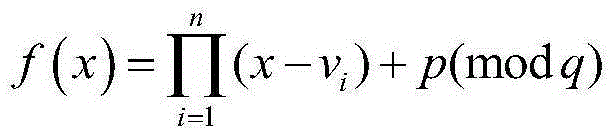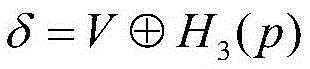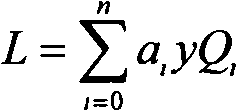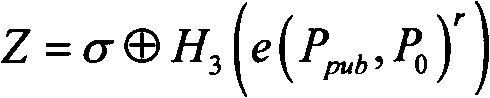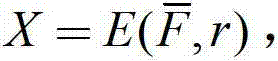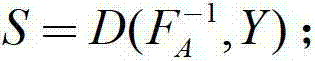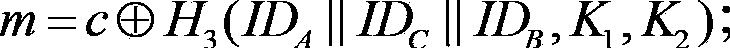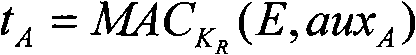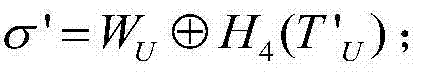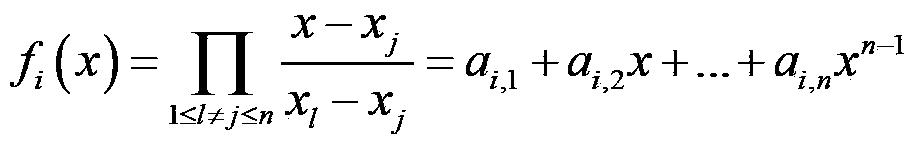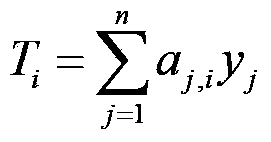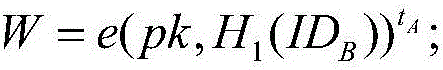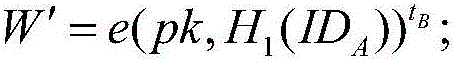Patents
Literature
243 results about "Signcryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
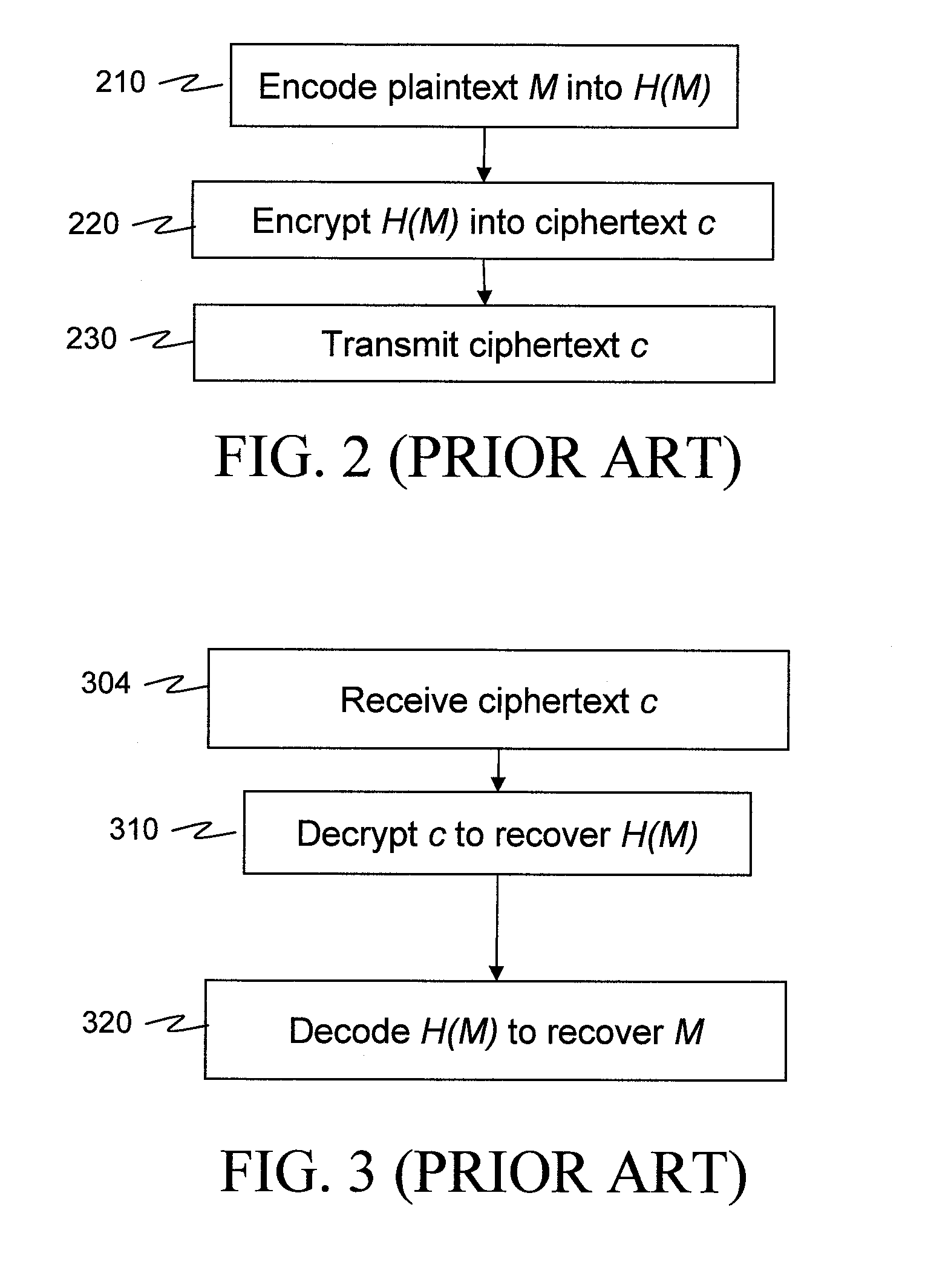
In cryptography, signcryption is a public-key primitive that simultaneously performs the functions of both digital signature and encryption. Encryption and digital signature are two fundamental cryptographic tools that can guarantee the confidentiality, integrity, and non-repudiation. Until 1997, they were viewed as important but distinct building blocks of various cryptographic systems. In public key schemes, a traditional method is to digitally sign a message then followed by an encryption (signature-then-encryption) that can have two problems: Low efficiency and high cost of such summation, and the case that any arbitrary scheme cannot guarantee security. Signcryption is a relatively new cryptographic technique that is supposed to perform the functions of digital signature and encryption in a single logical step and can effectively decrease the computational costs and communication overheads in comparison with the traditional signature-then-encryption schemes.
Signcryption method and device and corresponding signcryption verification method and device
InactiveUS20130051551A1Public key for secure communicationSecret communicationSigncryptionConcatenation
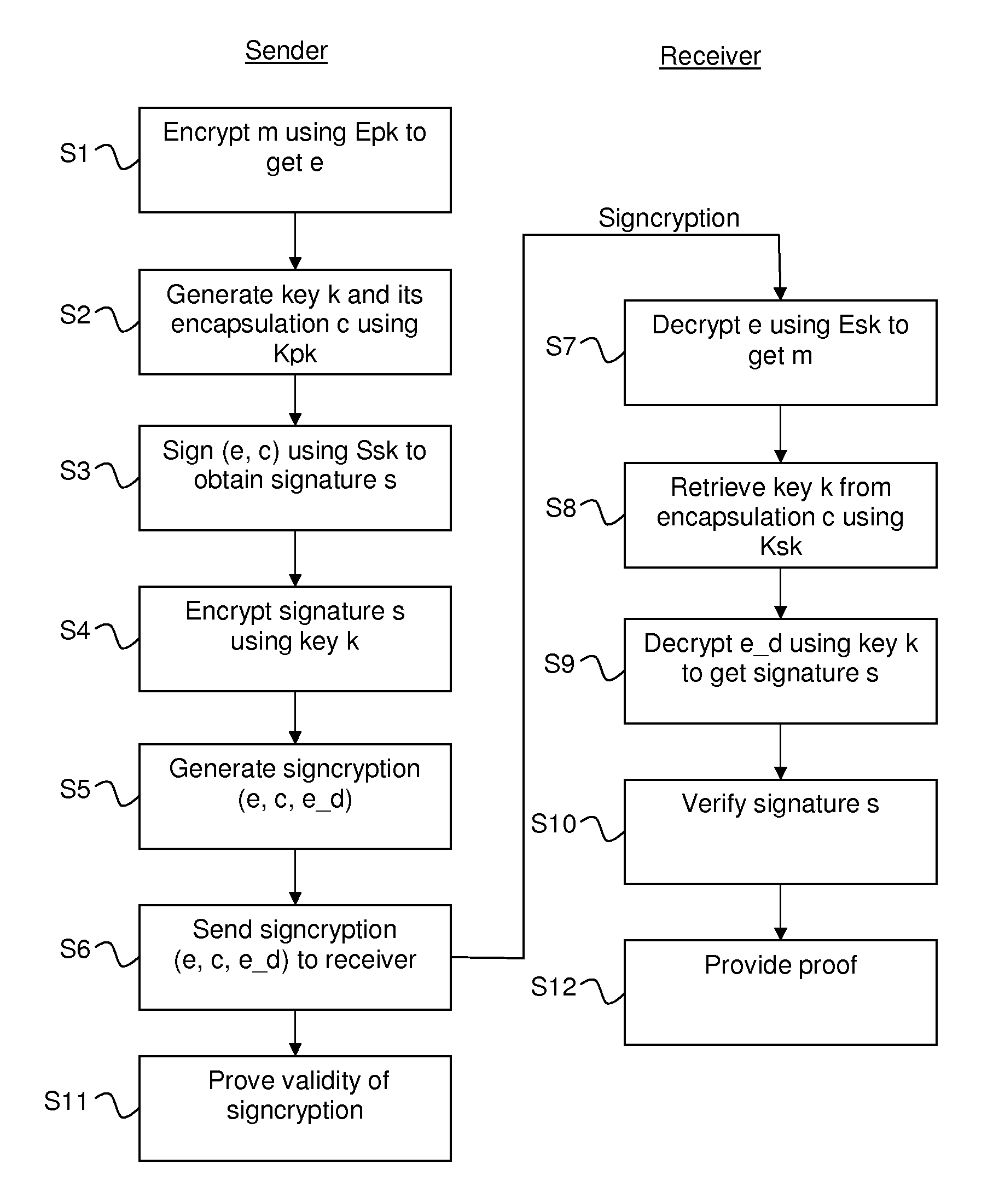
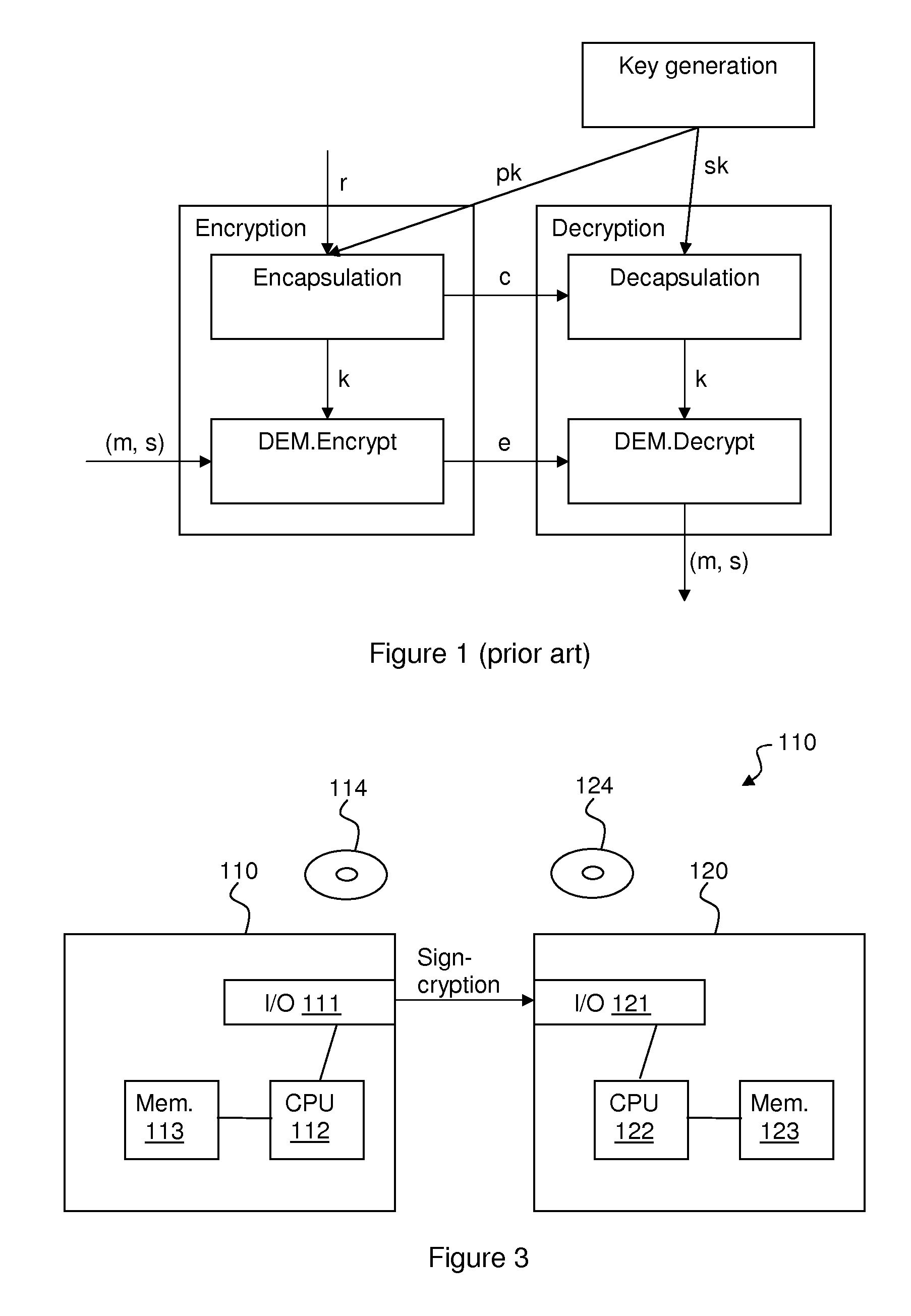
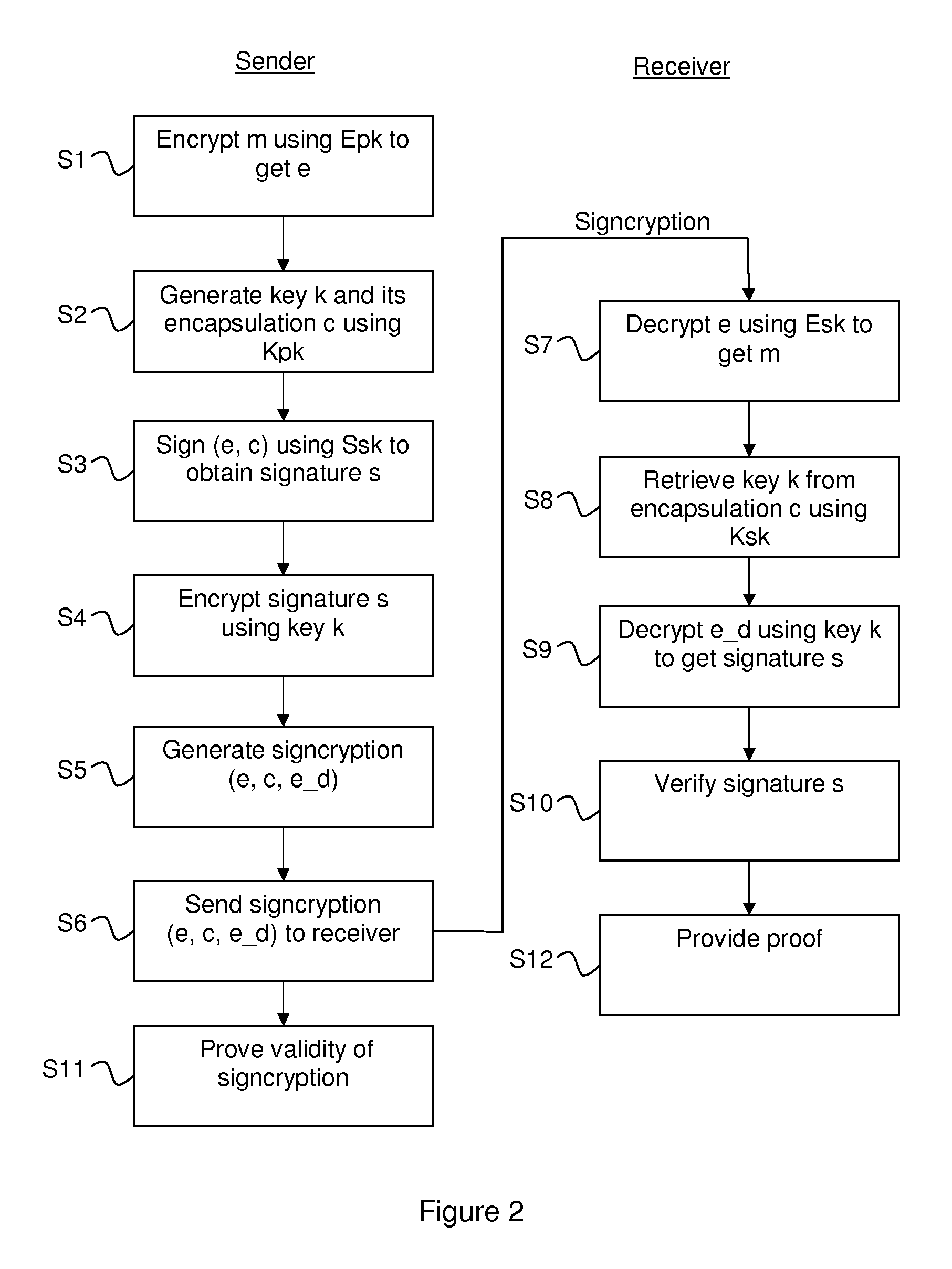
A signcryption is generated by a sender by using a first encryption algoritm to encrypt plaintext m with public key Epk to get ciphertext e, e=E.Encrypt(m); generating a key k and its encapsulation c using an encapsulation algoritm and public key Kpk, k,c=KD.Encapsulate() sign (e,c) using Ssk, s=S.sign(e,c); encrypt the signature s using a second encryption algoritm and the key k, e_d=D.Encrypt(s). The signcryption of m is formed by (e,c,e_d). The sender may also prove knowledge of the decryption of e, and that e_d encrypts a valid signature on the concatenation of c and e using the key of the encapsulation. Also provided are the corresponding signcryption verification device and method, and computer program products.
Owner:THOMSON LICENSING SA
Secure certificateless hybrid signcryption method without pairing
InactiveCN105024994AResistant to Substitution AttacksImprove security levelPublic key for secure communicationPlaintextSigncryption
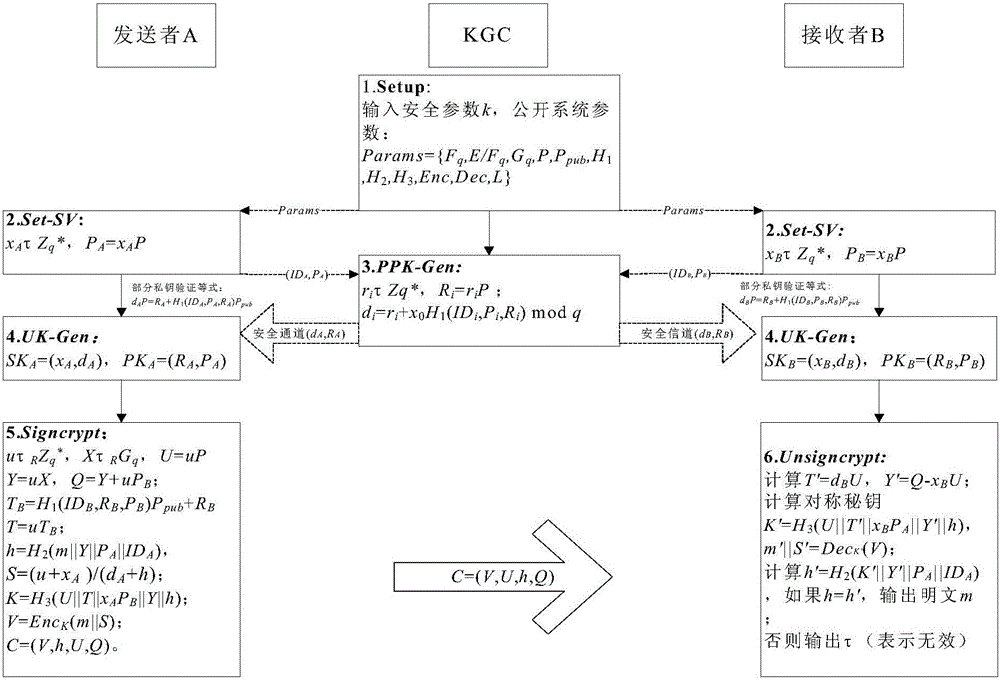
The invention discloses a secure certificateless hybrid signcryption method without pairing. The method is used for solving a technical problem of low efficiency of a conventional certificateless hybrid signcryption method. The method is characterized by a KGC is restricted by a user part public key in a stage of generating a part secret key by prescribing a fixed secret key generation sequence of a user so as to bind the user part public key when a signcryption user performs signcryption on a plaintext and guarantee enough resistance to public key replacing attack; before a user complete private key is generated, using a part private key bound with user identity information and a part public key to verify an equality in order that the user timely detects an invalid behavior of the active dishonest KGC, resists to malicious KGC attack, improves a system security level, and eliminates unnecessary computation consumption; in a unsigncryption stage, substituting scalar multiply operation on a elliptical curve to for expensive time-consuming bilinear pairings to complete message signcryption and unsigncryption processes, thereby improving computation efficiency.
Owner:东莞市三航军民融合创新研究院
Multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve
ActiveCN106027239AOvercome the problem of not being able to resist malicious KGC attacksResistance to malicious KGC attacks hasKey distribution for secure communicationPublic key for secure communicationSigncryptionKey escrow
This invention discloses a multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve, and solves the technical problem of private key trusteeship existed in the existing multi-receiver signcryption method. The method comprises the following steps: a user randomly selects a secret value as own private key, calculates a verification share according to own private key, and sends the verification share and own identity information to a private key generating center KGC; the private key generating center KGC generates a public key, a public key verification parameter and a public key hiding parameter of the user according to the verification share and the identity information sent by the user, and sends the public key, the public key verification parameter and the public key hiding parameter to the user; and after receiving the parameters sent by the private key generating center KGC, the user verifies the public key. Since the private key of the user is the secret value randomly selected by the user, the private key generating center KGC only knows the public key and corresponding identity information of the user, and cannot acquire the private key of the user to realize keyless trusteeship. Simultaneously, the signcryption efficiency is improved; and the bandwidth is reduced.
Owner:XIDIAN UNIV
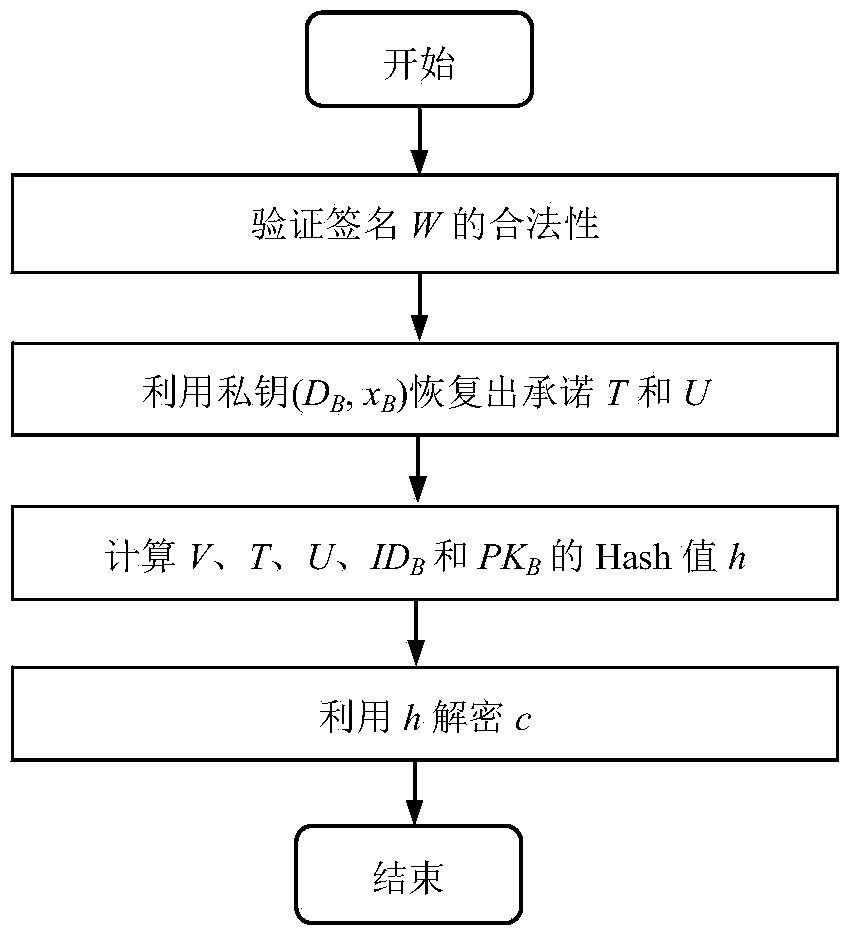
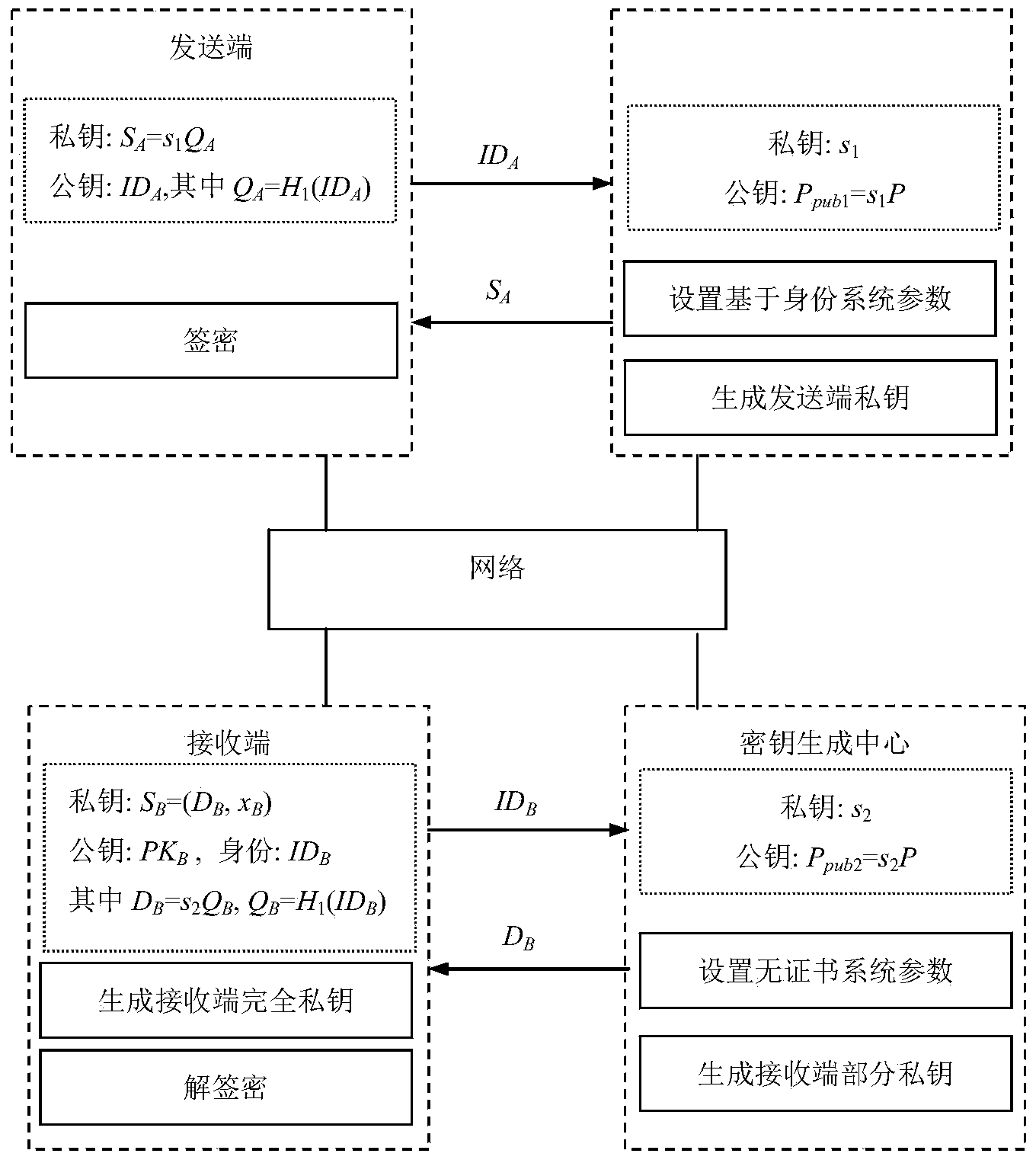
Signcryption method from certificateless environment to identity environment
InactiveCN104270249AProvide confidentialityProvide integrityUser identity/authority verificationSecure communicationCiphertext
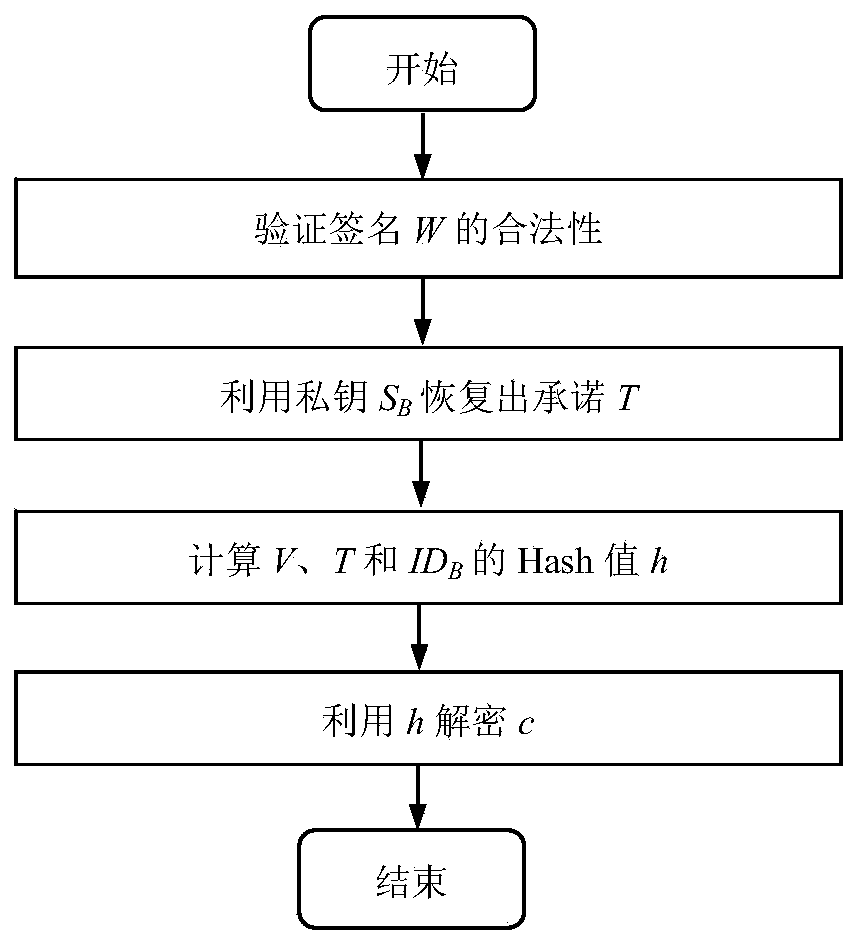
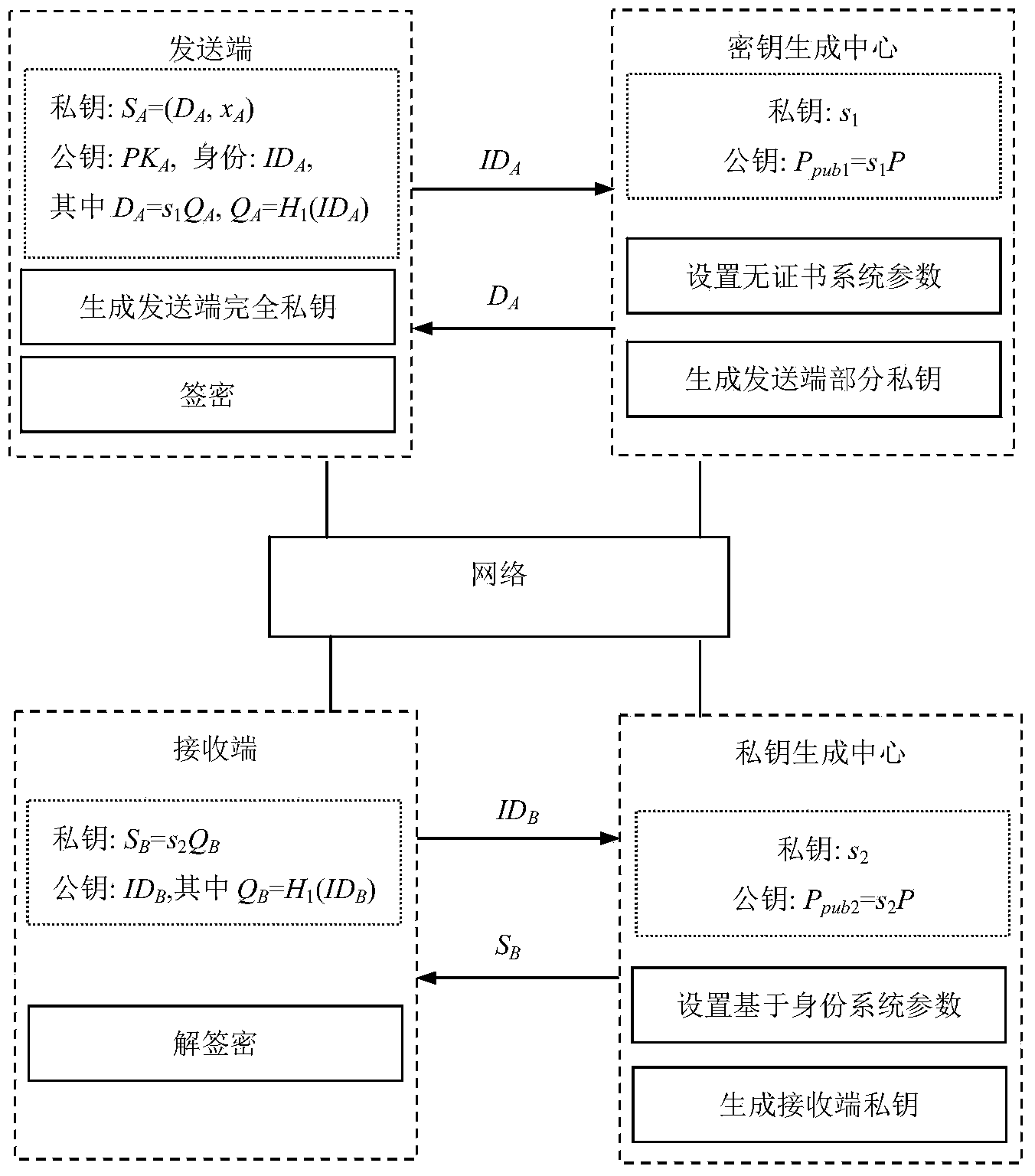
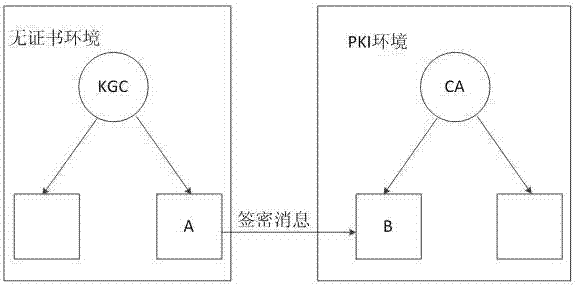
The invention discloses a signcryption method from a certificateless environment to an identity environment and belongs to the field of secure communication. In order to enable a sending end based on the certificateless environment to send messages to a receiving end based on the identity environment through the signcryption method, the signcryption method includes the steps that after system parameters are initialized, a key generation center generates a part private key DA and sends the part private key DA to the sending end, and the sending end generates a secrete value randomly based on the system parameters, and a complete private key SA and a public key PKA are arranged with the part private key DA; a private key generation center generates a private key SB and sends the private key SB to the receiving end; the sending end generates a signcryption ciphertext according to the system parameters, the identity of the sending end, the complete private key SA, the public key PKA, the identity of the receiving end and the messages m, and the ciphertext, the identity of the sending end and the public key PKA are sent to the receiving end to conduct signcryption treatment. The signcryption method is used for signcryption communication of a heterogeneous network, and end-to-end secrete, complete, certificated and undeniable services are provided for users in the certificateless environment and users based on the identity environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Multi-receiver identity anonymity signcryption method
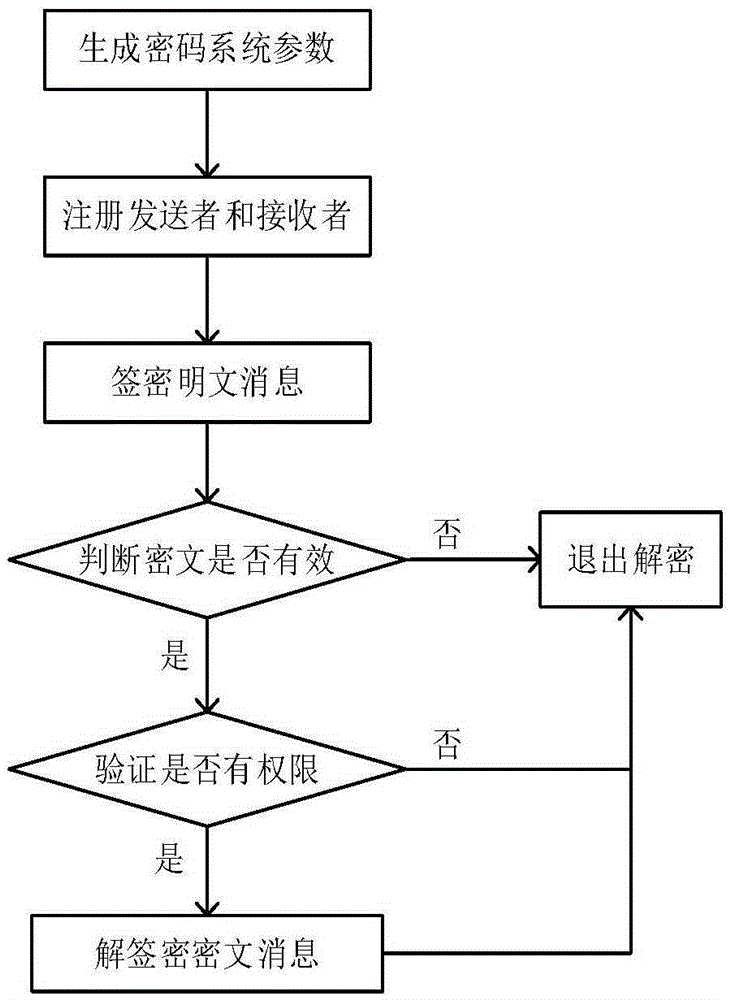
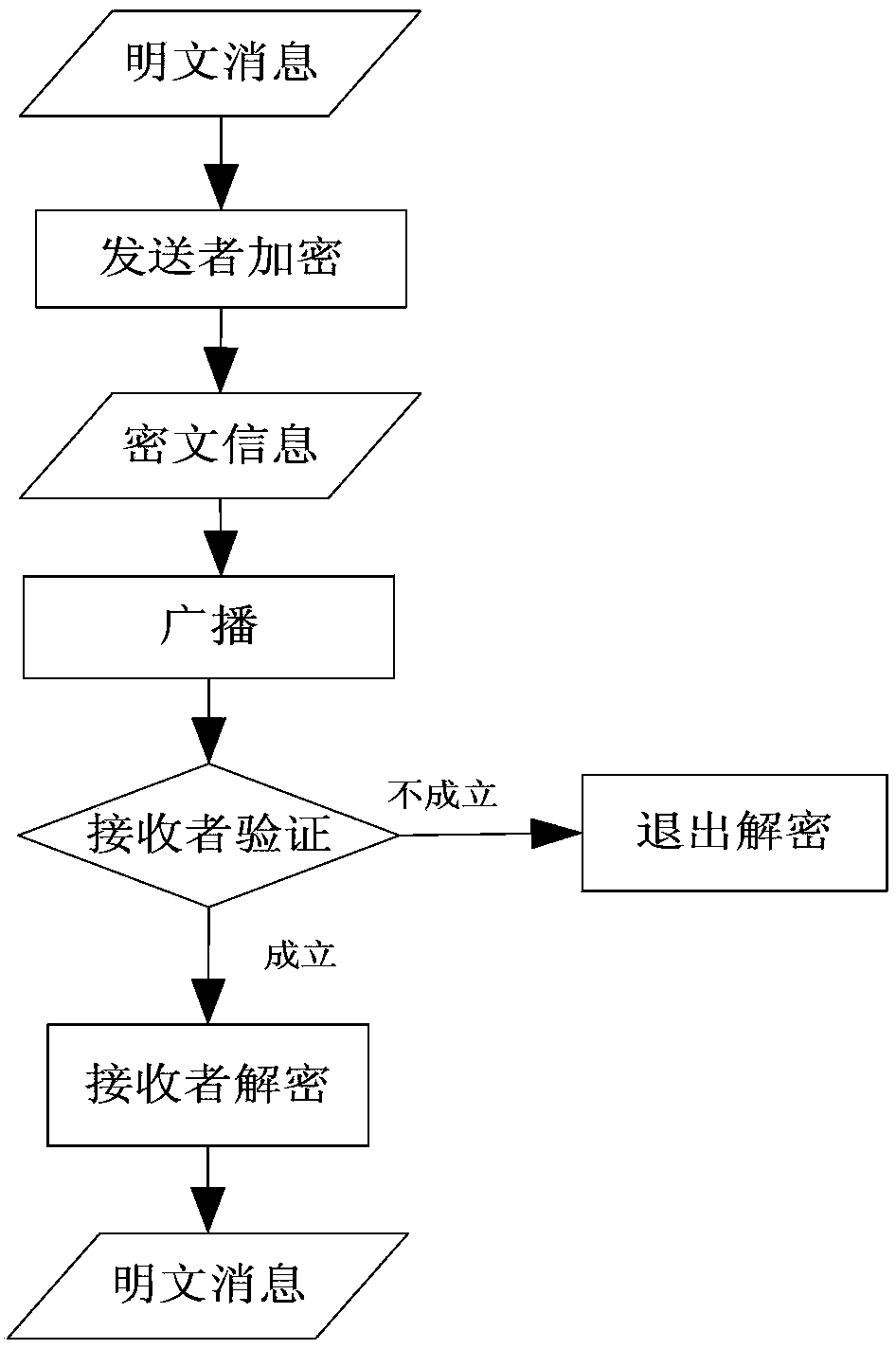
The invention discloses a multi-receiver identity anonymity signcryption method. The method specifically includes steps: 1, generating password system parameters; 2, registering senders and receivers; 3, performing signcryption of the senders; 4, determining whether a validity condition of a signcryption ciphertext is established; 5, determining whether a permission verification condition is established; 6, performing de-signcryption of the receivers; and 7, exiting the de-signcryption. According to the method, the LaGrange interpolation technique is replaced by the new polynomial technique, identity anonymity between registered receivers is realized, the calculation of intermediate parameters is reduced in a signcryption process, the efficiency of encryption and decryption is improved, the overall security and the anonymity of the system are improved, the receivers can no longer verify the identity of other receivers, and the method can be applied to the application field of distributed network.
Owner:XIDIAN UNIV
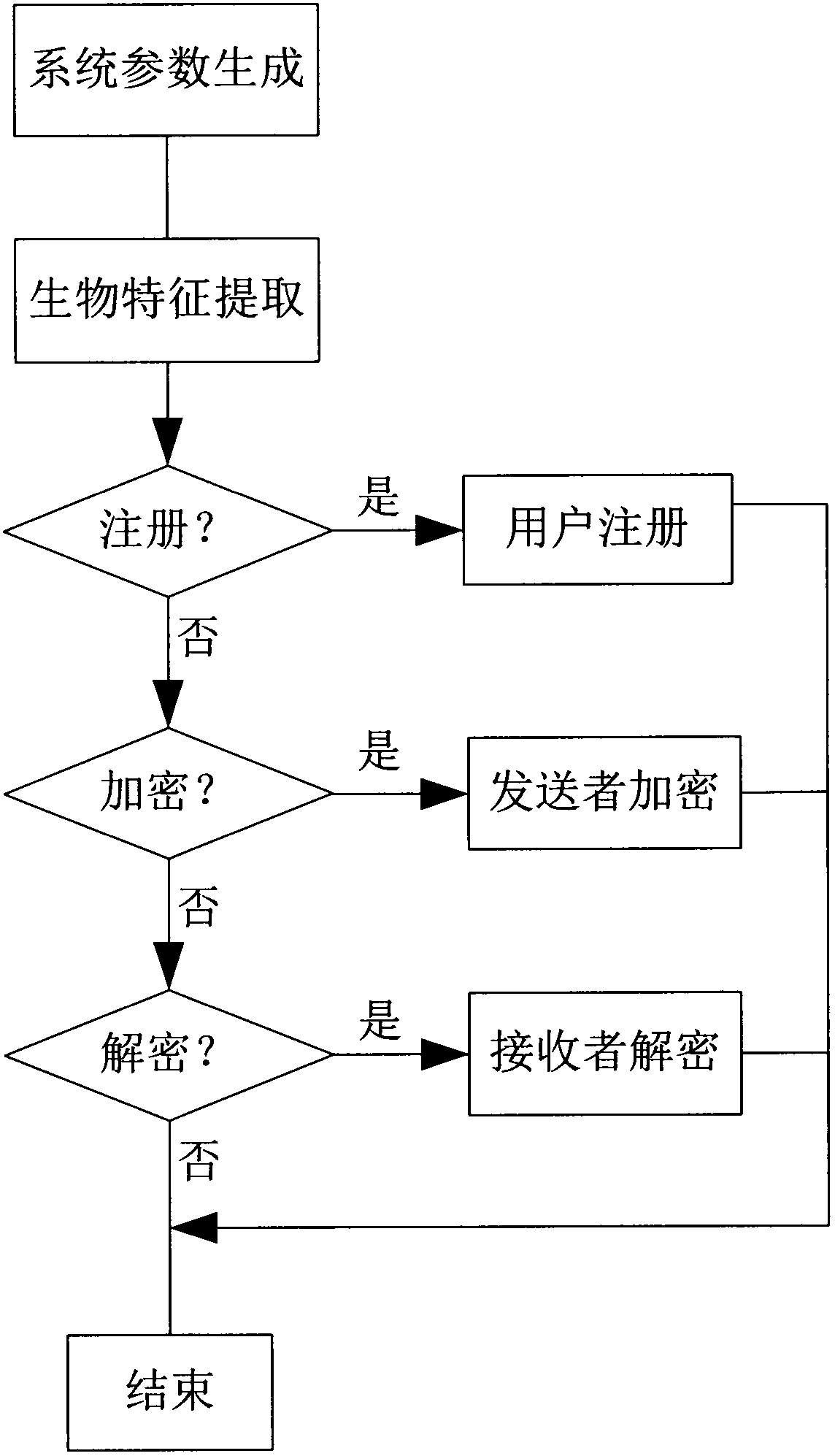
Signcryption method of biological features of a plurality of receivers
InactiveCN102710613AOvercome the problem of forgeryPrevent leakageTransmissionDigital signatureSigncryption
The invention discloses a signcryption method of biological features of a plurality of receivers, comprising generating system parameters; extracting features; performing user log-on; encrypting by a sender; and decrypting by receivers. The method employs fuzzy extractor technique to bind the biological features and user keys to protect keys, directly authenticates user identity through the biological features, solves the safety problems of key safety and key abuse in the conventional cryptography, adds digital signature of senders during encryption, verifies identity of senders through certification during decryption, and solves the problem of counterfeiting of senders. The method improves the safety and reliability of whole systems, has the advantages of high safety, high efficiency and no need for storing any secret information by users, and can be applied to the distributed network application field.
Owner:XIDIAN UNIV
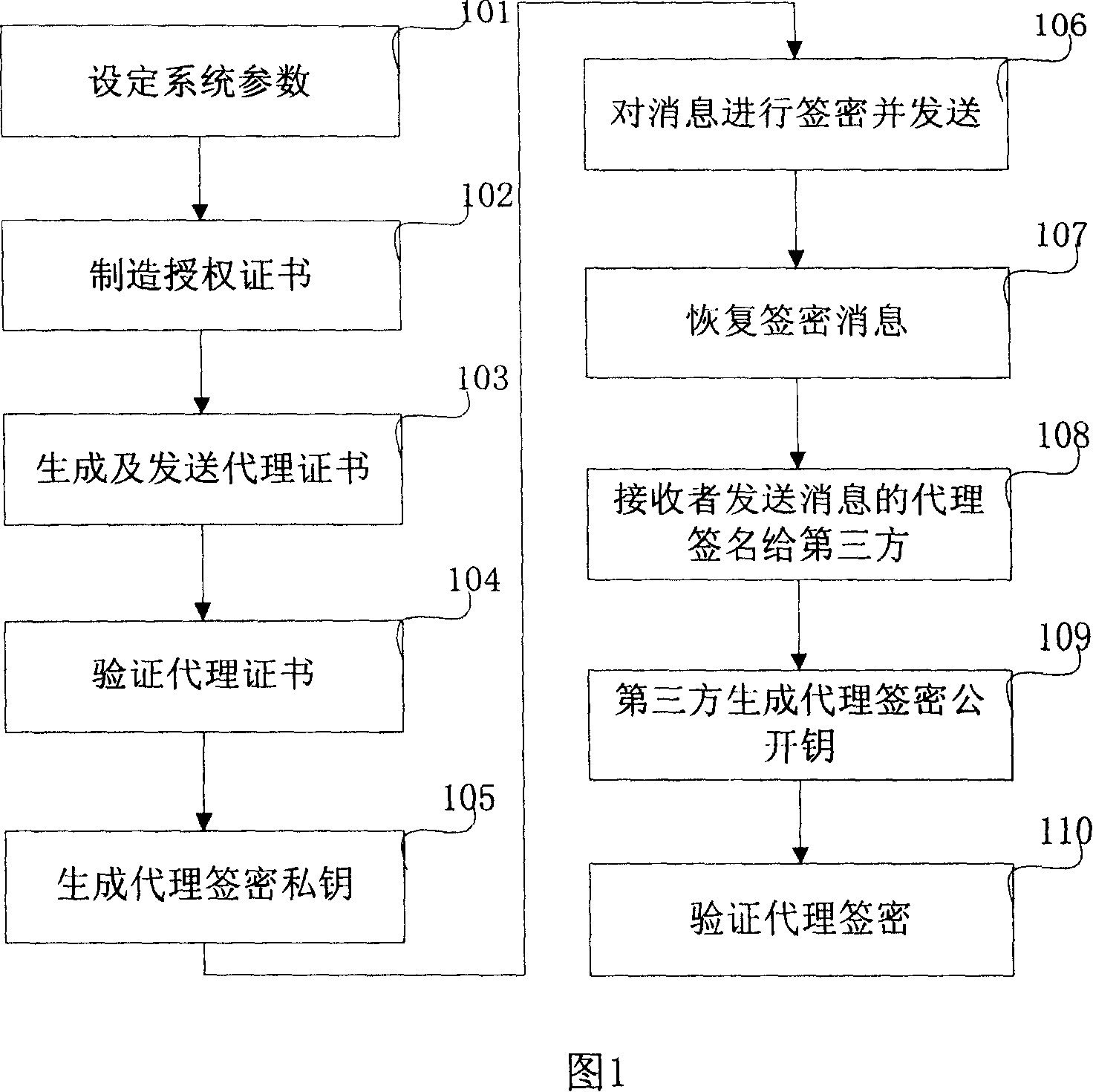
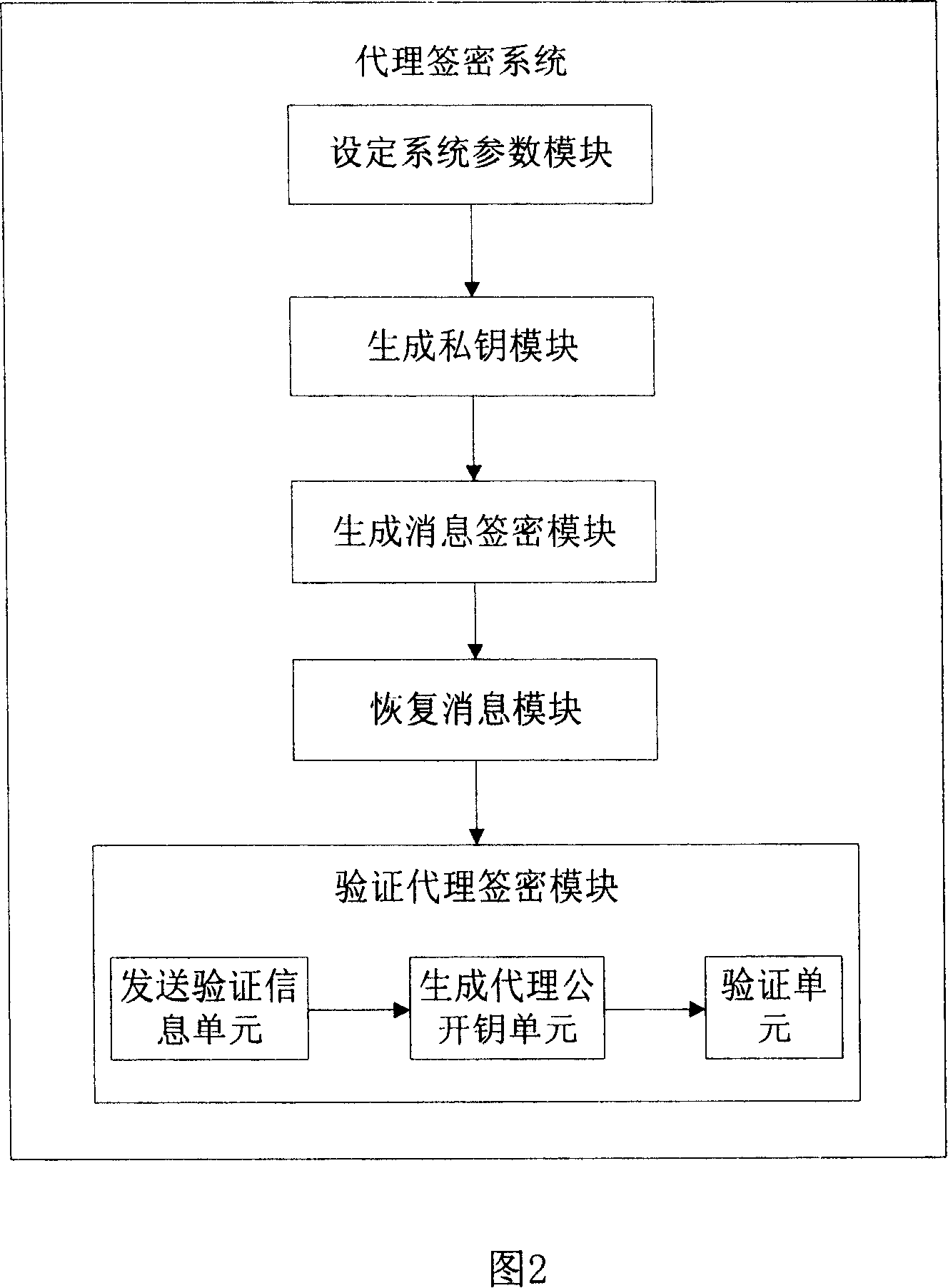
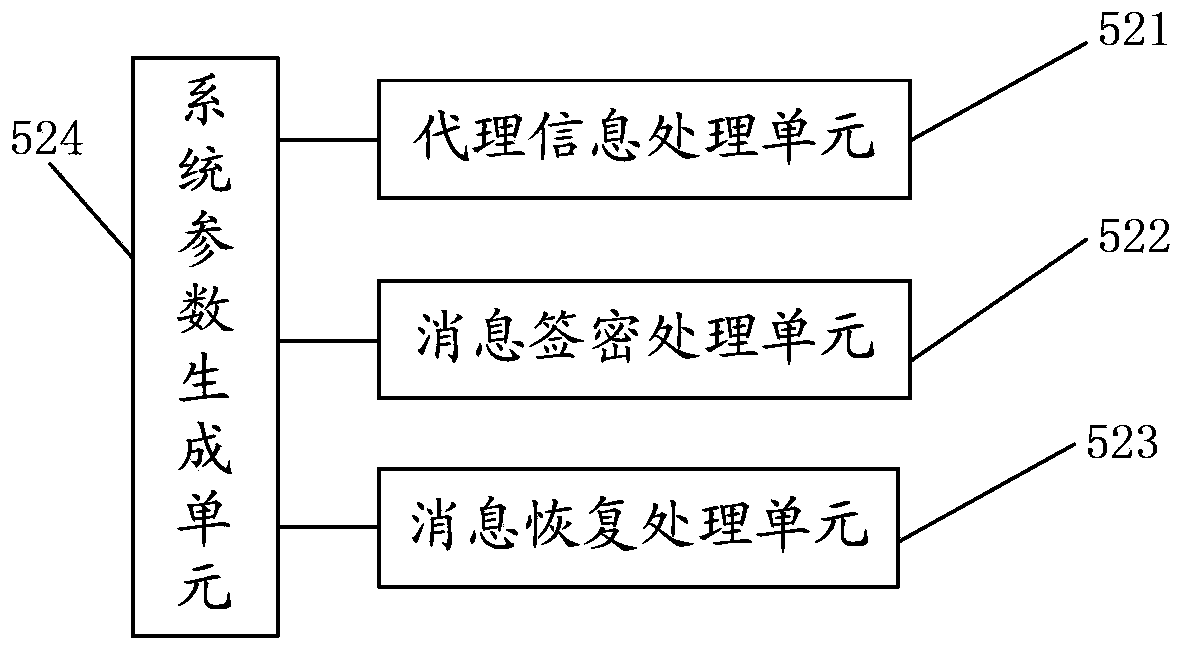
Agent signcryption method and system
InactiveCN101051902AEliminate dependenciesPractical application of proxy signcryption systemData taking preventionPublic key for secure communicationSigncryptionE-commerce
The invention solves issues that disadvantages of large amount of calculation and system security exist in current technique. The method includes steps: setting up system parameters, generating proxy cipher-signed private key, sending cipher-signed message, recovering cipher-signed message, and validating proxy cipher sign. The invention raises operation efficiency, and avoids dependence on secure channel.
Owner:SHANGHAI JIAO TONG UNIV +1
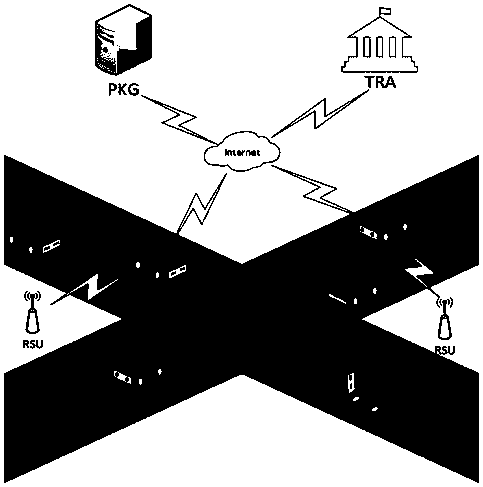
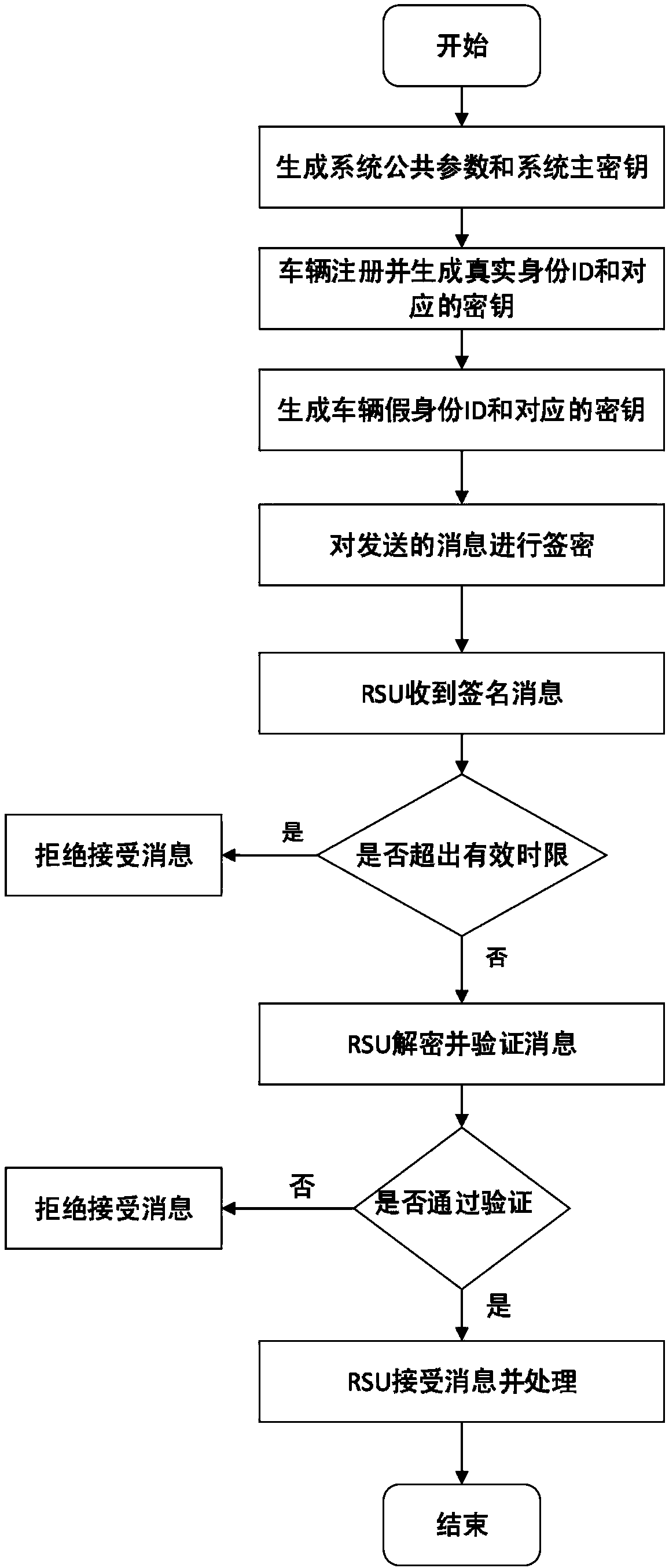
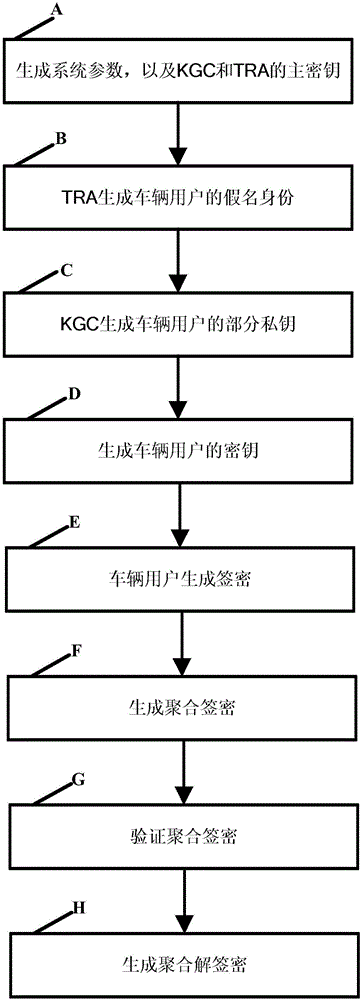
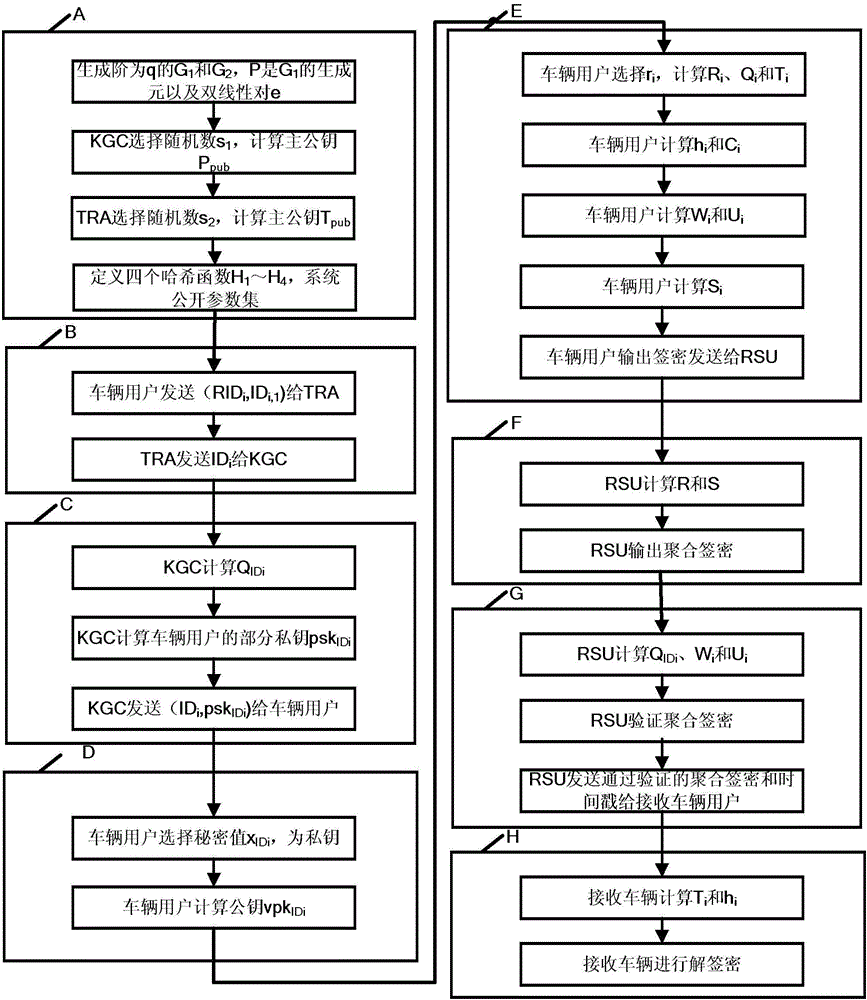
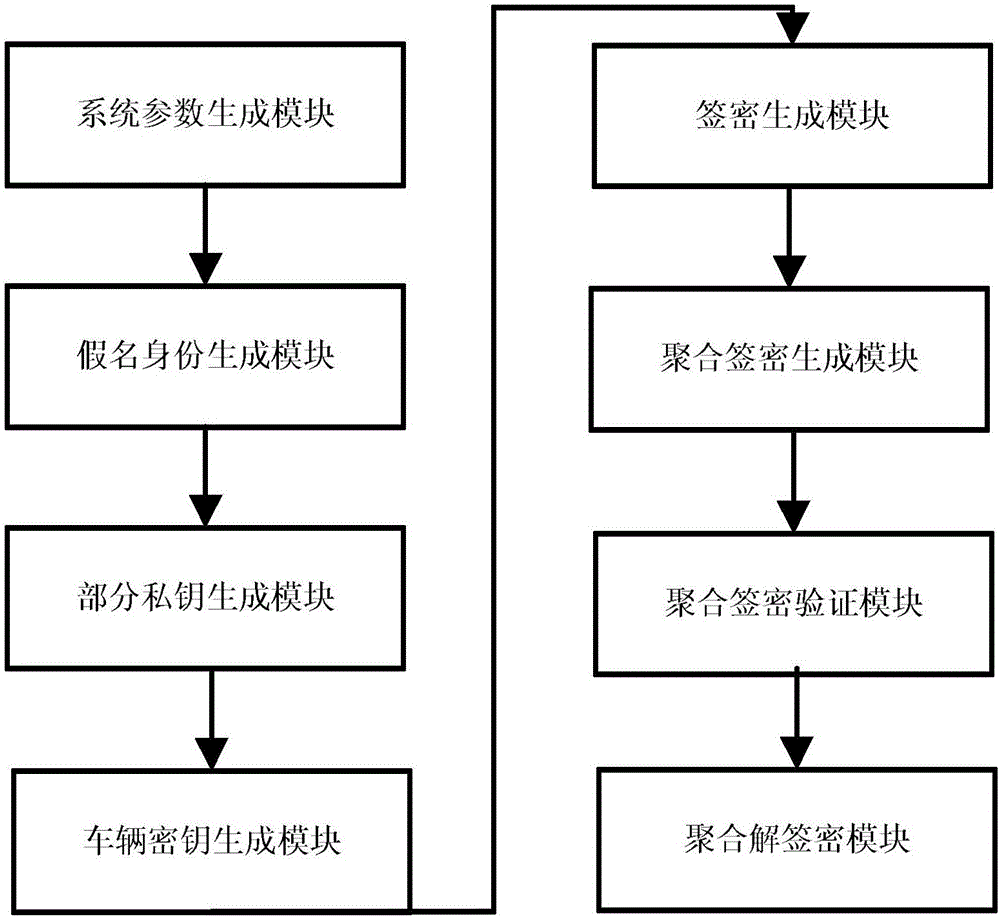
Method for protecting privacy of vehicle ad hoc network based on signcryption
InactiveCN107682149AEffective calculationProtect identity privacyKey distribution for secure communicationParticular environment based servicesDigital signatureSigncryption
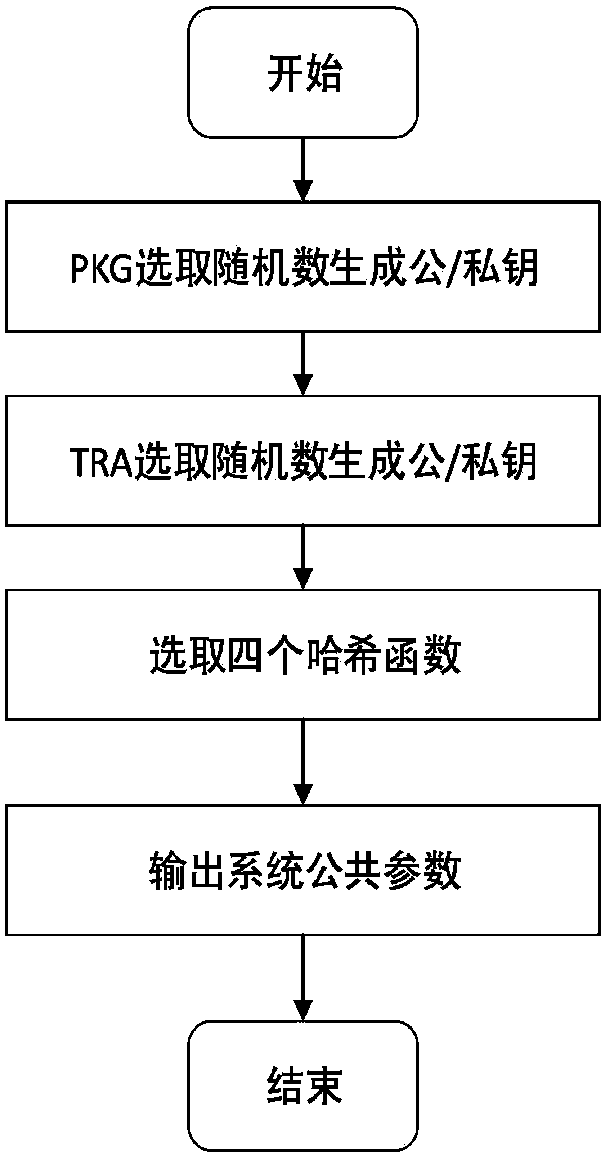
The invention request to protect a method for protecting privacy of a vehicle ad hoc network based on signcryption. The method is used for solving a privacy protection problem when a vehicle node (OBU) under an environment of the Internet of vehicles communicates with a road side unit (RSU). On the basis of a digital signature mechanism and a pseudonym mechanism, the invention provides a signcryption mechanism which is an integrated scheme synthesizing encryption and signature; in the method, privacy protection on the vehicle node is achieved via the pseudonym mechanism. Under the environmentof the Internet of vehicles, the vehicle node sends own identity information to a TRA to generate a pseudonym, a secret key generation center generates a secret key corresponding to a private key of the pseudonym, the vehicle node uses the generated pseudonym and the secrete key to perform signcryption on a message and sends the message to the road side unit, after receiving the message, the roadside unit uses the private key to decrypt the message and verify the same, and the message is accepted if the verification is passed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Block chain encryption method based on PKI-CLC heterogeneous aggregation signcryption algorithm
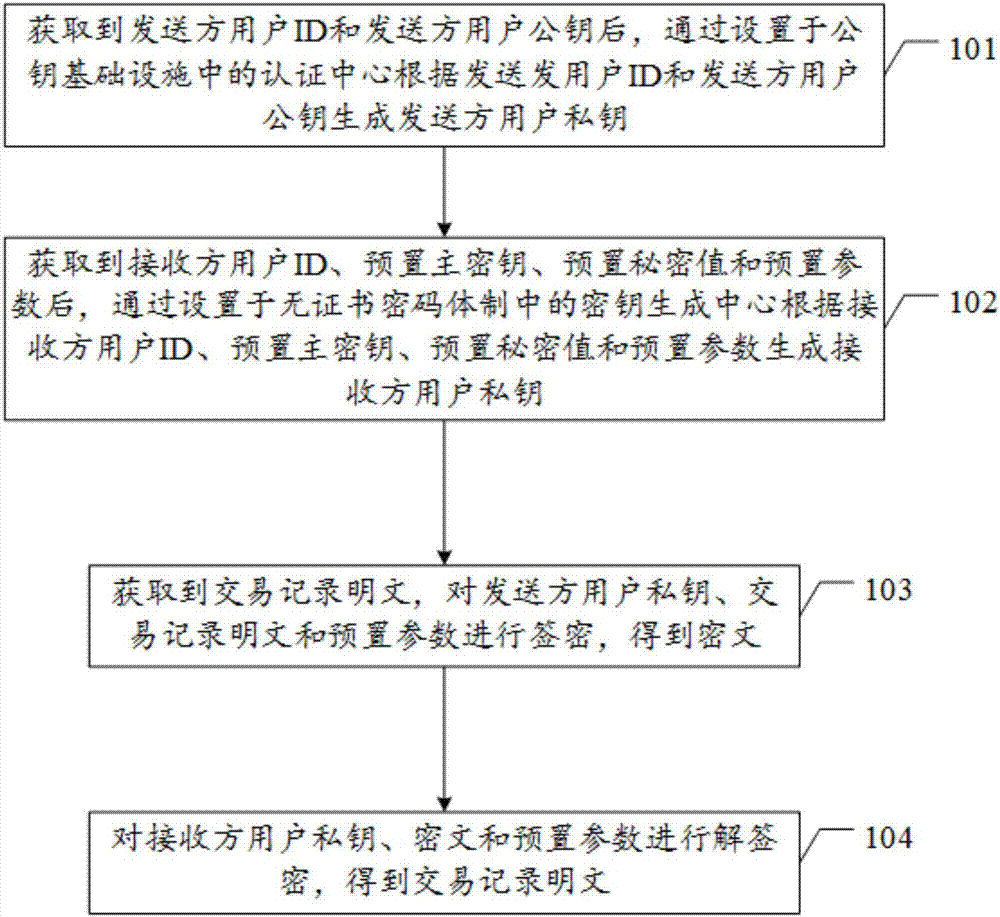
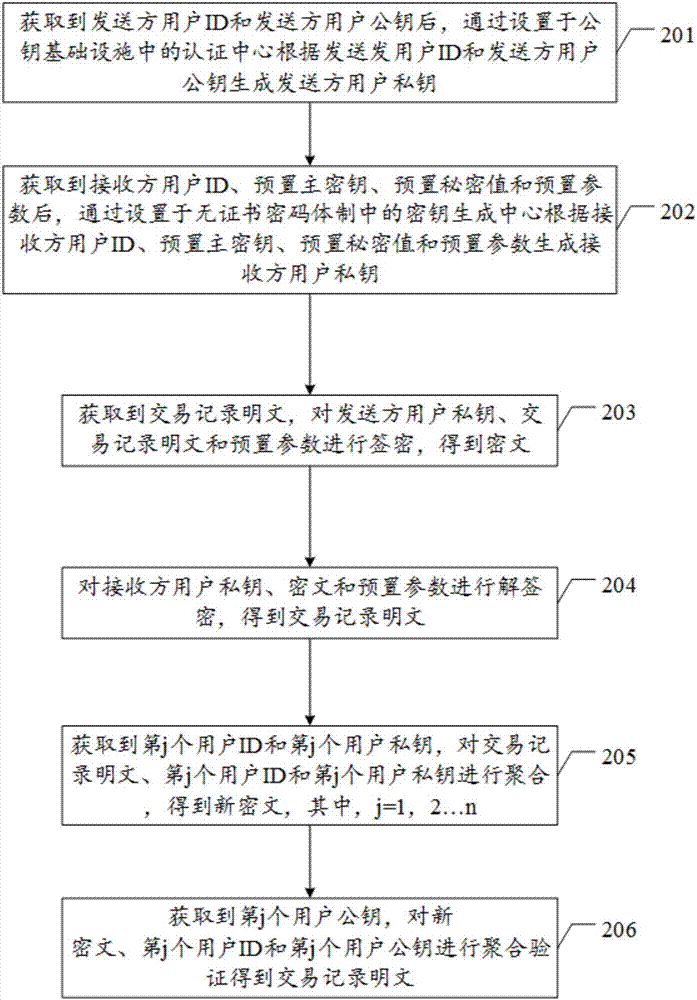
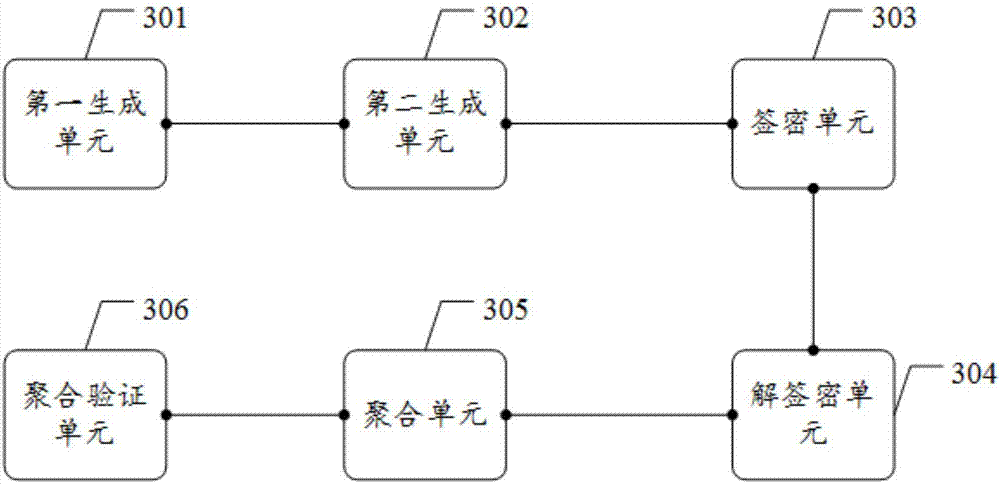
The embodiment of the invention discloses a block chain encryption method based on a PKI (public key infrastructure)-CLC (certificateless cryptography) heterogeneous aggregation signcryption algorithm. The method comprises: generating, after a sender user ID and a sender user public key are obtained, a sender user private key by using an authentication center in the PKI according to the sender user ID and the sender user public key; generating, after a receiver user ID, a preset master secret key, a preset secret value, and a preset parameter, a receiver user private key by using a secret key generation center in the CPC according to the receiver user ID, the preset master secret key, the preset secret value, and the preset parameter; obtaining a transaction record plaintext, subjecting the sender user private key, the transaction record plaintext, and the preset parameter to signcryption to obtain a ciphertext; and subjecting the receiver user private key, the ciphertext, and the preset parameter to unsigncryption to obtain the transaction record plaintext.
Owner:GUANGDONG UNIV OF TECH
Certificateless multi-receiver signcryption method with multivariate-based cryptosystem
InactiveCN102811125APrivacy protectionImprove securityPublic key for secure communicationUser identity/authority verificationCiphertextConfidentiality
The invention discloses a certificateless multi-receiver signcryption method with a multivariate-based cryptosystem. The certificateless multi-receiver signcryption method is used for solving the technical problem of poor security of an existing certificateless signcryption method. The technical scheme includes that the method includes: firstly, using a key generation center to generate system parameters, and selecting a secure multivariable encryption algorithm to generate keys; and enabling a user U to obtain system private keys of the key generation center and generate the private keys to user keys prior to that a user Alice with the identity IDA sends signcryption messages to a user group L={ID1, ID2,...,IDt}, and accepting or refusing ciphertext sigma by means of un-signcryption. By the aid of the multivariate-based cryptosystem, high security of anti-quantum computation is achieved, and the certificateless multi-receiver signcryption method is still high in security facing attack of a quantum computer. Compared with the background art, the certificateless multi-receiver signcryption method is small in computation and high in security, has the advantages of completeness, confidentiality, unforgeability, forward security, backward security, receiver privacy protection and the like and is capable of resisting existing known attack.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Method and system for certificateless and pairing-free identity-based proxy signcryption
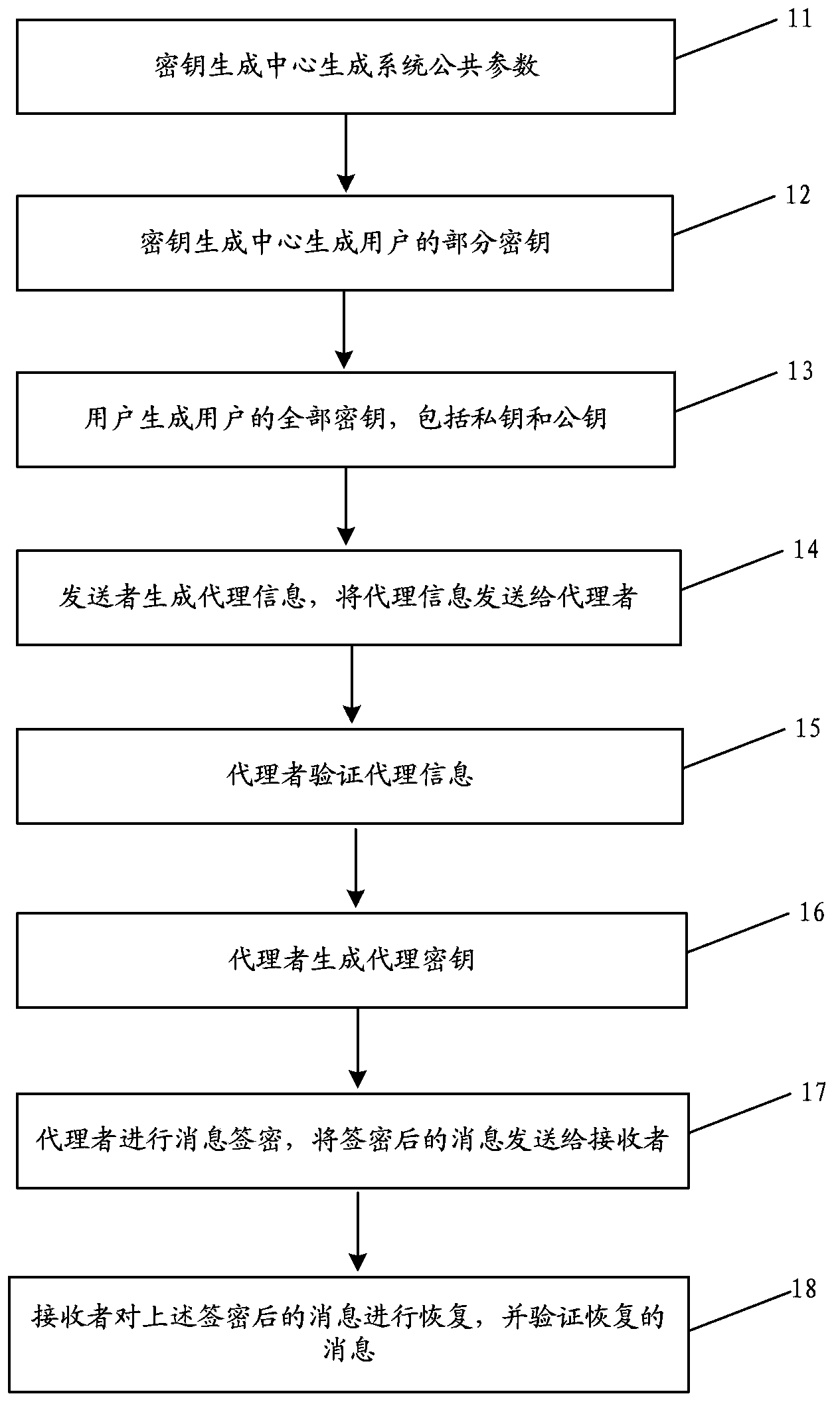
ActiveCN103905189ATroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationSurrogate keySigncryption
The embodiment of the invention provides a method and a system for certificateless and pairing-free identity-based proxy signcryption. The method mainly comprises the following steps: a sender generates a private key and a public key thereof according to common parameters of the system and identity information parameters of the sender, generates proxy information based on the private key and the public key thereof, and sends the proxy information to a proxy; after the proxy information passes verification of the proxy, the proxy generates a proxy key, performs signcryption on a message needing to be sent based on the proxy key and the common parameters of the system to obtain a signcrypted message and an intermediate parameter, and sends the signcrypted message and the intermediate parameter to a receiver; and the receiver recovers the signcrypted message with the use of the intermediate parameter and the common parameters of the system to obtain a recovered message, and verifies the recovered message. The certificateless and pairing-free identity-based proxy signcryption scheme provided by the embodiment of the invention has both signature and encryption characteristics and has the feature of proxy. A key generation center only generates part of keys of a user, no certificate is needed, and the problem of key escrow is solved.
Owner:AEROSPACE INFORMATION
Method for authentication for resisting secrete data disclosure and key exchange based on passwords
InactiveCN101626364AImprove computing efficiencyPrevention analysisPublic key for secure communicationUser identity/authority verificationKey exchangeCryptographic protocol
The invention belongs to a cryptographic protocol, and in particular relates to a method for authentication for resisting secrete data disclosure and key exchange based on passwords. The method is superior to correlative American or international current standard in the aspects of user password protection, secrete data disclosure resistance, better user privacy protection, better online efficiency calculation, less communication bandwidth and higher security. The method for the authentication and the key exchange comprises sub-methods of an innovative method for public key encryption and signcryption based on passwords, a method for knowledge binding certification, a method for resisting temporary secrete data disclosure, a method for awarding a public key certificate. The method has the advantages of good systematicness, adaptability and compatibility.
Owner:赵运磊 +3
Elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method
ActiveCN106936593AReduce multiplicationImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCiphertextSigncryption
The invention discloses an elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method. The method is used for solving the technical problem in the prior art that an existing certificateless multi-receiver signcryption method is low in operation efficiency. According to the technical scheme of the invention, firstly, a user public key and a partial private key, generated by a private key generation center PKG, are sent to a user. Secondly, after the user receives the user public key and the partial private key, the user calculates its own private key. Meanwhile, the user verifies whether the received user public key and the received partial private key are valid or not. If valid, the operation is continued. Otherwise, the operation is stopped. Thirdly, the signcryption algorithm is adopted to design an elliptic curve and the ciphertext information does not include the identity information of a sender and a recipient. Finally, the ciphertext information is broadcasted. Only authorized recipients can fairly decrypt and verify the ciphertext information. According to the technical scheme of the invention, the signcryption process is designed to conduct based on the elliptic curve. Therefore, the multiplication operation on the elliptic curve is reduced, and the calculation efficiency is improved.
Owner:XIDIAN UNIV
Internet of vehicle condition privacy protection method based on certificateless aggregate signcryption and system
ActiveCN106302406APublicly verifiableAvoid managementUser identity/authority verificationPasswordSigncryption
The invention discloses an Internet of vehicle condition privacy protection method based on certificateless aggregate signcryption and a system, wherein the method and the system have excellent performance based on a certificateless password system. According to the method, problems of certificate management and secret key escrow can be avoided, calculation efficiency of the Internet of vehicle during aggregate signcryption verification and aggregate signcryption efficiency during network transmission are improved, condition privacy protection of Internet-of-vehicle users is realized, and the method and the system can be safely utilized in the open Internet of vehicle.
Owner:HOHAI UNIV
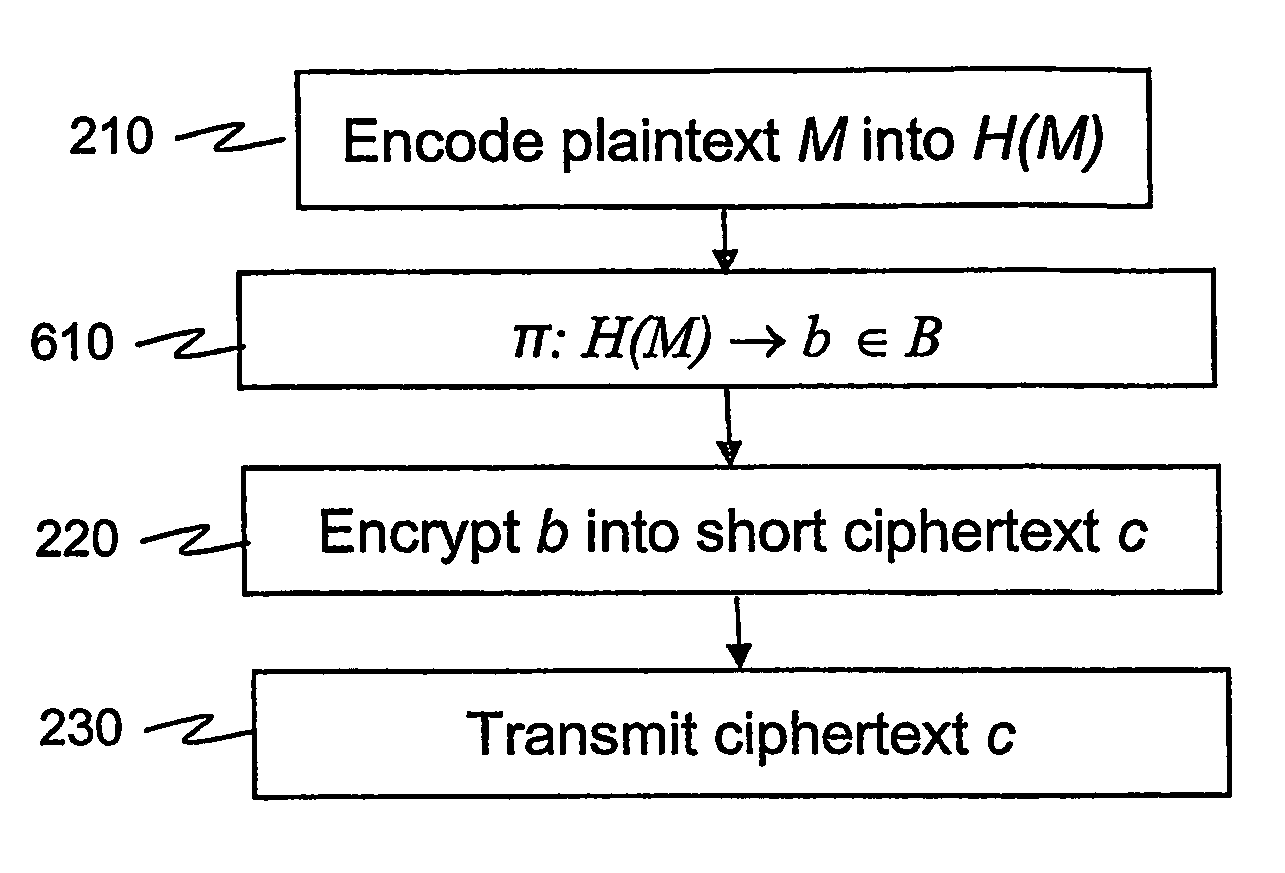
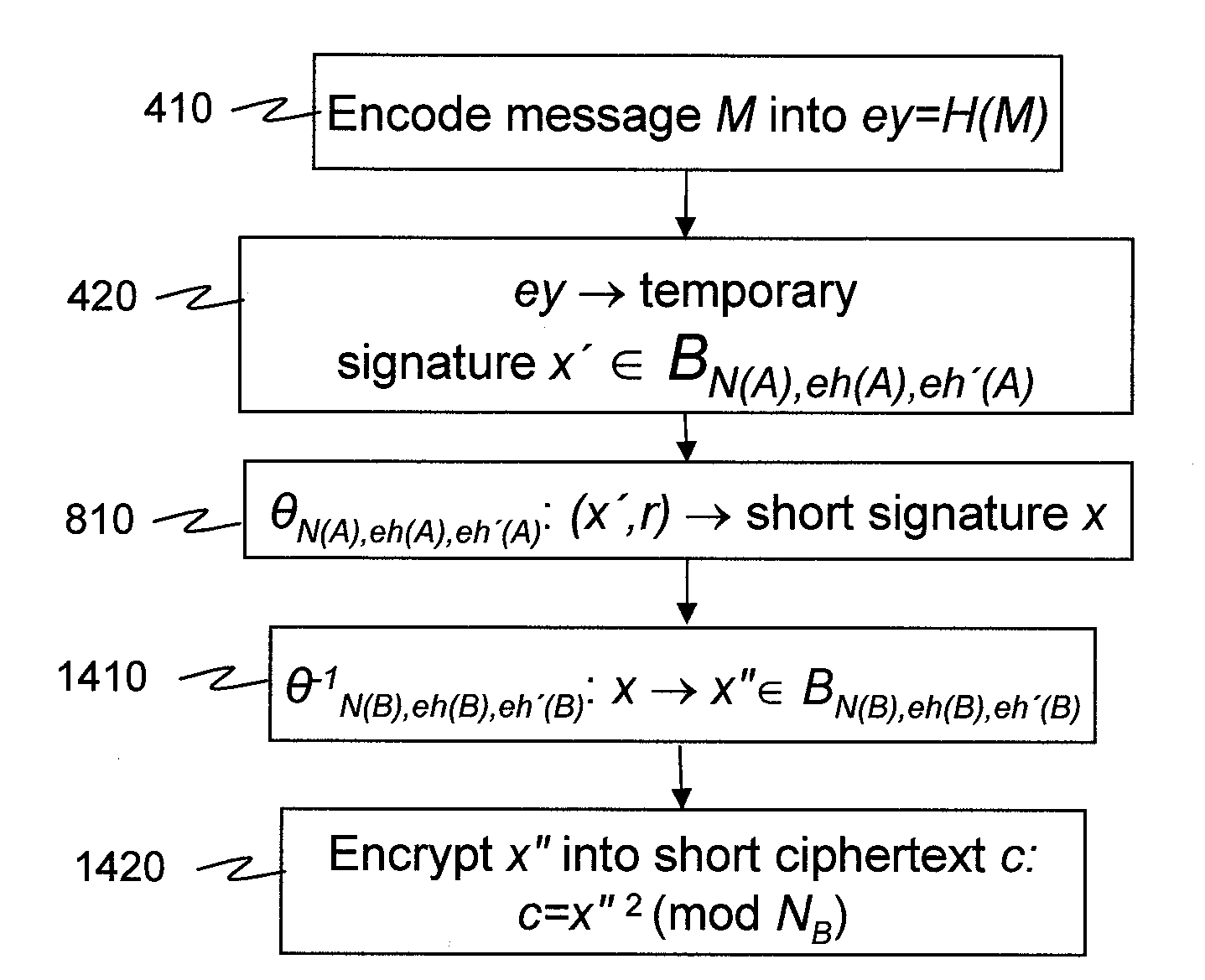
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20060159259A1Computationally efficientBandwidth-reduced ring signaturePublic key for secure communicationUser identity/authority verificationComputer hardwareRing signature
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h?] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Internet-of-vehicles-based auxiliary cloud traffic safety method
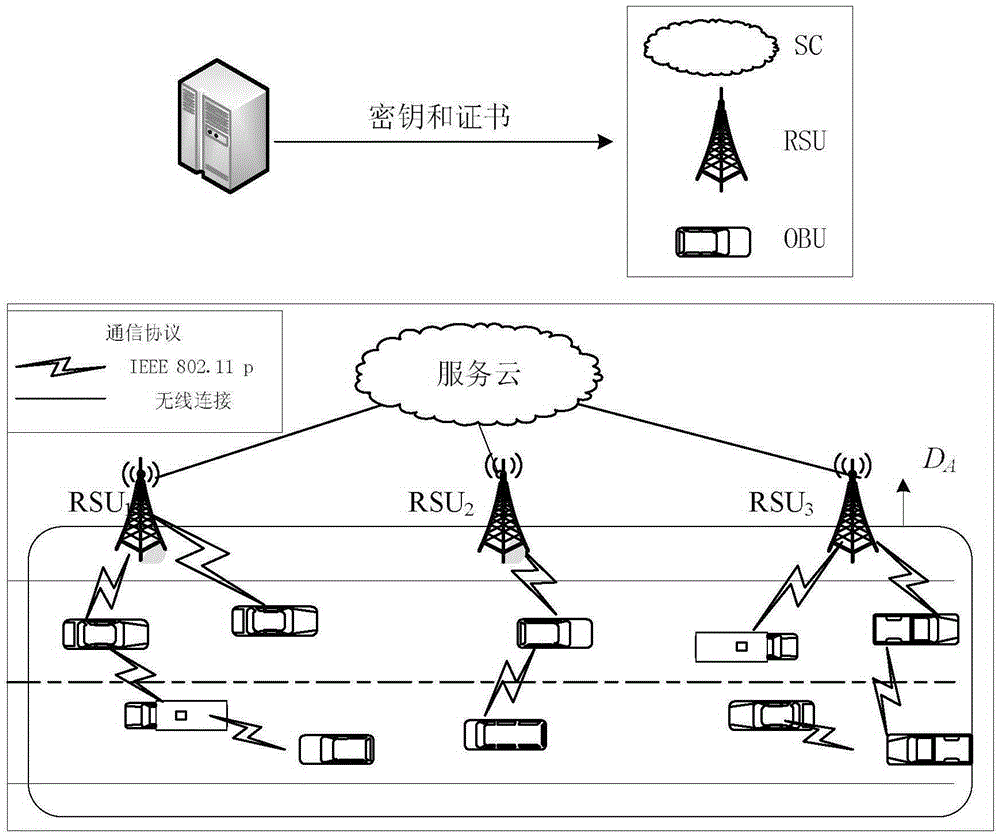
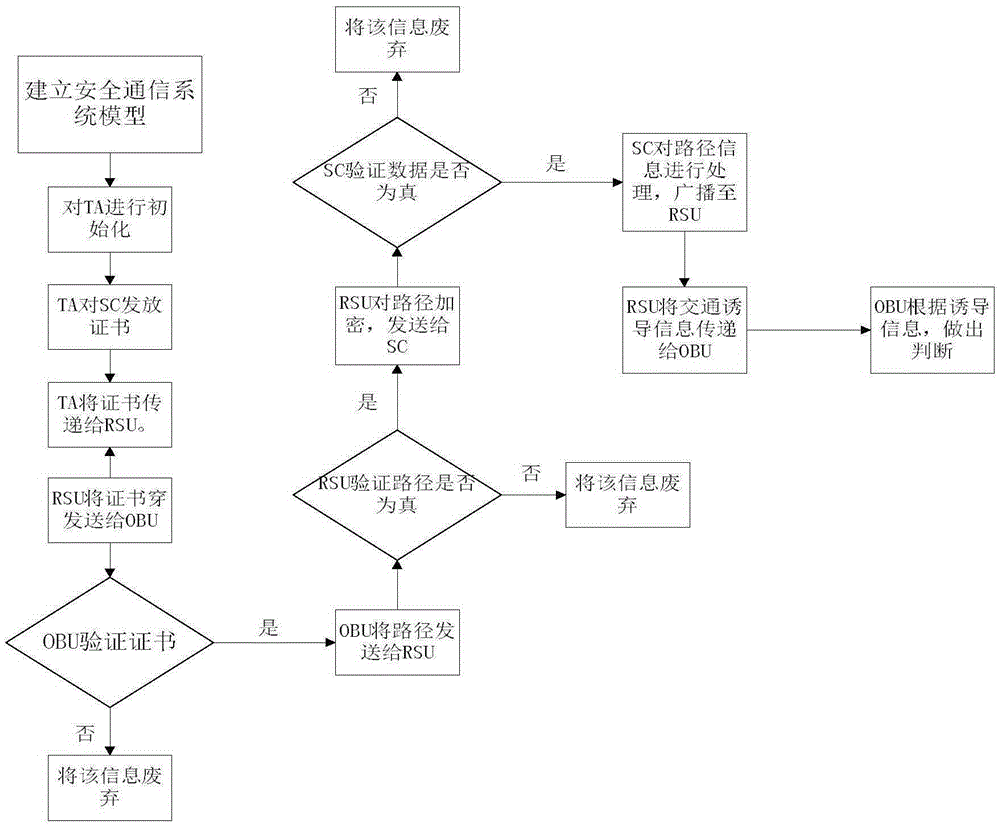
InactiveCN105427643APrevent leakageProtect personal privacyRoad vehicles traffic controlCommunications systemSigncryption
The invention discloses an internet-of-vehicles-based auxiliary cloud traffic safety method. With the method, defects of high cost and insecure communication of calculation and communication based on the existing method can be overcome. According to the technical scheme, the method comprises: firstly, a trust institution TA initializes a internet-of-vehicles communication system and issues a certificate to a service cloud (SC) and a road side unit (RSU); secondly, a user vehicle V identifies the RSU based on the certificate issued by the trust institution TA and sends encrypted route information; thirdly, the RSU verifies authenticity of the route and aggregates an actual route; fourthly, the SC decrypts the aggregated route to generate traffic guidance information; and fifthly, the user vehicle V selects a corresponding route based on the traffic guidance information. According to the invention, effectiveness of internet-of-vehicles communication can be guaranteed with less computation and communication costs; and the user route information is encrypted and signed by means of homomorphic signcryption algorithm, thereby guaranteeing privacy of the user route information. The provided method can be applied to intelligent management and intelligent dynamic information service of the traffic system.
Owner:XIDIAN UNIV
Real anonymous certificateless multi-message multi-receiver signcryption method
ActiveCN107682145AImprove practicalityImprove computing efficiencyKey distribution for secure communicationPublic key for secure communicationKey generationSigncryption
Owner:XIDIAN UNIV
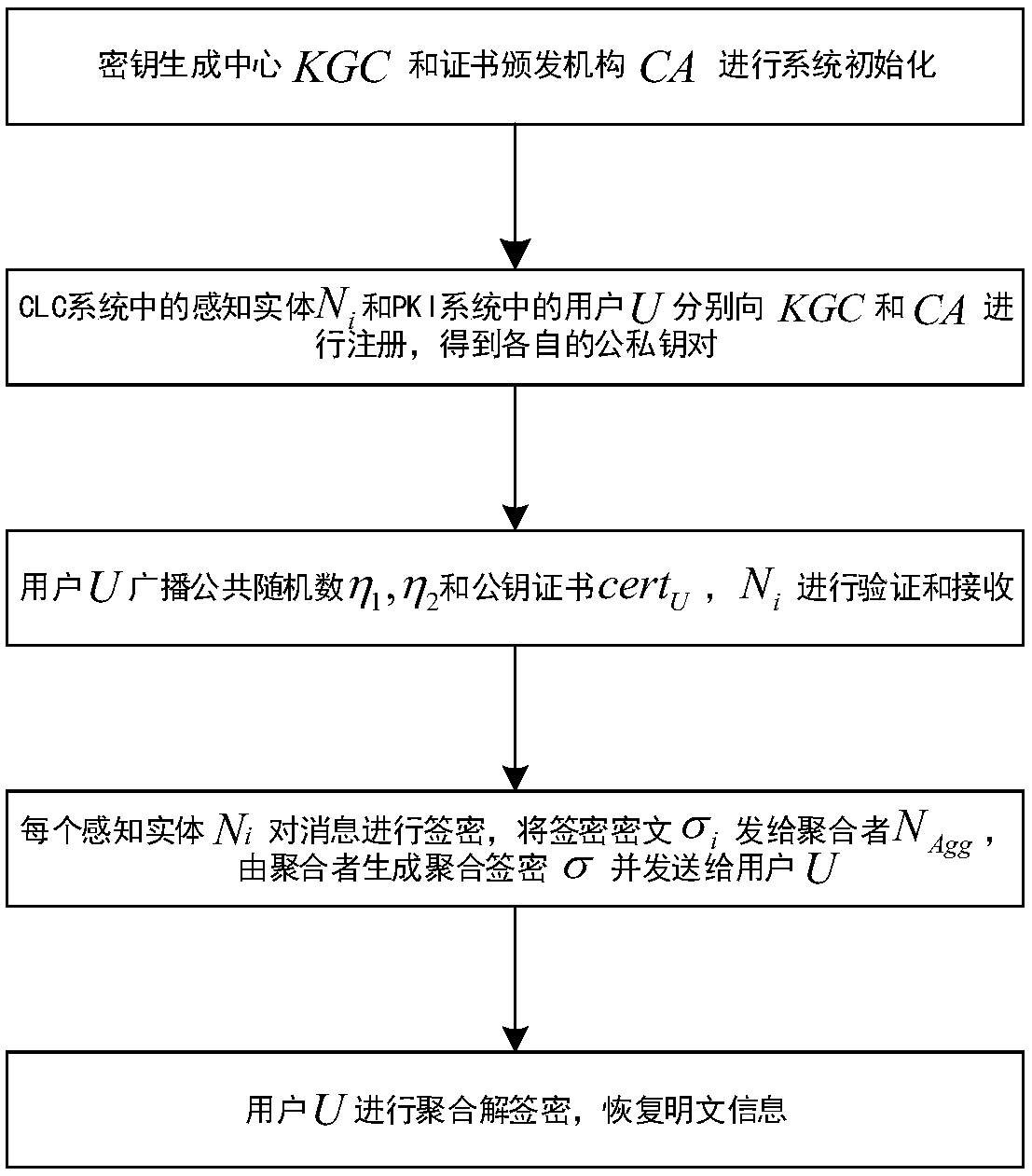
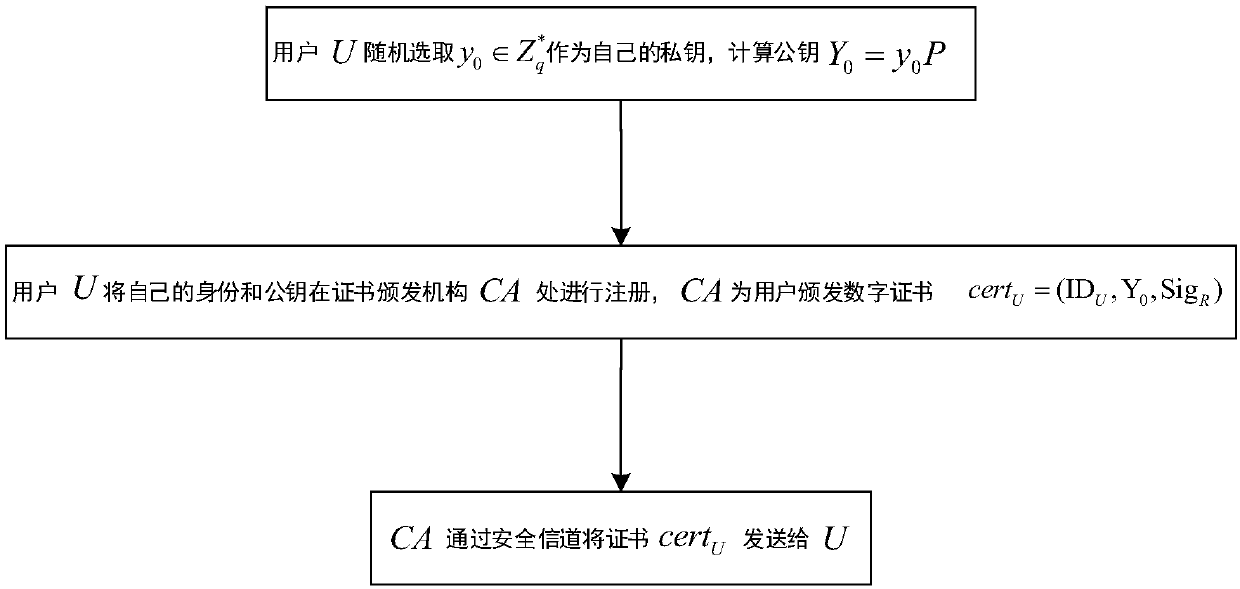
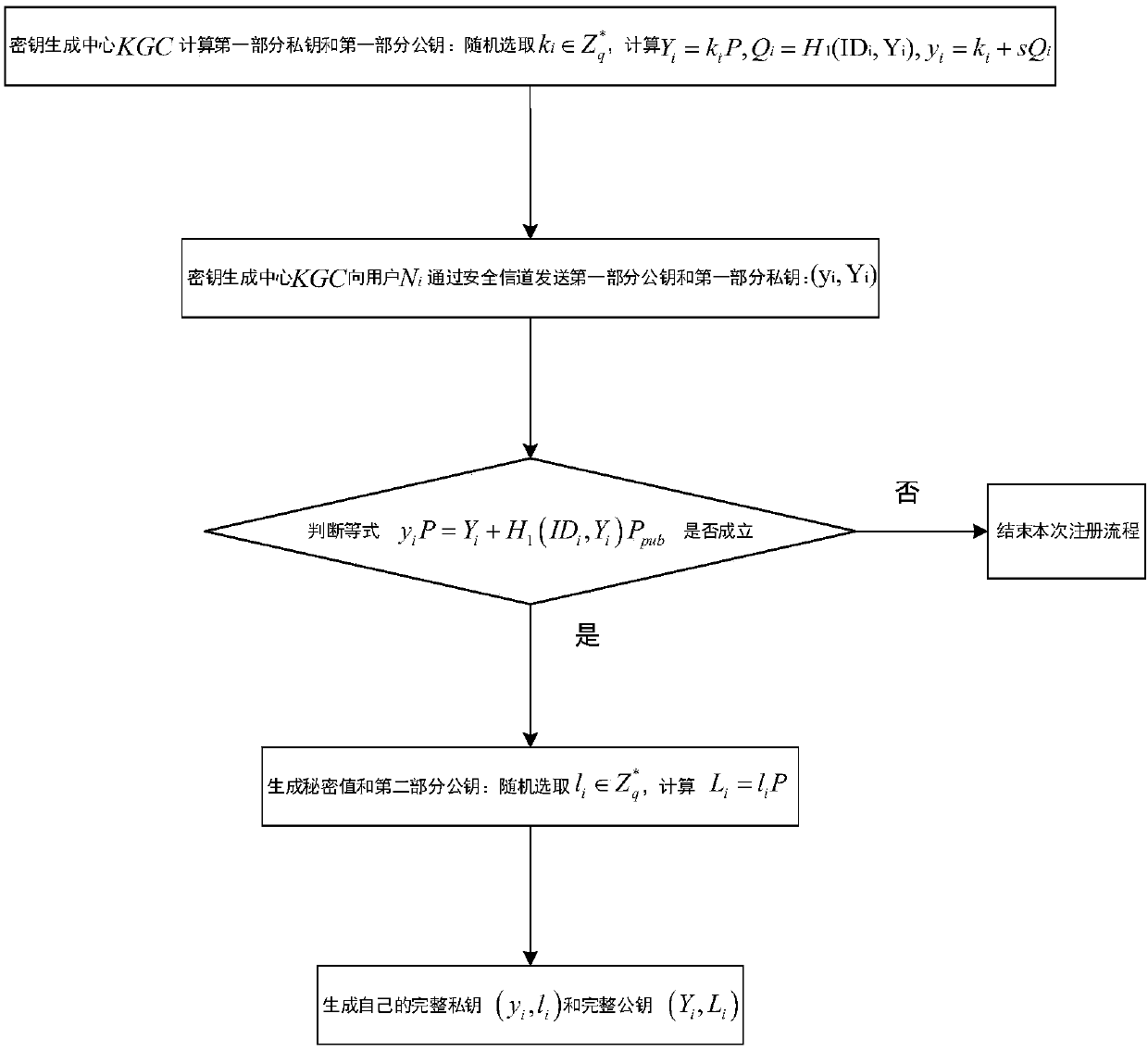
Heterogeneous polymerization signcryption method in Internet-of-things environment
ActiveCN107707360AReduce computational overheadImprove execution efficiencyKey distribution for secure communicationUser identity/authority verificationChemistrySigncryption
The invention discloses a high-efficiency polymerization signcryption solution in an Internet-of-things environment, wherein the high-efficiency polymerization signcryption solution mainly settles theproblems of relatively small application range and relatively low practicability caused by relatively high calculation expenditure in an existing polymerization signcryption solution. The high-efficiency polymerization signcryption solution comprises the following realizing steps of 1, performing system initialization by a secret key generating center KGG and a certificate issuing mechanism CA; 2, registering a perception entity Ni in a CLC system and a user U in a PKI system to KGC and CA; 3, broadcasting a common random number and a public key certificate by the user U in the PKI system, and performing verification and receiving by the Ni; 4, selecting a message generating signcryption cryptograph by the perception entity Ni in the CLC system, transmitting the message generating signcryption cryptograph to an aggregator Nn for forming aggregated signcryption, and transmitting the aggregated signcryption to the user U by the aggregator Nn; and 5, performing polymerization de-signcryption and restoring corresponding plaintext information. The high-efficiency polymerization signcryption solution has isomerism and higher practicability. The high-efficiency polymerization signcryption solution can be used for smart home, intelligent traffic, intelligent medical service and intelligent industrial detection.
Owner:陕西链诚致远科技有限公司
Multi-receiver hybrid signcryption algorithm without bilinear pairings
ActiveCN104734857APrevent forgeryDefend against forgery attacksKey distribution for secure communicationUser identity/authority verificationSigncryptionTwo-way communication
The invention discloses a multi-receiver hybrid signcryption algorithm without bilinear pairings. The multi-receiver hybrid signcryption algorithm includes the five processes of secret key generation center initialization, extraction of a part of private keys, secret key extraction, signcryption and unsigncryption. Two-way communication signcryption of multiple receivers is achieved, the signcryption algorithm in the scheme is achieved without the bilinear pairings, calculation expenses are greatly reduced, and universality is better; compared with traditional schemes, counterfeit attacks of a positive and dishonest secret key generation center can be defended, and safety is higher.
Owner:NANJING UNIV OF POSTS & TELECOMM
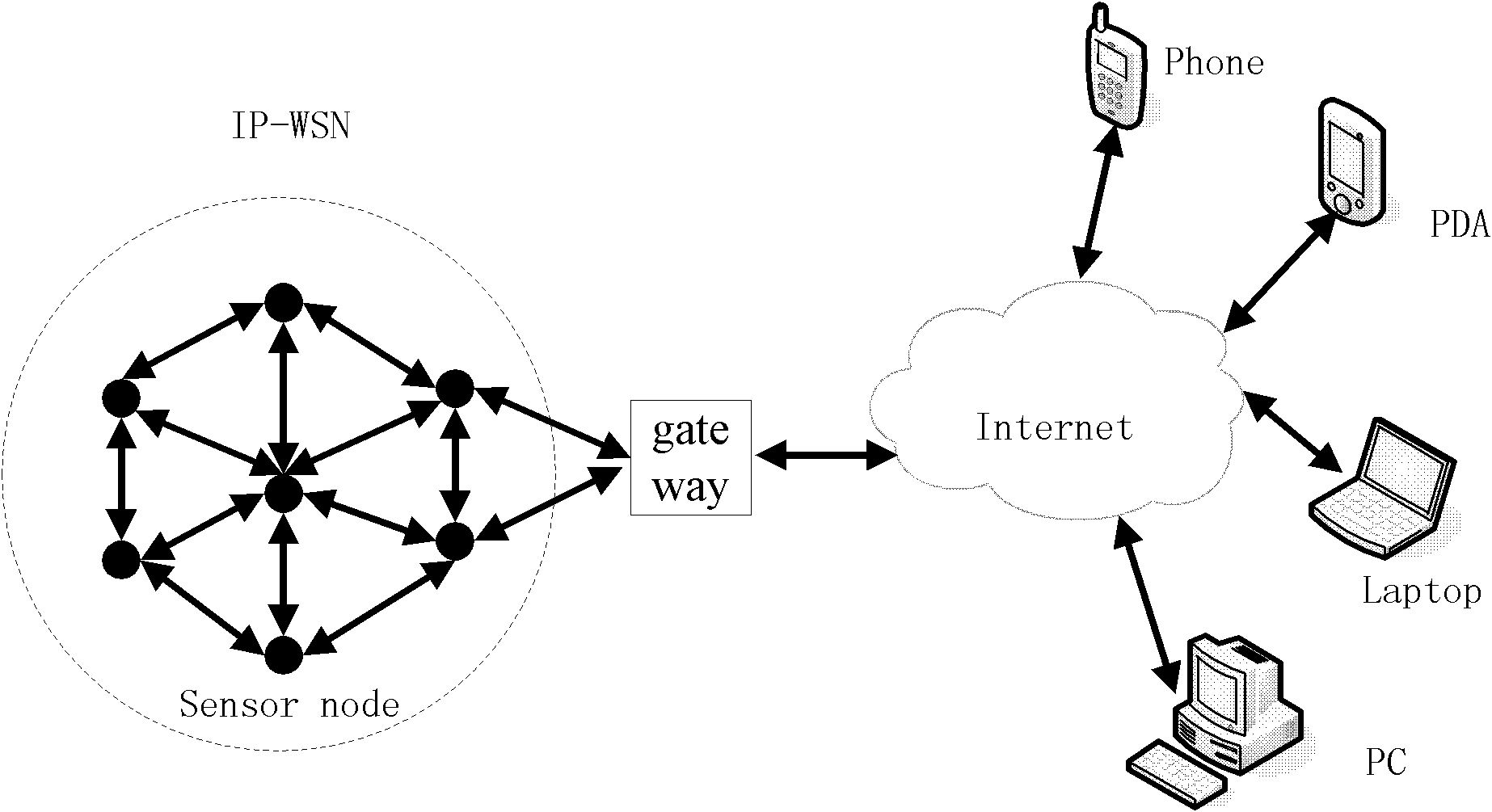
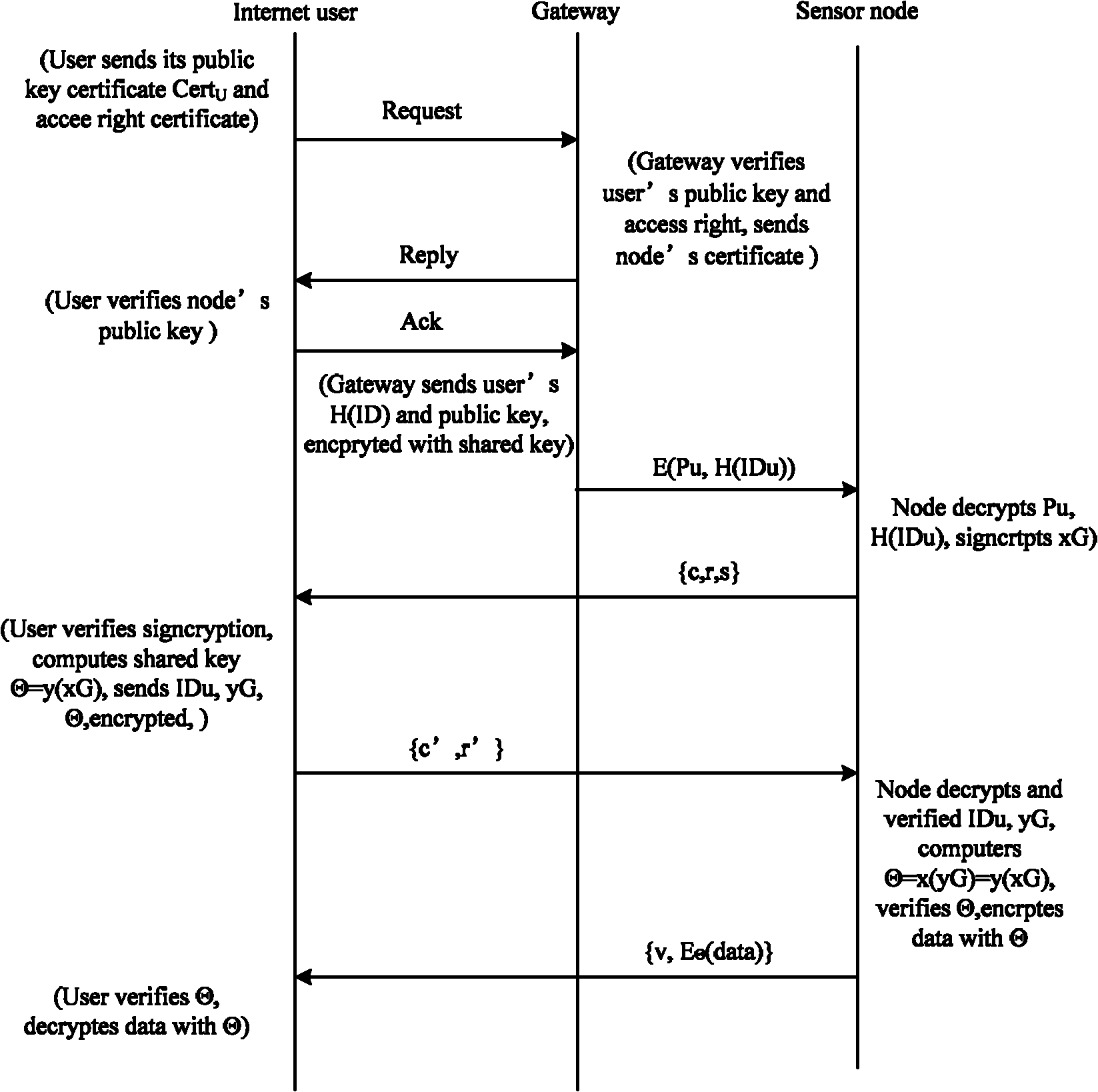
End-to-end safety control method for wireless sensor network and internet intercommunication
InactiveCN102546650AReduce energy consumptionEnhanced Access ControlKey distribution for secure communicationUser identity/authority verificationEnd to end securityWireless mesh network
The invention provides an end-to-end safety control method for wireless sensor network and internet intercommunication. Part of the certification and access control work is transferred to the gateway of the wireless sensor network, an asymmetric key negotiation mode based on elliptic-curve signcryption technology is adopted to place unsigncryption operation with large computing amount in an Internent remote terminal, and the symmetric key decryption operation is placed in the sensor nodes. Compared with the improved ECC (Elliptic Curve Cryptography)-based SSL (Security Socket Layer) protocol and the improved TLS (Transport Layer Security) protocol based on elliptic-curve identity, the energy consumption of the sensor nodes is effectively reduced, access control and privacy protection are enhanced and Dos (Disk Operating System) attack can be resisted.
Owner:BEIJING UNIV OF TECH
Anonymous participant identity-based signcryption method for multiple receivers
InactiveCN103368741AEnhanced anonymityPrivacy protectionUser identity/authority verificationPlaintextCiphertext
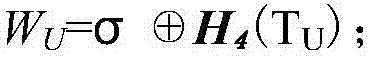
The invention discloses an anonymous participant identity-based signcryption method for multiple receivers, solving the technical problem that the safety of the current signcryption method for multiple receivers is poor. The technical scheme comprises the steps of (1) sender signcryption: a sender IDs selects n authorization receivers ID1, ID2, ellipsis, IDn, builds an authorization receiver identity information list L={ID1, ID2, ellipsis, IDn}, constructs a signcryption ciphertext C=<Y, X, U, sigma, W, T, J>, and broadcasts the signcryption ciphertext C so as to complete signcryption operation; and (2) receiver decryption: a receiver IDi calculates h'=H4 (sigma, X, U, T, J) according to elements in the signcryption ciphertext C firstly, then judges whether an equation e (W, P)=e (X+h'Y, Ppub) is workable, decodes a message ciphertext sigma by using a symmetrical decipherment algorithm Dk() to obtain a cleartext M=DK(sigma), and completes the decryption process. The sender is anonymous through constructing a pseudo public key, meanwhile Lagrange's interpolation is adopted for fusing identity information of all the authorization receivers to realize that the identities of the authorization receivers are anonymous for non-authorization receivers, and the safety of the signcryption method for multiple receivers is improved.
Owner:XIDIAN UNIV +1
Construction method for one-time anonymous signcryption of public key
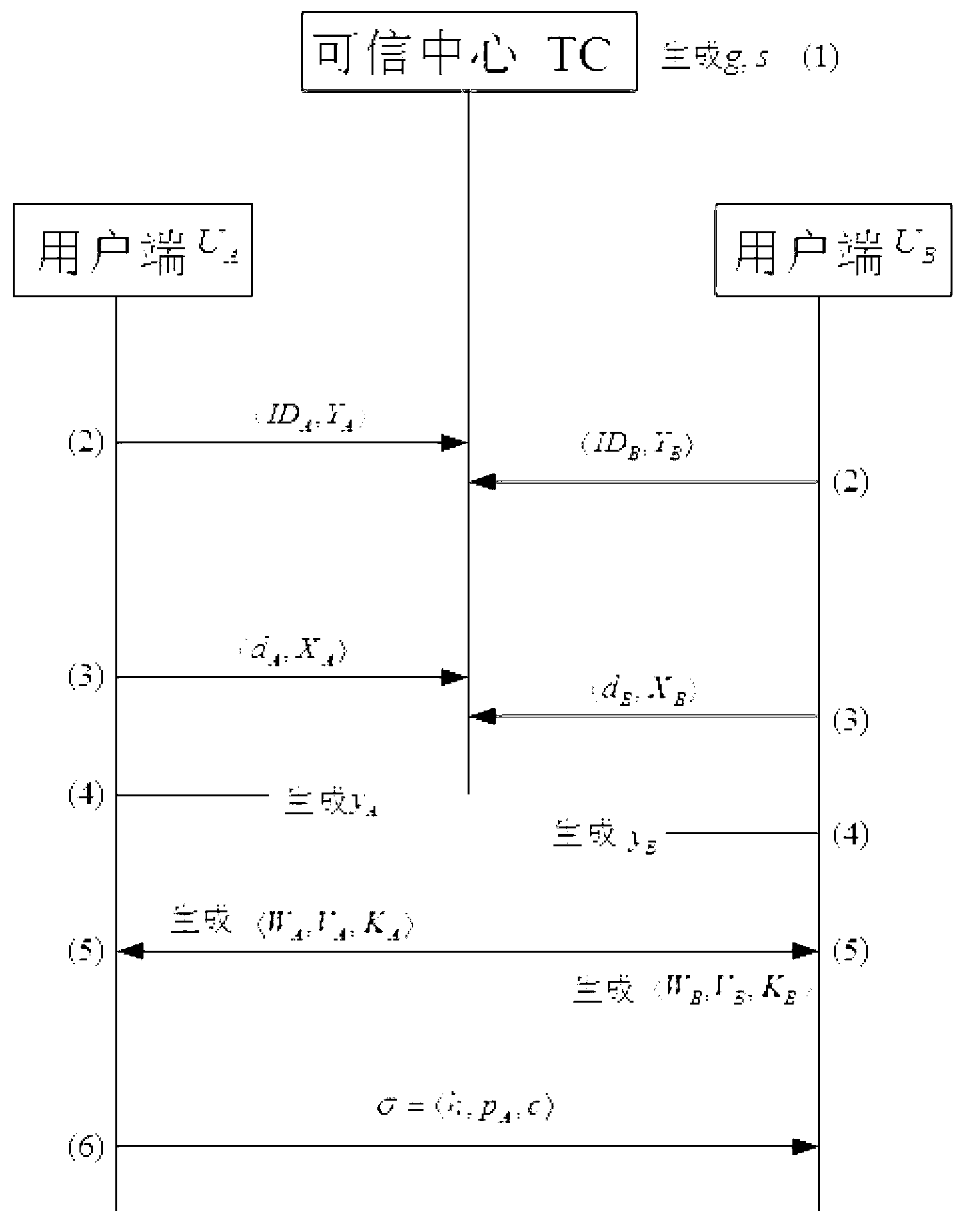
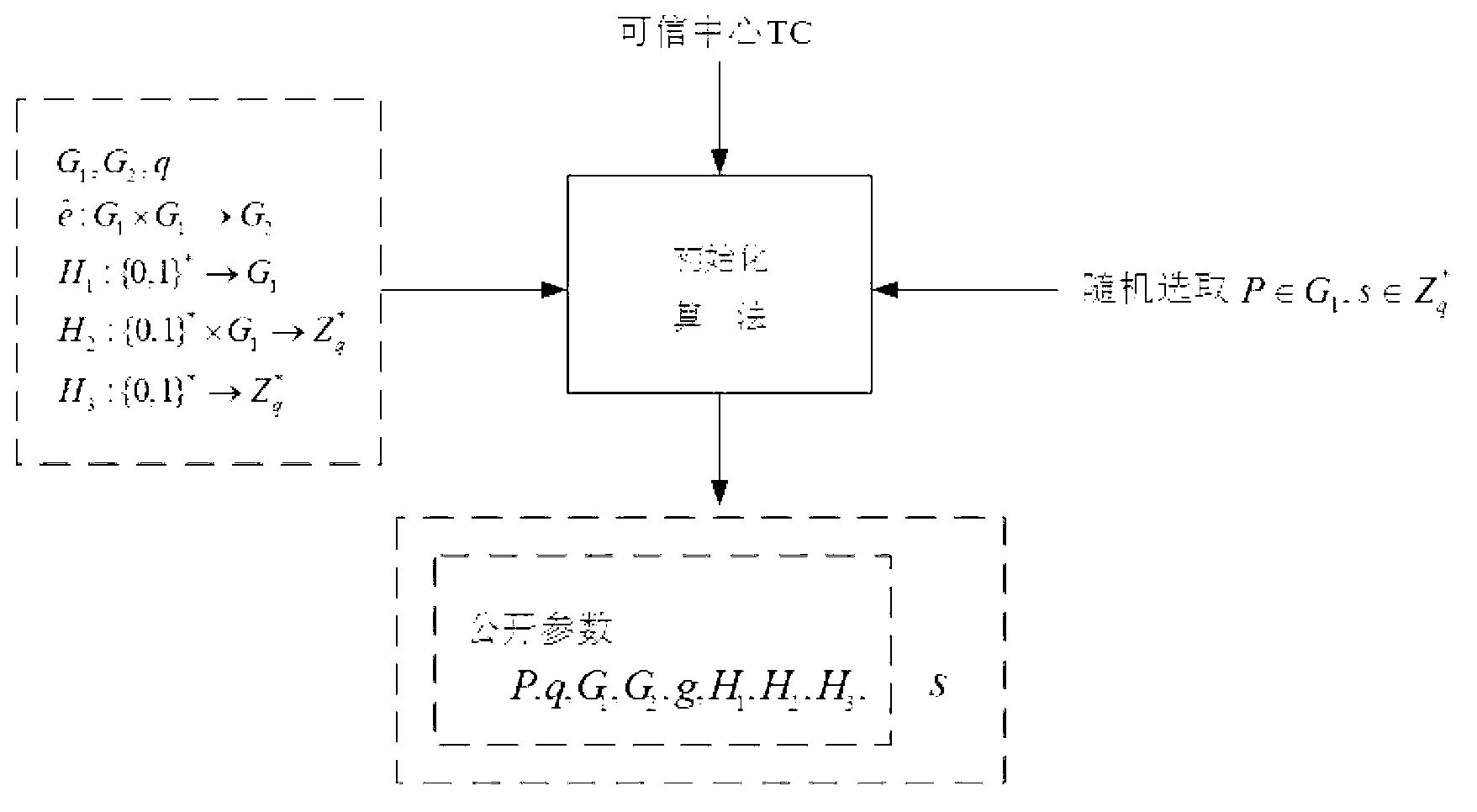
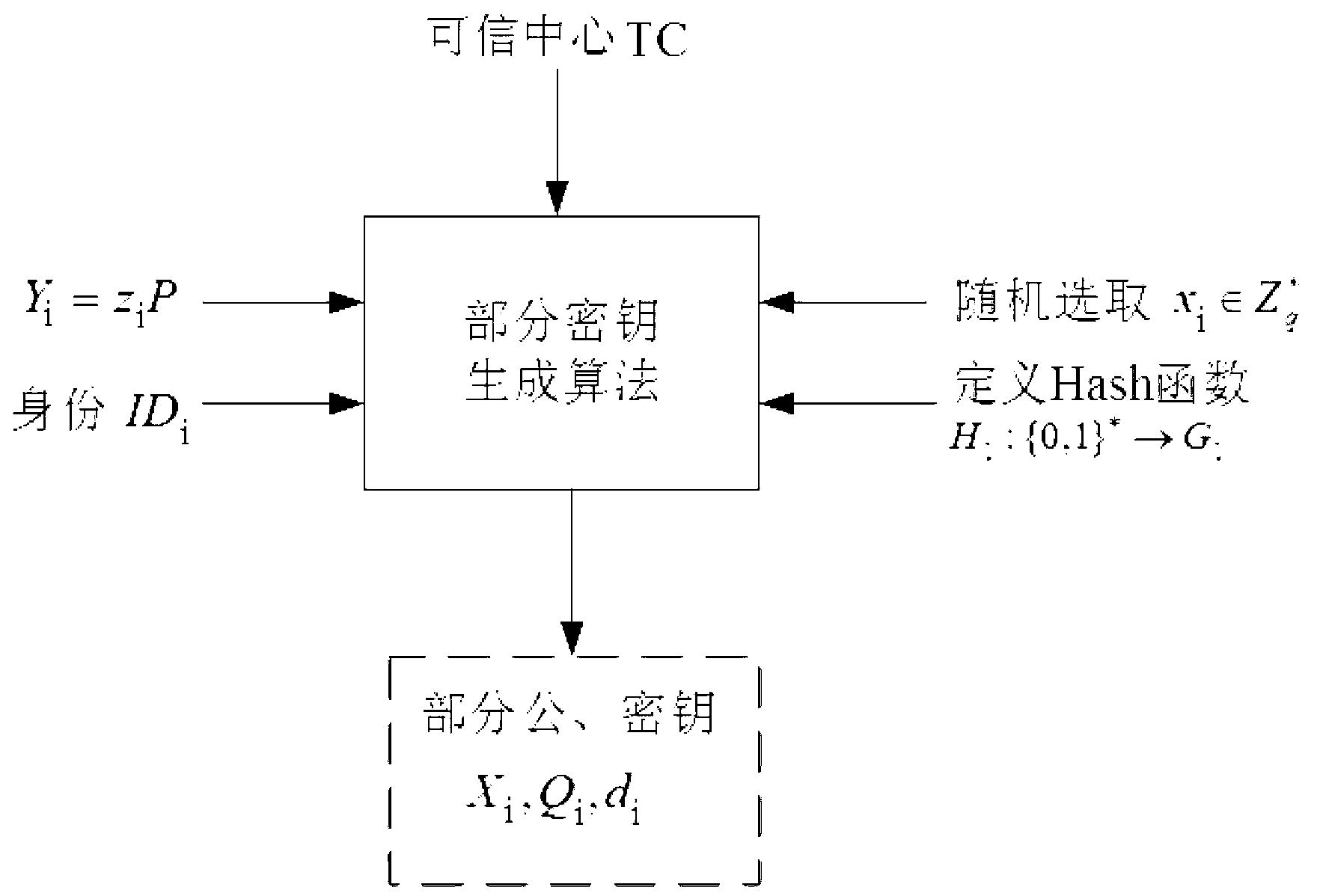
InactiveCN103297241APrevent one-off attacksPrevent untrusted attacksUser identity/authority verificationSigncryptionComputerized system
The invention discloses a construction method for one-time anonymous signcryption of public key and aims to complete the construction method for the one-time anonymous signcryption of the public key by the aid of a computer system. The computer system comprises a UA (user A), a UB (user B) and a TC (trusted center), and the UA, the UB and the TC are mutually communicated. The construction method includes seven steps of 1), generating computer system public key; 2), generating user partial secret key; 3), generating user secret key; 4), generating one-time public key; 5), subjecting the one-time public key to validity verification; 6), performing signcryption; 7), unsigncrypting. Compared with the prior art, the construction method has both anonymity and traceability, and can effectively prevent one-time attacks of malicious users and untrusted attacks from the TC inside a system. Meanwhile, the construction method has high computational efficiency and low communication costs as compared with conventional methods.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
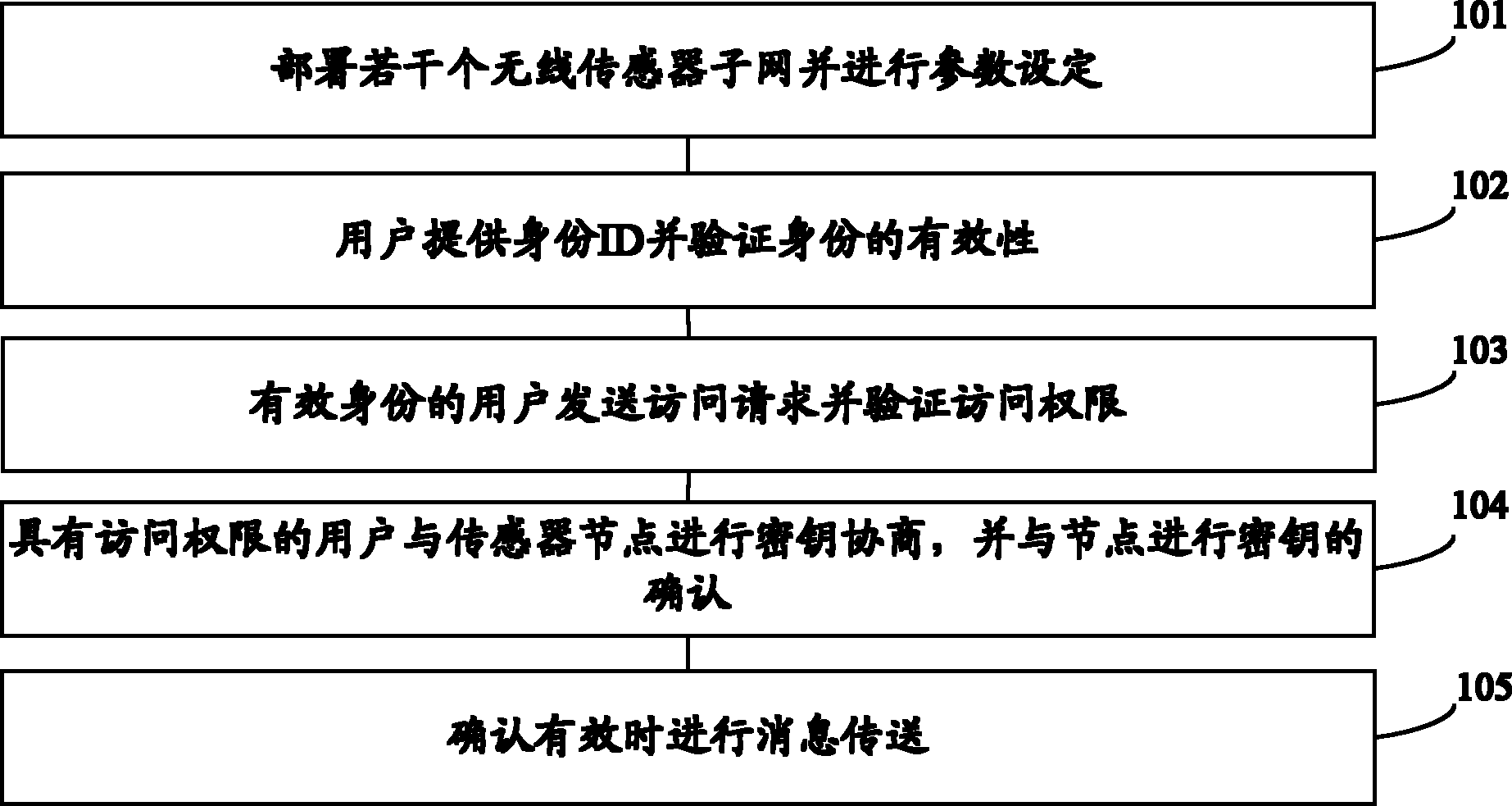
Safe positioning method in wireless sensor network
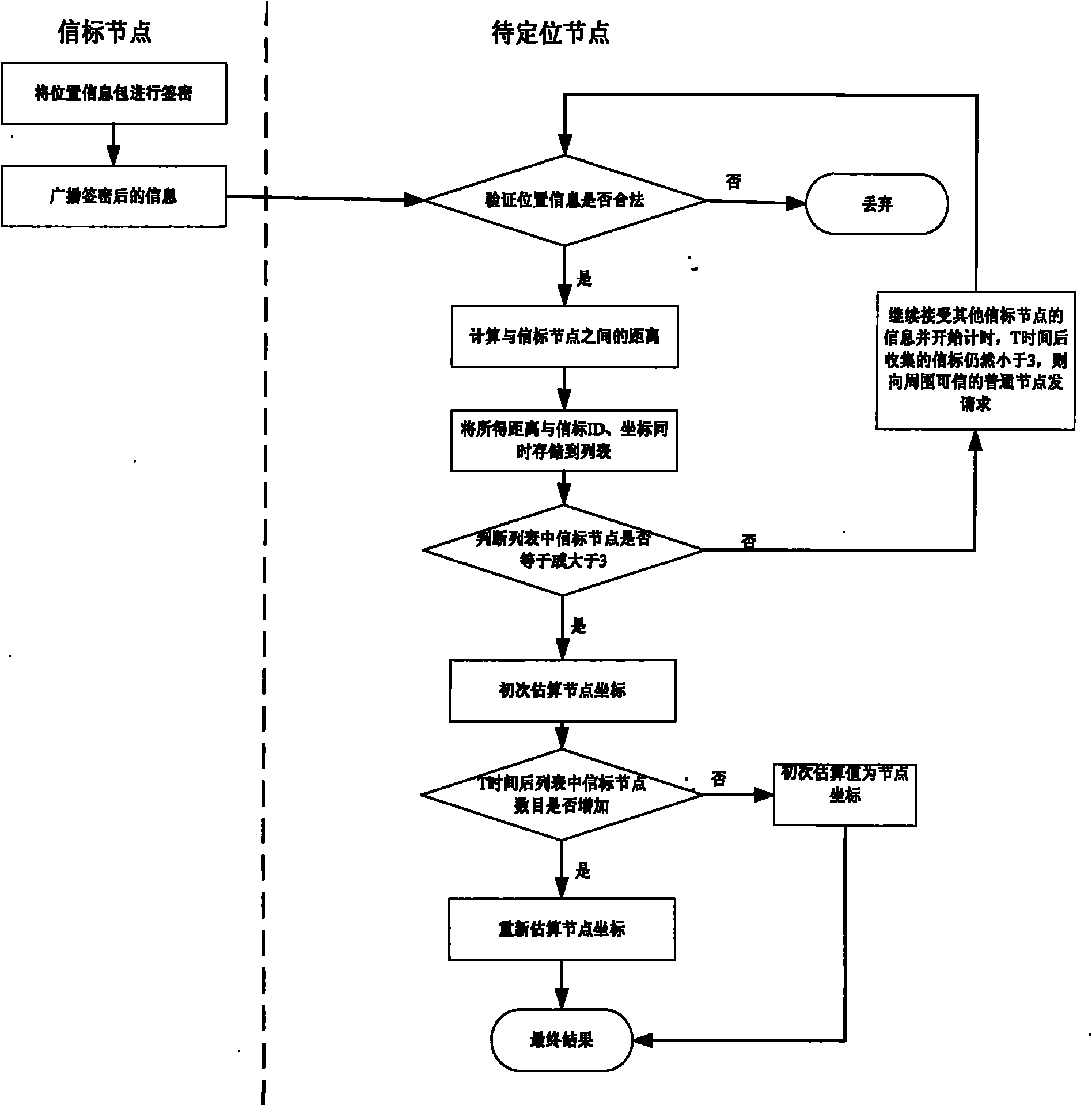
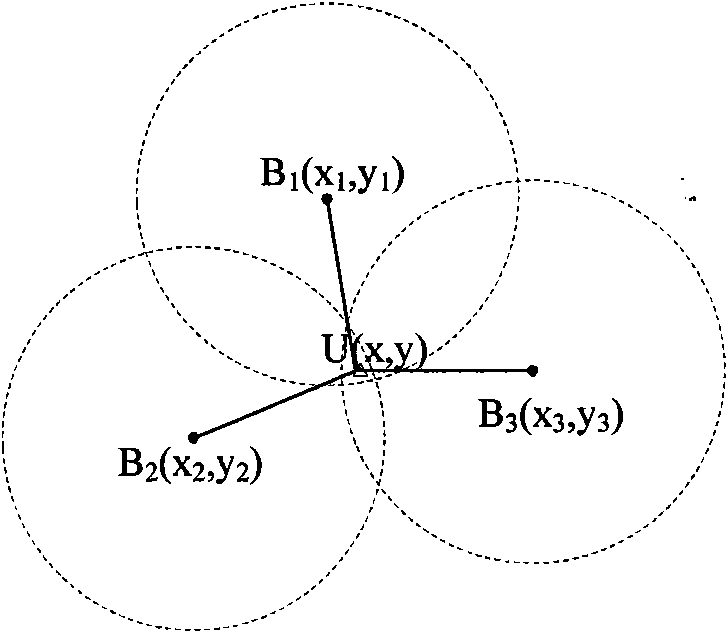
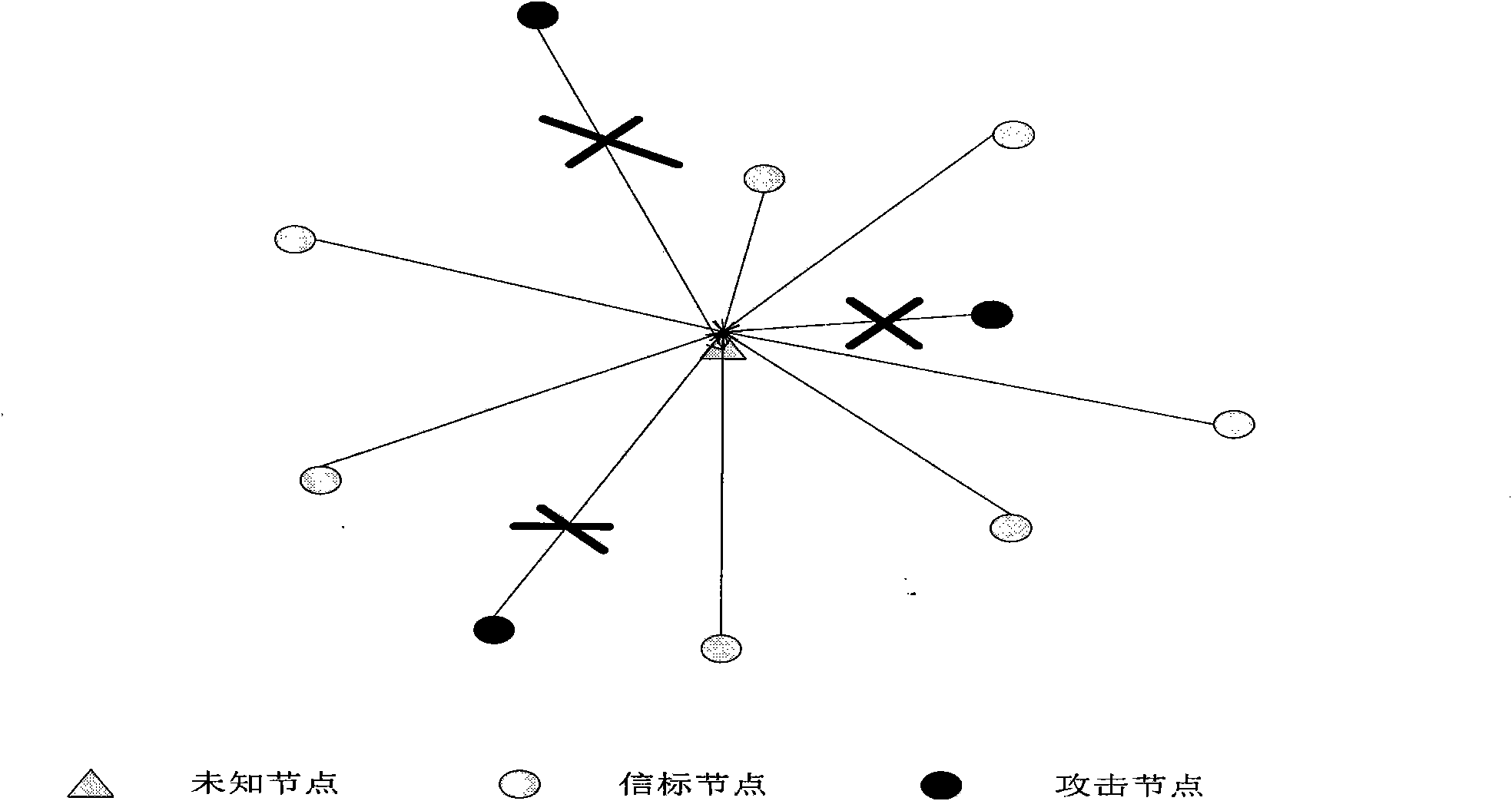
InactiveCN102006663AReduce computational costResource impactNetwork topologiesHigh level techniquesSigncryptionTransfer procedure
The invention belongs to the technical field of computer network security, relating to a safe positioning method in a wireless sensor network. The traditional positioning methods do not consider the security problems sufficiently, and the invention provides the positioning method based on a signcryption mechanism so as to ensure confidentiality of position information and integrity of the position information in the transmission process. The method comprises the following steps of: carrying out signcryption and broadcasting on the position information by a beacon node; carrying out unsigncryption and authentification on the received position information by an unknown node; calculating a self-position by the unknown node; and updating the self-position by the node. Compared with the prior art, the invention effectively protects the position information in the positioning process, completely considers the characteristic of limited energy of a wireless sensor node, and minimizes the communication cost and calculating cost of the node in the positioning method. The invention has flexible positioning and updating mechanism, and executors can adjust according to the specific circumstances of the network so as to achieve the satisfied positioning convergence time.
Owner:BEIJING UNIV OF TECH
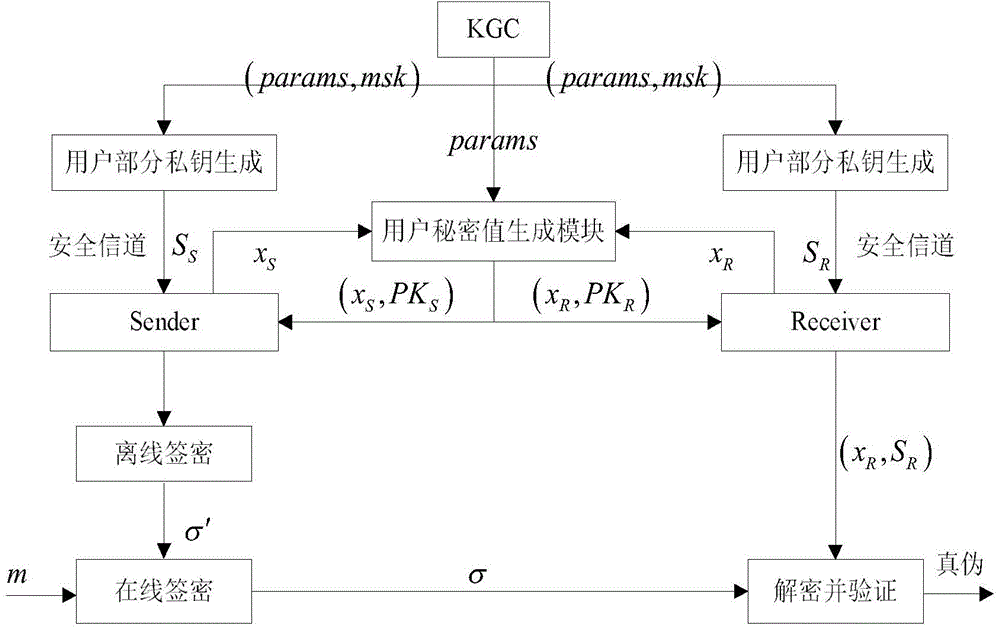
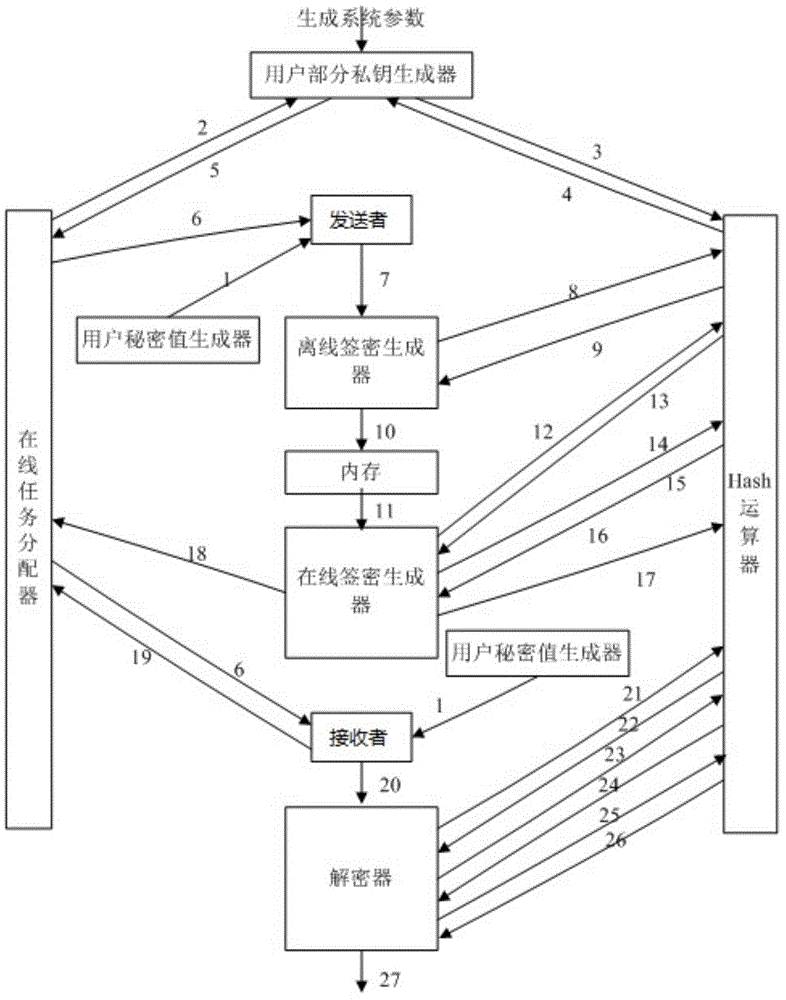
Certificateless-based signcryption method and certificateless-based signcryption system
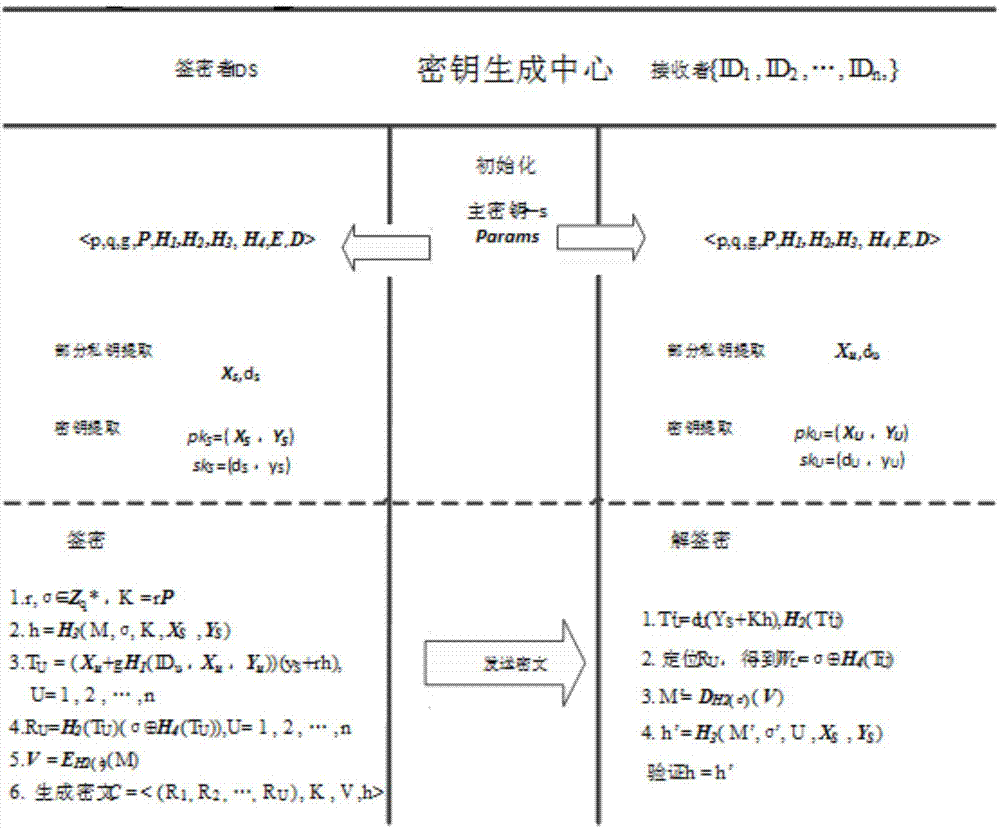
ActiveCN104393996AImprove securityIncrease flexibilityUser identity/authority verificationThird partySigncryption
The invention discloses a certificateless-based signcryption method and a certificateless-based signcryption system, belonging to the field of signcryption technologies. The certificateless-based signcryption method and the certificateless-based signcryption system comprise a third-party KGC (Key Generation Center partial private key generation center) and a user module, wherein the third-party module comprises an online task distributor, a partial private key generator and an Hash arithmetic unit which are connected through a secure channel; the user module comprises a user secret value generator, a user full private key generator, an offline signcryption machine, an online signcryption machine and a decipher, and the signcryption operation is carried out on a user through the steps of generating system parameters, generating a user secret value, generating a user partial private key, generating a user full private key, carrying out offline signcryption, carrying out online signcryption and decoding in sequence. According to the certificateless-based signcryption method and the certificateless-based signcryption system, signcryption effectively replaces a simple method of combining encryption and a signature through a logic unit, so that the online / offline signcryption can be implemented under the certificateless environment safely and effectively, and determination of identity of a receiver is not needed in an offline stage, and the certificateless-based signcryption method and the certificateless-based signcryption system have the advantages of high efficiency, good safety, large flexibility and strong applicability.
Owner:马鞍山城智信息技术有限公司
Oval curve mixing signcryption method based on certificateless effect
InactiveCN104811302ATo overcomeOvercome storageKey distribution for secure communicationPublic key for secure communicationKey generationSigncryption
The invention provides an oval curve mixing signcryption method based on a certificateless effect. The method consists of the steps including system initialization, user private key and public key generation, partial user public key and partial user private key generation, signcryption and unsigncryption. The method solves the problems of calculation cost for certificate generation, storage, issuing, withdrawal and certificate verification, and the like in a traditional public key basic facility. The inherent private key trusteeship problem in the identity-based cryptography is eliminated, safety signal channels are not needed, the confidentiality and authentication effects can be simultaneously achieved, and the signcryption of messages with any length can be realized. The oval curve mixing signcryption method has the advantages that the safety is high, the operation efficiency is high, the communication cost is low, and the like. The method can be used for a wireless sensor network with the limited resources.
Owner:SHAANXI NORMAL UNIV +1
Anonymous signcryption method from identity public key system to certificate public key system
ActiveCN103746811APrivacy protectionImprove securityUser identity/authority verificationCiphertextConfidentiality
The invention discloses an anonymous signcryption method from an identity public key system to a certificate public key system. The anonymous signcryption method specifically comprises the steps that parameters are randomly selected from a public key function database and system public keys and system private keys of the identity public key system and the certificate public key system are generated; a public key and a private key of a user are generated according to the public keys and the private keys and the system parameters; anonymous signcryption is performed to a message by using a bilinear pair, the private key of the user of the identity public key system and the public key of the user of the certificate public key system, and a ciphertext is sent to a receiver; the receiver performs designcryption to the ciphertext according to the bilinear pair and the private key of the receiver and simultaneously authenticates the identity of a sender. The anonymous signcryption method from the identity public key system to the certificate public key system has the advantages of simple implementation process and high transmission efficiency, and can be used for realizing the confidentiality, authentication and anonymity of information transmitted from the identity public key system to the certificate public key system.
Owner:西安千喜网络科技有限公司
Signcryption method from certificateless environment to public key infrastructure environment
InactiveCN104767612ANo public parameters requiredAchieving authenticityPublic key for secure communicationCiphertextConfidentiality
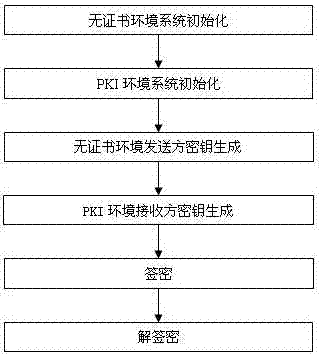
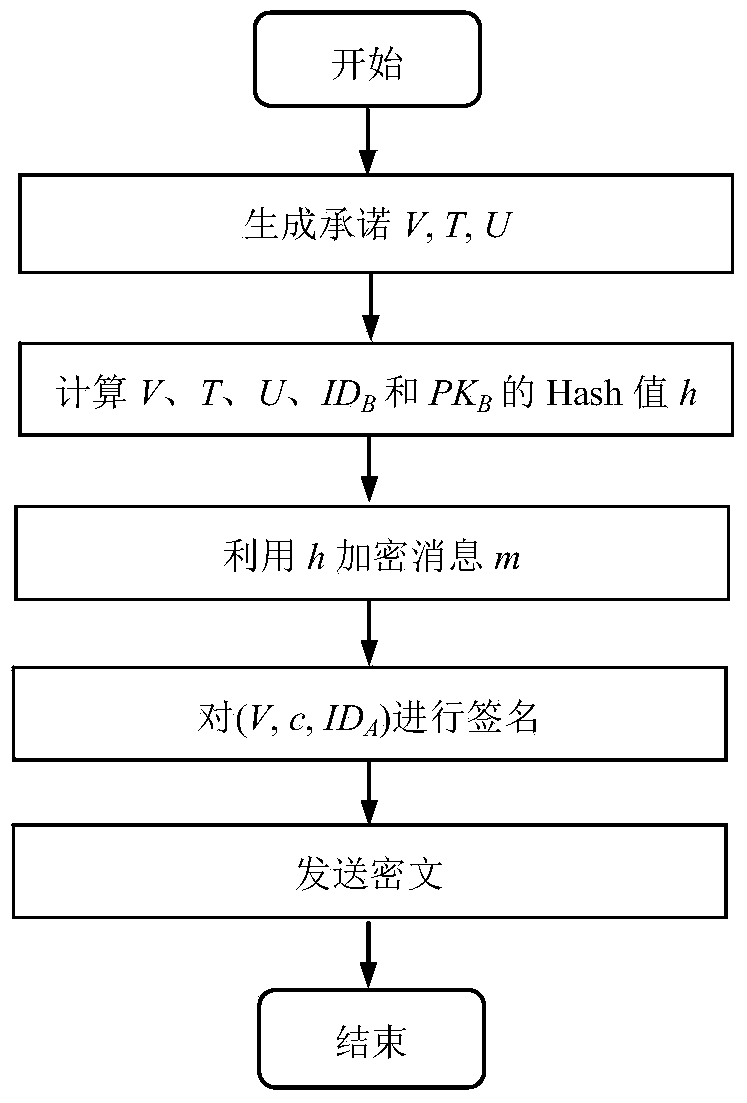
The invention discloses a signcryption method from a certificateless environment to a public key infrastructure environment, and belongs to the field of secret communications. The signcyption method comprises the steps that system initialization of the certificateless environment is conducted; system initialization of the public key infrastructure environment is conducted; a secret key of a certificateless environment sender is generated; a secret key of a public key infrastructure environment receiver is generated; the certificateless environment sender generates a signcryption text sigma according to system parameters, a complete private key and public key of the sender, a public key of the receiver and a message m and sends results to the receiver; the public key infrastructure environment receiver verifies the correctness of the signcryption text sigma according to the system parameters, an identity and the public key of the sender and the public key of the receiver and decrypts the signcryption text sigma by using a private key of the receiver. The signcryption method from the certificateless environment to the public key infrastructure environment can achieve that the sender of the certificateless environment sends the signcryption text to the receiver of the public key infrastructure environment and provides confidentiality and authentication for the receiver of the public key infrastructure environment; the features that the authentication can be verified publicly and a sharing system and common parameters of the receiver and the sender are not necessary are achieved.
Owner:JIUJIANG UNIVERSITY
Signcryption method based from identity environment to certificateless environment
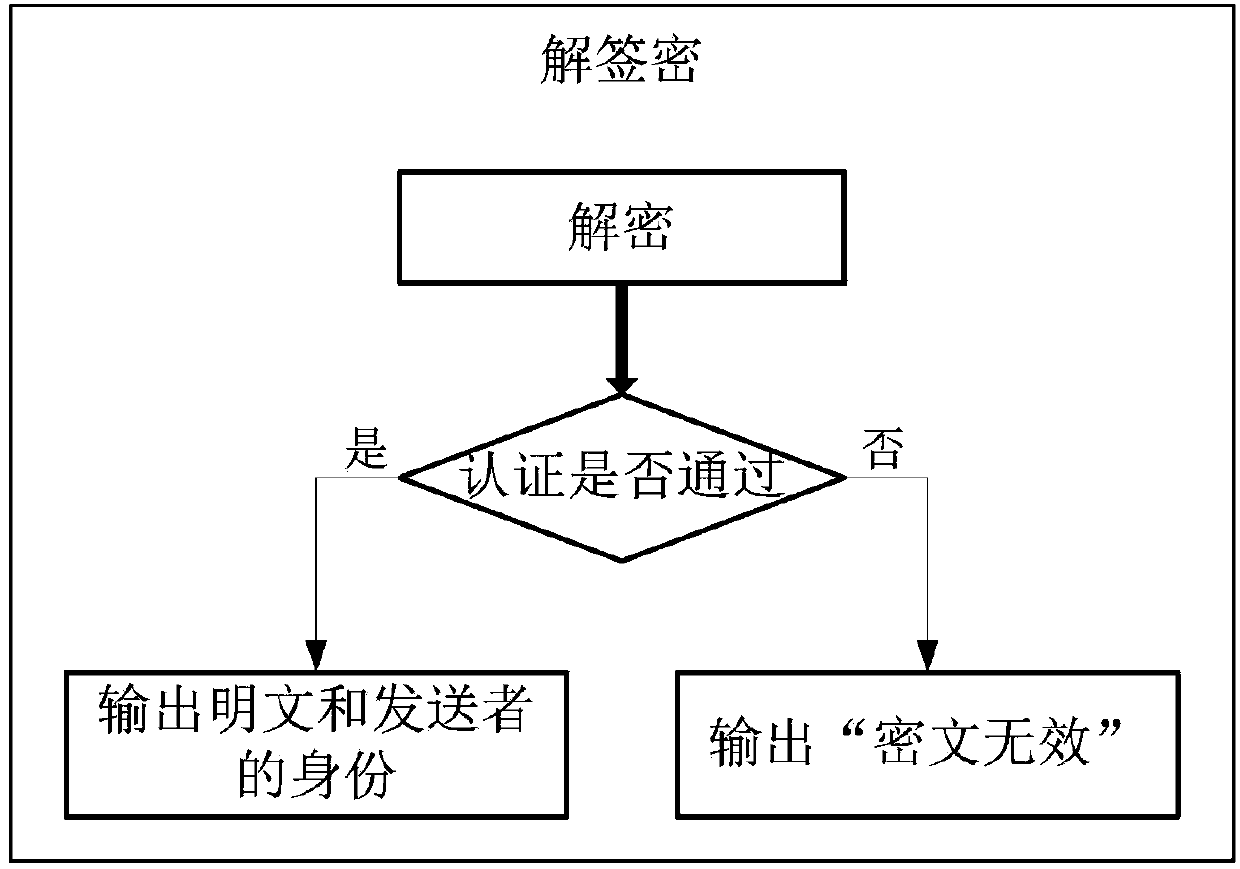
The invention discloses a signcryption method based from identity environment to certificateless environment, and belongs to the field of secret communication. In order to enable a sending end based on the identity environment to be capable of utilizing the signcryption method for sending messages to a receiving end based on the certificateless environment, the method comprises the steps that systematic parameters are initialized, and then a private key generation center generates a private key SA and sends the private key SA to the sending end; a secret key generation center generates a partial private key DB and sends the partial private key DB to the receiving end; the receiving end randomly generates a secrete value based on the systematic parameters, and a complete secrete key SB and a public key PKB are set according to the secrete value and the partial private key DB; the sending end generates signcryption ciphertexts according to the systematic parameters, the identity and the private key SA of the sending end, and the identity, the public key PKB and messages m of the receiving end, the ciphertexts and the identity of the sending end are sent to the receiving end, and then unsigncrypt treatment is carried out on the ciphertexts and the identity of the sending end. The method is used for signcryption communication of a heterogeneous network, and the end-to-end confidentiality, integrity, authentication and non-repudiation service is provided for a user based on the identity environment and a user based on the certificateless environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20100008496A1Computationally efficientBandwidth-reduced ring signatureKey distribution for secure communicationPublic key for secure communicationRing signatureCiphertext
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h″] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
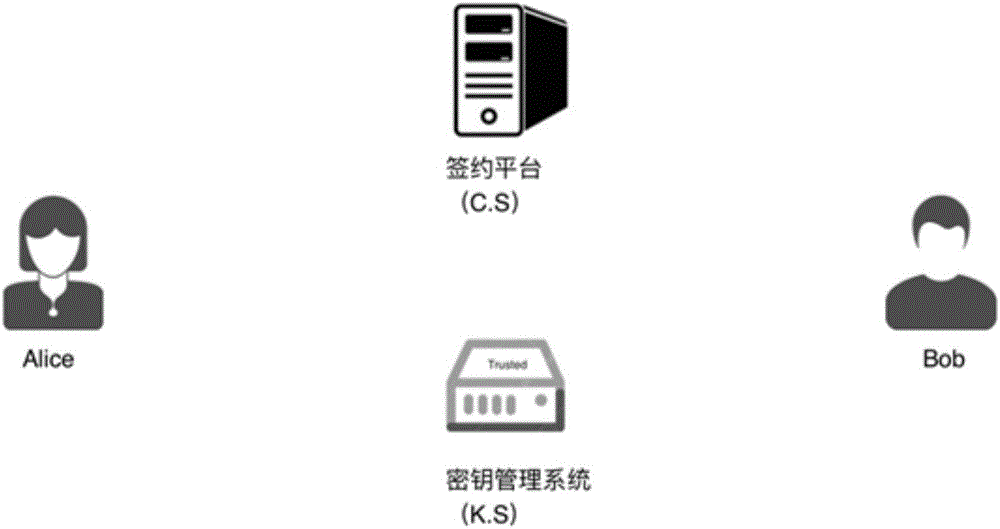
Electronic contract signing method based on certificateless signcryption
ActiveCN106789033AEasy to deploySimple identificationKey distribution for secure communicationPublic key for secure communicationElectronic contractsSigncryption
The invention provides an electronic contract signing method based on certificateless signcryption. A signing platform and a secret key management system are used. The method includes the steps that initialization of the secret key management system is conducted, user registering is conducted, a user initiates signing, and the user accepts signing. The system is easy to deploy, and system deployment does not depend on a CA center in a PKI; identity identification is easy, and recognition between users in the system only needs identity information of the other party and does not need to verify public-key certificates of the other party; use cost is lower, the user only needs to register in the system to obtain a corresponding system secret key, and the user does not need to purchase a Ukey hardware device to manage the certificate of the user.
Owner:江苏慧世联网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com