Patents
Literature
1198 results about "Network generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
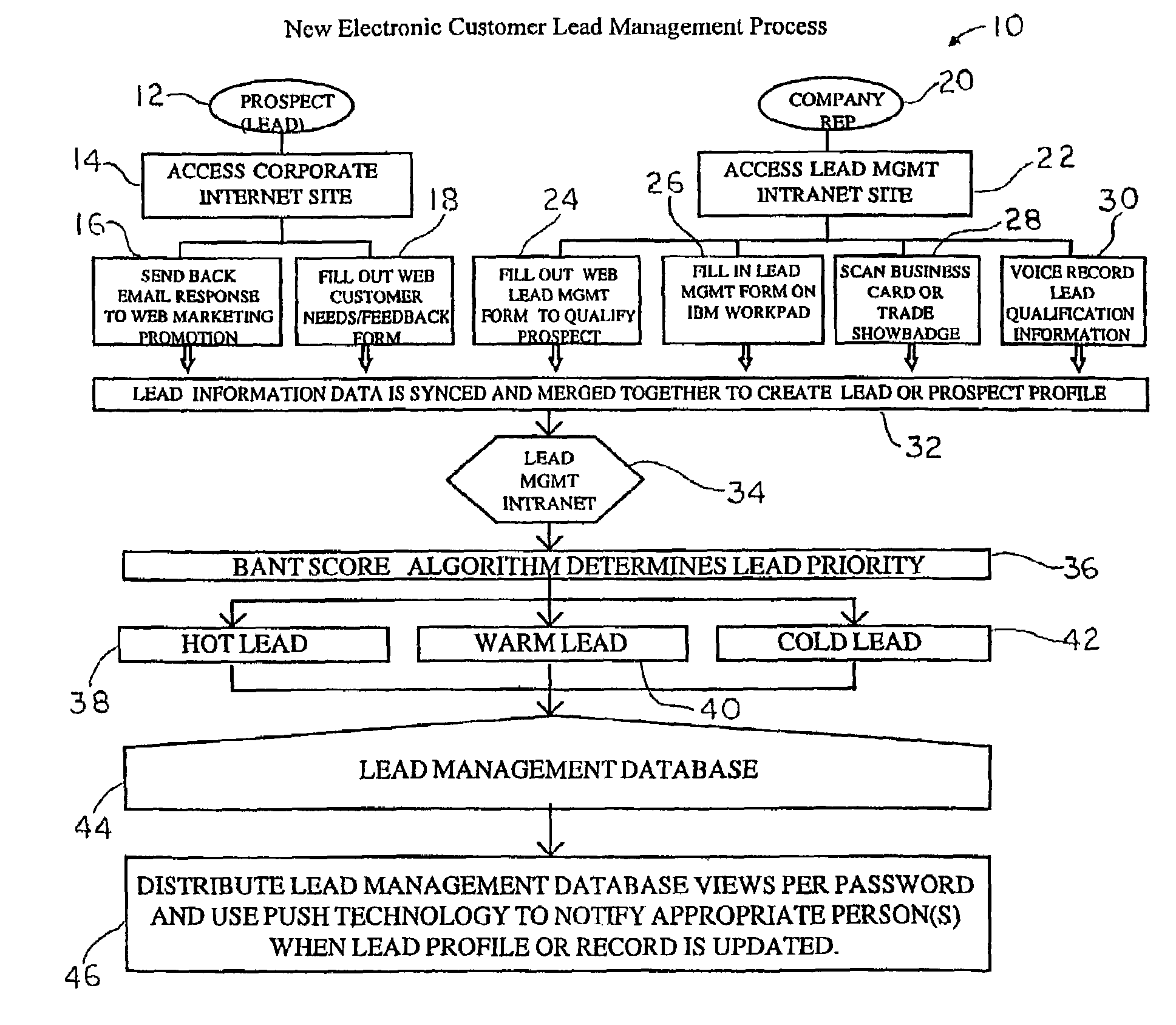
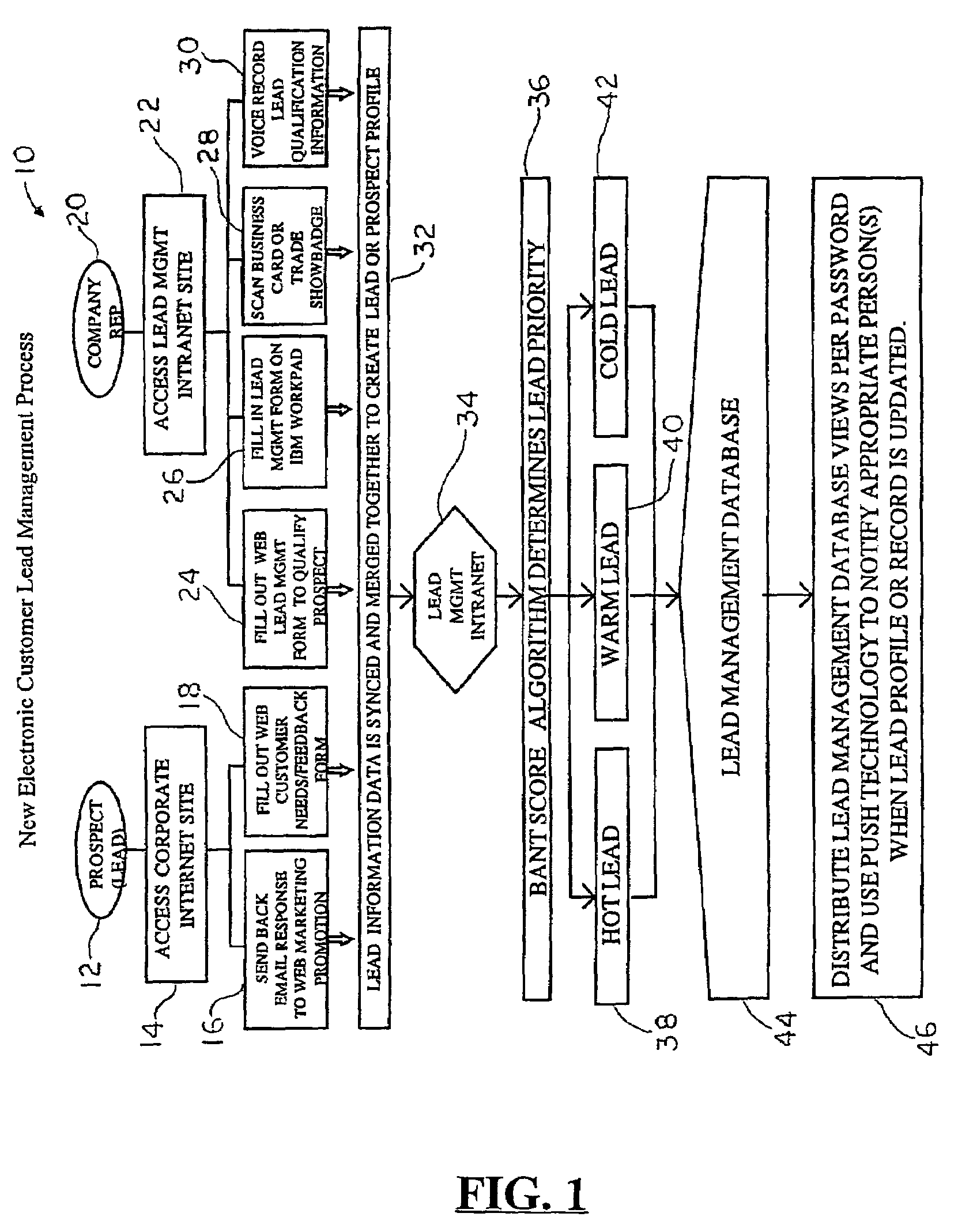
System and method for generating, capturing, and managing customer lead information over a computer network
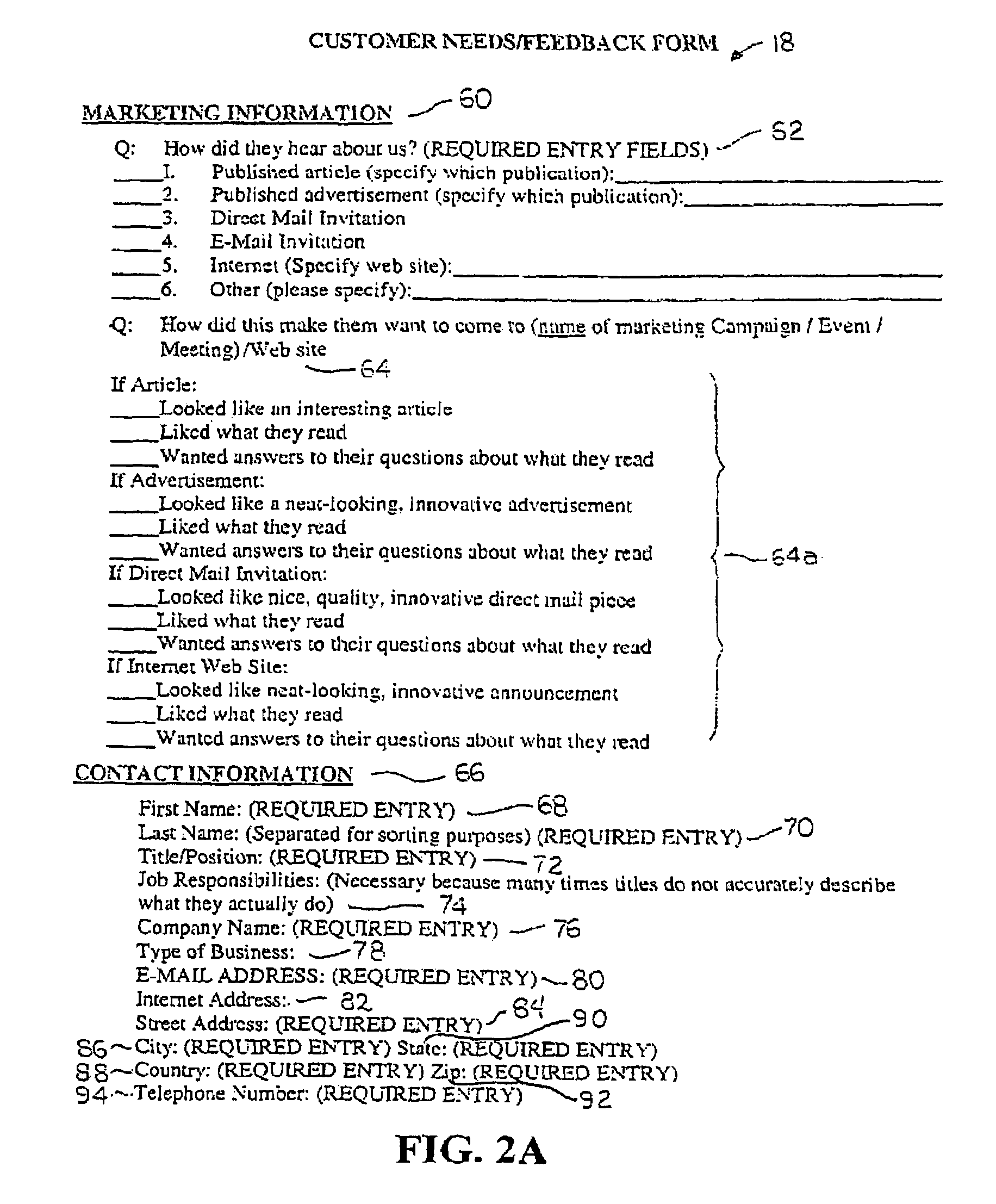
A customer lead management system that relates to a system and method for collecting and organizing customer-marketing data, which is then made available to business representatives to assess. Specifically, using a computer network, and data on a potential customer's Budget, Authority, Needs, Timeframe, and other related customer data is collected. While this data is being collected, the customer lead management system stores the customer lead data in real-time instantly, automatically ranking the viability of the customer lead on the interest level of the customer lead and other variable criteria used in the web-based algorithm calculation, and automatically electronically notifies the appropriate company and / or company representative about the customer lead. The resulting customer lead profile record is located in a web server database, and can be accessed and undated in real-time by a portable computer or electronic device that has been web-enabled. The customer lead data is then capable of being accessed via a computer network by various companies that have goods / services that satisfy the needs and requirements of the customer lead. A company representative can be automatically notified when a customer lead profile has been updated.
Owner:CXT SYST INC
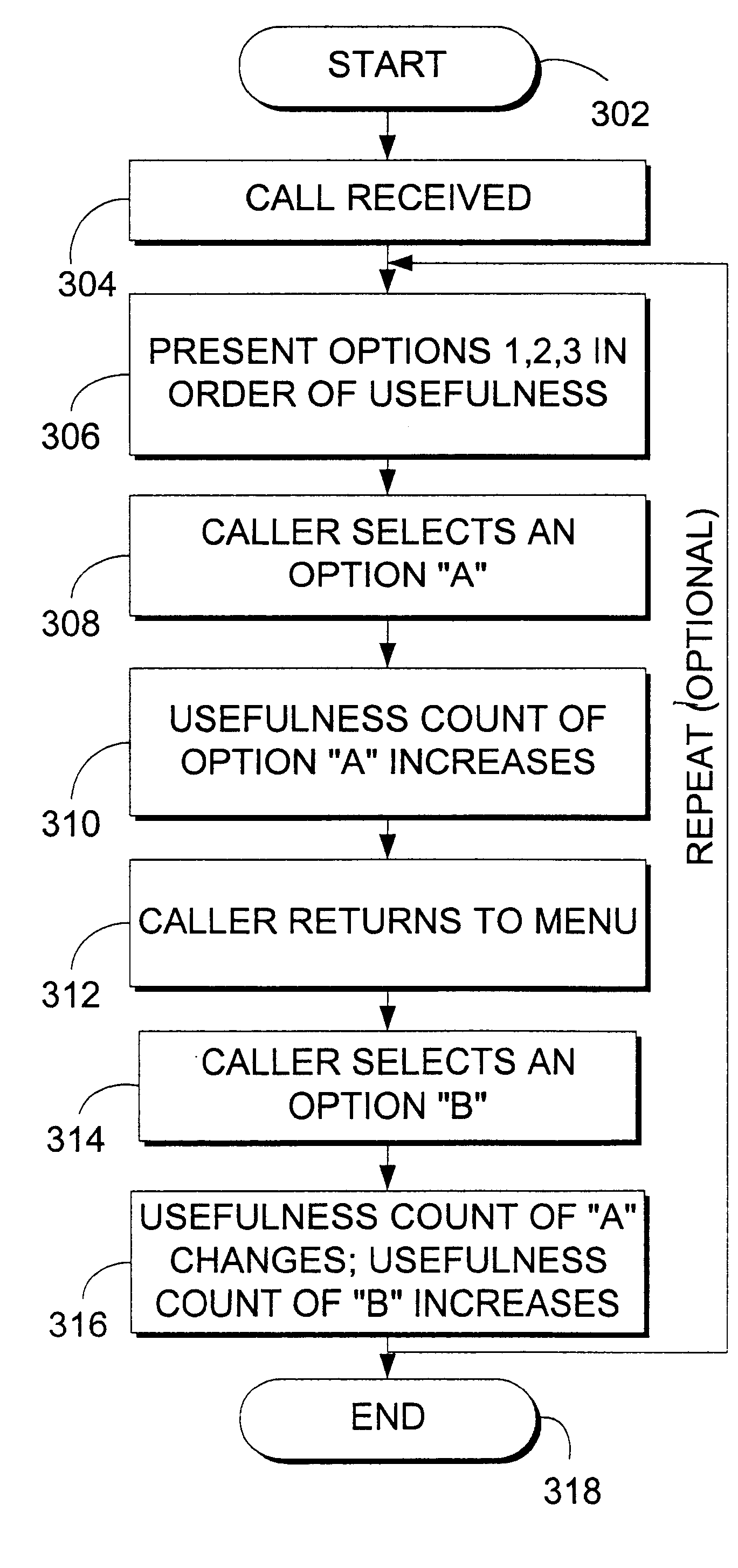
System and method for generating a dynamic interface via a communications network
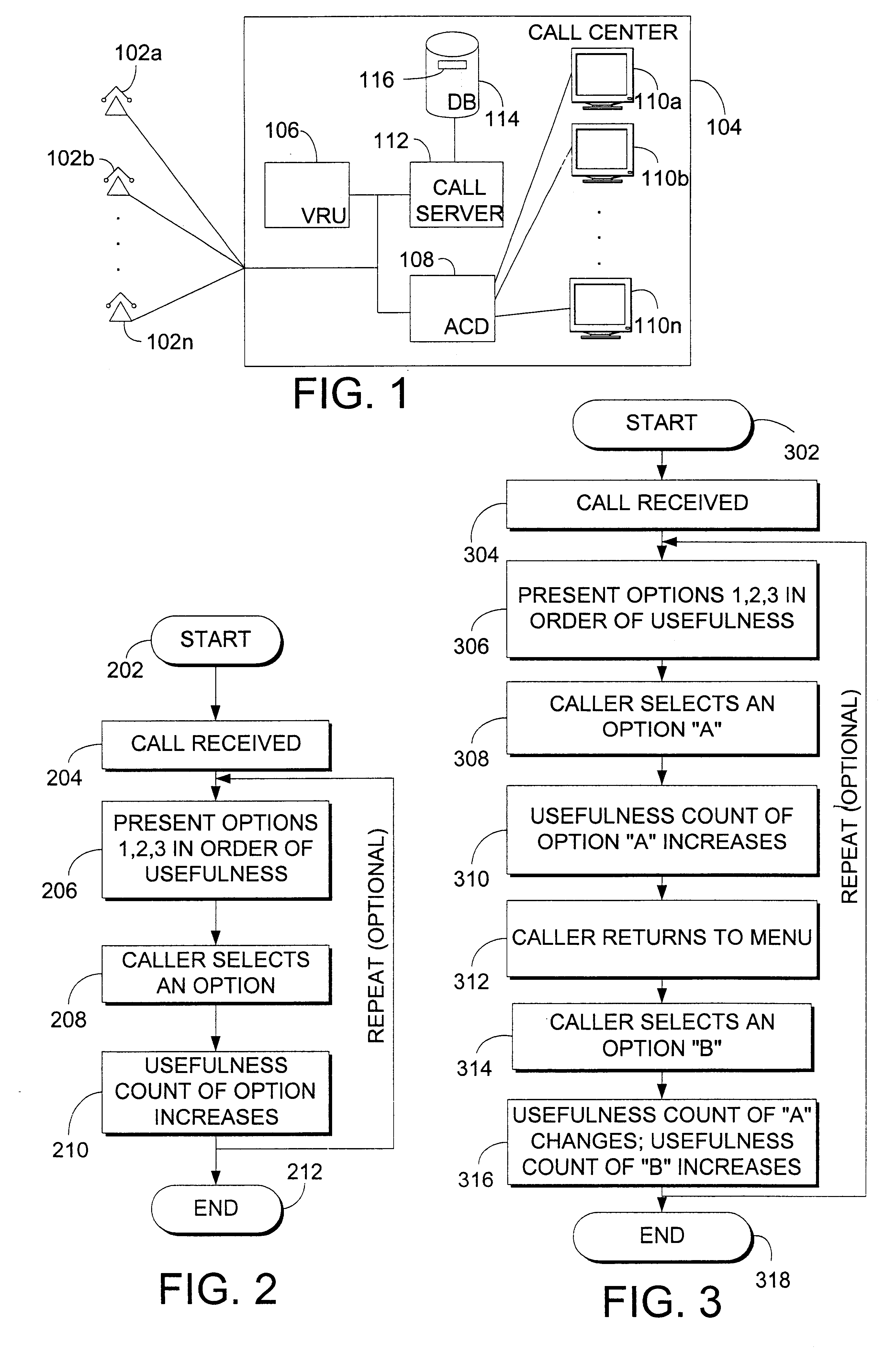
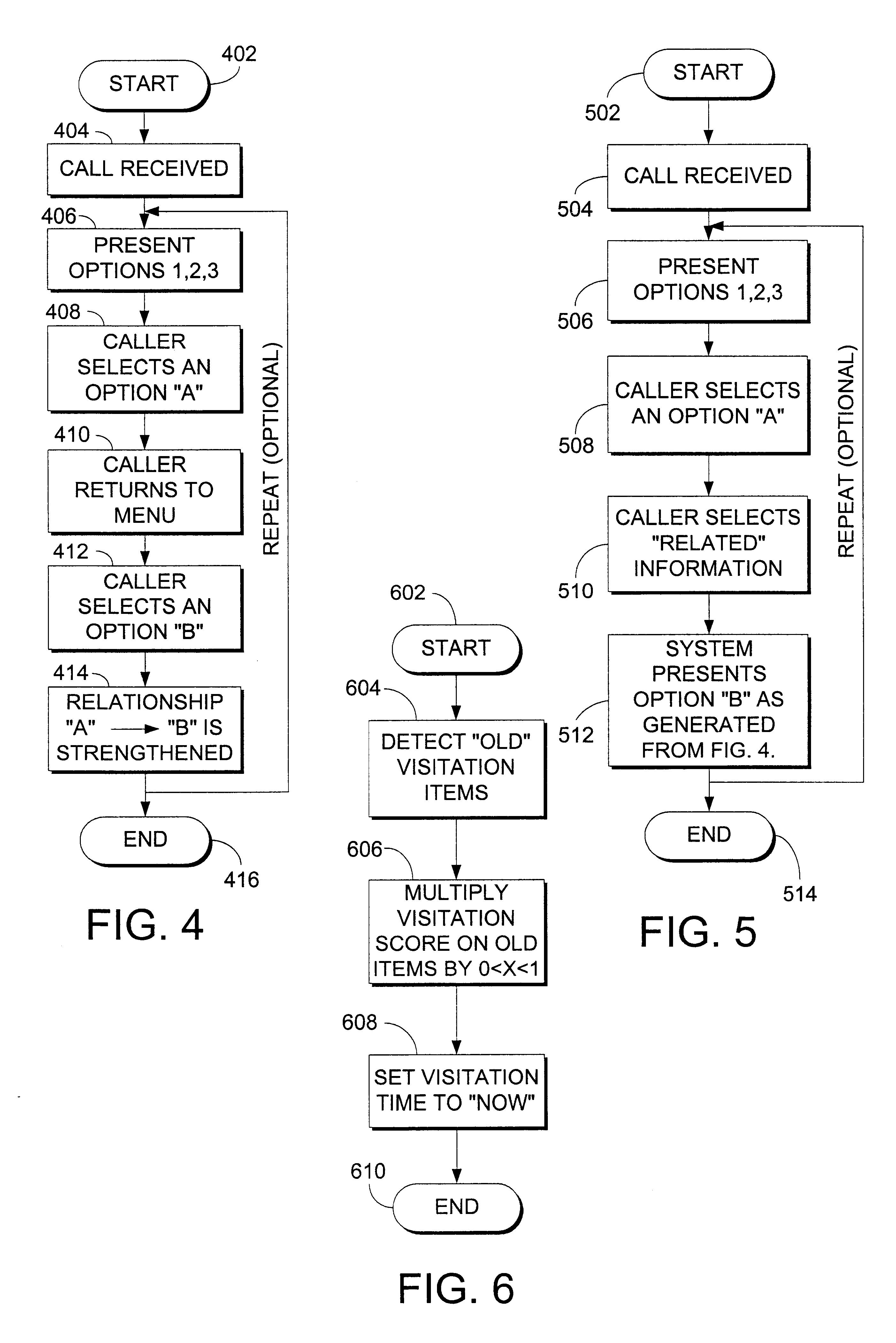
InactiveUS6850949B2Prevent excessive inputIncrease administrative overheadData processing applicationsDigital data processing detailsSupporting systemNetwork generation
A system, method, and computer program product for dynamically adapting selections in an automatic phone support system is described. The invention may integrate a dynamic knowledge base of responses with the menu selections on an automated phone system or other response system to present the most frequently used items earlier in the option list, or otherwise order options and information. Call data may be captured from single callers or historical ensembles of callers. An automatically generated similarity relationship may be used to initialize the system without historical call data, based on textual similarity or other techniques. Prioritization of options provides a more enjoyable, efficient experience for callers without increasing administrative overhead.
Owner:ORACLE OTC SUBSIDIARY
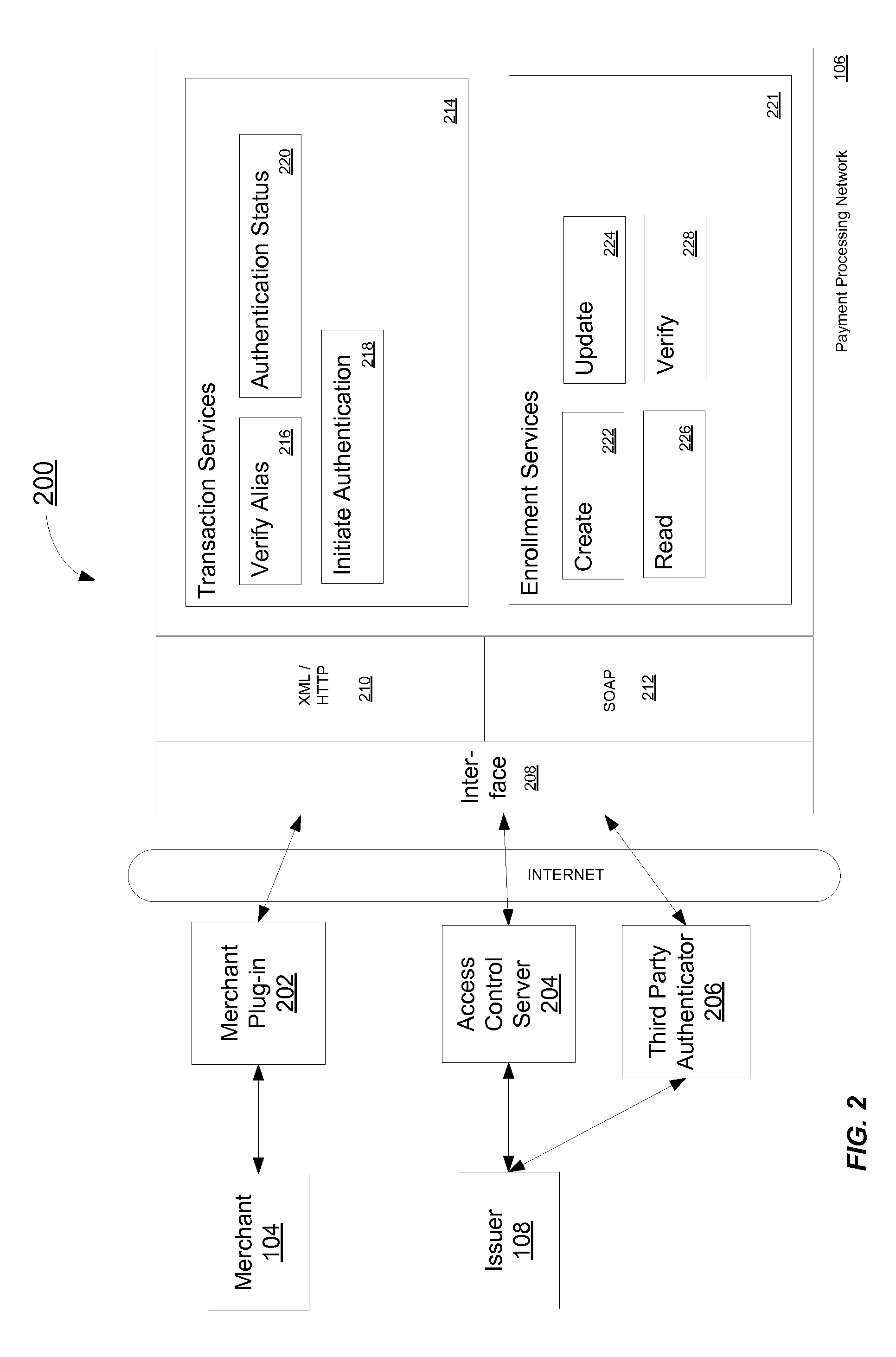
Network message generation for automated authentication
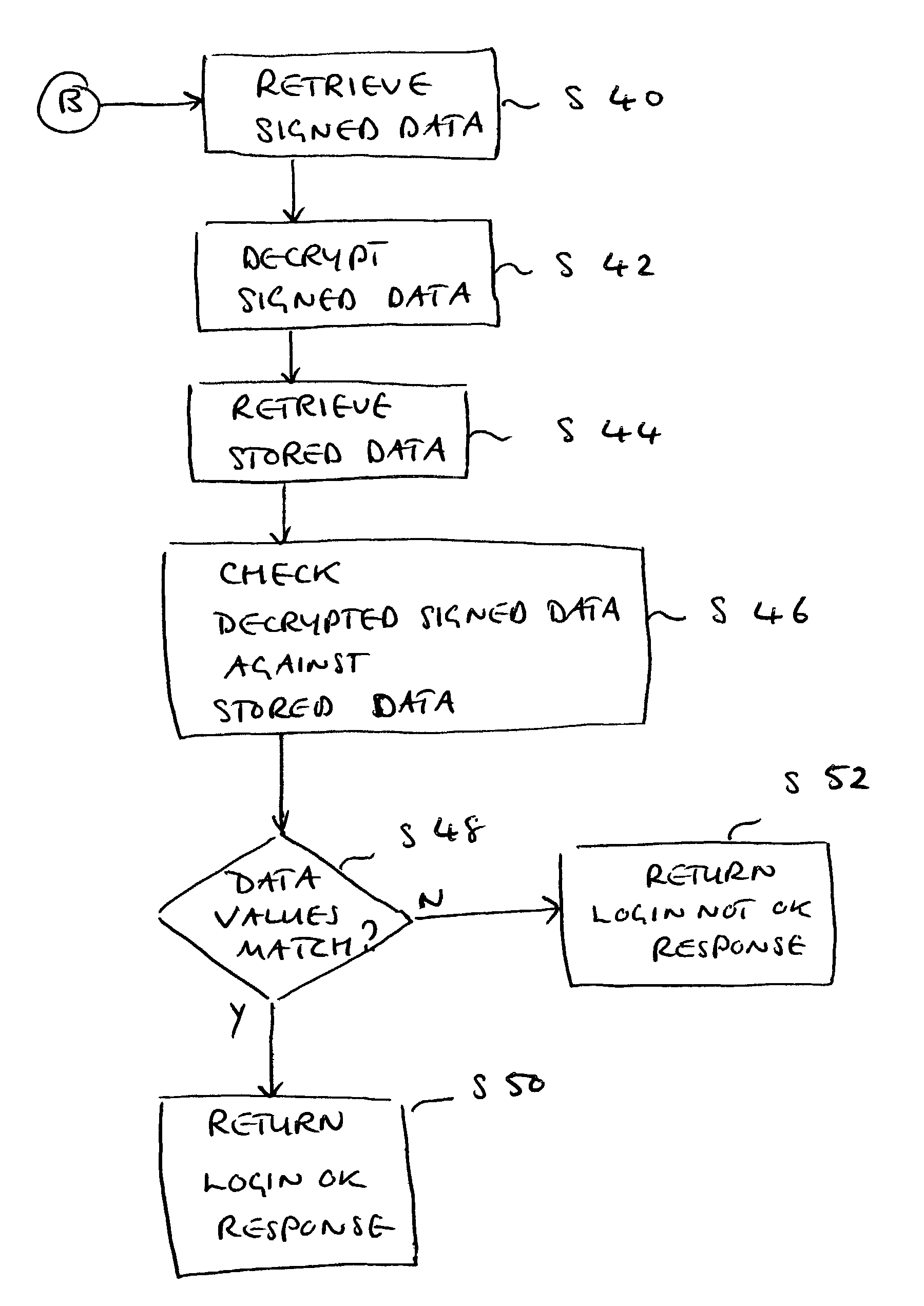
ActiveUS8819253B2Avoids presentationImprove user experienceDigital data processing detailsUser identity/authority verificationUser deviceNetwork generation
A message generation mechanism for a network interface is provided. The message generation mechanism is operable to generate a message which includes data for signing and authentication procedure instructions. The message is for conveying information to a user device for presentation to a user via a user interface of the user device. The data is arranged in the message in a manner which permits the user device to utilize the data in an automated signing procedure. The automated signing procedure may be a digital signing procedure. The data for signing may be random data, pseudo-random data or secure random data and may be arranged in the message in a manner which avoids presentation to the user.
Owner:ORACLE INT CORP
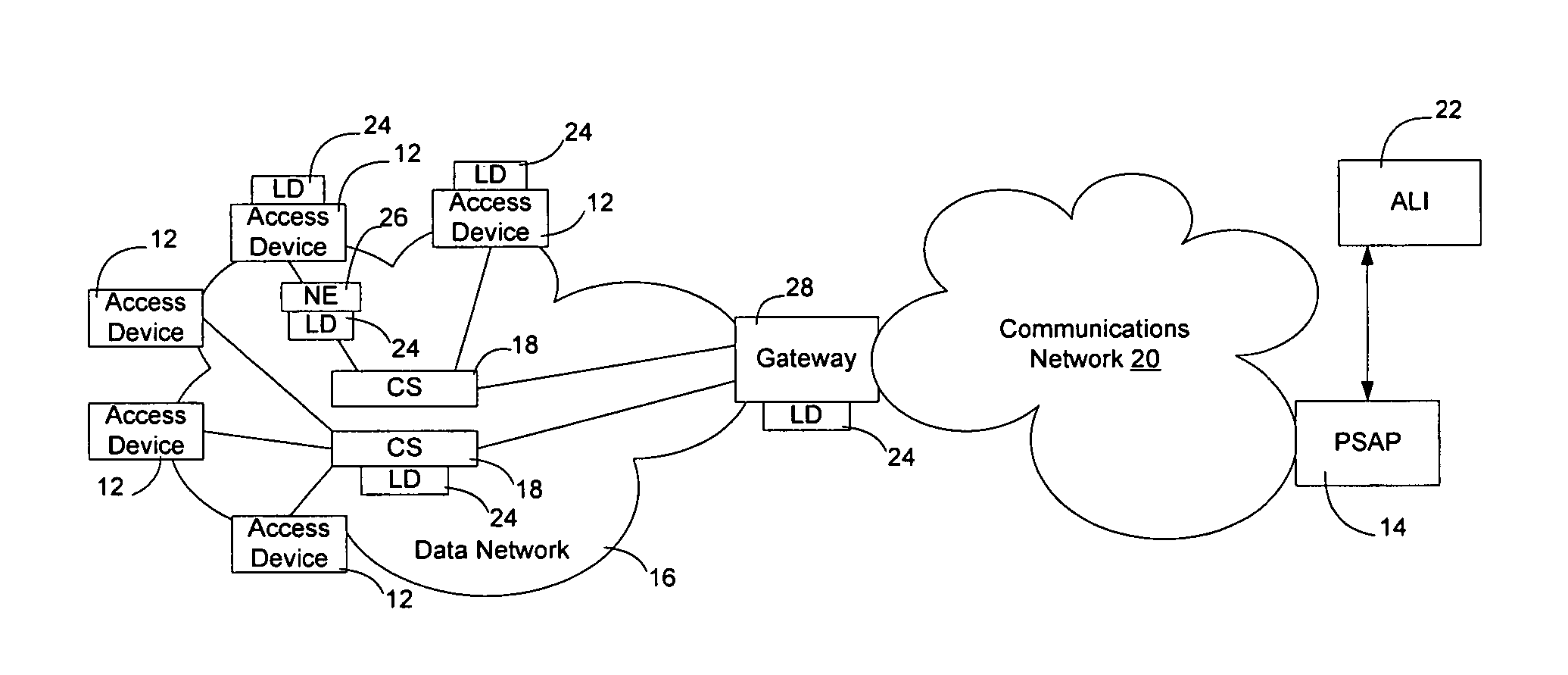
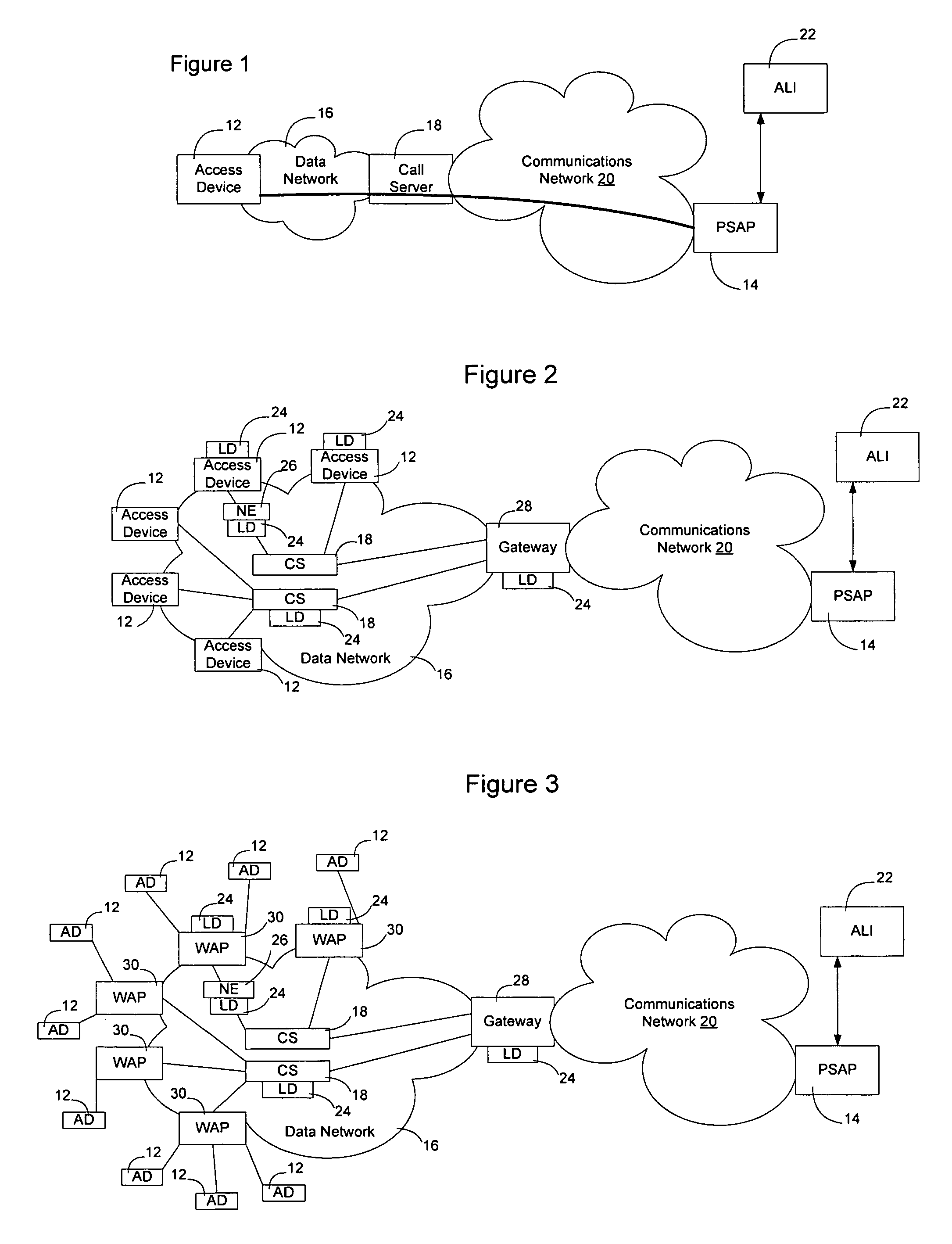
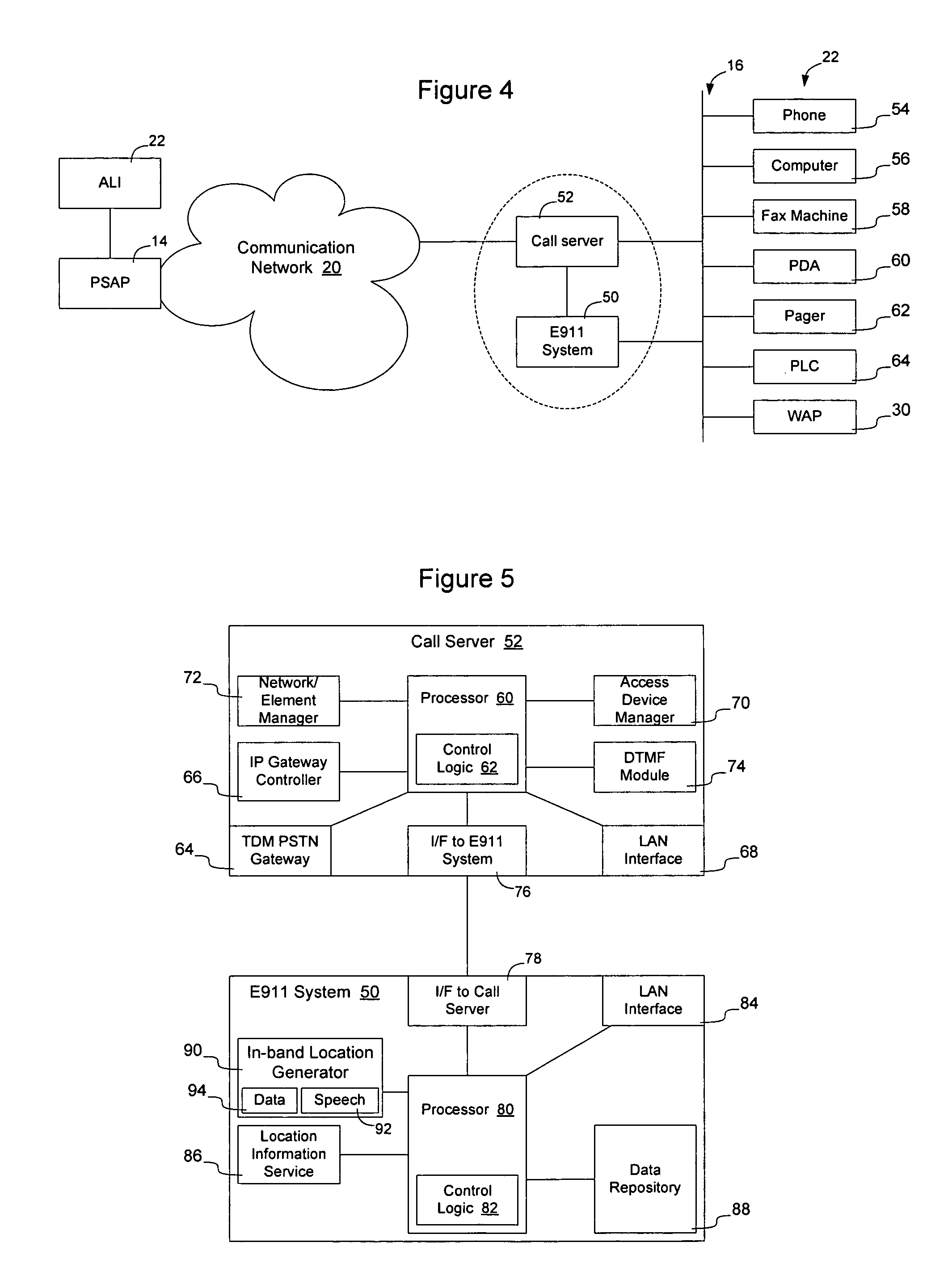
Method and apparatus for providing in-band location information in an emergency response network
InactiveUS20050169248A1Overcomes drawbackTelephone data network interconnectionsData switching by path configurationNetwork generationOn demand
Location information associated with an access device on a data network may be generated by the network and transmitted in-band on an emergency call to a PSAP to allow the PSAP operator to obtain the location of the caller for emergency services. The location information may be audible or may be generated in a form readable by a machine at the PSAP operator's station. The information may be provided automatically or on-demand. Enabling the data network to generate and transmit the location information enables the data network to provide more up-to-date location information than if the location information were required to be updated into the PSAP's ALI database. Additionally, mobility on the data network may be accommodated to enable the emergency location service to be provided on a wireless network. A database associated with the service may be configured to store the location information, which may then be provided in connection with emergency calls.
Owner:NORTEL NETWORKS LTD
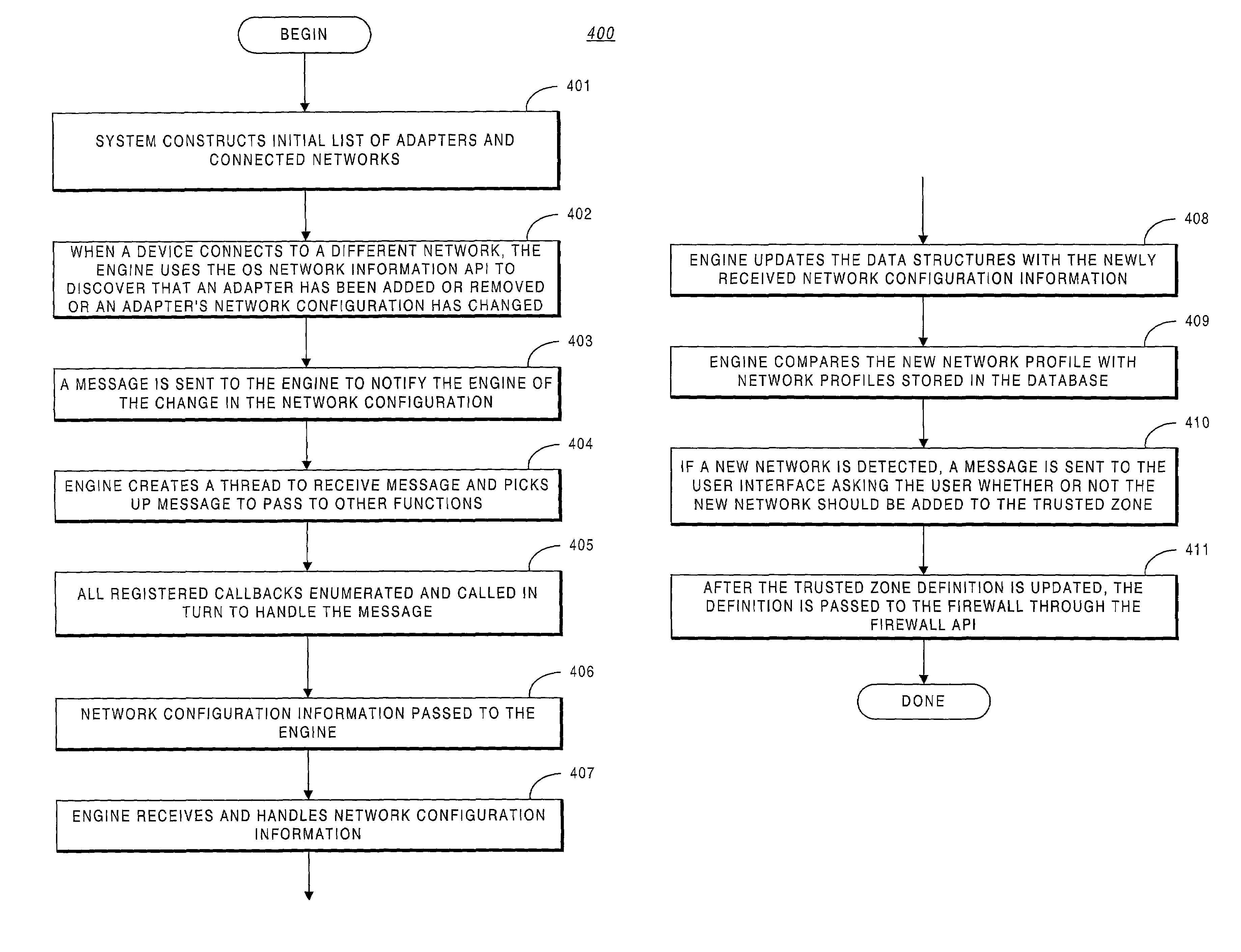
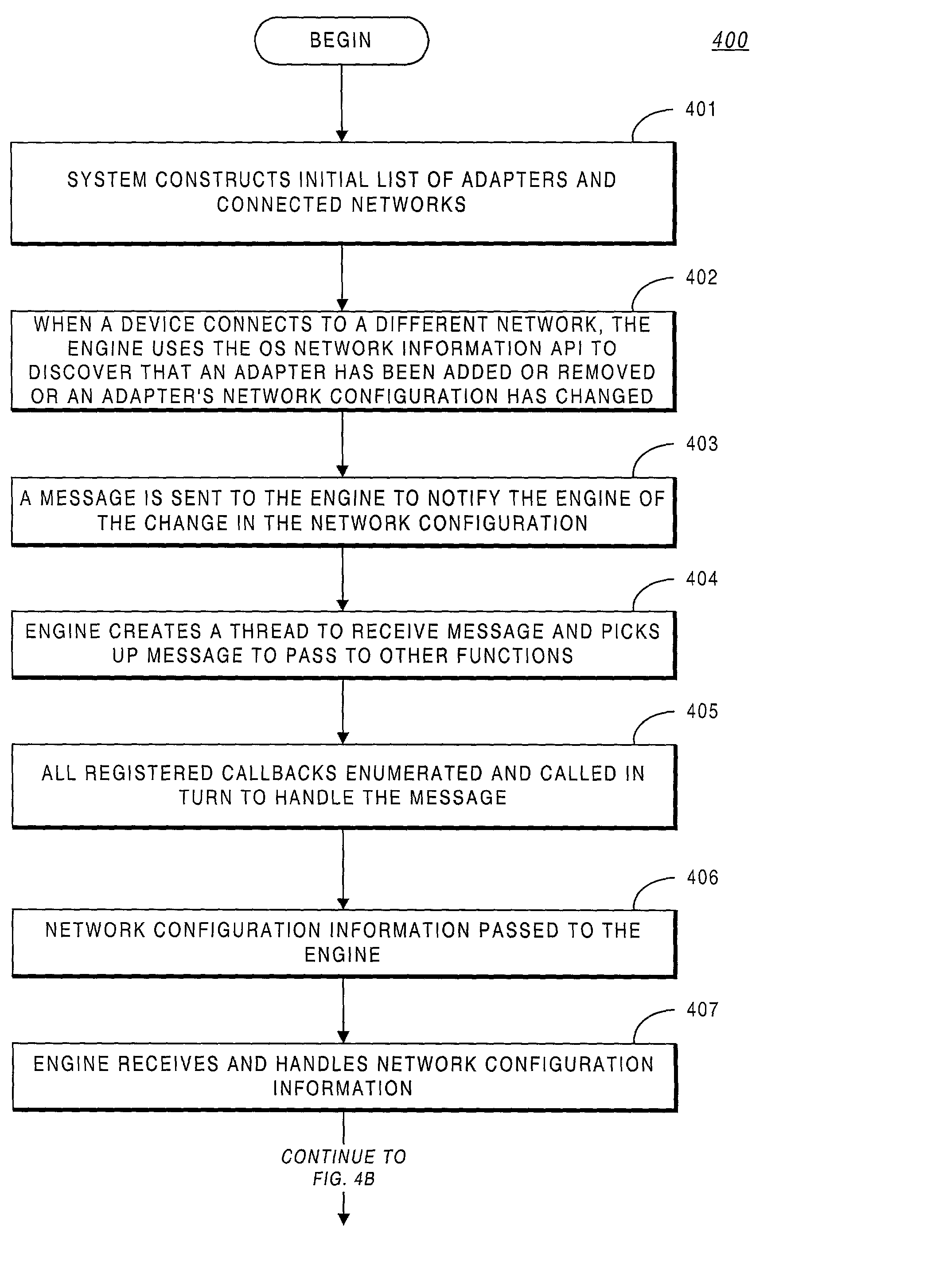
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS7222359B2Easy to detectDigital data processing detailsMultiple digital computer combinationsNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
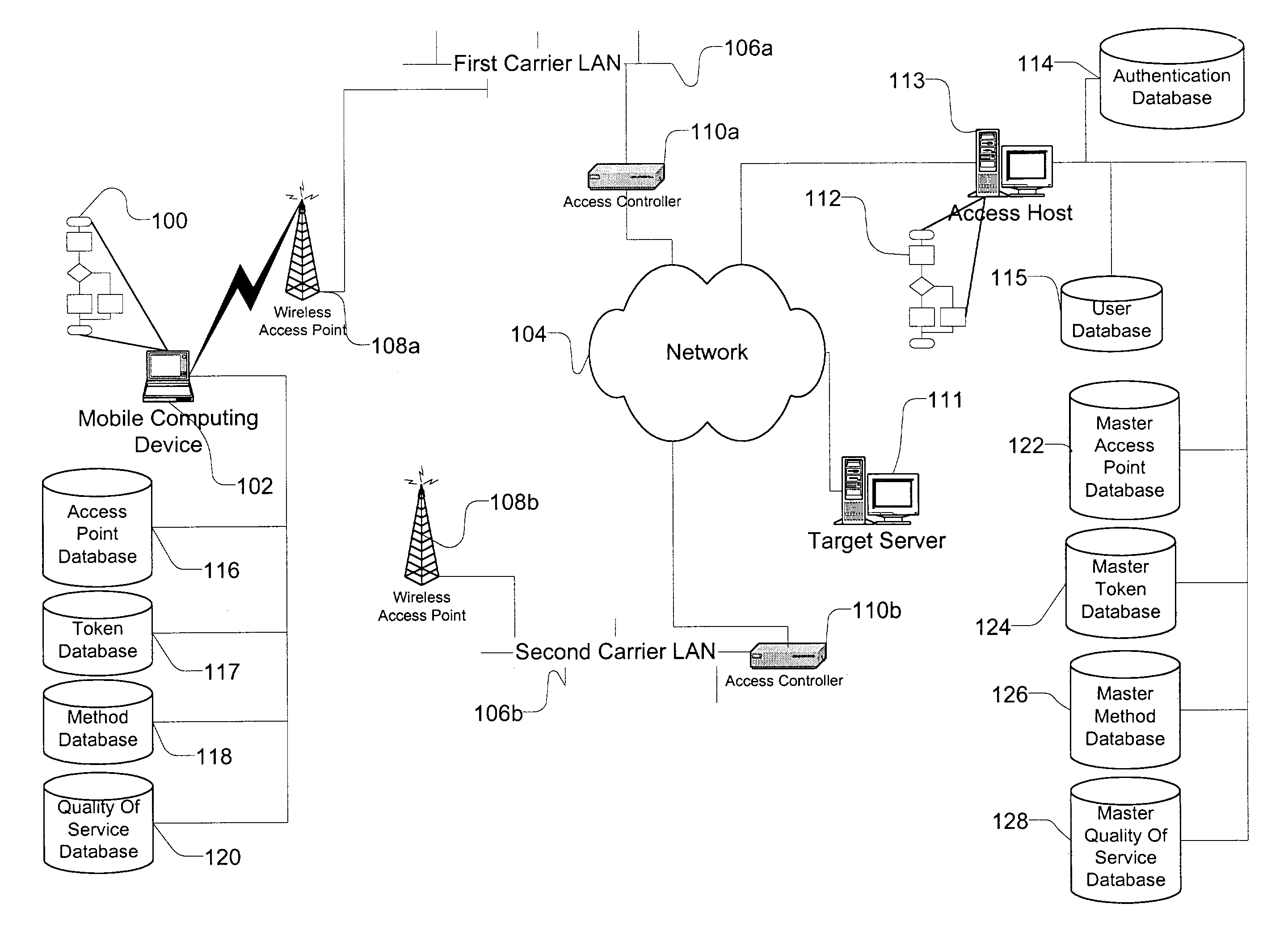
Method and apparatus for accessing networks by a mobile device
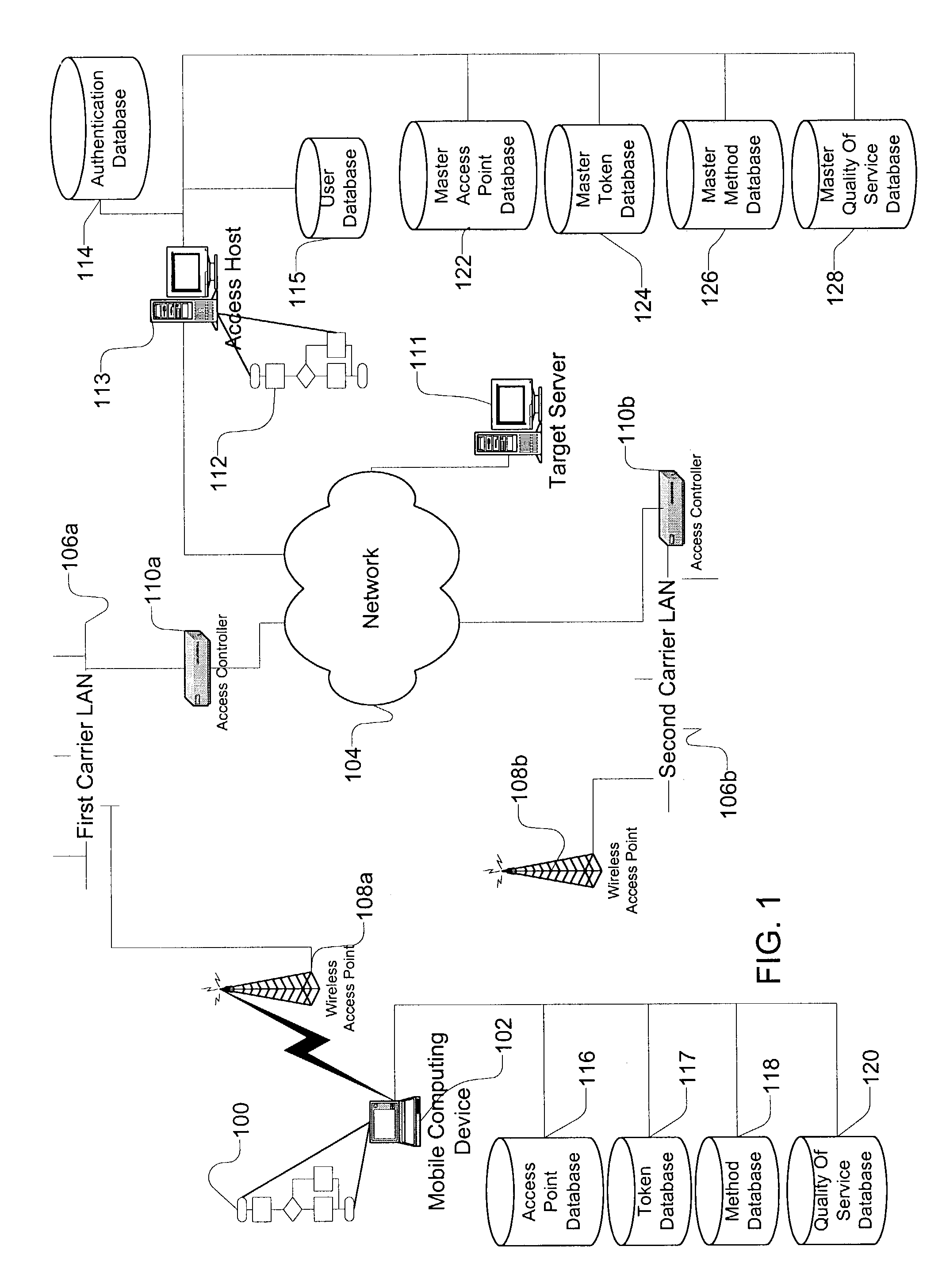
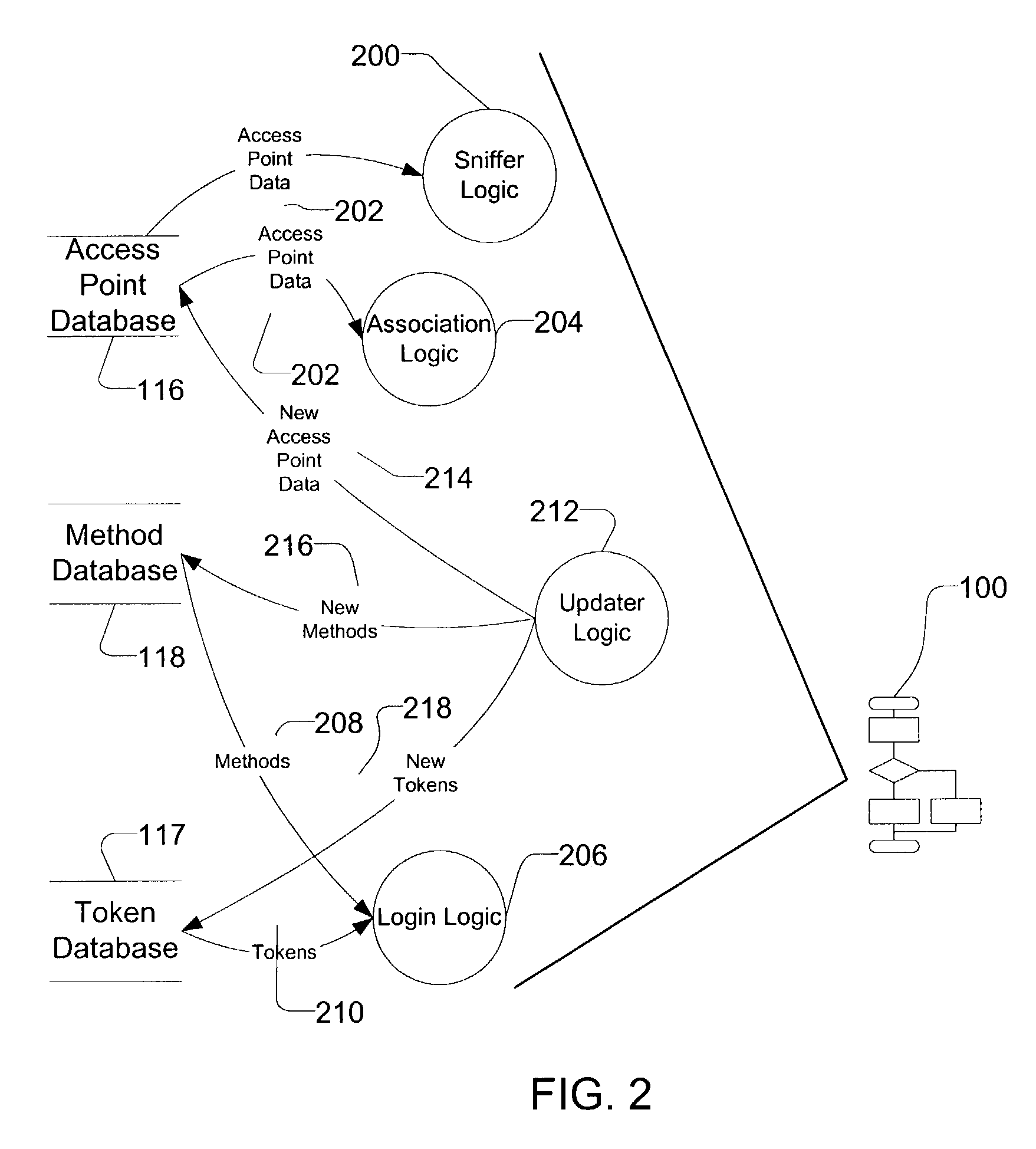
InactiveUS7483984B1Assess restrictionMultiple digital computer combinationsAccess networkNetwork generation
A method and apparatus for accessing wireless carrier networks by mobile computing devices. An access client hosted by a mobile computing device accesses carrier networks using wireless access points. The access client uses an access point database to identify access points and carrier networks. The access client uses a methods database and a tokens database to access the carrier networks. The access client updates the access point database, the methods database, and the token database using an access server when the access client is operably coupled to a carrier network. The access client transmits user information to the carrier network. The carrier network uses the user information to authenticate the user and to generate session data while the user is accessing the carrier network. The carrier network transmits the session data to the access server. The access server uses the session data to generate billing information for the user. The access client also collects network performance data for individual access points and carrier networks. The access client transmits the network performance data to the access server. The access server aggregates network performance data from a plurality of access clients to generate quality of server reports for both individual access points and carrier networks. The access client further includes access point detection and evaluation features for use by a user in selecting access points available at a single location.
Owner:BOINGO WIRELESS
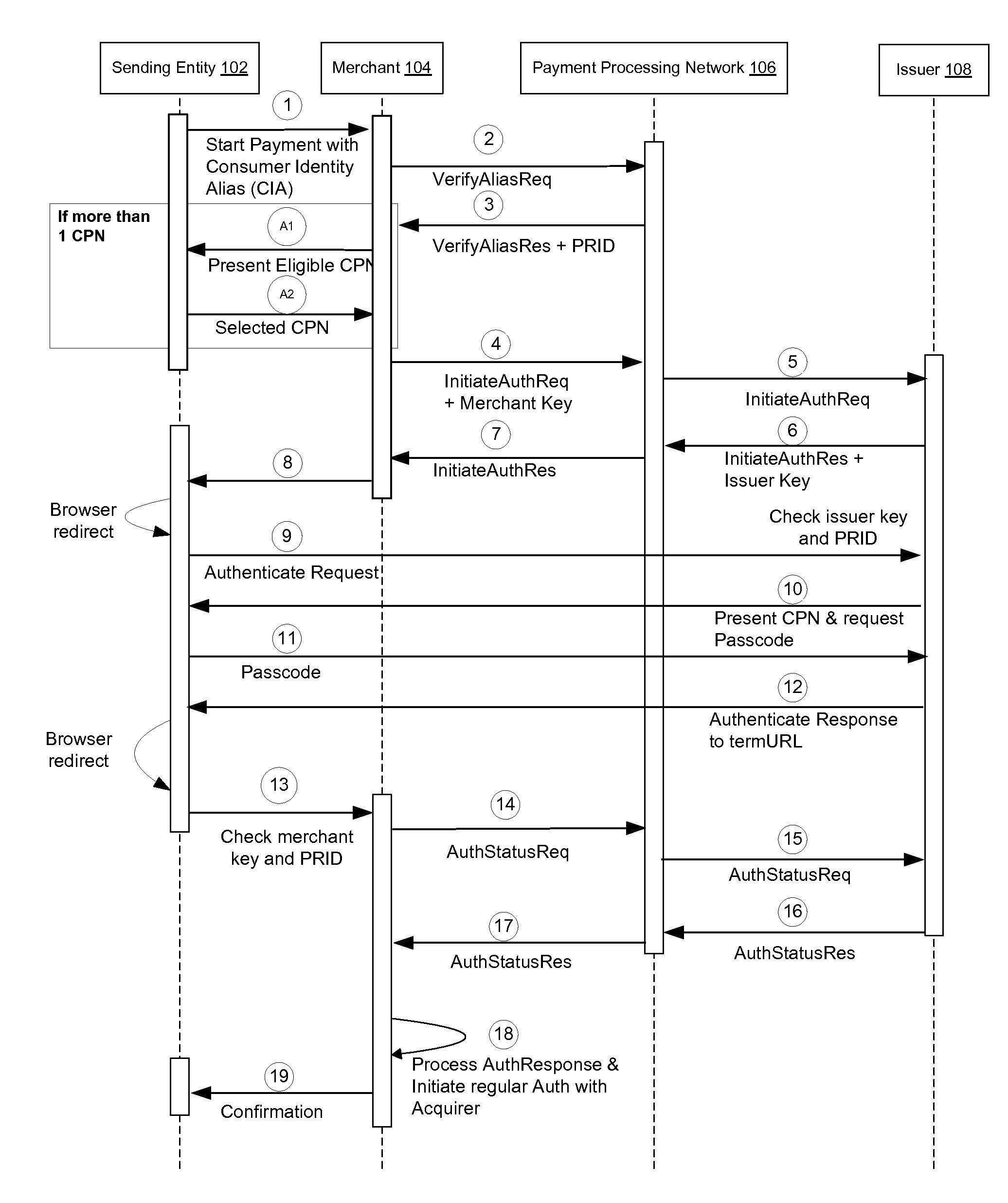
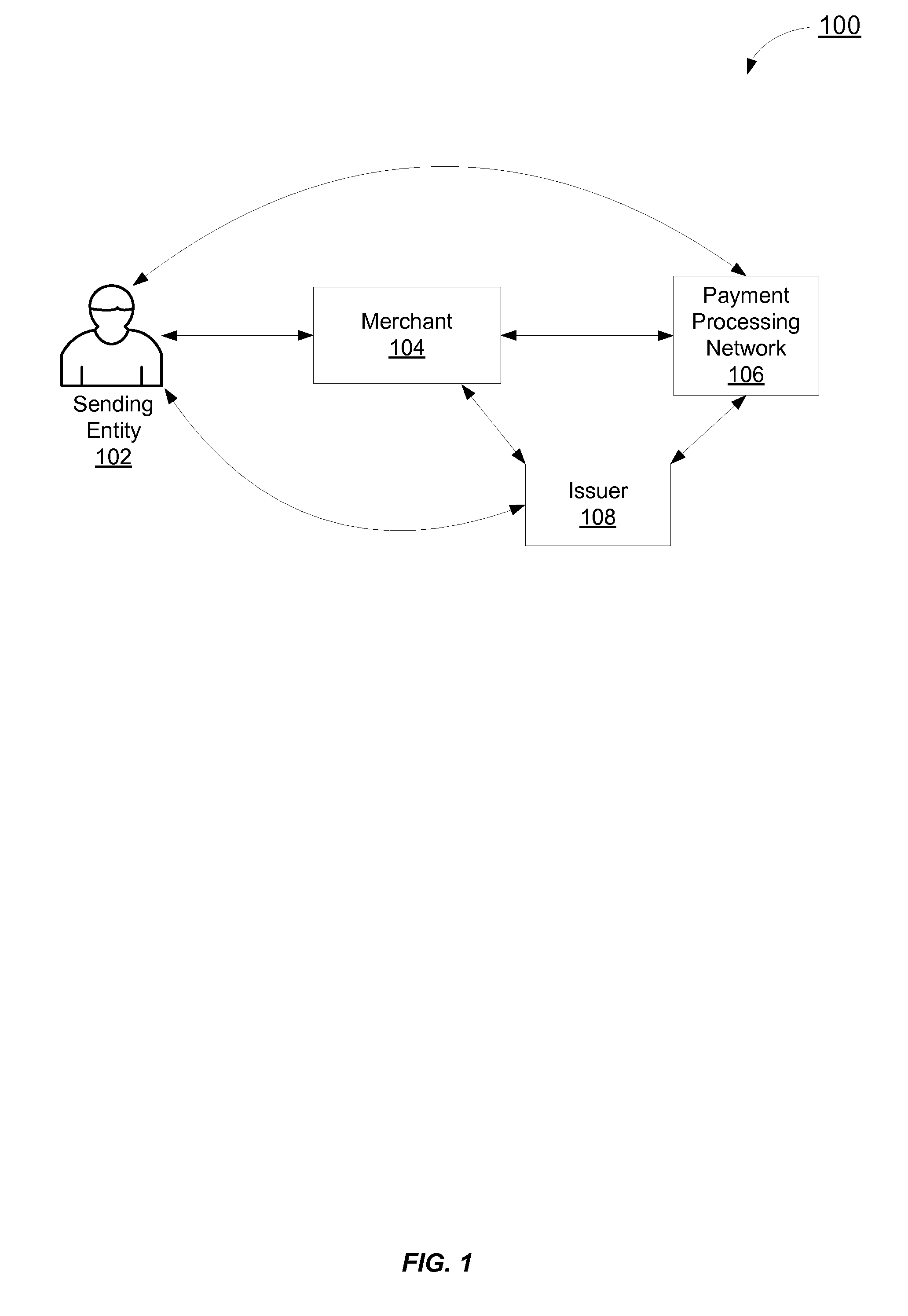
Token based transaction authentication
A token based transaction authentication system is disclosed. Issuer, merchants, and a payment processing network generate unique tokens or keys to authenticate messages between themselves and to authenticate a sending entity or consumer as they are redirected between entities. The tokens are also used to identify the particular authentication thread a message or sending entity is associated with. The sending entity authentication occurs over a web-based channel or a mobile based channel.
Owner:VISA INT SERVICE ASSOC
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS20030167405A1Easy to detectDigital data processing detailsHardware monitoringNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
End-to-end identification method for scene text with random shape
ActiveCN108549893AAccurate identificationAccurate detectionCharacter and pattern recognitionNeural architecturesNetwork generationTheoretical computer science
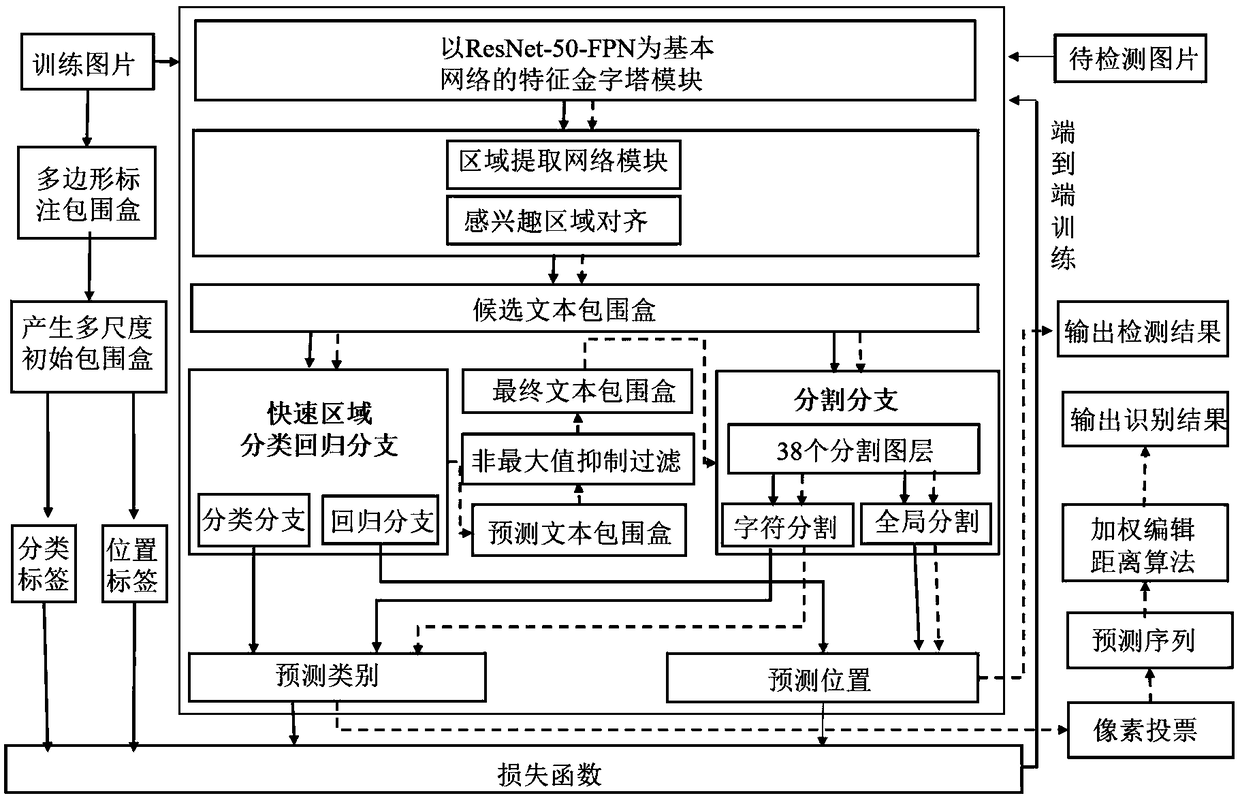
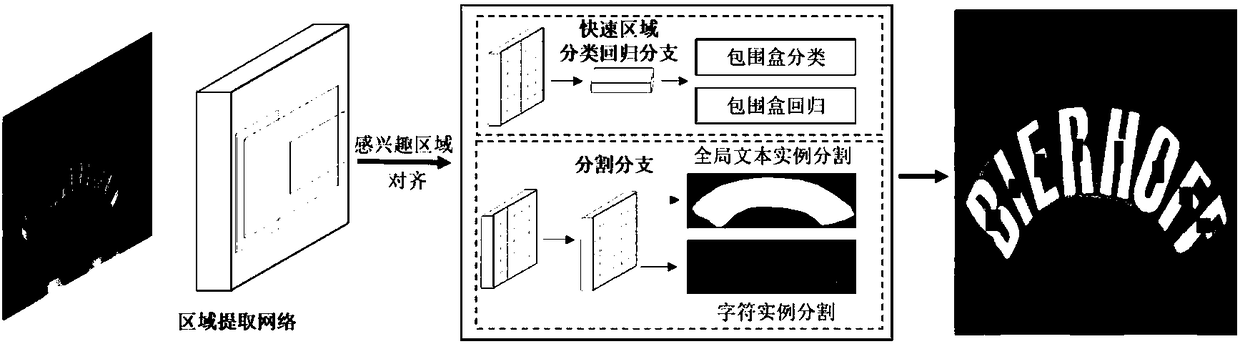
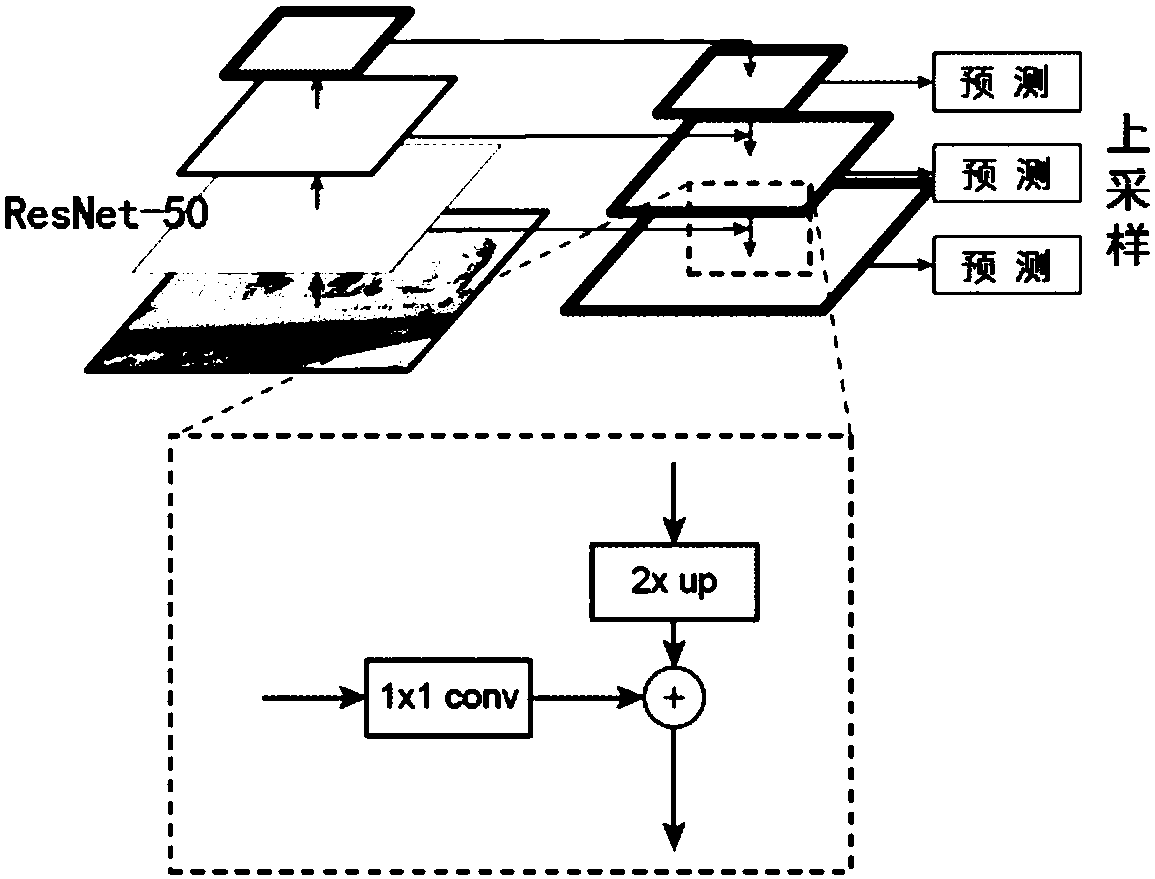
The invention discloses an end-to-end identification method for a scene text with a random shape. The method comprises the steps of extracting a text characteristic through a characteristic pyramid network for generating a candidate text box by an area extracting network; adjusting the position of the candidate text box through quick area classification regression branch for obtaining more accurate position of a text bounding box; inputting the position information of the bounding box into a dividing branch, obtaining a predicated character sequence through a pixel voting algorithm; and finally processing the predicated character sequence through a weighted editing distance algorithm, finding out a most matched word of the predicated character sequence in a given dictionary, thereby obtaining a final text identification result. According to the method of the invention, the scene texts with the random shape can be simultaneously detected and identified, wherein the scene texts comprisehorizontal text, multidirectional text and curved text. Furthermore end-to-end training can be completely performed. Compared with prior art, the identification method according to the invention has advantages of obtaining advantageous effects in accuracy and versatility, and realizing high application value.
Owner:HUAZHONG UNIV OF SCI & TECH
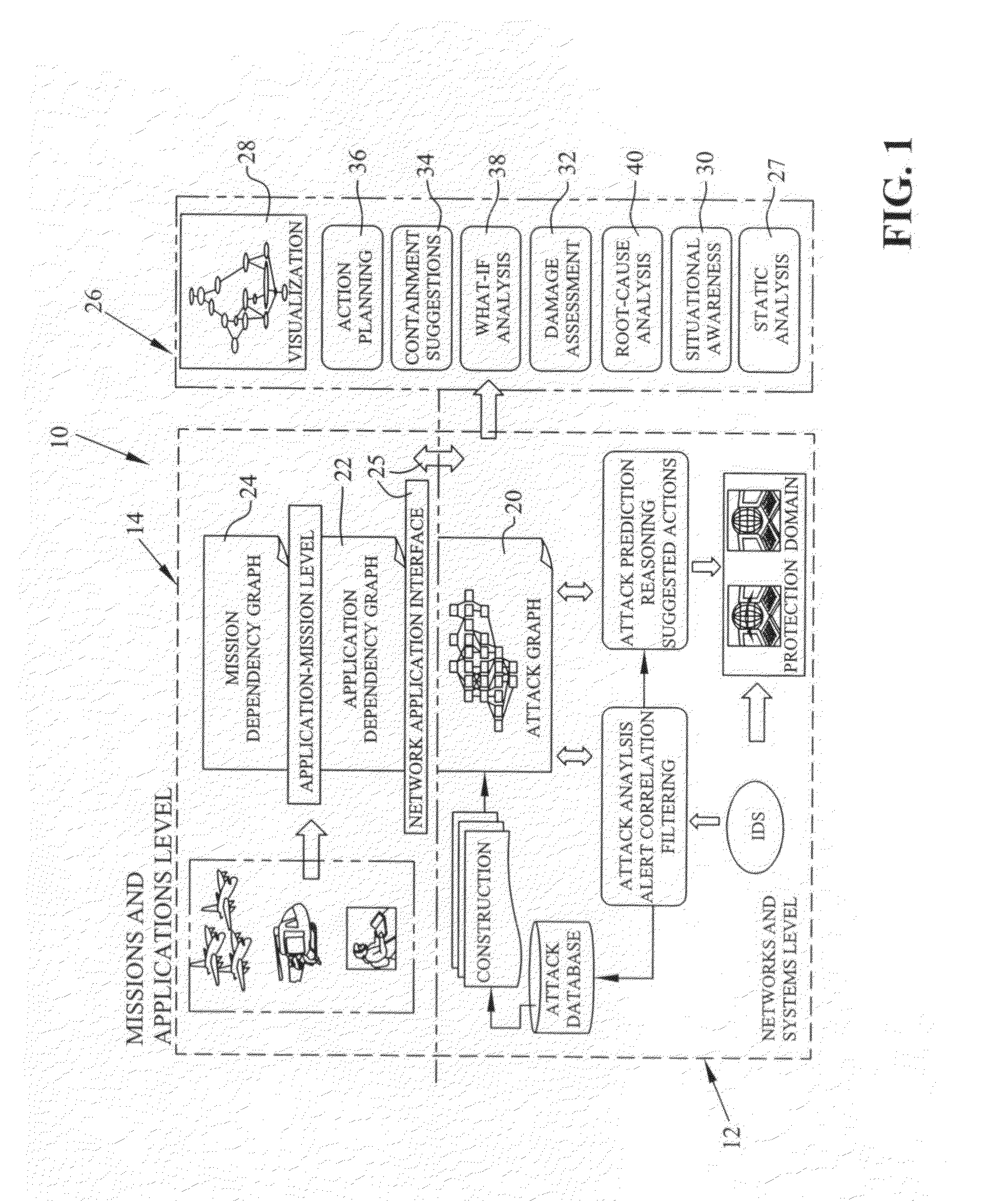
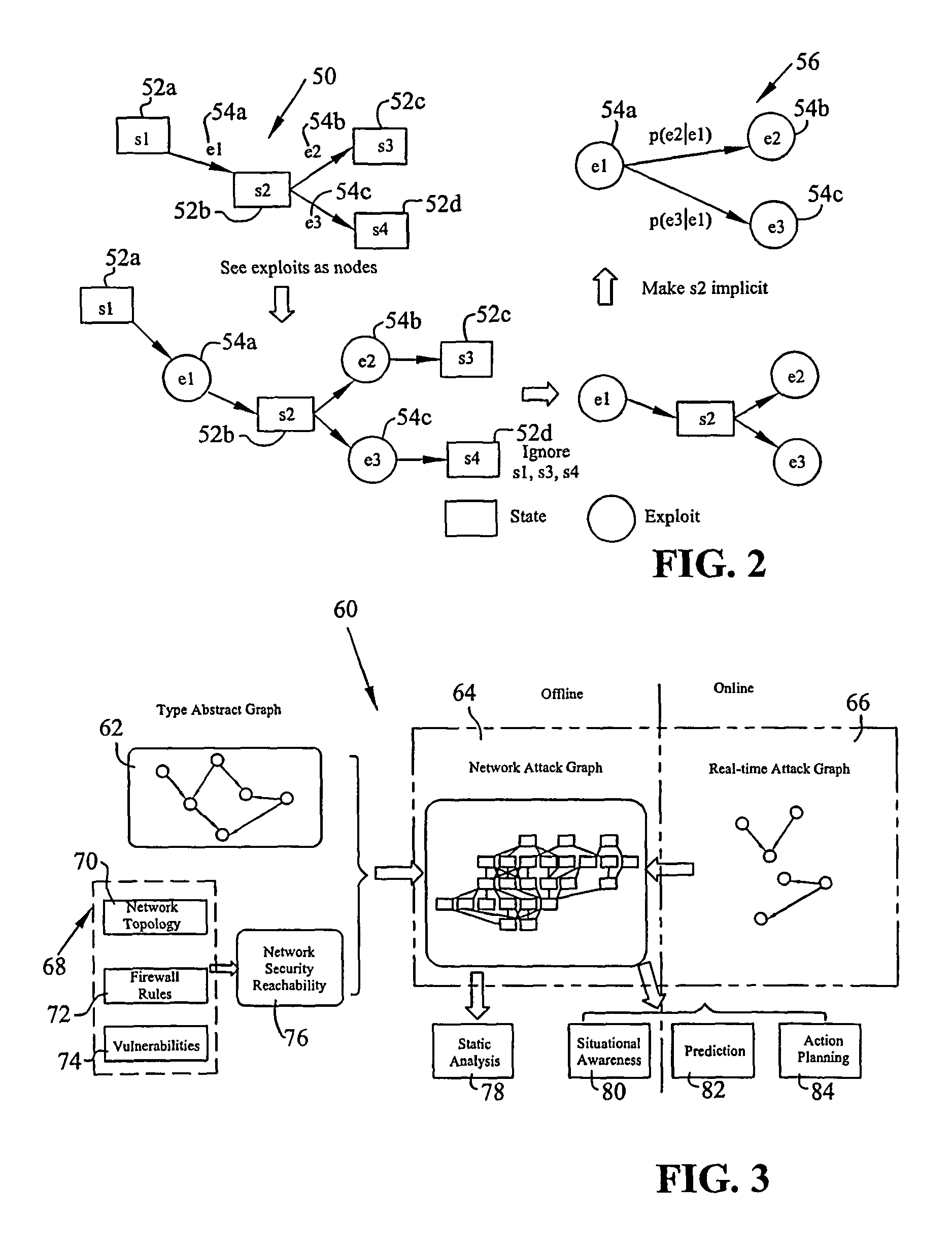
Graphical models for cyber security analysis in enterprise networks
ActiveUS8881288B1Accurate and efficientReduce and compress redundancyMemory loss protectionError detection/correctionGraphicsGaussian network model
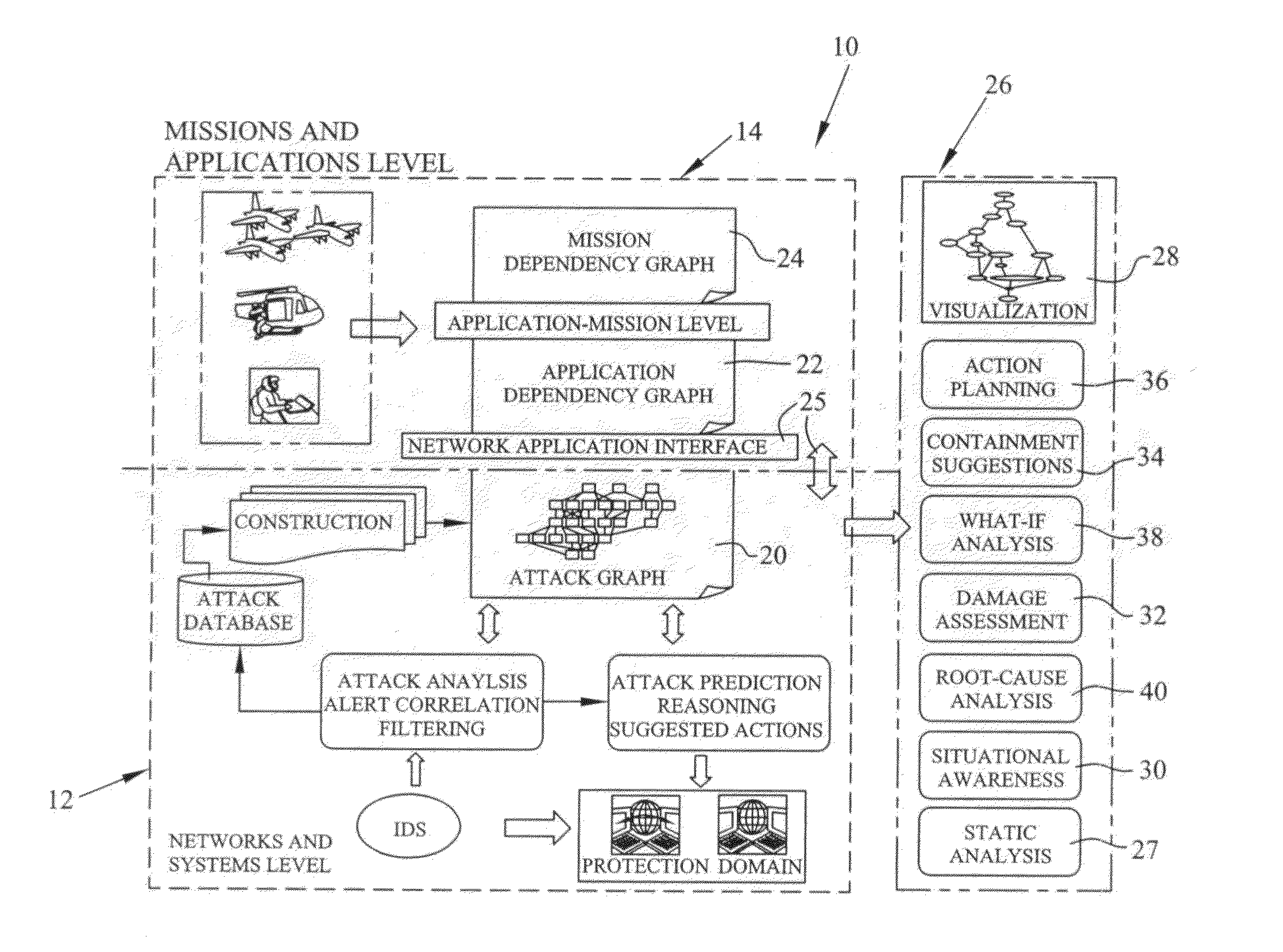
A method of generating graphical models for providing security analysis in computer networks that in one embodiment includes the steps of generating a type abstract graph independent of particular networks that models abstract dependency relationships among attributes and exploits; generating network-specific attack graphs by combining the type abstract graph with specific network information; monitoring an intruder alert; and generating a real-time attack graph by correlating the intruder alert with the network-specific attack graph. The real-time attack graph can be generated using reachability checking, bridging, and exploit prediction based on consequence alerts and may further include the step of calculating the likelihood of queries using a Bayesian network model. The method may also include the steps of inferring unobserved attacks that may have been missed by intrusion detection sensors, and projecting on which hosts and using what exploits additional intruder attacks may occur. The method may further include the step of comparing alternate actions by computation, wherein the alternate actions include the step of patching some vulnerabilities, and wherein the specific network information includes network topology. The specific network information may also include firewall rules.
Owner:INTELLIGENT AUTOMATION LLC
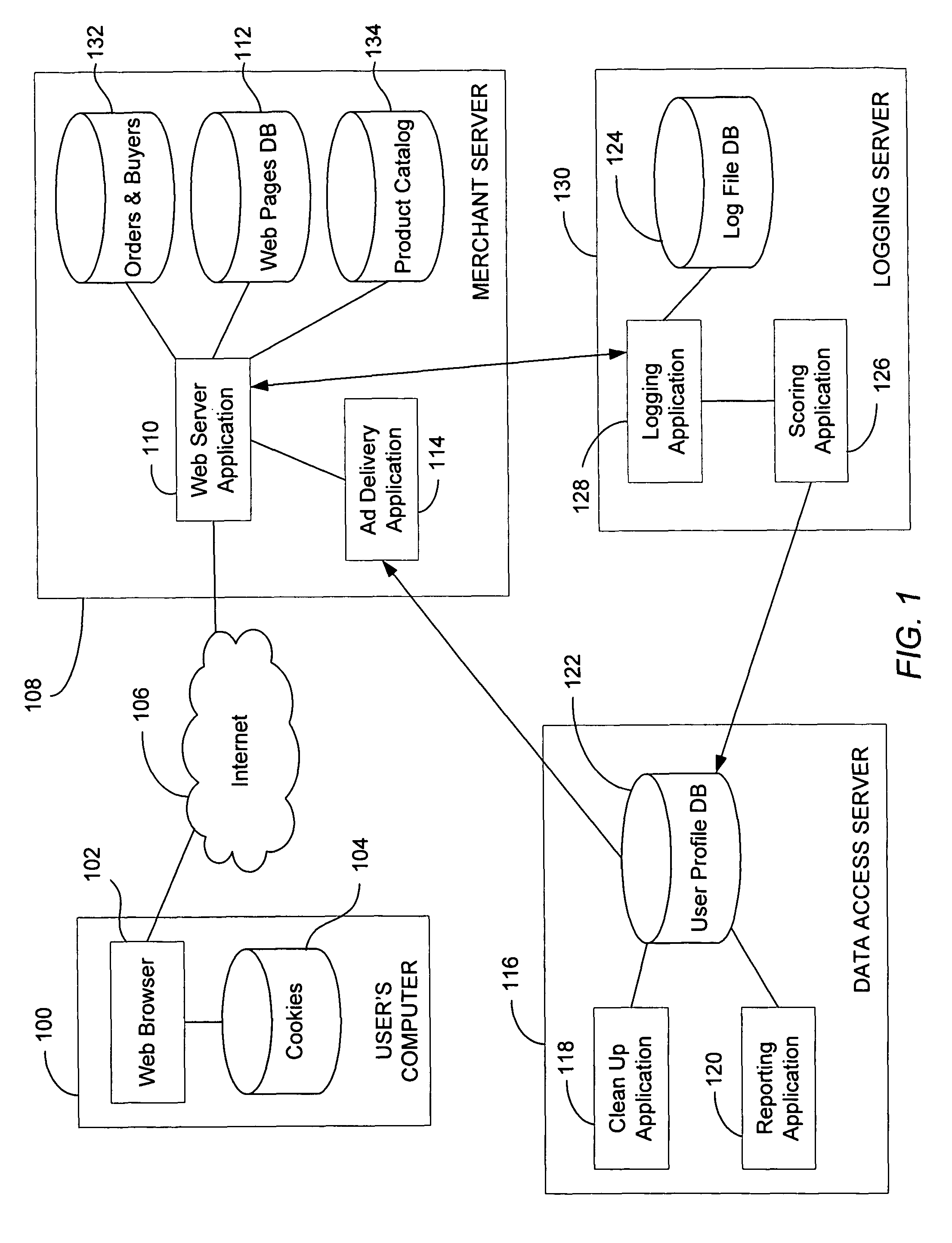
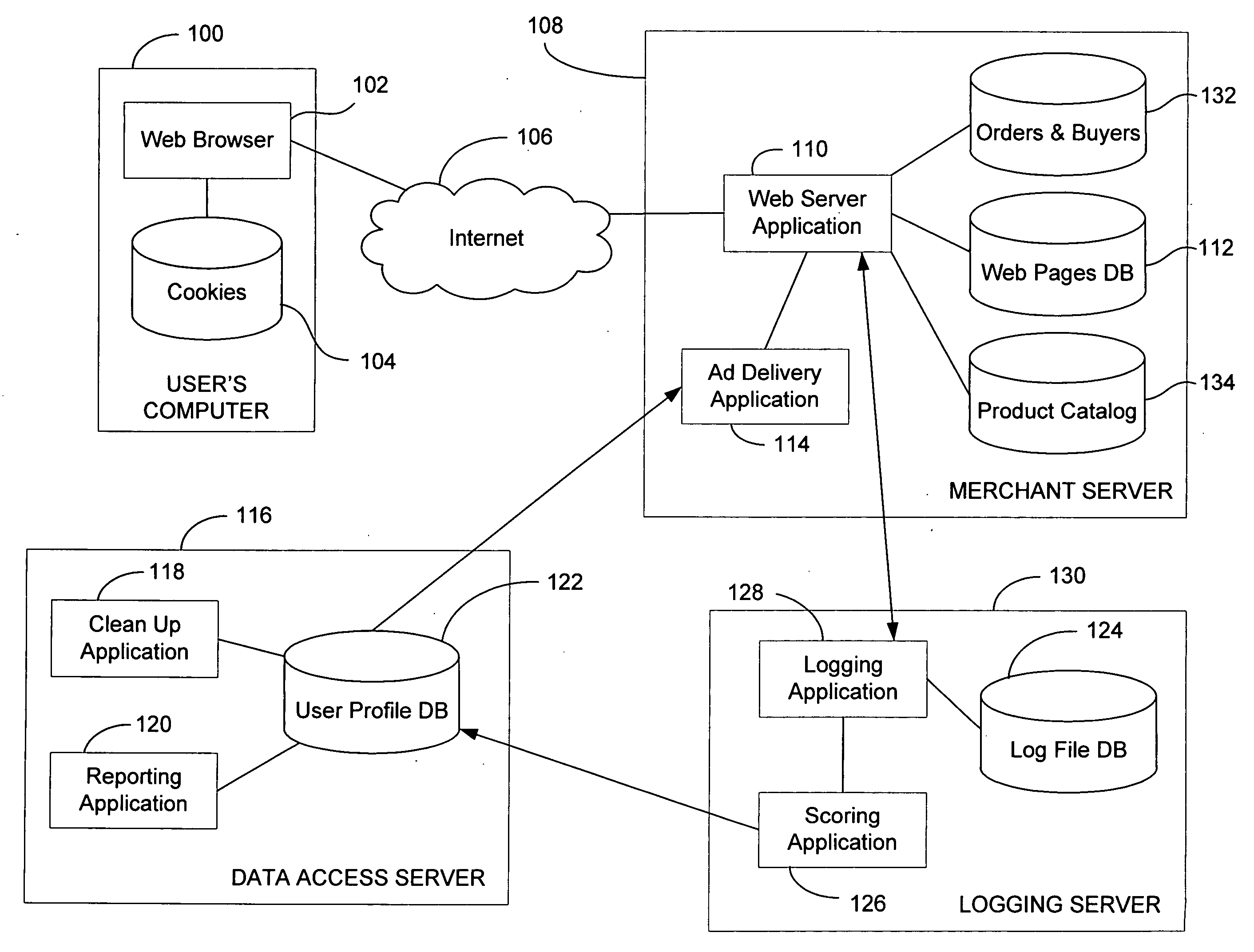
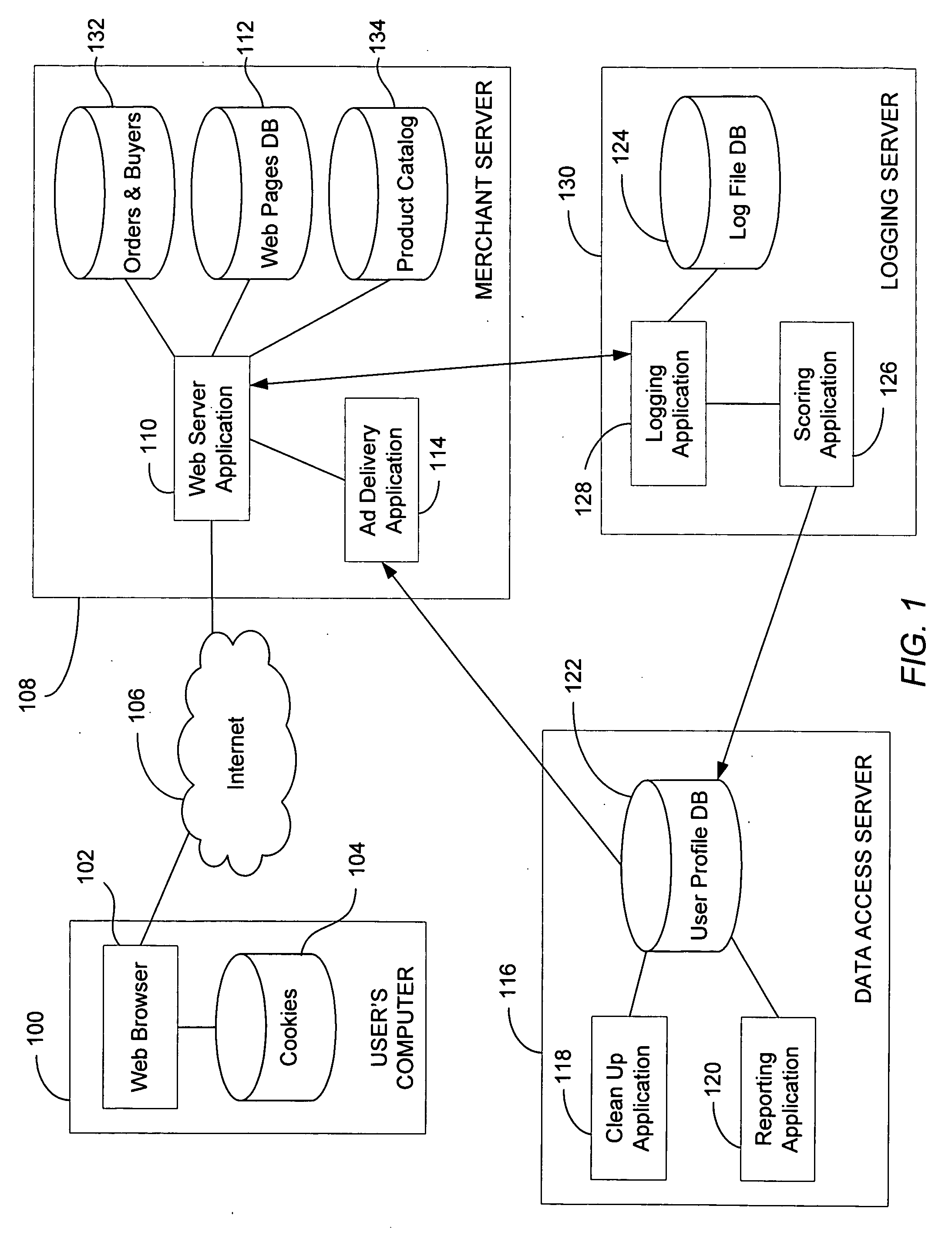
System and method for targeted ad delivery
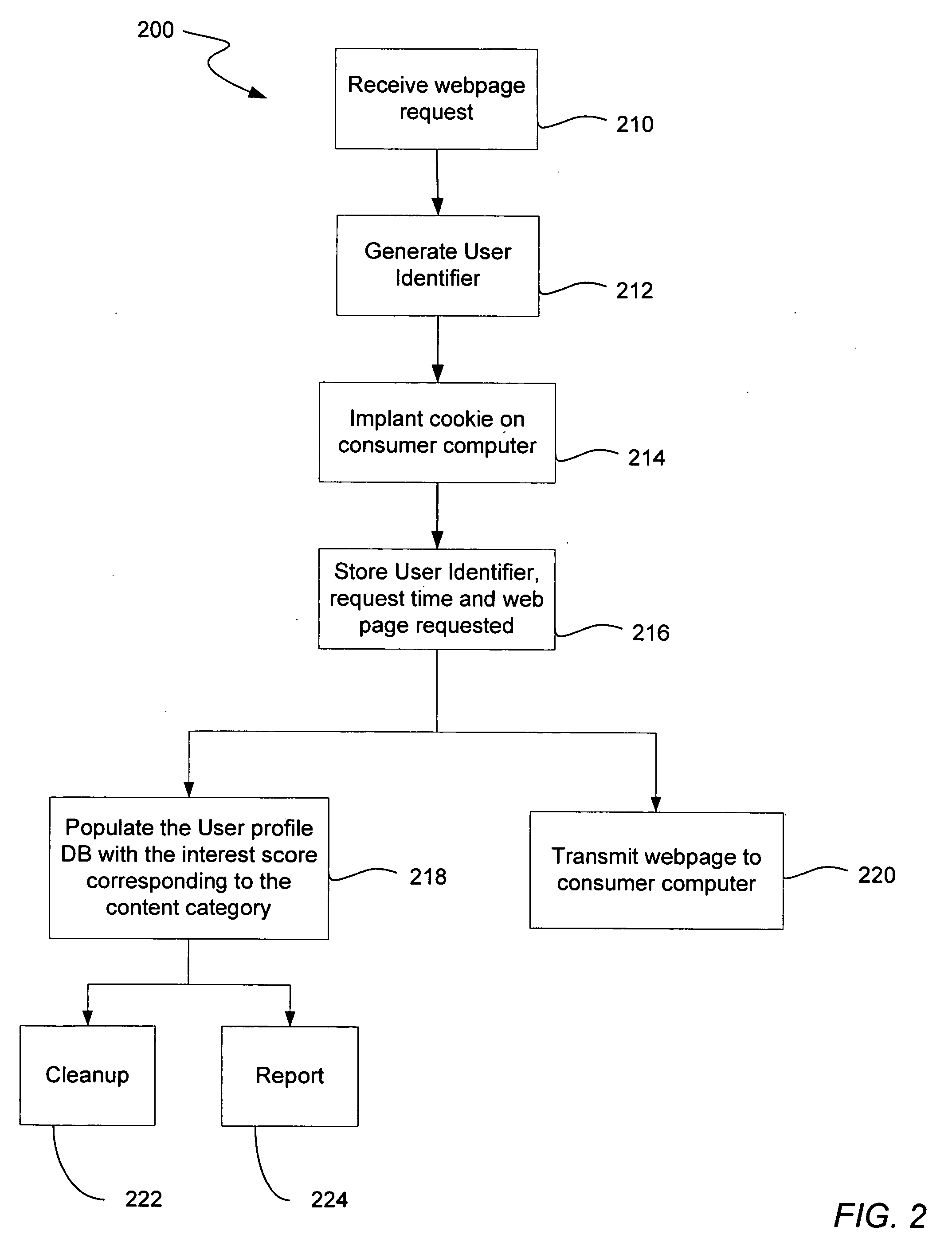
ActiveUS7734632B2User interest can be reducedDigital data processing detailsSpecial data processing applicationsNetwork generationWeb service
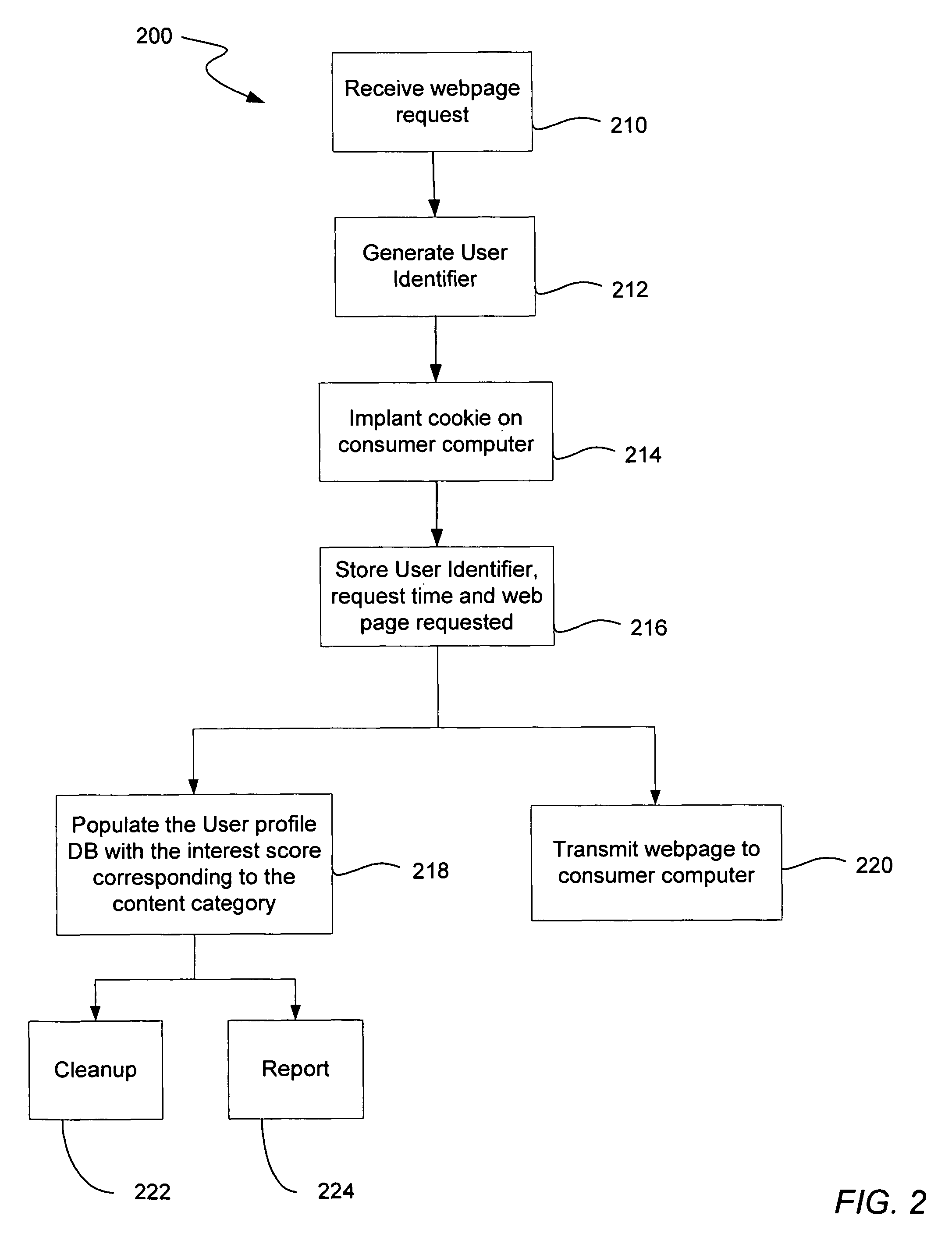
A method and system of generating a user profile for advertisement over a computer network is disclosed. A webpage identifier that identifies a webpage and a content category identifier that identifies a content category is generated. The webpage identifier is associated with the content category identifier if web content depicted in the webpage is relevant to the content category. A web server then receives a request for the webpage including the webpage identifier and a first user identifier from a client computer connected to the computer network. A user profile is located by determining whether the first user identifier matches a second user identifier corresponding to the user profile. The user profile includes at least one user content category identifier and a corresponding user interest score. The corresponding user interest score is increased by the predetermined amount if the content category identifier matches the user content category identifier.
Owner:DISNEY ENTERPRISES INC
System for real time transmission of variable bit rate MPEG video traffic with consistent quality
InactiveUS20020090029A1Quality improvementPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningReal time transmissionTransmission system
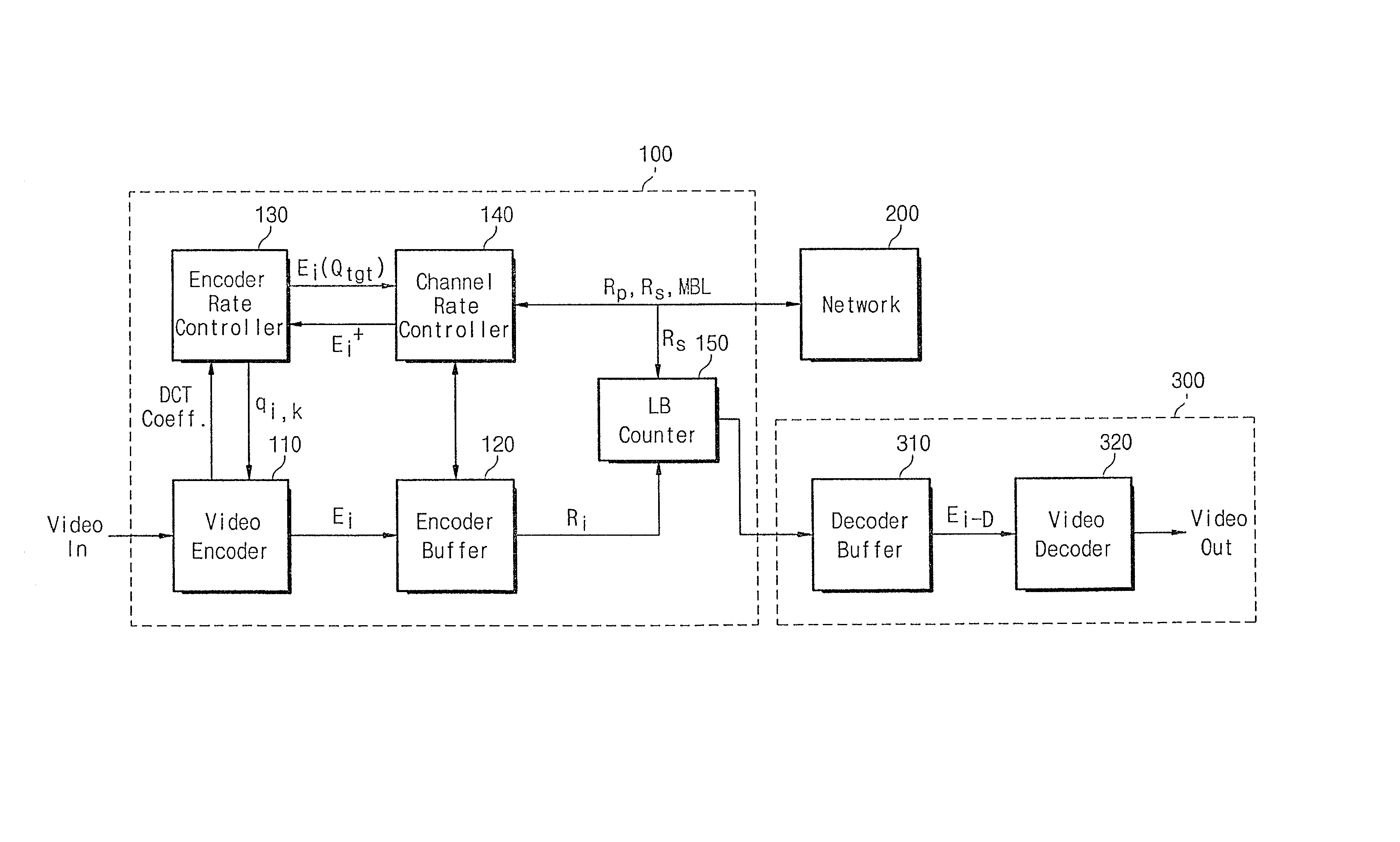
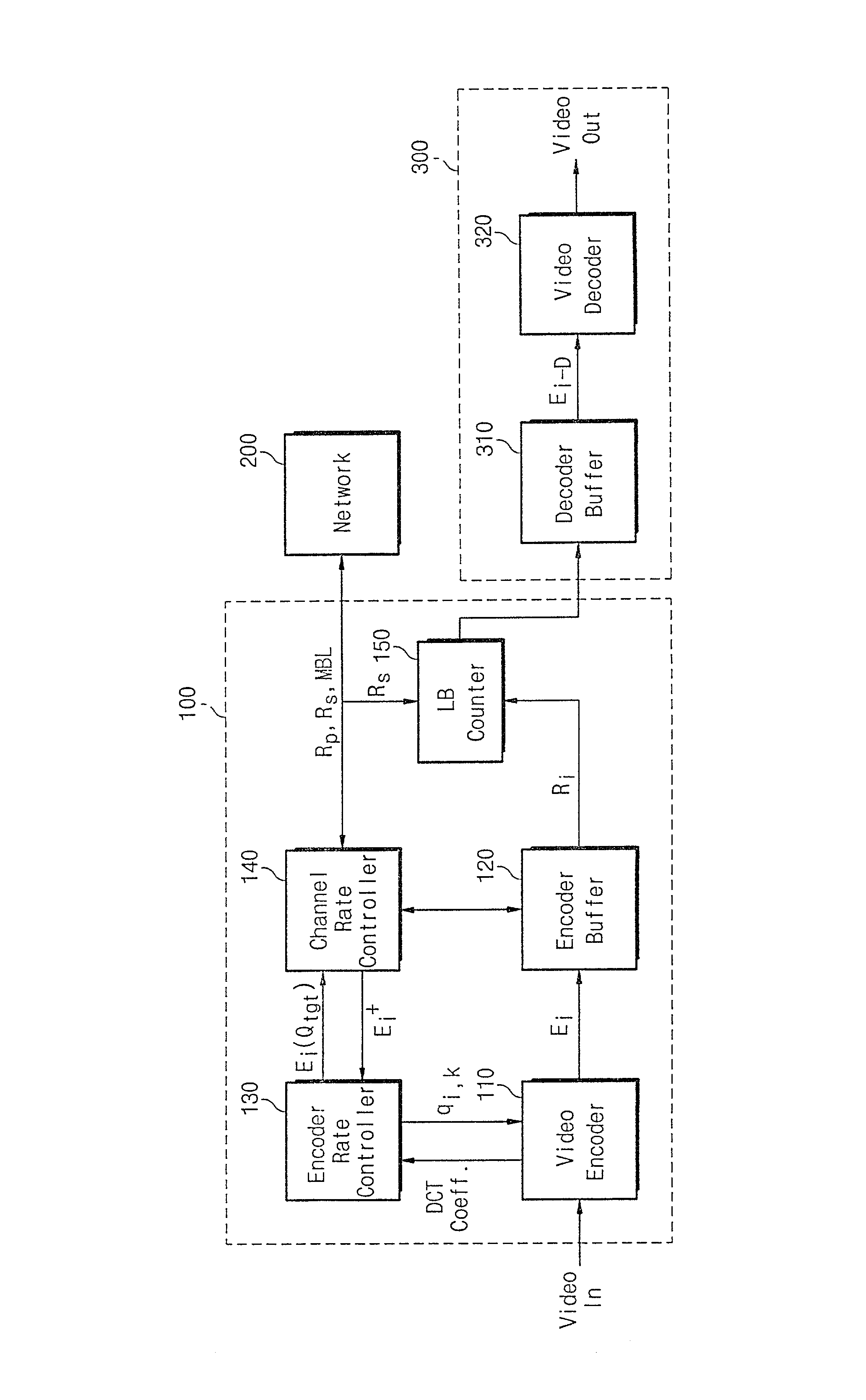
A system and method for real time transmission of variable bit rate MPEG video traffic with consistent quality, wherein each frame is encoded with quantization parameter generated from an encoder rate controller, and encoded data is transmitted to an encoder buffer. Transmission rate about each frame interval is determined by a channel rate controller at the beginning of the frame interval. Data transmission buffered at the encoder buffer is first regulated by Leaky Bucket counter, and the regulated data is transferred to a decoder buffer in a video receiving system through network. The encoder rate controller and channel rate controller included in the VBR video transmission system control the transmission rate generated from the video encoder and that from the network with satisfying imposed constrained conditions, respectively.
Owner:SAMSUNG ELECTRONICS CO LTD
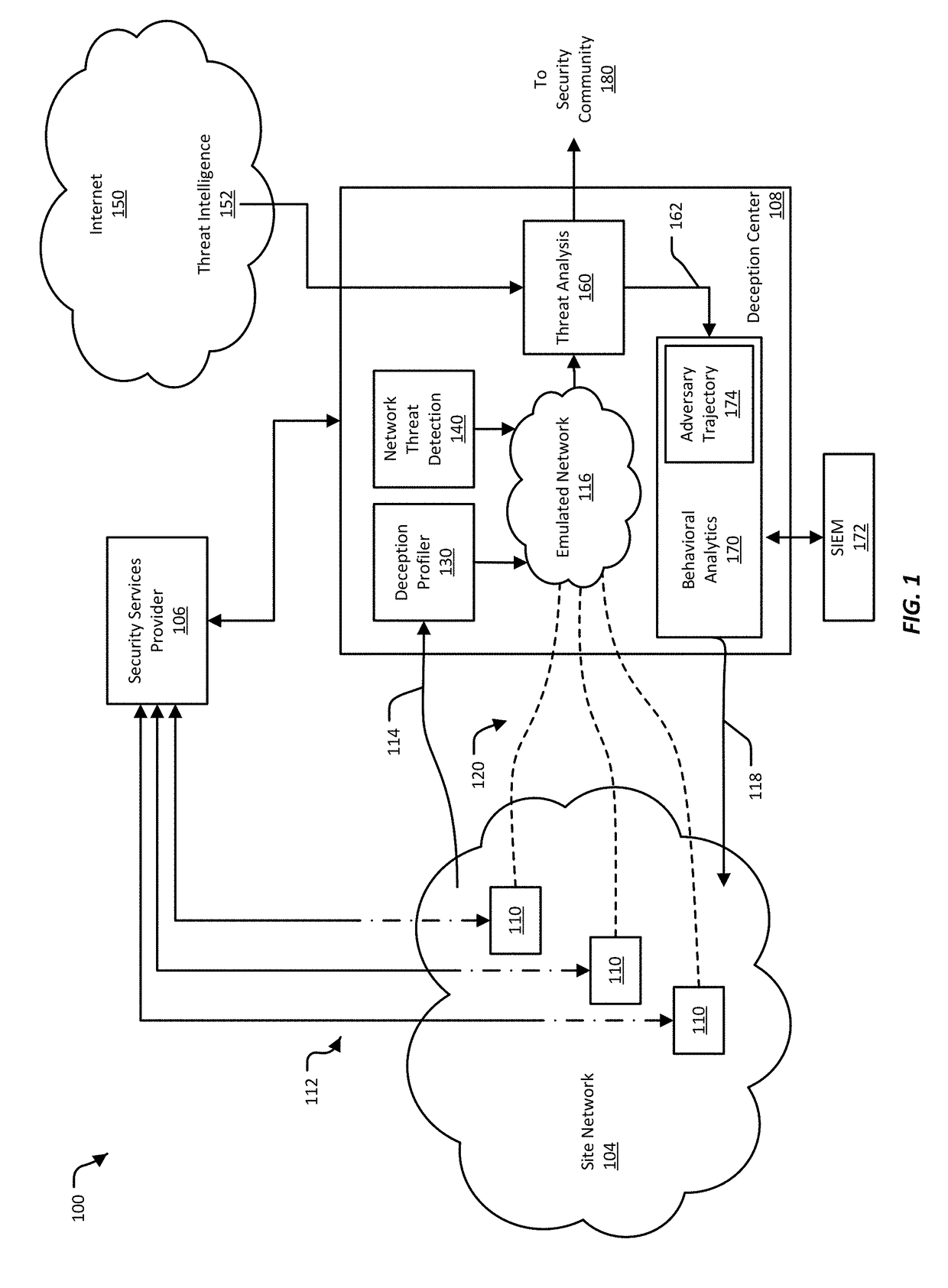
Systems and Methods for Detecting and Tracking Adversary Trajectory
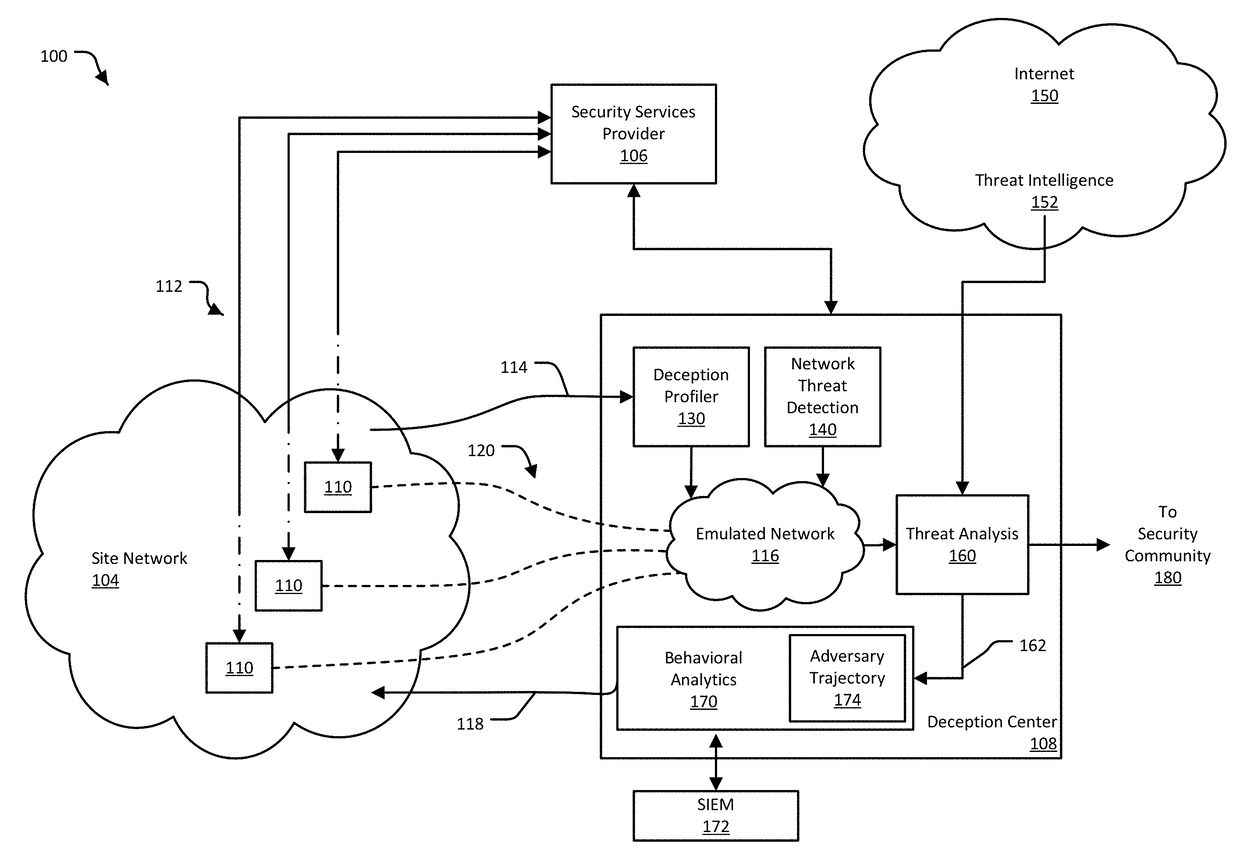
This disclosure is related to using network flow information of a network to determine the trajectory of an attack. In some examples, an adjacency data structure is generated for a network. The adjacency data structure can include a machine of the network that has interacted with another machine of the network. The network can further include one or more deception mechanisms. The deception mechanisms can indicate that an attack is occurring when a machine interacts with one of the deception mechanisms. When the attack is occurring, attack trajectory information can be generated by locating in the adjacency data structure the machine that interacted with the deception mechanism. The attack trajectory information can correlate the information from the interaction with the deception mechanism, the interaction information of the network, and machine information for each machine to determine a possible trajectory of an adversary.
Owner:ACALVIO TECH
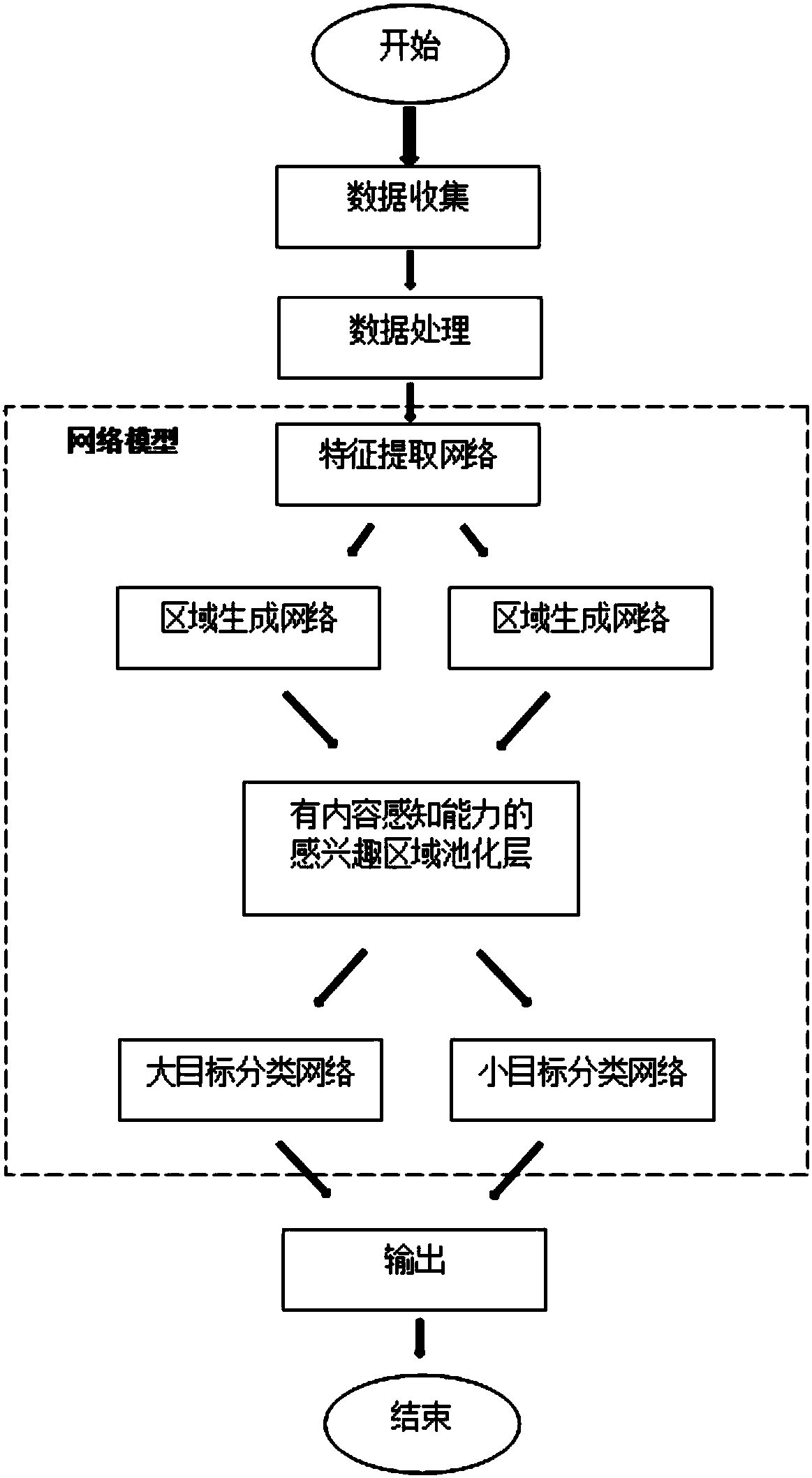
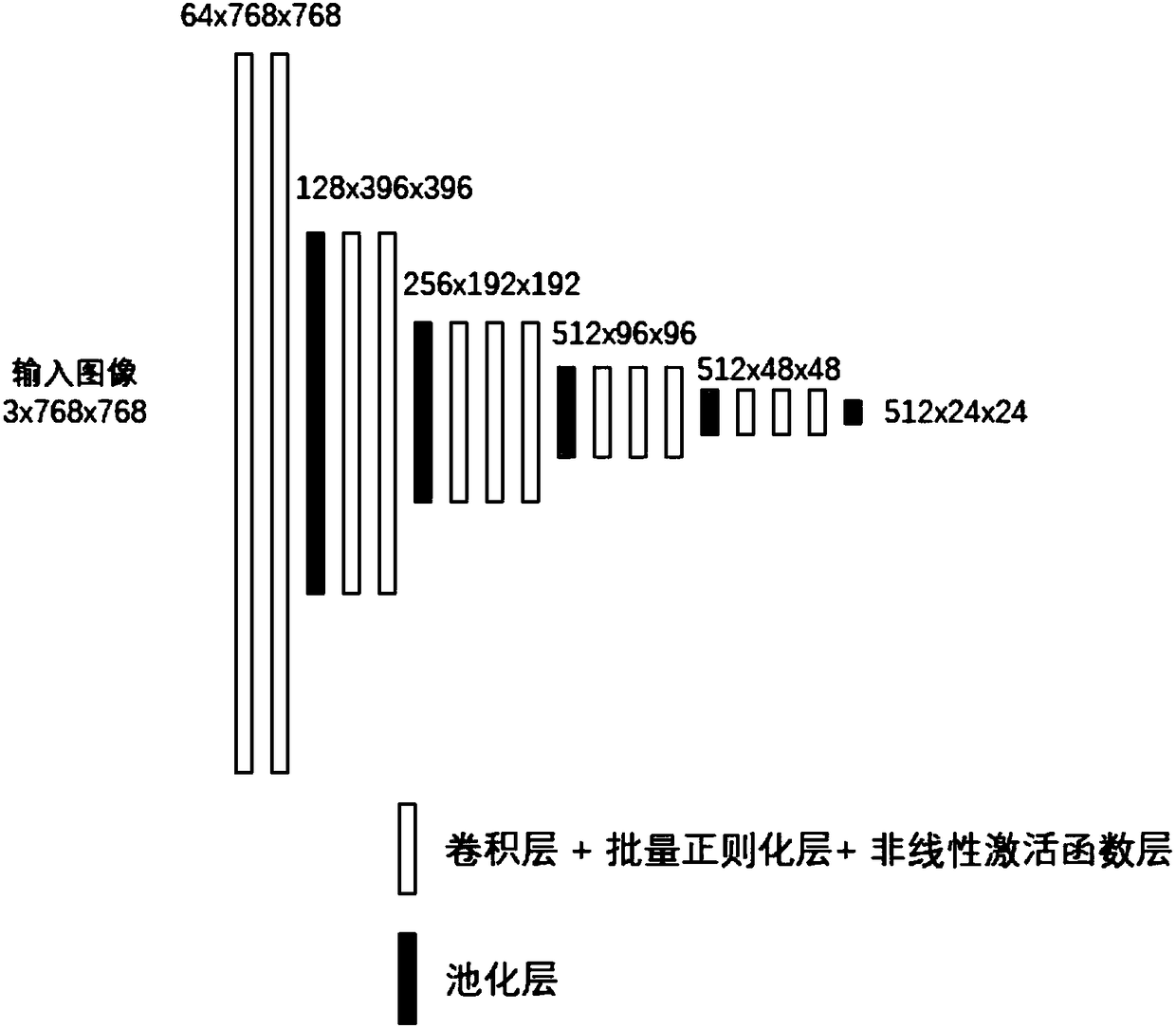
Multi-scale target detection method based on deep convolutional neural network
ActiveCN108564097AAccurate distinctionAccurate detectionCharacter and pattern recognitionNeural architecturesNerve networkNetwork generation
The invention discloses a multi-scale target detection method based on a deep convolutional neural network. The method comprises the steps of (1) data acquisition; (2) data processing; (3) model construction; (4) loss function definition; (5) model training; and (6) model verification. The method combines the ability of extracting image high-level semantic information of the deep convolutional neural network, the ability of generating candidate regions of region generation networks, the repair and mapping abilities of a content-aware region-of-interest pooling layer and the precise classification ability of multi-task classification networks, and therefore multi-scale target detection is completed more accurately and efficiently.
Owner:SOUTH CHINA UNIV OF TECH
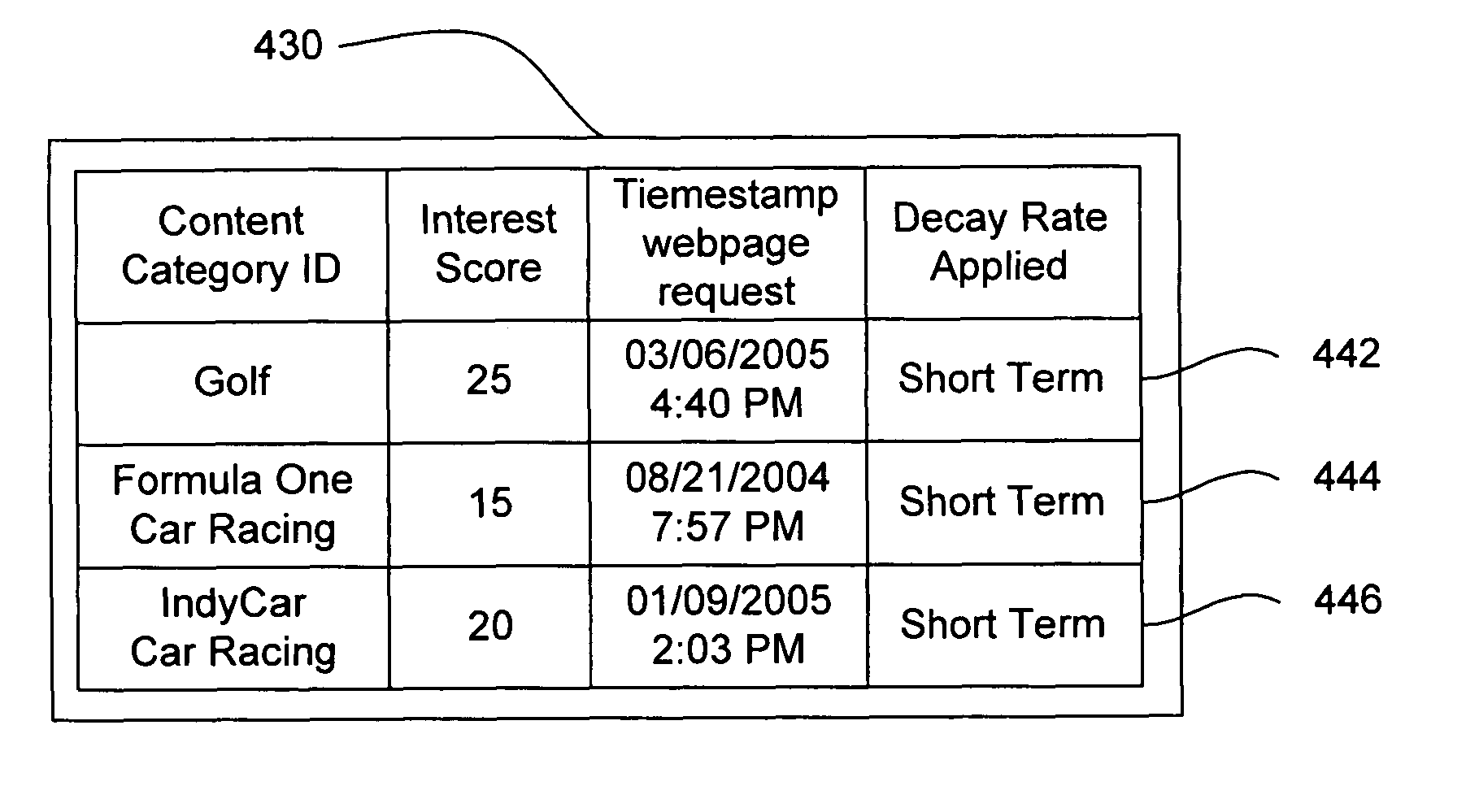
System and method for targeted ad delivery
ActiveUS20070100796A1User interest can be reducedDigital data processing detailsSpecial data processing applicationsTimestampWeb service
A method and system of generating a user profile for advertisement over a computer network is disclosed. A webpage identifier that identifies a webpage is generated. The webpage identifier can be a universal resource locator. A content category identifier that identifies a content category is generated. The webpage identifier is associated with the content category identifier if web content depicted in the webpage is relevant to the content category. A web server then receives a request for the webpage, the request including the webpage identifier and a first user identifier, the request being received from a client computer connected to the computer network. The webpage request can include a webpage request timestamp. A user profile is located by determining whether the first user identifier matches a second user identifier corresponding to the user profile. The user profile includes at least one user content category identifier and a corresponding user interest score. A predetermined amount is established independently from the web content depicted in the webpage being viewed by the user. The corresponding user interest score is increased by the predetermined amount if the content category identifier matches the at least one user content category identifier.
Owner:DISNEY ENTERPRISES INC
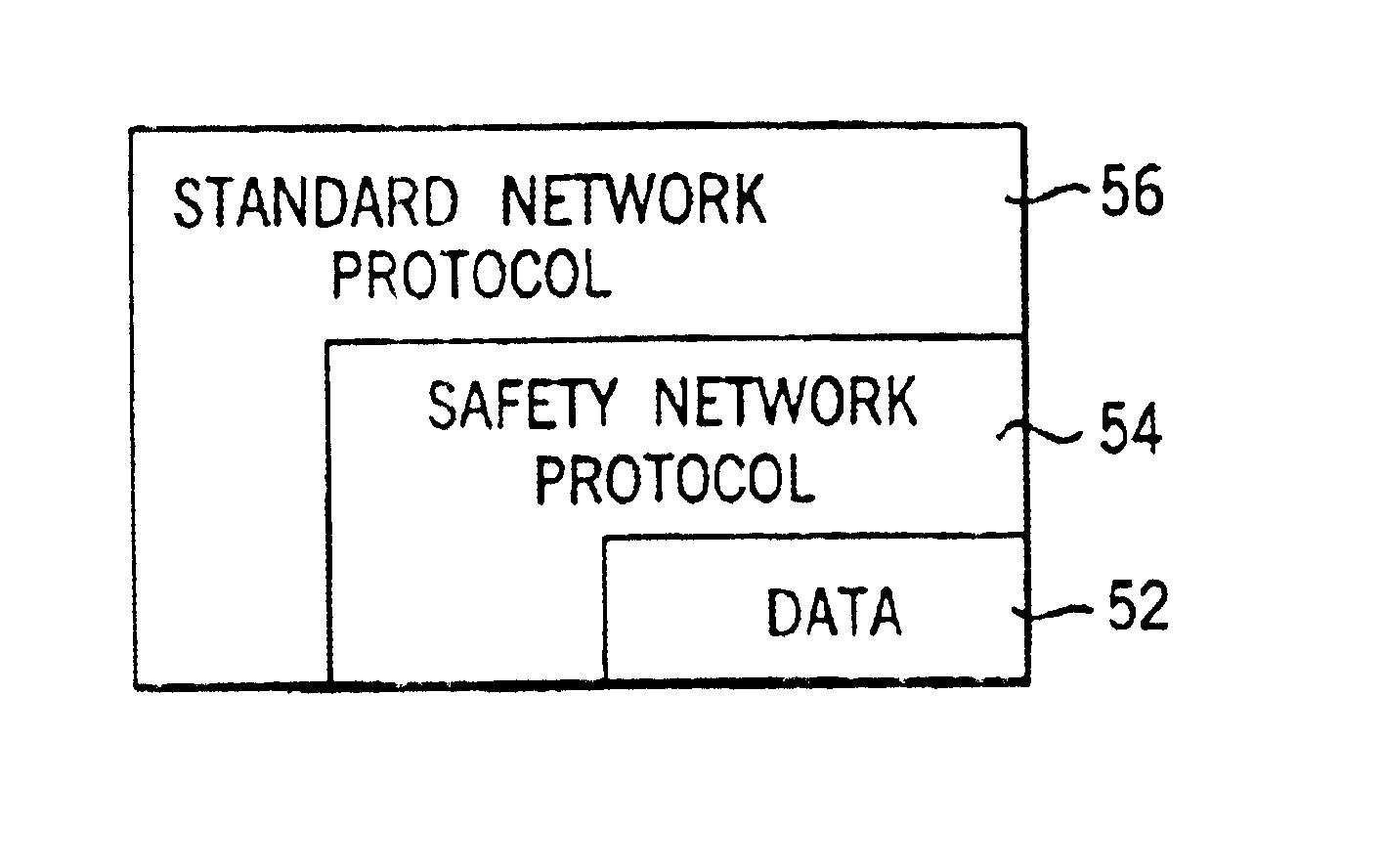
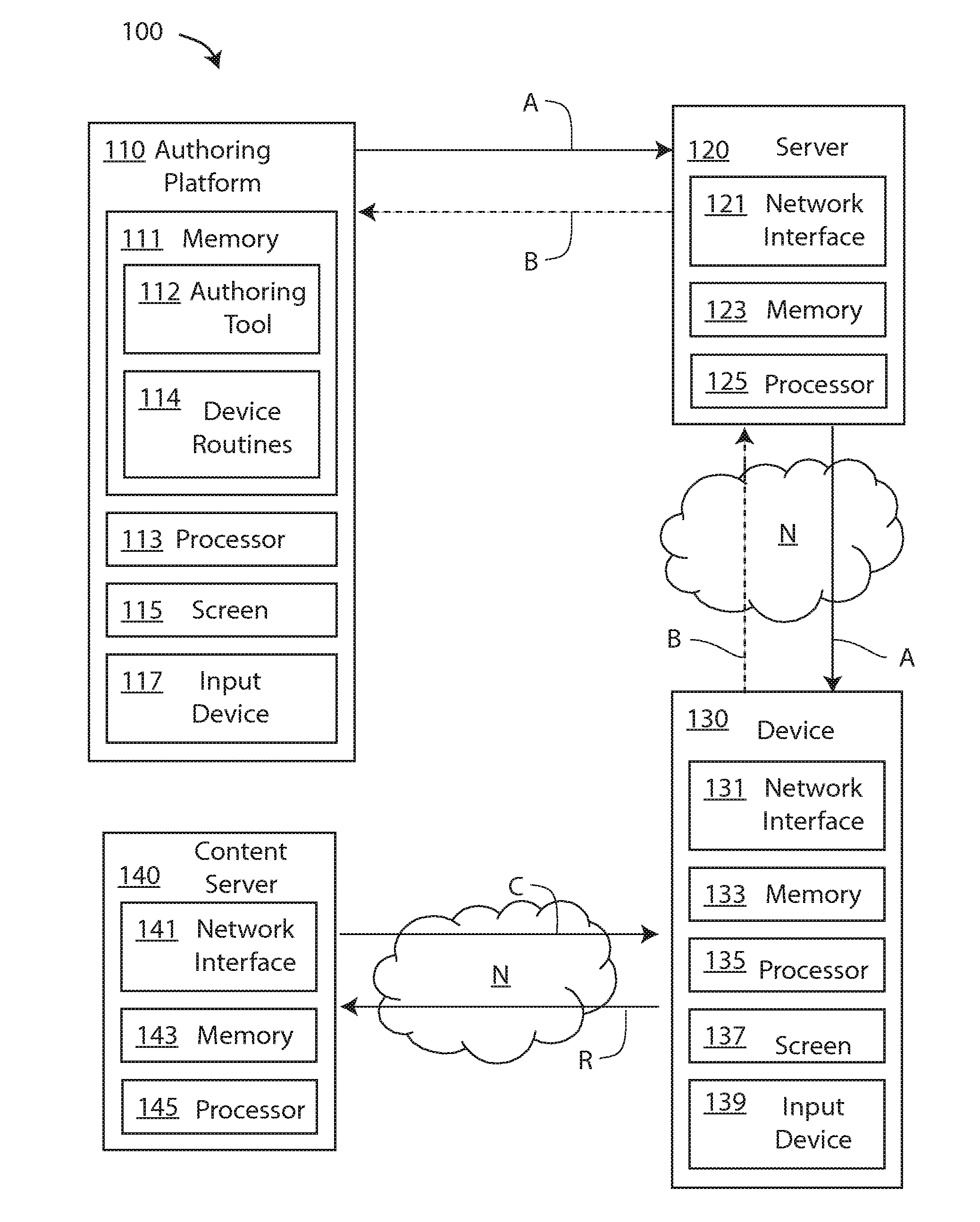
Network independent safety protocol for industrial controller
InactiveUS6891850B1Reduce errorsComputer controlSimulator controlNetworking protocolNetwork generation
A highly reliable industrial control system is produced using a network running a standard serial protocol. A safety protocol is embedded within the standard serial protocol by adding to special error detecting data redundant with the protocol of the standard serial network. In addition an overarching protocol involving timing of messages is imposed to provide the necessary level of reliability in the standard serial network. This approach allows the safety protocol to be used with a wide variety of commercially available serial communication standards without modification of the media or the specialized integrated circuits used for that communication. Safety protocol may be implemented in an additional level for integrated circuits or through firmware changes in programmable aspects of the industrial controller components.
Owner:ROCKWELL TECH
Systems and methods for presenting information on mobile devices
ActiveUS20110107227A1Light weightEfficient managementInput/output for user-computer interactionMultiple digital computer combinationsNetwork generationMobile device
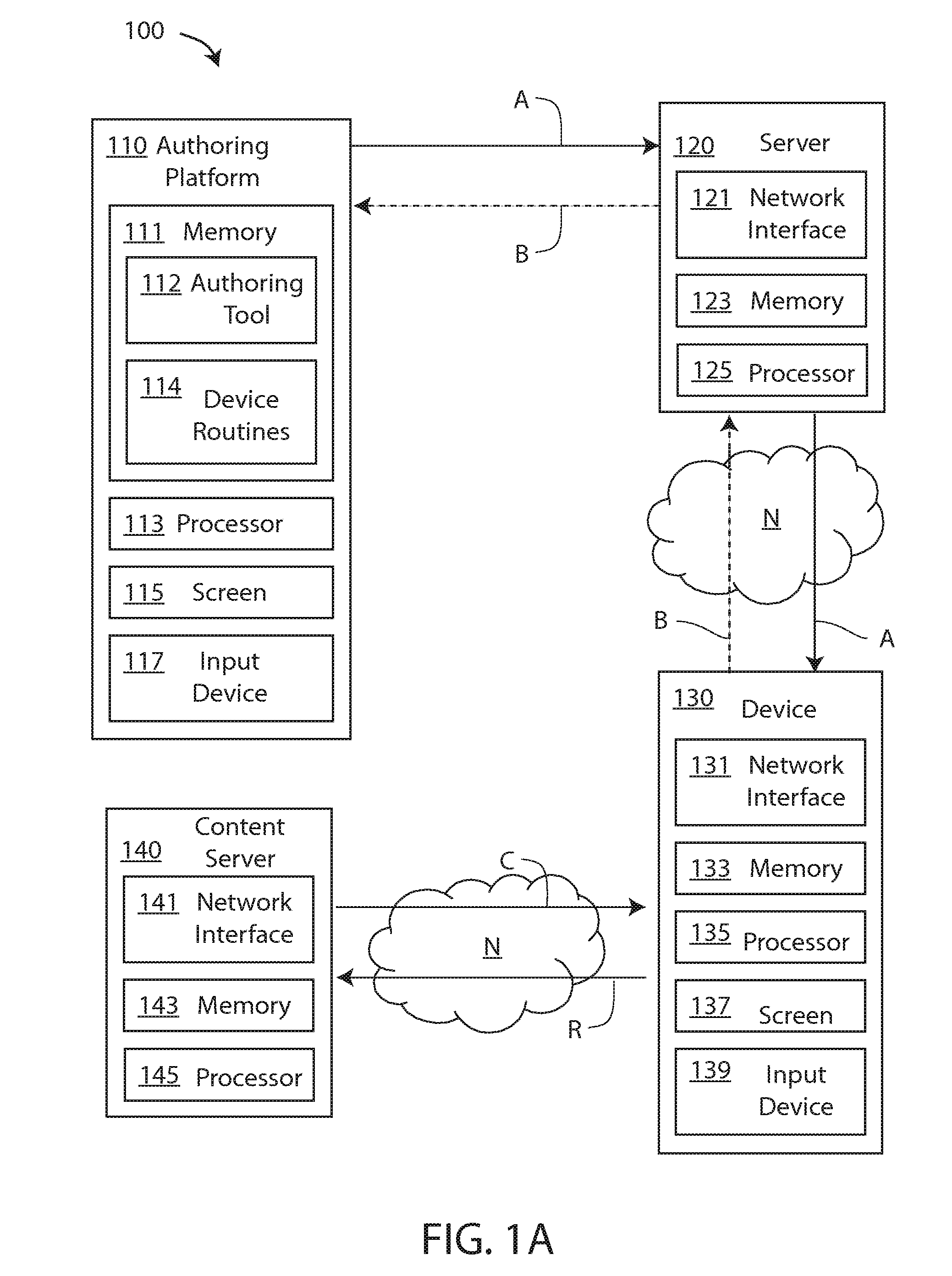
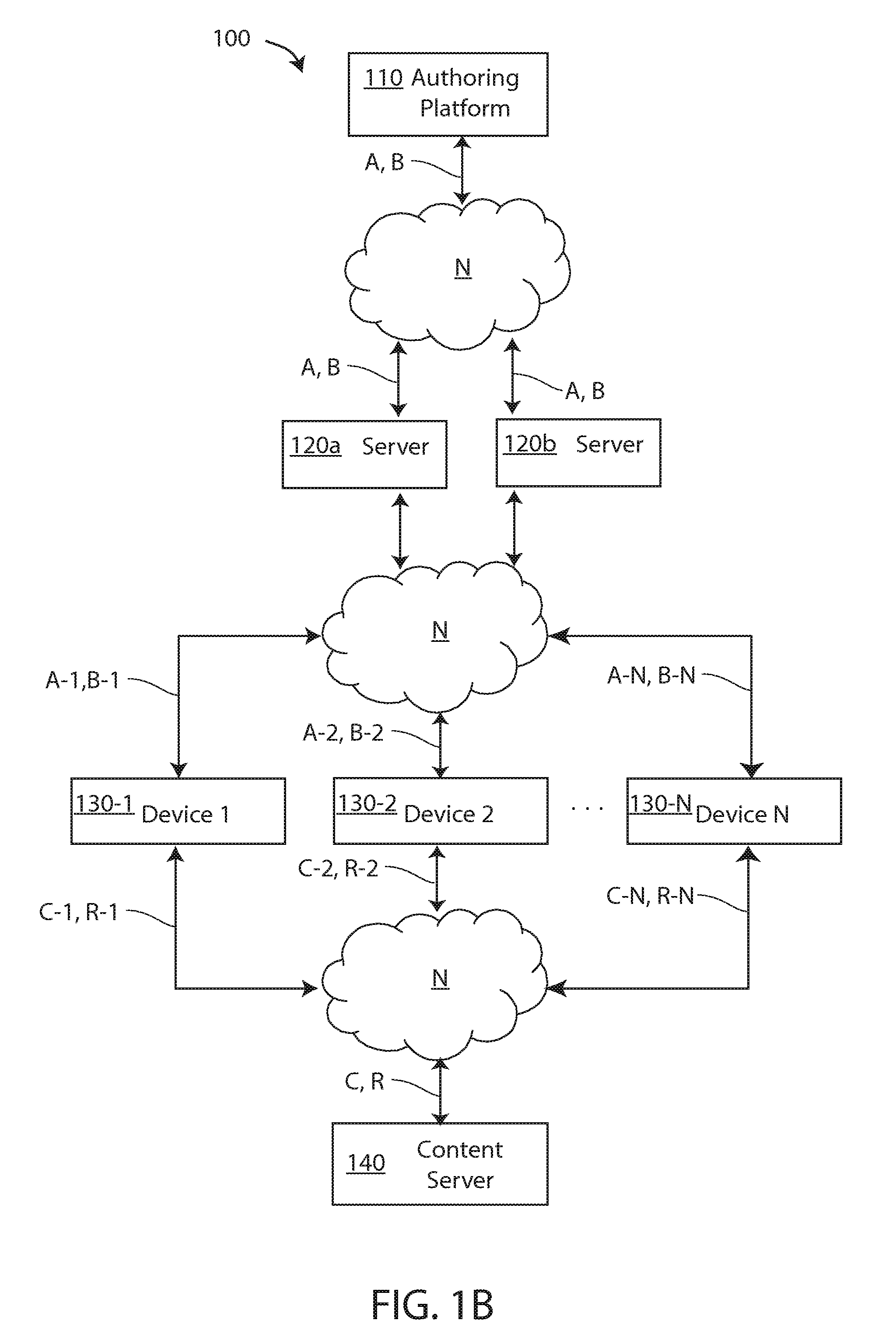
Embodiments of a system and method are described for generating and distributing programming to mobile devices over a network. Devices are provided with Players specific to each device and Applications that are device independent. Embodiments include a full-featured WYSIWYG authoring environment, including the ability to bind web components to objects.
Owner:EXPRESS MOBILE
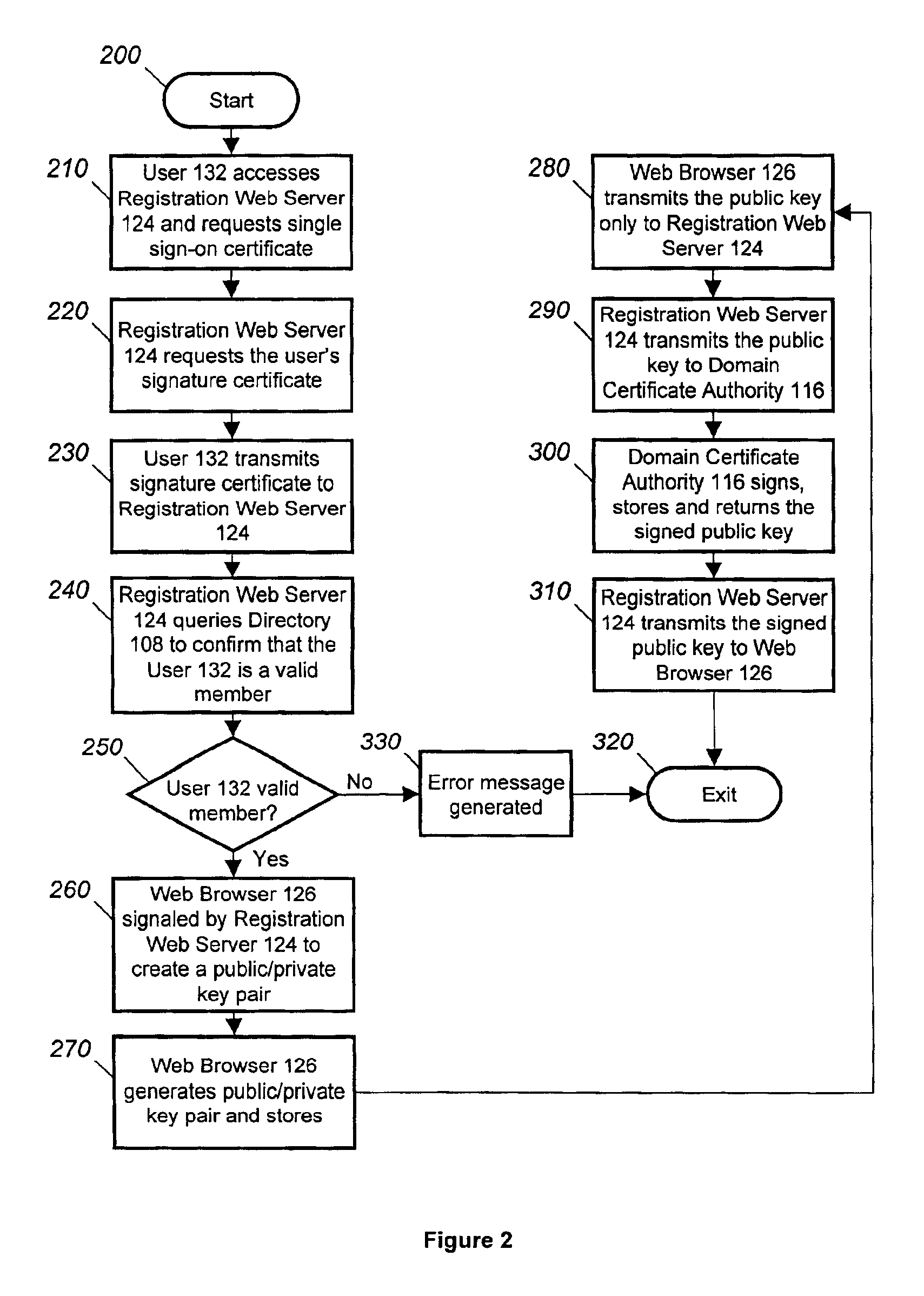
Technique for obtaining a single sign-on certificate from a foreign PKI system using an existing strong authentication PKI system
InactiveUS7069440B2Key distribution for secure communicationData processing applicationsNetwork generationStrong authentication
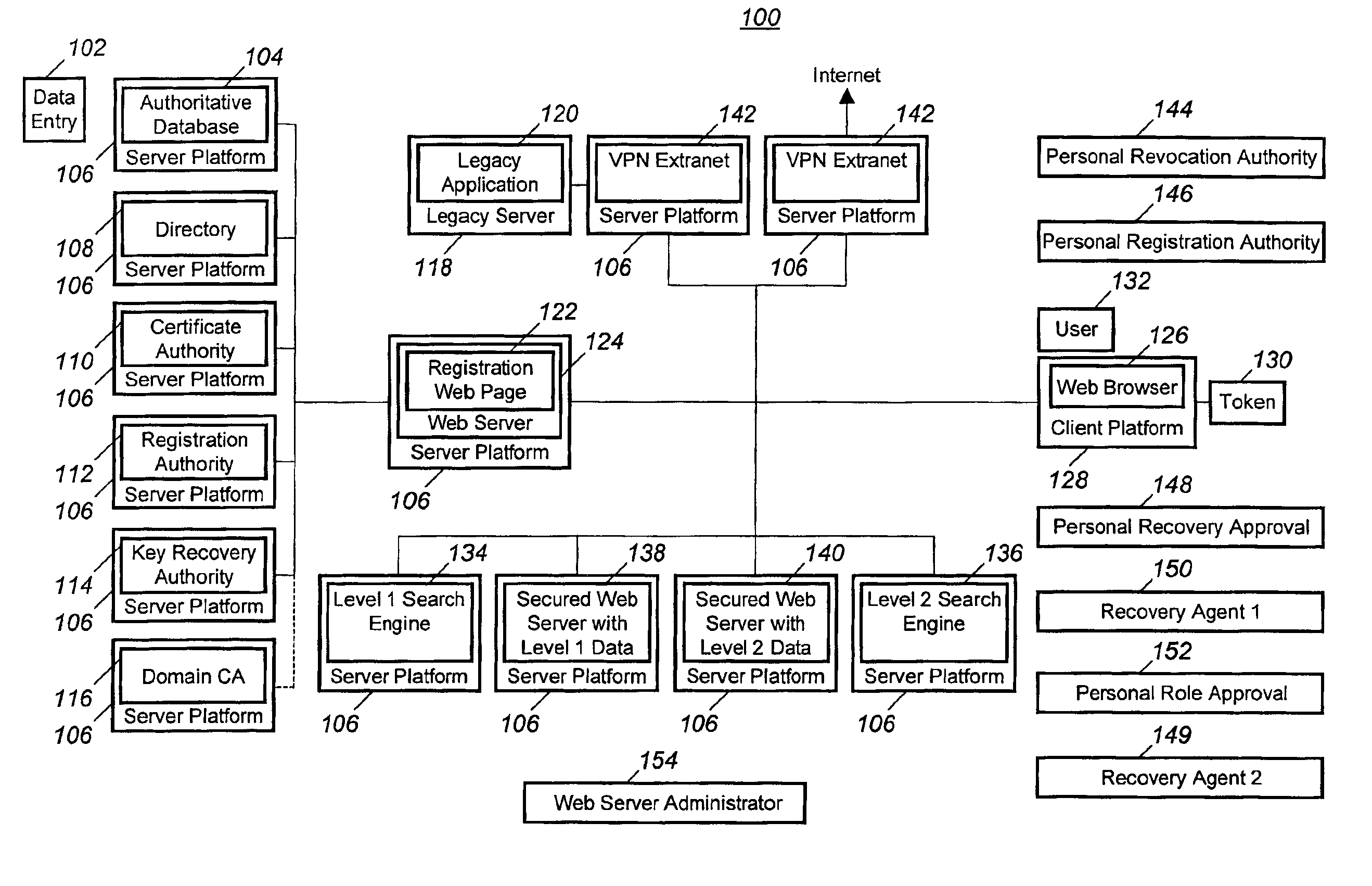
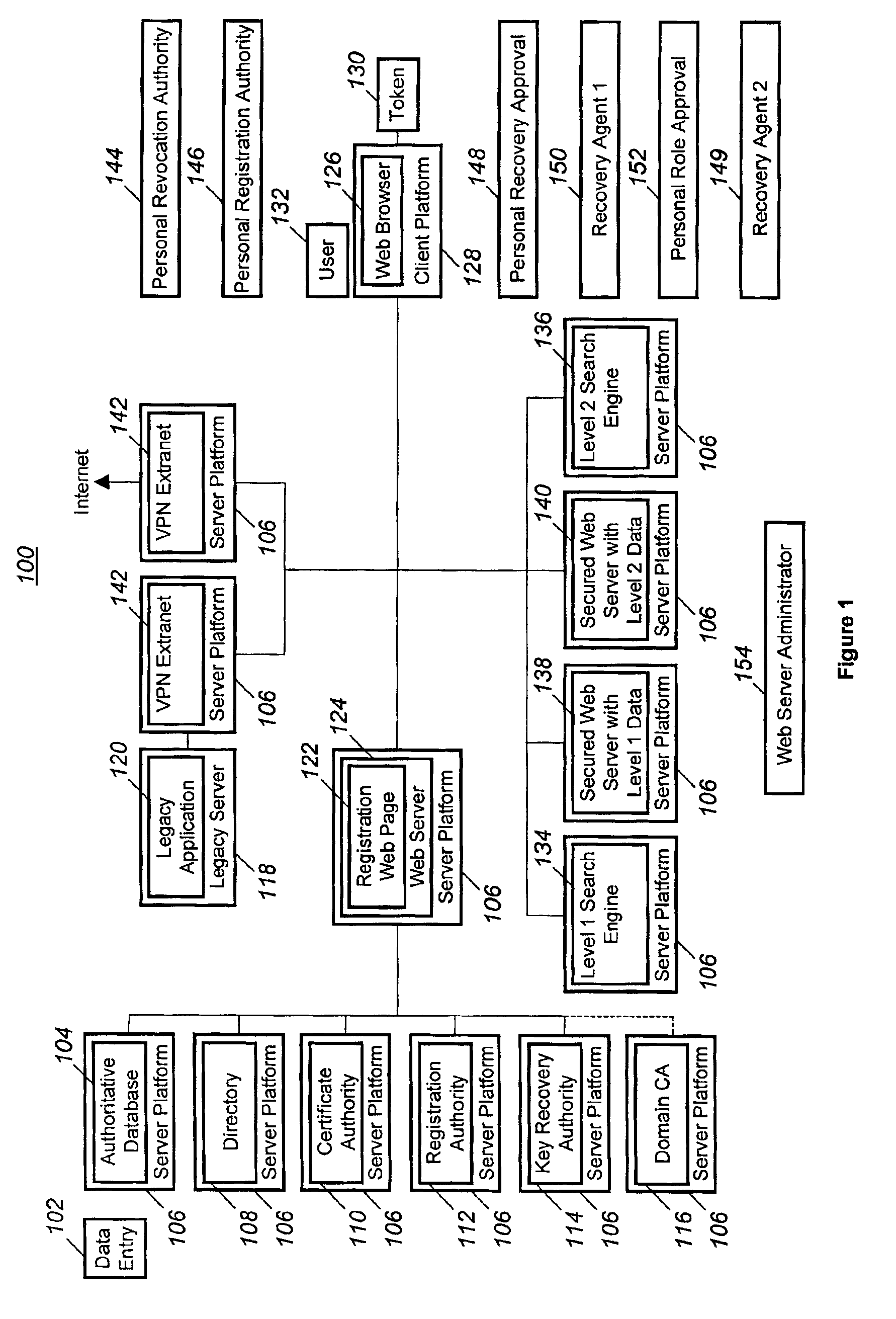
A method and computer program in which a user (132) may have a digital certificate created using a strong authentication technique. Once the user has the digital certificate he may then request the generation of a “single sign-on” certificate that will allow the user (132) access to a foreign computer networks. This is accomplished by the user (132) contacting a registration web server (124) and requesting the generation of “single sign-on” for the foreign computer network. Thereafter, the registration web server (124) may take a public key generated based on the digital certificate and request the creation of a “single sign-on” by simply creating a public key from the digital certificate.
Owner:NORTHROP GRUMMAN SYST CORP
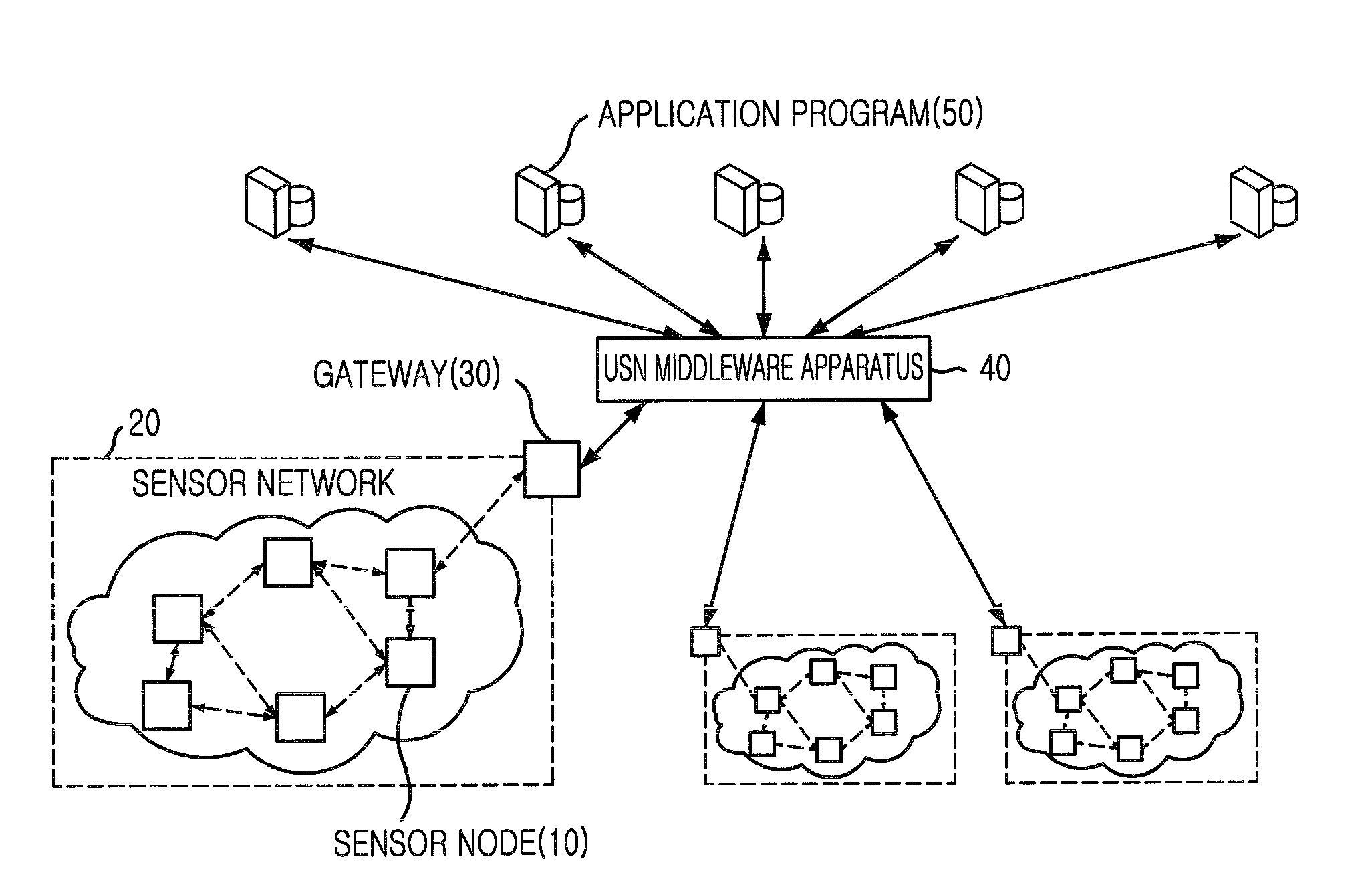
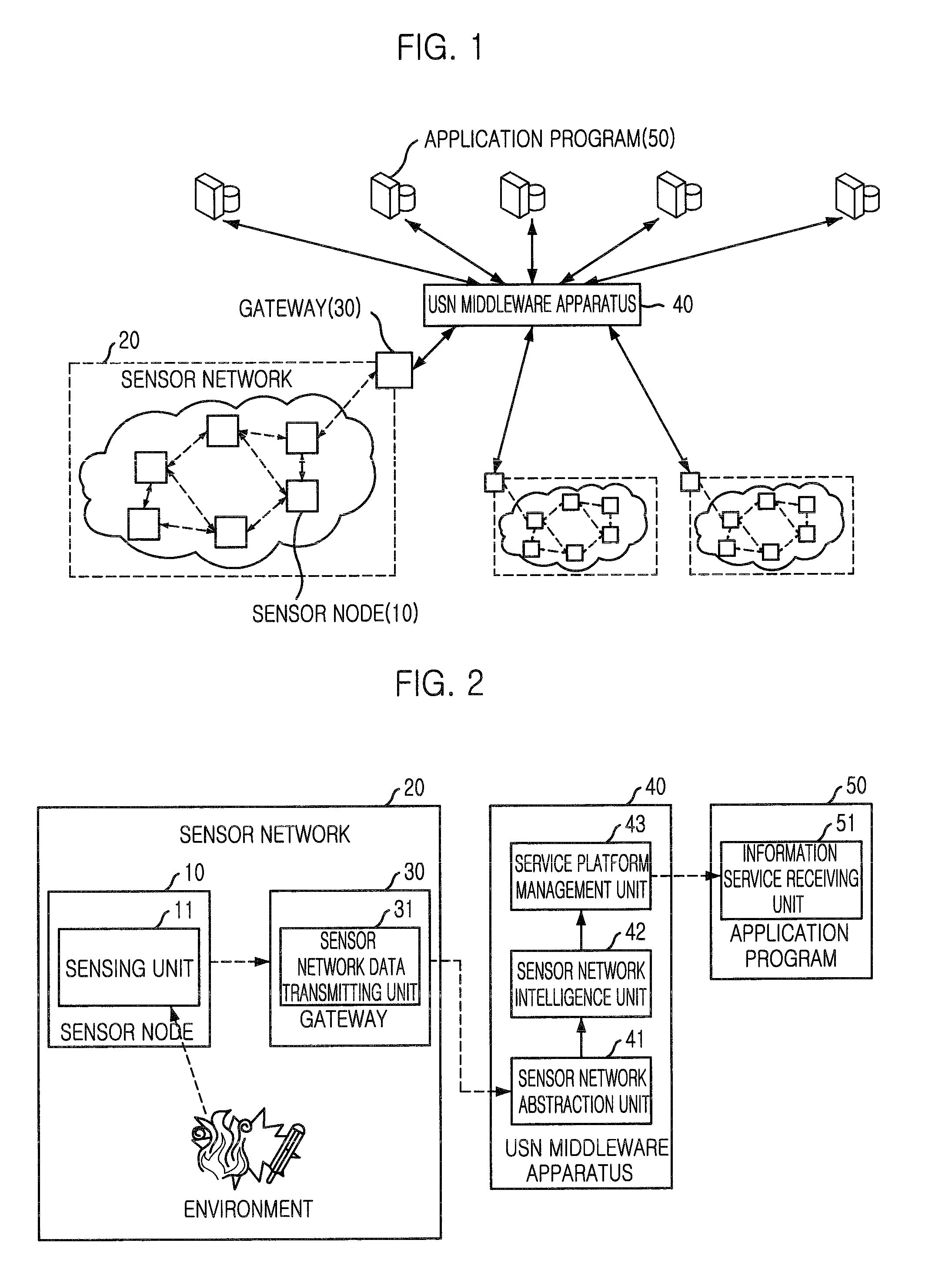
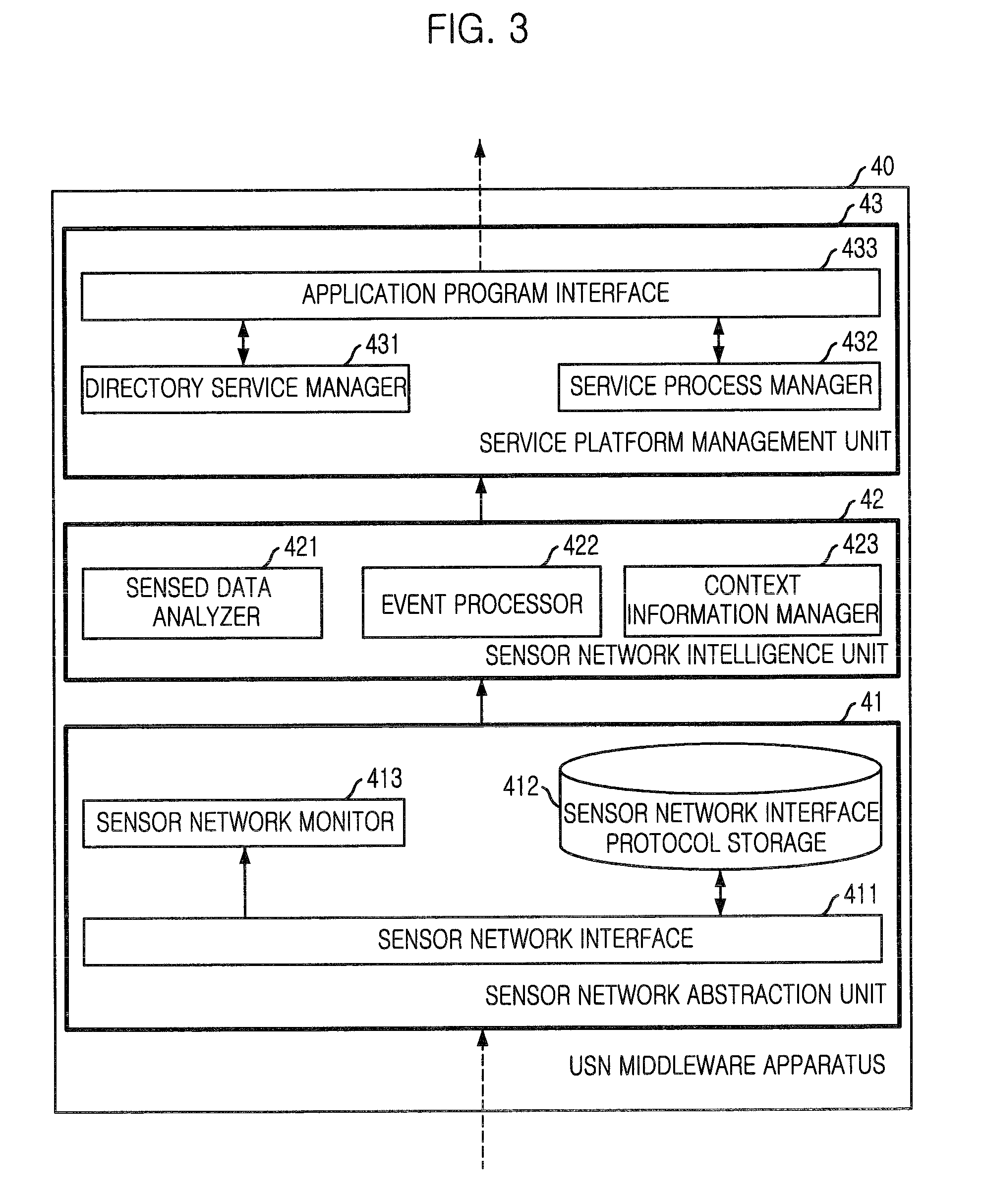
USN middleware apparatus and method for generating information based on data from heterogeneous sensor networks and information service providing system using the same
ActiveUS8040232B2Improve effectivenessImprove reliabilityFrequency-division multiplex detailsSubstation remote connection/disconnectionSensing dataNetwork generation
Owner:KAIFI LLC
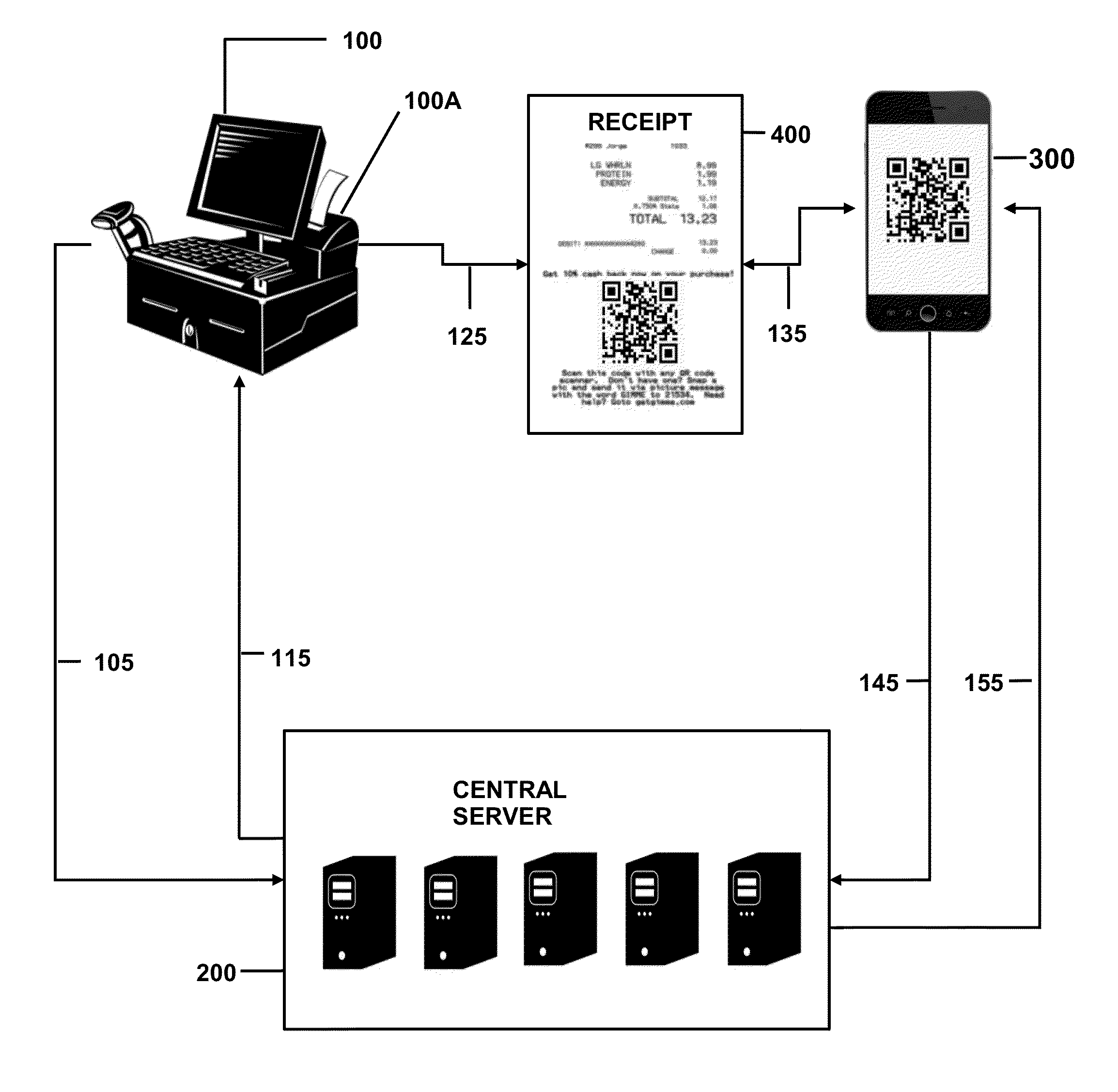
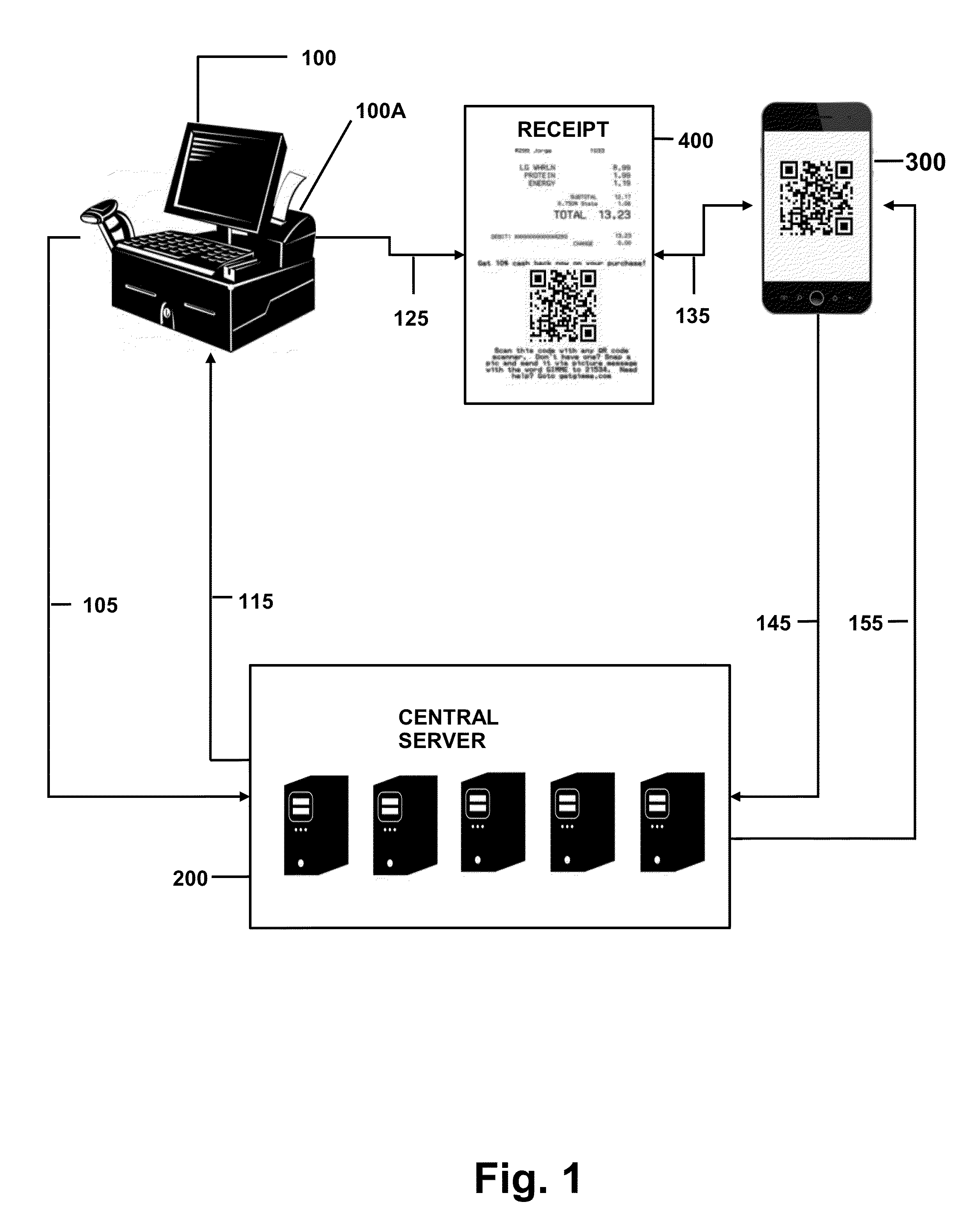
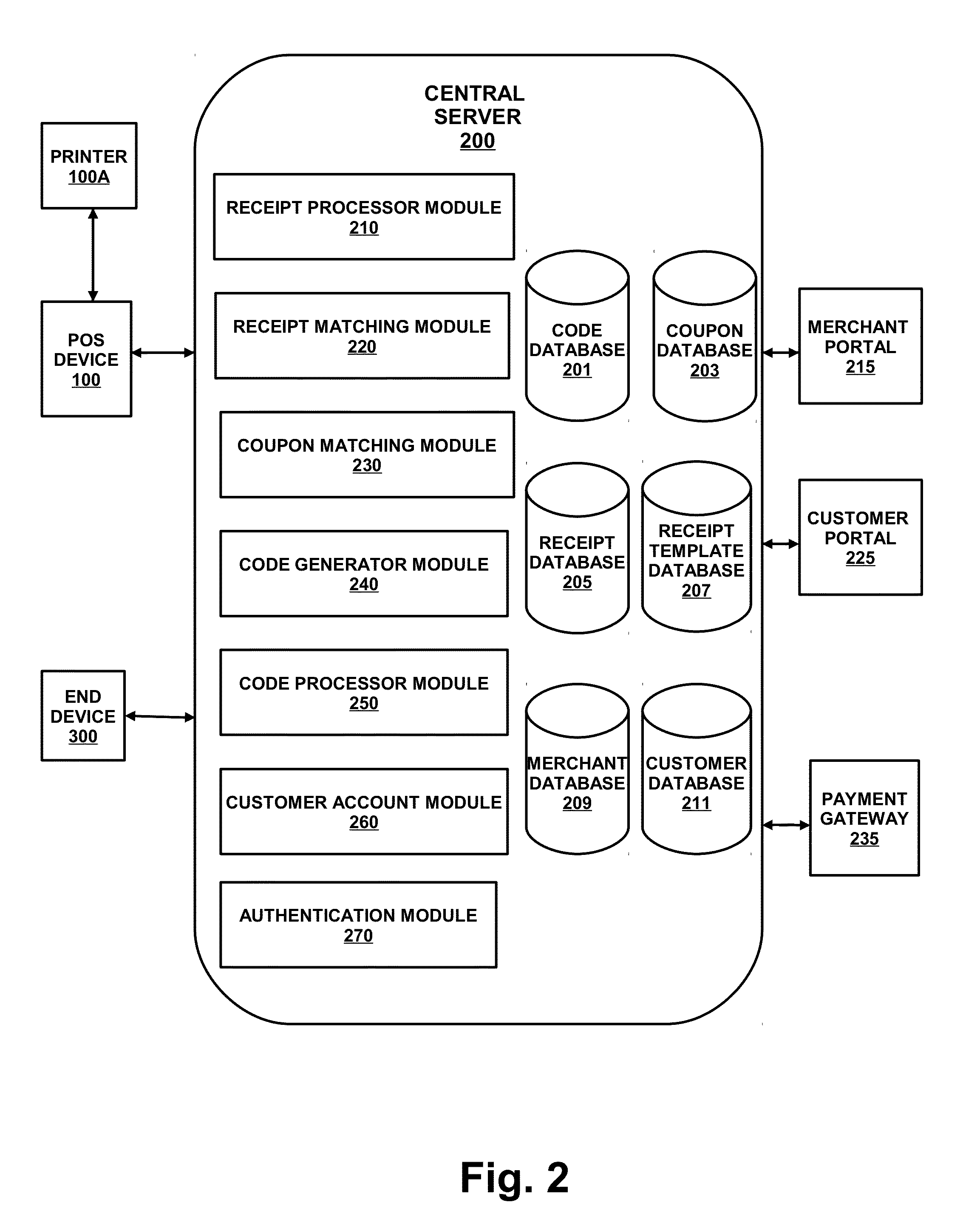
Coupon generation, authentication, and redemption via a network
A point-of-sale (POS) and mobile device implemented method of providing customer rebates via machine-readable codes, such as Quick Response (QR) codes. Specifically, a customer completes a transaction at a POS. The POS or remote servers determine if the transaction qualifies for a promotional credit or rebate. If the transaction qualifies for the promotional credit, then the POS generates the QR code, wherein the QR code includes the credit. Further, the customer captures the QR code with a mobile device or scanner and transmits the code to the POS or remote servers for authentication. Upon successful authentication, the POS or remote servers transfer the credit to the customer.
Owner:BASMAJIAN STEVEN ALLEN +2
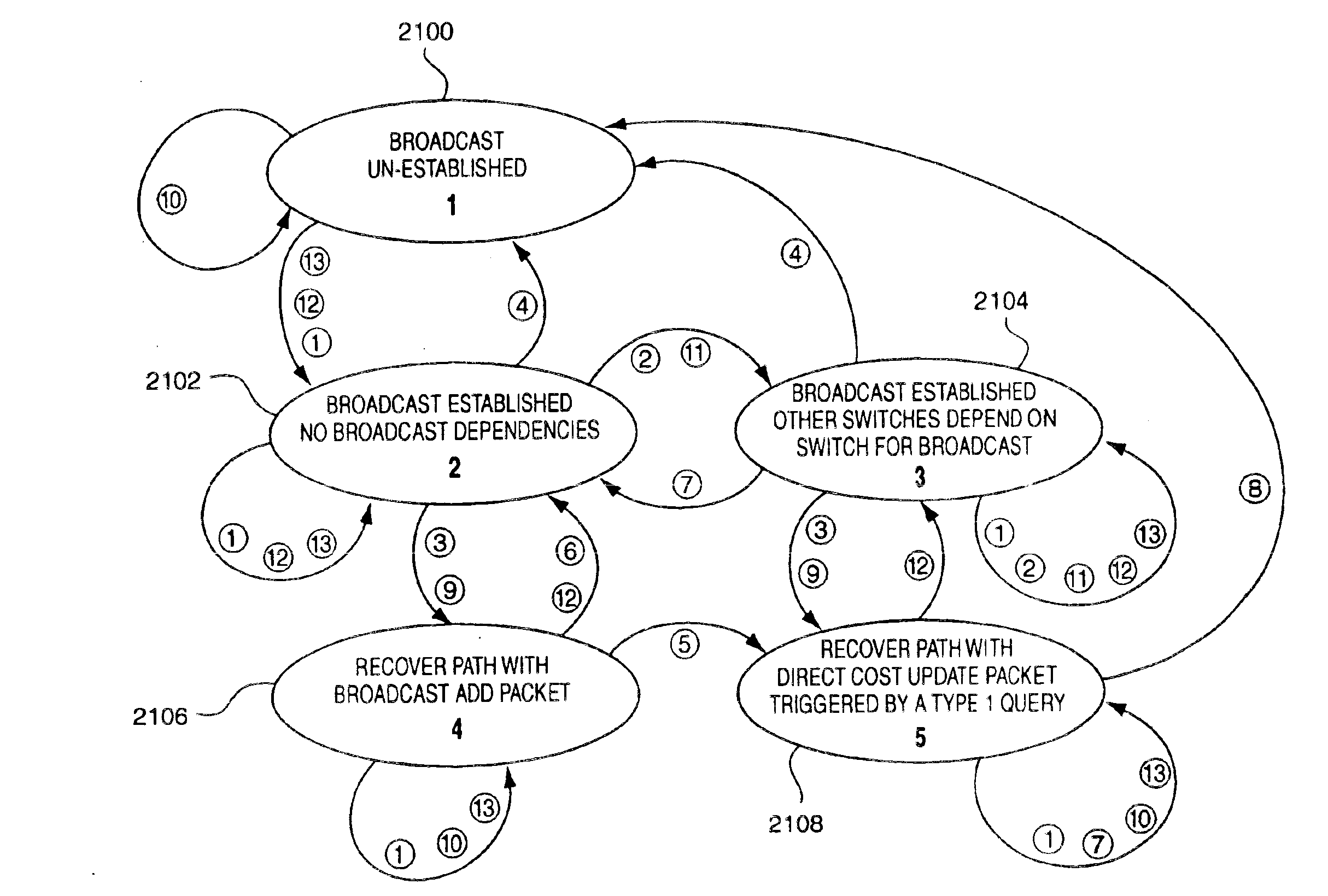
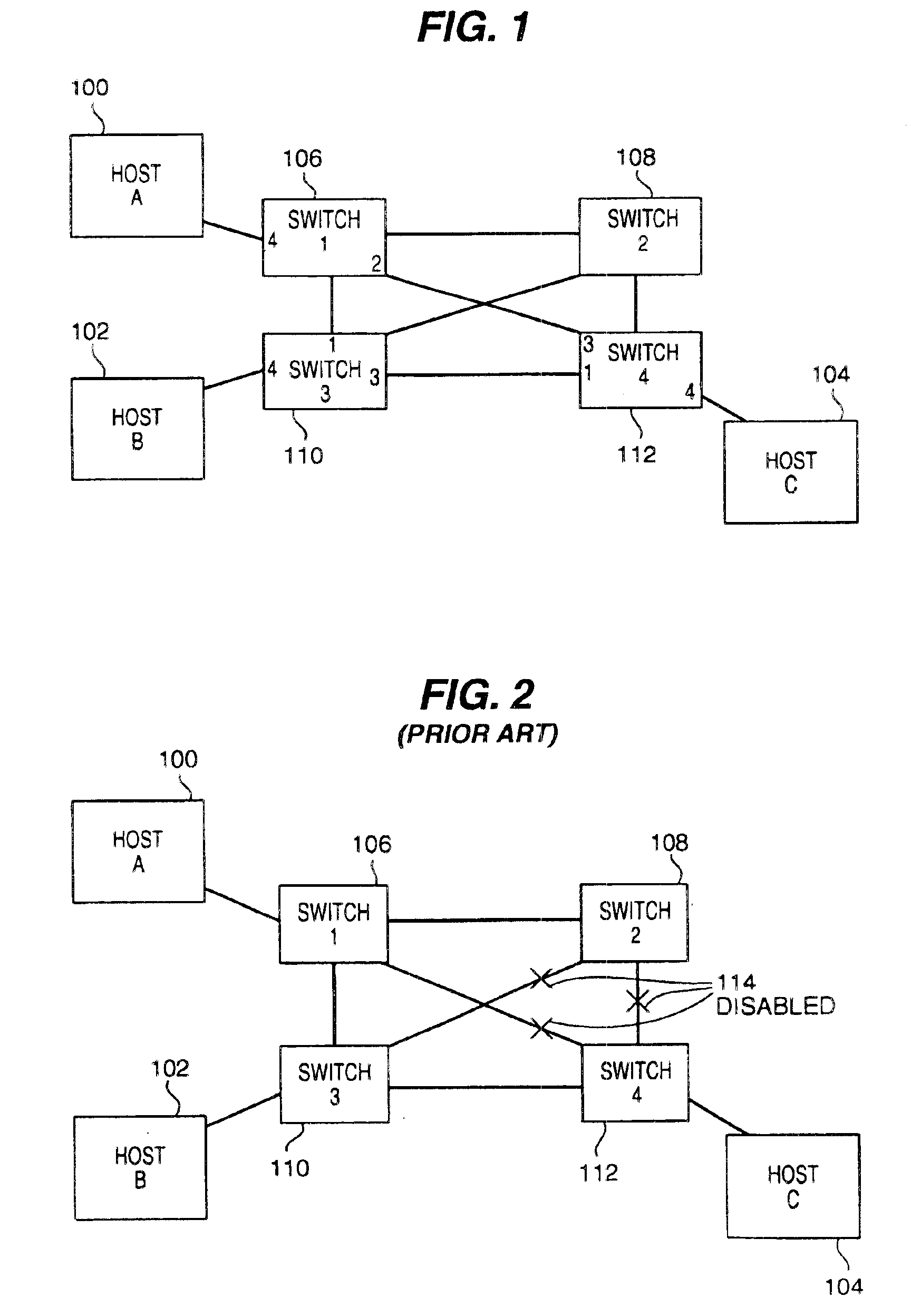
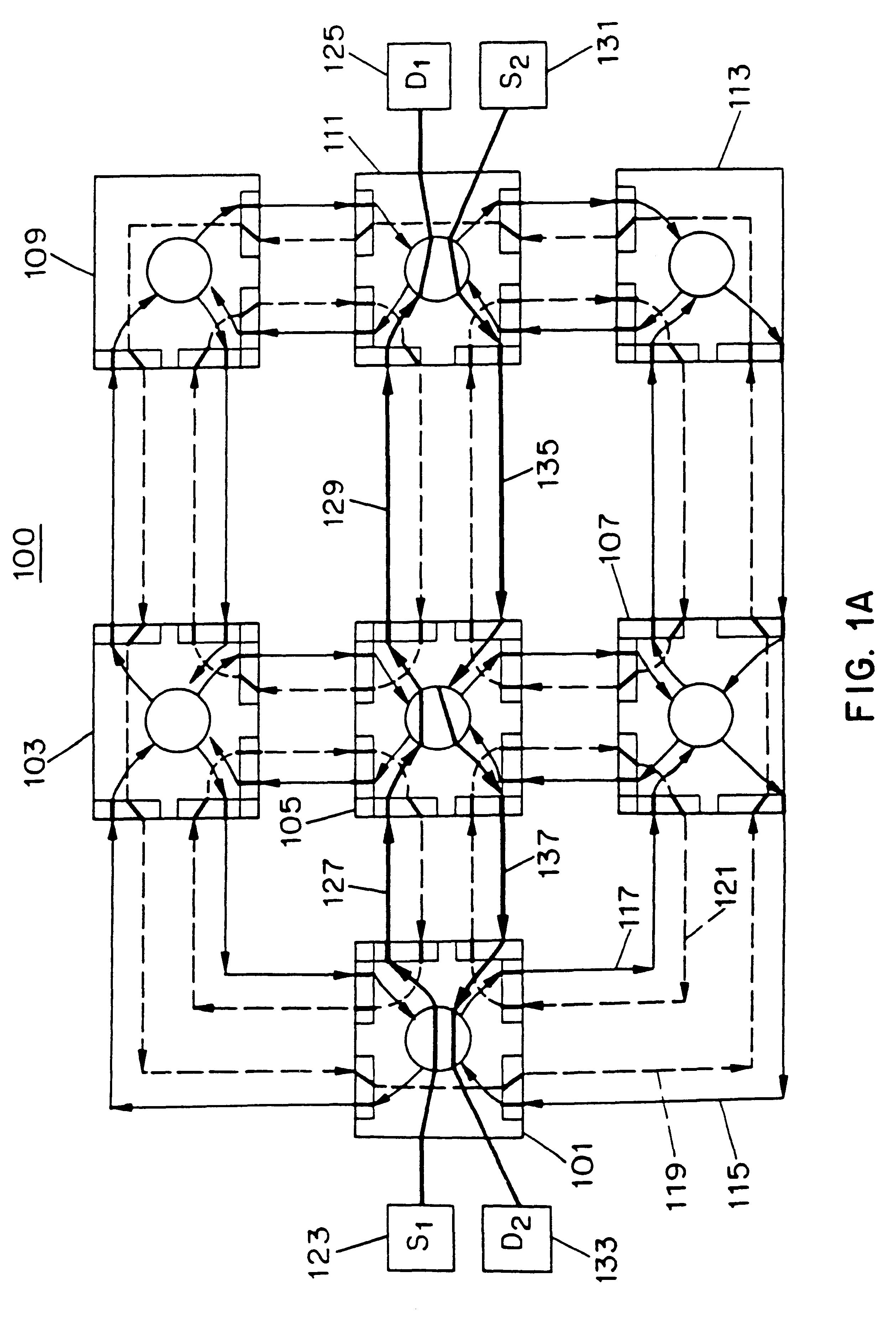
Broadcast tree determination in load balancing switch protocols
InactiveUS6865160B1Increase profitImprove scalabilitySpecial service provision for substationData switching by path configurationNetwork generationNetwork switch
A method for generating and maintaining a pruned broadcast tree for a network of switches operating multiple simultaneously active paths between devices with a load balancing family of protocols. The pruned broadcast tree is preferably generated as a by product of cost propagation aspects of the load balancing protocols exchanged among cooperating network switches. The load balance protocols operable within the network switches in association with the present invention permit multiple simultaneously active paths to be utilized among the network devices. The pruned broadcast tree is therefore used to reduce the latency of broadcast messages propagated within the network switches to reach all devices in the network. The broadcast tree defines a minimized set of devices to which a broadcast message need be forward to assure transmission to all network devices. The pruned broadcast tree, once established, is updated only in response to failure of a link and recovery of a failed link. A separate protocol of the present invention enables such pruned broadcast tree modifications and restoration.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
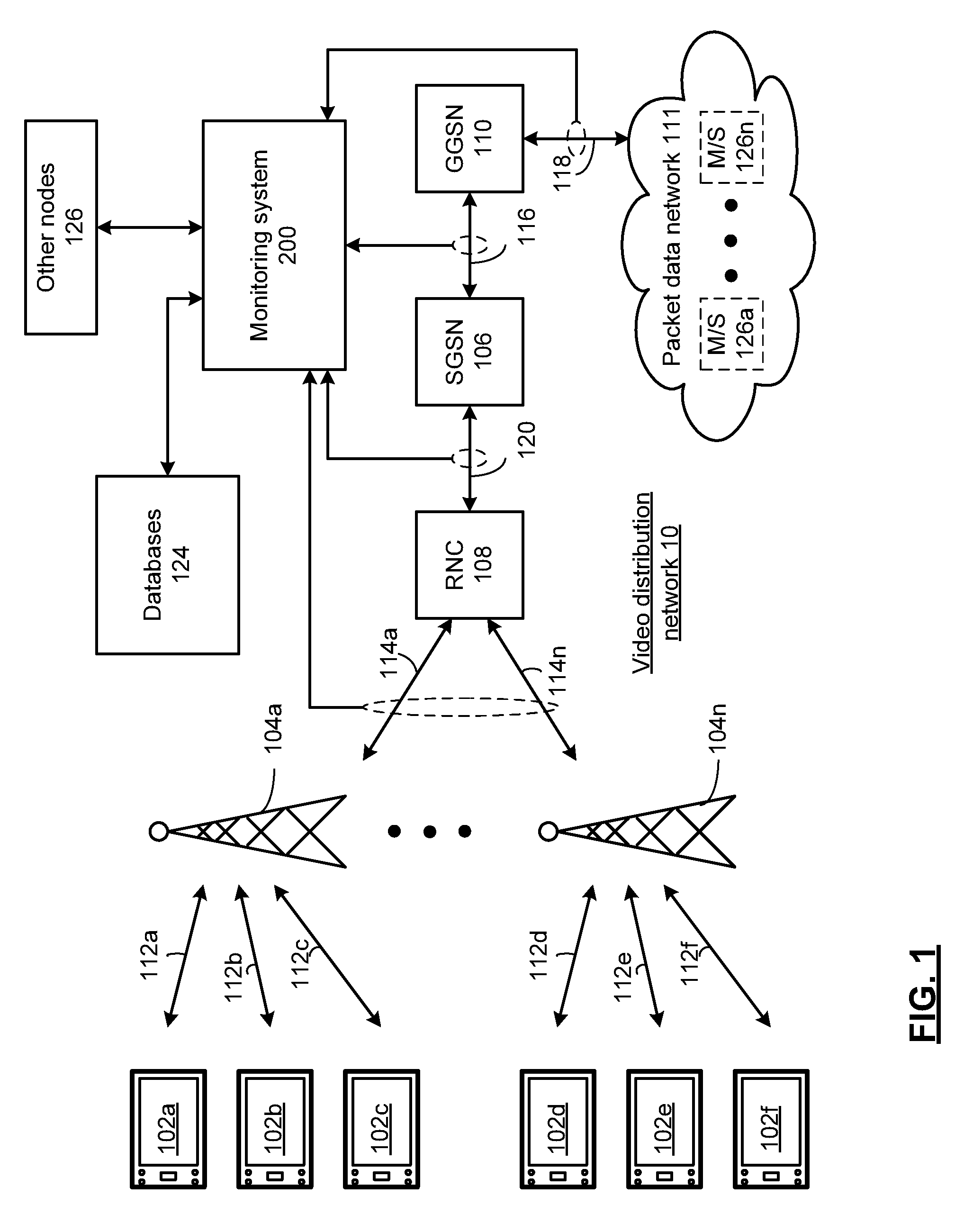
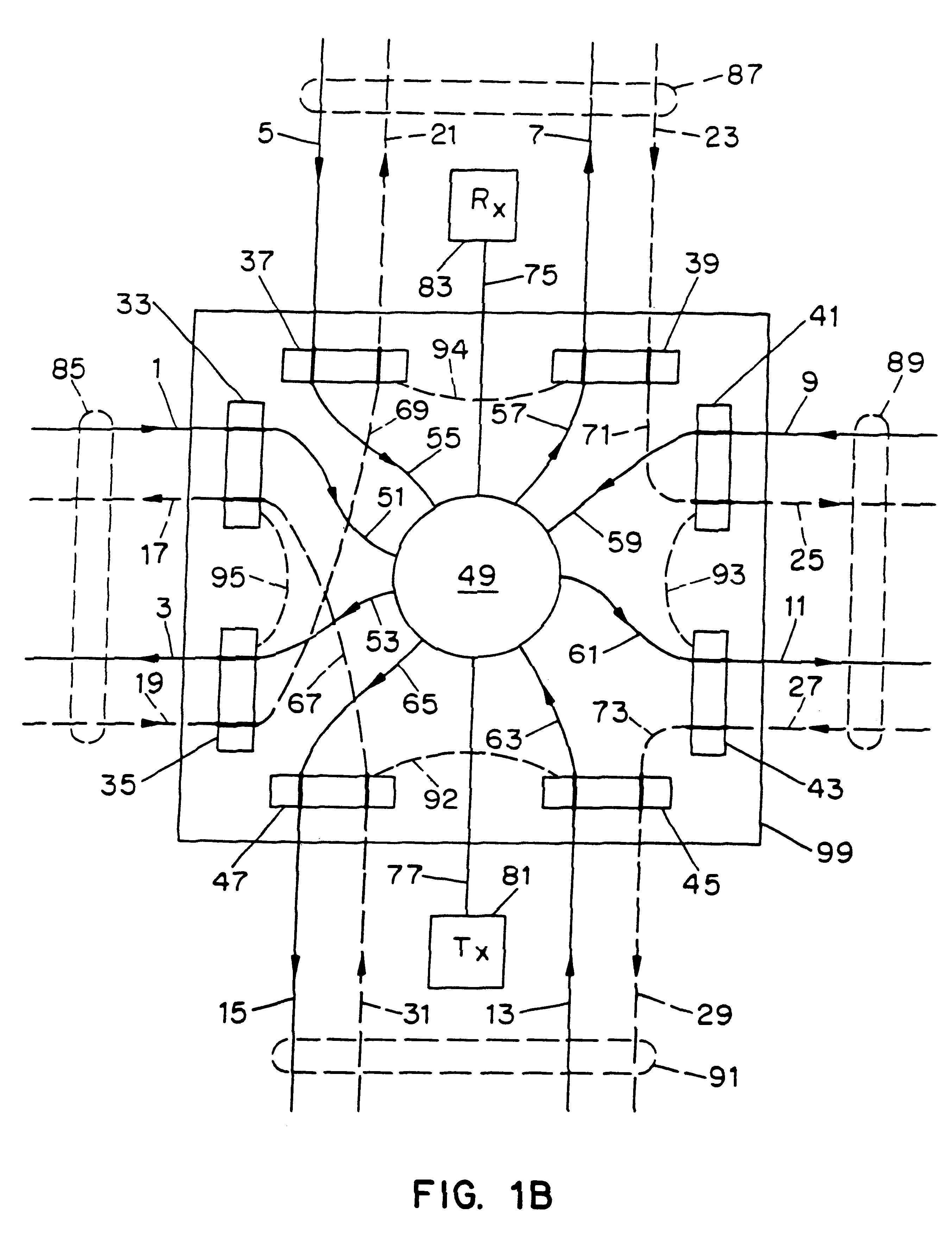
System for monitoring a video network and methods for use therewith
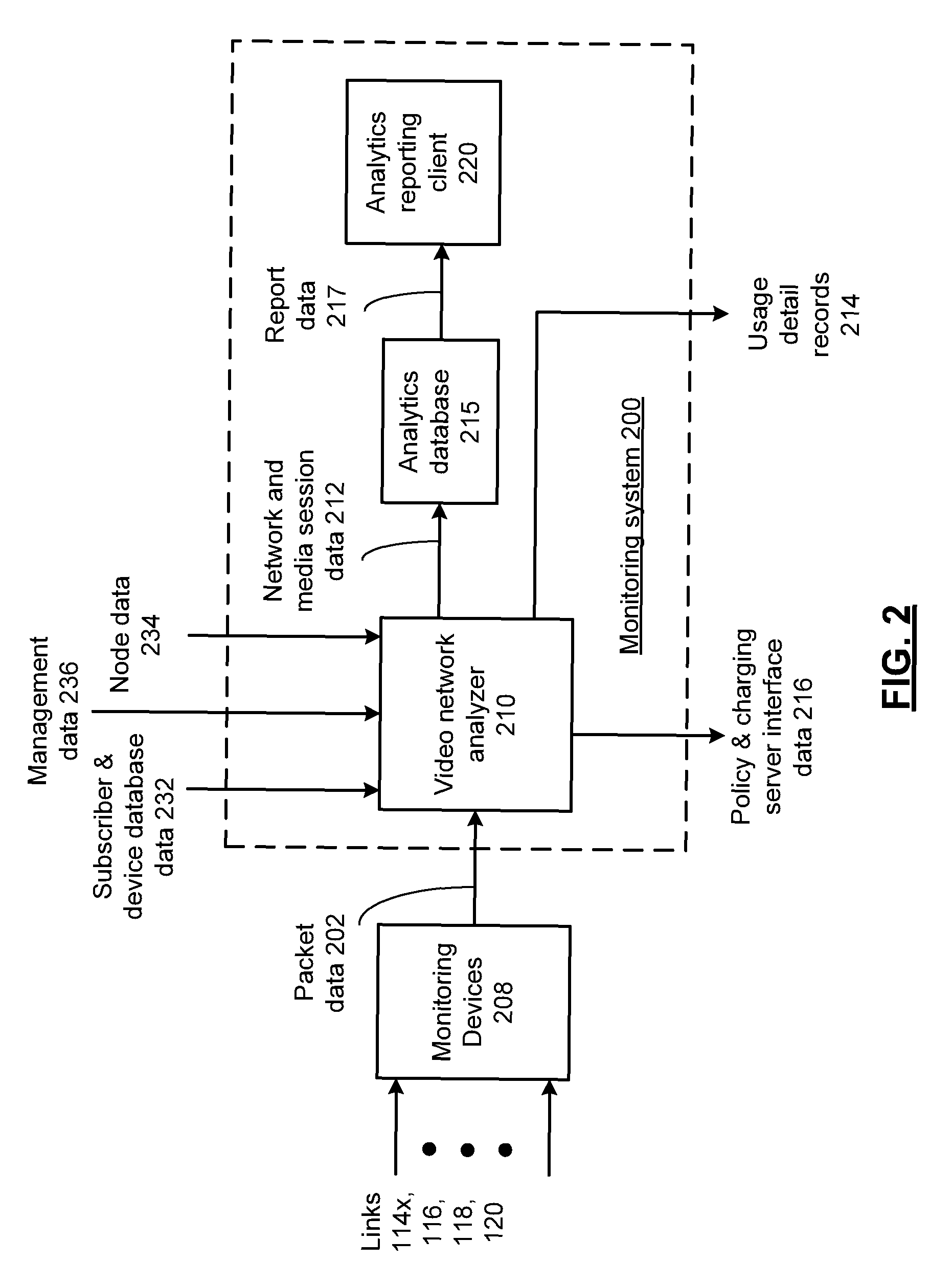
ActiveUS9032427B2Analogue secracy/subscription systemsBroadcast information monitoringComputer networkAnalysis data
A monitoring system includes a video network analyzer processes the packet data to generate network and media session data relating to the distribution of video content via the data distribution network in at least one media session, wherein the network and media session data includes at least one session metric, location data, protocol identification data, video encoding parameter data, and audio encoding parameter data. An analytics database stores the network and media session data for generation of report data.
Owner:NETSCOUT SYST TEXAS LLC
Method of generating a monitoring datagram
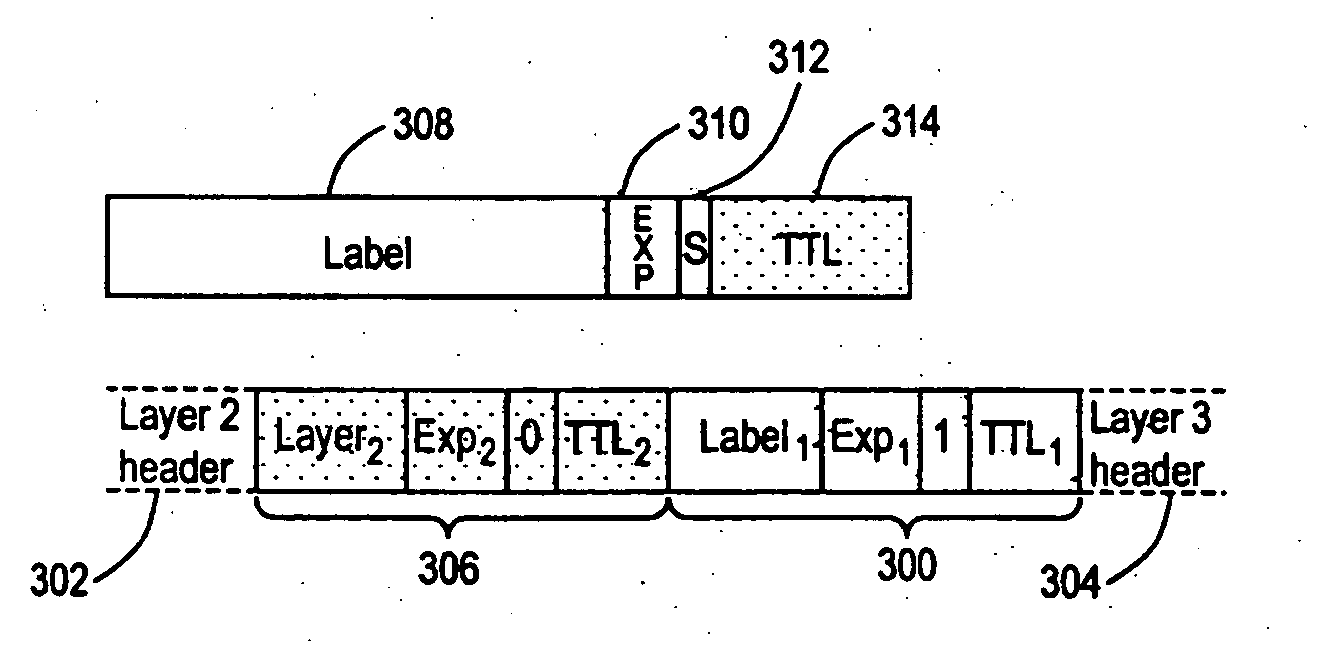
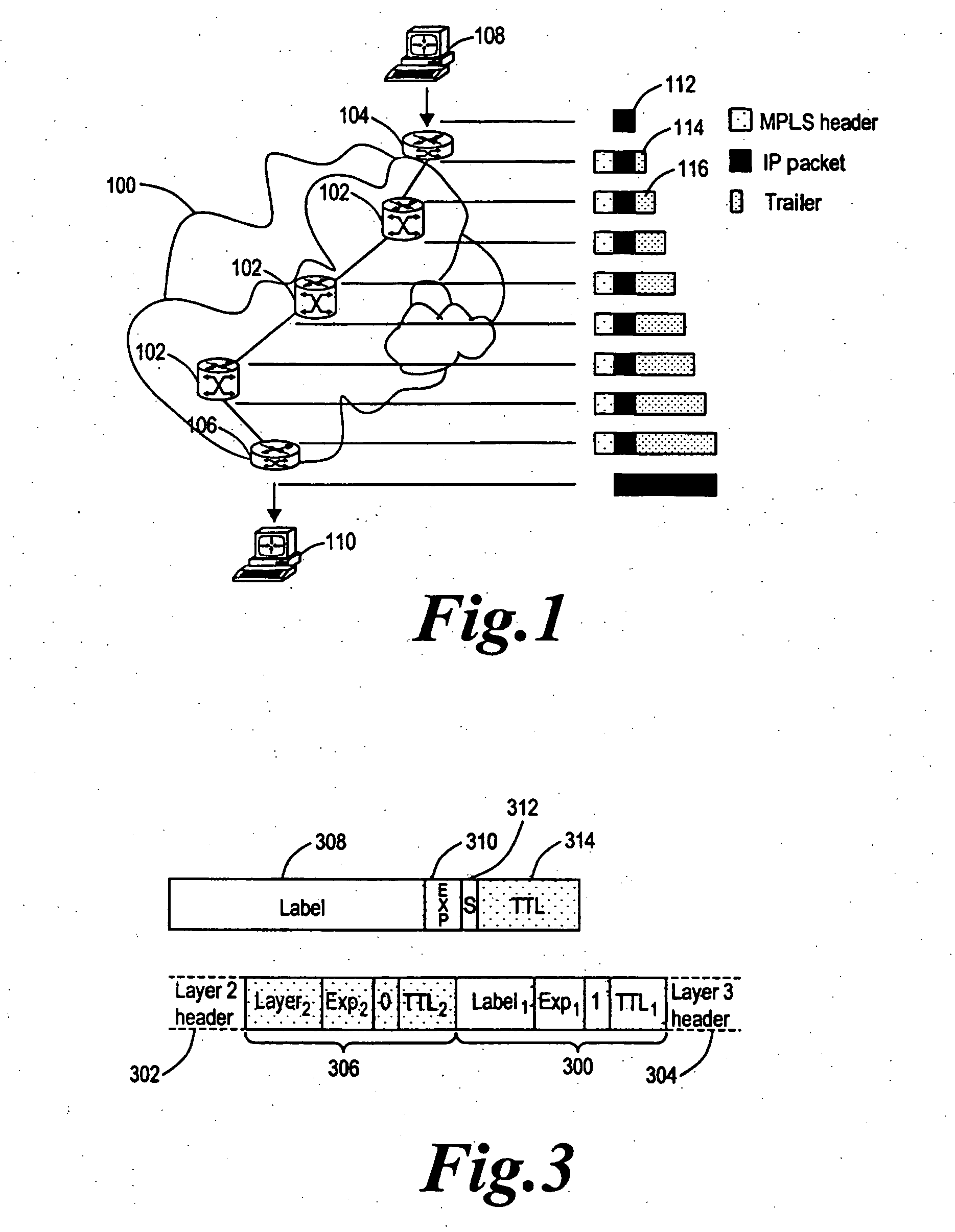
InactiveUS20050281259A1Improve accuracyPreserving confidentialityData switching by path configurationMonitoring statusNetwork generation
A method of generating a monitoring datagram for a predetermined network includes generating an initial datagram and encapsulating the initial datagram with a shim header, where the shim header has a first shim entry and a second shim entry, the first and second shim entries are associated with the predetermined network, the first shim entry is next to and follows the second shim entry, and where the first shim entry identifies the initial datagram as having a monitoring status.
Owner:AGILENT TECH INC
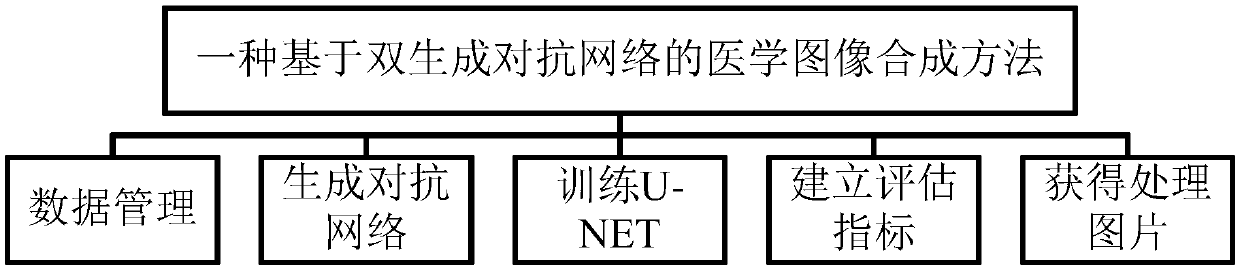
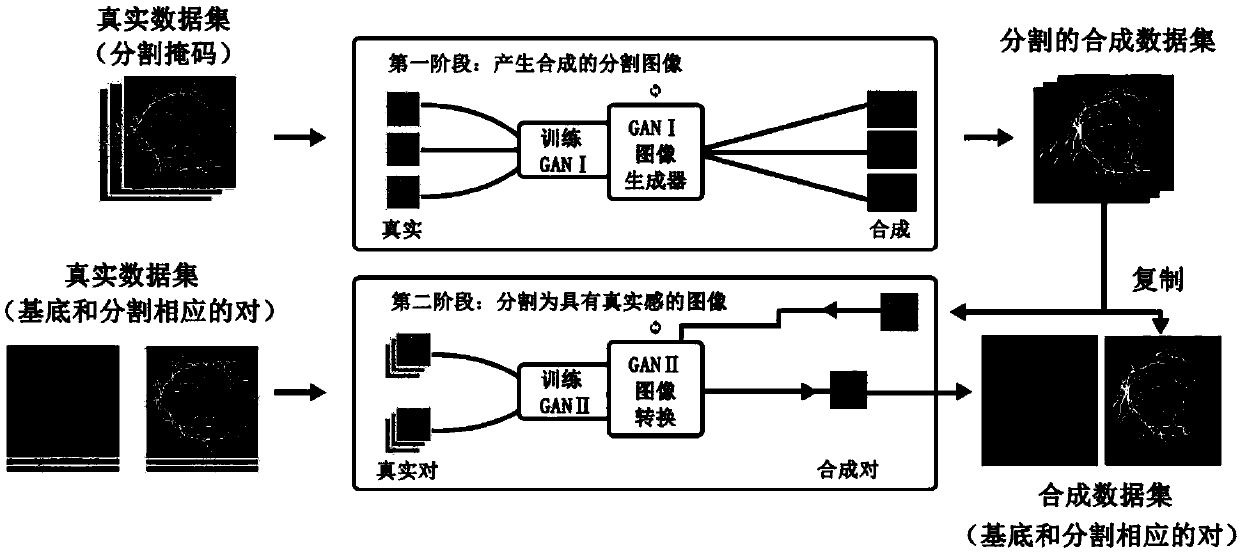
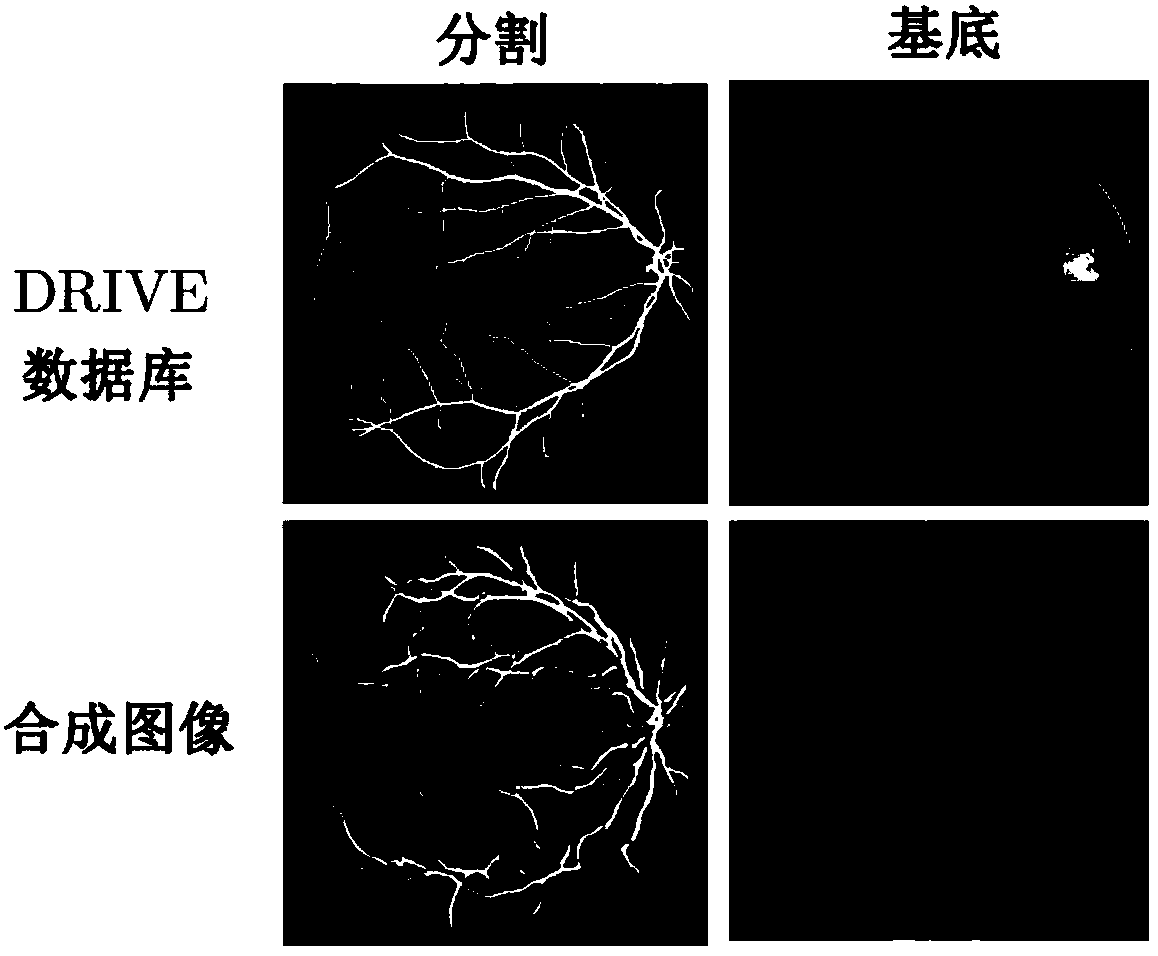
Medical image synthesis method based on double generative adversarial networks
The invention provides a medical image synthesis method based on double generative adversarial networks. The method comprises the main content of performing data management, generating the generativeadversarial networks, training a U-NET, establishing assessment indexes and obtaining processed pictures, wherein first, a DRIVE database is used to manage a first-stage GAN, then the first-stage GANgenerates a partitioning mask representing variable geometry of a dataset, a second-stage GAN converts the mask produced at the first stage into an image with a sense of reality, an generator minimizes a loss function of the true data in classification through a descriminator, then the U-NET is trained to assess the reliability of synthetic data, and finally the assessment indexes are establishedto measure a generated model. According to the method, by use of a pair of generative adversarial networks to create a new image generation path, the problem that the synthetic image contains a fake shadow and noise is solved, the stability and the sense of reality of the image are improved, and meanwhile image details are clearer.
Owner:SHENZHEN WEITESHI TECH
System for optimizing the performance of a smart advertisement
InactiveUS20080140508A1Improve performancePerformance rateMarket predictionsMarket data gatheringNetwork generationUser profile
A system is described for optimizing the performance of smart advertisements generated over a network for display to a user. The smart advertisements may adapt to specific user profile information and available advertising campaign information. The system may consume log data relating to previously displayed smart advertisements and compare the performance rates of the smart advertisements to determine relationships between controllable variables and the performance rates. The system may manipulate the controllable variables based on the relationships to optimize the performance of smart advertisements.
Owner:OATH INC
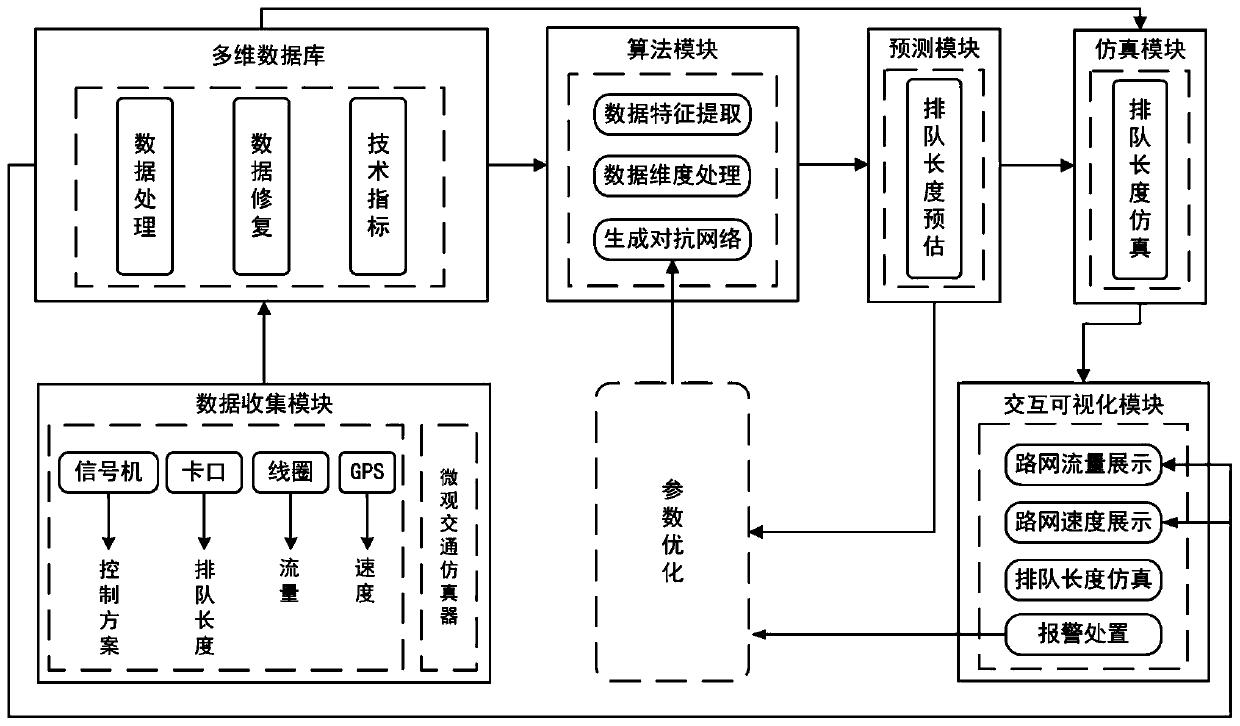
City-level intelligent traffic simulation system
ActiveCN110164128ASolve low work efficiencyDetection of traffic movementForecastingState predictionFeature extraction
The invention discloses a city-level intelligent traffic simulation system. With multi-source heterogeneous data as input, the vehicle queue length of each lane at an intersection can be predicted, the evolution of the vehicle queue length is further dynamically simulated, and the simulation system comprises a data collection module, a multidimensional database, an algorithm module, a traffic state prediction module, a traffic simulation derivation module and an interaction visualization module. In the data collection module, the collected data comprise traffic dynamic data and static data. The multidimensional database is used for receiving various traffic dynamic information in real time and storing road infrastructure configuration information. In the algorithm module, a generated confrontation network is used for data generation and state prediction on the vehicle queue length, and the processing process comprises data feature extraction, data dimension processing, confrontation network generation, and hyperparameter optimization. The vehicle queue length of each lane at the intersection can be predicted, and the evolution of the vehicle queue length is further dynamically simulated.
Owner:ENJOYOR COMPANY LIMITED
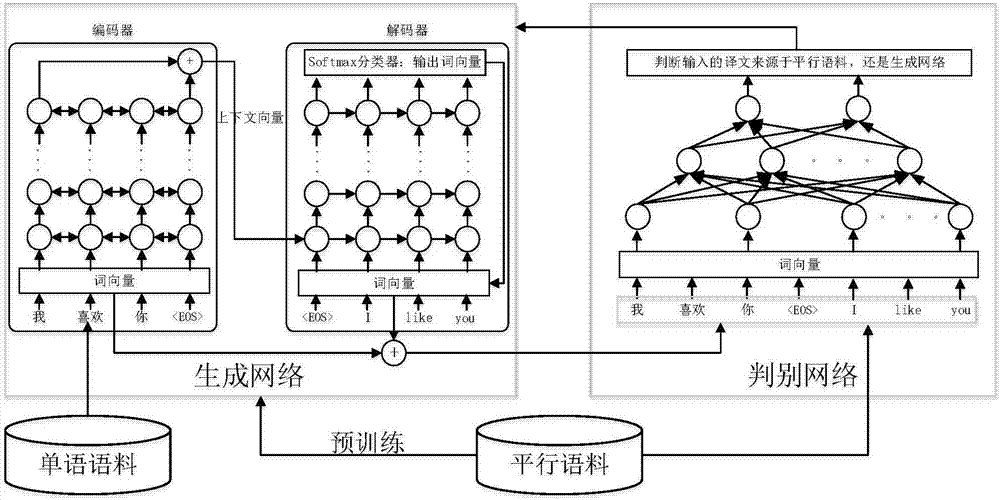
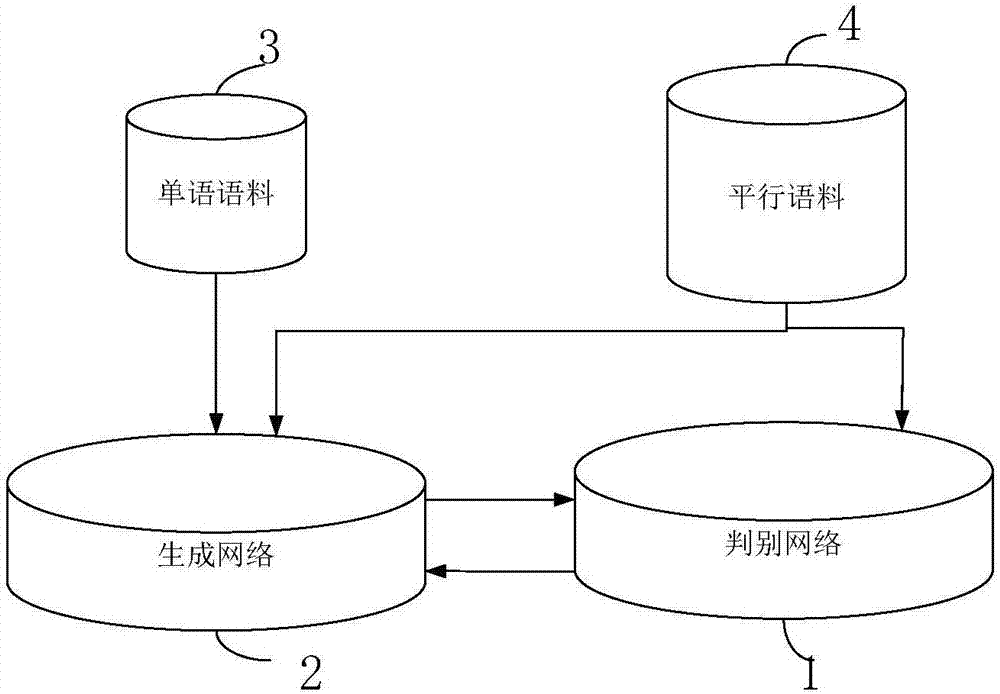
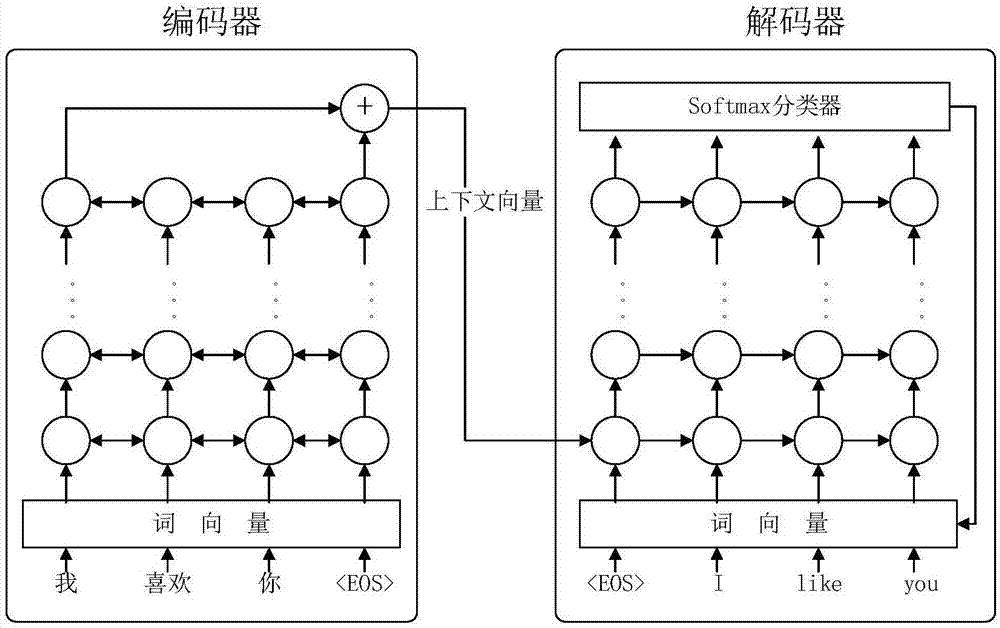
Machine translation method and system based on generative adversarial neural network
ActiveCN107368475AAddress the bottleneck of insufficientLow costNatural language translationSpecial data processing applicationsNerve networkCountermeasure
The invention belongs to the technical field of computers, and discloses a machine translation method and system based on a generative adversarial neural network. The method comprises the following steps that: on the basis of an original machine translation generation network, a discrimination network which generates network countermeasure with the original machine translation generation network is imported; a translation used for judging a target language is from a training parallel corpus and is a network machine translation result of the original machine translation generation network; and the discrimination network adopts a multi-layer sensor feedforward neural network model to realize binary classification. The system comprises the discrimination network, a generation network, a mono-lingual corpus and a parallel corpus. While manually annotated bilingual parallel corpus resources are fully utilized, and mono-lingual corpus resources also can be fully utilized to carry out semi-supervised learning; and the mono-lingual corpus resources are very rich and can be easily obtained, and the problem that required training corpora required by the neural network machine translation model are not sufficient is solved.
Owner:GLOBAL TONE COMM TECH
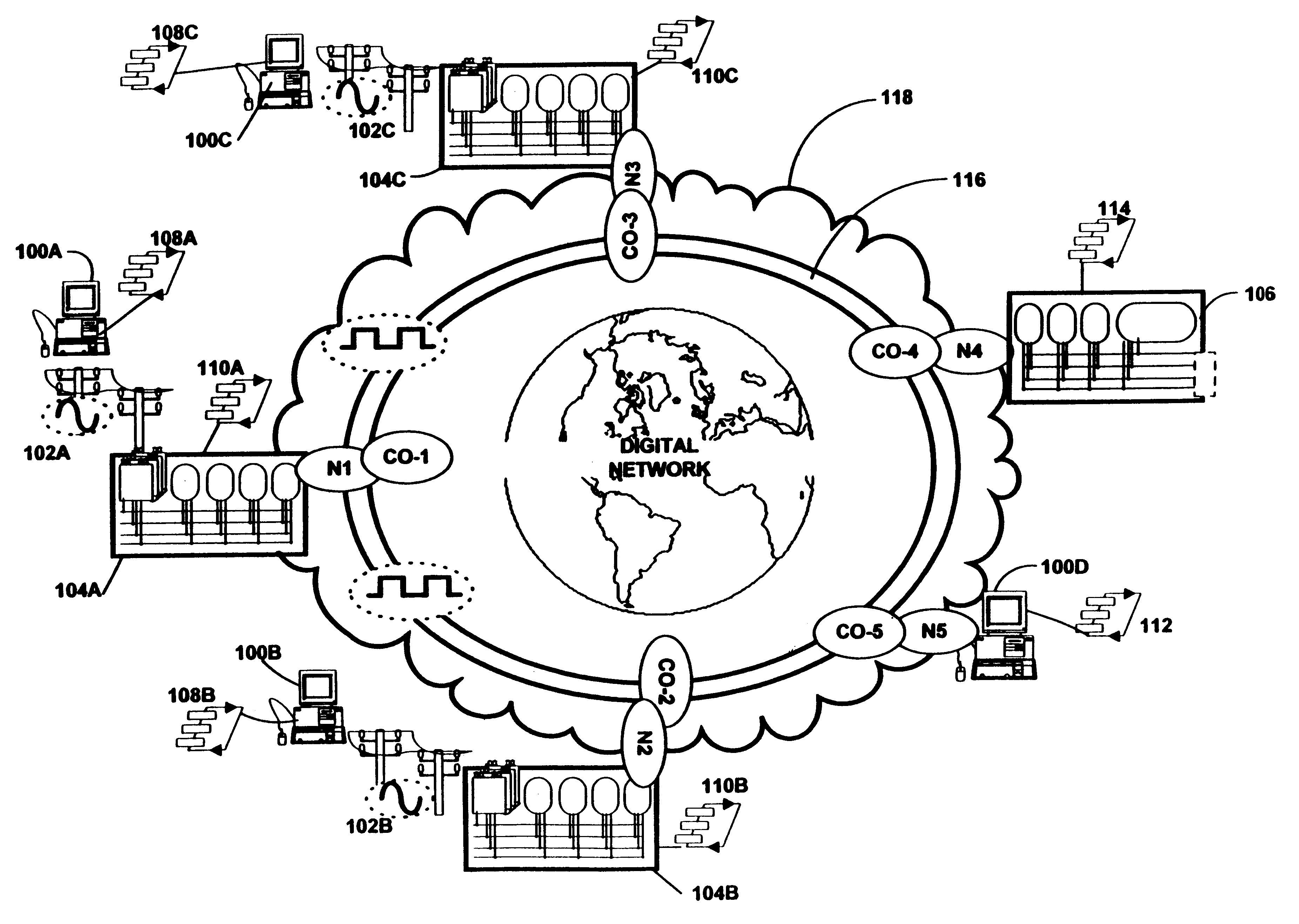
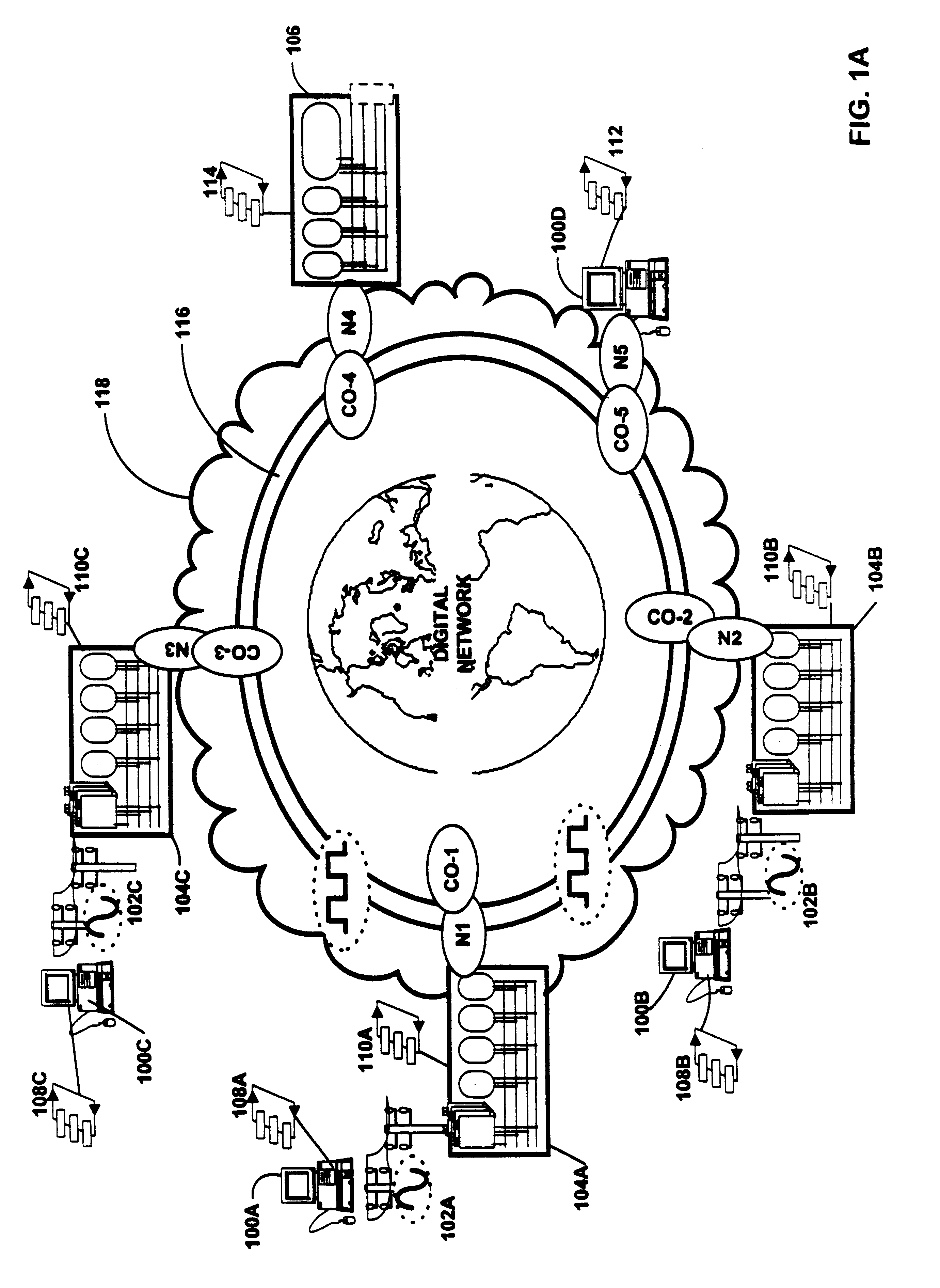
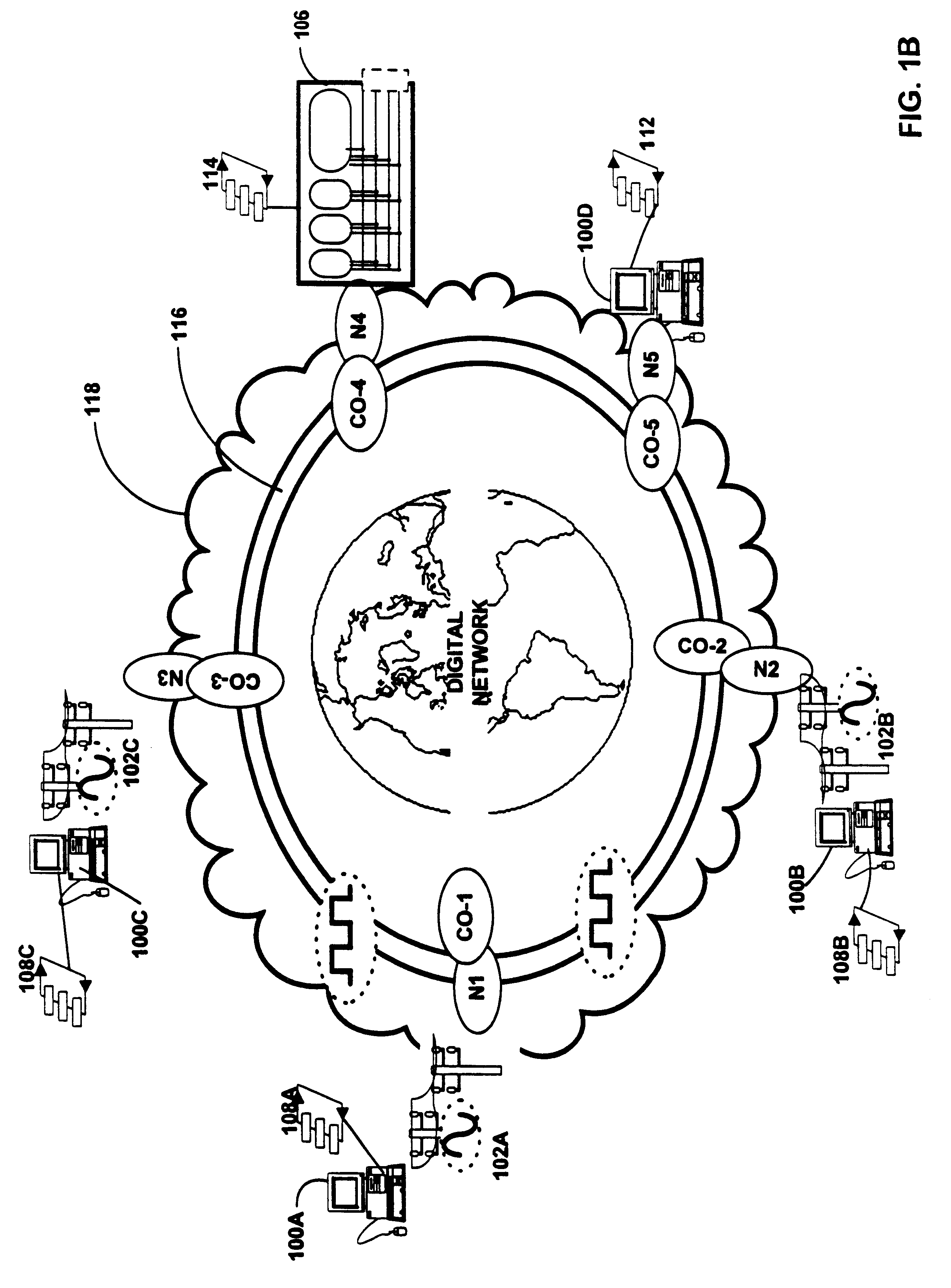
Method and apparatus for hierarchical management of subscriber link traffic on digital networks
InactiveUS6320867B1Time-division multiplexData switching by path configurationData terminalNetwork generation
The current invention provides apparatus for relieving congestion associated with interfacing voice-band data, and broad-band data, with a network such as the public switched telephone network (PSTN).A hierarchical system for converting digital transmissions on a network between a first protocol and a second protocol is disclosed. The transmissions are generated by data terminals communicating in a third protocol with the network. The hierarchical system includes: interface units, a local processor, a first remote processor and a first controller. The interface units are each coupled to corresponding ones of the data terminals and each signal a call session with the corresponding data terminal. The interface units convert the transmissions from the data terminal in the third protocol to the second protocol. The local processor is switchably coupled to the interface unit and communicates with the network. The local processor converts digital transmissions from the second protocol to the first protocol. The first remote processor is coupled to each of the interface units and communicates with the network. The first remote processor converts digital transmissions from the second protocol to the first protocol. The first controller detects the signaling from the interface units corresponding to the call session and allocates to an available one of the local processor and the first remote processor a conversion of digital transmissions associated with the call session from the second protocol to the first protocol.In an alternate embodiment of the invention, a hierarchical system includes remote control and processing capability.
Owner:UTSTARCOM INC
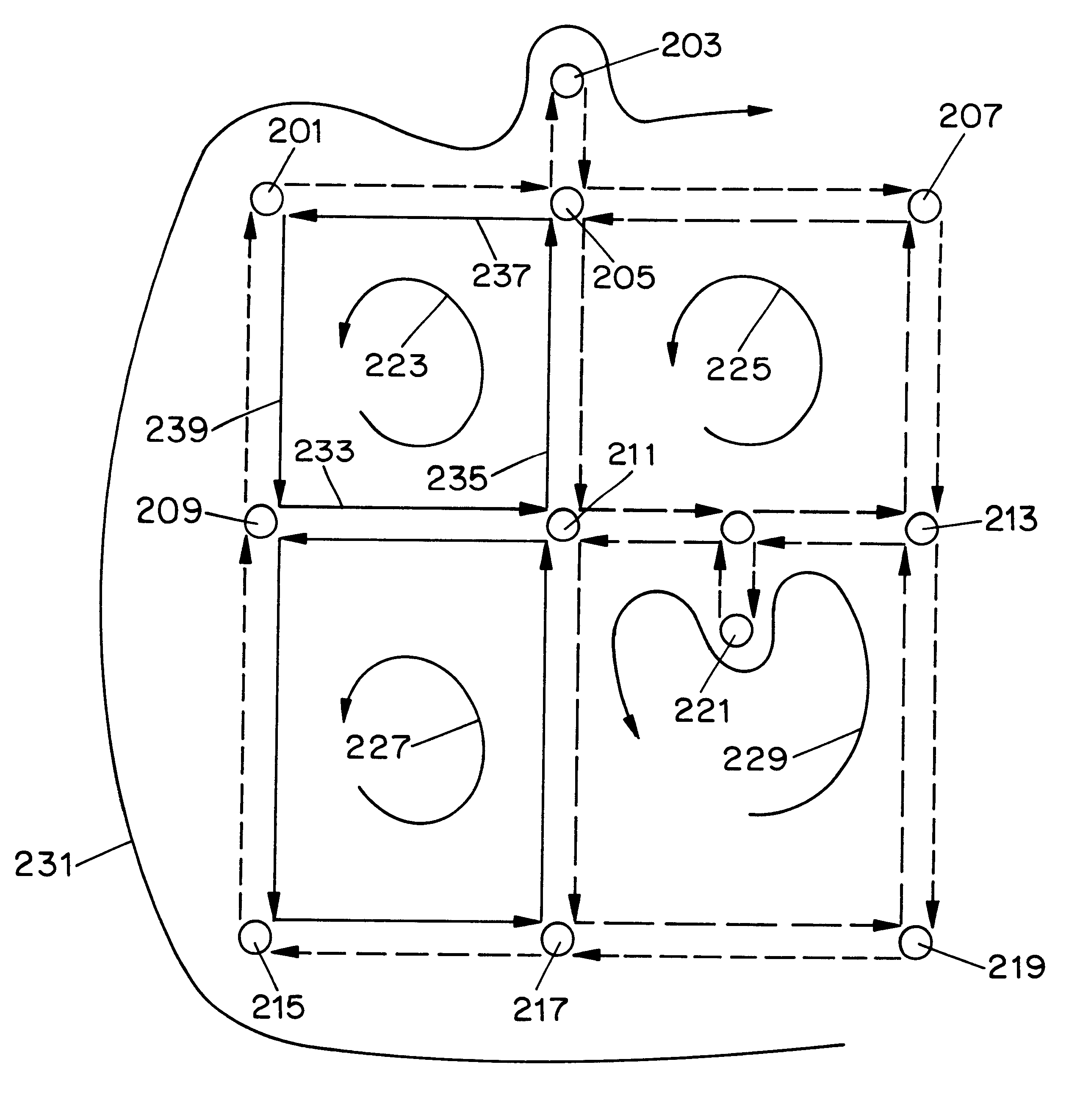
Network switch failure restoration
A system and method for automatically restoring a network which contains a node with a failed switch. Protection cycles are generated for the network to be restored and cyclegroups are generated from the protection cycles. Each node is provided with protection switches which internally interconnect the input / output ports to connecting links via interconnecting protection fibers. The selection of which internal protection fibers upon which to switch transmitted information onto allows the node to be configured to create merged cyclegroups. Thus if a failure in the central switch is detected, the transmitted information is diverted to a selected protection fiber corresponding to a merged cyclegroup so that the information can be automatically passed around the failed switch via the protection fibers. Each protection switch has associated mapping data which defines which protection fiber will be switched to based upon the input and output link for the transmission that is required to be sent through the node. The system and method applies to non-planar networks as well as planar networks.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
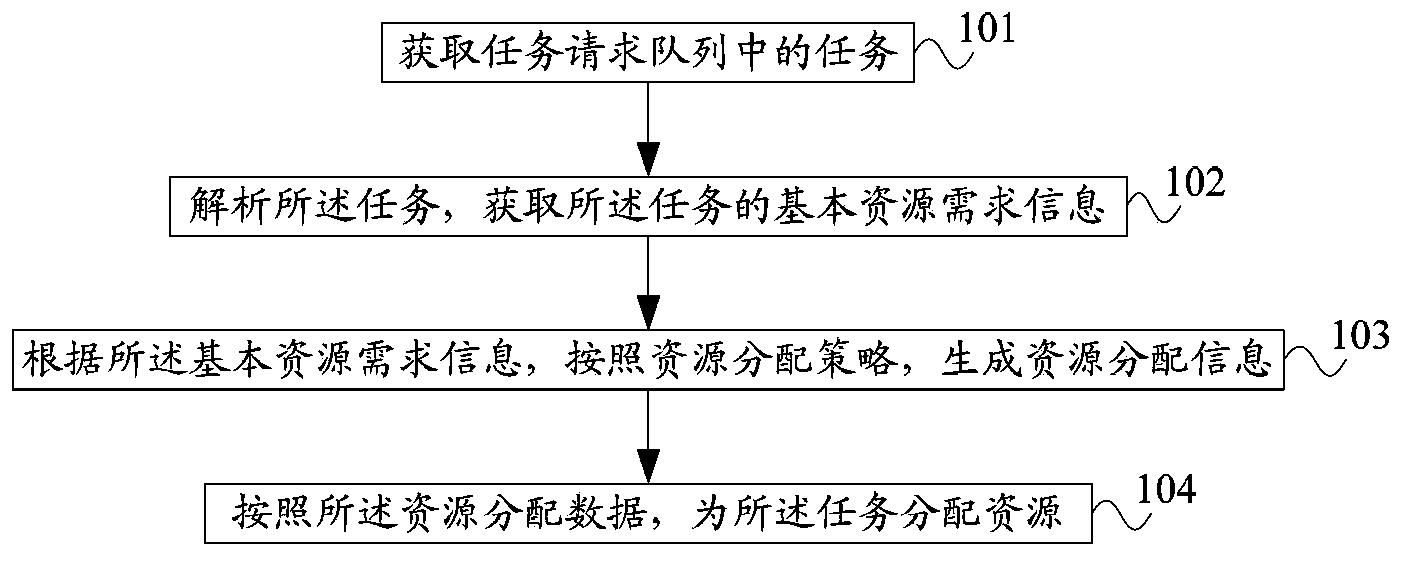
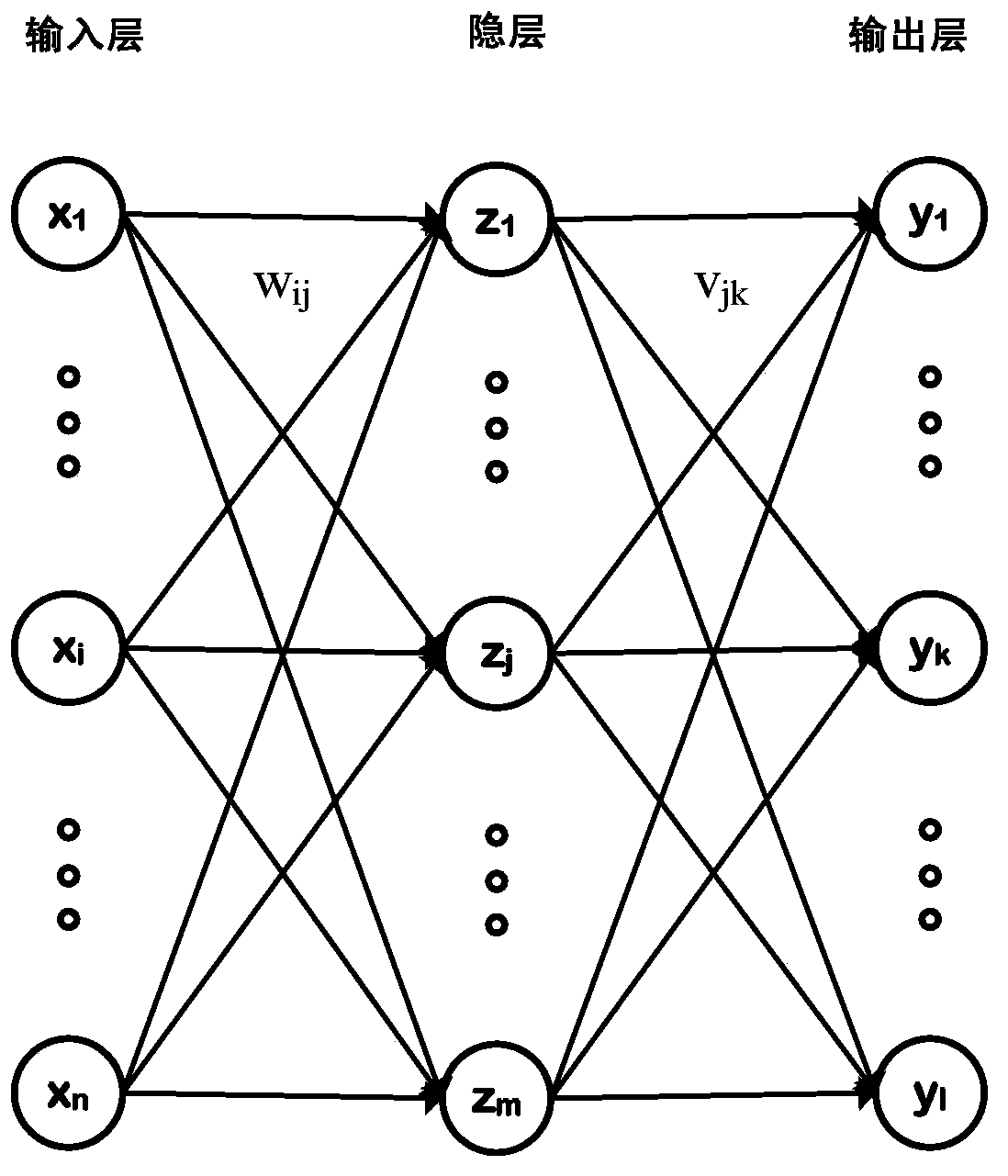
Method and device for cloud computing platform system to distribute resources to task
ActiveCN103699440AImprove resource utilizationIncrease the amount of concurrent tasksResource allocationNeural learning methodsNetwork generationResource utilization
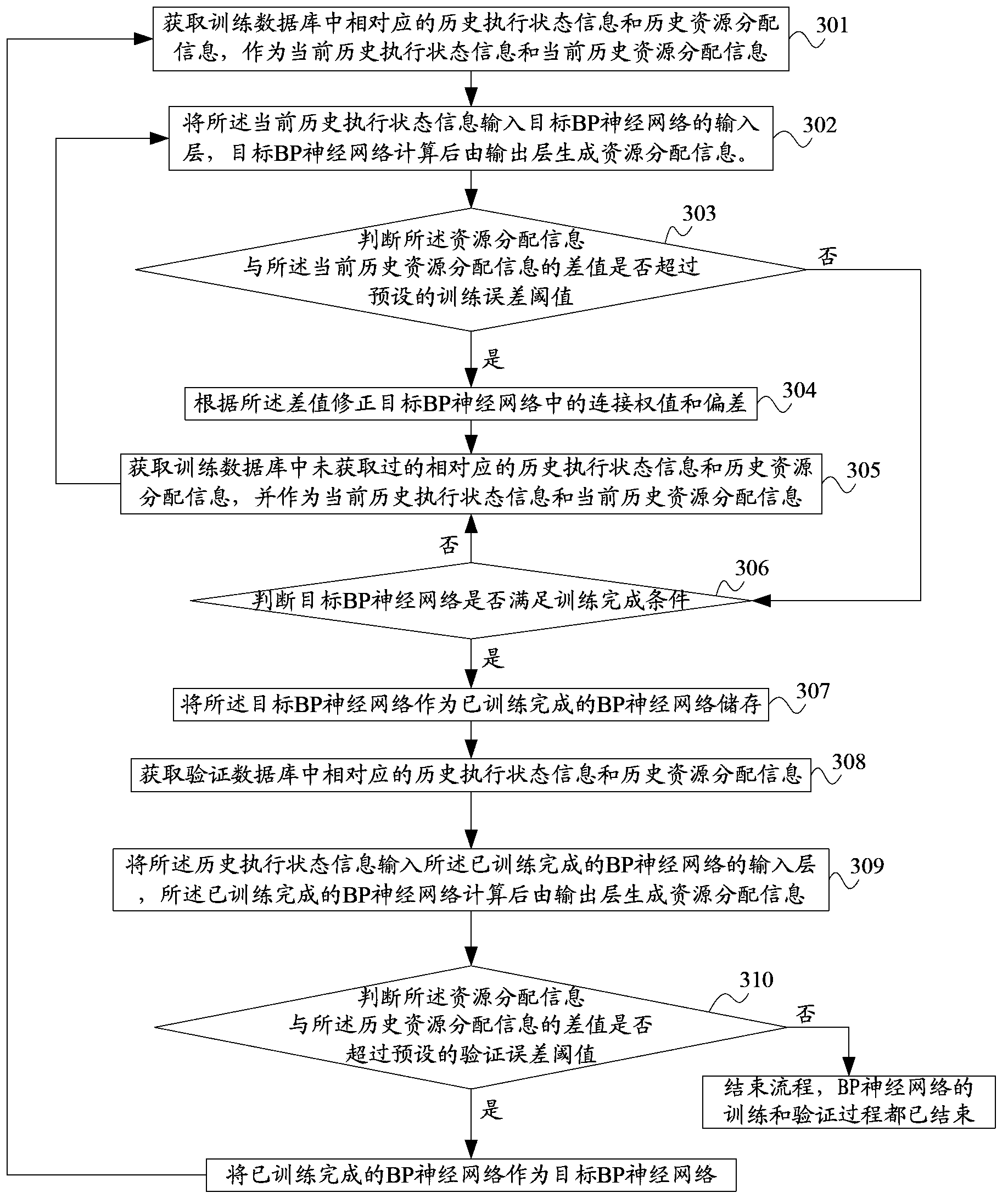
The invention discloses a method and a device for a cloud computing platform system to distribute resources to a task. The method comprises the steps that a task from a task request queue is obtained; the task is analyzed, and the basic resource requiring information of the task is obtained; resource distribution information is generated by a resource distribution strategy according to the basic resource requiring information; the resource distribution strategy is a trained back propagation (BP) neural network; the training is as follows: a historically executed state information is input into a target BP neural network; if the difference between the generated resource distribution information and historical resource distribution information exceeds a preset training error threshold, the target BP neural network is revised, so that the difference between resource distribution information which is output after the training and the historical resource distribution information does not exceed the training error threshold; the resources are distributed to the task according to the resource distribution information. According to the method and the device for the cloud computing platform system to distribute the resources to the task, the system distributes the resources according to the resource distribution information generated by the BP neural network, so that the resource utilization rate of the system is improved, and the number of concurrent tasks and the throughput of the tasks are increased.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com