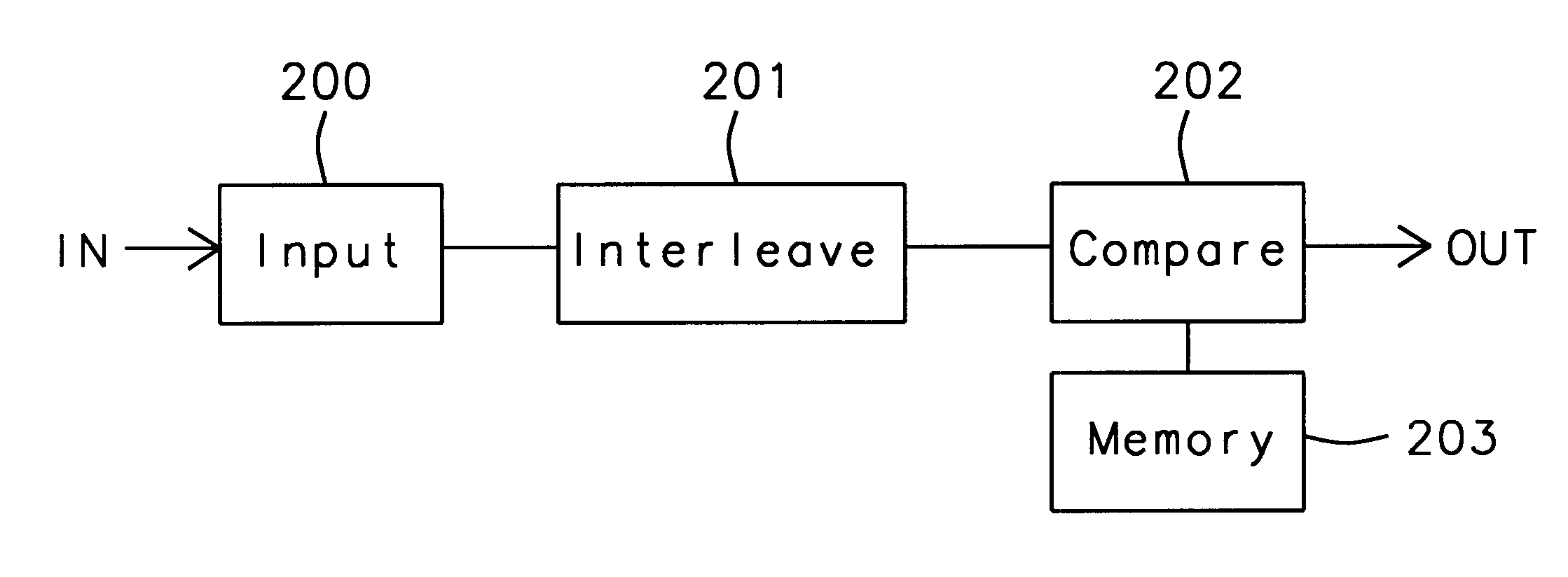
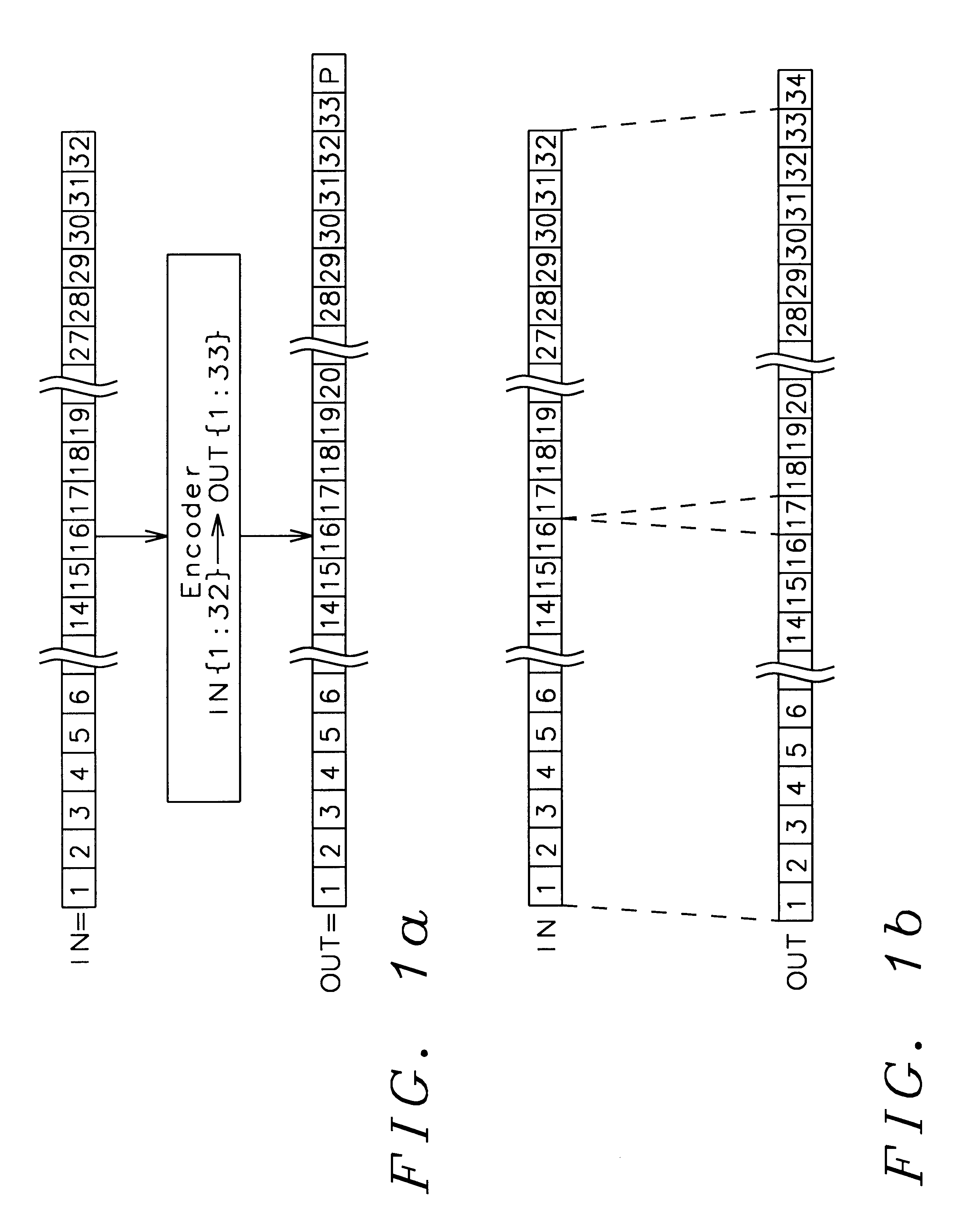
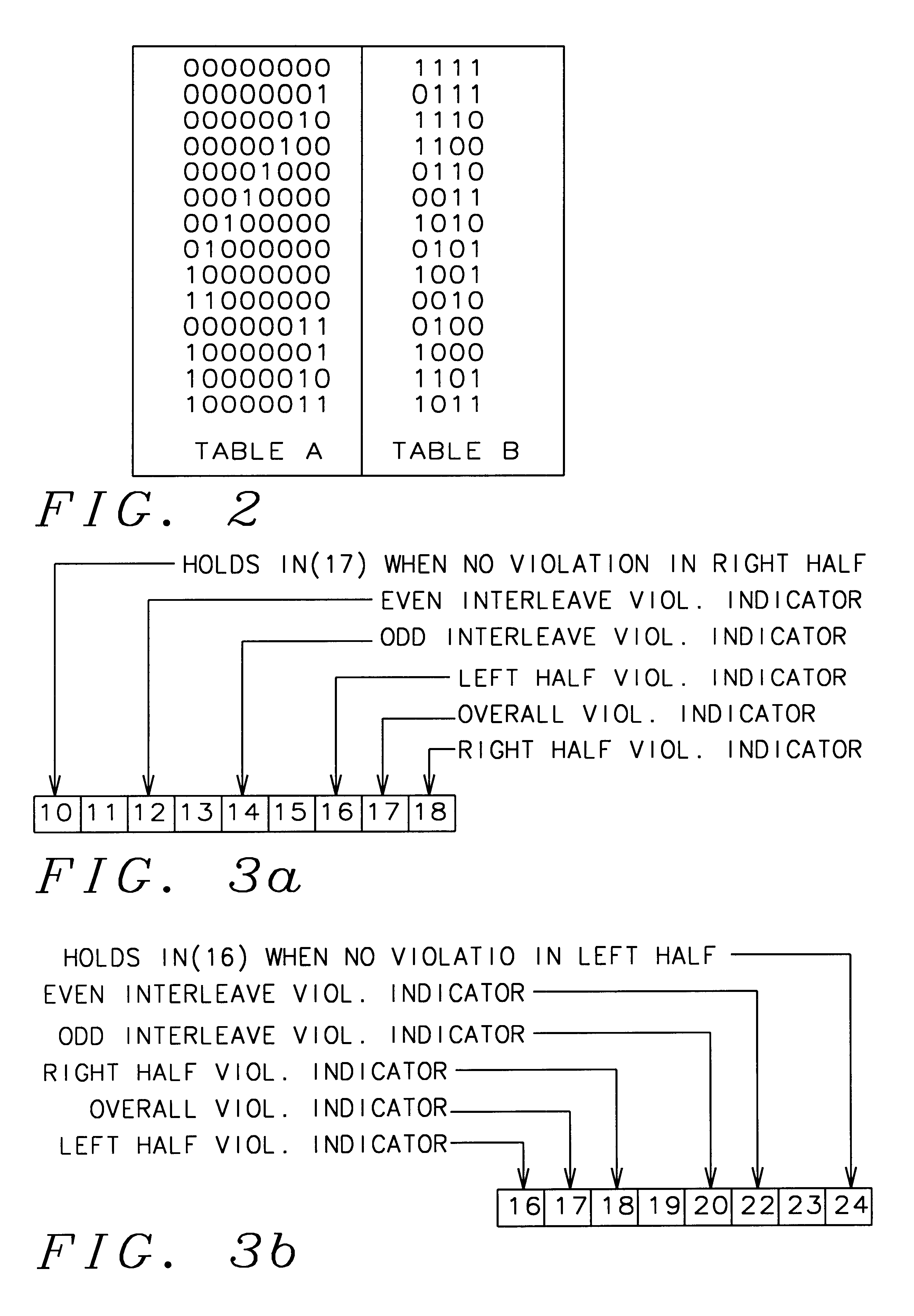
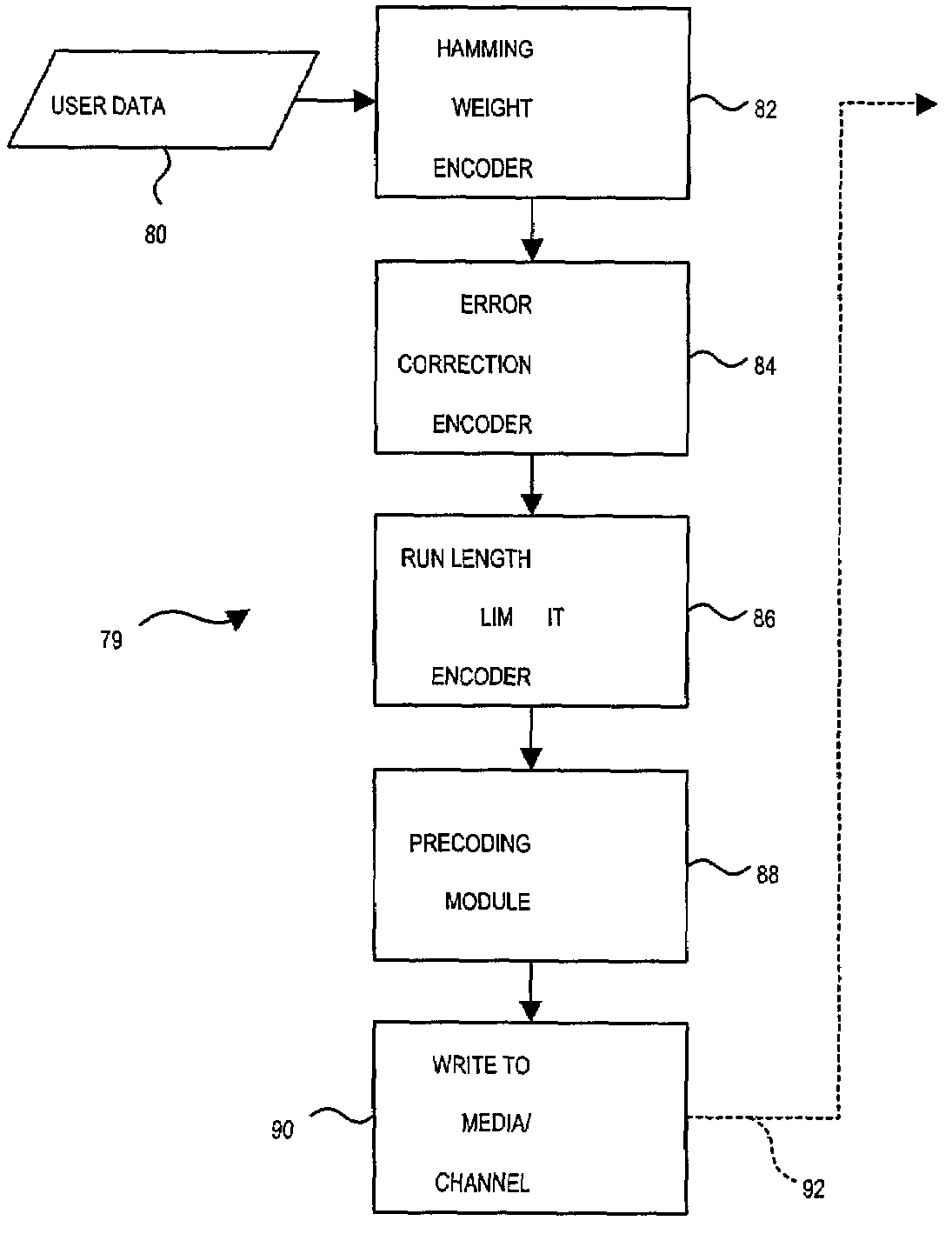
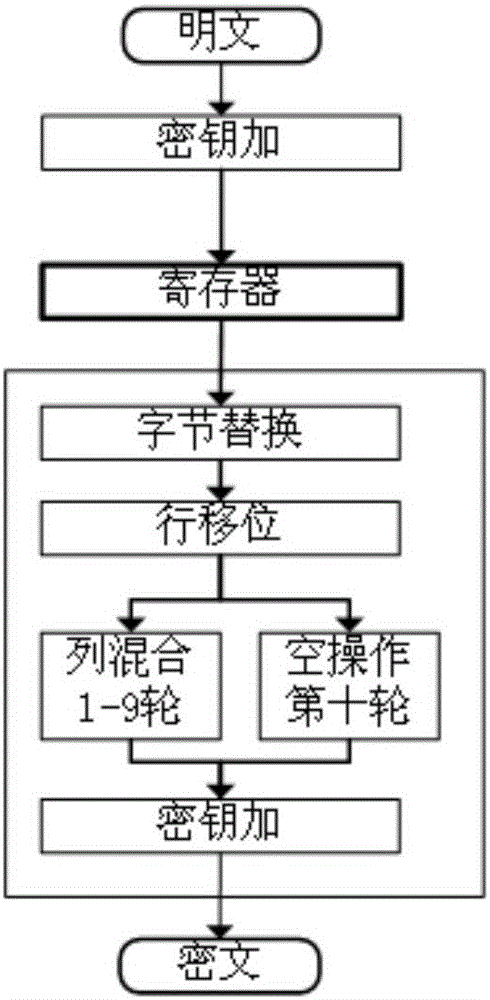
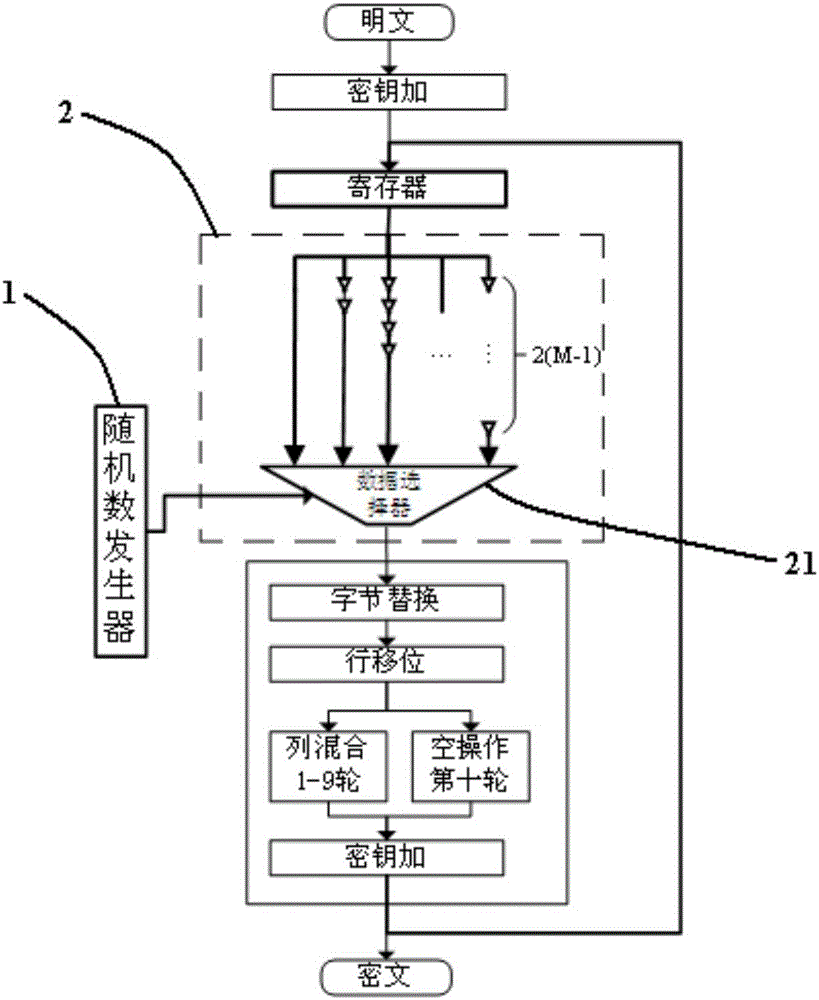
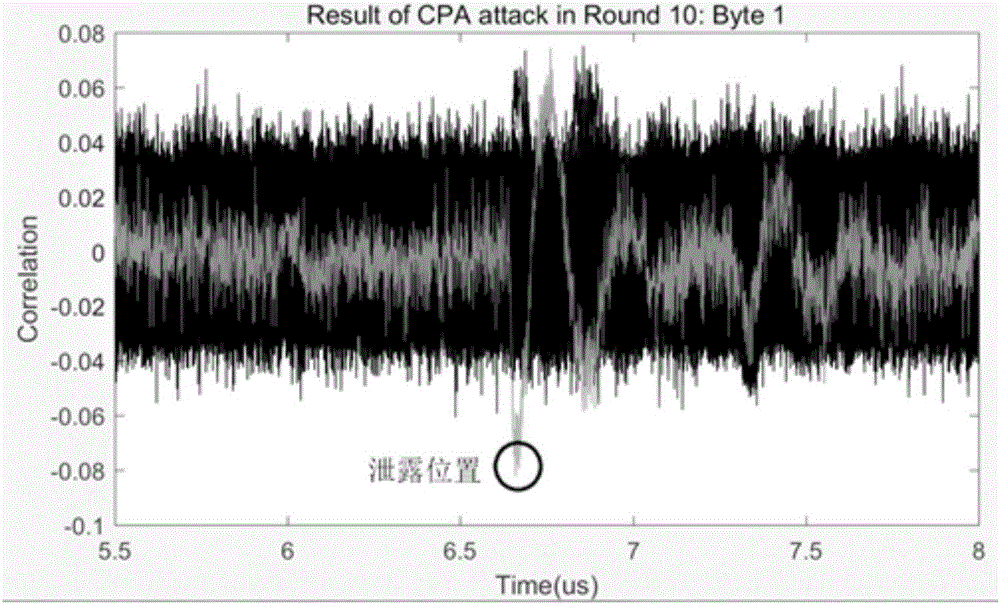
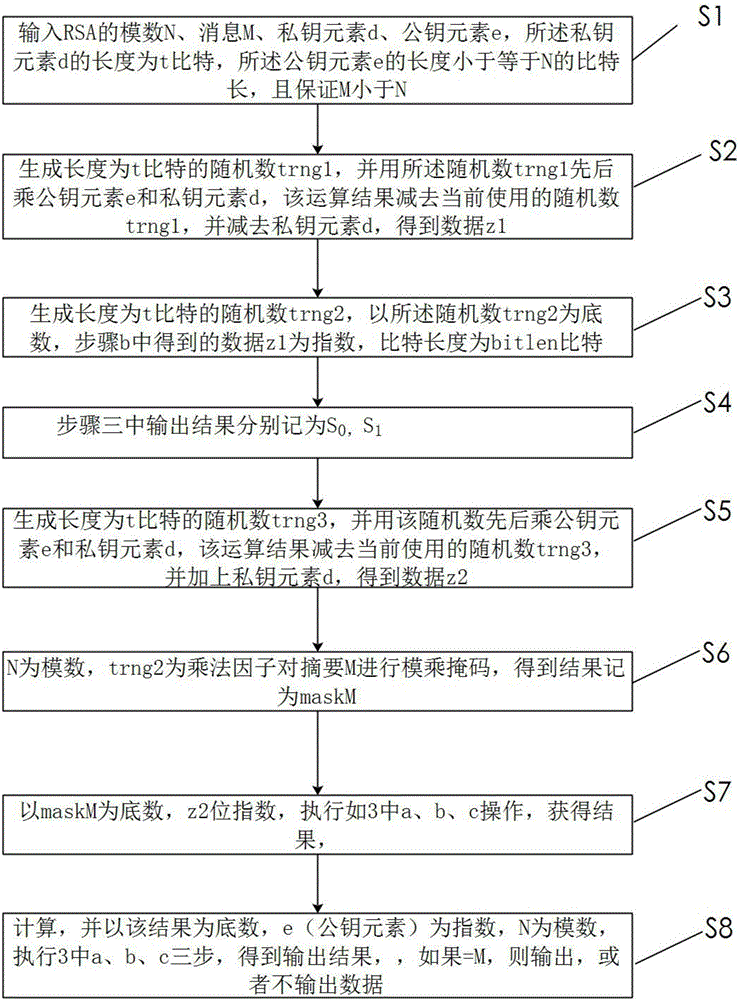
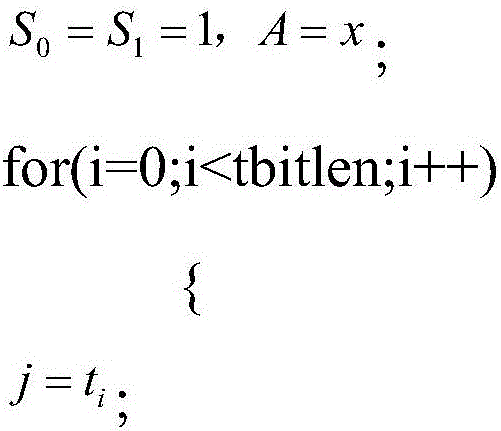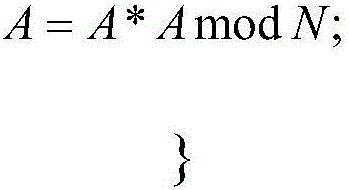Patents
Literature
115 results about "Hamming weight" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Hamming weight of a string is the number of symbols that are different from the zero-symbol of the alphabet used. It is thus equivalent to the Hamming distance from the all-zero string of the same length. For the most typical case, a string of bits, this is the number of 1's in the string, or the digit sum of the binary representation of a given number and the ℓ₁ norm of a bit vector. In this binary case, it is also called the population count, popcount, sideways sum, or bit summation.
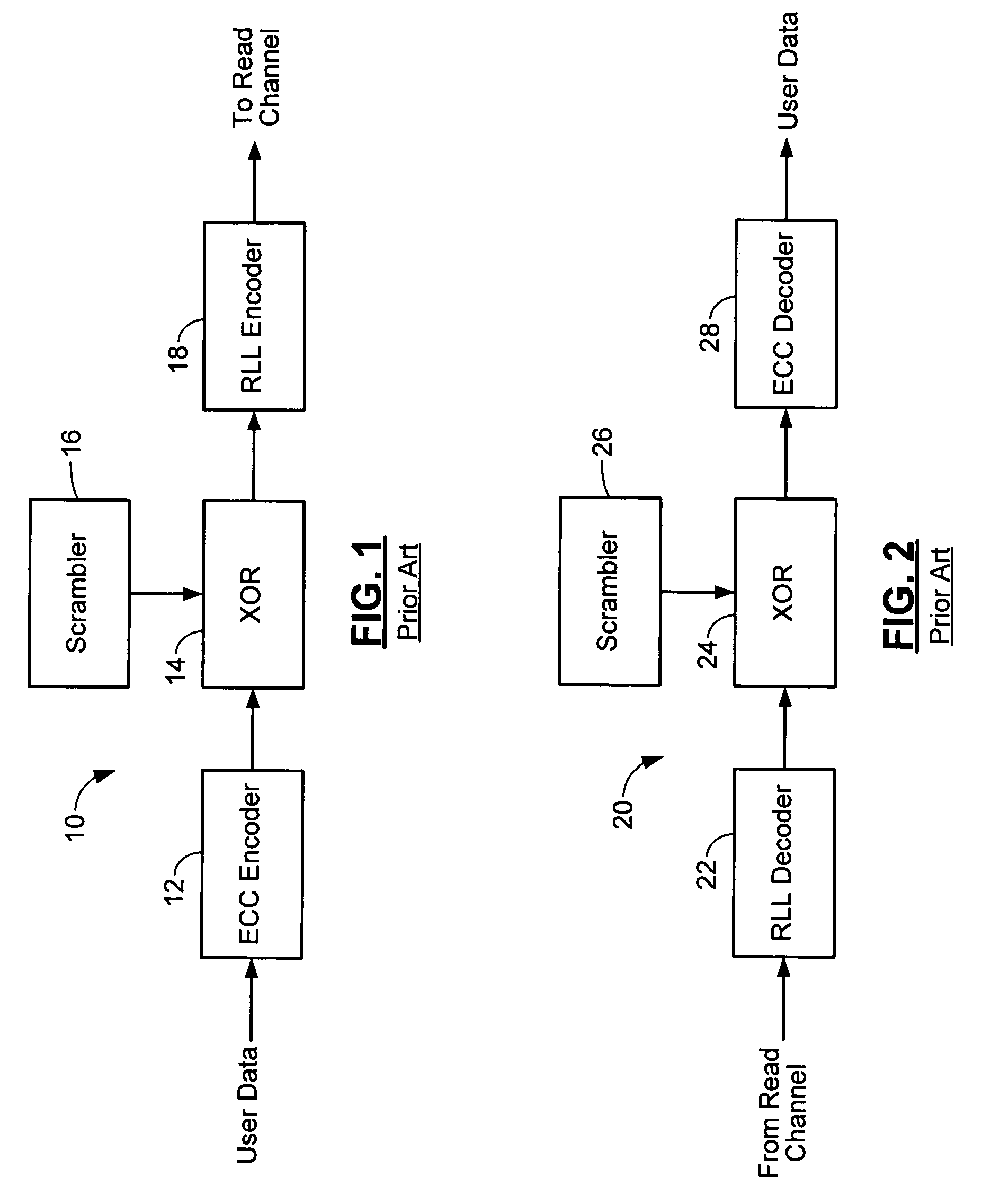
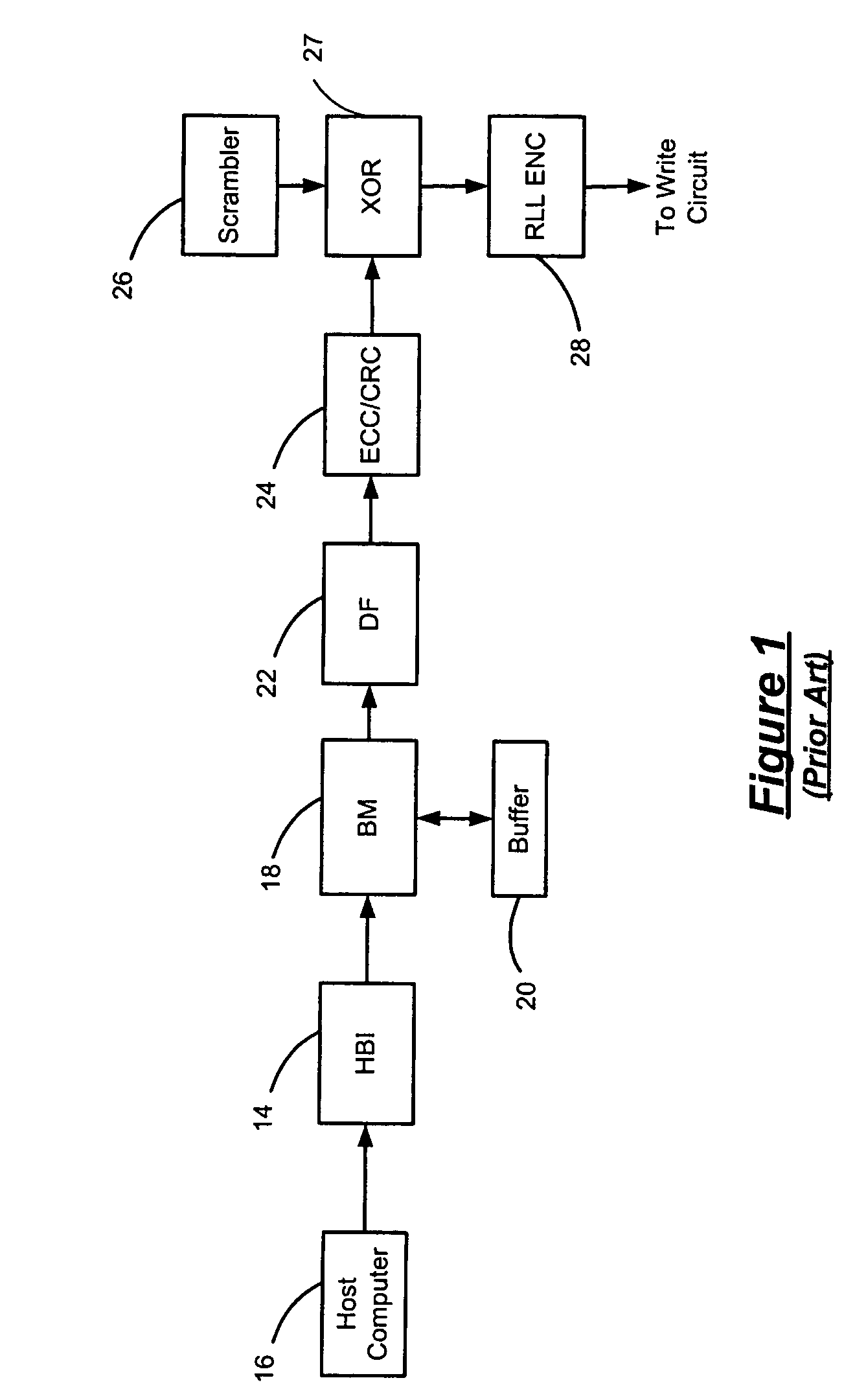
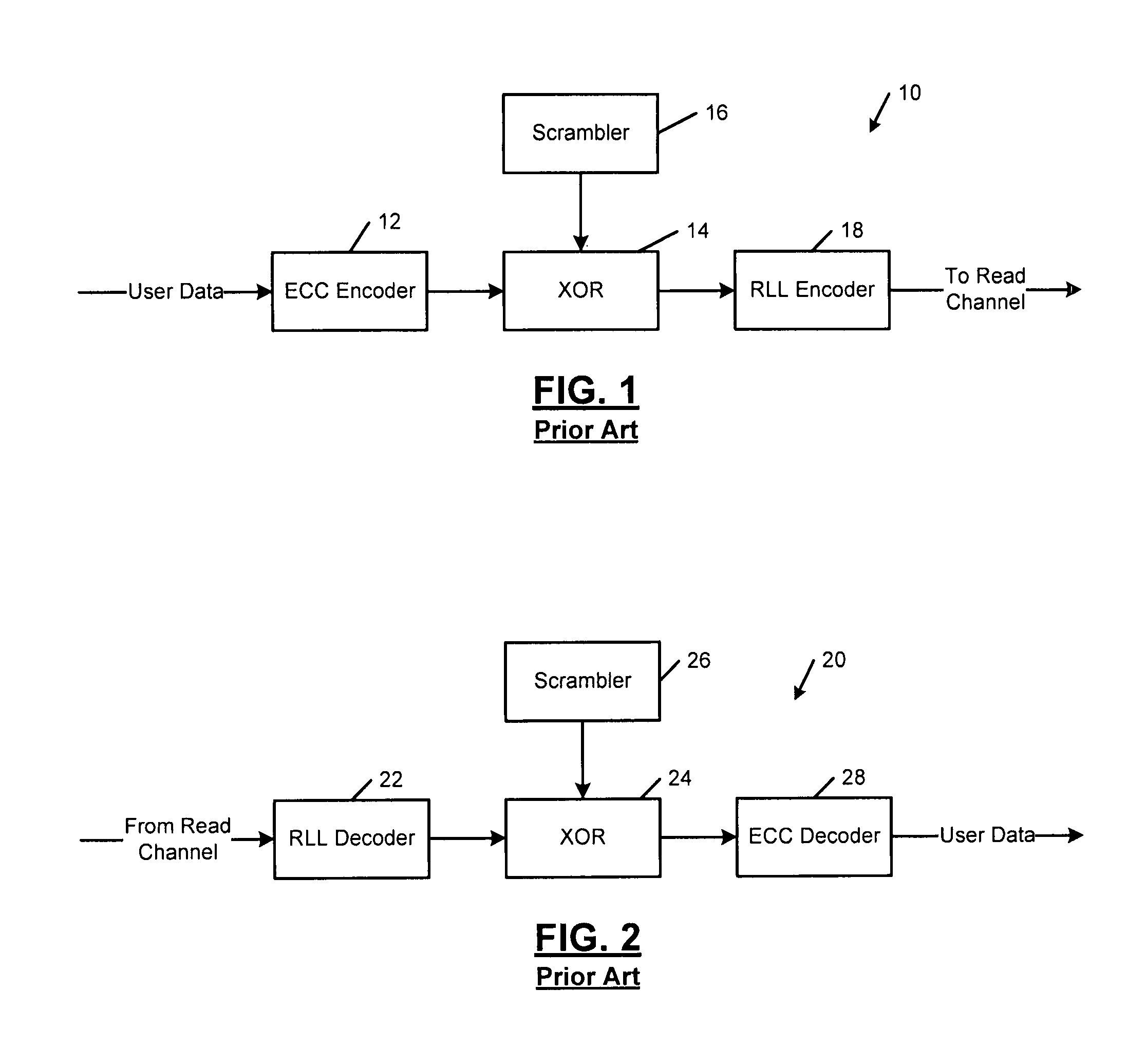
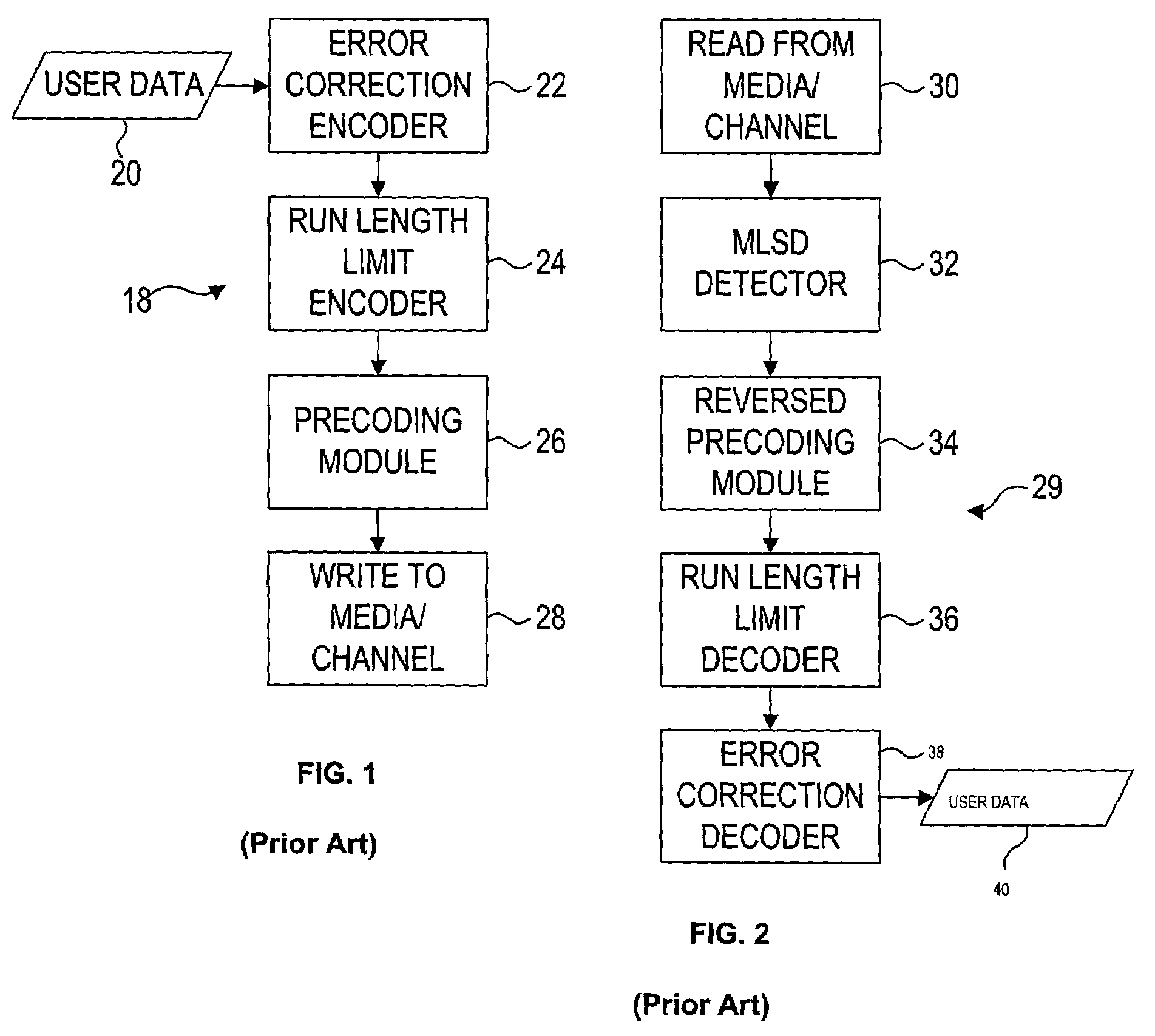
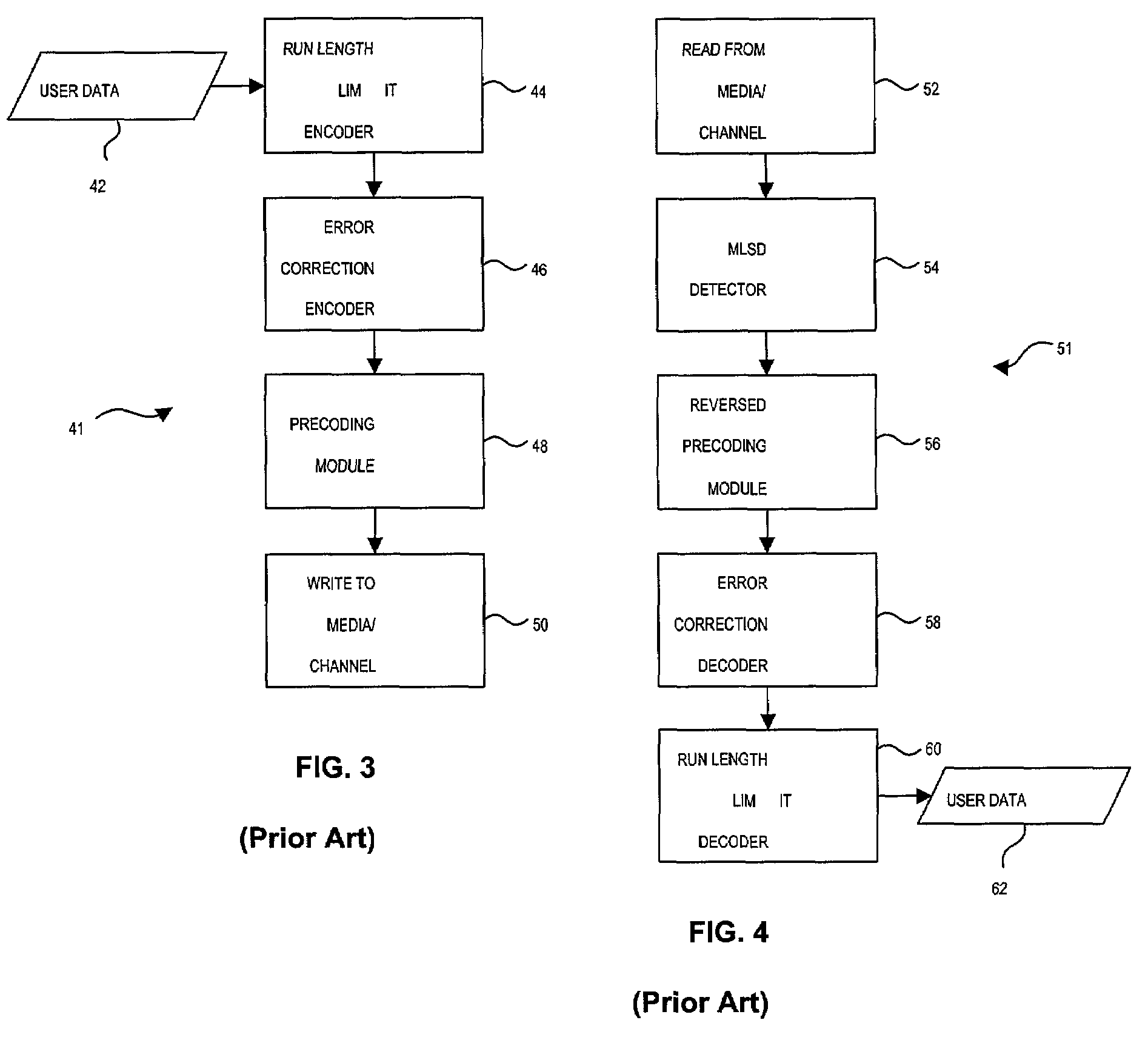
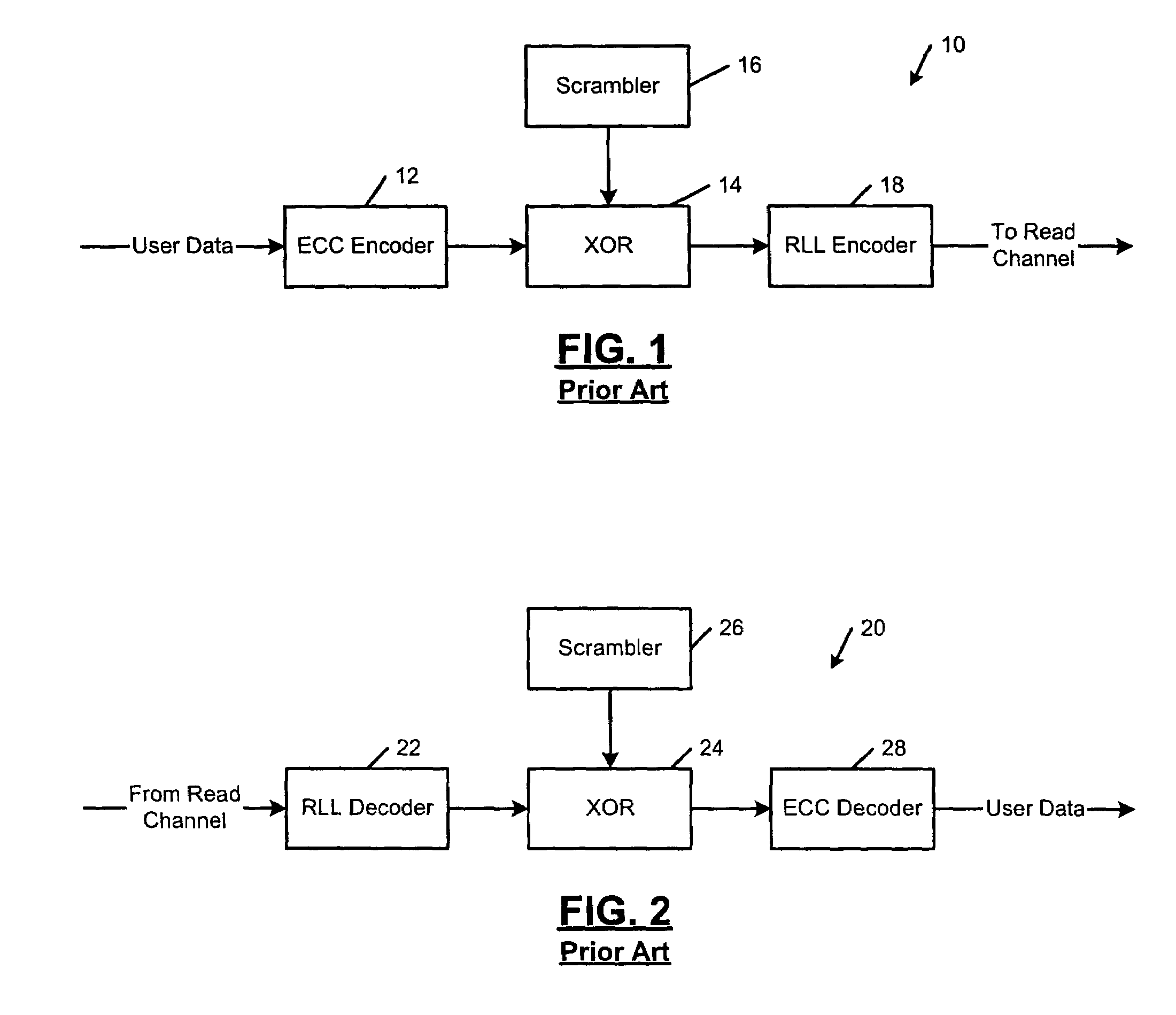
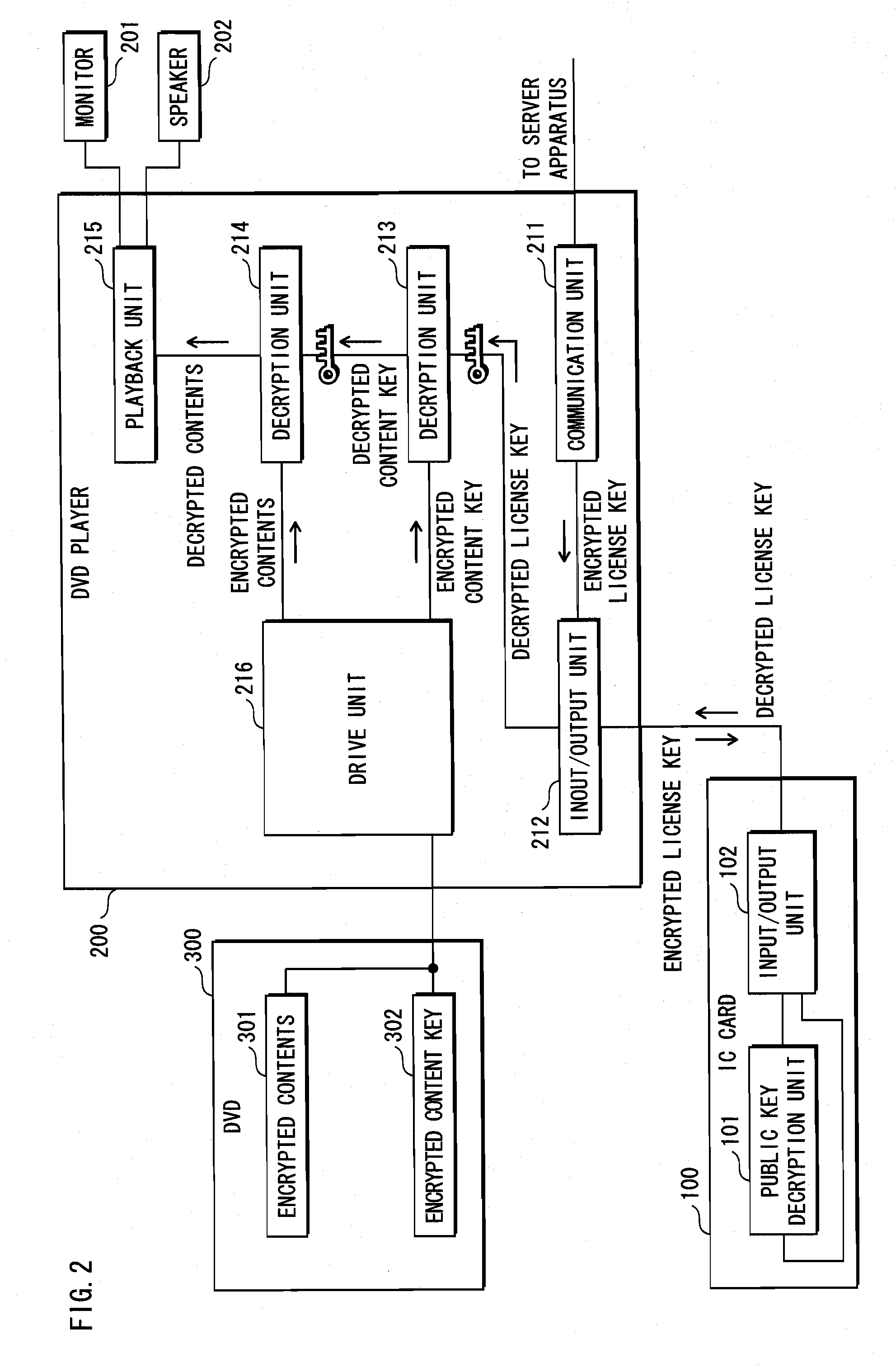
Ring arithmetic method, system, and apparatus
ActiveUS20030044004A1Public key for secure communicationData switching by path configurationComputer scienceBit numbering
A data encryption method performed with ring arithmetic operations using a residue number multiplication process wherein a first conversion to a first basis is done using a mixed radix system and a second conversion to a second basis is done using a mixed radix system. In some embodiments, a modulus C is be chosen of the form 2w-L, wherein C is a w-bit number and L is a low Hamming weight odd integer less than 2(w-1) / 2. And in some of those embodiments, the residue mod C is calculated via several steps. P is split into 2 w-bit words H1 and L1. S1 is calculated as equal to L1+(H12x1)+(H12x2)+ . . . +(H12xk)+H1. S1 is split into two w-bit words H2 and L2. S2 is computed as being equal to L2+(H22x1)+(H22x2)+ . . . +(H22xk)+H2. S3 is computed as being equal to S2+(2x1+ . . . +2xk+1). And the residue is determined by comparing S3 to 2w. If S3<2w, then the residue equals S2. If S3>2w, then the residue equals S3-2w.
Owner:NCIPHER LIMITED ACTING BY & THROUGH ITS WHOLLY OWNED SUBSIDIARY NCIPHER +1
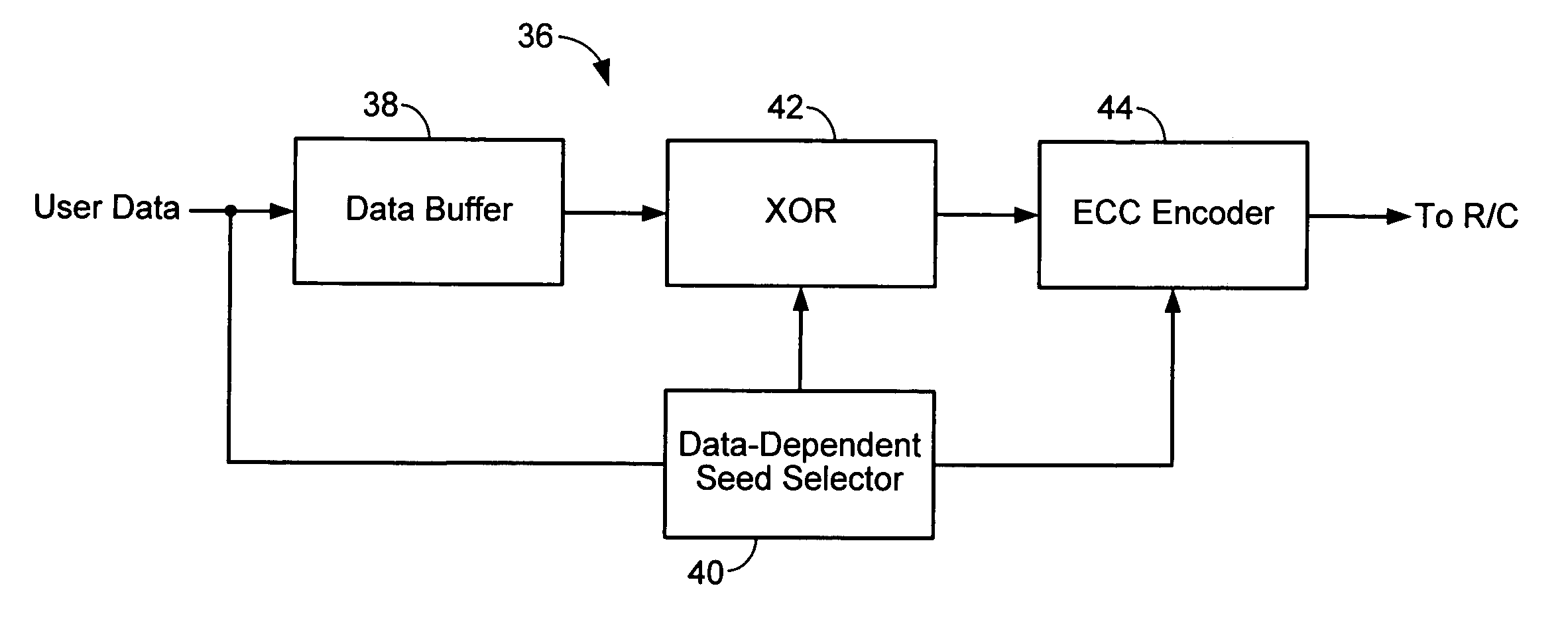
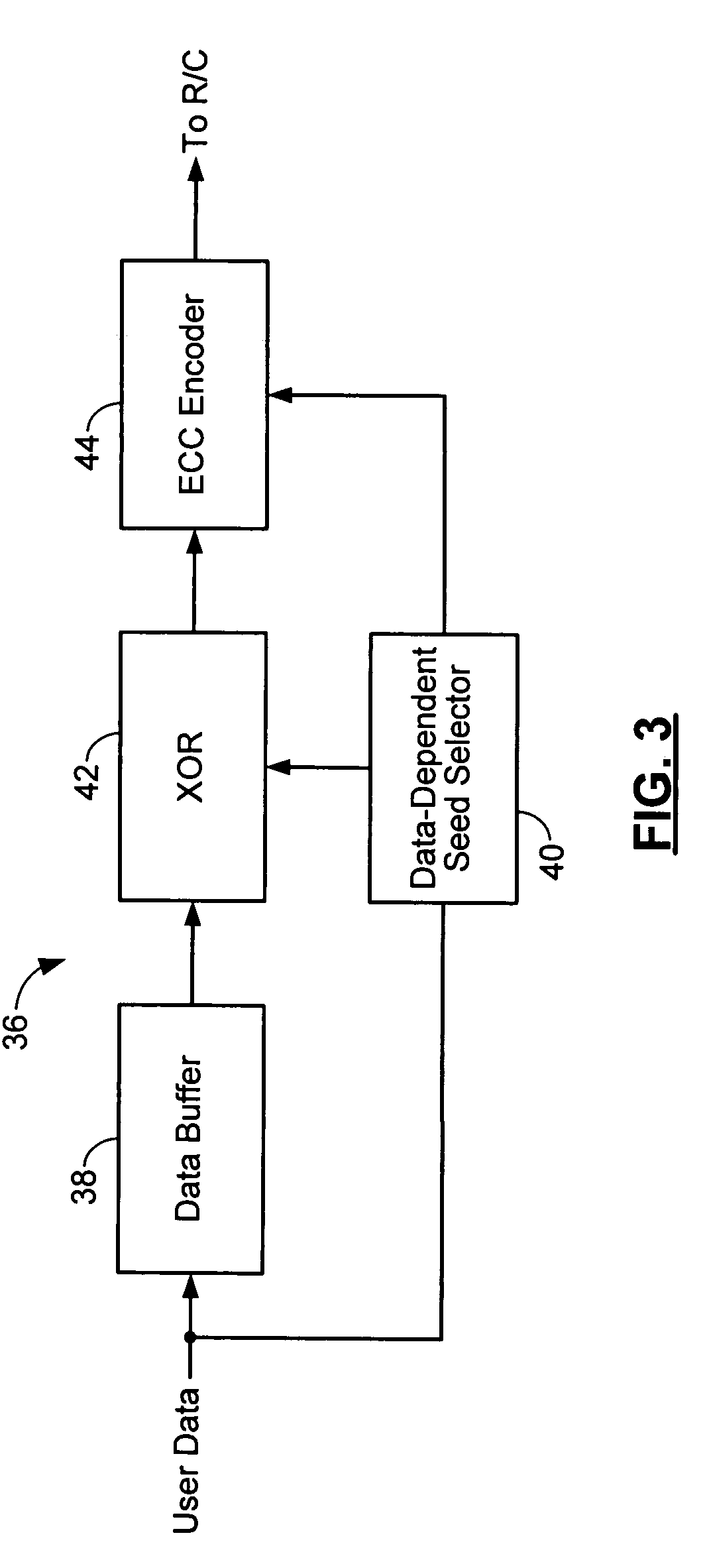
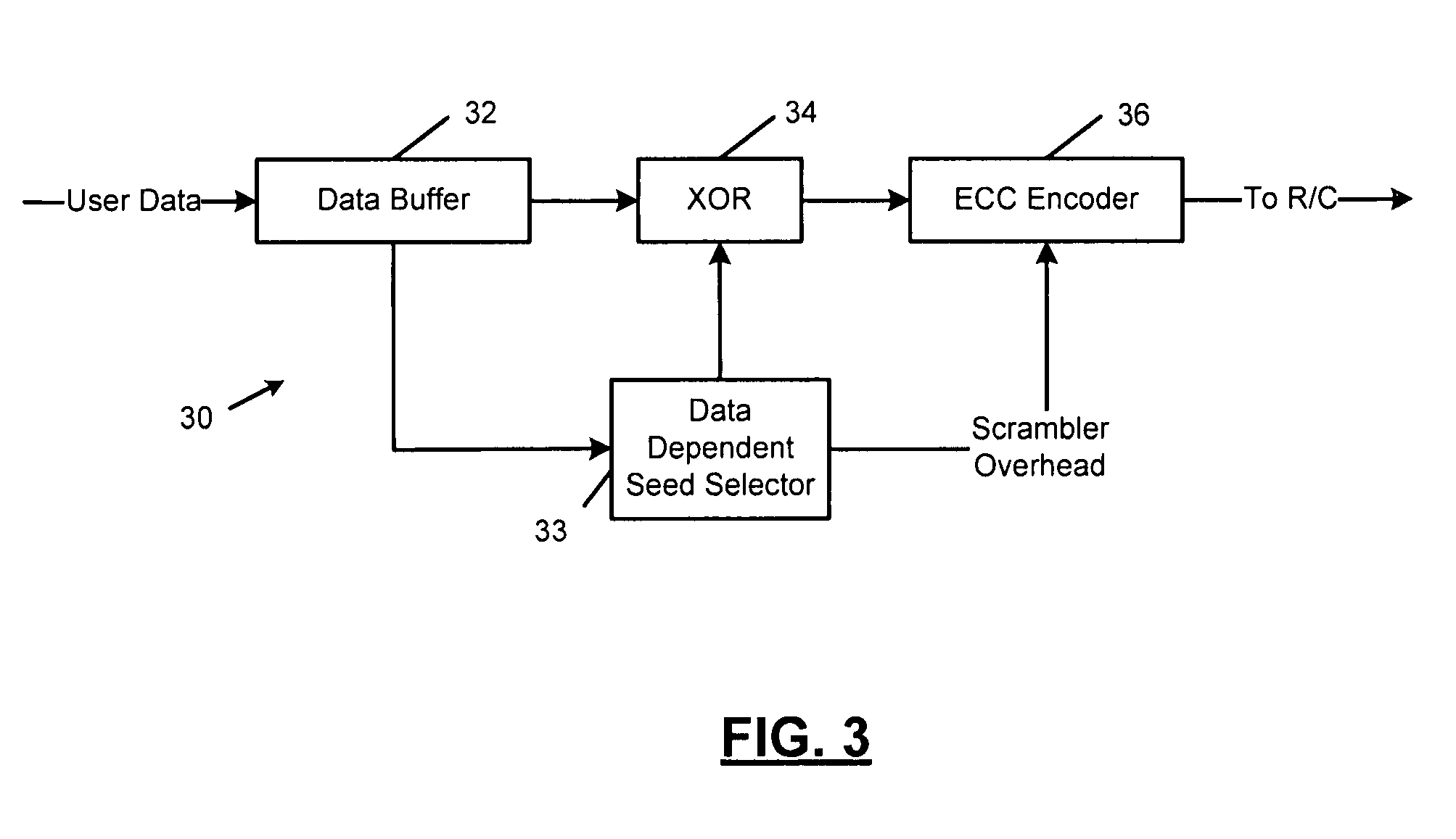
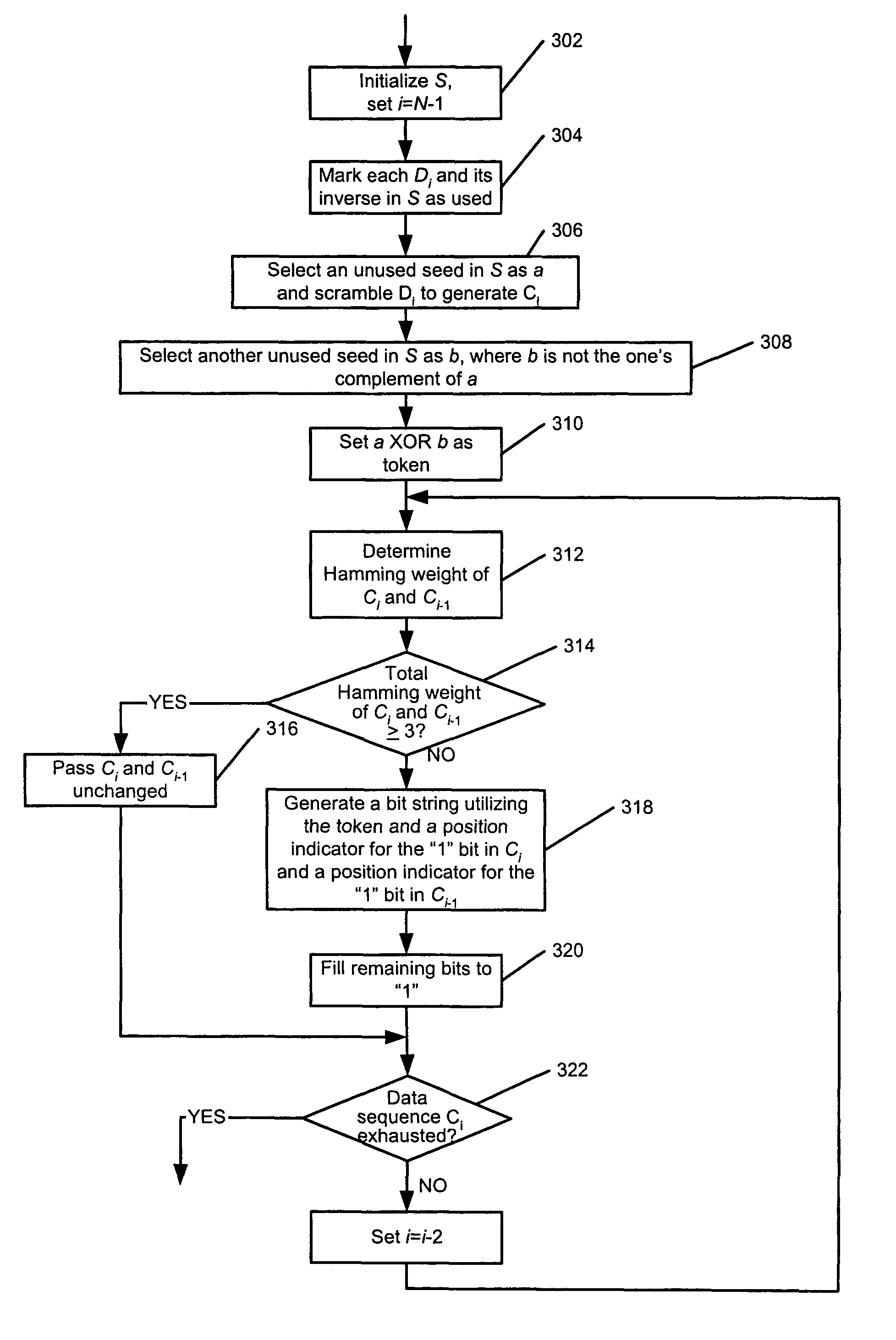
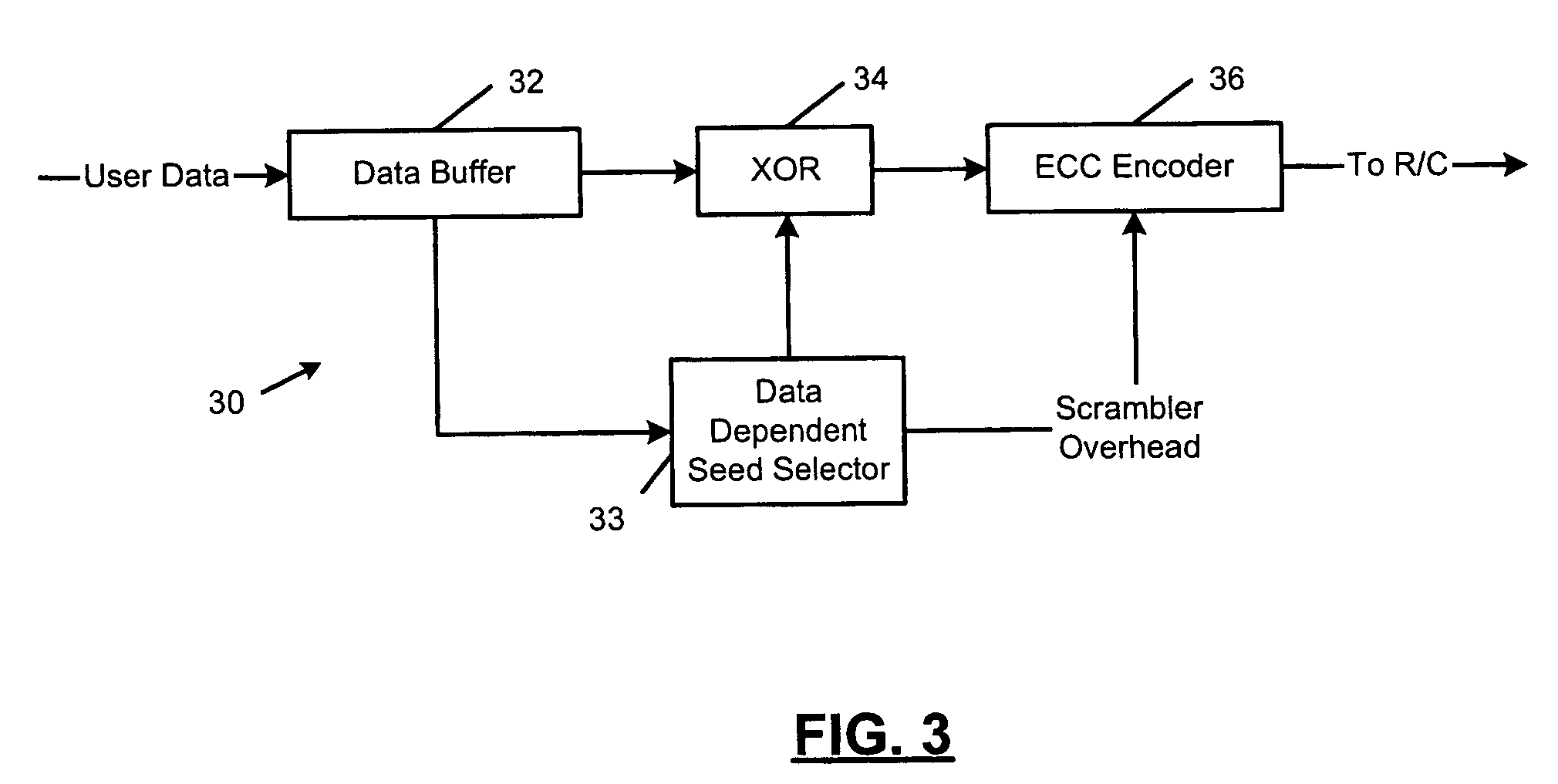
Method and apparatus for generating a seed set in a data dependent seed selector
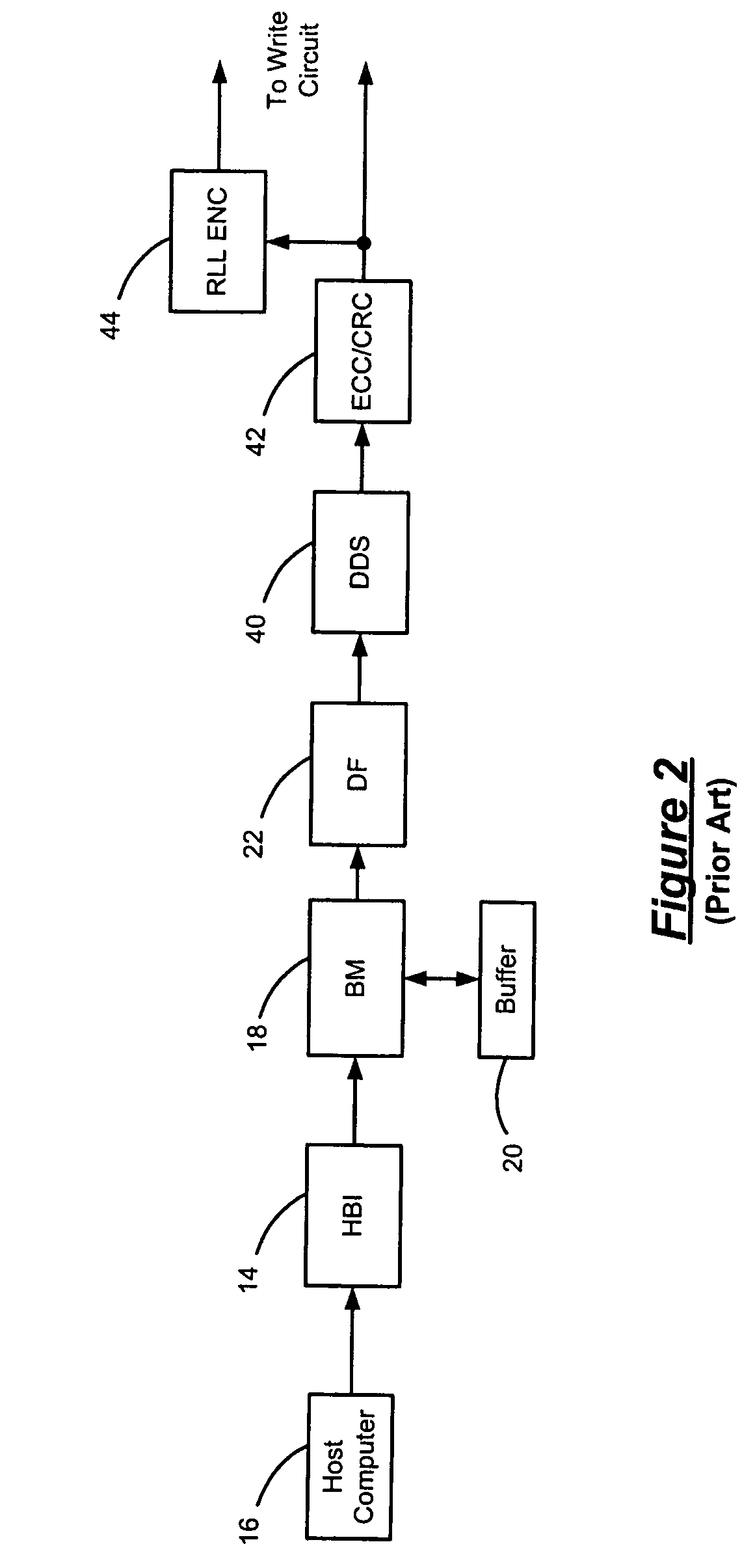
InactiveUS7158058B1Modification of read/write signalsRecord information storageComputer networkHamming distance
A communications channel includes a buffer that receives user data symbols including a plurality of M-bit symbols. A seed selector receives the plurality of M-bit symbols, selectively removes symbols from a seed set based on Hamming distances between at least two of the M-bit symbols, and selects a scrambling seed from remaining symbols in the seed set. A scrambling device that communicates with the seed selector and the data buffer generates scrambled user data based on the user data symbols and the scrambling seed. The communications channel is implemented in a data storage system. The seed selector ensures a minimum Hamming weight of 15 percent in the scrambled user data. The seed selector compares first and second user data symbols in the plurality of M-bit symbols.
Owner:MARVELL ASIA PTE LTD
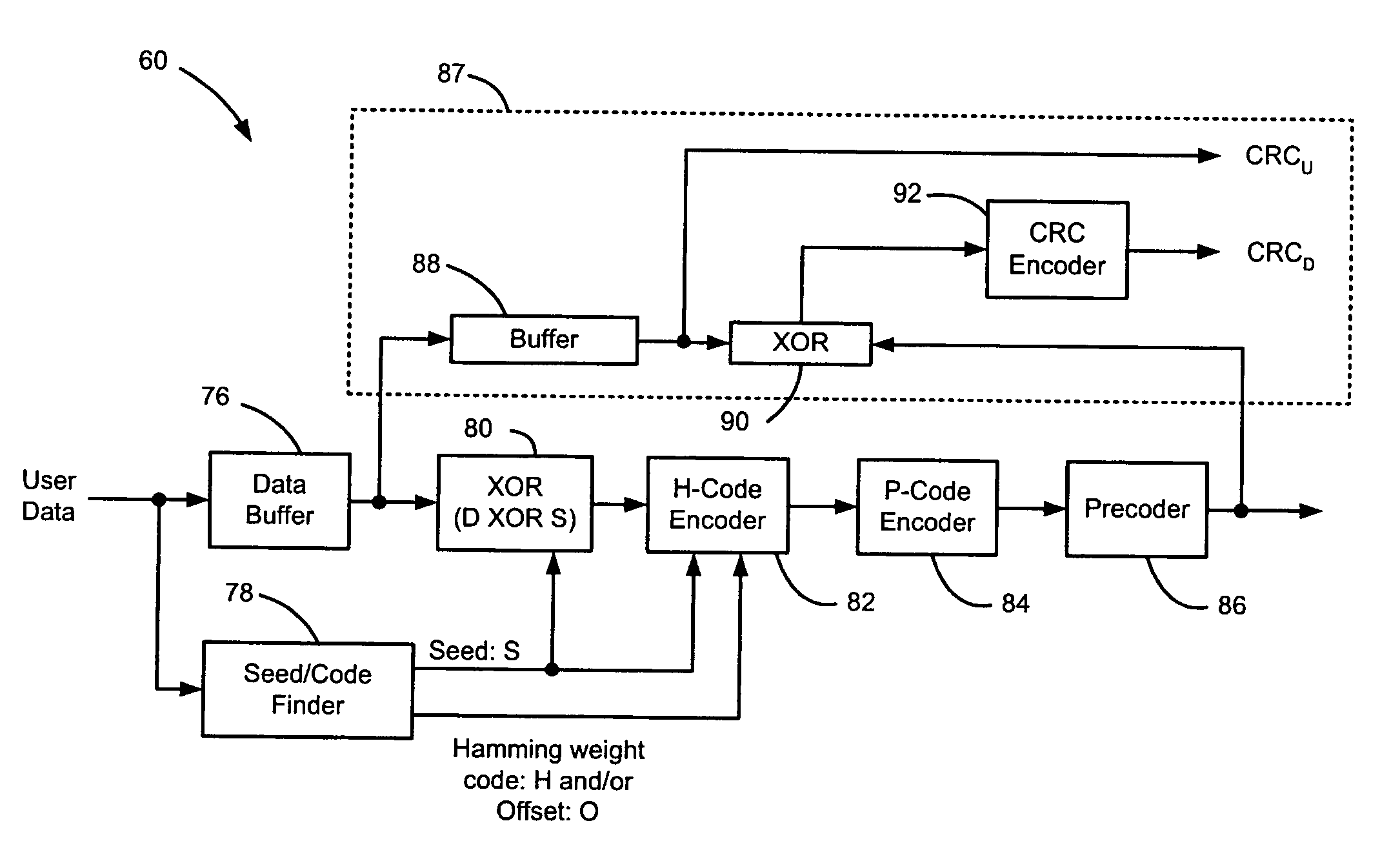
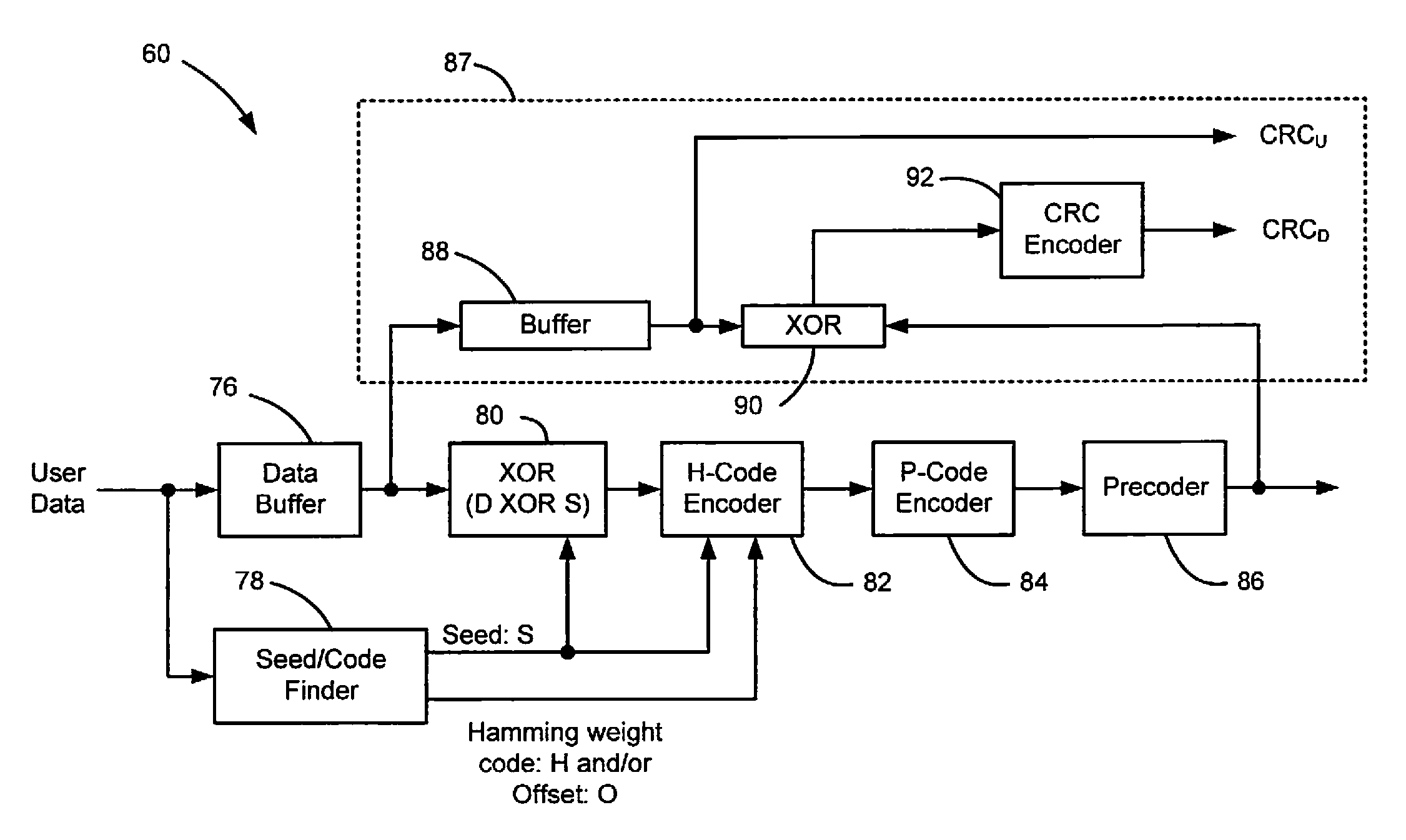
Data dependent scrambler with reduced overhead
ActiveUS7469049B1Data augmentationReduce in quantityTelevision system detailsUser identity/authority verificationData dependentComputer science
A data dependent scrambler for a communications channel that receives a user data sequence including X bits that are organized as N M-bit symbols includes a seed finder that generates a scrambling seed that is dependent upon the symbols in the user data sequence. A first scrambler receives the user data sequence from the data buffer and the scrambling seed from the seed finder and generates the scrambled user data sequence. An H-code finder generates at least one of an H-code token that is dependent upon the symbols in the user data sequence and an offset of the H-code token from the scrambling seed. An H-code encoder receives the scrambled user data sequence and at least one of the H-code token and the offset. The H-code encoder increases a Hamming weight of the scrambled user data sequence using the at least one of the H-code token and the offset.
Owner:MARVELL ASIA PTE LTD
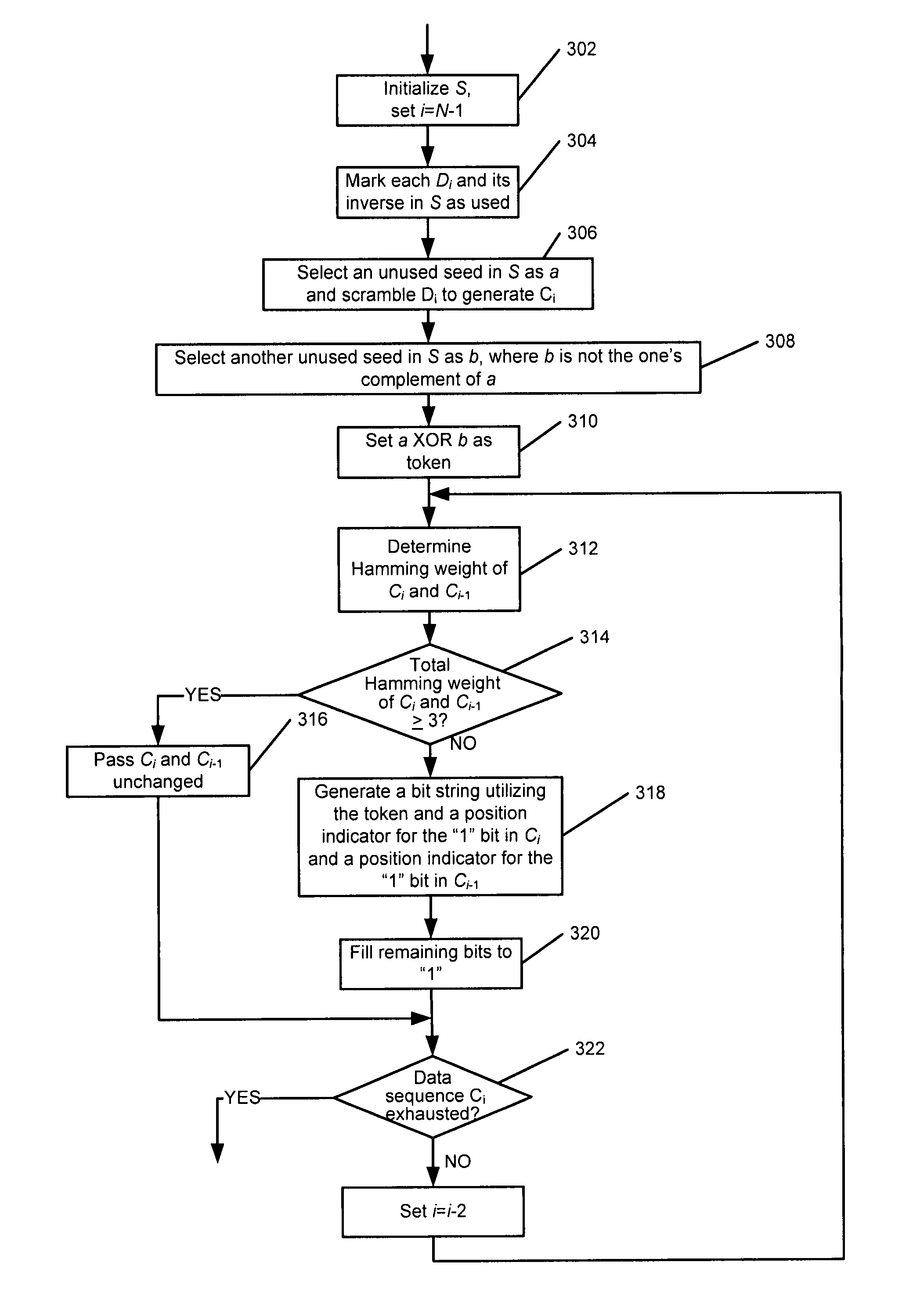
Methods and apparatus for improving minimum hamming weights of a sequence
A communications channel comprises a seed selector that selectively removes X M-bit symbols of user data from a seed set comprising Y M-bit symbols and that selects a scrambling seed from Y-X symbols remaining in the seed set, where X, Y and M are integers greater than one. A Hamming weight coding device that determines a Hamming weight of symbols of scrambled user data that are generated based on the user data and the selected scrambling seed and that selectively codes the symbols depending upon the determined Hamming weight.
Owner:MARVELL ASIA PTE LTD
Technique to construct 32/33 and other RLL codes
InactiveUS6456208B1Easy to analyzeMinimize constraintIndividual digits conversionError correction/detection using multiple codesLeft halfHamming weight
In this invention a thirty three bit word is encoded from a thirty two bit word to conform to RLL coding constraints. A parity bit is added to the coded word after coding is complete. With the parity bit inserted the code satisfies a minimum Hamming weight of nine and no more than eleven consecutive zeros and no more than eleven consecutive zeros in both the odd and even interleaves. A table of "bad" eight bit sequences is used to compare the odd and even interleaves of the right and left halves of the input word that is being encoded. If a "bad" sequence is found, its position in the table points to a second table containing a four bit replacement code that is inserted into the coded output word. Flag bits in the output coded word are set to indicate the violation of the coding constraints and provide a means by which a decoder can be used to reverse the process and obtain the original input word.
Owner:MARVELL ASIA PTE LTD
Encoding and decoding apparatus and method with hamming weight enhancement
InactiveUS7149955B1Improve reliabilityImprove efficiencyError preventionError detection/correctionComputer scienceHamming weight
A Hamming weight encoder includes an input that receives user data including P symbols and a Hamming weight module that determines a Hamming weight of N of said P symbols. N and P are integers greater than one and N is less than or equal to P. The Hamming weight encoder also includes a comparing module that compares the Hamming weight to a Hamming weight threshold and an inverting module that selectively bitwise inverts bits in said N symbols based on said comparison.
Owner:MARVELL ASIA PTE LTD
Generation of golay-based systematic block code supporting various sizes
ActiveUS20090217139A1Strong resistanceEffectively generating codesError preventionModulated-carrier systemsComputer hardwareBlock code
A method for generating block codes from Golay code and a method and apparatus for encoding data are provided. The method can effectively generate codes having various lengths, various dimensions, and superior hamming weight distribution, and encodes data such as control information having various lengths into codes having strong resistance to channel errors, resulting in an increase of error correction performance.
Owner:LG ELECTRONICS INC
Encryption processing circuit and encryption processing method
InactiveUS20080212776A1User identity/authority verificationSecret communicationHamming weightEncryption
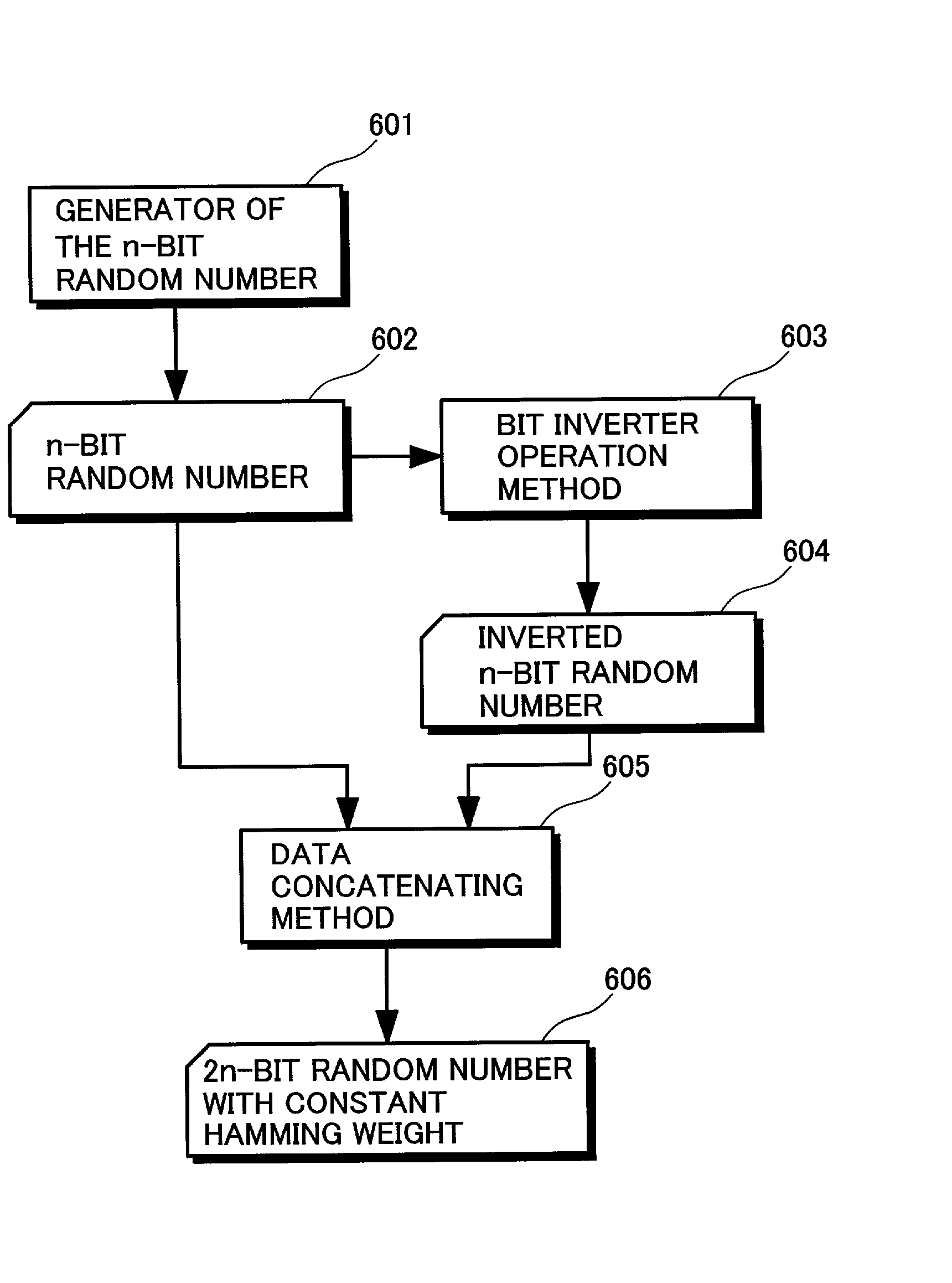
An encryption processing circuit includes: a decoder configured to convert a binary input data used for predetermined encryption computing into a first plurality of bit data of a constant hamming weight independently of a hamming weight of the input data; a wiring network configured to receive the first plurality of bit data converted by the decoder, the wiring network further configured, for the purpose of the predetermined encryption computing, to change a bit pattern of the received first plurality of bit data by replacing bit positions of the first plurality of bit data, and to generate a second plurality of bit data; and an encoder configured to convert the second plurality of bit data generated in the wiring network into a binary output data.
Owner:KK TOSHIBA
Tamper resistance device
InactiveUS20020154767A1Low degree of relationshipImprove securityEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionTamper resistanceCurrent consumption
It is an object of the disclosed technology to provide a tamper resistance device such as a card member having high security. The disclosed technology provides a solution to problems by reduction of the degree of relationship between information processed in the card member such as a chip for an IC card and current consumption for the processing. As a means for solving the problem, there is provided a method for reducing the degree of relationship between the magnitude of a current consumed by the chip for an IC card and information processed by the chip. In accordance with this method, information is transformed by using data for disturbance of the information prior to processing and, after the processing of the transformed data, the processed transformed information is subjected to inverse transformation using the data for disturbance of the information to result in correct processed information. The method is characterized in that the hamming weight of the data for disturbance of information is all but constant.
Owner:HITACHI LTD
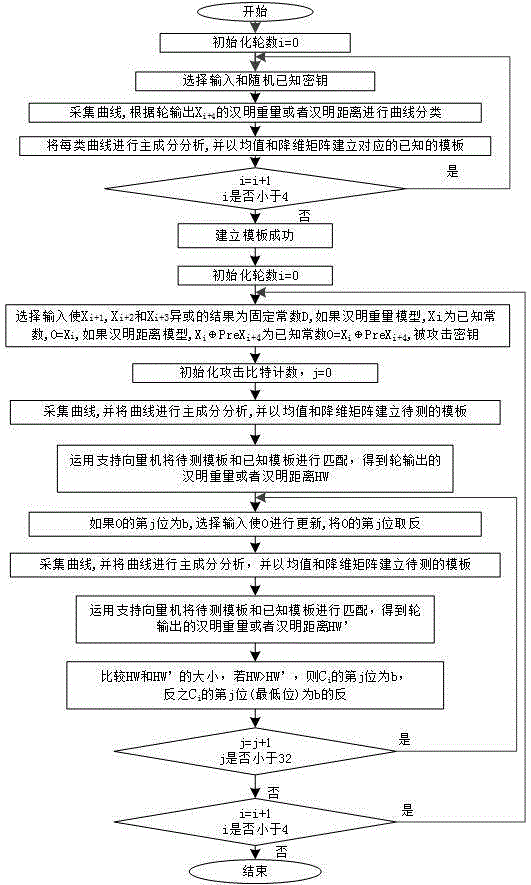
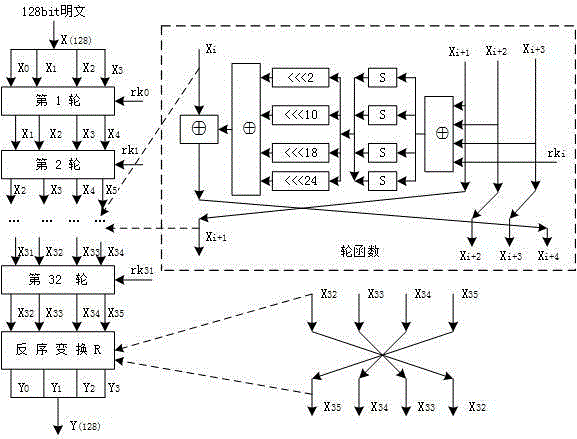
Template attack method in allusion to SM4 cipher algorithm round output
ActiveCN104868990AEncryption apparatus with shift registers/memoriesTemplate matchingSupport vector machine
The invention discloses a template attack method in allusion to SM4 cipher algorithm round output. According to the method disclosed by the invention, special channel input is taken as a premise, the SM4 algorithm round output is used as an attack point, the hamming weight or the hamming distance of the round output is selected to establish a template, and template attack in allusion to the SM4 cipher algorithm round output can be realized by a small number of templates. Meanwhile, selective input is taken as a basis in a template matching stage, a support vector machine is used to act as a tool for judgment and analysis, a bit of linear transformation output can be broken by only two times of matching, and then a round sub-key is reversely derived by inverse transformation of nonlinear transformation and linear transformation. The method disclosed by the invention effectively solves a problem that template attack in allusion to the SM4 cipher algorithm round number is infeasible at the present stage.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
Method for scalarly multiplying points on an elliptic curve
InactiveUS20090136025A1Optimal reduction attributesReduce weightPublic key for secure communicationDigital data processing detailsEllipsePolynomial representations of cyclic redundancy checks
A method performs scalar multiplication of points on an elliptic curve by a finite expandable field K of a first field Fp of a p>3 characteristic, wherein said characteristic p has low Hamming weight and the expandable field has a polynomF(X)+Xd−2 of order d in the polynomial representation thereof.
Owner:SIEMENS AG
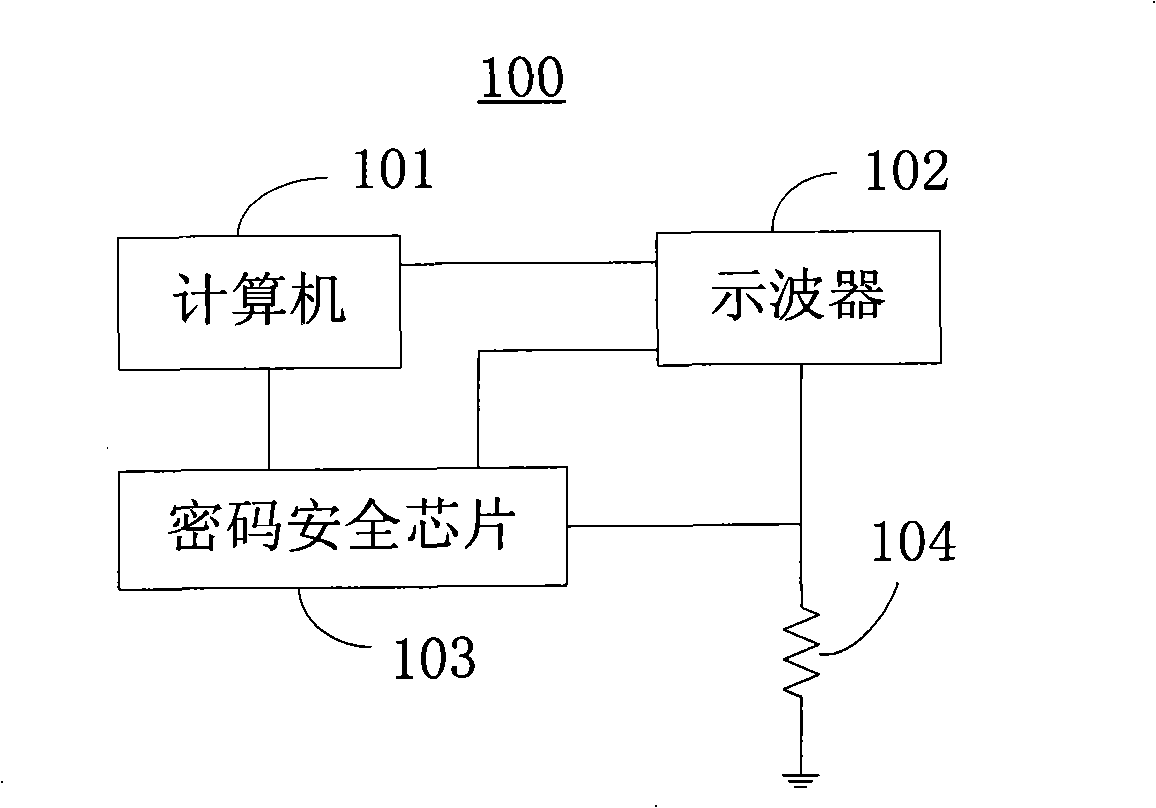
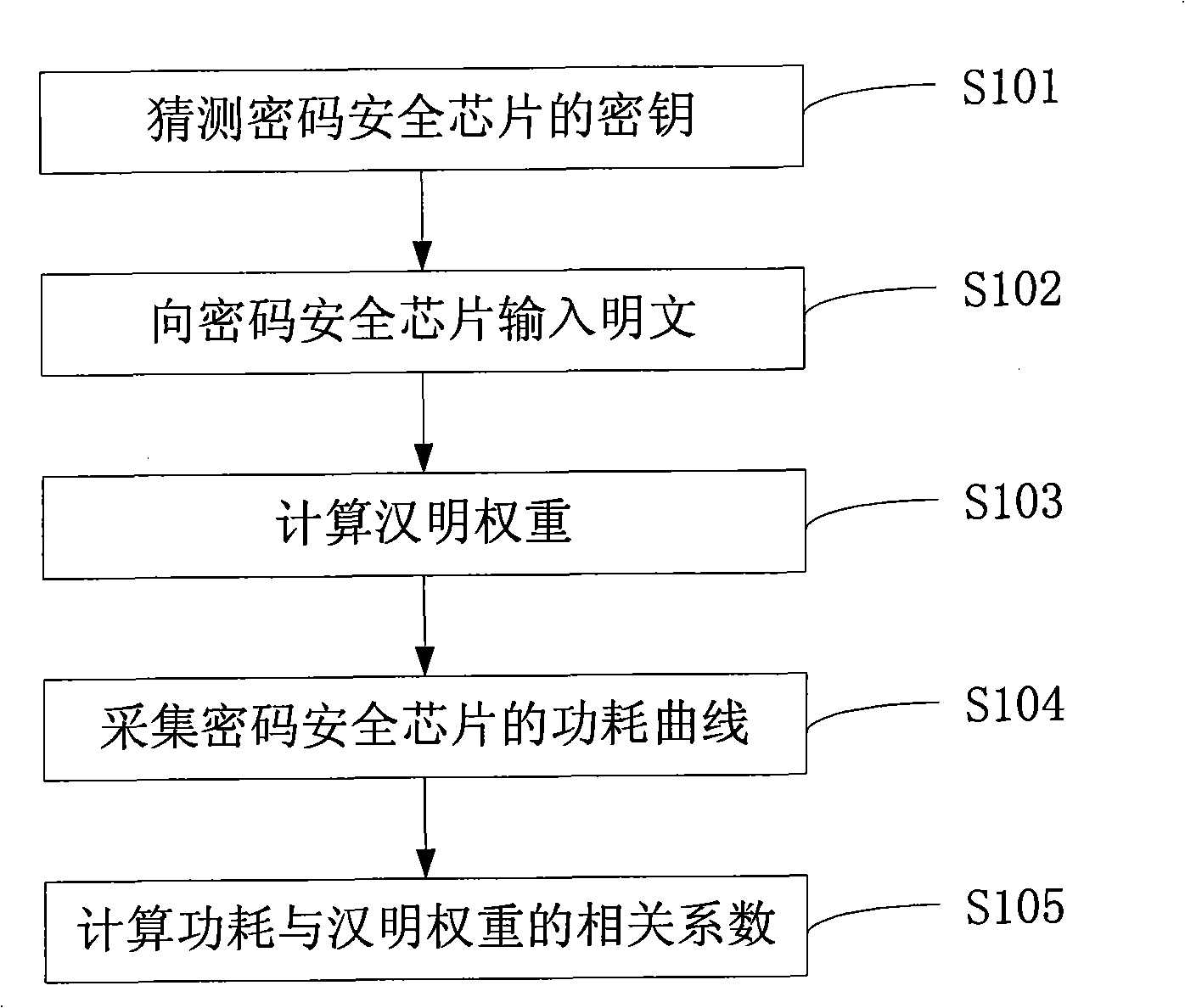
Quantification and evaluation method for cipher safe chip side channel safe degree
ActiveCN101494537AEncryption apparatus with shift registers/memoriesHamming weightSafety coefficient
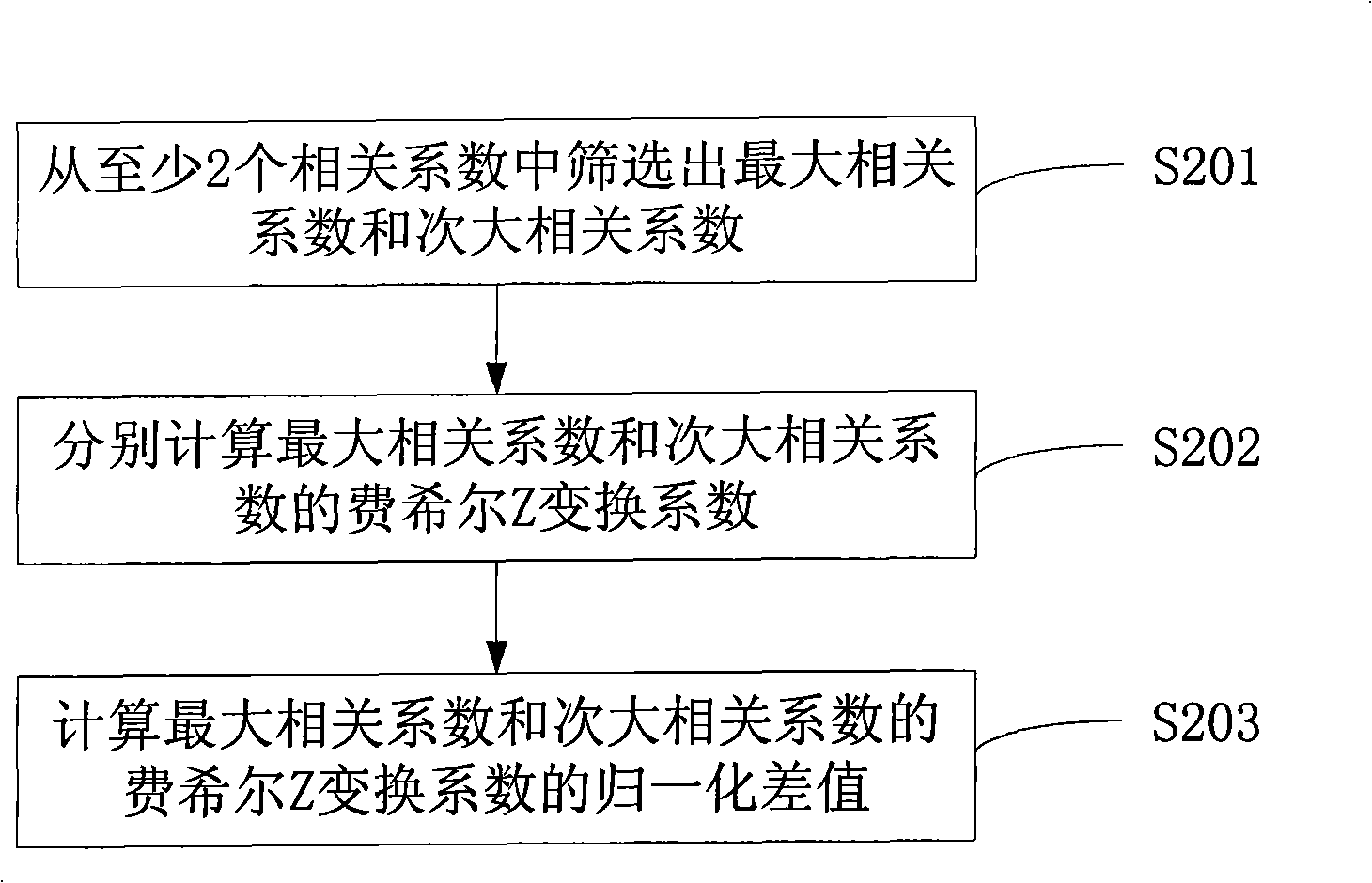
The invention relates to a quantitative evaluation method of safety degree of a side channel of a code safety chip. The method comprises the following steps of: obtaining at least two relevant coefficients of power consumption and Hamming weight; calculating a normalized difference value; and calculating the safety coefficient of the side channel of the code safety chip. The method can evaluate the safety degree under the analytical attack of the side channel of a key of the code safety chip.
Owner:SHENZHEN INST OF ADVANCED TECH
Hardening data transmissions against power side channel analysis
ActiveUS20150033338A1Memory loss protectionError detection/correctionComputer hardwareChannel analysis
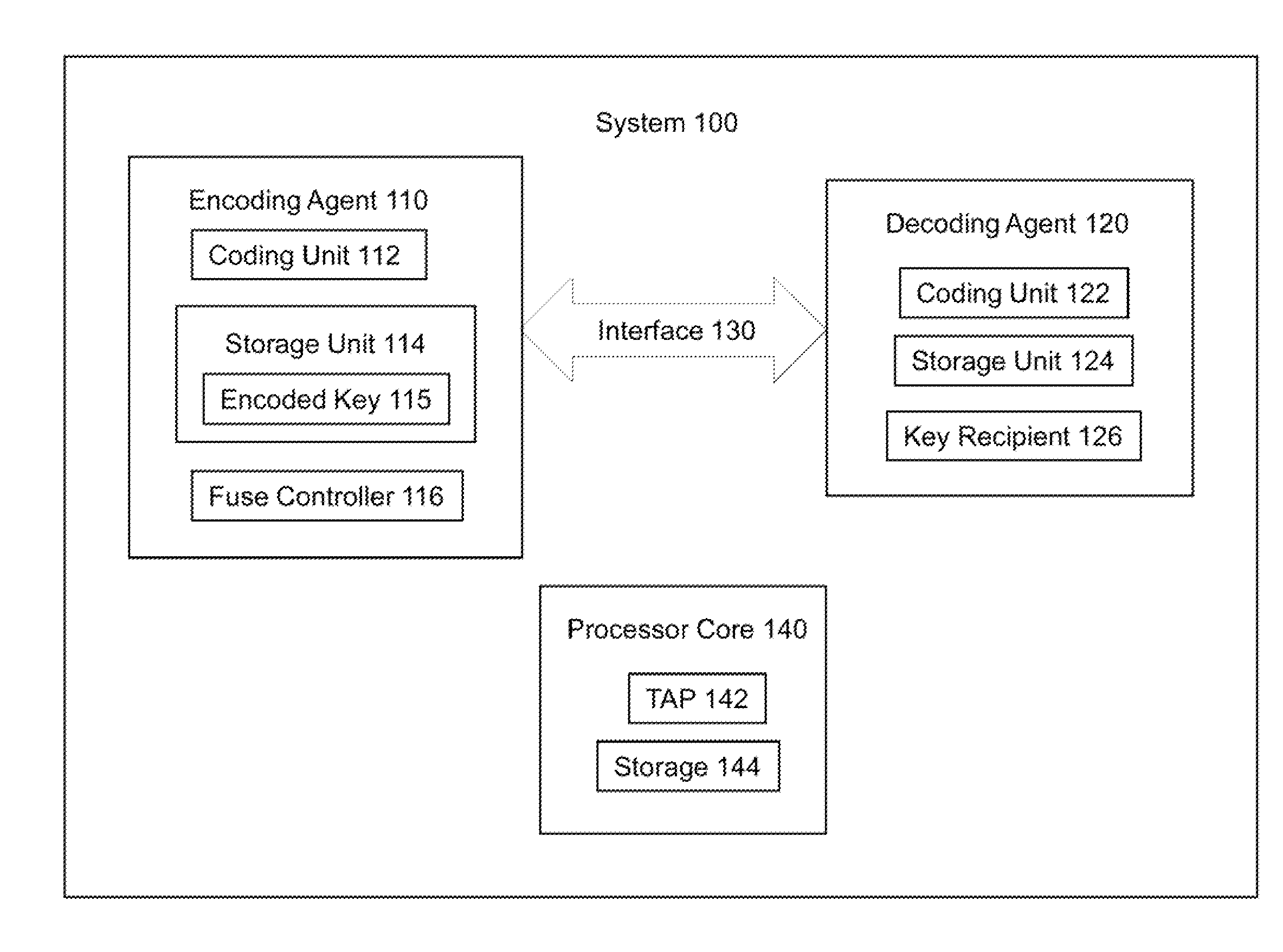
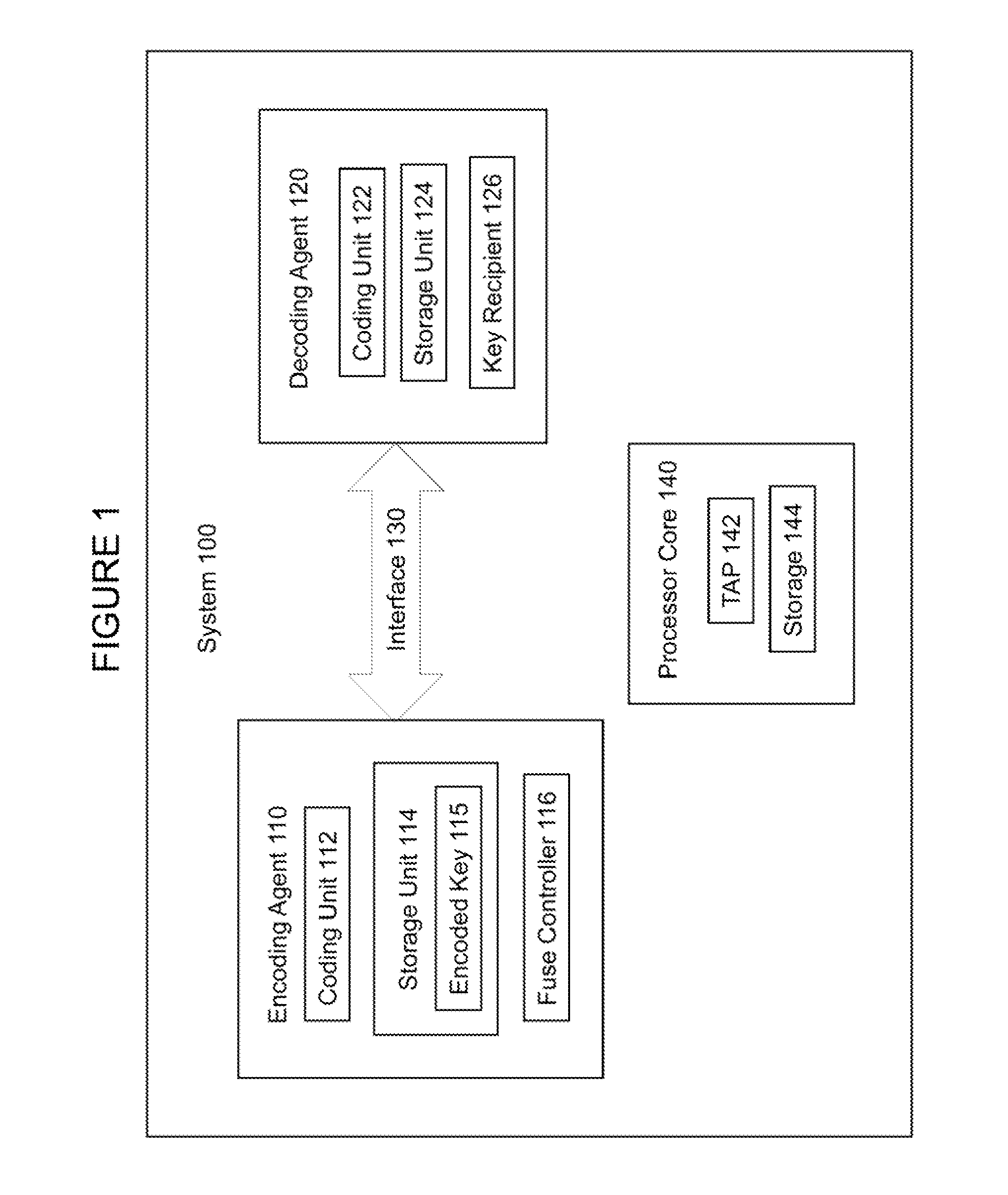
Embodiments of an invention for hardening data transmissions against power side channel attacks are disclosed. In one embodiment, a system includes a first agent and a second agent. The first agent is to transmit an encoded datum through an interface in a plurality of encoded packets. The second agent is to receive each of the plurality of encoded packets from the interface and decode each of the encoded packets to generate a plurality of decoded packets. Each of the encoded packets has the same Hamming weight. The Hamming distance between any two consecutively transmitted encoded packets is constant.
Owner:INTEL CORP
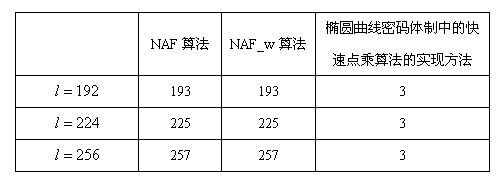
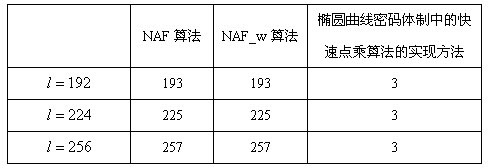
Implementation method for rapid scalar multiplication algorithm in elliptic curve cryptosystem
InactiveCN102393812AFast operationReduce the number of cyclesPublic key for secure communicationComputations using residue arithmeticCoordinate changeSymbol of a differential operator
The invention discloses an implementation method for a rapid scalar multiplication algorithm in an elliptic curve cryptosystem. The method at least comprises a scalar multiplication algorithm procedure of binary coding with the minimum Hamming weight and provided with symbols from left to right, and the method comprises the following steps of: arranging definitions on a finite prime number field, being arbitrary point, and being arbitrary integer; inputting'':''; outputting'':''; A. commanding '', ,''; B. decreasing progressively until, implementing: a. commanding; b. '', ,''; c. if, commanding; C. returning. The implementation method for the rapid scalar multiplication algorithm in the elliptic curve cryptosystem provided by the invention, the binary coding with the minimum Hamming weight and provided with the symbols from left to right is applied to the rapid scalar multiplication algorithm in the elliptic curve cryptosystem, a novel binary coding scalar multiplication algorithm with the symbols is created, which can be faster achieved. The novel binary coding scalar multiplication algorithm has the advantages that: arithmetic speed is high, additional memory plint space and coordinate change are not needed during calculation, calculation period is reduced, and the like.
Owner:四川卫士通信息安全平台技术有限公司
Methods and apparatus for improving minimum Hamming weights of a sequence
A communications channel includes a buffer that receives symbols of user data including a plurality of M-bit symbols. A seed selector receives the M-bit symbols of the user data, selectively removes symbols of the user data from a seed set, and selects a scrambling seed from symbols remaining in the seed set. A scrambling device that communicates with the seed selector and the data buffer generates scrambled user data using the user data and the selected scrambling seed. A Hamming weight coding device determines a Hamming weight of symbols of the scrambled user data and selectively codes the symbols depending upon the determined Hamming weight.
Owner:MARVELL ASIA PTE LTD
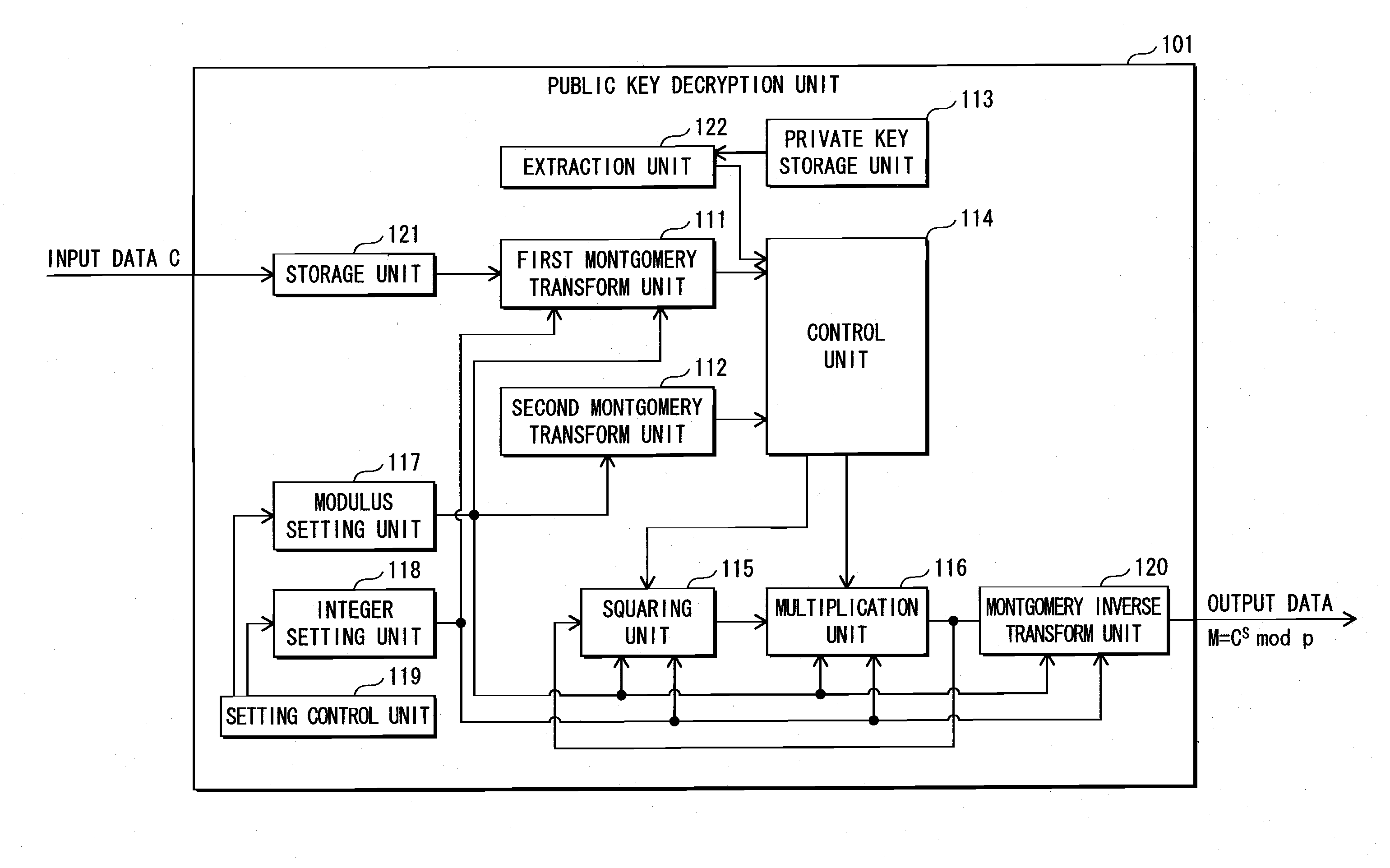
Information security device, information security method, computer program, computer-readable recording medium, and integrated circuit
ActiveUS20100064142A1Avoid weightDifficult to analyzeDigital data processing detailsUnauthorized memory use protectionPower analysisCryptosystem
The present invention aims to provide an information security apparatus that counters a simple power analysis attack (SPA) on an information security apparatus such as an RSA cryptosystem. The information security apparatus uses a multiplication with 1 in a Montgomery domain. 1 in the Montgomery domain is determined depending on a modulus and an integer k, which is greater than a number of bits of a modulus p. Therefore, it is hard for attackers who do not know p or k to analyze. Also, even if an analyzer can predict the Hamming weight, it is possible to further improve the safety against the SPA by modifying k or the modulus at random.
Owner:PANASONIC CORP
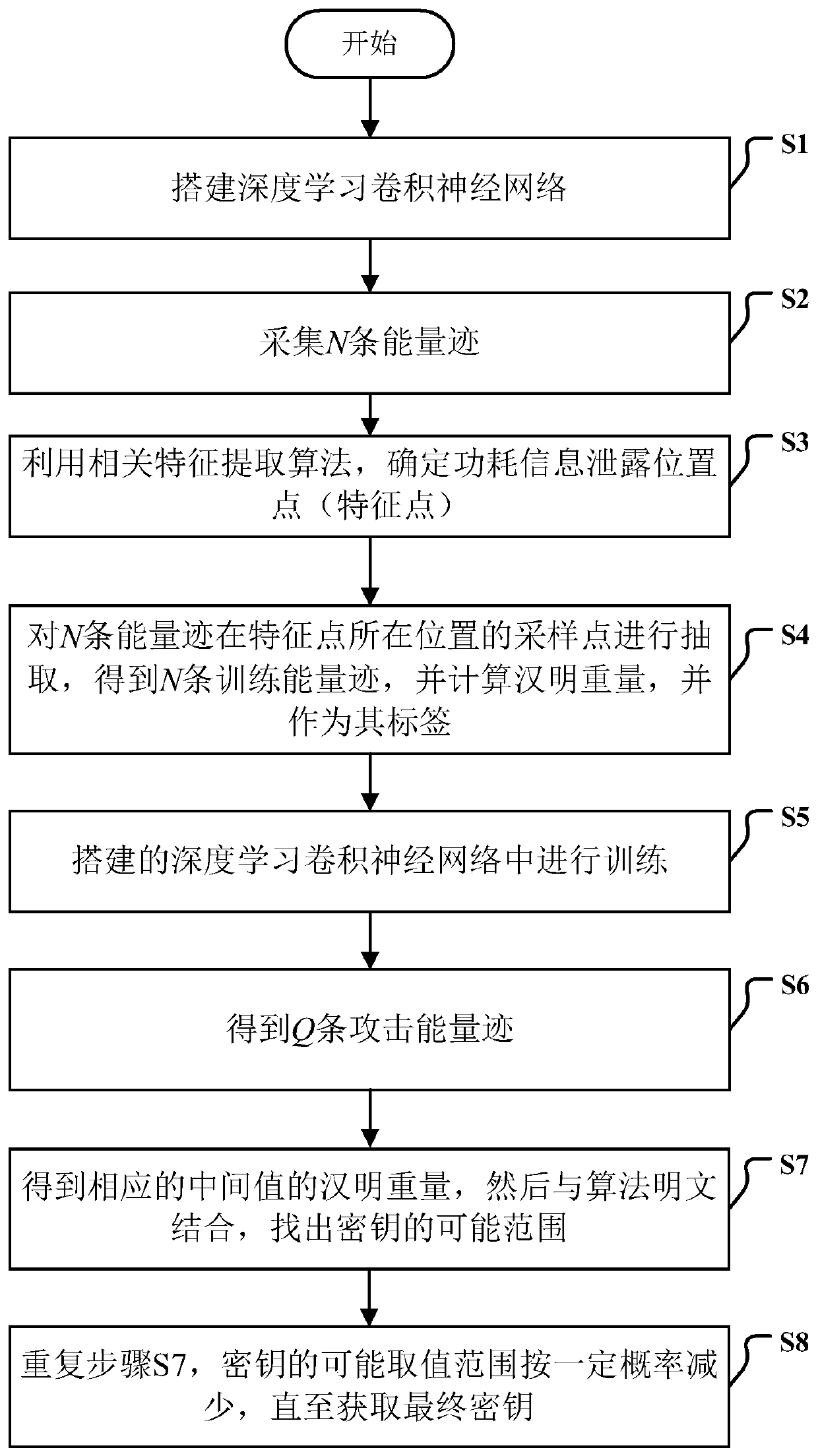
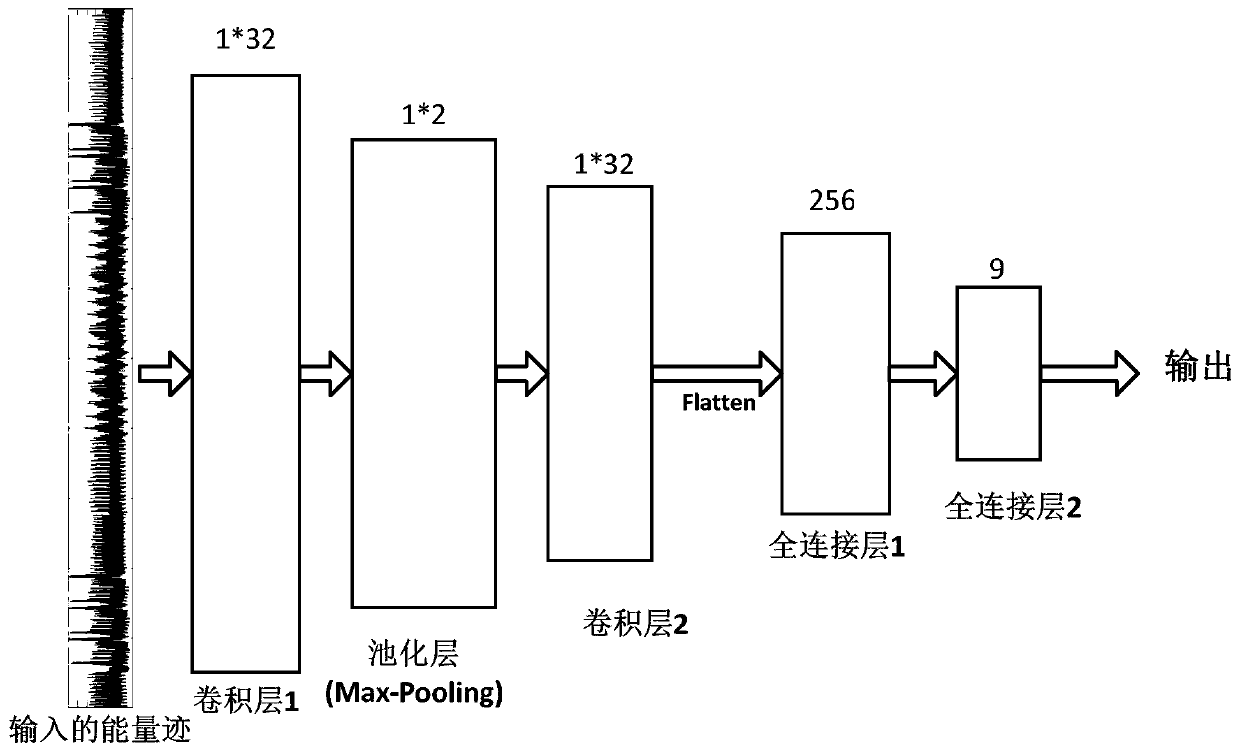
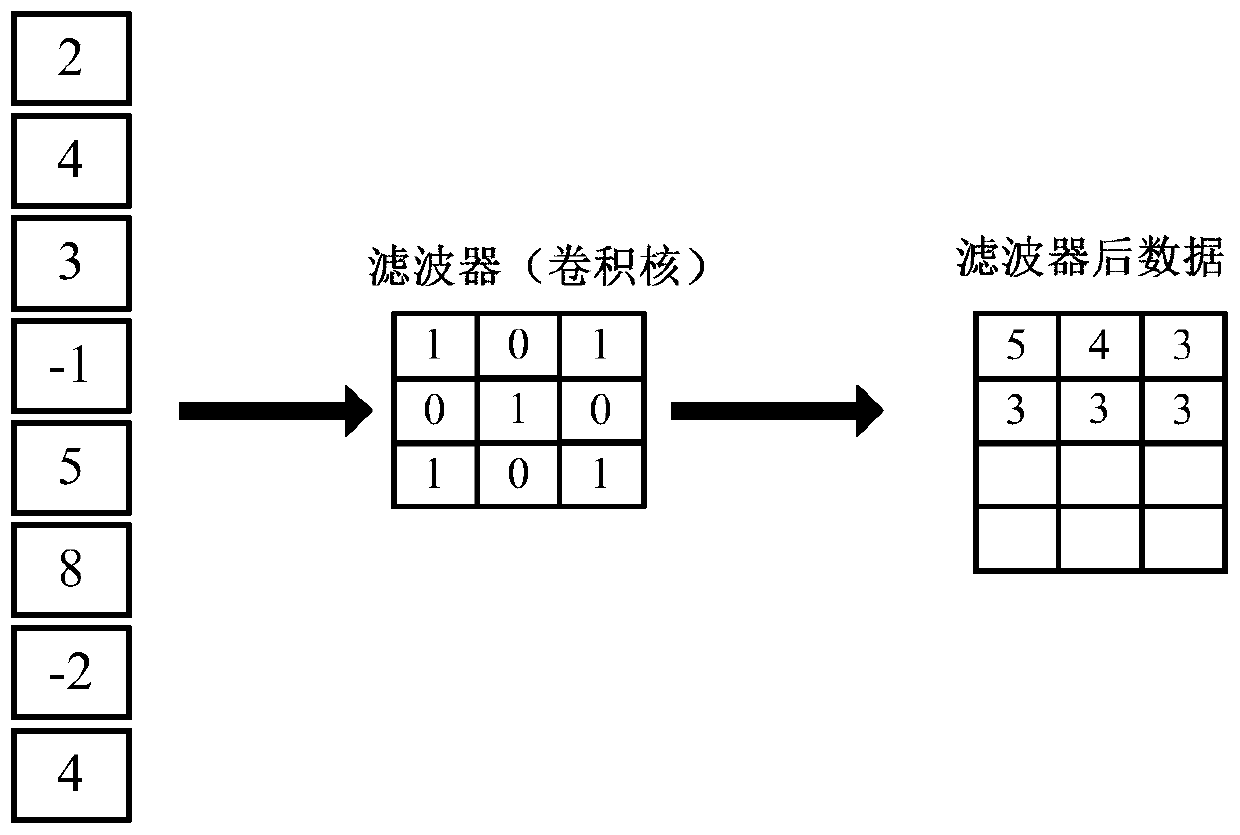
Class template attack method based on deep learning convolutional neural network
ActiveCN110048827AAvoid dependenceOvercome build imprecise issuesEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresHamming weightNeural network nn
The invention discloses a class template attack method based on a deep learning convolutional neural network. The method aims at characteristics of energy traces and types of Hamming weights, a deep learning convolutional neural network with a unique five-layer structure is built and is used for predicting Hamming weight of the attack energy trace; the dependence of traditional template attack ontemplate construction is well solved, the deep learning convolutional neural network is used as a class template for predicting the energy trace Hamming weight, the problem that template constructionis inaccurate is solved, the attack success rate is increased, and meanwhile the energy trace Hamming weight prediction method has high generalization capacity.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Encryption system side channel attack test method
InactiveCN103259647AImprove securityImprove developmentEncryption apparatus with shift registers/memoriesData switching networksPlaintextCryptosystem
The invention discloses an encryption system side channel attack test method and relates to information security technologies. The encryption system side channel attack test method includes the following steps: inputting a specific plaintext on a controlled device, using an attacked cryptosystem to conduct encryption, and capturing a power consumption curve. The encryption system side channel attack test method is characterized in that the inputted plaintext is a large number which is low in Hamming weight. The encryption system side channel attack test method has the advantages that attack efficiency is high, the method has certain universality, and attack cannot be prevented with utilization of a single method for shielding special numbers. The encryption system side channel attack test method is beneficial to promotion of development of an information security system with higher safety performance.
Owner:CHENGDU UNIV OF INFORMATION TECH
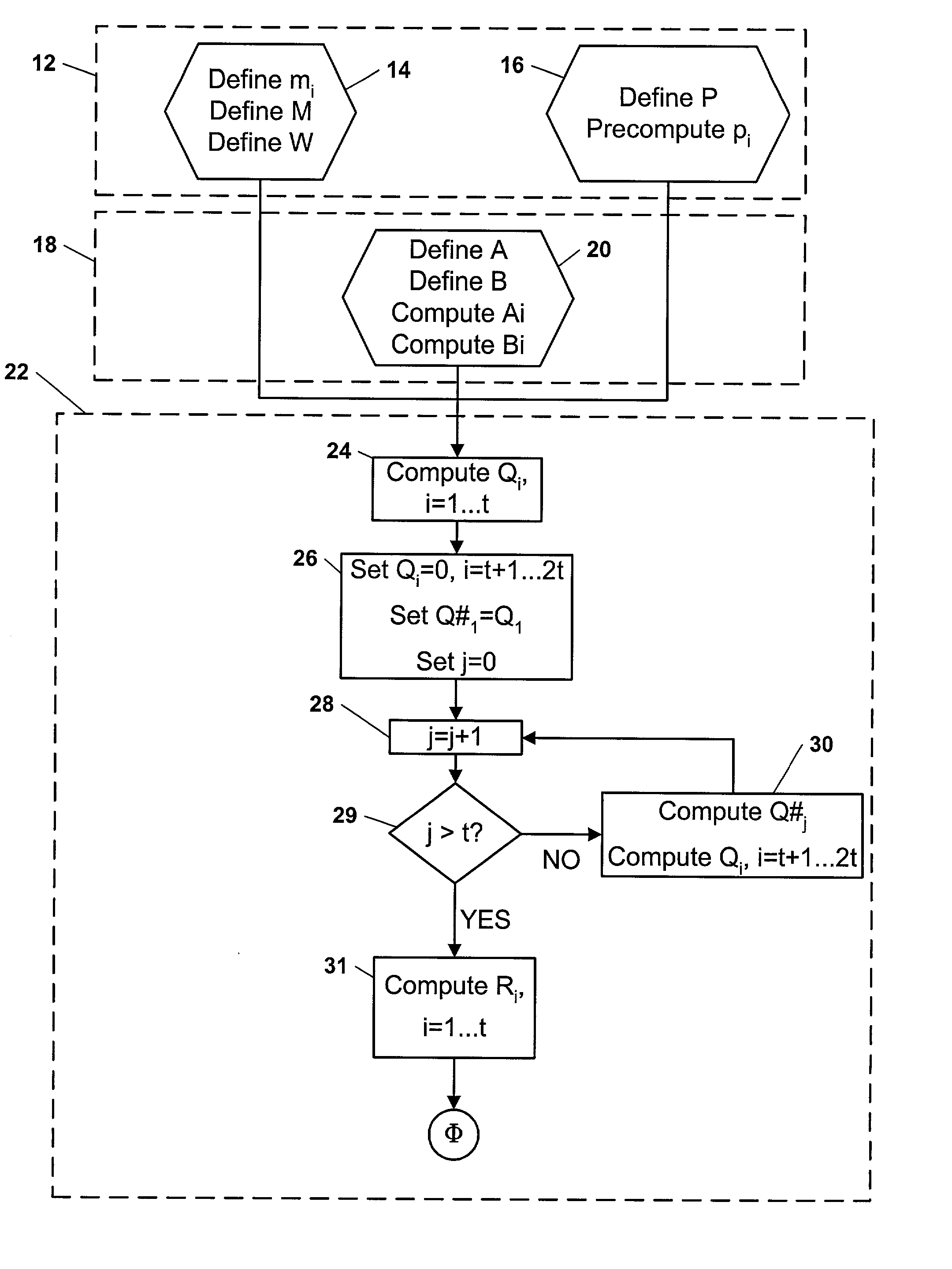
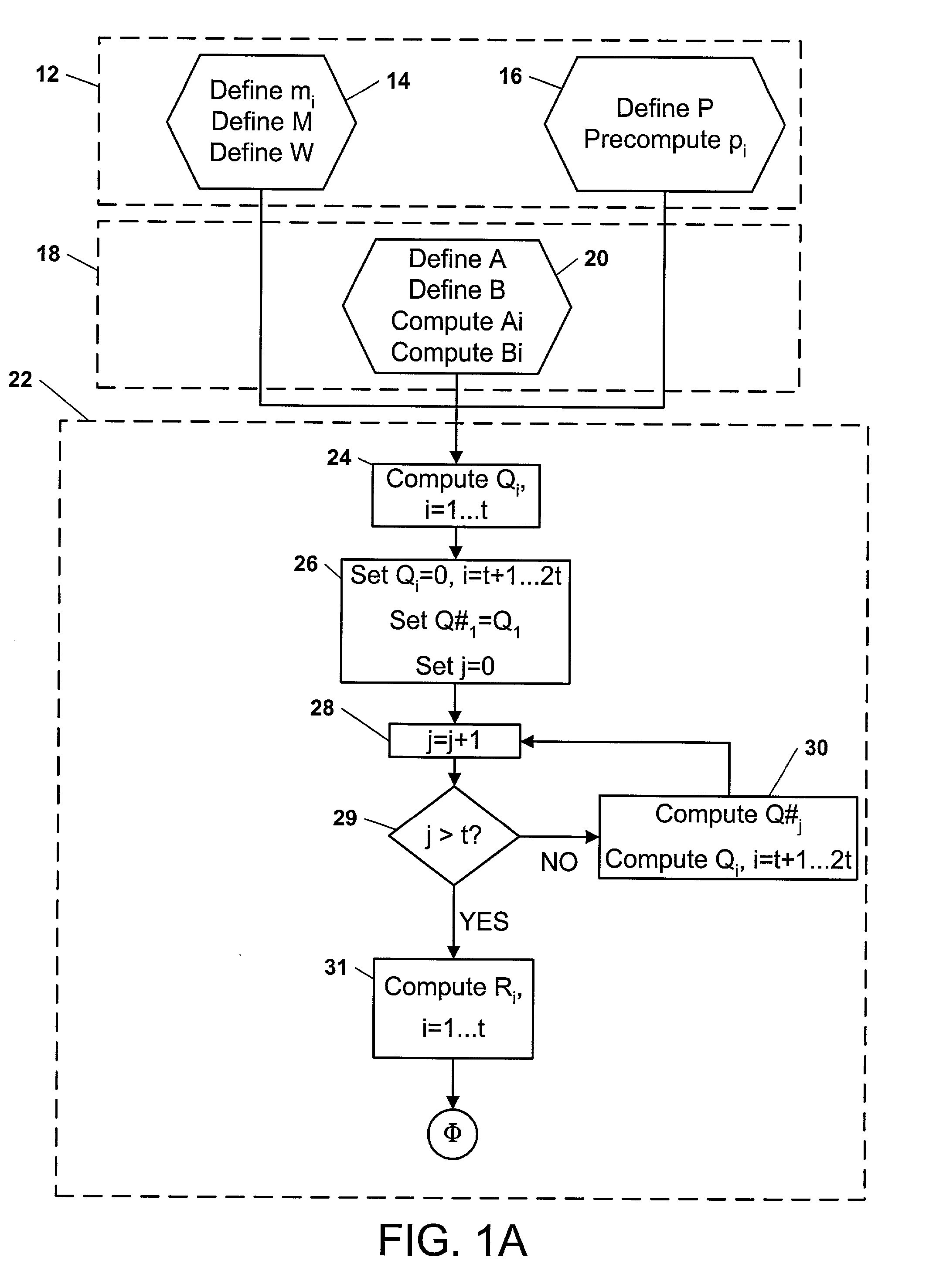
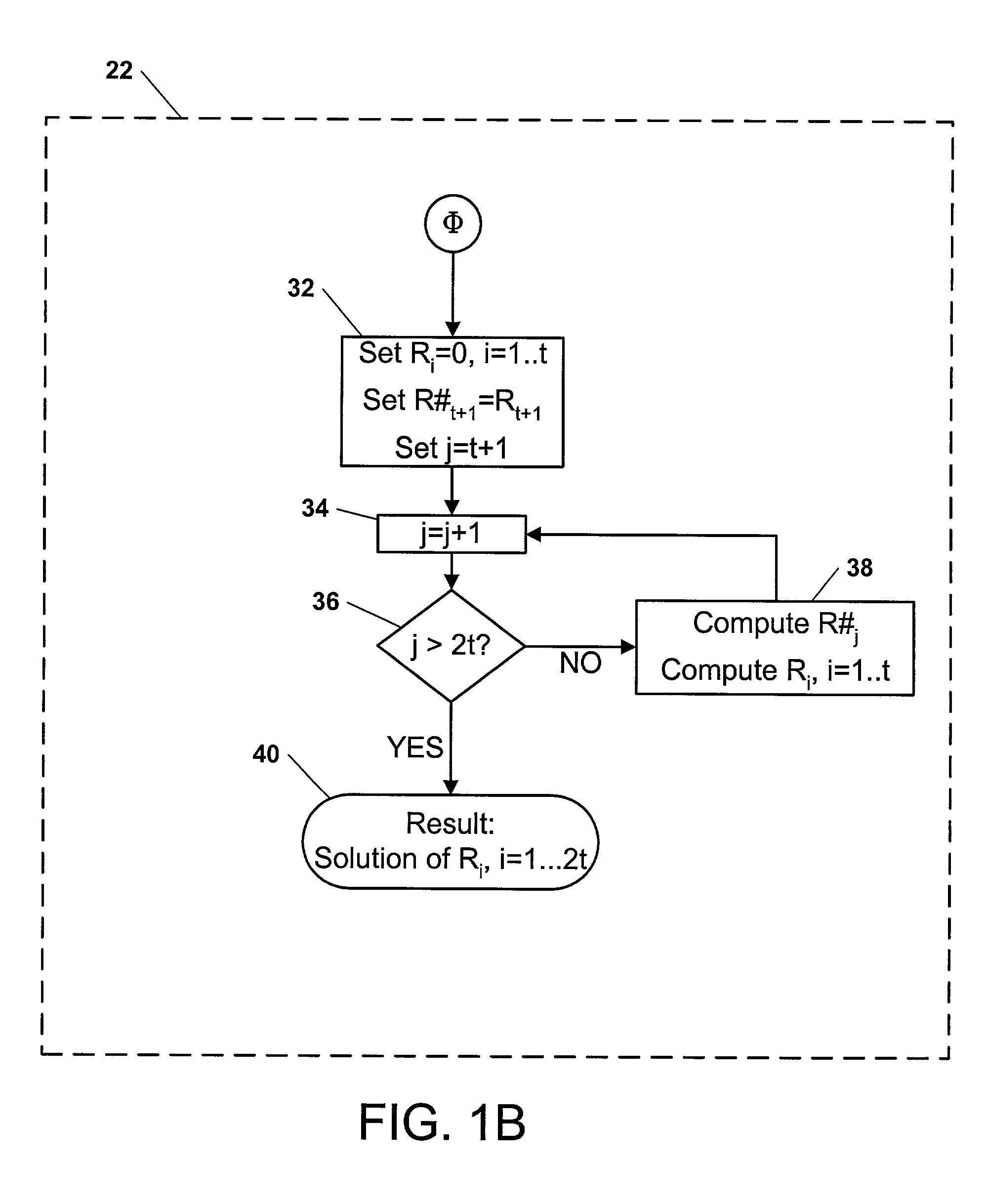
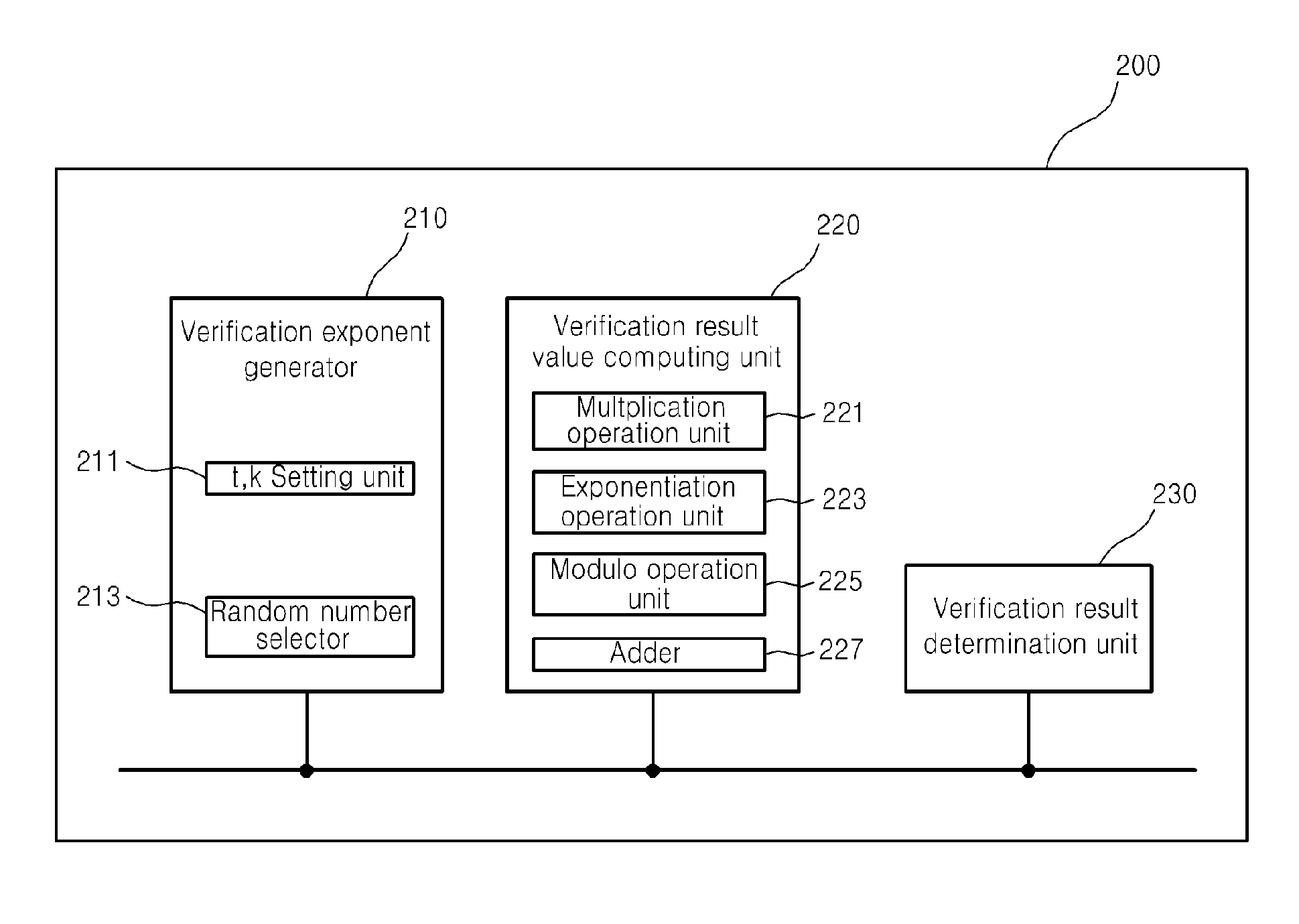
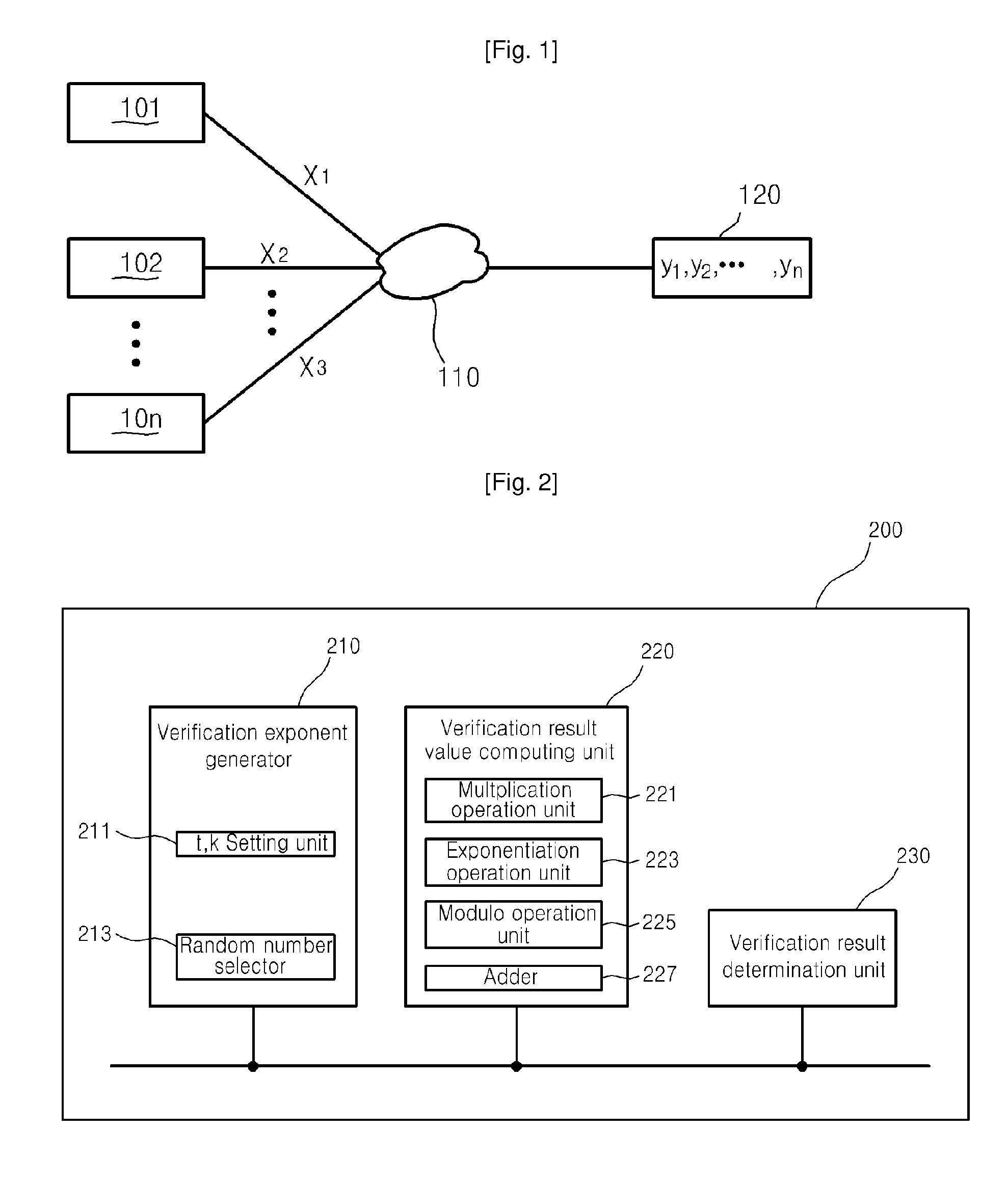
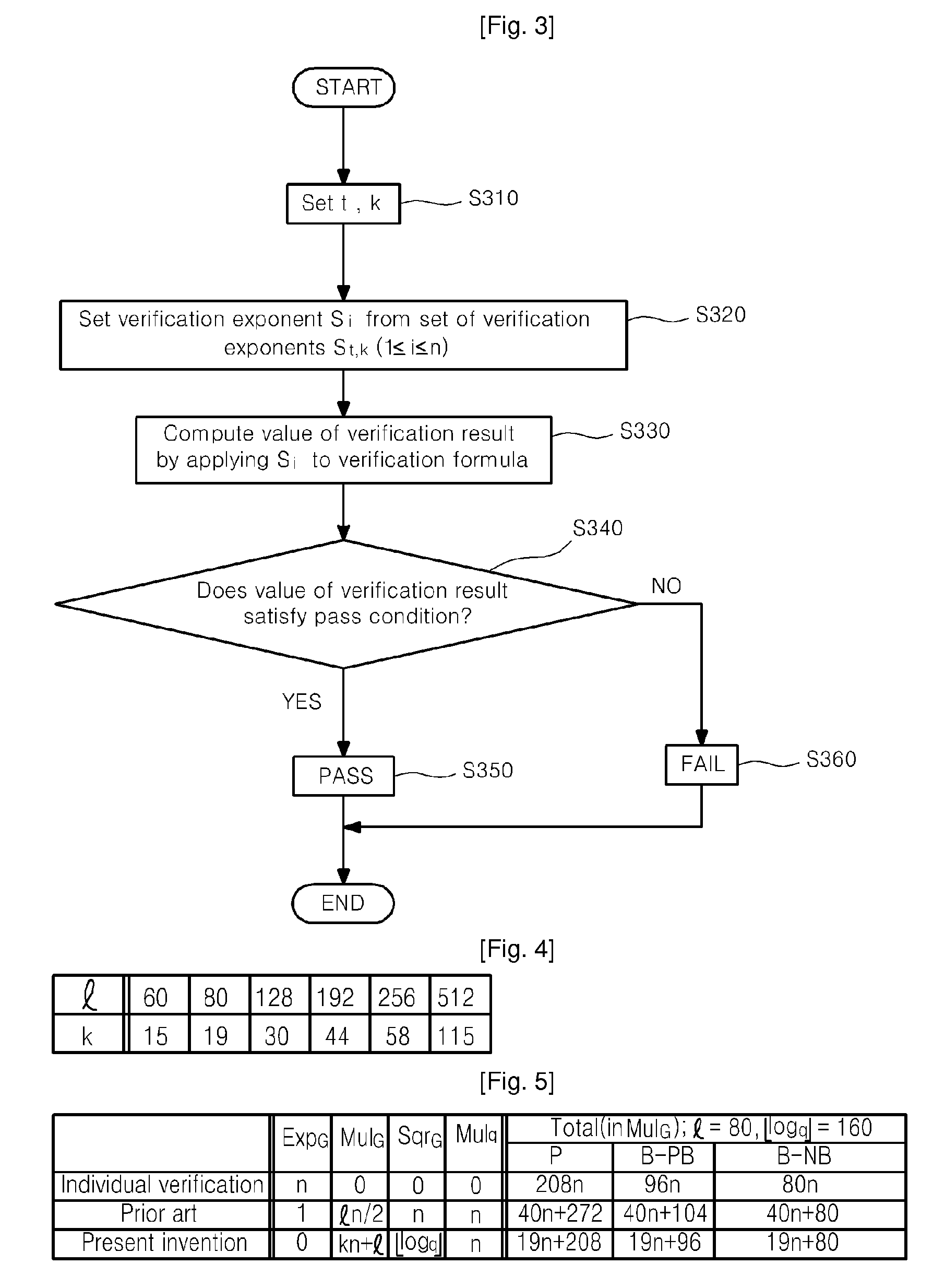
Fast Batch Verification Method And Apparatus There-of
ActiveUS20090112956A1Reduce the amount requiredIncrease speedUser identity/authority verificationDigital computer detailsComputer hardwareValidation methods
A fast batch verification method and apparatus are provided. In the method of batch-verifying a plurality of exponentiations, (a) a predetermined bit value t is set to an integer equal to or greater than 1; (b) a maximum Hamming weight k is set to an integer equal to or greater than 0 and less than or equal than the predetermined bit value t; (c) n verification exponents si are randomly selected from a set of verification exponents S (n is an integer greater than 1, i is an integer such that 1≦i≦n), where the set of verification exponents S include elements whose bit values are less than or equal to the predetermined bit value t and to which a Hamming weight less than or equal to the maximum Hamming weight k is allocated; (d) a value of verification result is computed by a predetermined verification formula; and (e) the verification of the signatures is determined to be passed when the value of verification result satisfies a pre-determined pass condition. Accordingly, it is possible to significantly reduce the amount of computation and particularly, the computation amount of multiplication, without increasing a probability that a verification error would occur, thereby significantly improving the speed of verifying a plurality of signatures.
Owner:SEOUL NAT UNIV R&DB FOUND
Data dependent scrambler with reduced overhead
InactiveUS7697685B1Data augmentationReduce in quantityTelevision system detailsUser identity/authority verificationData dependentData sequences
A scrambling system includes a seed finder that selects a scrambling seed. A first scrambler generates a scrambled sequence in response to a user data sequence and the scrambling seed. A code finder generates at least one of a token and an offset of the token from the scrambling seed. An encoder increases a Hamming weight of the scrambled sequence in response to at least one of the token and the offset.
Owner:MARVELL ASIA PTE LTD
AES-algorithm-oriented power analysis attack resistant method based on random time delay
ActiveCN105871536AGood resistance to attackResist Elastic AlignmentEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresPower analysisProcessor register
The invention discloses an AES-algorithm-oriented power analysis attack resistant method based on random time delay. A random number generator and a random time delay module are added in an AES algorithm; a plurality of different time delay paths are provided between a register and a wheel operation module; one path is randomly selected through the random number generated by the random number generator, so that the power consumption generation time point generated by the wheel operation module trends to randomization in one clock period. The method has the advantages that the dependency of the supposed power and practical power consumption track based on hamming weight in the AES algorithm can be effectively reduced; the power analysis attack based on the hamming weight module can be effectively resisted.
Owner:SOUTHEAST UNIV
Signature method of preventing side-channel attack from multi-azimuth
ActiveCN106452789APrevent inversionAvoid time consuming inversionUser identity/authority verificationCryptographic attack countermeasuresModular exponentiationOnes' complement
The invention discloses a signature method of preventing side-channel attack from multi-azimuth. The signature method of preventing side-channel attack from multi-azimuth is characterized in that the technology or similar technology contained in the signature method masks the base, and an RSA signature or other public key system signatures are obtained; in the signature method of preventing side-channel attack from multi-azimuth, two module exponentiation results are obtained at the same time, and the power exponents are radix minus one complement for each other; when modular exponentiation is realized, the verification technology of preventing outputting error data is used; and for the modular exponentiation algorithm which does not use the jump statement, the signature method of preventing side-channel attack from multi-azimuth is the technology that during the operation process, the data or the operation result data is equal to the Hamming weight. The signature method of preventing side-channel attack from multi-azimuth effectively protects the step which is known and is easy to be attacked during the RSA STD operation process. The modular exponentiation provided by the signature method of preventing side-channel attack from multi-azimuth can be fully applied to the RSA CRT operation, and can realize that the algorithm of the modular exponentiation algorithm and the complementary power can be transplanted to the point multiplication operation of SM2 at the same time. The test that whether the module exponentiation is attacked can be similarly transplanted in the point multiplication operation of SM2.
Owner:BEIJING HONGSI ELECTRONICS TECH
Encryption and decryption data processing method, device and system
ActiveCN104954124AImprove encryption efficiencyPublic key for secure communicationComputer hardwarePlaintext
The embodiment of the invention provides an encryption and decryption data processing method, device and system. The method comprises the steps that first equipment obtains a public key generated by second equipment; the first equipment selects one random bit string; the first equipment employs the public key to encrypt the random bit string, and obtains a first cryptograph; the first equipment employs a one-way function to achieve the mapping of the random bit string; the first equipment employs the decimal numerical value of the random bit string, the Hamming weight of the random bit string and the mapped random bit string to achieve the encryption of cleartext, and obtains a second cryptograph; and the first equipment transmits the cryptographs to the second equipment, wherein the cryptographs comprises the first cryptograph and the second cryptographs. According to the embodiment of the invention, the encryption for a plurality of bits is achieved, and the defect that the encryption efficiency of the cleartext in a single-bit mode is low is ironed out.
Owner:HUAWEI TECH CO LTD +1
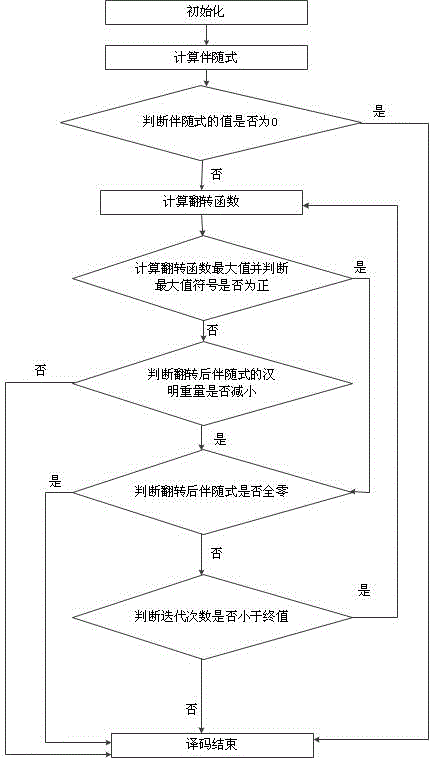
Hybrid advanced iteration-stopping method of weighted bit-flipping decoding method of LDPC (low-density parity-check) codes
ActiveCN104796159AEasy to implementImprove applicabilityError correction/detection using multiple parity bitsDecoding methodsLow density
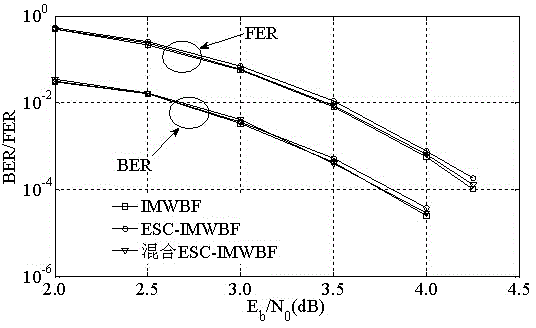
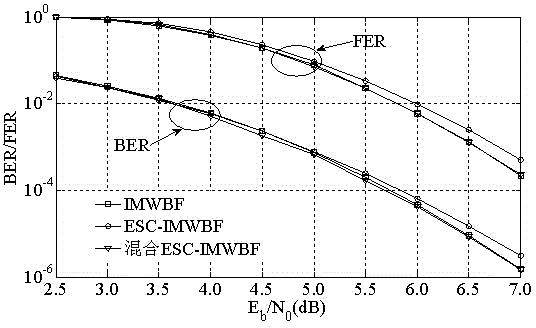
The invention discloses a hybrid advanced iteration-stopping method of a weighted bit-flipping decoding method of LDPC (low-density parity-check) codes. The method includes the steps of S1, performing hard decision and S2, decoding a sequence subjected to hard decision. The step S2 includes sub-steps of S21, performing initializing; S22, calculating a syndrome; S23, judging whether a value of the syndrome is 0; S24, calculating a flipping function; S25, calculating a maximum value of the flipping function, and jointly judging a symbol to the maximum value of the flipping function and post-flipping changes in the Hamming weight of the syndrome; S26, judging whether the syndrome is all-zero after flipping and whether the number of iterations is less than a final value; S27, ending decoding. The method has the advantages that the probability of correct judging is increased, decoding performance loss is decreased, and no decoding performance loss is caused during the use of the method in the IMWBF (improved modified weighted bit-flipping) algorithm.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
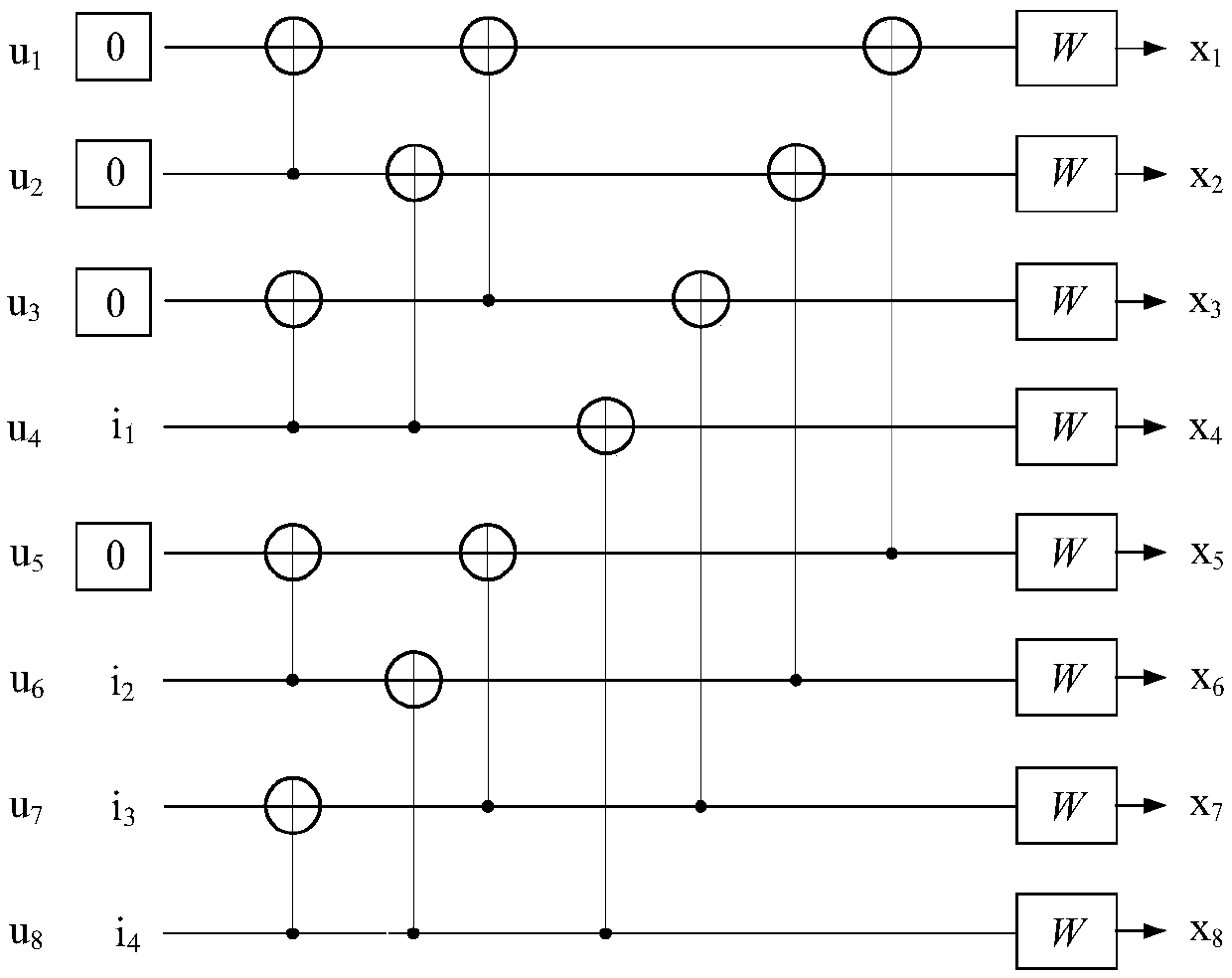
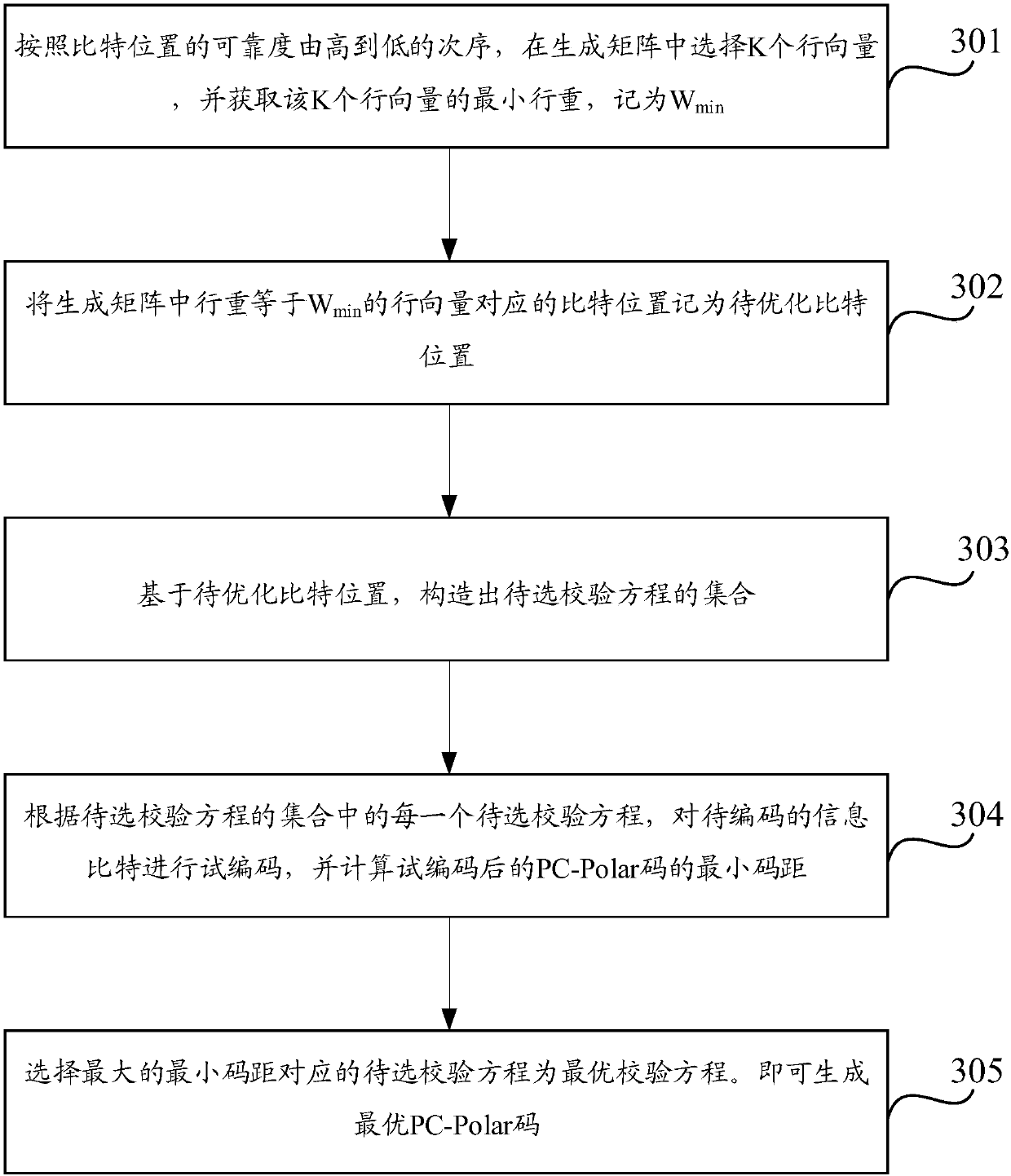
Coding method and device
The invention discloses a coding method and device, and aims to unifying coding methods of ultrashort codes. The method comprises the following steps that: a transmitting end acquires an information bit to be coded; and the transmitting end performs PC-Polar code coding on the information bit to be coded according to a first construction parameter to obtain and transmit a coded bit sequence, wherein a check equation in the first construction parameter include a first element representing the bit location of the check information and a second element representing a check bit location; the firstelement corresponds to a first vector in a generation matrix of a PC-Polar code; the second element corresponds to a second vector in the generation matrix; if the first Hamming weight of the first vector is the same as the second Hamming weight of the second vector, the third Hamming weight of a modular two vector is greater than the first Hamming weight and greater than the second Hamming weight; and if the first Hamming weight is different from the second Hamming weight, the third Hamming weight is greater than a smaller value in the first Hamming weight and the second Hamming weight.
Owner:HUAWEI TECH CO LTD
Viterbi decoding with channel and location information
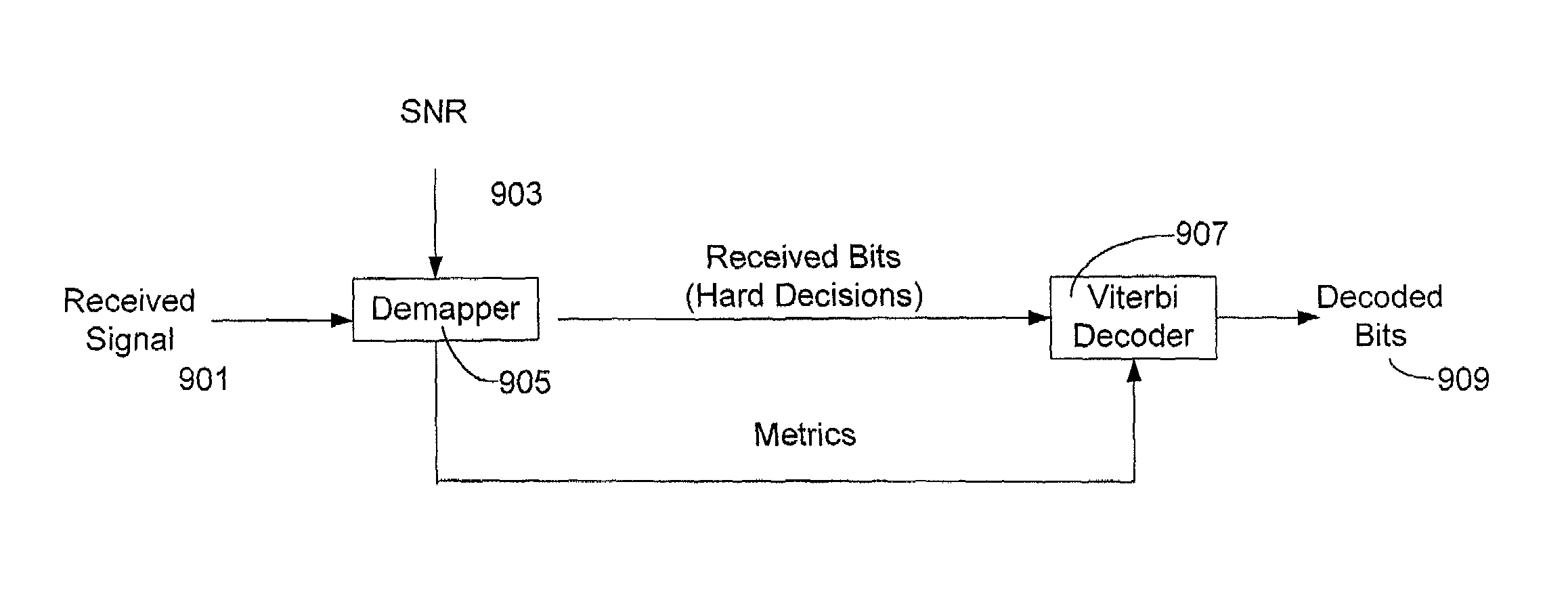
InactiveUS7027532B2Improvement in decoder performanceImprove performanceError preventionOther decoding techniquesErrors and residualsComputer science
A method for exploiting location information inherent in the location of points within a transmitted signal constellation. A common method for assigning weights to branch metrics in a Viterbi decoder is to assign Hamming weights which are summations of the number of places in which a received bit pattern differs from the bit pattern assigned to a branch metric. Signal strength information may be incorporated into the weight assigned to a branch metric in the Viterbi decoder. Additionally information-inherent in the location of the points within a constellation may be taken into account. Bit errors which require a larger deviation to occur are given higher weights, and bit errors which require less deviation to occur are given lower weights. By taking into account signal strength and location information up to 2 dB of coding gain can be realized.
Owner:AVAGO TECH INT SALES PTE LTD
Decoding method and error correction method of a cyclic code decoder
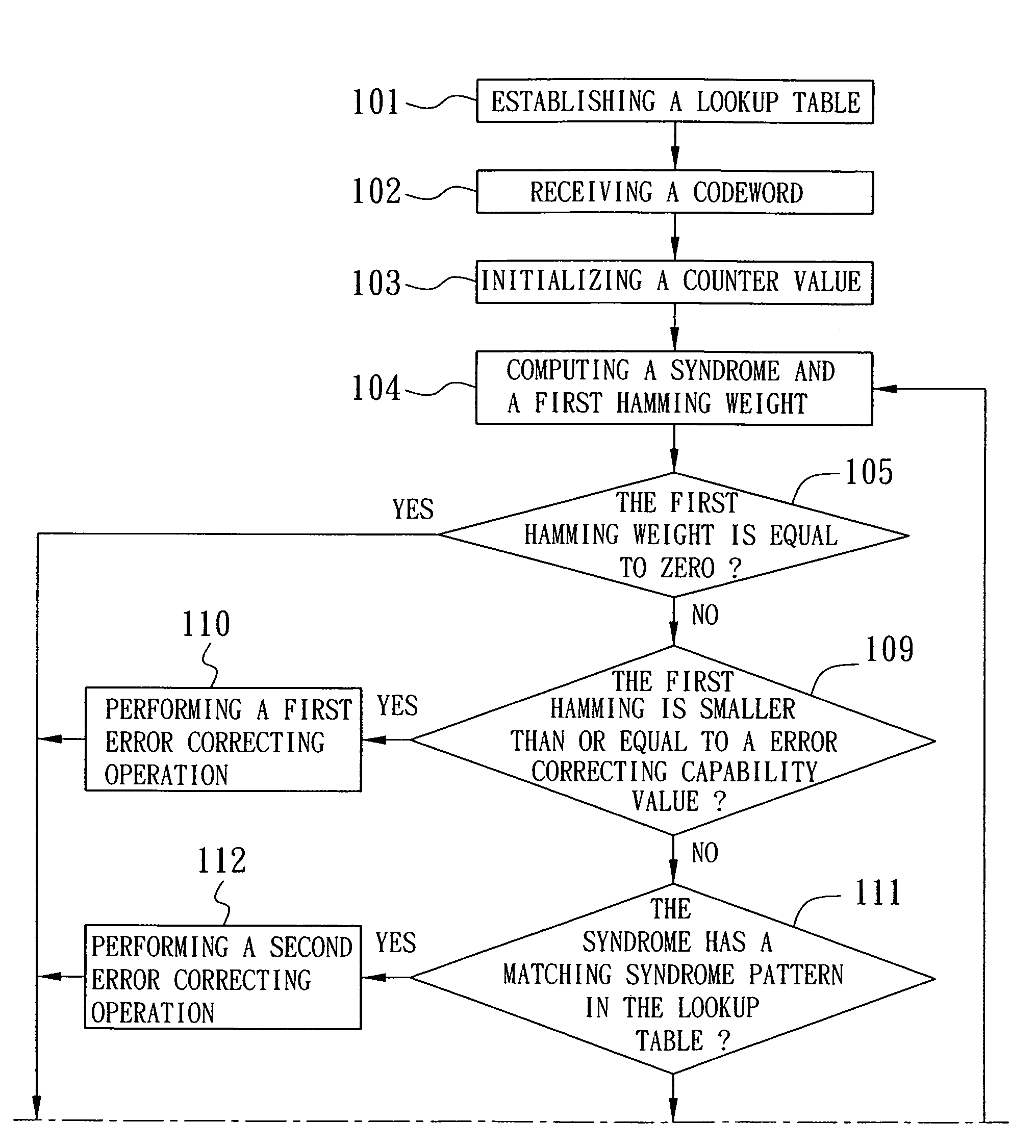
ActiveUS20090287983A1Reduce size requirementsSmall sizeCode conversionCyclic codesDecoding methodsComputer hardware
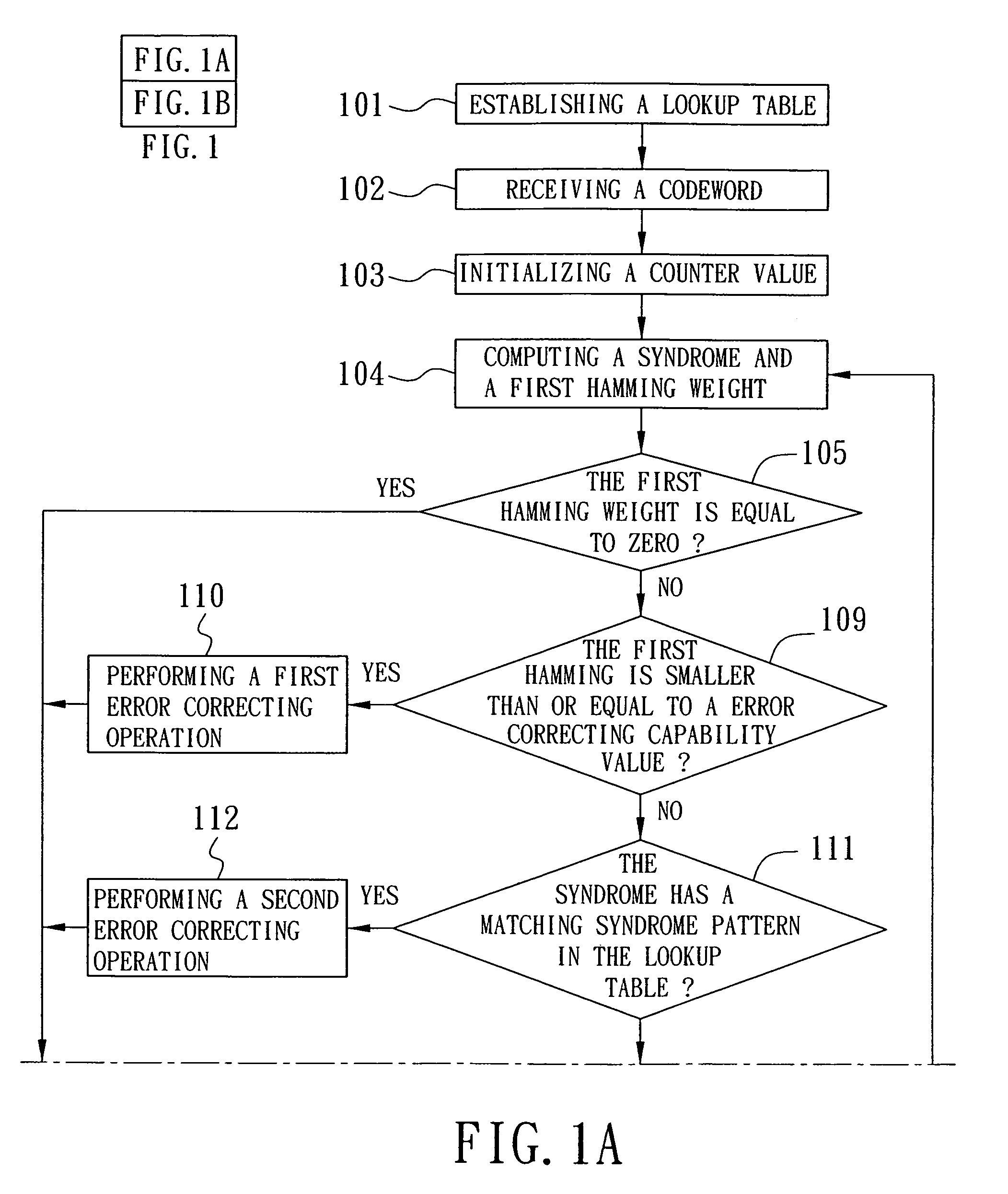
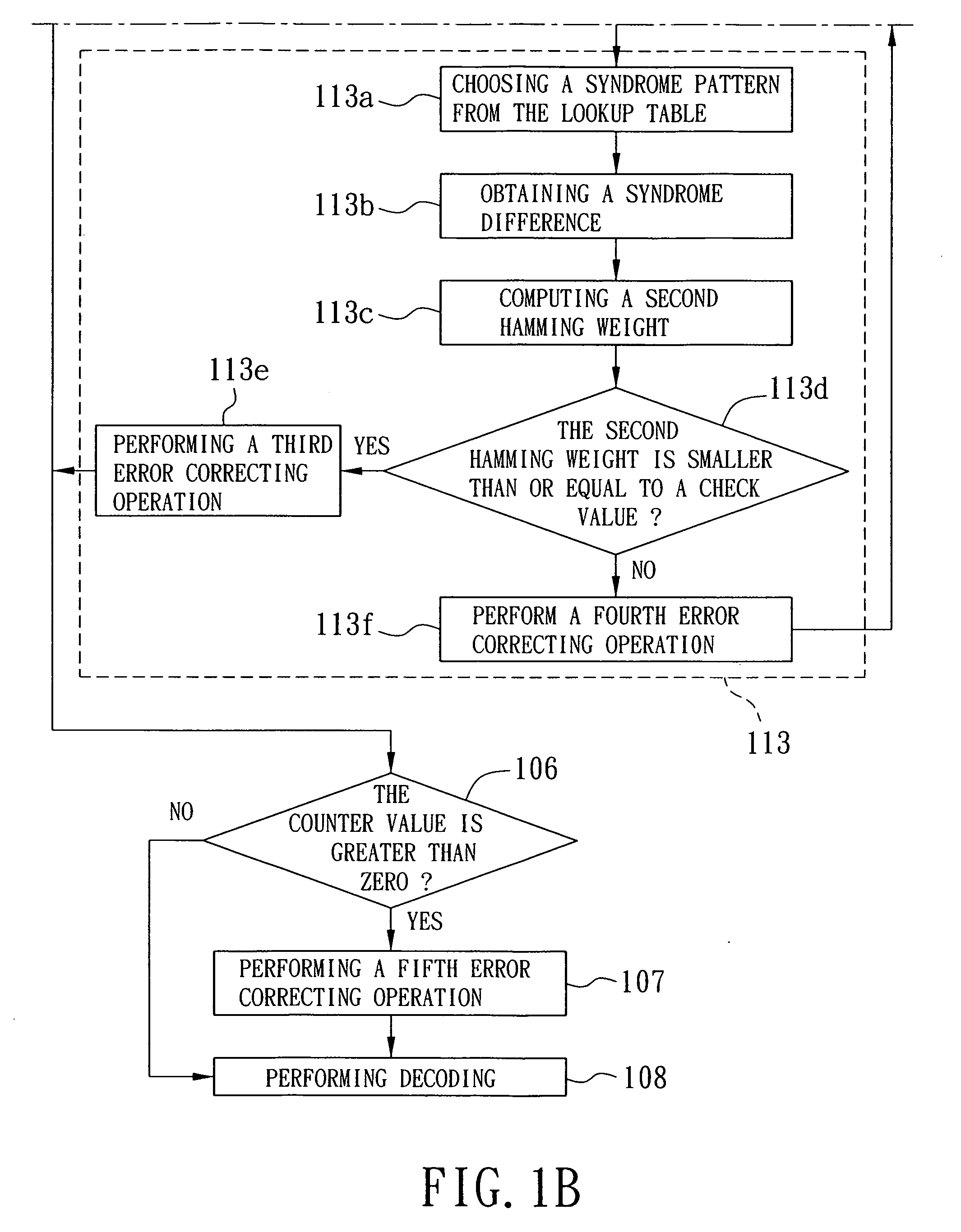
A decoding method of a cyclic code decoder includes the machine-implemented steps of: establishing a lookup table; receiving a codeword; computing a syndrome and a Hamming weight; if the Hamming weight is not equal to zero and not greater than an error correcting capability value, performing a first error correcting operation; if the Hamming weight is greater than the error correcting capability value, and if the syndrome has a matching syndrome pattern in the lookup table, performing a second error correcting operation; if a second Hamming weight corresponding to a syndrome difference is smaller than a check value, performing a third error correcting operation, otherwise performing a fourth error correcting operation; and if a counter value is greater than zero, performing a fifth error correcting operation before decoding a corrected codeword.
Owner:I-SHOU UNIVERSITY
Method and apparatus for transmitting hamming weight and codeword
ActiveUS10075197B1Reduce signaling overheadJoint error correctionError preventionComputer hardwareCommunications system
Owner:LG ELECTRONICS INC
Hardware security assessment method for chaotic cryptosystem
PendingCN110263586AEncryption apparatus with shift registers/memoriesDigital data protectionNetwork structureSecret code
The invention discloses a hardware security evaluation method for a chaotic cipher system, which comprises the following steps of 1) analyzing the structure of the chaotic block cipher system applying a replacement-replacement network structure, and judging the possible bypass information leakage; 2) comparing the links with bypass information leakage in the SP structure, and selecting the attack points; 3) modeling the energy consumption information corresponding to the intermediate data generated at the attack point, wherein the adopted energy consumption model is a Hamming weight model; 4) performing the correlation energy analysis attack on the chaotic cryptographic algorithm of the SP structure according to the energy consumption model; and 5) evaluating the security of the chaotic cryptographic algorithm of the SP structure during hardware implementation according to the attack result. According to the method, the hardware security of the chaotic cryptosystem passing the statistical test can be verified, whether the cryptosystem has the possibility of being cracked by a side channel attack or not is verified, and a necessary method and a necessary detection means are provided for the design, analysis and evaluation of the cryptosystem.
Owner:GUANGXI NORMAL UNIV
A block password fault-tolerant algebraic bypass analysis method based on multi-inference utilization
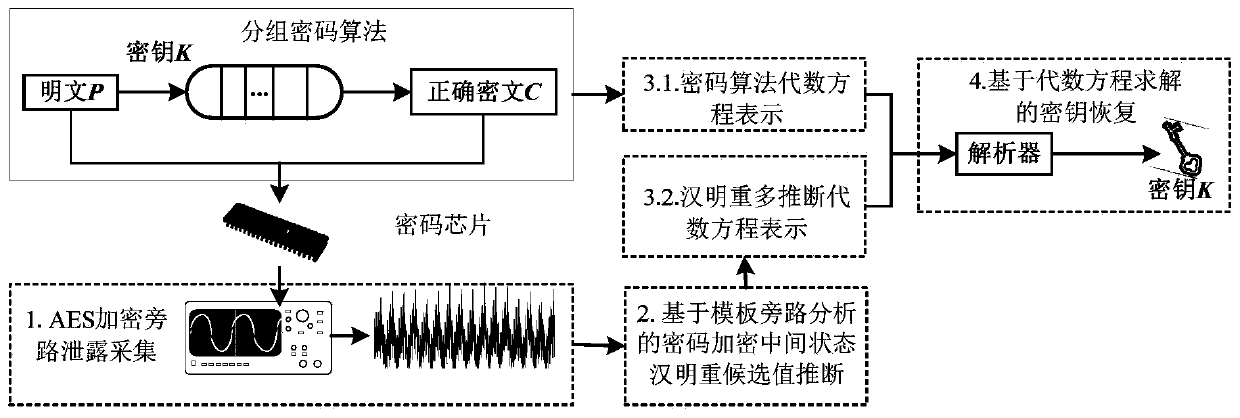
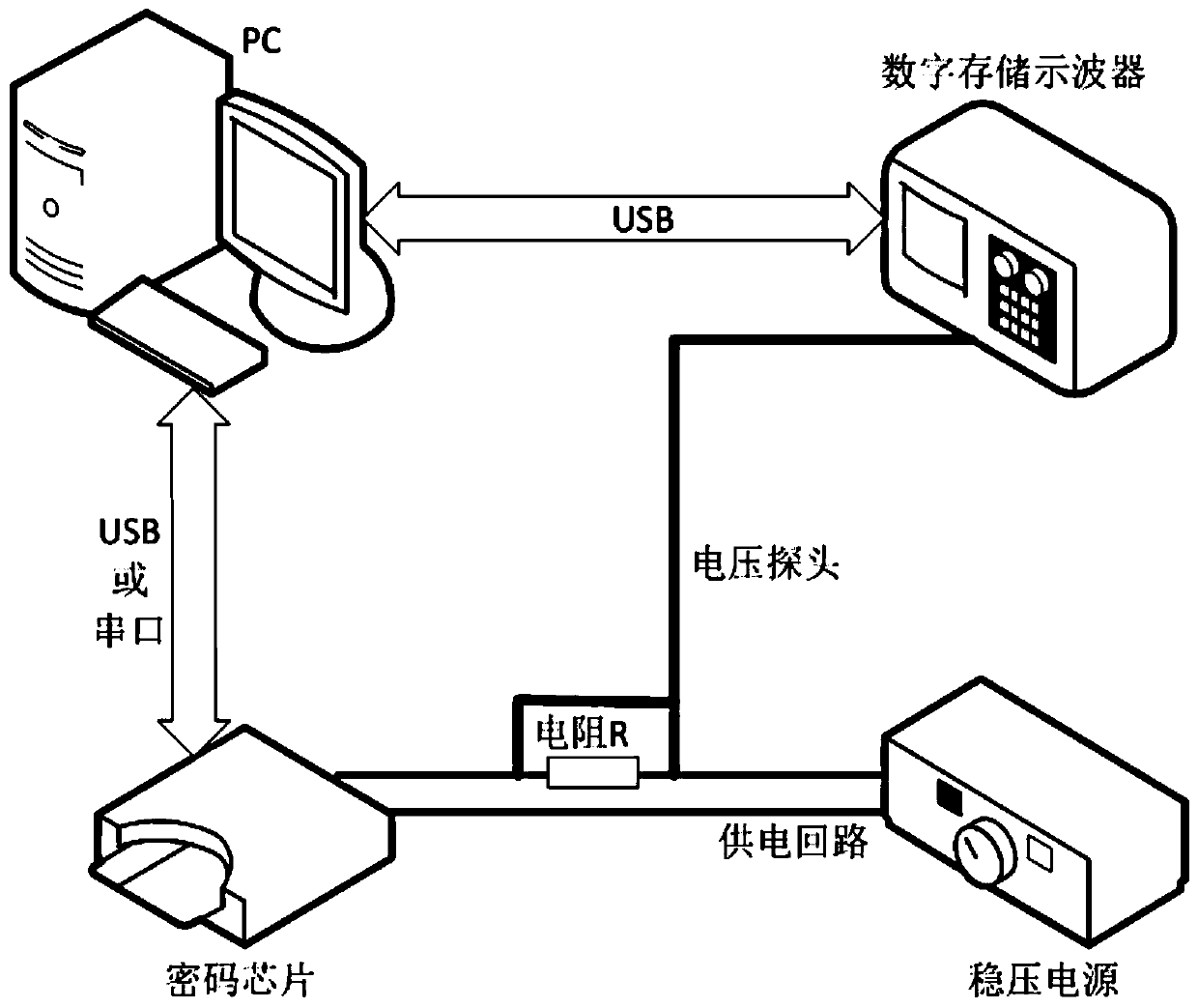
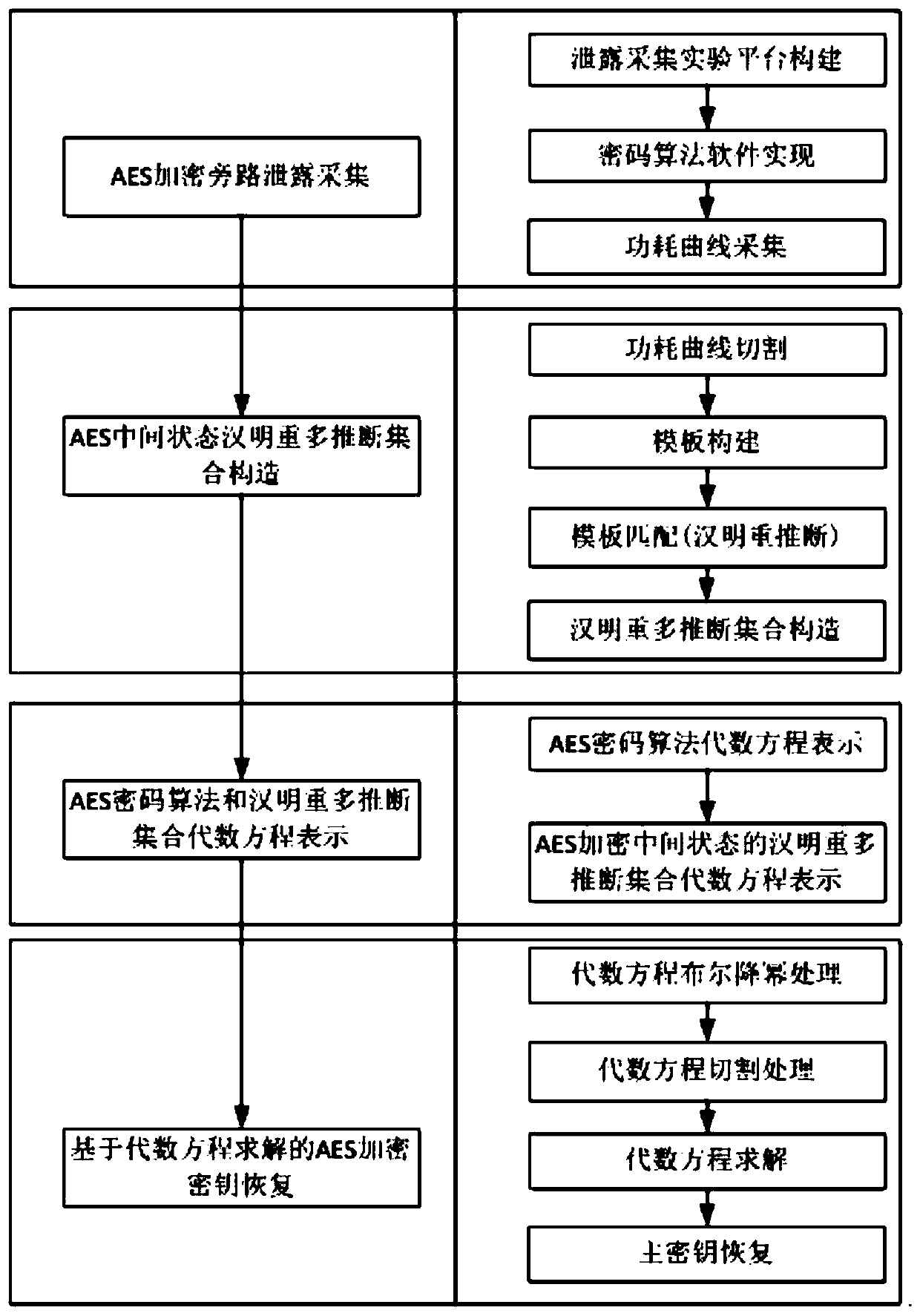
InactiveCN109787745AImprove fault toleranceEncryption apparatus with shift registers/memoriesMicrocontrollerValue set
The invention provides a block password fault-tolerant algebraic bypass analysis method based on multi-inference utilization, which comprises the following steps of: when a key is known, constructinga power consumption track template corresponding to a Hamming weight candidate value in an encryption intermediate state according to a plurality of power consumption tracks in a block password encryption process executed by a controlled password chip; Executing a power consumption track in a block password encryption process by utilizing the power consumption track template and a password chip tobe attacked to obtain a Hamming weight multi-inference value set in an encryption intermediate state; Representing the block cipher algorithm and the Hamming weight multi-inference value set by usingan algebraic equation; And using an analyzer to solve the algebraic equation, and recovering the encrypted master key. It can be seen that for AES block password implementation on the microcontroller, the master key recovery can be achieved through one power consumption track. Moreover, a plurality of Hamming weight inference values corresponding to one power consumption track exist in the actualattack, so that the fault-tolerant capability of the algebraic bypass attack can be greatly improved by utilizing the plurality of inference values.
Owner:中国人民解放军32082部队
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com