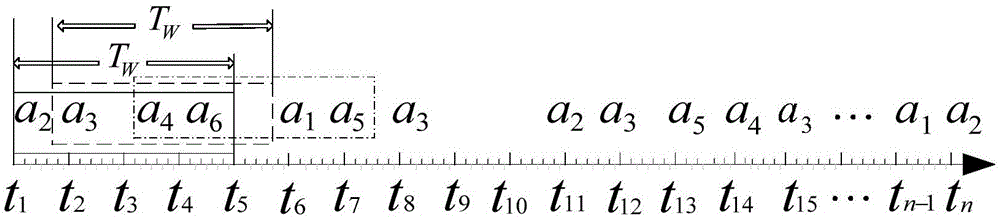Bayesian network-based multi-step attack security situation assessment method
A technology of Bayesian network and security situation, which is applied in the direction of computer security devices, instruments, platform integrity maintenance, etc., and can solve problems such as lack of multi-step correlation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
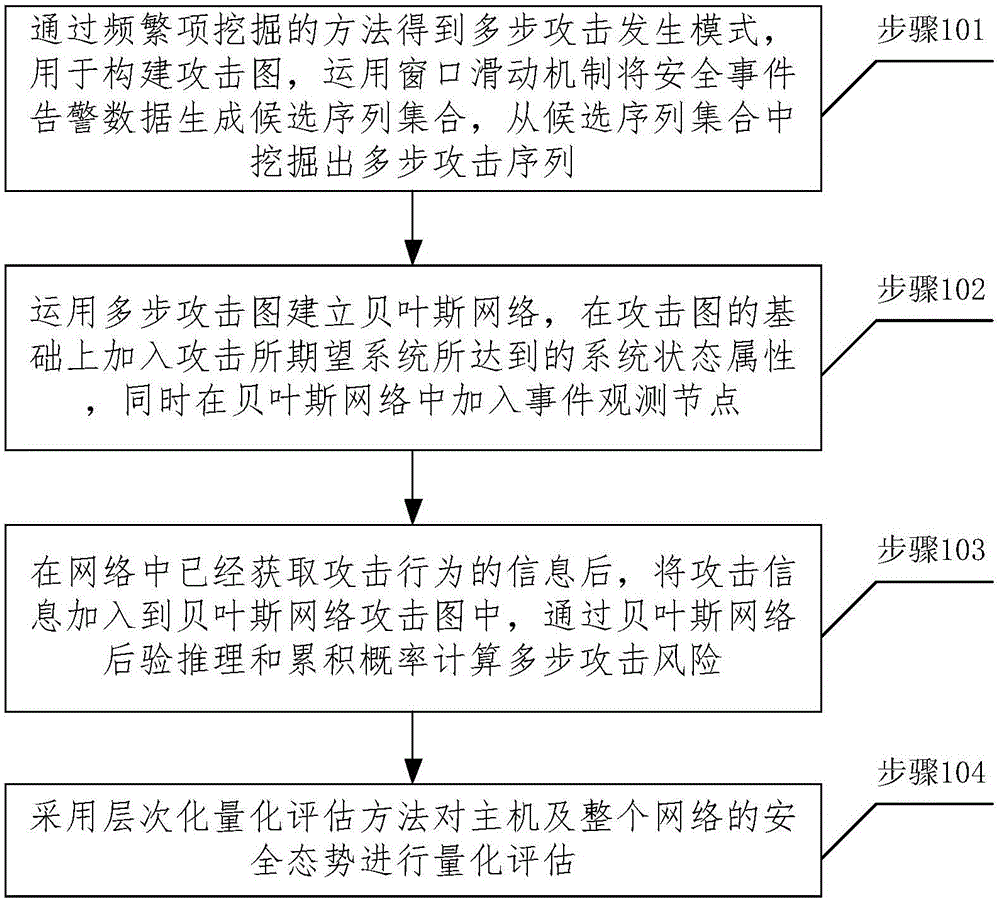
[0055] figure 1 It is a flow chart of the network security situation assessment method provided by the present invention, including the following steps:
[0056] In step 101, a multi-step attack occurrence pattern is obtained by mining frequent items, which is used to construct an attack graph, and a set of candidate sequences is generated from security event alarm data by using a window sliding mechanism, and multi-step attack sequences are mined from the set of candidate sequences.
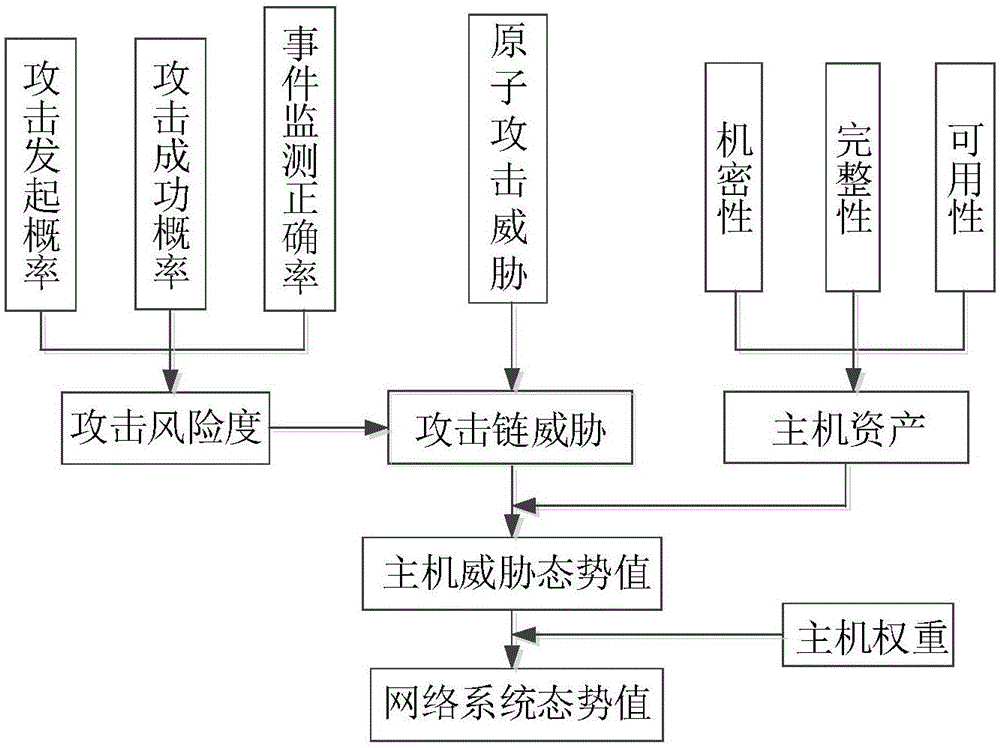
[0057] Step 102, using the multi-step attack graph to establish a Bayesian network, adding the system state attributes achieved by attacking the expected system on the basis of the attack graph, and adding event observation nodes to the Bayesian network.
[0058] Step 103, after the attack behavior information has been obtained in the net...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com