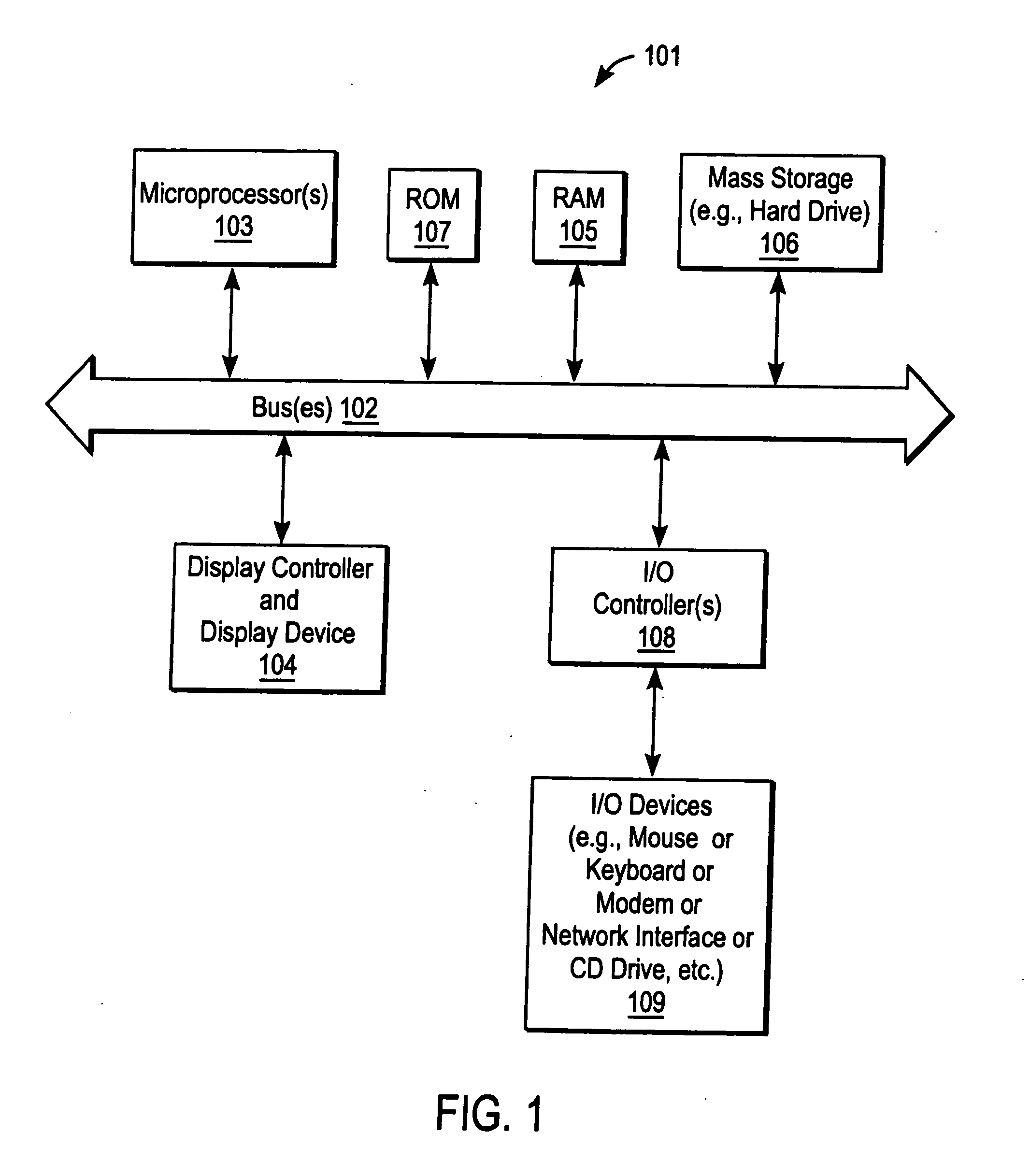
Patents
Literature
4490results about How to "Avoid access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
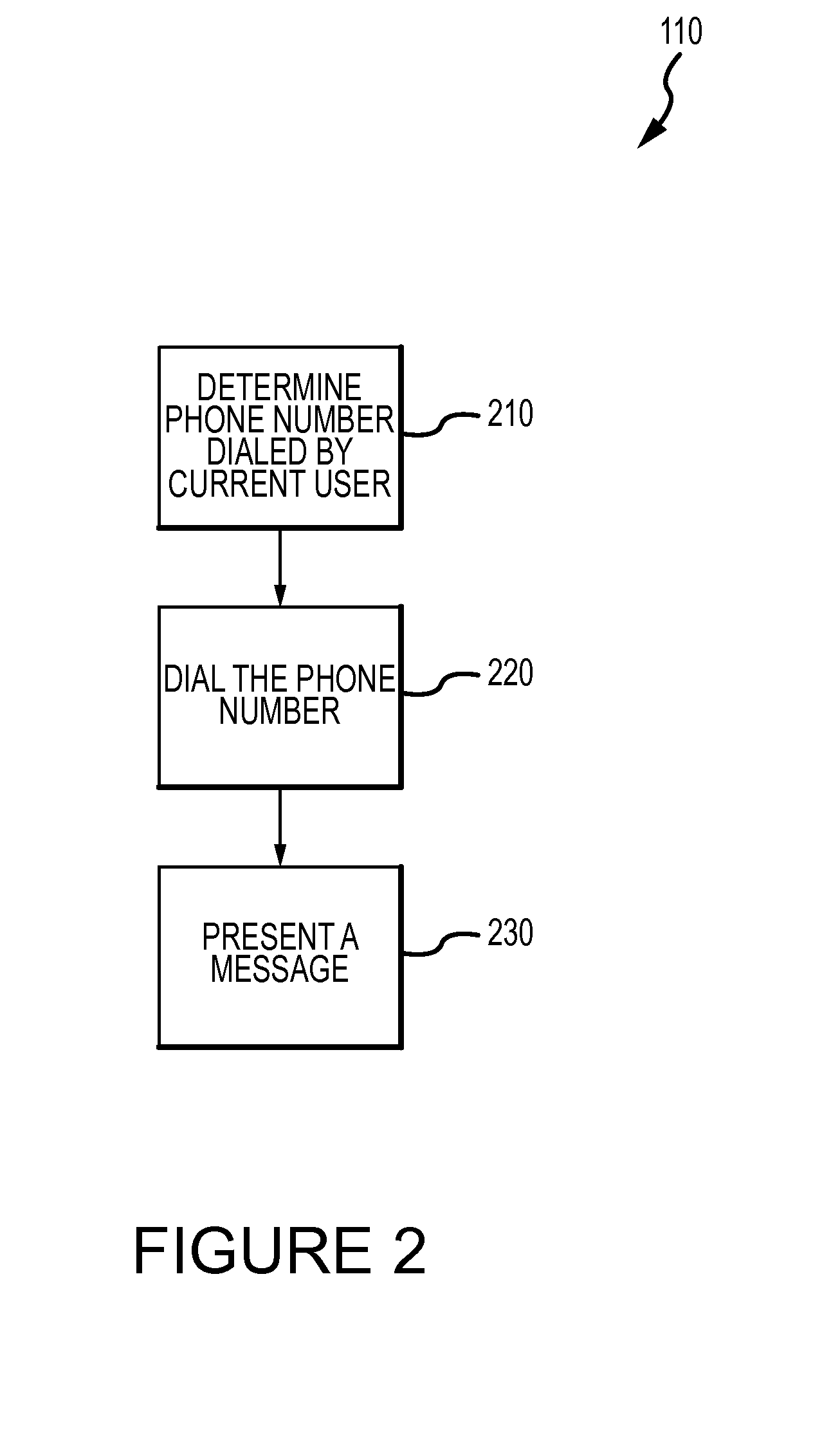
Flexible instrument
InactiveUS7090683B2Small diameterSufficient flexibilitySuture equipmentsProgramme-controlled manipulatorEngineeringComputer algorithm
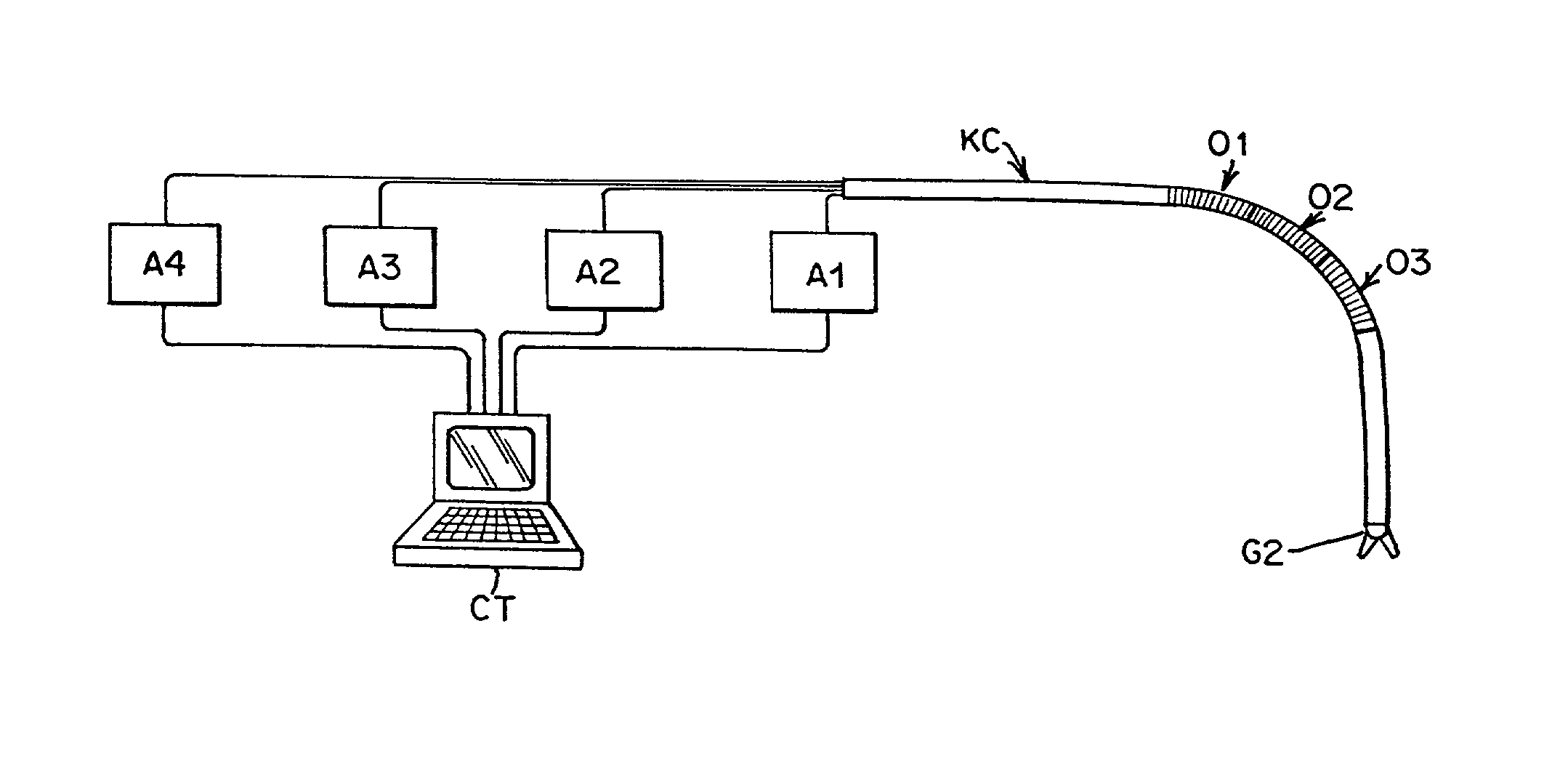
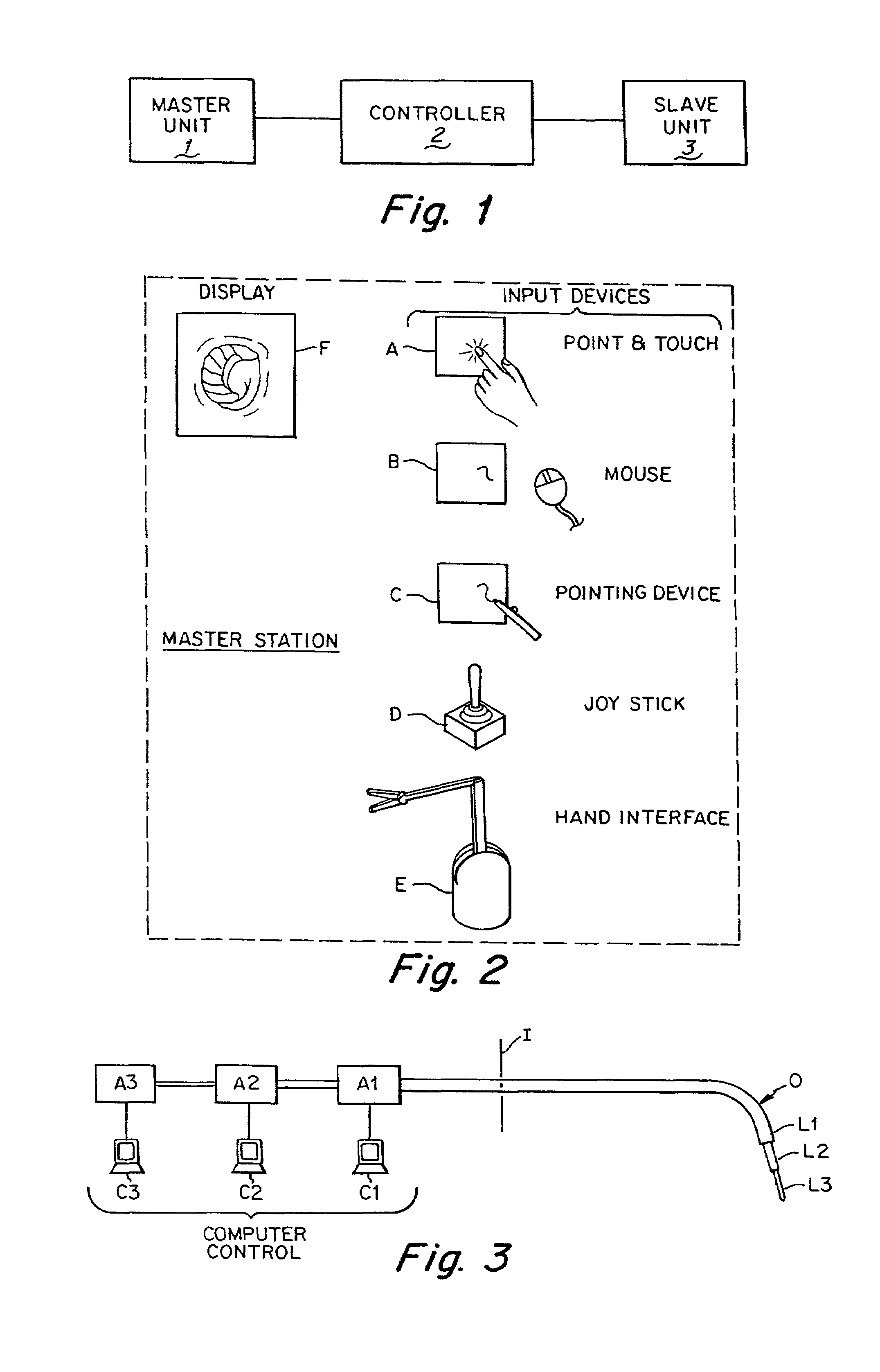
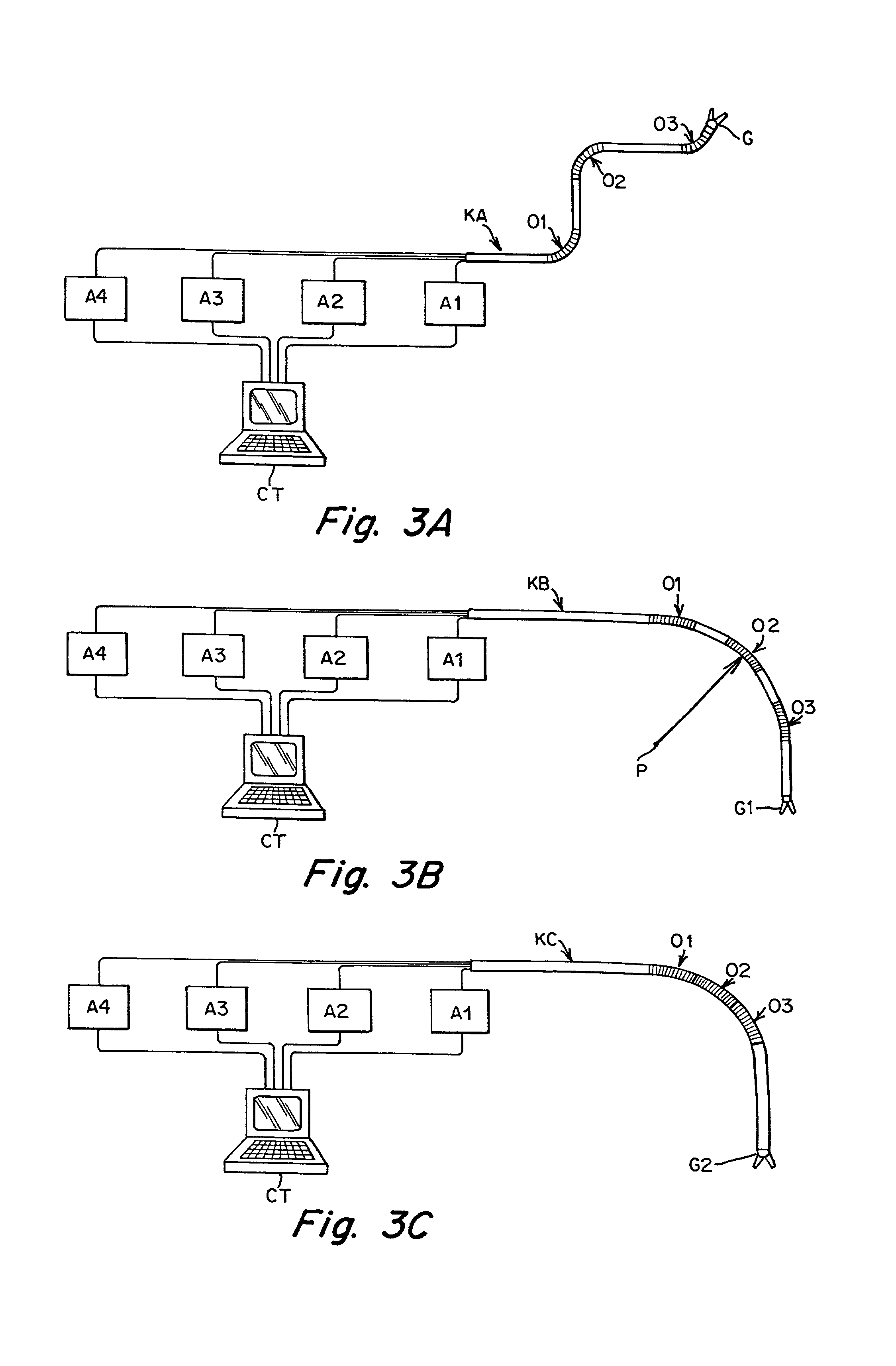
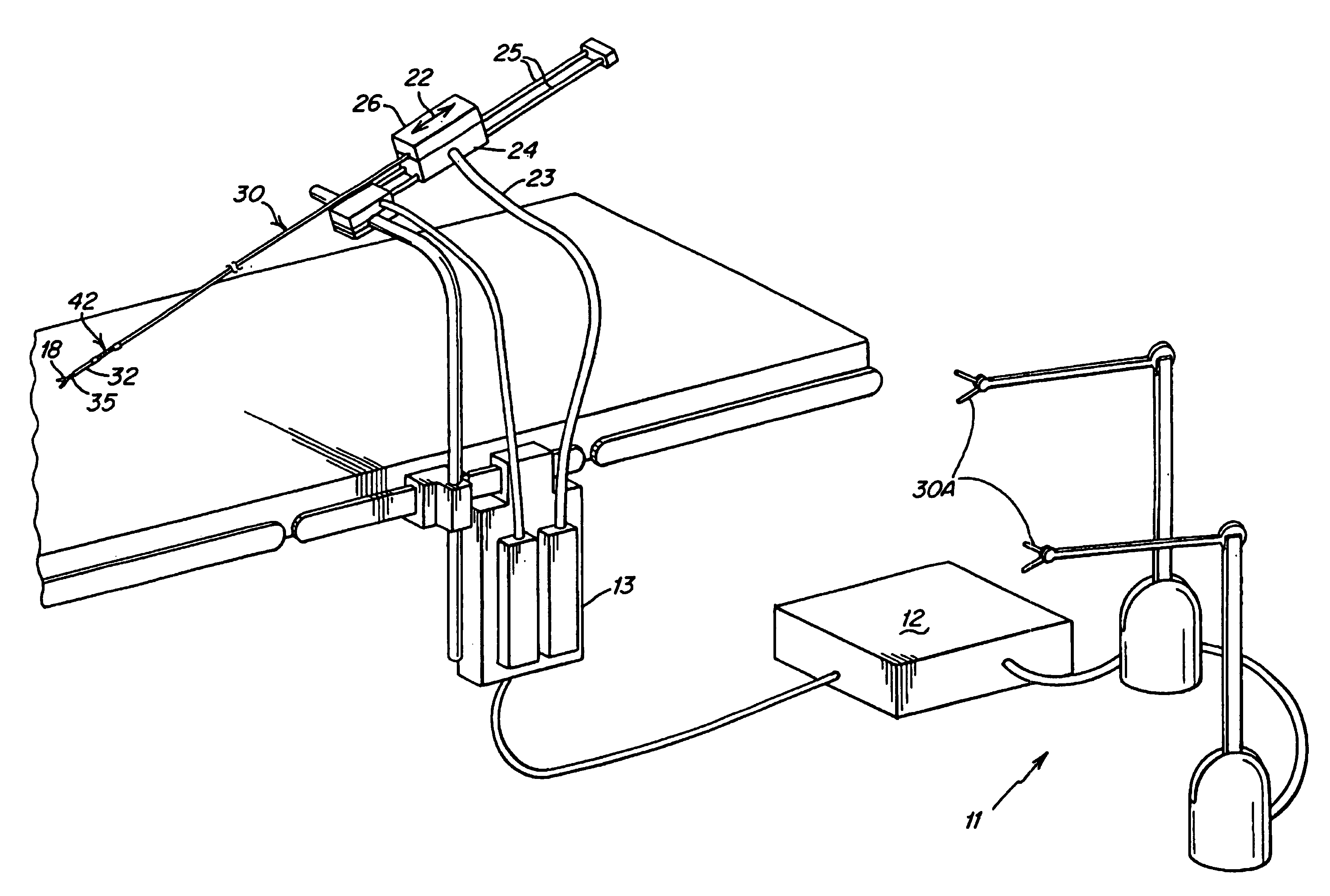
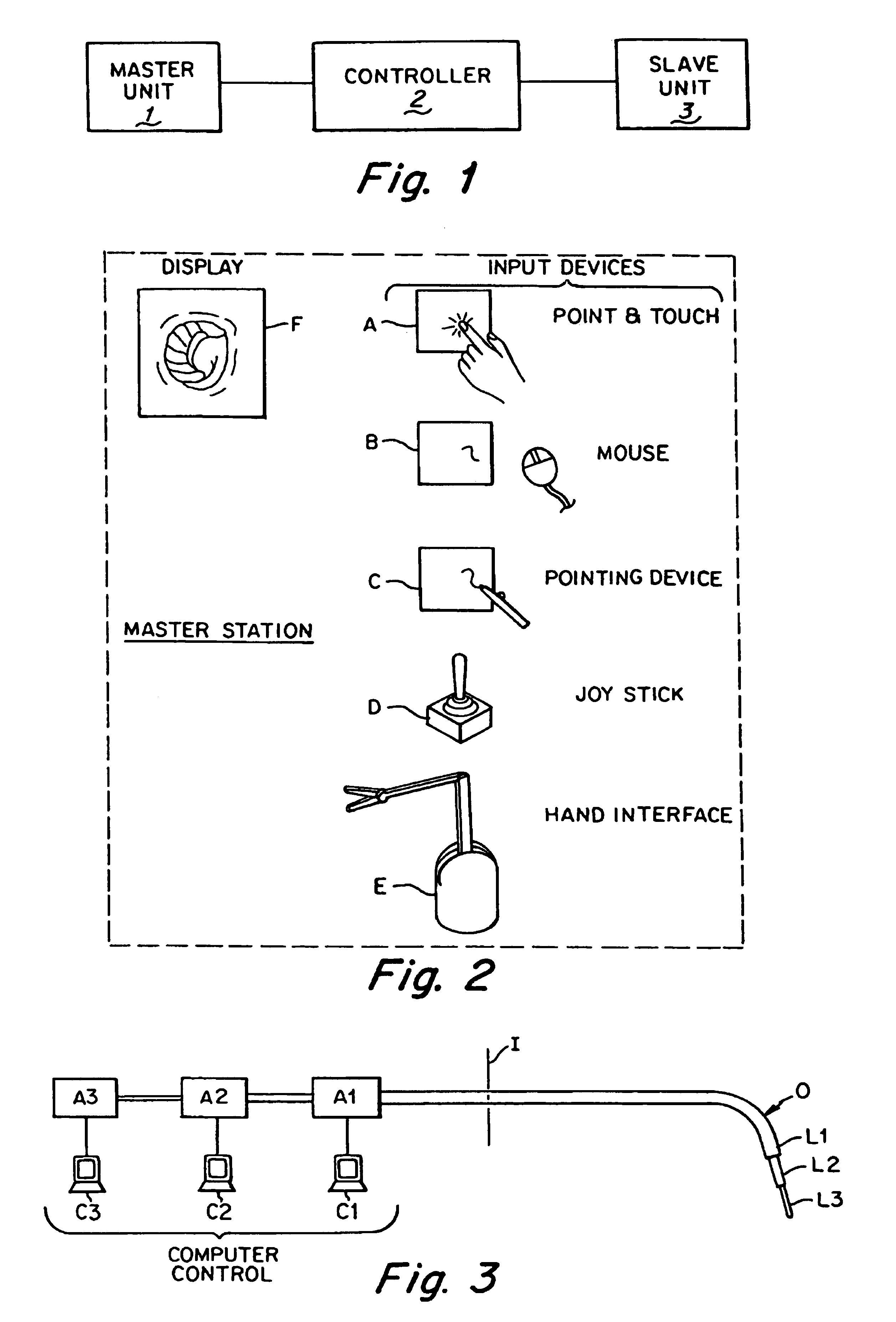
A remote control flexible instrument system, employing a shaft which supports a tool, is described in which the has proximal and distal ends with at least a portion thereof extending through a lumen of the human body so as to locate the shaft at an internal target site. A master station including an input device provides control of the instrument situated at a slave station. The master station can control at least one degree-of-freedom of the flexible instrument. A controller intercouples the master and slave stations and is operated in accordance with a computer algorithm that receives a command from the input device for controlling at least one degree-of-freedom of the catheter so as to respond in accordance with action at the input device. The flexible instrument further comprises a controlled flexible segment along the shaft, for controlled bending at the flexible segment to guide the shaft and to dispose the tool at an operative site.
Owner:HANSEN MEDICAL INC
Flexible instrument
InactiveUS7214230B2Small diameterSufficient flexibilitySuture equipmentsProgramme-controlled manipulatorRemote controlMaster station
A remote control flexible instrument system, employing a shaft which supports a tool, is described in which the has proximal and distal ends with at least a portion thereof extending through a lumen of the human body so as to locate the shaft at an internal target site. A master station including an input device provides control of the instrument situated at a slave station. The master station can control at least one degree-of-freedom of the flexible instrument. A controller intercouples the master and slave stations and is operated in accordance with a computer algorithm that receives a command from the input device for controlling at least one degree-of-freedom of the catheter so as to respond in accordance with action at the input device. The flexible instrument further comprises a controlled flexible segment along the shaft, for controlled bending at the flexible segment to guide the shaft and to dispose the tool at an operative site.
Owner:AURIS HEALTH INC
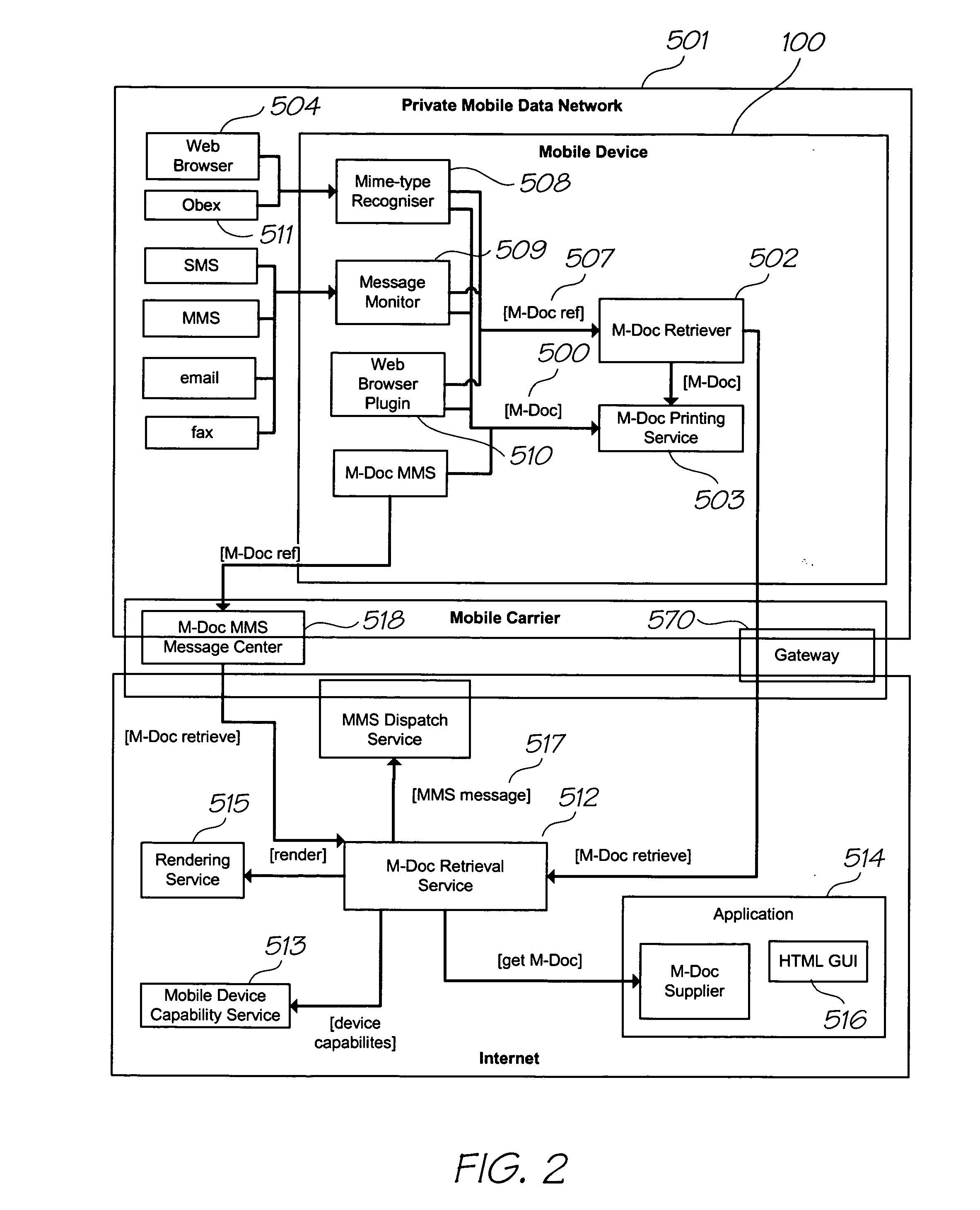
Managing a global namespace for a distributed filesystem
ActiveUS20140006465A1Outweigh additional overheadIncreasing file access performanceDigital data information retrievalSpecial data processing applicationsFile systemCloud storage system
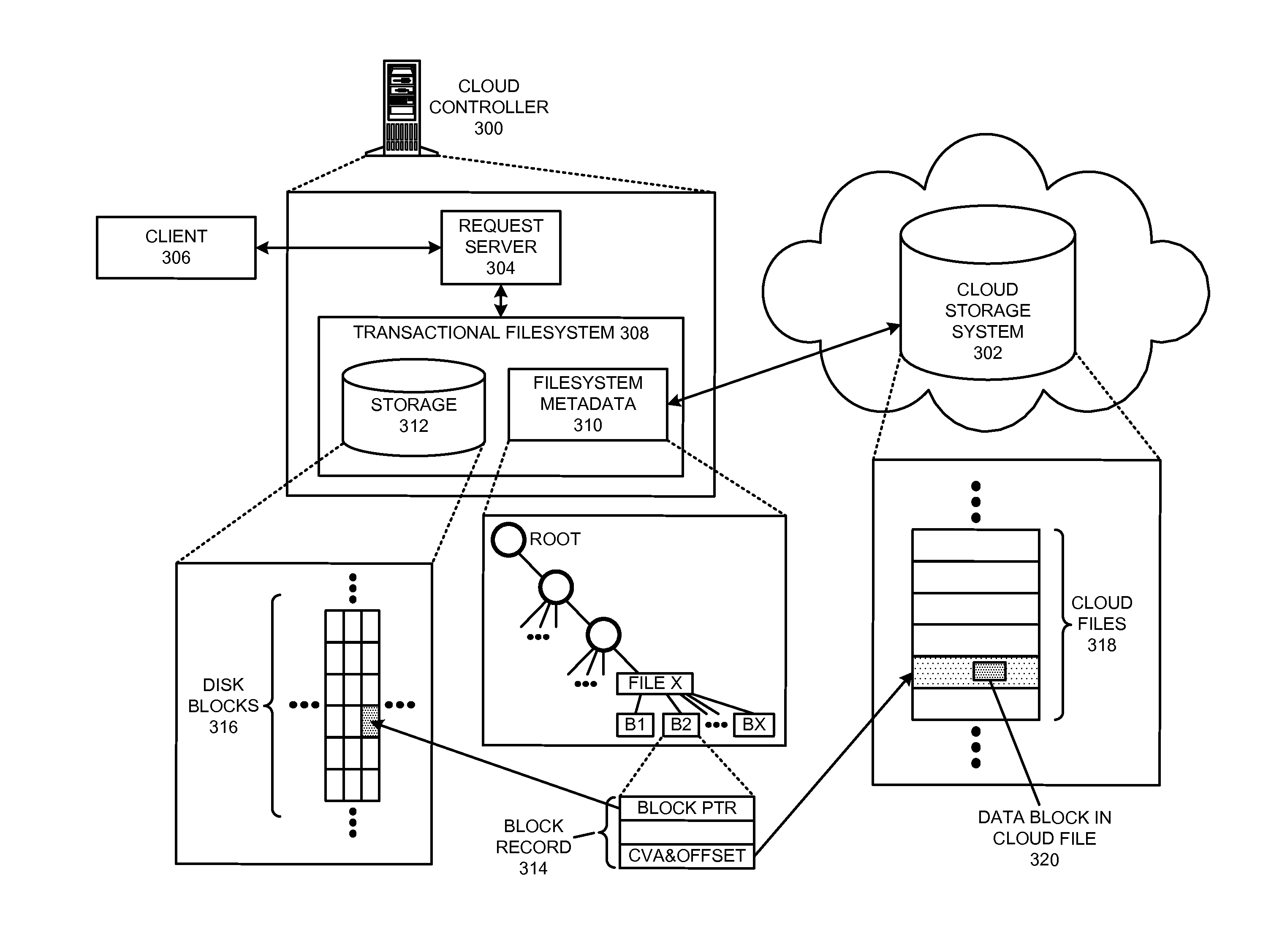
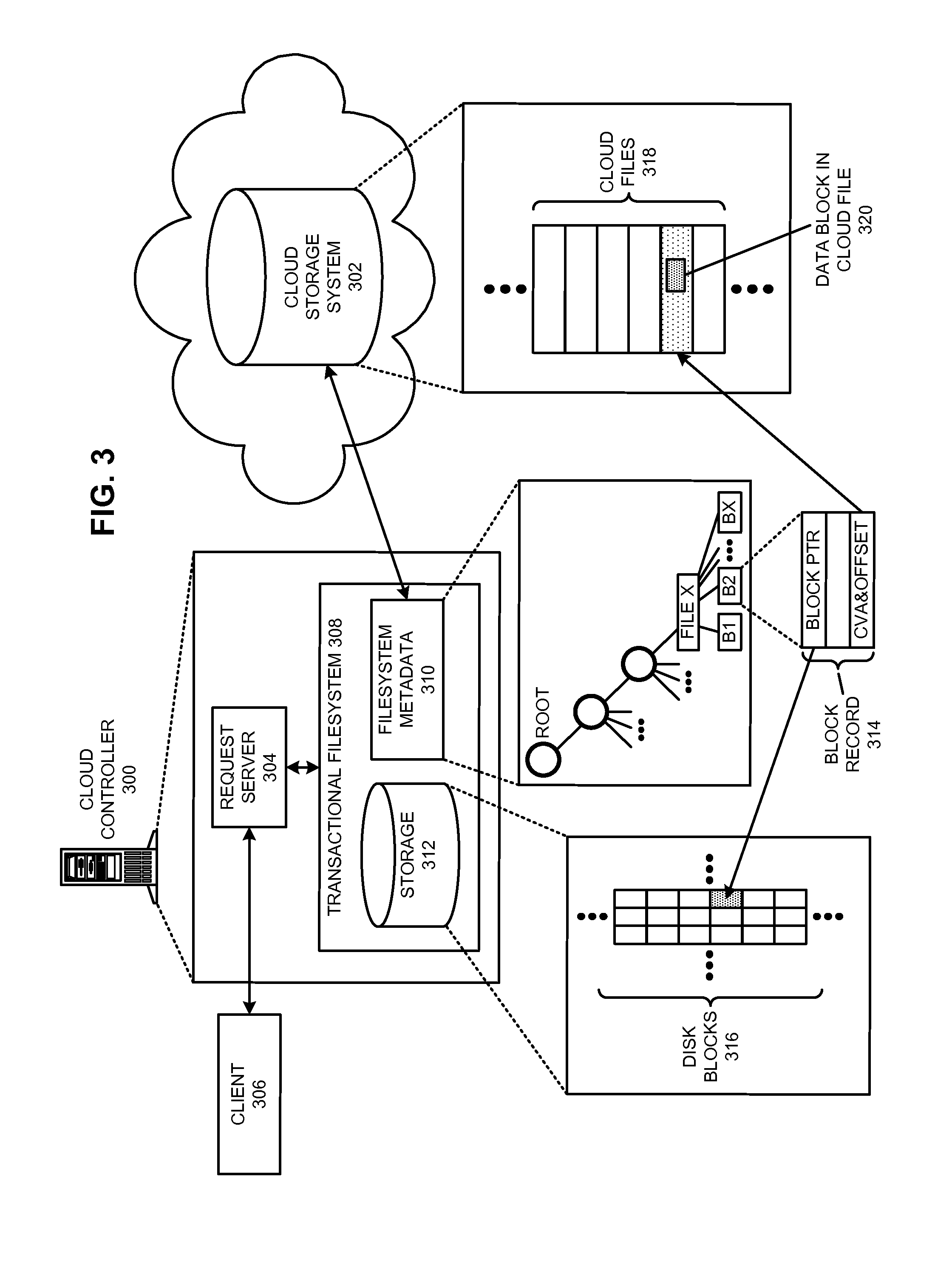
The disclosed embodiments disclose techniques for managing a global namespace for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in a cloud storage system; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. Furthermore, a global namespace for the distributed filesystem is also split across these cloud controllers, with each cloud controller “owning” (e.g., managing write accesses for) a distinct portion of the global namespace and maintaining a set of namespace mappings that indicate which portion of the namespace is assigned to each cloud controller. During operation, an initial cloud controller receives a request from a client system to access a target file in the distributed system. This initial cloud controller uses the namespace mappings for the global namespace to determine a preferred cloud controller that will handle the request.
Owner:PANZURA LLC
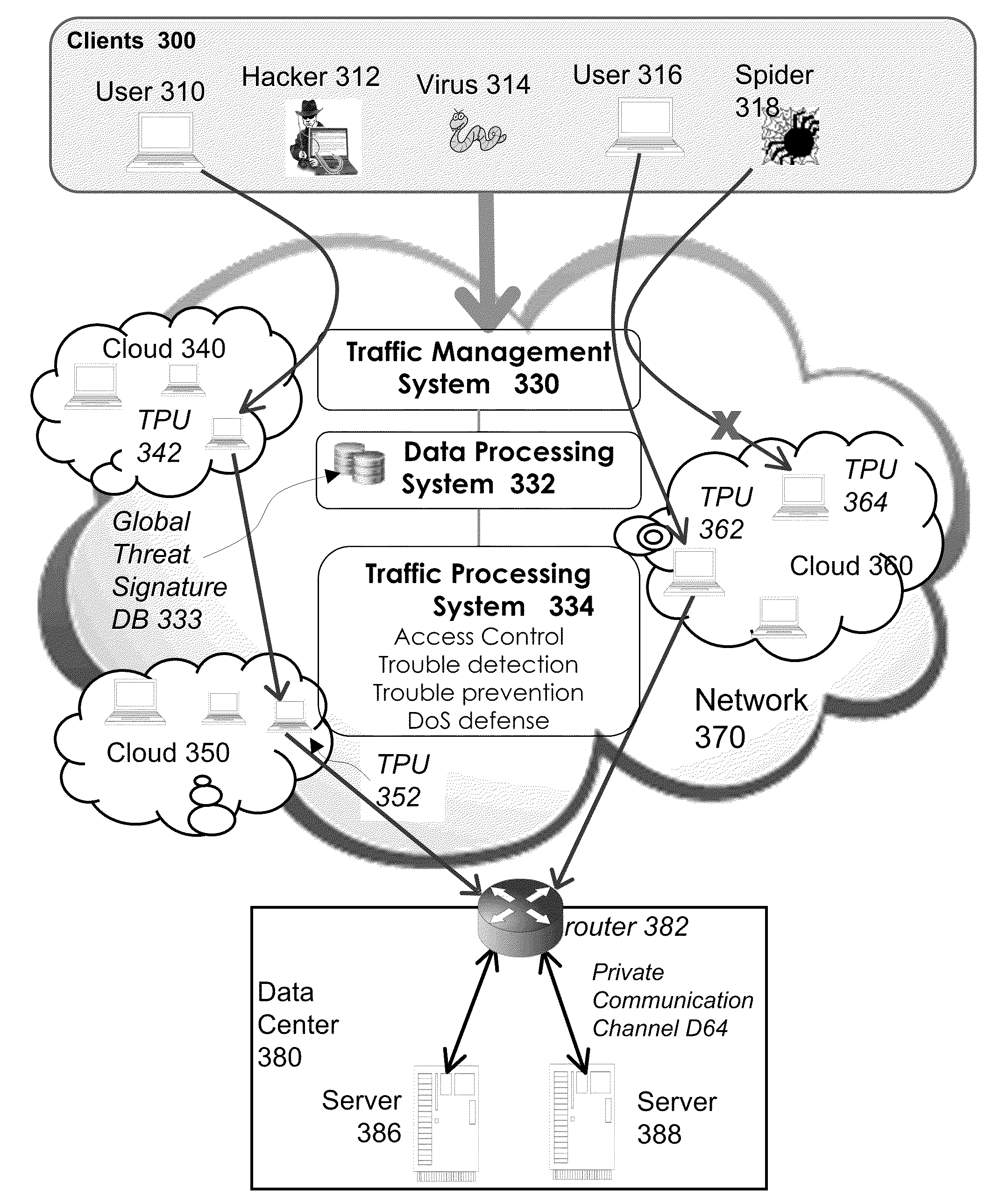
System and method for access management and security protection for network accessible computer services
InactiveUS20100251329A1Detection problemGrows and shrinks capacity and bandwidth capacityMemory loss protectionError detection/correctionTraffic capacityService provision
A method for providing access management and security protection to a computer service includes providing a computer service that is hosted at one or more servers and is accessible to clients via a first network, providing a second network that includes a plurality of traffic processing nodes and providing means for redirecting network traffic from the first network to the second network. Next, redirecting network traffic targeted to access the computer service via the first network to a traffic processing node of the second network via the means for redirecting network traffic. Next, inspecting and processing the redirected network traffic by the traffic processing node and then routing only redirected network traffic that has been inspected, processed and approved by the traffic processing node to access the computer service via the second network.
Owner:YOTTAA
Method and system for data backup
ActiveUS20070100913A1Cost-effectiveAvoid accessMemory loss protectionError detection/correctionWeb serviceApplication software
Embodiments of the present invention are directed to Web-Services-based data backup and data-archiving applications that provide remote data backup and data archiving to private individuals, small businesses, and other organizations that need reliable, secure, geographically remote, and cost-effective data backup, data archiving, and backed-up and archived-data retrieval. In one embodiment of the present invention, a private or small-business client contracts with a service provider for data-backup and data-archiving services. The service provider, in turn, contracts with a remote data-storage facility to provide secure, reliable data backup and data archiving to the personal or small-business client. A client-side application is downloaded to the client computer and configured to allow the client to store locally encrypted data at the remote, data-storage facilities. Neither the service provider nor the data-storage facility can decrypt or otherwise access the information stored by the client. In addition, the encryption key or encryption keys used by the client to encrypt the data for remote storage are securely stored at the remote, data-storage facility for subsequent recovery by the client, should the client suffer damage or loss to a local computer system. However, the client encryption key is stored in a doubly encrypted fashion, preventing access to the client's encryption key by either the service provider or the data-storage facility. Certain embodiments of the present invention also provide local indexing for remotely stored, encrypted data and efficient storage of updates to already remotely stored data.
Owner:CARBONITE GMBH
Printing a gambling ticket using a mobile device
InactiveUS20070064074A1Accurate explanationEasy to getTypewritersPayment architecturePrint mediaMobile device
A system for printing a gambling ticket on a print medium, the system comprising: a mobile telecommunications device which comprises: a printer module to print the ticket on the print medium; and, a sensor module to sense a print media identifier of the print medium.
Owner:SILVERBROOK RES PTY LTD
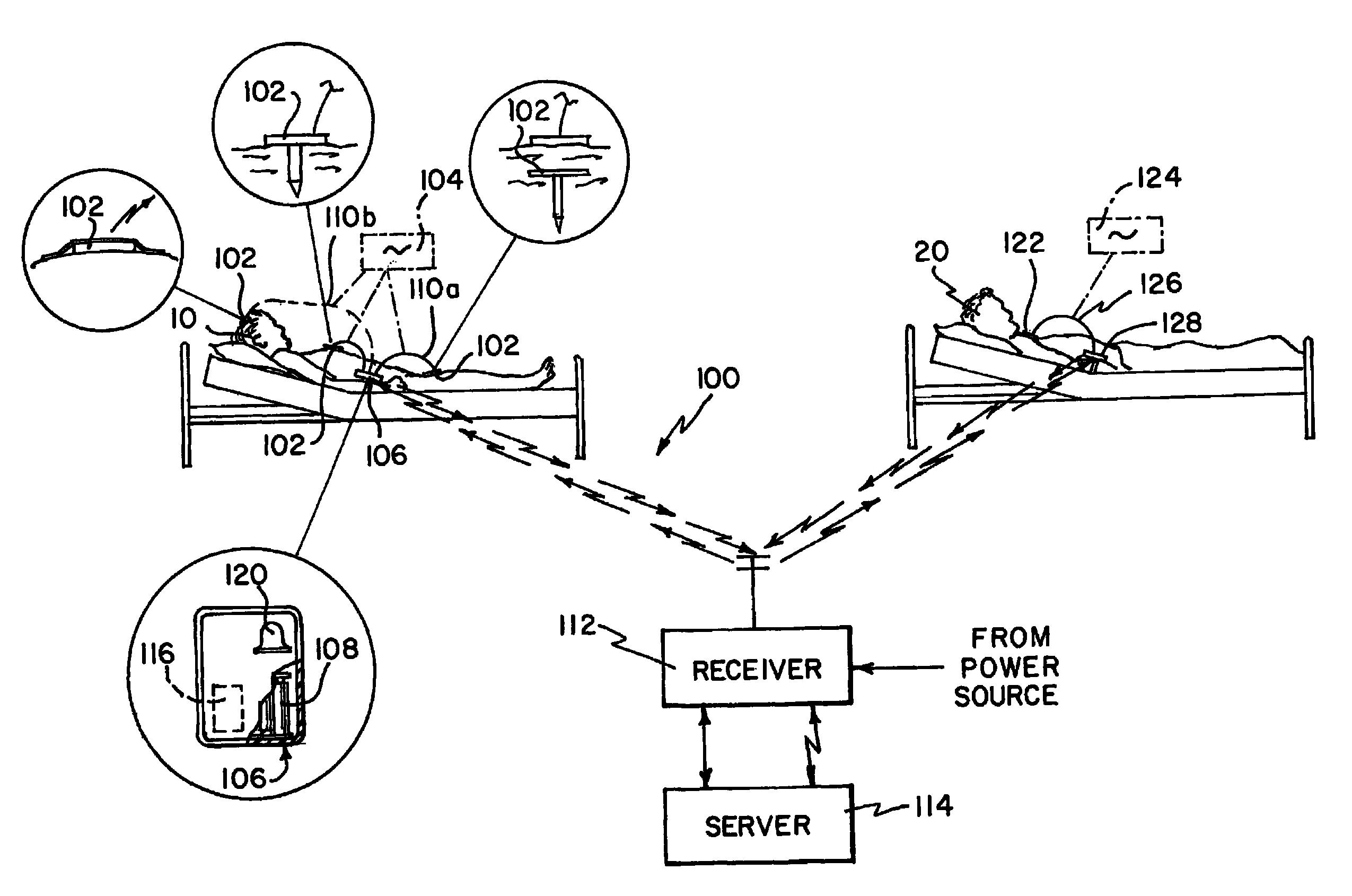
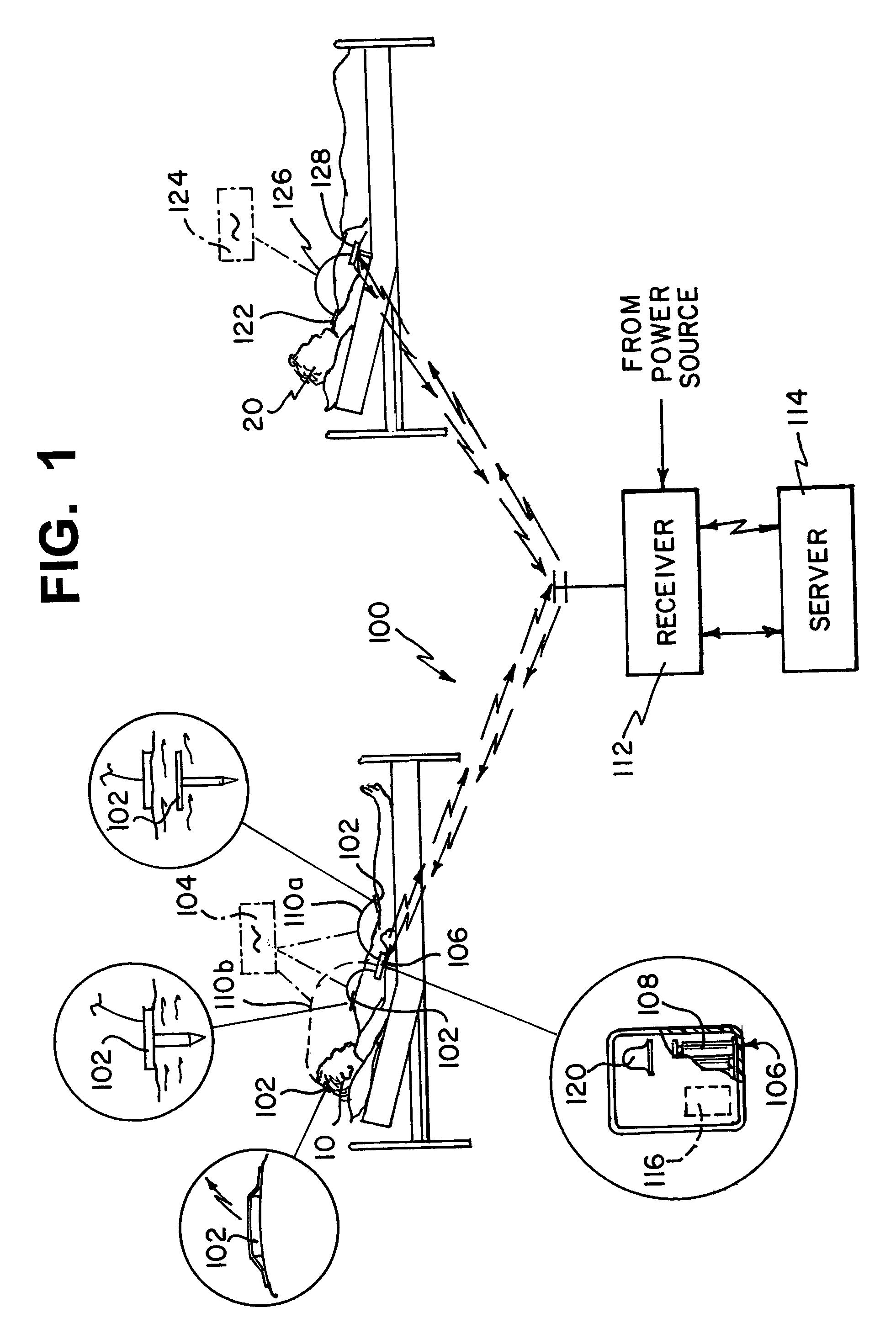
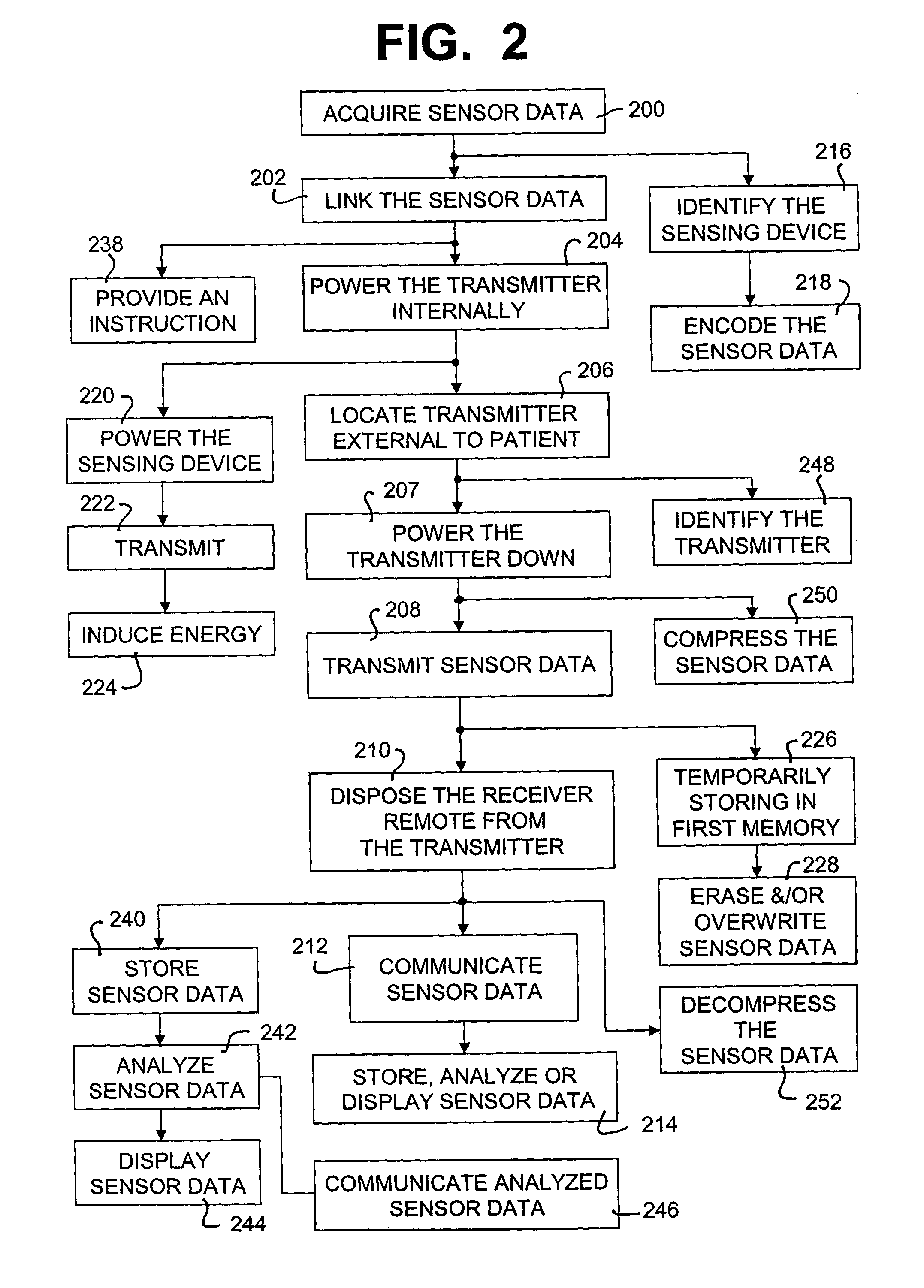
Wireless patient monitoring system
A device and method for monitoring a patient having a sensing device taking sensor data continuously and a transmitter located on the patient and internally powered. The transmitter is normally in a power-down state and powered-up for transmitting the sensor data. A receiver is located remote from the patient and receives the sensor data transmitted wirelessly from the transmitter. The transmission is typically a burst and can also be initiated on a command. For the burst, the sensor data is accumulated over a first period. The transmitter can transmit the sensor data over a second period of time. The second period of time is shorter than the first period of time. Once the transmission is complete, transmitter can be powered down. A further step displays the sensor data at the receiver in pseudo real-time. The display is shifted by a sum of the first and the second period of time.
Owner:INTEGRA LIFESCI
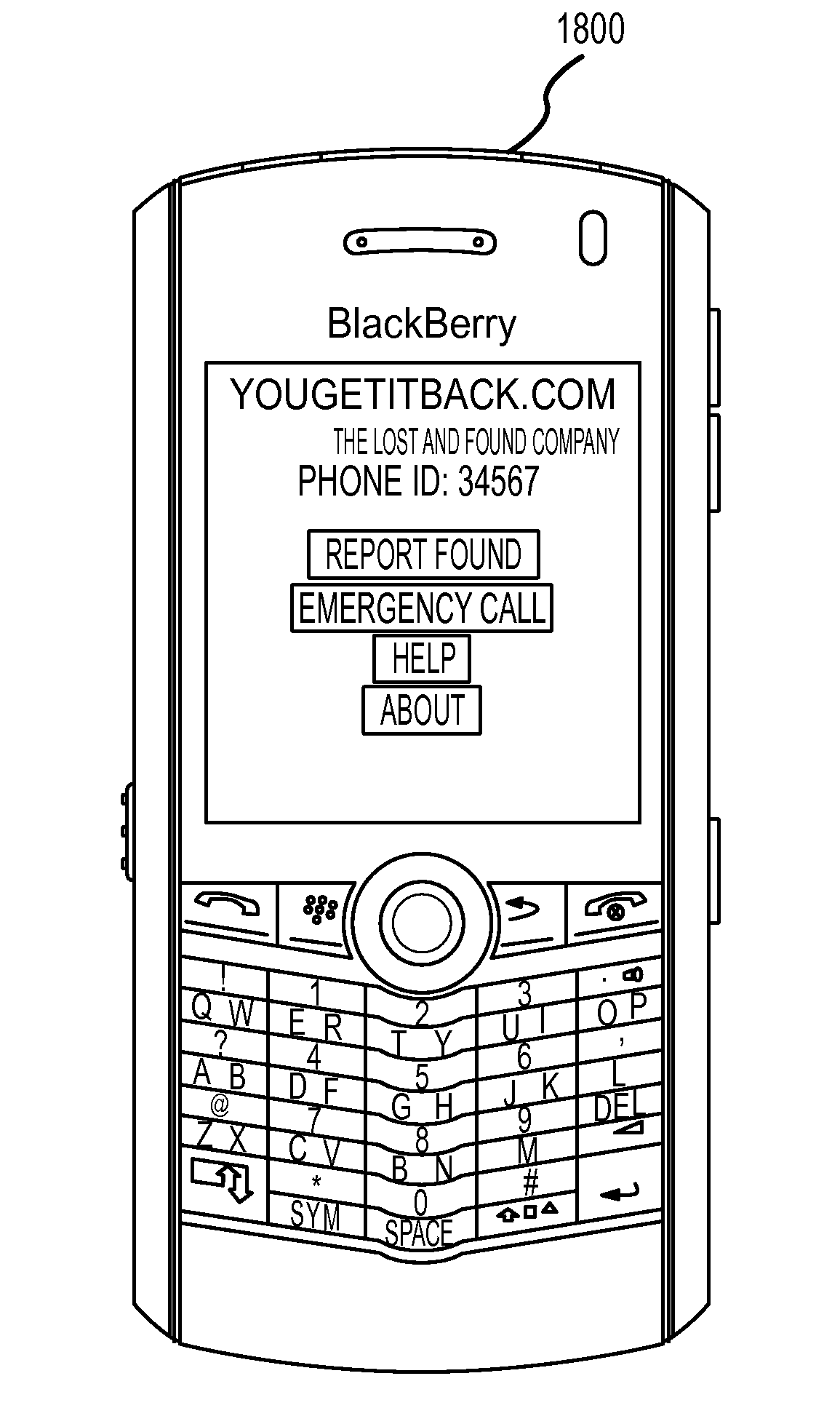
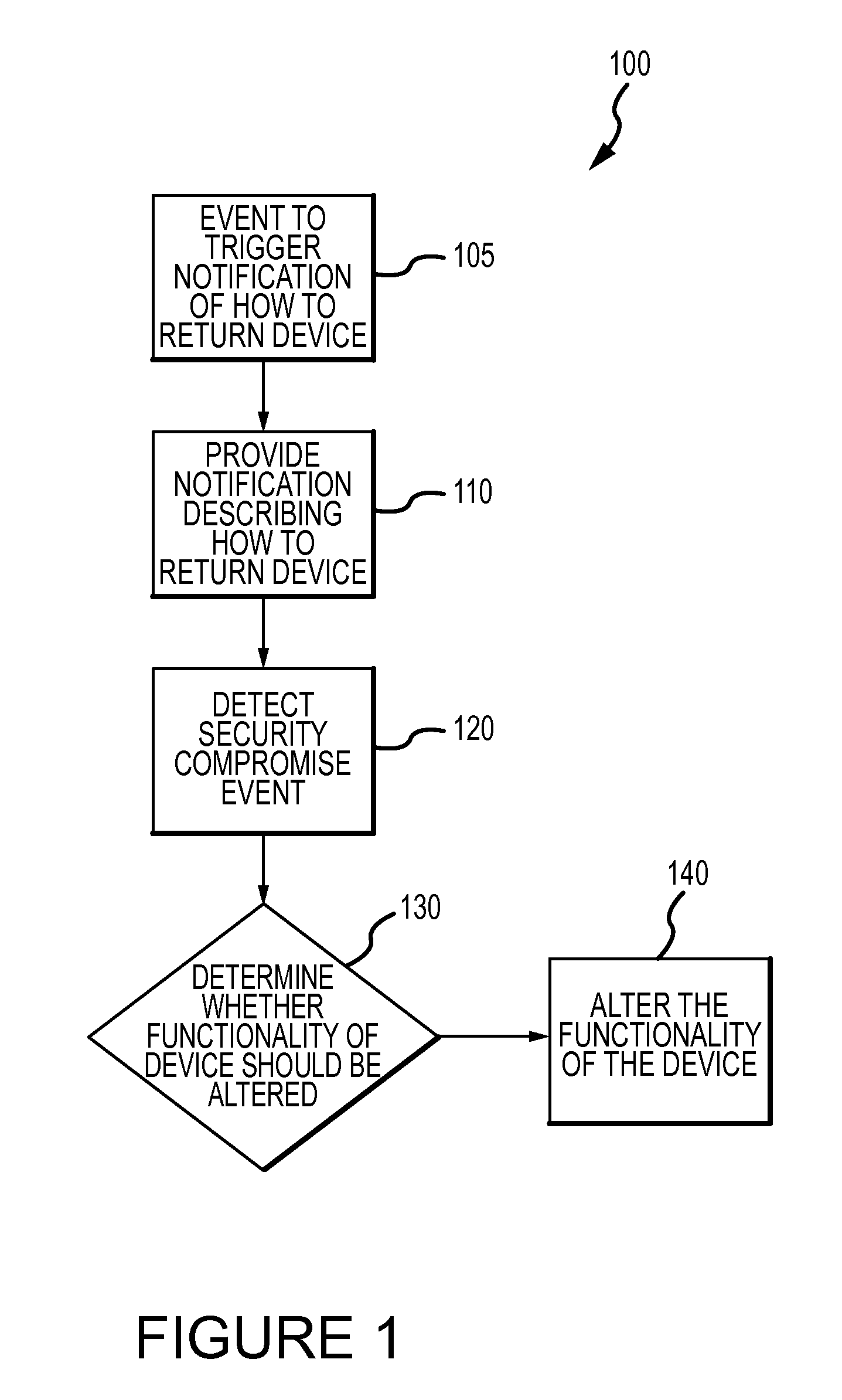
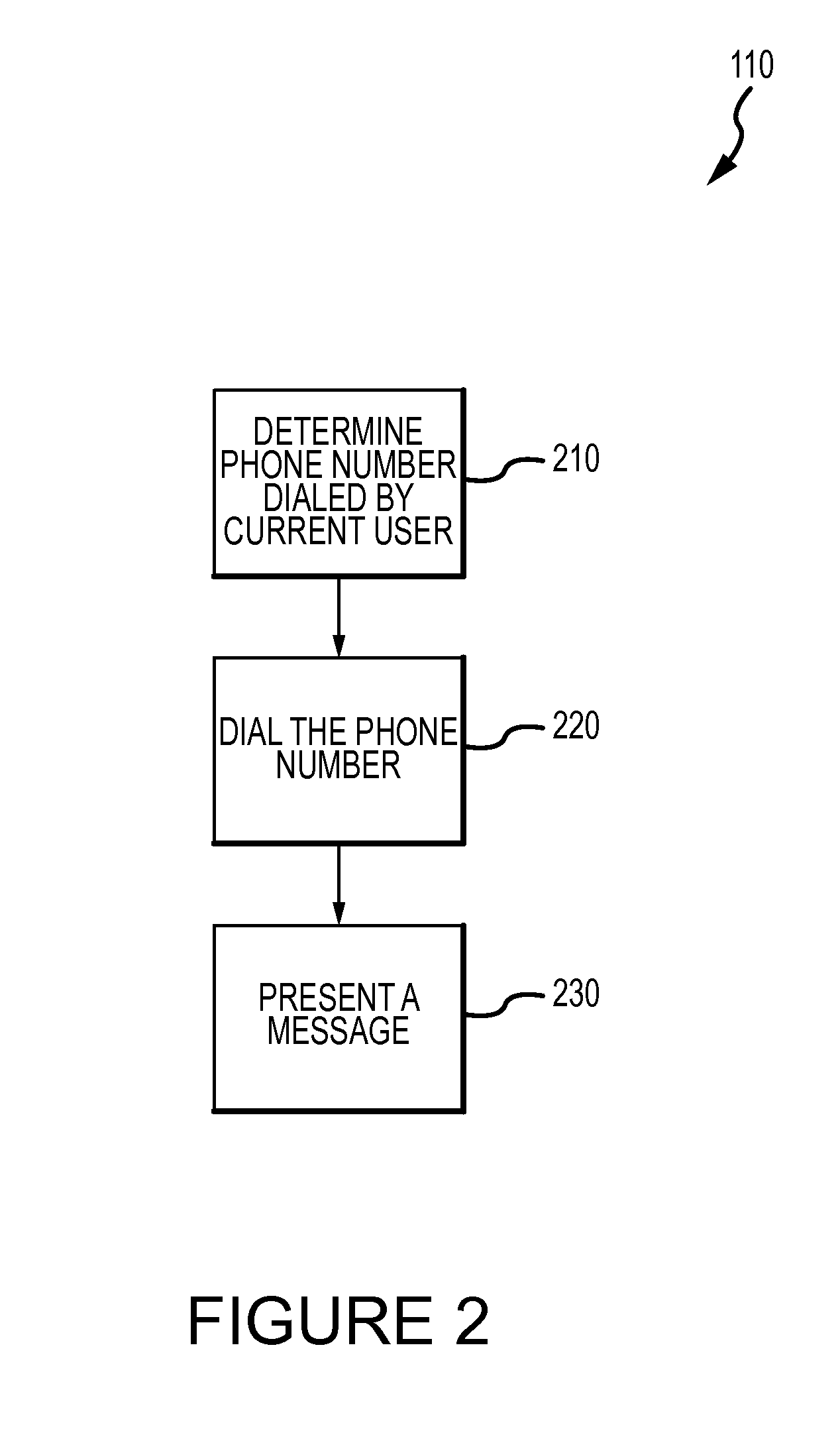
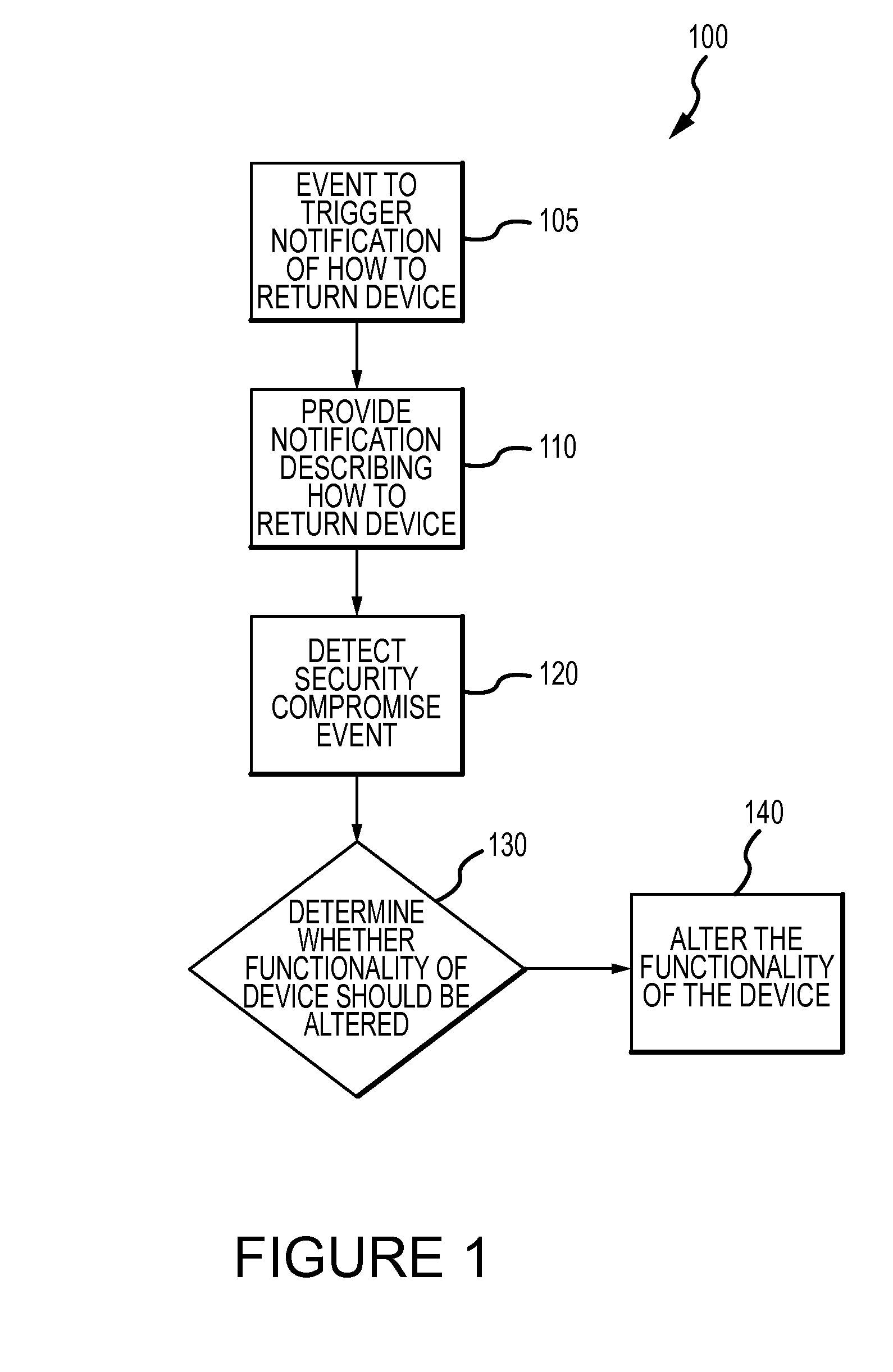
Method for mitigating the unauthorized use of a device
ActiveUS20090253410A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
Over-wire rotation tool
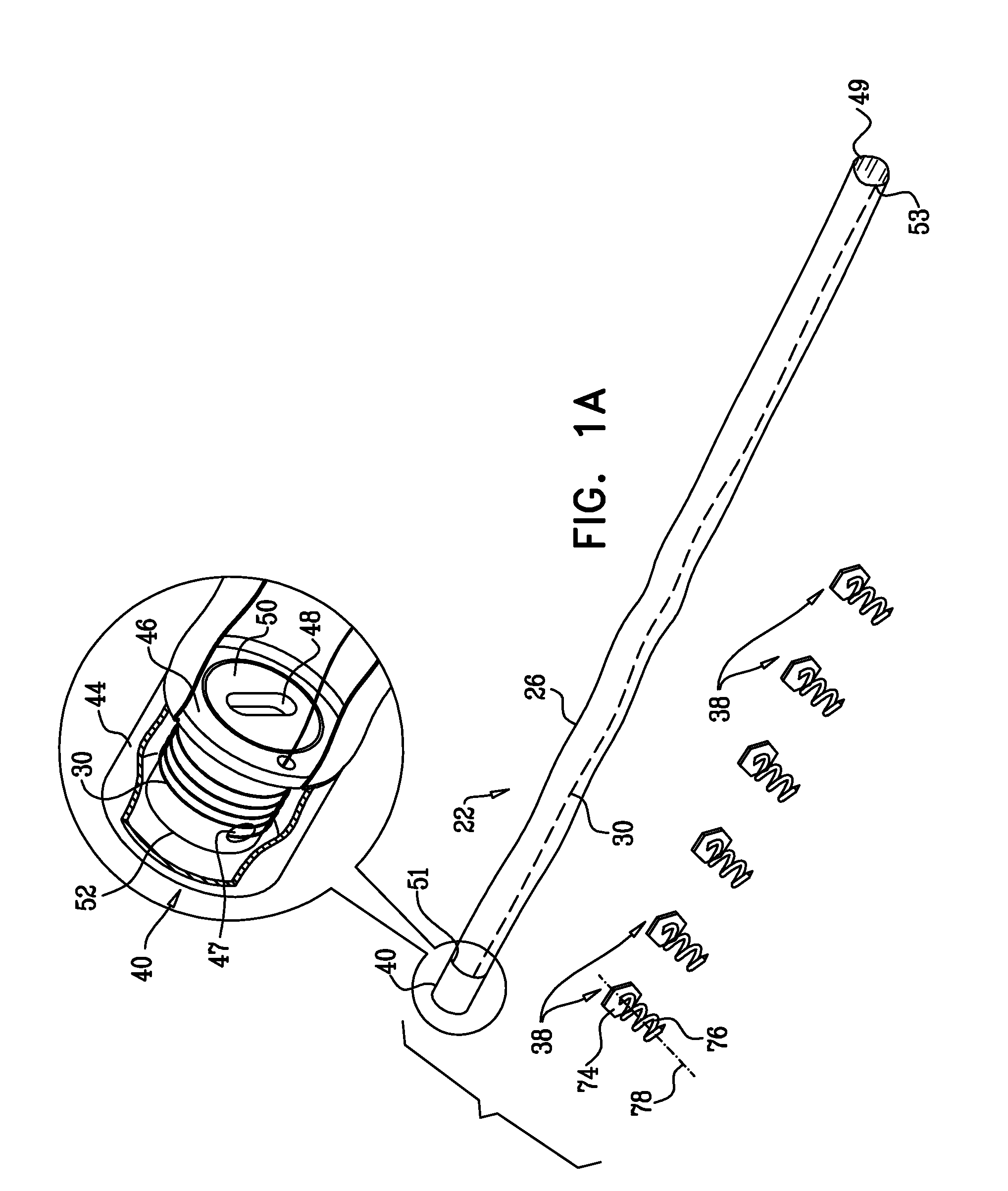
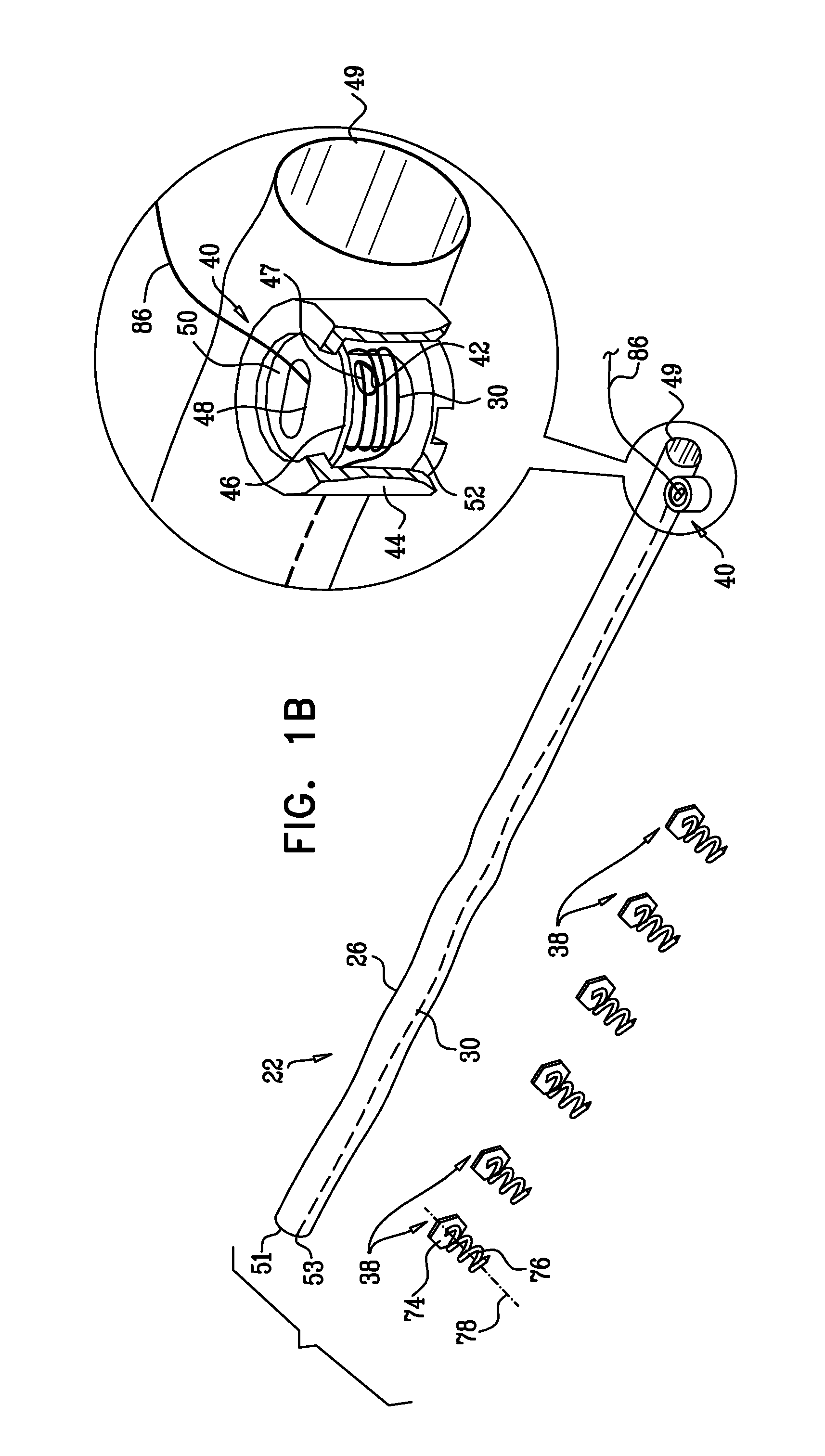
ActiveUS20100280604A1Avoid accessEasy accessSuture equipmentsAnnuloplasty ringsEngineeringMechanical engineering
Apparatus is provided that includes an implant structure, which includes a contracting mechanism, which includes a rotatable structure, arranged such that rotation of the rotatable structure contracts the implant structure. A longitudinal member is coupled to the contracting mechanism. A tool for rotating the rotatable structure is configured to be guided along the longitudinal member, to engage the rotatable structure, and to rotate the rotatable structure in response to a rotational force applied to the tool. Other embodiments are also described.
Owner:VALTECH CARDIO LTD
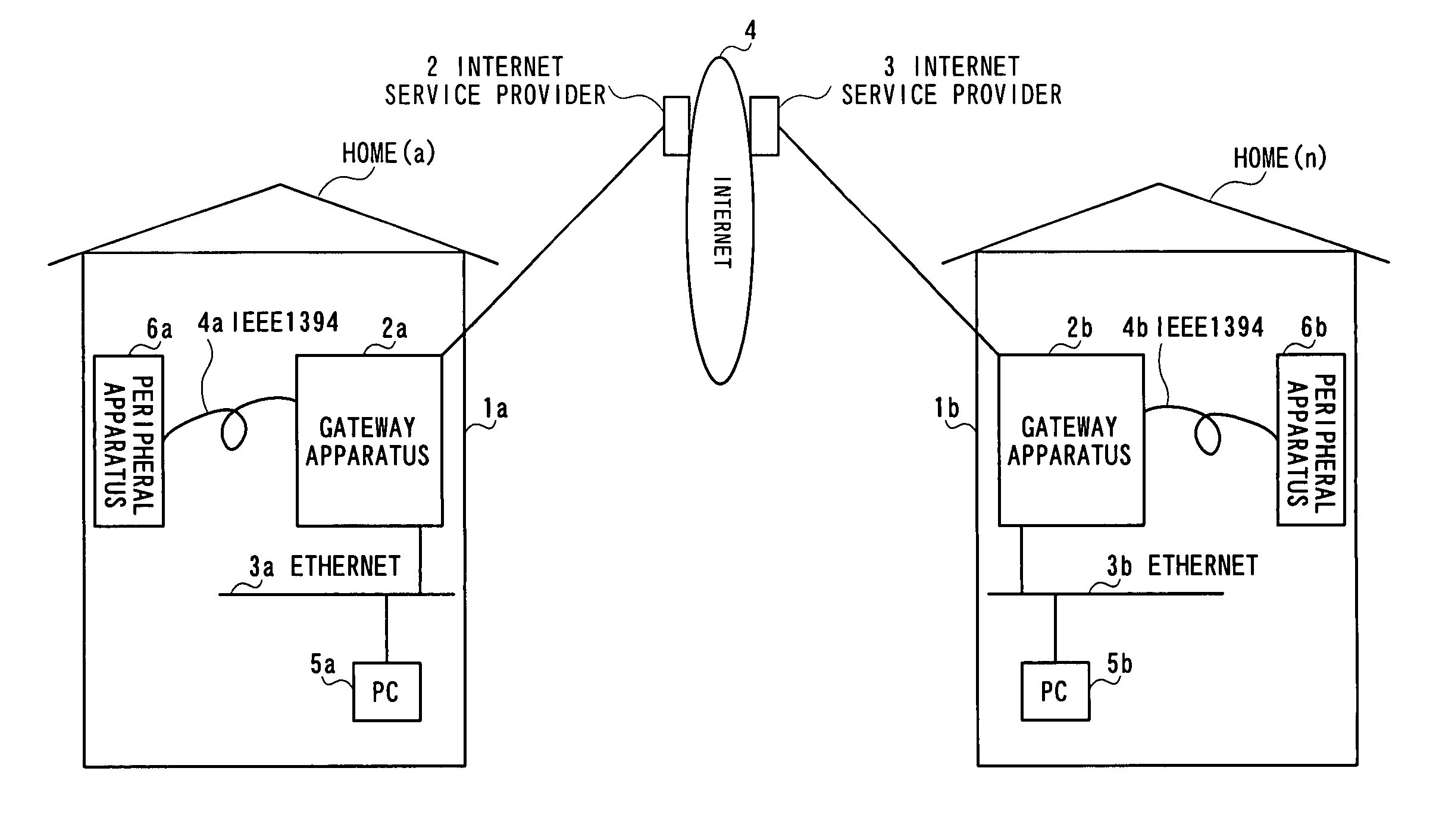
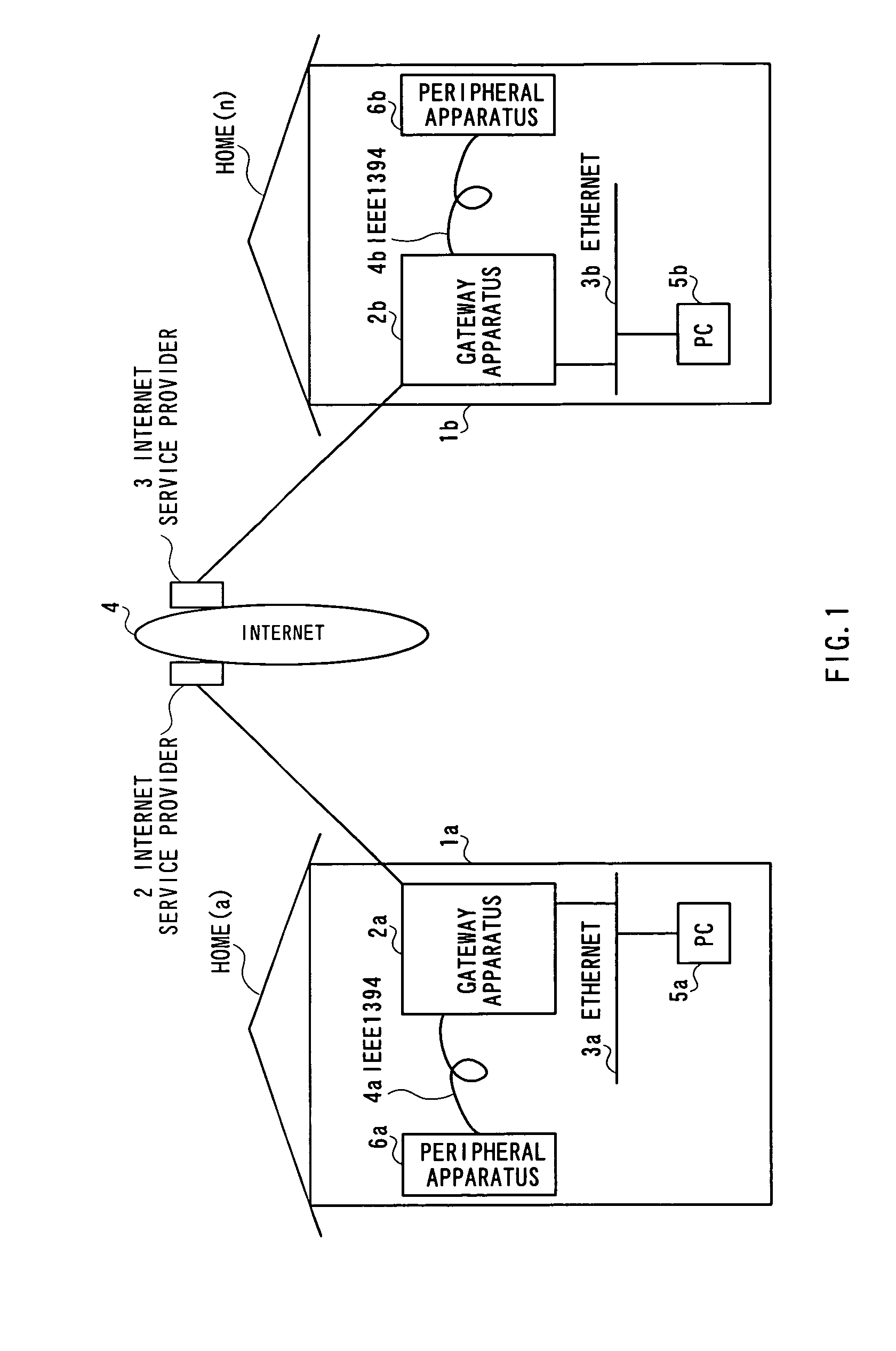
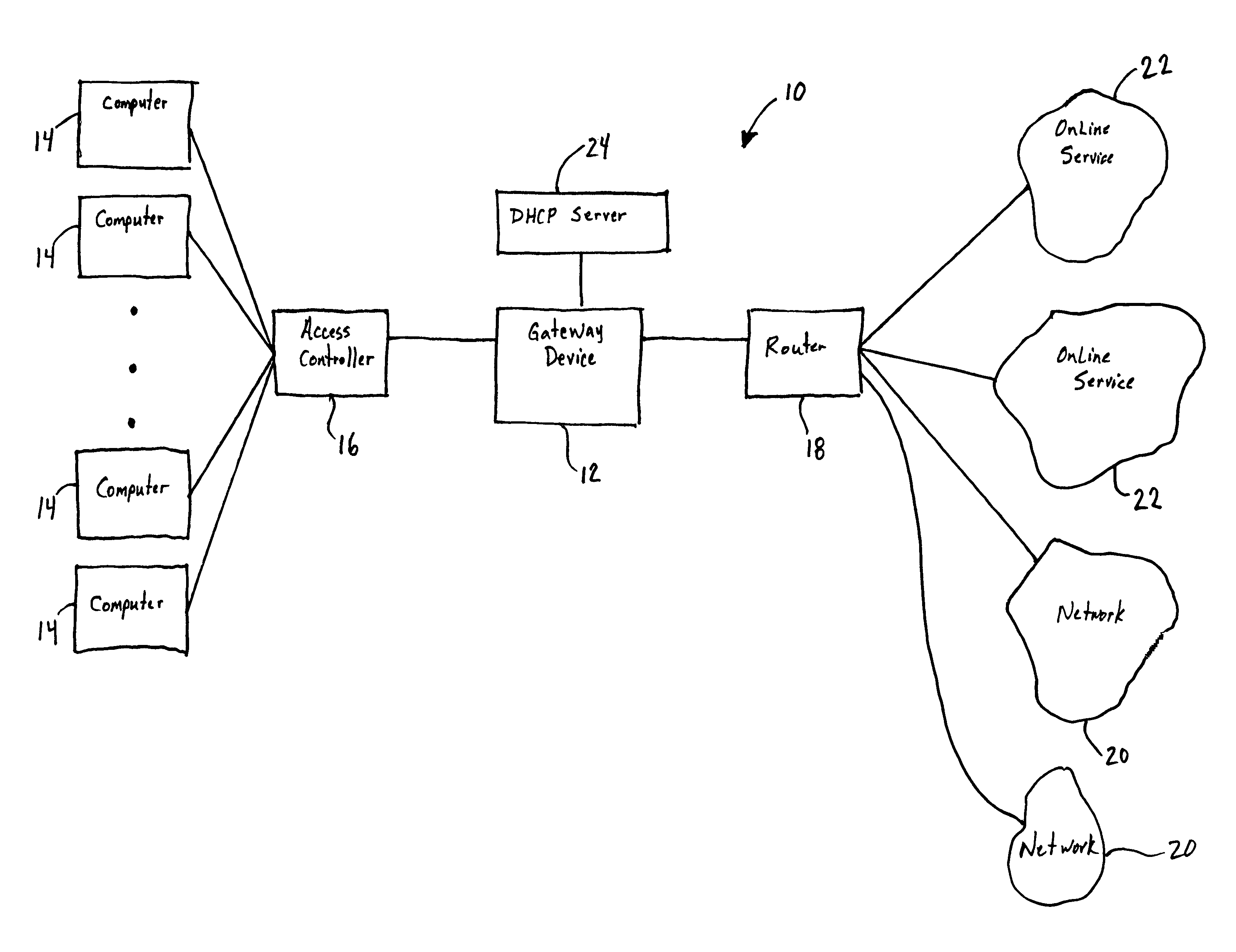
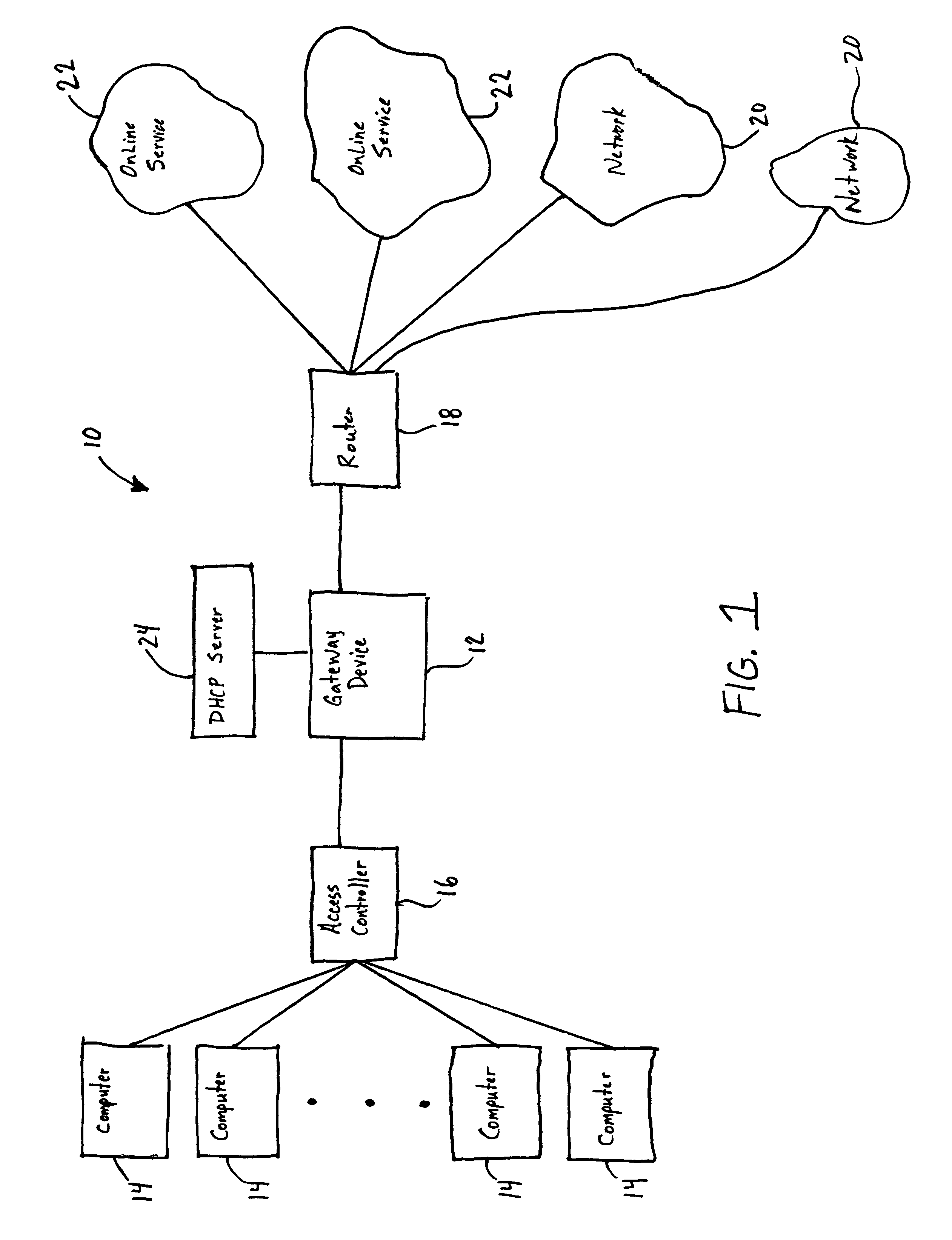
Gateway apparatus for controlling apparatuses on home network
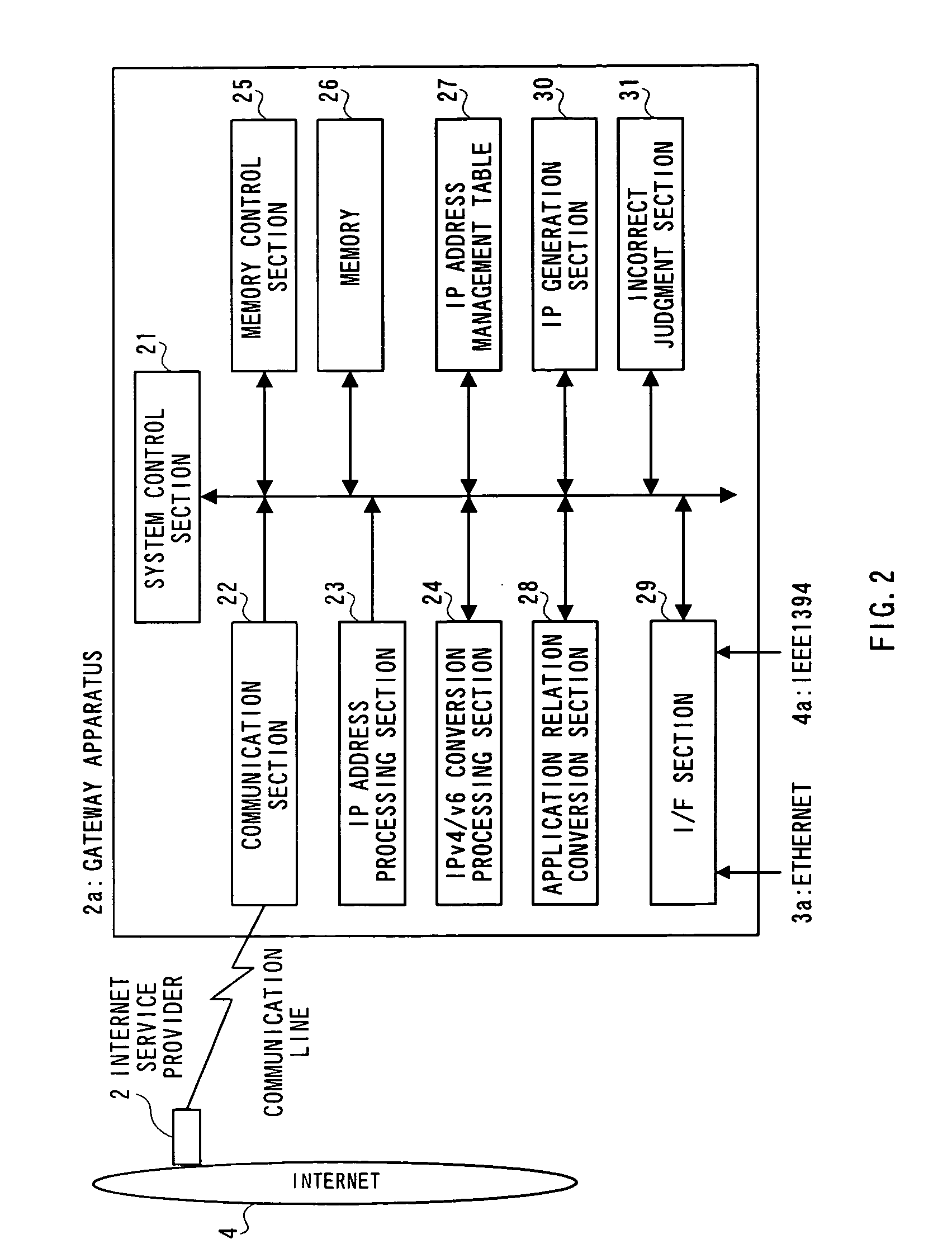
InactiveUS6957275B1Easy to controlAvoid accessMultiple digital computer combinationsNetworks interconnectionIp addressIdentification device
The gateway apparatus has an IP address table that relates a plurality of apparatuses, each of which is one of components constructing a home network, to IP addresses respectively assigned to the apparatuses to store, a reception section that receives data with a destination indicative of one of the apparatuses constructing the home network, a recognition section that recognizes the apparatus with an IP address matching the IP address indicative of the destination contained in received data using the IP address table, and a distribution section that transmits the received data to the recognized apparatus.
Owner:MATSUSHITA GRAPHIC COMM SYST INC
Transformer antenna device and method of using the same
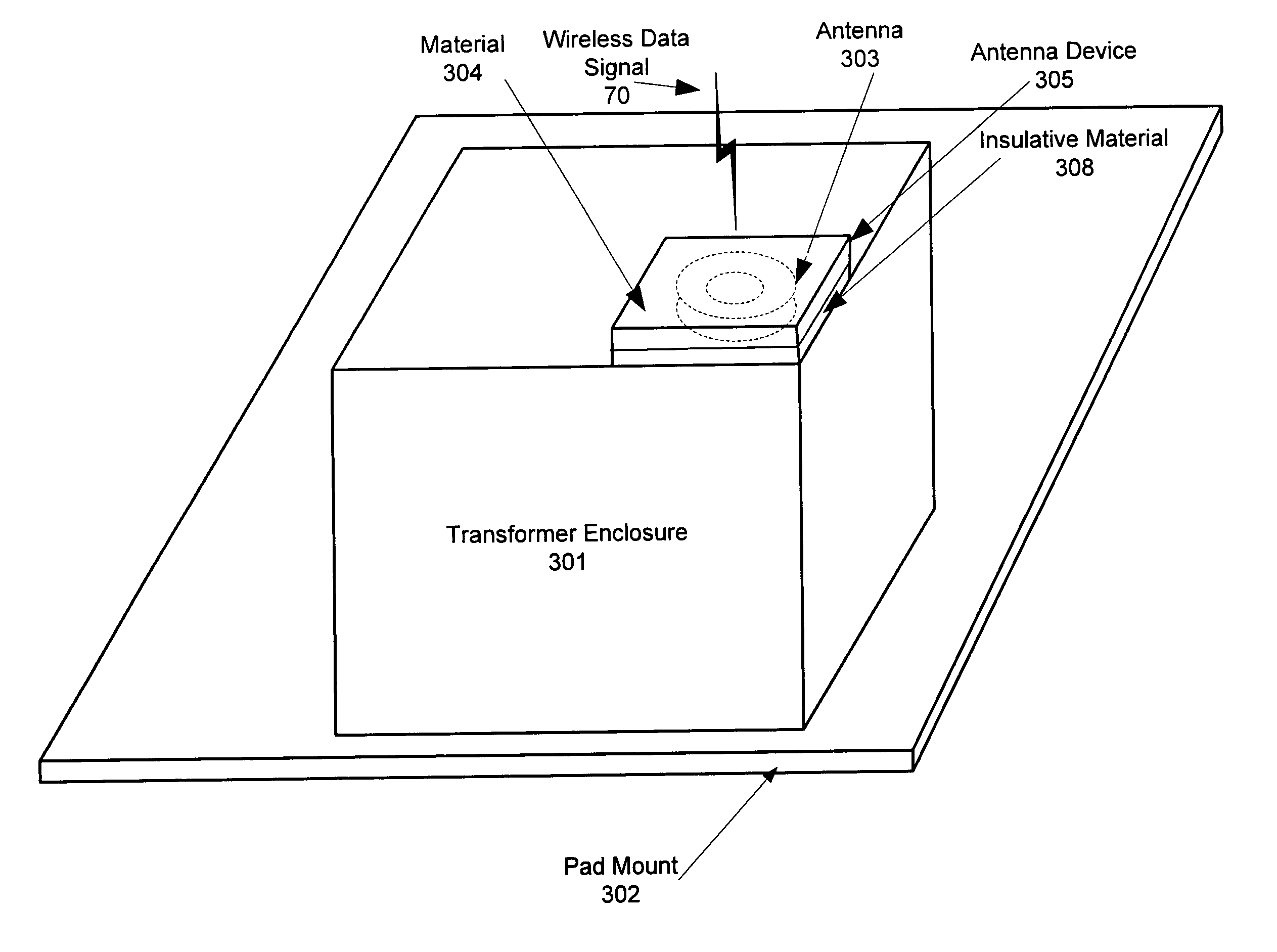
InactiveUS7113134B1Good adhesionAvoid accessAntenna supports/mountingsProtective material radiating elementsElectricityElectrical conductor
The invention contemplates an antenna device, system and method of installing the antenna device for receiving a wireless signal at a pad mounted electrical transformer. The novel device includes an antenna capable of communicating the wireless signal and a material located around the antenna. The material facilitates attachment to the pad mounted electrical transformer as well as preventing access to the antenna. The antenna may be covered by or embedded within the material. The material may be emissive and / or insulative. In addition, the device may include a conductor that passes through an enclosure of the pad mounted transformer. The conductor may be communicatively coupled to a first communication device that provides communication to a customer premise that is electrically coupled to the pad mounted electrical transformer.
Owner:CURRENT TECH
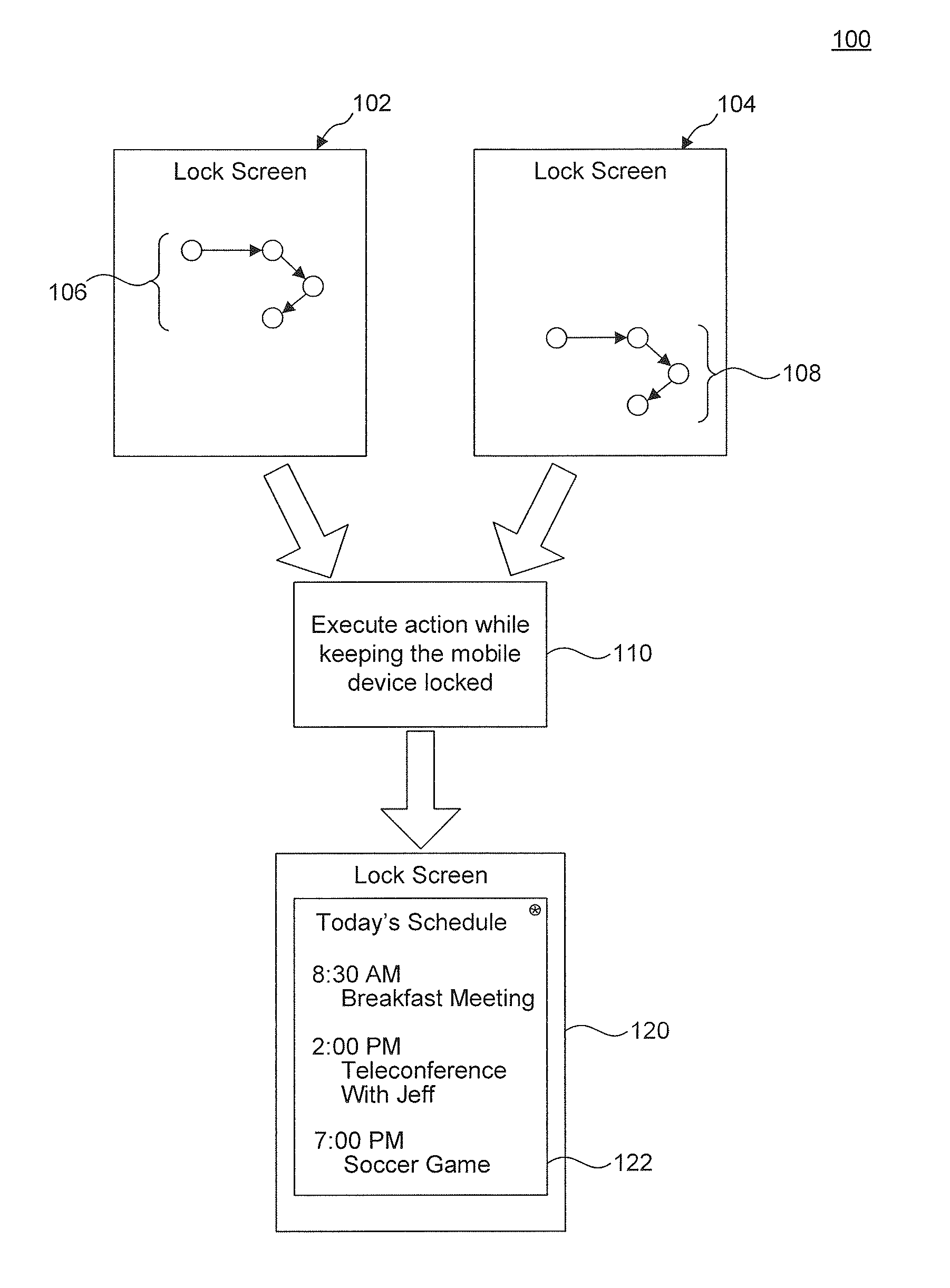
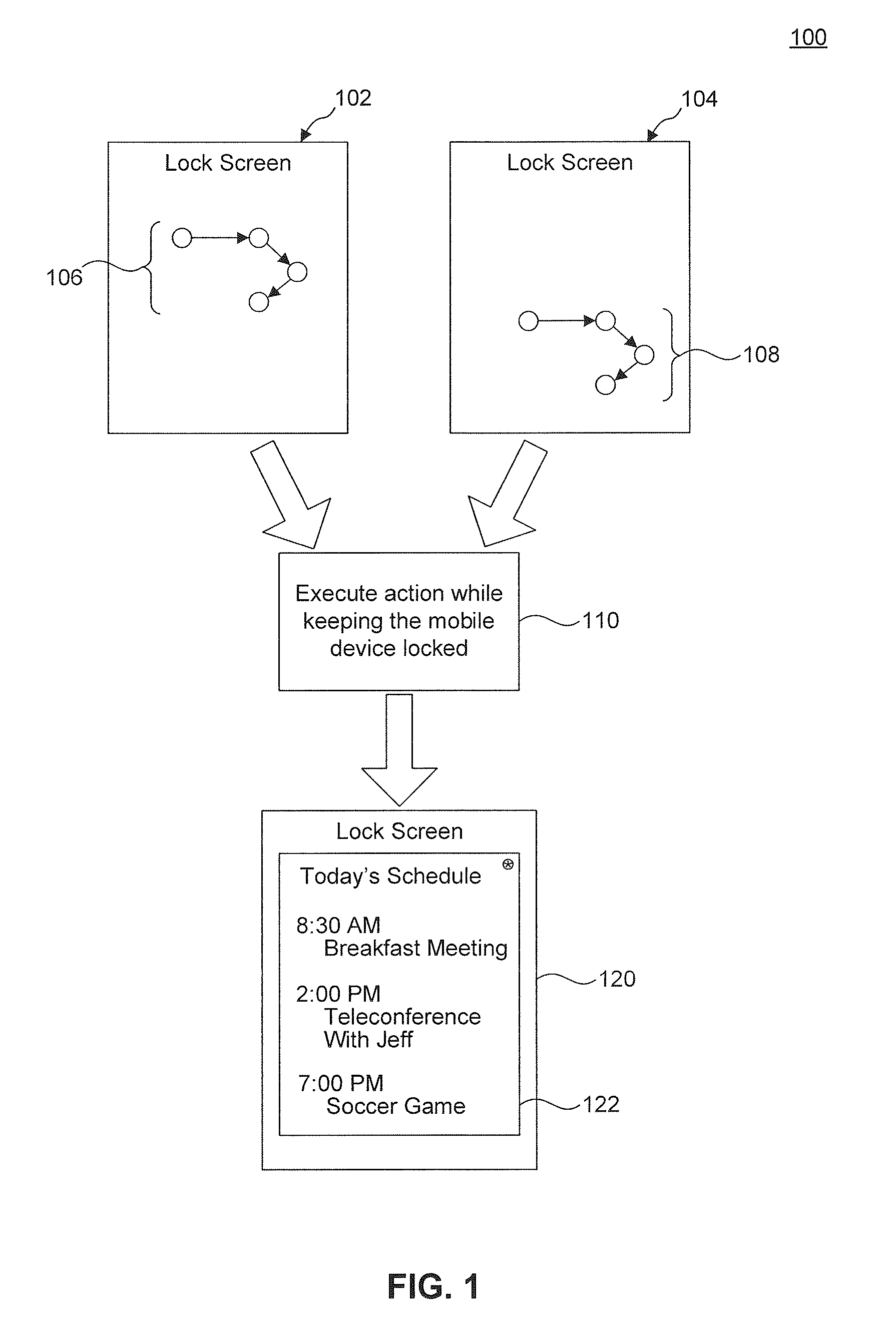
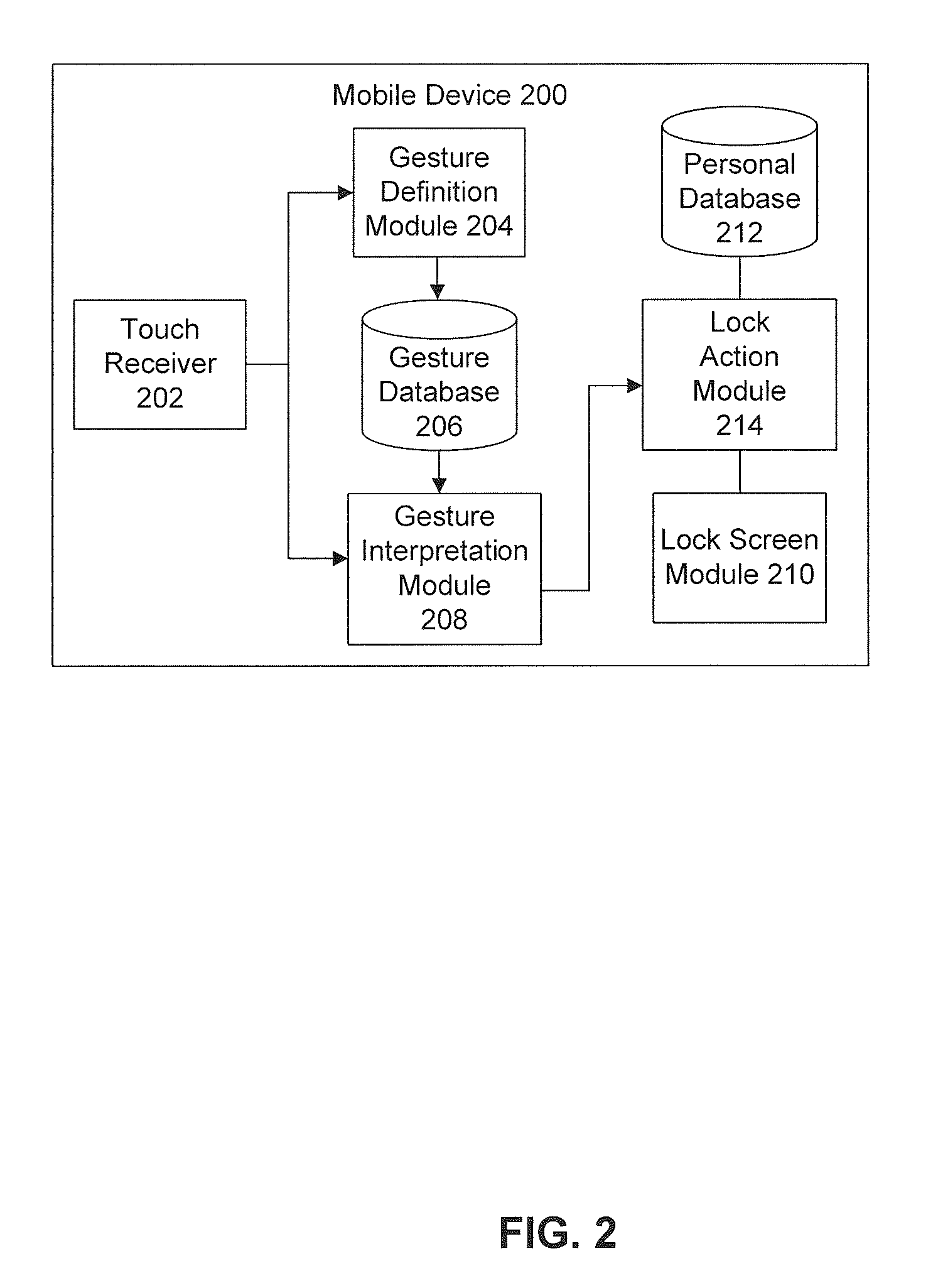
Touch Gesture Actions From A Device's Lock Screen
InactiveUS20110283241A1Avoid accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsLock screenTouchscreen
Embodiments enable a mobile device to execute an action analogous to a user-defined action in response to receipt of a gesture analogous to a user-defined gesture. In a first embodiment, a computer-implemented method executes an action on a mobile device. A lock screen view is displayed on the mobile device to prevent unauthorized and inadvertent access to the mobile device's data. While the mobile device is locked, a touch gesture having a pre-defined shape is detected on a touch screen of the mobile device independently of the initial position of the touch gesture on the touch screen. In response to detection of the touch gesture, a particular action is executed on the mobile device while the mobile device stays locked. The particular action determined according to the pre-defined shape. In this way, detection of the touch gesture causes the particular action to execute while keeping the mobile device locked.
Owner:GOOGLE LLC
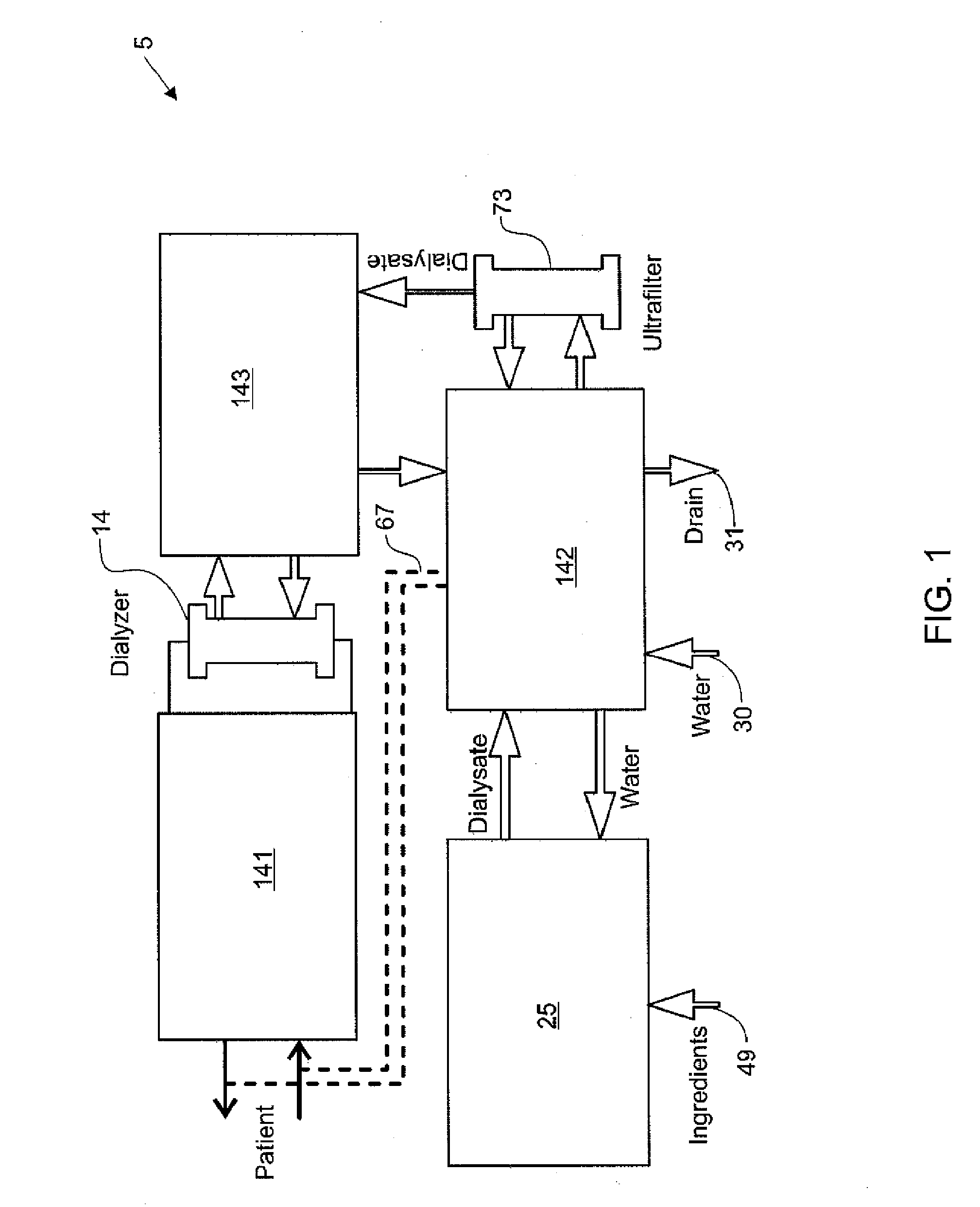
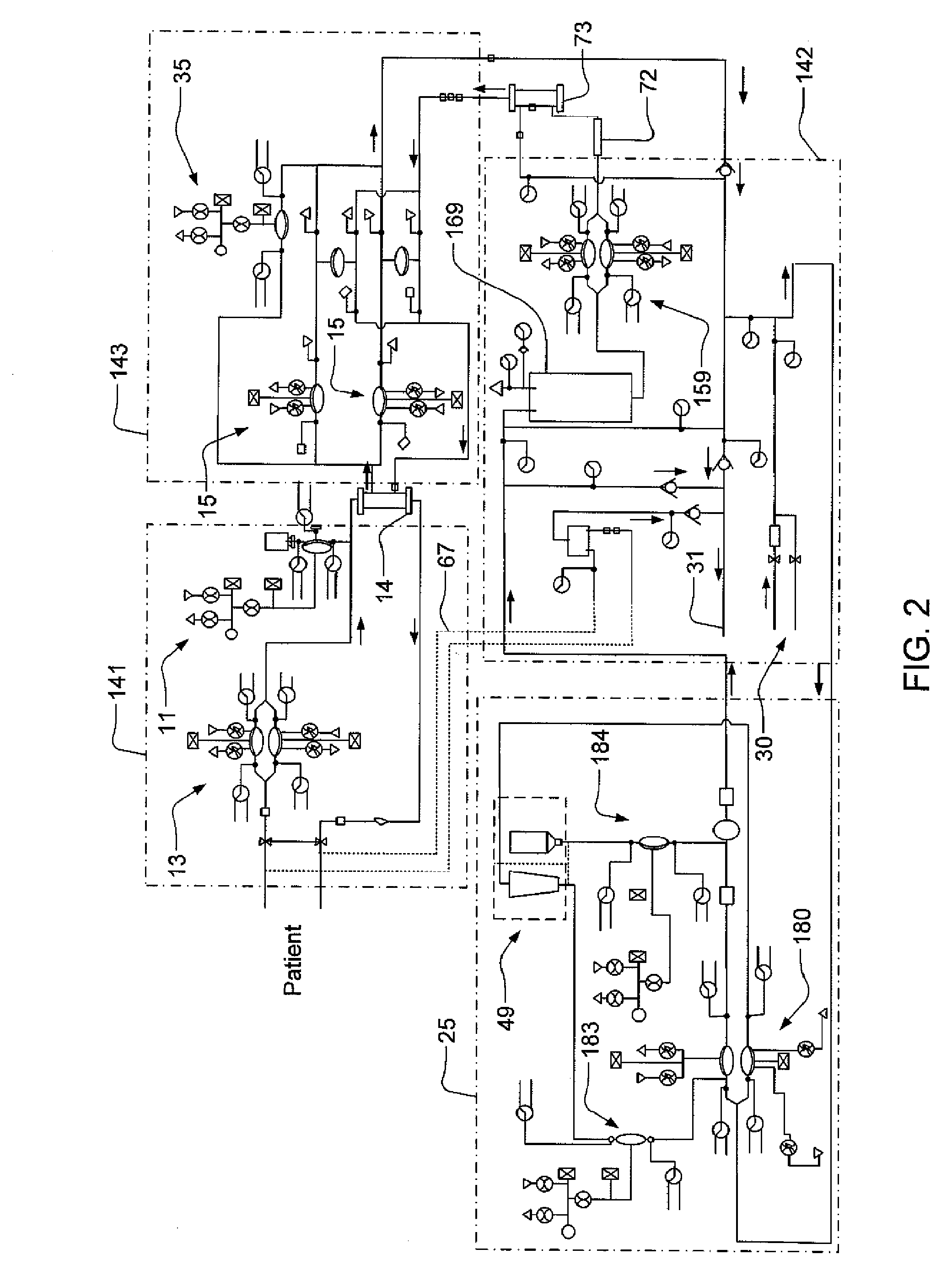
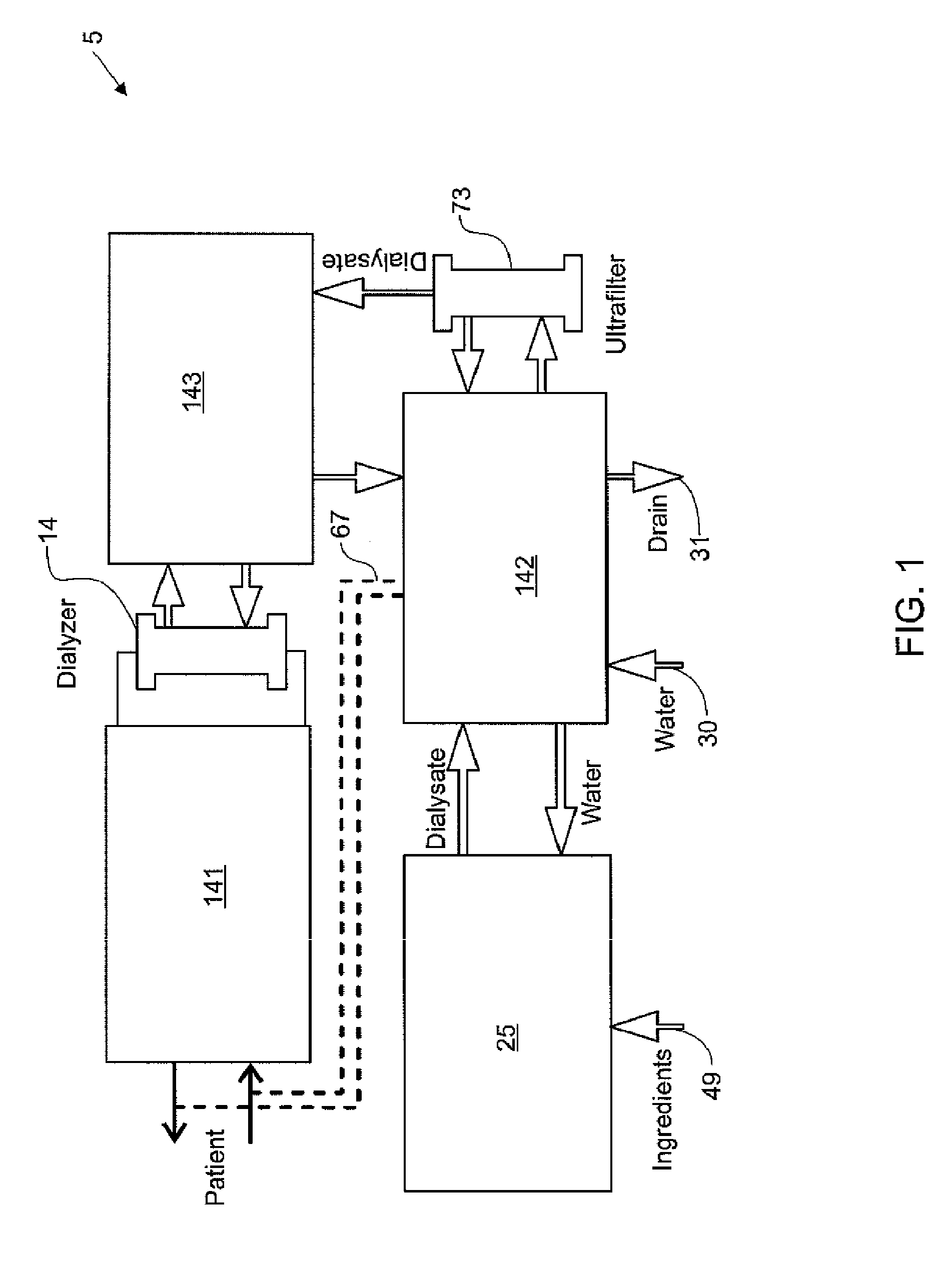
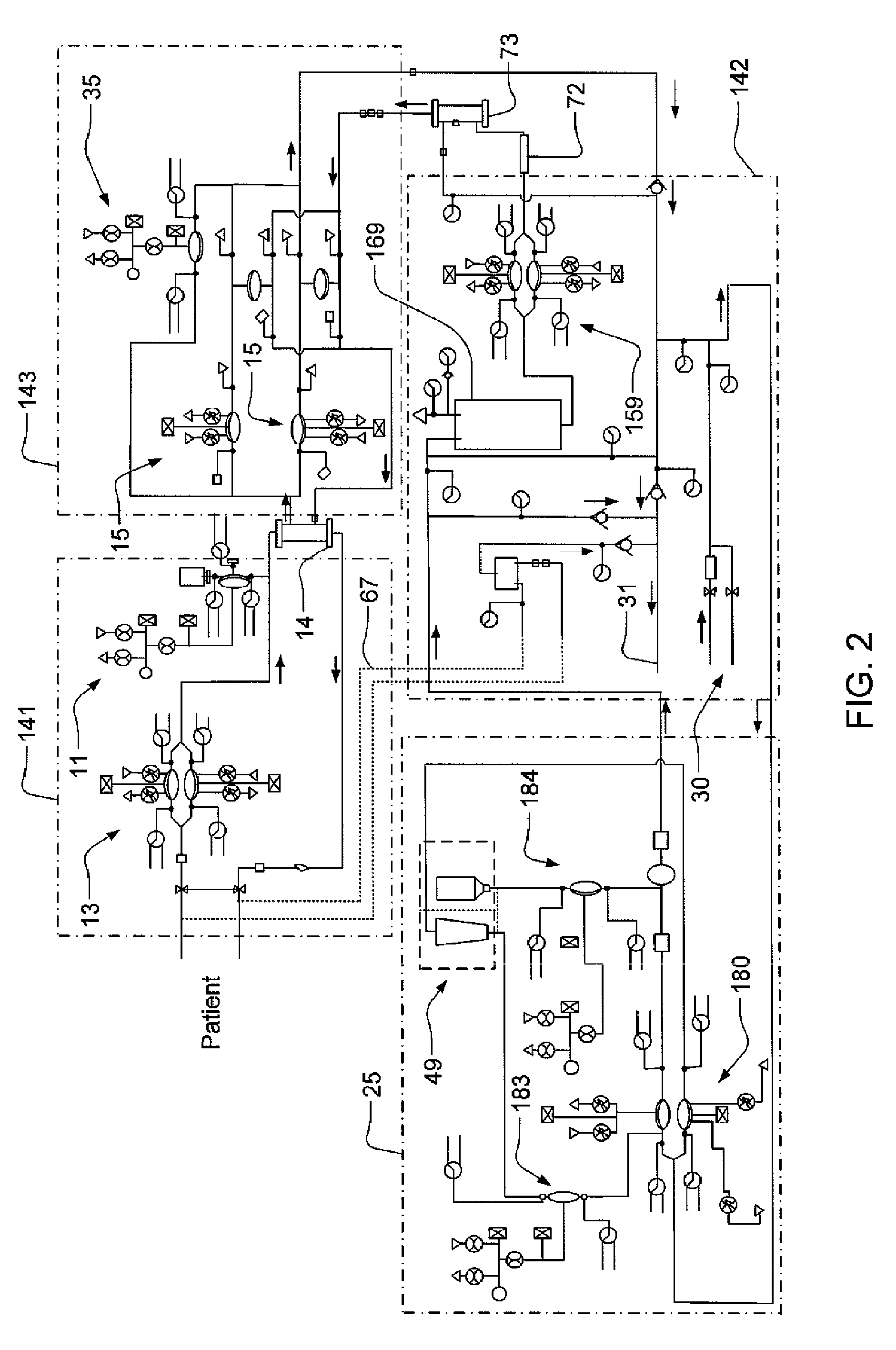
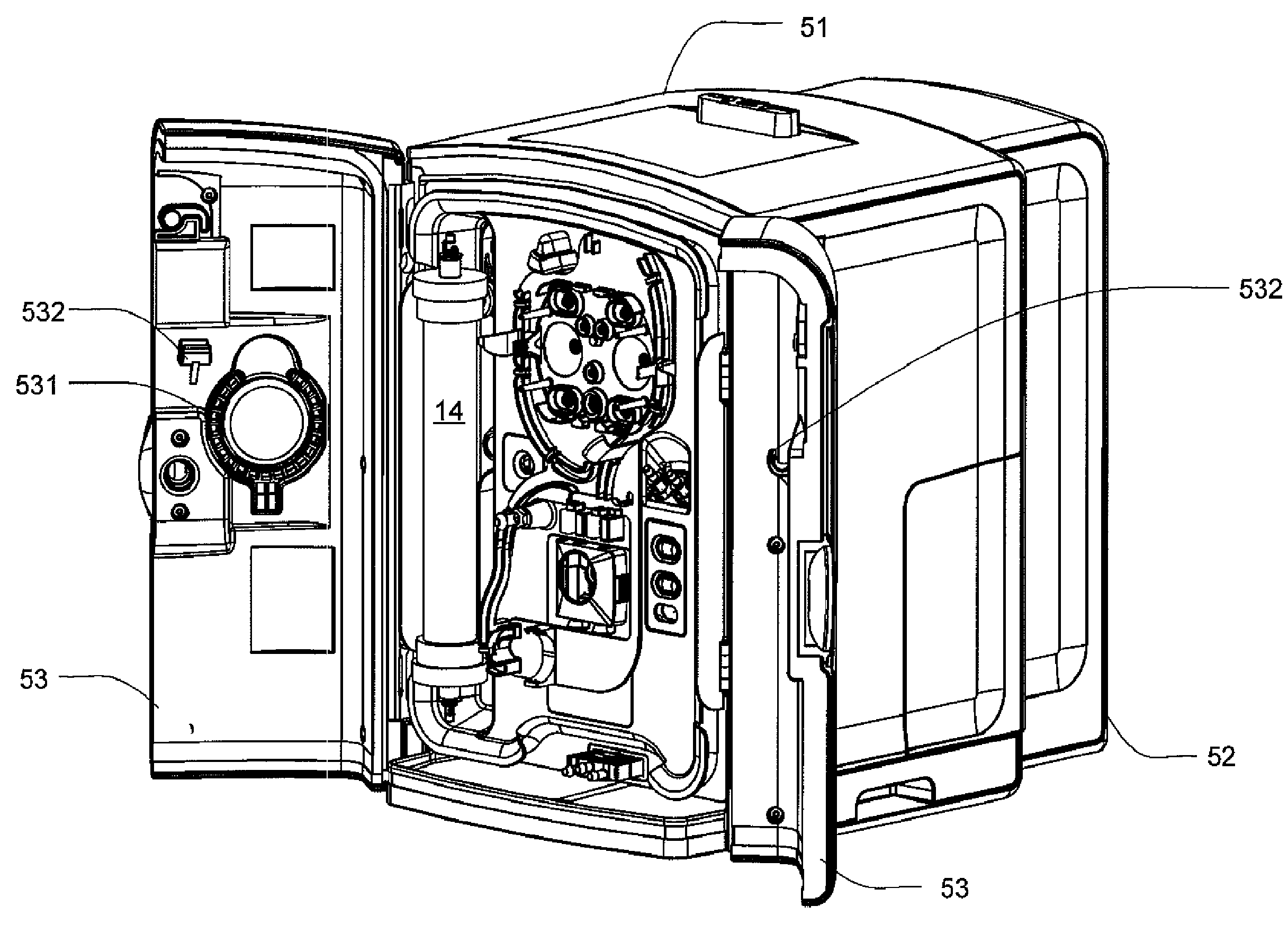
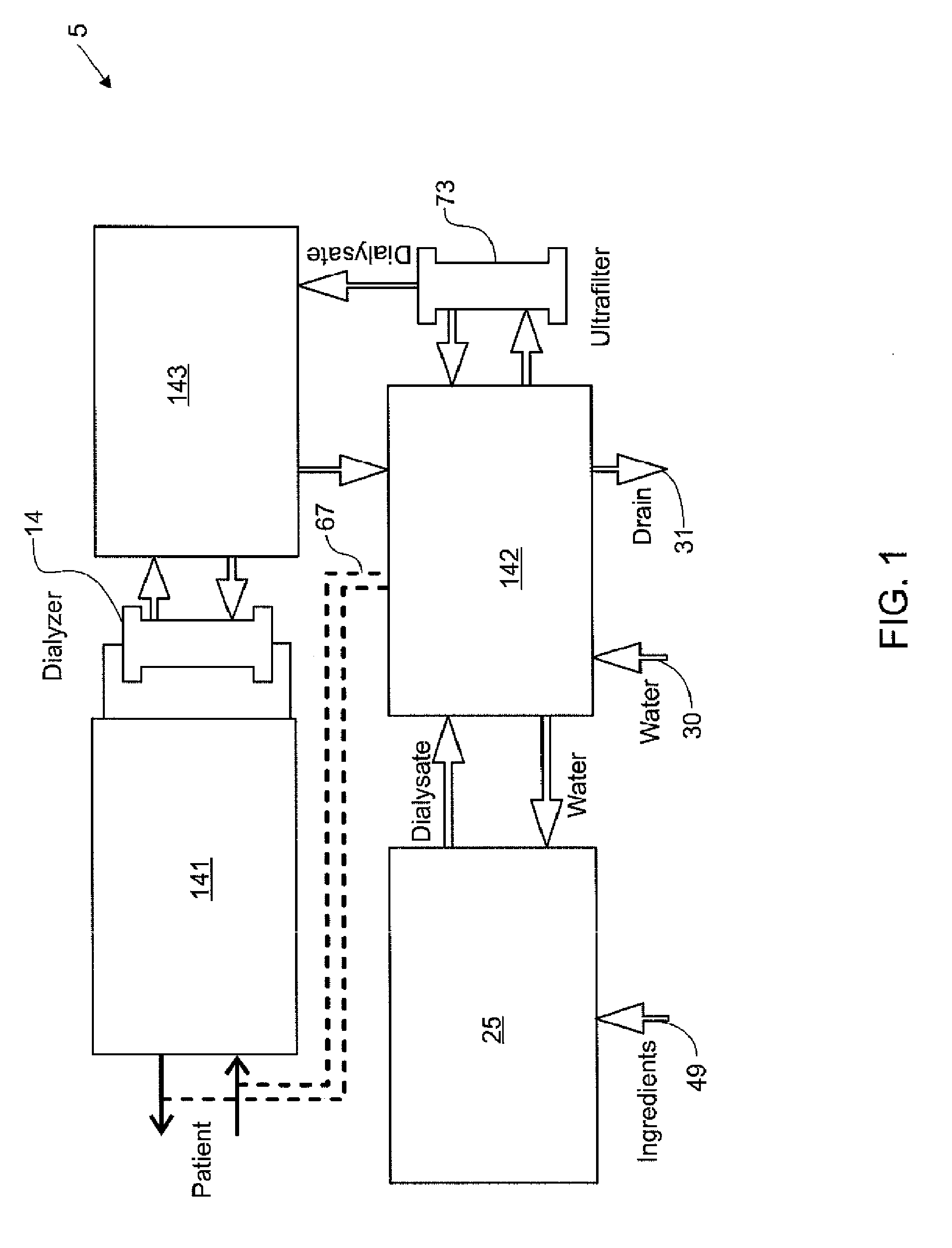
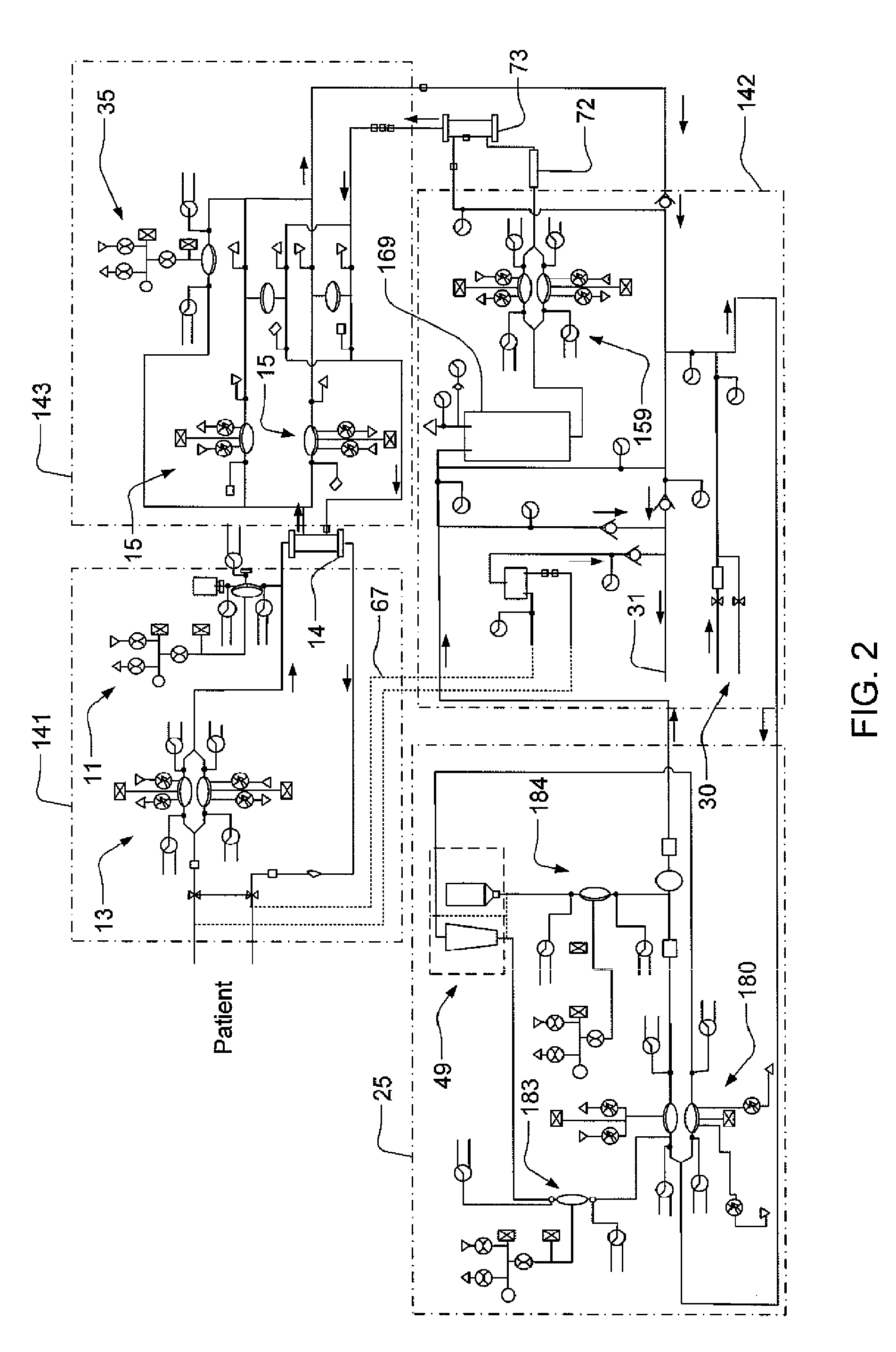
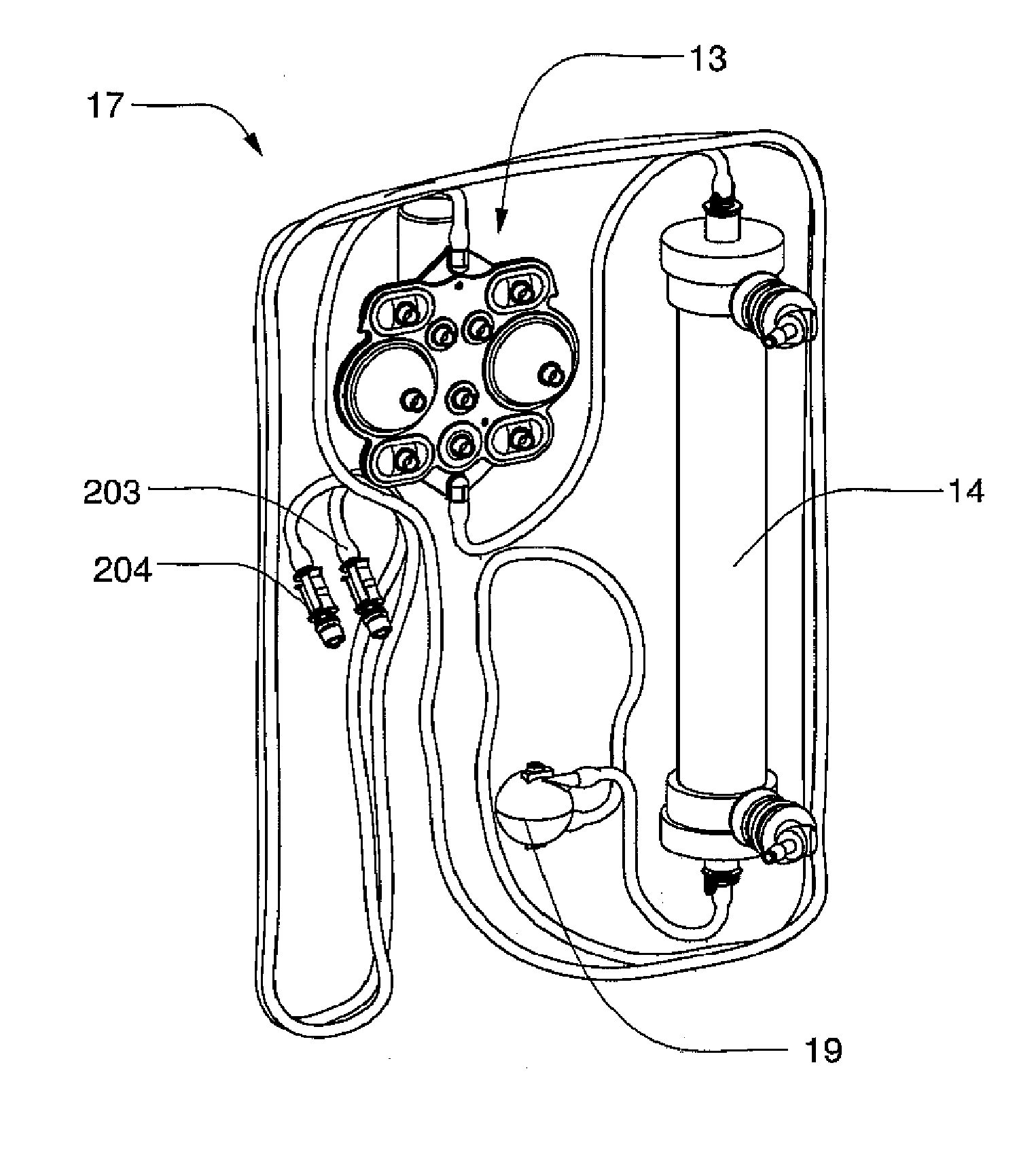
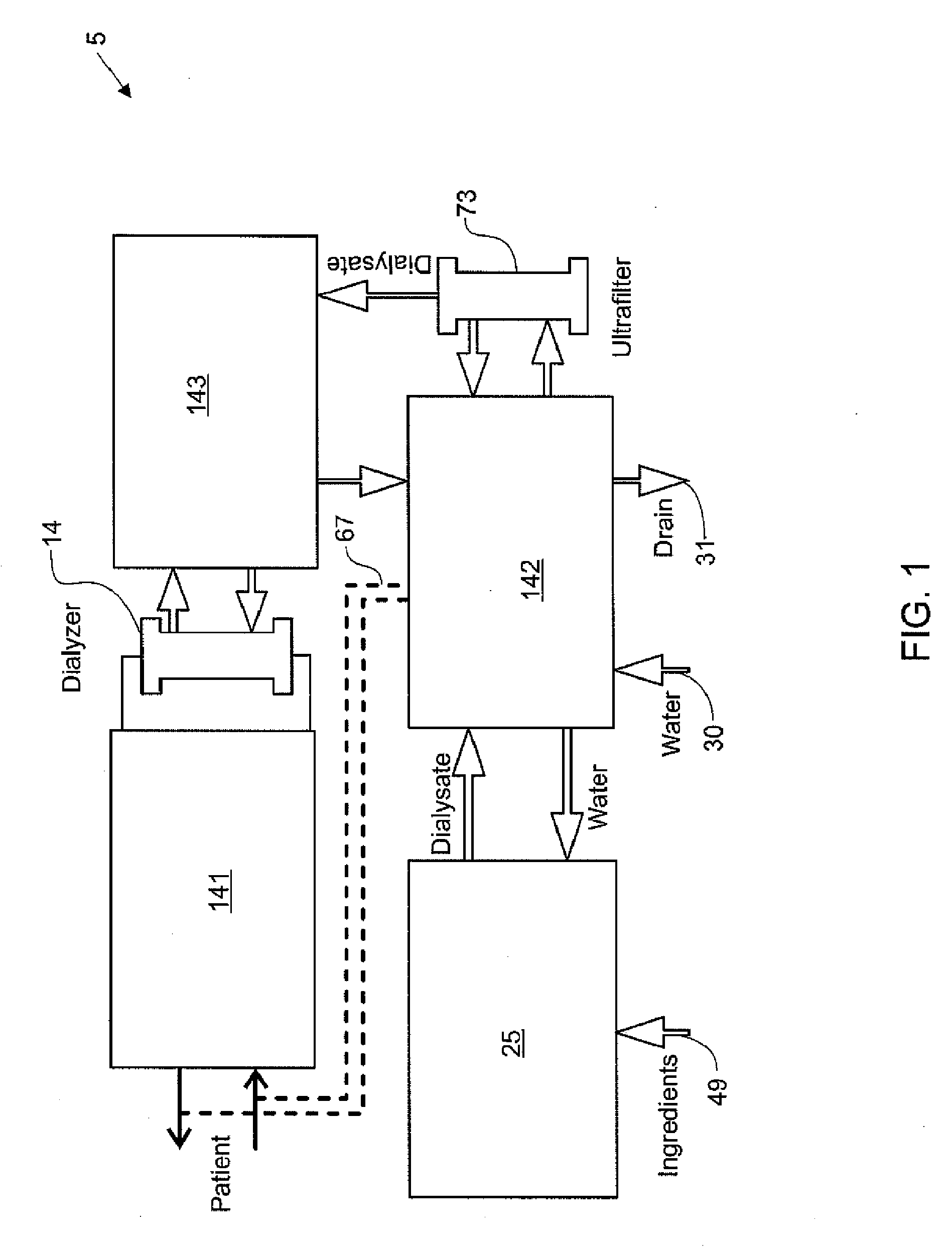
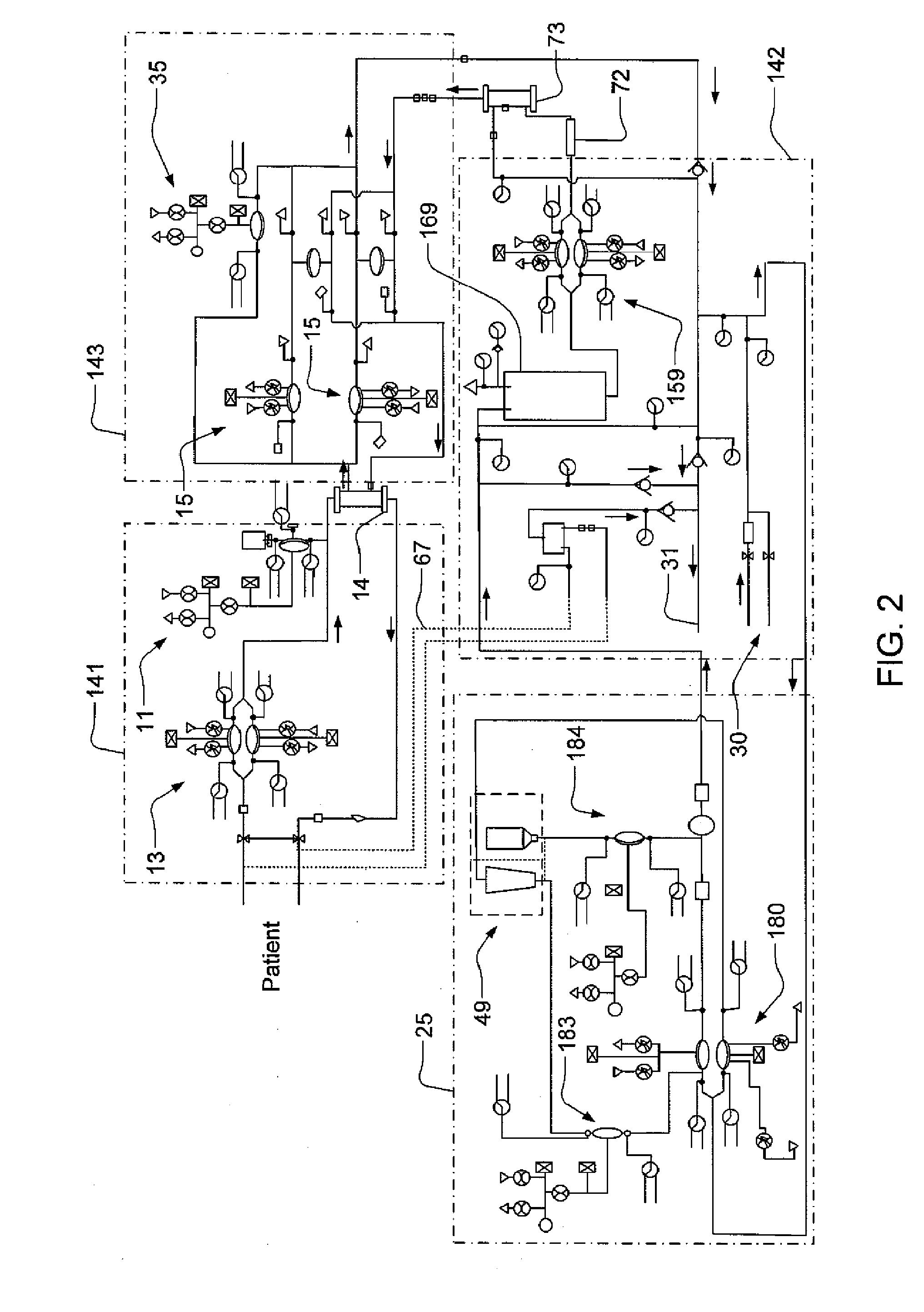
Modular assembly for a portable hemodialysis system
ActiveUS20090101549A1Easy to useOptimize locationMechanical/radiation/invasive therapiesOther blood circulation devicesHaemodialysis machineModularity
A modular assembly for a portable hemodialysis system may include a dialysis unit, e.g., that contains suitable components for performing hemodialysis, such as a dialyzer, one or more pumps to circulate blood through the dialyzer, a source of dialysate, and one or more pumps to circulate the dialysate through the dialyzer, and a power unit having a housing that contains suitable components for providing operating power to the pumps of the dialysis unit. The power unit may be selectively connected to the dialysis unit and provide power (e.g., pneumatic power in the form of pressure and / or vacuum) to the dialysis unit for the pumps when connected to the dialysis unit, but may be incapable of providing power to the dialysis unit when disconnected from the dialysis unit. The dialysis unit and the power unit are sized and weighted to each be carried by hand by a human.
Owner:DEKA PROD LLP
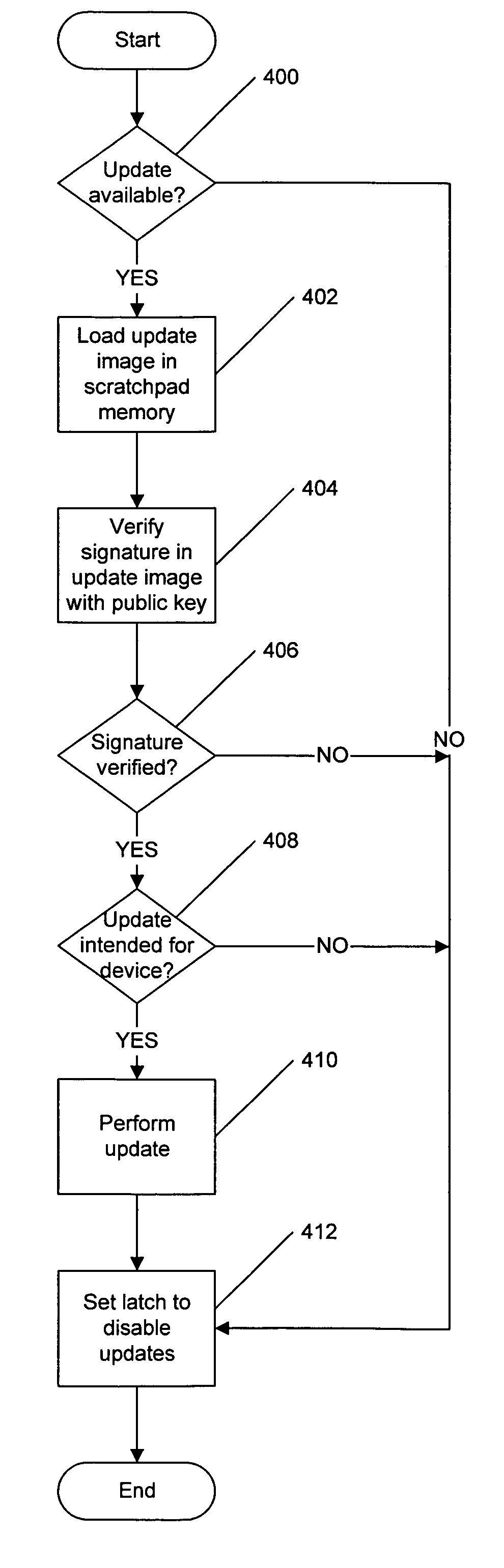
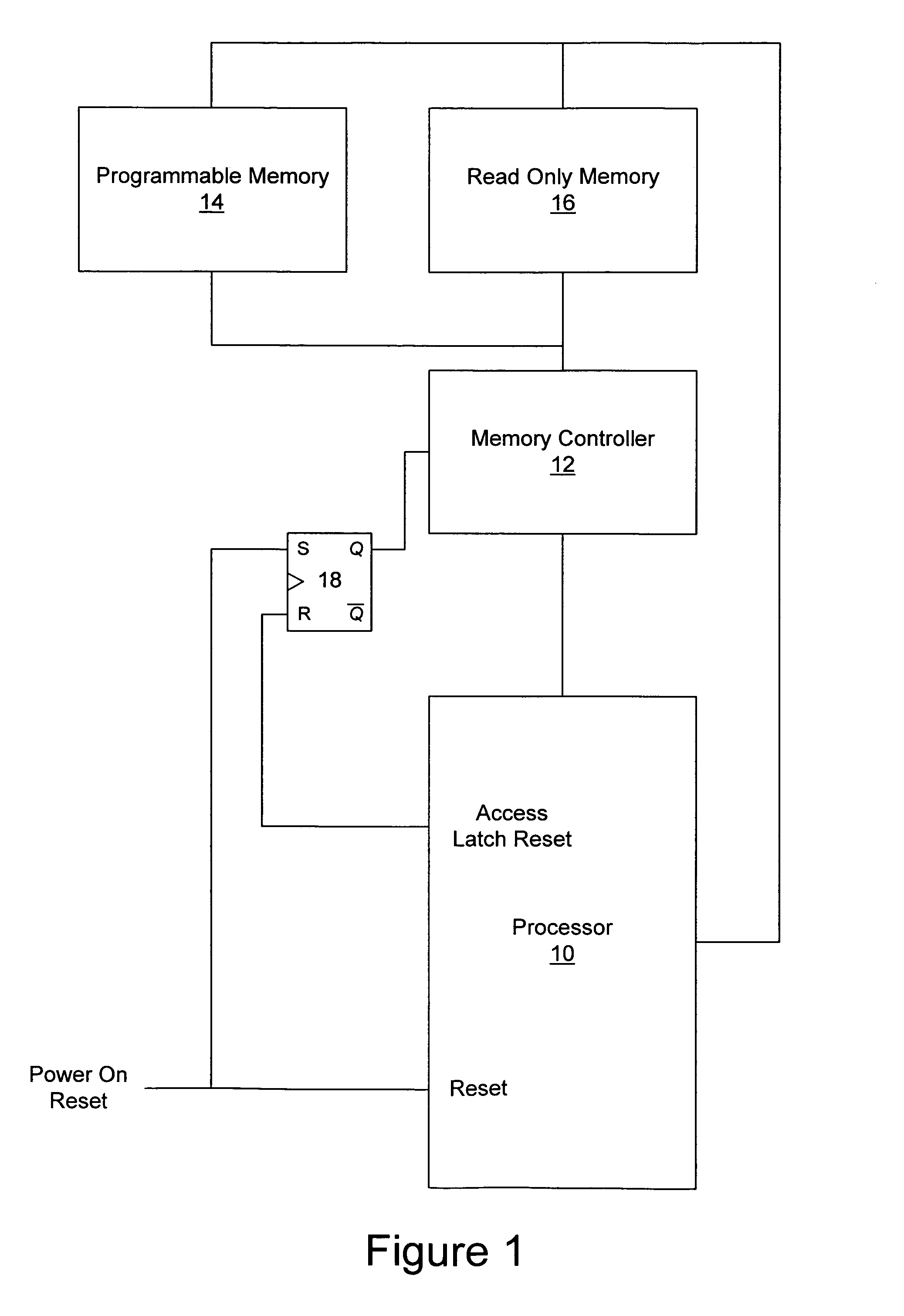
Methods, systems and computer program products for secure firmware updates
ActiveUS7069452B1Avoid accessReduce stepsDigital computer detailsUnauthorized memory use protectionData storeControl equipment
Methods, systems and computer program products which provide secure updates of firmware (i.e. data stored in a programmable memory device of a processing system) are disclosed. Updates of a programmable memory of a device may be controlled by providing an update window of finite duration during which the programmable memory may be updated. Access to the programmable memory may be based on the state of an access latch. The access latch may be set to allow access after a hardware reset of the device. An update control program may be executed to control access to the programmable memory and the latch reset to prevent access upon completion of the update control program. Verification of the update may be provided through encryption techniques and rules incorporated in certificates for application of updates to provide for selectively updating devices. Also disclosed are methods of securely providing differing functionality to generic devices.
Owner:IBM CORP
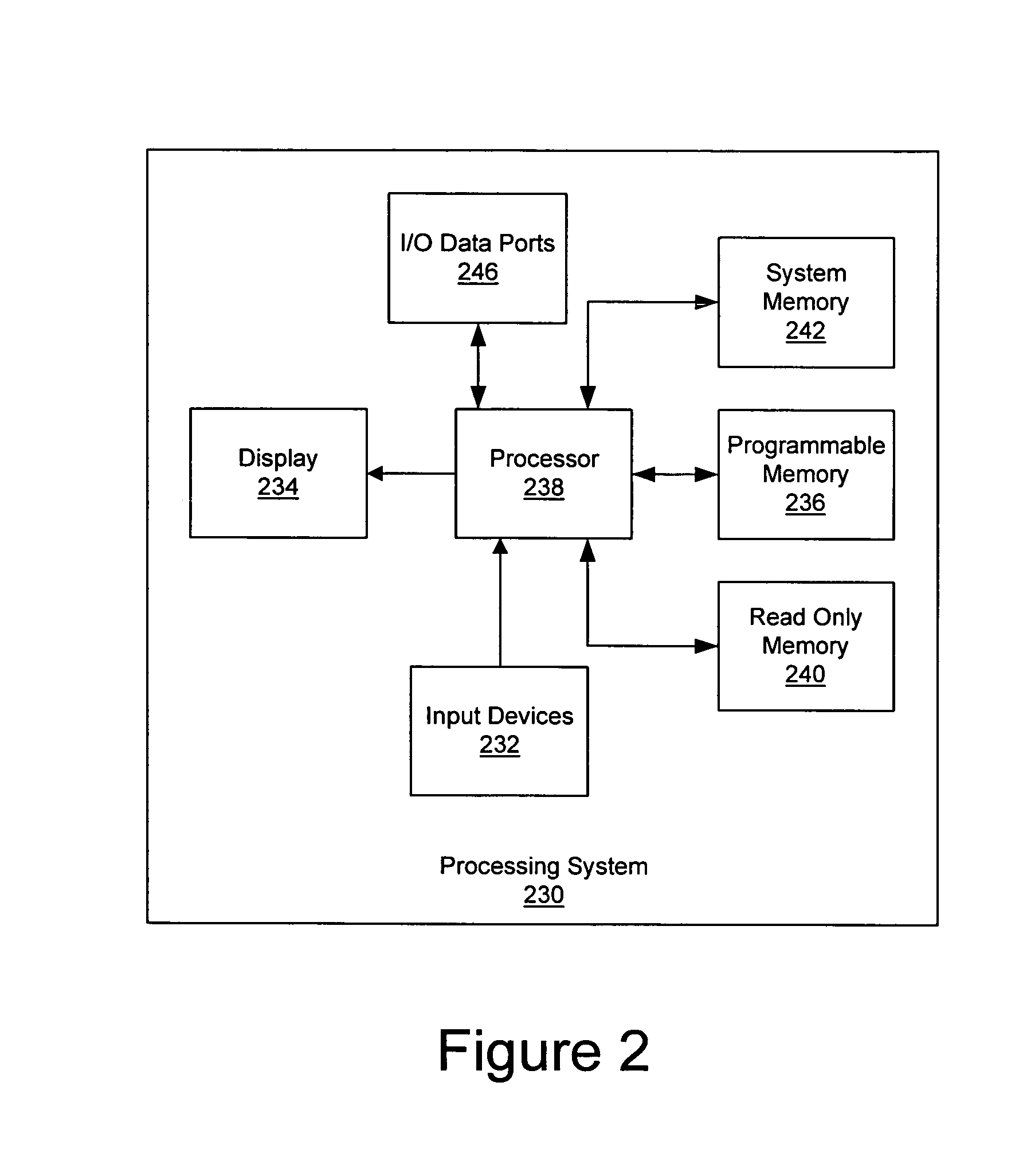
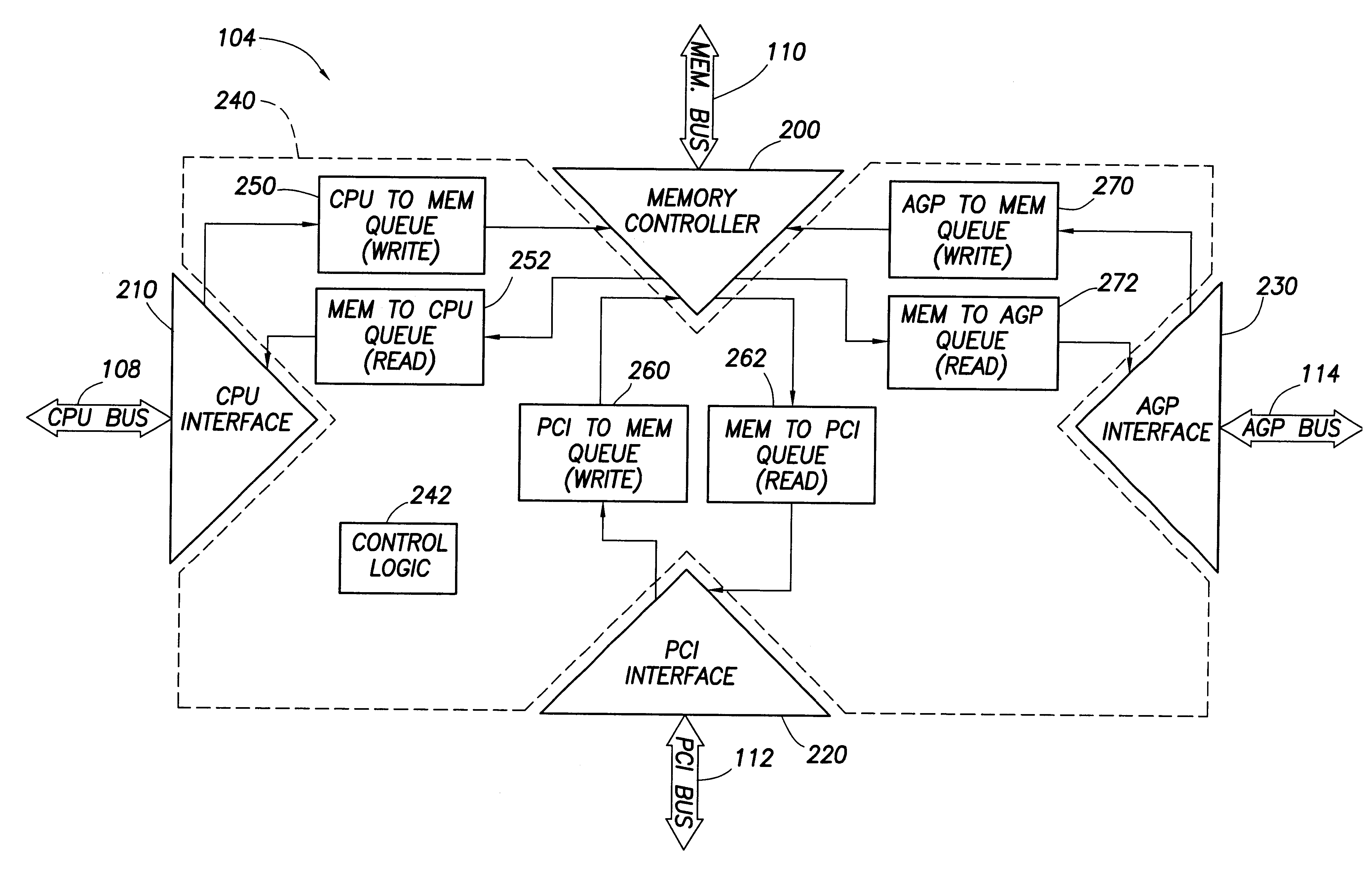
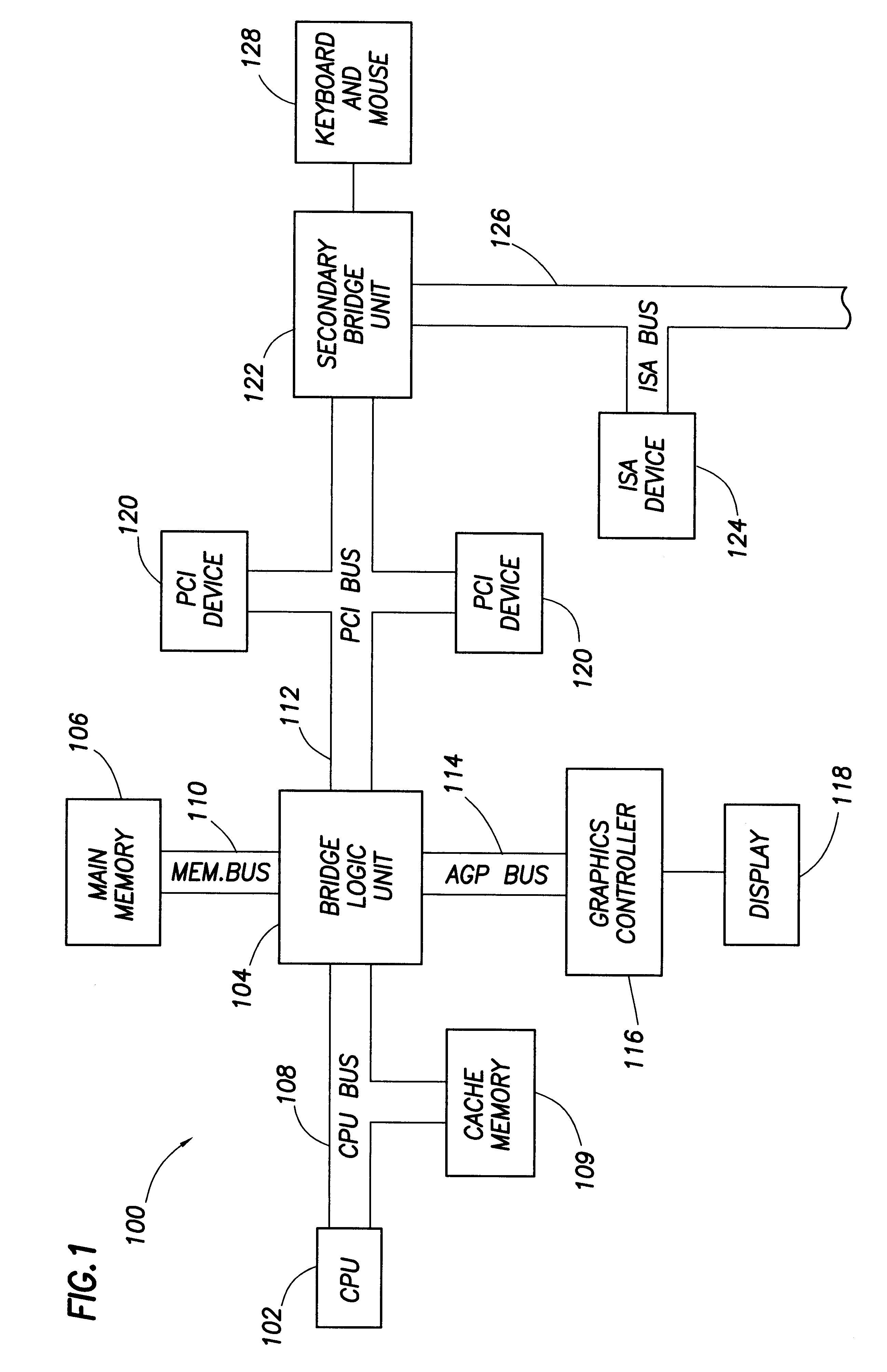
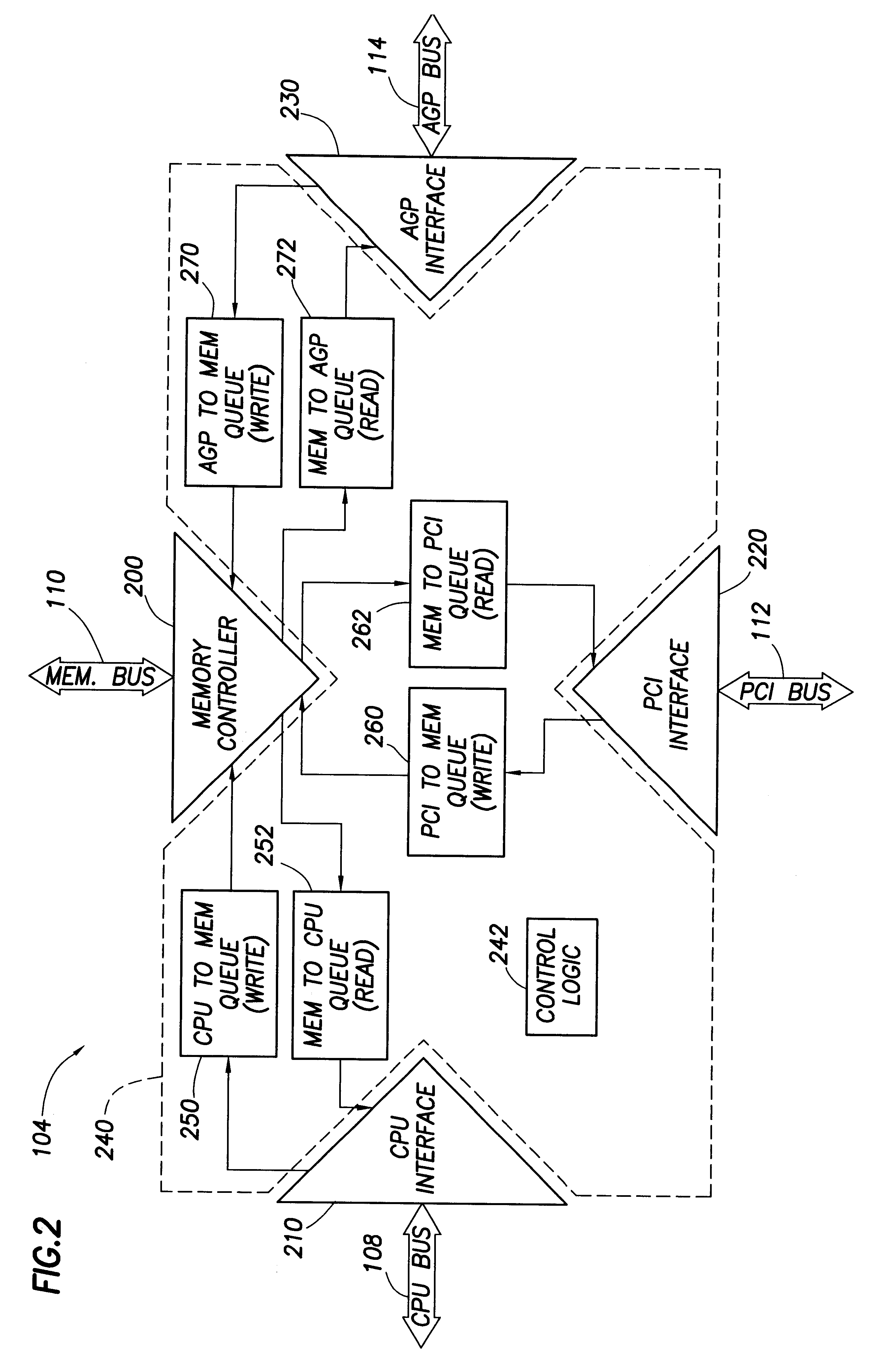
Computer system with adaptive memory arbitration scheme
InactiveUS6286083B1Raise priorityAvoid accessMemory systemsInput/output processes for data processingOut of memoryParallel computing
A computer system includes an adaptive memory arbiter for prioritizing memory access requests, including a self-adjusting, programmable request-priority ranking system. The memory arbiter adapts during every arbitration cycle, reducing the priority of any request which wins memory arbitration. Thus, a memory request initially holding a low priority ranking may gradually advance in priority until that request wins memory arbitration. Such a scheme prevents lower-priority devices from becoming "memory-starved." Because some types of memory requests (such as refresh requests and memory reads) inherently require faster memory access than other requests (such as memory writes), the adaptive memory arbiter additionally integrates a nonadjustable priority structure into the adaptive ranking system which guarantees faster service to the most urgent requests. Also, the adaptive memory arbitration scheme introduces a flexible method of adjustable priority-weighting which permits selected devices to transact a programmable number of consecutive memory accesses without those devices losing request priority.
Owner:HEWLETT PACKARD DEV CO LP
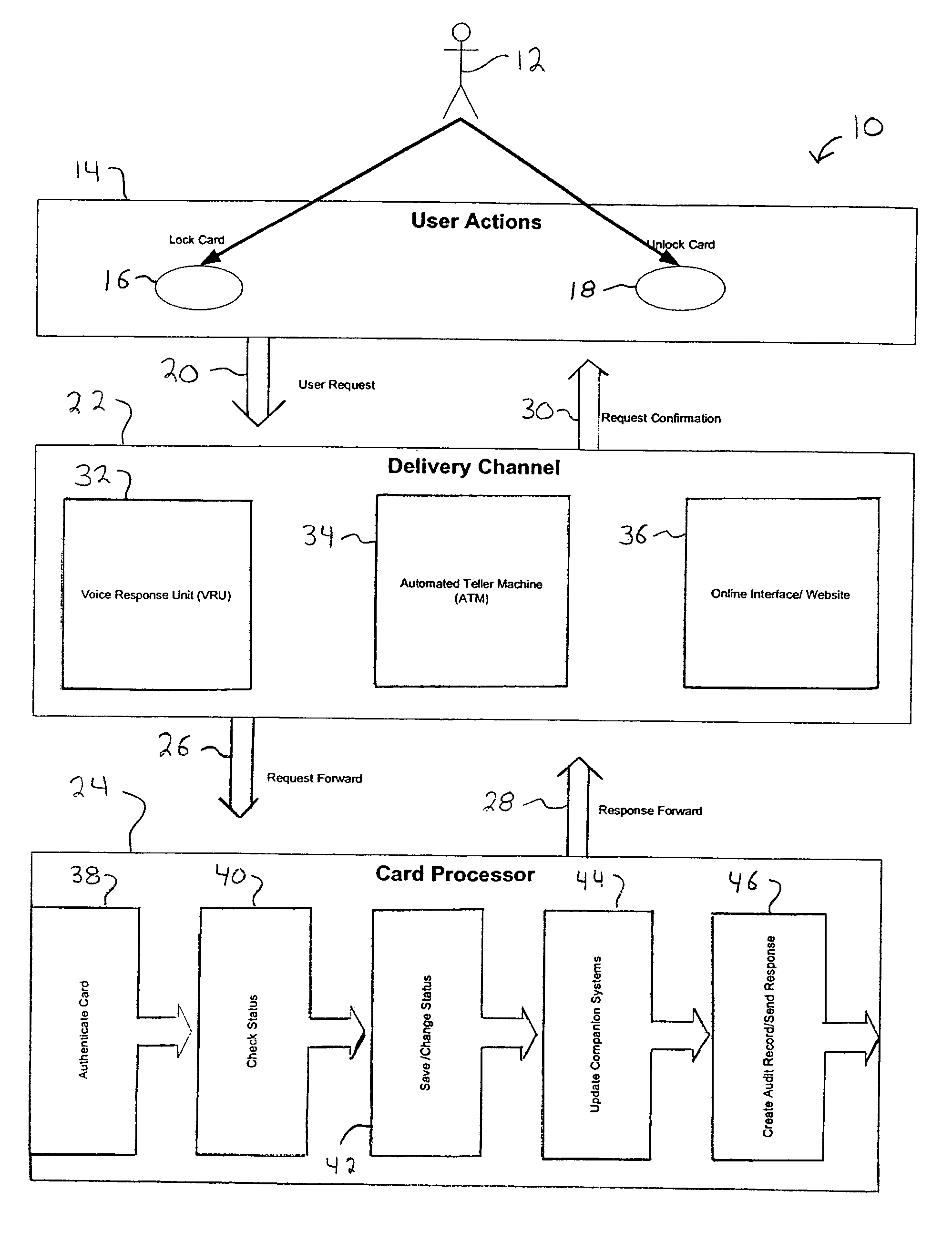
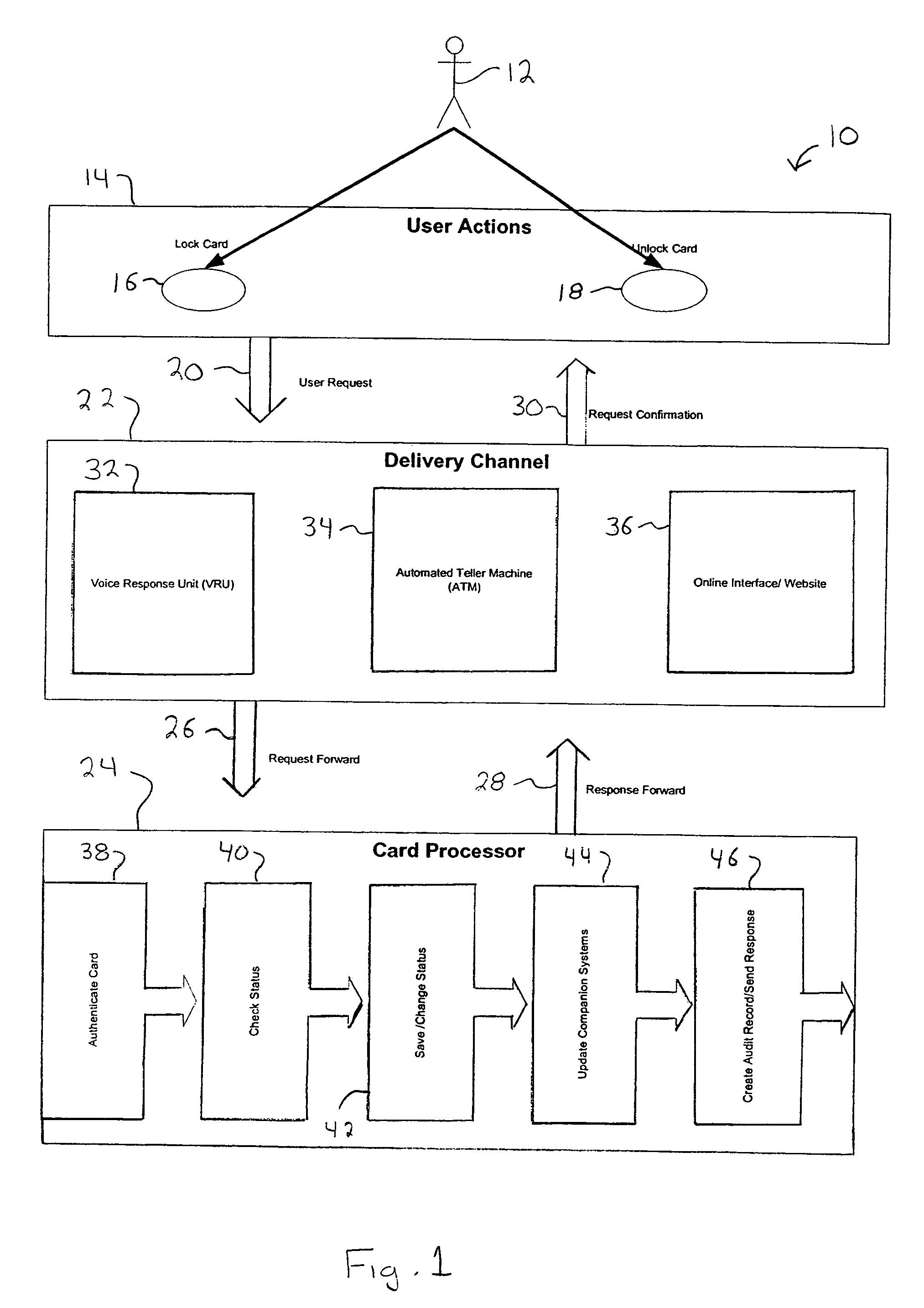
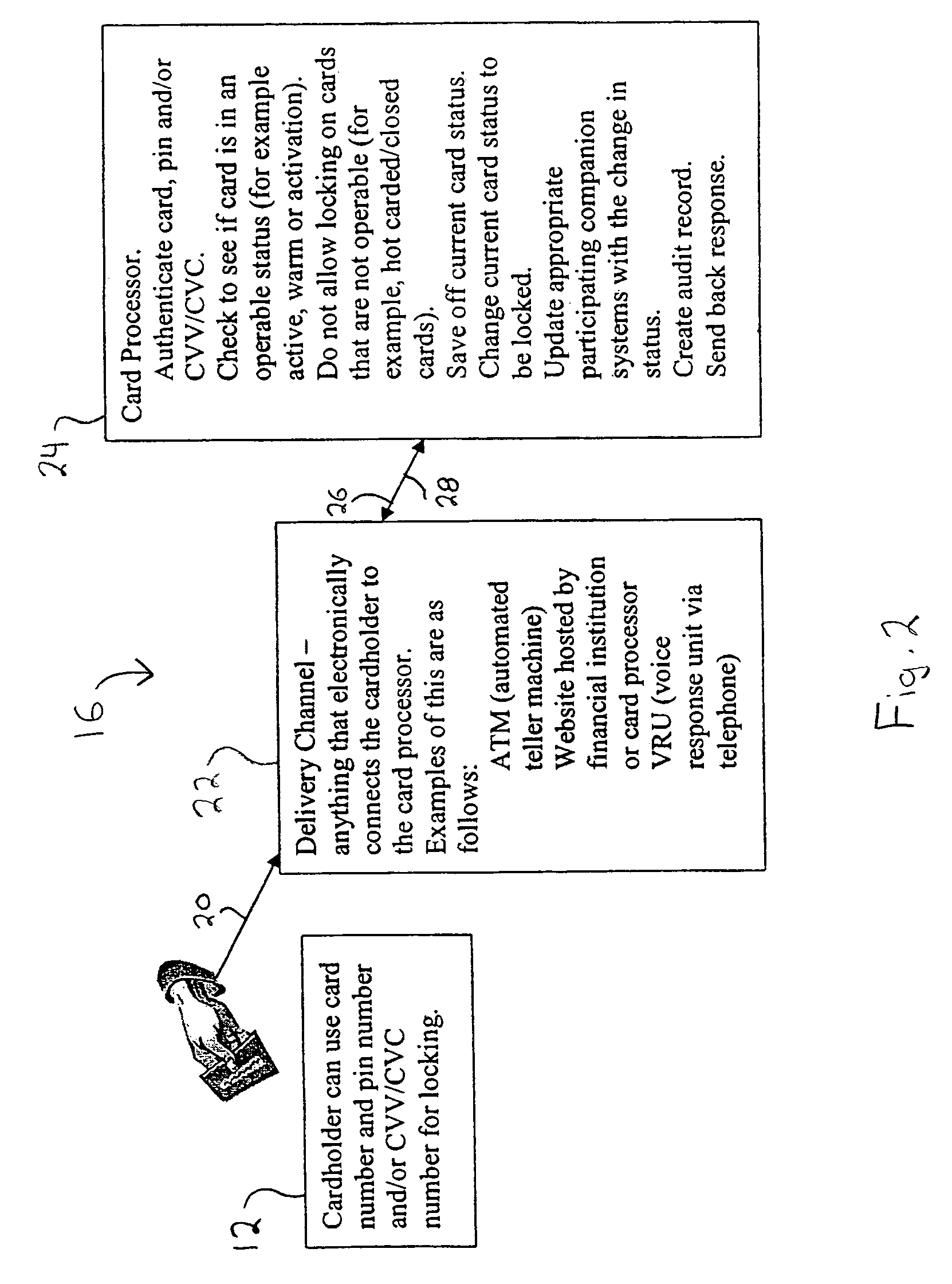
System and method for locking and unlocking a financial account card
Owner:FIDELITY INFORMATION SERVICES LLC
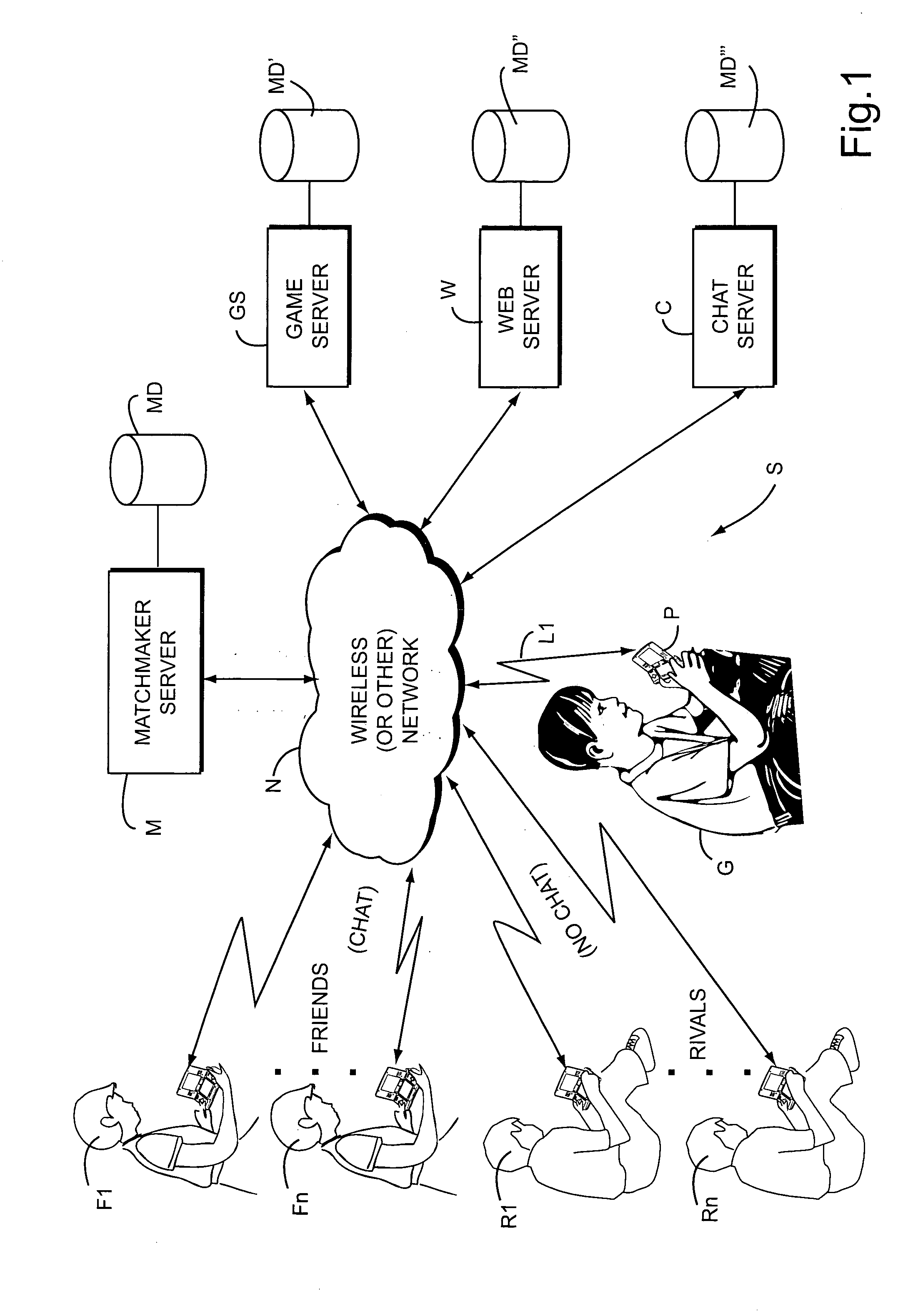
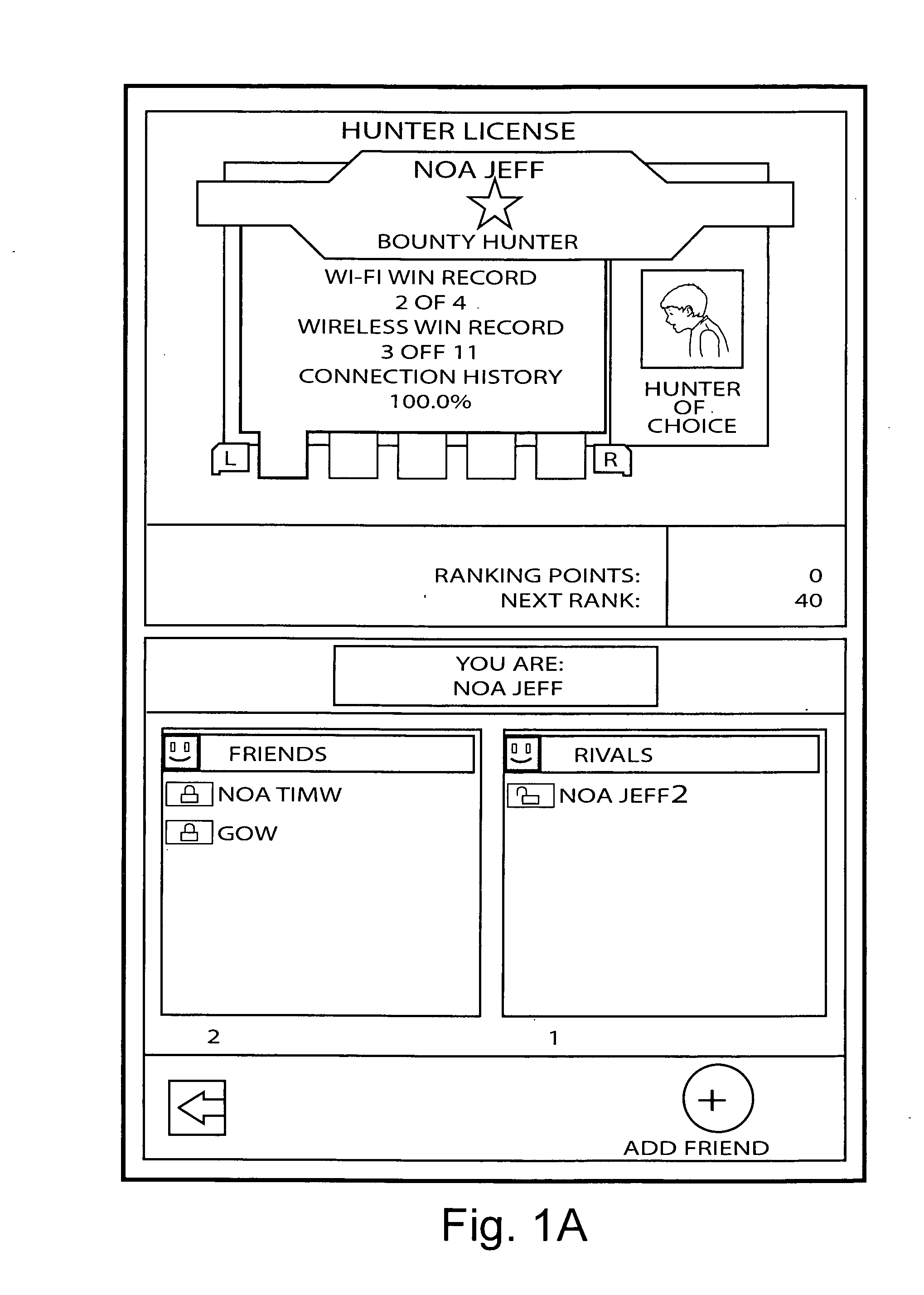
Systems, methods and techniques for safely and effectively coordinating video game play and other activities among multiple remote networked friends and rivals
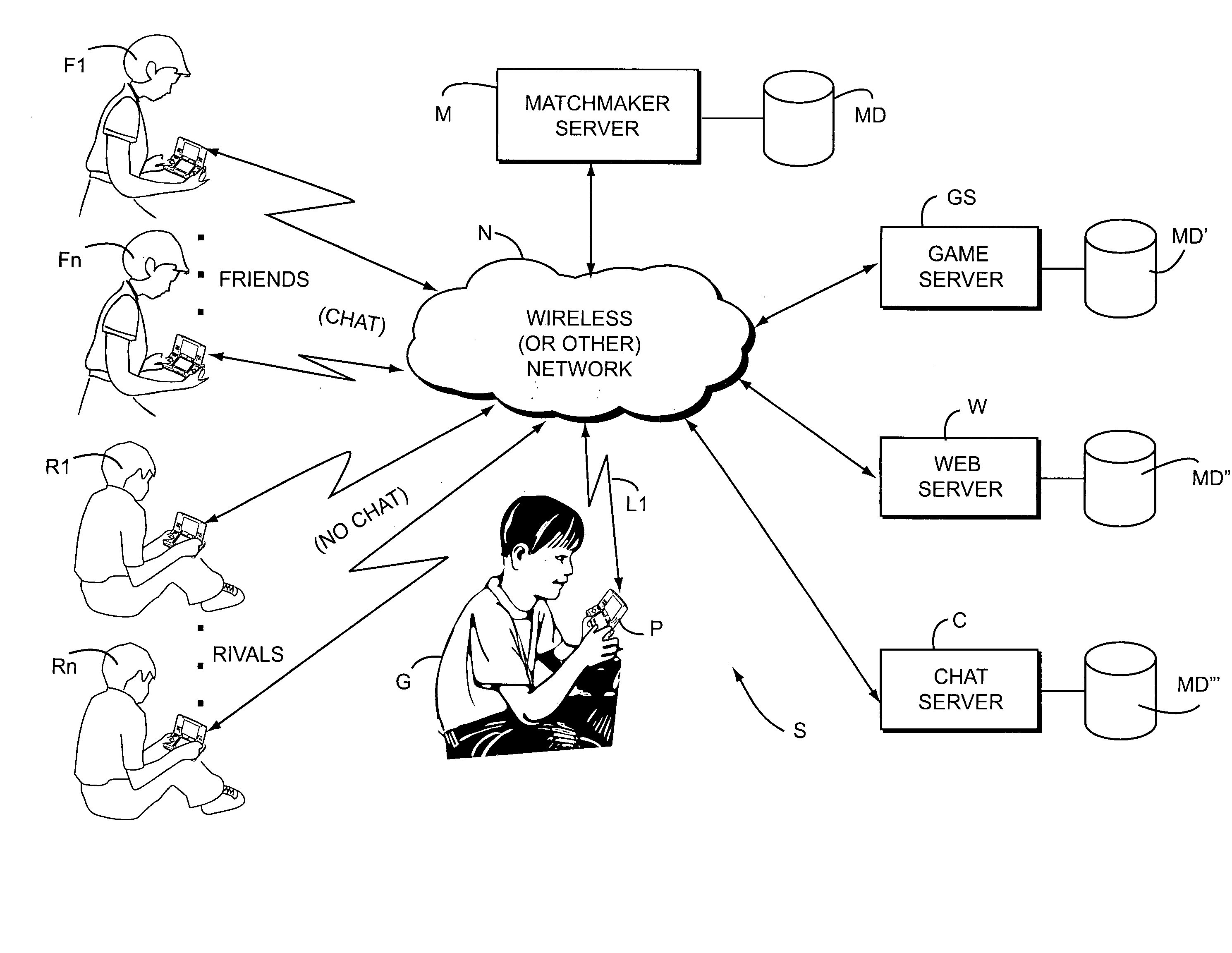
ActiveUS20070218997A1Meet the selection requirementsEnsuring privacyVideo gamesSpecial data processing applicationsGame playerDirect communication
Real time interactive networked gaming is provided with two different classes of bookmarked online game players: “Friends” and “Rivals.”“Friends” are game players that are known personally. “Rivals” are game players who are not known personally but whom one has played against in the past in an online gaming scenario. Game software may allow chatting or other direct communication with “Friends” but not with “Rivals.” Rivals may be tracked to a limited degree so that for example it is possible to play against the Rival when he or she is online. Rivals may for example be players who you wish to track or keep track of, but in a manner that is safe for both you and the “rival.” When a player goes online again, he or she can see whether his or her Rivals are online and invite them to play another game. Inviting Rivals to play may be selectable, so an online player can invite Friends, Rivals or both to play.
Owner:NINTENDO CO LTD
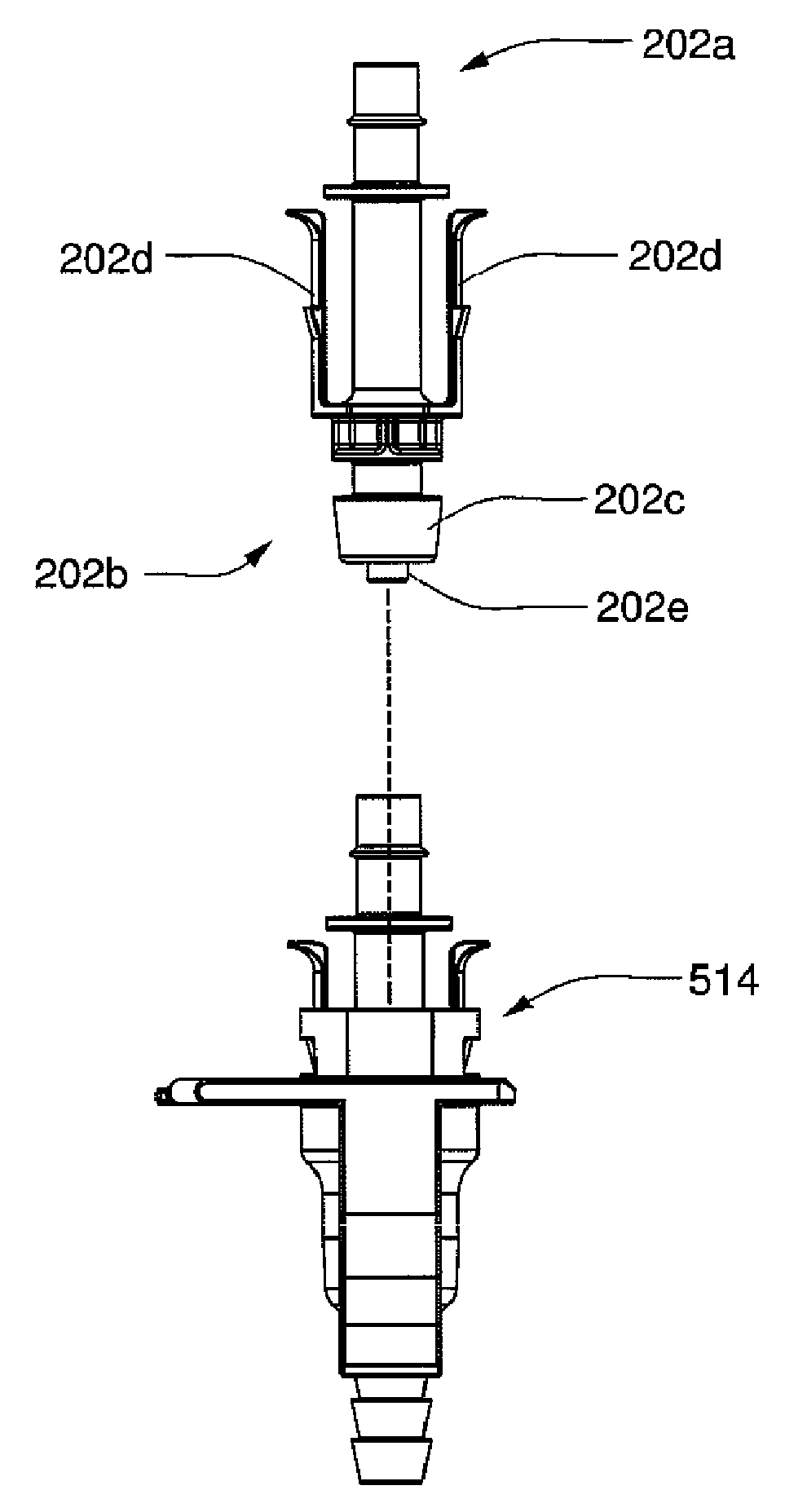
Blood line connector for a medical infusion device
InactiveUS20100056975A1Easy to useOptimize locationDialysis systemsMedical devicesLine tubingDialysis fluid
A blood line connector for a blood circuit of a hemodialysis unit with an ability to make two different types of fluid tight connections, e.g., a screw-type connection with a luer connector at a patient access and a press-in type connection with a dialysate circuit. The blood line connector may include a tube connection end arranged to sealingly engage with a blood circuit tube, and a patient access connection end with a frustoconical member having an internally threaded portion arranged to engage with an externally threaded patient access, and a pair of locking arms extending rearwardly from the frustoconical member. The locking arms may each have a finger depression portion and a barbed portion, and may be arranged to engage with a mating connector on the dialysis unit at the barbed portions to lock the frustoconical member in sealing engagement with the mating connector when making a press-in type connection.
Owner:DEKA PROD LLP
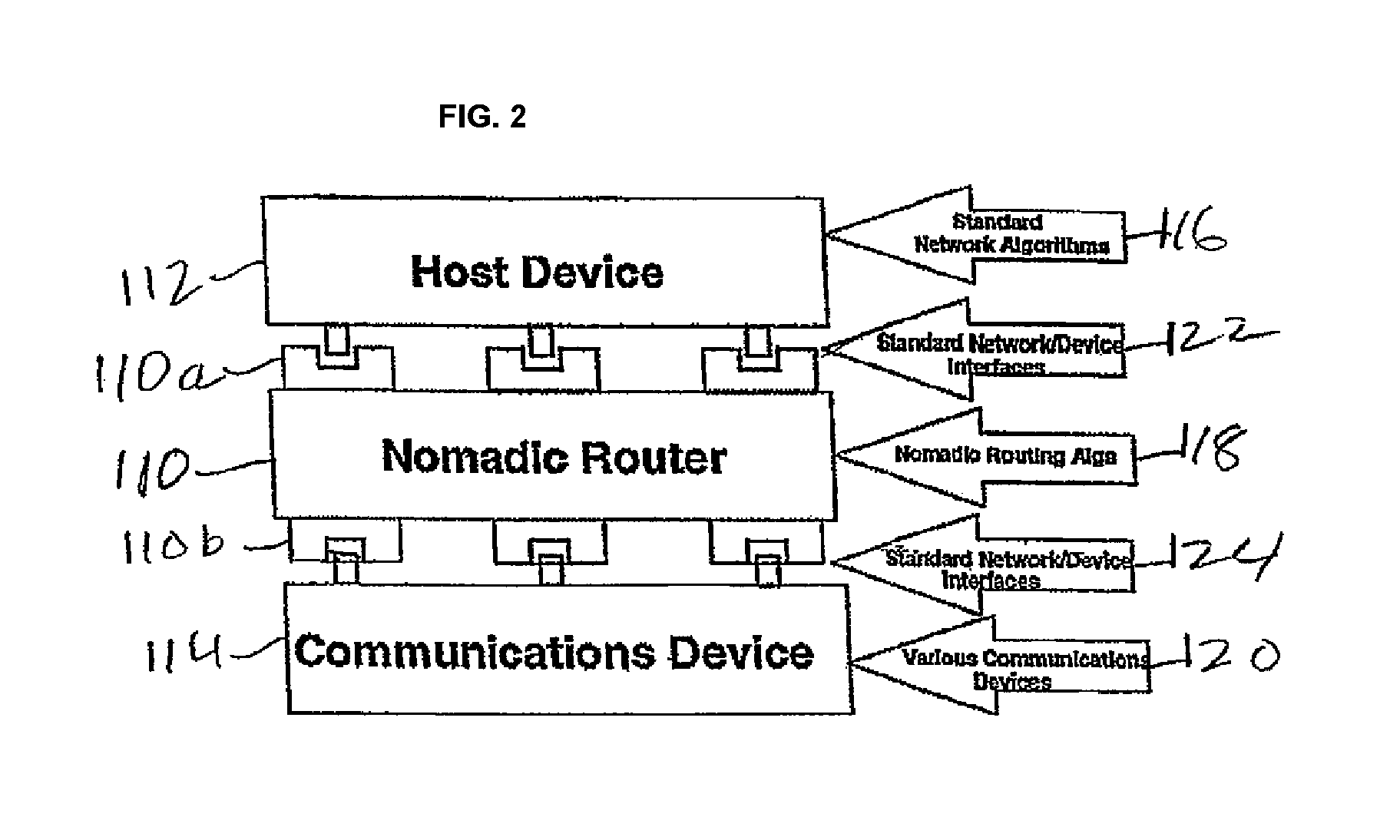
Systems and methods for authorizing, authenticating and accounting users having transparent computer access to a network using a gateway device
InactiveUS8713641B1Avoid accessDigital data processing detailsMultiple digital computer combinationsComputer networkTransparent computing
A system and method for authorizing, authenticating and accounting users having transparent access to a destination network, wherein the users otherwise have access to a home network through home network settings resident on the user's computers, and wherein the users can access the destination network without altering the home network settings and without installing software on the user's computer. The system includes a gateway device for receiving a request from a user for access to the destination network, and means for identifying an attribute associated with the user based upon a packet received by the gateway device, wherein the packet is transmitted from the user's computer, and wherein the user's computer is configured for accessing the home network.
Owner:NOMADIX INC
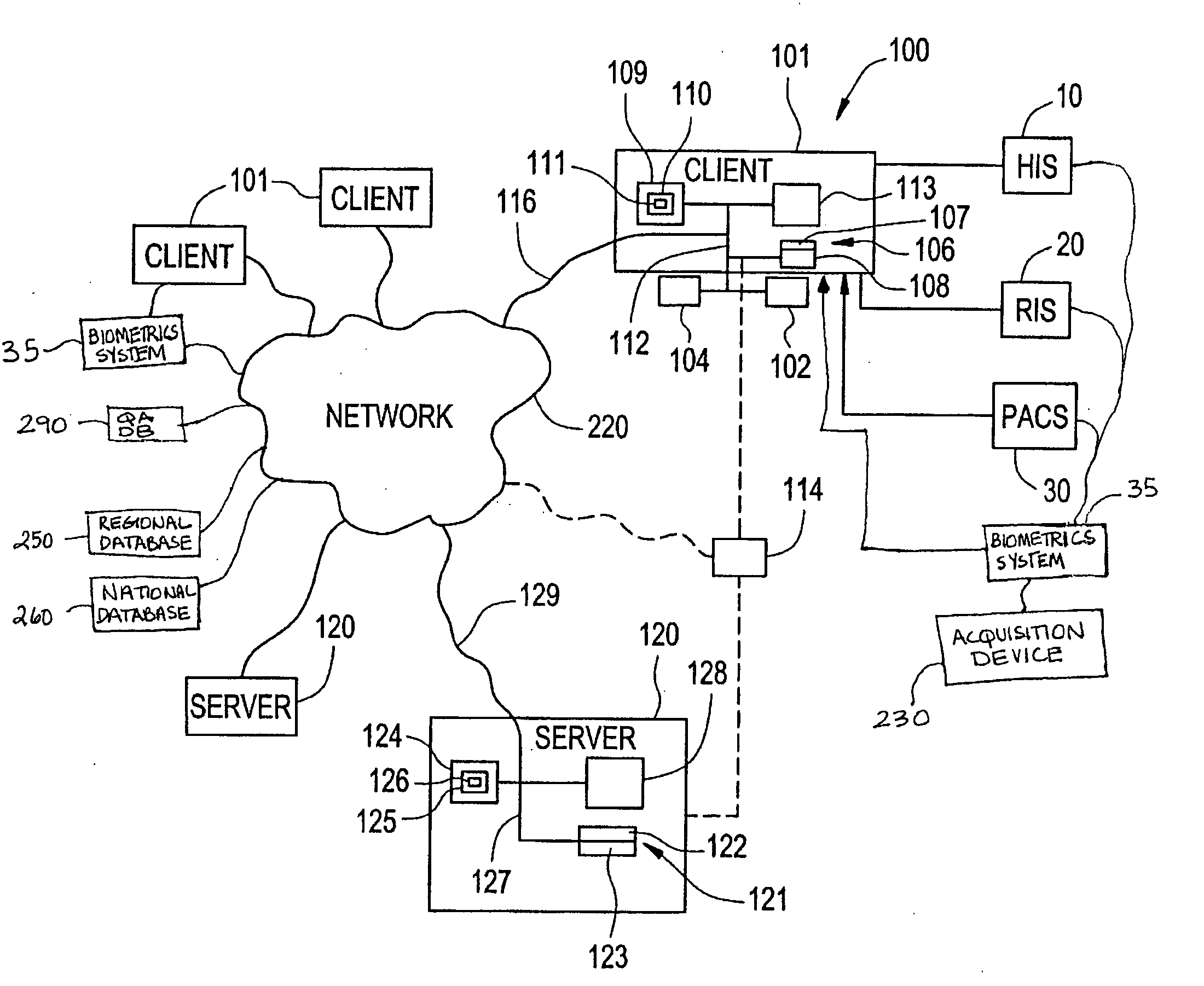
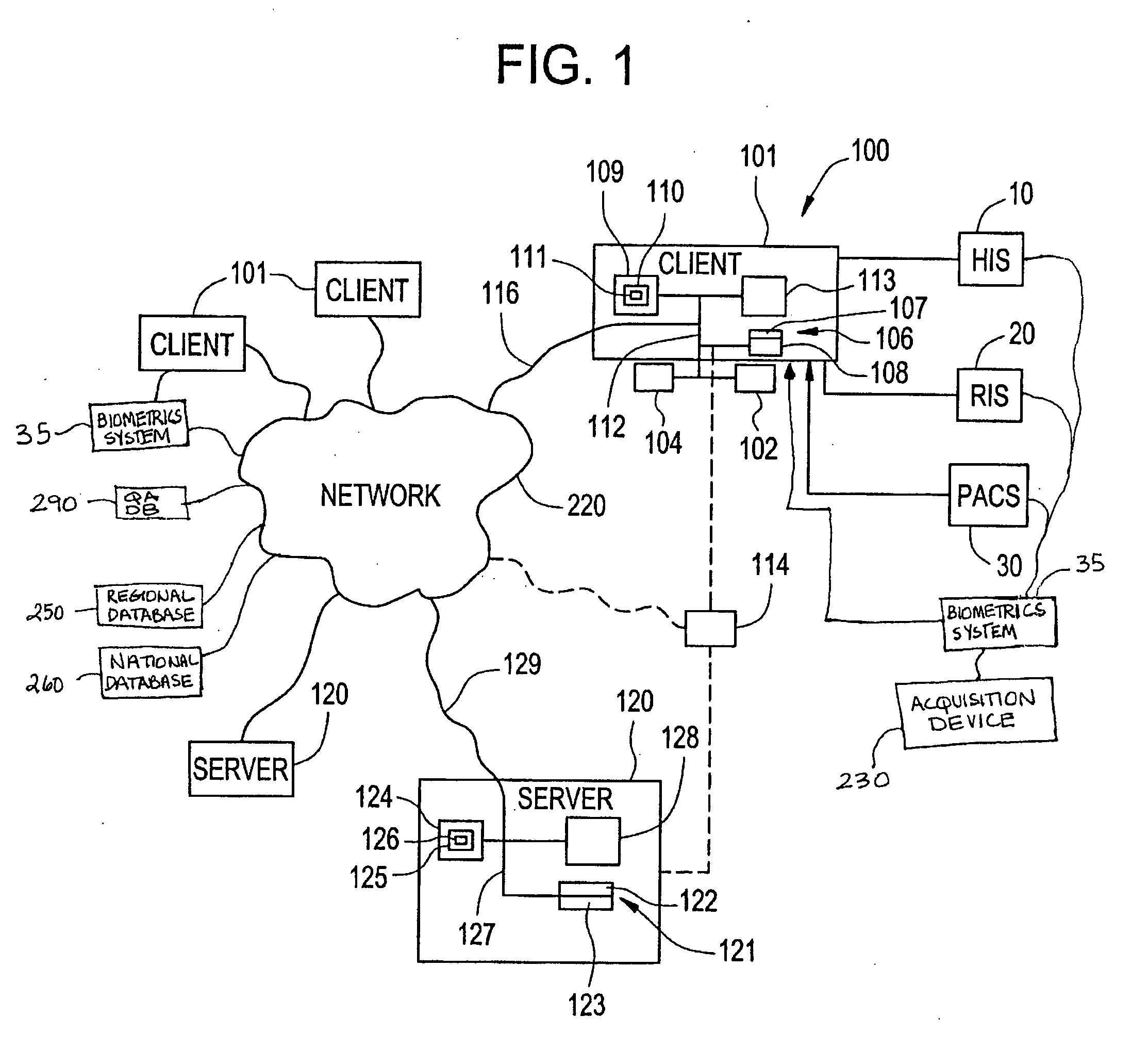
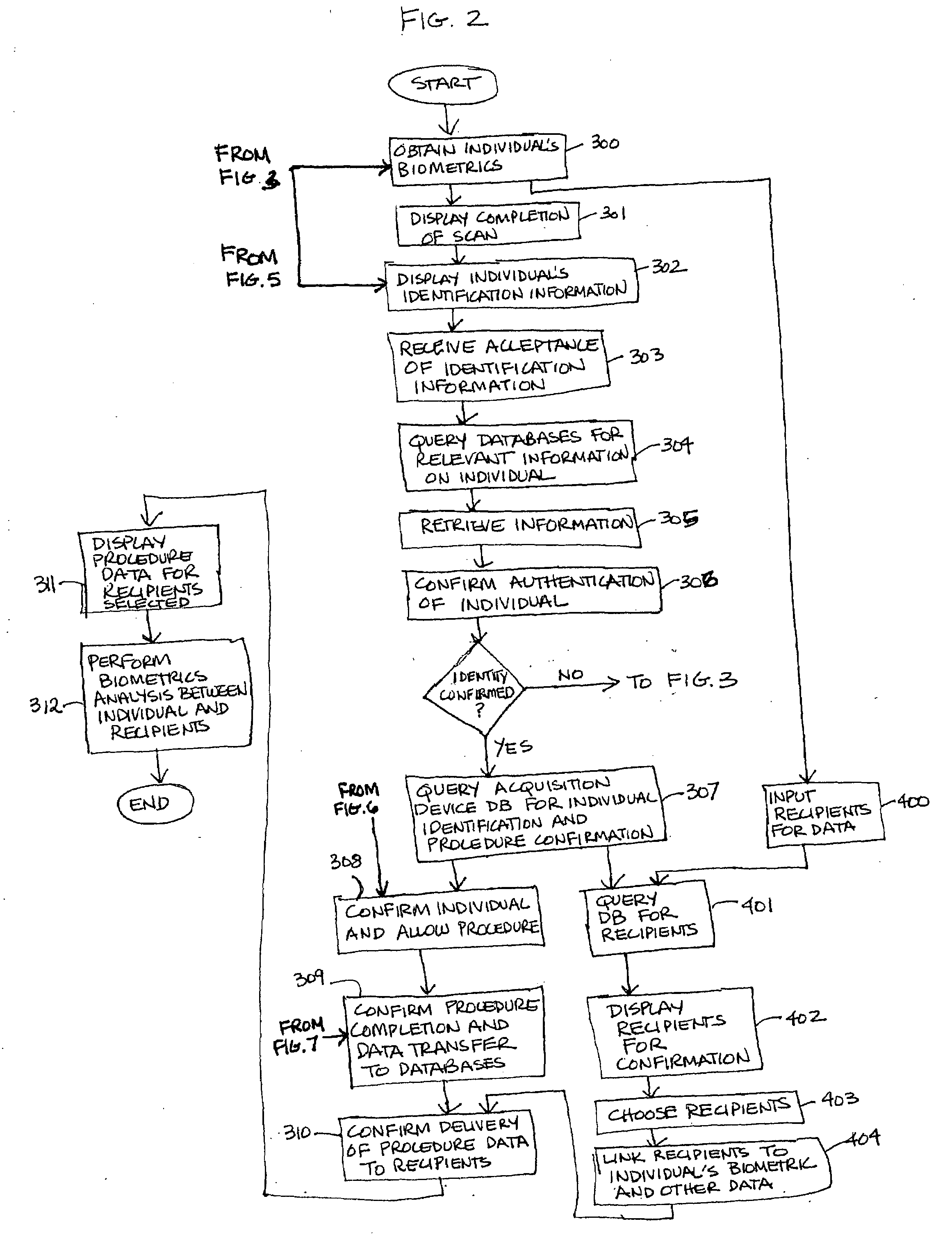
Apparatus and method for utilizing biometrics in medical applications
ActiveUS20070258626A1Avoid mistakesAvoid accessDigital data processing detailsDrug and medicationsPharmacyBiometrics
In the present invention, the user will sign onto a system, utilizing a biometrics authentication or identification procedure. Once authentication and identification takes place, local, regional, and centralized medical databases can be automatically queried using the identification-specific biometrics signature. All data intrinsic to the medical procedure or examination being performed will be automatically tagged and downloaded into that specific patient's electronic medical database. At the same time, that patient's medical database is queried to provide all historical data relevant to the medical examination or procedure being performed to assist with planning, protocol, and analysis of the data being collected. The biometrics authentication can be performed at patient intake, at an imaging device, at a pharmacy, or in the operating room, to ensure that the personnel and the patient are correctly identified before any procedure is performed or drug administered.
Owner:IMPRIVATA
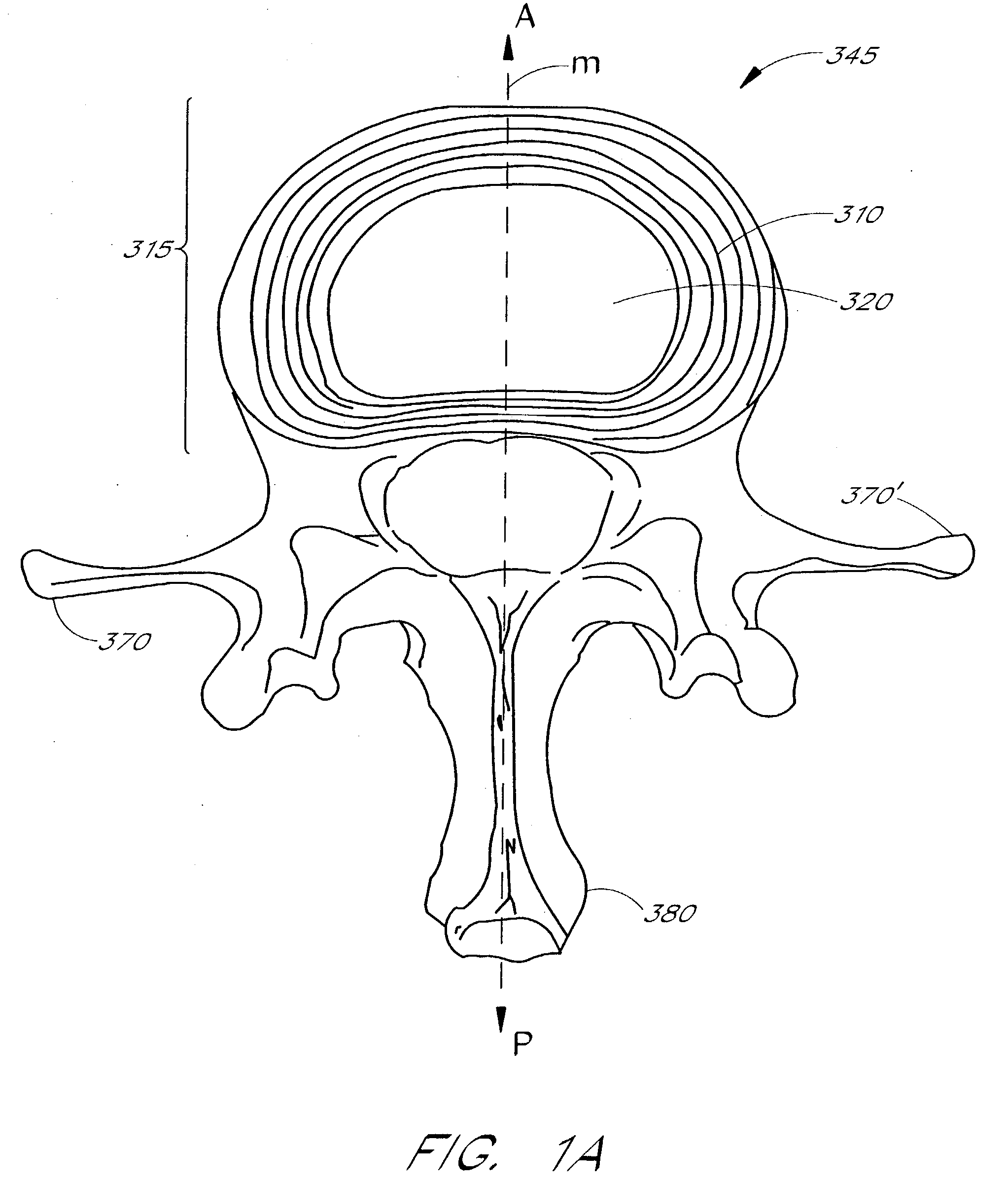
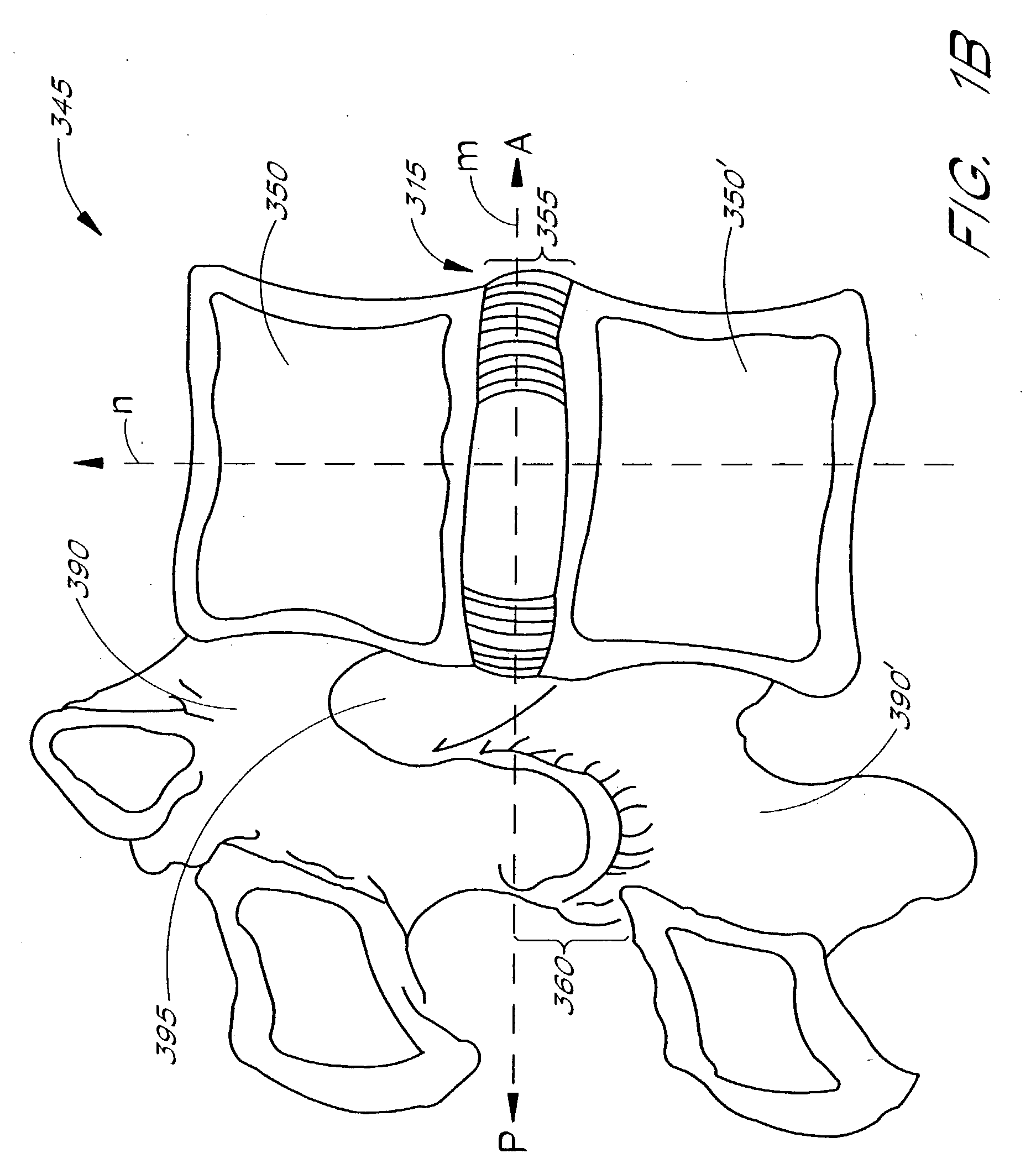
Apparatus delivery in an intervertebral disc
ActiveUS20050004578A1Convenient and reliable and accurateConvenient guidanceInternal osteosythesisCannulasDiagnostic agentIntervertebral disc
The present invention relates generally to intervertebral disc devices and methods and instrumentation for intervertebral disc procedures. Methods include performing procedures such as implant delivery, tissue manipulation, tissue diagnostics, and therapeutic and diagnostic agent delivery at selected locations within intervertebral discs.
Owner:INTRINSIC THERAPEUTICS
Enclosure for a portable hemodialysis system
ActiveUS20090114582A1Easy to useResist entry of dustSolvent extractionHaemofiltrationDialysis fluidBlood circulation
An enclosure for containing a portable hemodialysis unit includes a housing suitable to support components for performing hemodialysis including a dialyzer, one or more pumps to circulate blood through the dialyzer, a source of dialysate, and one or more pumps to circulate the dialysate through the dialyzer. The housing may have a front panel at which blood circuit connections and dialysate fluidic connections are located, e.g., blood line connections for patient blood access, connections for a reagent supply, dialyzer connections for both blood flow and dialysate, etc. The enclosure may also include a pair of vertical, side-by-side doors hingedly mounted to the housing. With the doors in the closed position, access to the patient access and dialysate fluidic connections may be blocked, and the doors may allow for the retention of heat in the housing suitable for disinfection during a disinfection cycle.
Owner:DEKA PROD LLP
Security method and apparatus for controlling the data exchange on handheld computers
InactiveUS7346778B1Avoid accessTransparent to userDigital data processing detailsUnauthorized memory use protectionData transmissionAuthorization
A method and system for protecting portable computer data from unauthorized transfer or using portable computers to download unauthorized data. The invention is applicable to any computer capable of transferring data, but in one embodiment a portable computer is described. Authorization is enabled by an interface permitting synchronization of the portable computer with a host computer by authentication of the particular portable computer identity. For instance, in one embodiment, when a portable computer is docked with a compatible interface connected to a host desktop computer, it is sensed and identified by the interface. If the particular portable computer identity is authenticated as authorized for that desktop, then synchronization will be enabled by the interface. The computers may then transfer data. However, if the identity is not an authorized one, then authentication will not occur, synchronization is correspondingly disabled, and data transfer is prevented. Various systems can enable the identity authentication.
Owner:ACCESS
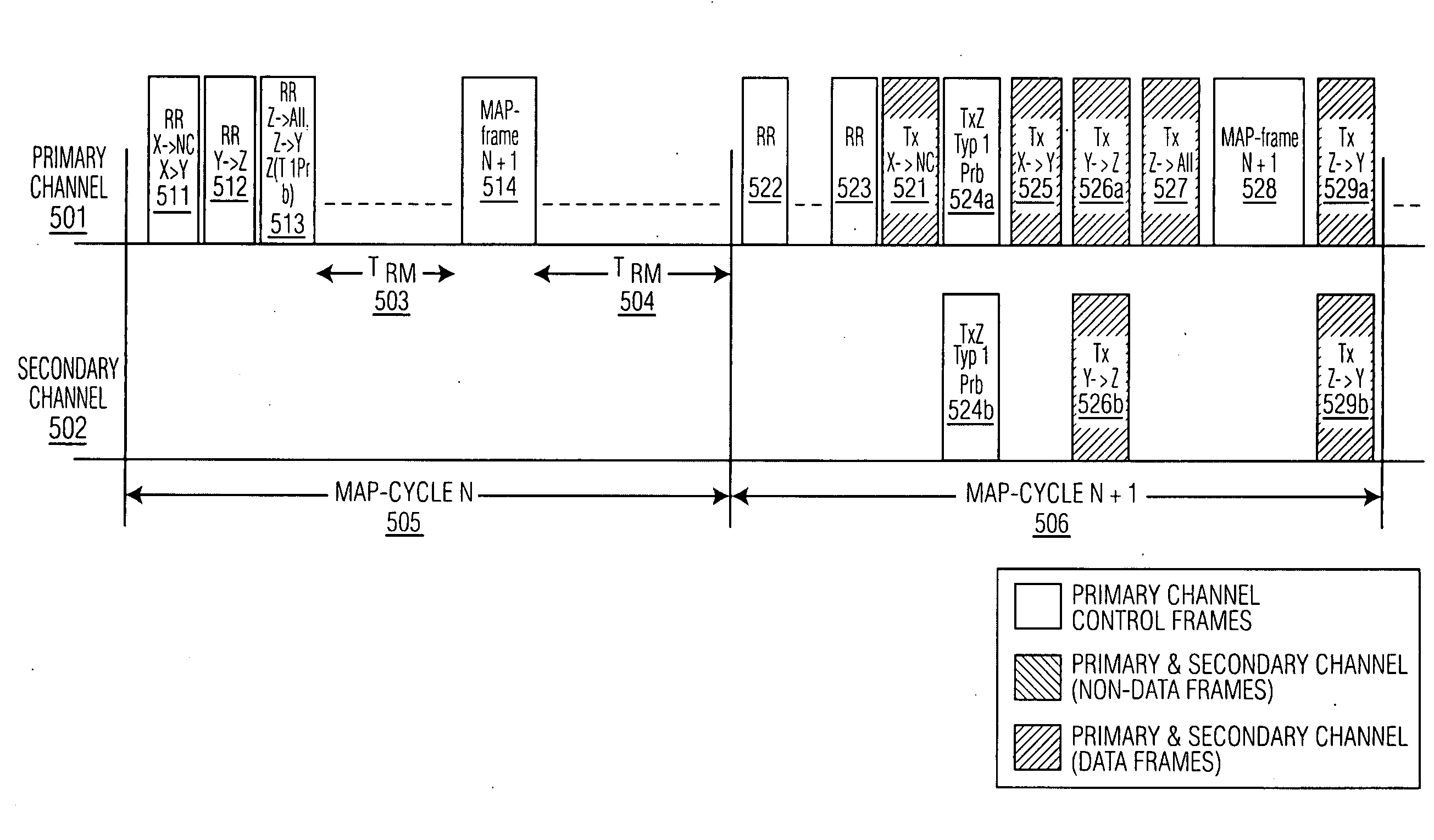
Method, system, and apparatus for extended rate/range communication over a communication network
ActiveUS20090092154A1High data rateImprove reliabilityFrequency-division multiplexRadio transmissionCoaxial cableMedia access control
A technique for communicating multimedia data between nodes over coaxial cable, wherein the nodes are connected via a coaxial cable network, is disclosed. In an embodiment, the technique involves establishing a primary channel for communicating between first and second nodes of the coaxial cable network, establishing a secondary channel for communicating between the first and second nodes of the coaxial cable network, wherein the primary and secondary channels are in different frequency bands and wherein the primary channel is used for communicating media access control frames, and communicating a time series of data frames between the first and second nodes using both the primary channel and the secondary channel.
Owner:ENTROPIC COMM INC
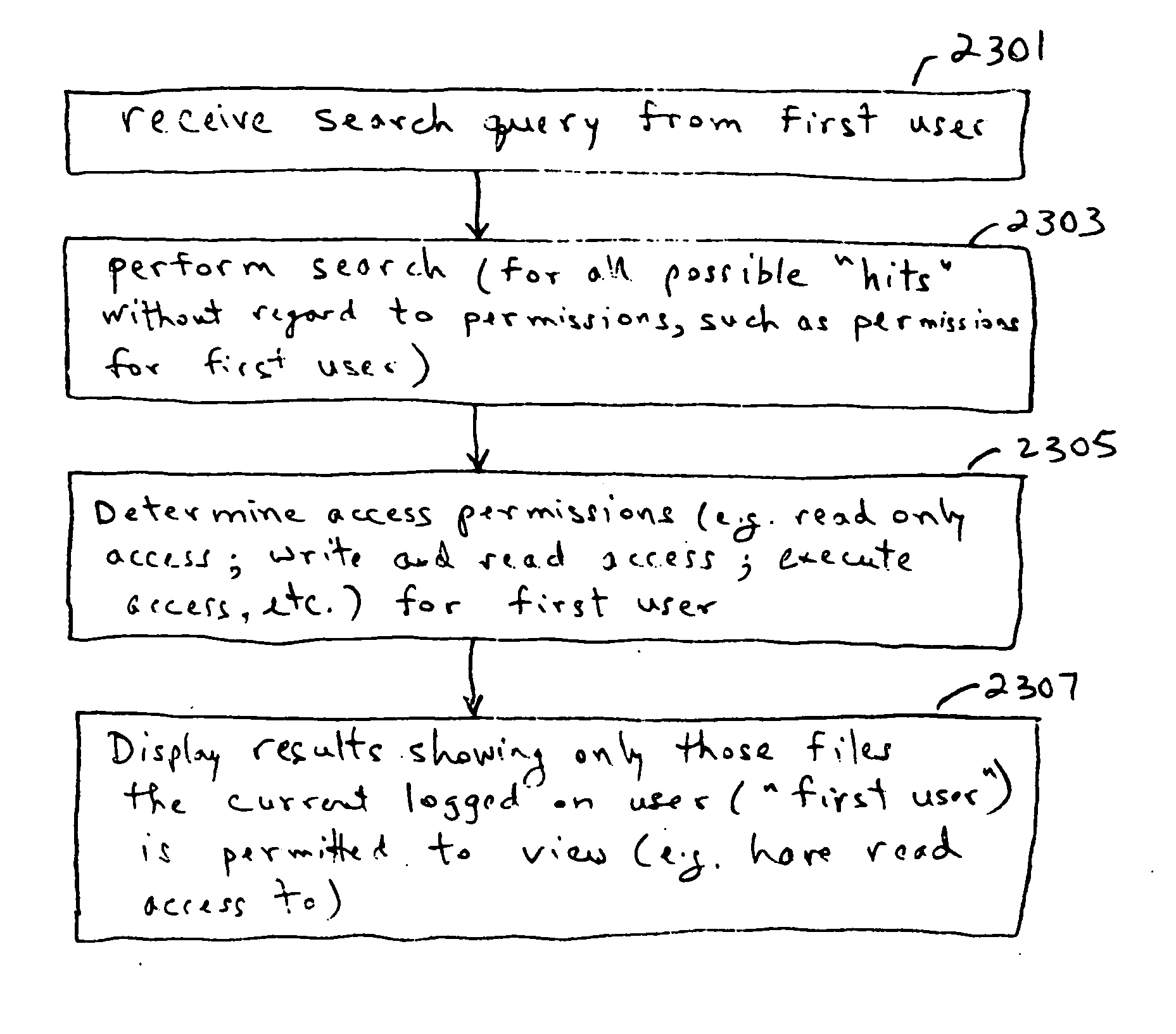
Methods and systems for managing permissions data and/or indexes
ActiveUS20070033191A1Data augmentationSpeed up searchDigital data processing detailsFile access structuresIndex systemDatabase
Systems and methods for indexing and searching data, such as file contents and / or metadata. In one exemplary method, an index corresponding to files on a storage device is created. Index is partitioned into subindexes according to certain criteria, such as the location of files or exclusivity of access to files. Subindex contains the entire content of files or metadata describing files, in addition to identifiers leading back to files' physical storage. Index is maintained by moving files' index entries from one subindex to another as files change in relation to the partition criteria, such as changing location. Searching some subindexes, like one corresponding to files in a shared folder, is done with permission checking. Searches of certain other subindexes, like one corresponding to the home folder of the user searching, are done without permission checking the underlying files resulting in a performance improvement.
Owner:APPLE INC
System for monitoring the unauthorized use of a device
ActiveUS20090247122A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
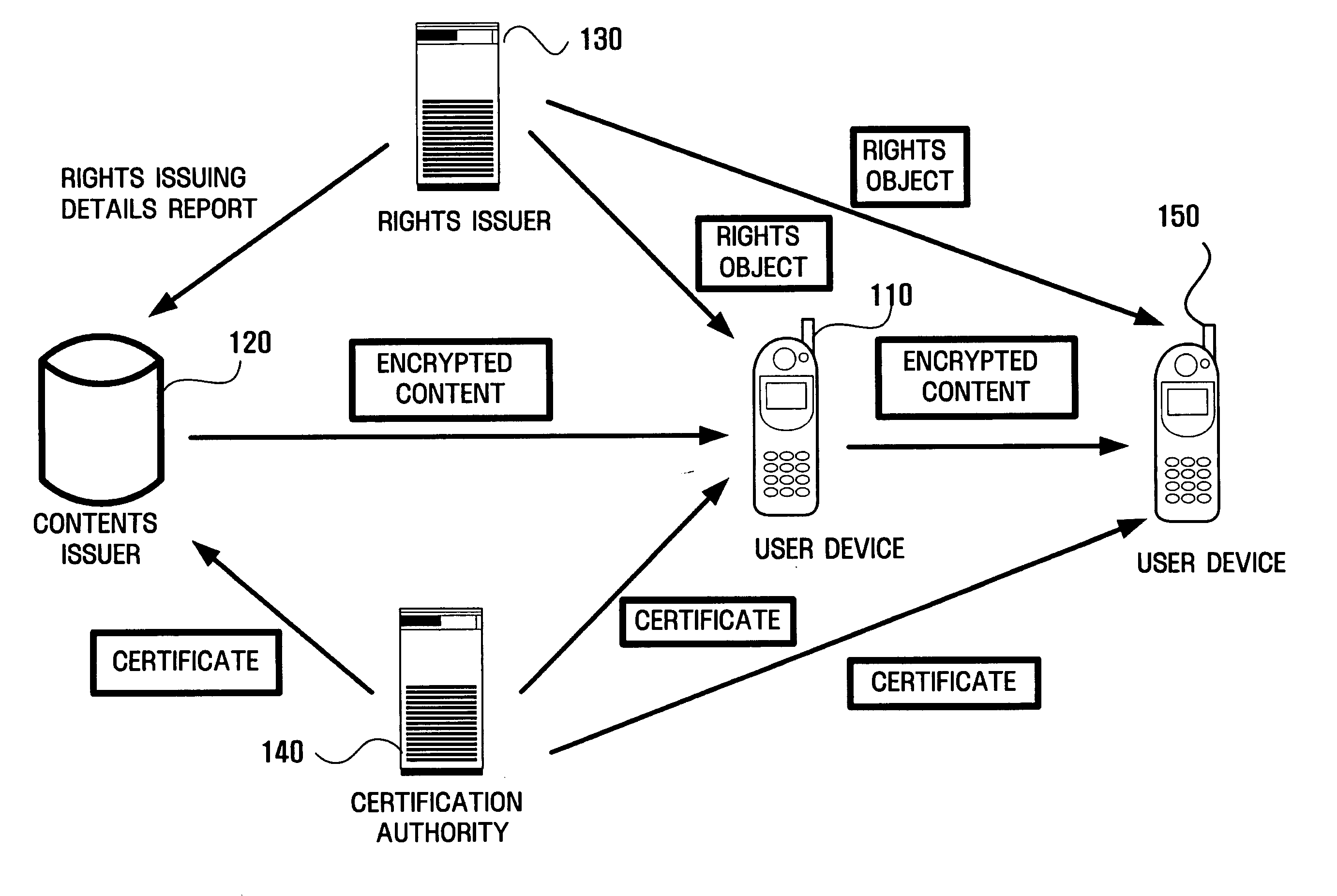
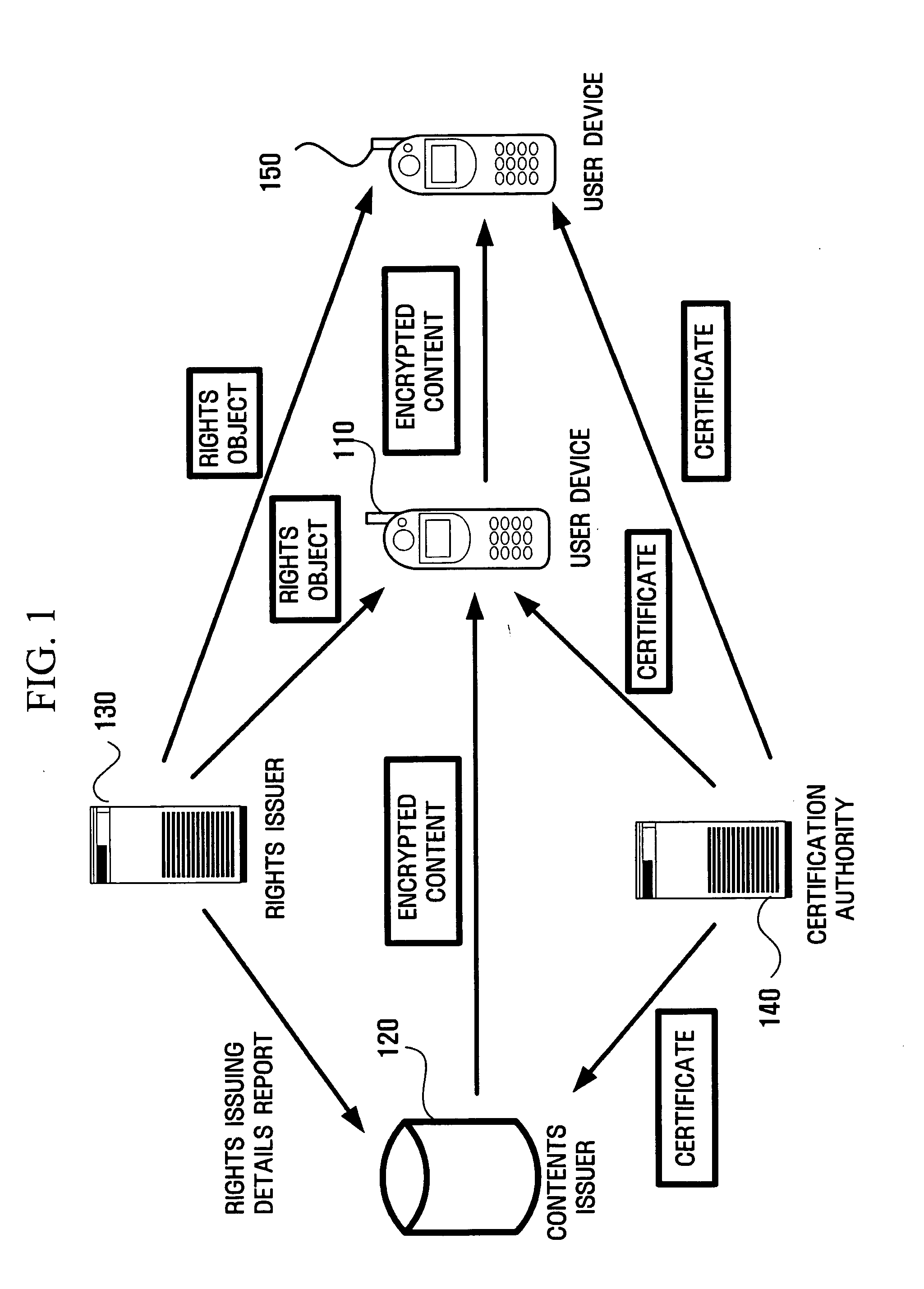
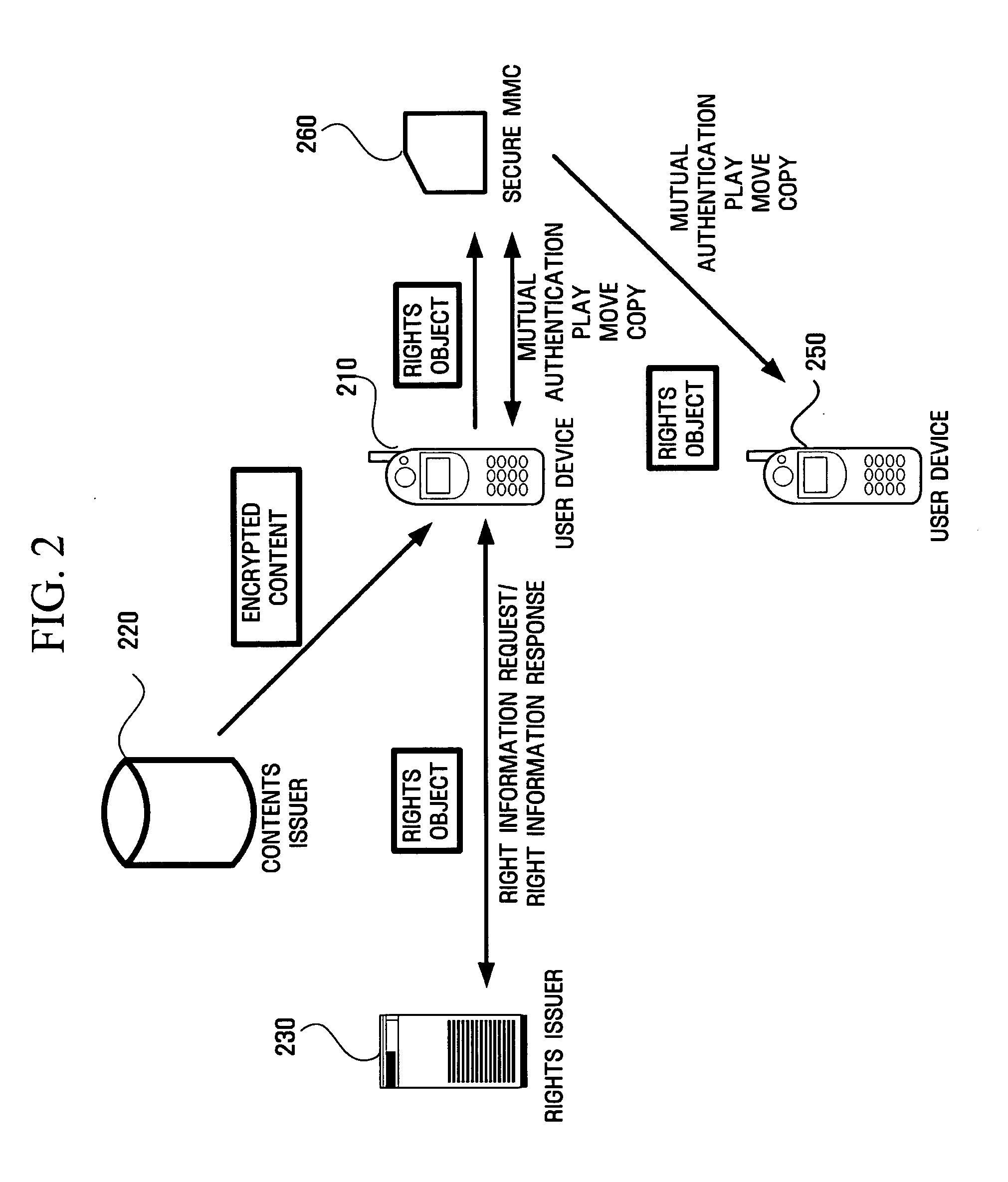
Apparatus and method for moving and copying rights objects between device and portable storage device
InactiveUS20050210249A1Efficient of digital contentEfficient managementKey distribution for secure communicationDigital data processing detailsComputer hardwareDigital content
A method and apparatus for copying or moving a rights object having right information regarding digital contents between a device and a portable storage device to copy or move the digital contents there between are provided. According to the method and apparatus, the digital works can be prevented from being recklessly and randomly copied and moved, and therefore, copyright can be protected. In addition, data loss or unauthorized access can be prevented.
Owner:SAMSUNG ELECTRONICS CO LTD
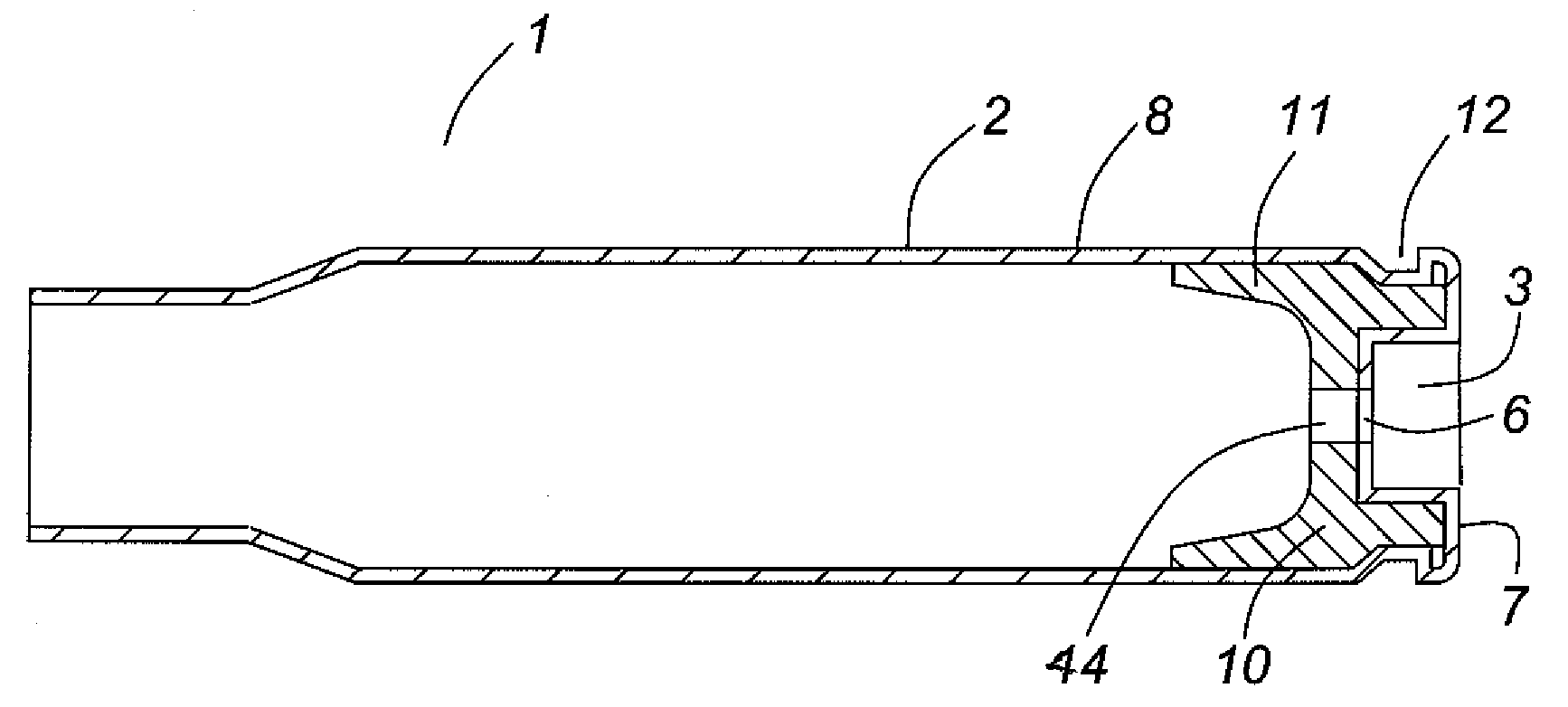
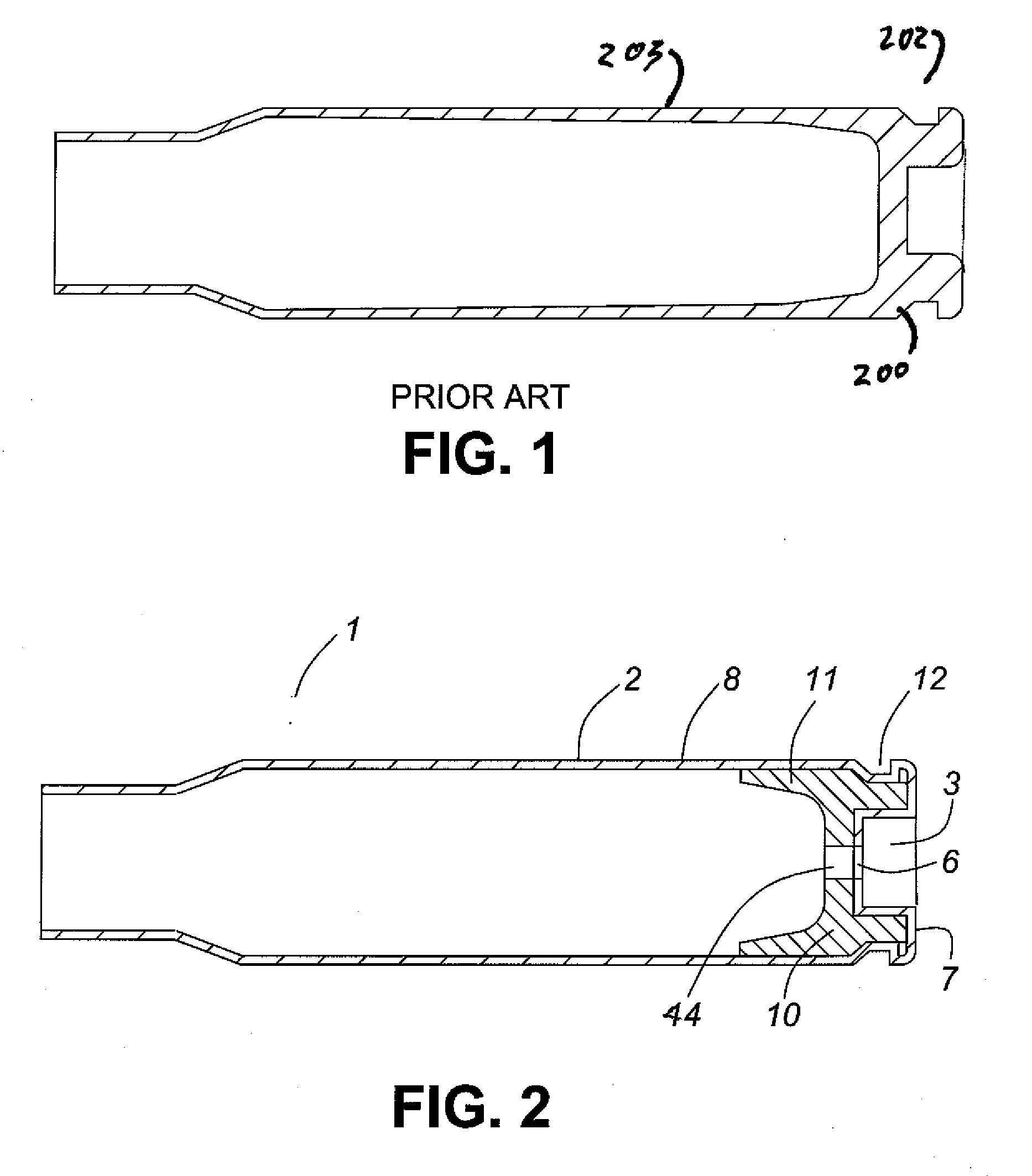
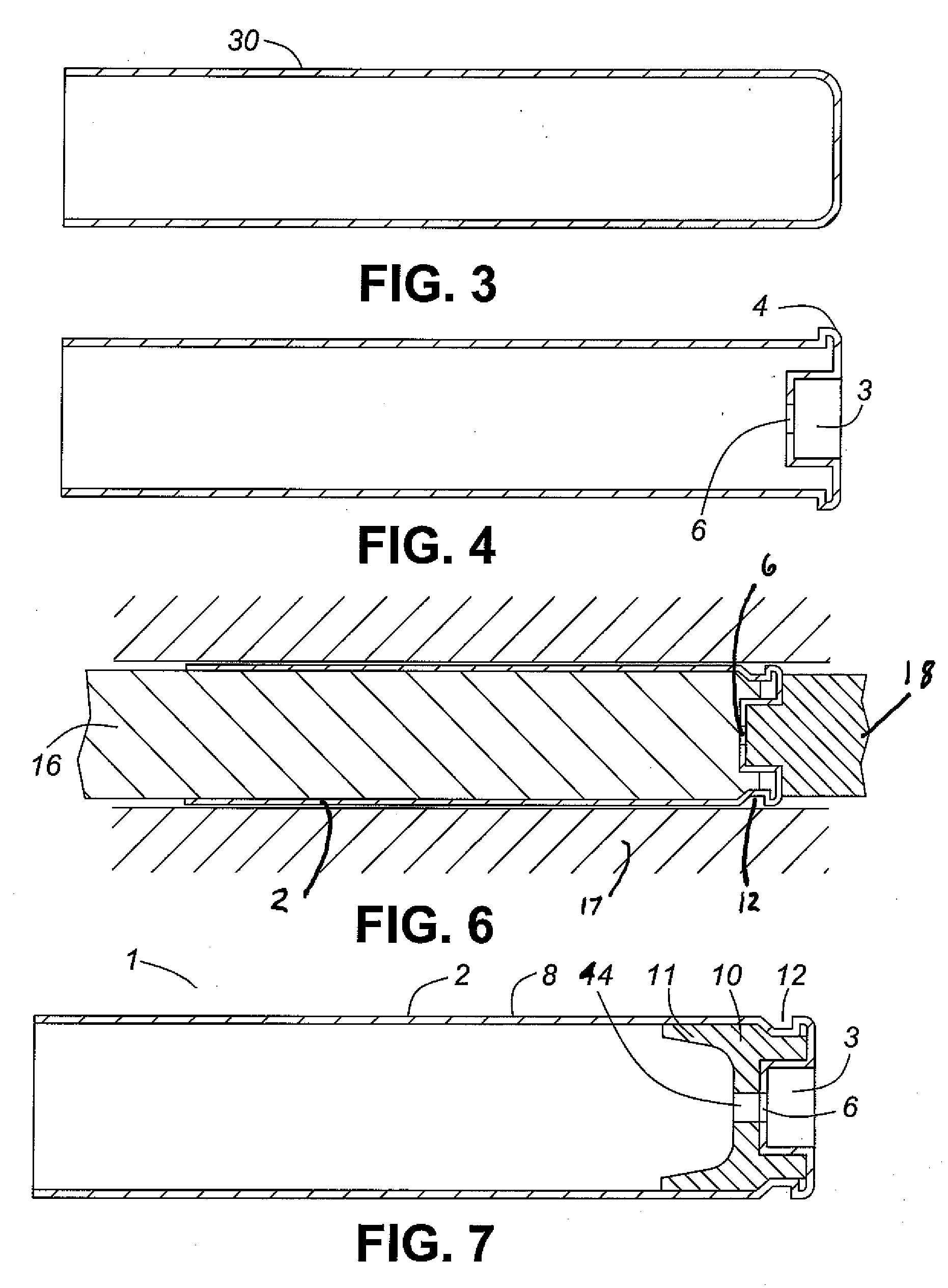
Thin walled, two component cartridge casing
A cartridge or ammunition casing is made of two components, one forming the outer casing sleeve and head end and the other comprising a plug seated within the head end to protect the outer casing material from propellant gases. The outer cylindrical sidewall and end panel of the casing may be made of a material selected from the group consisting of stainless steel, steel, pre-coated carbon steel, brass or brass-type alloys, aluminum, hardened aluminum alloys, and suitable polymeric plastic material such as nylon derivatives and VECTRA™. The inner plug may be made of a material selected from the group consisting of aluminum, brass, steel, stainless steel, and suitable polymeric materials.
Owner:TECH CORPORATION CO LTD
Air trap for a medical infusion device
InactiveUS20090107335A1Easy to useOptimize locationLiquid degasificationDialysis systemsEngineeringVertical axis
An air trap for a blood circuit and method for removing air from blood in a dialysis unit. The air trap may include a blood inlet supply line, a blood outlet supply line, and a container having an approximately spherical internal wall, an inlet at a top end of the container connected to the blood inlet supply line, and an outlet at a bottom end of the container connected to the blood outlet supply line. The inlet may be offset from a vertical axis of the approximately spherical internal wall such that blood entering the container is directed to flow in a spiral-like path. The inlet port may be arranged to introduce blood into the container in a direction that is approximately tangential to the approximately spherical inner wall of the container and / or in a direction that is approximately perpendicular to the vertical axis of the container.
Owner:DEKA PROD LLP
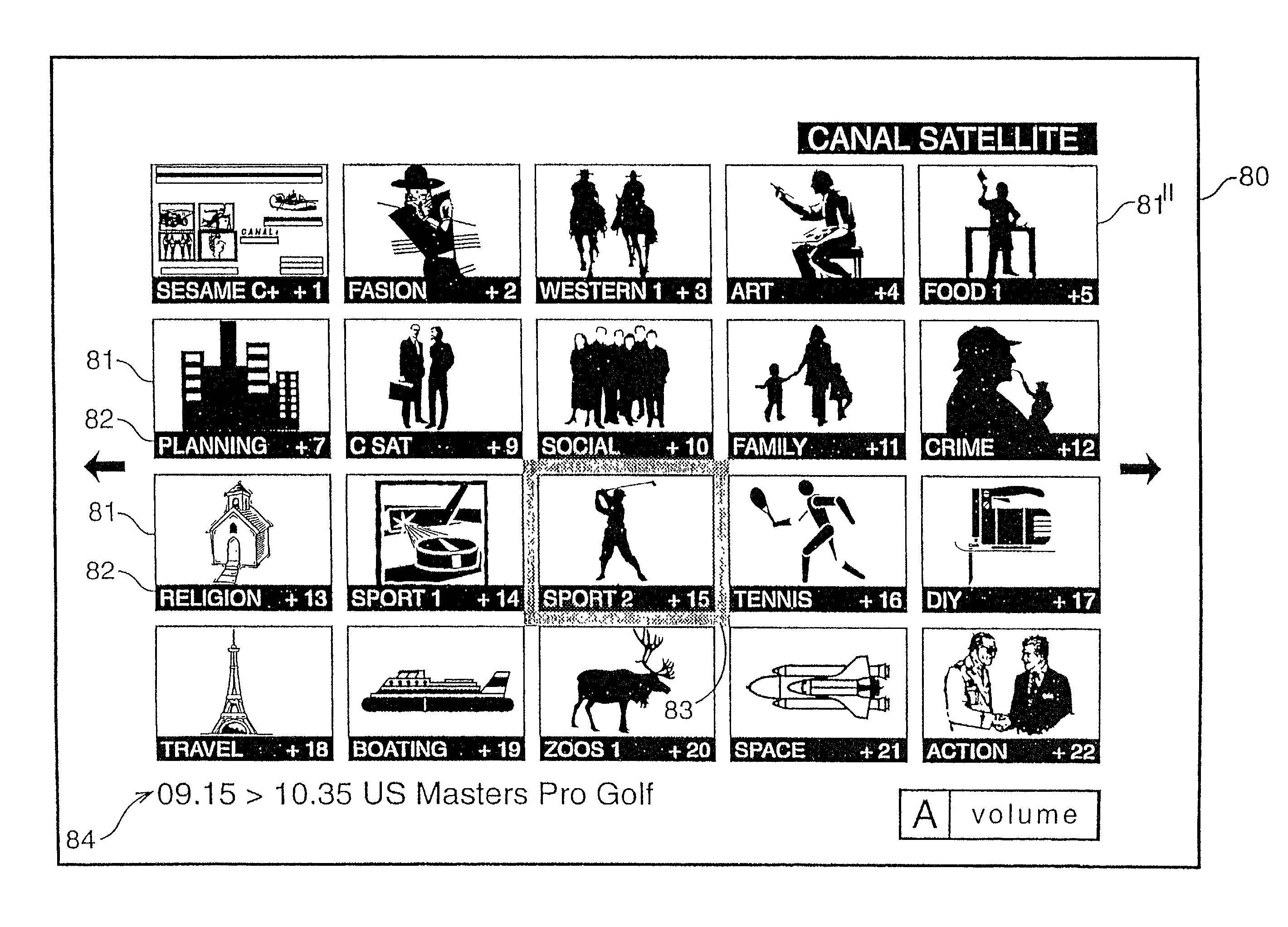
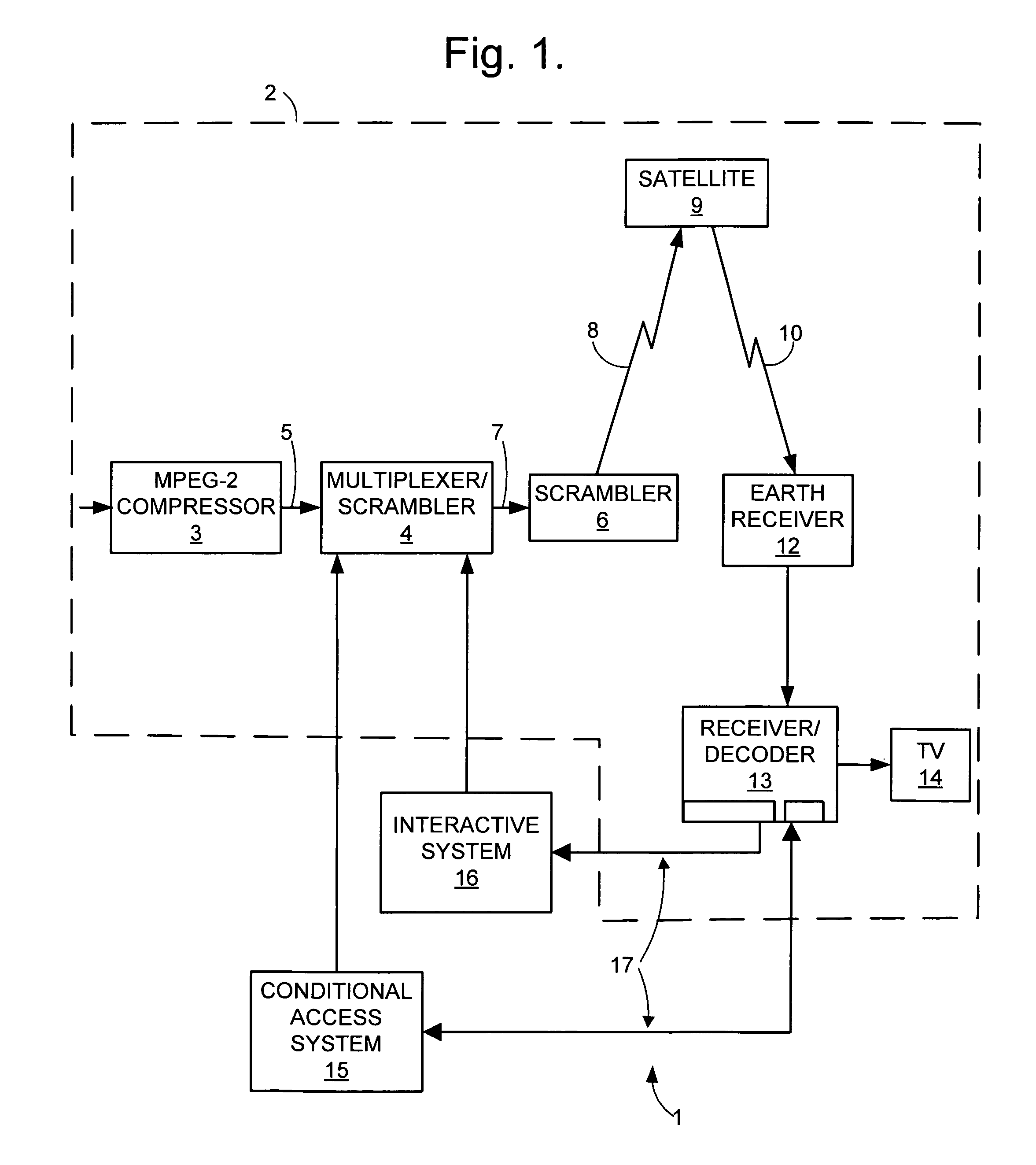
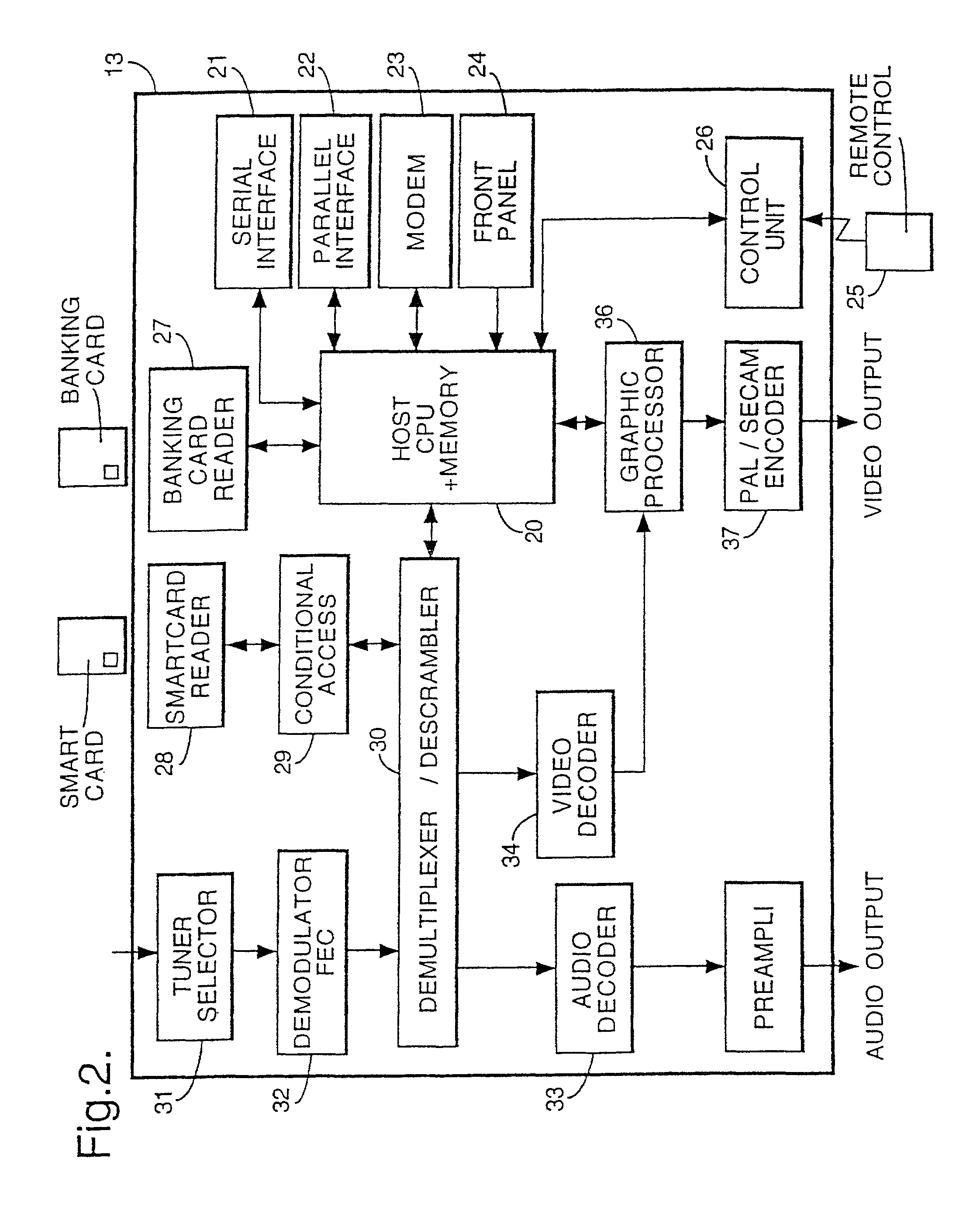
Navigation system for a multichannel digital television system
InactiveUS7757252B1Prevent videoPrevent audio accessTelevision system detailsAnalogue secracy/subscription systemsTelecommunicationsNavigation system
The present invention provides a digital television system where access rights to a programme or channel are received analyzed by the decoder in determining whether to permit or prohibit full audio and visual access by the user to that programme or channel when displayed in respective windows of a mosaic formation.
Owner:INTERDIGITAL CE PATENT HLDG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com