Patents
Literature
47 results about "Administrative controls" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Administrative controls are training, procedure, policy, or shift designs that lessen the threat of a hazard to an individual. Administrative controls typically change the behavior of people (e.g., factory workers) rather than removing the actual hazard or providing personal protective equipment (PPE).
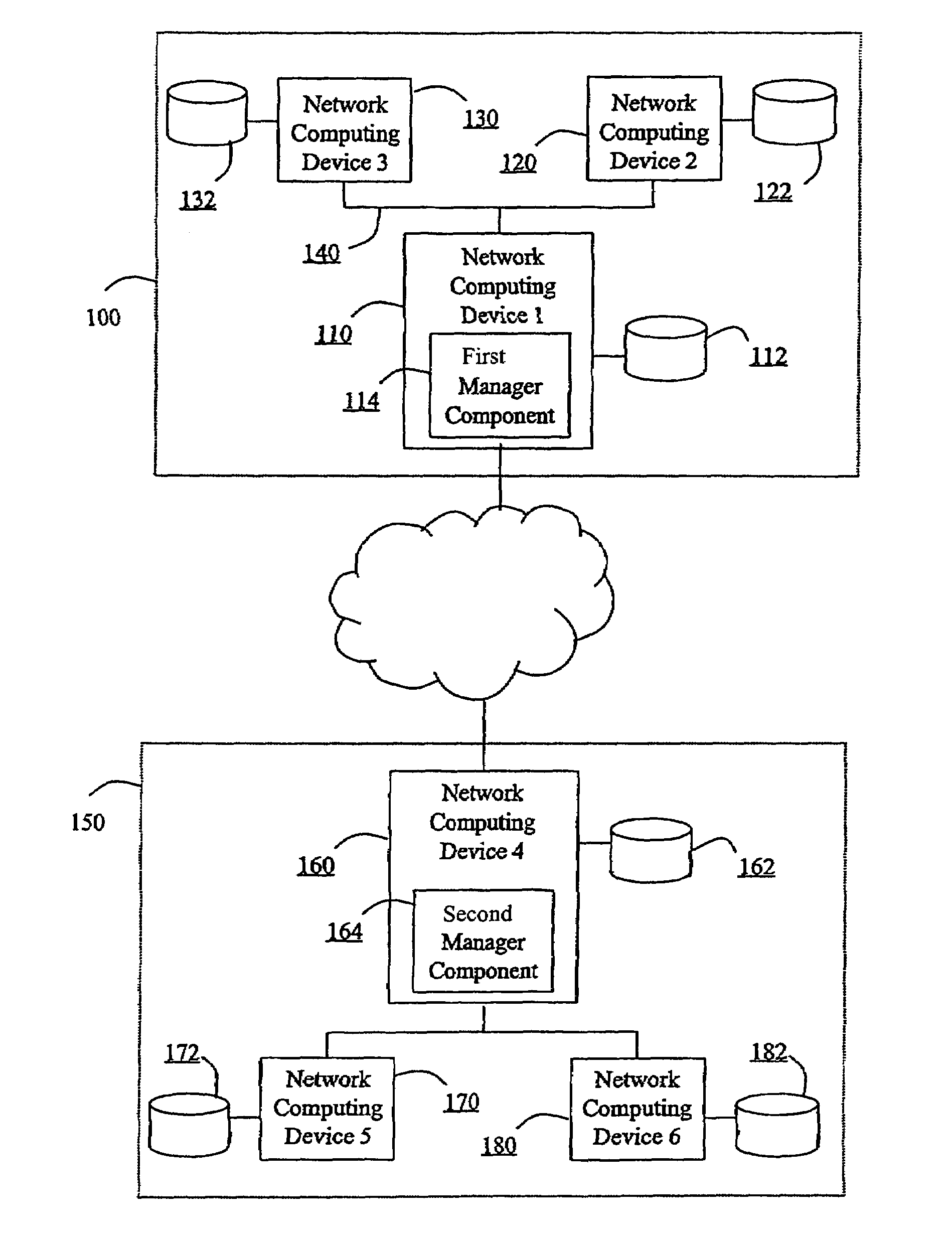
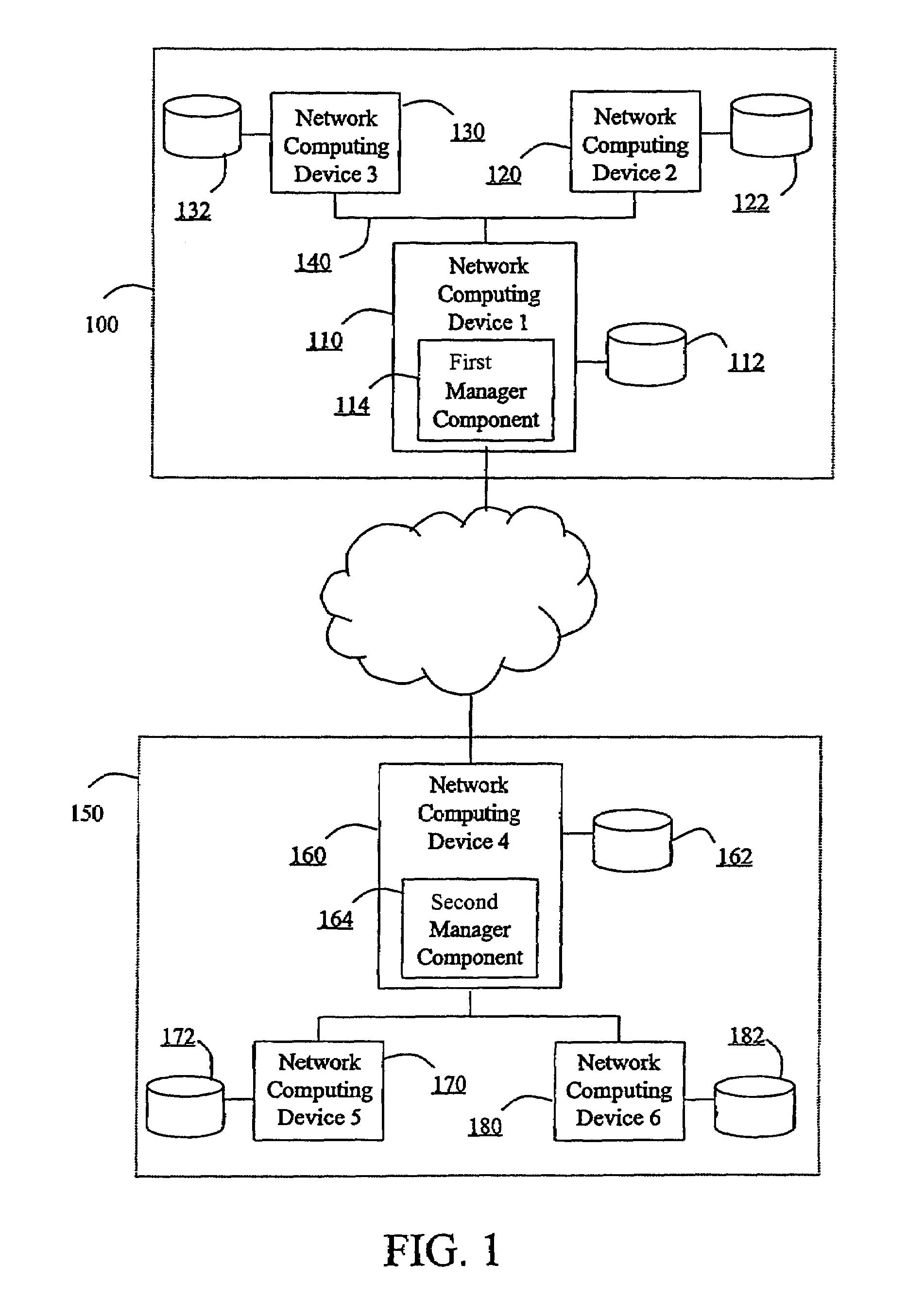
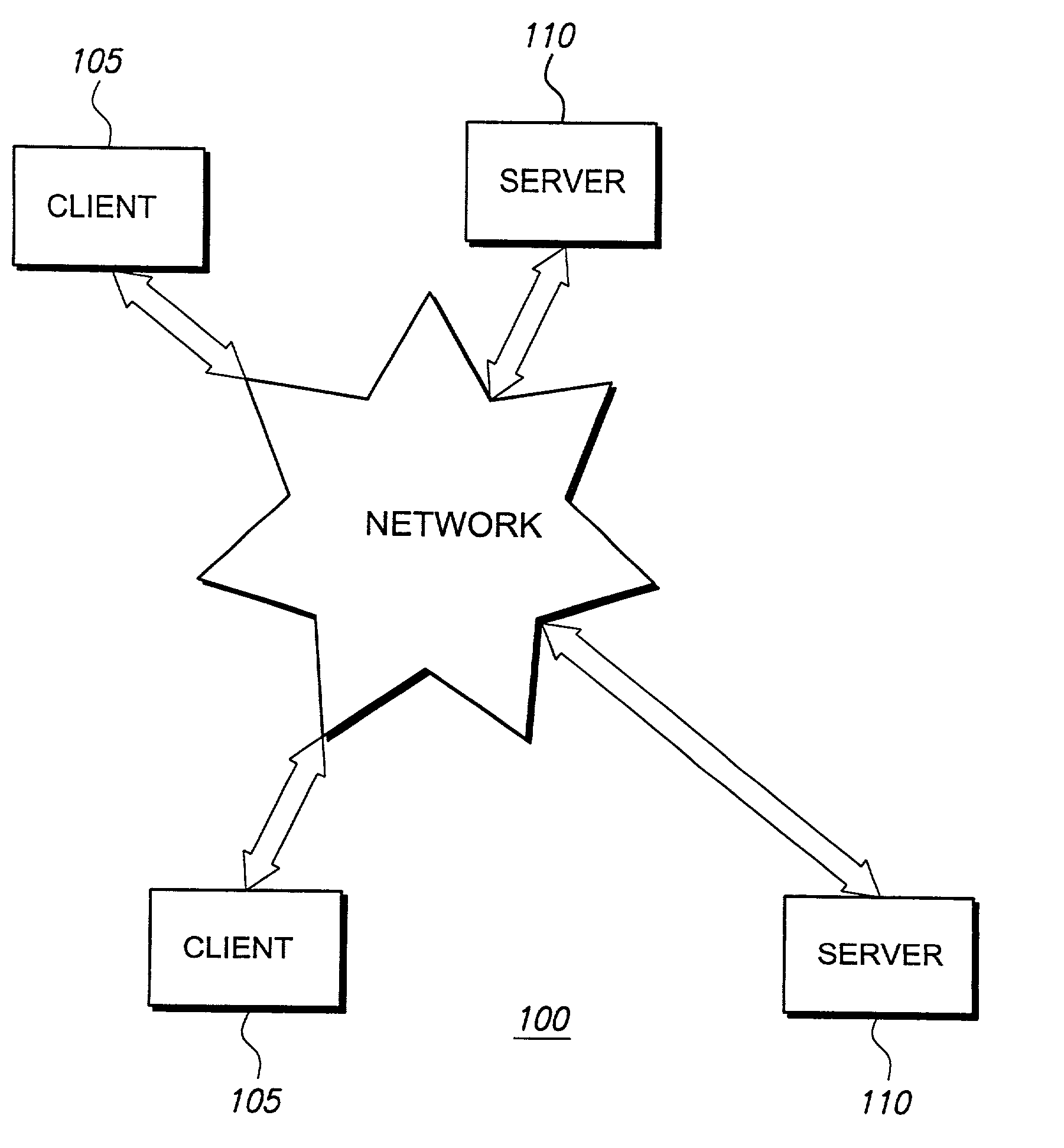
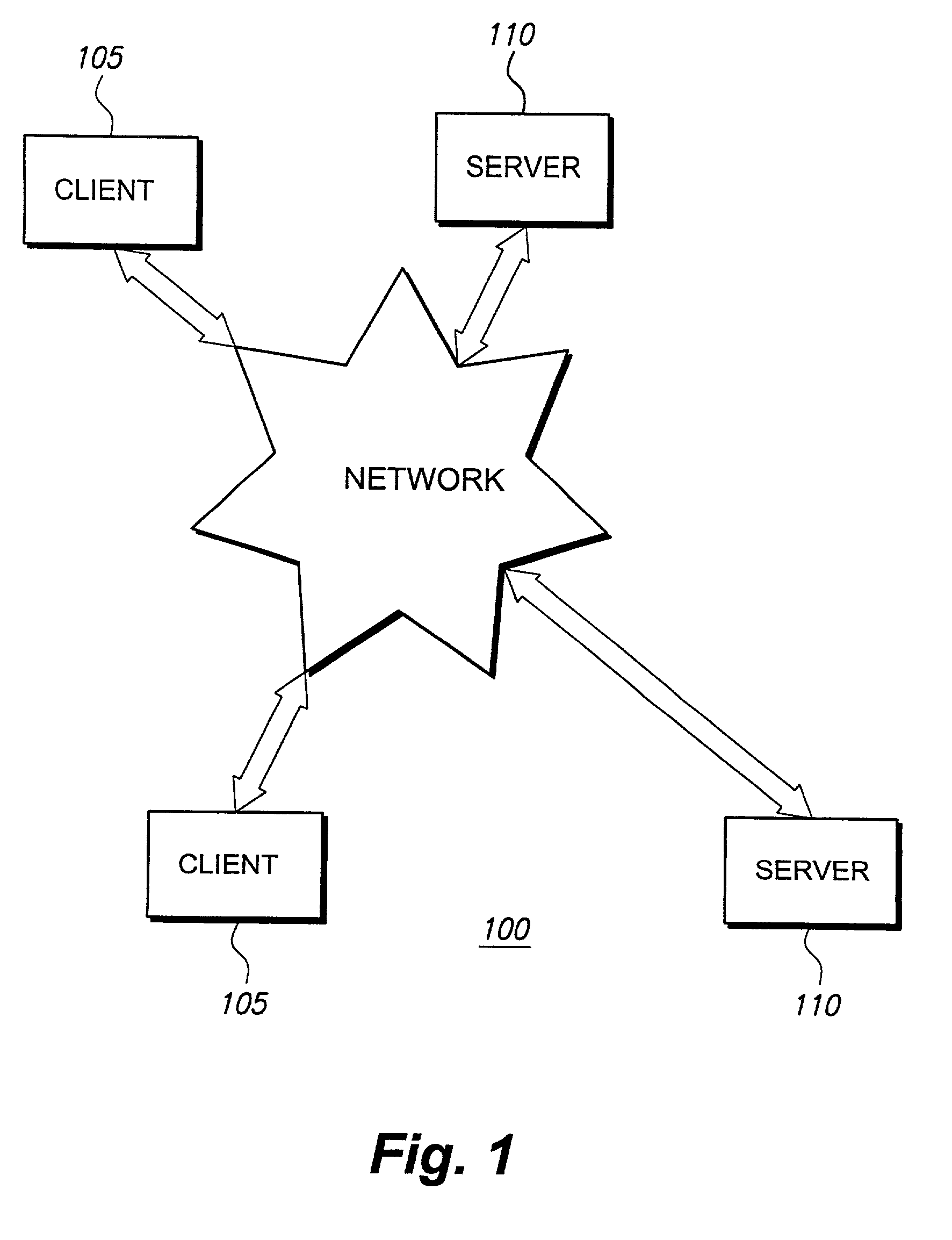
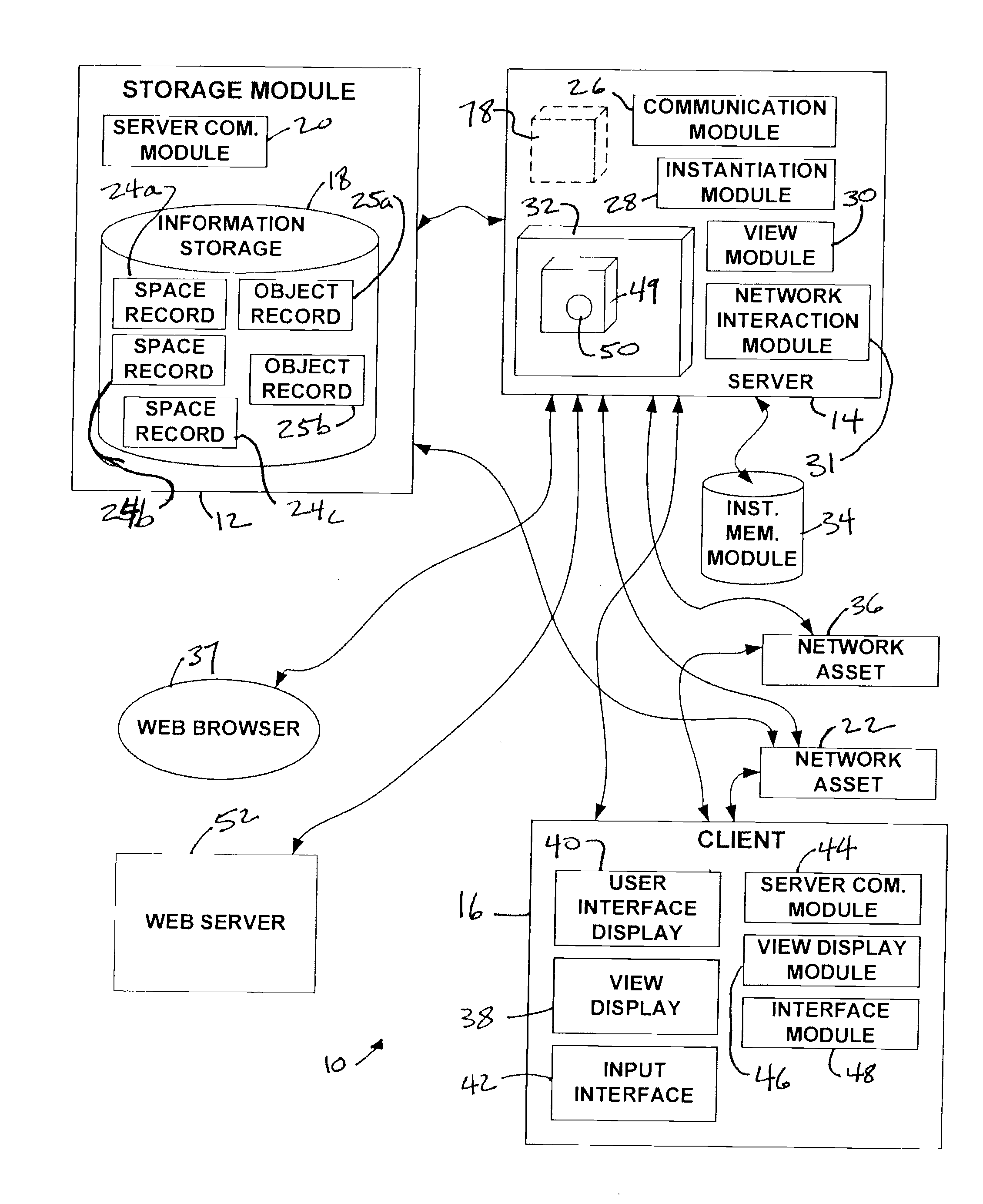
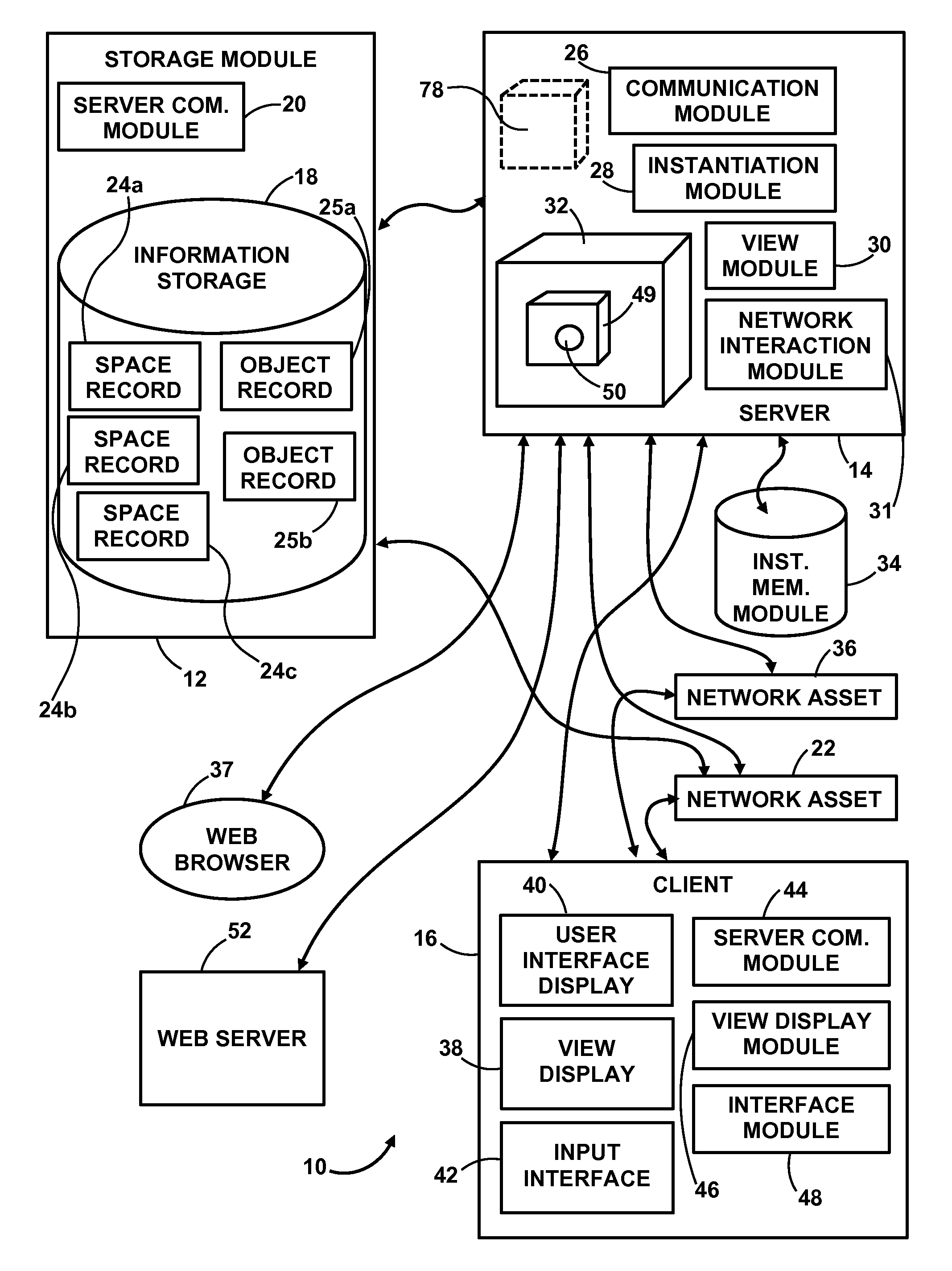
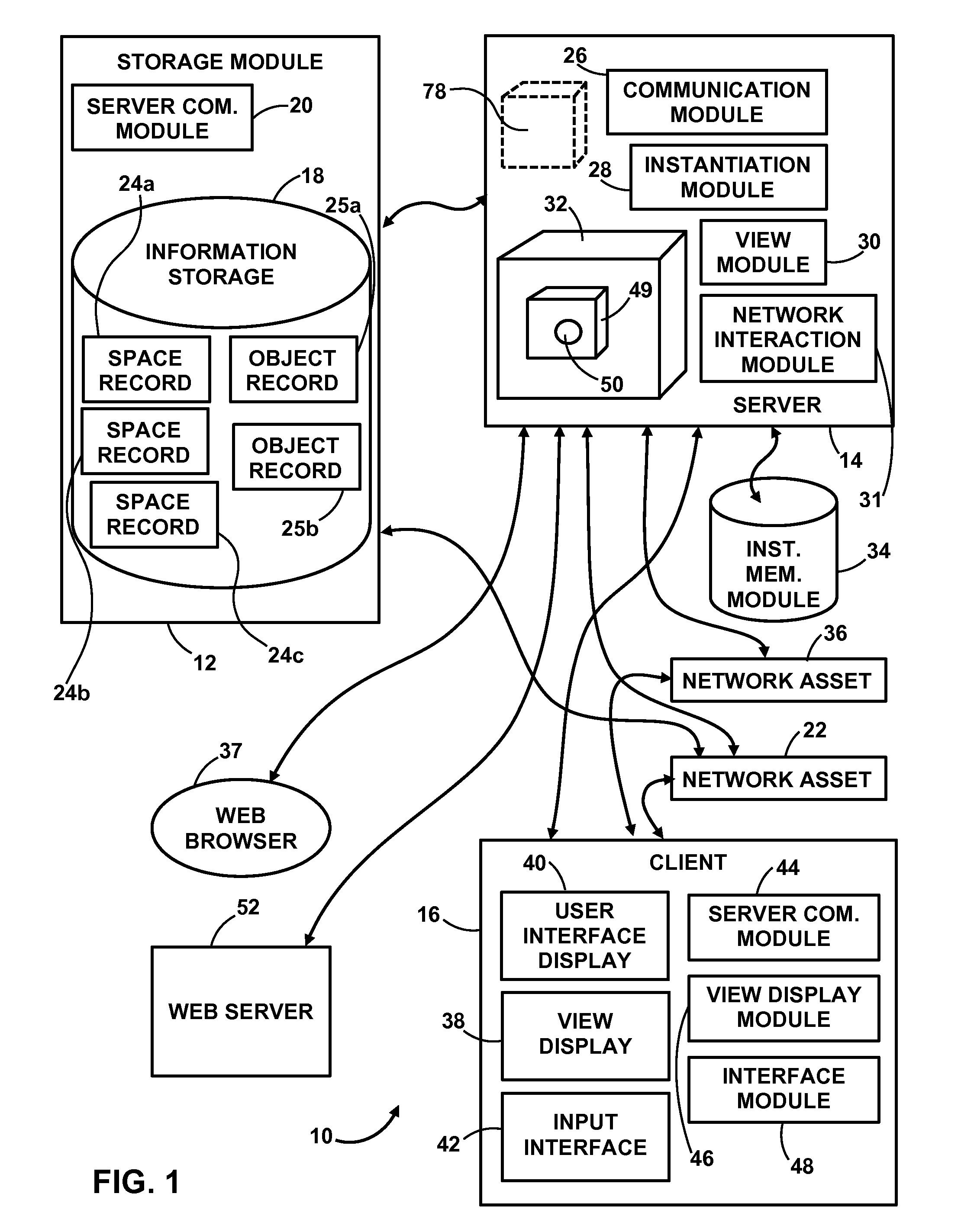
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
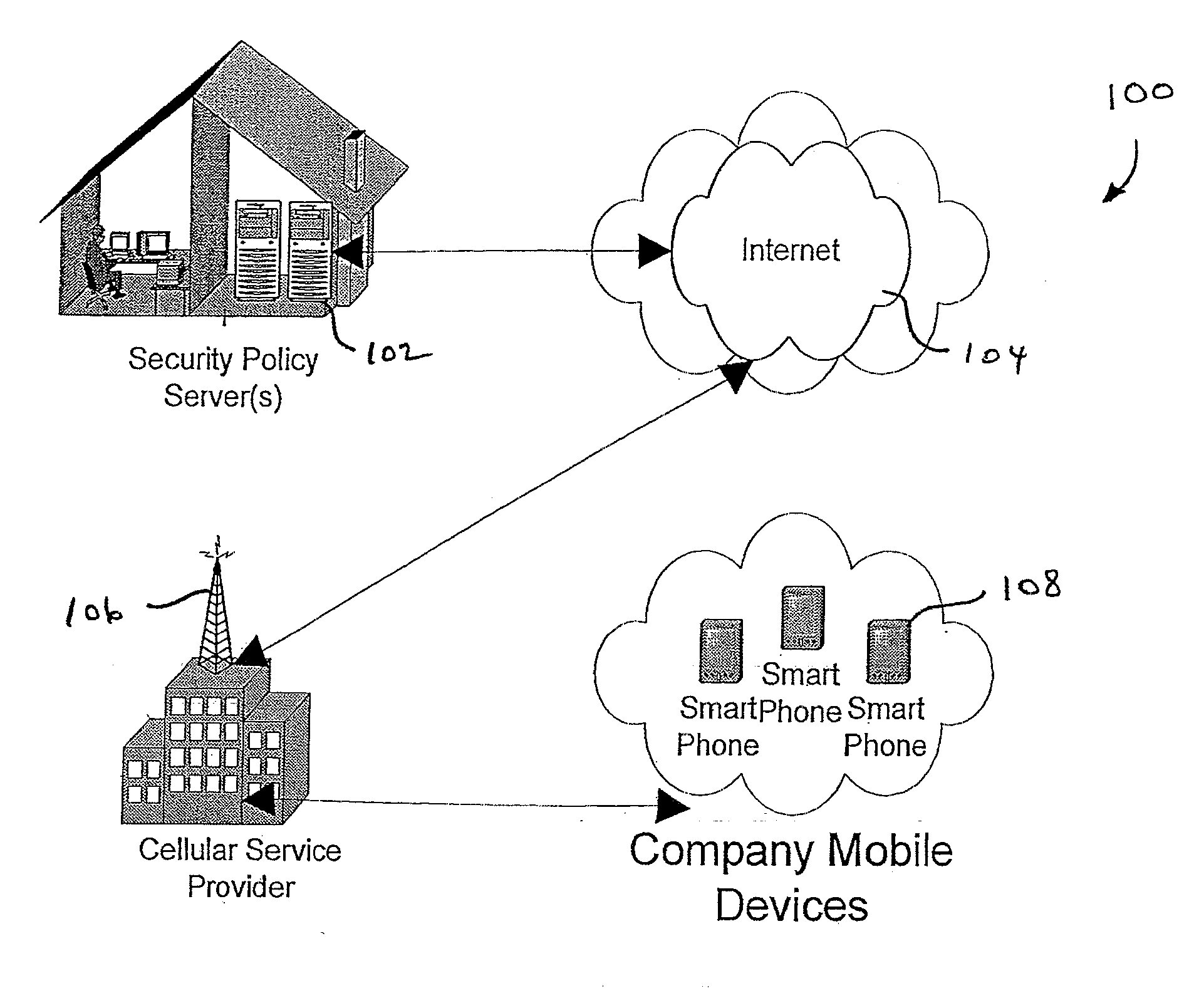
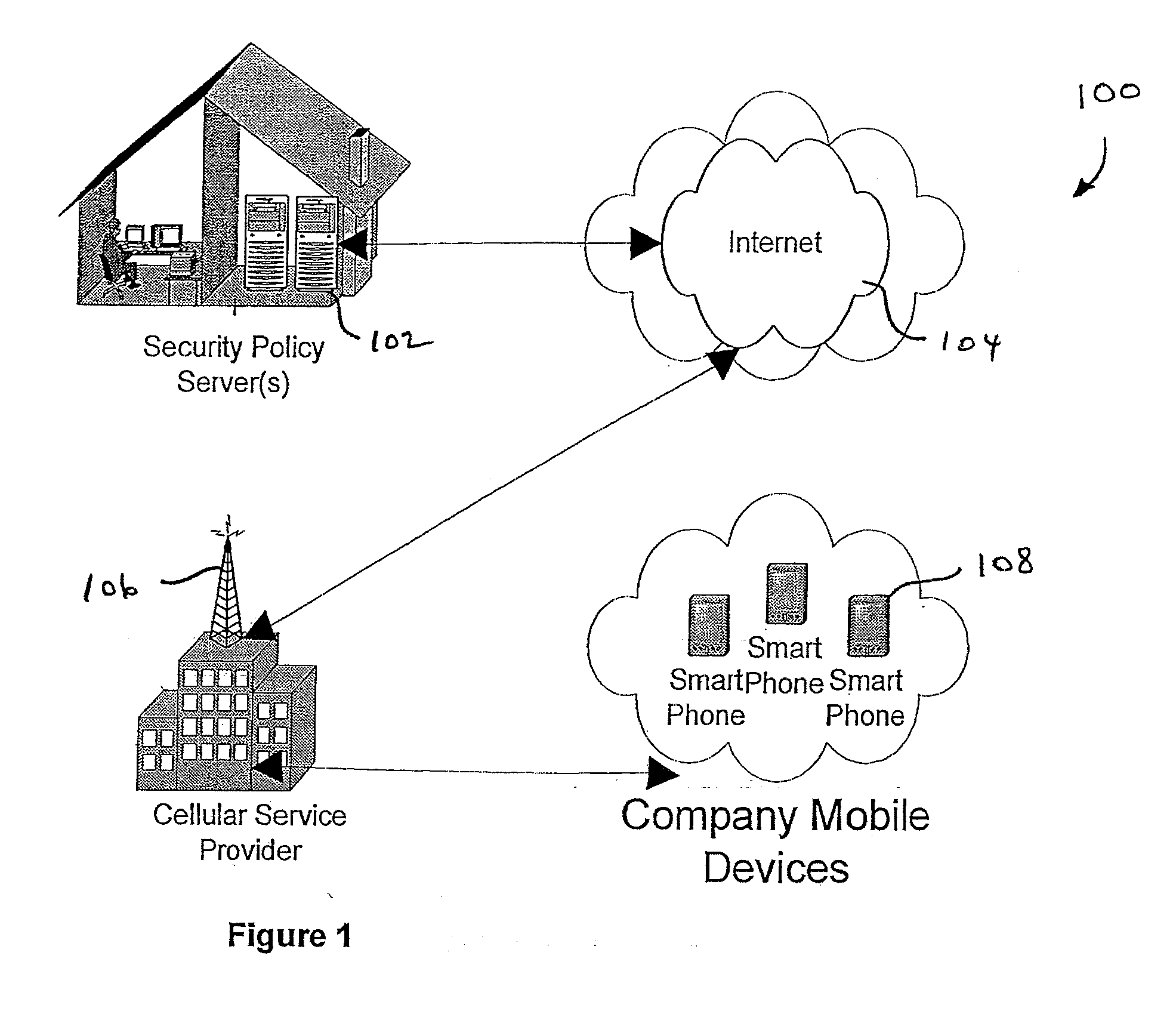
Centralized Dynamic Security Control for a Mobile Device Network
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
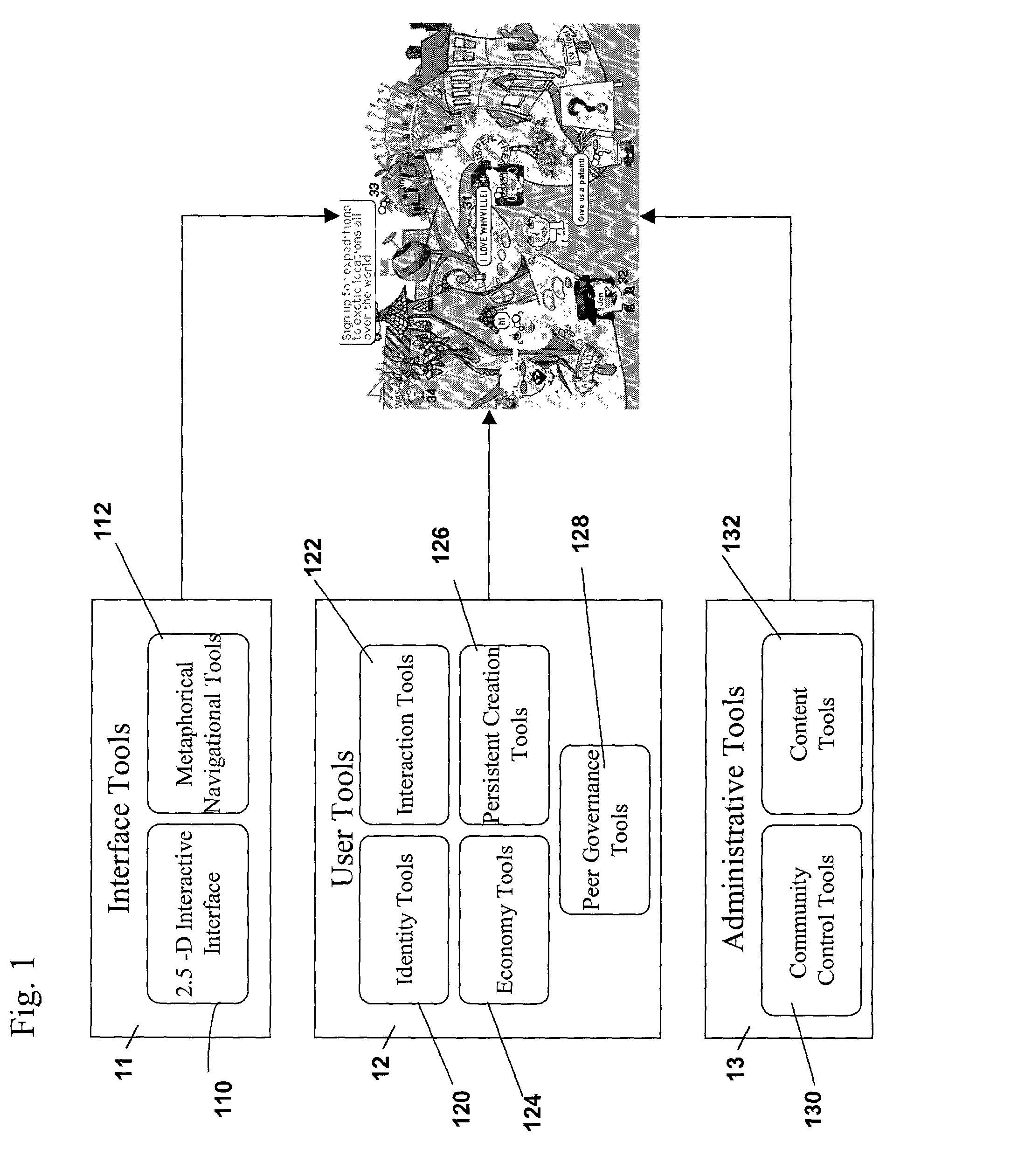
Graphical interactive interface for immersive online communities
ActiveUS7925703B2Low bandwidth connectionMinimal sizeIndoor gamesMultiple digital computer combinationsGraphicsTime response
The present invention discloses a computer system within a computer network having multiple computers connected together using telecommunications mechanisms for graphically interacting within immersive online communities. A user selects a set of desired characteristics associated with a personality for creation of a first intelligent virtual object. The first intelligent virtual object interacts with other intelligent virtual objects within the immersive online community utilizing predetermined interface tools such that said other intelligent virtual objects receive real-time responses to stimuli initiated by said other intelligent virtual objects. The first intelligent virtual object interactively passes user generated content between said other intelligent virtual objects and said user under administrative controls.
Owner:NUMEDEON
Classified ads software program
InactiveUS20020120506A1Easy to useInexpensive, dependableMarketingSpecial data processing applicationsWeb siteExtensibility
A method and system for electronic classified advertising, including in a sophisticated edition, a seven-step installation wizard, portability to web servers, scalability, an intuitive and easy to use layout, customization features, fee-based options and features, ad display options and features, selected expiration of ads with optional notification, user set-up personal search agent which will automatically notify the user with new ads matching the database search criteria specified by the user, private messaging, a search engine for seven types of searches including browsing, keyword searches, retrieval of a specific ad by its database ID number, retrieval of all of a specific user's ads, retrieval of one specific ad for modification, and full database power searches, user registration, additional user posting and searching options, E-mail, Antispamming, detailed administrative controls, and security. Also available are banner ad modules, affiliate web sites, and internationalization features.
Owner:HAGEN PHILIP A
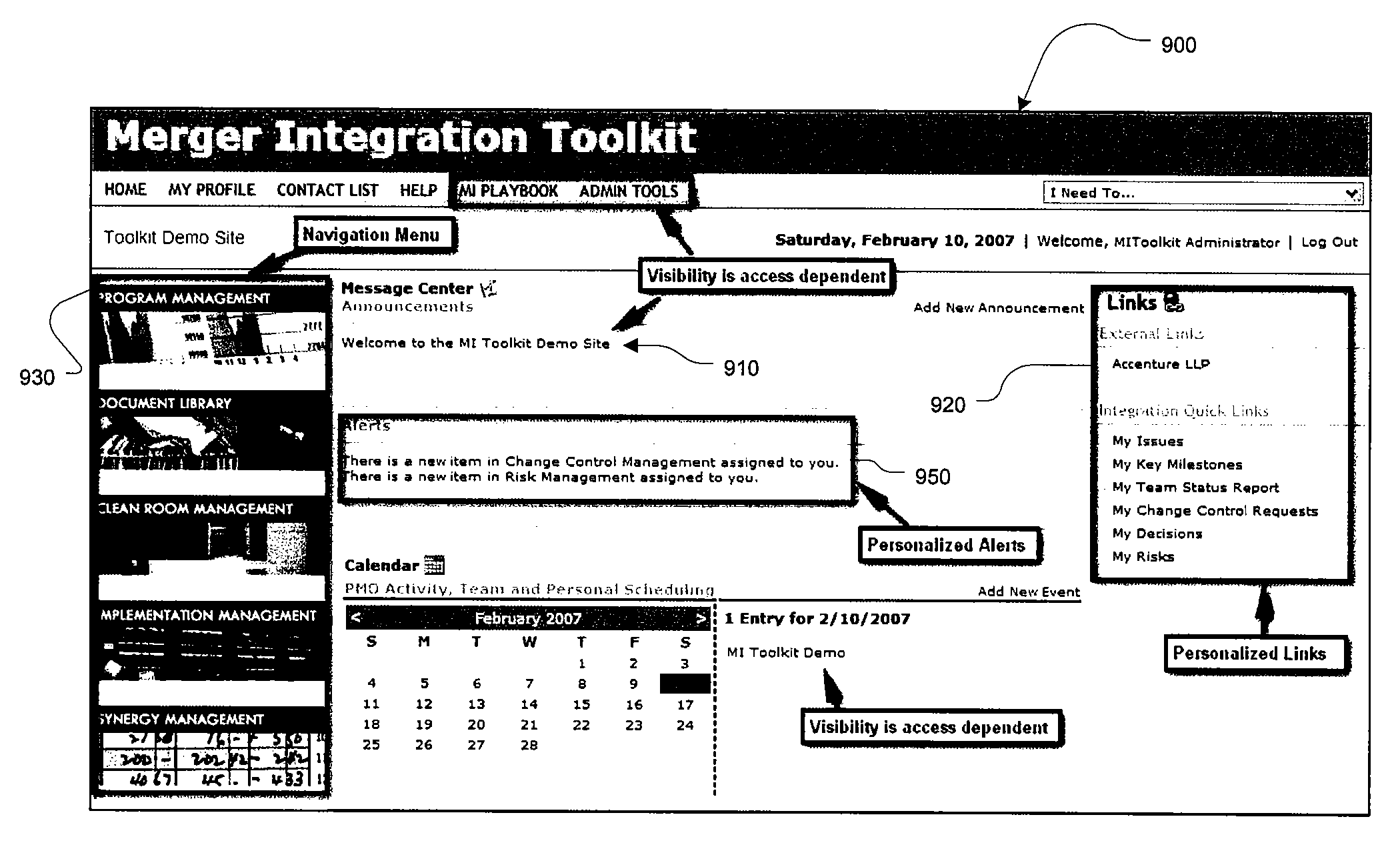
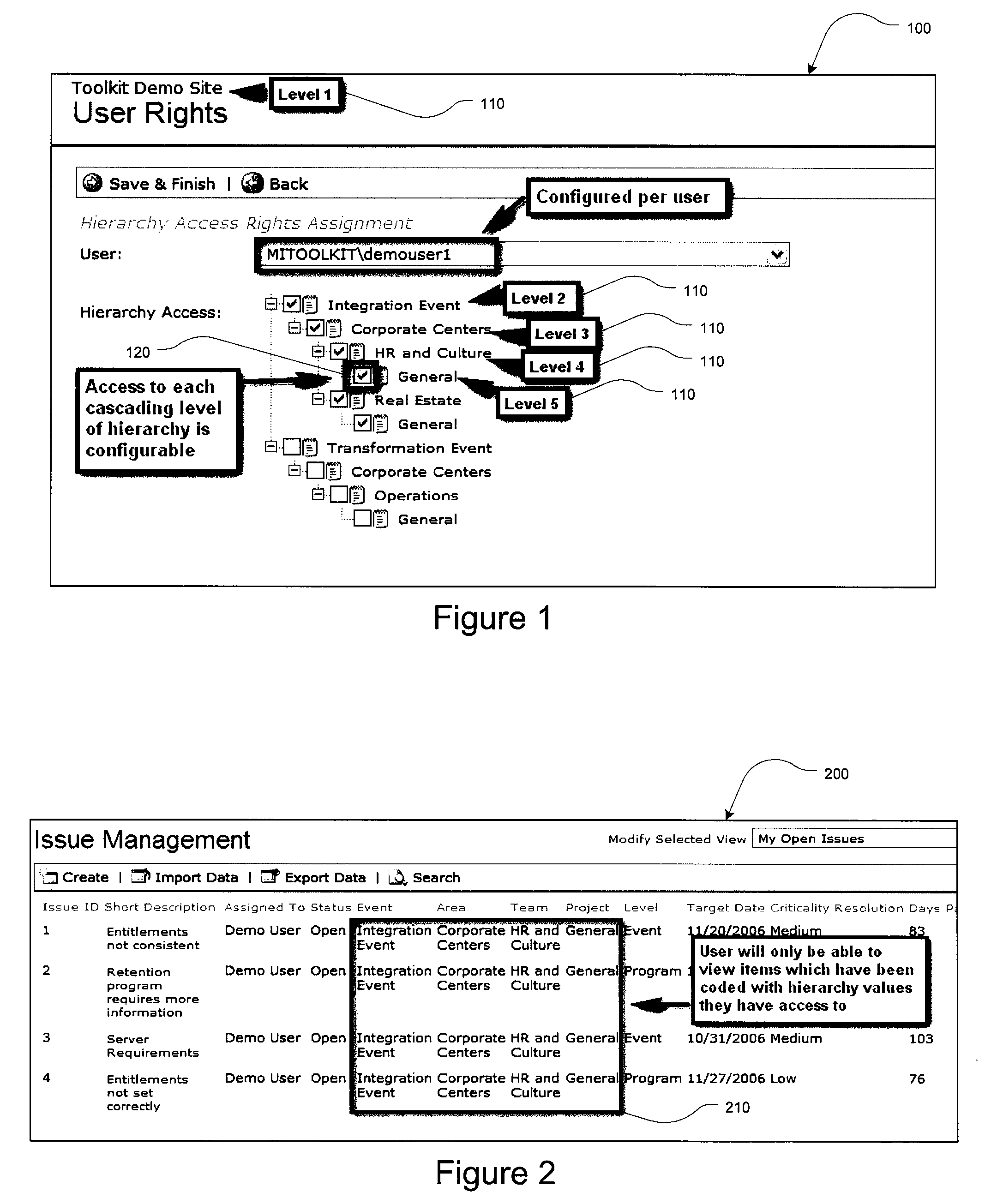
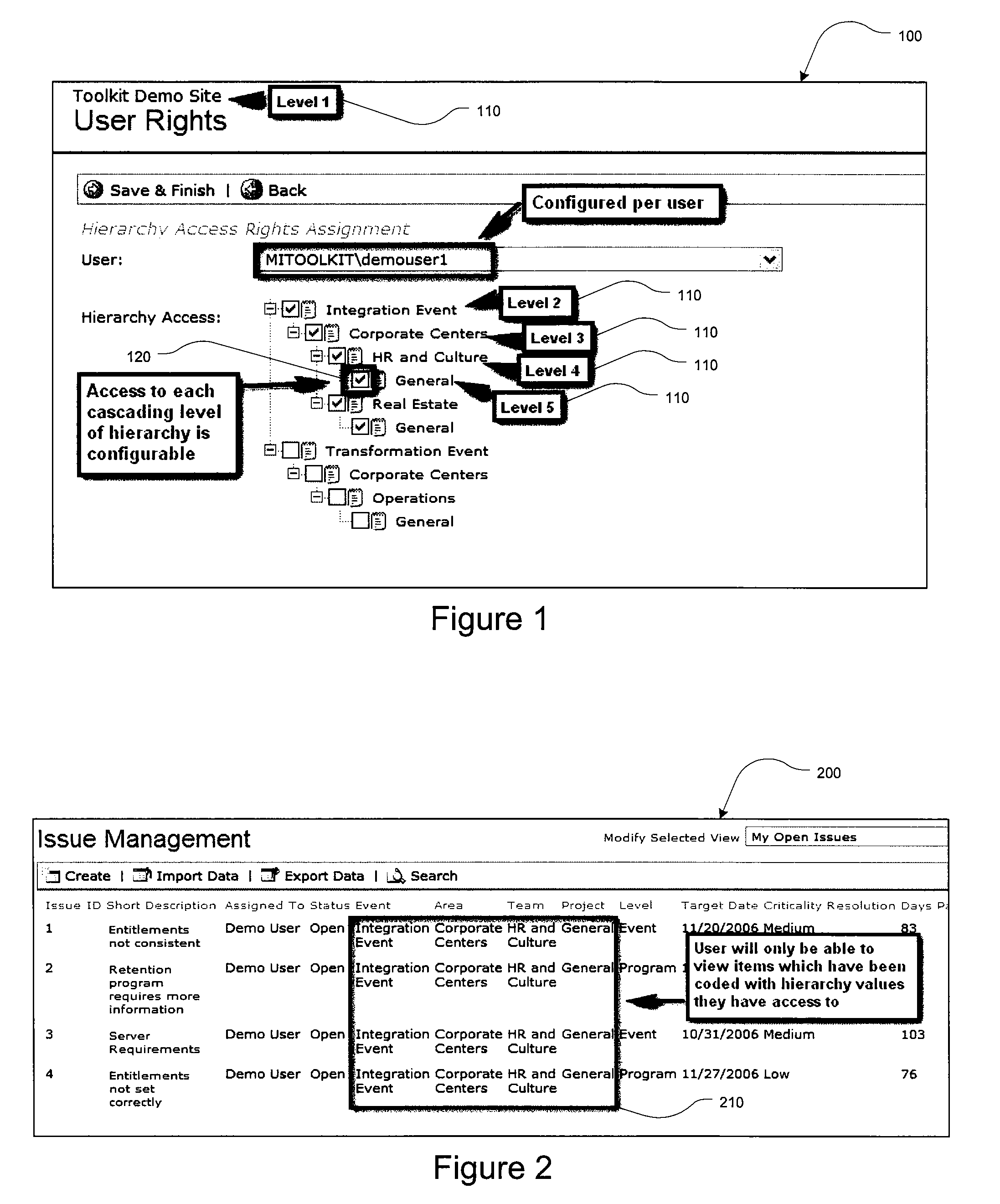
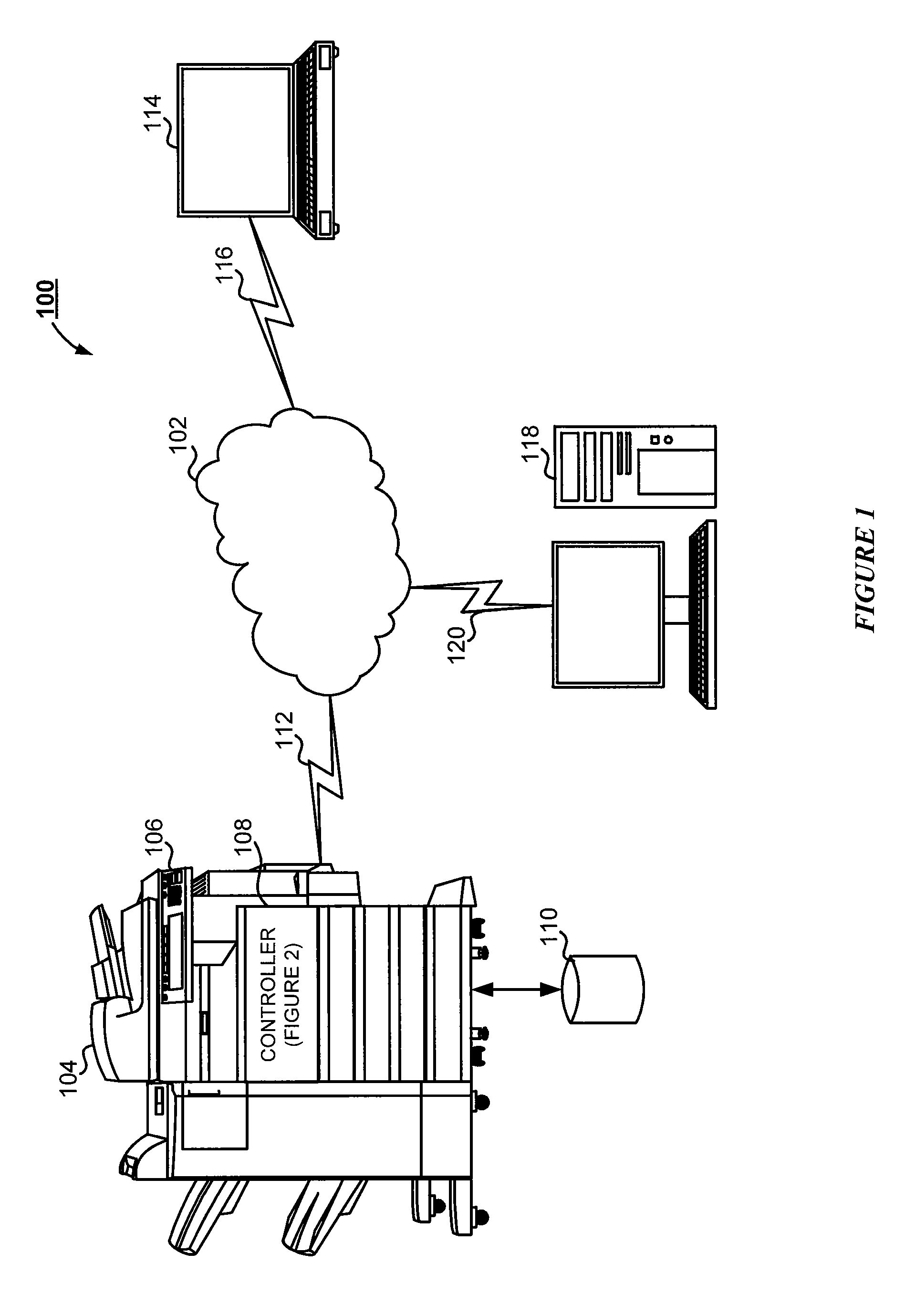
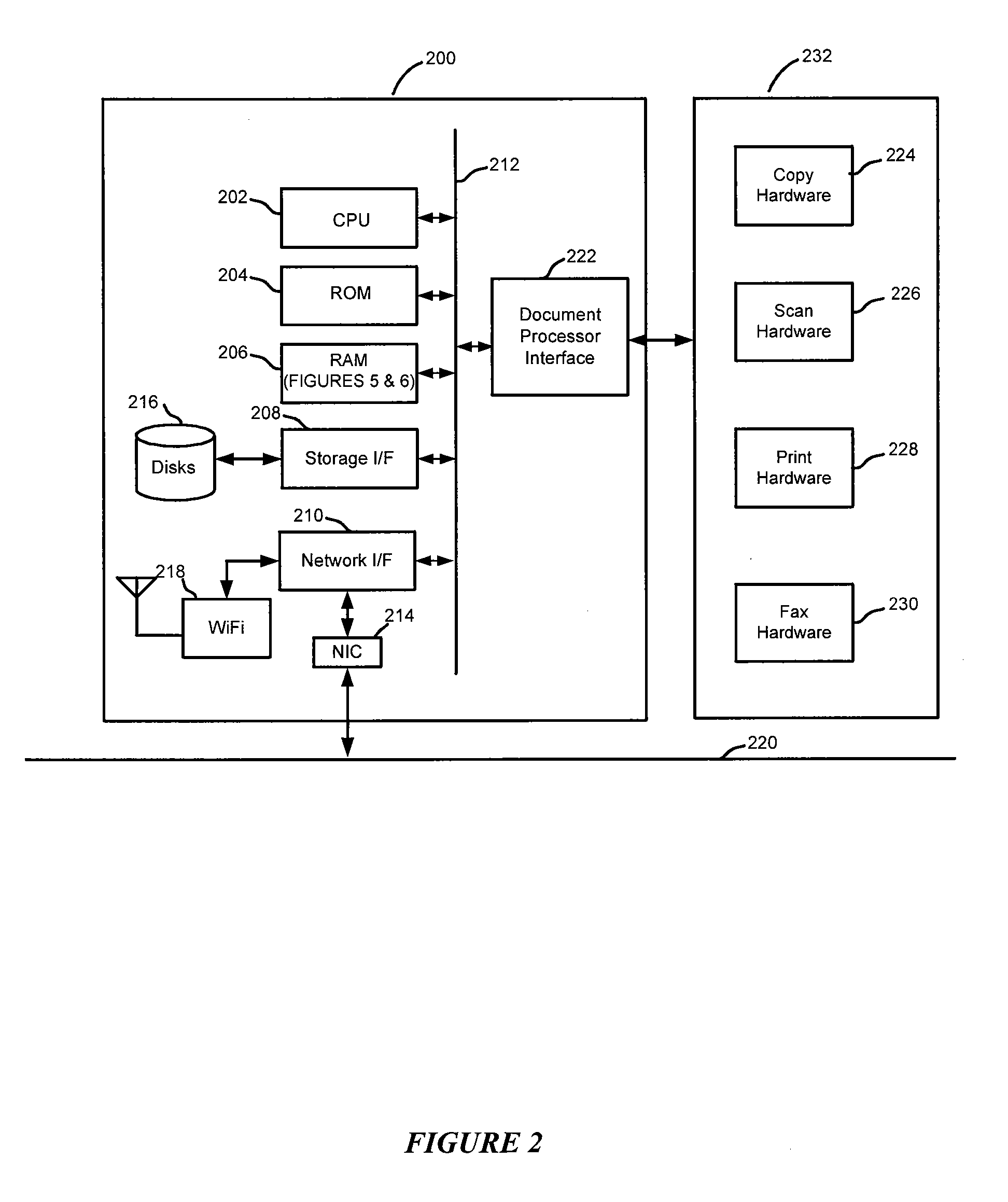
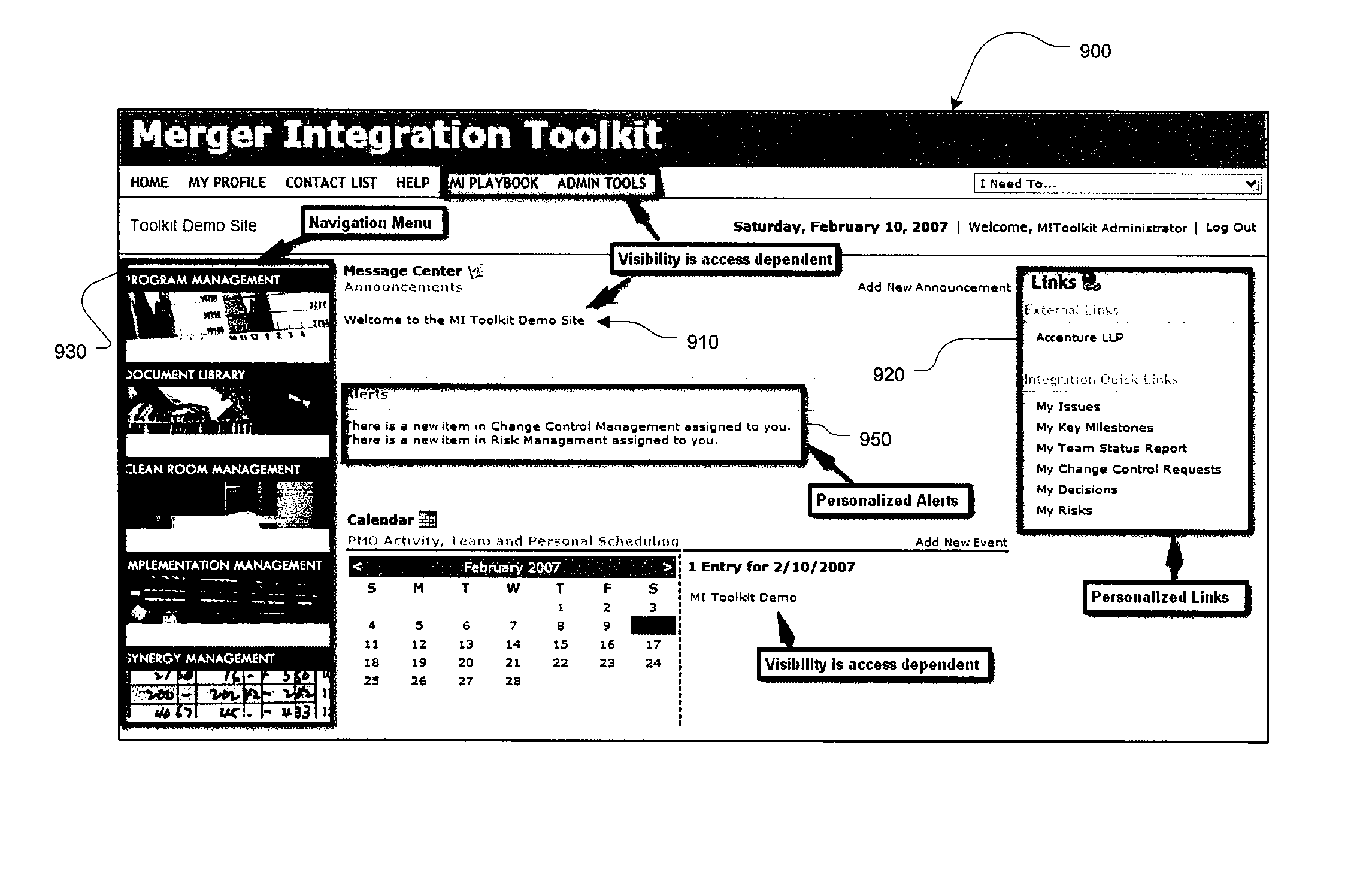
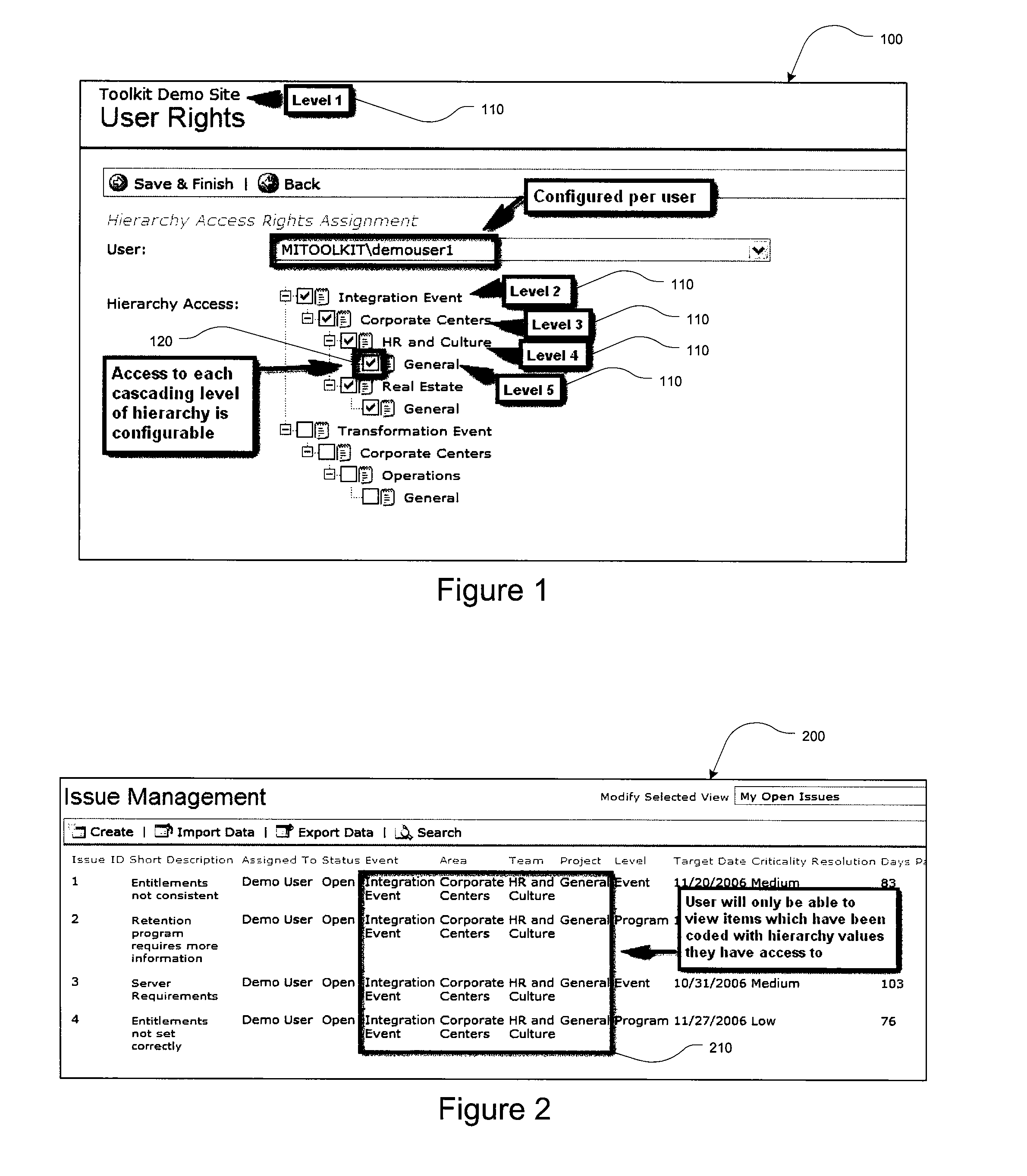
Merger integration toolkit system and method for secure navigation hierarchy and workflow functionality
InactiveUS20080040173A1Provide functionalityProvide securityResourcesSpecific program execution arrangementsVisibilityEnterprise integration
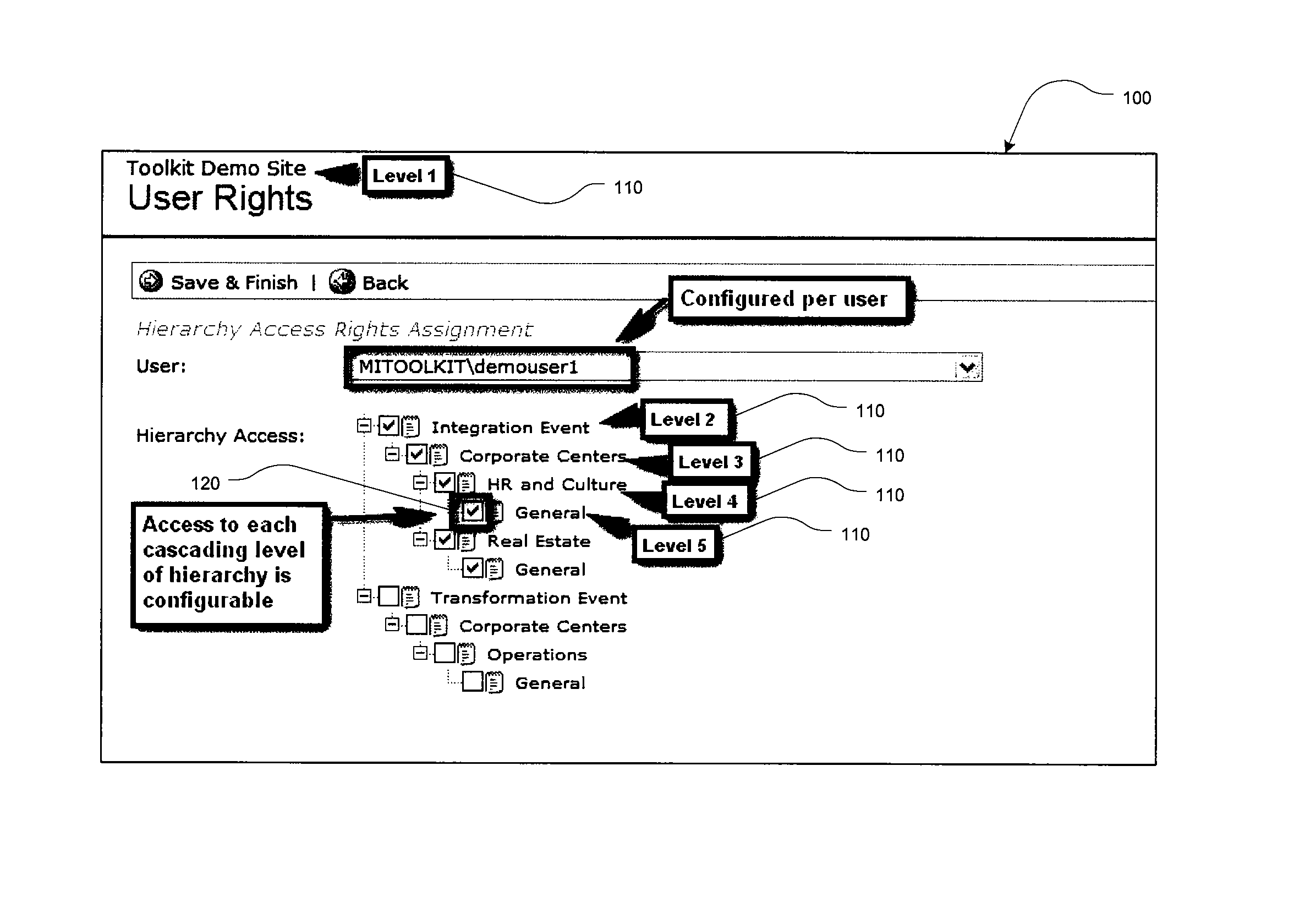
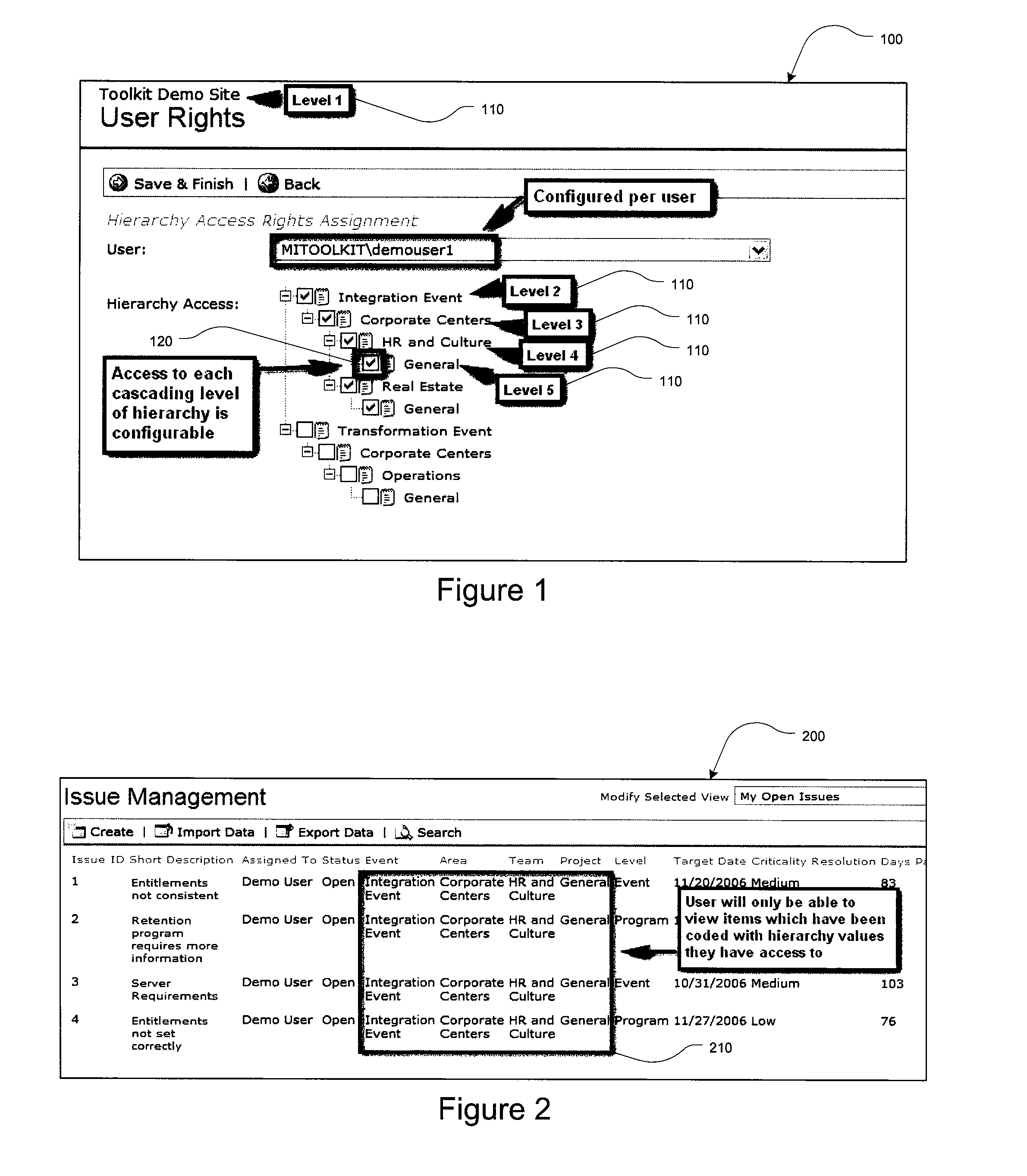
The present invention provides for a method and a computer system for electronically managing and supporting a merger integration of businesses. In one aspect, the invention provides program-level hierarchy and security with a collaboration environment computer program for assisting a group of individuals performing the integration, such that the collaboration environment is an electronic tool configured to provide administrative controls and communication among the group of individuals performing the integration. A management and security layer is established for the collaboration environment computer program. The management and security layer is configurable to control access to content in the collaboration environment computer program independently for each of the individuals, and access to the content is controlled with a plurality of hierarchy levels that are defined and applied to designate the portions of the content to which each individual has access. An individual interfaces with the management and security layer such that the individual's access or visibility of the content is controlled based on the plurality of hierarchy levels. In other aspects of the invention, the method and computer system for an integration of businesses provides a user portal and customizable workflow.
Owner:ACCENTURE GLOBAL SERVICES LTD
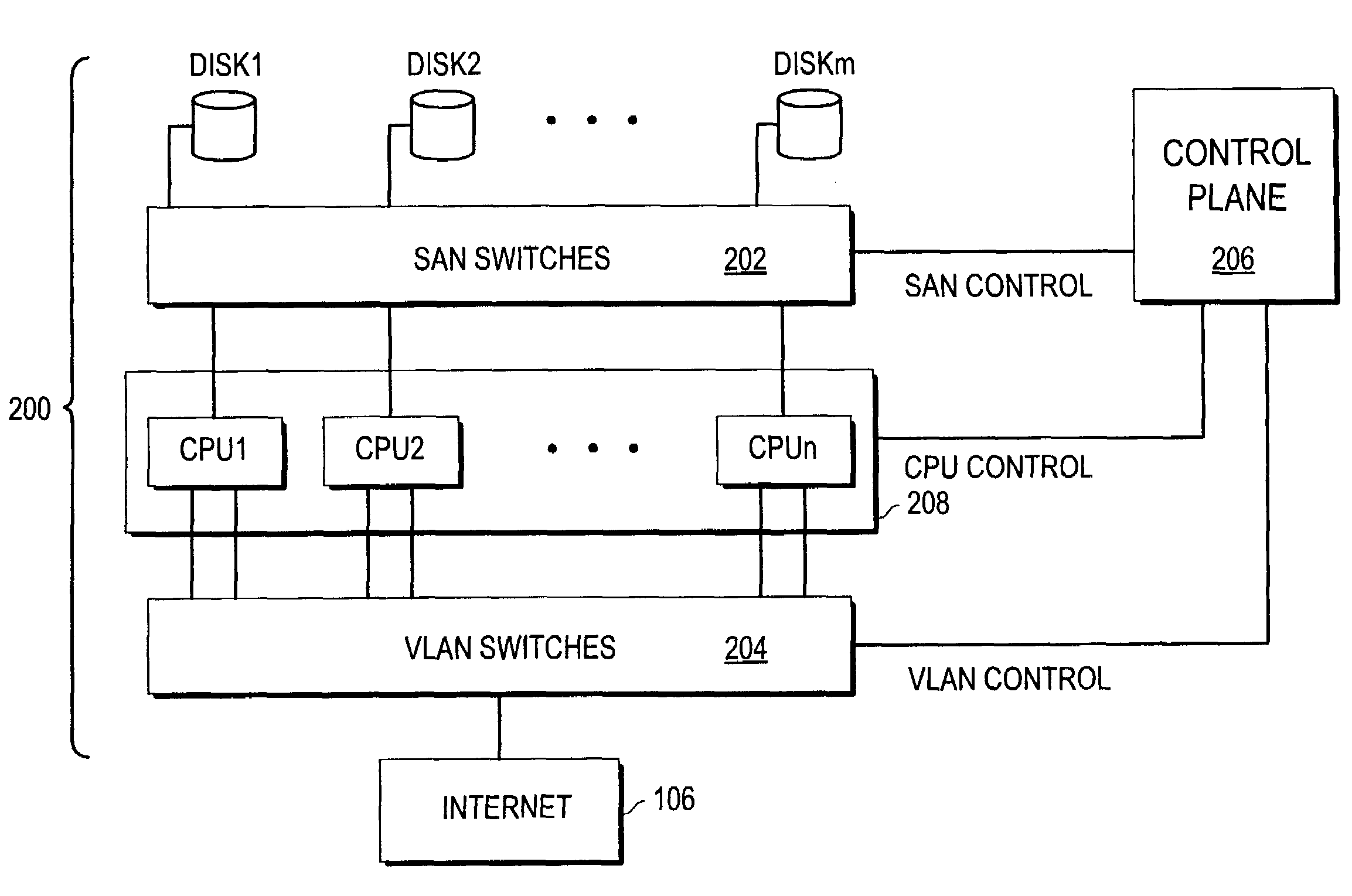
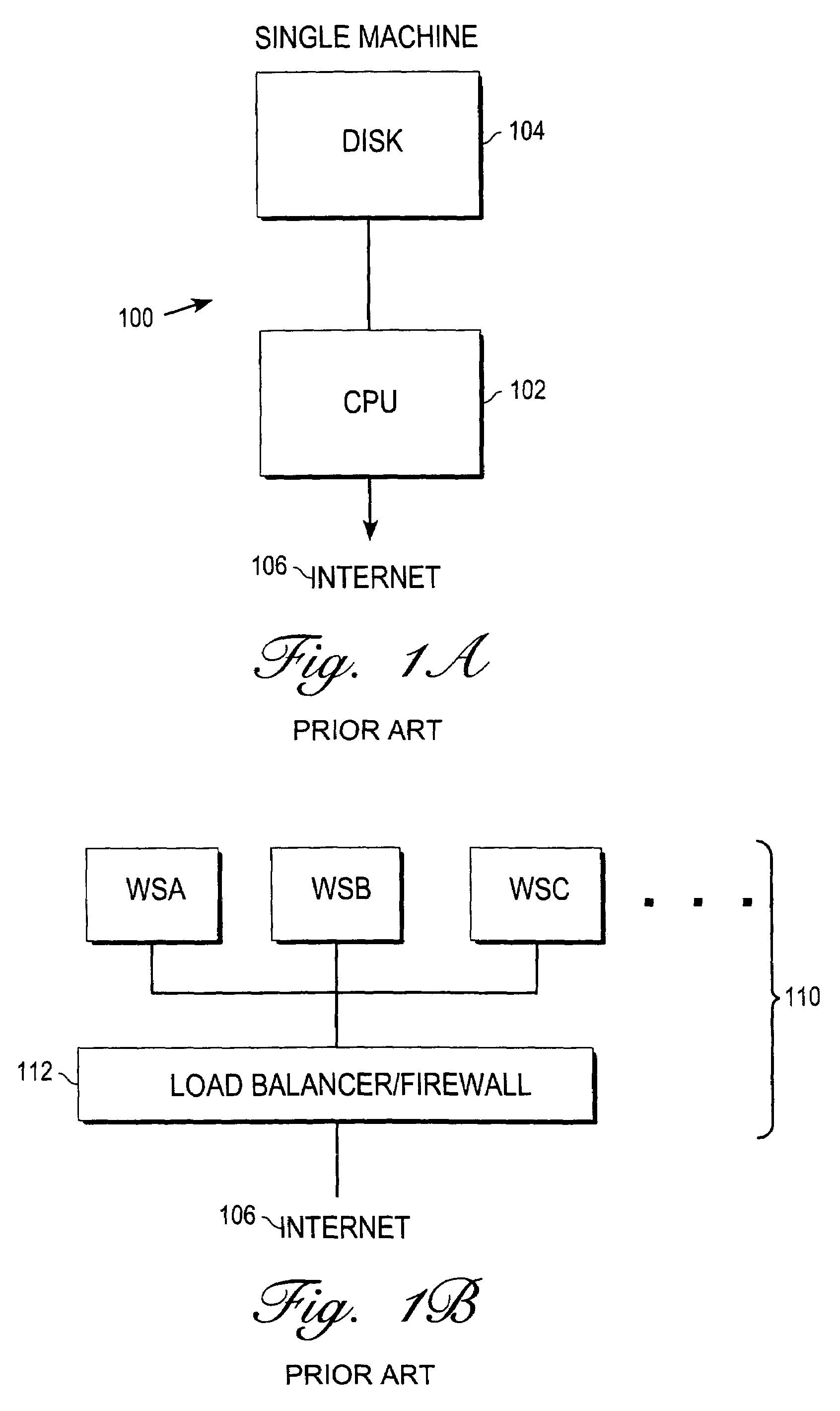
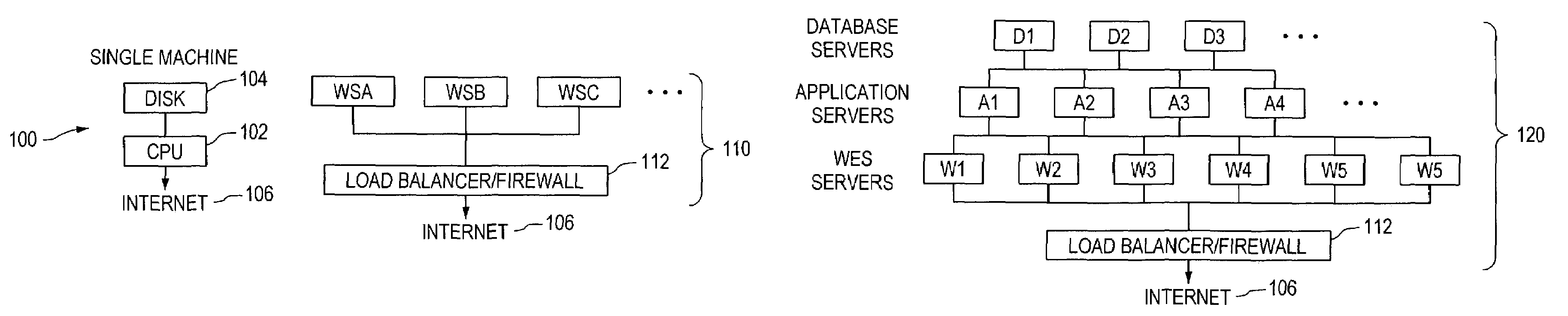
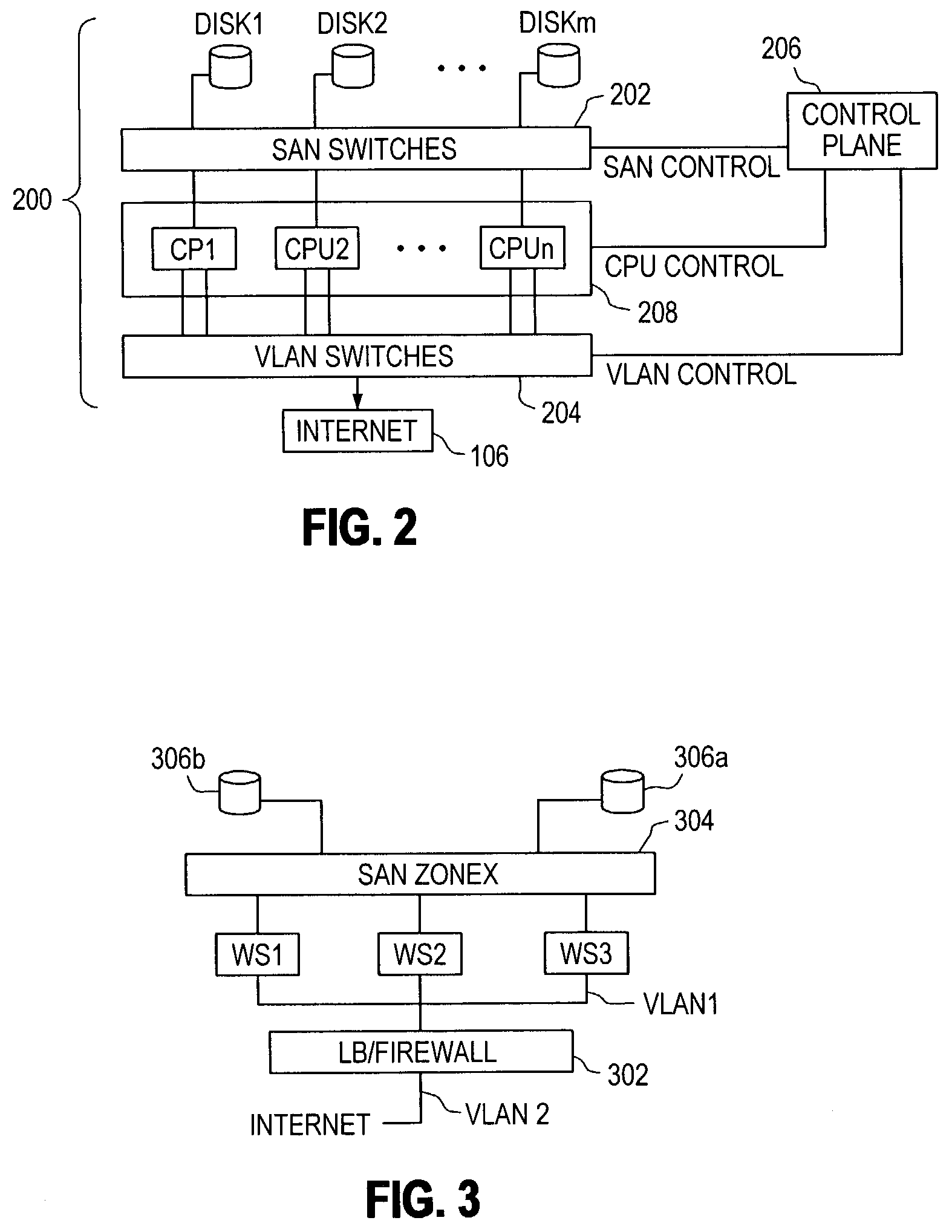
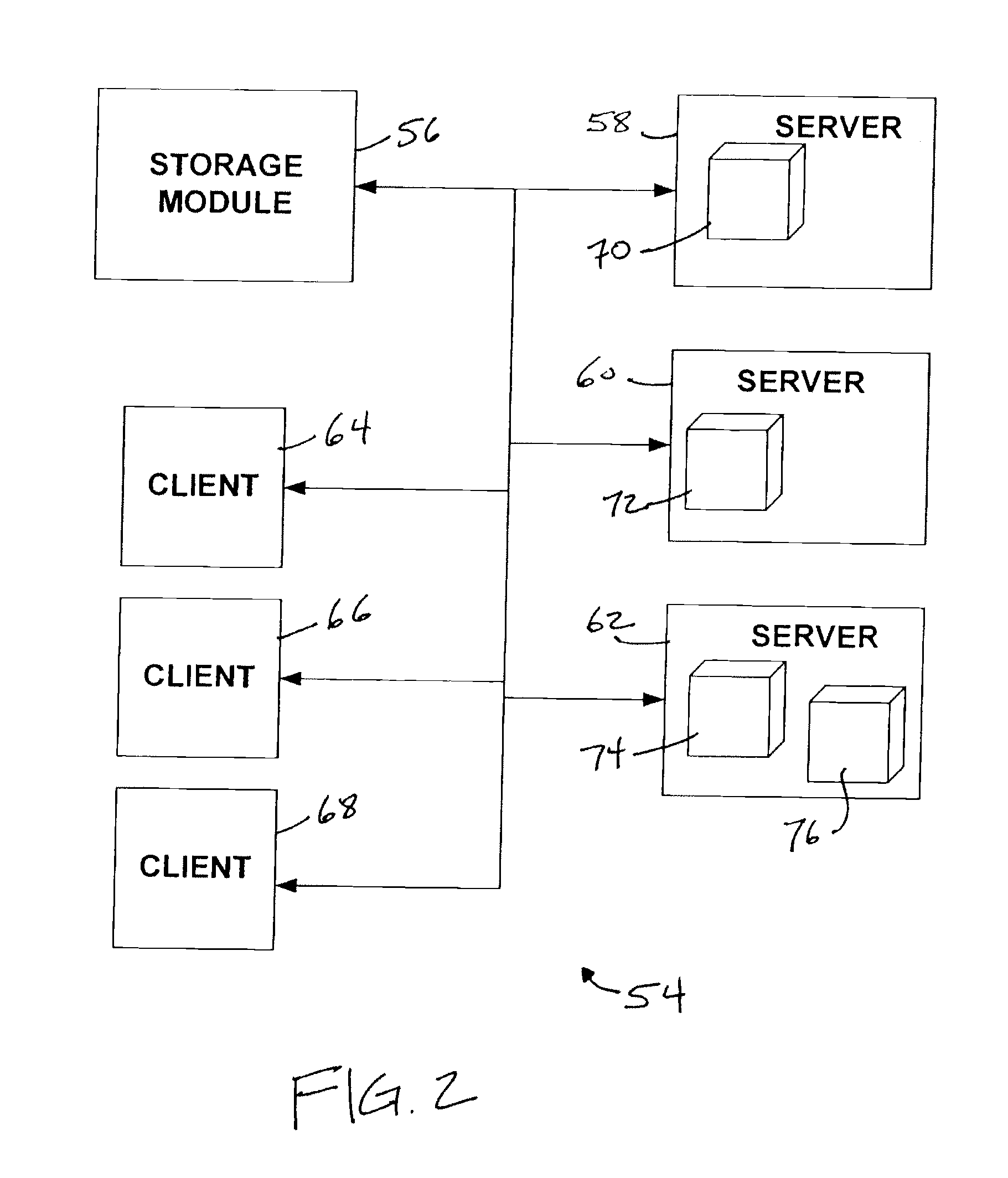
Extensible computing system
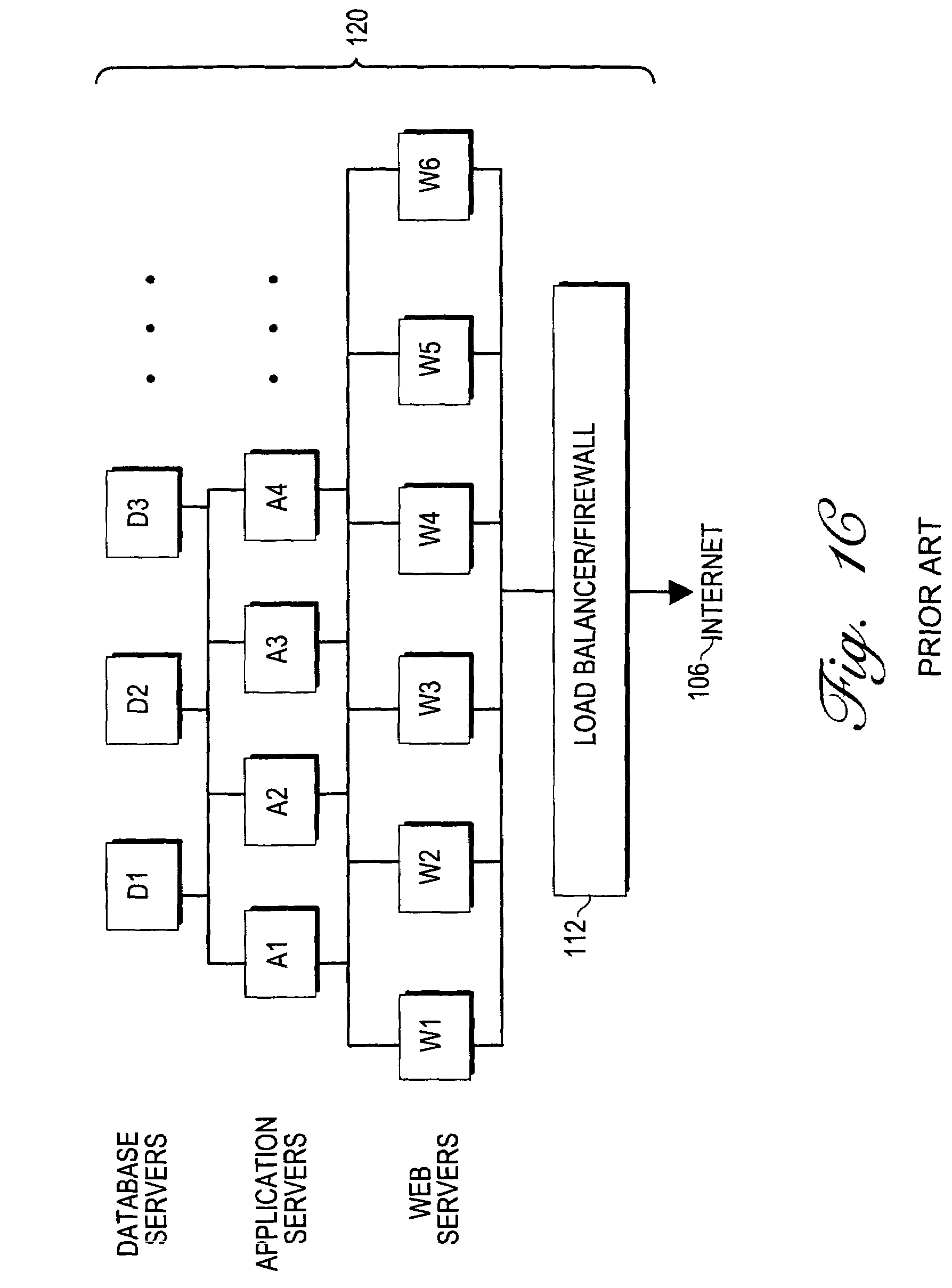
Methods and apparatus providing a dynamically sized, highly scalable and available server farm are disclosed. A Virtual Server Farm (VSF) is created out of a wide scale computing fabric (“Computing Grid”) which is physically constructed once and then logically divided up into VSFs for various organizations on demand. Each organization retains independent administrative control of a VSF. A VSF is dynamically firewalled within the Computing Grid. Allocation and control of the elements and topology in the VSF is performed by a Control Plane connected to all computing, networking, and storage elements in the computing grid through special control ports. No physical rewiring is necessary in order to construct VSFs in many different configurations, including single-tier Web server or multi-tier Web-server, application server, database server configurations.
Owner:ORACLE INT CORP
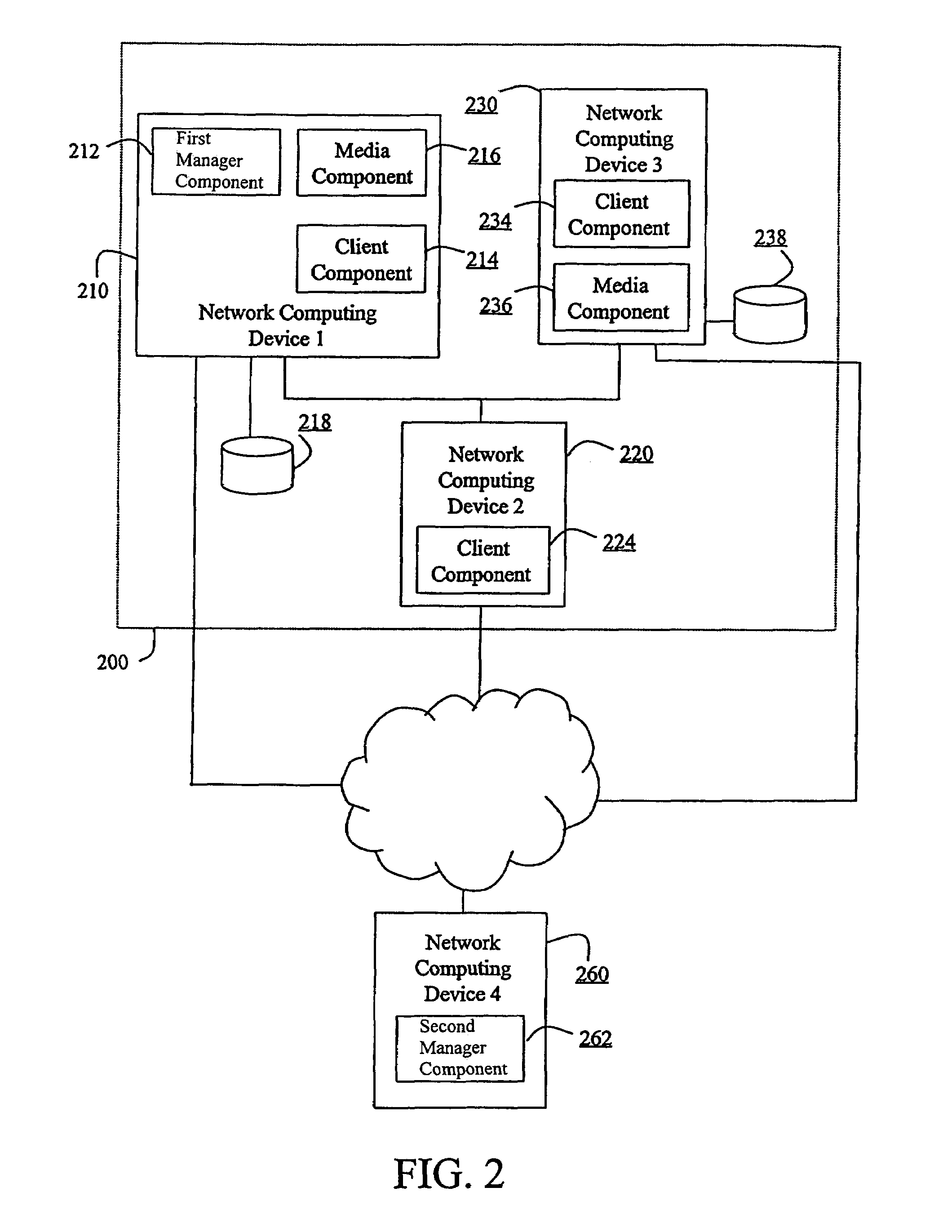
Method and apparatus for connecting a secure peer-to-peer collaboration system to an external system
InactiveUS7139798B2Digital data processing detailsMultiple digital computer combinationsMonitoring systemSoftware development
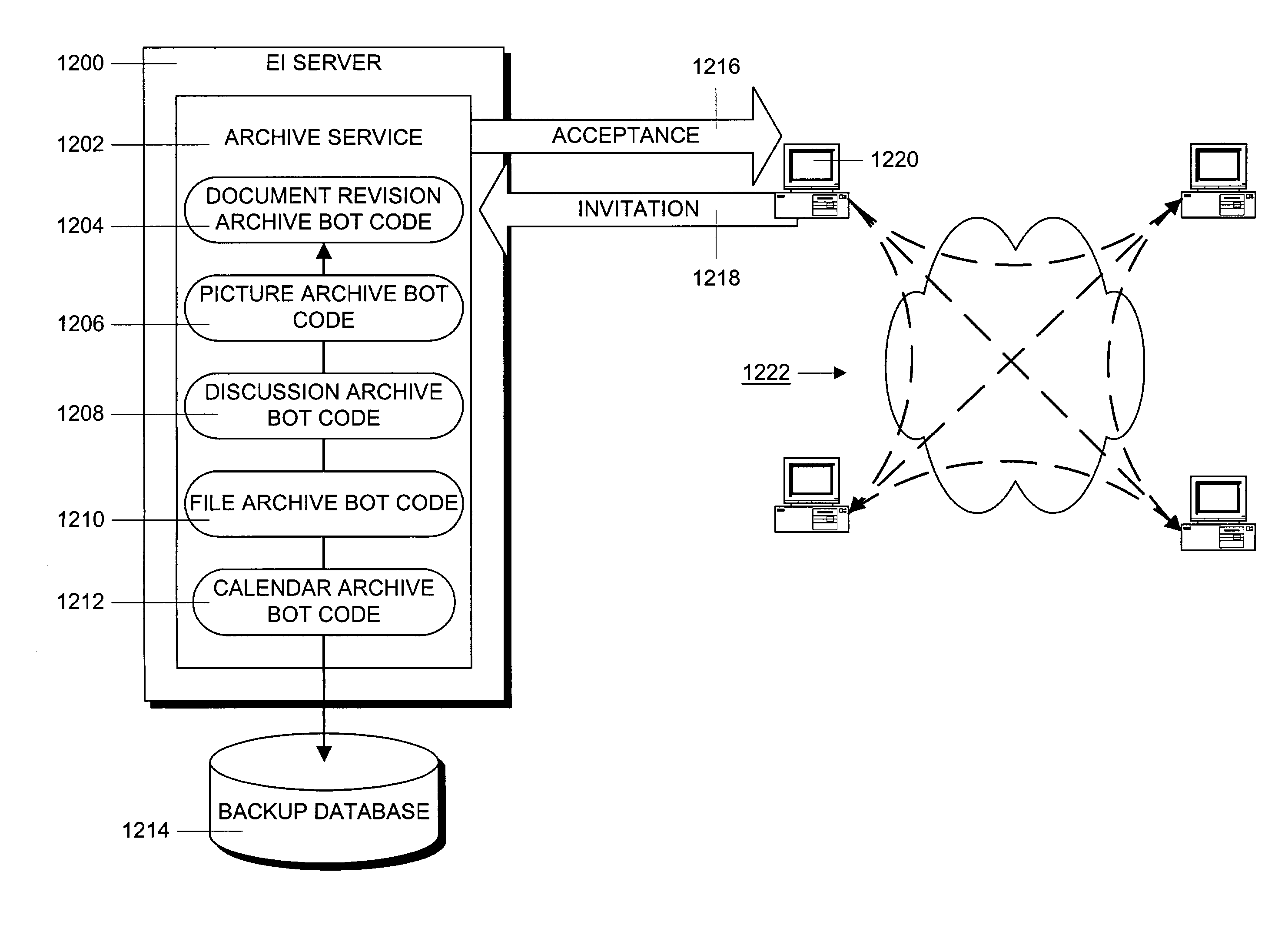
A connection between a secure shared space and an external system is created with a connector tool. The connector tool code is included in an independent agent called a “bot” that is created by a software developer. Bots run in the background in an automated and unattended manner in a specialized enterprise integration server. Each bot has a unique identity and runs under an account assigned to the enterprise integration server. A bot can be invited to a shared space much as another collaborator. Bots can also invite others to shared spaces. All bots running in the enterprise integration server are administered by a centralized administrative control. This allows account and identity policies to be established and global behaviors, including authentication settings, startup options and scope to be determined centrally. The centralized control allows simple installation, configuration and deployment and administrative control of bot operation and access. It also allows for logging and monitoring of system behavior.
Owner:MICROSOFT TECH LICENSING LLC
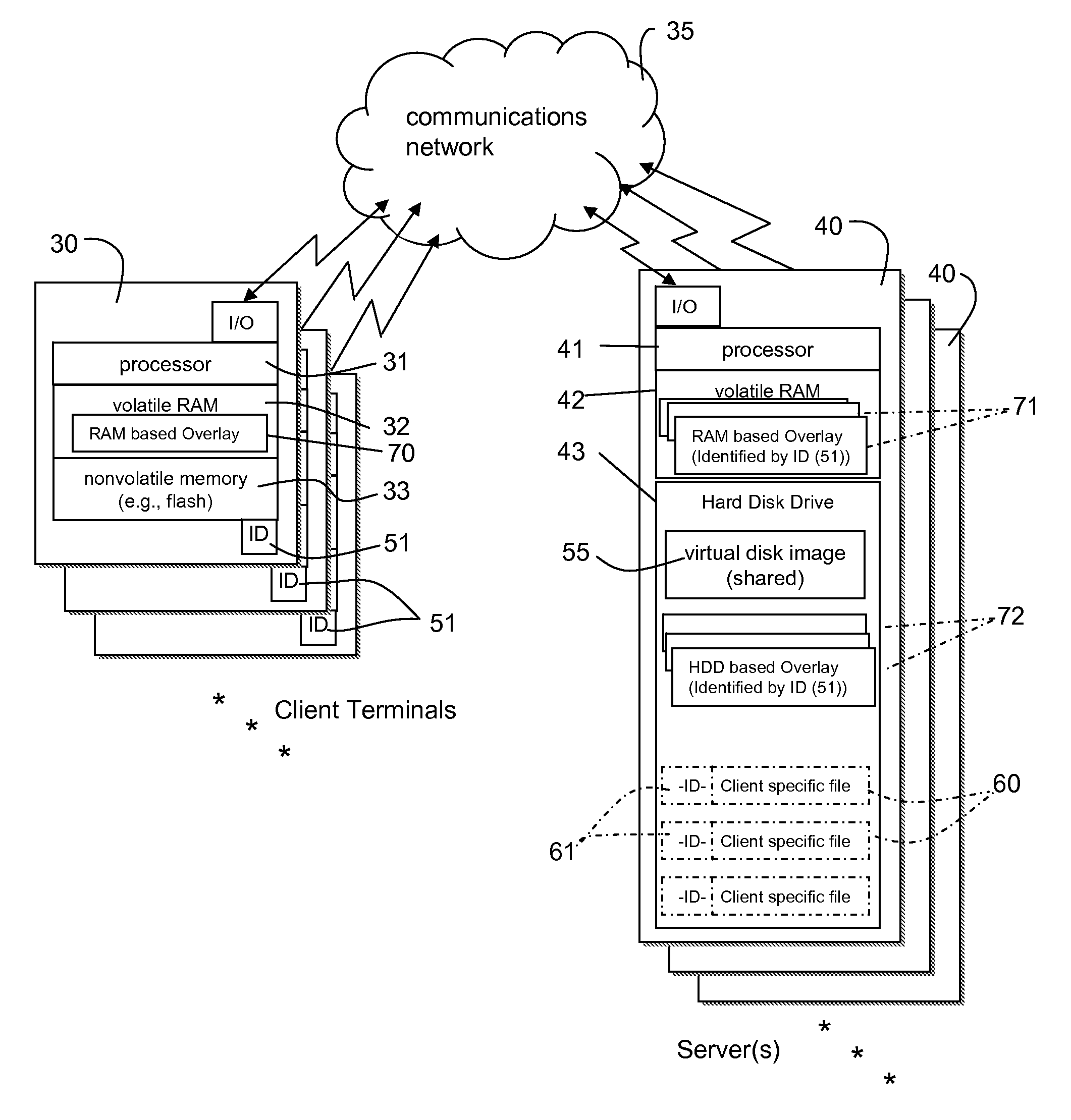
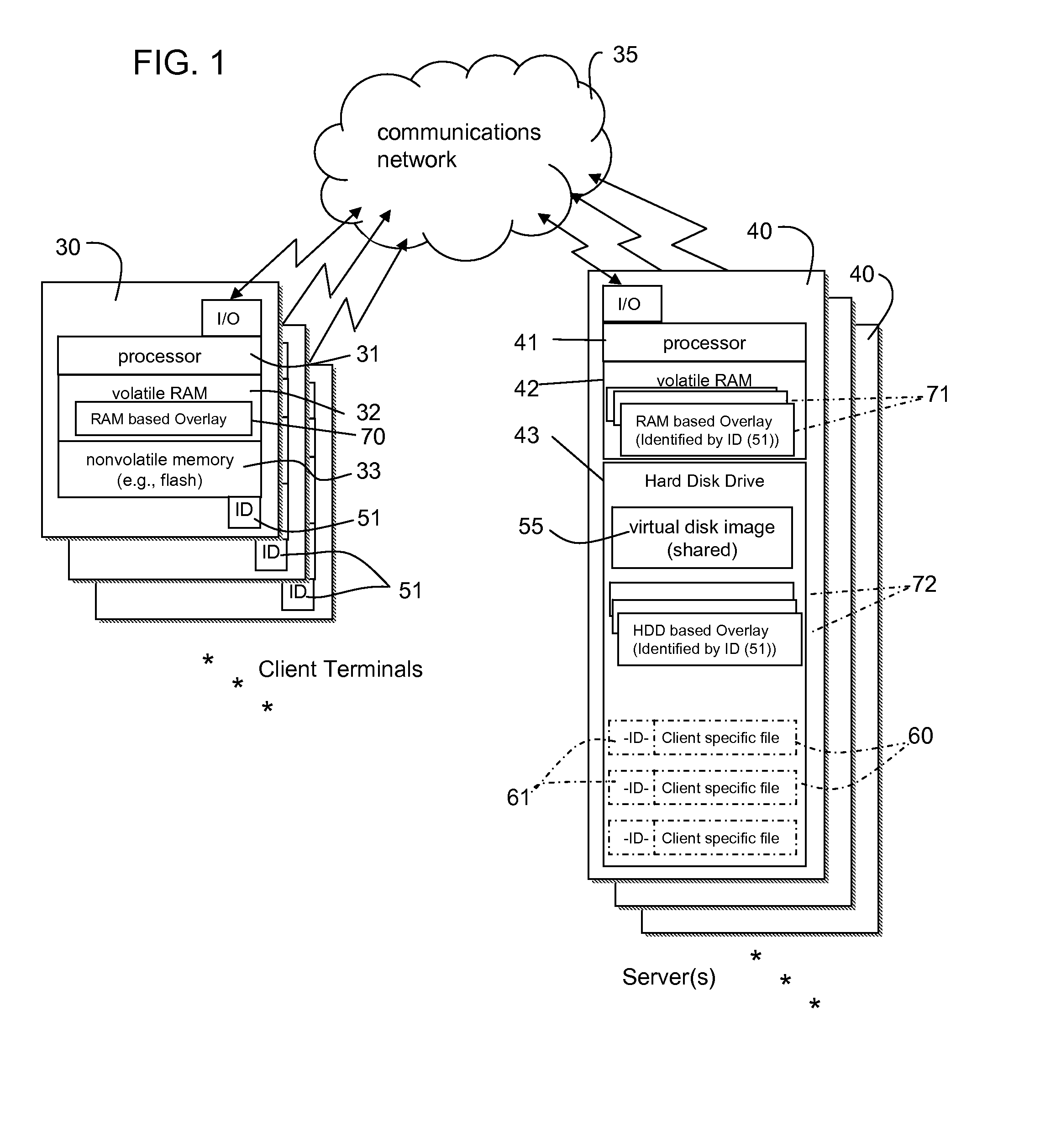
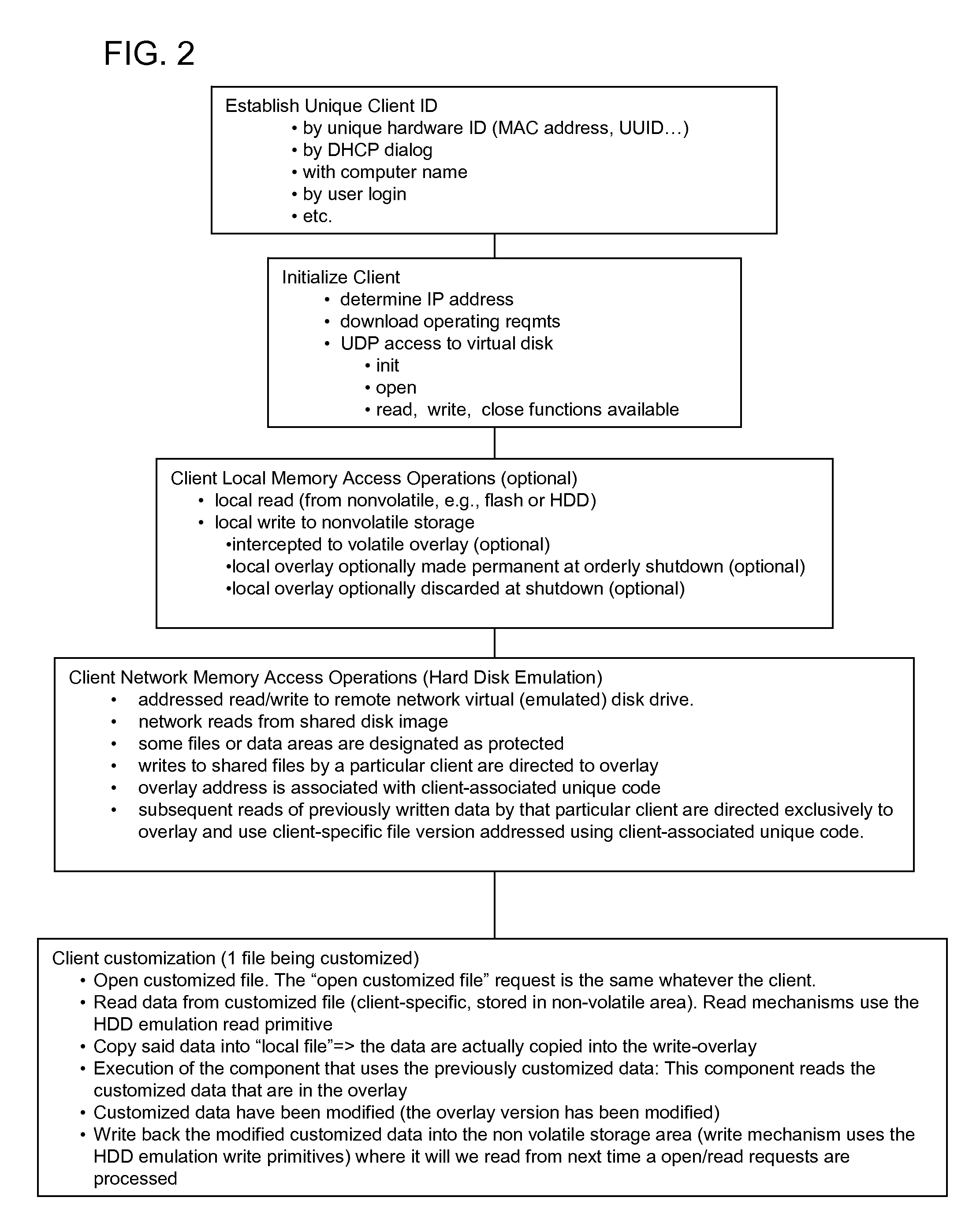
Maintaining commonly named client-specific file content in hard disk drive emulation
InactiveUS20070266027A1Most efficientMaximum versatilityRecording carrier detailsDisc-shaped record carriersHard disc driveOperational system
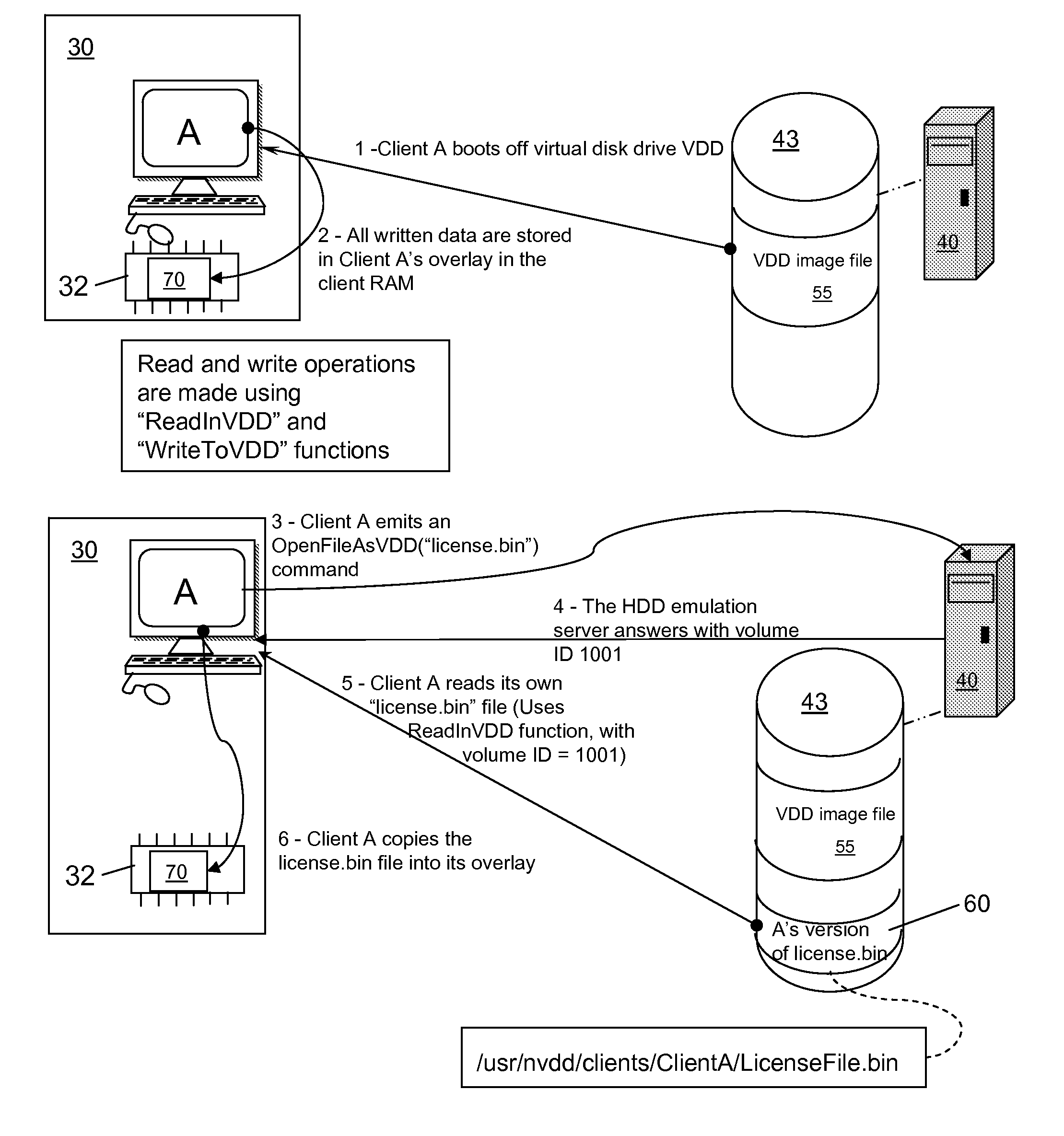
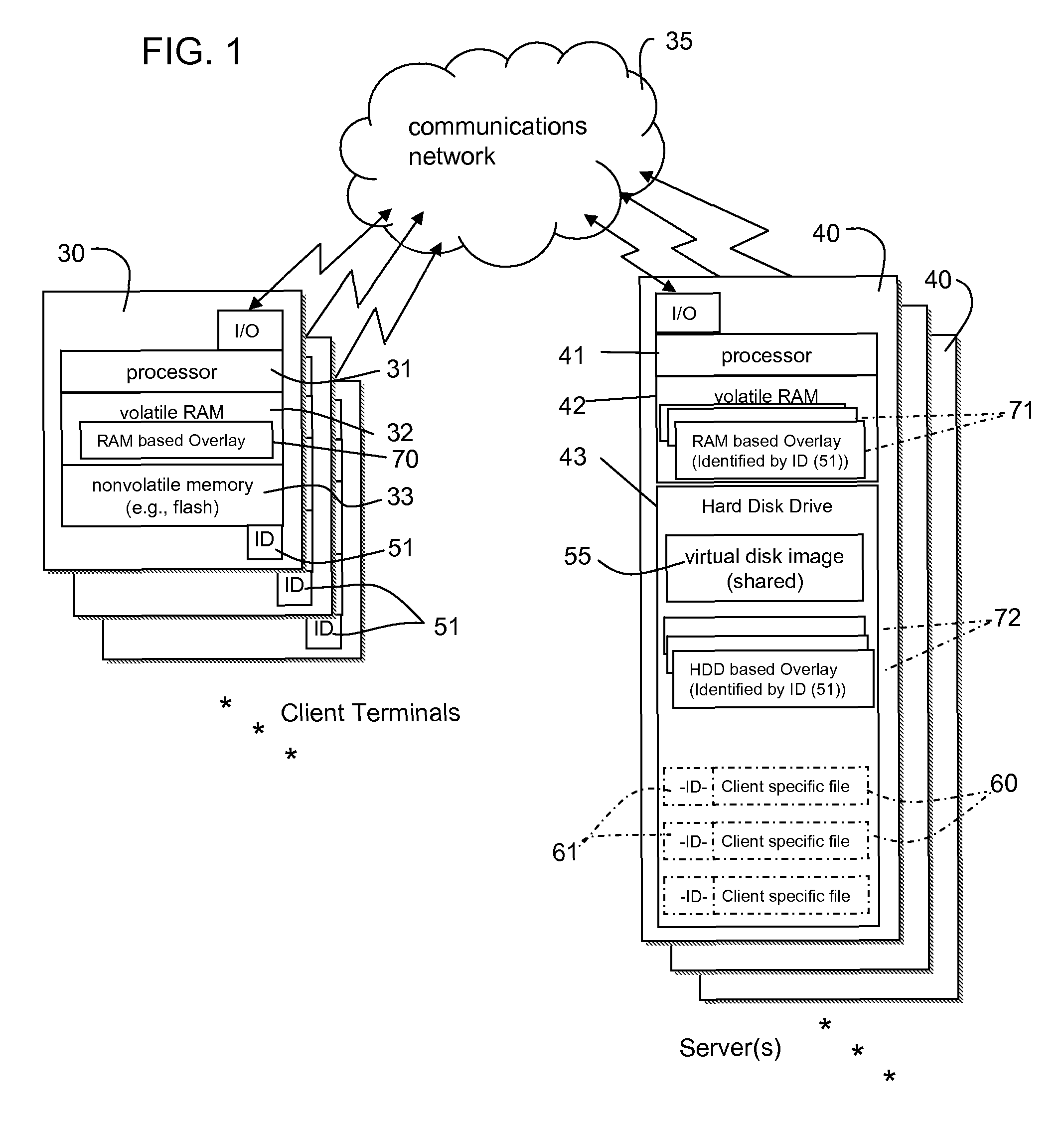
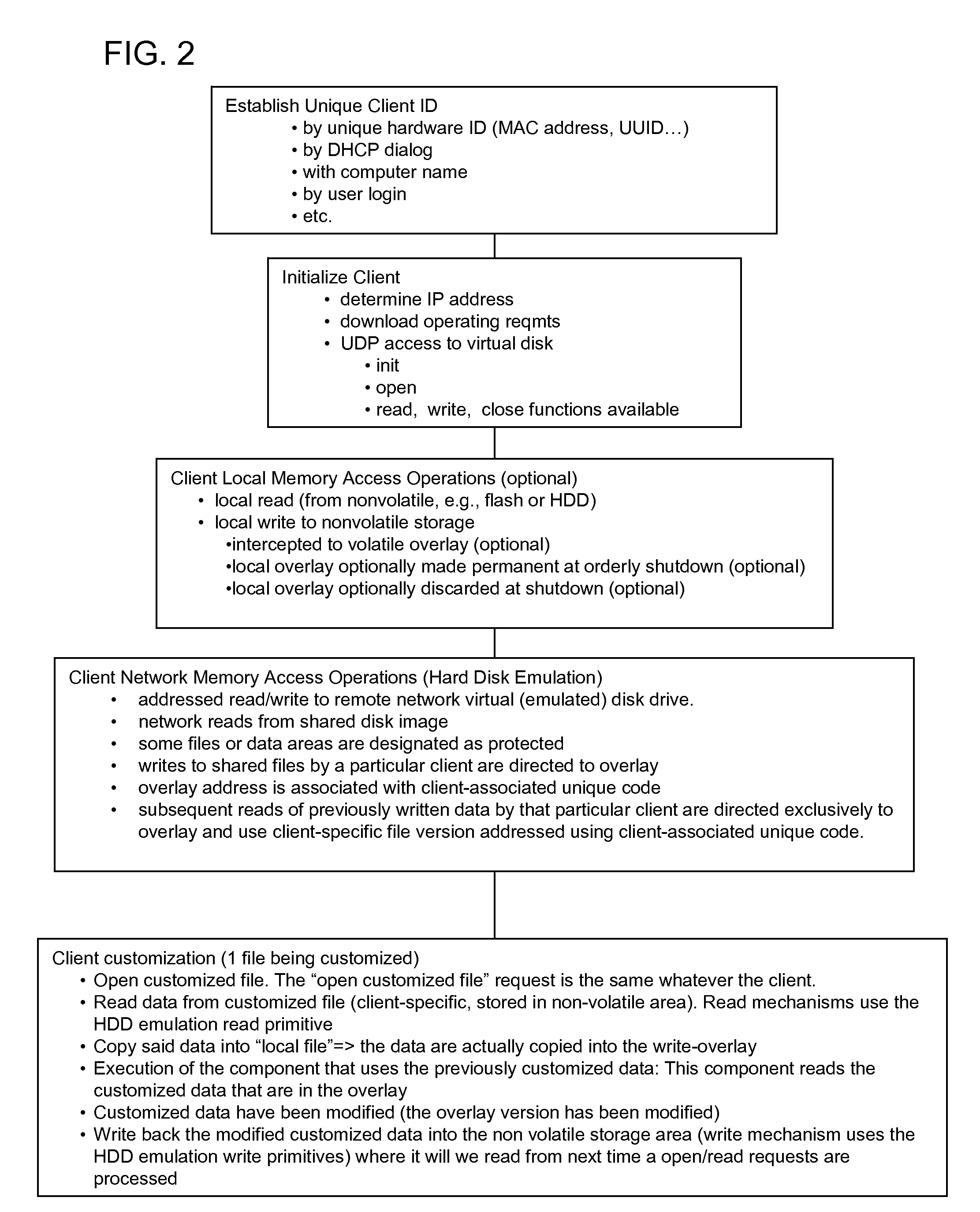
A data processing network has a virtual hard drive emulator and client terminals that share a virtual disk image. Client-specific read-write versions of selected files or directories are supported. All clients access the client-specific versions using the same name and address identifiers (for example, the same file name for a given configuration file), but each client has an exclusive version. A file ID distinguishes respective clients. These files are maintained alongside other files of other types and attributes. The selection of files to be client-specific can be predetermined, or a client-specific version of a file can be generated if the client executes a write operation to a client-specific file or area, the written data containing data read by the client in any of memory area available to the clients (RAM, Virtual Disk Drive, Hard Disk drive etc.). The technique supports customization while maximizing administrative control of operating system versions and minimizing redundant storage. File access for client terminals can be made close to systems having local hard drives.
Owner:HEWLETT PACKARD DEV CO LP
Electronic computer system secured from unauthorized access to and manipulation of data
ActiveUS20060069692A1Improve isolationFacilitate redirectionDigital data processing detailsDigital computer detailsSystem callAuthentication
A software security application for a Windows® OS based electronic computer system provides an isolated User environment which protects a User from unauthorized access to and manipulation of data on the system. The security software implements an isolated User file system and provides process / IPC isolation, Windows® registry isolation, network interface isolation, and isolated administrative control on the computer system. Interactive components of the system include an execution hook component that traps system calls, a job object component that creates / destructs, manages and manipulates job objects, a system call hook component for trapping and filtering all Windows registry I / O requests, a file system block device driver for mounting / unmounting the isolated User file system, a file system / filter driver, a network interface / NDIS hook component, and an environment handler. The environment handler provides the overall management interface for other system components, allowing definition of rules, managing authentication and other control / management functions.
Owner:VIIRII LLC
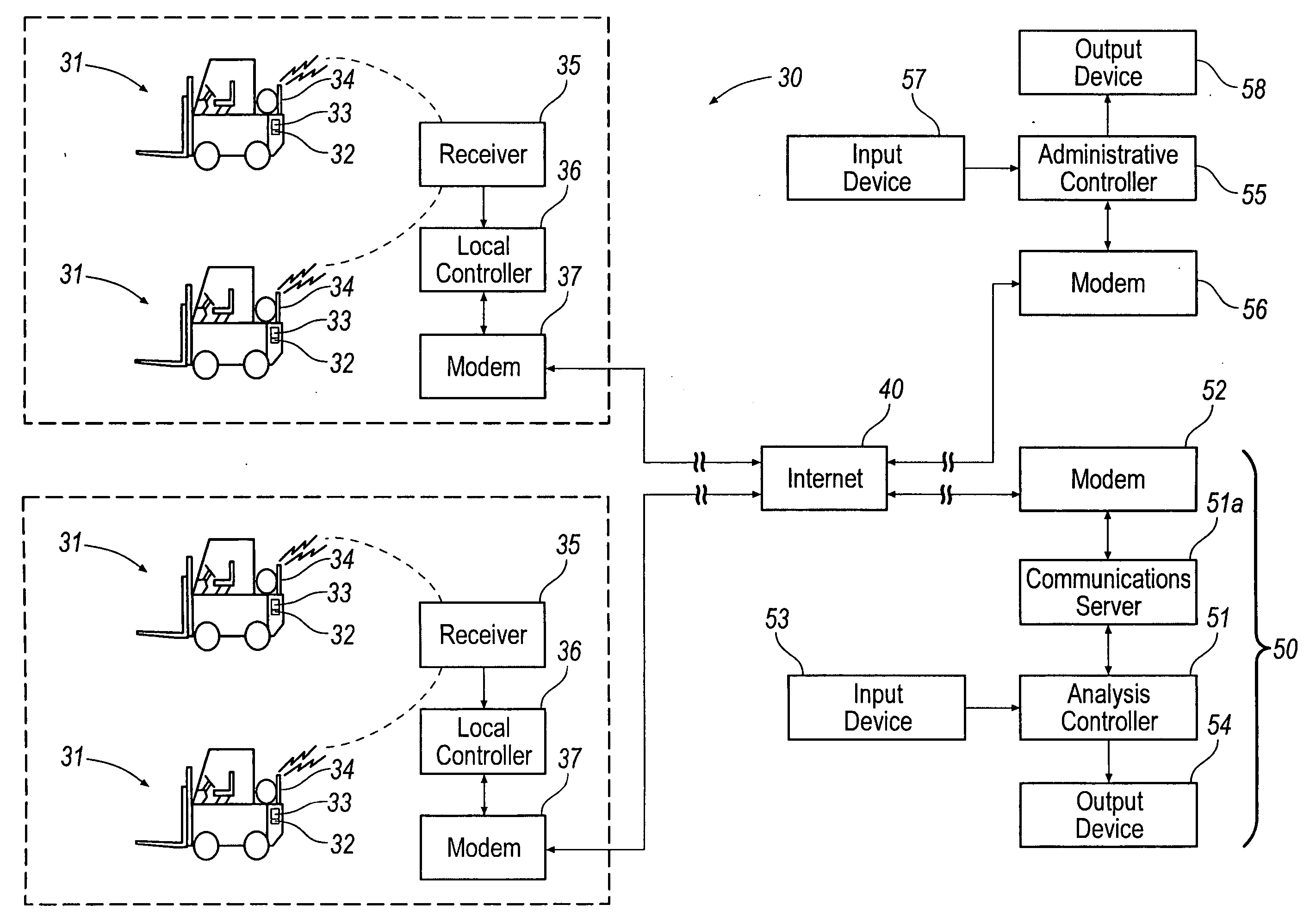
Apparatus and method for tracking and managing physical assets
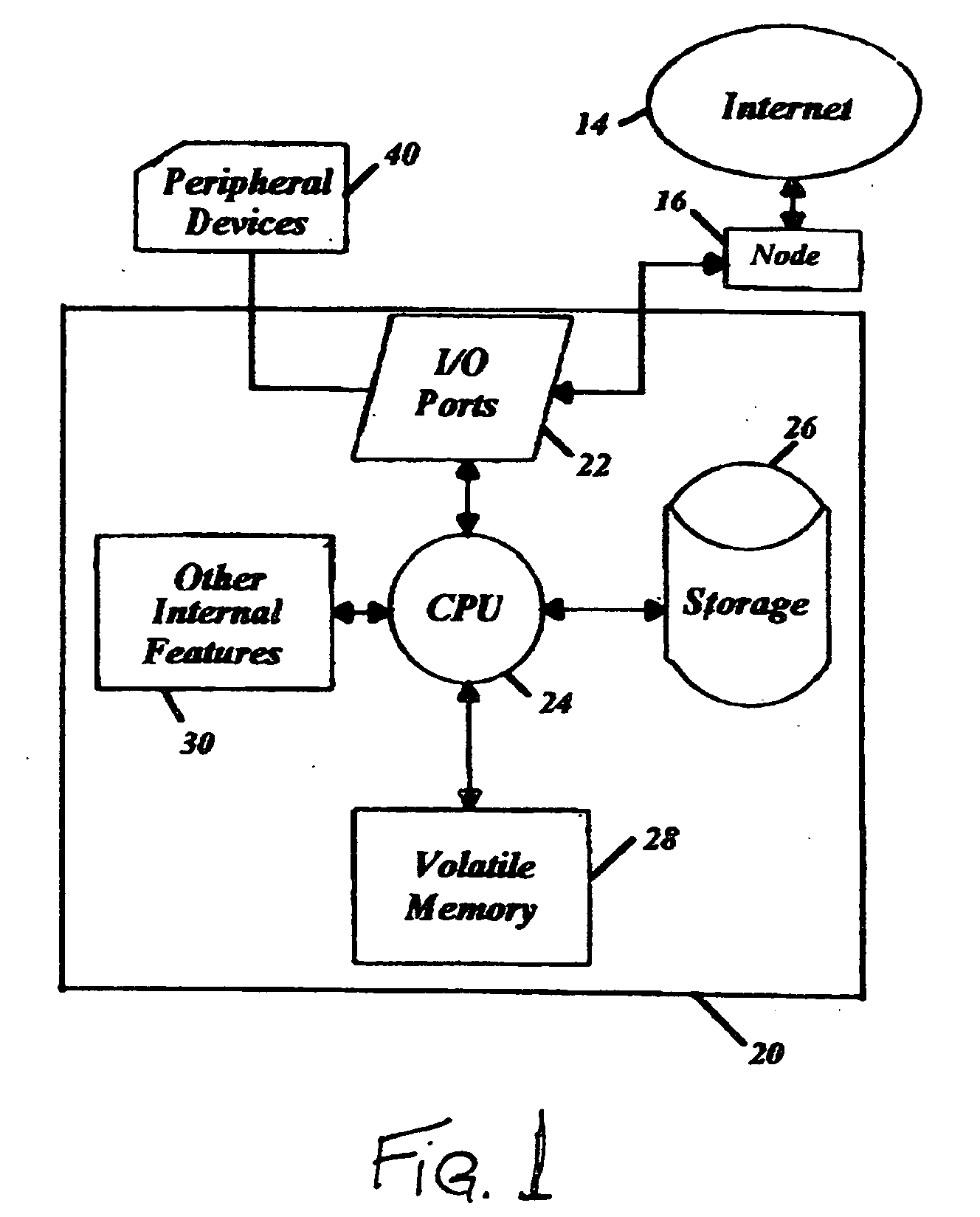
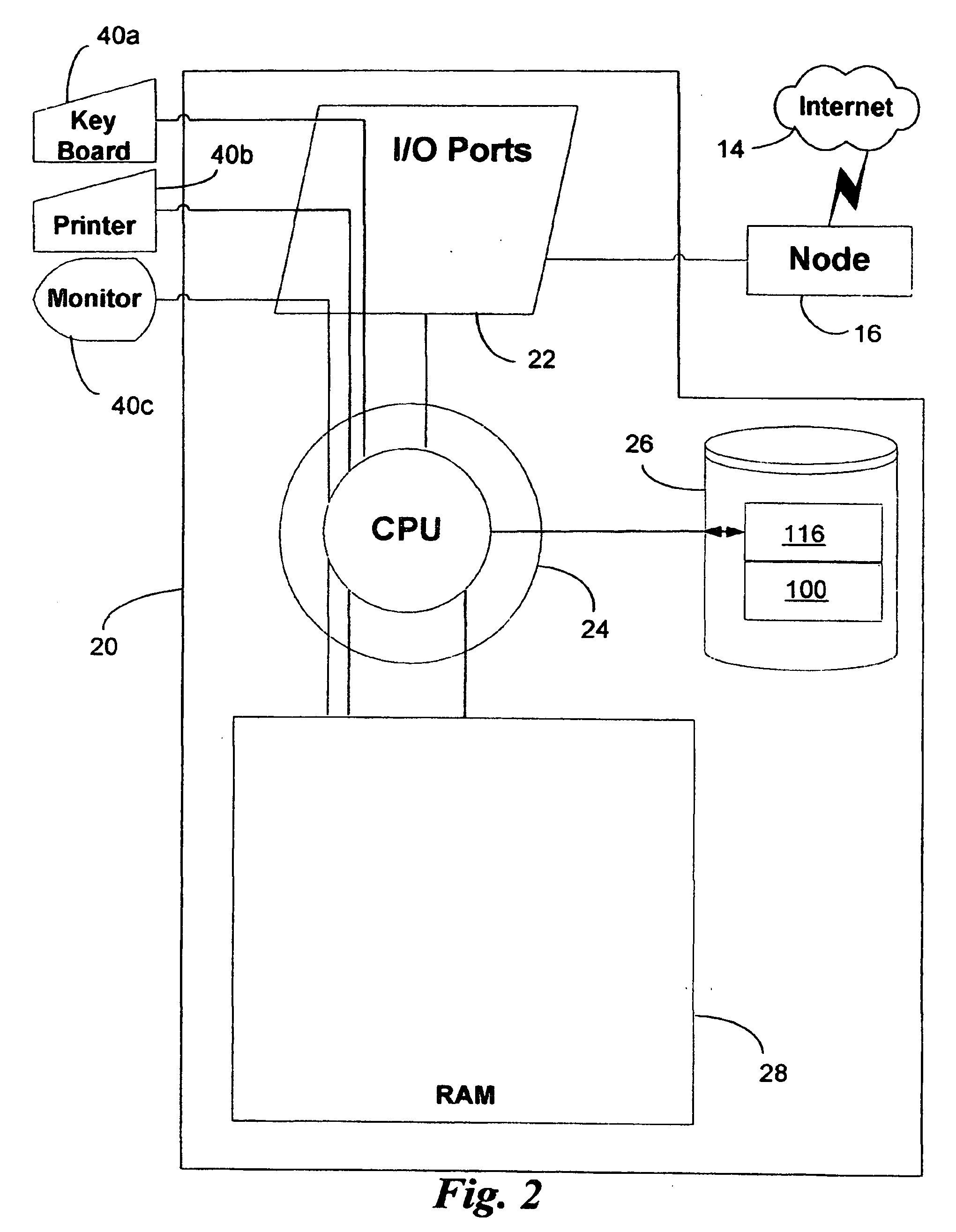
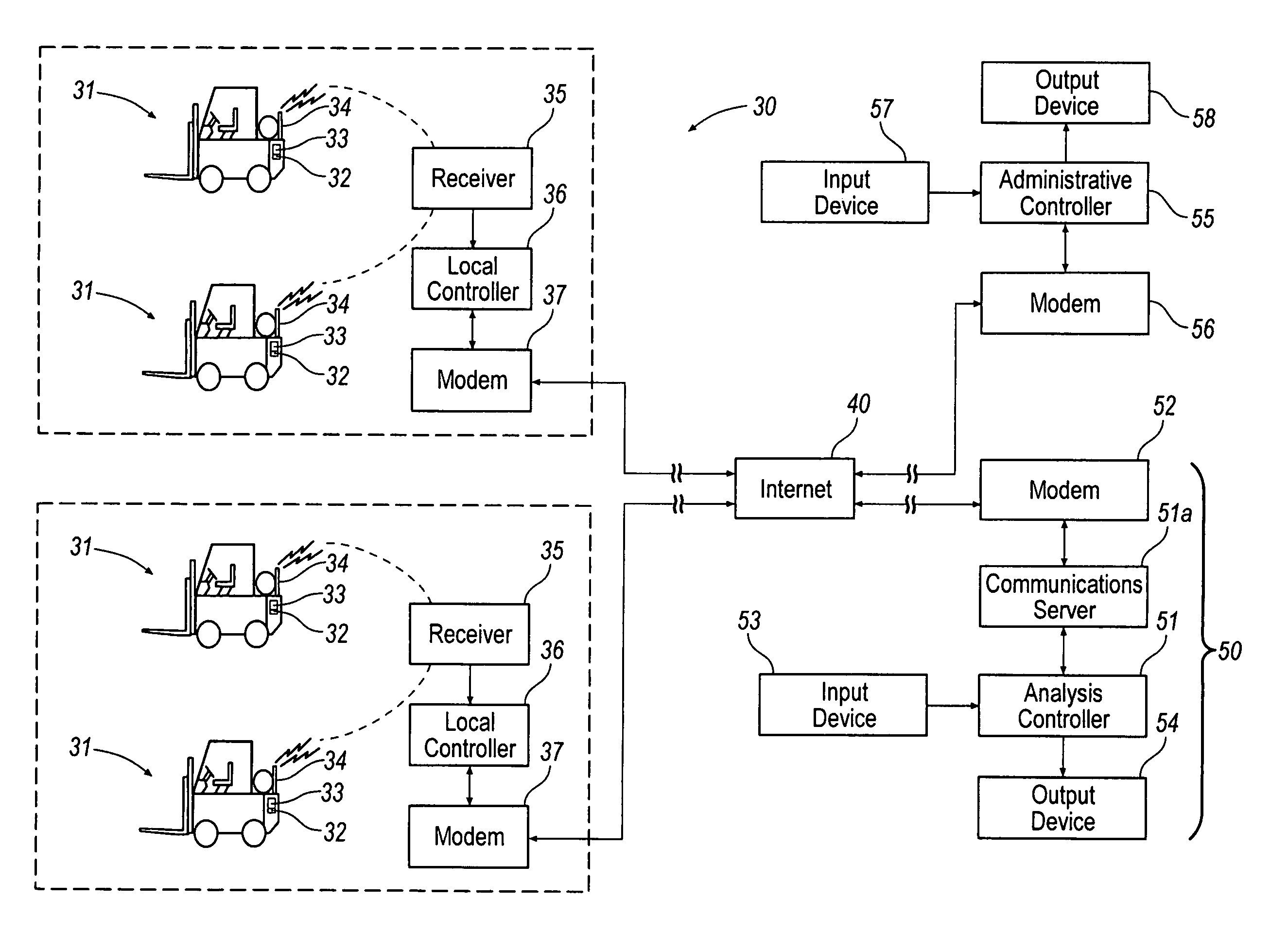
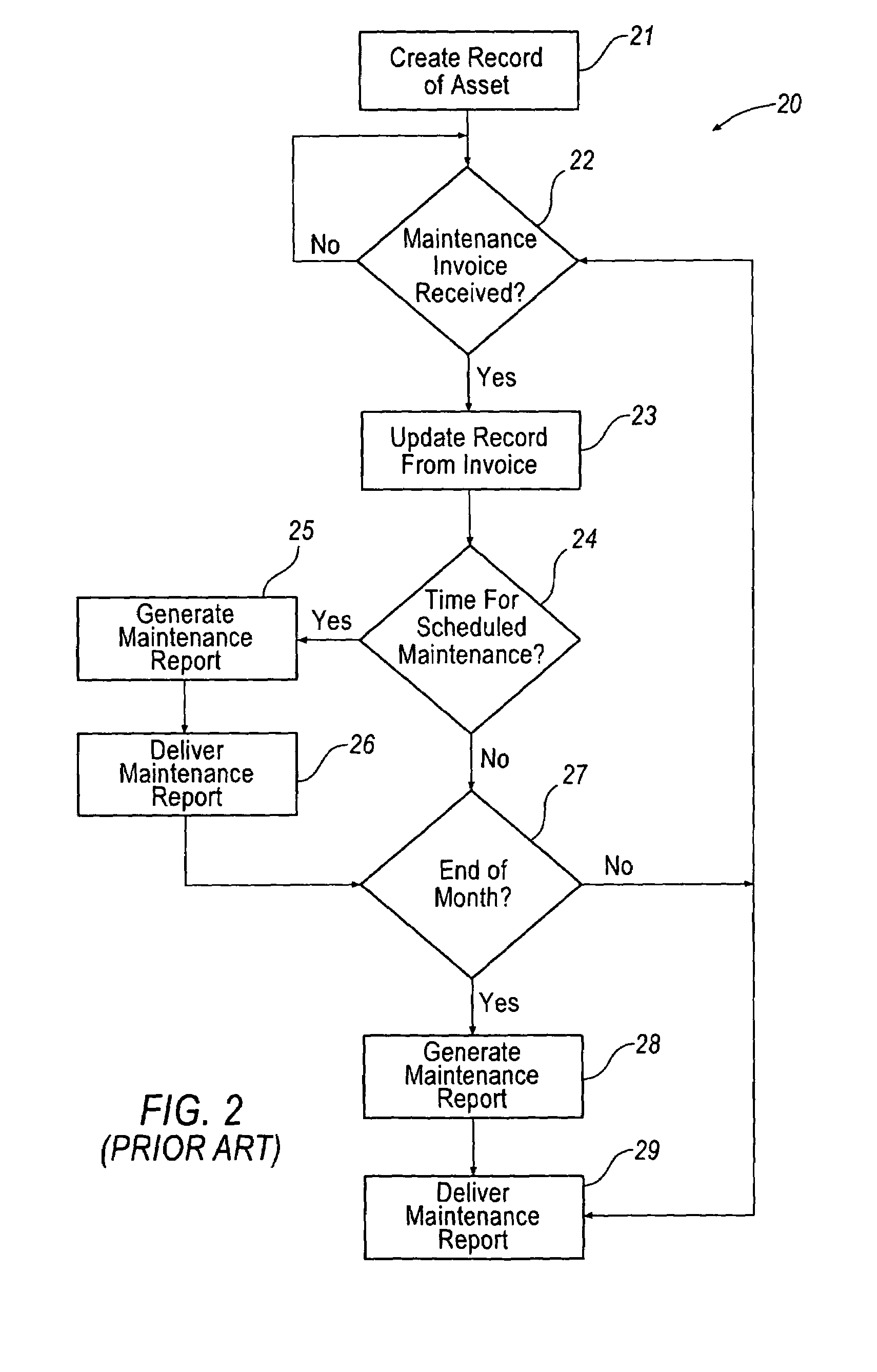
InactiveUS7062446B1Maximize productivityReduce operating costsTechnology managementCommerceProduction rateData acquisition
A computer based system automatically gathers, analyzes, and delivers information relating to the procurement and utilization of a plurality of such assets, such as a fleet of industrial equipment, so as to maximize productivity and to reduce operating costs and administrative burdens. Each of the assets is preferably provided with a data acquisition device for sensing and storing one or more operating characteristics associated therewith. That information can be transmitted through space to a receiver connected to a local controller for storing such information and for transmitting such information over the internet to a remote analysis system. The remote analysis system automatically updates individual records associated with each of the assets with the information received from the internet. In response to such information, the remote analysis system automatically analyzes the newly provided information and generates reports regarding scheduled maintenance, warranty coverage, and other management information. These reports can be transmitted back over the internet to an administrative controller for review by one or more persons responsible for managerial review. Additionally or alternatively, the remote analysis system can automatically post such reports on a website and, thus, be made available to one or more of such persons upon request.
Owner:DANA AUTOMOTIVE SYST GRP LLC
Maintaining commonly named client-specific file content in hard disk drive emulation
InactiveUS8332370B2Easy to manageEfficiently customizedDisc-shaped record carriersRecording carrier detailsHard disc driveOperational system
A data processing network has a virtual hard drive emulator and client terminals that share a virtual disk image. Client-specific read-write versions of selected files or directories are supported. All clients access the client-specific versions using the same name and address identifiers (for example, the same file name for a given configuration file), but each client has an exclusive version. A file ID distinguishes respective clients. These files are maintained alongside other files of other types and attributes. The selection of files to be client-specific can be predetermined, or a client-specific version of a file can be generated if the client executes a write operation to a client-specific file or area, the written data containing data read by the client in any of memory area available to the clients (RAM, Virtual Disk Drive, Hard Disk drive etc.). The technique supports customization while maximizing administrative control of operating system versions and minimizing redundant storage. File access for client terminals can be made close to systems having local hard drives.
Owner:HEWLETT PACKARD DEV CO LP
Request queue management
InactiveUS7146233B2Digital data information retrievalResource allocationQueue management systemVirtual servers
Methods and apparatus providing, controlling and managing a dynamically sized, highly scalable and available server farm are disclosed. A Virtual Server Farm (VSF) is created out of a wide scale computing fabric (“Computing Grid”) which is physically constructed once and then logically divided up into VSFs for various organizations on demand. Each organization retains independent administrative control of a VSF. A VSF is dynamically firewalled within the Computing Grid. Allocation and control of the elements in the VSF is performed by a control plane connected to all computing, networking, and storage elements in the computing grid through special control ports. The internal topology of each VSF is under control of the control plane. A request queue architecture is also provided for processing work requests that allows selected requests to be blocked until required human intervention is satisfied.
Owner:ORACLE INT CORP
Method and apparatus for connecting a secure peer-to-peer collaboration system to an external system
InactiveUS20060075024A1Multiple digital computer combinationsOffice automationMonitoring systemSoftware development
A connection between a secure shared space and an external system is created with a connector tool. The connector tool code is included in an independent agent called a “bot” that is created by a software developer. Bots run in the background in an automated and unattended manner in a specialized enterprise integration server. Each bot has a unique identity and runs under an account assigned to the enterprise integration server. A bot can be invited to a shared space much as another collaborator. Bots can also invite others to shared spaces. All bots running in the enterprise integration server are administered by a centralized administrative control. This allows account and identity policies to be established and global behaviors, including authentication settings, startup options and scope to be determined centrally. The centralized control allows simple installation, configuration and deployment and administrative control of bot operation and access. It also allows for logging and monitoring of system behavior.
Owner:MICROSOFT TECH LICENSING LLC
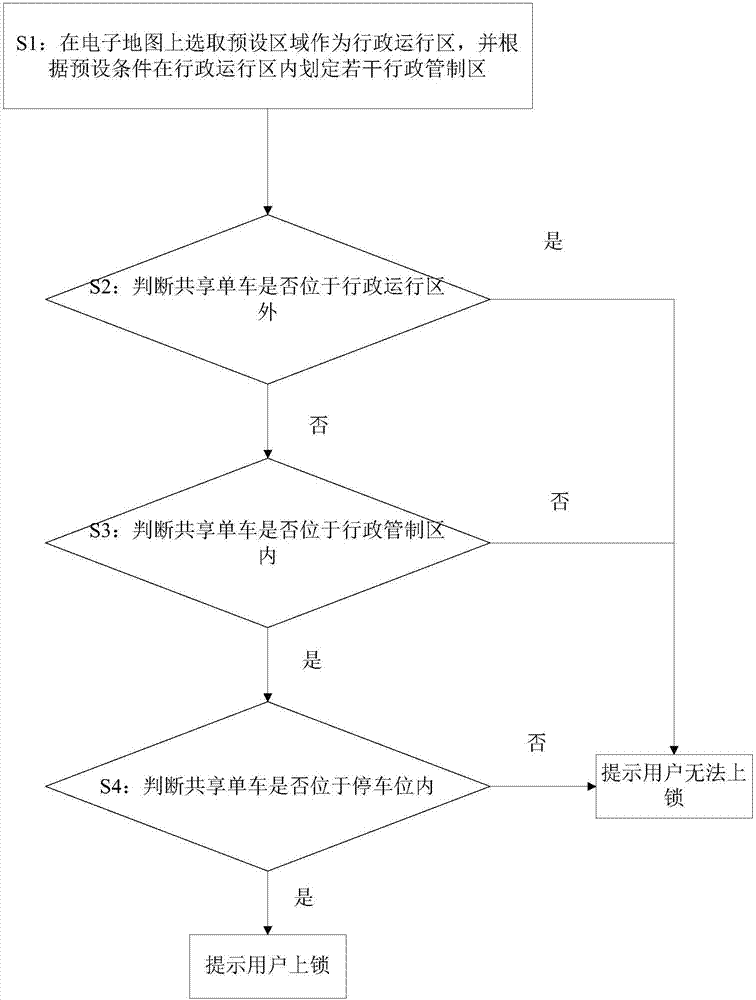
Driving area alarm method and device for shared bicycle
InactiveCN106898135AEasy to guideArrangements for variable traffic instructionsParking areaSingle vehicle
The invention discloses a driving area alarm method and device for a shared bicycle. The method includes the steps of selecting a preset area on an electronic map as an administrative operation area, and in accordance with preconditions, designating a plurality of administrative control areas in the administrative operation area; and obtaining GPS information of a user, determining whether a shared bicycle is located outside the administrative operation area according to the GPS information, if so, reminding the user of failure to lock, otherwise, further determining whether the shared bicycle is located in one of the administrative control areas, if so, reminding the user of locking, and otherwise, reminding the user of failure to lock. According to the invention, it is possible to better guide the user to park the shared bicycle in the legal position by designating the driving areas of the shared bicycle and by setting the legal parking areas of the shared bicycle in the legal driving areas and positioning the shared bicycle.
Owner:SURE RICH ELECTRONICS TECH LTD
System and method for providing virtual spaces for access by users via the web
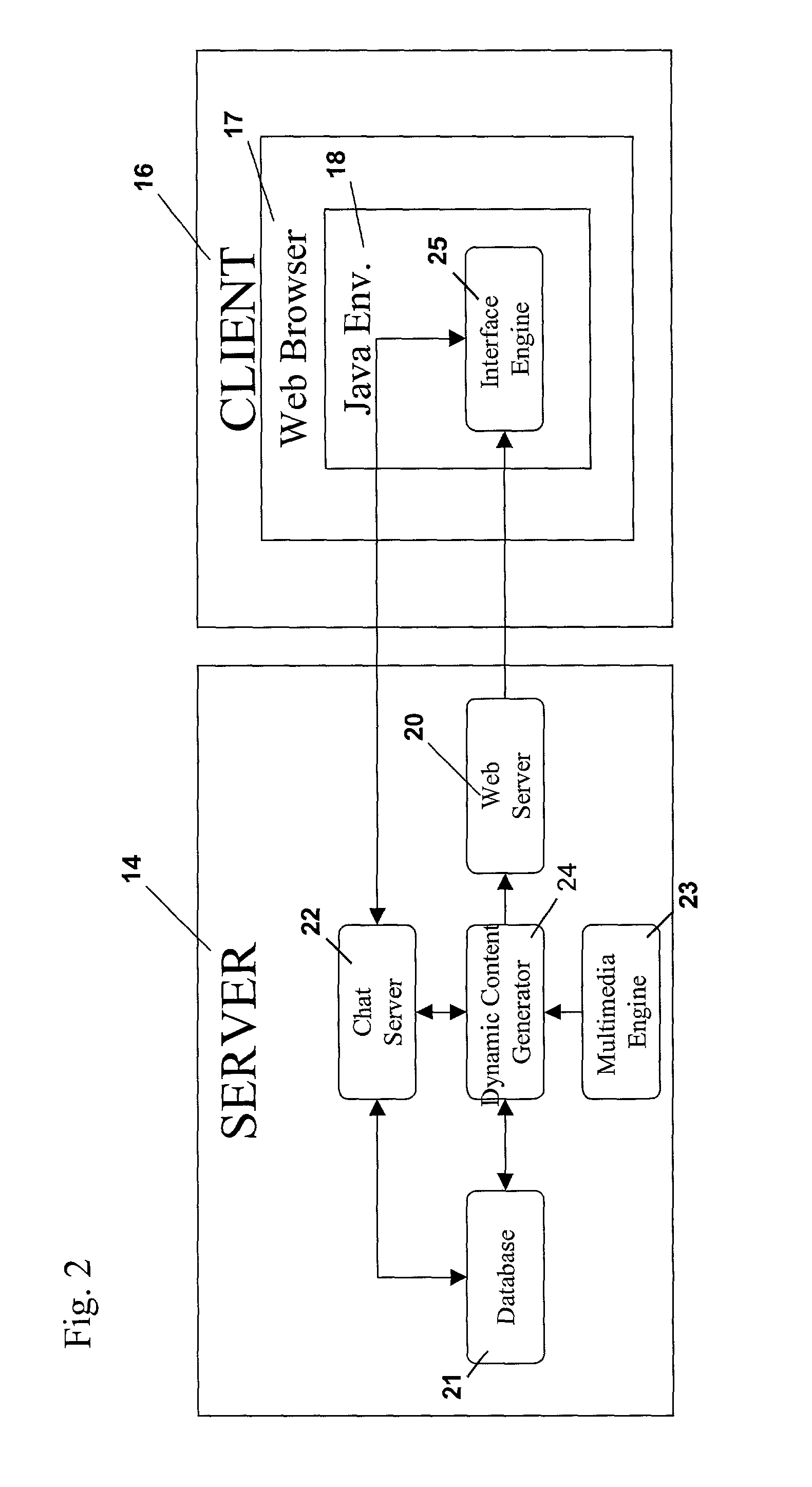
ActiveUS20100095213A1Improve interactivityIndoor gamesTransmissionVirtual spaceHypertext Transfer Protocol over Secure Socket Layer
A system configured to provide one or more virtual spaces that are accessible to users. The virtual spaces may be provided such that an enhanced level of interactivity between the virtual spaces and the Web, including resources that communicate with the system via the Internet (e.g., via users, websites, webpages, other web resources, etc.) and / or other networks. To provide this enhanced level of interactivity, the system may enable interactions between an instance of a virtual space and the Web (e.g., queries, commands, communication, administrative controls, etc.) via a standard web protocol, such as a HyperText Transfer Protocol (e.g., http, https, etc.) and / or other standard web protocols. Since interactions take place between the instance of the virtual space and the Web via a standard web protocol, the instance of the virtual space may interact directly with Web resources such as web servers, web browsers, websites, webpages, and / or other Web resources.
Owner:DISNEY ENTERPRISES INC
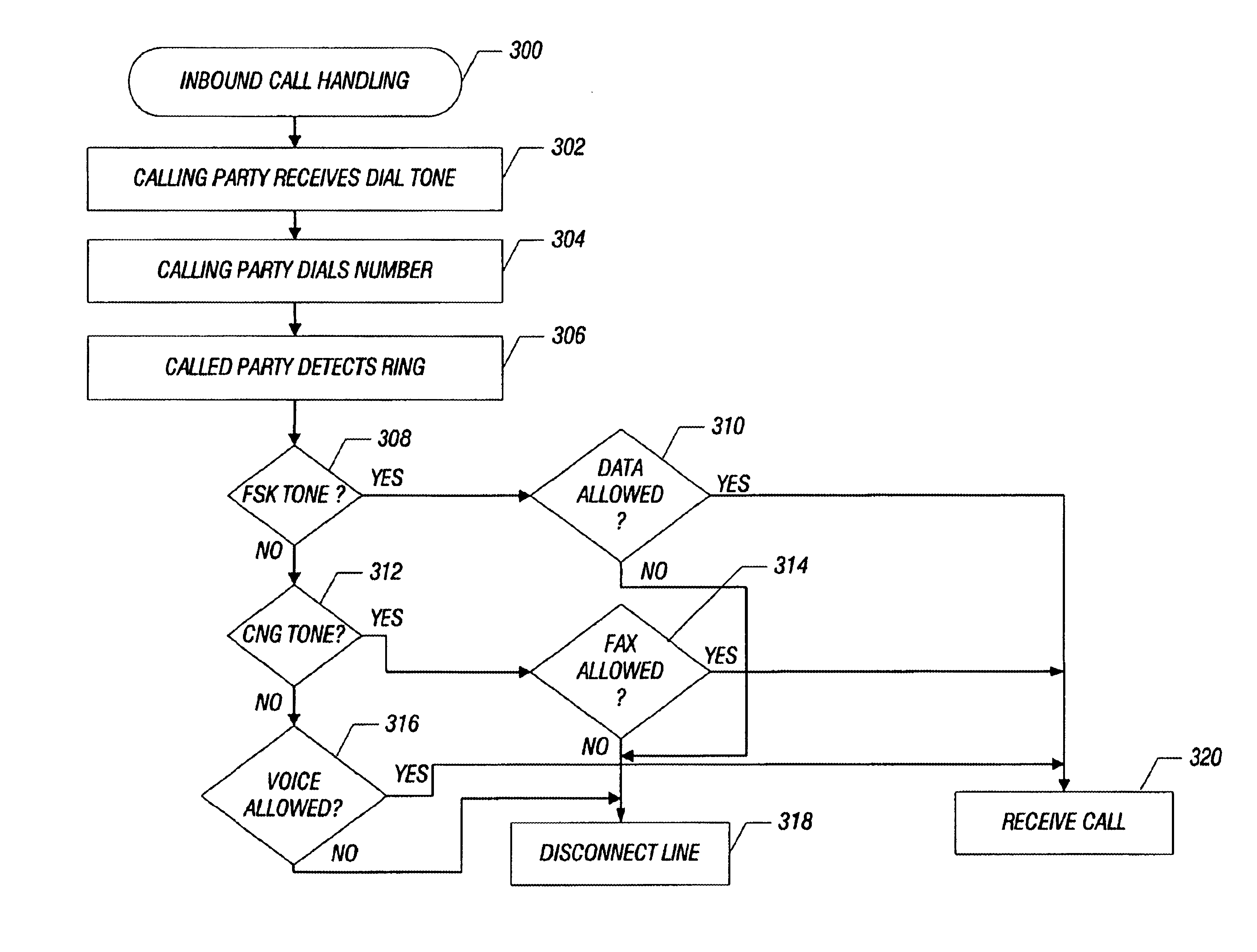
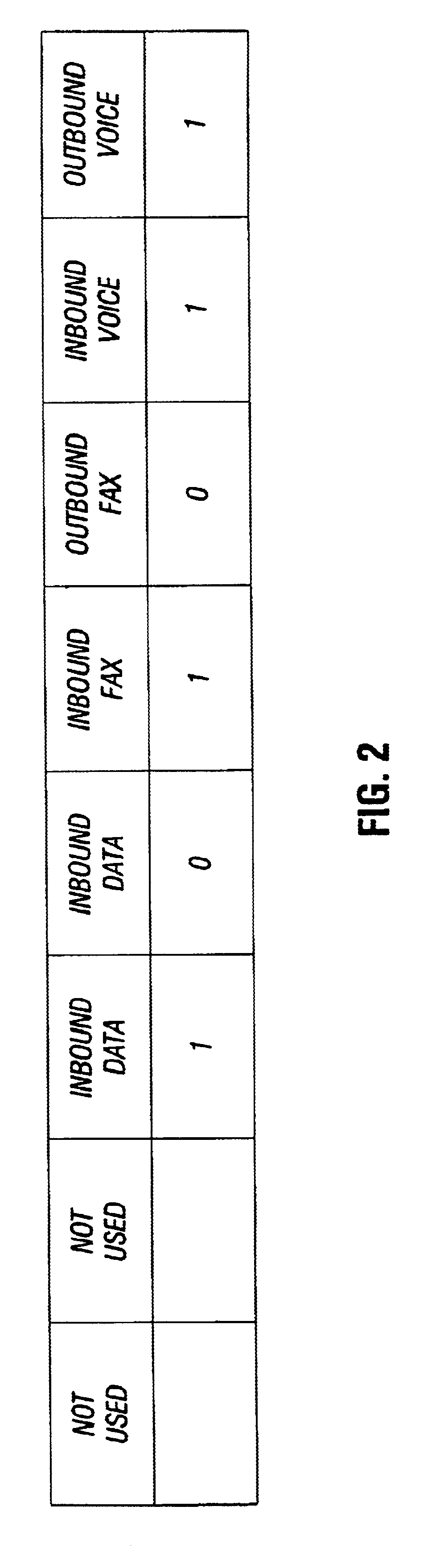
Administrative control and security of modems
A modem or modem driver includes the ability to individually enable or disable inbound data, outbound data, inbound fax, outbound fax, inbound voice, and outbound voice. These capabilities may be individually enabled or disabled by an administrator thereby controlling and authorizing user operations. In one embodiment, a bit mask representing permission states is stored in modem associated memory. Each feature has an assigned bit in the bit mask. The modem associated memory may be RAM, ROM, EPROM, EEPROM or flash ROM. When the modem memory is flash ROM the states may be changed by an administrator via software.
Owner:HTC CORP
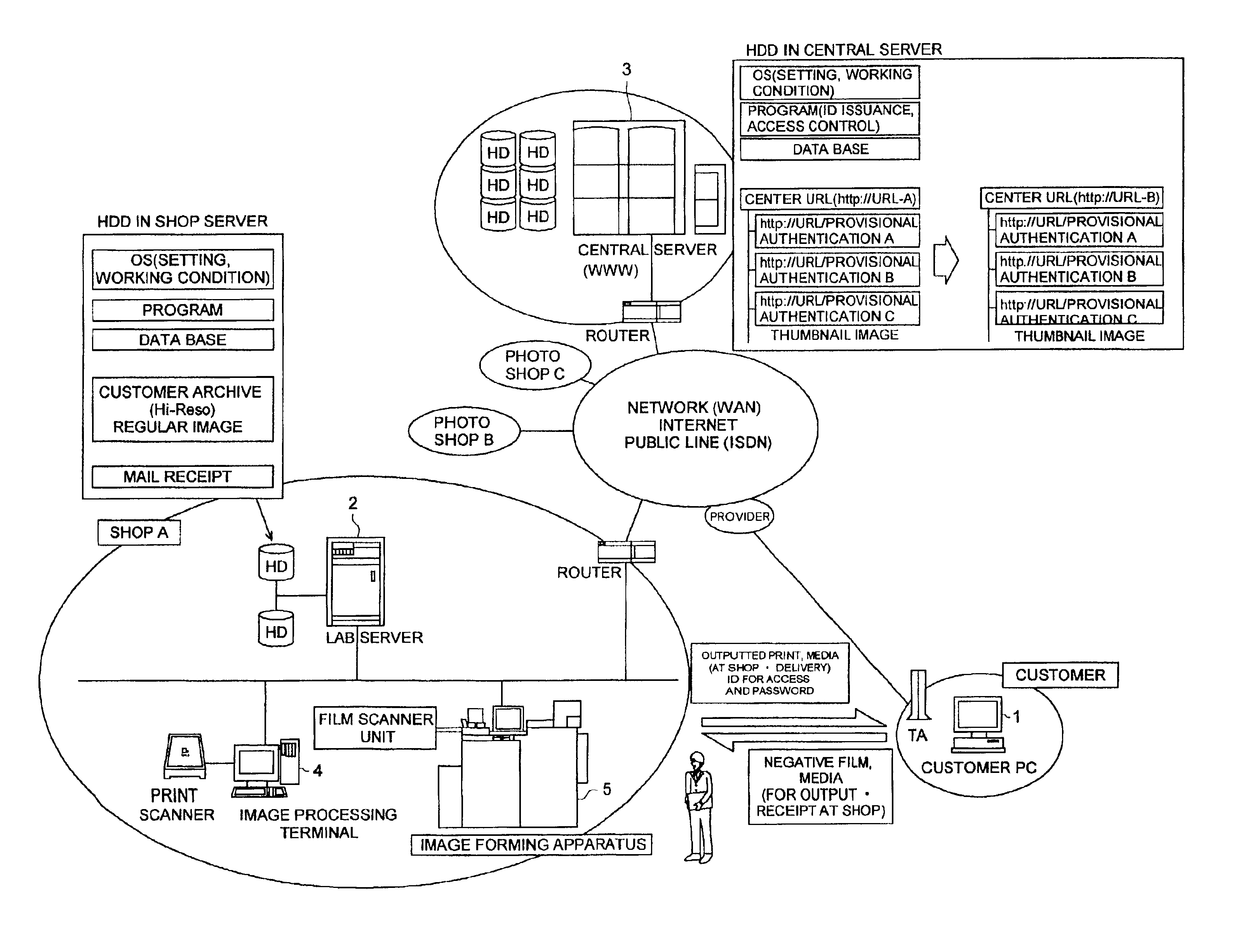
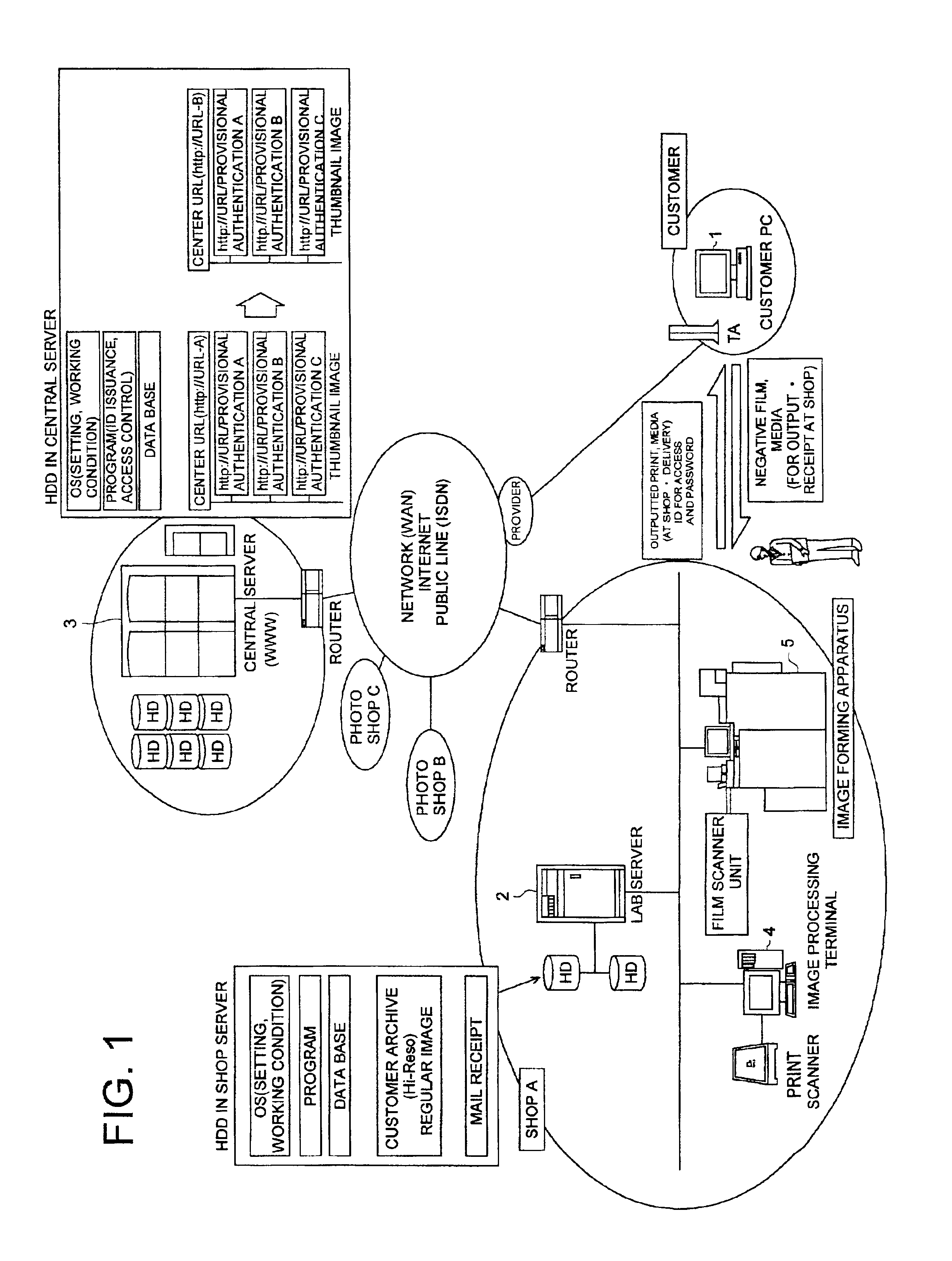
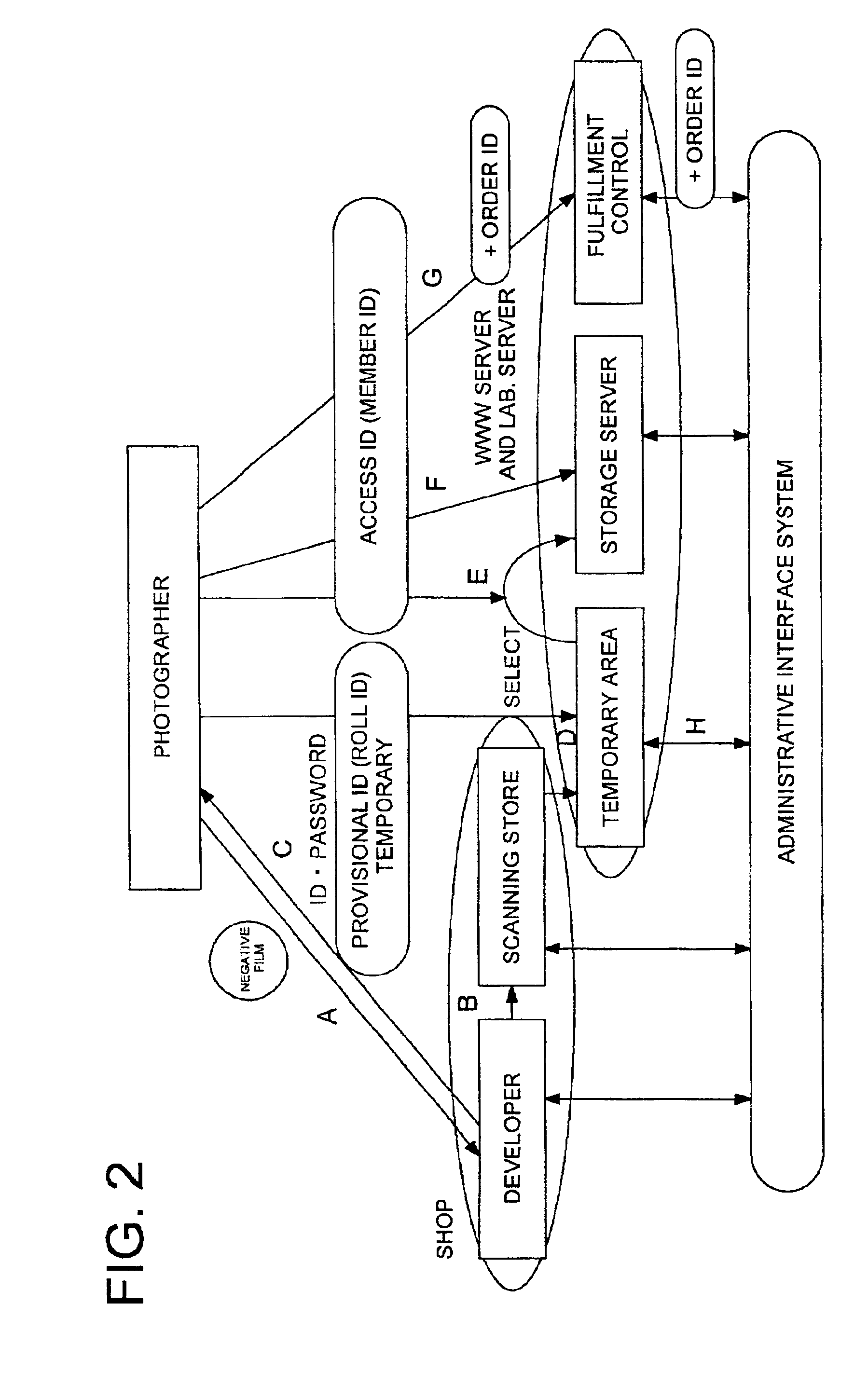
Image data processing system and server system
InactiveUS6934048B2Easy to useDigital computer detailsVisual presentationData processing systemComputer science
An image data processing system, comprises first and second storing sections; an administrative control section to administrate the image data stored in the first storing section or the reduced image data stored in the second storing section; an authenticating section to conduct an authenticating process for an access from a customer terminal on a network; the administrative control section making it possible for the customer to peruse the reduced image data when the authenticating section is accessed with the provisional ID and the administrative control section capable of conducting a receiving process for a member ID; and the administrative control section making it possible to receive an operation for at least one of the reduced image data in the second storing section and the image data stored in the first storing section.
Owner:KONICA CORP
Apparatus and method for tracking and managing physical assets
InactiveUS20060229906A1Maximize productivityReduce the burden onTechnology managementCommerceProduction rateThe Internet
Owner:DANA AUTOMOTIVE SYST GRP LLC
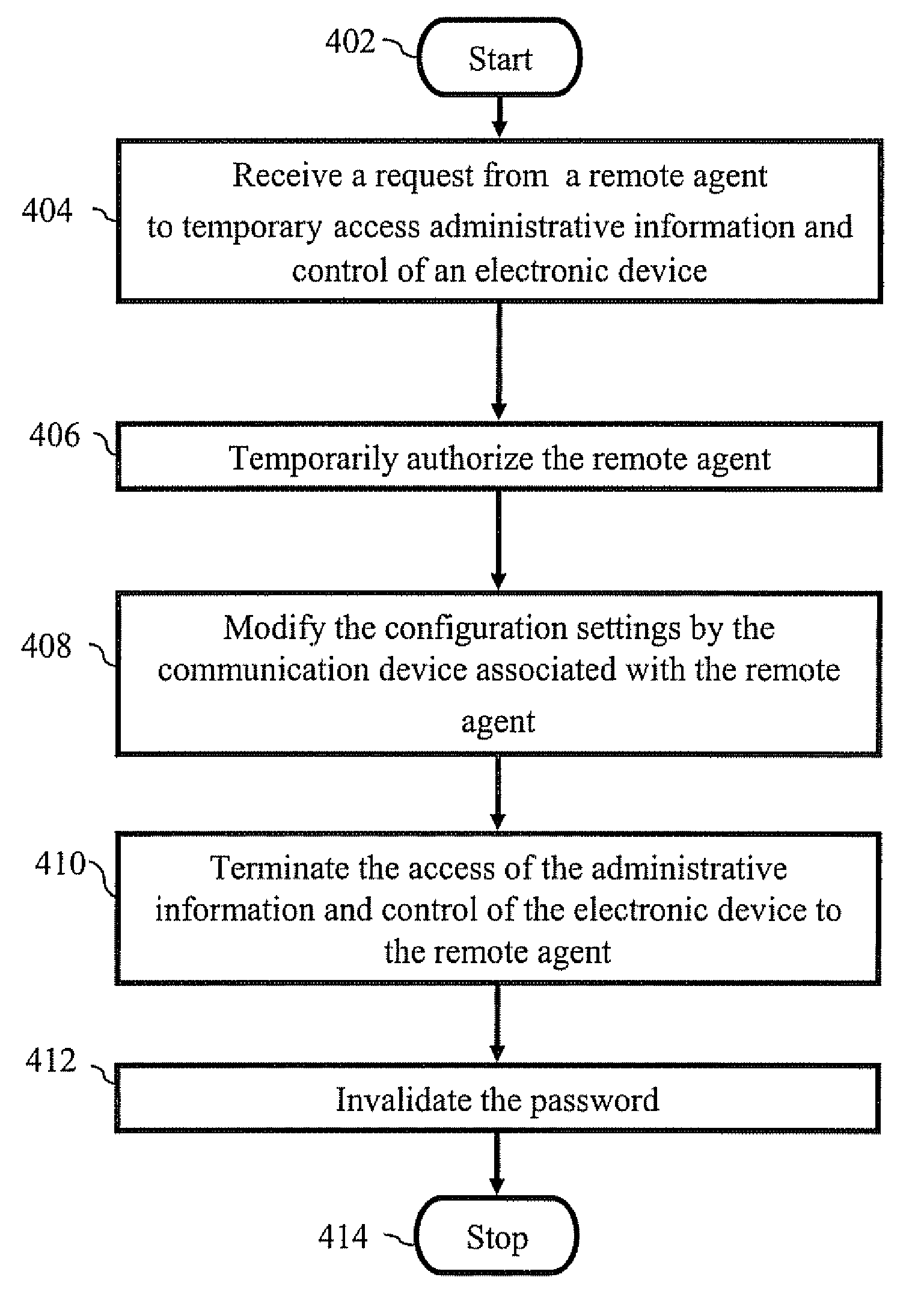
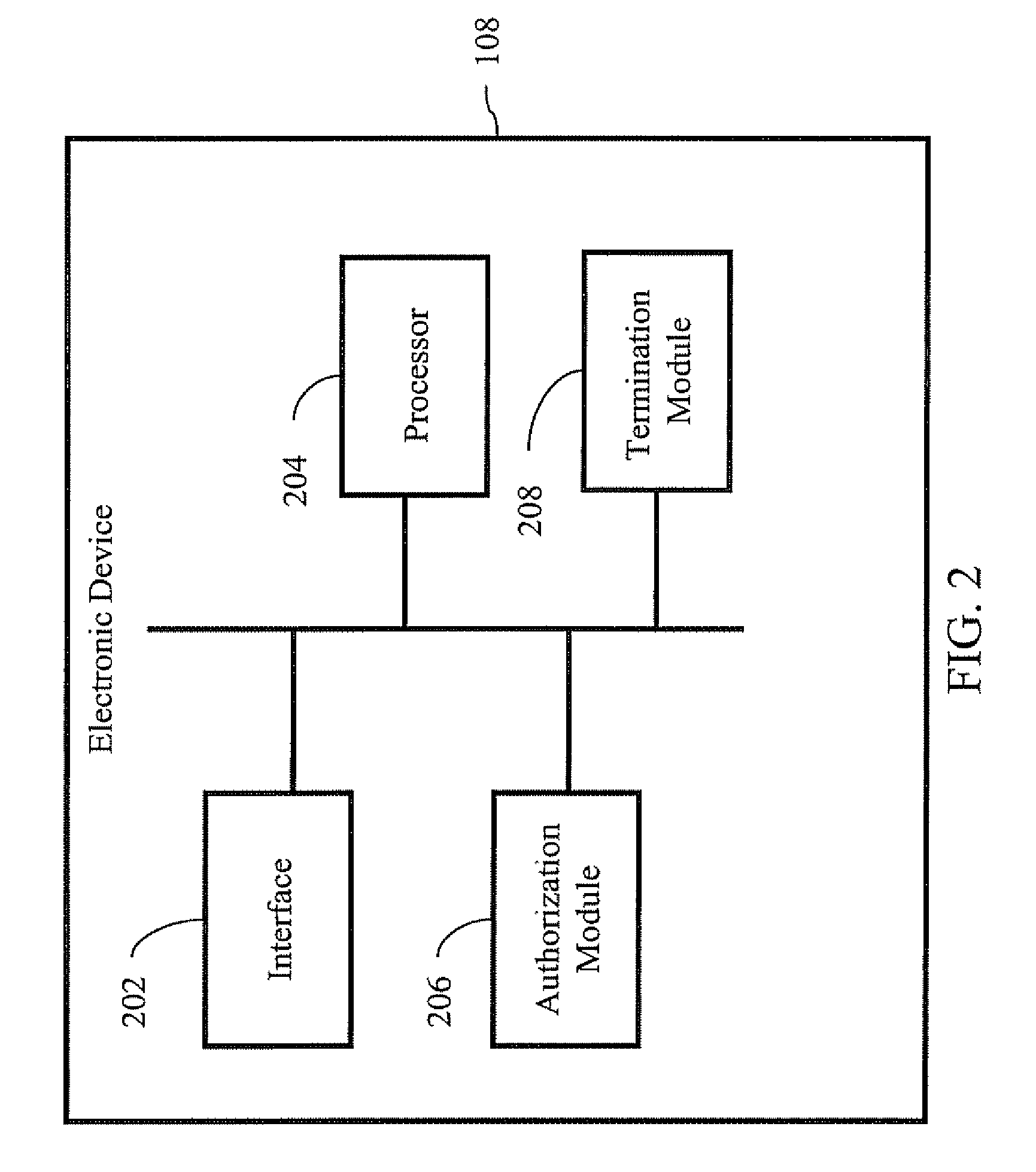
System authorizing a remote agent using a temporary password to manage configuration settings of a device and invalidating it after a fixed time interval
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
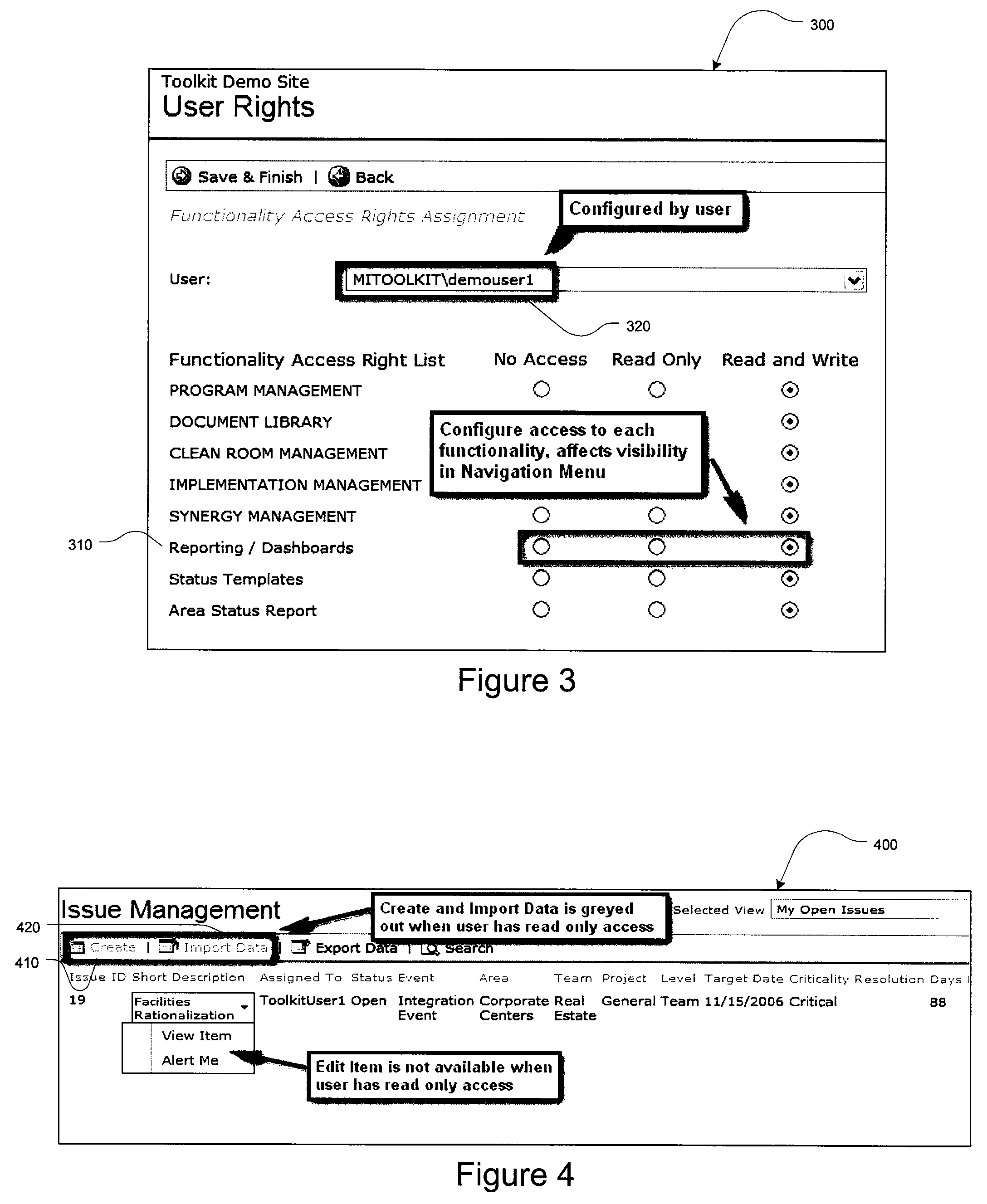
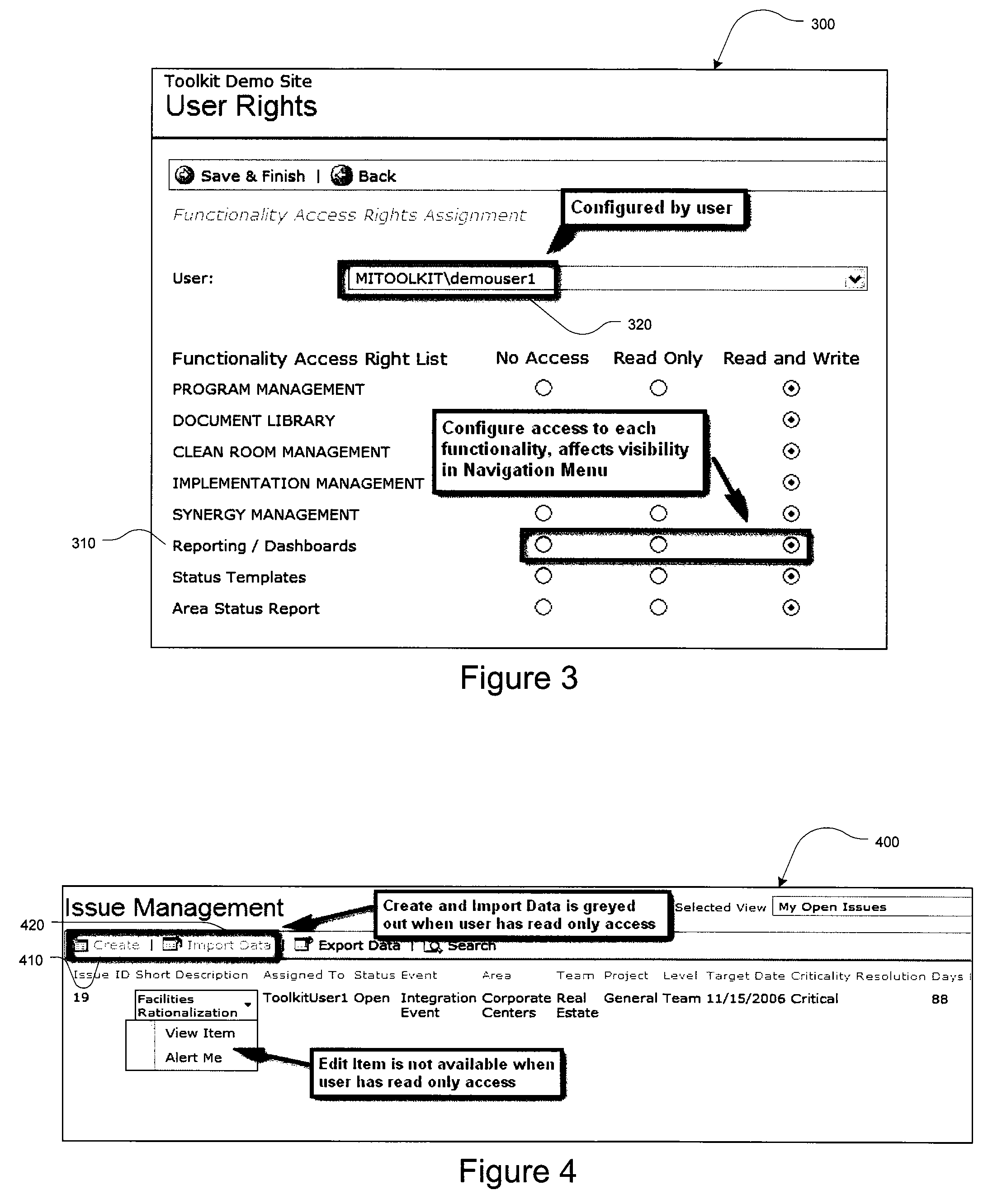
Merger integration toolkit system and method for merger-specific functionality
The present invention provides for a method and a computer system for providing functionality for electronically managing and supporting a merger integration of businesses, using software and other computer-implemented tools. In one aspect of the invention, the method and system provide merger-specific implementation functionality for an integration of businesses, where the businesses are subject to a merger or acquisition. The invention provides a collaboration environment computer program for assisting a group of individuals performing the integration of businesses. The collaboration environment computer program provides administrative controls and communication among the group of individuals performing the integration. Merger-specific implementation functionality, which is executable in conjunction with the collaboration environment computer program, is provided and arranged to manage detailed tasks and incidents of transition events associated with the merger or acquisition. The merger-specific implementation functionality includes detailed schedule tracking, incident tracking, KPI monitoring, and communications tracking.
Owner:ACCENTURE GLOBAL SERVICES LTD
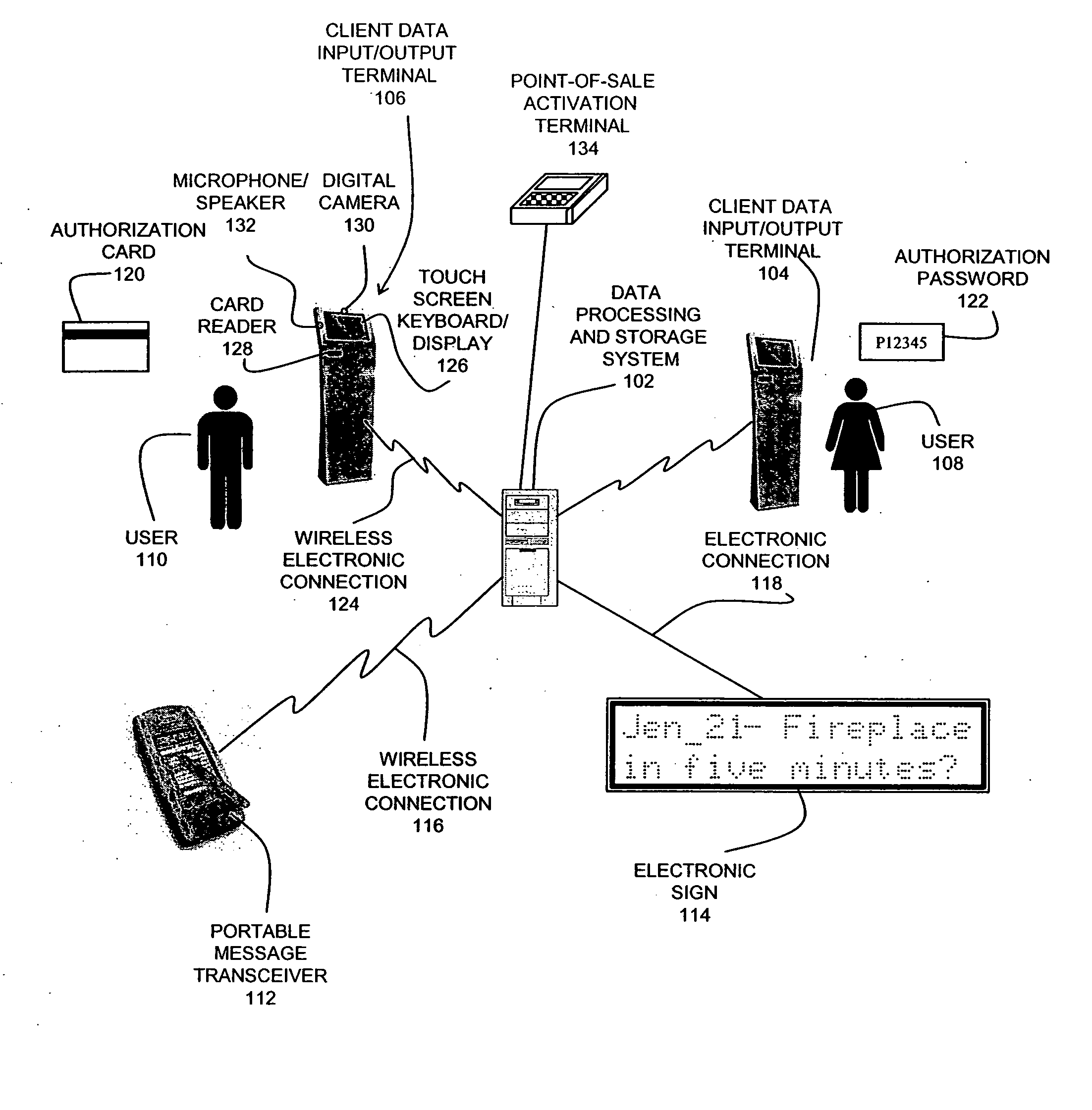
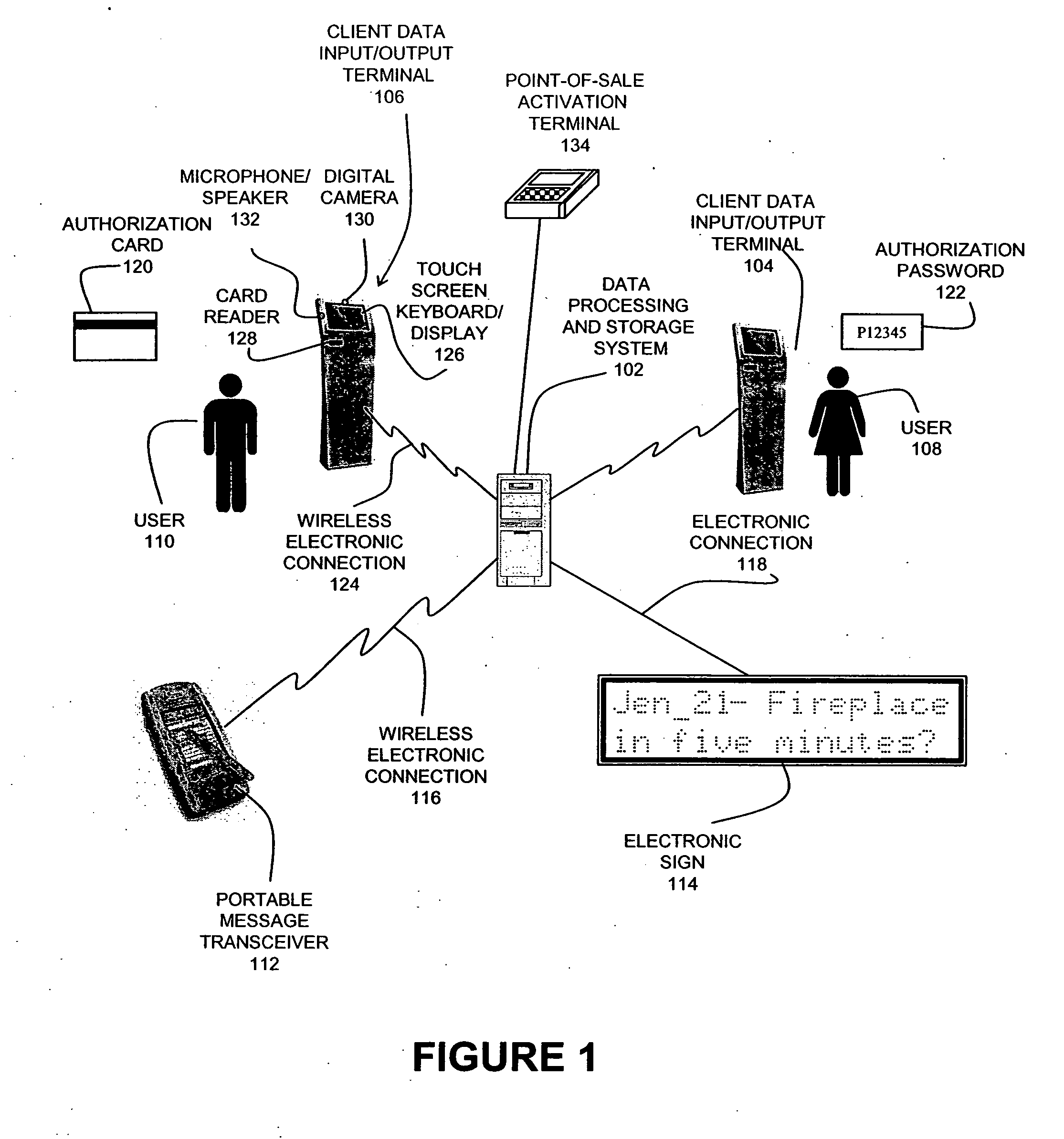
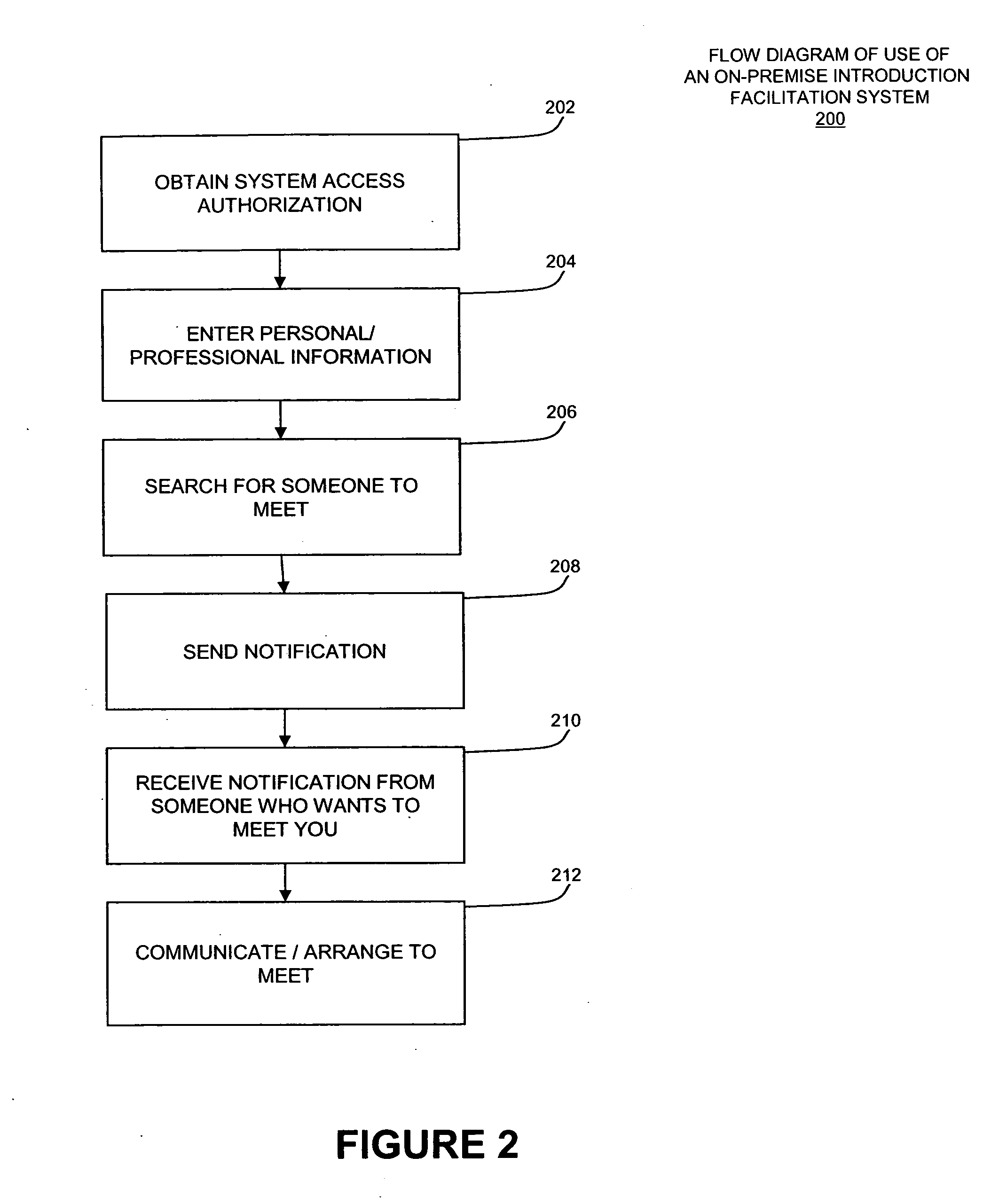
System and method for facilitating on-premise personal introductions
InactiveUS20050154911A1Digital data processing detailsAnalogue secracy/subscription systemsTransceiverUser input
The present invention disclosed overcomes the disadvantages of existing introduction systems and methods by providing an on-premise personal introduction facilitation system and a method for using an on-premise personal introduction facilitation system to facilitate personal introductions in a variety of venues and applications. Various embodiments of the system allow a user to enter and search for personal / professional information relevant to a desired on-premise personal introduction. The system may be disposed at locations to facilitate timely personal introductions. The system may utilize various electronic technologies including portable message transceivers, data processing and storage systems, data acquisition and display devices to facilitate timely interactive communications. The system includes administrative controls and authentication terminals and software modules that allow an administrator to control who uses the system and the duration of use.
Owner:SOFT SHOULDER
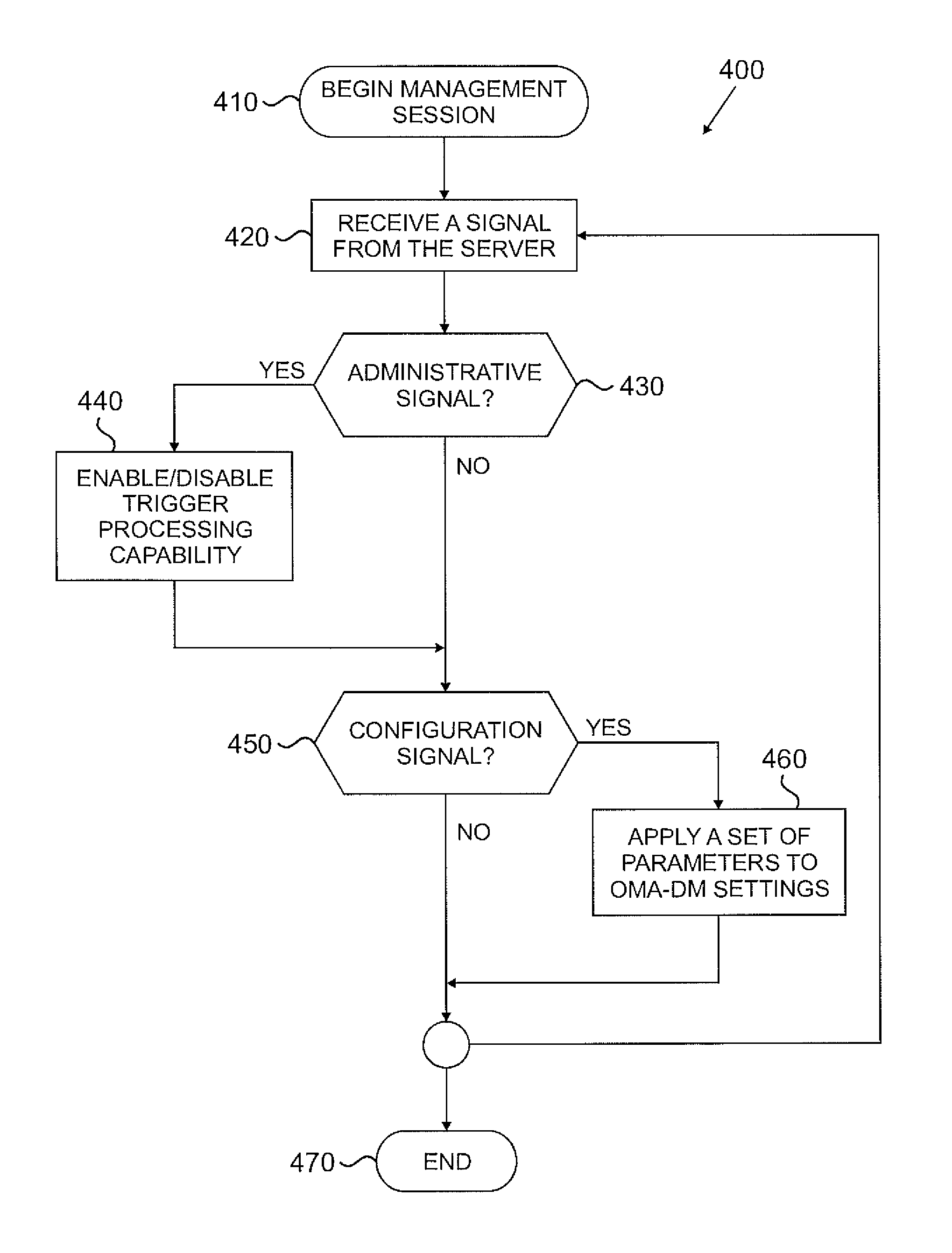
Configuration and administrative control over notification processing in oma dm
InactiveUS20100299418A1Network traffic/resource managementAssess restrictionComputer hardwareAdministrative controls
A method and a device are configured to receive a signal from a server to perform administrative and configuration control. During Open Mobile Alliance (OMA) Device Management (DM) session, the device receives either an administrative or configuration signal from the server. The administrative signal may instruct the device to inhibit or allow a trigger processing capability. The configuration signal may instruct the device to apply a set of parameters to the device settings that are related to notification processing.
Owner:SAMSUNG ELECTRONICS CO LTD
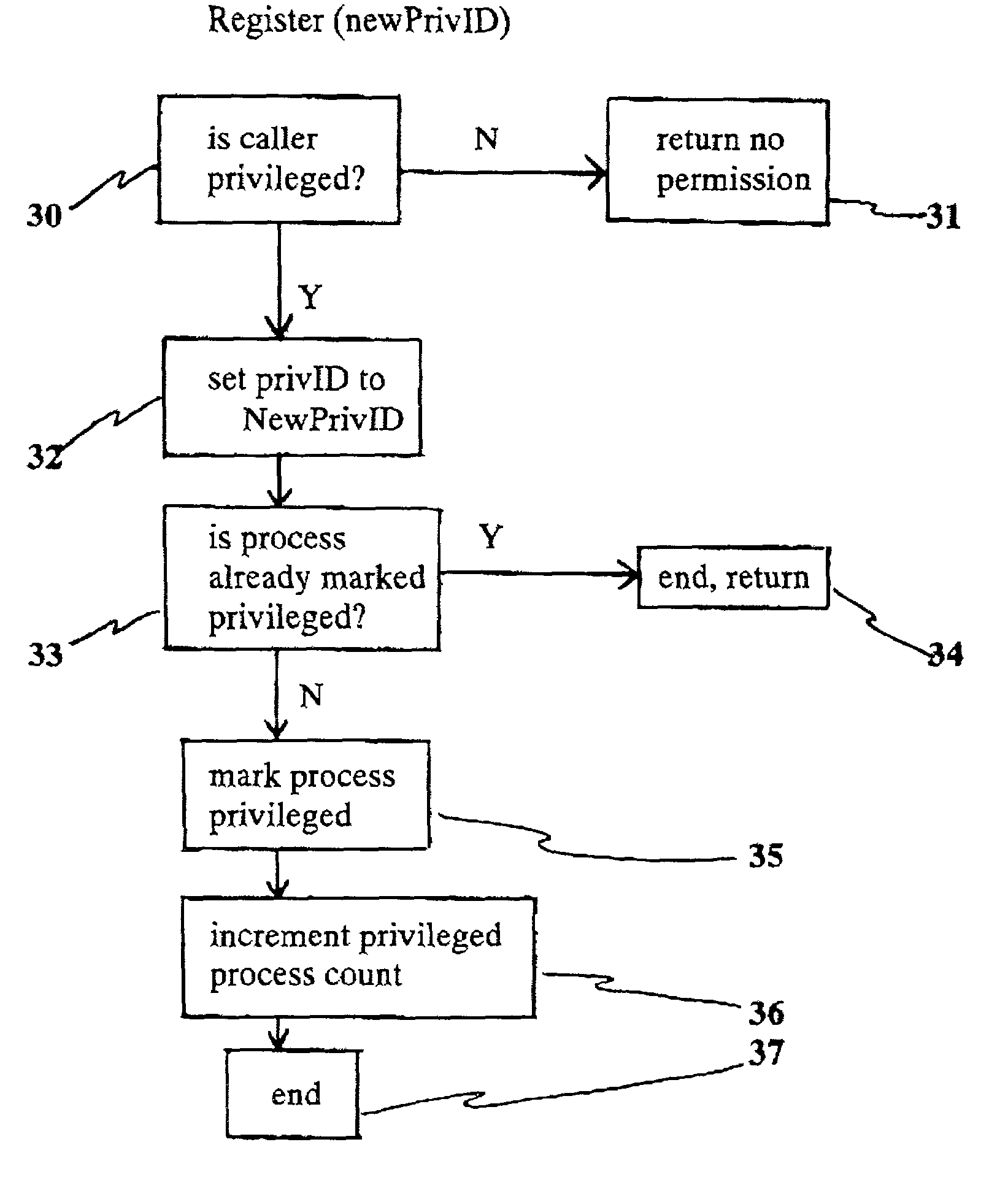
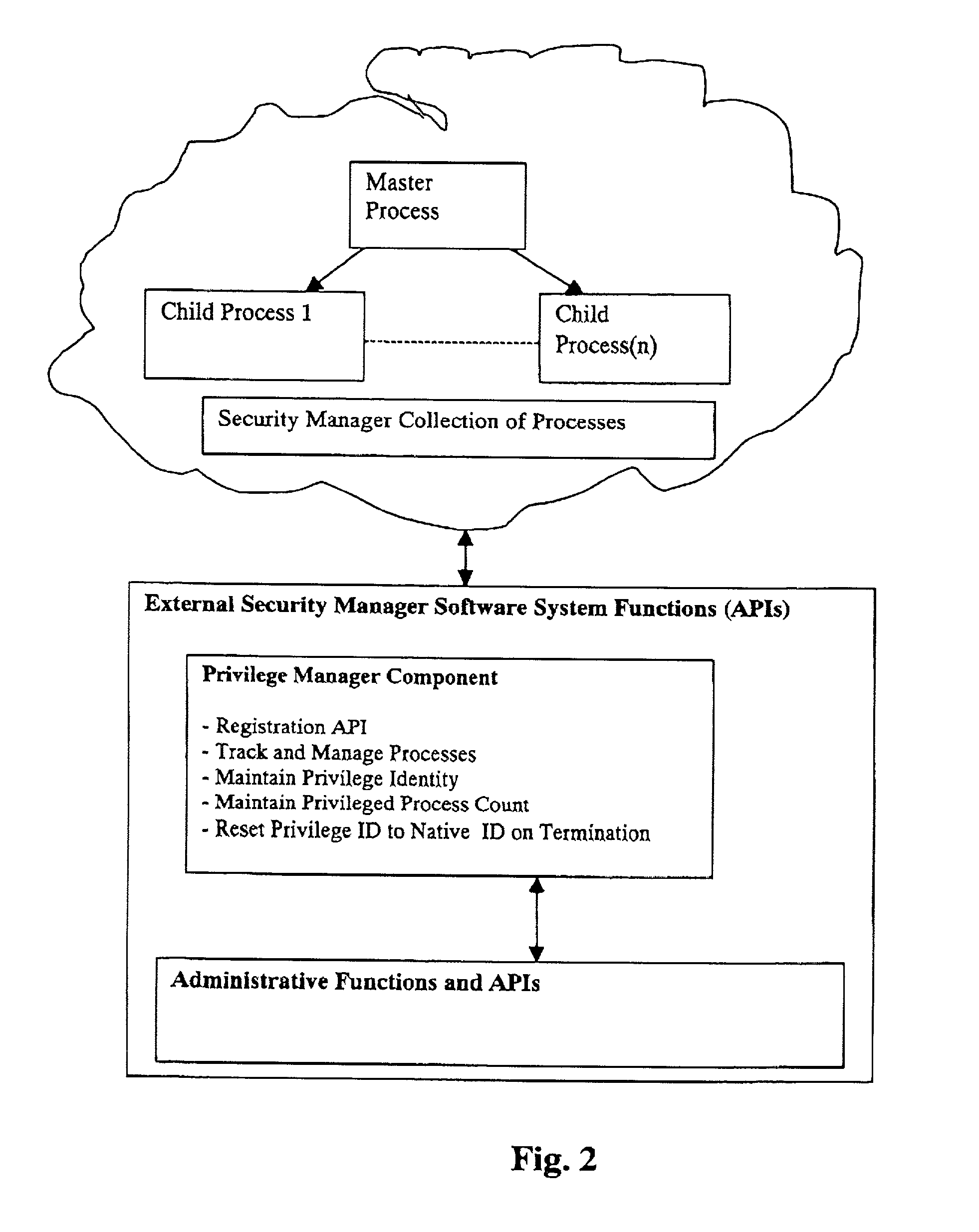
Method for transferring privilege access to a resource manager with subsequent loss of privilege by the initiating identity
InactiveUS7080406B2Data processing applicationsDigital data processing detailsComputer networkResource management
The present invention describes a privilege transfer method between programs in a computing system. This transfer method allows a resource manager such as a security manager to be initially started on the system by the system's native privileged user. This user has the needed native privilege to add it to the system. Subsequently the privilege to administer the security manager is transferred from the native privileged identity to a designated user identity. Once transferred, the initial privileged identity, the system's native privileged user, losses privilege with respect to the security manager and the new registered identity gains administrative control over the security manager. Since the new registered identity is not the native root identity, the security of the native system is not compromised.
Owner:LINKEDIN
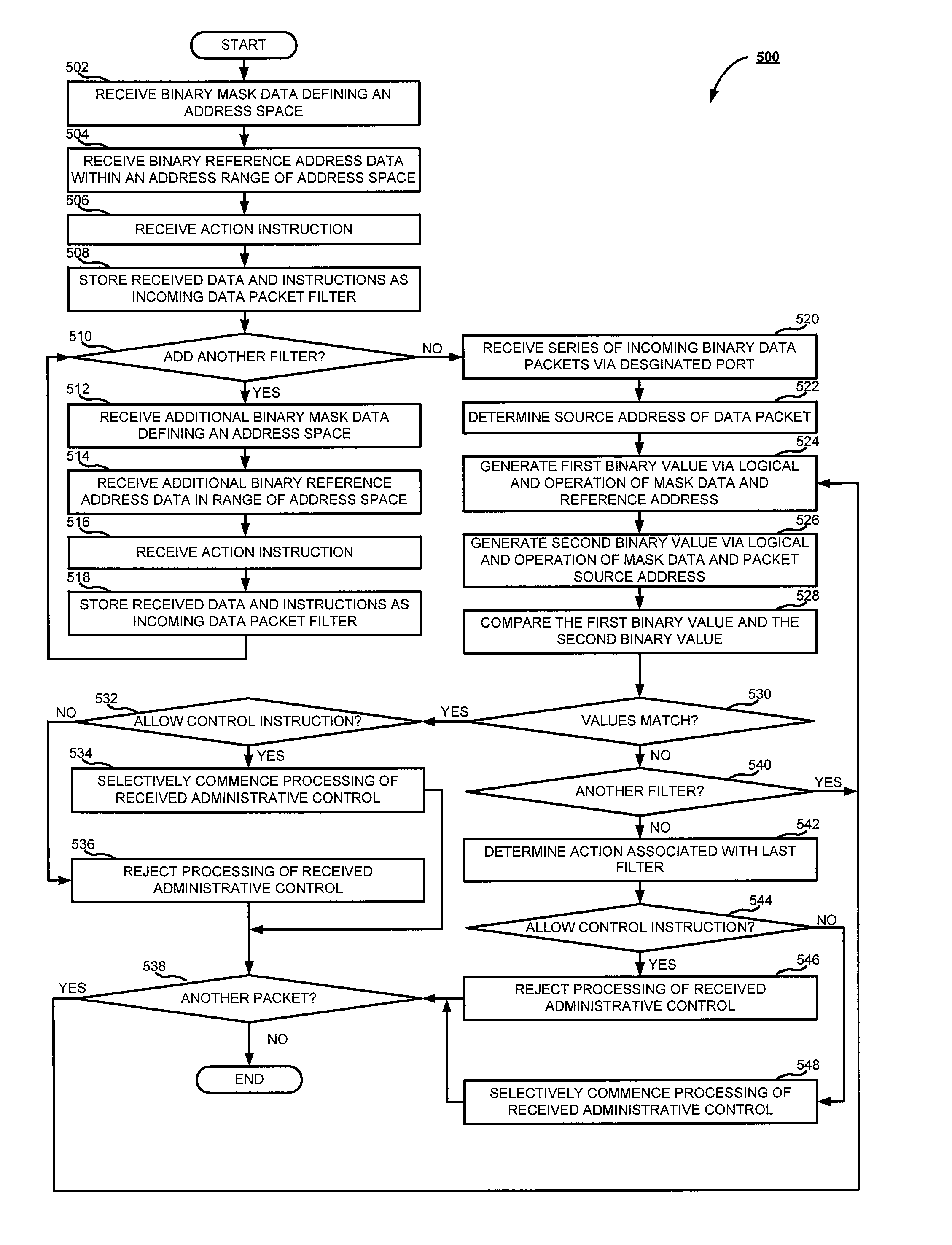
System and method for securing remote administrative access to a processing device
The subject application is directed to a system and method for securing remote administrative access to a processing device. Incoming data packets, including source data, destination data, and a data portion for administrative control of a processing device are received at a designated port associated with administrative control. Binary mask data defining an address space from which control is acceptable is then received. Binary reference address data representing an address with an address range within the address space is received. A first binary value is generated via a comparison of the reference data and the mask data. A second binary value is generated via a comparison of an incoming data packet and the mask data. The acceptability of the packet is determined based on comparing the first value with the second value. Processing of received administrative control by the processing device is then selectively commenced based on the value comparison.
Owner:KK TOSHIBA +1
Merger integration toolkit system and method for milestone tracking
The present invention provides for a method and a computer system for providing functionality for electronically managing and supporting a merger integration of businesses, using software and other computer-implemented tools. In one aspect of the invention, the method and system provide program milestone tracking for an integration of businesses, where the businesses are subject to a merger or acquisition. The system provides a collaboration environment computer program for assisting a group of individuals performing the integration of businesses. The collaboration environment computer program provides administrative controls and communication among the group of individuals. A project management computer program assists the group of individuals and is configured to manage project schedules, budgets, and timeframes. A program milestone component is established and configured to facilitate creating and tracking program milestones for the collaboration environment computer program. The program milestone component also configured to interface the collaboration environment computer program and the project management computer program such that the collaboration environment computer program directly links to the project management computer program and receive program milestone updates.
Owner:ACCENTURE GLOBAL SERVICES LTD
System and method for handling media streams
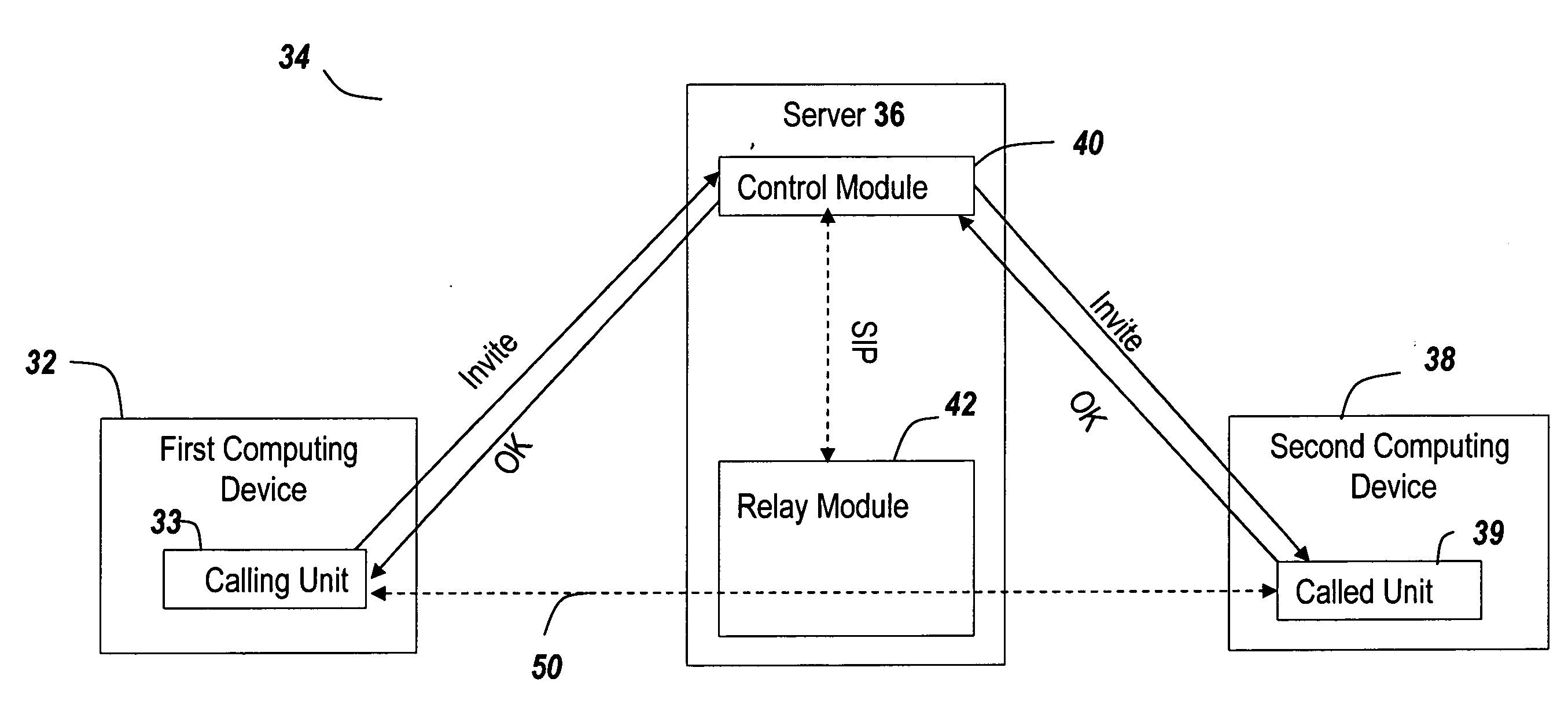
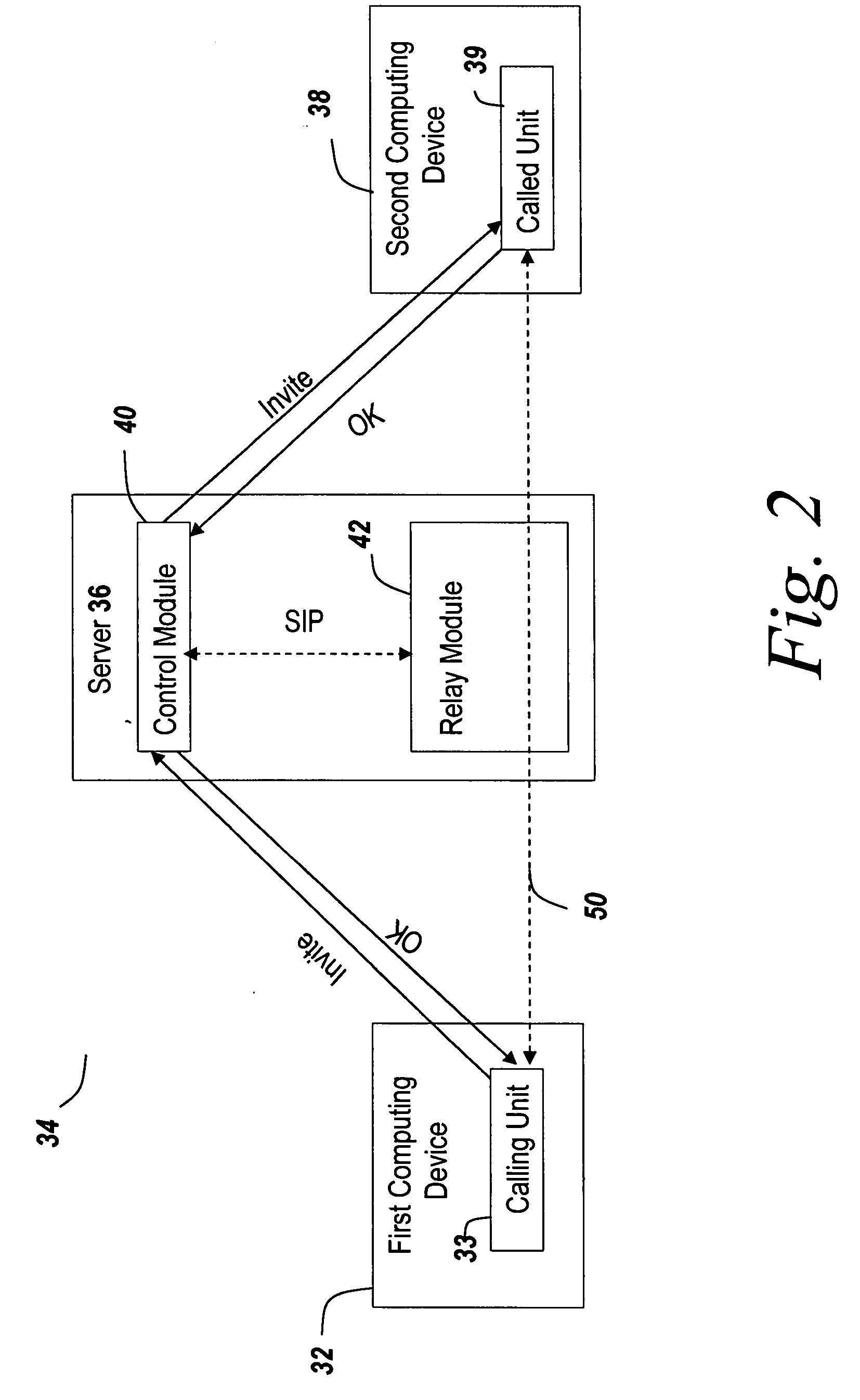
ActiveUS20080031231A1Facilitate communicationGood serviceSpecial service provision for substationMultiplex system selection arrangementsEnhanced serviceService use
A mechanism for managing and enhancing communication streams in a VOIP service using SIP is discussed. SIP is used to manage and enhance a communication stream at a centralized switching element in the VoIP environment rather than at the communication stream endpoints. The communication stream set up by SIP is directed through a central switching element under administrative control rather than traveling directly between the stream endpoints. As a result, the media stream may be conditioned with treatments and may be provided with enhanced services at the central switching element without the specific treatments and services being supported at both stream endpoints. The use of the centralized switching element allows full administrative control of the VoIP environment.
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT +1
System and method for providing virtual spaces for access by users via the web
A system configured to provide one or more virtual spaces that are accessible to users. The virtual spaces may be provided such that an enhanced level of interactivity between the virtual spaces and the Web, including resources that communicate with the system via the Internet (e.g., via users, websites, webpages, other web resources, etc.) and / or other networks. To provide this enhanced level of interactivity, the system may enable interactions between an instance of a virtual space and the Web (e.g., queries, commands, communication, administrative controls, etc.) via a standard web protocol, such as a HyperText Transfer Protocol (e.g., http, https, etc.) and / or other standard web protocols. Since interactions take place between the instance of the virtual space and the Web via a standard web protocol, the instance of the virtual space may interact directly with Web resources such as web servers, web browsers, websites, webpages, and / or other Web resources.
Owner:DISNEY ENTERPRISES INC
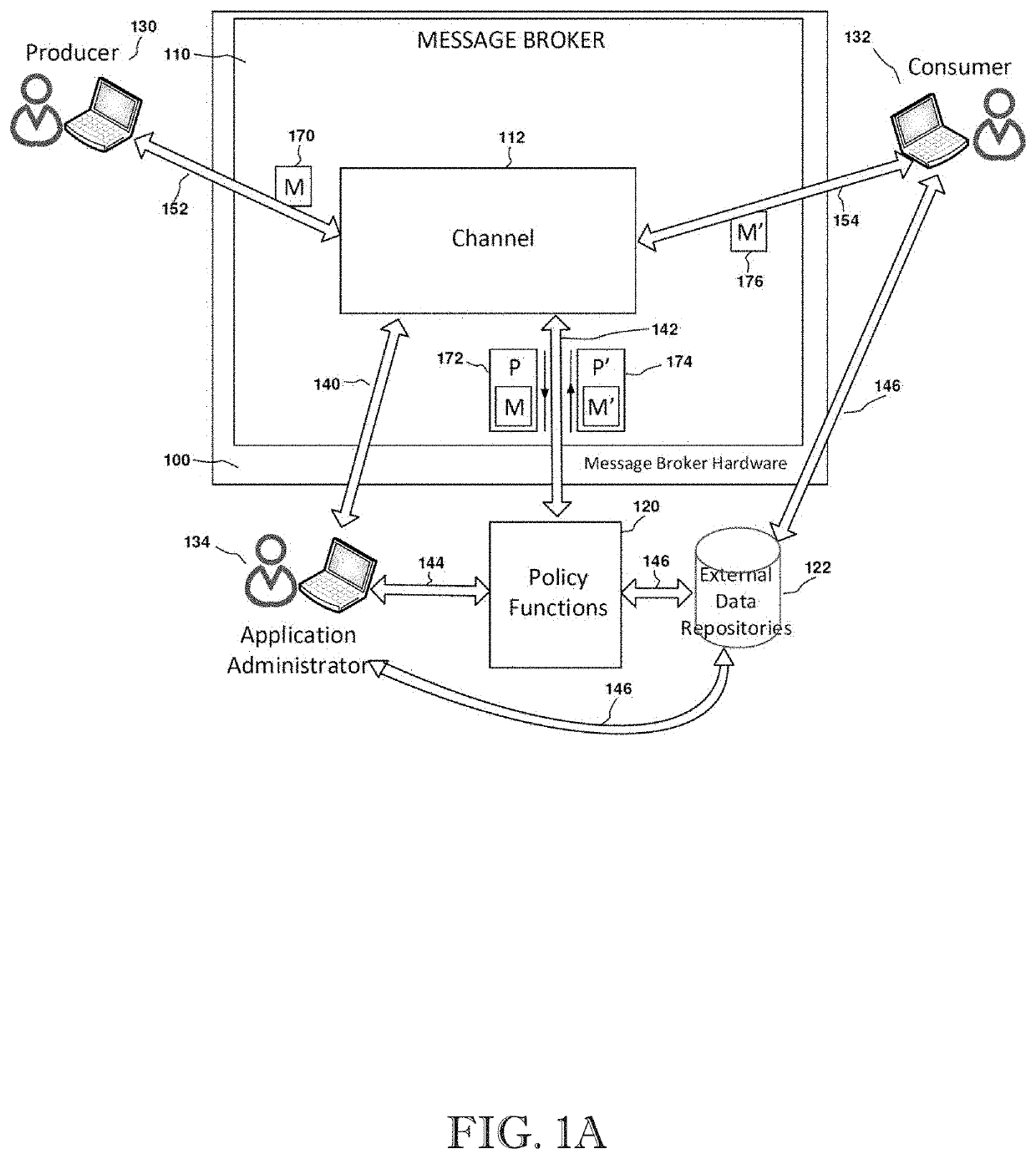
Message broker customization with user administered policy functions
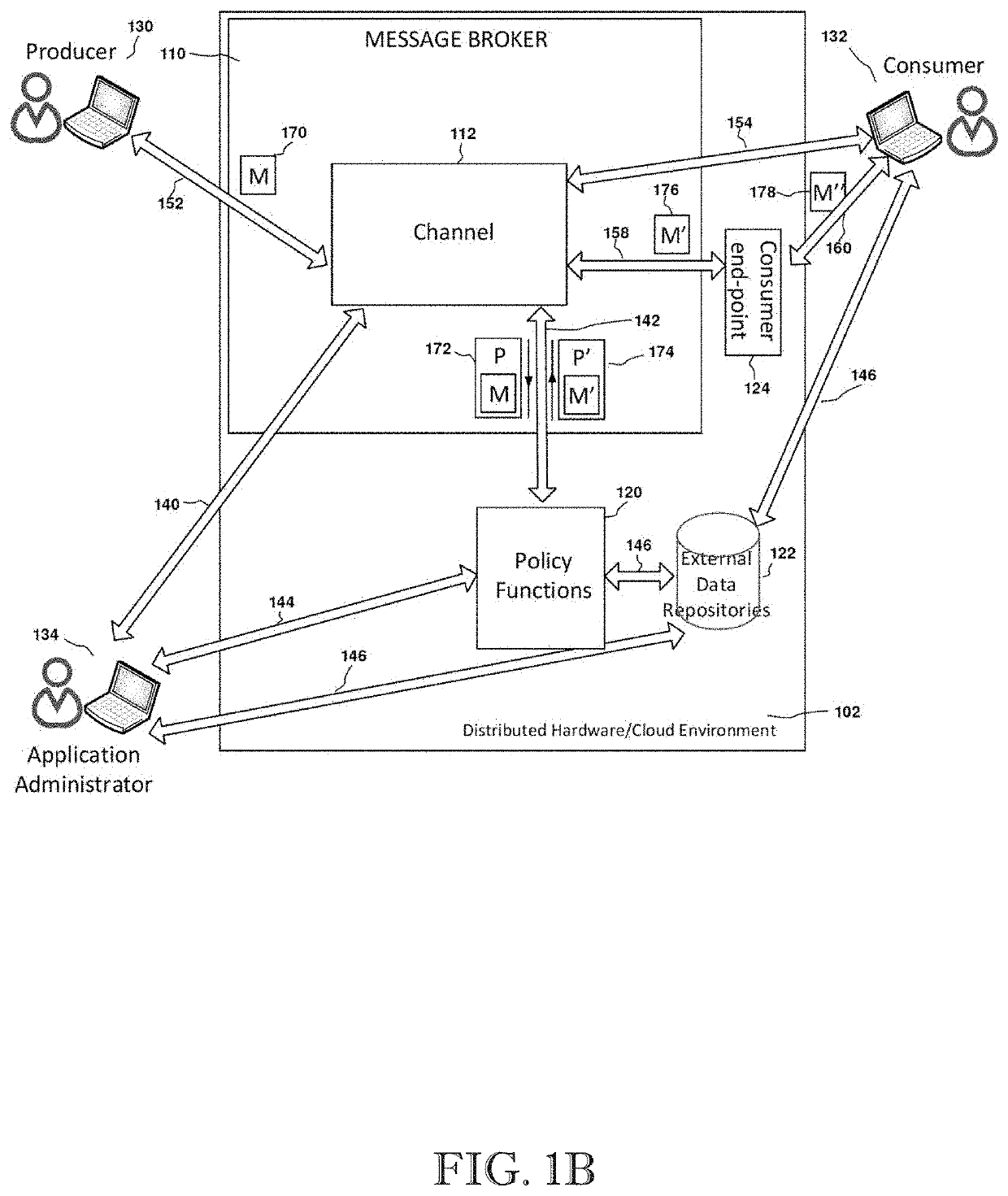
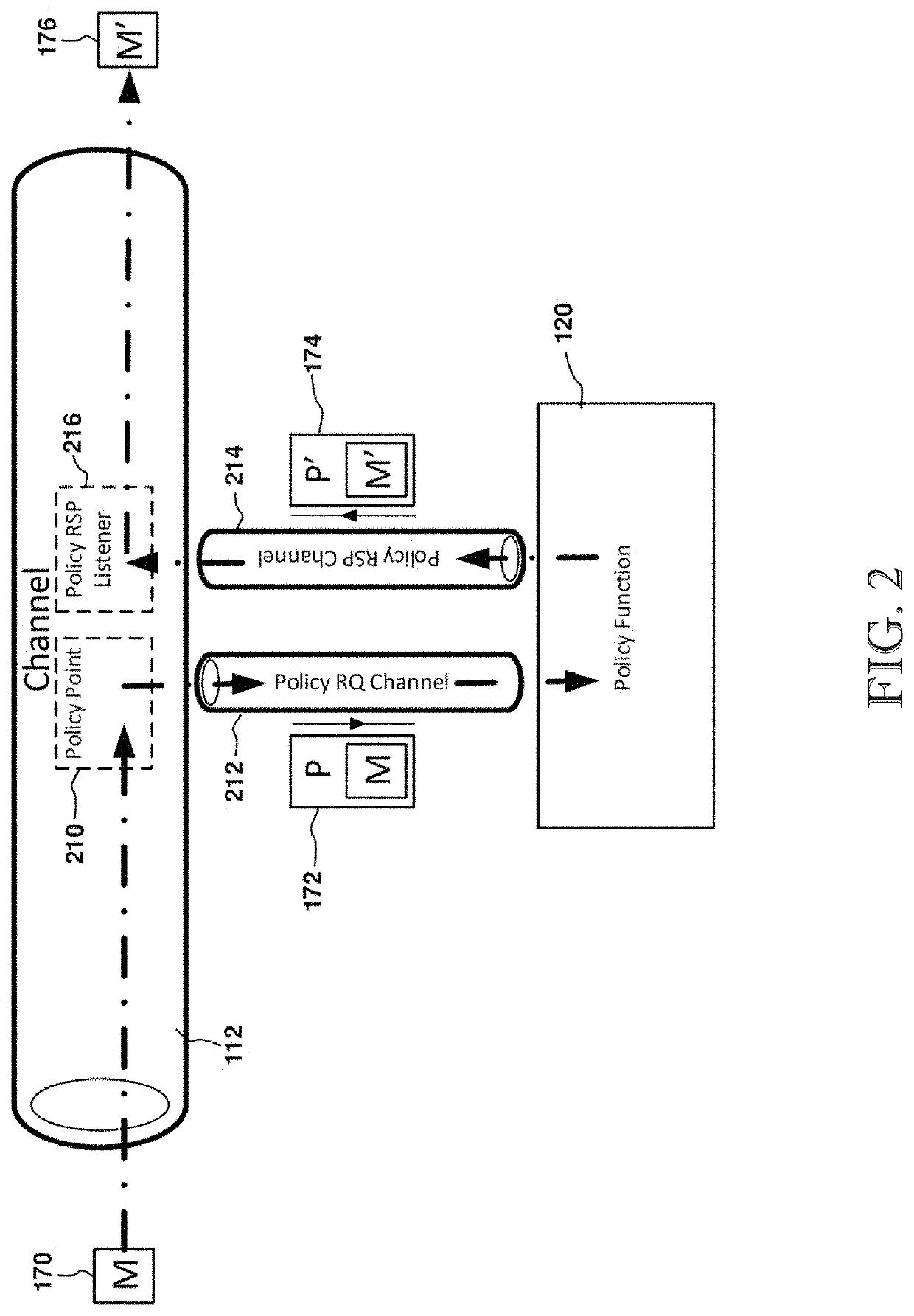
ActiveUS20210176326A1Limited customizationProgram controlData switching networksEngineeringUser management
A message broker customization system and method with user administered policy functions. The system uses user defined and controlled policy functions to programmatically, customize the behaviors of a message broker's processing of messages and further allowing for that customization to take place on a per channel basis. This provides for greater functionality and flexibility to the users of a message system, especially when the users of the message system do not have administrative control over the message broker.
Owner:CARLEY JEFFREY ALAN
Merger integration toolkit system and method for milestone tracking
The present invention provides for a method and a computer system for providing functionality for electronically managing and supporting a merger integration of businesses, using software and other computer-implemented tools. In one aspect of the invention, the method and system provide program milestone tracking for an integration of businesses, where the businesses are subject to a merger or acquisition. The system provides a collaboration environment computer program for assisting a group of individuals performing the integration of businesses. The collaboration environment computer program provides administrative controls and communication among the group of individuals. A project management computer program assists the group of individuals and is configured to manage project schedules, budgets, and timeframes. A program milestone component is established and configured to facilitate creating and tracking program milestones for the collaboration environment computer program. The program milestone component also configured to interface the collaboration environment computer program and the project management computer program such that the collaboration environment computer program directly links to the project management computer program and receive program milestone updates.
Owner:ACCENTURE GLOBAL SERVICES LTD
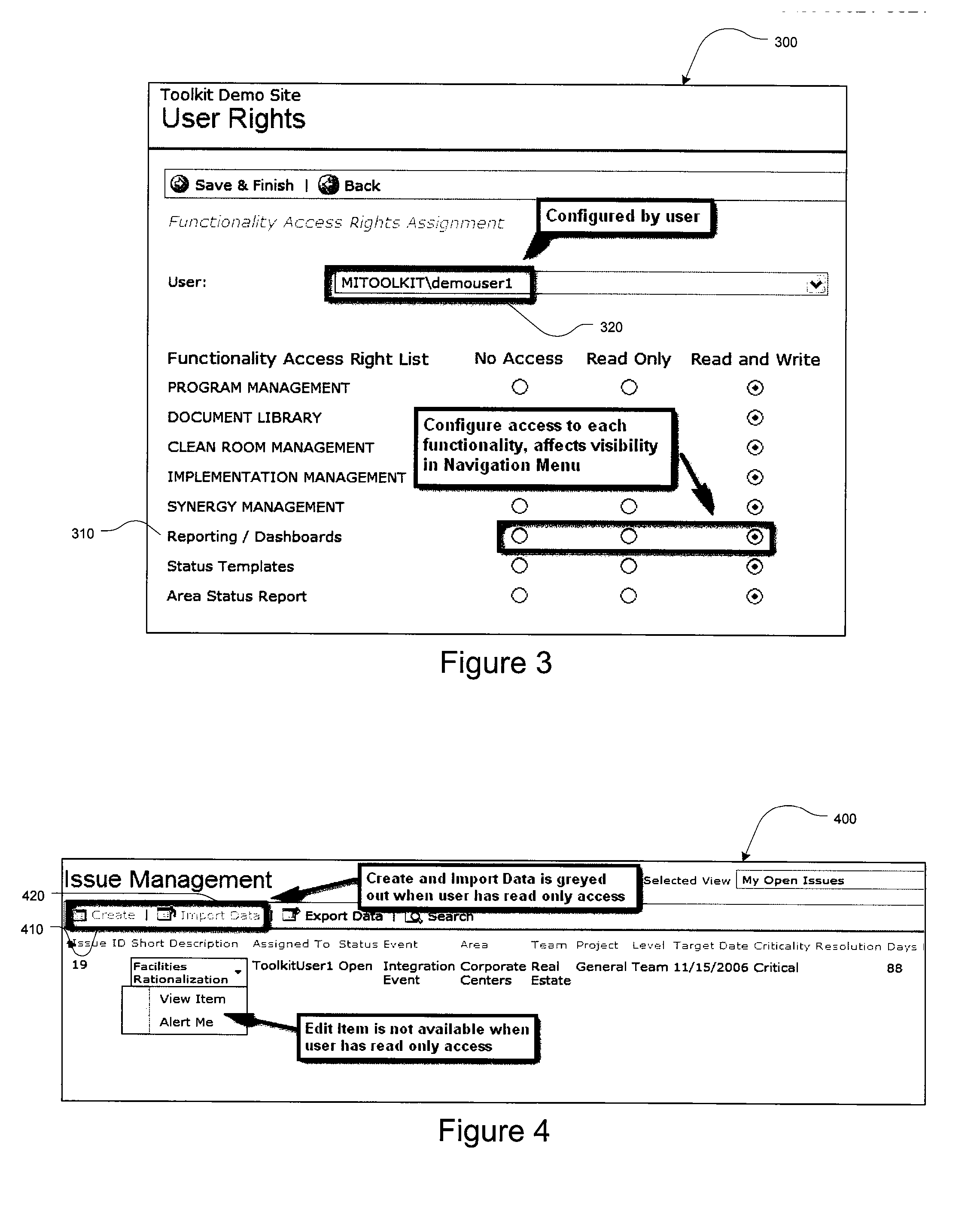
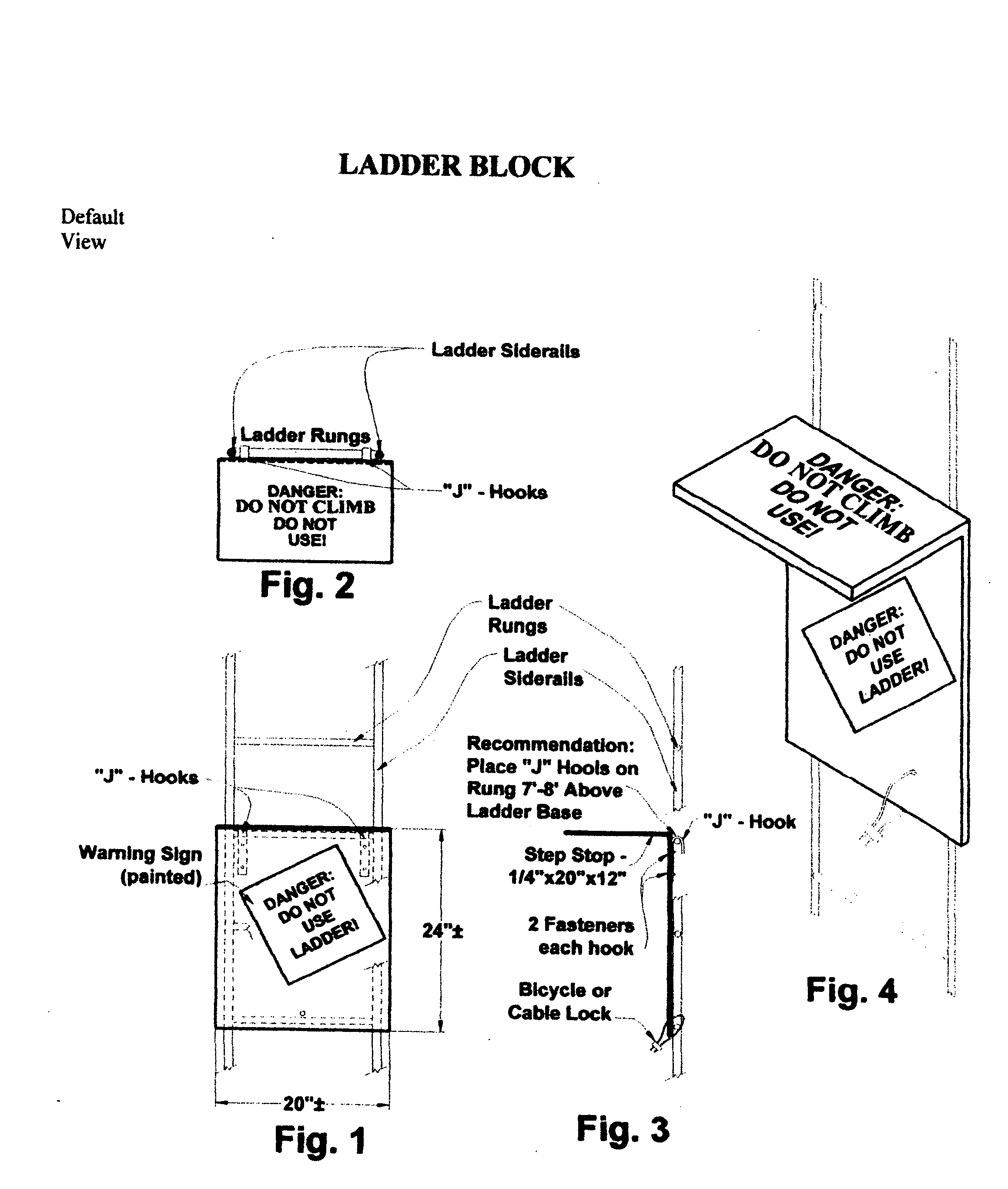
Ladder block
InactiveUS20050241199A1Avoid accessProhibition of useAdvertisingBoardsCombined useEngineering controls
The LADDER BLOCK is an innovative engineering control device that when used properly will prohibit access to and use of incomplete or unsafe scaffolds and work platforms. The LADDER BLOCK should be used in conjunction with administrative controls and safety policy and procedures that provide the user with an additional method for the prevention of falls from elevations. The LADDER BLOCK offers the construction industry a ladder access prevention device that has heretofore been unavailable. This device will help reduce personal injury to workers and minimize direct and indirect costs to employers.
Owner:GHORMLEY ARNOLD BENNETT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com