Patents
Literature
4625results about "Eavesdropping prevention circuits" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
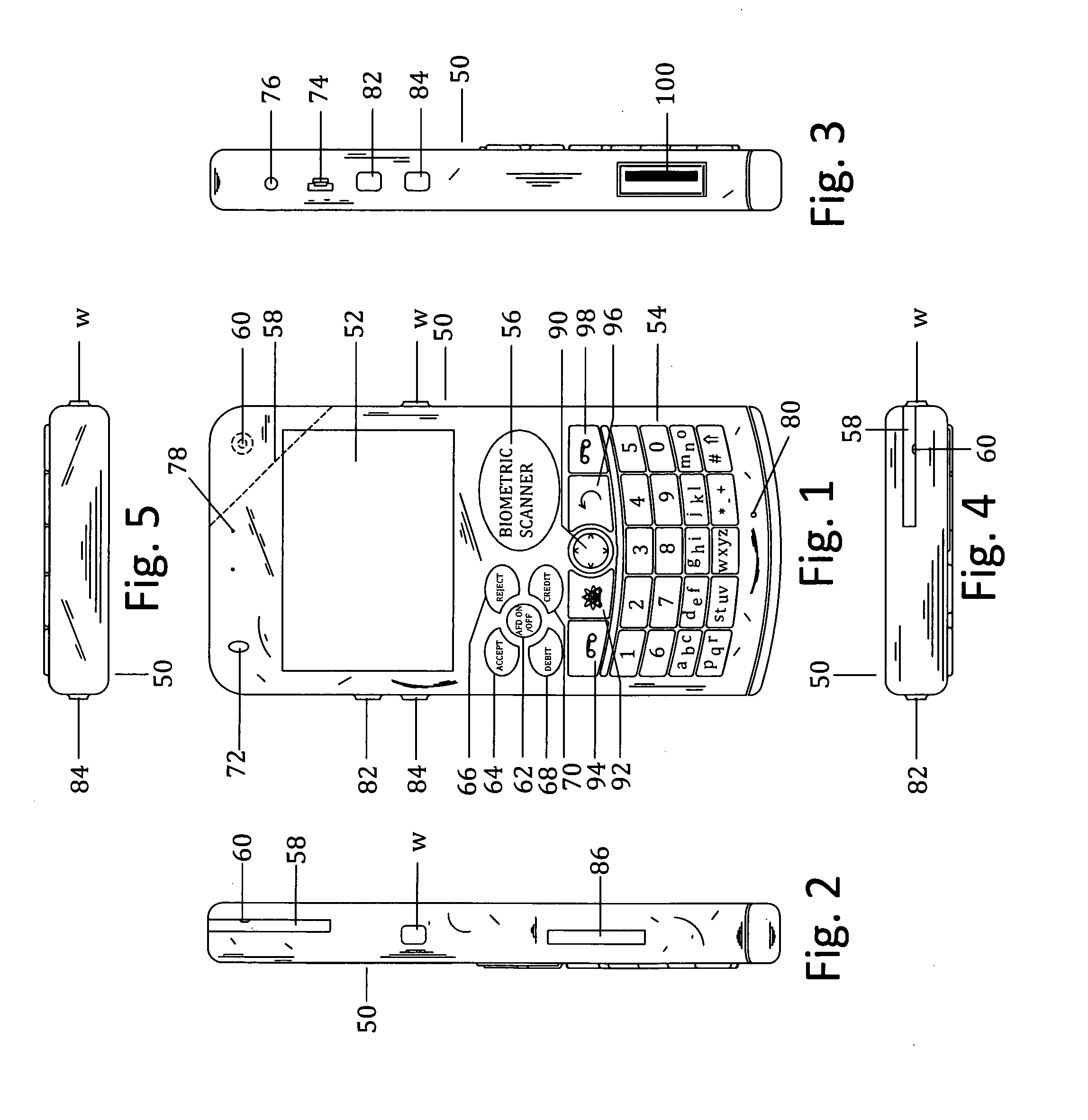
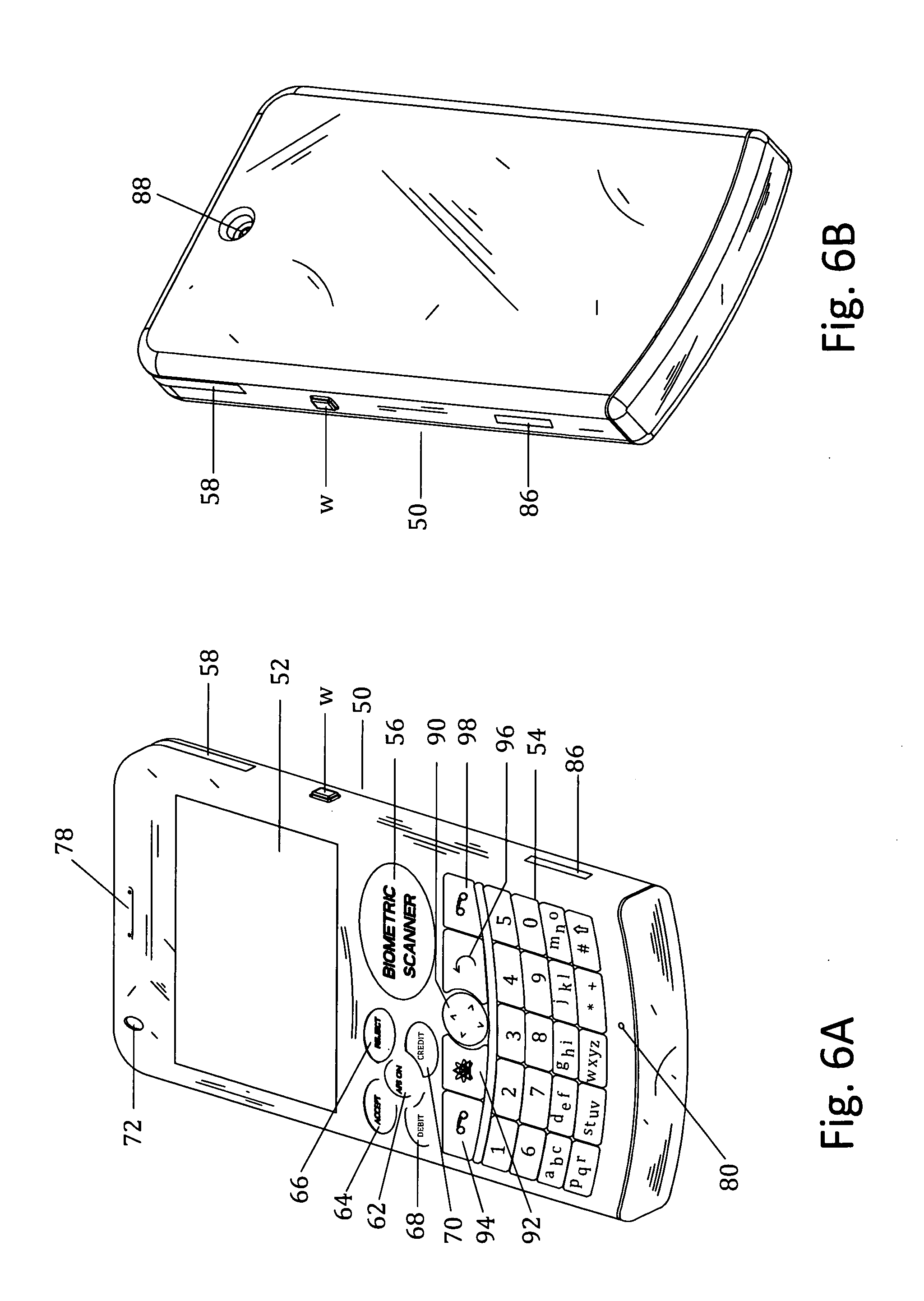
Method and apparatus for controlling and securing mobile phones that are lost, stolen or misused
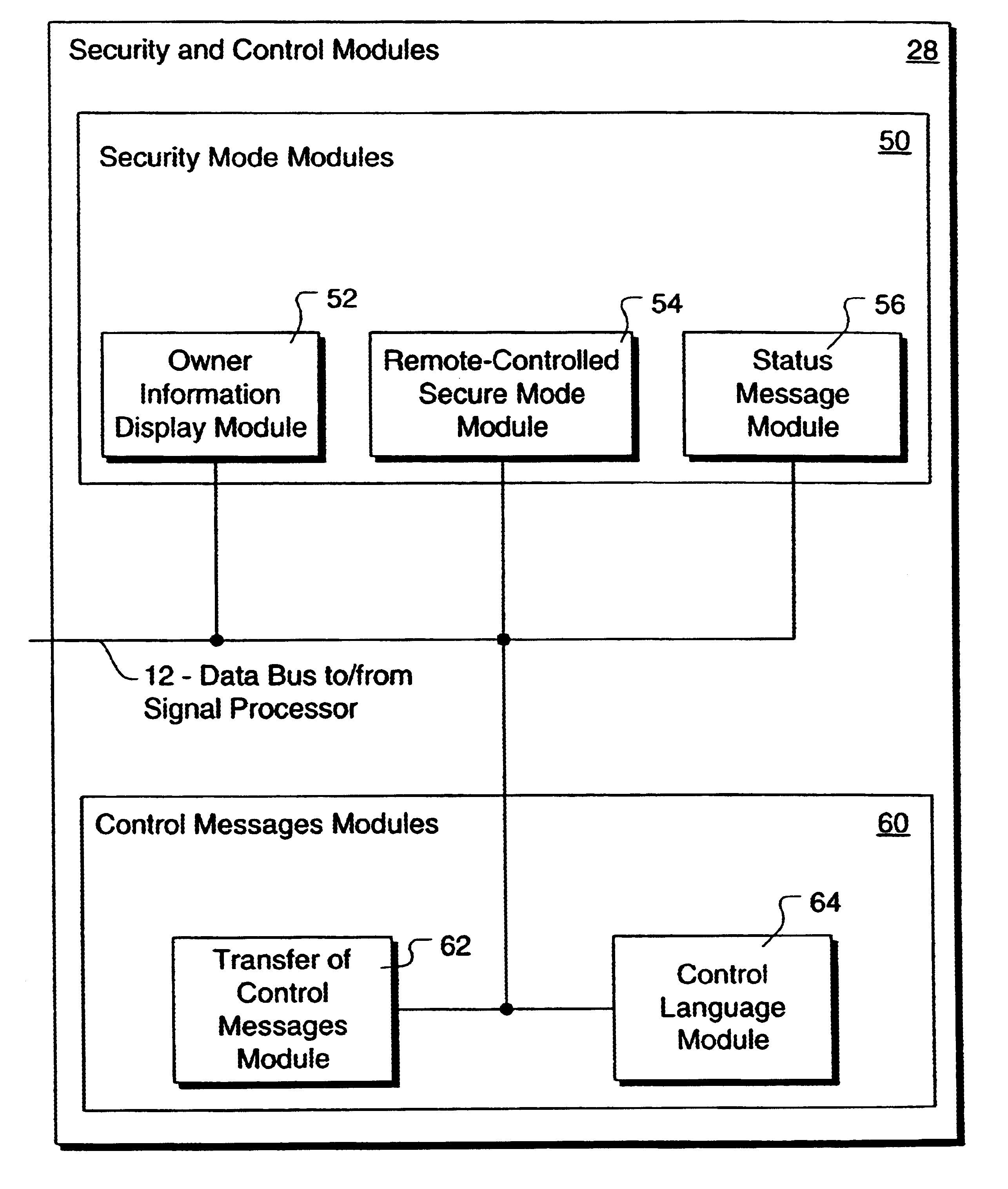
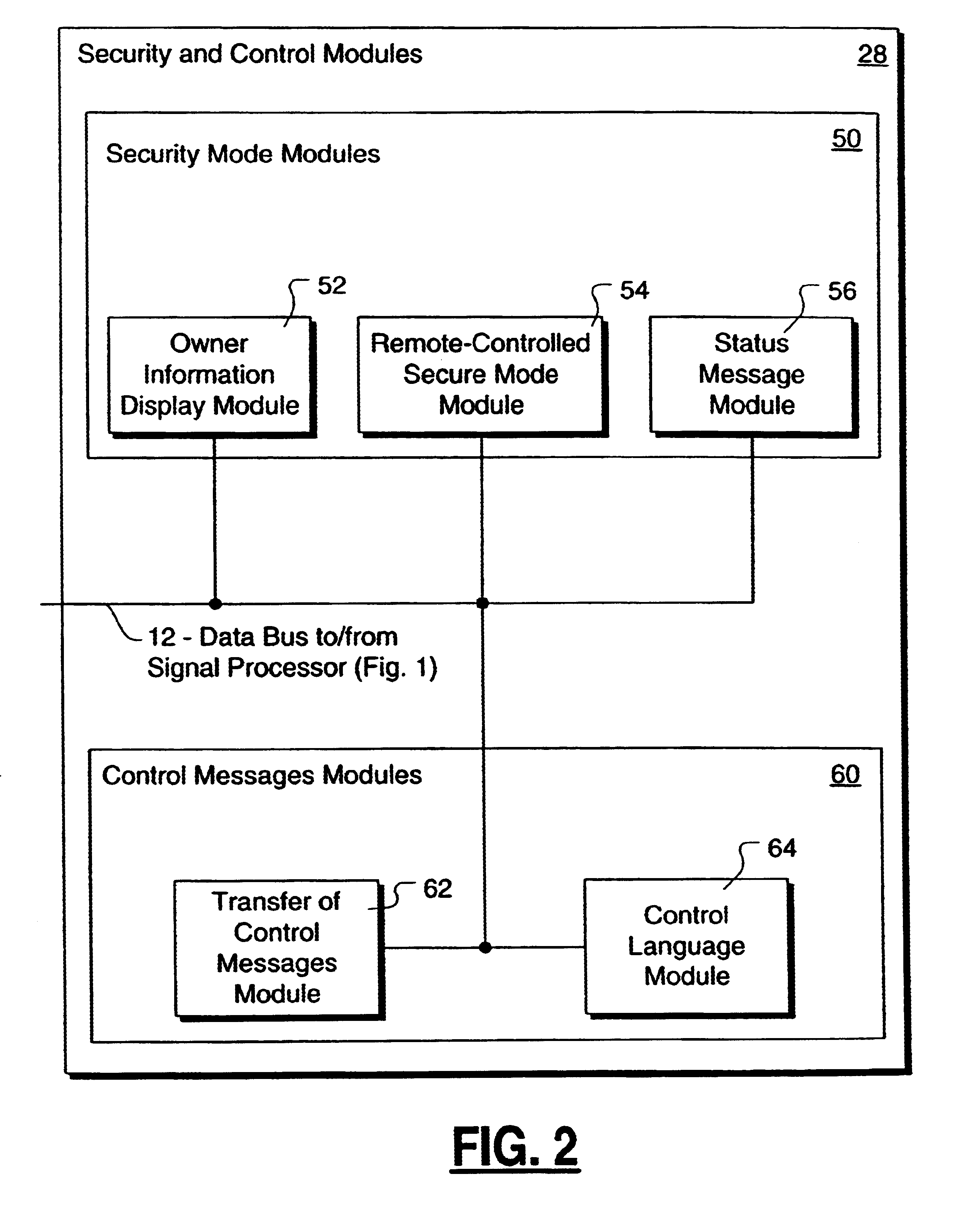
InactiveUS6662023B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure stateStart up
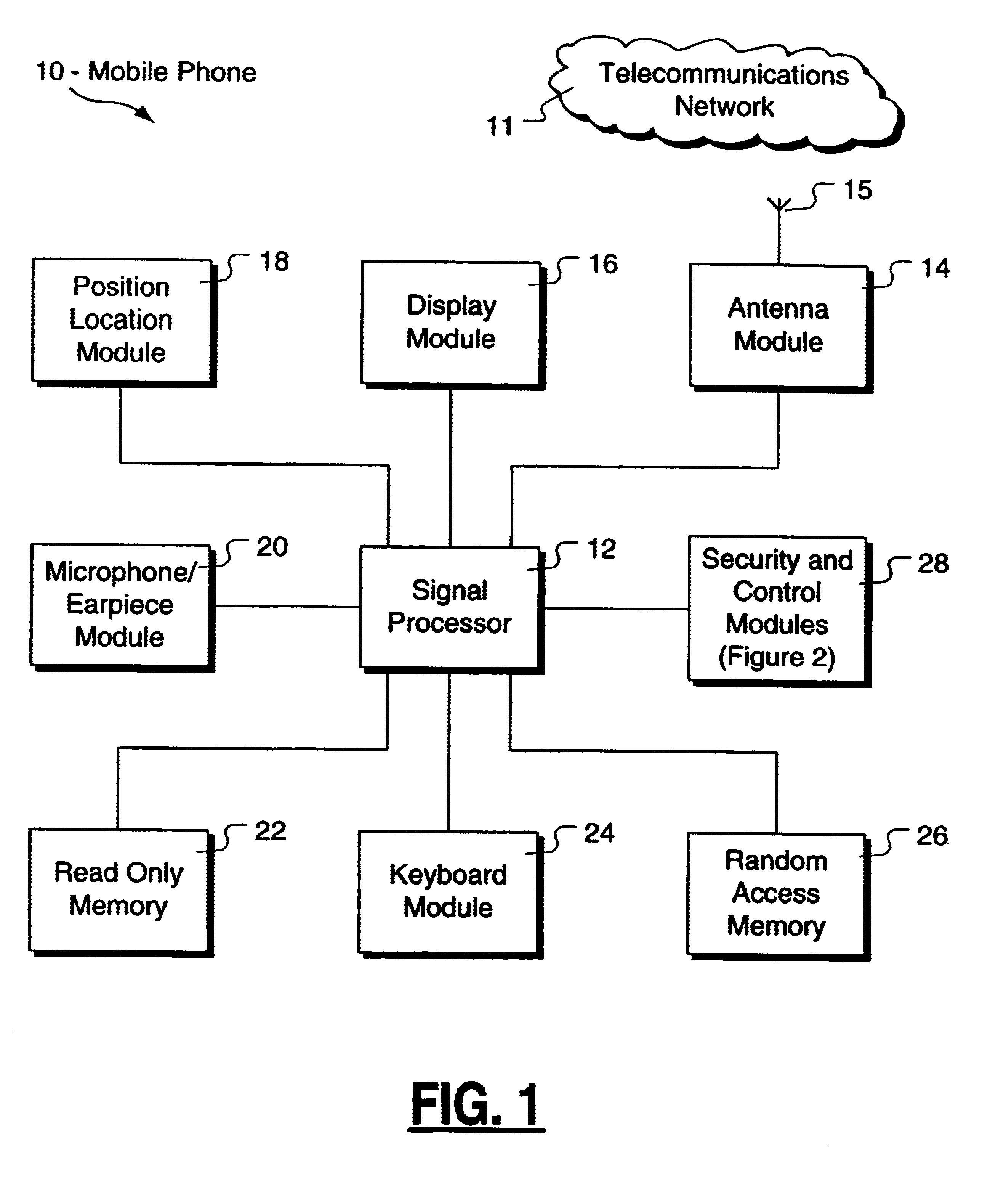
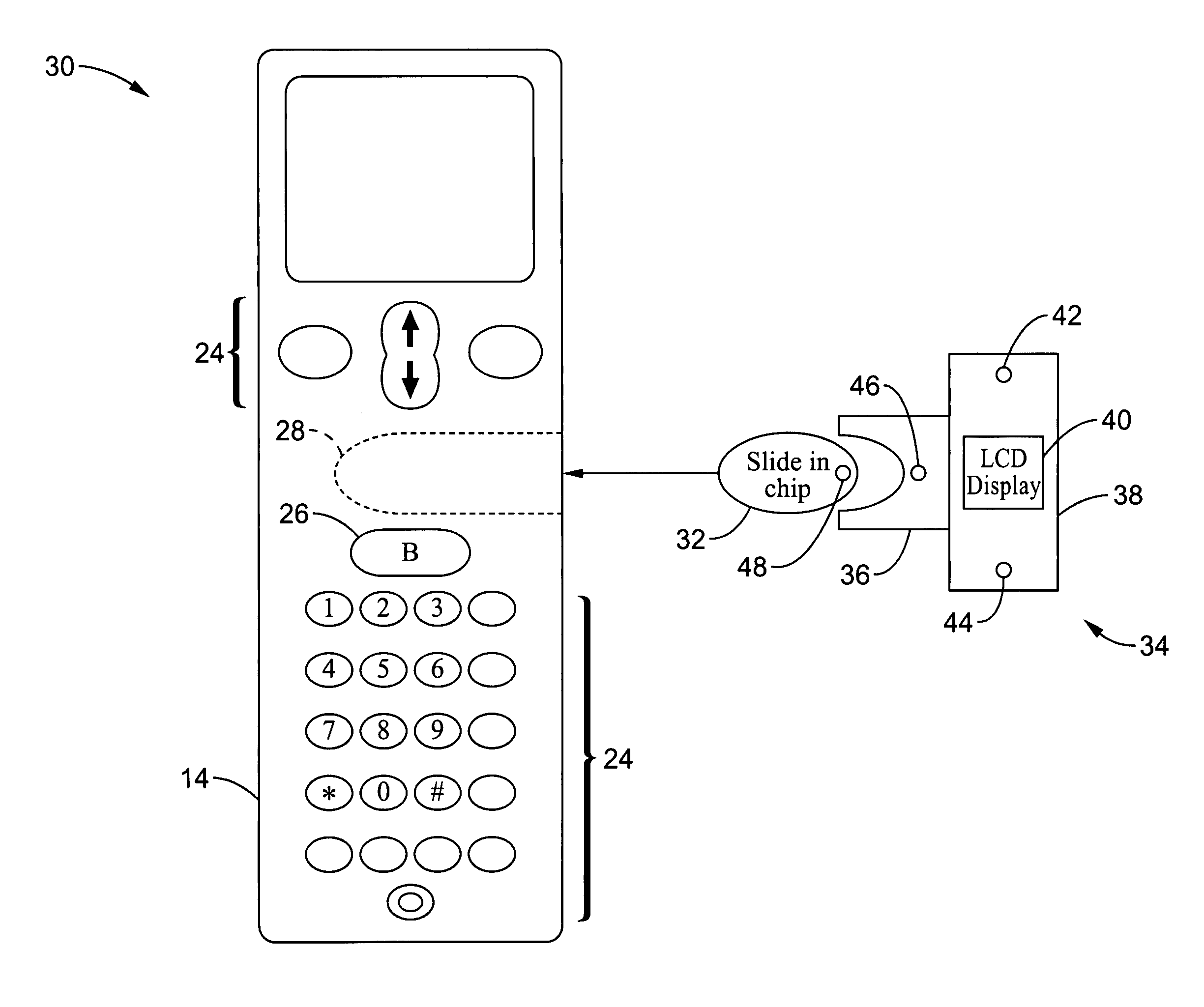
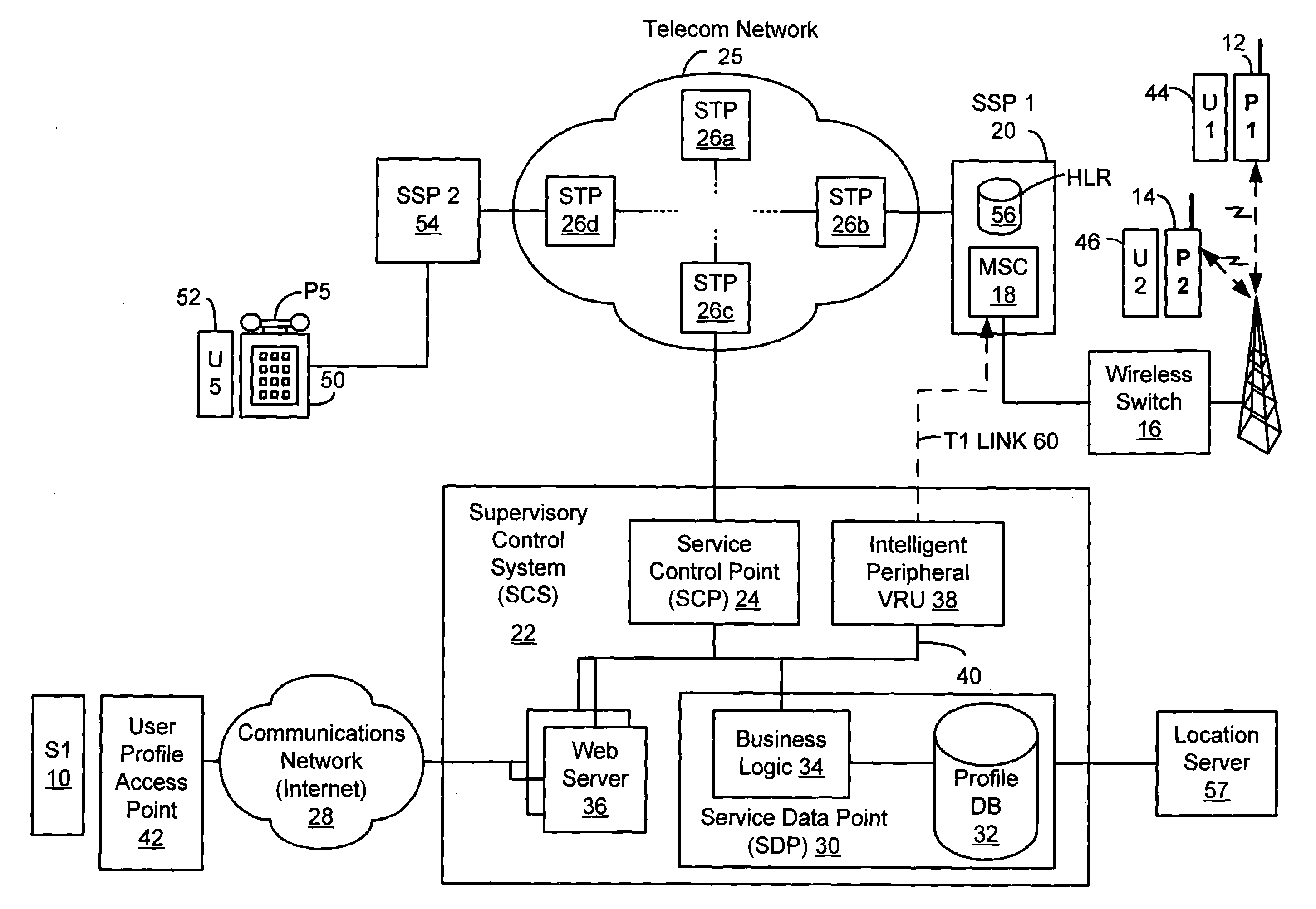
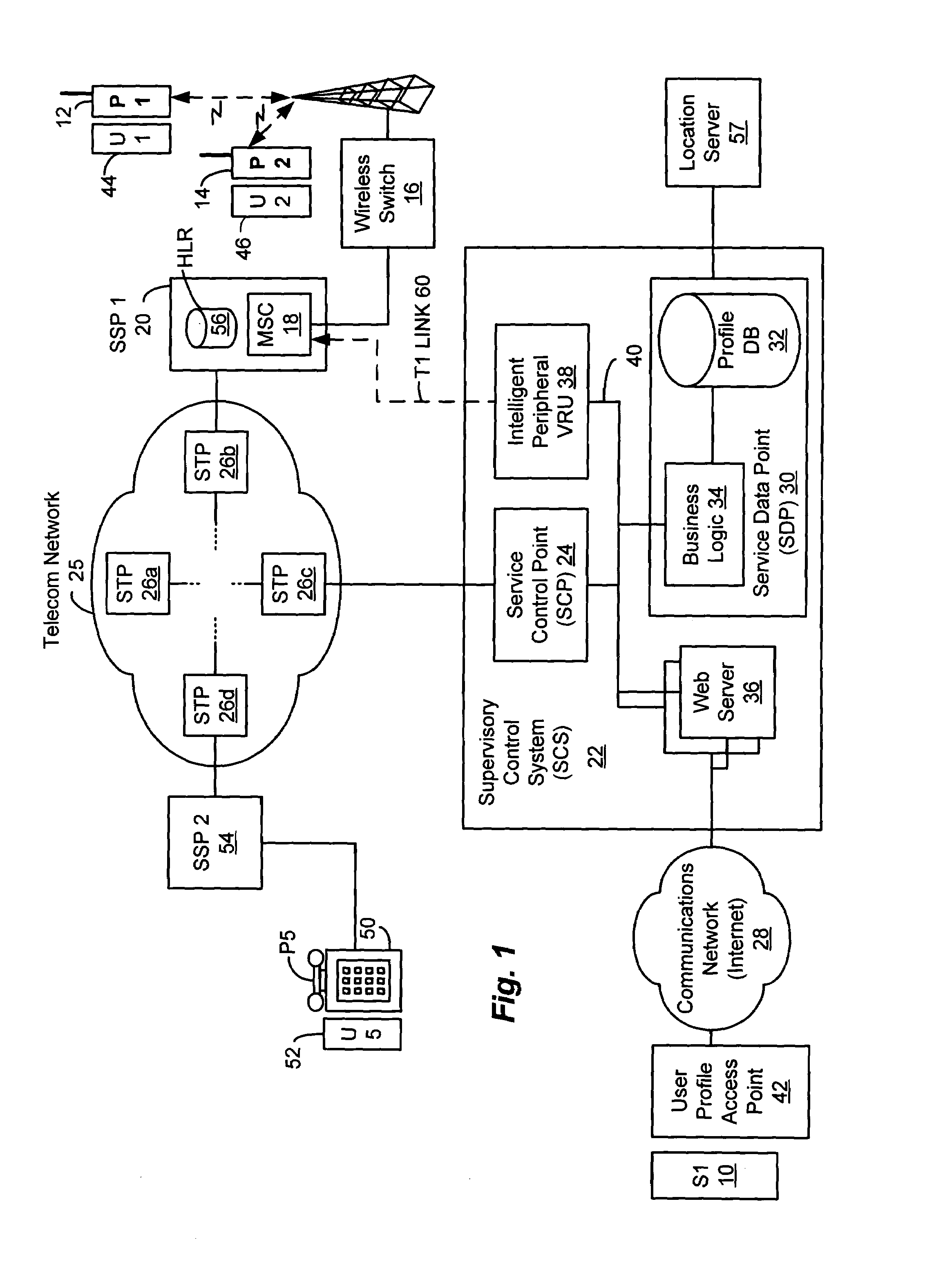
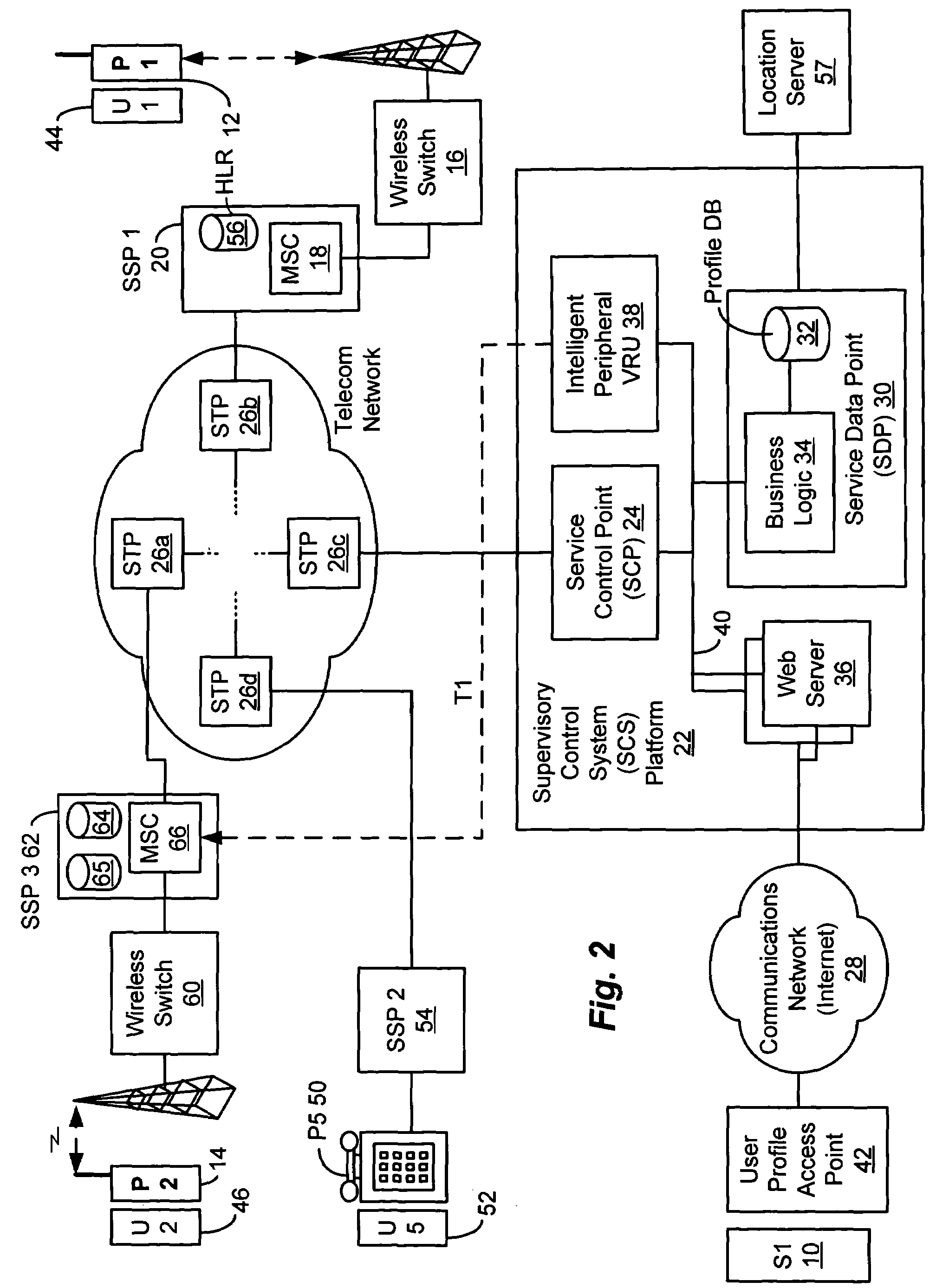
A method and apparatus is provided for controlling a mobile phone when it has been lost or stolen in order to prevent its use except to help the owner find it. Controlling the phone remotely may be implemented via a known Short Messaging System, for example. The security features provided are as follows: (1) Displaying contact information (phone number) of the owner on screen when the mobile phone can not start up normally, for example, due to an incorrect security code entry; (2) Setting the mobile phone in a secure state where it can only be used to call one number (Emergency calls are of course always possible.); and (3) Commanding the mobile phone to send information about its location and usage via SMS to a given number.
Owner:NOKIA TECHNOLOGLES OY
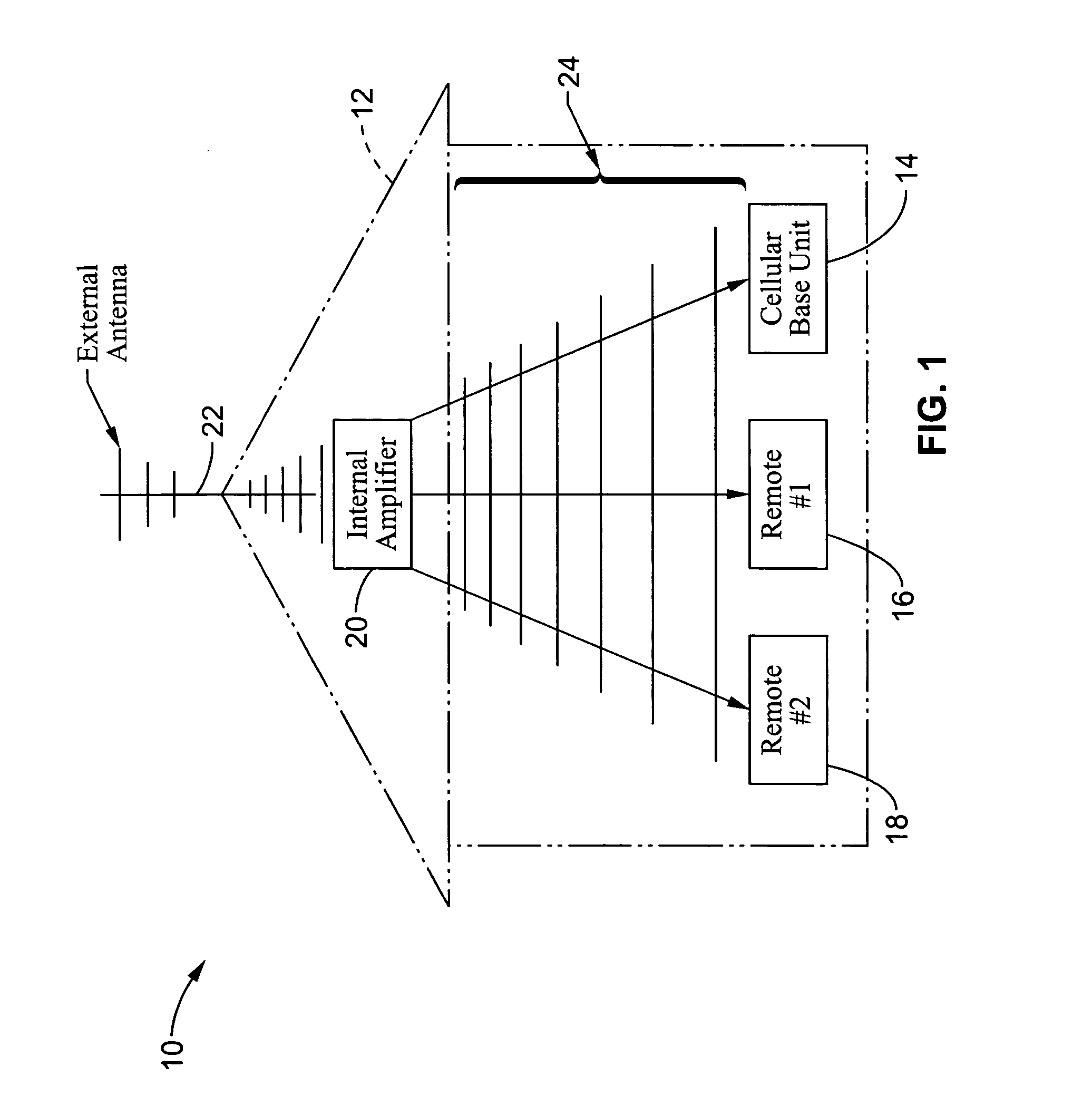
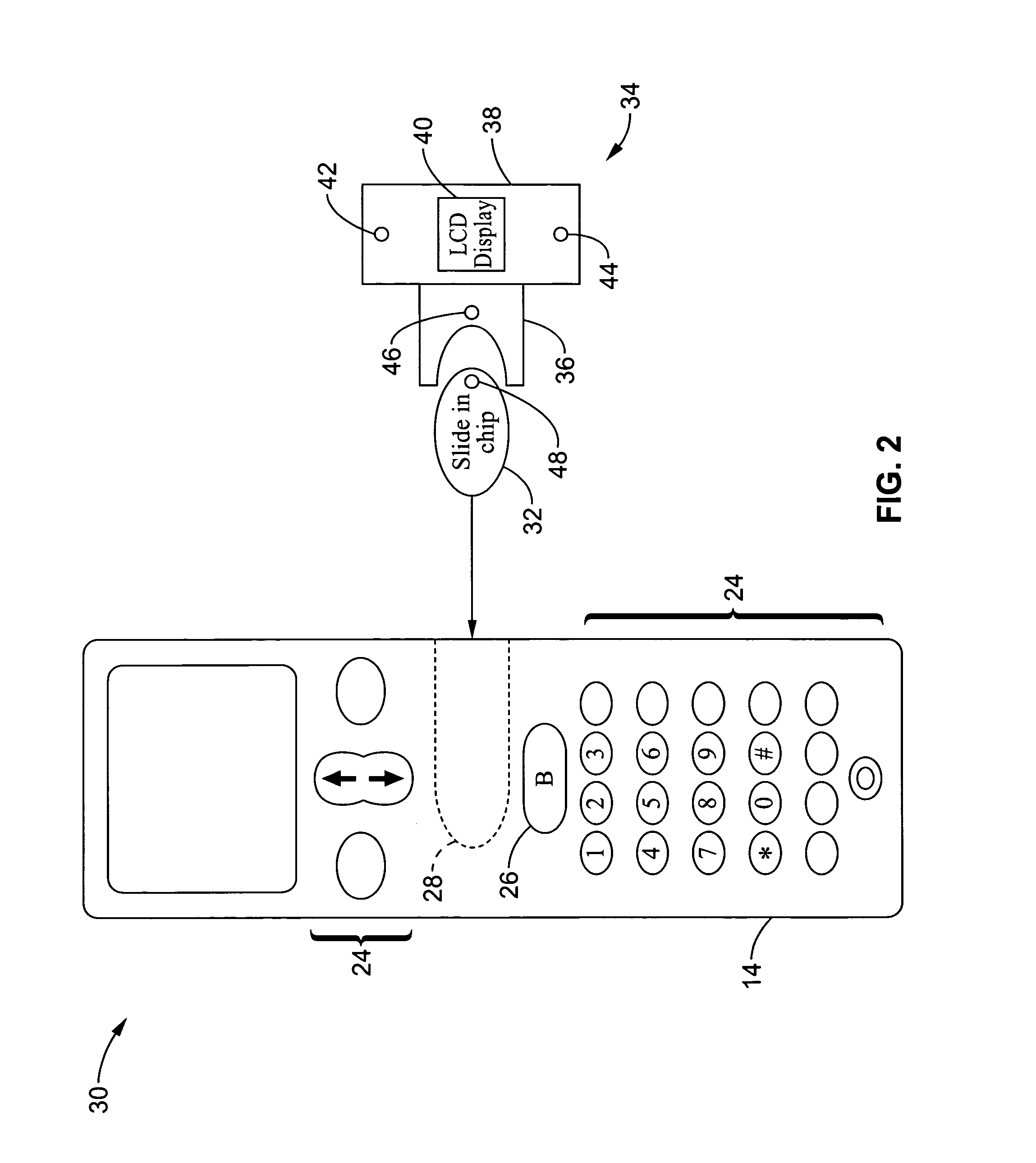
Wireless communications apparatus and method
InactiveUS7146191B2Easy to be stolenProcess safetyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInterconnectivityDisplay device
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
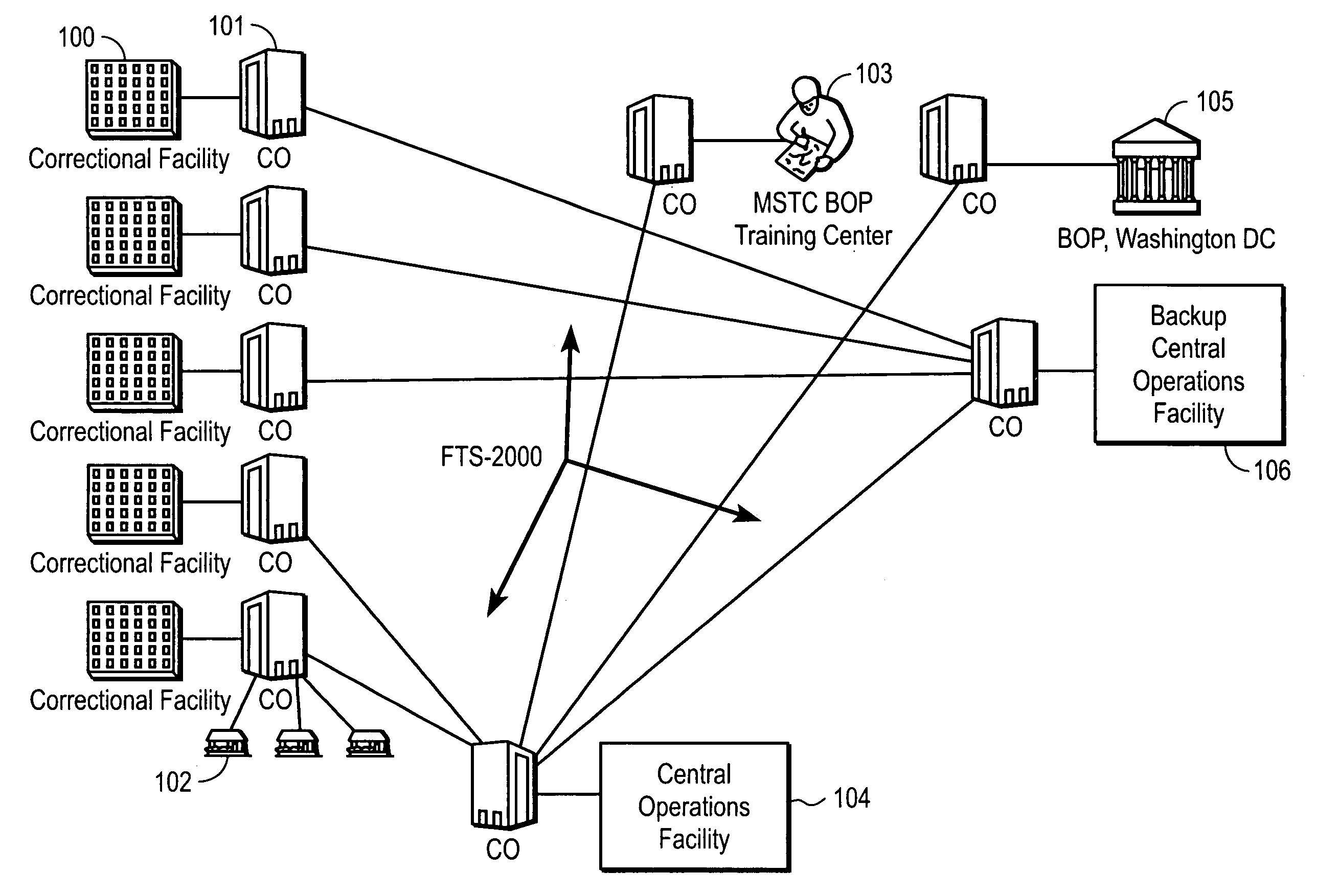
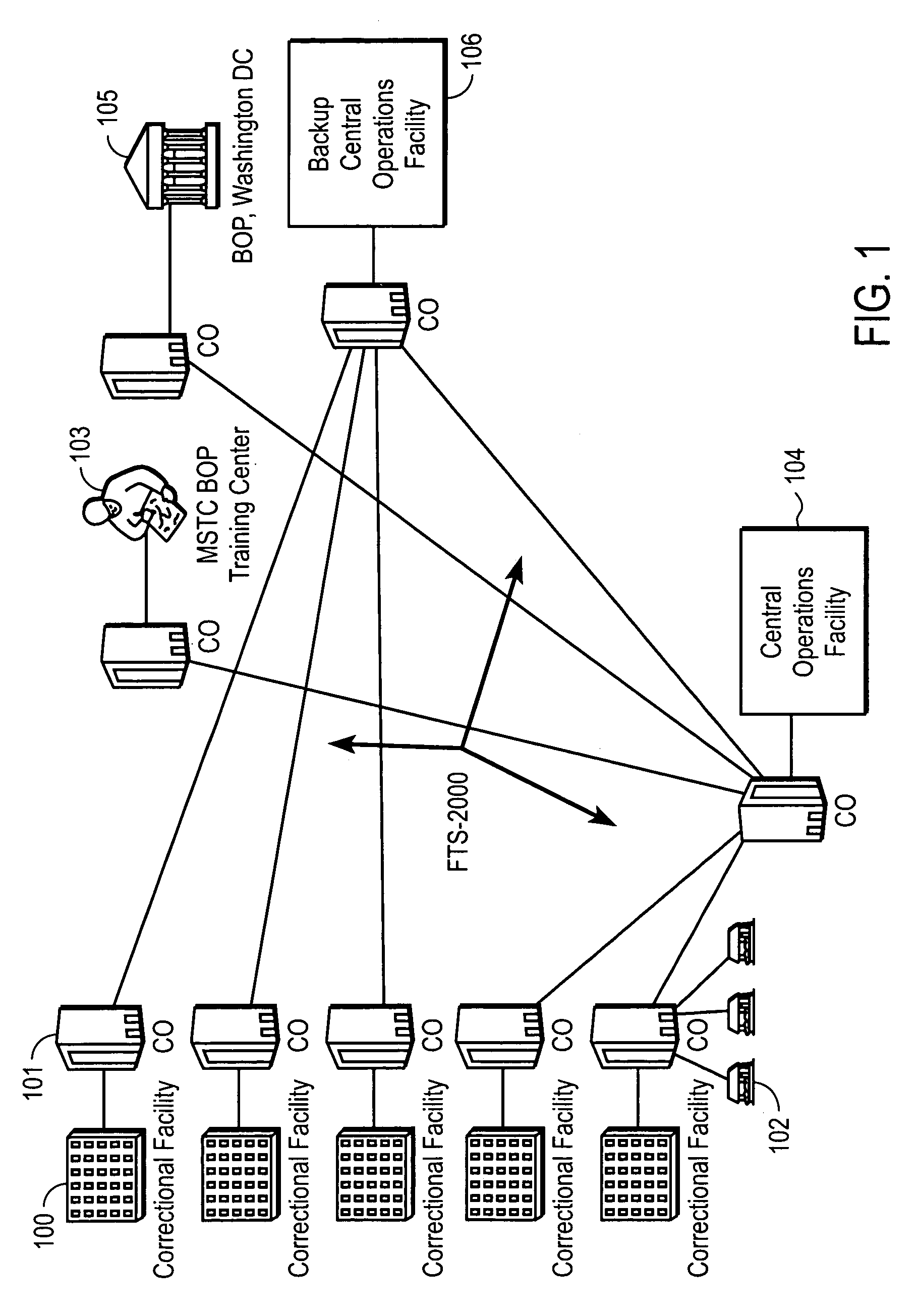
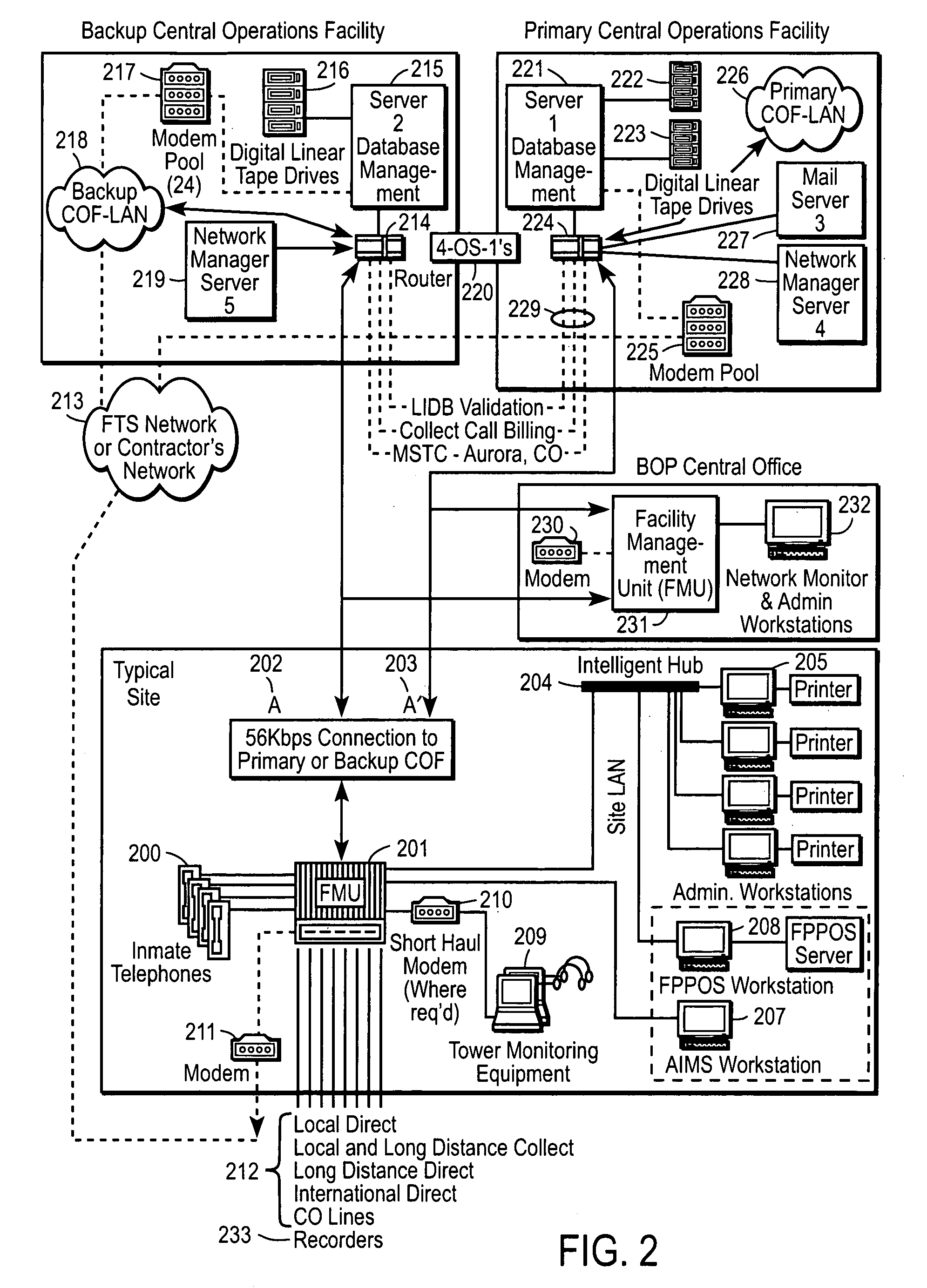
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
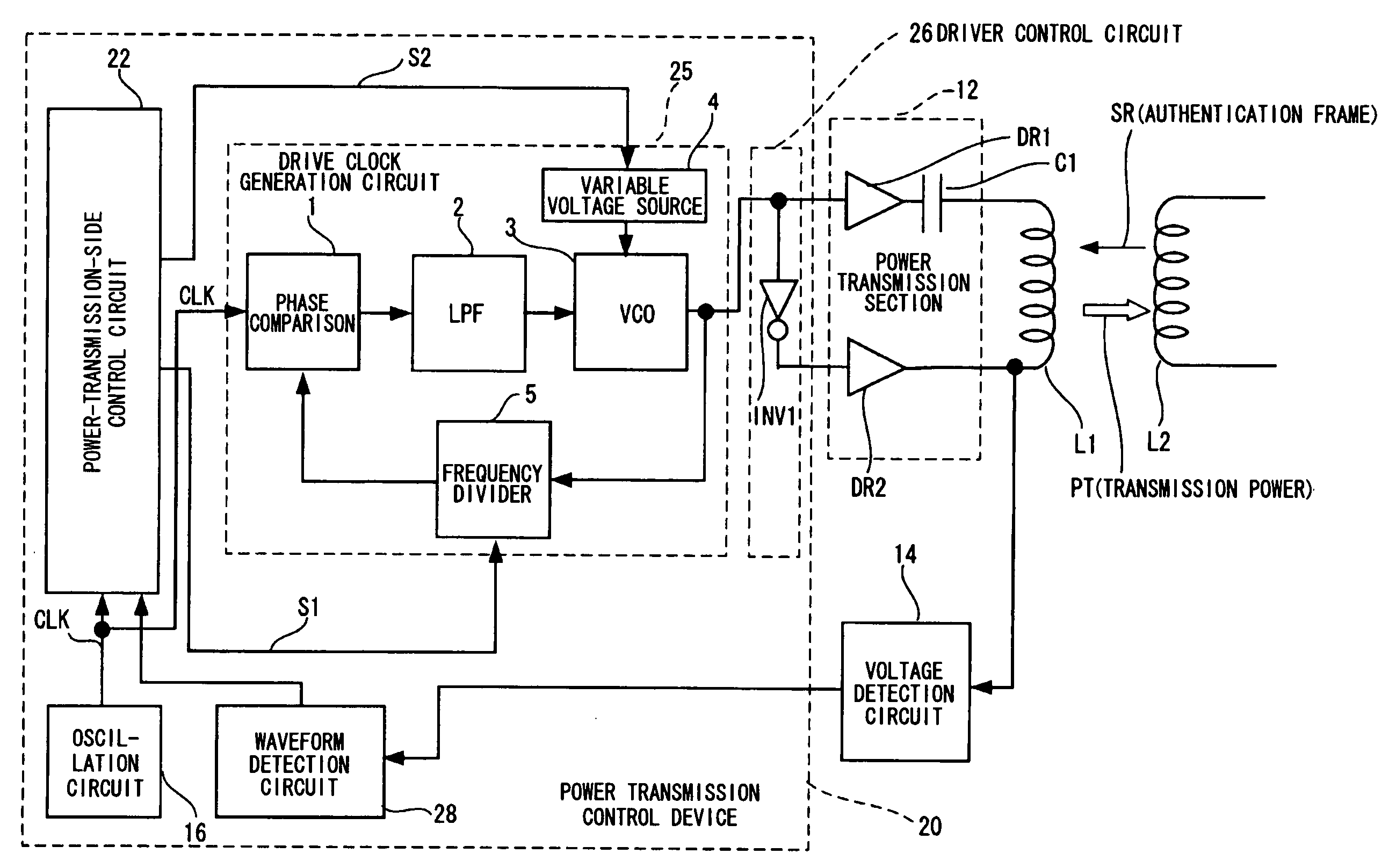
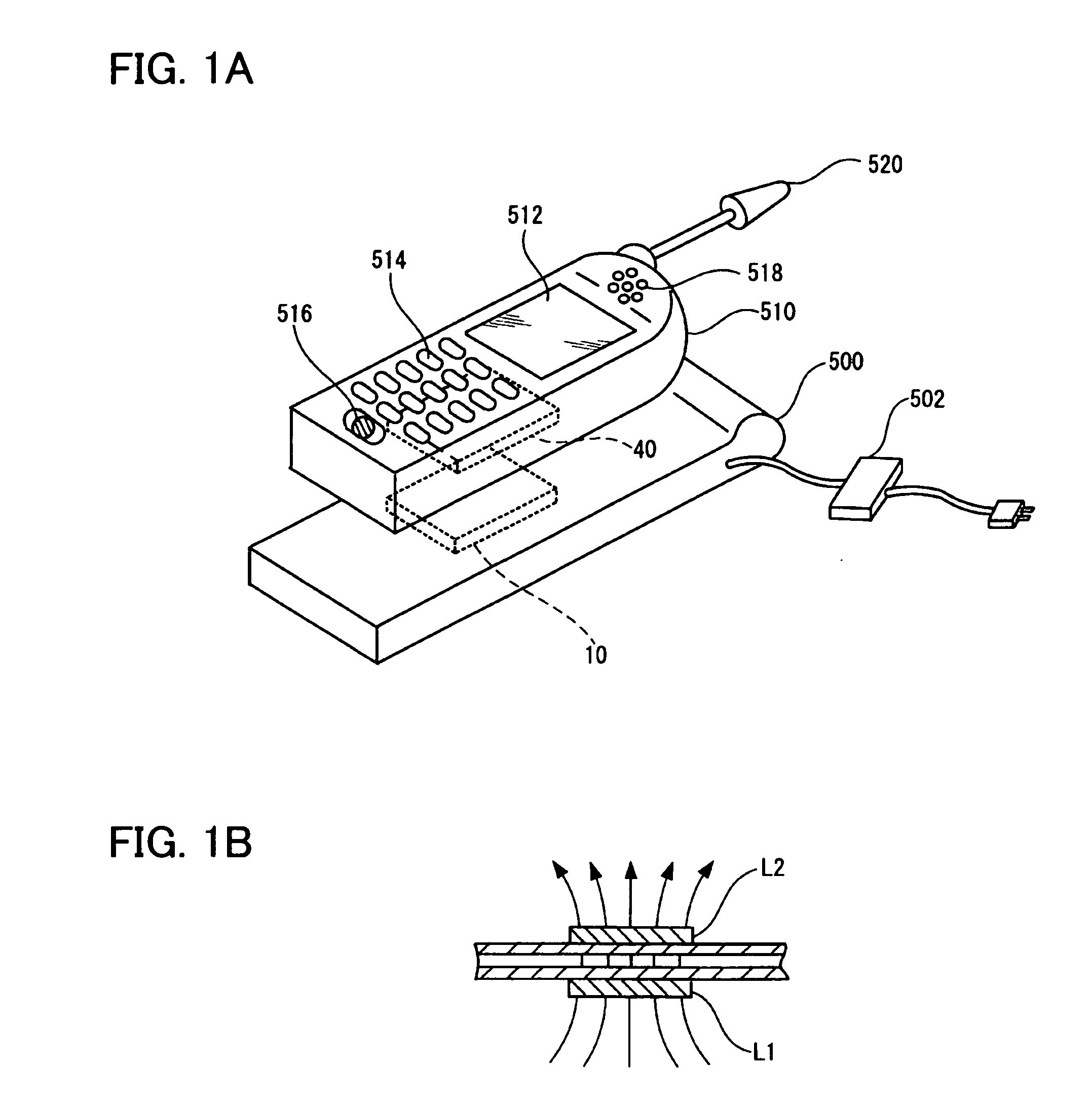
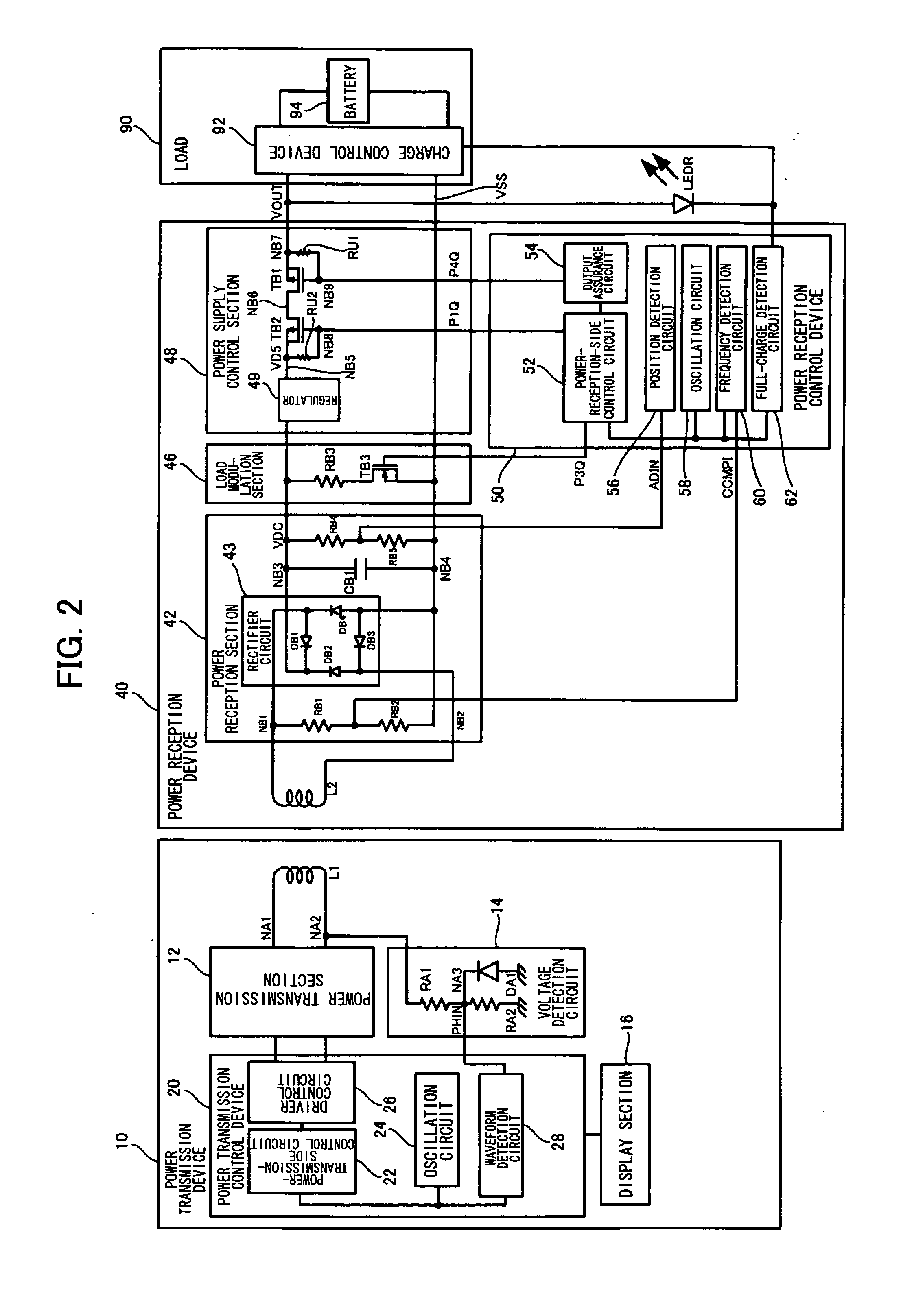
Power transmission control device, power reception control device, non-contact power transmission system, power transmission device, power reception device, and electronic instrument
ActiveUS20080197802A1Circuit authenticationInterconnection arrangementsElectric power transmissionResonance
A power reception device transmits authentication information (e.g., start code, manufacturer ID, product ID, rated power information, and resonance characteristic information) to a power transmission device before starting normal power transmission by a non-contact power transmission system. The power transmission device performs instrument authentication based on the received authentication information, and regulates the maximum transmission power is regulated to conform to a power-reception-device side rated power. The power transmission device then performs normal power transmission.
Owner:SEIKO EPSON CORP +1
Authentication services using mobile device
InactiveUS7606560B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet Authentication ServiceMobile device
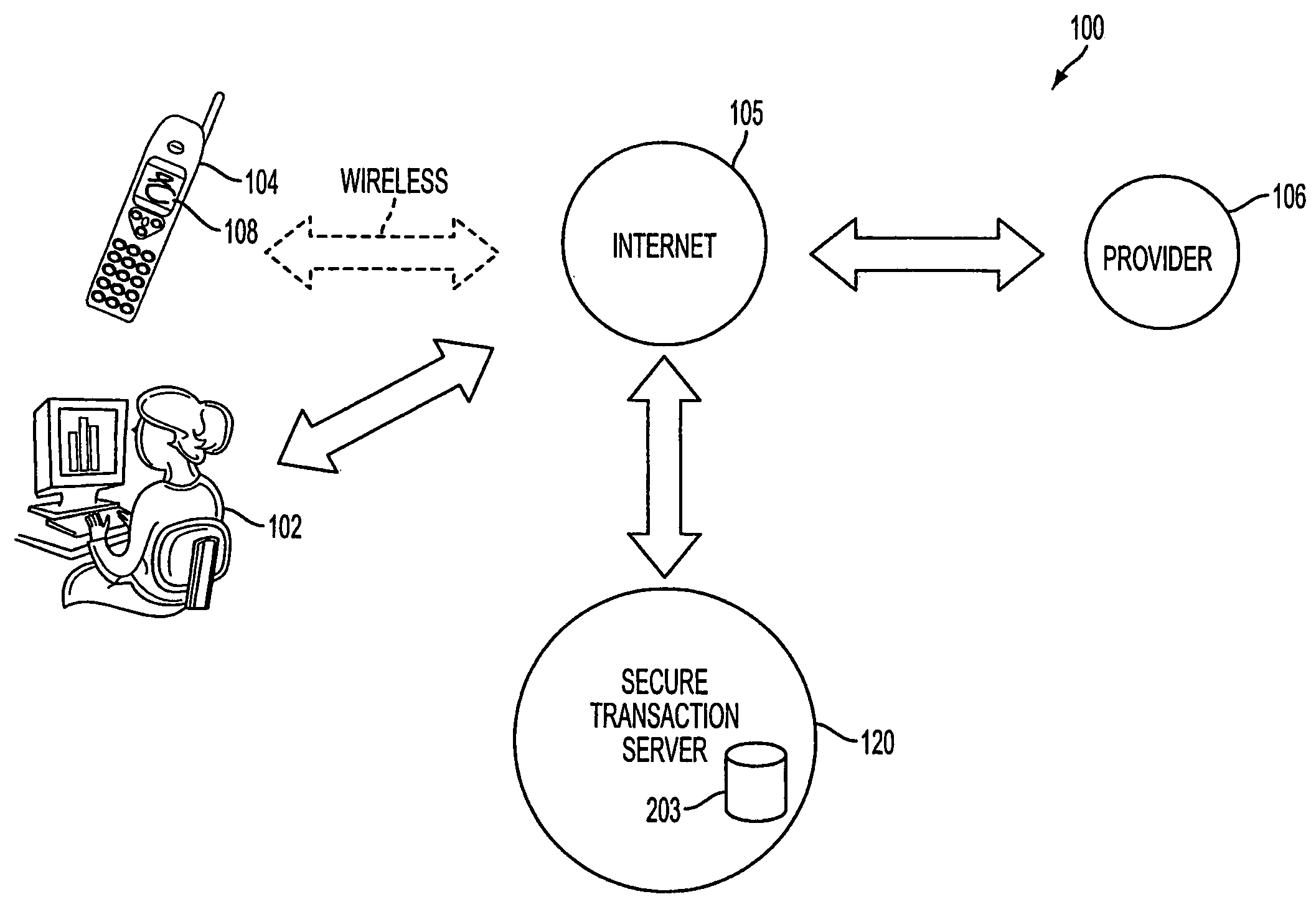
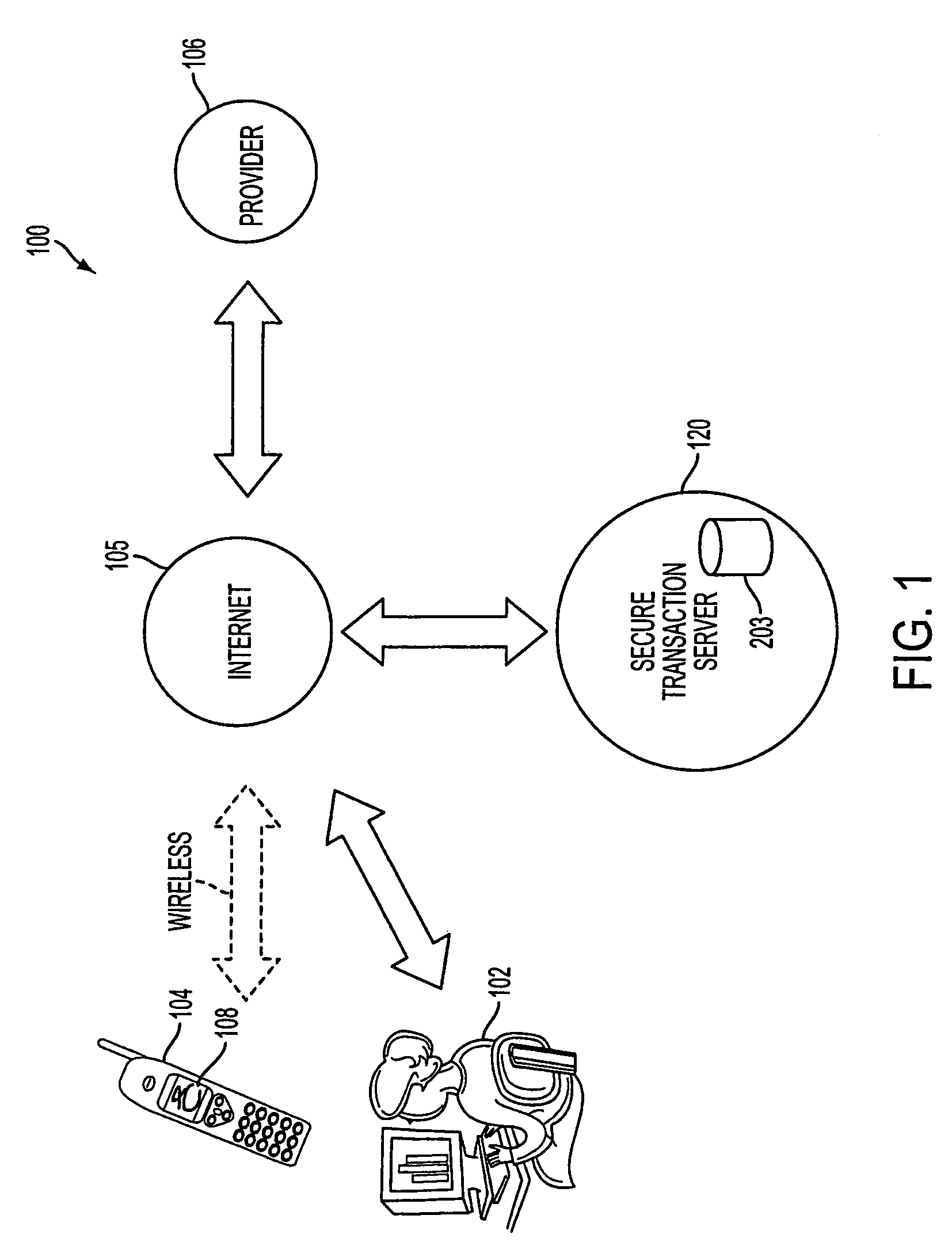
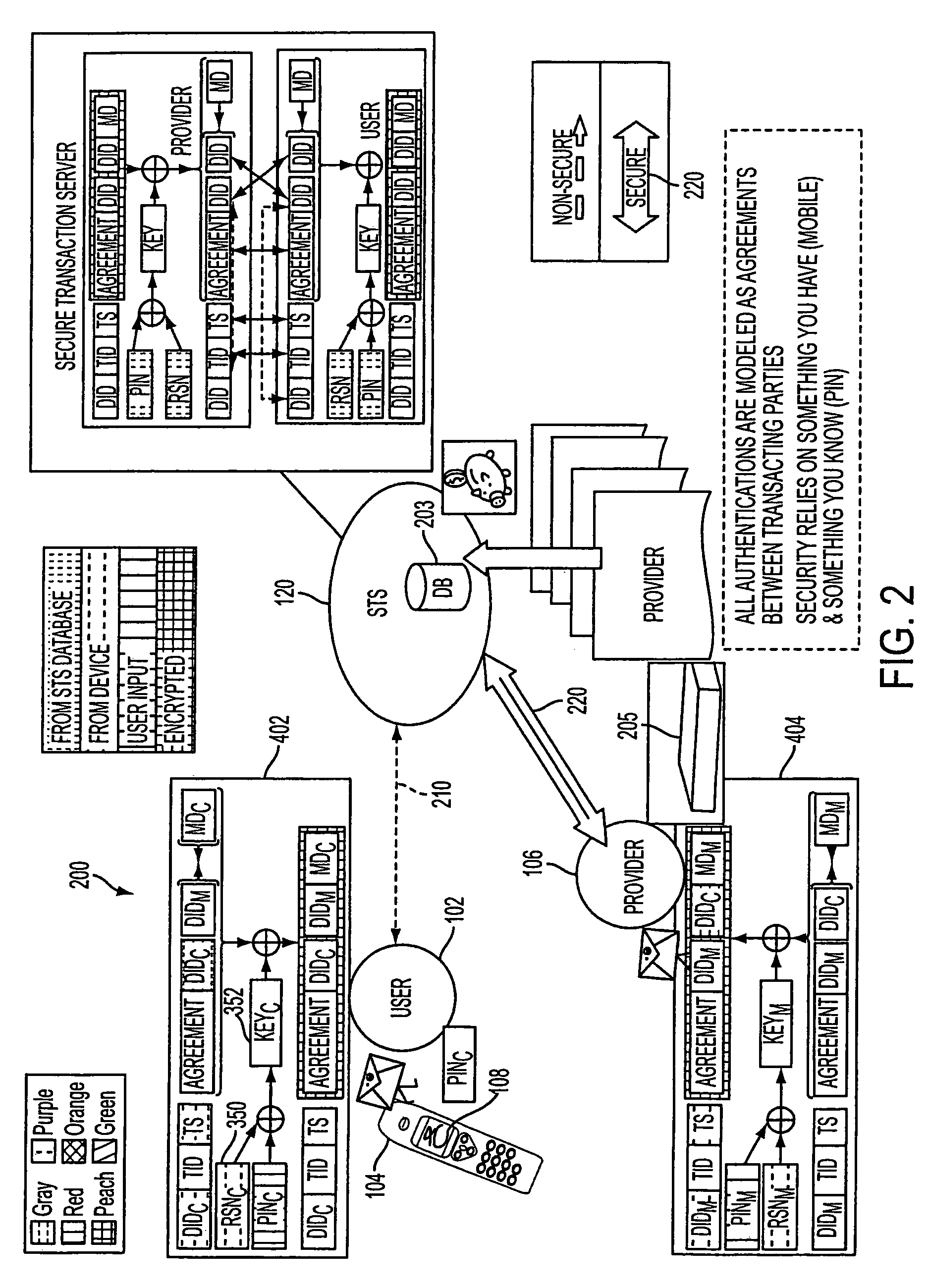
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
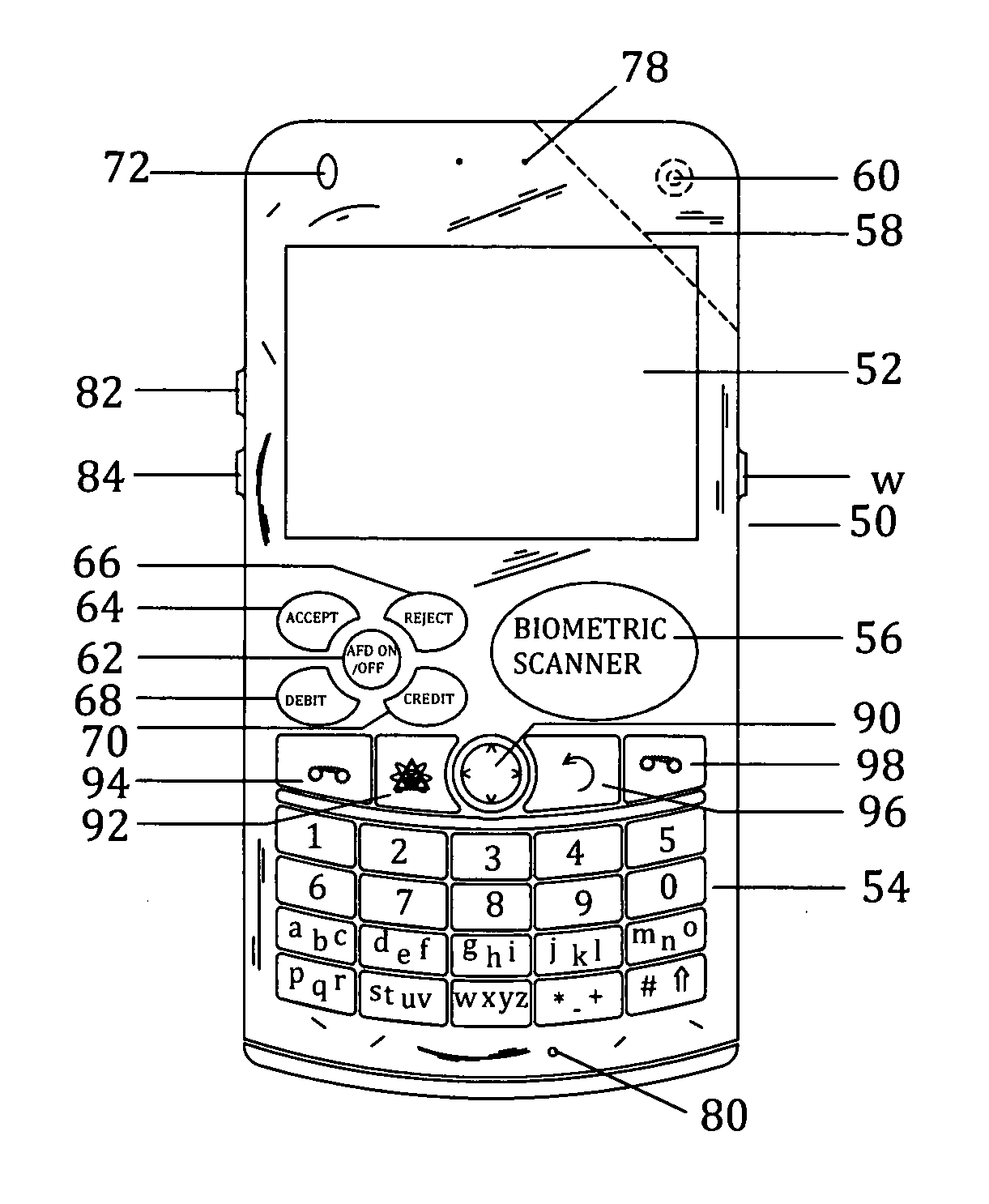
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
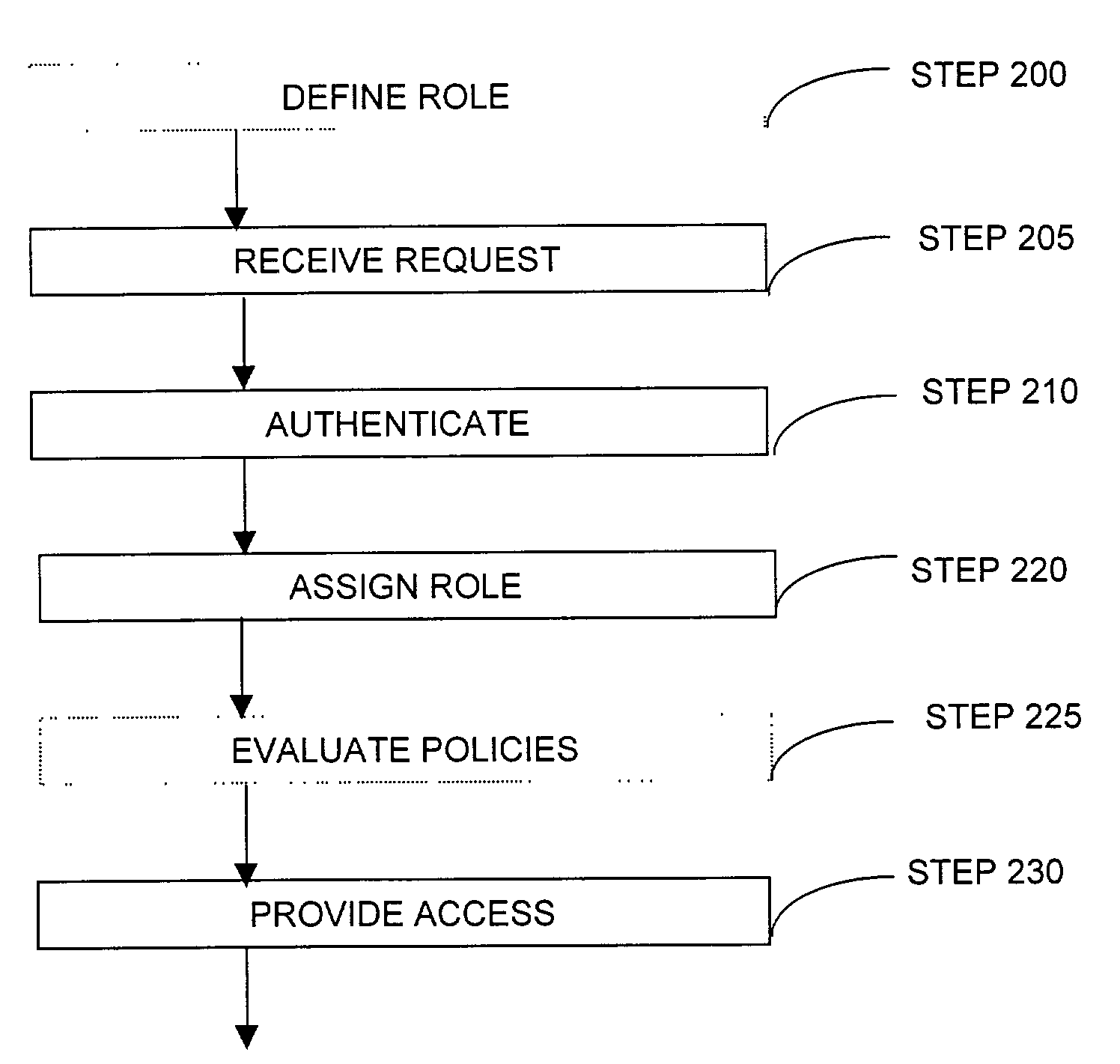
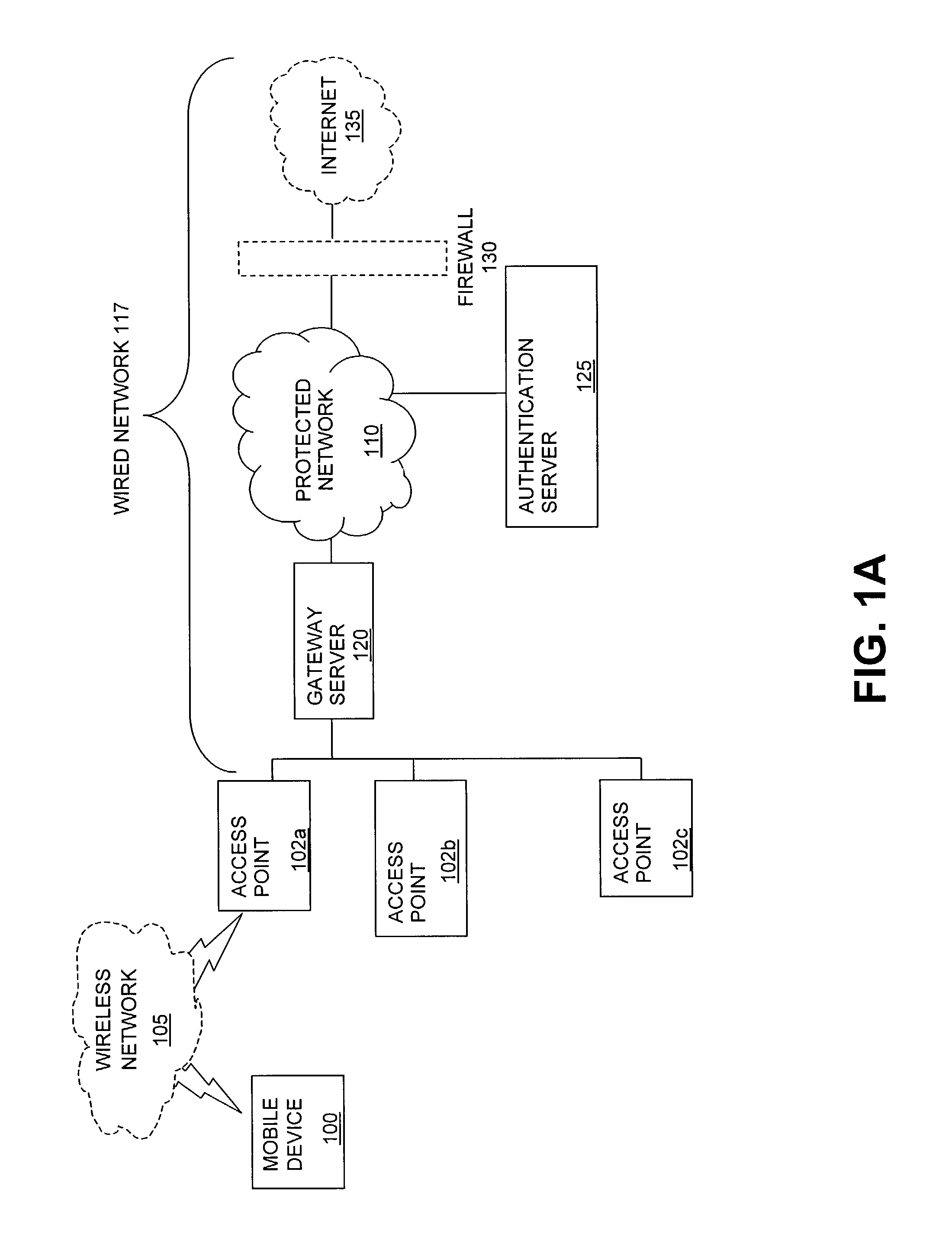
Method and system for managing data traffic in wireless networks
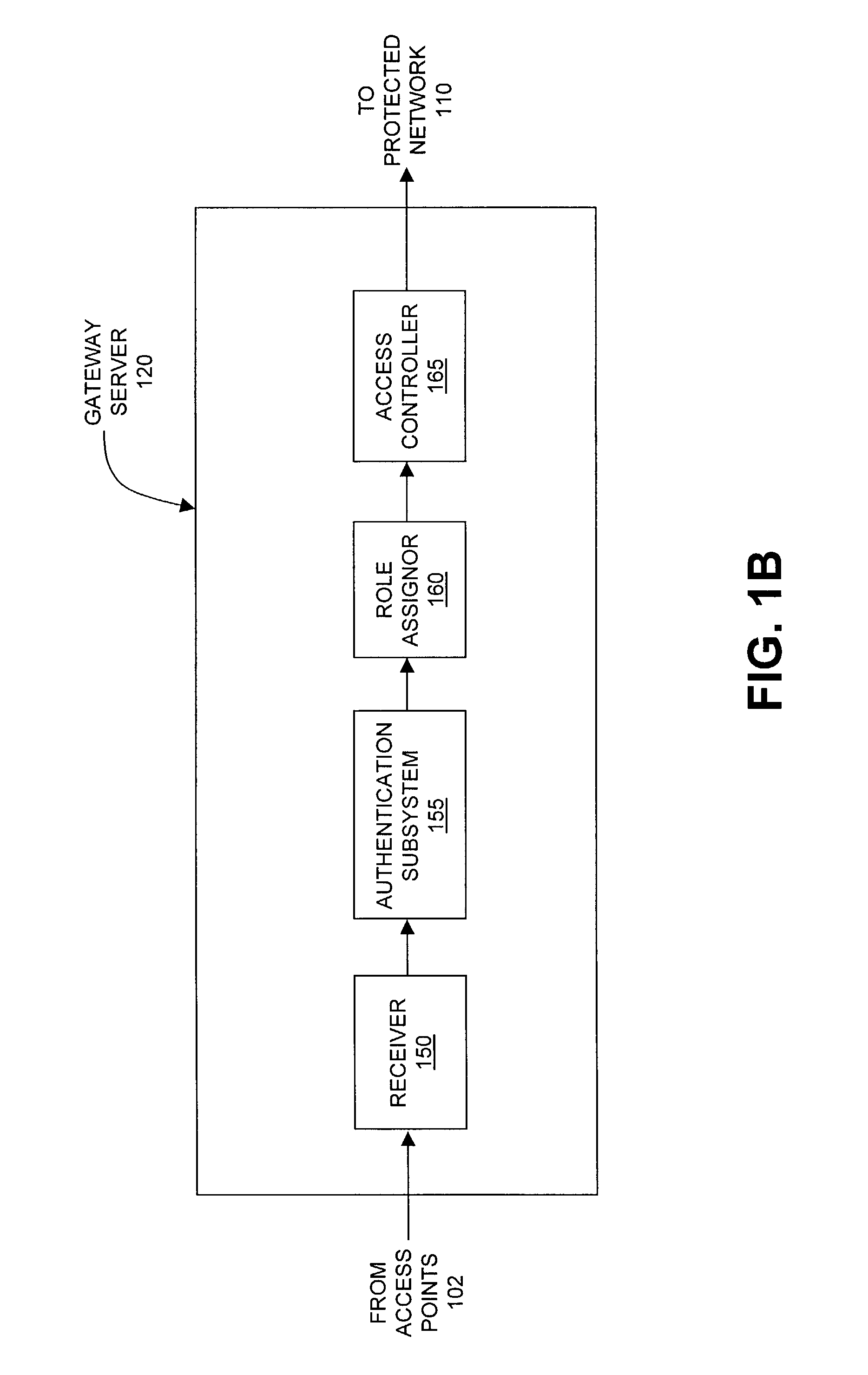
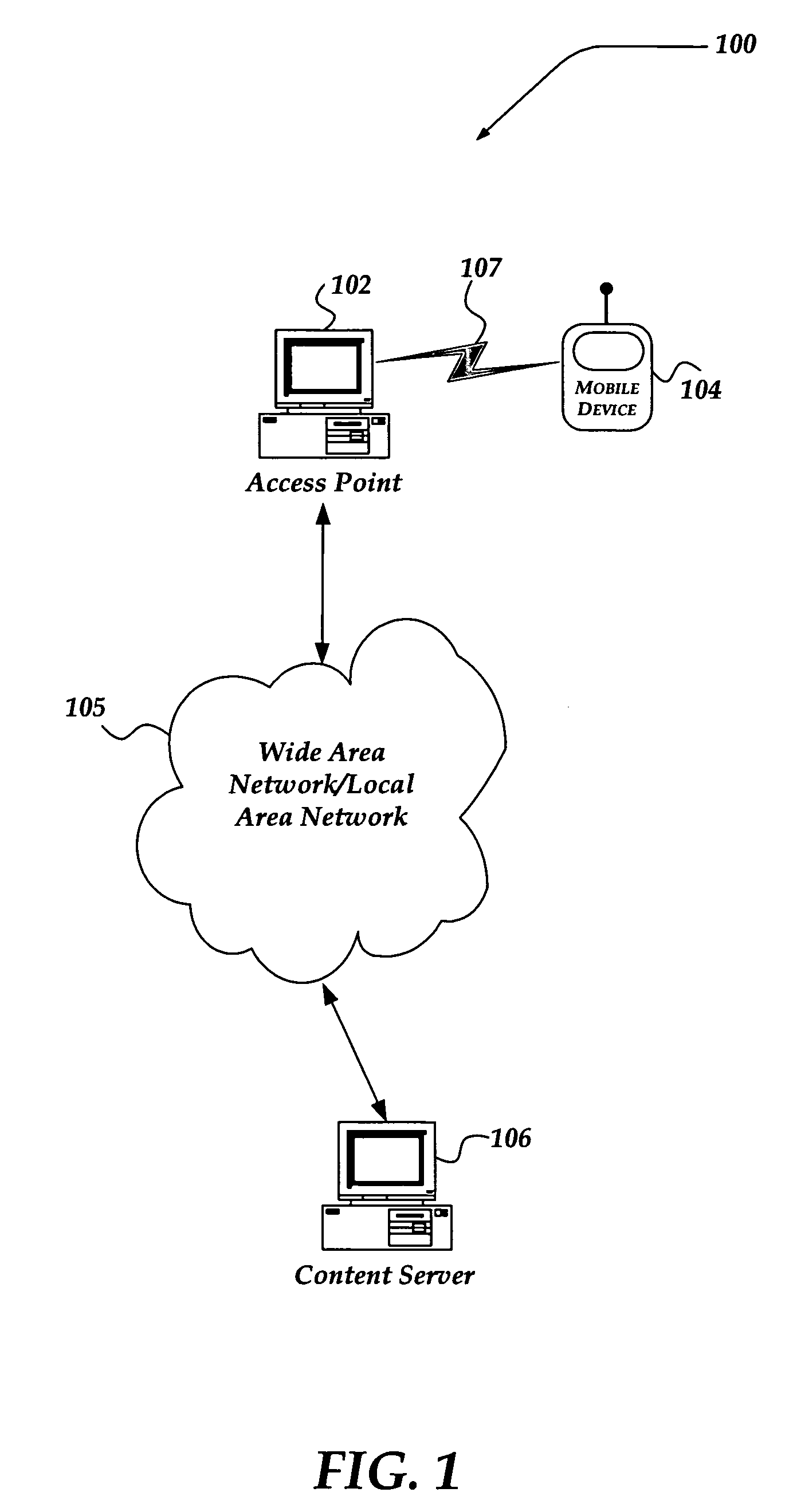
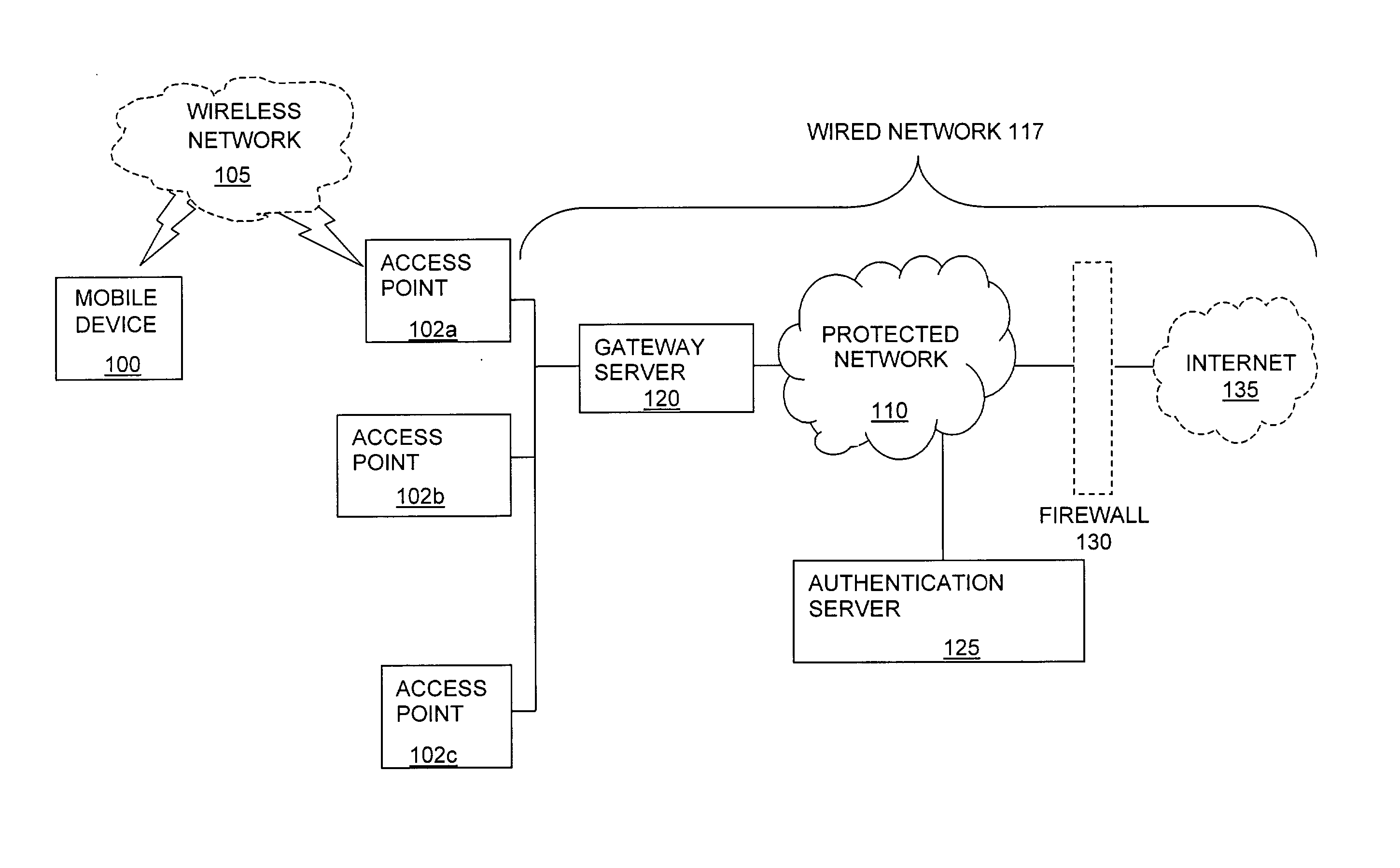
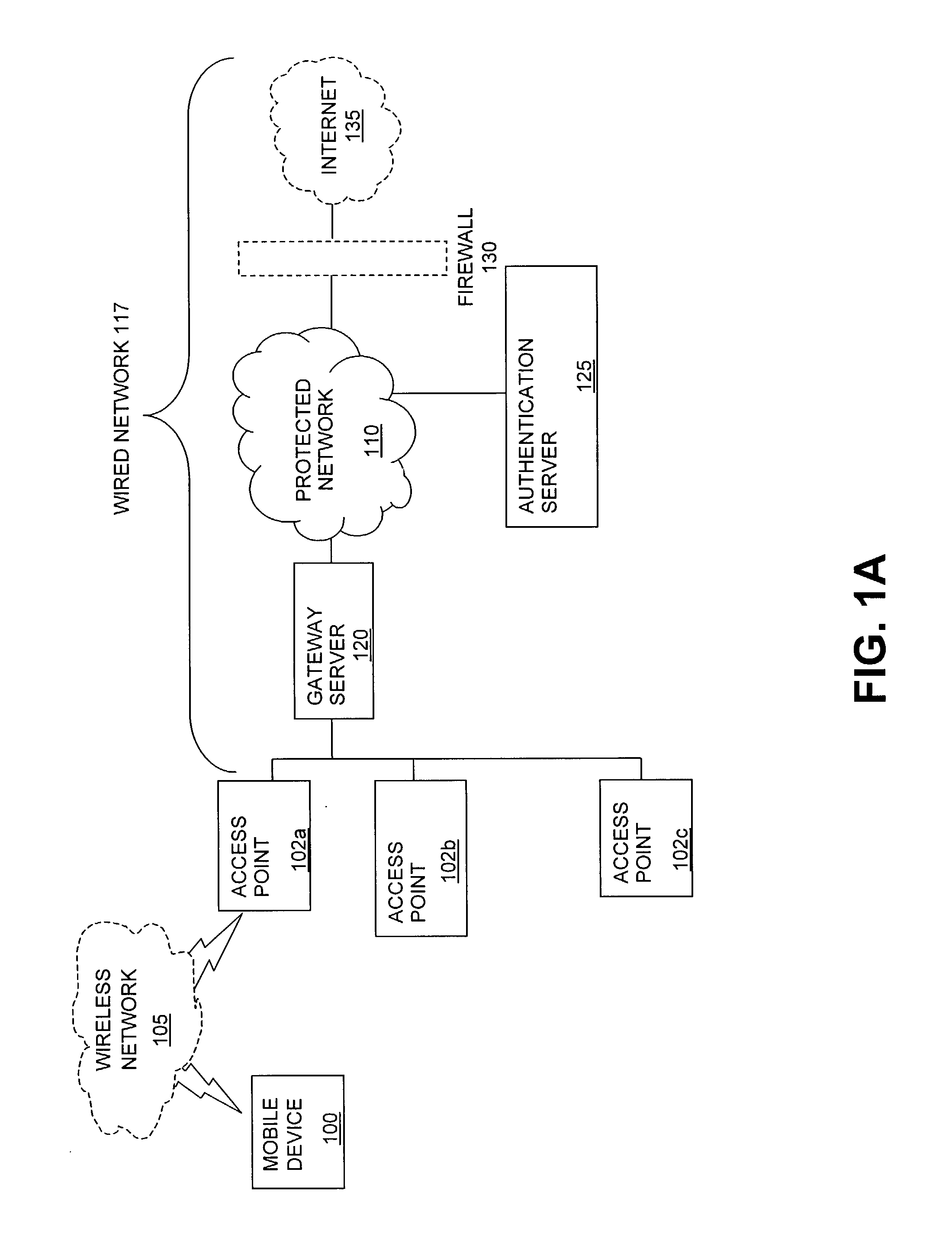
ActiveUS7042988B2Facilitate secure integrationExtensive controlError preventionUnauthorised/fraudulent call preventionWireless mesh networkNetwork architecture
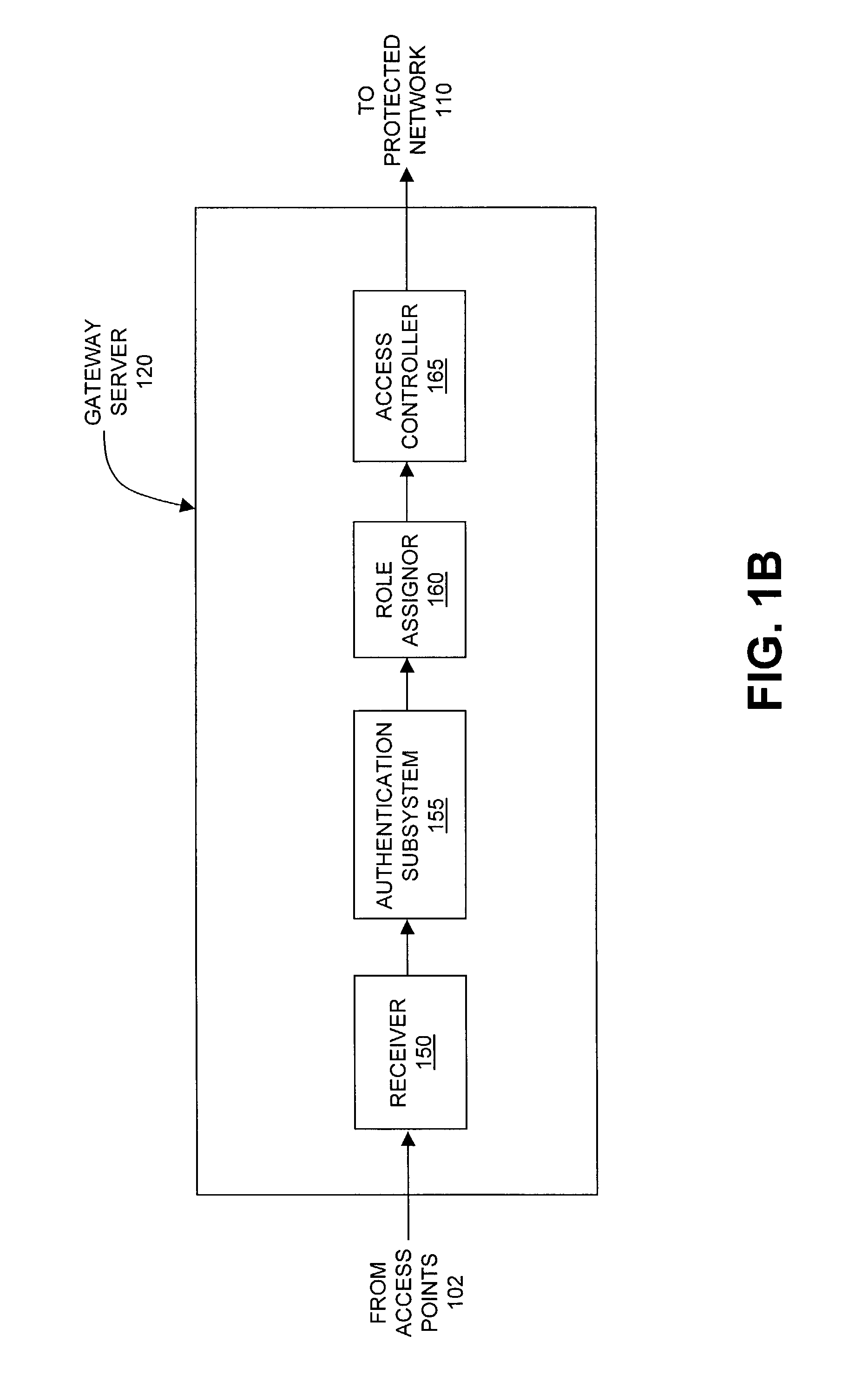
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
Mobile data security system and methods
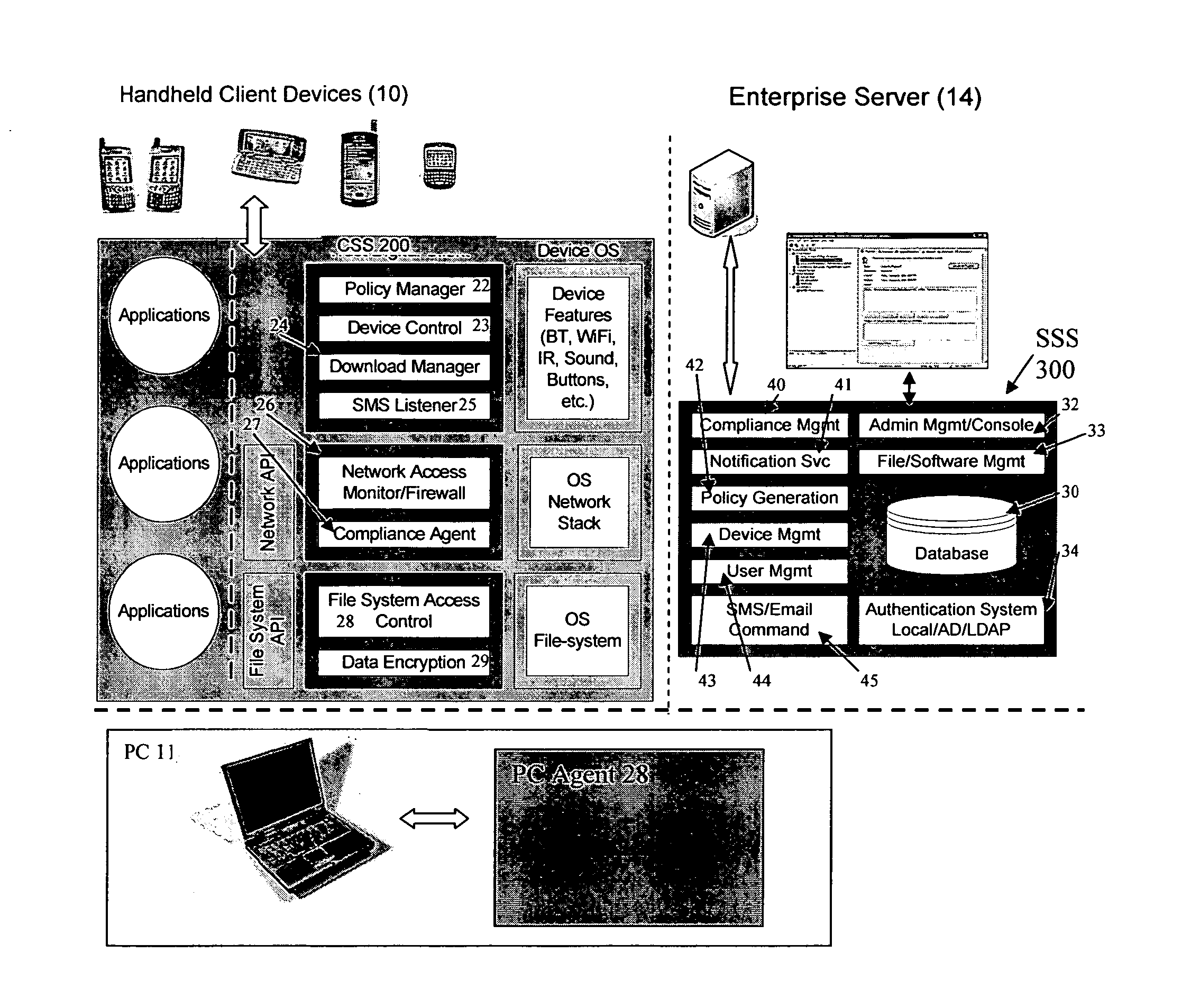
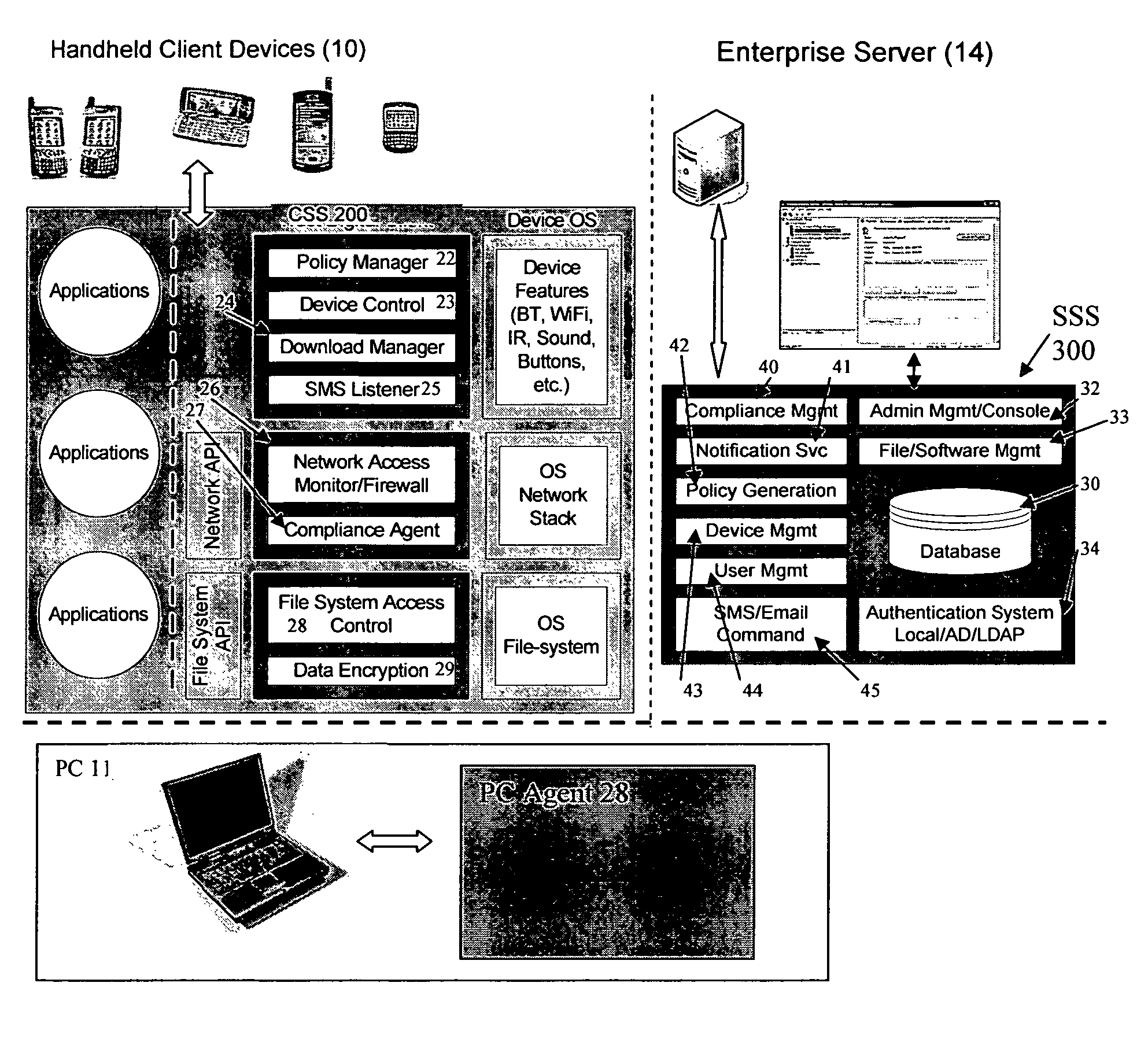
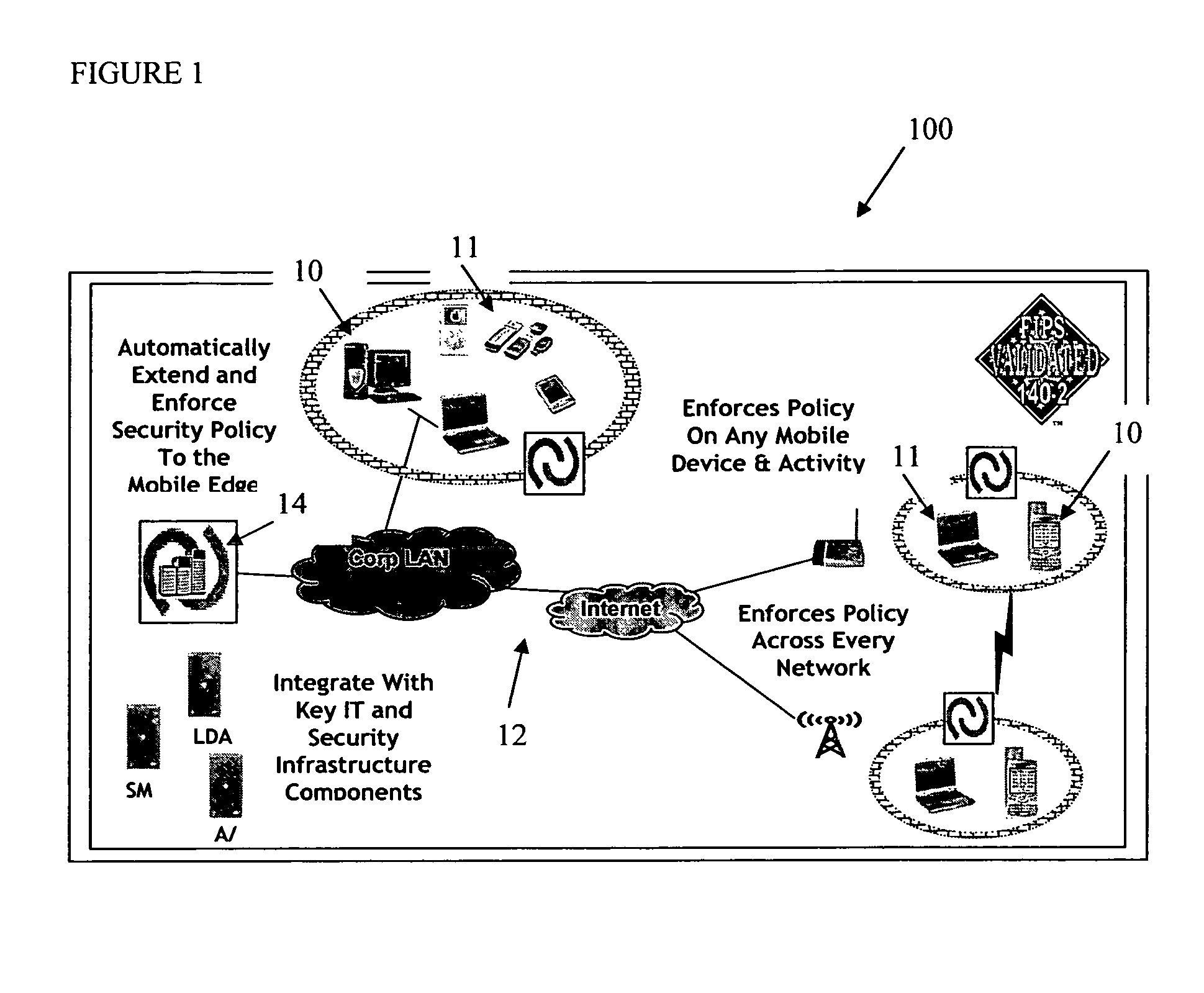
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
Onetime passwords for smart chip cards
ActiveUS8095113B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDisplay deviceFinancial transaction
A financial transaction card is provided according to various embodiments described herein. The financial transaction card includes a card body with at least a front surface and a back surface. The financial transaction card may also include a near field communications transponder and / or a magnetic stripe, as well as a digital display configured to display alphanumeric characters on the front surface of the card body. The financial transaction card may also include a processor that is communicatively coupled with the near field communications transponder or magnetic stripe and the digital display. The processor may be configured to calculate one-time passwords and communicate the one-time passwords to both the near filed communications transponder or magnetic stripe and the digital display.
Owner:FIRST DATA
Mobile mesh Ad-Hoc networking
InactiveUS6879574B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCyber operationsAccess network
An architectural solution in which standalone ad-hoc network cells are used as an extension of the backbone infrastructure in terms of network architecture or / and its service capabilities is provided. These Ad-Hoc networks will integrate to the Internet via cellular and other access networks. This integration brings new possibilities to network operators and ISP's. In its extended architecture, it is envisaged that the mobility issues are handled by utilizing the IP mobility capabilities, taking into account the mobile mesh Ad-Hoc specific requirements.
Owner:NOKIA TECHNOLOGLES OY
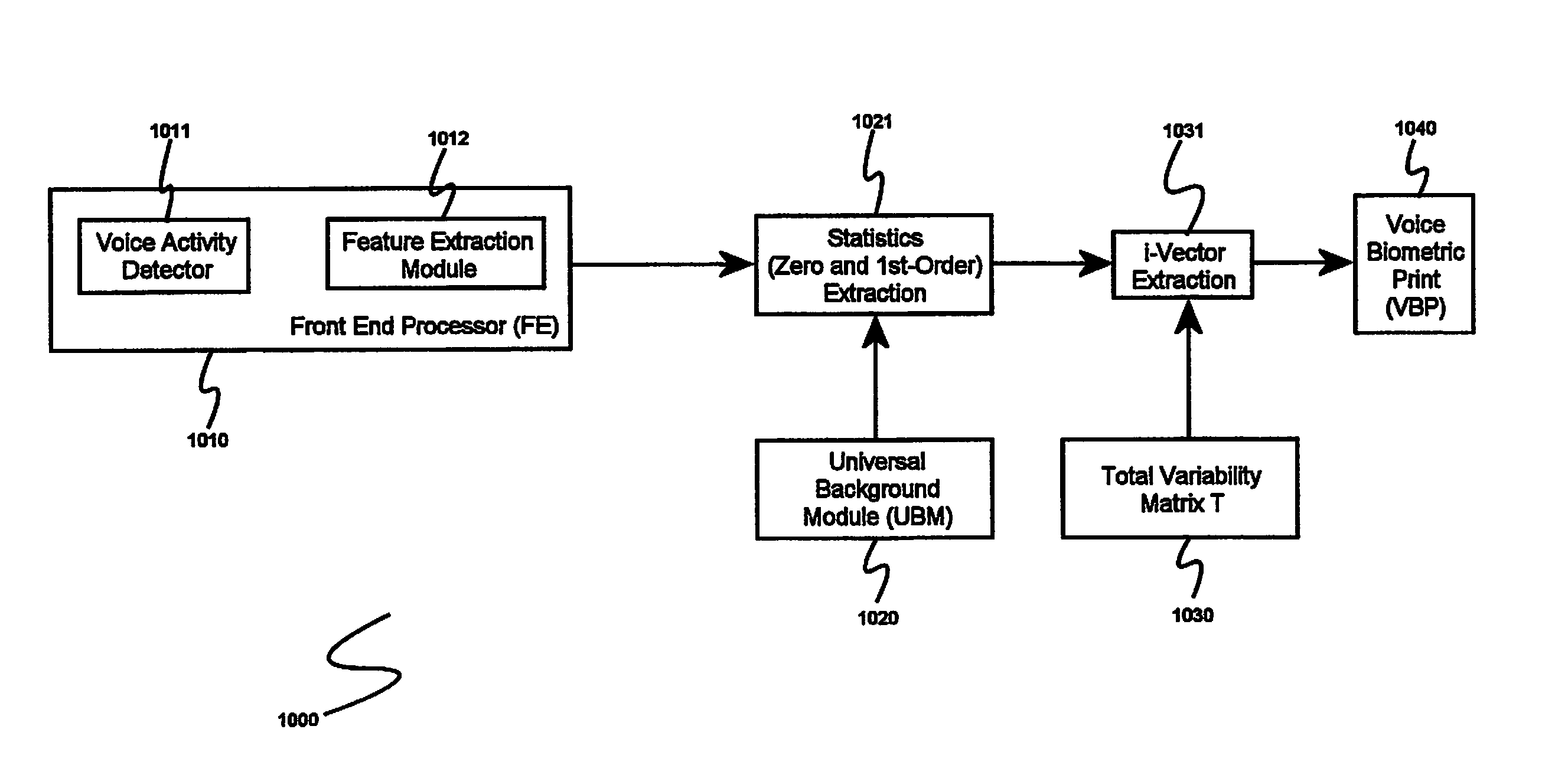
System and method for speaker recognition on mobile devices
InactiveUS20130225128A1Reduce storageReduce processUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSpeaker recognition systemMobile device
A speaker recognition system for authenticating a mobile device user includes an enrollment and learning software module, a voice biometric authentication software module, and a secure software application. Upon request by a user of the mobile device, the enrollment and learning software module displays text prompts to the user, receives speech utterances from the user, and produces a voice biometric print. The enrollment and training software module determines when a voice biometric print has met at least a quality threshold before storing it on the mobile device. The secure software application prompts a user requiring authentication to repeat an utterance based at least on an attribute of a selected voice biometric print, receives a corresponding utterance, requests the voice biometric authentication software module to verify the identity of the second user using the utterance, and, if the user is authenticated, imports the voice biometric print.
Owner:CIRRUS LOGIC INC
System, method and apparatus for federated single sign-on services
ActiveUS20030163733A1Unauthorised/fraudulent call preventionDigital data processing detailsCyber operationsService domain
The advent of new and sophisticated web services provided by Service Providers to users, services that individually require authentication of user and authorization of access, brings the needs for a new service to facilitate such authentication and access, a service referred to as Single Sign-On (SSO). The basic principle behind SSO is that users are authenticated once at a particular level, and then access all their subscribed services accepting that level of authentication. The present invention provides a system, method and apparatus wherein a cellular Federation of mobile network operators becomes an SSO authentication authority for subscribers of this Federation accessing Service Providers having such agreement with a mobile network operator of the Federation. In accordance with this invention, mobile network operators can leverage their operator-subscriber trust relationship in order to act as SSO authentication authority for those subscribers accessing Service Providers in a service domain other than the mobile network domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
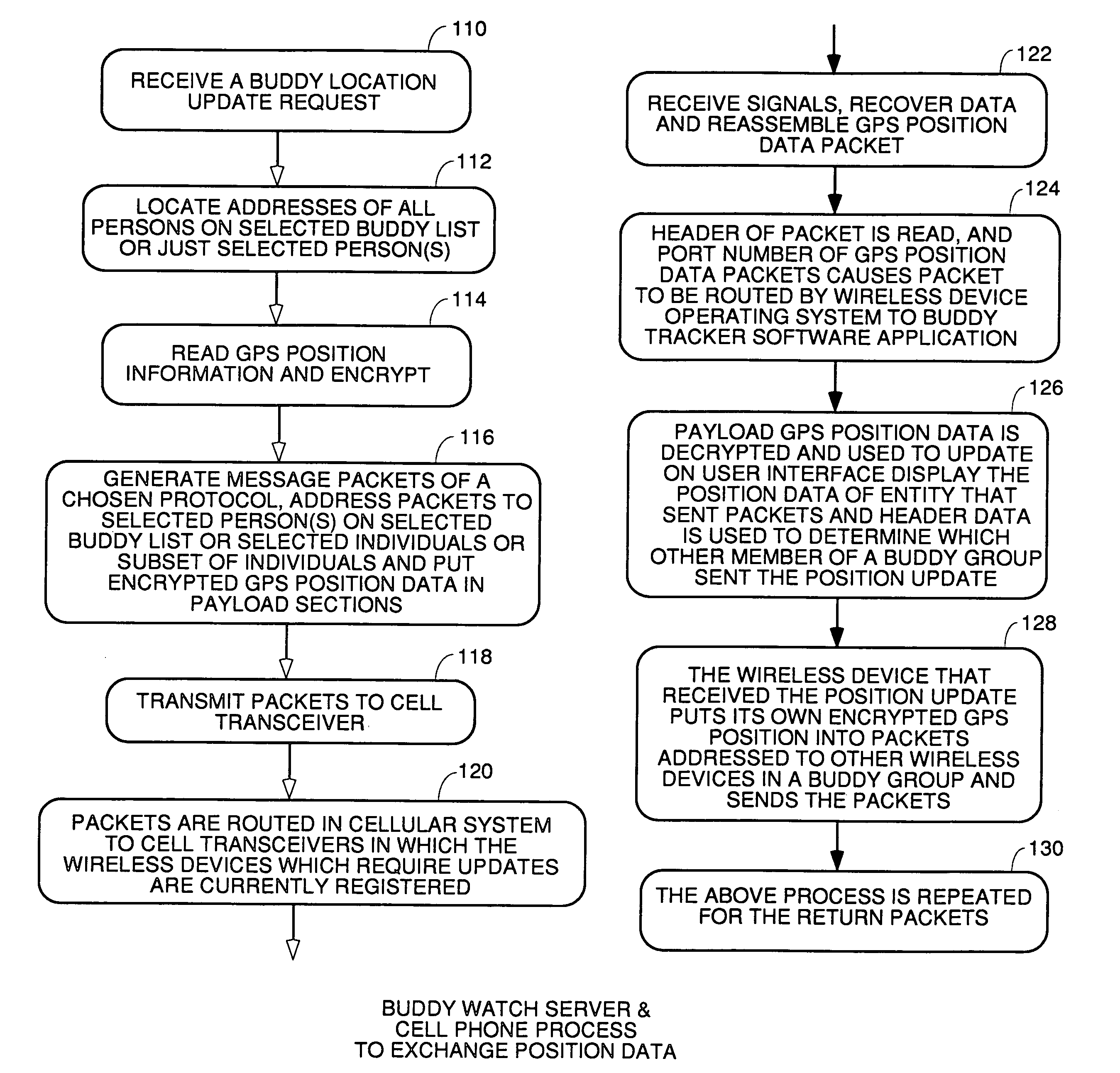
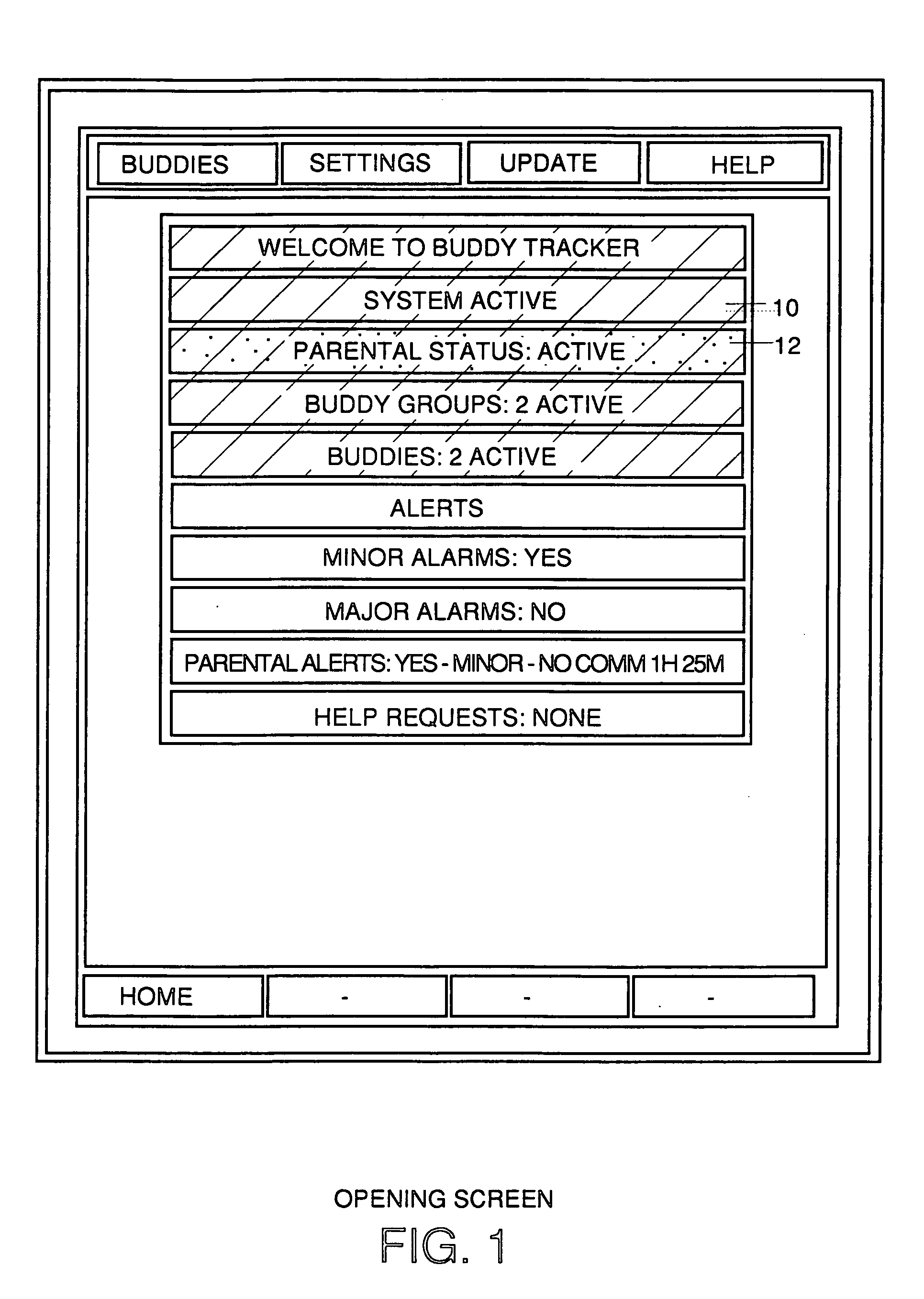
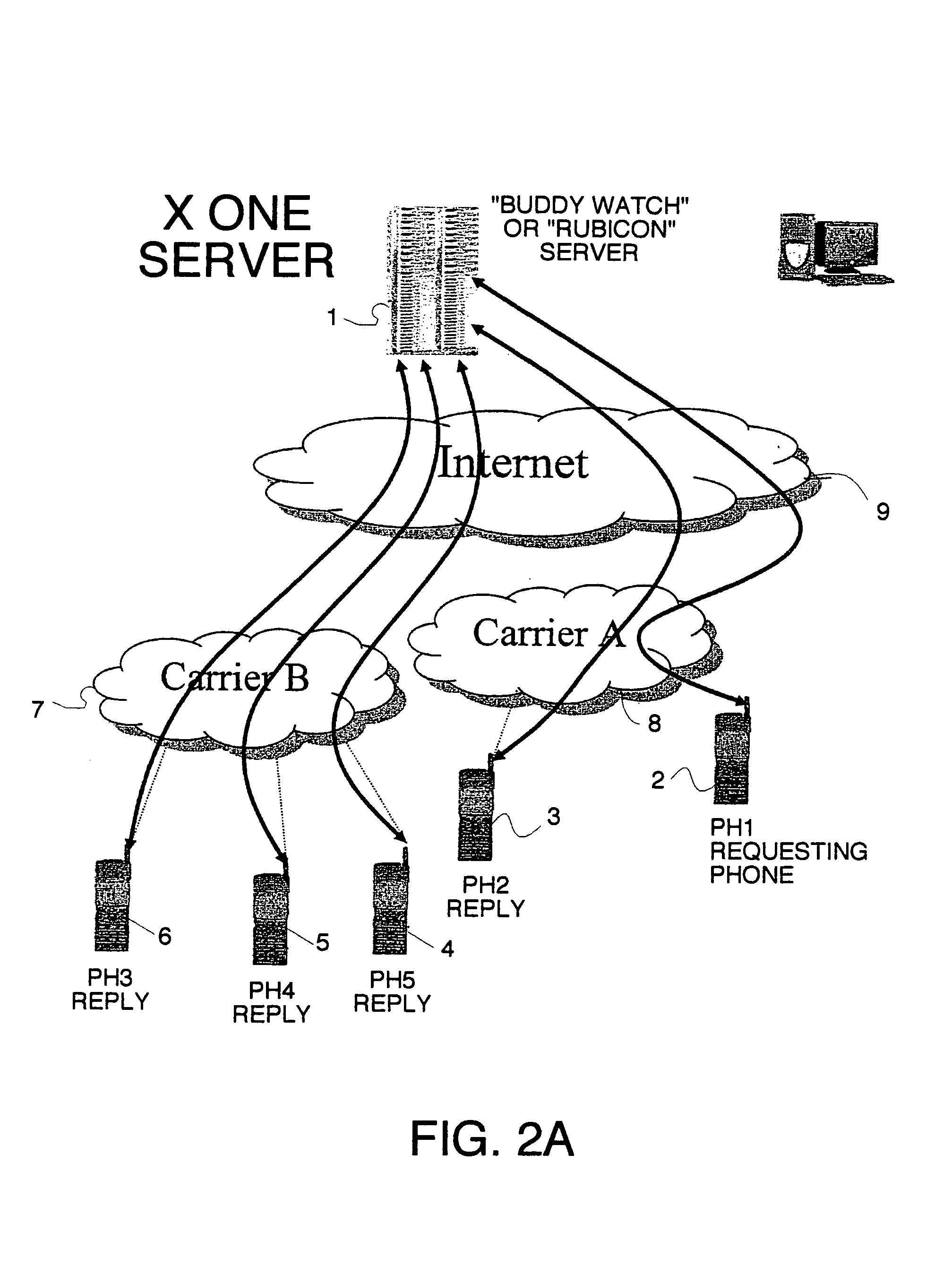
Location sharing and tracking using mobile phones or other wireless devices
ActiveUS7353034B2Easy to manageEasy SetupNavigational calculation instrumentsUnauthorised/fraudulent call preventionLocation sharingGroup coordination
A system for exchanging GPS or other position data between wireless devices for purposes of group activities, child location monitoring, work group coordination, dispatching of employees etc. Cell phones and other wireless devices with GPS receivers have loaded therein a Buddy Watch application and a TalkControl application. The Buddy Watch application communicates with the GPS receiver and other wireless devices operated by buddies registered in the users phone as part of buddy groups or individually. GPS position data and historical GPS position data can be exchanged between cell phones of buddies and instant buddies such as tow truck drivers via a buddy watch server. Emergency monitoring services can be set up with notifications to programmable individuals in case an individual does not respond. Positions and tracks can be displayed. TalkControl simplifies and automates the process of joining talk groups for walkie talkie services such as that provided by Nextel.
Owner:X ONE
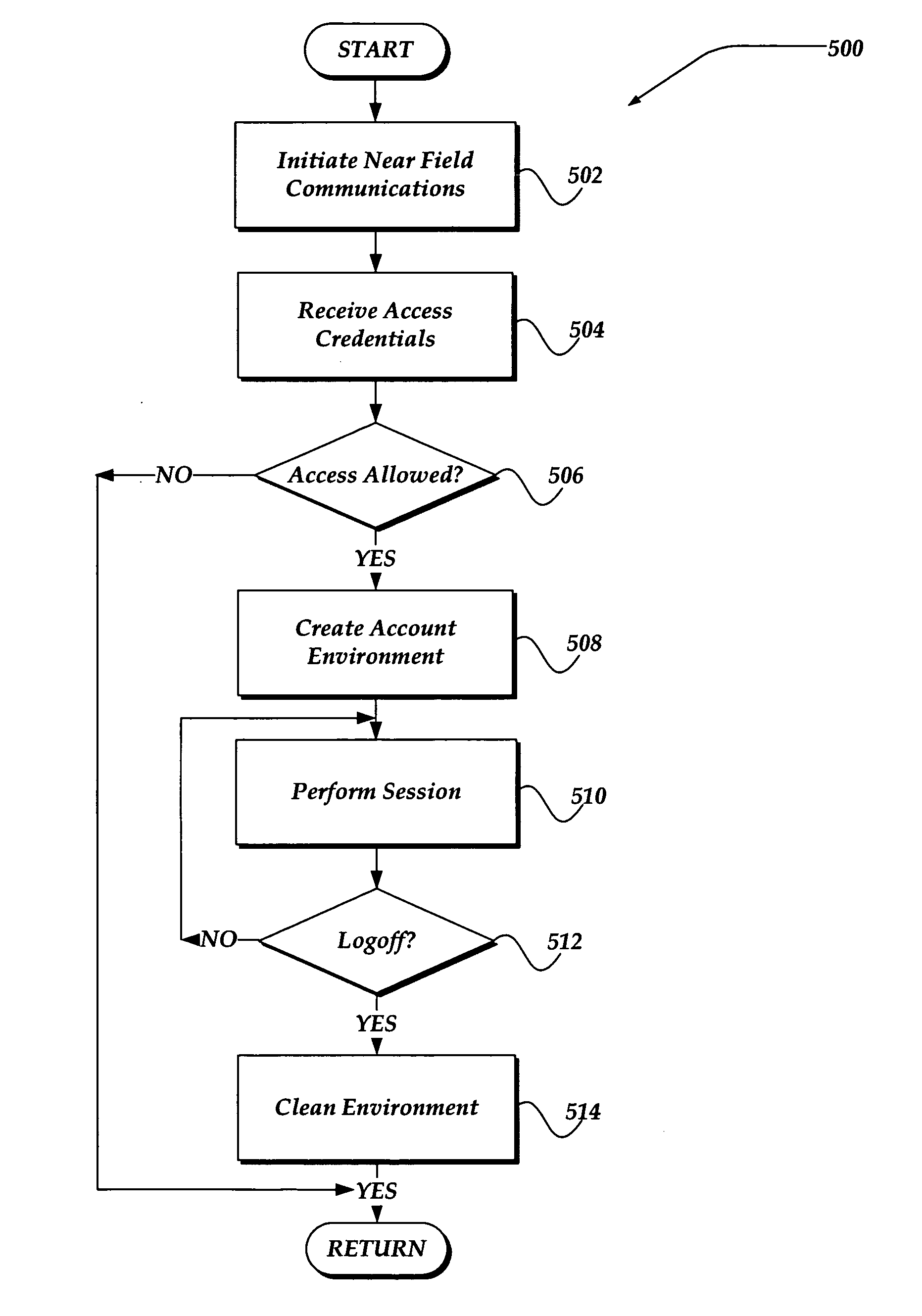
Managing an access account using personal area networks and credentials on a mobile device
InactiveUS20060183462A1Near-field transmissionUnauthorised/fraudulent call preventionAccess networkRelevant information
A system, apparatus, and method are directed towards automatically managing an access account at an access point using near field communications and credentials stored on a mobile device. The mobile device receives, out-of-band, information for use in creating an account for accessing network resources from the access point. As the mobile device is brought into proximity with the access point, a wireless network connection is established using a near field communication (NFC) protocol. The information, which may include a user credential, account information, and so forth, is communicated to the access point. The access point employs the information to establish an account and create an environment from which access to the network resources may be obtained. Upon termination, the access point removes from itself any user specific data. The access point may provide also session related information useable in billing the user of the mobile device.
Owner:NOKIA CORP
Method and system for managing data traffic in wireless networks
ActiveUS20030087629A1Reduce capacityEasy networkingError preventionUnauthorised/fraudulent call preventionEnterprise computingNetwork architecture
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
Method and apparatus for wireless network security
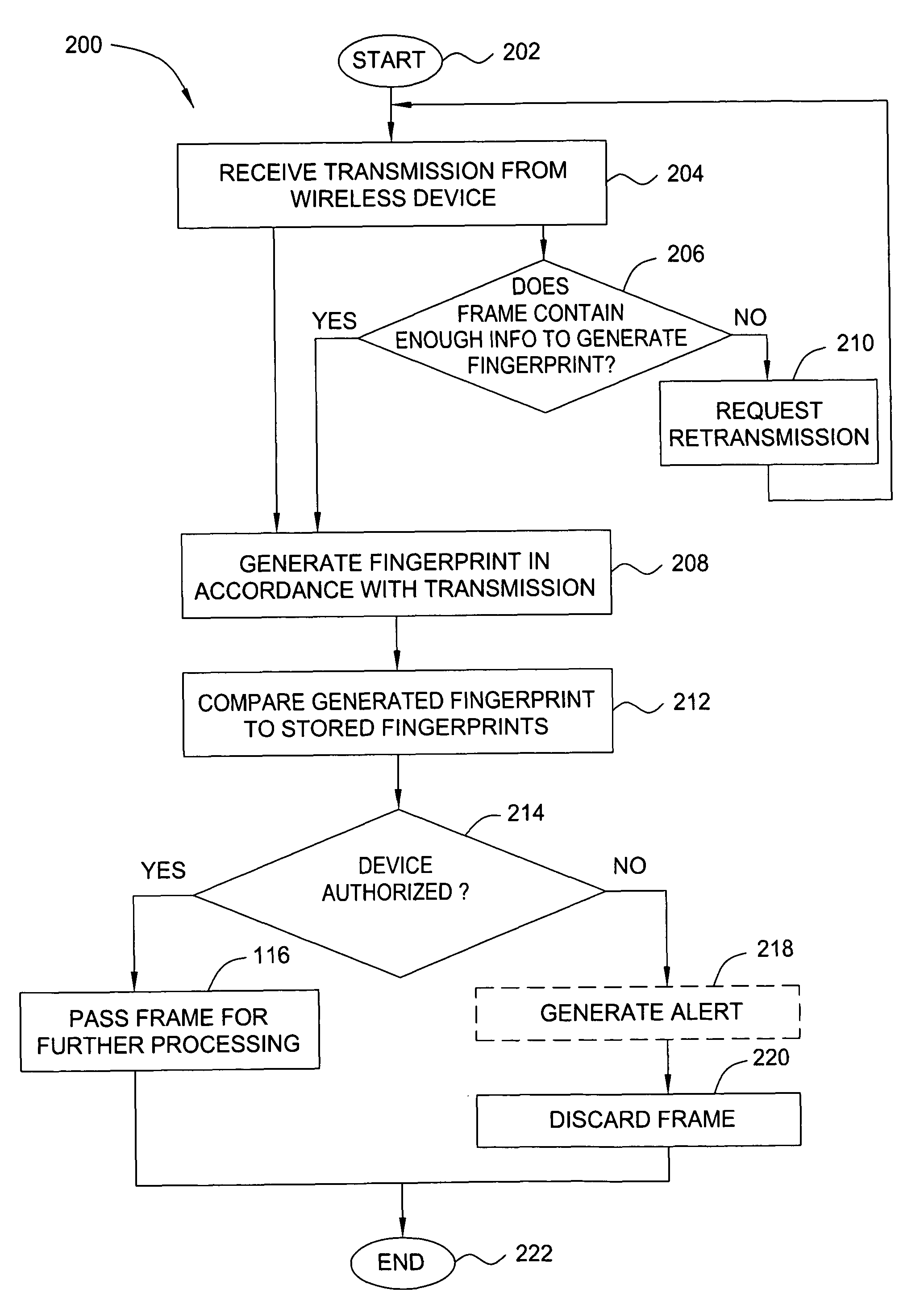
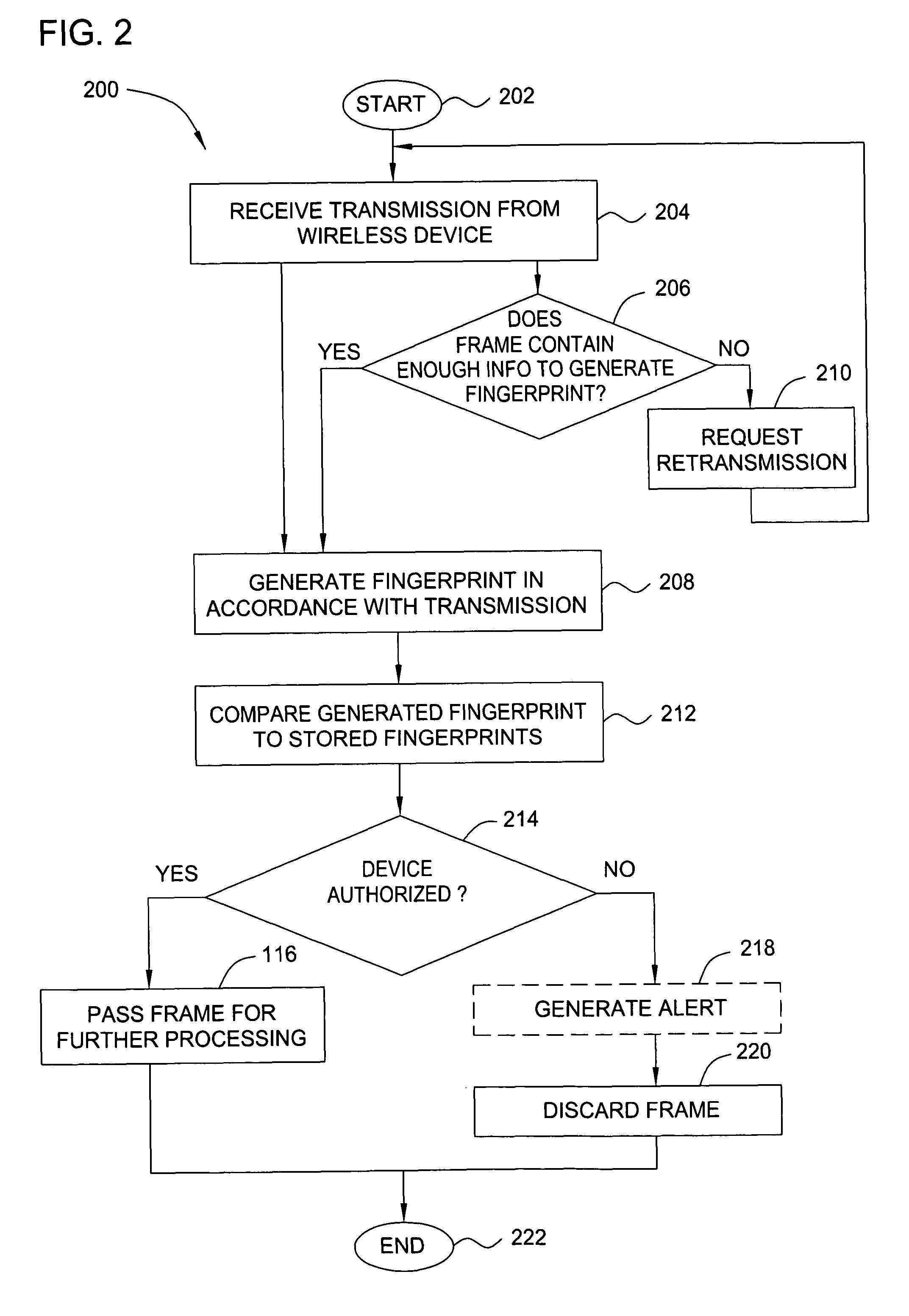
ActiveUS20070025265A1Error preventionFrequency-division multiplex detailsRadio frequency signalEngineering
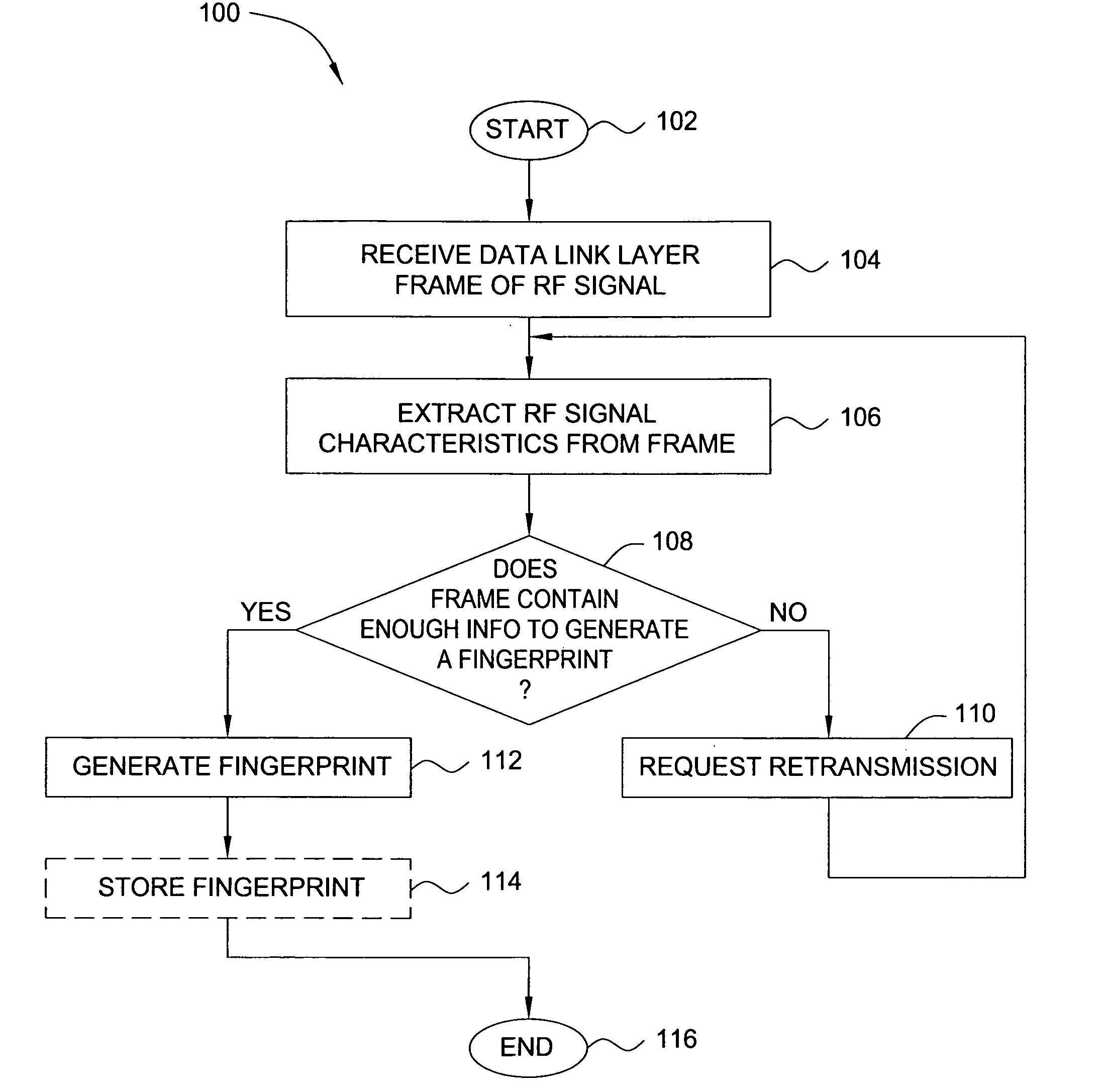
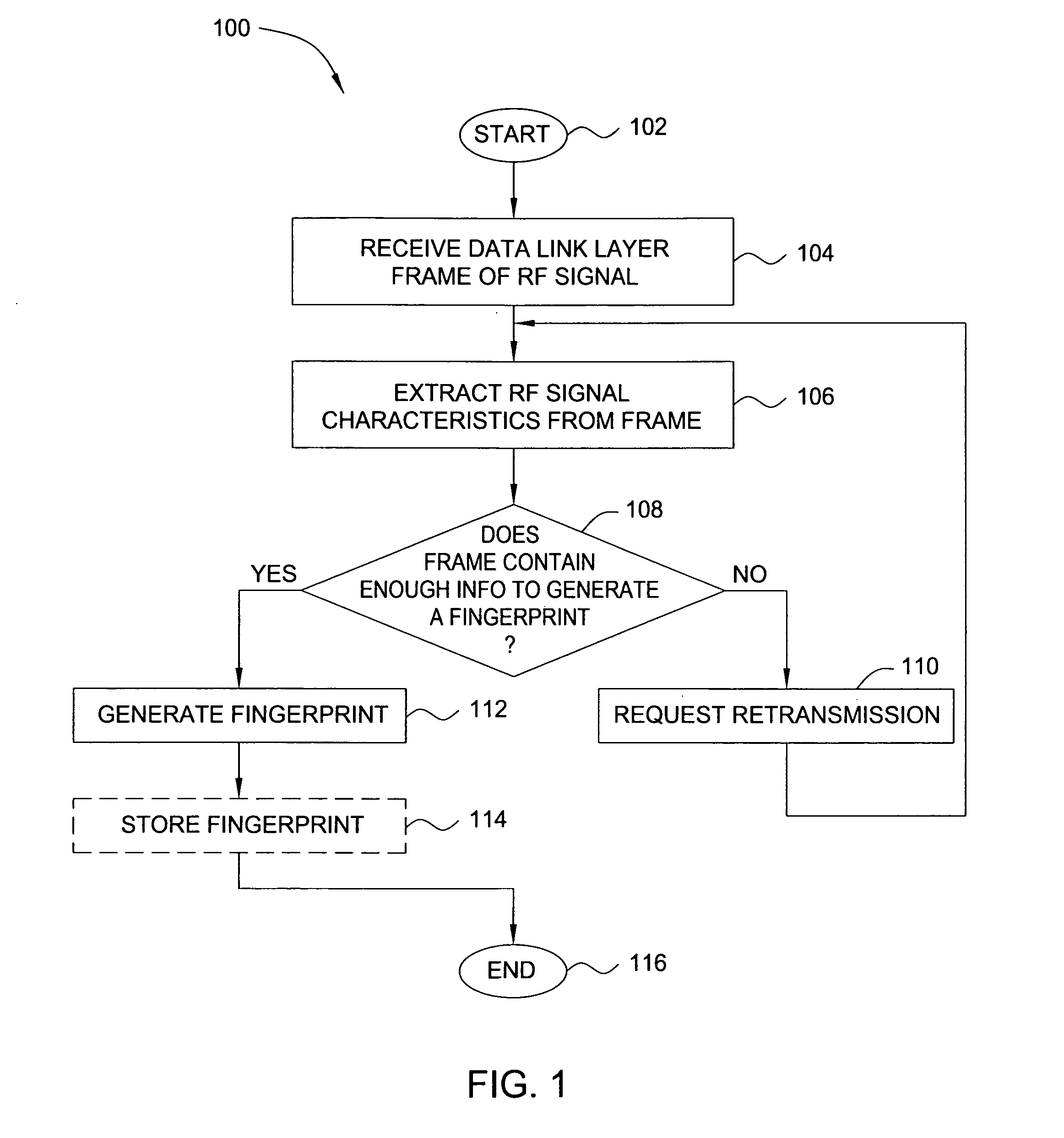
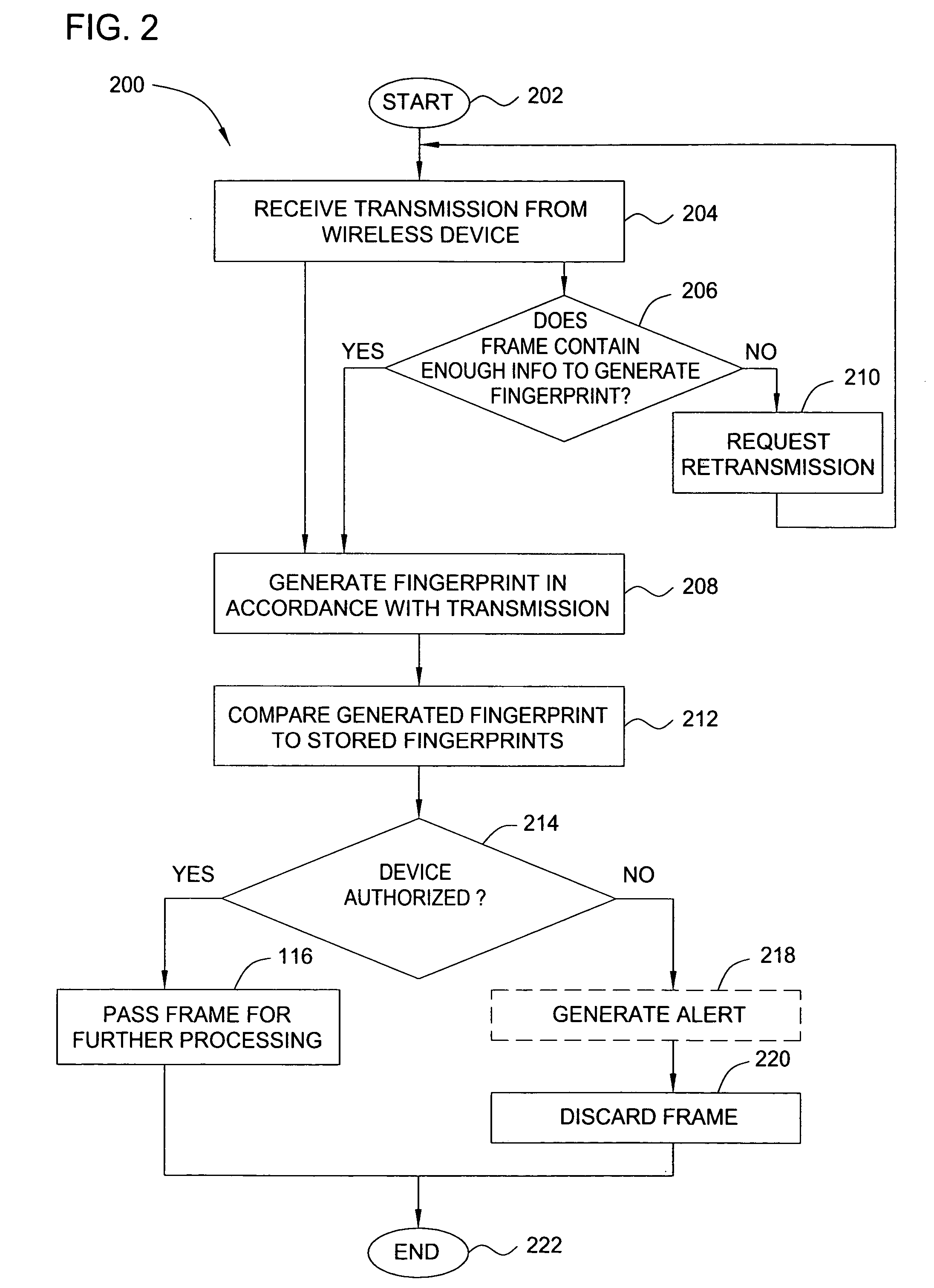
In one embodiment, the present invention is a method and apparatus for wireless network security. In one embodiment, a method for securing a wireless computing network includes receiving a communication from an unidentified transmitter, identifying the transmitter in accordance with a fingerprint generated from one or more radio frequency signal characteristics extracted from the communication, and taking action in response to an identity of the transmitter.
Owner:SRI INTERNATIONAL
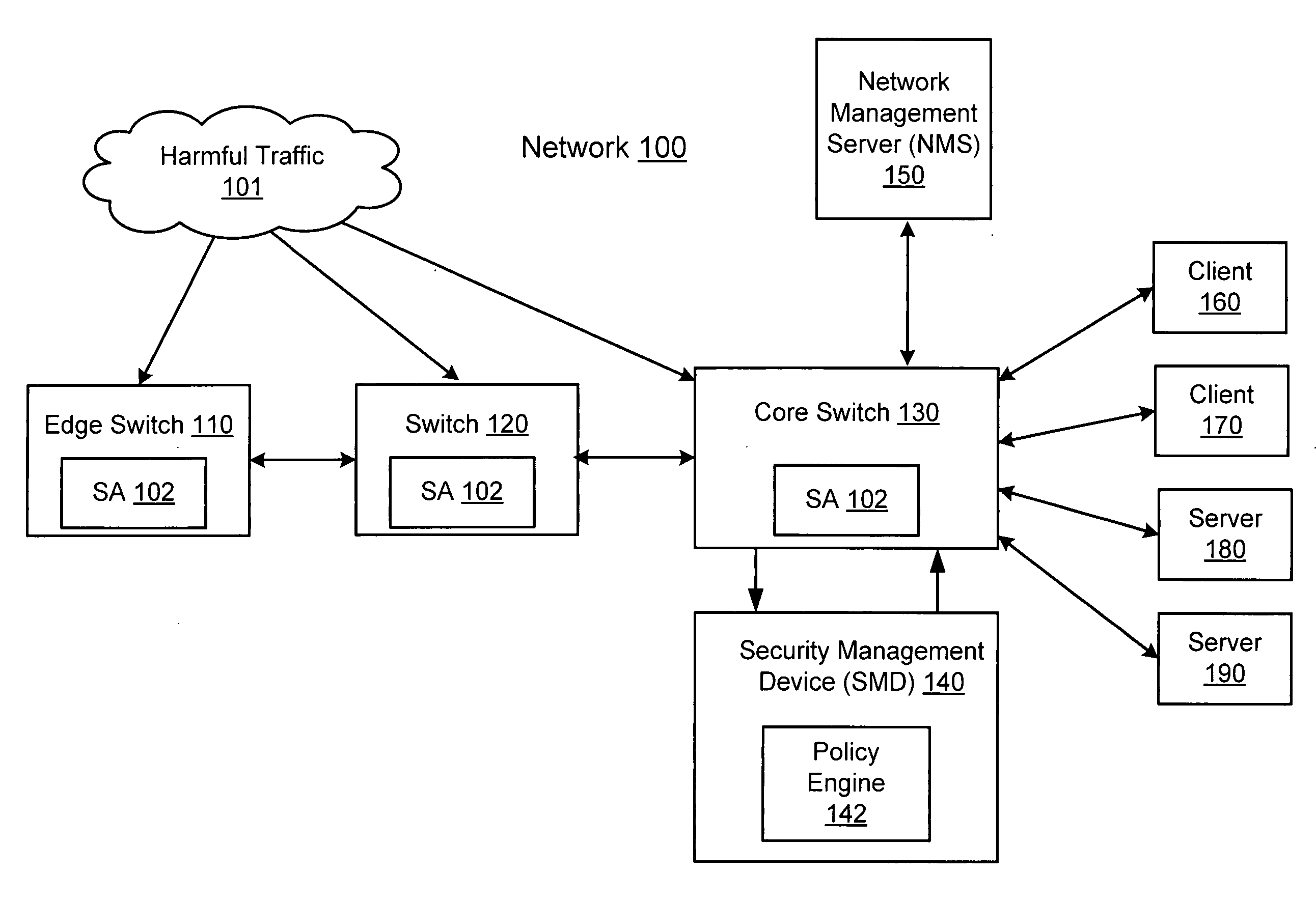
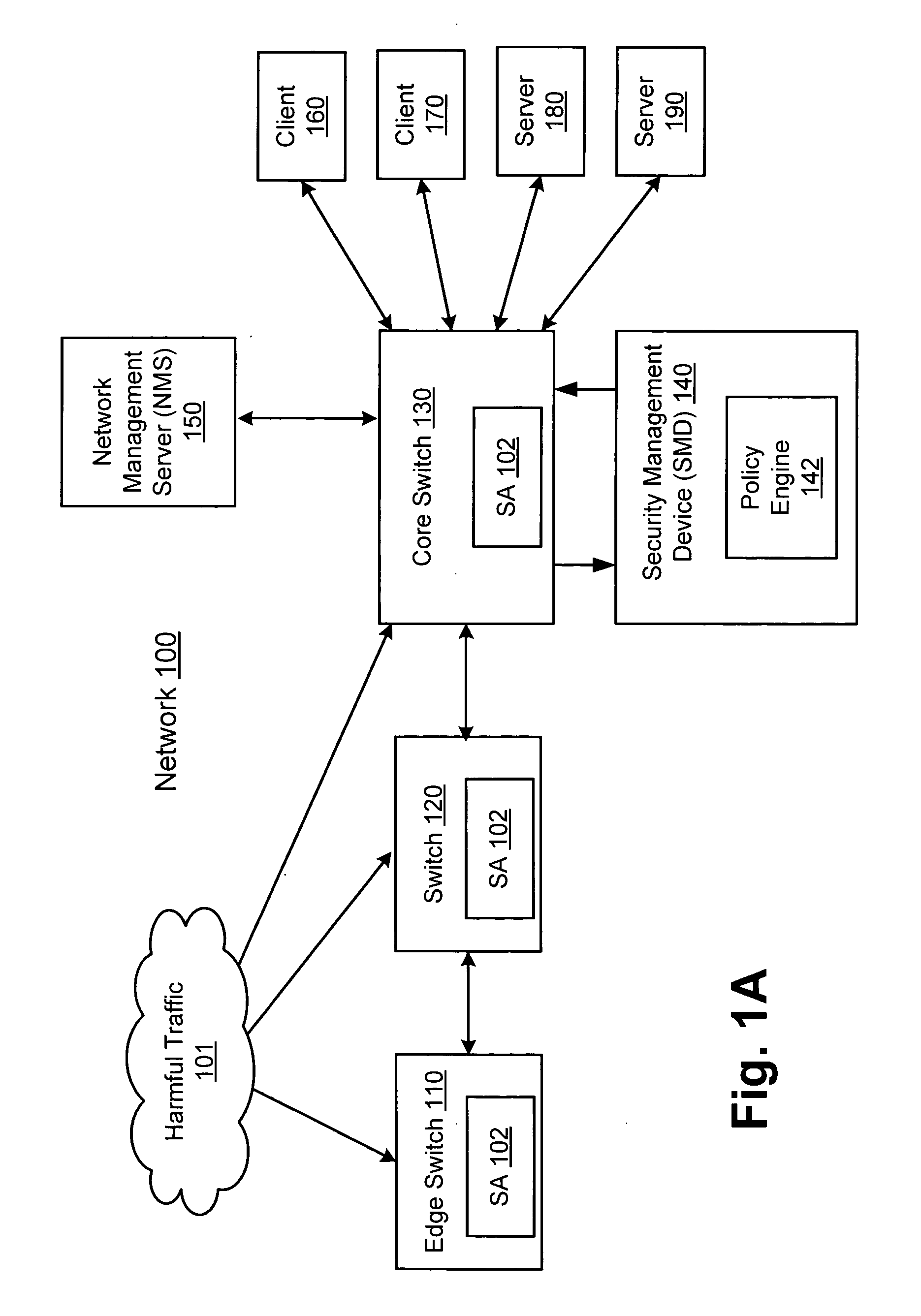
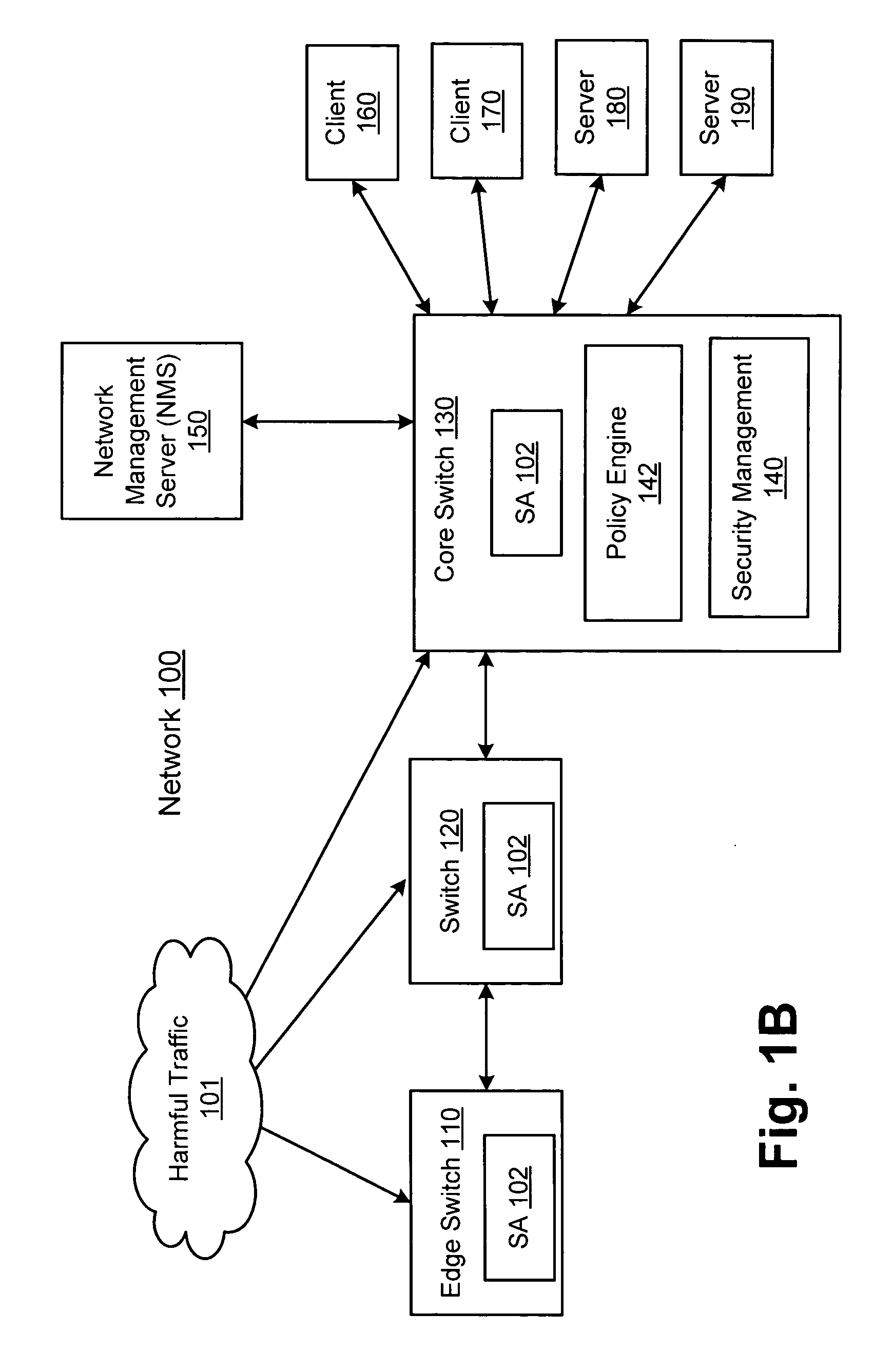
Network threat detection and mitigation
ActiveUS20070157306A1Error preventionFrequency-division multiplex detailsInternet trafficNetwork switch
A network switch automatically detects undesired network traffic and mirrors the undesired traffic to a security management device. The security management device determines the source of the undesired traffic and redirects traffic from the source to itself. The security management device also automatically sends a policy to a switch to block traffic from the source.
Owner:EXTREME NETWORKS INC
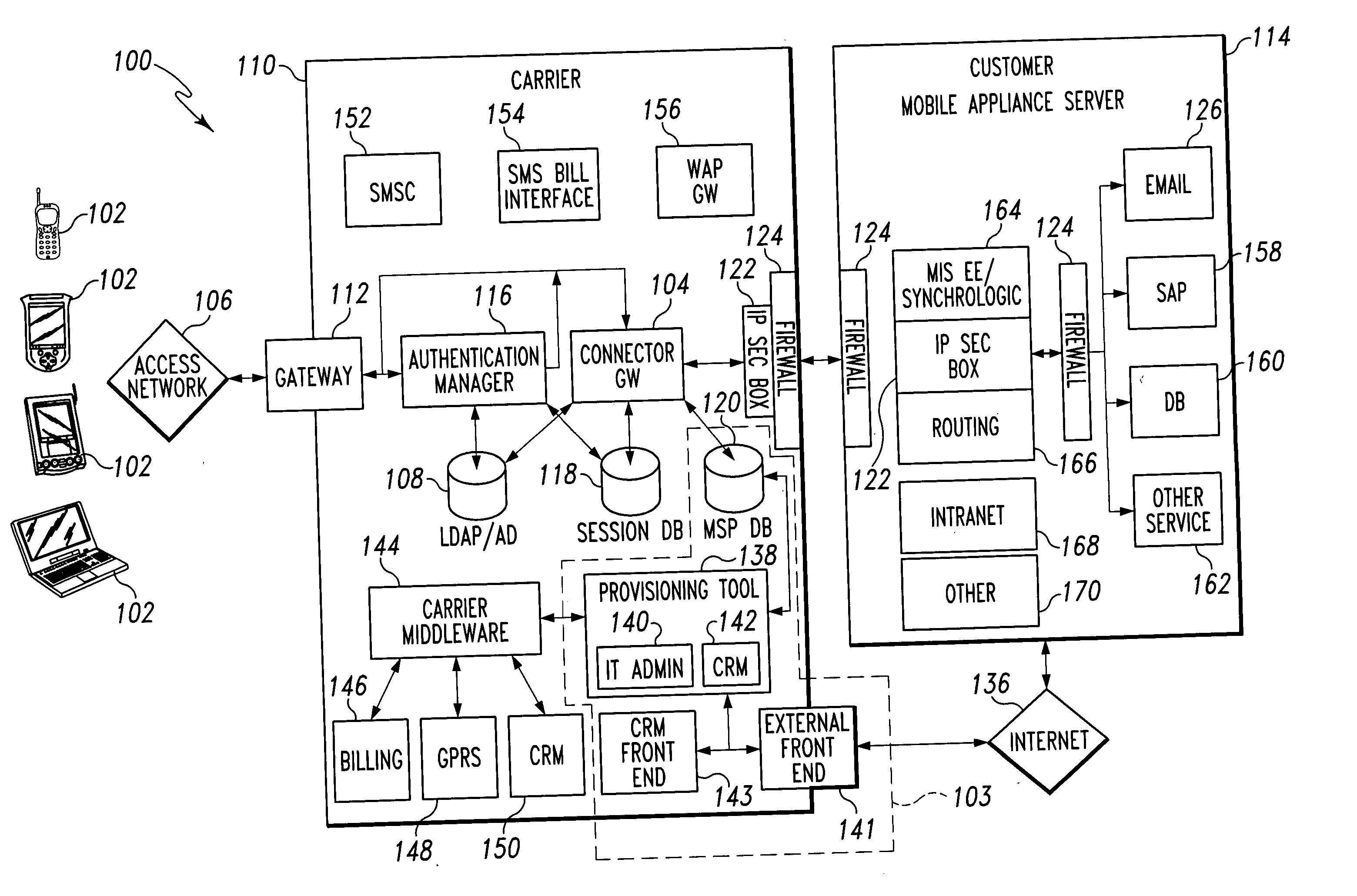
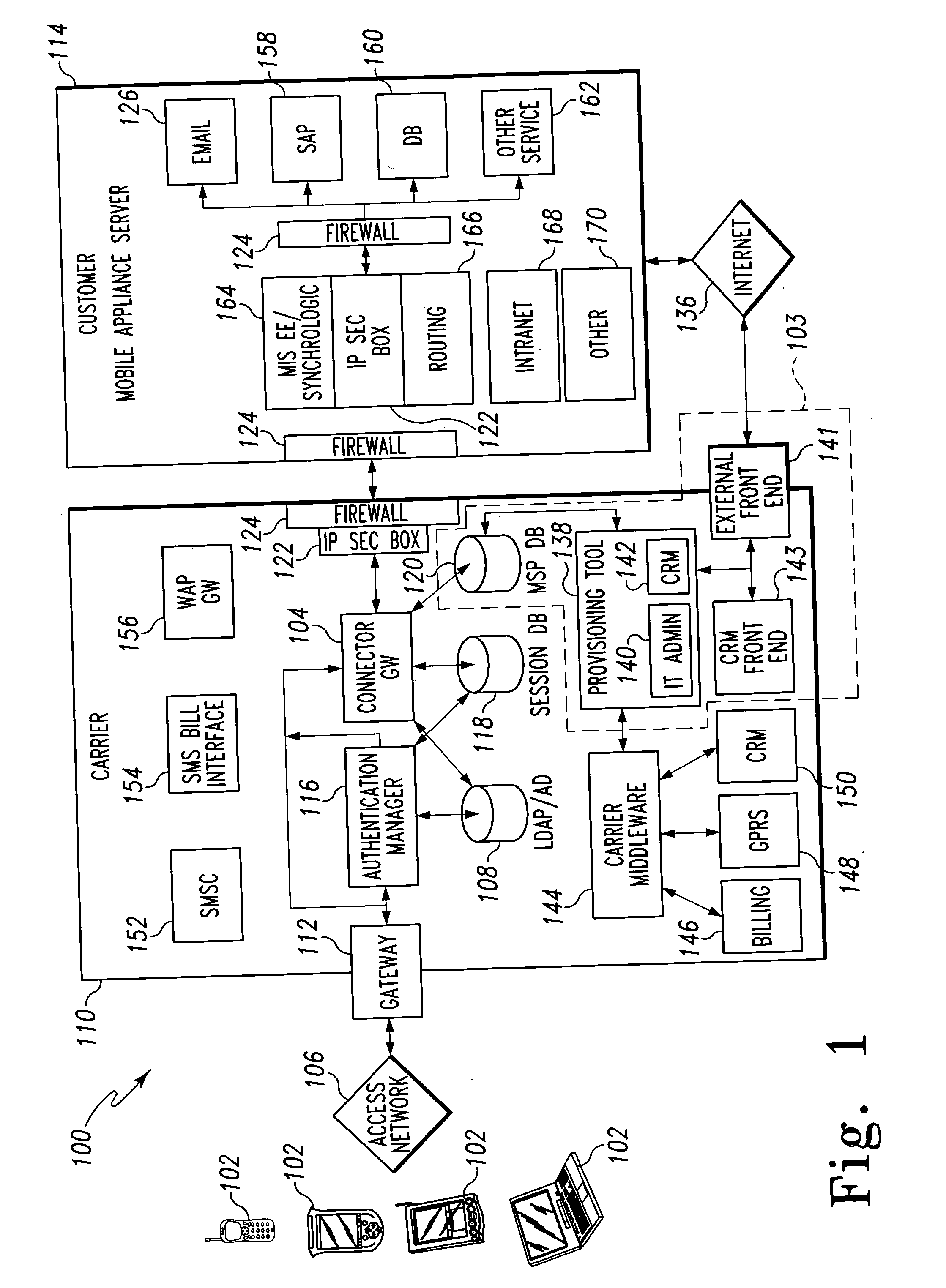
Mobile provisioning tool system
ActiveUS20050075115A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessWorkstation
A mobile provisioning tool system including a software provisioning tool application. The mobile provisioning tool system includes mobile devices capable of conducting wireless communication with wireless access points. A carrier network is connected with the wireless access points and a customer network that includes at least one business application. A provisioning tool application is located on a provisioning server. The provisioning tool application includes a CRM Rep component and an IT Admin component. A software provisioning tool application allows the provisioning workstation to automatically install mobile business services and configure network configuration settings on the mobile device.
Owner:ACCENTURE GLOBAL SERVICES LTD
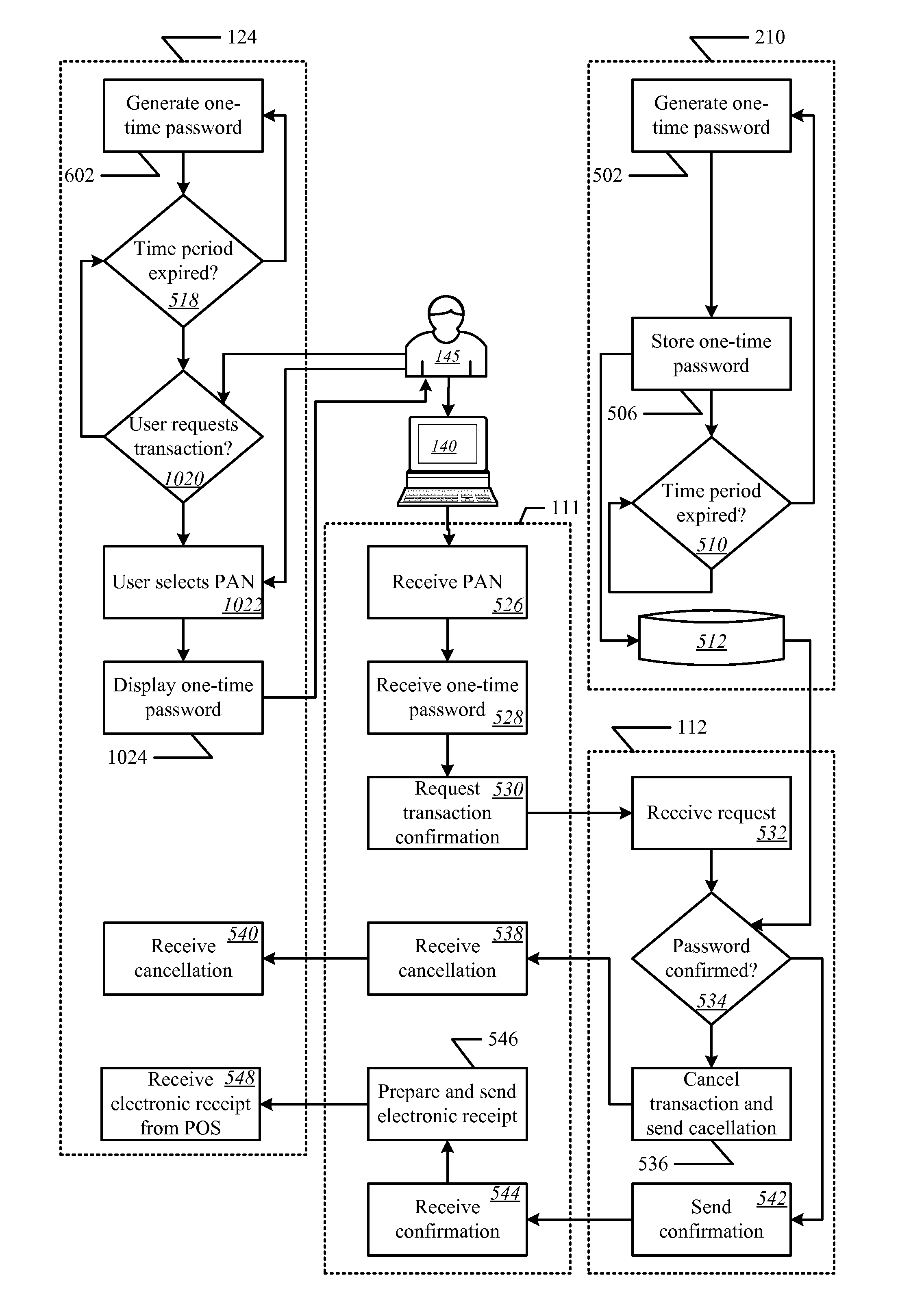
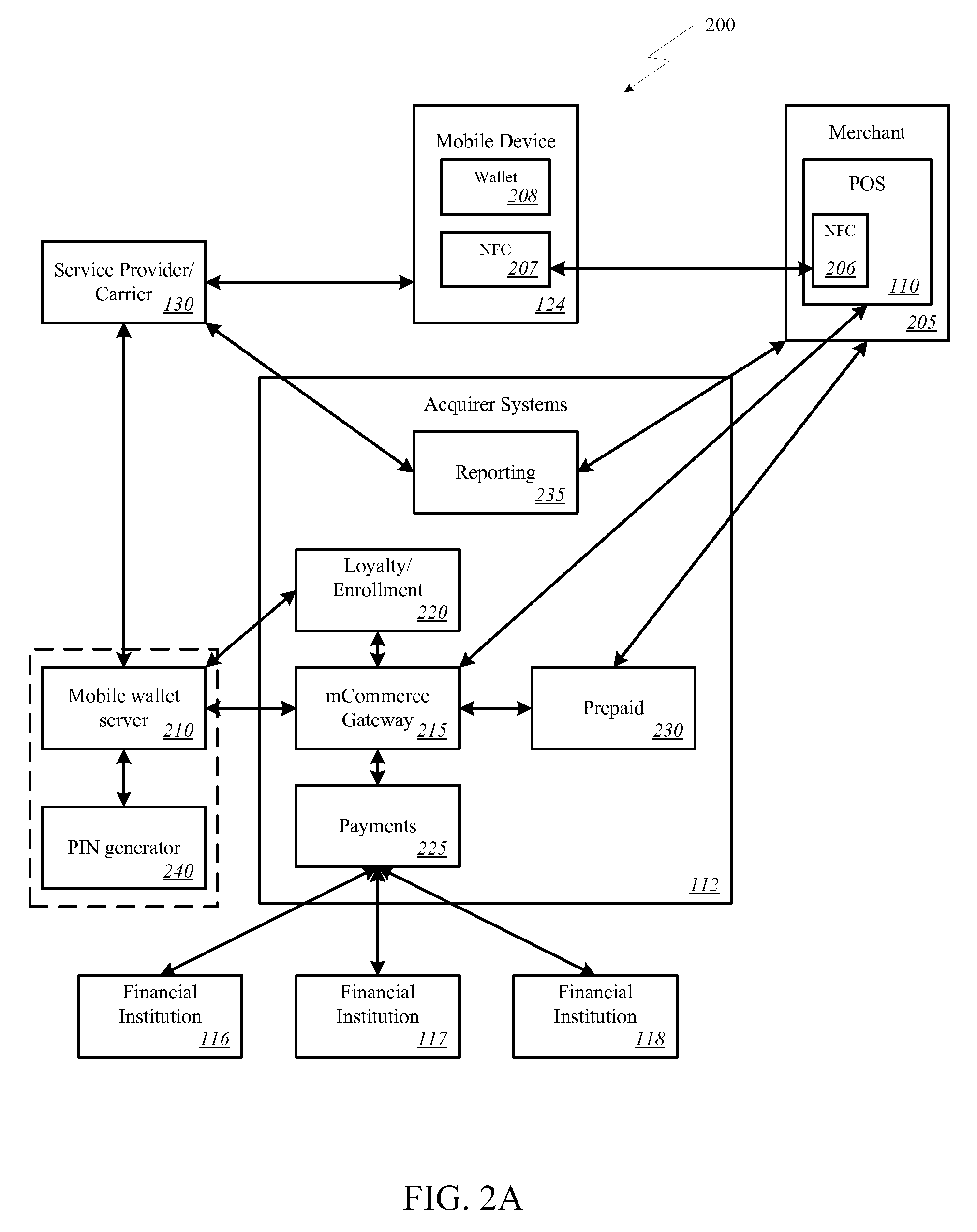
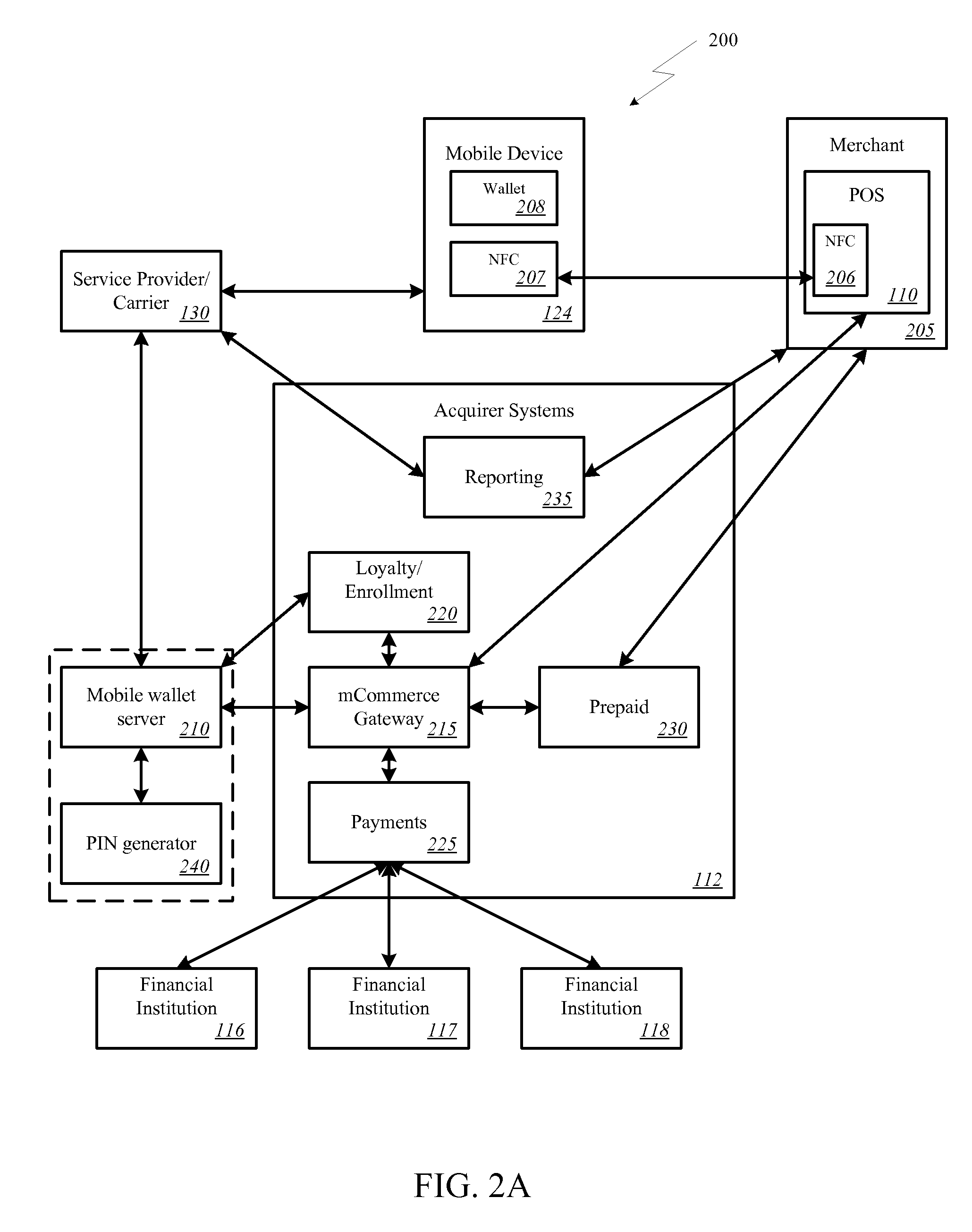
Onetime Passwords For Mobile Wallets
ActiveUS20090104888A1Near-field transmissionUnauthorised/fraudulent call preventionNetworked systemOne-time password
A mobile wallet and network system using onetime passwords for authentication is disclosed according to one embodiment of the invention. A onetime password may be generated at a mobile wallet server and transmitted to the mobile device. The onetime password may then be used to authenticate the user of the mobile wallet when completing a transaction. Authentication may require entry of the onetime password and confirmation that the onetime password entered matches the onetime password sent by the mobile wallet server. In other embodiments of the invention, a mobile wallet and a mobile wallet server are in sync and each generate the same onetime password at the same time. These onetime passwords may then be used to authenticate the user of the mobile wallet.
Owner:FIRST DATA
Hand-ear user interface for hand-held device
InactiveUS6978127B1Small sizeInput/output for user-computer interactionInterconnection arrangementsInformation processingPersonalization
A hand-held information processing device, such as a mobile phone, has a thumb wheel that lets the user scan a circular array of options. Each respective one of the options is represented by a respective audio output that gets played out when the wheel is turned a notch up or down. This enables the user to select an option with one hand and without having to look at the device. It also allows for a form factor smaller than that of a conventional mobile phones since a keypad is not needed for entering digits to make a call from a personalized directory.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method and system for providing supervisory control over wireless phone usage
InactiveUS7197321B2Reduce usageAccounting/billing servicesUnauthorised/fraudulent call preventionUser profileControl period
A system for controlling wireless phone usage enables a supervisor to establish user profiles for supervised users of wireless phones across a range of parameters which are stored in a user profile database. Such parameters may include one or more locations at which use of the wireless phone is restricted or permitted. In addition, restrictions on phone use may be provided based upon total phone usage within a specified control period, time periods, dates or days of the week during which phone use is restricted or permitted. One or more lists including numbers that are always-accessible may be provided and one or more lists including numbers that are never-accessible may also be provided. In the event a call does not satisfy predefined criteria, the call is blocked. Predetermined messages may be played to the called or calling party as applicable when a call is blocked. Boolean combinations of restrictions and permissive use criteria for the wireless phone may be specified to provide for flexibility when establishing use criteria for the wireless phone.
Owner:BOSTON COMM GROUP
Active ticket with dynamic characteristic such as appearance with various validation options
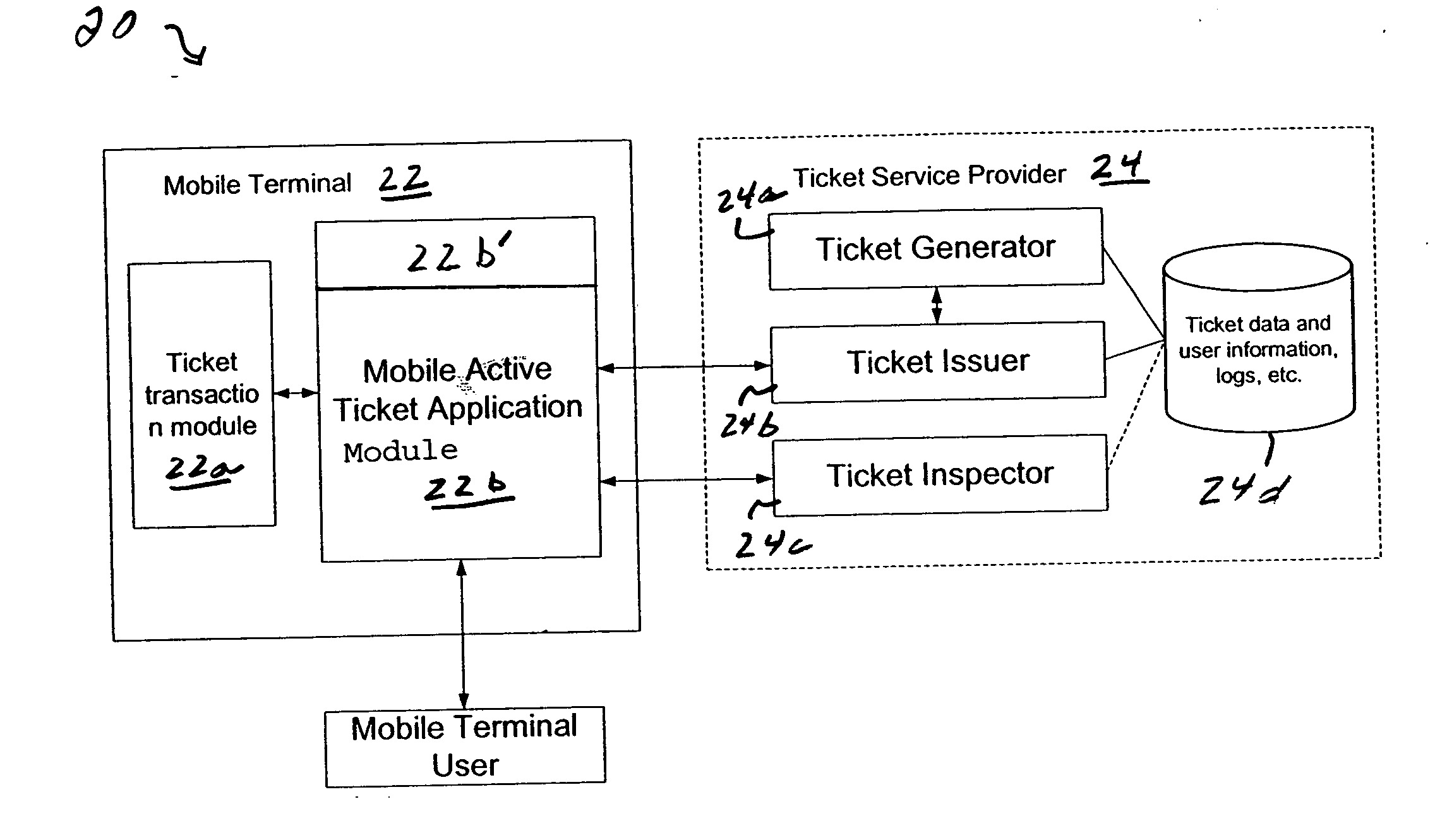
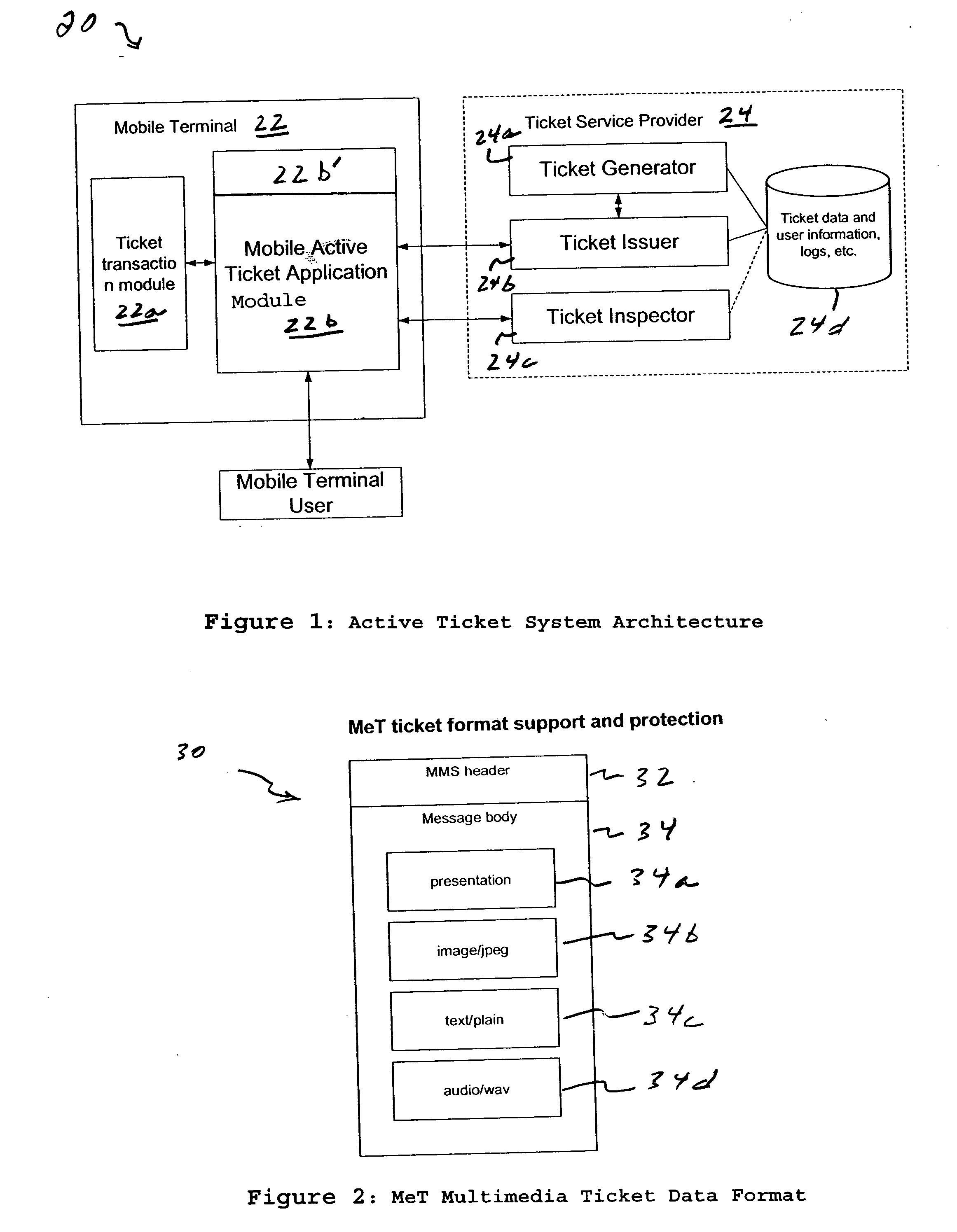
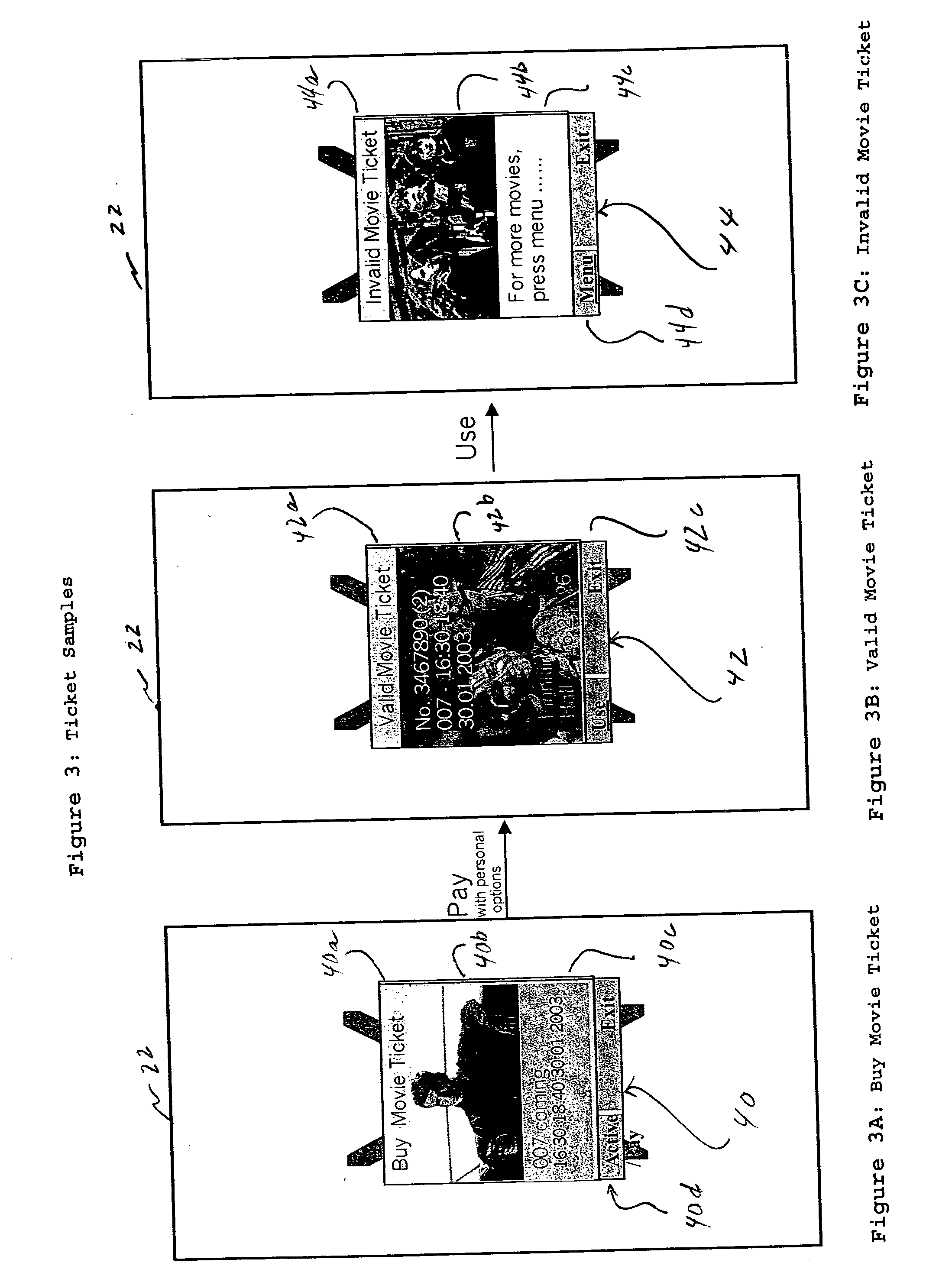
InactiveUS20050070257A1Validate easilyValidation without machine is easyTicket-issuing apparatusUnauthorised/fraudulent call preventionService provisionAnimation
A method and apparatus is provided for providing an active ticket in a mobile terminal for use by a mobile terminal user, wherein at least one active ticket has a ticket characteristic that dynamically changes based on one or more states in a life cycle of the active ticket. Dynamic changes to the ticket characteristic include multimedia changes or other presentation data, including text, sound (audio), animation, video, still pictures, or some combination thereof. The active ticket can have different states in it's life cycle, such as purchased, validated, invalid for certain events. Also the ticket service provider or issuer can send new control data to change the characteristic and / or contents of the active ticket.
Owner:NOKIA TECHNOLOGLES OY
Onetime passwords for smart chip cards
ActiveUS20090200371A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDisplay deviceFinancial transaction
A financial transaction card is provided according to various embodiments described herein. The financial transaction card includes a card body with at least a front surface and a back surface. The financial transaction card may also include a near field communications transponder and / or a magnetic stripe, as well as a digital display configured to display alphanumeric characters on the front surface of the card body. The financial transaction card may also include a processor that is communicatively coupled with the near field communications transponder or magnetic stripe and the digital display. The processor may be configured to calculate one-time passwords and communicate the one-time passwords to both the near filed communications transponder or magnetic stripe and the digital display.
Owner:FIRST DATA
Vehicle monitoring system
InactiveUS20120209634A1Vehicle testingUnauthorised/fraudulent call preventionMonitoring systemRemovable media
A data logging device tracks the operation of a vehicle or driver actions. The device includes a storage device, which may be removable or portable, having a first memory portion that may be read from and may be written to in a vehicle and a second memory portion that may be read from and may be written to in the vehicle. The second memory portion may retain data attributes associated with the data stored in the first removable storage device. A processor reads data from an automotive bus that transfers data from vehicle sensors to other automotive components. The processor writes data to the first memory portion and the second memory portion that reflect a level of risk or safety. A communication device links the storage device to a network of computers. The communication device may be accessible through software that allows a user to access files.
Owner:PROGRESSIVE CASUALTY INSURANCE
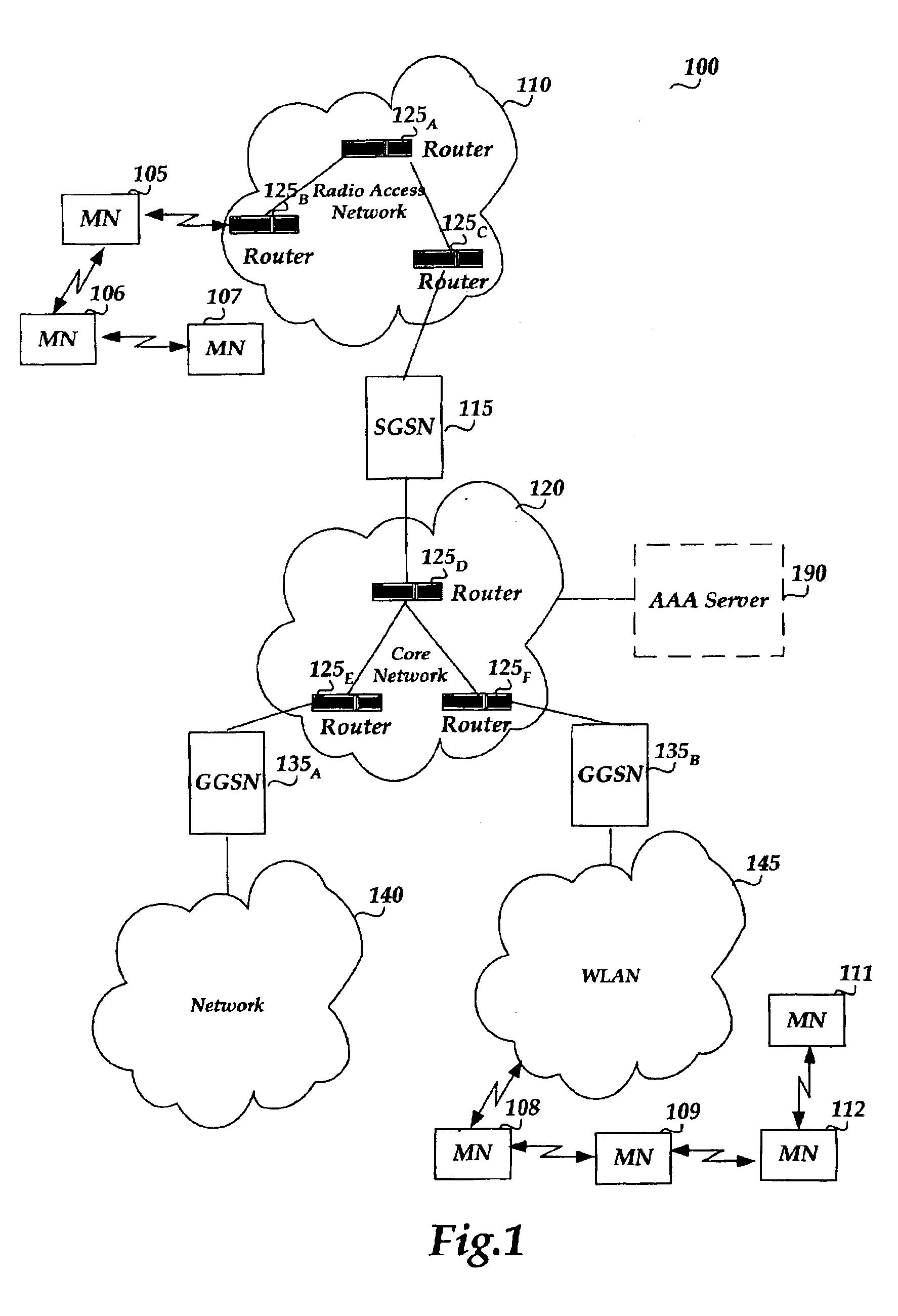
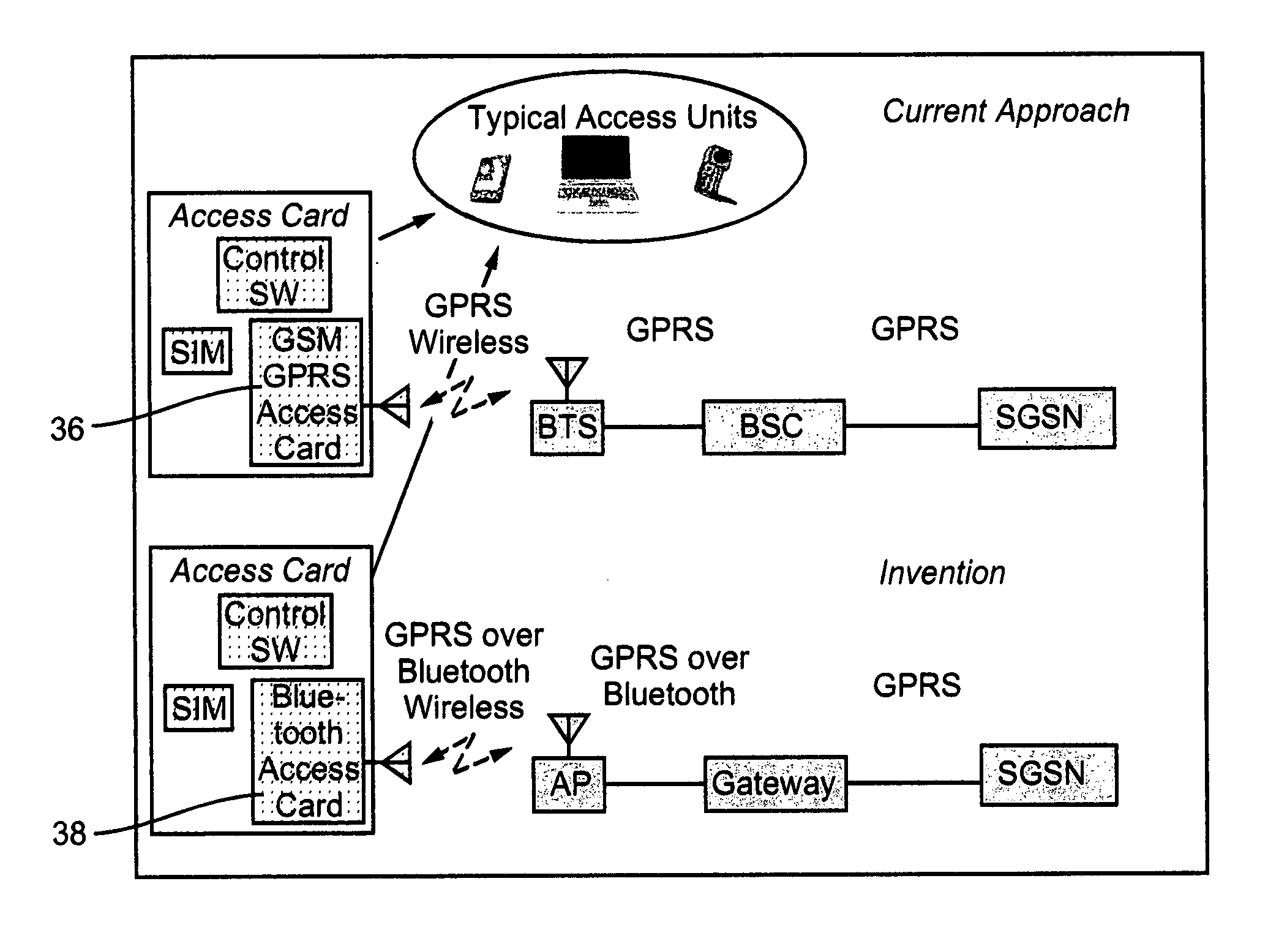
Access to plmn networks for non-plmn devices, and to issues arising in interfaces in general between plmn and non-plmn networks
ActiveUS20060291455A1Reduce quality of connectionLower Level RequirementsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsNetwork interface deviceMobile device
Interface device for interfacing between a PLMN network and a non-PLMN network, the PLMN network being configured to recognize cellular base stations as nodes thereof through which to mediate connections to cellular mobile devices, the non-PLMN networks each comprising a plurality of access points for mediating connections to network compatible mobile devices, and for which the network compatible mobile devices are not required to be cellular devices. The interface device is configured as a node of the PLMN network to appear to the PLMN network as a standard cellular base station, and comprises functionality to make non-cellular devices connecting to the non-PLMN network and attempting to access the PLMN network through the non-PLMN network appear as cellular devices to the PLMN network.
Owner:FLASH NETWORKS
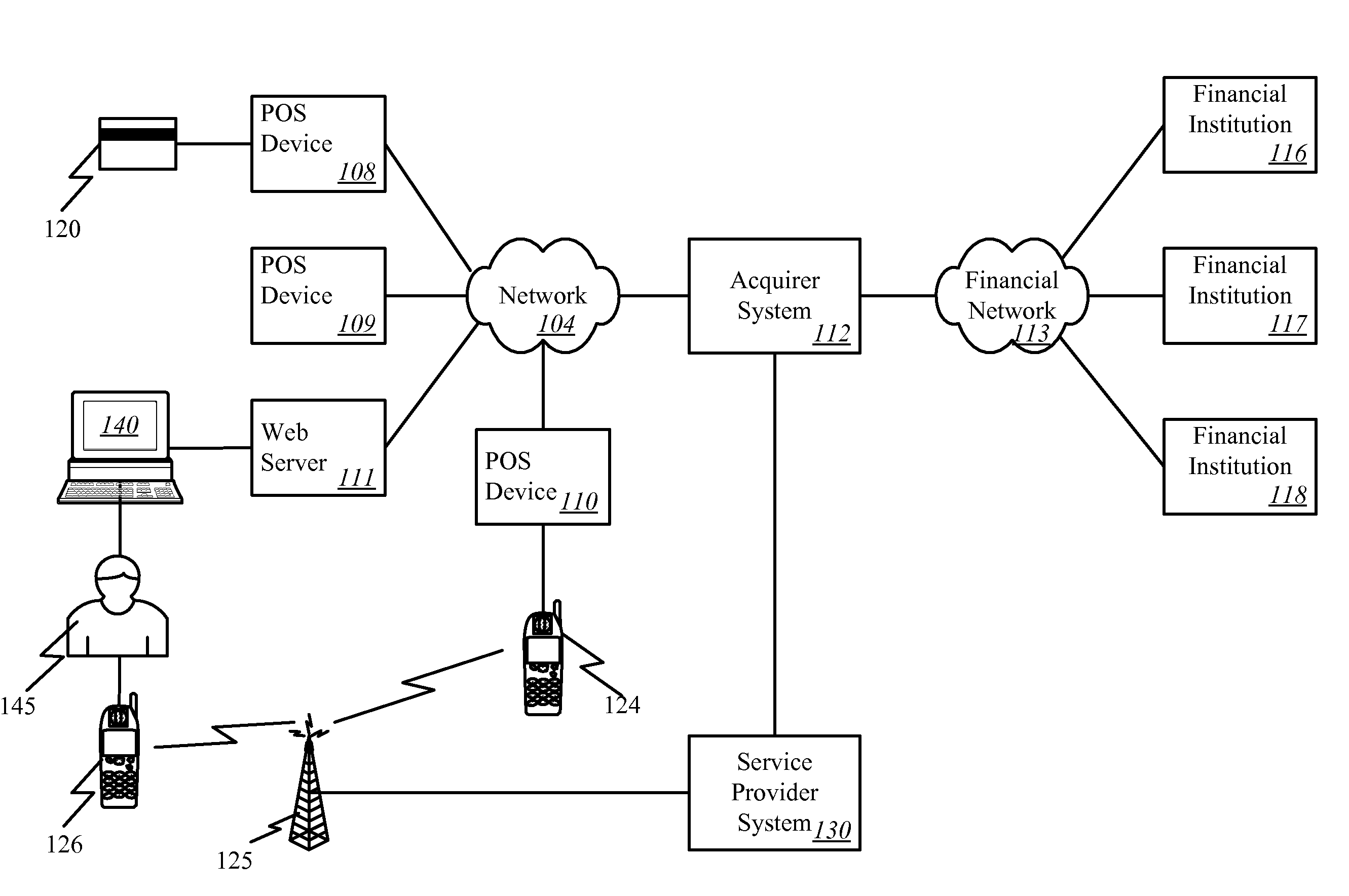
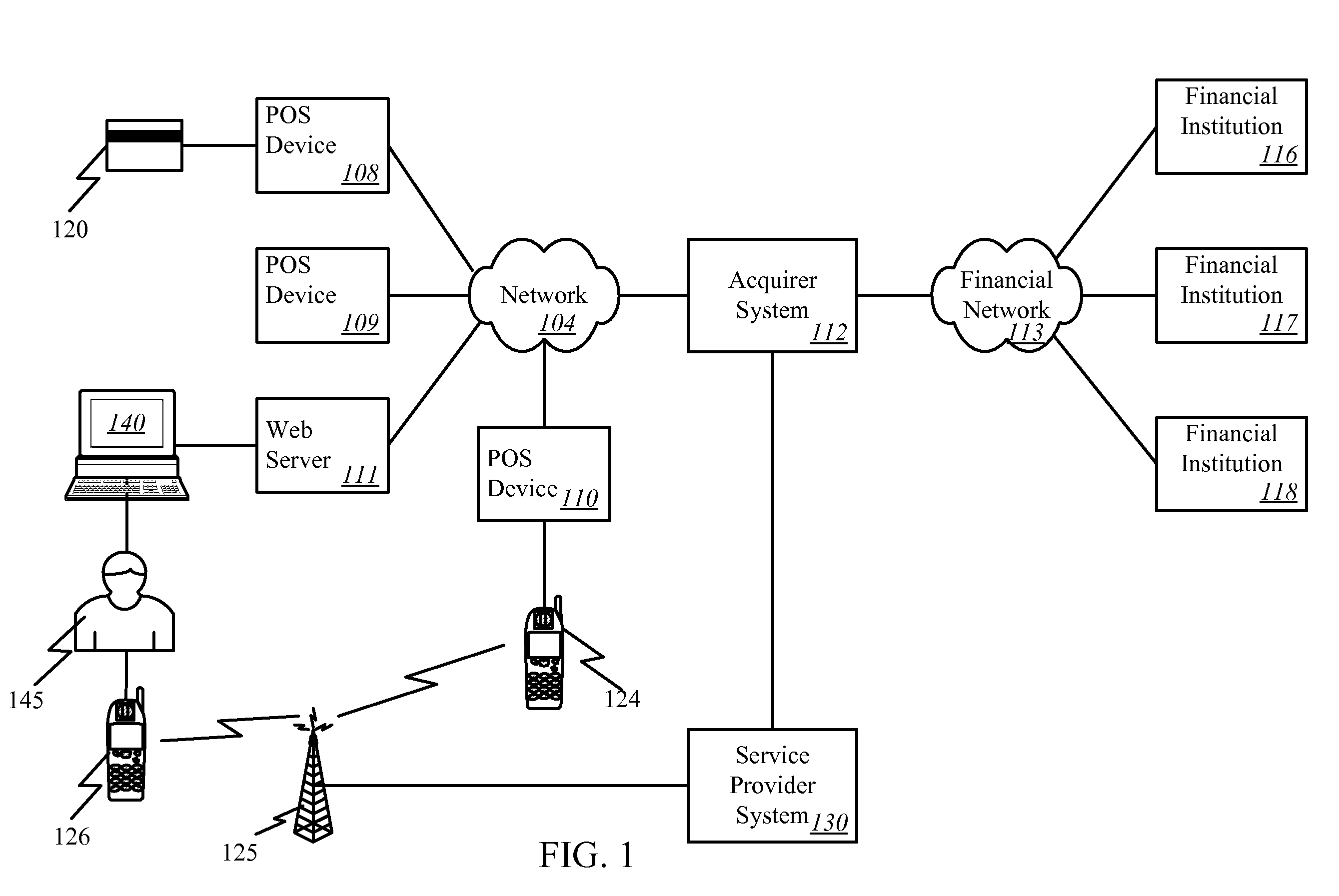
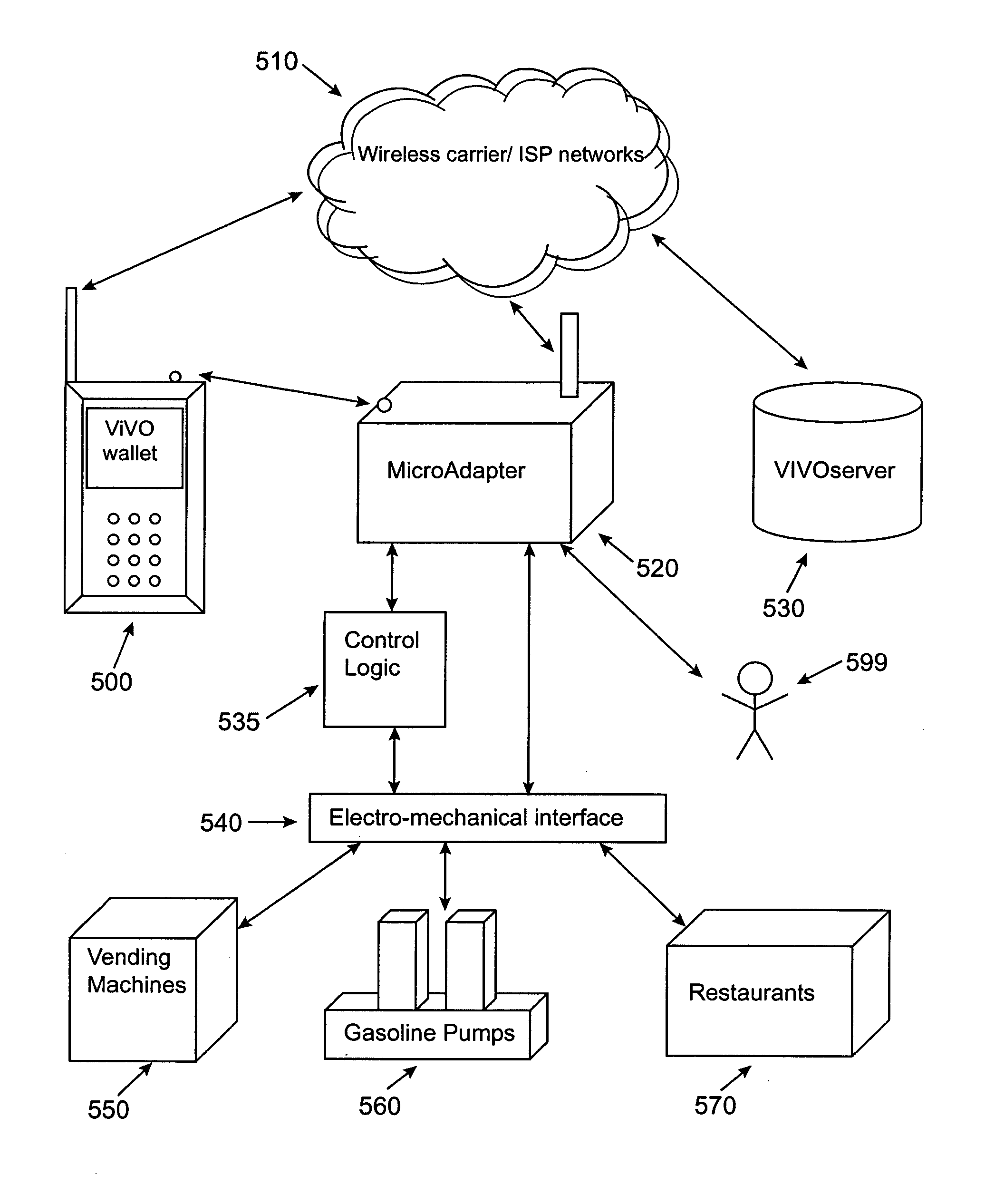
Micropayment financial transaction process utilizing wireless network processing
InactiveUS7127236B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyTransceiver
A MicroAdapter device enables payment transactions to be effected through a purchaser's personal trusted device (PTD) without relying upon tokens or prepayment cards. In one embodiment, the MicroAdapter includes a transceiver configured to receive a purchase signal from the PTD including order and payment information. In response, the MicroAdapter communicates via wireless telephony with a transaction authorizer to receive authorization for effectuating the purchase transaction. The MicroAdapter may be particularly suited to effectuate micropayment transactions authorized by a Billing On Behalf of Others (BOBO) program administered through a wireless carrier / ISP or third party.
Owner:MASTERCARD INT INC
Femtocell Integration into the Macro Network
ActiveUS20080207170A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemNetwork control
Some embodiments of the invention provide a communication system that includes a first communication network, a second communication network, and a core network. The second communication network includes a network controller and a group of two or more access areas that are communicatively coupled to the core network by the network controller. Some embodiments service the second network access areas by providing access area identifiers to each access area while communicating with the first network or core network using a single are identifier assigned to the network controller. Some embodiments provide access control by sending a series of invalid messages to a user equipment (UE) that is not authorized to access services of the second network to reject the UE. Some embodiments reject the UE by sending a message to ban a UE from an access area with a particular access area identifier.
Owner:RIBBON COMM OPERATING CO INC
Method and apparatus for identifying wireless transmitters
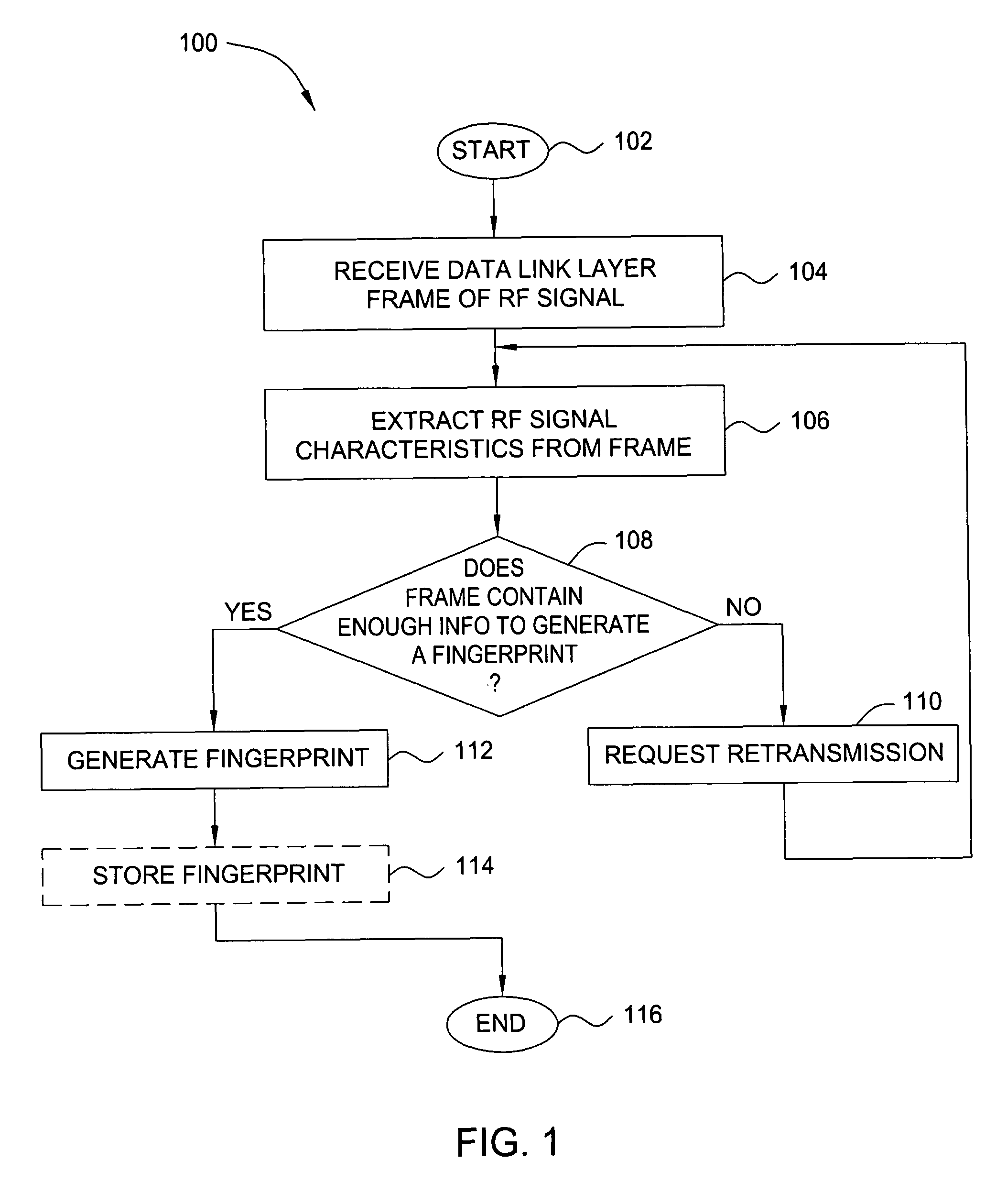
ActiveUS8249028B2Error preventionFrequency-division multiplex detailsRadio frequency signalWireless computing
In one embodiment, the present invention is a method and apparatus for identifying wireless transmitters. In one embodiment, a method for identifying a transmitter in a wireless computing network includes extracting one or more radio frequency signal characteristics from a communication from the transmitter and generating a fingerprint of the transmitter in accordance at least one of the extracted radio frequency signal characteristics.
Owner:SRI INTERNATIONAL
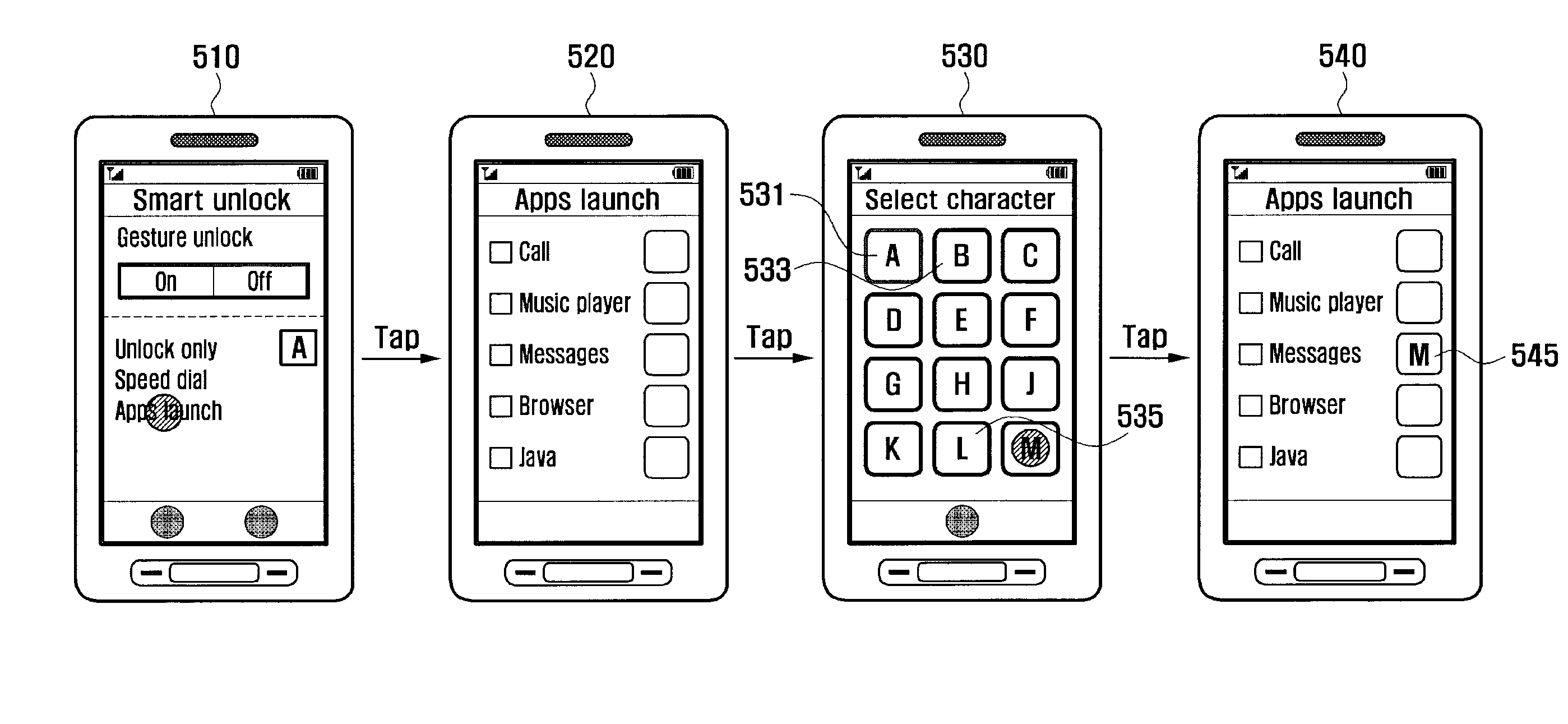
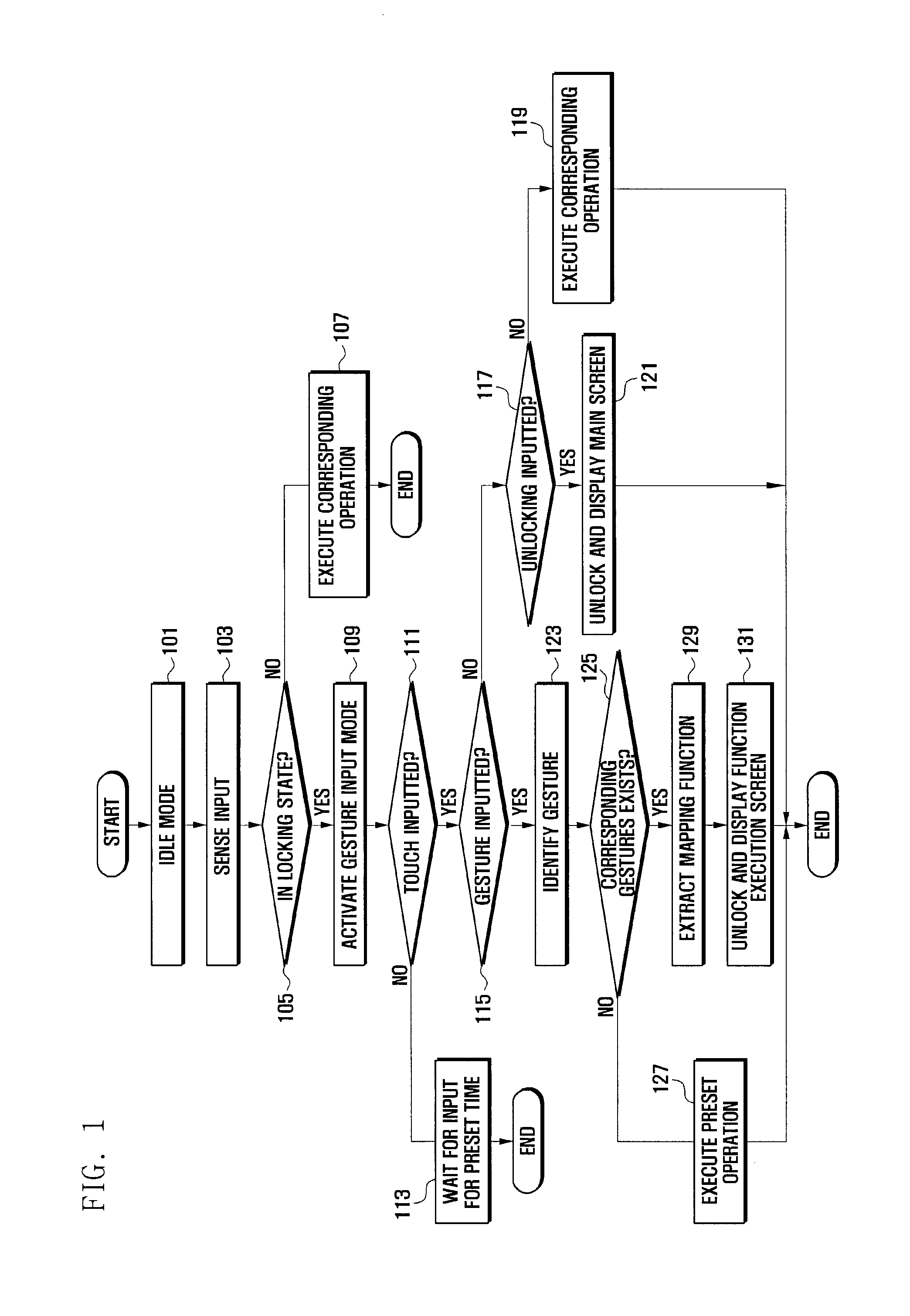
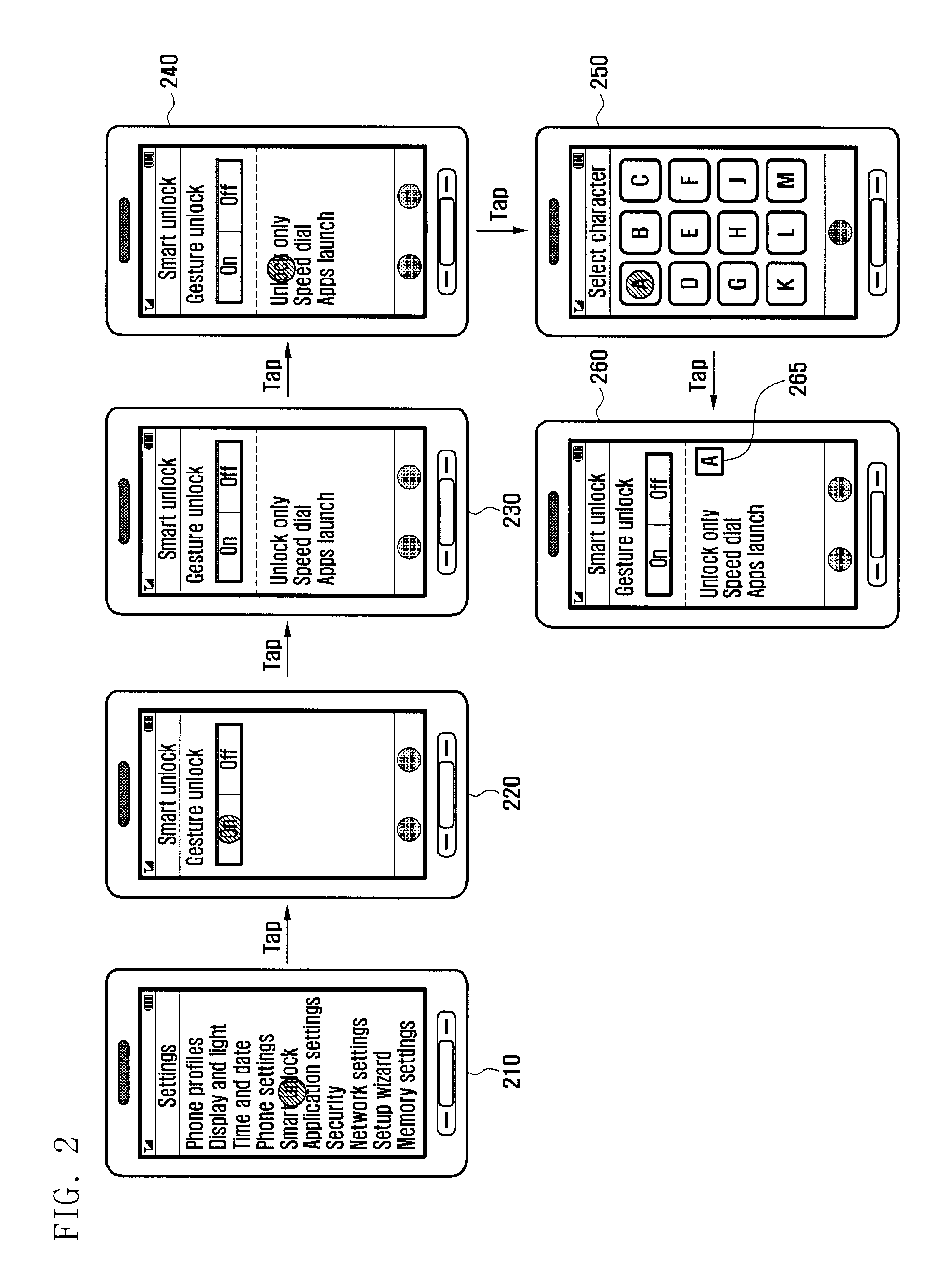
Apparatus and method for unlocking a locking mode of portable terminal
ActiveUS20100306718A1Easy to unlockEasy to implementUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer terminalHuman–computer interaction
Owner:ROVI GUIDES INC
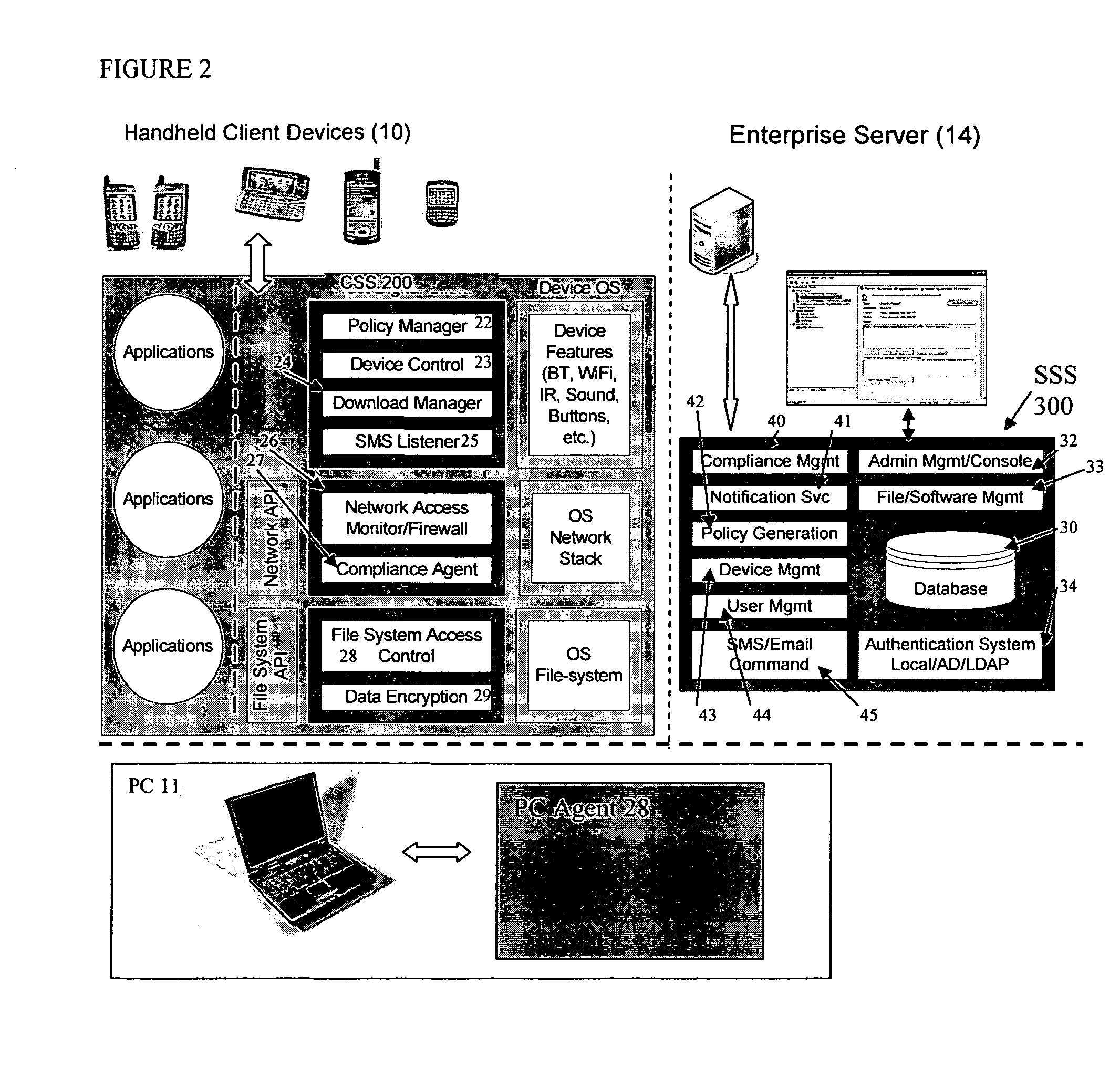
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com