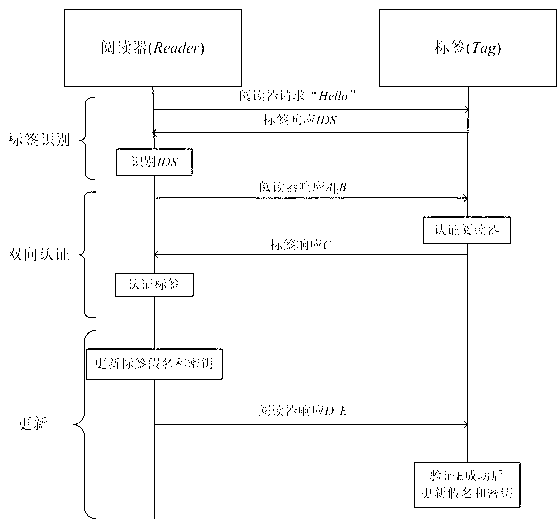
RFID (radio frequency identification) mutual authentication protocol method
A two-way authentication and protocol technology, which is used in collaborative devices, user identity/authority verification, instruments, etc., and can solve the problems of large storage space for tags, no forward security, weak authentication and data integrity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention and its advantages will be further described below in conjunction with the accompanying drawings and its embodiments.
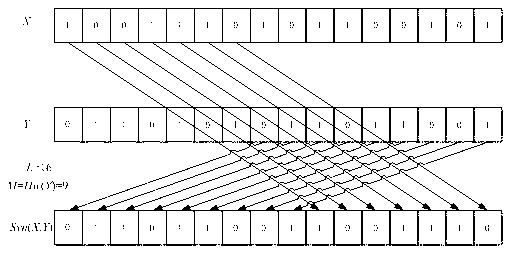
[0034] In order to be suitable for low-cost labels, the present invention newly defines word synthesis operation Syn ( X , Y ): Syn ( X , Y ) by the array Y after the M Bit and X before L - M made up of bits L A new array of bits. in X , Y Two binary arrays required for word synthesis operations, , , ;one of them M set as: M=Hw ( Y ), can also be M = L - hw ( Y );or M = hw ( X ), can also be M = L - hw ( X );or M = HD ( X , Y ), can also be M = L - HD ( X , Y ); hw ( X )for X The Hamming weight of hw ( Y ) for Y The Hamming weight, HD ( X , Y )for X and Y The Hamming distance of .
[0035] For example, take L =16, set X =1001110101100101, Y =0110101011011001, set M = hw ( Y )=9, then according to the above word synthesis operation, get Syn ( X , Y )=01101...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com