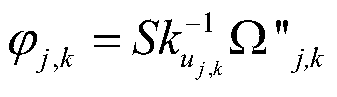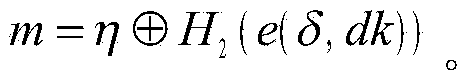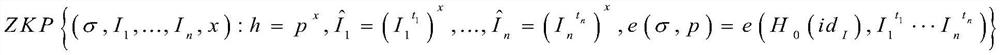Patents
Literature
42 results about "Short signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
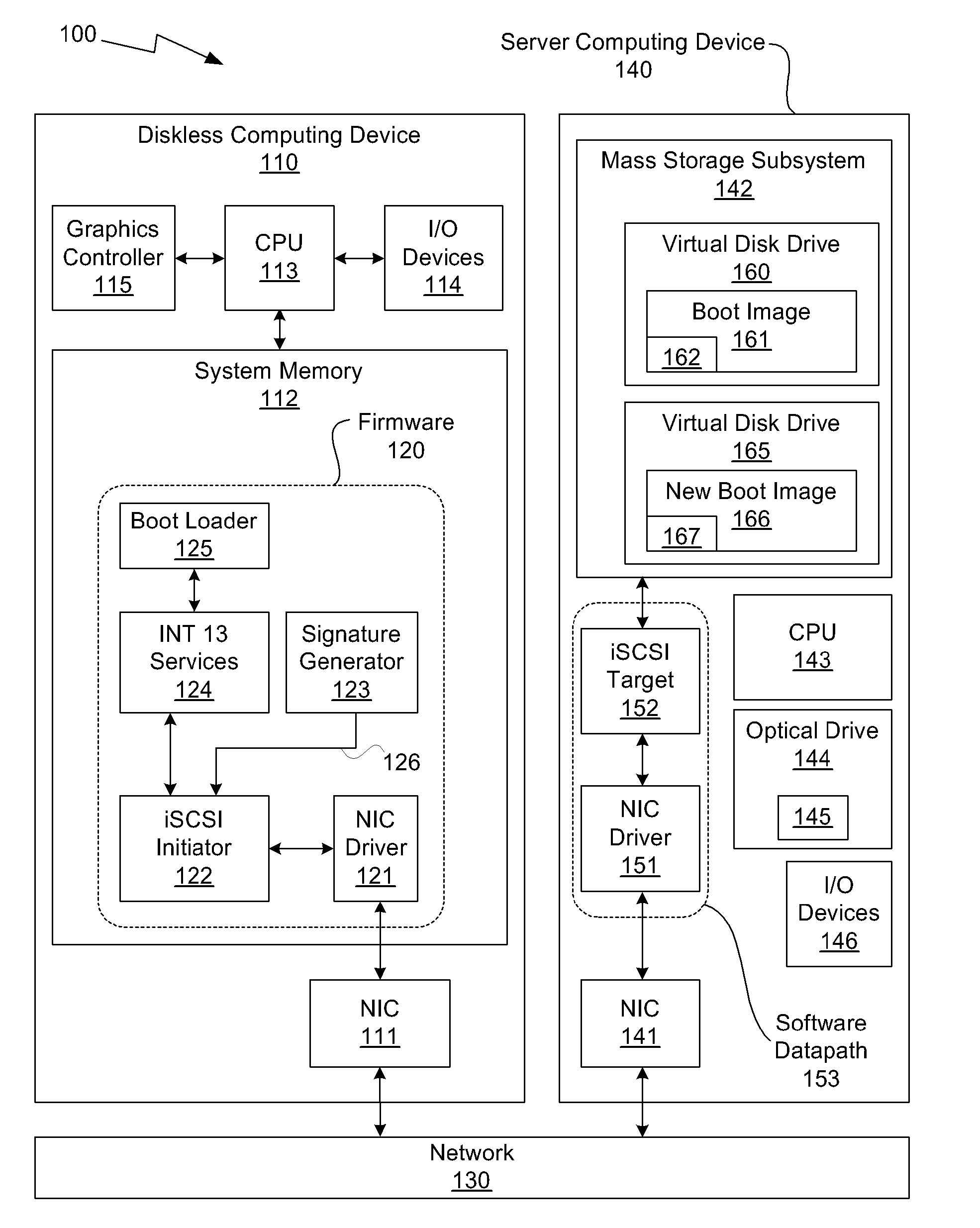
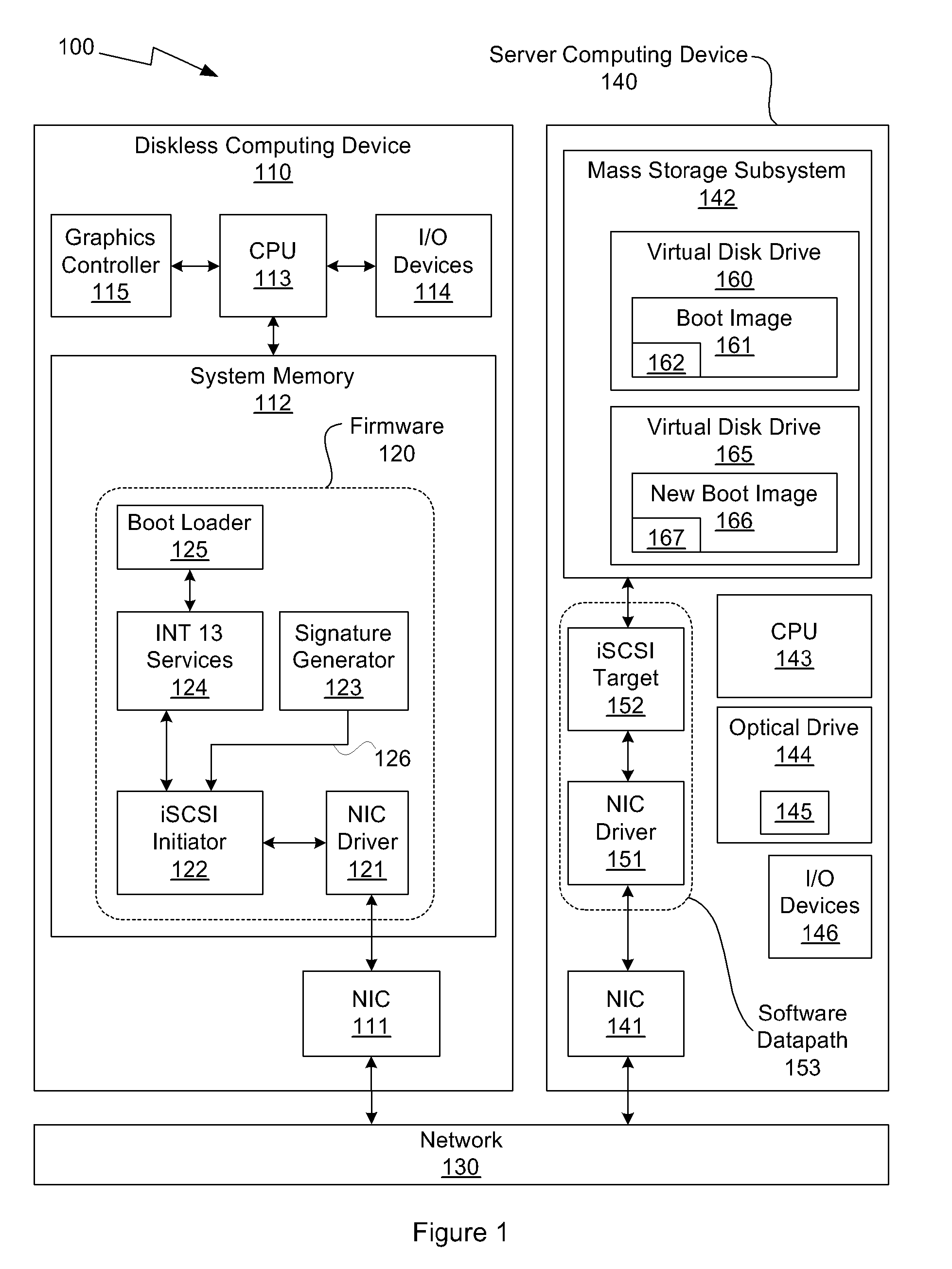
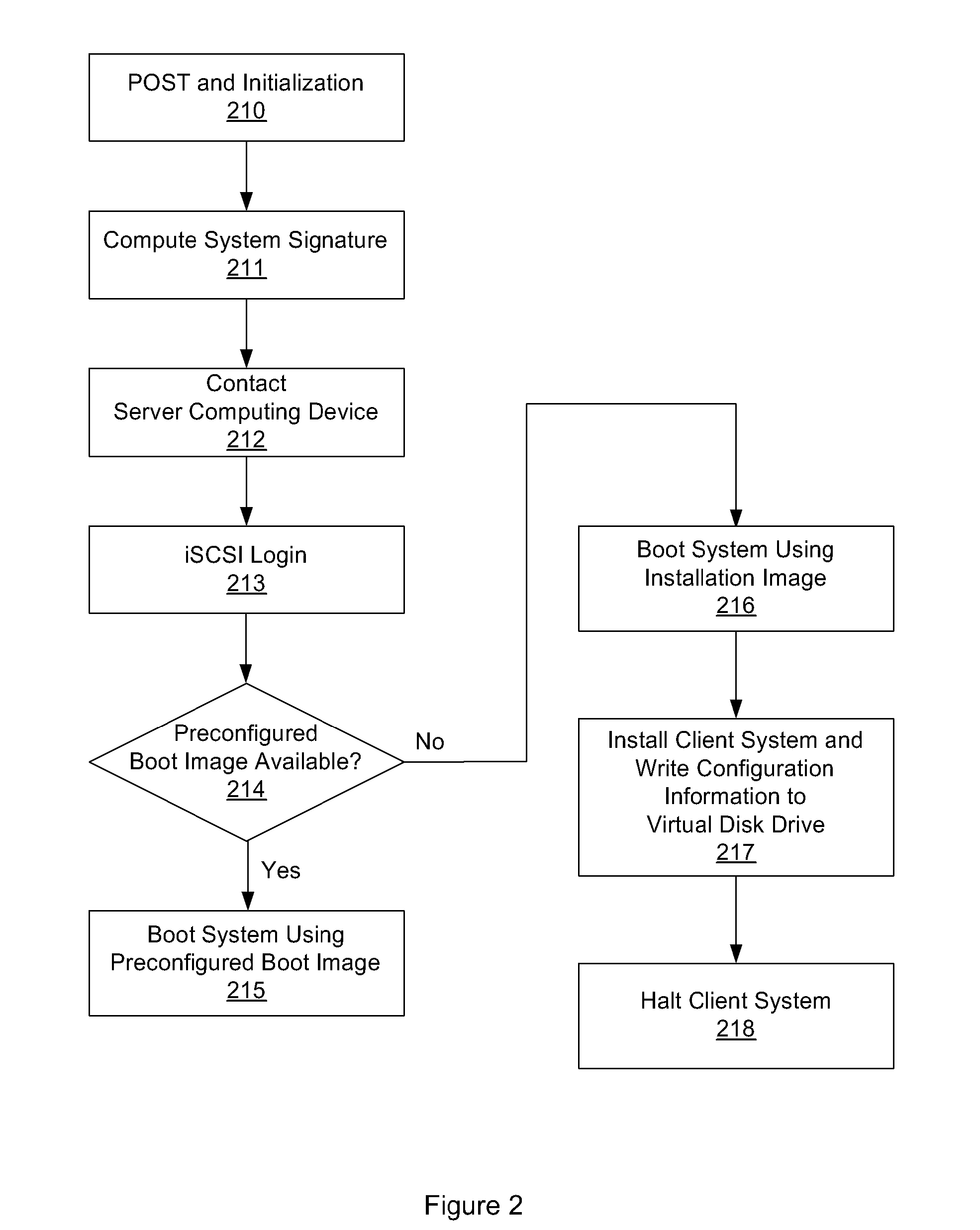
System and method for operating system installation on a diskless computing platform
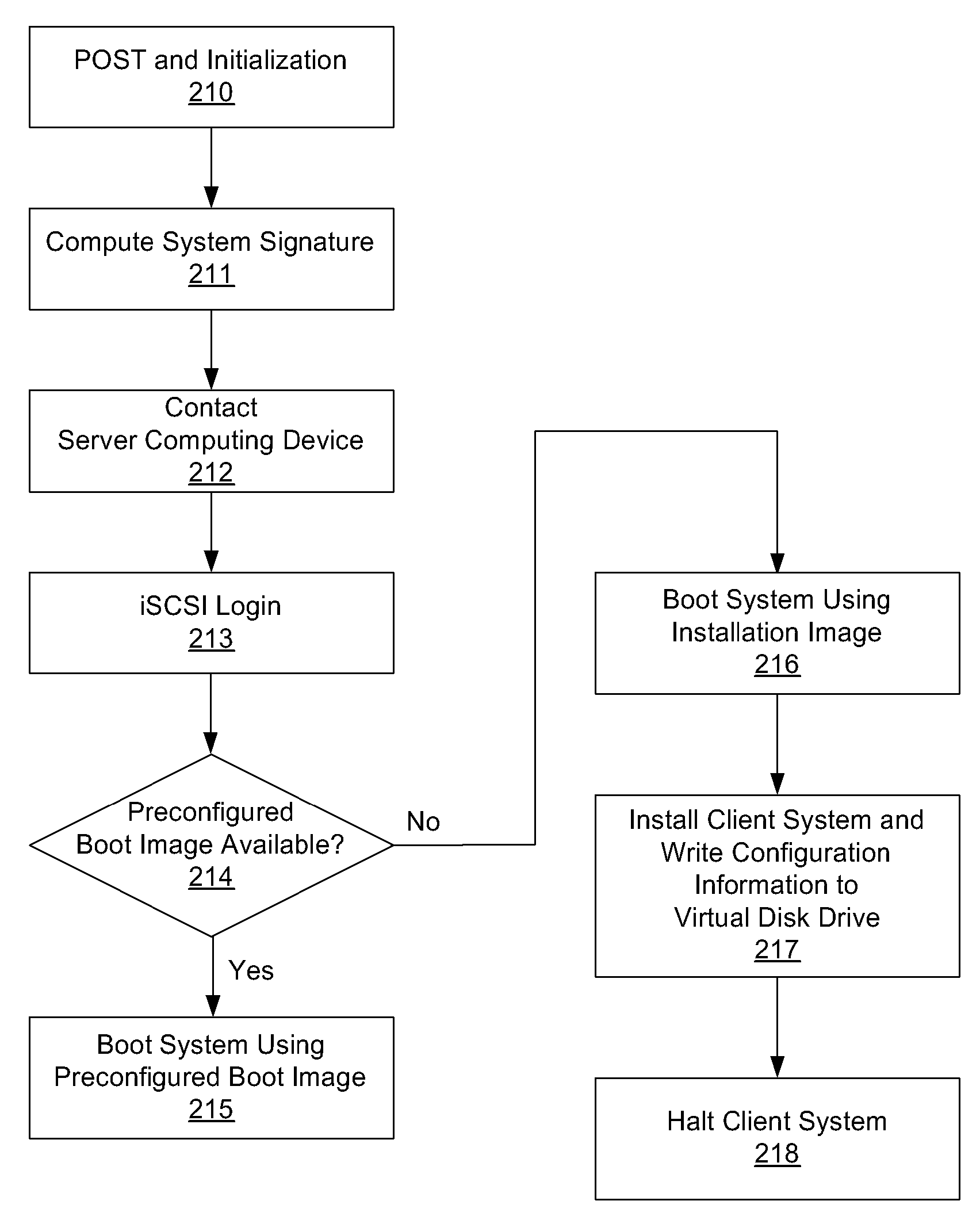
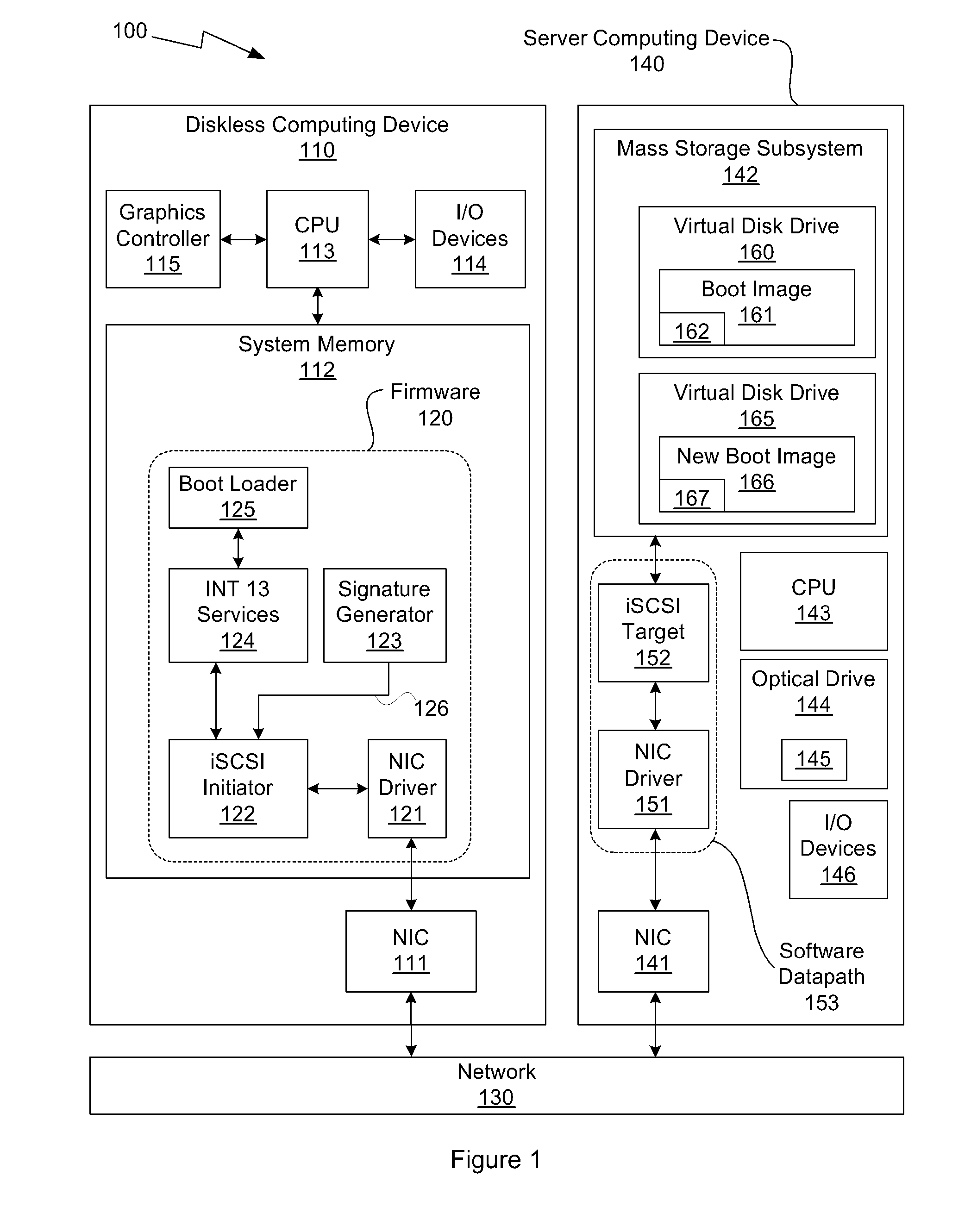
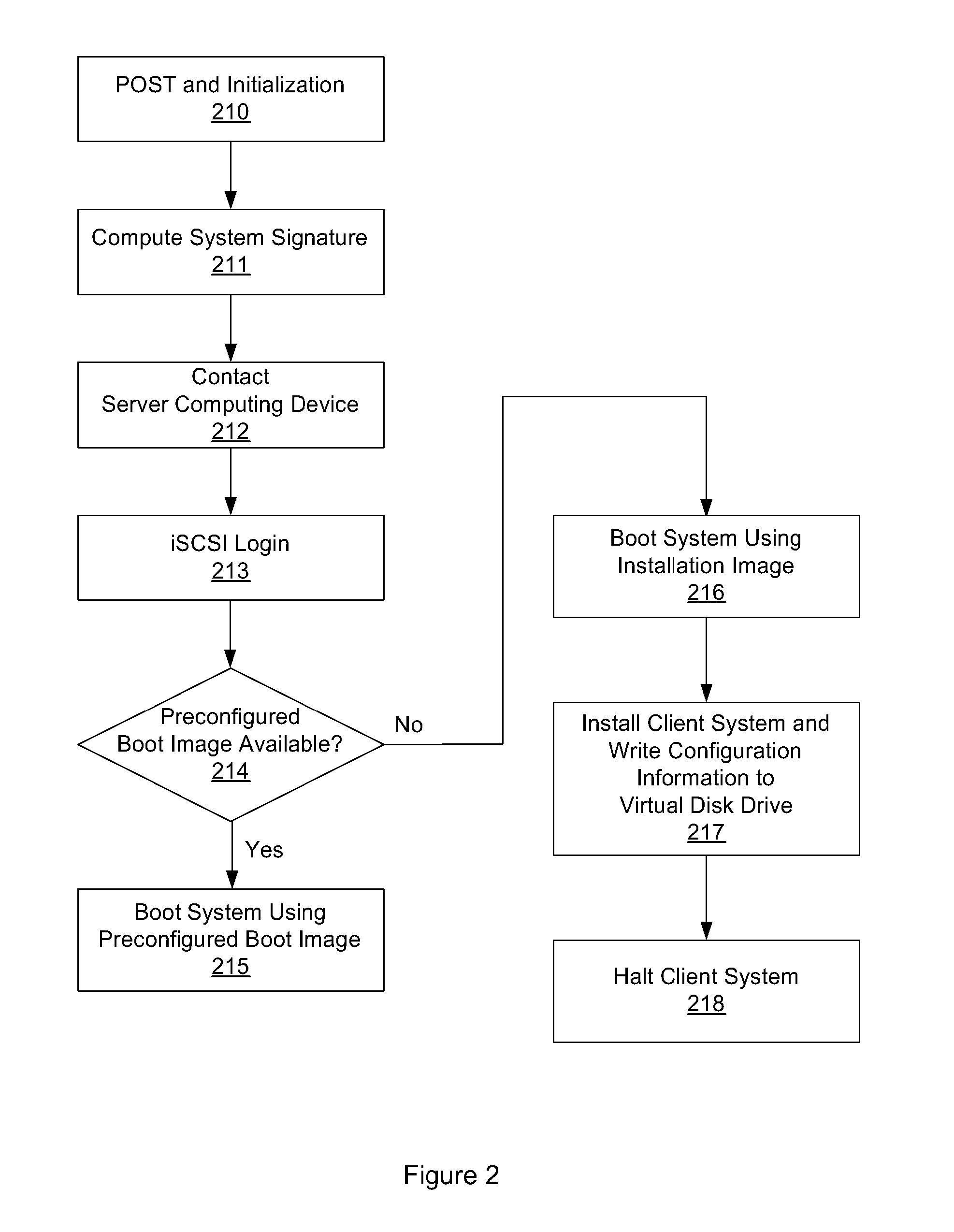
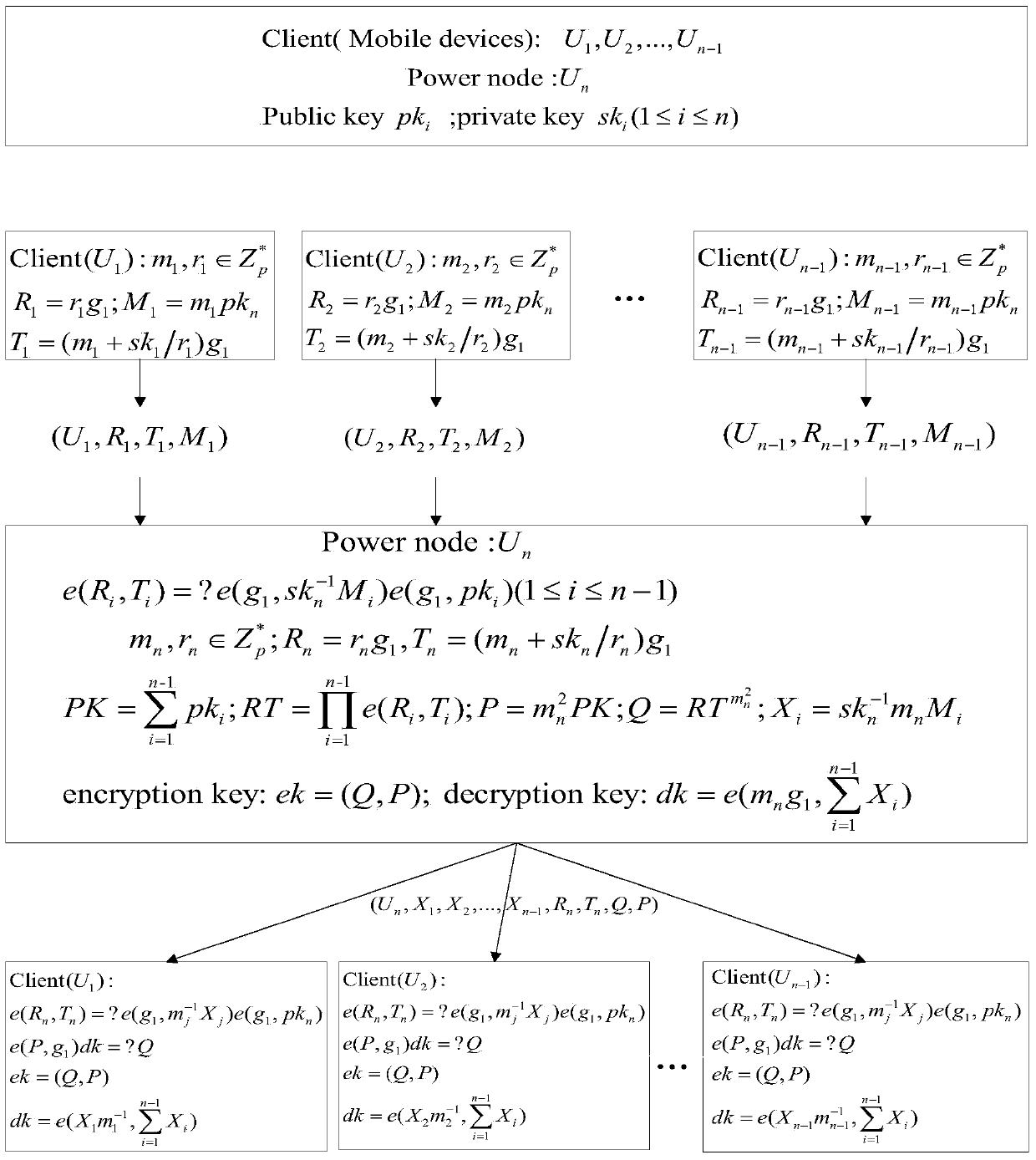
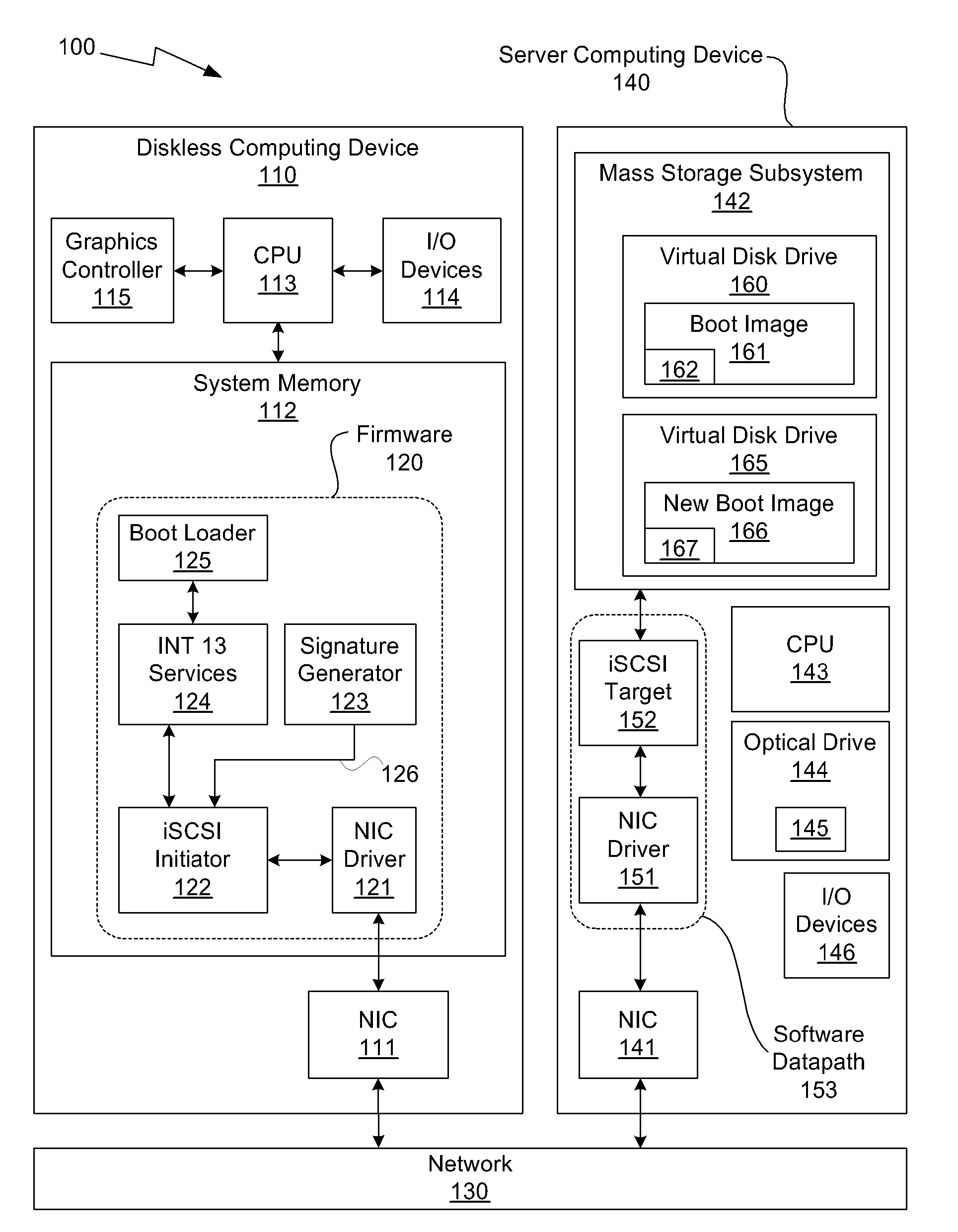
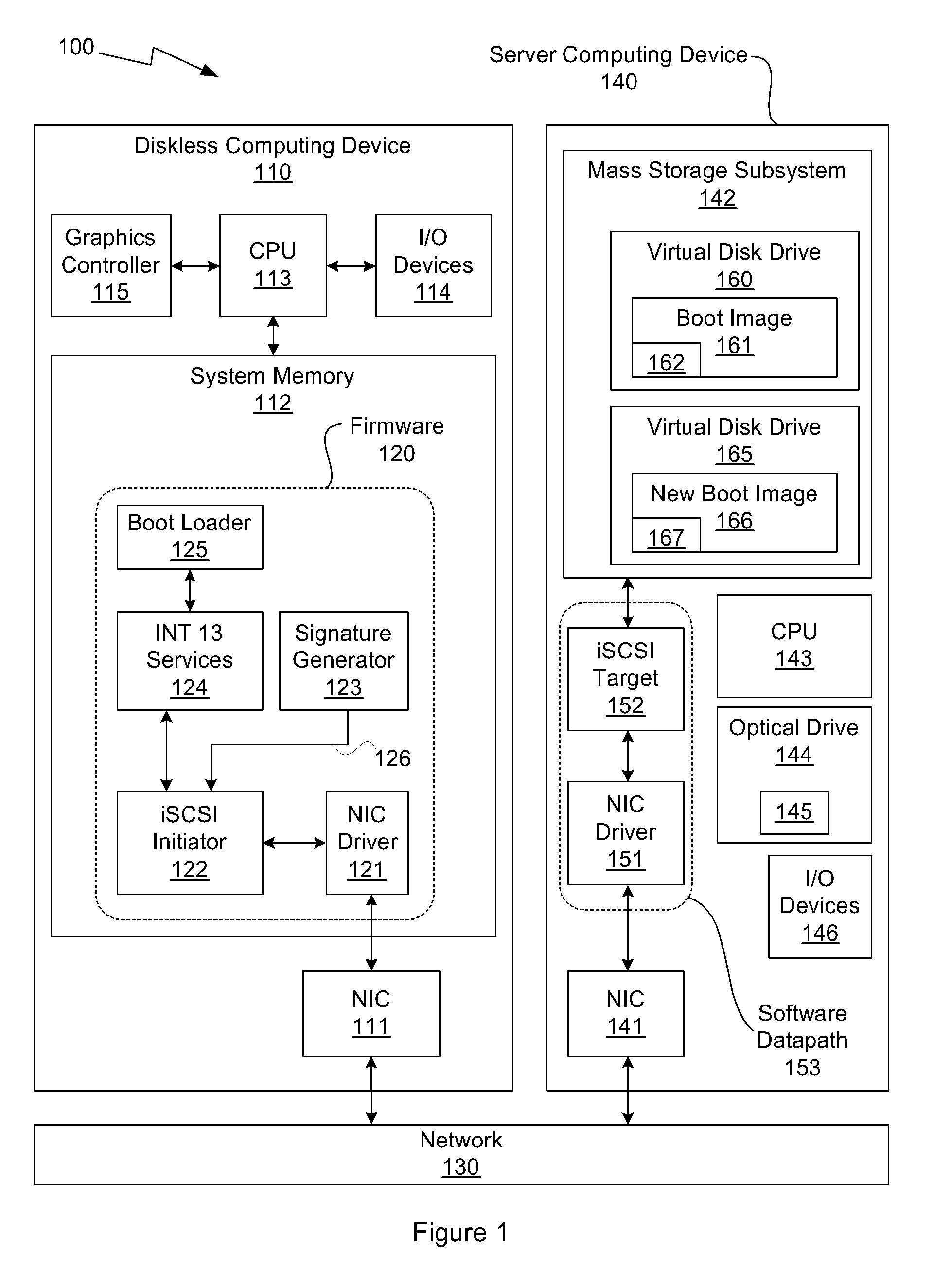
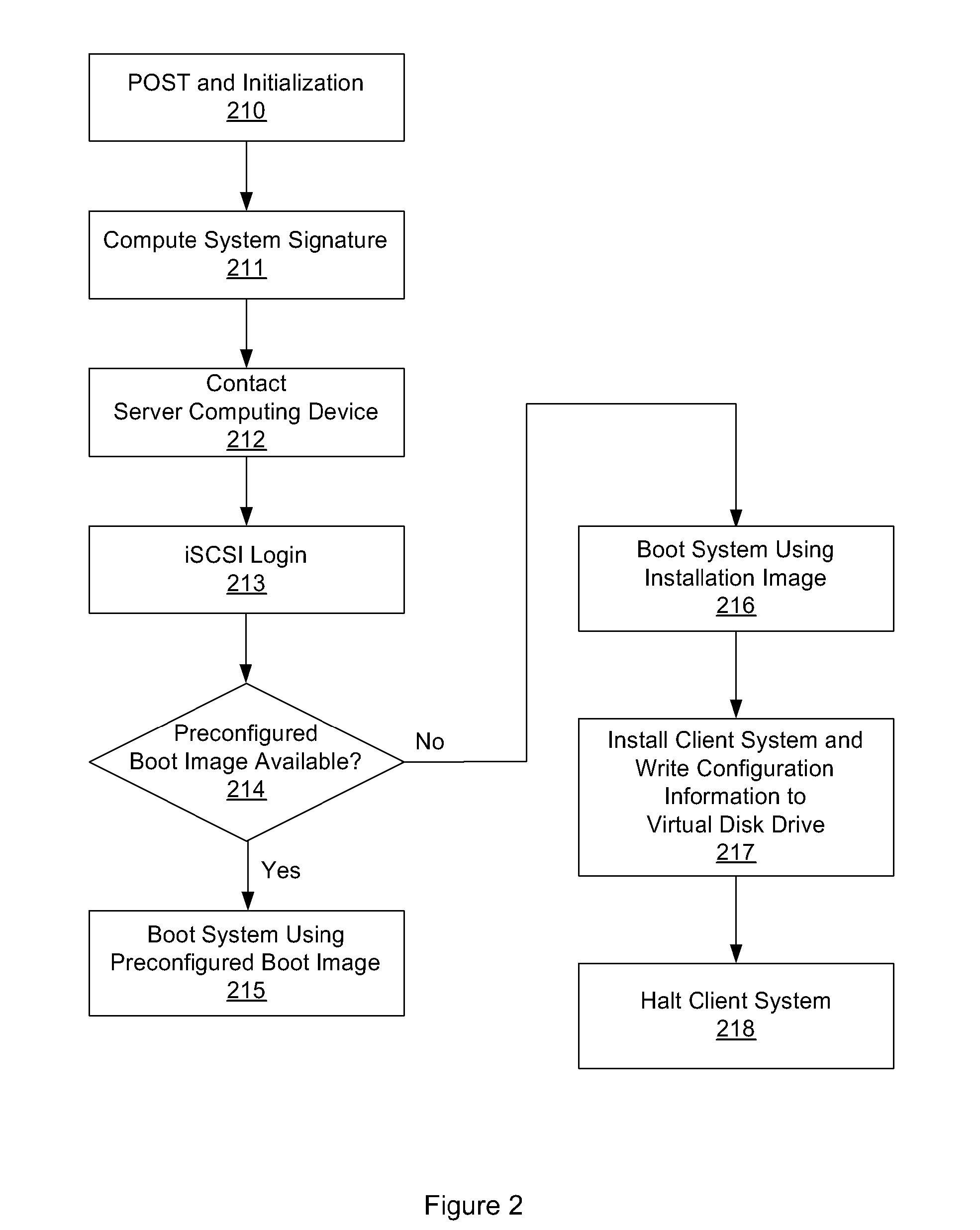
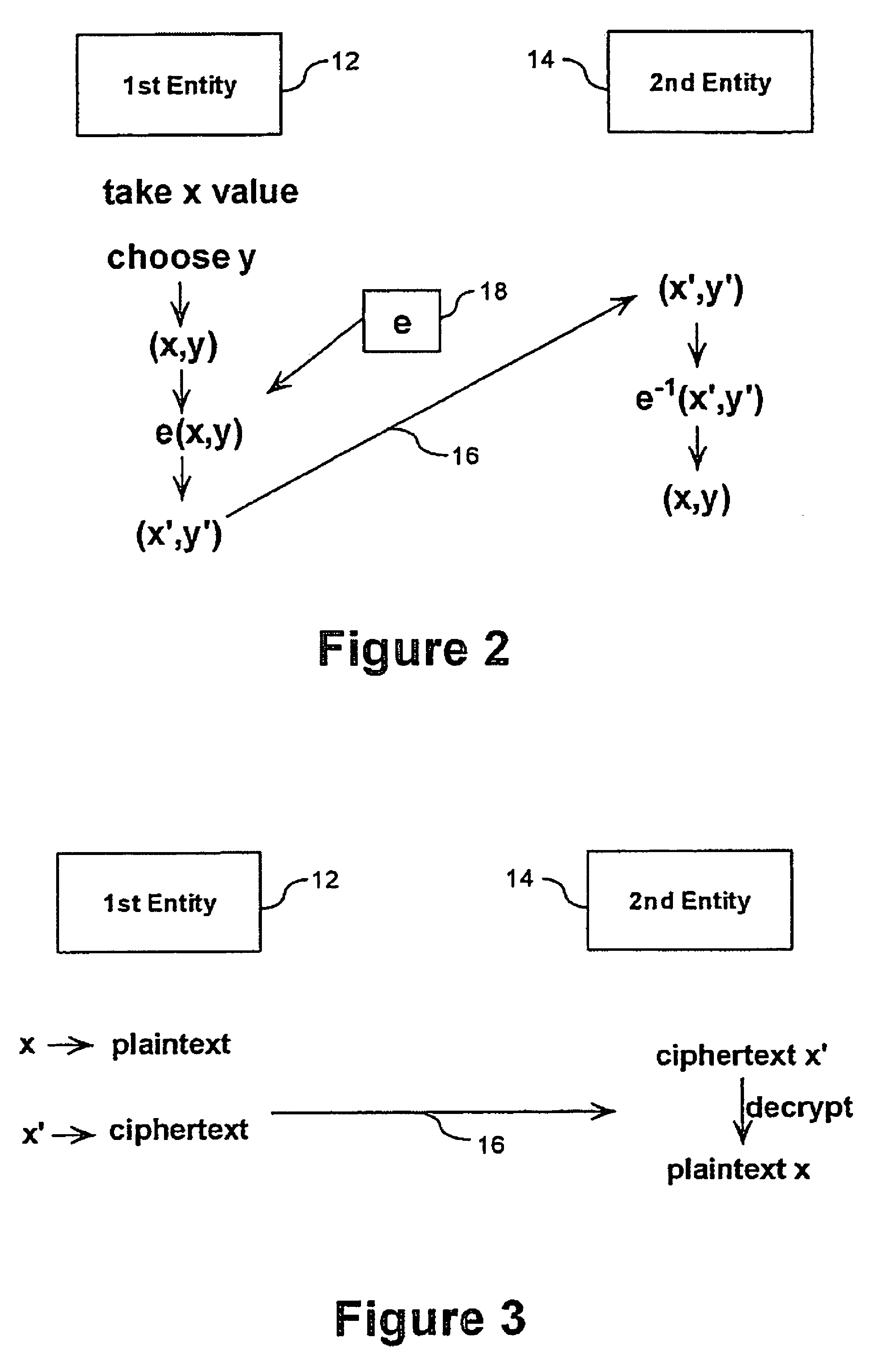
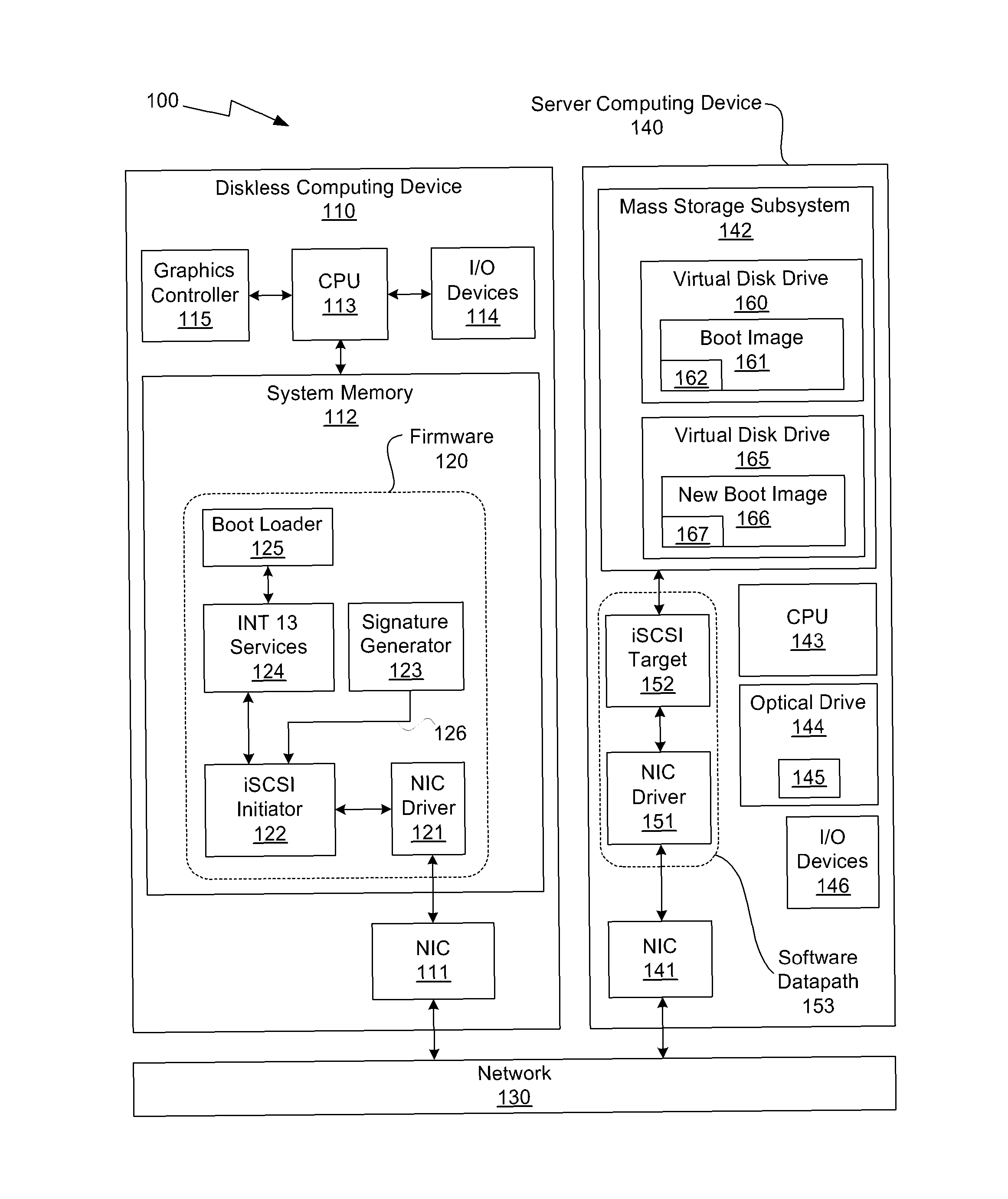
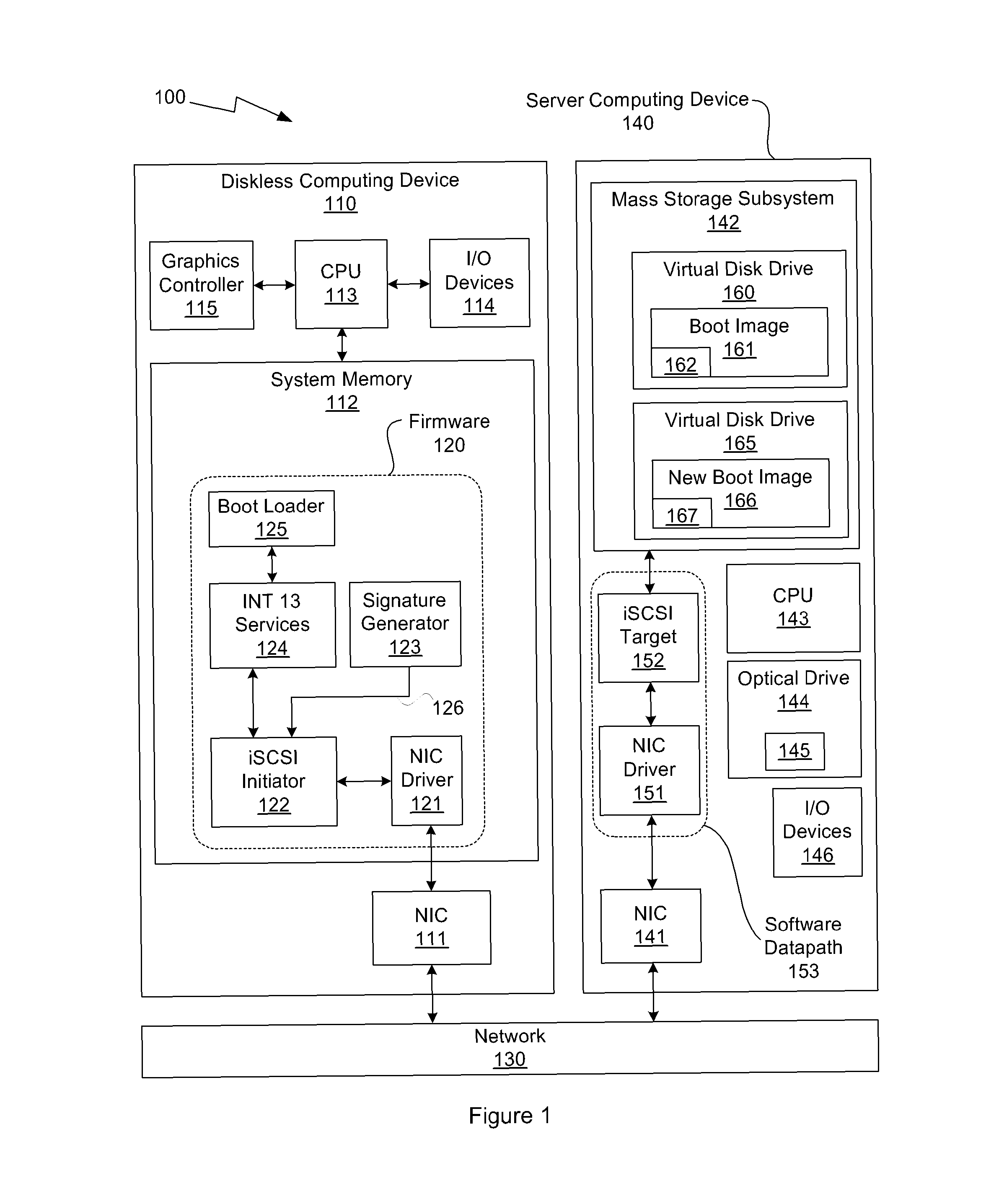
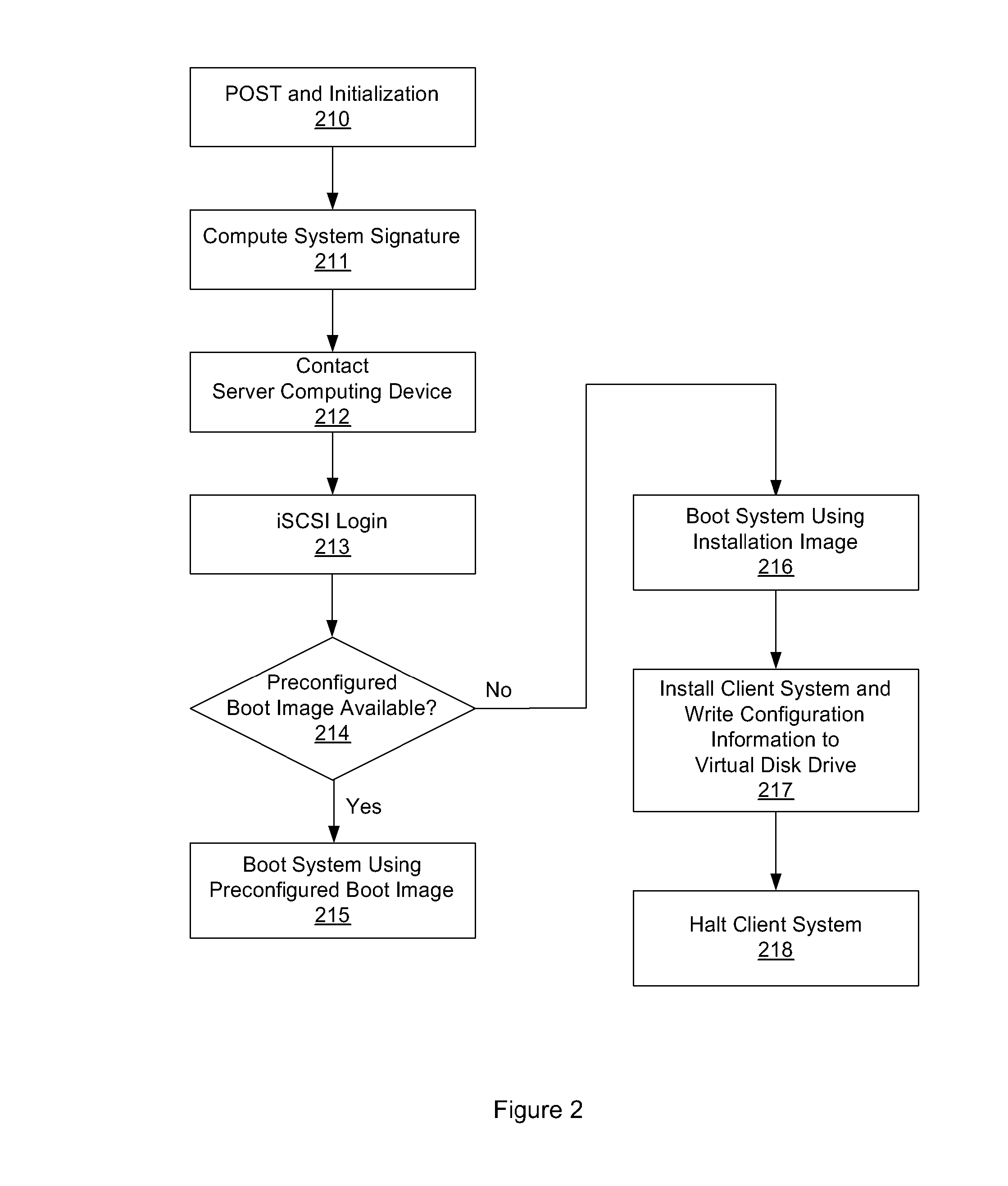
One embodiment of the present invention sets forth a technique for automatically provisioning a diskless computing device and an associated server system. A diskless computing device client incorporates an iSCSI initiator that is used to access resources provided by an iSCSI target that is resident on a server computing device. The iSCSI initiator is implemented in the client firmware, providing INT13 disk services entry points, thereby enabling the client to transparently access virtual storage devices at boot time. The client device conducts an apparently local installation using the virtual storage devices provided by the server computing device. A short signature value is associated with the boot image, uniquely associating the boot image with the specific client hardware configuration. When the client device boots normally, the signature value of the client device is presented to the server computing device to automatically reference the appropriate boot image.
Owner:NVIDIA CORP
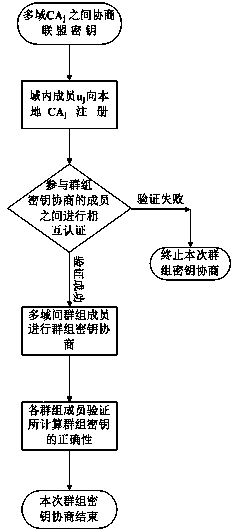
Multi-inter-domain asymmetric group key agreement protocol method in mobile cloud computing environment
ActiveCN104660415AWide distributionNetwork heterogeneityKey distribution for secure communicationUser identity/authority verificationMobile cloudConfidentiality
The invention discloses a multi-inter-domain asymmetric group key agreement protocol method under the mobile cloud computing network environment. The method comprises the following steps: adopting a bilinear mapping technology and a blind secret key technology to realize a short signature mechanism between a domain secret key management center and a domain terminal; using a short signature technology to realize a multi-inter-domain group key agreement authentication mechanism of terminals distributed in different domains, and further realize asymmetric group key agreement of the terminals distributed in multiple domains. The protocol method disclosed by the invention has the anonymity and the authentication, supports dynamic group key updating of nodes, and realizes the security of forward confidentiality and backward confidentiality of the group keys; on the hypothesis of the Diffe-Hellman bilinear computing problem, the security of the protocol is proved; the computing and communication energy consumption of the protocol is low; the method is good in flexibility, security and practicability, and suitable for cross-domain group key agreement of the terminals distributed in the multiple domains under the mobile cloud computing network environment.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
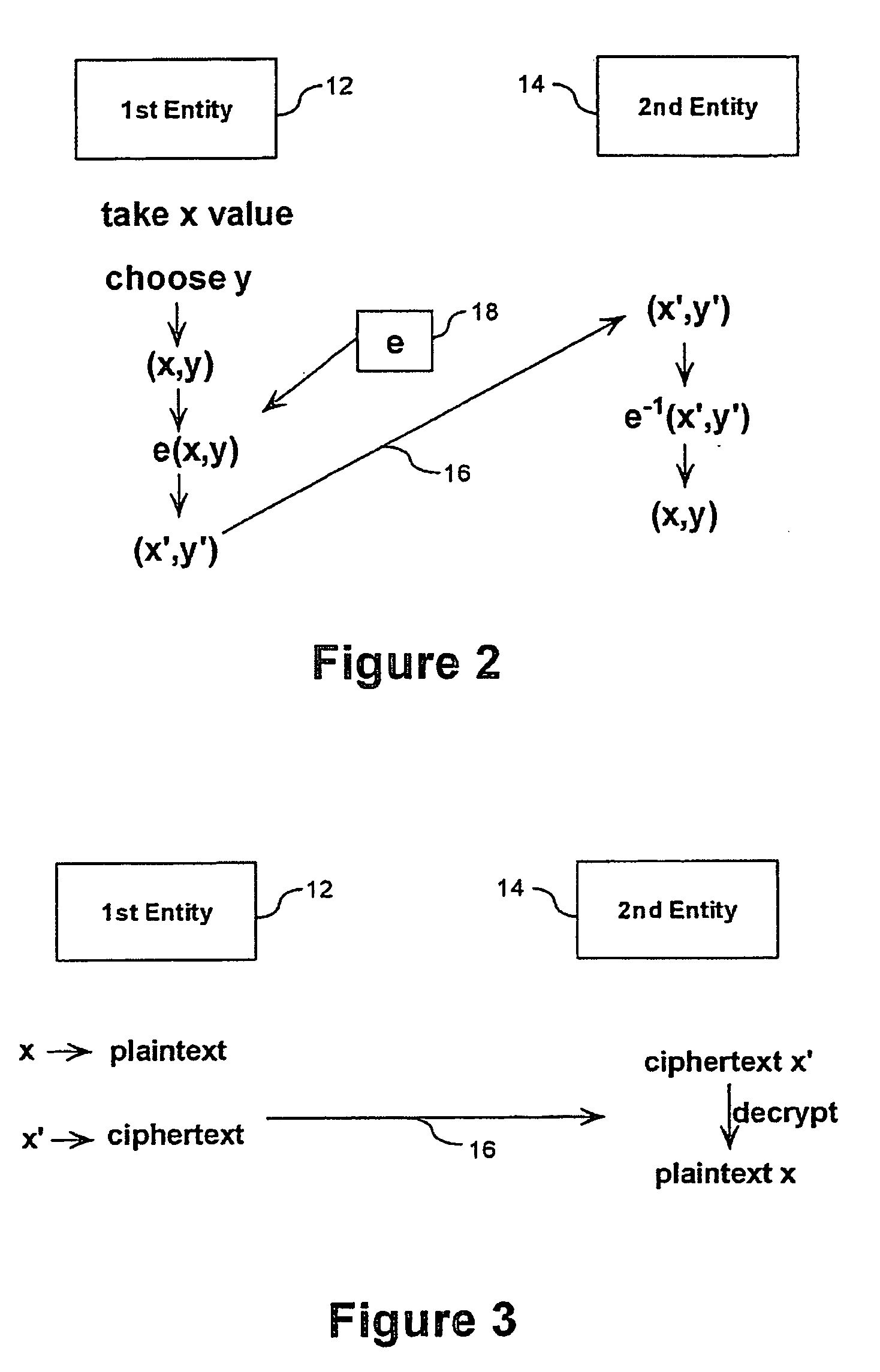
Trapdoor one-way functions on elliptic curves and their application to shorter signatures and asymmetric encryption
ActiveUS20060140400A1Reduced bandwidthPublic key for secure communicationUser identity/authority verificationEllipseShort signature
The present invention provides a new trapdoor one-way function. In a general sense, some quadratic algebraic integer z is used. One then finds a curve E and a rational map defining [z] on E. The rational map [z] is the trapdoor one-way function. A judicious selection of z will ensure that [z] can be efficiently computed, that it is difficult to invert, that determination of [z] from the rational functions defined by [z] is difficult, and knowledge of z allows one to invert [z] on a certain set of elliptic curve points. Every rational map is a composition of a translation and an endomorphism. The most secure part of the rational map is the endomorphism as the translation is easy to invert. If the problem of inverting the endomorphism and thus [z] is as hard as the discrete logarithm problem in E, then the size of the cryptographic group can be smaller than the group used for RSA trapdoor one-way functions.
Owner:MALIKIE INNOVATIONS LTD
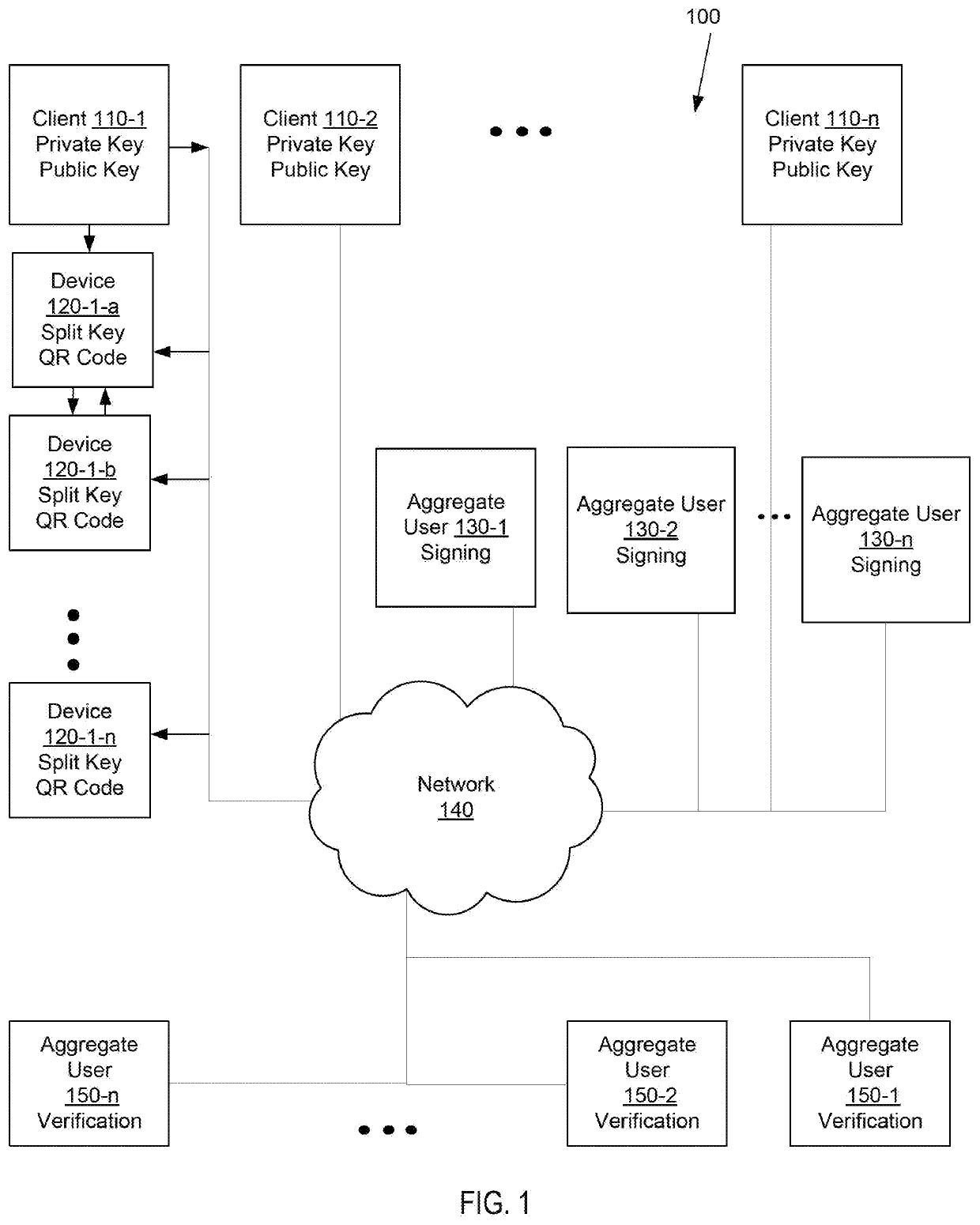
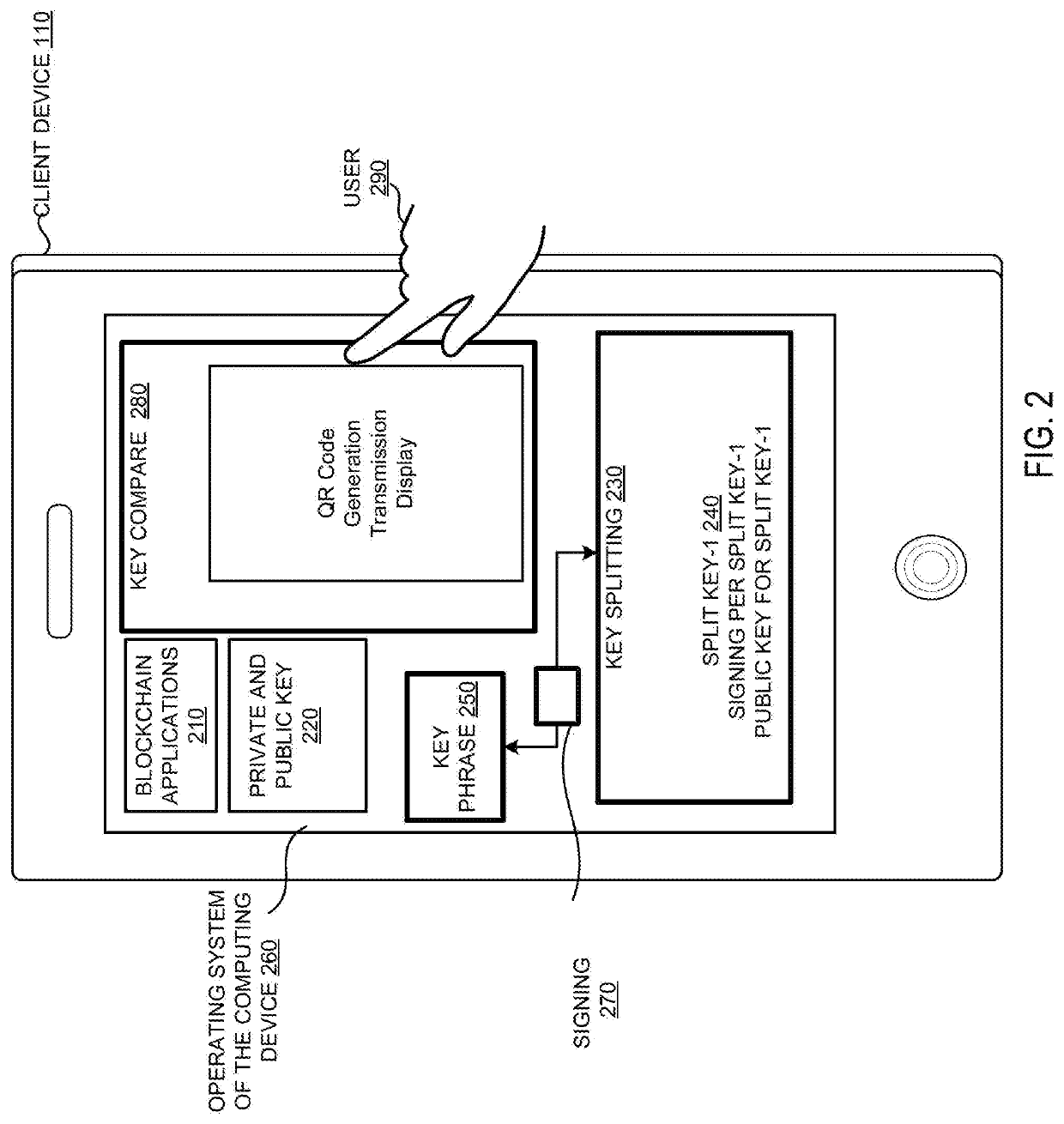
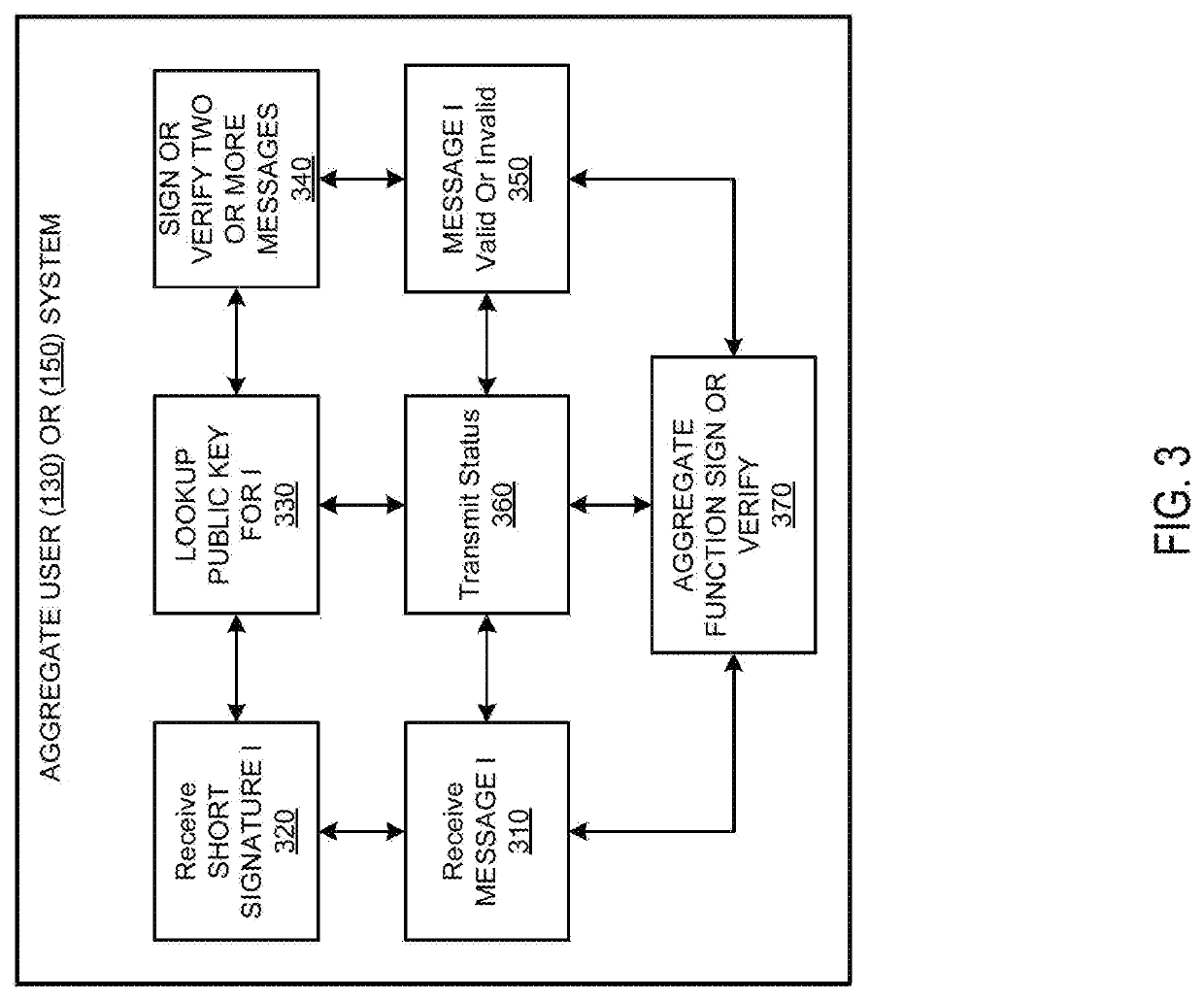
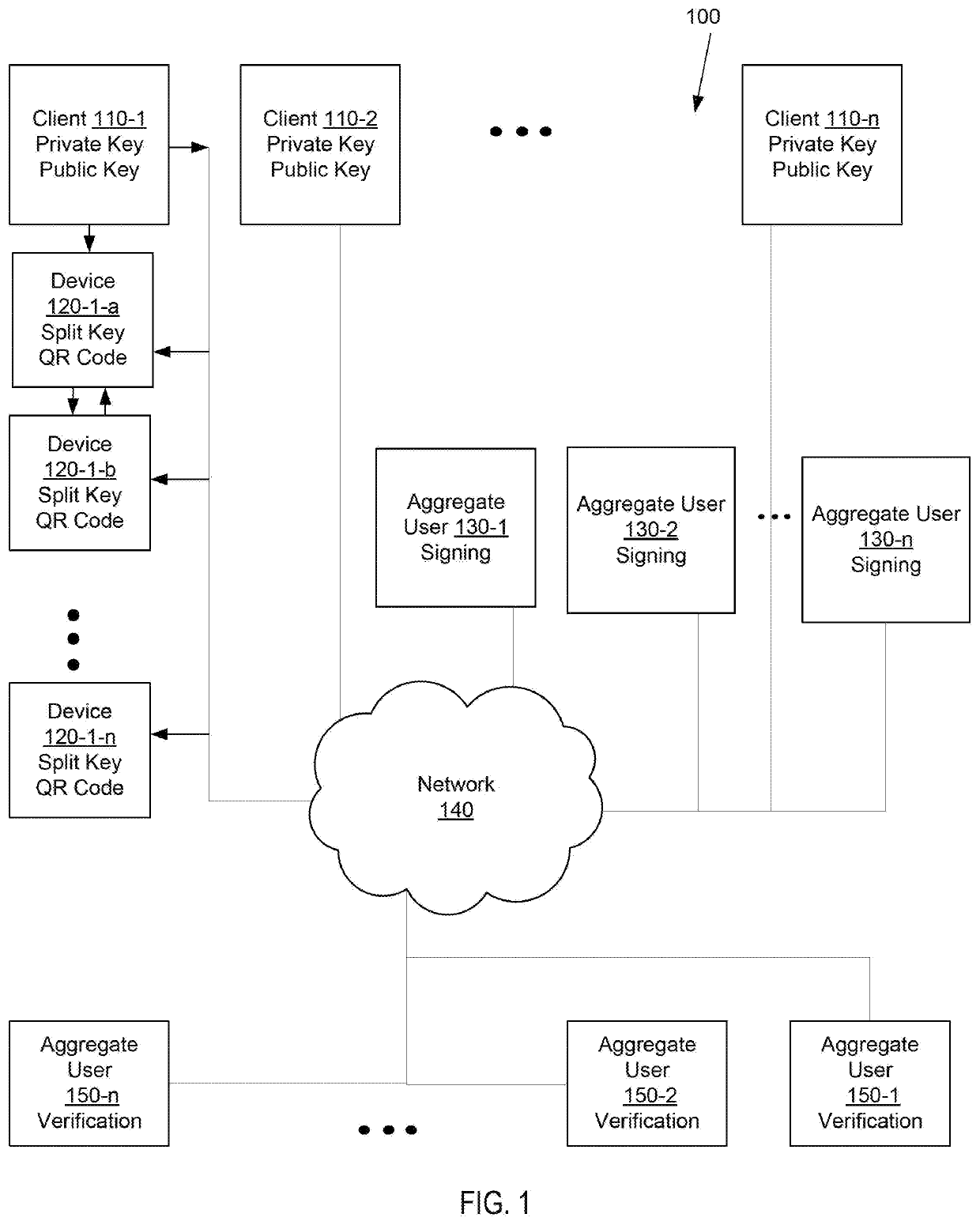
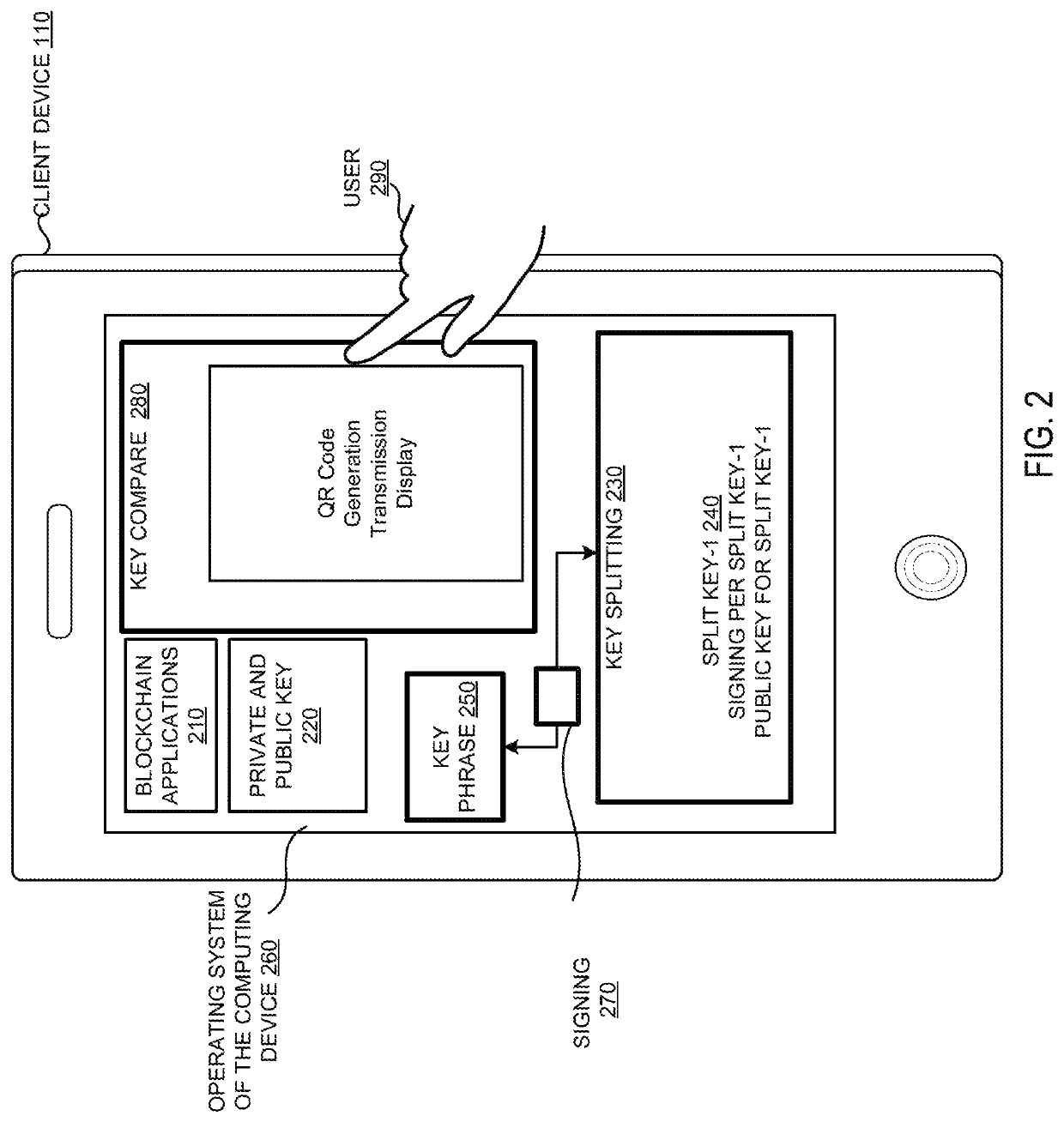
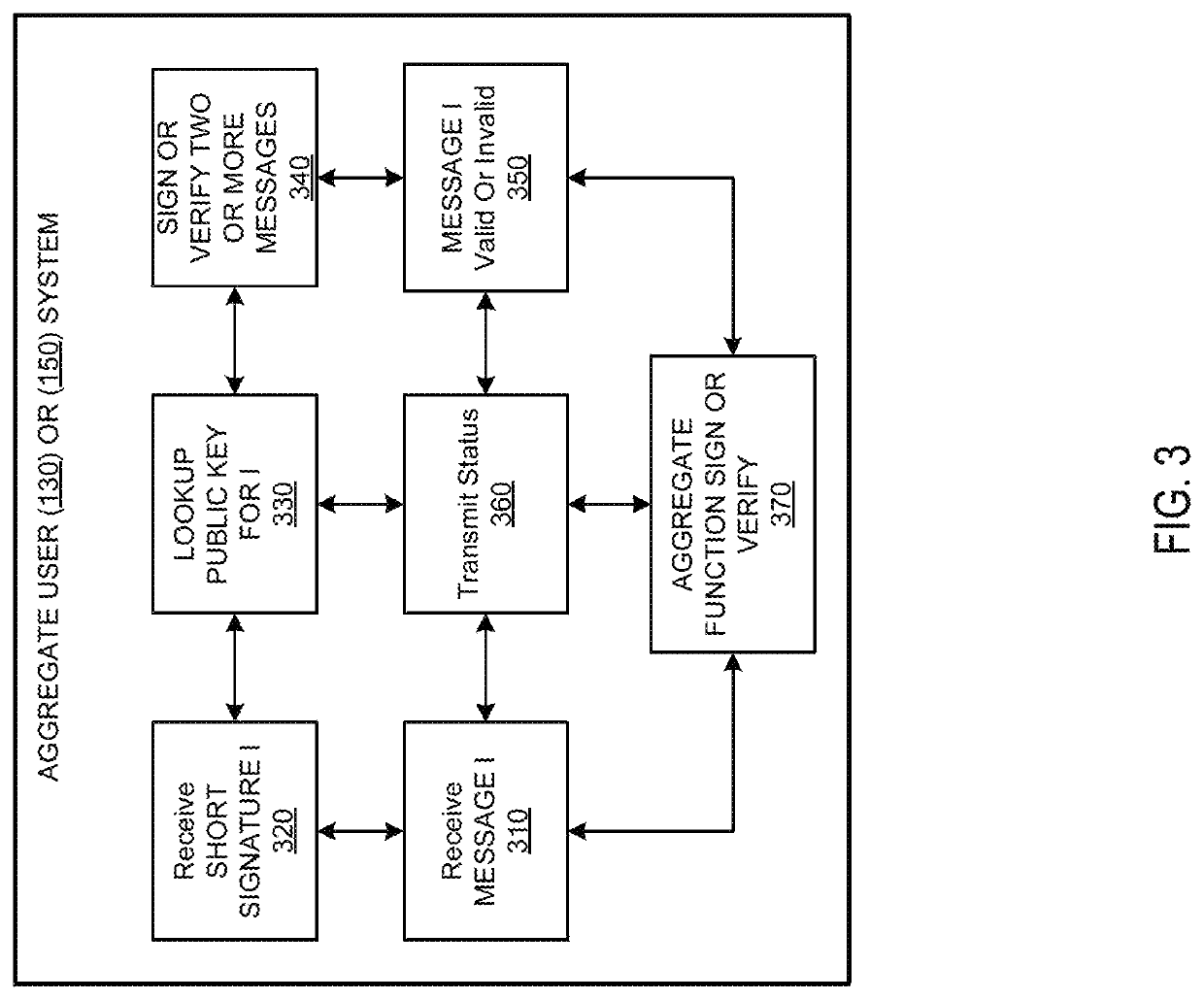
Systems and methods of aggregate signing of digital signatures on multiple messages simultaneously using key splitting
ActiveUS20200228349A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkInternet privacy
The systems and methods of aggregate signing of digital signatures on multiple messages simultaneously, comprising: receiving two or more digital messages wherein each message is signed using two or more digitally split keys from a private key and the two or more digital signatures of the message using the split key are combined to get a compressed short signature; receiving the compressed short signature for each message; receiving a public key associated with the private key for each message; aggregate signing the messages to output an aggregate signature. The aggregate signature can be further verified against any or all of the messages.
Owner:0CHAIN LLC
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20060159259A1Computationally efficientBandwidth-reduced ring signaturePublic key for secure communicationUser identity/authority verificationComputer hardwareRing signature
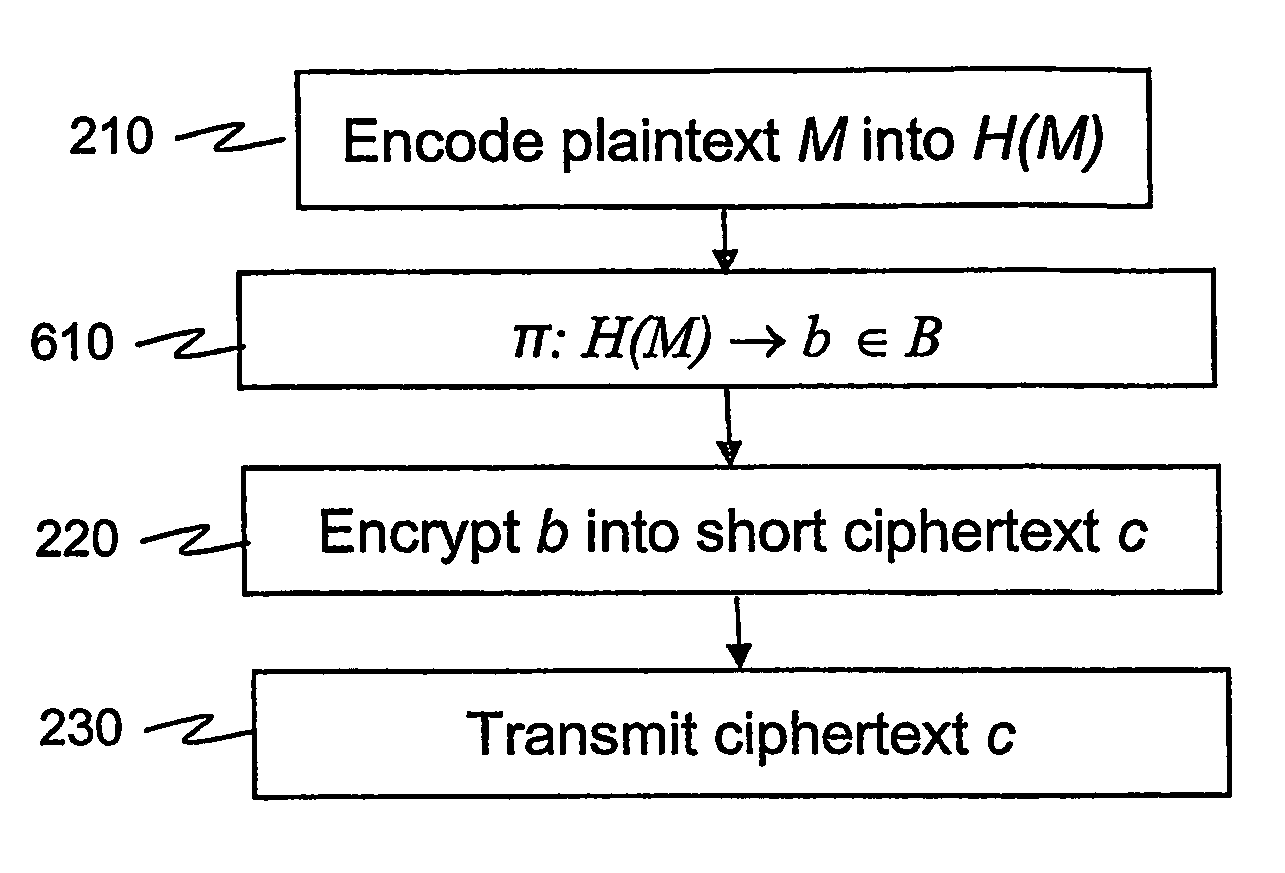
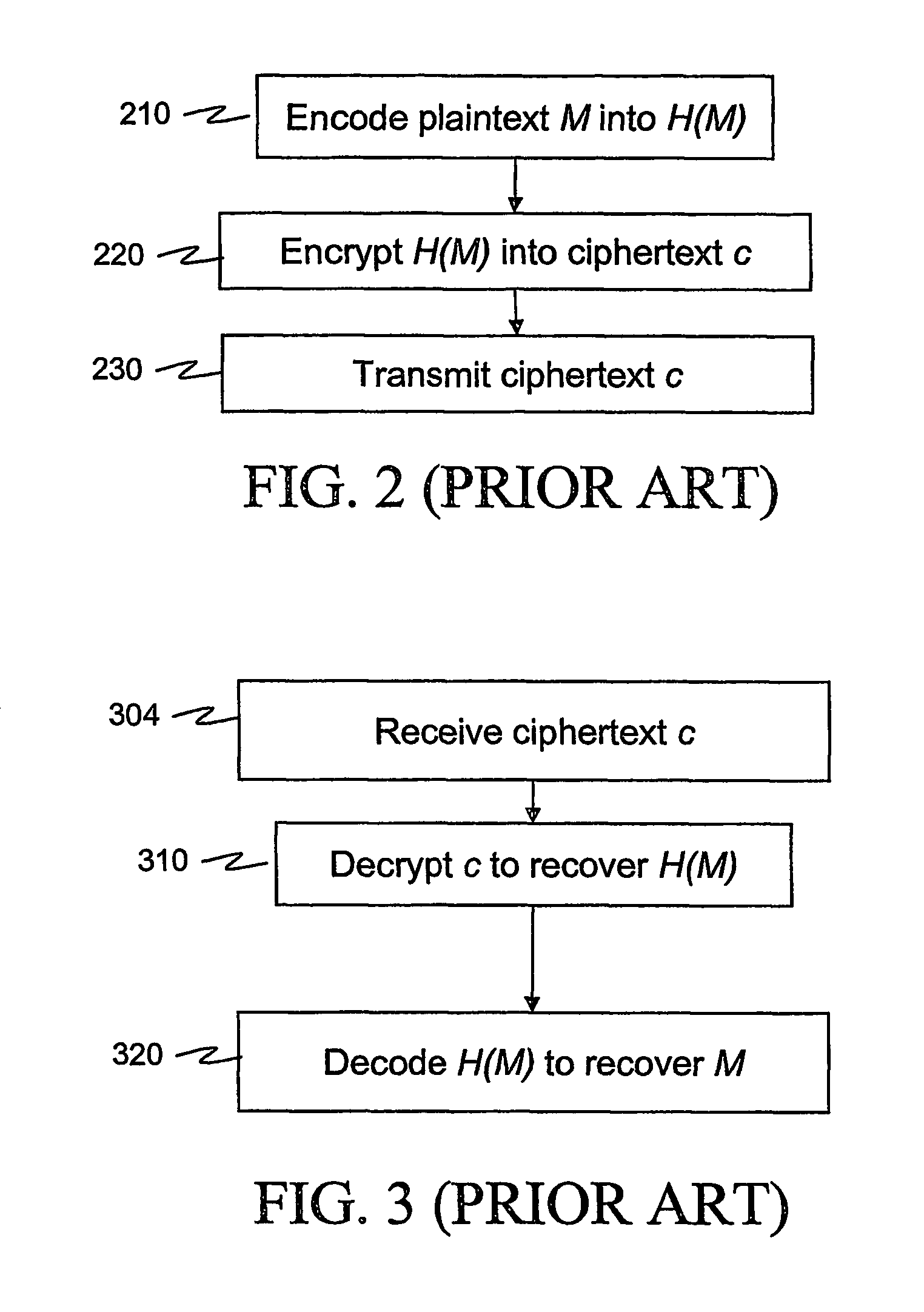
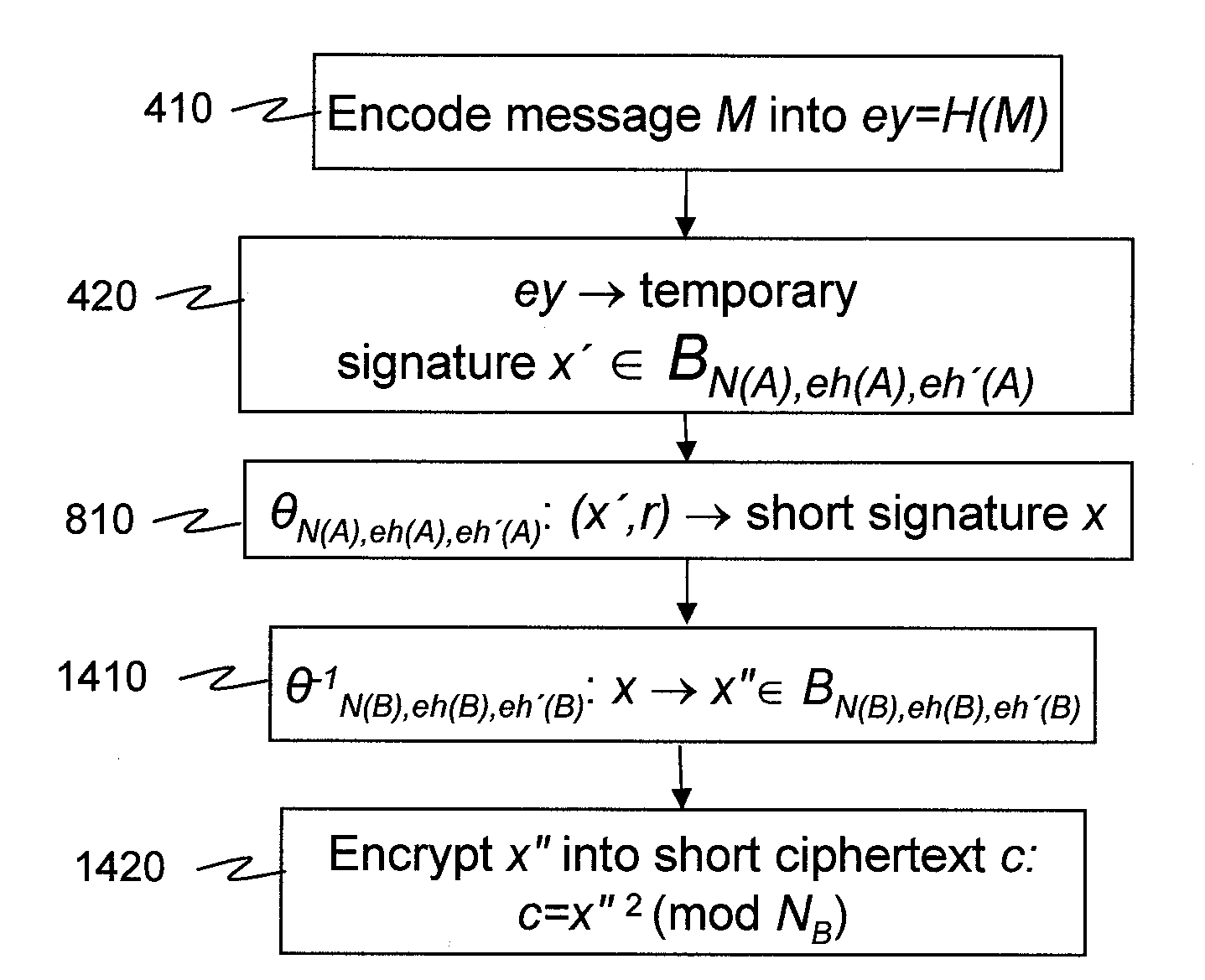
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h?] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Authenticable asymmetrical group secret key negotiation method in mobile unbalanced network
ActiveCN103796199AGuaranteed freshnessEnsure secure communicationSecurity arrangementBalancing networkSecure communication
The invention relates to an authenticable asymmetrical group secret key negotiation scheme in a mobile unbalanced network. The scheme comprises the steps that signature and authentication of group members are carried out, group members negotiate an asymmetrical shared secret key, and consistency verification of the shared secret key is carried out. According to the signature and authentication, a short signature mechanism of mobile equipment in a network is achieved by adopting a bilinear mapping technology, and members of mobile groups provide identify authentication by using the signature before the group secret key is negotiated to defense active attack of adversaries. According to step that the group members negotiate the asymmetrical shared secret key, all mobile equipment in the mobile unbalanced network negotiates a pair of asymmetrical group communication encryption / decryption secret keys, and members outside the group can send secret messages to members inside the group by encrypting the secret messages through a public key without the necessary of joining the group. According to the consistency verification of the shared secret key, after the group members negotiate the group secret key, the accuracy and the consistency of the calculated group secret key can be guaranteed. According to the authenticable asymmetrical group secret key negotiation scheme in the mobile unbalanced network, when secret communication is carried out among mobile group equipment in the mobile network environment, safe communication among the group equipment can be guaranteed, energy consumption of calculation and communication is quite low, and good flexibility, safety and practicability are achieved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
System and method for operating system installation on a diskless computing platform
ActiveUS20080028035A1Multiple digital computer combinationsProgram controlOperational systemEntry point
One embodiment of the present invention sets forth a technique for automatically provisioning a diskless computing device and an associated server system. A diskless computing device client incorporates an iSCSI initiator that is used to access resources provided by an iSCSI target that is resident on a server computing device. The iSCSI initiator is implemented in the client firmware, providing INT13 disk services entry points, thereby enabling the client to transparently access virtual storage devices at boot time. The client device conducts an apparently local installation using the virtual storage devices provided by the server computing device. A short signature value is associated with the boot image, uniquely associating the boot image with the specific client hardware configuration. When the client device boots normally, the signature value of the client device is presented to the server computing device to automatically reference the appropriate boot image.
Owner:NVIDIA CORP
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20100008496A1Computationally efficientBandwidth-reduced ring signatureKey distribution for secure communicationPublic key for secure communicationRing signatureCiphertext
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h″] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
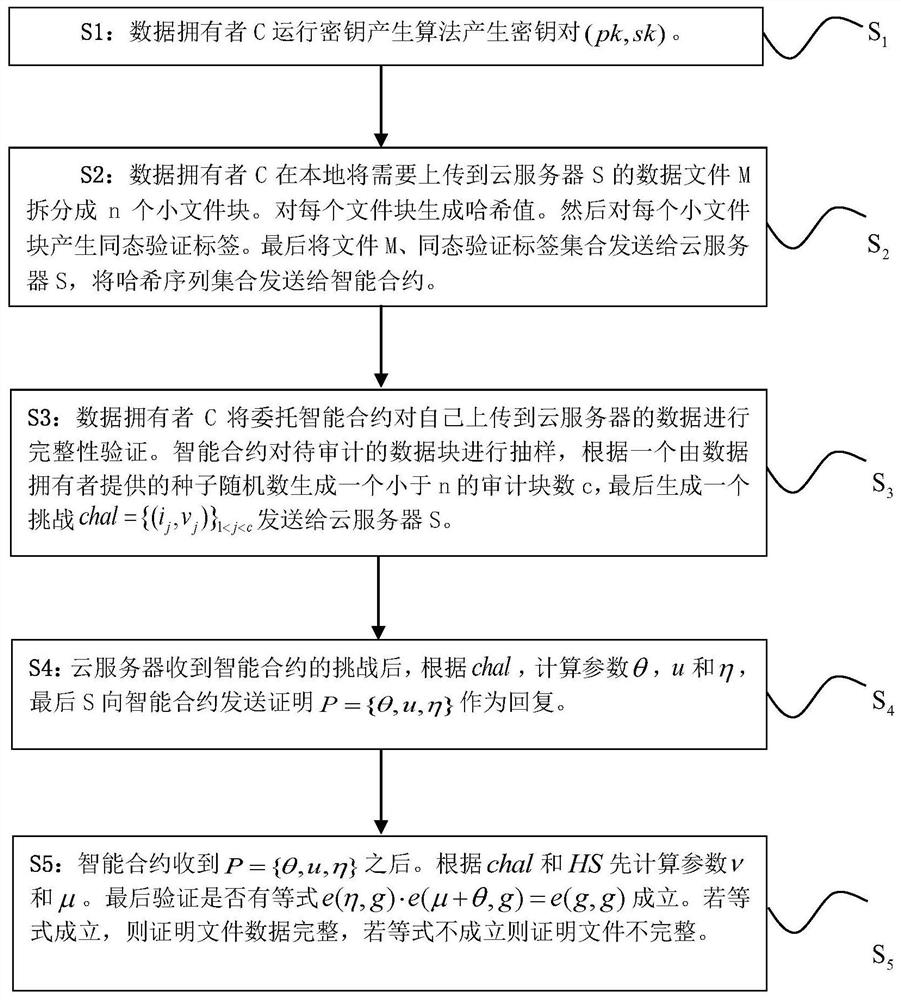
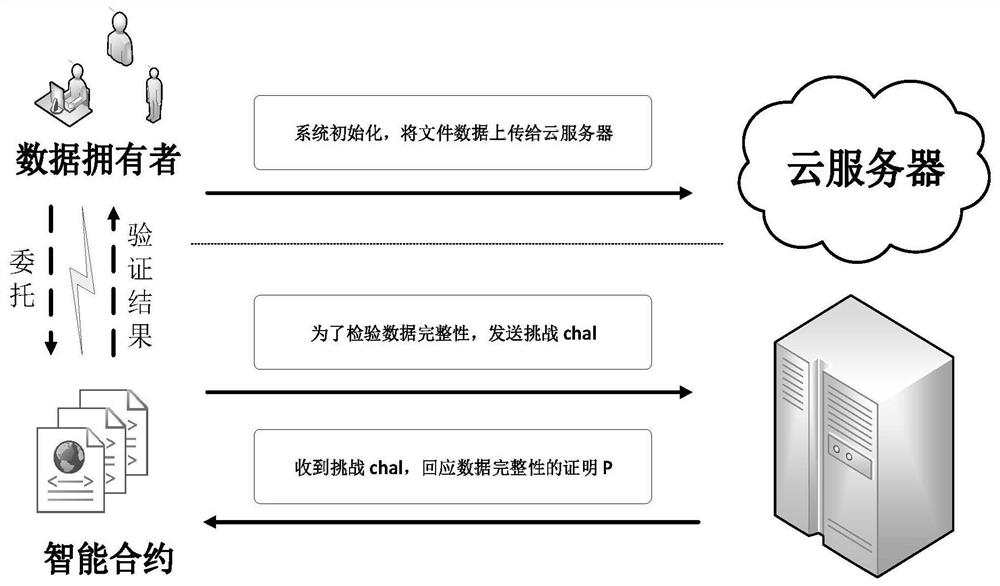
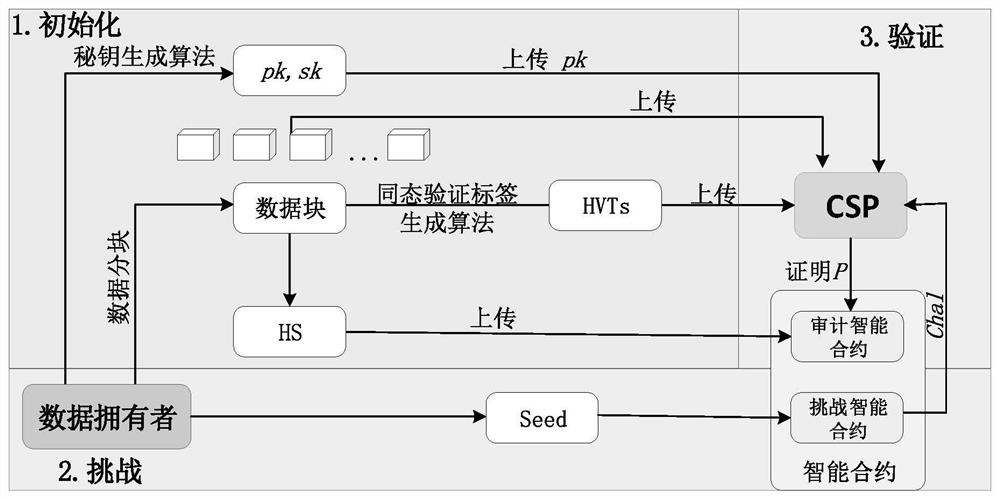
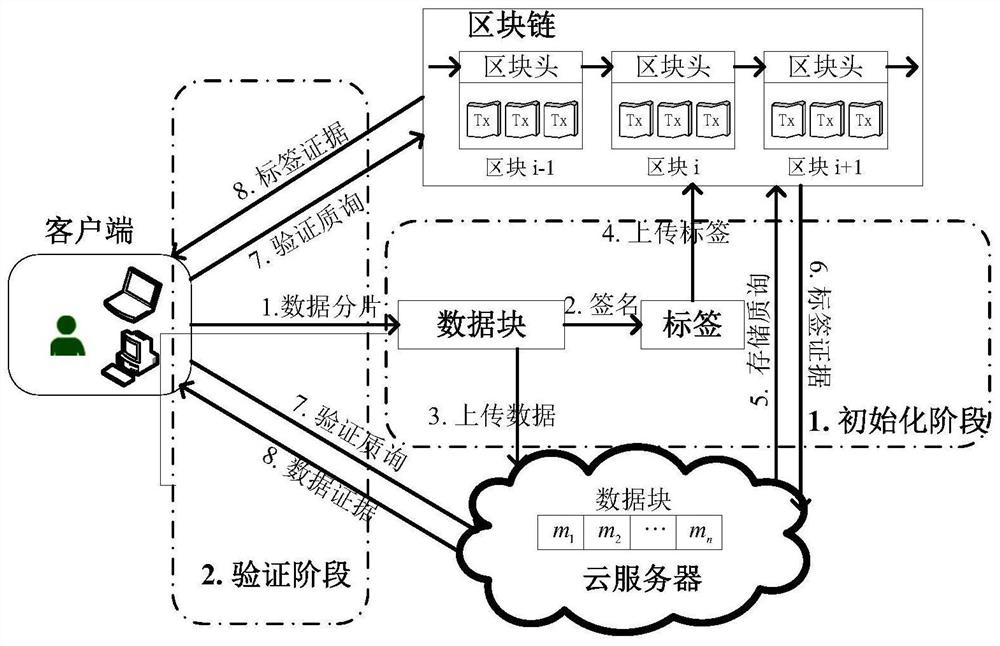
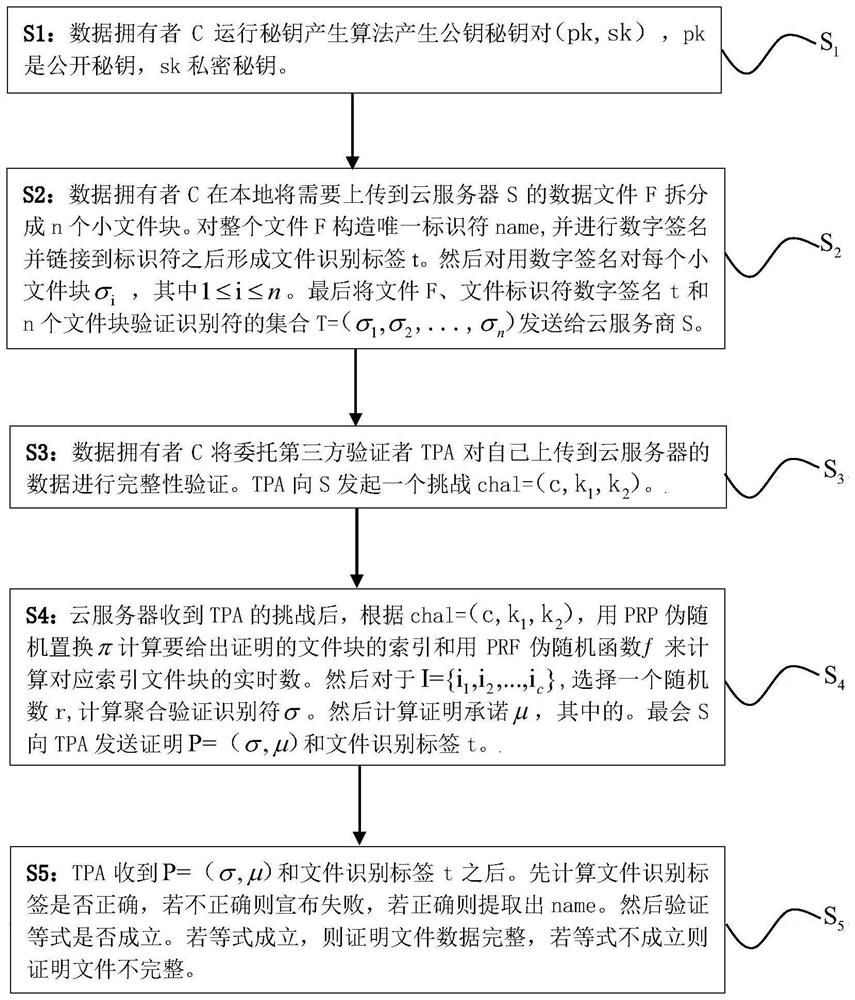
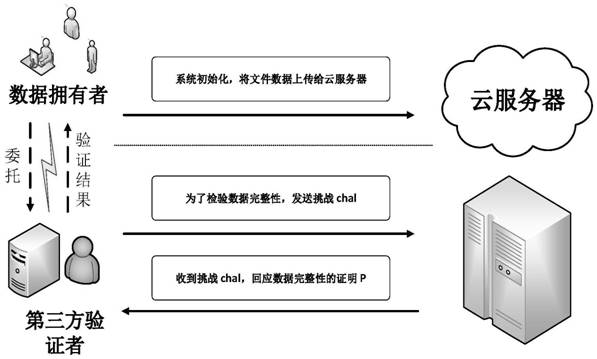
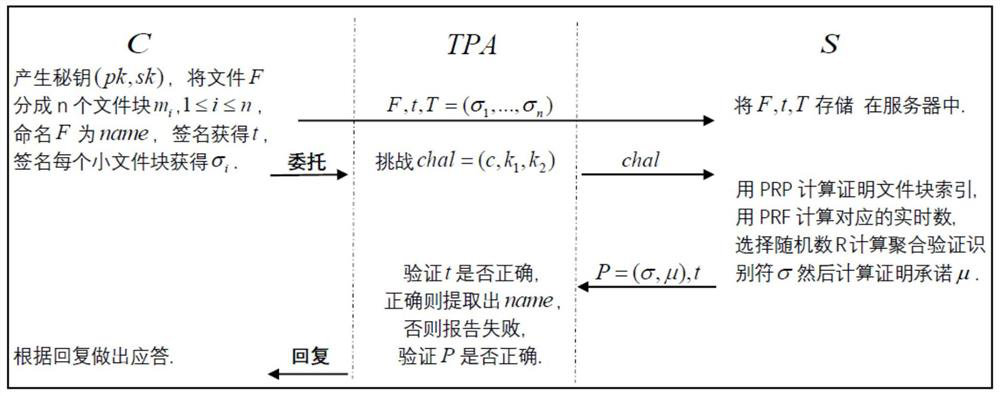
Cloud data integrity verification scheme based on blockchain
ActiveCN113556322AReduce complexityReduce computational complexityKey distribution for secure communicationPublic key for secure communicationData integrityValue set
The invention relates to a cloud data integrity verification scheme based on a blockchain, which uses the technical means of digital short signature, bilinear mapping, the blockchain and the like to solve the problems of integrity of cloud storage data, uncredibility of a third-party auditor and the like at present. When a data owner interacts with a cloud server, the data owner C generates a key pair, performs block processing on its own data and generates a homomorphic verification tag by using a digital signature. The data owner C uploads the data block and a homomorphic verification tag set to the cloud server S, and uploads a hash value set corresponding to the data block to a smart contract on the blockchain, and the smart contract verifies the data of the data owner. The smart contract sends a challenge to verify whether the integrity of the data, and S generates a response proof according to the challenge. Finally, the smart contract verifies whether the proof is correct. Due to the fact that the blockchain has the characteristics of non-tampering, decentration and the like, the integrity and privacy of the scheme are strongly guaranteed.
Owner:BEIHANG UNIV
Symbolism stamping method based on public key system
InactiveCN101414908AMaintain majestyImprove securityUser identity/authority verificationOffice automationDigital signatureShort signature
The invention discloses a symbol seal method based on a public key system, belonging to the cryptographic technology and computer technology field; the invention leads the unforgeability of a seal to be corresponding to the security of a public key digital signature system, comprising four parts: database creating of symbolized seal, key controlling, seal stamping and seal authentication, wherein, the database creating part is used for creating three relevant databases, the key controlling part is used for generating and managing a pair of private keys and public keys of a document (certificate) issuing unit, the seal stamping part is used for the document (certificate) issuing unit to generate a 64 system short signature character string to the Hash summary of a document or a certificate and stamp a seal image, and the seal authentication part is used for a document (certificate) receiving unit to judge the authenticity of source of the document or the certificate by the short signature character string; the method has low cost and easy operation, not only retains the appearance style of the traditional seal, but also greatly improves the security thereof, and can be widely applied in the issuing and transferring business of various paper documents or certificates, and electronic version documents or certificates of various units.
Owner:苏盛辉 +2
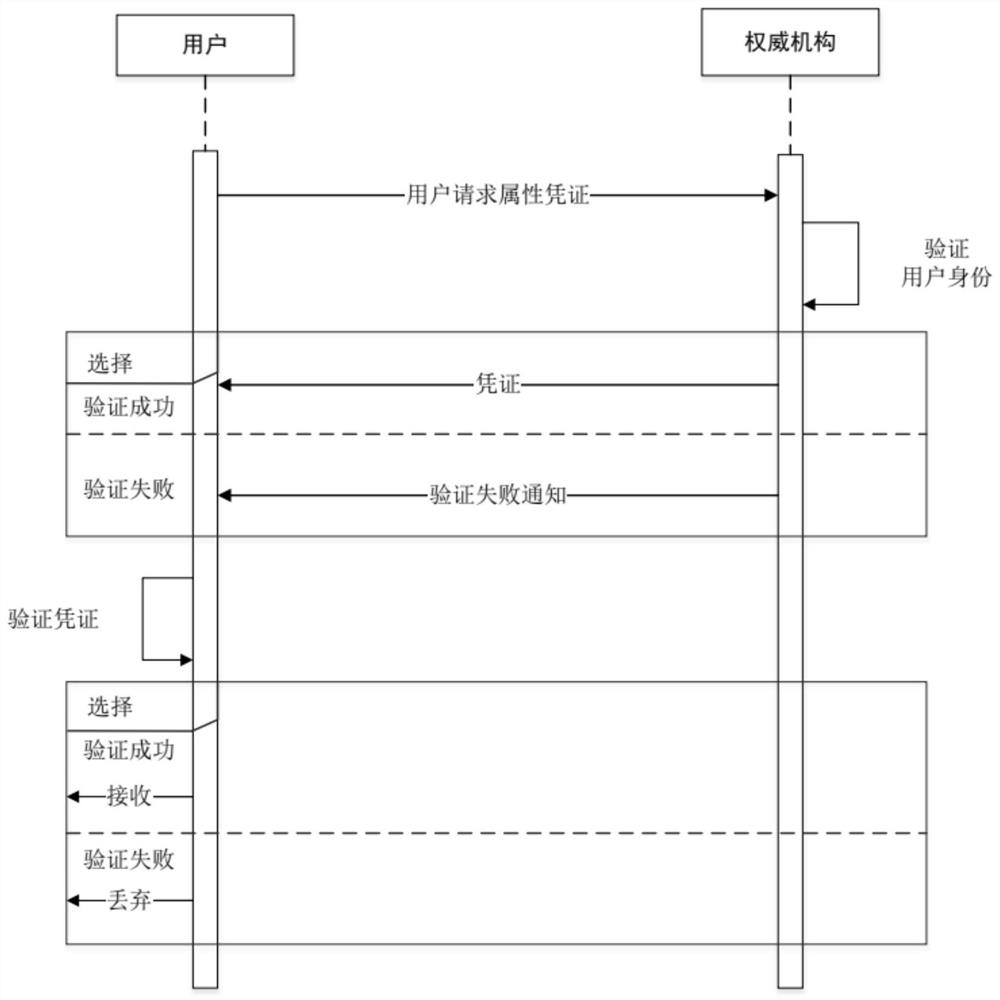
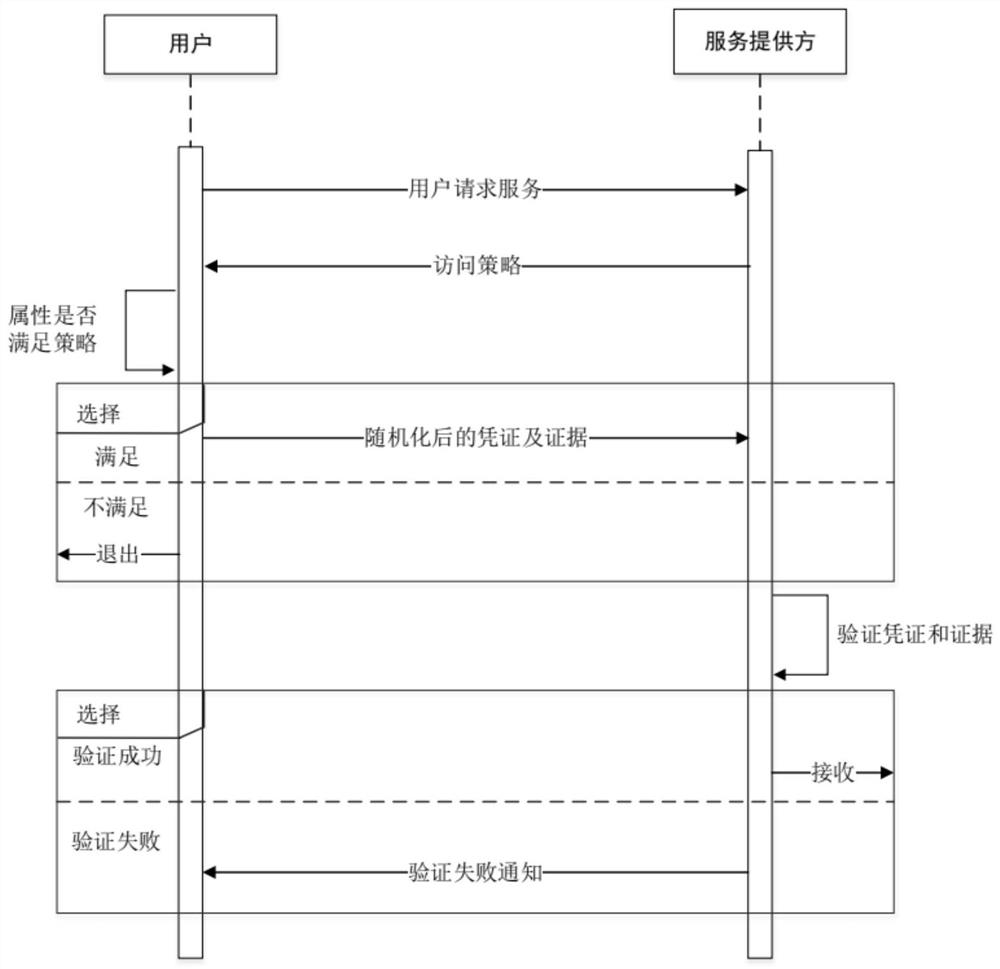
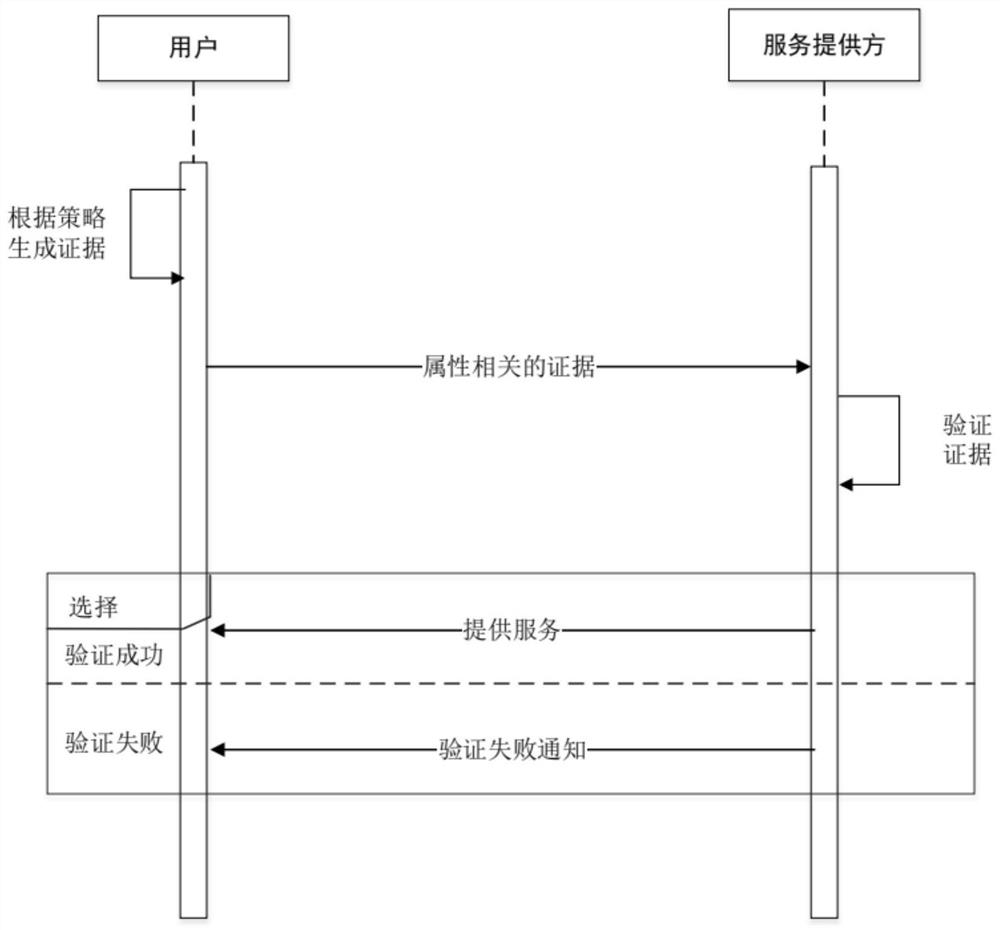
Privacy protection attribute authentication system and method based on verifiable declaration
PendingCN113221089APrivacy protectionPrivacy securityDigital data protectionDigital data authenticationPrivacy protectionShort signature
The invention provides a privacy protection attribute authentication system and method based on a verifiable declaration, and relates to the technical field of privacy protection in identity authentication. The method comprises the following steps: firstly, designing a data structure of a voucher by adopting a verifiable declaration of W3C, and verifying a signature of the data structure to confirm whether the declarated content is valid or not, thereby standardizing an identity verification standard; for the privacy problem existing in the verifiable declaration, expanding the structure of the verifiable declaration, and adding corresponding fields, so that the verifiable declaration has anonymity. Interval certification, non-relation certification and or relation certification of attribute values are realized by adopting a BB short signature scheme and a non-interactive zero-knowledge certification technology; detailed designs of protocols are given, including initialization, a certificate issuing protocol, a certificate showing protocol and an attribute proving protocol, and a verifiable declaration is applied to the protocols; and privacy protection authentication of the user is realized.
Owner:NORTHEASTERN UNIV
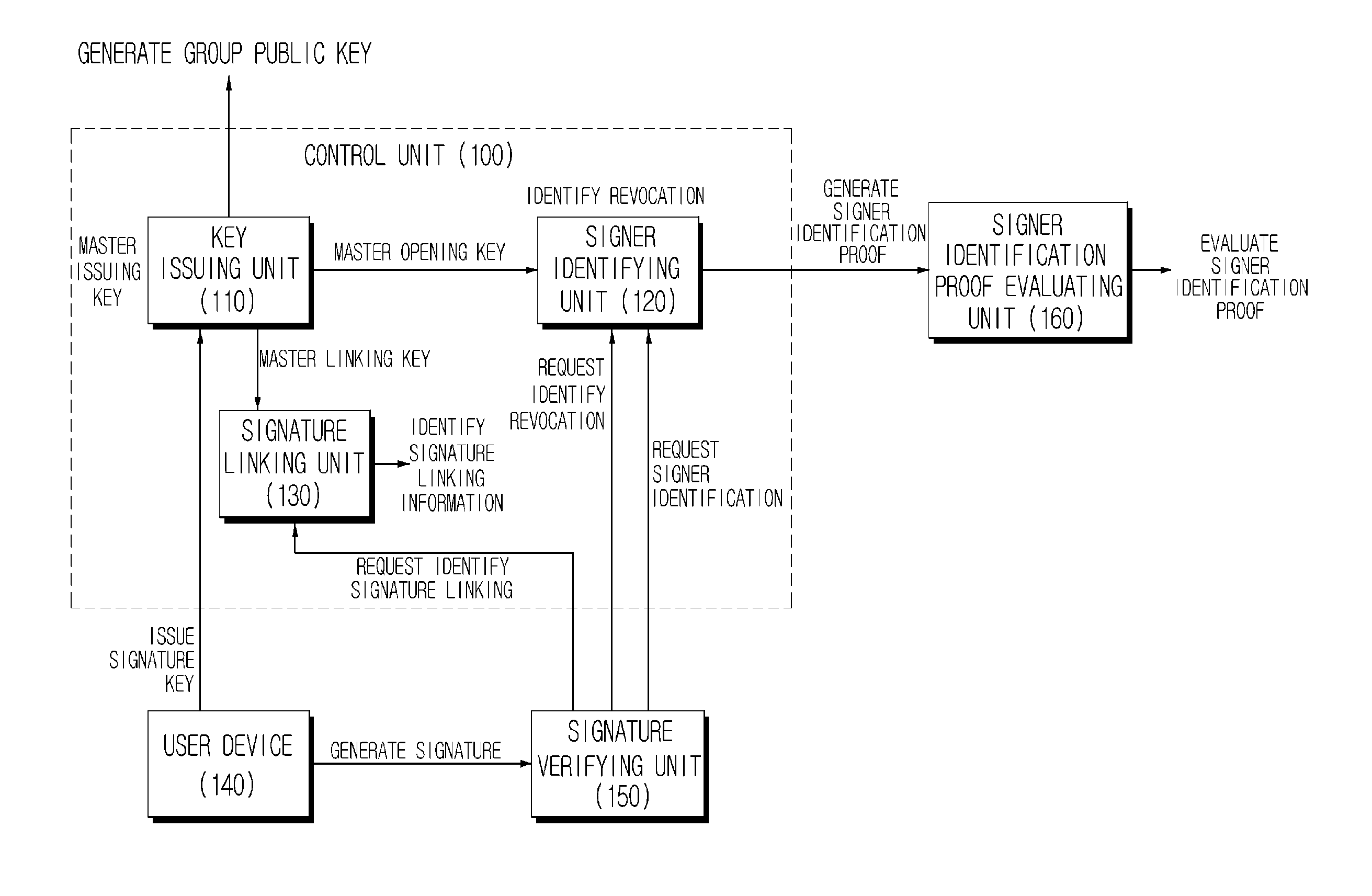
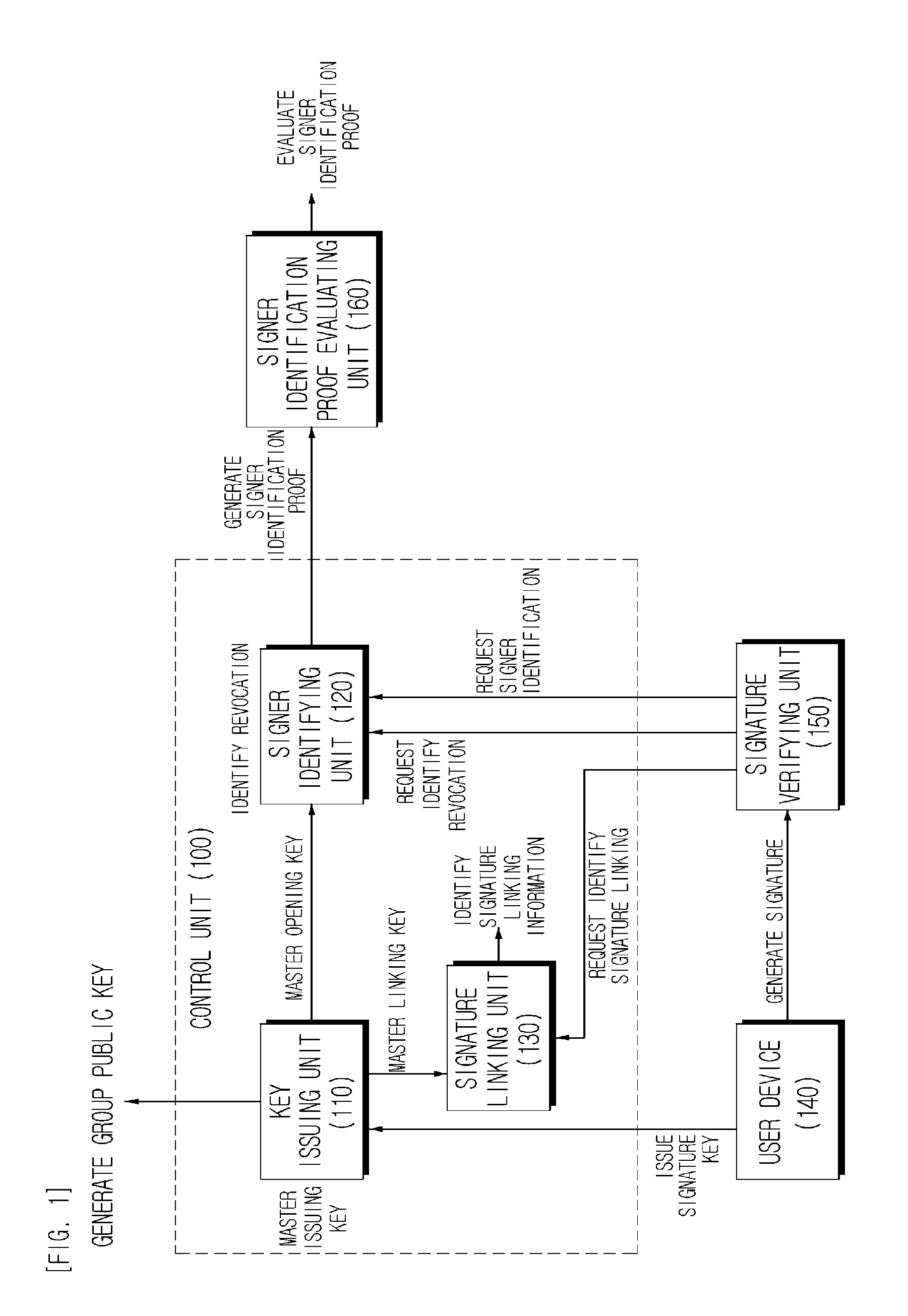
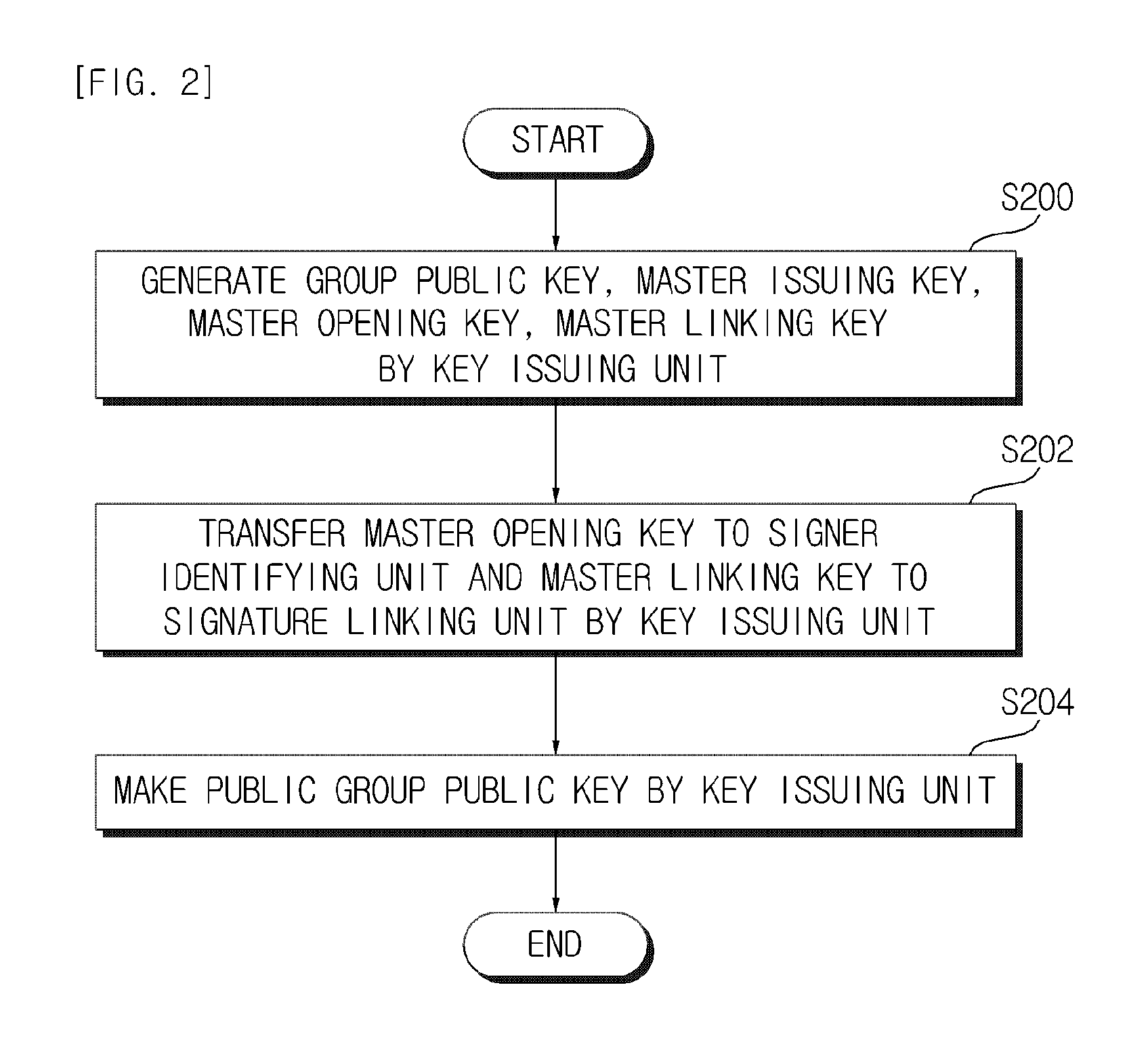
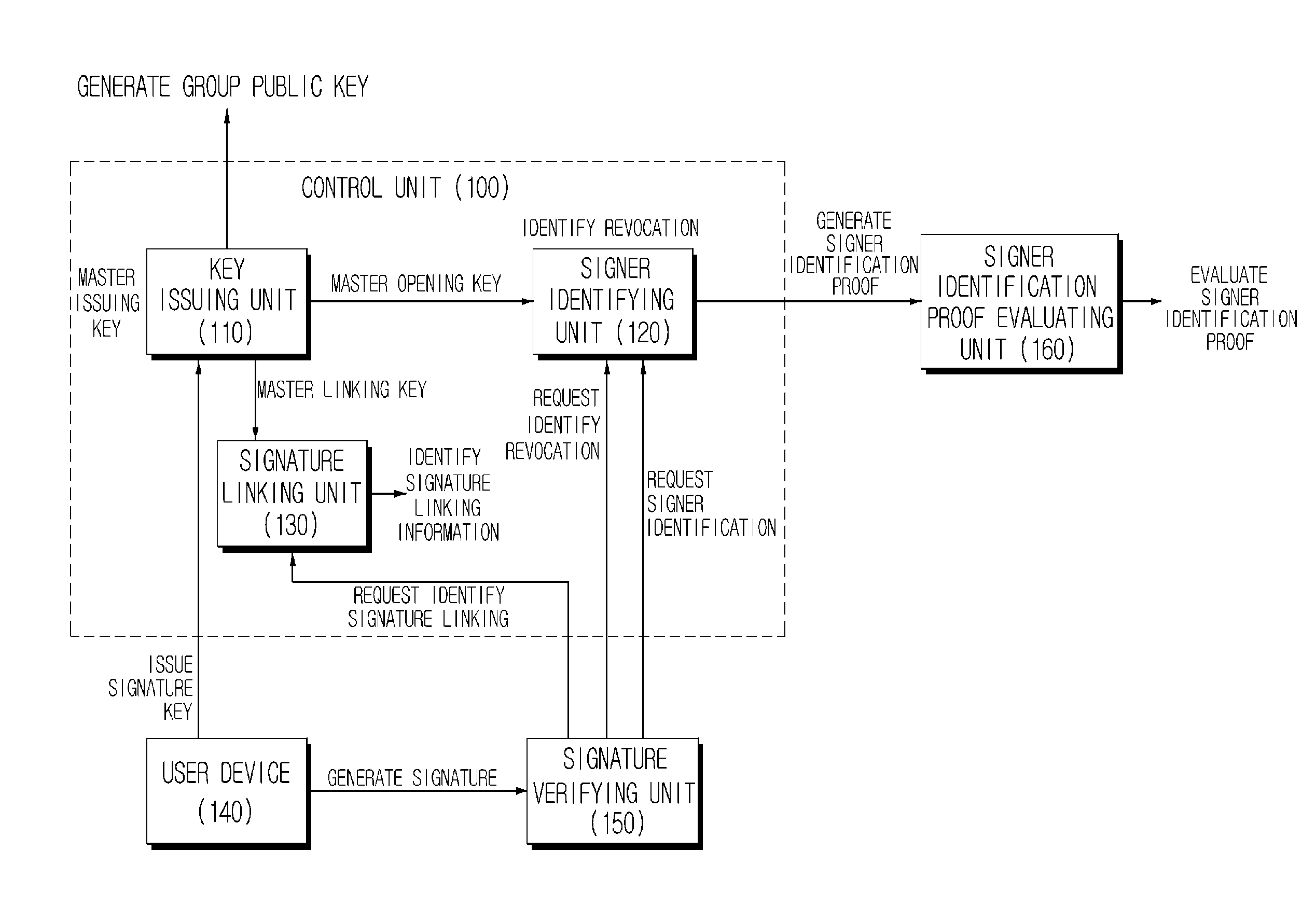
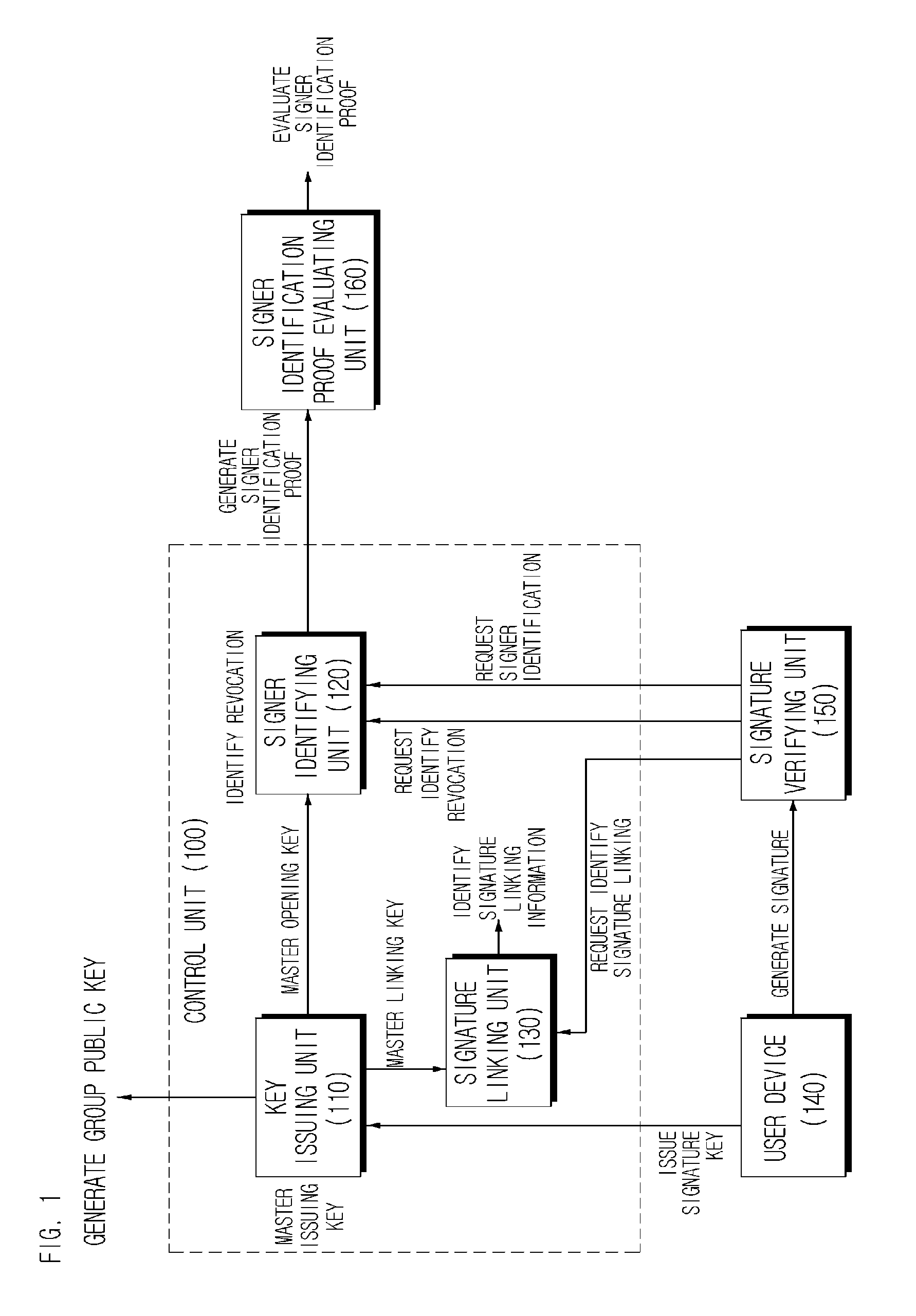
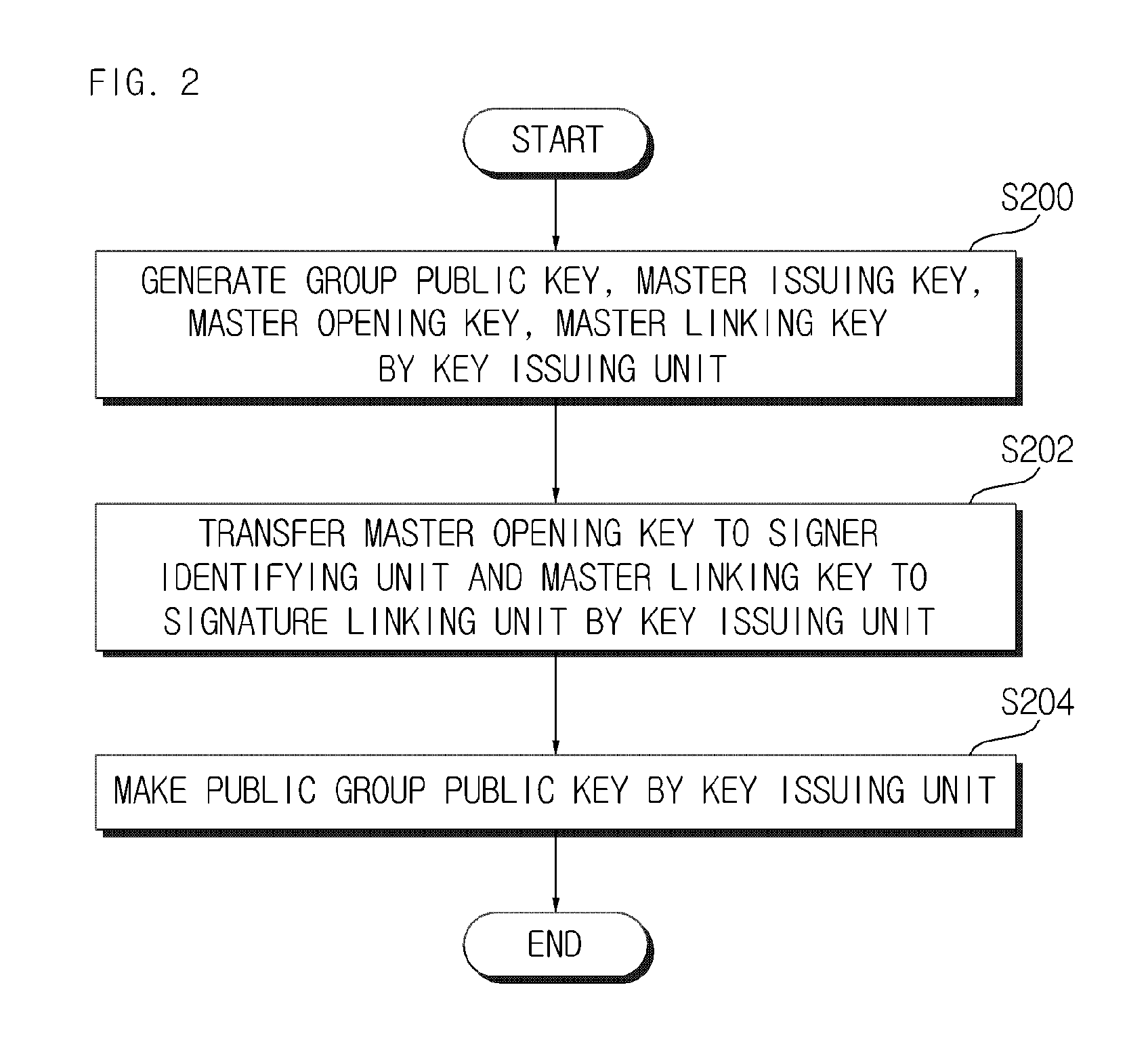
Lightweight group signature system and method with short signature
ActiveUS20130091360A1Improve performanceImprove featuresKey distribution for secure communicationUser identity/authority verificationShort signatureAnonymity
A lightweight group signature system and method with short signatures according to the exemplary embodiments of the present invention can provide security characteristics similar to group signature mechanisms providing the existing known controllable linkability but can make a revocation method simple by outputting a short signature and providing excellent operation efficiency at the time of signature generation, signature verification, and revocation on smart terminals, and can be widely applied to various anonymity-based application environments, making by making operation efficiency excellent at the time of signature generation and verification and outputting very short signature lengths.
Owner:ELECTRONICS & TELECOMM RES INST
Lightweight group signature system and method with short signature
ActiveUS8966273B2Improve performanceImprove featuresUser identity/authority verificationWeighing apparatus detailsShort signatureAnonymity
A lightweight group signature system and method with short signatures according to the exemplary embodiments of the present invention can provide security characteristics similar to group signature mechanisms providing the existing known controllable linkability but can make a revocation method simple by outputting a short signature and providing excellent operation efficiency at the time of signature generation, signature verification, and revocation on smart terminals, and can be widely applied to various anonymity-based application environments, making by making operation efficiency excellent at the time of signature generation and verification and outputting very short signature lengths.
Owner:ELECTRONICS & TELECOMM RES INST
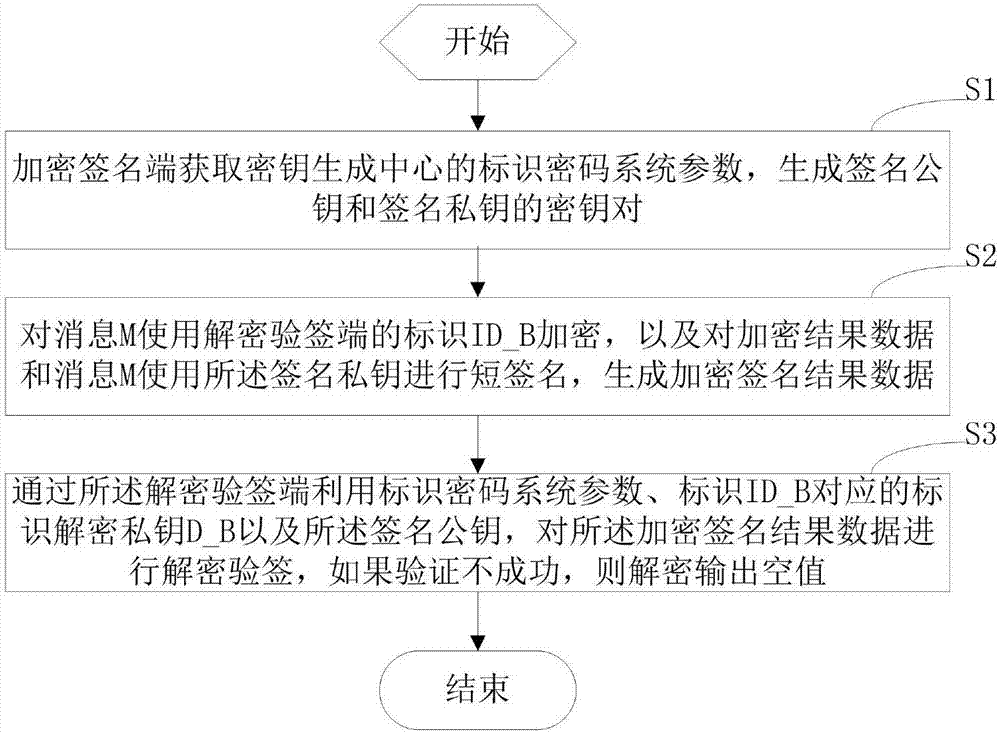
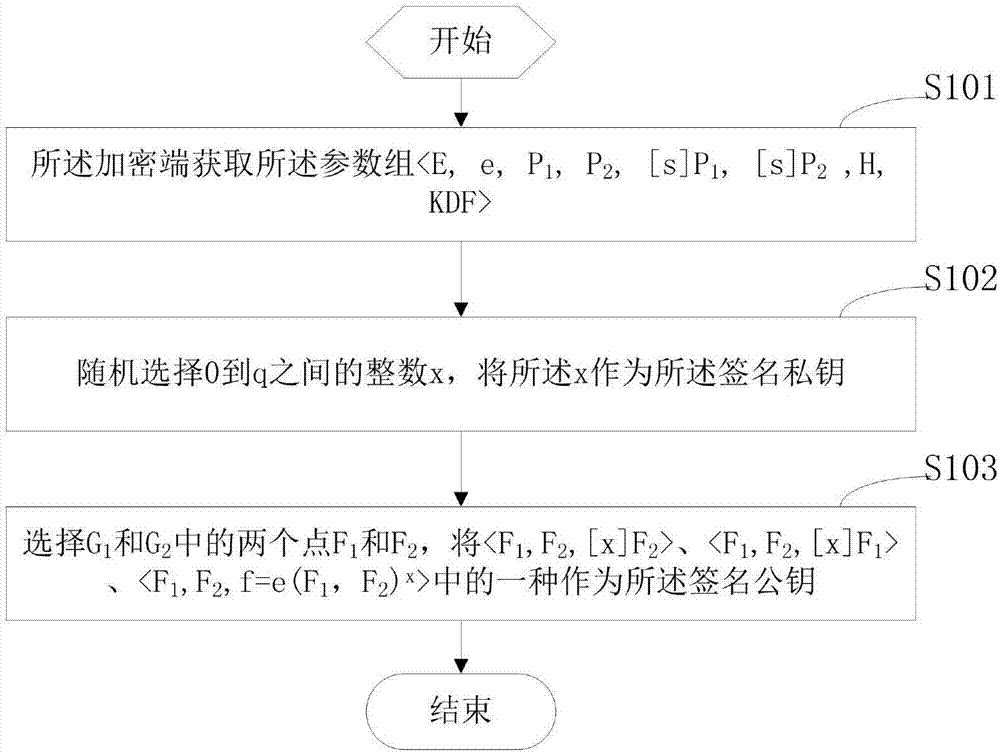
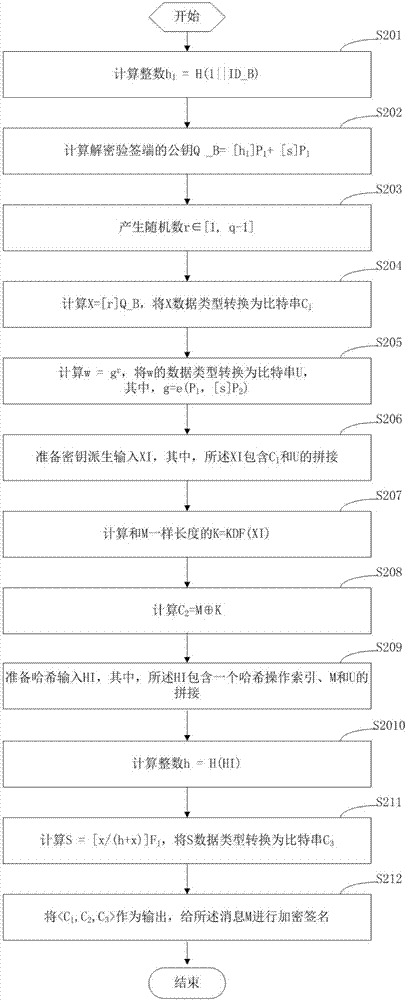
Terminal and non-repudiation encrypted signature method and device thereof
ActiveCN107104788AGuaranteed privacyGuarantee authenticityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesShort signatureNon-repudiation
The invention relates a terminal and a non-repudiation encrypted signature method and device thereof. The method comprises that an encrypted signature end obtains parameters of an identification cipher system of a secret key generating center, and generates a key pair including a public signature key and a private signature key; a message M is encrypted by utilizing an identification ID_B of a decrypted signature verification end, short signature is carried out on encryption result data and the message M by utilizing the private signature key, and encrypted signature result data is generated; and the decrypted signature verification end carries out decrypted signature verification on the encrypted signature result data by utilizing the parameters of the identification cipher system, an identification decrypting private key D_B corresponding to the identification ID_B and the public signature key, and if verification fails, an output null is decrypted. According to the invention, the encrypted signature result data is generated via short signature, an output result of the encrypted signature end is short, verification is simple, and both the data privacy and authenticity can be ensured.
Owner:SHENZHEN OLYM INFORMATION SECURITY TECHOLOGY CO LTD
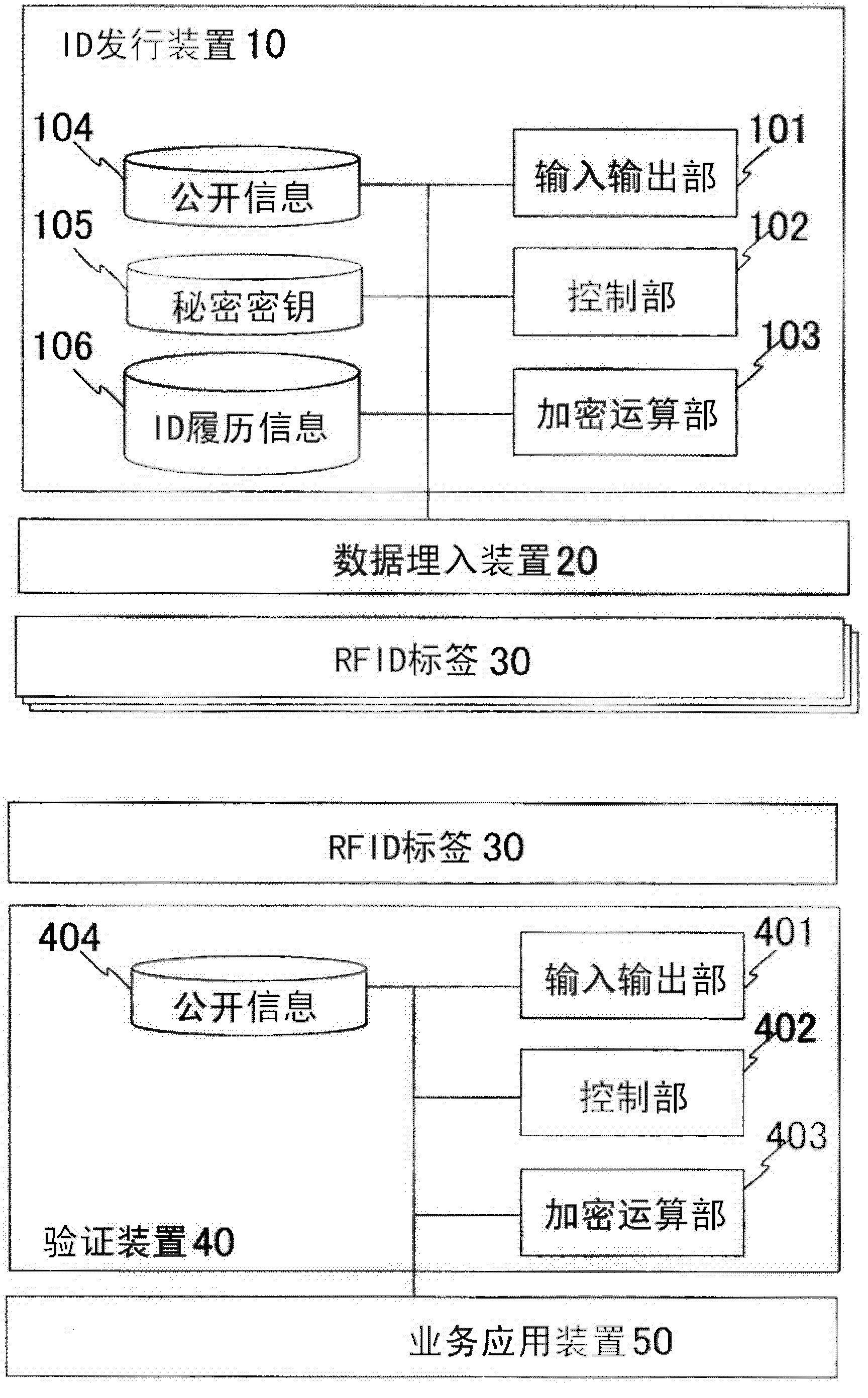
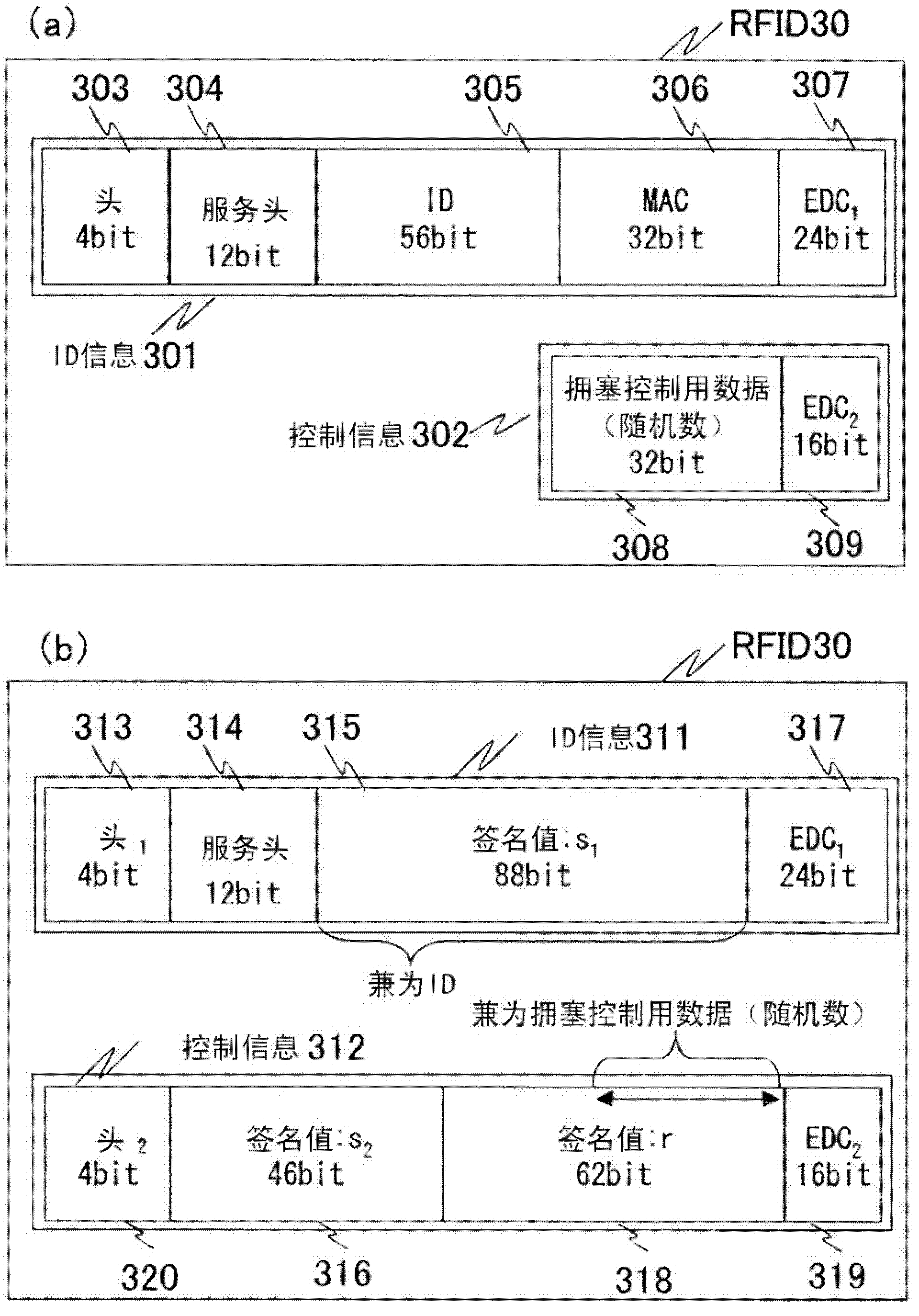
Method of generating id with guaranteed validity, and validity legitimacy guarantying rfid tag
InactiveCN102326355AReduce data sizeGuaranteed legalityUser identity/authority verificationCo-operative working arrangementsShort signatureDigital Signature Algorithm
A portion of a digital signature value for authenticating the validity of ID information is also used as an ID so as to reduce the amount of data. This is achieved by using a digital signature scheme with a short signature length obtained by transforming a Schnorr signature, which is a typical example of a digital signature scheme.
Owner:HITACHI LTD
Trapdoor one-way functions on elliptic curves and their application to shorter signatures and asymmetric encryption
ActiveUS7844051B2Reduced bandwidthPublic key for secure communicationUser identity/authority verificationEllipseShort signature
The present invention provides a new trapdoor one-way function. In a general sense, some quadratic algebraic integer z is used. One then finds a curve E and a rational map defining [z] on E. The rational map [z] is the trapdoor one-way function. A judicious selection of z will ensure that [z] can be efficiently computed, that it is difficult to invert, that determination of [z] from the rational functions defined by [z] is difficult, and knowledge of z allows one to invert [z] on a certain set of elliptic curve points. Every rational map is a composition of a translation and an endomorphism. The most secure part of the rational map is the endomorphism as the translation is easy to invert. If the problem of inverting the endomorphism and thus [z] is as hard as the discrete logarithm problem in E, then the size of the cryptographic group can be smaller than the group used for RSA trapdoor one-way functions.
Owner:MALIKIE INNOVATIONS LTD
System and method for operating system installation on a diskless computing platform
ActiveUS9003000B2Multiple digital computer combinationsProgram/content distribution protectionOperational systemEntry point
One embodiment of the present invention sets forth a technique for automatically provisioning a diskless computing device and an associated server system. A diskless computing device client incorporates an iSCSI initiator that is used to access resources provided by an iSCSI target that is resident on a server computing device. The iSCSI initiator is implemented in the client firmware, providing INT13 disk services entry points, thereby enabling the client to transparently access virtual storage devices at boot time. The client device conducts an apparently local installation using the virtual storage devices provided by the server computing device. A short signature value is associated with the boot image, uniquely associating the boot image with the specific client hardware configuration. When the client device boots normally, the signature value of the client device is presented to the server computing device to automatically reference the appropriate boot image.
Owner:NVIDIA CORP
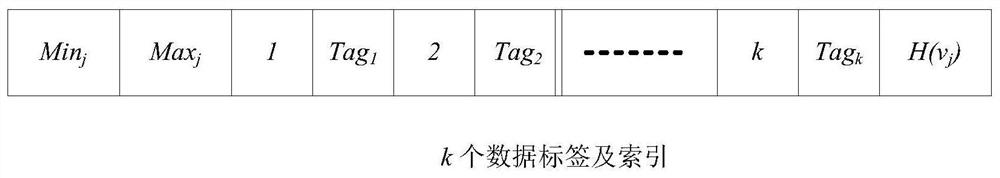
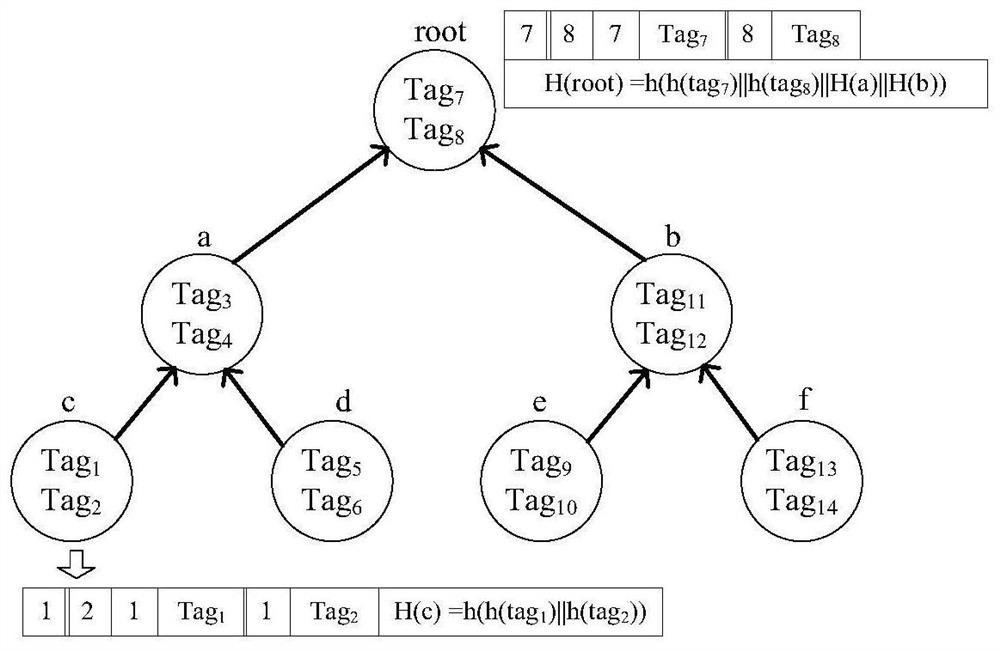
Data integrity auditing method supporting tag block chain storage and query
PendingCN111898164AImprove storage scalabilitySave storage spaceDigital data protectionData integrityCiphertext
The invention discloses a data integrity auditing method supporting tag block chain storage and query, which comprises the steps that a client blocks a data file and generates a data tag, data is stored on a cloud server, and the data tag is stored on a block chain platform in a T-Merkle tree structure; an auditor sends a sampling auditing inquiry to the cloud server and the block chain platform;the block chain platform executes a query algorithm to obtain the data tag, calculates ciphertext label evidence and returns the ciphertext tag evidence to the auditor, and meanwhile, the cloud servercalculates ciphertext data evidence and returns the ciphertext data evidence to the auditor; and the auditor directly verifies the integrity of the data through the double-line pair property on the premise that decryption is not needed. According to the invention, the block chain platform is used for storing data tags, a corresponding block chain storage structure and a query method are provided,and a bilinear pair verification method based on ZSS short signatures is designed, so that the expandability of the system and the security and high efficiency of data integrity auditing are improved.
Owner:WUHAN TEXTILE UNIV
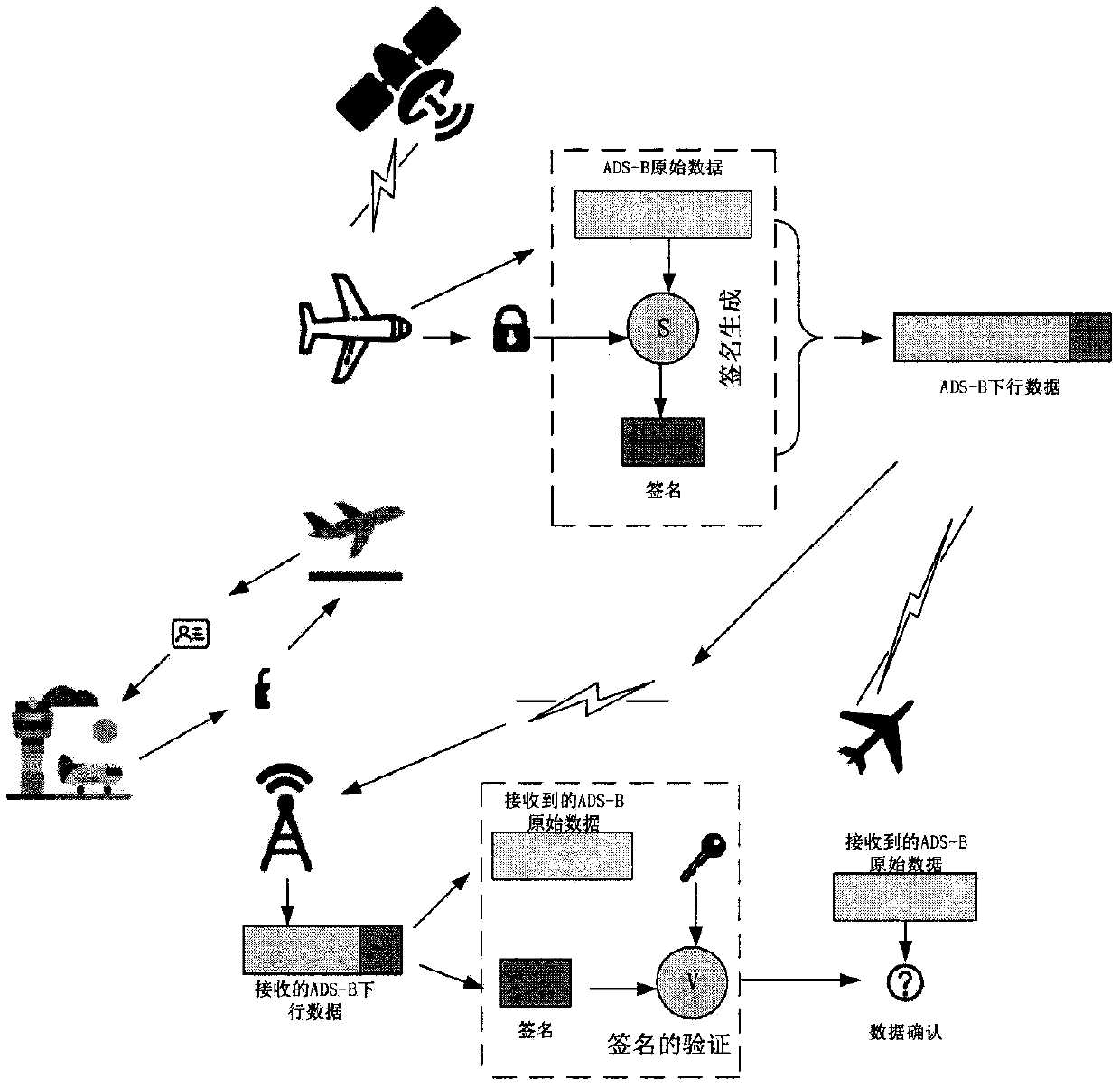
ADS-B message authentication method based on certificateless short signature
The invention relates to the technical field of information security, in particular to a broadcast type automatic correlation monitoring system (ADS-B) message authentication scheme based on certificateless short signatures. Aiming at potential safety hazards of ADS-B, by utilizing the characteristics of low bandwidth and less available data bits, the invention provides the ADS-B message authentication method based on the certificateless short signature. Compared with the current similar methods, the signature length is reduced by 3 / 4, the overall performance is improved to a certain extent, and the signature periodical performance is improved by nearly 1 time. In addition, the method does not need to manage certificates, eliminates the problem of secret key hosting, and greatly reduces the burden of the system ADS-B. And the availability and the overall safety of the system are enhanced. In order to further analyze the performance of the authentication method, NS2 is used to simulatethe ADS-B network, and the result shows that on the premise of guaranteeing ADS-B data integrity, identity authentication and non-repudiation, the influence on the network is very small, and the minimum operation function standard specification of 1090ES is met.
Owner:CIVIL AVIATION UNIV OF CHINA
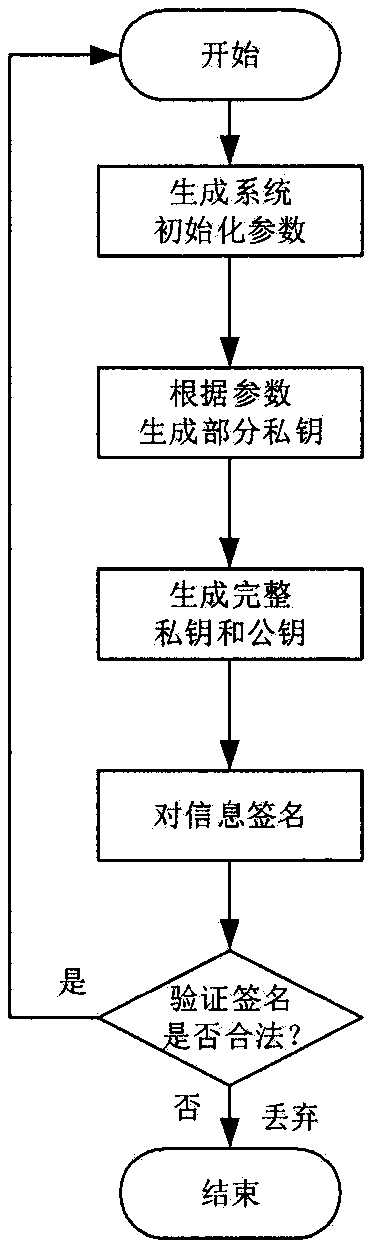
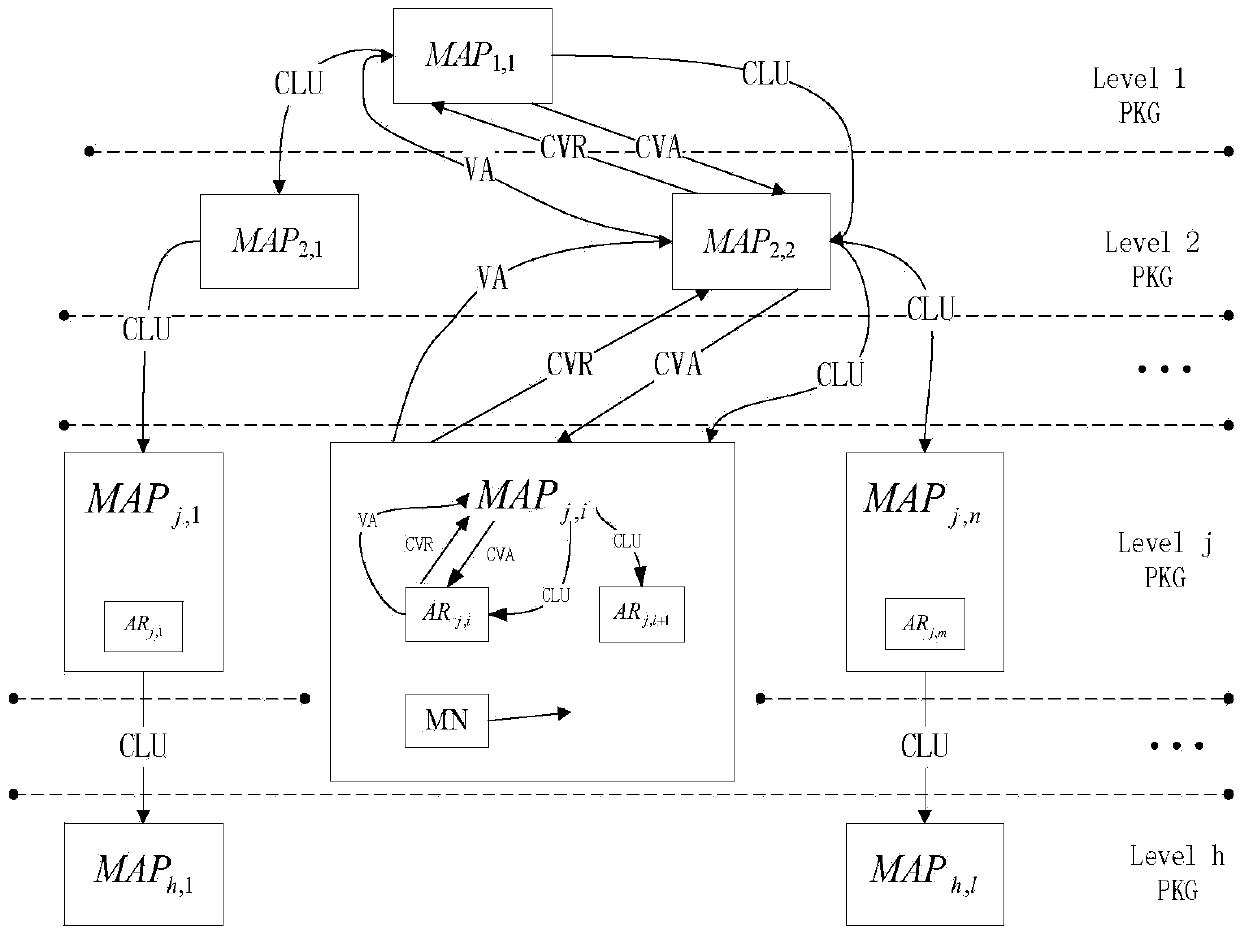
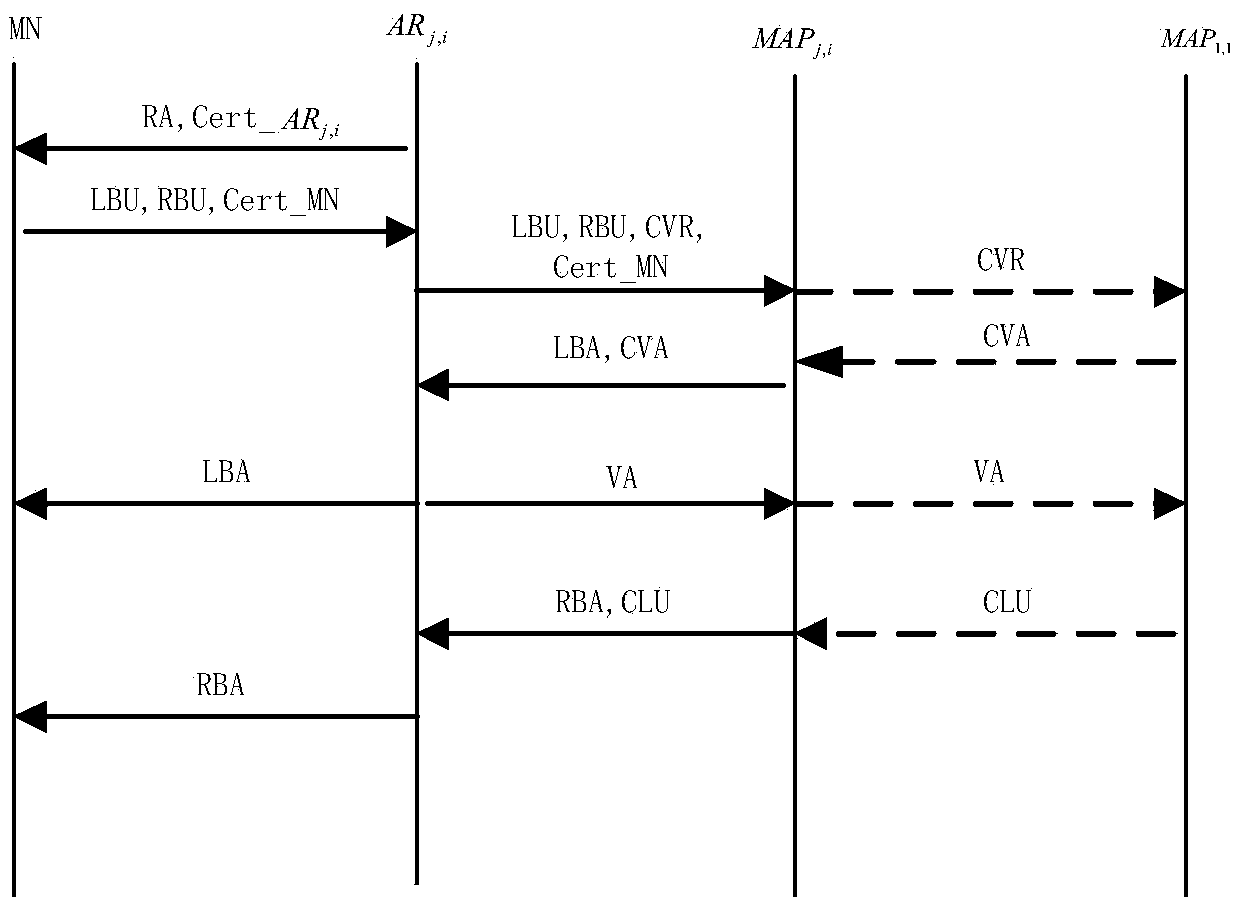
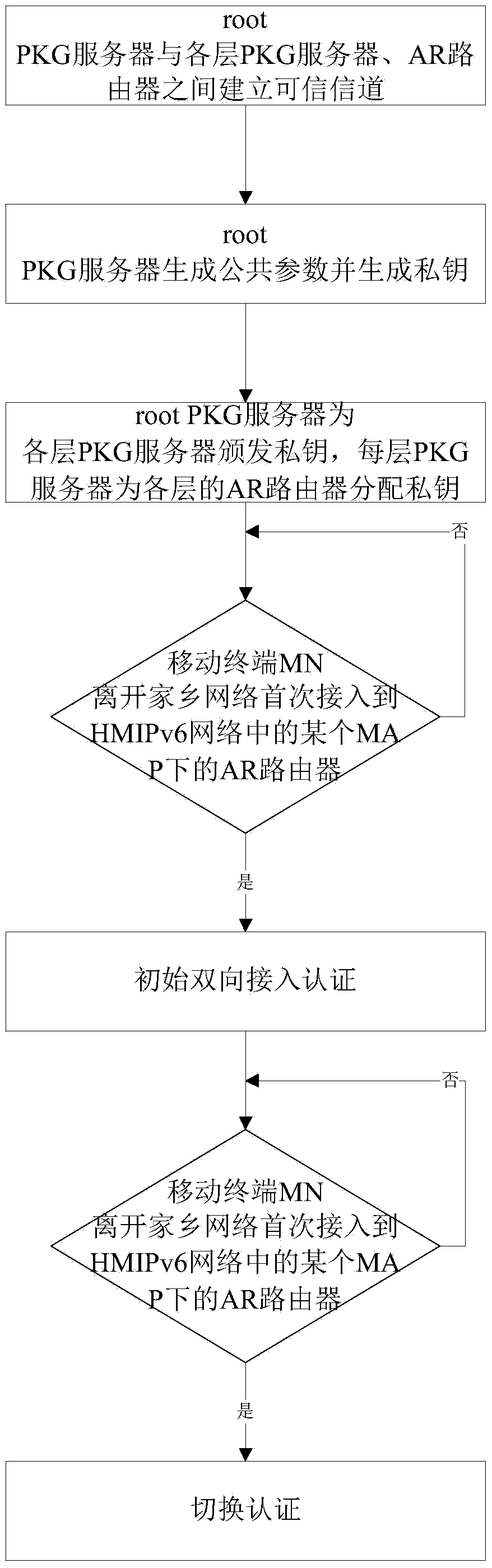
Two-way access authentication method for multi-layer-MAP oriented HMIPv6 network
ActiveCN105376230AShorten the lengthImplement two-way authenticationTransmissionSecurity arrangementShort signatureTrusted third party
The invention provides a two-way access authentication method for a multi-layer-MAP oriented HMIPv6 network. The two-way access authentication method comprises the following steps that: a root PKG server is used as a trusted third party; a trusted channel is established among the root PKG server, PKG servers and AR routers in various layers; the root PKG server generates common parameters and private keys; the root PKG server issues the private keys to the PKG servers in the various layers according to identity information of the PKG servers in the various layers; the PKG server in each layer distributes the private key to the AR router in this layer according to identity information of the AR router in this layer; when a mobile node MN leaves a home homework and is accessed to the AR router under a certain MAP in the HMIPv6 network for the first time, initial two-way access authentication is carried out; and, when the mobile node MN is in a currently accessed foreign network and the AR router in the current MAP domain is switched into another MAP domain or another AR router, switching authentication is carried out. The invention provides a short signature scheme based on node certificate hierarchical identity; the security is based on the h-CDH problem; the short signature scheme has the advantages that: the lengths of the private keys are reduced along with increasing of hierarchical levels; and the lengths of the private keys are independent of the hierarchical levels.
Owner:NORTHEASTERN UNIV
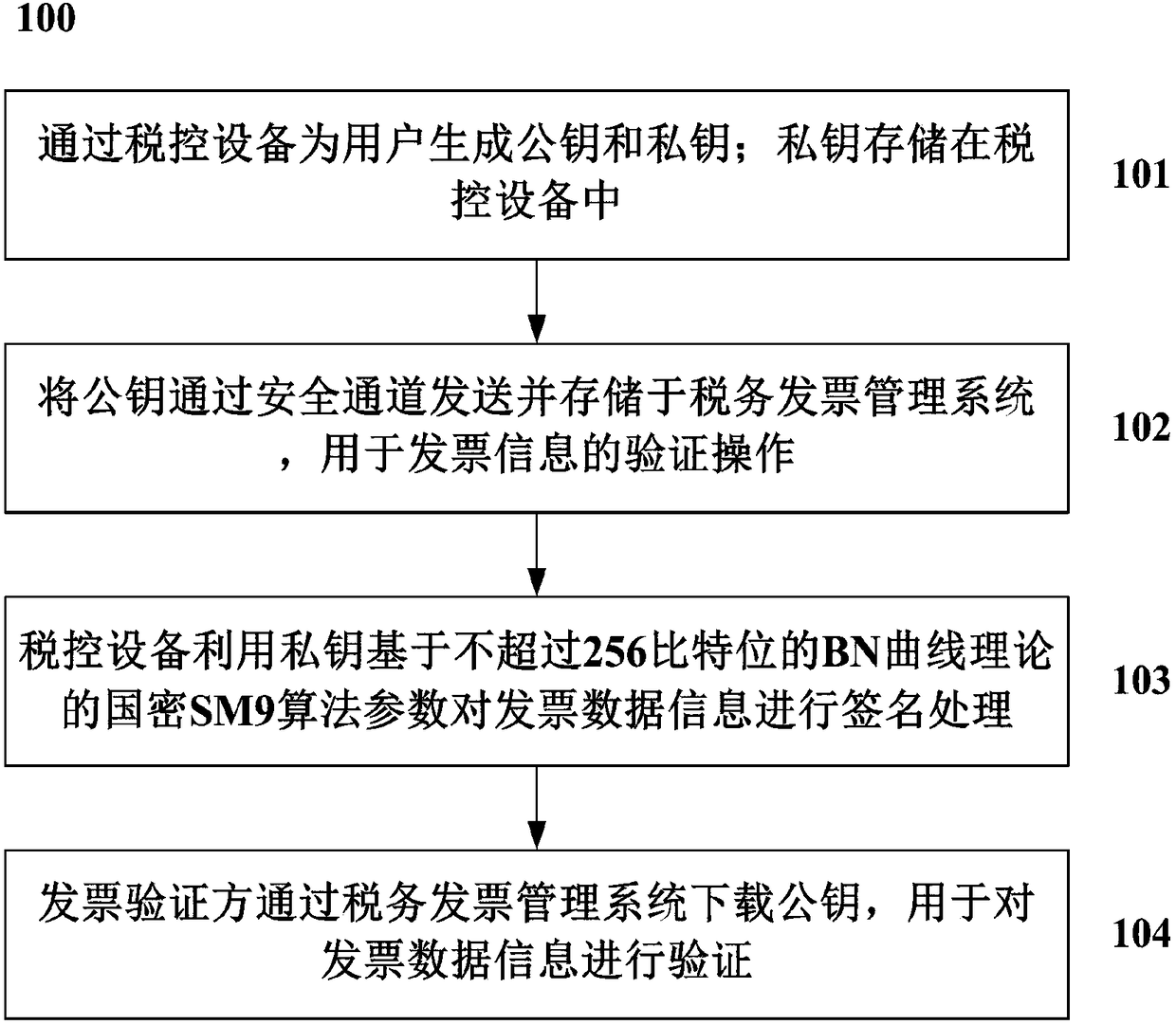
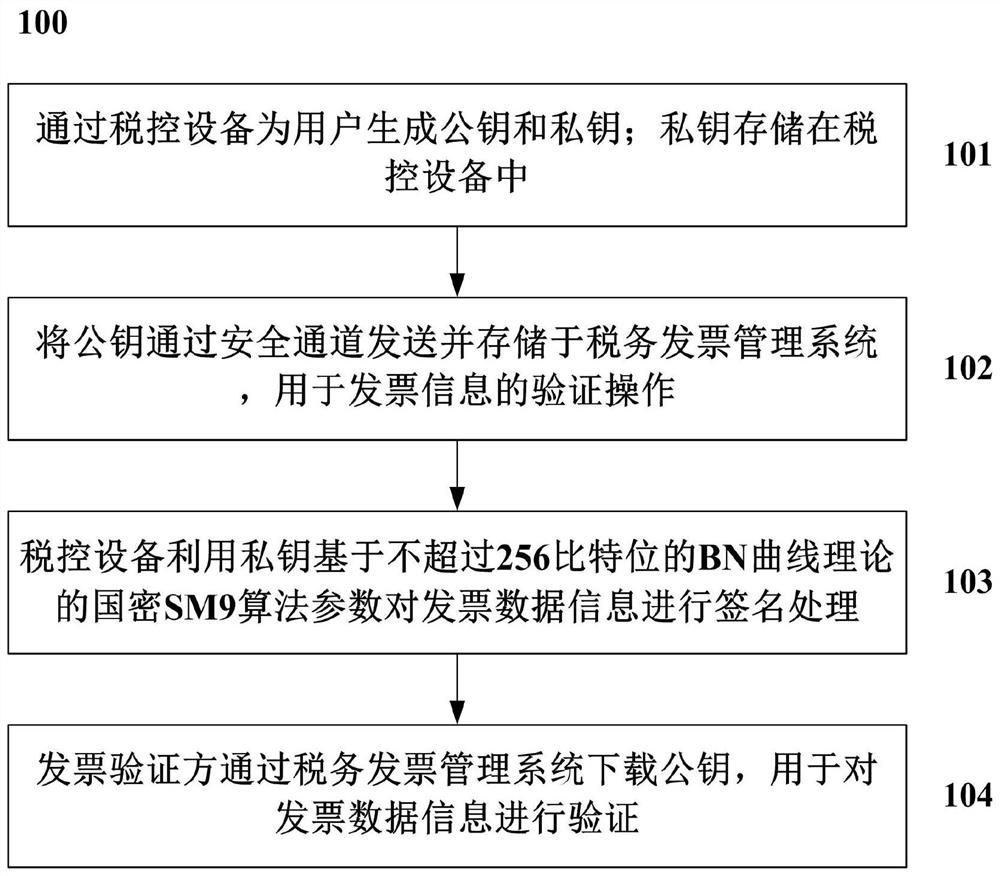
Method and system for processing short ciphertext signature of invoice
ActiveCN108268779AAchieve self-controlEnsure safetyDigital data protectionBilling/invoicingData informationCiphertext
The invention discloses a method for processing short ciphertext signature of an invoice. The method comprises: through a tax-control device, generating a public key and a private key for a user, andstoring the private key in the tax-control device; through a safe channel, sending the public key to a tax invoice management system and storing the public key in the tax invoice management system, sothat the tax invoice management system performs verification operation on invoice information; the tax-control device using the private key, and based on parameters of a BN curve domestic cryptographic SM9 algorithm, the parameters not exceeding 256 bits, to perform signature processing on invoice information; and an invoice verifying party downloading the public key through the tax invoice management system, and using the public key to verify the invoice data information. The short signature method can satisfy requirement of length of a current invoice password region.
Owner:AEROSPACE INFORMATION
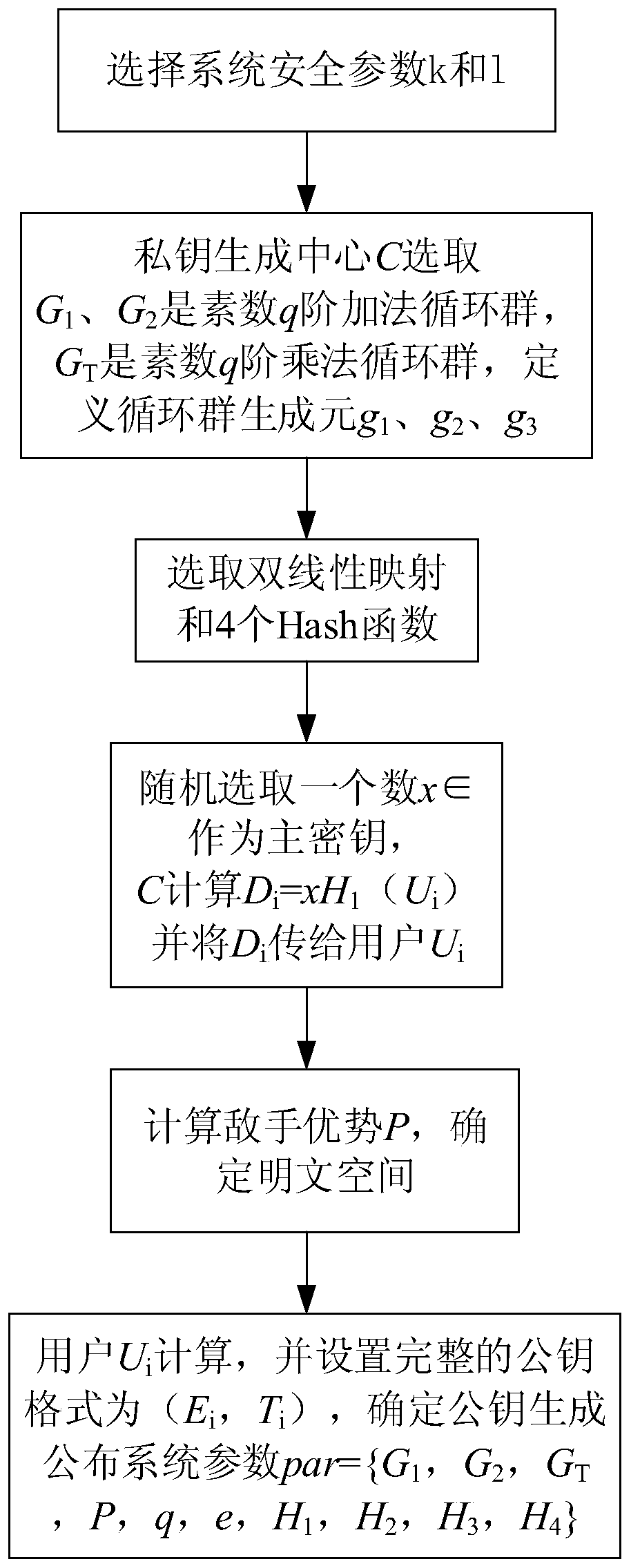
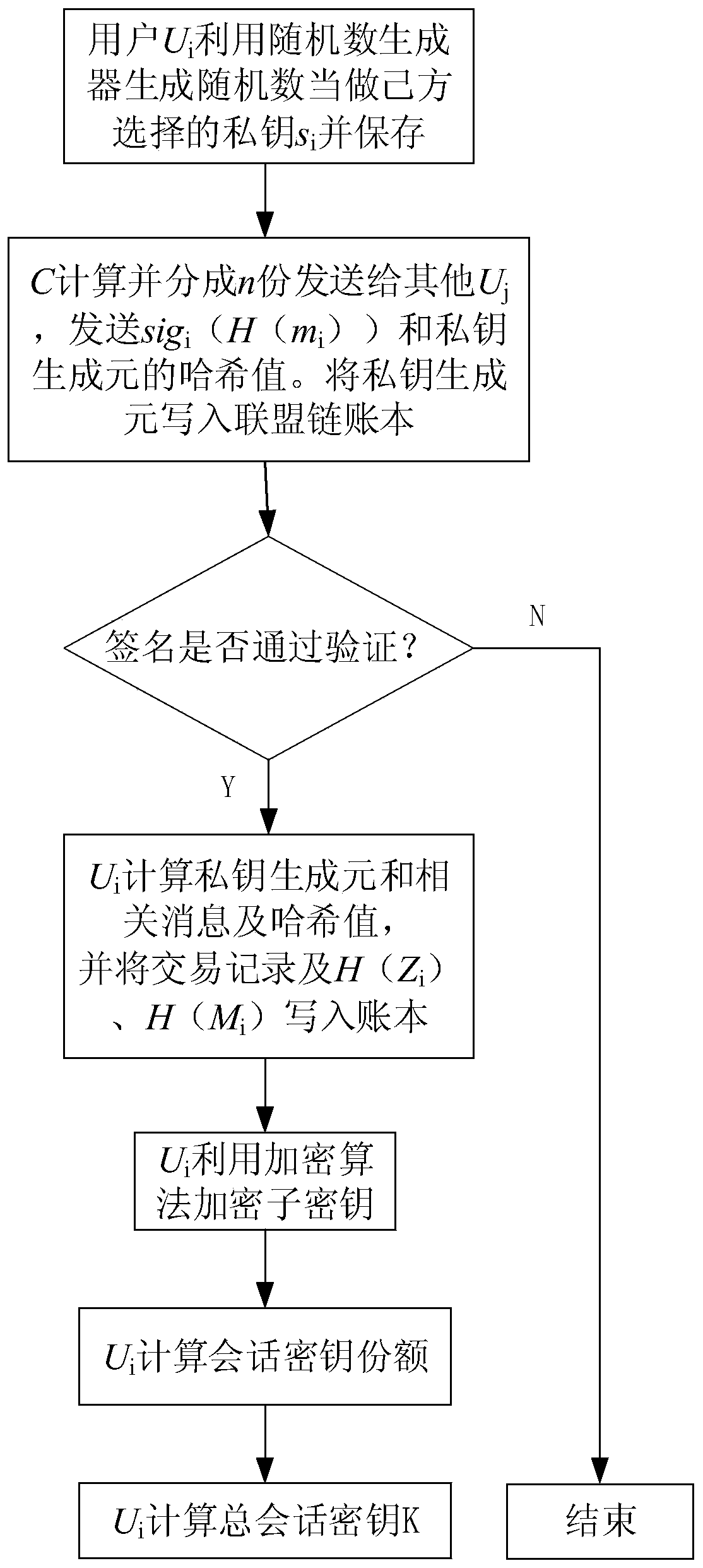
Alliance chain encryption method based on bilinear mapping technology
ActiveCN111030821AImprove production efficiencyImprove distribution efficiencyKey distribution for secure communicationFinanceKey exchangeHash function
The invention discloses an alliance chain encryption method based on a bilinear mapping technology. The method comprises the steps of (1) achieving the construction of an alliance chain encryption system based on the bilinear mapping technology, including the generation and setting of a public key and a private key, and the selection of an encryption function; (2) encrypting a secret key based ona bilinear mapping technology, and distributing the secret key in a secret key negotiation mode; and (3) based on the model and the secret key distribution method, realizing secret key exchange, plaintext encryption and digital signature processes based on the bilinear mapping technology. According to the invention, the bilinear mapping technology is an encryption technology commonly used in cryptology; in combination with a hash function, a signature scheme with the characteristics of short signature, safety, high efficiency and the like is constructed for encryption, and signature verification is carried out on signatures; the encryption efficiency is improved; and the function of improving the overall working efficiency of the system is achieved.
Owner:HANGZHOU YUNXIANG NETWORK TECH
TCP search optimization method under high performance calculating network
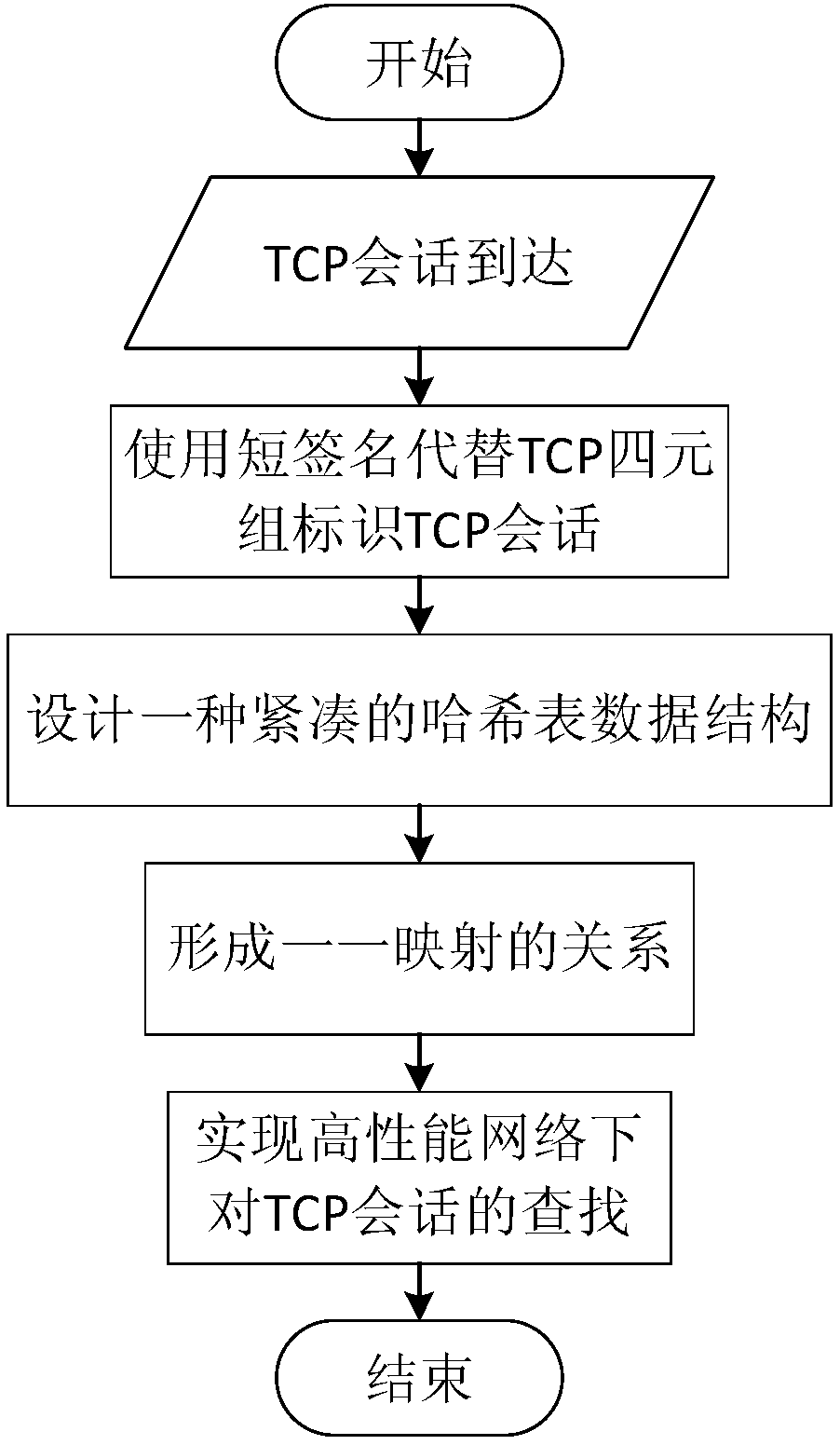
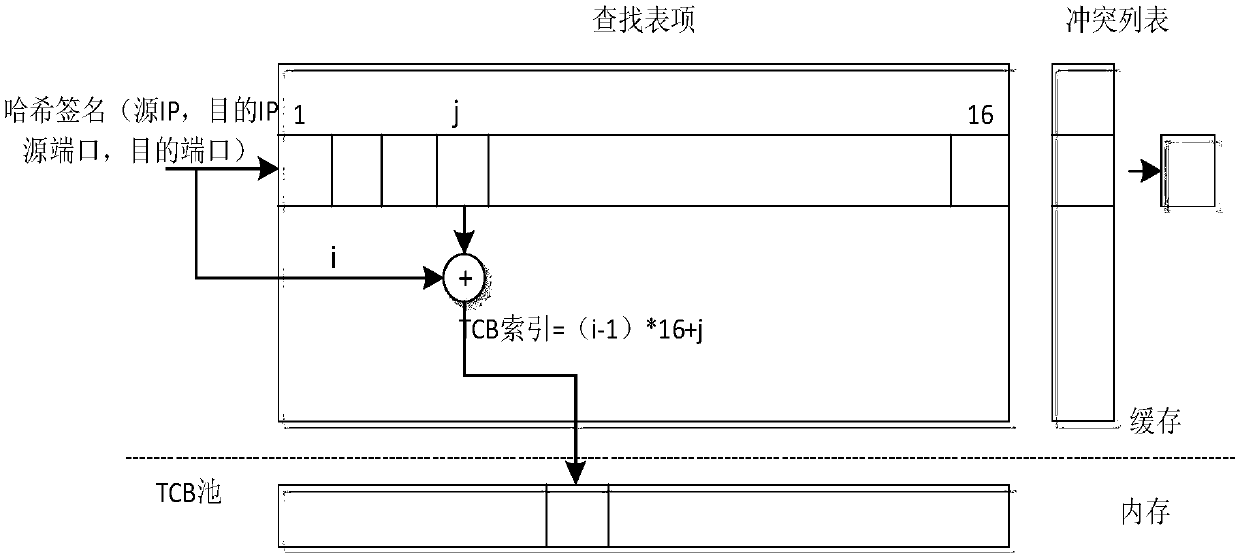
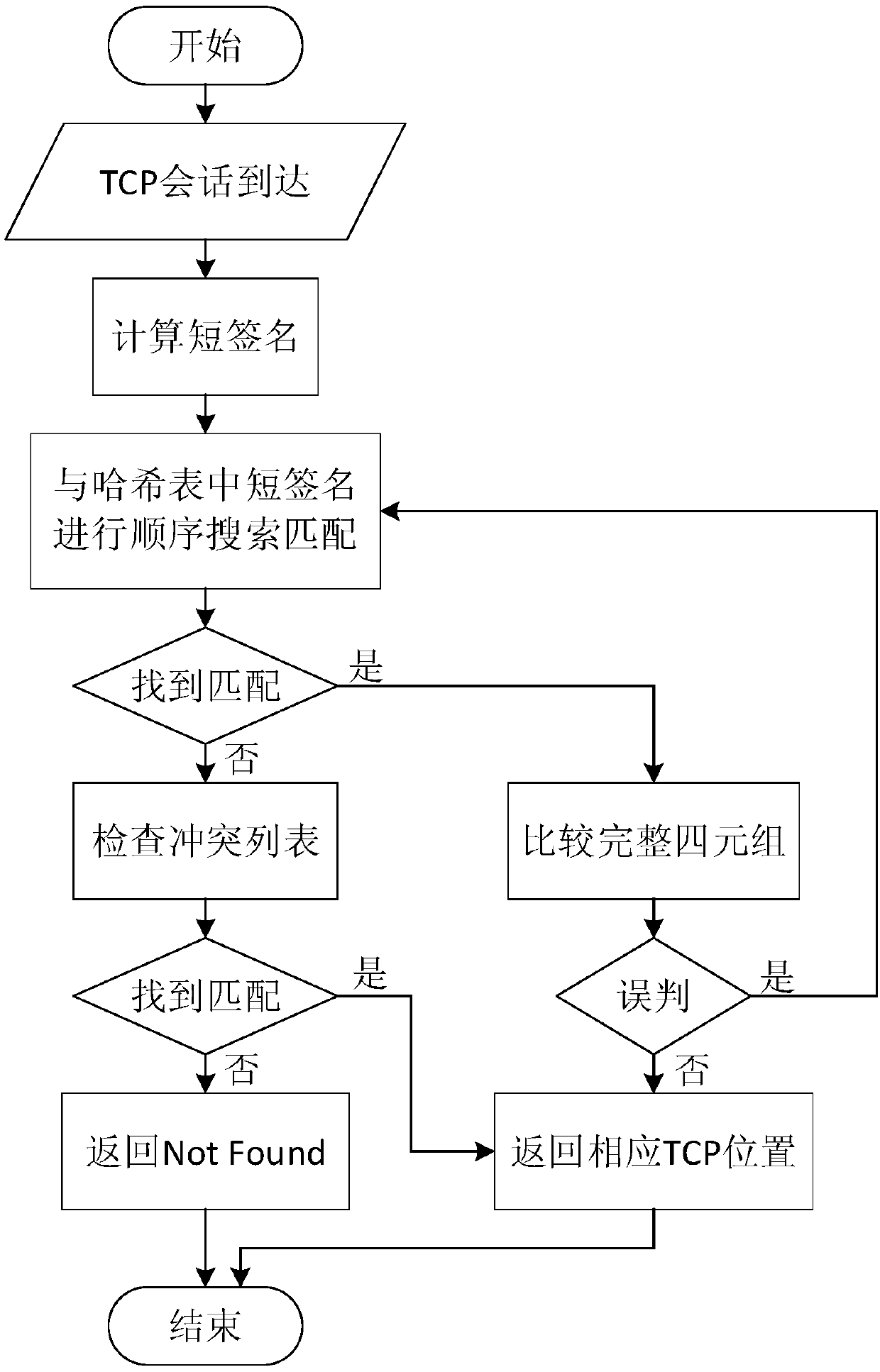
ActiveCN107294855AImprove the ability to handle millions or even billions of TCP sessionsImprove performanceData switching networks16-bitShort signature
The invention discloses a TCP search optimization method under a high performance calculating network; the method comprises the following steps: 1, in TCP conversation processing, preferably calculating TCP conversations to obtain 32-bit short signatures if the TCP conversation order of magnitude is at the million level, carrying out XOR for the front 16-bit and rear 16-bit of the 32-bit short signatures obtained on the previous basis if the TCP conversation order of magnitude is at 100-million level, thus obtaining 16-bit short signatures; 2, respectively using the 32- bit short signatures and the 16-bit short signatures to replace a TCP tetrad identification TCP conversations; 3, building corresponding relations between the front P TCP conversation short signatures and Hash slots one by one; mapping the front P TCP conversation short signatures and Hash slots one by one if arrived TCP conversations exceed P, and assigning the TCP conversation short signatures (starting from P+1) from a TCB pool to a conflict list. The method can reduce the searching taken cache size, and can reduce the Hash conflict probability.
Owner:STATE GRID CORP OF CHINA +3
Systems and methods of aggregate signing of digital signatures on multiple messages simultaneously using key splitting
ActiveUS11171791B2Key distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkInternet privacy
The systems and methods of aggregate signing of digital signatures on multiple messages simultaneously, comprising: receiving two or more digital messages wherein each message is signed using two or more digitally split keys from a private key and the two or more digital signatures of the message using the split key are combined to get a compressed short signature; receiving the compressed short signature for each message; receiving a public key associated with the private key for each message; aggregate signing the messages to output an aggregate signature. The aggregate signature can be further verified against any or all of the messages.
Owner:0CHAIN LLC
System and method for operating system installation on a diskless computing platform
Owner:NVIDIA CORP
Method and equipment for originating and detecting reverse access
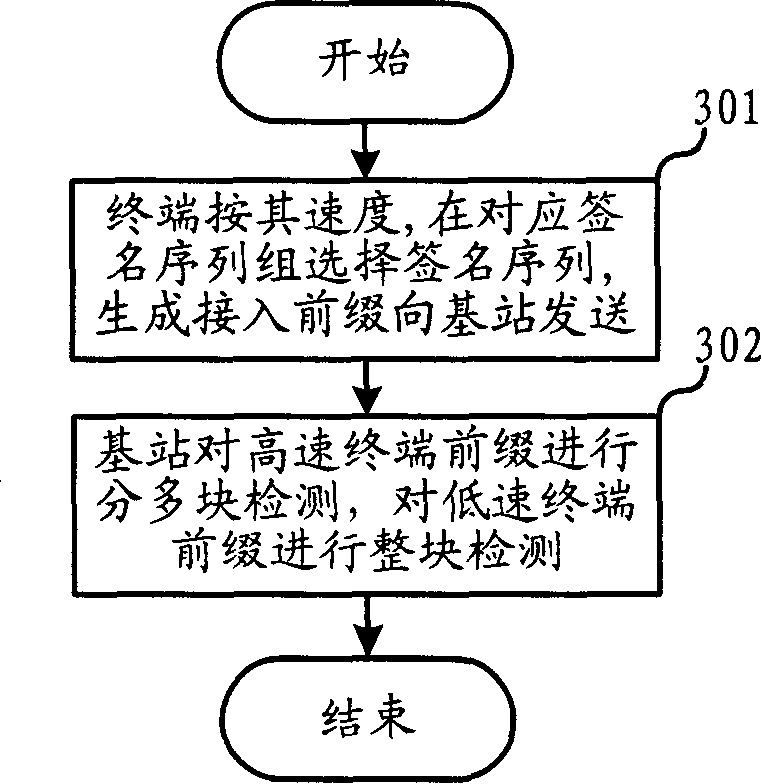
InactiveCN101166362AReduce the probability of packet lossImprove performanceRadio/inductive link selection arrangementsTransmissionLow speedShort signature
The invention improves capability for wireless terminal moved in high speed to reverse access channel. The method groups signature sequences. Different groups of signature sequences are utilized in different speed ranges. Using blocked mode, network side receives signed signature sequence groups in high speed so as to raise performance of reverse access channel. Different blocked modes are utilized to detect groups of signature sequences in different speed ranges. The blocked mode is not utilized for the signature sequence group in lowest speed; and the signature sequence group in higher speed utilizes smaller block. Using only one signature sequence group under one blocked mode carries out correlation detection. Partitioned blocks can be superposed each other. Shorter signature sequence can be selected for wireless terminal closer to base station; and longer signature sequence can be selected for wireless terminal farther to base station.
Owner:STATE GRID CORP OF CHINA +1
Safe and effective cloud data integrity verification scheme with privacy protection
InactiveCN111934880AIntegrity guaranteedGuaranteed privacyUser identity/authority verificationData integritySource Data Verification
The invention relates to a safe and effective cloud data integrity verification scheme with privacy protection, and aims to solve the problems of integrity, privacy and the like of current cloud storage data by adopting technical means such as digital short signature, bilinear mapping, zero knowledge proof and the like. When a data owner interacts with the cloud server, the data owner C generatesa secret key pair, carries out technical processing on own data and carries out digital signature to generate an identifier identifier. After uploading the data and the identifier to a cloud server S,the data owner C requests a third-party verifier TPA to verify own data. The TPA sends out a challenge to verify whether the data is complete, and S generates a response proof according to the challenge. And finally, the TPA verifies and proves whether the data is correct or not, and the TPA cannot obtain any private information in the data verification process. Therefore, the integrity and the privacy of the method are strongly guaranteed.
Owner:BEIHANG UNIV
Contact person tracking privacy protection method based on aggregation signature
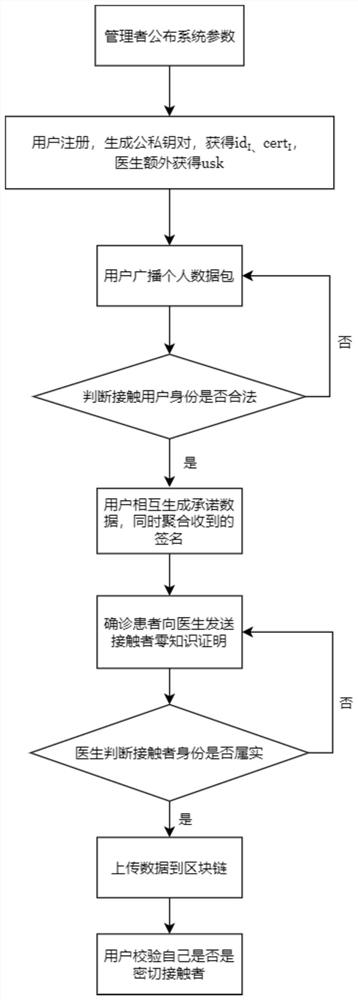
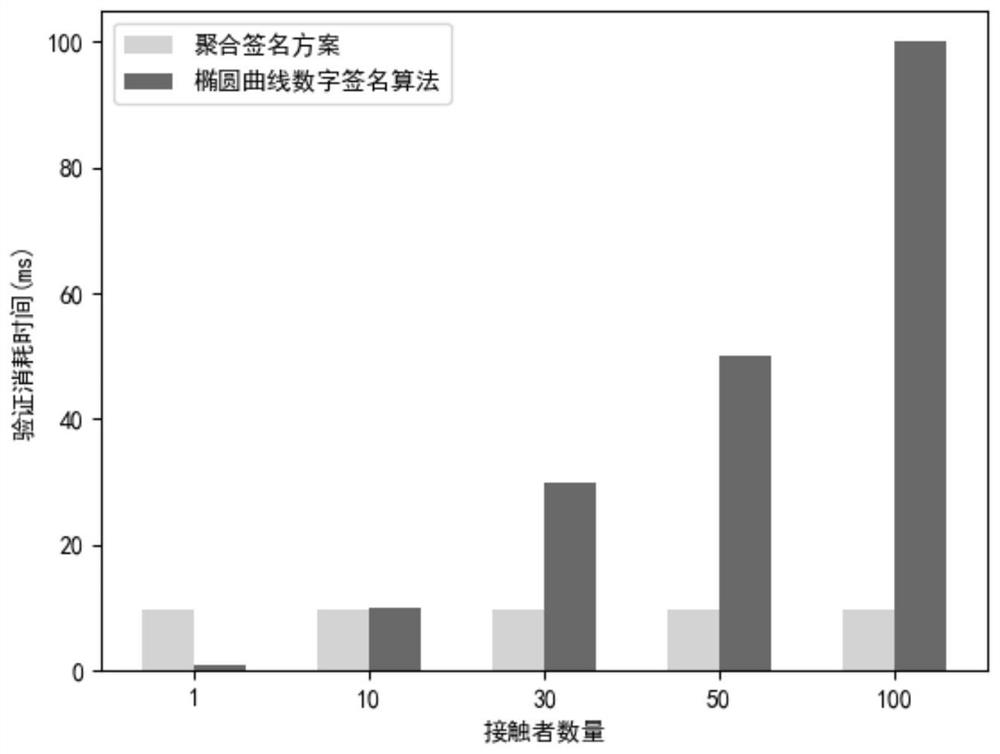
ActiveCN113395691ASave storage spacePrevent Identity LeakageUser identity/authority verificationSecurity arrangementData packPrivacy protection
The invention discloses a contact person tracking privacy protection method based on an aggregation signature. The method specifically comprises the steps: firstly, generating public and private key pairs of a manager, a user and a doctor; the user broadcasts the hash value of the personal data packet, and when the users meet, whether the opposite side is a legal user is authenticated; after the authentication succeeds, mutual commitments are generated among the users; the user aggregates the signatures of the data packets of other users stored in the commitment process into a single short signature; then, the diagnosers create respective false identities for the contact persons of the diagnosers; the diagnoser sends the false identity information to the doctor, and after the doctor verifies the identity of the contact person, a group signature is generated, and the data packet is uploaded to the block chain; the doctor reports a definite diagnosis state of the user to a manager; and finally determining a close contact person. By adopting the aggregation signature technology, the local storage space of the user is saved, the privacy of the contact person can be protected by the aggregation zero-knowledge proof generated by the diagnoser to the contact person. Meanwhile, the identity authentication speed of the doctor to the contact person can be increased.
Owner:XI'AN POLYTECHNIC UNIVERSITY
A processing method and system for performing short ciphertext signatures on invoices
ActiveCN108268779BAchieve self-controlEnsure safetyDigital data protectionBilling/invoicingCiphertextData information
Owner:AEROSPACE INFORMATION
Trusted authentication and safe access control method of MPLS network
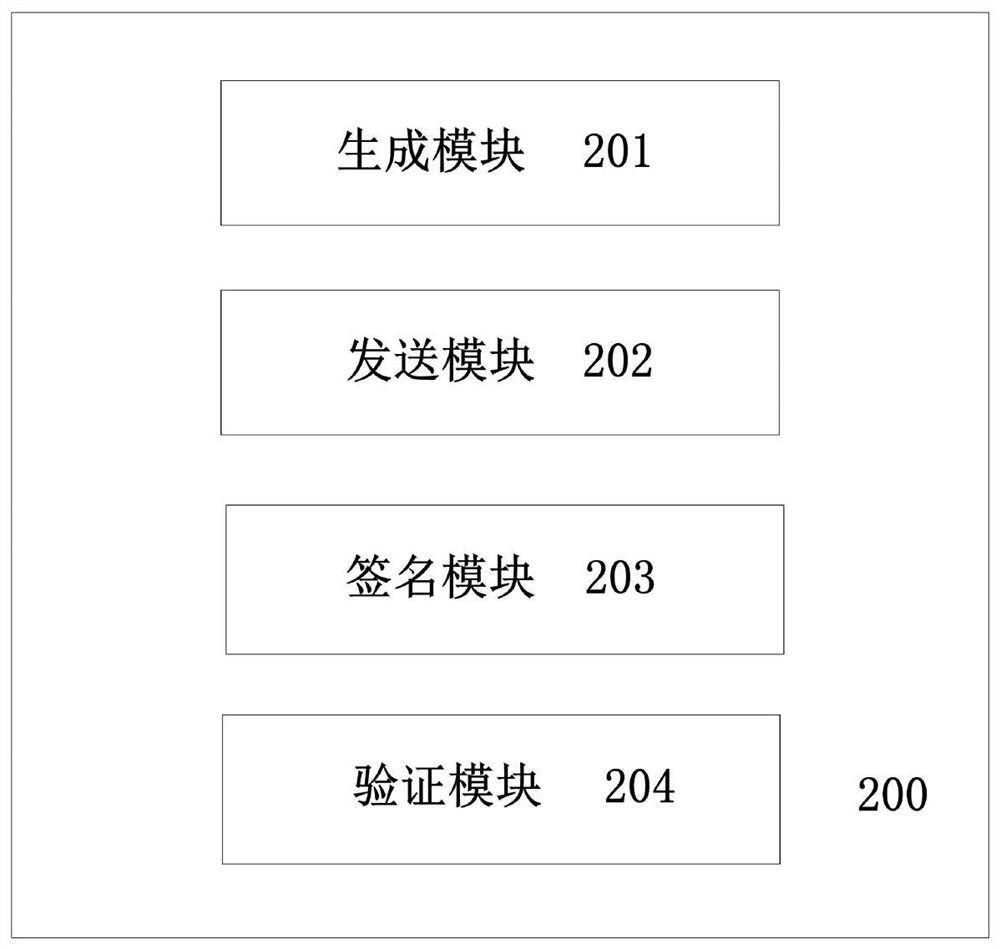
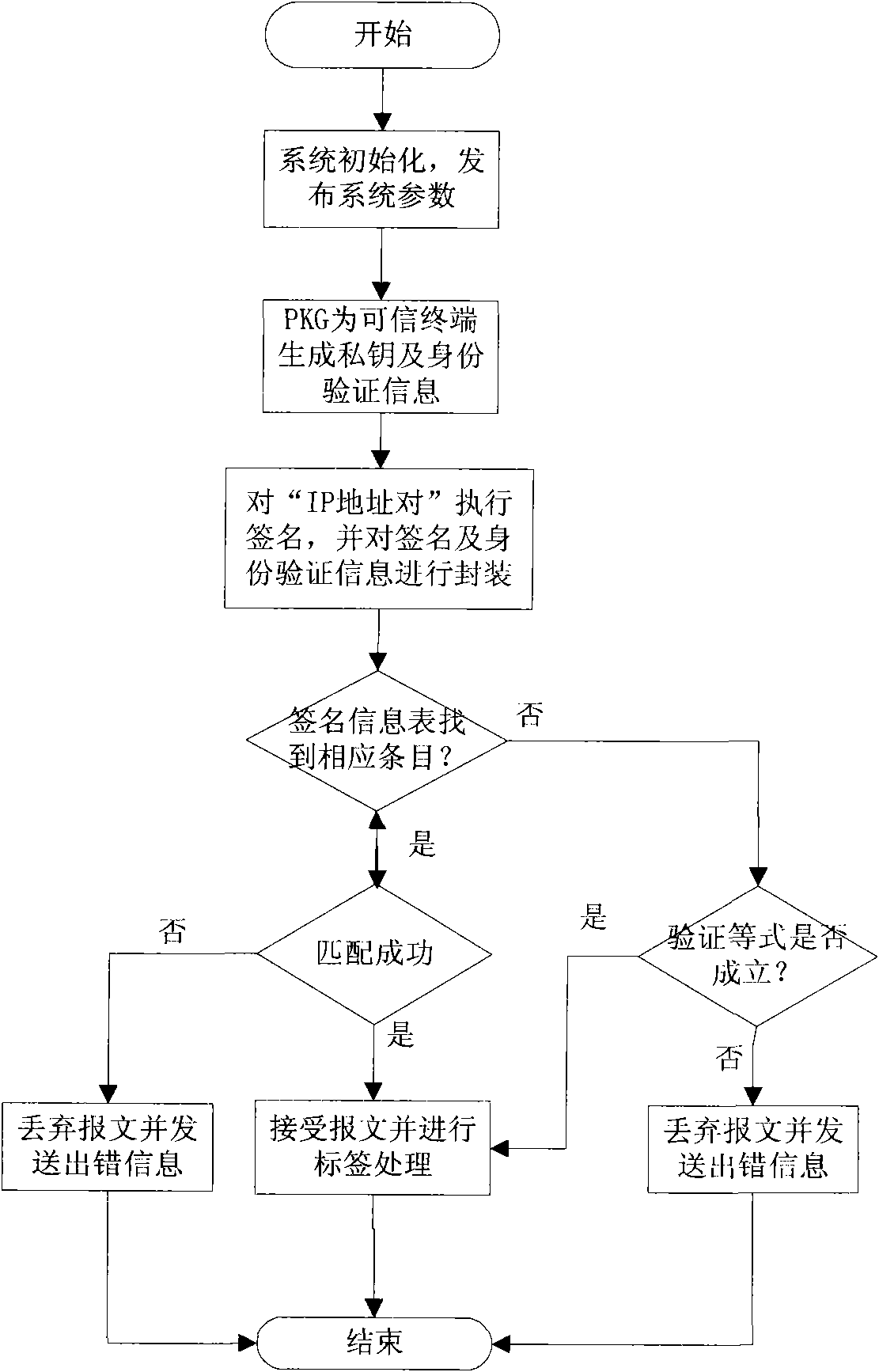
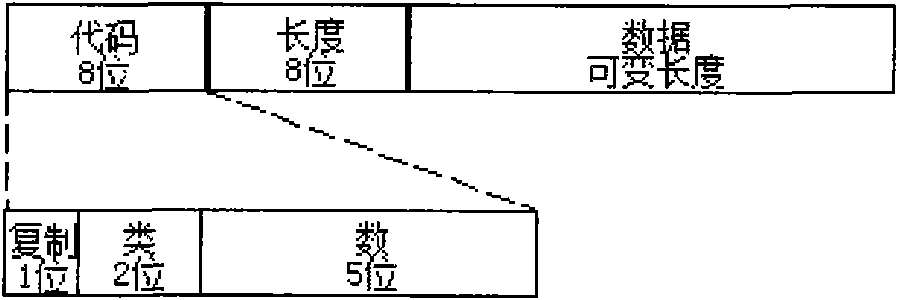
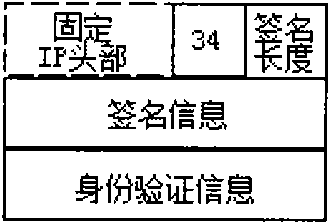
InactiveCN101977189BShort signatureReduce computational overheadUser identity/authority verificationNetwork terminationTTEthernet
The invention discloses a trusted authentication and safe access control method of an MPLS network, which realizes the trusted authentication and safe access control of the MPLS network and improves the credibility of Internet backbone. The method comprises four parts as follows: microcode implementation of digital short signature, microcode implementation of IP head signature option format, microcode implementation of signature verification based on IP address pair and TCAM design of signature information table. The method comprises the following steps that: the terminal node signs for source target IP address pair and packages signature associated information in the option field of the IP head; and verification of the signature is implemented through microcode design on a network processor, wherein the signature information table stores and searches based on TCAM technology. The invention is adapted to access control to MPLS backbone networks by various wire park networks, government affairs networks, campus networks and network terminal nodes such as wireless Mesh and WLAN. As an effective and practical technical scheme, the method has good application prospect.
Owner:QINGHAI NORMAL UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com