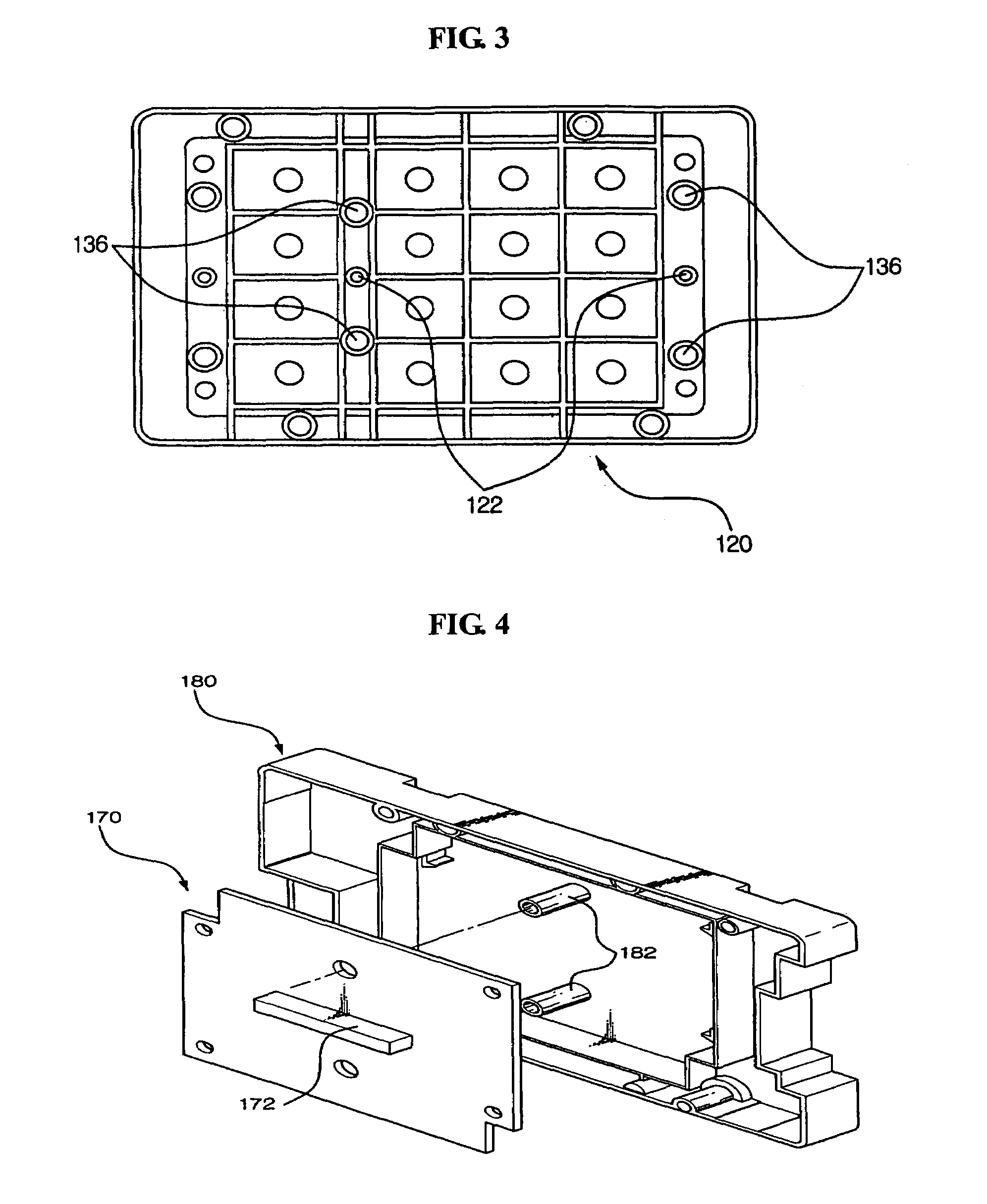
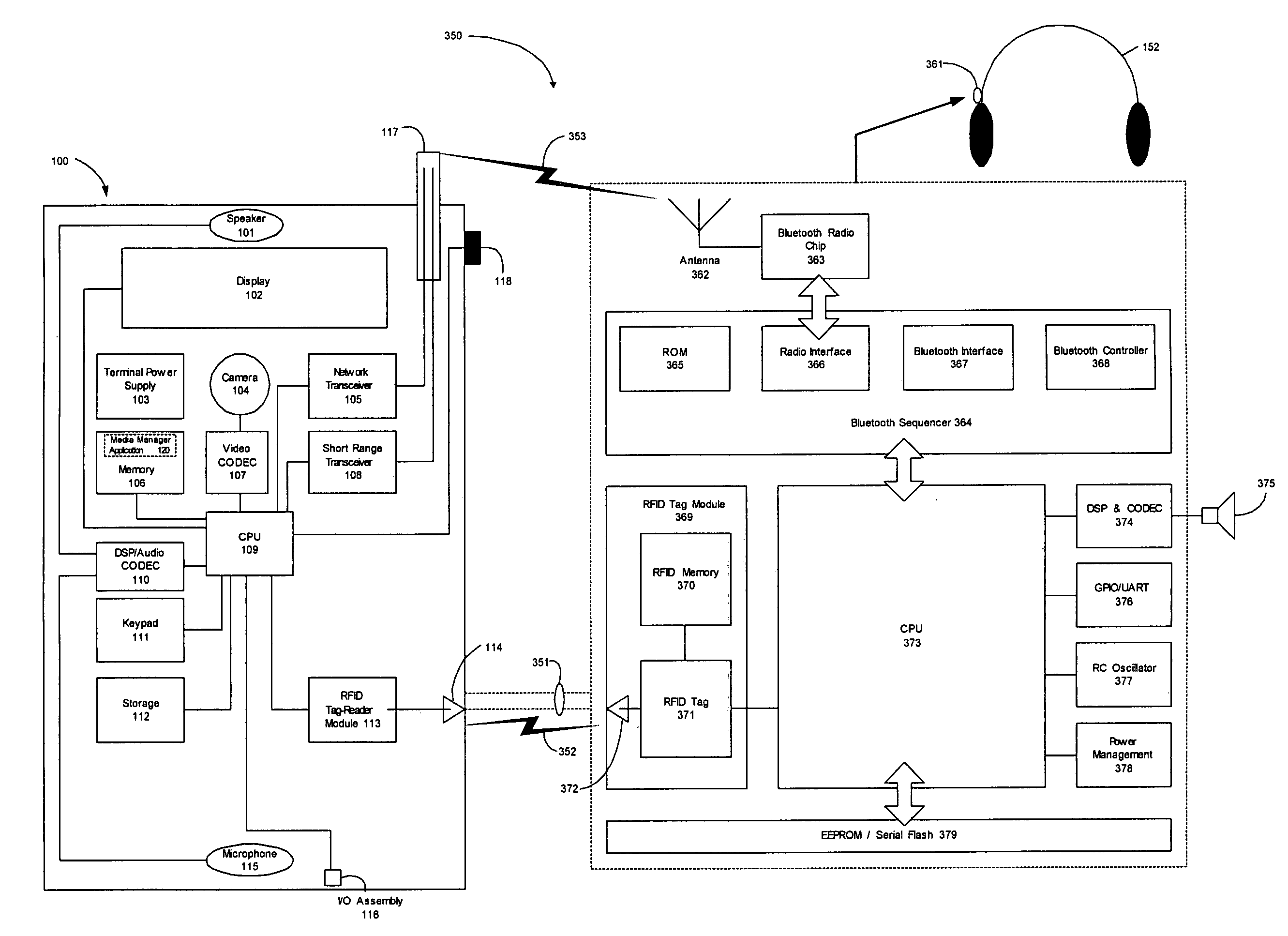
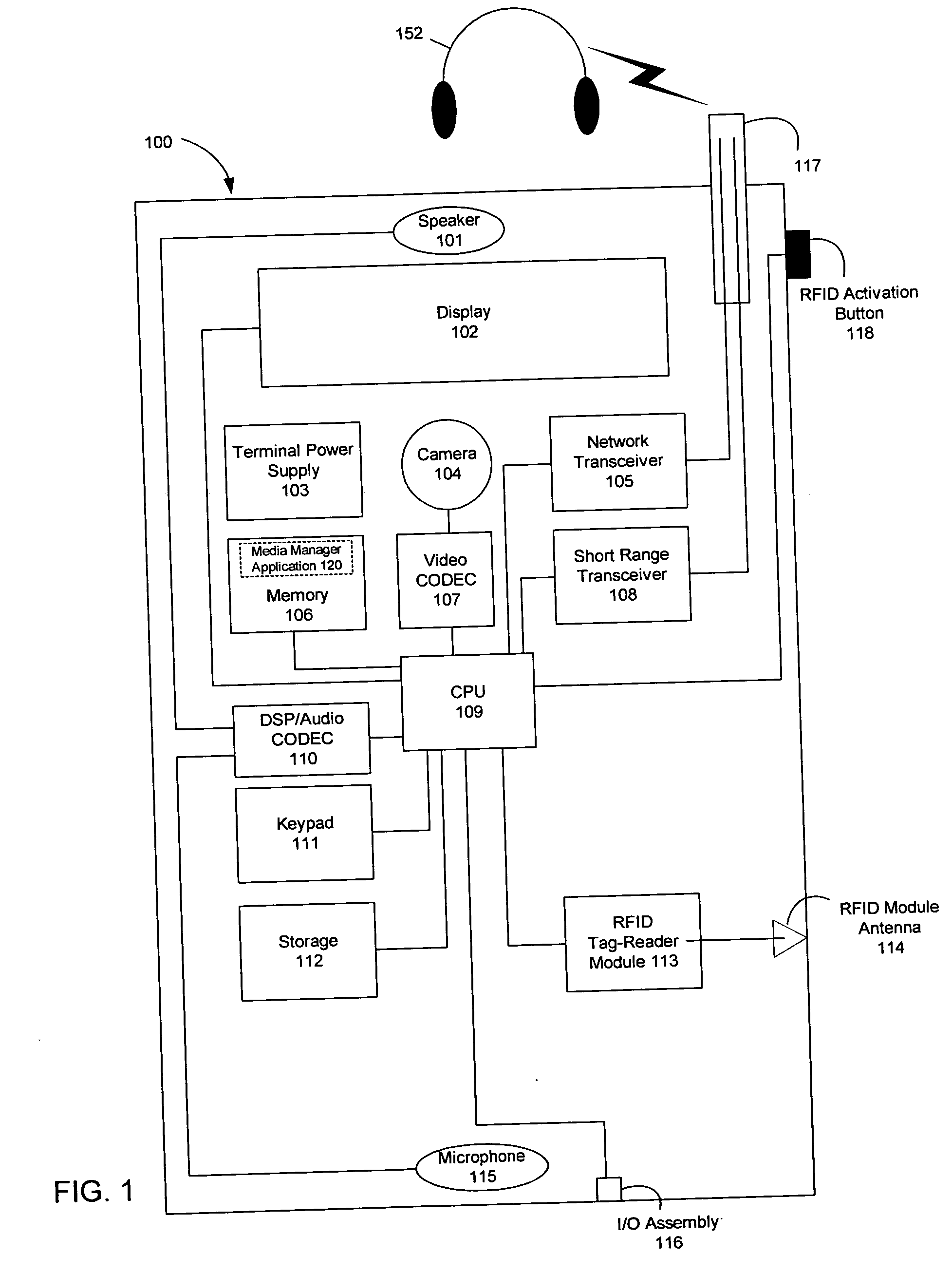
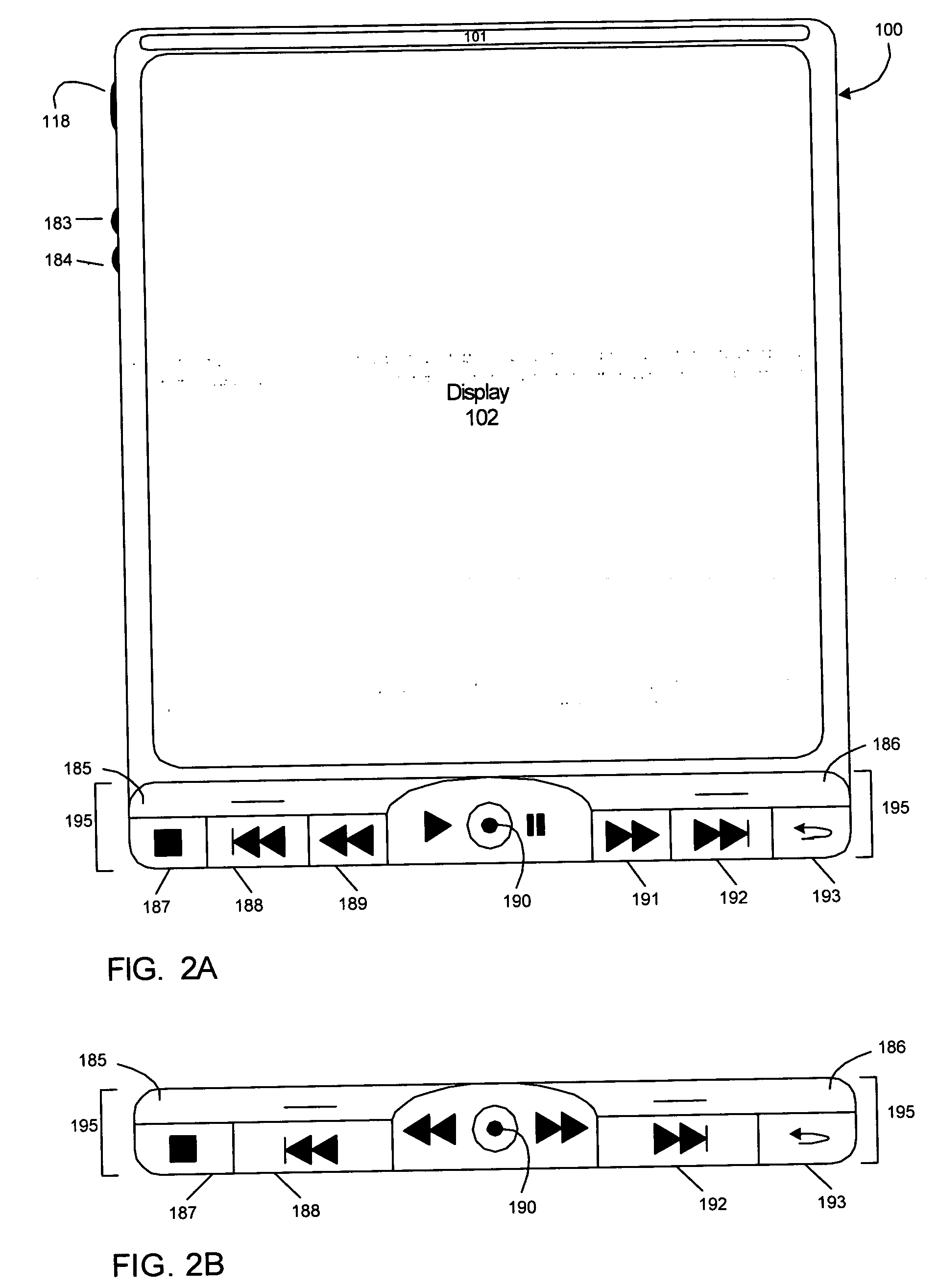
Patents
Literature
110746 results about "Software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer software, or simply software, is a collection of data or computer instructions that tell the computer how to work. This is in contrast to physical hardware, from which the system is built and actually performs the work. In computer science and software engineering, computer software is all information processed by computer systems, programs and data. Computer software includes computer programs, libraries and related non-executable data, such as online documentation or digital media. Computer hardware and software require each other and neither can be realistically used on its own.
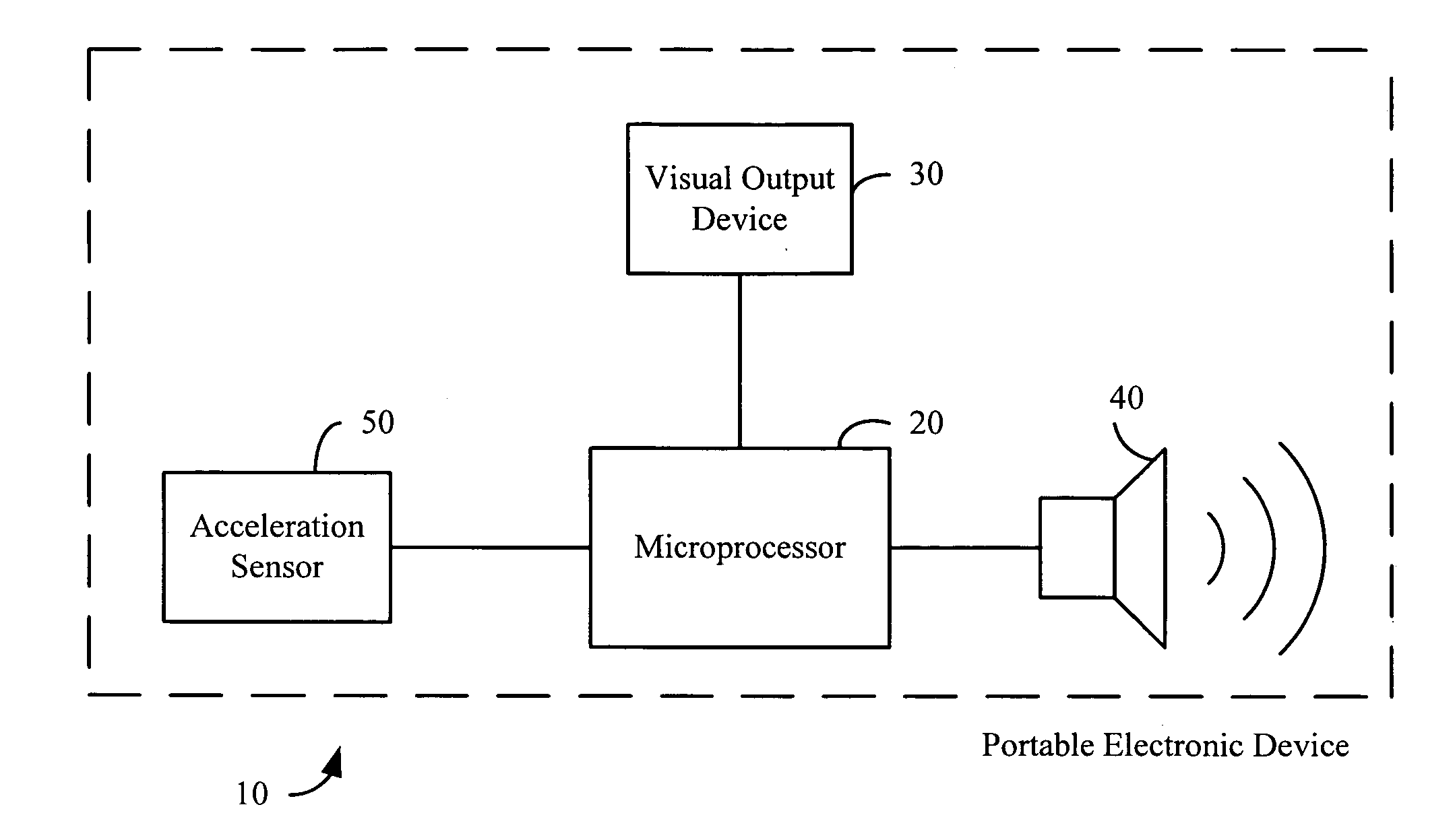
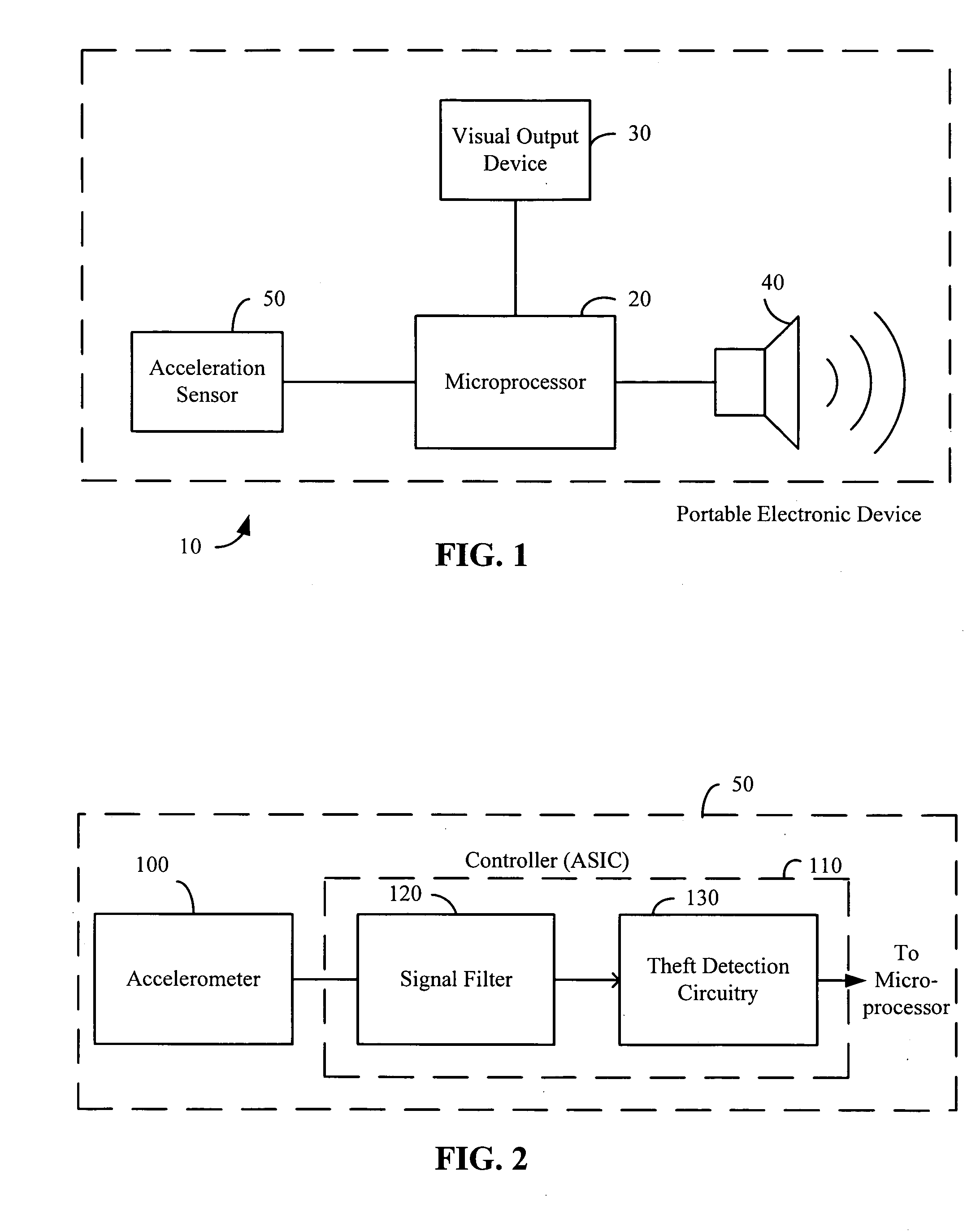
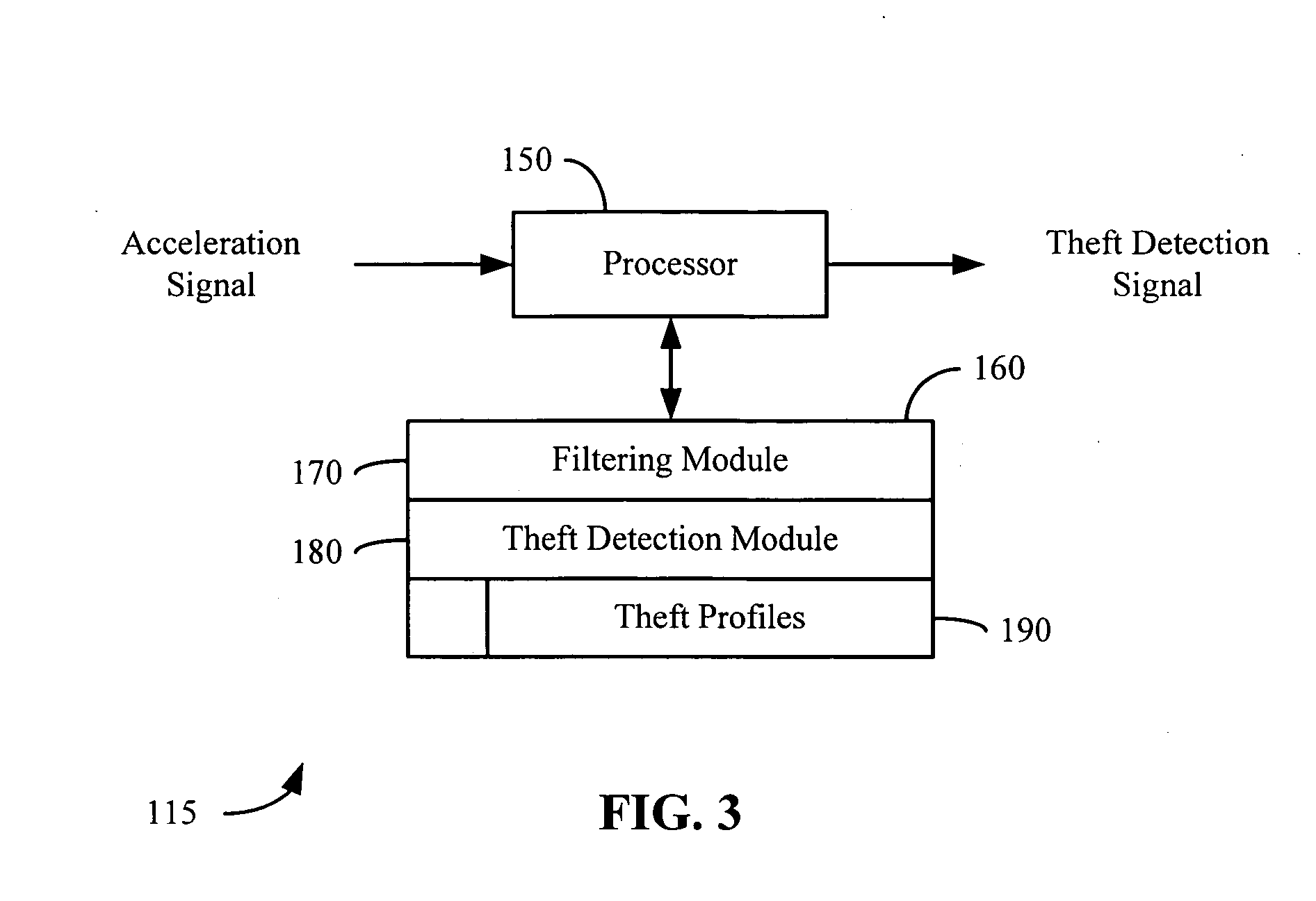
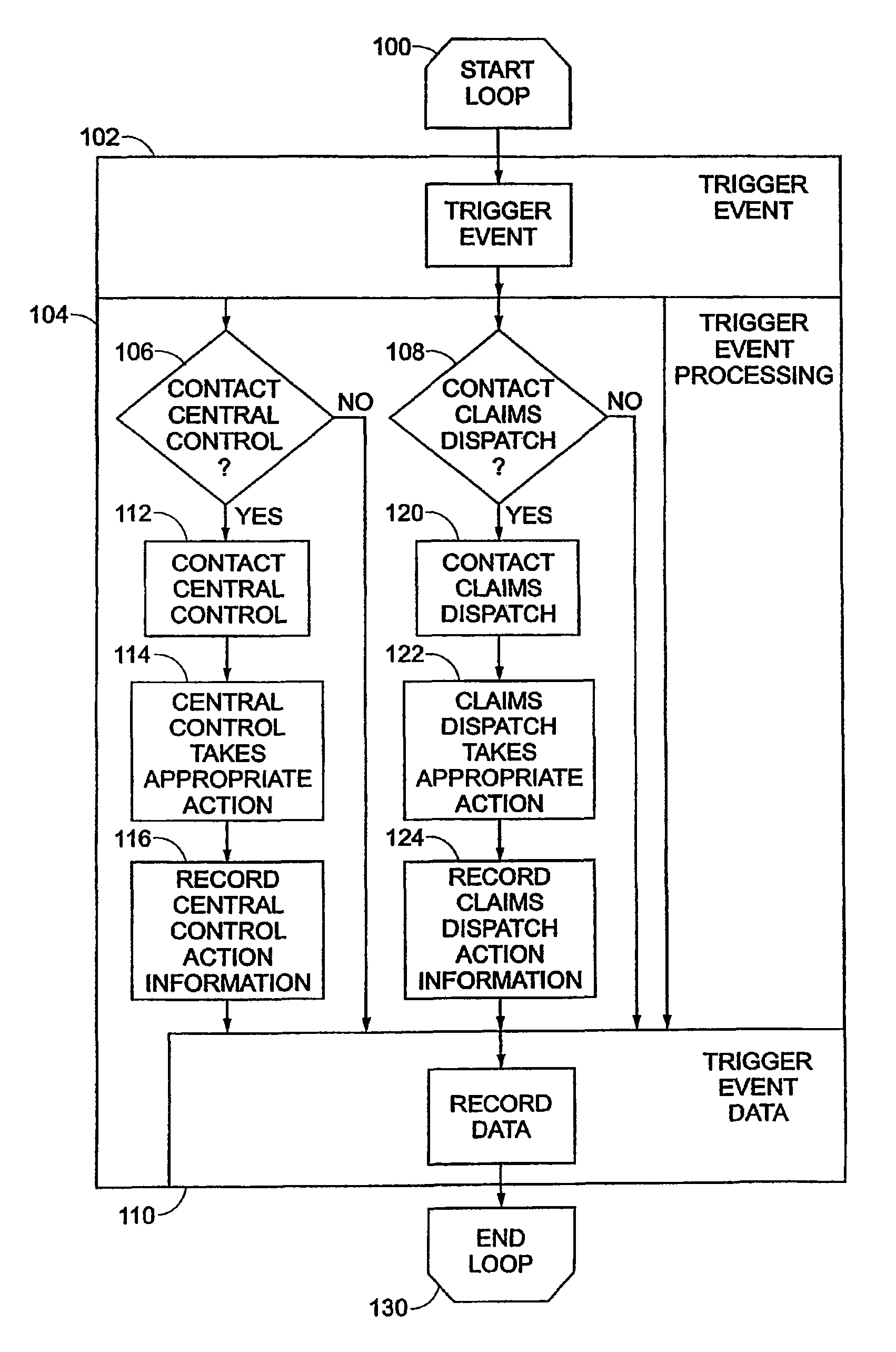
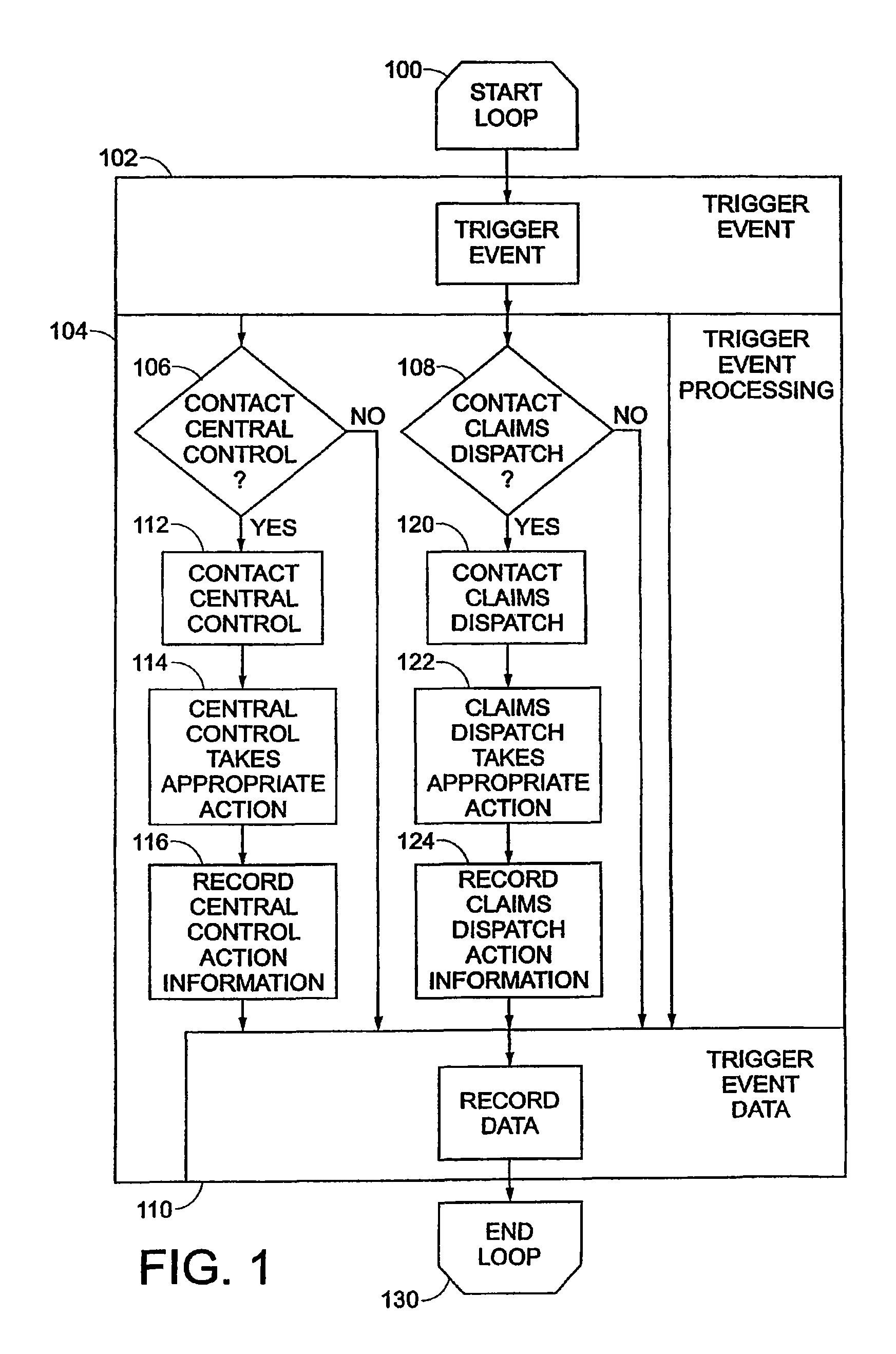
Acceleration-based theft detection system for portable electronic devices
InactiveUS20050190059A1Prevent theftElectric signalling detailsBurglar alarm by hand-portable articles removalGraphical user interfaceEngineering
A theft prevention system for protecting portable electronic devices is disclosed. An acceleration sensor detects the acceleration of a portable electronic device, and a controller analyzes this acceleration to determine whether a theft condition is present. If so, an alarm can be initiated. The theft prevention system can include a filter for attenuating irrelevant acceleration frequencies and isolating those representative of theft, and comparison hardware / software for determining whether the detected acceleration matches a known acceleration profile characteristic of theft. Various parameters of the theft prevention system can also be set by a user through mechanisms such as a graphical user interface.
Owner:APPLE INC
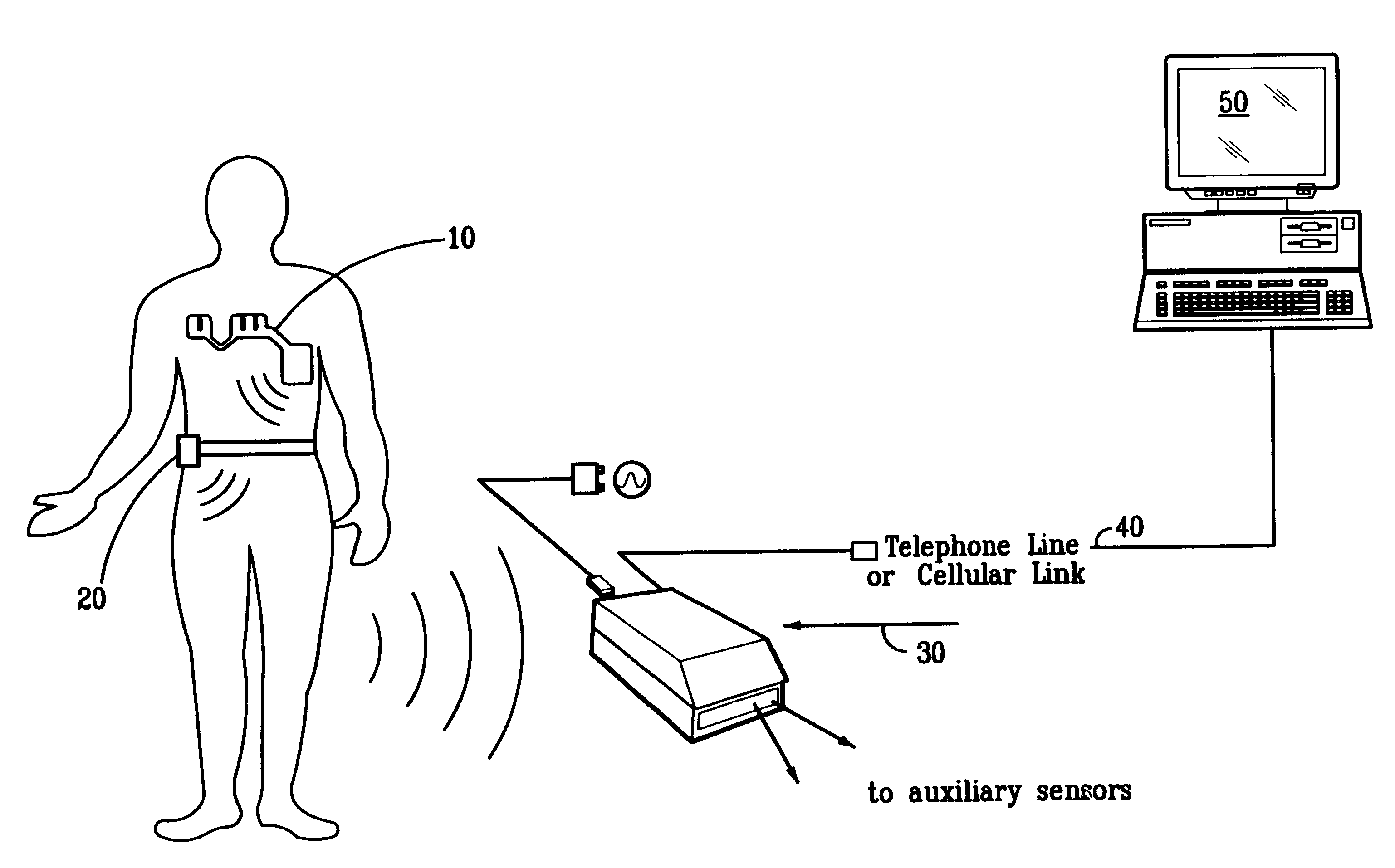
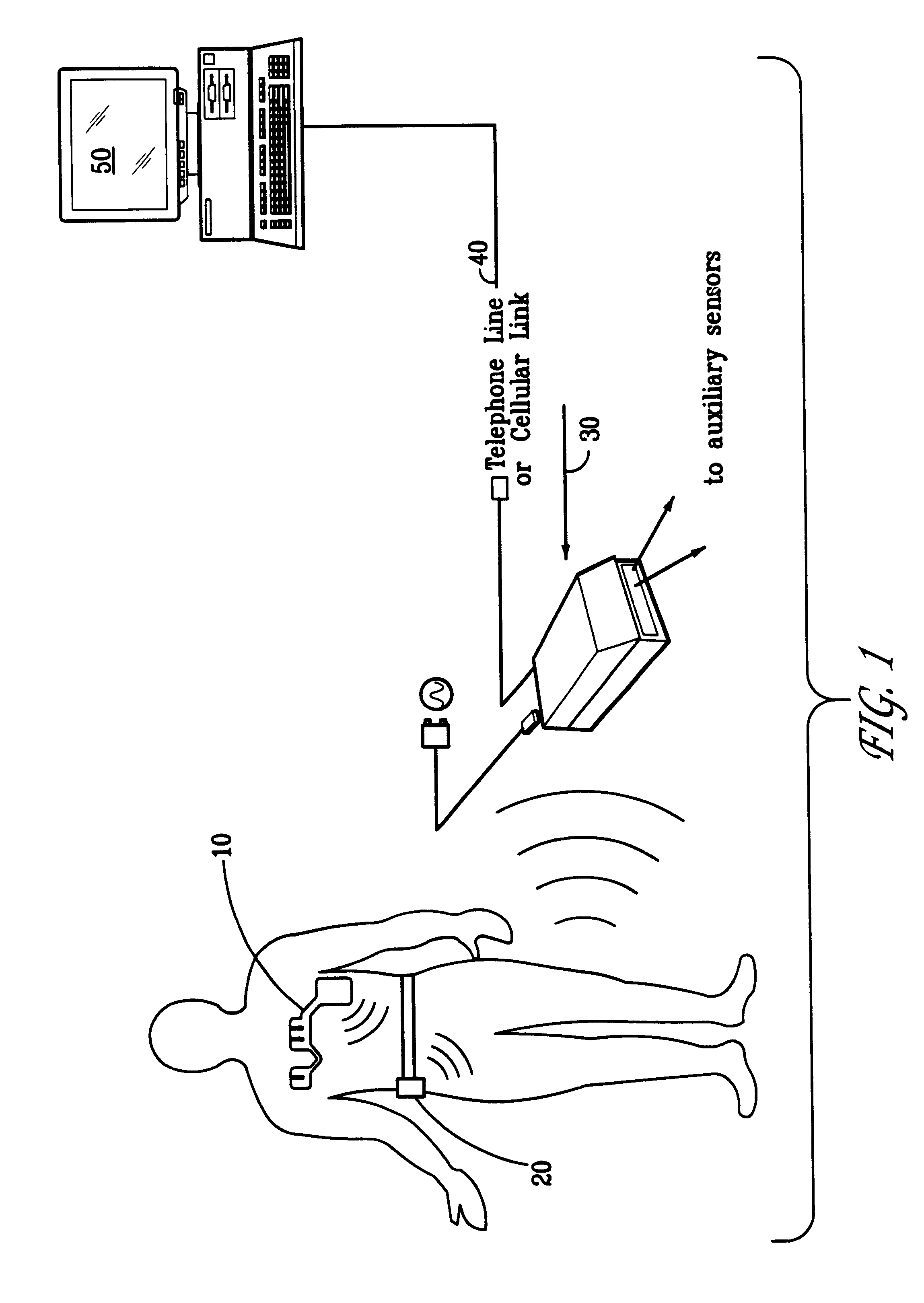
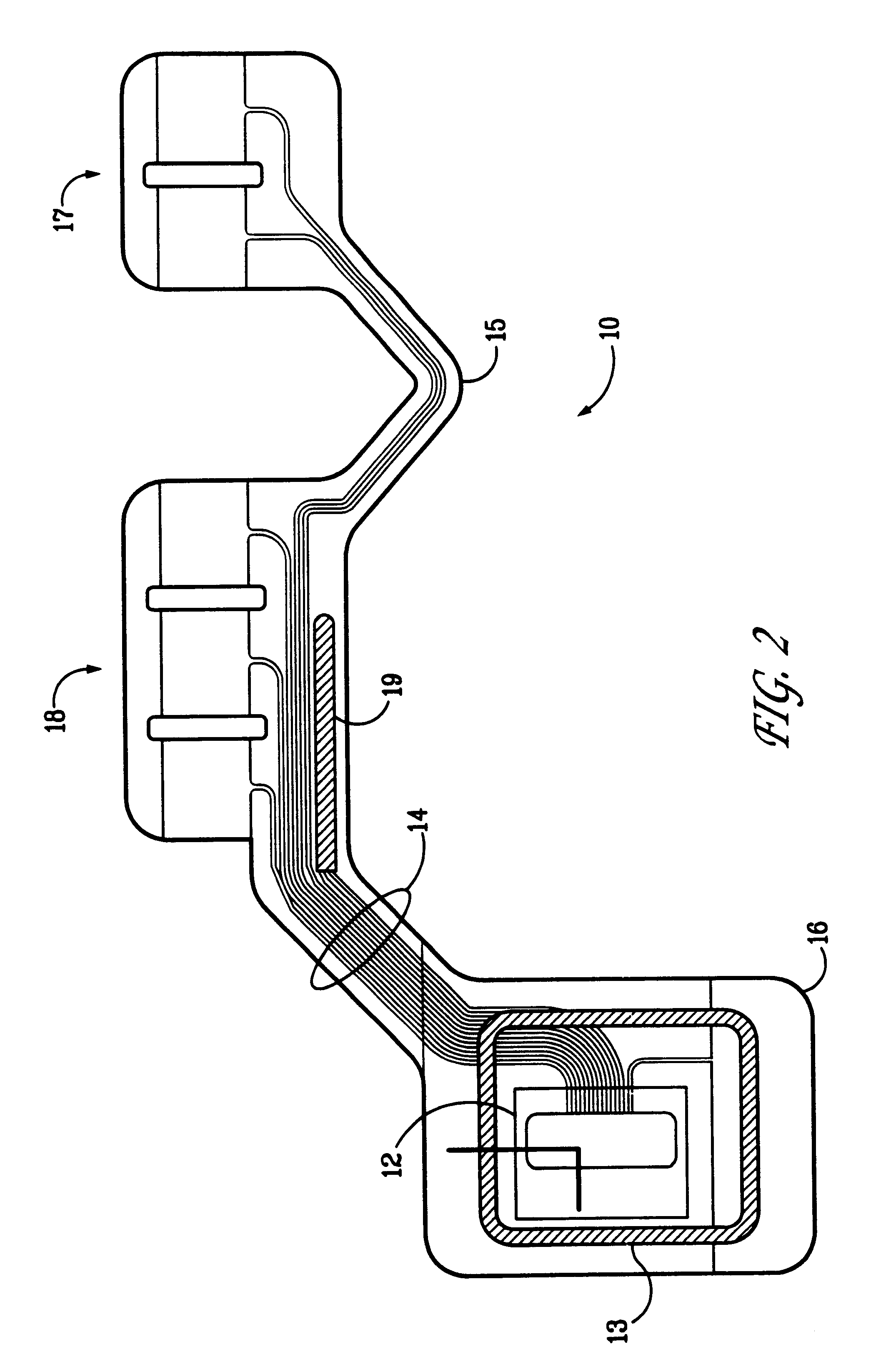
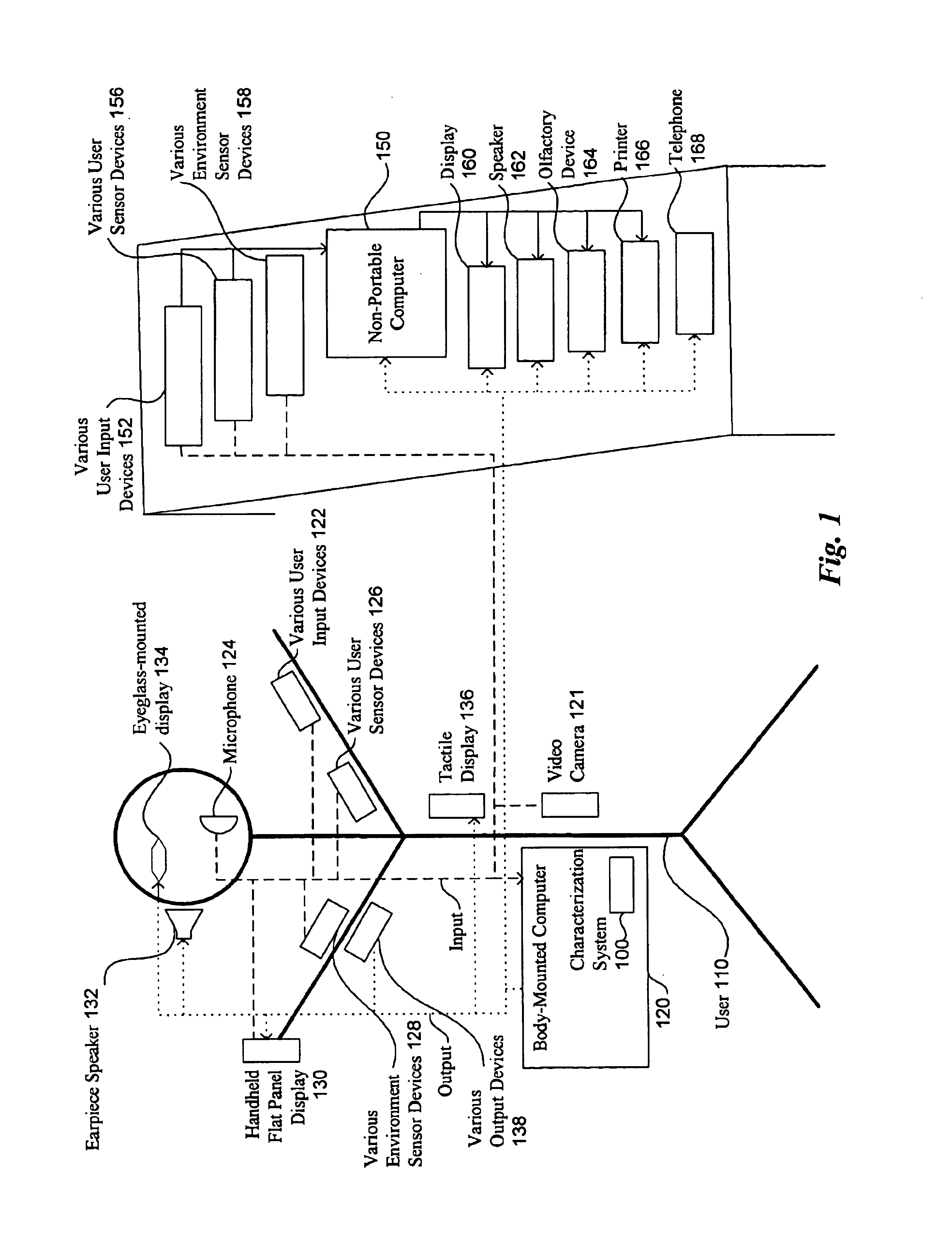
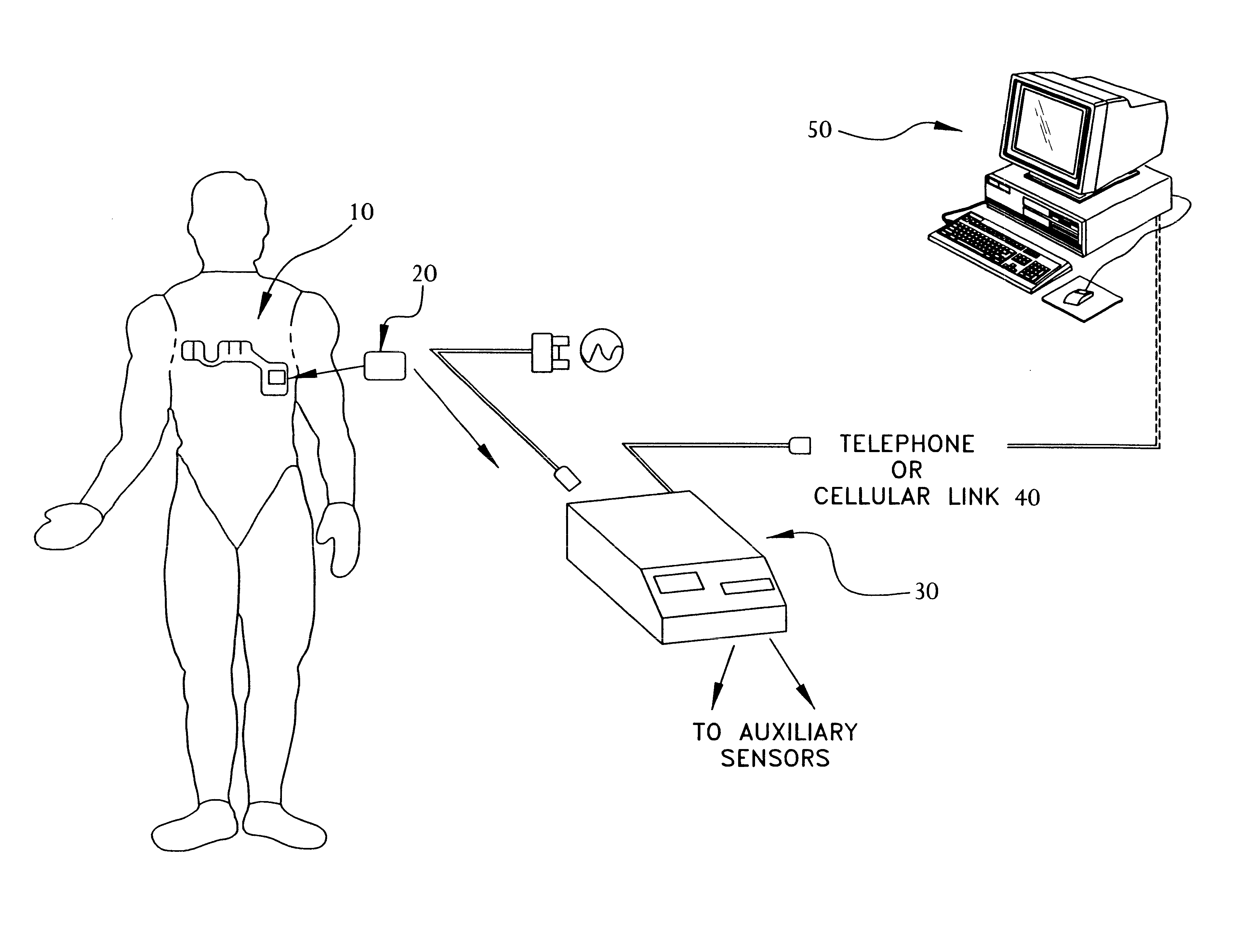
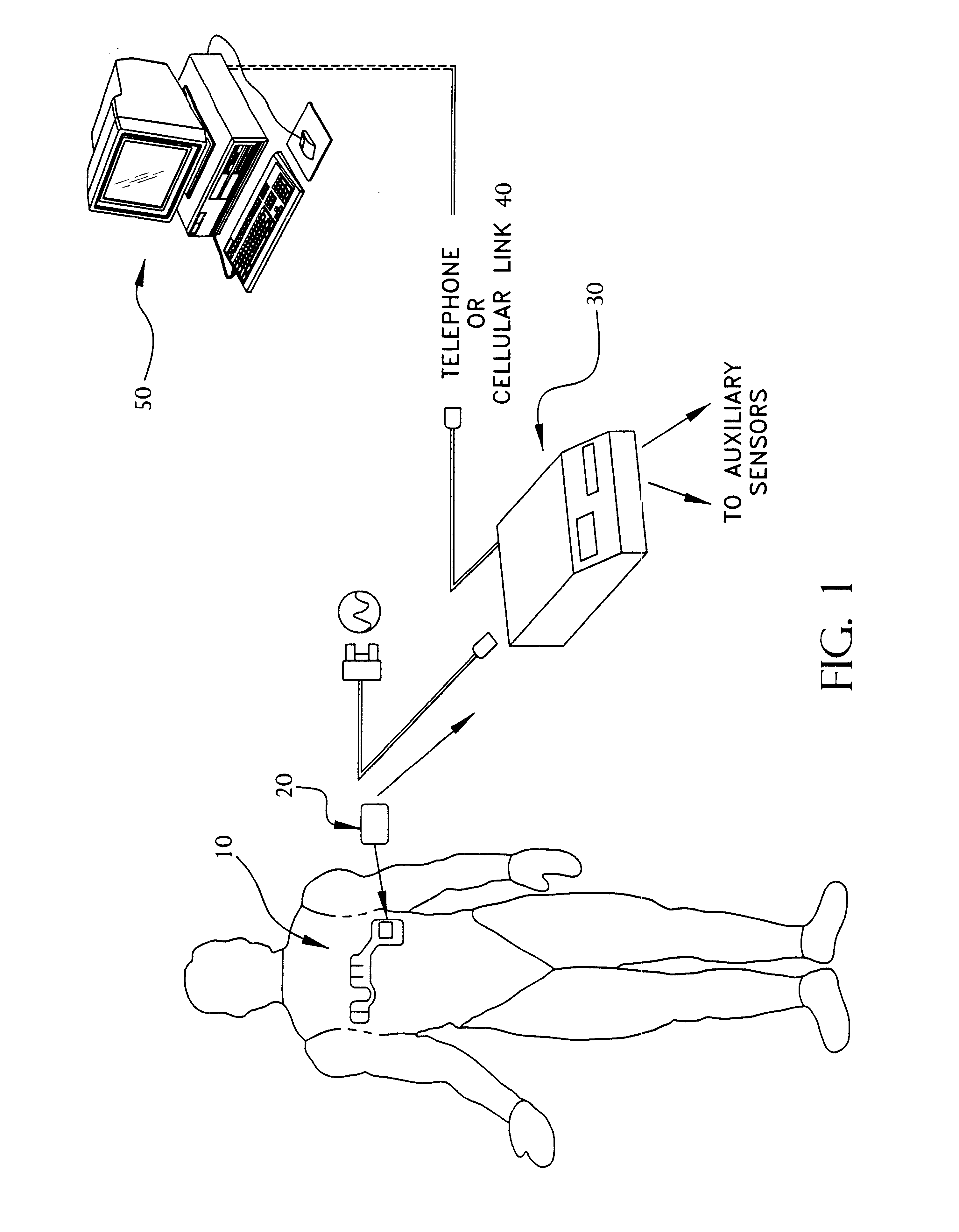
Portable remote patient telemonitoring system
A system and method for monitoring vital signs and capturing data from a patient remotely using radiotelemetry techniques. The system is characterized by a cordless, disposable sensor band with sensors form measuring full waveform ECG, full waveform respiration, skin temperature, and motion, and transmission circuitry for the detection and transmission of vital signs data of the patient. A small signal transfer unit that can either be worn by the patient, e.g., on his or her belt, or positioned nearby receives data from the sensor band, which it then forwards by e.g., radio transmission to a base station that can be located up to 60 meters away. The base station receives data transmissions from the signal transfer unit and is designed to connect to conventional phone lines for transferring the collected data to a remote monitoring station. The base station may also capture additional clinical data, such as blood pressure data, and to perform data checks. Patient safety is enhanced by the ability of the base station to compare clinical data, e.g., ECG, against given profiles and to mark events when appropriate or when the base station is programmed to do so. Such events are indicated to the physician and could be indicated to the patient by reverse transmission to the signal transfer unit. A remote monitoring station allows the presentation and review of data (including events) forwarded by the sensor band. ECG analysis software and a user-friendly graphical user interface are provided to remotely analyze the transmitted data and to permit system maintenance and upkeep. The system of the invention has useful application to the collection of patient clinical data during drug trials and medical testing for regulatory approvals as well as management of patients with chronic diseases.
Owner:CLEARPATH PARTNERS
Systems and methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS6112181AIncrease success rateCostly and inefficientUser identity/authority verificationSignalling system detailsRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
Automated generation of dynamic data entry user interface for relational database management systems
InactiveUS7062502B1Easy to navigateData processing applicationsMultiple digital computer combinationsRelational database management systemComputer software
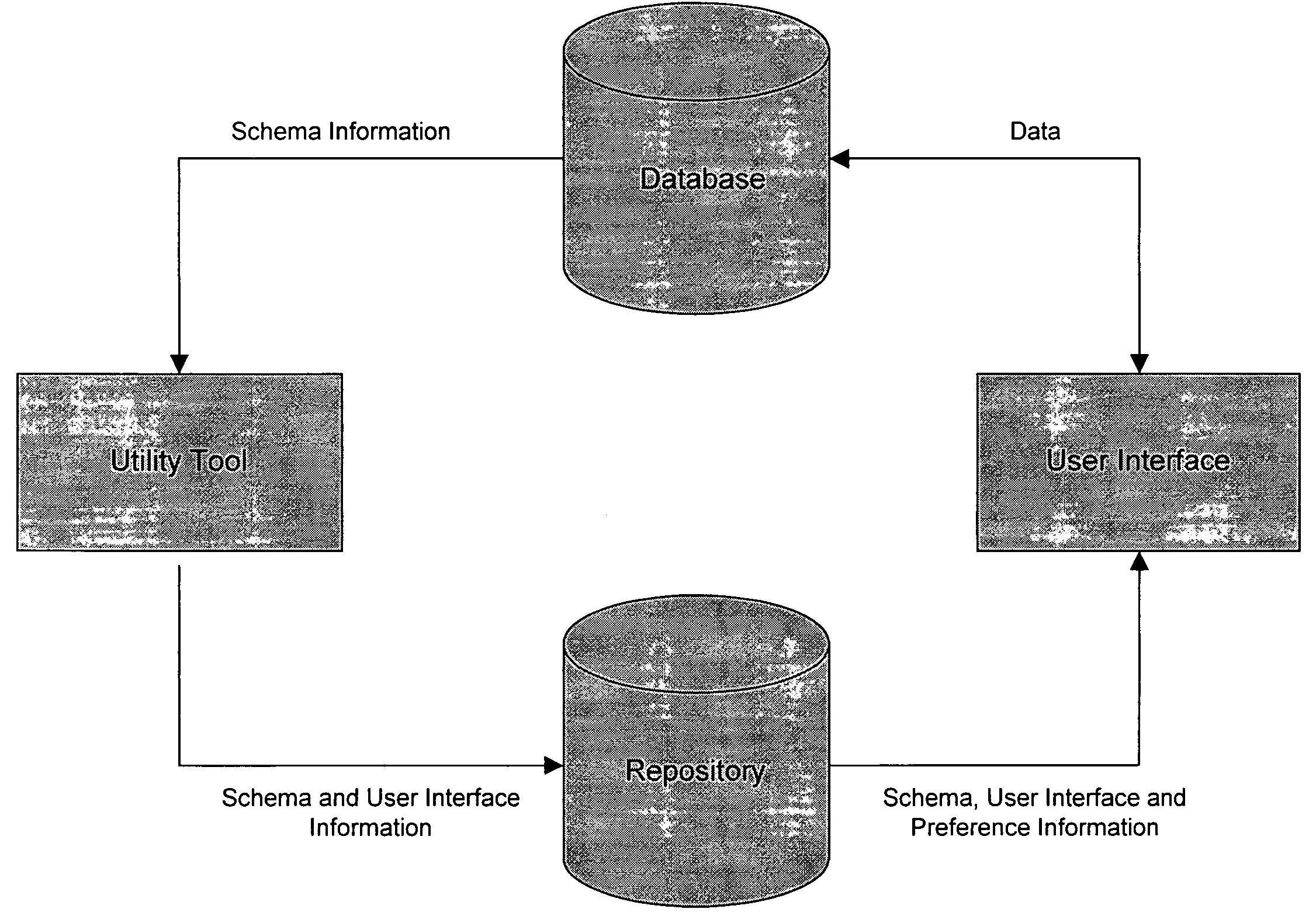
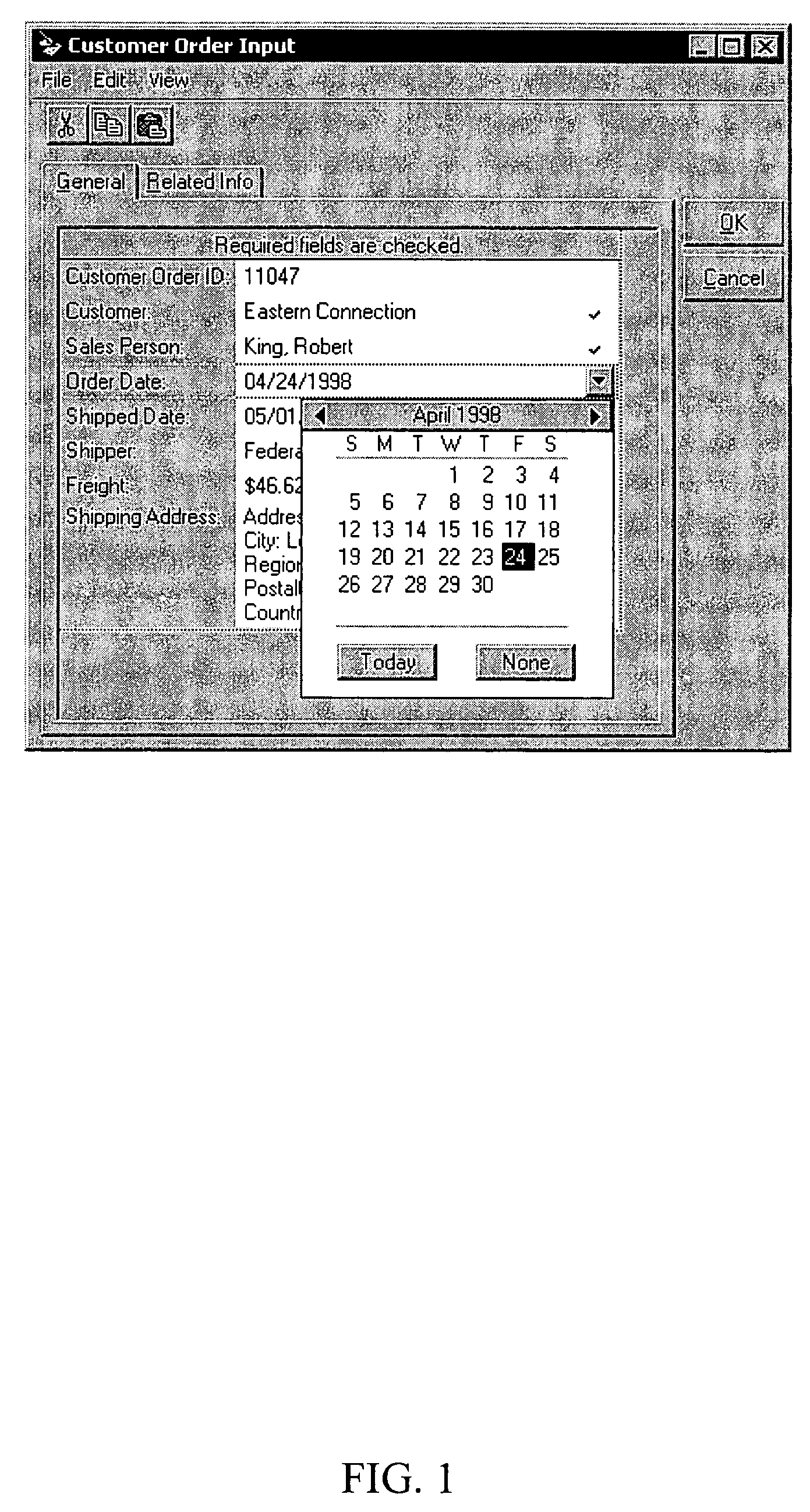
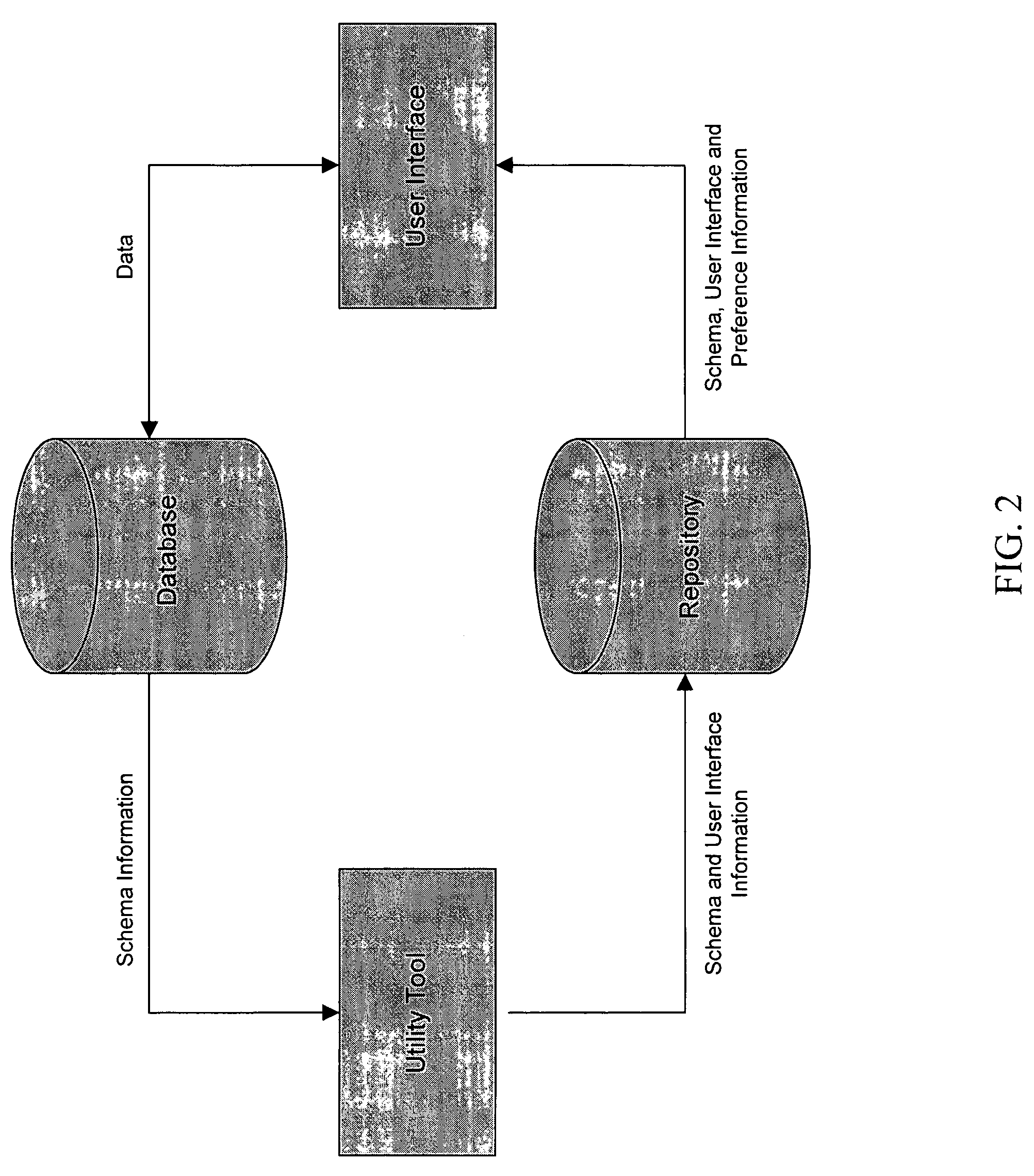
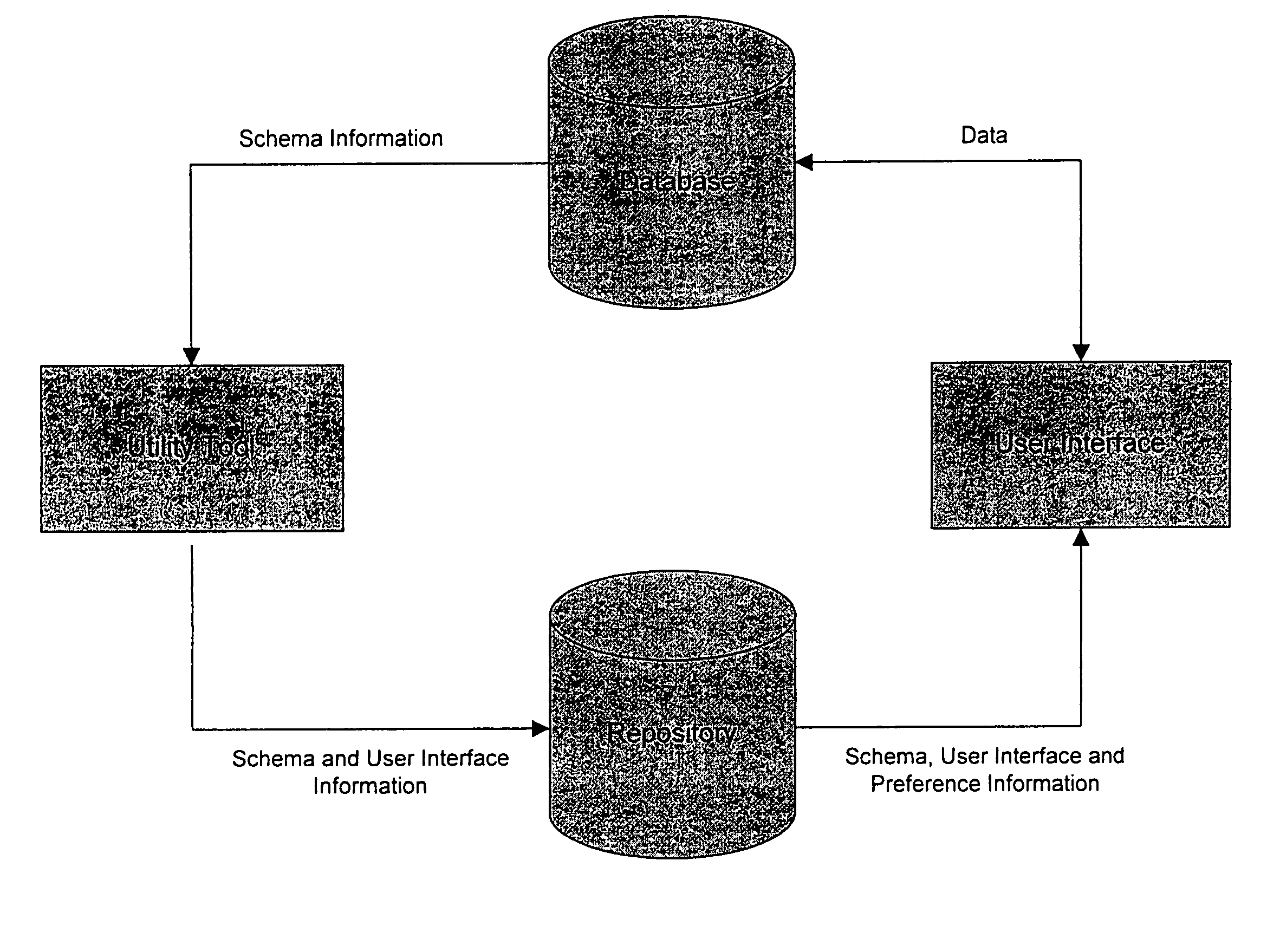
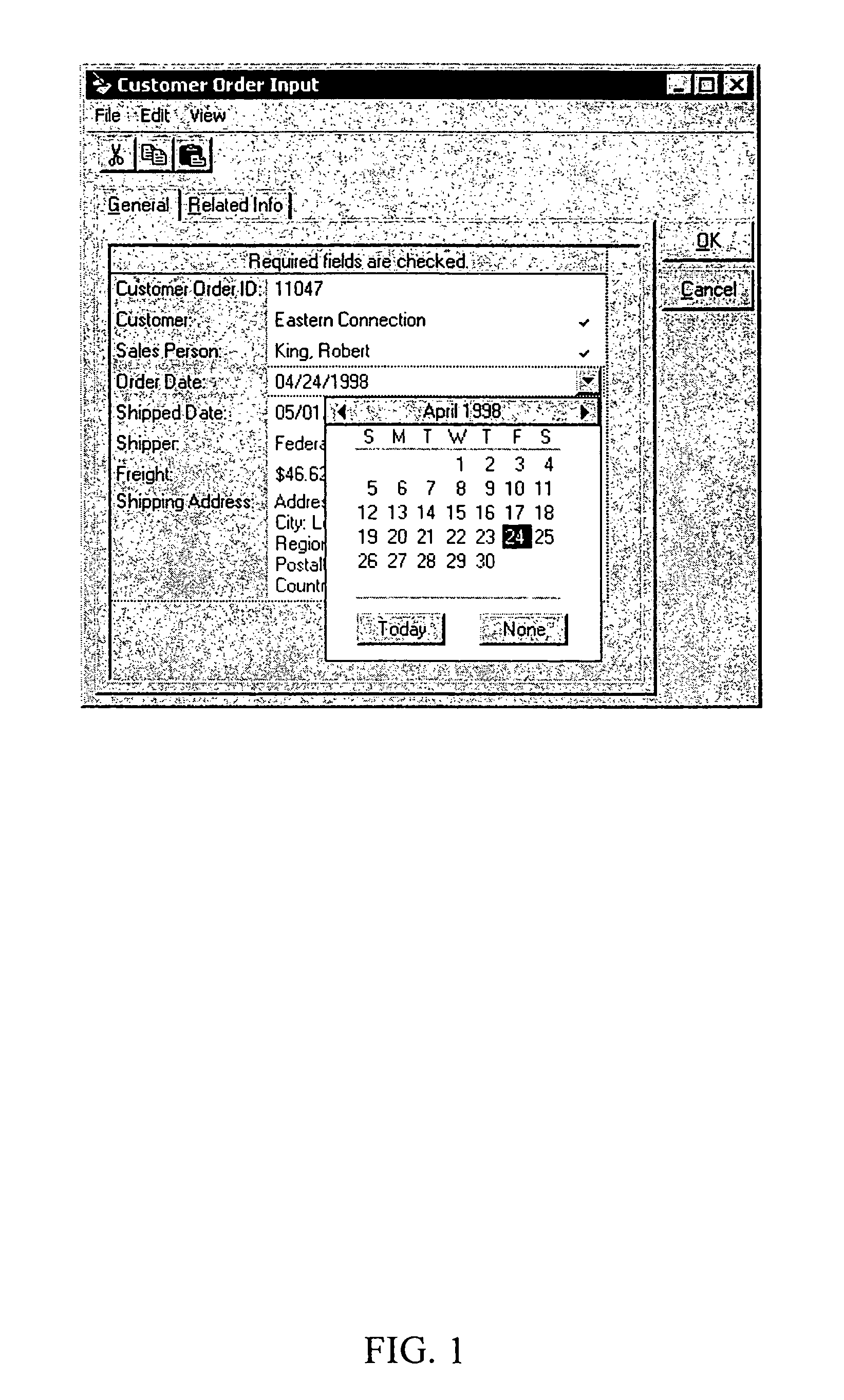
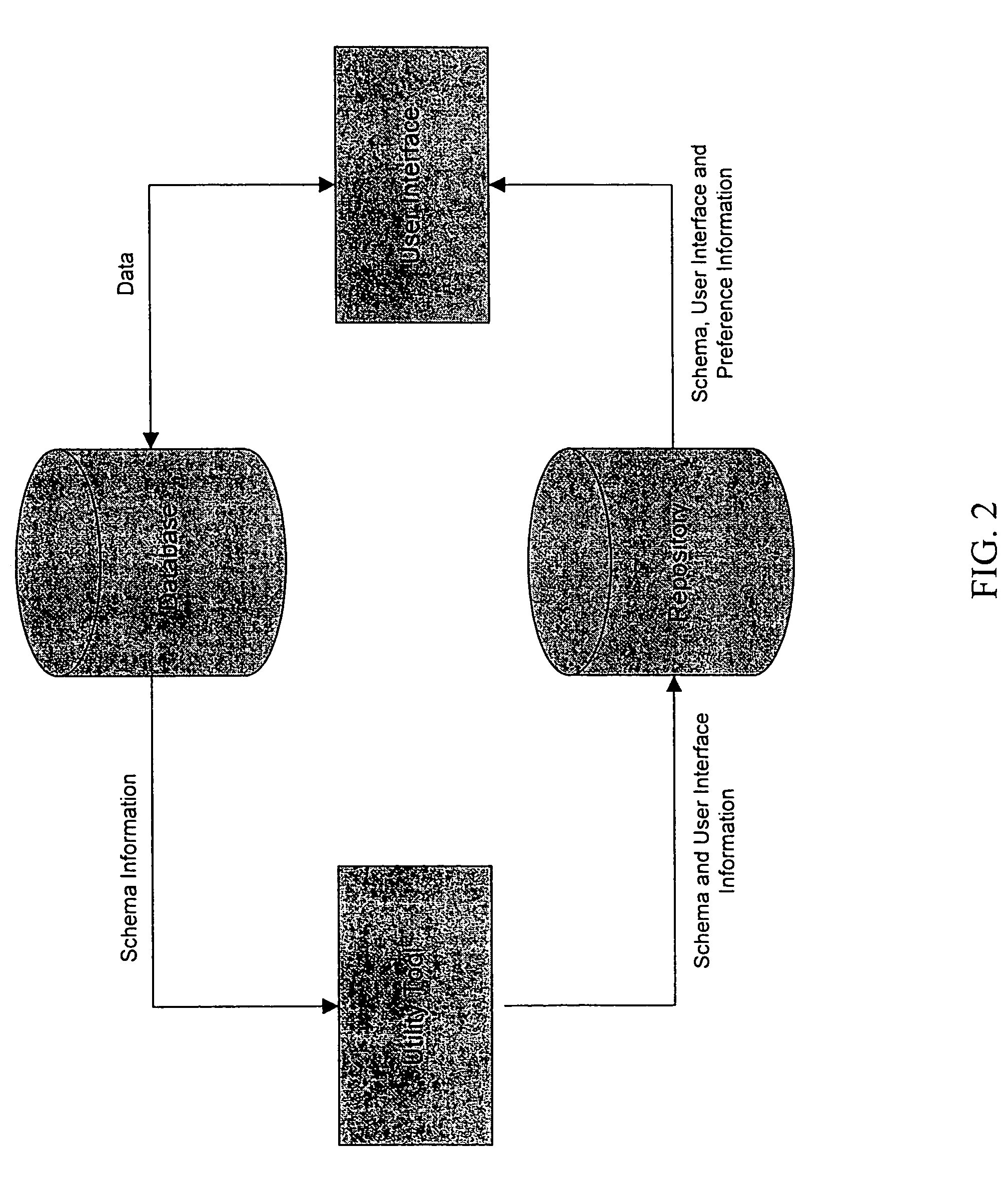
Computer software for, computer apparatus for, and a method of automatically generating a user interface for a relational database comprising extracting schema information from the relational database and automatically generating corresponding schema and user interface metadata, storing the metadata in a repository, and automatically developing from the metadata a user interface appropriate to the relational database.
Owner:ADVANCED DYNAMIC INTERFACES
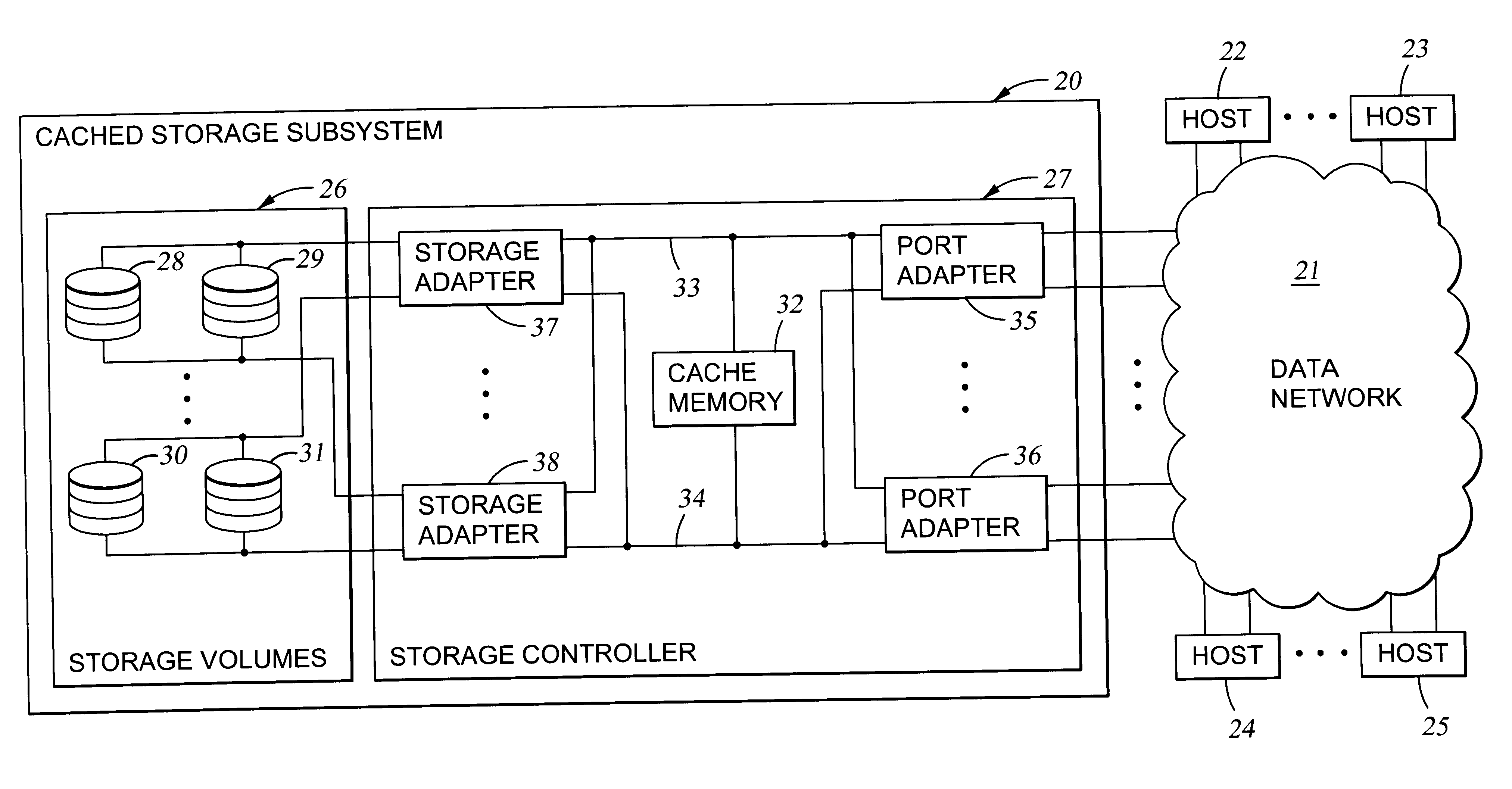
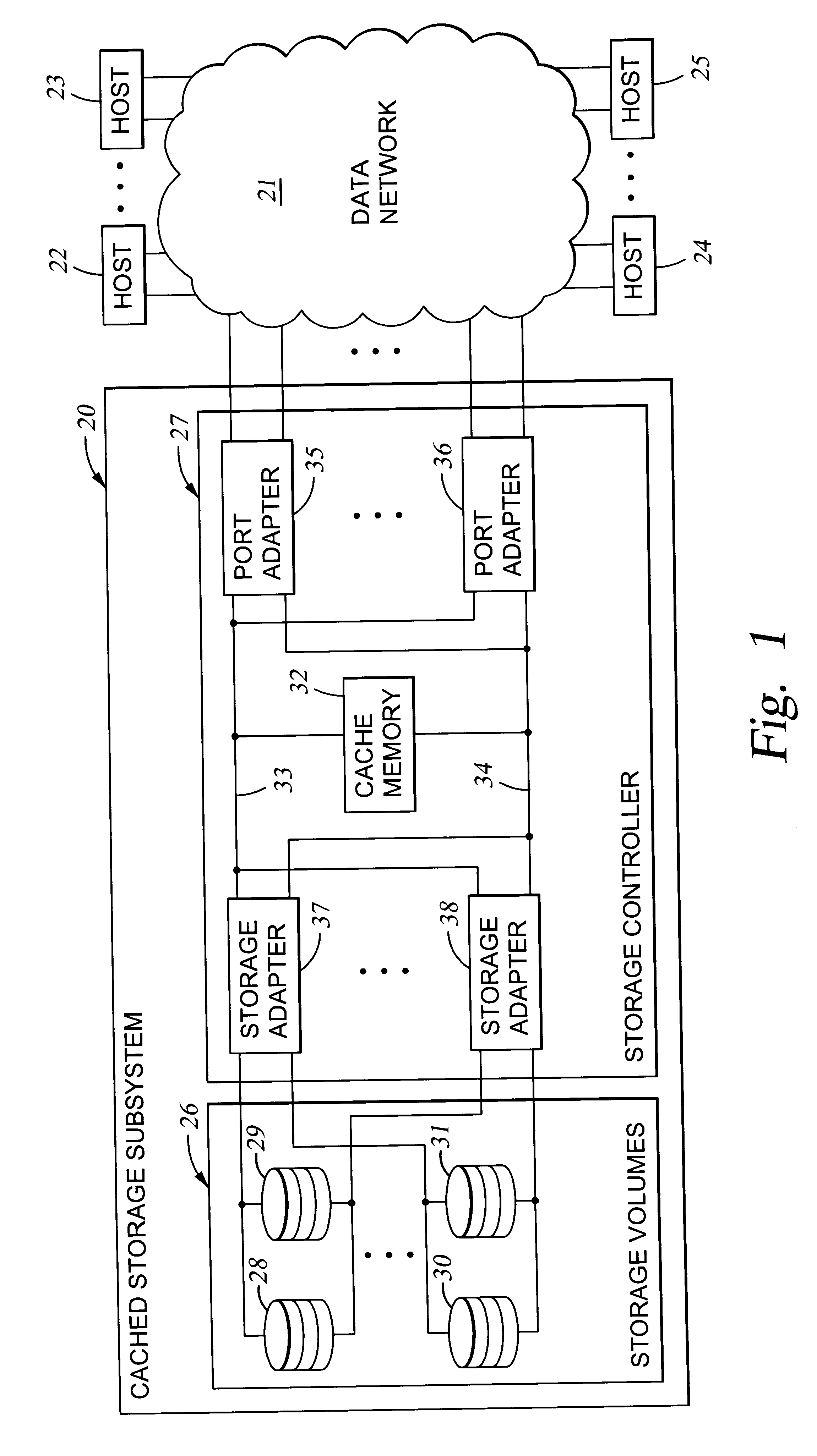
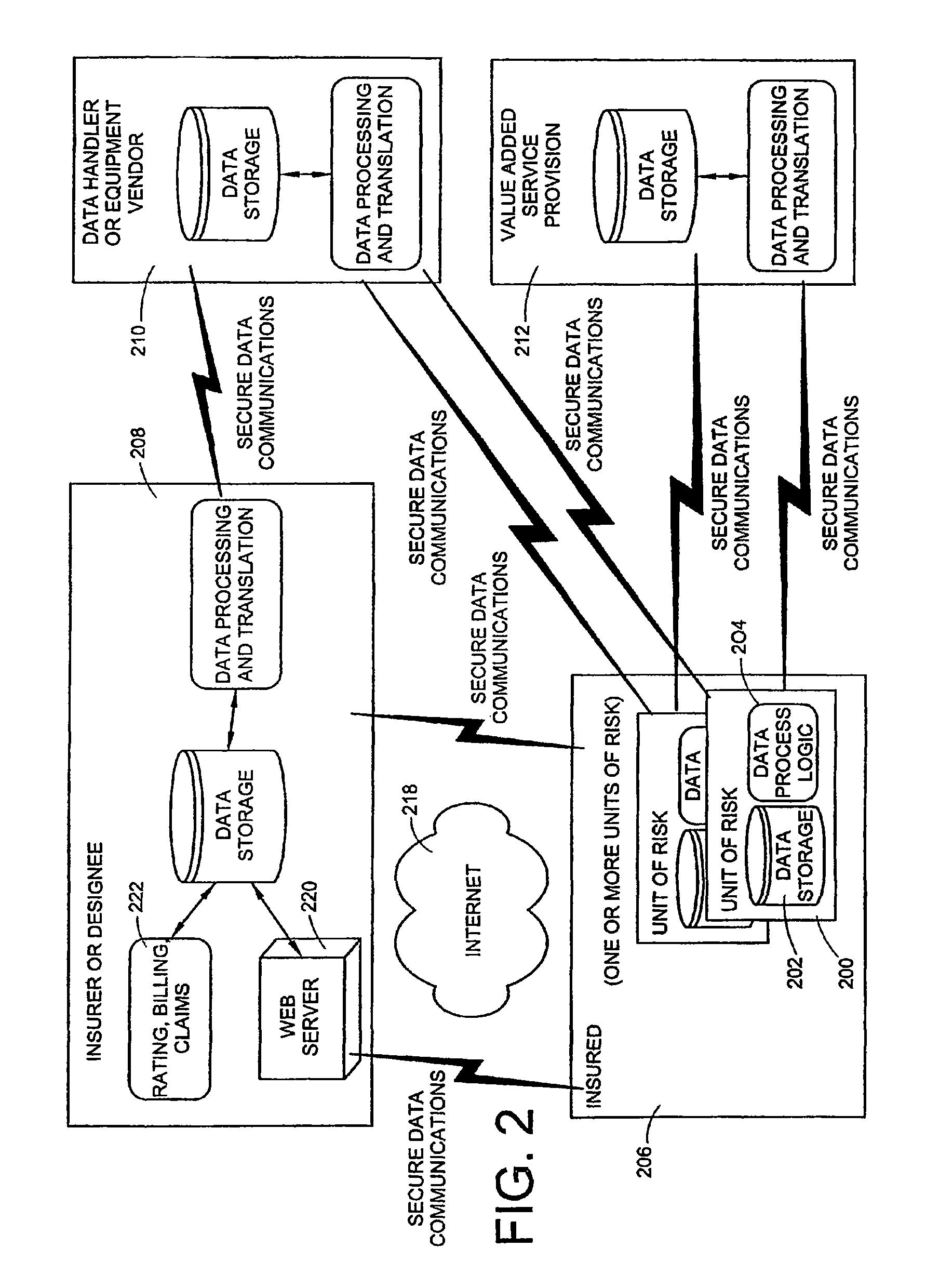
Virtual ports for data transferring of a data storage system
A storage controller has at least one physical data port for a data network including host processors. The storage controller is programmed to provide a plurality of virtual ports for access to storage, and a virtual switch for routing storage access requests from the physical port to the virtual ports. The virtual ports and the virtual switch are defined by software. The virtual ports appear to the hosts as physical ports in the data network. For example, in a Fiber-Channel network, the virtual ports have World Wide Names (WWNs) and are assigned temporary addresses (S_Ds), and the virtual switch provides a name server identifying the WWNs and S_IDs of the virtual ports. For convenient partitioning of storage among host processors, one or more virtual ports are assigned to each host, and a set of storage volumes are made accessible from each virtual port. A host can access storage at a virtual port only if the virtual port has been assigned to the host. Preferably, storage can be accessed through each virtual port by no more than one assigned host, although a shared volume may be accessible from more than one virtual port. The storage controller may provide a service for reporting to a host the virtual ports through which the host can access storage, and the storage volumes that are accessible to the host through each of the virtual ports.
Owner:EMC IP HLDG CO LLC
Multi-dimensional data protection and mirroring method for micro level data
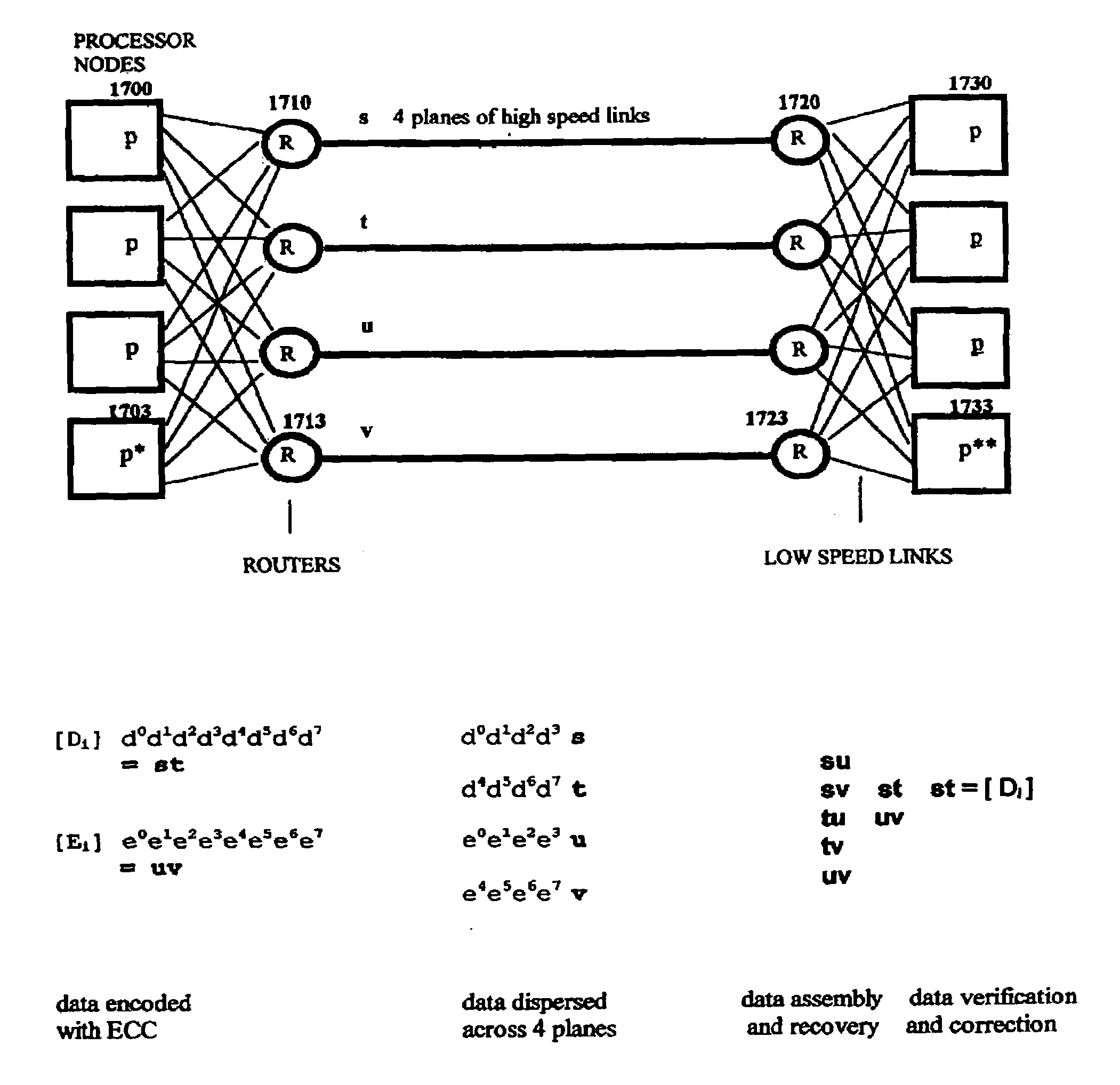
ActiveUS7103824B2Detection errorLow common data sizeCode conversionCyclic codesData validationData integrity
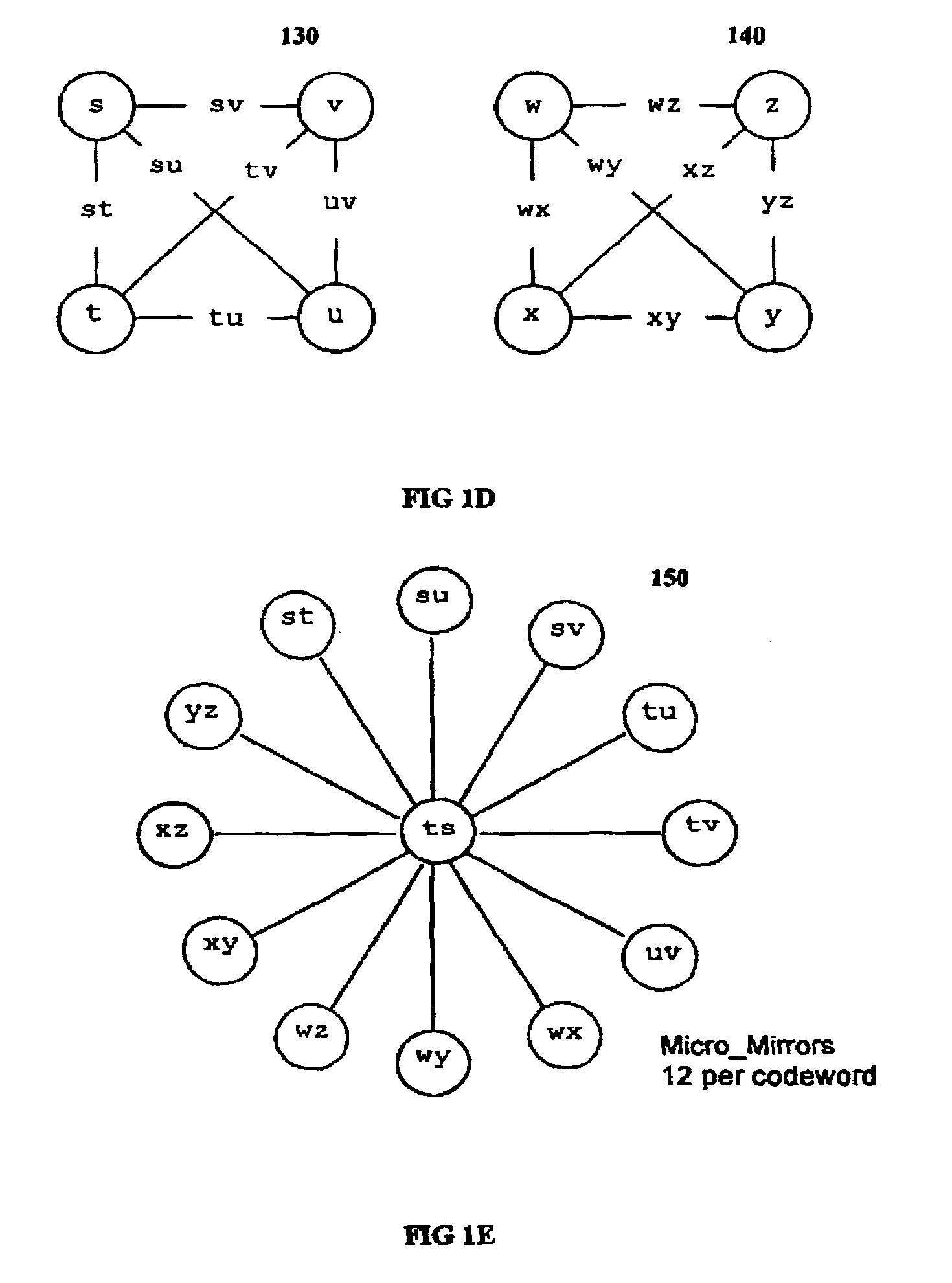
The invention discloses a data validation, mirroring and error / erasure correction method for the dispersal and protection of one and two-dimensional data at the micro level for computer, communication and storage systems. Each of 256 possible 8-bit data bytes are mirrored with a unique 8-bit ECC byte. The ECC enables 8-bit burst and 4-bit random error detection plus 2-bit random error correction for each encoded data byte. With the data byte and ECC byte configured into a 4 bit×4 bit codeword array and dispersed in either row, column or both dimensions the method can perform dual 4-bit row and column erasure recovery. It is shown that for each codeword there are 12 possible combinations of row and column elements called couplets capable of mirroring the data byte. These byte level micro-mirrors outperform conventional mirroring in that each byte and its ECC mirror can self-detect and self-correct random errors and can recover all dual erasure combinations over four elements. Encoding at the byte quanta level maximizes application flexibility. Also disclosed are fast encode, decode and reconstruction methods via boolean logic, processor instructions and software table look-up with the intent to run at line and application speeds. The new error control method can augment ARQ algorithms and bring resiliency to system fabrics including routers and links previously limited to the recovery of transient errors. Image storage and storage over arrays of static devices can benefit from the two-dimensional capabilities. Applications with critical data integrity requirements can utilize the method for end-to-end protection and validation. An extra ECC byte per codeword extends both the resiliency and dimensionality.
Owner:HALFORD ROBERT
Automated generation of dynamic data entry user interface for relational database management systems
InactiveUS7401094B1Easy to navigateData processing applicationsDigital data processing detailsRelational database management systemComputer software
Owner:ADVANCED DYNAMIC INTERFACES
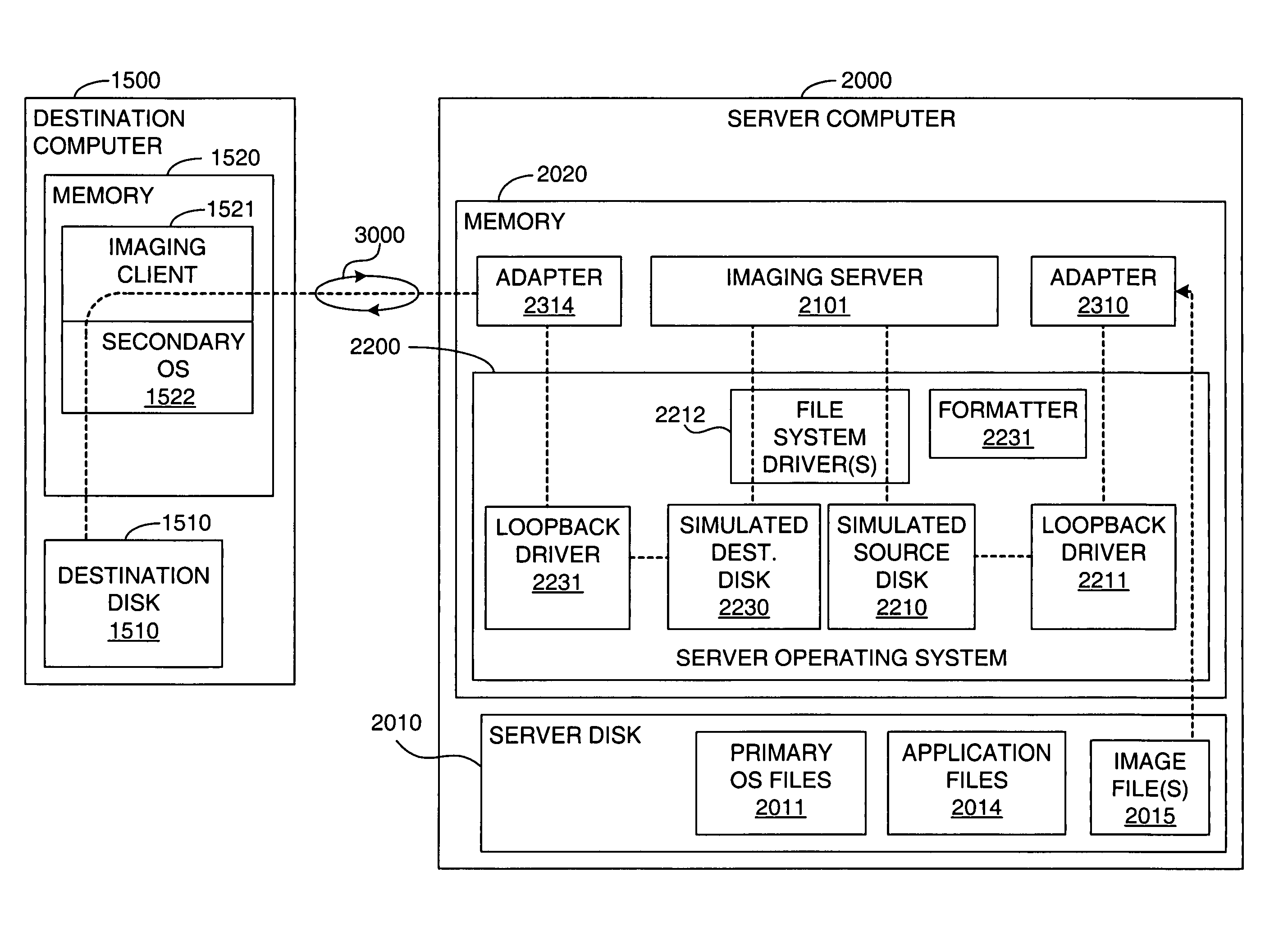
Computer image capture, customization and deployment
ActiveUS7356679B1Increased riskDigital computer detailsProgram loading/initiatingVirtual machineSoftware
Owner:VMWARE INC
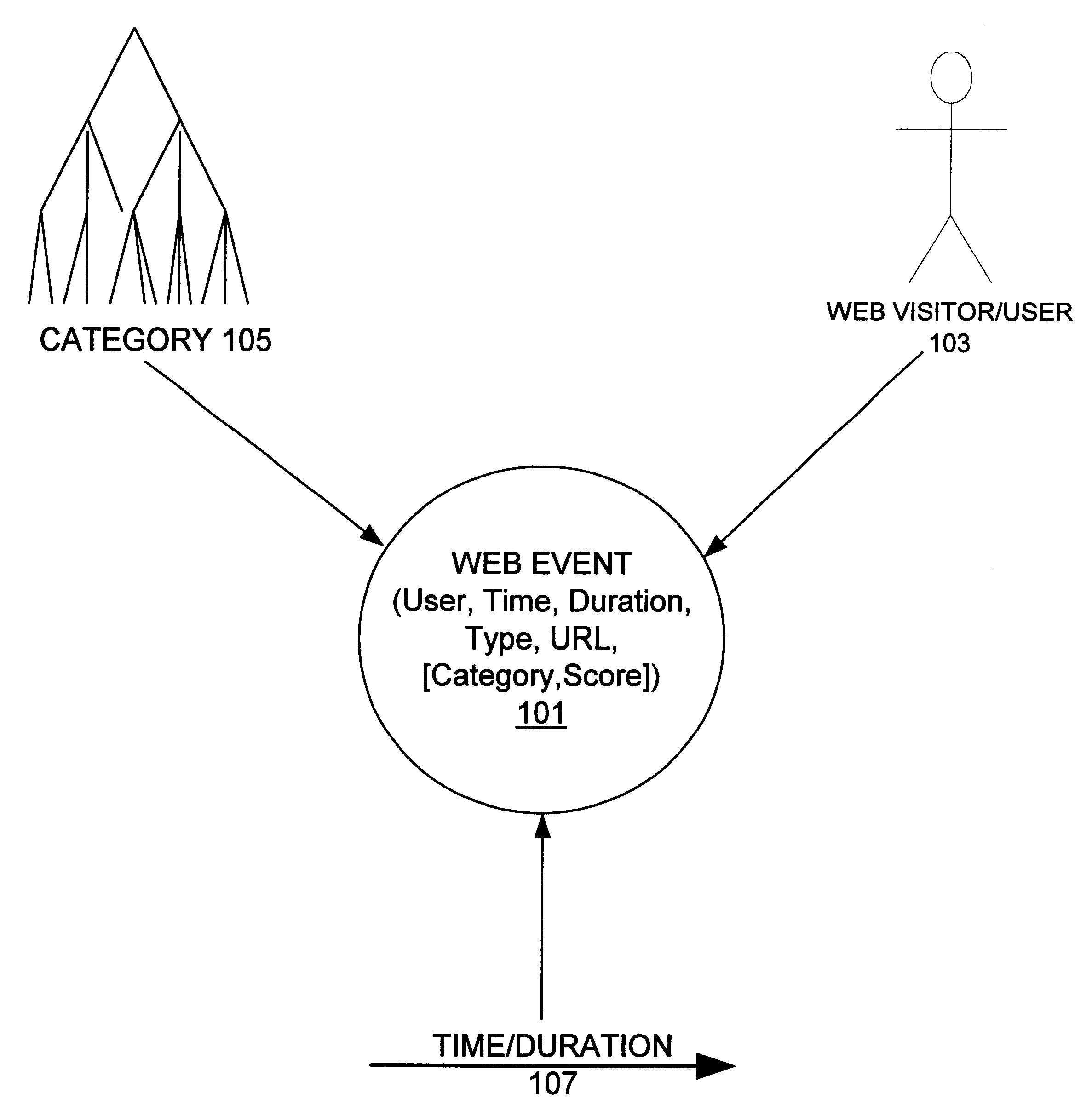
Internet profiling
InactiveUS6839680B1Quick applicationEasy to shareMarket predictionsSpecial data processing applicationsWeb serviceStandardization
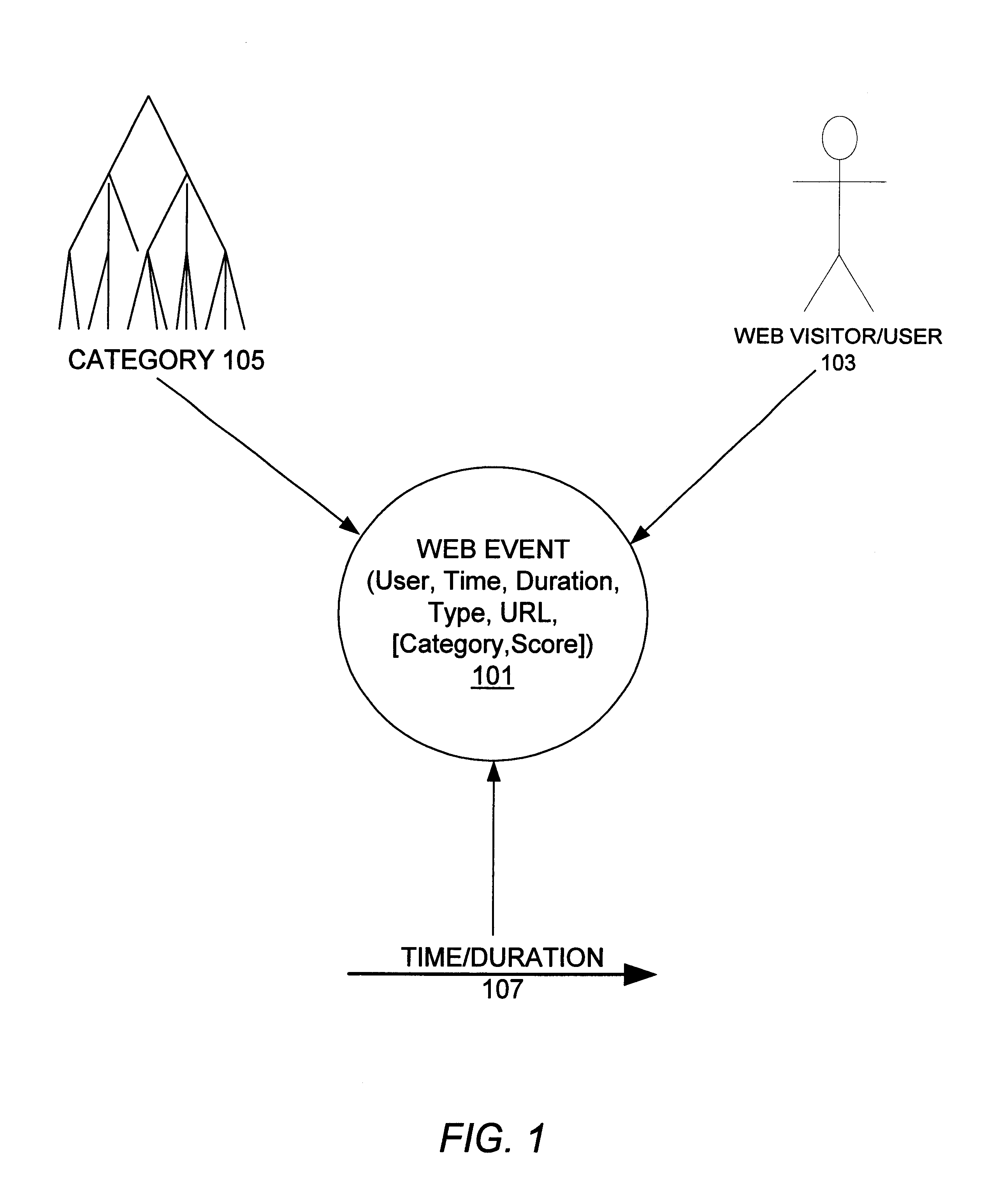
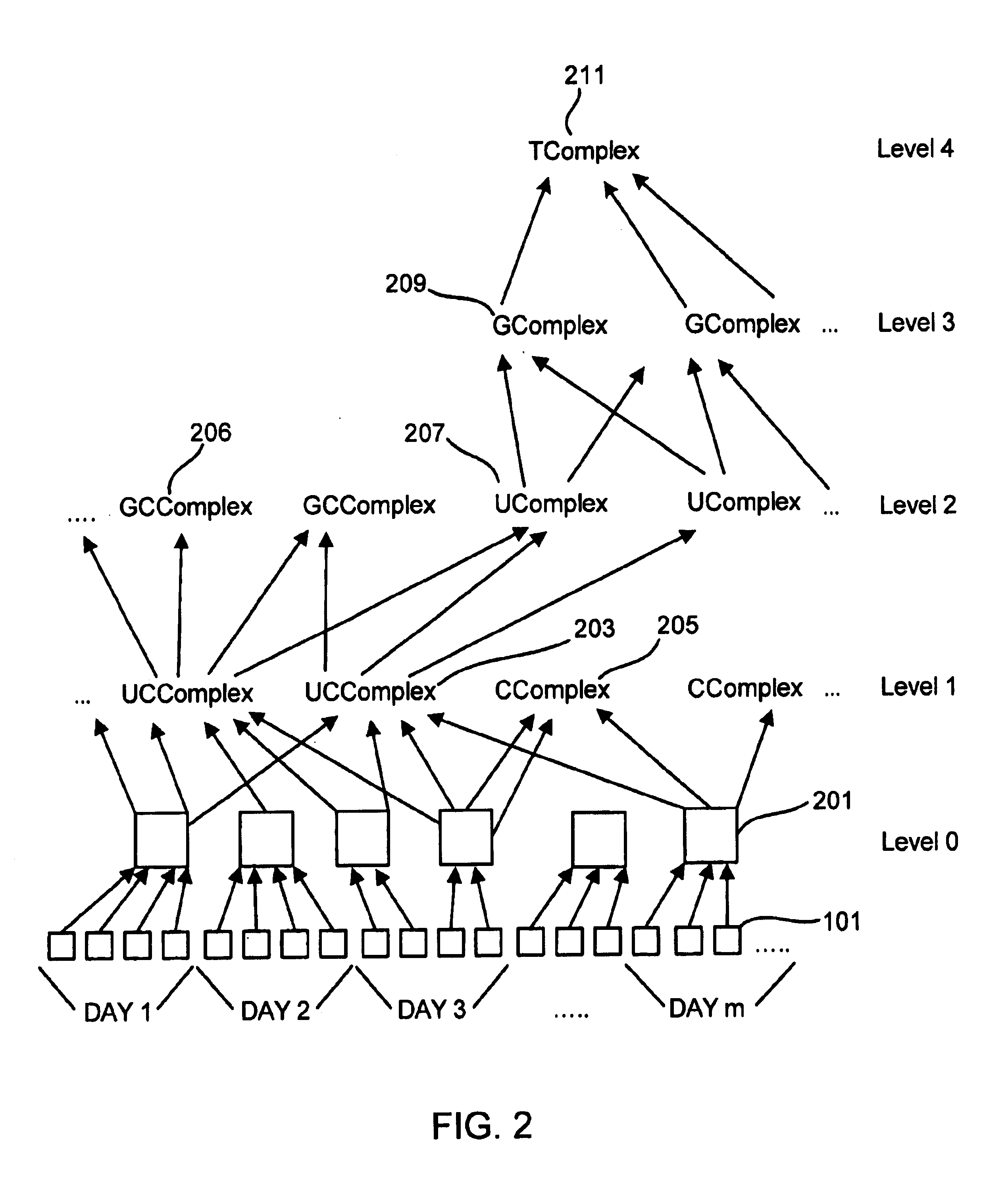
A system, method, and various software products provide for consistent identification of web users across multiple web sites, servers and domains, monitoring and capture of data describing the users' web activities, categorization of the web activity data, aggregation of the data into time dependent models describing interest of users and groups over time. Categorization is made with respect to a category tree which may be standardized or customized for each web site. User groups may be defined based on membership rules for category interest information and demographics. Individual user profiles are then created for users automatically based on satisfaction of the user group membership rules. As new data is collected on a user over time, the category interest information extracted from the user's web activity is updated to form a current model of the user's interests relative to the various categories. This information is also used to automatically update group membership and user profile information. Identification of users across multiple sites is provided by a global service that recognizes each user and provides a globally unique identifier to a requesting web server, which can use the identifier to accumulate activity data for the user. Client side user identification is provided to track user activity data on web servers that do not communicate with the global service and do not process activity for category information. User profiles may be shared among web sites that form alliances. User activity data may be aggregated along various dimensions including users / user groups, categorization, and time to provide robust models of interest at any desired time scale.
Owner:FUJITSU LTD
Methods and systems for monitoring user, application or device activity
InactiveUS20050183143A1Improve securityMemory loss protectionUnauthorized memory use protectionWorking environmentComputer usage
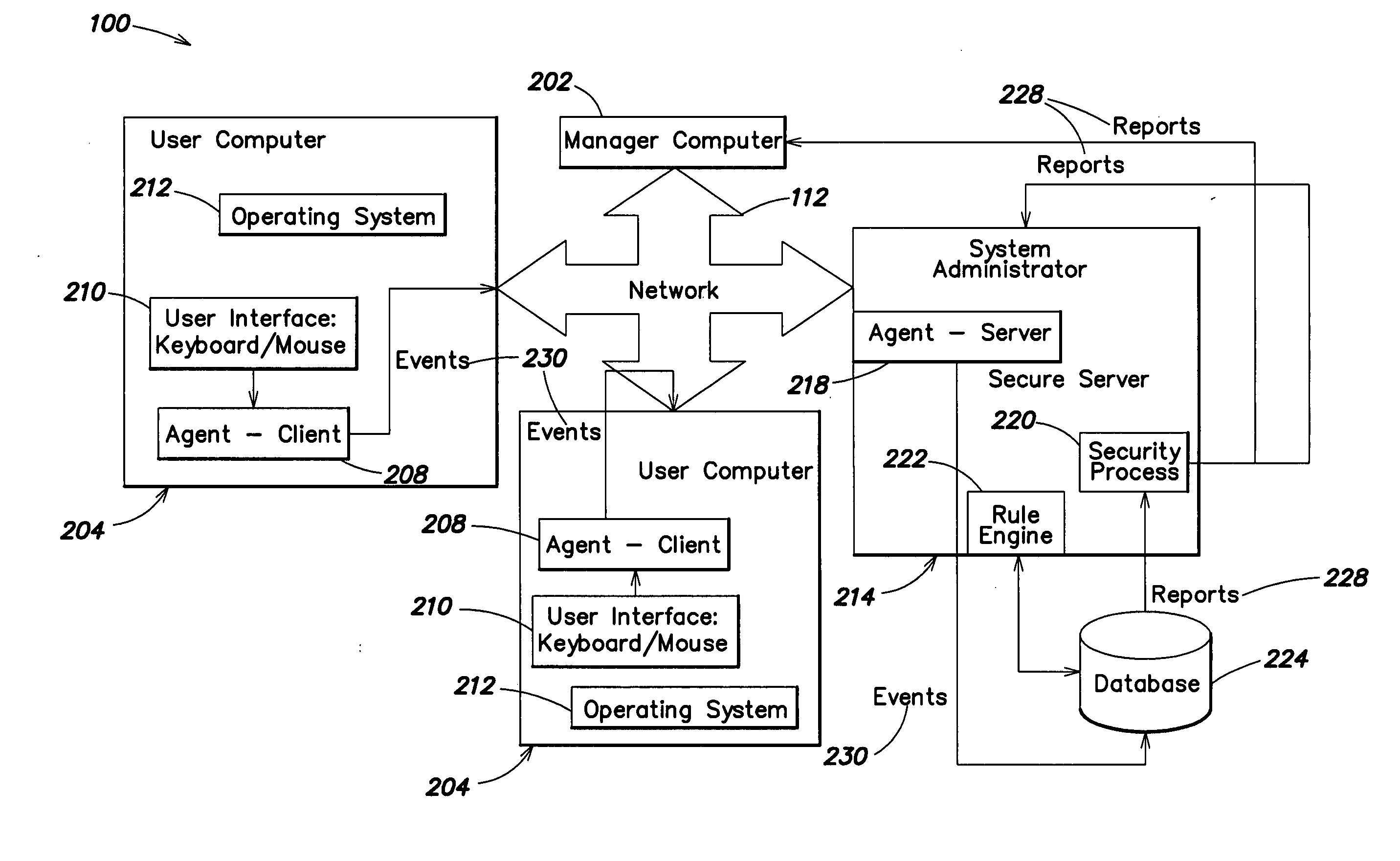
Methods and systems are provided for capturing usage data from a user computer, processing a subset of such data to form output, and offering access to selective views of such output, such as to assist a company's management in monitoring computer usage in a work environment. The output may be processed and viewed according to software application, device, or specified user. The output, or a report generated therefrom, may be accessible in differing degrees to individuals having appropriate levels of permission.
Owner:SERGEANT LAB
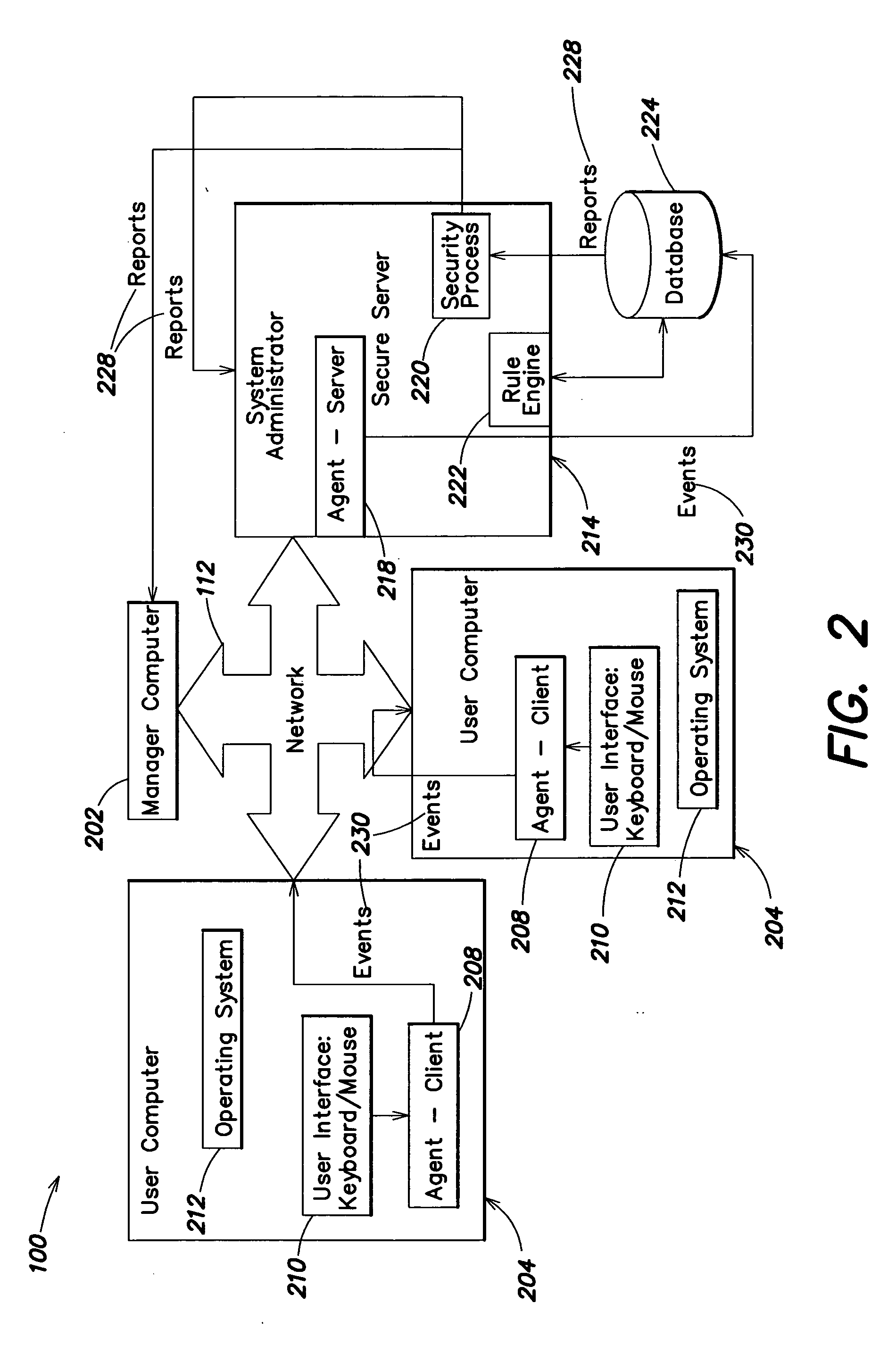
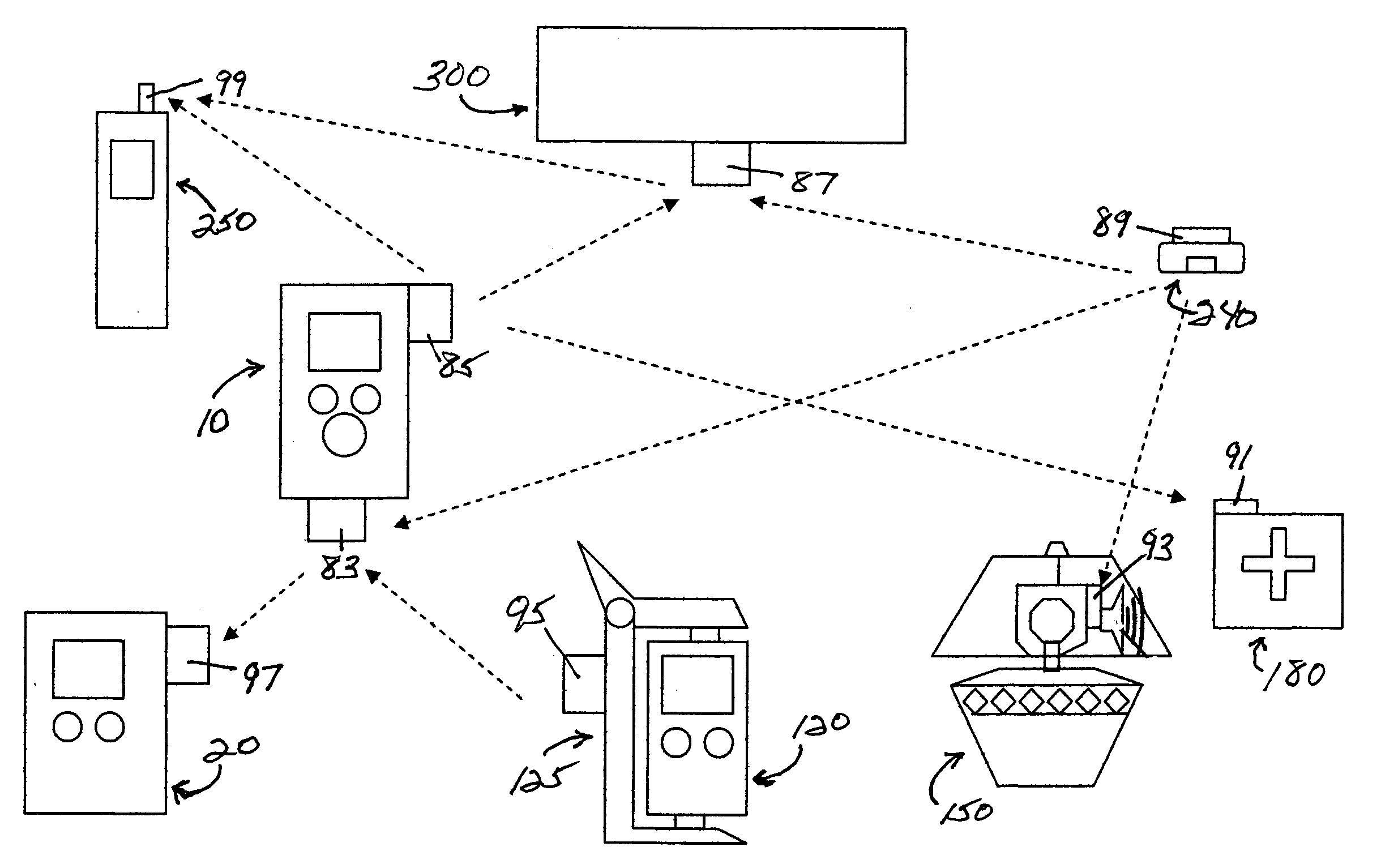
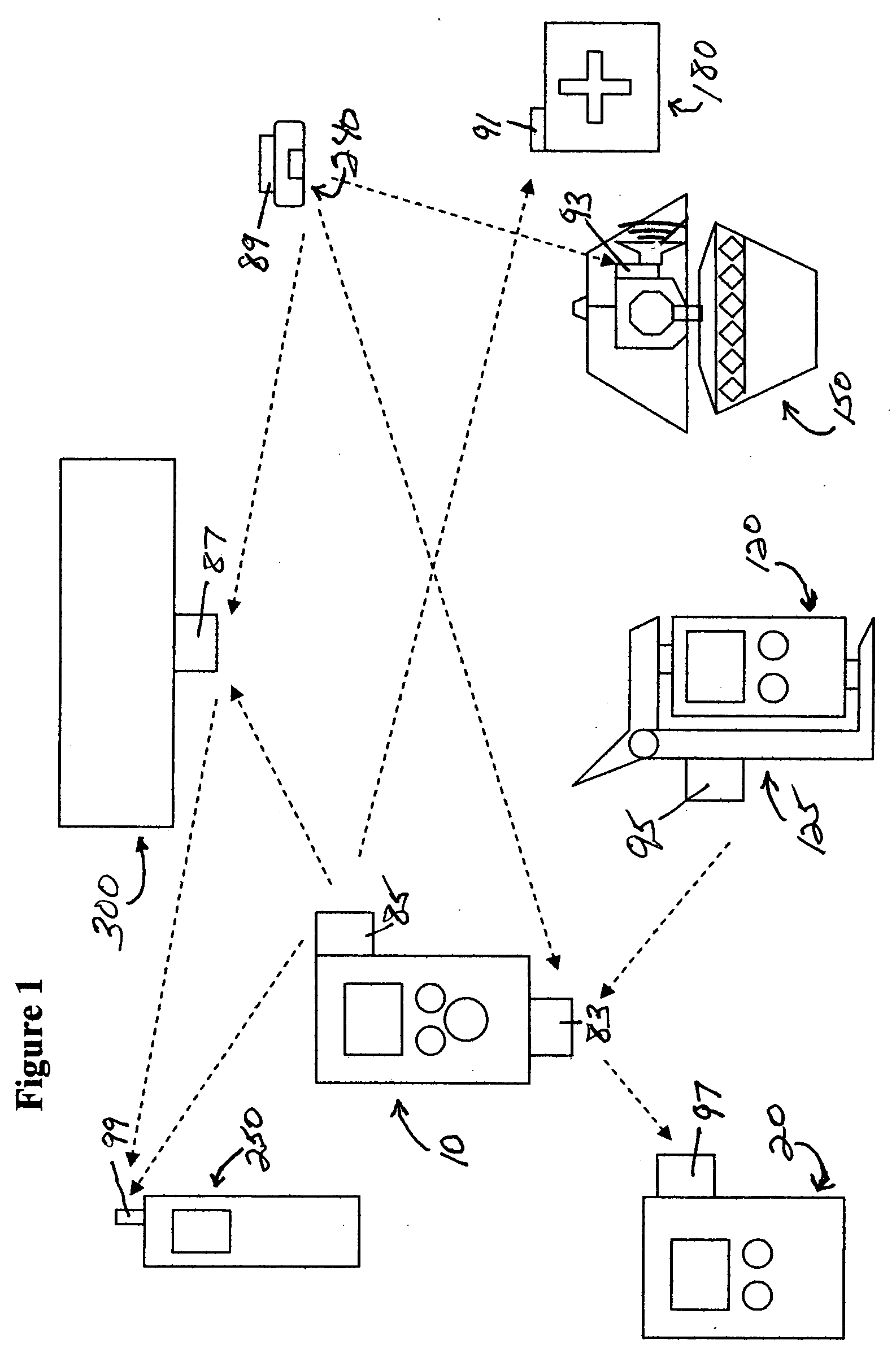
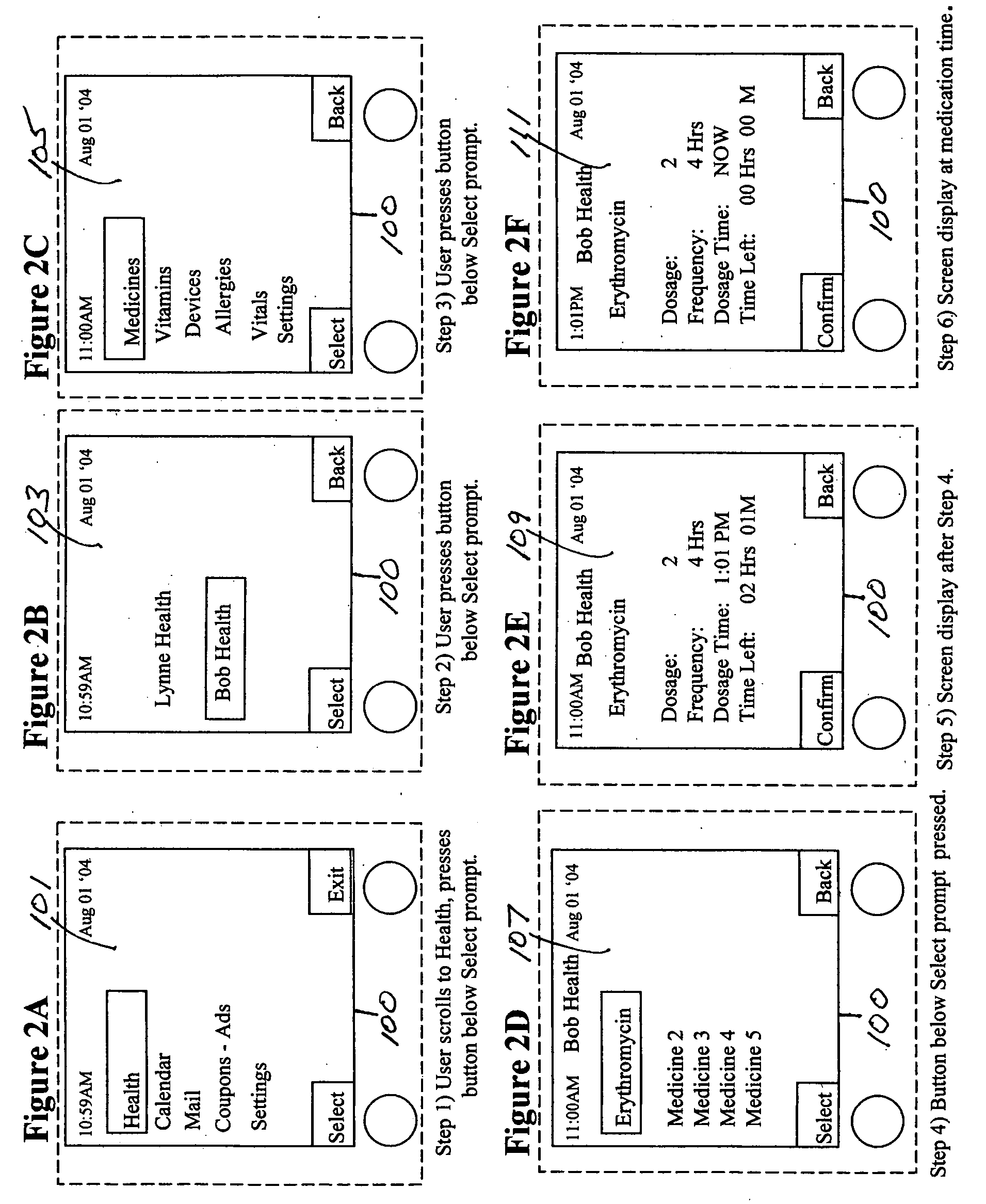
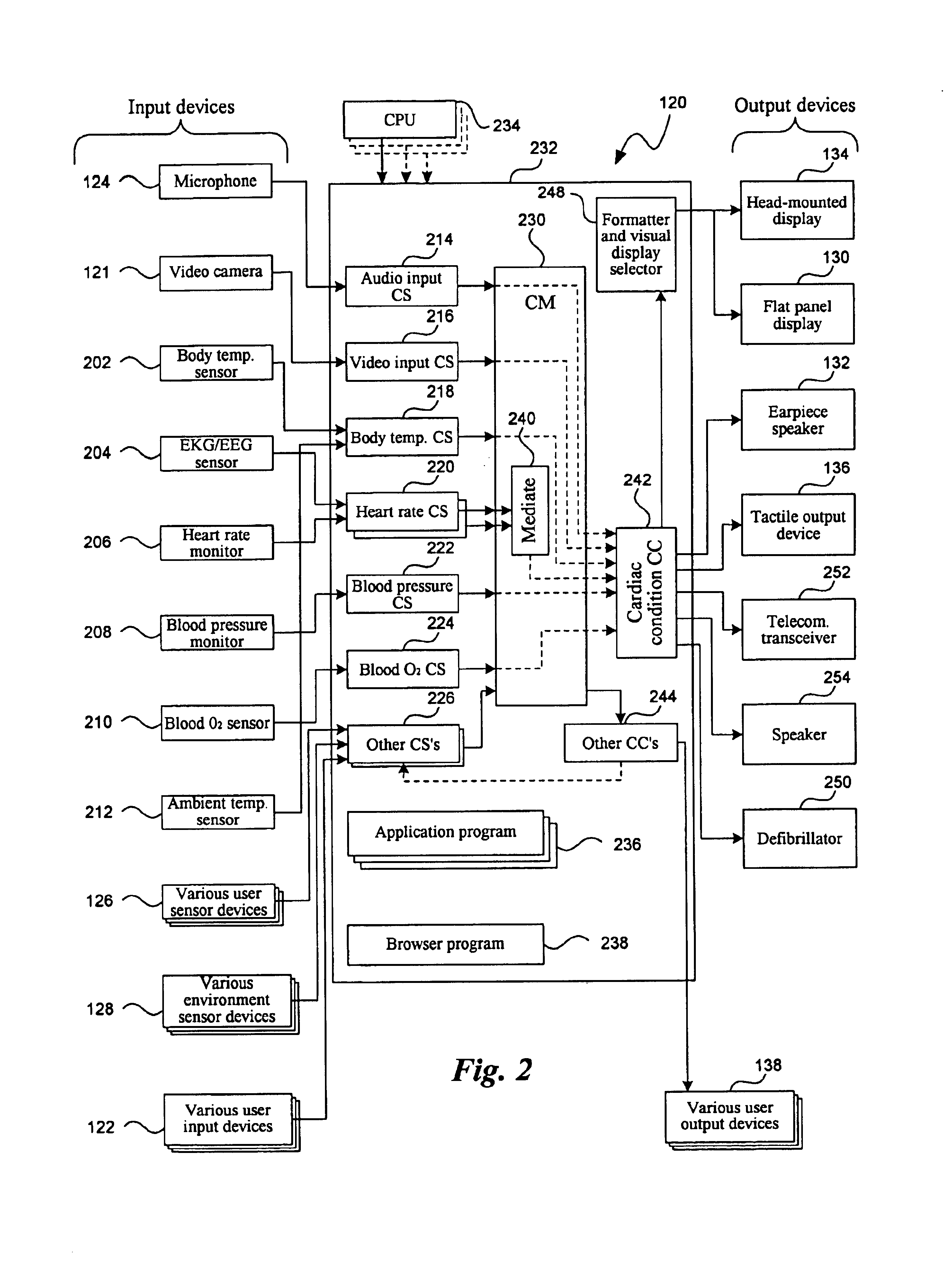
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
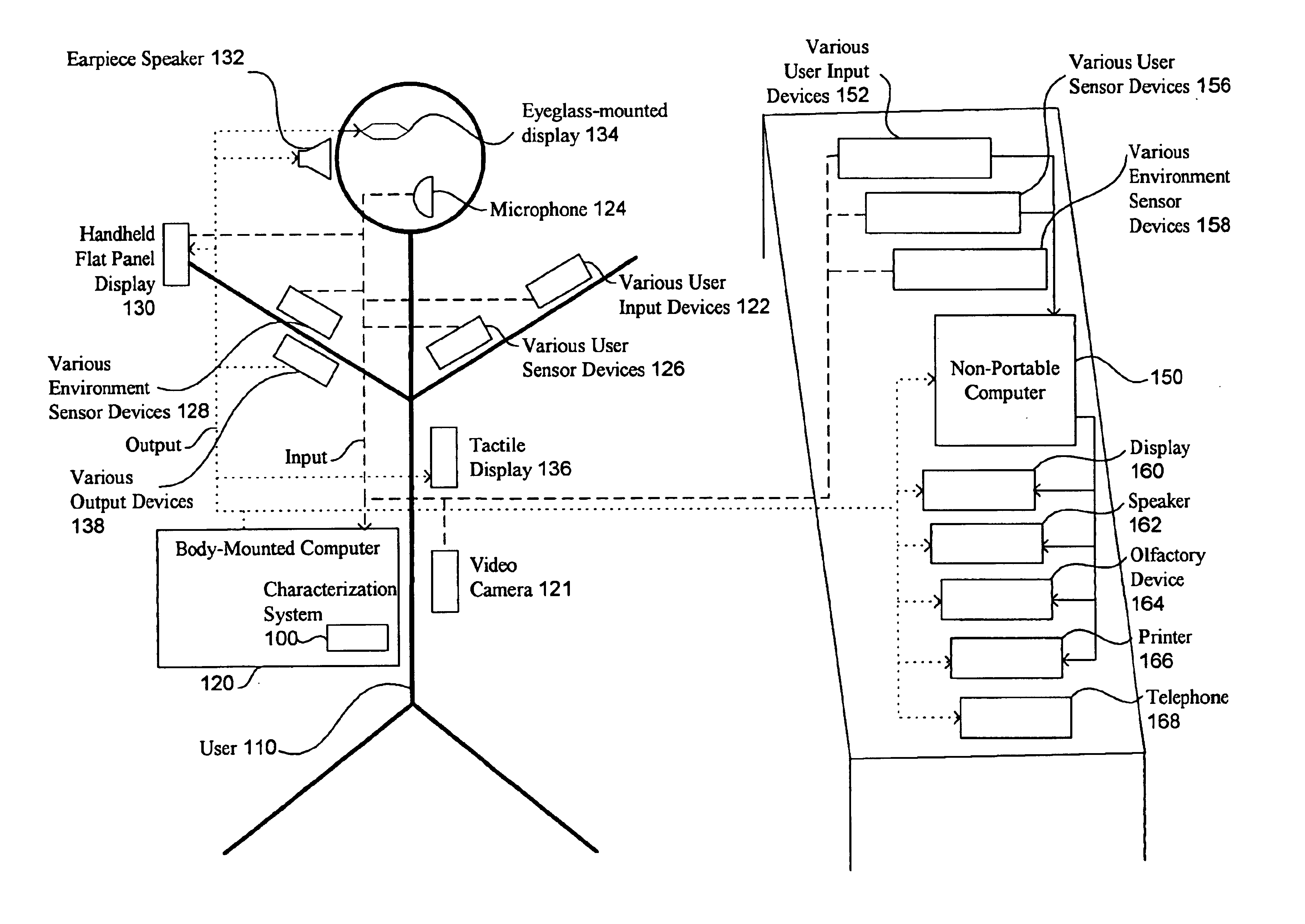
Microprocessor controlled ambulatory medical apparatus with hand held communication device
InactiveUS6873268B2Enhance user interfaceReduce system sizeEnergy efficient ICTElectrotherapyDrugs infusionHand held
An implantable infusion pump possesses operational functionality that is, at least in part, controlled by software operating in two processor ICs which are configured to perform some different and some duplicate functions. The pump exchanges messages with an external device via telemetry. Each processor controls a different part of the drug infusion mechanism such that both processors must agree on the appropriateness of drug delivery for infusion to occur. Delivery accumulators are incremented and decremented with delivery requests and with deliveries made. When accumulated amounts reach or exceed, quantized deliverable amounts, infusion is made to occur. The accumulators are capable of being incremented by two or more independent types of delivery requests. Operational modes of the infusion device are changed automatically in view of various system errors that are trapped, various system alarm conditions that are detected, and when excess periods of time lapse between pump and external device interactions.
Owner:MEDTRONIC MIMIMED INC
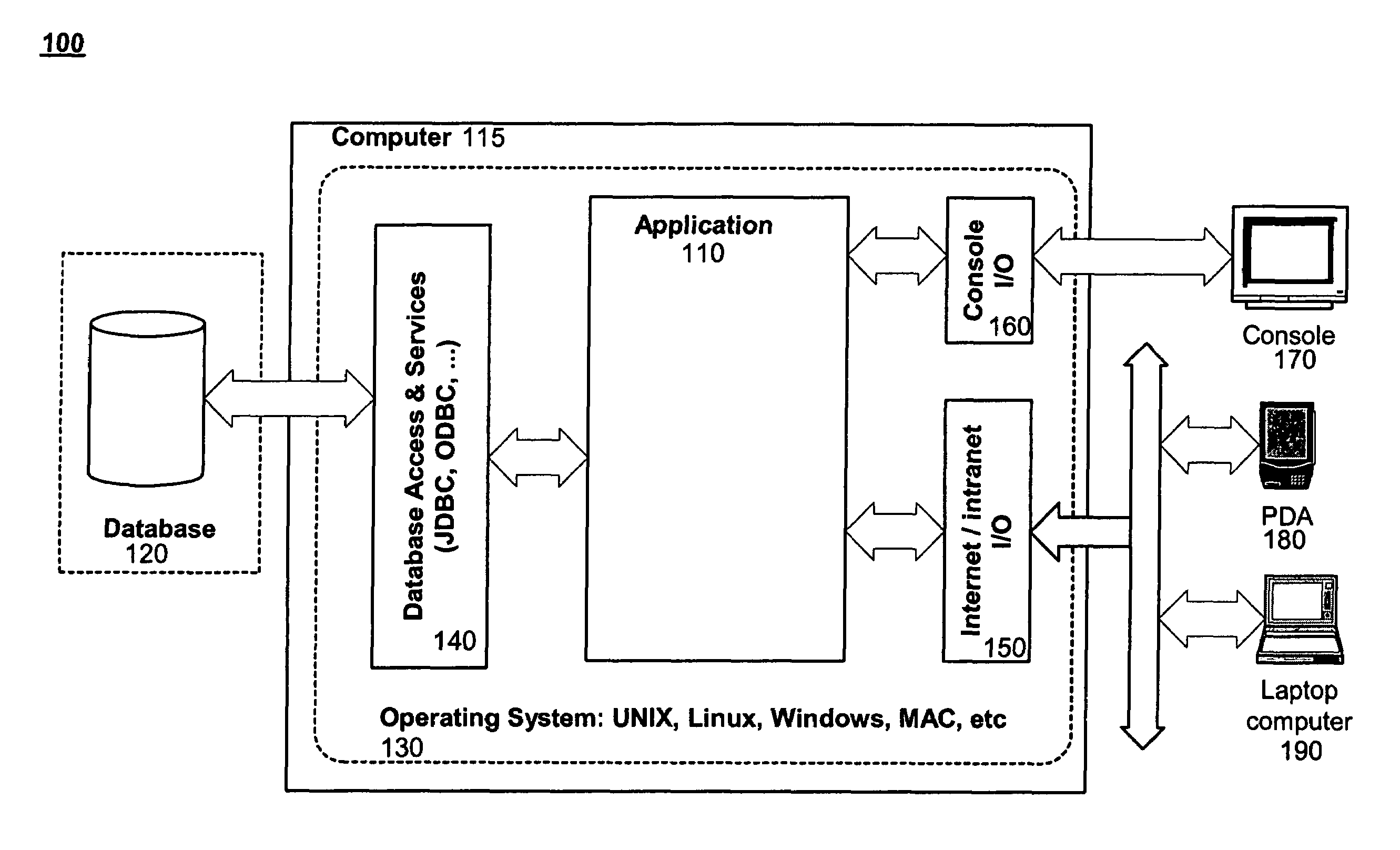
Software framework that facilitates design and implementation of database applications
InactiveUS7412455B2Facilitates efficient design and implementationData processing applicationsDigital data information retrievalSoftware engineeringDatabase application
An intelligent framework is provided that is disposed between a high-level language environment and a database system environment. According to one embodiment, the framework programmatically receives information regarding definitions of data structures of objects participating in a software application and information regarding relationships among the objects. Based upon the particular request from the high-level language environment and upon the definitions and relationships, the framework programmatically and dynamically generates appropriate statements associated with the database system environment that accomplish the request. For example, the framework may issue statements to define the structure of a database, access information from the database, and / or manipulate information within the database.
Owner:RPX CORP
Systems and methods for use of structured and unstructured distributed data
InactiveUS20070061487A1Increase flexibilityDigital data processing detailsDatabase distribution/replicationDistributed databaseComputer science
The invention relates to hardware, software and electronic service components and systems to provide large-scale, reliable, and secure foundations for distributed databases and content management systems, combining unstructured and structured data, and allowing post-input reorganization to achieve a high degree of flexibility.
Owner:NEWSILIKE MEDIA GROUP
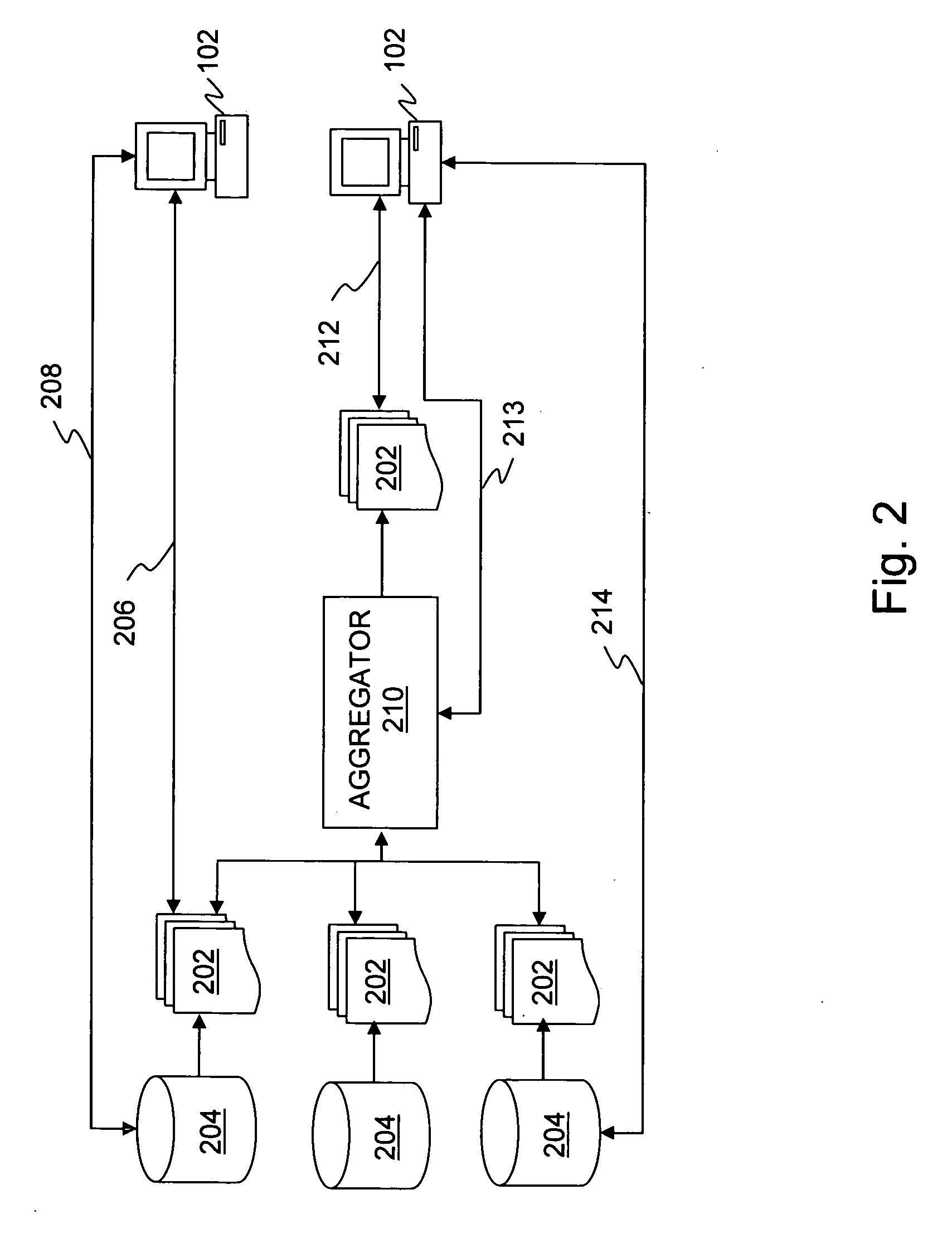
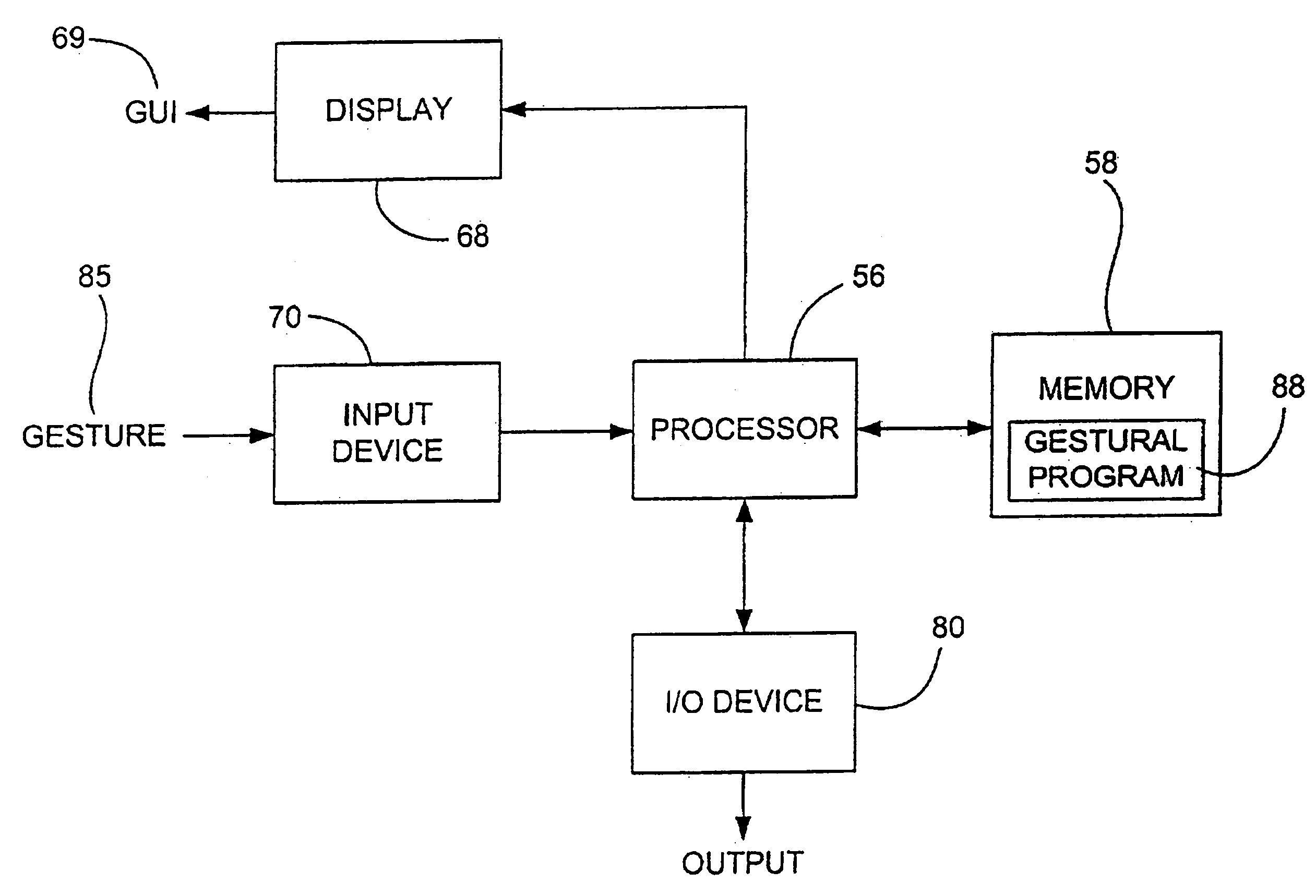
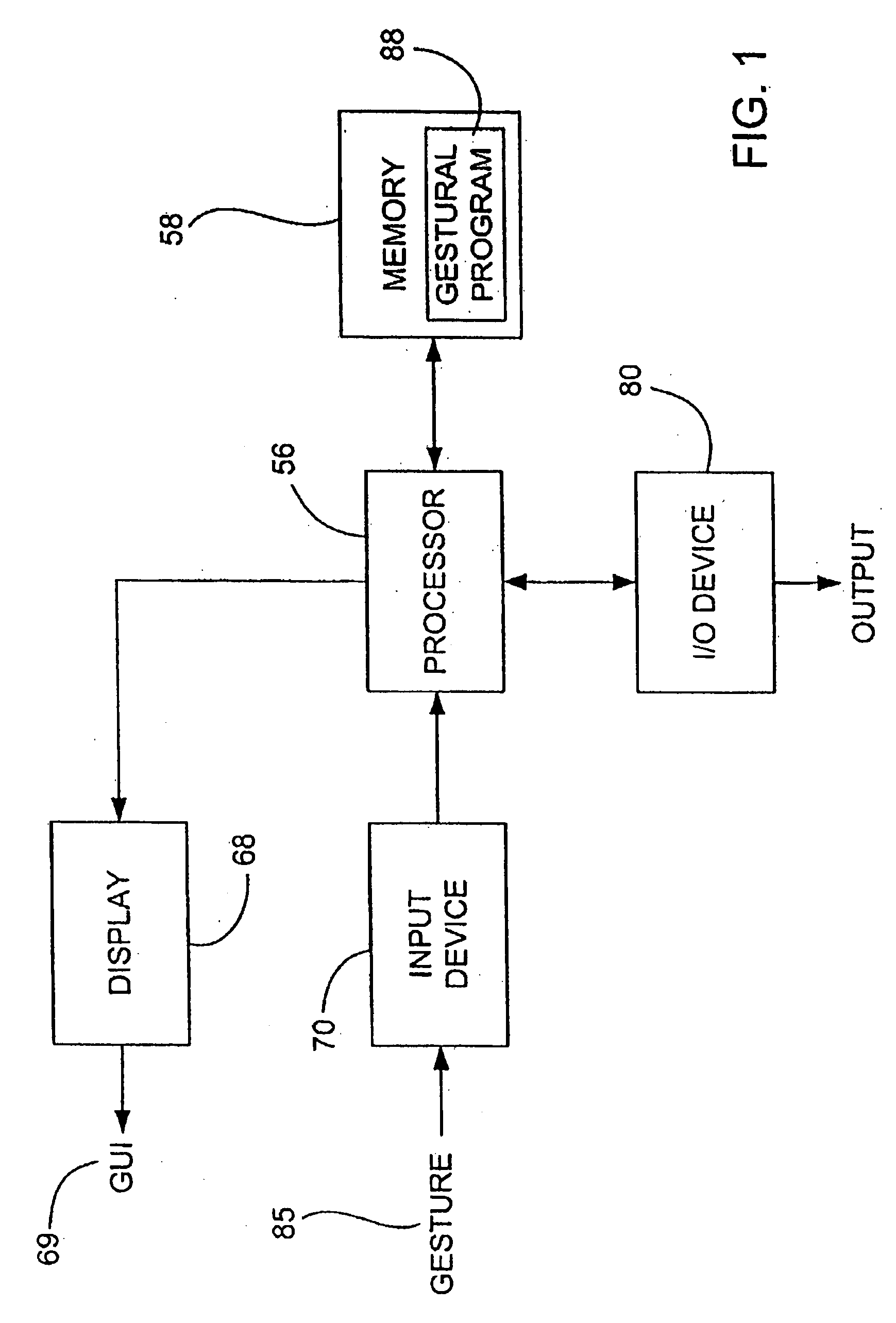
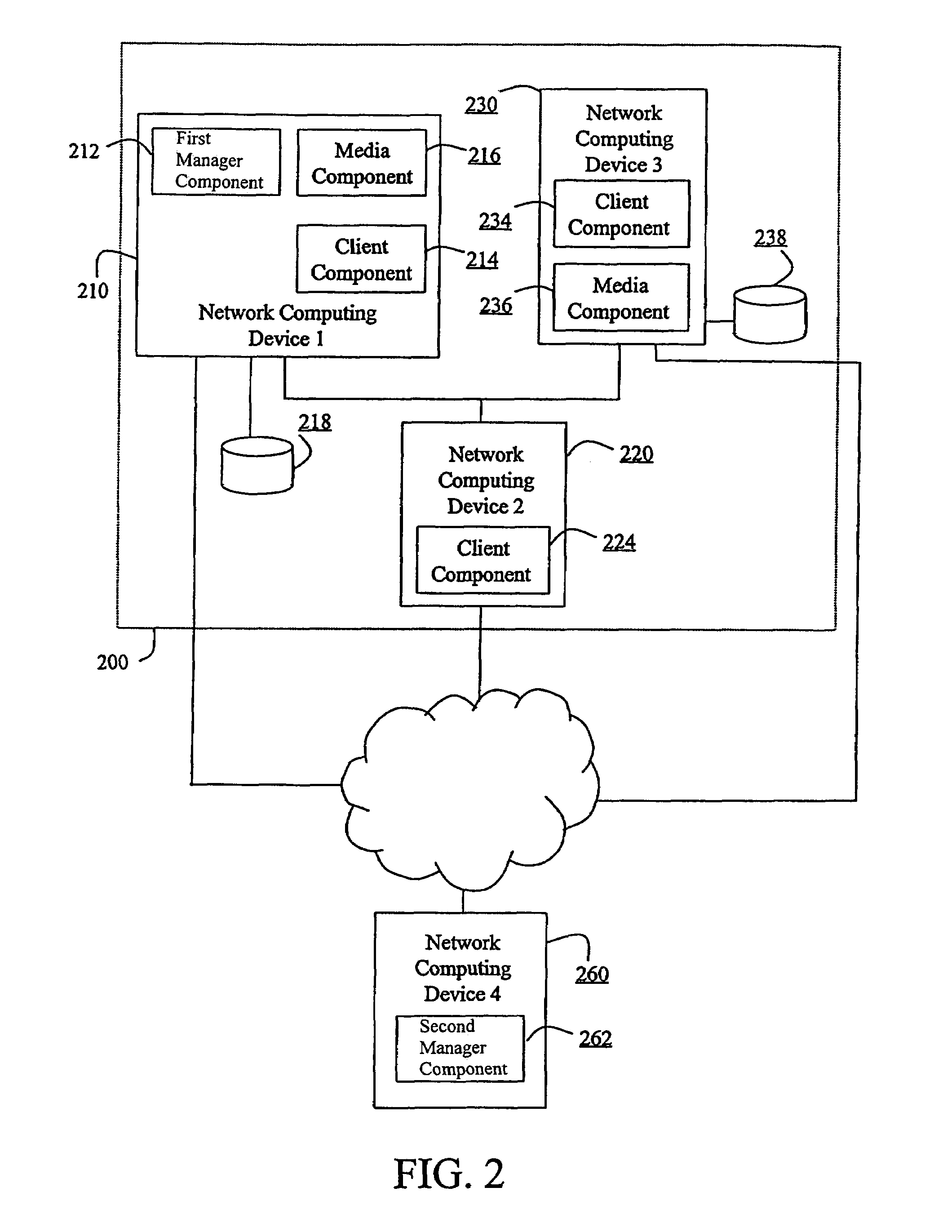
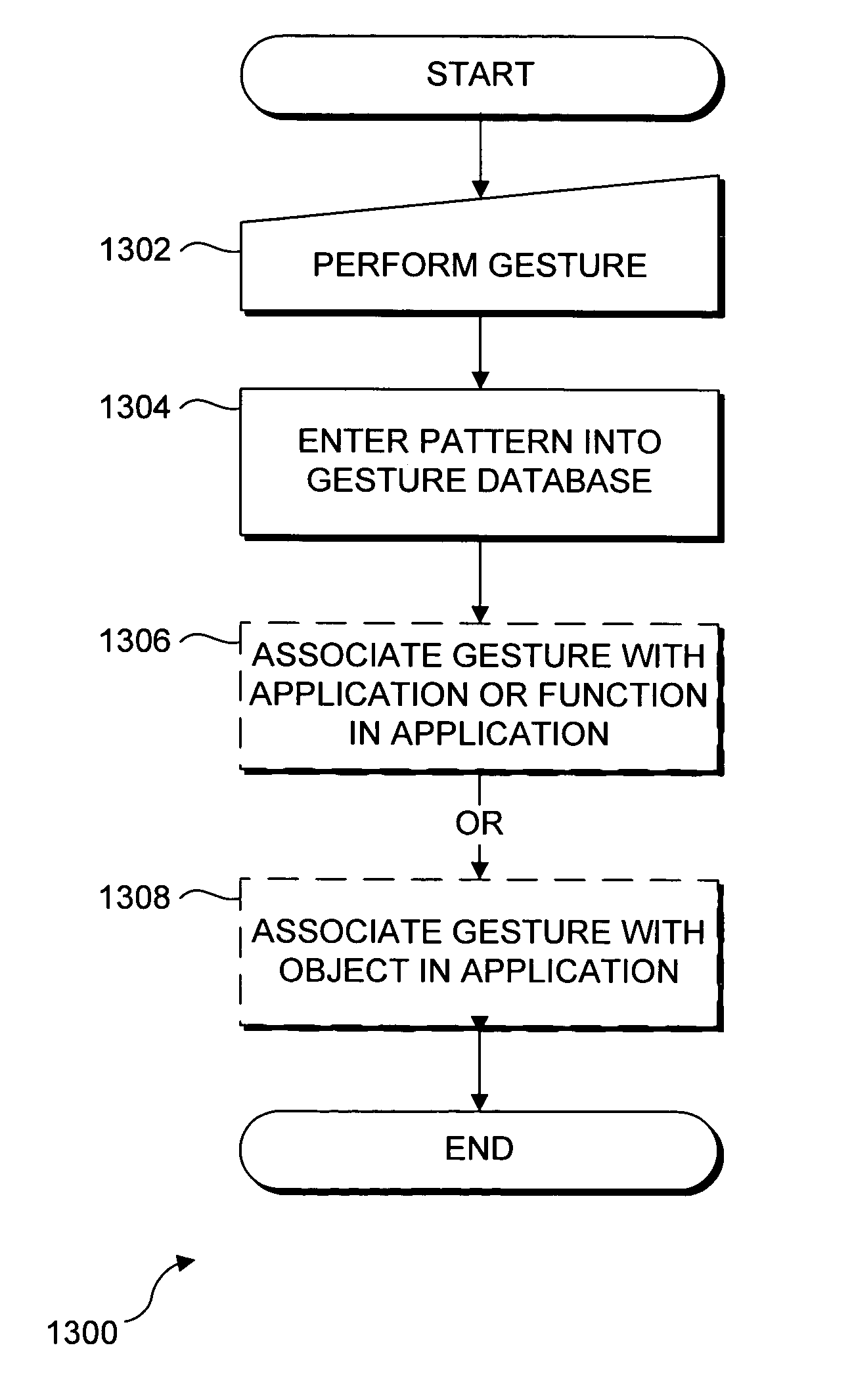
Gestures for controlling, manipulating, and editing of media files using touch sensitive devices
ActiveUS20080165141A1Electronic editing digitised analogue information signalsCarrier indicating arrangementsGraphicsSoftware
Embodiments of the invention are directed to a system, method, and software for implementing gestures with touch sensitive devices (such as a touch sensitive display) for managing and editing media files on a computing device or system. Specifically, gestural inputs of a human hand over a touch / proximity sensitive device can be used to control, edit, and manipulate files, such as media files including without limitation graphical files, photo files and video files.
Owner:APPLE INC
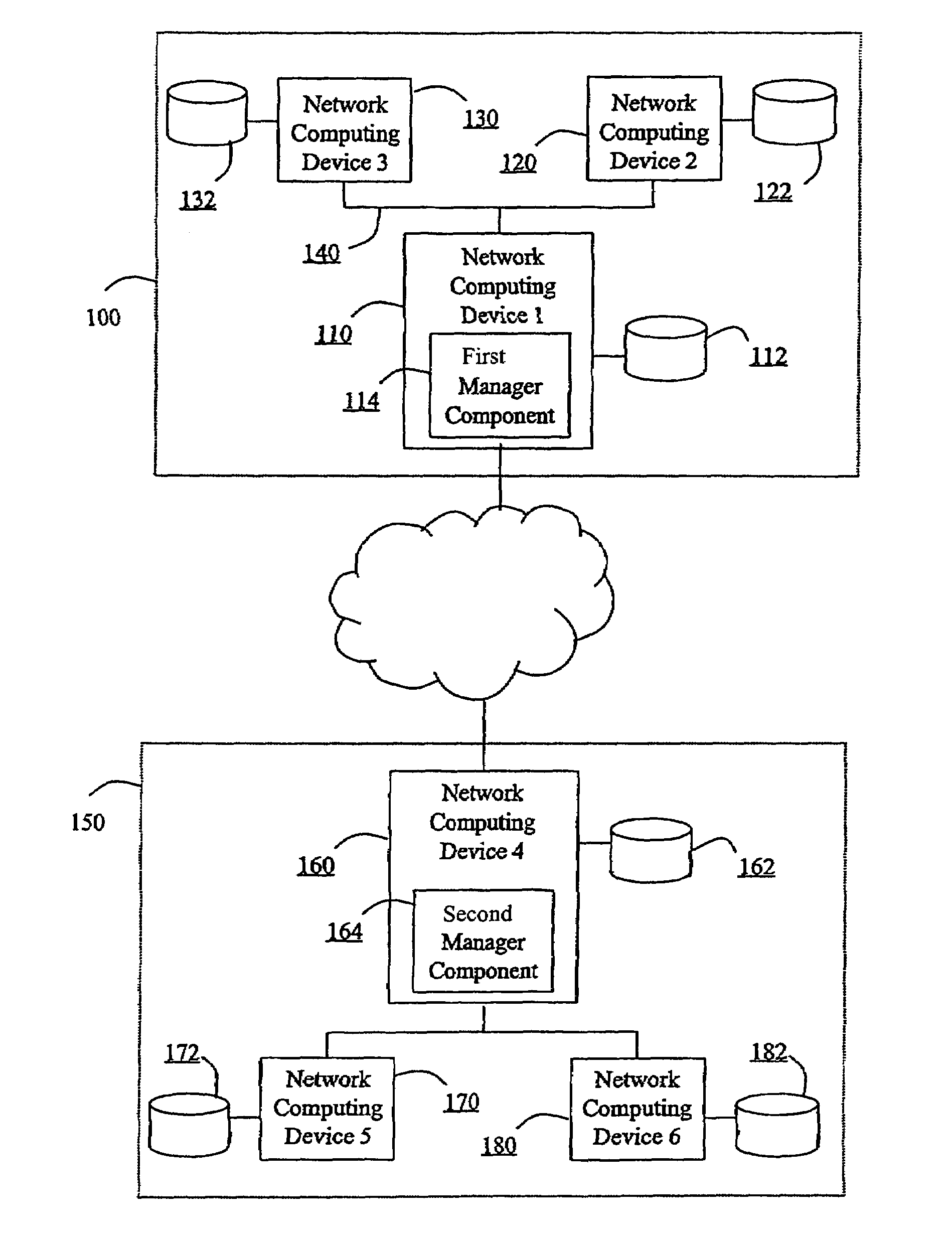
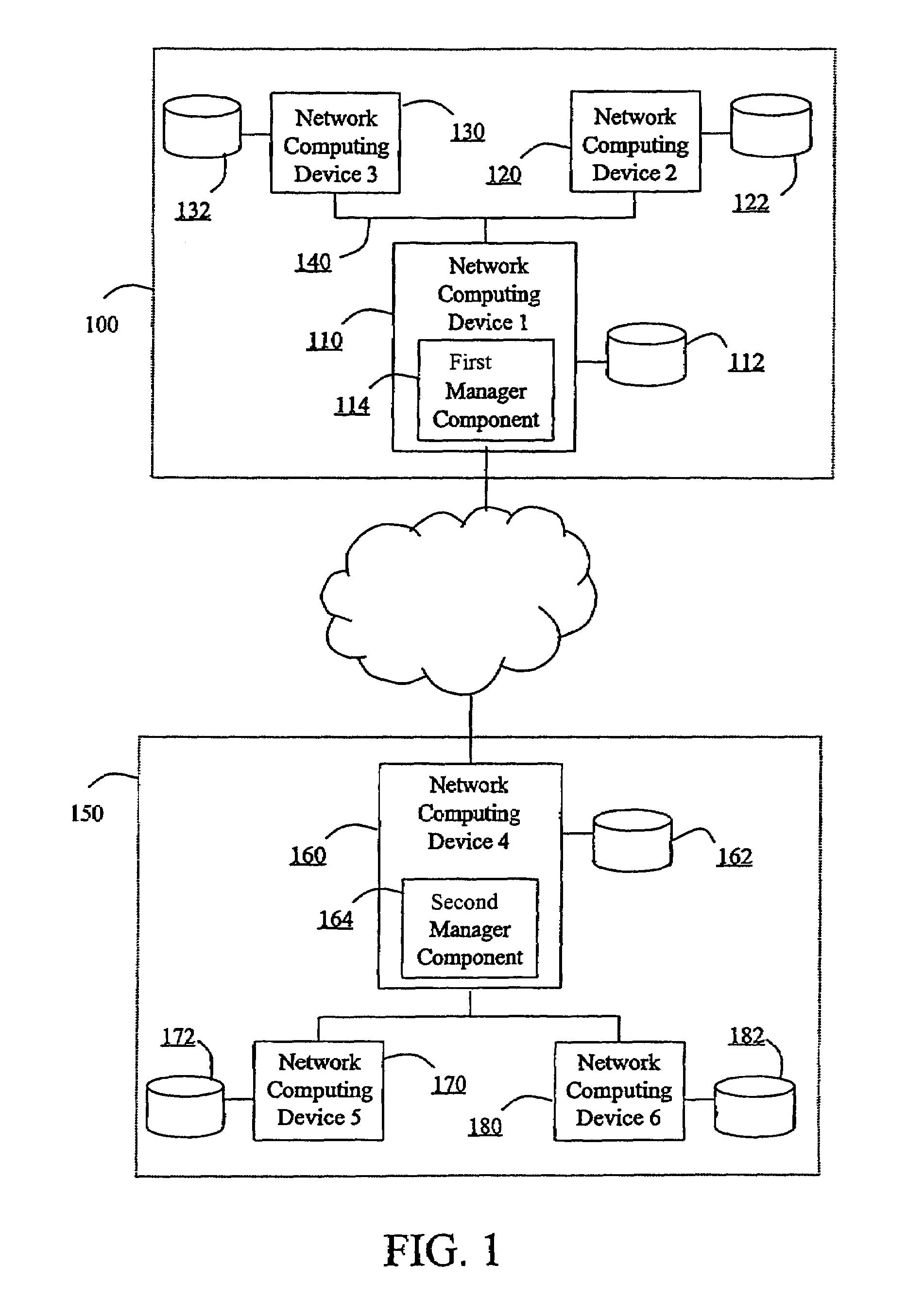
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
Contextual responses based on automated learning techniques
InactiveUS6842877B2Input/output for user-computer interactionComputer security arrangementsRepetitive taskUser interface
Techniques are disclosed for using a combination of explicit and implicit user context modeling techniques to identify and provide appropriate computer actions based on a current context, and to continuously improve the providing of such computer actions. The appropriate computer actions include presentation of appropriate content and functionality. Feedback paths can be used to assist automated machine learning in detecting patterns and generating inferred rules, and improvements from the generated rules can be implemented with or without direct user control. The techniques can be used to enhance software and device functionality, including self-customizing of a model of the user's current context or situation, customizing received themes, predicting appropriate content for presentation or retrieval, self-customizing of software user interfaces, simplifying repetitive tasks or situations, and mentoring of the user to promote desired change.
Owner:MICROSOFT TECH LICENSING LLC
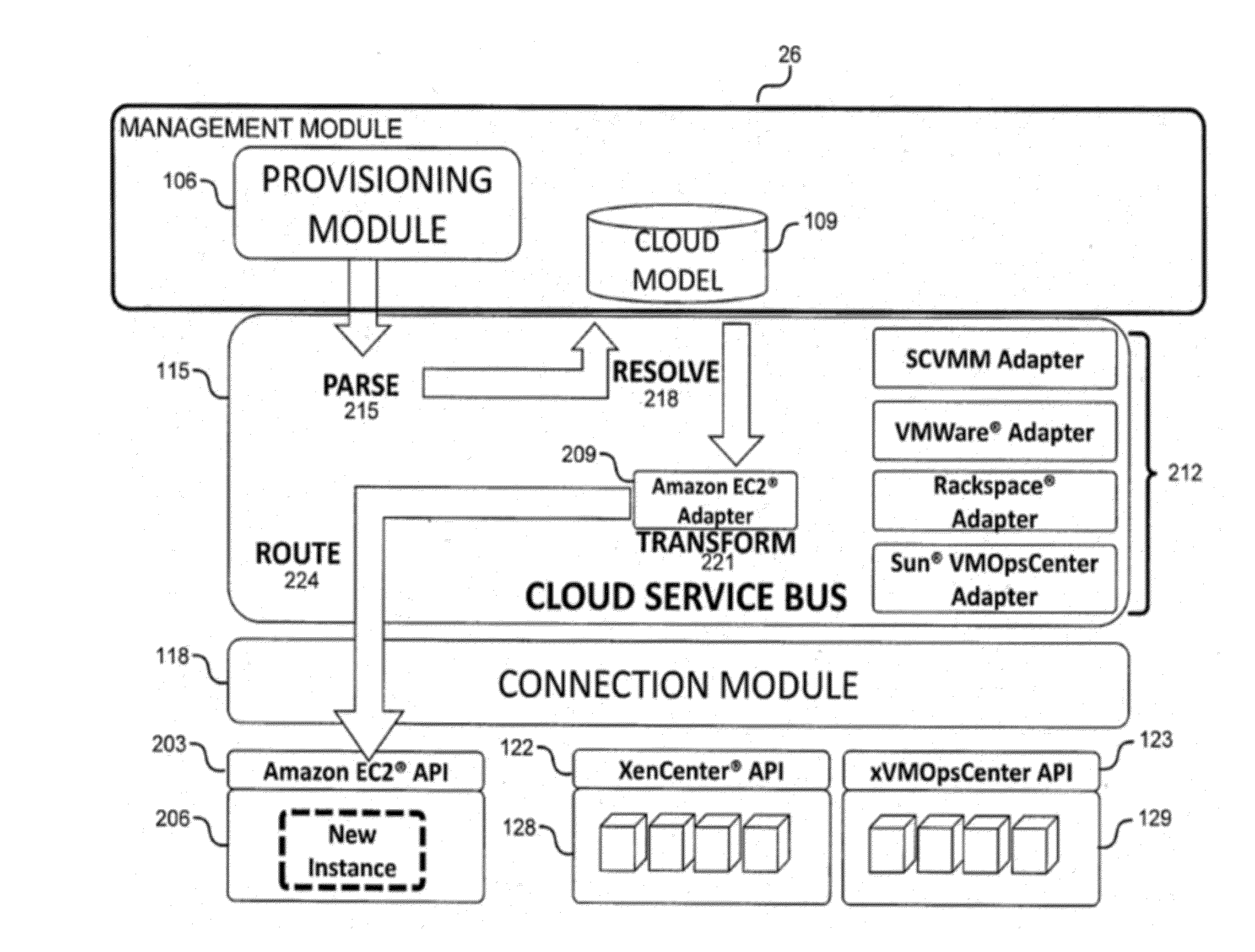
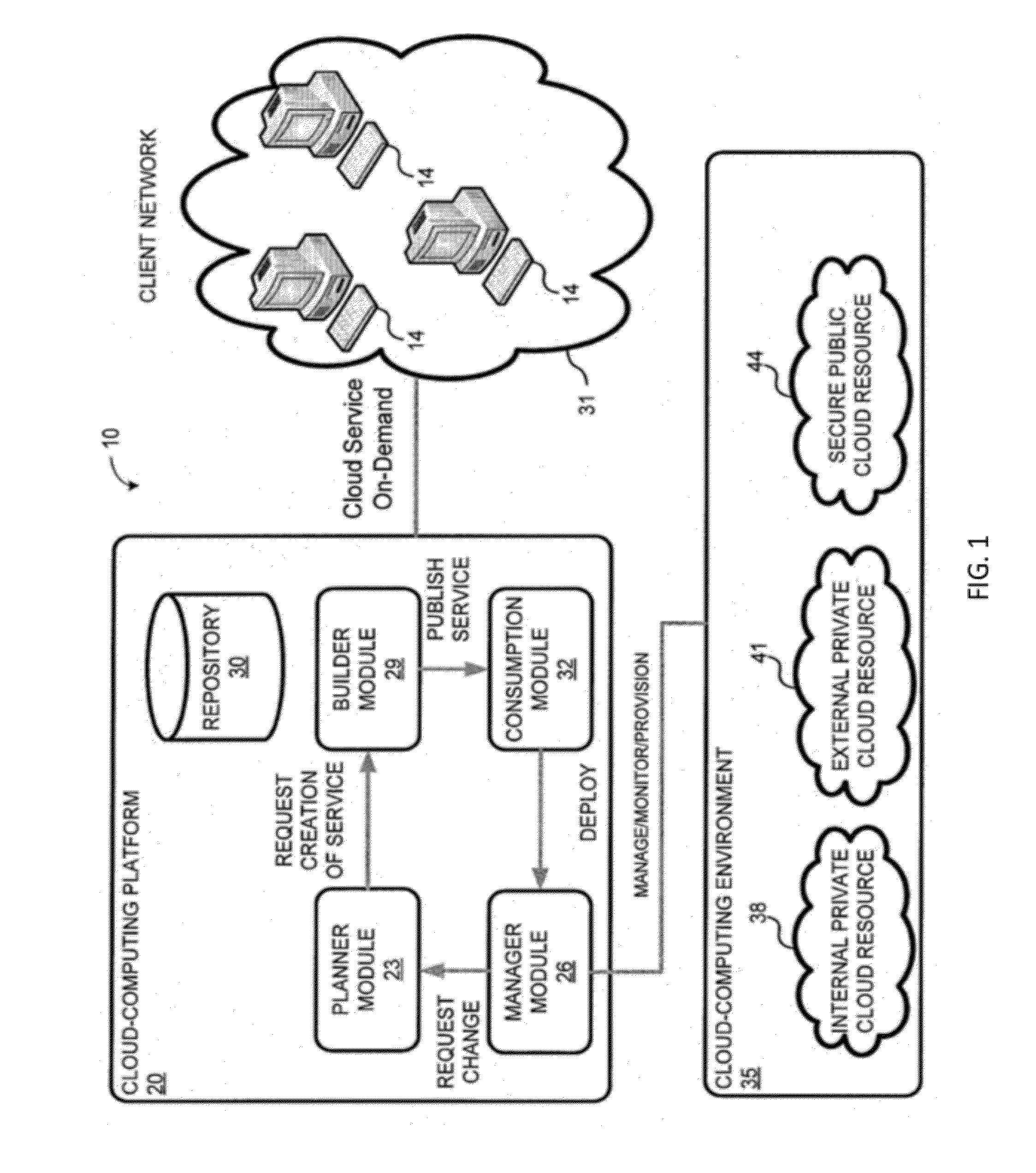
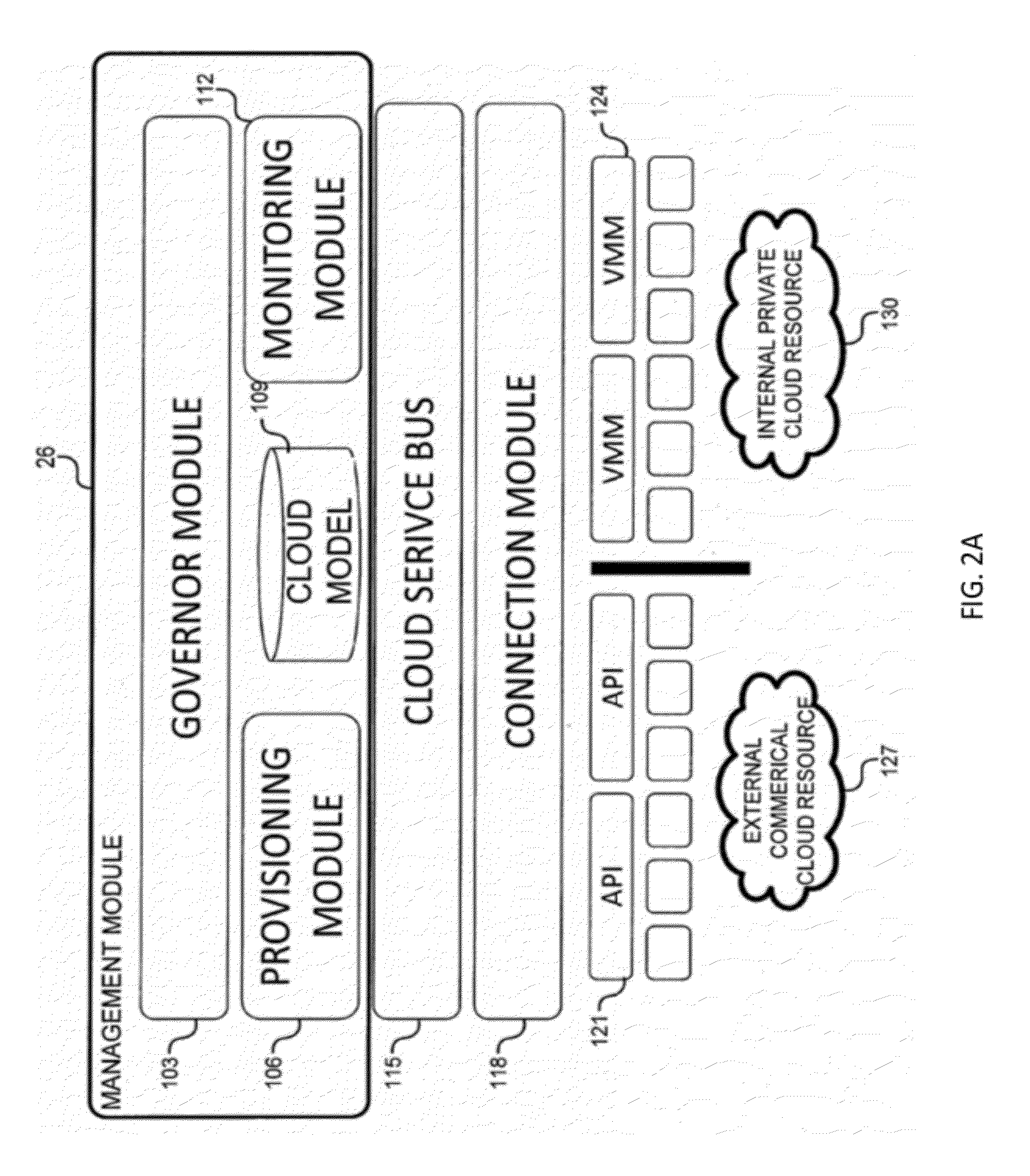
System and method for a cloud computing abstraction layer with security zone facilities
ActiveUS20120185913A1Rapid and dynamic deployment and scalingShorten the timeComputer security arrangementsHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
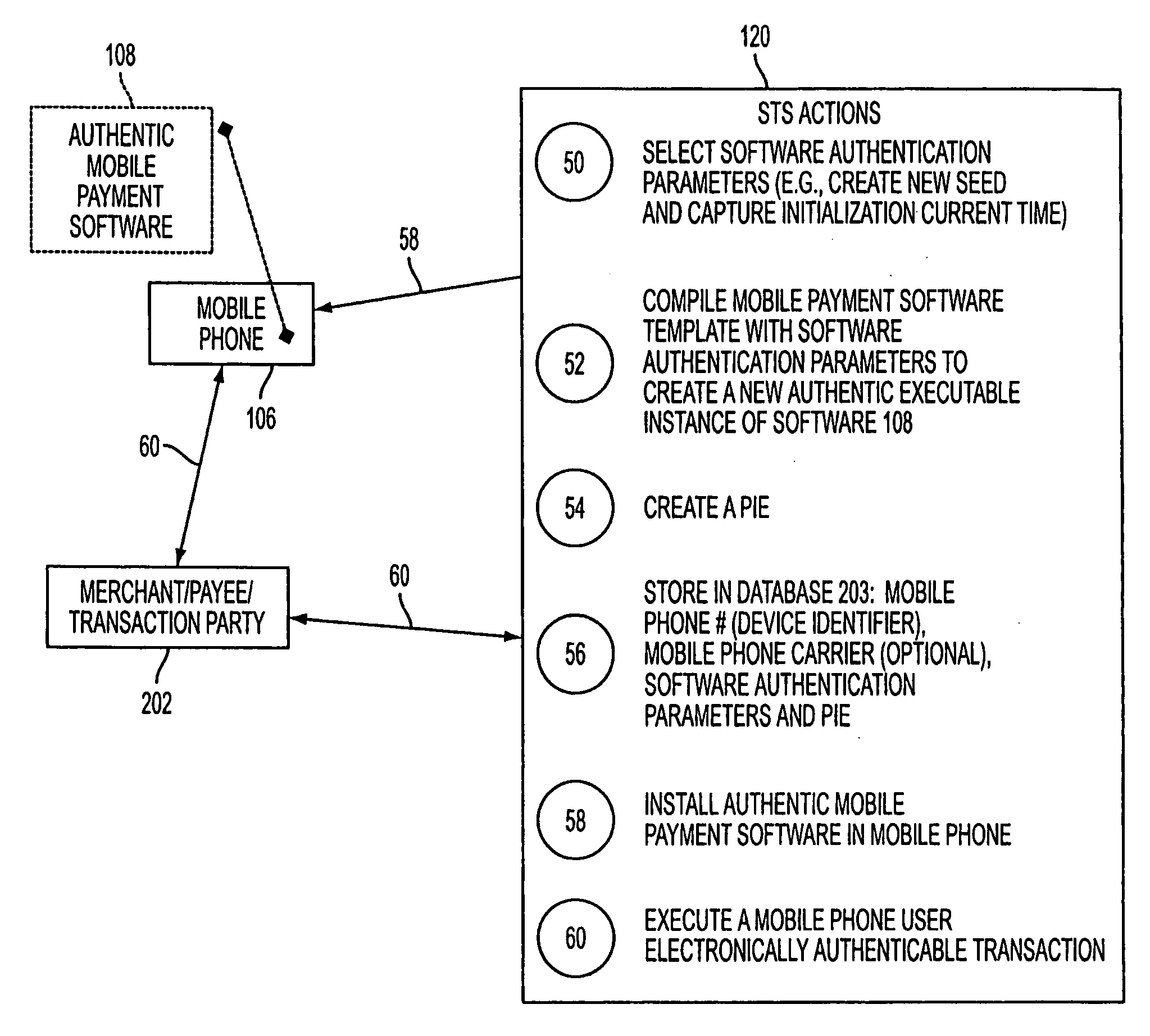
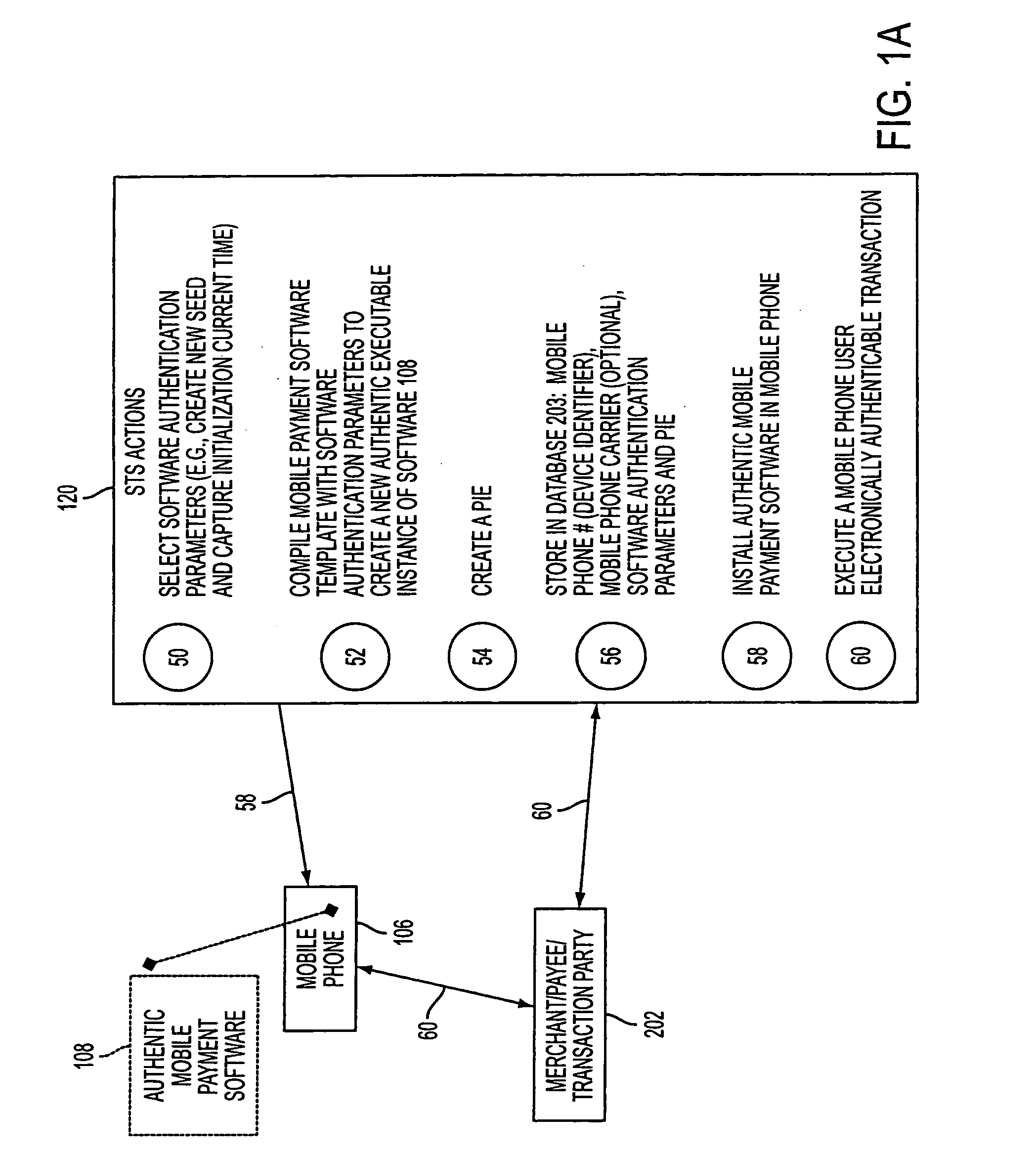
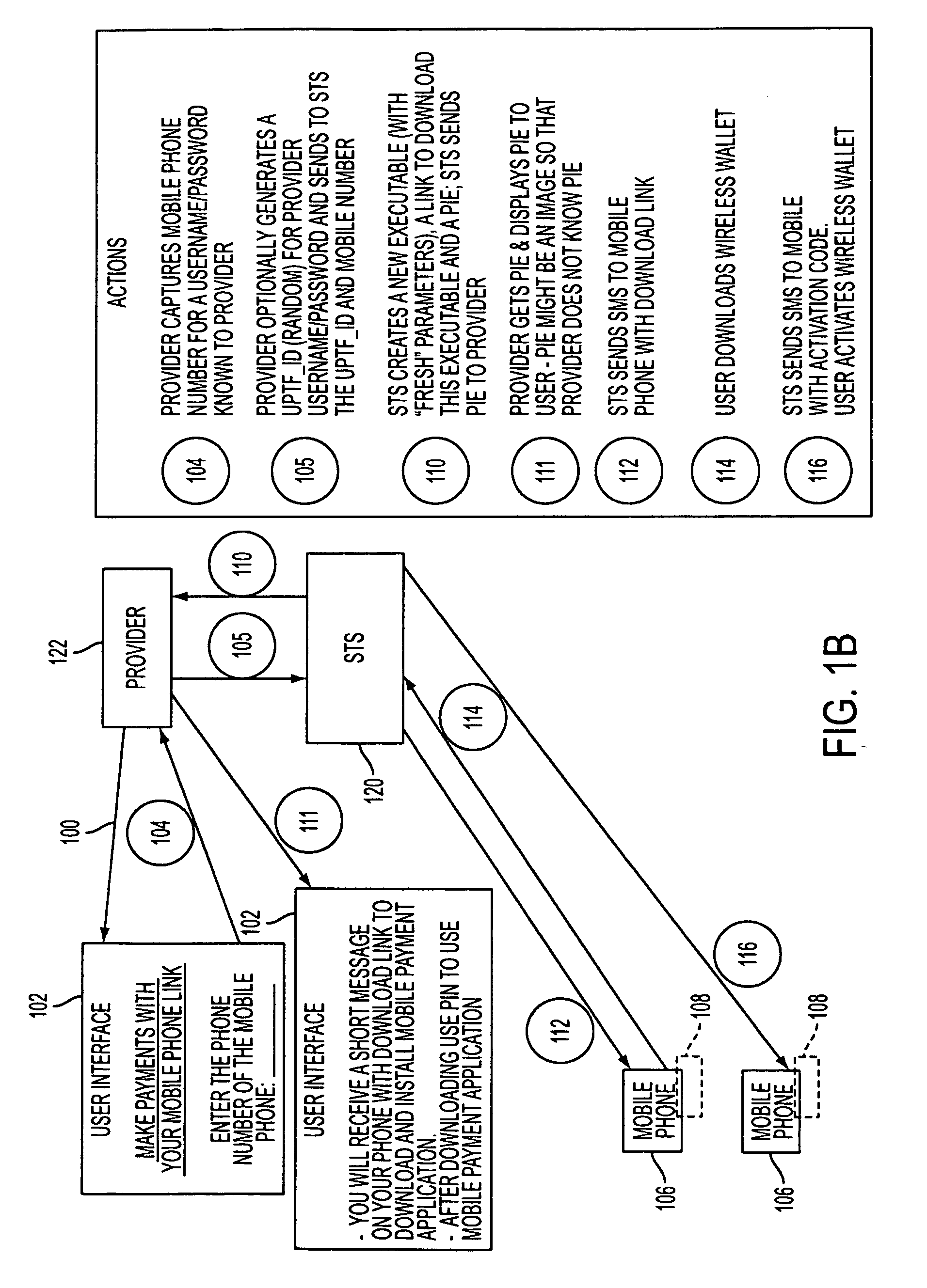
Wireless wallet
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
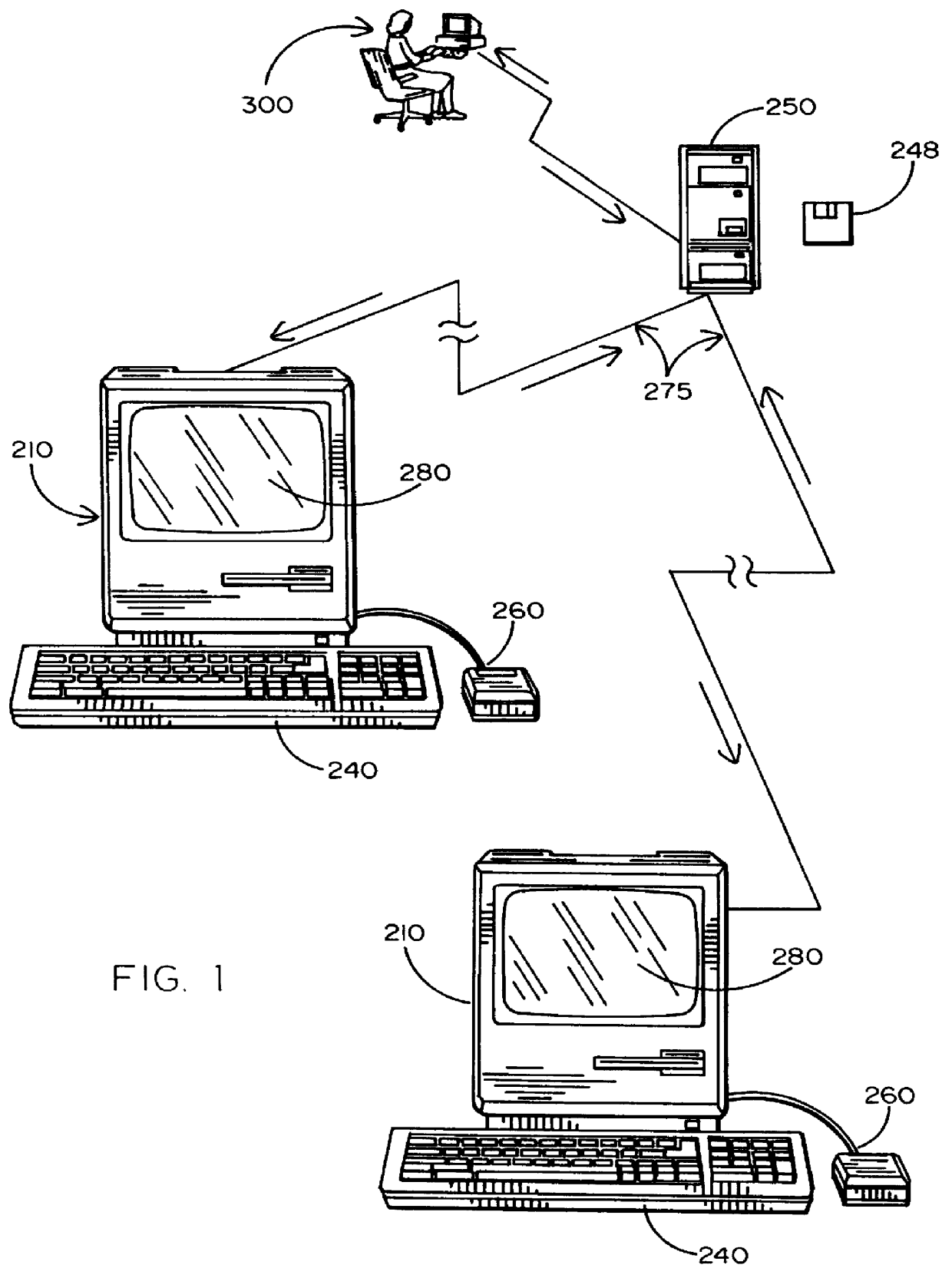
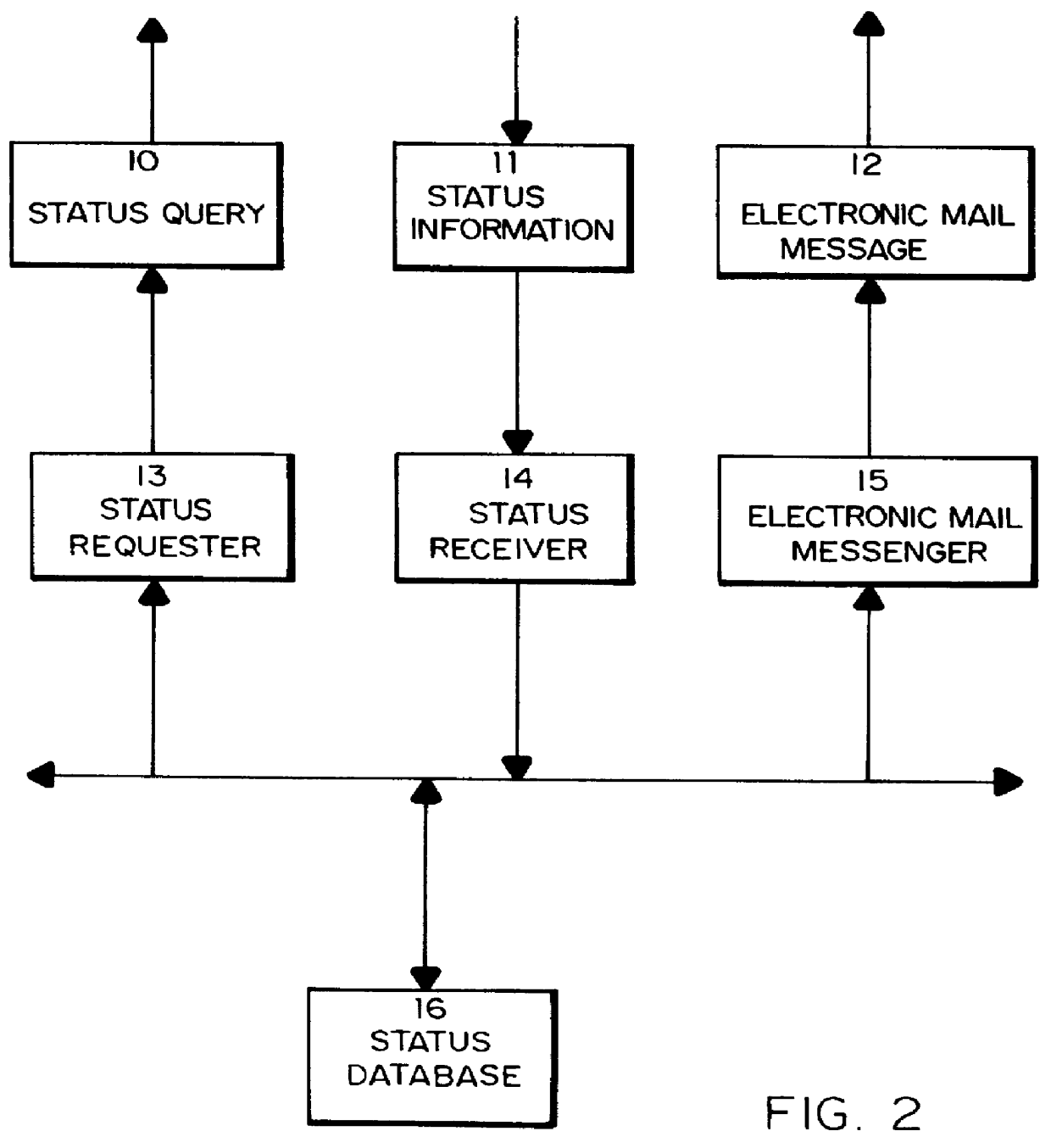
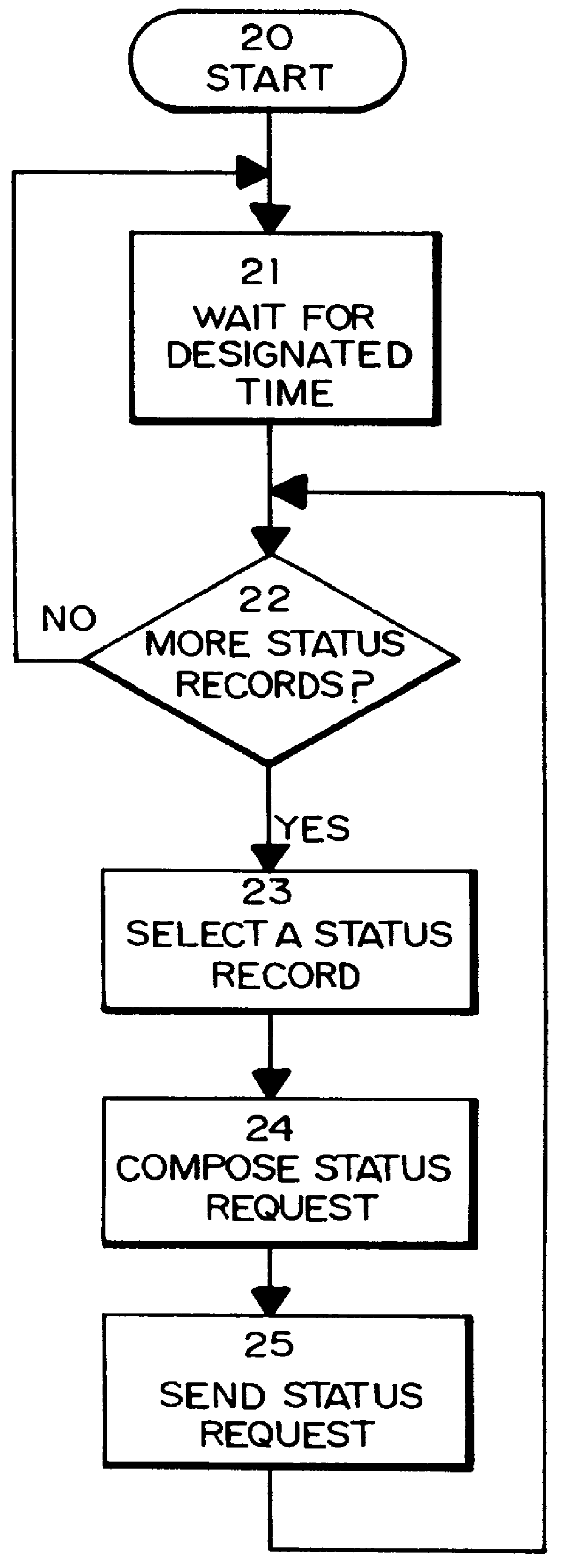
Method for supplying automatic status updates using electronic mail
A method is disclosed for automatically updating the status of customers' orders and shipments via electronic mail without using a human attendant to create and send the electronic mail messages. Preferably implemented in software, the updating method allows a large set of customers to be periodically updated over a computer or communications network via electronic mail. The method utilizes a database for maintaining order and shipping status and other relevant information.
Owner:EBAY INC
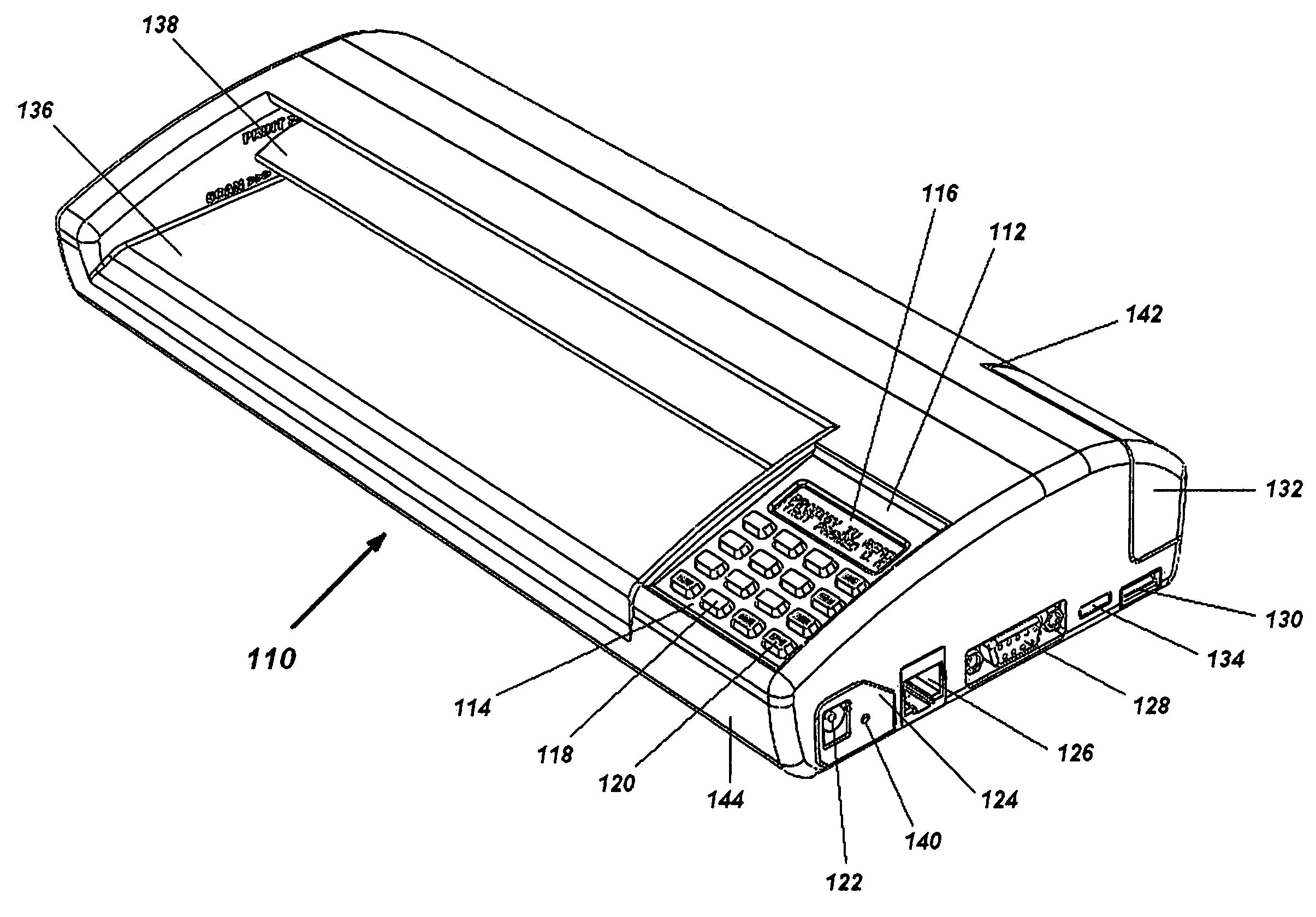
Portable electronic faxing, scanning, copying, and printing device
A lightweight, battery operated, portable, personal electronic device capable of faxing, scanning, printing and copying media as a standalone device or in cooperation with other electronic devices including PCs, mobile telephones, PDAs, etc. is provided. The device automatically detects the presence of fax-capable devices and reconfigures the software for compatibility with the fax-capable device eliminating the need for user programming. The device's ergonomic design, intrinsic physical stability, and same side paper feeds and user interface provide use in work areas having limited space. The device includes unidirectional, independent pathways for original and recording media such that paper jams are minimized. Portability is maximized through innovative power management software and hardware.
Owner:SCI FORGE
Tamper resistant pin entry apparatus
ActiveUS7238901B2Prevent leakagePrevent penetrationComplete banking machinesEmergency casingsPasswordElectric power system
Disclosed is a tamper resistant PIN entry apparatus for input of a key and for encryption of a password in a cash transaction machine. The PIN entry apparatus supplies the electric power to a memory of an electric circuit section, in such a manner that a first rod and a second rod of a rear case connect contacts of a key scan board, wherein the first rod is protruded on the rear of a key module including a button provided substantially on the front of the key module and the second rod of the rear case is coupled with the rear of the key module. At this time, in case that the rear case is removed from the key module or damaged, thereby changing the location of any one of the first and the second rods at the contact, the electric circuit section detects the event and destroys the memory itself physically. Otherwise, the electric circuit section makes information stored in the memory physically or softwarely unreadable, thereby preventing the leakage of the information.
Owner:NAUTILUS HYOSUNG
Wireless media system and player and method of operation
ActiveUS20060258289A1Easy to useMultimedia data browsing/visualisationPayment architectureUltra-widebandSecure communication
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
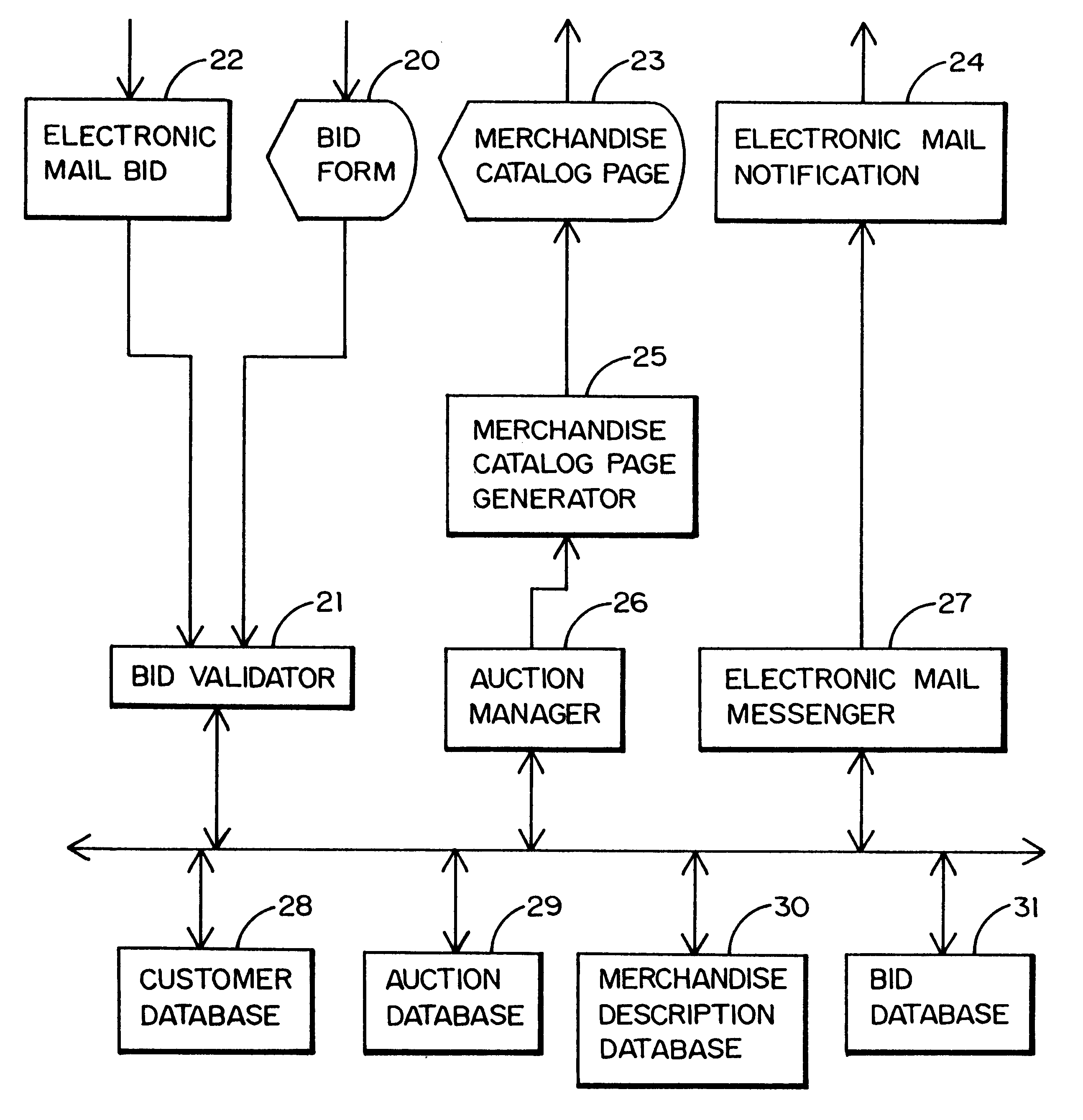
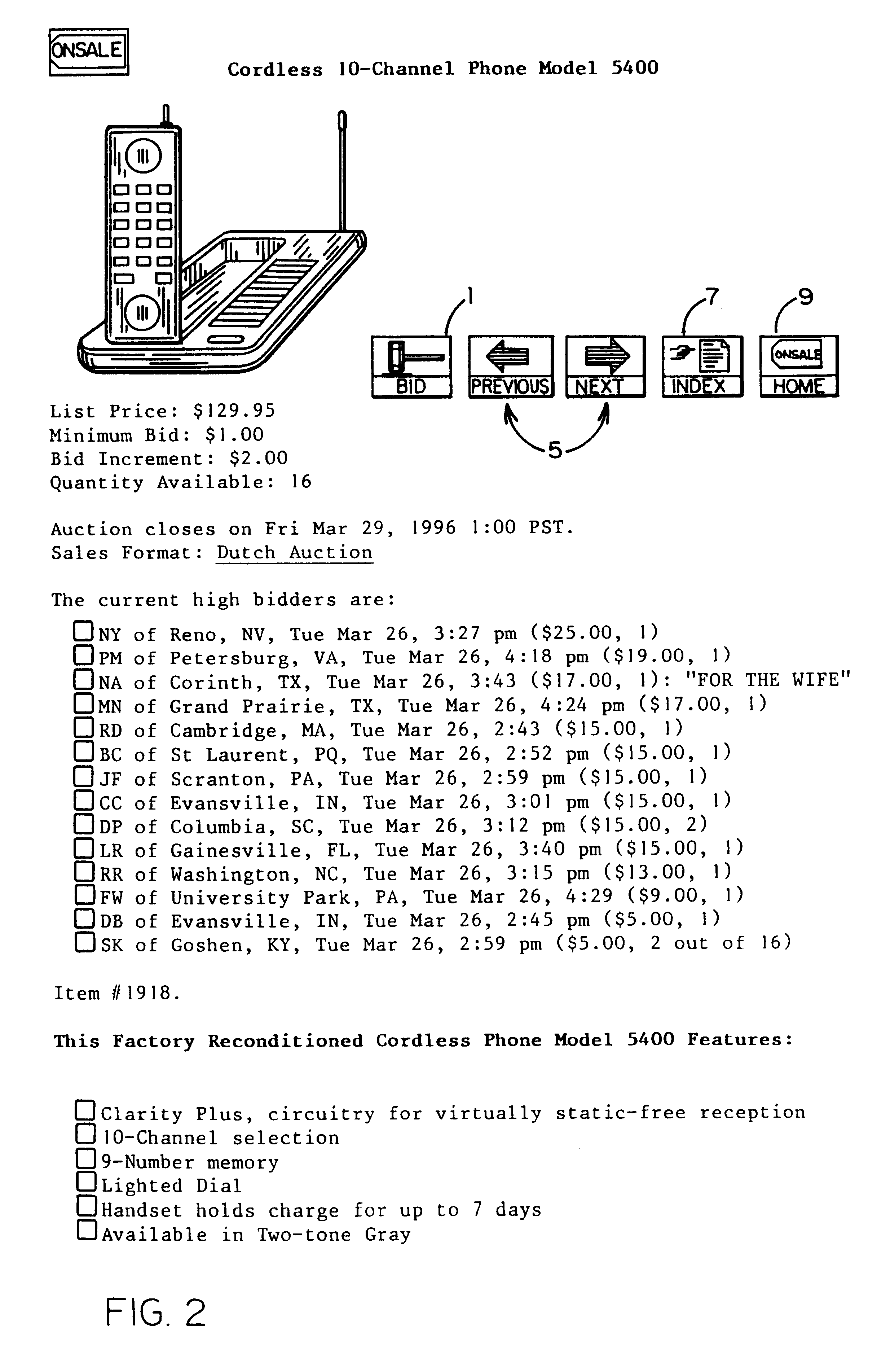
Method and system for processing and transmitting electronic auction information
InactiveUS6243691B1Good priceHigh priceFinanceBuying/selling/leasing transactionsComputer scienceSoftware
A system and method for conducting a multi-person, interactive auction, in a variety of formats, without using a human auctioneer to conduct the auction. The system is preferably implemented in software. The system allows a group of bidders to interactively place bids over a computer or communications network. Those bids are recorded by the system and the bidders are updated with the current auction status information. When appropriate, the system closes the auction from further bidding and notifies the winning bidders and losers as to the auction outcome.
Owner:EBAY INC
Program guide on a remote control display
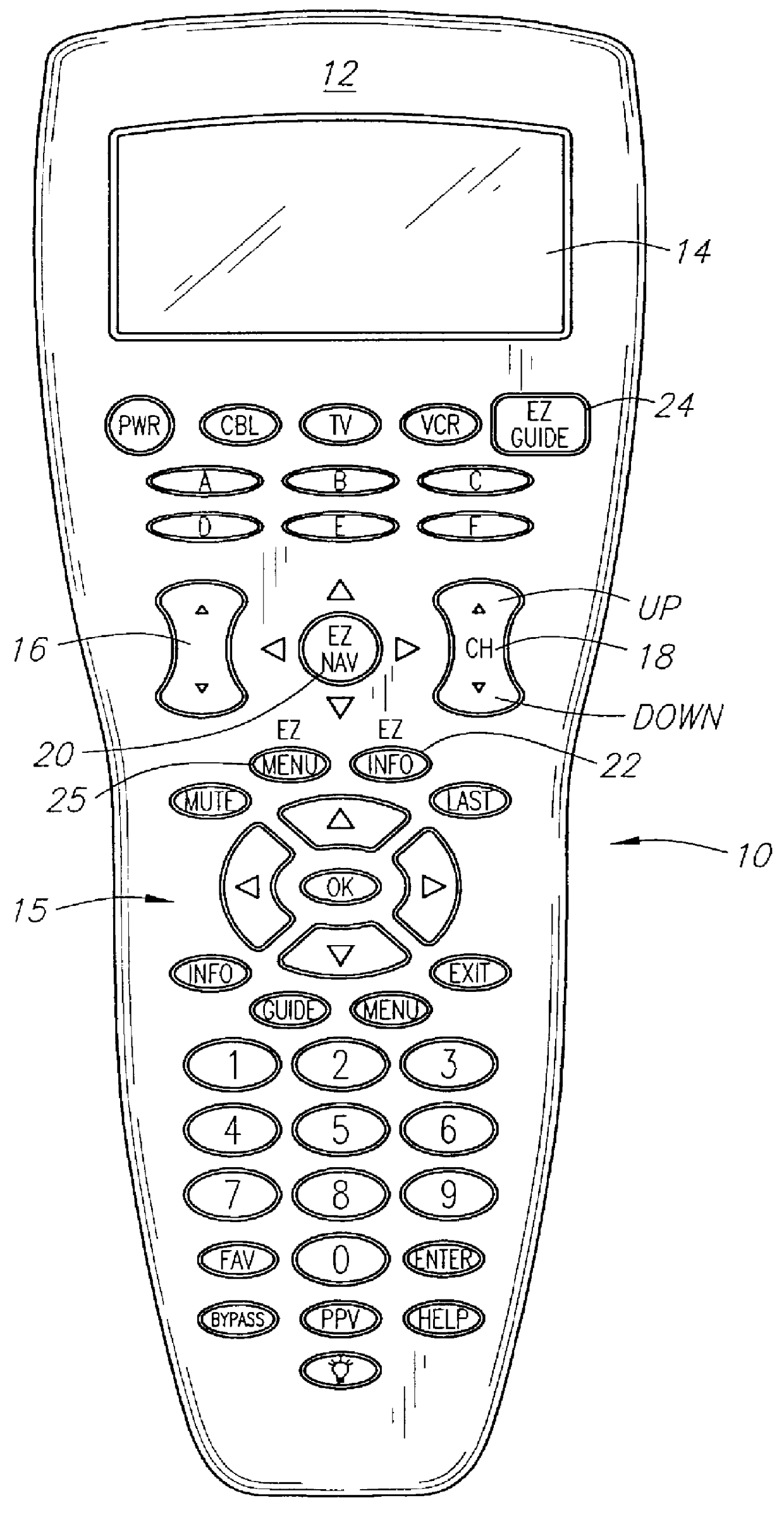
InactiveUS6130726AEliminate needTelevision system detailsSpecific information broadcast systemsData setRemote control
A remote control for operating a consumer electronic device. The remote control device may comprise a housing providing a mounting for a visual display and a keyboard including a plurality of keys; electrical circuitry in the housing including a microprocessor, at least one of an IR or RF receiver circuit coupled to the microprocessor, keyboard circuitry coupled between the microprocessor and the keyboard, a memory coupled to the microprocessor, and at least one of an IR or RF transmitter circuit coupled to the microprocessor. Program guide software is stored in the memory and executable by the microprocessor for causing to be displayed on the visual display, upon actuation of one or more of the keys, a program guide, advertising and / or other content contained in a data set received by the receiver.
Owner:LOGITECH EURO SA
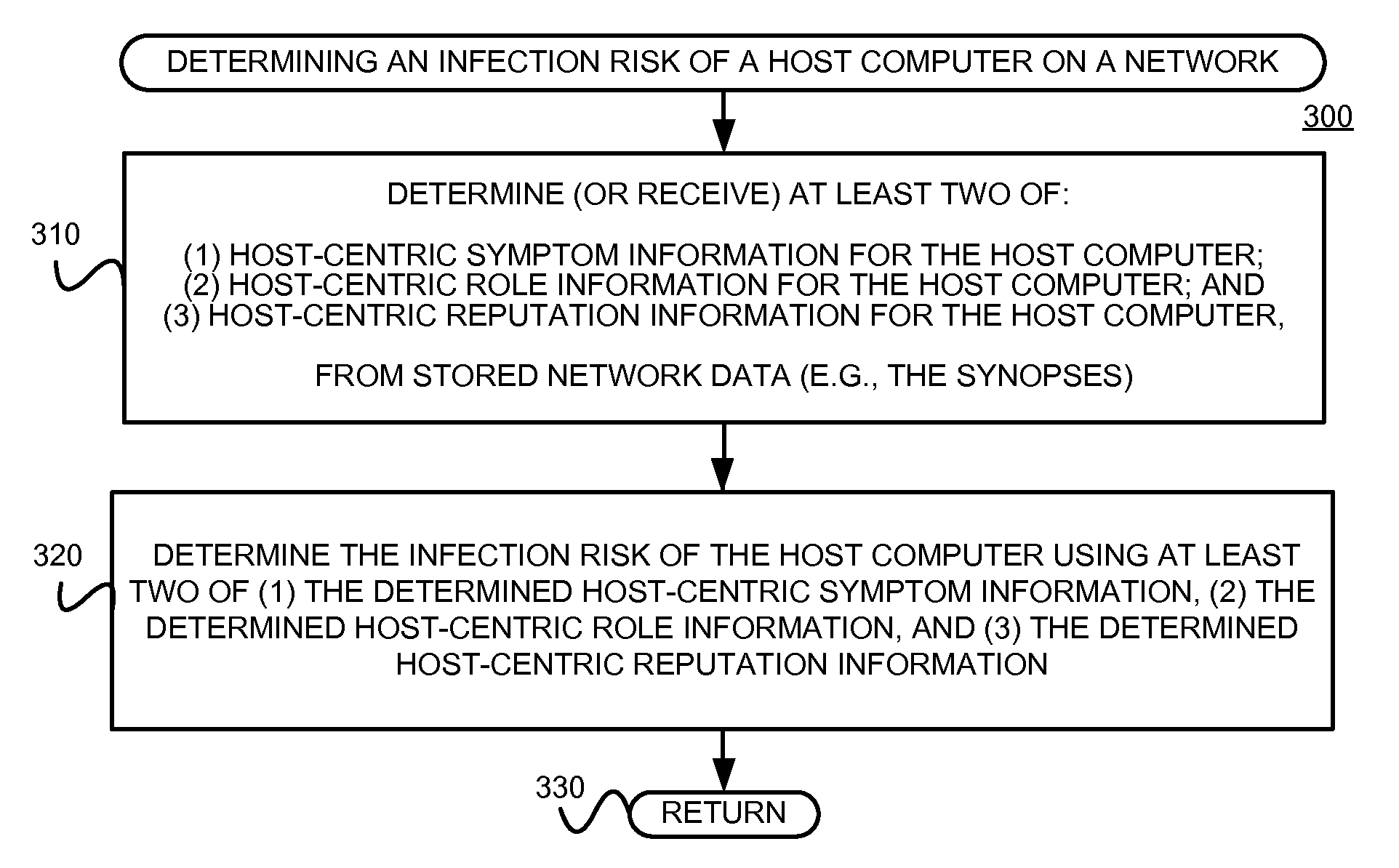
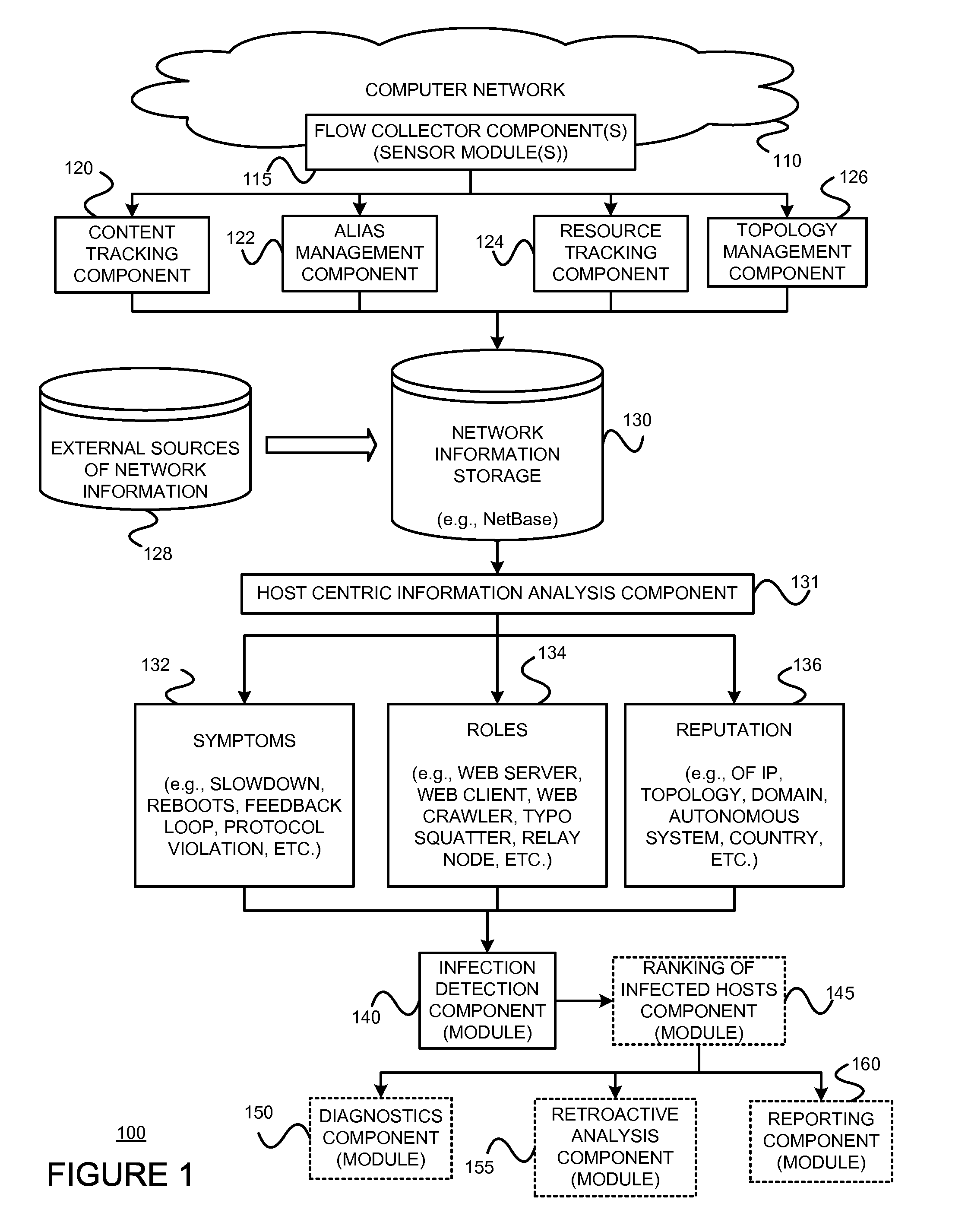
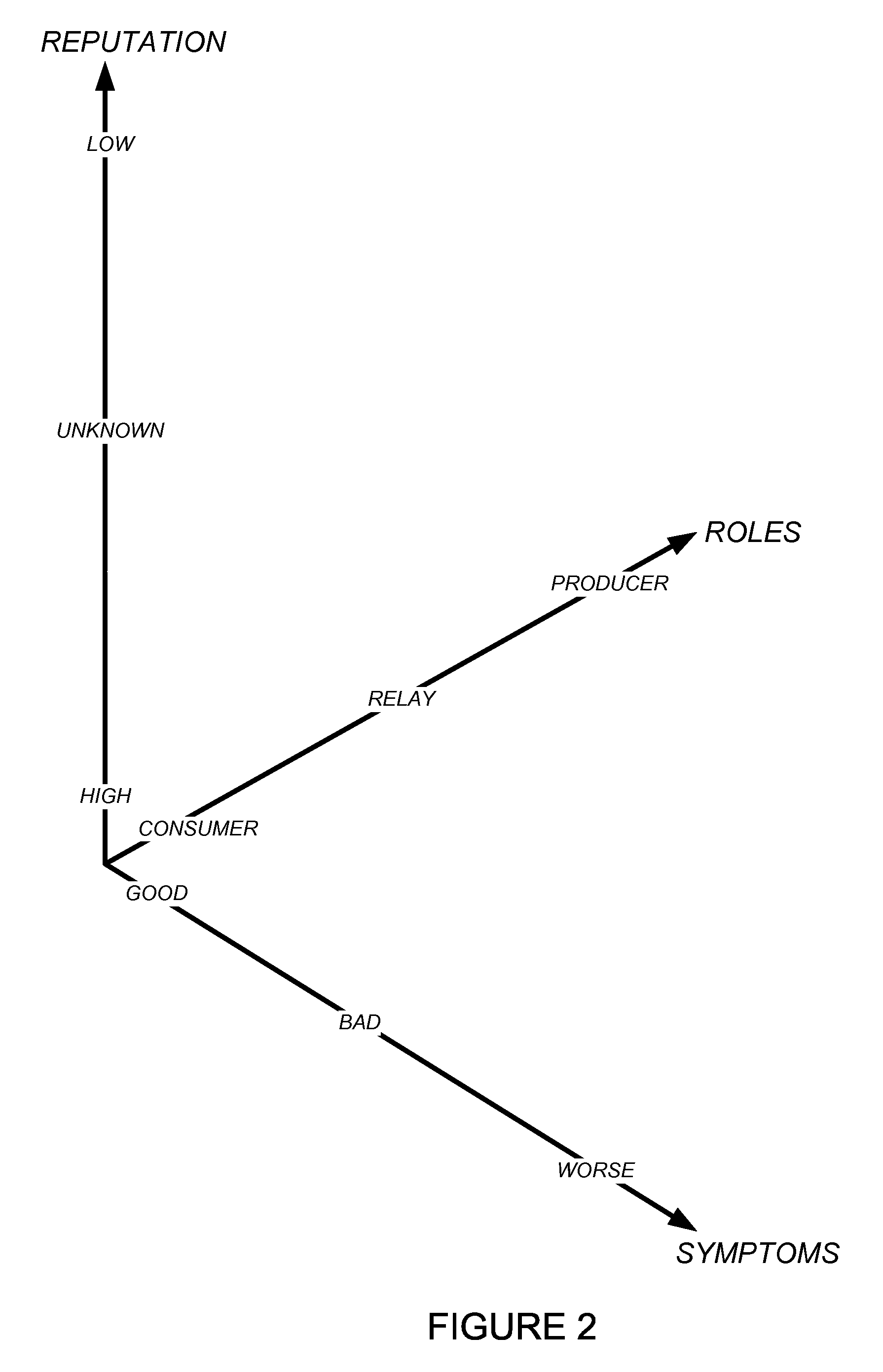
Using host symptoms, host roles, and/or host reputation for detection of host infection
InactiveUS20100235915A1Memory loss protectionError detection/correctionMalwareIntrusion prevention system
Detecting and mitigating threats to a computer network is important to the health of the network. Currently firewalls, intrusion detection systems, and intrusion prevention systems are used to detect and mitigate attacks. As the attackers get smarter and attack sophistication increases, it becomes difficult to detect attacks in real-time at the perimeter. Failure of perimeter defenses leaves networks with infected hosts. At least two of symptoms, roles, and reputations of hosts in (and even outside) a network are used to identify infected hosts. Virus or malware signatures are not required.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Vehicle monitoring system
InactiveUS8140358B1FinanceRegistering/indicating working of vehiclesDriver/operatorMonitoring system
A data logging device tracks the operation of a vehicle or driver actions. The device includes a storage device, which may be removable or portable, having a first memory portion that may be read from and may be written to in a vehicle and a second memory portion that may be read from and may be written to in the vehicle. The second memory portion may retain data attributes associated with the data stored in the first removable storage device. A processor reads data from an automotive bus that transfers data from vehicle sensors to other automotive components. The processor writes data to the first memory portion and the second memory portion that reflect a level of risk or safety. A communication device links the storage device to a network of computers. The communication device may be accessible through software that allows a user to access files related to a level of risk or safety and other software that may be related to those files.
Owner:PROGRESSIVE CASUALTY INSURANCE
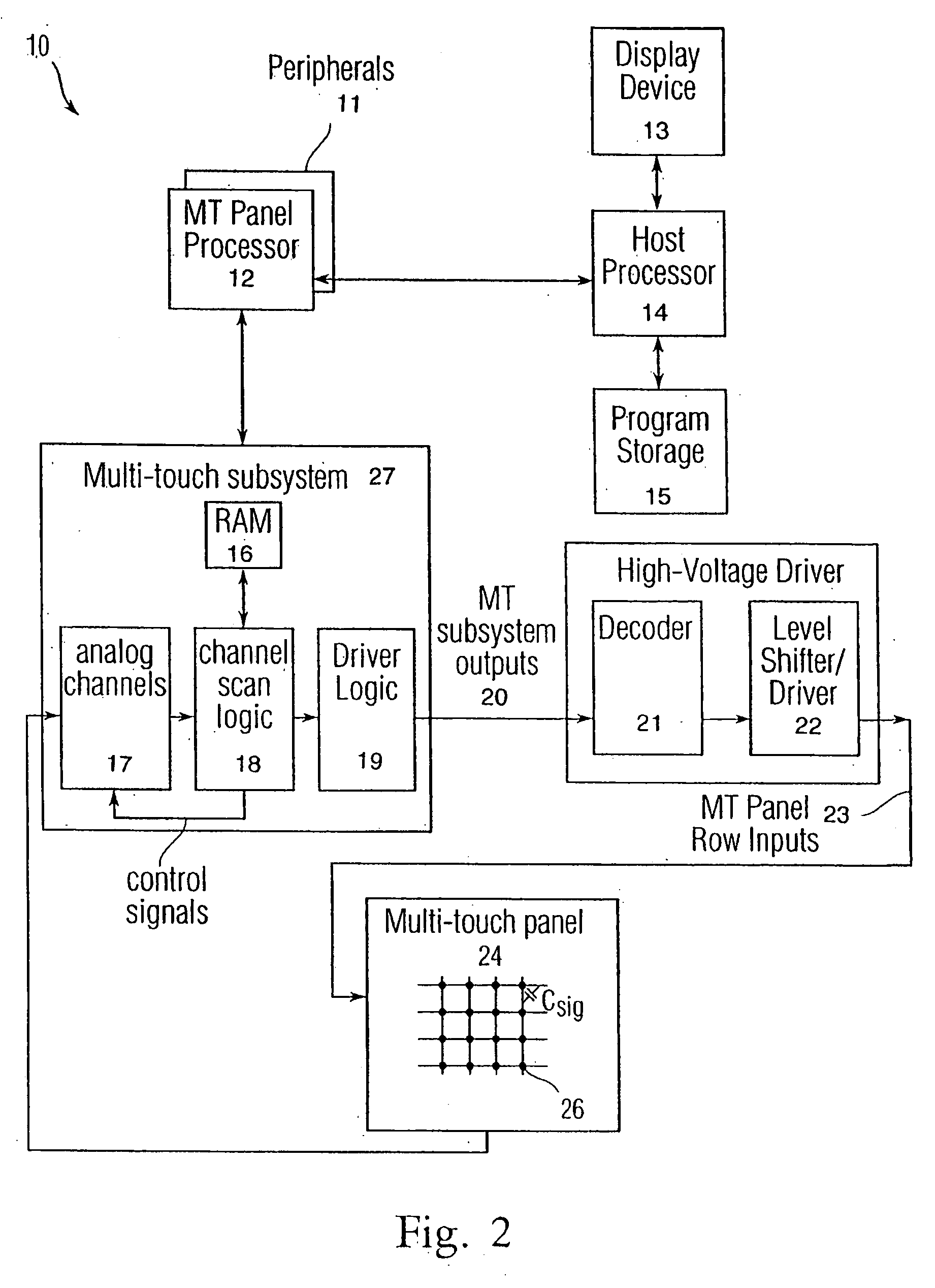
Recognizing gestures and using gestures for interacting with software applications
InactiveUS20060010400A1Character and pattern recognitionColor television detailsInteractive displaysHuman–computer interaction
An interactive display table has a display surface for displaying images and upon or adjacent to which various objects, including a user's hand(s) and finger(s) can be detected. A video camera within the interactive display table responds to infrared (IR) light reflected from the objects to detect any connected components. Connected component correspond to portions of the object(s) that are either in contact, or proximate the display surface. Using these connected components, the interactive display table senses and infers natural hand or finger positions, or movement of an object, to detect gestures. Specific gestures are used to execute applications, carryout functions in an application, create a virtual object, or do other interactions, each of which is associated with a different gesture. A gesture can be a static pose, or a more complex configuration, and / or movement made with one or both hands or other objects.
Owner:MICROSOFT TECH LICENSING LLC
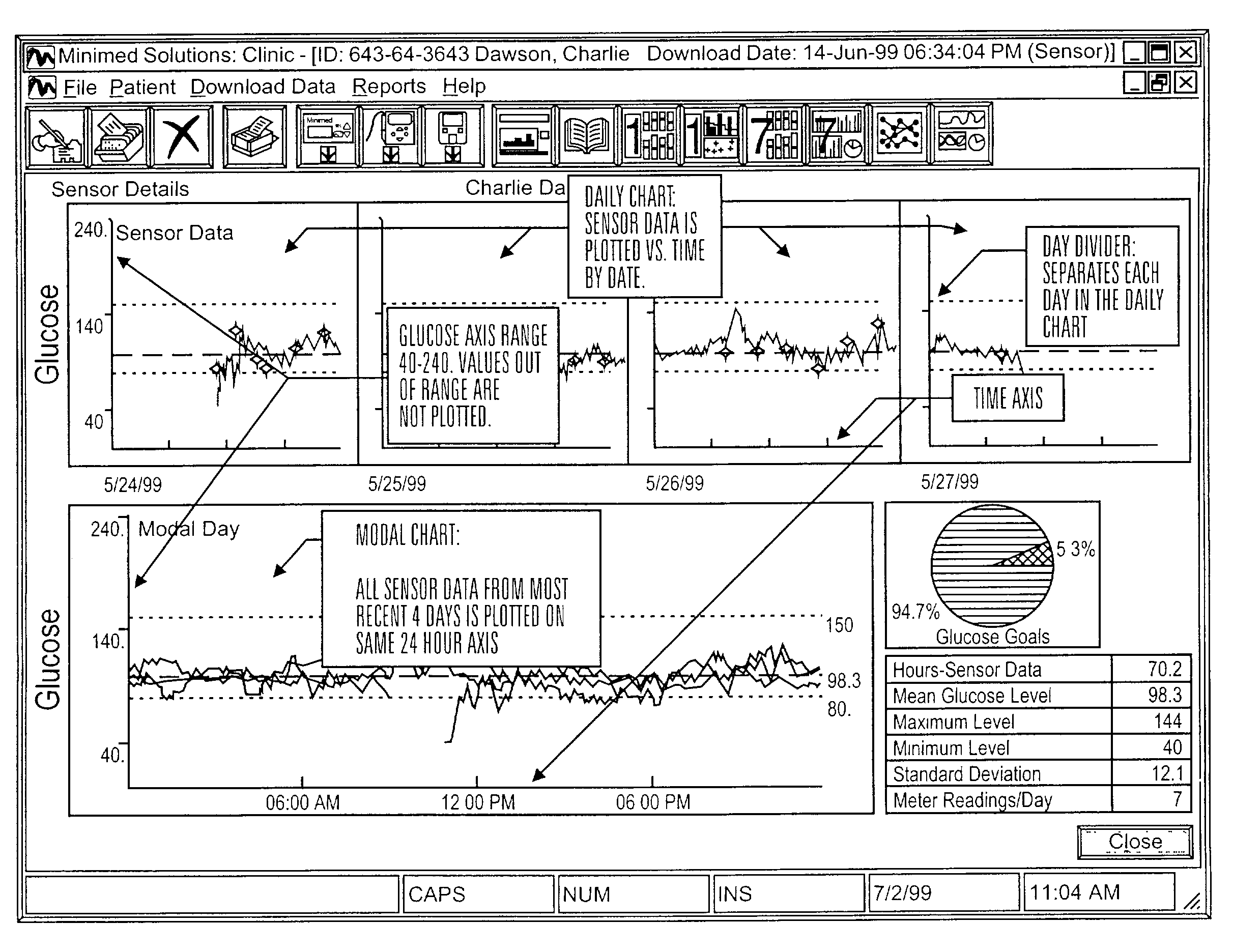
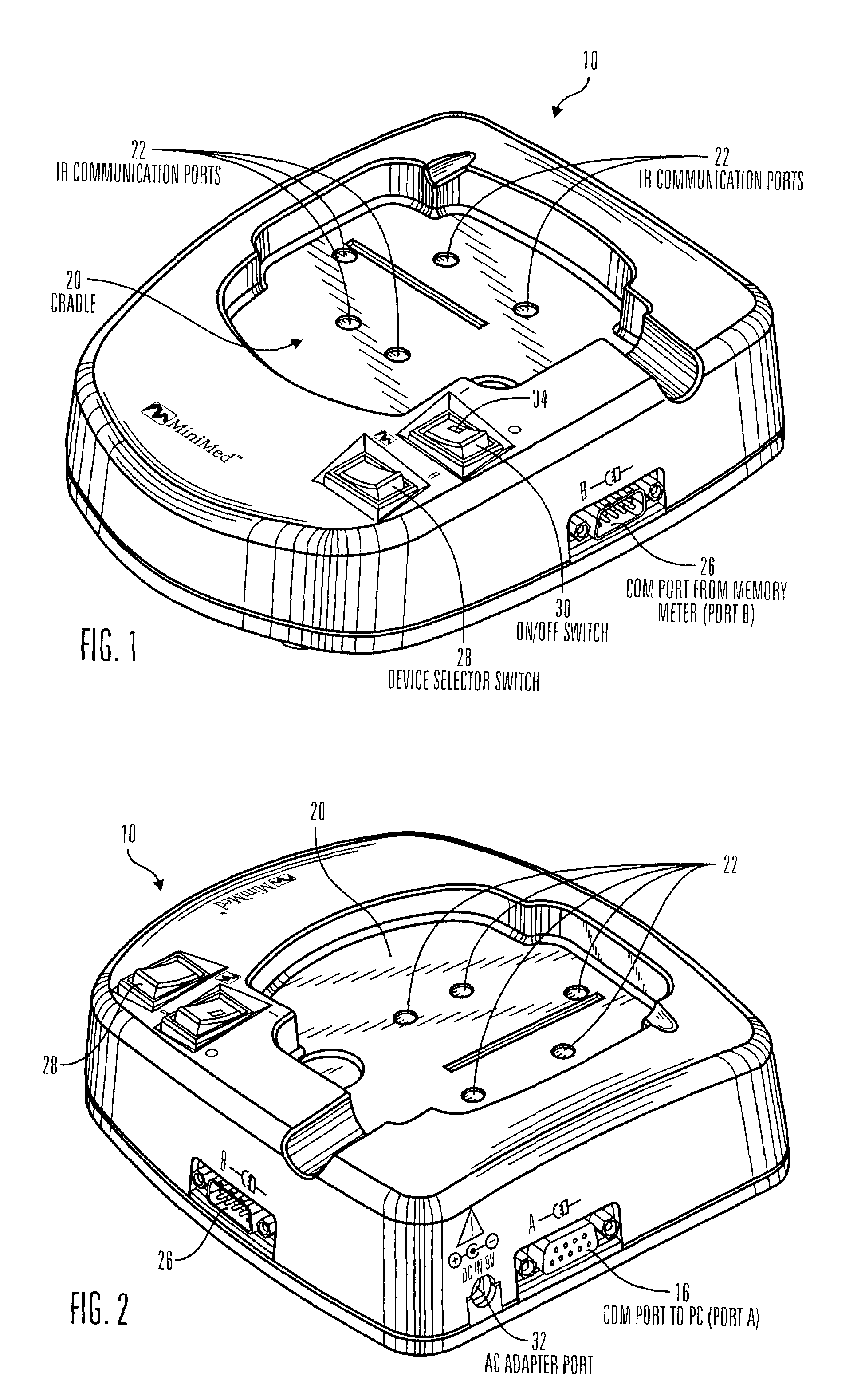
Communication station and software for interfacing with an infusion pump, analyte monitor, analyte meter, or the like
InactiveUS7647237B2Peptide/protein ingredientsDigital data processing detailsAnalyteSystem combination
A communication station is for use with a medical device (such as an infusion pump) and a processing device (such as a computer). The communication station includes a housing, a medical device interface coupled to the housing, a processing device interface coupled to the housing and a processor coupled to the housing. The device interface interfaces with the medical device, and the processing device interface interfaces with the processing device. The processor provides a communication path between the medical device and the processing device such that programming and instructions may be communicated from the processing device to the medical device and data may be transferred from the medical device to the processing device. The communication station may be combined with a system that is capable of generating reports either locally or remotely. In addition, the medical device interface may be a cradle that is configurable to attach to different shaped medical devices.
Owner:MINIMED
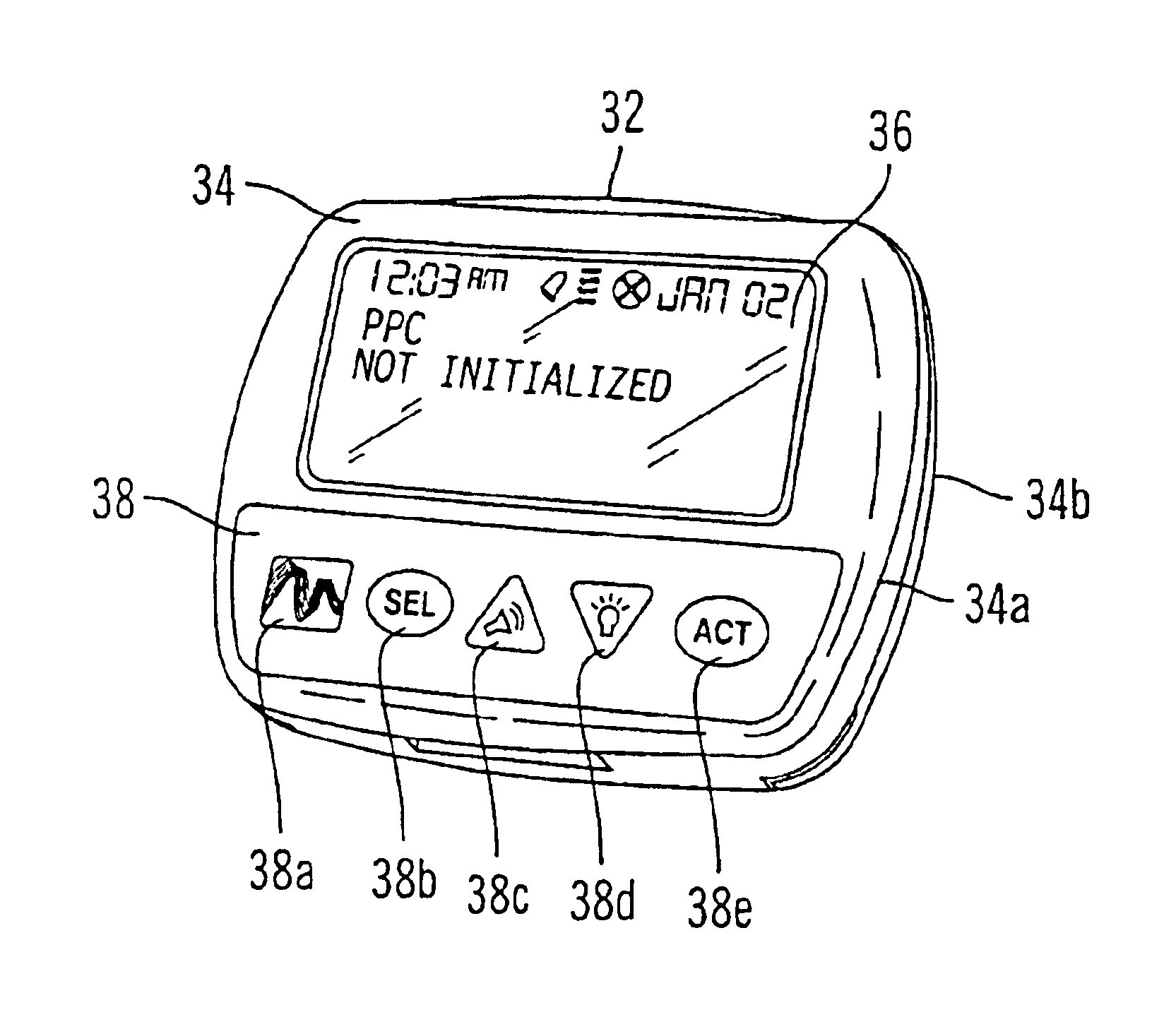
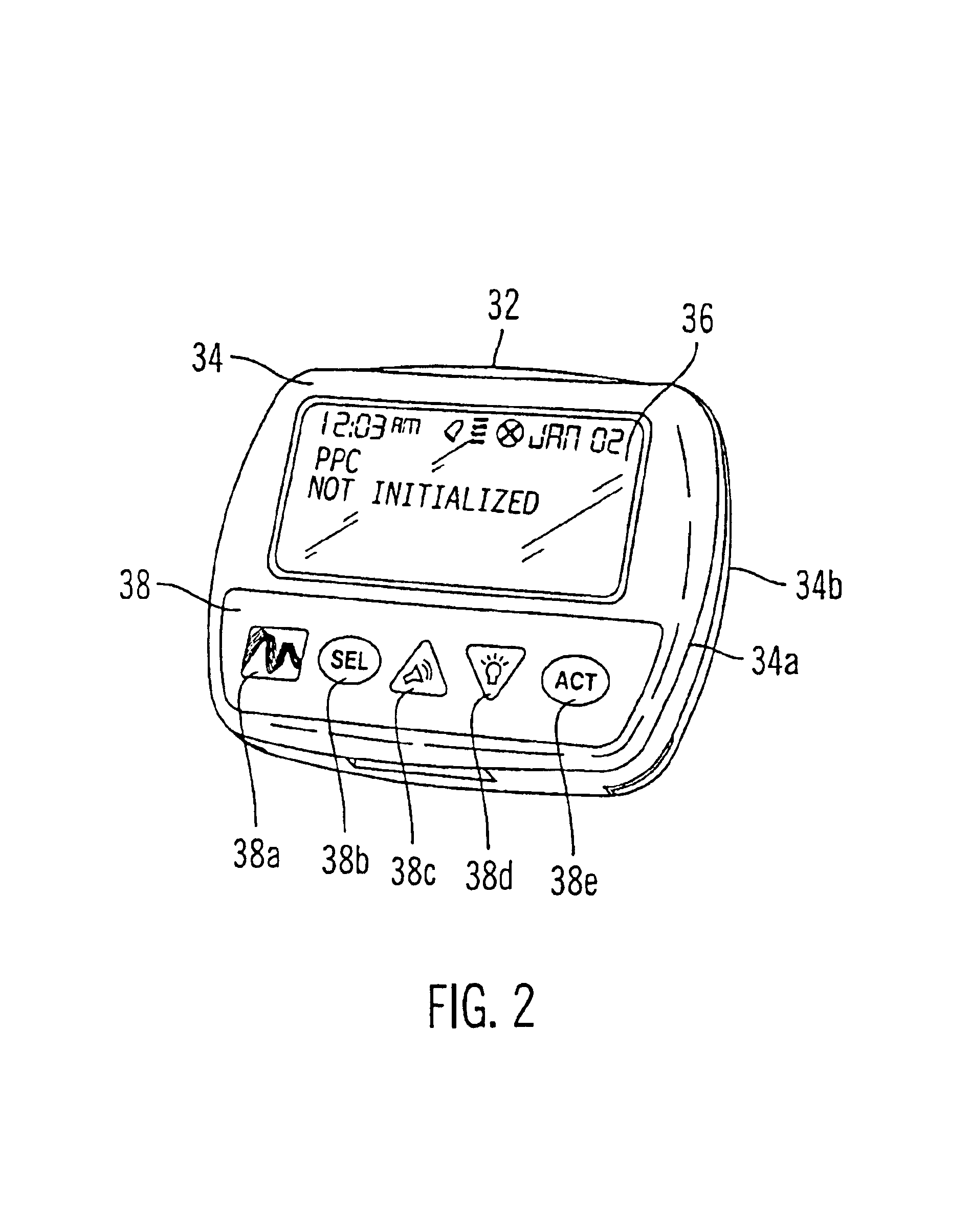
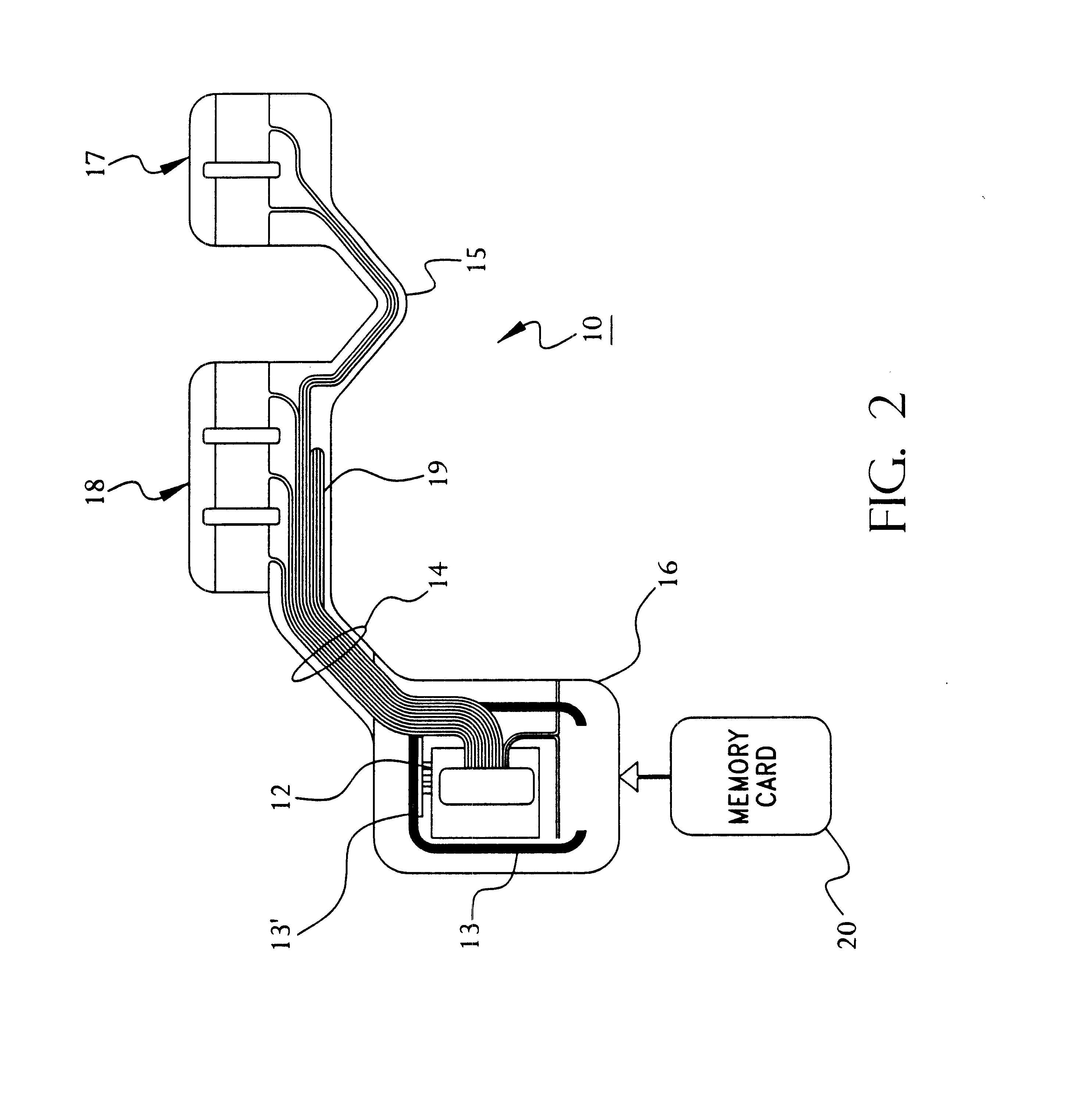
Portable remote patient telemonitoring system using a memory card or smart card
InactiveUS6454708B1Low costIncrease the number ofSurgeryRespiratory organ evaluationSmart cardFull waveform
A system and method for monitoring health parameters and capturing data from a subject. The system is characterized by a cordless, disposable sensor band with sensors for measuring full waveform ECG, full waveform respiration, skin temperature, and motion, and a connector which accepts a memory card or a smart card for storage of the measured data. After a predetermined period of time, such as when the sensor band is removed, the memory card or smart card is removed and inserted into a monitoring device which reads the stored health parameter data of the subject. The monitoring device includes a base station that includes a memory / smart card reader and is connected to conventional phone lines for transferring the collected data to a remote monitoring station. The base station may also capture additional clinical data, such as blood pressure data, and to perform data checks. Subject safety is enhanced by the ability of the base station to compare clinical data, e.g. ECG, against given profiles and to mark events when appropriate or when the base station is programmed to do so. The remote monitoring station allows the presentation and review of data (including events) forwarded by the sensor band. ECG analysis software and a user-friendly graphical user interface are provided to remotely analyze the transmitted data and to permit system maintenance and upkeep. In alternative embodiments, a smart card includes the sensor band's electronics and / or signal transmission circuitry in conjunction with a portable data logger so that the electronics may be reused from one disposable sensor band to the next without limiting the patient's range of movement. The system of the invention has useful application to the collection of subject clinical data during drug trials and medical testing for regulatory approvals as well as management of subjects with chronic diseases.
Owner:CLEARPATH PARTNERS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com