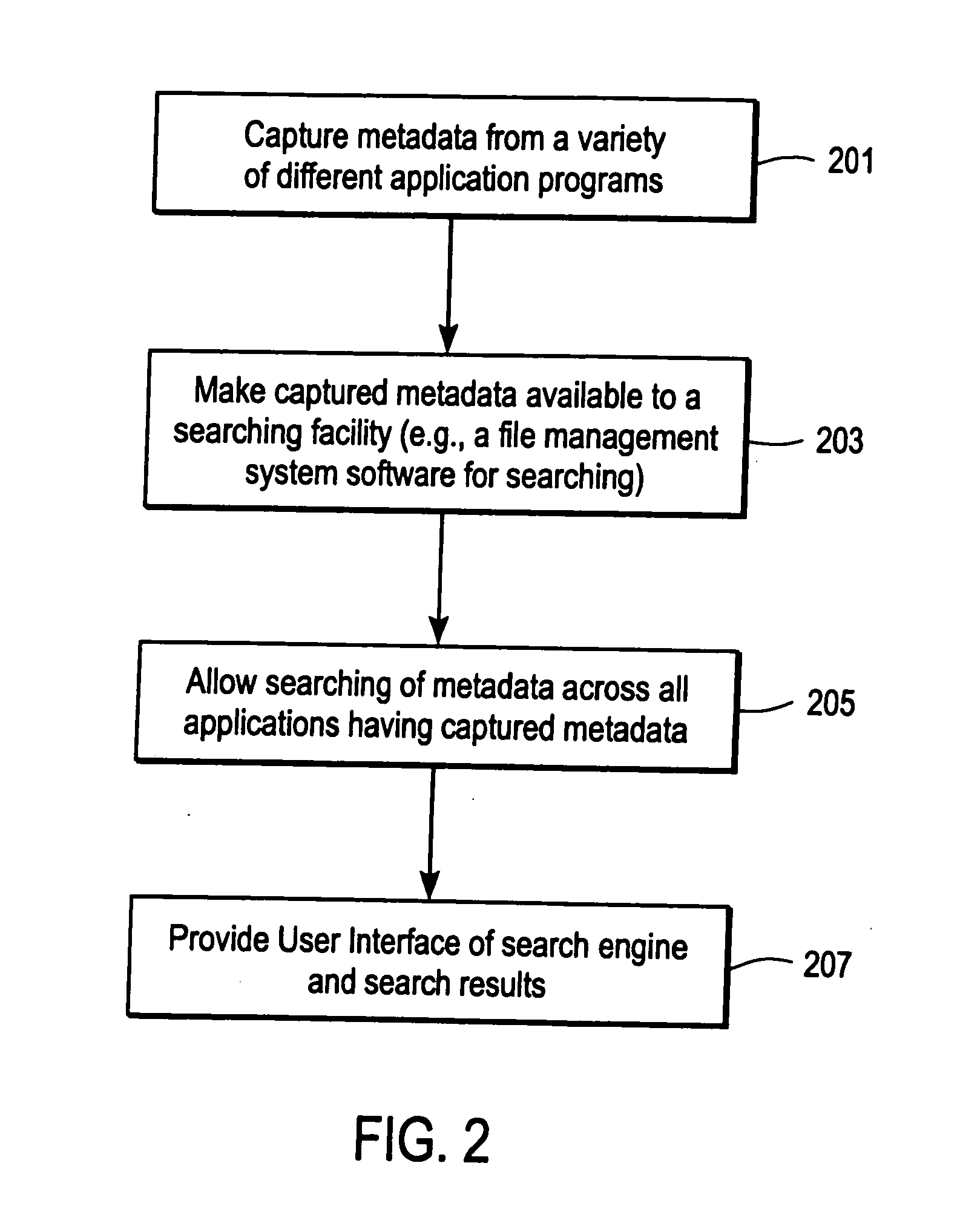
Patents
Literature
5414results about "File access structures" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
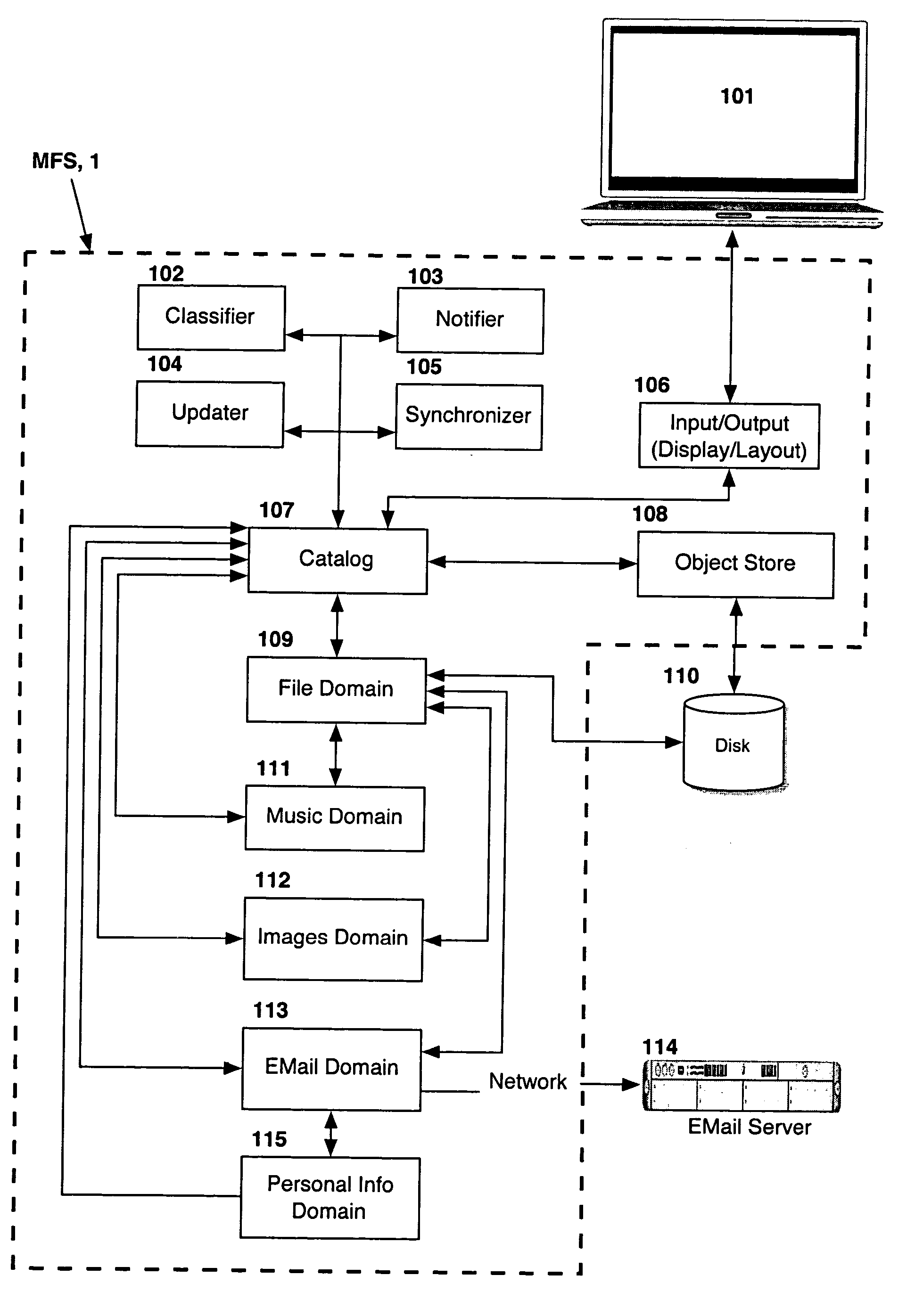
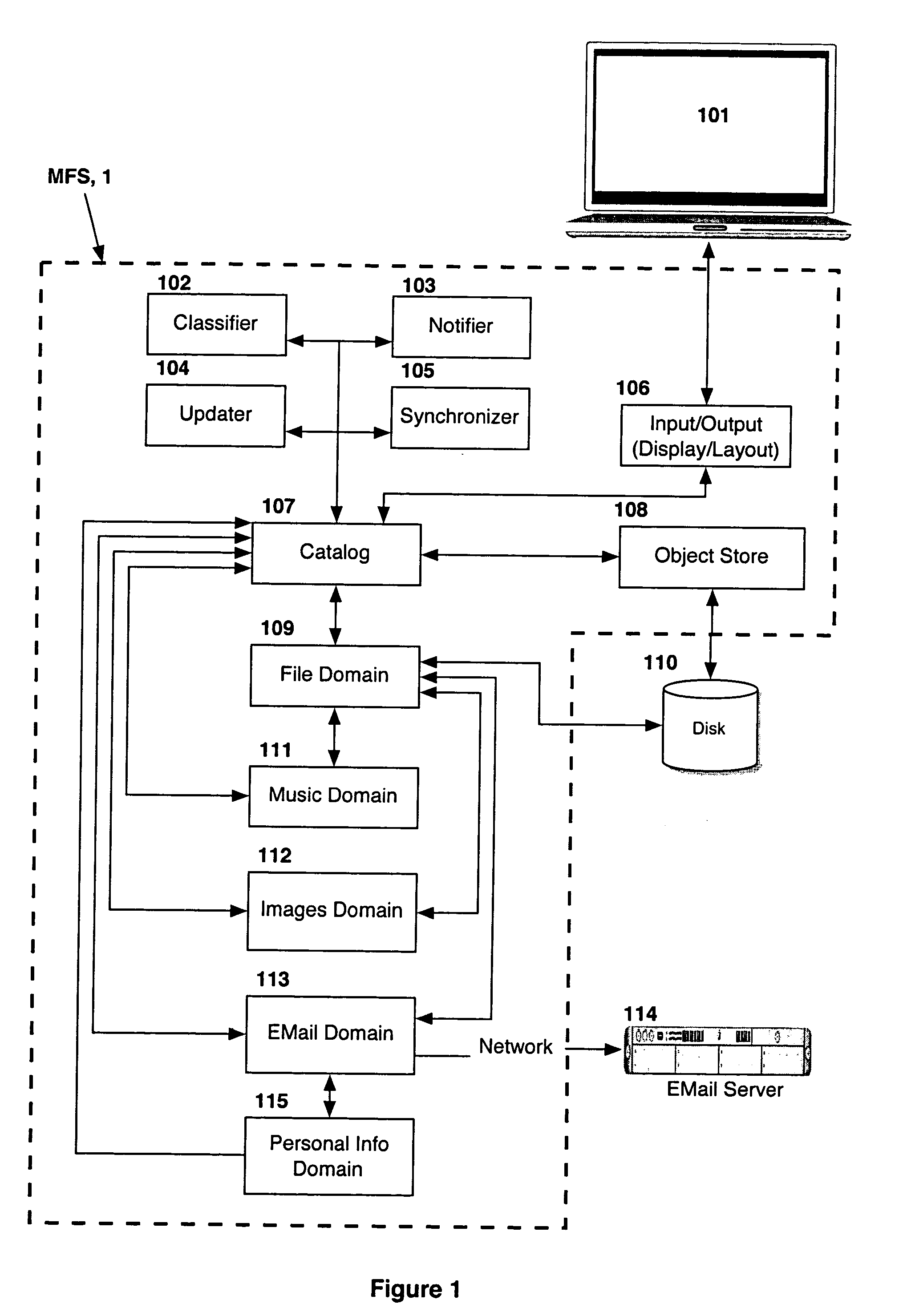
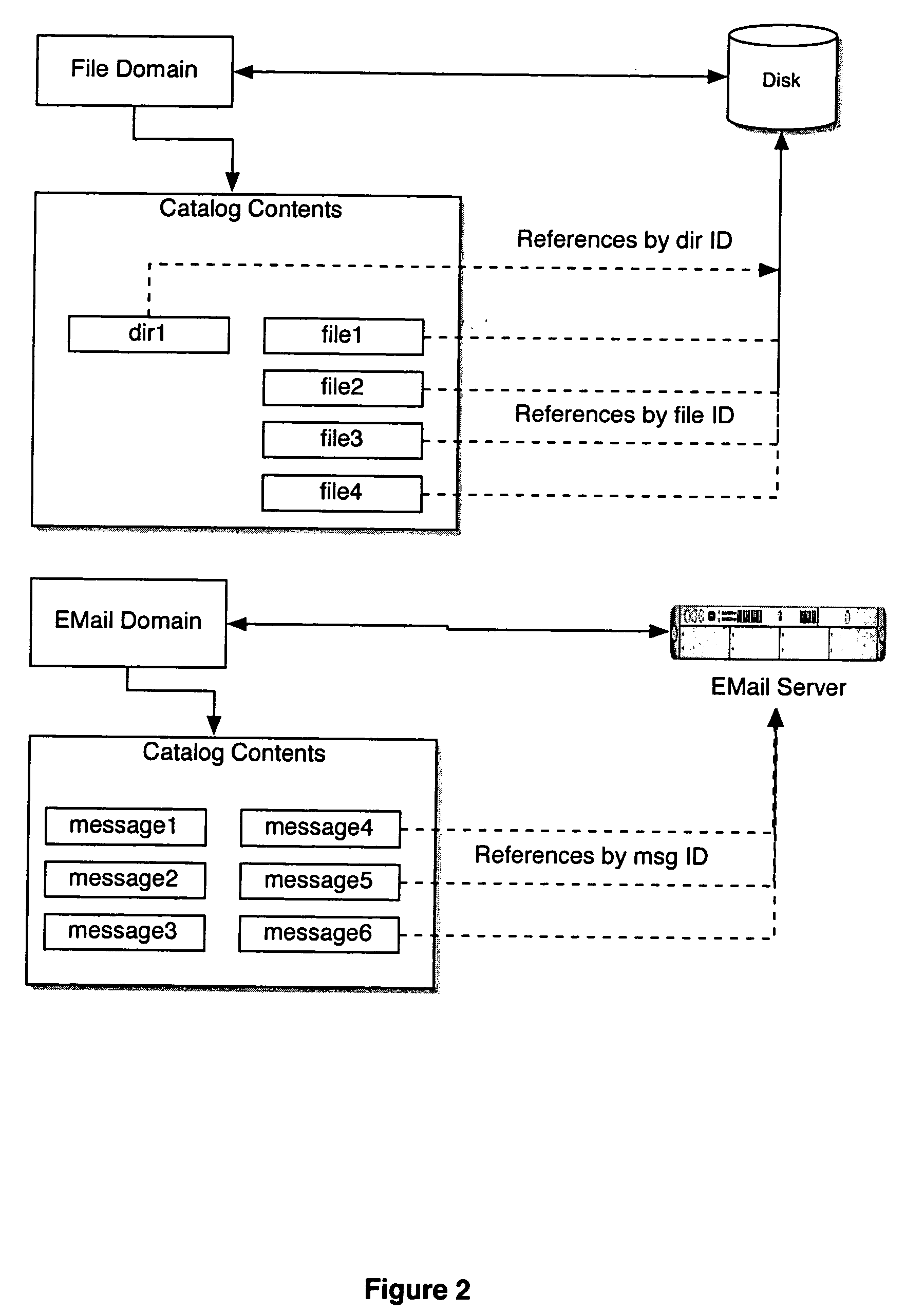
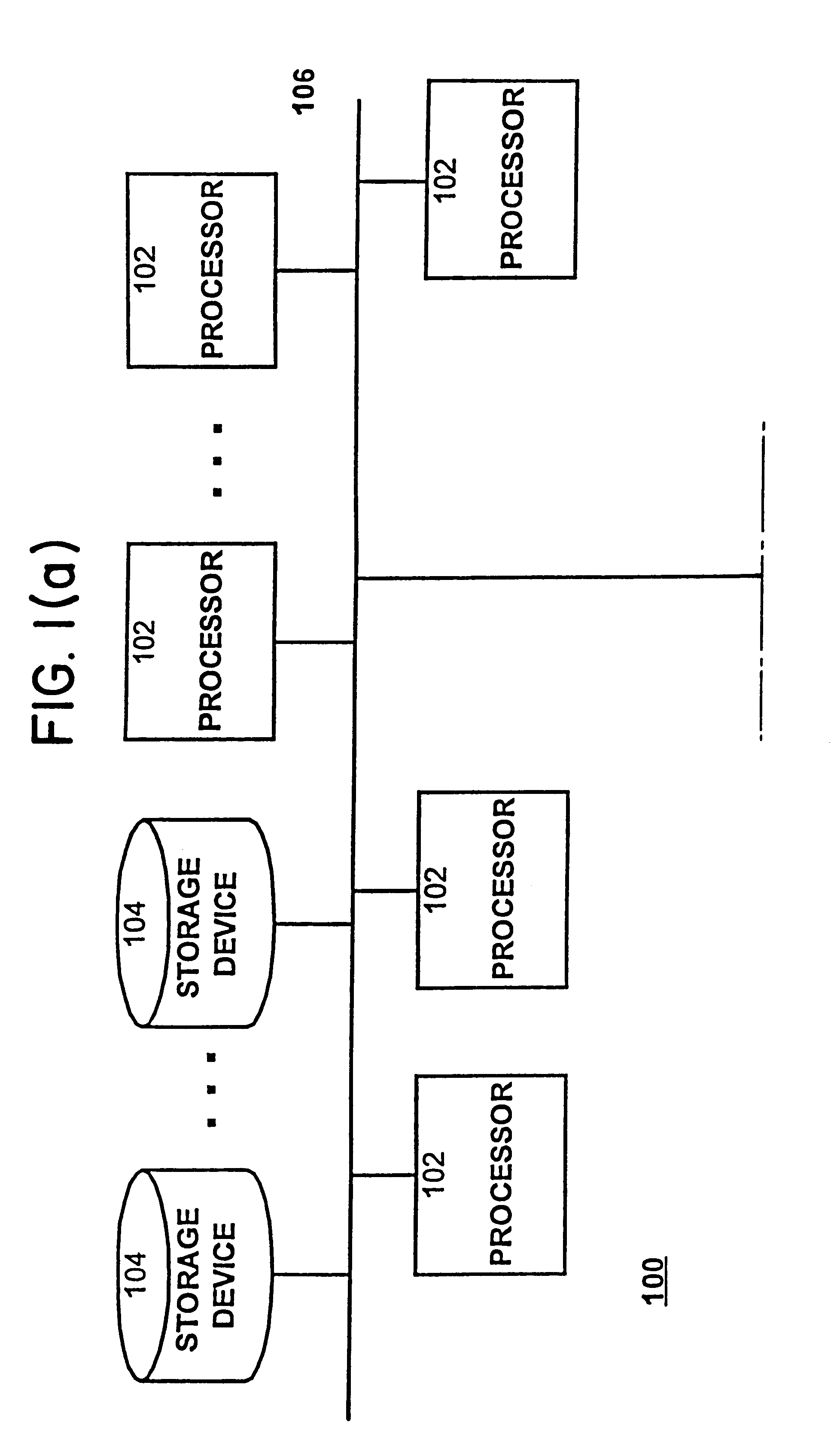
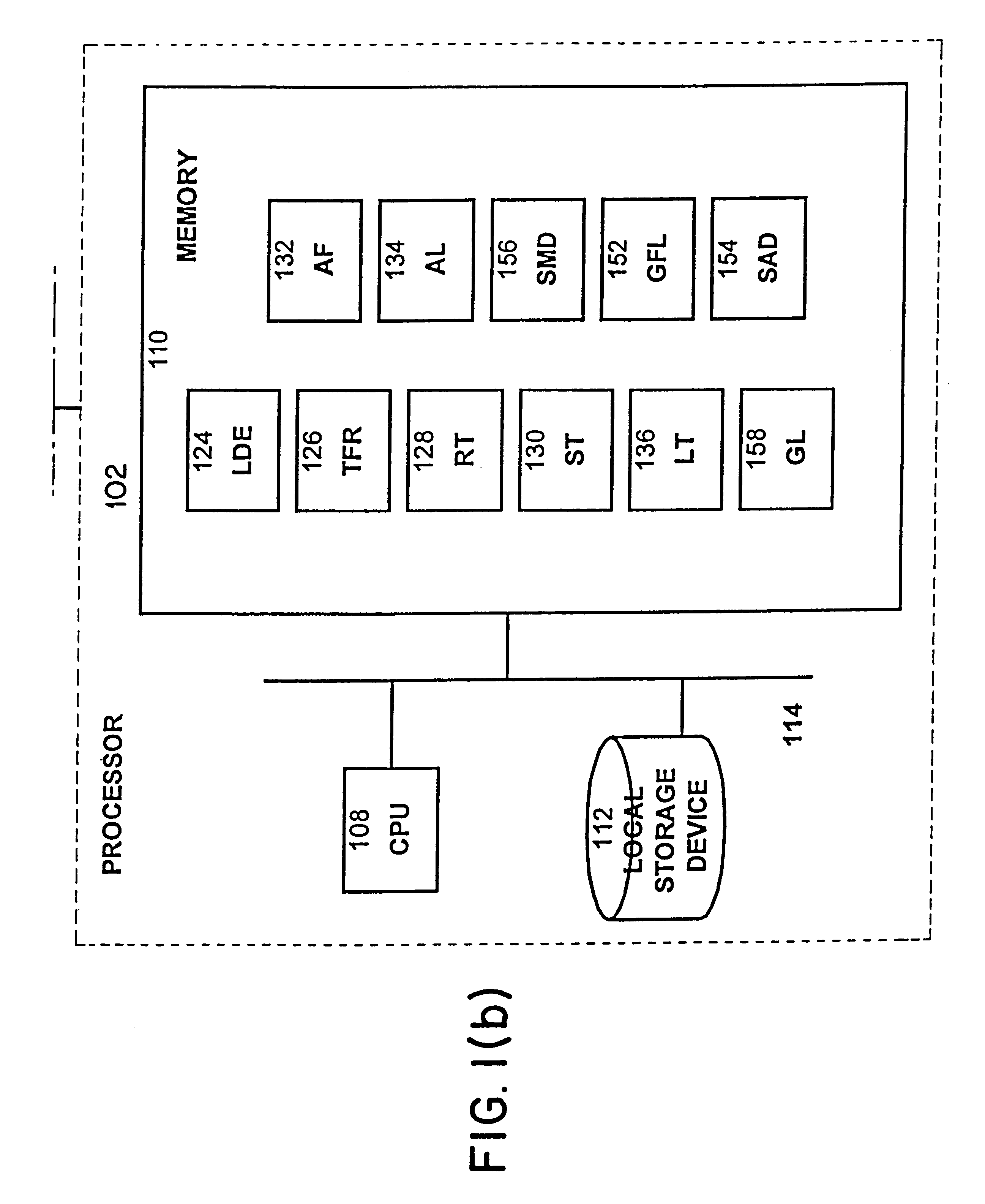
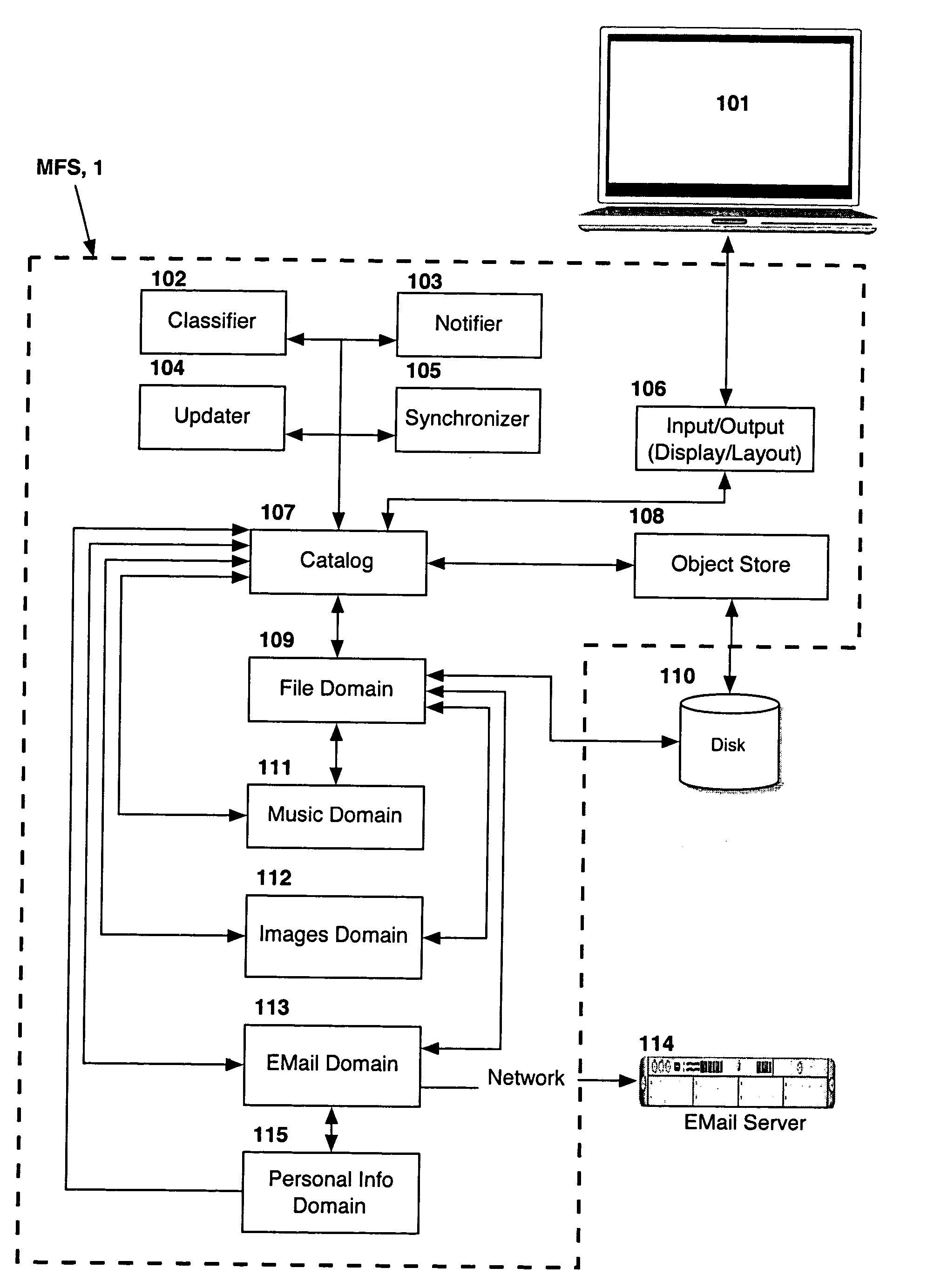
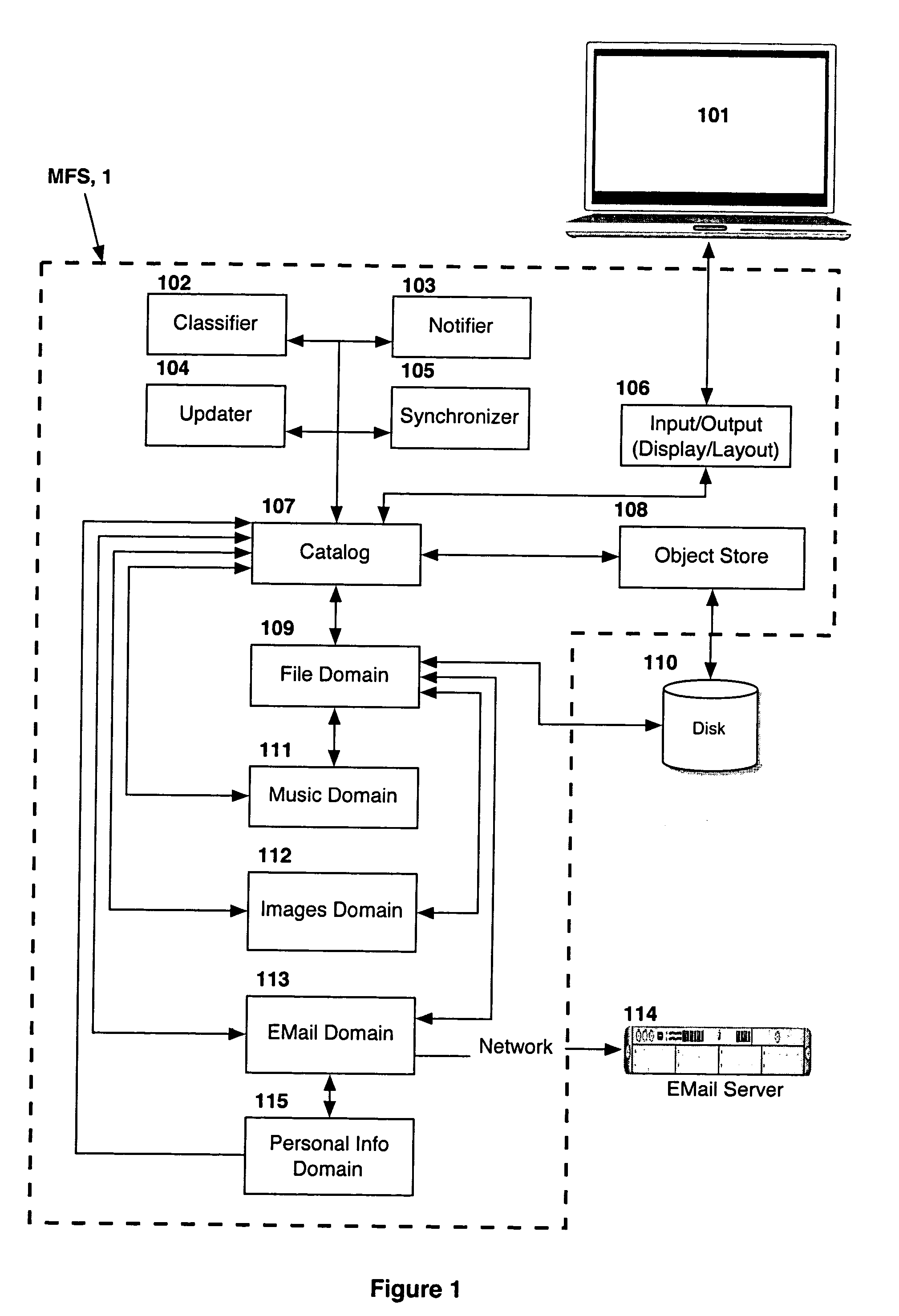
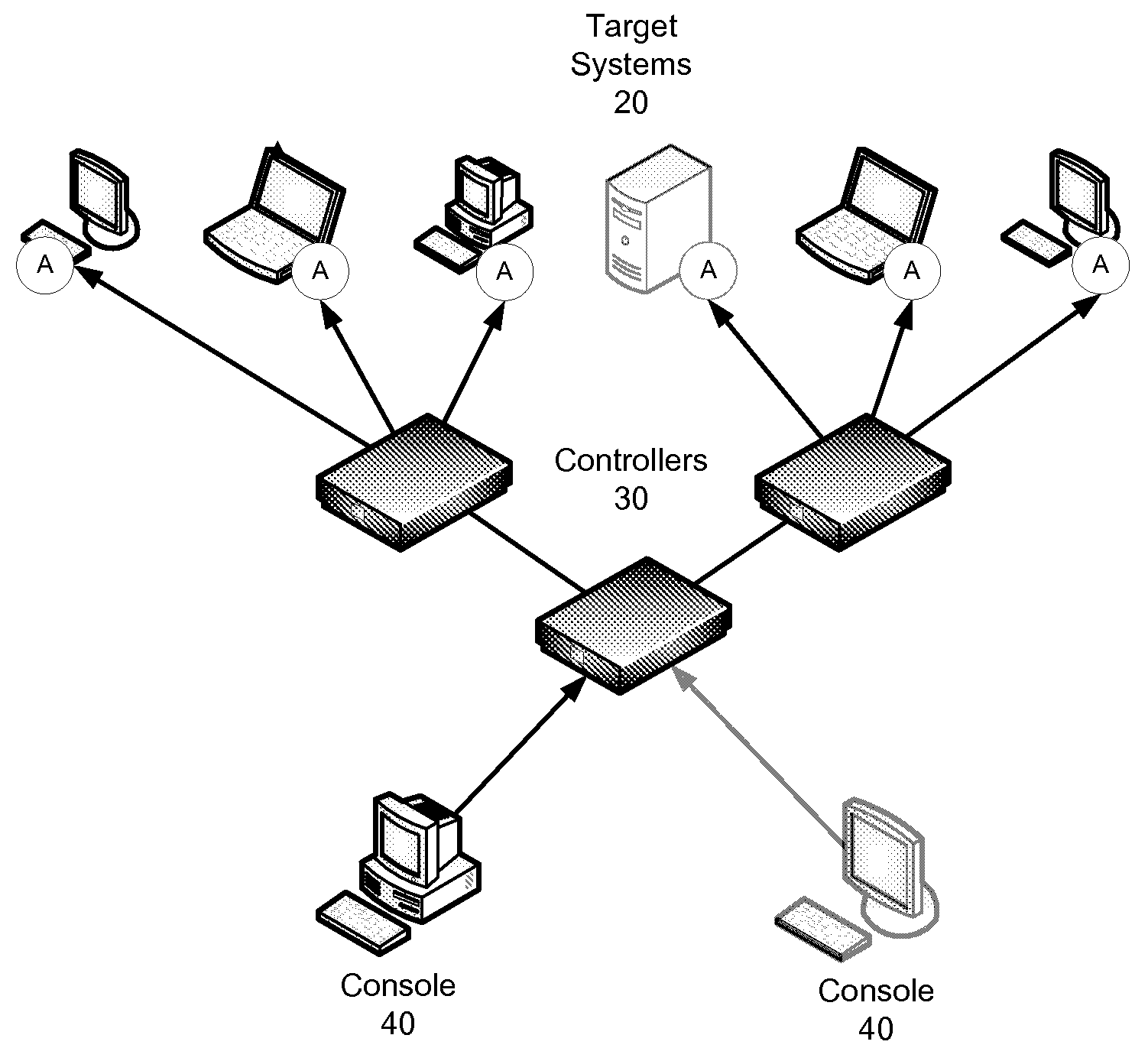
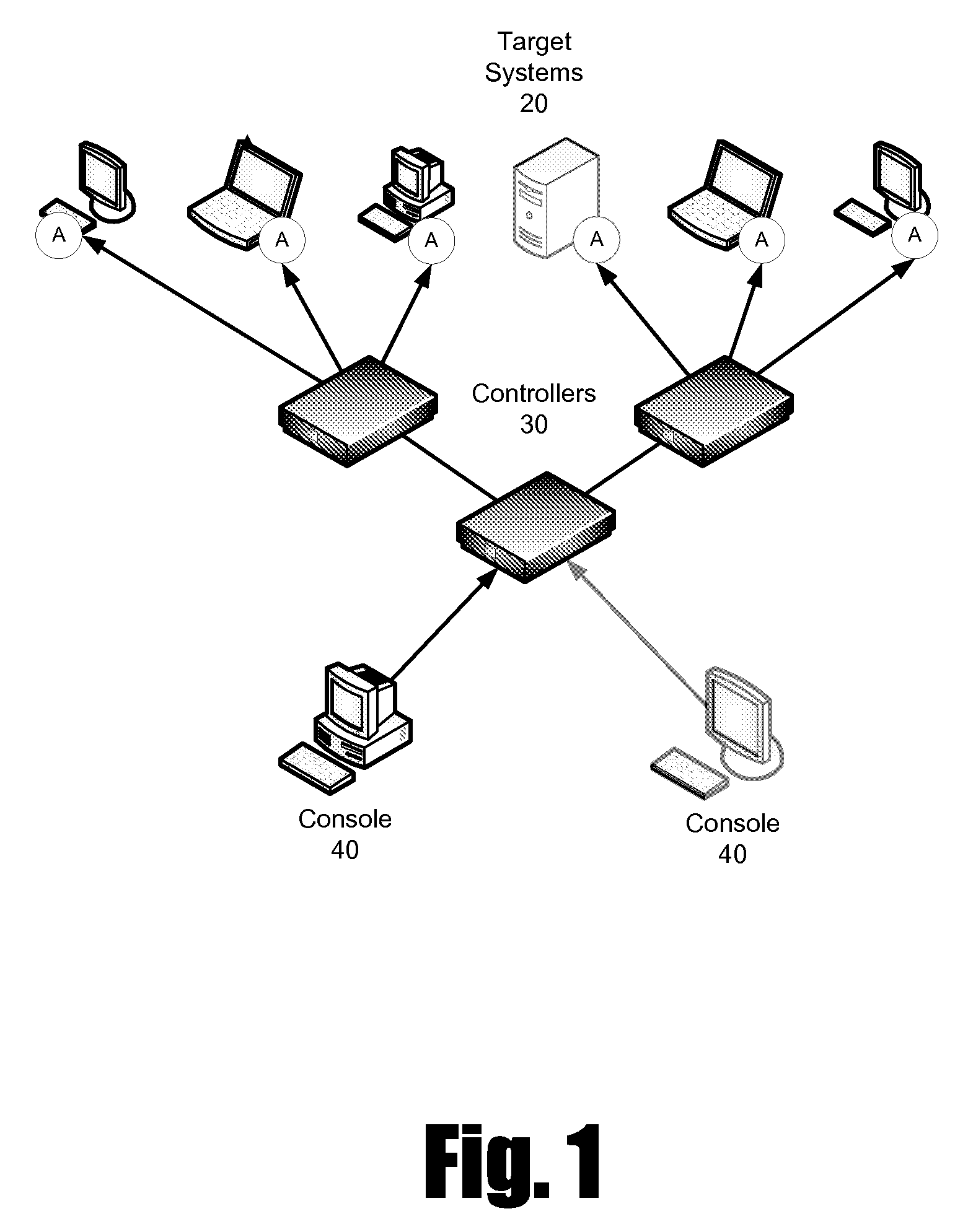
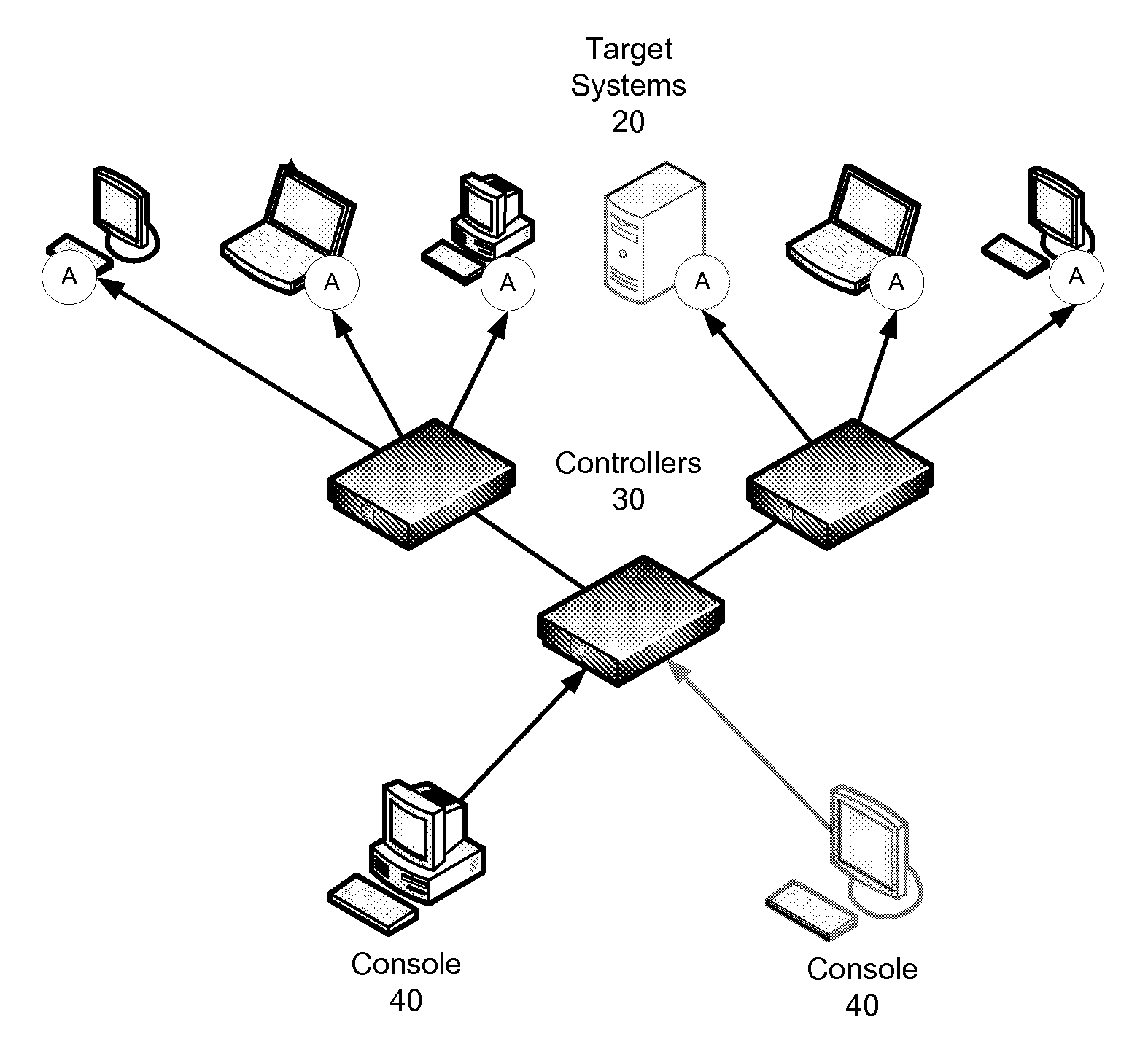
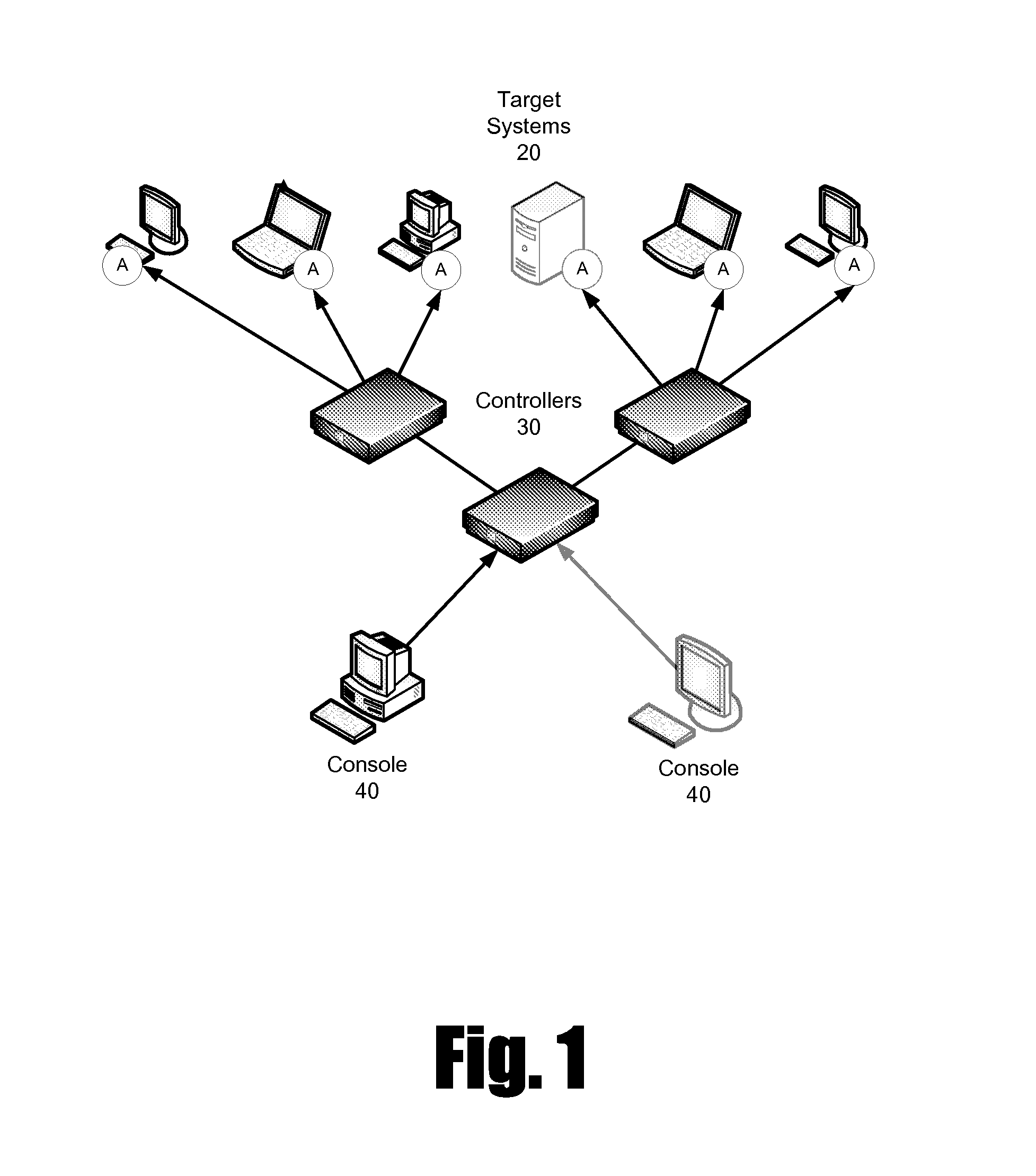
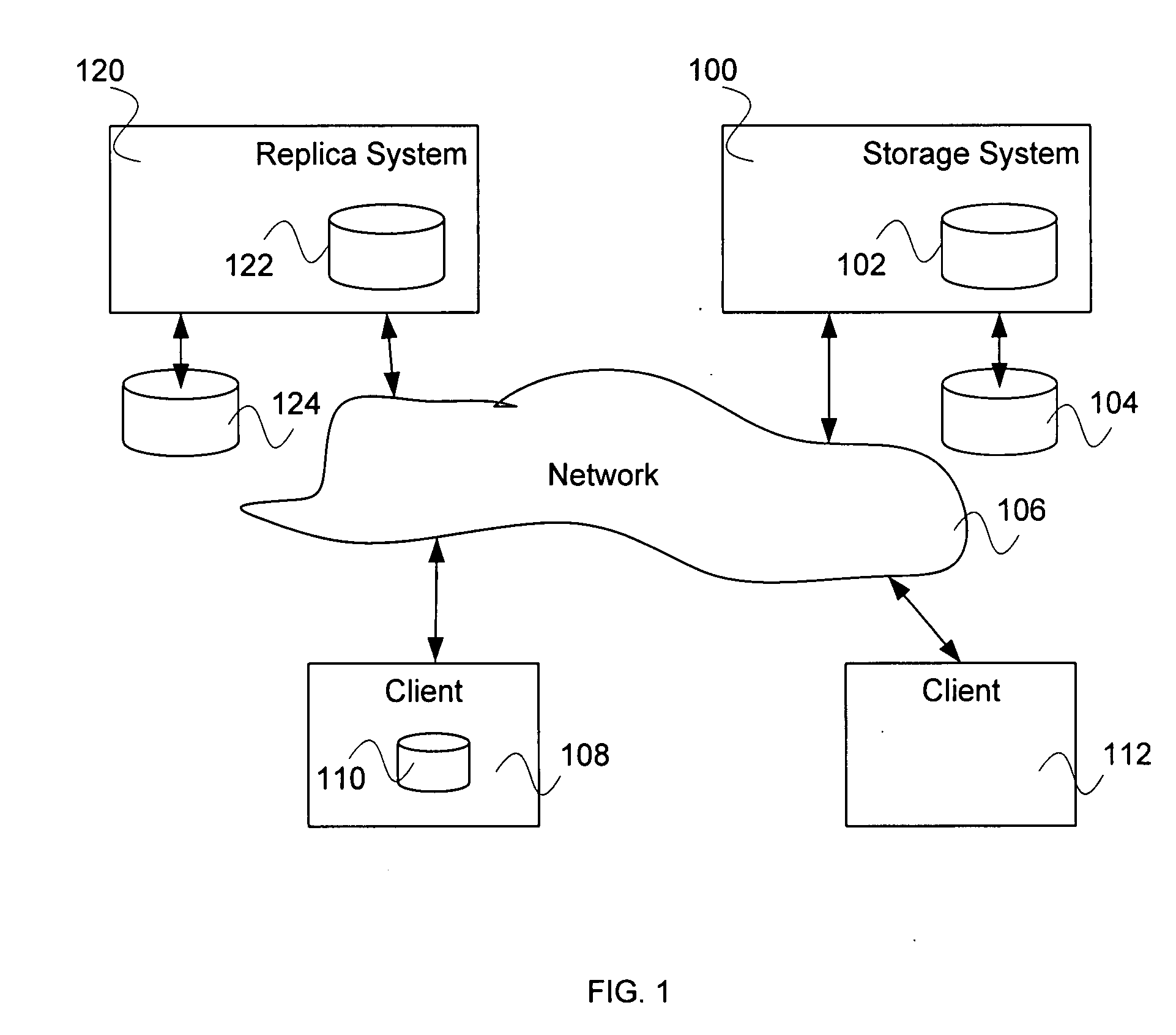
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS20040177319A1Efficient storageMultimedia data indexingFile access structuresComputer data processingData processing
A computer data processing system including a central processing unit configured with a novel integrated computer control software system for the management of data objects including dynamic and automatic organization, linking, finding, cross-referencing, viewing and retrieval of multiple objects regardless of nature or source. The inventive system provides underlying component architecture having an object-oriented database structure and a metadata database structure which is unique in storing only one instance of each object while linking the object to multiple collections and domains by unique metadata links for the grouping into and retrieval from any of the collections. The system employs configurable, extensible attribute / properties of data objects in metadata format, and a truly user-friendly configurable interface that facilitates faster, more unified, comprehensive, useful and meaningful information management. Additional features include a sticky path object hierarchy viewing system, key phrase linking, viewing by reference, and drag-and-drop relationship link creation.
Owner:EHIERARCHY LLC
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS6415280B1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsHash functionData content
In a system in which a set of data items are distributed across a network of servers, at least some of the data items being cached versions of data items from a source server, a content delivery method includes determining a data identifier for a particular data item, the data identifier being determined using a given function of the data comprising the particular data item; and responsive to a request for the particular data item, the request including at least the data identifier of the particular data item, providing the particular data item from a given one of the servers of the network of servers. The request for the particular data item may be resolved based on a measure of availability of at least one of the servers, where the measure of availability may be a measurement of bandwidth to the server; a measurement of a cost of a connection to the server, and / or a measurement of a reliability of a connection to the server. The function used to determine the identifier may be a message digest function or a hash function.
Owner:LEVEL 3 COMM LLC +1
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS7275063B2Facilitate communicationMultimedia data indexingFile access structuresPathPingSoftware system
Owner:EHIERARCHY LLC
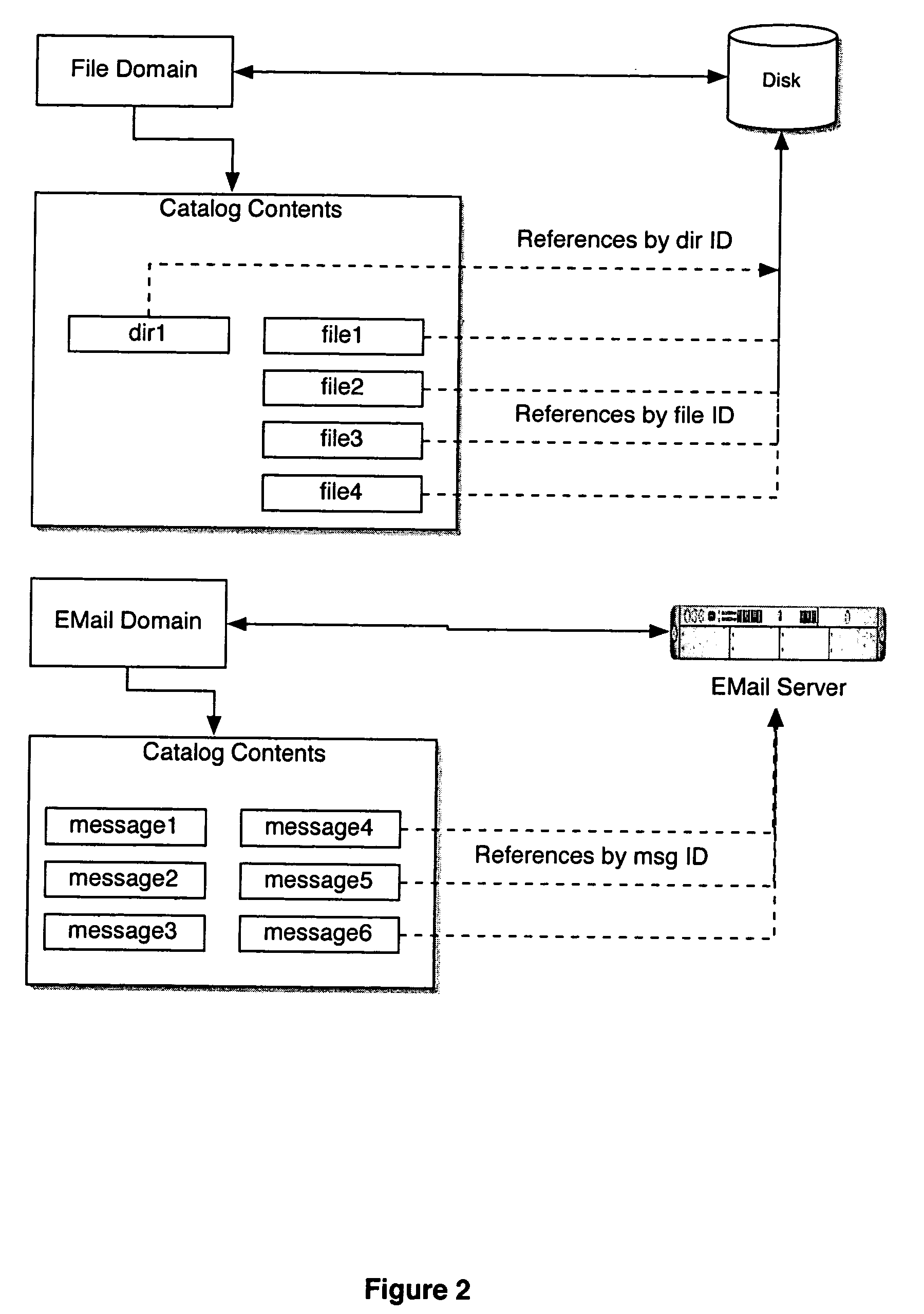
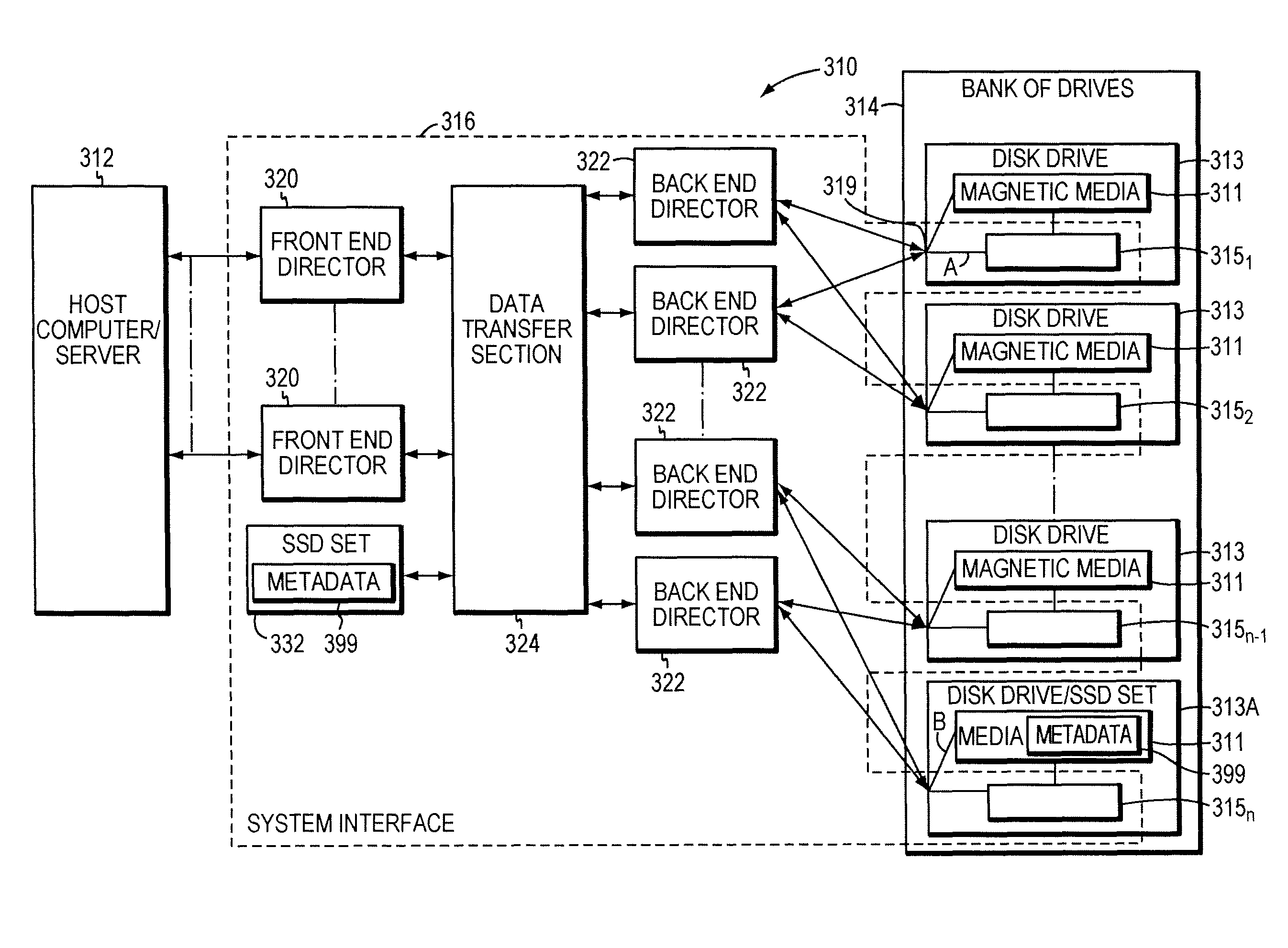
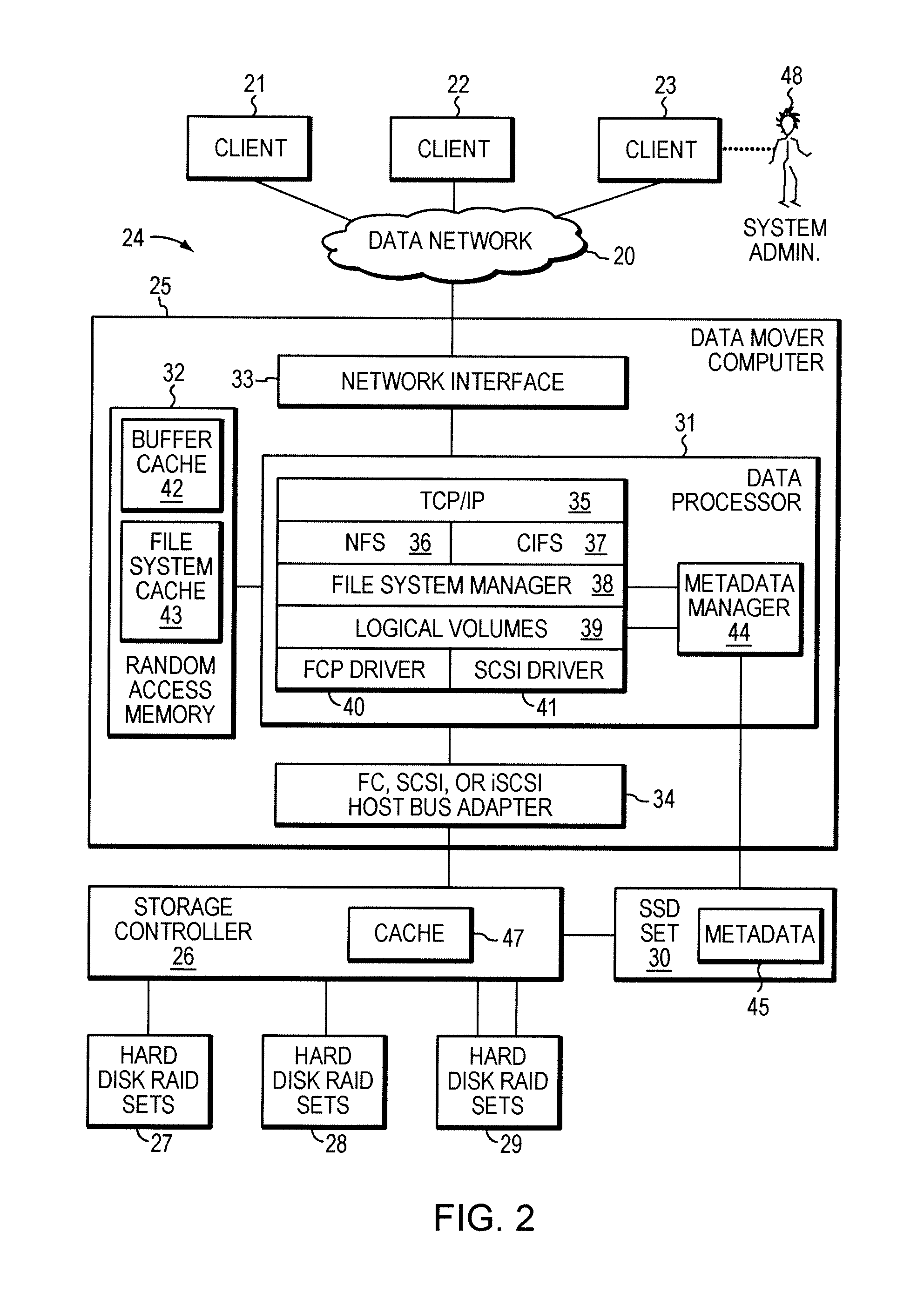
Managing metadata
A method is used in managing metadata. Data of an object is stored in a magnetic hard disk set in an object addressable data storage system. Metadata for the object is stored in an SSD set in the object addressable data storage system. The metadata includes information necessary for determining the location of the data of the object in the magnetic hard disk set.
Owner:EMC IP HLDG CO LLC
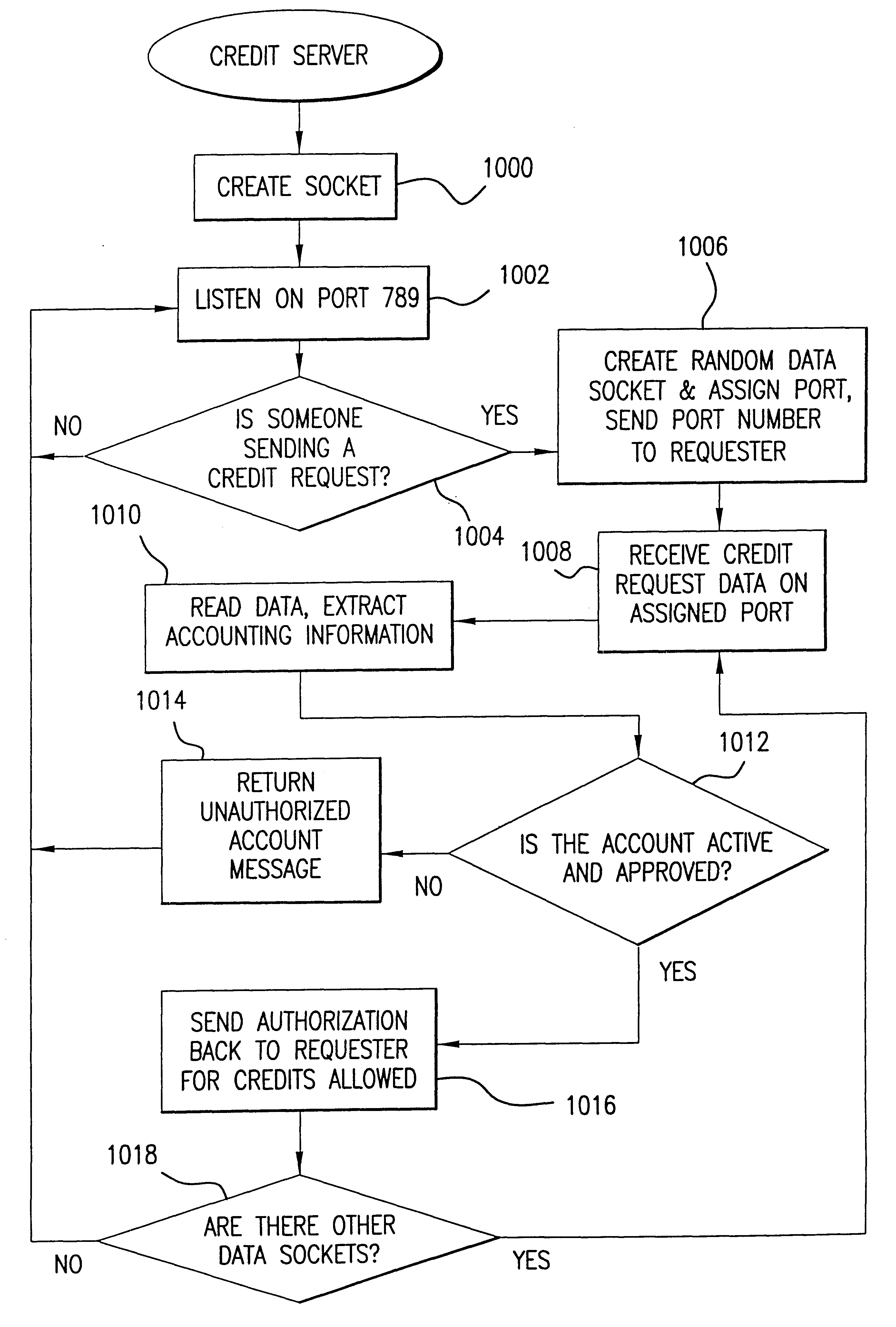
File transfer system using dynamically assigned ports
InactiveUS6219669B1Data processing applicationsFile access structuresData transmissionVariable number
A computer data signal embodied in a propagation medium is provided. The signal enables a variable number of data transfers and includes an initial connection source code segment and a data transfer source code segment. The initial connection source code segment establishes a connection between at least two devices via predetermined listening ports, with at least one predetermined listening port residing within each device. The initial connection source code segment also dynamically assigns a first data port within a first device, and transmits the address of the first data port to a remaining device via the predetermined listening ports. The data transfer source code segment is for each of the variable number of data transfer operations. The data transfer source code segment dynamically assigns a corresponding second data port within the remaining device and transfers data between the connected devices via the data ports so that the data is substantially simultaneously transferred between a variable number of devices via the data ports. Each pair of first and second data ports is established in response to each listening port connection.
Owner:INTELLECTUAL VENTURES I LLC
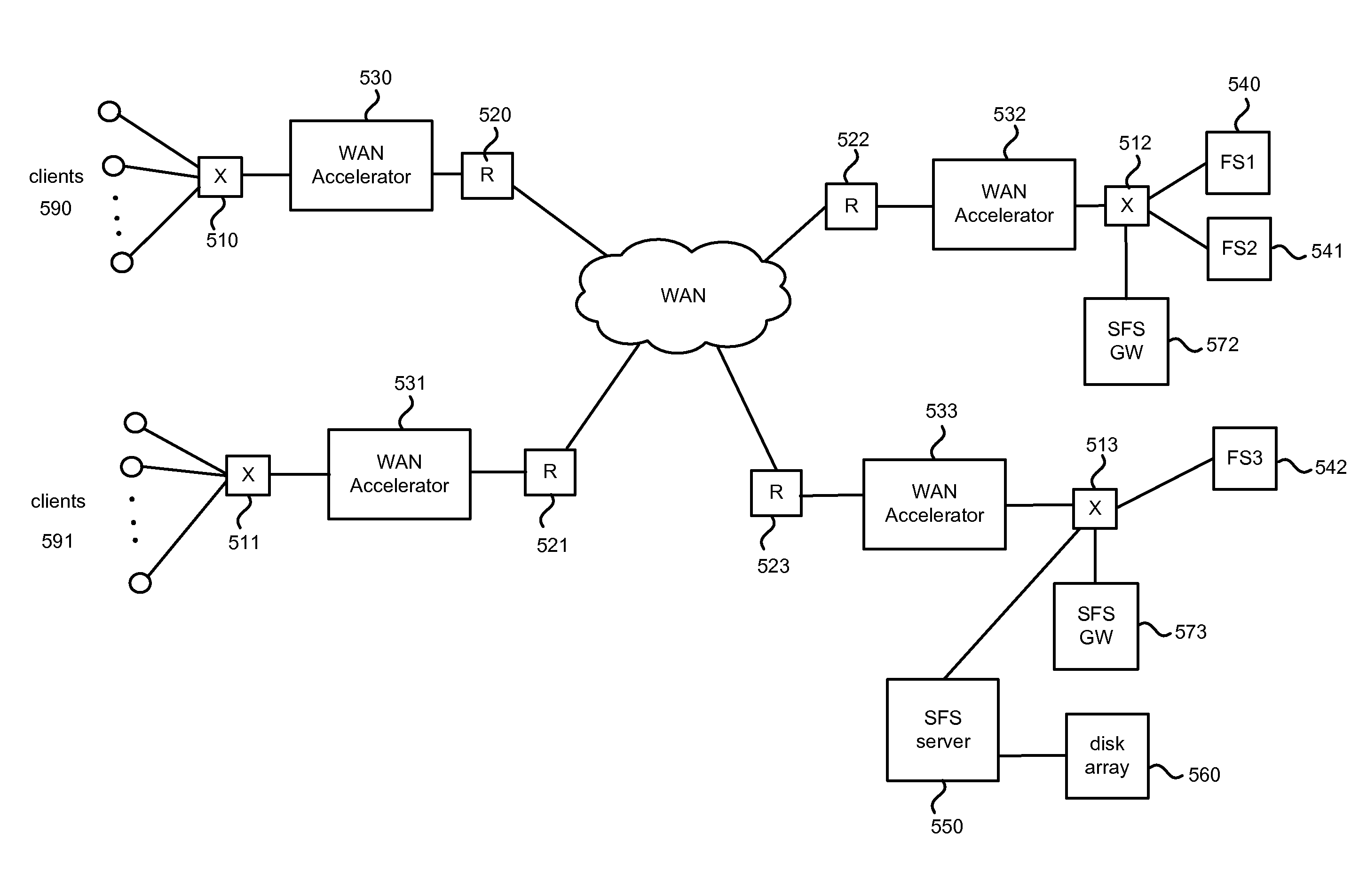
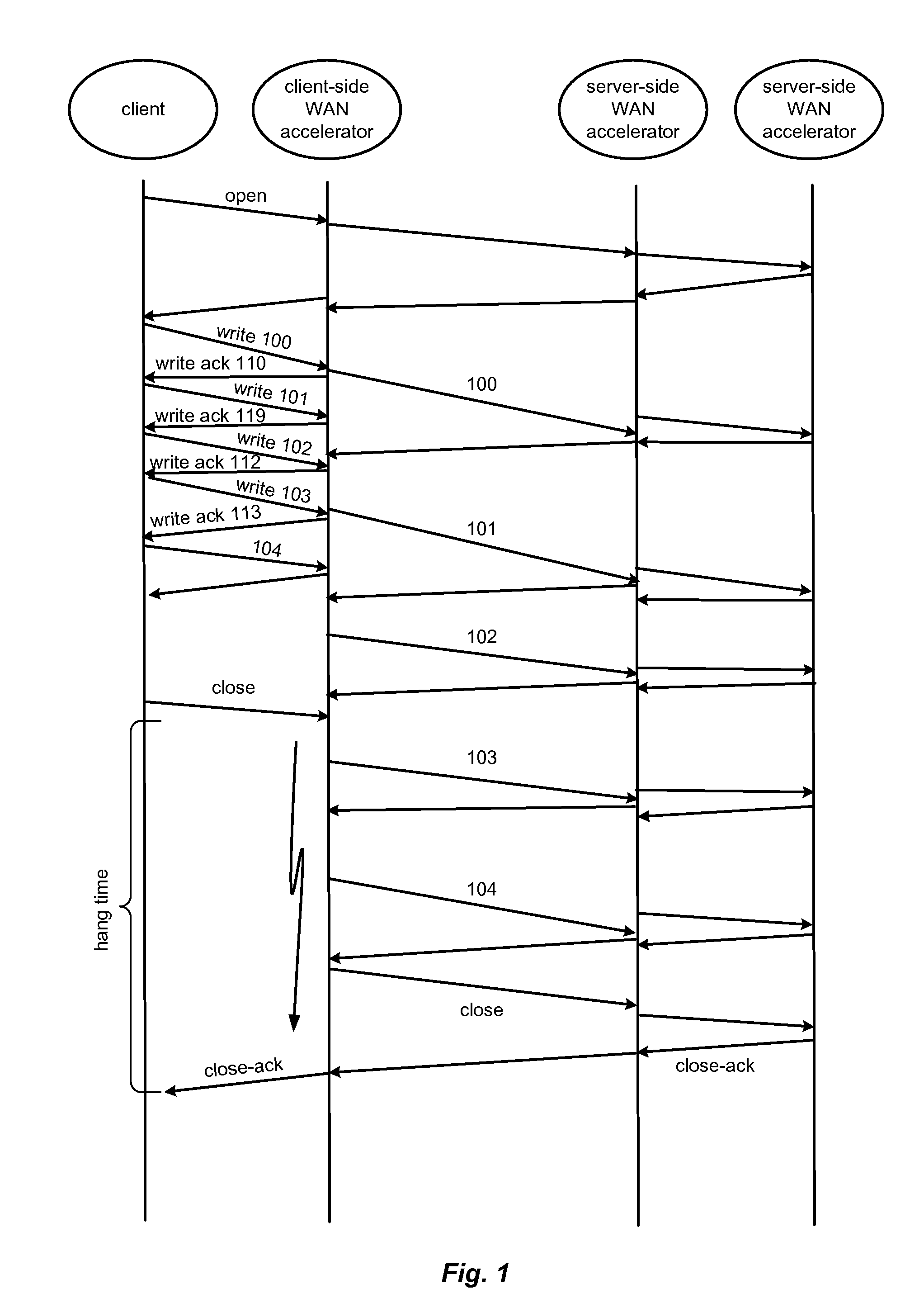
Hybrid segment-oriented file server and wan accelerator
ActiveUS20080281908A1Error detection/correctionComputer security arrangementsFile serverProtocol for Carrying Authentication for Network Access
In a network including WAN accelerators and segment-oriented file servers, a method comprises responding to a client request to manipulate a file via a network file protocol by receiving a first request at a first WAN accelerator, wherein the request is a request to open a file located at a file server that is a segment-oriented file server, sending a local request for the file, corresponding to the first request, from the WAN accelerator to the file server, using a segment-aware network request protocol, returning at least a portion of the requested file in the form of a representation of a data map corresponding to the at least a portion of the requested file stored on the file server and using a data map for reconstruction of the requested file.
Owner:RIVERBED TECH LLC
Methods and apparatus for secure electronic, certified, restricted delivery mail systems
A computer data signal embodied in a propagation medium is provided. The signal enables a variable number of data transfers and includes an initial connection source code segment and a data transfer source code segment. The initial connection source code segment establishes a connection between at least two devices via predetermined listening ports, with at least one predetermined listening port residing within each device. The initial connection source code segment also dynamically assigns a first data port within a first device, and transmits the address of the first data port to a remaining device via the predetermined listening ports. The data transfer source code segment is for each of the variable number of data transfer operations. The data transfer source code segment dynamically assigns a corresponding second data port within the remaining device and transfers data between the connected devices via the data ports so that the data is substantially simultaneously transferred between a variable number of devices via the data ports. Each pair of first and second data ports is established in response to each listening port connection.
Owner:INTELLECTUAL VENTURES I LLC
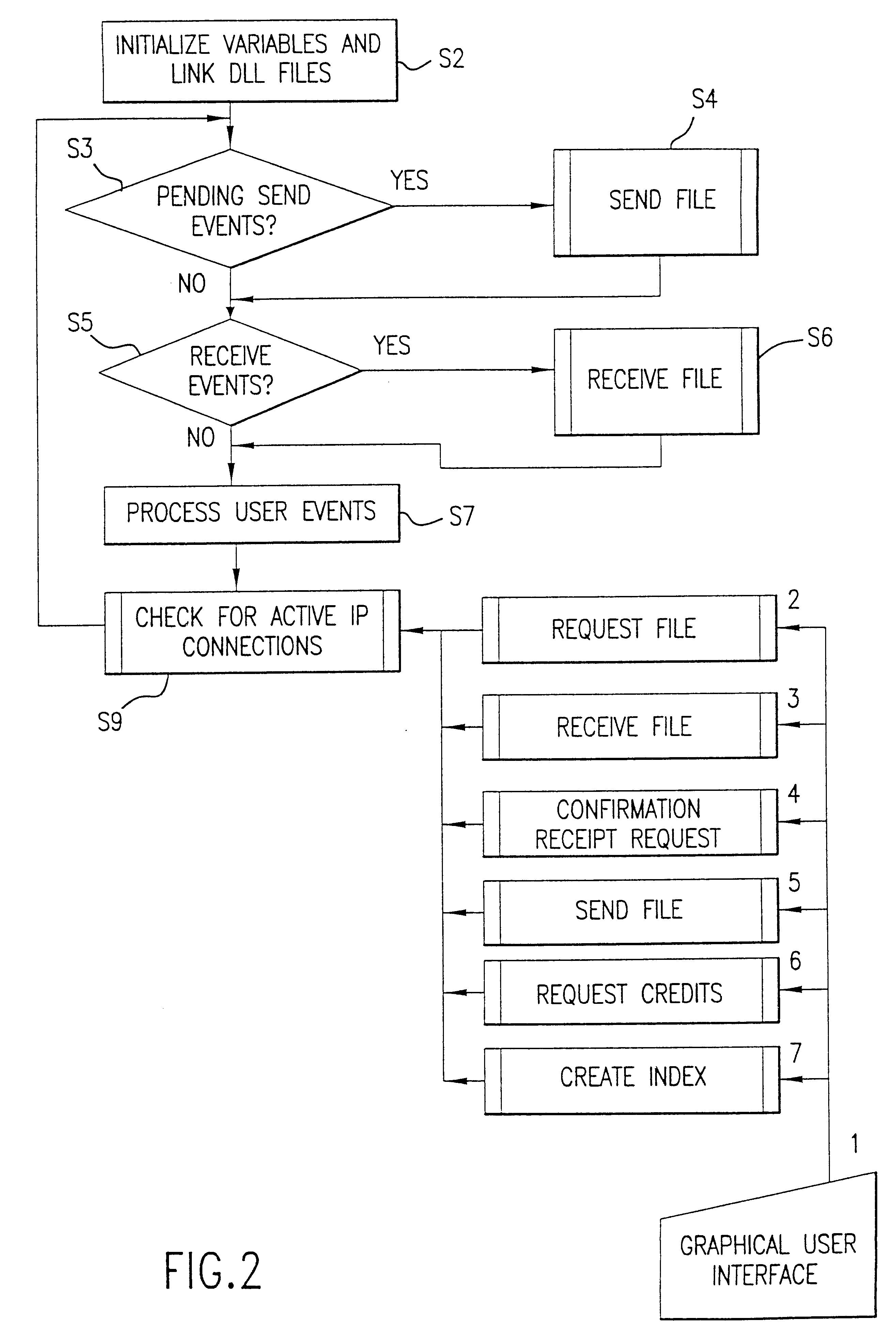
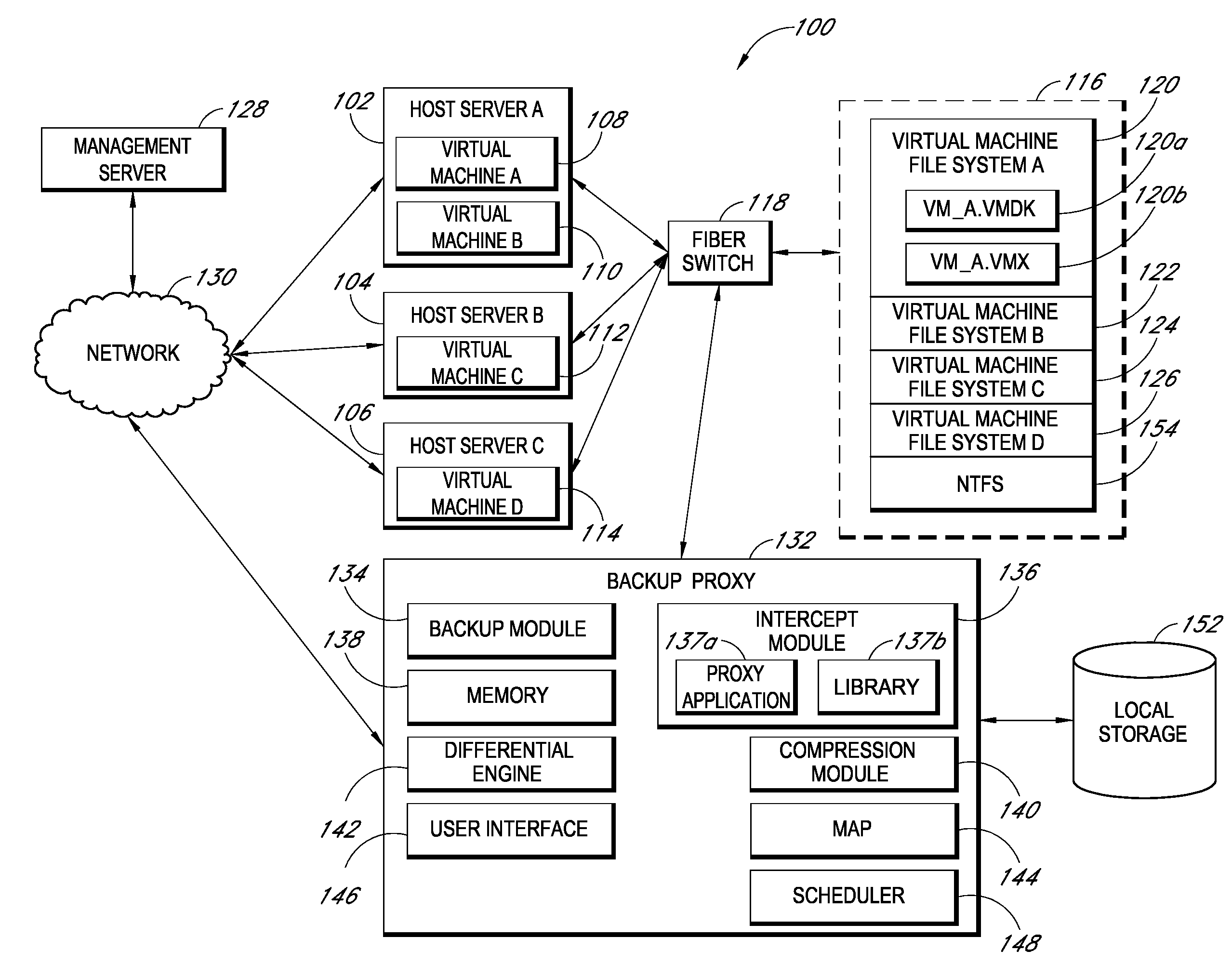
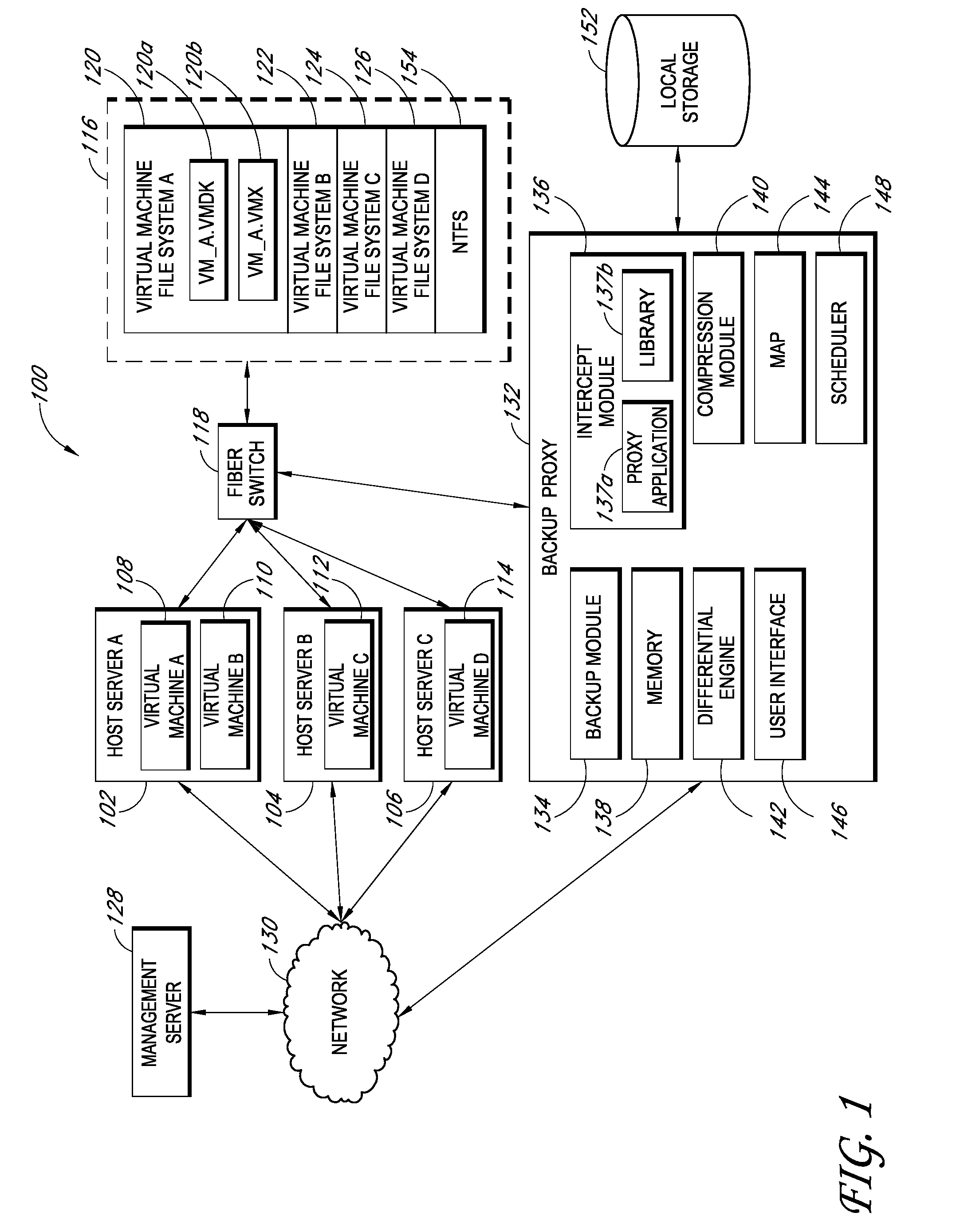
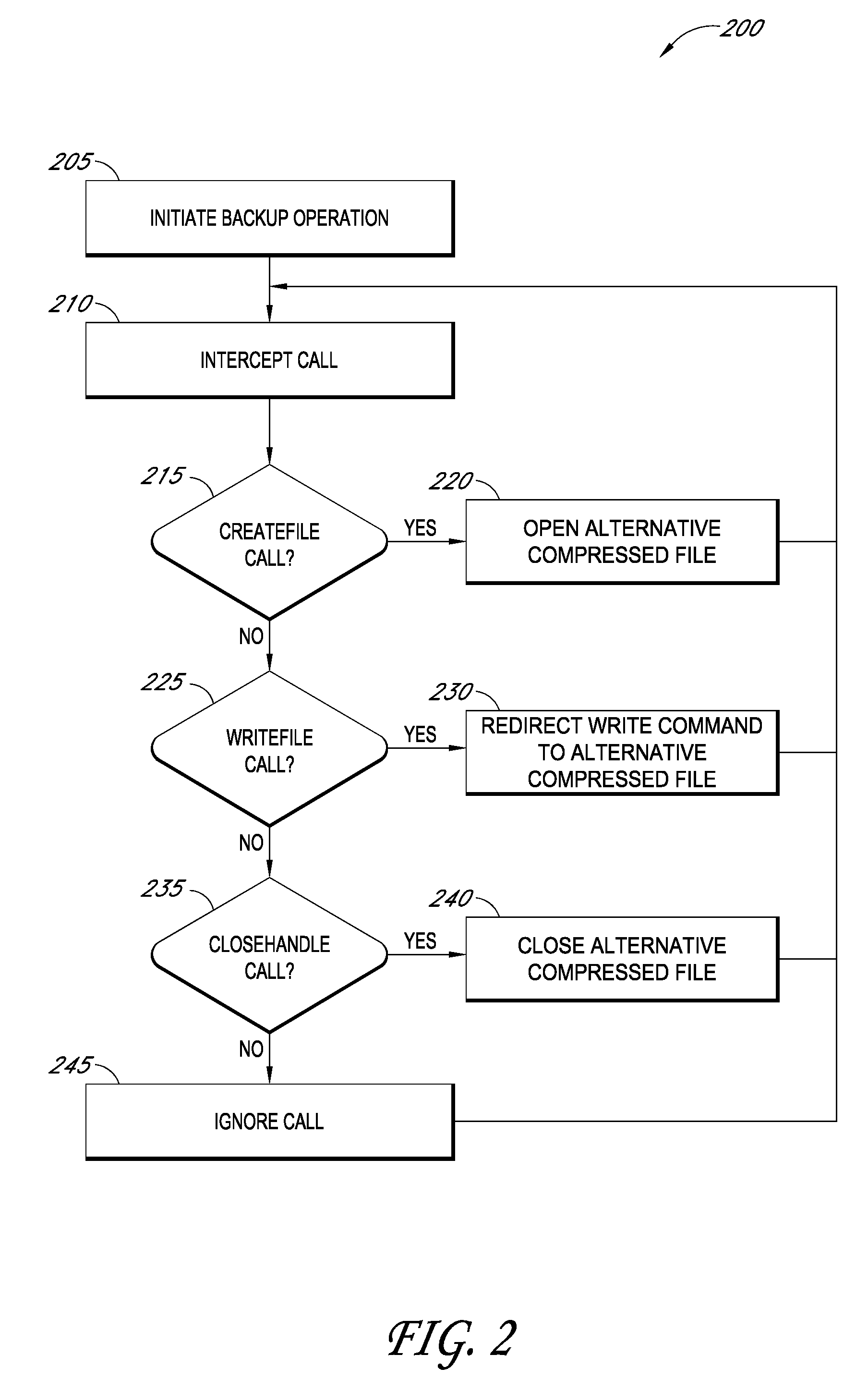
Backup systems and methods for a virtual computing environment
ActiveUS8060476B1Reduce the amount requiredReduce image sizeError detection/correctionDigital data processing detailsApplication programming interfaceApplication software
Improved backup and storage operations are disclosed for virtual computing environments using a backup proxy server to perform storage operations on one or more virtual machine disks. The proxy server can include a module that intercepts application programming interface (API) calls, for writing backup data to a first location, prior to the data arriving on the proxy disk. During the intercept process, the data can be compressed in memory pages of the proxy server and redirected to an alternative backup disk location. The proxy server can also include a differential engine that identifies changes to the virtual machine disk at the block level since the last full backup. The differential engine can advantageously leverage memory pages of the proxy server to compare differences between signatures of blocks of the last full backup with signatures of new blocks. Subsequently, only blocks with non-matching signatures are processed for backup.
Owner:QUEST SOFTWARE INC
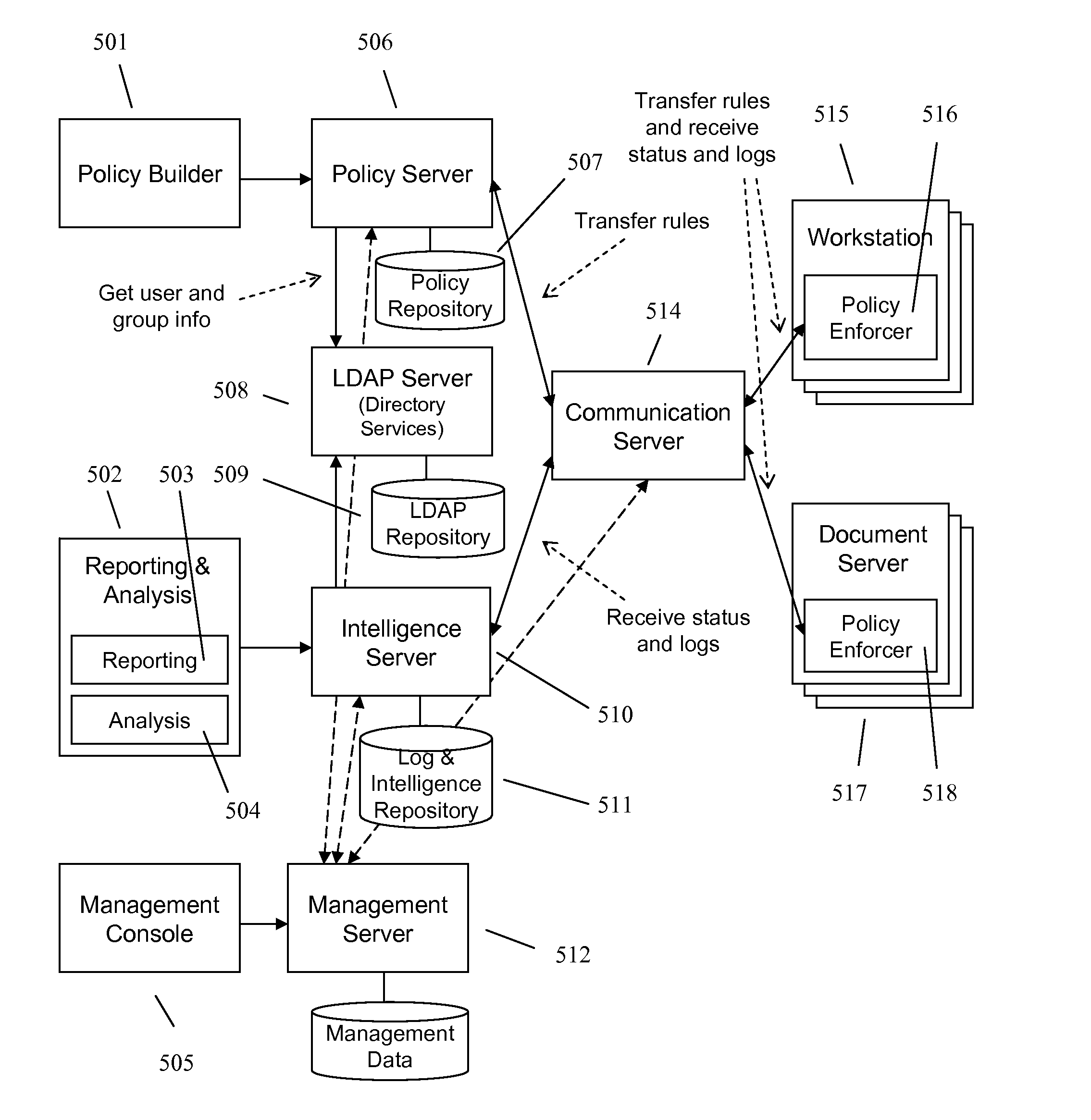
Techniques of optimizing policies in an information management system
In an information management system, policies are optimized before they are associated to a device in order to increase evaluation speed or reduce space requirements, or both. Optimization techniques may include common subexpression elimination, constant folding, constant propagation, comparison optimization, dead code or subexpression removal, map or lookup table generation, policy rewriting, redundant policy elimination, heuristic-based policy ordering, or policy-format transformation, and combinations of these.
Owner:NEXTLABS
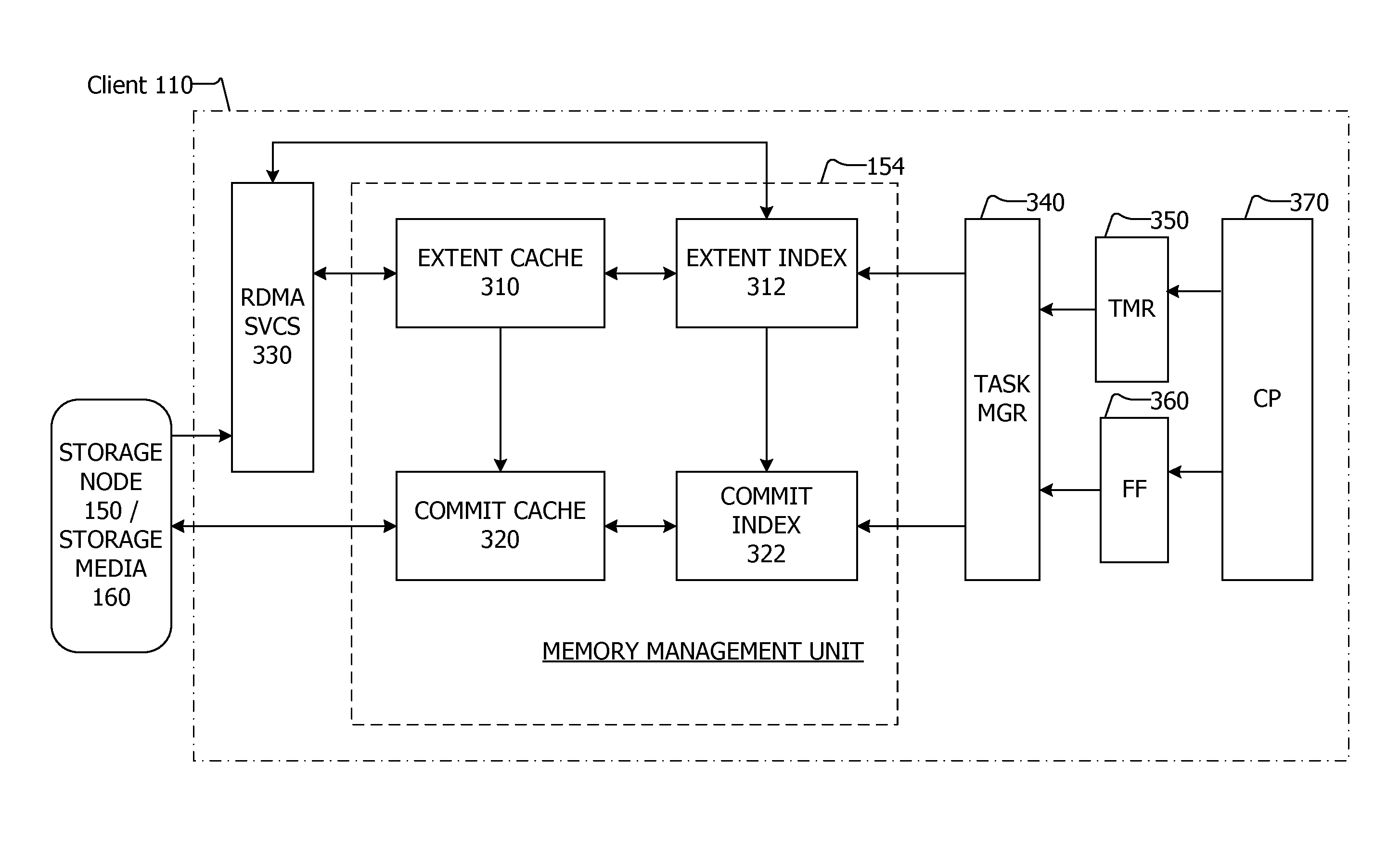
Reducing metadata in a write-anywhere storage system
ActiveUS9116819B2Memory architecture accessing/allocationMemory adressing/allocation/relocationManagement unitData retrieval
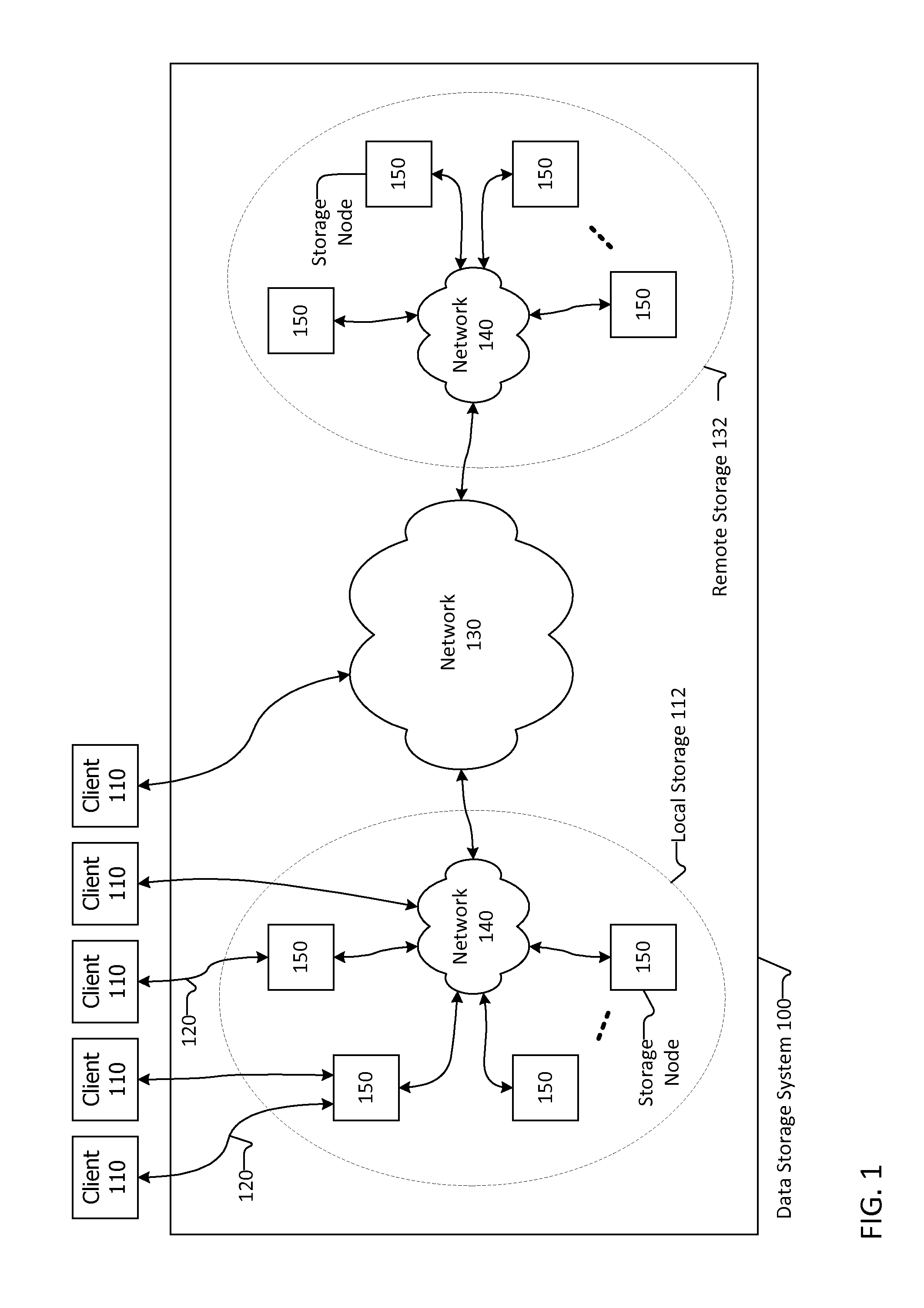
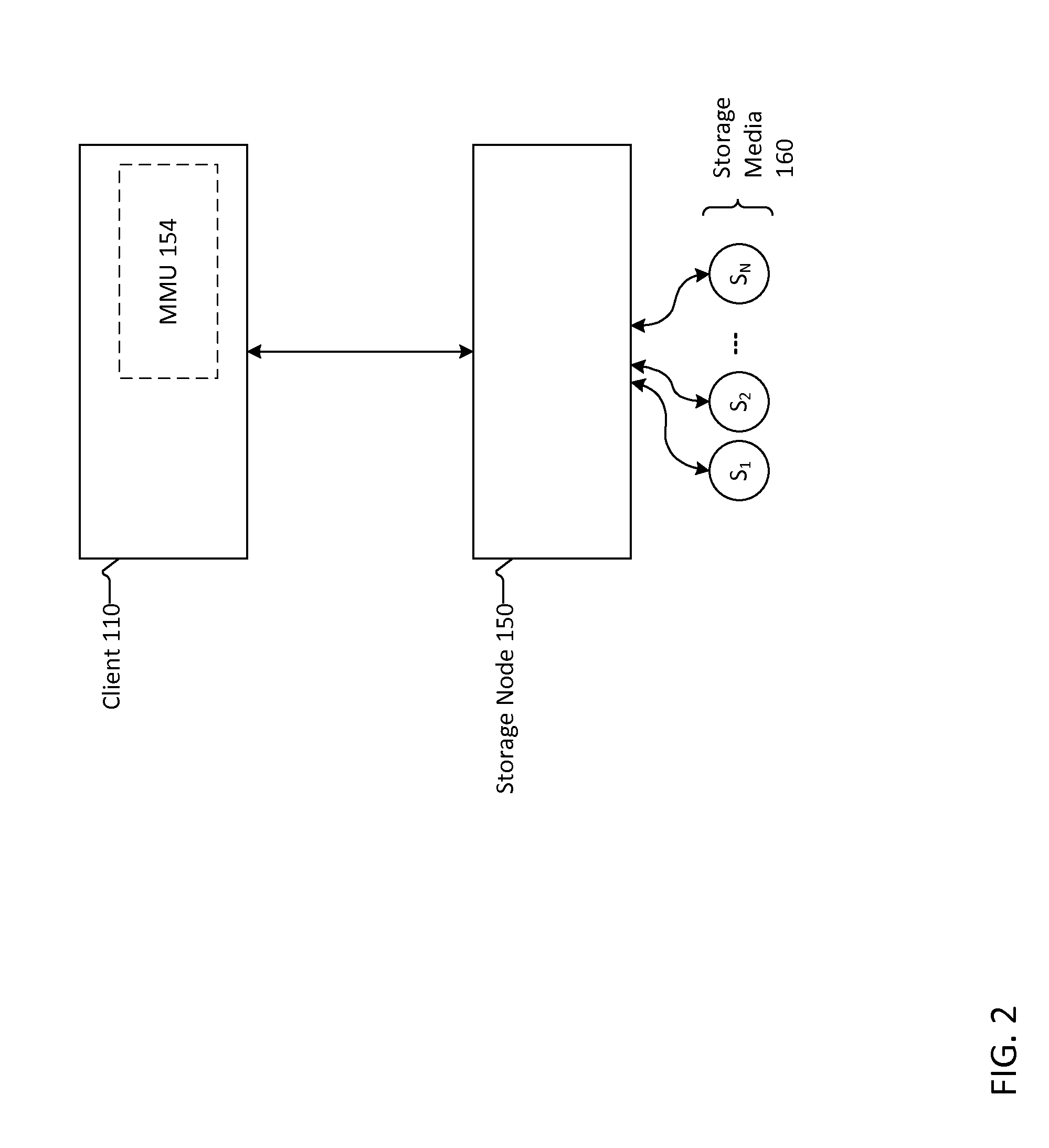
Systems and methods for reducing metadata in a write-anywhere storage system are disclosed herein. The system includes a plurality of clients coupled with a plurality of storage nodes, each storage node having a plurality of primary storage devices coupled thereto. A memory management unit including cache memory is included in the client. The memory management unit serves as a cache for data produced by the clients before the data is stored in the primary storage. The cache includes an extent cache, an extent index, a commit cache and a commit index. The movement of data and metadata is by an interval tree. Methods for reducing data in the interval tree increase data storage and data retrieval performance of the system.
Owner:DATADIRECT NETWORKS
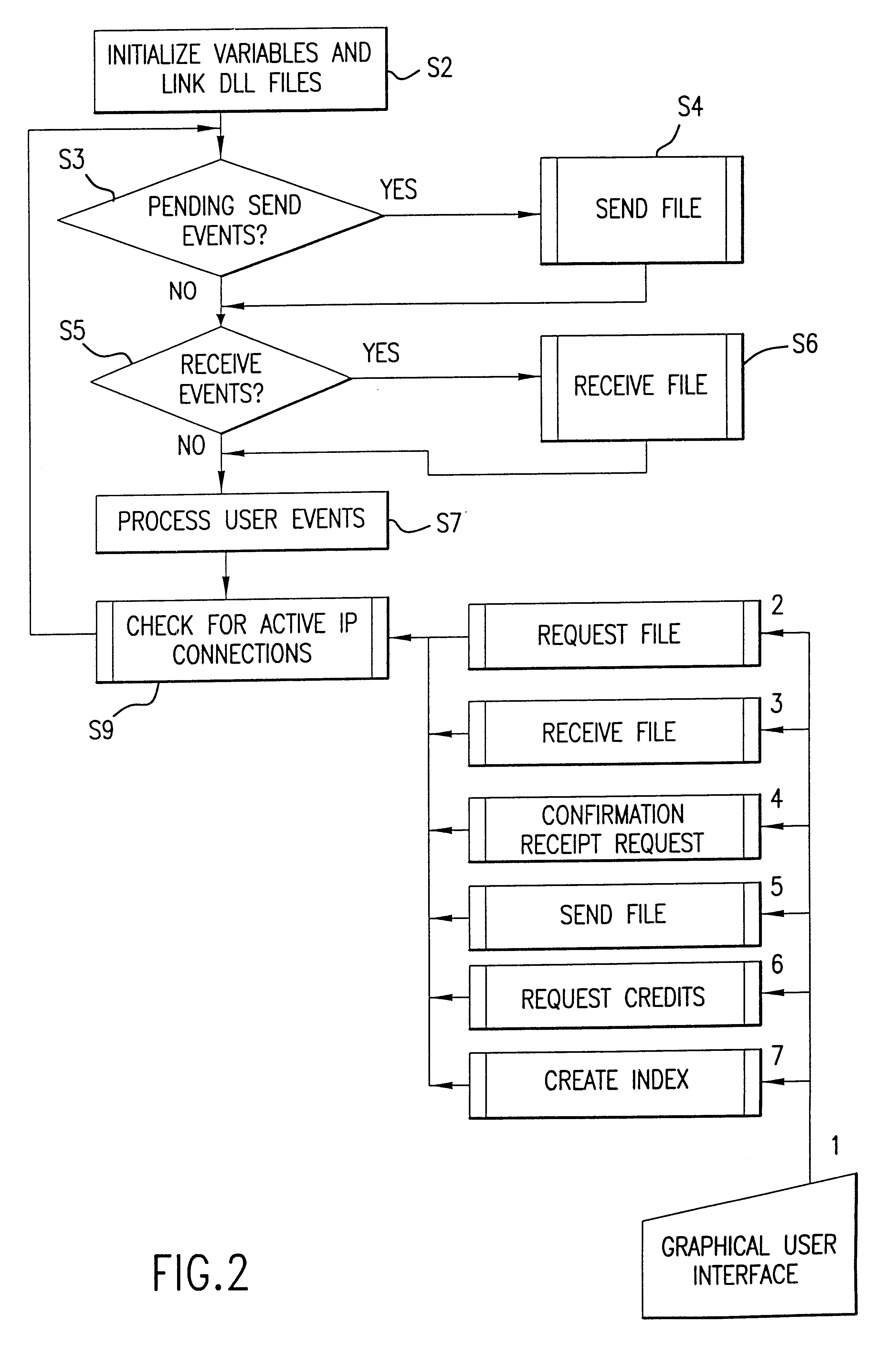
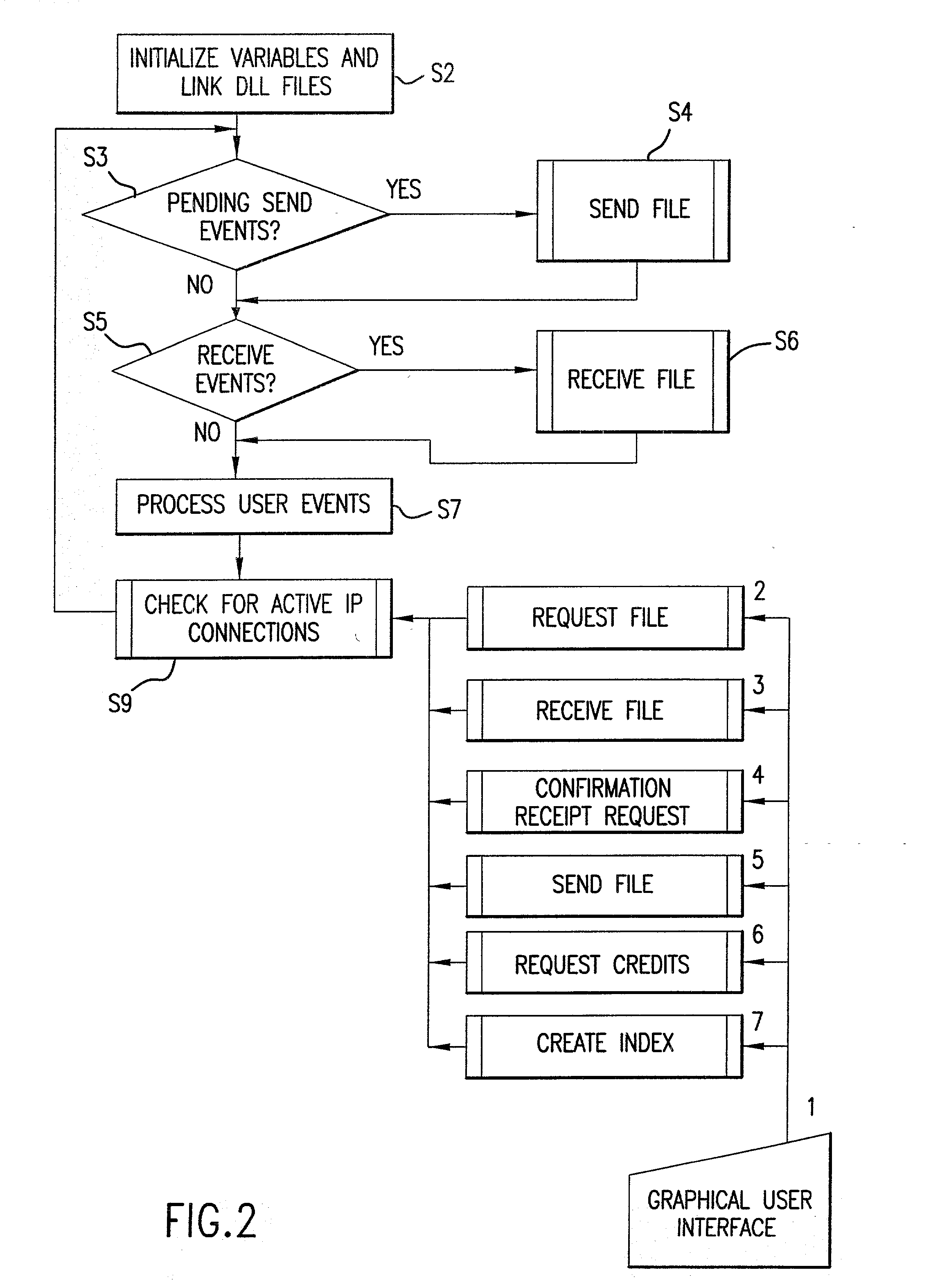
File transfer system
InactiveUS20020184224A1Data processing applicationsDigital data processing detailsDEVICE EVALUATIONComputer science
A file transfer system includes peer devices, including an index creating device and at least one requesting peer device. The index creating device creates an index of stored files that can be requested by peer devices. The index creating device evaluates communications requests from the peer devices and accepts communications requests in accordance with user defined criteria. The index creating device communicates with a requesting peer device when the communications request from the requesting peer device has been accepted, and also stores the index, which is linked to an identification. The requesting peer device requests files that are listed in the index linked to the identification. The requesting peer device also creates the file request, which includes a list of the selected files and the identification, transmits the file request to the index creating device, and receives the requested files listed in the index.
Owner:INTELLECTUAL VENTURES I LLC
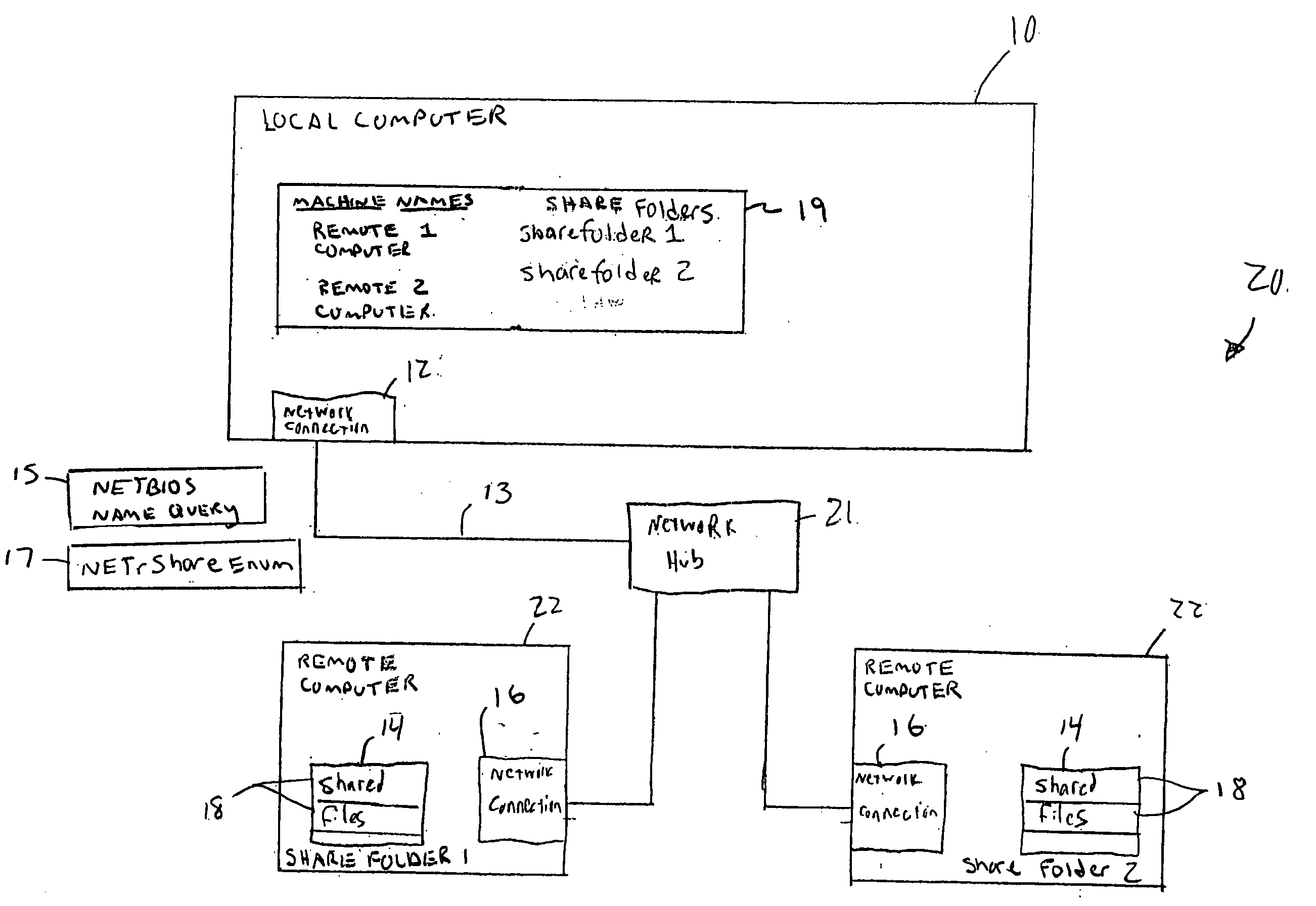
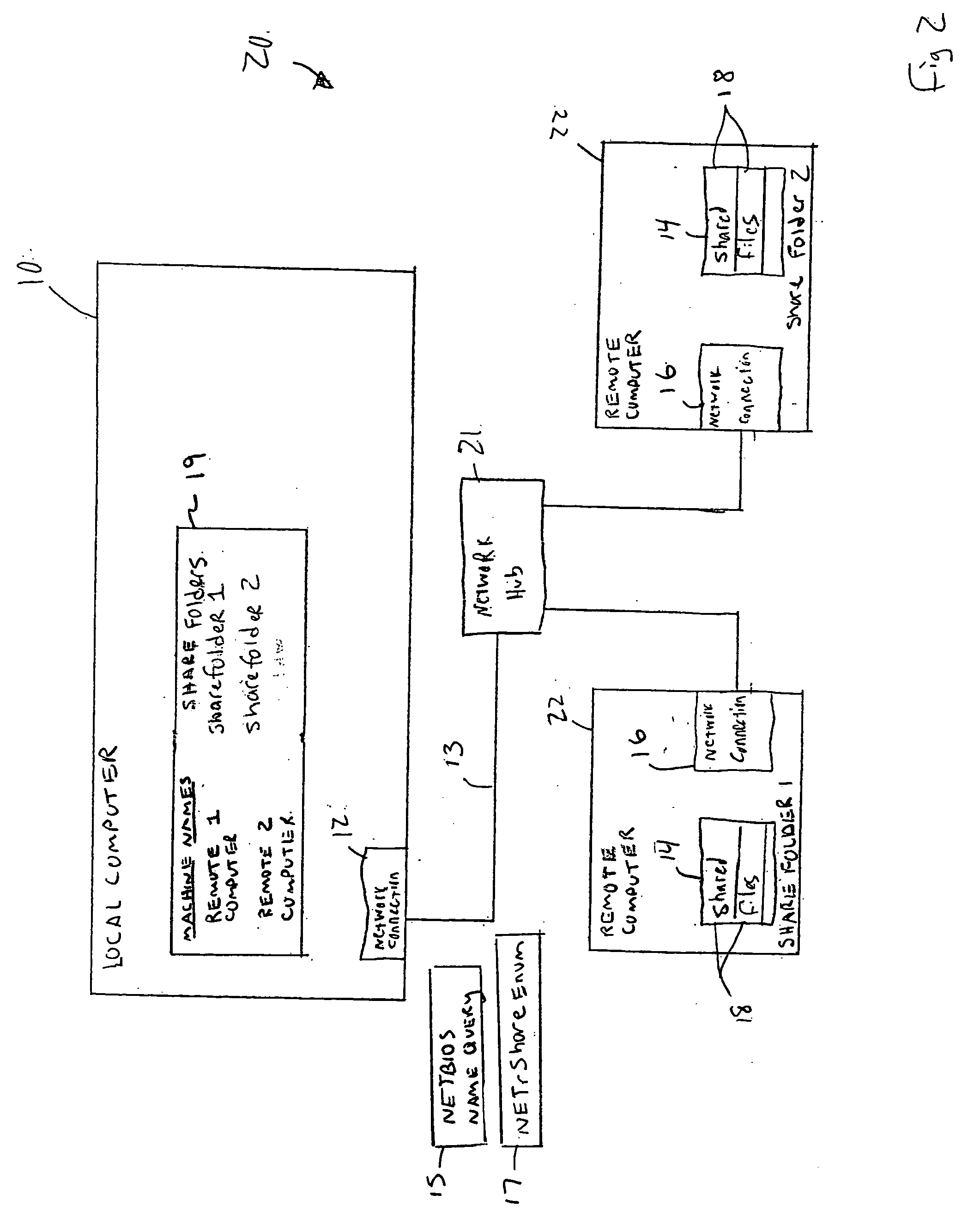
System for remote share access
InactiveUS20050149508A1Data processing applicationsDigital data processing detailsDistributed computingDevice name
A distributed share folder & file discovery system allows different local computers to discover hosts and share folders without having to go through a central master browser. The local computer sends a device name query directly to any remote devices connected to a same network. The local computer then sends out a share query to the remote devices identified during the device name query to identify any folders or files that are available for sharing (shares). The local computer assembles a list of shares available on the remote devices and mounts any of the shares that are selected from the list.
Owner:SHARP KK
System and method for data preservation and retrieval
ActiveUS20090198689A1Digital data processing detailsComputer security arrangementsComputerized systemSearch computing
A system and method for searching for computer environments, authenticating the computer environments, and copying data from the authenticated computer environments to a memory location. The data is marked or bound to the computer system it was copied from which provides a user with assurance that the data was obtained from a specific, authenticated source. The computer environments and the memory location may be coupled over a network.
Owner:FIREEYE SECURITY HLDG US LLC
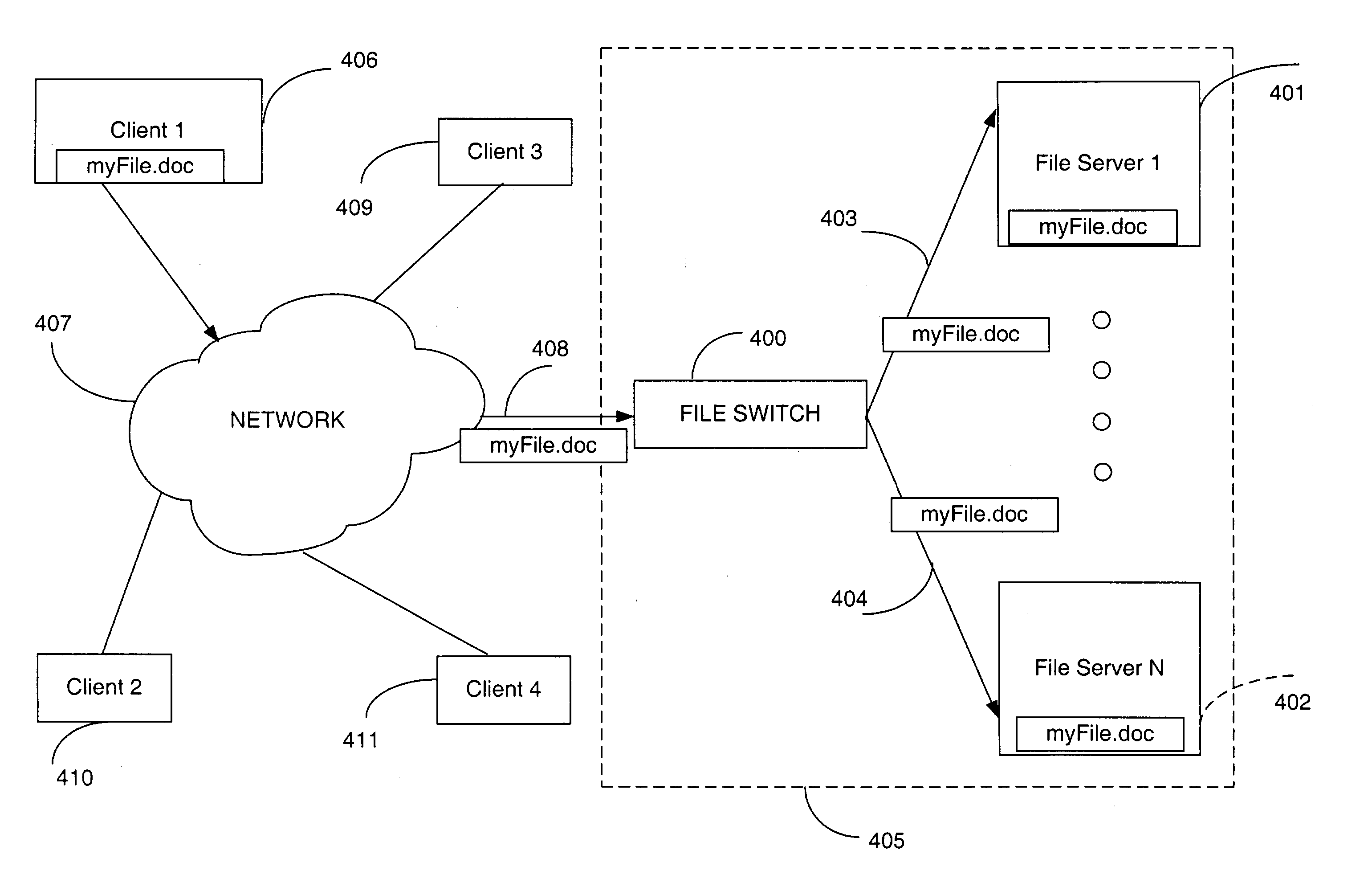
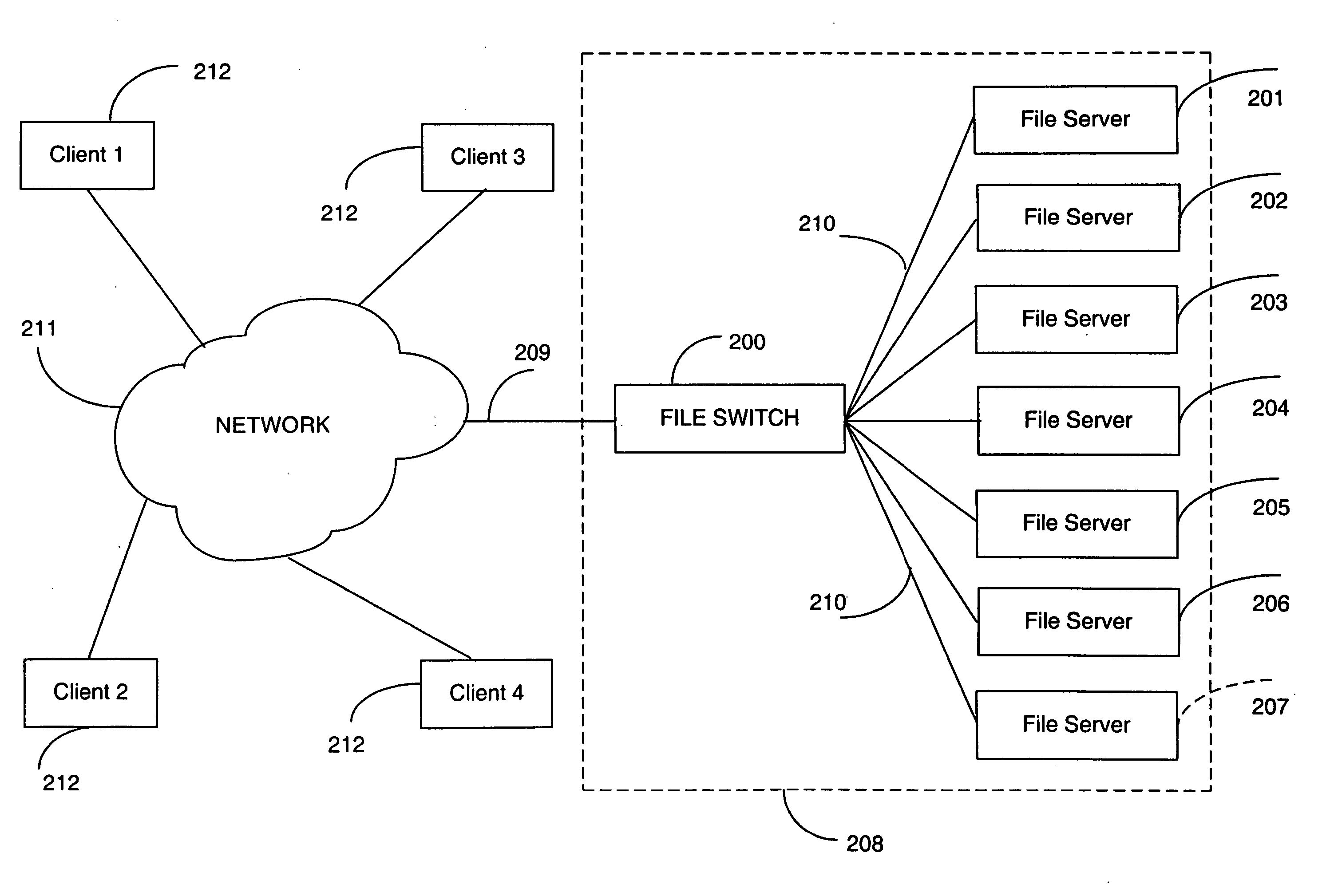
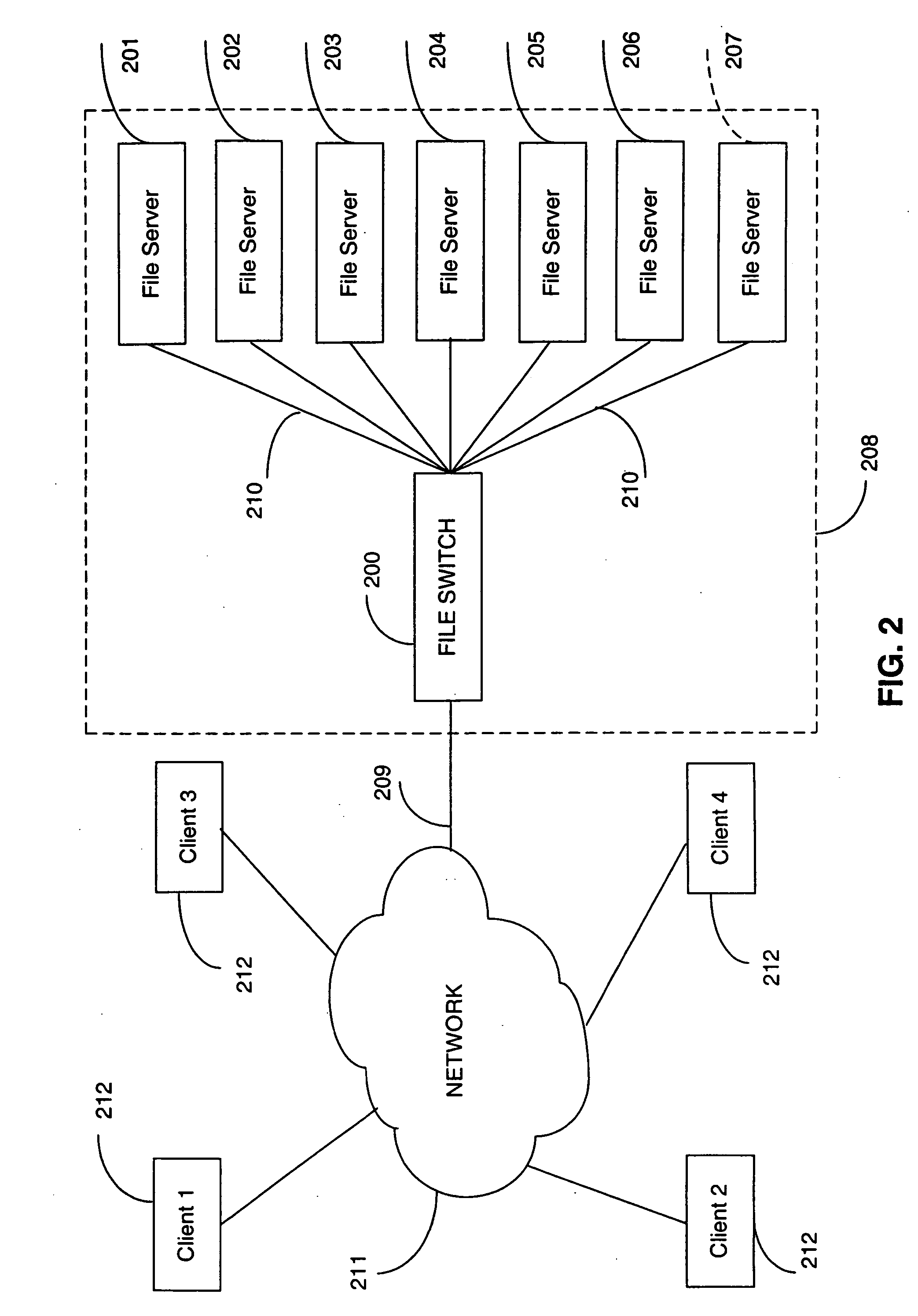
Directory aggregation for files distributed over a plurality of servers in a switched file system
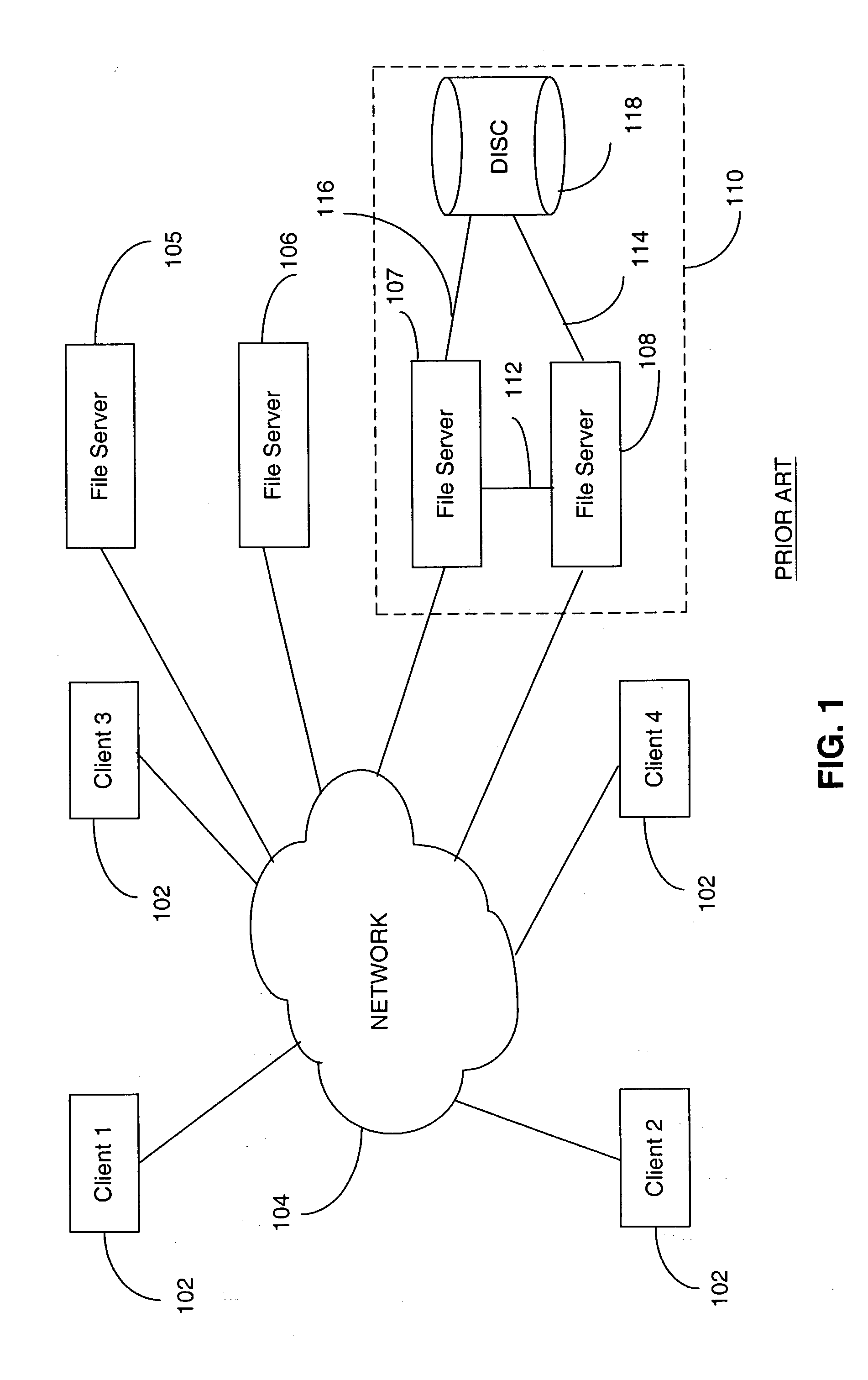
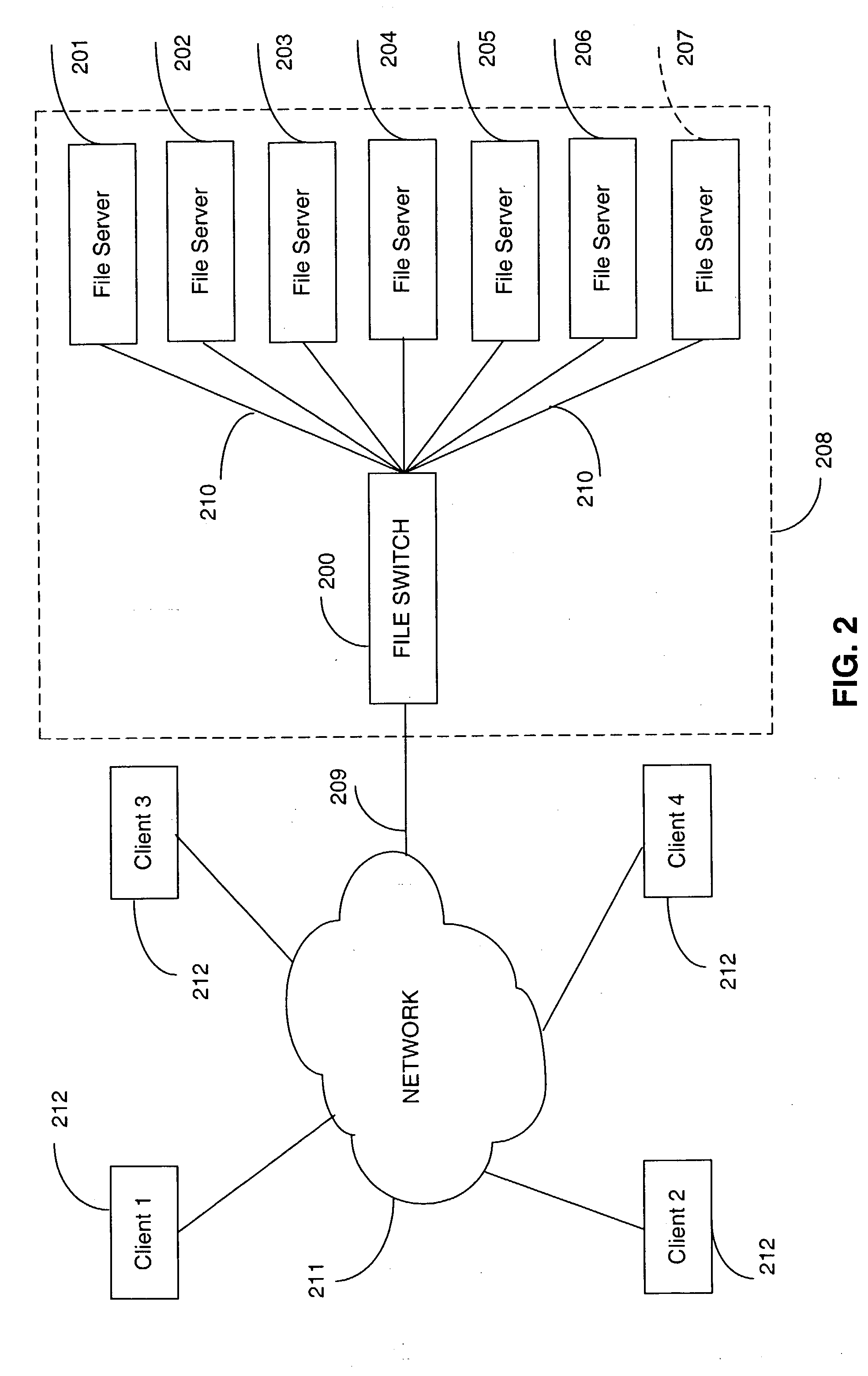
InactiveUS20040133606A1Improve throughputImprove toleranceFile access structuresSpecial data processing applicationsFile systemData file
A file switch, logically positioned between client computers and file servers in a computer network, distributes user files among multiple file servers using an aggregated directory mechanism. A hierarchical directory structure is created on the file servers and used to store metadata files, which store metadata for each user file to indicate where data files, containing portions of the user file, are stored. The file switch automatically spreads the data files and metadata files over a large number of distinct directories on multiple file servers, preventing large number of data files from being stored in a single directory on a single file server. In response to a directory enumeration request from a client computer, one or more directories of metadata files on one or more of the file servers is enumerated, instead of enumerating the data file that store the user file portions.
Owner:RPX CORP
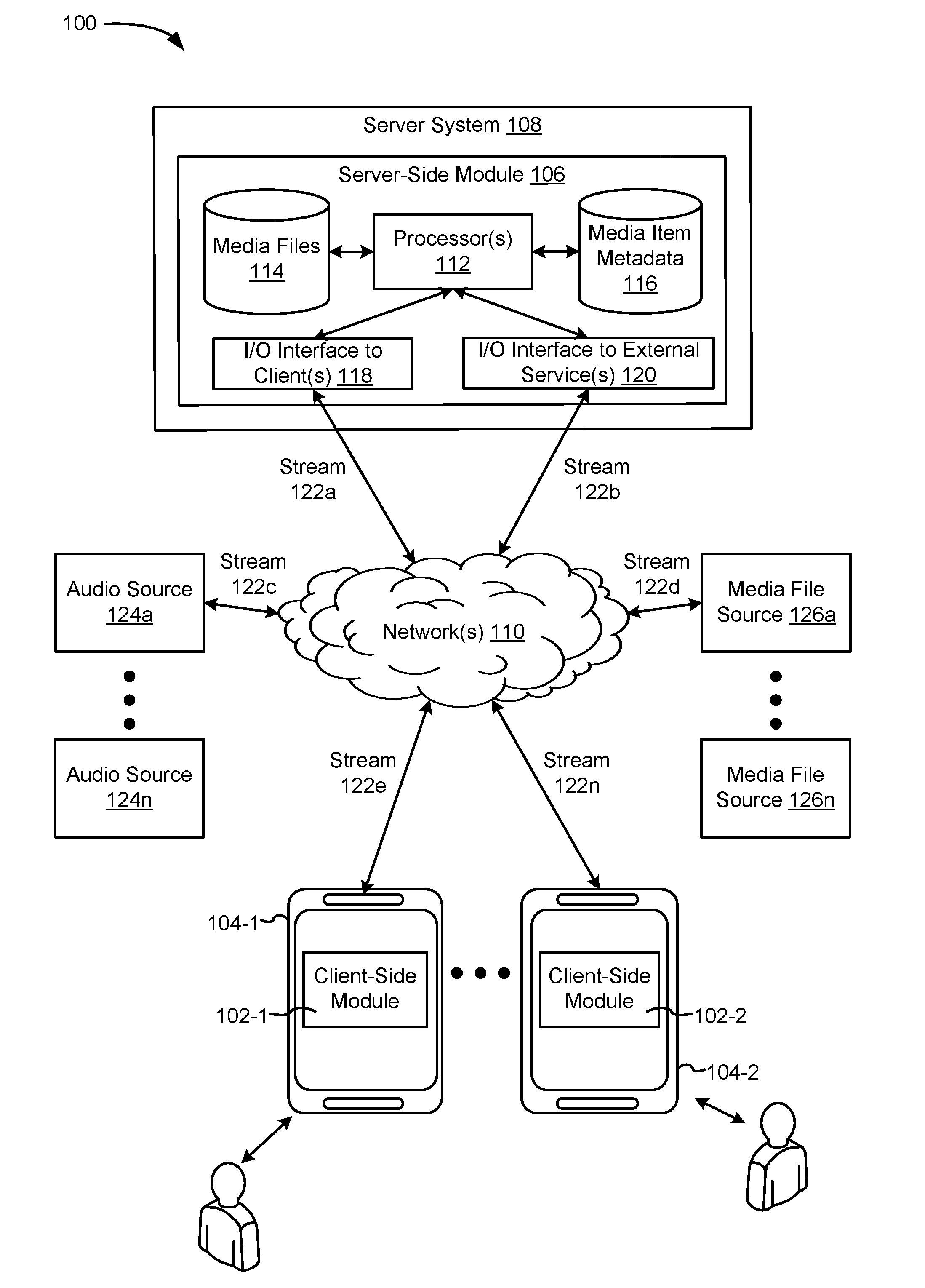
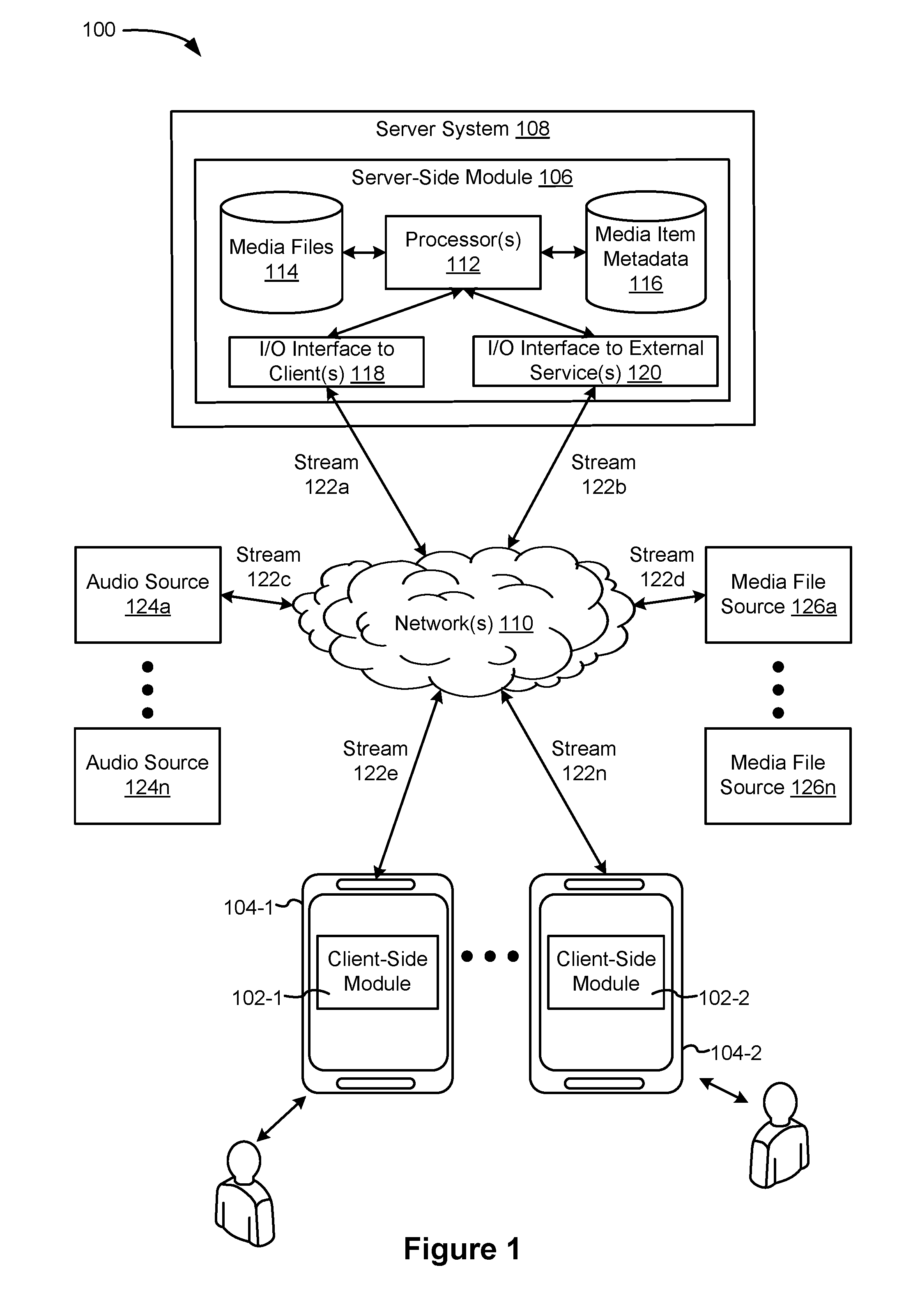
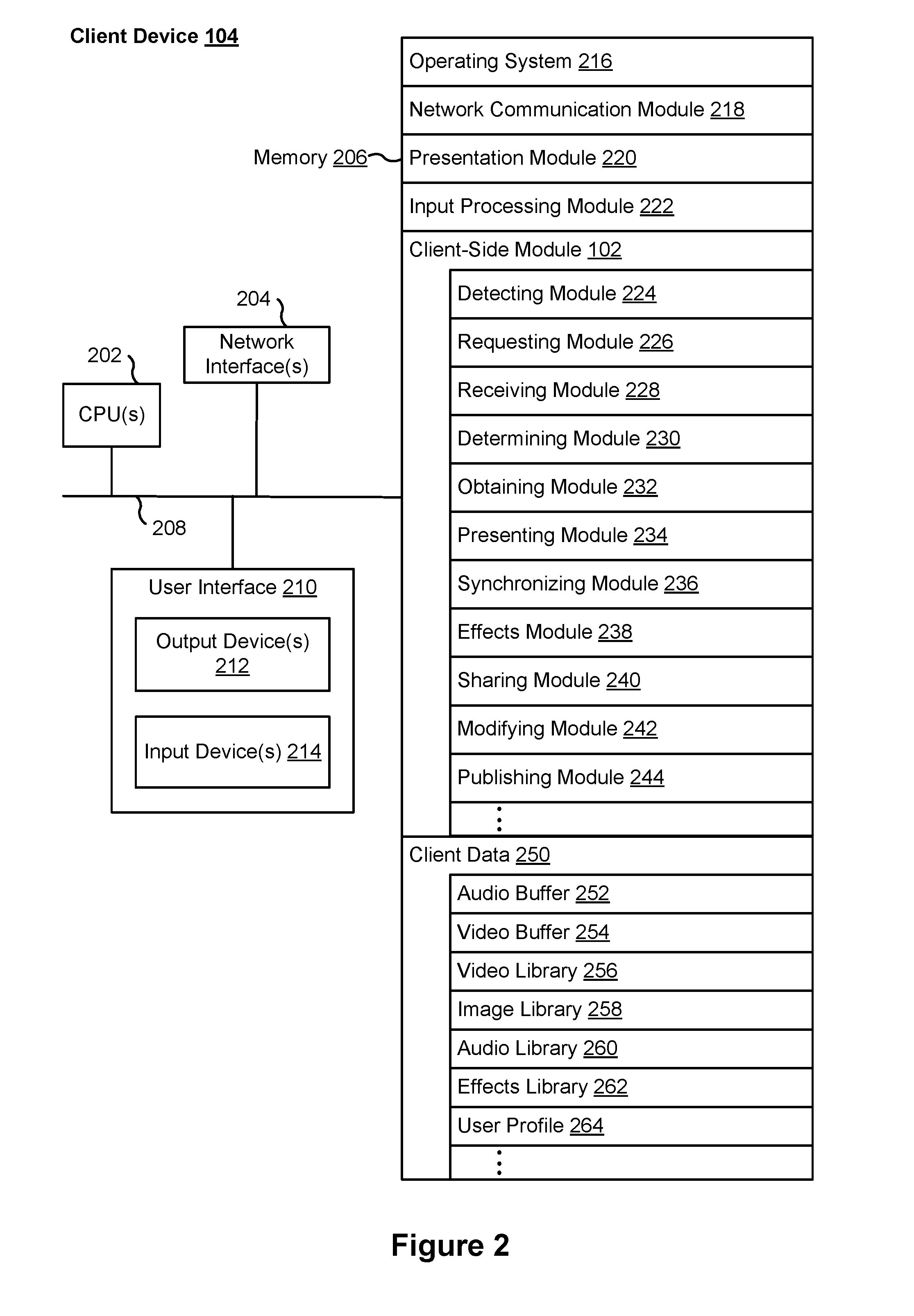
Methods and systems for generating audiovisual media items
The various embodiments described herein include methods and systems for generating an audiovisual media item. In one aspect, a method is performed at a server system. The method includes: (1) receiving, from a first electronic device associated with a first user, a creation request to create the media item, the creation request including information identifying one or more audio files and one or more visual media files; (2) obtaining the visual media files; (3) requesting at least one audio file from a server in accordance with the information identifying the audio files; (4) in response to the request, receiving at least one audio file from the server; (5) obtaining any remaining audio files; (6) in response to receiving the creation request, generating the audiovisual media item based on the audio files and the visual media files; and (7) storing the generated audiovisual media item in a media item database.
Owner:META PLATFORMS INC
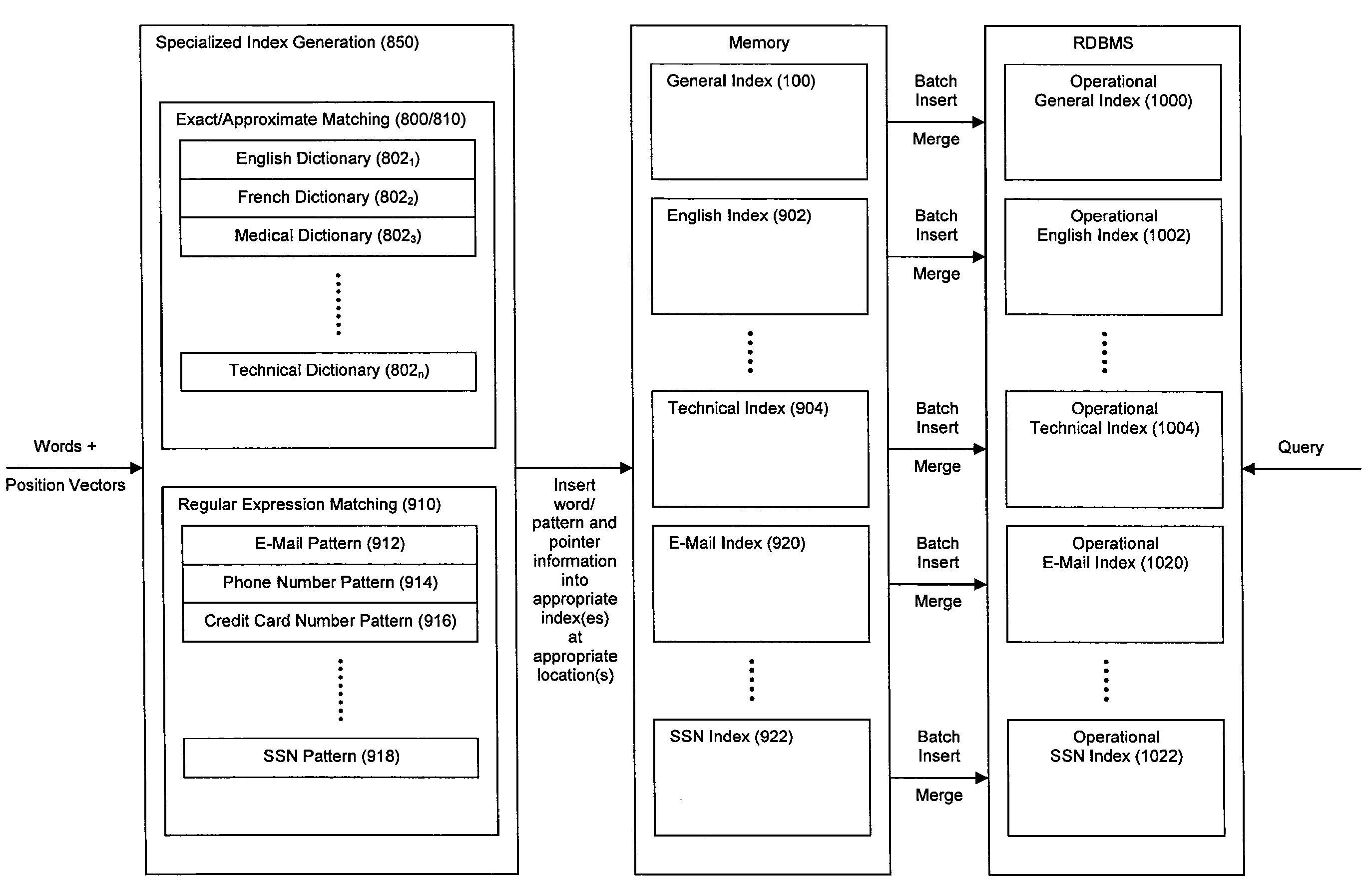
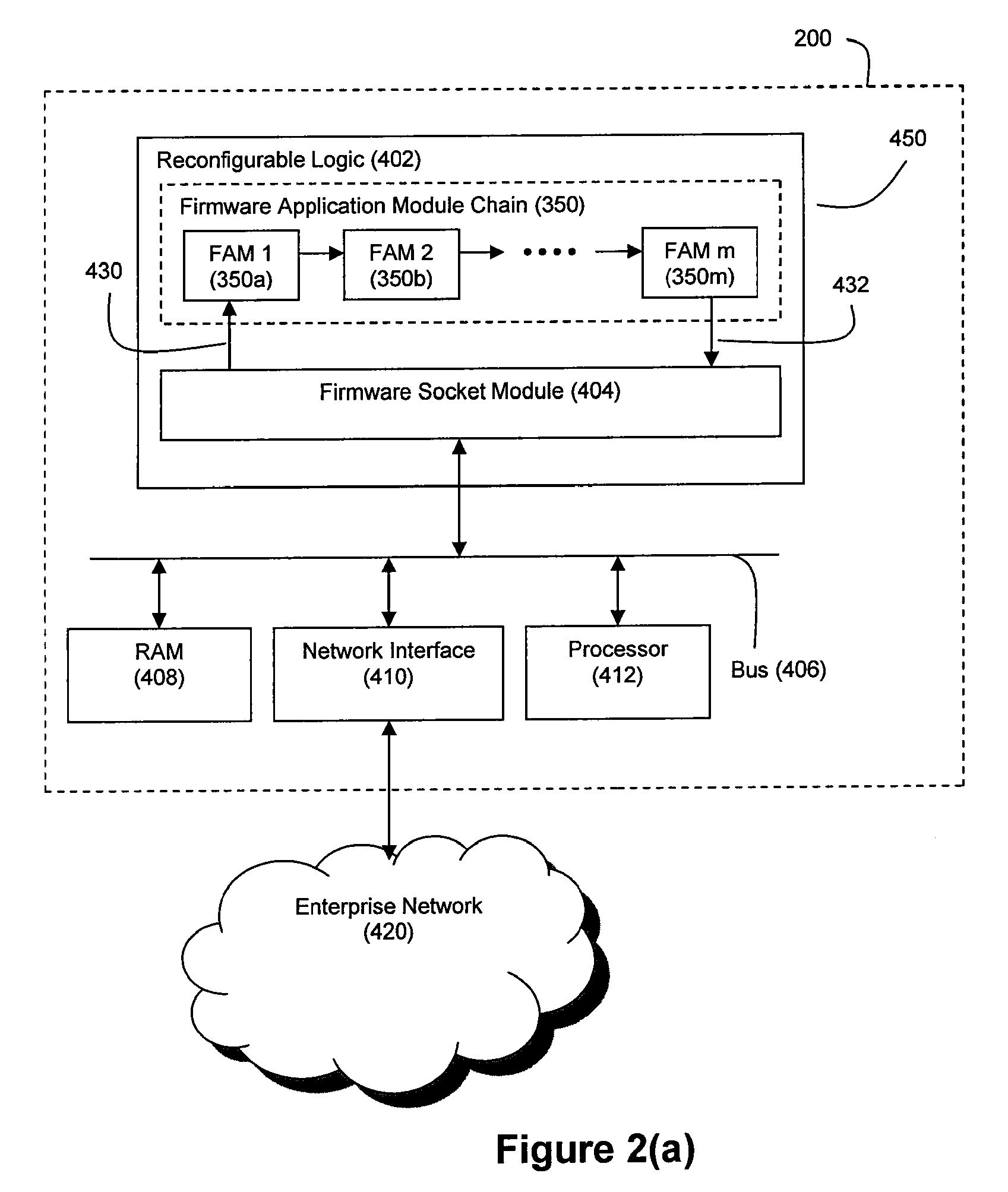
Method and System for High Performance Data Metatagging and Data Indexing Using Coprocessors
ActiveUS20080114725A1Robust and high performance data searchingHigh indexWeb data indexingFile access structuresData streamCoprocessor
Disclosed herein is a method and system for hardware-accelerating the generation of metadata for a data stream using a coprocessor. Using these techniques, data can be richly indexed, classified, and clustered at high speeds. Reconfigurable logic such a field programmable gate arrays (FPGAs) can be used by the coprocessor for this hardware acceleration. Techniques such as exact matching, approximate matching, and regular expression pattern matching can be employed by the coprocessor to generate desired metadata for the data stream.
Owner:IP RESERVOIR
Directory aggregation for files distributed over a plurality of servers in a switched file system
A file switch, logically positioned between client computers and file servers in a computer network, distributes user files among multiple file servers using an aggregated directory mechanism. A hierarchical directory structure is created on the file servers and used to store metadata files, which store metadata for each user file to indicate where data files, containing portions of the user file, are stored. The file switch automatically spreads the data files and metadata files over a large number of distinct directories on multiple file servers, preventing large number of data files from being stored in a single directory on a single file server. In response to a directory enumeration request from a client computer, one or more directories of metadata files on one or more of the file servers are enumerated, instead of enumerating the data file that store the user file portions.
Owner:RPX CORP
File system
ActiveUS20110022566A1Improve performanceLow costDigital data processing detailsFile access structuresDigital signatureFile system
A digitally signed file system in which data, metadata and files are objects, each object having a globally unique and content-derived fingerprint and wherein object references are mapped by the fingerprints; the file system has a root object comprising a mapping of all object fingerprints in the file system, such that a change to the file system results in a change in the root object, and tracking changes in the root object provides a history of file system activity.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
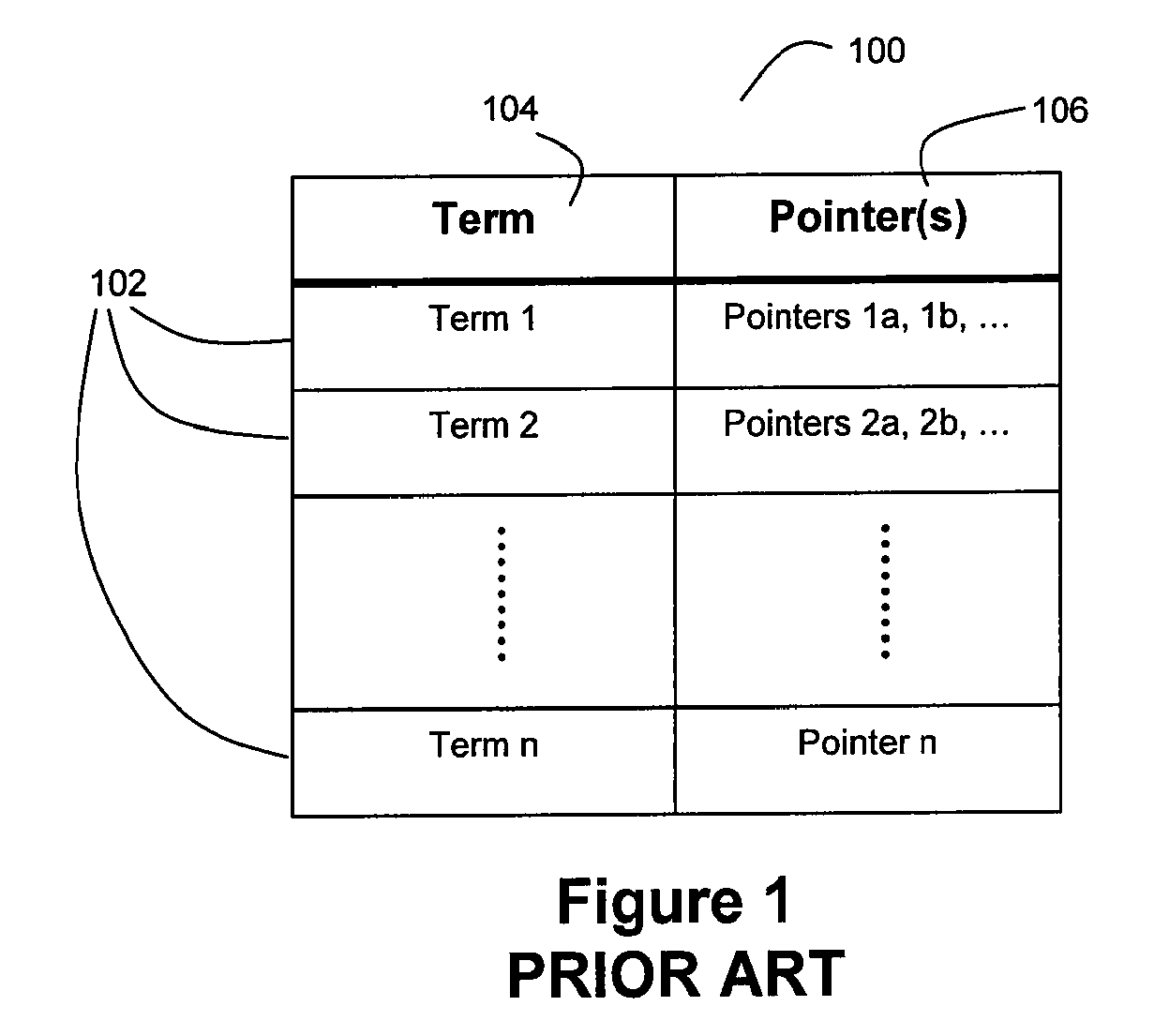
Methods and systems for managing permissions data and/or indexes
ActiveUS20070033191A1Data augmentationSpeed up searchDigital data processing detailsFile access structuresIndex systemDatabase
Systems and methods for indexing and searching data, such as file contents and / or metadata. In one exemplary method, an index corresponding to files on a storage device is created. Index is partitioned into subindexes according to certain criteria, such as the location of files or exclusivity of access to files. Subindex contains the entire content of files or metadata describing files, in addition to identifiers leading back to files' physical storage. Index is maintained by moving files' index entries from one subindex to another as files change in relation to the partition criteria, such as changing location. Searching some subindexes, like one corresponding to files in a shared folder, is done with permission checking. Searches of certain other subindexes, like one corresponding to the home folder of the user searching, are done without permission checking the underlying files resulting in a performance improvement.
Owner:APPLE INC
Managing dependencies between operations in a distributed system
InactiveUS20150172412A1Reduce transaction overheadSaving synchronizationFile access structuresTransmissionSemanticsSerialization
An efficient fault-tolerant event ordering service as well as a simplified approach to transaction processing based on global event ordering determines the order of interdependent operations in a distributed system. The fault-tolerant event ordering service externalizes the task of tracking dependencies to capture a global view of dependencies between a set of distributed operations in a distributed system. A novel protocol referred to as linear transactions coordinates distributed transactions with Atomicity, Consistency, Isolation, Durability (ACID) semantics on top of a sharded data store. The linear transactions protocol achieves scalability by distributing the coordination task to only those servers that hold relevant data for each transaction and achieves high performance by serializing only those transactions whose concurrent execution could potentially yield a violation of ACID semantics.
Owner:CORNELL UNIVERSITY
System and method for data preservation and retrieval
ActiveUS7937387B2Digital data processing detailsComputer security arrangementsComputerized systemSearch computing
A system and method for searching for computer environments, authenticating the computer environments, and copying data from the authenticated computer environments to a memory location. The data is marked or bound to the computer system it was copied from which provides a user with assurance that the data was obtained from a specific, authenticated source. The computer environments and the memory location may be coupled over a network.
Owner:FIREEYE SECURITY HLDG US LLC
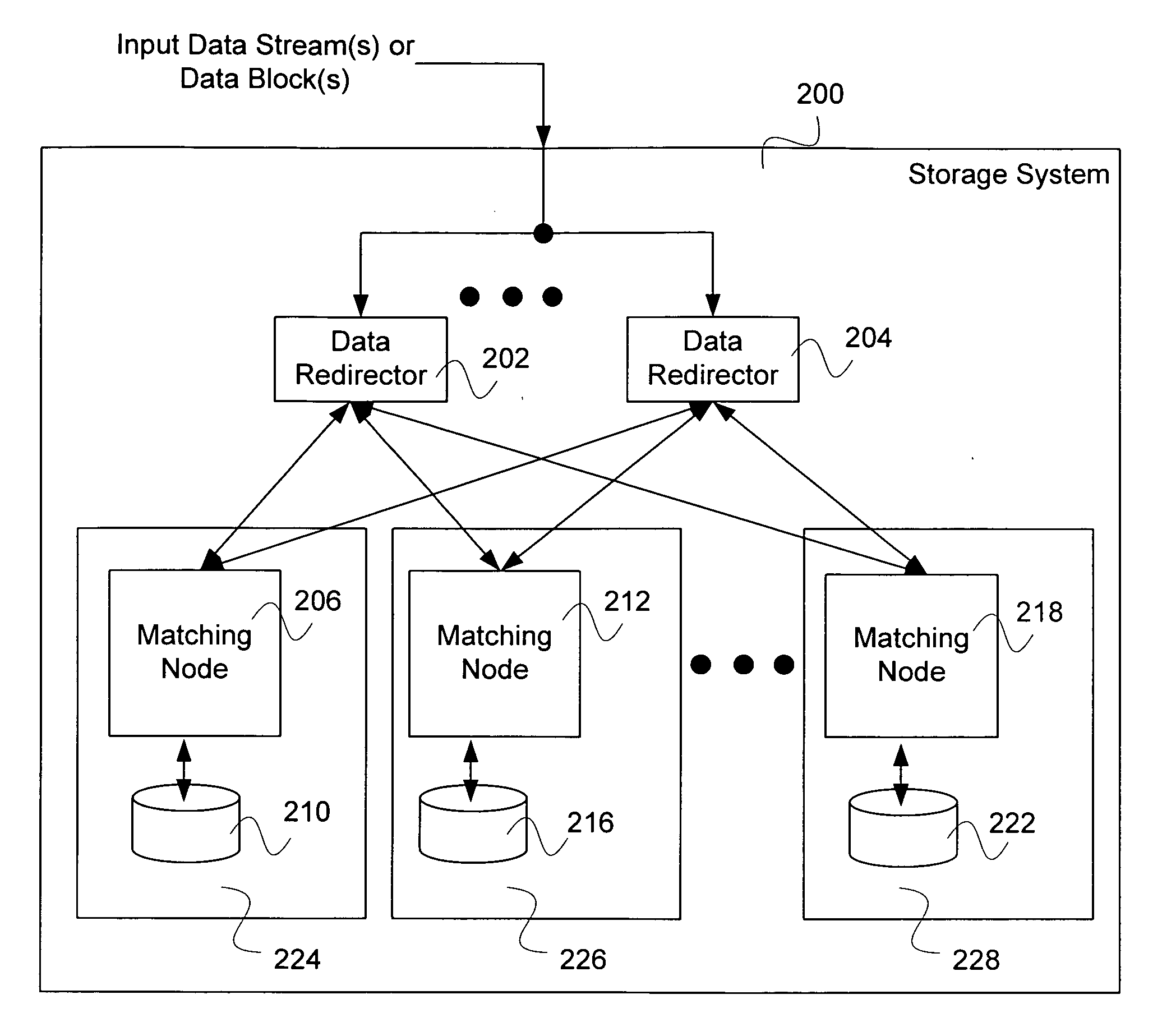
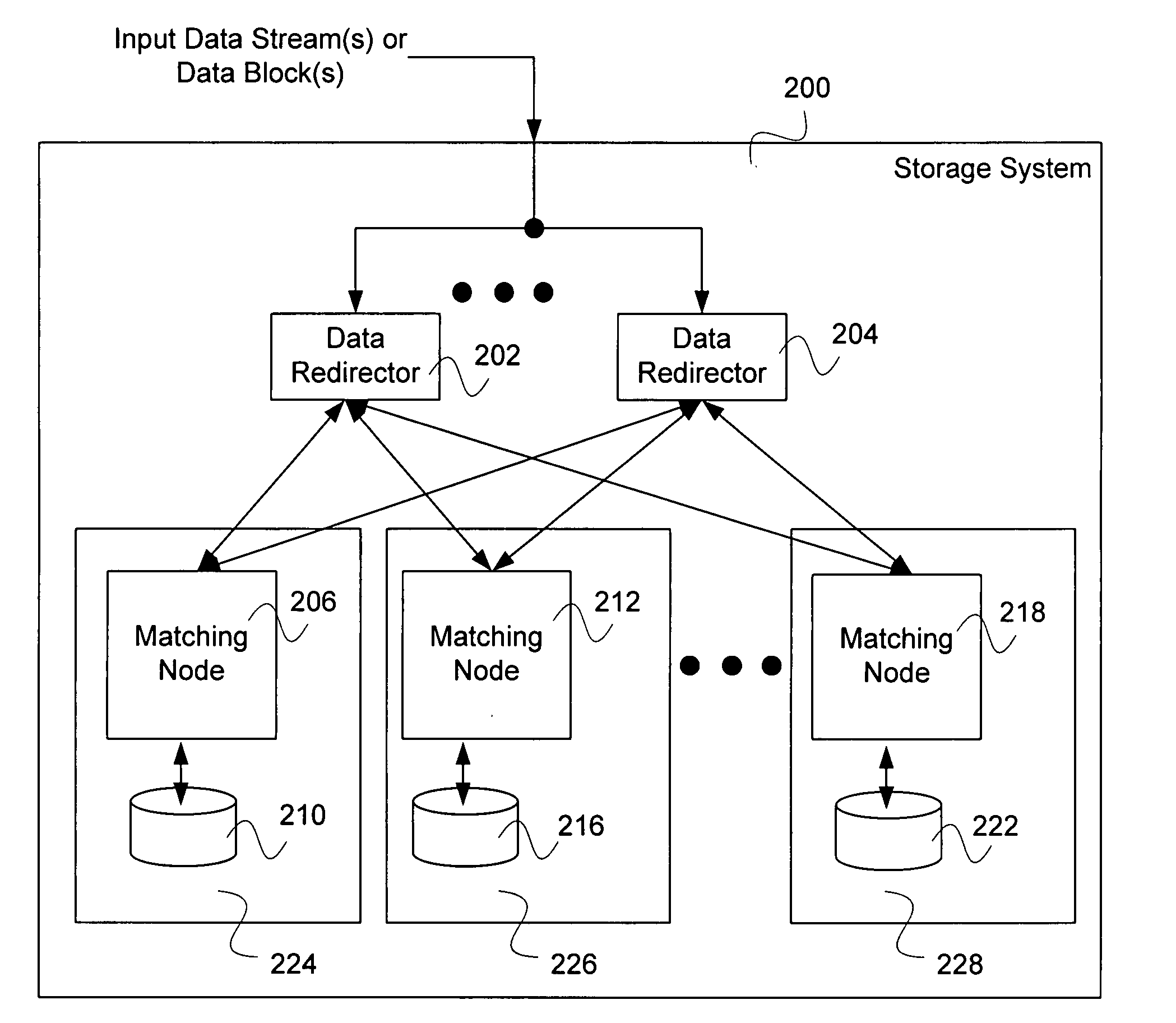
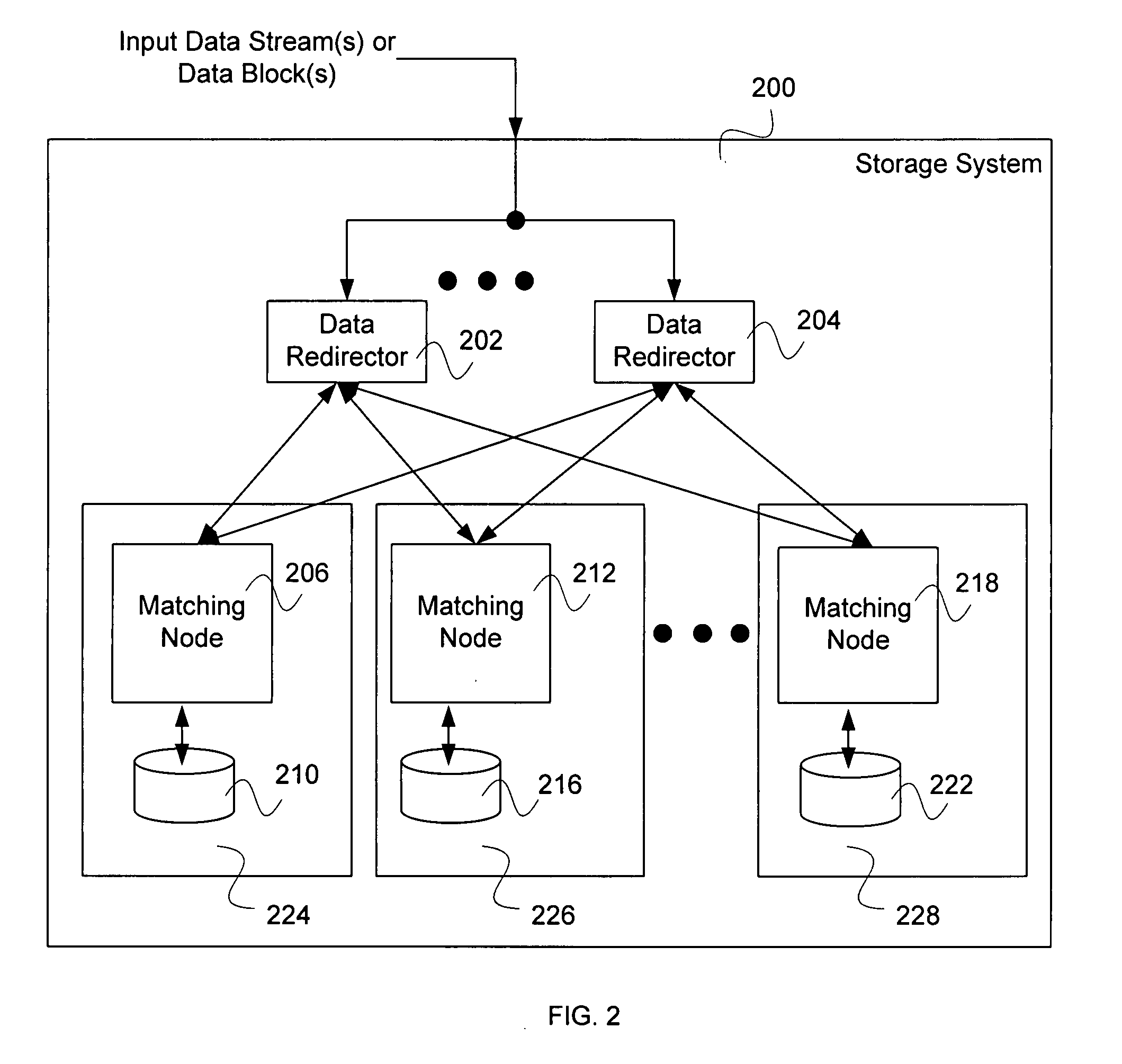
Cluster storage using delta compression
Cluster storage is disclosed. A data stream or a data block is received. The data stream or the data block is broken into segments. For each segment, a cluster node is selected, and in the event that a similar segment to the segment is identified that is already managed by the selected cluster node, a reference to the similar segment and a delta between the similar segment and the segment is caused to be stored on the selected cluster node.
Owner:EMC IP HLDG CO LLC
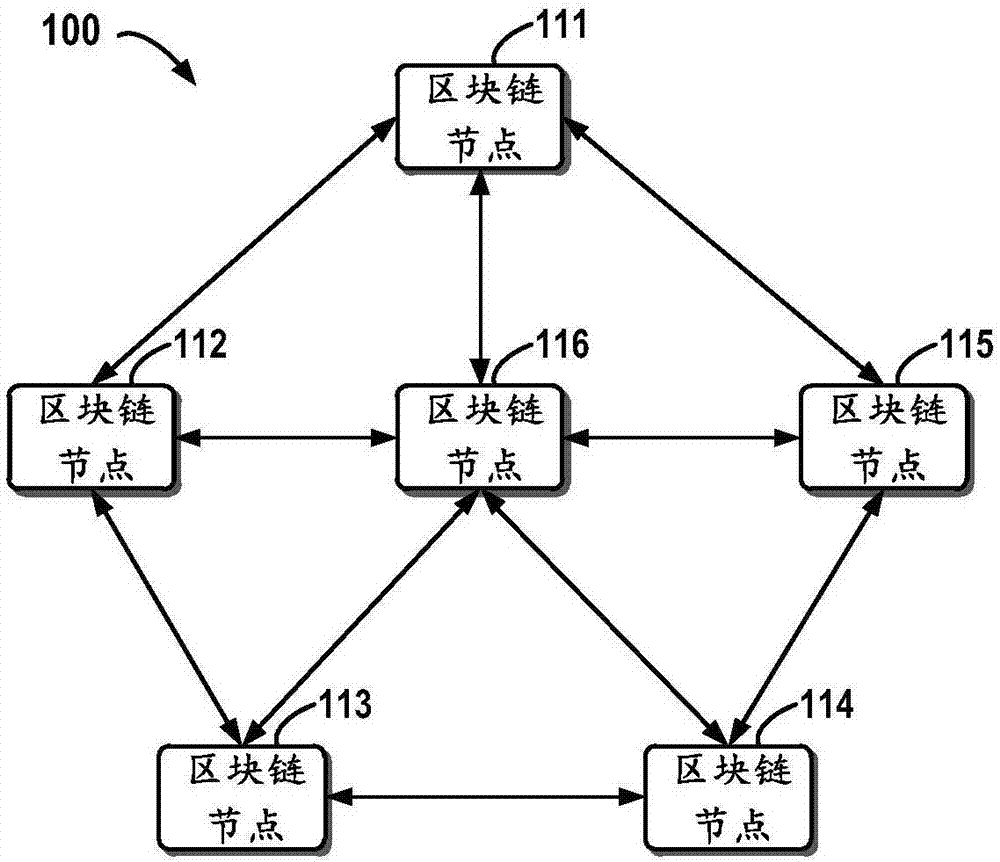
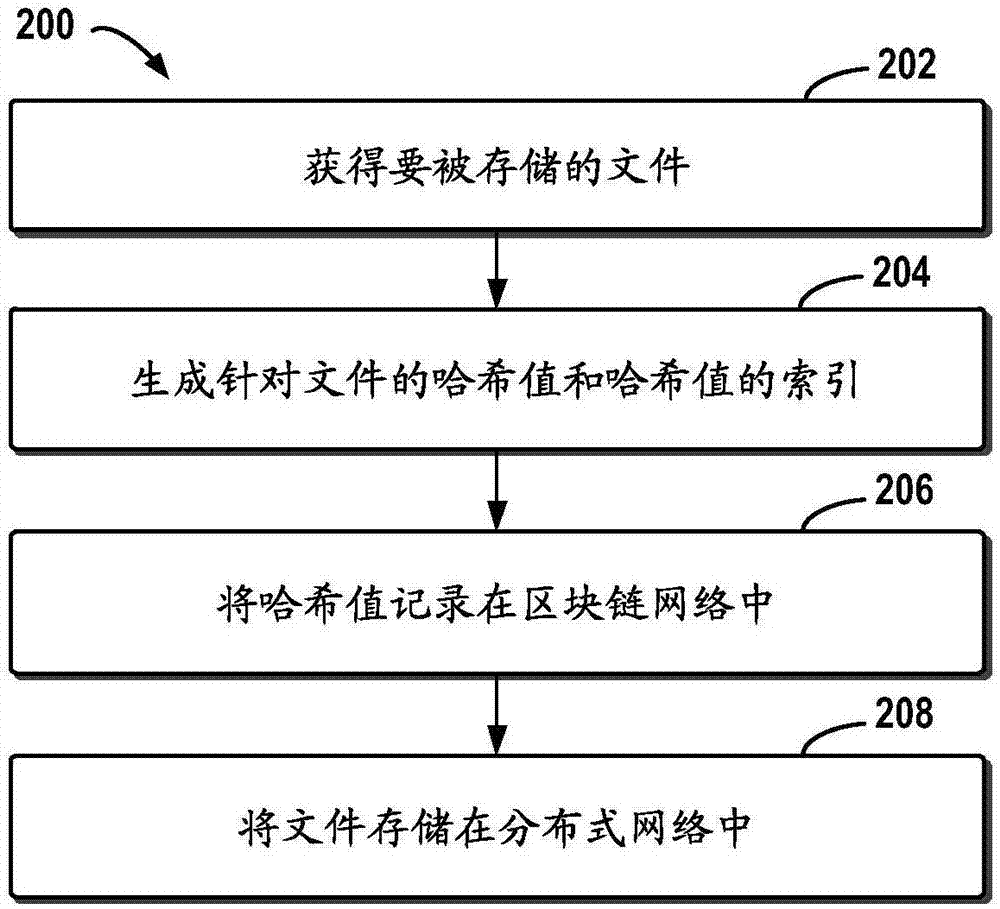
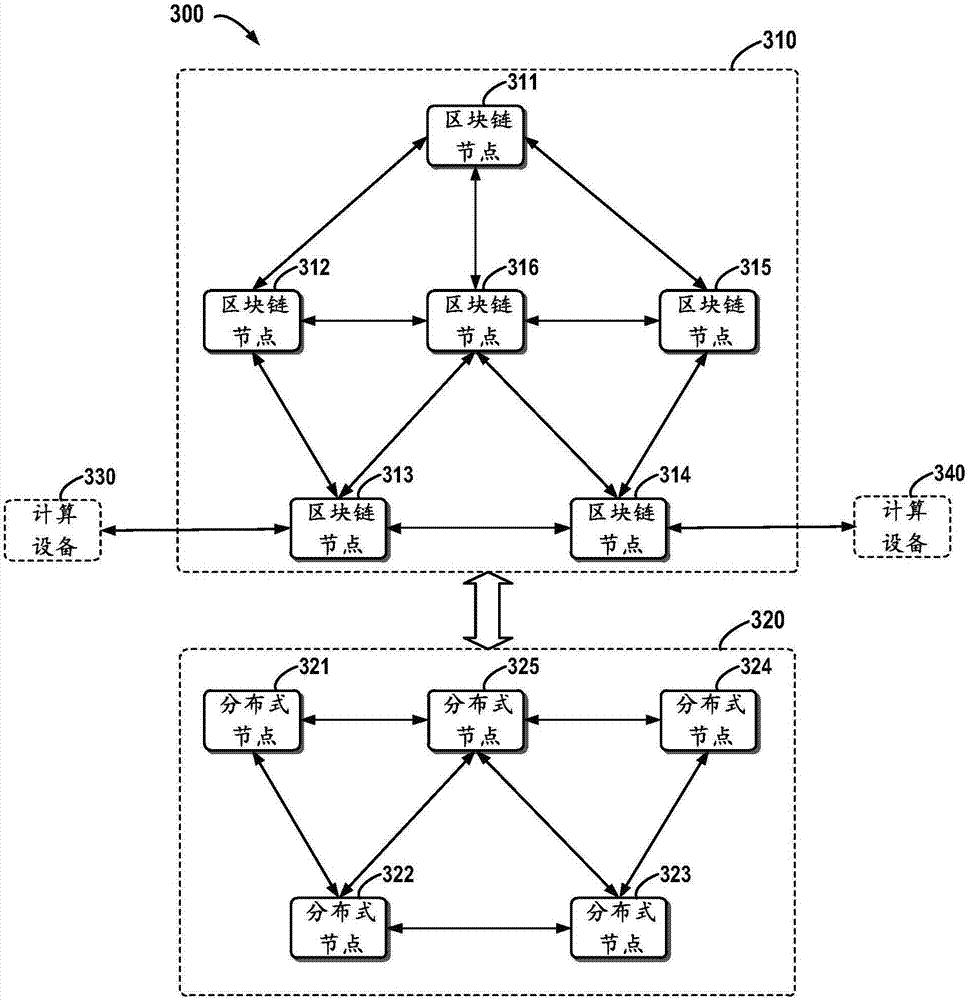
Block chain-based distributed storage
InactiveCN107273410ASolve the problem of limited node capacityAchieve tamper resistanceFile access structuresSpecial data processing applicationsTamper resistanceDistributed File System
The embodiment of the disclosure relates to block chain-based distributed storage, and discloses a block chain-based distributed storage method. The method includes: obtaining a file which needs to be stored, and generating a hash value and an index of the hash value for the file. The method also includes: recording the hash value in a block chain network, and storing the file in a distributed network, wherein the file is located on the basis of the hash value in the distributed network. Therefore, according to the embodiment of the disclosure, tampering proofing and the distributed storage of the file can be realized through combining a block chain and a distributed file system, thus the problem of the limited capacity of block chain nodes is solved, and the authenticity and the availability of the stored file are effectively guaranteed.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS20020052884A1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsData processing systemUnique identifier
In a data processing system, a mechanism identifies data items by substantially unique identifiers which depend on all of the data in the data items and only on the data in the data items. Existence means determine whether a particular data item is present in the system, by examining the identifiers of the plurality of data items.
Owner:LEVEL 3 COMM LLC +1
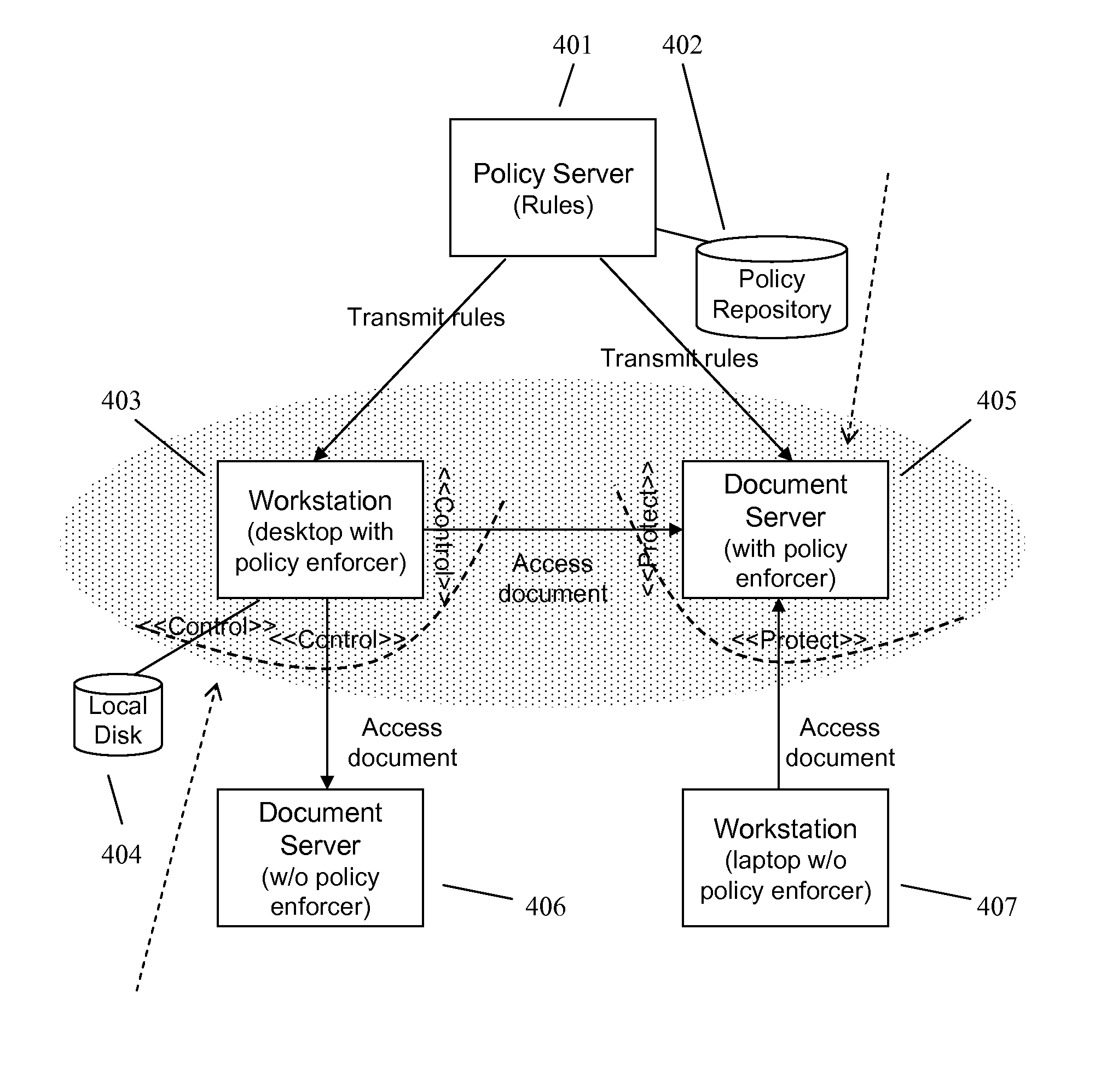
Techniques and System for Specifying Policies Using Abstractions
ActiveUS20070157287A1Specific access rightsError detection/correctionHuman languageComputer security
A policy language for an information management system allows specifying or more policies using policy abstractions. The policies and policy abstractions are decoupled from one another, so policies and policy abstractions may be specified and altered separately from each other. A policy may refer to any number of policy abstractions. Multiple policies may reference a single policy abstraction, and a change to that policy abstraction will result in multiple policies being changed. Further, policy abstractions may be nested, so one policy abstraction may reference another policy abstraction, and so forth.
Owner:BLUE JUNGLE
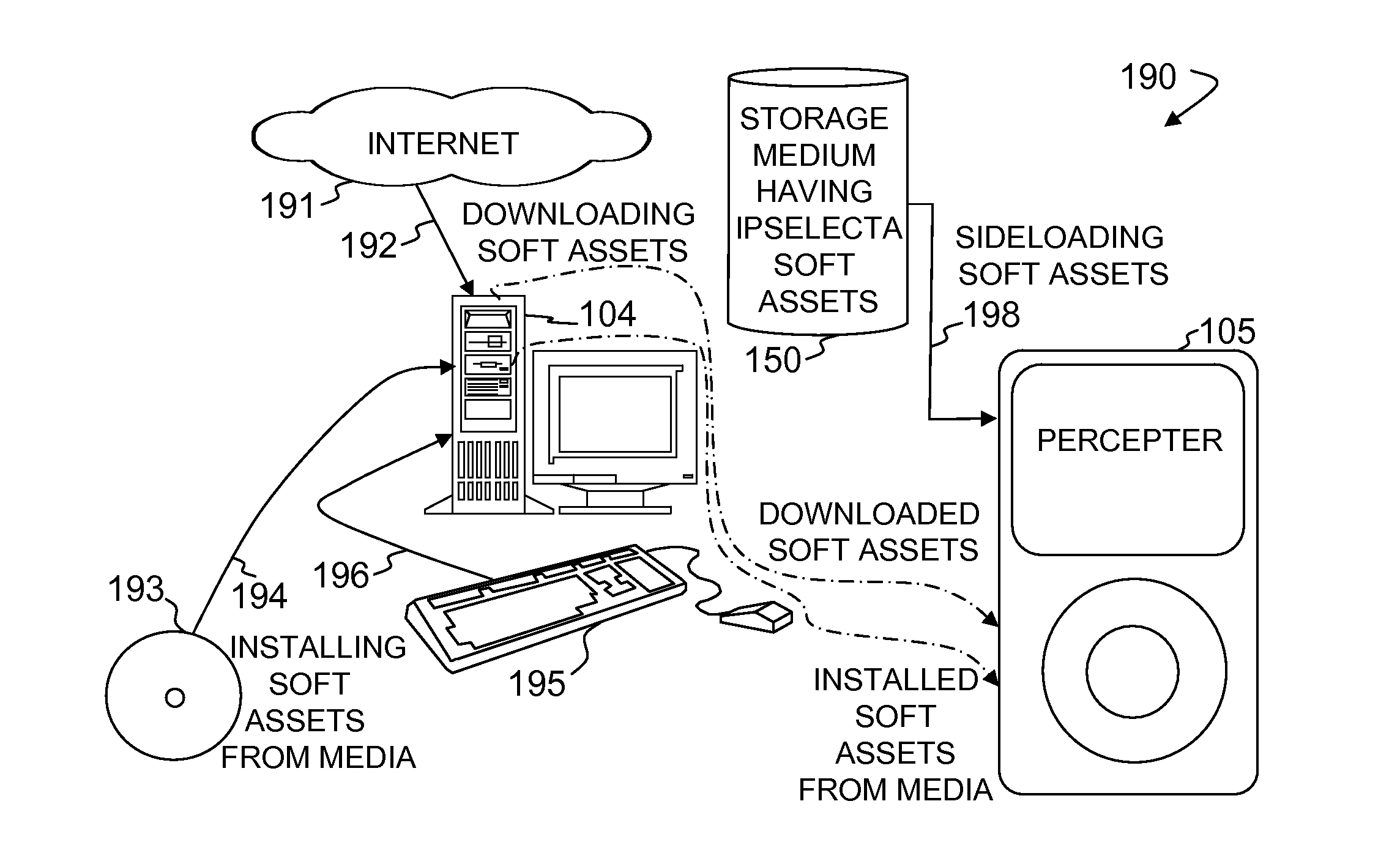
Method and apparatus for delivering percepta
InactiveUS20080141242A1Enhanced couplingOptimizationPayment architectureAutomatic exchangesOperating systemNew device
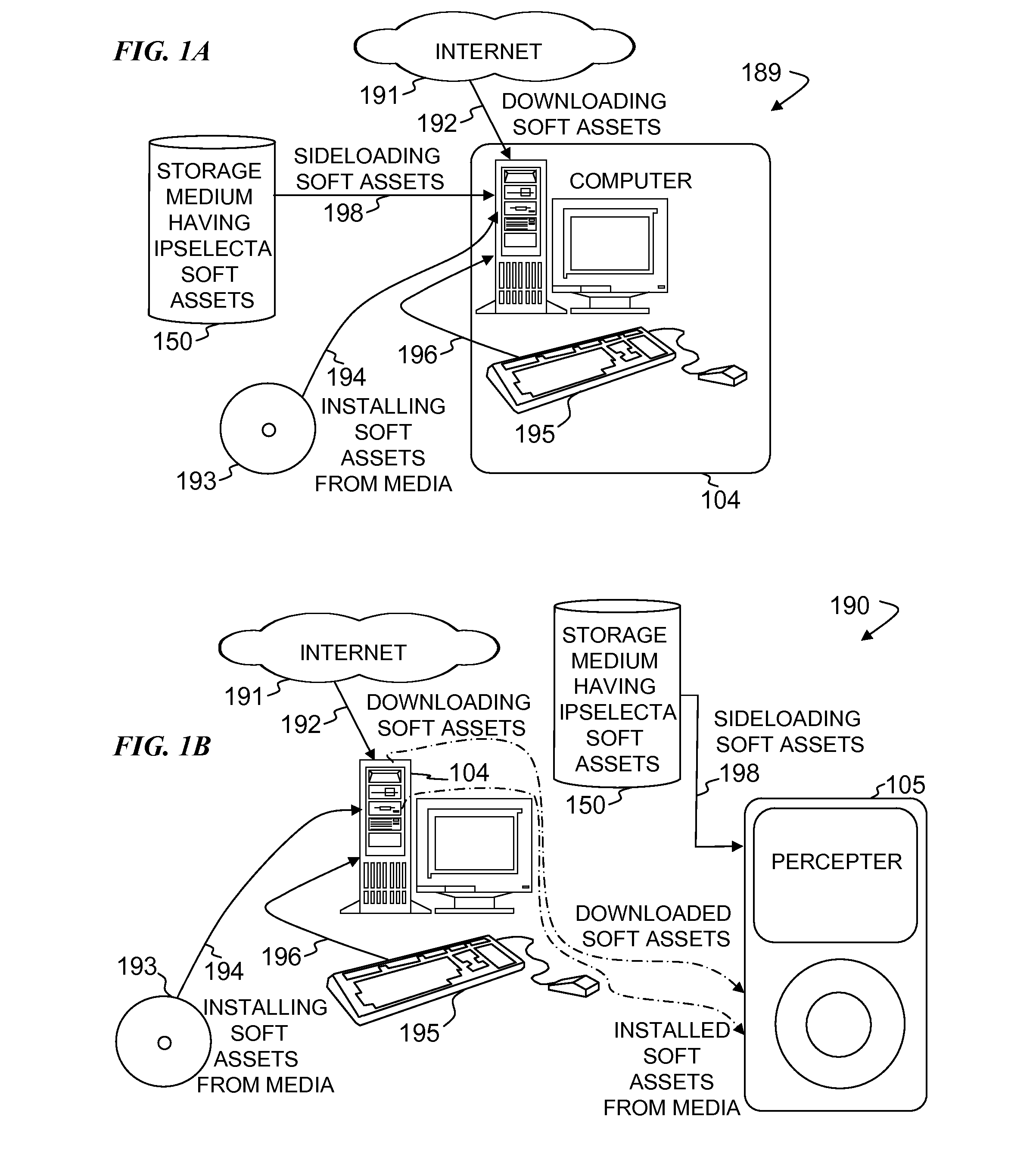
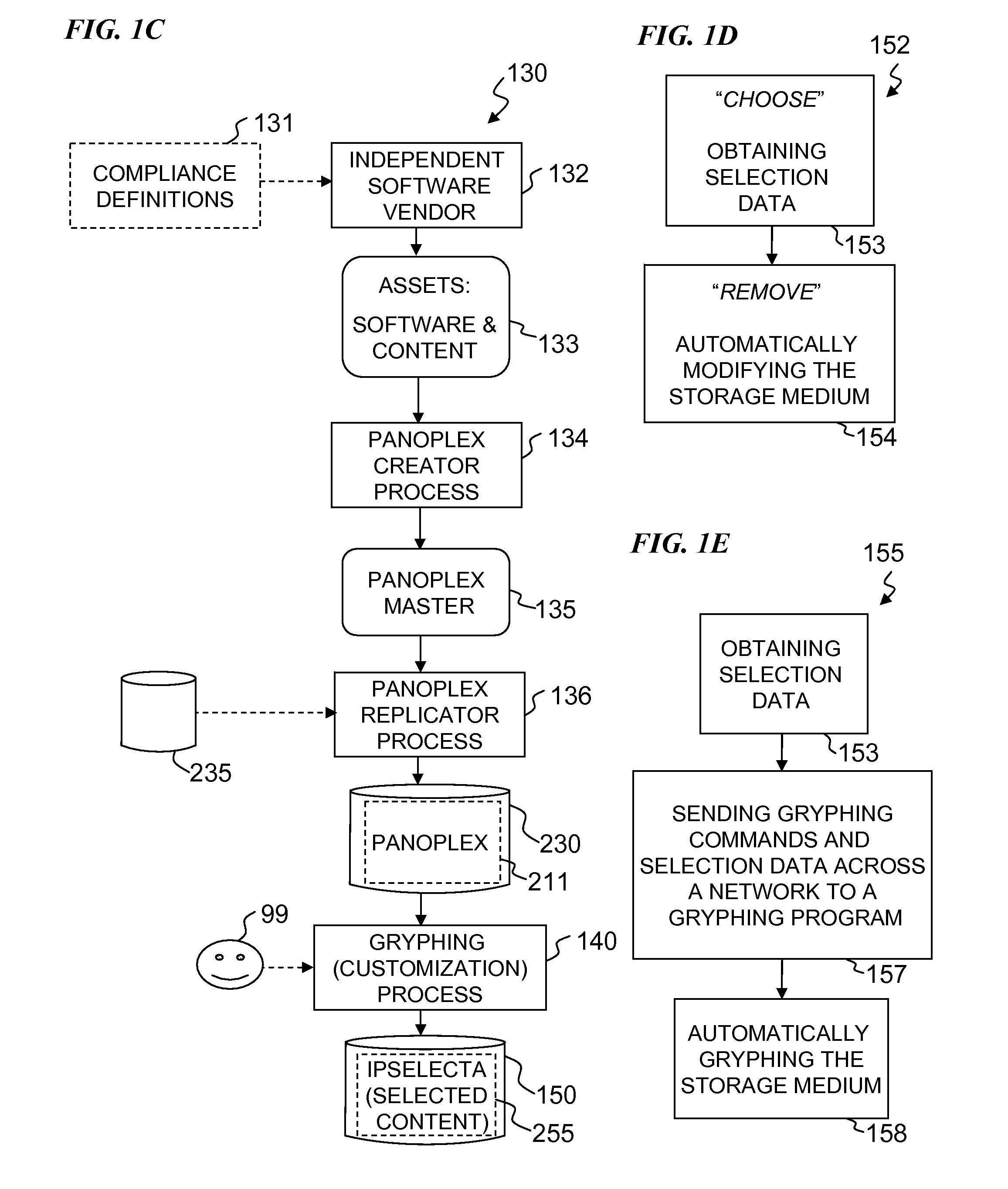
An apparatus and method for obtaining a storage medium with a deeply customizable set of installed content. Soft assets (e.g., programs, songs, videos, etc.) that form the content are selected from among a much larger set of preinstalled soft assets previously stored on storage media, such as disk drives. In some embodiments, based on a user's selections, the non-selected assets are permanently erased from a storage medium, while the remaining assets are available as installed (wherein substantially no further processing is required to install them). In some embodiments, a new device uses the storage medium to provide its user with a fully functional device without the need to separately install the soft assets from a plurality of sources (e.g., from program-distribution CDROMS and the like). Some embodiments include the storage medium having the soft assets installed, and including a program that elicits selections from a user and erases non-selected assets.
Owner:SHAPIRO ALAN JOSHUA
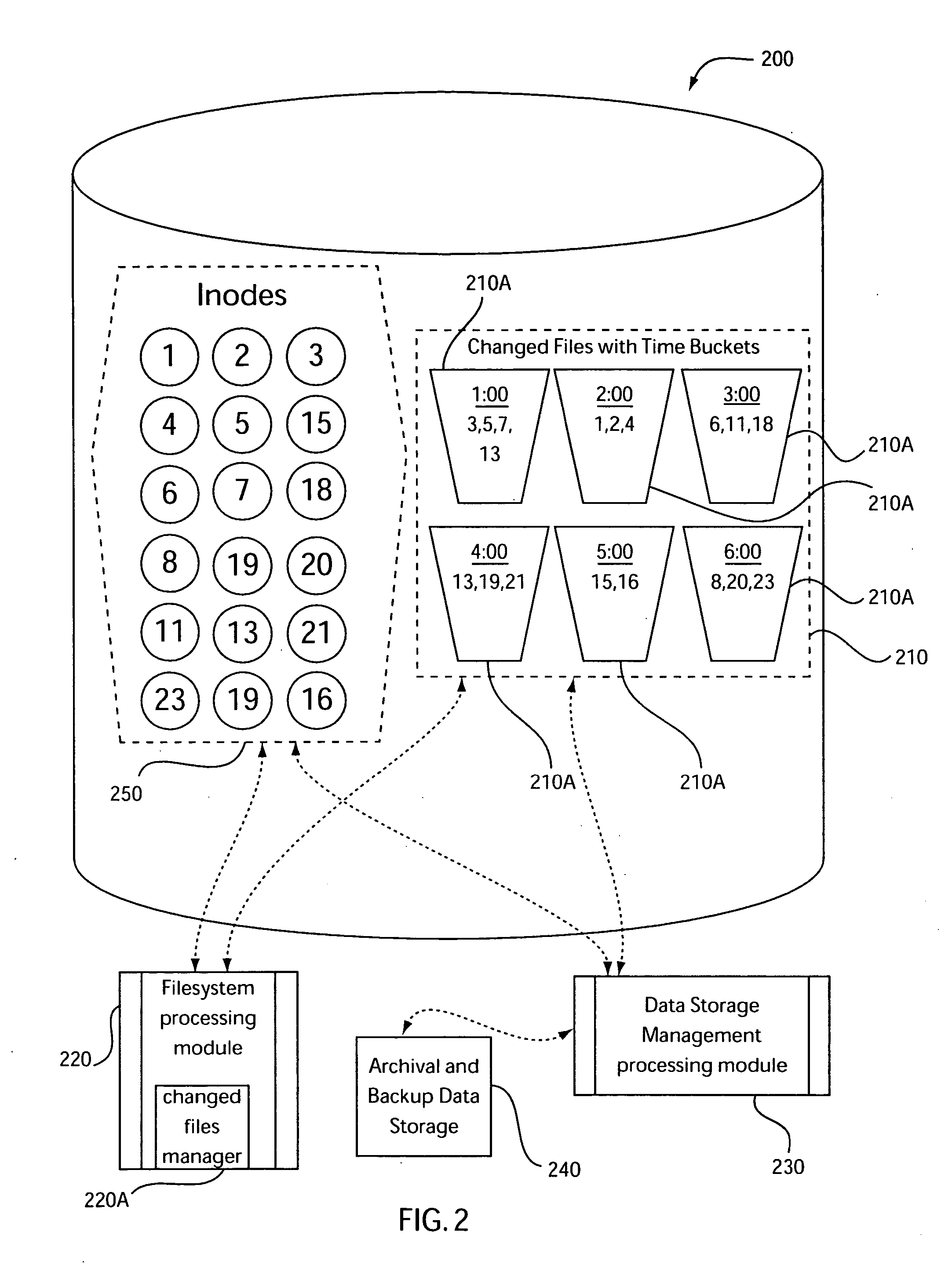
Changed files list with time buckets for efficient storage management
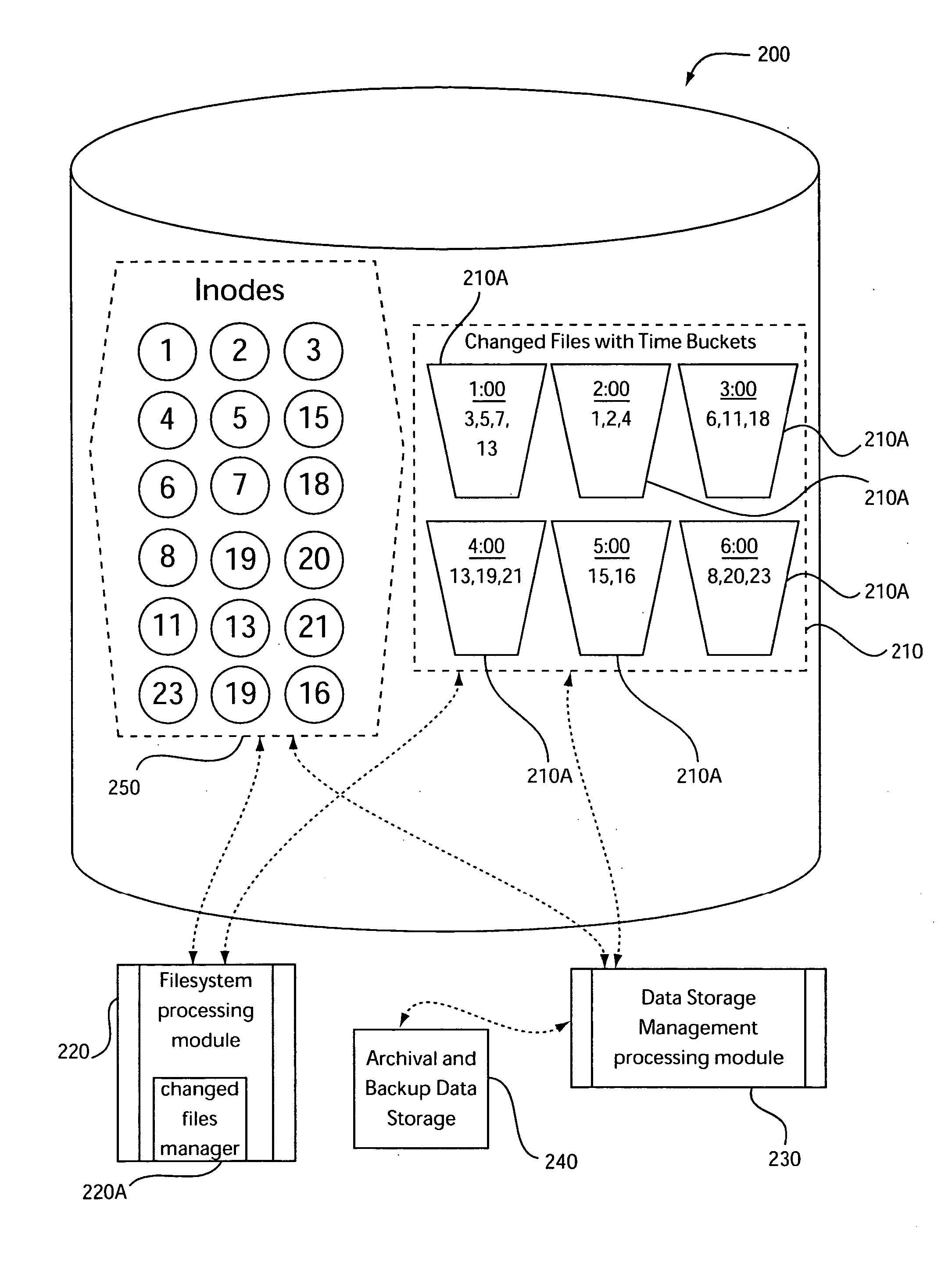
InactiveUS20060259527A1File access structuresSpecial data processing applicationsTimestampManagement object
There is provided, in a computer processing system, an apparatus for managing object data. The apparatus includes a changed objects manager for creating and managing a changed objects list that at least identifies the objects that have changed based on time of change. The changed objects list is associated with a plurality of time buckets. Each of the plurality of time buckets is associated with a respective date and time period and with object change records for objects having a timestamp falling within the respective date and time period. Each of the object change records is associated with a unique object identifier and the timestamp for a corresponding one of the objects. The timestamp specifies a date and a time corresponding to a latest one of a creation time or a most recent update time for the corresponding one of the objects.
Owner:IBM CORP
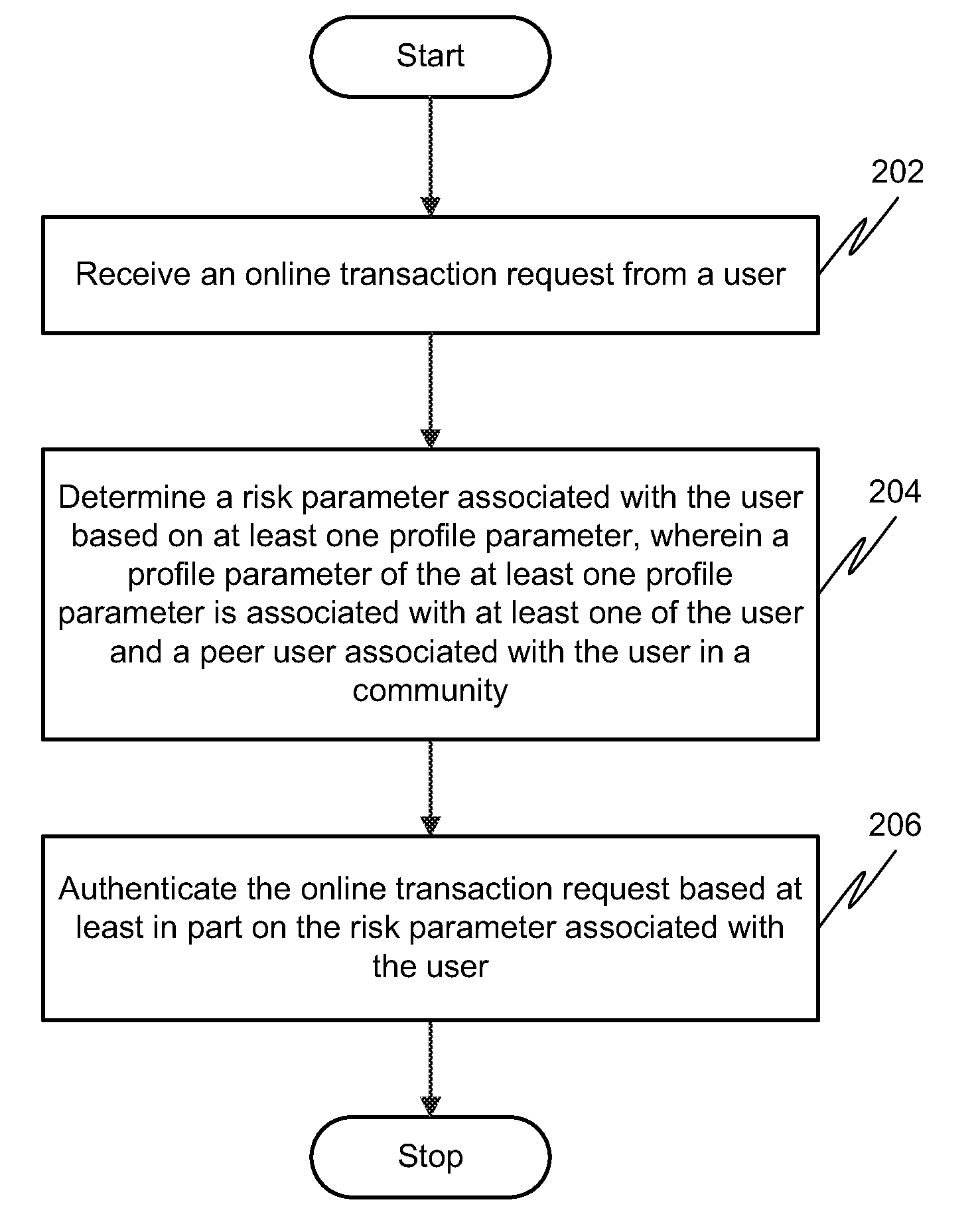
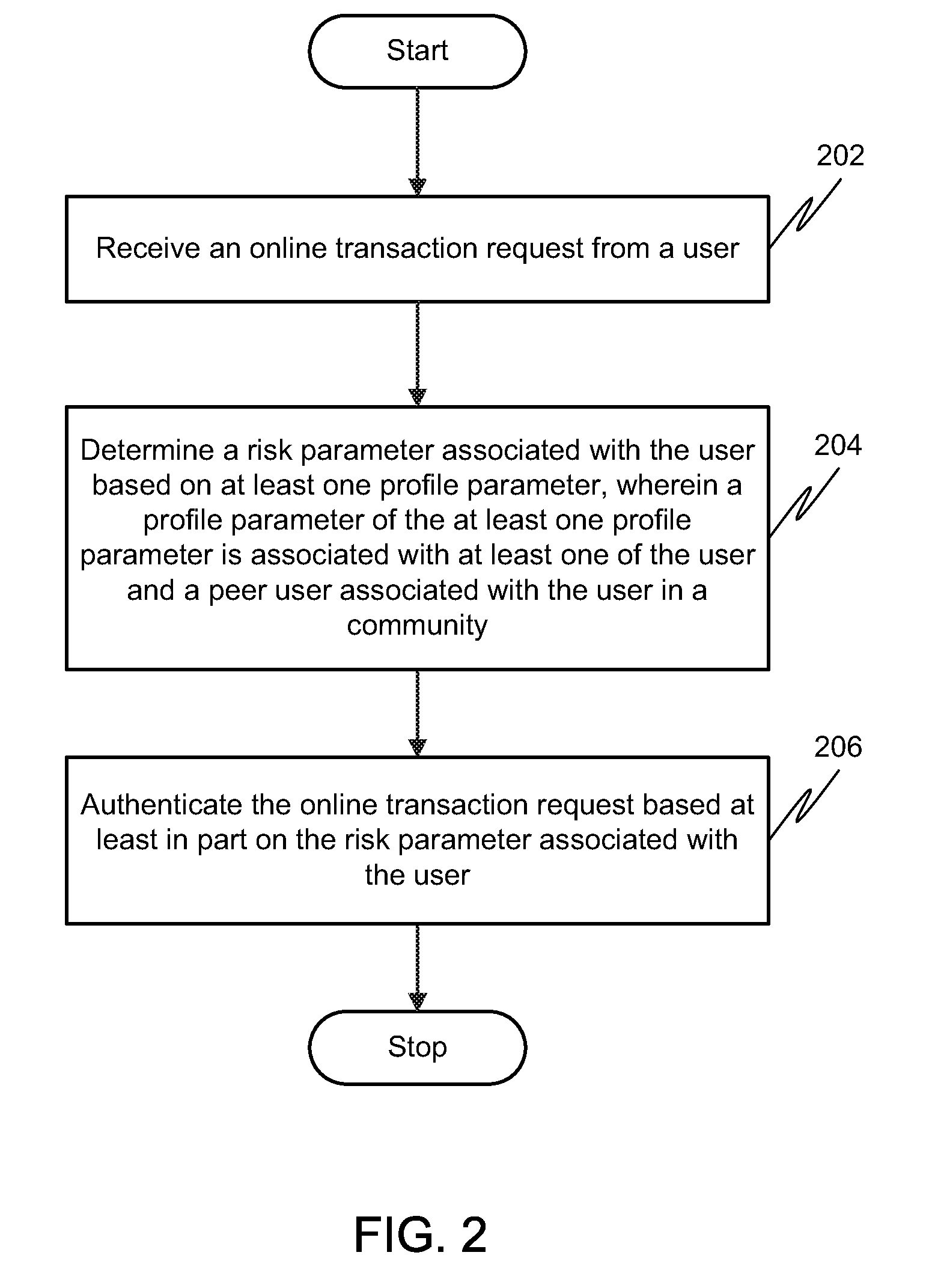
Method and system for authenticating online transactions
The present invention generally relates to authenticating online transactions, and more specifically, to method and system for determining a potentially fraudulent online transaction request based on a risk parameter associated with a user in a networking platform such as, a social networking platform. The method comprises receiving an online transaction request from a user. Thereafter, determining the risk parameter of the user based on one or more profile parameters associated with the user or one or more peer users associated with the user in the community. Based on the risk parameter of the user the online transaction request of the user is authenticated.
Owner:VISA INT SERVICE ASSOC
Transaction-based storage system and method that uses variable sized objects to store data
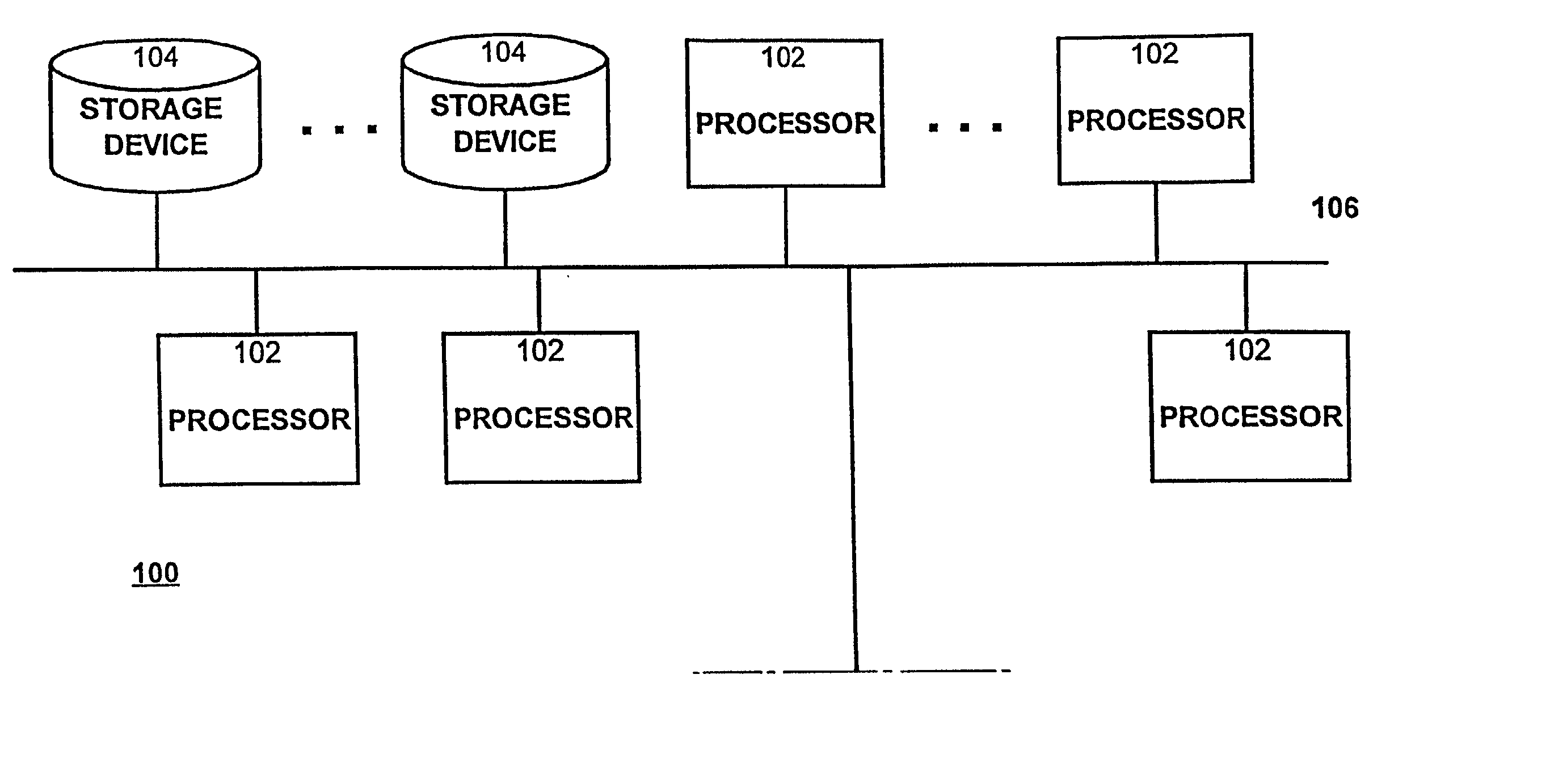
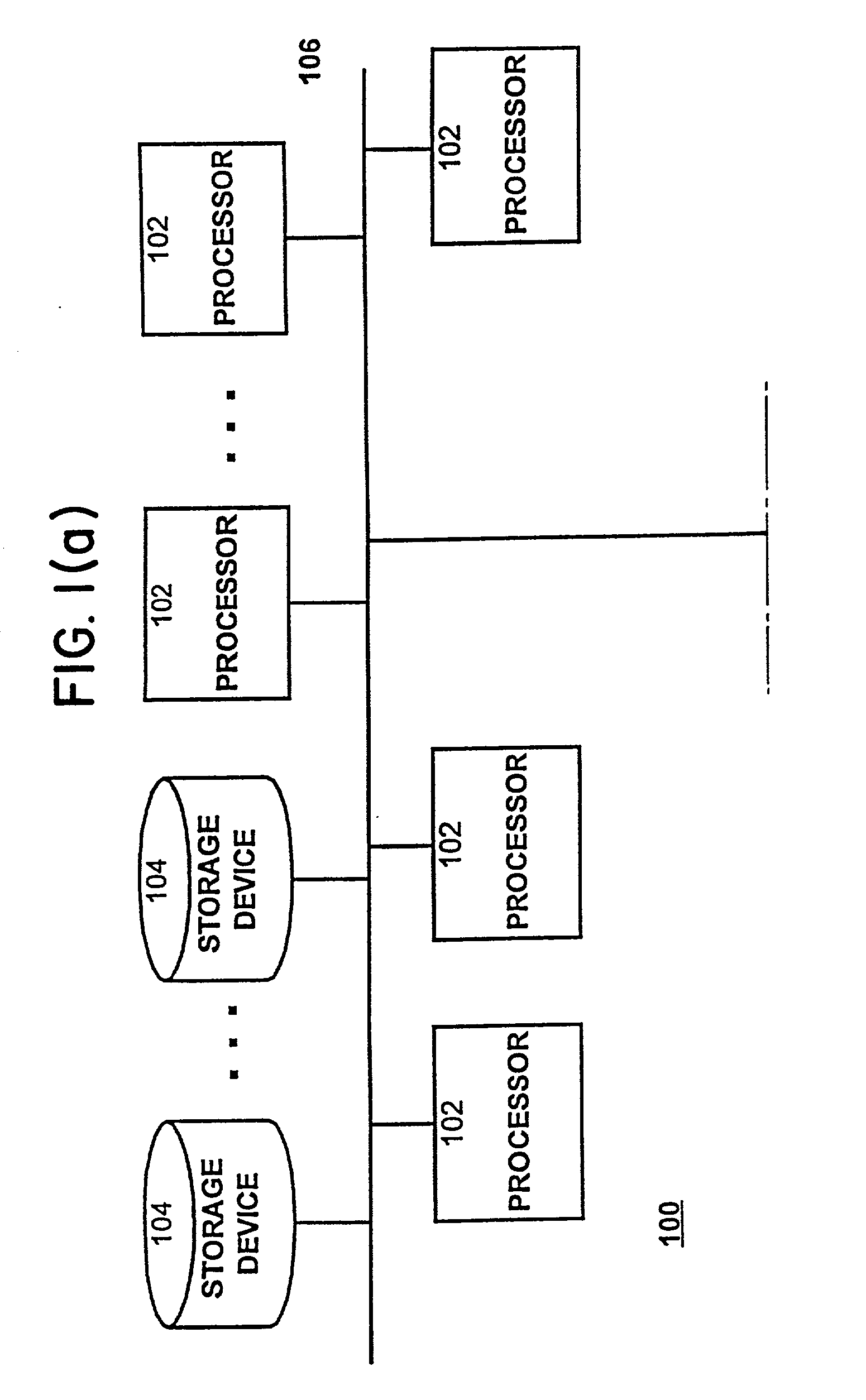
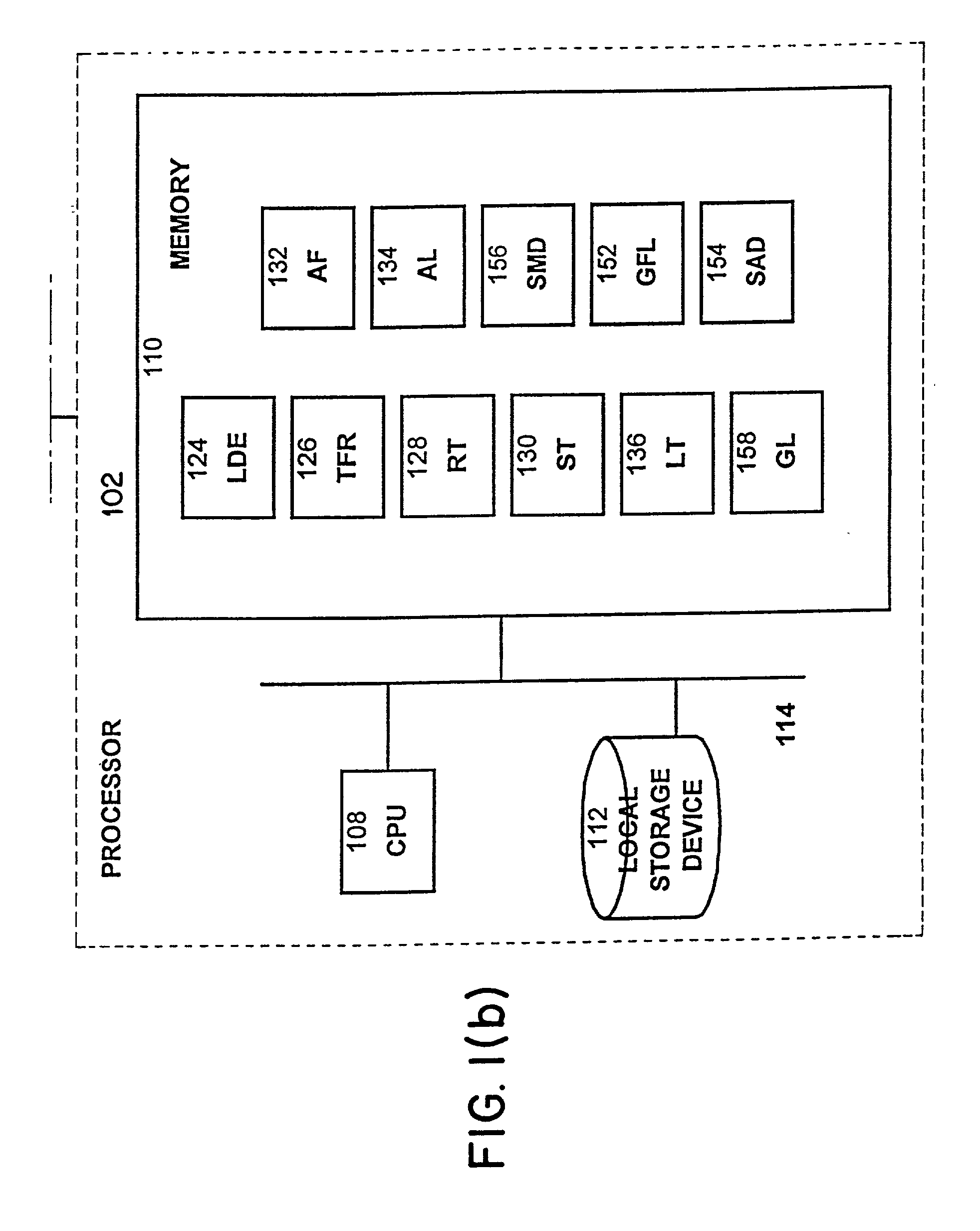
ActiveUS20050257083A1Increase write speedImprove reading speedMemory loss protectionError detection/correctionExtendible hashingBinary tree
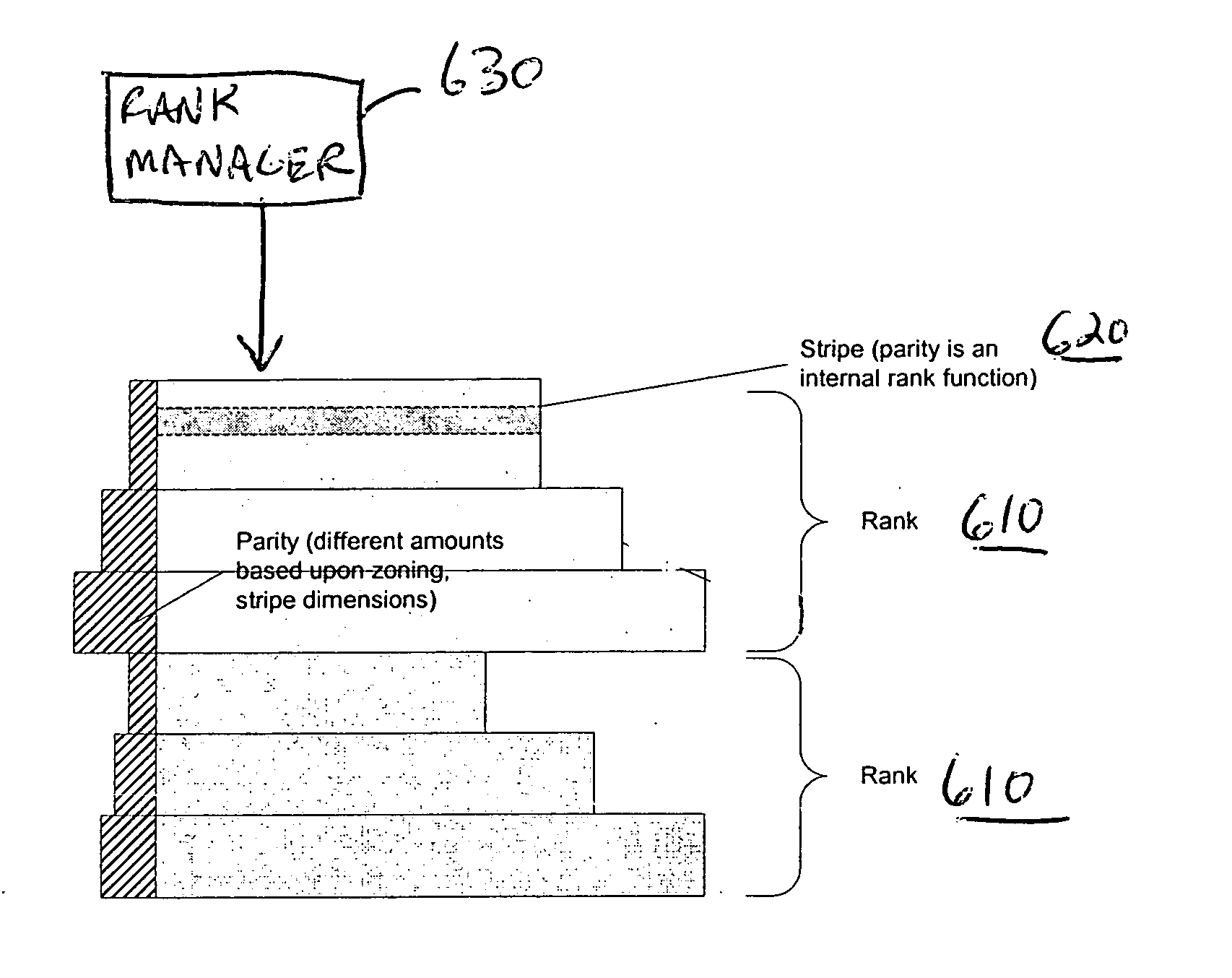
The present invention provides a storage system for storing variable sized objects. The storage system is preferably a transaction-based system that uses variable sized objects to store data. The storage system is preferably implemented using arrays disks that are arranged in ranks. Each rank includes multiple stripes. Each stripe may be read and written as a convenient unit for maximum performance. A rank manager is able to dynamically configure the ranks to adjust for failed and added disks by selectively shortening and lengthening the stripes. The storage system may include a stripe space table that contains entries describing the amount of space used in each stripe. An object map provides entries for each object in the storage system describing the location (e.g., rank, stripe and offset values), the length and version of the object. A volume index translates regions of logical storage into object identifiers. The storage system may implement various types of formats such as I-node, binary tree and extendible hashing formats.
Owner:COUSINS ROBERT E
Cluster storage using subsegmenting
Cluster storage is disclosed. A data stream or a data block is received. The data stream or the data block is broken into segments. For each segment, a cluster node is selected, and a portion of the segment smaller than the segment is identified that is a duplicate of a portion of a segment already managed by the cluster node.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com