Image encryption and decryption method based on probability interval division and dynamic probability events
A technology of probability interval and encryption method, which is applied in the direction of encryption device with shift register/memory, image data processing, image data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0171] The present invention is described below in conjunction with specific embodiment:
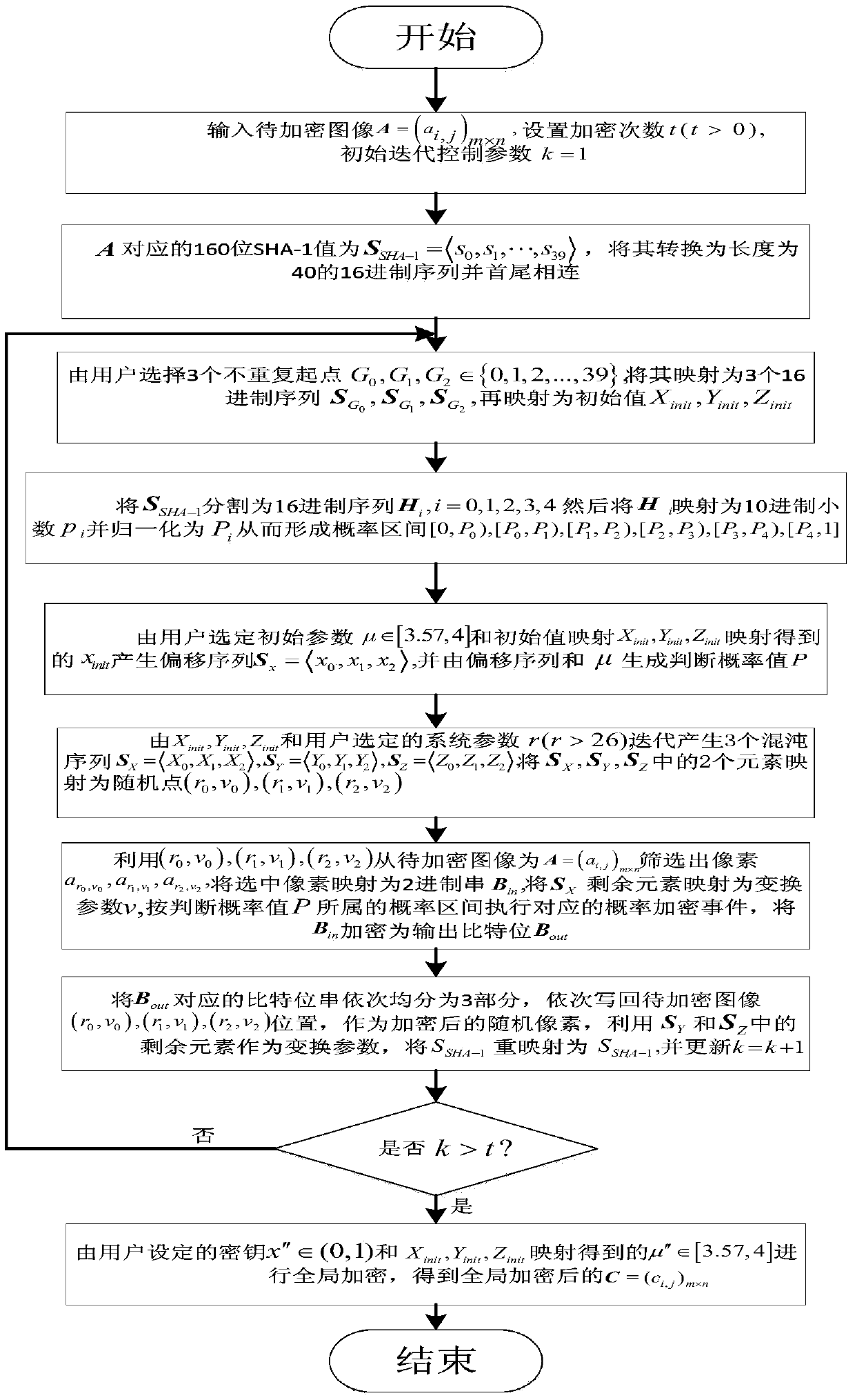
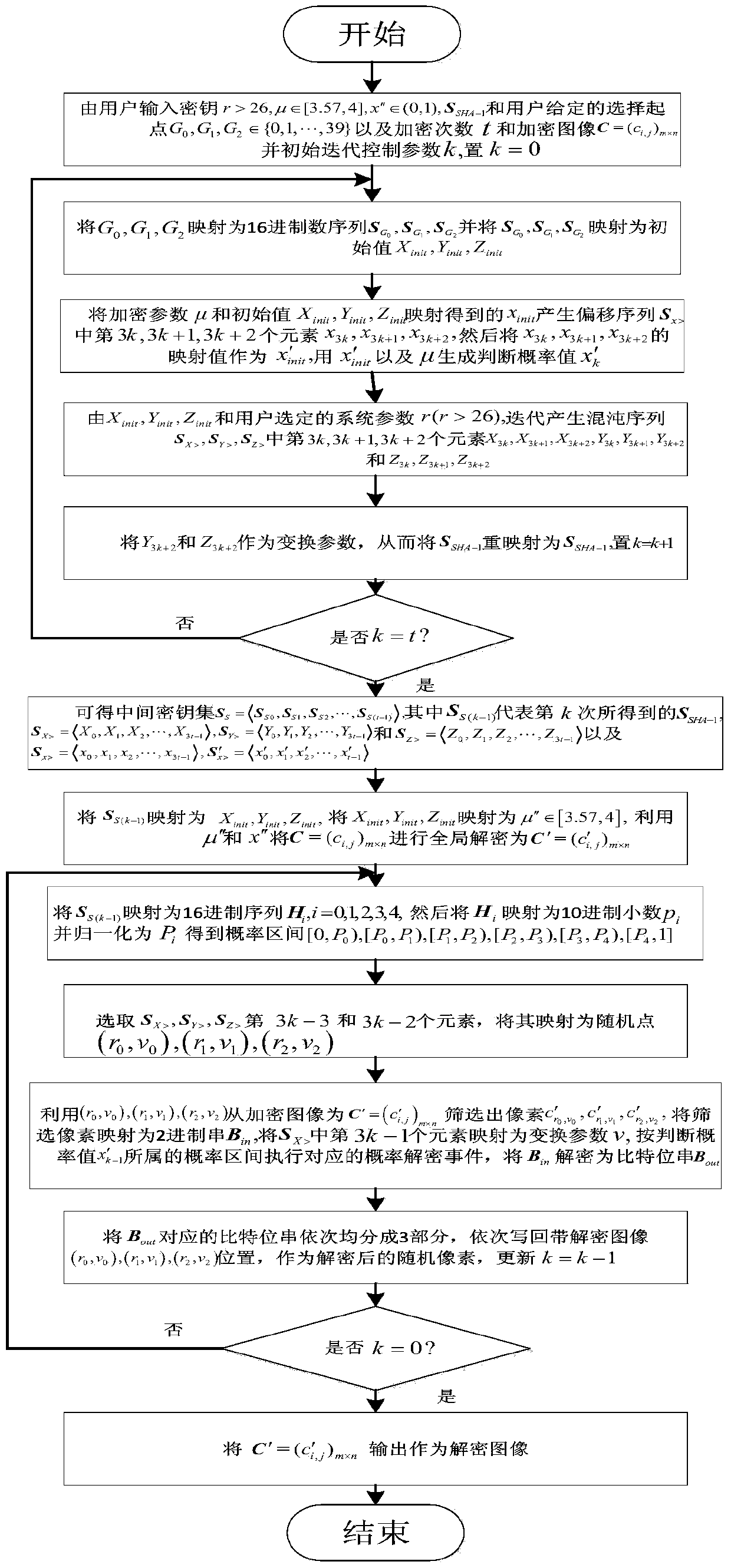
[0172] Taking JAVAjdk1.8.0_20 as the case implementation environment, the implementation of the present invention will be described in detail in conjunction with the accompanying drawings, but not limited to this implementation case, where figure 1 is the flowchart of the encryption method, figure 2 is the flowchart of the decryption method.
[0173] Encryption process:
[0174] Step 1: Select image A, such as image 3 As shown, it is a 256×256 grayscale image Lena, and the encrypted image A=(a i,j ) m×n The corresponding 40-bit hexadecimal SHA-1 value is S SHA-1 =4D27B479AC001B2D07EB2D784659E520DD2E6672, and connect them end to end. Determined by the user not to repeat the starting point G 0 ,G 1 ,G 2 ∈ {0,1,2,...,39}, map it to a sequence of hexadecimal numbers
[0175] For example: G 0 =8,G 1 =16,G 2 = 36 S G 0 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com