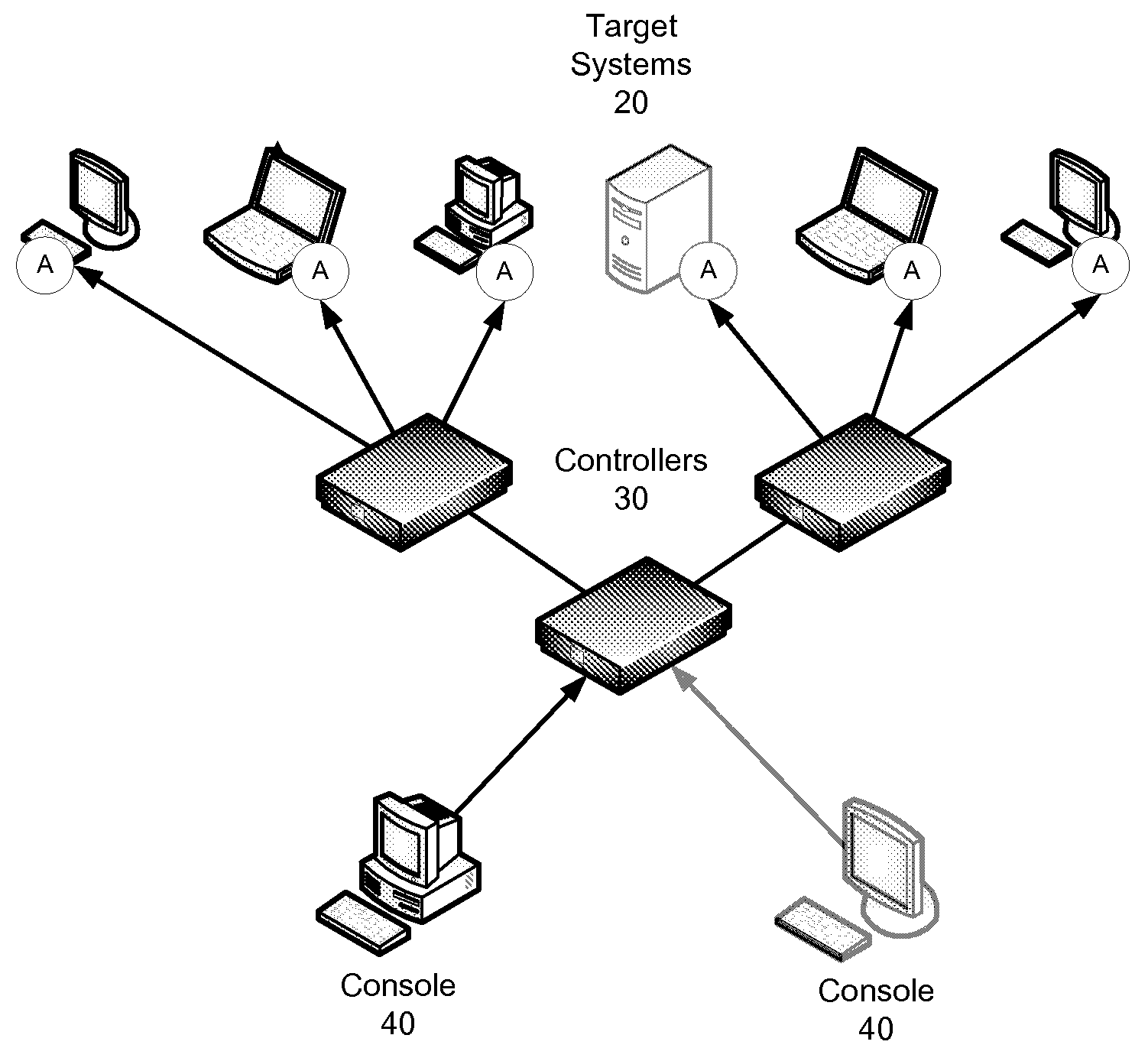
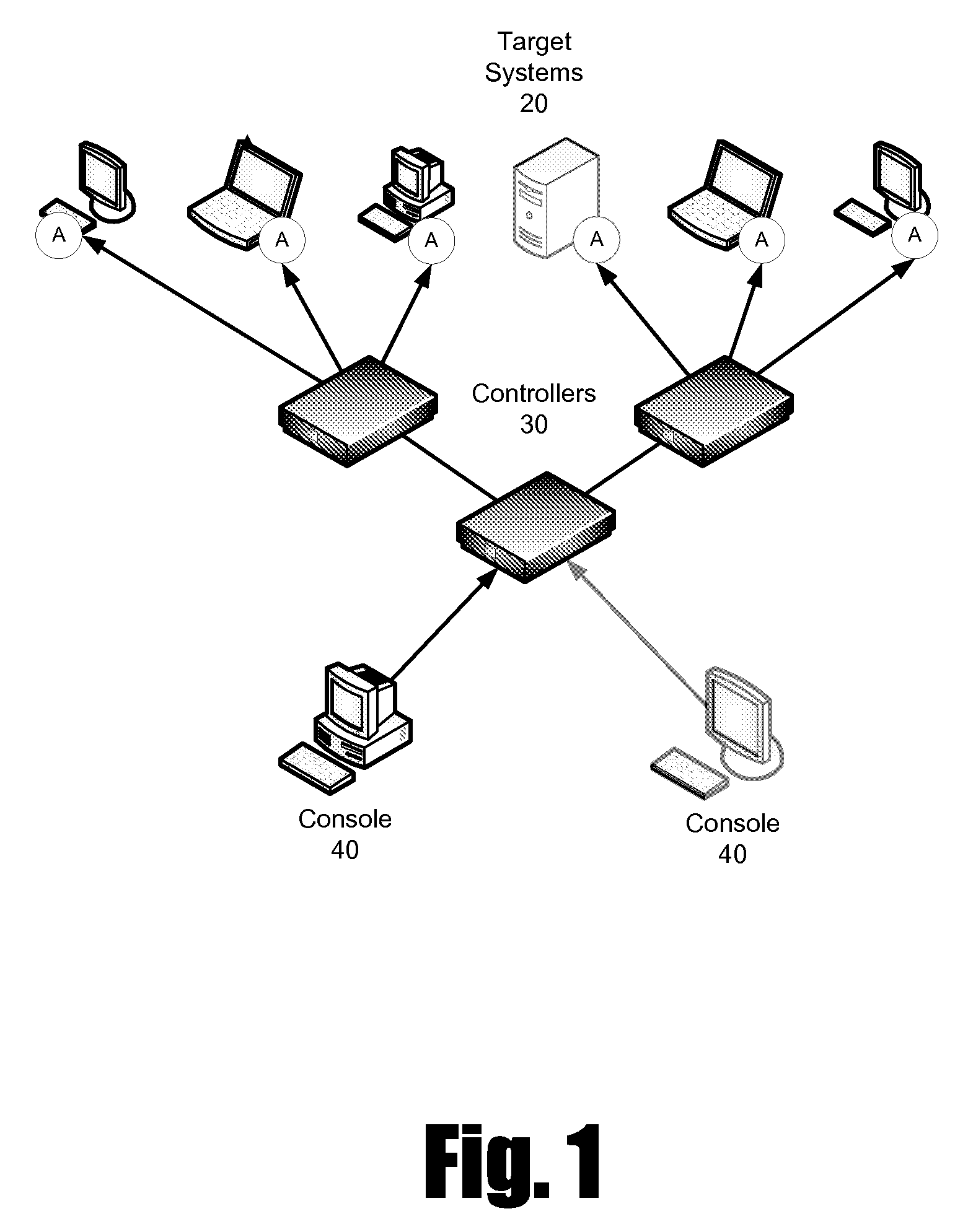
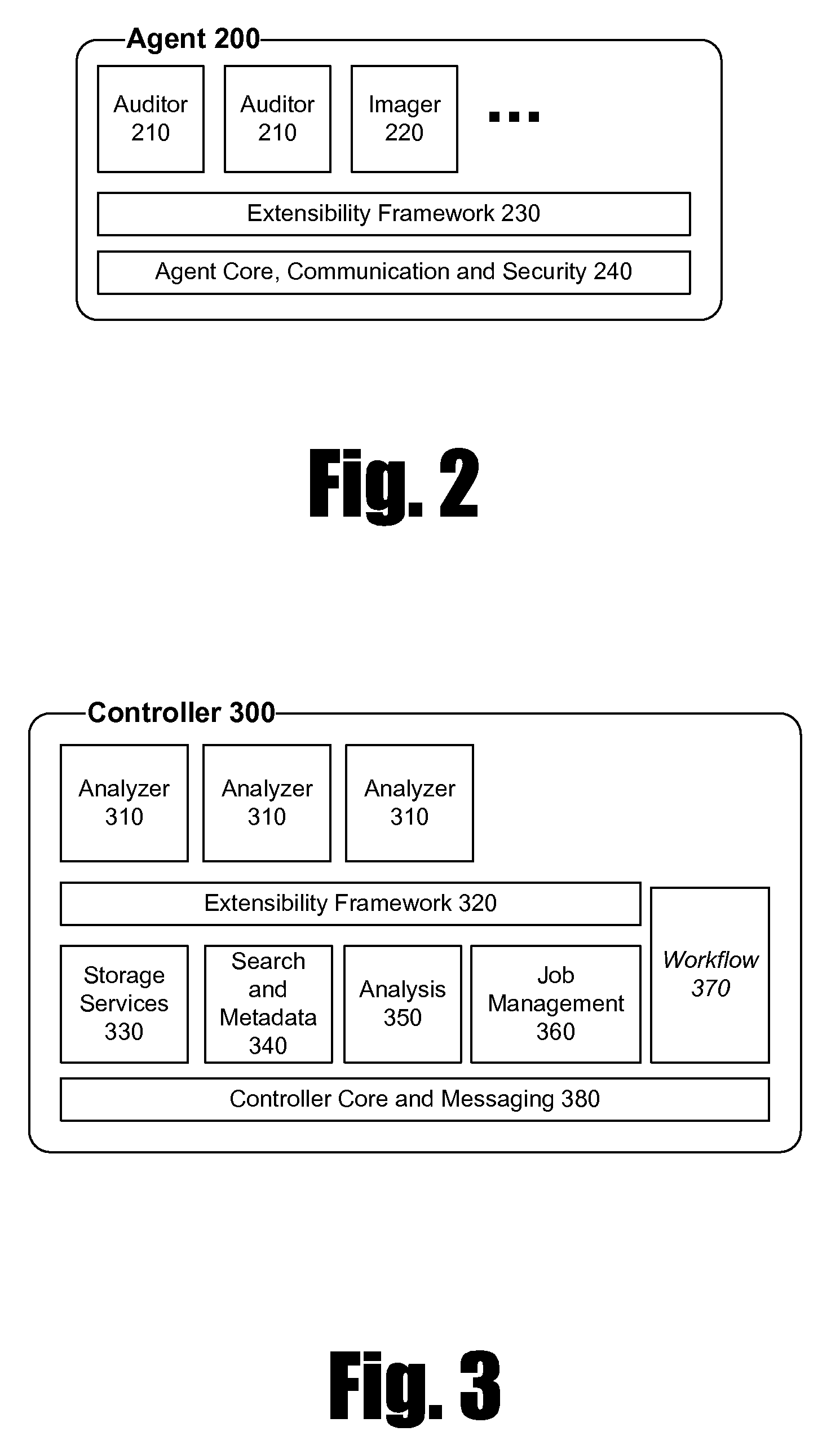
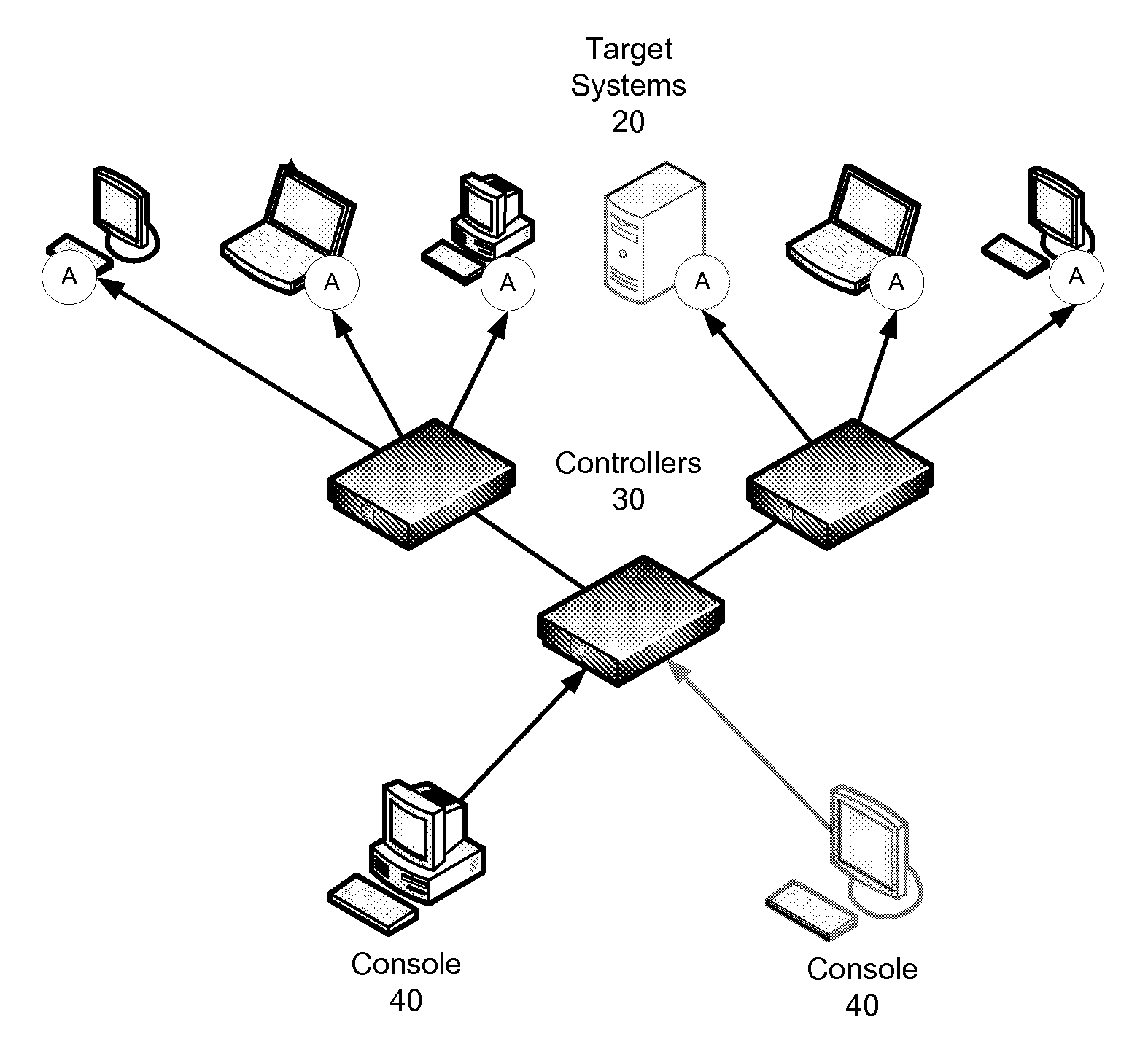
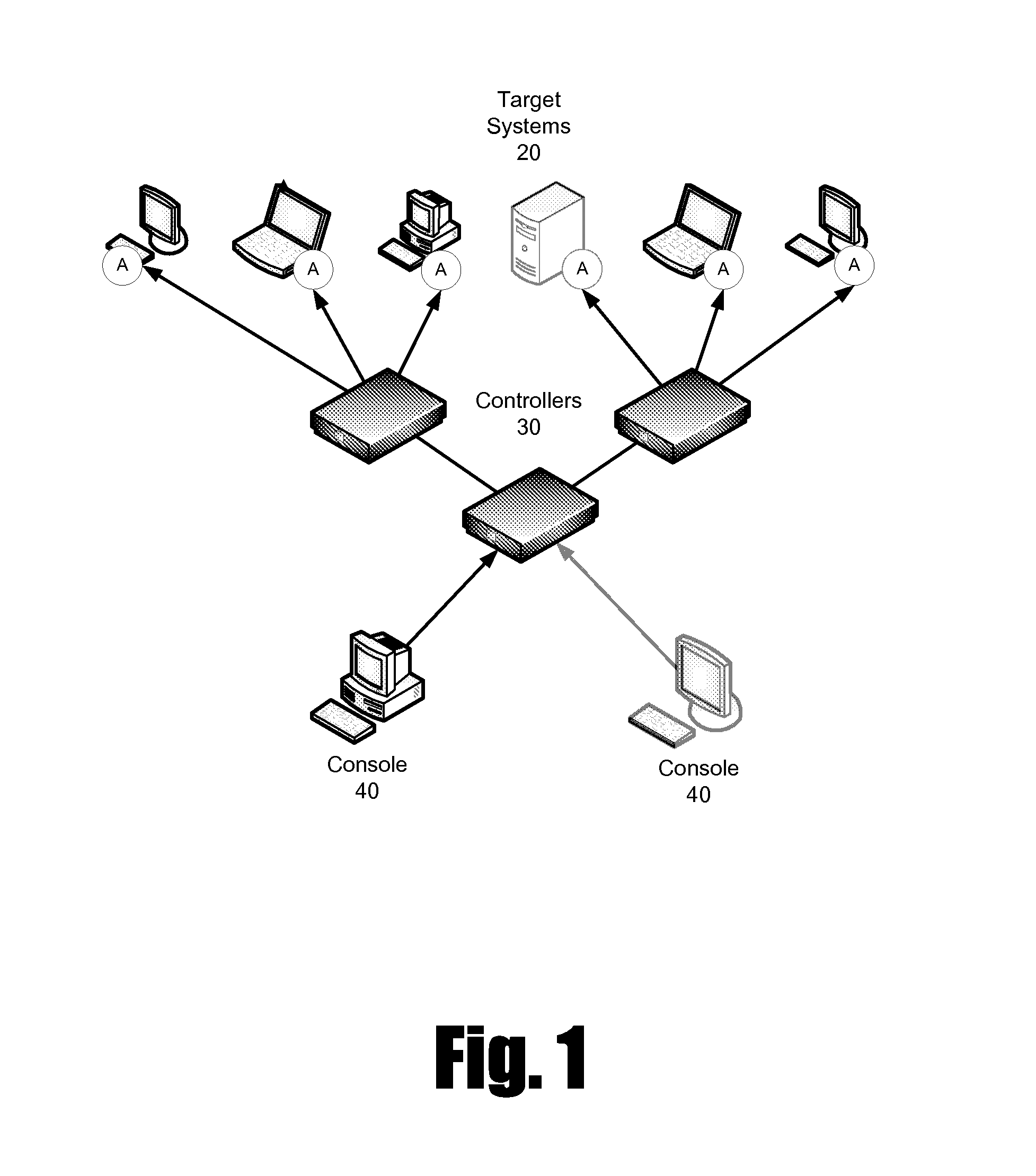
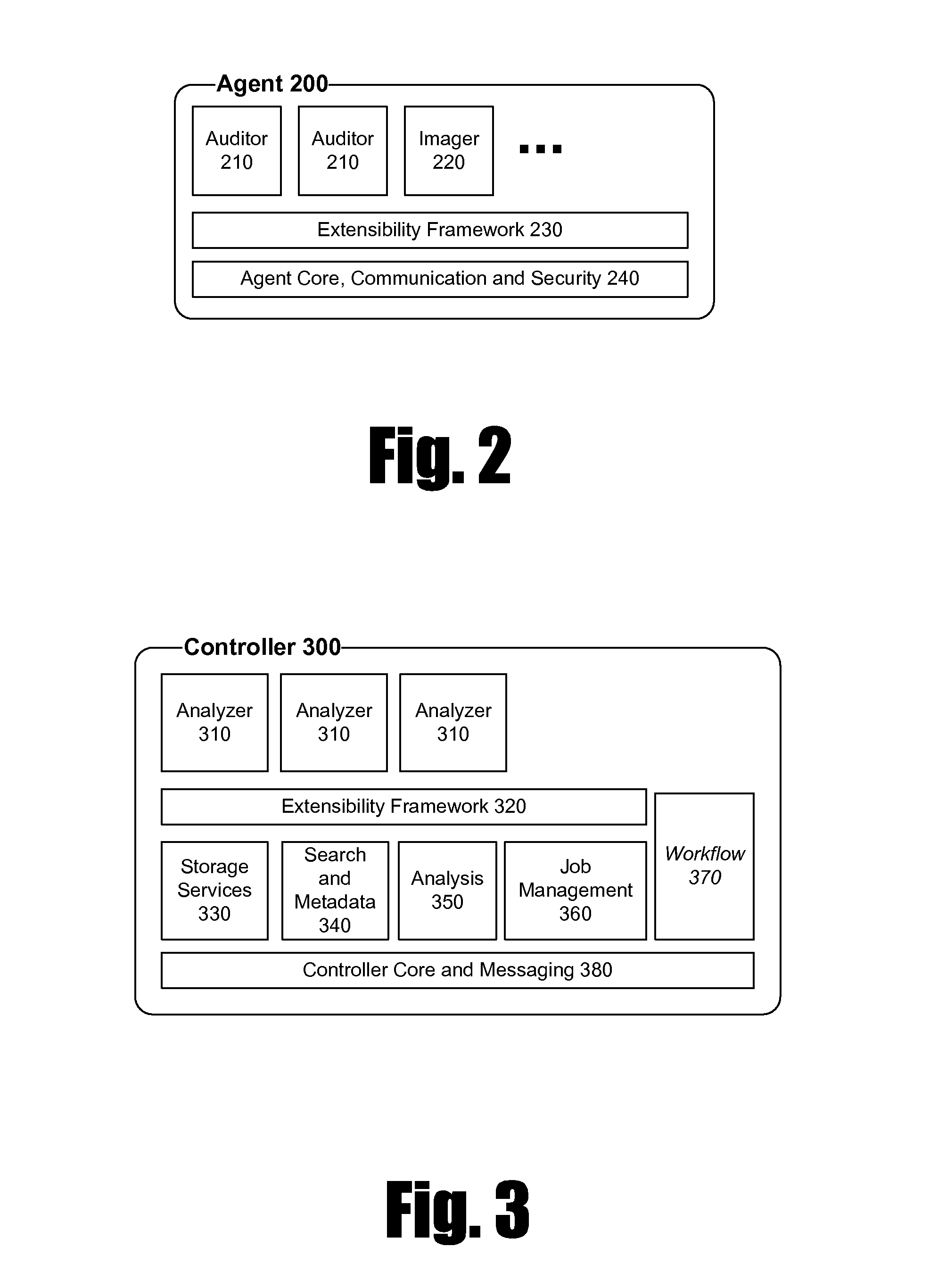
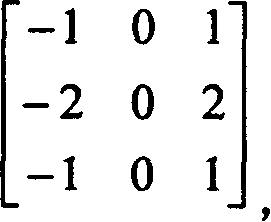Patents
Literature
107 results about "Search computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for data preservation and retrieval
ActiveUS20090198689A1Digital data processing detailsComputer security arrangementsComputerized systemSearch computing
A system and method for searching for computer environments, authenticating the computer environments, and copying data from the authenticated computer environments to a memory location. The data is marked or bound to the computer system it was copied from which provides a user with assurance that the data was obtained from a specific, authenticated source. The computer environments and the memory location may be coupled over a network.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for data preservation and retrieval
ActiveUS7937387B2Digital data processing detailsComputer security arrangementsComputerized systemSearch computing
A system and method for searching for computer environments, authenticating the computer environments, and copying data from the authenticated computer environments to a memory location. The data is marked or bound to the computer system it was copied from which provides a user with assurance that the data was obtained from a specific, authenticated source. The computer environments and the memory location may be coupled over a network.
Owner:FIREEYE SECURITY HLDG US LLC
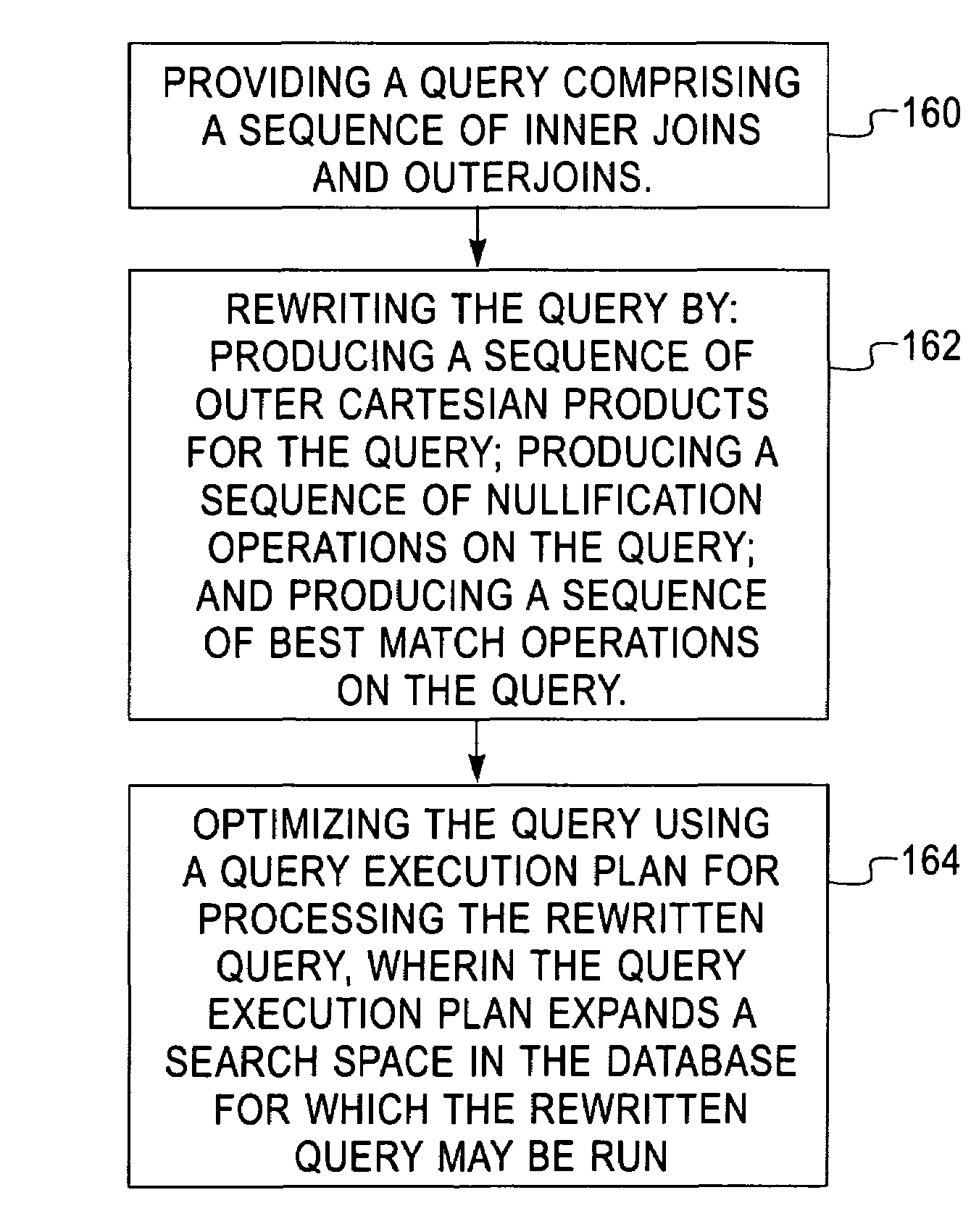
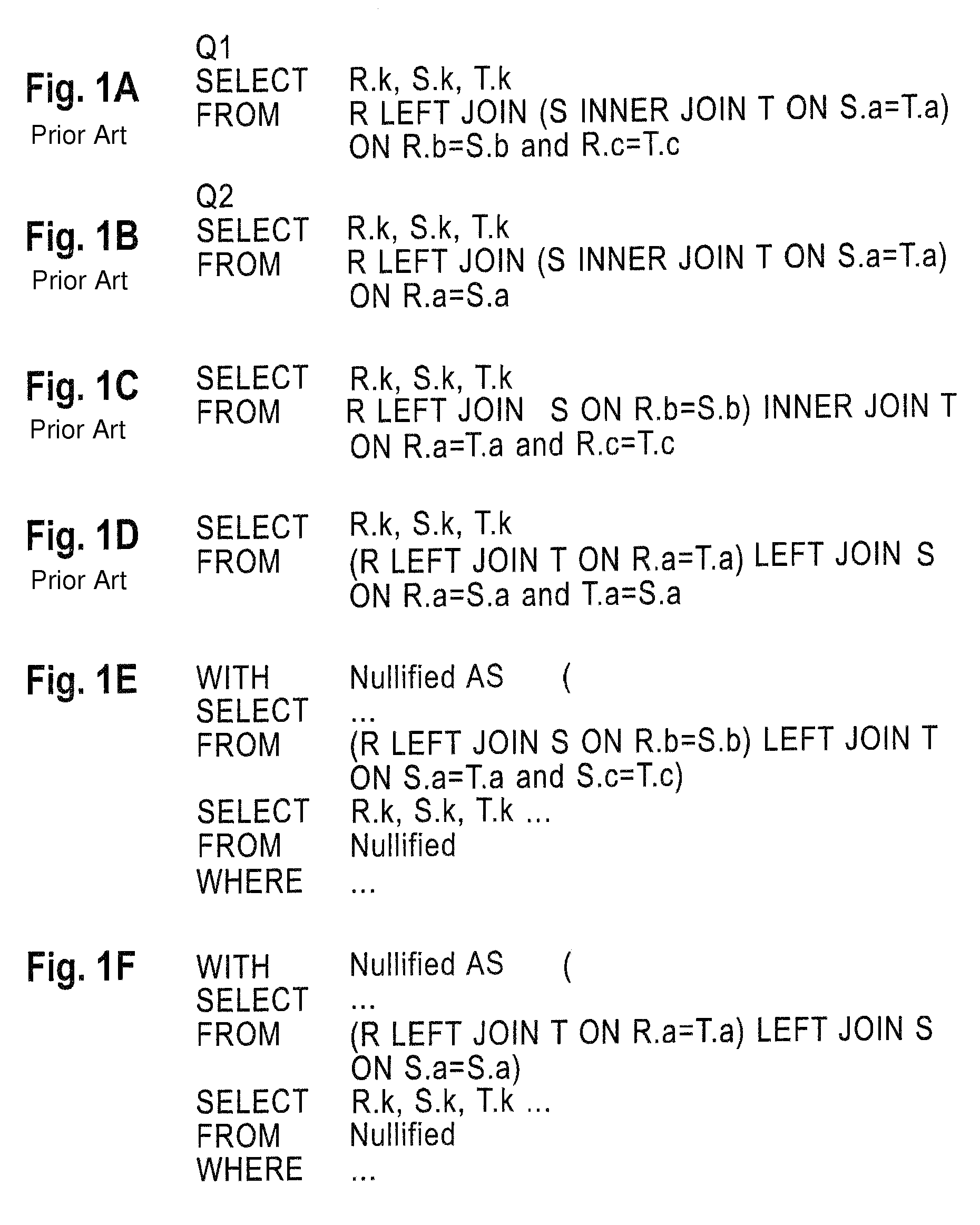
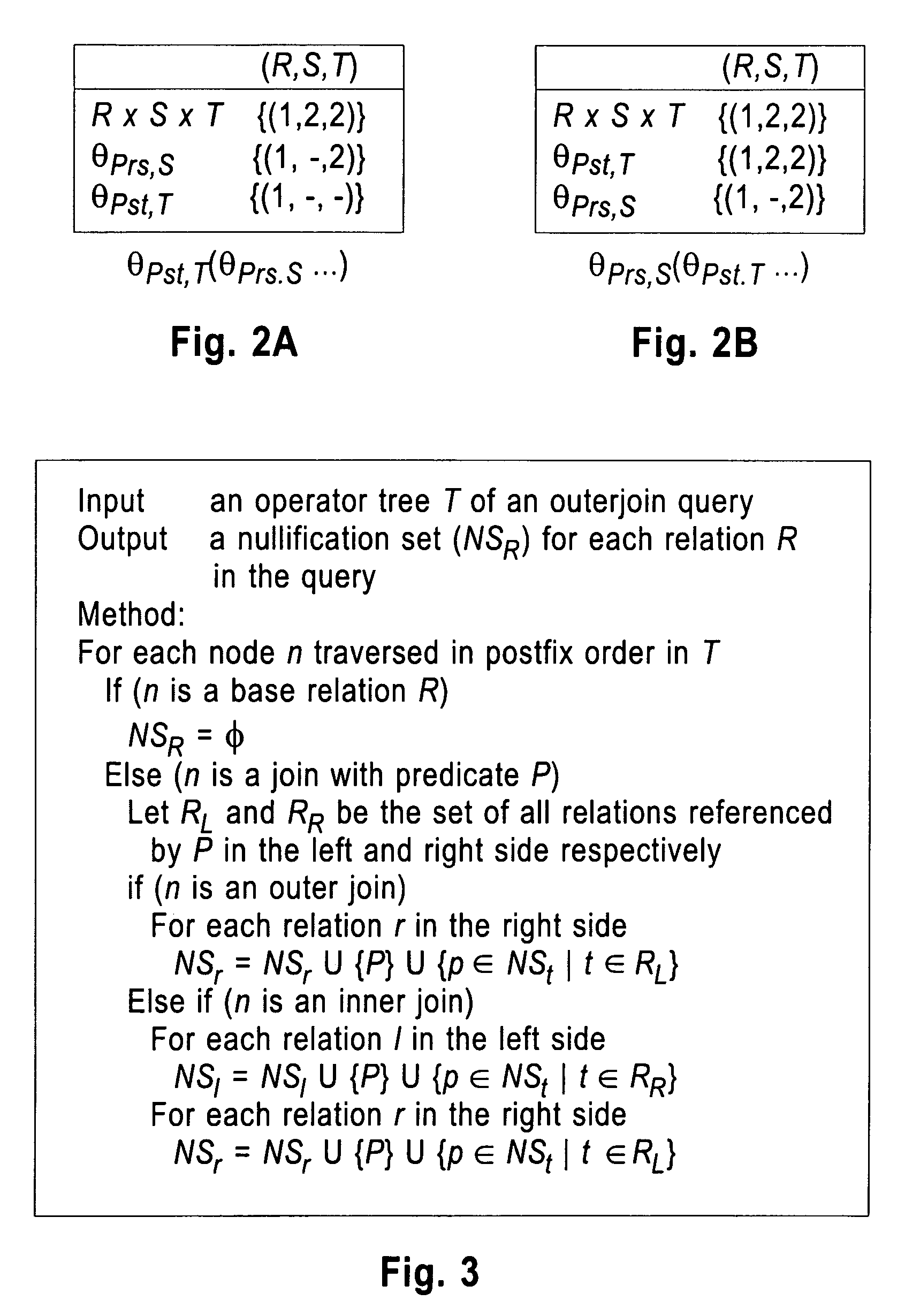
Canonical abstraction for outerjoin optimization
InactiveUS20060074901A1Efficient implementationData processing applicationsDigital data information retrievalExecution planProgramming language
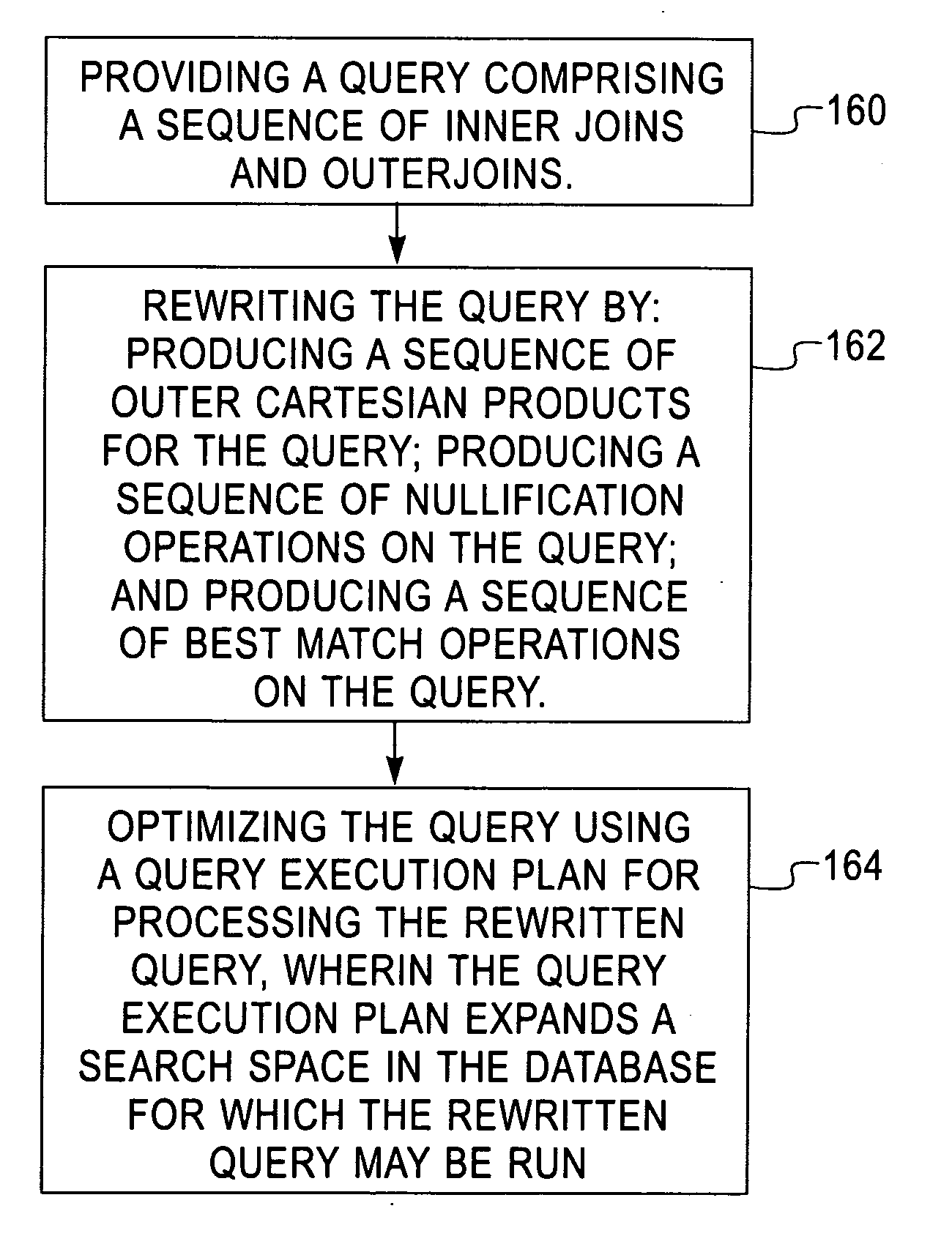
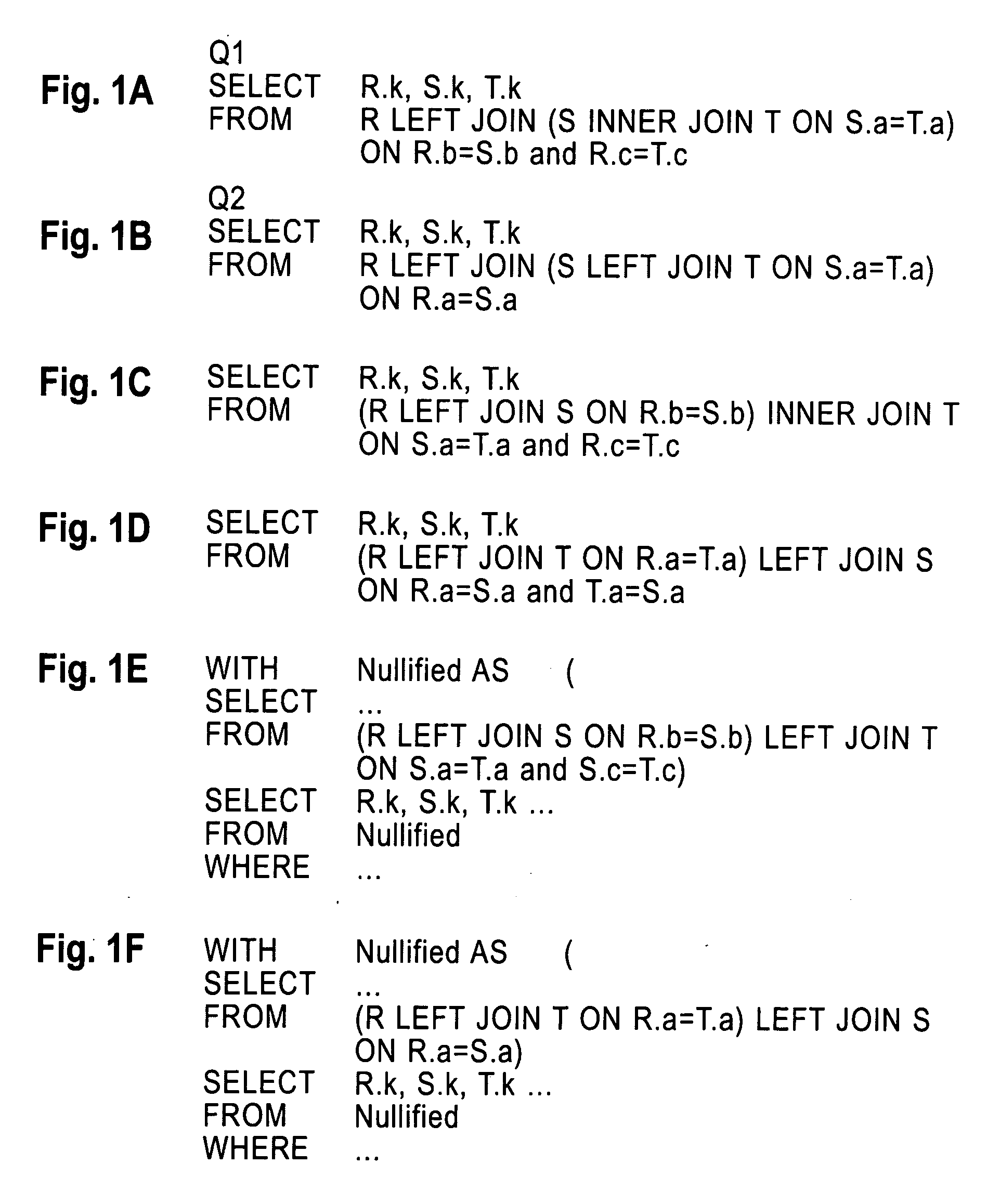
A system, apparatus, and program storage device implementing a method of optimizing queries used for searching a computerized database, wherein the method comprises providing a query comprising a sequence of inner joins and outerjoins; and rewriting the query by producing a sequence of outer Cartesian products for the query; producing a sequence of nullification operations on the query; and producing a sequence of best match operations on the query. The method further comprises optimizing the query using a query execution plan for processing the rewritten query, wherein the query execution plan expands a search space in the database for which the rewritten query may be run.
Owner:IBM CORP
Method and apparatus for indexing, searching and displaying data
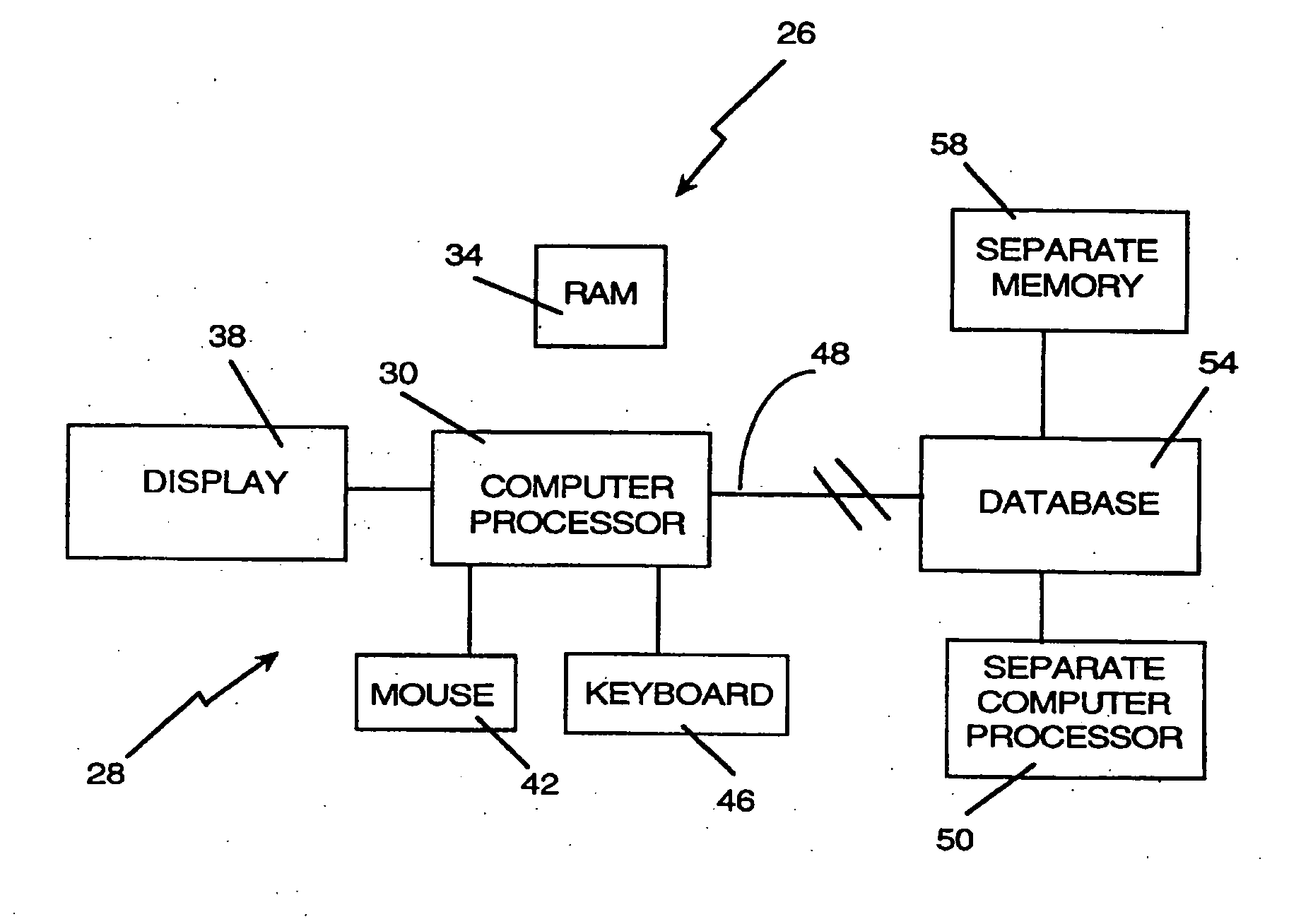
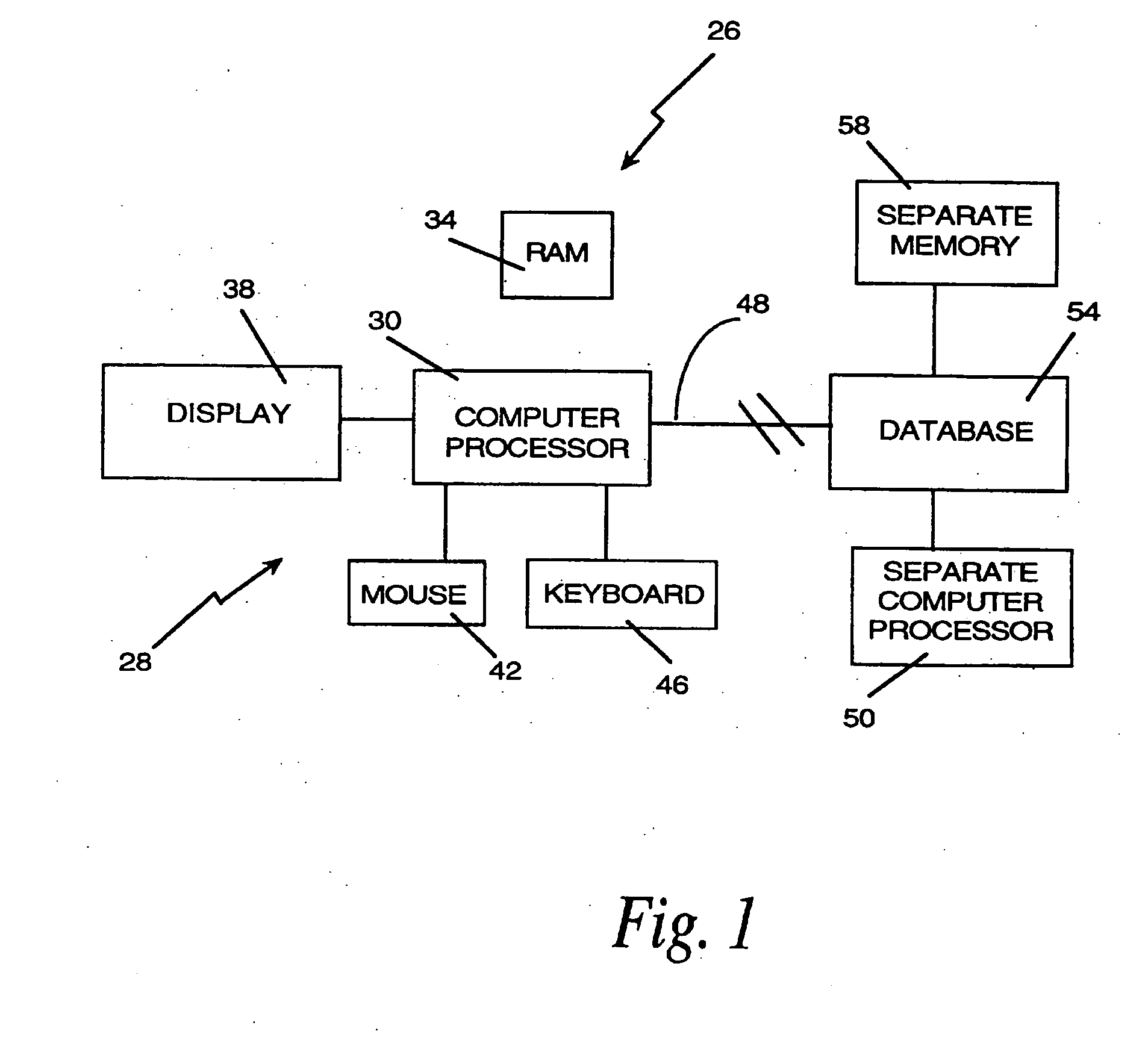
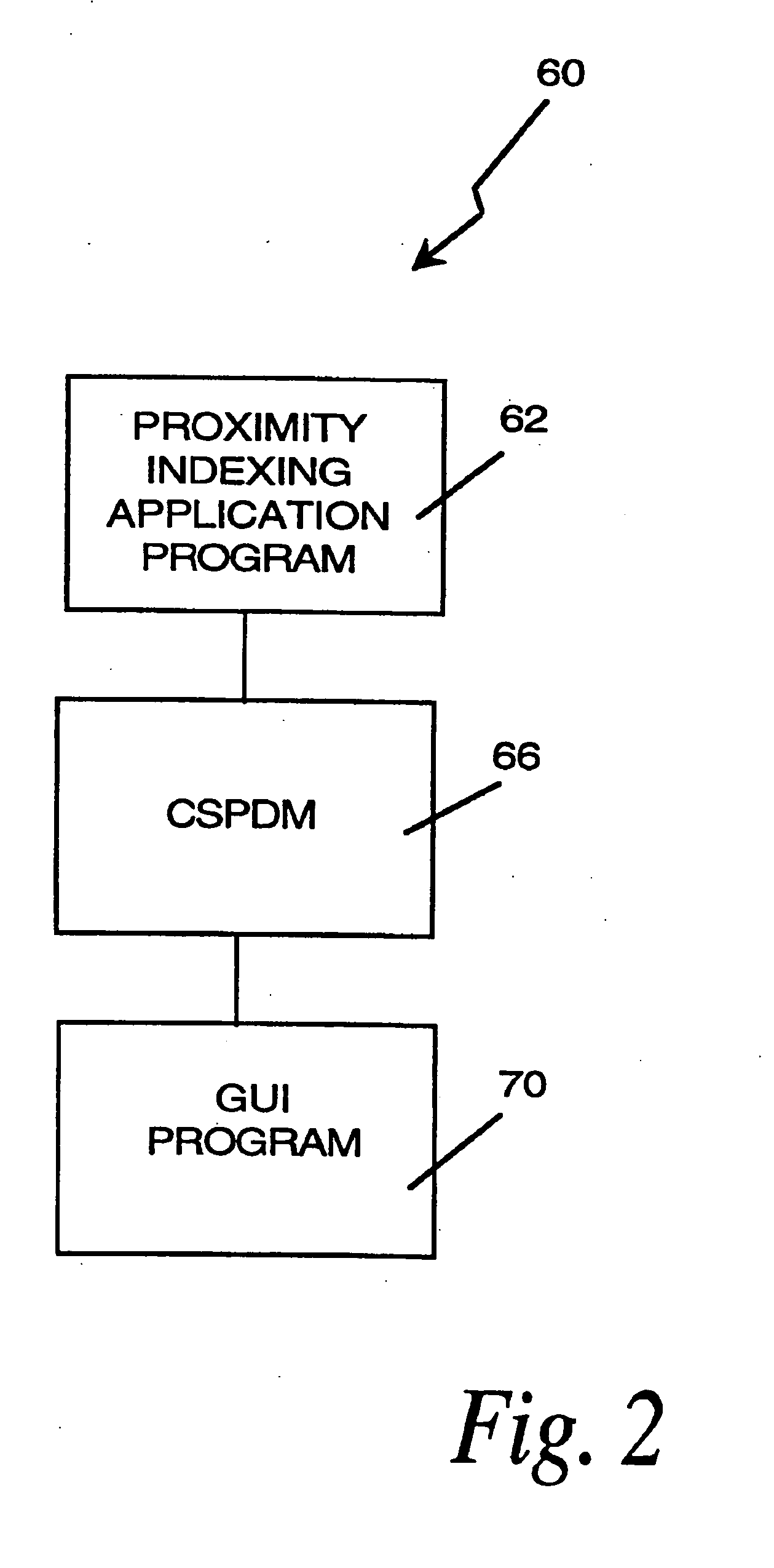
InactiveUS20060242564A1Simplifies research taskEasy to demonstrateData processing applicationsWeb data indexingSpatial OrientationsGraphics
A computer research tool for indexing, searching and displaying data is disclosed. Specifically, a computer research tool for performing computerized research of data including textual objects in a database or a network and for providing a user interface that significantly enhances data presentation is described. Textual objects and other data in a database or network is indexed by creating a numerical representation of the data. The indexing technique called proximity indexing generates a quick-reference of the relations, patterns and similarity found among the data in the database. Proximity indexing indexes the data by using statistical techniques and empirically developed algorithms. Using this proximity index, an efficient search for pools of data having a particular relation, pattern or characteristic can be effectuated. The Computer Search program, called the Computer Search Program for Data represented in Matrices (CSPDM), provides efficient computer search methods. The CSPDM rank orders data in accordance with the data's relationship to time, a paradigm datum, or any similar reference. An alternative embodiment of the invention employs a cluster link generation algorithm which uses links and nodes to index and search a database or network. The algorithm searches for direct and indirect links to a search node and retrieves the nodes which are most closely related to the search node. The user interface program, called the Graphical User Interface (GUI), provides a user friendly method of interacting with the CSPDM program and prepares and presents a visual graphical display. The graphical display provides the user with a two or three dimensional spatial orientation of the data.
Owner:LIBERTECH
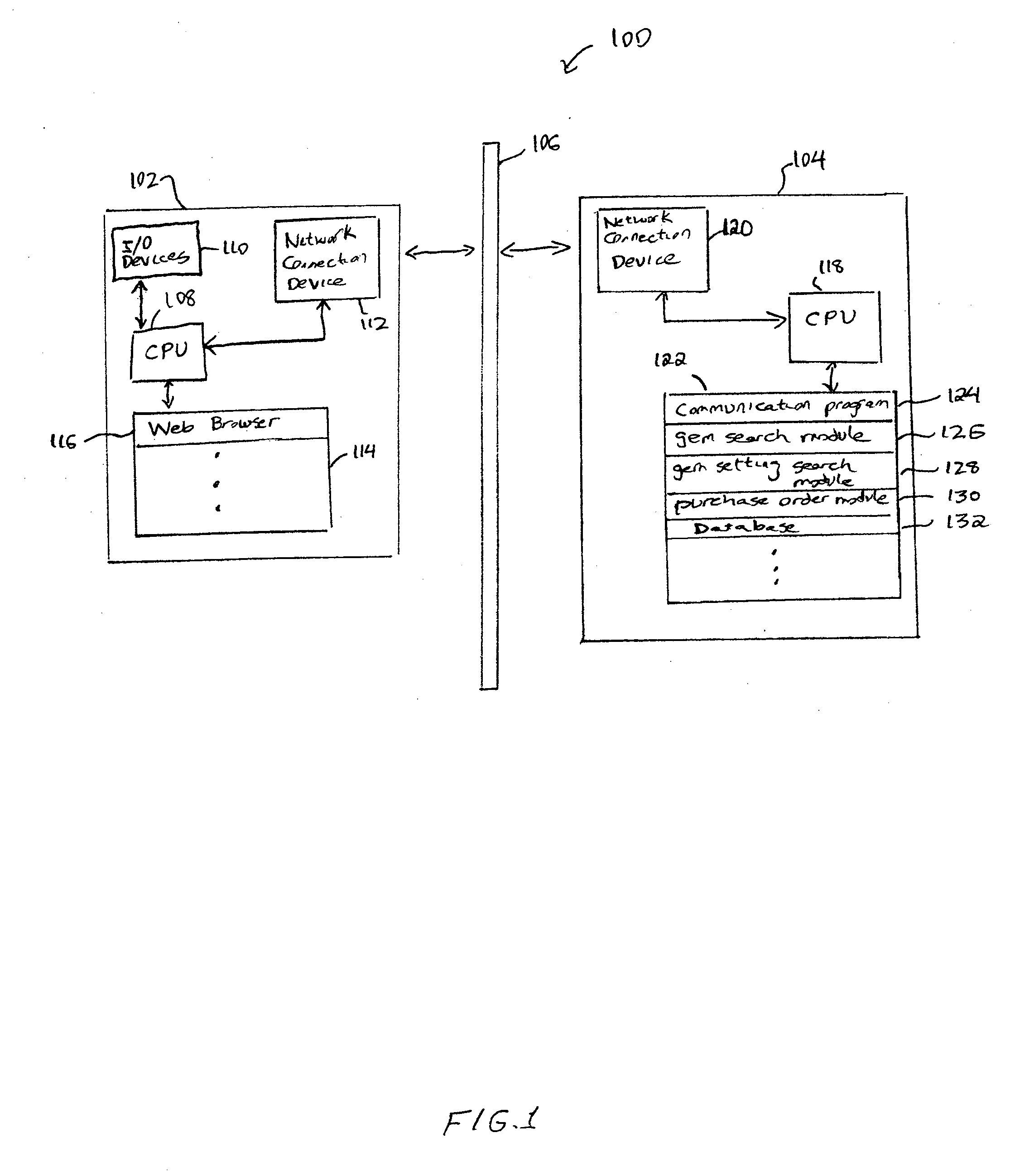
Apparatus and method for facilitating a search for gem settings
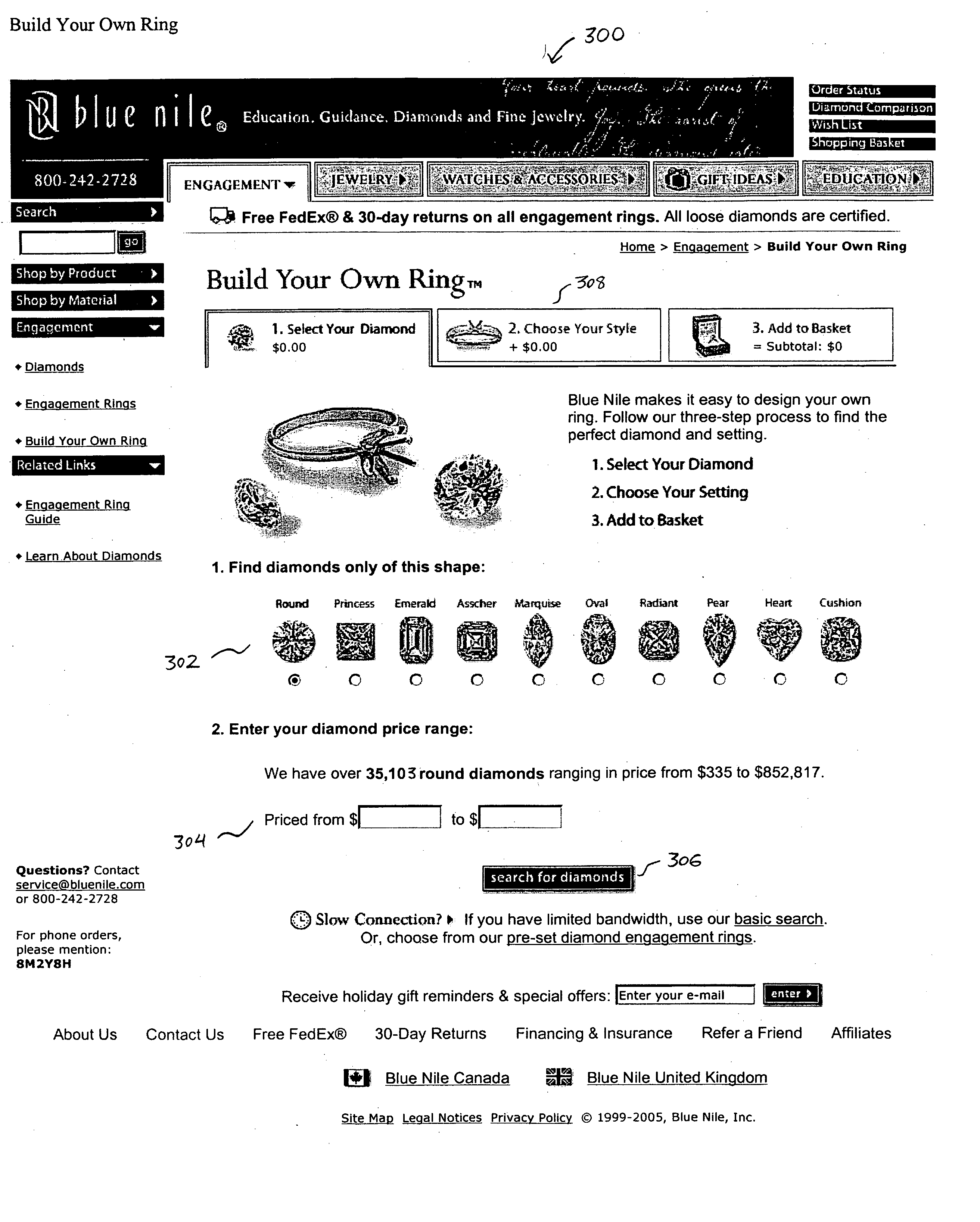
InactiveUS20050261989A1Easy searchCommerceSpecial data processing applicationsSearch computingInformation retrieval
Owner:BLUE NILE INC
High-Speed MAC Address Search Engine
InactiveUS20090031044A1Multiple digital computer combinationsData switching networksSearch computingDatabase
Disclosed is an apparatus and method for storing and searching computer node addresses in a computer network system. In one embodiment, the apparatus comprises a frame forwarding device such as a switch. The switch includes two MAC address tables including a primary MAC address table and secondary MAC address table both for storing and searching MAC addresses. The primary table stores records that contain compressed values of MAC addresses. The records are contained in storage locations that are referenced using the compressed value of the MAC address as a search index. In order to account for searching collisions that may result from different MAC addresses compressing to the same value, each record in the primary address table is linked to a chain of records in the secondary table. The records in the secondary table store the full value of the MAC address. Each chain of records in the secondary address table contains MAC addresses the present invention.
Owner:IKANOS COMMUNICATIONS
Method and system for generating a real estate title report
InactiveUS20060026136A1Easy to prepareReduce the possibilityData processing applicationsData acquisition and loggingA* search algorithmSearch computing
A method for generating a title report for a target real estate parcel includes the steps of gathering data records pertaining to real estate parcels from a plurality of disparate sources, storing the gathered data records in a common format within a computer database, indexing the commonly formatted data records within the computer database to facilitate searching, searching the indexed data records within the computer database for data records pertaining to a target real estate parcel, selecting at least one record of data pertaining to the target real estate parcel, electronically abstracting pre-selected data directly into an associated file while simultaneously viewing said record and generating a title report containing the pre-selected data in a predefined format. A system for generating a title report for a target real estate parcel includes a computer database containing data records from a plurality of disparate sources, wherein the data records pertain to real estate parcels and are commonly formatted within the database. The system further includes a search algorithm for searching the computer database for data records pertaining to a target real estate parcel and a report building algorithm for electronically abstracting pre-selected data directly into an associated file and generating a title report containing said pre-selected data.
Owner:REALTYDATA
Methodology, system, and computer-readable medium for collecting data from a computer
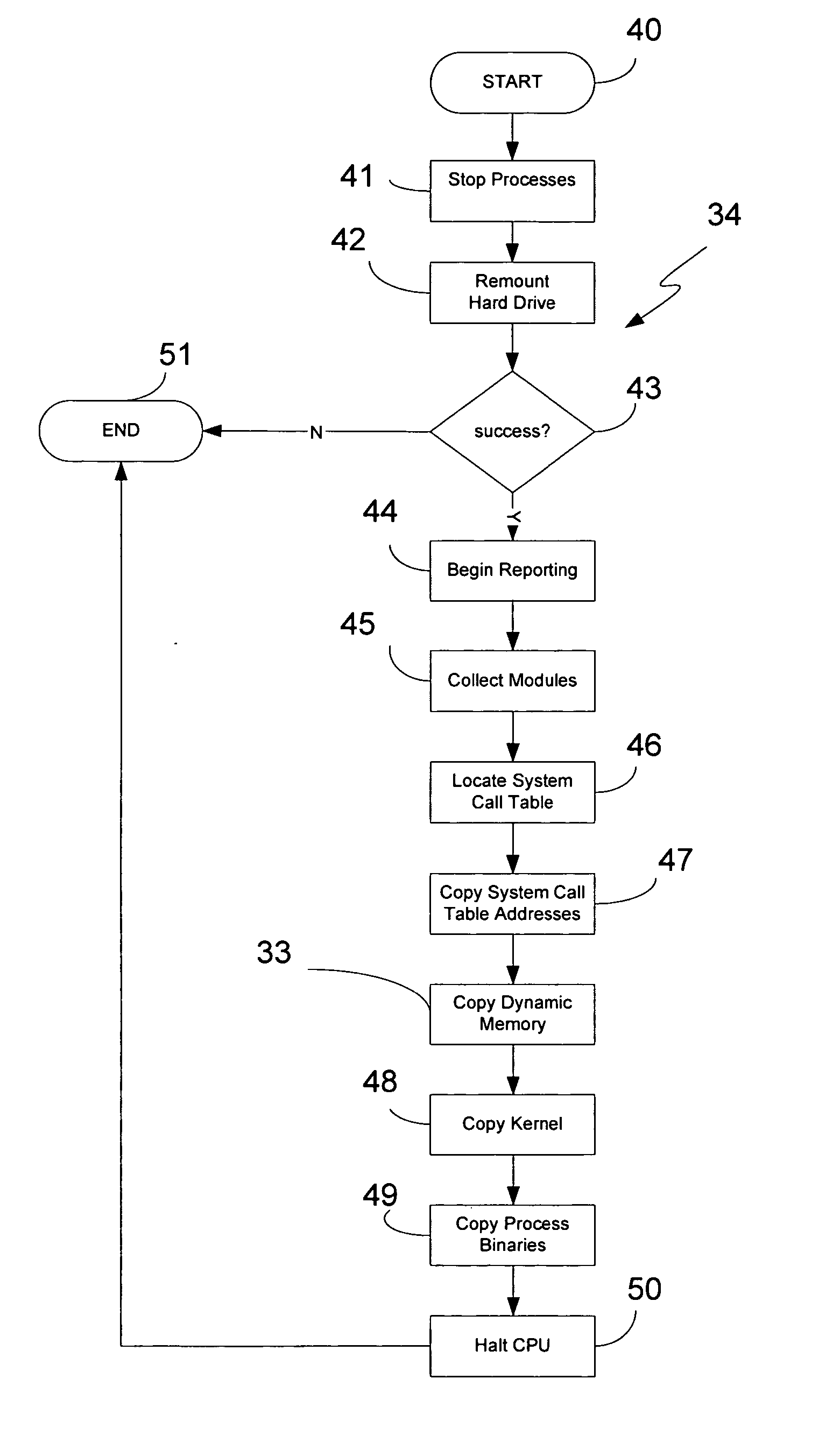
InactiveUS20050193173A1Avoid writingError detection/correctionUnauthorized memory use protectionShort-term memoryTerm memory
A computerized method for collecting suspected data of interest from a computer comprises searching the computer's shot-term memory to locate at least one target memory range containing the suspected data of interest, and copying the suspected data of interest within the target memory range to an alternate data storage location in a manner which avoids writing the suspected data to the computer's long-term memory. Alternatively, the suspected data of interest can be copied to a previously unused data storage location while preserving integrity of non-volatile memory resources. A computer-readable medium and a system for collecting target forensics data are also provided.
Owner:RING SANDRA E +1
Method for prioritizing content
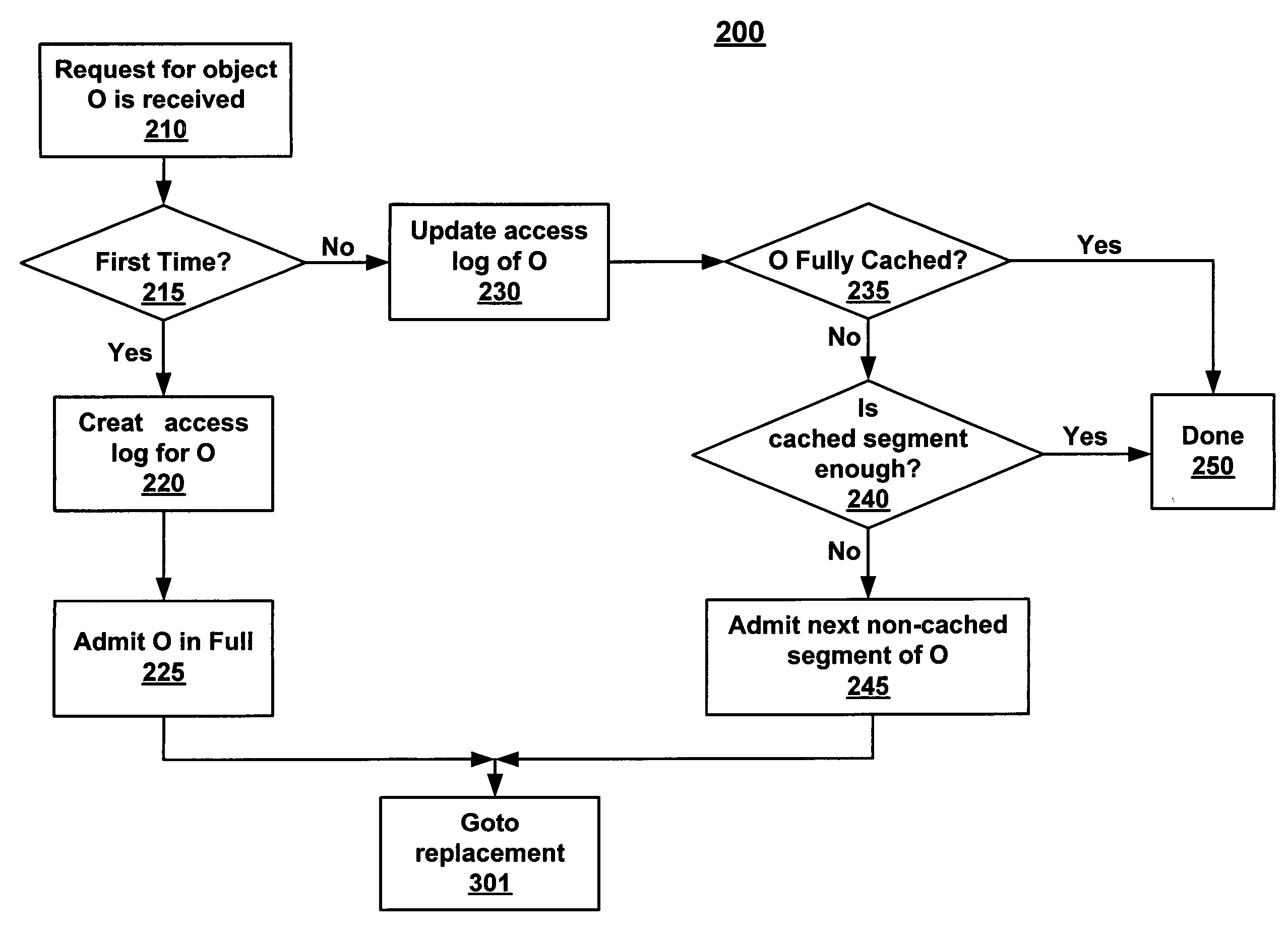
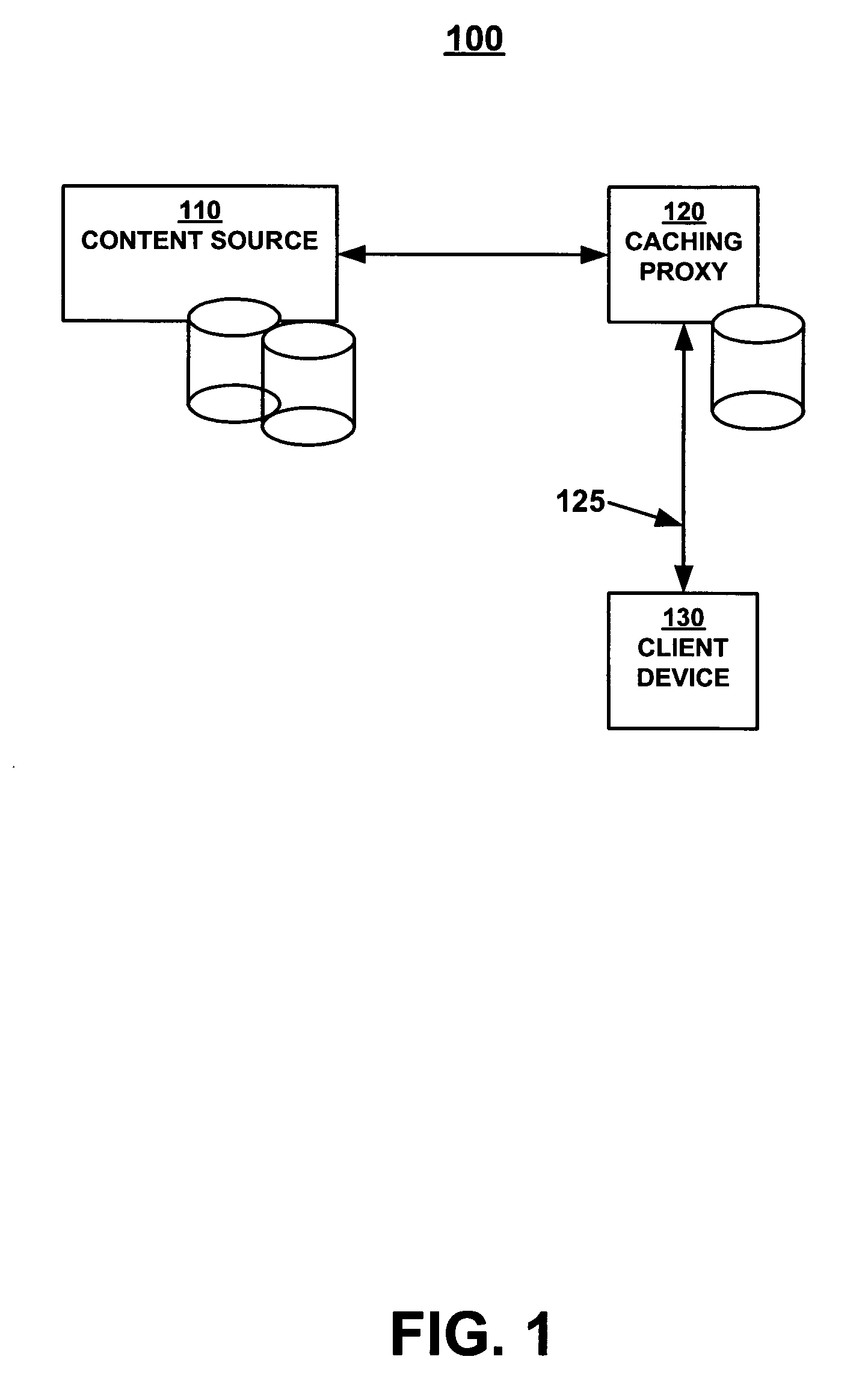
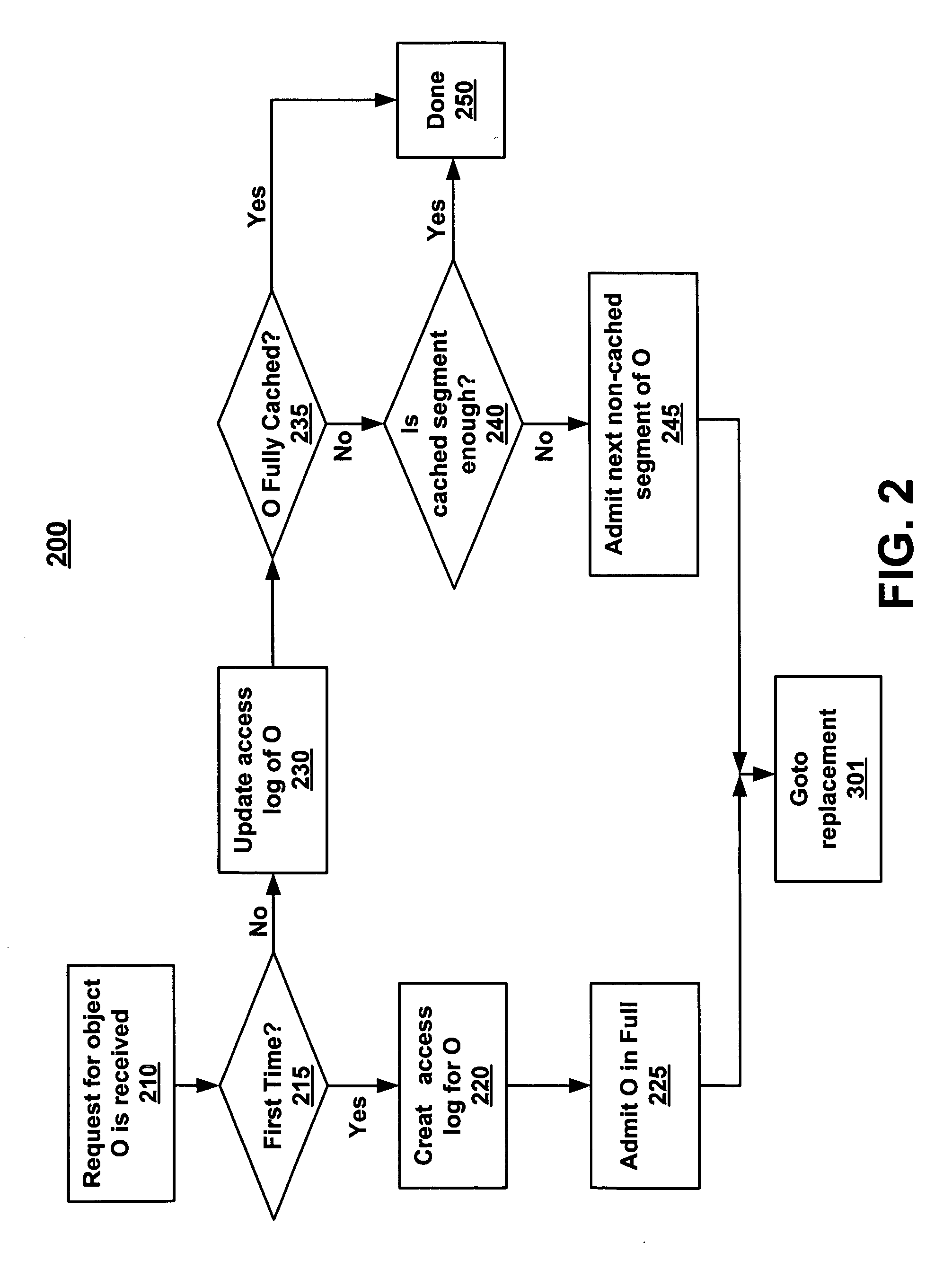
InactiveUS20050097085A1Data processing applicationsDigital data information retrievalParallel computingSearch computing
Methods and systems for prioritizing content are described. A request for a first content object is received at a caching proxy. A search of an access log of the proxy cache for a portion of the first content object is then performed. The size of the portion of the first content object on the proxy cache is calculated and the normally utilized size of the segment of the first content object is derived. A comparison is then made between the size of the portion of the first content object on the proxy cache and the normally utilized size of the first content object requested.
Owner:HEWLETT PACKARD DEV CO LP
Video compression coding-decoding method
InactiveCN1658673ALess importantRaise the importanceTelevision systemsDigital video signal modificationMotion vectorVideo encoding
A compressing encoding and decoding method which includes the following: encode the video compressed signals with the programs, discrete cosine transform DCT; transform and quantitate; set the channel buffer storage before the encoding bit flow gets into the channel; the buffer storage must have a control mechanism; movement estimate; the position excursion is described by the movement vector, and a movement vector represents the displacement in the two actinic and vertical directions; as movement estimating, the P frame image uses the former most recent decoded I frame or P frame as the referenced image called the forward forecast; the movement compensation; the movement vector calculated by the movement estimate moves the macro piece in the referenced image to the corresponding position in the actinic and vertical direction, then namely produce the forecast to the compressed image; and search and calculate the subpels; the quantitation, storage and movement search after the sampling signals are made the discrete cosine transform DCT transform are all completed in the frequency field. The video encoder finishes all the calculation in the frequency field. The compressed rate is high, and the calculating quantity is small.
Owner:NANJING UNIV
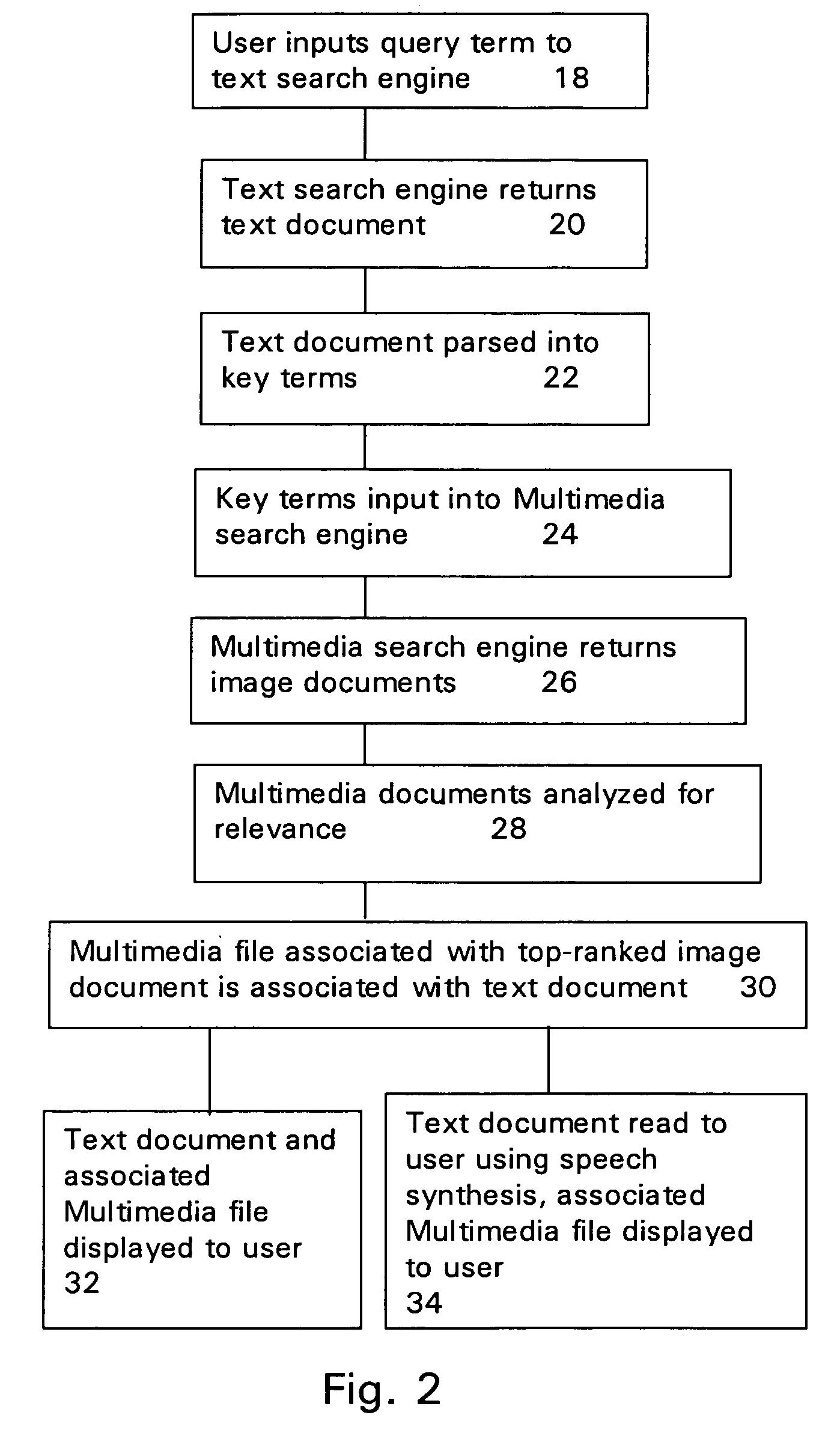
Method and apparatus for correlating the results of a computer network text search with relevant multimedia files
InactiveUS20080086453A1Web data indexingSpecial data processing applicationsMultimedia searchData display
The Invention is a method and apparatus for automatic retrieval, organization, correlation and presentation of text, image, audio, or video data in a sequential manner. A user searches a database available on a computer network using a text search engine to locate a text document. The text document is automatically read and parsed to identify text portions and key phrases. The key phrases are used to automatically search a multimedia file database available on the computer network using a multimedia search engine, such as an image search engine. Multimedia documents containing multimedia files are retrieved. Text in the multimedia documents is compared to the key terms and to the query terms and the multimedia documents are ranked by relevance using a variety of techniques including ranking, indexing, statistical analysis and natural language processing. Each text portion in the text document is stored in association with the most relevant multimedia file for that text portion. The resulting correlated information is displayed to the user in a sequence of text, audio, image or video data.
Owner:FABIAN BABER
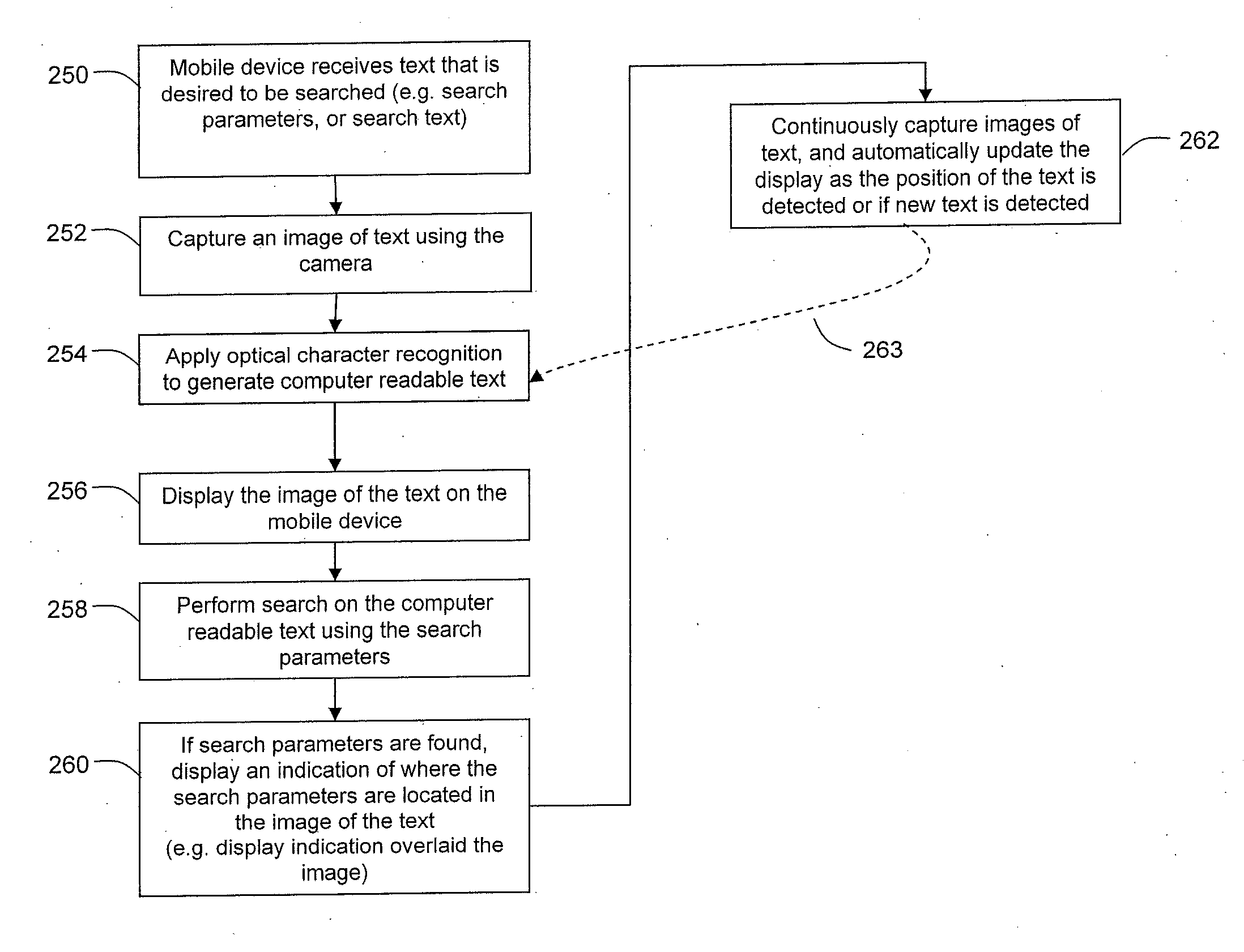
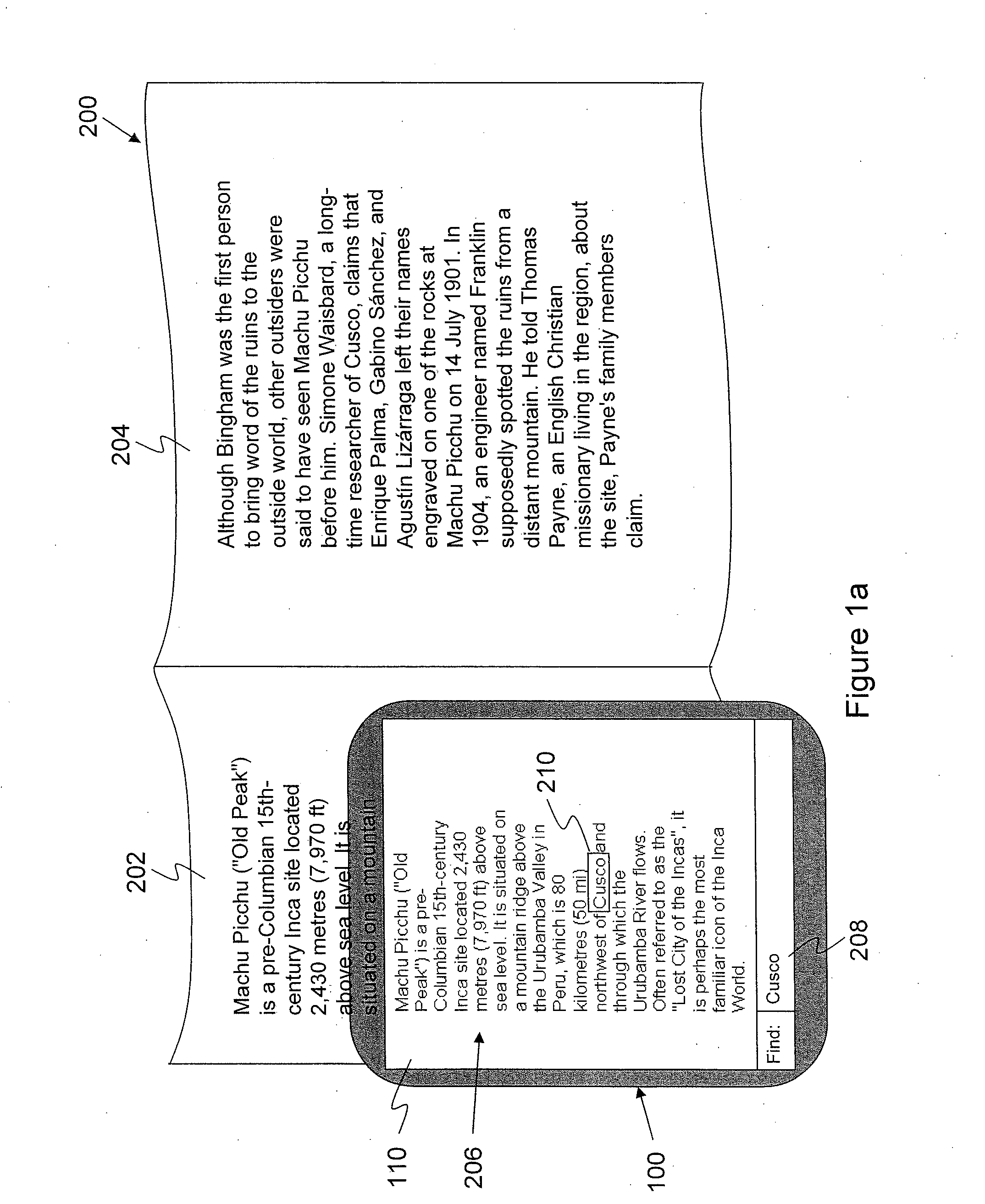
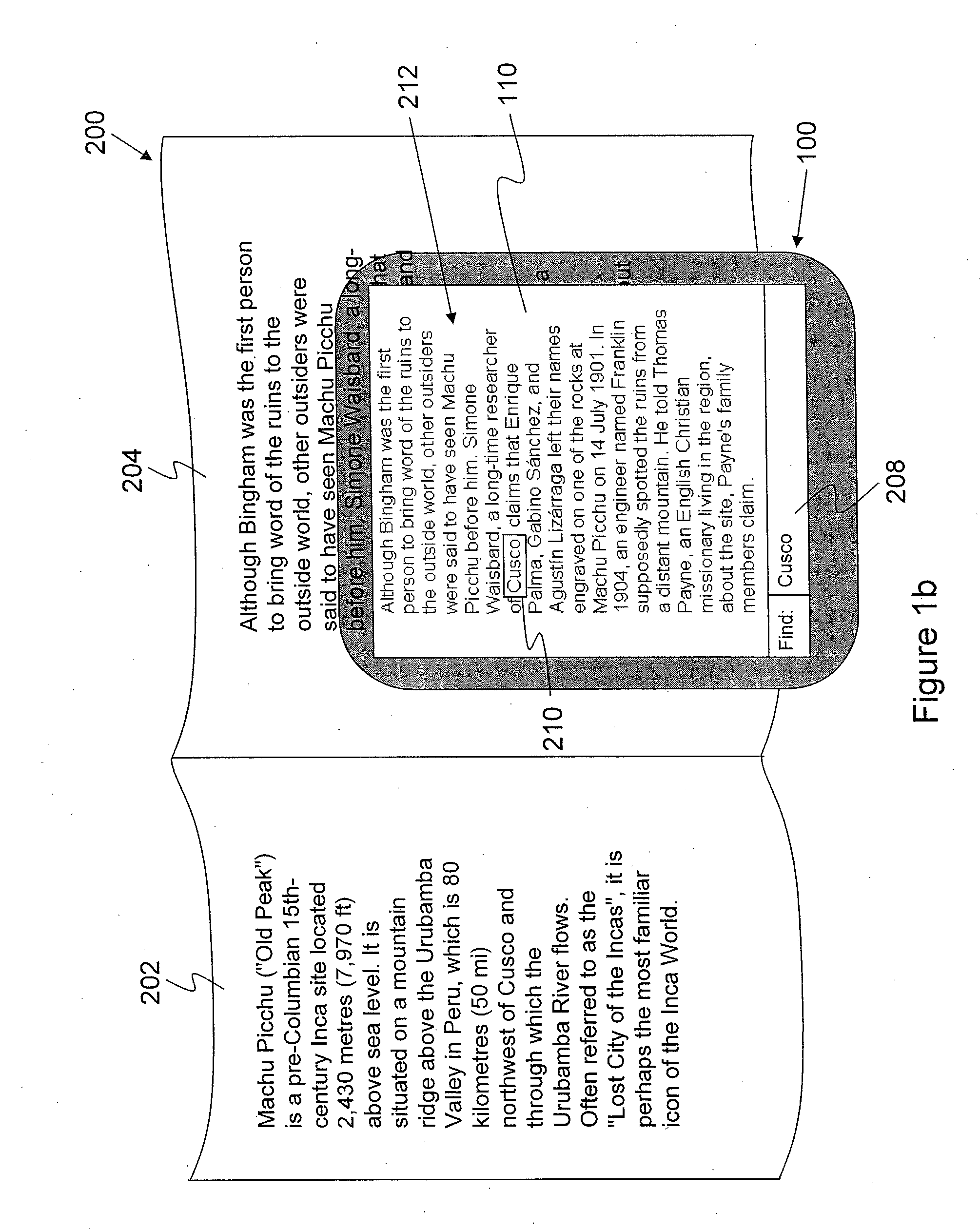
System and Method for Searching for Text and Displaying Found Text in Augmented Reality
InactiveUS20130113943A1Navigation instrumentsGeographical information databasesSearch computingOptical character recognition
A system and a method for searching for text in one or more images are provided. The method, performed by a computing device, comprises receiving an input. The computing device generates a search parameter from the input, the search parameter comprising the text. Optical character recognition is applied to the one or more images to generate computer readable text. The search parameter is applied to search for the text in the computer readable text and, if the text is found, an action is performed.
Owner:BLACKBERRY LTD
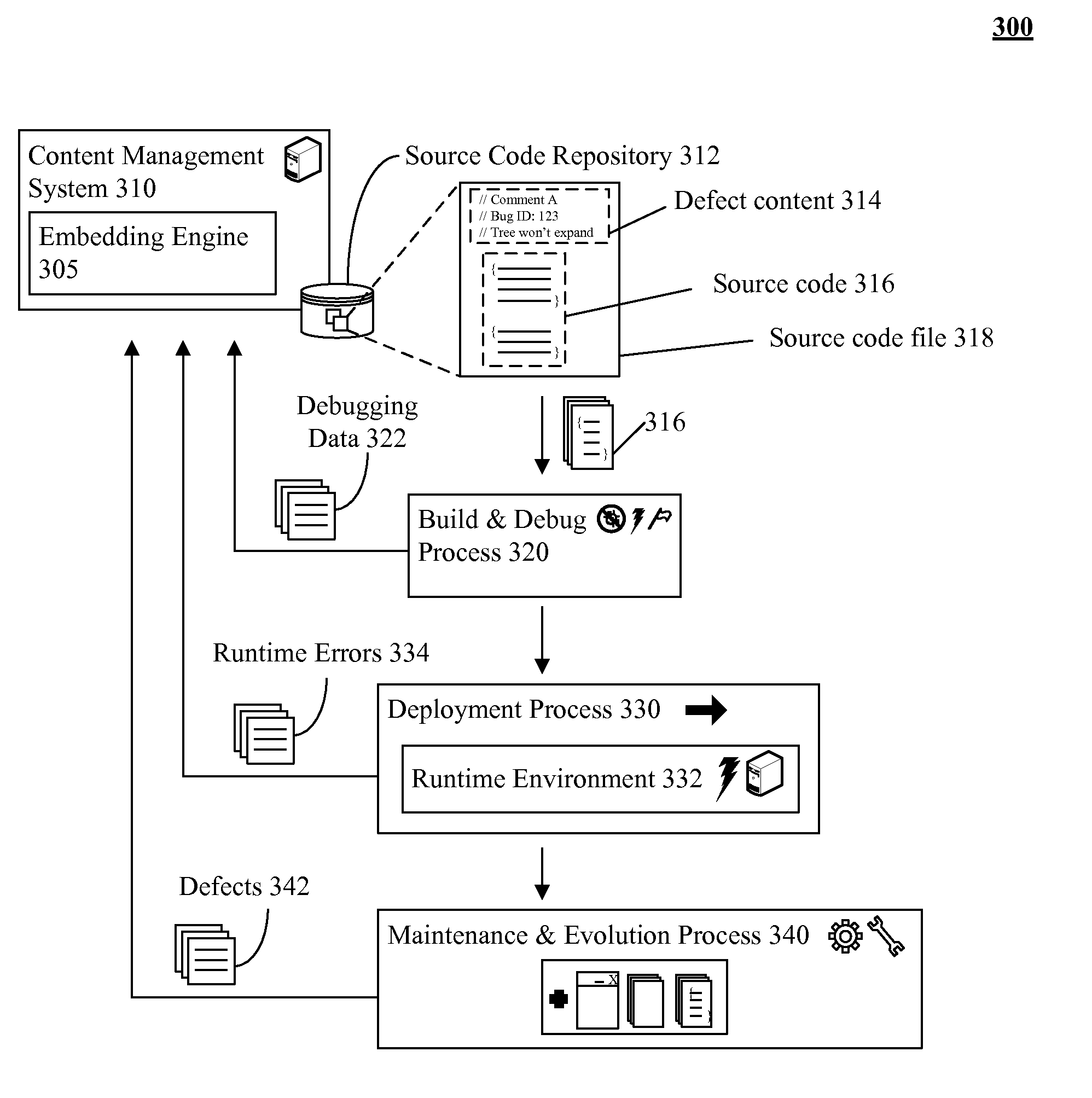
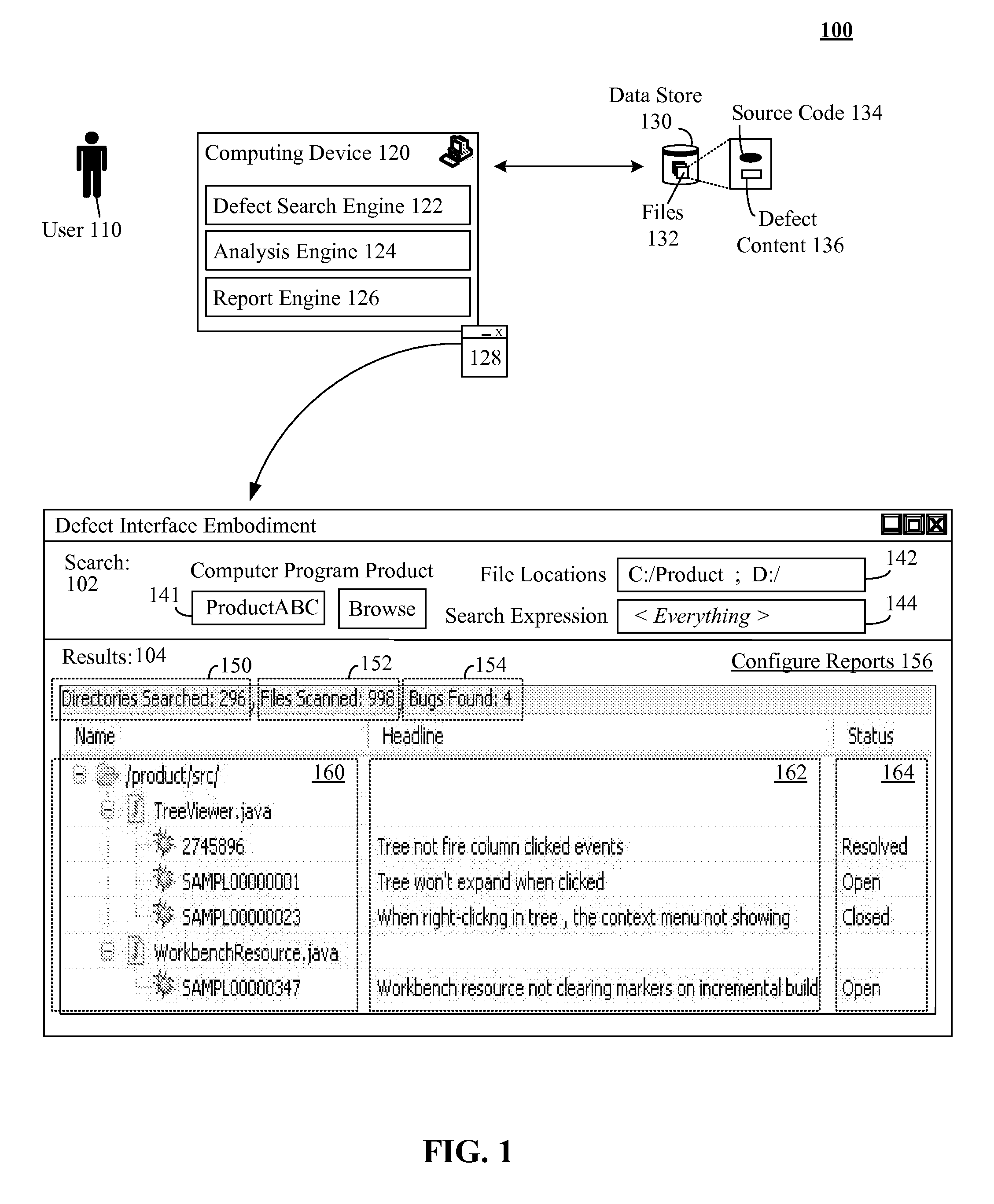
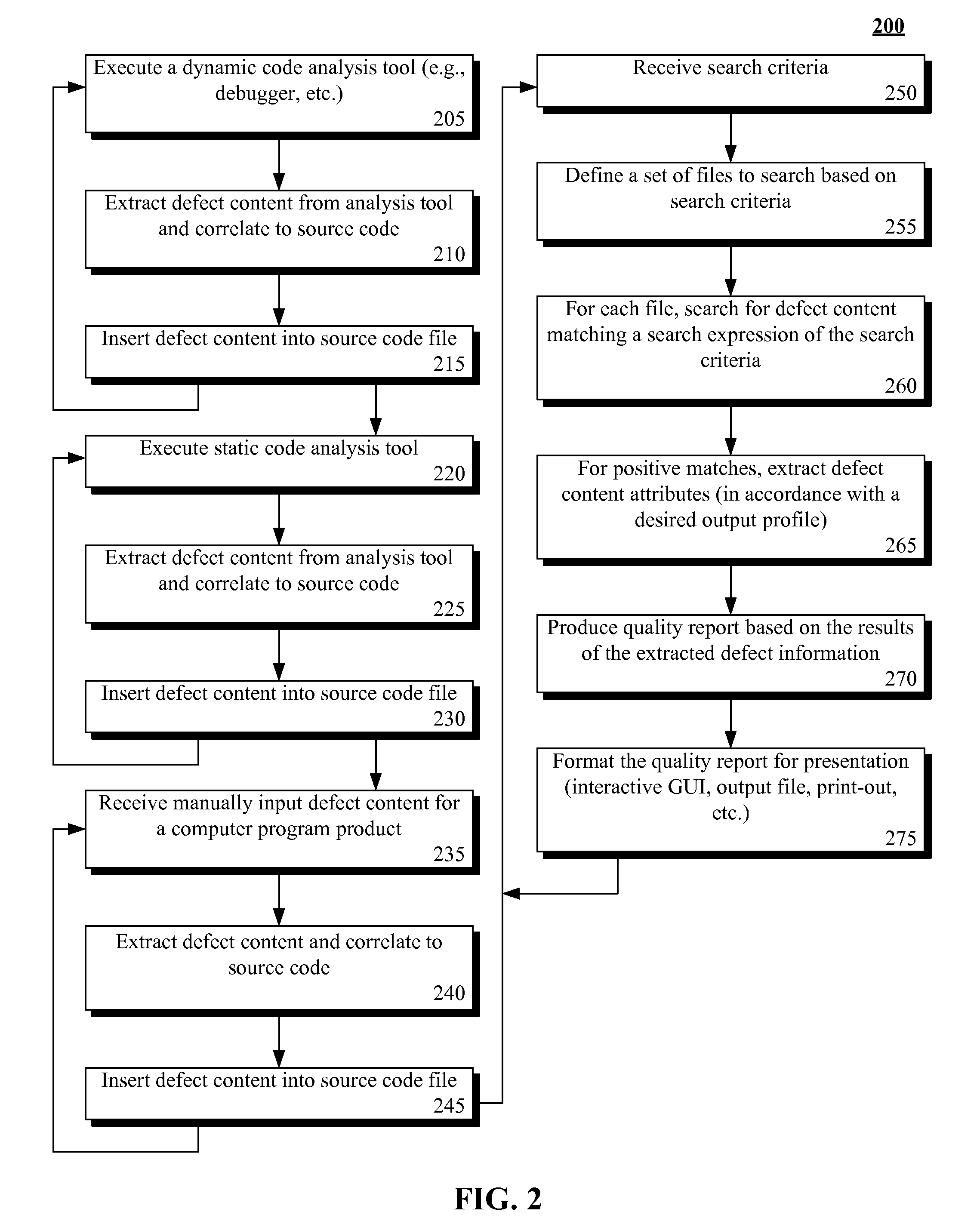
Including defect content in source code and producing quality reports from the same
InactiveUS20110161938A1Digital data processing detailsSoftware metricsGraphicsGraphical user interface
Defect content for a computer program product can be stored with source code of the computer program product. A computer program product analysis tool having a graphical user interface can be provided. Search criteria for defect content for the computer program product can be specified by a user via the graphical user interface. The stored defect content of the source code of the computer program product can be searched based on the search criteria. A computer program product quality report can be produced for the computer program product based on results of the searching of the stored defect content.
Owner:IBM CORP
Search capability implementation for a device
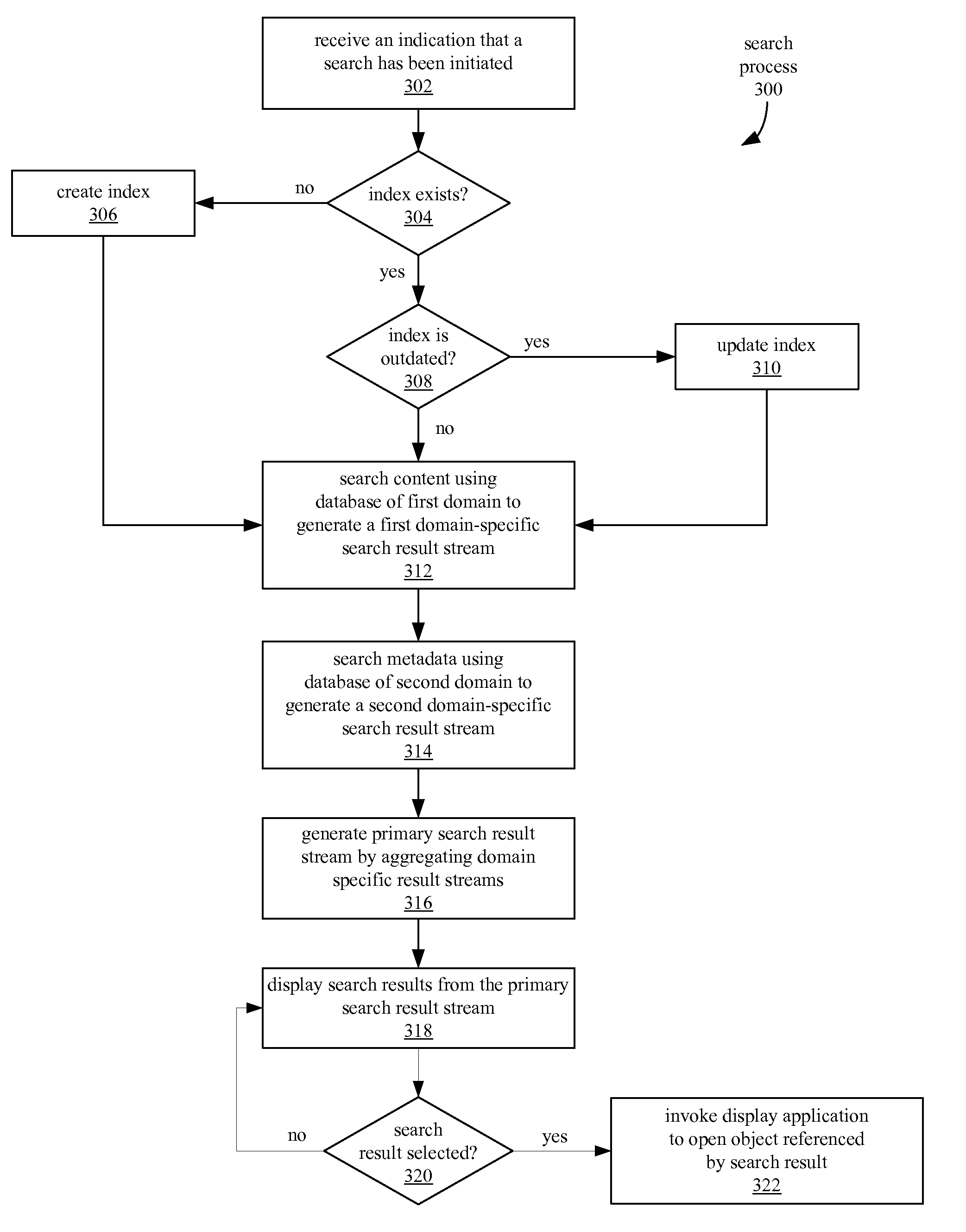
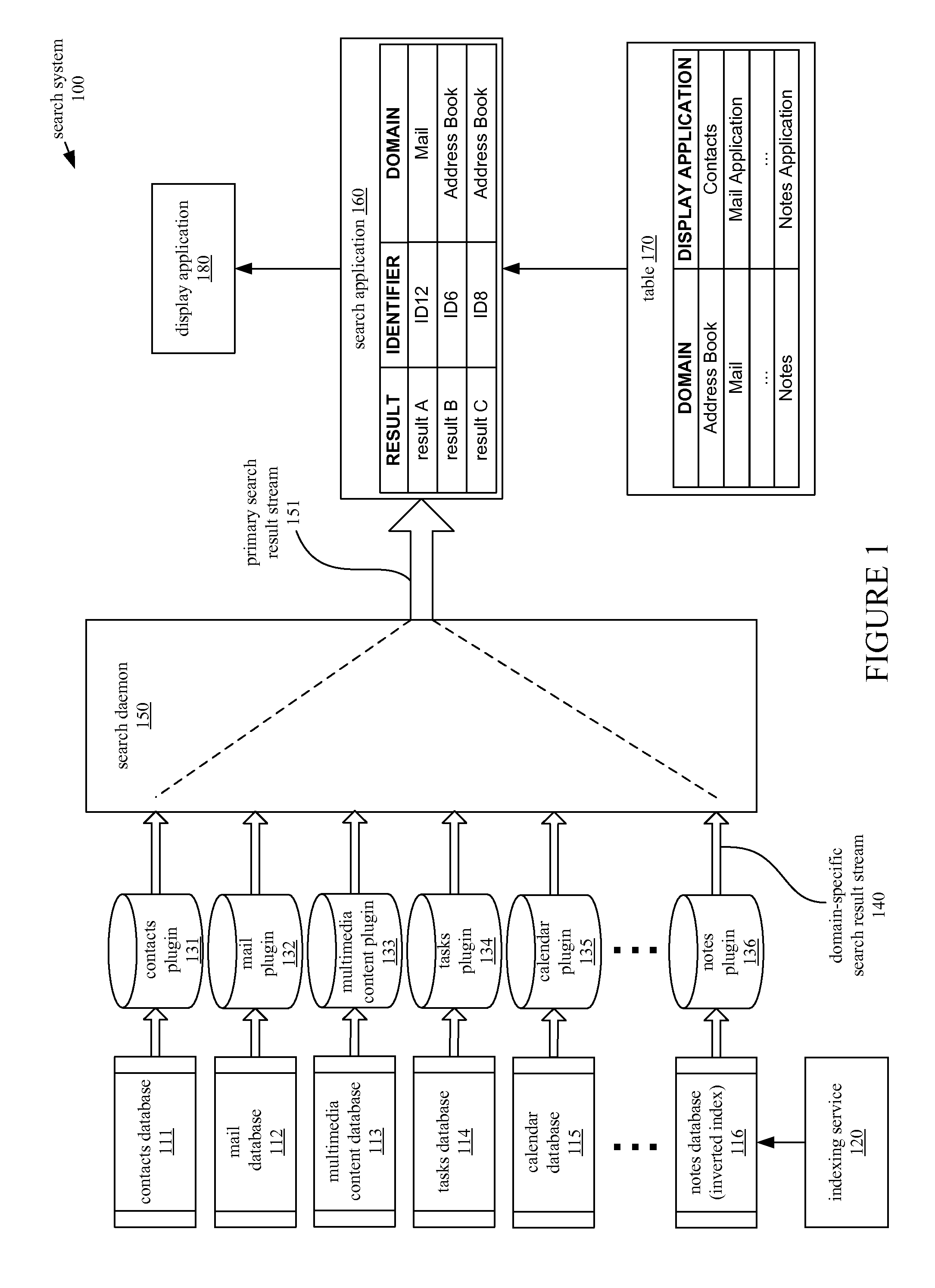
ActiveUS20100228724A1Digital data processing detailsSpecial data processing applicationsSearch computingMetadata
In a method of searching for data objects in a computer system, a content-based search of a first database generates a first domain-specific search result stream and a metadata-based search of a second database generates a second domain-specific search result stream. The first and second domain-specific search result streams are aggregated into a primary search result stream, and search results from the primary search result stream are displayed.
Owner:APPLE INC
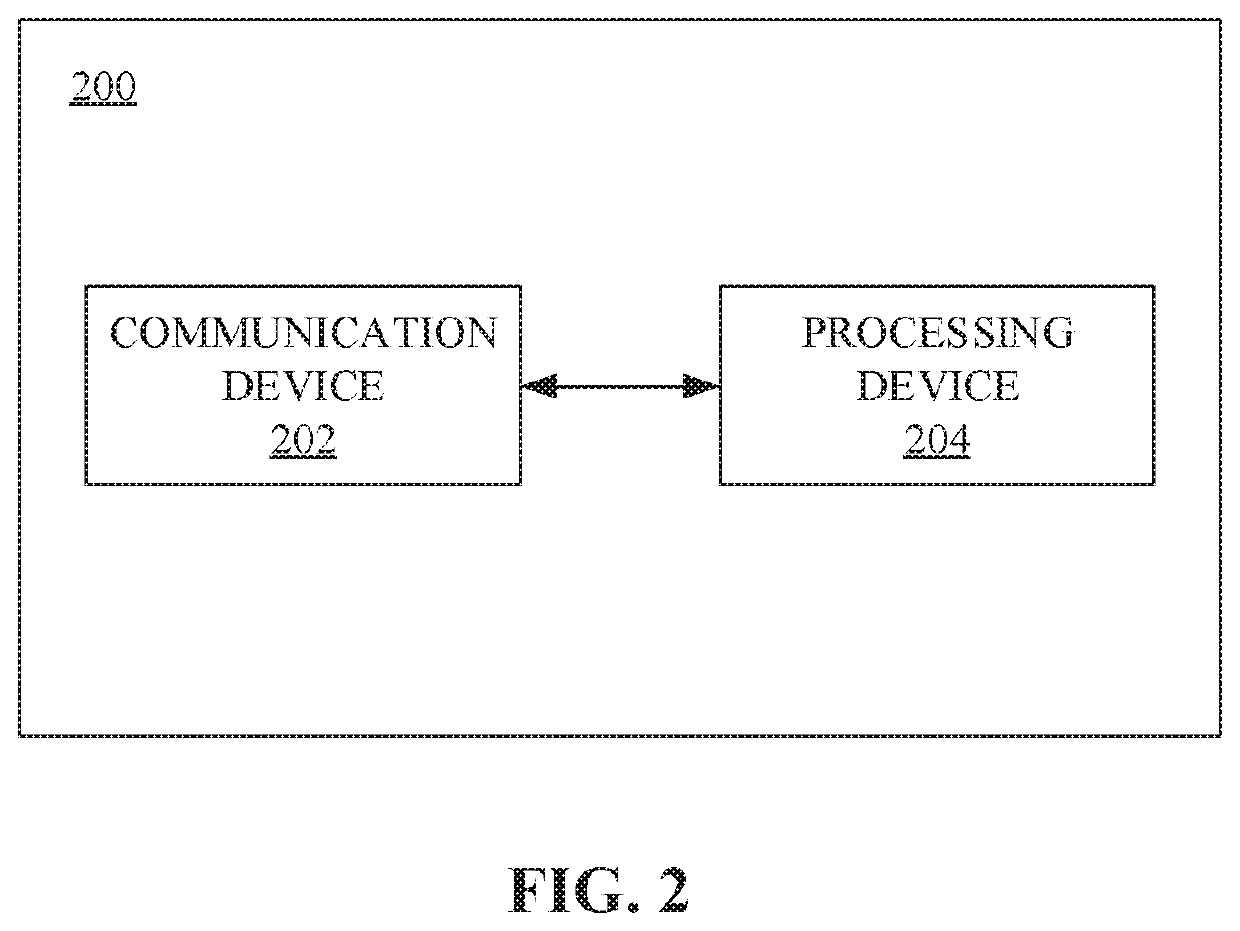
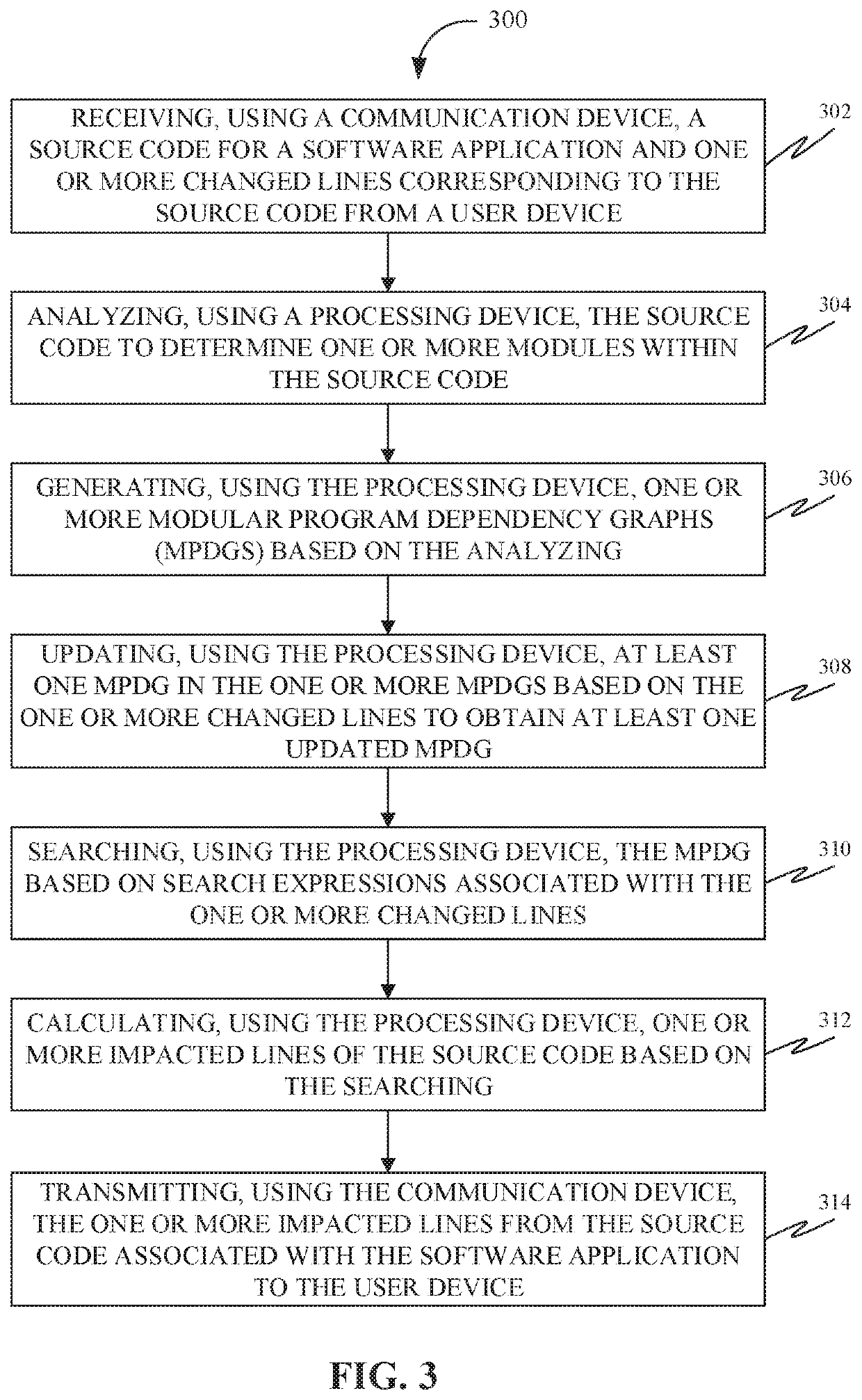
Methods, systems, apparatuses and devices for facilitating change impact analysis (CIA) using modular program dependency graphs
Disclosed herein is a system for facilitating Change Impact Analysis (CIA) using modular program dependency graphs. Further, the system may include a communication device configured for receiving a source code for a software application and one or more changed lines corresponding to the source code from a user device, and transmitting one or more impacted lines from the source code associated with the software application to the user device. Further, the system may include a processing device configured for analyzing the source code to determine one or more modules, generating one or more modular Program Dependency Graphs (mPDGs) based on the analysis, updating at least one mPDG based on the one or more changed lines to obtain the at least one updated mPDG, searching the mPDG based on search expressions associated with the one or more changed lines, and calculating one or more impacted lines based on the searching.
Owner:FIND IT EZ SOFTWARE CORP
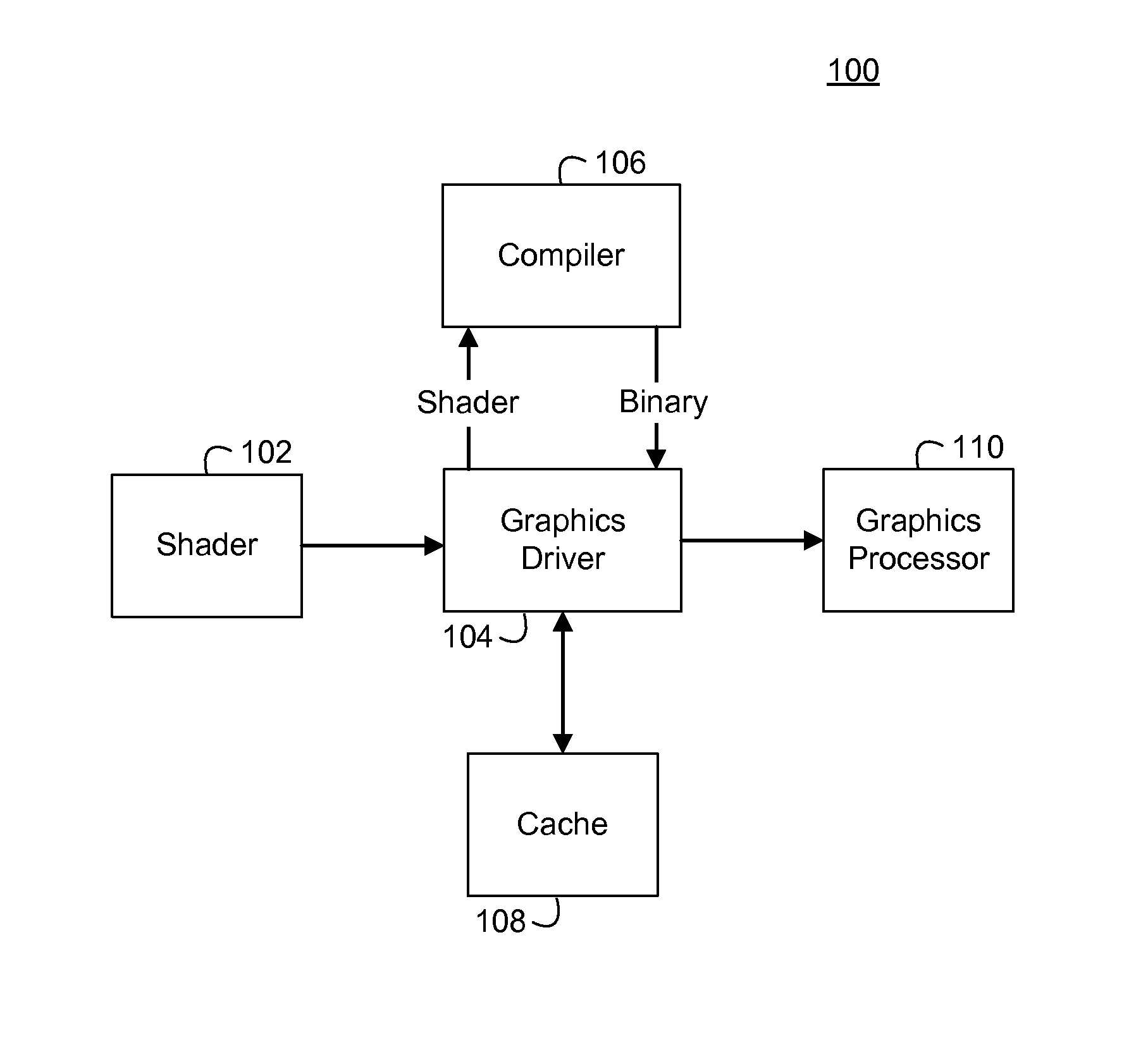
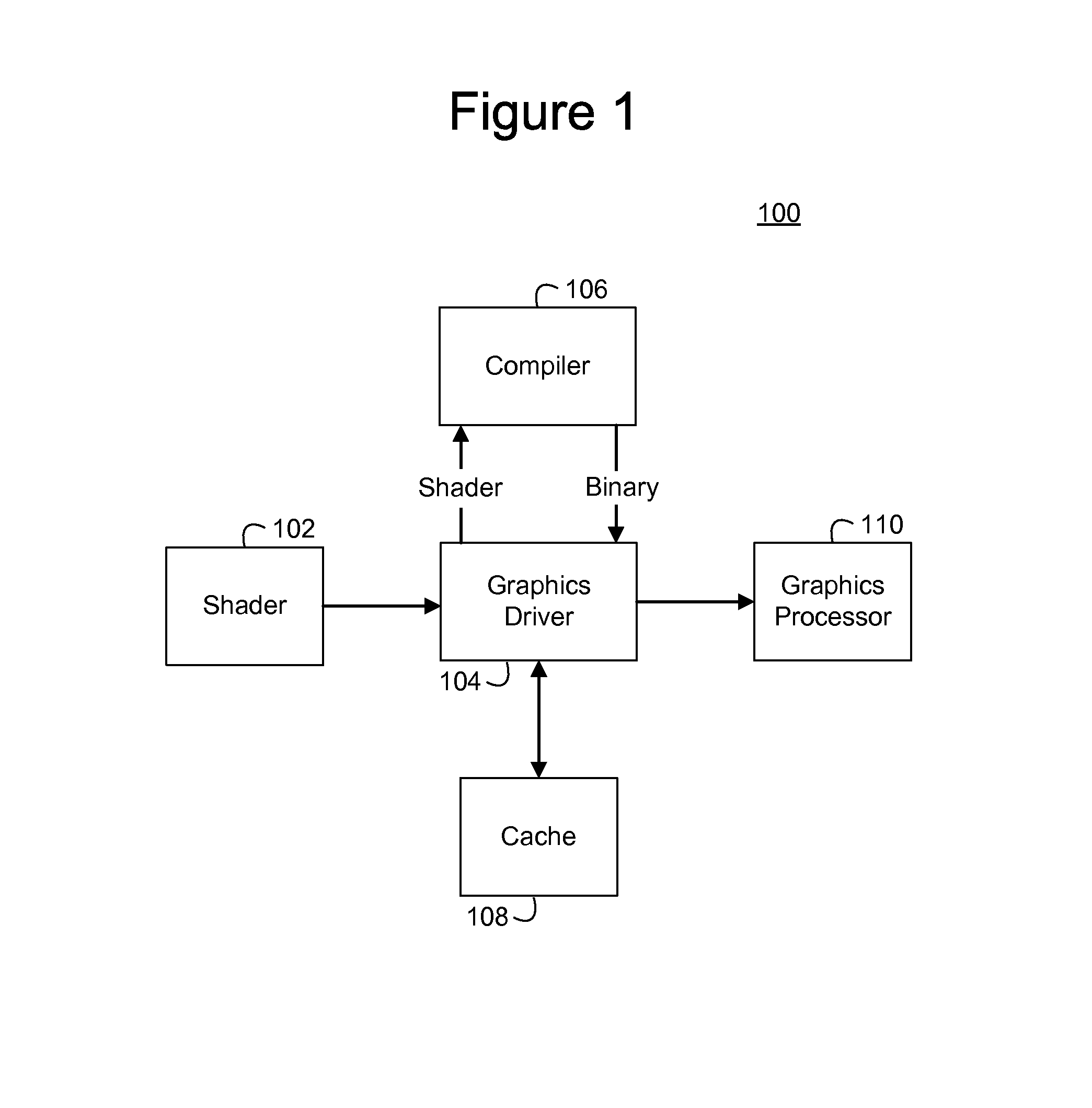
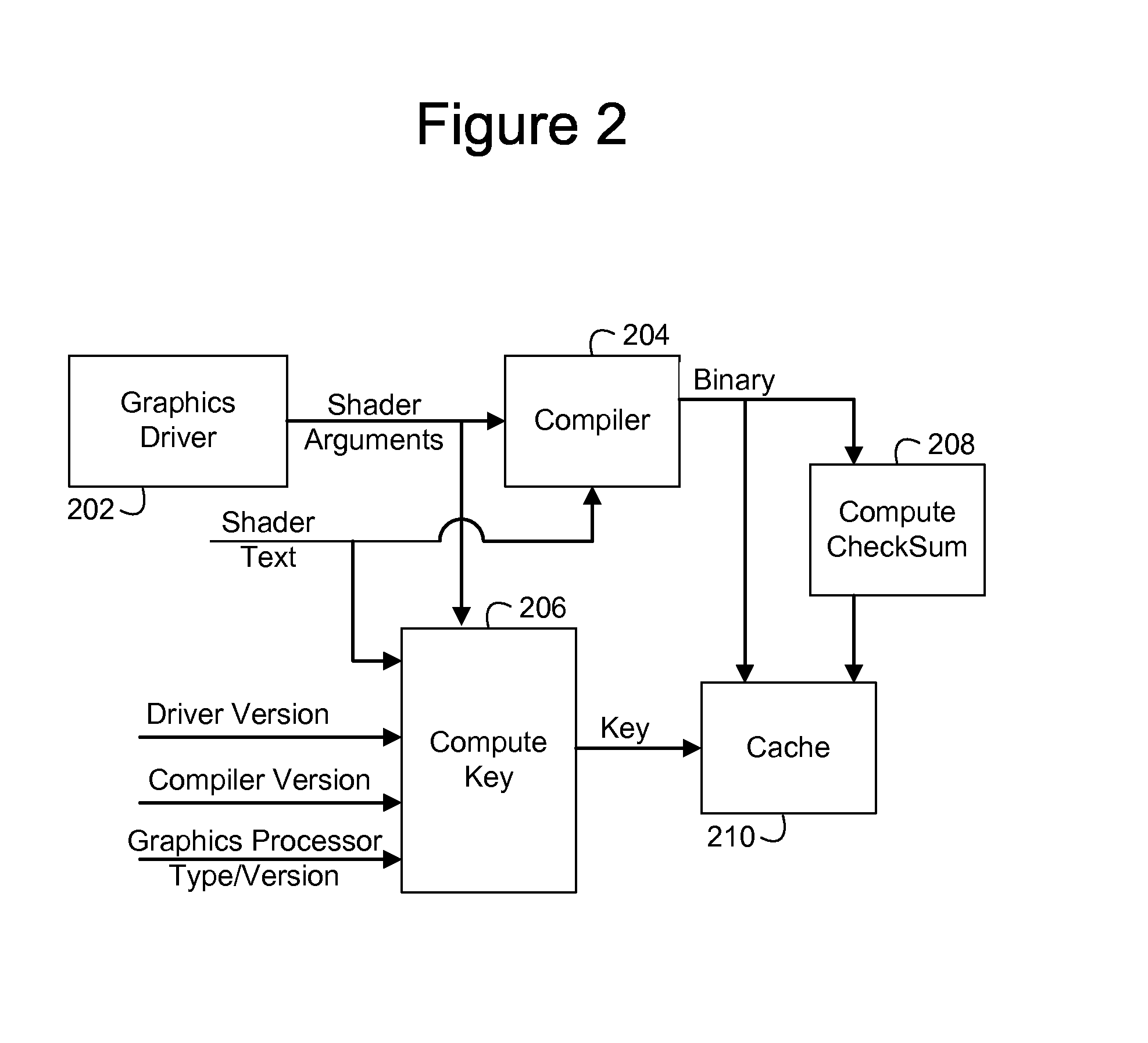
Application load times by caching shader binaries in a persistent storage
InactiveUS20140043333A1Efficiently compiledError detection/correctionDigital data processing detailsComputational scienceLoad time
A method for compiling a shader for execution by a graphics processor. The method comprises selecting a shader for execution. A key is computed for the selected shader. A memory is searched for a copy of the computed key. A shader binary stored in the memory is passed to the graphics processor for execution if the copy of the computed key is located in the memory. Otherwise, the shader is compiled to produce the shader binary for execution by the graphics processor and storing the shader binary in the memory. The shader binary is associated with the computed key and the copy of the computed key.
Owner:VERIZON PATENT & LICENSING INC +1
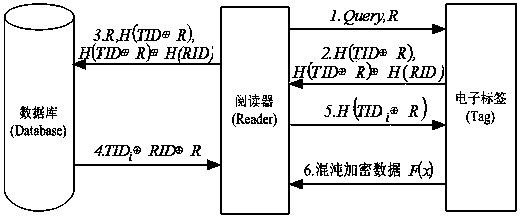
Bidirectional authentication method of radio frequency identification system
ActiveCN103413109AImprove securityHigh utility valueUser identity/authority verificationSensing record carriersHash functionAttack
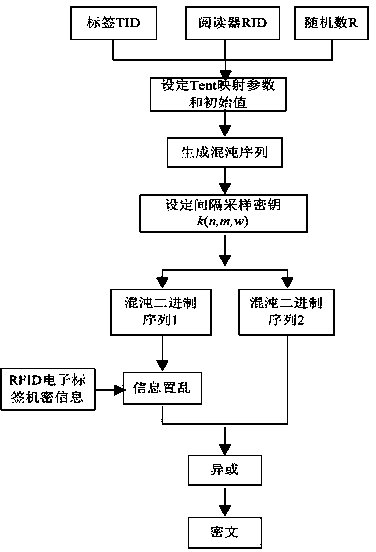
Disclosed is a bidirectional authentication method of a radio frequency identification system. The simple and rapid method with chaotic mapping combined with the Hash function, the exclusive-or operation and the like is adopted, filter operation is conducted together with bidirectional authentication, search and computing loads of a back-end data base are reduced, the safety problems of impersonation, retransmission attack, tracing and the like are avoided, a label of the radio frequency identification system and TID and RID of the unique mark amount of a reader are used as an initial value and parameters of the chaotic mapping, and chaotic scrambling and exclusive-or encryption are performed on confidential information of the label by being combined with the authentication process. On the basis of taking full consideration of saving the cost of the passive radio frequency identification label, data encryption and safety authentication are organically combined, and accordingly the safety problems such as illegal access, counterfeiting and cheating and data leakage in the radio frequency identification system can be solved.
Owner:徐州虹智智能科技有限公司
System and method for handling data requests
InactiveUS20090150622A1Memory architecture accessing/allocationDigital computer detailsComputerized systemMemory controller
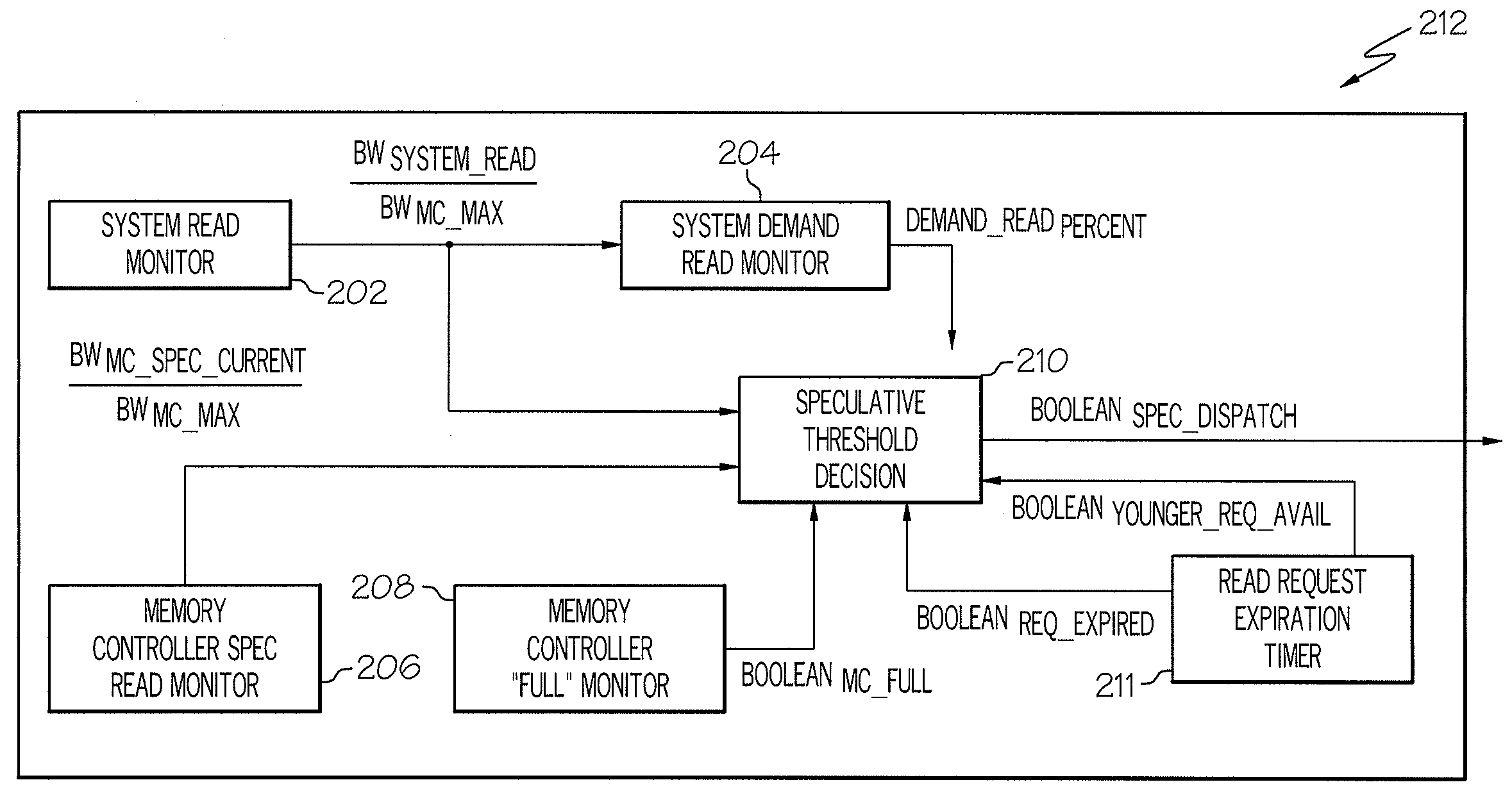
A system and method for handling speculative read requests for a memory controller in a computer system are provided. In one example, a method includes the steps of providing a speculative read threshold corresponding to a selected percentage of the total number of reads that can be speculatively issued, and intermixing demand reads and speculative reads in accordance with the speculative read threshold. In another example, a computer system includes a CPU, a memory controller, memory, a bus connecting the CPU, memory controller and memory, circuitry for providing a speculative read threshold corresponding to a selected percentage of the total number of reads that can be speculatively issued, and circuitry for intermixing demand reads and speculative reads in accordance with the speculative read threshold. In another example, a method includes the steps of providing a speculative dispatch time threshold corresponding to a selected percentage of a period of time required to search a cache of the computer system, and intermixing demand reads and speculative reads in accordance with the speculative dispatch time threshold.
Owner:IBM CORP
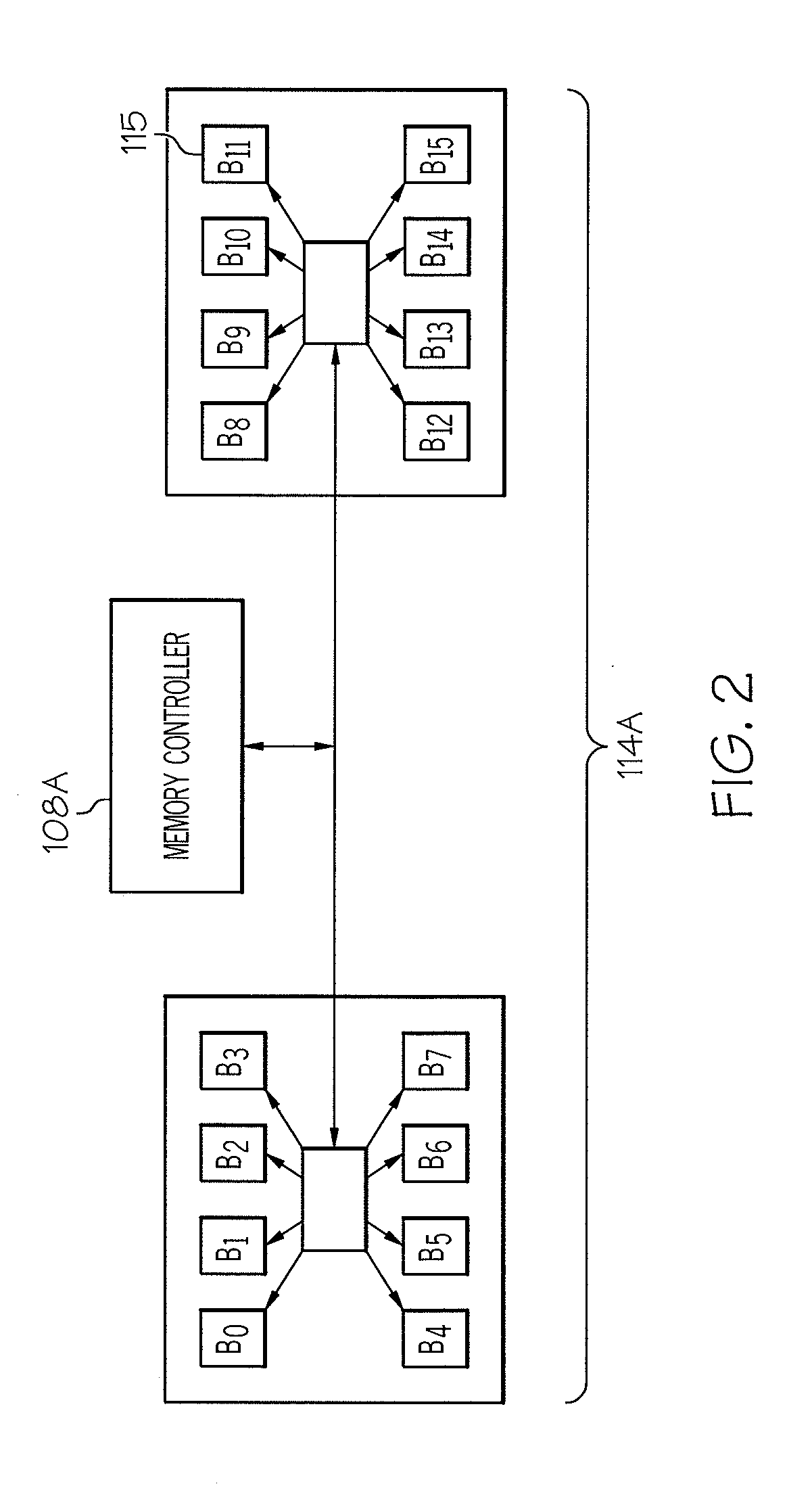
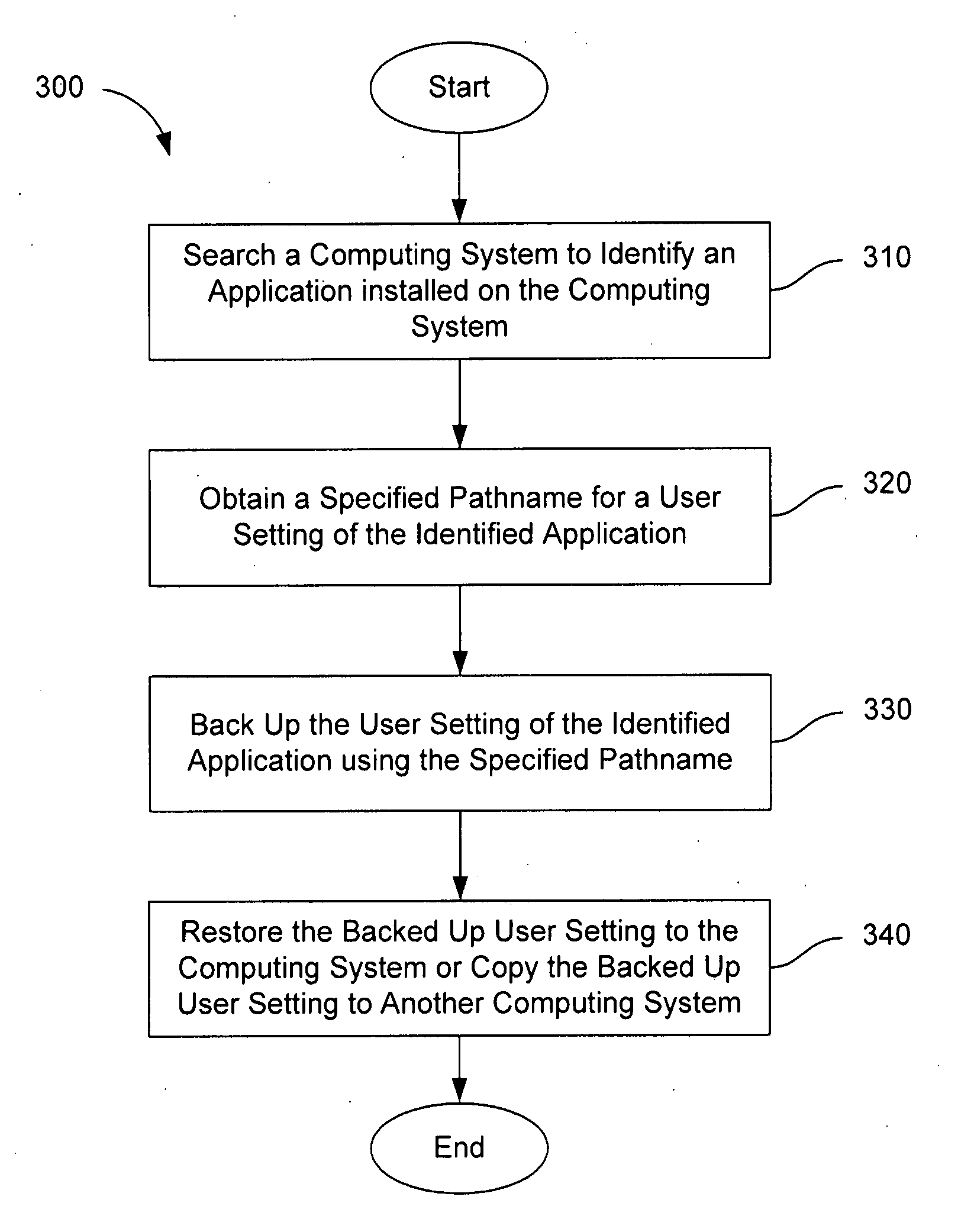
Systems and methods for backing up user settings
InactiveUS20080126446A1Error detection/correctionSpecial data processing applicationsApplication softwareSearch computing
Systems and methods are provided for backing up the user settings of a computing system. The computing system is searched to identify an installed application, a known pathname for a user setting of the identified application is then obtained, and then the user setting is backed up by using the specified pathname to find the user setting on the computing system. User settings can be backed up for one or more user accounts of the computing system, and later the user settings for any of the backed up user accounts can be restored to the computing system, or copied to another computing system. In this way, a user's customization of the computing system can be restored to the computing system at a later time or provided to another computing system.
Owner:STORAGE APPLIANCE CORP
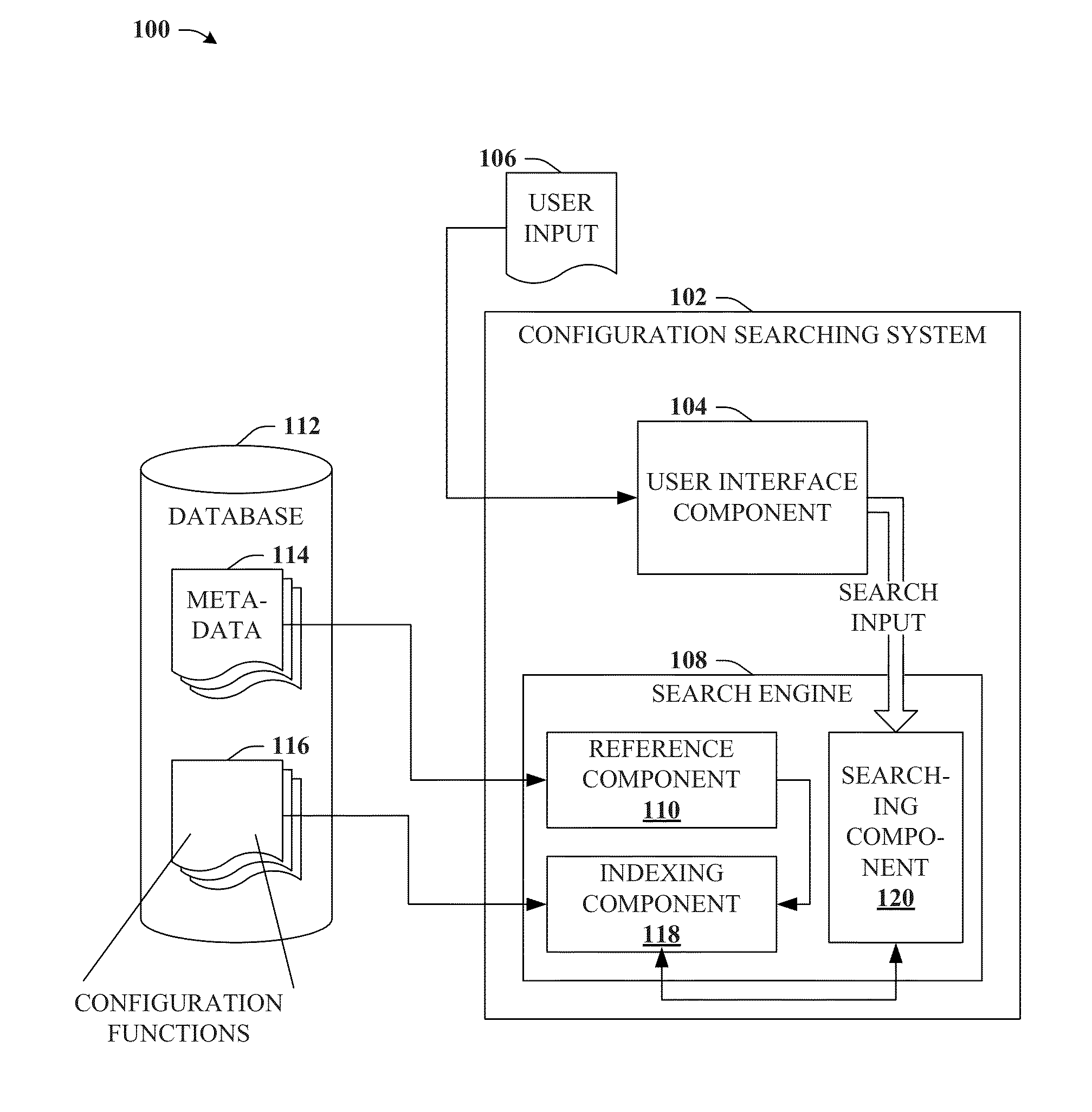
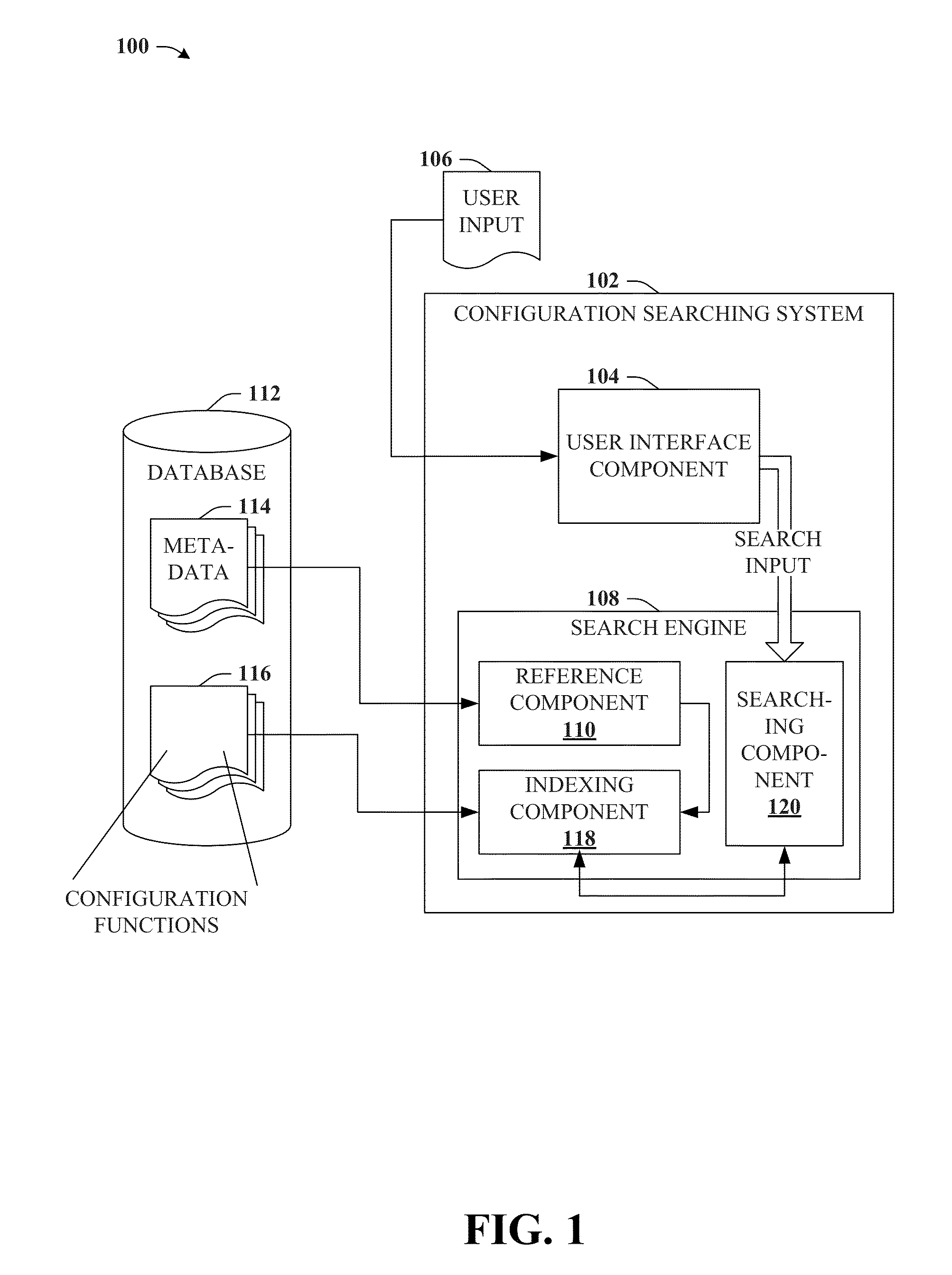
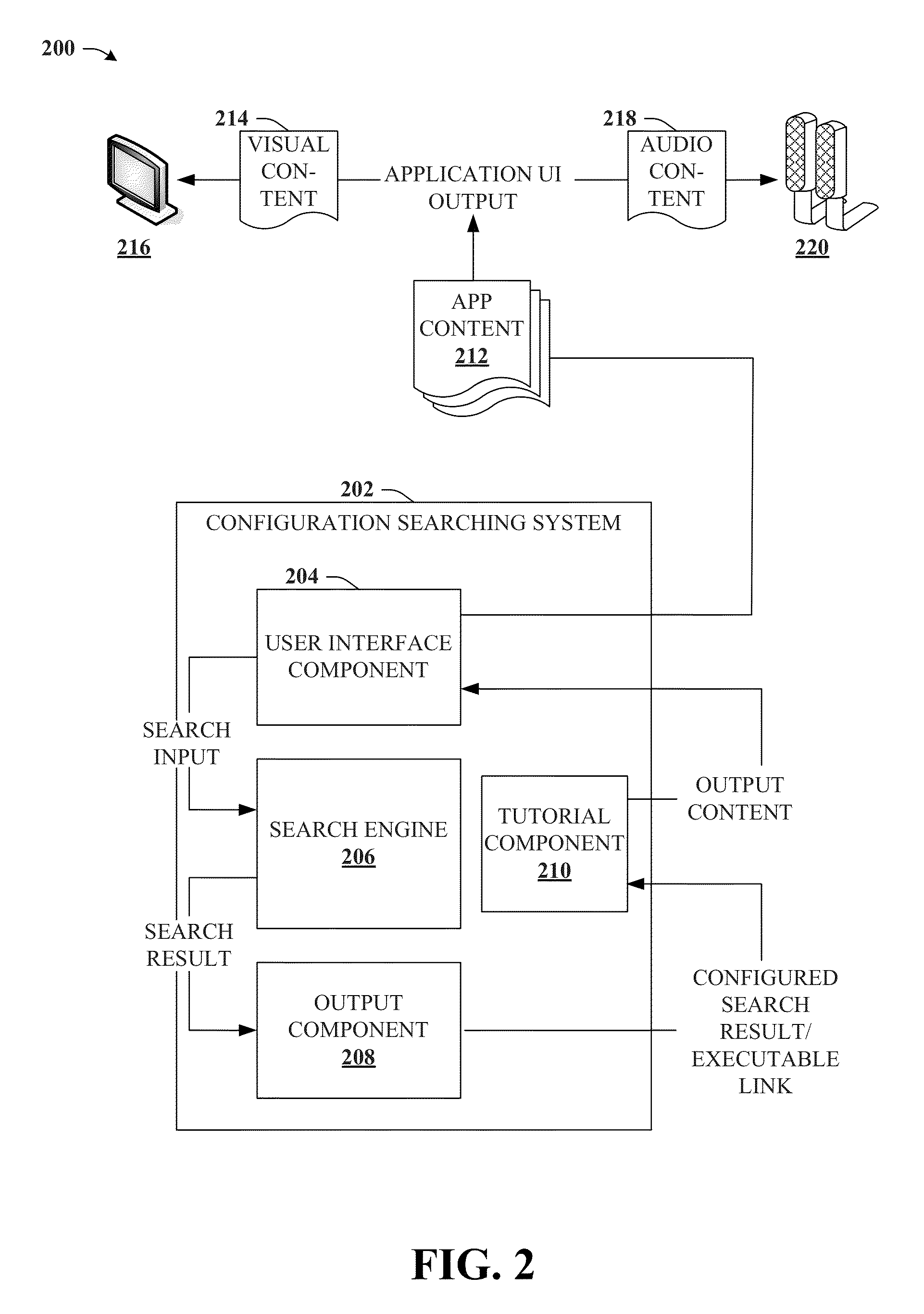
Search augmented menu and configuration for computer applications
ActiveUS20130124529A1Facilitate rapid accessImprove productivityDigital data processing detailsRelational databasesData matchingApplication software
Providing for search to facilitate discovery or access to configuration functions of a computer application is described herein. By way of example, metadata can be appended to configuration functions of the computer application. A matrix correlating subsets of metadata with related configuration functions can facilitate distinguishing respective configuration functions, or groups of related configuration functions based on the subsets of metadata. User search data can be referenced against the subsets of metadata. Respective subsets of metadata that satisfy a condition defined by a data matching function can be returned as a match, and configuration functions associated with matching metadata can be output in response to the search data. In some aspects, user-appended metadata is provided for user customization of configuration function searching, and in other aspects machine learning can be employed to derive user preferences from usage activity and search history, and tailor search results to predicted user preferences.
Owner:MICROSOFT TECH LICENSING LLC
Canonical abstraction for outerjoin optimization
InactiveUS7478080B2Efficient implementationData processing applicationsDigital data information retrievalExecution planProgramming language
A system, apparatus, and program storage device implementing a method of optimizing queries used for searching a computerized database, wherein the method comprises providing a query comprising a sequence of inner joins and outerjoins; and rewriting the query by producing a sequence of outer Cartesian products for the query; producing a sequence of nullification operations on the query; and producing a sequence of best match operations on the query. The method further comprises optimizing the query using a query execution plan for processing the rewritten query, wherein the query execution plan expands a search space in the database for which the rewritten query may be run.
Owner:IBM CORP
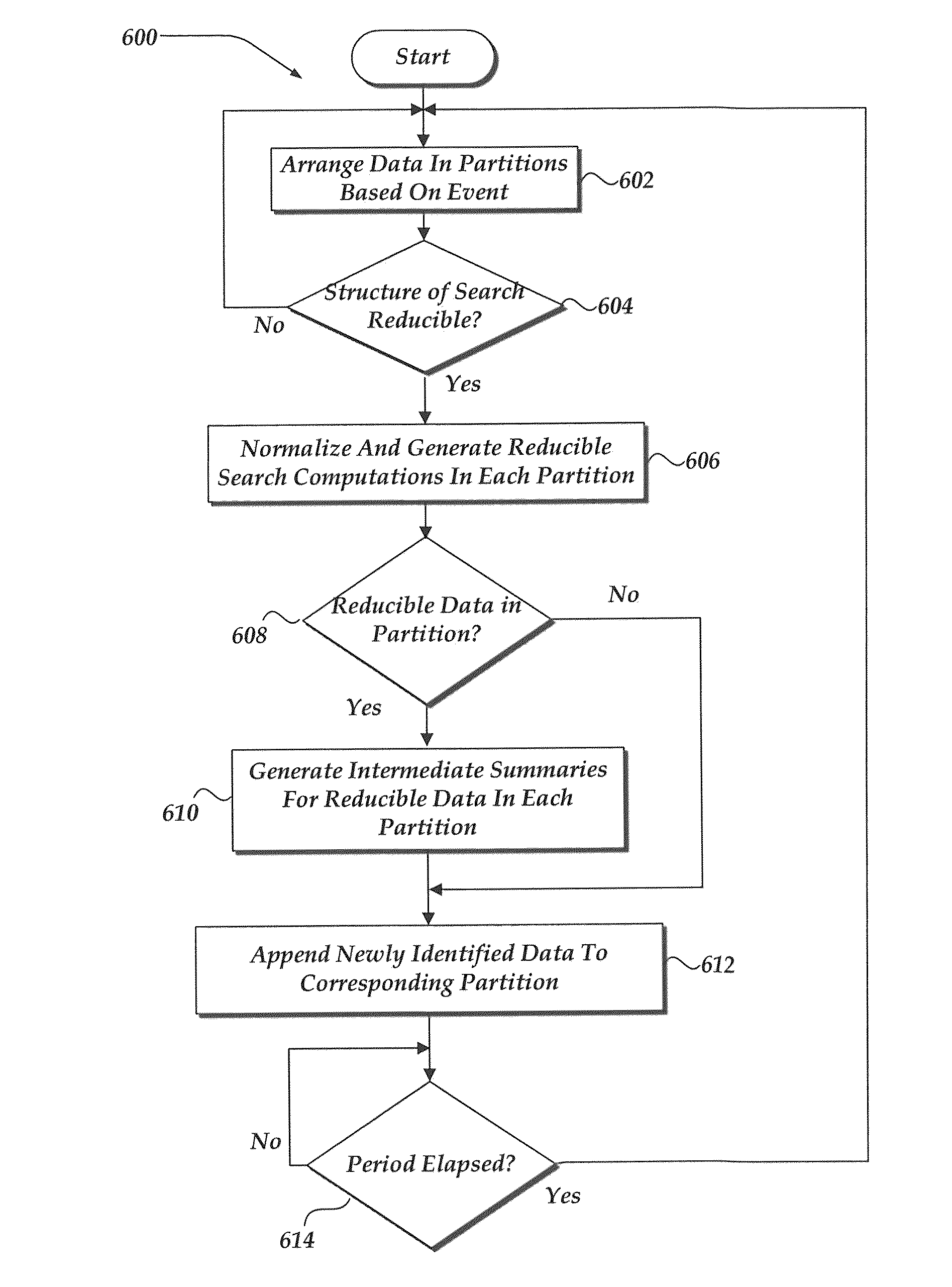
Transparent index summarization
A method and system for managing searches of a data set that is partitioned based on a plurality of events. A structure of a search query may be analyzed to determine if logical computational actions performed on the data set is reducible. Data in each partition is analyzed to determine if at least a portion of the data in the partition is reducible. In response to a subsequent or reoccurring search request, intermediate summaries of reducible data and reducible search computations may be aggregated for each partition. Next, a search result may be generated based on at least one of the aggregated intermediate summaries, the aggregated reducible search computations, and a query of adhoc non-reducible data arranged in at least one of the plurality of partitions for the data set.
Owner:SPLUNK INC
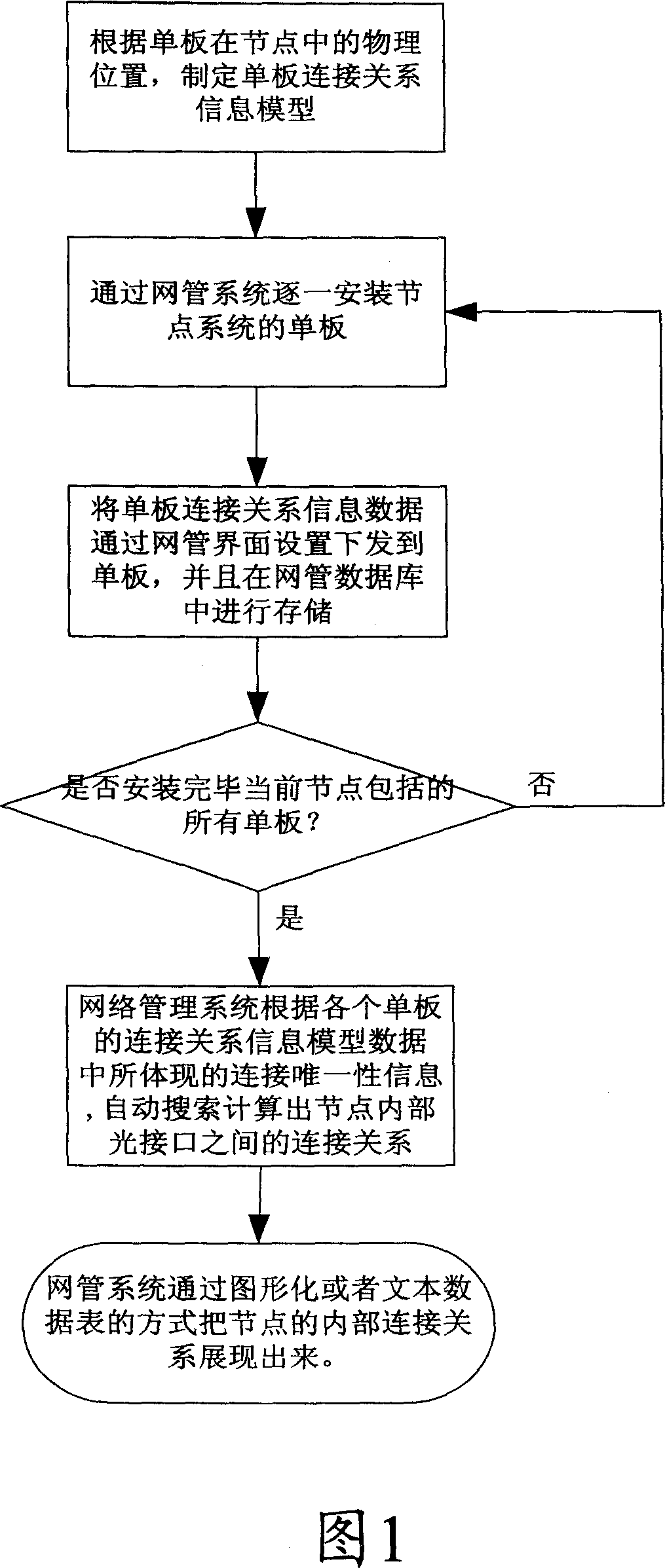
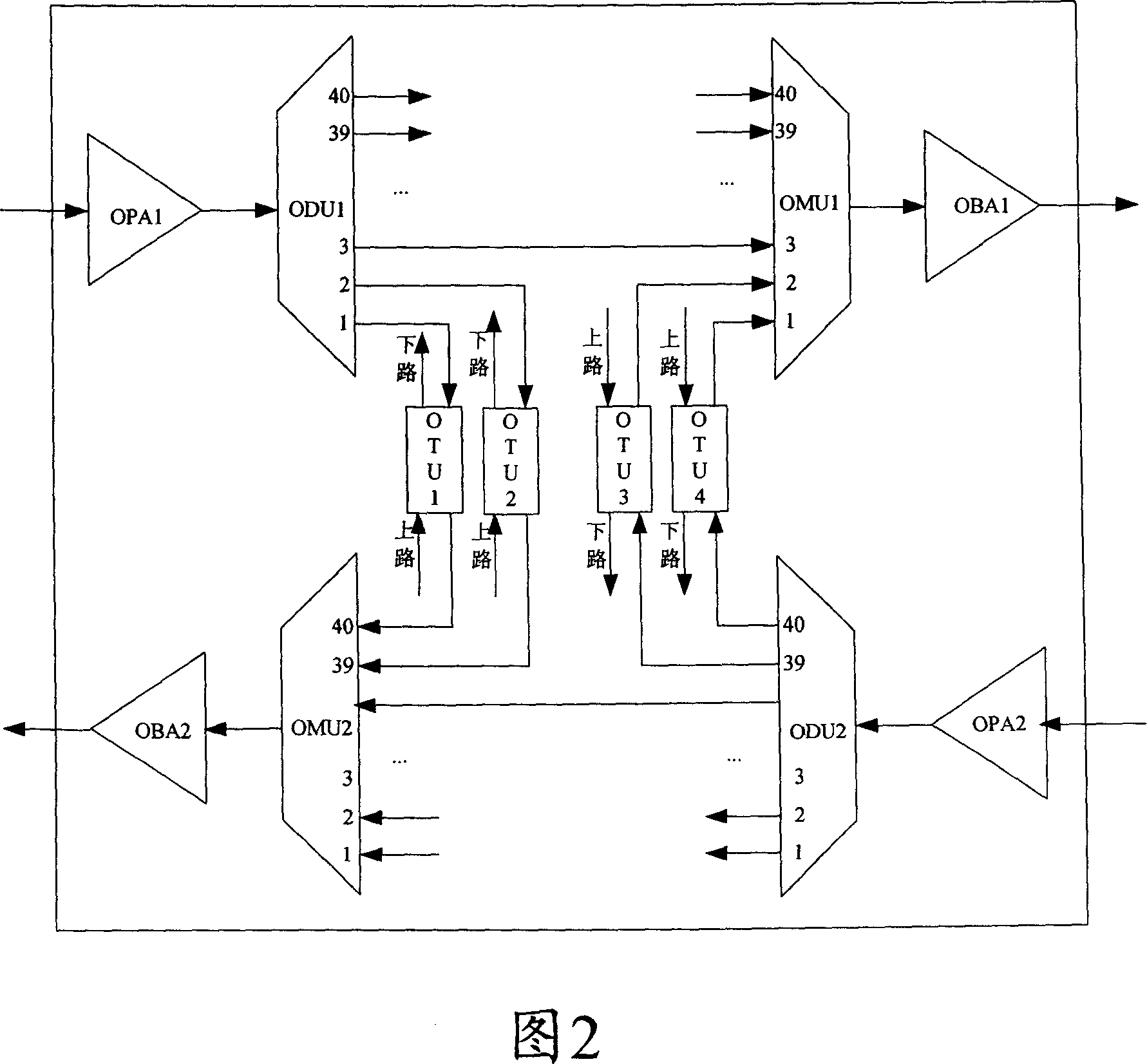
A method to automatically obtain inner connection relation of optical network node
ActiveCN1964283ARealize automatic configuration establishmentPrecise positioningWavelength-division multiplex systemsElectromagnetic transmissionNetwork managementSearch computing
The disclosed method for automatic acquiring inner connection relation for optical network node comprises: the network management system builds connection relation model for every function single board of node; according to the unique information in the model data, it matches inner port to automatic search all inner connection relation; then, it shows the connection result in figure or text table. This invention is convenient to reduce maintenance cost.
Owner:ZTE CORP
Web-based method of rendering indecipherable selected parts of a document and creating a searchable database from the text
InactiveUS20070150163A1Reduce morbidityImprove accuracyAnalogue computers for vehiclesComputer security arrangementsWord processingPaper document
A method and apparatus for uploading and storing a document created in a word processing program (such as MS Word, Claris Works, WordPad, WordPerfect, etc.) onto a networked server in a way that preserves the “look and feel” of the uploaded document and allows users to select, classify, and conceal various blocks of text contained within the document so that a confidential or secure version of the document can be displayed on the Internet and the classified blocks of text can become the basis of a searchable computer database.
Owner:AUSTIN DAVID J
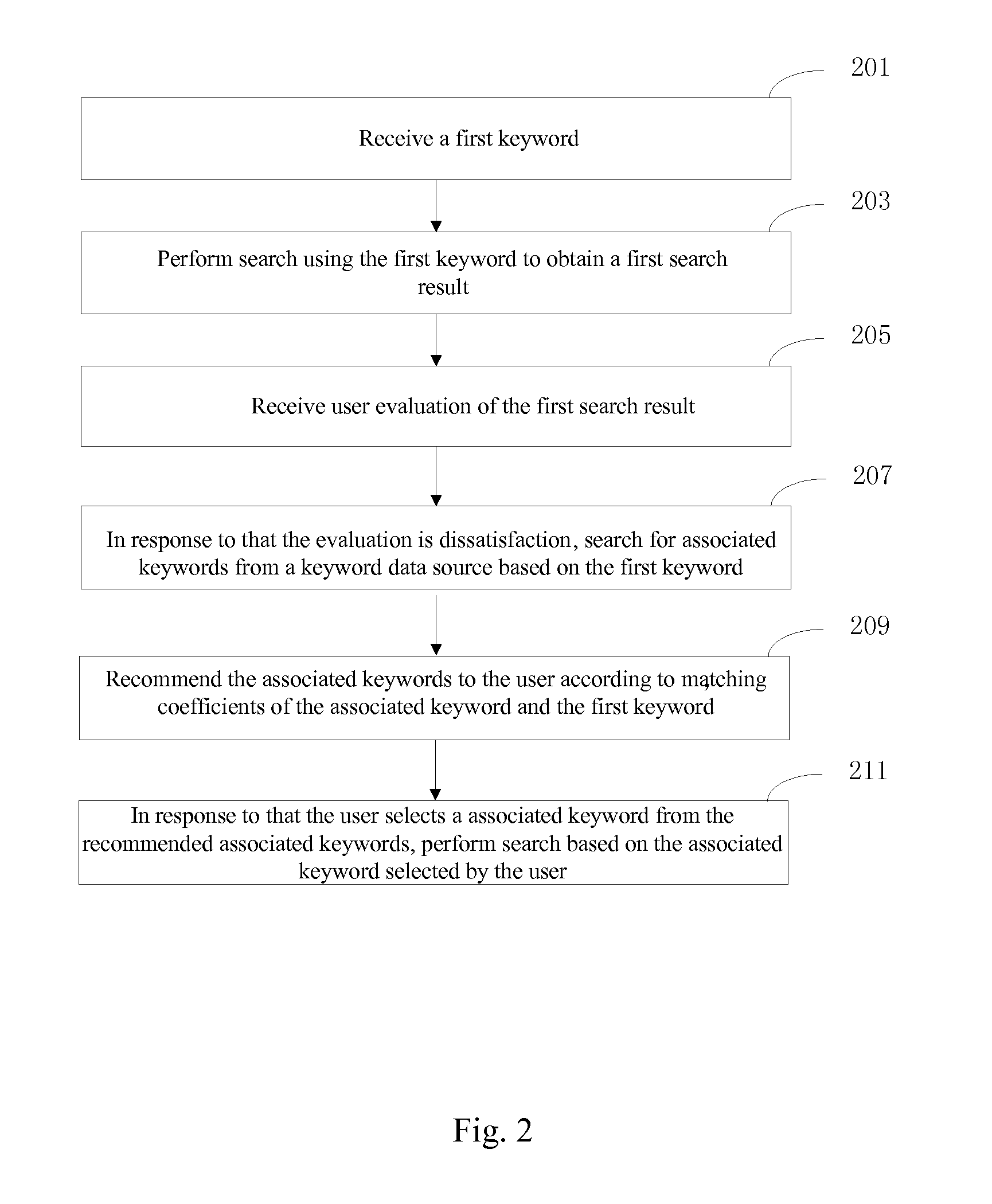
Computer Processing Method and System for Searching
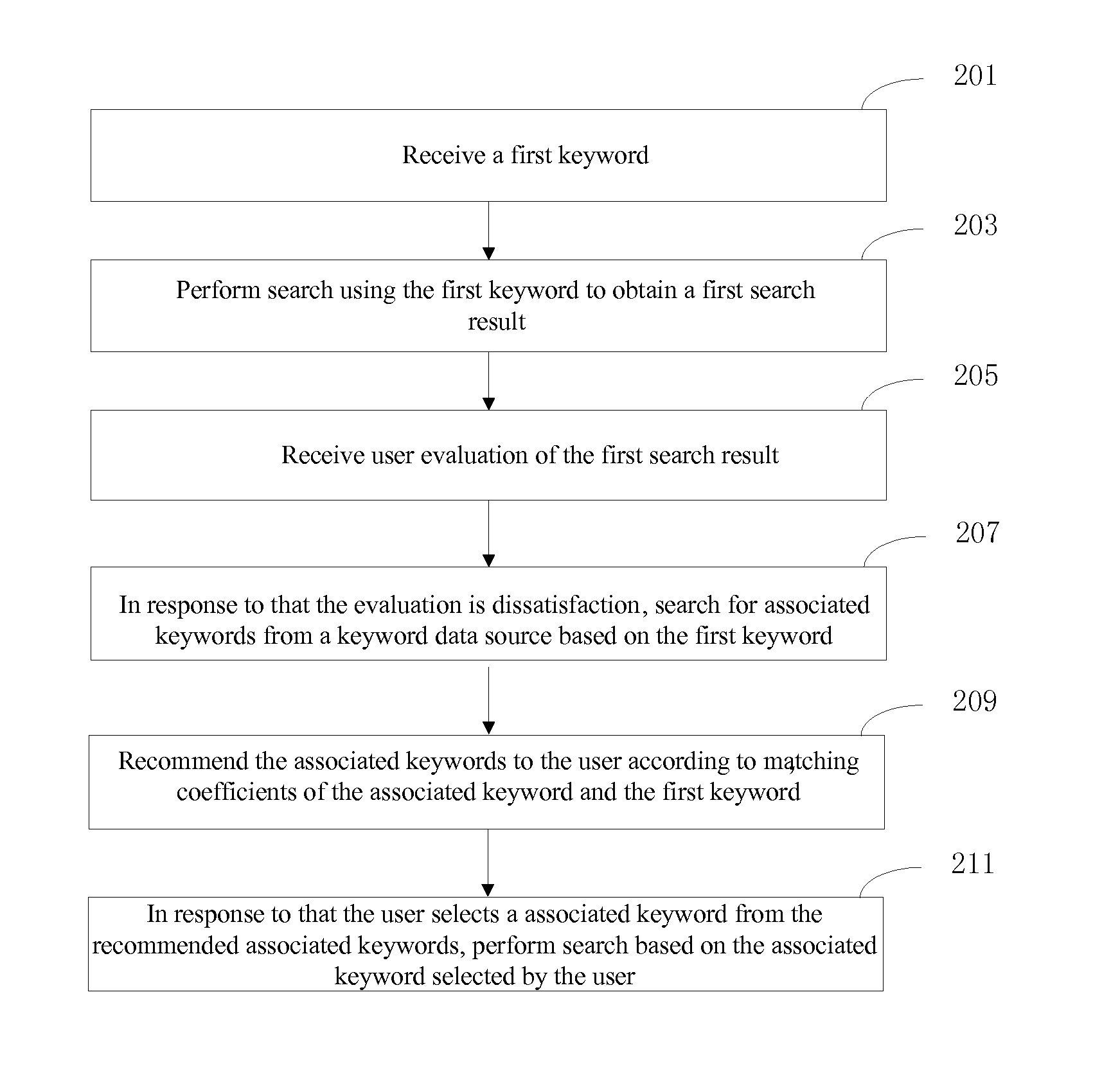
InactiveUS20120271843A1Digital data information retrievalDigital data processing detailsData sourceData mining
The present invention provides a computer processing method and a system thereof for searching. The computer processing method includes: receiving a first keyword; performing search using the first keyword to obtain a first search result; receiving user evaluation of the first search result; in response to the evaluation being unsatisfactory, searching for associated keywords from a keyword data source based on the first keyword; recommending associated keywords to the user according to matching degrees of the associated keywords and the first keyword; and in response to that the user selects an associated keyword from the recommended associated keywords, performing search based on the associated keyword selected by the user. The related specific implementation of the present application will help a user to find an input keyword more effectively during a search so as to enable him / her get more satisfactory search result.
Owner:IBM CORP
Information directory system
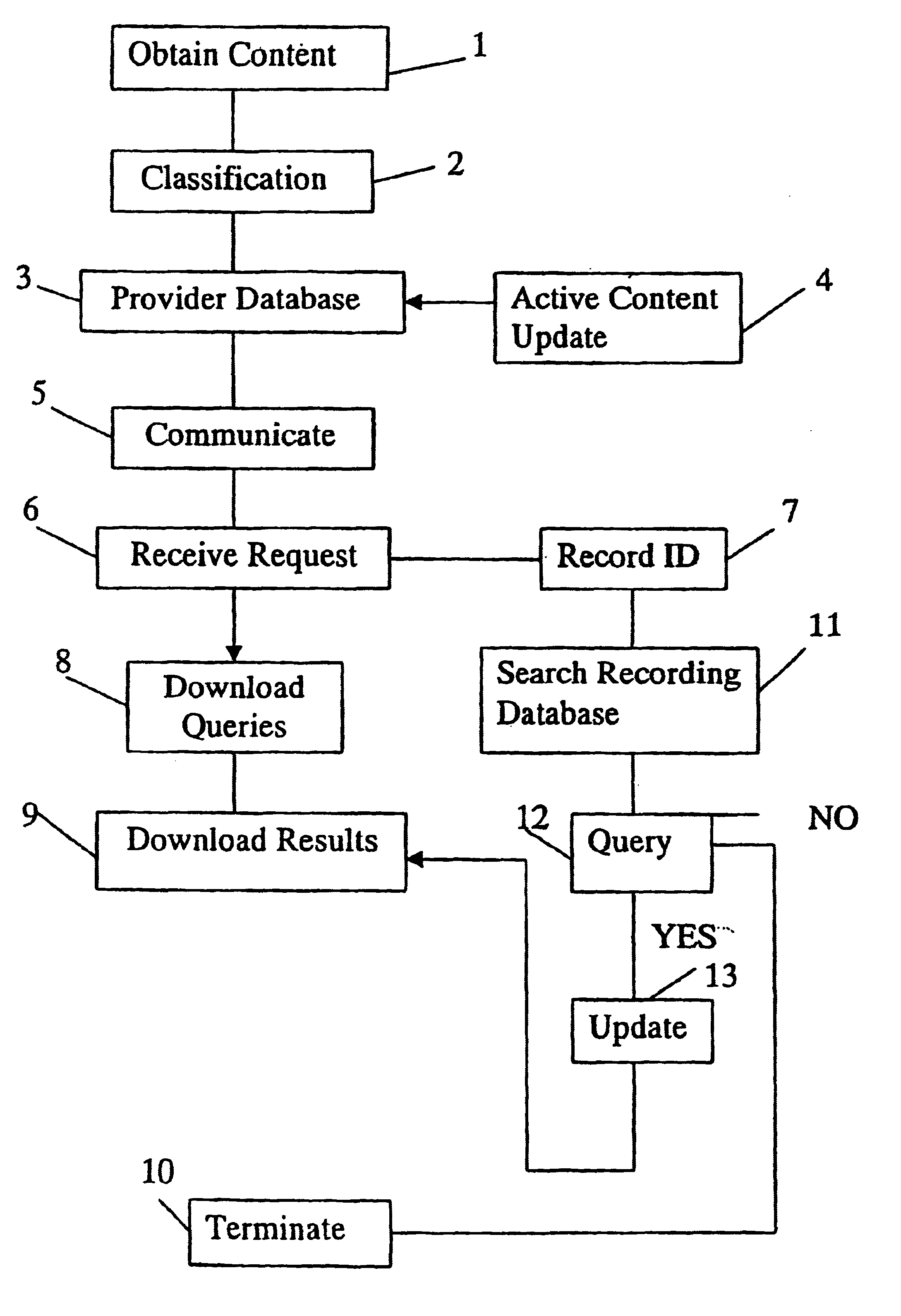
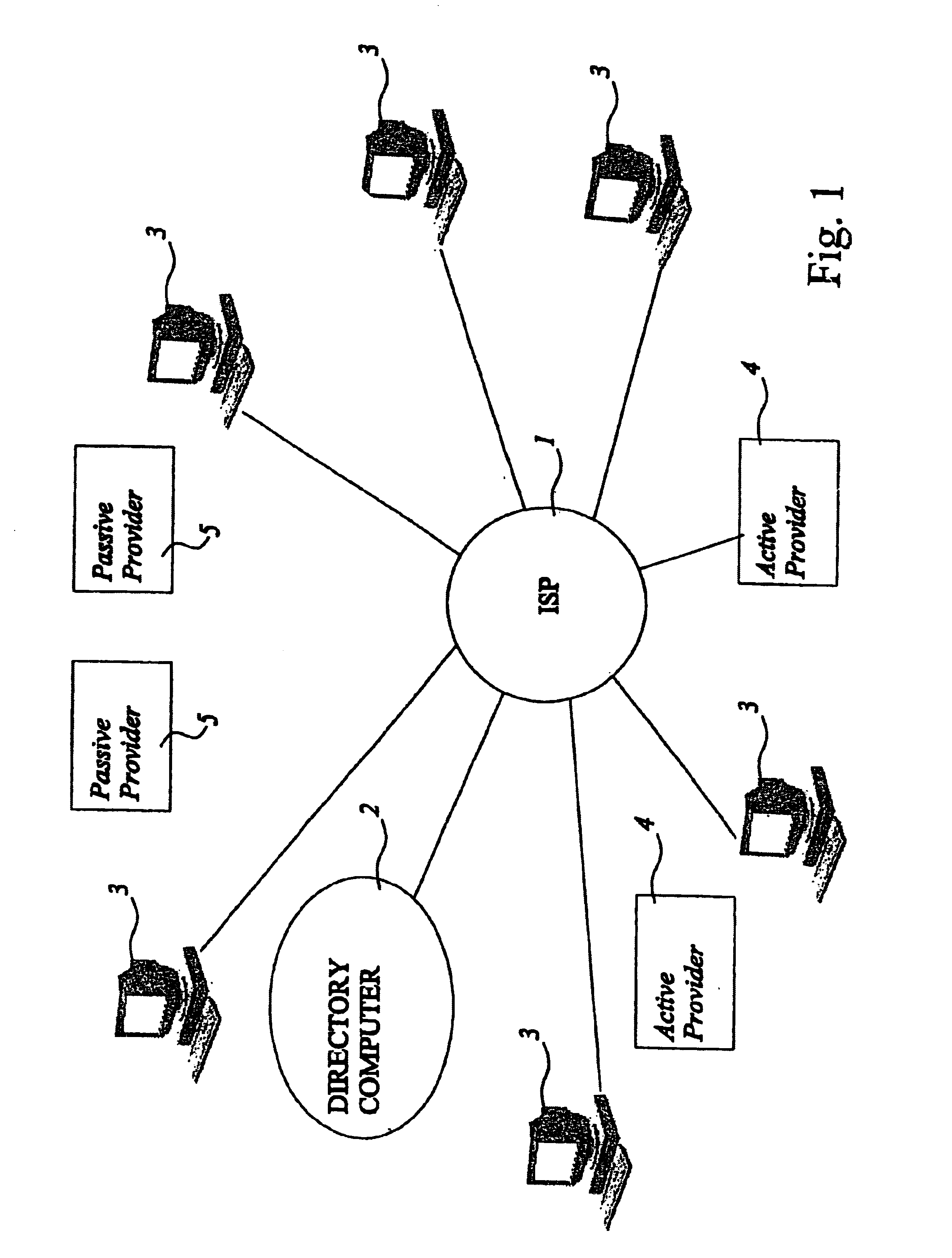
InactiveUS7047233B1Web data indexingDigital data processing detailsUnique identifierDirectory system
A method of providing information in a directory system comprising a directory for company information, goods and services; a communications network; a directory computer operated by a directory provider; a plurality of search computers operated by enquirers which search computers are connected within the network; and a plurality of active content providers operating active content provider computers, at least some of which are connected to the directory computer. The company information, goods and services are classified by unique identifiers. Lists of goods and services and company information are provided as provider content from both active and passive content providers. These are stored in a provider database with unique identifiers. The directory computer on request downloads to the search computer one or more queries to allow the search computer specify the search correctly and then the directory computer downloads the search result. The active content provider computers update the search from time to time. The purpose is to provide a comprehensive listing of useful information to an enquirer in an easily searched form while simultaneously allowing the active content providers to tailor the information supplied.
Owner:TODAYS PAGES
Report acceleration using intermediate summaries of events
A method and system for managing searches of a data set that is partitioned based on a plurality of events. A structure of a search query may be analyzed to determine if logical computational actions performed on the data set is reducible. Data in each partition is analyzed to determine if at least a portion of the data in the partition is reducible. In response to a subsequent or reoccurring search request, intermediate summaries of reducible data and reducible search computations may be aggregated for each partition. Next, a search result may be generated based on at least one of the aggregated intermediate summaries, the aggregated reducible search computations, and a query of adhoc non-reducible data arranged in at least one of the plurality of partitions for the data set.
Owner:SPLUNK INC
Zero-search, zero-memory vector quantization
ActiveUS20050004795A1Improve fidelityReduce calculationCode conversionSpeech recognitionData compressionAdaptive coding
The invention comprises a method for lossy data compression, akin to vector quantization, in which there is no explicit codebook and no search, i.e. the codebook memory and associated search computation are eliminated. Some memory and computation are still required, but these are dramatically reduced, compared to systems that do not exploit this method. For this reason, both the memory and computation requirements of the method are exponentially smaller than comparable methods that do not exploit the invention. Because there is no explicit codebook to be stored or searched, no such codebook need be generated either. This makes the method well suited to adaptive coding schemes, where the compression system adapts to the statistics of the data presented for processing: both the complexity of the algorithm executed for adaptation, and the amount of data transmitted to synchronize the sender and receiver, are exponentially smaller than comparable existing methods.
Owner:PROMPTU SYST CORP
Method for Improving the Performance of Computers
ActiveUS20110321034A1Improve performanceSystem resourceError detection/correctionBootstrappingComputer resourcesSystem requirements
In a method for improving the performance of a computer system by releasing computer resources, a list P of programs installed on a computer system is determined. All relevant extension points EP of the computer system are searched for registered entries. A list A of automatically starting programs is generated by assigning the registered entries at the relevant extension points EP to the installed programs, respectively. The list A of the automatically starting programs is compared with a list S of system-required programs and a list V of used programs. Programs that are not system-required and programs that have not been used for a longer period of time are deactivated and computer resources that have been used by the deactivated programs are released. The deactivation of programs can be done by the user or automatically and can be cancelled when necessary.
Owner:AVAST SOFTWARE
Control Object Model Generation Device And Generation Method
InactiveUS20070293957A1Simulator controlComputation using non-denominational number representationMathematical modelControl system
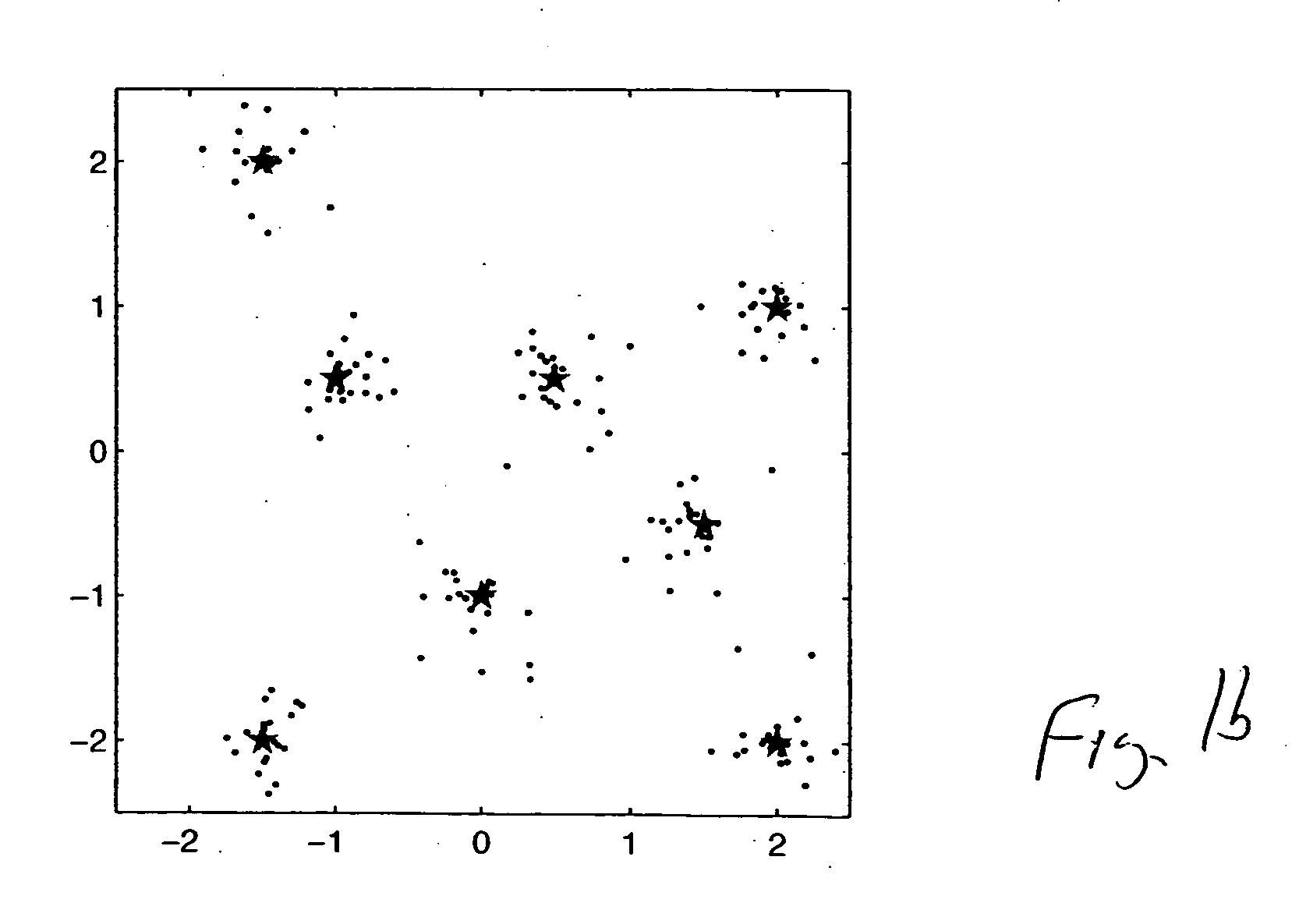
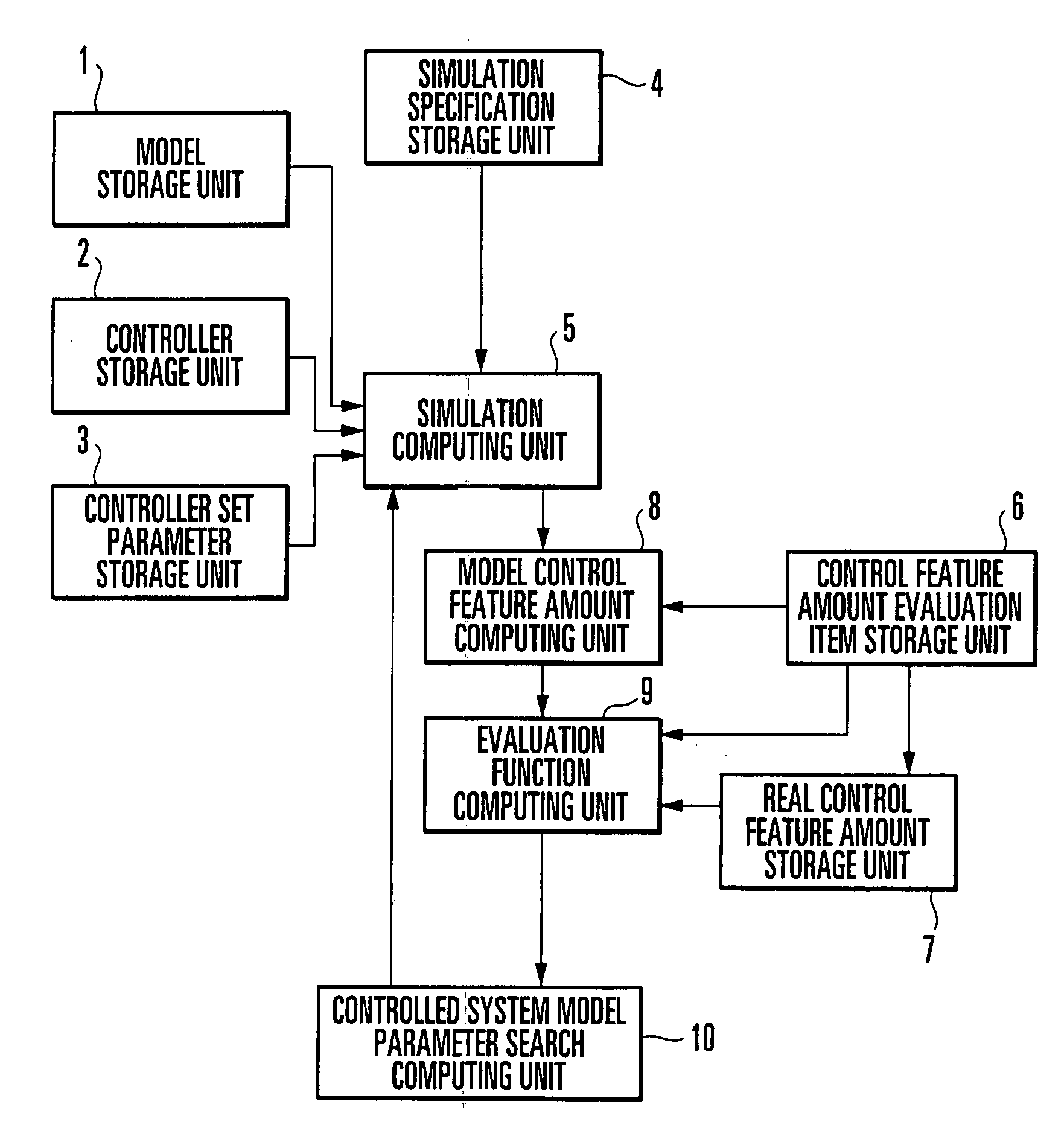
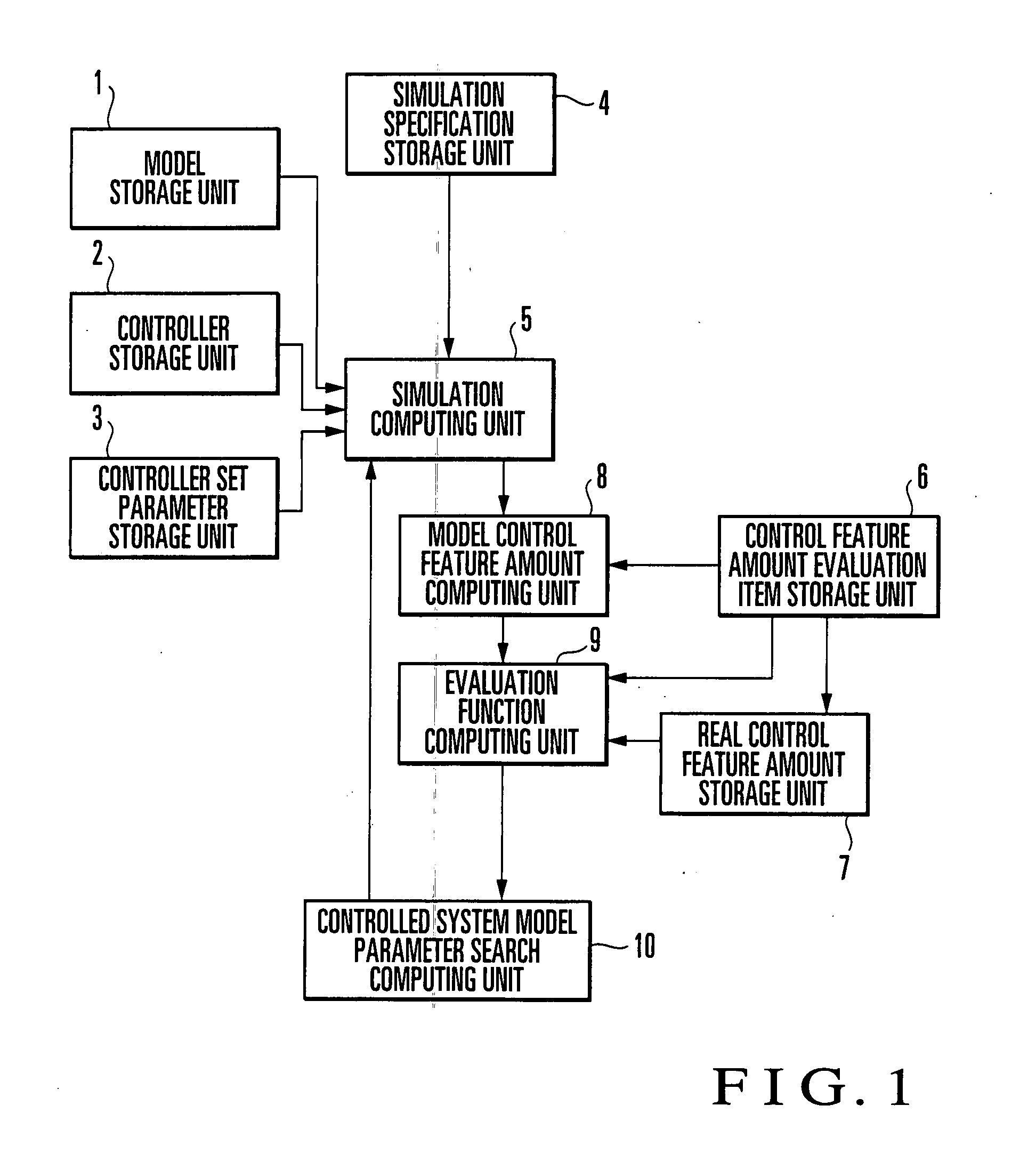
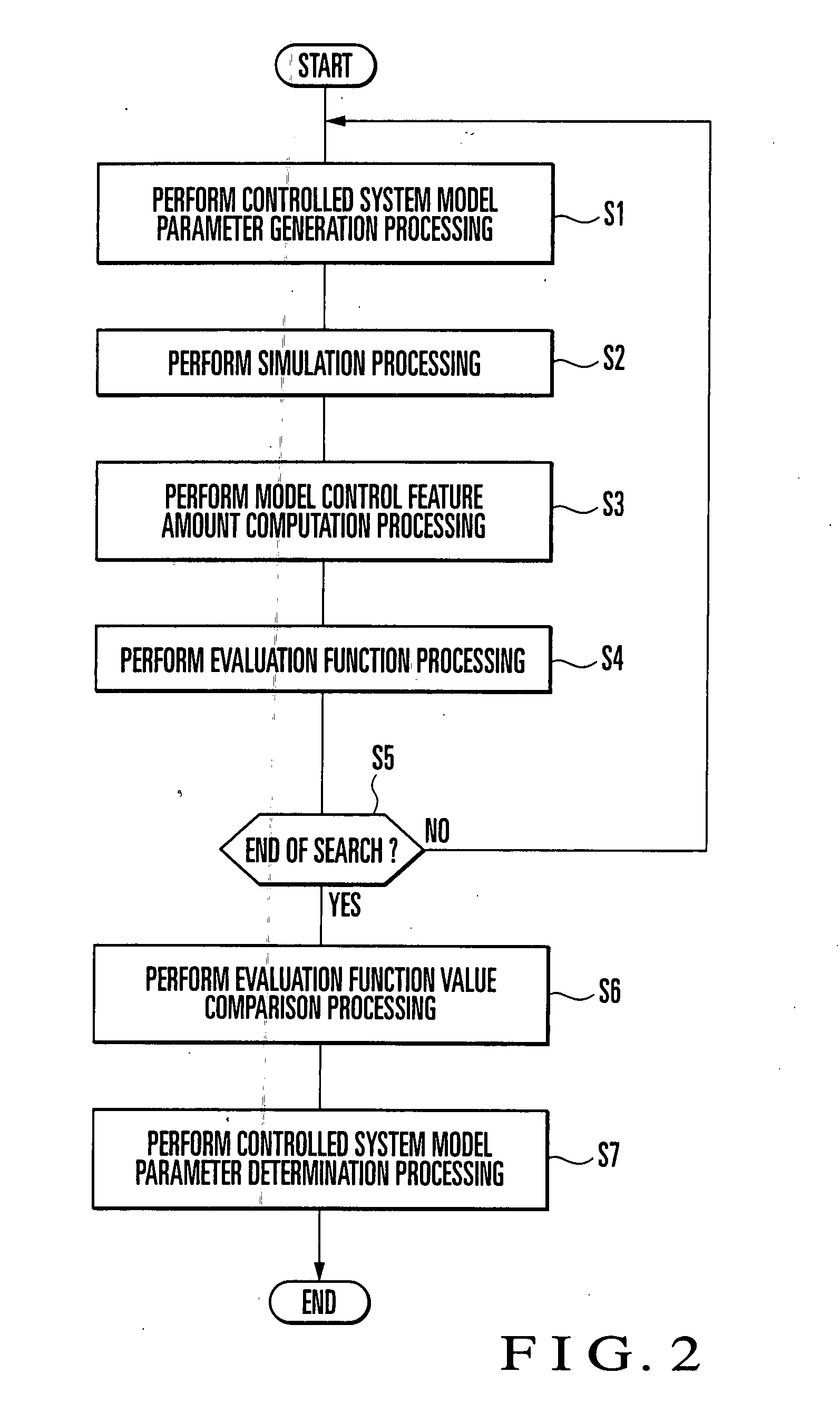
A control object model generation device of this invention includes a simulation computing unit (5) which executes simulation of a control system including a controlled system represented by a mathematical model and a controller represented by a controller algorithm, a model control feature amount computing unit (8) which computes a model control feature amount from the simulation result, an evaluation function computing unit (9) which computes an evaluation function value indicating the similarity between a real control feature amount obtained from a control result on an actual controlled system and a model control feature amount, and a controlled system model parameter search computing unit (10) which executes simulation while sequentially changing the values of controlled system model parameters set in the mathematical model, and obtains controlled system model parameters which optimize the evaluation function value. This makes it possible to reduce the time and labor which are required to acquire time-series data and eliminate the necessity of expert knowledge about control and modeling.
Owner:YAMATAKE HONEYWELL CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com