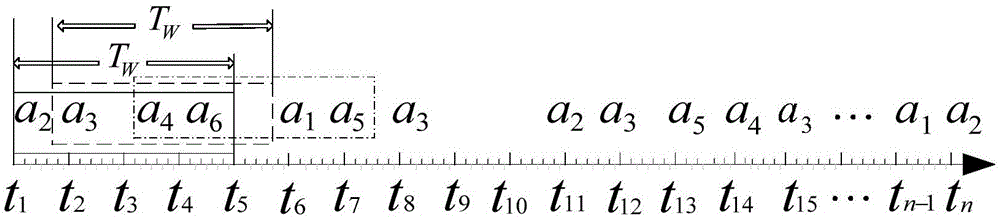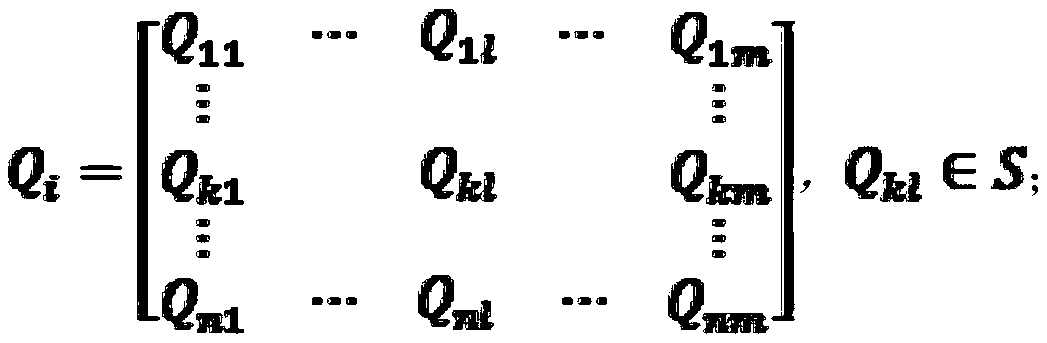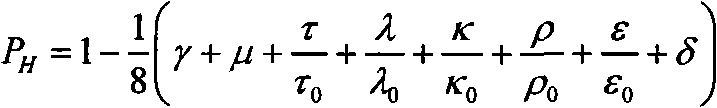Patents
Literature
174 results about "Attack graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
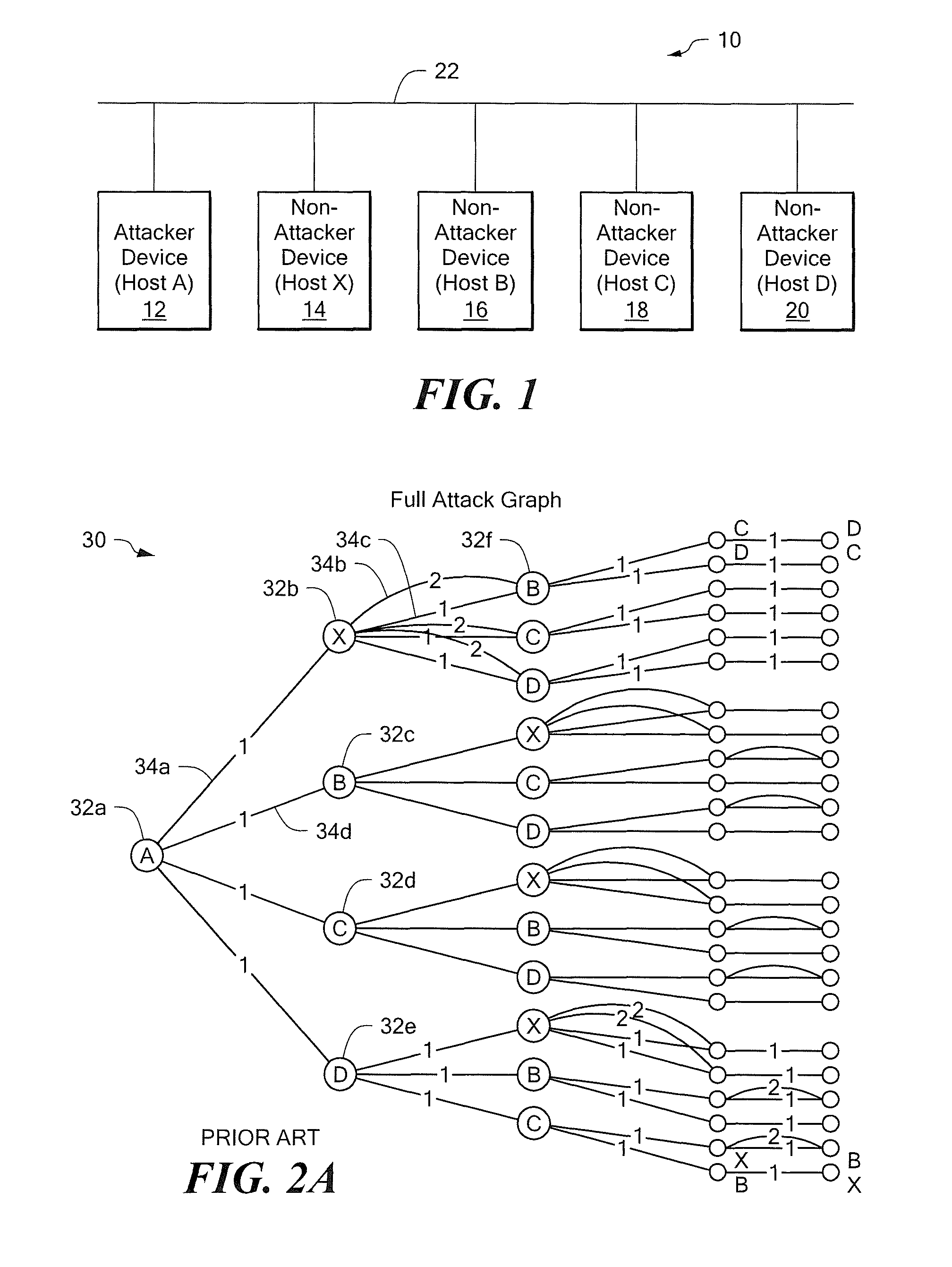
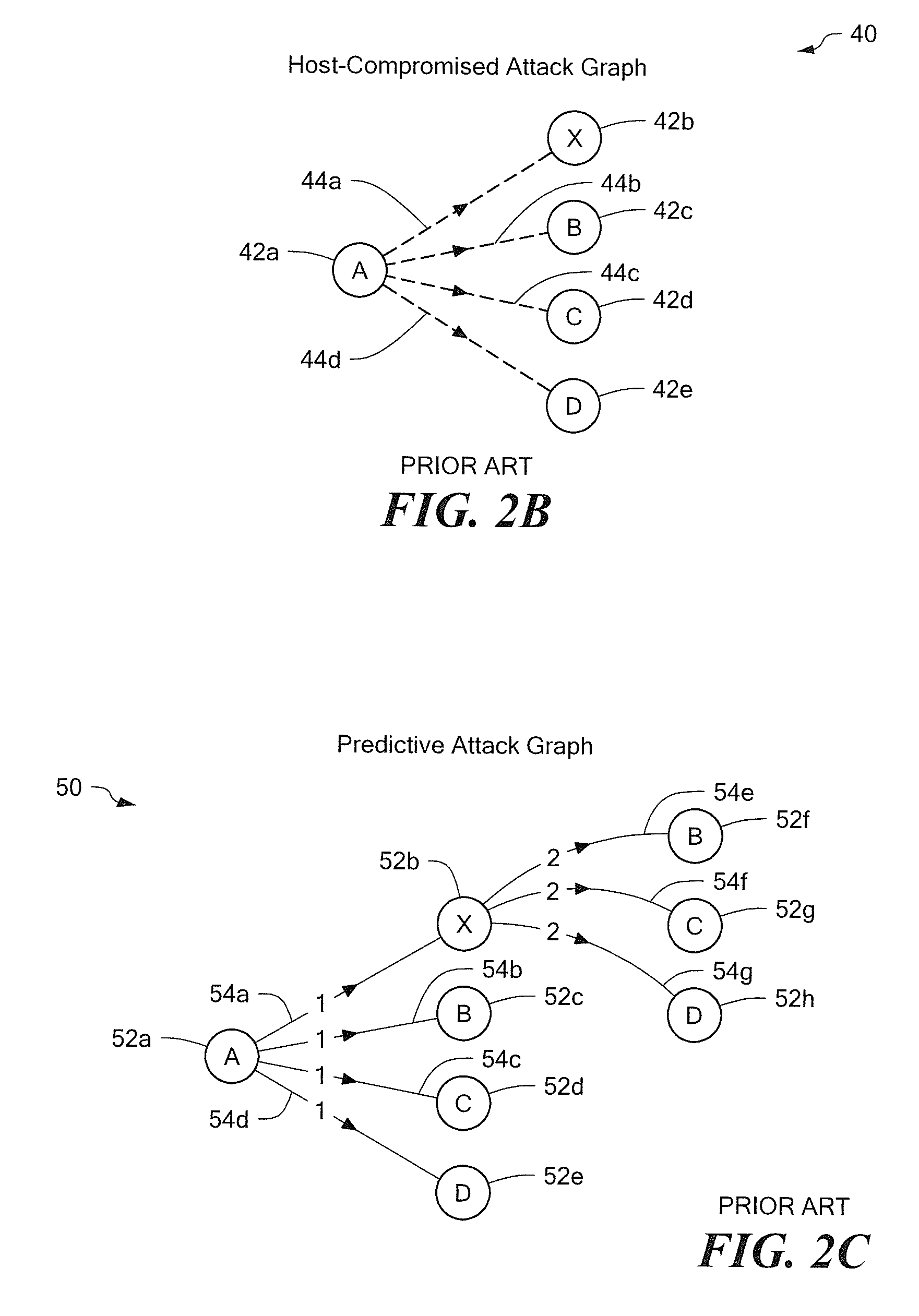
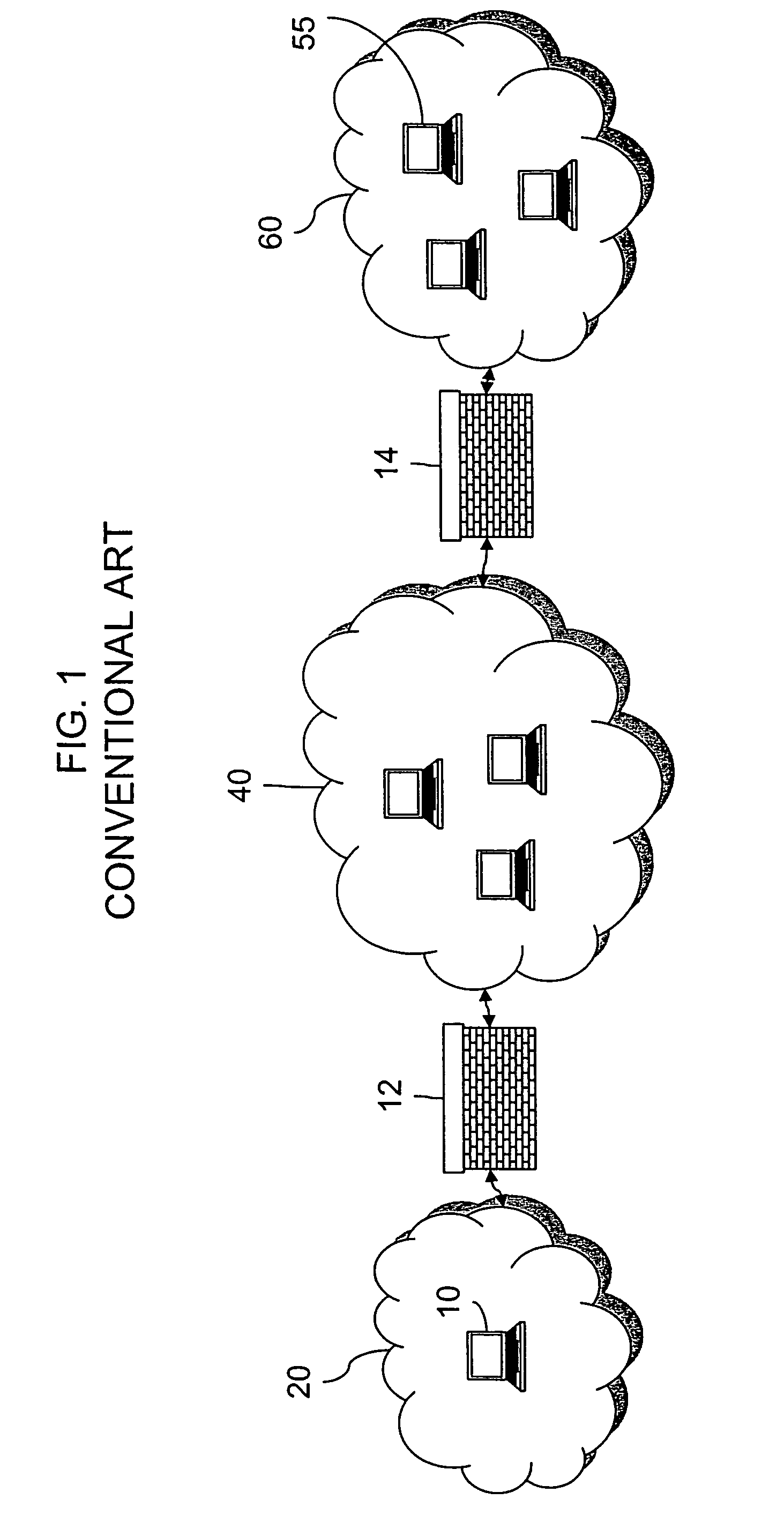
Method and tool for network vulnerability analysis
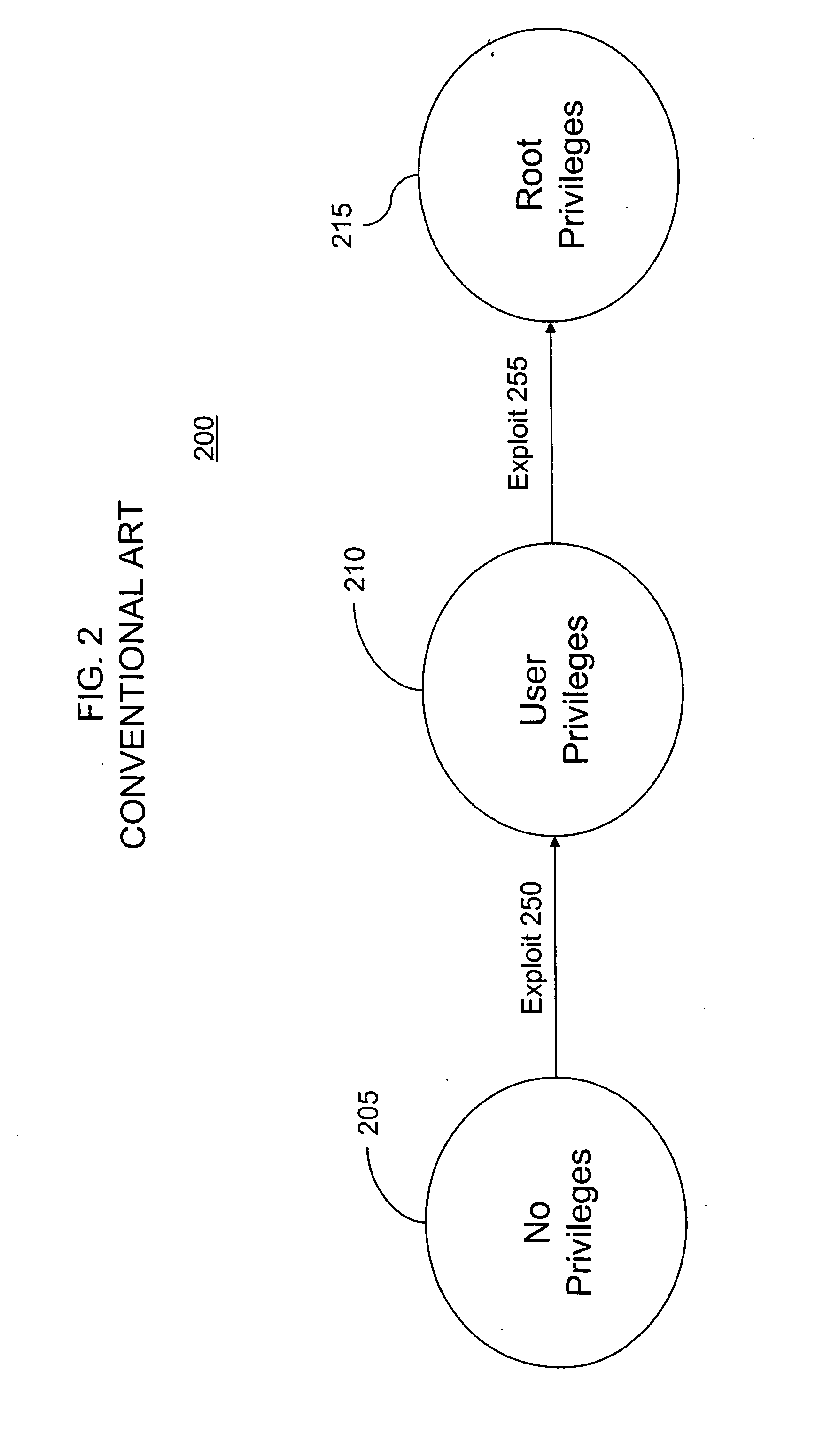
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
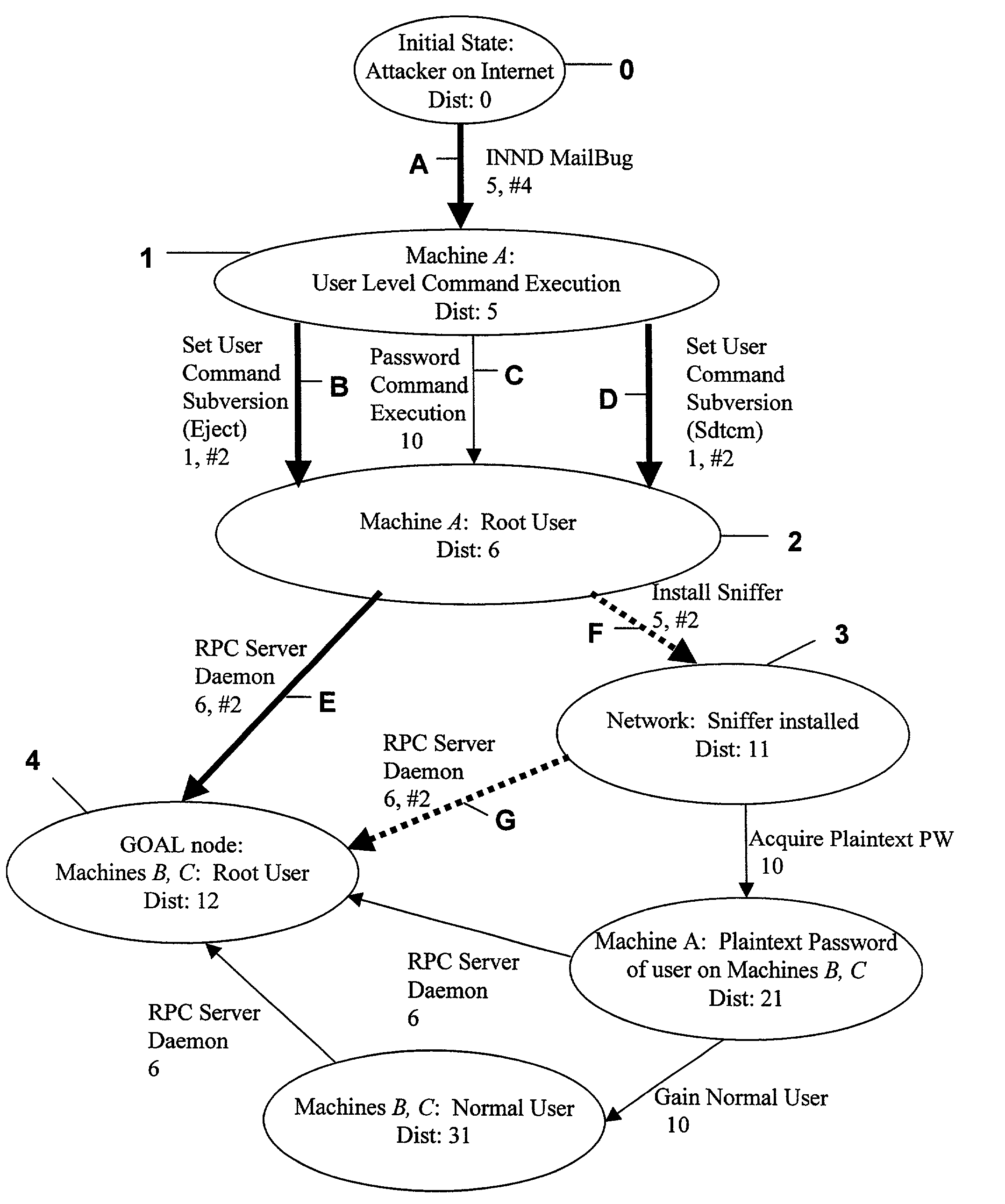
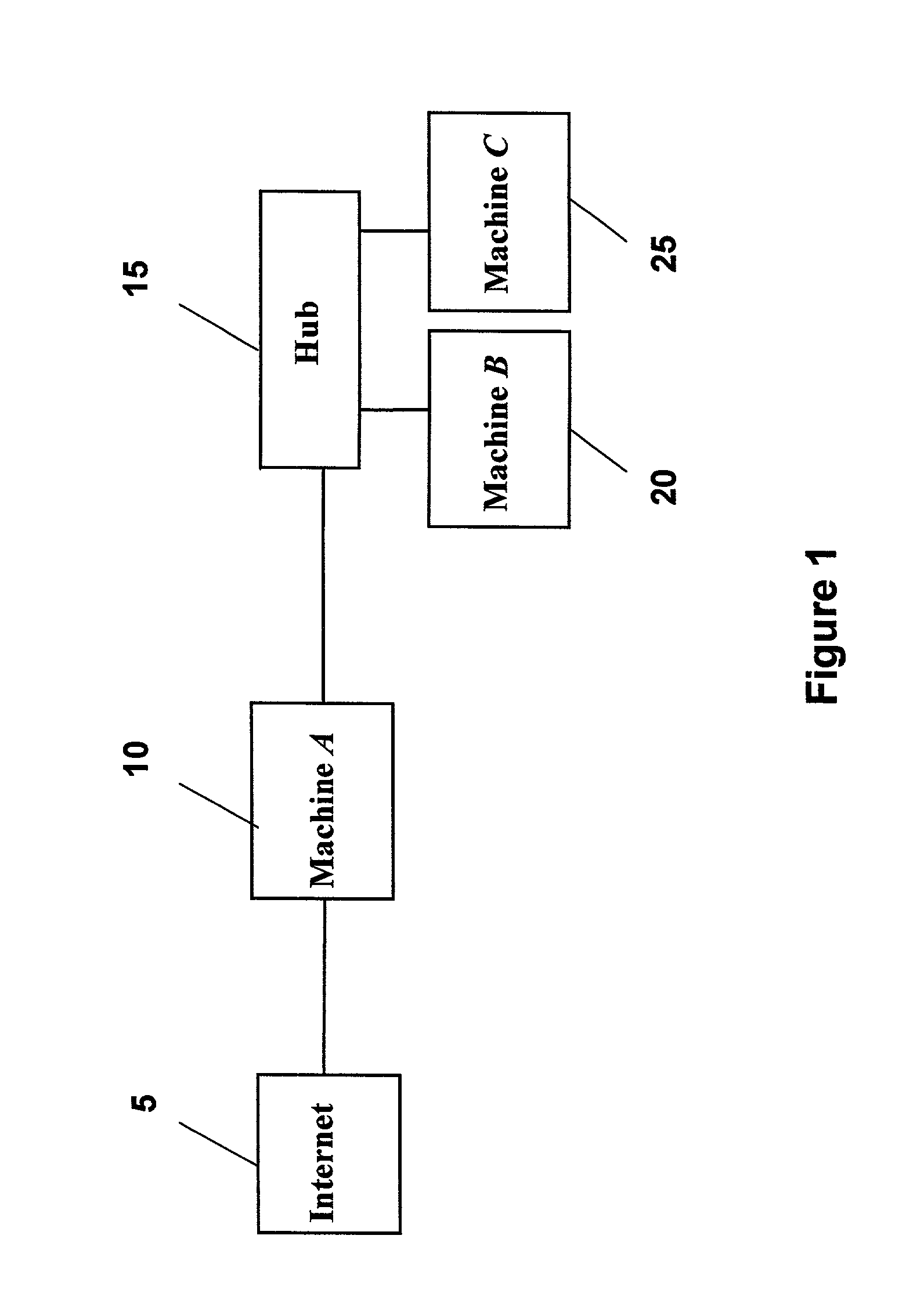
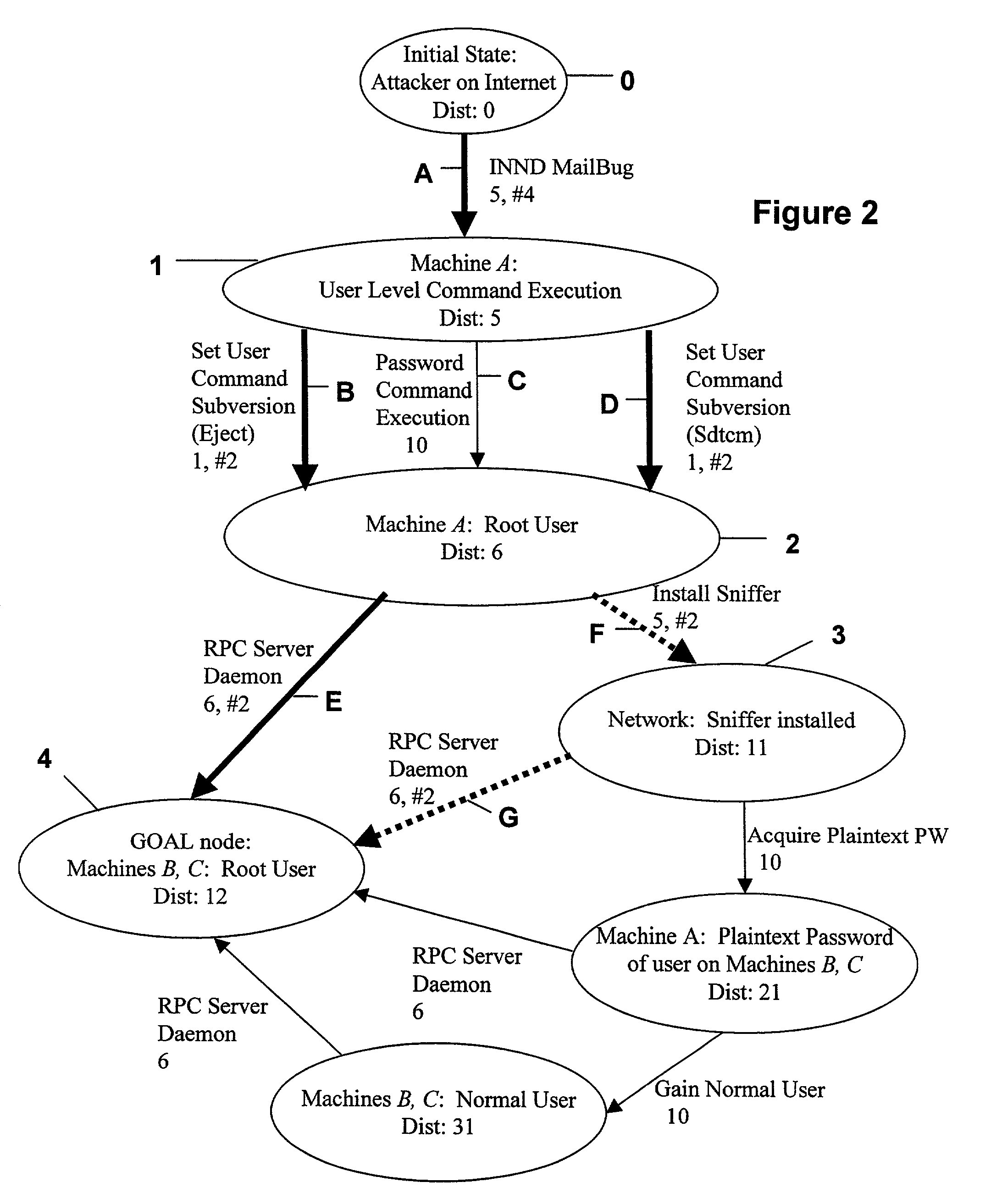
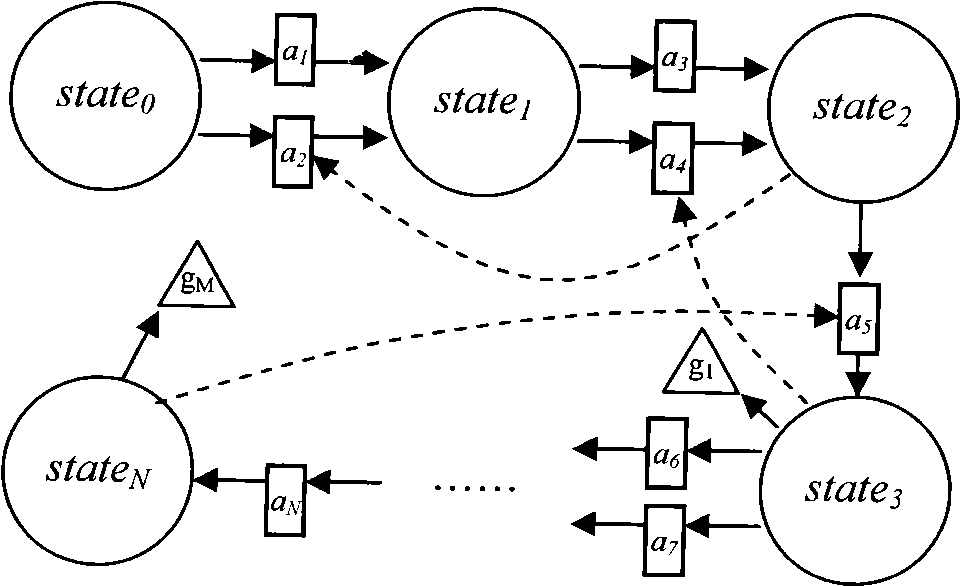
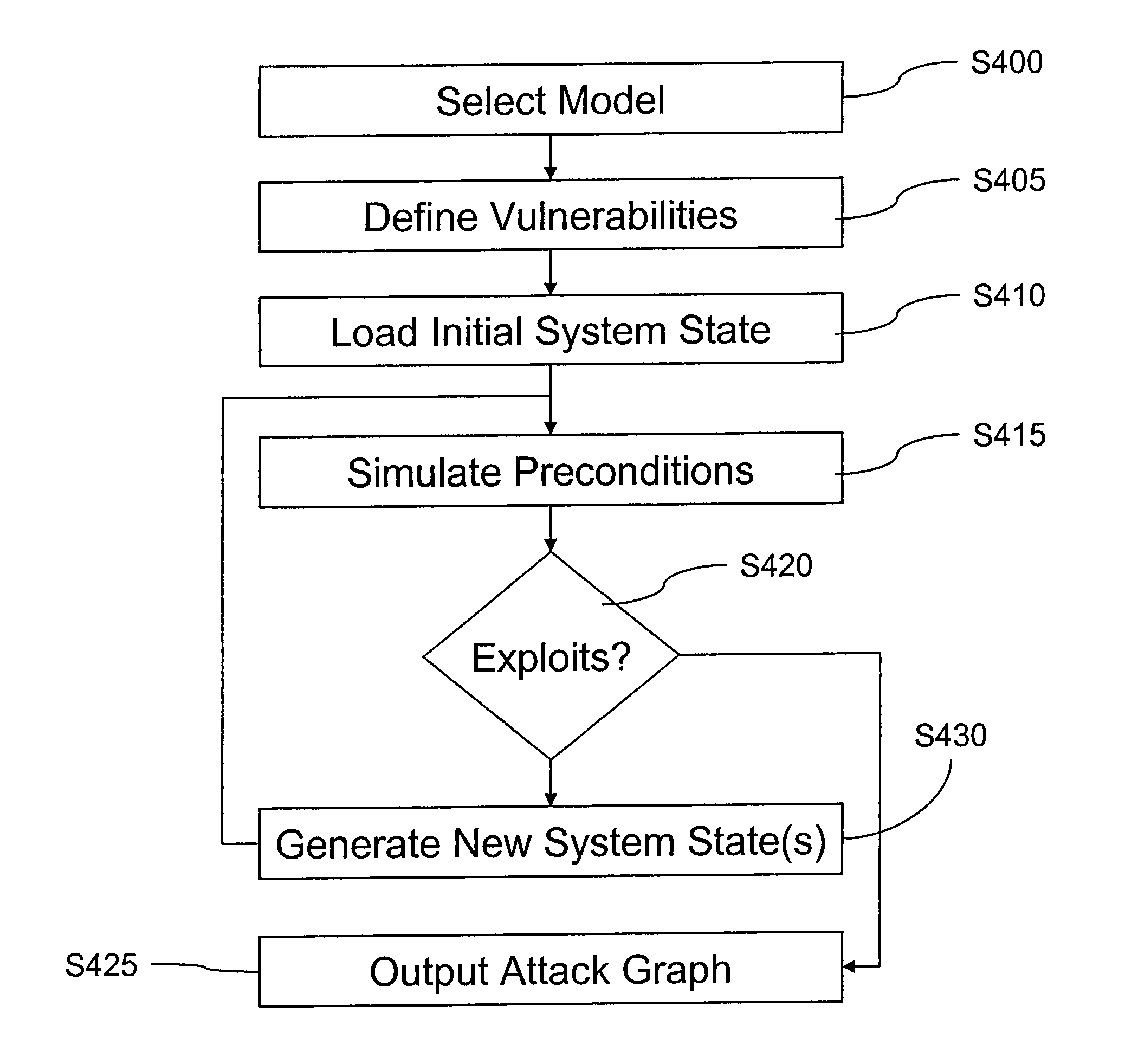
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
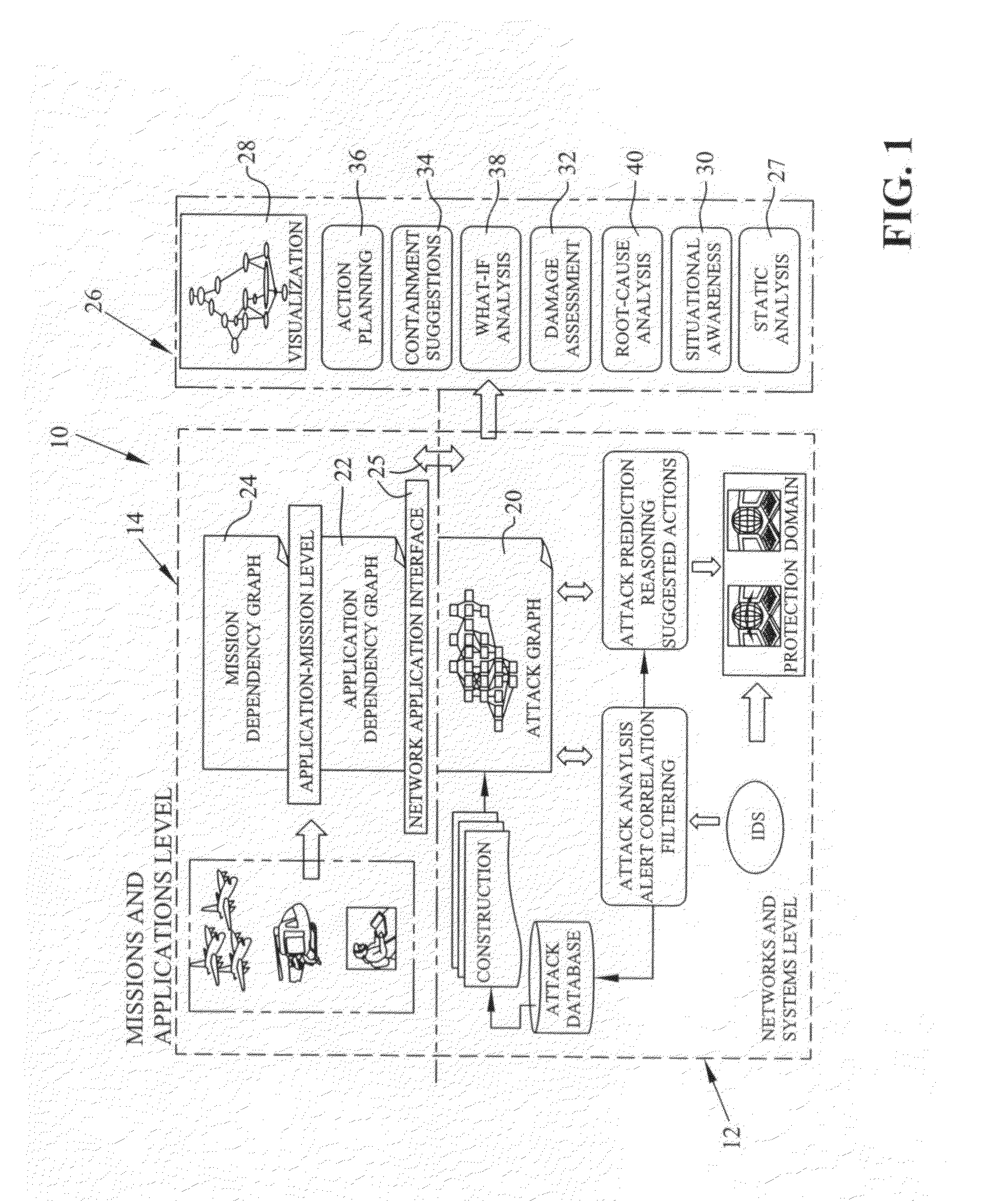
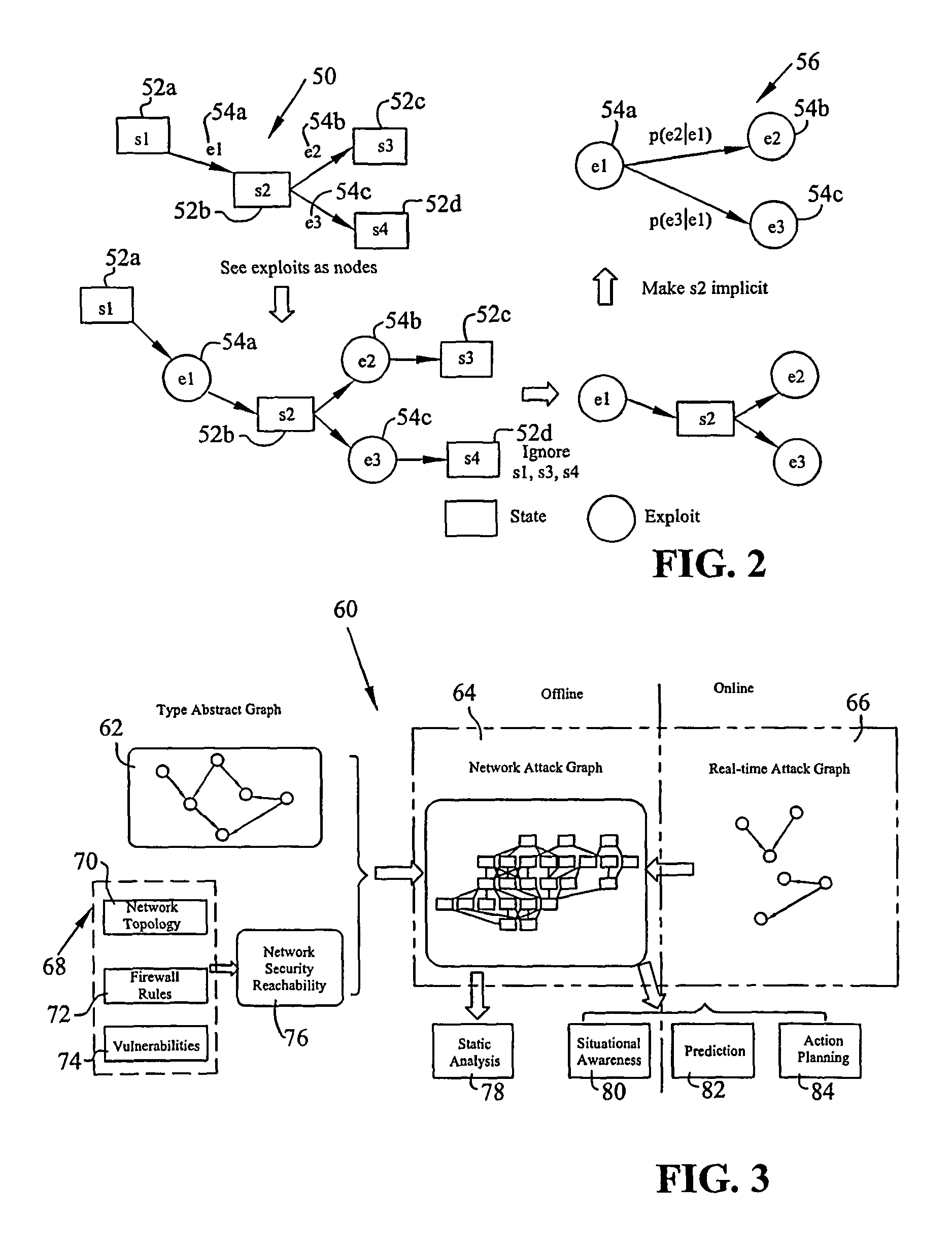
Graphical models for cyber security analysis in enterprise networks
ActiveUS8881288B1Accurate and efficientReduce and compress redundancyMemory loss protectionError detection/correctionGraphicsGaussian network model
A method of generating graphical models for providing security analysis in computer networks that in one embodiment includes the steps of generating a type abstract graph independent of particular networks that models abstract dependency relationships among attributes and exploits; generating network-specific attack graphs by combining the type abstract graph with specific network information; monitoring an intruder alert; and generating a real-time attack graph by correlating the intruder alert with the network-specific attack graph. The real-time attack graph can be generated using reachability checking, bridging, and exploit prediction based on consequence alerts and may further include the step of calculating the likelihood of queries using a Bayesian network model. The method may also include the steps of inferring unobserved attacks that may have been missed by intrusion detection sensors, and projecting on which hosts and using what exploits additional intruder attacks may occur. The method may further include the step of comparing alternate actions by computation, wherein the alternate actions include the step of patching some vulnerabilities, and wherein the specific network information includes network topology. The specific network information may also include firewall rules.
Owner:INTELLIGENT AUTOMATION LLC
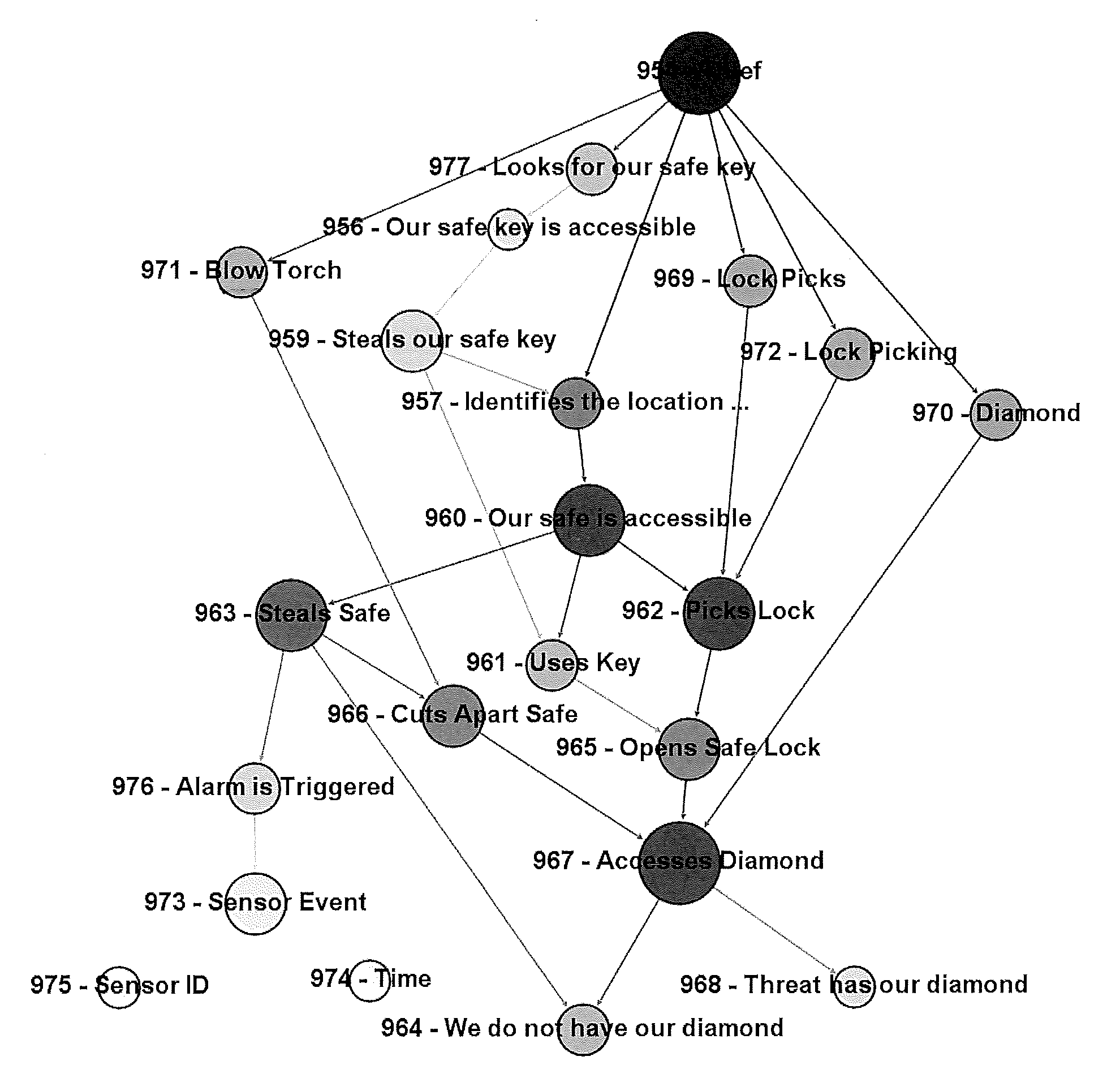
System and Method for Cyber Security Analysis and Human Behavior Prediction
ActiveUS20160205122A1Simple conditionsMemory loss protectionError detection/correctionHuman behaviorAttack graph
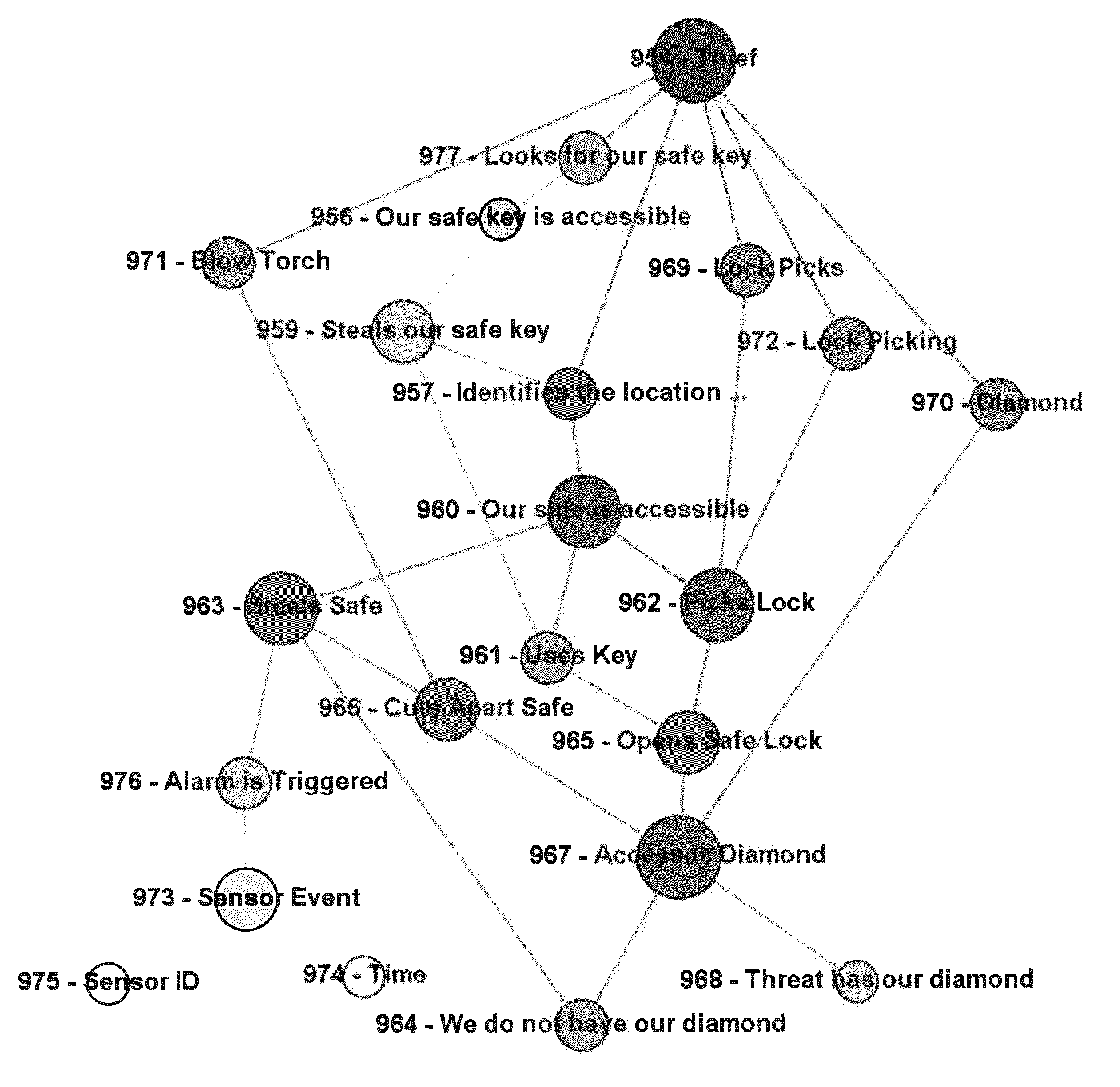
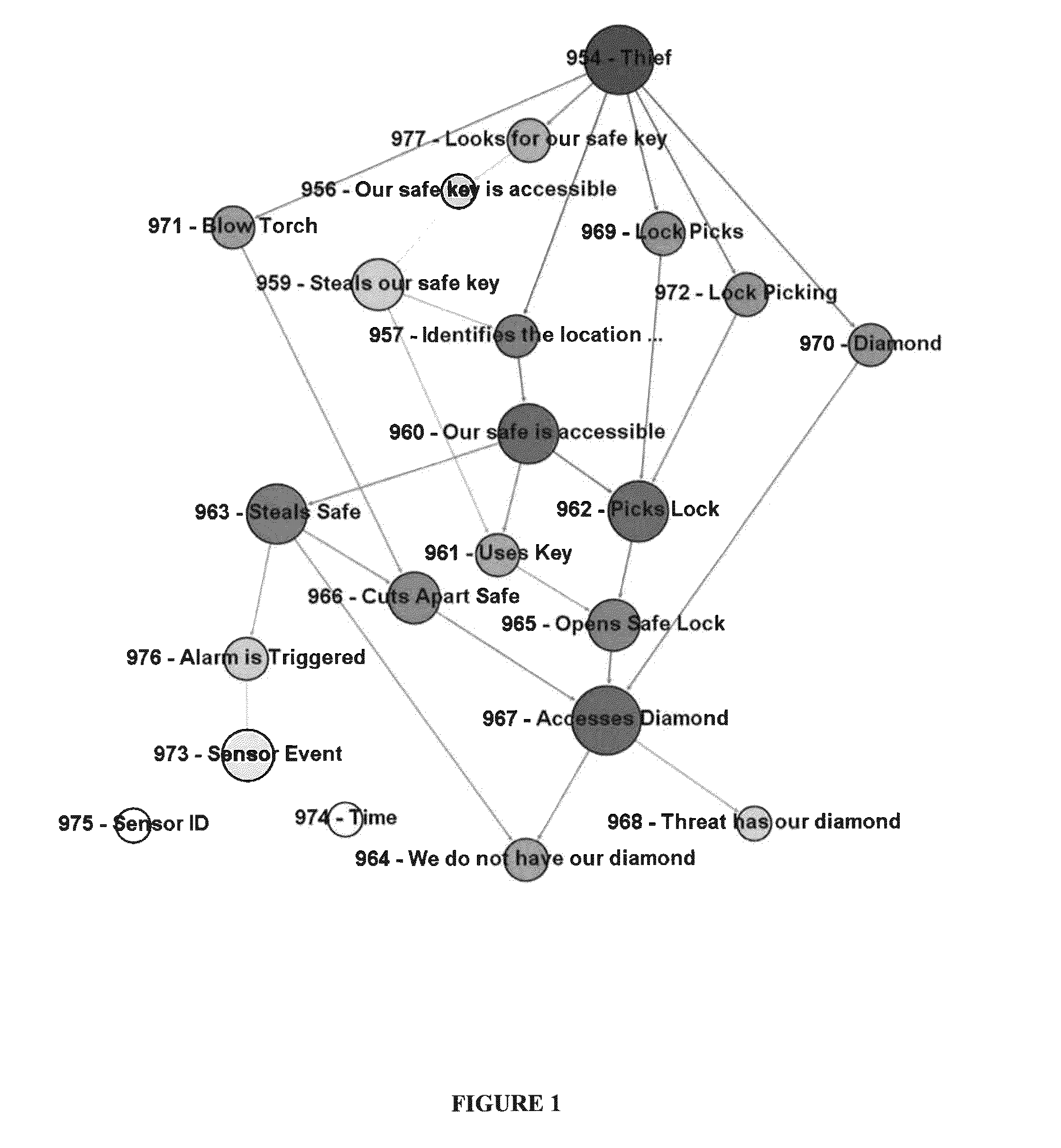
An improved method for analyzing computer network security has been developed. The method first establishes multiple nodes, where each node represents an actor, an event, a condition, or an attribute related to the network security. Next, an estimate is created for each node that reflects the ease of realizing the event, condition, or attribute of the node. Attack paths are identified that represent a linkage of nodes that reach a condition of compromise of network security. Next, edge probabilities are calculated for the attack paths. The edge probabilities are based on the estimates for each node along the attack path. Next, an attack graph is generated that identifies the easiest conditions of compromise of network security and the attack paths to achieving those conditions. Finally, attacks are detected with physical sensors on the network, that predict the events and conditions. When an attack is detected, security alerts are generated in response to the attacks.
Owner:BASSETT GABRIEL
System and method for cyber security analysis and human behavior prediction
ActiveUS9292695B1Attacked easilyError detection/correctionPlatform integrity maintainanceHuman behaviorAttack graph
A method for analyzing computer network security has been developed. The method first establishes multiple nodes, where each node represents an actor, an event, a condition, or an attribute related to the network security. Next, an estimate is created for each node that reflects the case of realizing the event, condition, or attribute of the node. Attack paths are identified that represent a linkage of nodes that reach a condition of compromise of network security. Next, edge probabilities are calculated for the attack paths. The edge probabilities are based on the estimates for each node along the attack path. Finally, an attack graph is generated that identifies the easiest conditions of compromise of network security and the attack paths to achieving those conditions.
Owner:BASSETT GABRIEL
Attack-oriented network security situation prediction method, device and system
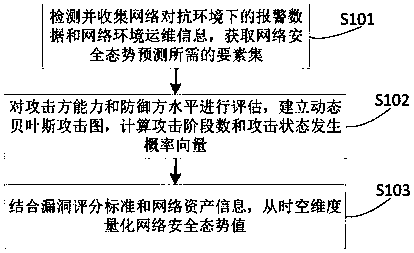
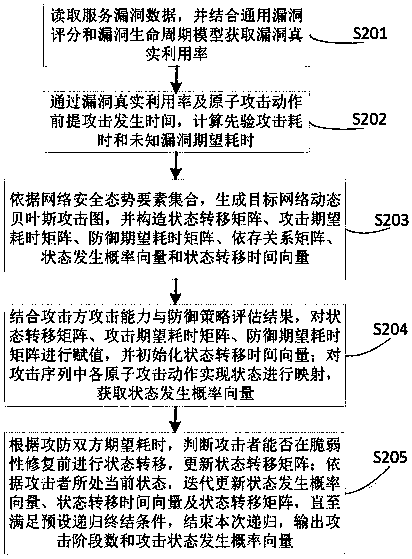
ActiveCN108494810ARealize dynamic associationIn line with the actual environmentData switching networksSecuring communicationCountermeasureAttack graph
The invention belongs to the technical field of network security and particularly relates to an attack-oriented network security situation prediction method, device and system. The method comprises the following steps: detecting and collecting alarm data and network environment operation and maintenance information in a network countermeasure environment, obtaining an element set required by network security situation prediction, wherein the element set comprises three types of information of an attacker, a defense party and a network environment; evaluating the attacker capability and the level of the defense party, establishing a dynamic Bayesian attack graph, and calculating an attack phase number and an attack state occurrence probability vector; and combining a vulnerability scoring standard and network asset information, and performing time-space dimension quantification on the network security situation value. According to the method, dynamic association of the situation elements of the defense party, the attacker, the environment information and the like is achieved, the actual environment of the network is better conformed to, the future situation and the attack occurrencetime can be accurately predicted, higher prediction efficiency is achieved, and storage scale and timeliness of network security situation awareness are optimized, so as to provide more effective guidance for network protection.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Methods of simulating vulnerability
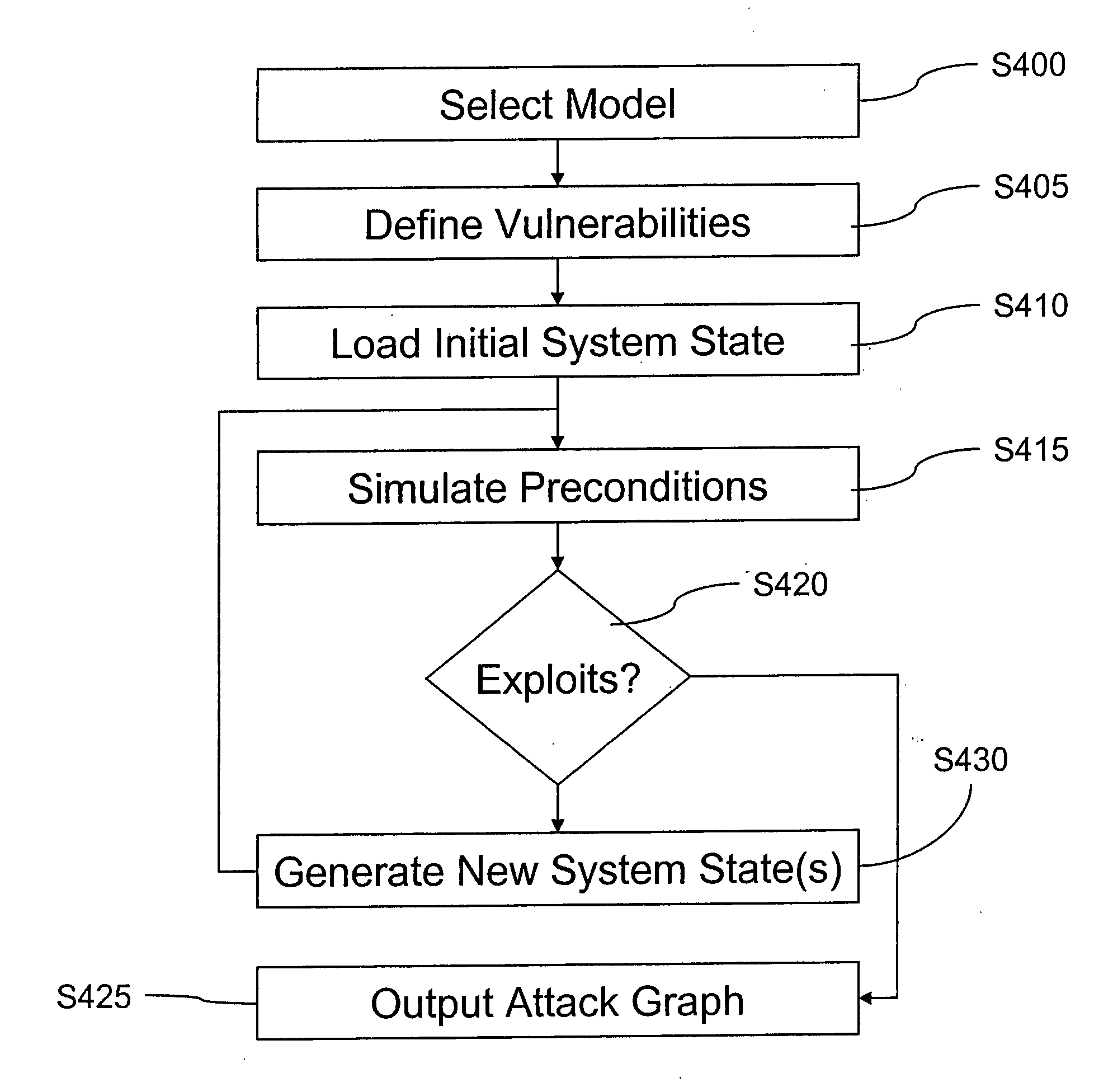
Methods of simulating vulnerability are provided. In an example, multi-stage vulnerability across multiple systems may be simulated by first simulating a probing of at least one intermediate entity, the at least one intermediate entity connected to a target system, second simulating a probing of the target system if the first simulated probing is successful and generating an attack graph based on the results of the first and second simulating steps. In another example, multi-system vulnerability may be simulated by receiving a plurality of attributes associated with vulnerabilities of a plurality of systems within a network, the plurality of systems including at least one target system and generating an attack graph including one or more attack chains based at least in part on the received plurality of attributes. In another example, system (e.g., single-system) vulnerability may be simulated by first simulating whether vulnerabilities exploited from a first system state cause a transition to a second system state, the second system state having a higher-privilege level than the first system state within a target system and generating an attack graph based at least in part on the results of the simulation.
Owner:LGS INNOVATIONS
Bayesian network-based multi-step attack security situation assessment method
ActiveCN106341414AReal-time assessmentEffective assessmentPlatform integrity maintainanceTransmissionAttack graphCorrelation analysis
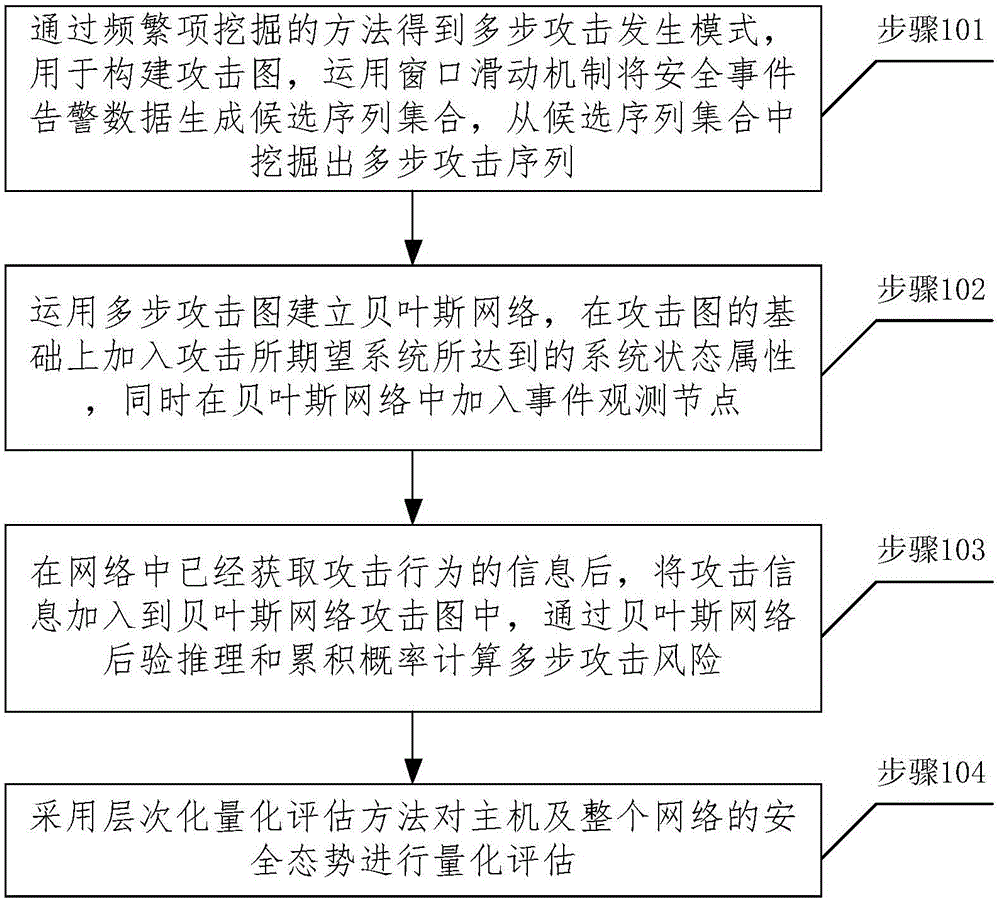
The invention relates to a network security situation assessment method, in particular, a Bayesian network-based multi-step attack security situation assessment method. The method includes the following steps that: multi-step attack generating patterns are mined through association analysis, so that an attack graph can be constructed; a Bayesian network is established according to the multi-step attack graph, attack wills, probability of success of attacks and the accuracy of event monitoring are defined as the probability attributes of the Bayesian network; based on the event monitoring, a multi-step attack risk is calculated according to the posterior reasoning and cumulative probability of the Bayesian network; and the security situations of a host and the whole network are quantitatively assessed according to a hierarchical quantitative assessment method. With the method of the invention adopted, the problem of lack of correlation analysis in a network security situation assessment process can be solved. According to the method of the invention, monitoring events are taken into risk assessment, and a network security situation assessment model is accurately established, and therefore, the effectiveness and real-time performance of the method of the invention can be enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
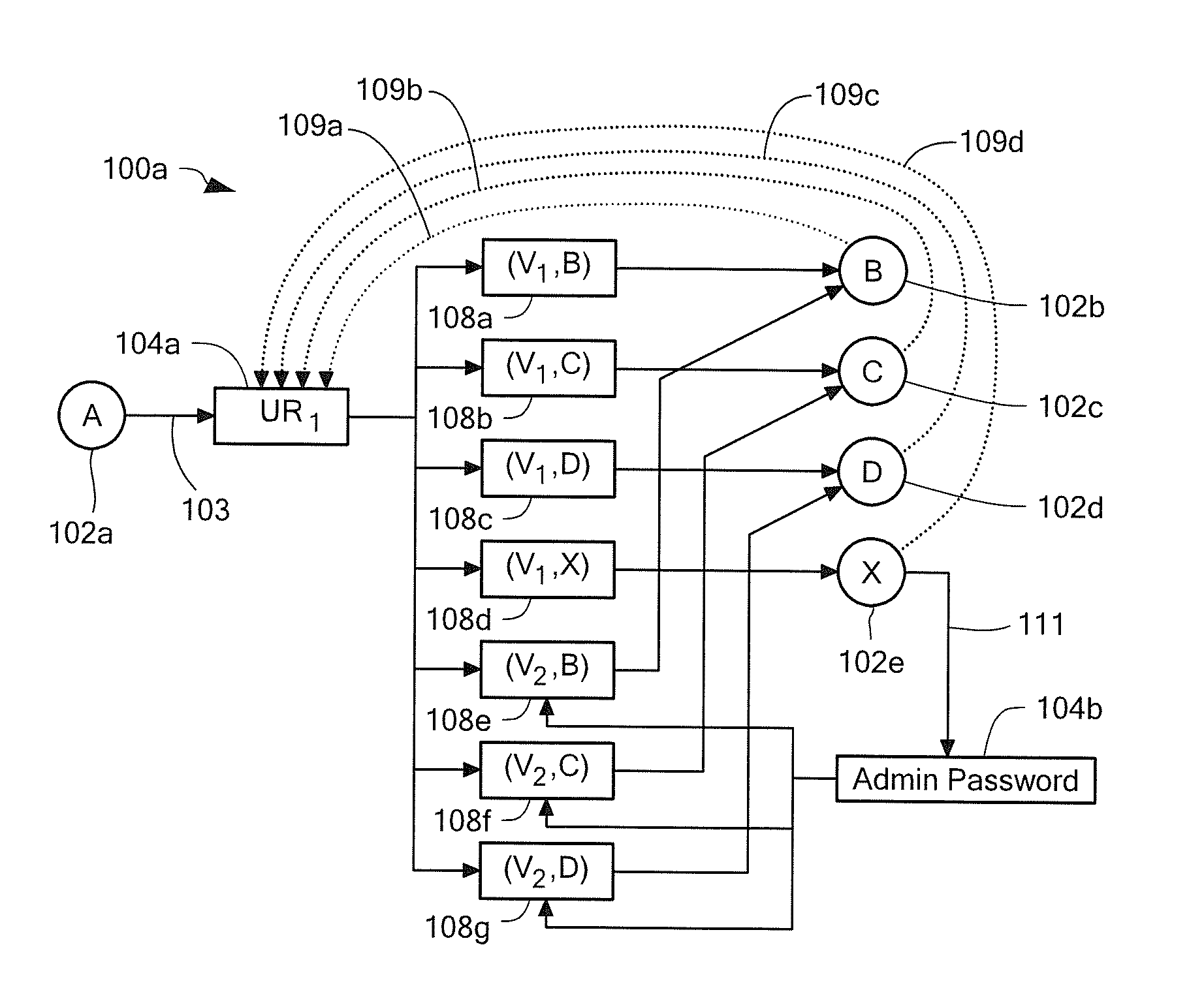
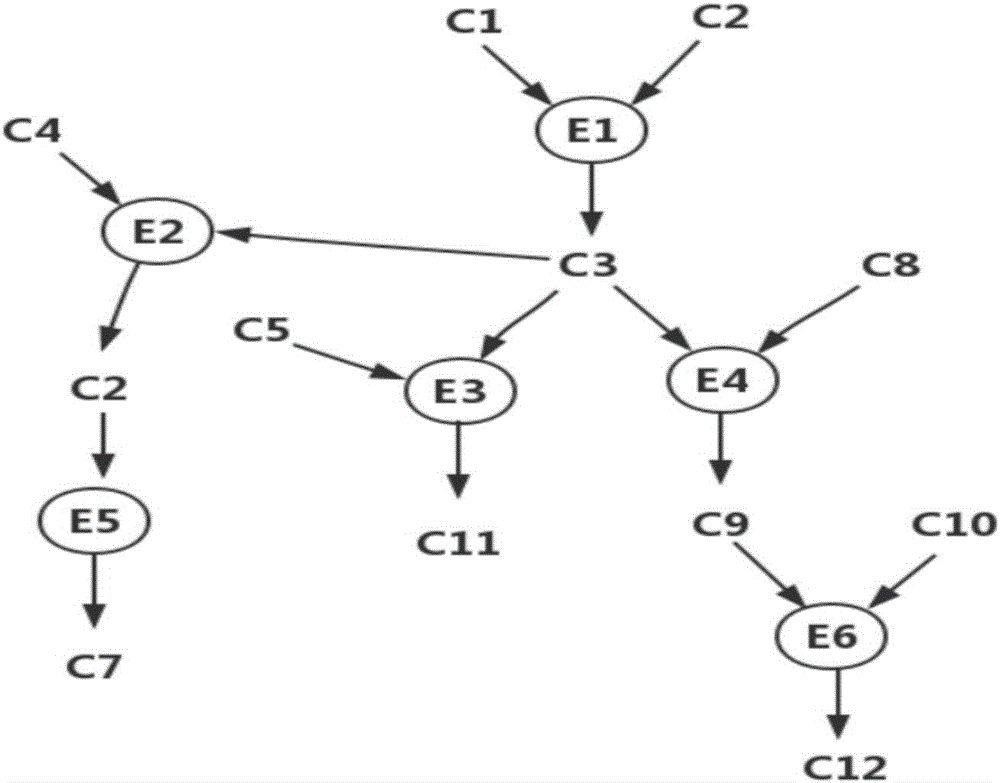
Generating a multiple-prerequisite attack graph
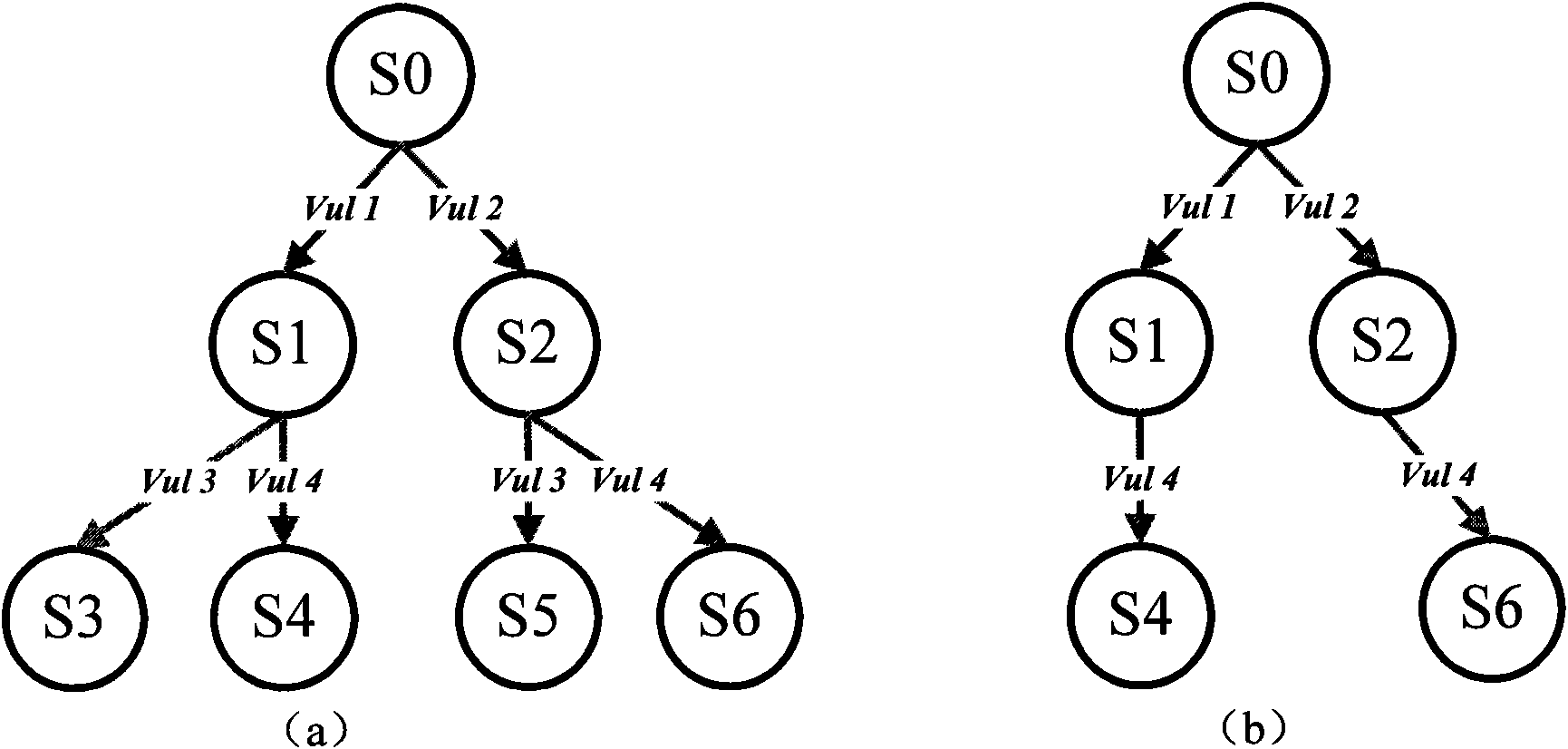
In one aspect, a method to generate an attack graph includes determining if a potential node provides a first precondition equivalent to one of preconditions provided by a group of preexisting nodes on the attack graph. The group of preexisting nodes includes a first state node, a first vulnerability instance node, a first prerequisite node, and a second state node. The method also includes, if the first precondition is equivalent to one of the preconditions provided by the group of preexisting nodes, coupling a current node to a preexisting node providing the precondition equivalent to the first precondition using a first edge and if the first precondition is not equivalent to one of the preconditions provided by the group of preexisting nodes, generating the potential node as a new node on the attack graph and coupling the new node to the current node using a second edge.
Owner:MASSACHUSETTS INST OF TECH
Network security situation awareness model and method based on attack graph
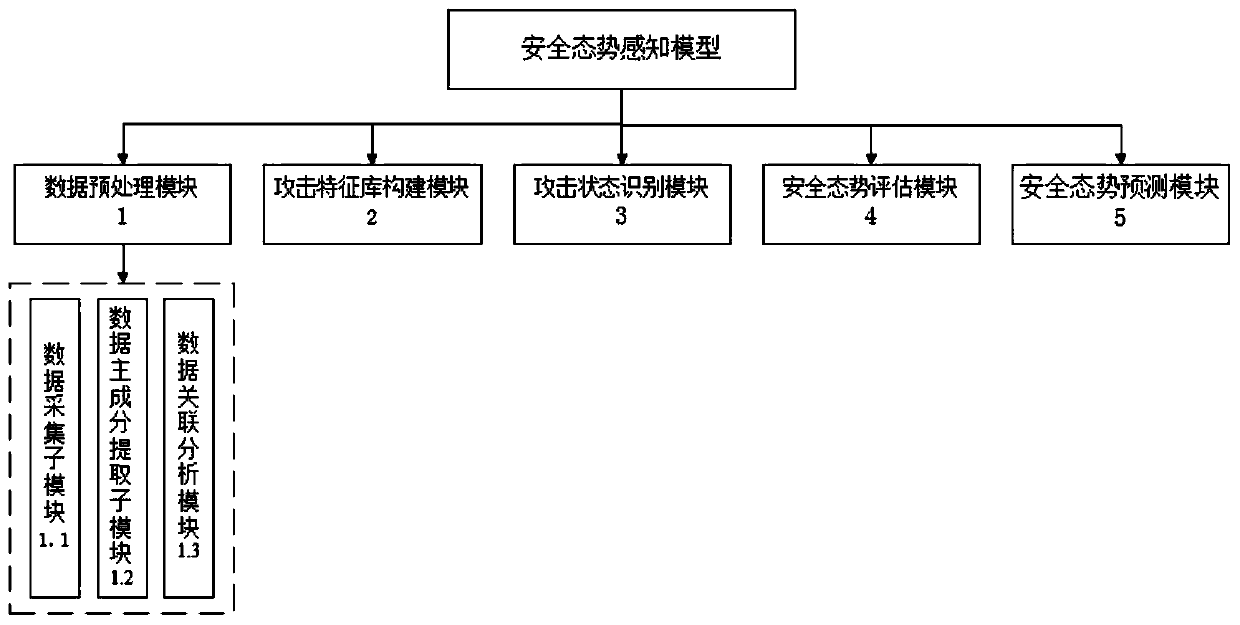
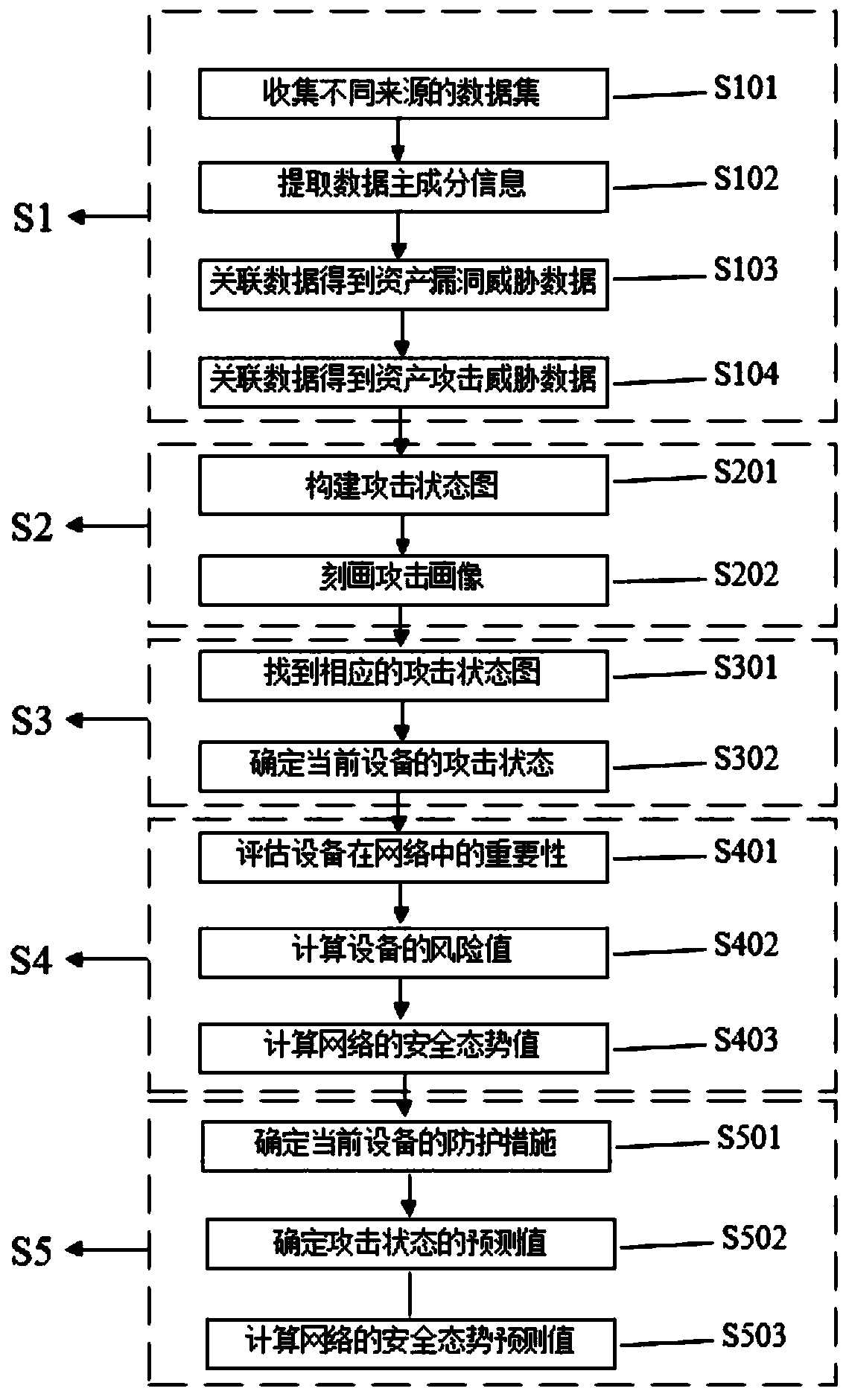
ActiveCN110380896AMining relevanceEliminate redundancyData switching networksData setPredictive function
The invention discloses a network security situation awareness model and method based on an attack graph. The model comprises a data preprocessing module, an attack feature library construction module, an attack state identification module, a security situation evaluation module and a security situation prediction module. The method comprises: firstly, collecting data sets of different sources, and obtaining asset vulnerability threat data and asset attack threat data after preprocessing; further analyzing and training by utilizing the asset attack threat data and the principal component dataof the attack information, and establishing an attack feature library; matching the attack portrait, and determining the attack state of the current equipment; then, calculating a security situation value of the whole network by utilizing the asset attack threat data; and finally, predicting the next attack state through the attack and defense game matrix of the attack state diagram so as to predict the network security situation. A good situation awareness effect and a network security situation evaluation and prediction function are realized, and the model and the method have relatively goodpracticability, high efficiency and expansibility.
Owner:湖北央中巨石信息技术有限公司
Method and device for evaluating system security based on correlation analysis
InactiveCN104348652AAccurate Security AssessmentEfficient Safety AssessmentData switching networksAttackTheoretical computer science
The invention discloses a method and a device for evaluating system security based on correlation analysis. The method comprises the following steps of using an attack graph model to perform the correlation analysis on the network security condition, adopting an attack graph generation algorithm based on breadth-first search, introducing a PageRank calculation model to quantize the weights of state nodes of the attack graph, utilizing the difference of the weights to judge the critical attack nodes of the attack graph, utilizing a depth-first search algorithm to find the critical attack path in the attack graph, finally providing the network security amount based on the attack graph, quantizing the risk value of the critical attack path of the attack graph, and quantizing the security of the whole network.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
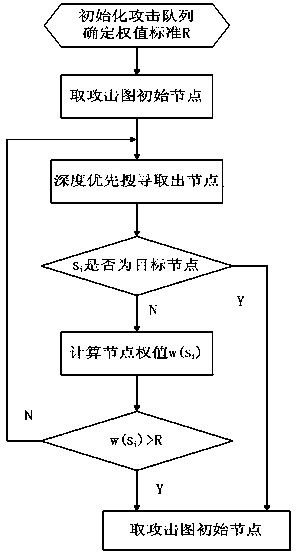
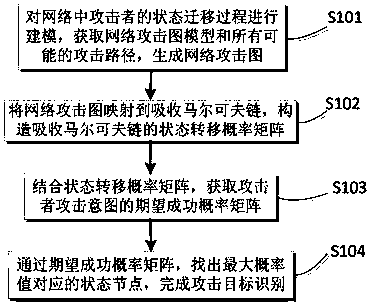
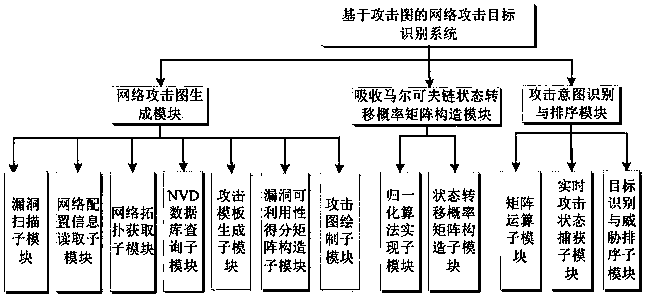
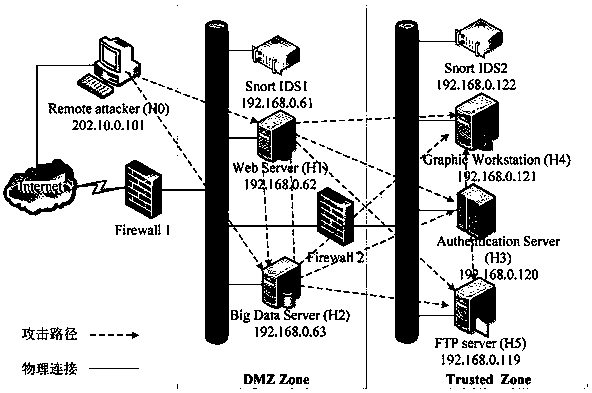
Network attack target identification method and network attack target identification system based on attack graph
ActiveCN108418843AObjective assessmentAccurate assessmentData switching networksNODALComputation complexity
The invention belongs to the technical field of network security, and particularly relates to a network attack target identification method and a network attack target identification system based on an attack graph, wherein the method comprises the following steps: modeling for a state migration process of an attacker in a network, acquiring a network attack graph model and all possible attack paths, and generating a network attack graph; mapping the network attack graph to a Markov chain, and constructing a state transition probability matrix which absorbs the Markov chain; and in combinationwith the state transition probability matrix, acquiring an expectancy for success probability matrix of attack intention of the attacker; through the expectancy for success probability matrix, finding out a state node corresponding to the maximum probability value, and completing attack target identification. With the method and the system provided by the invention, an average probability value of realizing different intentions of the attacker can be evaluated more objectively and accurately, a problem that the conventional method is limited by ideal cumulative probability when evaluating probability of occurrence of attacks is solved, computation complexity is low, operations are simple and convention to execute, and more reliable guidance is provided for assisting a security administrator to make a decision and improving network security performance.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Network security evaluation device based on attack graph adjacent matrix
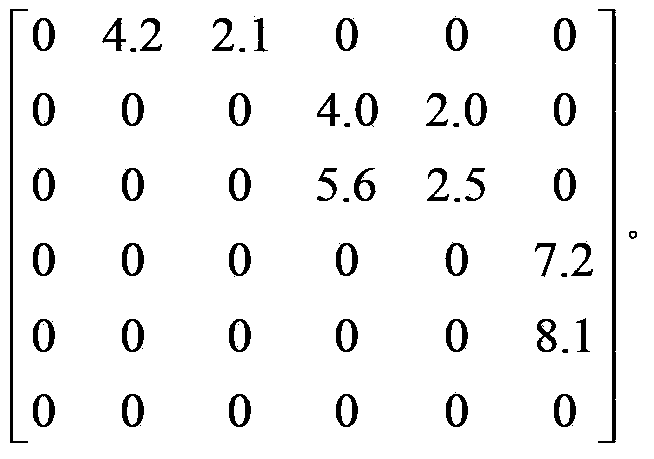
The invention provides a network security evaluation device based on an attack graph adjacent matrix. The network security evaluation device comprises an information collection device, an atom attack graph generation device, a matrix calculation device, a network safety analyzing device and a result appearing device, wherein the information collection device is used for collecting all information in a network; the atom attack graph generation device is used for generating an initial atom attack graph between a main engine pair needed for carrying out subsequent analysis on network safety; the matrix calculation device is used for converting the generated atom attack graph into the corresponding adjacent matrix and is also used for calculating a corresponding iteration matrix of the adjacent matrix through setting iteration times; the network safety analyzing device is used for obtaining information including a key main engine, a key path and the like on the basis of the finally-generated iteration matrix; the result appearing device is used for visually appearing the found key main engine and key path and a network vulnerability index. The network security evaluation device disclosed by the invention is high in efficiency and is suitable for large-scale and high-speed networks. The network security evaluation device can improve the instantaneity of evaluating a target network. The evaluation accuracy rate is high, and the key path and the key main engine can be accurately recognized. The visualization degree is high so that the network security evaluation device is convenient for a manager to check, analyze and maintain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Network security situation evaluating method
InactiveCN101867498AReflect security postureAccurate analysisData switching networksCorrelation analysisAttack graph
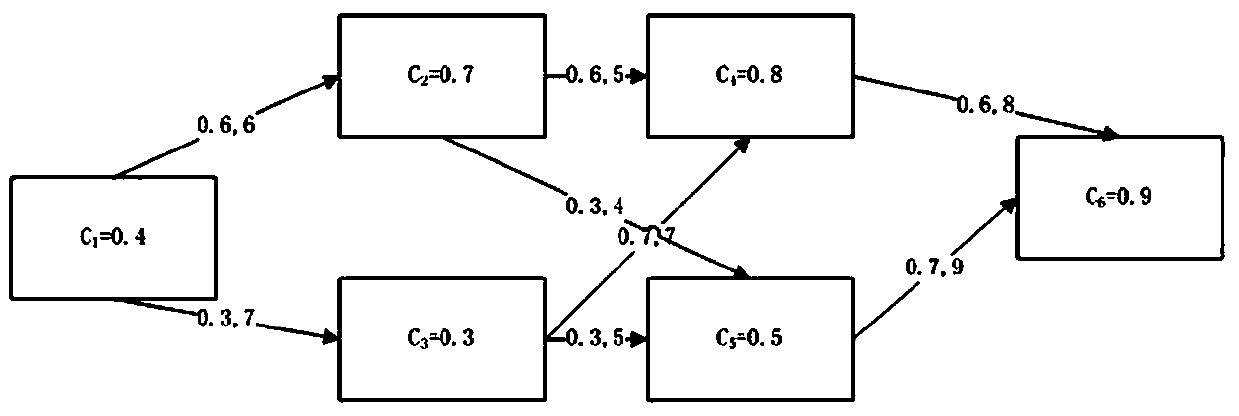
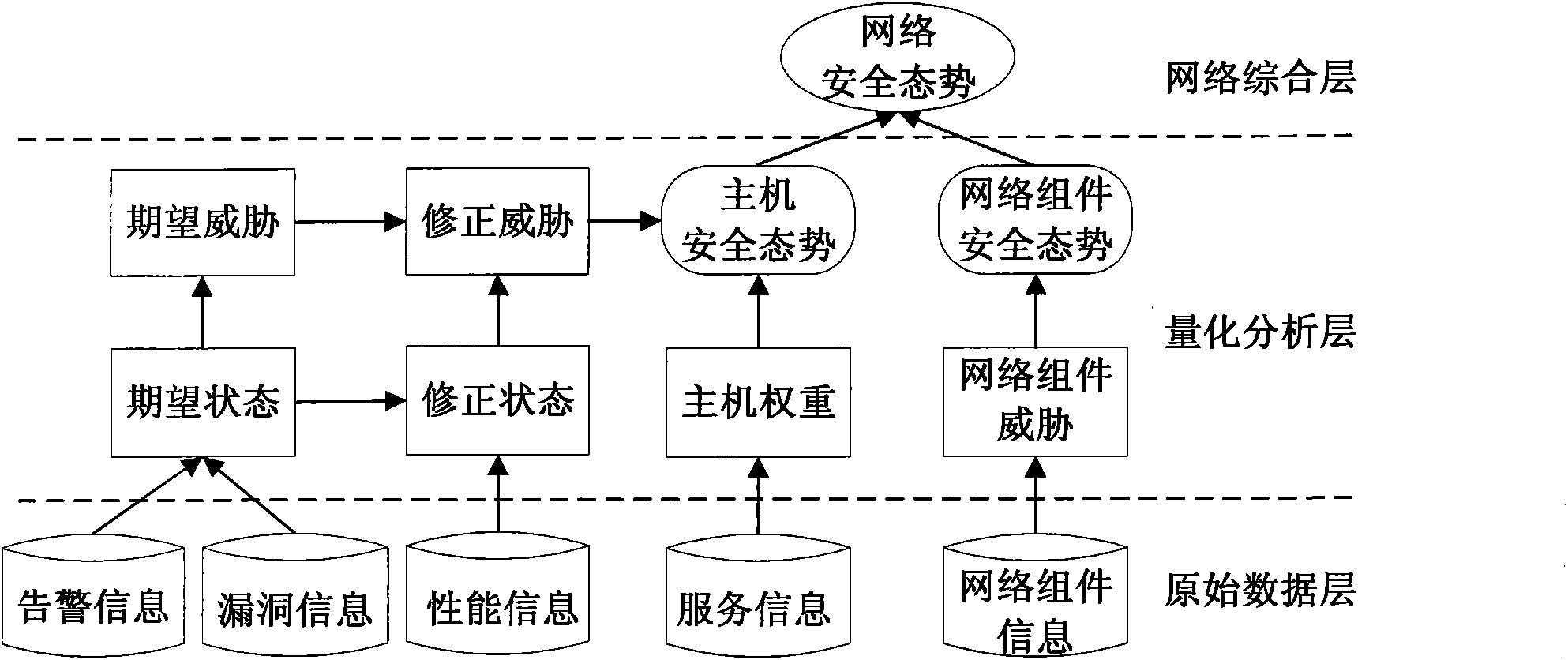
The invention discloses a network security situation evaluating method, and belongs to the technical field of network security. The method comprises the following steps of: 1) performing correlation analysis on input alarm information to obtain a host attack graph; 2) performing association analysis on the host attack graph according to input host vulnerability information to obtain a host expectation state graph; 3) calculating a host threat value by utilizing intrusive expectant threat and the host expectation state graph; 4) calculating a host comprehensive security situation by utilizing weight information of services provided by hosts and threat values of the hosts; 5) calculating a network component comprehensive security situation by utilizing network component performance information and weight values of network components; and 6) performing weighted calculation by utilizing the host comprehensive security situation and the network component comprehensive security situation to obtain a network security situation. The method can more accurately analyze the actual influence of attacks on the network hosts and the network components, analyzes threat caused by unknown attacks, and reflects the network security situation more accurately compared with the traditional method.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
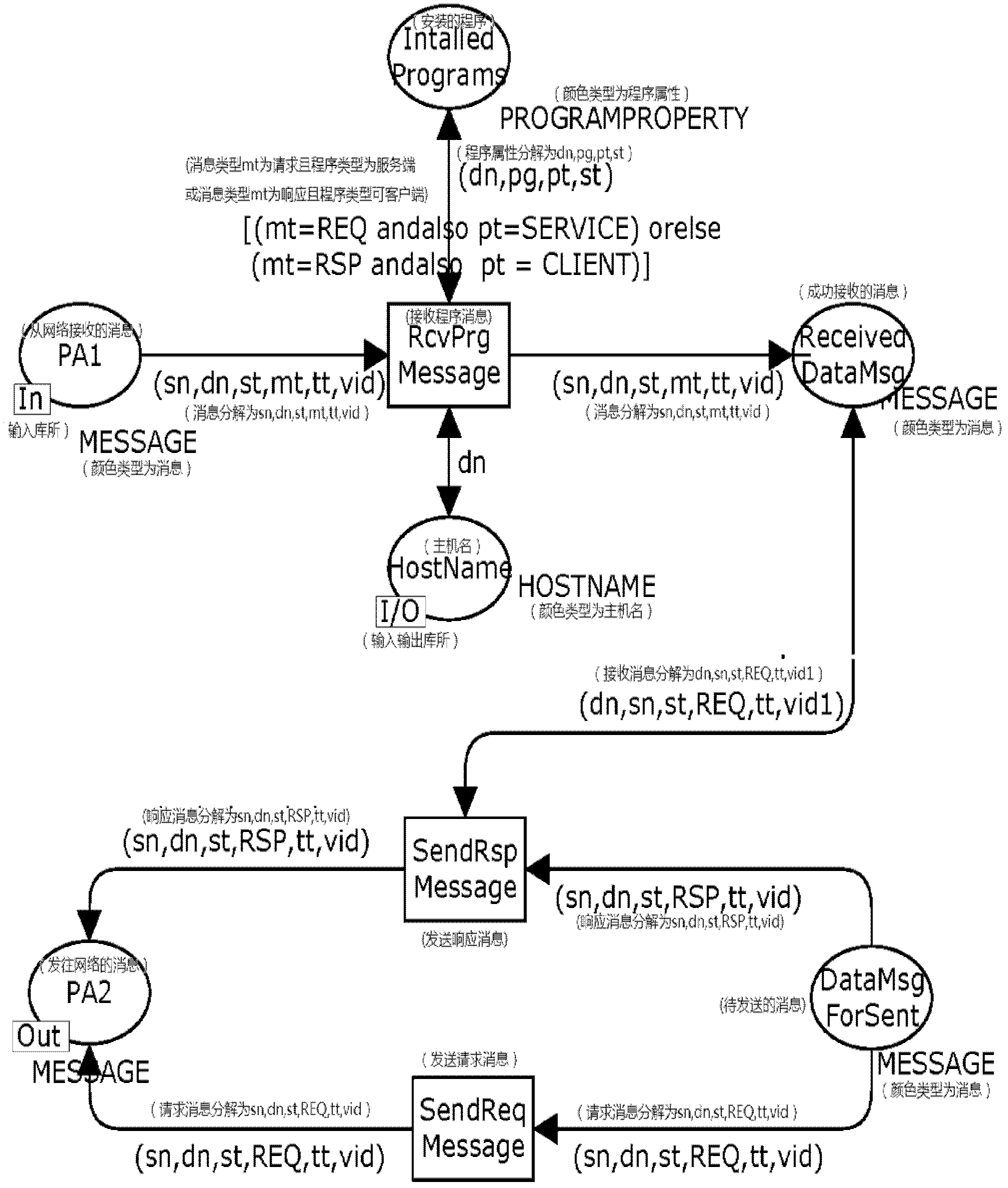
Method for identifying key attack path in service system
InactiveCN102447695AAchieving Unified ModelingAttack graph simplificationTransmissionComputation complexityDirected graph
The invention discloses a method for identifying the key attack path in a service system and belongs to the technical field of network information safety. The method comprising the steps as follows: 1, synthesizing data stream of the service system, vulnerability of the system, security threat, security measures and other factors to establish an attack model of the service system; 2, analyzing the established attack model and building a vulnerability exploitation map comprising all attack paths based on the model analysis result; and 3, converting the vulnerability exploitation map into a standard directed graph and analyzing the standard directed graph through a shortest path method to identify the key attack path that an attacker can reach all targets. The method has the advantages that the expandability is better than that of a traditional attack map, and the computation complexity of identification of the key attack path can be reduced effectively.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Attack path analysis method based on hierarchical attack graph
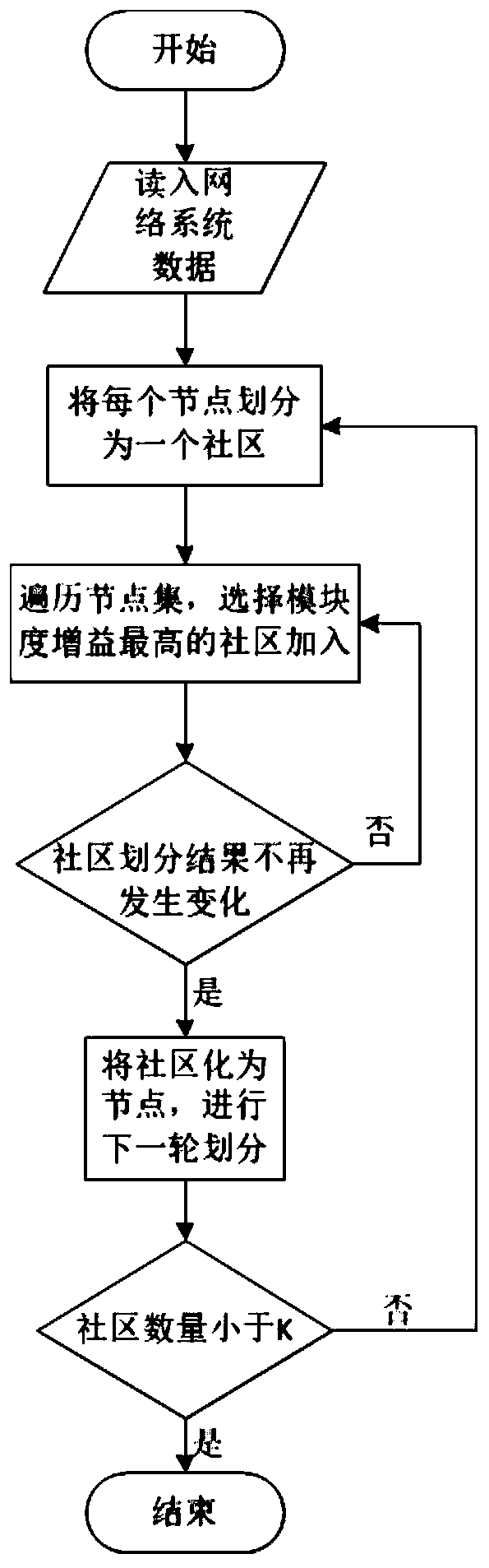
ActiveCN110138764ADownsizingImprove analysis efficiencyPlatform integrity maintainanceData switching networksPath generationAttack graph
The invention belongs to the technical field of network security, and discloses an attack path analysis method based on a hierarchical attack graph. Firstly, dividing an original network into a plurality of logic subnets through a community discovery algorithm, wherein the logic subnets and connection relations thereof form a network logic structure; generating two layers of attack graphs based onthe network logic structure and the network basic information; and finally, reducing an attack path on the two layers of attack graphs by utilizing monotonicity of attack behaviors. The method comprises the following specific steps: (1) realizing community discovery; (2) establishing a hierarchical attack graph model; (3) generating an attack path; (4) analyzing the attack path to provide a defense strategy. According to the attack path analysis method, unreasonable attack path generation is avoided from the perspective of attackers, the real-time performance of attack path analysis is effectively improved, and the problem that an existing attack path analysis method is poor in real-time performance when the network scale is large and the vulnerability is high is solved.
Owner:山西佳瑞通科技有限公司
Method and system for detecting network security
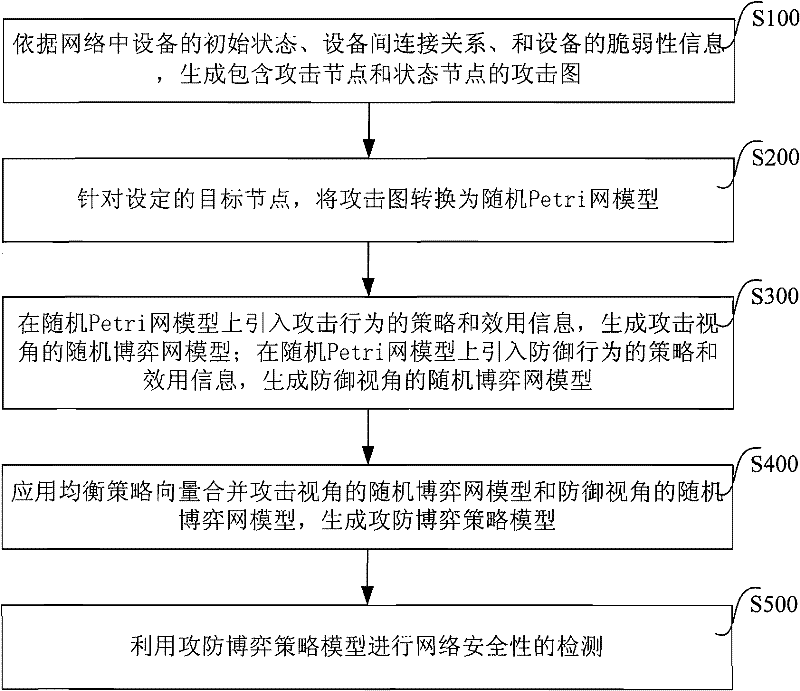
ActiveCN102413003AEnhanced description abilityAccurate descriptionData switching networksAttack graphNetwork security policy
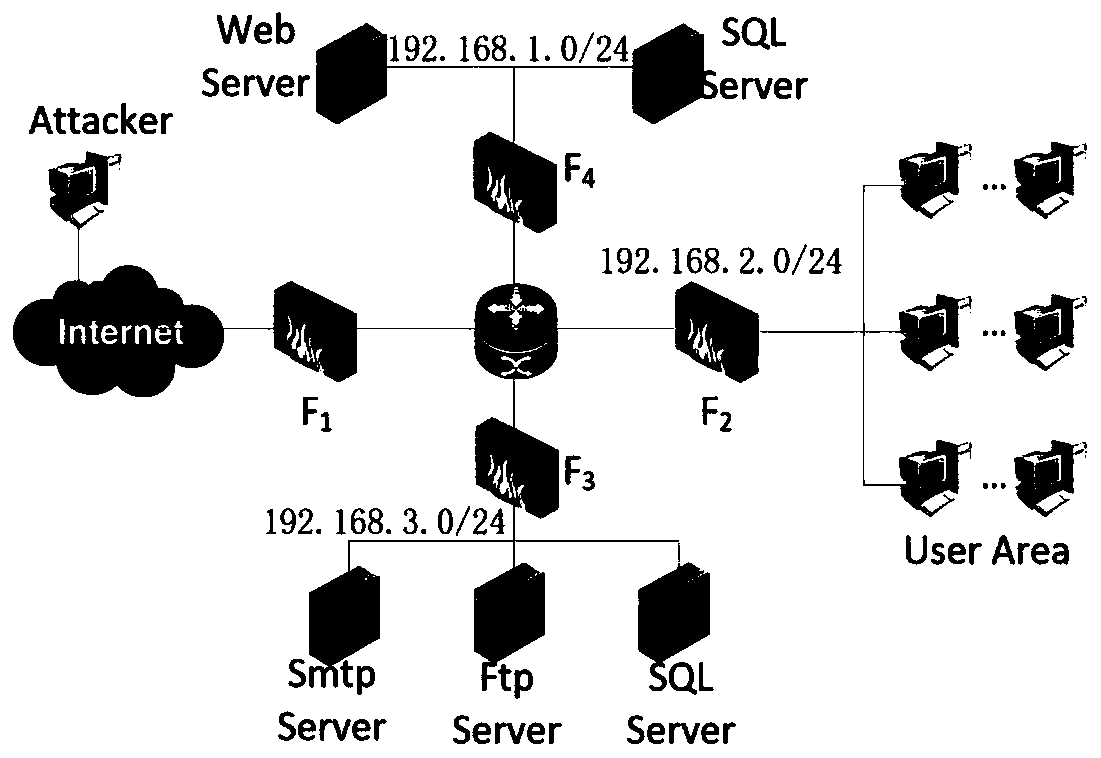
The invention discloses a method and a system for detecting network security. The method comprises the following steps: 1) according to the initial state of equipment in a network, connection relationships among different pieces of equipment and the vulnerability information of the equipment, generating an attack graph comprising an attack node and a state node; 2) by aiming at a set target node, converting the attack graph into a stochastic Petri net model; 3) introducing the strategy and utility information of an attack behavior on the stochastic Petri net model, generating the stochastic game net model of an attack visual angle, and introducing the strategy and utility information of a defensive behavior on the stochastic Petri net model to generate the stochastic game net model of a defensive visual angle; 4) combining the stochastic game net model of the attack visual angle with the stochastic game net model of the defensive visual angle to generate an attack-defense game strategy model; and 5) detecting network security by the attack-defense game strategy model. According to the method and the system, the accuracy for detecting the network security can be improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
APT attack scene mining method based on intrusion kill chain and fuzzy clustering
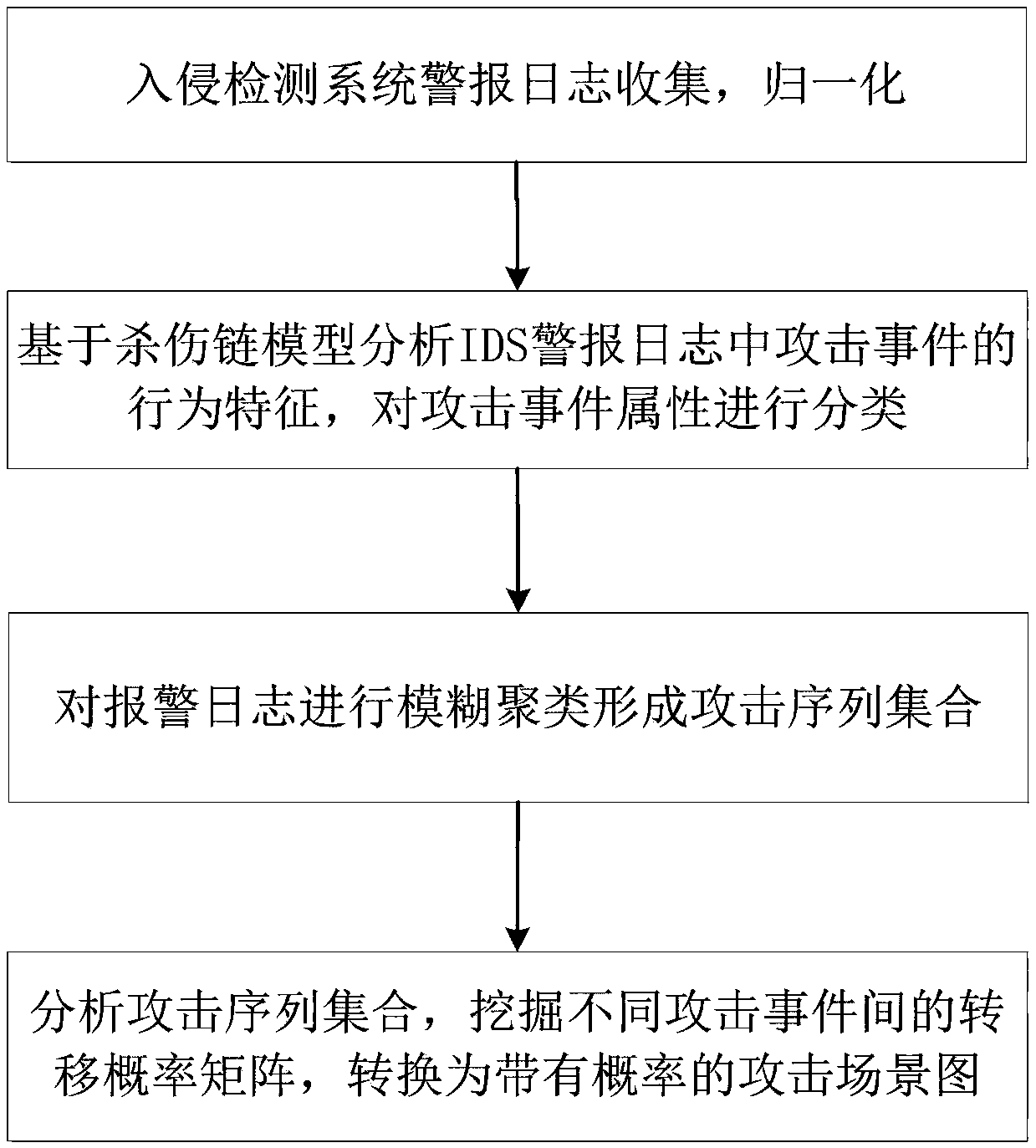
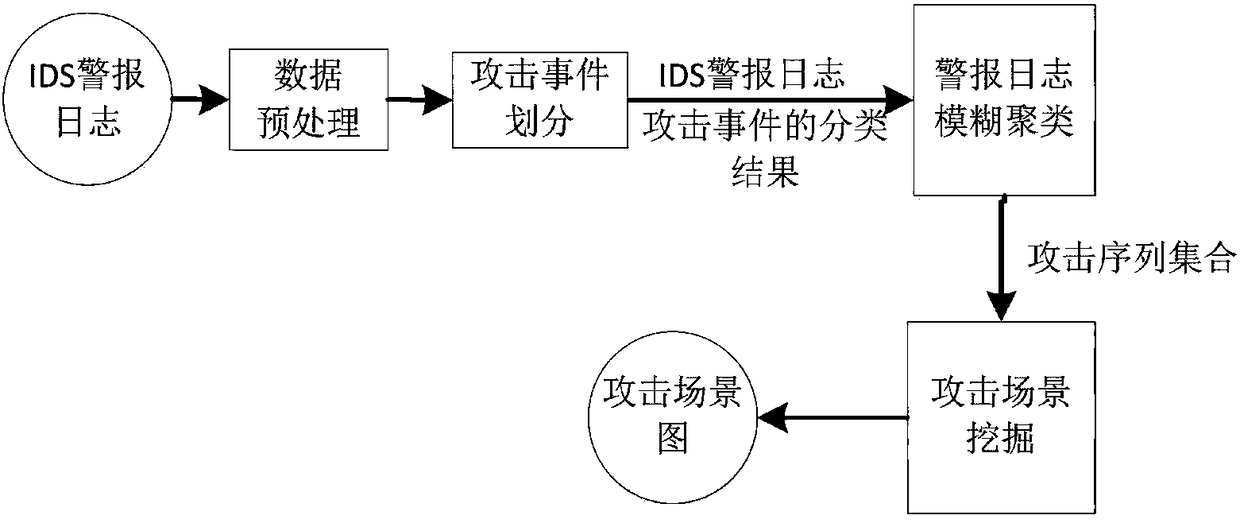
ActiveCN108076040AImprove accuracyImprove relevanceTransmissionDirected graphTransition probability matrix
The invention discloses an APT attack scene mining method based on an intrusion kill chain and fuzzy clustering. The method can be used for mining an APT attack scene in an intrusion detection system(IDS) log. The method comprises the steps of collecting and normalizing alert of the intrusion detection system; analyzing behavior characteristics of attack events in alert logs based on an intrusionkill chain model and classifying the attack events; carrying out fuzzy clustering on the alert logs to form an attack sequence set; and analyzing the attack sequence set, deleting incomplete sequences, converting each attack sequence into a directed graph, mining a transition probability matrix among different attack events, and converting the transition probability matrix into an APT attack scene graph with the probability. According to the method, the APT attack graph in true alert can be mined, and the theoretical foundation for APT detection and defense is provided.
Owner:BEIJING UNIV OF POSTS & TELECOMM
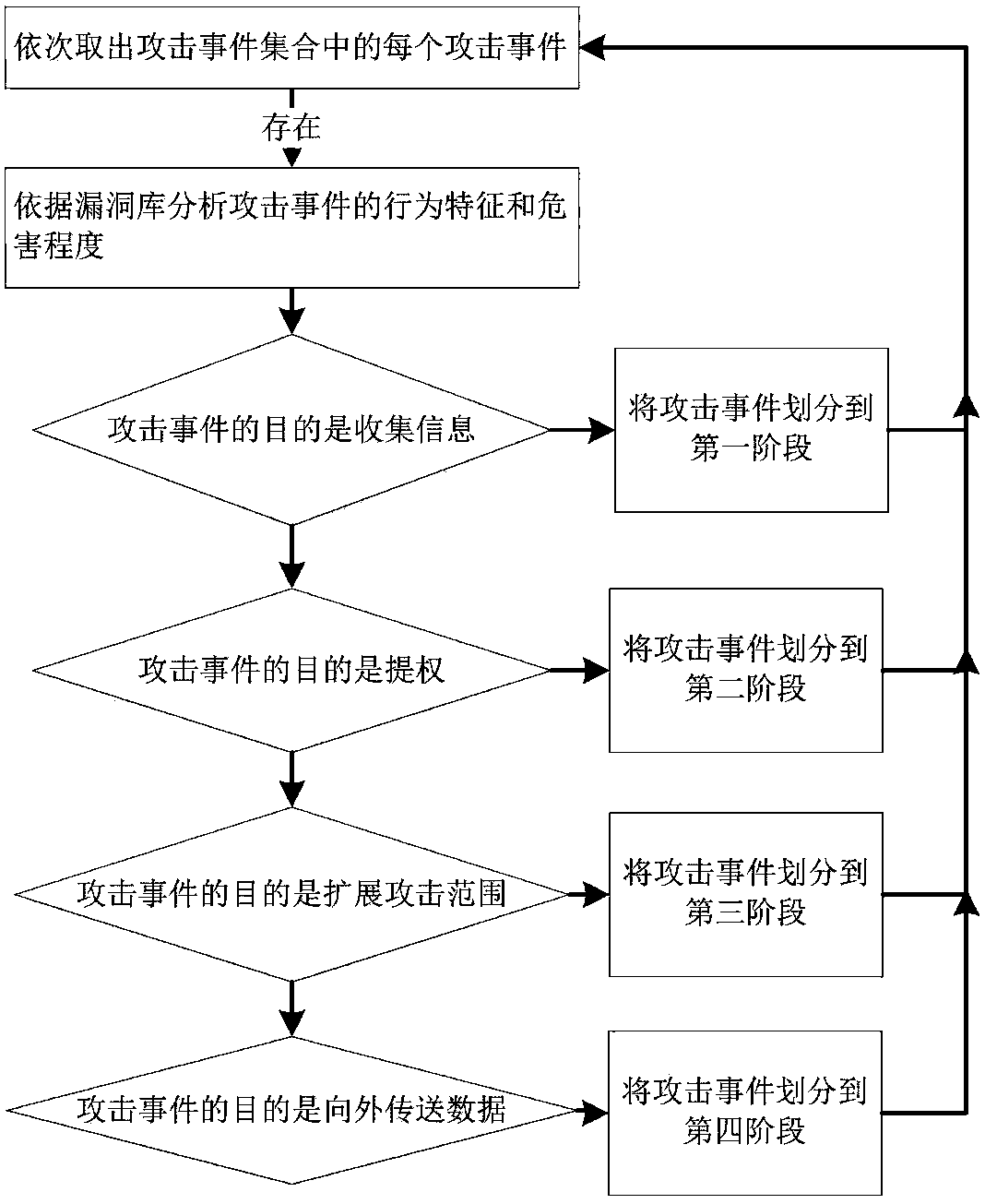
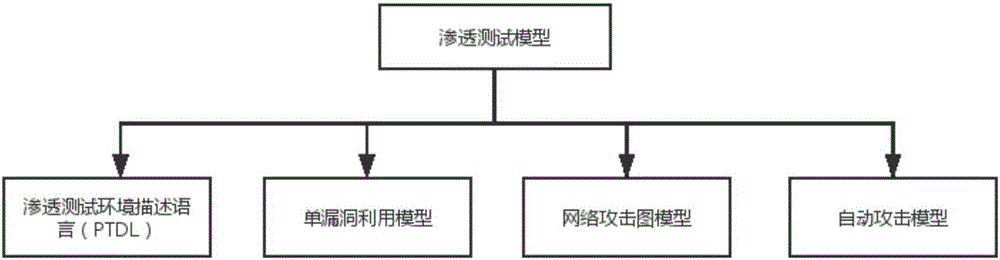
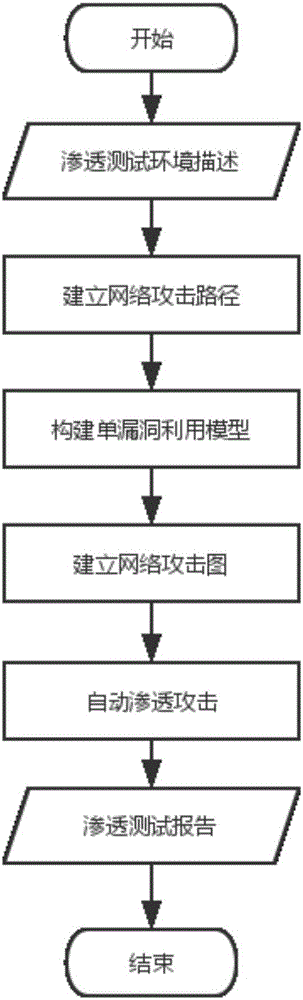
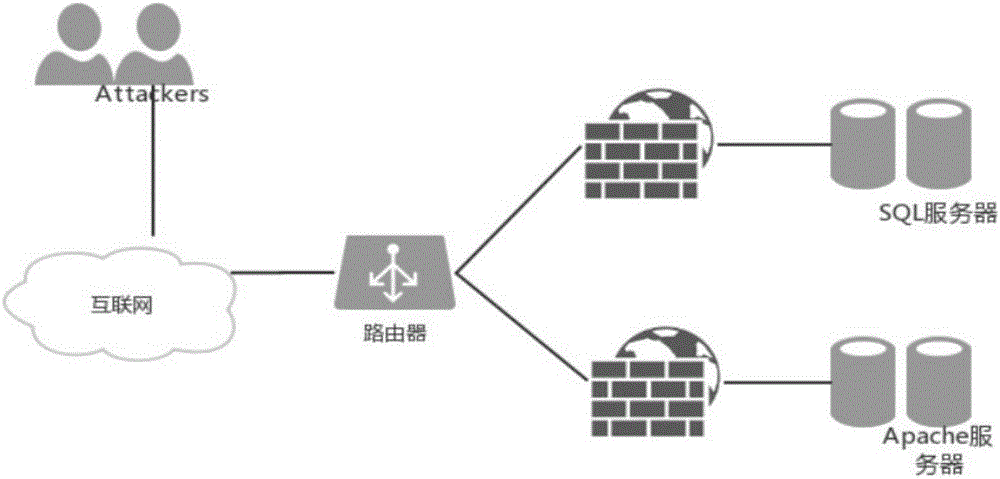
Network penetration testing method
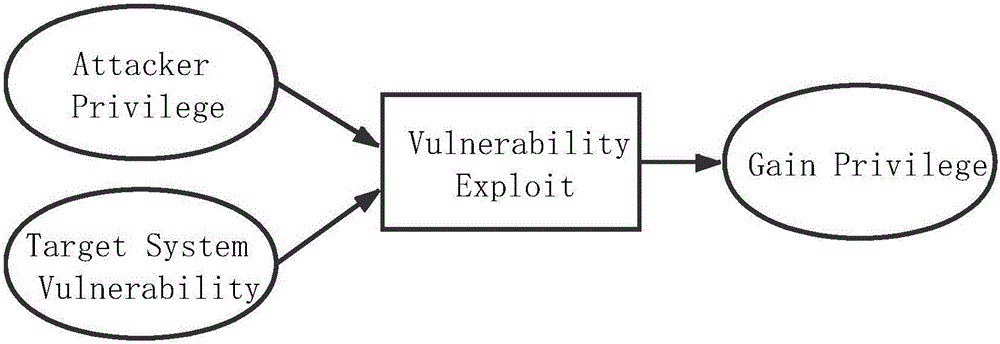
The invention provides a network penetration testing method. The method comprises the steps that 1, a network attack path is established according to the accessibility among different network segments on the basis of an existing network topology and vulnerability information list; 2, the network attack path is traversed, every two adjacent network segments belong to a group, and a single-vulnerability exploitation model (SVEM) is constructed for each vulnerability of an attack target by taking one host in the previous network segment as an attacker and taking one host in the latter network segment as the attack target; 3, the SVEM is synthesized on the basis of a backward search algorithm, and an attack graph from the attaching host to the target host is constructed; 4, all possible attack paths are decomposed according to the attack graph, and attacking is conducted for vulnerabilities in all the paths to obtain an effective attack path. According to the network penetration testing method, the attack path can be automatically planned according to a network environment, an automatic penetration attacking scheme can be achieved, penetration testing is rapidly and efficiently conducted on a target system, and a large quantity of manpower and material resources are saved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
System for generating assaulting chart facing network safety alarm incident
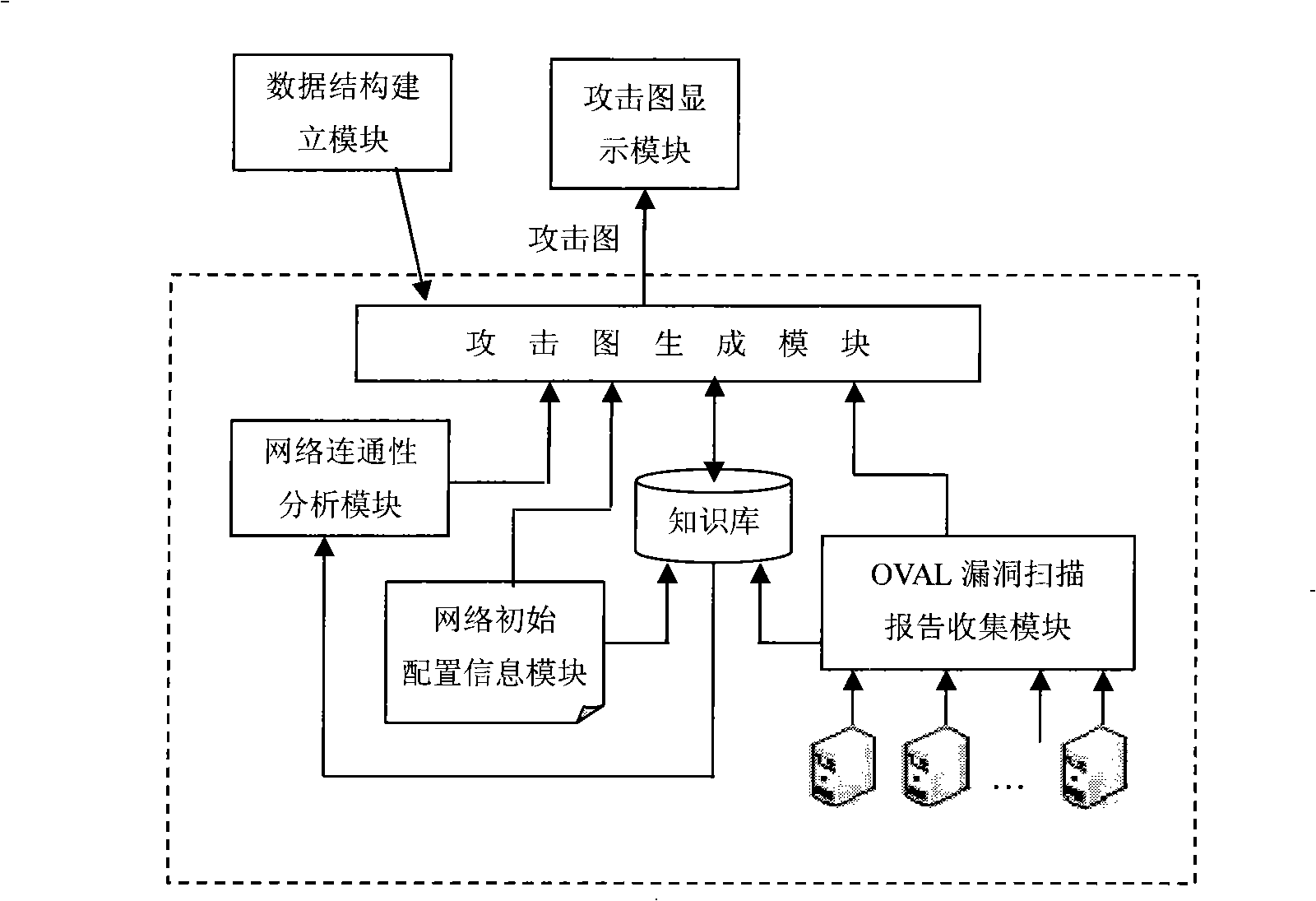
InactiveCN101282332AEasy to implementNetwork connectionsSpecial data processing applicationsUser inputComputer module
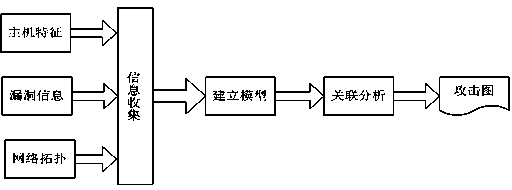
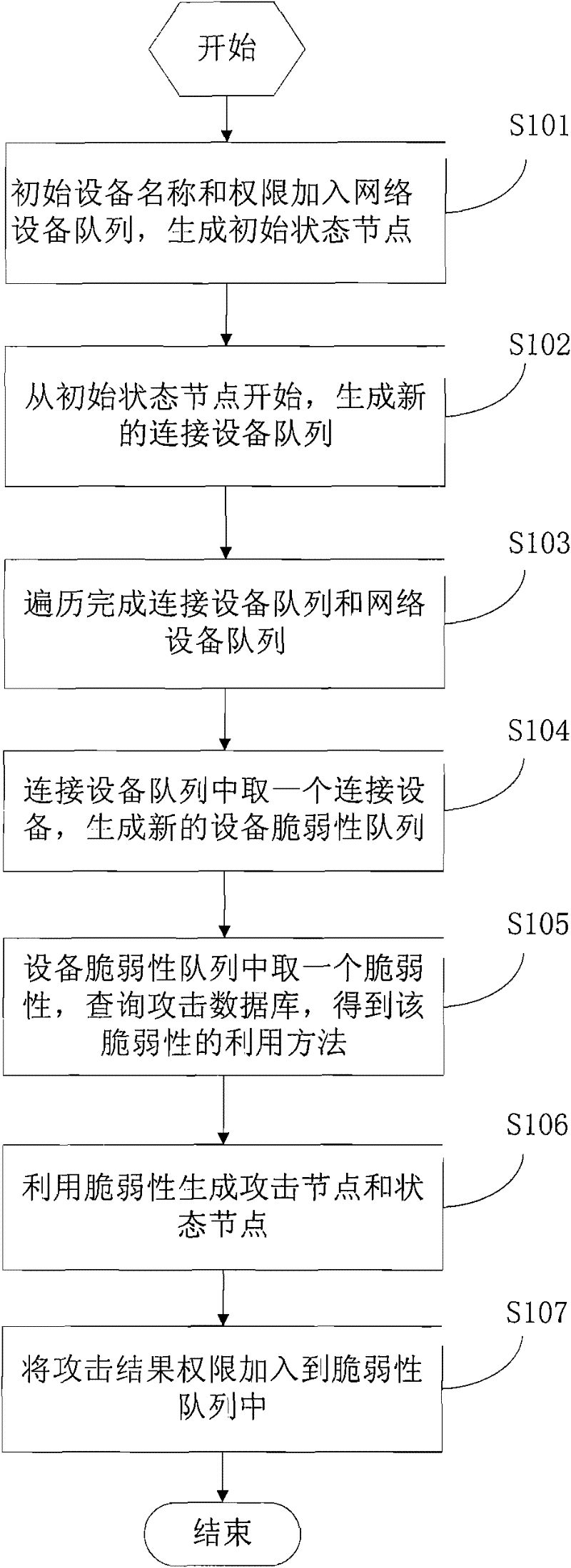
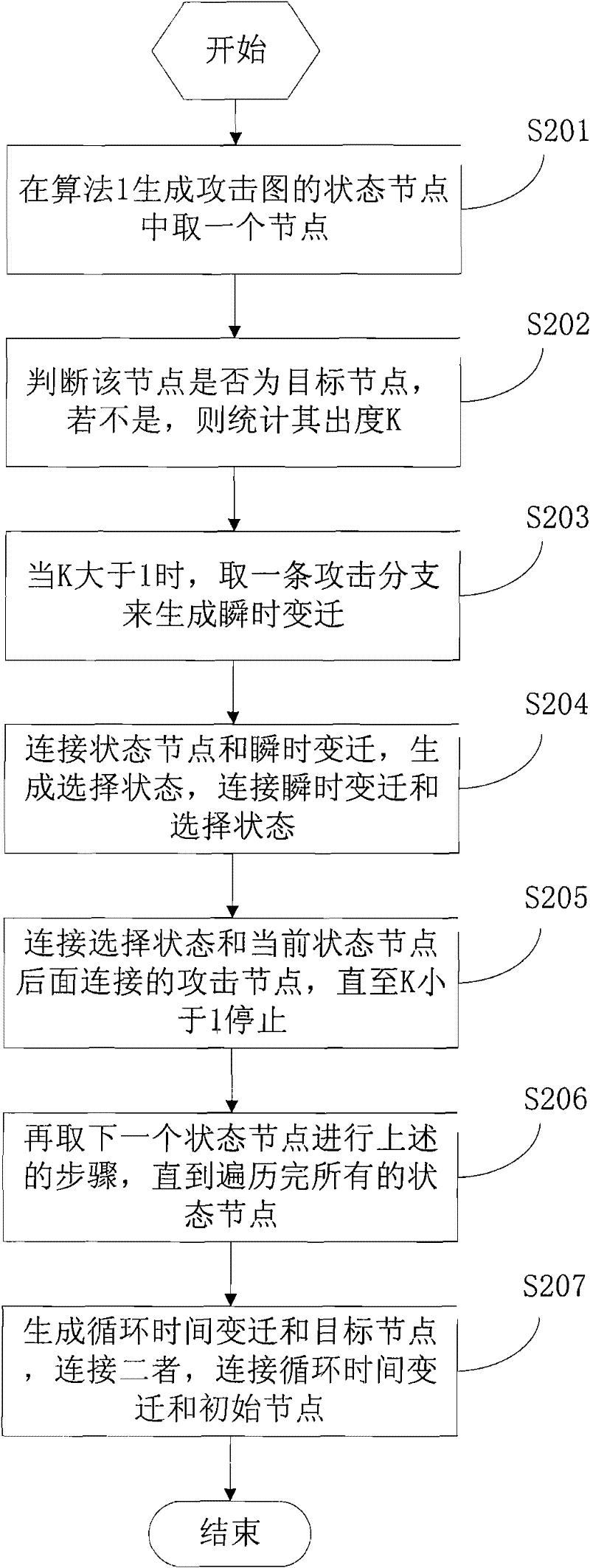
An attack graph generation system facing to network security alarm association in the field of computer network, in the present invention, the network initial configuration information module receives the network topological structure, gateway filtering rule input by the users; OVAL vulnerability scanning report collecting module collects the vulnerabilities in all the apparatuses in the network; the network connectivity analyzing module transmits connectivity between ant two apparatuses to the attack graph generation module; the data structure establishing model respectively establishes a kind of data to describe aiming at the attacker state, apparatus state, implantation vulnerability behavior, atom attack action, system state in the network; the knowledge base stores the network topological structure, gateway filtering rule, vulnerability to transfer by the attack graph generation module; the attack graph generation module transfers the information in the knowledge base, generates the network attack graph and transmits the generated attack graph to the attack graph displaying module to visually display to the user; the system work complexity of the present invention is O(N<5>) and is easy to realize the project.
Owner:SHANGHAI JIAO TONG UNIV +1
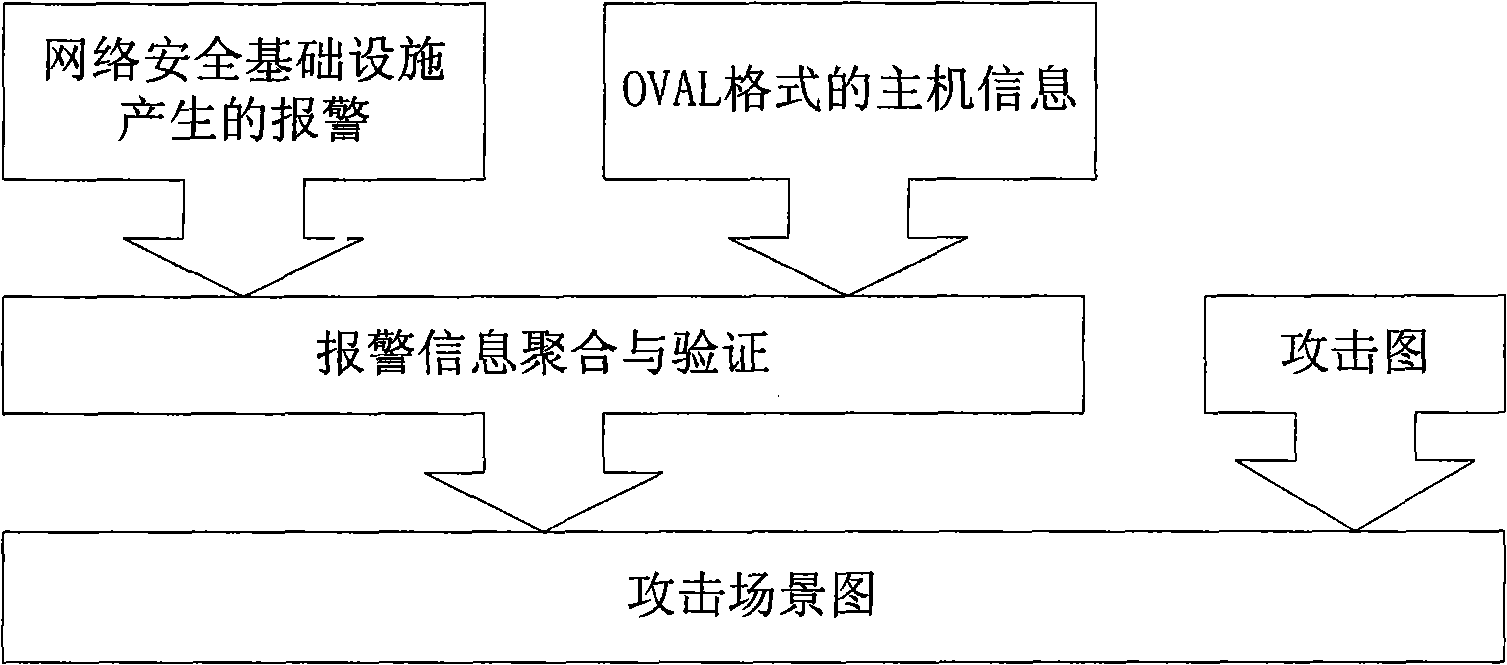
Network attack detection method
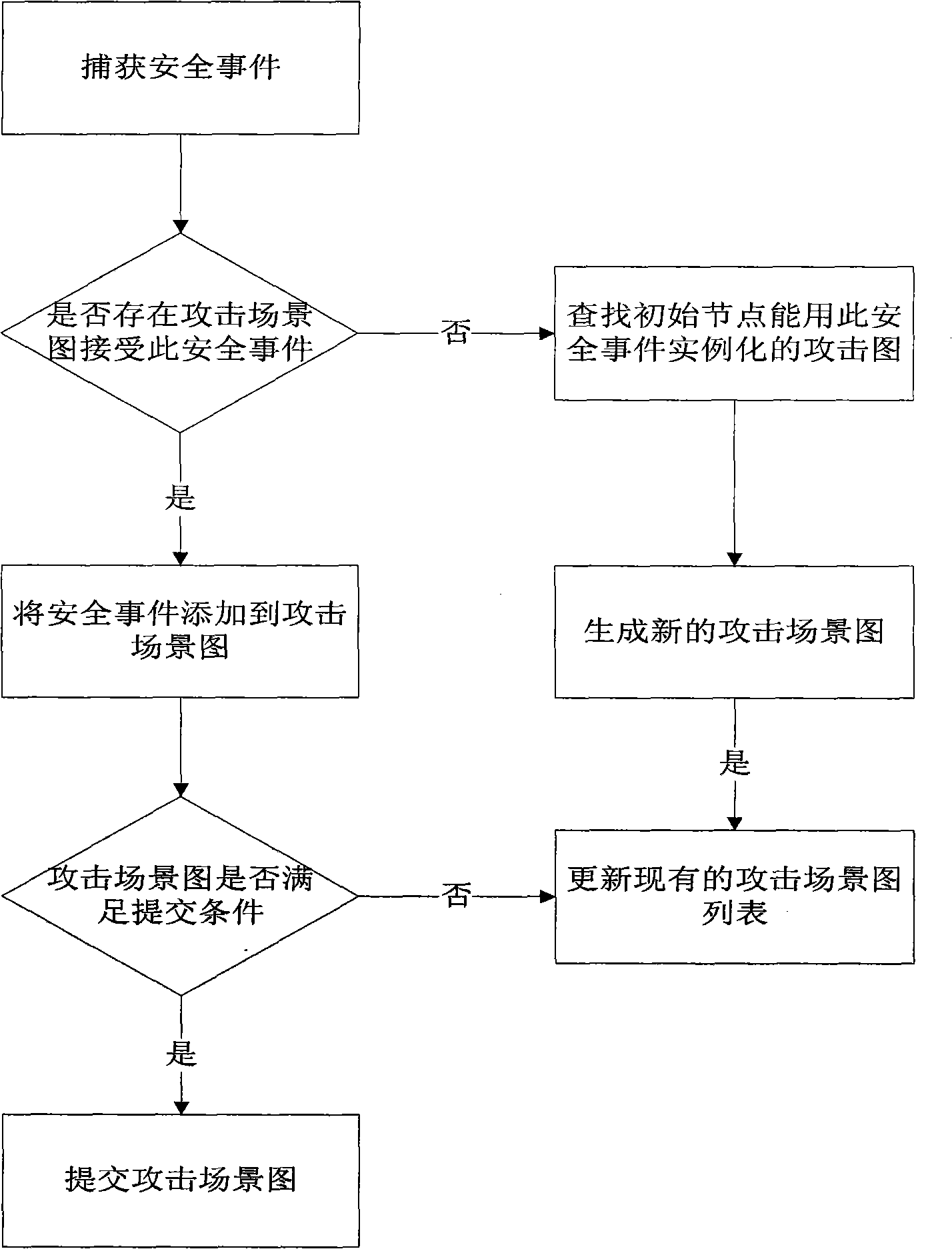
The invention discloses a network attack detection method, which belongs to the technical field of the network safety, and comprises the following steps: 1) alarm which is obtained from a network safety infrastructure is converted to an alarm in a uniform form; 2) the status information of a host computer which is associated to the alarm action is obtained, the alarm association action is judged whether to take effect according to the status information, and when one alarm association action is invalid, the alarm is abandoned, otherwise the alarm is marked as valid; and when the status information of the host computer which is associated to the alarm action cannot be obtained, the alarm is marked as undetermined; 3) valid alarm and undetermined alarm are aggregated to generate a safety event; 4) the attack graph is instantiated by the generated safety event to obtain an attack scene graph; 5) and the attach scene graph which satisfies the conditions is outputted, and the attack type is determined. The method effectively reduces the expenditure of the attack graph algorithm, and is free from reducing the timeliness of the discovering process while improving the network attack accuracy.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Lateral movement detection
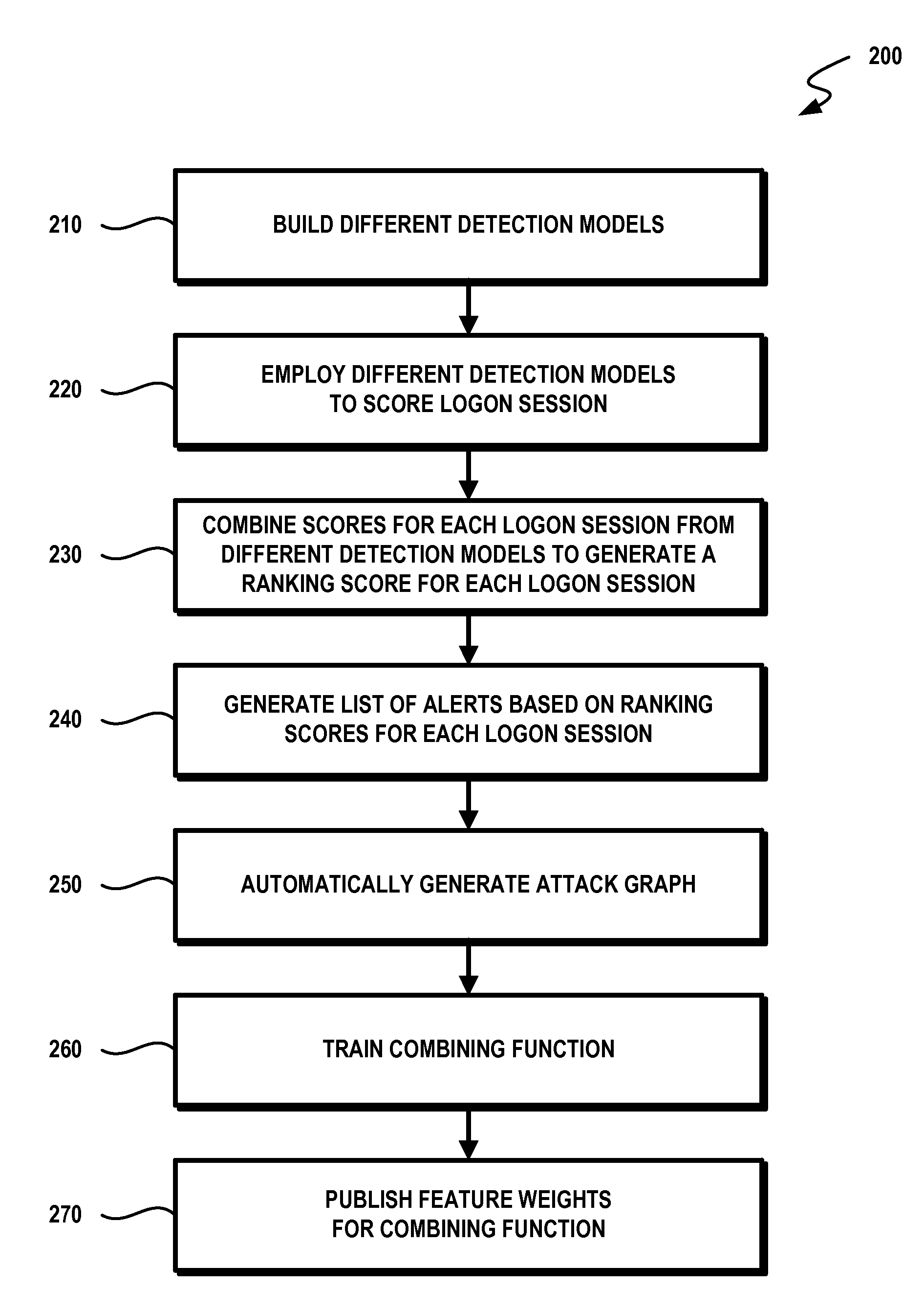
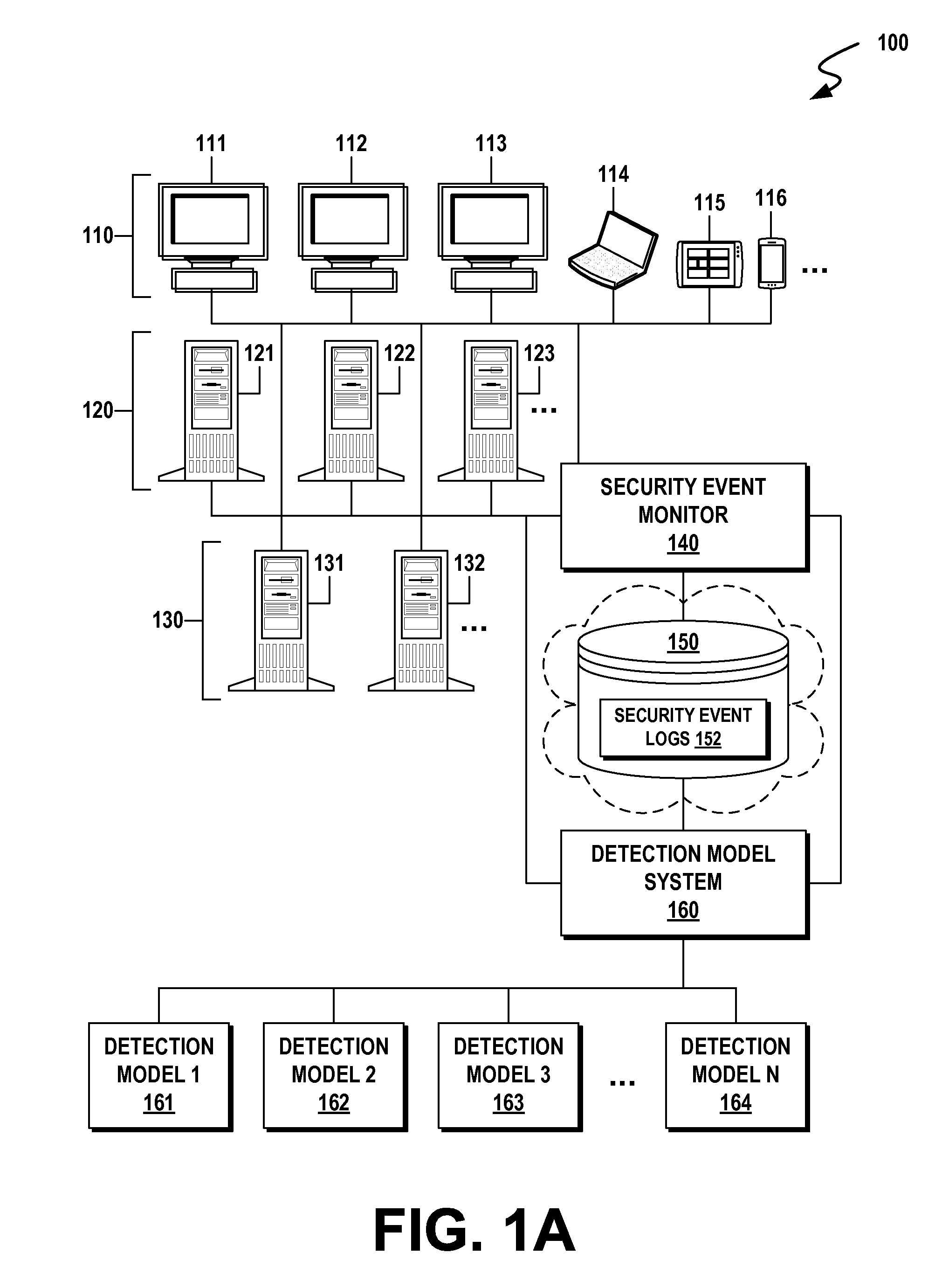
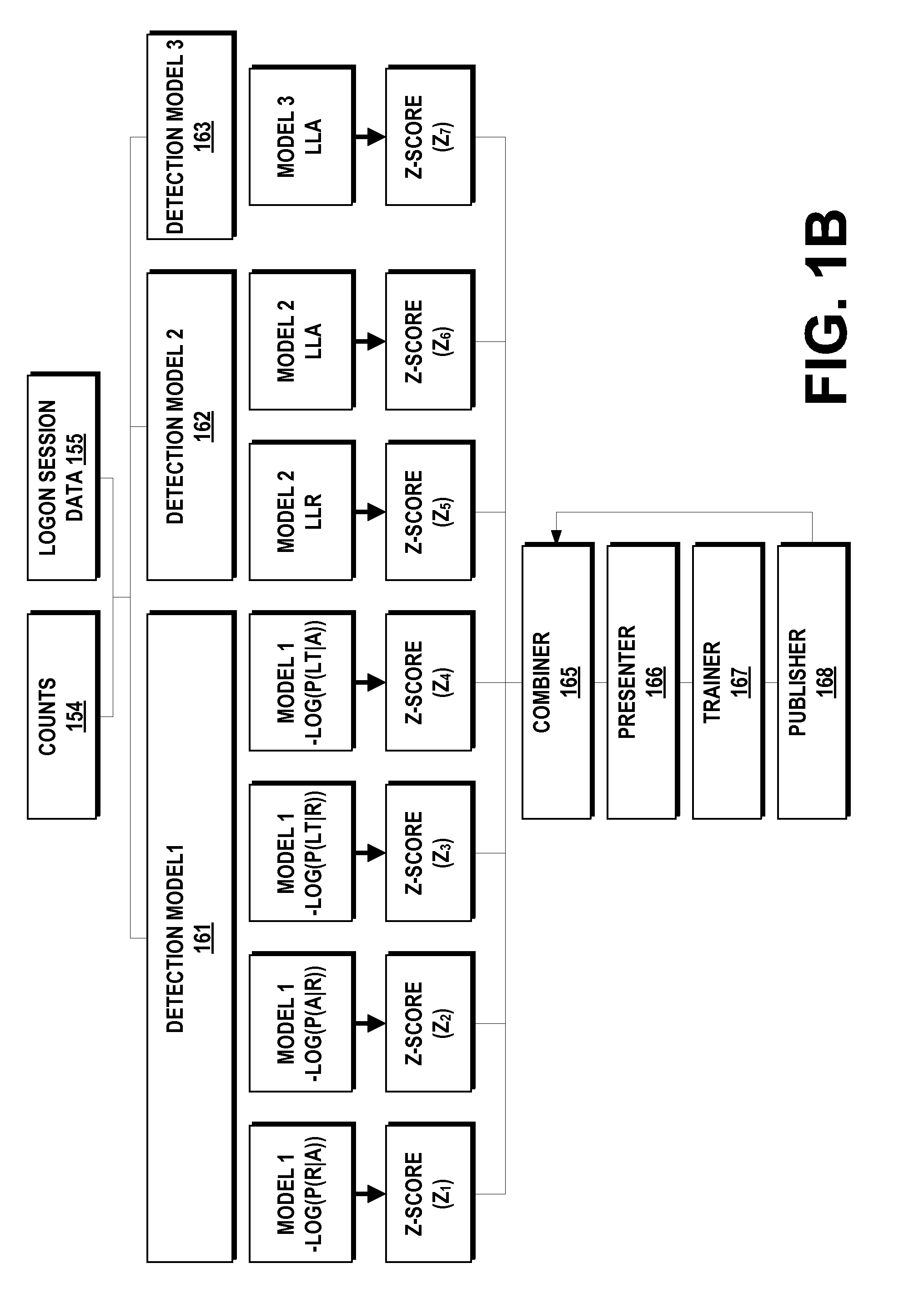
Lateral movement detection may be performed by employing different detection models to score logon sessions. The different detection models may be implemented by and / or utilize counts computed from historical security event data. The different detection models may include probabilistic intrusion detection models for detecting compromised behavior based on logon behavior, a sequence of security events observed during a logon session, inter-event time between security events observed during a logon session, and / or an attempt to logon using explicit credentials. Scores for each logon session that are output by the different detection models may be combined to generate a ranking score for each logon session. A list of ranked alerts may be generated based on the ranking score for each logon session to identify compromised authorized accounts and / or compromised machines. An attack graph may be automatically generated based on compromised account-machine pairs to visually display probable paths of an attacker.
Owner:MICROSOFT TECH LICENSING LLC
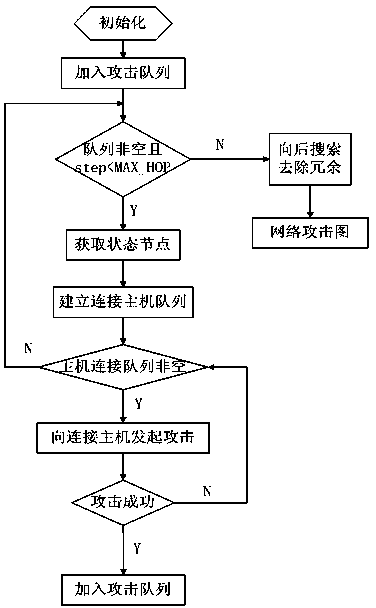
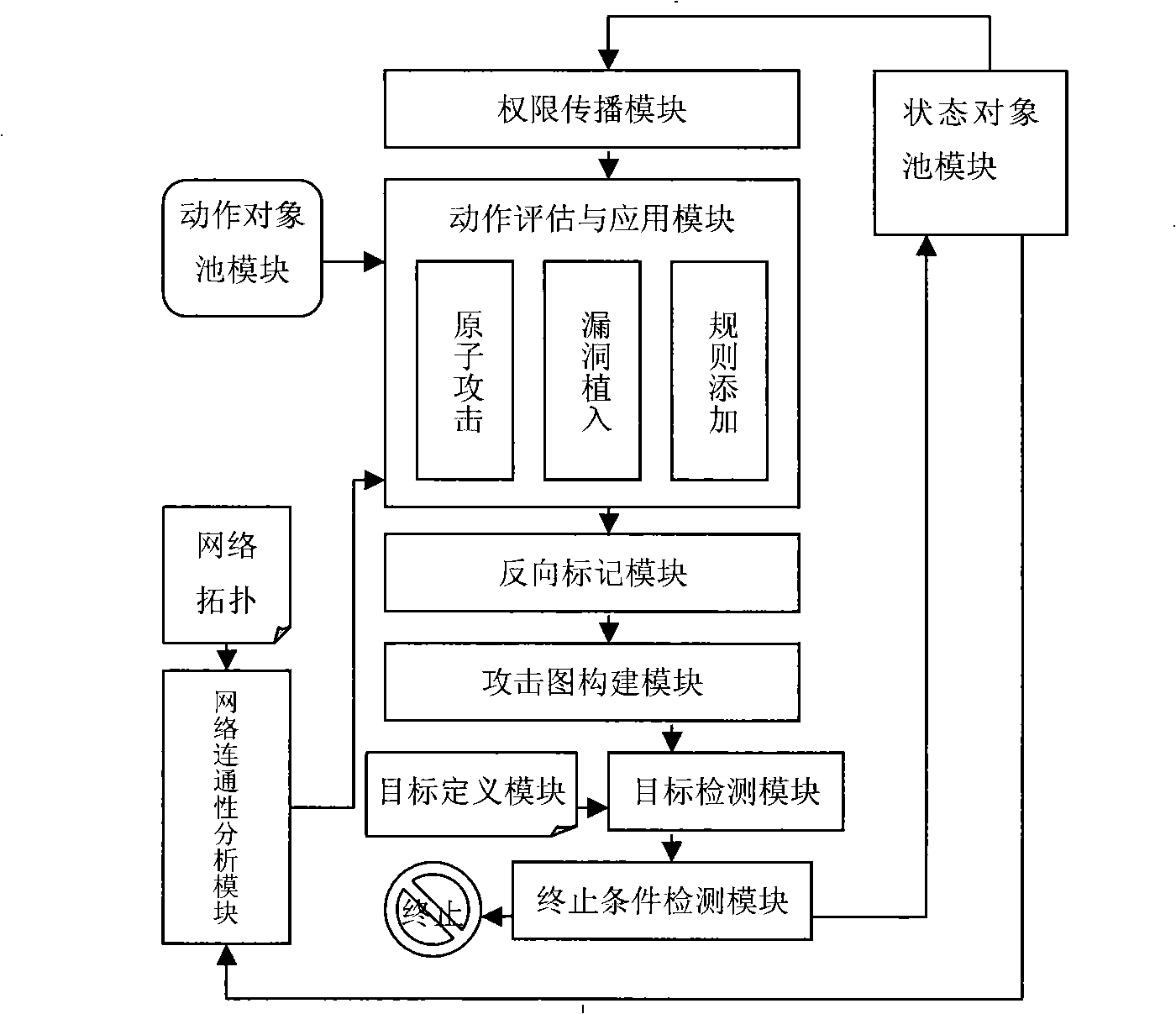
Depth-first attack drawing generating method
The invention provides a depth-first attack graph generation method. The steps are as follows: (1) the entire safety factors of the current network are collected to form an initial network state; (2) a prolog system is used to search the entire network states that an attacker is possible to pass through before a target state is reached; (3) attack routes are constructed according to the searched dependency relations among the network states; (4) the constructed attack routes are combined into a network attack graph. The invention has the advantages that: the depth-first generation algorithm decreases the scale of the attack graph, and can ensure that no non-target leaf node exists in the attack graph.
Owner:HARBIN ENG UNIV
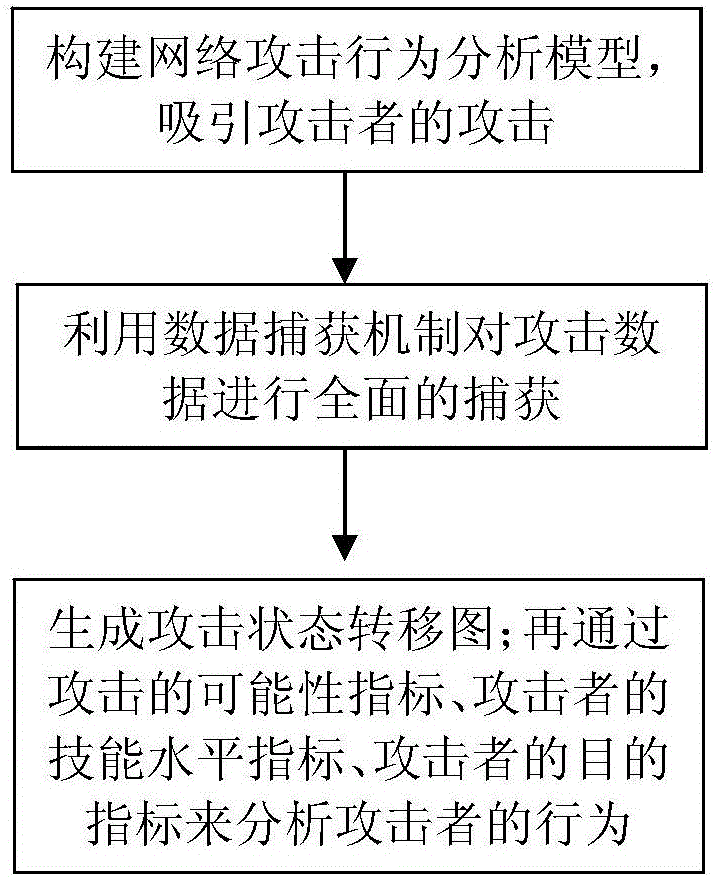
Network attacker behavior analyzing method based on attack graph
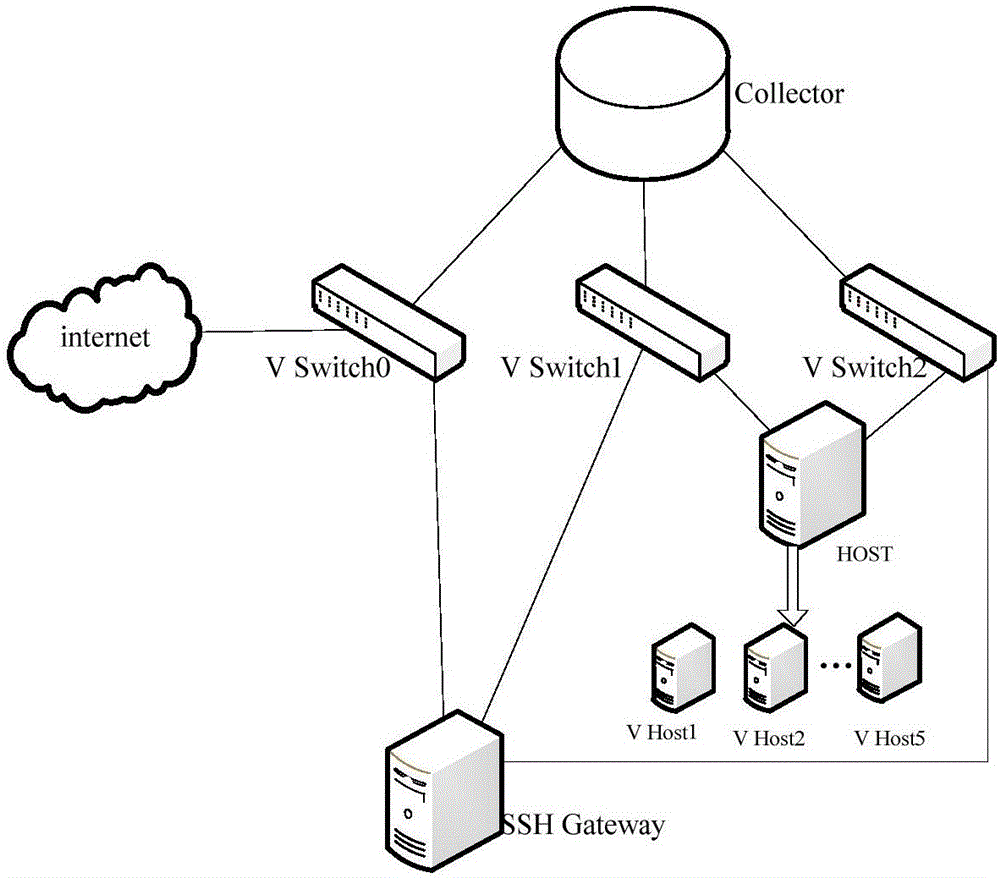
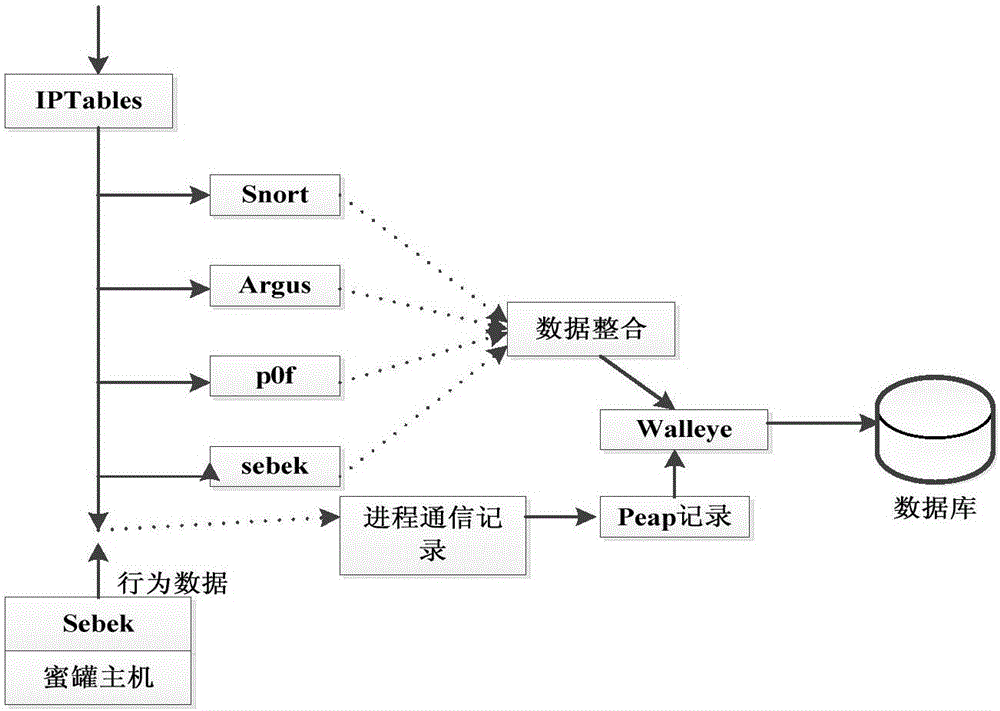
The invention discloses a network attacker behavior analyzing method based on an attack graph. The method comprises the steps of establishing a network attacker behavior analyzing model and attracting attacks of attackers; carrying out comprehensive capturing on attack data through a data capturing mechanism; and generating an attack state transfer graph through combination of a finite-state machine and analyzing behaviors of the attackers according to possibility indexes of attack behaviors, skill level indexes of the attackers and destination indexes of the attackers. According to the network attacker behavior analyzing method based on the attack graph provided by the invention, the good foundation can be laid for design of an active defense system, the network attacks can be defended, the attacks can be prevented before the network attacks occur, one part of the attacks are screened, a cybercrime can be effectively prevented, the defense efficiency is improved, and the defense cost is reduced.
Owner:HANGZHOU SUNYARD DIGITAL SCI
Methods of simulating vulnerability
Owner:LGS INNOVATIONS
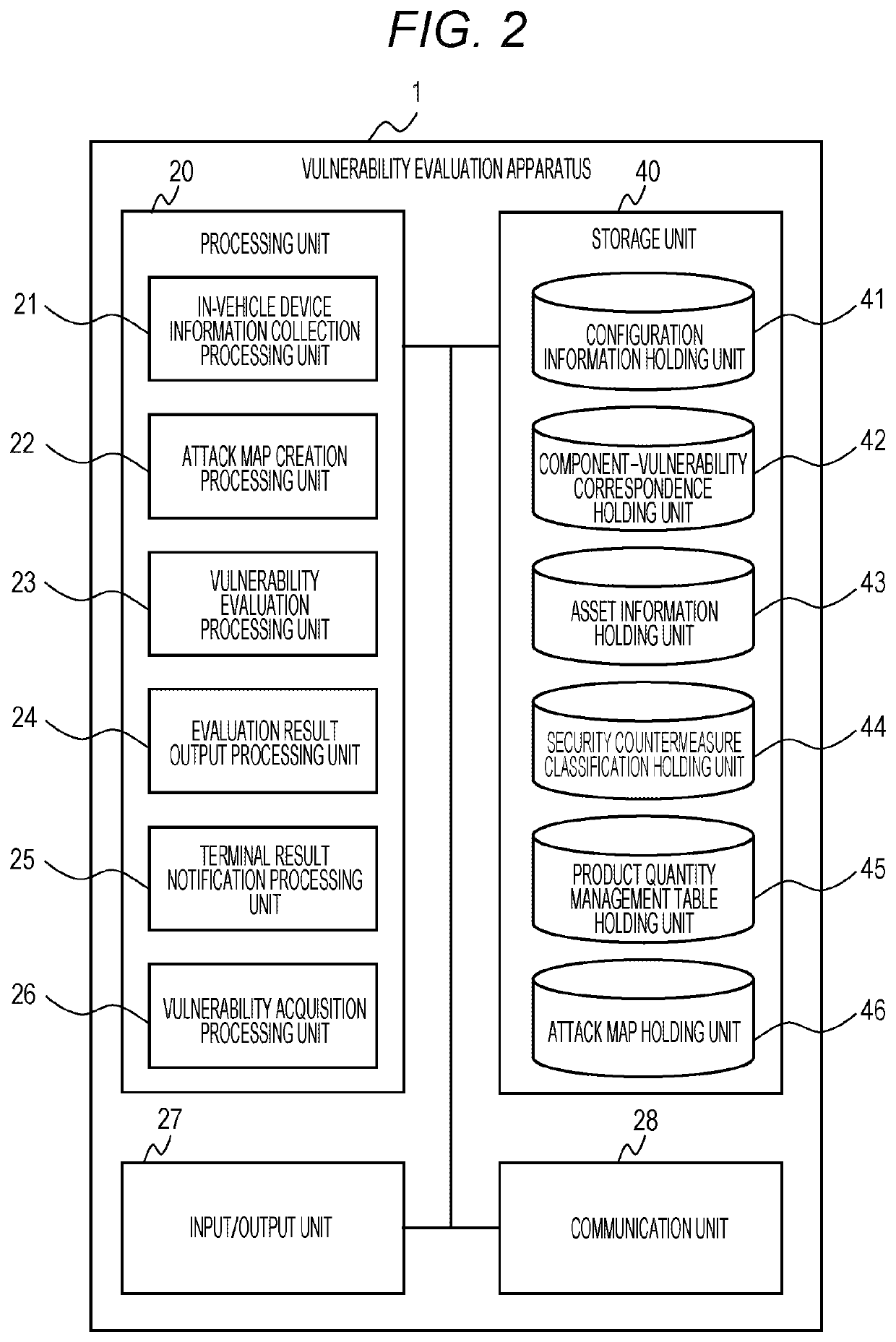
Vulnerability evaluation apparatus, vulnerability evaluation system, and vulnerability evaluation method
InactiveUS20200097663A1Improve quality controlCharacter and pattern recognitionPlatform integrity maintainanceAttackProcessing element
A storage unit of a computer includes: a product configuration information holding unit; a component-vulnerability correspondence holding unit indicating security holes; an asset information holding unit that stores asset values of the respective component of the product; a security countermeasure classification holding unit that stores defense target components for the respective security countermeasures and coefficients of countermeasure effects; and an attack map holding unit that stores attack maps indicating attack paths. A processing unit executes a program, to form: an information collection processing unit; an attack map creation processing unit that creates an attack map for each product; and a vulnerability evaluation processing unit that calculates priority order among countermeasures from threat levels of security holes of the respective components on the basis of the asset values.
Owner:CLARION CO LTD
Network spoofing performance evaluation method based on dynamic Bayesian attack graph
ActiveCN111371758AGuaranteed availabilityDefense Effectiveness Efficiently AssessedMathematical modelsTransmissionAttackTheoretical computer science
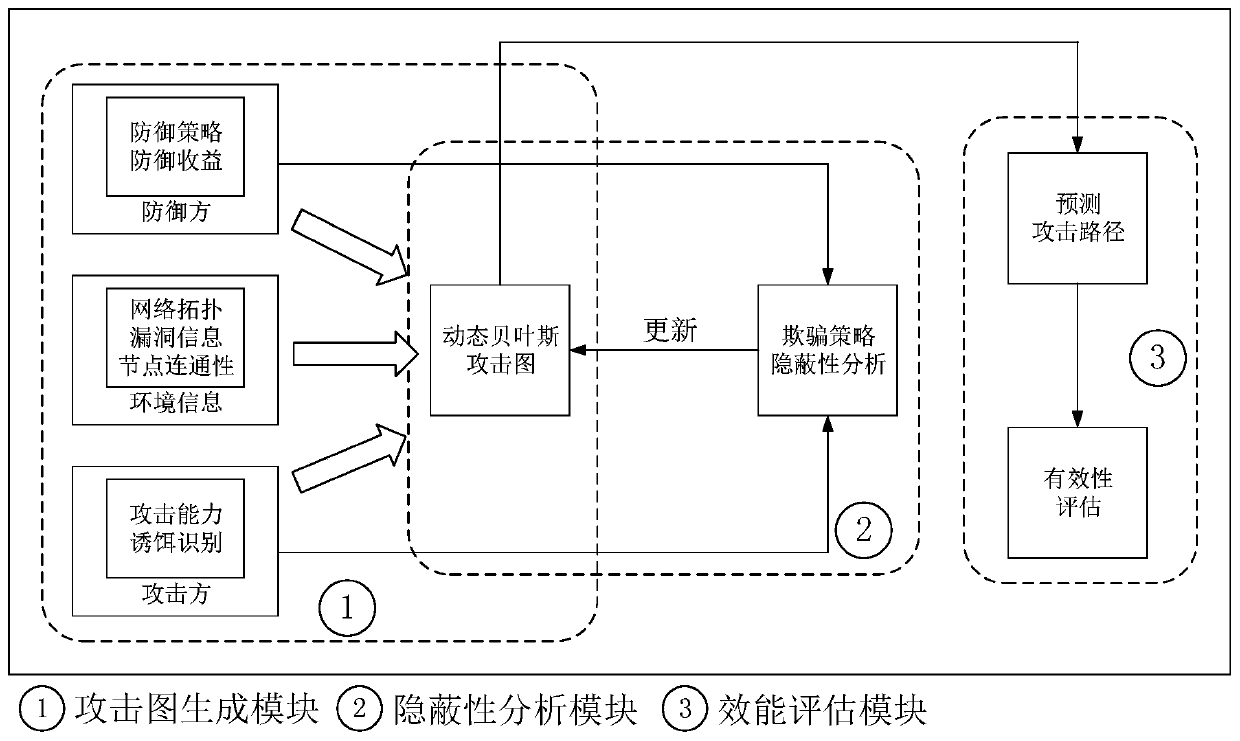
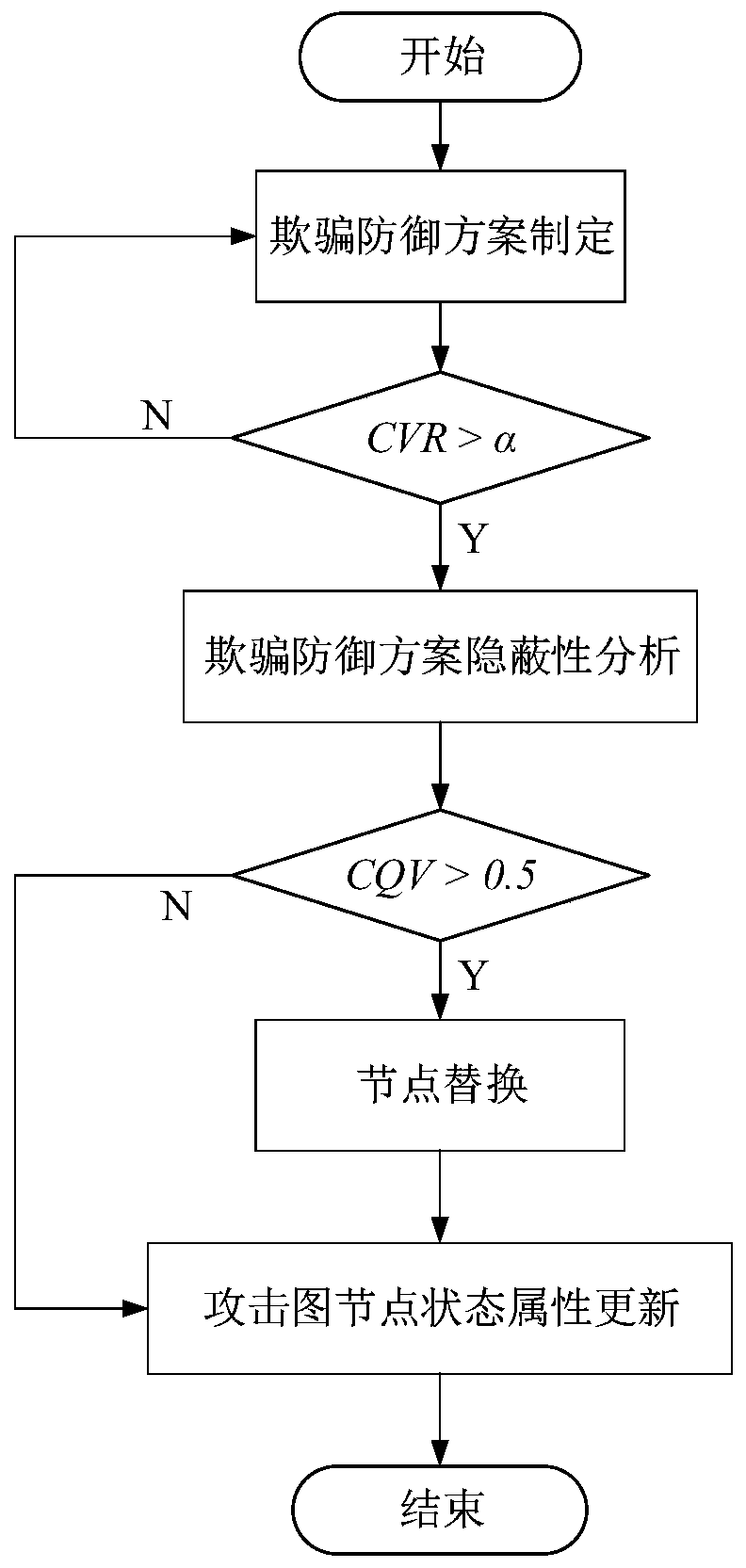
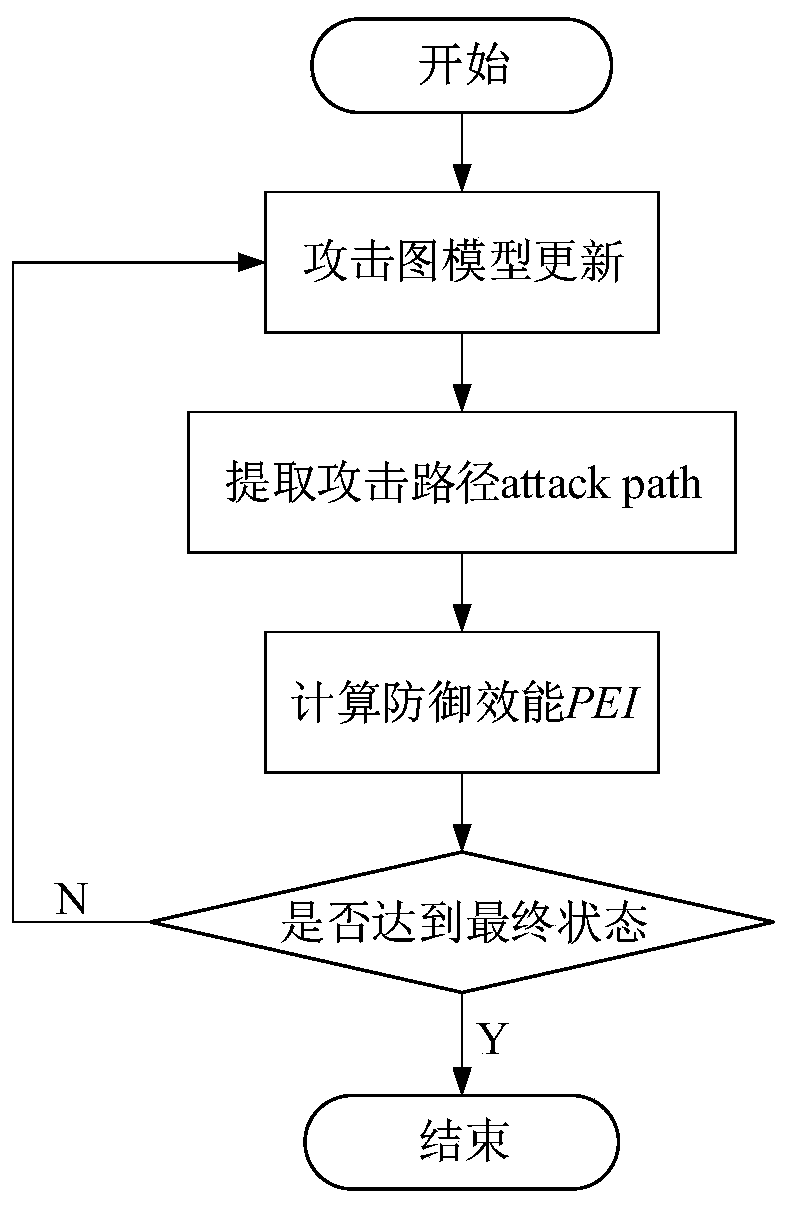
The invention discloses a network spoofing defense efficiency evaluation method based on a dynamic Bayesian attack graph, and belongs to the field of network space security. The method comprises the following steps: speculating attacker ability by analyzing vulnerability elements in a current network, and constructing a dynamic Bayesian attack graph model; aiming at the defense characteristics ofnetwork spoofing and counterfeiting real assets, the consistency of real nodes and bait nodes in the aspects of network characteristics, equipment fingerprints, file attributes and the like is comprehensively compared, so that a spoofing scheme is subjected to concealment analysis, and whether a defense strategy can achieve an expected effect or not is judged; and updating the attack graph model according to the analysis result and the attack and defense confrontation information, and giving a quantitative index to evaluate the effectiveness of deception defense. The method can be integrated on a server serving as a control center, other nodes in the network do not need to be modified, and the method has good applicability.
Owner:SOUTHEAST UNIV
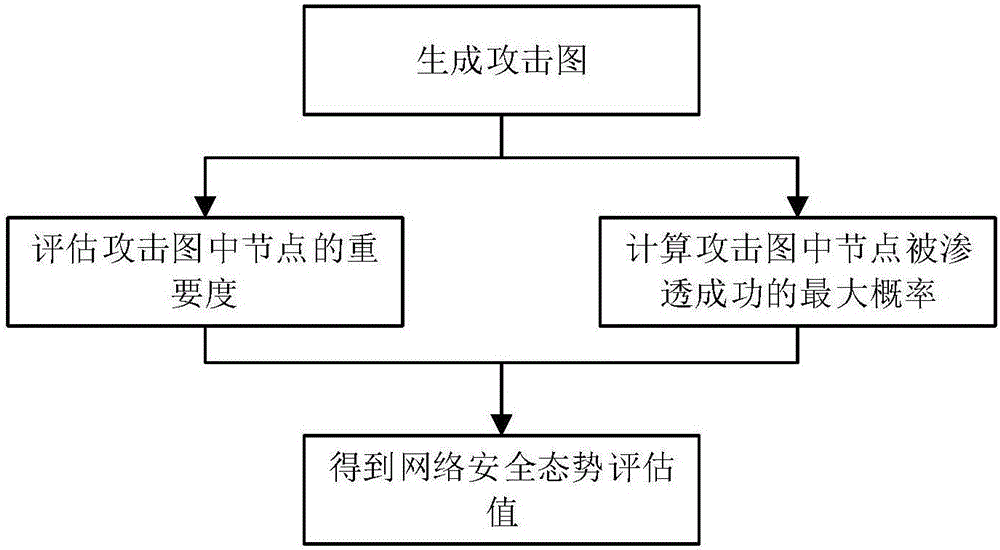
Quantitative evaluation method of network security situation based on attack graph
The invention relates to a quantitative evaluation method of a network security situation based on an attack graph, and belongs to the field of information security technology. The method specifically comprises the following steps: step 1, generating the attack graph; step 2, evaluating the importance of nodes in the attack graph G; step 3, on the operation basis of step 1, calculating the maximum probability that the nodes in the attack graph G are successfully permeated; and step 4, obtaining an evaluation value of the network security situation. Compared with the prior art, the method provided by the invention has the following advantages: (1) by adoption of the evaluation method based on the attack graph, the intention of multi-step attacks of an attacker using the loopholes in the network can be reflected. (2) The data used in the evaluation method are easy to collect and are operable. (3) The protection conditions of the nodes in the network obtained in the evaluation process reflect the protection conditions of the nodes in the network. (4) In the evaluation method, the topological information of the network, loophole association information and the attack intention of the attacker are comprehensively considered, and thus the precision of the evaluation result is high.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
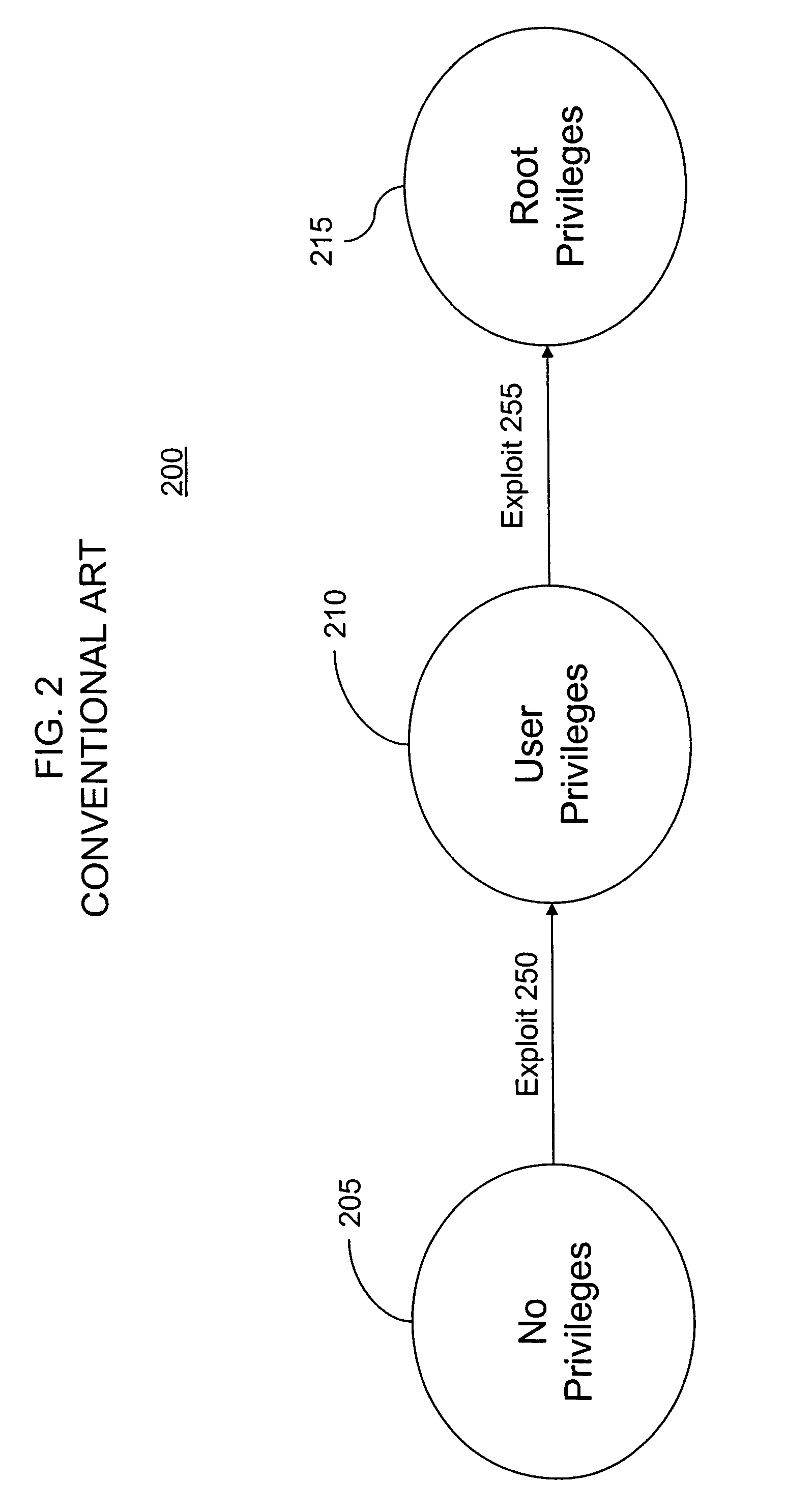
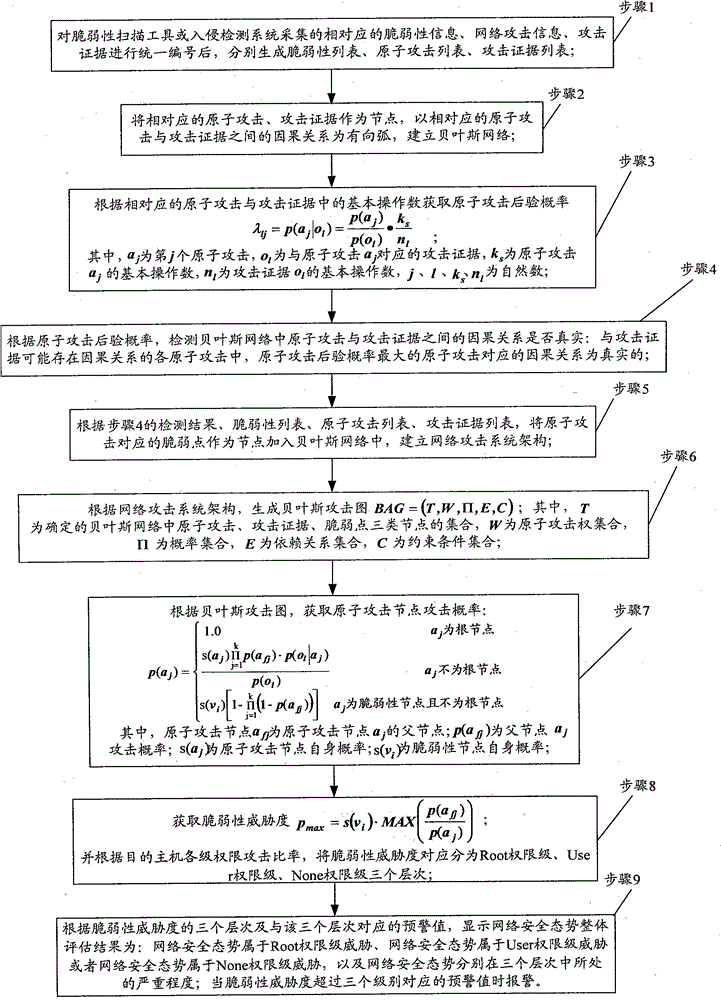
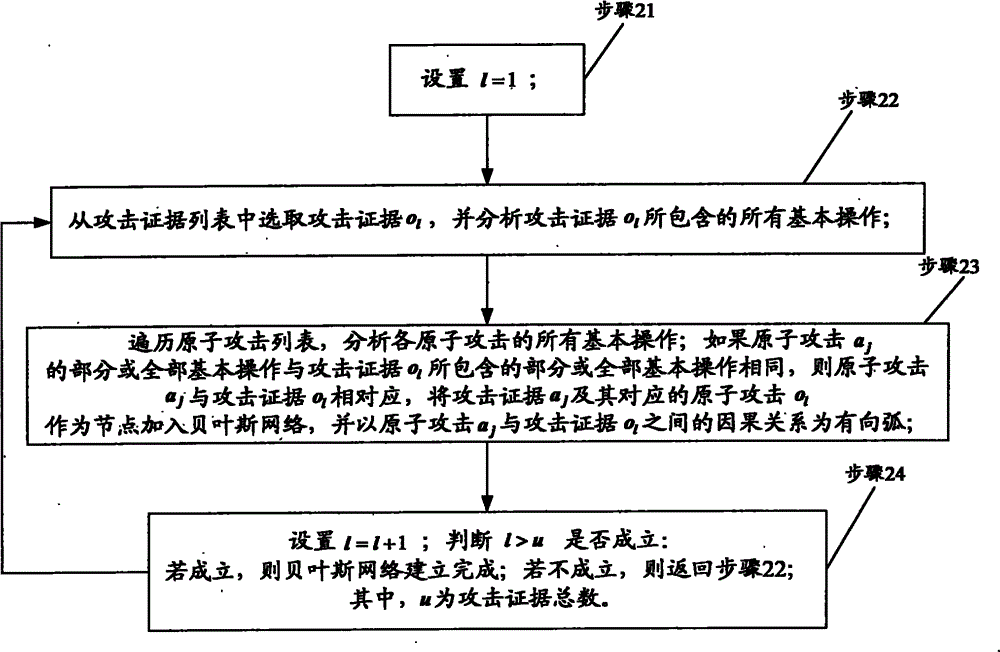
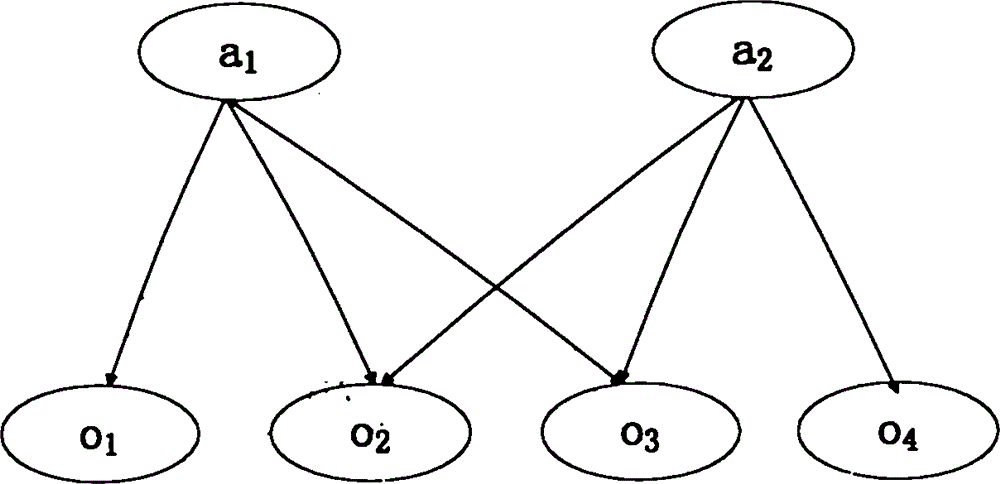
Network security posture assessment method
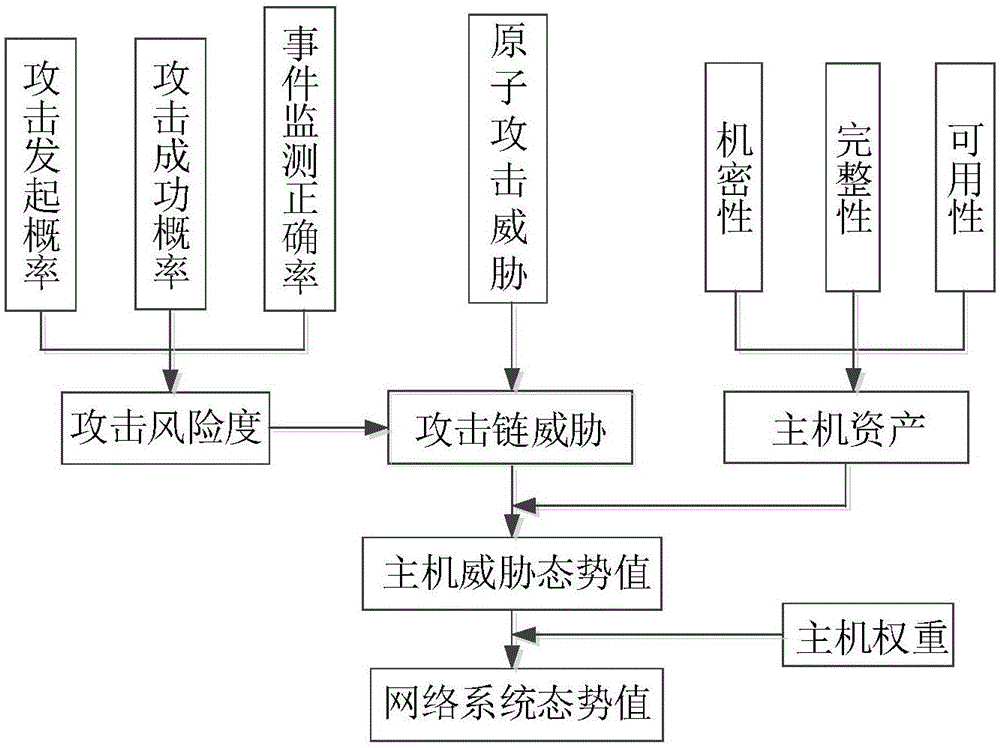
The invention provides a network security posture assessment method. The method comprises the following steps: producing a vulnerability list, an atomic attack list and an attack evidence list according to the acquired vulnerability information, network attack information and attack evidence; creating a bayesian network; acquiring atomic attack posterior probability; detecting the authenticity of the causal relationship between the atomic attack and the attack evidence in the bayesian network; building a network attack system framework and producing a bayesian attack graph; acquiring node attack probability of atomic attack; acquiring vulnerability threat degree and dividing into three levels, namely, Root authority level, User authority level and None authority level; displaying the overall assessment result of the network security posture according to the three levels of the vulnerability thread degree and early warning values corresponding to the three levels; performing early warning when the vulnerability thread degree exceeds the early warning levels corresponding to the three levels. The network security posture assessment method has the characteristics of being simple in model, accurate in assessment result and wide in applicable scope, and can be widely applied to the field of network security.
Owner:HENAN POLYTECHNIC UNIV
Network security analytical method for solving K maximum probability attack graph
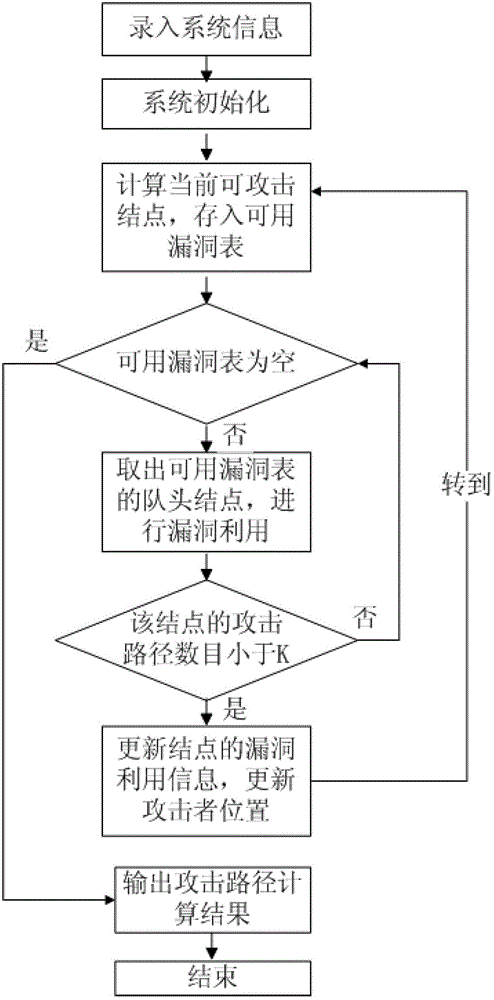
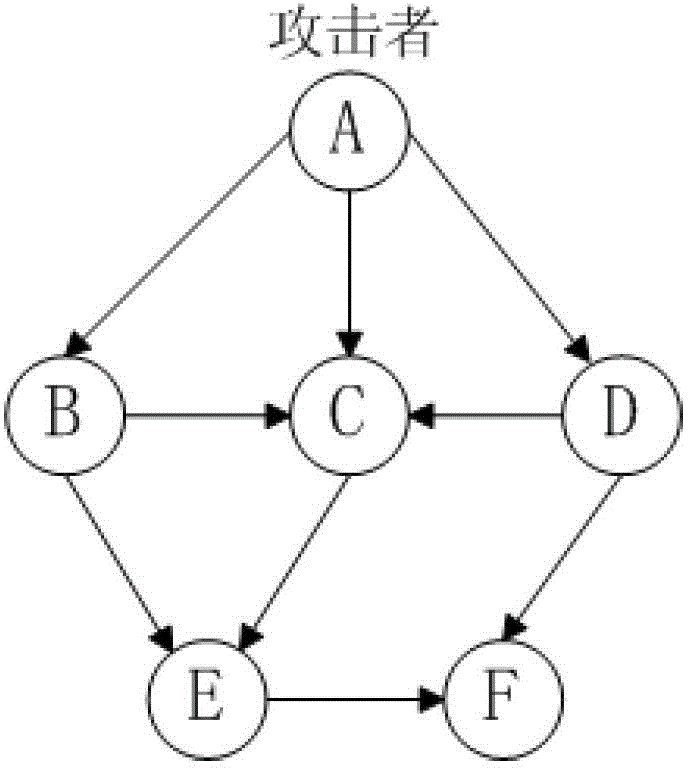
ActiveCN102724210ADifferentiate the degree of riskRich guidance informationTransmissionAlgorithmAttack graph
The invention disclose a network security analytical method for solving a K maximum probability attack graph. The method specially includes: step (1) typing in system information and inputting the value of a parameter K; step (2) initializing a system; step (3) counting nodes which can be attacked by an attacker currently; step (4) judging whether a loophole table is empty, entering the step (5) if the loophole table is empty, taking out head-of-line nodes of an available loophole table otherwise for loophole using, judging whether the number of existing attack paths of the nodes is smaller than K, updating loophole using information and the position of the attacker and entering the step (3) for executing if the number of existing attack paths of the nodes is smaller than K, and entering the beginning position of the step (4) for continuing executing otherwise; and step (5) generating front K paths with the maximum probability of all attack nodes and finishing operation. By storing and accumulating the front K attack paths with the maximum probability at the nodes, the problem of the front K attack paths with the maximum probability at the attack nodes is solved.
Owner:SHANGHAI MARITIME UNIVERSITY
Network intrusion situation intention evaluation method based on alarm integration
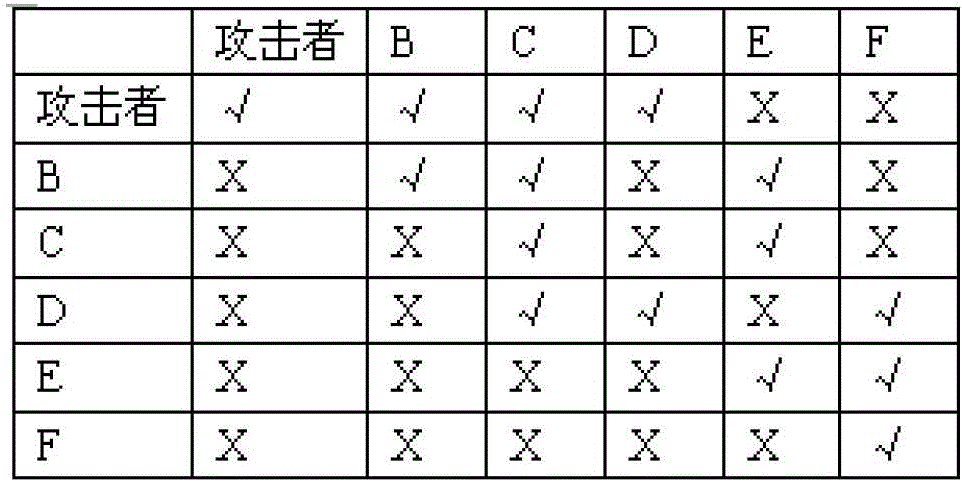
ActiveCN108769051AReduce computational complexityEasy to operateData switching networksComputation complexityDecision taking
The invention belongs to the technical field of the network security, and especially relates to a network intrusion situation intention evaluation method based on alarm integration. The method comprises the following steps: collecting network environment information, generating a Bayes attack graph model, wherein the network environment information at least comprises network connectivity, networkservice loopholes, host network configuration and access policy information, and the Bayes attack graph model comprises an attack state node, an atom attack node and an alarm evidence node; setting alarm confidence and association strength through the Bayes attack graph model, extracting effective alarm evidence; respectively computing the alarm confidence of the effective alarm evidence for eachattack state node; and evaluating the intruded probability of the effective node, and outputting the threaten order of all situation intention nodes. The method disclosed by the invention is low in computation complexity, not overly dependent on the historic data, simple and convenient for operation, capable of improving the node attack probability prediction accuracy, thereby providing reliable and effective data reference for defense decision and providing reliable guidance for the safety defense decision of the auxiliary network.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com