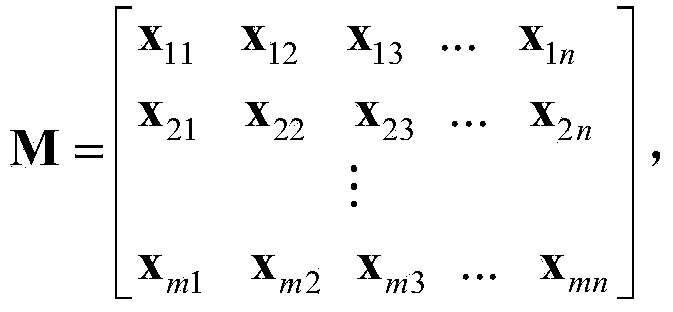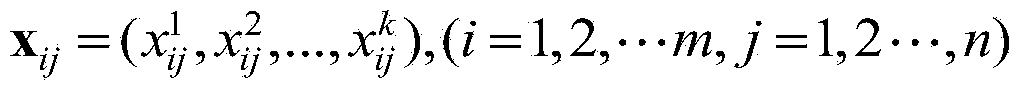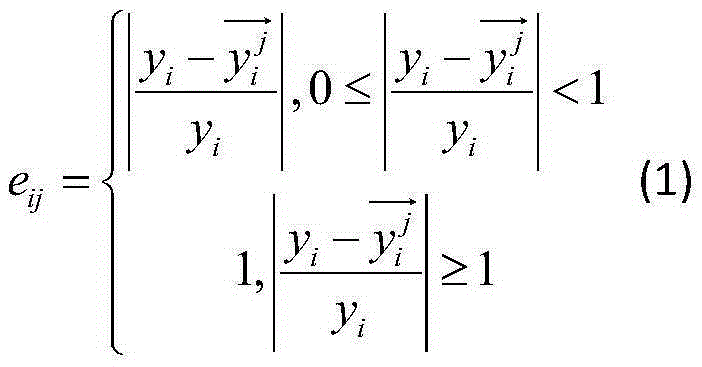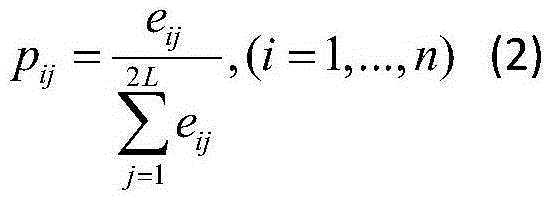Patents
Literature
246results about How to "Solve redundancy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
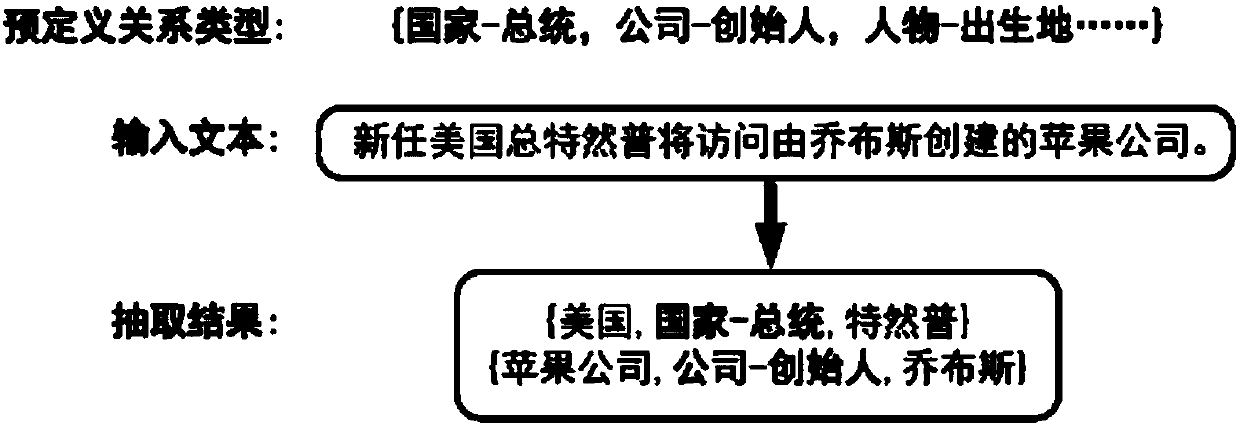
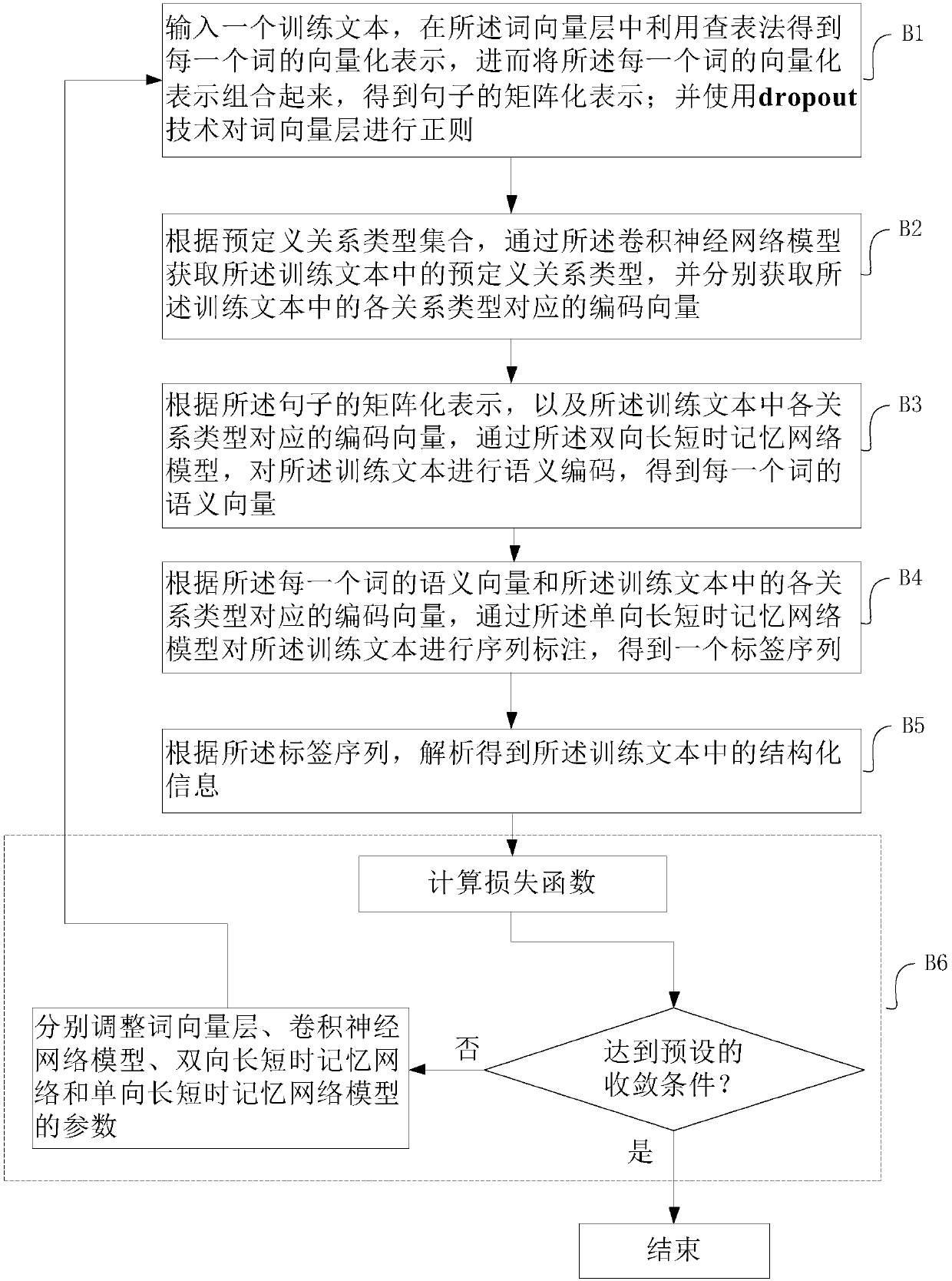
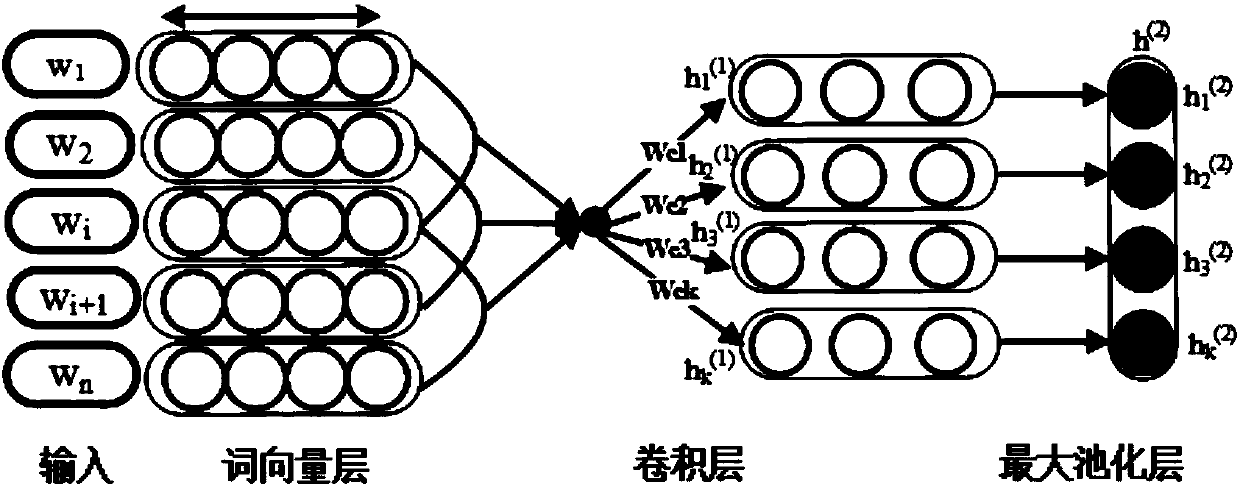
Knowledge extraction method and system based on memory neural network and device
ActiveCN108304911APrevent overloadImprove extraction efficiencySemantic analysisBiological neural network modelsSemantic vectorNetwork structure
The invention relates to the field of knowledge extraction and particularly relates to a knowledge extraction method and system based on a memory neural network and a device. The invention aims to solve the problem of information redundancy existing in the prior art. The method comprises a step of obtaining a possible relationship type in an input text and a semantic coding vector by using a convolutional neural network under the premise of giving a predefined relationship type, a step of carrying out semantic encoding by using a two-way long and short time memory neural network and obtaininga semantic vector, a step of taking the relationship type as an initial value of the two-way long and short time memory network and a first label in a decoding module and thus fusing the relationshiptype information into encoding information and label information of the decoding module, and a step of obtaining a label sequence by using a decoding module of a single-way long and short time memorynetwork and then obtaining structured information by parsing the label sequence. According to the knowledge extraction method and system and the device, the efficiency of structured information extraction is greatly improved, and the problem of information redundancy existing in the prior art is solved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Industrial control network redundancy fault-tolerant system
ActiveCN101907879AAvoid network conflictSolve redundancyError preventionTotal factory controlComputer monitorComputer monitoring
The invention discloses an industrial control network redundancy fault-tolerant system, belonging to the industrial control field. The system of the invention comprises four parts, namely a main controller redundancy system, a slave redundancy system, a fault log system and a host computer monitoring interface, wherein the main controller redundancy system is composed of two main controllers which provide redundancy; each main controller carries a control network to form network redundancy or the two main controllers share one control network; the slave redundancy system is composed of a main controller and a pair of slaves; the main controller monitors the communication condition of the current line and selects the best communication path in real time; the fault log system records the fault message of the device; and the host computer monitoring interface provides communication response for a monitoring computer and processes input operation to control the operation of the redundancy system. The system of the invention can ensure that the resources of the control network of the two redundancies synchronize automatically; the fault can be judged automatically; and when the network has a failure, the network can be switched to a backup control network within 300 milliseconds to operate continuously.
Owner:DALIAN UNIV OF TECH
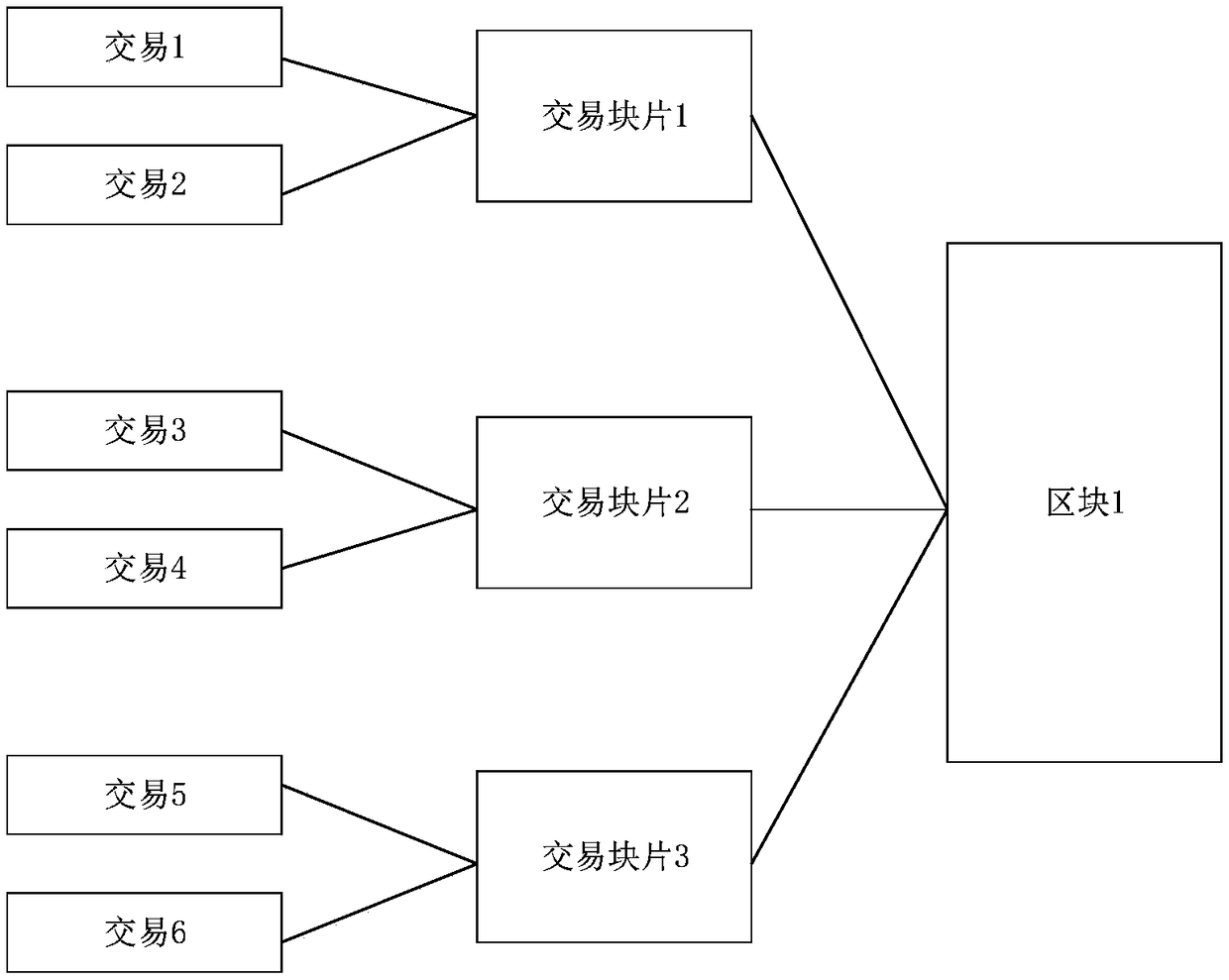
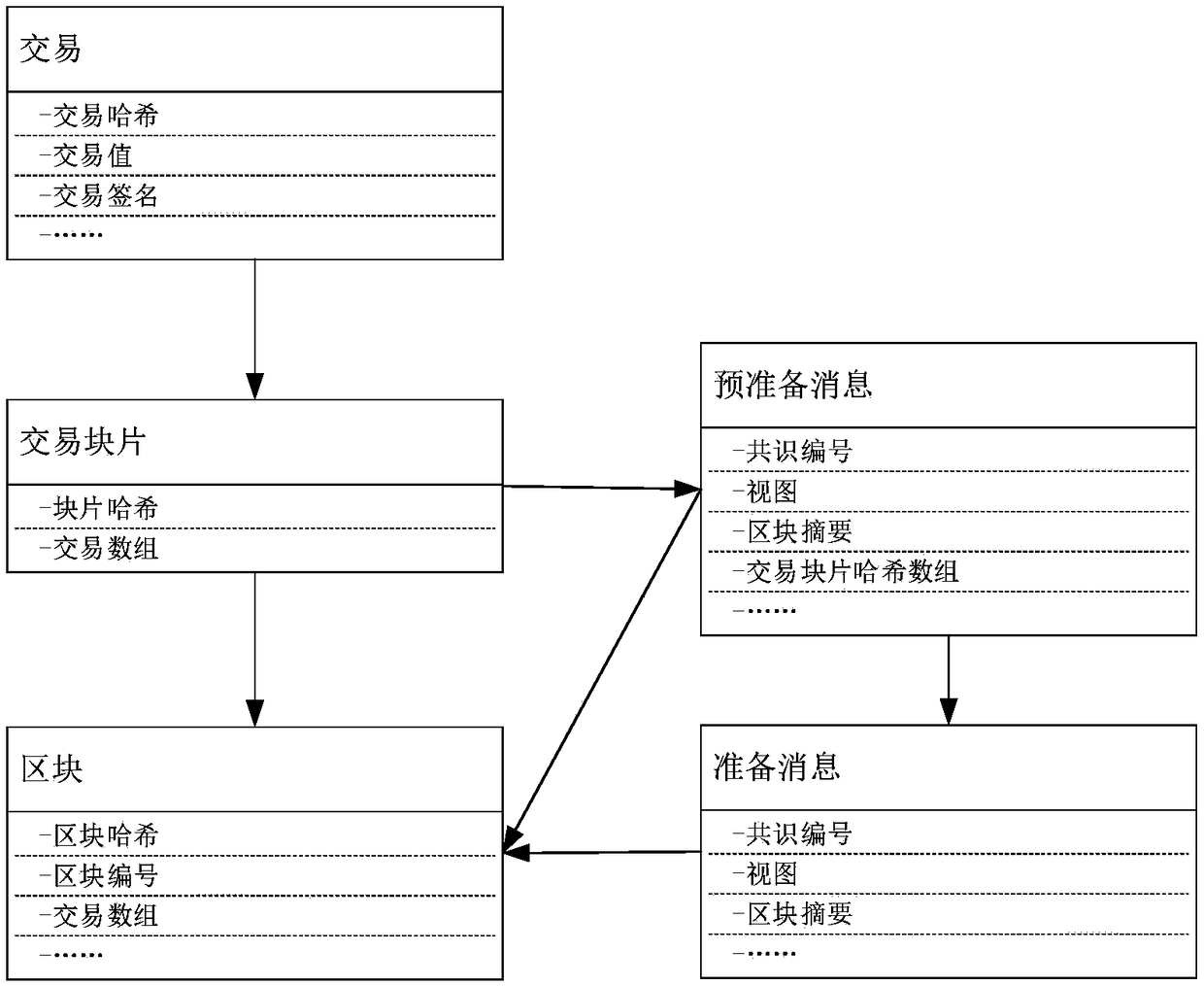
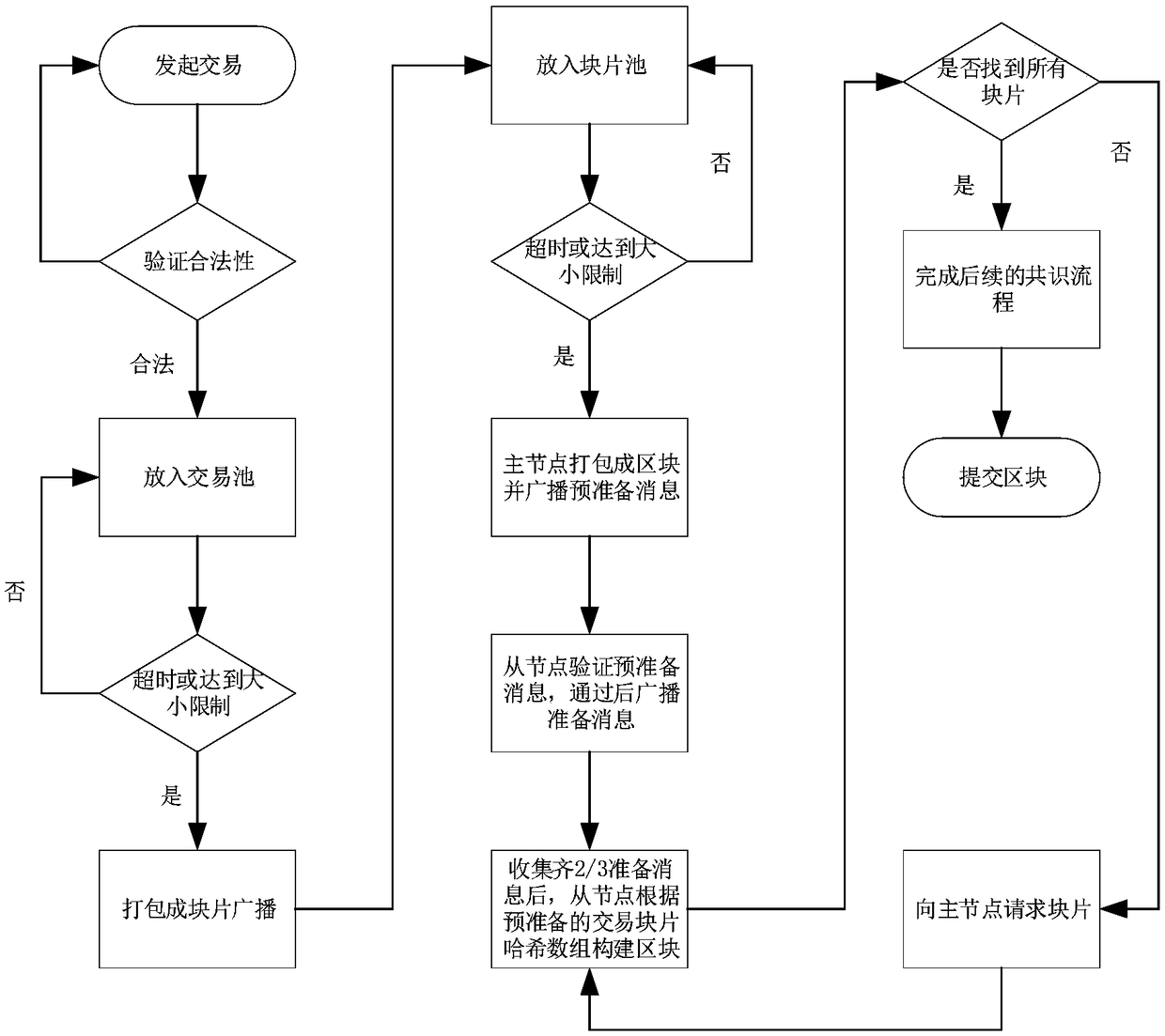
Method for improving bandwidth utilization rate of BFT consensus algorithm based on block piece
ActiveCN109150598AGuaranteed validitySolve redundancyFinanceUser identity/authority verificationFinancial transactionBroadcasting
The invention discloses a method for improving the bandwidth utilization rate of a BFT consensus algorithm based on a block piece. In one blockchain network, when a node receives new transaction, andthe new transaction passing through the verification will be cached till a certain number of transactions are obtained or there is no new transaction in a specified time window, so the transactions will be taken as one block piece and broadcast is transmitted to other nodes, and other nodes will put the block piece into respective transaction block piece pools; For a main node, after a certain number of transaction block pieces are obtained or there is no new block piece in the specified time window, the block pieces are packaged into one block for consensus, and a prepared message sent by themain node just needs to transmit the Hash of the block pieces, and other nodes organizes the required blocks for consensus in the respective block pieces according to the block piece Hash table of the main node. The method guarantees the effectiveness of the BFT algorithm, also solves a problem of redundancy of the broadcast mechanism of the BFT algorithm, and improves the bandwidth utilization rate of the blockchain node.
Owner:上交所技术有限责任公司 +1
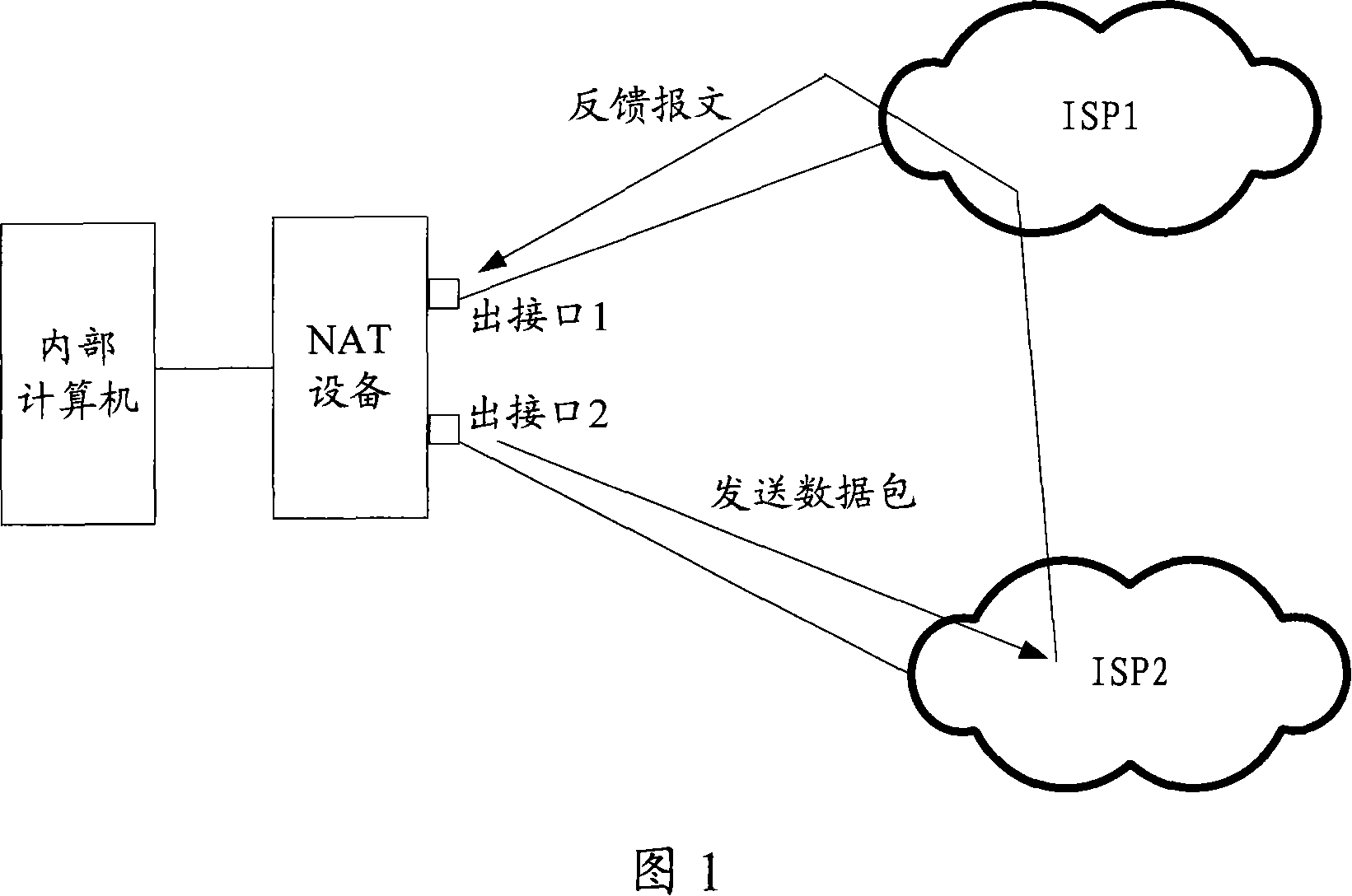
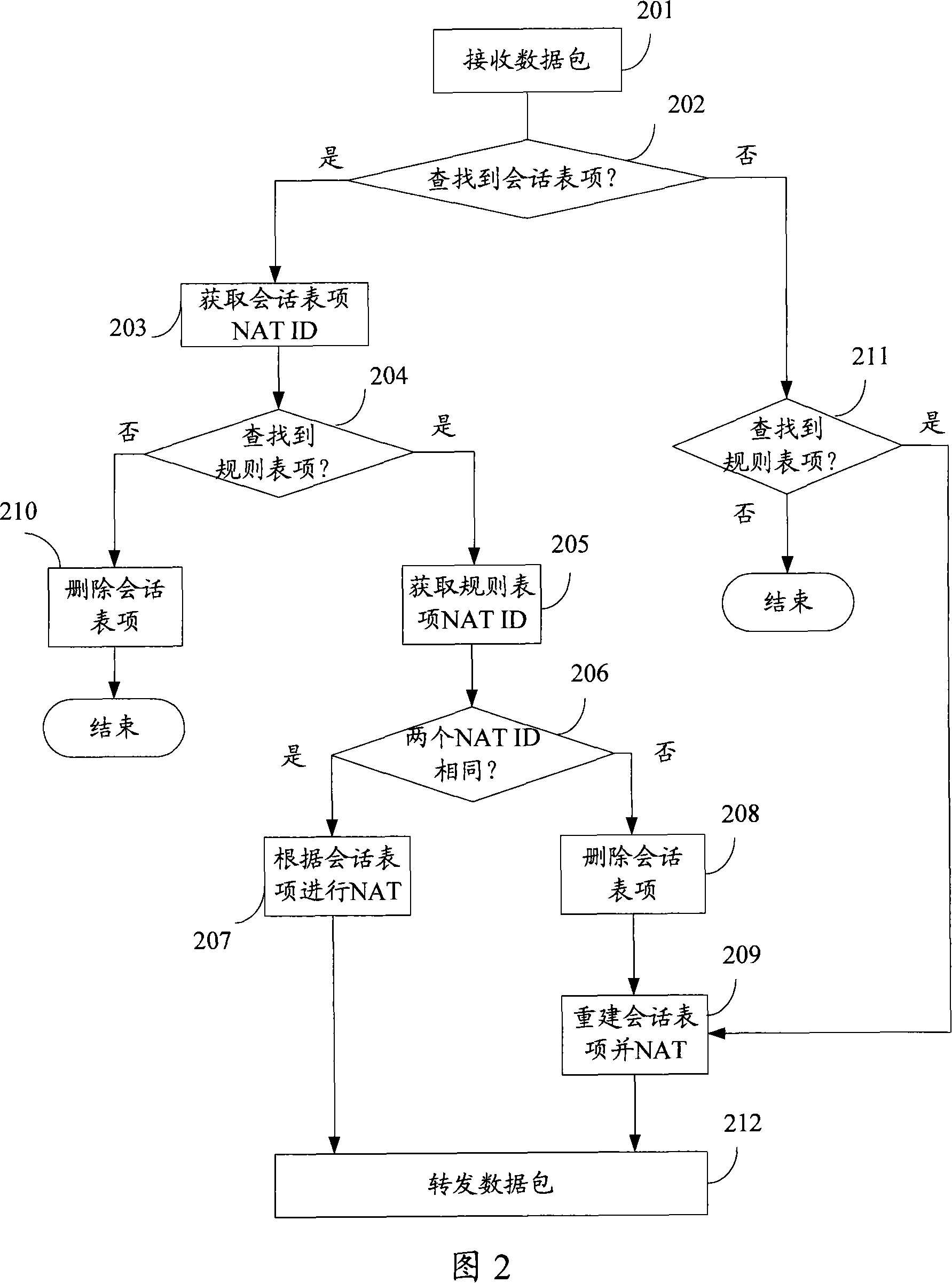
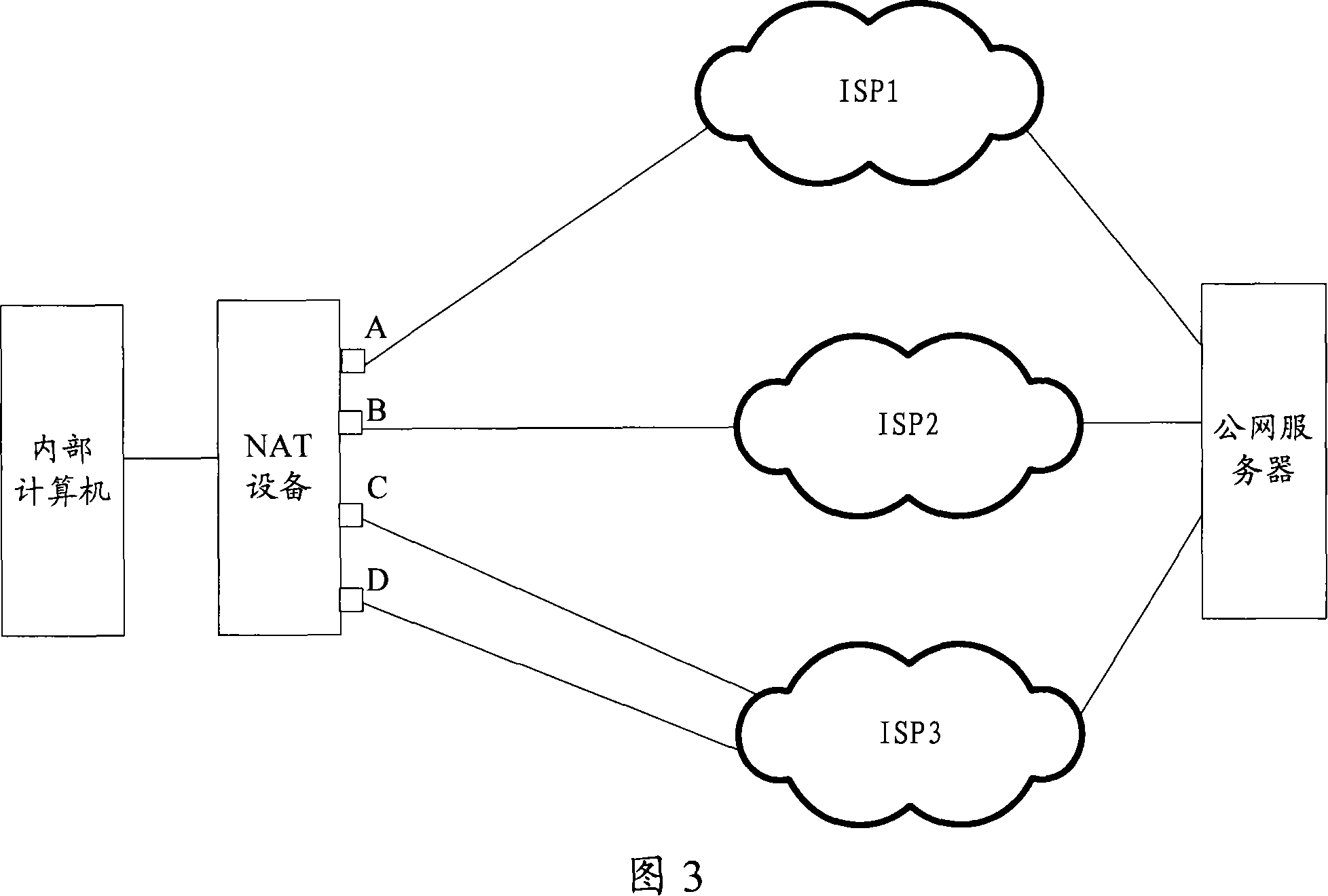
Network address converting attribute self-adaptive method and apparatus
ActiveCN101119324ASolve redundancyAchieve adaptiveData switching networksNetwork addressingNetwork address
The present invention discloses a NAT characteristic self adapting method, which comprises the following steps; looking for dialogue table using data packet IP five tuple or part of IP five tuple as index to match the dialogue tables items that contains NAT_ID; besides looking for the regulation table using the data packet as key works to match the regulation table items that contains NAT_ID; judging the NAT_ID in the dialogue tables items and regulation table items, if is the same, processing NAT according to the dialogue tables items; otherwise, deleting dialogue tables items and building new dialogue tables items according to the regulation table items and processing the NAT according to the new dialogue tables items. The present invention can renew the dialogue tables immediately after the NAT regulations changing, so as to realize NAT attribution self adapting. Corresponding to the above method, the present invention also provides a NAT charactersitic self adapting device.
Owner:北京紫光通信科技集团有限公司
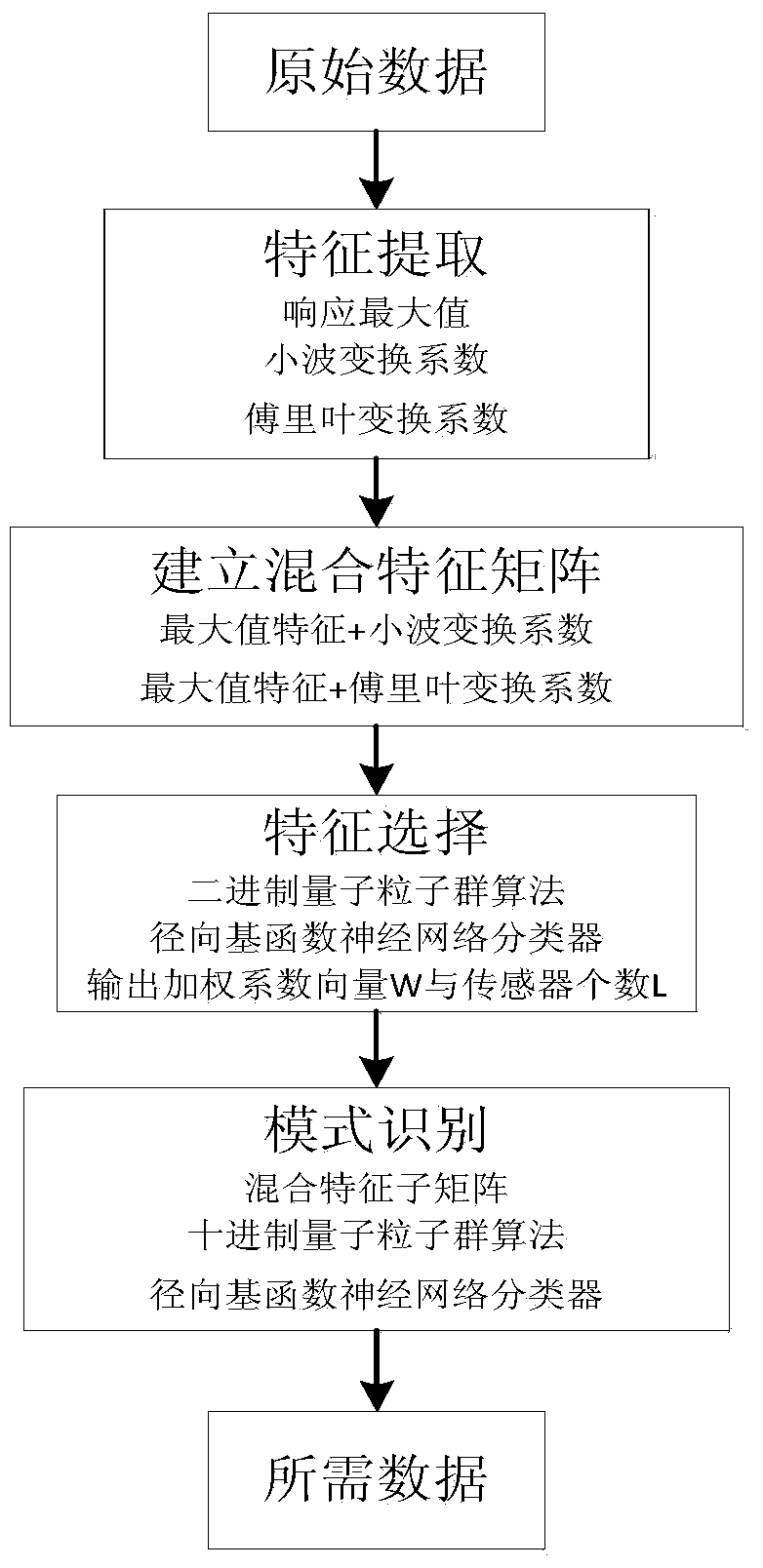
Electronic nose signal processing method based on mixing characteristic matrix
InactiveCN104268575ASolve redundancyImprove recognition rateCharacter and pattern recognitionFeature extractionOriginal data
The invention discloses an electronic nose signal processing method based on a mixing characteristic matrix. The method comprises the steps that first, characteristic extraction is conducted on an original data matrix to establish the mixing characteristic matrix, then a binary quantum particle swarm optimization algorithm is used for conducting characteristic selection on the mixing characteristic matrix, at last, the mixing characteristic matrix is fed into a classifier, a decimal quantum particle swarm optimization algorithm is used for conducting synchronous optimization on mixing characteristic sub matrixes and the parameters of the classifier, mode recognition is conducted to determine the mixing characteristic sub matrix with the highest recognition rate, and the sensor characteristic corresponding to the mixing characteristic sub matrix is selected to be used as the optimized characteristic of an electronic nose signal for conducting mode recognition. The electronic nose signal processing method based on the mixing characteristic matrix has the advantages that the defect that the complete information of an entire response curve can not be reflected only by extracting a single characteristic is overcome; the operation complexity is lowered, the problem of redundancy between sensors is effectively solved, the recognition rate of wound infection detection of an electronic nose is improved, and beneficial guidance can be provided for a doctor to choose a proper treatment method.
Owner:SOUTHWEST UNIV
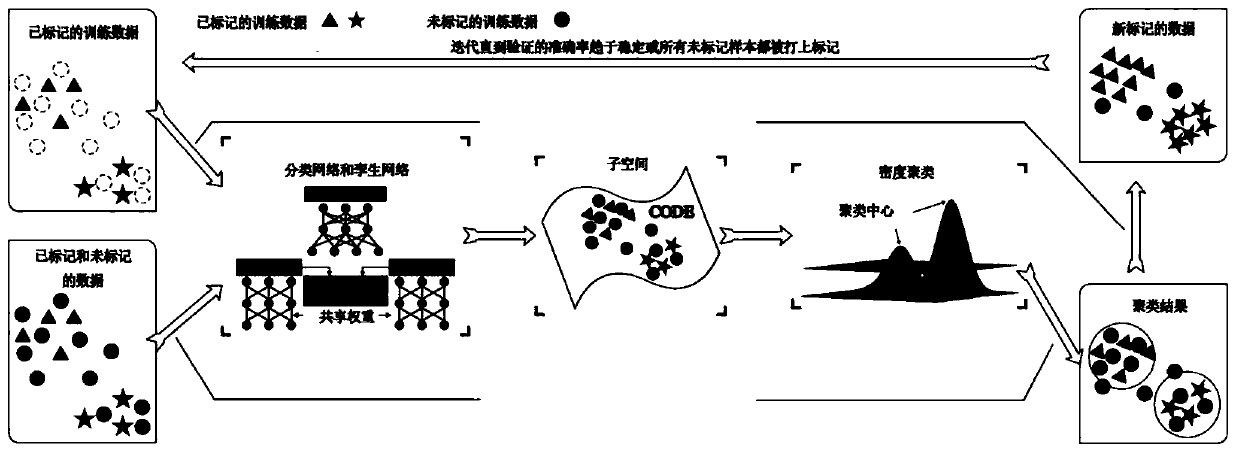
Webpage classification method for semi-supervised multi-view learning
ActiveCN110413924ASolve redundancyEfficient divisionCharacter and pattern recognitionWebsite content managementWeb page categorizationAlgorithm
The invention relates to the technical field of Internet, in particular to a webpage classification method for semi-supervised multi-view learning which comprises the following steps of: obtaining data from a webpage, and establishing a training set; training a classifier through the marked training set; encoding the marked training set and the unmarked training set through a trained classifier toobtain sample features; performing density clustering on the sample features to obtain a clustering result; and classifying the samples of the unmarked training set according to a clustering result.According to the scheme, the marked training set is used for training the classifier; orthogonal constraints and adversarial similarity constraints are added on the basis of an existing multi-view classification method, density clustering marking is carried out on all data in a training set through a trained classifier, finally, accuracy verification is carried out on the classifier, and the classification performance of the classifier can be improved through multiple iterations of the process.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
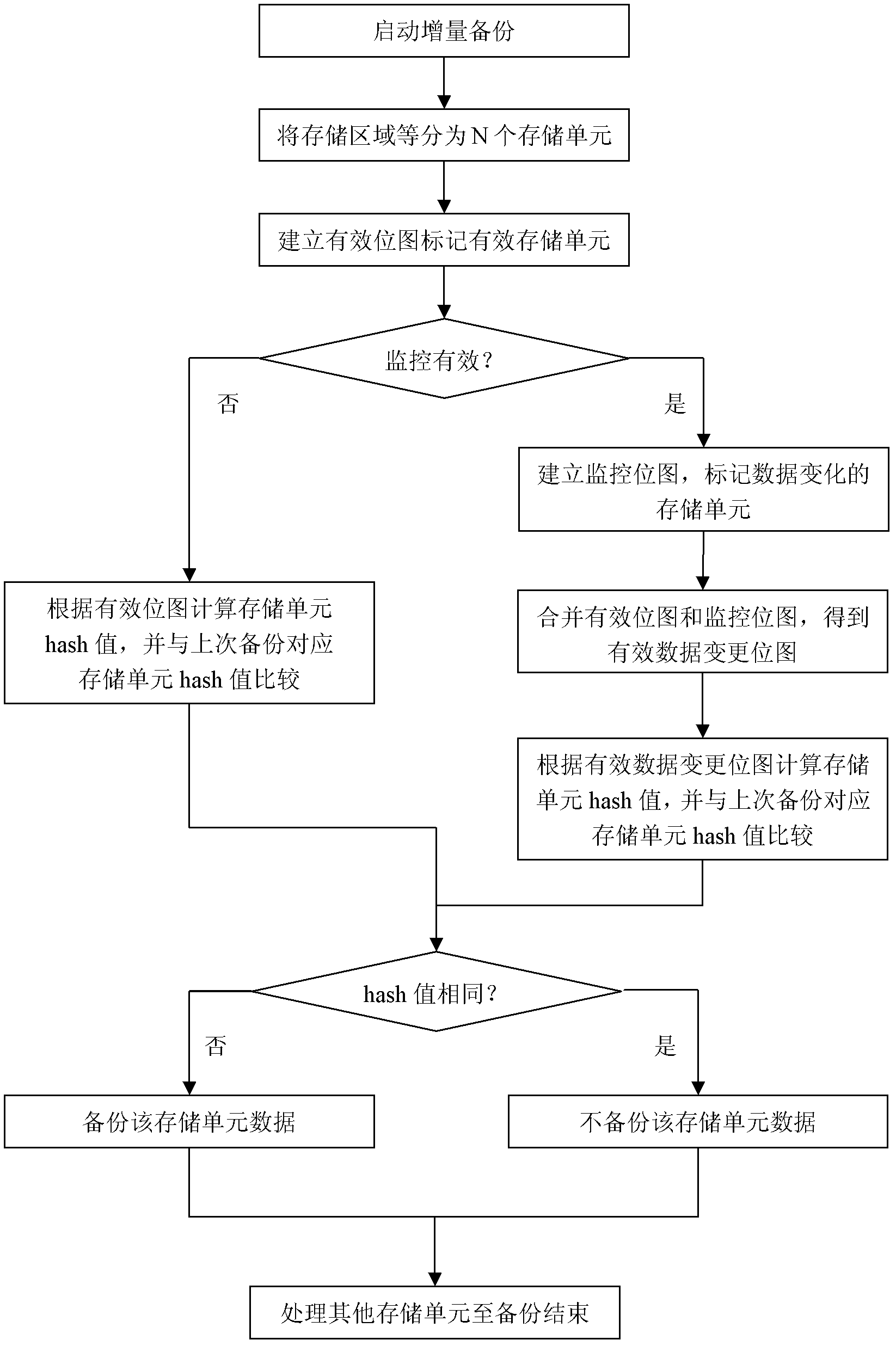
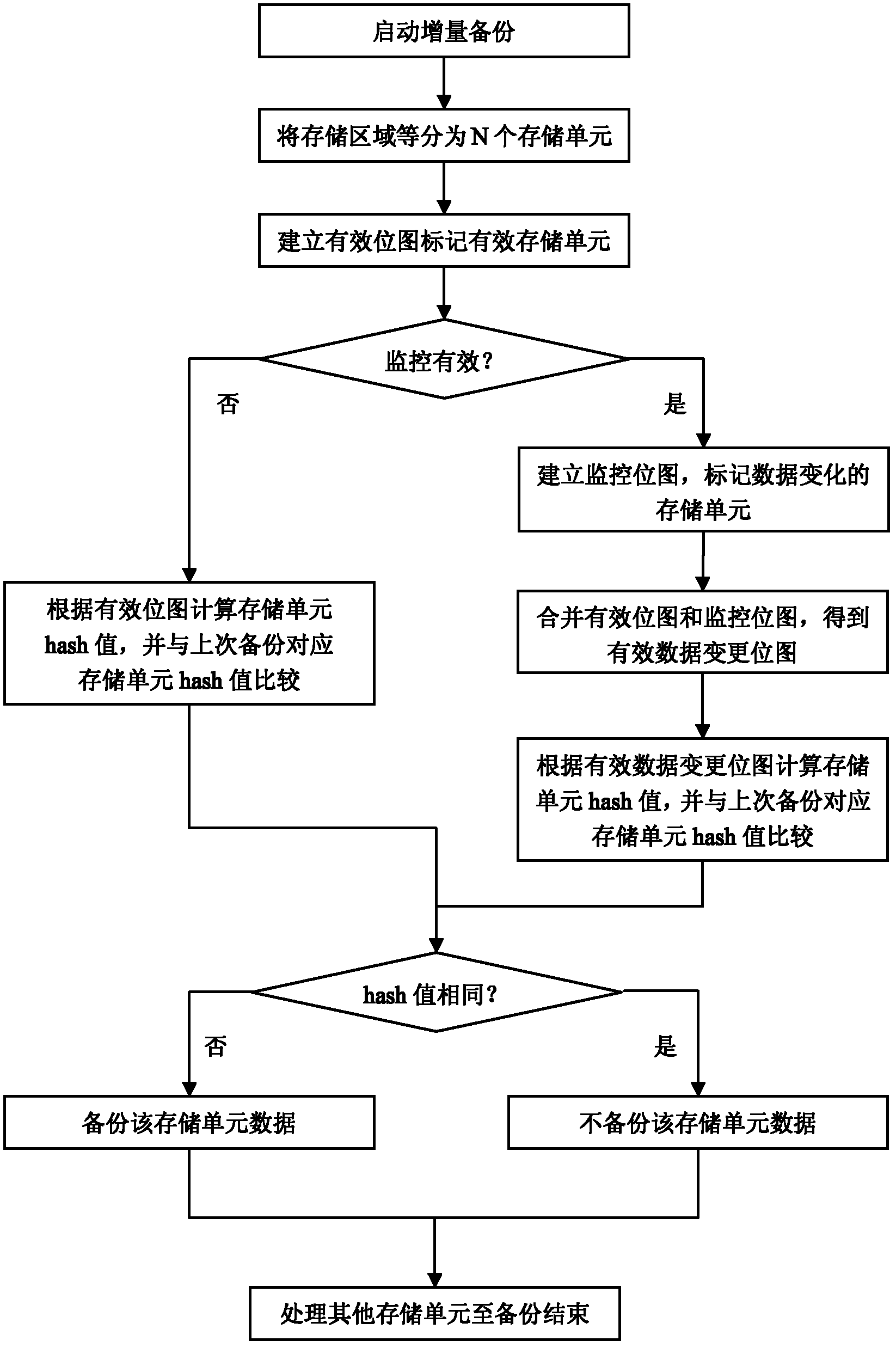
Incremental backup method
ActiveCN102207897AIncomplete solutionSolve redundancyRedundant operation error correctionData memoryLabeled data
The invention relates to a data backup technology, in particular to a disk incremental backup technology in a computer system. An incremental backup method comprises the following steps of: adding a valid bitmap into an incremental backup program to mark a valid data memory unit; only backing up the increment of valid data during incremental backup to reduce data redundancy and improve backup efficiency; adding a monitoring bitmap into the incremental backup program to mark a data change memory unit; backing up the increment of the valid data when monitoring is valid; and backing up all validdata when the monitoring is invalid. When the program is totally normal, the incremental backup is efficiently finished, and when the monitoring program is abnormal, no loss of increment of the validdata can be also guaranteed.
Owner:CHENGDU YIWO TECH DEV CO LTD
Park power system net load combined prediction method based on adaptive error feedback
ActiveCN110909912AAchieving Net Load Combination ForecastingImprove accuracyForecastingCharacter and pattern recognitionLeast squares support vector machineEngineering
The invention discloses a park power system net load combined prediction method based on adaptive error feedback, and the method comprises the steps: determining sample data according to a to-be-predicted date, and carrying out the abnormality recognition and data preprocessing; adaptively selecting characteristic indexes; training various methods based on the similarity set, and selecting an individual prediction model under the evaluation system; respectively combining the selected individual prediction models, performing combined regression on each independent prediction value by using a particle swarm optimization-least square support vector machine algorithm, and comparing an error with an actual historical training value to obtain a fitted optimal variable weight; and finally, executing an adaptive combined prediction method based on historical data. According to the method, the accuracy of predicting the net load of the park power system can be improved, and the method is more reliable and effective than an individual prediction method.
Owner:XI AN JIAOTONG UNIV
BOQ (bill of quantities) information and WBS information coupling method and system for technical improvement overhaul engineering of power grid
ActiveCN107818427ADirect useReduce data volumeCo-operative working arrangementsOffice automationCouplingPower grid
The invention relates to a BOQ (bill of quantities) information and WBS information coupling method and system for the technical improvement overhaul engineering of a power grid. Compared with the prior art, the invention irons out the defect that a WBS element architecture is not correspondingly coupled with a BOQ. The method comprises the following steps: constructing a WBS recognition code treestructure: setting a WBS recognition code format, constructing a WBS data dictionary of a WBS recognition code, and constructing the WBS recognition code tree structure according to the WBS data dictionary; constructing a BOQ coding tree structure: obtaining the list item codes of the technical improvement overhaul engineering of the power grid, and analyzing and constructing the BOQ coding treestructure; carrying out the coupling of the BOQ information and the WBS information, and enabling the WBS recognition code tree structure to be correspondingly correlated with the BOQ coding tree structure. The method can achieve the effective correlation of the BOQ information and the WBS information.
Owner:EAST INNER MONGOLIA ELECTRIC POWER COMPANY +1
Shiro authentication method based on Redis storage
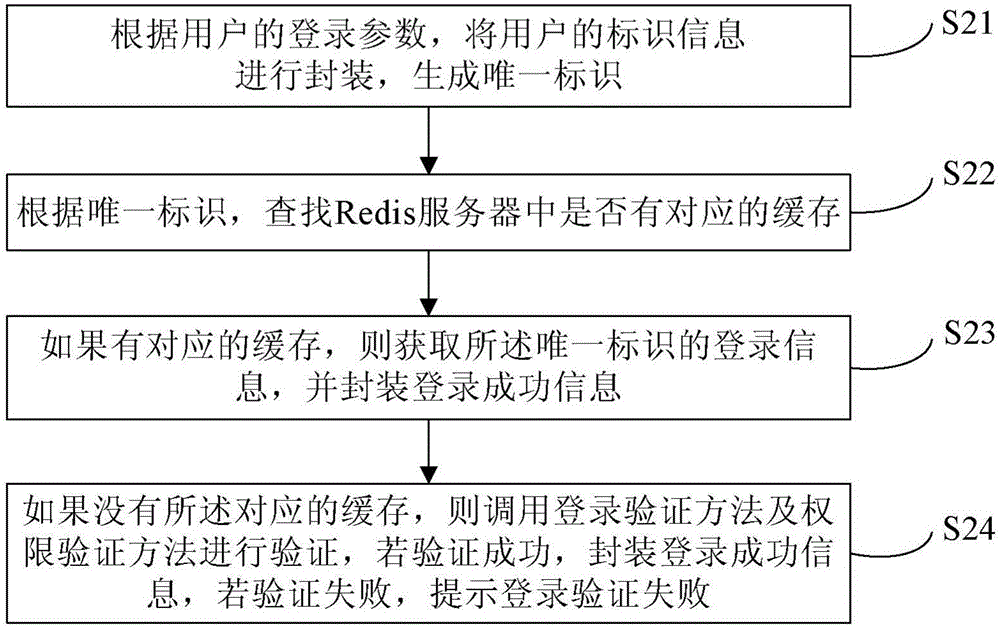
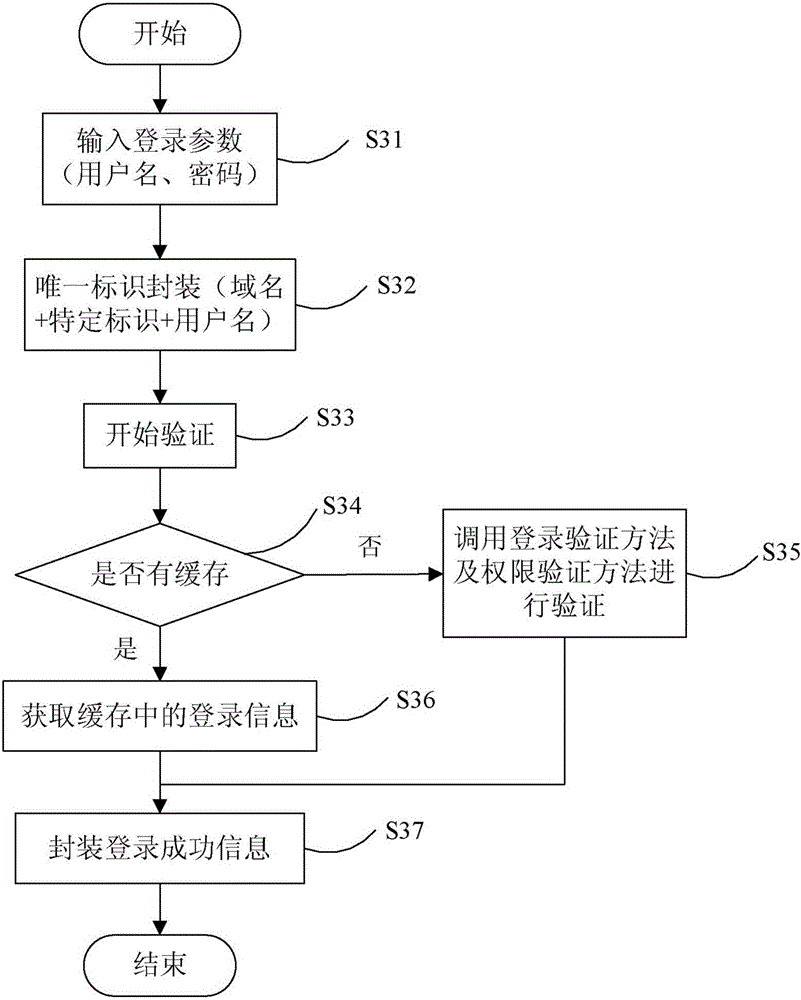
ActiveCN106487744AEasy to operateImprove efficiencyTransmissionHigh level techniquesExpiration TimeValidation methods
The invention provides a Shiro authentication method based on Redis storage. Through placing a session into an Redis for caching, the memory consumption can be reduced to solve the problem of memory overflow; and as an expiration time algorithm is introduced to automatically eliminate a cache, the efficiency and the hit rate of the cache are improved, thereby guaranteeing data to be stored efficiently and reliably. The method comprises the steps of carrying out encapsulation on identification information of a user according to login parameters of the user to generate a unique identifier; according to the unique identifier, finding whether the corresponding cache exists in an Redis server; if the corresponding cache exists, obtaining login information of the unique identifier and encapsulating login successful information; and if the corresponding cache does not exist, calling a login authentication method and an authority authentication method for authentication, if the authentication is passed, encapsulating the login successful information, and if the authentication is failed, prompting the login authentication is failed.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Method and system for solving equipment redundant in industrial control network
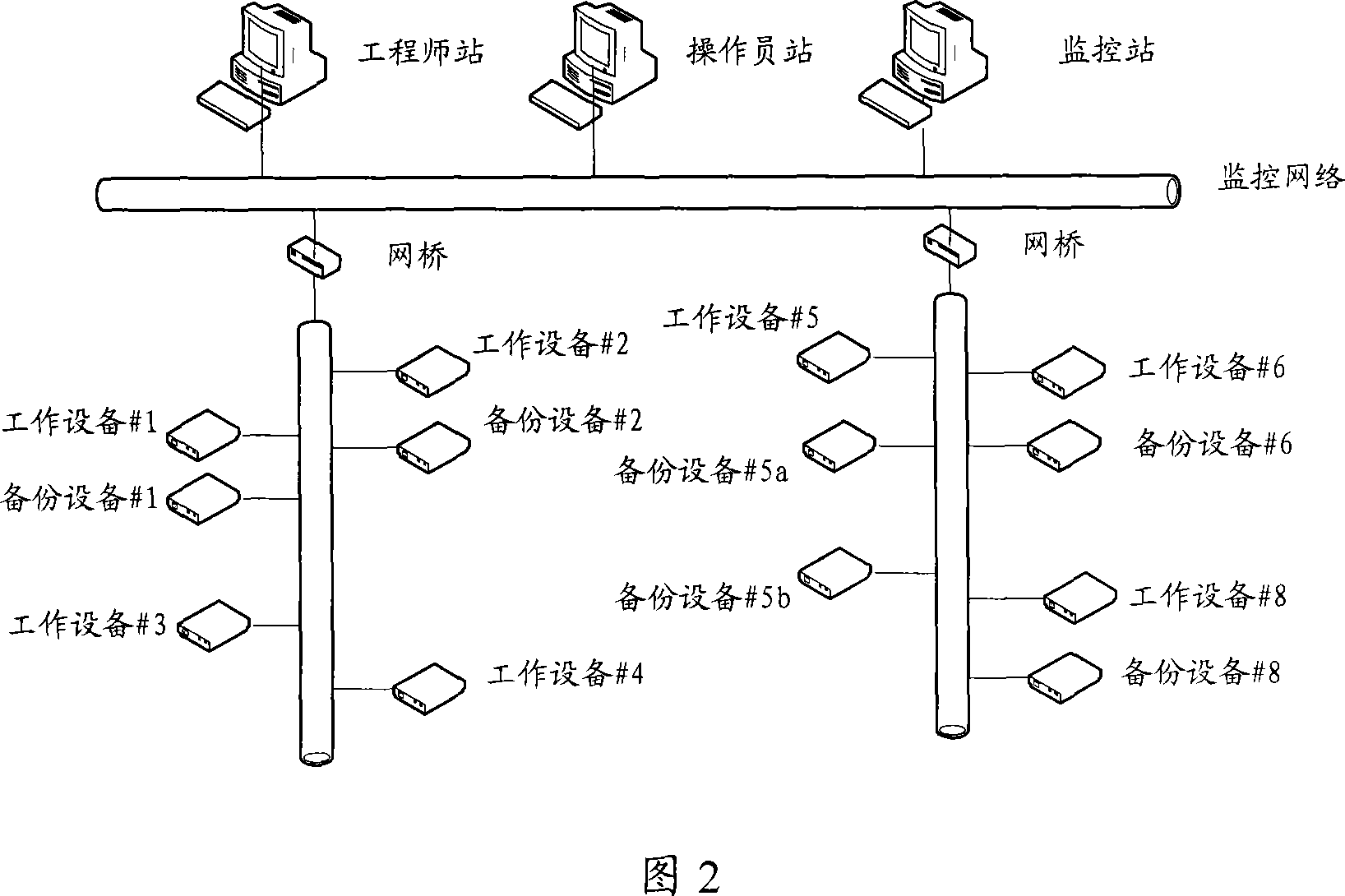
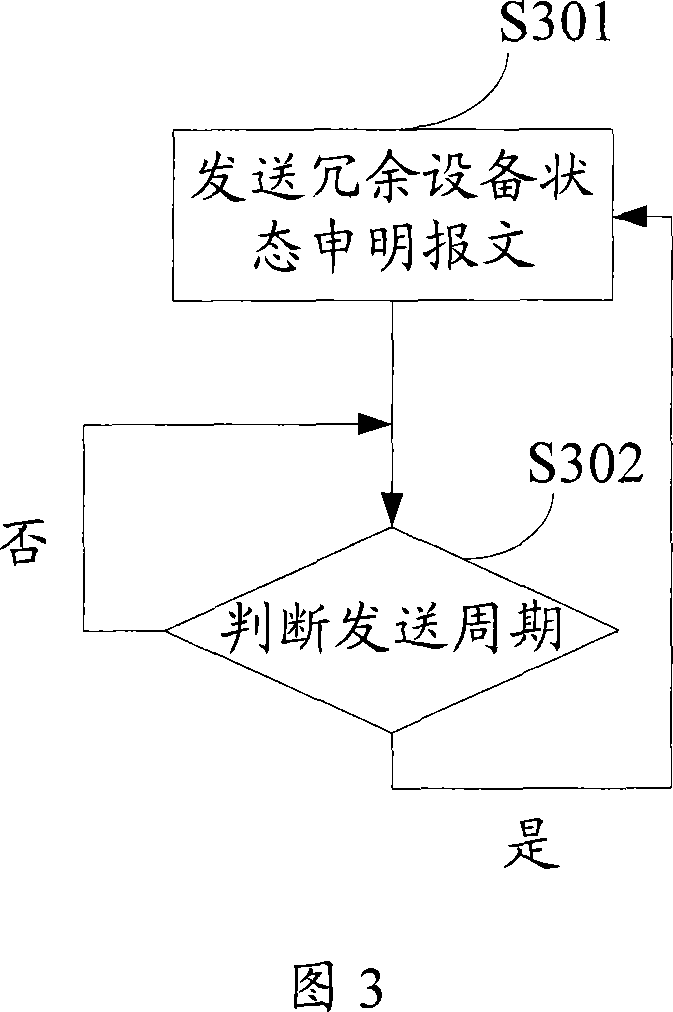
InactiveCN101047487ASolve redundancyStart fastError preventionData switching by path configurationBroadcastingControl network
A method for realizing device redundancy in industrial control network includes broadcasting declaration message of redundant device state in network periodically by operation device, switching itself state over on operation state by back-up device if said declaration message is not received by back-up device of operation device and broadcasting switchover message of redundant device in network, updating communication connection of operation device to be communication connection with said back-up device by device received said switchover message and set in network.
Owner:SUPCON GRP +1
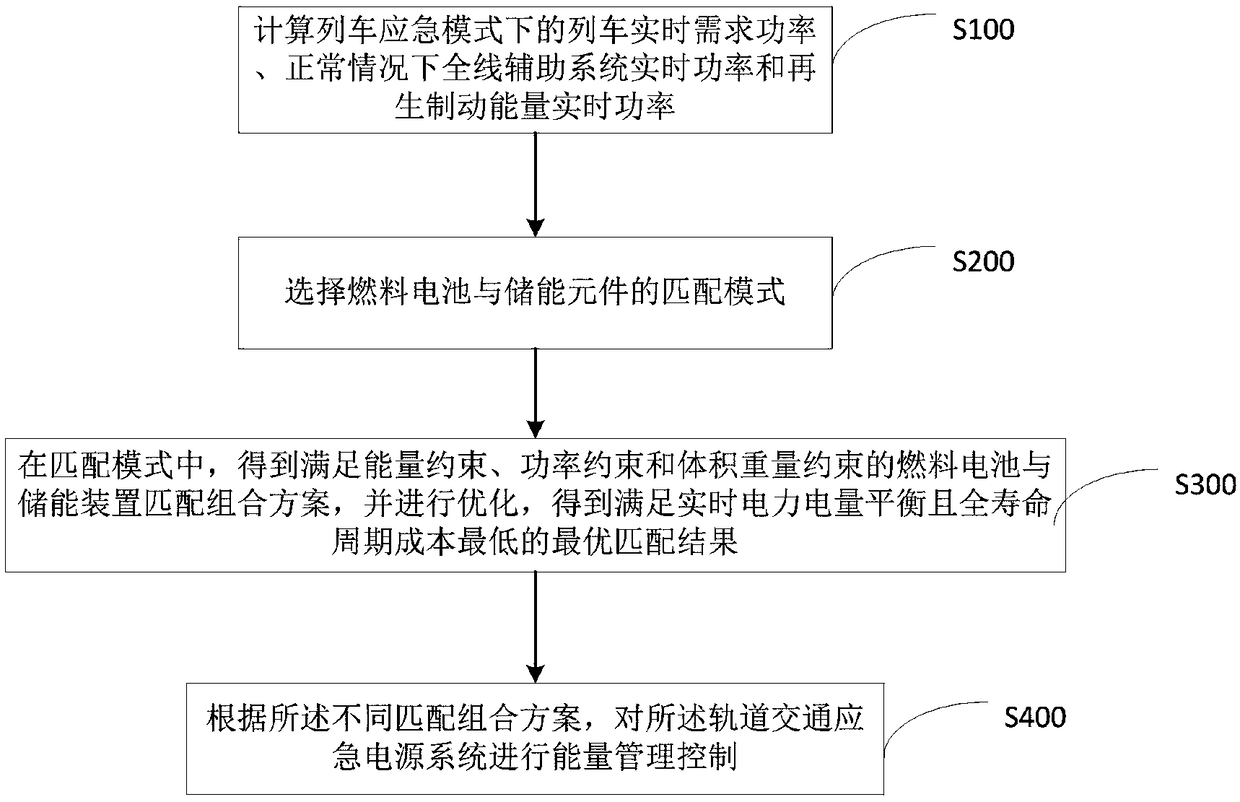
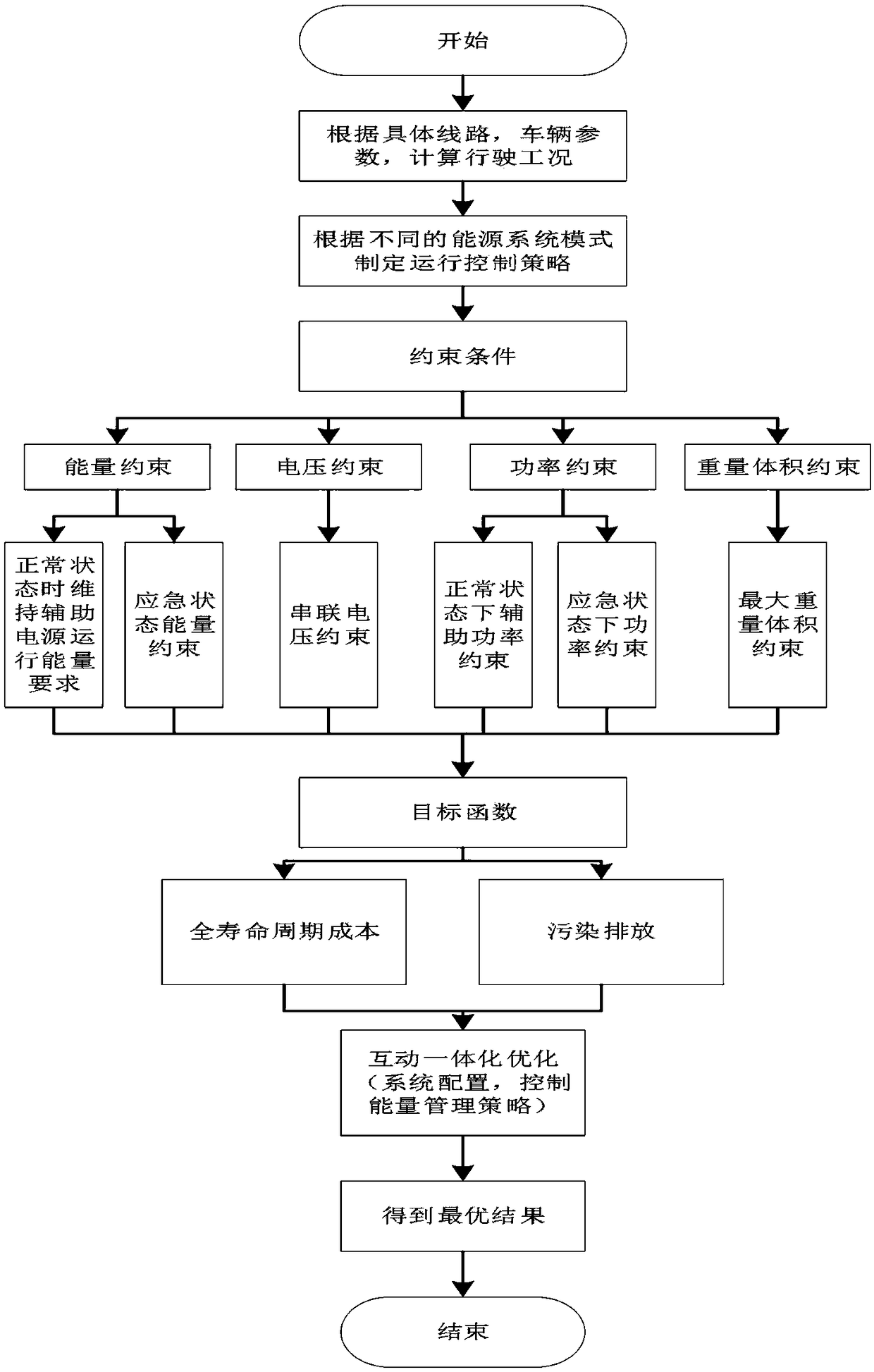
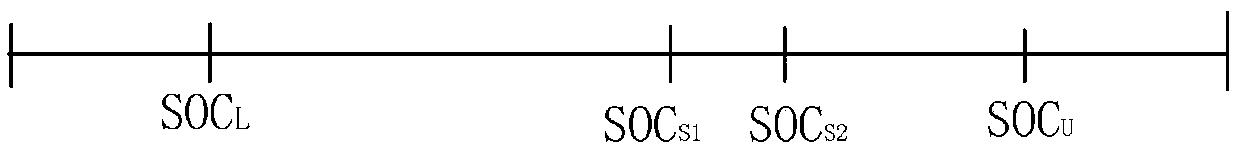
Rail transit emergency power supply system and control method
ActiveCN108832611ASolve redundancySolve energy wasteDc network circuit arrangementsBatteries circuit arrangementsFuel cellsEnergy control
The invention discloses a rail transit emergency power supply system and a control method, belonging to the technical field of rail transit power supply. The invention mainly comprises a matching design of a D-series high-speed train emergency power supply system and a hybrid power control method, wherein the emergency power supply system mainly comprises a fuel cell system, an energy storage device, an energy controller and the like. The matching design is mainly based on the running line of D-series high-speed trains under the emergency mode and the power and energy under vehicle parametersas constraint conditions, and the volume cost is used as the objective function for performing matching design to obtain a scheme of D-series high-speed train emergency power system. According to theinvention, the emergency power supply system of the D-series high-speed train can be effectively designed and controlled, the electric energy demand under the emergency situation is satisfied, and theenergy utilization efficiency is improved.
Owner:SOUTHWEST JIAOTONG UNIV
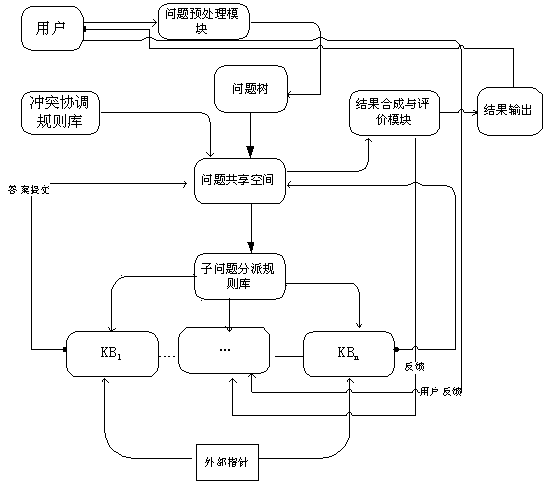
Multi-user repository cooperation method
ActiveCN103425776AAddressing Redundancy and StalenessImprove accuracySpecial data processing applicationsProblem resolutionData science
The invention provides a multi-user repository cooperation method, which comprises the following steps: firstly, converting a problem into a problem tree; assigning a subproblem into a corresponding repository by a subproblem dispatching rule to solve the subproblem; after the subproblem is solved, carrying out answer integration by a blackboard mechanism; and finally, obtaining a final answer, and submitting the final answer to a user by the cooperation of a coordinating rule repository and a knowledge evaluation system. According to the multi-user repository cooperation method disclosed by the invention, the knowledge updating deficiency is solved by the multi-repository real-time relevance, and a rigorous knowledge evaluation system is established to guarantee the accuracy and the reliability degree of an answer fed back to the user finally. Meanwhile, according to the user feedback, the evaluation score of the knowledge is revised in real time to optimize the knowledge structure and the knowledge depth, multi-repository cooperation parallel processing is utilized to solve the problem, and the problem solving capability and efficiency can be improved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
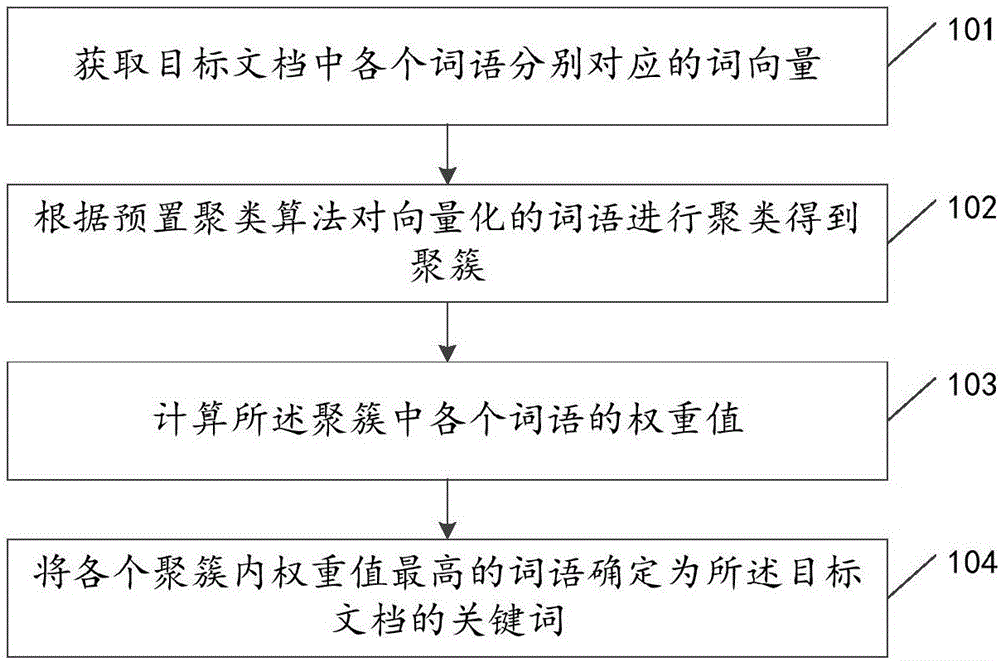
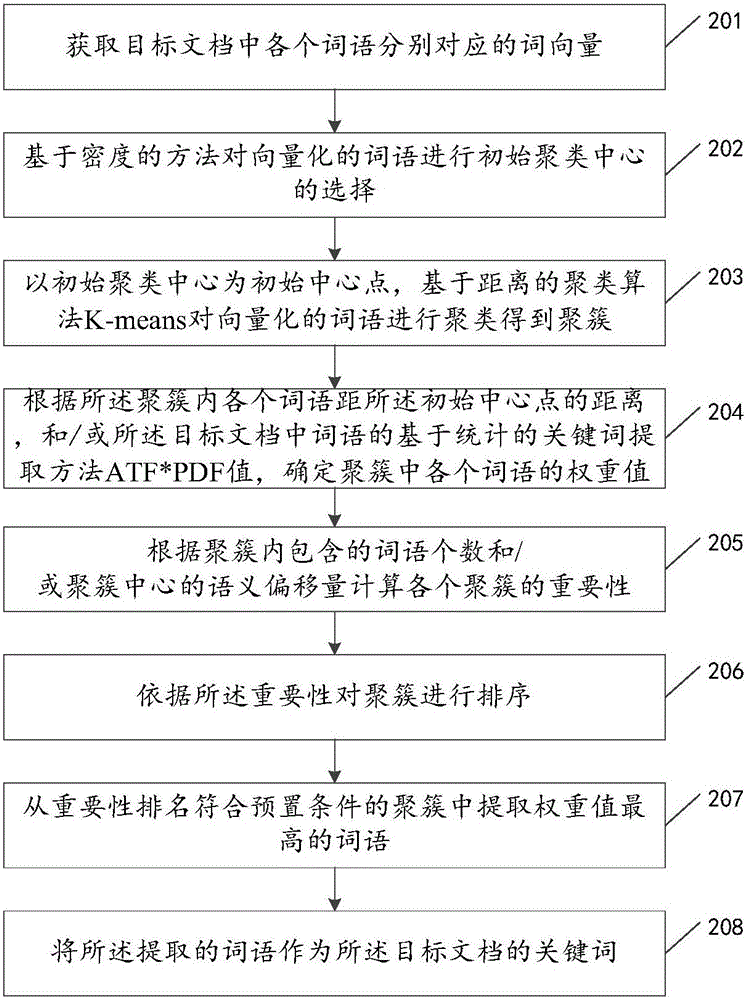
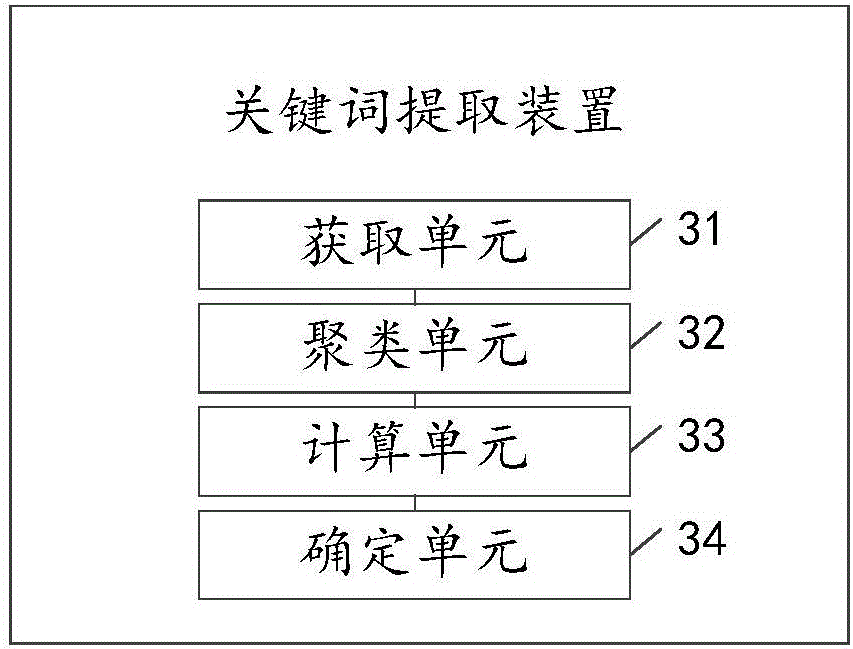
Keyword extracting method and device
ActiveCN106599269ASolve redundancySpecial data processing applicationsText database clustering/classificationWeight valueAlgorithm
The invention discloses a keyword extracting method and device, and relates to the technical field of text processing. The method mainly aims at solving the problem that the keyword extracting redundancy is high. The main technical scheme disclosed by the invention is as follows: acquiring a word vector corresponding to each word in a target document; clustering the vectorized words according to a preset clustering algorithm to obtain a cluster, wherein the semantics of the words in the cluster are the same or similar to each other; computing a weighted value of each word in the cluster; and determining the word with the highest weighted value in the each cluster as the keyword of the target document. The method and device disclosed by the invention are mainly used for extracting the keyword from the target document.
Owner:NEUSOFT CORP
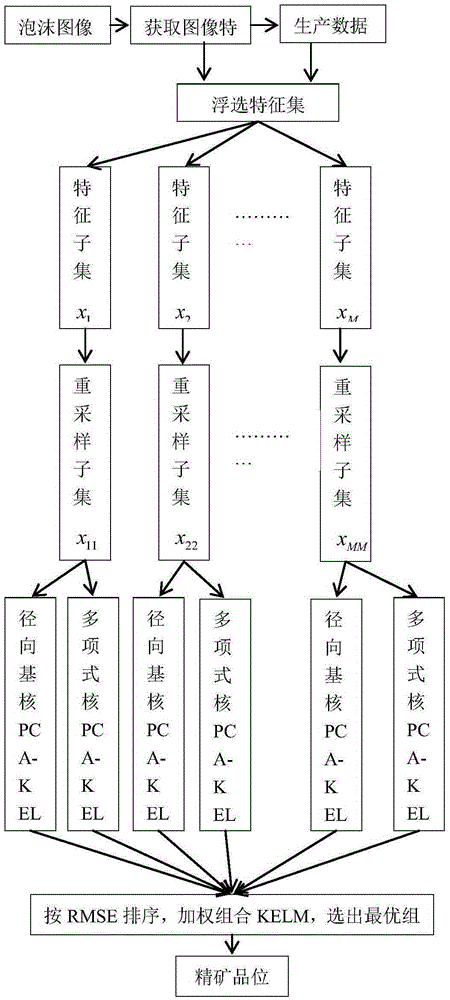
Antimony ore grade soft-measurement method based on selective fusion of heterogeneous classifier
ActiveCN105260805ASolve the problem of difficult online detectionSolve redundancyForecastingModel compositionOptimal weight
The invention provides an antimony ore grade soft-measurement method based on the selective fusion of a heterogeneous classifier. The method comprises the step of together forming a feature space based on the pretreatment of antimony flotation froth image feature data and production data related to the grade of the antimony ore. According to the method, firstly, some feathers are randomly selected to form a plurality of sub-sample spaces. Secondly, a plurality of different sub-samples in each sub-sample space are sampled through the bootstrap sampling process. At the same time, the PCA analysis is conducted on each sub-sample to obtain key features that are high in sensitivity to grade change and free of / weak in dependency. Thirdly, two KELMs are conducted respectively for each sub-sample set to construct a candidate sub-model, based on an RBF kernal of better learning ability and a polynomial kernel type KELM of better generalization ability. Fourthly, each candidate sub-model is endowed with a weight based on the method of information entropy. Finally, all candidate sub-models are sorted from small to large based on the RMSE, and then an optimal weighted sub-model combination is selected as a final model for the prediction on the grade of the antimony ore.
Owner:CENT SOUTH UNIV
Design method of software defect prediction model based on kernel principal component analysis algorithm
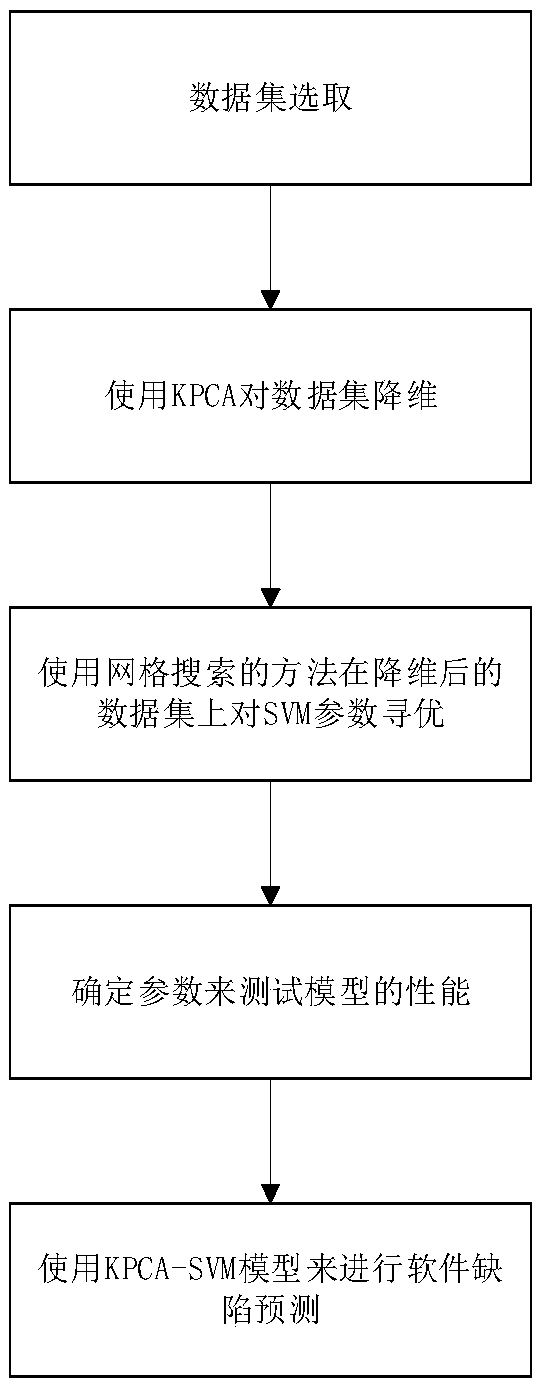
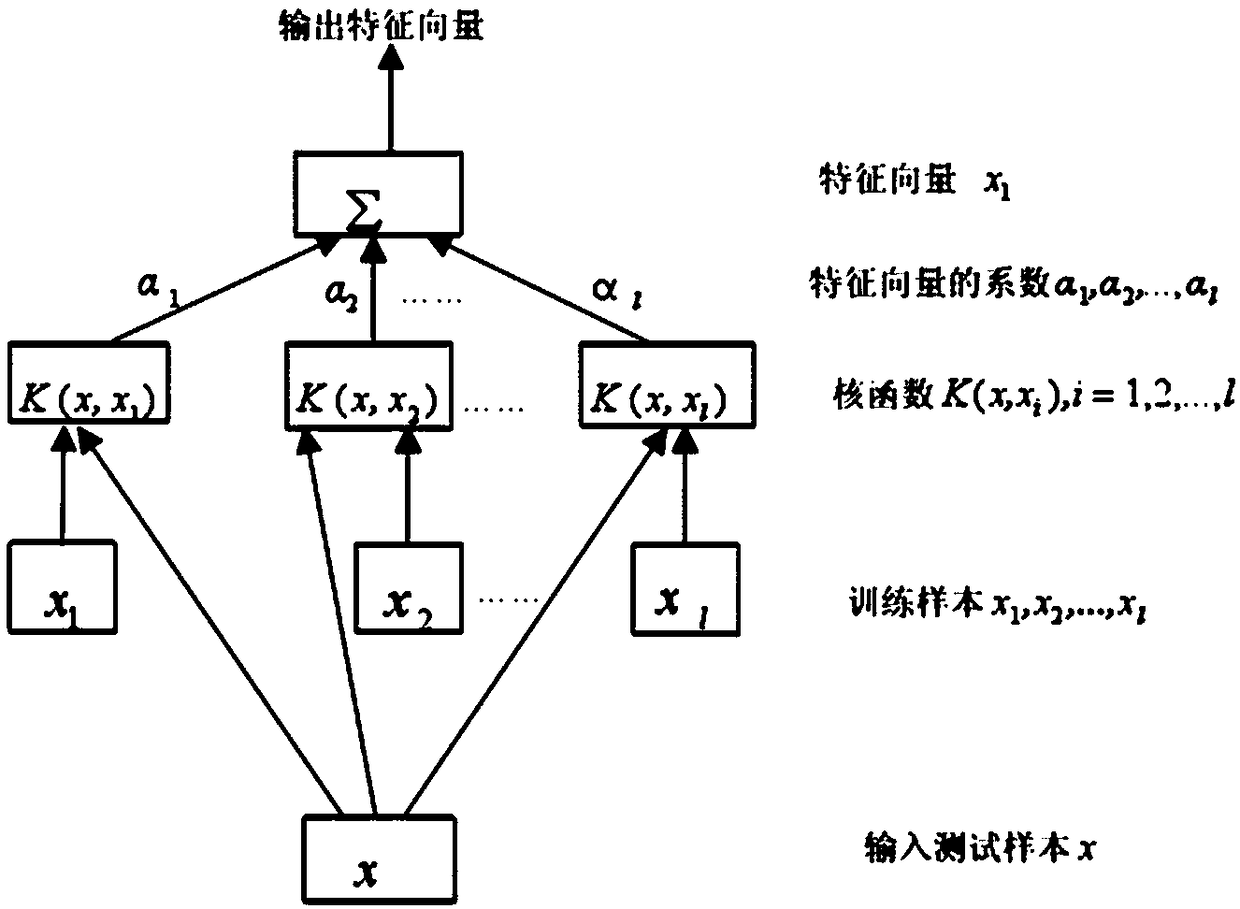
InactiveCN109165160ASolve redundancyMaintain global featuresCharacter and pattern recognitionSoftware testing/debuggingKernel principal component analysisData set
The invention discloses a design method of a software defect prediction model based on a kernel principal component analysis algorithm. The method includes: step 1, determining a data set for traininga model, and dividing the data set into a training set and a test set; step 2, carrying out dimensionality reduction treatment on that training set by using a kernel principal component analysis algorithm: selecting kernel functions and determining parameter of the kernel functions, selecting dimensionality reduction dimensions, and then reducing the dimensionality of the training set; step 3, taking the reduced-dimension training set as input, selecting Gauss (RBF) function as SVM kernel function, defining value interval and step size, and using grid search to find the optimal solution of SVM parameter penalty factor C and kernel function parameter sigma through cross-validation experiment method of ten fold; step 4, testing the performance of the model through a test set, and completingthe design of the software defect prediction model. The invention can solve the problem of redundant data in the measurement element of the software defect, and improve the accuracy rate of the machine learning algorithm.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
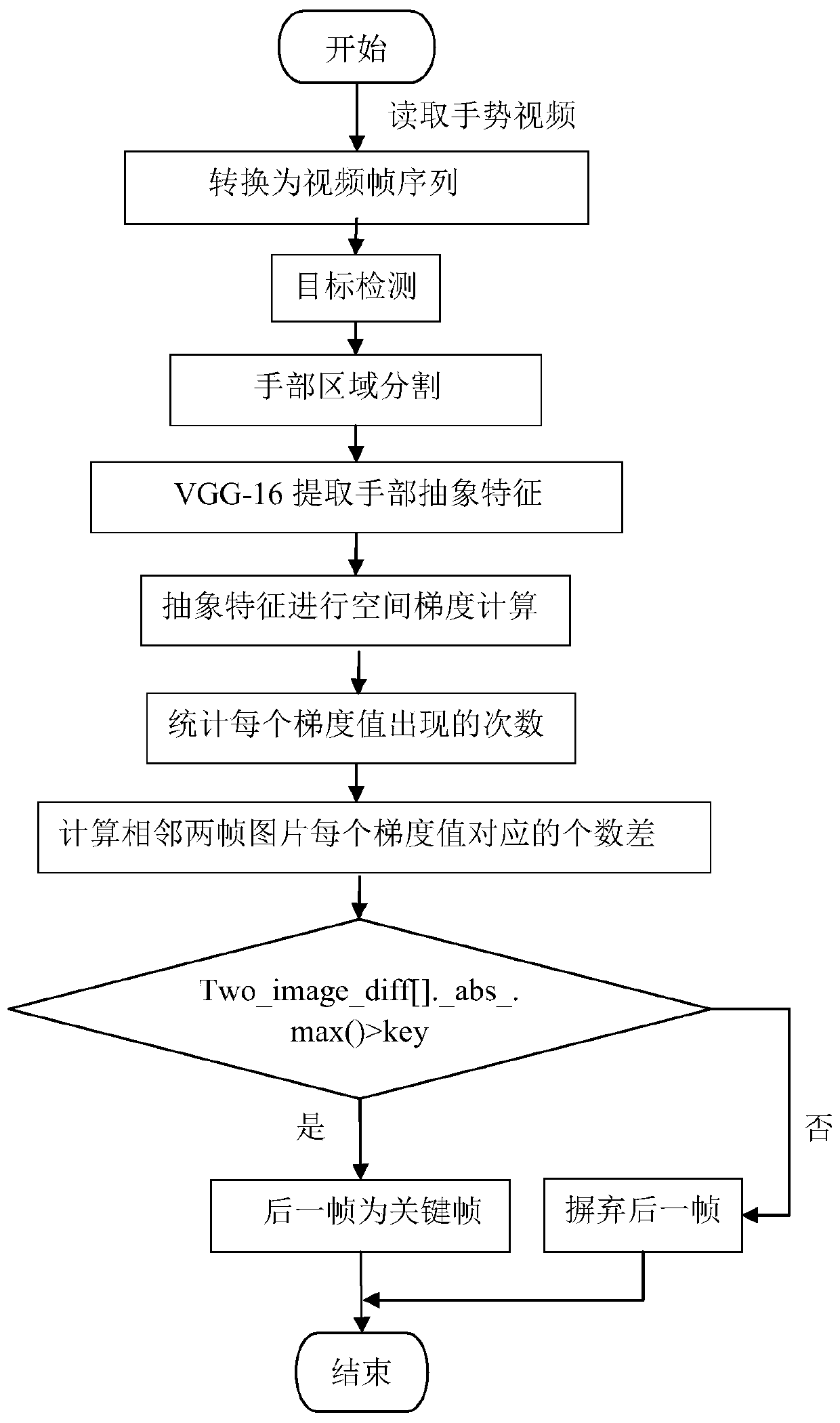
Gesture image key frame extraction method based on deep learning
ActiveCN110110646AReduce complexityReduce the amount of parametersCharacter and pattern recognitionNeural architecturesSmall amplitudeComputer vision
The invention discloses a gesture image key frame extraction method based on deep learning. The method comprises the following steps: reading an input gesture video, and converting the input gesture video into a video frame image; detecting a gesture in a video frame image by adopting a Mobilenet-SSD target detection model, and segmenting the detected gesture; and training a gesture segmentation image by adopting a VGG16 training model to obtain a corresponding abstract feature, calculating a spatial gradient, and setting an appropriate threshold value to judge a key frame according to a gradient difference between two adjacent frames of images. The Mobilenet-SSD target detection model is used to detect and segments a hand area, background area noise is removed; hand abstract features areaccurately extracted by utilizing VGG-16, so that the expression capability of the picture is greatly enhanced;, the parameter quantity is reduced, the model complexity is reduced, and the method is suitable for small-amplitude changing video key frame extraction.
Owner:康旭科技有限公司
Light field camera internal parameter calibration device and method
InactiveCN109615661AImprove calibration accuracyCounteract refractionImage analysisLight-field cameraMotion controller
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Gesture image key frame extraction method based on image similarity
ActiveCN110245593AHigh precisionGood effectCharacter and pattern recognitionCosine similarityRadiology
The invention discloses a gesture image key frame extraction method based on image similarity. The method comprises the steps of firstly, converting an input gesture video into a video frame image; classifying the video frame images into the static gesture images and the dynamic gesture images by adopting a Mobilenet-SSD target detection model; for the dynamic gesture image, adopting the cosine similarity to judge an image key frame; for the static gesture image, firstly adopting the cosine similarity for pre-extracting the key frame, then using a VGG16 network model for extracting the abstract features, carrying out the space gradient calculation, and according to the gradient difference of two adjacent frames of images, setting a self-adaptive threshold value to complete the judgment of the final key frame of the static image. According to the method, the problems of missing detection and redundancy of the video key frames are effectively solved, and by adopting the VGG-16 network model, the expression capability of the image is greatly enhanced, and the pre-extracted static gestures can be extracted again, so that the number of the static gesture key frames is reduced.
Owner:康旭科技有限公司
Stratum fracture monitoring and pre-warning system and method
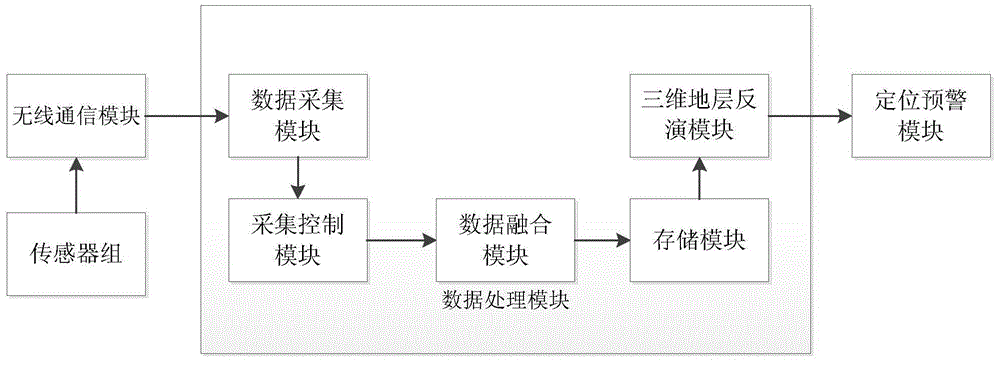
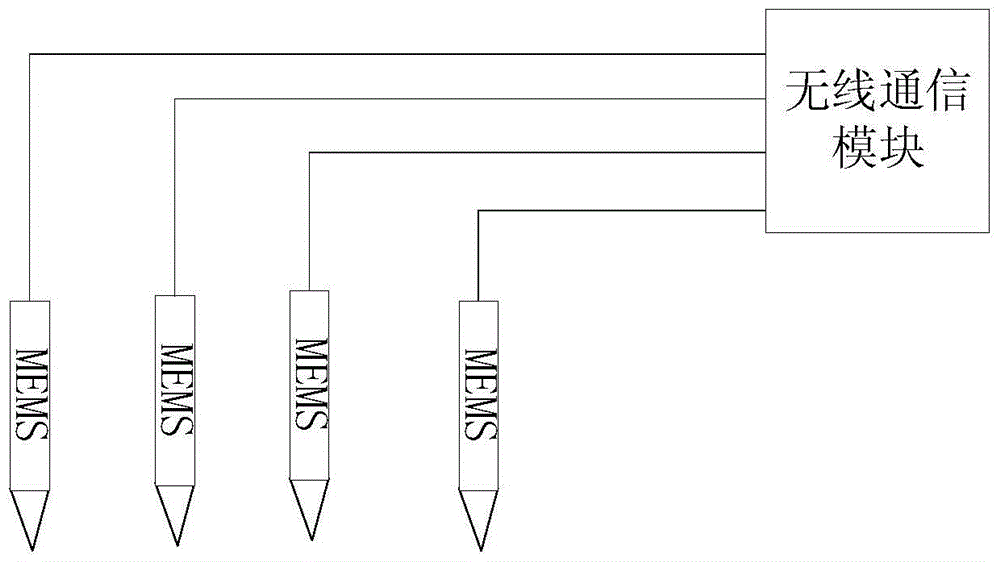
InactiveCN104483700AReduce use costConvenient post-debuggingSeismic signal processingData processingProspecting
The invention discloses a stratum fracture monitoring and pre-warning system and method, and relates to the technical field of geological prospecting. The system comprises a sensor module, a wireless communication module, a data processing module and a positioning pre-warning module, wherein the sensor module consists of a plurality of MEMS (Micro-electromechanical System) digital acceleration sensors; the wireless communication module is used for transmitting feedback electromotive force generated by the sensor set to the data processing module; the data processing module is used for processing acquired data, comparing monitored earthquake impact with a set pre-warning threshold value and then transmitting a pre-warning signal to the positioning pre-warning module to prompt a worker. The system and the method have the beneficial effects that the data is acquired and processed by using the wide MEMS digital acceleration sensors, the cost is low, the later debugging and maintenance of the system are extremely convenient, the stratum fracture condition can be monitored in real time, the position of a stratum fracture is accurately positioned and the worker is timely prompted to achieve a pre-warning effect, and the monitoring accuracy is high.
Owner:CHINA MERCHANTS CHONGQING COMM RES & DESIGN INST +1
Block-level snapshot system and user reading and writing method based on same
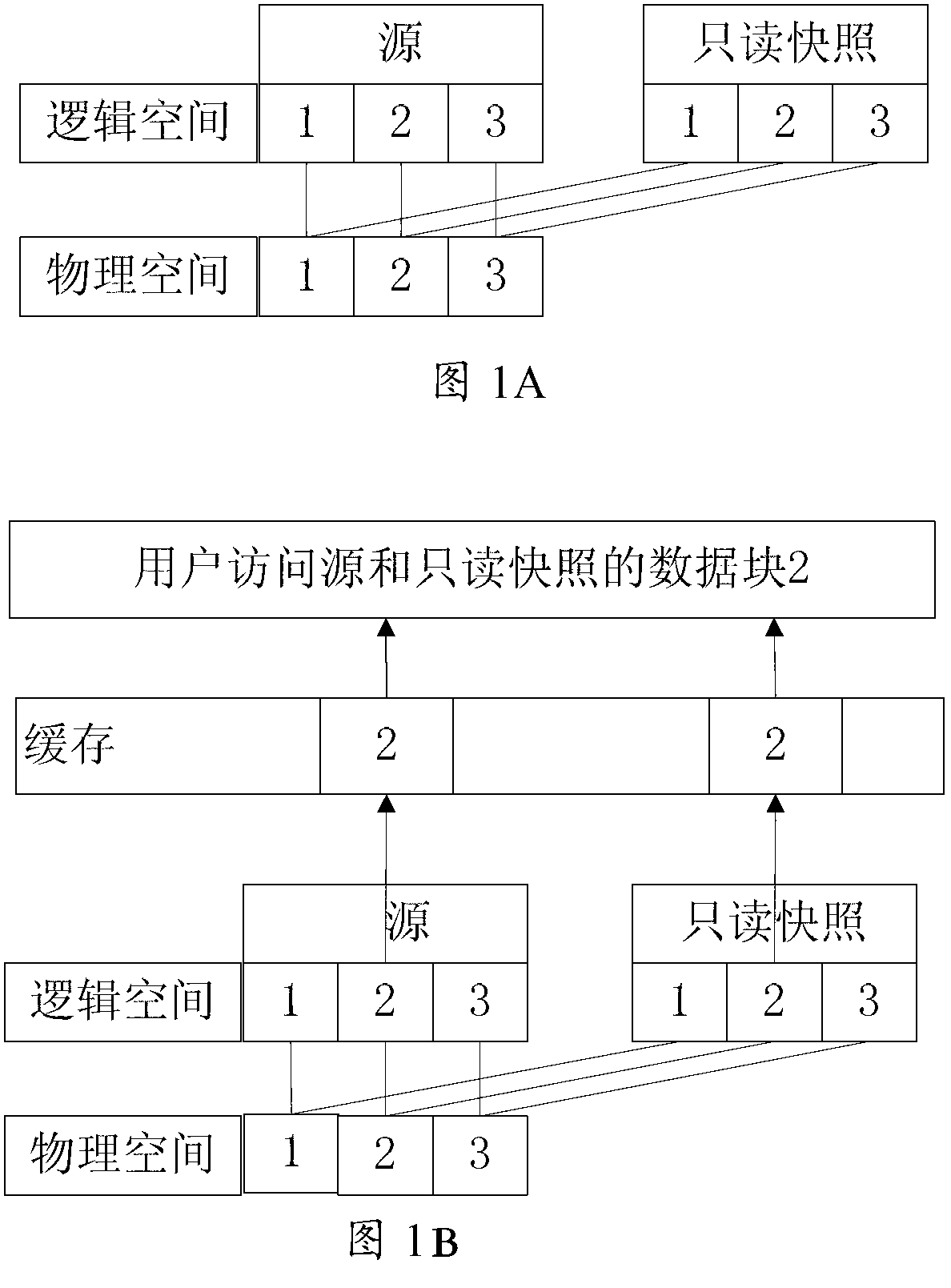
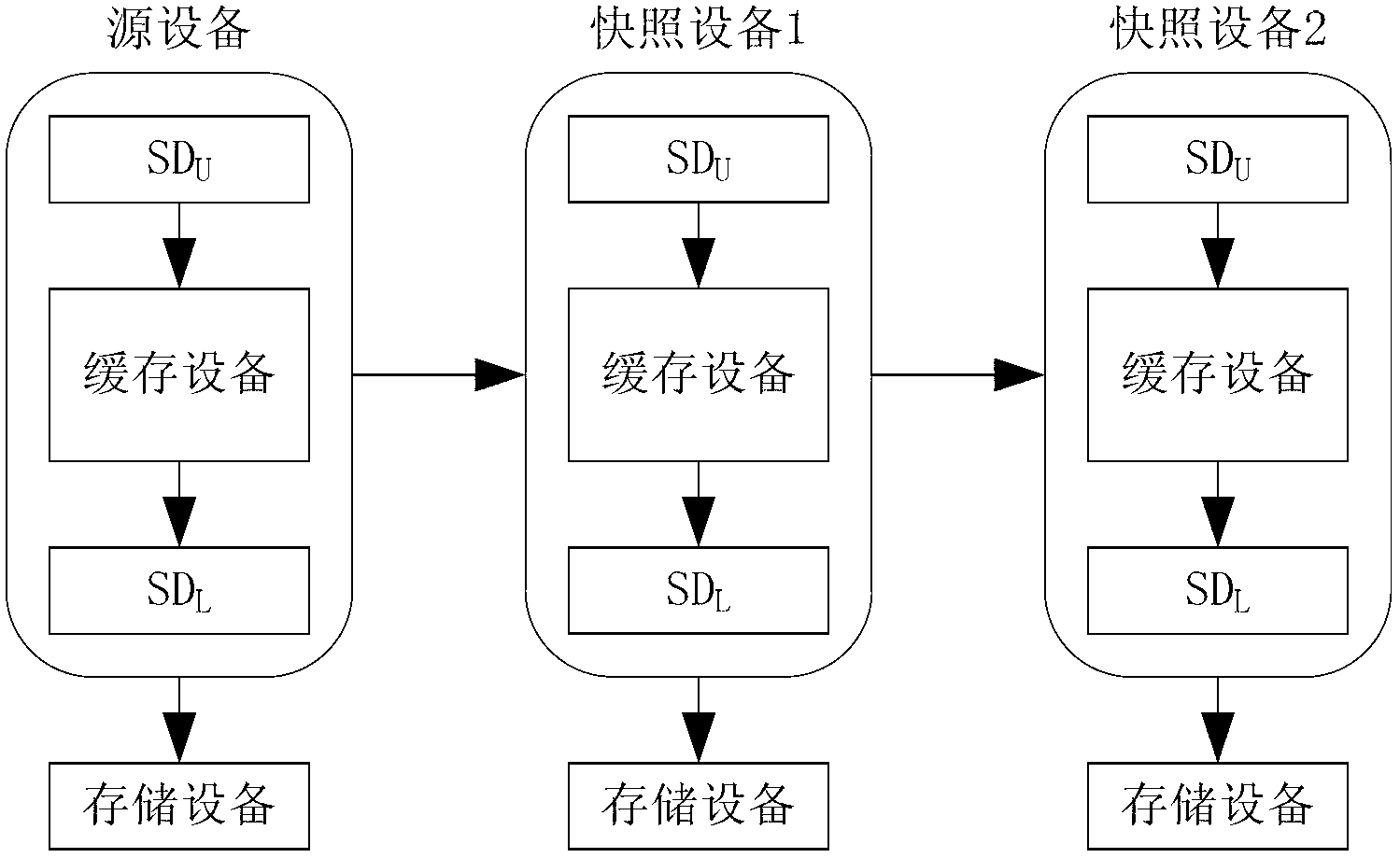
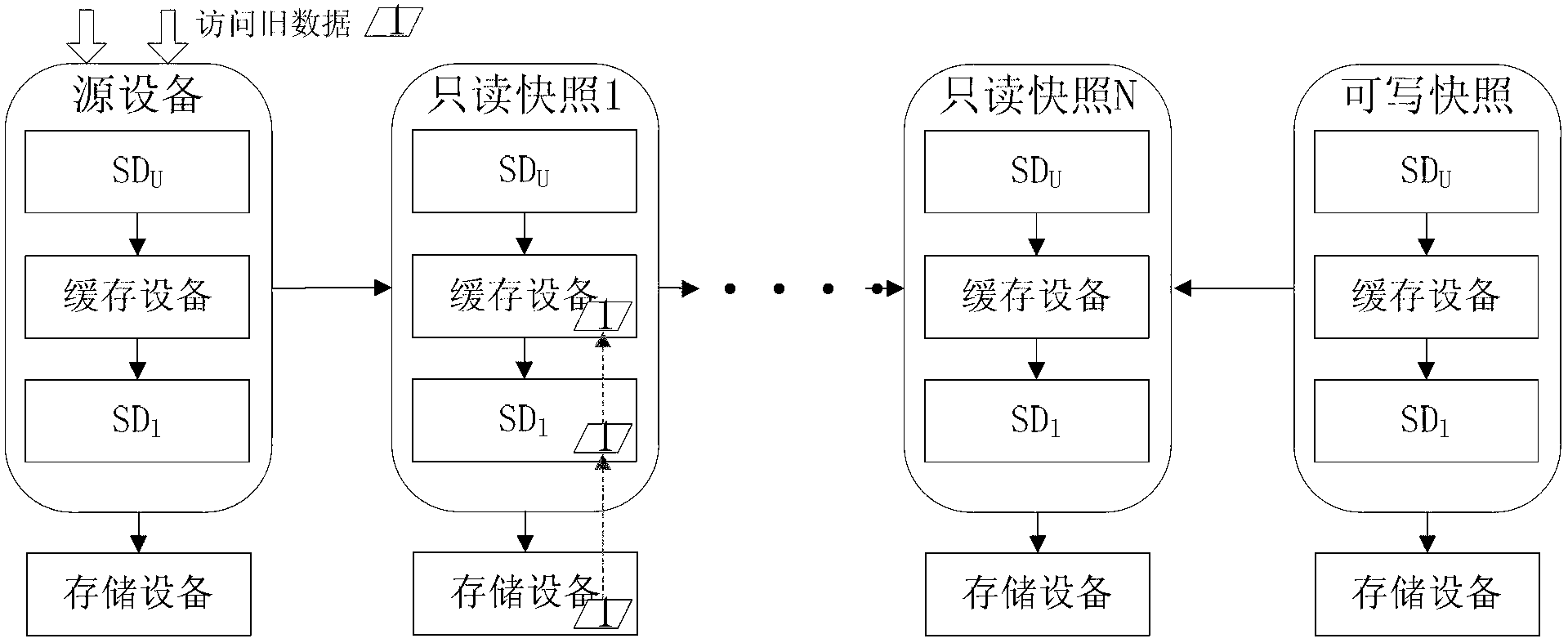
ActiveCN103077099ASolve redundancyIncrease profitMemory adressing/allocation/relocationRedundant operation error correctionBlock levelService data unit
The invention provides a block-level snapshot system, which comprises a snapshot device chain formed by a source device and one or more than one snapshot device, wherein the source device and the snapshot device consist of a cache device, a pair of block devices SDU (service data unit) and SDL (standard description language), and a storage device. The block device SDU is used for receiving and processing a reading and writing request of a user on a system, the cache device is used for processing the reading and writing request of the user forwarded from the block device SDU and is used for caching data, and the block device SDL is used for processing a reading request forwarded from the cache device. When the reading request of the user is received by the system, the reading request which is not of local data is forwarded to the block device SDU of a previous time point by the block device SDU; and the reading request which is of local data is read from the storage device and is returned to the cache device for caching by the block device SDL. The cache device is only used for caching the data locally stored, and thus the problem of the redundancy of cache resource is solved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
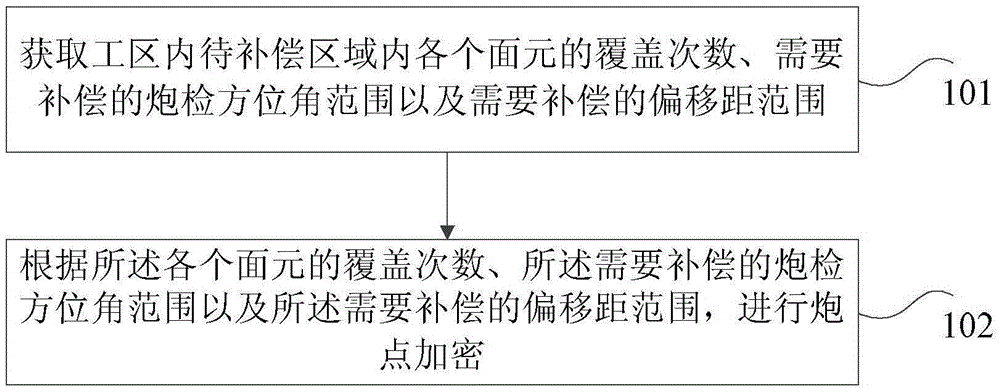
Shot point arrangement method and device
ActiveCN105607115ASurf properties are reasonable and reliableCoverage is evenly distributedSeismic energy generationOffset distanceSurface element
The invention provides a shot point arrangement method and device, wherein method comprises the steps: acquiring covering times, an offset azimuth coverage needing to be compensated and a offset distance range needing to be compensated of every surface element in a to-be-compensated area in a work area; and encrypting the shot point according to the above values. In the embodiment of the invention, the arrangement of the covering times, the offset azimuth and the offset distance of every surface element is comprehensively considered, the covering times compensation is performed in the offset azimuth coverage and offset distance range, and an optimal encrypted shot point position is automatically obtained. The covering times, and the arrangement of the offset azimuth and the offset distance are considered for the arrangement of the encrypted shot point, therefore the finally obtained compensated work area surface element attributes are more reasonable and reliable than before, so that the redundancy problem of the surface element attributes is solved, the possibility of the appearance of the redundant encrypted shot point is reduced, and the work efficiency is greatly improved.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
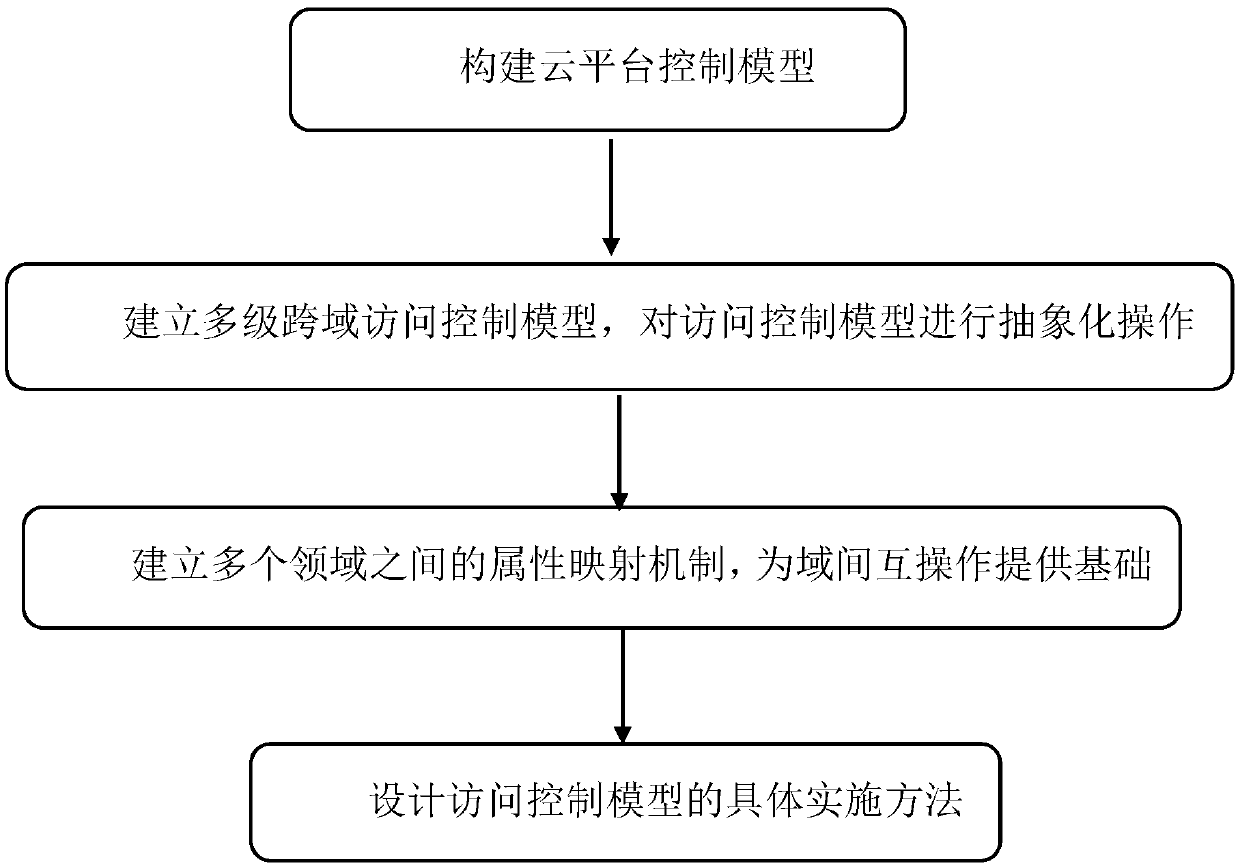
A multi-core mesh multi-level cross-domain access control method based on cloud platform
ActiveCN109257364ASolve complexityIncrease or decrease access control impactData switching networksInter-domainInteroperability Problem
The invention discloses a multi-core mesh multi-level cross-domain access control method based on a cloud platform, which comprises building a cloud platform control model, addressing the complexitiesof multilevel cross-domain access and privilege management;anaccess control model is establish, abstraction operations are performed on the access control model; attribute mapping mechanism is established between multiple domains, providing a basis for interdomain interoperability;the concrete implementation method of access control model is designed; rules for multilevel cross-domain accessare established; managers are established;the establishment of cloud platform access control model provides some possibilities and approaches for multi-level and cross-domain access, cloud platforms are highly modifiable and scalable. The multi-level cross-domain access control model has good scalability and high flexibility. The multi-core mesh processing method is adopted to process the cross-domainaccess request, which improves the processing efficiency of the multi-level cross-domain access request.
Owner:CHENGDU UNIV OF INFORMATION TECH
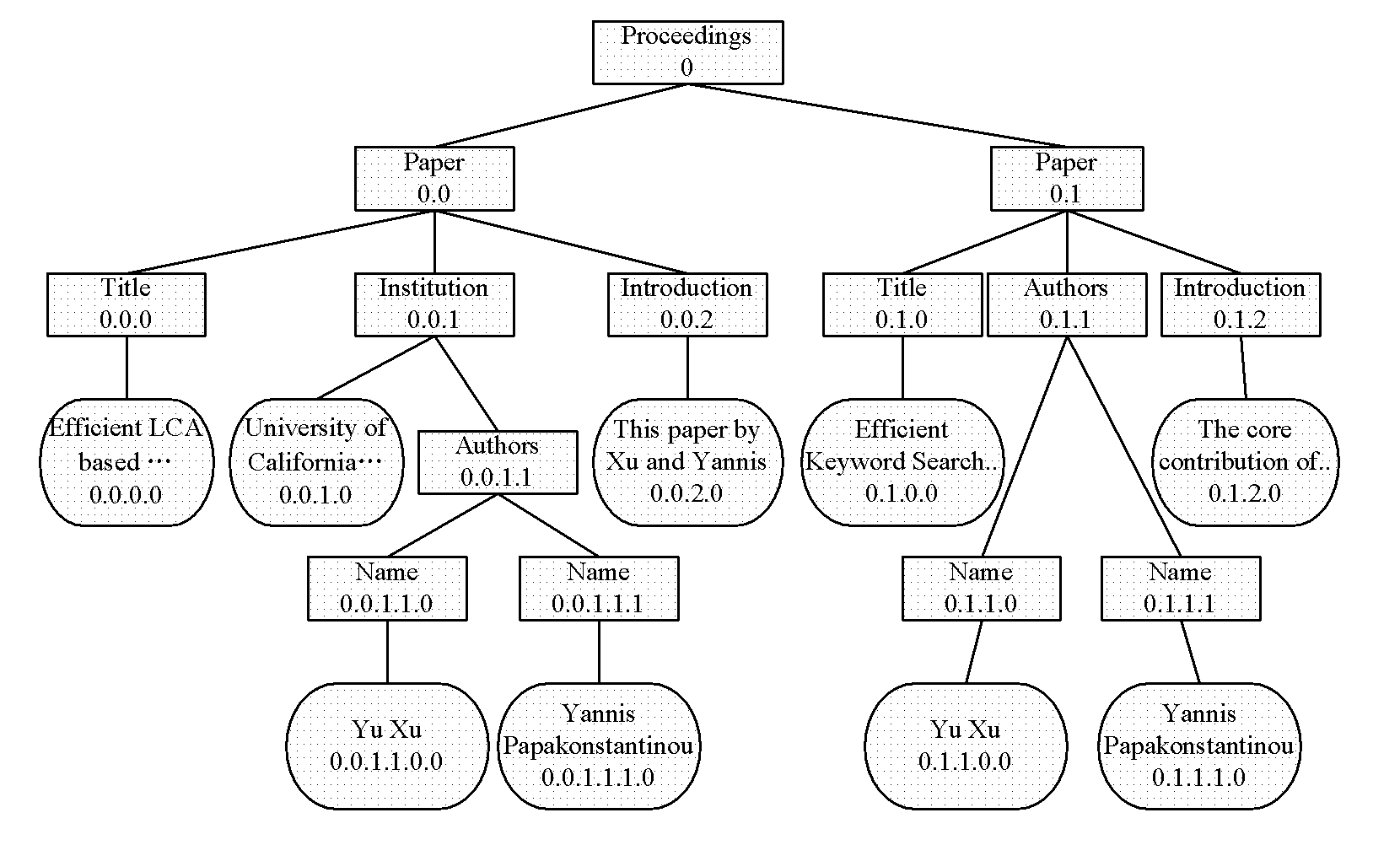
Indexing structure of XML (Extensive Markup Language) document
InactiveCN101833588ASolve redundancyReduce processingSpecial data processing applicationsRelationship - FatherData retrieval
The invention discloses a new indexing structure of an XML (Extensive Markup Language) document, belonging to the field of data retrieval. For nodes in the XML document, LAF (Layer order And Father numbering) coding is defined into three parts: a hierarchy traversal number of the nodes, a hierarchy traversal number of father nodes of the nodes and depths at which the nodes locate. The invention further provides a two-stage indexing structure based on the LAF coding; in the indexing structure, the plain text attribute of the XML document is stored in a primary index, and the semi-structure attribute of the XML document is stored in a secondary index, and the primary index and the secondary index are associated together through a pointer. The invention provides the two-stage indexing technology, which can not only avoid the redundancy problem possibly brought by the traditional indexing method, but also support a more-efficient retrieval algorithm and reduce the treatment frequency to invalid elements by the retrieval algorithm.
Owner:PEKING UNIV
Software defect prediction method for support vector machine based on neighborhood preserving embedding algorithm
ActiveCN107957946ASolve redundancyImprove accuracyCharacter and pattern recognitionSoftware testing/debuggingSupport vector machineData set
The invention provides a software defect prediction method for a support vector machine based on a neighborhood preserving embedding algorithm. The method is used for solving the problem of data redundancy of software metrics. The method comprises the steps that a training set X1 and a testing set X2 are selected from a software defect prediction data set; the NPE algorithm is adopted for conducting dimension reduction on the training set X1 and the testing set X2; a training set Y1 after dimension reduction is used as a training input set, the support vector machine (SVM) is used for training, and a trained defect prediction model is obtained; a testing set Y2 after dimension reduction is used as a testing input set, the trained defect prediction model is used for prediction, a predictionresult is compared with an actual result, and if the prediction result meets a stopping condition, the software defect prediction model at this time is an optimum software defect prediction model; ifnot, SVM training is executed again, and optimization is conducted.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Millimeter wave radar and video monitoring camera combined calibration method
InactiveCN113012237AImprove reliabilityImprove accuracyImage enhancementImage analysisVideo monitoringVideo sensors
The invention provides a millimeter wave radar and video monitoring camera combined calibration method. According to the invention, the video detection technology is utilized to accurately identify the types of traffic participants, and the millimeter wave radar detection technology is combined to monitor the target in the positioning range in real time, so that the two technologies complement each other. A multi-sensor fusion model is utilized to establish an accurate coordinate transformation matrix among a radar coordinate system, a video sensor coordinate system, an image coordinate system and a pixel coordinate system, and spatial fusion of multi-sensor data is realized.
Owner:WUHAN UNIV
Unmanned aerial vehicle safety certifiable information communication processing method based on cloud platform
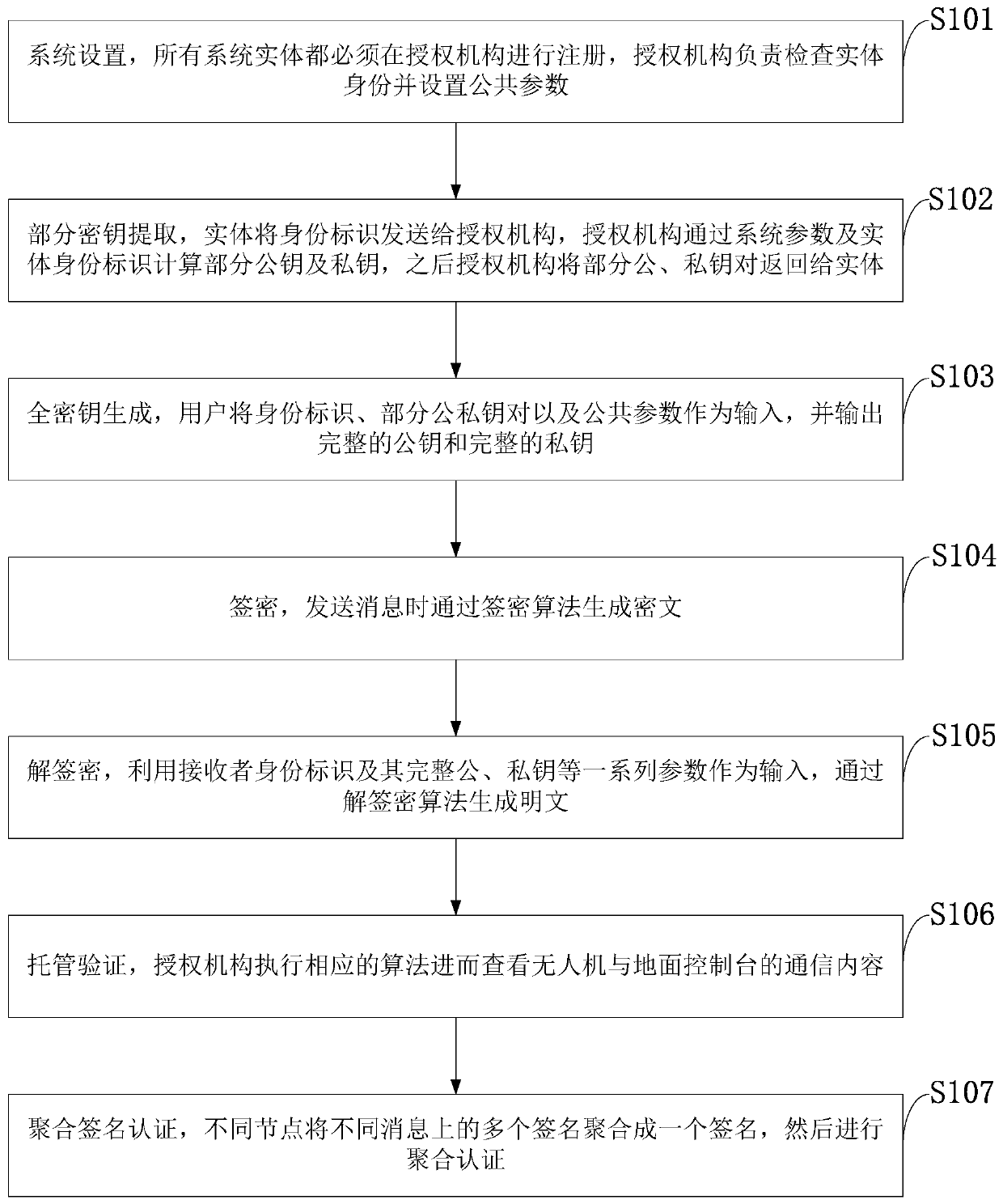
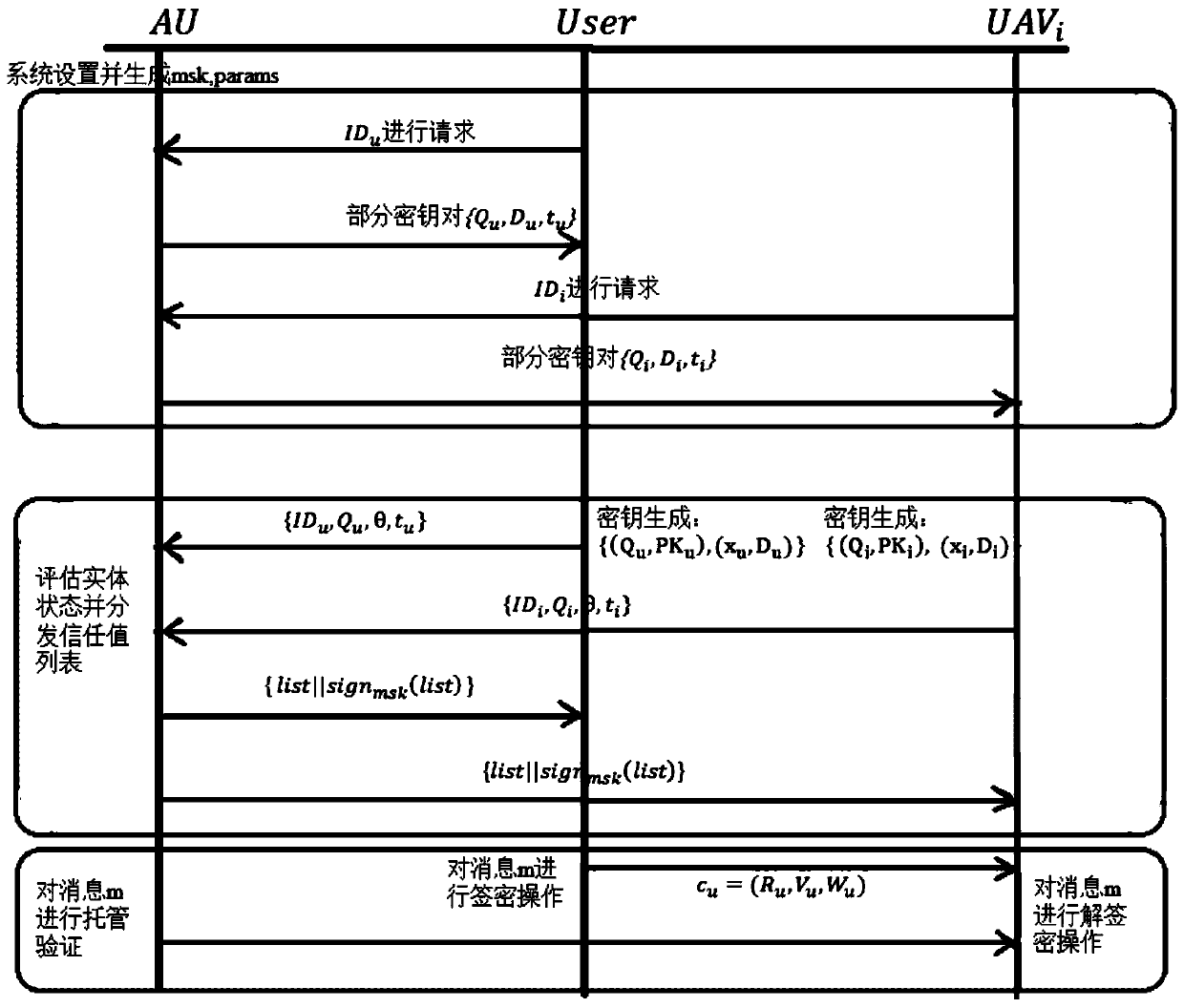
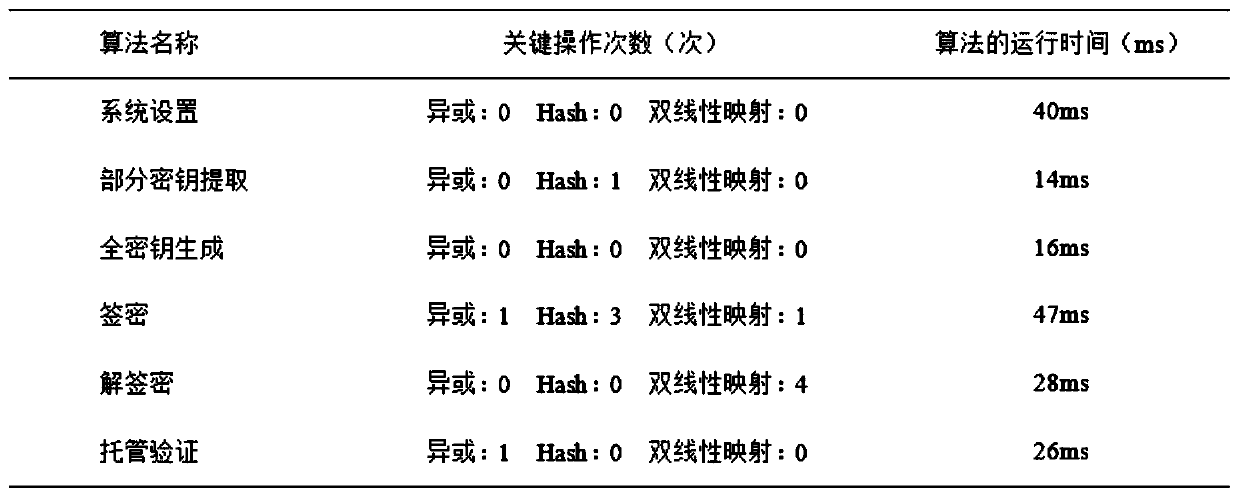
ActiveCN110690959AReduce overheadSolve redundancyKey distribution for secure communicationTransmission systemsPlaintextAlgorithm
The invention belongs to the technical field of unmanned aerial vehicle communication, and discloses an unmanned aerial vehicle safety certifiable information communication processing method and system setting based on a cloud platform. The method includes: setting a system; extracting a part of secret keys; generating a full key; generating a ciphertext through a signcryption algorithm when a message is sent; generating a plaintext through an unsigncryption algorithm by taking the receiver identity label and the parameters thereof as input; enabling the authorization mechanism to execute a corresponding algorithm so as to check and supervise the communication content of the unmanned aerial vehicle and the ground console; and enabling different nodes to aggregate a plurality of signatureson different messages into one signature for aggregation authentication, so as to reduce the authentication overhead. According to the invention, confidentiality, authentication, non-repudiation and unforgeability are realized; public key encryption and digital signature are combined, and confidentiality and identity authentication can be achieved at the same time. The authorization mechanism provides part of the key through the secure channel, and can check the access command and the location information. The control command and the position information cannot be forged under the condition ofno other part of private keys.
Owner:XIDIAN UNIV
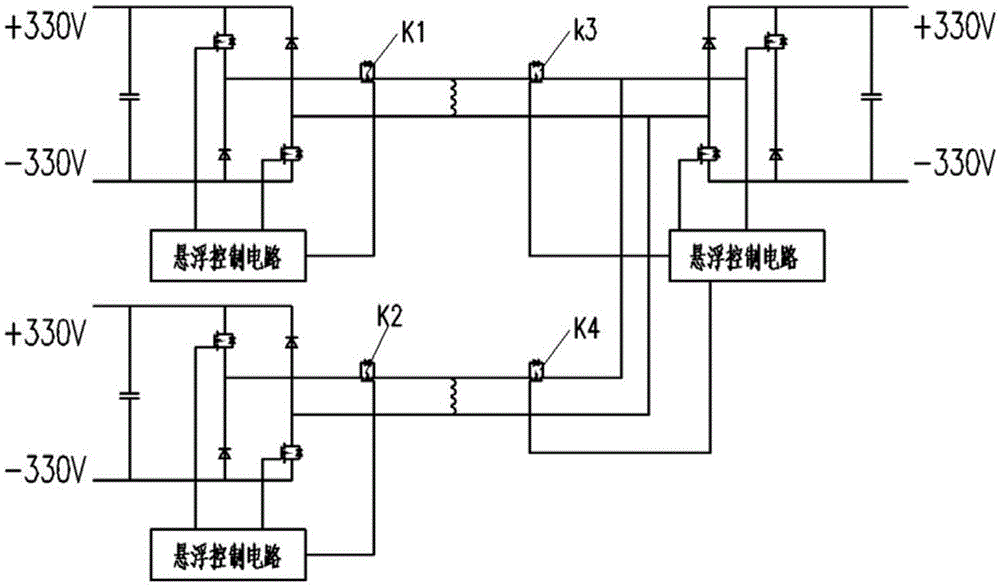
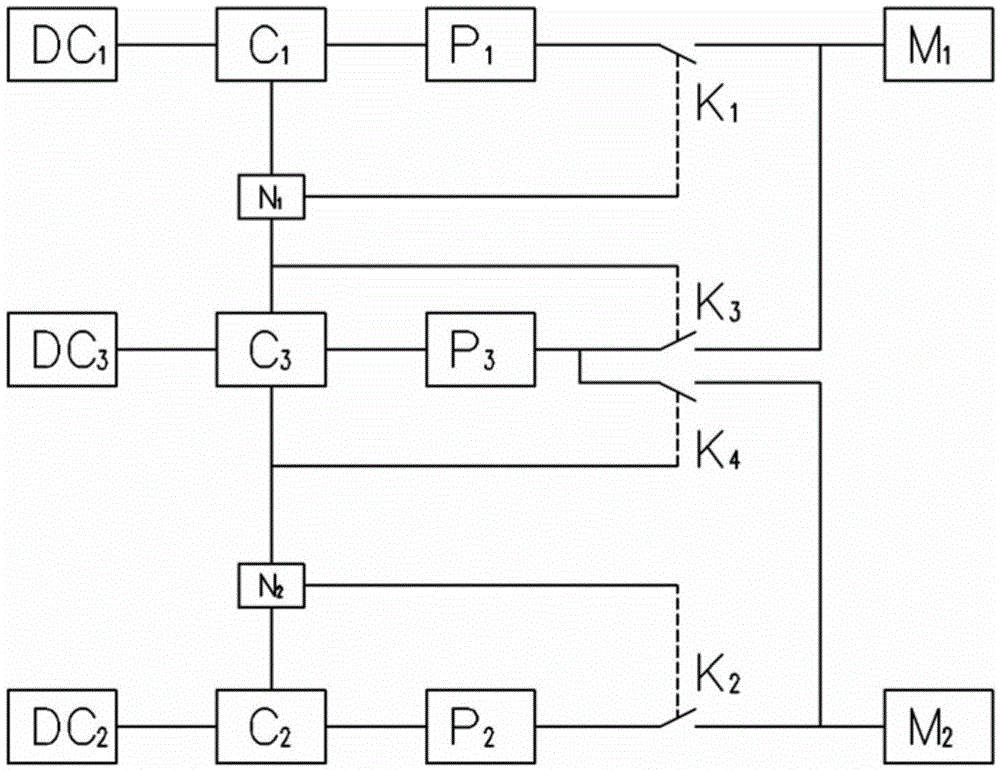
Levitation controller of magnetic-levitation train
ActiveCN105667338AImprove availabilitySimple circuit structureElectric propulsionLevitationLow speed
The invention relates to a levitation controller of a magnetic-levitation train. The levitation controller is used for controlling an electromagnet of the magnetic-levitation train, and comprises three control units, wherein the first main control unit and the second main control unit have the same structures; each of the first main control unit and the second main control unit comprises a main control circuit (C1 / C2), a main gating power switch (K1 / K2), a main power conversion circuit (P1 / P2) and a main auxiliary power supply (DC1 / DC2); a redundancy control unit comprises a redundancy control circuit (C3), two redundancy gating power switches (K3 and K4), a redundancy power conversion circuit (P3) and a redundancy auxiliary power supply (DC3); and the redundancy control circuit (C3) communicates with the two main control circuits (C1 and C2) to form the redundancy control. Compared with the prior art, the levitation controller has the advantages that through the redundancy structure design, the redundancy control circuit is enabled to communicate with the two main control circuits; the redundancy problem of a levitation control system of a medium-and-low-speed magnetic-levitation train is solved; when the levitation controller partially fails, the magnetic-levitation train can normally work; and the availability of the magnetic-levitation train is improved.
Owner:TONGJI UNIV
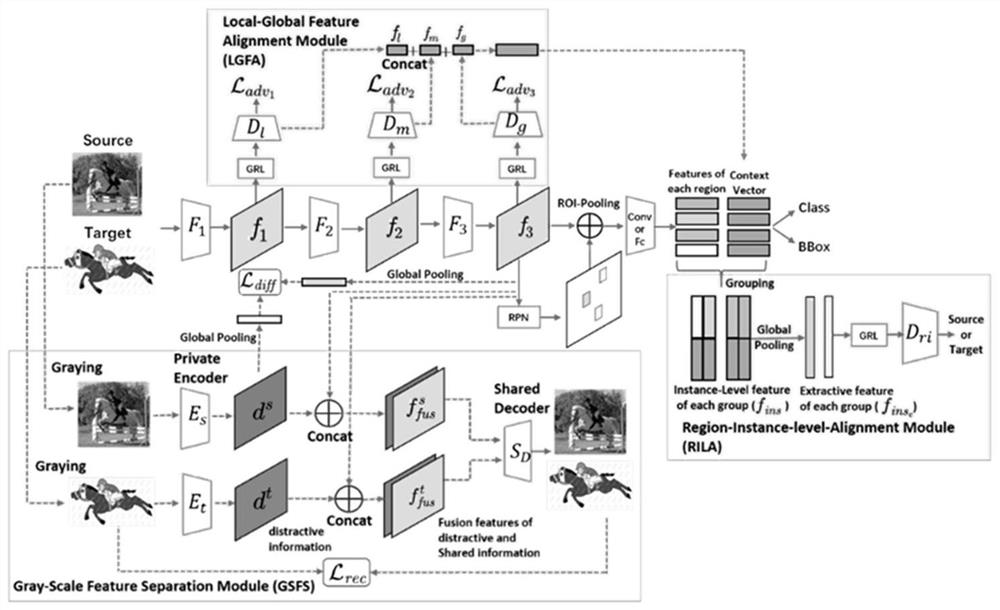
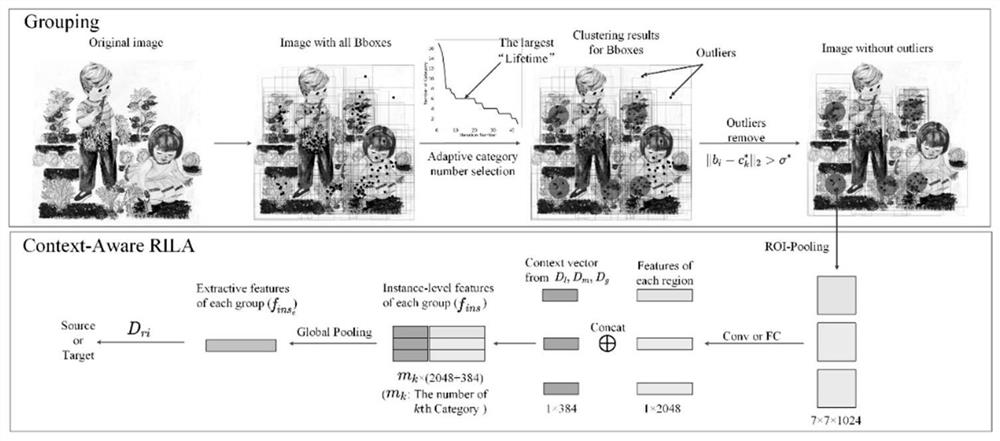
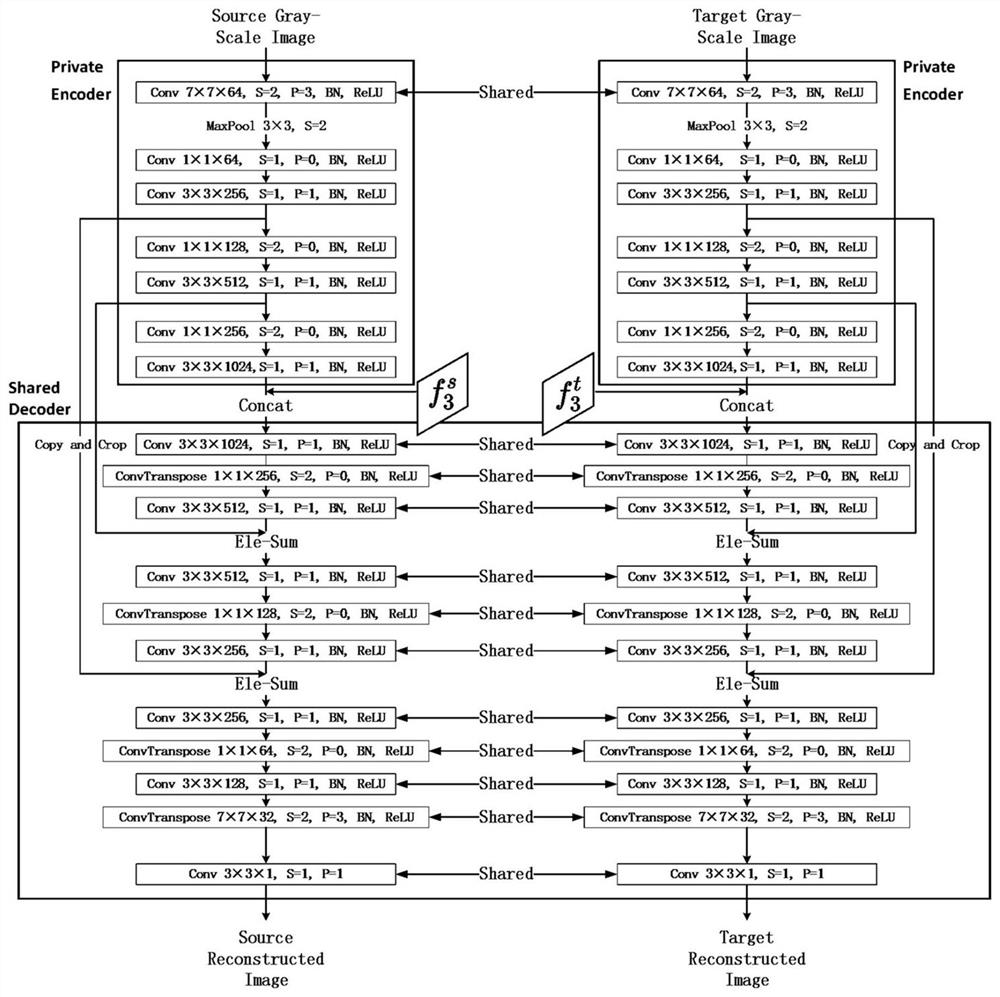
Domain adaptive unsupervised target detection method based on feature separation and alignment
PendingCN112488229ASolve the noiseImprove portabilityCharacter and pattern recognitionInternal combustion piston enginesPattern recognitionA domain
The invention discloses a domain adaptive unsupervised target detection method based on feature separation and alignment, and the method comprises the following steps: inputting paired RGB samples ofa source domain and a target domain into a two-stage target detection framework, calculating the detection loss through the label of the source domain, training the target detection framework, and obtaining a learned target detection model, wherein in the training process, the multi-level high-dimensional features are aligned; aligning the regional instance features of each group; graying the RGBsamples of the source domain and the target domain which are paired, carrying out feature separation, and separating out high-dimensional features related to detection and disturbance features irrelevant to detection. The invention provides an unsupervised domain self-adaptive target detection method based on feature separation and alignment, which can effectively solve the problems of backgroundinformation noise and candidate region redundancy in domain self-adaptive target detection.
Owner:XI AN JIAOTONG UNIV
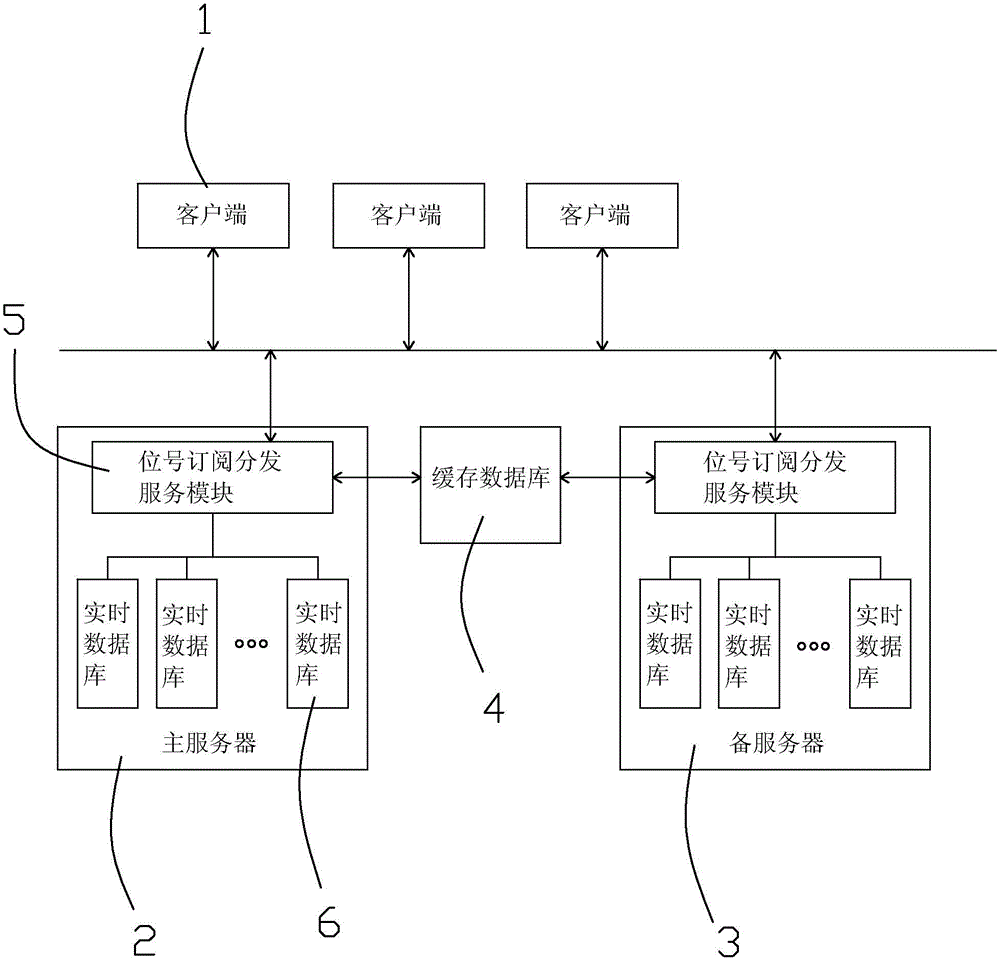
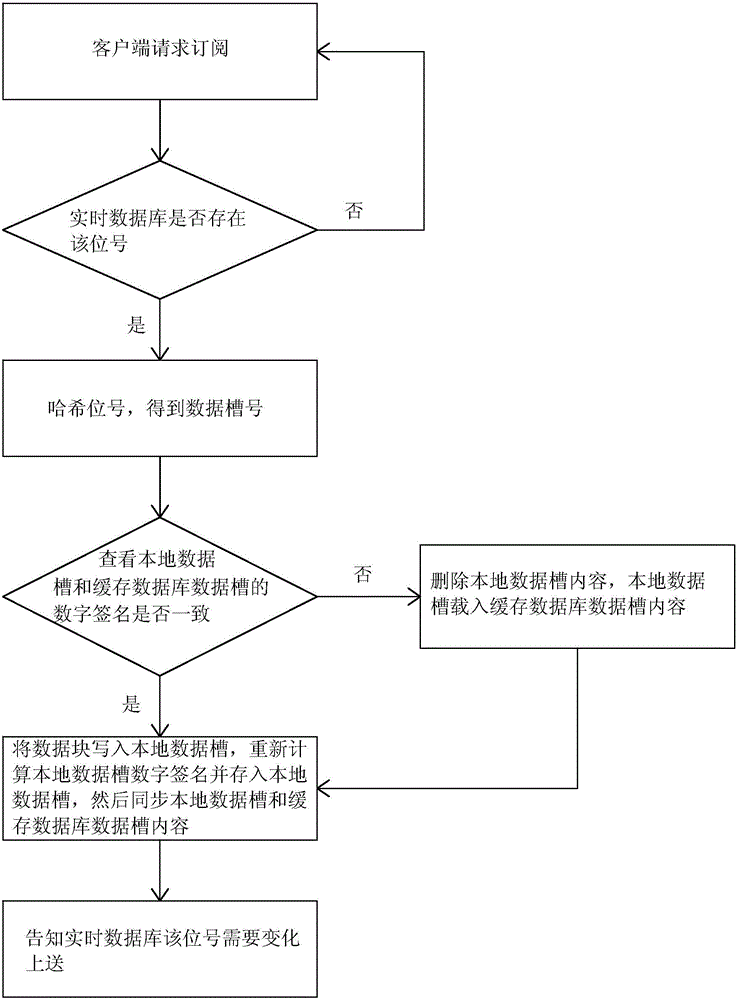
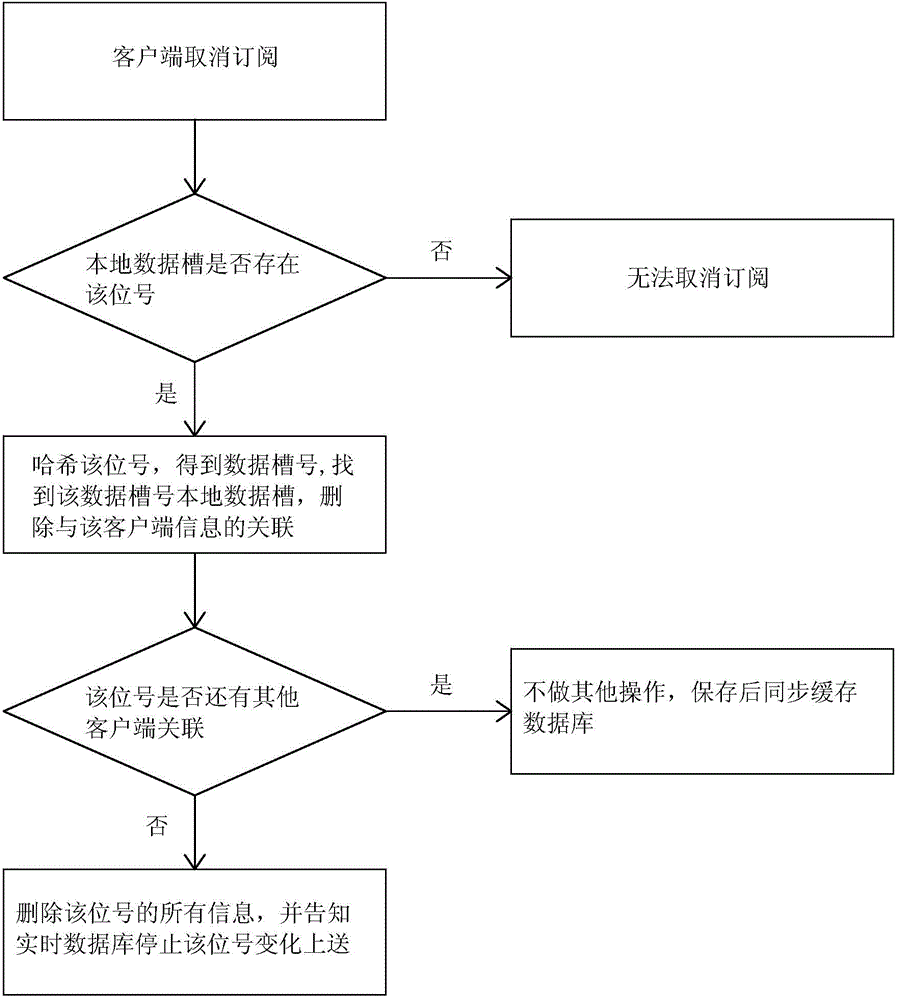
Real-time database subscription system and method
ActiveCN104539583ASolve redundancySolve storage problemsTransmissionSpecial data processing applicationsTraffic volumeClient-side
The invention relates to a real-time database subscription system and method, and aims to solve the problems of waste of network flow, waste of spatial efficiency and increase of cost in a bit number subscription system in the prior art. The system comprises a plurality of clients, a master server and a cache database, wherein the master server comprises a plurality of real-time databases and a bit number subscription and distribution service modules; the clients are connected with the bit number subscription and distribution service modules respectively through system buses; the real-time databases are connected with the bit number subscription and distribution service modules respectively; and the bit number subscription and distribution service modules are connected with the cache database. The subscription method comprises a subscription step, an un-subscription step and a change and up-transmission step. The real-time database subscription system and method have the advantages that subscription information is placed into different slots, so that the redundancy and storage problems of the subscription information are solved, and the efficiency is increased. A multi-service-coexistence hot standby mode is adopted, so that the security is enhanced. The network and calculated amount loads are mean, and resources are fully utilized.
Owner:ZHEJIANG SUPCON INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com