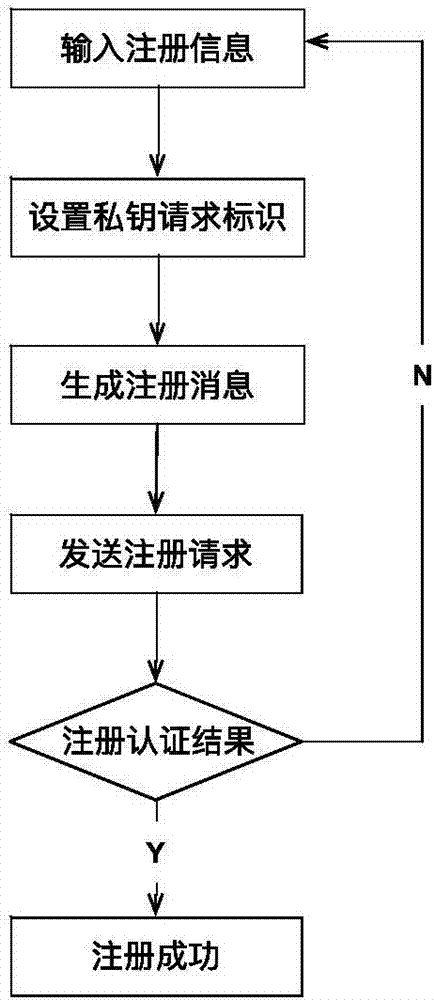
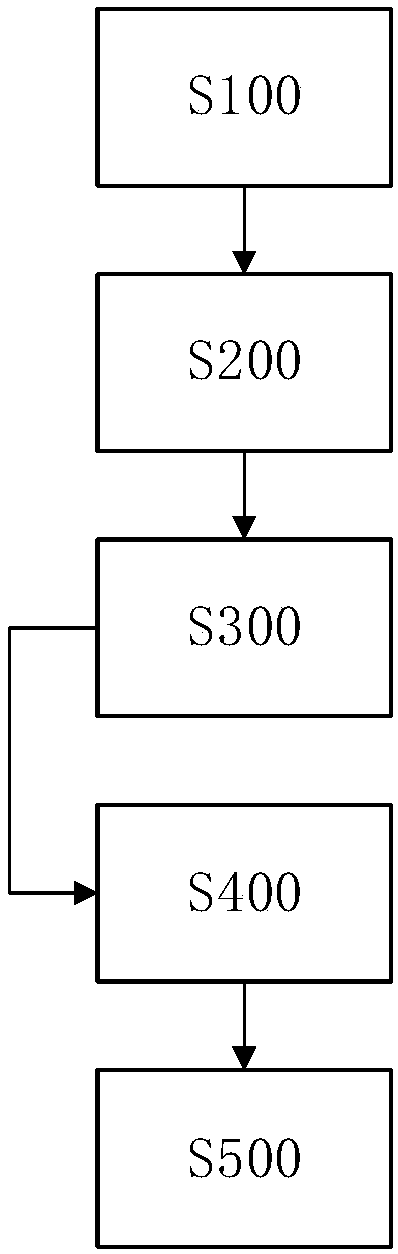
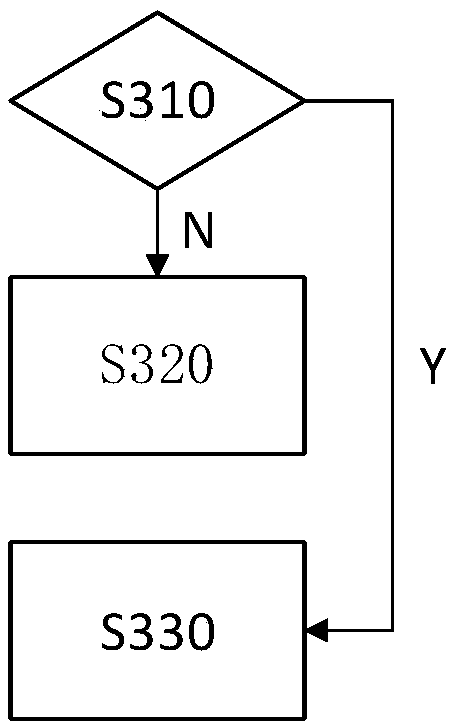
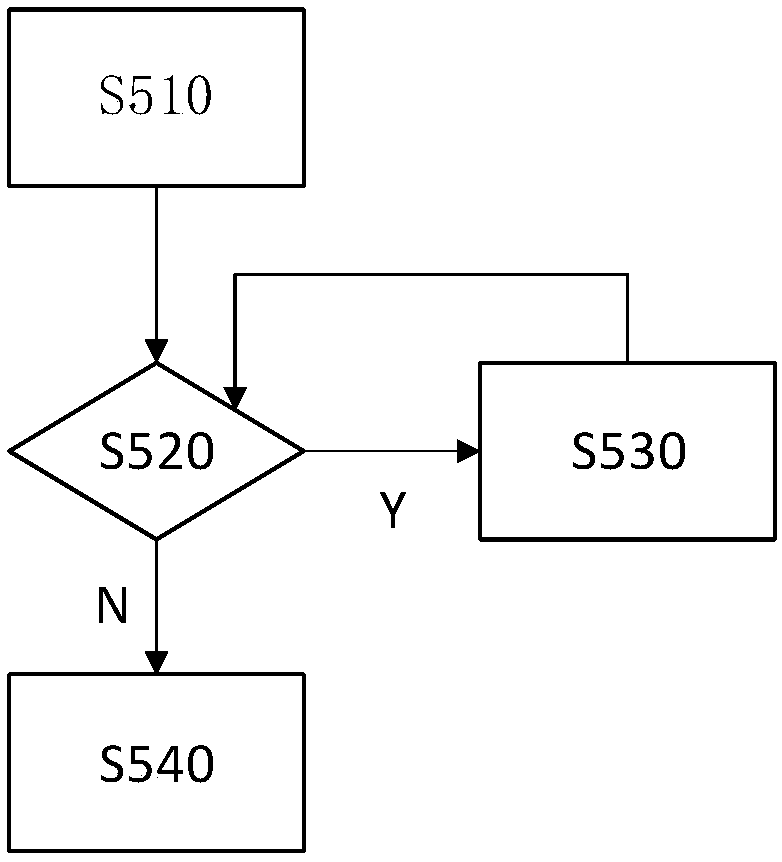
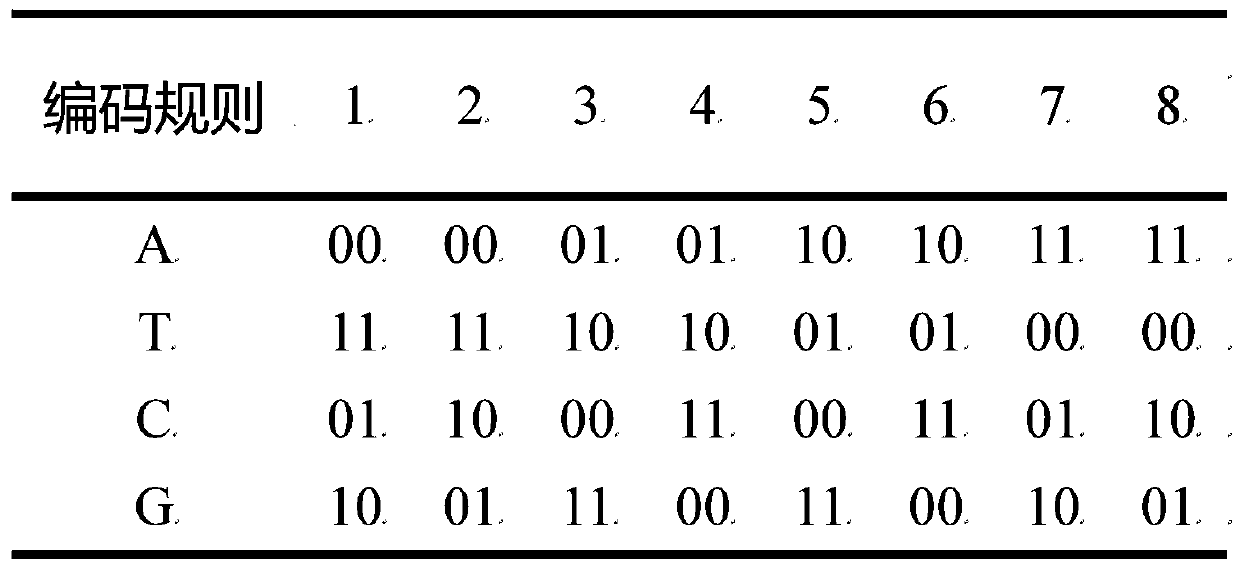
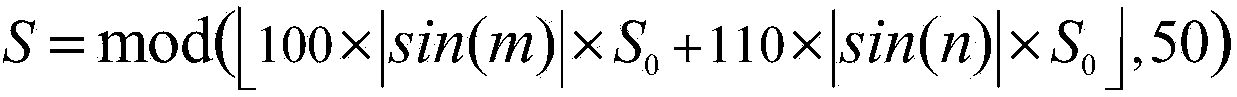Patents
Literature
367results about How to "Improve encryption efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
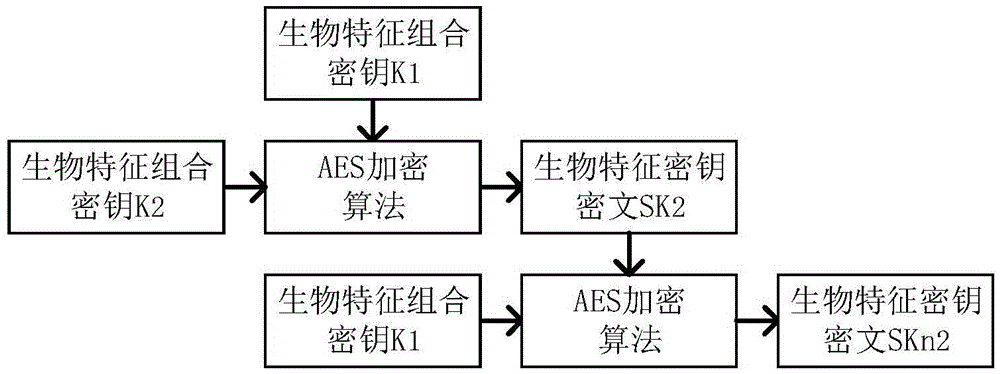
File encryption method and electronic device
ActiveCN105260668AEnsure safetyImprove confidentialityDigital data protectionComputer hardwareEncrypted file system
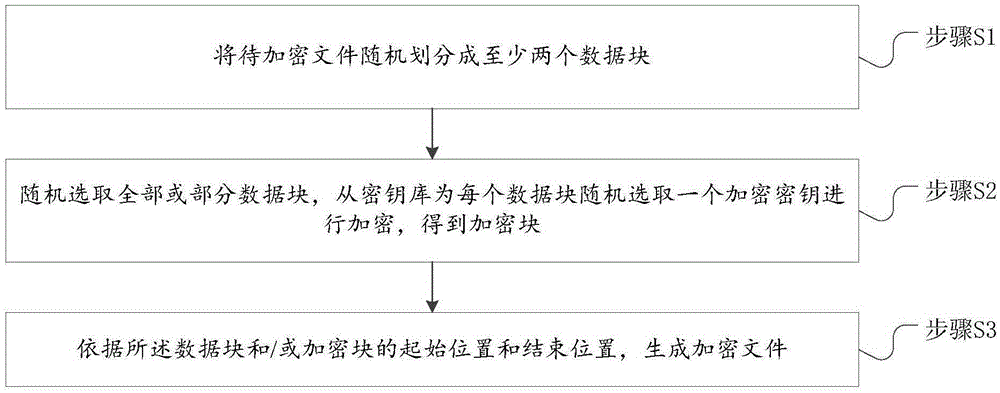
The present invention discloses a file encryption method and an electronic device. The method comprises: after determining a to-be-encrypted file, randomly dividing the to-be-encrypted file into at least two data blocks; then randomly selecting all or a part of the data blocks, and randomly selecting one encryption key from a key library for each data block to perform encryption to obtain an encrypted block; and then generating an encrypted file according to starting locations and ending locations of the data blocks and / or the encrypted blocks. According to the file encryption method and the electronic device provided by the present invention, the whole to-be-encrypted file is divided, thereby increasing the encryption efficiency; and during encryption, selection of the data blocks and selection of the encryption key are both random, so that the secrecy of the encrypted file is improved, the decryption difficulty is increased, and the security of the encrypted file is ensured.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Encryption and decryption method for numeric type data
ActiveCN103532701AEnsure safetyGuaranteed feasibilityEncryption apparatus with shift registers/memoriesOriginal dataCiphertext
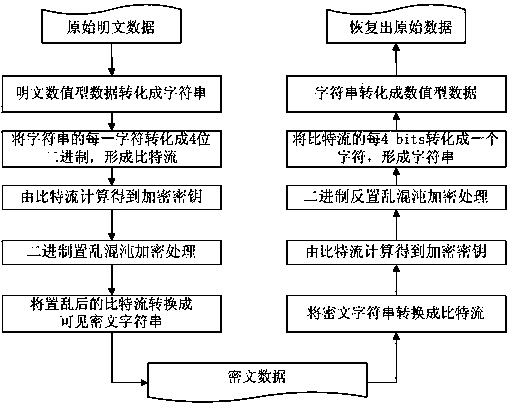
The invention discloses an encryption and decryption method for numeric type data. The method comprises the following steps that the numeric type data is converted into character strings; each character is sequentially converted into 4 bits according to the correspondence relationship between the numeric characters and the binary system, and a bit stream is formed; the number of 0 and 1 in the bit stream is counted, and an encryption secret key is obtained through calculation; the encryption secret key is utilized, a chaotic sequence with the pseudo-random property is generated by a chaotic system, in addition, chaotic signals are taken from the chaotic sequence and are sequenced in an ascending sequence, and the bit stream is scrambled according to the positions in accordance with the scrambling rule; the corresponding relationship between the four-digit binary coding mode and the visible ciphertext characters is utilized for converting the scrambled bit stream into the visible ciphertext character strings, and the ciphertext can be decrypted and recovered into the original data type data through adopting the similar method. According to the method provided by the invention, the corresponding table customization is adopted, the numeric type data is subjected to binary scrambling chaotic encryption processing, the safety and the feasibility of the data encryption are ensured, and in addition, the encryption efficiency is also greatly improved.
Owner:南通九盛软件有限公司
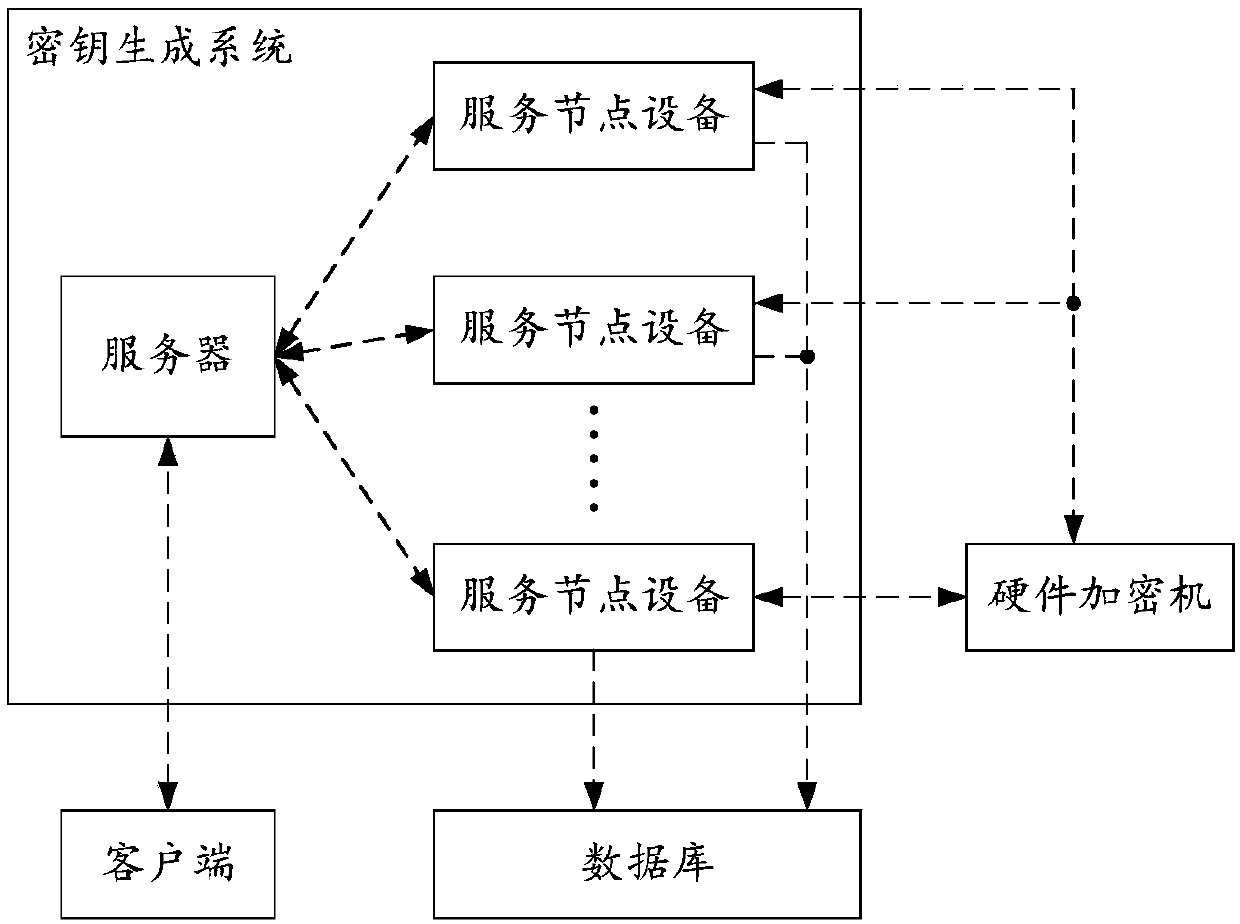
Method for generating key, service node device and computer readable medium
InactiveCN107786328AImprove encryption efficiencyLow costKey distribution for secure communicationPlaintextClient-side
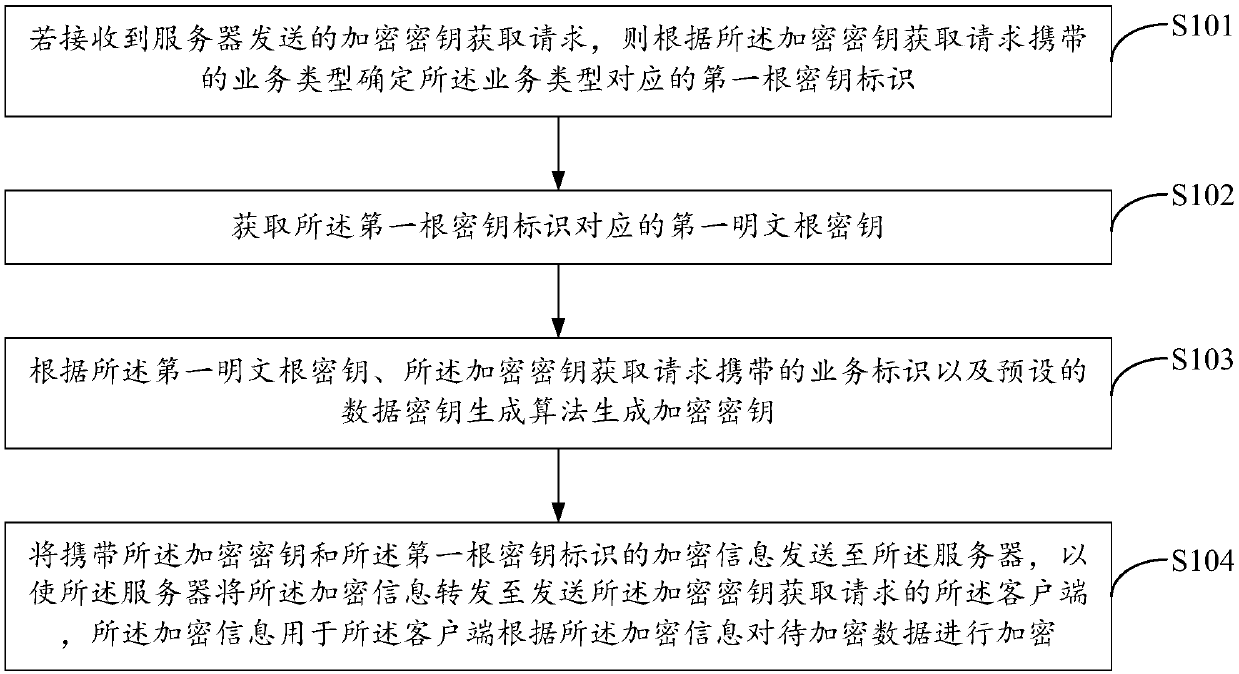
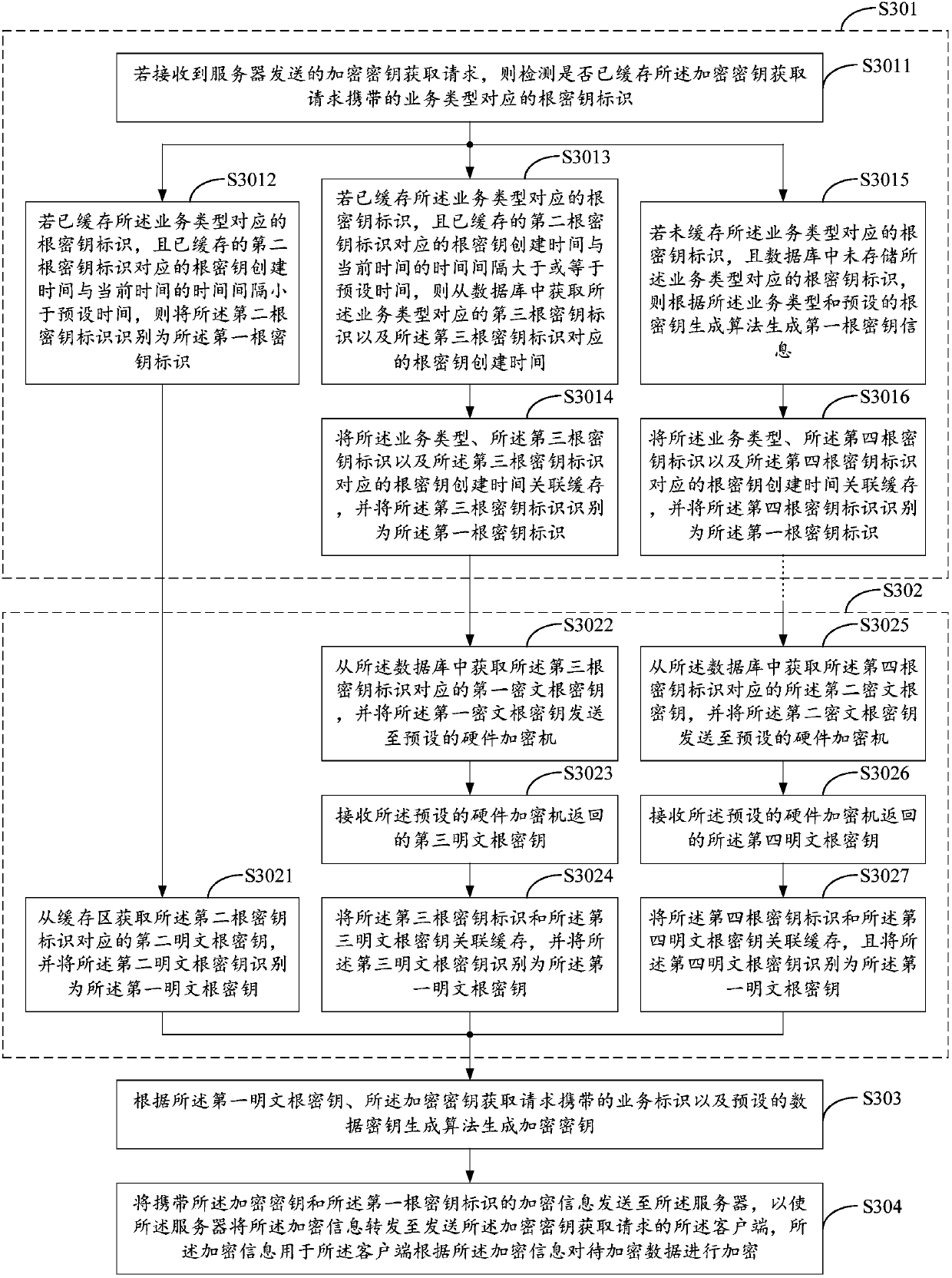
The embodiment of the invention discloses a method for generating a key, a service node device and a computer readable storage medium. The method comprises the steps of if receiving an encryption keyobtaining request sent by a server, according to a service type carried by the encryption key obtaining request, determining a first root key identifier corresponding to the service type, wherein theencryption key obtaining request is sent from a client to the server; obtaining a first plaintext root key corresponding to the first root key identifier; generating an encryption key according to thefirst plaintext root key, the service identifier carried by the encryption key obtaining request and a preset data key generation algorithm; and sending encryption information carrying the encryptionkey and the first root key identifier to the server, such that the server forwards the encryption information to the client. According to the method for generating the key, the service node device and the computer readable medium disclosed by the embodiment of the invention, the cost of data encryption can be saved, and the efficiency of data encryption is improved.
Owner:SHENZHEN GIONEE COMM EQUIP
Digital copyright protection method and system for media network application
InactiveCN1937495AIn line with psychological characteristicsGreat authorityPublic key for secure communicationProgram/content distribution protectionAuthorization ModeThe Internet
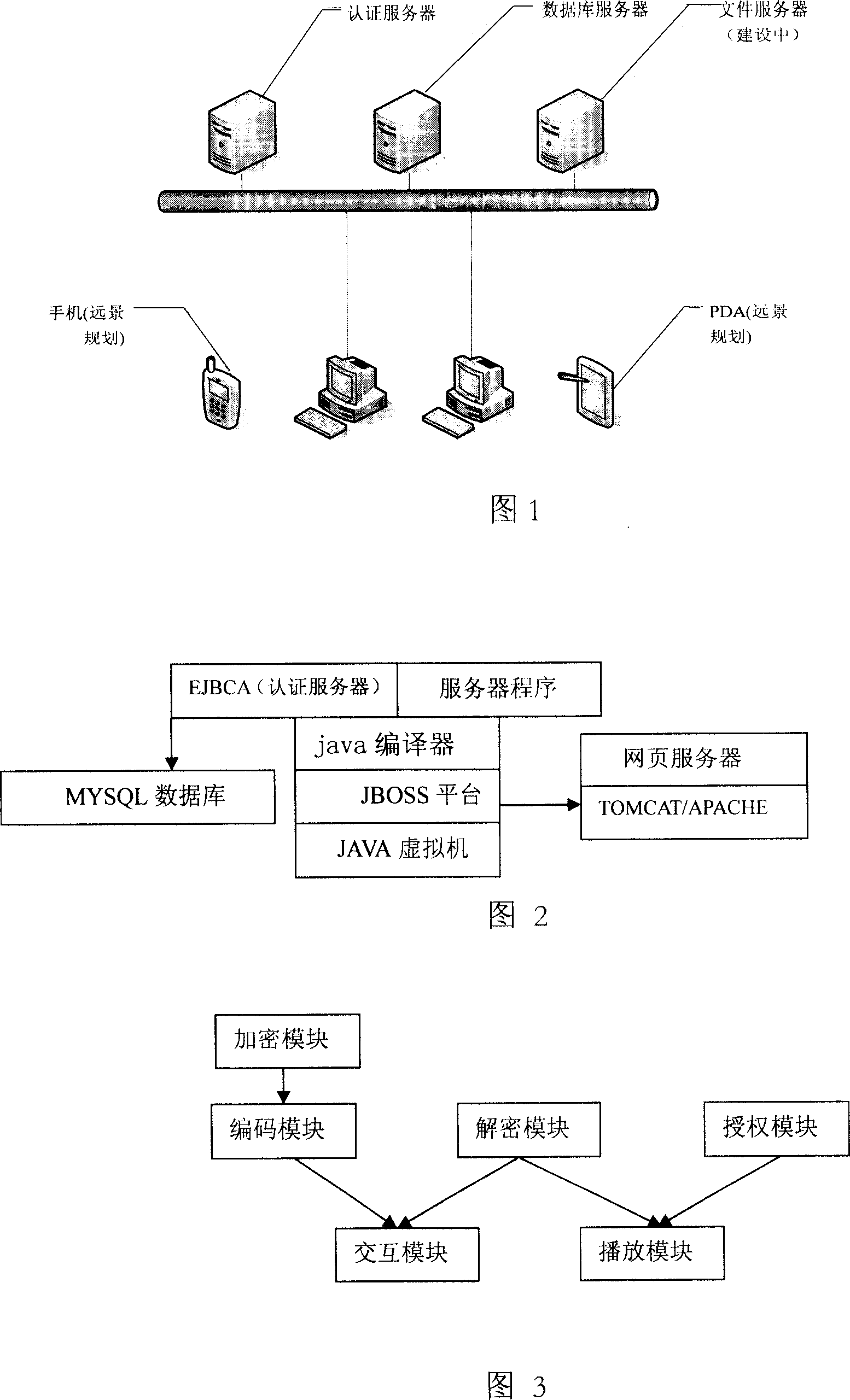
The media document owner encrypts his media documents via a encrypt module on the user end, and then uploads the encrypted documents to the data server via network. The owner manages the use right of these encrypted document by himself. This system includes the authentication server connected to the Internet, the data server and several user ends. Every user end has encryption module, authorization module, decoder module and playback module. The media document owner encrypts and authorizes their documents at the user end. It decreases the load of system server, increases the encryption efficiency. It is easy to renew the algorithm and is flexible and easy to use. The user will feel more confident by possessing the power of authorization.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Data encrypting method and device and data decrypting method and device
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
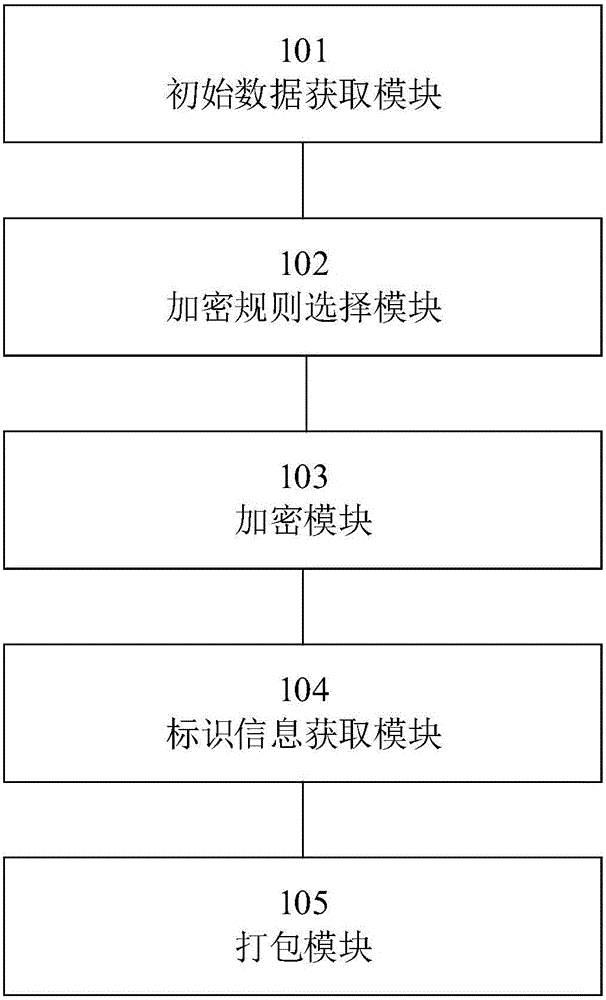
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
Design method for chaos digital secret communication system based on FPGA
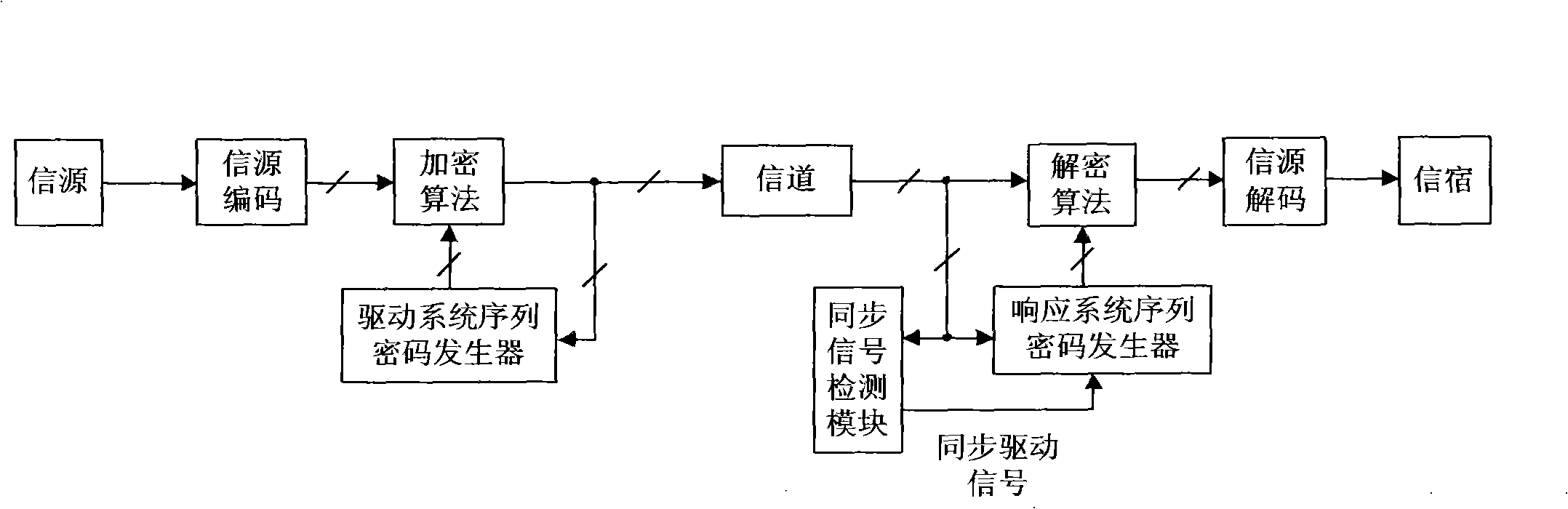
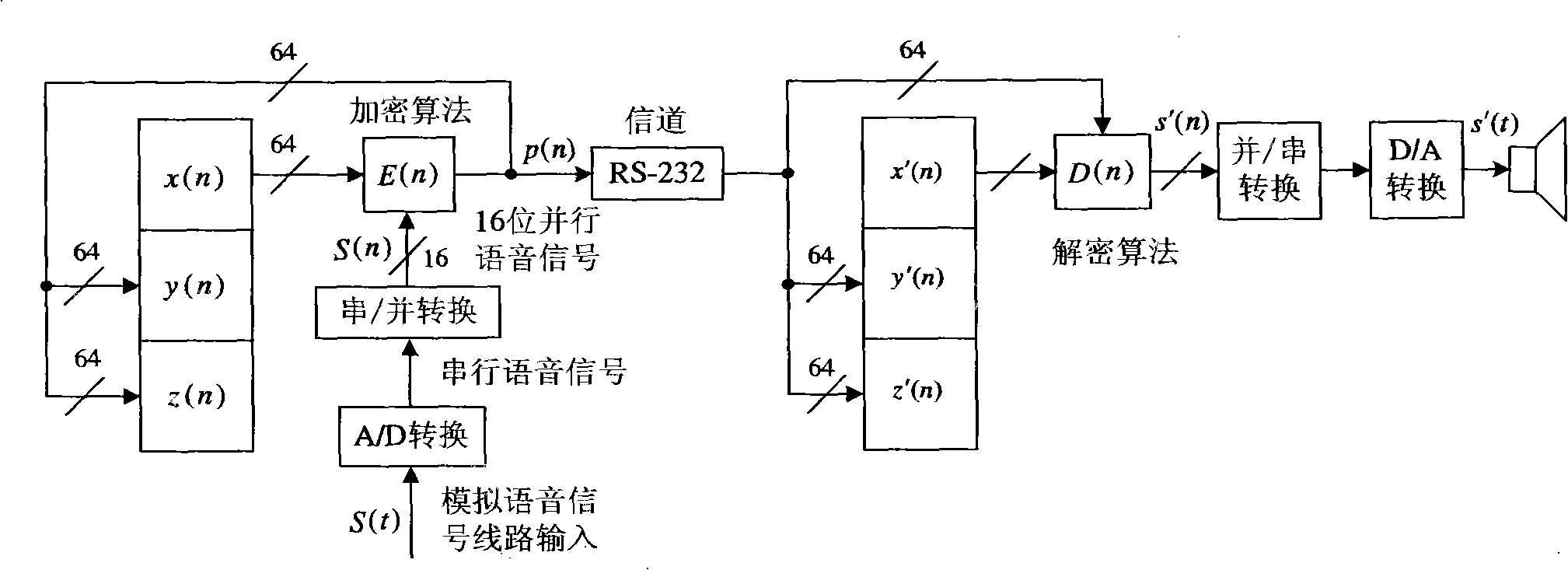
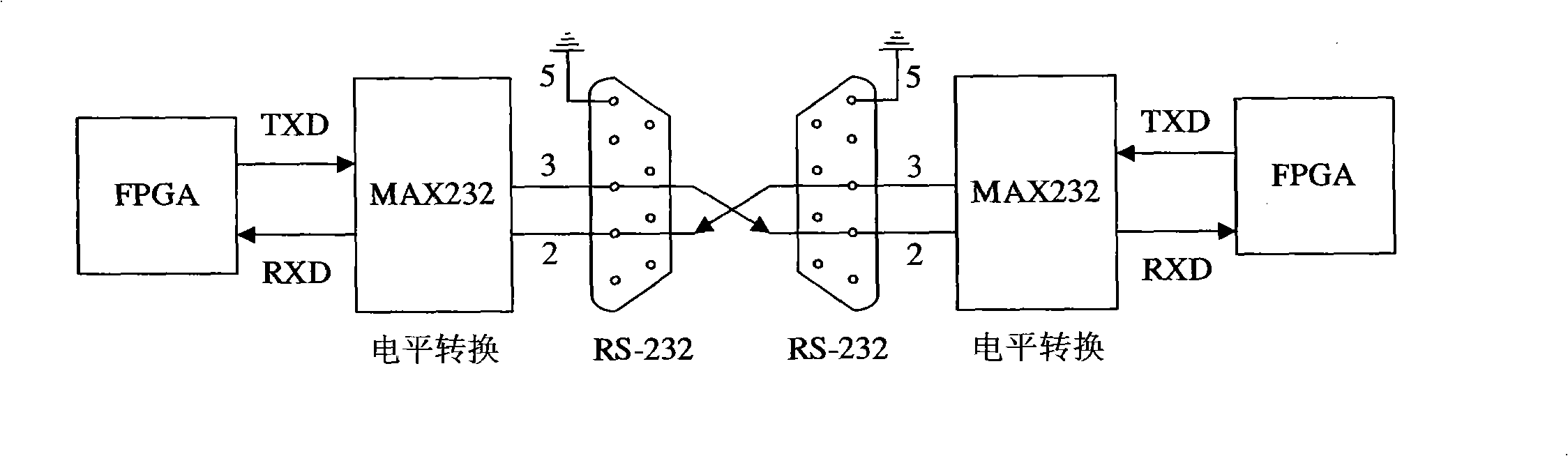
InactiveCN101345615AIncreased complexityImprove real-time performanceSecuring communicationComputer architectureCommunications system
The invention relates to design method for FPGA based chaos digital secure communication system comprising following steps: executing discrete process for continuous chaos system by FPGA hardware, designing chaos discrete system by FPGA hardware and make it produce digital chaos sequence in a certain accuracy, adopting the digital chaos sequence as key, designing drive response type synchronous secure communication system based on choas discrete system, constructing a closed loop with interior signal, accomplishing two block FPGA development board finite digital voice communication using lattice type Cai chaos and real time voice secure communication system design based on lattice type Cai chaos. The invention is highly secure and accomplishes combination of chaos encryption system and traditional cipher system. The inventive secure communication system not only serve voice secure communication, but transmit confidential binary file. As long as data can be represented as binary data, it can execute secure communication. The inventive system can employ graph encryption / decryption and transmit over Ethernet.
Owner:GUANGDONG UNIV OF TECH
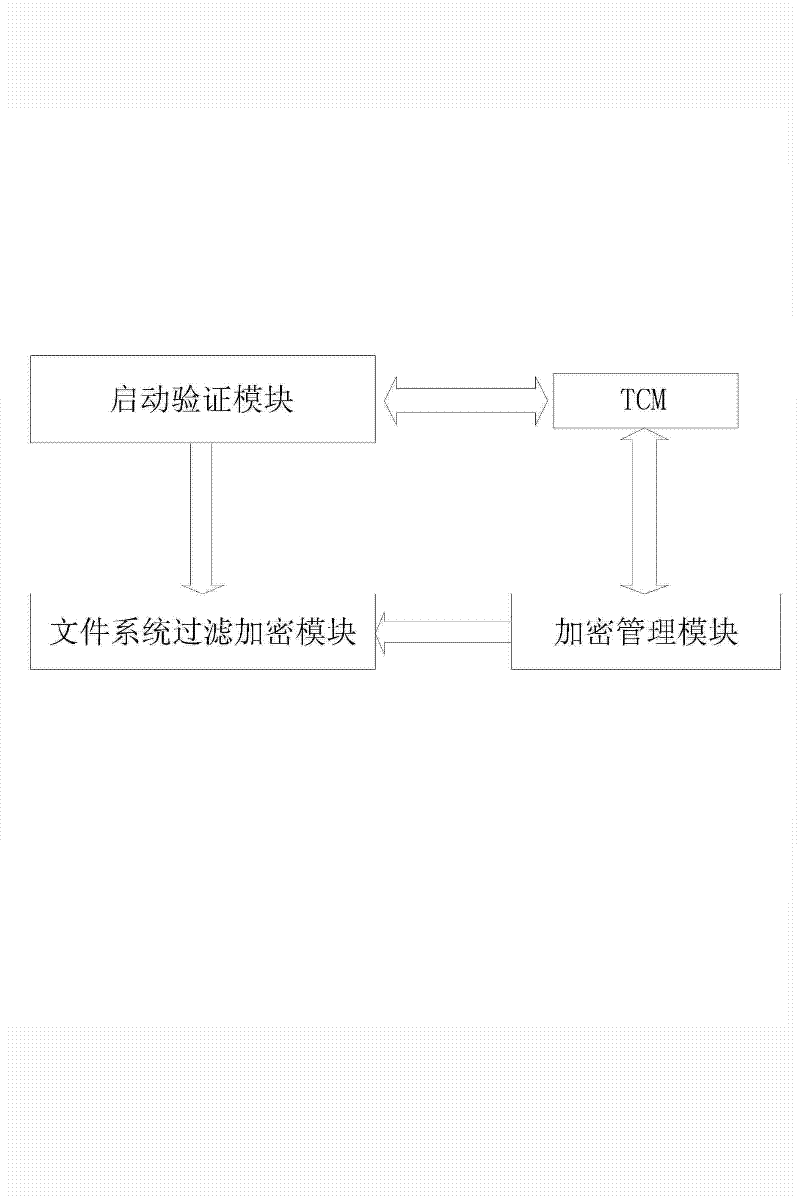
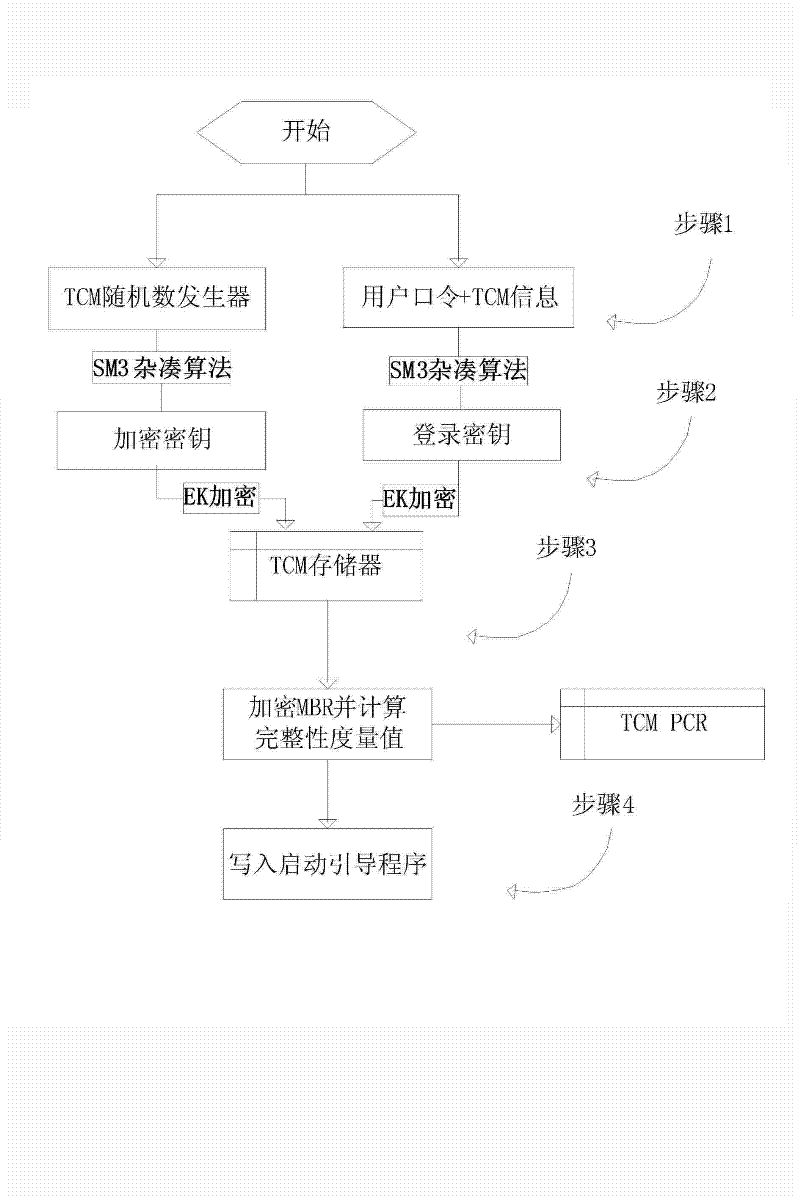
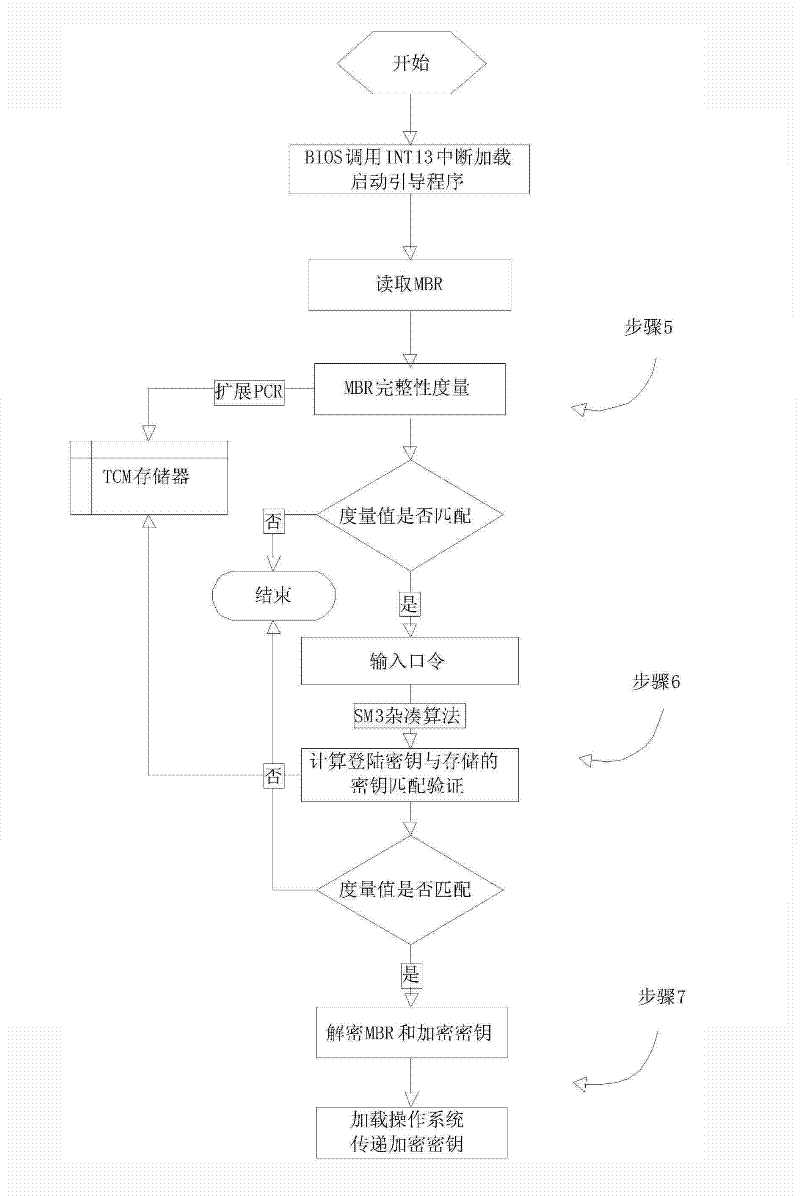
Method for full-disk encryption based on trusted cryptography module
ActiveCN102646077AImprove securityImprove encryption efficiencyUnauthorized memory use protectionInternal/peripheral component protectionFile systemPassword
The invention provides a method for full-disk encryption based on a trusted cryptography module. A logging-in key and a storage key are protected by a trusted cryptography module, a file system is designed for filtering and driving an encryption module to encrypt or decrypt the I / O data of a disk, the real-time transparent encryption of full-disk data is realized, the trusted cryptography module (TCM) is invoked to carry out authentication and integrality verification on an encryption system by adding a starting and verifying module into a first magnetic track of the disk, and the keys and integrality verification information are stored in the TCM. Compared with the prior art, the operation of storage is not carried out in the disk according to the method for the full-disk encryption based on the trusted cryptography module, so that the safety is high; and TCM authentication and integrality inspection are needed for logging in a system, so that the condition that a user password is intercepted by implanting a malicious program can be prevented.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Novel authentication mechanism for encrypting vector
InactiveCN101355422AObvious superiorityImmune to cryptographic attack methodsPublic key for secure communicationUser identity/authority verificationCryptosystemKey generation
The invention discloses a novel vector encryption authentication mechanism and relates to a vector cryptography method, belonging to the technical field of information security. The method comprises the following steps: a cipher system selects a large number encryption key space M which is twice divided into 2*2 encryption key subspaces which are provided with 2 vectors with different orientations in order that each cipher system of the system possesses a unique encryption key subspace and a unique decryption key subspace; according to the method, the novel vector encryption authentication mechanism can be constructed; the mechanism adopts a hardware tamperproof encryption key generation / regeneration technology to realize the secondary division of the large number encryption key space and endow the encryption key with vector property; and the mechanism adopts a dissymmetrical symmetric algorithm array for encryption / decryption, thereby realizing high strength security, anti-replay, integral control, identity authentication and digital signature and having no problem of the management of the encryption key.
Owner:冯振周
Encryption method and system based on data attributions
InactiveCN104063334AReduce processingImprove securityUnauthorized memory use protectionComputer hardwareEncryption
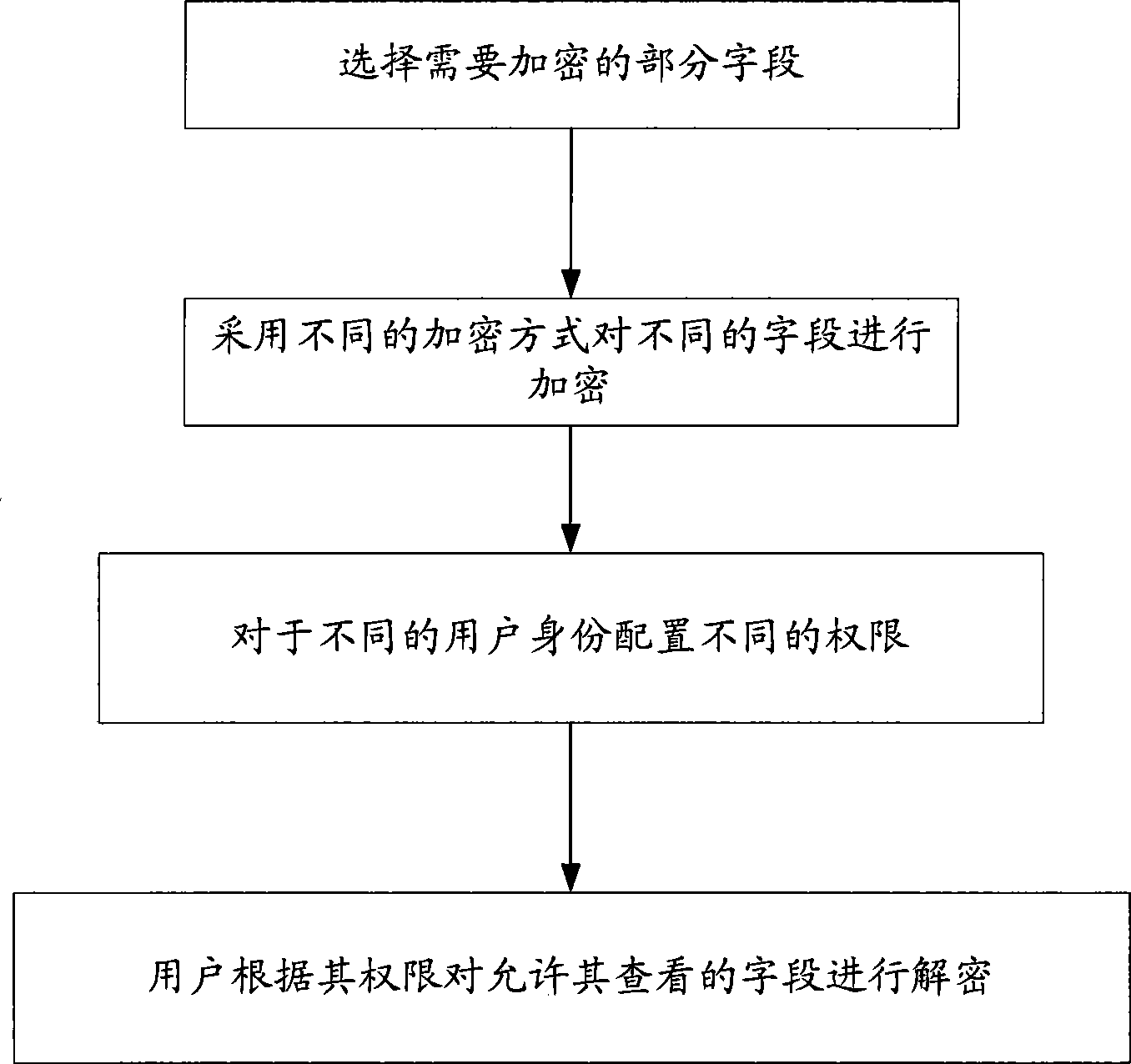
The invention provides an encryption method based on data attributions. The encryption method comprises the steps of choosing parts of fields needing encrypting, and encrypting different fields through different encryption modes; configuring different permissions to different user identifications, wherein users decrypt the fields allowing the users to look over according to the permissions. By means of the encryption method, parts of fields in a database are encrypted, parts of fields in files in the database or parts of fields in structural data can be encrypted according to needs, and therefore, encryption speed is increased. Different fields can be encrypted through different encryption modes, therefore, different permissions are configured according to user identifications conveniently, encryption modes can be selected flexibly, working efficiency is increased, and safety of data during usage is improved.
Owner:CHINESE PEOPLE'S PUBLIC SECURITY UNIVERSITY
Method and device for file encrypting/decrypting
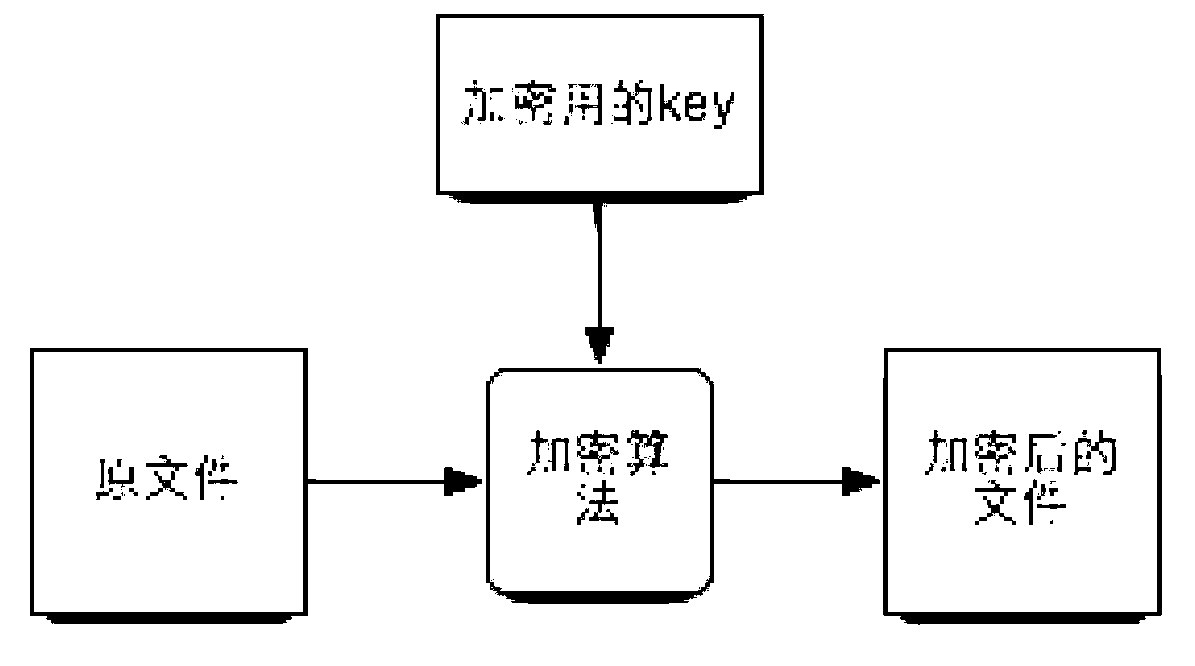
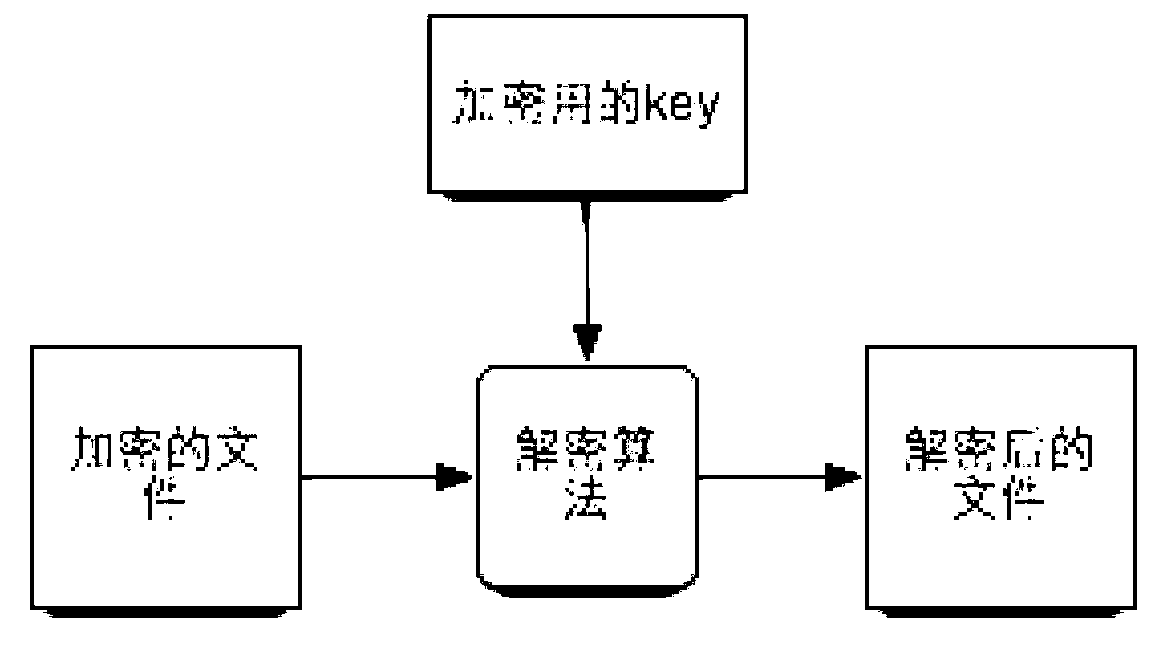
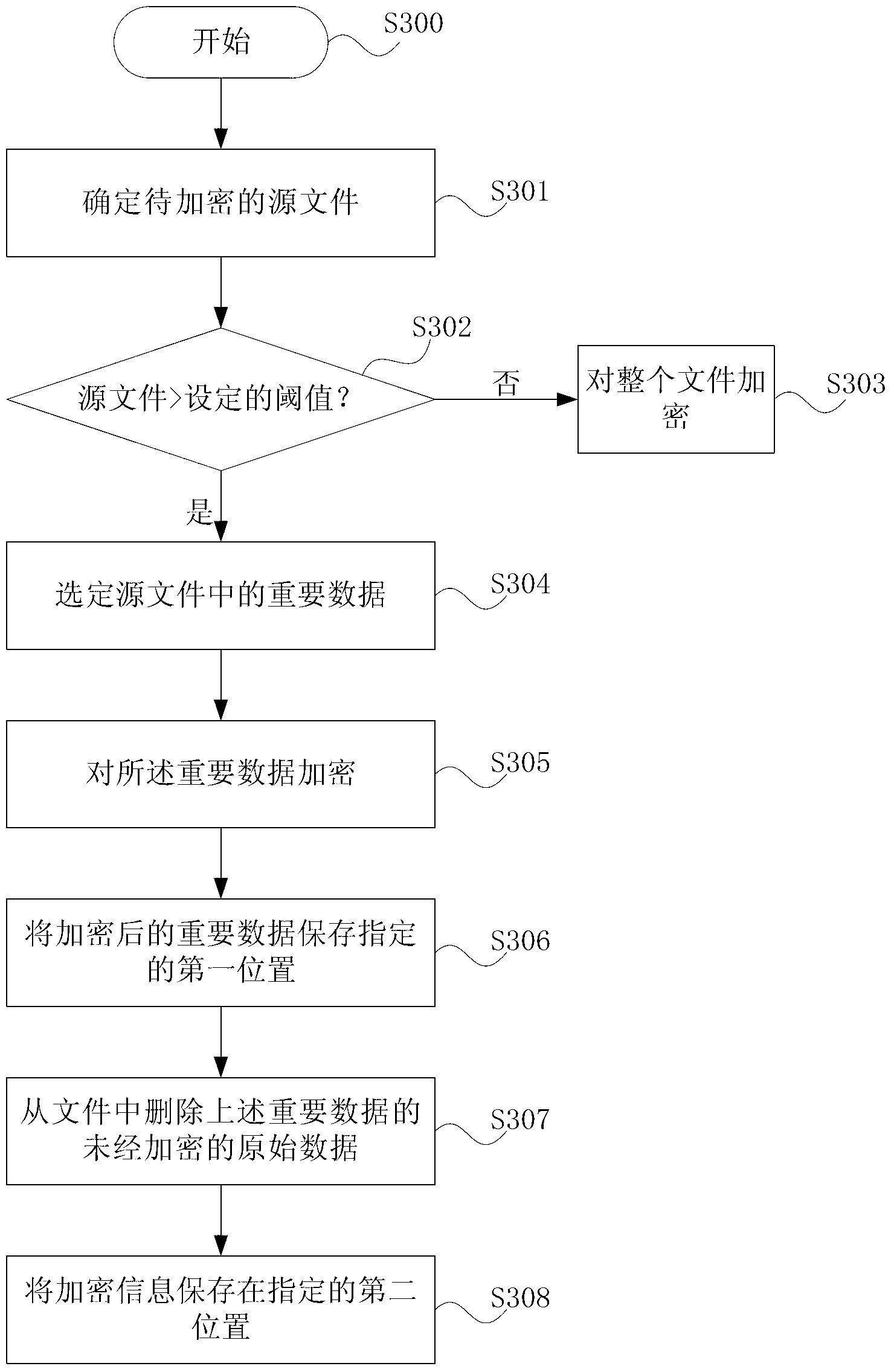
InactiveCN103294961AIncrease the difficultyReduce the amount of encryption operationsPublic key for secure communicationDigital data protectionComputer hardwareUser needs
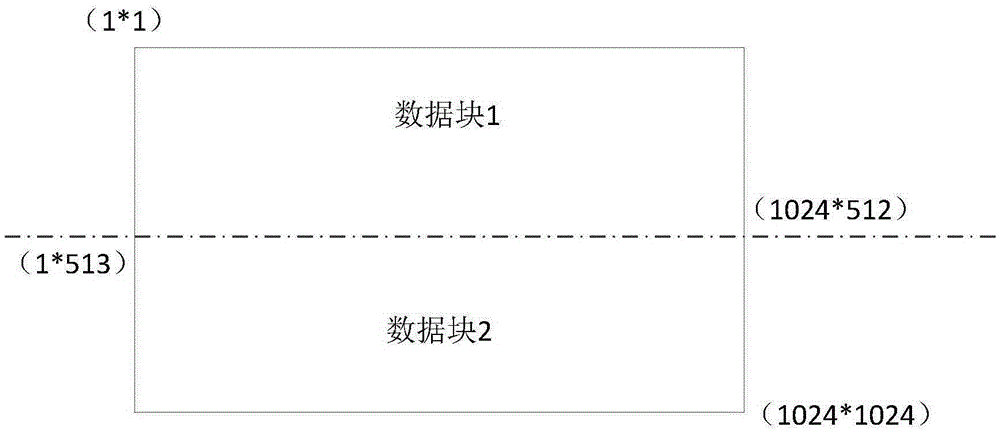
The invention provides a method and device for file encrypting / decrypting. The encrypting method includes the steps that a source file to be encrypted is determined; important data in the source file are selected; encrypting is carried out on the important data according to a set encryption algorithm; at a specified first position, the encrypted important data are stored; unencrypted important data in the source file are deleted; encrypted information is stored at a specified position; the encrypted information at least includes original positions of the important data in the source file. Relative to the encrypting method, a decrypting method, an encrypting device and a decrypting device are further provided, due to the fact that local encrypting is achieved, when decrypting is carried out, a user needs to know whether the encrypted important data exist in the source file or not and needs to know the storage position of the encrypted data, and therefore decrypting difficulty is increased.
Owner:BEIJING QIHOO TECH CO LTD +1
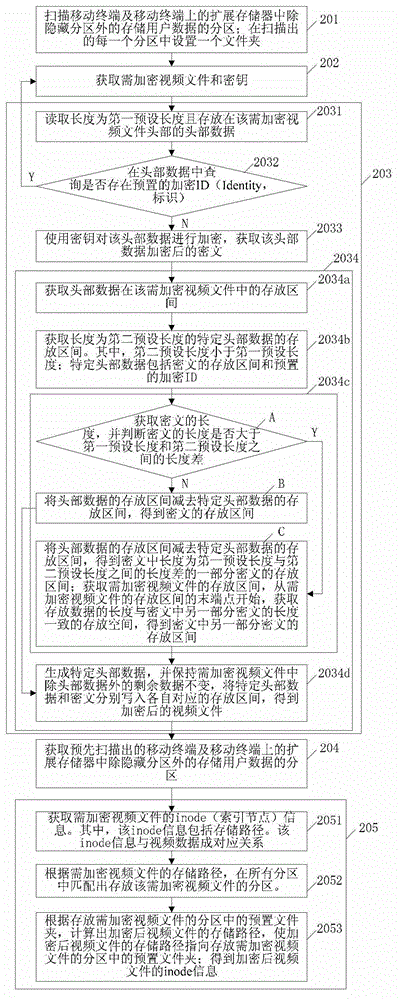
Methods and devices for encrypting and decrypting video file and mobile terminal
ActiveCN102867153AImprove securityImprove encryption efficiencyTelevision system detailsData processing applicationsComputer terminalEncryption
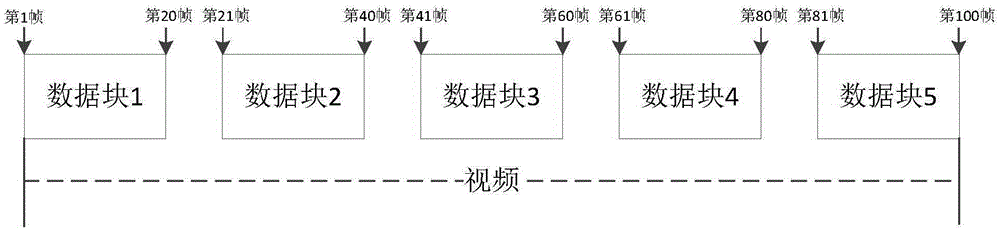
The invention discloses a method for encrypting a video file, a method for decrypting the video file, a device for encrypting the video file, a device for decrypting the video file, and a mobile terminal, and belongs to the field of mobile terminals. The method for encrypting the video file comprises the following steps of: acquiring the video file to be encrypted and a key; encrypting the video file to be encrypted by using the key to obtain an encrypted video file; acquiring a pre-scanned mobile terminal and partitions storing user data except hidden partitions in an extended memory on the mobile terminal; and determining a partition storing the video file to be encrypted in all the partitions, and moving the encrypted video file into a preset folder in the partition storing the video file to be encrypted. The method for decrypting the video file comprises the following steps of: acquiring a video file to be decrypted and the key; decrypting the video file to be decrypted by using the key to obtain a decrypted video file; and determining the storage position of the video file to be decrypted before encryption, and moving the decrypted video file to the storage position before encryption. The video file can be quickly encrypted.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
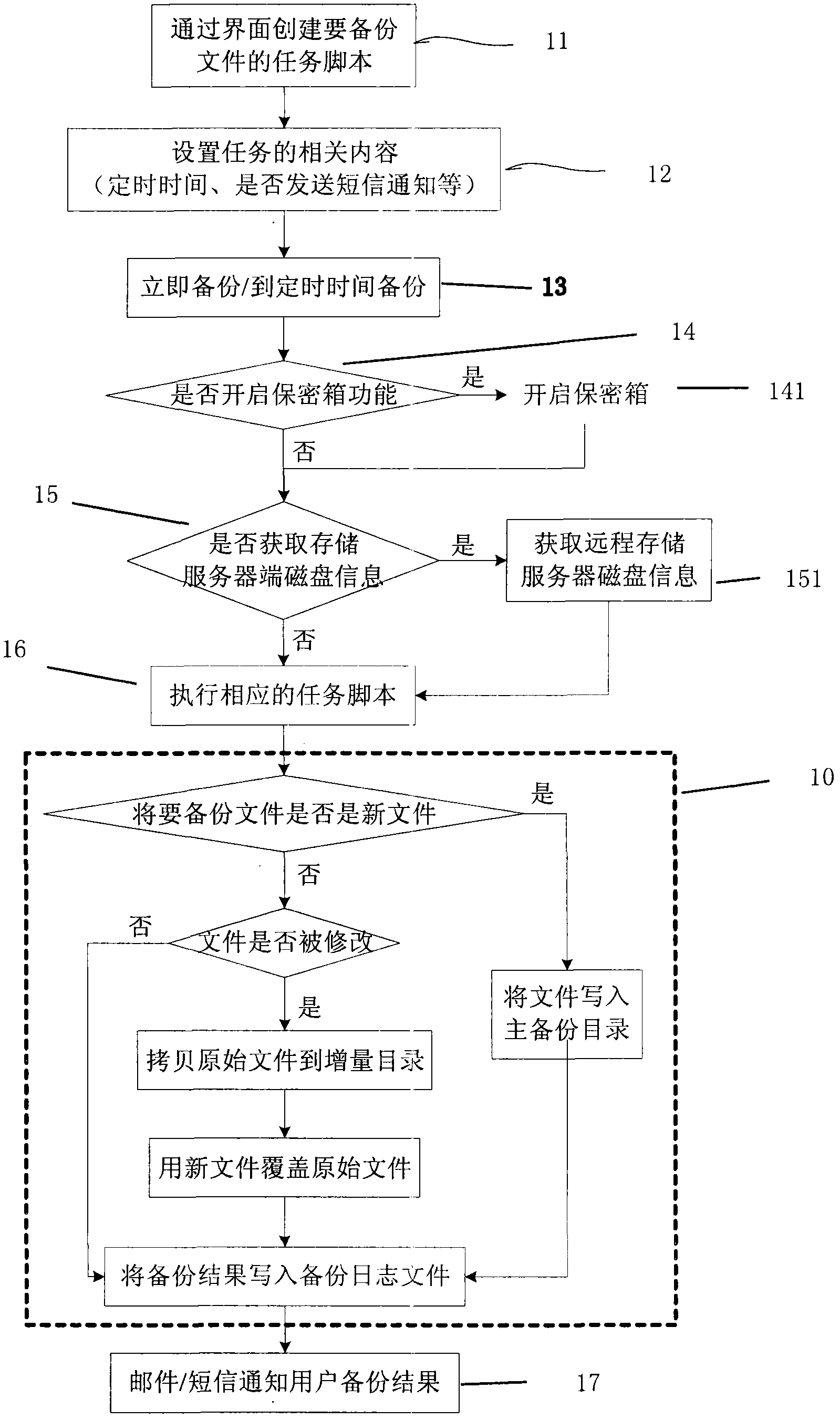
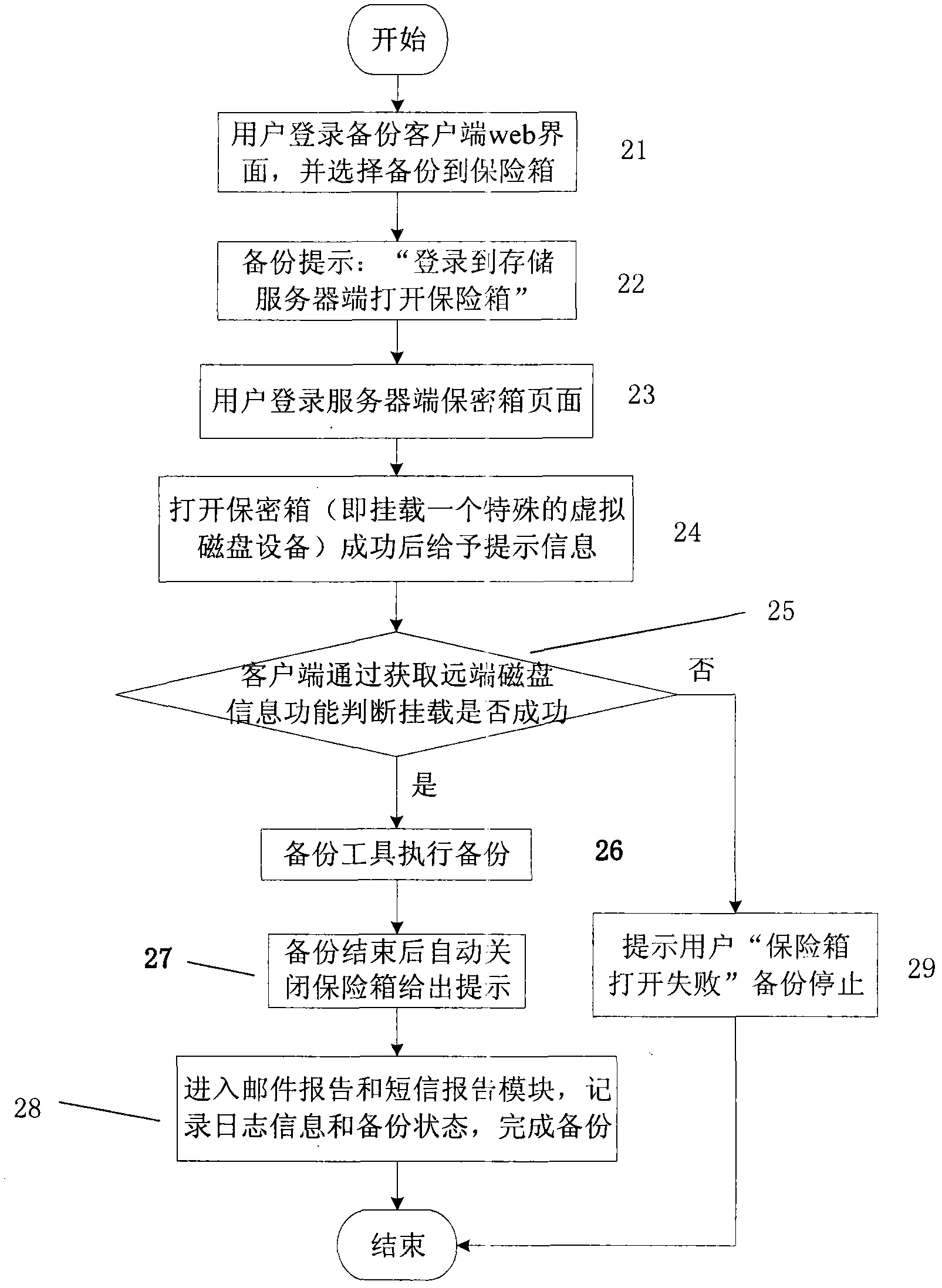
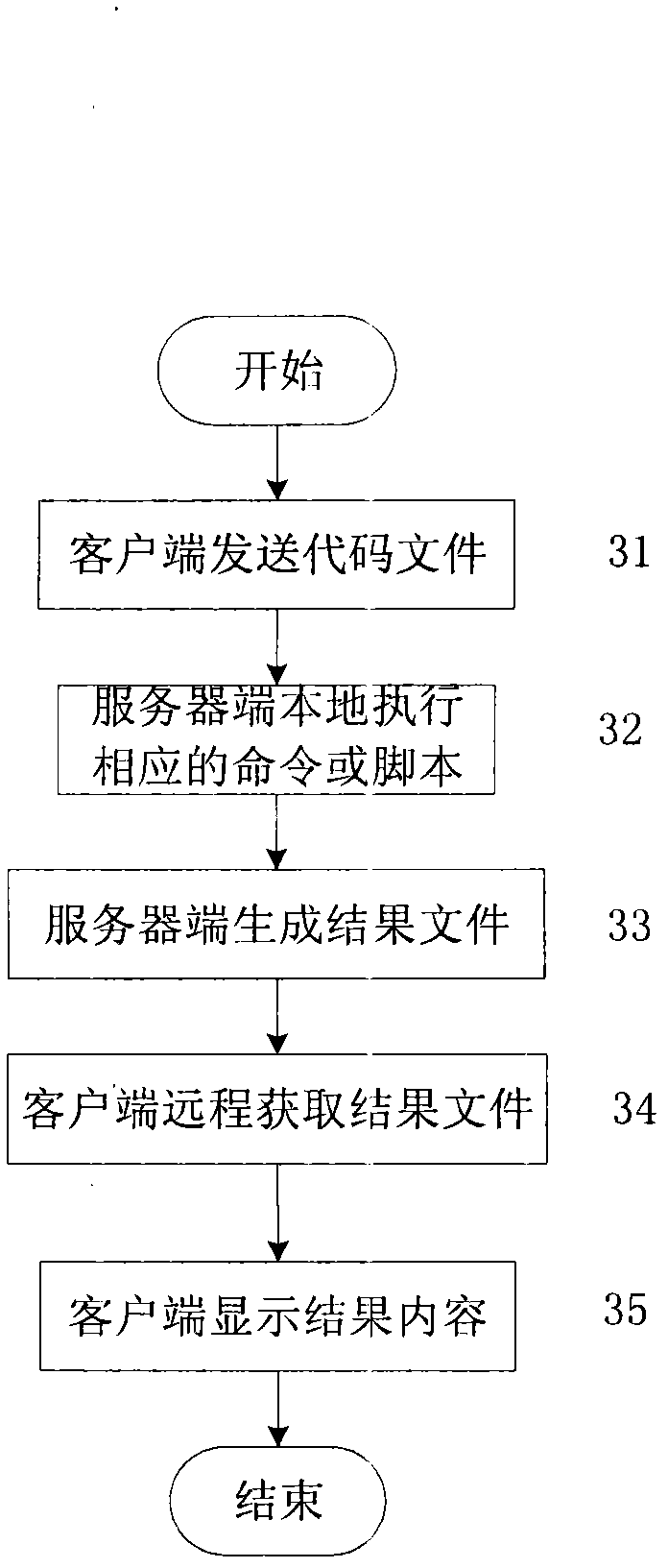
Mirror image backup/recovery method and tool of web management mode
ActiveCN102457567AReduce transfer timeImprove backup efficiencyTransmissionNetwork managementSystem Management Mode
The invention discloses a mirror image backup / recovery method and tool of a web management mode. A mirror image backup / recovery file is stored in a privacy box created by a server. The mirror image backup / recovery method comprises the following steps of: creating tasks on an interface of a client and backs up the tasks into the privacy box; indicating a user to log in a storage server and open the privacy box; enabling the user to log in a configuration webpage of the privacy box of the server; and opening the corresponding privacy box distributed to the user, wherein virtual disk equipment is mounted to be used as the privacy box for storage. The tool comprises a backup guide, a task manager, the privacy box, a recovery manager, a timing manager, a mail reporter, a short message reporter, system resources, a superior network manager, historical logs and a client remote storage server disk information acquisition module. By a privacy box encryption technology, the backup transmission efficiency cannot be influenced and overmuch resources of the storage server cannot be consumed; therefore, the data encryption storage is realized under the condition that any backup efficiency is not influenced.
Owner:CHINA STANDARD SOFTWARE
Cryptographic method and computer program product for use in wireless local area networks
InactiveUS7277548B2Improve encryption efficiencySecret communicationSecuring communicationComputer hardwareInitialization vector
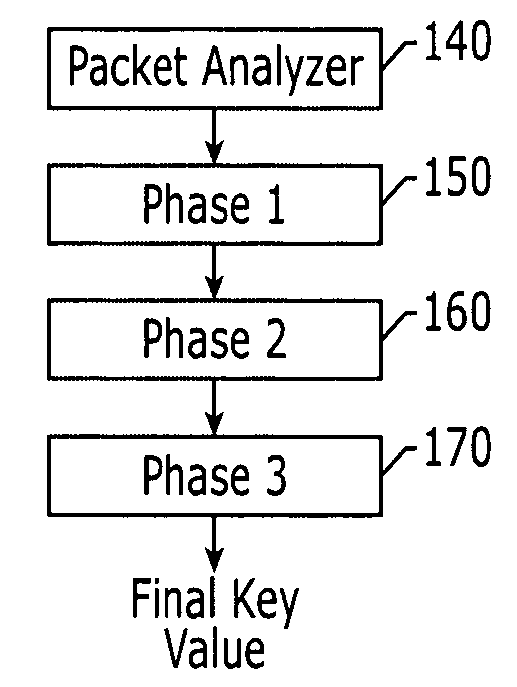
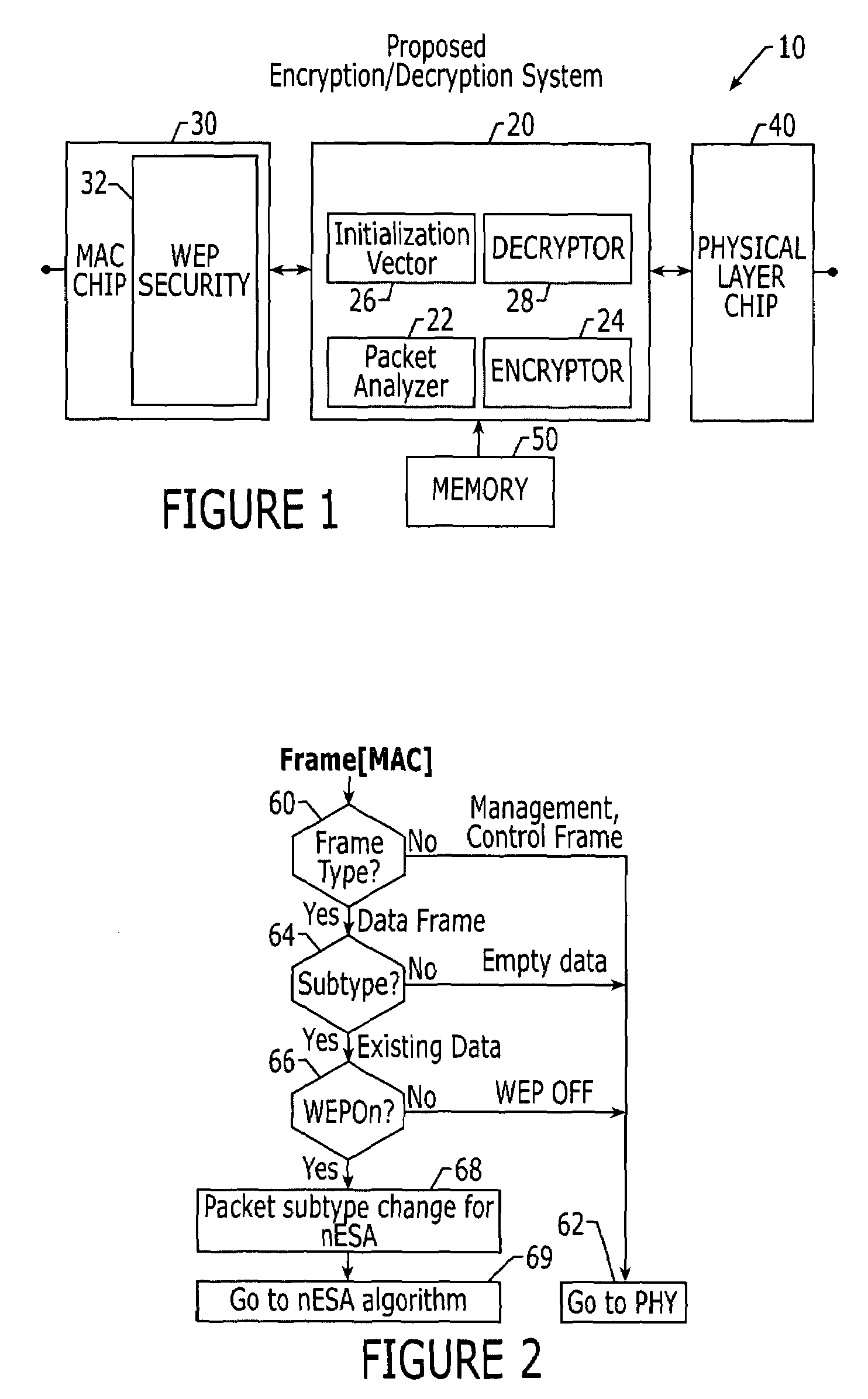
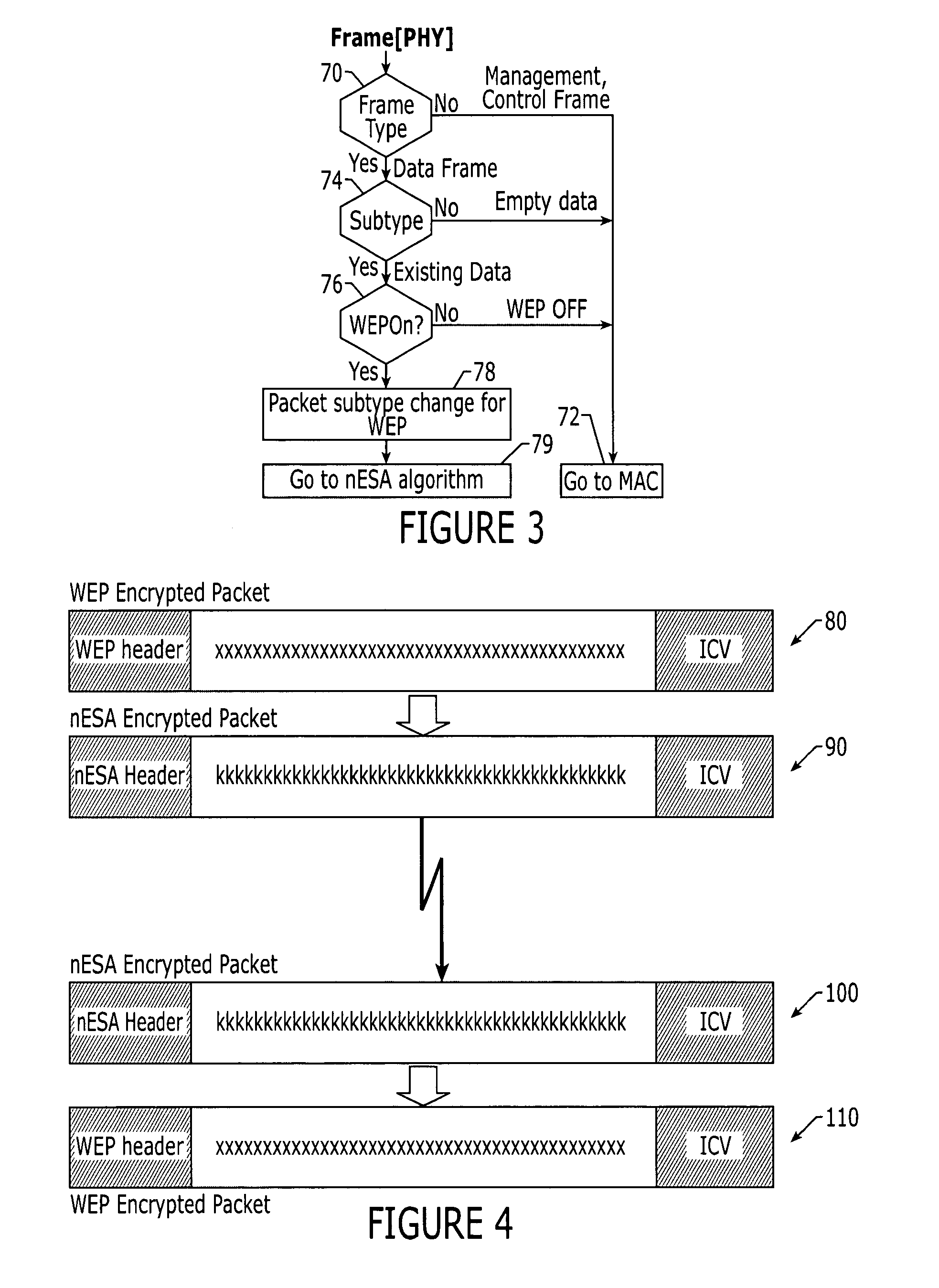
An encryption system and method that may encrypt all of the transmitted and received data packets on the data link layer without collisions on the Initialization Vector (IV). In the encryption system and method a new final key value may be generated and applied to every transmitted and received data packet. The encryption system and method provide for a novel three phase algorithmic process for generating a final secret key.
Owner:NDOSA TECH
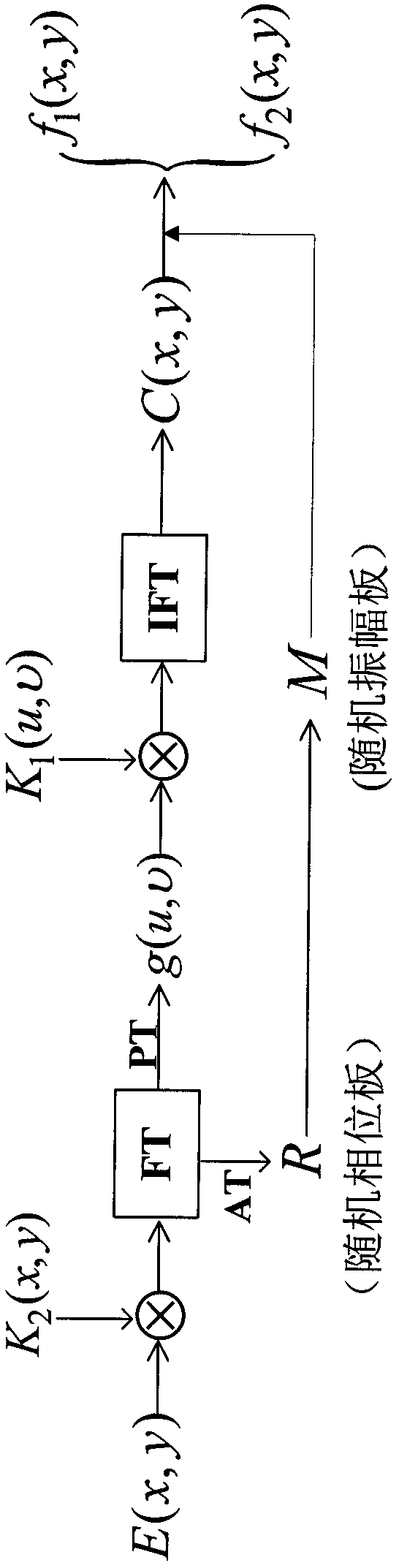
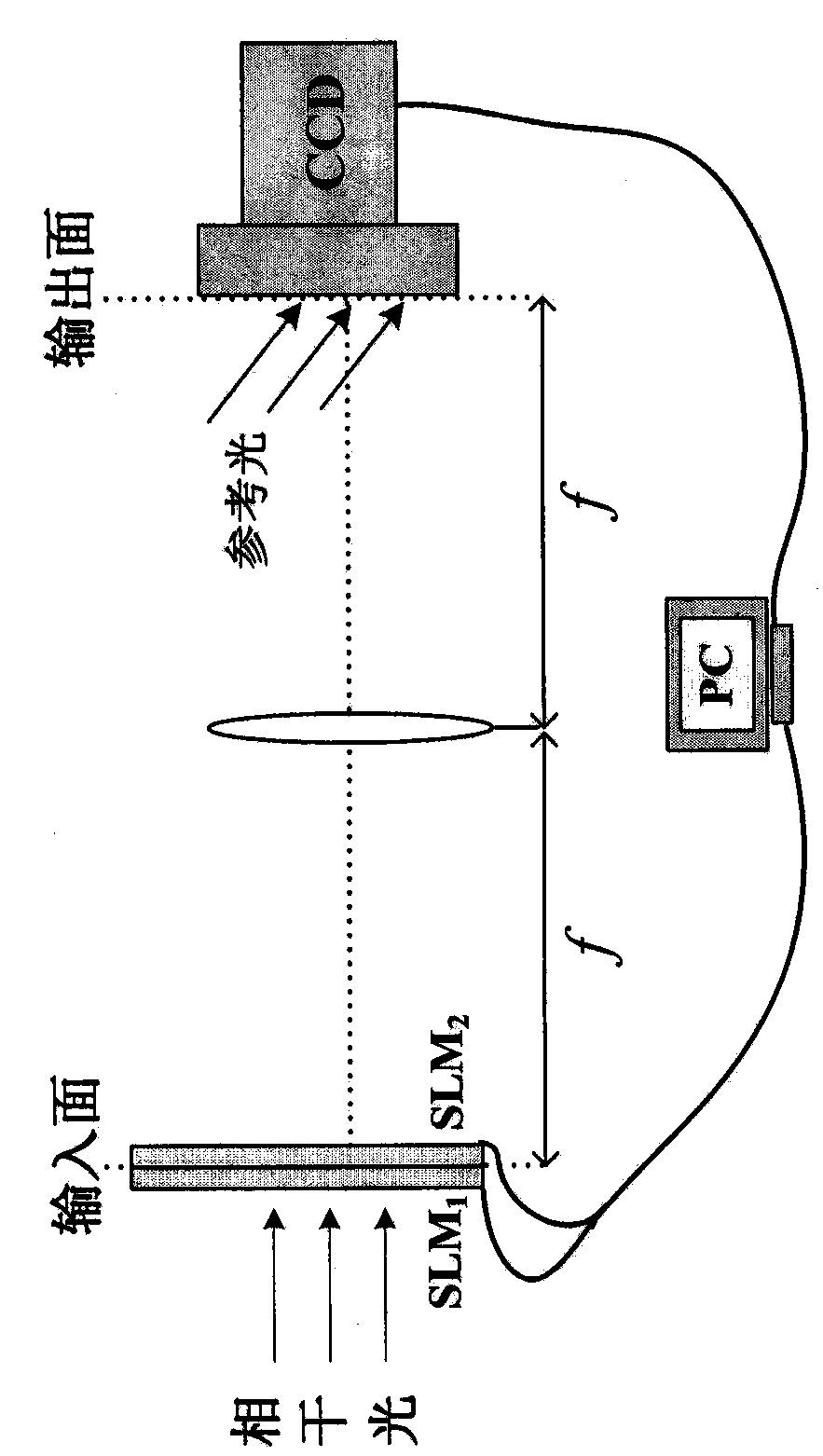
Spatial domain and Fourier frequency domain double encryption-based dual image encryption method
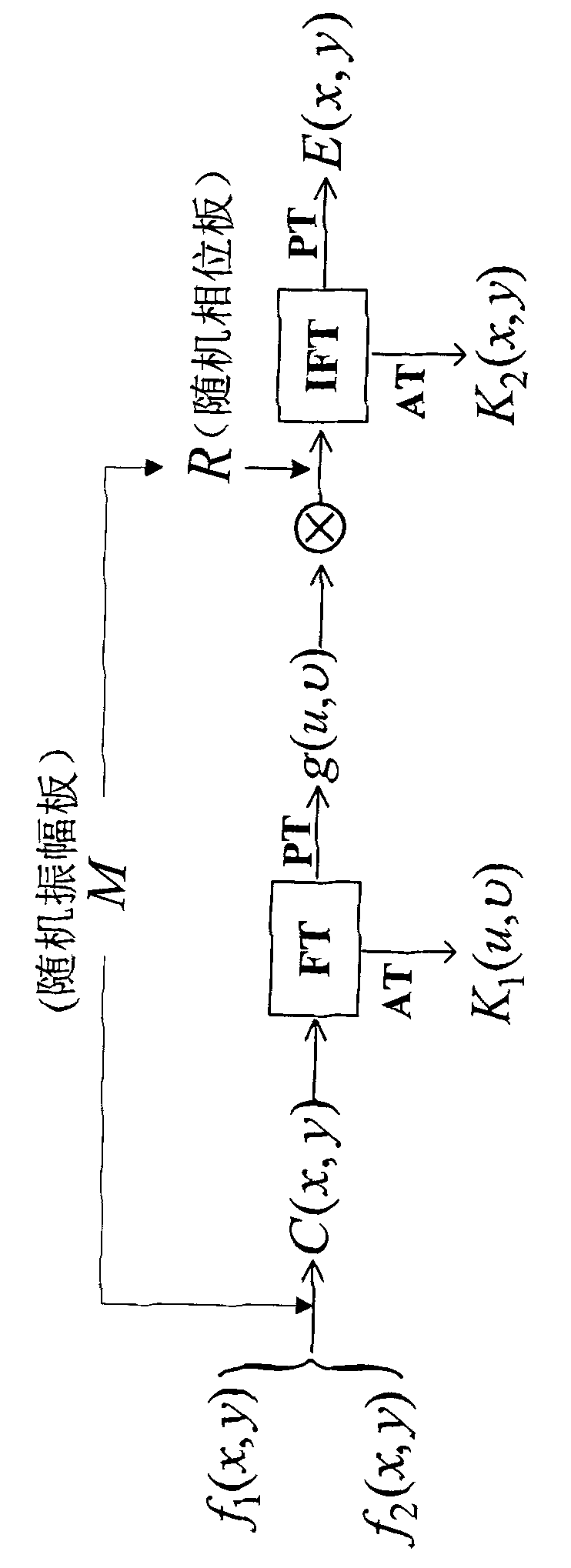
ActiveCN103402040ASimultaneous encryptionImprove encryption efficiencyPictoral communicationComplex amplitudePlaintext
The invention discloses a spatial domain and Fourier frequency domain double encryption-based dual image encryption method. The method comprises the following two major steps: 1, encrypting, i.e., encrypting two normalized original images in spatial domain by using a random amplitude plate generated by a computer to obtain an encrypted result, i.e., complex amplitude, and encrypting the encrypted result in frequency domain by using a random phase plate generated by the random amplitude plate; 2, decrypting, i.e., recovering the random amplitude plate and the image obtained by encryption in spatial domain by using two private keys, and decrypting in spatial domain by using the random amplitude plate to obtain a decryption result, i.e., two original images. The method is used for encrypting and decrypting images; only the random amplitude plate is used for encrypting the images in spatial domain and frequency domain during decryption, and simultaneous encryption of a plain text and encryption key information is realized; the double encryption in spatial domain and frequency domain is adopted in the image encryption method, and two private keys are generated during the encryption, so that the safety of the system is high.
Owner:JIAXING NIYA OPTOELECTRONICS CO LTD
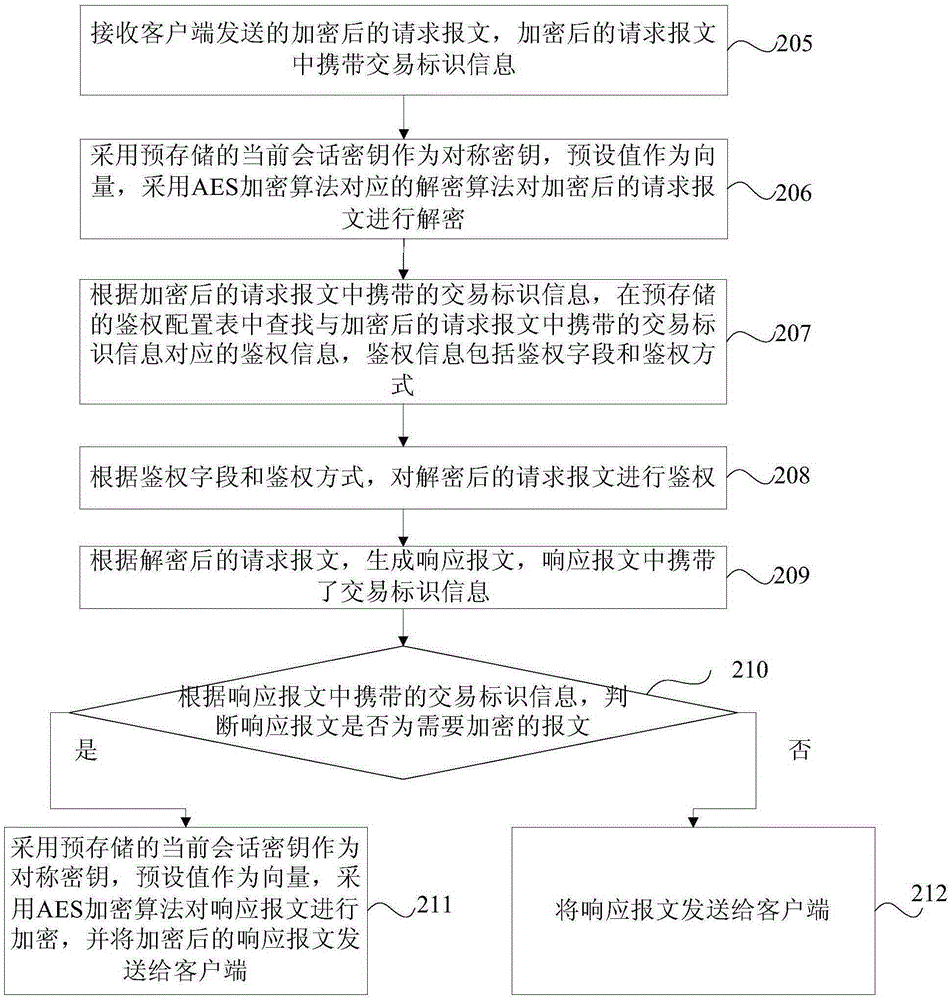
Communication method based on mobile application, server and client
ActiveCN105307165AImprove encryption efficiencyAvoid the risk of replay attacksSecurity arrangementCiphertextClient-side
The invention provides a communication method based on a mobile application, a server and a client. The method comprises the following steps: receiving a current session key acquisition request sent by the client, wherein the current session key acquisition request comprises a first encrypted ciphertext, and the first encrypted ciphertext is generated by the client by using a RSA encryption algorithm to encrypt a randomly generated first encryption factor; generating a current session key according to the first encrypted ciphertext and a randomly generated second encryption factor; using an AES encryption algorithm to encrypt the current session key to generate a ciphertext of the current session key; and sending current session key acquisition response to the client, wherein the current session key acquisition response comprises the ciphertext of the current session key, so that after decrypting the ciphertext of the current session key, during the current session, the client uses the current session key as a symmetric key, uses a preset value as a vector and uses the AES encryption algorithm to encrypt a request message needing to be encrypted.
Owner:MINSHENG BANKING CORP
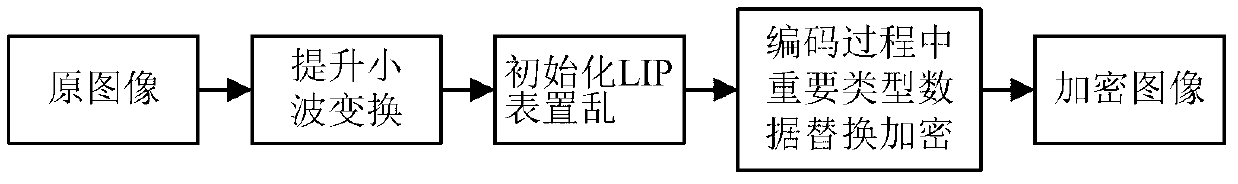
Hyper-spectral image compression and encryption method
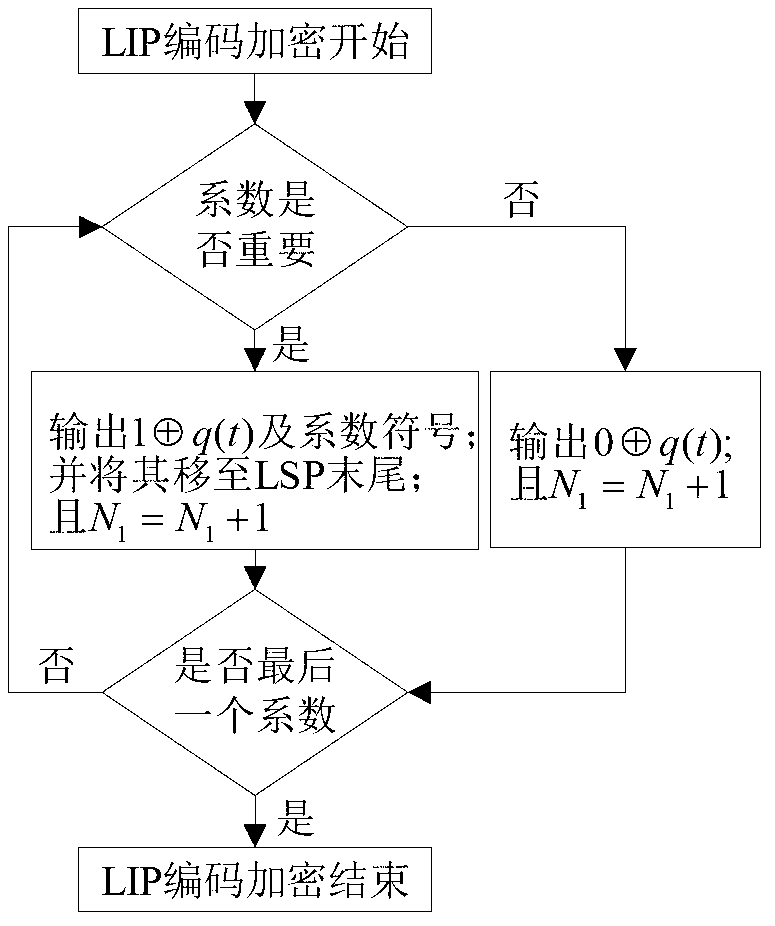
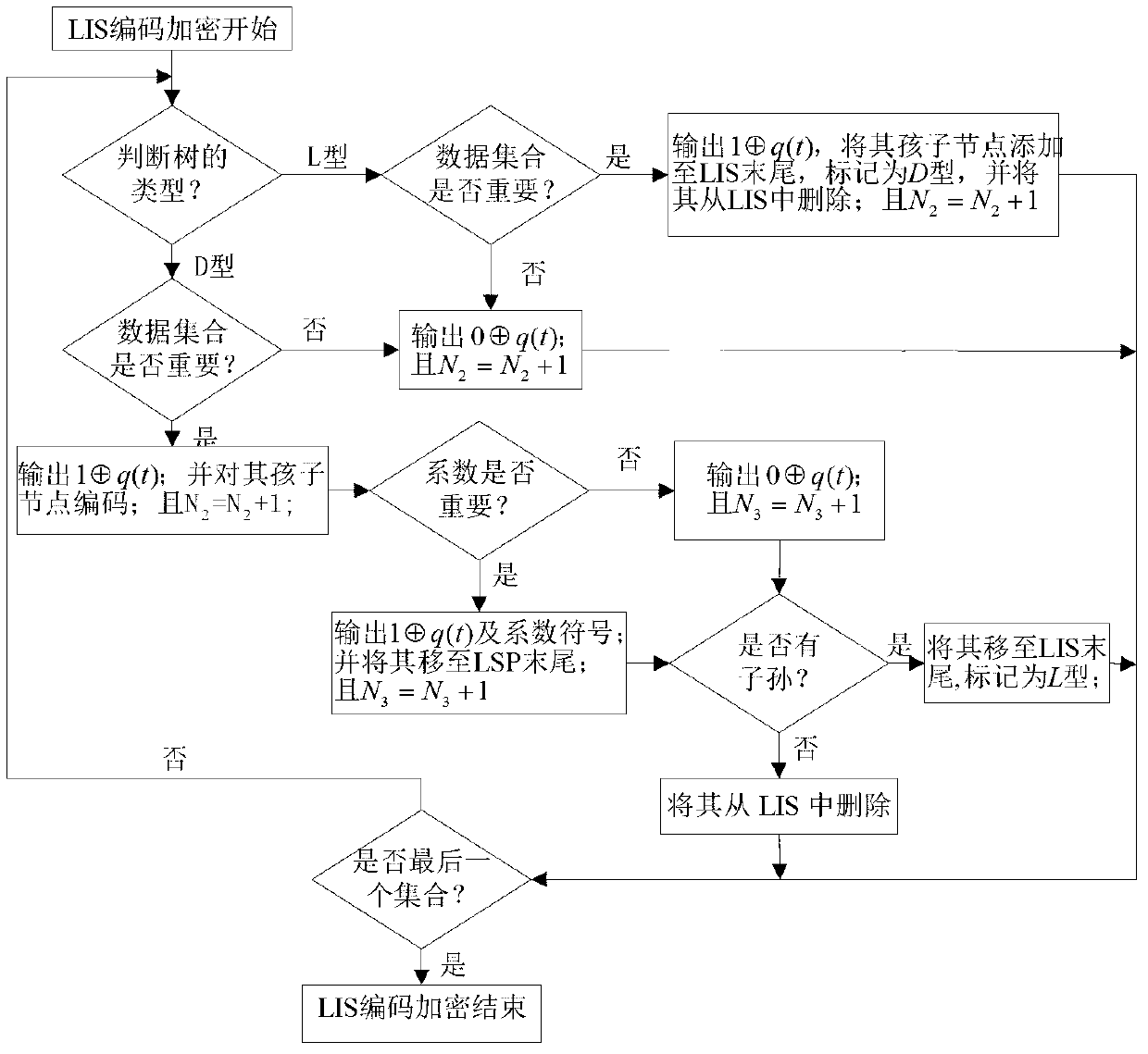
InactiveCN103281534AReduce the amount of encrypted dataImprove transmission efficiencyTelevision systemsComputer hardwarePlaintext
The invention provides a hyper-spectral image compression and encryption method. The method comprises the following steps of performing coding in a wavelet transform three-dimensional set partitioning in hierarchical trees (3DSPIHT) coding way, simultaneously performing encryption, constructing a scrambling table in a Logistic mapping way to scramble an initial list of insignificant pixels (LIP), continuously iterating a Chen's model until all bits of data of significant types are encrypted, and in a decryption process which is the inverse operation of encryption, continuously updating an initial value of the Chen's model to decrypt the data of the significant types to make the decrypted data gradually approximate to an original image and finally reproduce the original image. According to the method, forward dependence of a 3DSPIHT coding method is utilized, and the data of the significant types is selectively encrypted in real time in a compression process, so that the encrypted data volume of the image is reduced, and the image transmission and encryption efficiency is improved; and the encrypted data volume of each significant type in a bit plane is calculated, and an initial key is scrambled after preprocessing, so that the sensitivity of the coding method to a plaintext is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Implementation method for specific security terminal system based on iOS system
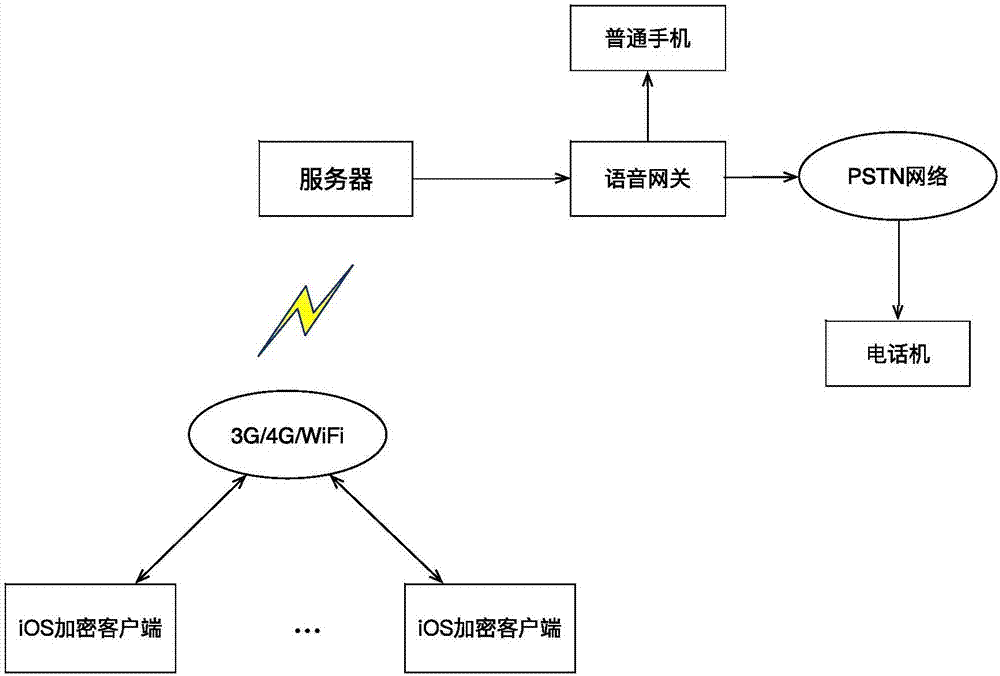
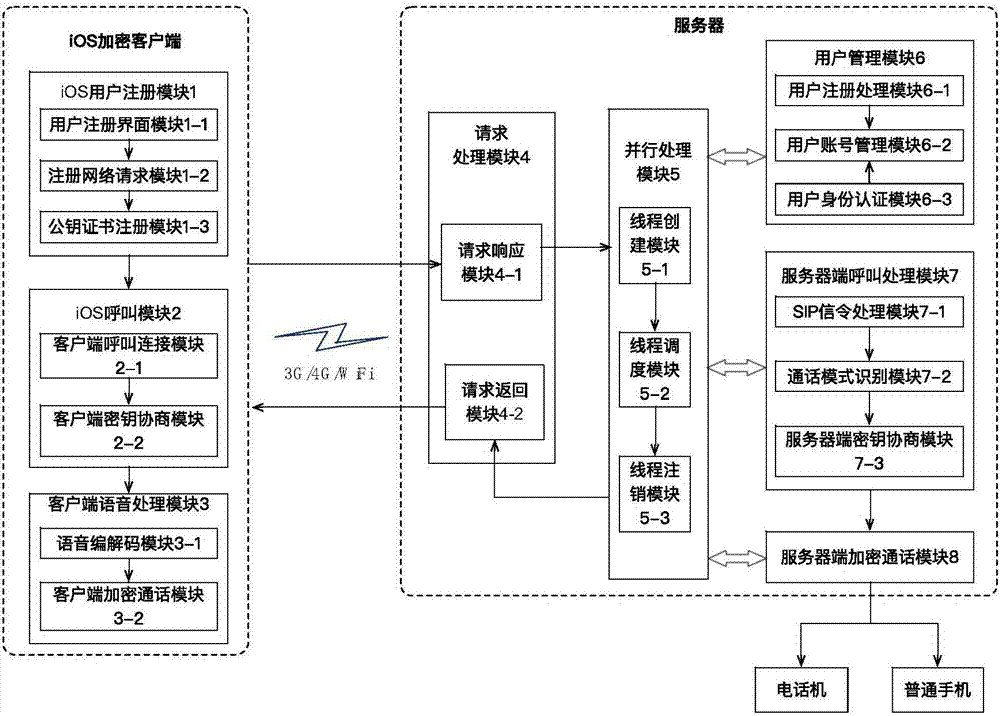
InactiveCN106899969AImplement voice encryptionImprove encryption efficiencySubstation equipmentSecurity arrangementThird generationComputer terminal
The invention provides an implementation method for a specific security terminal system based on an iOS system, which is suitable for WiFi / 3G / 4G networks and comprises eight modules including an iOS user registration module, an iOS calling module, a client voice processing module, a request processing module, a parallel processing module, a user management module, a server side call processing module and a server side voice encryption and decryption module, wherein a client of the specific security terminal firstly registers with a server and initiates a call based on a client-server (C-S) framework, the server carries out authentication on identity of the client, and after the authentication is successful, the server carries out corresponding encryption and decryption processing on call voice through identifying whether a calling party and a called party establish different call modes for the security terminal, so that the voice encryption transmission from the specific security terminal to the server side is guaranteed. The invention provides an efficient and convenient method, and the method only encrypts one side with the security requirement, so that the call efficiency and the practicability are improved.
Owner:东南大学常州研究院 +1
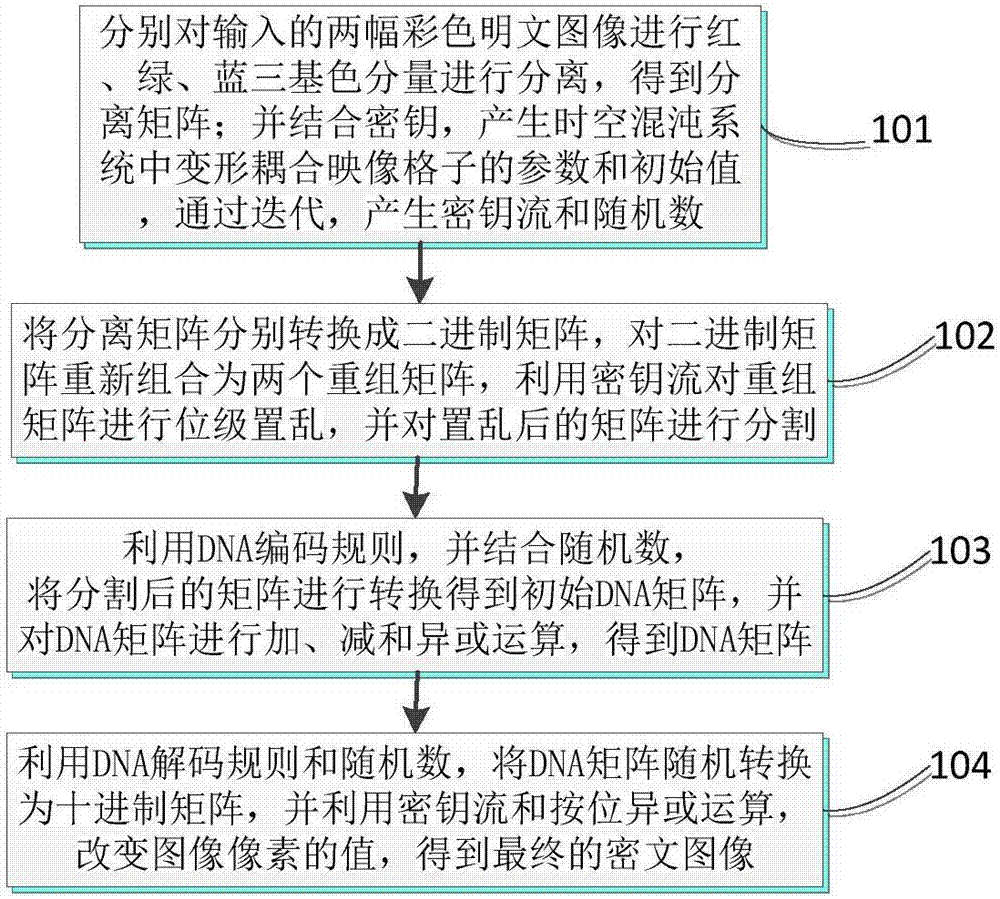
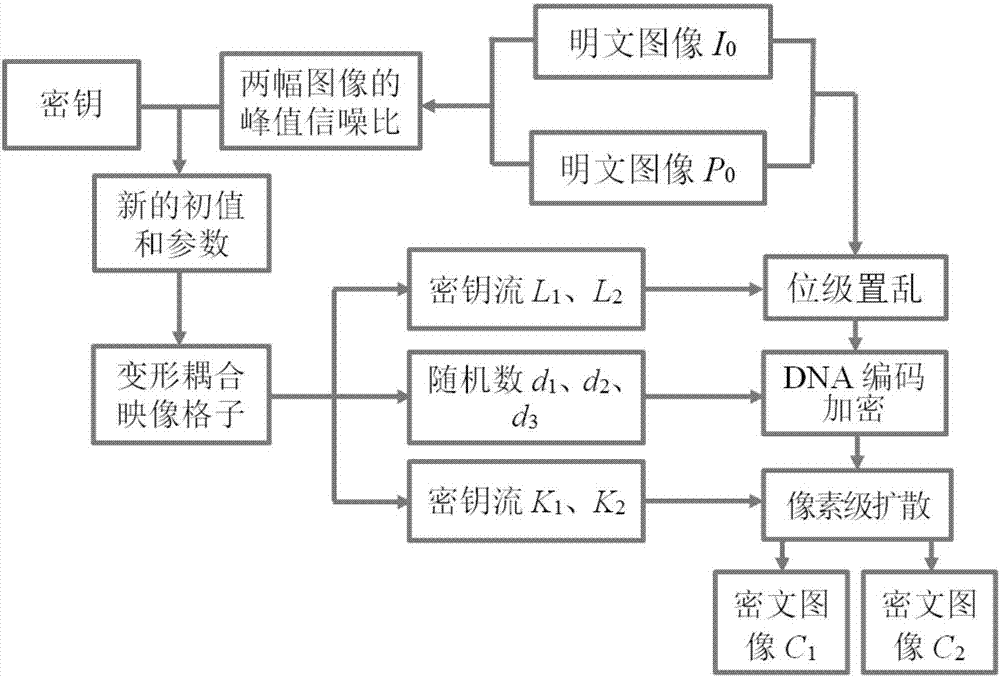
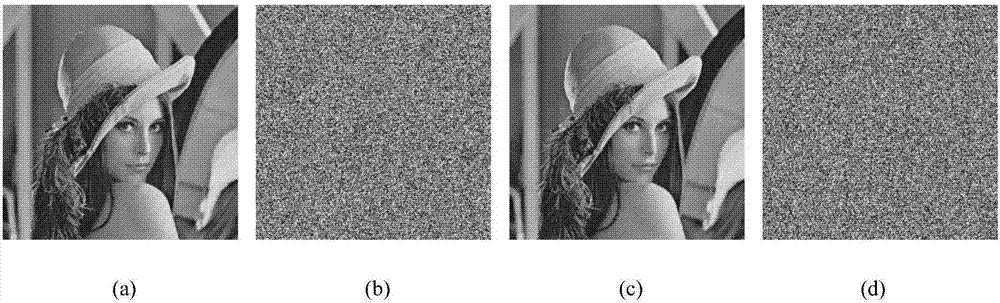
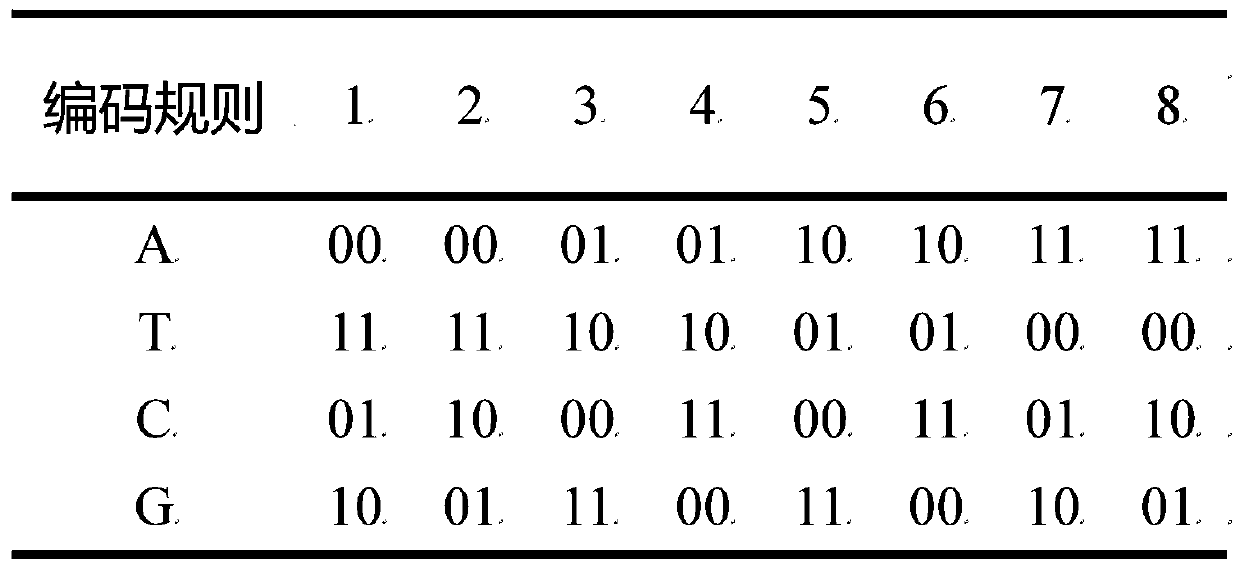
Double color image encryption method based on DNA sequence operation and deformed coupled map lattices
The invention discloses a double color image encryption method based on DNA sequence operation and deformed coupled map lattices. The method comprises: utilizing a secret key and two color plaintext images to generate parameters and initial values of iterating the deformed coupled map lattices, and generating secret key streams of L1, L2, K1 and K2 and random numbers of d1, d2 and d3 through iteration; separating red, green and blue trichromatic components of the plaintext images, transforming the components into binary matrices, and recombining the six binary matrices to obtain recombination matrices of A and B, utilizing the secret key streams of L1 and L2 to carry out bit-level scrambling on the matrices of A and B, and dividing the same into six binary matrices; utilizing a DNA encoding rule and combining the random numbers of d1, d2 and d3 to transform the binary matrices into DNA matrices, and executing DNA addition, subtraction and exclusive OR operations; and utilizing a DNA decoding rule to transform the DNA matrix into decimal matrices, utilizing the secret key streams of K1 and K2 and the bitwise exclusive OR operation to change values of image pixels, and obtaining ciphertext images of C1 and C2. The method can encrypt the two plaintext images at the same time, and has the advantages of high security, good encryption effect, no information loss, fast encryption speed and the like.
Owner:HENAN UNIVERSITY
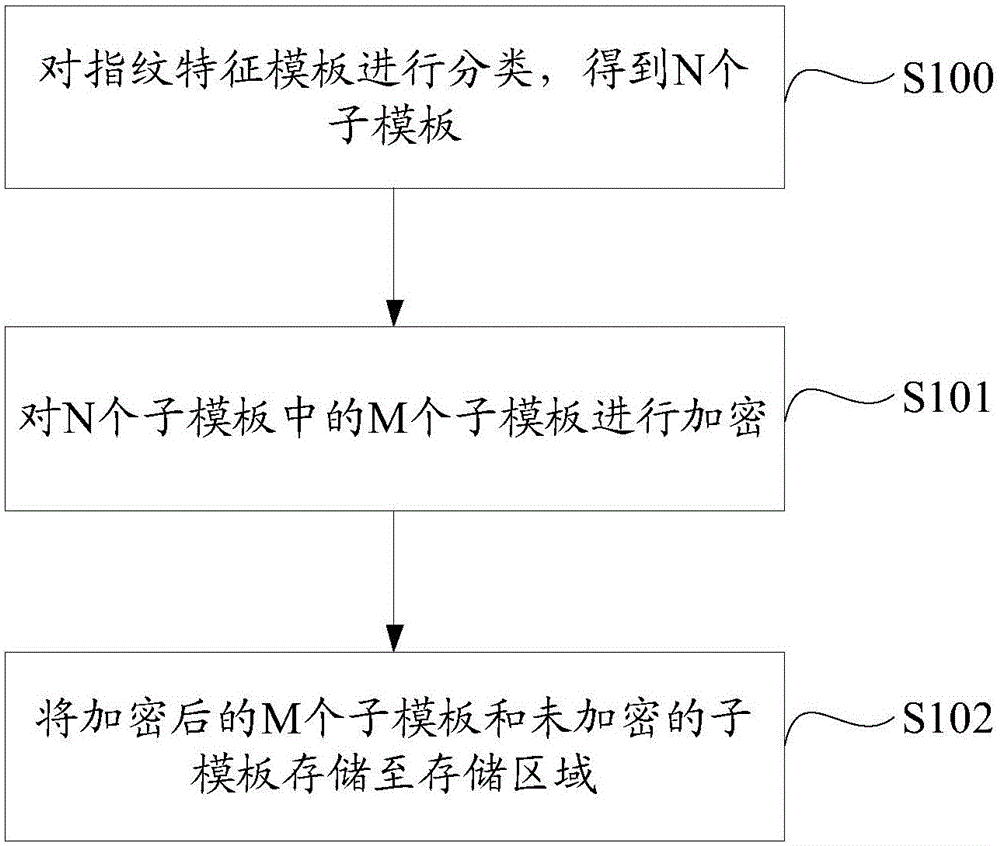
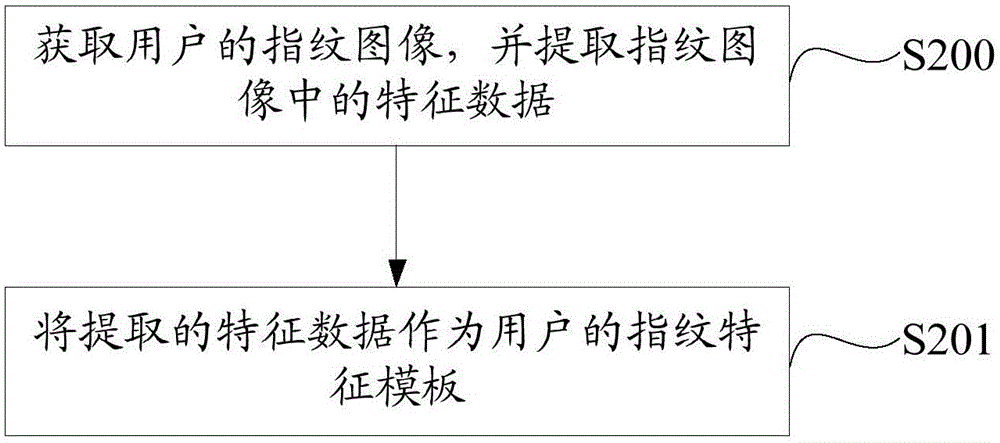
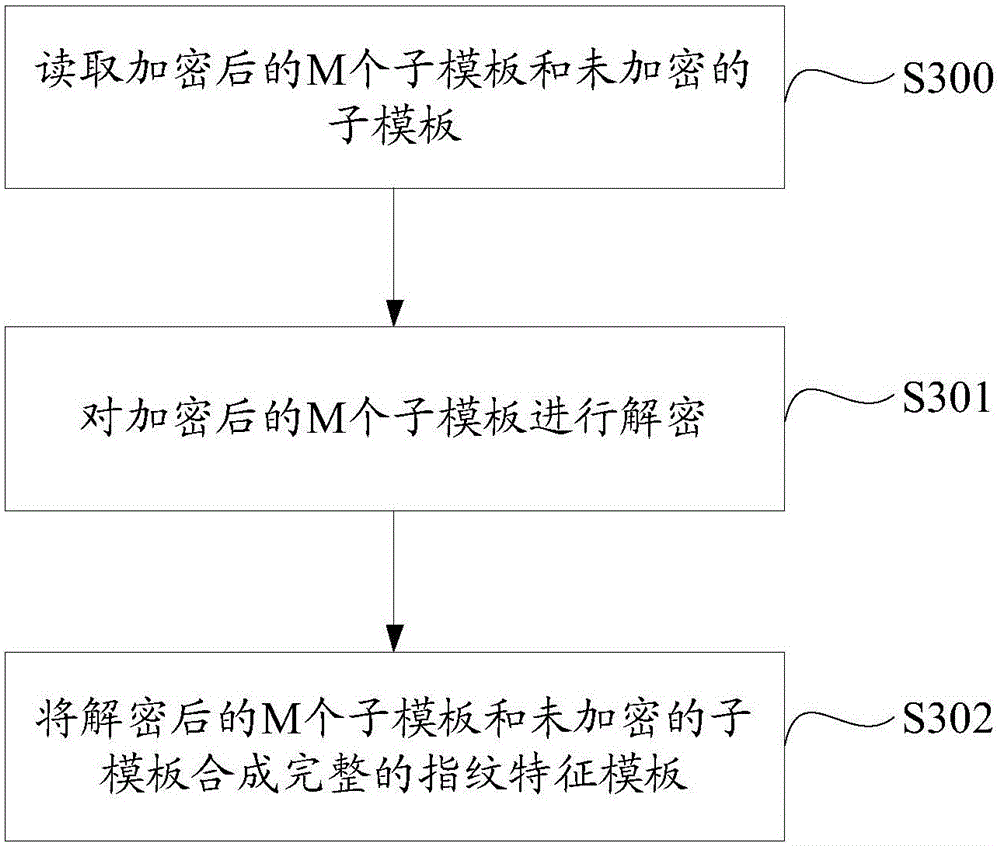
Fingerprint feature template encrypted storage method and system of mobile terminal
ActiveCN105160316AEnsure safetySmall amount of calculationDigital data protectionAcquiring/reconising fingerprints/palmprintsFeature dataEncryption
The invention discloses a fingerprint feature template encrypted storage method and system of a mobile terminal. The method comprises the following steps: classifying fingerprint feature templates to obtain N sub-templates, wherein N is greater than or equal to 2 and each sub-template in the N sub-templates corresponds to fingerprint feature data of a different type; encrypting M sub-templates in the N sub-templates, wherein M is smaller than N; and storing the encrypted M sub-templates and the unencrypted sub-templates to a storage area. Compared with encrypting the whole fingerprint feature templates in the prior art, in the fingerprint feature template encrypted storage method, only partial sub-templates in the N sub-templates are encrypted, and therefore, the calculation amount is remarkably reduced under the premise that the data security is guaranteed, and the encryption efficiency is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Format-preserving data desensitization method
InactiveCN105426445AAvoid loading errorsEnsure safetySpecial data processing applicationsProcess mechanismChinese characters
The invention discloses a format-preserving data desensitization method, which relates to a data desensitization method, in particular to a format-preserving data processing method. The method aims to solve the problems that data accuracy is seriously affected since data missing happens when a traditional protection method of client sensitive data carries out a data association operation, an algorithm is easy in cracking since the adopted algorithm is too simple and no effective historical data processing mechanism is provided after a key is exposed. A GB2312 Chinese character set is divided into 72 isometric unit intervals on the basis of the coding structure of the GB2312 Chinese character set within a range of B0A0, and the code distribution of each unit interval is the same. The method comprises the coding structure of the GB2312 Chinese character set, a GBK (Guo-Biao Kuozhan) isometric encryption algorithm, a GBK isometric decryption algorithm, a number scrambling algorithm and a number descrambling algorithm. The method belongs to the field of computer software.
Owner:TIANJIN JIANING KUNXIANG TECH CO LTD
Image encryption and decryption method based on probability interval division and dynamic probability events
ActiveCN105577354AIncrease tight couplingImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPattern recognitionProbabilistic encryption
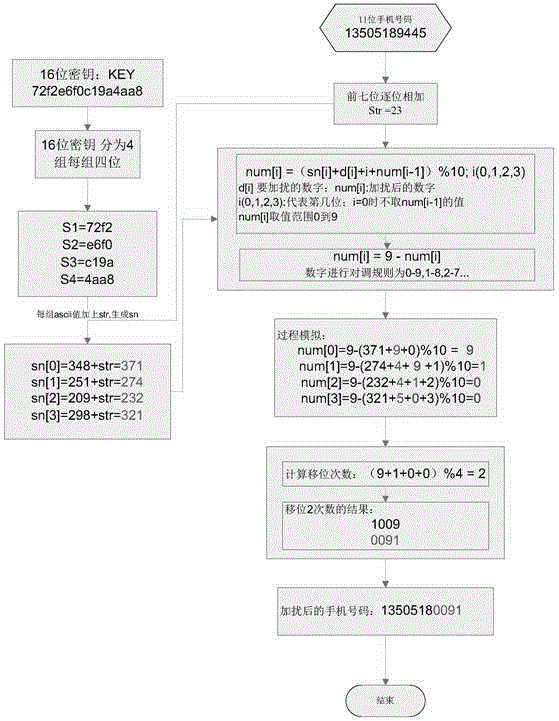
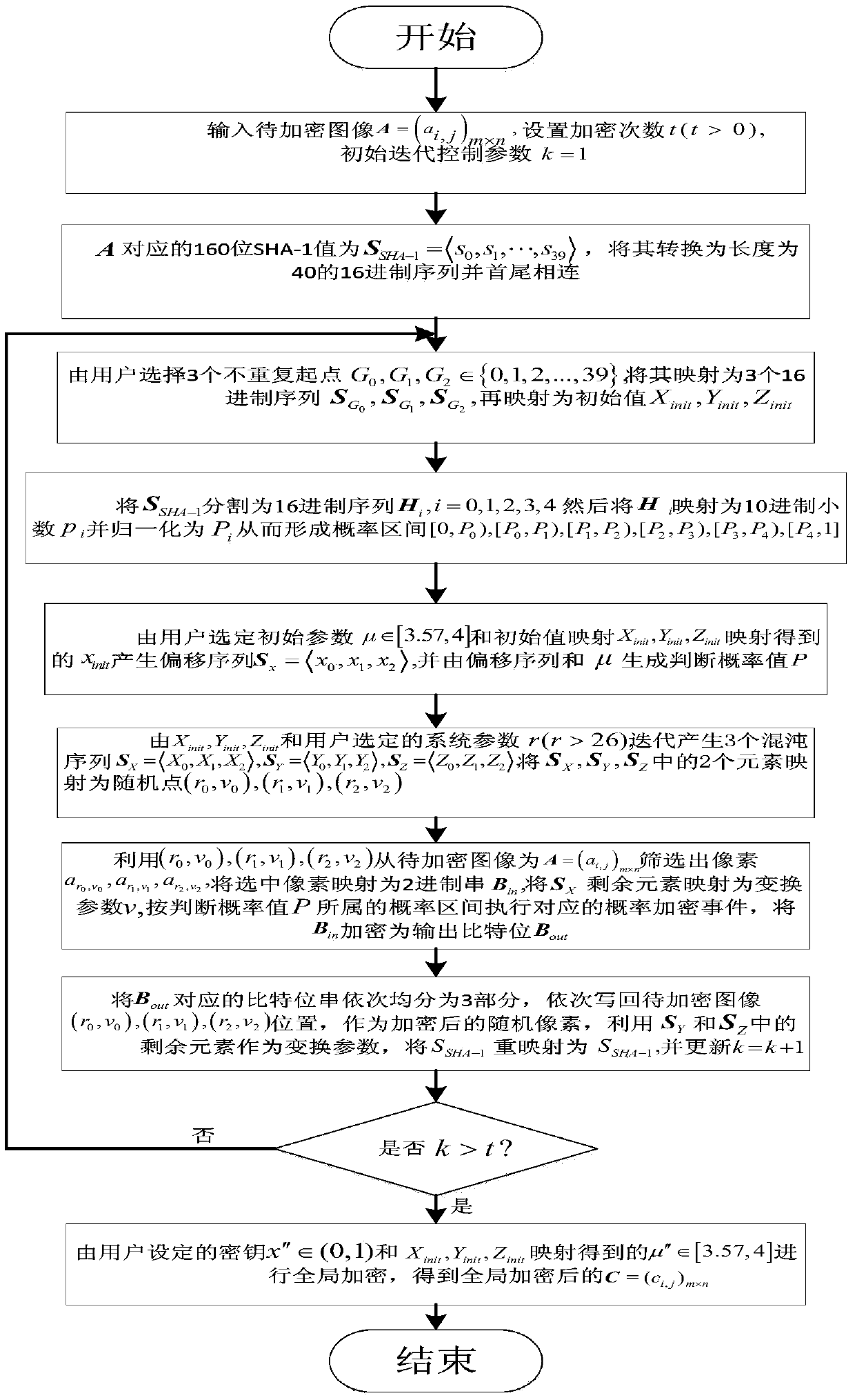
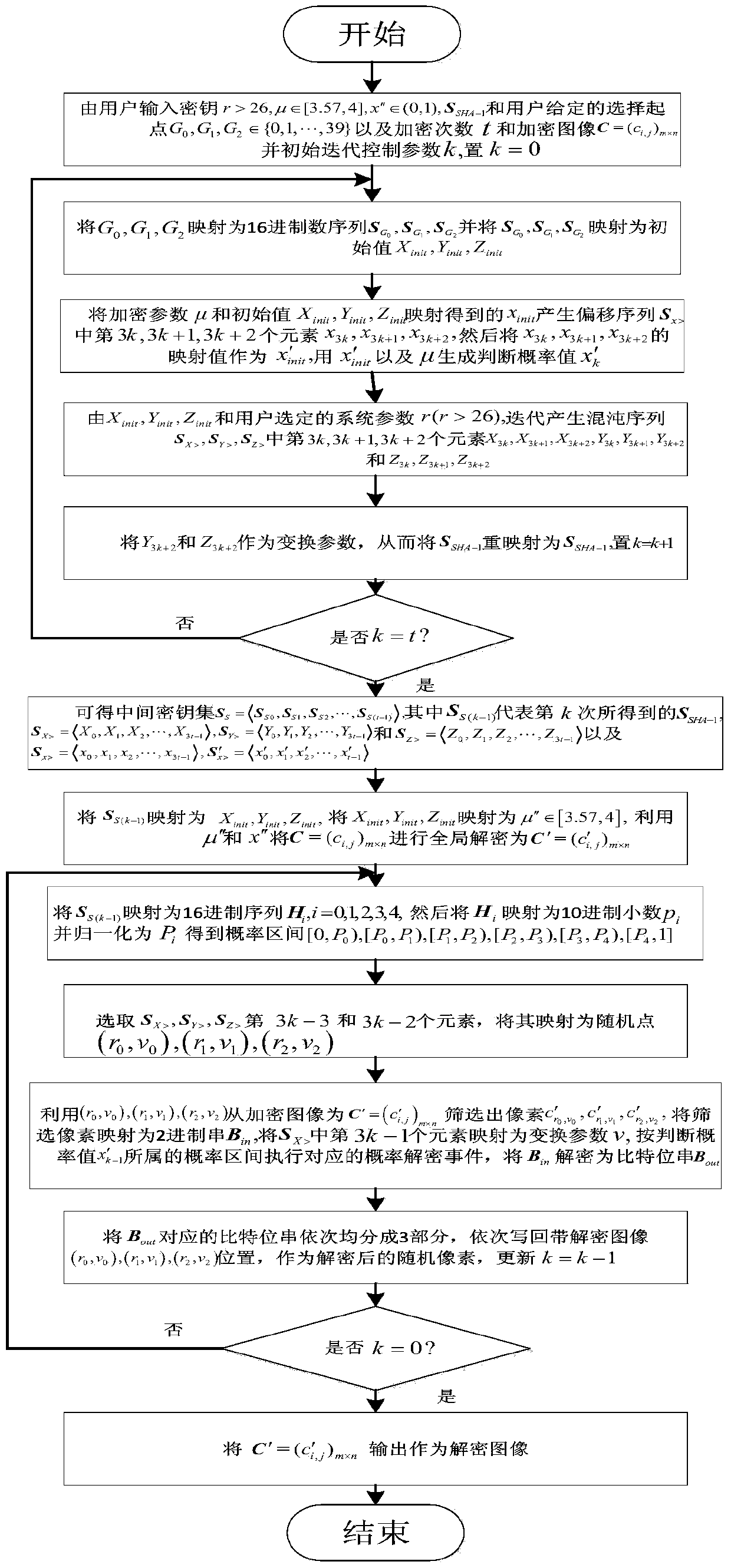
The invention provides an image encryption and decryption method based on probability interval division and dynamic probability events. The method comprises steps of during encryption, firstly mapping secret key parameters and SHA-1 values of to-be-encrypted images to different probability encryption sections; carrying out random screening on to-be-encrypted pixels based on the secret key parameters and the SHA-1 values; and executing and writing different probability encryption events into corresponding pixel positions according to the probability sections where the probability encryption events fall. In order to improve safety, an SHA-1 value remapping process is added for dividing the probability sections, screening the to-be-encrypted pixels and carrying out stochastic disturbance on encryption; and by adding an overall situation encryption process related to SHA-1 update values and user secret keys, performance of an image encryption algorithm is enhanced. The method also comprises steps of during decryption, firstly recovering encrypted parameters; then finishing overall decryption; and at last executing inverse decryption operation on randomly screened pixels. Compared with the prior art, different pixels and secret keys correspond to different encryption processes, so the method is highly safe.
Owner:SHAANXI NORMAL UNIV
Multi-image encryption method based on DNA encoding and chaos
ActiveCN107659752AAchieve protectionImprove encryption efficiencyPictoral communicationDna encodingImage content
The invention provides a multi-image encryption method based on DNA encoding and chaos, and belongs to the field of information encryption. For mass digital images generated in big data, not only doesthe security of image content need to be guaranteed, but also the high encryption efficiency is needed. Multi-image encryption has the high efficiency characteristic by serving as a novel multimediasecurity technology. Some existing multi-image encryption methods have the defects that the encryption efficiency and the security are low, and decrypted images are obviously distorted and unsatisfactory. According to the multi-image encryption method, multiple original images are encoded into a corresponding DNA sequence matrix. The DNA sequence matrix is scrambled by a chaotic sequence, and a DNA sequence diffusion operation is conducted on a scrambling result. Encrypted images are obtained through a DNA decoding operation. The multi-image encryption method based on DNA encoding and chaos isproposed to serve as the main innovation content. Experiment results show that the method has the excellent encryption effect and is high in security and suitable for practical image encryption application.
Owner:CHINA UNIV OF MINING & TECH
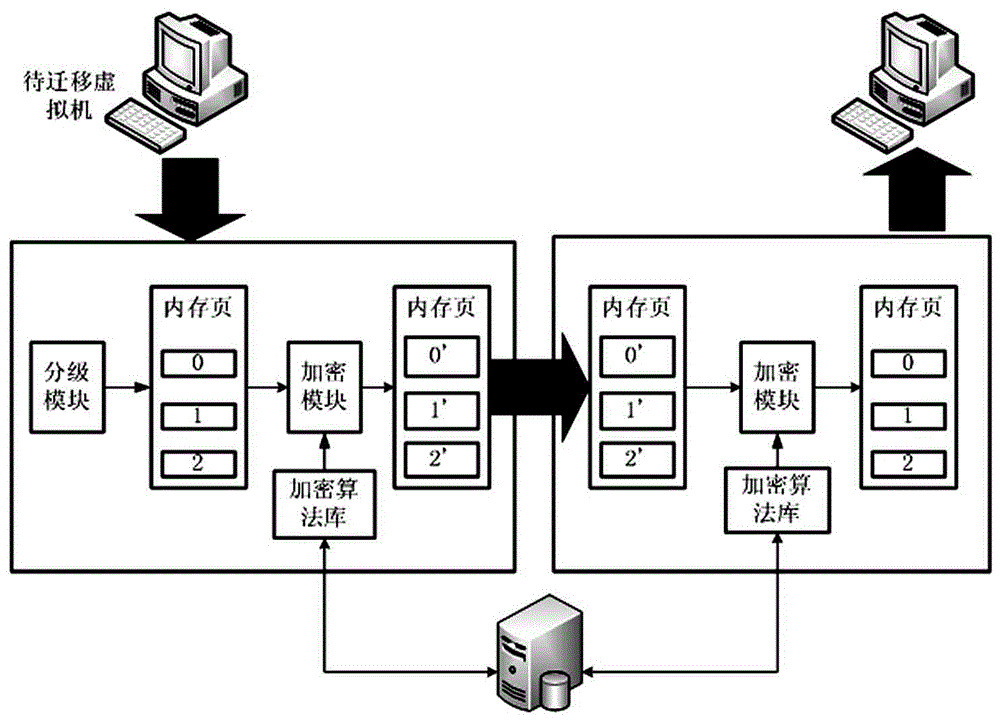
Virtual machine dynamic migration security protection method
InactiveCN106095525AEnables fine-grained processingFlexible security protectionProgram initiation/switchingSoftware simulation/interpretation/emulationData informationConfidentiality
The invention discloses a virtual machine dynamic migration security protection method. The virtual machine dynamic migration security protection method comprises the following steps of adding a security level division module and an encryption module based on a traditional migration mechanism, performing level division and marking on information of an emigrated virtual machine by the security level division module, enabling a marked memory page to enter the encryption module, and performing encryption of a corresponding level on data by utilizing an encryption algorithm; and at an immigrated host end, performing decryption on the encrypted data to recover the virtual machine. The method has the following beneficial effects: 1) the virtual machine information is subjected to the level division, so that fine-granularity processing of data information is realized and the security protection is more flexible; 2) different encryption algorithms are adopted according to different importance degrees of the information, so that the encryption efficiency is improved while the data security is ensured; and 3) the encryption algorithm and the confidentiality level can be dynamically updated, so that the system migration security is improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Video-encryption camera and encryption method thereof
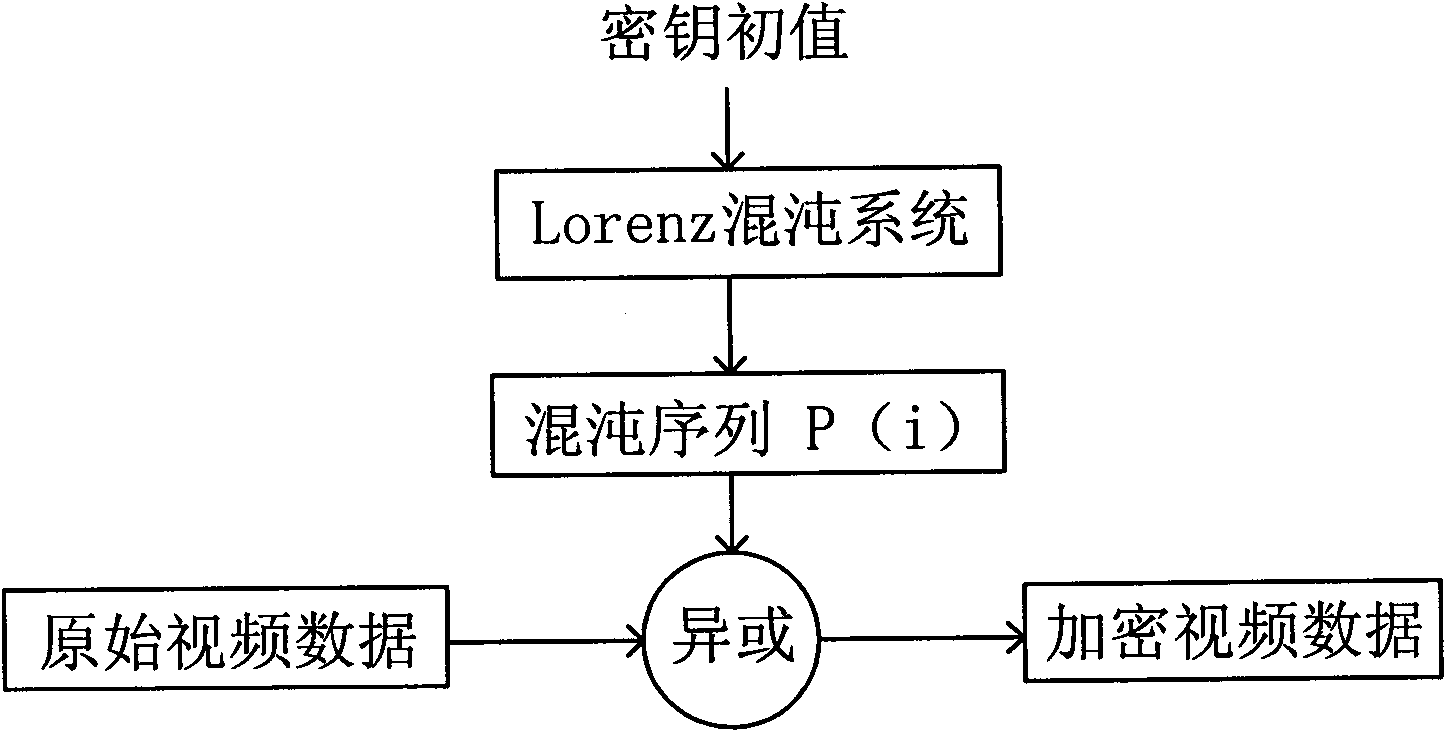
ActiveCN101902576AEasy to crackImprove securityTelevision system detailsColor television detailsVideo storageChaotic encryption
The invention relates to a video-encryption camera comprising a video acquisition module, a video pre-processing and encrypting module and a video storage module, wherein the video acquisition module is used for transmitting video data to the video pre-processing and encrypting module upon the completion of video acquisition; the video pre-processing and encrypting module is used for pre-processing each frame of video data, making calculations by calling a chaotic encryption system in the video storage module to generate chaotic sequences and further carrying out the XOR operations on the chaotic sequences and each frame of video data to encrypt the video data; and the video storage module is used for storing the encrypted video data on a real-time basis. Compared with the prior art, the invention encrypts the video data while acquiring and pre-processing the video data, and stores the encrypted video data in the video storage module on a real-time basis, thus avoiding the consequences that the raw video data are illegally stolen or falsified.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Data encryption and decryption methods and devices
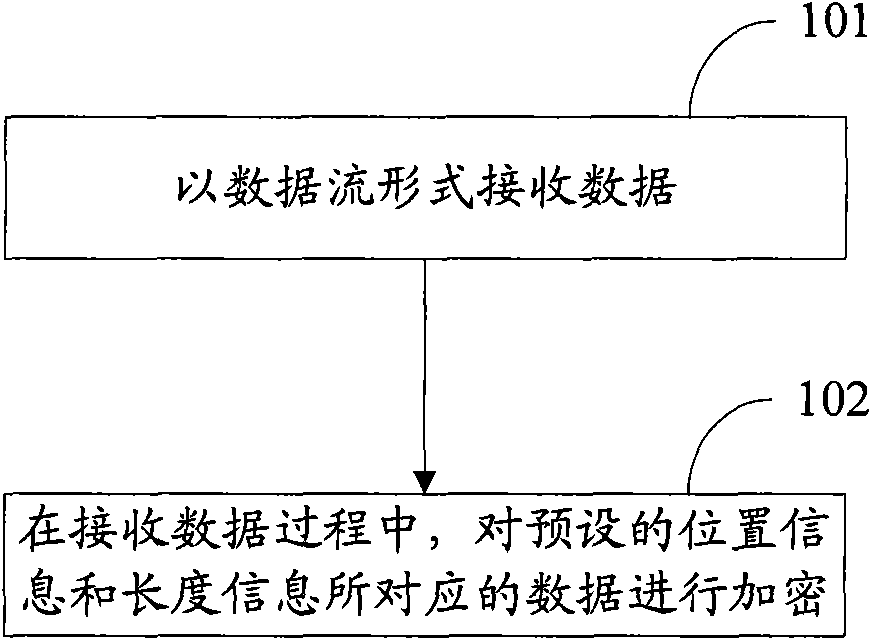
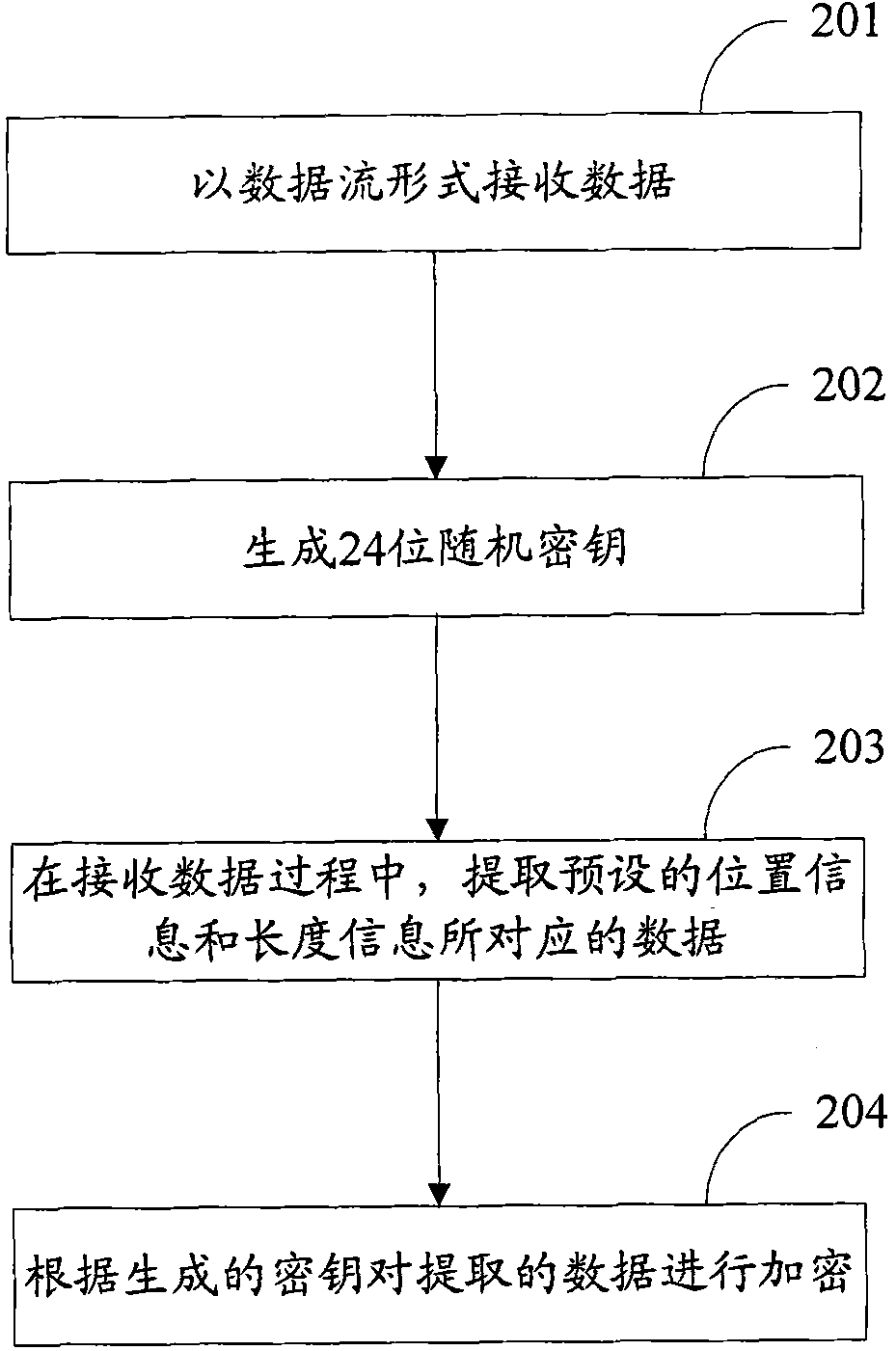
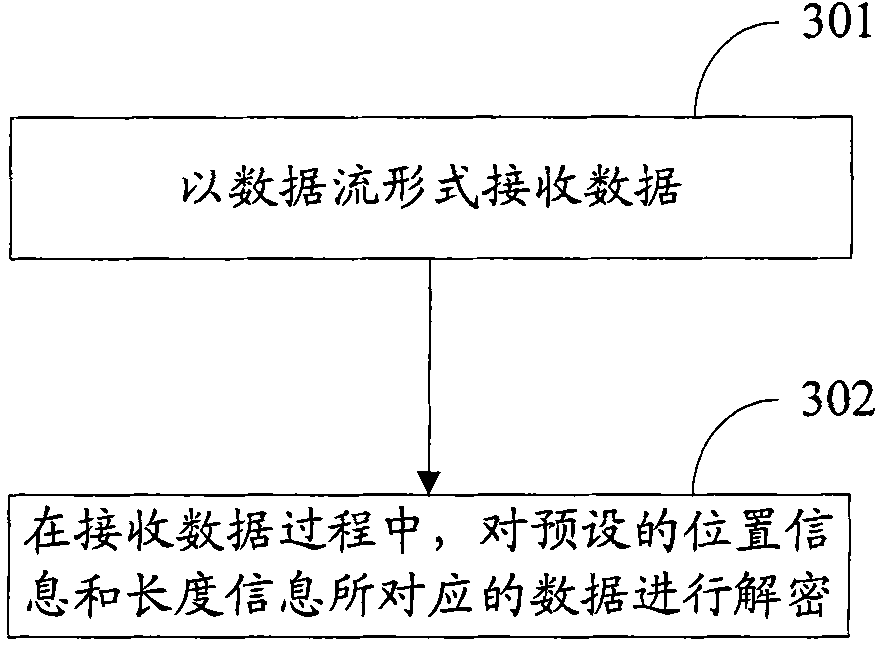
InactiveCN102063598AAvoid problems with encryptionFor encryption purposeDigital data protectionData streamData decryption
The invention discloses data encryption and decryption methods, which are used for locally encrypting data to improve encryption efficiency and realizing a corresponding decryption scheme. The data encryption method comprises the following steps of: receiving data in a data stream form; and in the process of receiving data, encrypting data corresponding to preset position information and length information, wherein the data to be encrypted is partial data in file data. The data decryption method comprises the following steps of: receiving data in a data stream form; and in the process of receiving the data, decrypting data corresponding to preset position information and length information, wherein the data to be decrypted is partial data in file data. The invention also discloses devices for implementing the methods.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Color image encryption method based on Latin square scrambling
ActiveCN108696666AImprove resistance to attackReduce strong correlationSecuring communication by chaotic signalsPictoral communicationPlaintextComputer hardware
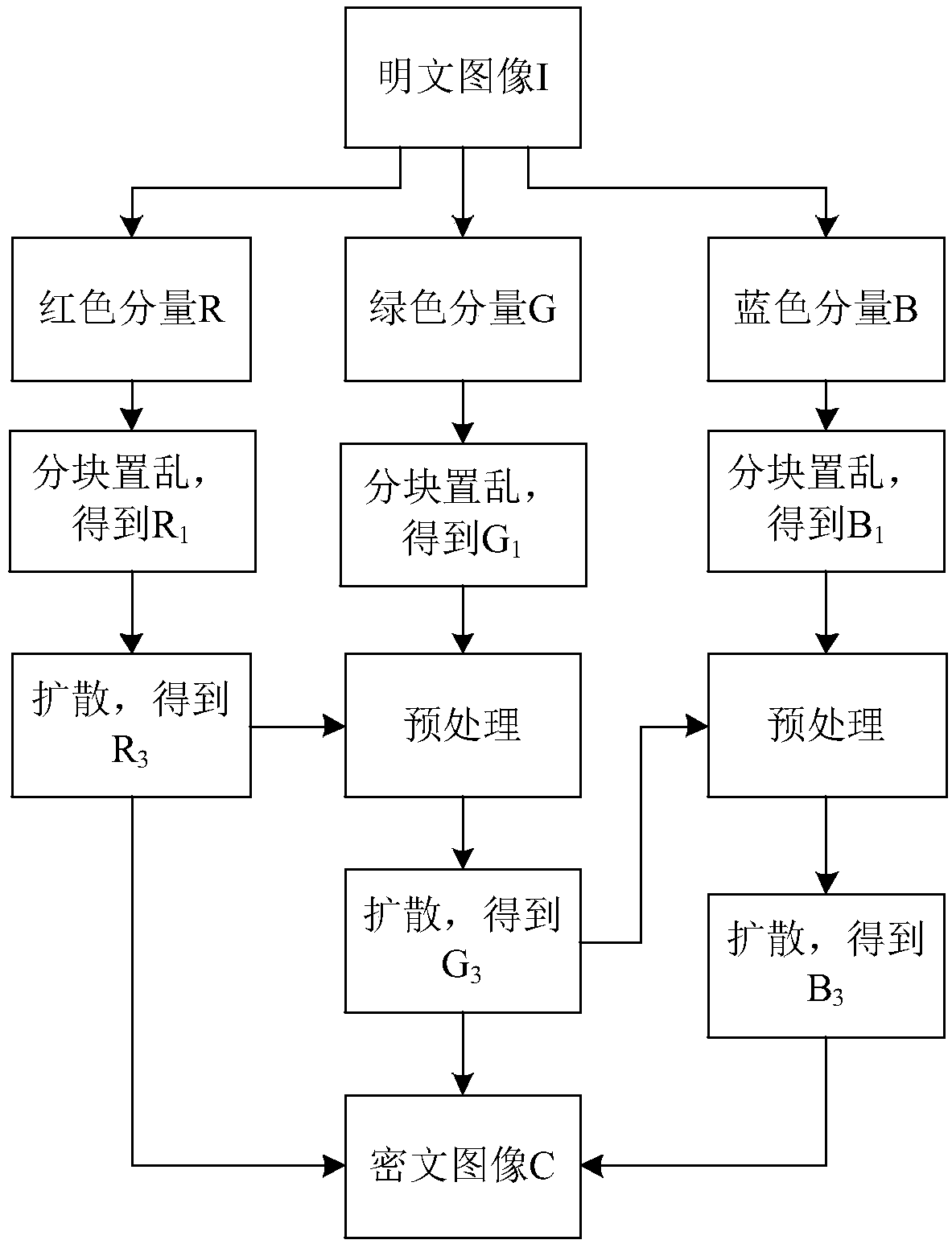
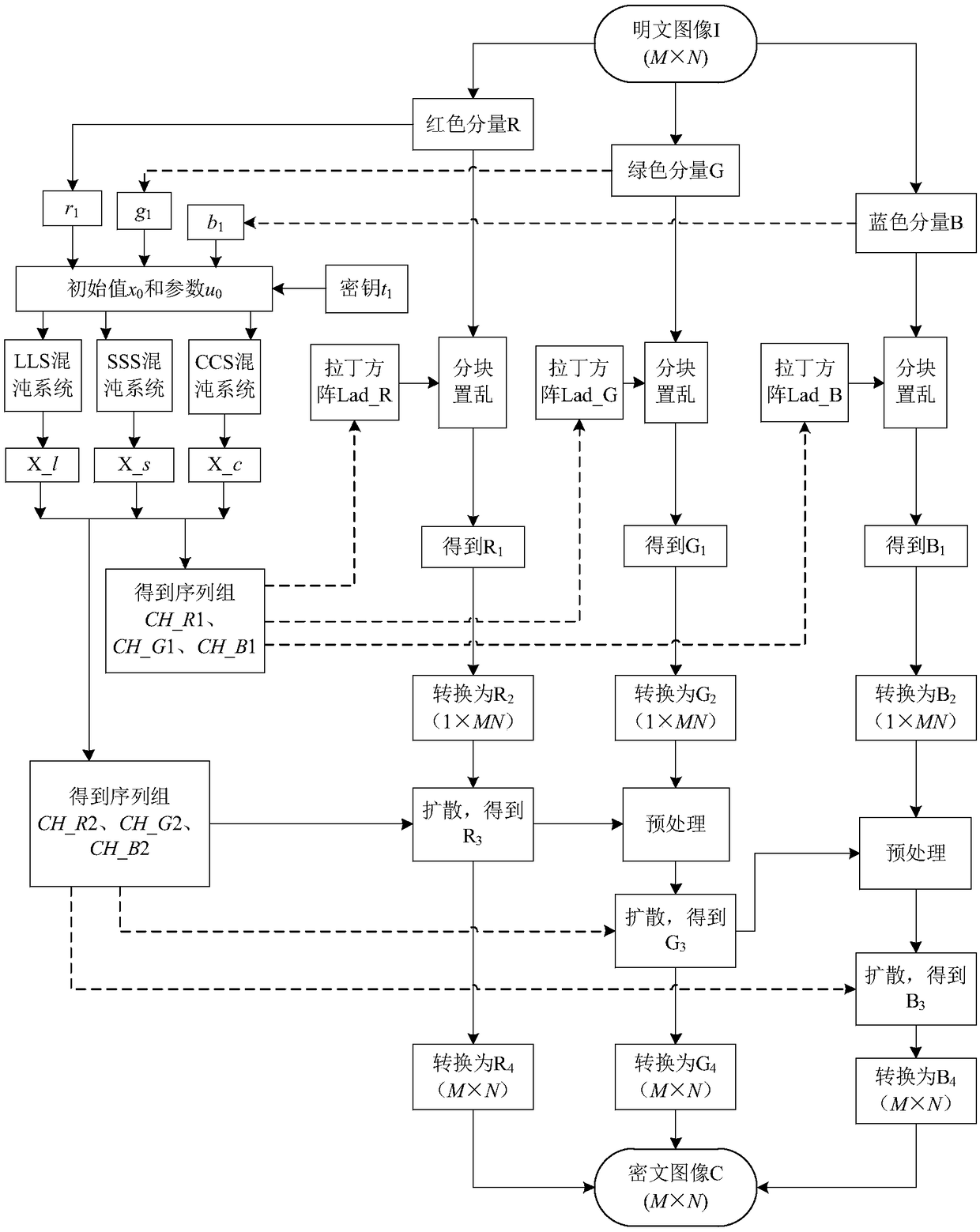
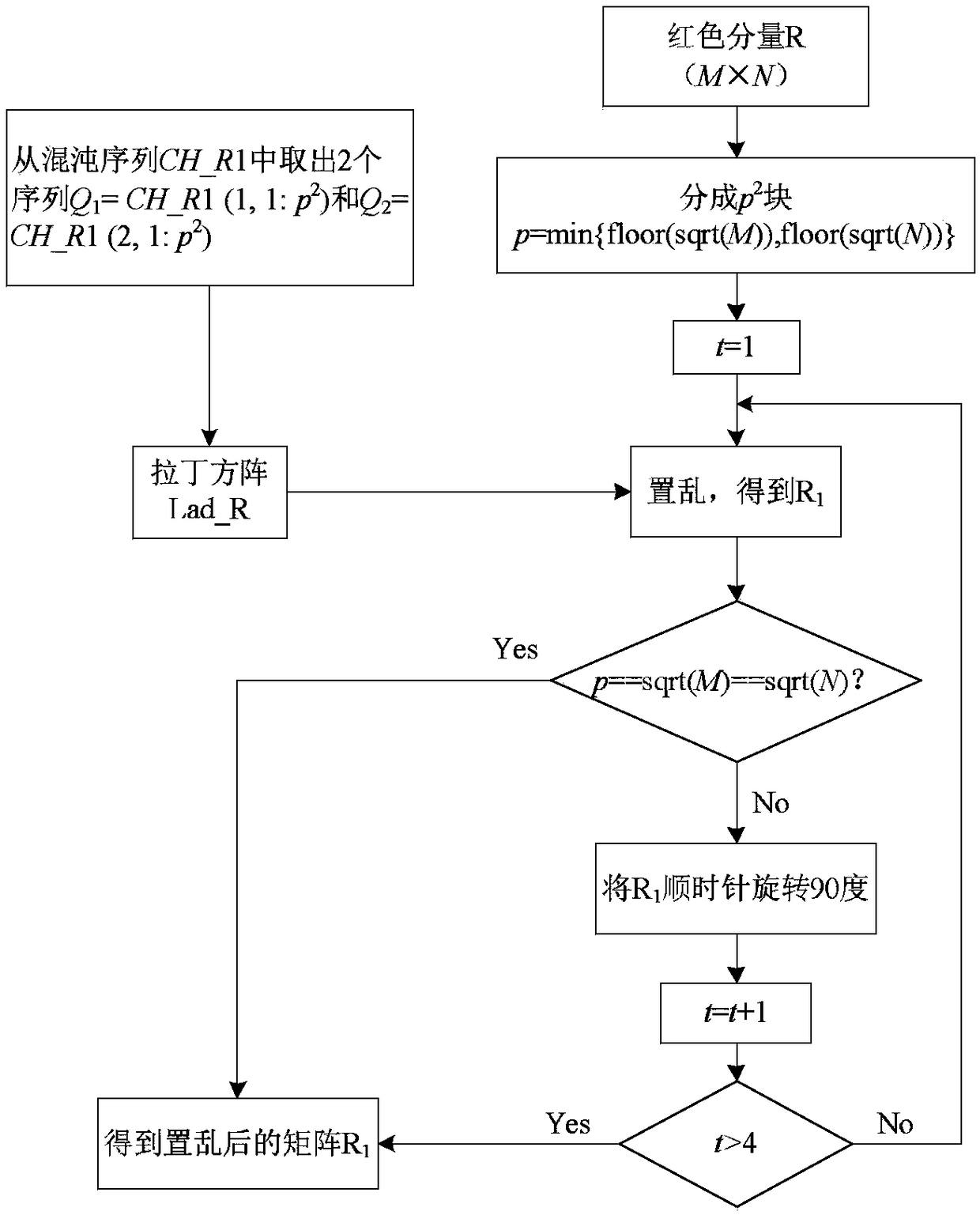
The invention relates to a color image encryption method based on Latin square scrambling. Plaintext keys r1, g1 and b1 are calculated through utilization of R, G and B components of a color plaintextimage, an initial value and a parameter obtained through calculation based on the keys are substituted into a chaotic system, and three groups of chaotic sequences are generated; the chaotic sequences for scrambling and diffusion are selected through utilization of a chaotic sequence selection mechanism based on the plaintext and digital arrangement; and a final ciphertext image is obtained through adoption of a block scrambling policy based on a Latin square and the chaotic sequences, and diffusion operation based on the plaintext and a scrambled image. The encryption method is closely related to the plaintext, so the plaintext attack resistance is improved. The employed chaotic system is an improved chaotic system, a chaotic characteristic is good, the randomness is high and a key spaceis great, so a security level is further improved. A simulation result and safety analysis show that according to the encryption provided by the invention, an image complete encryption demand can besatisfied, the encryption efficiency is high, and the robustness is high.
Owner:HENAN UNIVERSITY
Searchable public key encryption method, system employing method and server
ActiveCN108200063ASafe retrievalImprove encryption efficiencyKey distribution for secure communicationMultiple keys/algorithms usageCiphertextSecurity parameter
The invention relates to a searchable public key encryption method, a system employing the method and a server. The method comprises the following steps that bilinear mapping is established accordingto a preset security parameter, and a public parameter PK and a private key SK are output; a sender initializes a searchable ciphertext structure according to the public parameter PK, and outputs a public part Pub of the structure and a private part Pri of the structure; the sender inputs a keyword W, the public parameter PK and the private part Pri of the structure, generates a corresponding searchable ciphertext for the keyword W through utilization of an encryption algorithm, and uploads the searchable ciphertext to the server; a receiver inputs the keyword W and the private key SK, outputsa search trap door TW and submits the search trap door TW to the server; and the server inputs the search trap door TW, the public parameter PK and a searchable ciphertext set composed of a pluralityof searchable ciphertext, performs a search algorithm, finds the searchable ciphertext corresponding to the keyword W generated through one-time bilinear mapping operation based on a first encryptionalgorithm, and finds other searchable ciphertexts based on an implication relationship.
Owner:HUAZHONG UNIV OF SCI & TECH
Multiple-image encryption method based on DNA coding and chaos
ActiveCN107659751AAchieve protectionImprove encryption efficiencySecuring communication by chaotic signalsPictoral communicationDna encodingDigital image
The invention discloses a multiple-image encryption method based on DNA coding and chaos, belonging to the field of information encryption. The massive digital image produced in the large data age should not only ensure the security of the image content, but also have high encryption efficiency. As a new multimedia security technology, the multiple-image encryption has the characteristic of high efficiency. A number of multiple-image encryption methods in the prior art have low encryption efficiency, weak security and obvious distortion in decrypted images, which are difficult to satisfy. Themultiple-image encryption method based on the DNA coding and the chaos comprises the following steps: encoding a number of original images into corresponding DNA sequence matrices; disordering the DNAsequence matrices by means of the chaos sequence; performing the DNA sequence diffusion operation on the disordered results; and obtaining the encrypted image by the DNA decoding operation. The maininnovation is that the invention provides a multiple-image encryption method based on the DNA coding and the chaos. The experimental results show that the method has excellent encryption effect and high security, and is suitable for the practical application of image encryption.
Owner:CHINA UNIV OF MINING & TECH
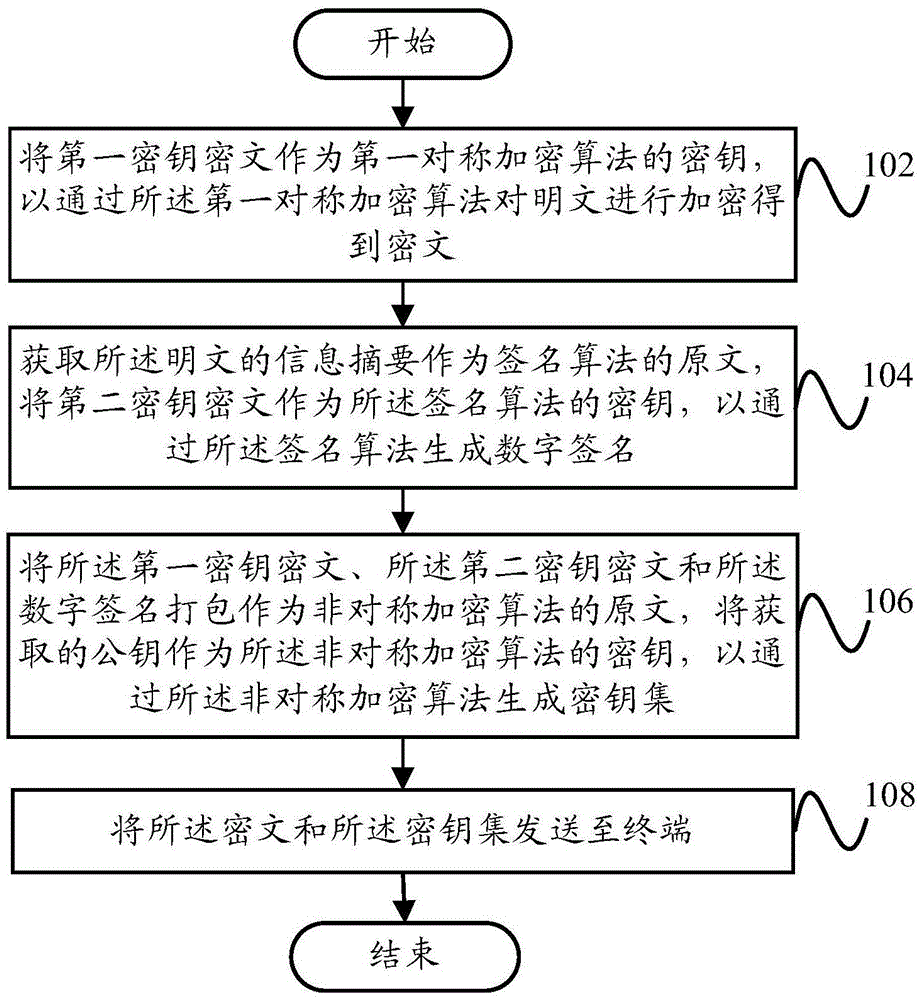
Encryption method, encryption apparatus, decryption method, decryption apparatus and terminal
InactiveCN105554031AImprove encryption efficiencyReduce resource usageTransmissionPlaintextDigital signature
The invention discloses an encryption method, an encryption apparatus, a decryption method, a decryption apparatus and a terminal. The encryption method comprises: using a first secret key cipher text as a secret key of a first symmetric encryption algorithm so as to encrypt a clear text by the first symmetric encryption algorithm to obtain a cipher text; acquiring an informative abstract of the clear text, using the informative abstract as an original text of a signature algorithm, and using a second secret key cipher text as a secret key of the signature algorithm so as to generate a digital signature by the signature algorithm; packaging the first secret key cipher text, the second secret key cipher text and the digital signature to form an original text of an asymmetric cryptographic algorithm, and using an acquired public key as a secret key of the asymmetric cryptographic algorithm so as to generate a secret key set by the asymmetric cryptographic algorithm; and sending the cipher text and the secret key set to the terminal. According to the technical scheme of the invention, the encryption method, the encryption apparatus, the decryption method, the decryption apparatus and the terminal can be simultaneously guaranteed to have the characteristics of high encryption efficiency, small system resource occupation and encrypted data safety when data is encrypted.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
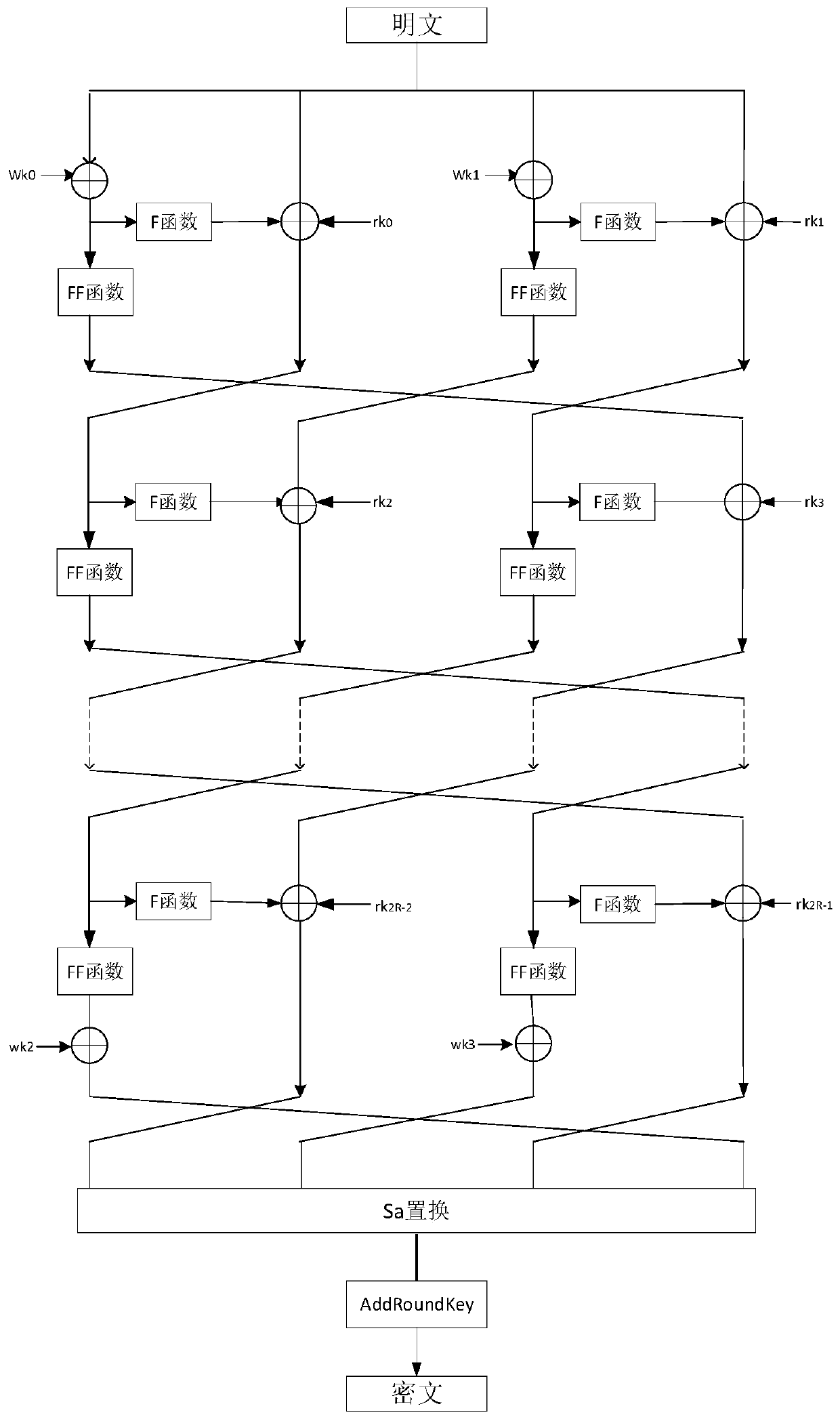
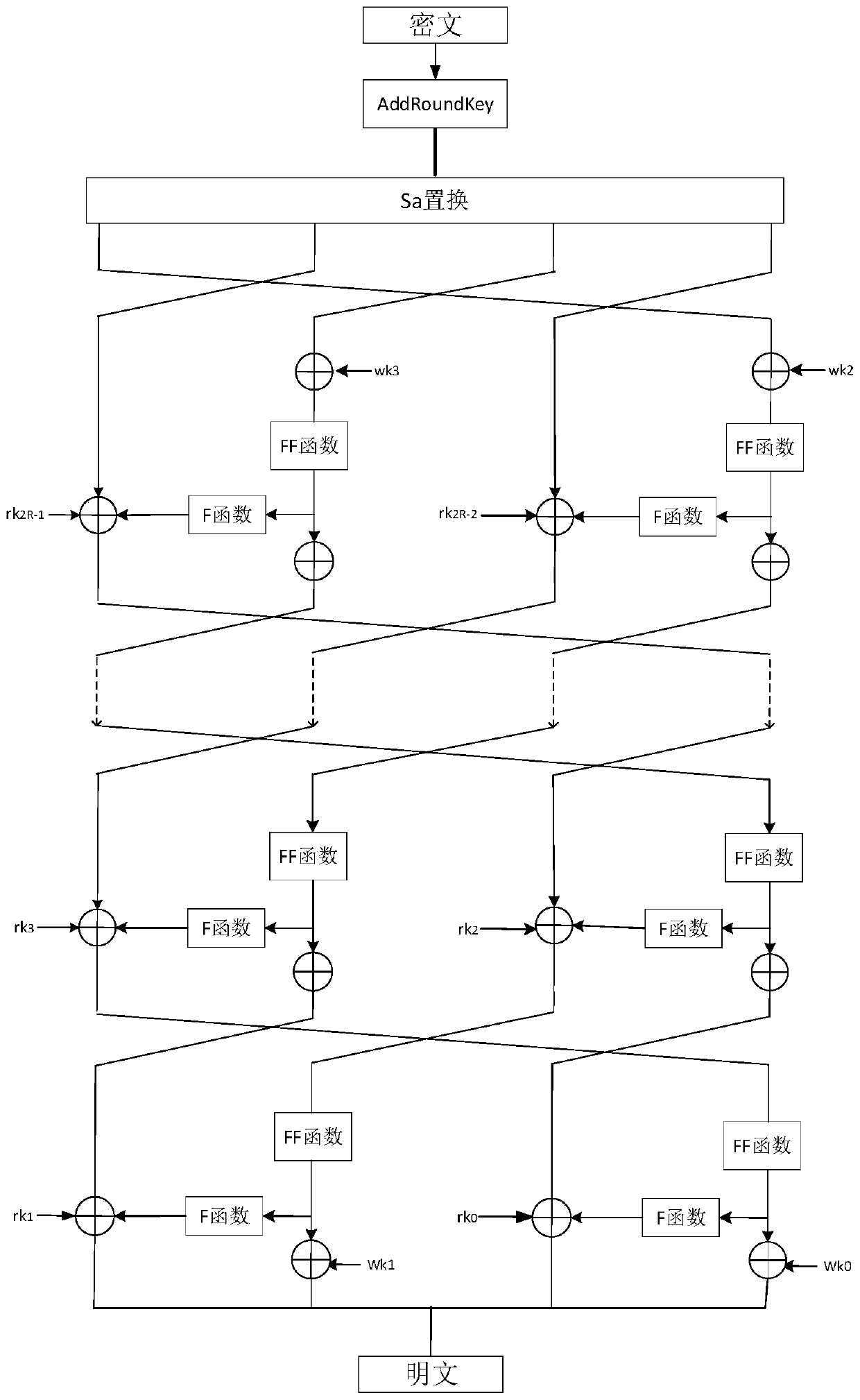
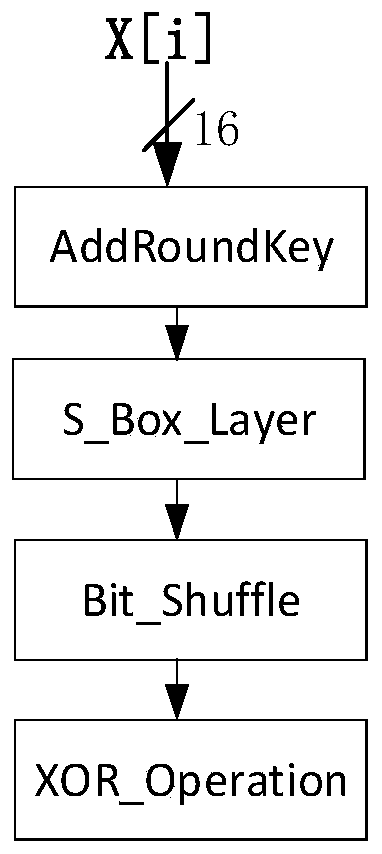
Implementation method of a lightweight block cipher algorithm Wheel
ActiveCN109768854AFix security issuesImprove efficiencyEncryption apparatus with shift registers/memoriesPlaintextExclusive or
The invention discloses an implementation method of a lightweight block cipher algorithm Wheel, which comprises the following steps of: calculating the number of turns by utilizing an initial encryption key, and sequentially obtaining an intermediate key and a whitening key by utilizing the initial encryption key; wherein each round of operation is composed of an F function operation, an FF function operation and a bitwise exclusive OR operation, each round of operation is used for processing N sets of encrypted information, and N sets of encrypted information corresponding to each next roundof operation are output information of the previous round of operation; and finally, performing Sa replacement operation on the output data subjected to round operation to obtain output data, and performing round encryption operation on the output data and the low bit of the initial encryption key to obtain encrypted plaintext information. According to the method, the encryption security and efficiency are improved.
Owner:HENGYANG NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com