Patents
Literature
7466 results about "Unique identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
With reference to a given (possibly implicit) set of objects, a unique identifier (UID) is any identifier which is guaranteed to be unique among all identifiers used for those objects and for a specific purpose. The concept have been formalized early in Computer science and Information systems, in general associating it to an atomic data type.
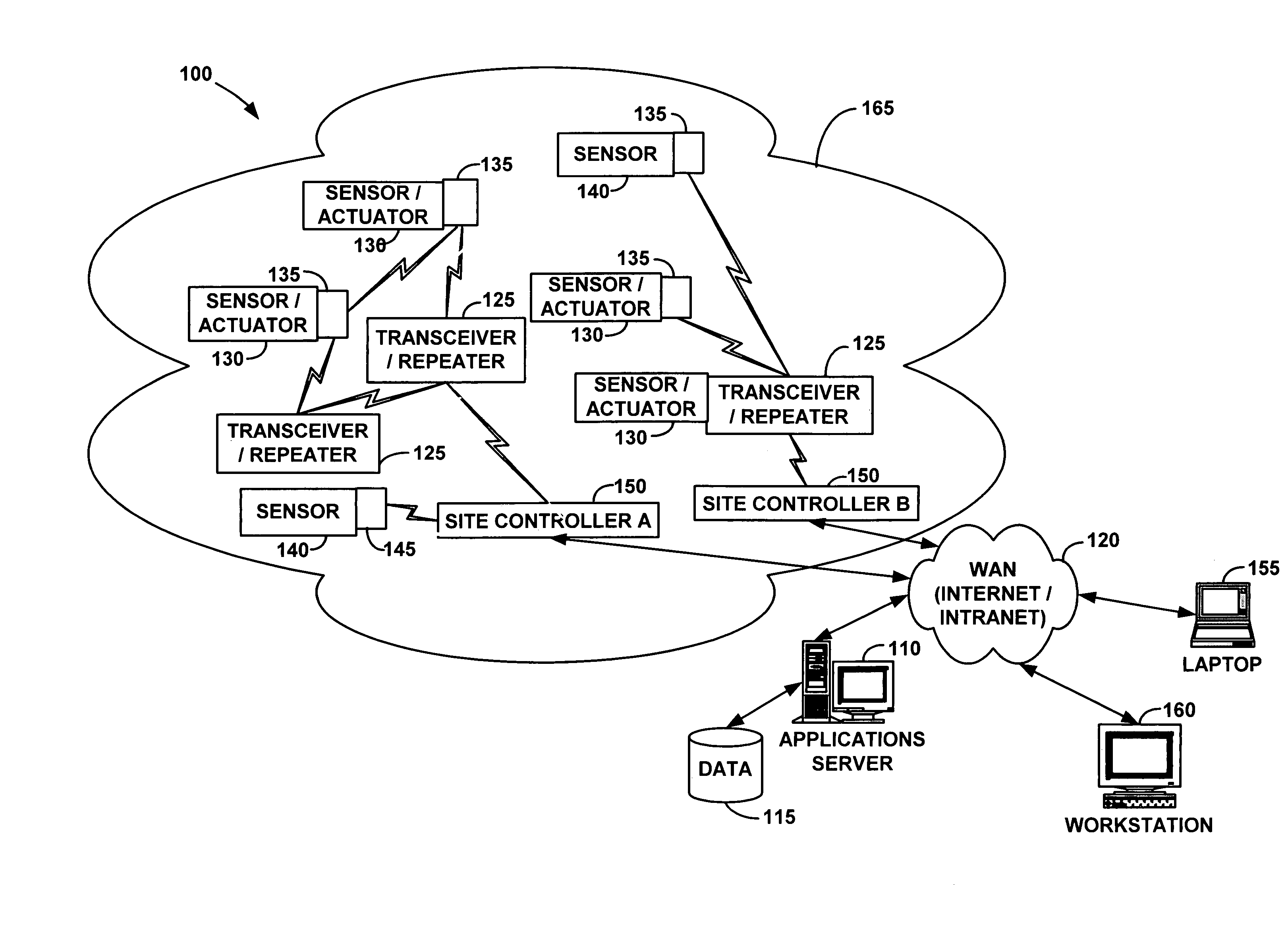
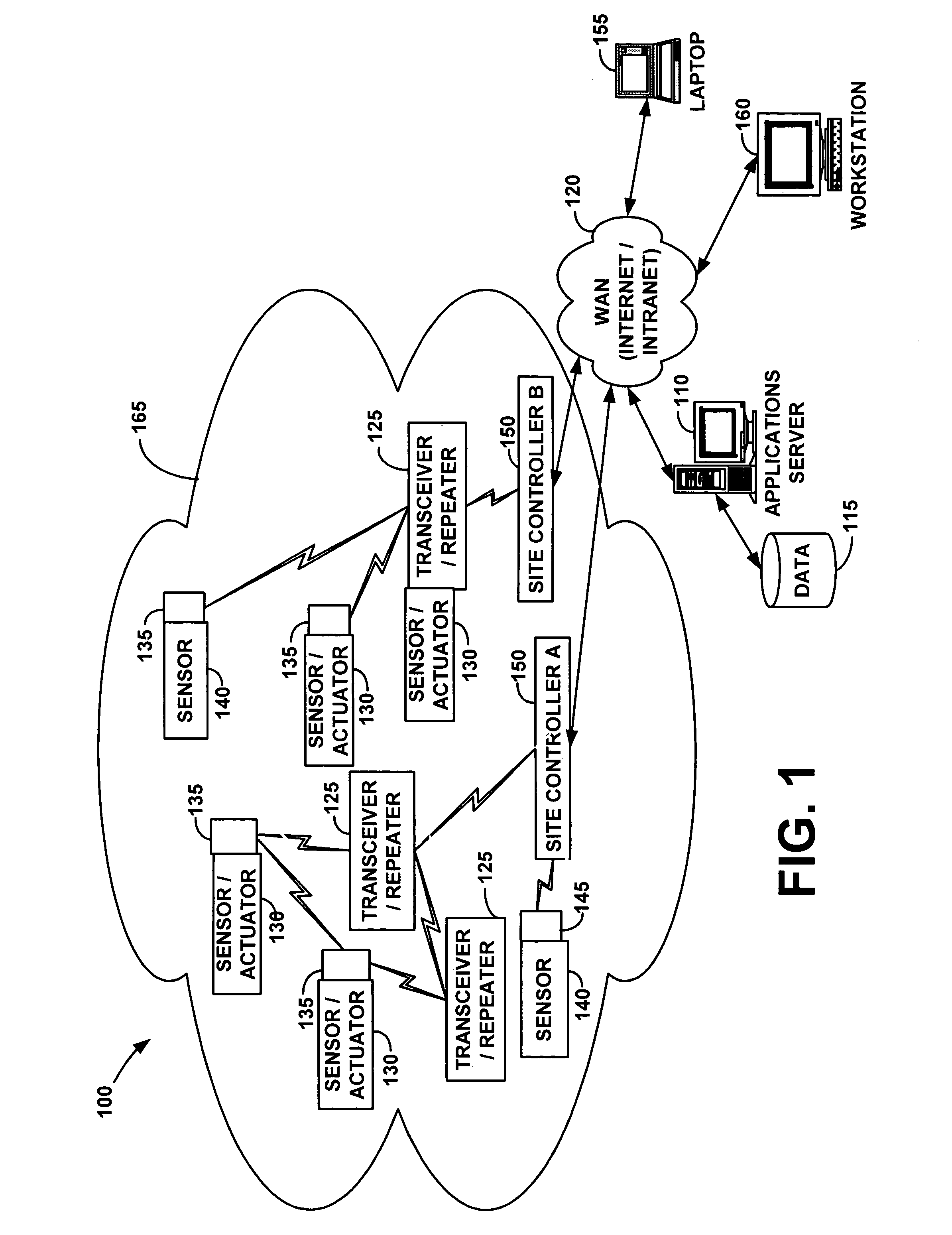
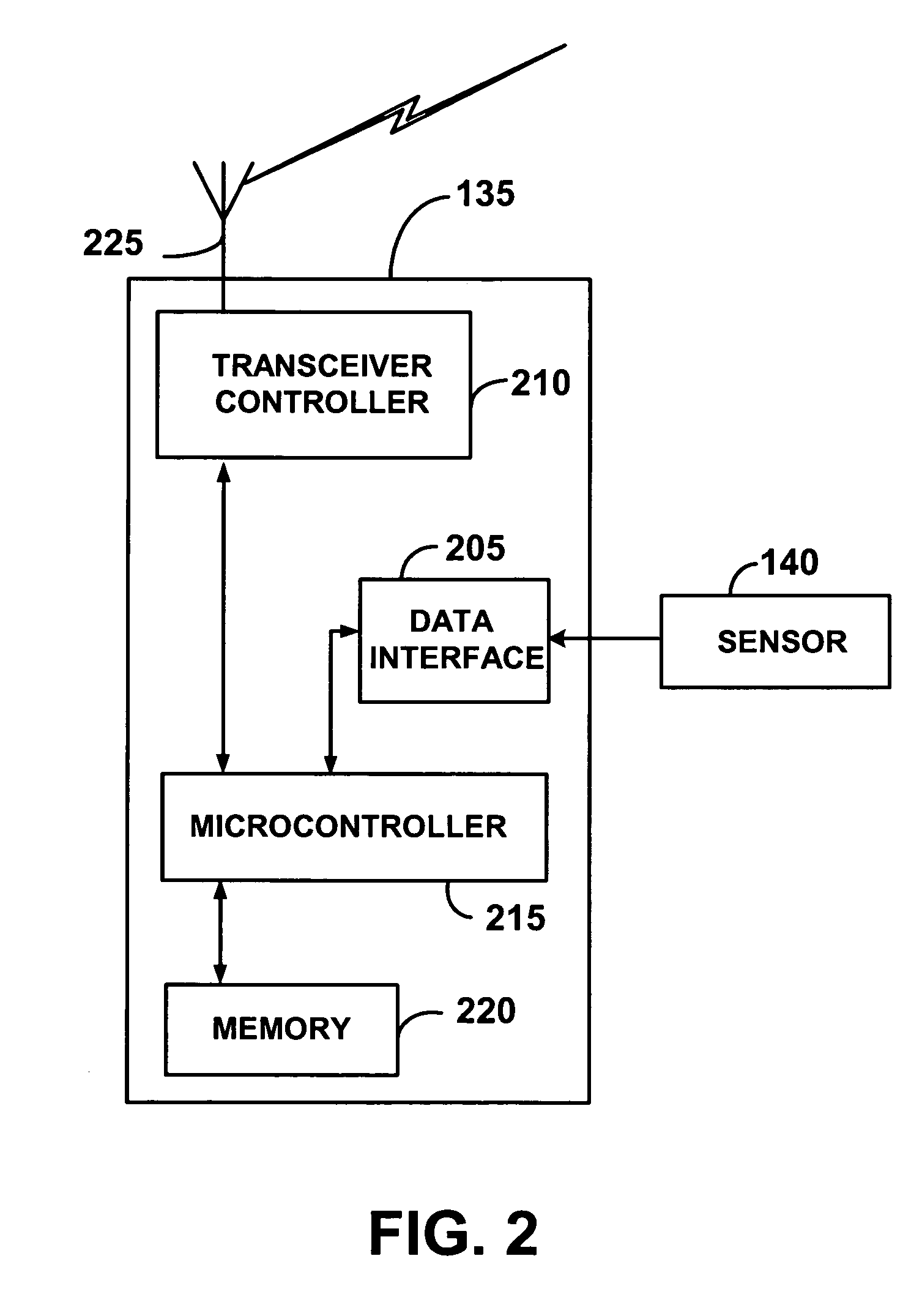
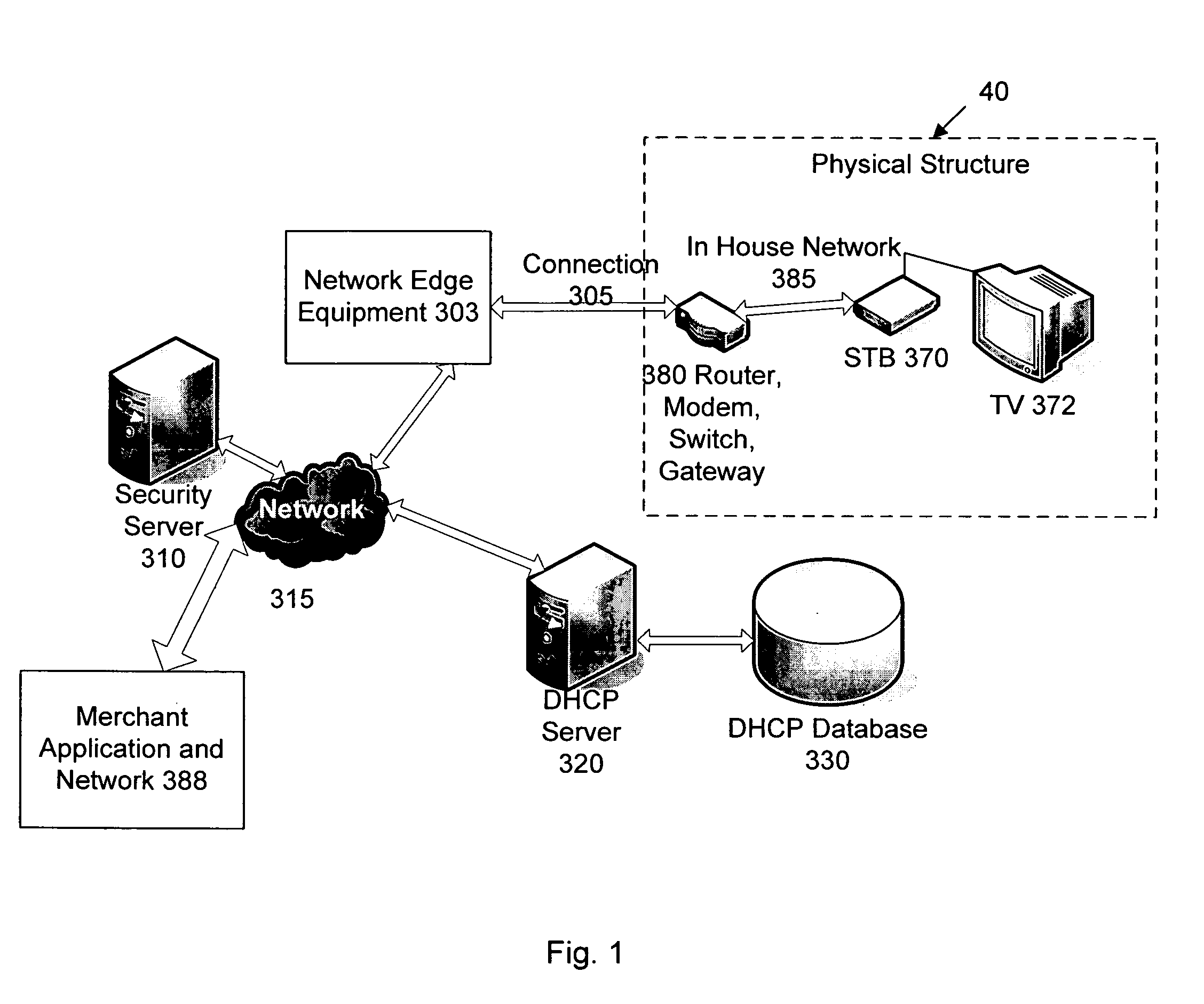
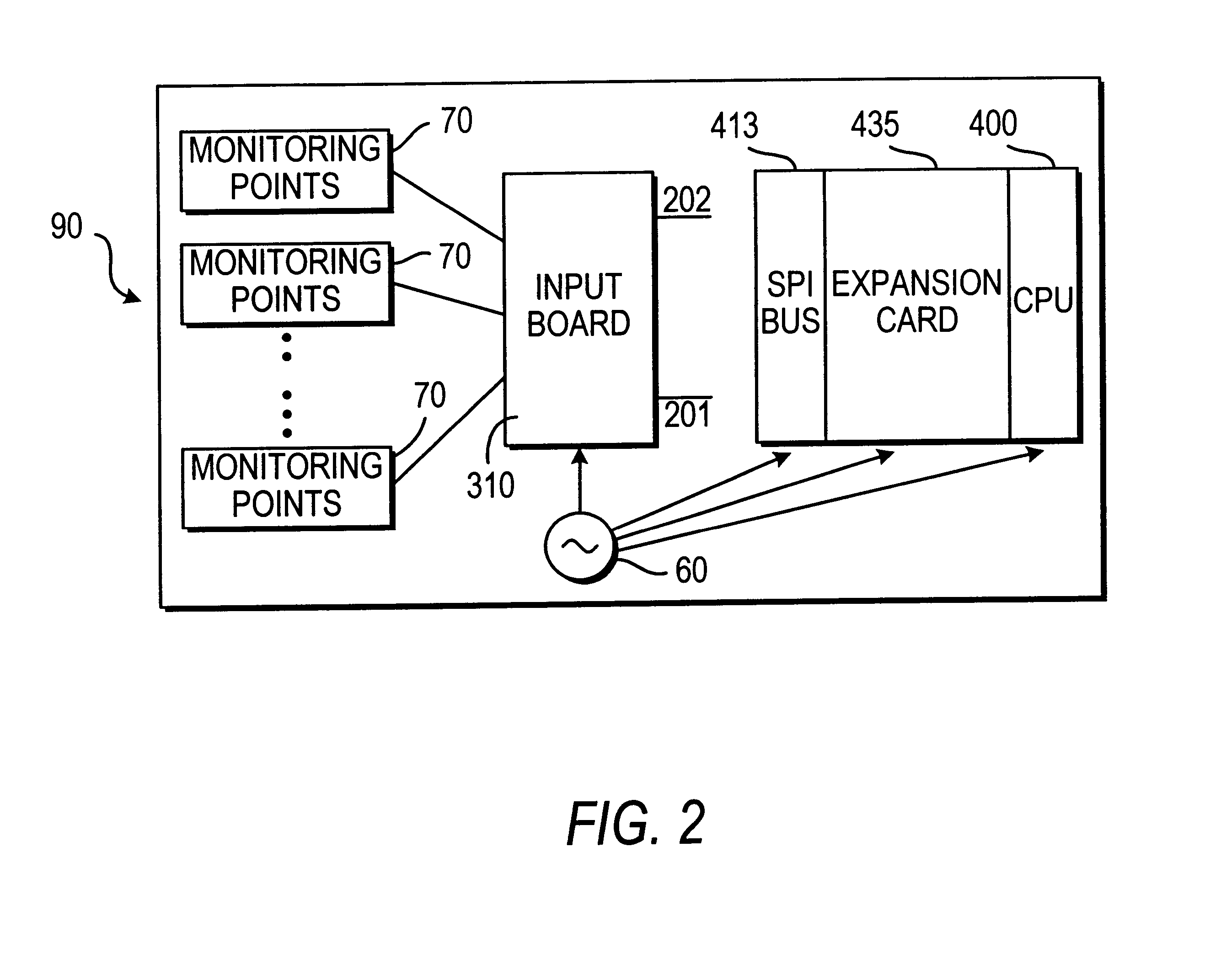
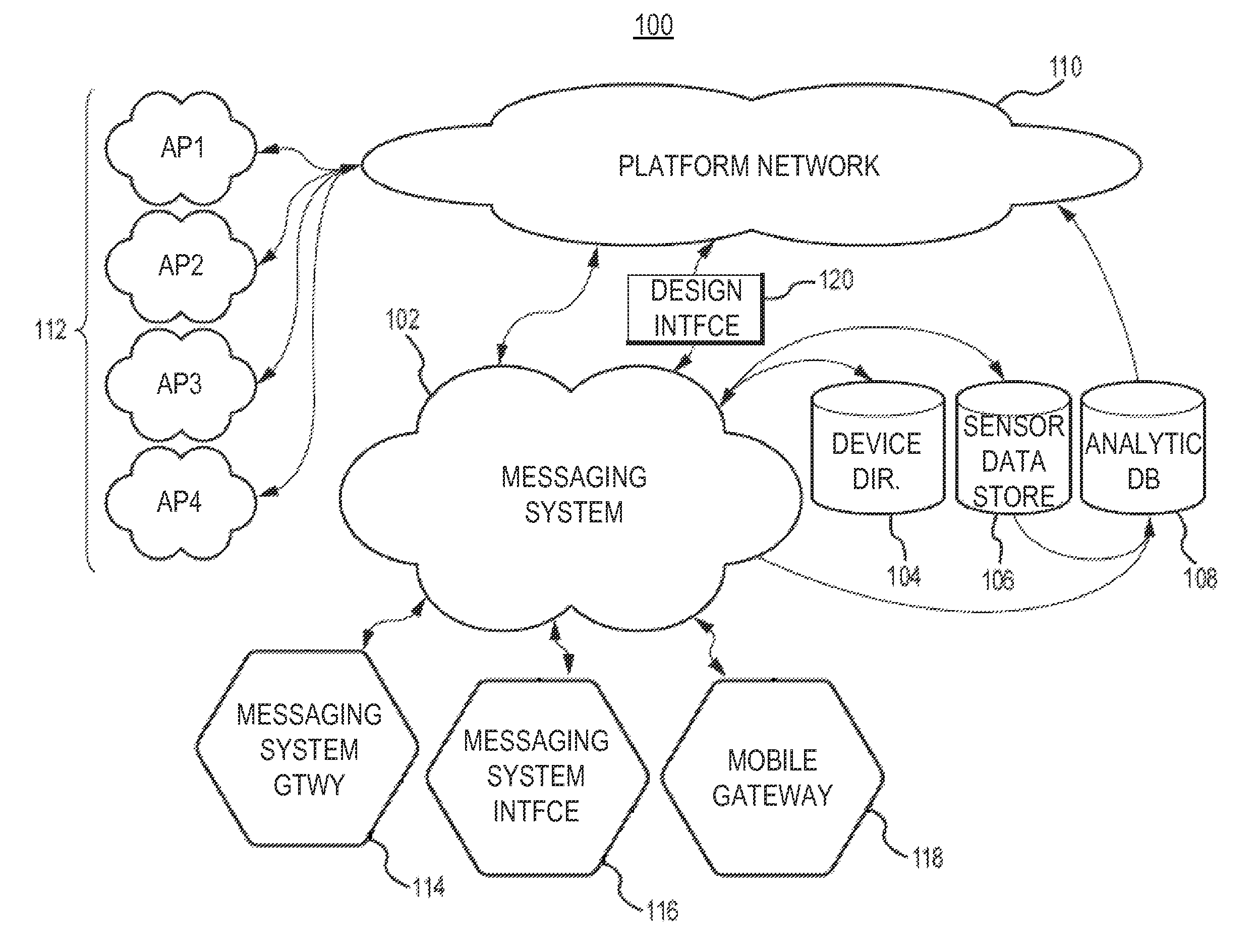
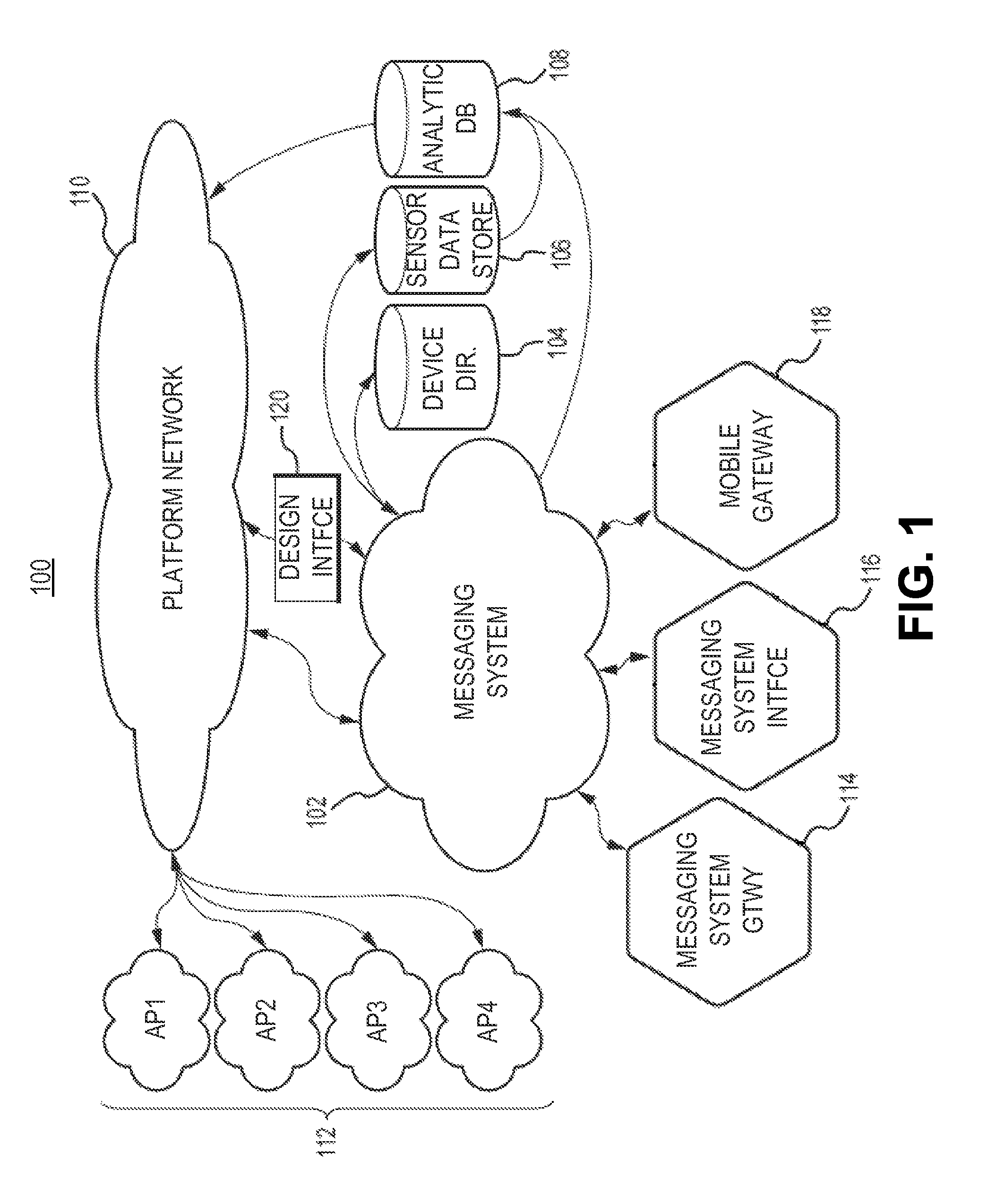
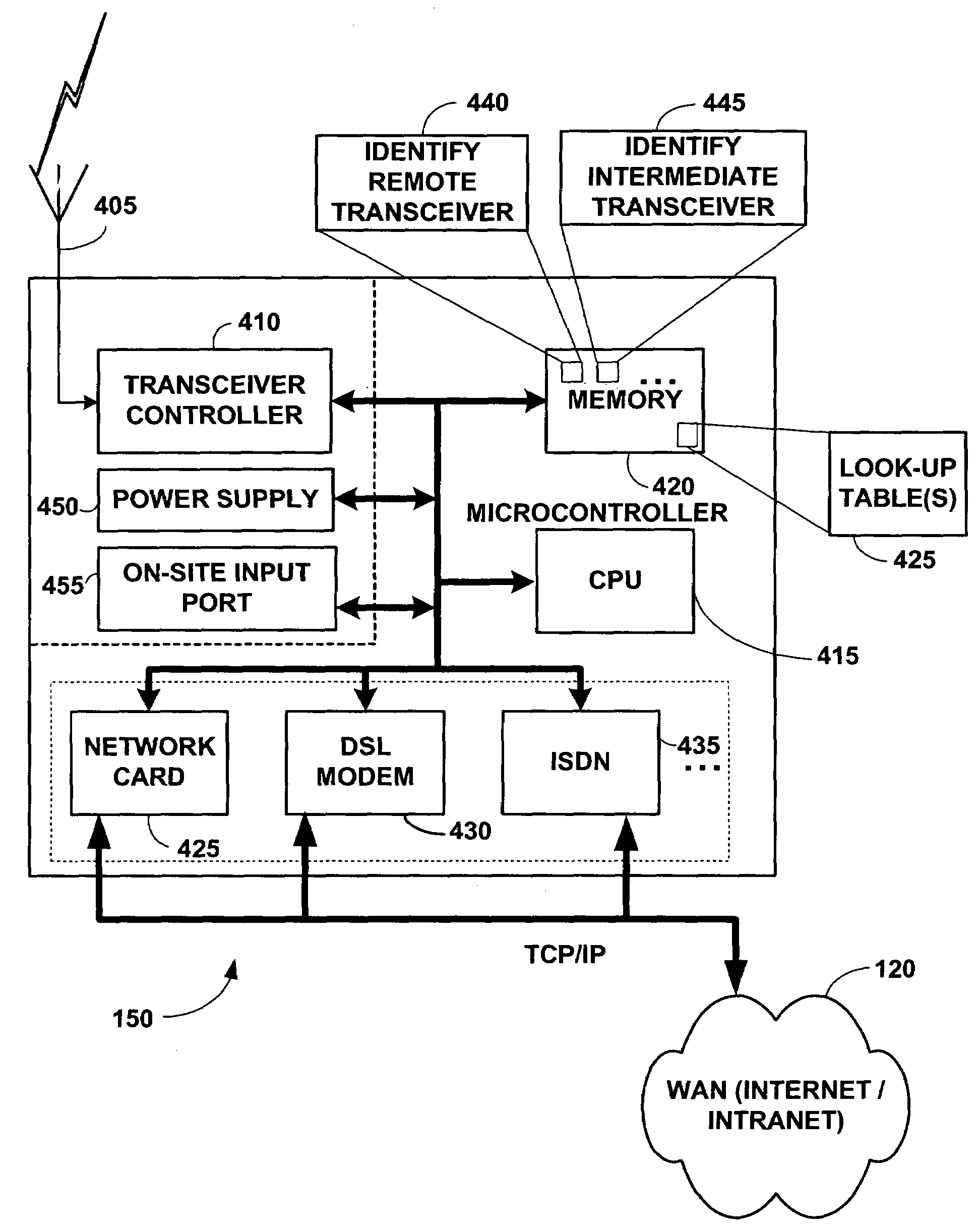
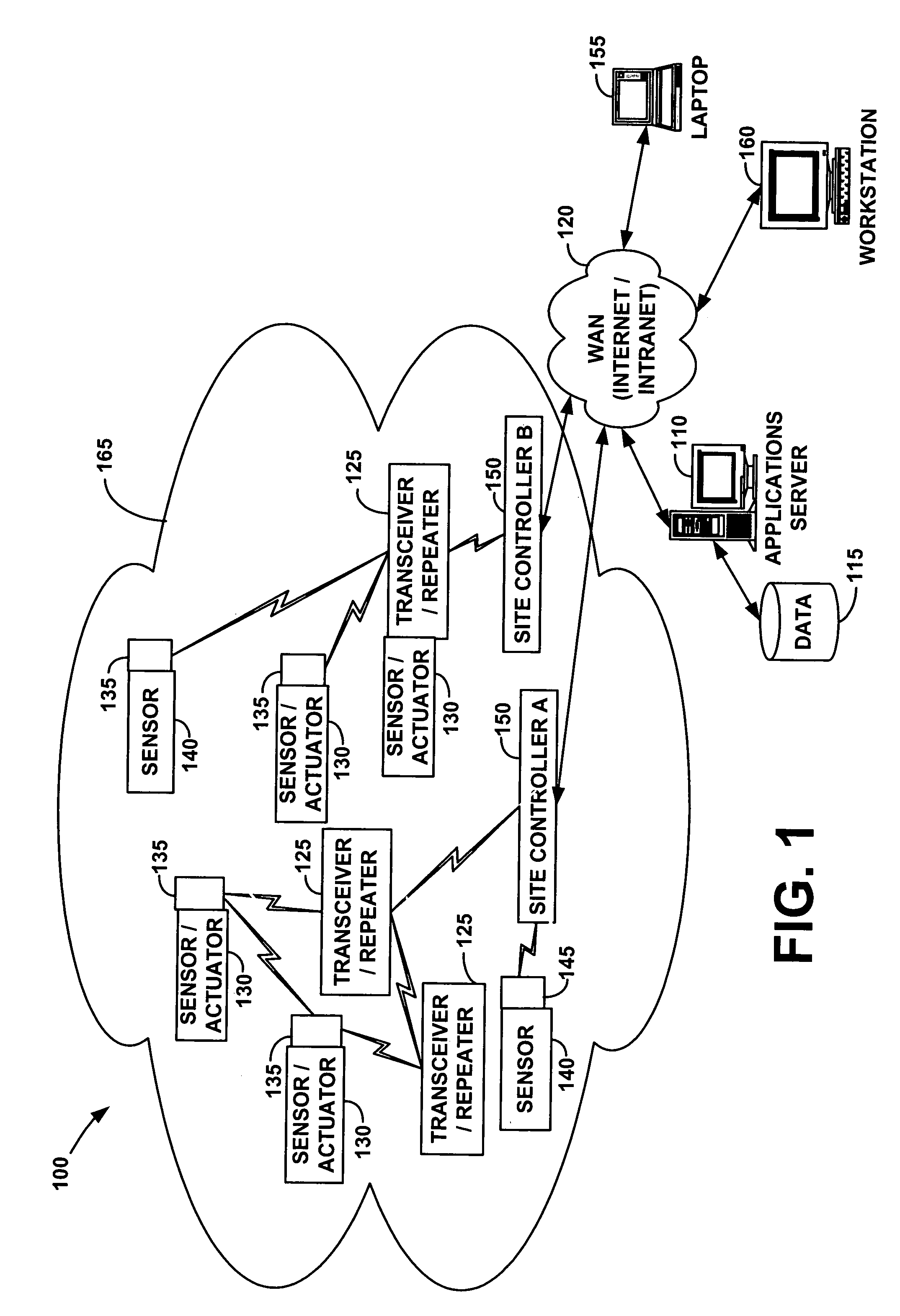
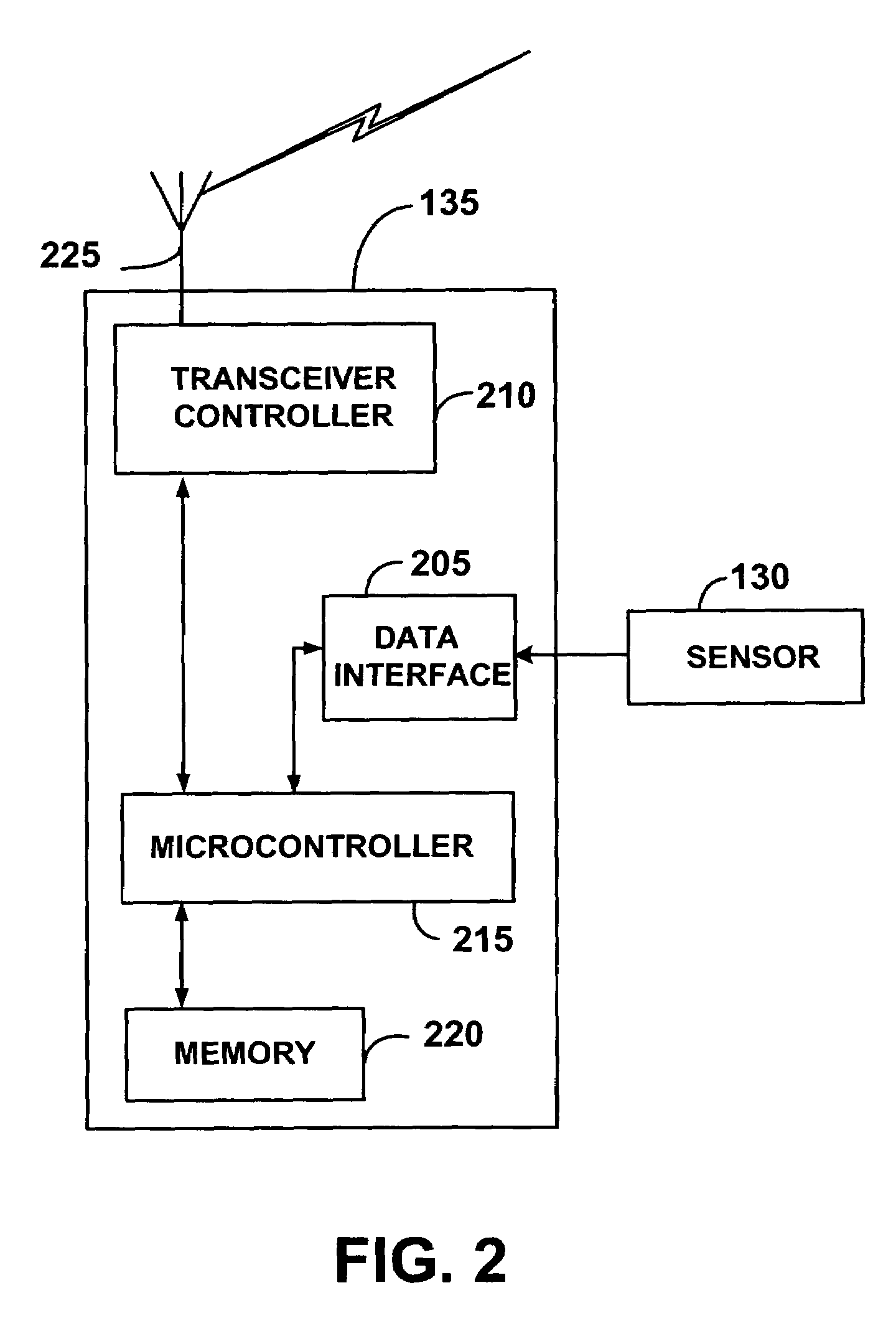
Wireless communication networks for providing remote monitoring of devices
InactiveUS7103511B2Cost-effectiveElectric signal transmission systemsError detection/correctionWireless communication protocolTransceiver
Wireless communication networks for monitoring and controlling a plurality of remote devices are provided. Briefly, one embodiment of a wireless communication network may comprise a plurality of wireless transceivers having unique identifiers. Each of the plurality of wireless transceivers may be configured to receive a sensor data signal from one of the plurality of remote devices and transmit an original data message using a predefined wireless communication protocol. The original data message may comprise the corresponding unique identifier and sensor data signal. Each of the plurality of wireless transceivers may be configured to receive the original data message transmitted by one of the other wireless transceivers and transmit a repeated data message using the predefined communication protocol. The repeated data message may include the sensor data signal and the corresponding unique identifier. Furthermore, at least one of the plurality of wireless transceivers may be further configured to provide the original data messages and the repeated data messages to a site controller connected to a wide area network. The site controller may be configured to manage communications between the wireless communication network and a host computer connected to the wide area network.
Owner:SIPCO
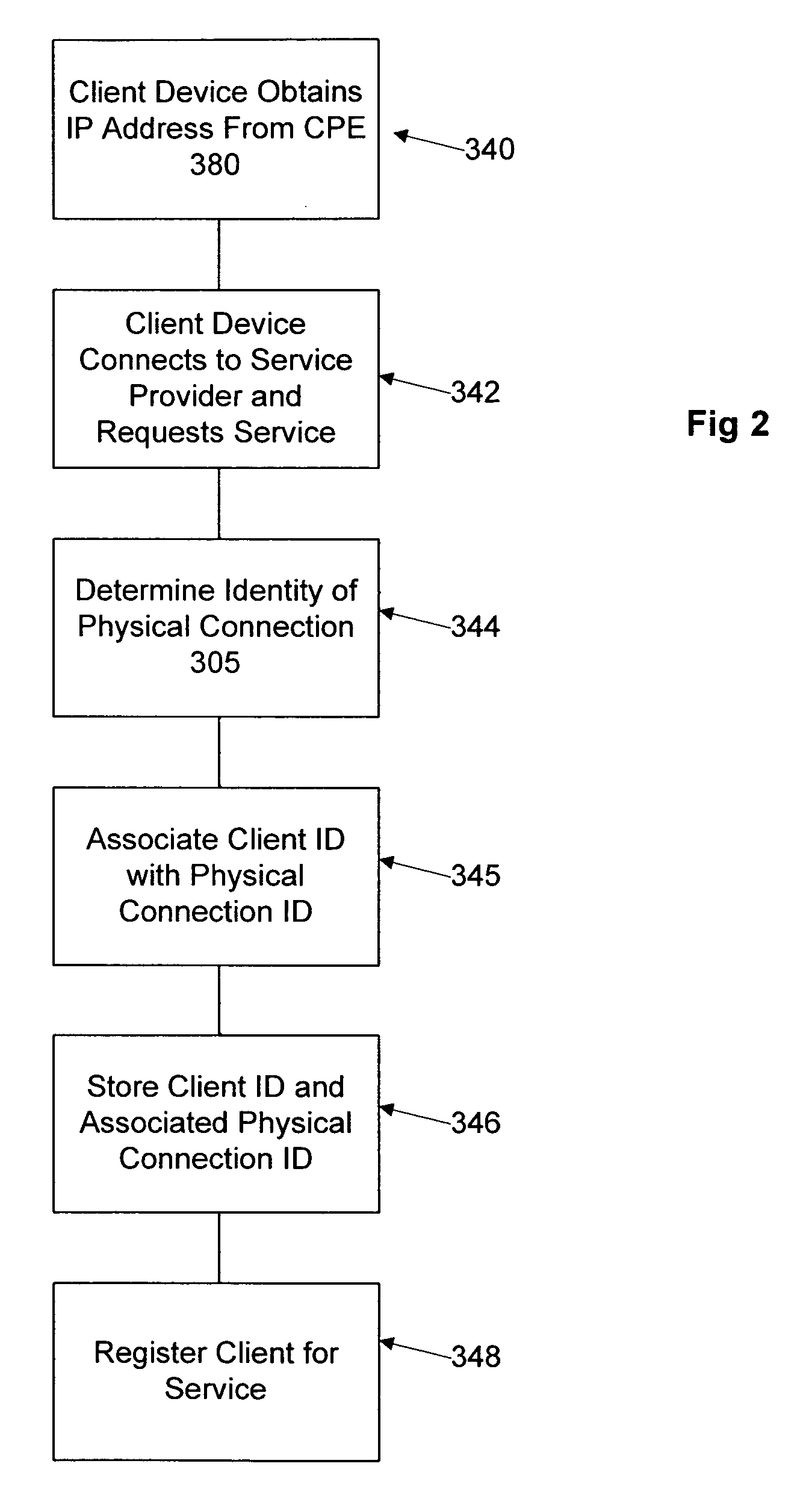
Network user authentication system and method
ActiveUS20070022469A1Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationUnique identifierAuthentication server
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
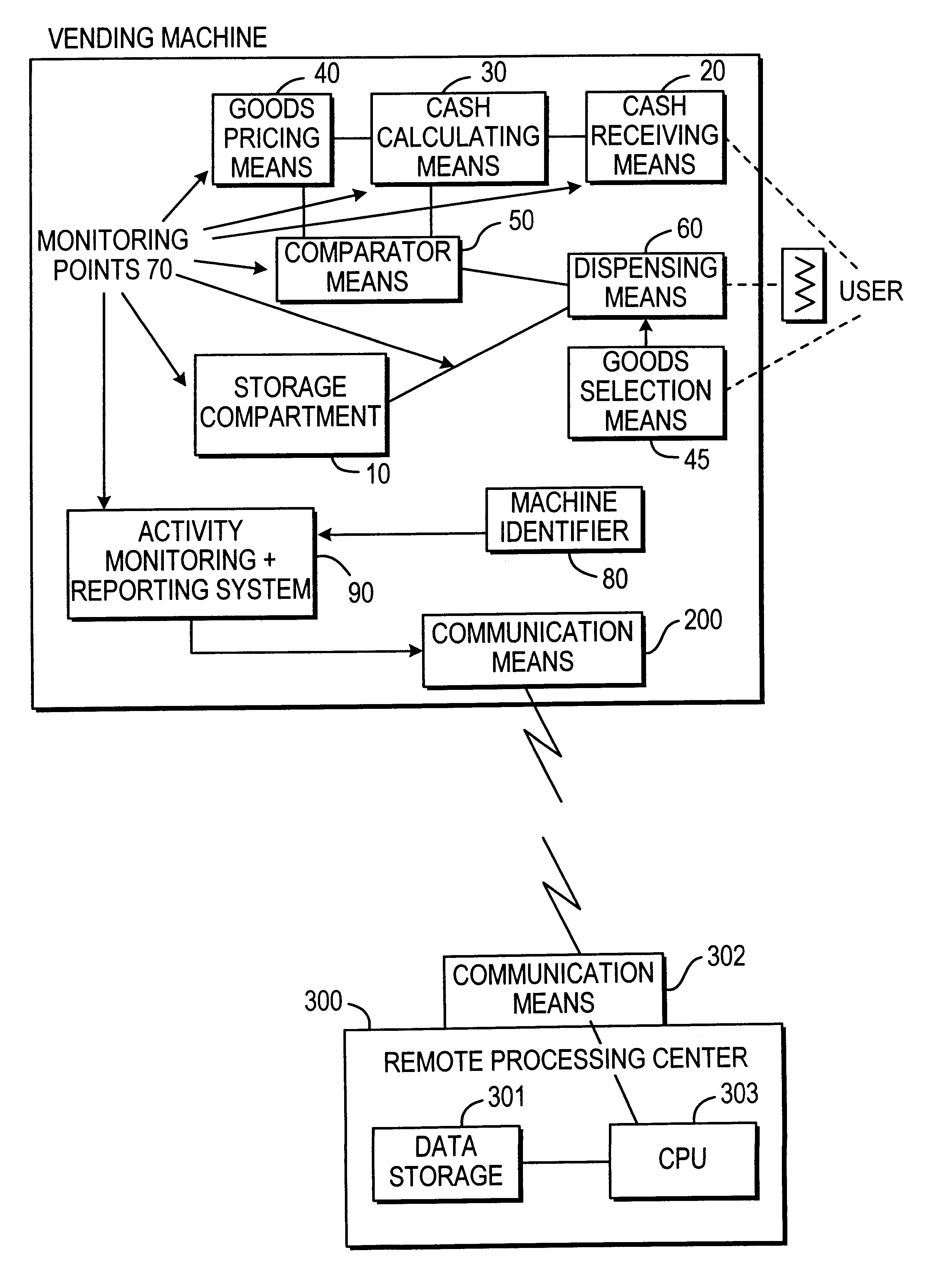
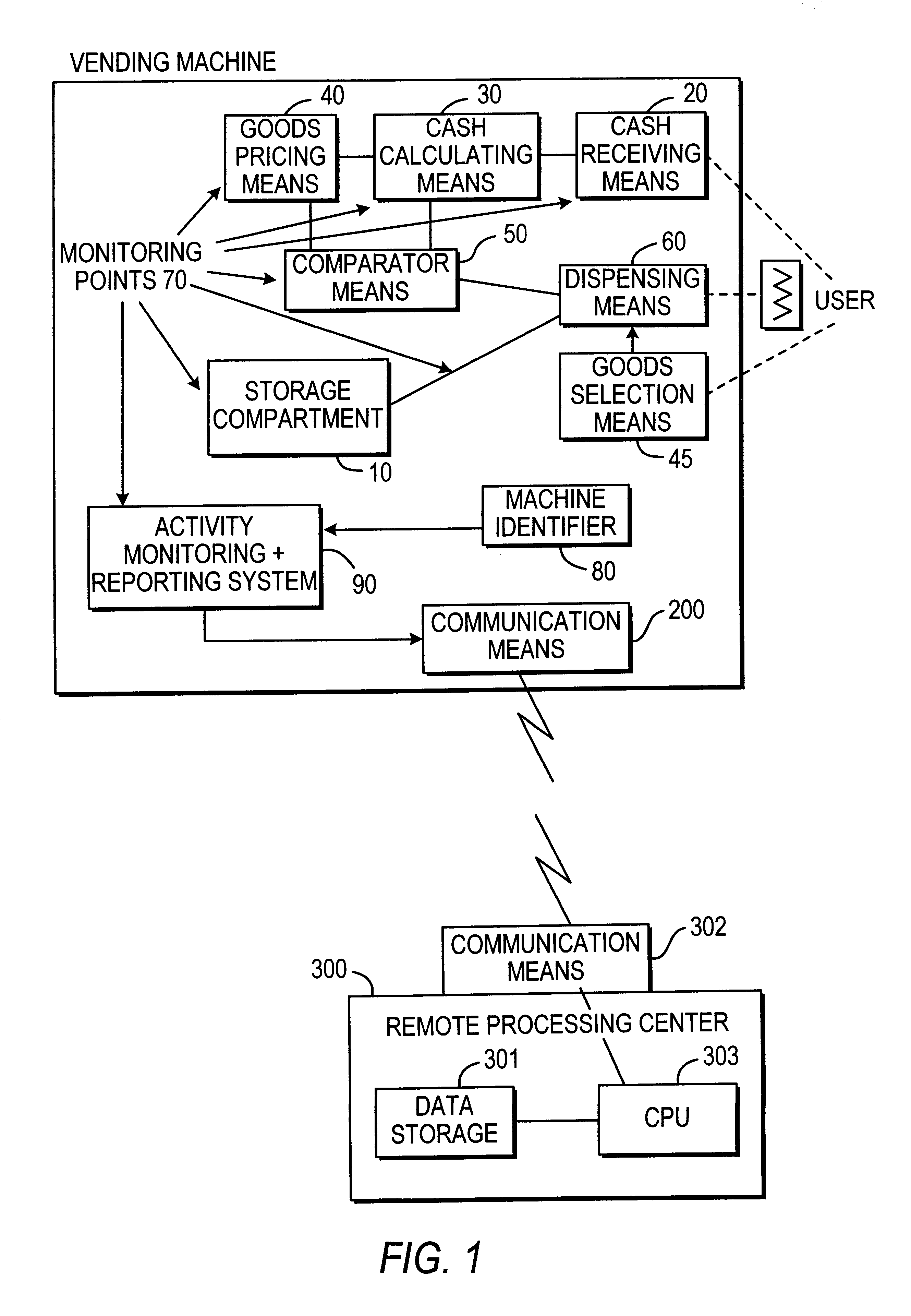
Apparatus and method for improved vending machine inventory maintenance
InactiveUS6181981B1Efficient schedulingEfficient restockingControlling coin-freed apparatusCoin-freed apparatus detailsTime scheduleUnique identifier
Inventory maintenance is improved for a system of one or more vending machines by providing one or more vending machines with unique identifiers, and means for collecting and transmitting information concerning goods dispensed and other status to a remote location where processing means provide an efficient service schedule.
Owner:VENDING MANAGEMENT SERVICES
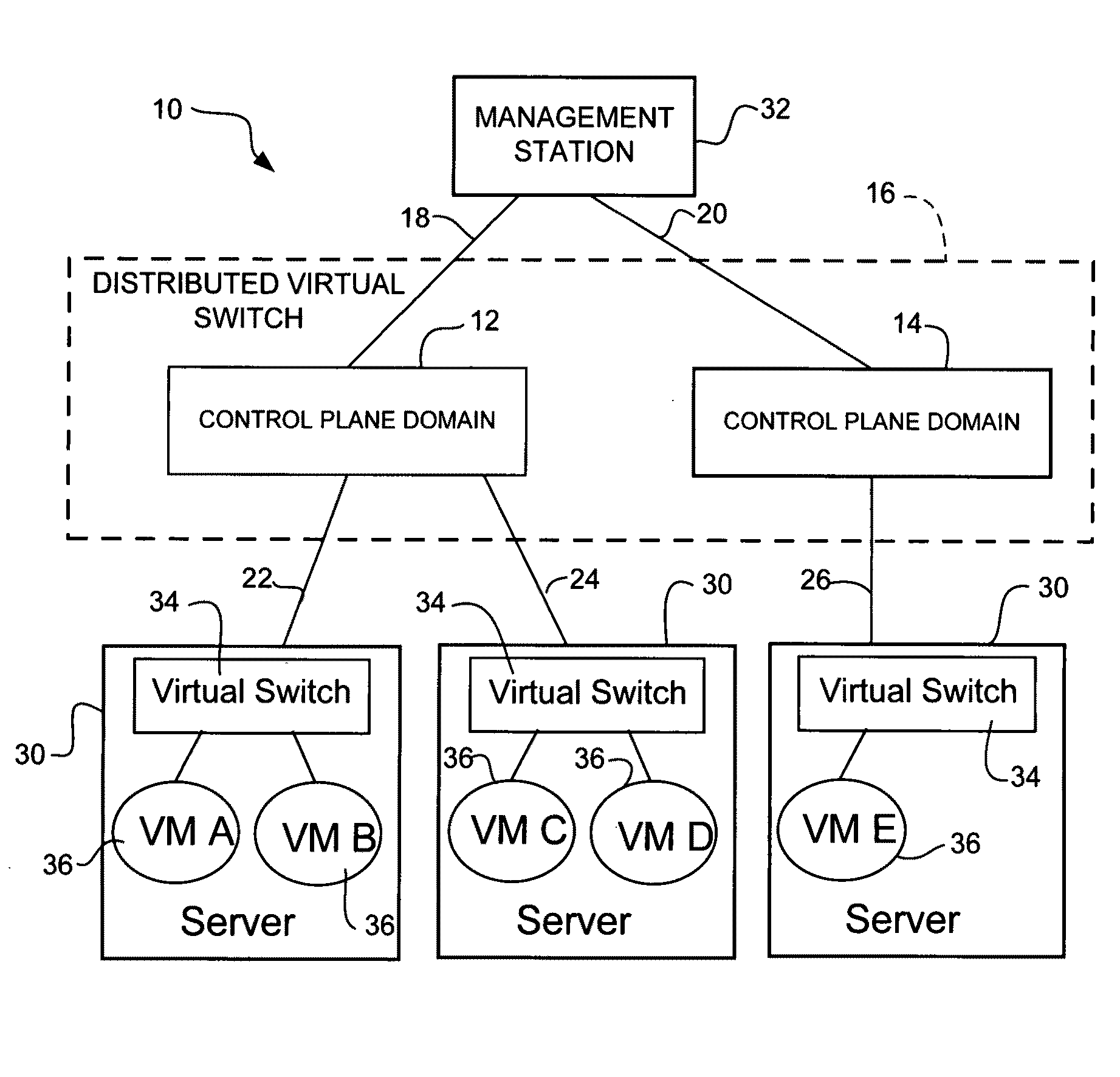
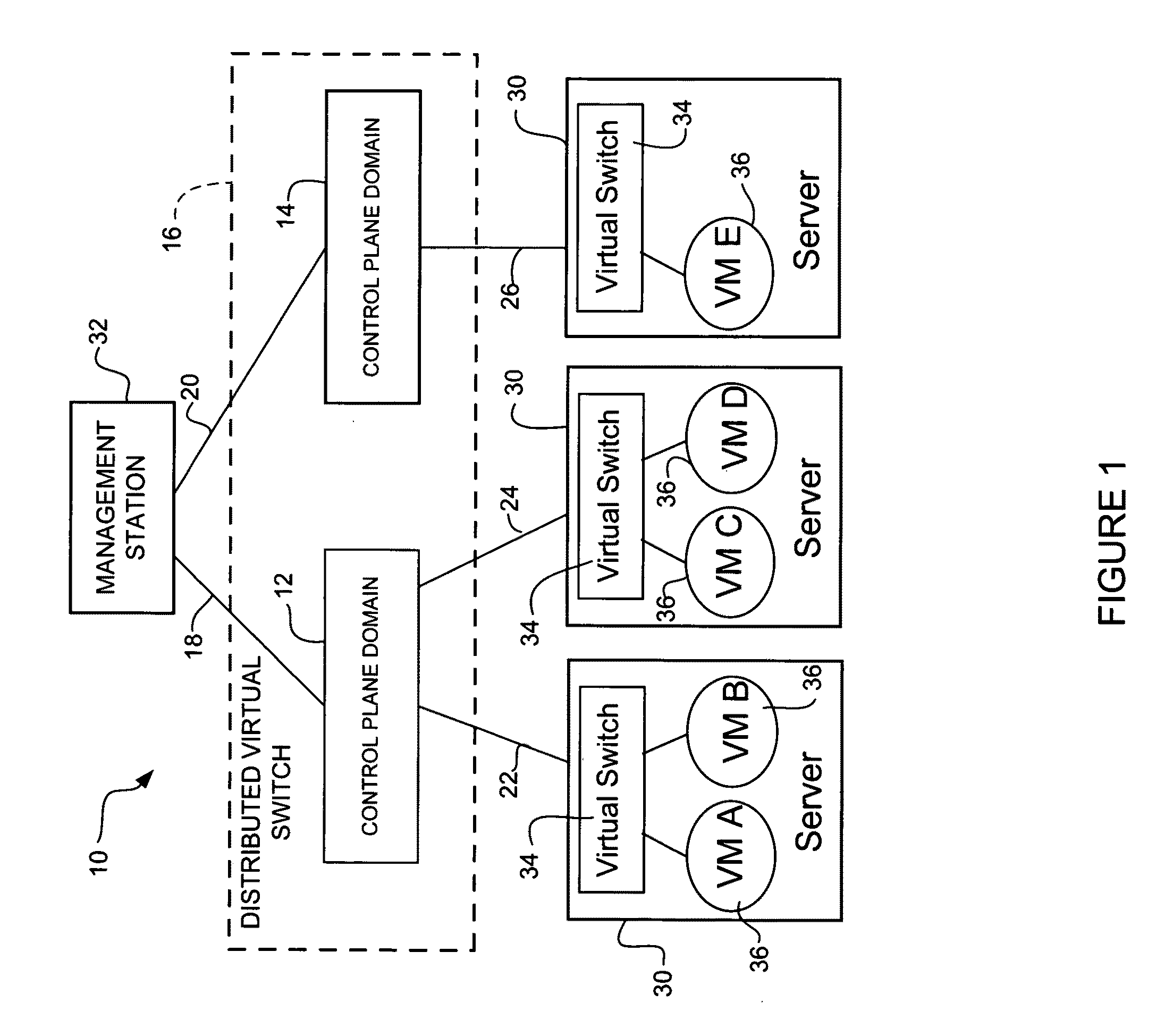
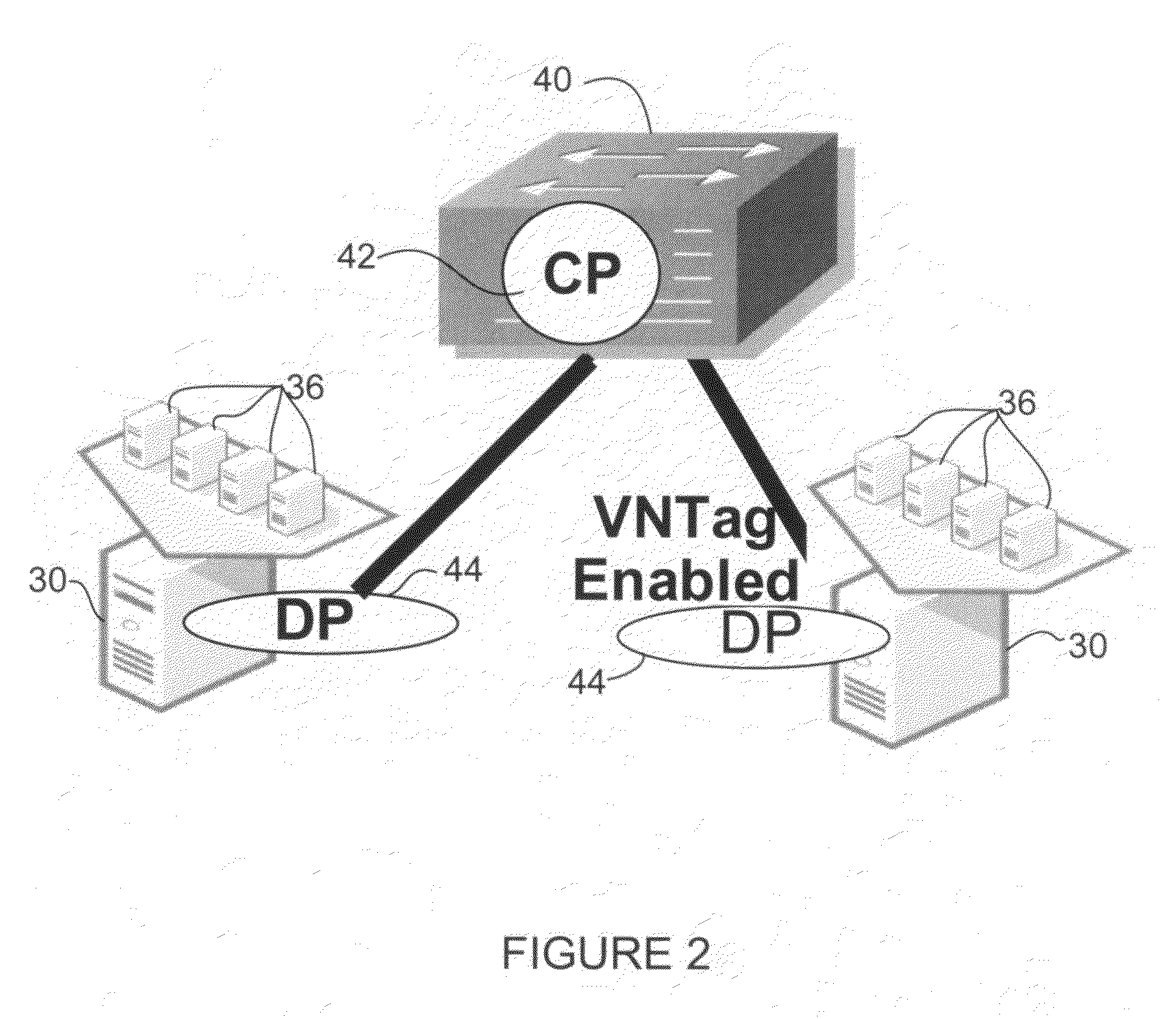
Distributed data center access switch
ActiveUS20100214949A1Data switching by path configurationNetwork connectionsData centerUnique identifier
In one embodiment, an apparatus includes a processor configured for operation in a control plane in a distributed virtual switch in communication with a plurality of virtual machines each having a virtual interface. The processor is operable to identify other control planes in the distributed virtual switch, assign a virtual interface identifier to one of the virtual interfaces, receive a configuration for the virtual interface, and share the configuration with the other control planes in the distributed virtual switch. The virtual interface identifier provides a unique identifier for the virtual interface across all of the control planes. The apparatus further includes memory for storing the configuration of the virtual interface. A method for operating a network device associated with a control in the distributed virtual switch is also disclosed.
Owner:CISCO TECH INC
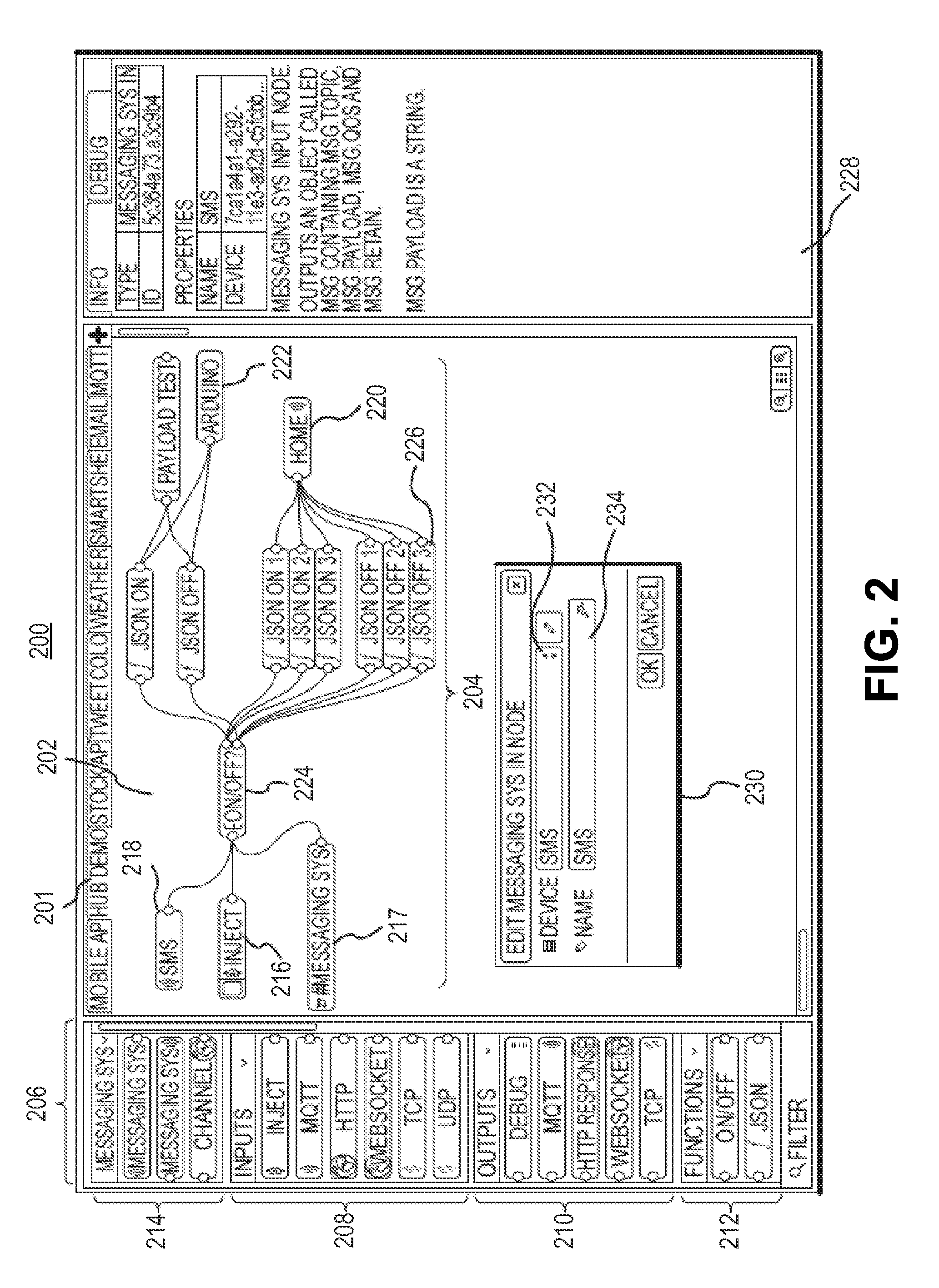
Security and rights management in a machine-to-machine messaging system
Techniques for providing security and rights management in a machine-to-machine messaging system are provided, such as a computing device, a method, and a computer-program product for detecting unauthorized message attempts. For example, the method may receive a communication sent from a first Internet of Things (IoT) device and destined for a second IoT device. The first IoT device is assigned a first universally unique identifier, and the communication includes a second universally unique identifier assigned to the second IoT device. The method may further include obtaining the second universally unique identifier, determining that the second universally unique identifier is assigned to the second IoT device, and determining, using the second universally unique identifier, that the communication received from the first IoT device is an unauthorized message attempt by the first IoT device to exchange a message with the second IoT device.
Owner:CITRIX SYST INC
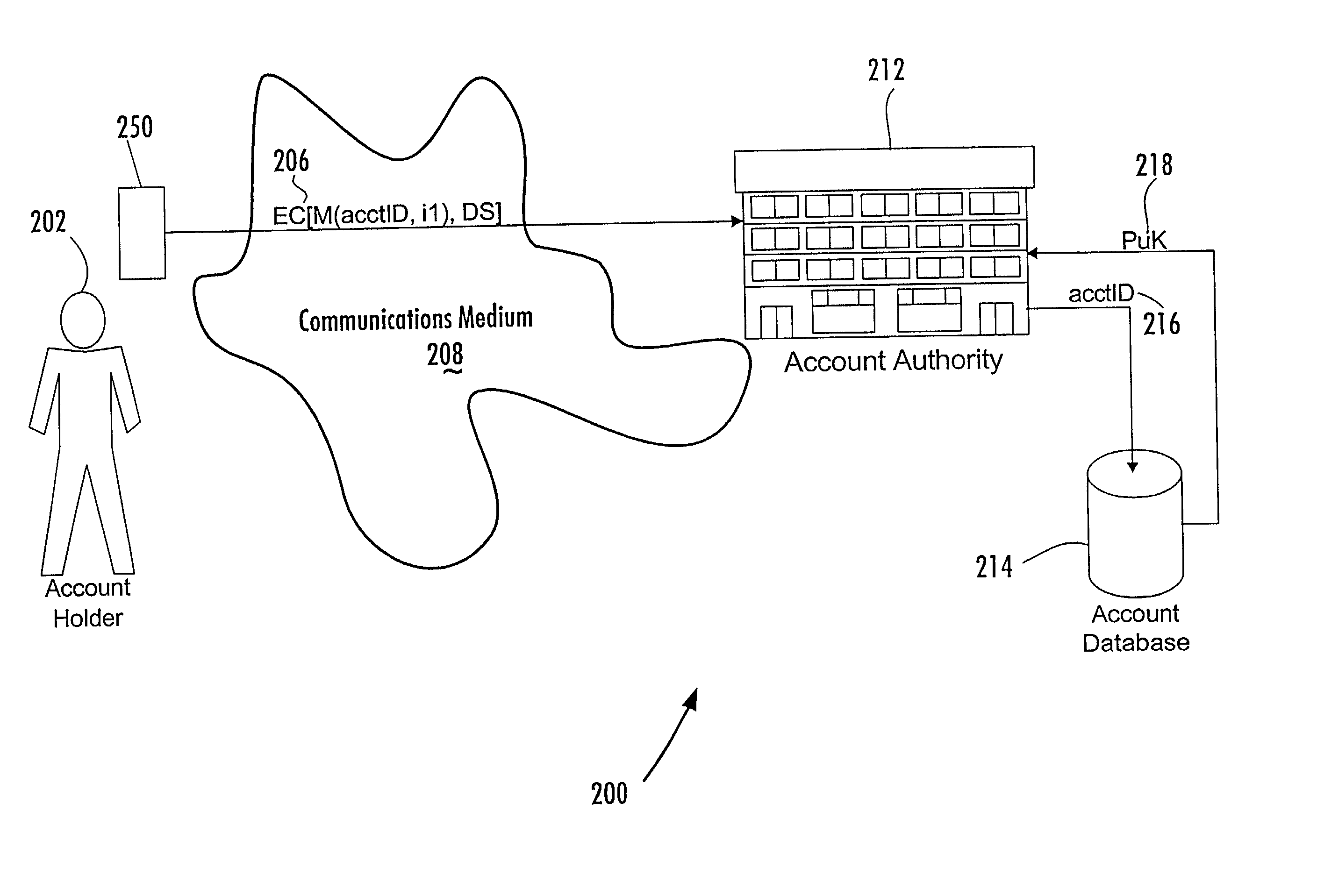
Account-based digital signature (ABDS) system
InactiveUS20020026575A1Key distribution for secure communicationFinanceDigital signatureElectronic communication
A method of authenticating an entity by a receiving party with respect to an electronic communication that is received by the receiving party and that includes both a unique identifier associated with an account maintained by the receiving party and a digital signature for a message regarding the account, consists of the steps of, before receipt of the electronic communication, first associating by the receiving party a public key of a public-private key pair with the unique identifier and, thereafter, only conducting message authentication using the digital signature received by the receiving party in the electronic communication and the public key associated with the account identifier.
Owner:FIRST DATA
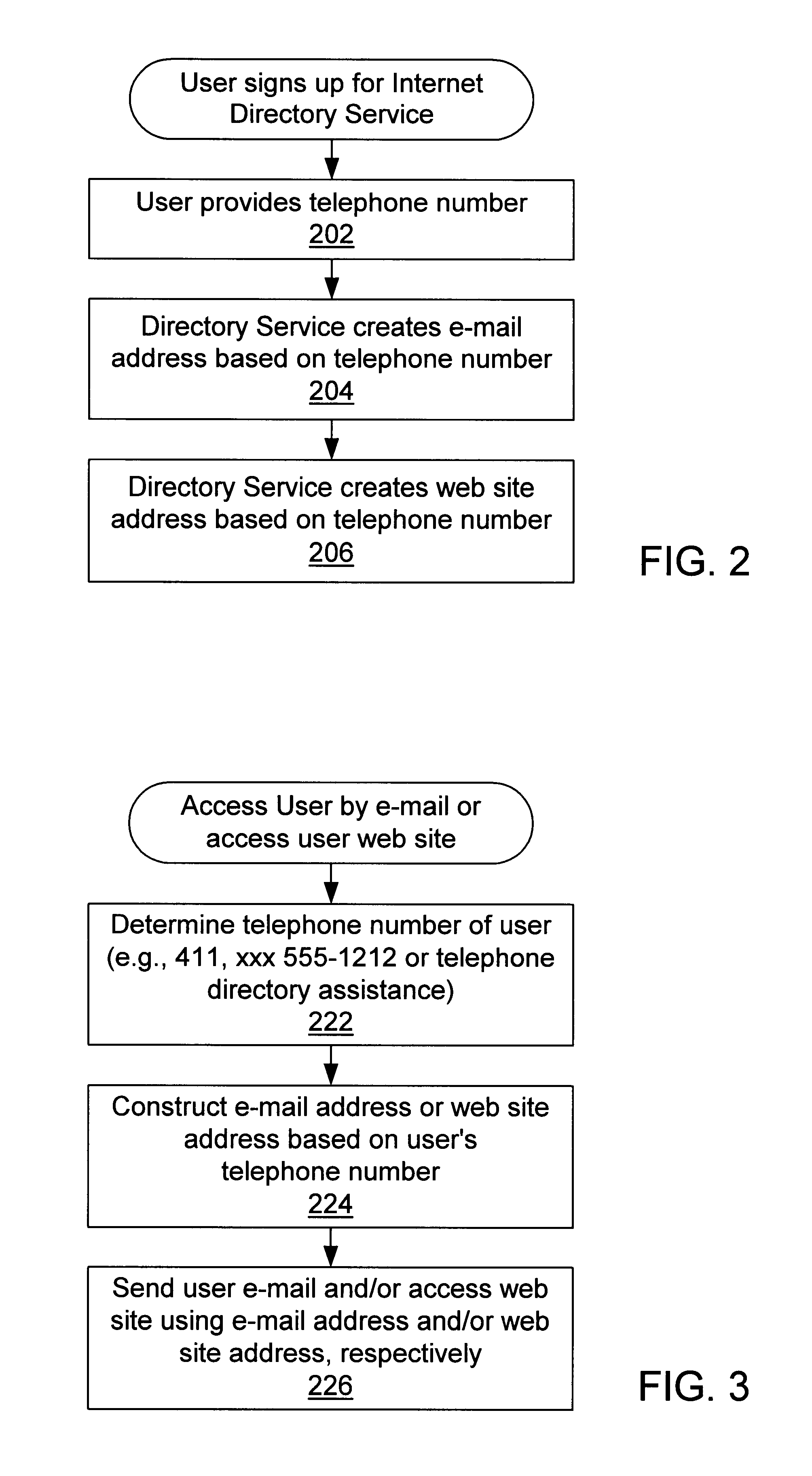
Internet directory system and method using telephone number based addressing
InactiveUS6788769B1Searches may be more readilyEasy to implementTelephone data network interconnectionsSpecial service for subscribersDomain nameEmail address
An Internet directory system and method that is based on user telephone number addressing. The system includes an interactive white and yellow pages directory that is based on telephone numbers. Thus, a user's telephone number is a unique identifier used to key other information within the directory. The telephone number may also be used as the primary component of an email address, domain name, or web site URL for the user. The use of a telephone number as the primary component of an e-mail address or domain name greatly simplifies the process of locating a user. E-mail addresses and domain names may be readily found using standard telephone information services, such as "411", as well as other telephone-based methods for obtaining telephone directory information. This Internet directory system and method brings all communication methods and directory services together using one searchable key, a user's telephone number. The directory entry page may be created, edited and updated by the subscriber using simple html editing or using a voice telephone call or via fax, without the use of a personal computer. Thus, the present invention provides an open directory model wherein the end users construct the directory, and the directory is "living", i.e., dynamically changeable and updateable. The power of the directory is thus placed in the users' hands. The telephone based Internet directory system of the present invention also provides addressing for unified messaging as well as locality in addressing.
Owner:WEISMAN SANFORD P
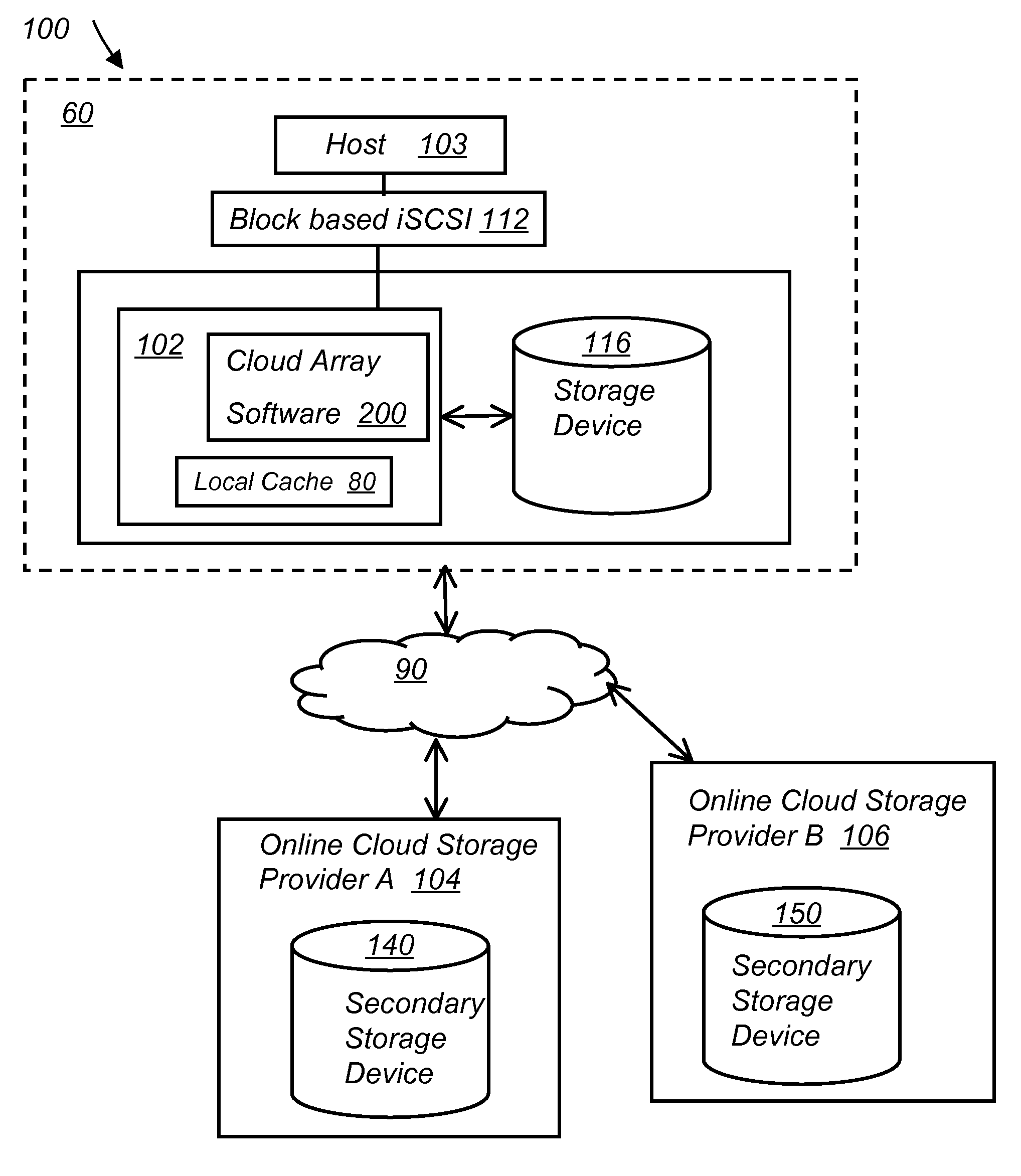
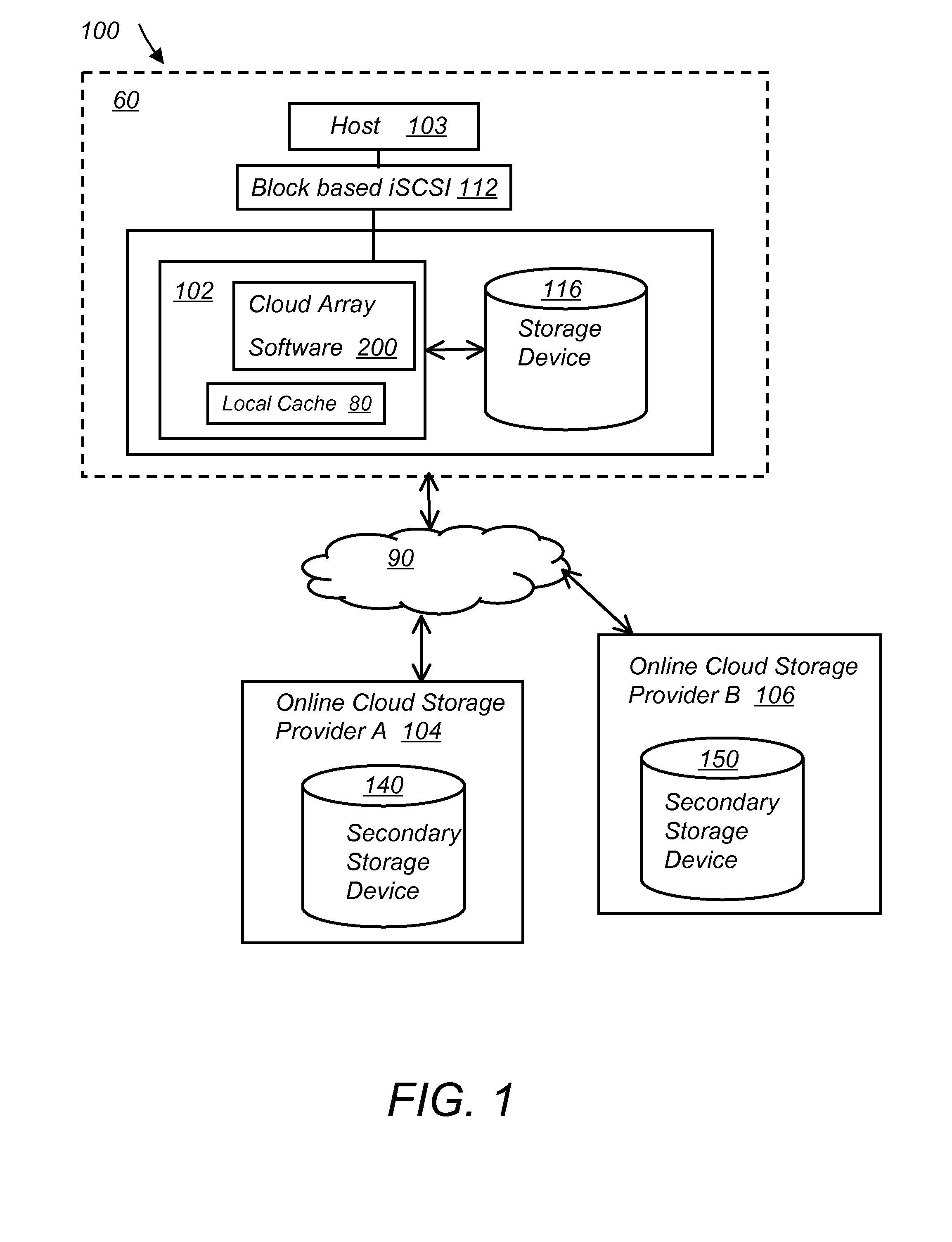
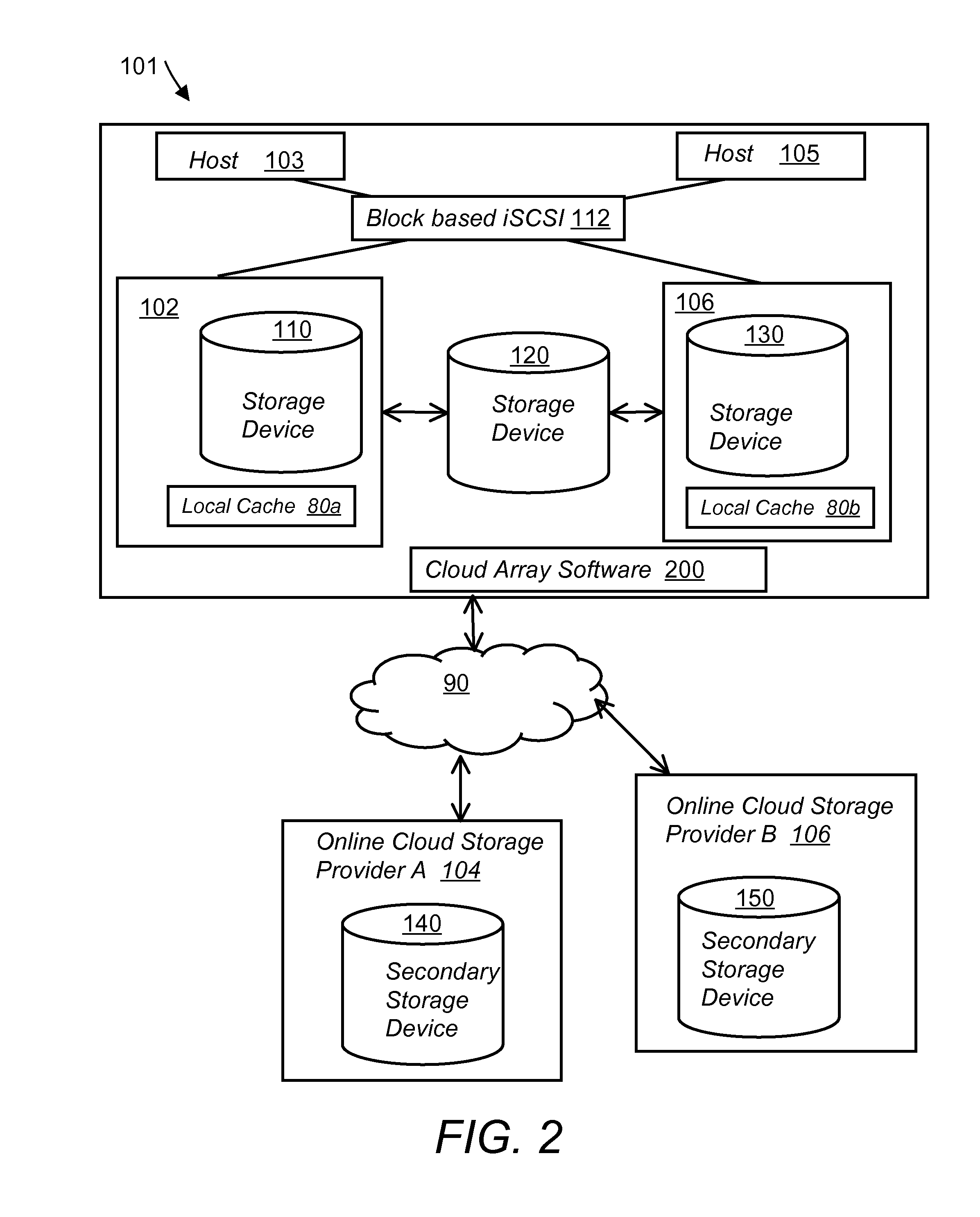
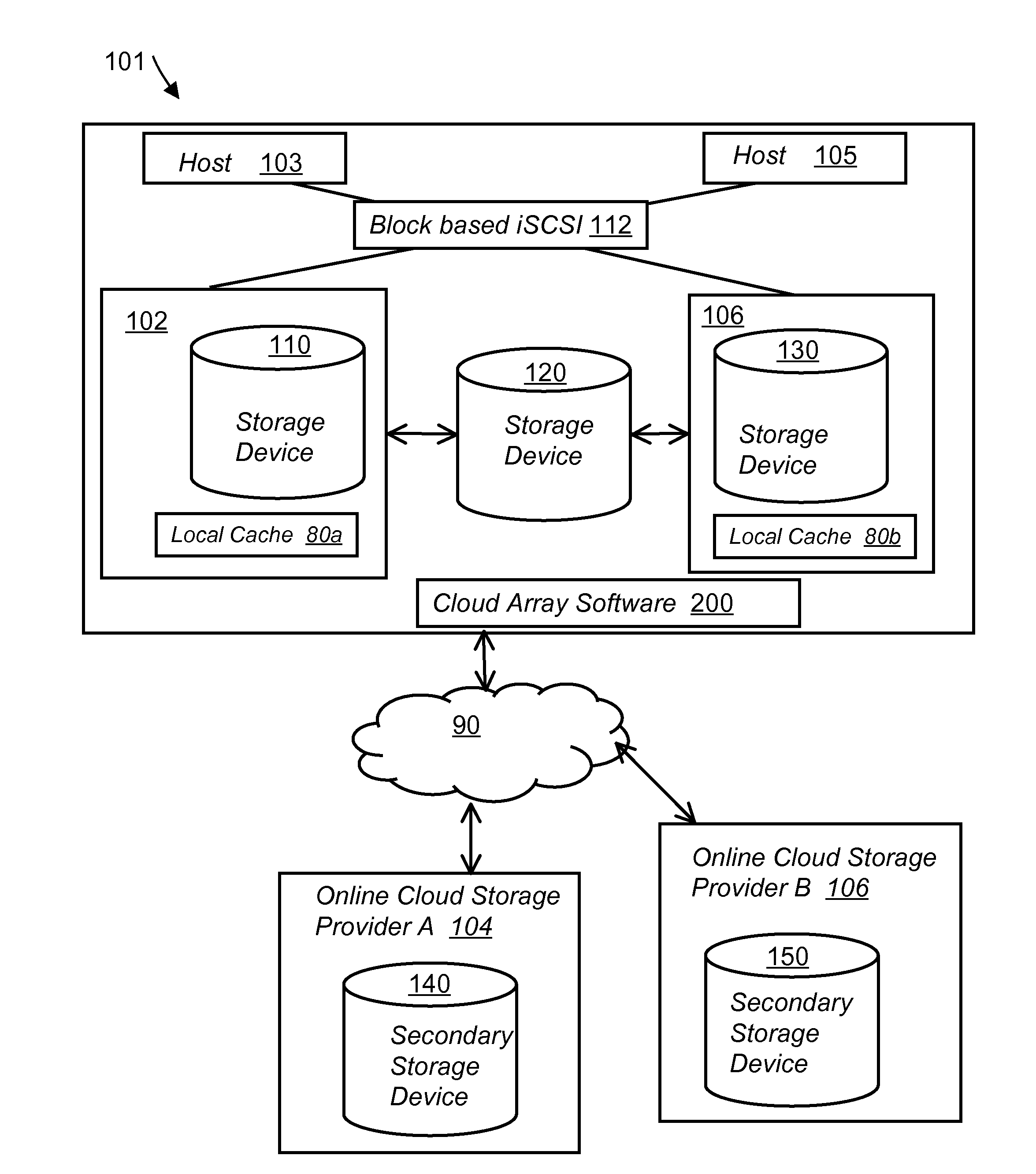
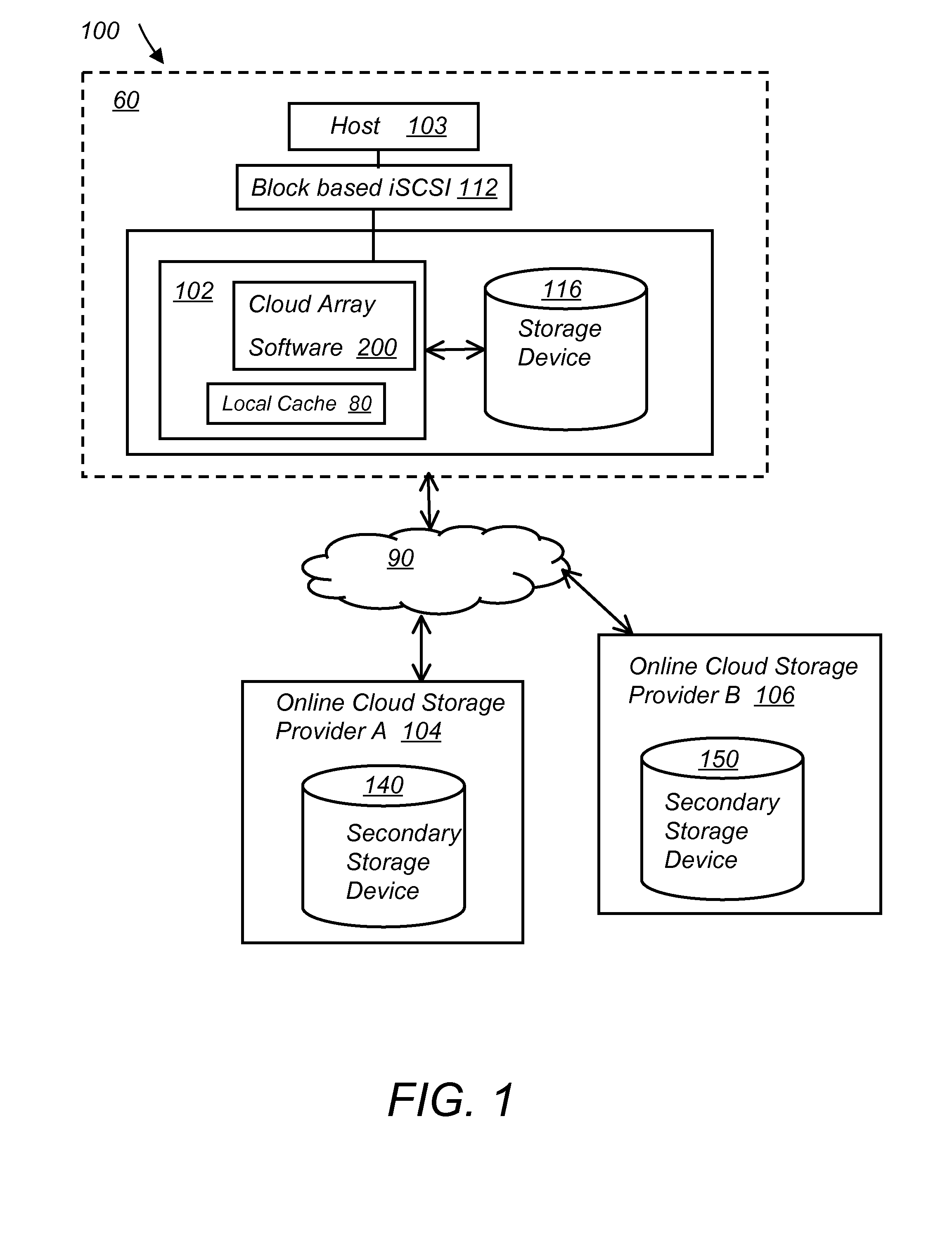
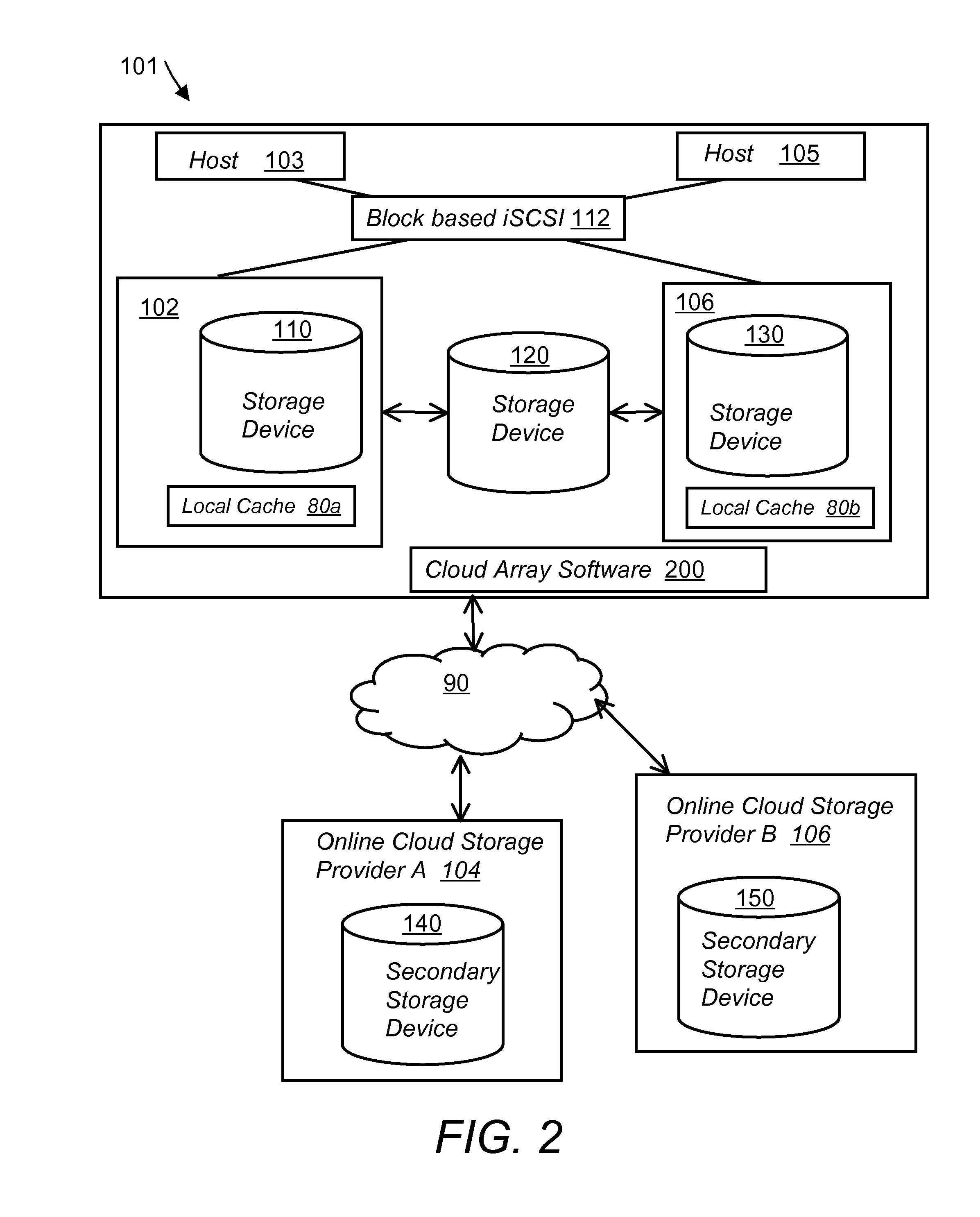
System and method for secure and reliable multi-cloud data replication
ActiveUS8762642B2Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationUnauthorized memory use protectionReliable computingNetwork connection
Owner:EMC IP HLDG CO LLC
System and method for secure and reliable multi-cloud data replication
ActiveUS20100199042A1Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationMemory loss protectionReliable computingReplication method
A multi-cloud data replication method includes providing a data replication cluster comprising at least a first host node and at least a first online storage cloud. The first host node is connected to the first online storage cloud via a network and comprises a server, a cloud array application and a local cache. The local cache comprises a buffer and a first storage volume comprising data cached in one or more buffer blocks of the local cache's buffer. Next, requesting authorization to perform cache flush of the cached first storage volume data to the first online storage cloud. Upon receiving approval of the authorization, encrypting the cached first storage volume data in each of the one or more buffer blocks with a data private key. Next, assigning metadata comprising at lest a unique identifier to each of the one or more buffer blocks and then encrypting the metadata with a metadata private key. Next, transmitting the one or more buffer blocks with the encrypted first storage volume data to the first online cloud storage. Next, creating a sequence of updates of the metadata, encrypting the sequence with the metadata private key and then transmitting the sequence of metadata updates to the first online storage cloud.
Owner:EMC IP HLDG CO LLC
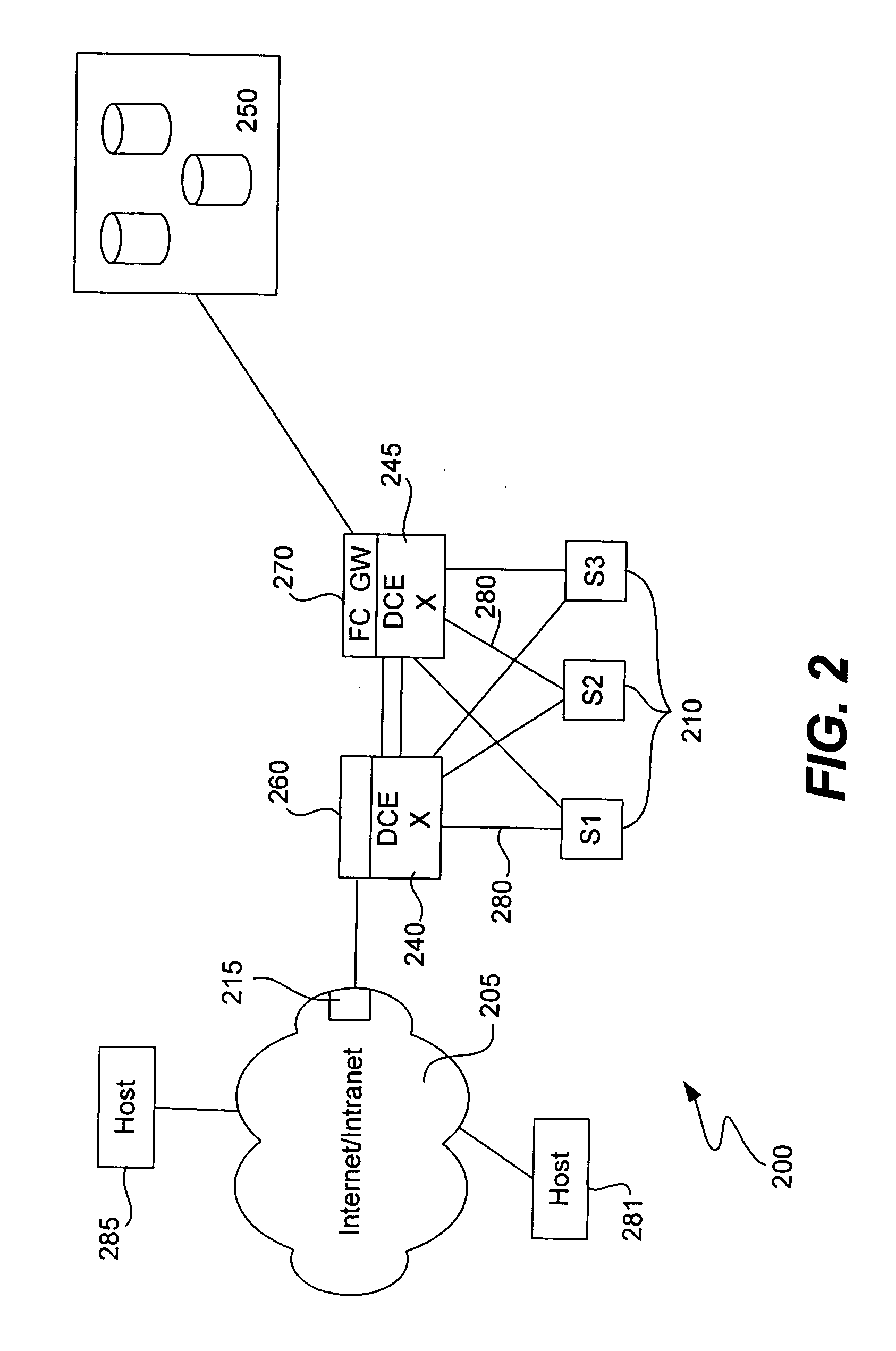
Fibre channel over ethernet
ActiveUS20060251067A1Improve reliabilityLower latencyTime-division multiplexData switching by path configurationHigh bandwidthData center
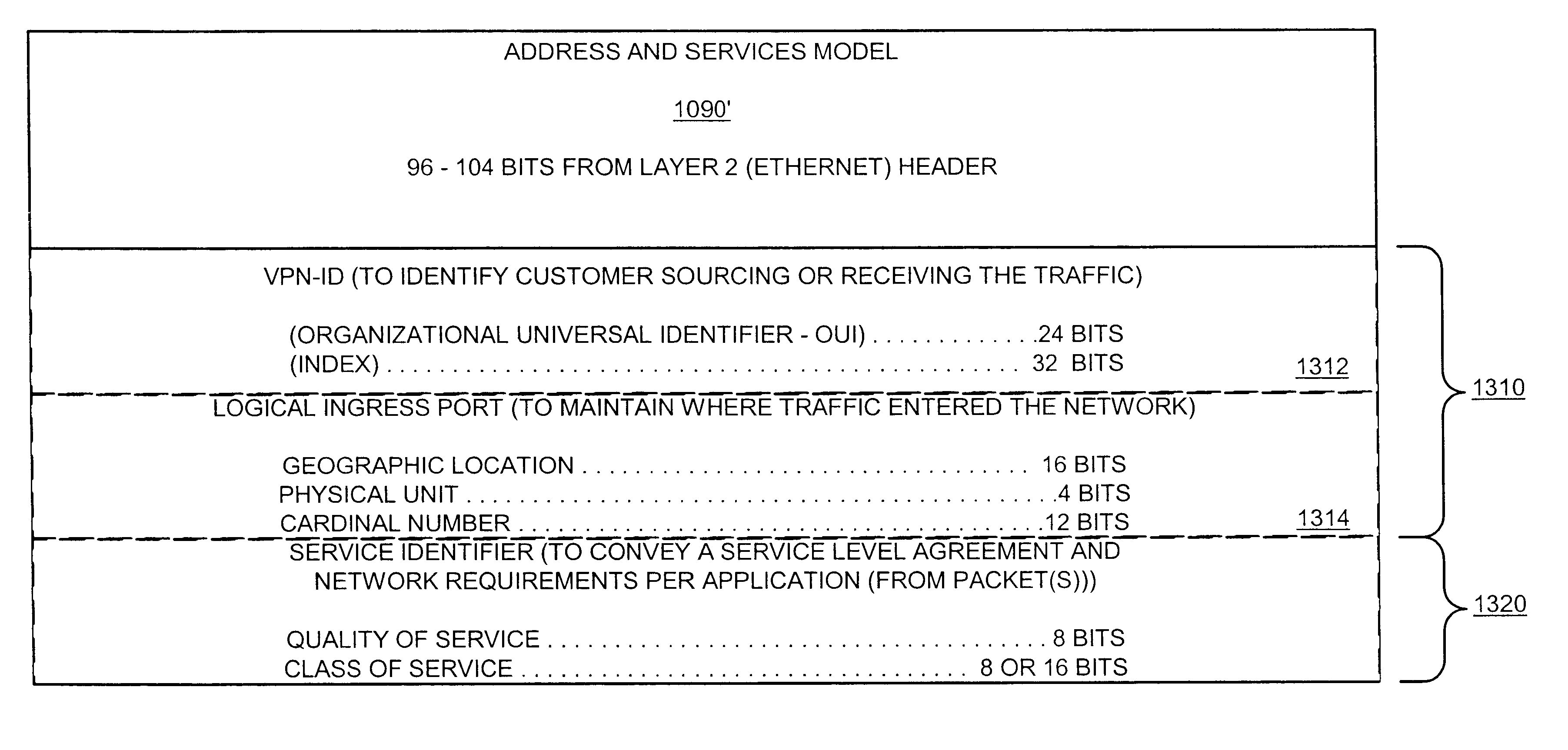
A Data Center Ethernet (“DCE”) network and related methods and device are provided. A DCE network simplifies the connectivity of data centers and provides a high bandwidth, low latency network for carrying Ethernet, storage and other traffic. A Fibre Channel (“FC”) frame, including FC addressing information, is encapsulated in an Ethernet frame for transmission on a Data Center Ethernet (“DCE”) network. The Ethernet address fields may indicate that the frame includes an FC frame, e.g., by the use of a predetermined Organization Unique Identifier (“OUI”) code in the D_MAC field, but also include Ethernet addressing information. Accordingly, the encapsulated frames can be forwarded properly by switches in the DCE network whether or not these switches are configured for operation according to the FC protocol. Accordingly, only a subset of Ethernet switches in the DCE network needs to be FC-enabled. Only switches so configured will require an FC Domain_ID.
Owner:CISCO TECH INC
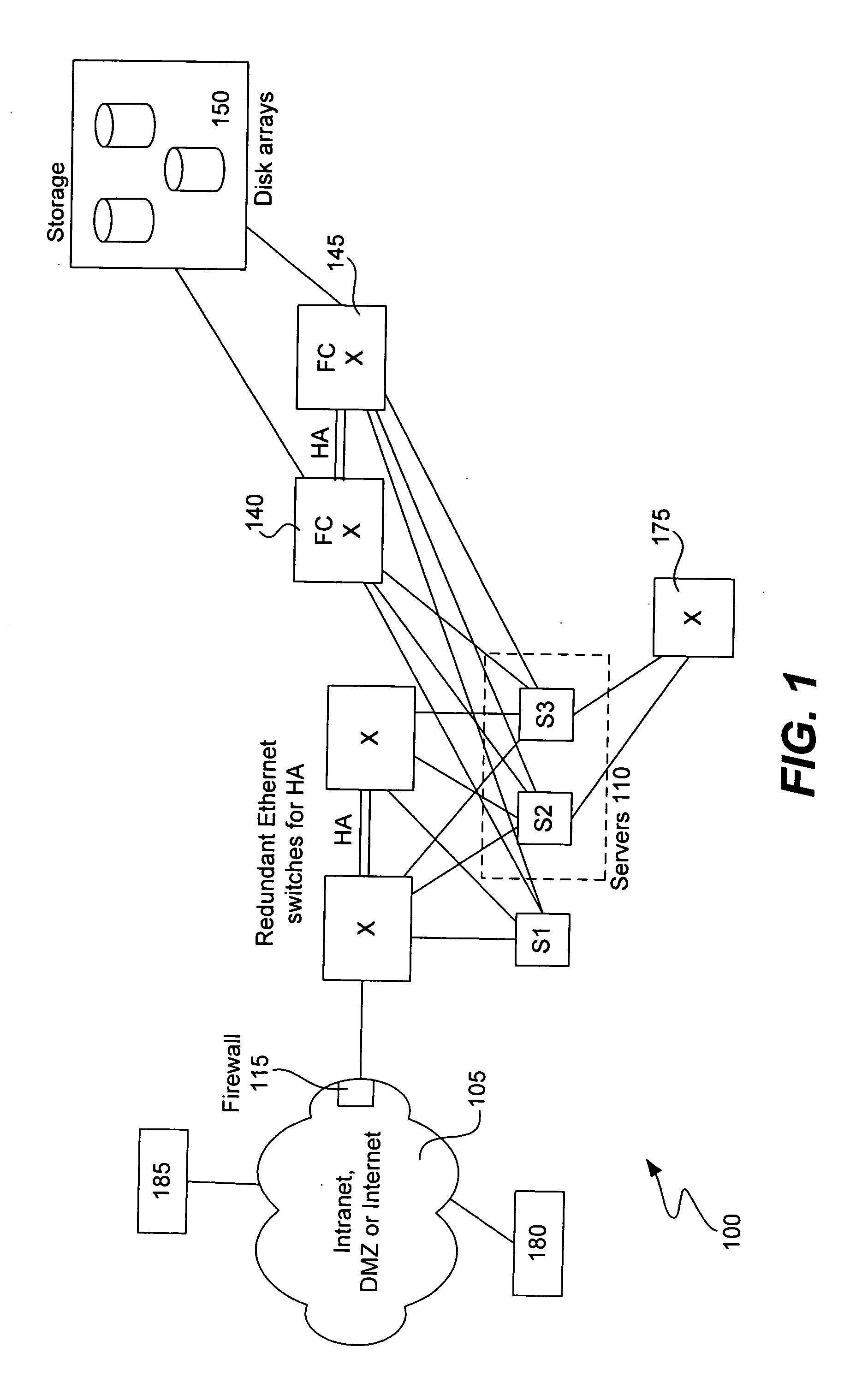
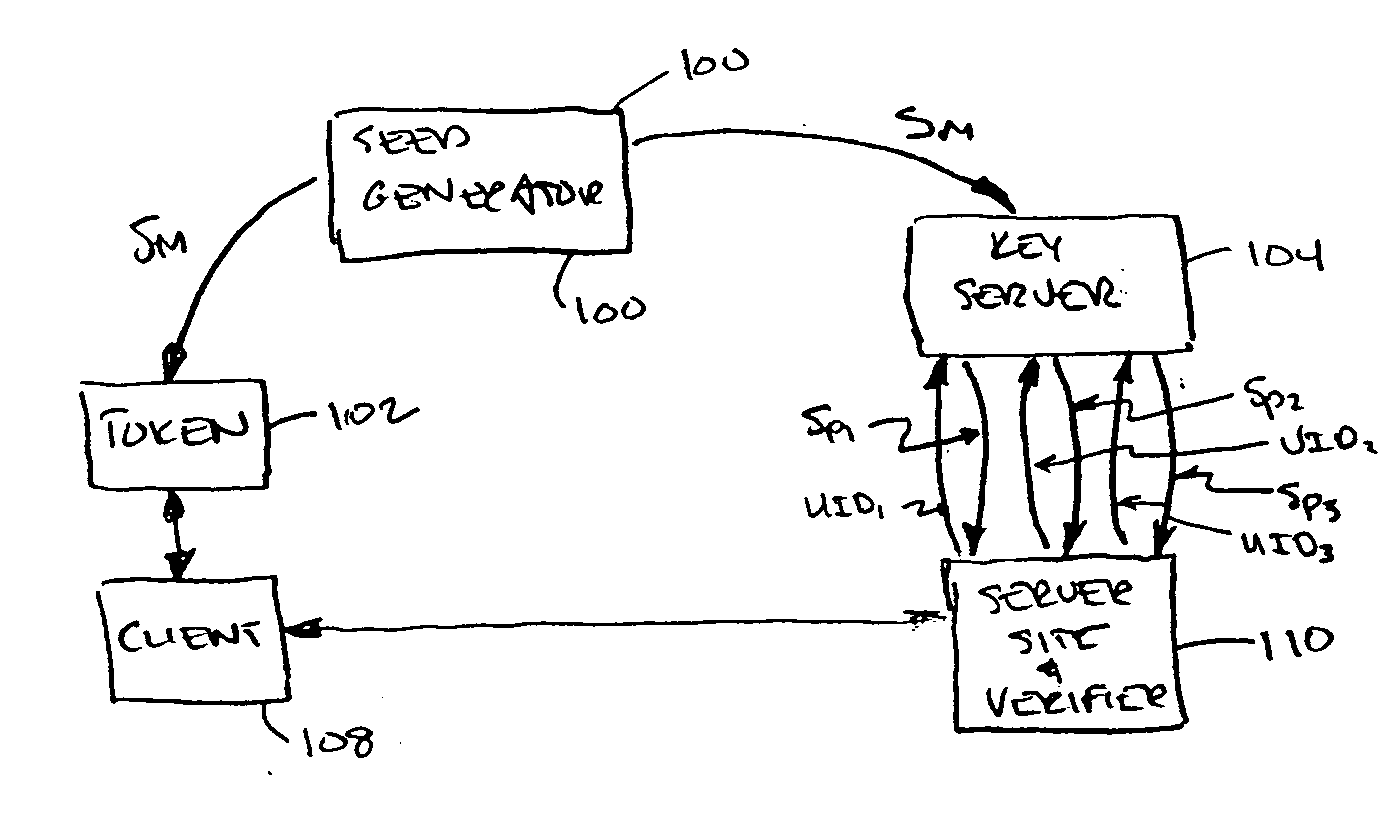
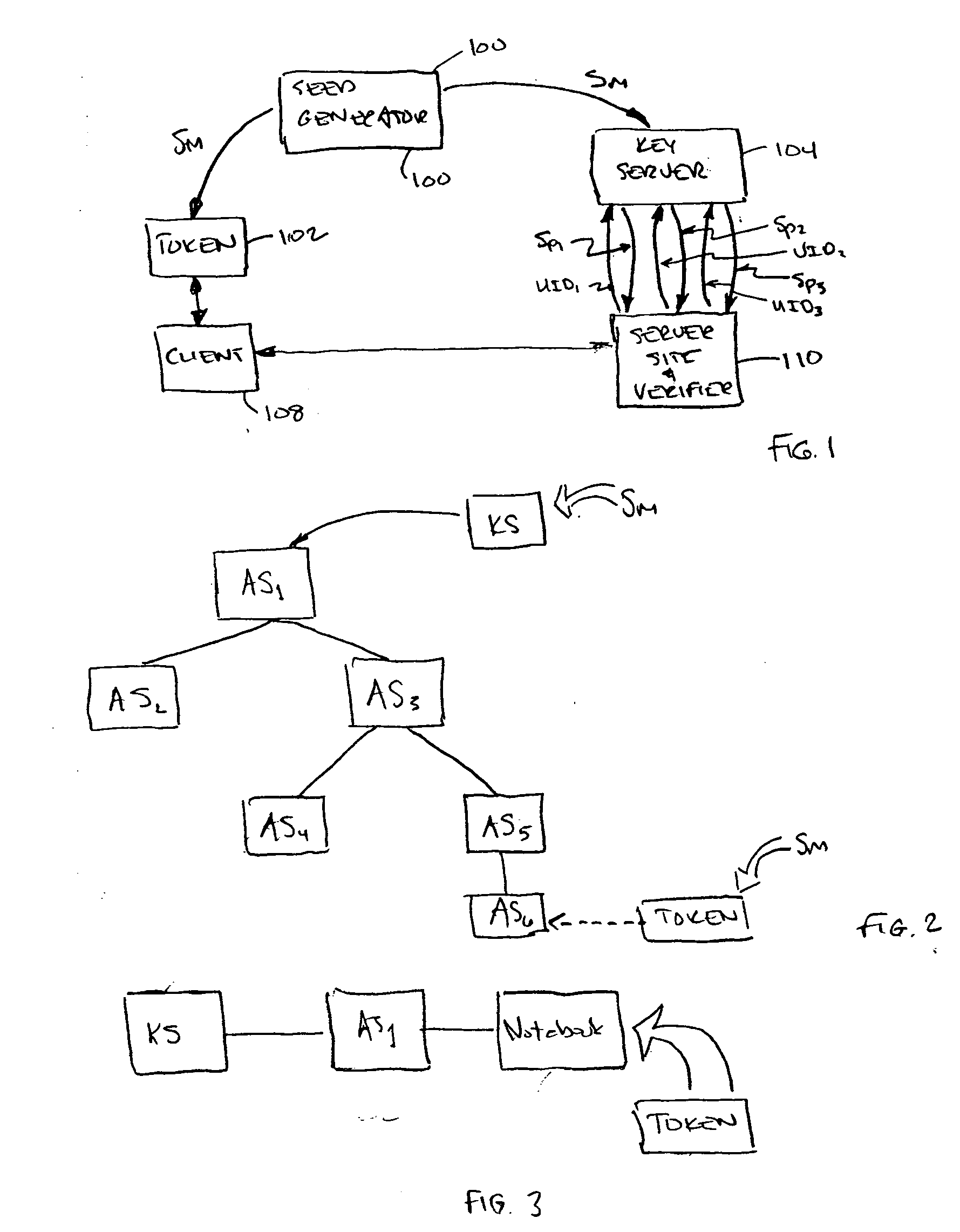
Derivative seeds
ActiveUS20070174614A1Simplify the distribution processImprove securityDigital data processing detailsUser identity/authority verificationUnique identifierComputer science
A method of generating authentication seeds for a plurality of users, the method involving: based on a single master seed, generating a plurality of derivative seeds, each one for a corresponding different one of a plurality of users; and distributing the plurality of derivative seeds to a verifier for use in individually authenticating each of the plurality of users to that verifier, wherein generating each one of the plurality of derivative seeds involves mathematically combining the master seed and a unique identifier identifying the corresponding user.
Owner:EMC IP HLDG CO LLC
System and method for single-action energy resource scheduling and participation in energy-related securities
InactiveUS20100217642A1Circuit arrangementsDigital data processing detailsCommunication interfaceInformation transmission
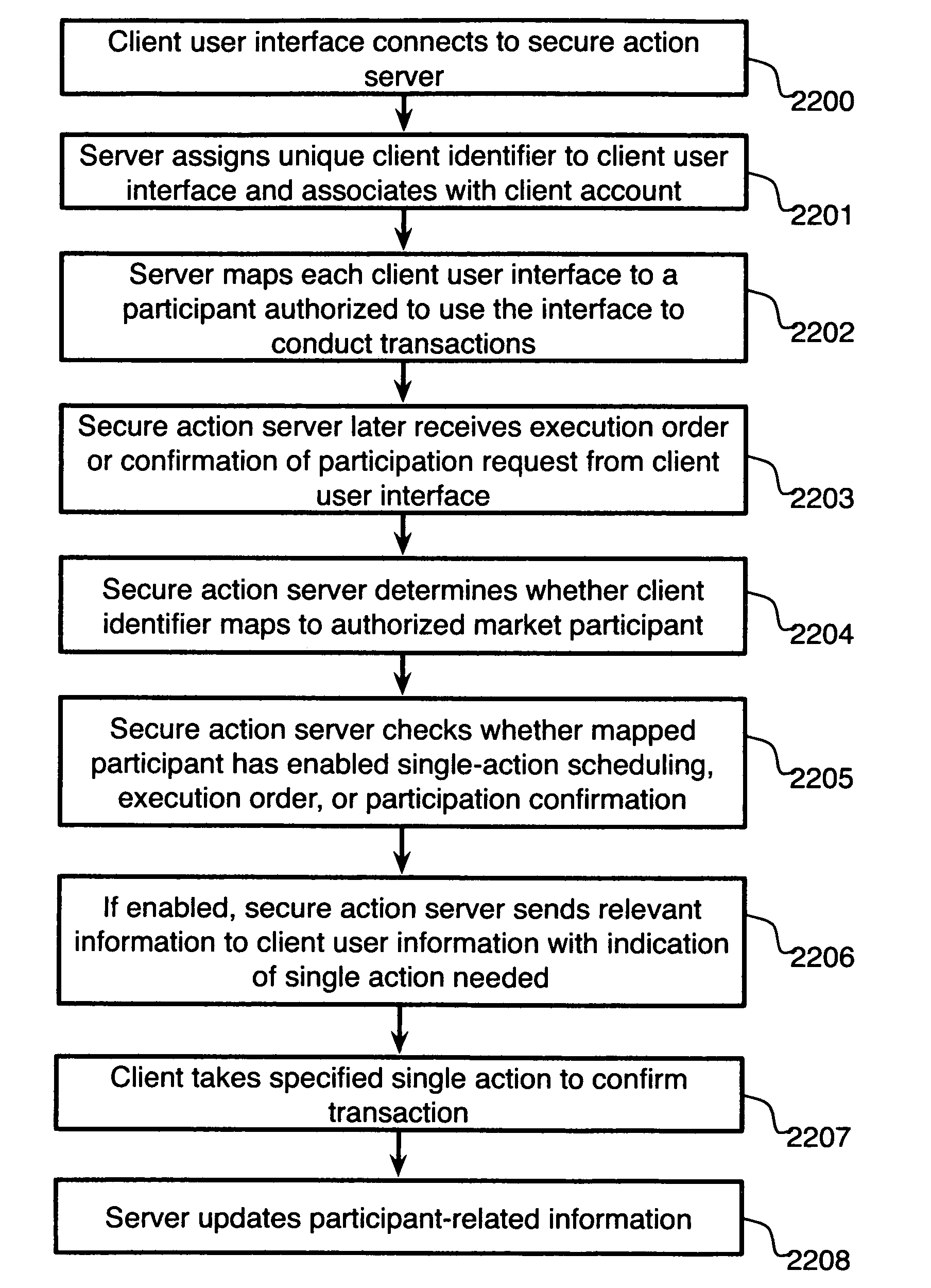
A system for single-action energy resource scheduling and participation in energy-related securities, comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of client user interfaces and a secure action server coupled to the communications interface, wherein the secure action server, on receiving a connection from a client user interface, assigns a unique client identifier to the client user interface and associates the unique identifier with a client account, and wherein the secure action server, on receiving a request from a client user interface, determines whether the client user interface is mapped to an authorized market participant who has enabled single-action scheduling, execution order, or participation confirmation functionality for the client user interface, and passes information to the client user interface pertaining at least to a single action needed to confirm scheduling, execution order, or participation and wherein the secure action server, on receiving indication from the communications interface that a required single action has been taken, at least updates information about the market participant who took the action, is disclosed.
Owner:CRUBTREE JASON +4
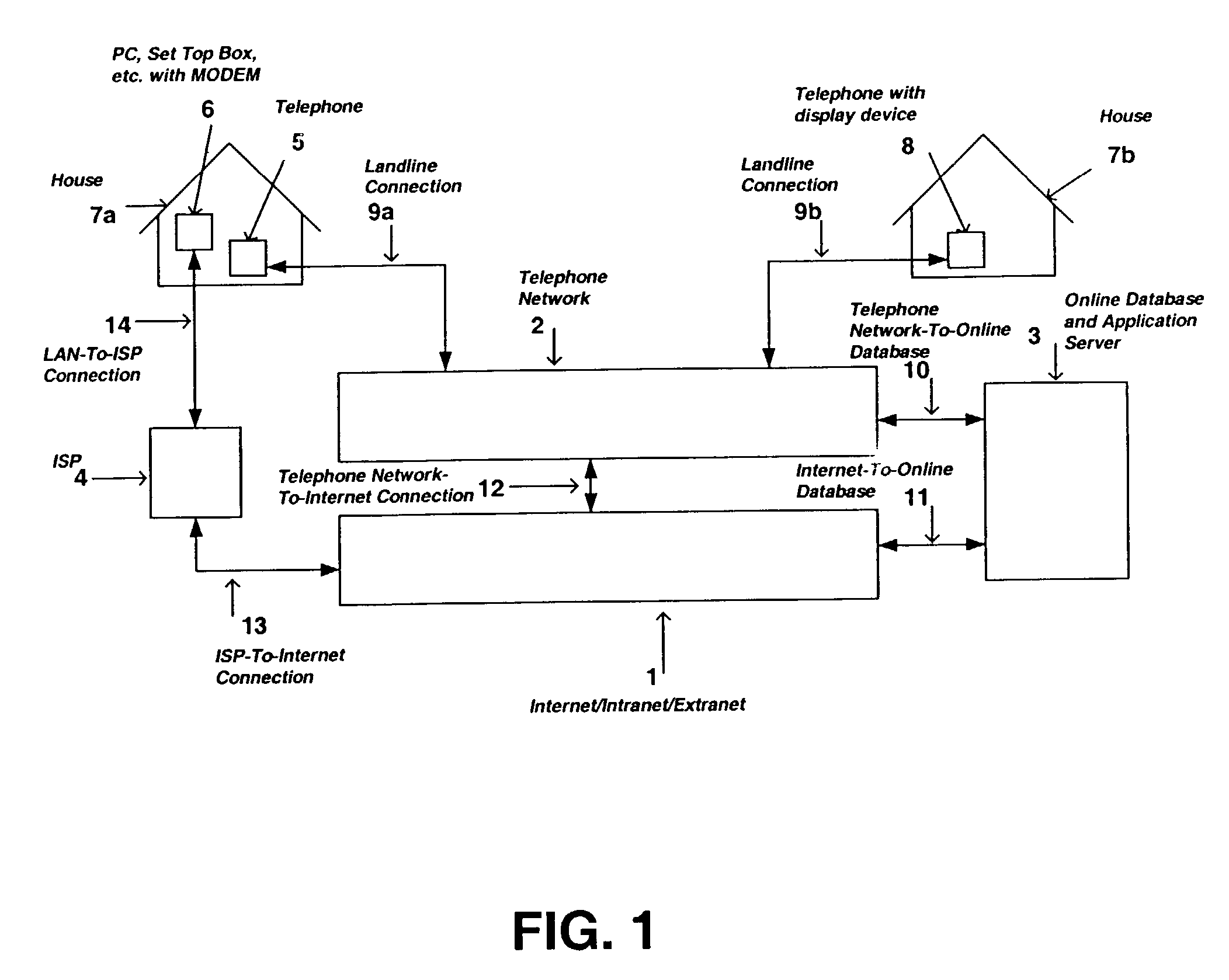
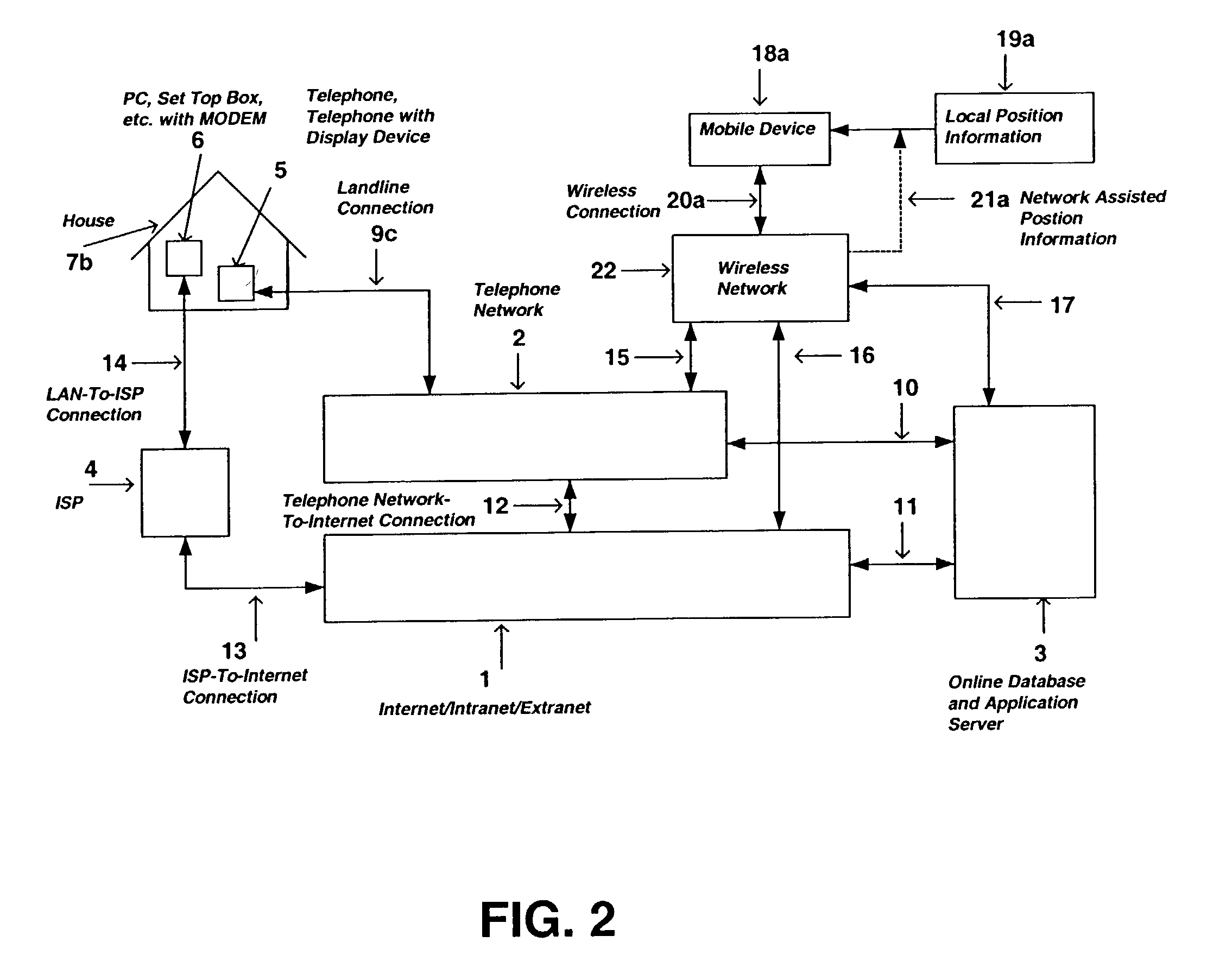
Position determination system
InactiveUS20030016804A1Limited resourceReduce areaInstruments for road network navigationDevices with GPS signal receiverTelecommunications networkThe Internet
The present invention is directed to a system and method for providing real-time position information of one party to another party by utilizing a conventional telecommunication network system such as the convention telephone network, a mobile telecommunications network, a computer network, or the Internet. More specifically, the preferred embodiments of the present invention allow a caller and a receiver of a telephone call to provide to and receive from each other position information related to the caller and / or receiver's physical location, including address information, GPS coordinates, nearby fixed locations such as a parking structure, etc. Additionally, the preferred embodiments of the present invention allow a caller and receiver to retrieve routing instructions or maps for traveling to or from each other. In another embodiment of the present invention, a party may locate the position of another party via the entry of the other party's unique identifier such as a phone number of the other party's mobile phone. In yet another embodiment of the present invention, the position information of a party may be concurrently delivered to another party's computer terminal whereby the other party can process the information in further detail.
Owner:ARTAX LLC
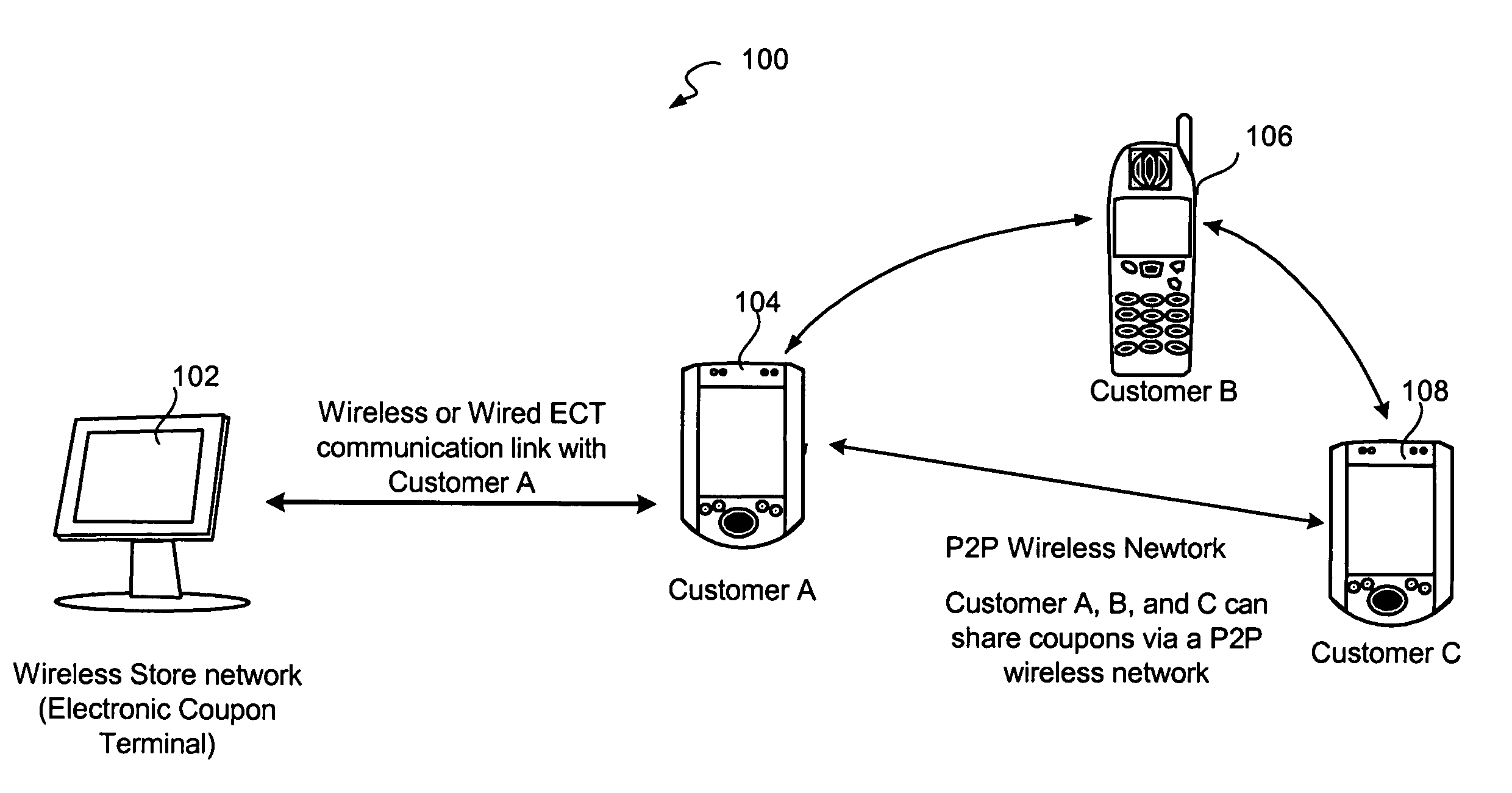
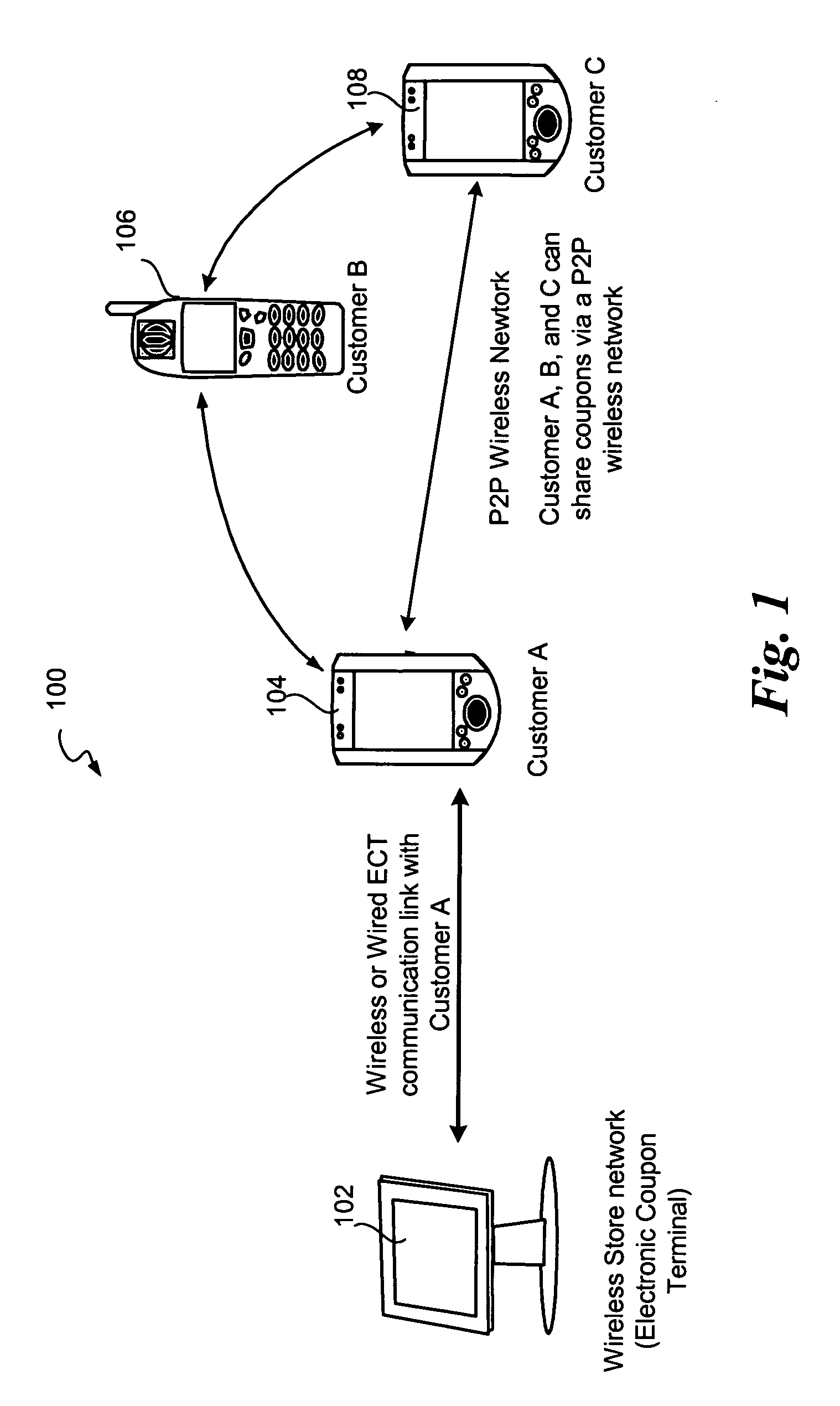
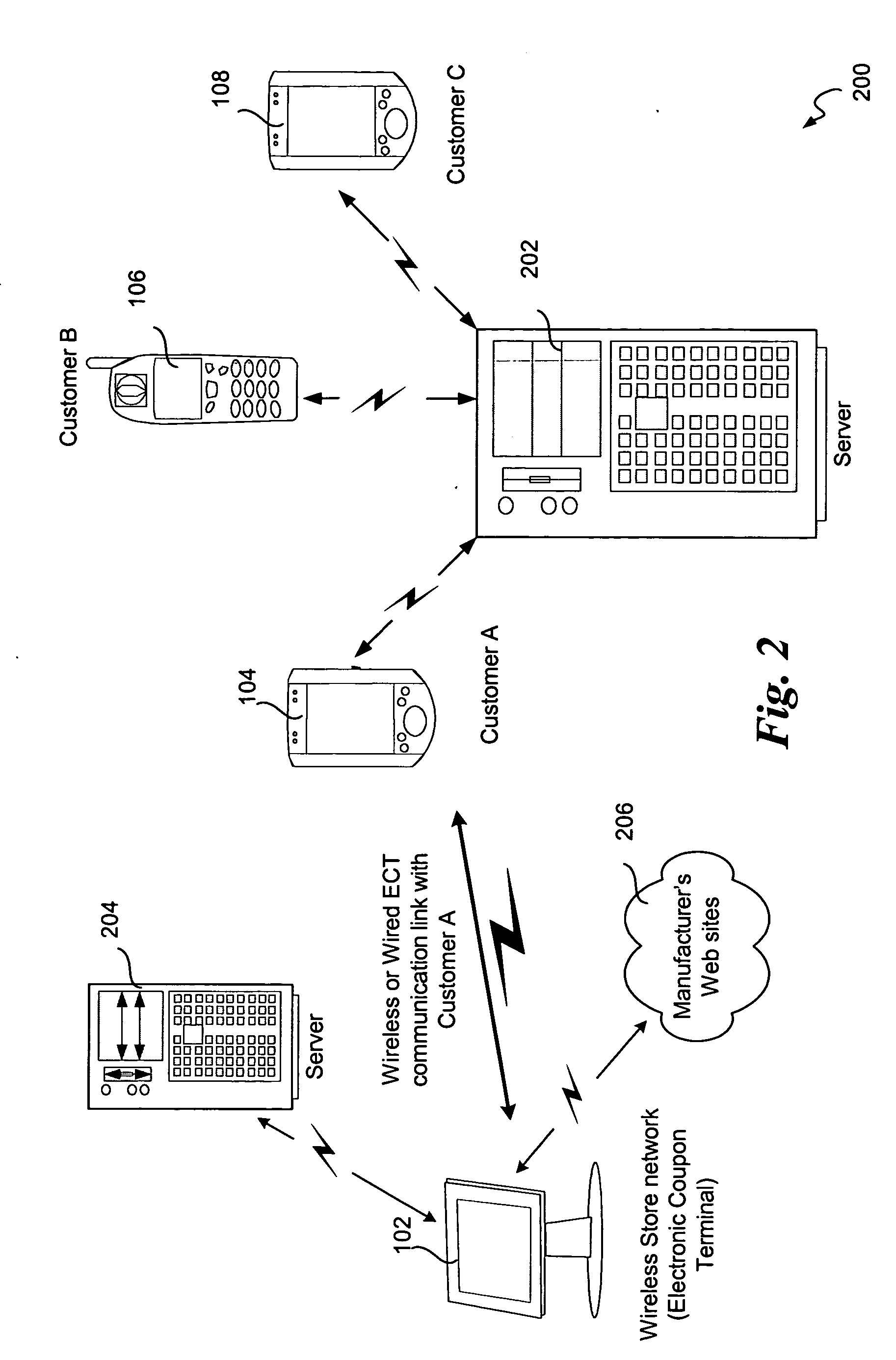
Mobile digital coupons
A system and method is disclosed for providing a reward-based digital mobile coupon environment, where the digital coupons may be shared among peers. Consumers utilize mobile digital coupon carriers having digital representations of coupons. Sharing of coupons among peers may be rewarded with additional discounts or points. The digital coupon carriers communicate with electronic coupon terminals at retail locations for automatic coupon redemption. A coupon may correspond to a globally unique identifier in order to track usage, sharing and redemption. Coupon use and sharing may be dependent upon stored user profiles, merchant profiles and policies, or programs embedded in the coupon.
Owner:INTEL CORP
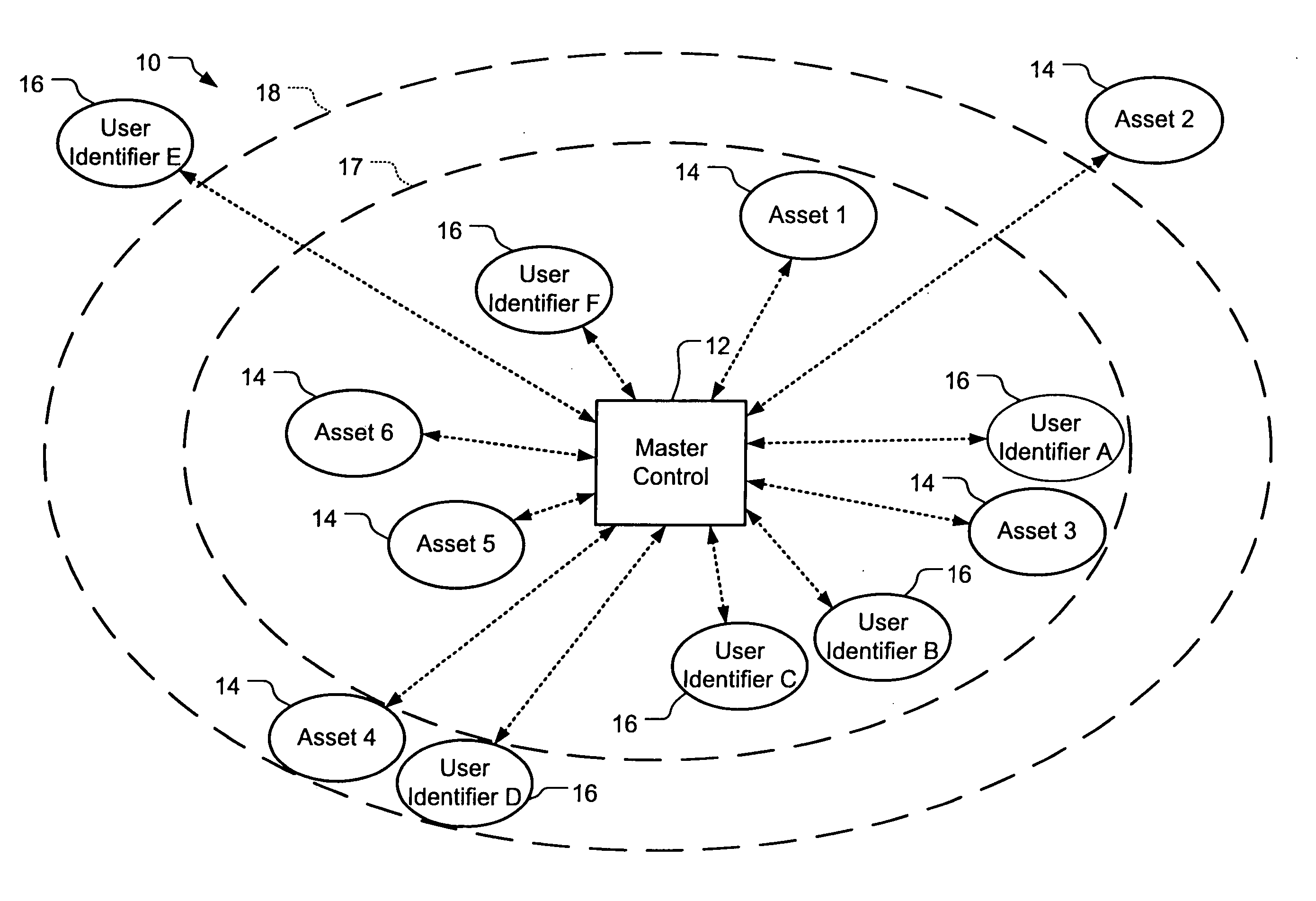
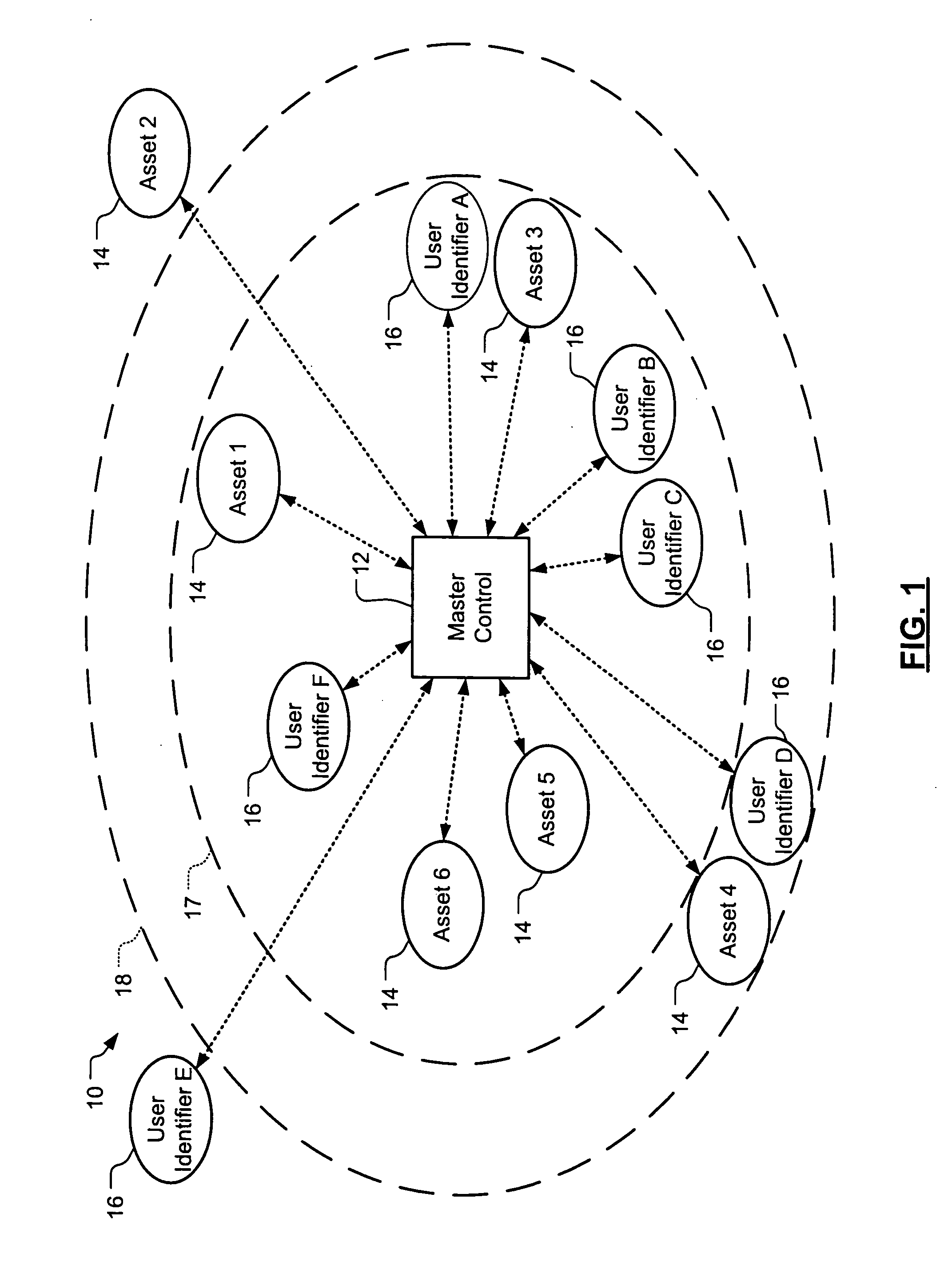
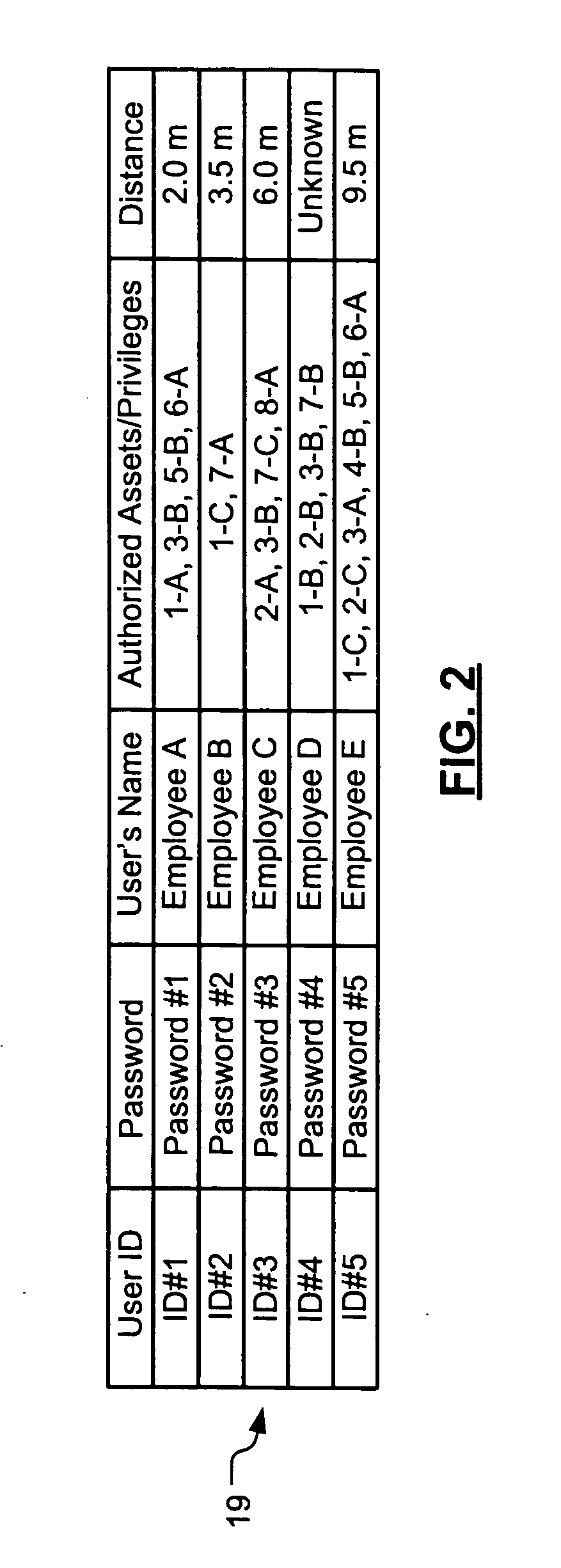
Wireless asset monitoring and security system
InactiveUS20050128083A1Electric signal transmission systemsMultiple keys/algorithms usageLocking mechanismUnique identifier
An asset monitoring and security system includes at least one asset assigned a unique identifier and operable wirelessly transmit an identification signal embodying the identifier. A data store maintains a list of the assets and privileges associated with the assets for authorized users of the assets. A control unit is adapted to receive identification signals from the assets and monitor positions of the assets within a defined area. The control unit communicates with the data store and is further operable to initiate an alarm event when privileges associated with a given asset for authorized users of the asset are exceeded. Each of the assets includes a lock-out mechanism that impedes use of the asset when the lock-out mechanism is activated. The control unit activates the lock-out mechanism of a given asset when the privileges associated with the asset for authorized users of the asset are exceeded.
Owner:BLACK & DECKER INC
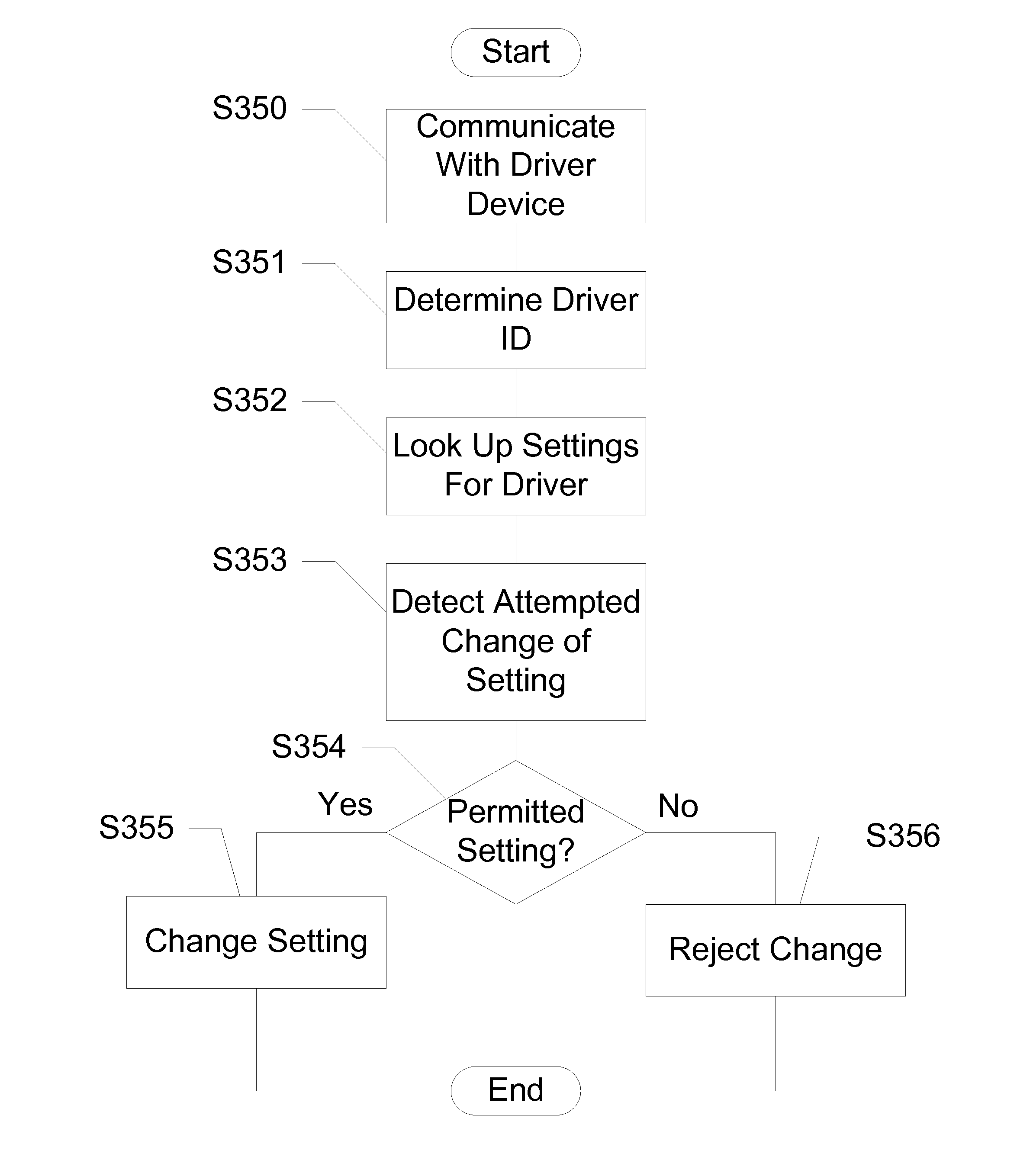
Devices, Systems and Methods for Controlling Permitted Settings on a Vehicle
ActiveUS20110137520A1Limiting distractionNetwork traffic/resource managementAnalogue computers for trafficDistractionDriver/operator
Devices, systems, and methods are disclosed for altering permitted settings of a vehicle according to a driver identified through short range wireless communication. The vehicle captures a unique identifier from a wireless communication device of the driver of the vehicle. This unique identifier is used to reference a database to determine the identity of the driver as well as settings for the driver created by a controlling authority. The controlling authority may be, for instance, a parent or employer of the driver. The settings may limit certain devices within the vehicle and / or the vehicle itself. Speed control settings, radio settings, wireless communication device settings, and various other settings are all possible to limit distractions to the driver. Further, the settings may be influenced by the number or identities of passengers within the vehicle.
Owner:HYUNDAI MOTOR CO LTD +1
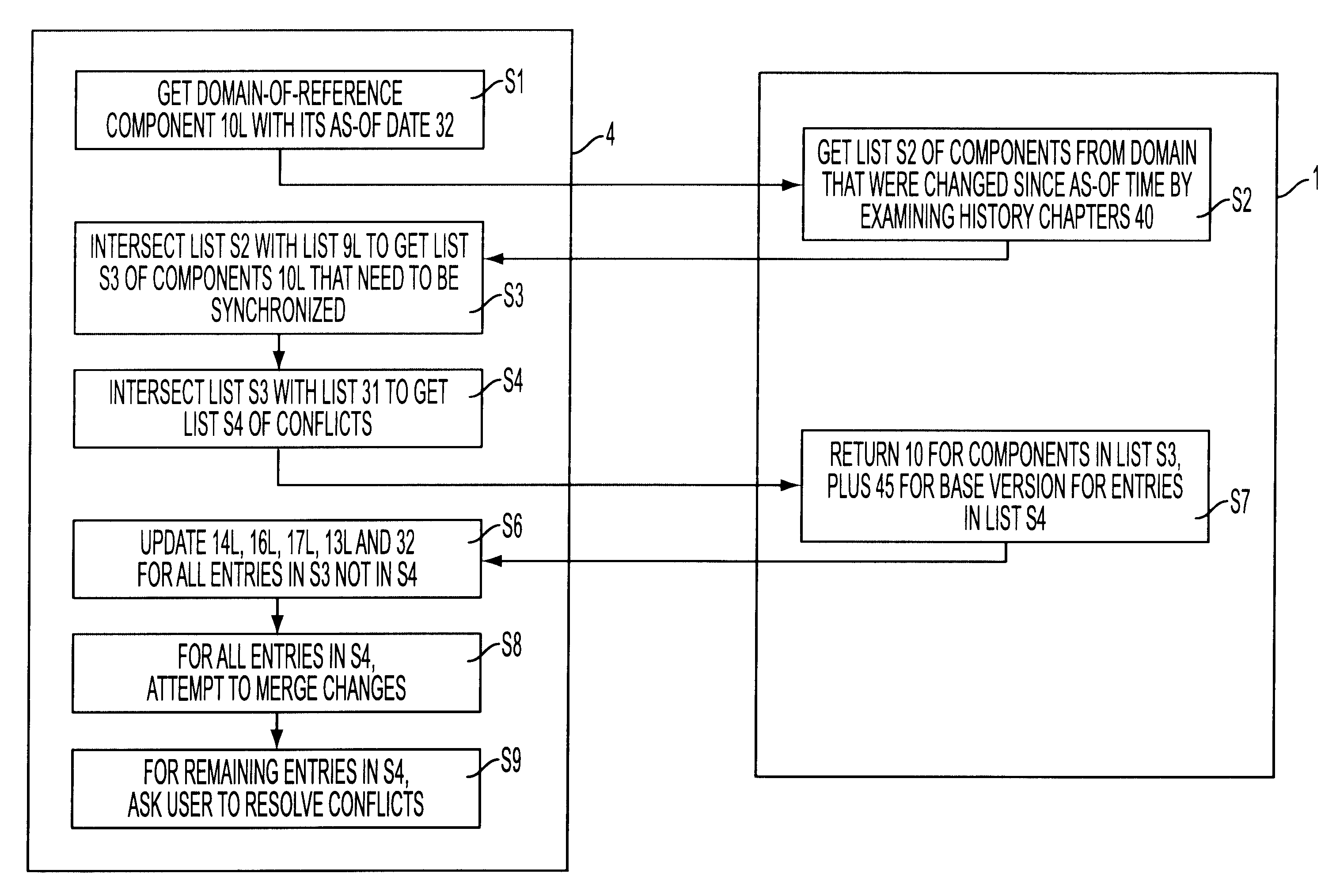
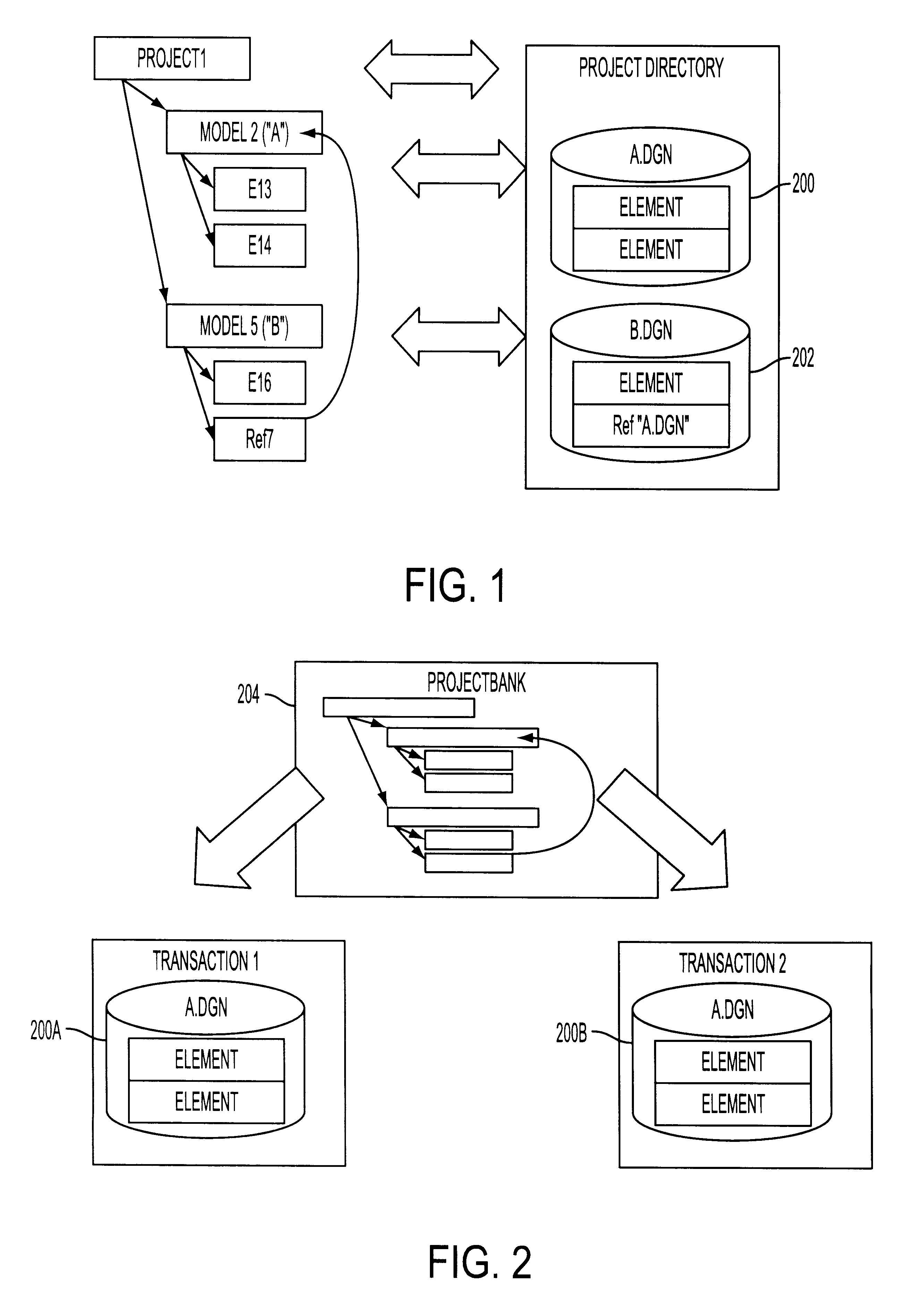
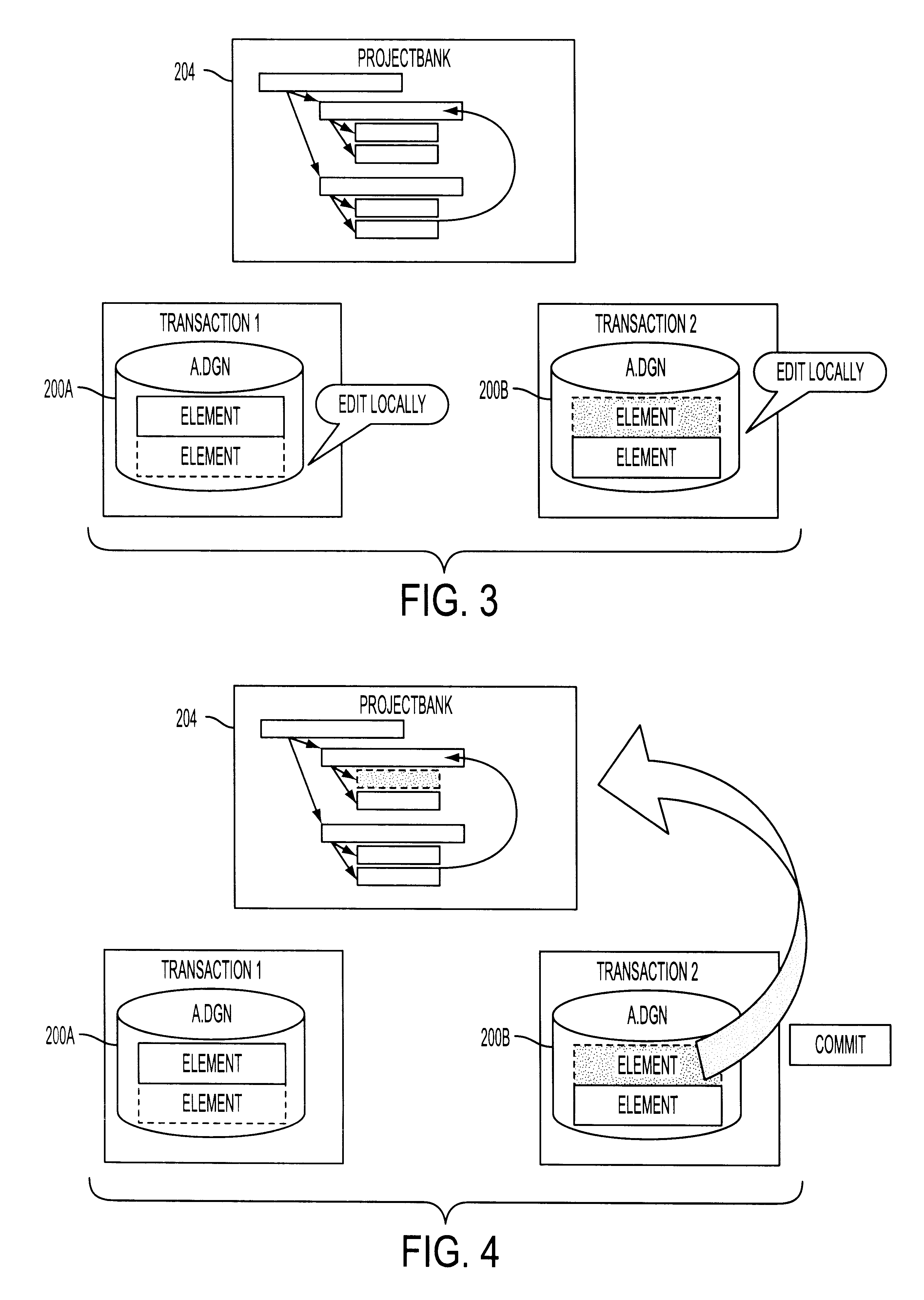
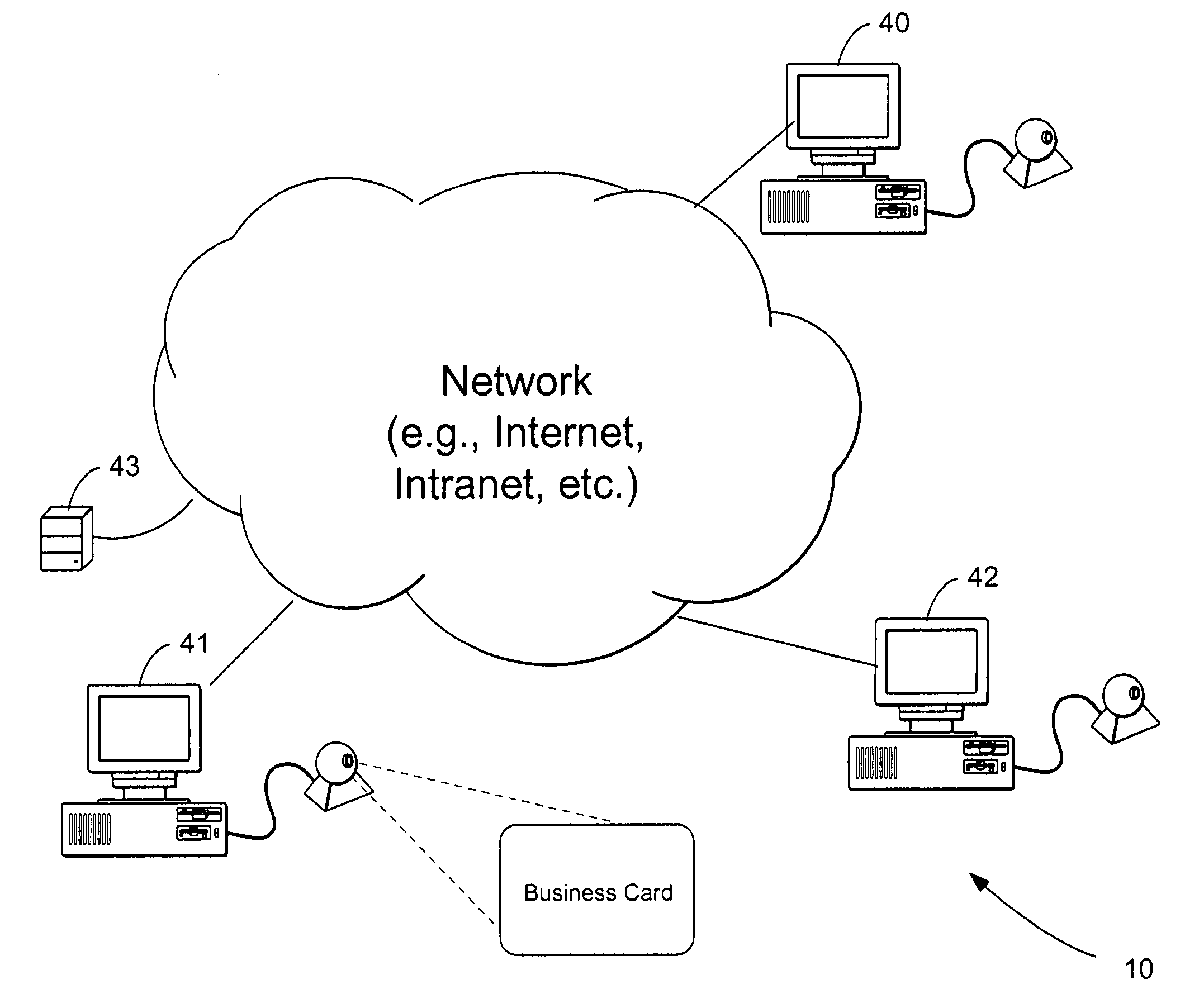
System for collaborative engineering using component and file-oriented tools
InactiveUS6341291B1Improve the level ofHigh currentData processing applicationsCAD network environmentSoftware engineeringIdenticon
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. Each component has a unique identifier, a set of fields, each field having a data type and a data value, and a program which interprets and modifies the fields. The plurality of components are stored in a repository of a server. The repository also stores a history of any changes made to the components. A plurality of client computers are bidirectionally connected to the server. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the server to replace the current versions in the repository. At the client computer, the user interacts with the components using conventional file-based software. Before locally edited versions of the components are committed to the server to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts therebetween. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to "wrap" each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
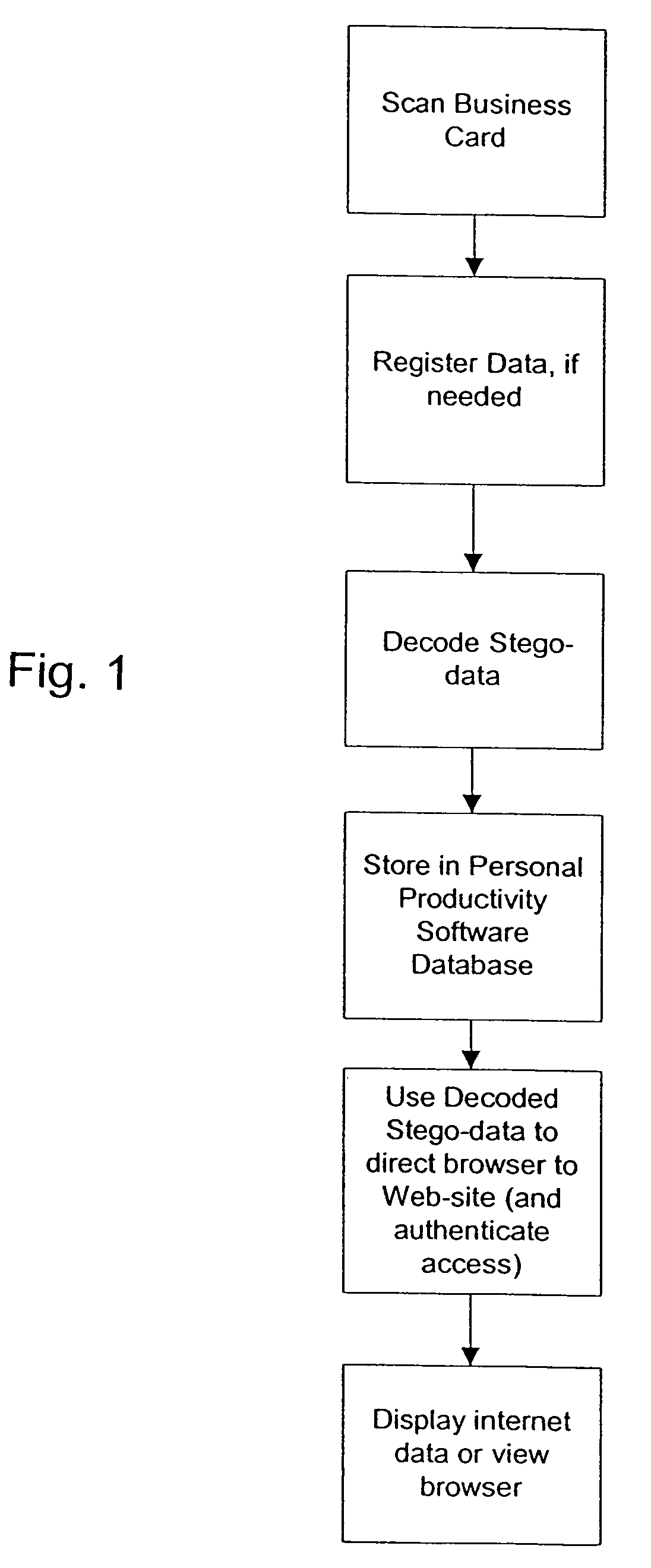
Method of linking on-line data to printed documents
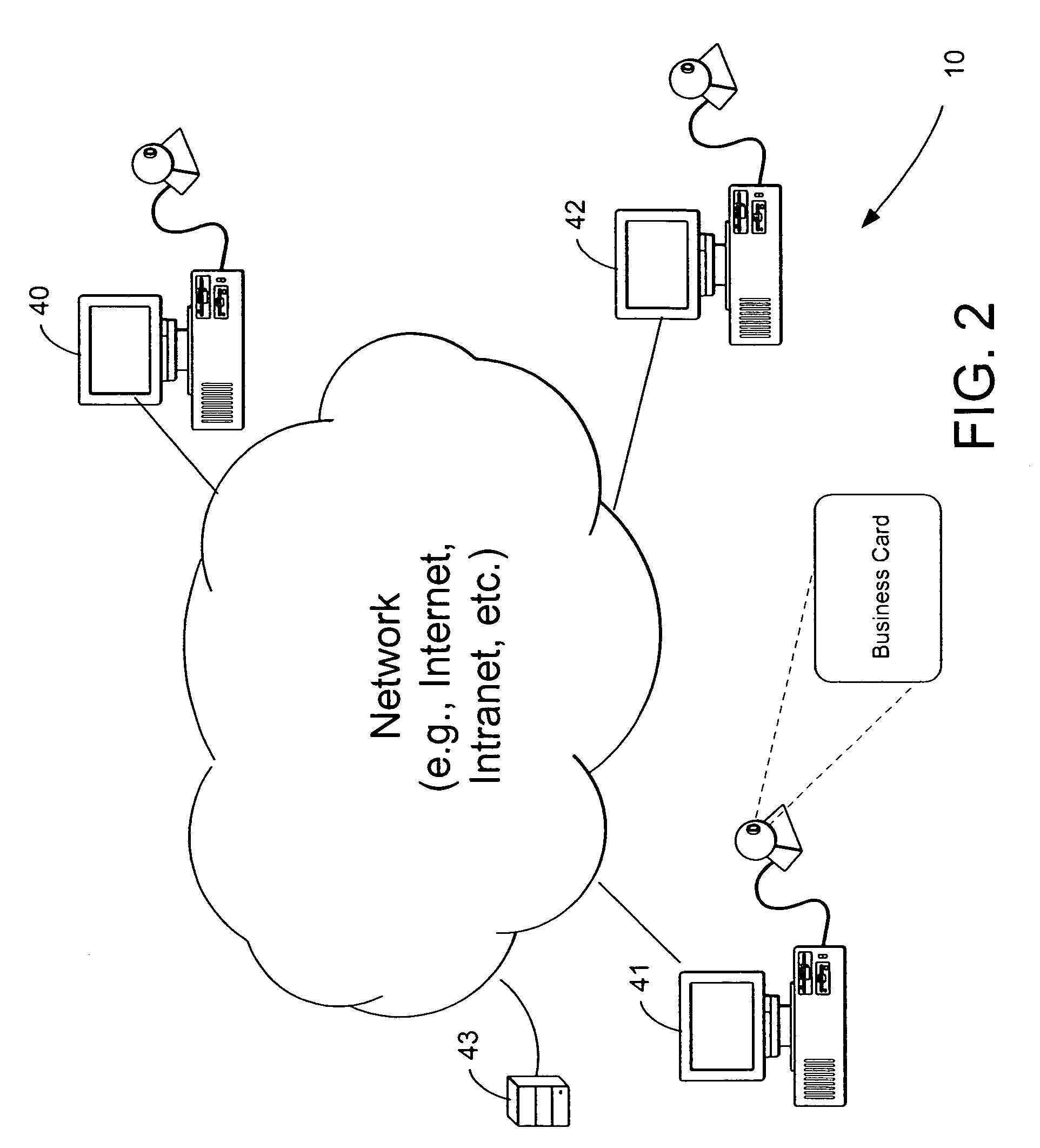
InactiveUS7051086B2Readily apparentRecord information storageMultiple digital computer combinationsGraphicsBusiness card
The present invention relates to linking on-line data to printed documents, such as business cards, envelopes, stickers, stationary, letterhead, résumés, etc. In one embodiment, a card-user registers with an on-line database and receives a gallery item including a steganographically-embedded unique identifier. The gallery item, such as a graphical background, text, shading, graphic, etc., is integrated and then printed with a document. The printed document can then be presented an optical-scanner, which outputs data. The output data is decoded to identify the unique identifier. The unique identifier is then used to index into the on-line database to retrieve information related to the proprietor of the document. In one embodiment, the on-line database includes features such as providing an immediate contact number, translation and / or pronunciation ability, and storage of audio / video files.
Owner:DIGIMARC CORP
System and method for secure electronic communication services
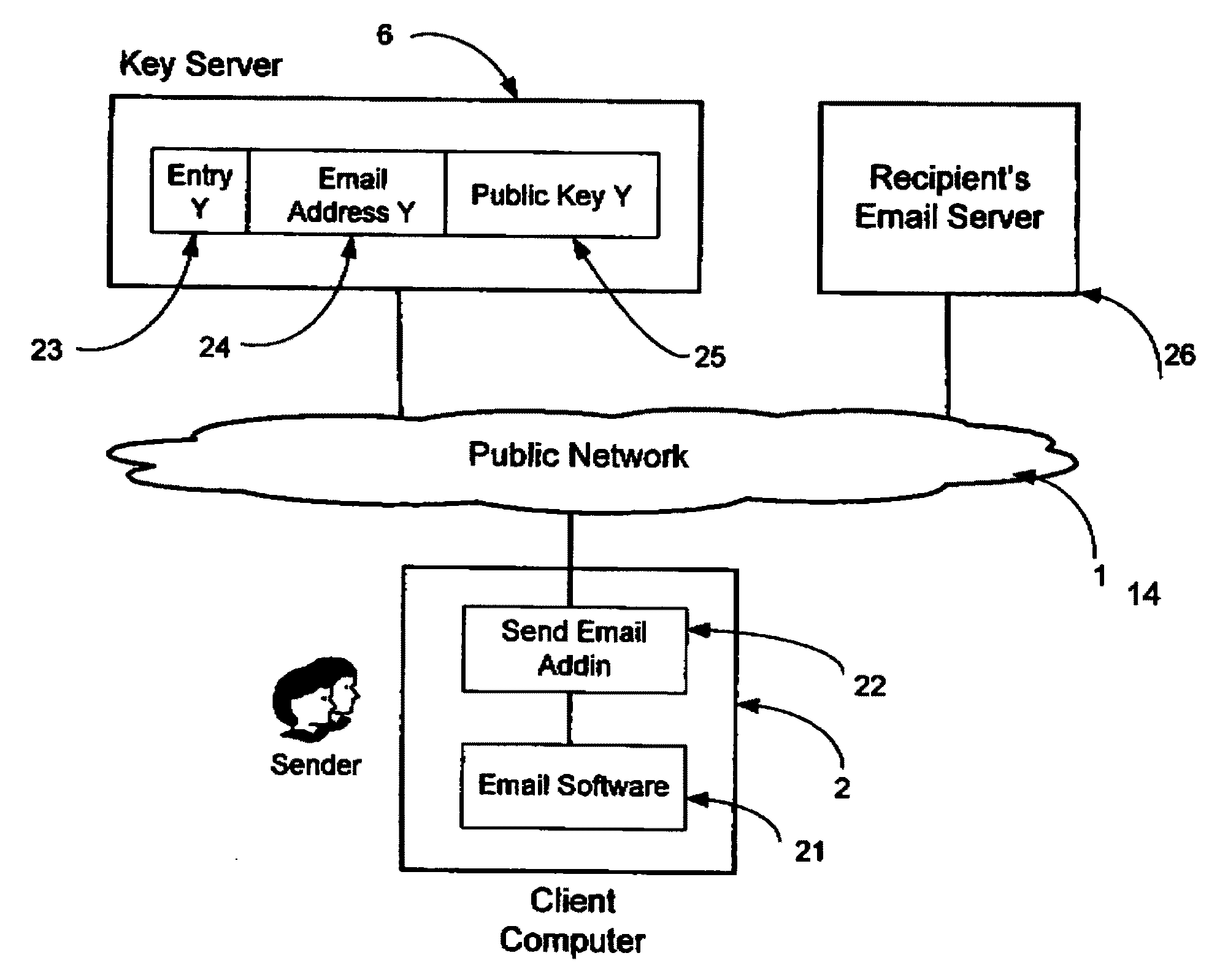
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
Systems and methods for providing remote monitoring of electricity consumption for an electric meter
InactiveUS7209840B2Electric signal transmission systemsCircuit arrangementsElectricityUnique identifier
A system for providing remote monitoring of electricity consumption is provided. In one embodiment the system may comprise electric meters, communication devices having a unique address and defining a wireless communication network, and a site controller. Each electric meter may be configured to measure electricity consumption of a load. Each communication device may be associated with one of the electric meters and configured to receive electricity consumption data and generate a transmit message using a predefined communication protocol being implemented by the wireless communication network. The transmit message may comprise the unique identifier and electricity consumption data. The site controller may be configured for communication with the wireless communication network and configured to receive the transmit message from one of the communication devices, identify the electric meter associated with the transmit message, and provide information related to the transmit message to a WAN for delivery to a computer.
Owner:LANDISGYR TECH
Method, a device and computer program products for protecting privacy of users from web-trackers
InactiveUS20170142158A1Protect user privacyPrivacy protectionTransmissionSecurity arrangementWeb siteNetwork behavior
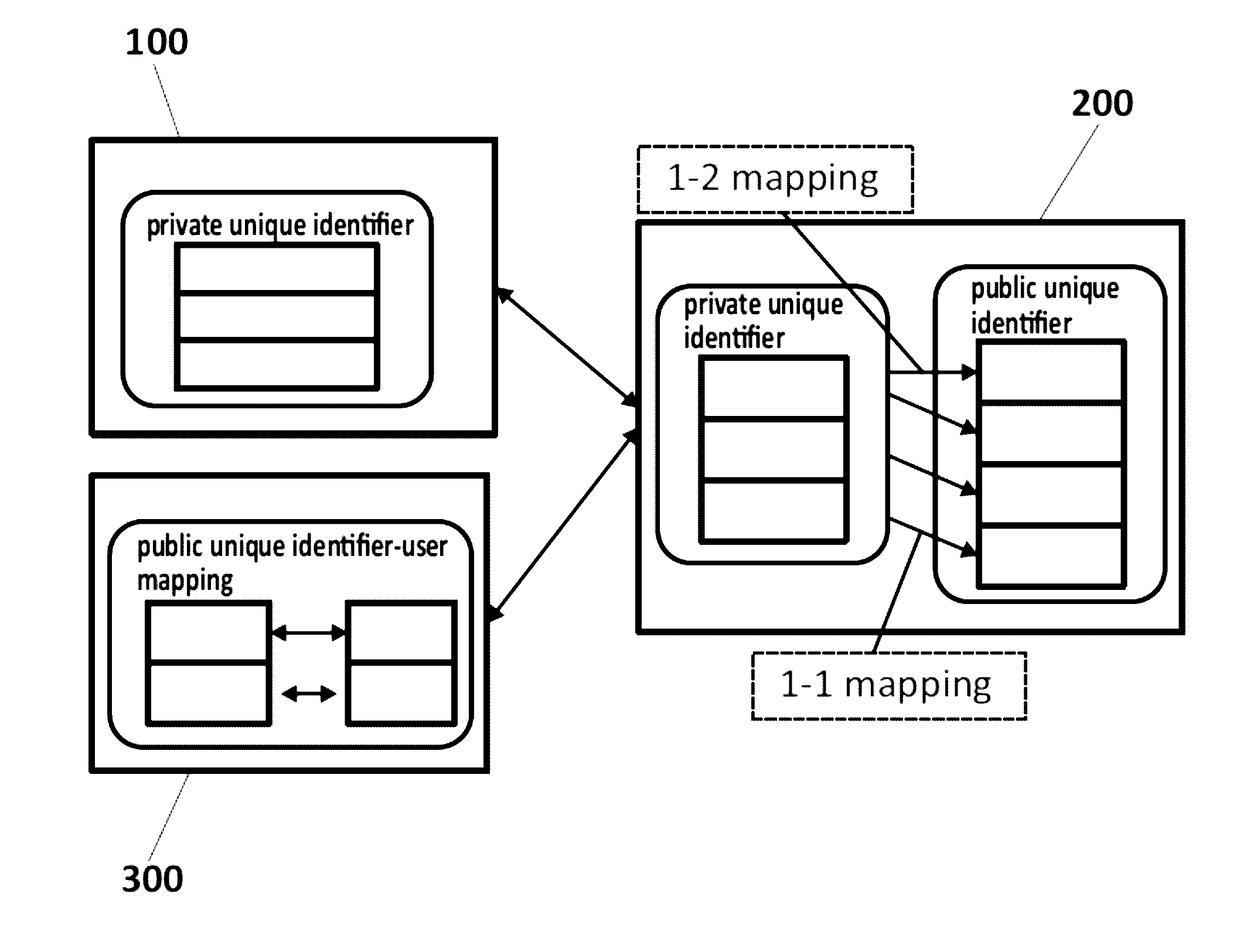
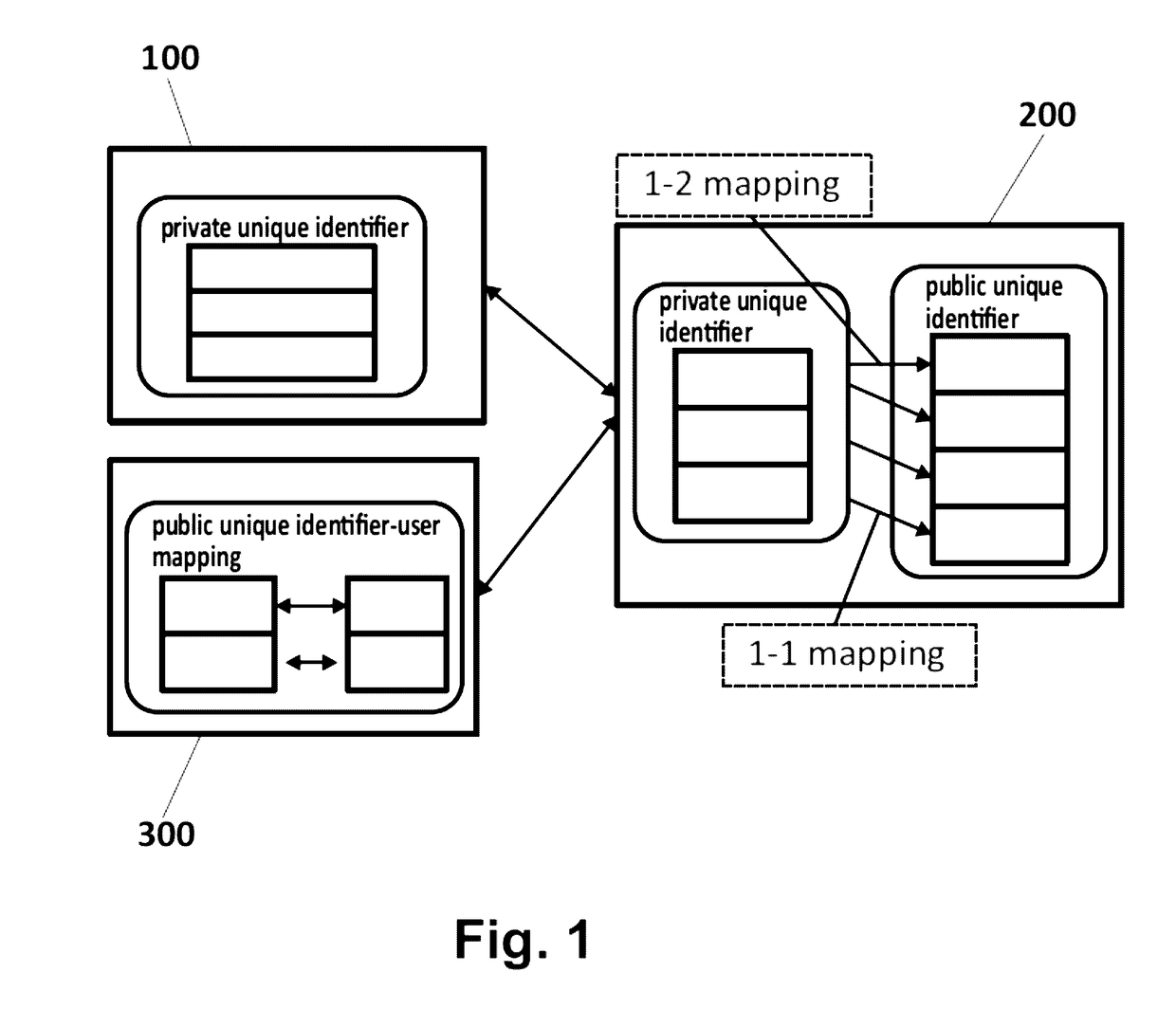
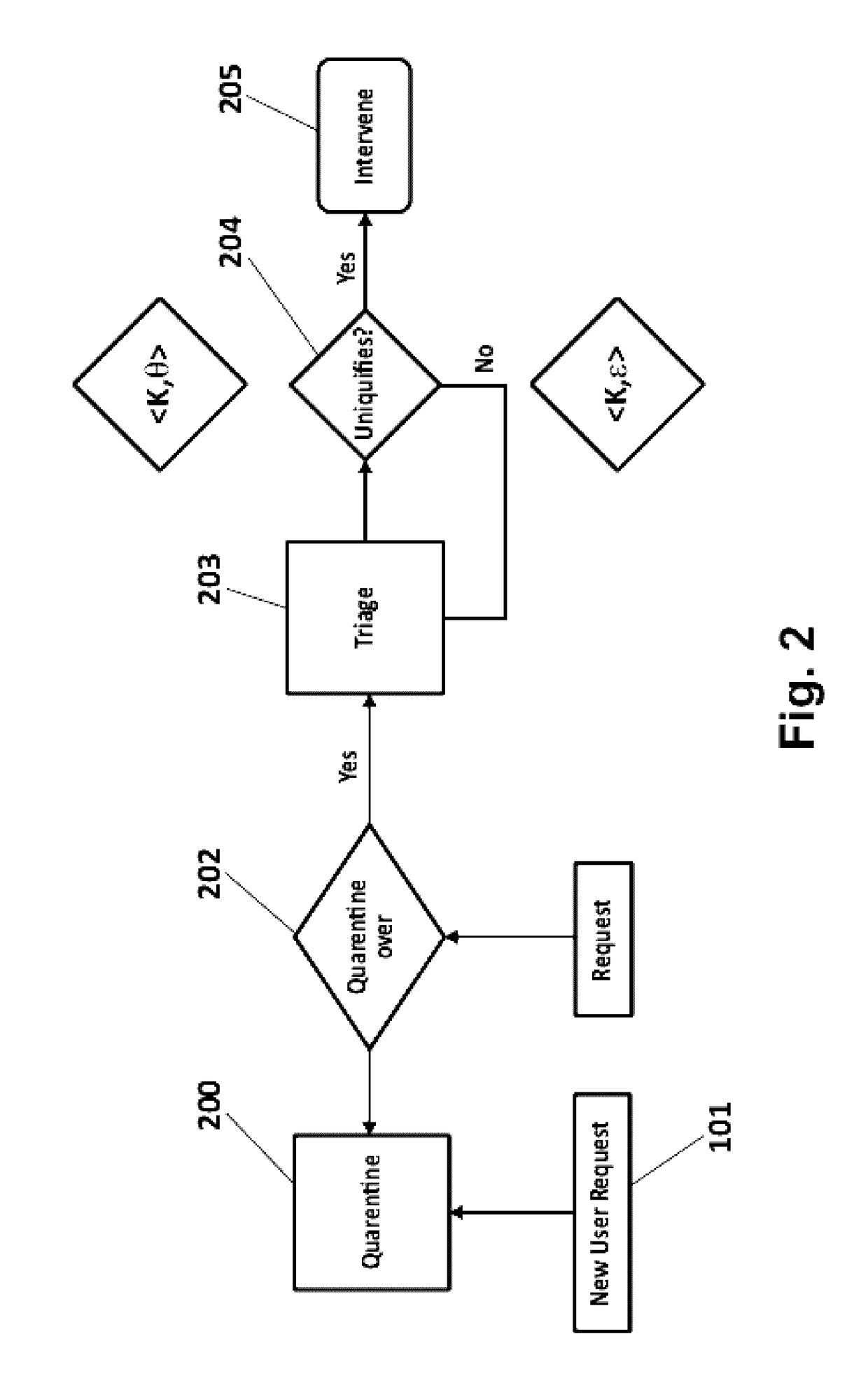
A method, a device and computer program products for protecting privacy of users from web-trackersThe method comprising:capturing and removing a public unique identifier set by a Website (300) in a computing device (100D) of a user (100);monitoring, during a first time-period, web-requests the user (100) makes to obtain a web-behavioral profile of the user (300), and storing the obtained web-behavioral profile as a first vector;tracking, during a second time-period, the web-requests to examine the effect each web-request has on assisting the de-anonymization of the user (100), obtaining a second vector;classifying, the obtained second vector taking into account a computed similarity score parameter;creating and mapping, a corresponding private unique identifier for said captured public identifier; andexecuting, based on said mapping between the private and the public unique identifiers, an intervention algorithm for said web-tracker, that considers a configured intervention policy.
Owner:TELEFONICA SA
Wireless Device Enabled Locking System
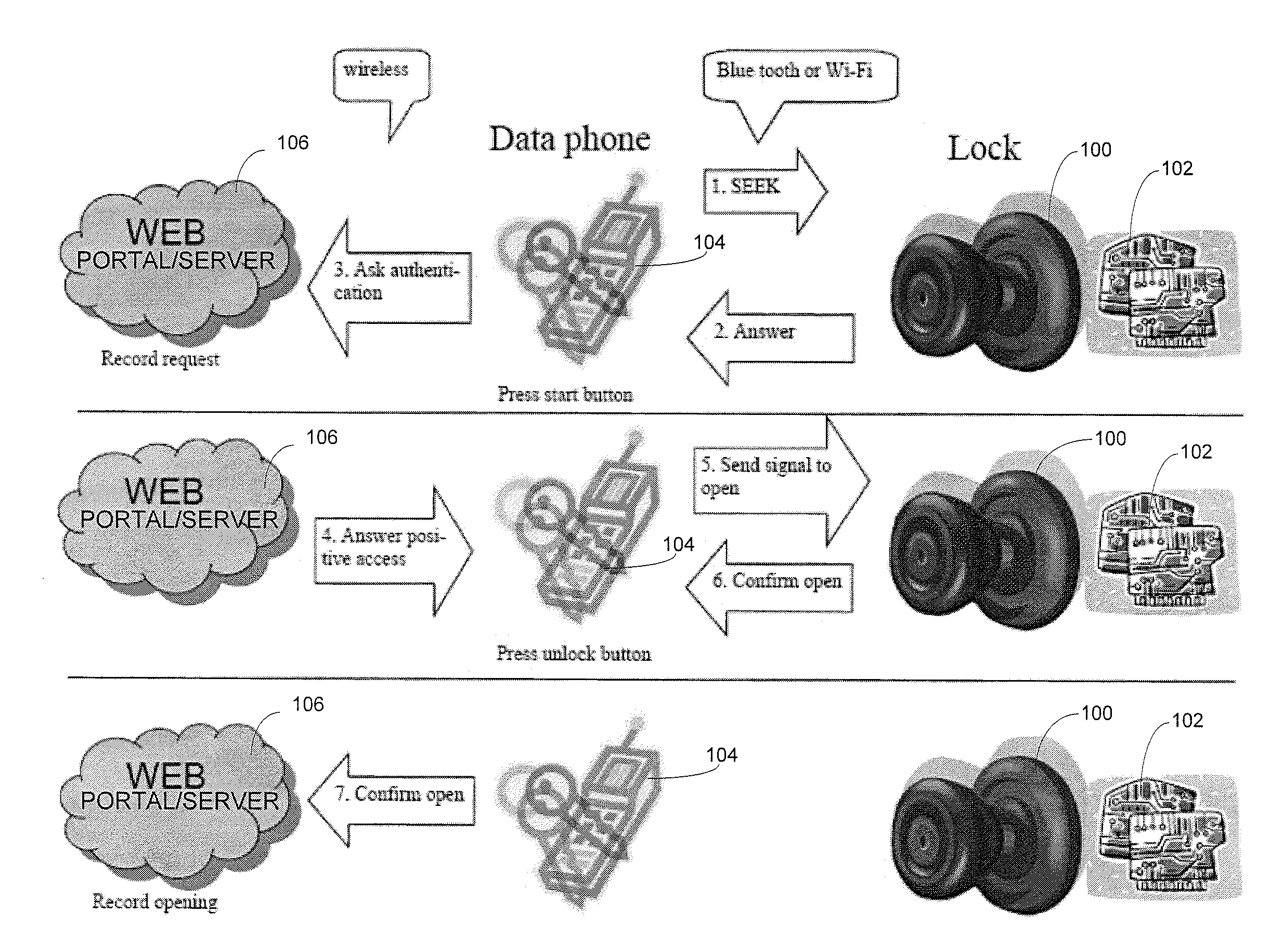
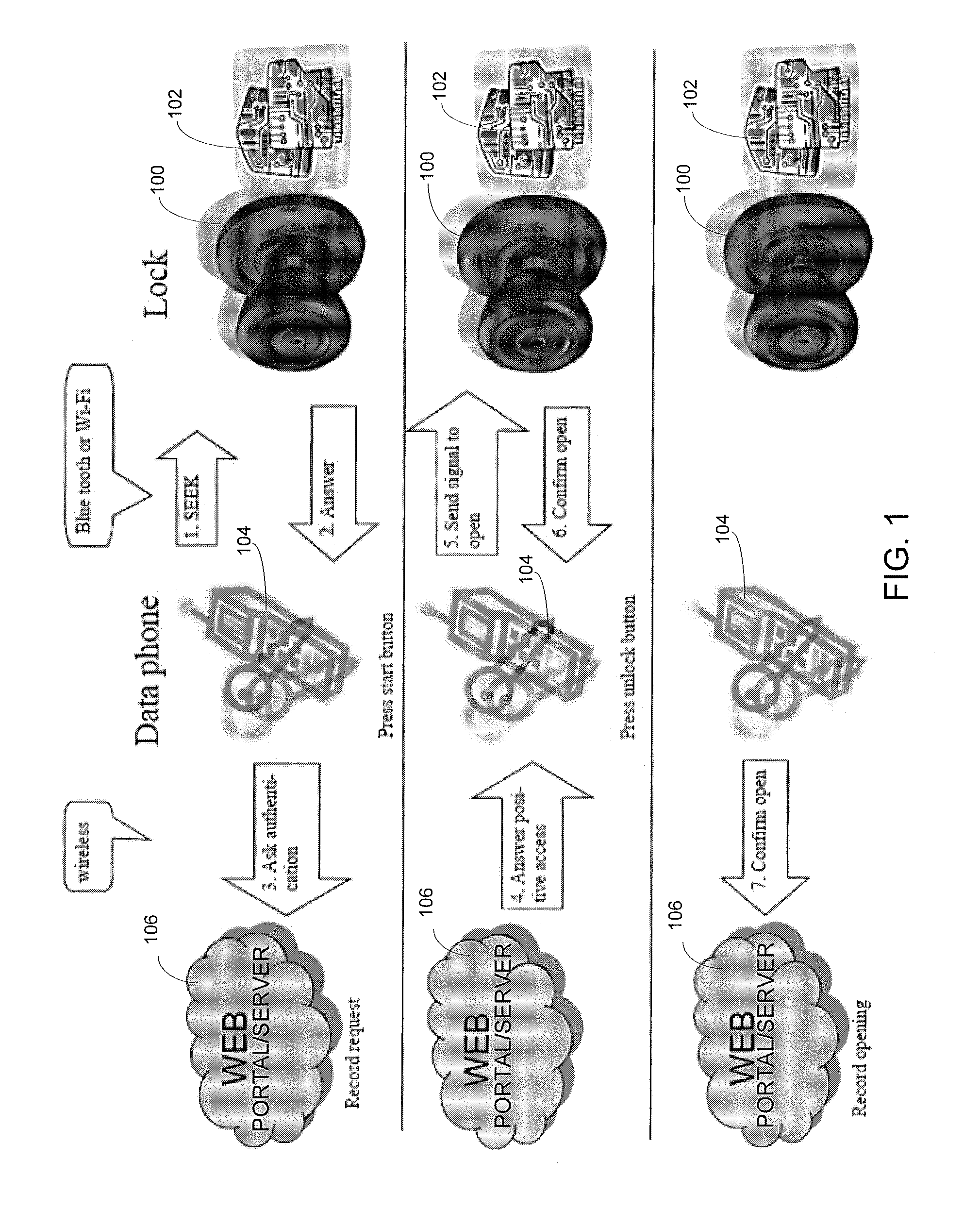
ActiveUS20110311052A1Provide securityDigital data authenticationSecret communicationUnique identifierMobile device
An encrypted security system and associated methods for controlling physical access. The system includes a security server configured to receive a request for authentication from a mobile device, the request comprising information identifying the mobile device and a physical access control device. The security server forwards an encryption message comprising a plurality of unique identifiers to the physical access control device via the mobile device. The physical access control device is configured to authenticate the plurality of unique identifiers in the encryption message and operate an access control mechanism.
Owner:DELPHIAN SYST
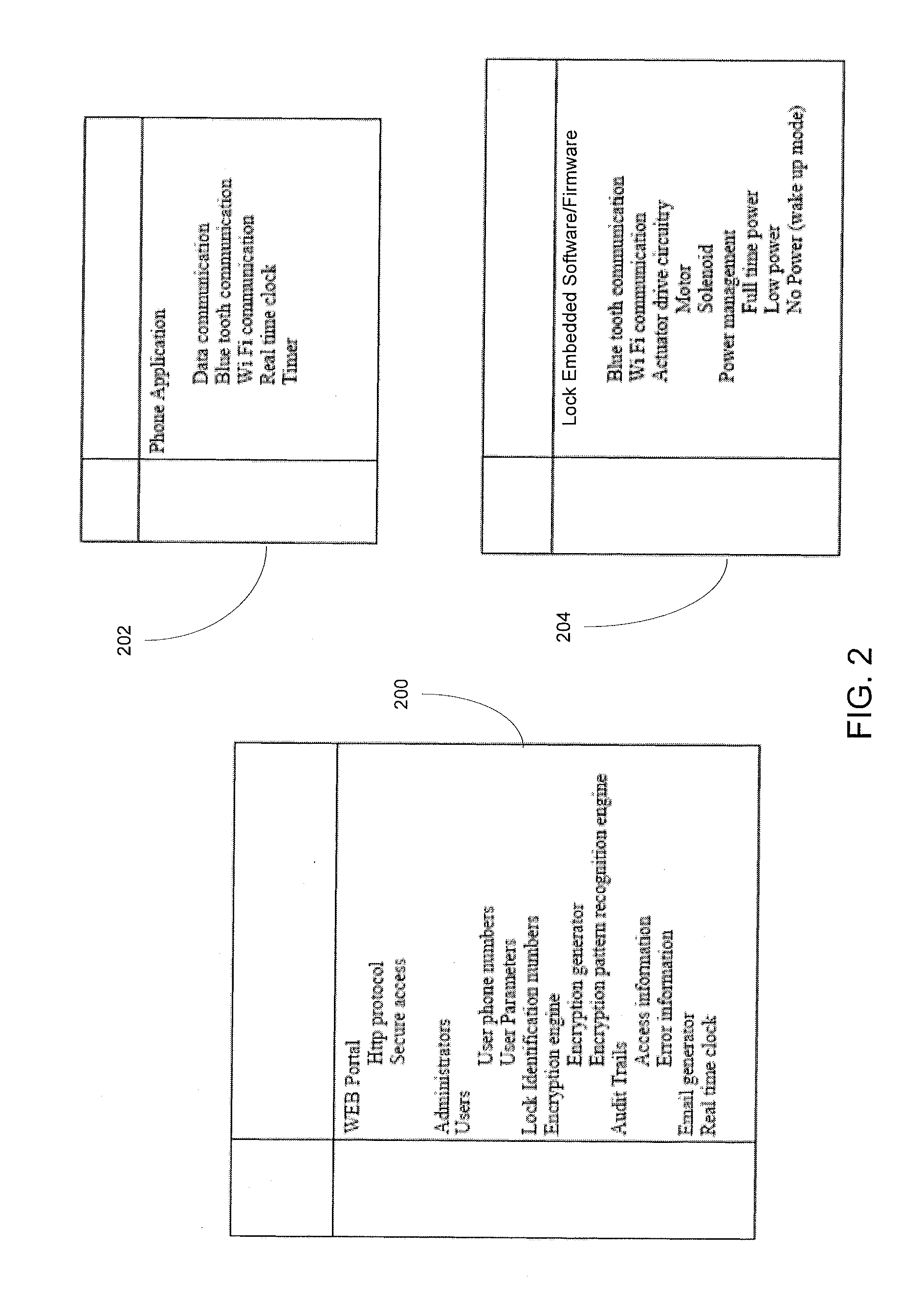
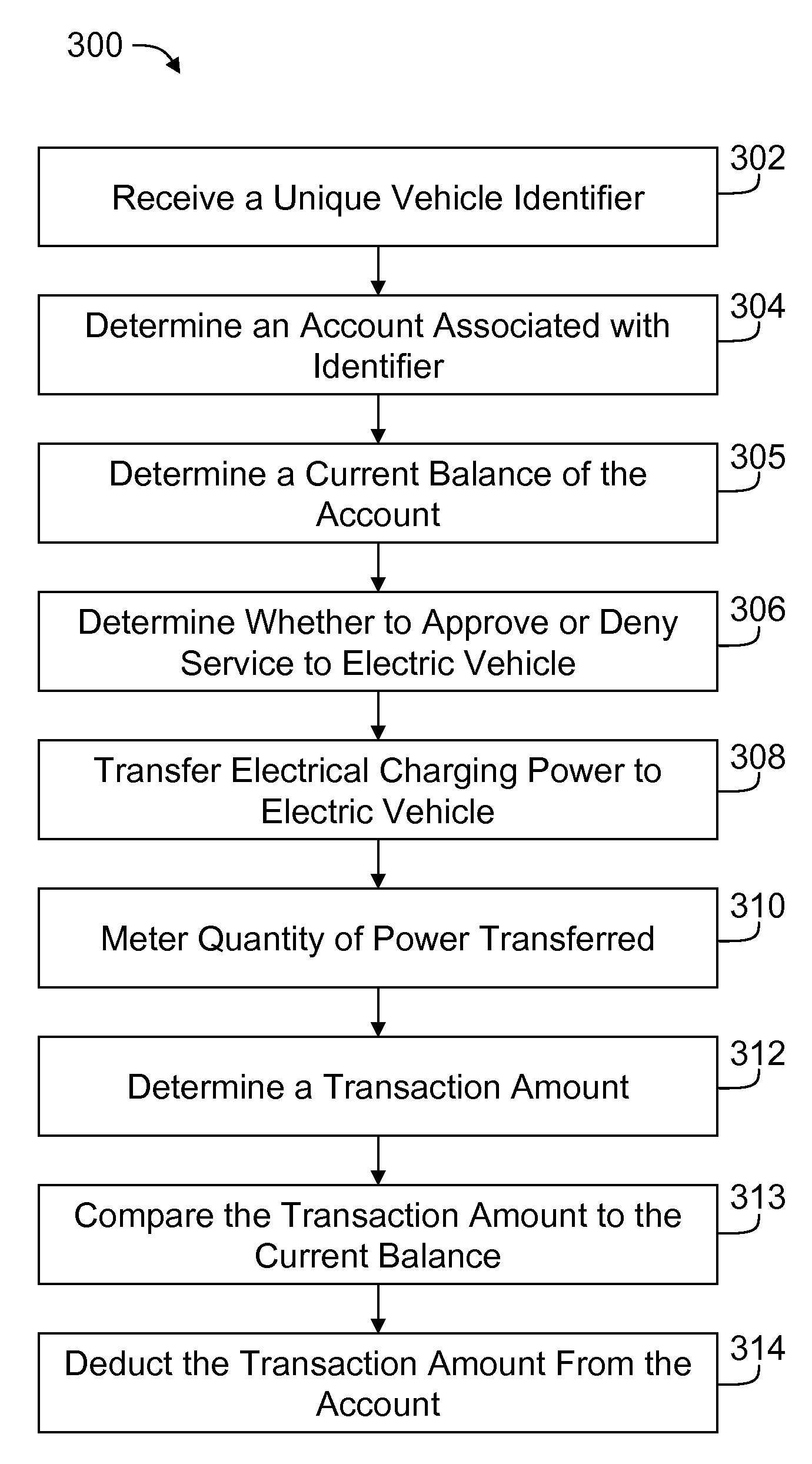
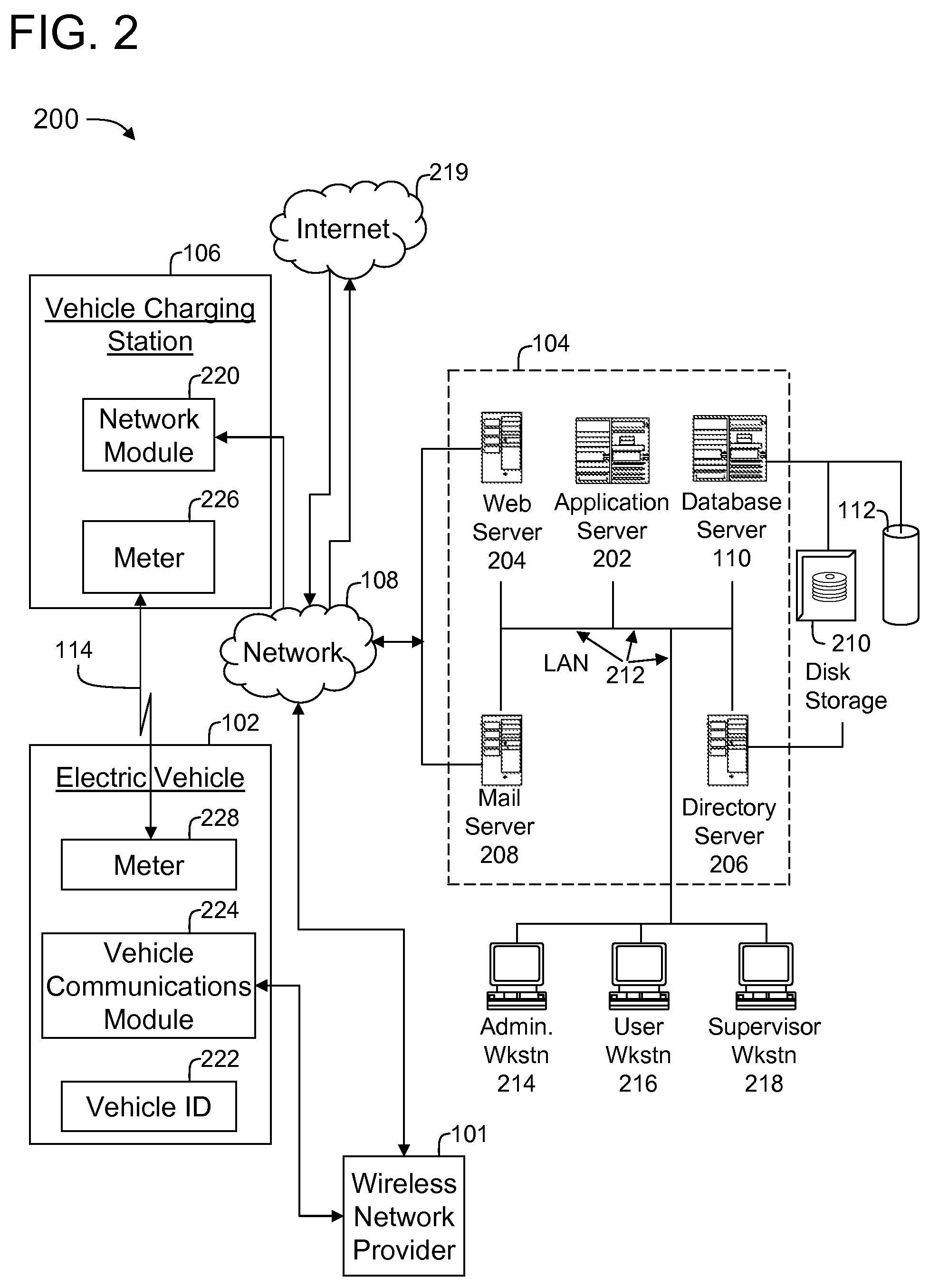
System and method for electric vehicle charging and billing using a wireless vehicle communciation service
ActiveUS20100161481A1Batteries circuit arrangementsSpecial tariff metersElectricityNetwork connection
A vehicle charging station for use in transmitting charging power to an electric vehicle for use in charging the vehicle is configured to communicatively couple to the electric vehicle via a network connection to a wireless network provider and electrically couple to the electric vehicle via a connector. Vehicle charging station is further configured to receive a unique identifier from the electric vehicle via the network connection, deliver a quantity of electrical charging power to the electric vehicle via the connector, and meter the quantity of electrical charging power delivered to the electric vehicle
Owner:GENERAL ELECTRIC CO
Safe sequencing system
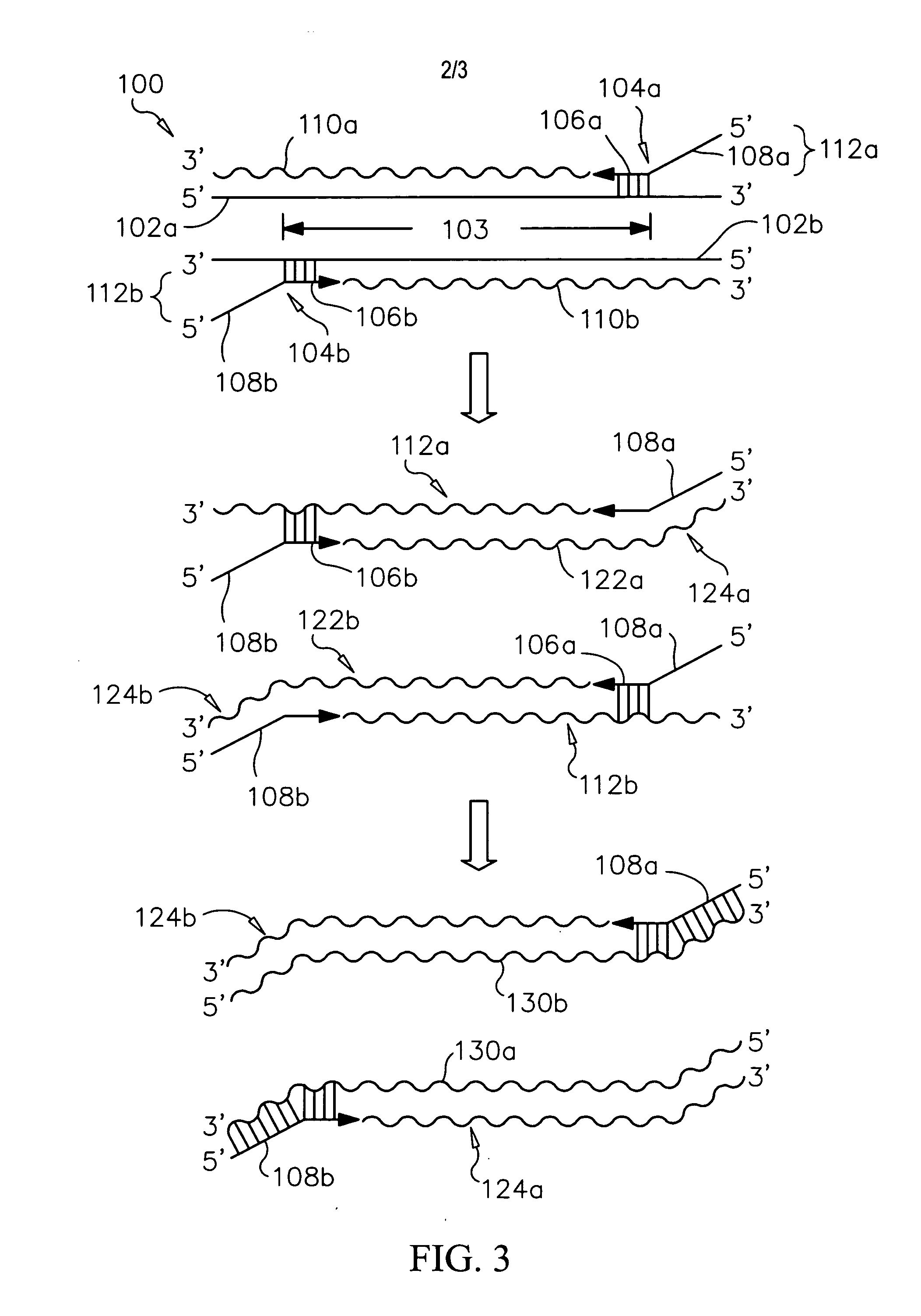
ActiveUS20140227705A1Sensitively accurately determiningMicrobiological testing/measurementOligonucleotideInstrumentation
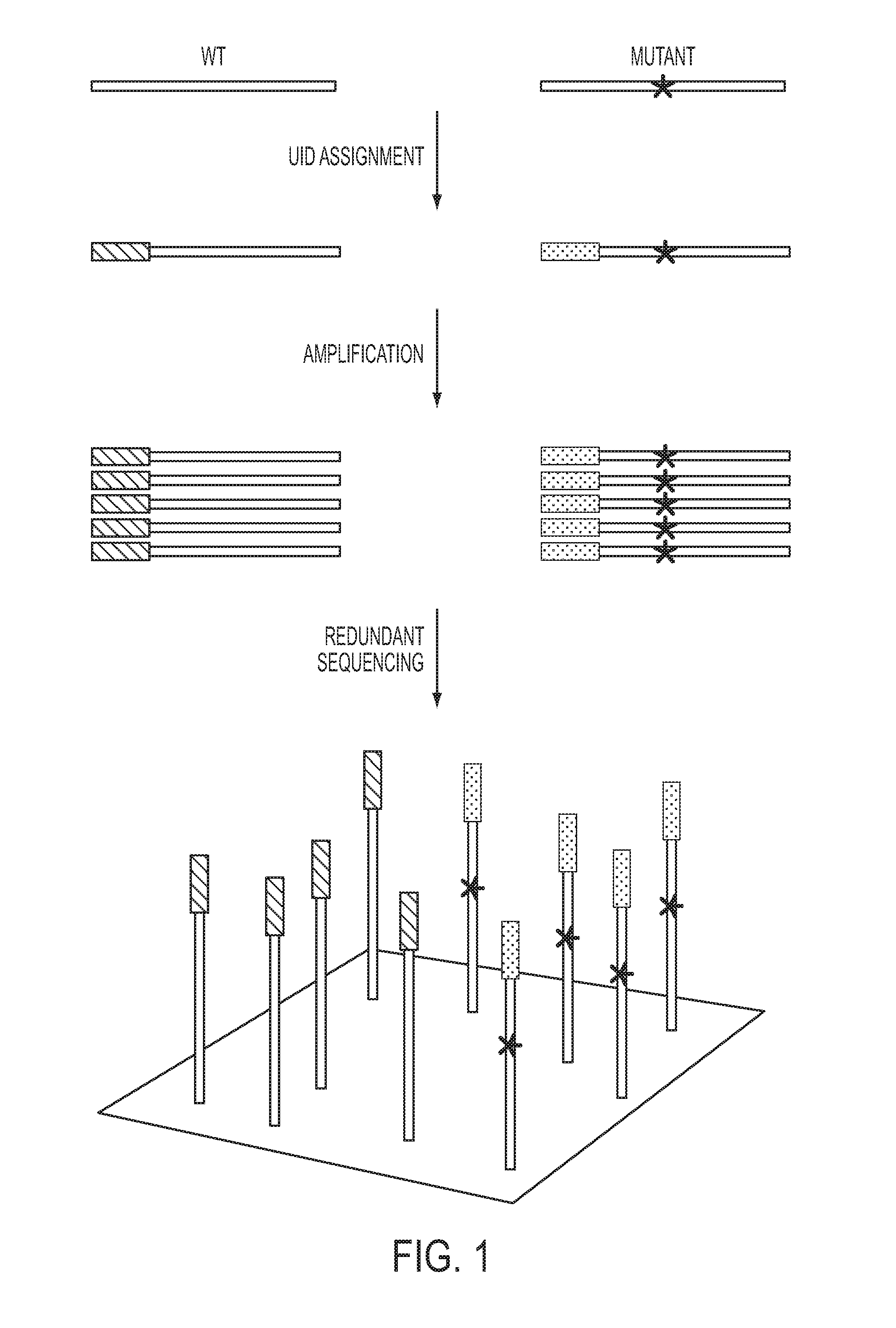
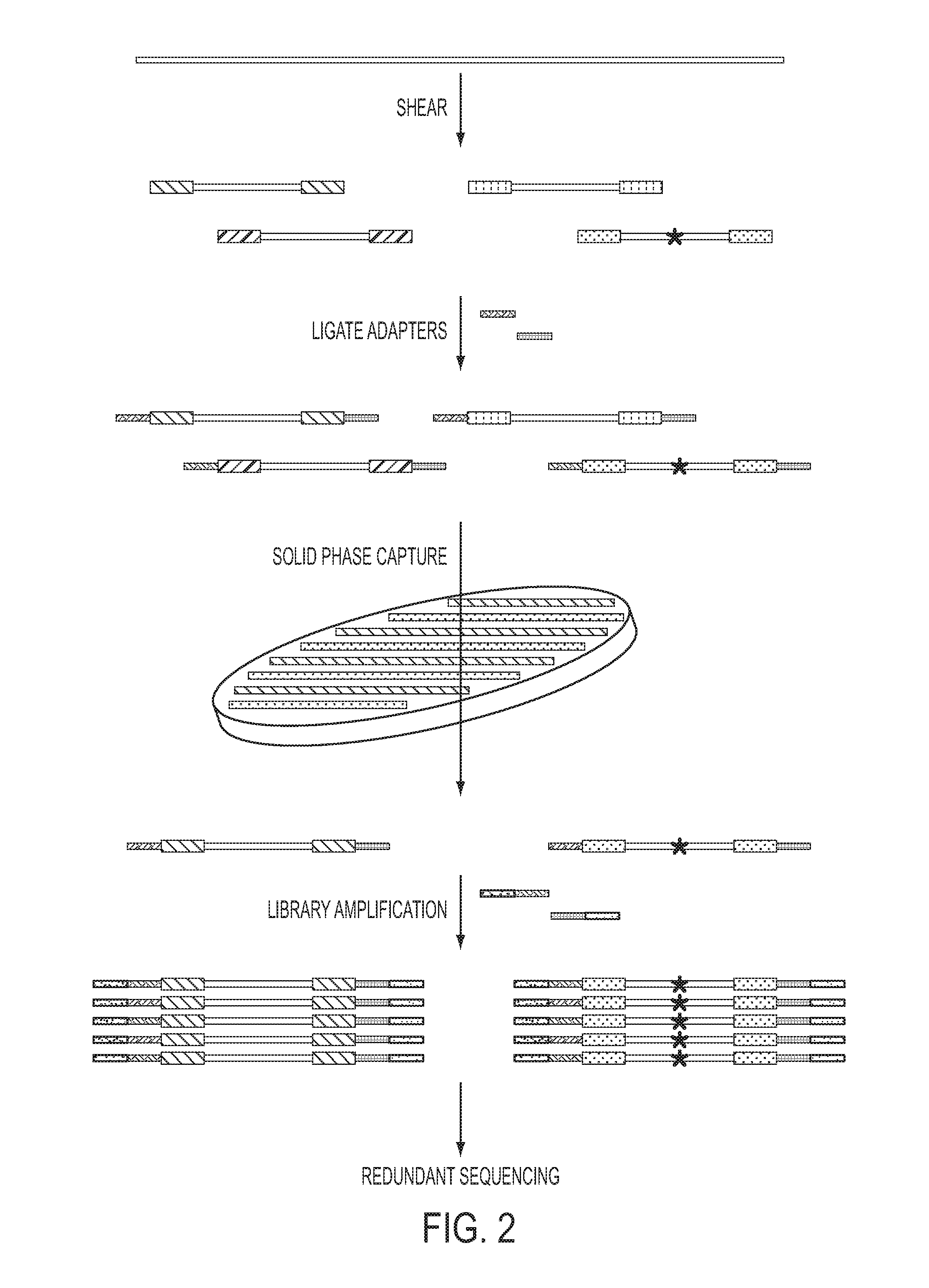
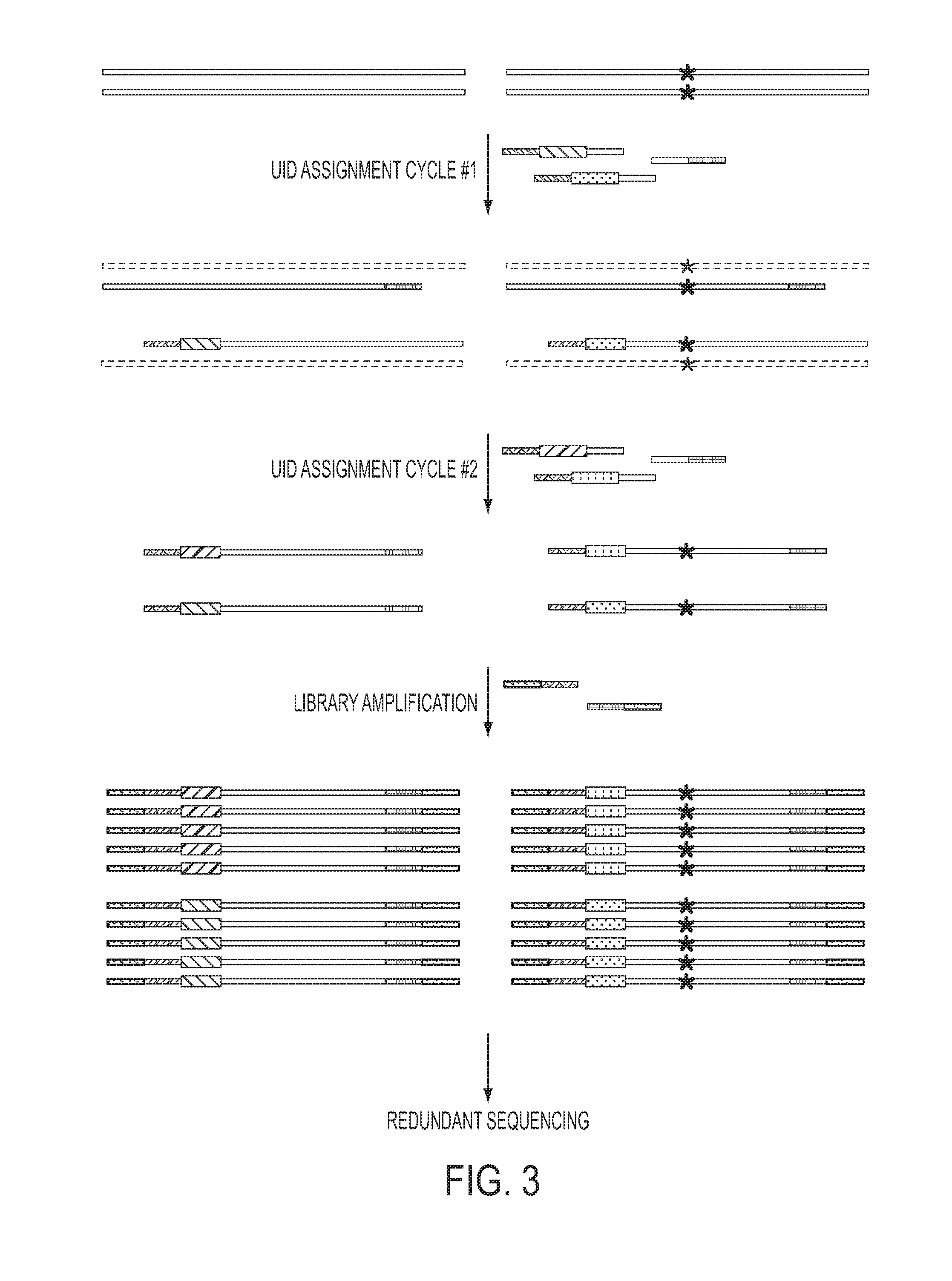
The identification of mutations that are present in a small fraction of DNA templates is essential for progress in several areas of biomedical research. Though massively parallel sequencing instruments are in principle well-suited to this task, the error rates in such instruments are generally too high to allow confident identification of rare variants. We here describe an approach that can substantially increase the sensitivity of massively parallel sequencing instruments for this purpose. One example of this approach, called “Safe-SeqS” for (Safe-Sequencing System) includes (i) assignment of a unique identifier (UID) to each template molecule; (ii) amplification of each uniquely tagged template molecule to create UID-families; and (iii) redundant sequencing of the amplification products. PCR fragments with the same UID are truly mutant (“super-mutants”) if ≧95% of them contain the identical mutation. We illustrate the utility of this approach for determining the fidelity of a polymerase, the accuracy of oligonucleotides synthesized in vitro, and the prevalence of mutations in the nuclear and mitochondrial genomes of normal cells.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
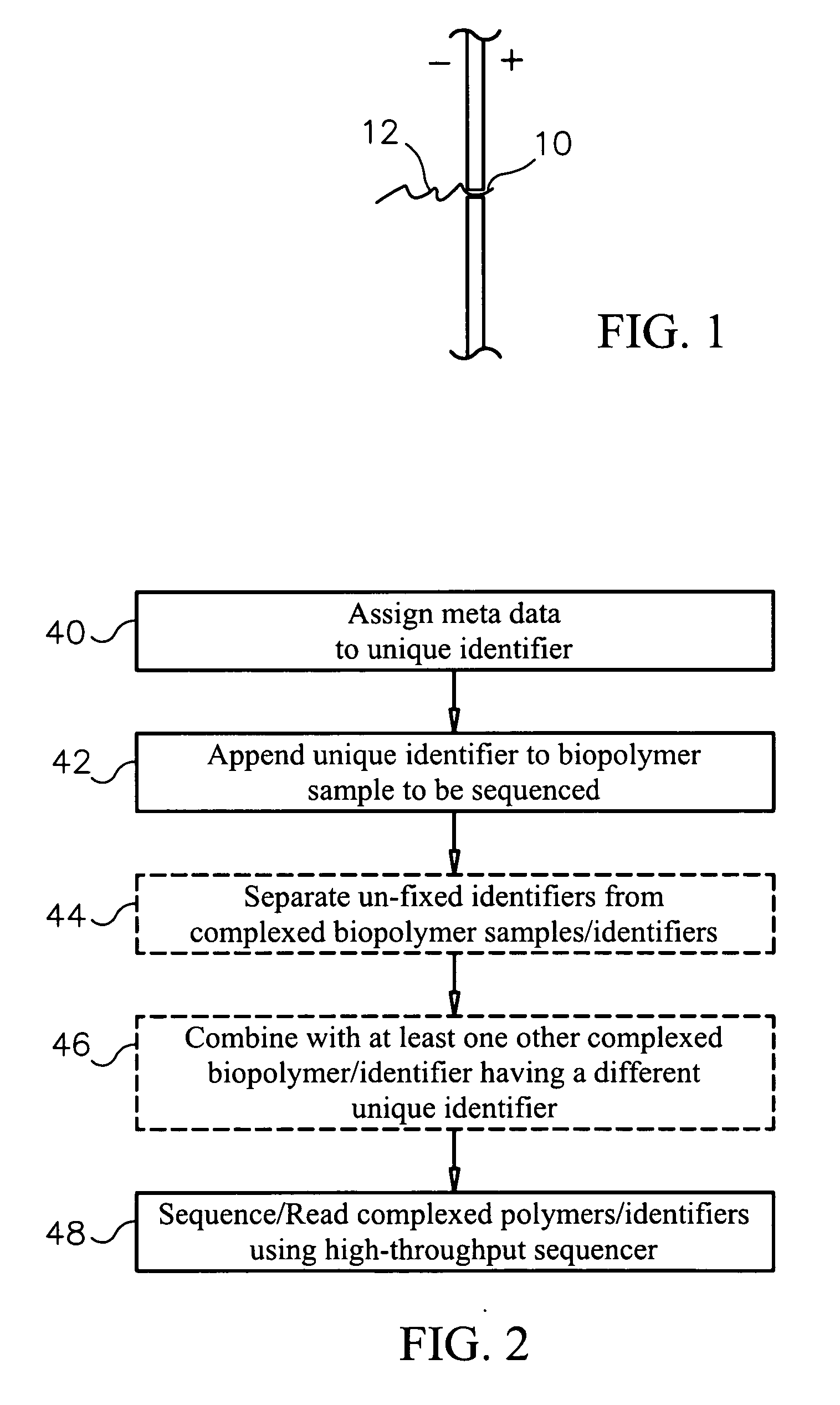
Unique identifiers for indicating properties associated with entities to which they are attached, and methods for using
InactiveUS20060263789A1Efficiently sequencingMicrobiological testing/measurementBiological testingBiopolymerUnique identifier
Methods, systems and computer readable media for sequencing a biopolymer specimen and tracking a source from which the specimen was derived. Methods, systems and computer readable media for multiplex sequencing biopolymer samples. Methods, systems and computer readable media for efficiently sequencing biopolymeric specimens through a high-throughput sequencer. Methods, systems and computer readable media for performing ratio-based analysis with a high throughput sequencer.
Owner:AGILENT TECH INC
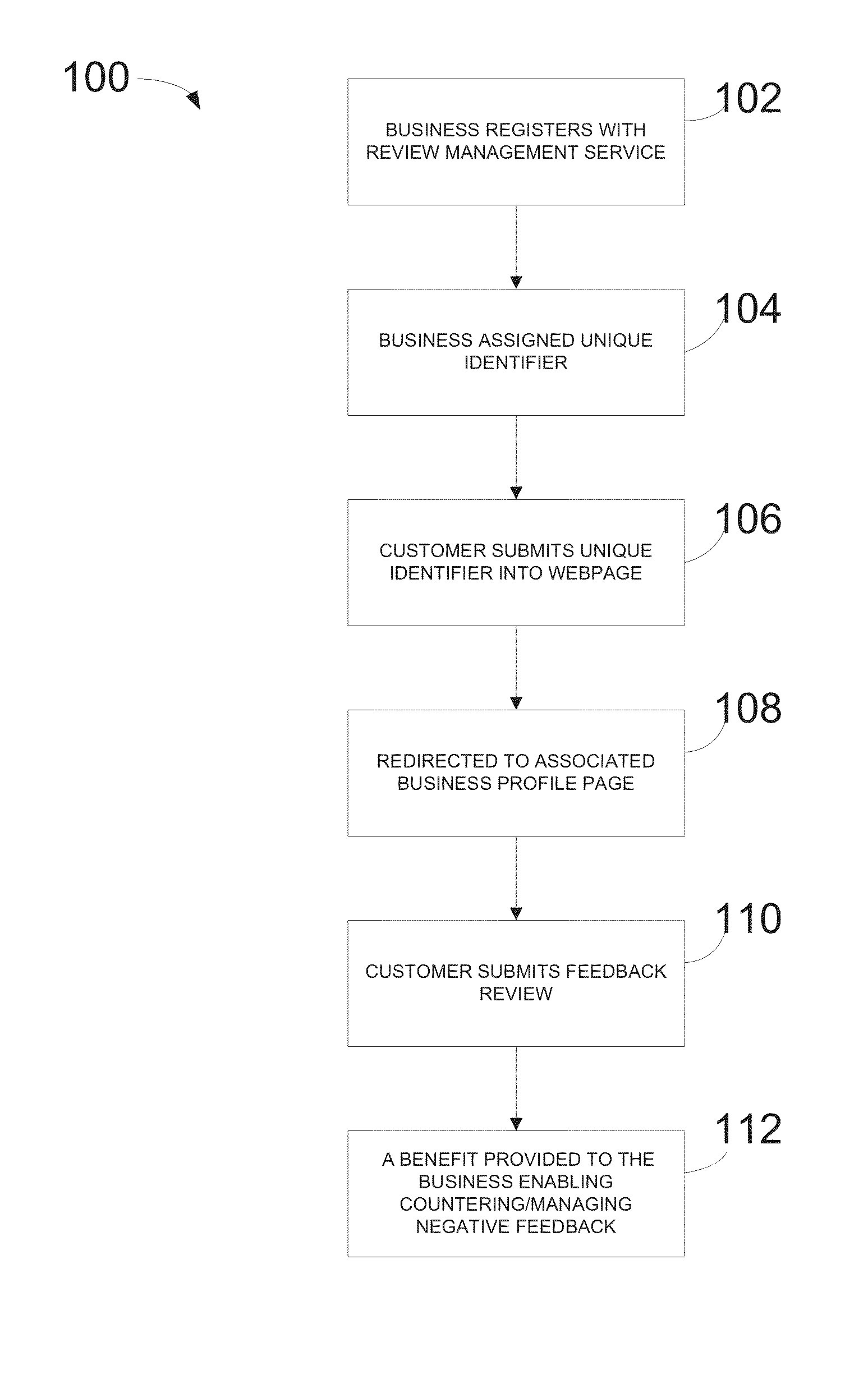
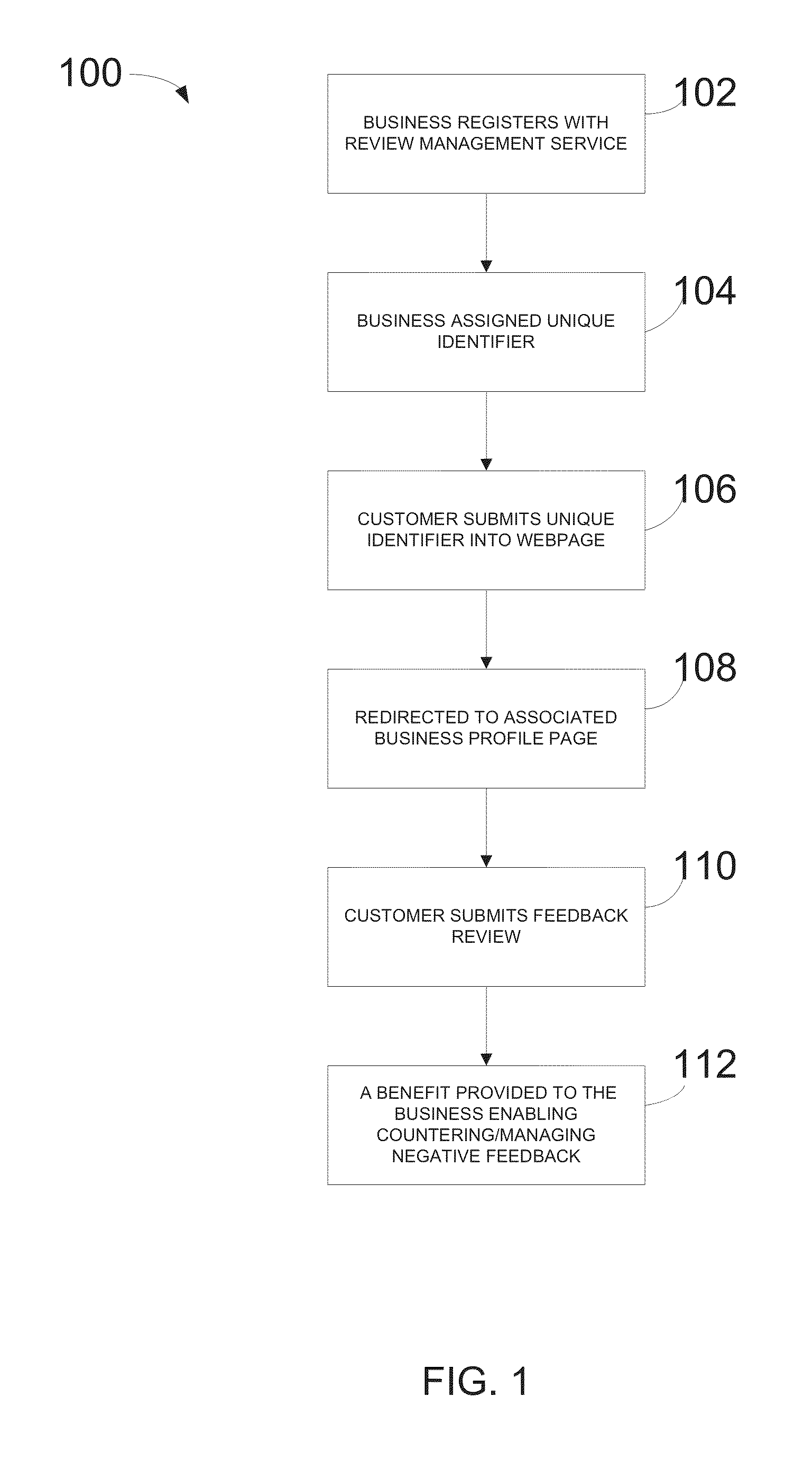
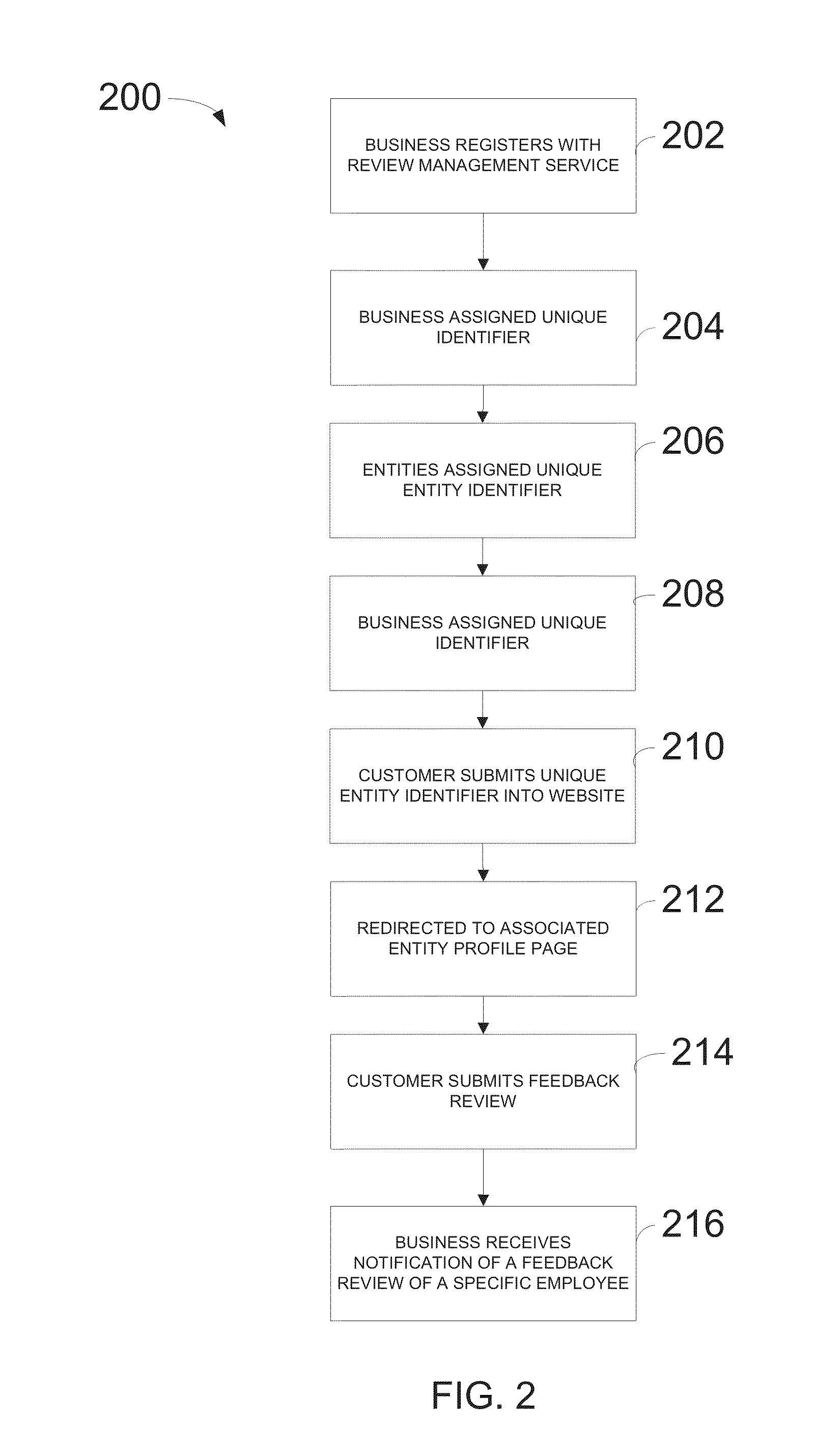
Method and system for managing business feedback online
A method and system for a business to manage negative feedback reviews submitted on a public review webpage by a customer. The method includes registering with a review management service, assigning a unique identifier and a profile page to the business, encouraging a customer to submit a review of the business using the unique identifier, and providing, to the business, information from the review management service which enables the business to counter or manage negative reviews. Thereby, a business can be notified when a negative feedback review is submitted by a customer prior to the negative feedback review being submitted to a public review webpage. The method also includes enabling businesses to receive notification of feedback for individual employees to take appropriate corrective action. Further, the business can provide customers with rewards as an incentive or encouragement to complete reviews with the goal of obtaining positive reviews from satisfied customers.
Owner:BERLIN JASON
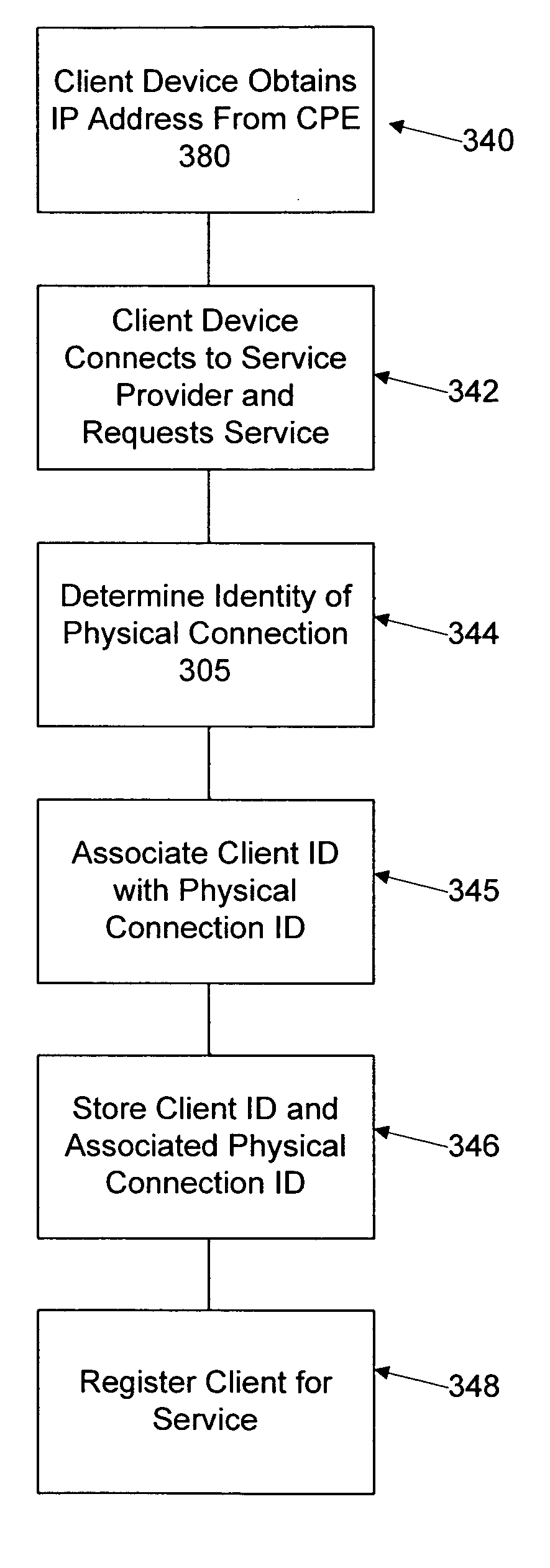
Methods and apparatus and data structures for providing access to an edge router of a network
Aggregating physical connections from customers for presentation to an access router and de-aggregating traffic from a shared link(s) from the access router. Ports of an aggregation unit may be configured such that each has a unique identifier in the place of information (e.g., the layer 2 address) originally in the layer 2 header. The layer 2 (e.g., MAC) address of the customer device connected with the port can be associated with, and therefore determined from, the IP address of the attached device. When a packet is received from a customer, information in the layer 2 header is changed to a unique identifier assigned to a logical port or interface associated with the physical port. When a packet is received from the access router, it is placed on the port assigned to the logical port associated with the destination layer 2 address (or associated with other bits of the unique bit string and at least some of those bits are replaced with the destination layer 2 address of the device associated with the port.
Owner:VERIZON PATENT & LICENSING INC
Method and system for granting access to personal information
InactiveUS20070130101A1Modified easily and seamlesslyOvercome disadvantagesDigital data processing detailsSpecial data processing applicationsWeb siteThird party
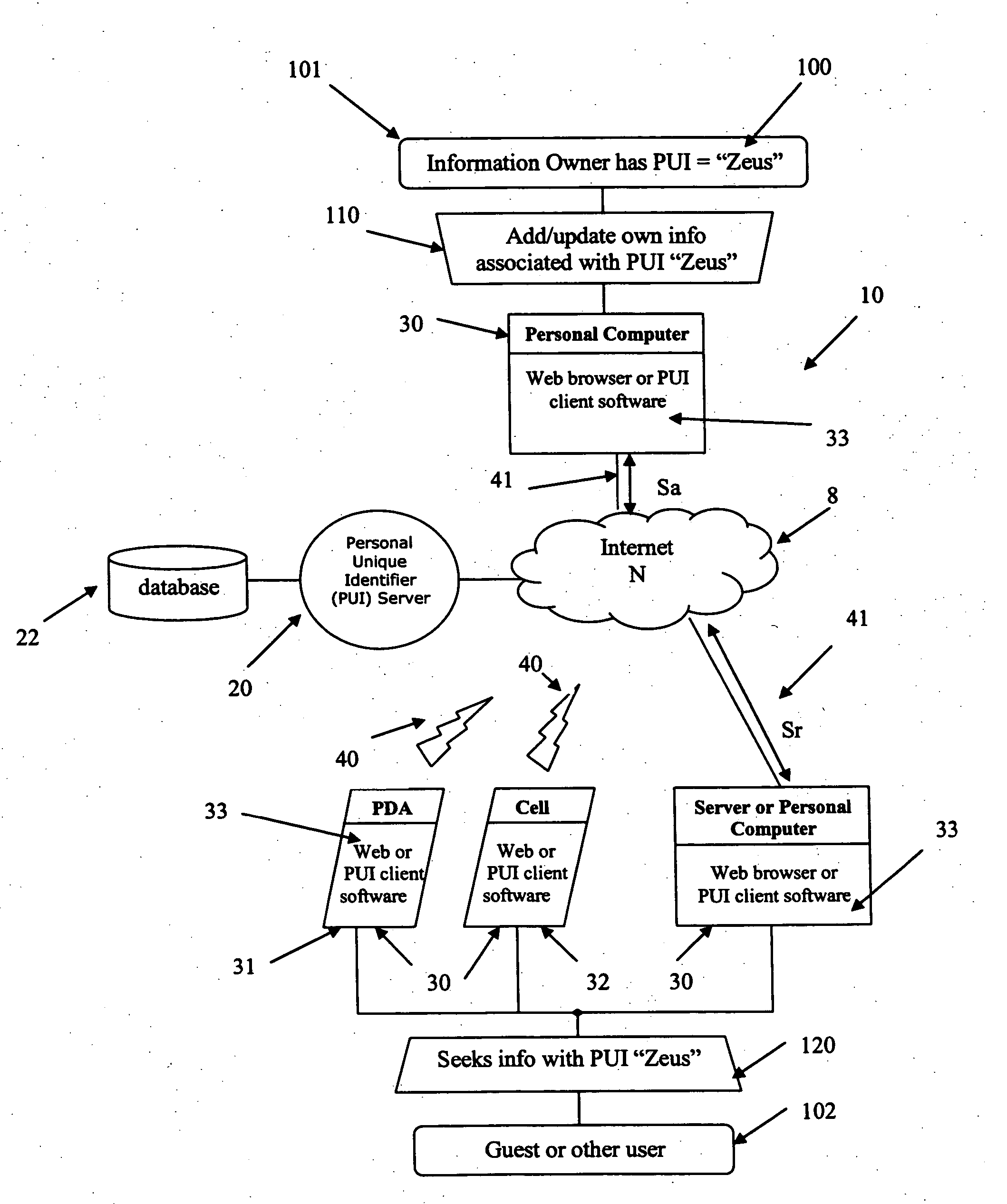
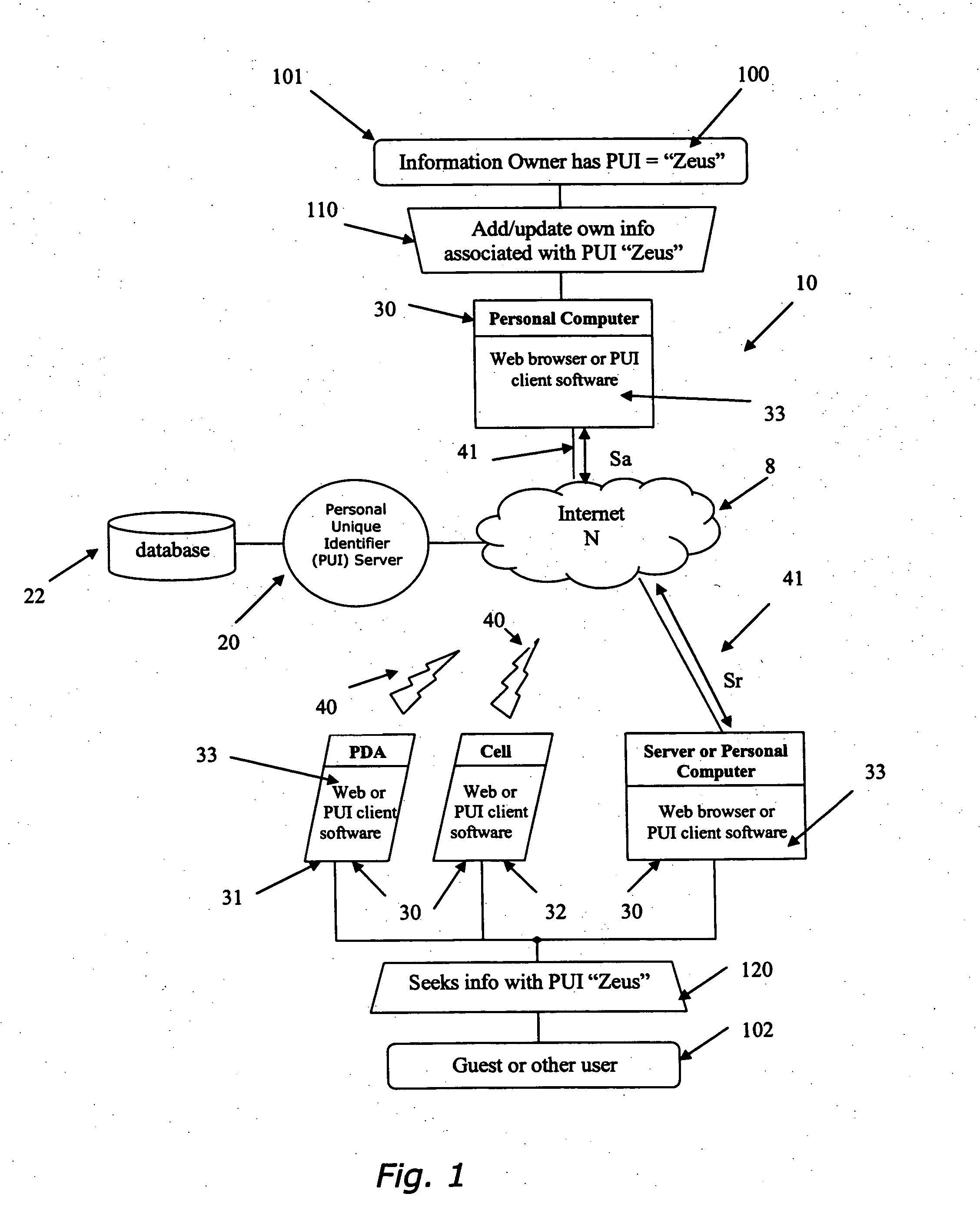
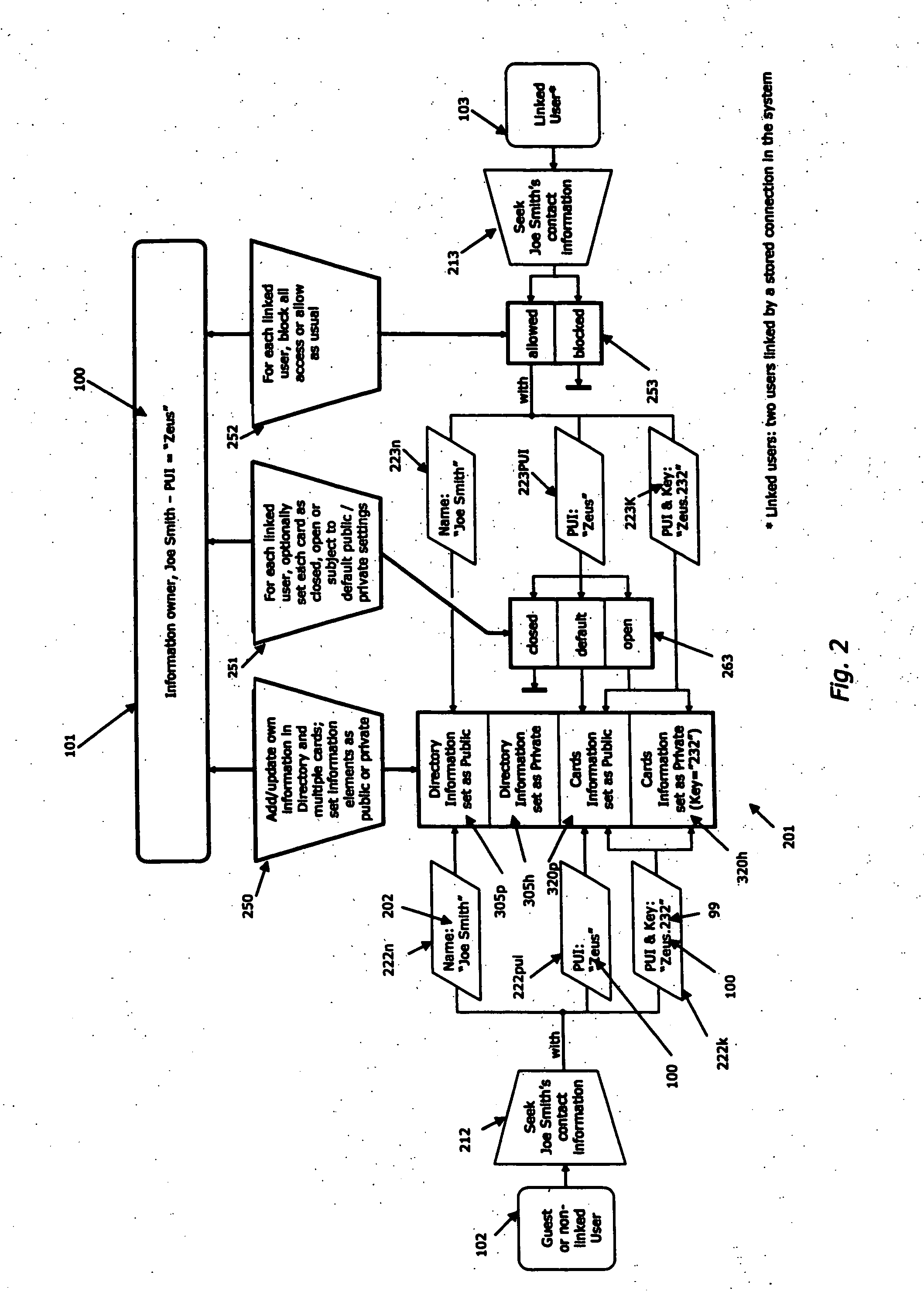
A system and method to permit users to have personal unique identifiers associated with personal information stored on a database accessed by an identity server is disclosed. The identity server is connected to one or more networks including the Internet. Users can distribute the personal unique identifier to third parties who can then obtain the personal information by accessing the server through the network. The users may modify the information stored in the database, which can then assist third parties in obtaining the modified information by inputting the personal unique identifier, or permitting client software to do so automatically on their behalf, in turn making updates to that information for the third party. This can be done over a large period of time such that third parties can easily access personal information of the user even if that information changes. The third parties may also be organizations or corporations with extensive customer lists that wish to update their client contact information with minimum interference to the customers and at minimal costs to the organization. Furthermore, users can use the personal unique identifier to populate electronic forms, such as web forms, provided on web sites hosted by organization or corporation, for the convenience of the organization or corporation and the use. The personal information of the user may also be organized in different cards having a variety of reveal and hidden status levels permitting access to additional information if a key, comprising an alphanumeric code, is entered together with the unique identifier.
Owner:ANDERSON TERRY PAUL +1
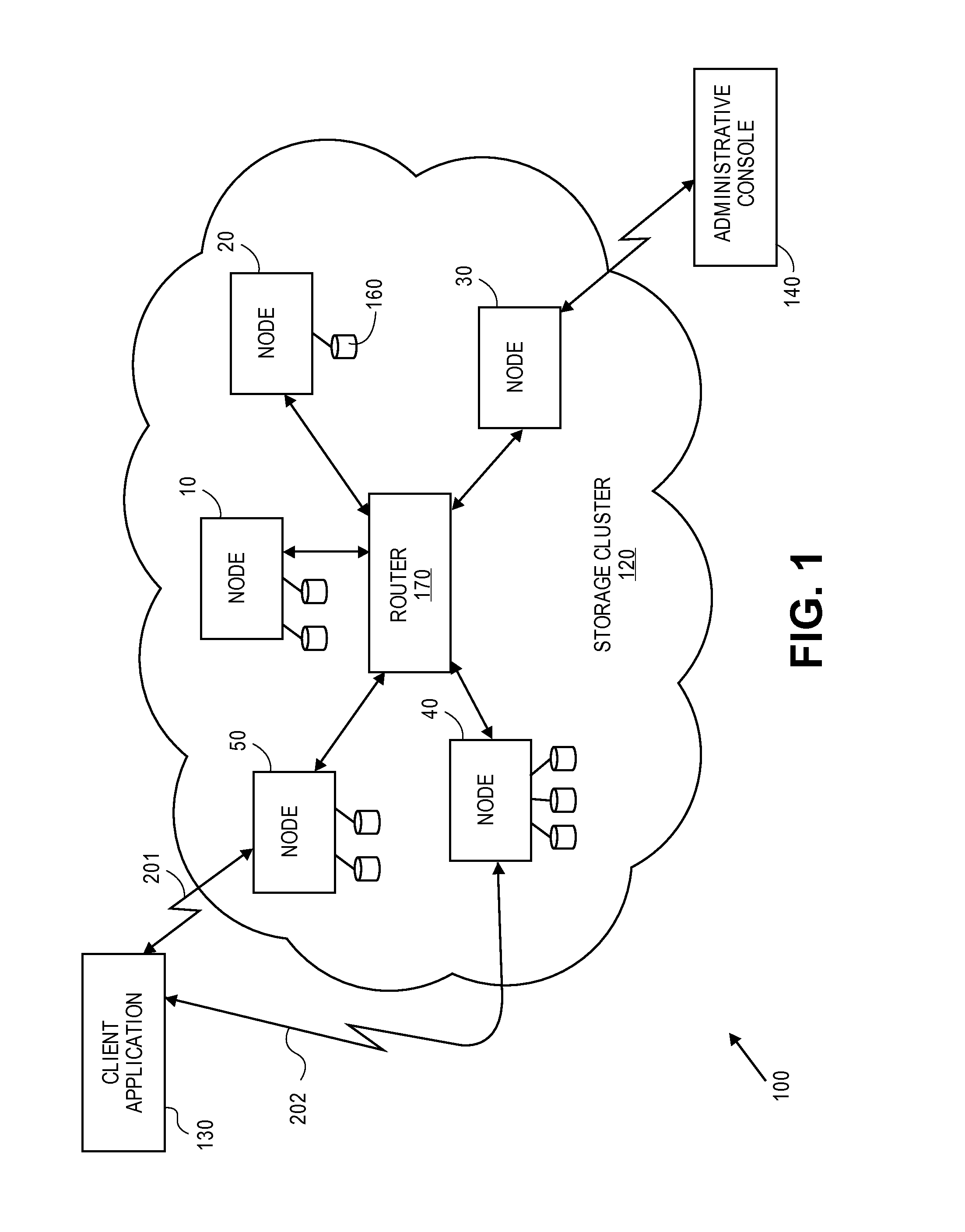
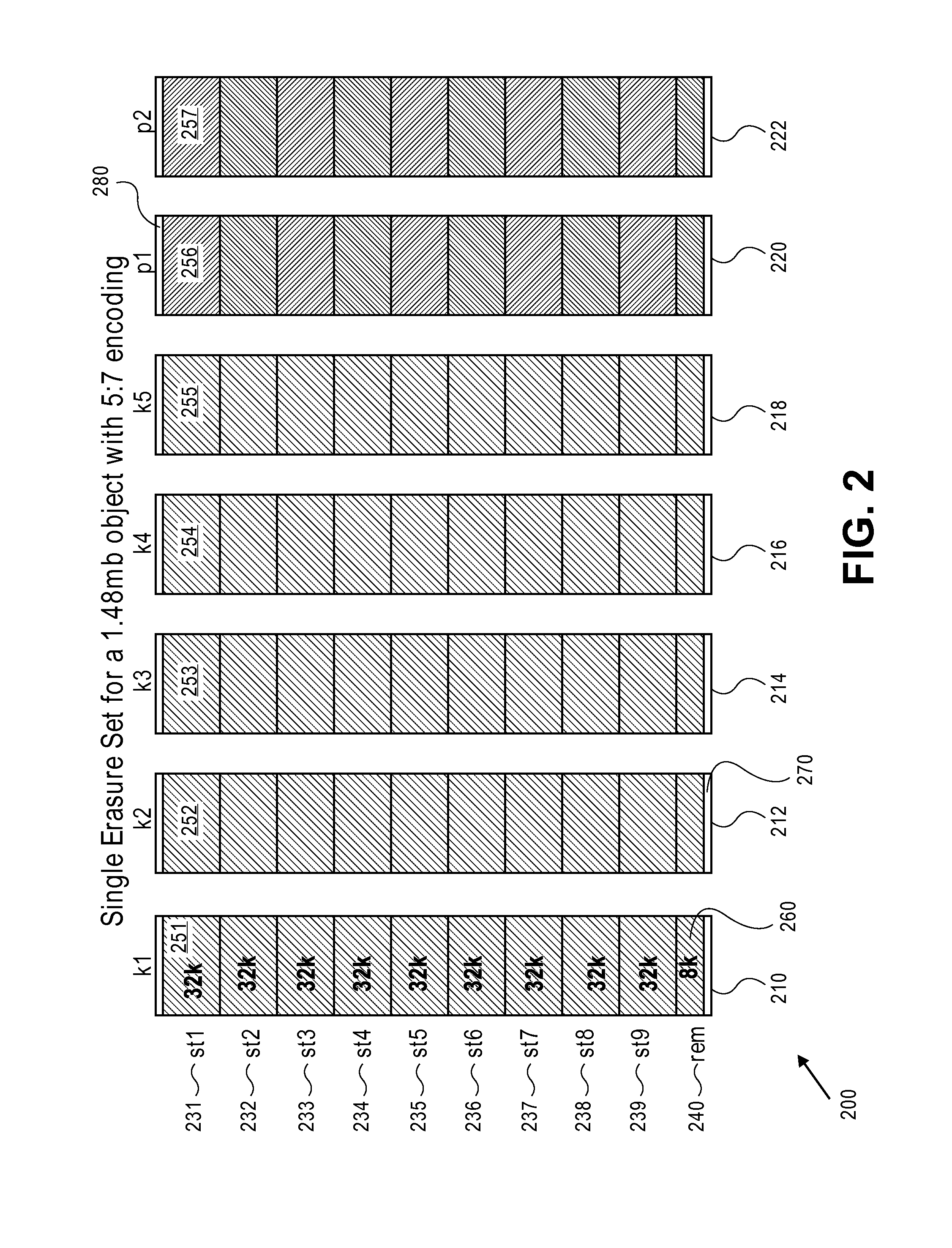
Erasure coding and replication in storage clusters
ActiveUS20130339818A1Error correction/detection using block single space codingCode conversionUnique identifierOperating system
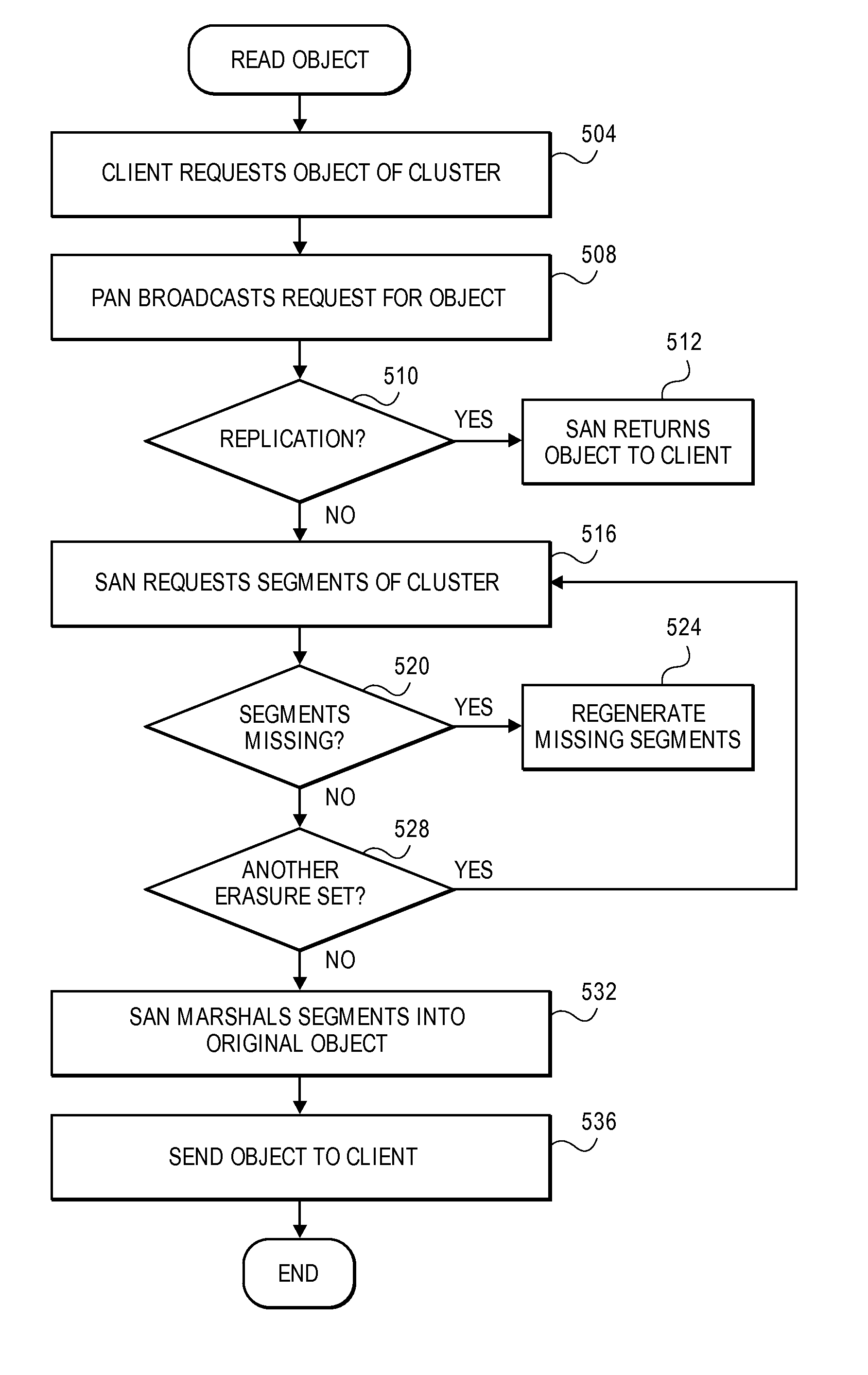
A cluster receives a request to store an object using replication or erasure coding. The cluster writes the object using erasure coding. A manifest is written that includes an indication of erasure coding and a unique identifier for each segment. The cluster returns a unique identifier of the manifest. The cluster receives a request from a client that includes a unique identifier. The cluster determines whether the object has been stored using replication or erasure coding. If using erasure coding, the method reads a manifest. The method identifies segments within the cluster using unique segment identifiers of the manifest. Using these unique segment identifiers, the method reconstructs the object. A persistent storage area of another disk is scanned to find a unique identifier of a failed disk. If using erasure coding, a missing segment previously stored on the disk is identified. The method locates other segments. Missing segments are regenerated.
Owner:DATACORE SOFTWARE
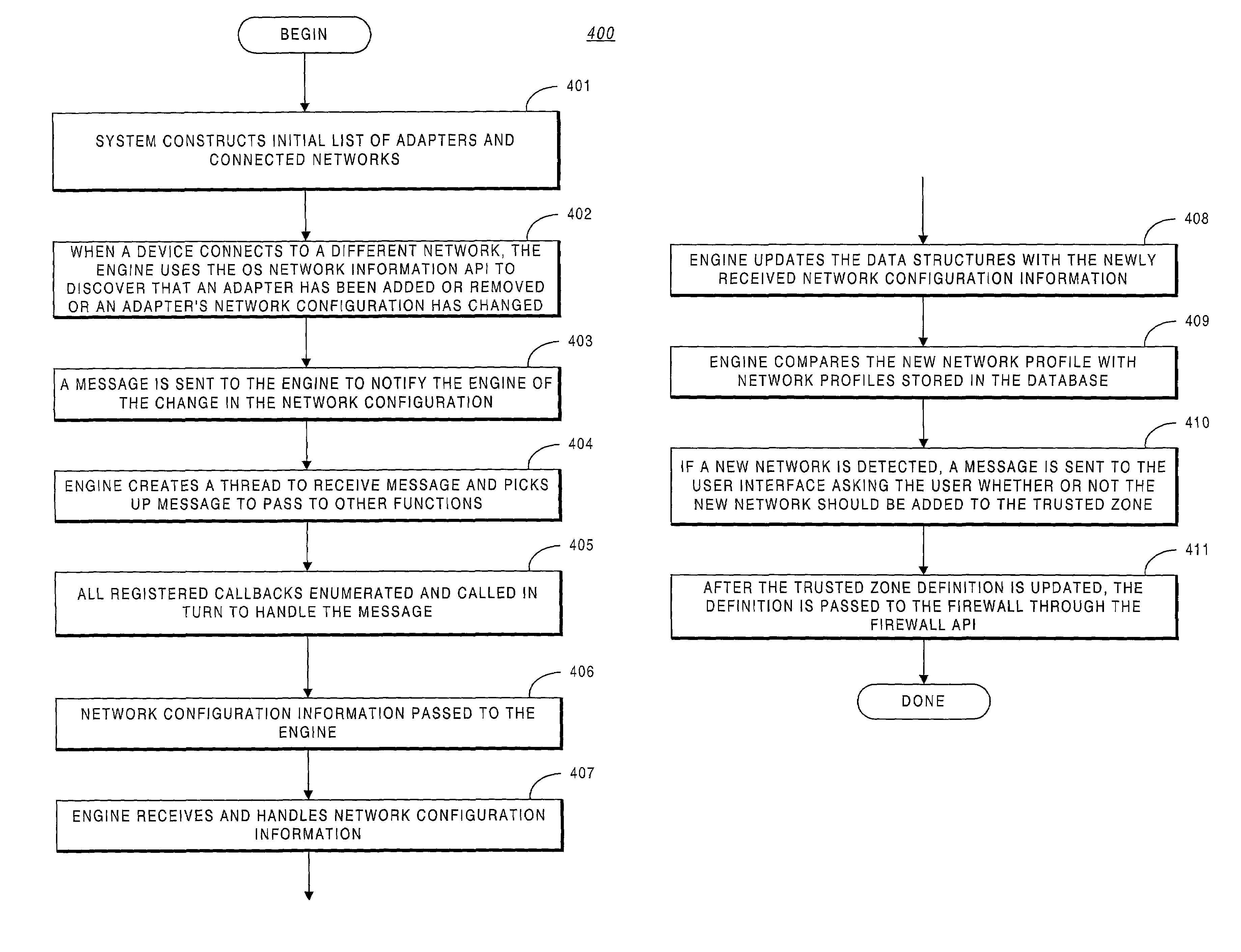
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS7222359B2Easy to detectDigital data processing detailsMultiple digital computer combinationsNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com