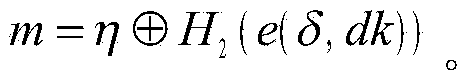Authenticable asymmetrical group secret key negotiation method in mobile unbalanced network
An unbalanced network and secret key negotiation technology, which is applied in the field of secure group secret key negotiation schemes and certifiable asymmetric group secret key negotiation schemes, and can solve problems such as large amount of calculation and unsuitable communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
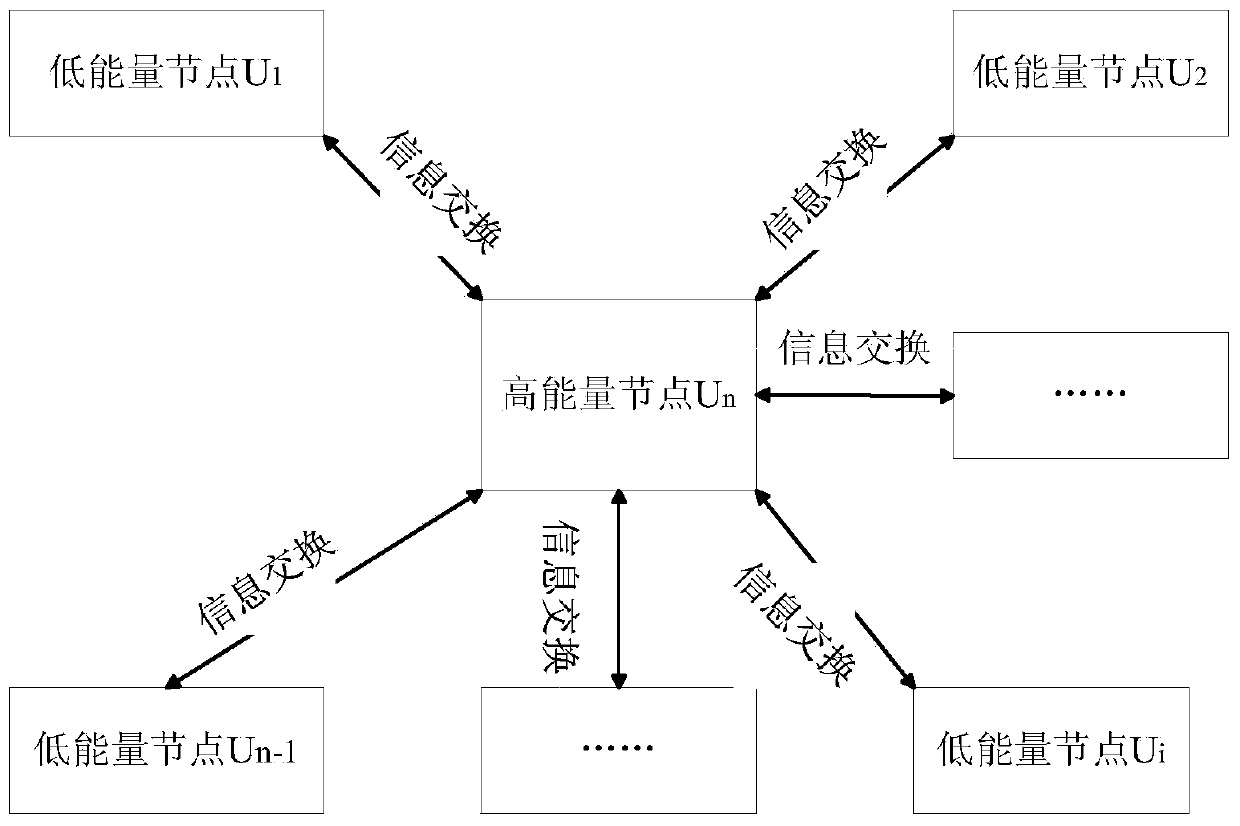
[0065] In this embodiment, the unbalanced mobile network consists of a high-energy node and multiple low-energy nodes, such as figure 1 shown. The resources of low-energy nodes are limited, and the amount of calculation and communication should be reduced as little as possible. High-energy nodes have more resources, and they share as much computing and communication traffic as possible for low-energy nodes. Group key negotiation can be divided into two stages: one is identity authentication before negotiation, and the other is group key negotiation.
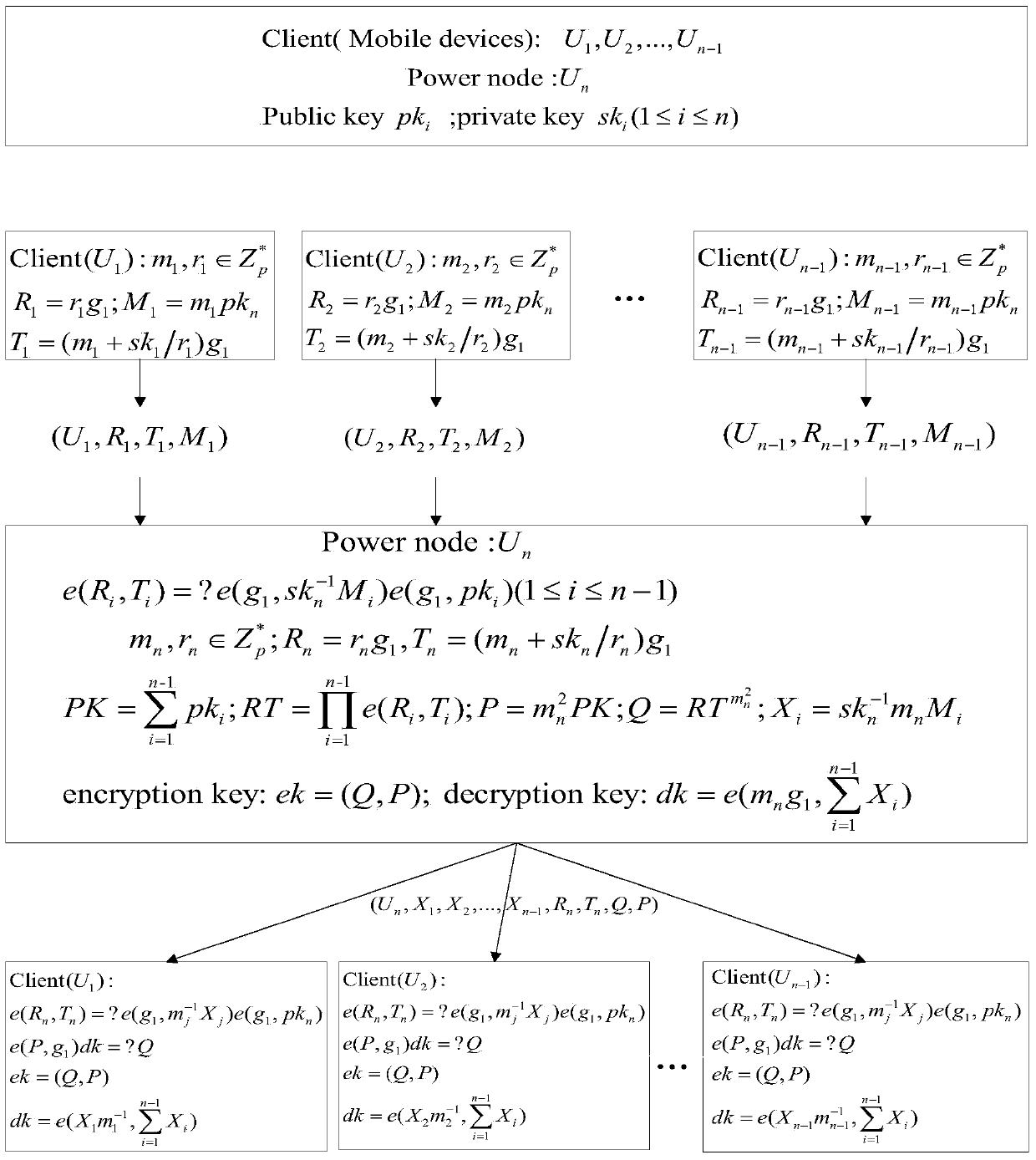
[0066] Such as figure 2 As shown, this embodiment implements the authentication of the asymmetric group key negotiation in the mobile unbalanced network according to the following steps.
[0067] 1. Signature and authentication of group members
[0068] A) Initialize the system
[0069] Suppose the group has 8 members U i (1≤i≤8), where U 8 is a high-energy node, and pk i (pk i =sk i g 1 ) is a group member U i (1≤...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com