other networks.
Owner:SCHNEIDER ELECTRIC SYST USA INC
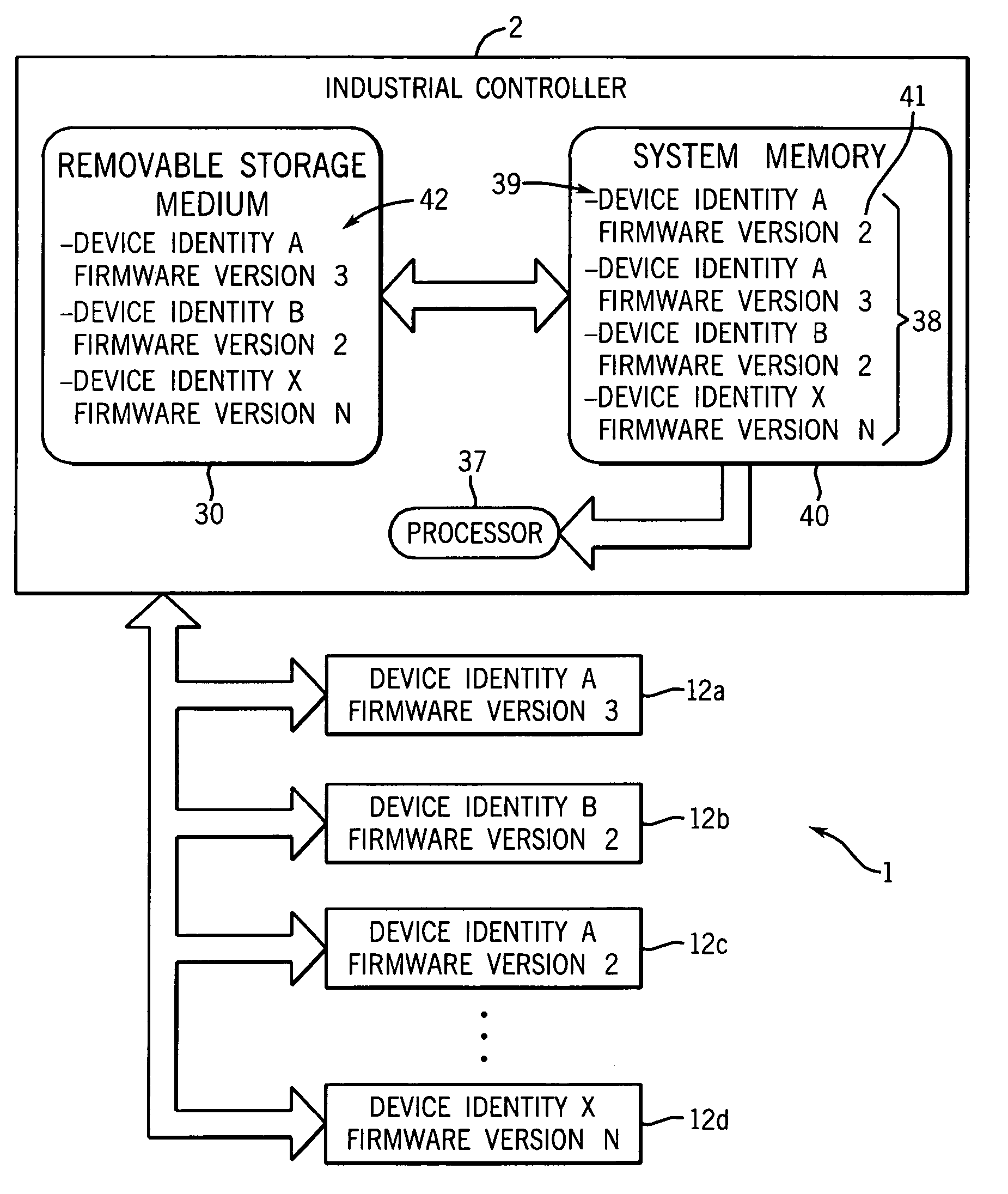
System and method for automatically matching programmable data of devices within an industrial control system
ActiveUS20060178757A1Effectively and efficiently clonedOvercomes drawbackComputer controlSimulator controlIndustrial control systemEmbedded system
An industrial control system includes a central controller having a memory containing programmable data including operating programs for operating the controller, control program for controlling an industrial process, and configuration data configuring values used by the operating program and control program. The central controller is designed to control multiple devices also having memory holding programmable data including operating programs and configuration data. A program is executable by the central controller that causes the central controller to identify memories distributed through the industrial control system having programmable data and collect the programmable data from the memories. Accordingly, the collected programmable data may be used to substantially recreate operation of the industrial control system in a second industrial control system having another central controller substantially identical to the industrial controller and multiple devices connected to the central controller.
Owner:ROCKWELL AUTOMATION TECH
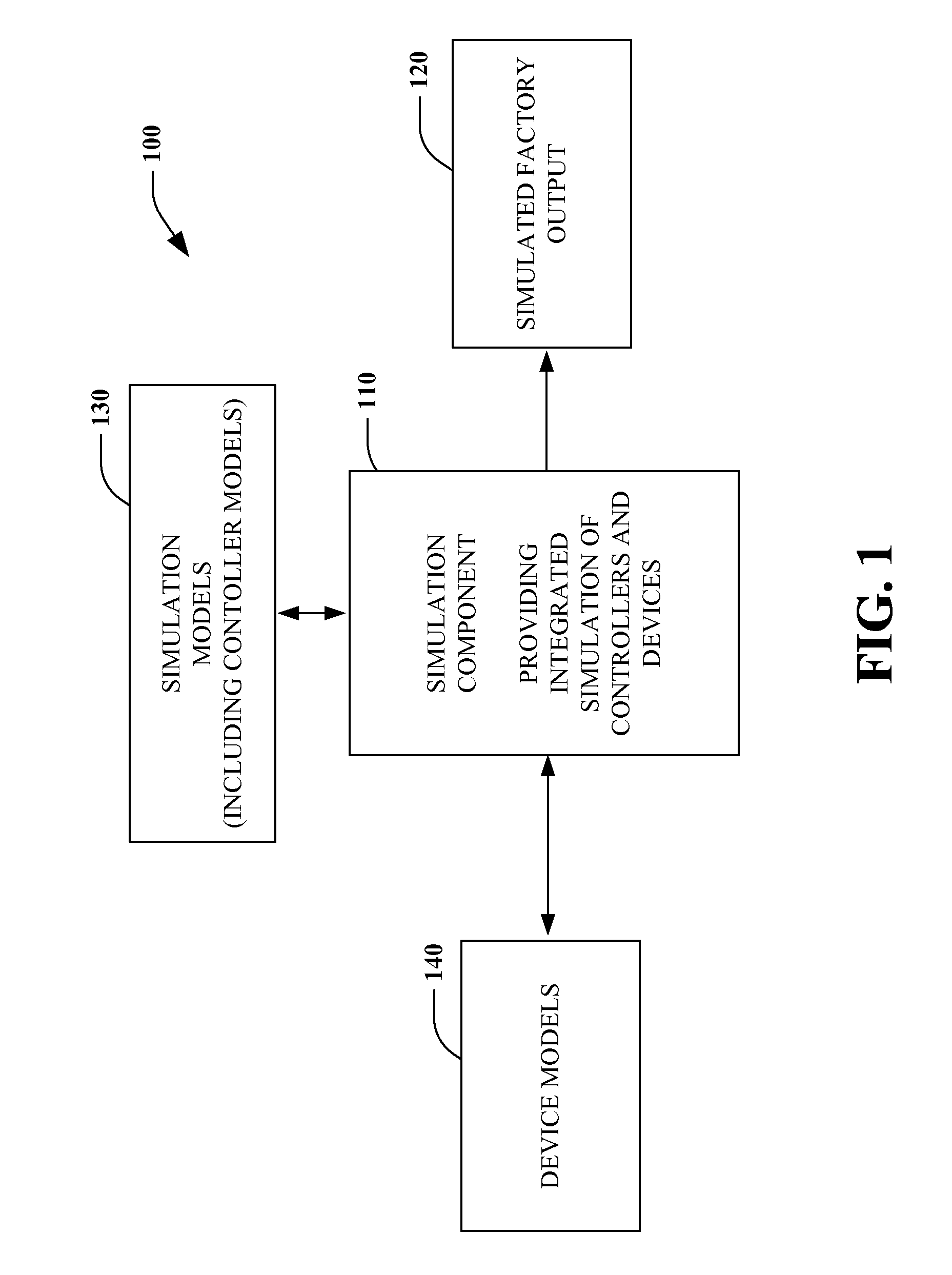
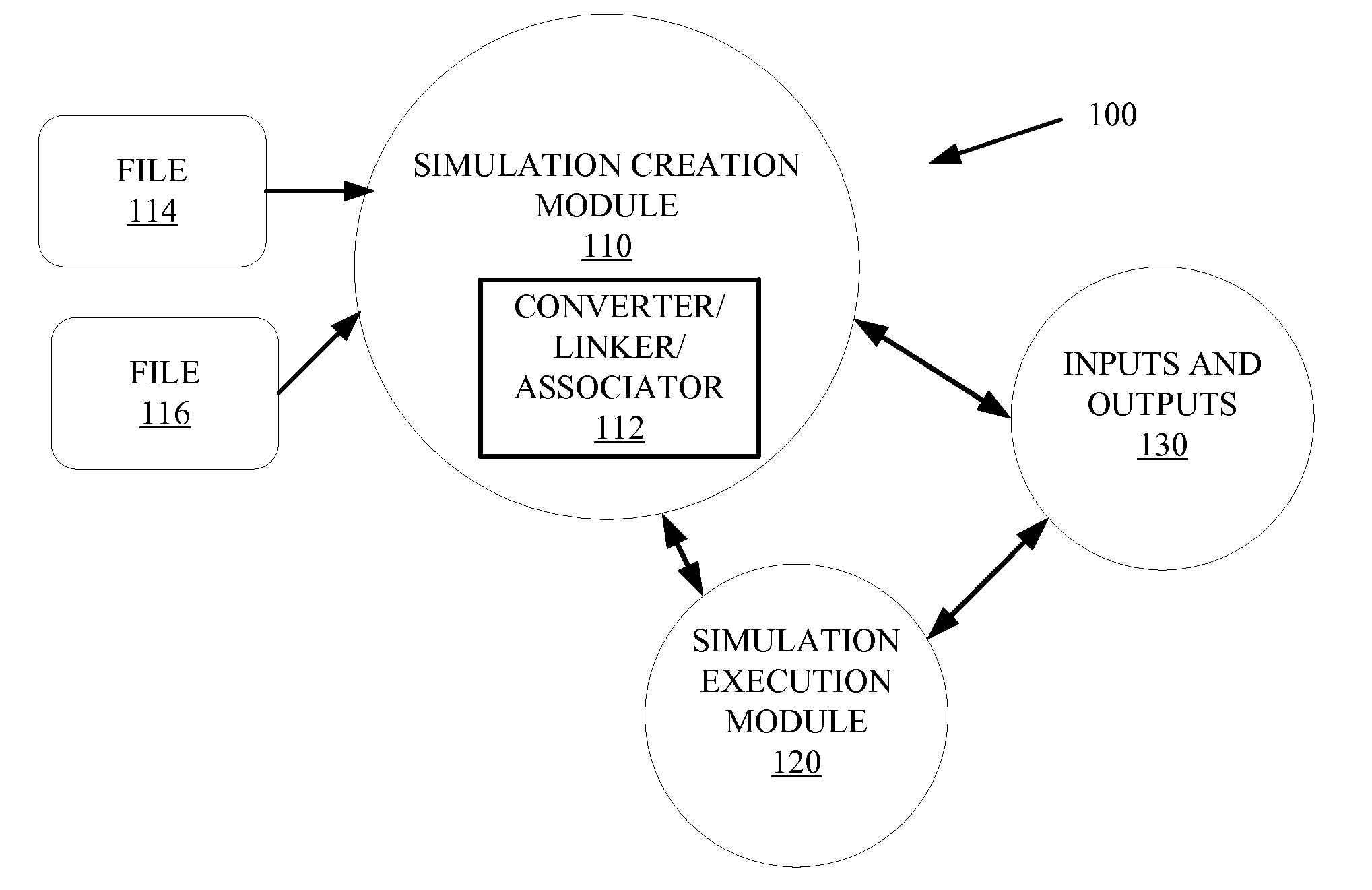
Integration of simulation of a machine for industrial automation
Methods and systems for creating and running and industrial control system simulation are described herein. The simulation may include animation of a complex machine linked with the industrial control device controlling the complex machine. The simulation may also include links to the physical I / O and other modules of the industrial controller to enhance the functionality of the simulation. This may increase the likelihood that the timing and functionality of the simulation may be more like real-time operation of the industrial control system. This may enhance the system design and save time of system design and start-up and troubleshooting of the operational industrial control system.
Owner:ROCKWELL AUTOMATION TECH
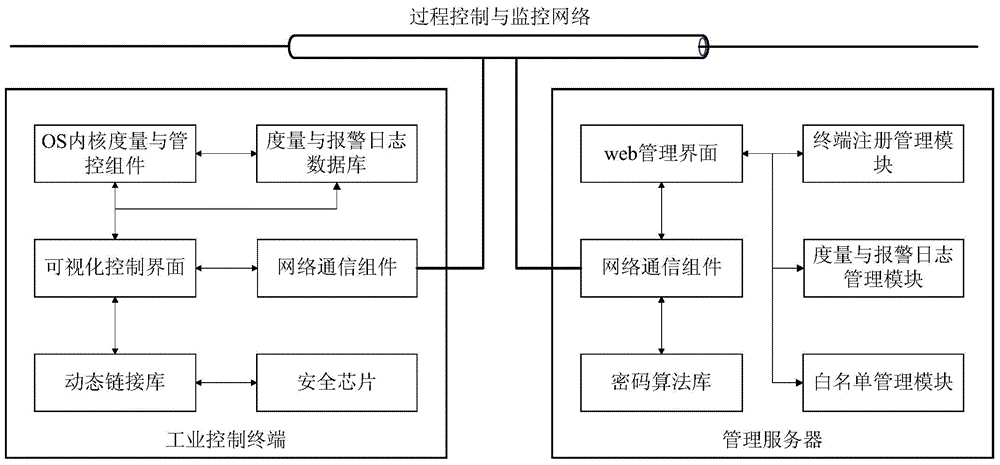
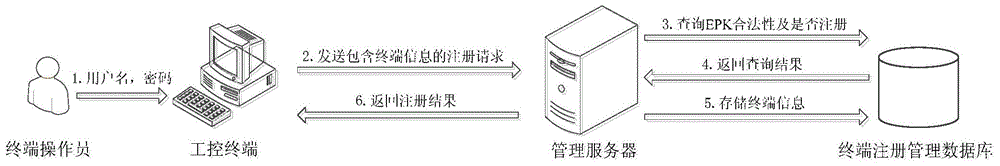
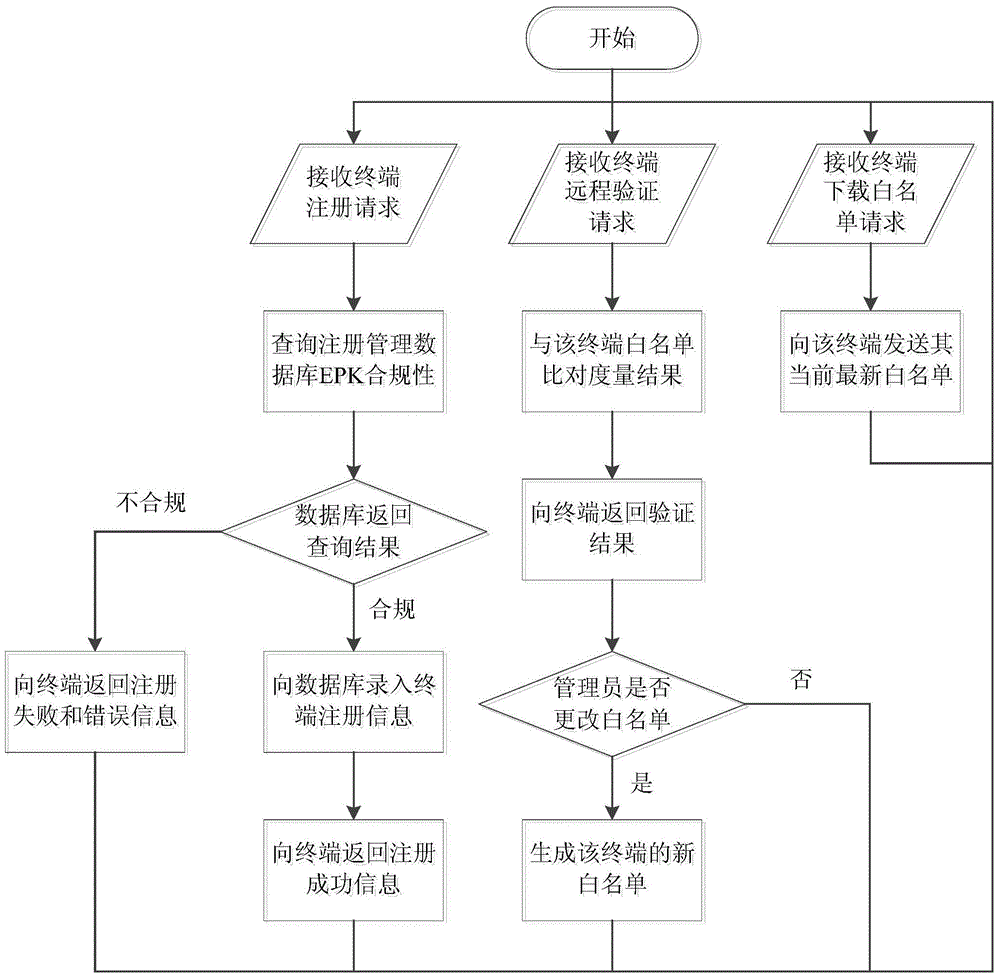
Industrial control system trusted environment control method and platform based on safety chip
ActiveCN104573516AGood cryptographic function serviceImprove security defense performanceDigital data protectionPlatform integrity maintainanceComputer terminalComputer science
The invention provides an industrial control system trusted environment control method and platform based on a safety chip. The method comprises the steps: (1) registering an industrial control terminal to a management server on the basis of the safety chip; (2) carrying out complete measurement on each operating process by adopting the industrial control terminal; (3) checking the measurement information by the management party on the management server, and forming a white list; (4) downloading the white list formed by the management party from the management server by the industrial control terminal, leading the white list into an operating system core, and then carrying out the control on the process to be operated. By adopting the method and platform, malicious code of an untrusted, unknown and uncontrollable program process is prevented from damaging the system of the industrial control terminal, from stealing the confidential information and damaging the industrial production, so that the safety defense capacity of the industrial control system can be improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
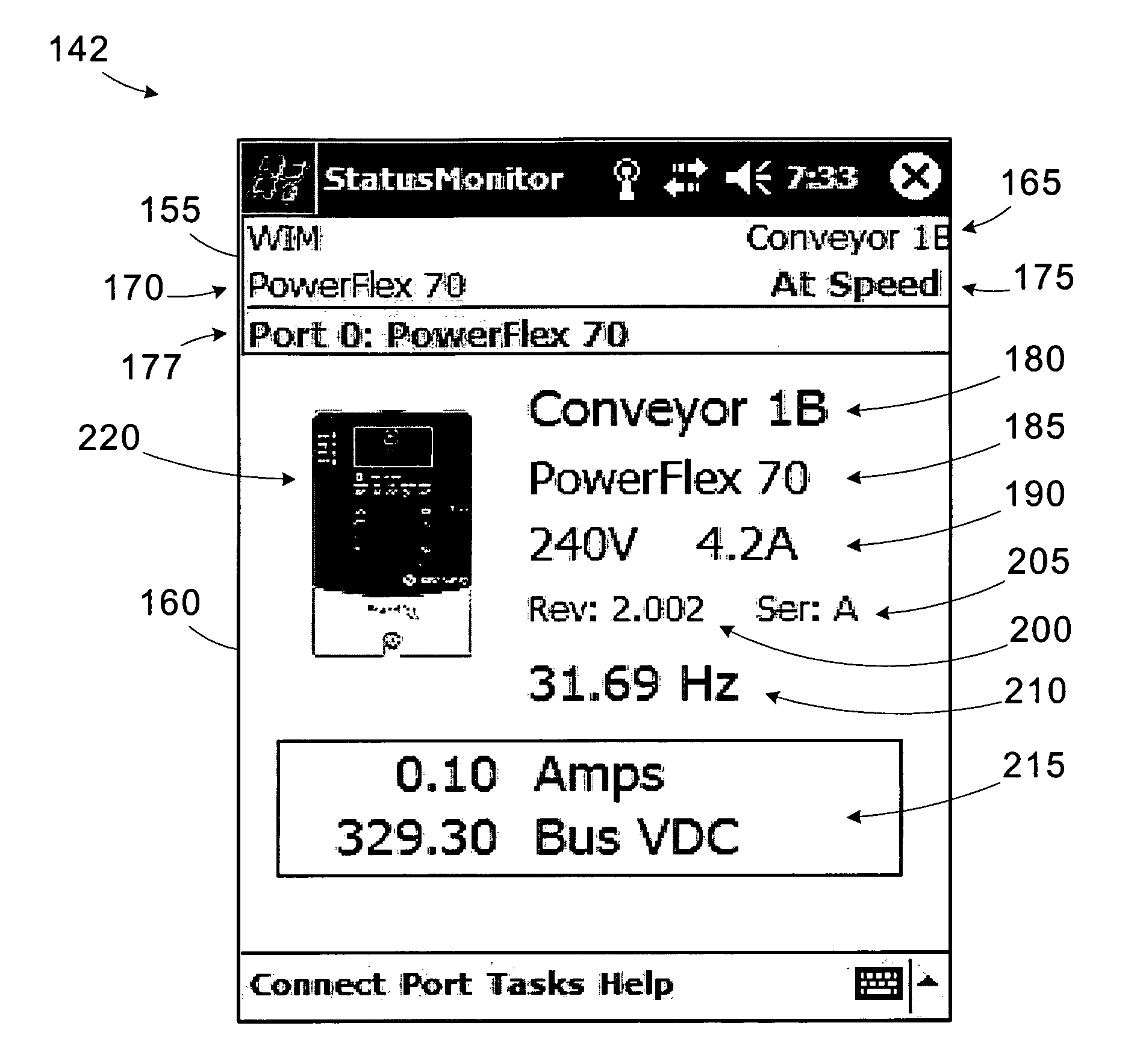
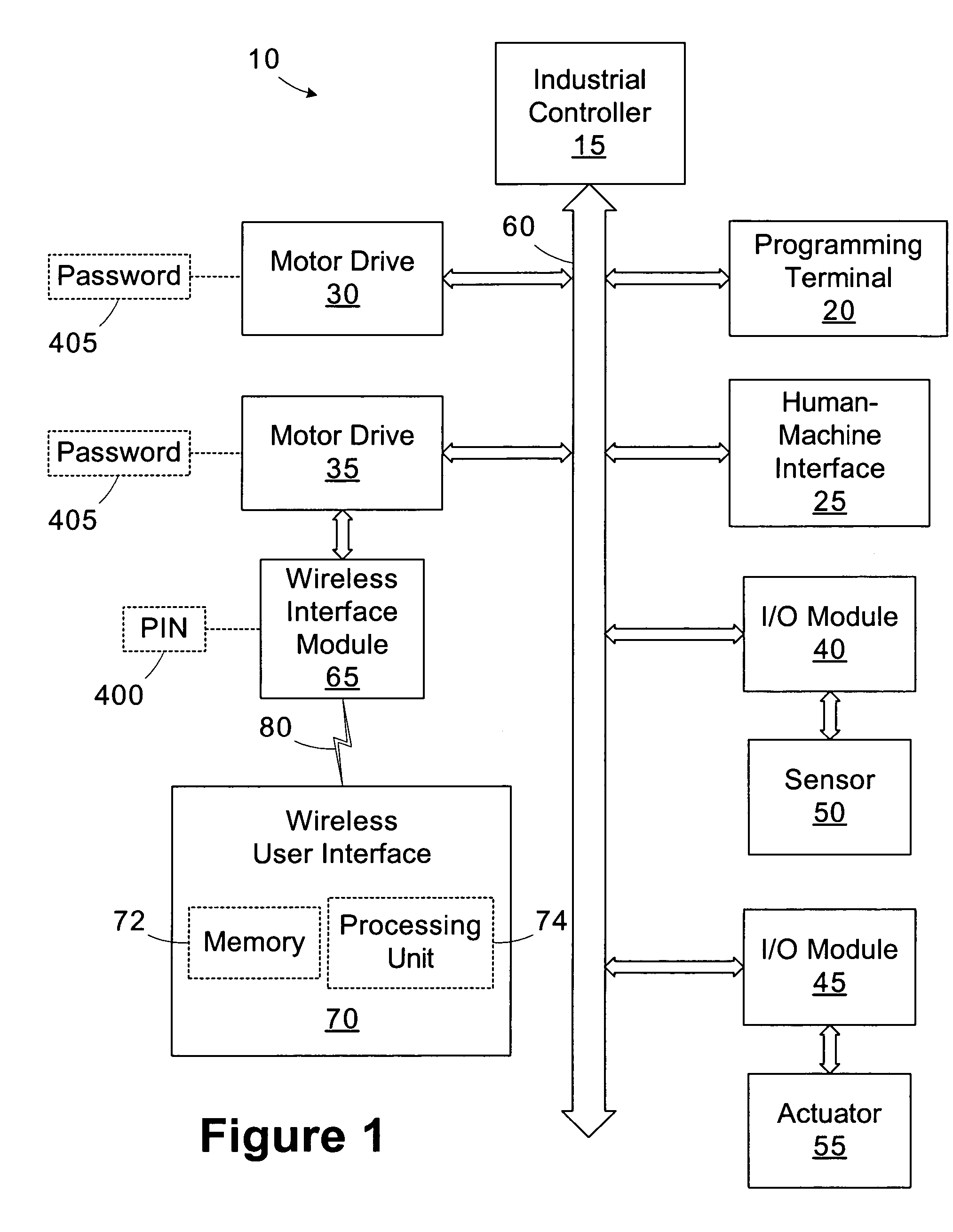
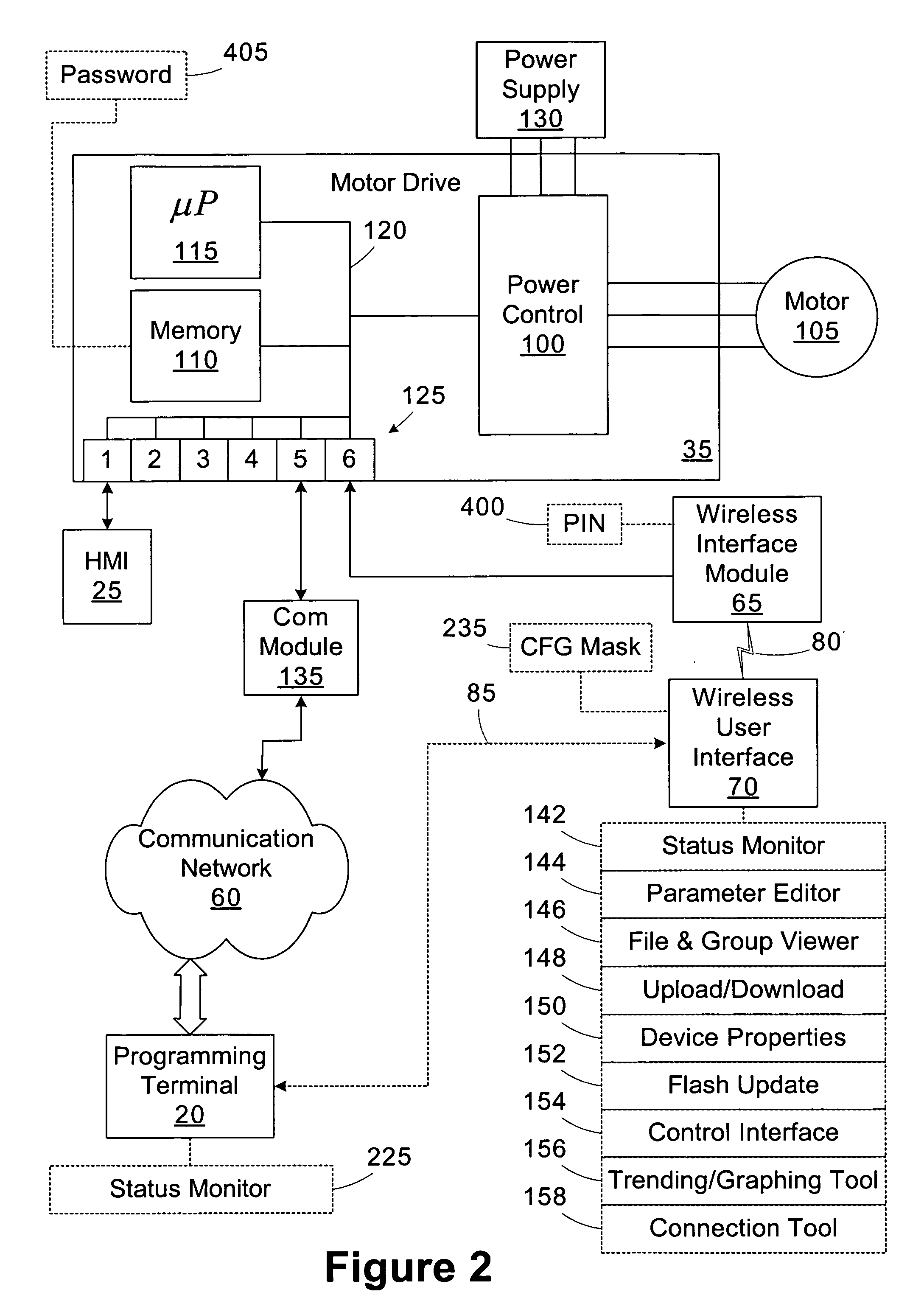
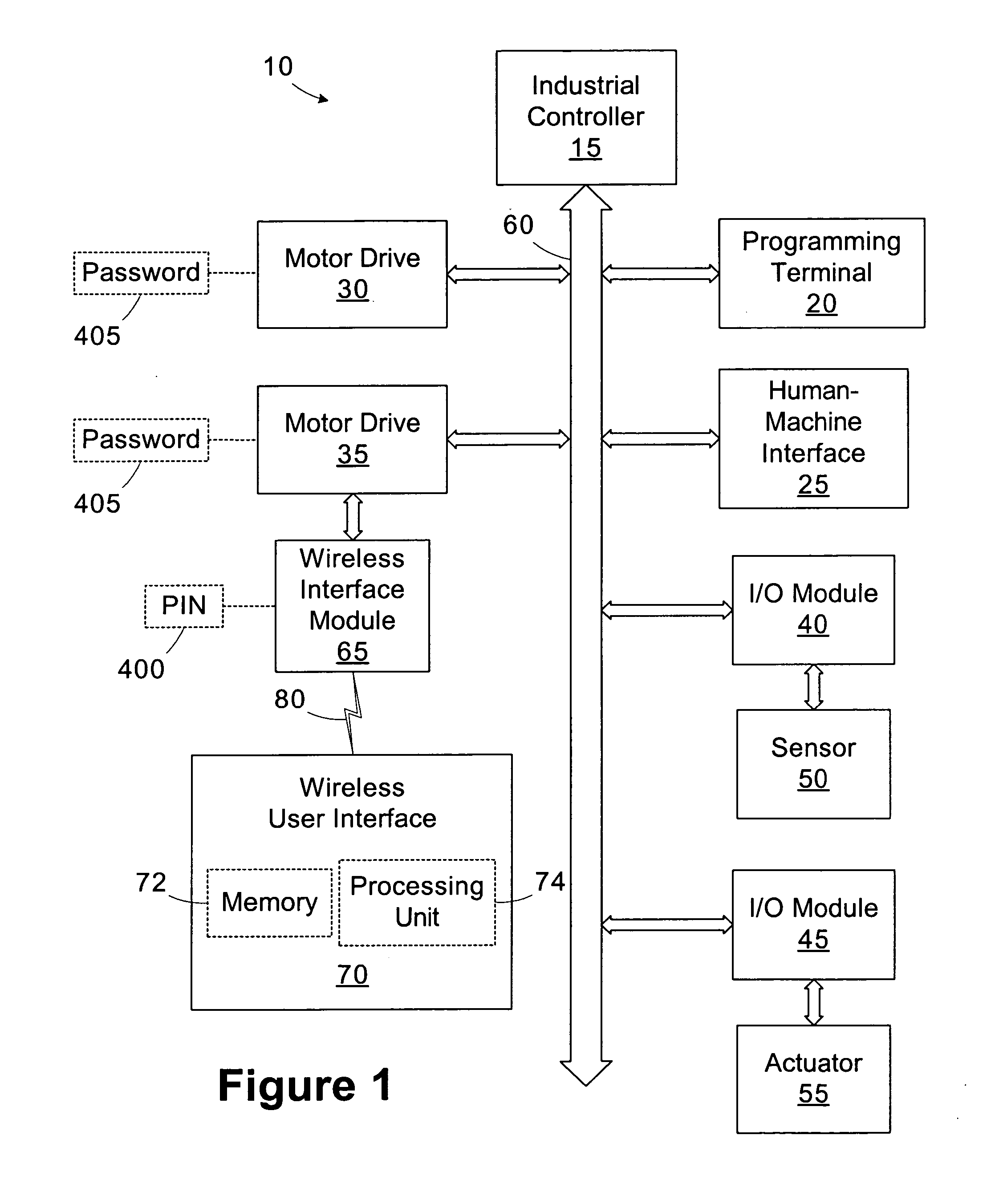
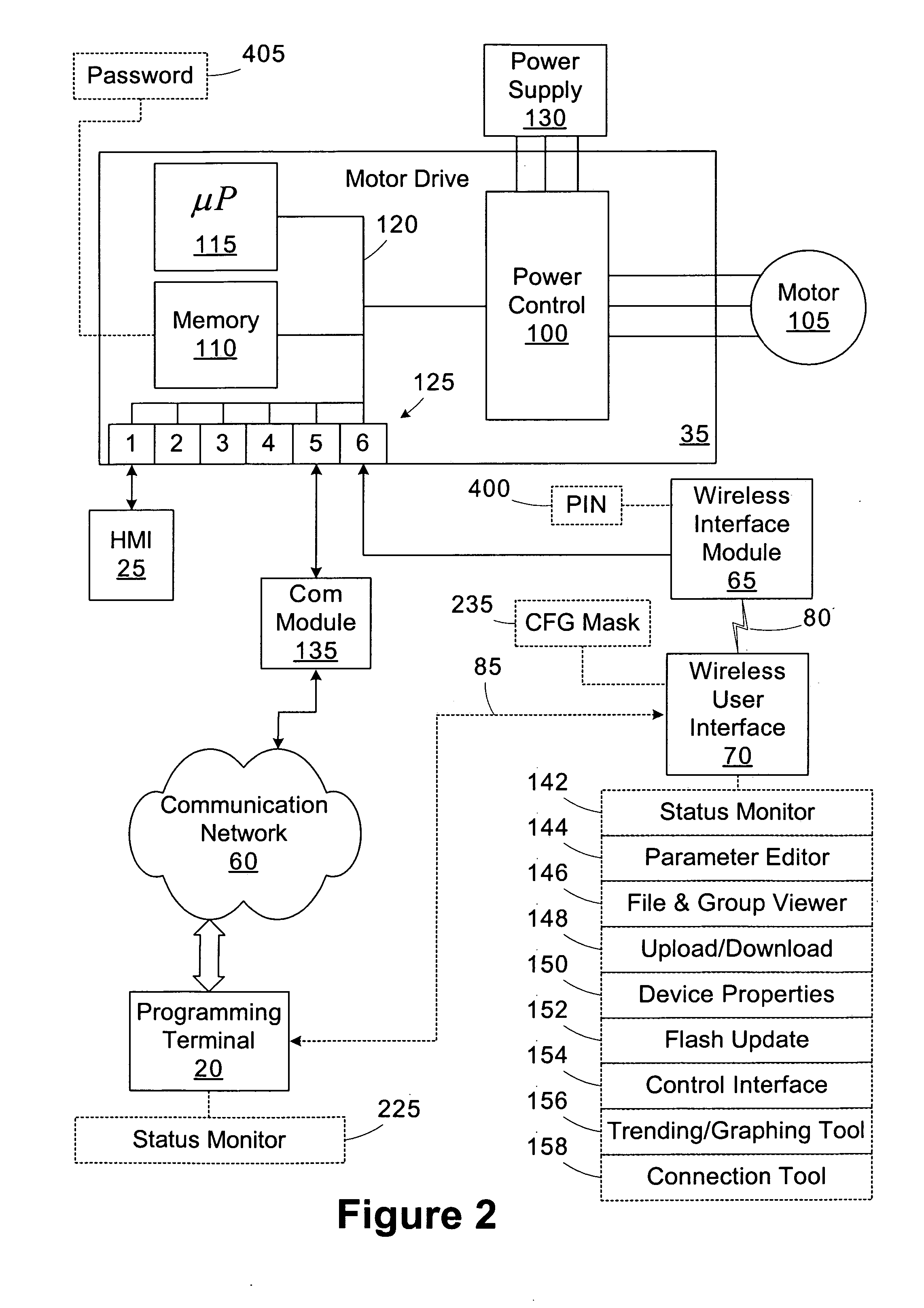
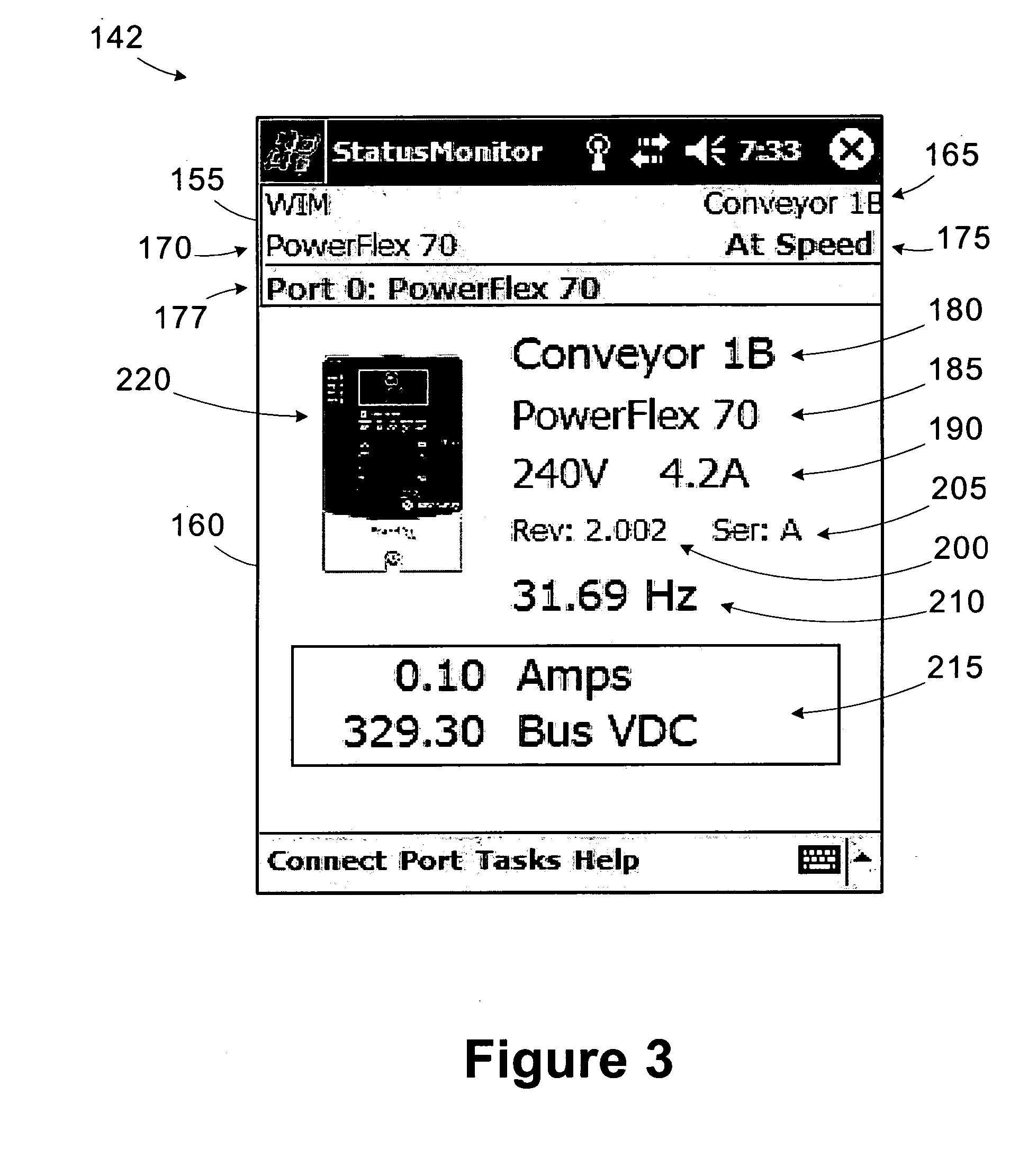
Wireless industrial control user interface
An industrial control system includes a motor drive, a wireless interface module, and a wireless user interface. The motor drive has at least a first port. The wireless interface module is coupled to the first port of the motor drive. The wireless user interface is operable to connect to the wireless interface module and establish a first connection through the wireless interface module to access the motor drive. A user interface operable to connect to a device within an industrial control system includes a display and a processing unit operable to establish a connection with the device and display an image representative of the device on the display responsive to establishing the connection.
Owner:ROCKWELL AUTOMATION TECH
Method and system for generating a control system user interface
ActiveUS20100017746A1Fast loadingHeavy demandComputer controlExecution for user interfacesGraphicsControl system software
A method for providing a user interface for an industrial control system including a computer and a plurality of process graphics including software objects for controlling and / or monitoring real world objects controlled by the control system. A display of selected process graphics, a designated view arranged with a tab or another selector, is automatically generated. The designated view may be generated dependent on selecting one or more logical groupings to which control system software objects representing the real world objects belong. At least one tab on a designated view, or an active link, is arranged to display a small visual representation of a second process graphic to which it is linked on detection of a computer input on or near the at least one tab, or link.
Owner:ABB (SCHWEIZ) AG
Bridge for an industrial control system using data manipulation techniques
ActiveUS7107358B2Improve security levelTransmission systemsComputer controlNetwork Communication ProtocolsComputer module
A bridge usable in a highly reliable industrial control system provides an interface between a producer module transmitting redundant messages in accordance with a communication protocol and a consumer module receiving the messages in accordance with a different communication protocol. The bridge includes a first network interface receiving two messages from the producer, a microprocessor capable of converting the messages from the producer communication protocol to consumer communication protocol, and a second network interface transmitting the messages to the consumer. One of the messages is reversible altered with respect to the other message. The altered message is uninverted in the consumer module, and compared to the other message to ensure that no transmission errors have occurred.
Owner:ROCKWELL AUTOMATION TECH
Industrial control system based on field bus and control network
ActiveCN101976074AReduce performance requirementsLow costTotal factory controlProgramme total factory controlNetwork Communication ProtocolsMaster station
Owner:无锡苏惠信息技术服务有限公司
Network independent safety protocol for industrial controller using data manipulation techniques
InactiveUS6915444B2Imposing level of safetyReduce decreaseError prevention/detection by using return channelComputer controlNetworked Transport of RTCM via Internet ProtocolNetworking protocol
A highly reliable industrial control system is produced using a network running a standard serial protocol on two redundant messages. A safety protocol is embedded within the standard serial protocol by adding to special error detecting data redundant with the protocol of the standard serial network. In addition, only a single network protocol module (CAN) is necessary to transfer two logical messages of data between modules. In order to still provide redundancy, the data on one of the messages is encoded in a predetermined manner, such as by inverting each bit of data, prior to transmission over the network. The data is then decoded at the destination module and compared to the data on the other logical message to determine whether a transmission error has occurred. Safety protocol may be implemented in an additional level for integrated circuits or through firmware changes in programmable aspects of the industrial controller components.
Owner:ROCKWELL AUTOMATION TECH
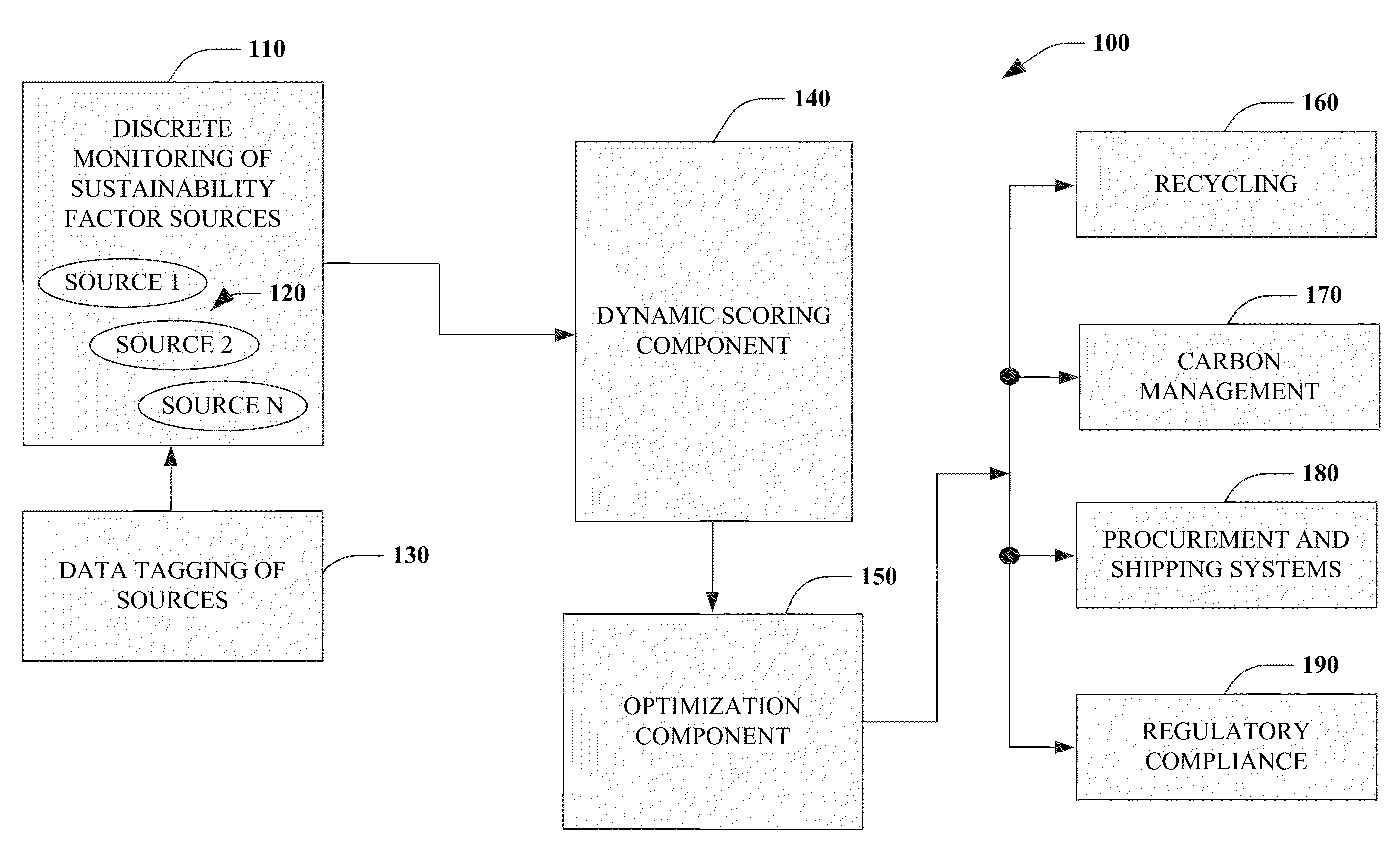
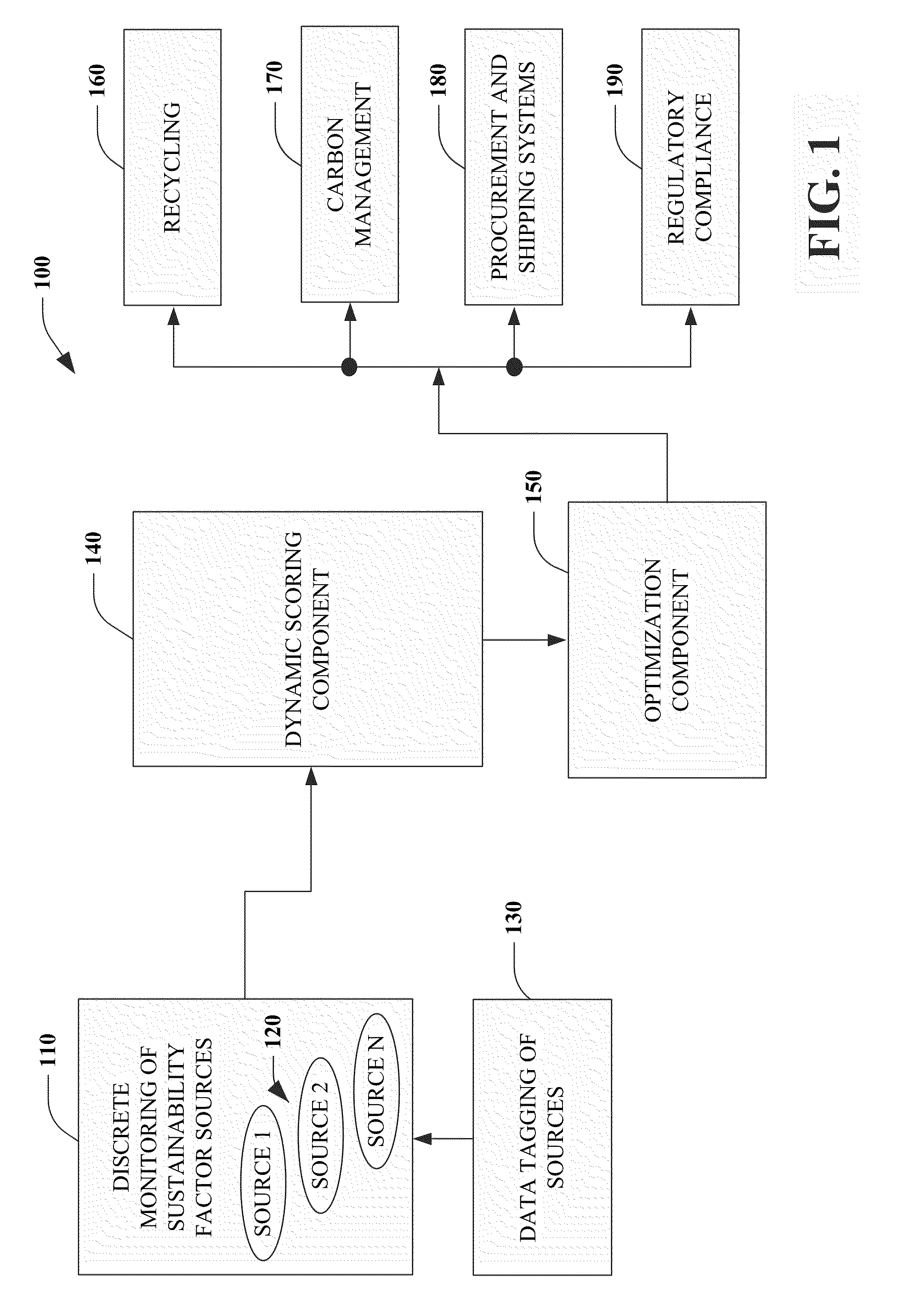
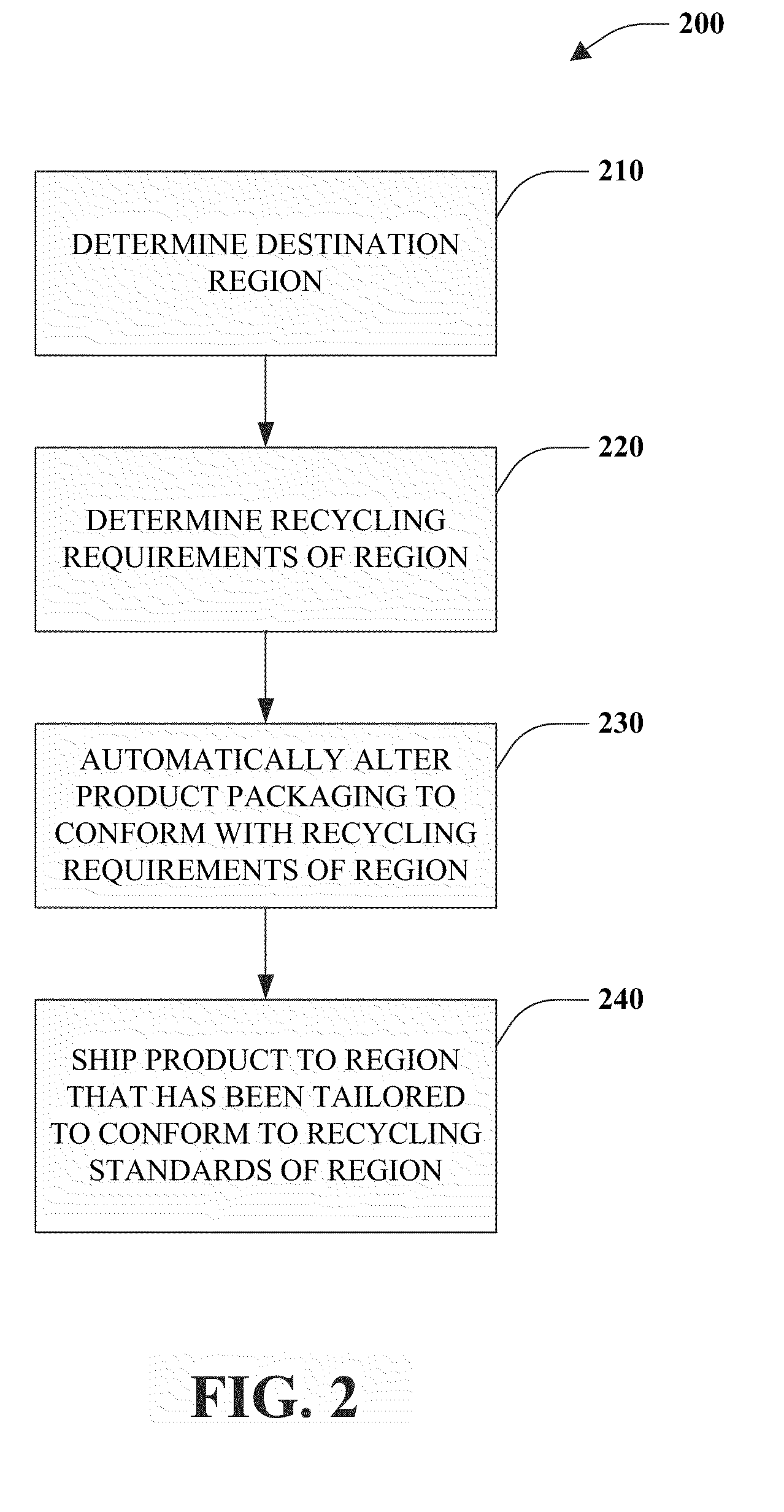
Utilizing sustainability factors for product optimization
InactiveUS20100274612A1Improve sustainabilityEasy to operateProgramme controlMechanical power/torque controlProcess optimizationCarbon footprint
An industrial control system is provided. The system includes a processor to analyze one or more sustainability factors and a scoring component to assign a weight to the sustainability factors. An optimizer automatically adjusts a production process in view of the sustainability factors, the weight, and at least one of a recycling requirement, a carbon footprint, a procurement process, a shipping process, or a regulatory requirement.
Owner:ROCKWELL AUTOMATION TECH
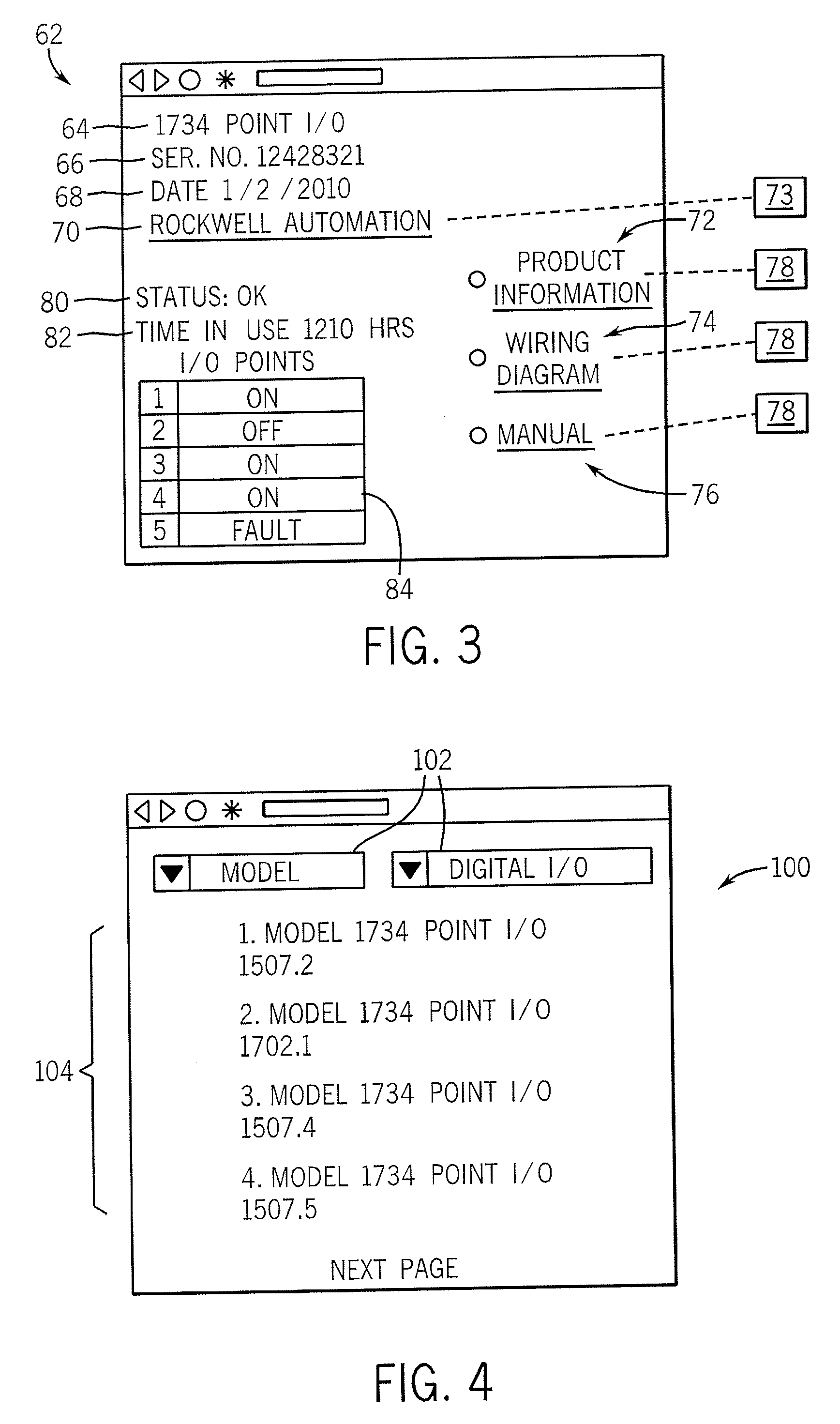
I/O Module with Web Accessible Product Data
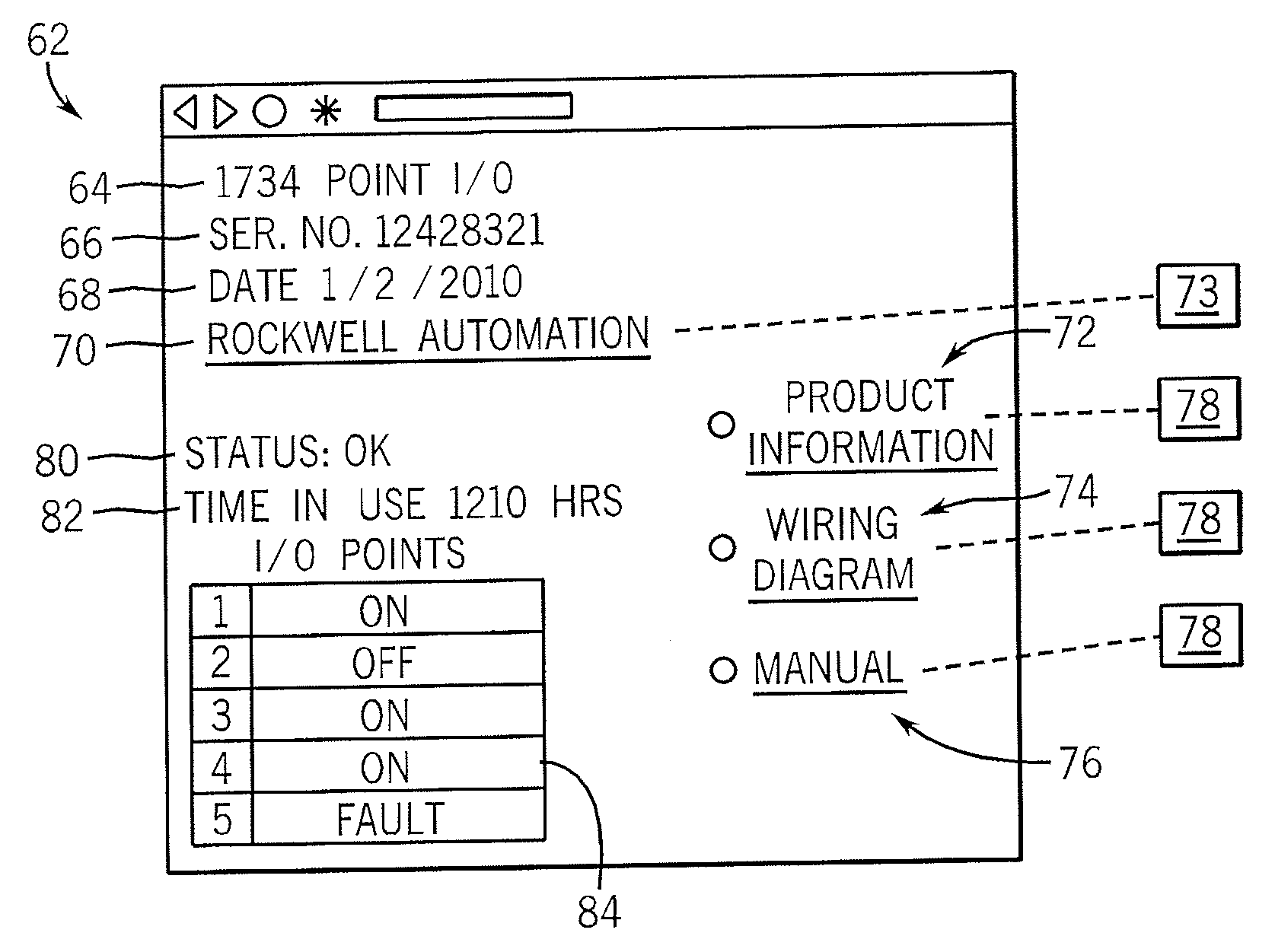
InactiveUS20070130310A1Programme controlDigital computer detailsNetwork serviceIndustrial control system
An industrial control system provides I / O modules with web-servers and dual protocol ports so that product information stored in the I / O modules can be served over the same network interface used by the industrial control system to any Internet ready browser.
Owner:ROCKWELL AUTOMATION TECH
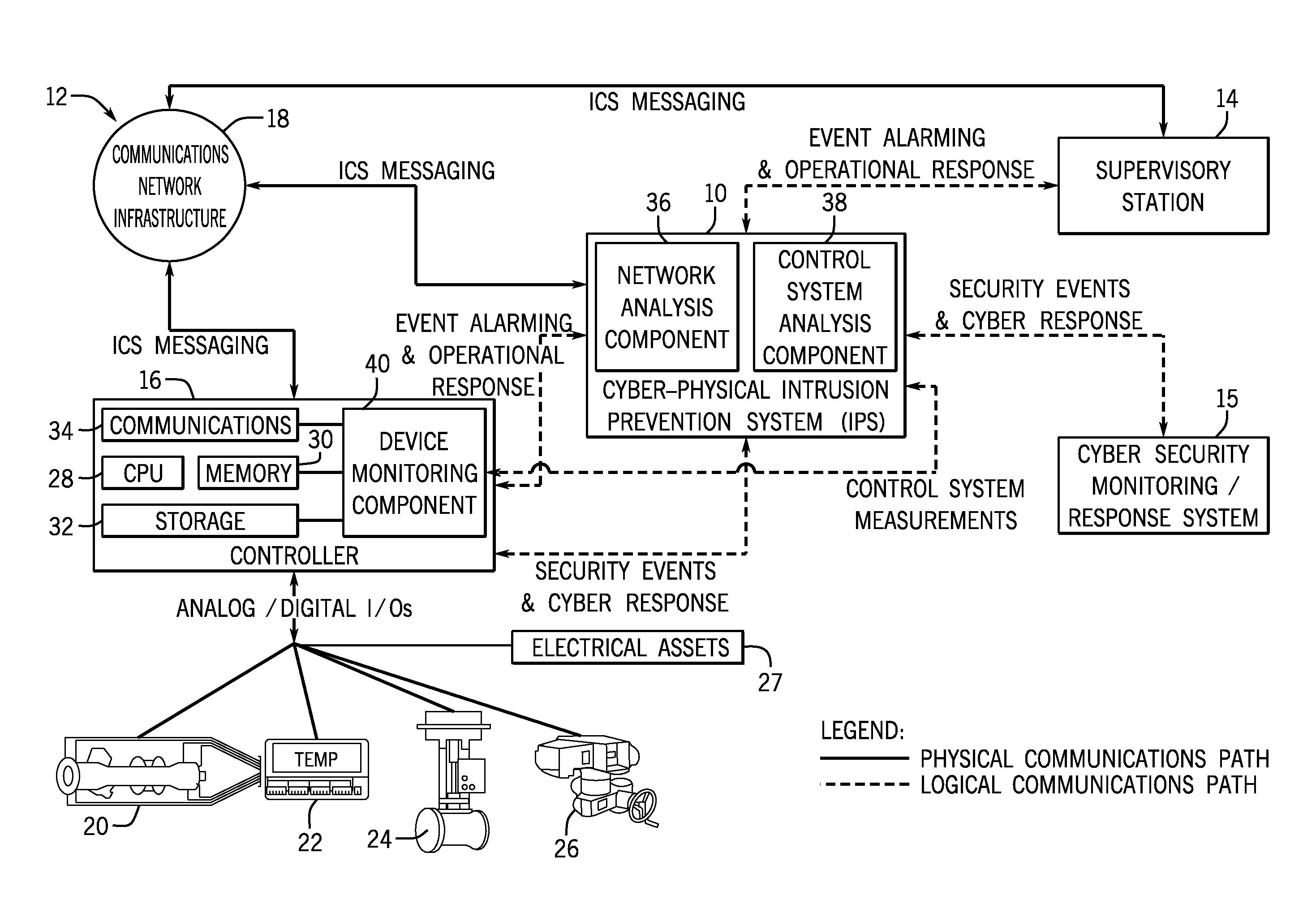
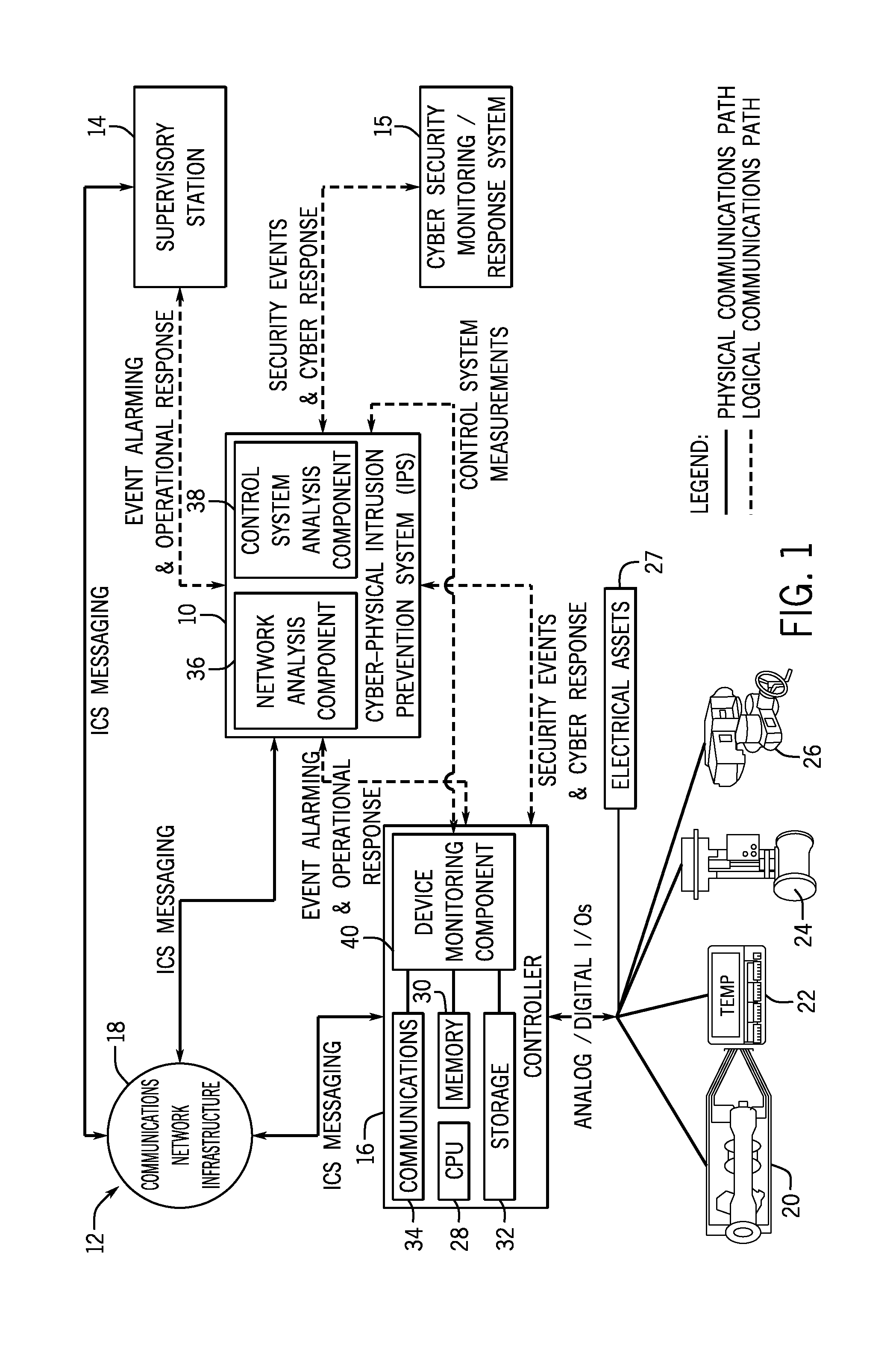
Intelligent cyberphysical intrusion detection and prevention systems and methods for industrial control systems
ActiveUS20140283047A1Memory loss protectionPower network operation systems integrationIntrusion detection and preventionIndustrial control system
The embodiments described herein include a system and a method. In one embodiment, a system includes a device monitoring component configured to measure control system behavior and an intrusion prevention system communicatively coupled to the device monitoring component and a communications network. The intrusion prevention system includes a control system analysis component configured to analyze the control system behavior measured by the device monitoring component against a first rule set to determine whether an anomaly, an intrusion, or both are present.
Owner:GENERAL ELECTRIC CO
Threat detection and defense device, system and method for industrial control system
InactiveCN103944915AWill not affect normal workEasy to detectTransmissionIndustrial control systemSafe operation
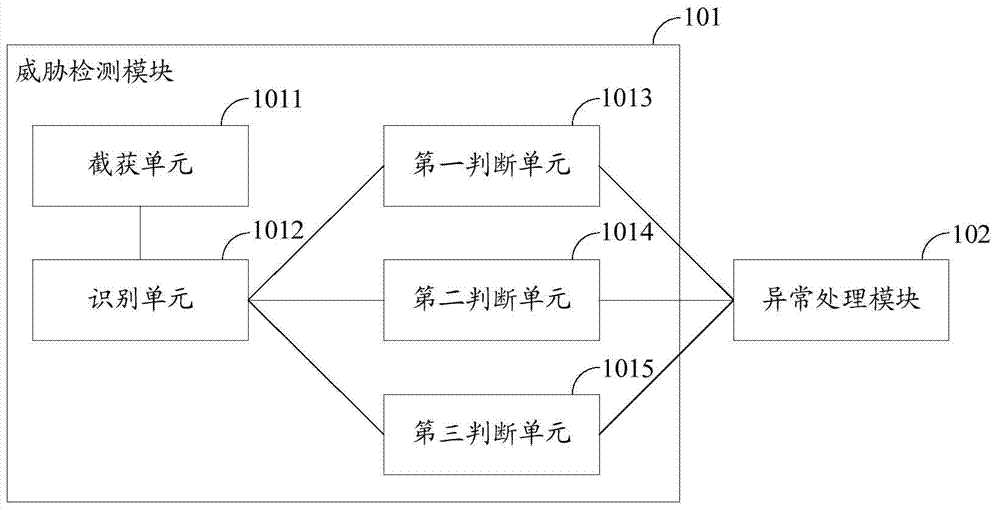
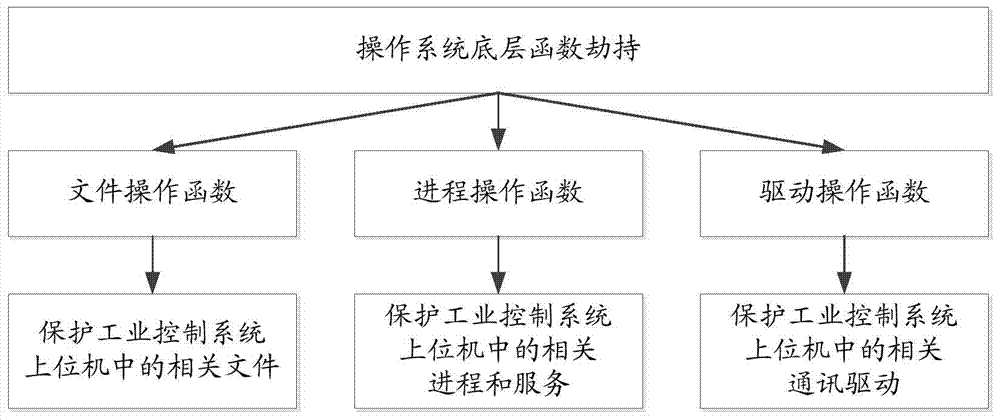
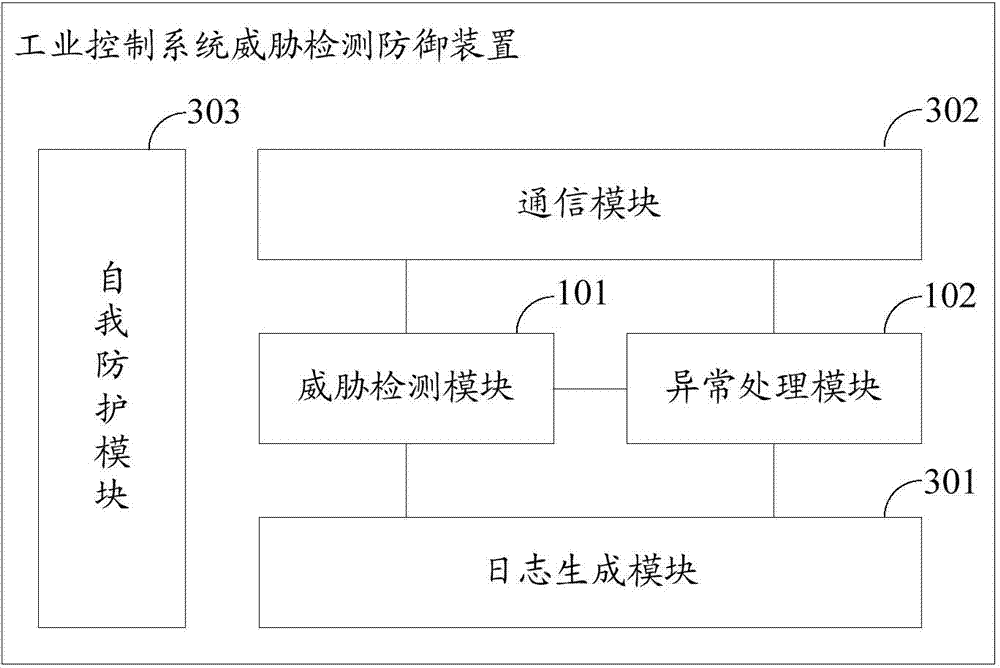
The invention discloses a threat detection and defense device, system and method for an industrial control system. The threat detection and defense device, system and method is used for protecting safety of the industrial control system. The threat detection and defense device comprises a threat detection module and an exception handling module, wherein the threat detection module is used for intercepting and capturing a communication data message, identifying message field information in the communication data message, judging whether the communication data message is the malicious message according to the message field information, judging whether malicious act against a local upper computer or malicious act initiated by the local upper computer exists according to the message field information and message field information in a communication massage recorded in a local communication log database and detecting whether malicious operation against a control program in the local upper computer exists; the exception handling module is used for triggering and performing corresponding safety operation according to safety configuration files if one or more of the malicious message, the malicious act against the local upper computer, the malicious act initiated by the local upper computer and the malicious operation against the control program in the local upper computer exist.
Owner:ZHEJIANG UNIV
Wireless industrial control user interface with configurable software capabilities
A user interface operable to connect to a device within an industrial control system includes a memory and a processing unit. The memory is operable to store a plurality of software applications for interfacing with the device and a configuration mask including access rights for at least a subset of the software applications. The processing unit is operable to establish a first connection with the device and disable selected software applications based on the configuration mask.
Owner:ROCKWELL AUTOMATION TECH
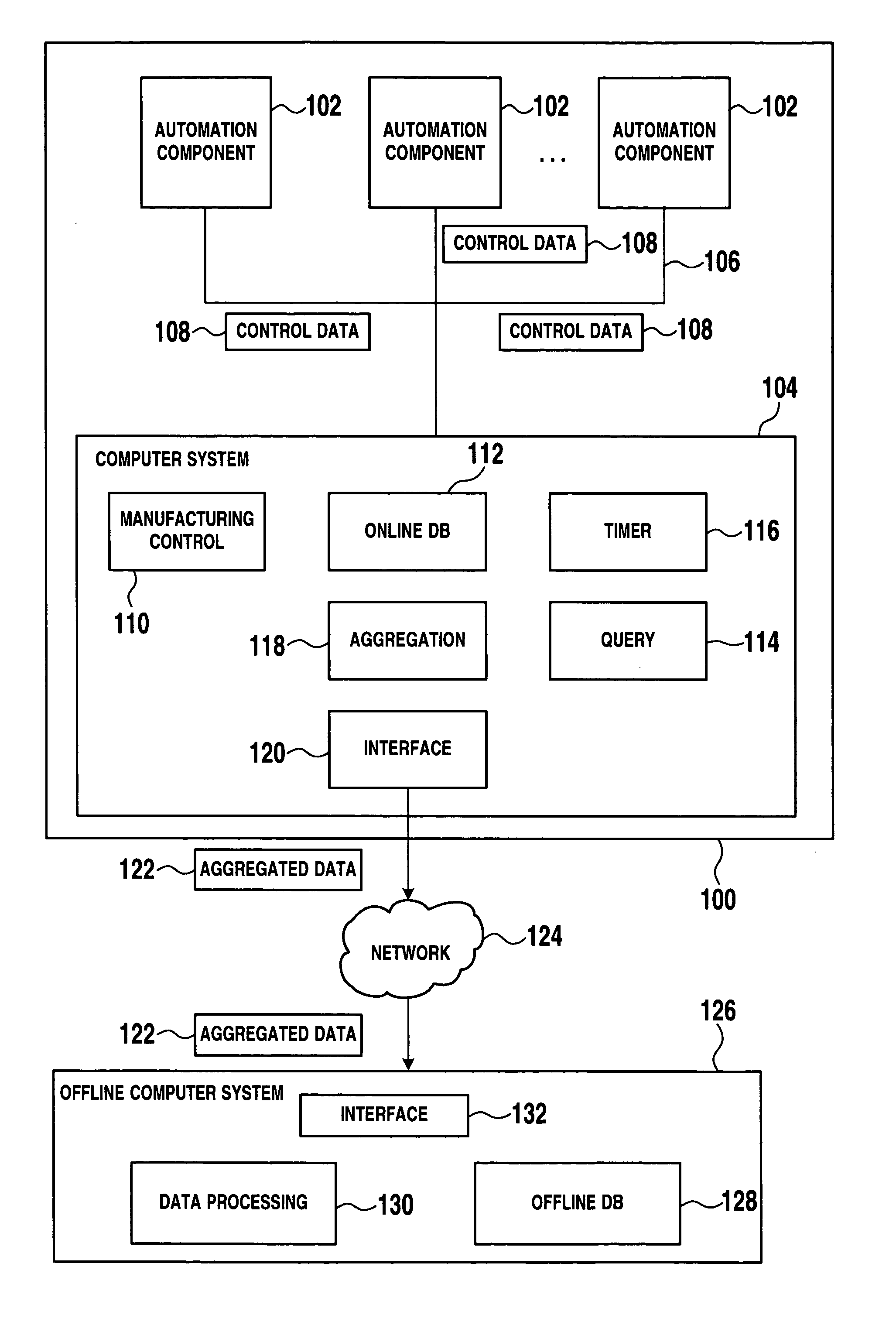
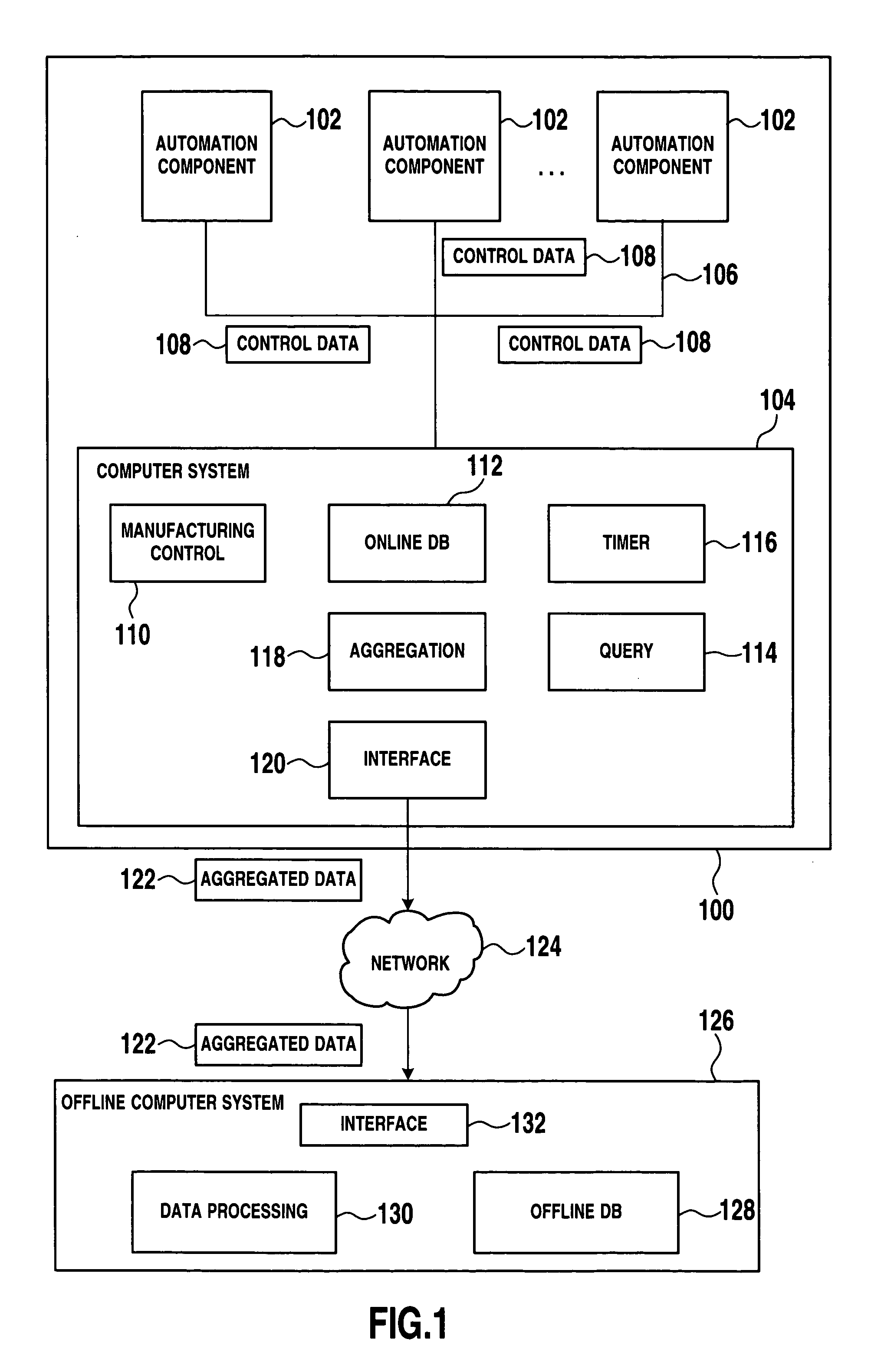
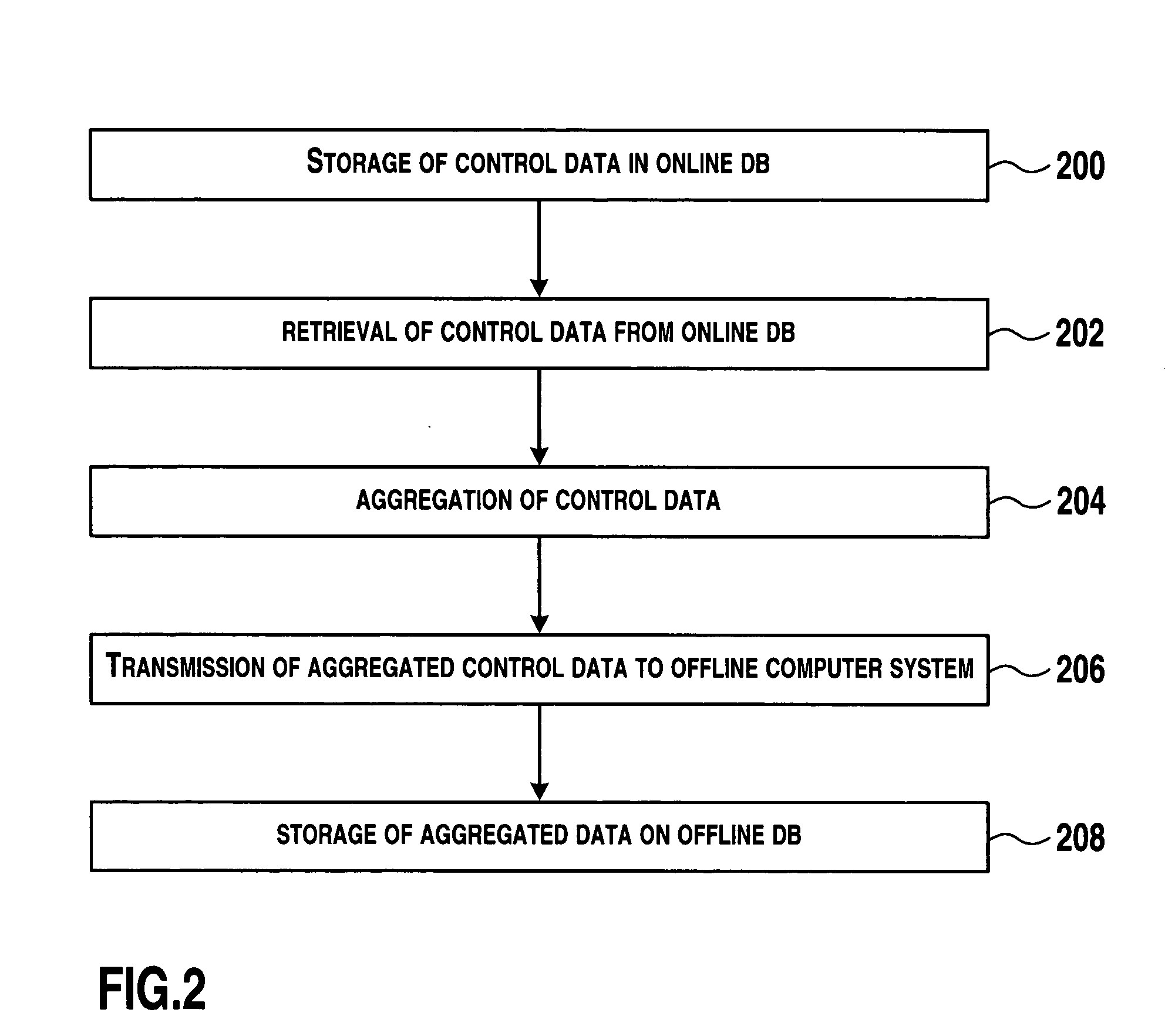
Data processing methods and systems for use in industrial control
ActiveUS20050125441A1Reduce loadLimit amount of dataDigital data processing detailsElectric testing/monitoringControl dataIndustrial control system
Data processing methods and systems are disclosed for use in industrial control. The methods and systems may include receiving control data from automation components of an industrial control system by a first computer system, the first computer system being coupled to the automation components by means of a first network, storing at least some of the control data in a first database by the first computer system, performing a database query of the first database for determination of a subset of the control data, aggregating the control data of the subset, and transmitting the aggregated control data to a second computer system over a second network.
Owner:SAP AG
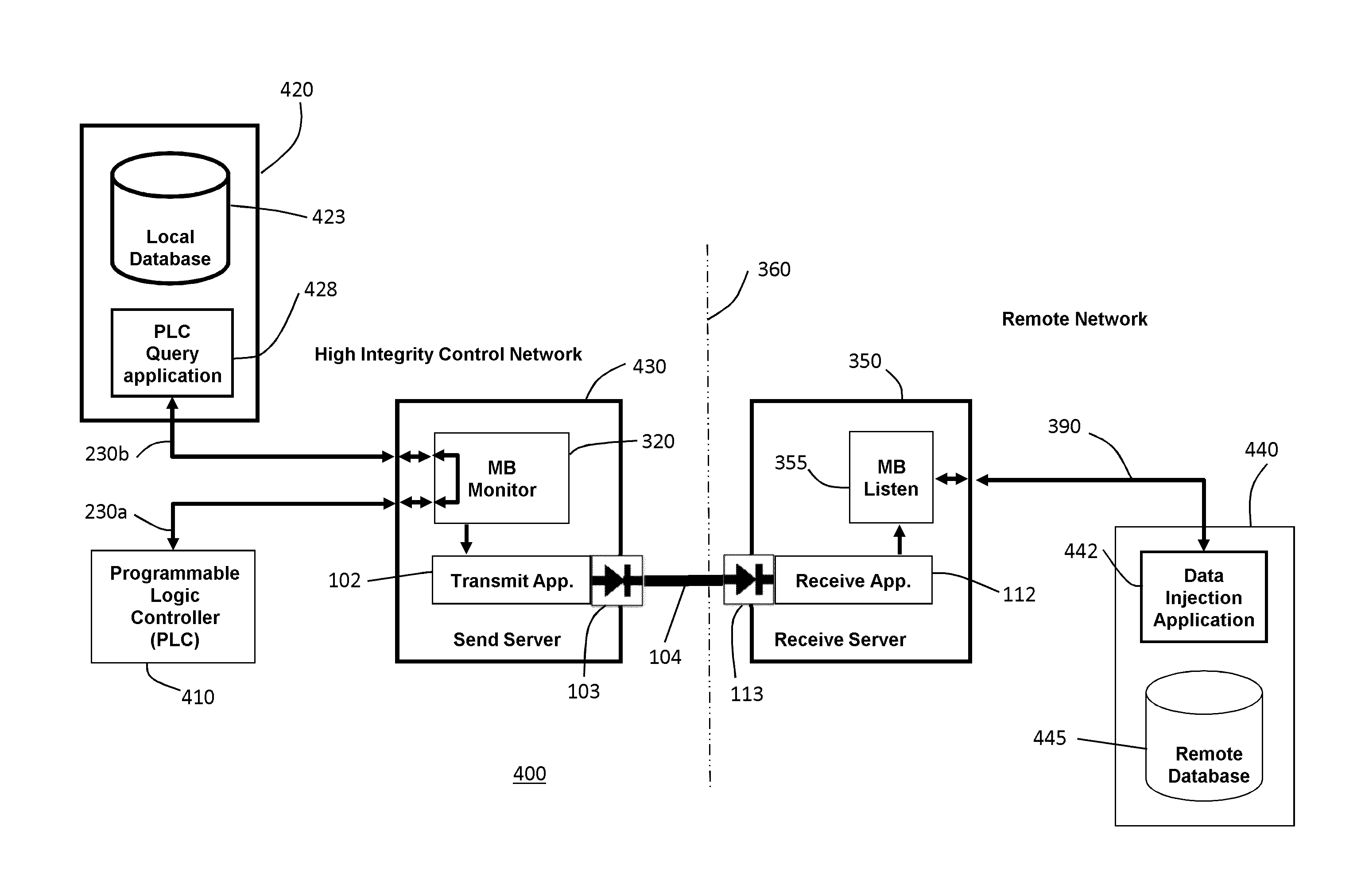
System for secure transfer of information from an industrial control system network
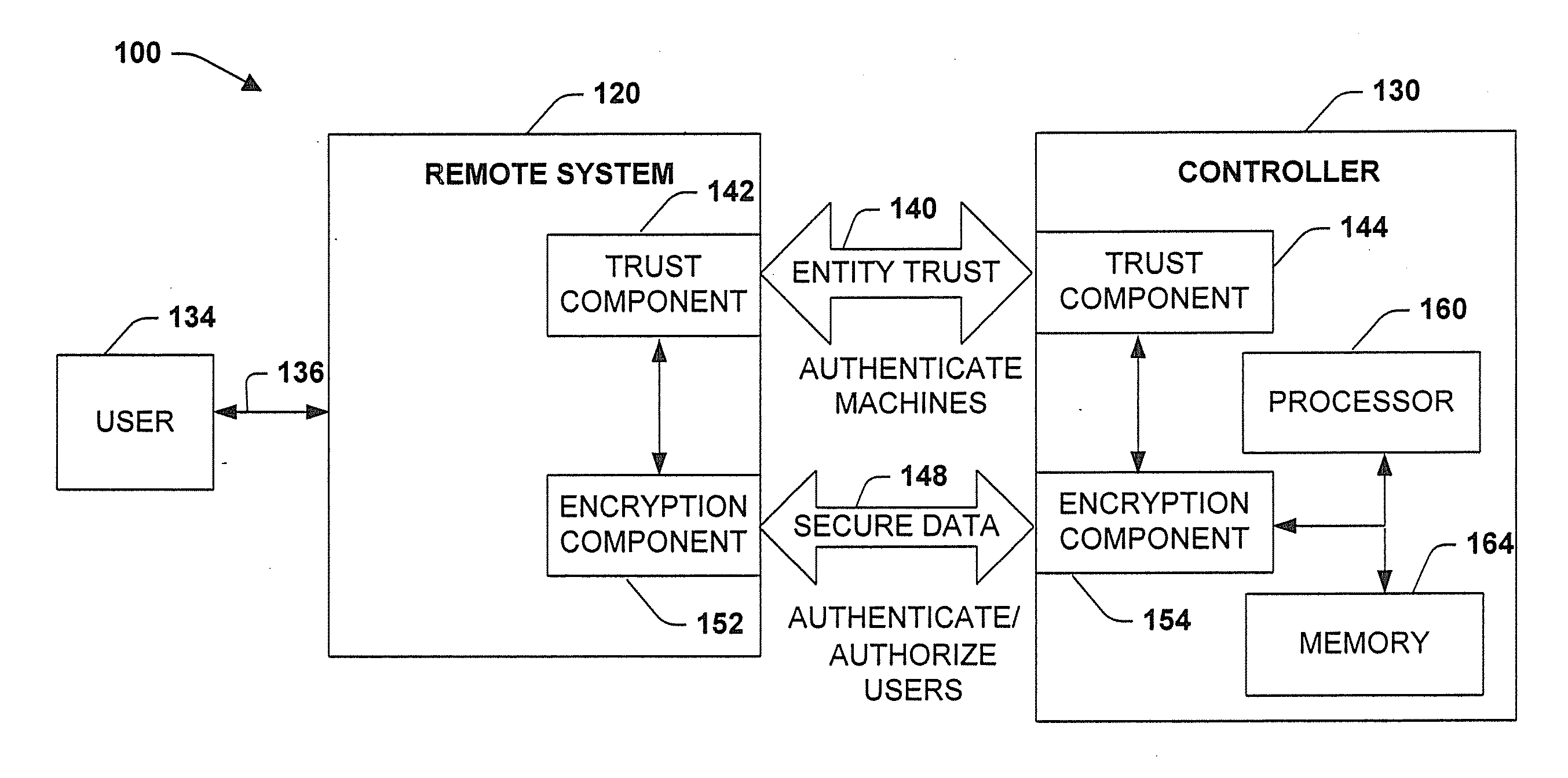
ActiveUS20140165182A1Multiple digital computer combinationsProgram controlSecure transmissionComputer terminal
A system for securely transferring information from an industrial control system network, including, within the secure domain, one or more remote terminal units coupled by a first network, one or more client computers coupled by a second network, and a send server coupled to the first and second networks. The send server acts as a proxy for communications between the client computers and the remote terminals and transmits first information from such communications on an output. The send server also transmits a poll request to a remote terminal unit via the first network and transmits second information received in response to the poll on the output. The system also includes, outside the secure domain, a receive server having an input coupled to the output of the send server via a one-way data link. The receive server receives and stores the first and second information provided via the input.
Owner:OWL CYBER DEFENSE SOLUTIONS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com