Patents
Literature
399 results about "Mail address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
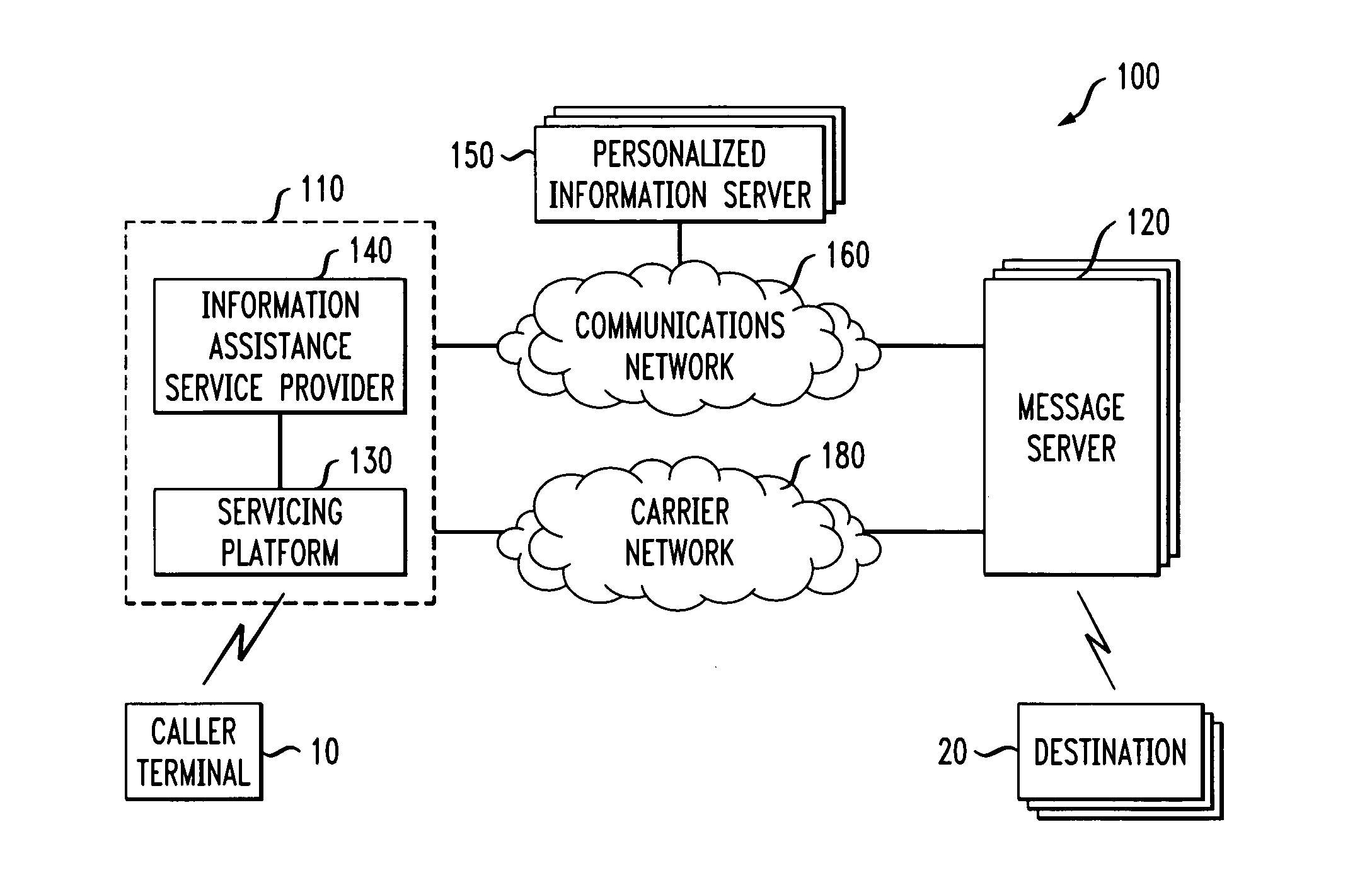
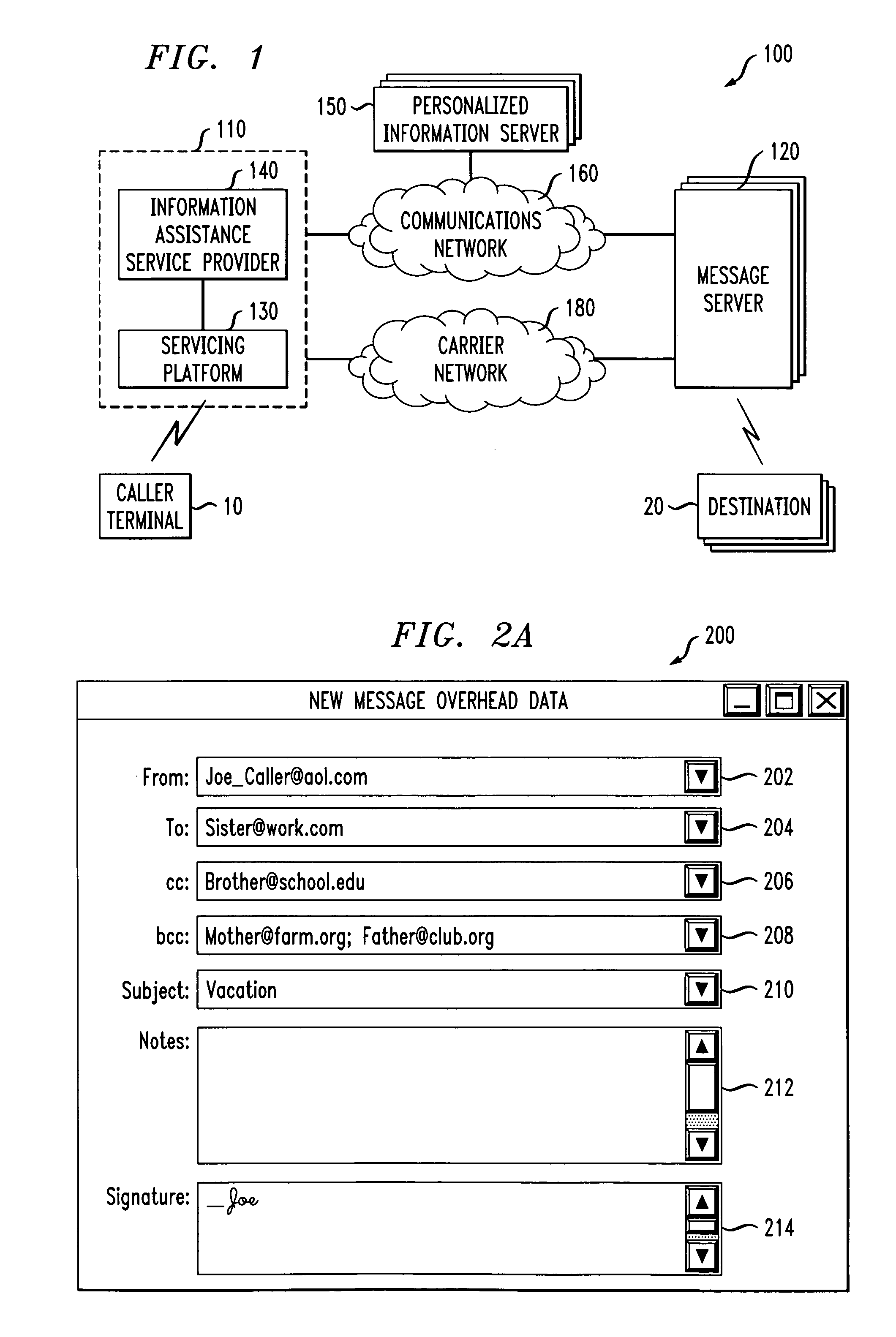
System for timely delivery of personalized aggregations of, including currently-generated, knowledge
InactiveUS20040059705A1Shorten the timeEffectively and efficiently aggregate and delivers personalized informationDigital data processing detailsSpecial data processing applicationsPersonalizationDatasheet
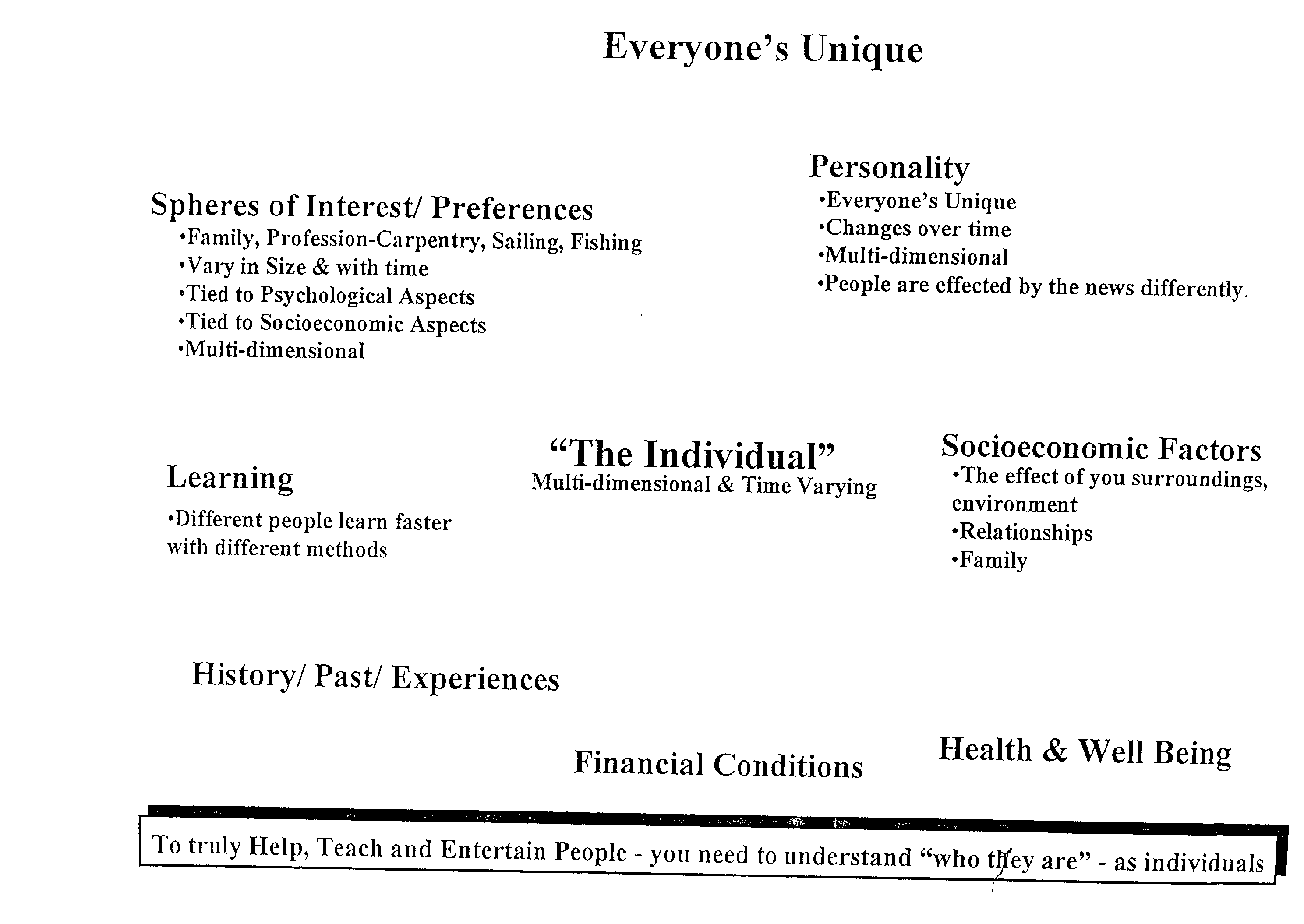
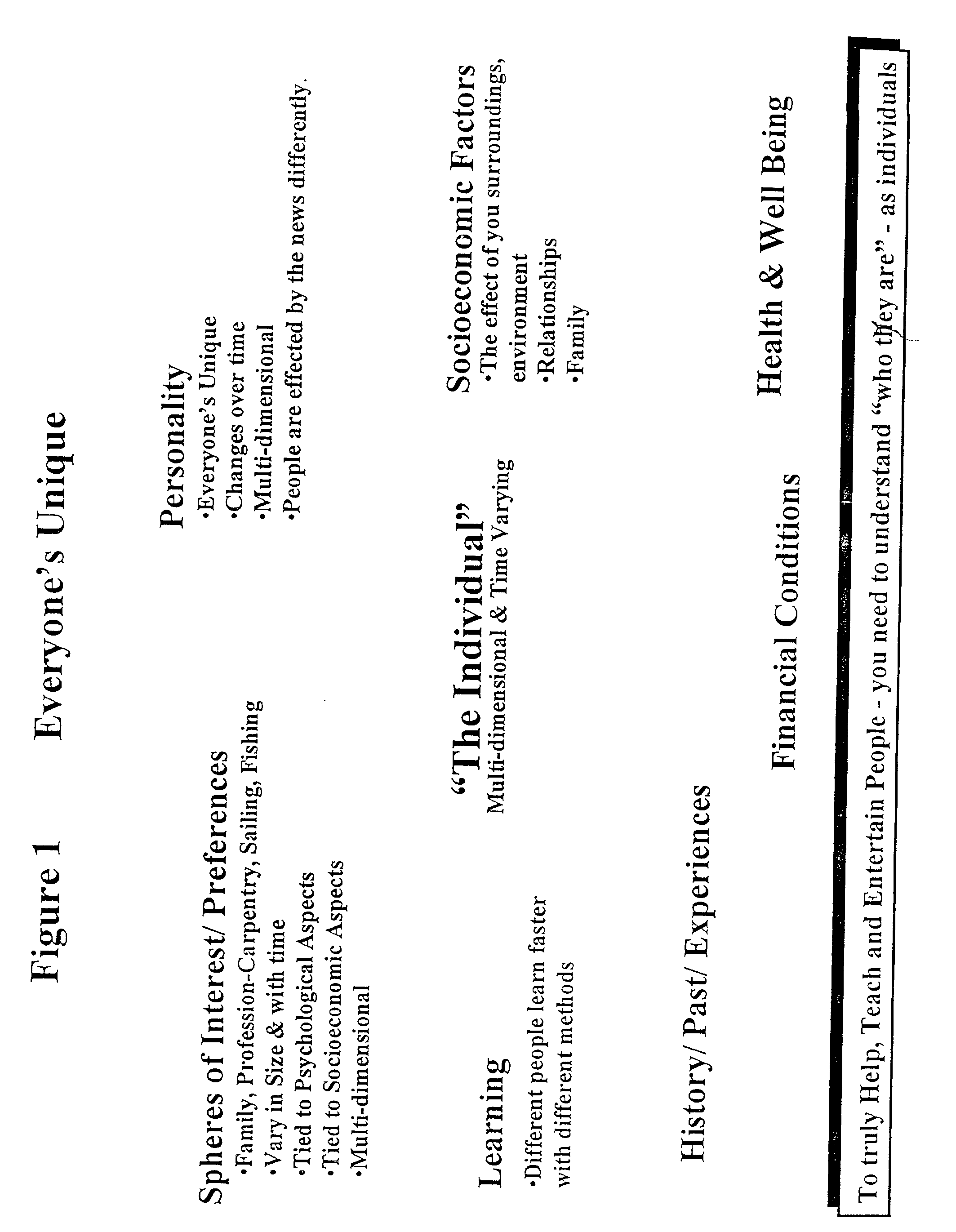
A multidimensional method and apparatus for adaptively characterizing and aggregating data through a secure automated means of database modification, a prioritization and weighting system, a third party enhanced metadata entry and classification mechanism, adaptive and time varying individual personality and preference characterization, and an aggregation and delivery capability which allows for multiple data formats and mediums. Individual characterization incorporates an inference engine which formulates client composite images which vary with time. Asynchronous data interchanges enabled through the use of XML allow for more efficient and effective resource utilization and time. The knowledge system of this invention A) effectively integrates information from diverse sources, B) verifies, adds to or enhances source metadata (product data sheet; article title), and C) searches, queries, retrieves, and aggregates information. Selected product information can be obtained by e-mail without exposure to spamming by using e-mail address translation.
Owner:MINDAGENT
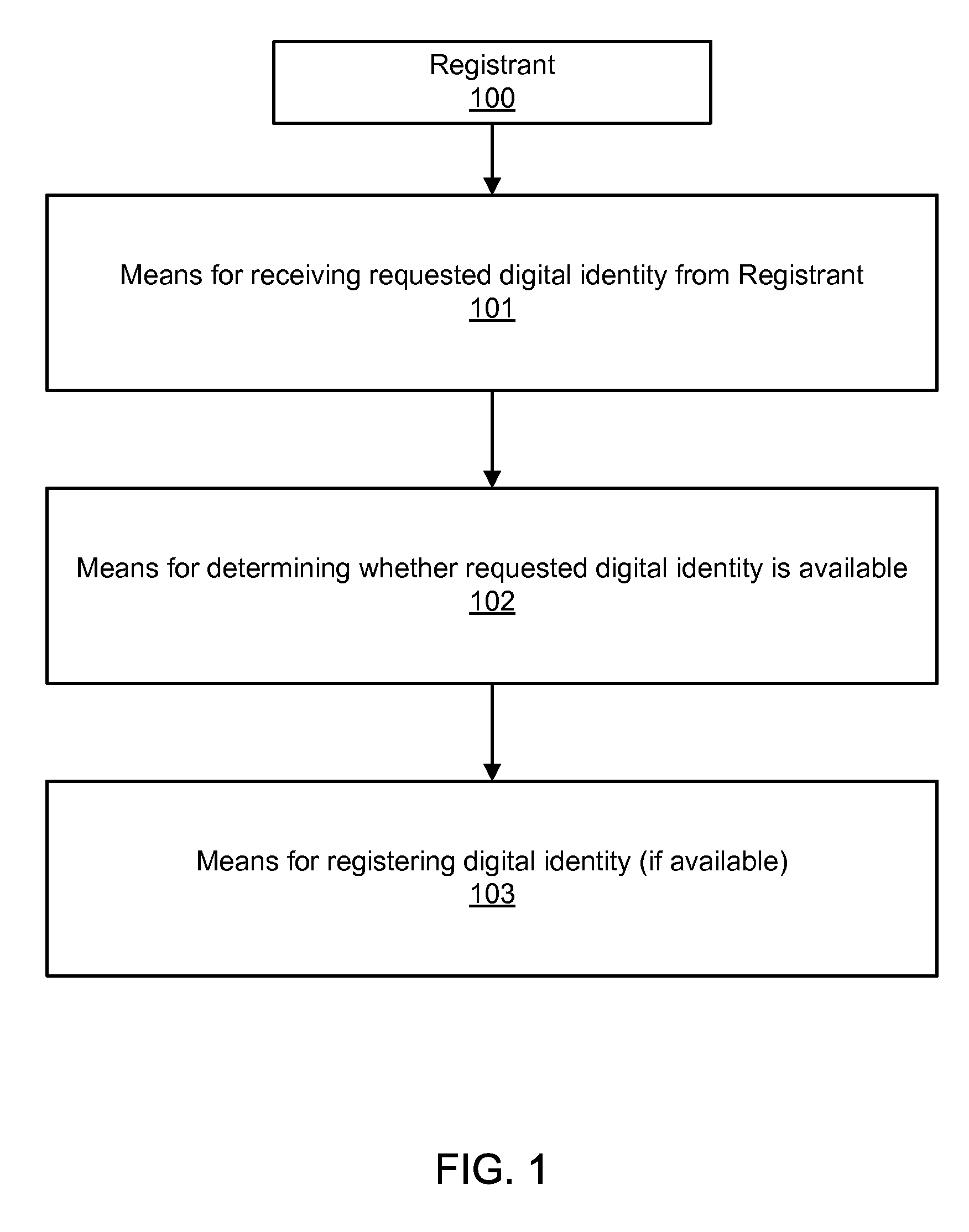
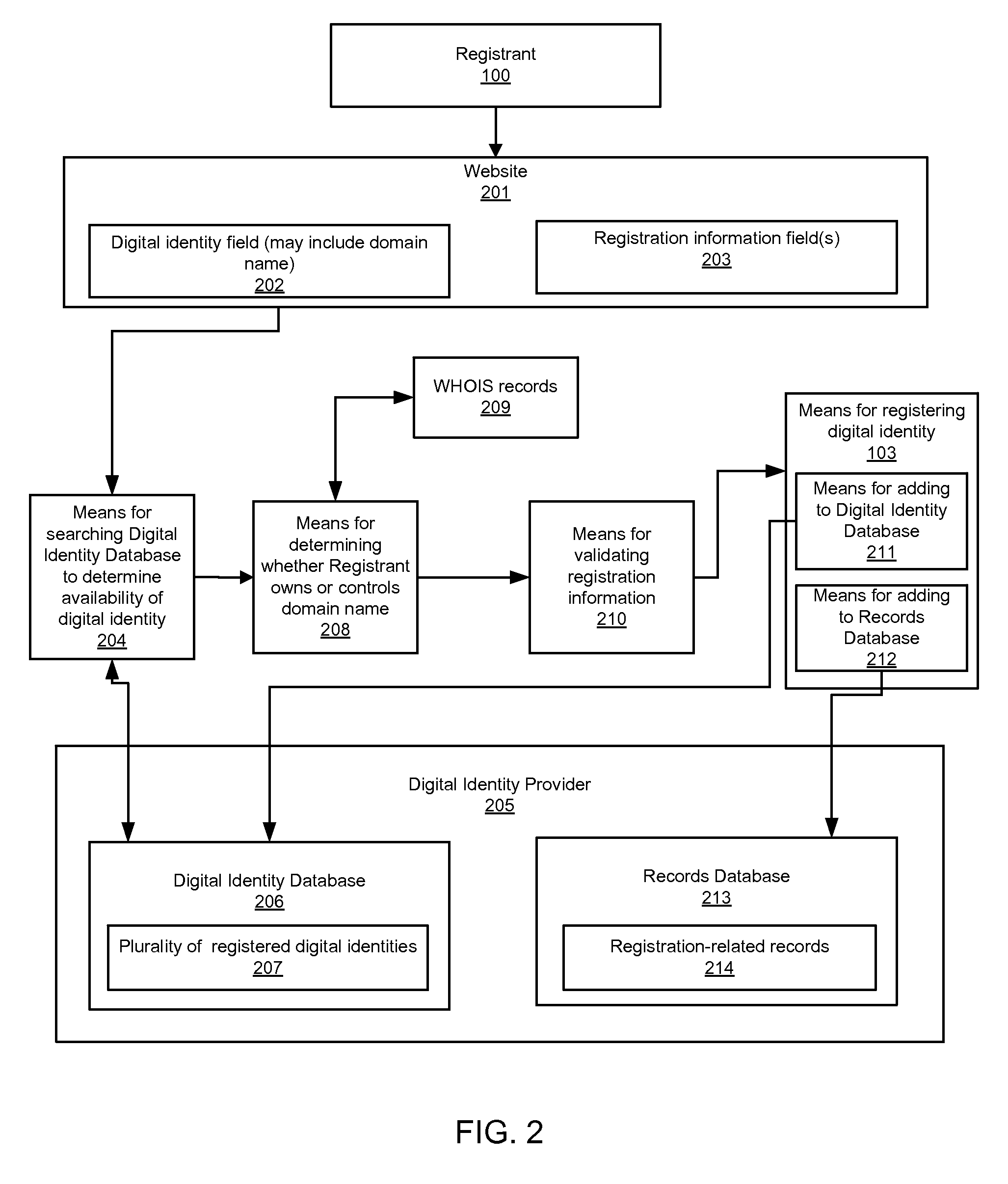
Digital identity validation
ActiveUS20070294431A1Effective registrationMultiple digital computer combinationsData switching networksDigital identityEmail address
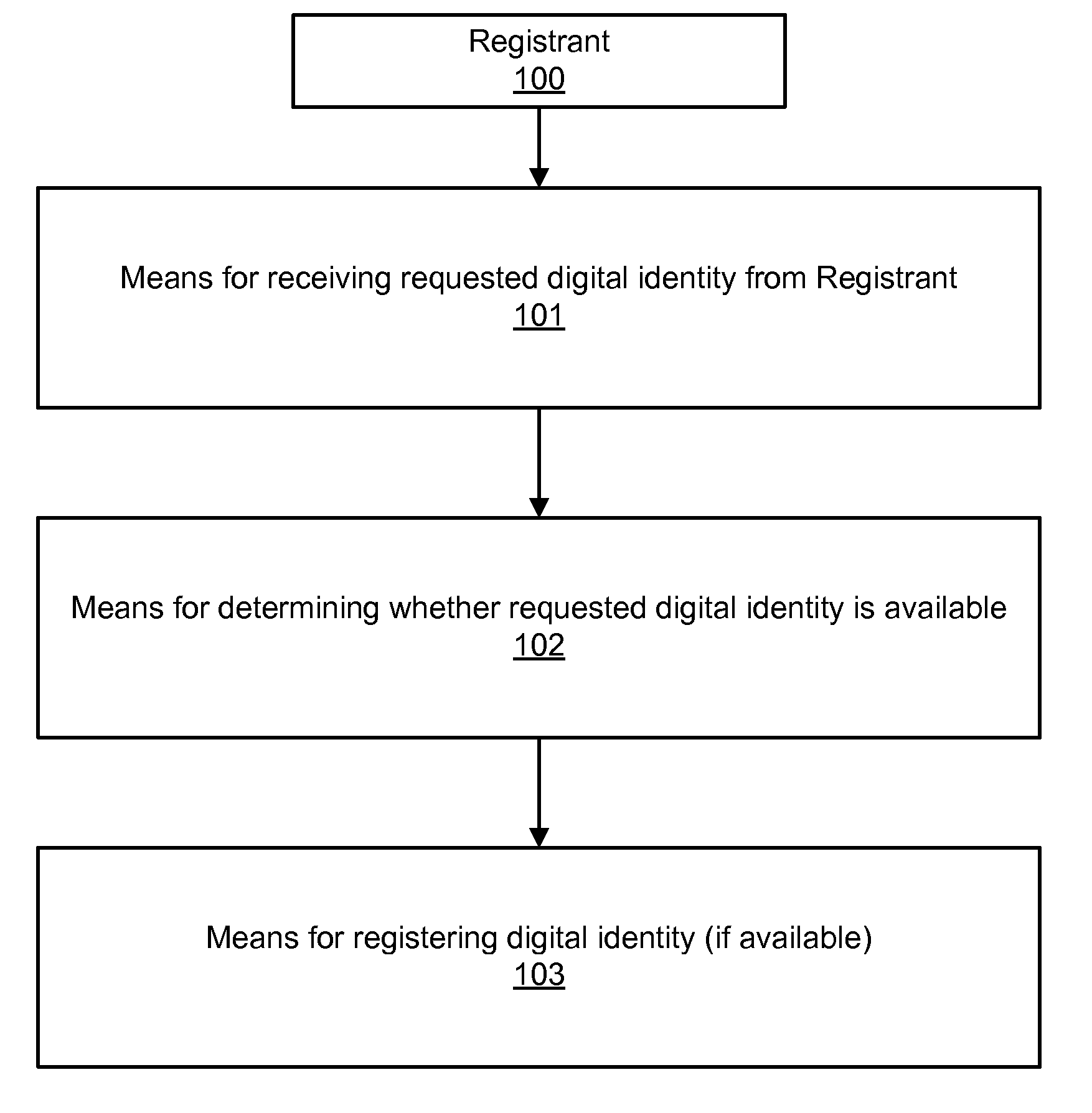
Systems and processes of the present invention allow for digital identity validation. In an example embodiment, a digital identity is registered to a Registrant. During the registration process, one or more registration records are collected from the Registrant and stored in a Records Database. The registration records may include information regarding a digital identity, its Registrant, or another person or entity associated with the digital identity. They may also include name, address, phone number, email address, website, URL, or other information. The information is then verified, possibly by contacting a Registrant, administrative contact, technical contact, or another contact to confirm at least some information in the records. If the information is verified, the Digital Identity Provider may provide the Registrant with a Validation Marker indicating that the digital identity has been validated.
Owner:GO DADDY OPERATING
System and method for identifying alternate contact information
ActiveUS20040133561A1Reducing possible errorSimplify the search processDigital data processing detailsTelephonic communicationEmail addressAutomated database
A method and system for identifying alternate contact information of a specific type; particularly, by providing an inputted Email address in a query, one or more alternate Email addresses can be returned to the query, using an automated database. The system is queried using an entity's known Email address, which, in turn, is associated with other contact information for the entity, such as name and postal address, and the other contact information is then used to identify alternative Email addresses for the targeted entity either at the time of the query or in preparation of the database, and the alternative Email address(es) are then outputted to the requestor from the system. The method uses knowledge of contact points of different types for the same entity to identify alternate contact points of a single type, within a database of contact information.
Owner:ATDATA LLC
Systems and methods for identifying and mitigating information security risks
ActiveUS20120124671A1High level of realismRaise the possibilityDigital data processing detailsAnalogue secracy/subscription systemsUnique identifierPhishing
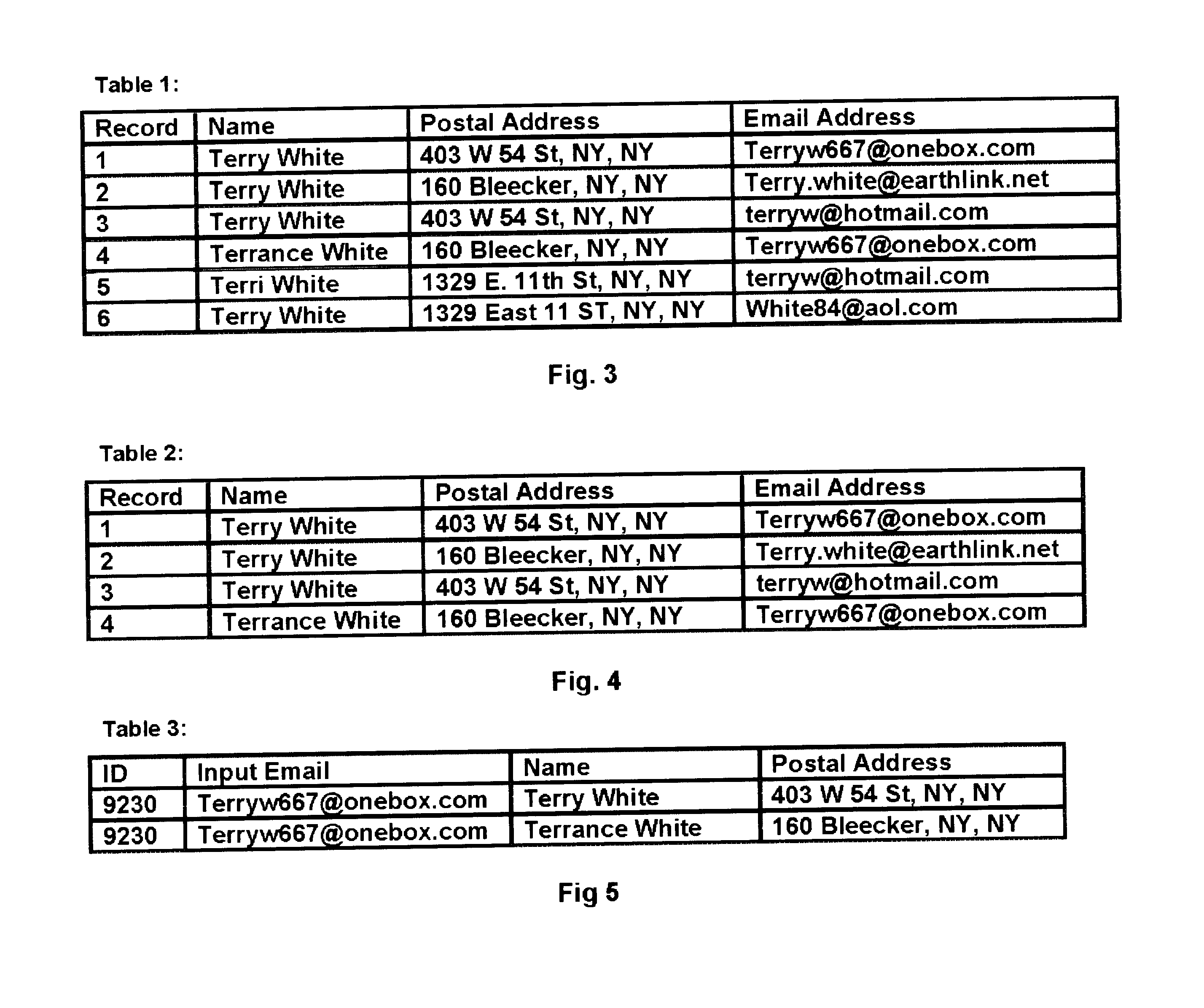
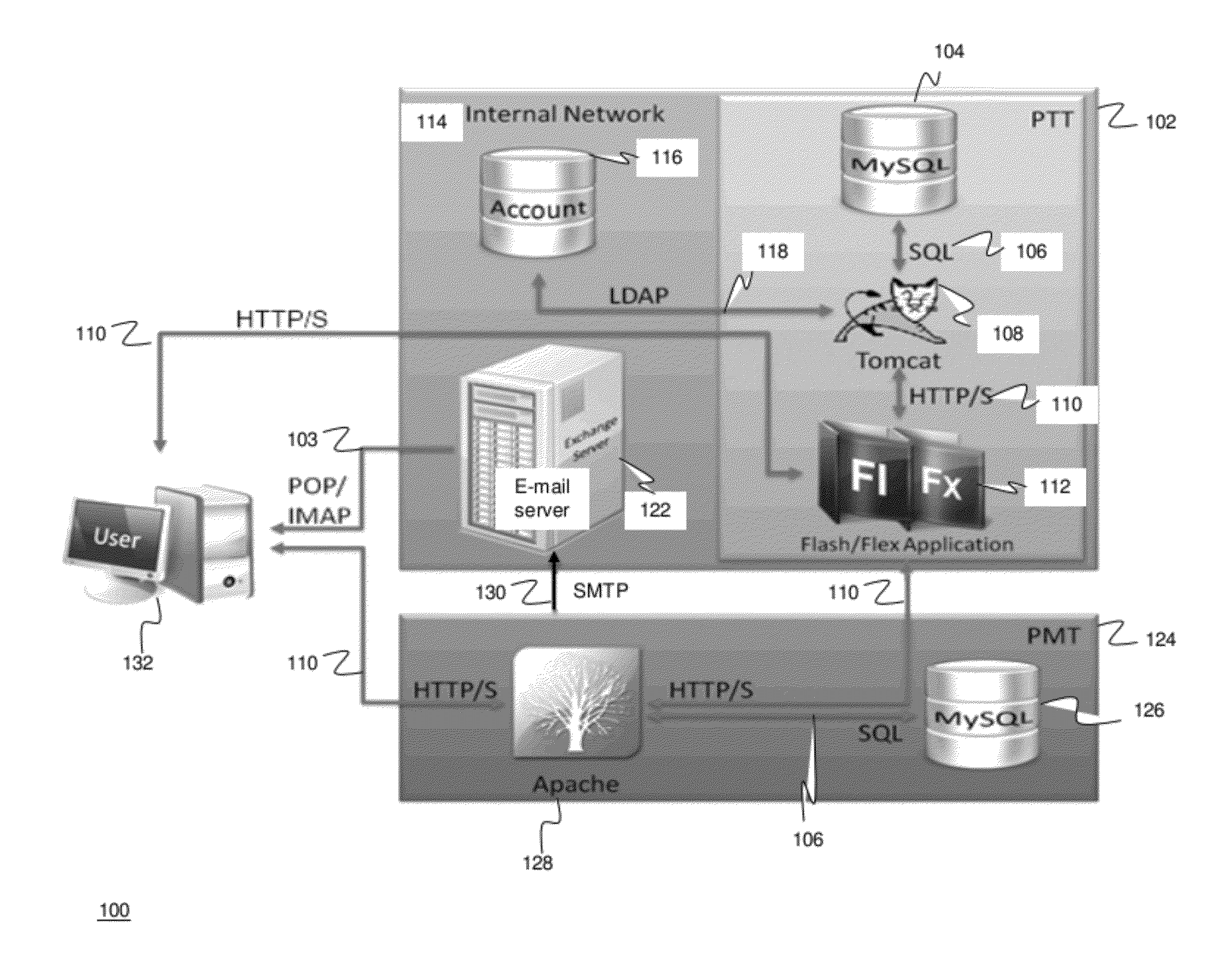
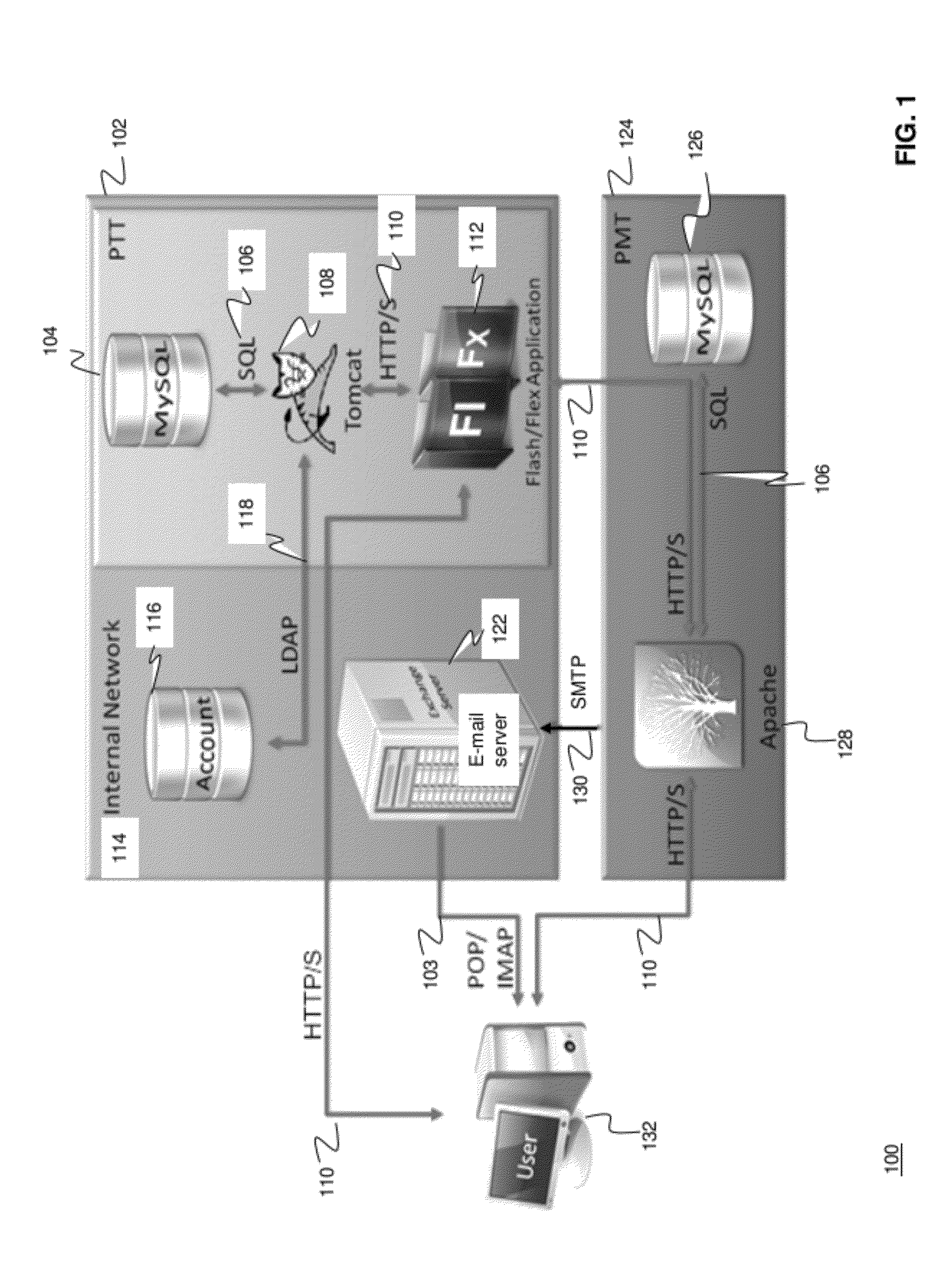
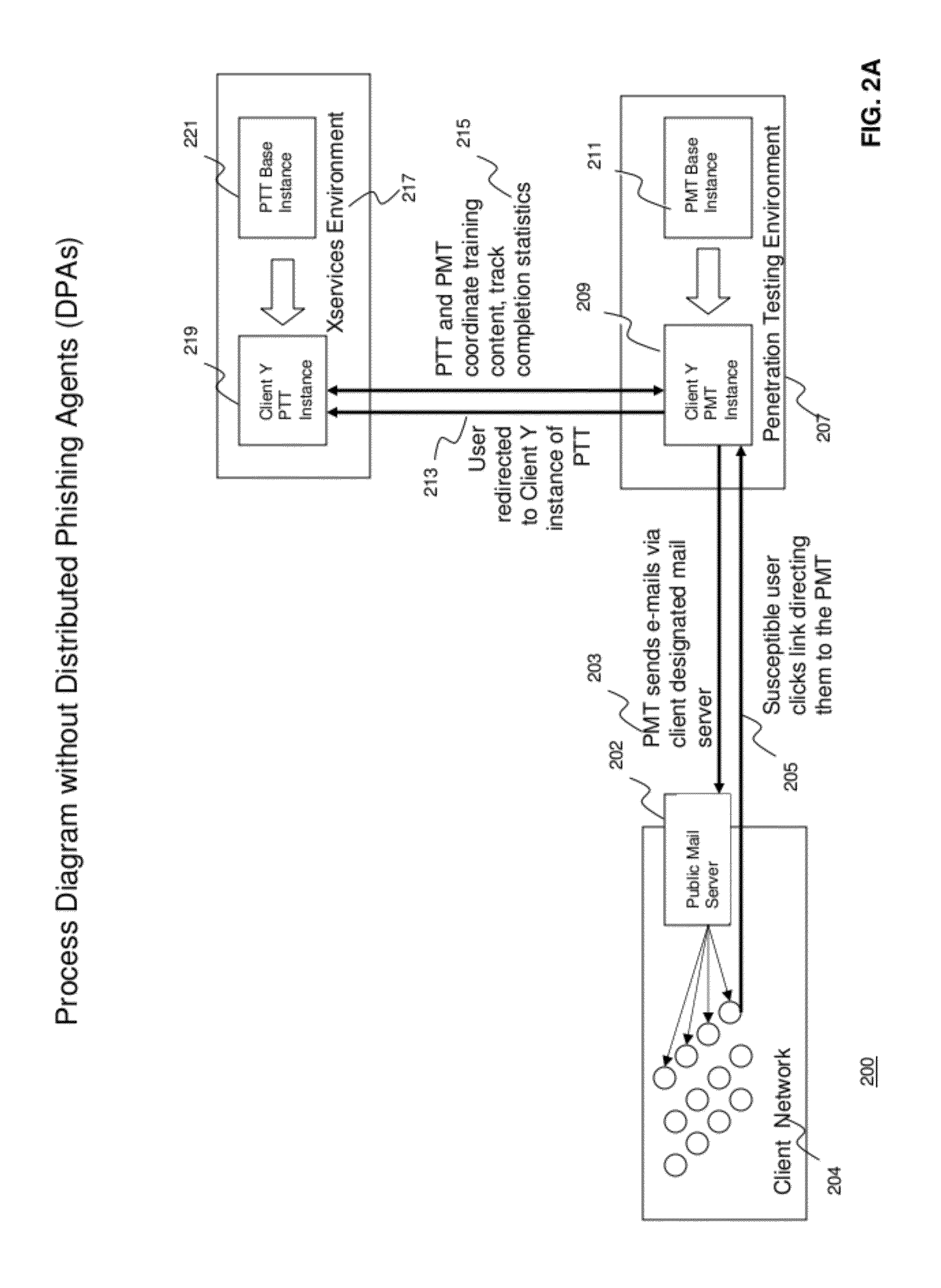
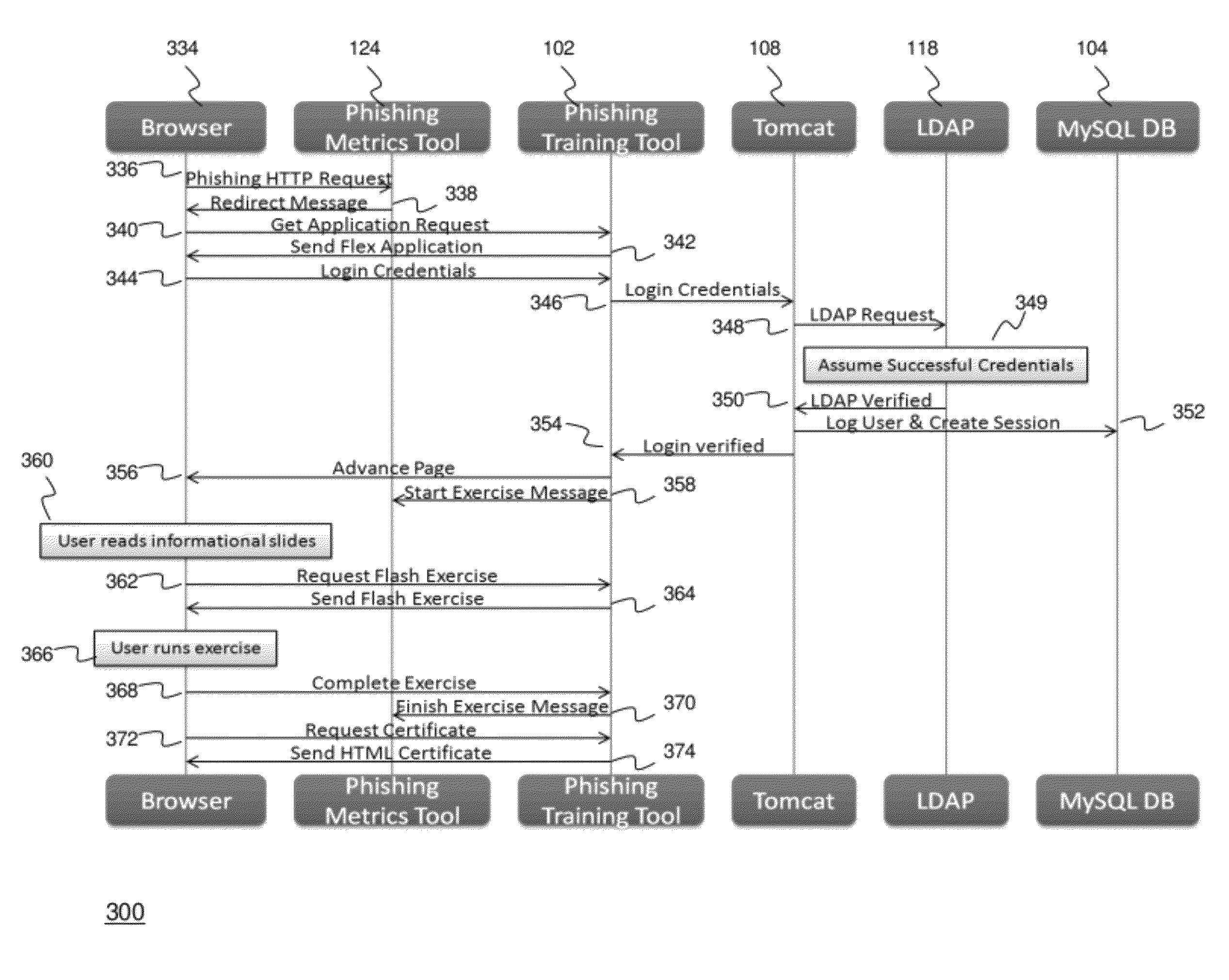
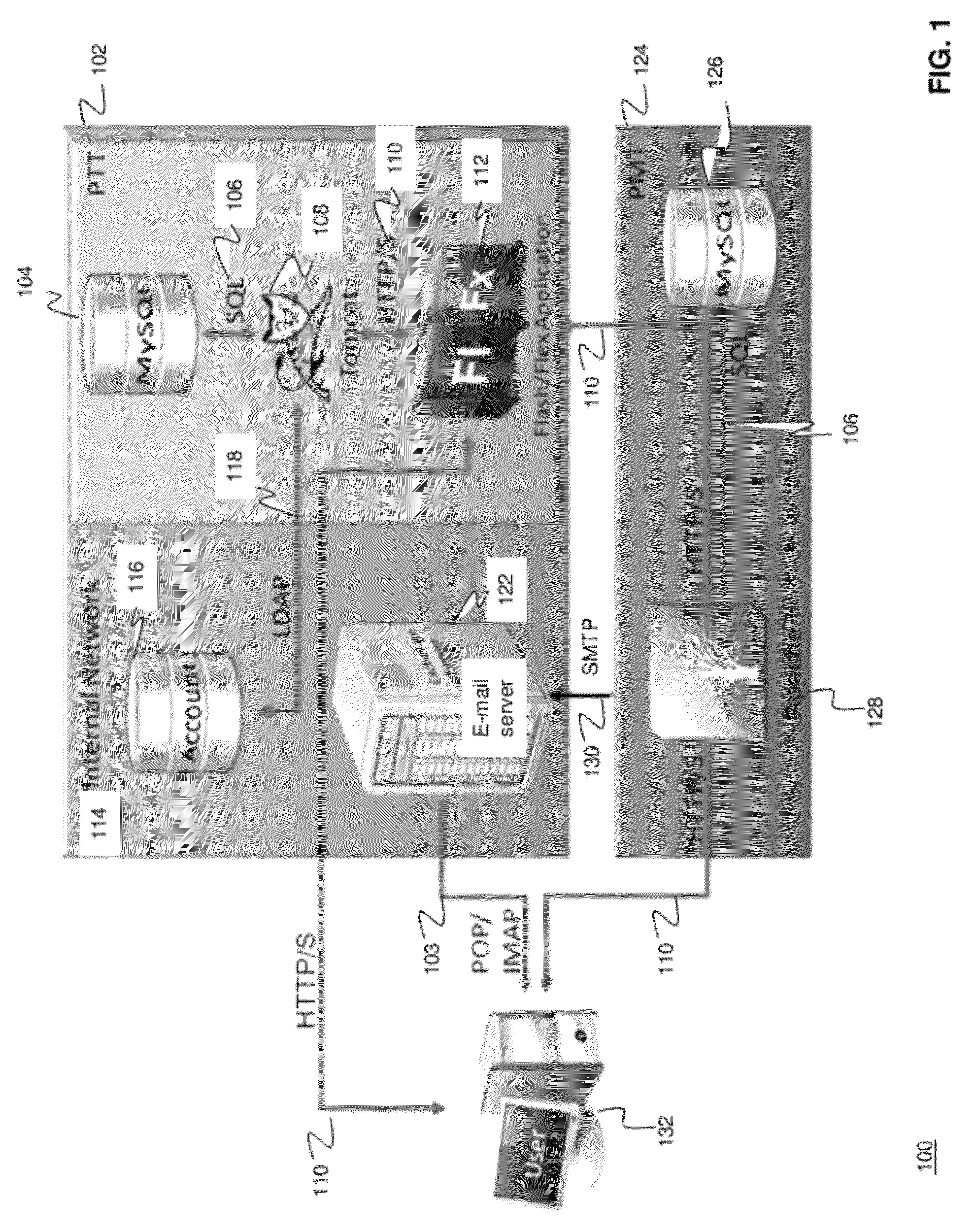
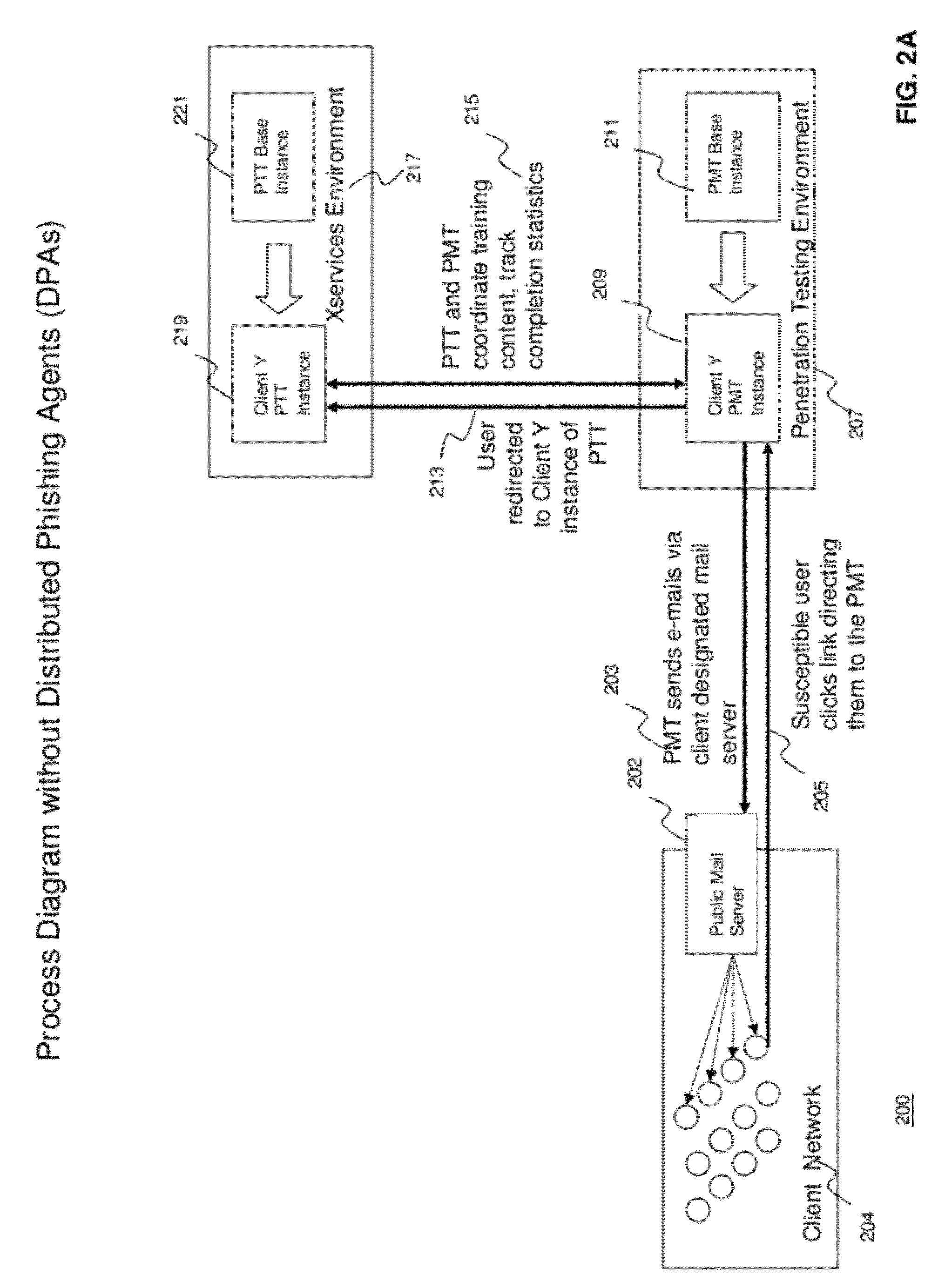
Methods and systems for Sustained Testing and Awareness Refresh against Phishing threats (STAR*Phish™) are disclosed. In an embodiment, a method assigns schemes and unique identifiers to target e-mail addresses associated with a user accounts. The method delivers e-mail messages to the targeted e-mail addresses, the e-mail messages comprising an HTTP request and a unique identifier associated with each of the user accounts. The method then receives, at a Phishing Metric Tool (PMT), a response including the unique identifier. The PMT logs training requirements for the user accounts, tracks response metrics for the training requirements, and redirects the respective HTTP requests to a phishing training tool (PTT). The PTT sends a notification of the user account identities and the unique identifiers to the PMT and returns a status for the training requirements for the user accounts. Upon completion of the training, the PMT sends completion notifications for the user accounts.
Owner:BOOZ ALLEN HAMILTON INC
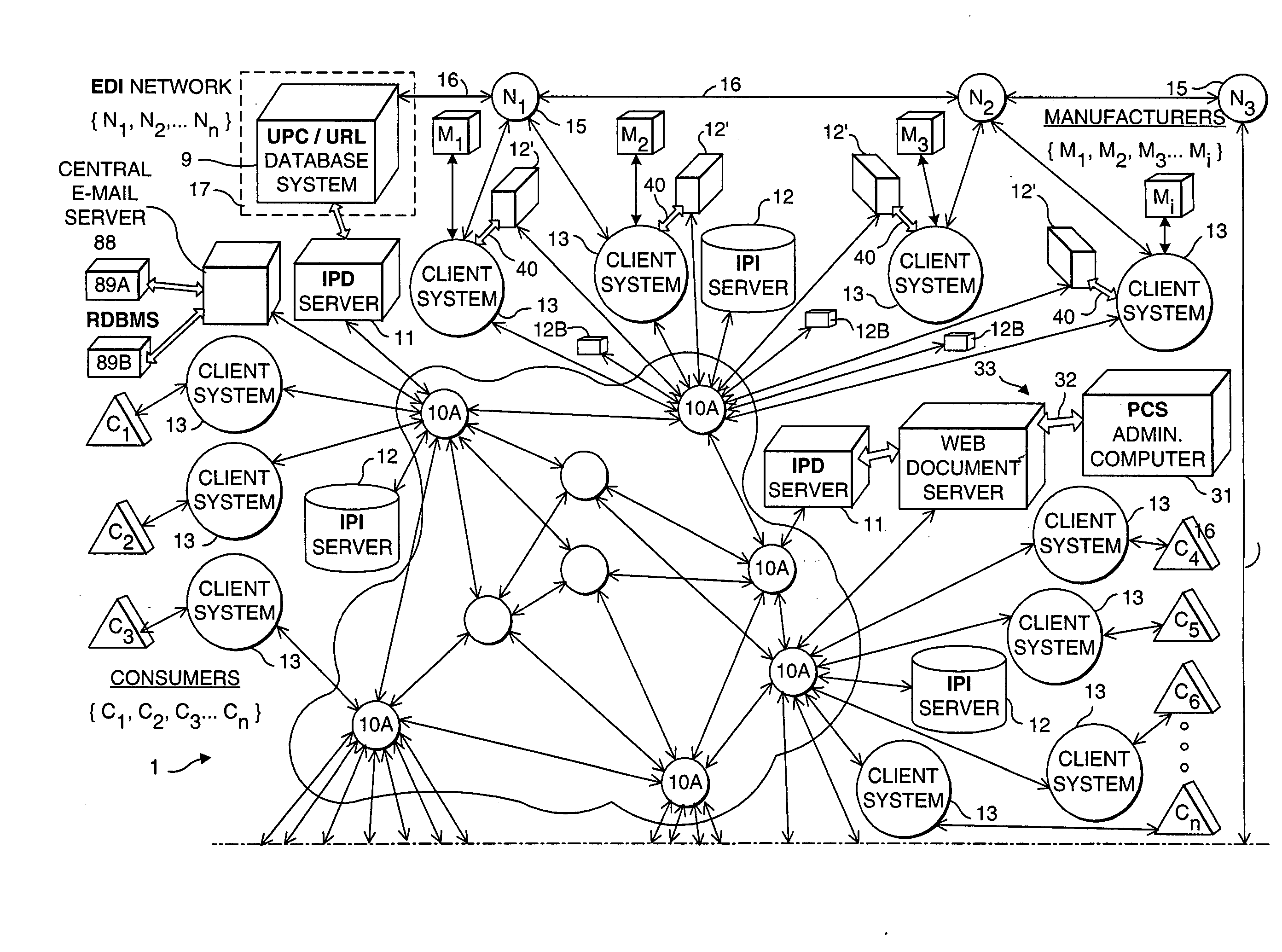
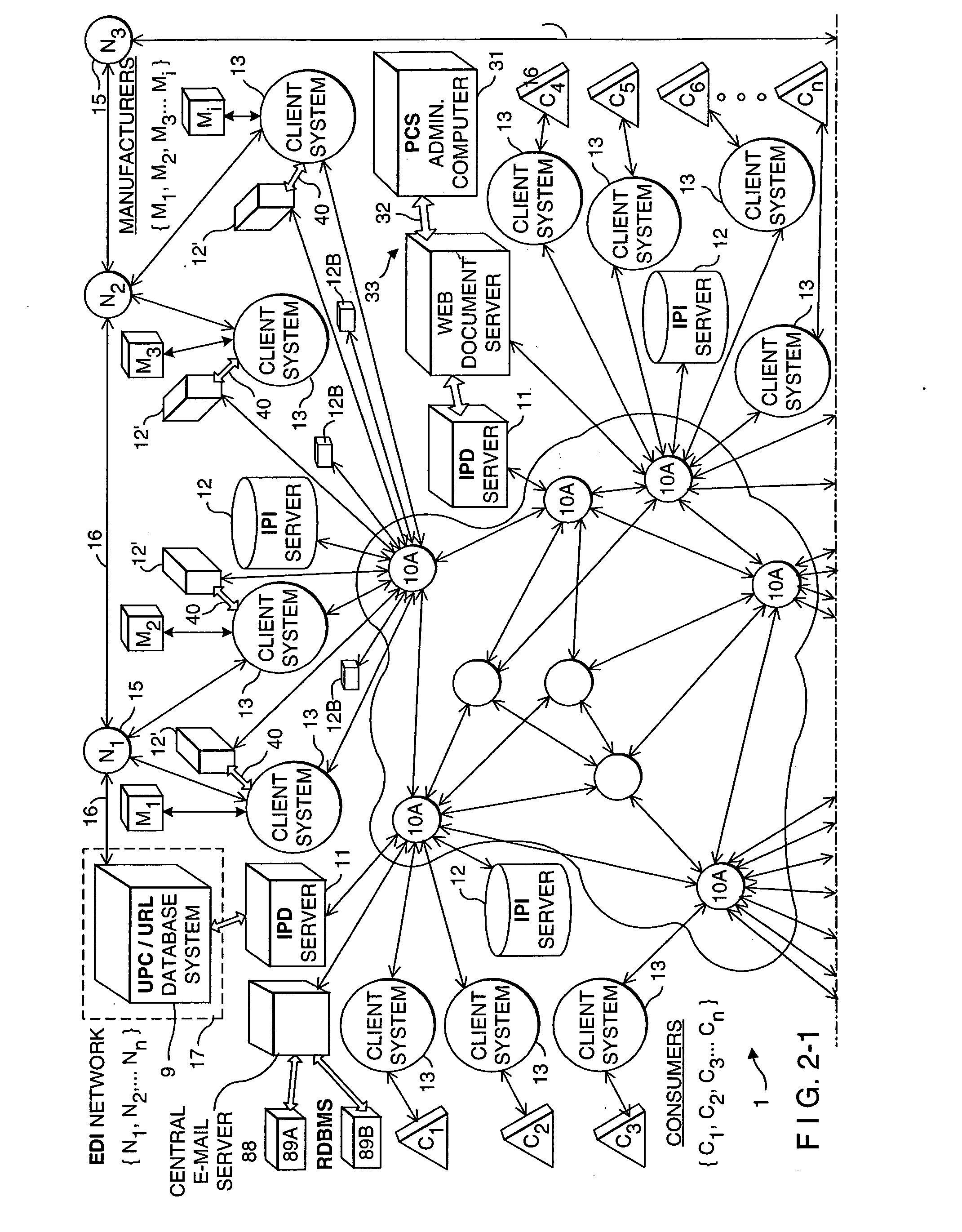
Internet-based method of and system for managing, distributing and serving consumer product related information to consumers in physical and electronic streams of commerce
InactiveUS20060011716A1Digital data processing detailsSpecial data processing applicationsEmail addressInformation analysis
A novel Internet-based consumer product information system and method for use in retail shopping environments, wherein each Web-enabled bar code driven consumer product information kiosk deployed therewithin embodies e-mail messaging capabilities which enable consumers to automatically save and record the URLs of CPI-related Web documents within the message field of a preformatted e-mail message that is transmitted from a retailer-operated e-mail server, to a remote e-mail address specified by the consumer within the retail shopping environment. One or more central e-mail servers are used to collect copies of e-mail documents (and records thereof) transmitted from the Web / e-mail enabled kiosks within each retail shopping environments, for consumer and demographic information analysis, compilation, and storage within RDBMSs that are made accessible to retailers and manufacturers alike for use in product marketing, sales forecasting, customer intelligence, and like operations which enable more effective marketing of consumer products and services in both physical and electronic forms of commerce.
Owner:PERKOWSKI THOMAS J
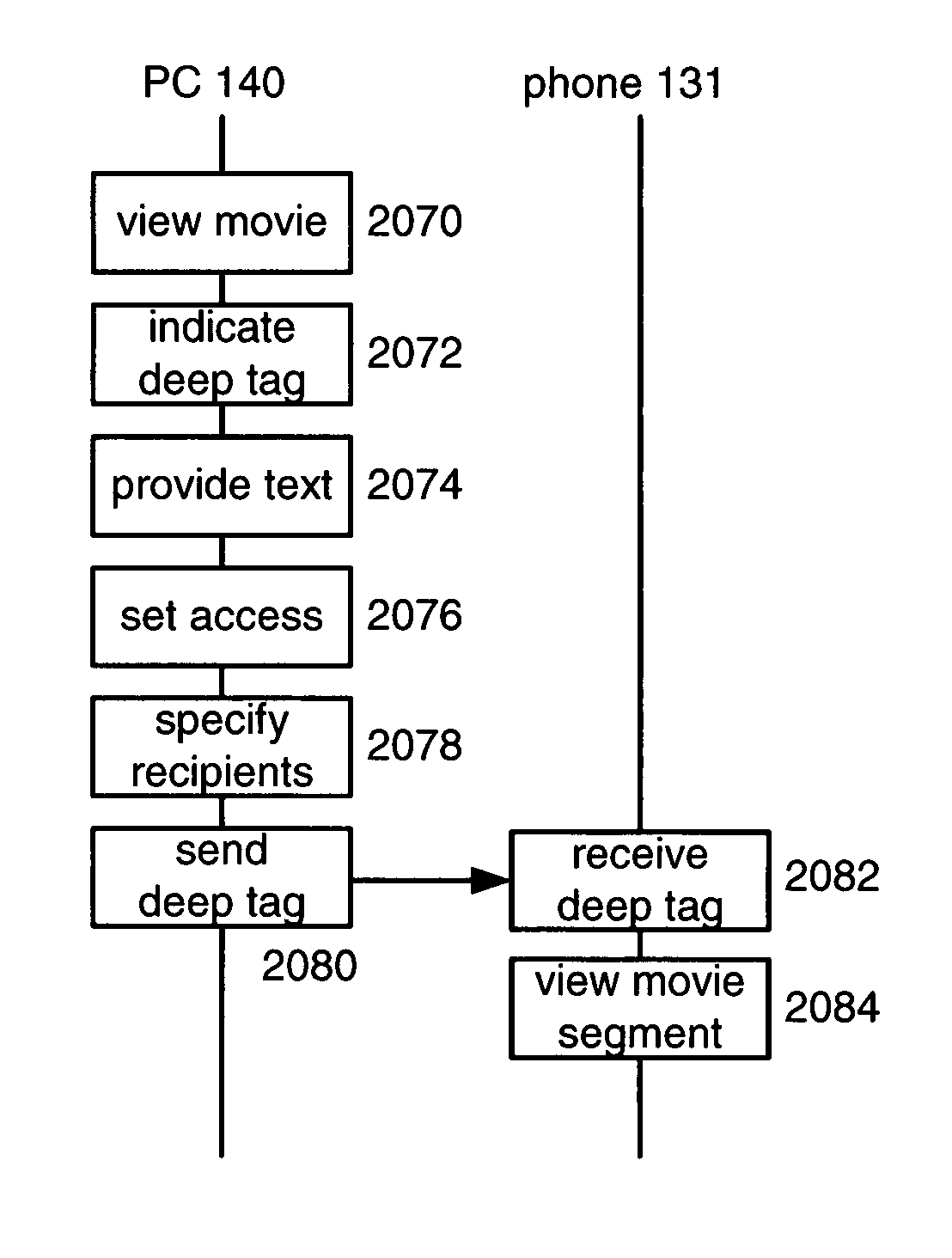
Content tracking for movie segment bookmarks
ActiveUS20070154190A1Television system detailsElectronic editing digitised analogue information signalsEmail addressBookmarking
Several ways are provided for a viewer of a movie to create a deep tag, that is, a bookmark for a segment of the movie. The deep tag can be associated with descriptive text and sent to an address provided by the viewer, either an e-mail address or an instant messaging address. Additionally, before the deep tag is created, it can be checked whether the content owner of the movie is known. If known, the content owner's rules, if any, regarding deep tagging are followed. If unknown, a set of registered content owners can be alerted of the presence of new content. When ownership of the new content is established, the already-created deep tags can be updated in accordance with the content owner's rules, if any, regarding deep tagging.
Owner:OPEN TEXT SA ULC
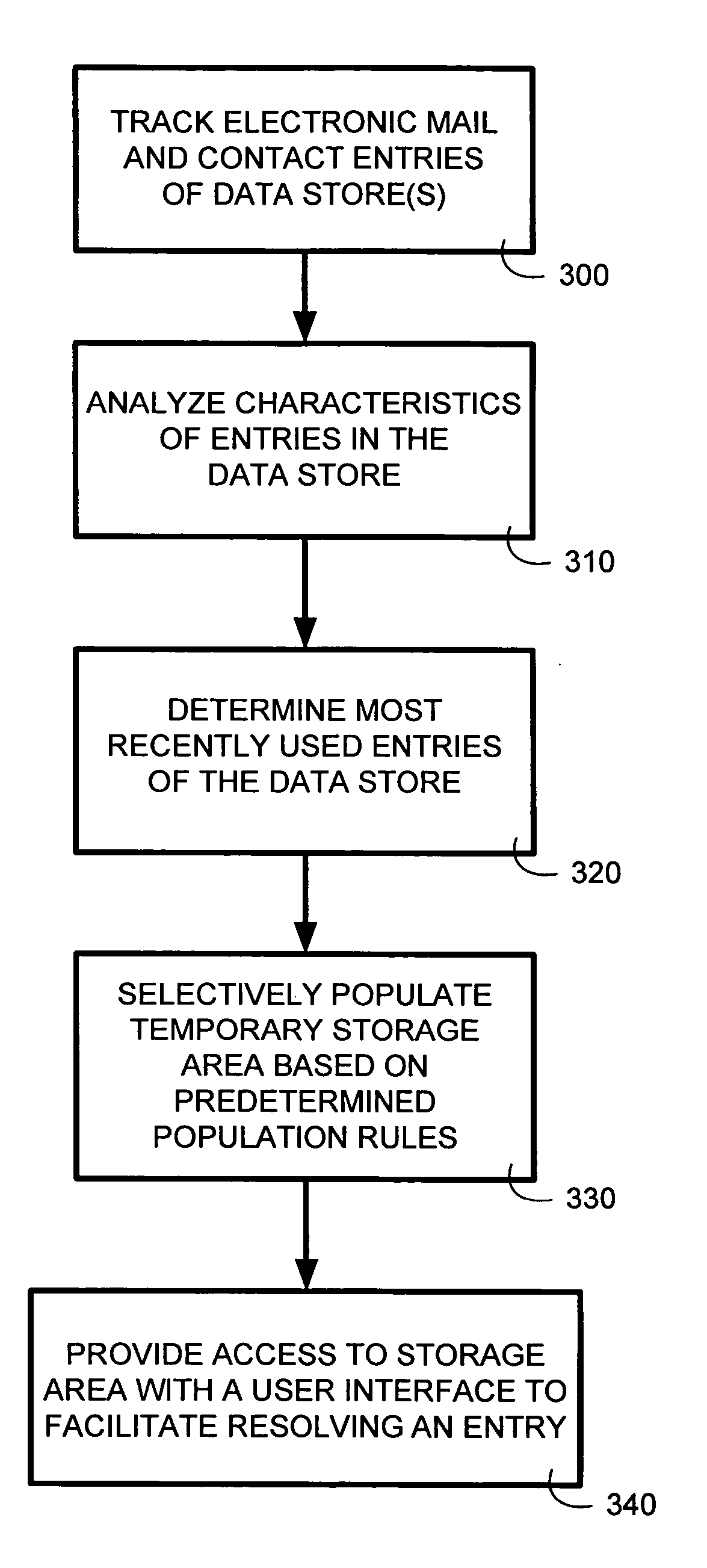
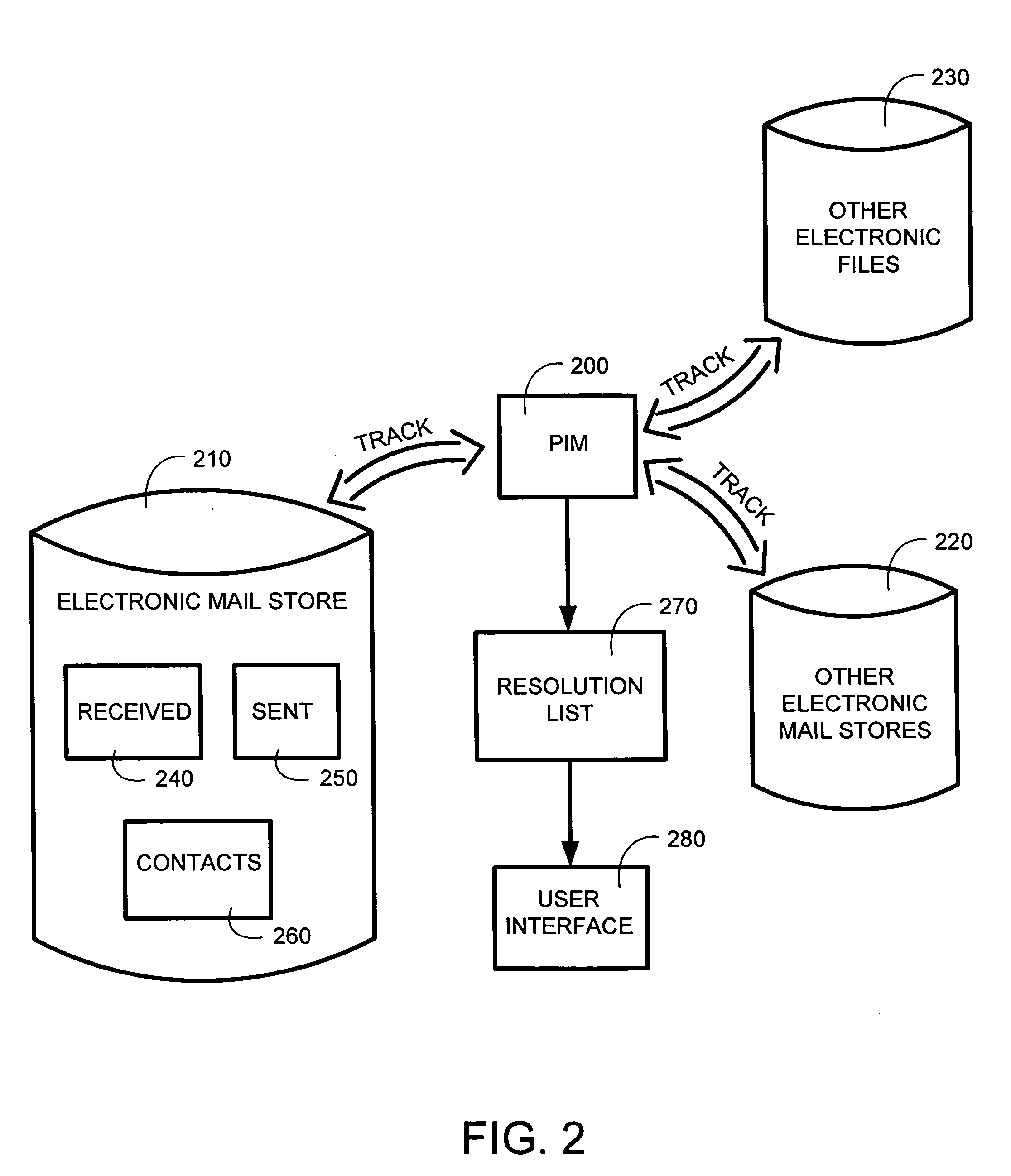
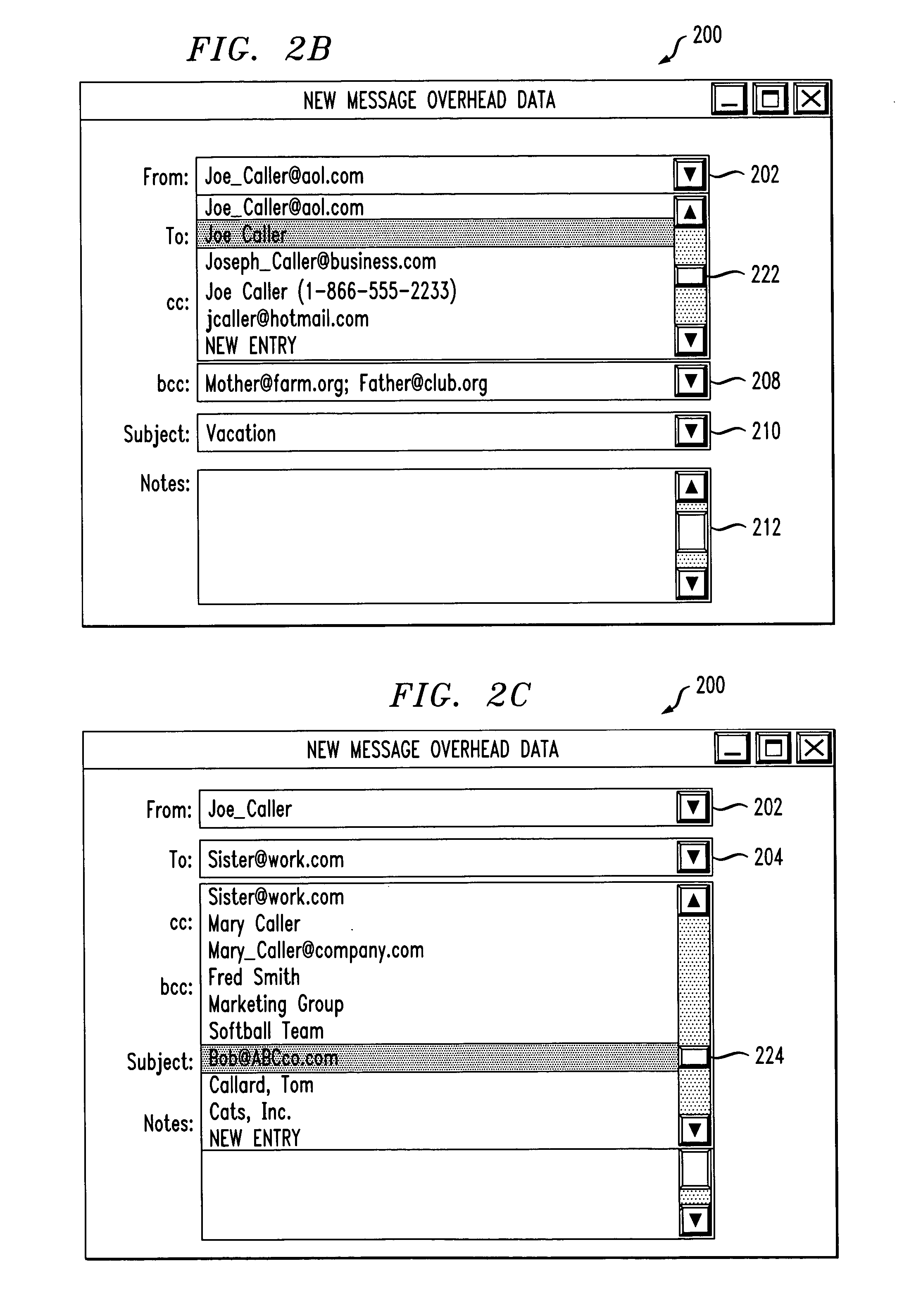
System and method for automatically populating a dynamic resolution list
InactiveUS20050131888A1Facilitate user inputDigital data processing detailsText processingEmail addressUser input
The system and method of the present invention automatically provides dynamically generated completion information for facilitating user input of email addresses or contact information. This completion information is developed from a “data store” comprised of multiple data sources such as previously sent or received email, and other types of electronic files such as word processor or spreadsheet files. The present invention monitors and uses the information in the data store to automatically store, track, maintain, and organize data entries in a dynamic “resolution list”. As a user begins to input an email address or contact, the present invention can either automatically complete the entry using a most probable result from the resolution list, or can display a list of likely matches from which the user may select the desired email address or contact.
Owner:MICROSOFT TECH LICENSING LLC
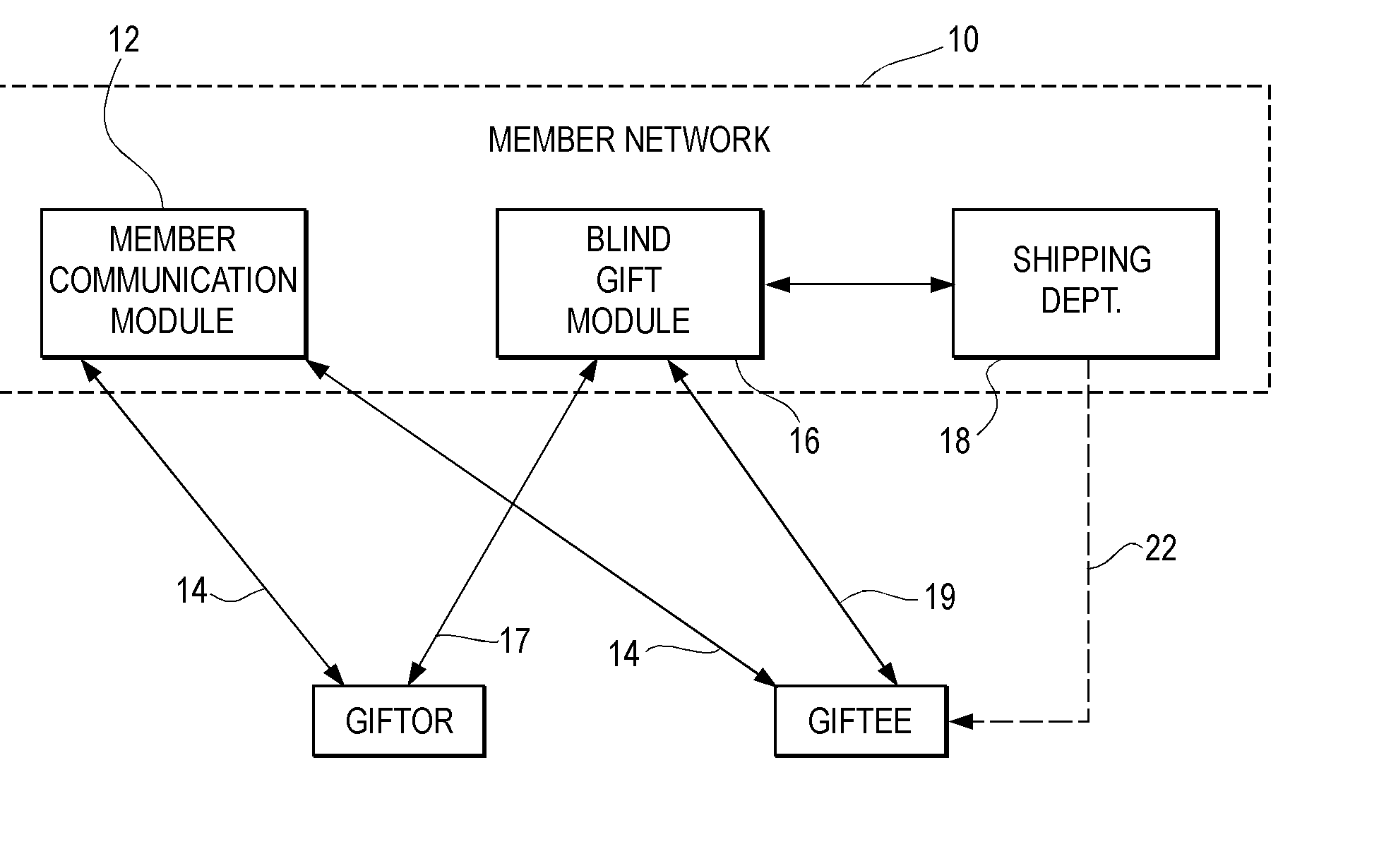
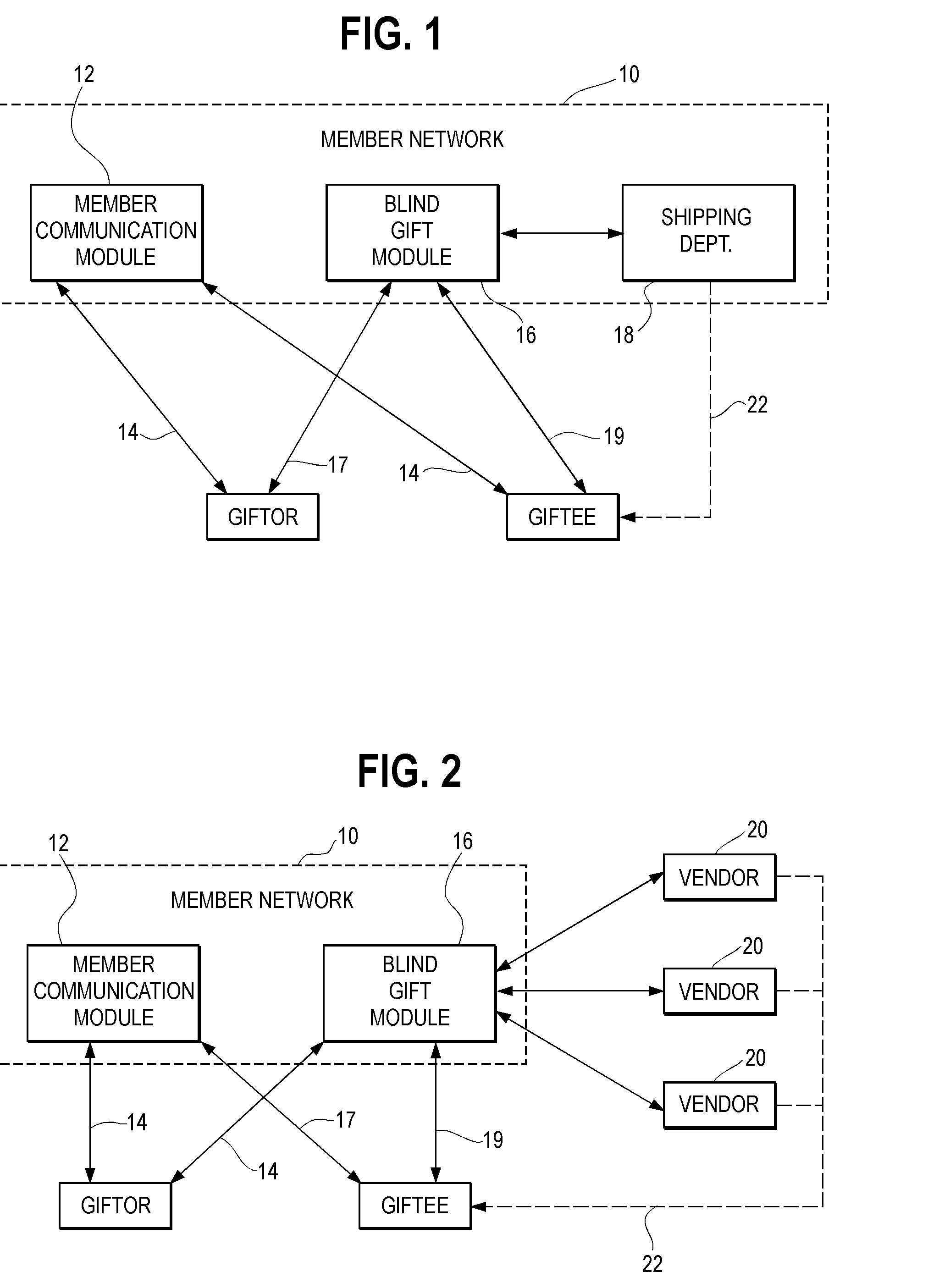
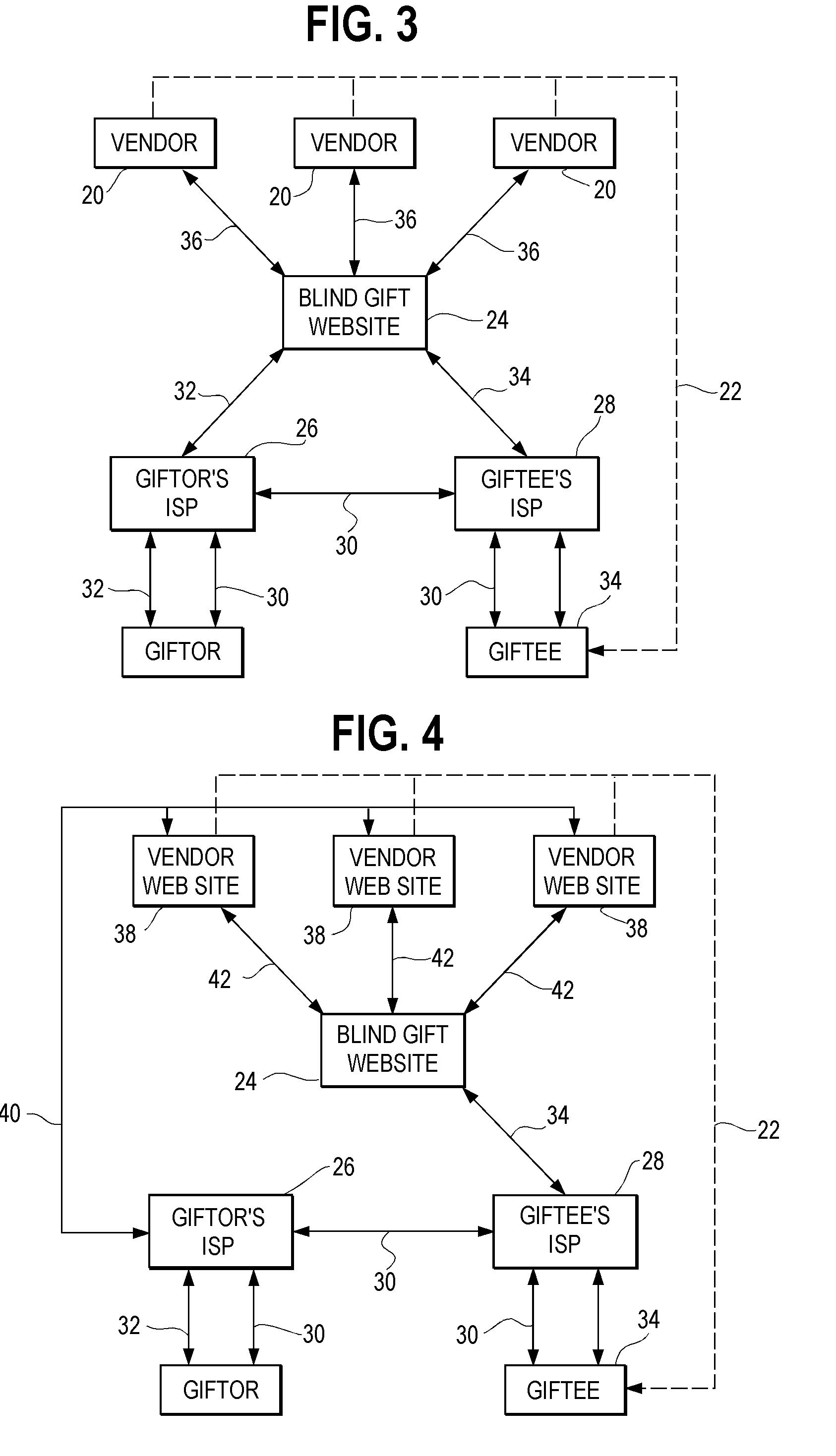
Blind Gift Method and System
InactiveUS20020095298A1Overcomes shortcomingAvoid disadvantagesBuying/selling/leasing transactionsMarketingThe InternetComputer science
<heading lvl="0">Abstract of Disclosure< / heading> This is a method and system whereby parties who know each other only by pseudonyms, such as by Internet e-mail addresses, may send and receive gifts while maintaining anonymity behind their pseudonyms. Steps of the method include receiving a request from a first pseudonymous party to take an order for a gift to be sent to a second party; obtaining from the first party an identification of the intended gift, and the pseudonym of the second party; and, looking up a non-pseudonymous name and address associated with the second in a database. Alternatively, the second party may be contacted and asked to confidentially reveal his or her name and mailing address for gift delivery purposes. While the second party's information is kept confidential from the first party, the second party has various choices including accepting the gift, accepting it upon certain conditions, or refusing it. The system of the invention includes components for permitting the first party to enter the second party's pseudonym; for determining the second party's true name and mailing address from his or her pseudonym; and, for sending the gift to the second party's true name and mailing address.
Owner:JOVIAN HLDG
Systems and methods for identifying and mitigating information security risks
ActiveUS8793799B2High level of realismRaise the possibilityMemory loss protectionDigital data processing detailsUnique identifierPhishing
Methods and systems for Sustained Testing and Awareness Refresh against Phishing threats (STAR*Phish™) are disclosed. In an embodiment, a method assigns schemes and unique identifiers to target e-mail addresses associated with a user accounts. The method delivers e-mail messages to the targeted e-mail addresses, the e-mail messages comprising an HTTP request and a unique identifier associated with each of the user accounts. The method then receives, at a Phishing Metric Tool (PMT), a response including the unique identifier. The PMT logs training requirements for the user accounts, tracks response metrics for the training requirements, and redirects the respective HTTP requests to a phishing training tool (PTT). The PTT sends a notification of the user account identities and the unique identifiers to the PMT and returns a status for the training requirements for the user accounts. Upon completion of the training, the PMT sends completion notifications for the user accounts.
Owner:BOOZ ALLEN HAMILTON INC
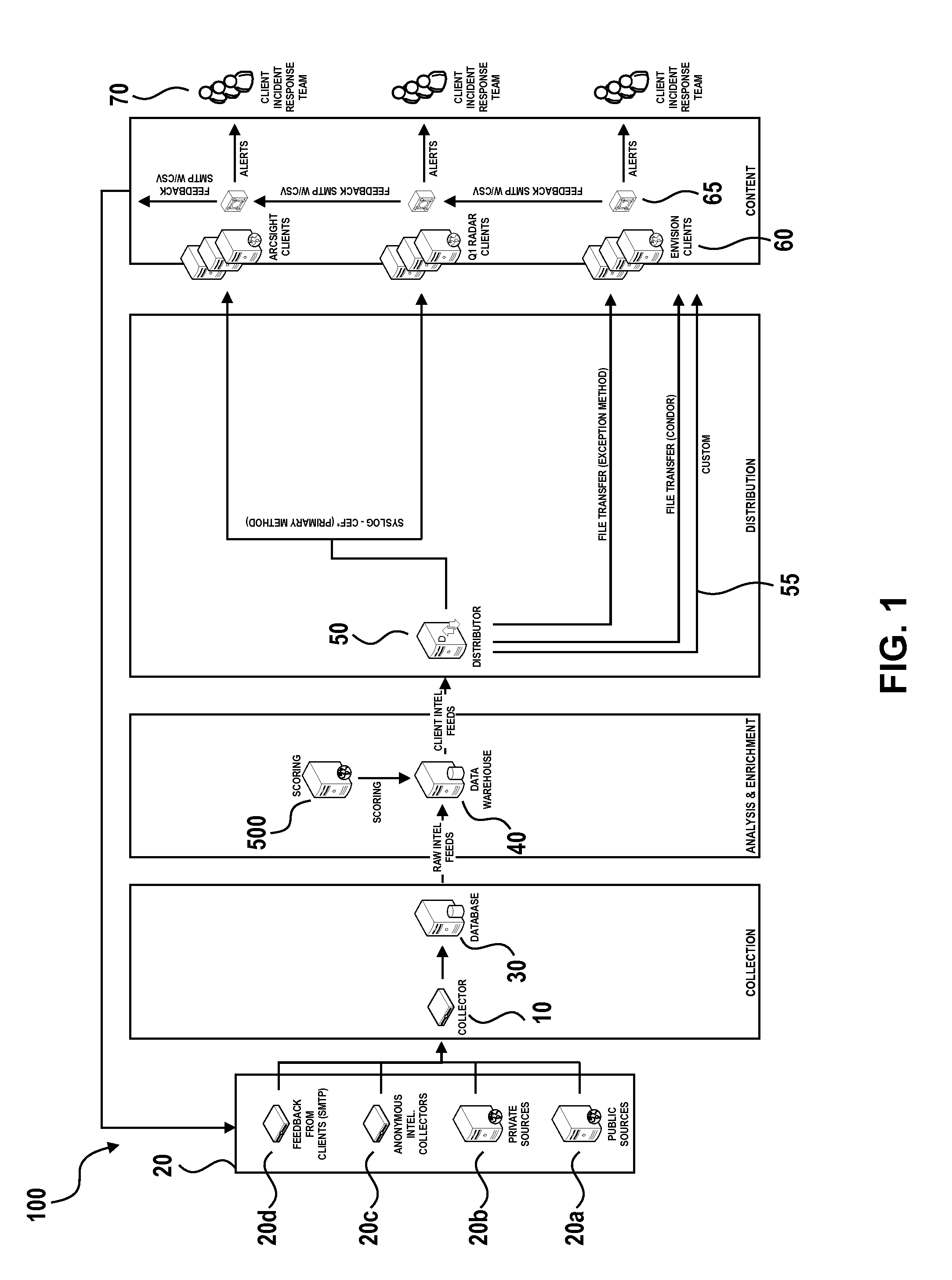
Collective threat intelligence gathering system
ActiveUS8813228B2Quality improvementMemory loss protectionUnauthorized memory use protectionIp addressInternet privacy
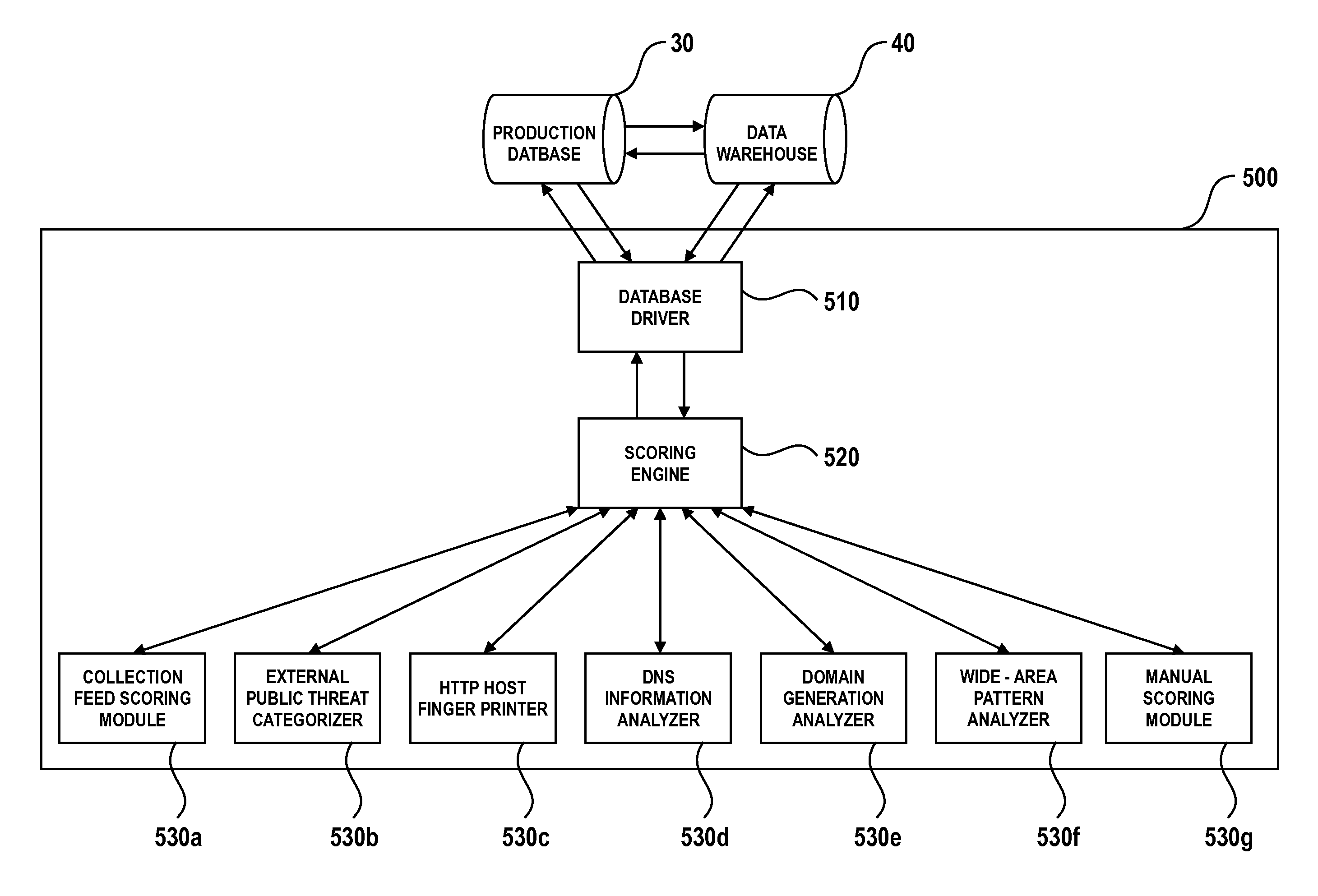
Threat intelligence is collected from a variety of different sources. The threat intelligence information is aggregated, normalized, filtered and scored to identify threats to an information network. Threats are categorized by type, maliciousness and confidence level. Threats are reported to network administrators in a plurality of threat feeds, including for example malicious domains, malicious IP addresses, malicious e-mail addresses, malicious URLs and malicious software files.
Owner:DELOITTE DEV
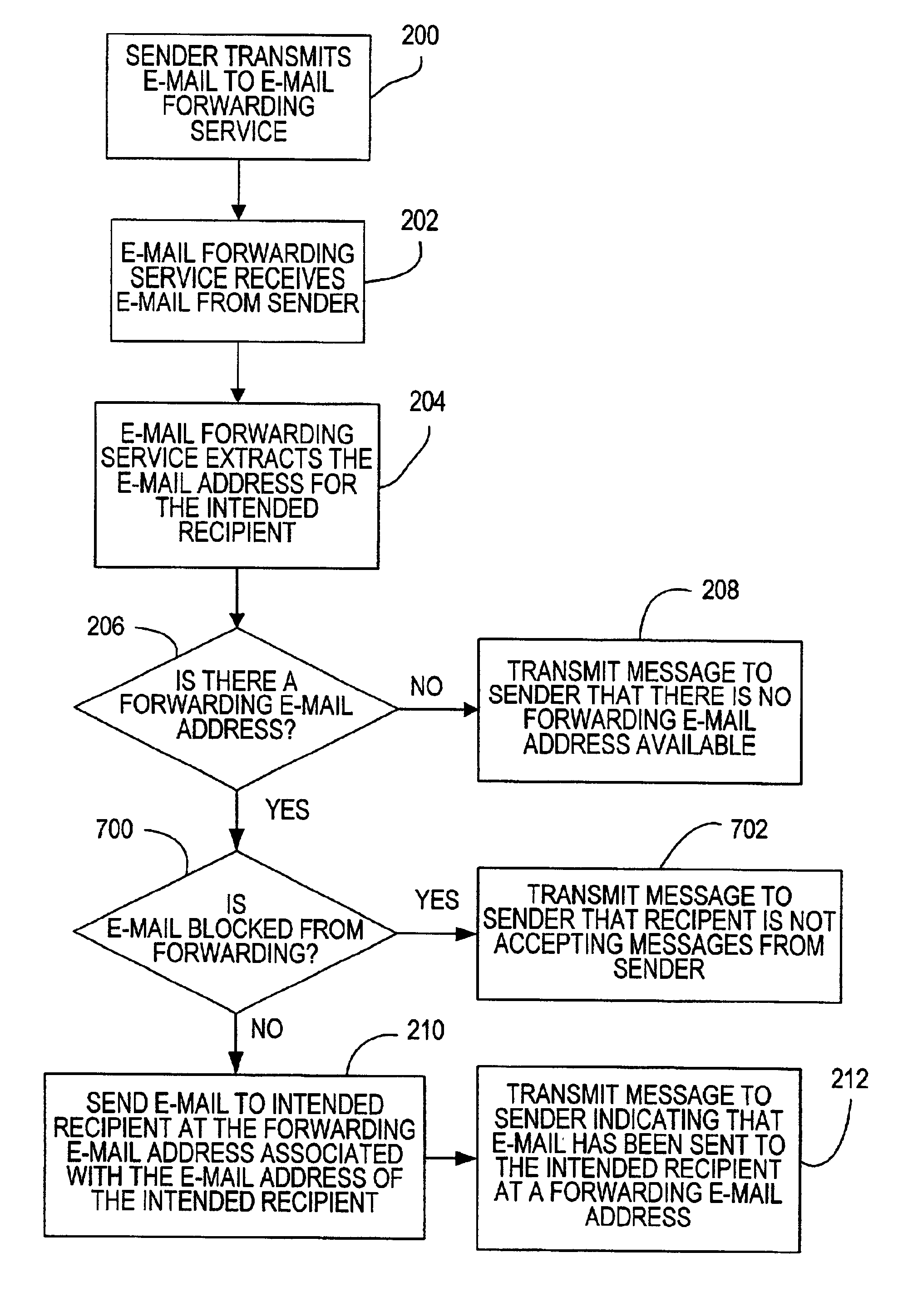
System and method for forwarding electronic messages
InactiveUS6957248B2Function increasePrivacy protectionMultiple digital computer combinationsOffice automationEmail addressInternet privacy
A method and system for forwarding an e-mail message addressed to a first disfavored e-mail address to a second preferred forwarding e-mail address. A message is received at an e-mail forwarding computer, the message identifying the first disfavored e-mail address. The e-mail forwarding computer parses the first e-mail address from the message to determine if there is a second preferred forwarding e-mail address associated with the first e-mail address. If there is a second e-mail address associated with the first e-mail address, the e-mail forwarding computer sends the e-mail message to a third computer associated with the second e-mail address.
Owner:CUFER ASSET LTD LLC
System and method for creating and managing forwarding email address
InactiveUS6973481B2Created quickly and easilyQuick and easy to createMultiple digital computer combinationsOffice automationEmail addressThe Internet
A system and method of creating an email forwarding address during an Internet session where a user is viewing a web page that includes a prompt for an email address includes creating and storing an email forwarding address for the user that is automatically associated with the web page. The email forwarding address re-directs email addressed thereto to a target email address associated with the user. The email forwarding address is sent to the user to enable the user to use the email forwarding address to satisfy the email address prompt.
Owner:WEBZERO
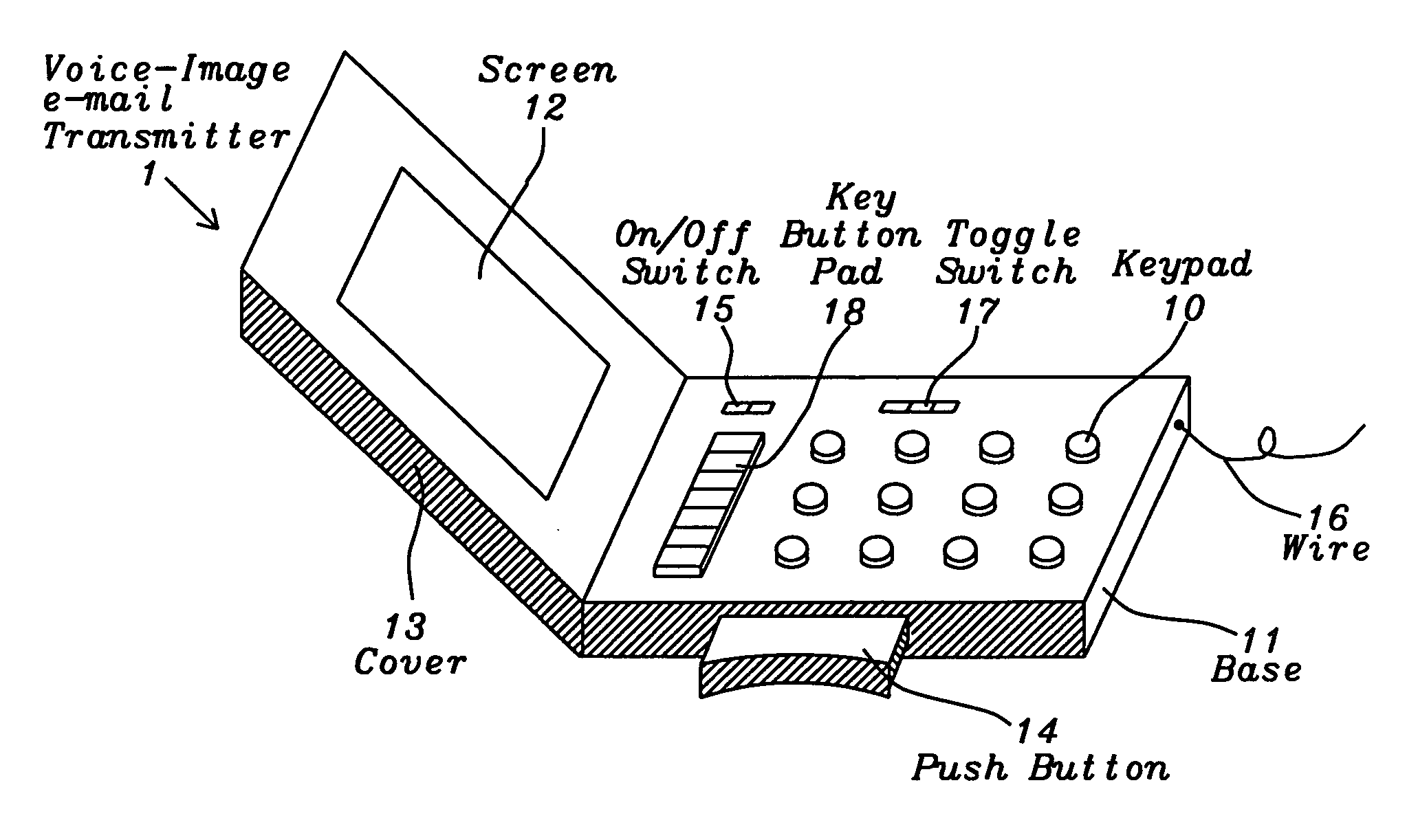
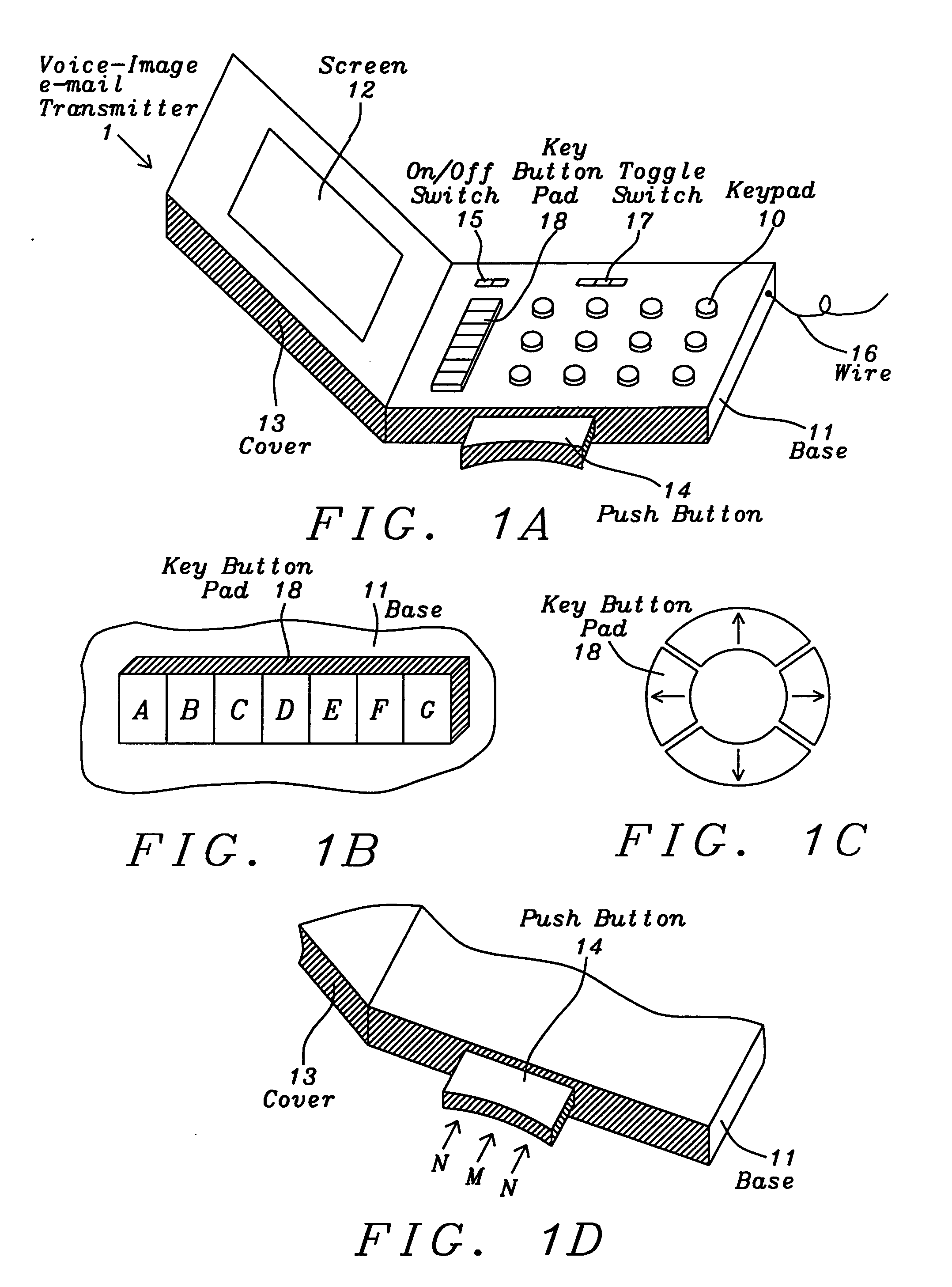
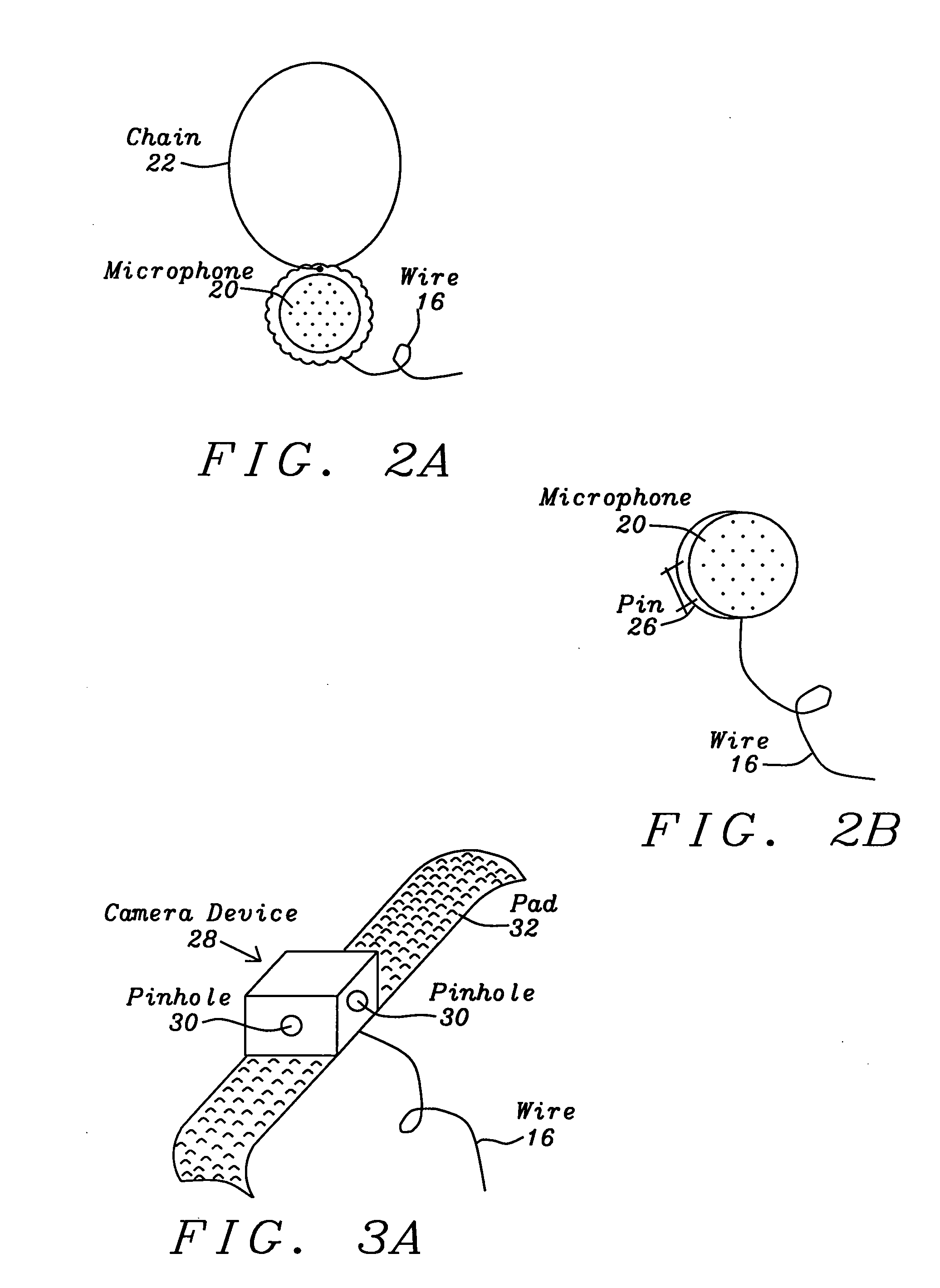
System and method for the emergency voice and image e-mail transmitter device
InactiveUS20120282884A1Justice be serveEasy and fastDevices with GPS signal receiverSubstation equipmentElectronic equipmentDigital signal
A voice and image e-mail transmitter device with an external camera attachment that is designed for the emergency and surveillance purposes is disclosed. The device converts voice signals and photo images into digital format, which are transmitted to the nearest voice-image message receiving station from where the digital signal strings are parsed and converted into voice, image, or video message files which are attached to an e-mail and delivered to user pre-defined destination e-mail addresses and a 911 rescue team. The e-mail also includes the caller's voice and personal information, photo images of a security threat, device serial number, and a GPS location map of the caller's location. The digital signal data may be recorded and transmitted within few seconds. The victim's family or police may either check the GPS location map in an e-mail or apply a new GPS based people tracking system of the present invention to search for a missing victim.
Owner:SUN NICHOLAS
Web based email control center for monitoring and providing a sumary of the detected event information organized according to relationships between the user and network sites
InactiveUS6874023B1Multiple digital computer combinationsData switching networksWeb siteEmail address
Accessing web sites on which the user has an account and providing notification of changes at the site, and improved electronic mail management is provided, allowing all email to be collected and forwarded from a central site to other email addresses or allowing for the user to view the email at the central site. The user may assign individual email addresses to any number of uses, for example, an individual email address for use in communicating with a particular commercial web site.
Owner:HANGER SOLUTIONS LLC
Apparatus and method for precluding e-mail distribution
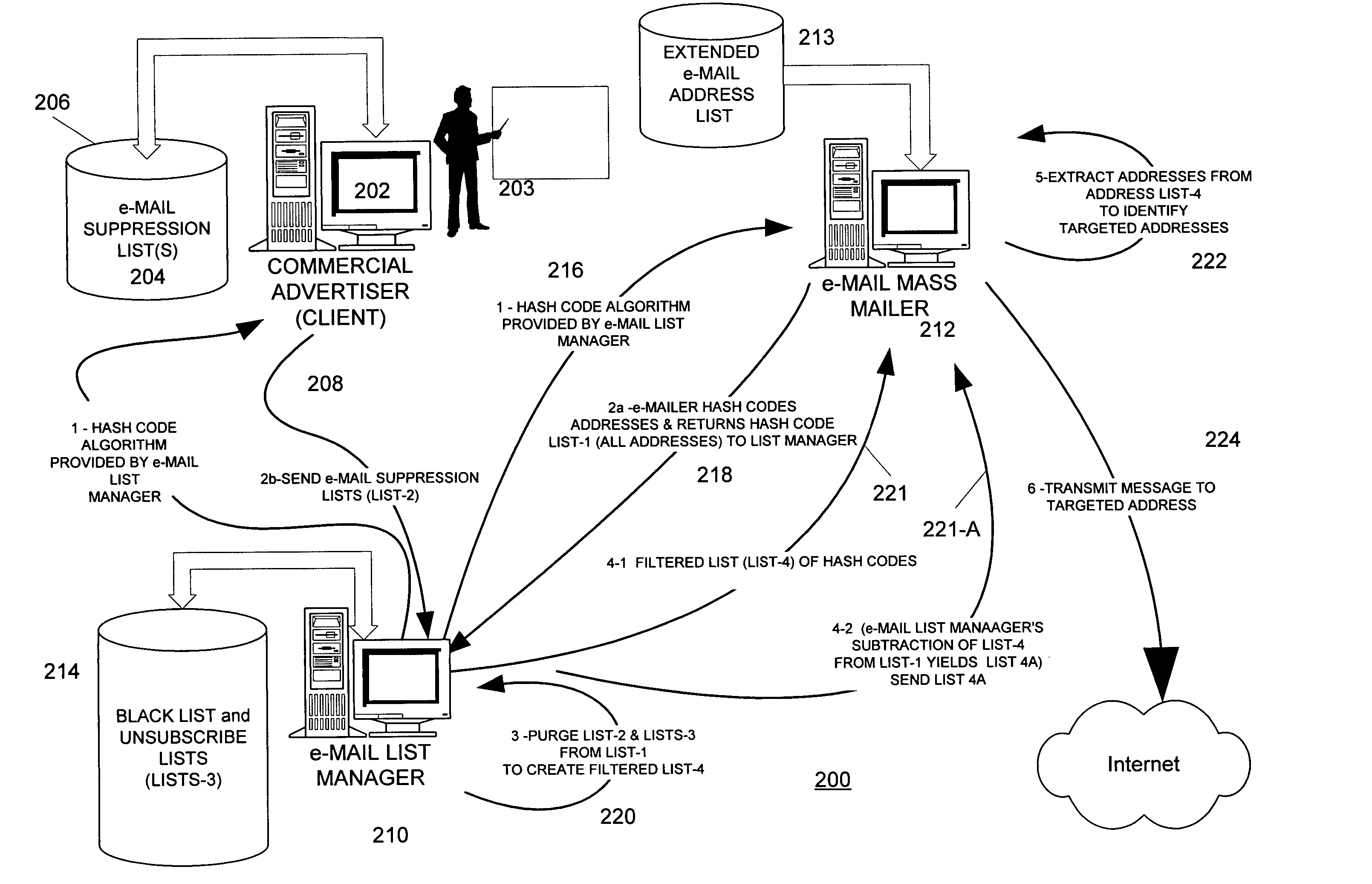
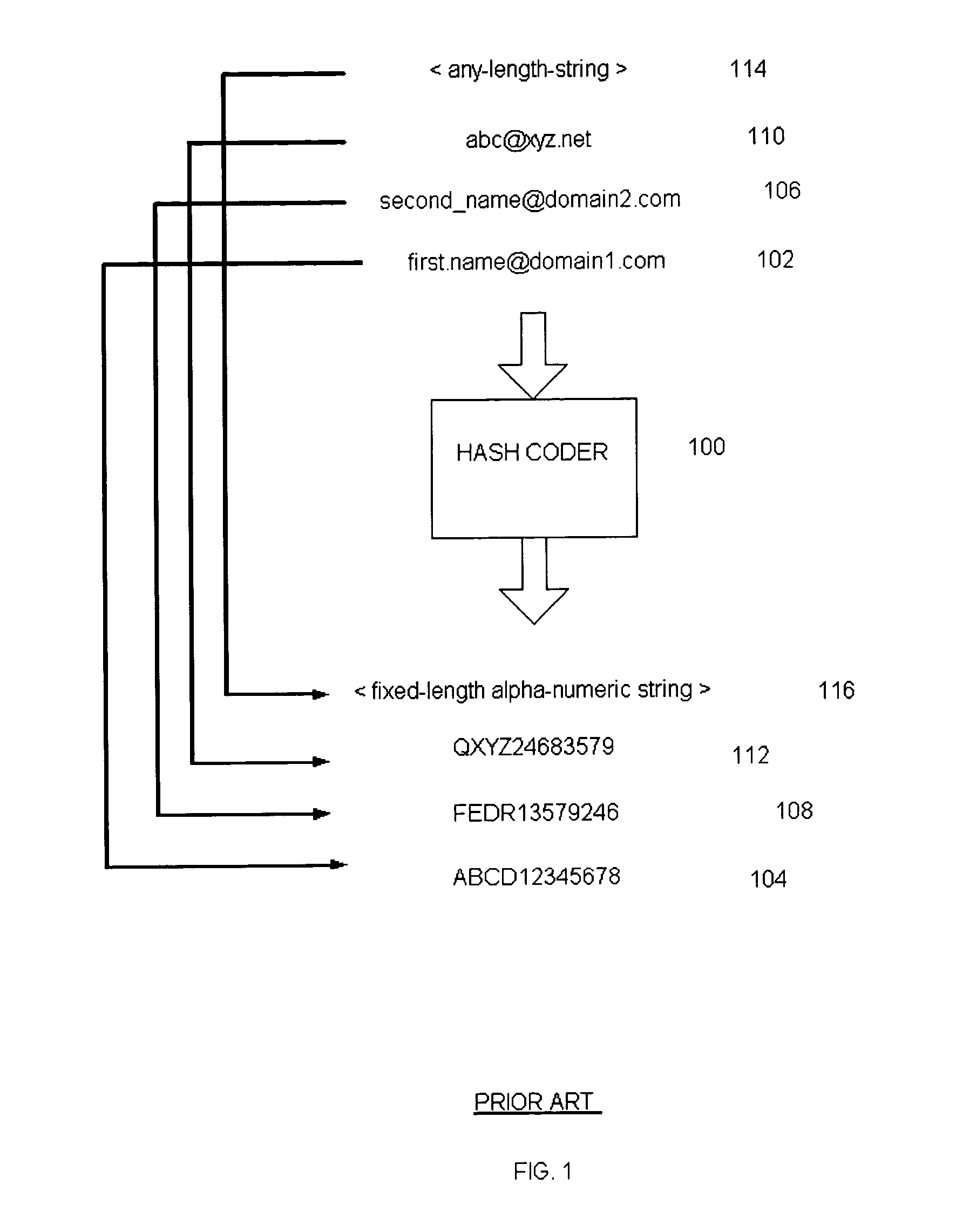
InactiveUS20050005164A1Digital data processing detailsUser identity/authority verificationComputer hardwareEmail address
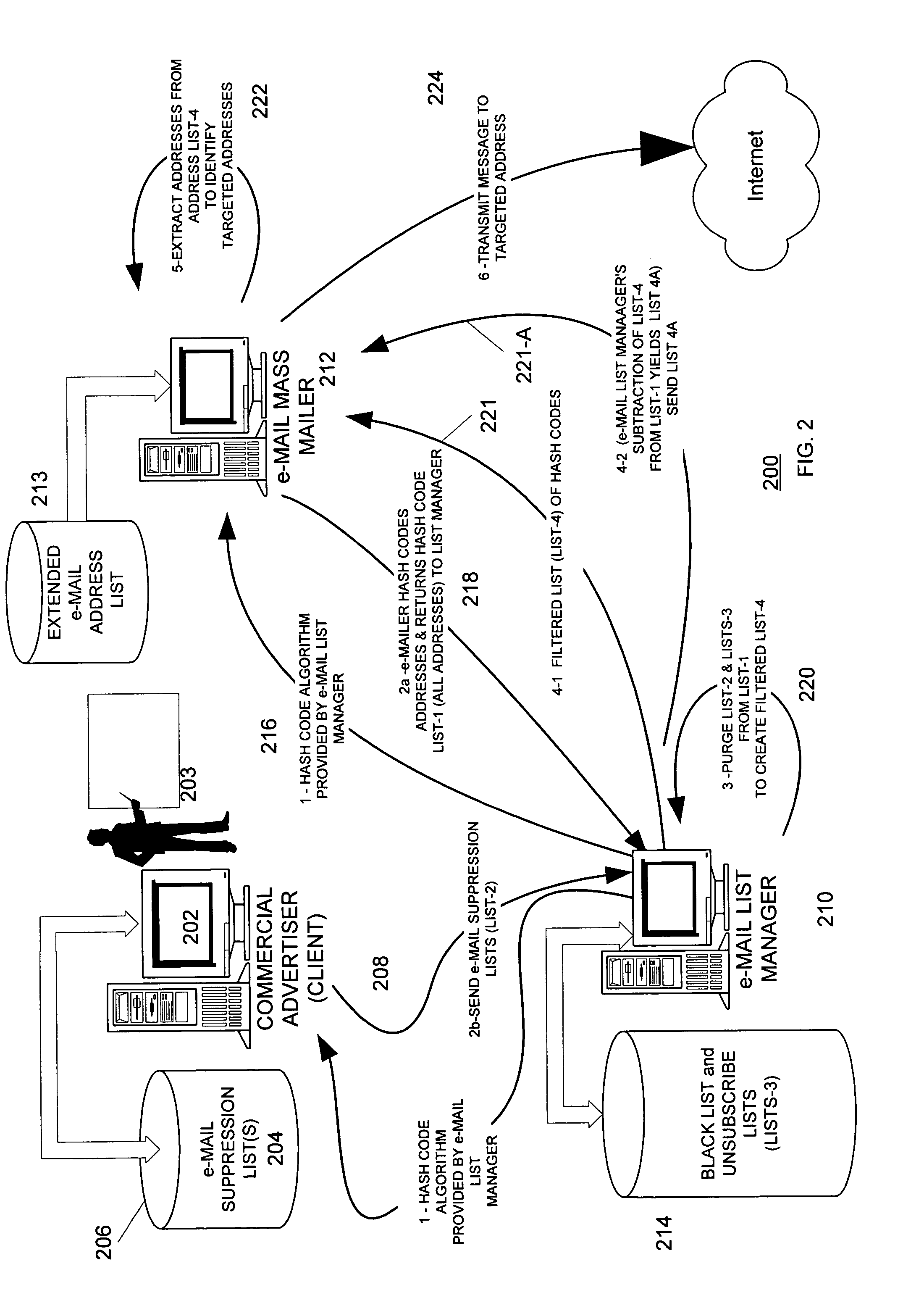
E-mail addresses are converted by a hashing function into hash codes. An e-mail mass mailer that can have millions of addresses hash codes all addresses to which a message might be sent to form a first list. An entity that wishes to exclude delivery of a message to various e-mail addresses, hash codes such addresses to form a second list. Hash codes in the first list that are also in the second list are purged from the first list to yield a third list of hash codes, each of which represents an e-mail address to which a message may be sent.
Owner:QUINSTREET
System of central signature verifications and electronic receipt transmissions
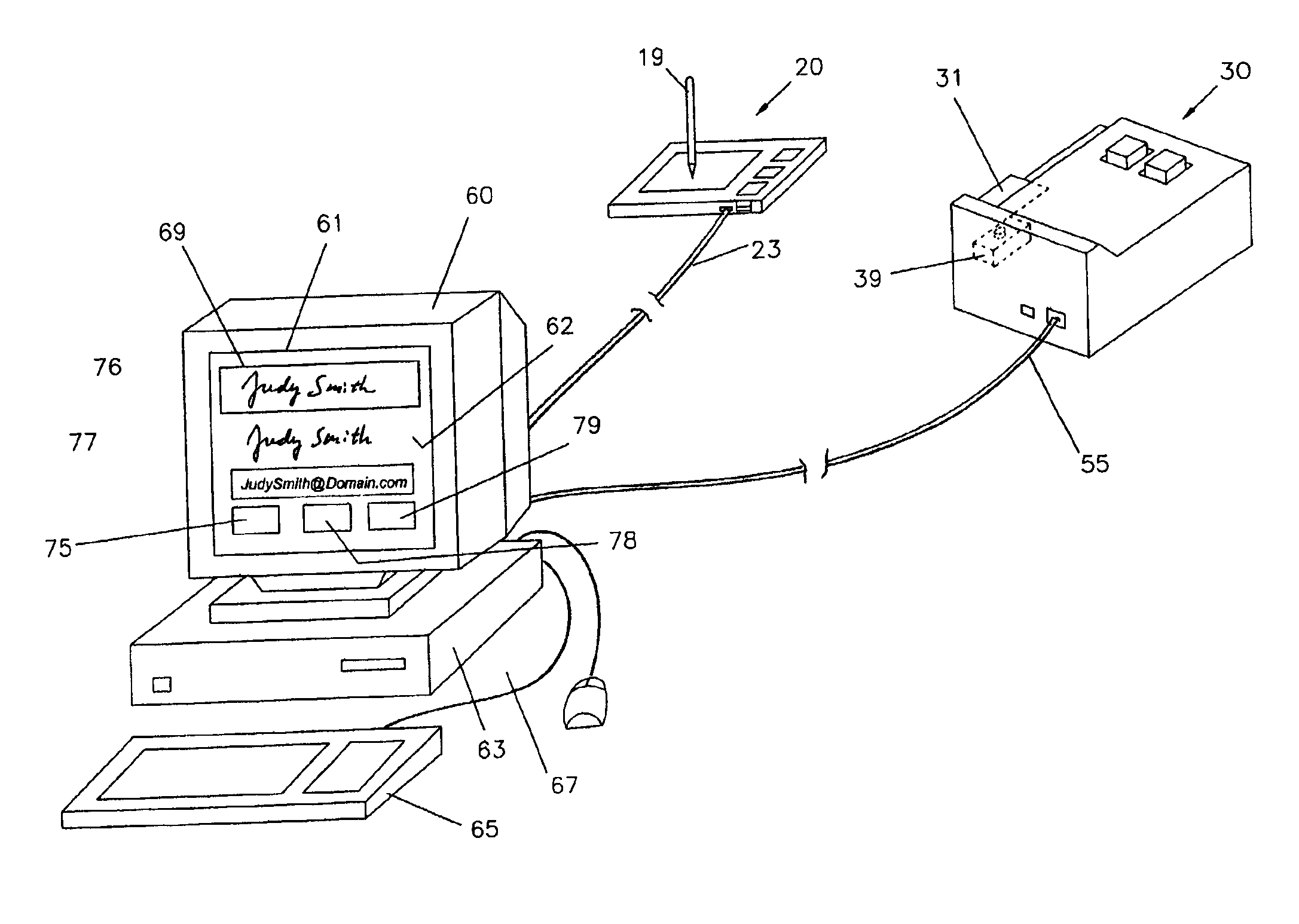
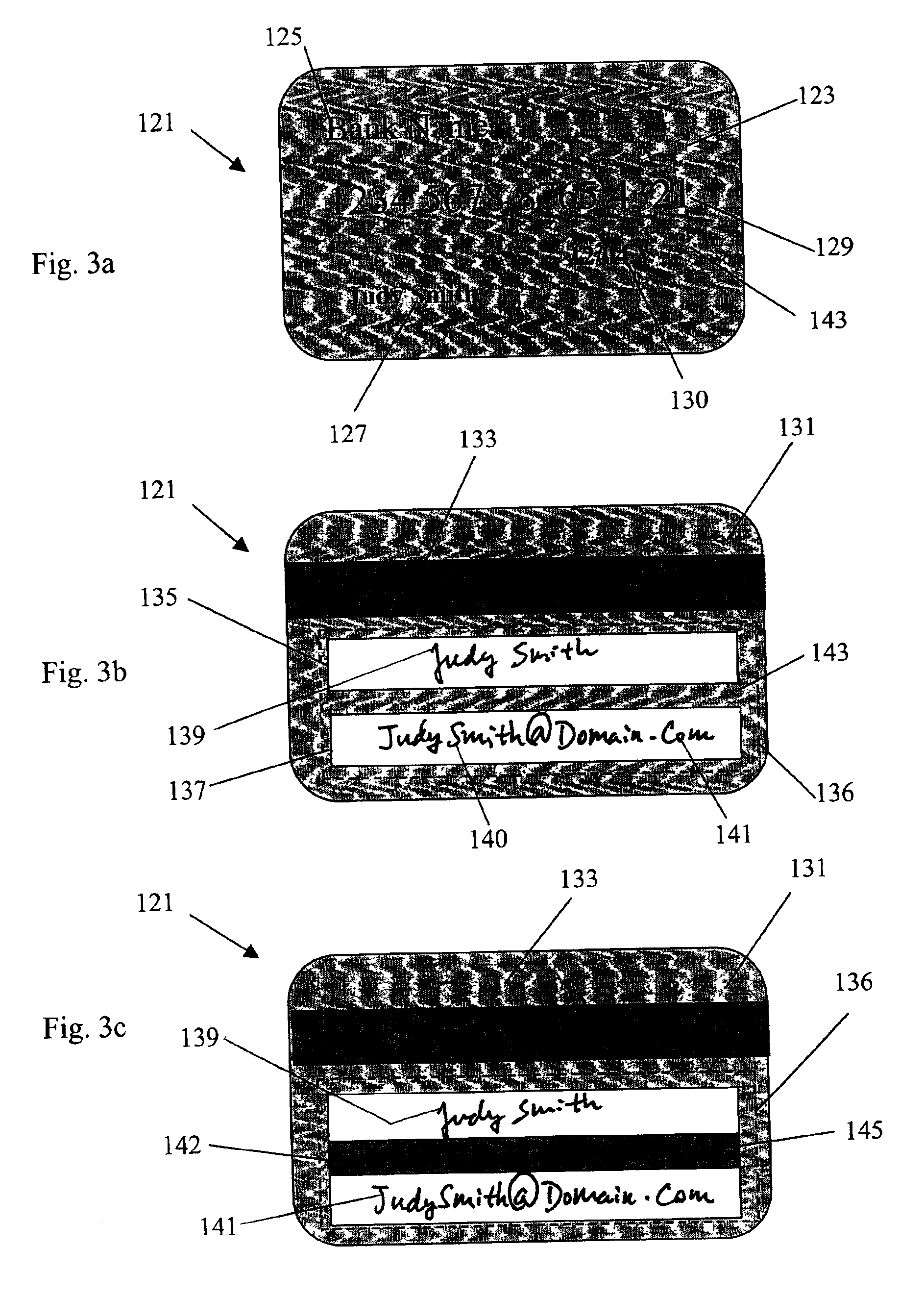
InactiveUS6873715B2Eliminate needElectric signal transmission systemsMultiple keys/algorithms usageCredit cardEmail address
A credit-card reader having a built-in digital camera for capturing a template signature and an email address on a credit card. The email address is identified by an optical character recognition program and input to an email system. A test signature is entered on a touch-pad input device and both the test and the template signatures are normalized and displayed for verification. Action buttons are provided on the display screen for enforcing the signature verification actions. The system enables the transmission of an electronic receipt selectively controlled by the customer and eliminates the needs of physically handling a credit card for signature verification and manual input or pre-registration of an email address for an electronic receipt. The computer-assisted features enables a central system of signature verification for purchase transactions at self-service check-out counters.
Owner:KUO YOU TI +1
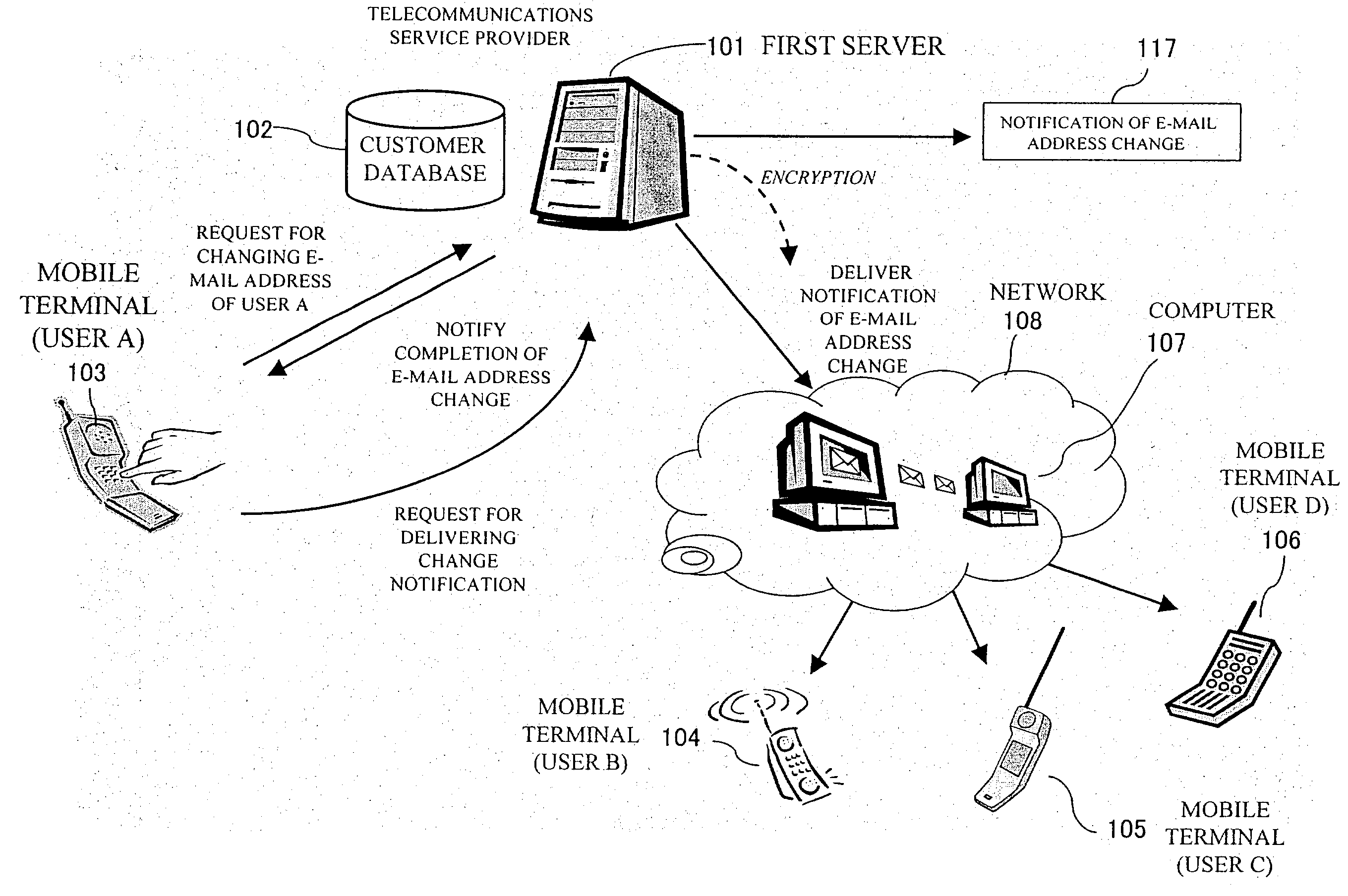
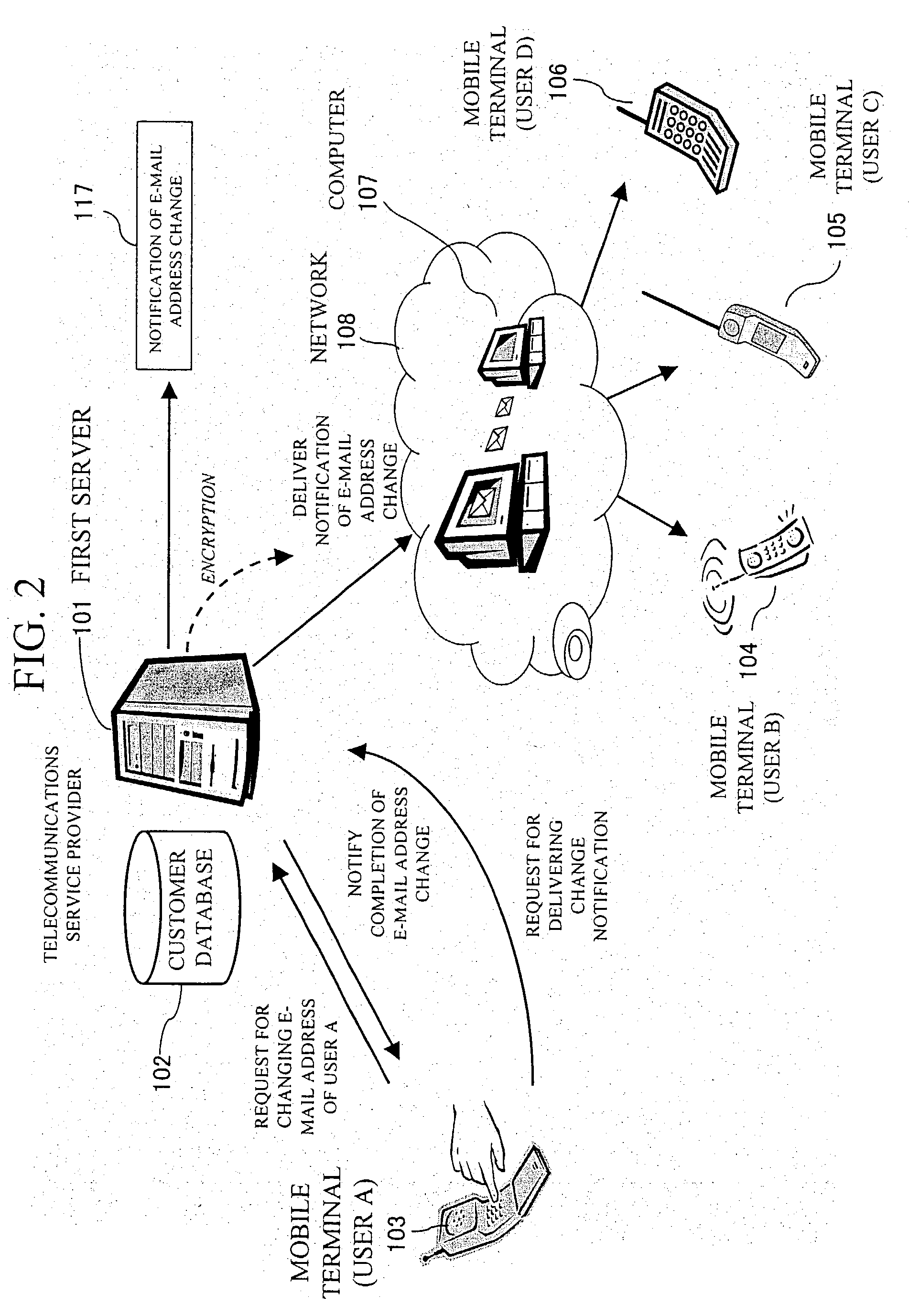
System and method for automatically changing user data
InactiveUS20030211844A1Special service for subscribersSubstation equipmentInternet privacyElectronic mail
A system automatically changes the user data such as e-mail address registered in reception designation lists used in a reception designation service according to notification of user data change. Reception designation service lists are provided for storing user data of each of users of a reception designation service. A first server has a capability of sending a notification of user data change according to a request from a terminal device of a user, the notification containing a change from a former user data to a new one. A second server has a capability of receiving the notification and changing the former user data to the new one in a corresponding one of the lists to the terminal device according to the notification. When the corresponding one of the lists is set to be changeable, the second server changes automatically the former user data to the new one in the corresponding one of the lists.
Owner:NEC CORP
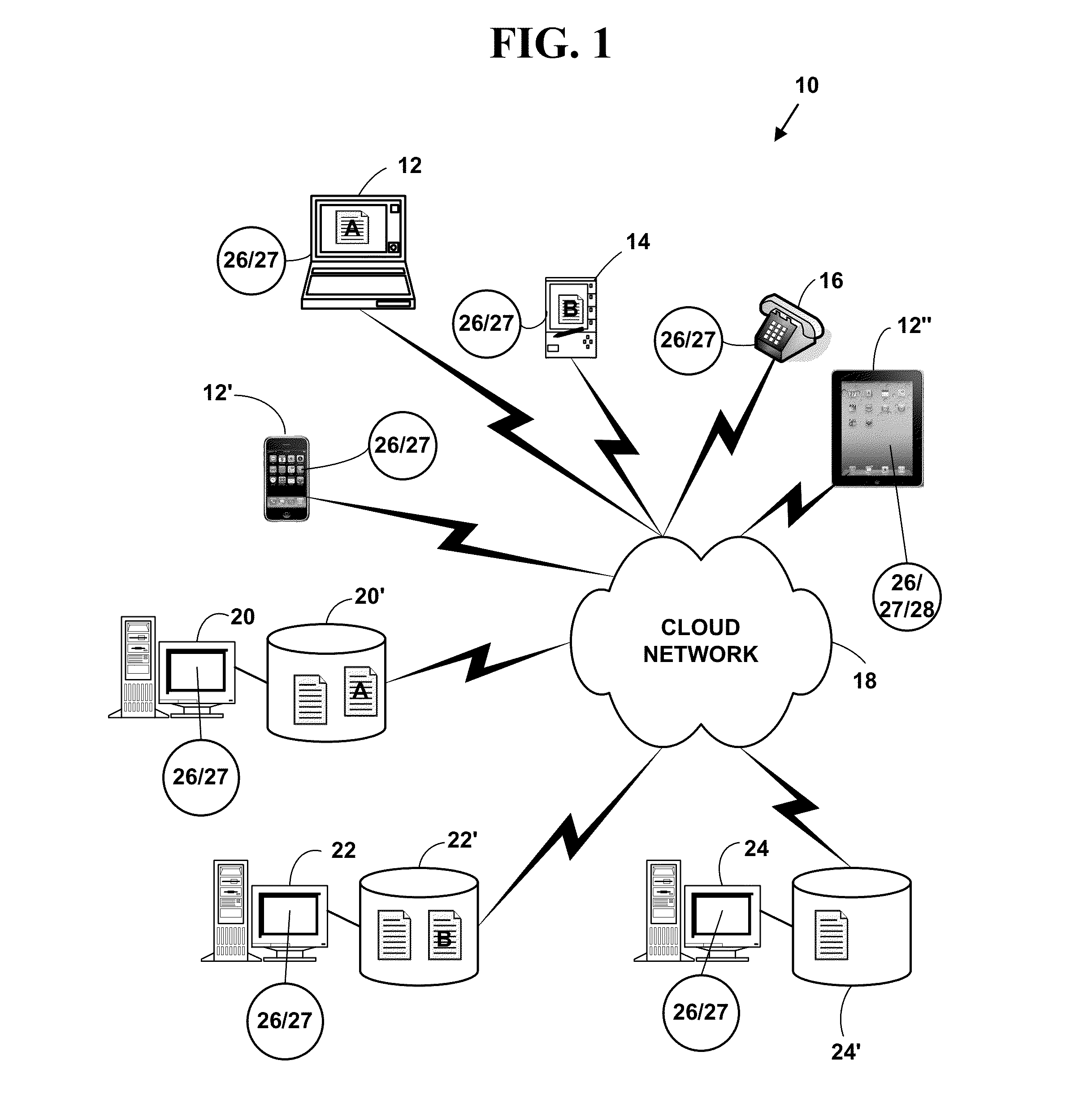
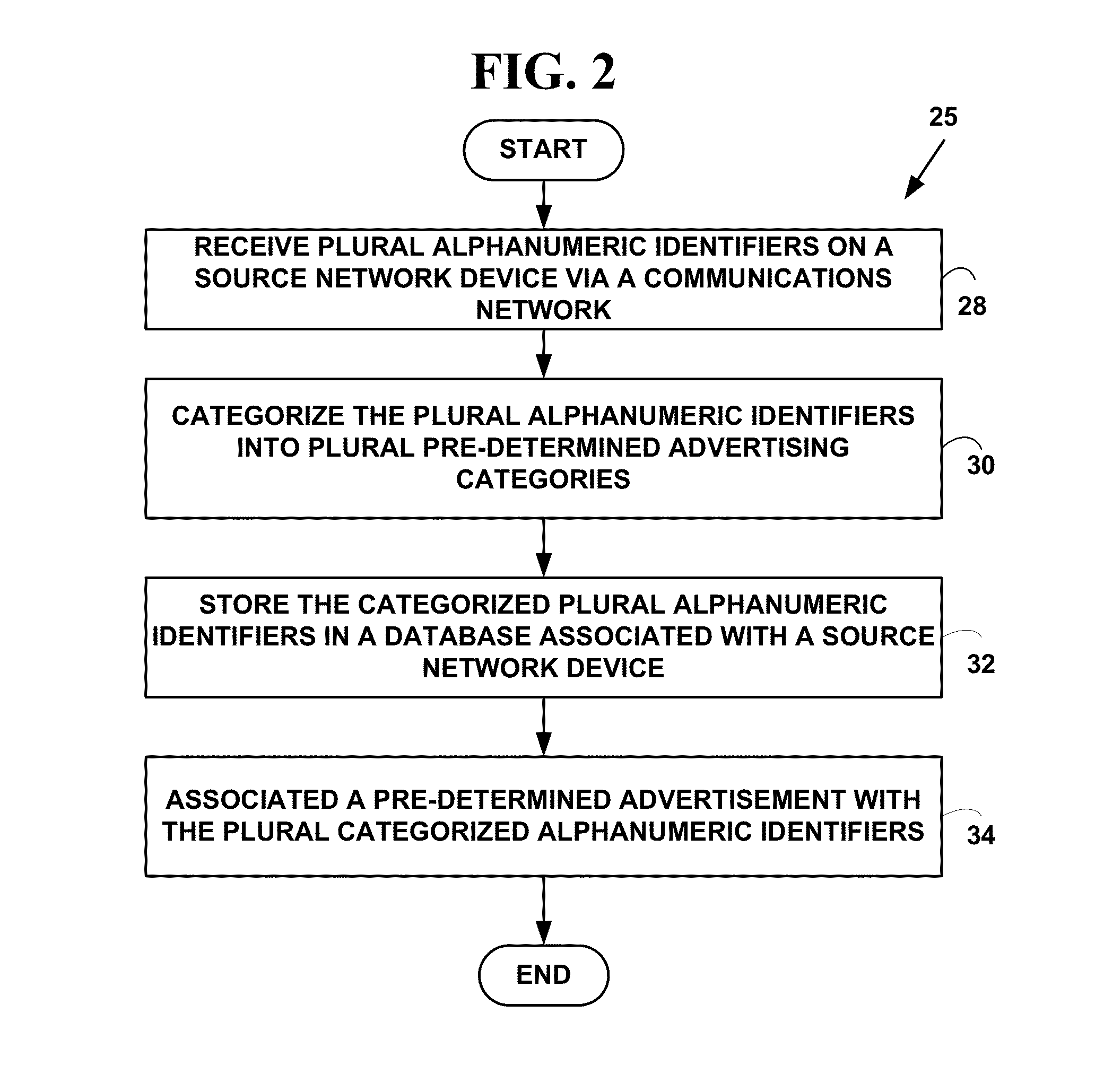
Method and system for automated intellegent advertising on wearable devices
A method and system for automated intelligent advertising on wearable devices. The wearable devices includes digital eyewear, clothing, jewelry, watches, etc. Messages sent to an invalid alphanumeric identifier (e.g., WiFi addresses, e-mail address, text message address, social networking identifier, etc.) for a desired network service are returned including a notification that an attempt to connect to the desired network service has failed and also includes electronic advertising information that allows a network device to view and display a retrieved pre-determined advertisement or the dynamically generated advertisement and make a selection input to automatically connect to another network device associated with the retrieved pre-determined or dynamically advertisement to obtain additional electronic advertising information.
Owner:BOOKSTAFF BLAKE
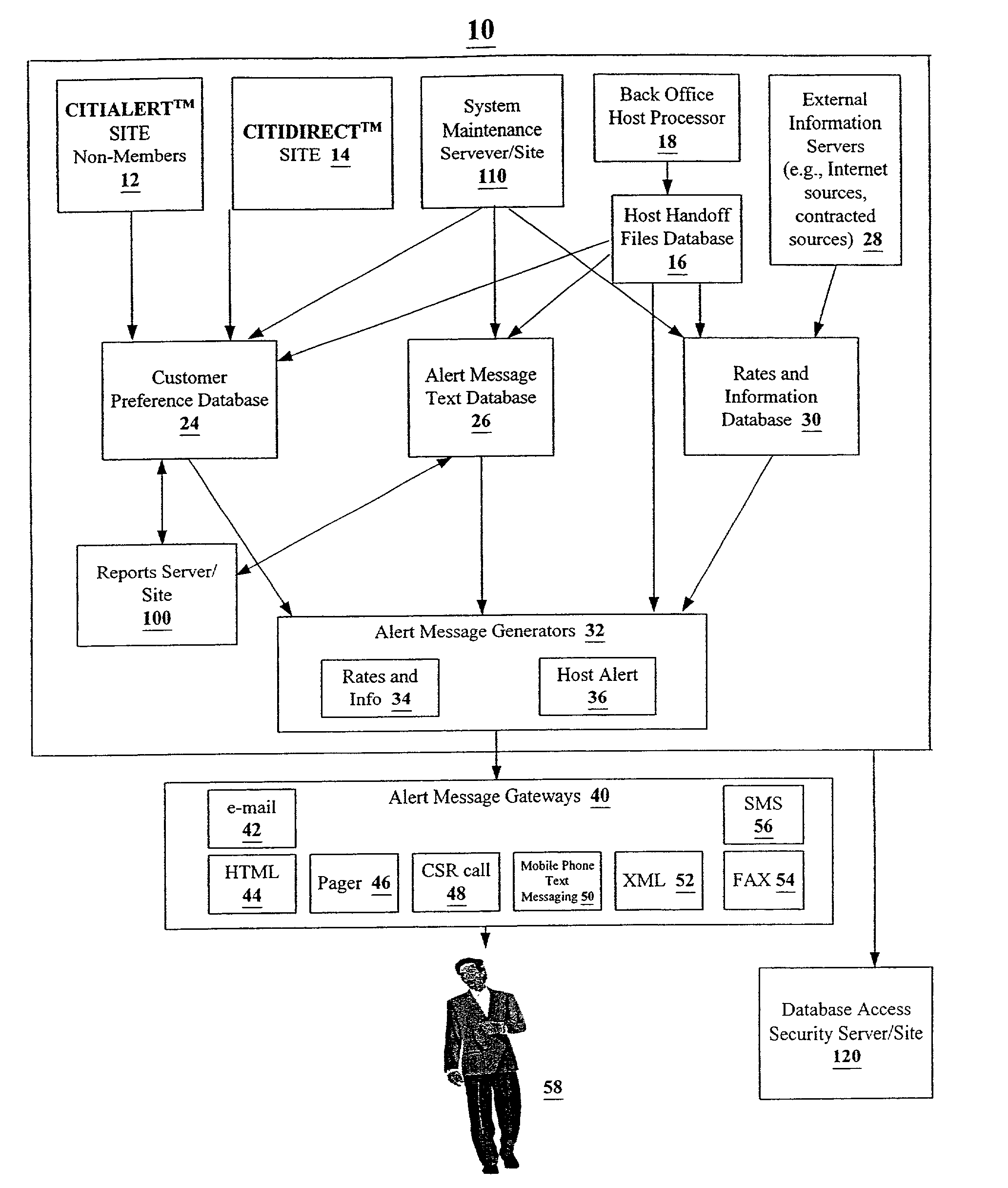
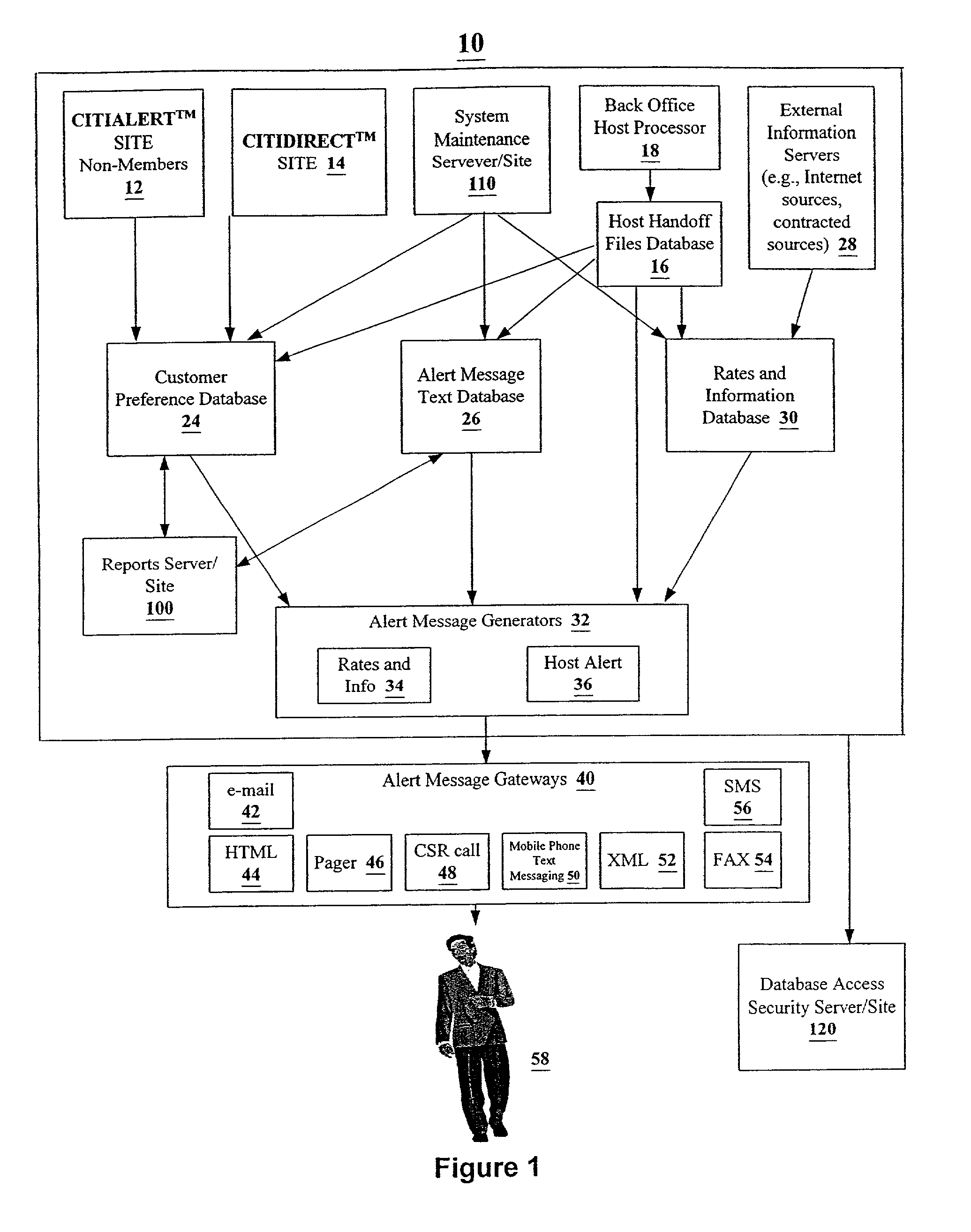
Method and system for notifying customers of transaction opportunities
A standalone notification system, including a notification server which generates electronic messages to registered customers upon their request or upon a host business request. The customer provides the system with his / her messaging identification (“ID”), e.g. e-mail address, GSM (global system for mobile communications) or other mobile phone numbers that are able to accept, e.g., short message service (“SMS”) messages, facsimile number, and / or telephone number. Customers can register with the host notification server without having any relationship, banking or otherwise, with the host. Customers can choose between different notification channels such as e-mail, SMS message, fax or pager.
Owner:CITICORP CREDIT SERVICES INC (USA)
System for timely delivery of personalized aggregations of, including currently-generated, knowledge
InactiveUS7668885B2Shorten the timeEffectively and efficiently aggregate and delivers personalized informationDigital data processing detailsSpecial data processing applicationsPersonalizationEmail address
A multidimensional method and apparatus for adaptively characterizing and aggregating data through a secure automated means of database modification, a prioritization and weighting system, a third party enhanced metadata entry and classification mechanism, adaptive and time varying individual personality and preference characterization, and an aggregation and delivery capability which allows for multiple data formats and mediums. Individual characterization incorporates an inference engine which formulates client composite images which vary with time. Asynchronous data interchanges enabled through the use of XML allow for more efficient and effective resource utilization and time. The knowledge system of this invention A) effectively integrates information from diverse sources, B) verifies, adds to or enhances source metadata (product data sheet; article title), and C) searches, queries, retrieves, and aggregates information. Selected product information can be obtained by e-mail without exposure to spamming by using e-mail address translation.
Owner:MINDAGENT
System and method for secure communications
InactiveUS20050278533A1Avoid accessAvoid problemsUser identity/authority verificationComputer networkEmail address
Like Microsoft's call for trustworthy computing, there are similarly a few inherent problems in communications between computers and / or between other electronic devices (such as for example Fax machines), which can initiate a similar call for trustworthy communications. These problems are caused mainly by various limitations in the currently employed communication protocols, for example over the Internet, or in Fax transmissions. The two main problems are: Verification by the sender that the user indeed received the message, and verification by the receiver that the purported sender indeed is the one who initiated the message. Both of these features are currently lacking for example in normal Fax communications and in normal email communications. In electronic communications over the Internet for example normal email communications allow users very easily to falsify the sender's email address, as happens for example many times when spam (unsolicited junk mail) is sent, or when various viruses, such as for example the Klez worm, spread themselves. A deeper issue in preventing the faking of email addresses is preventing the faking of IP addresses, since, clearly, making sure that the IP address is not forged can help considerably for verifying also the email address. Similarly, when sending normal email messages, the user cannot be sure that the receiver indeed received the message and / or if he / she opened it or read it. Although there are already some solutions to this 2nd problem, these solutions still have various remaining problems, so the problem has not been completely solved yet. The present invention solves the above problems by providing various solutions that preferably include improvement of the protocols and preferably include also methods for preventing theft of digital signatures.
Owner:MAYER YARON
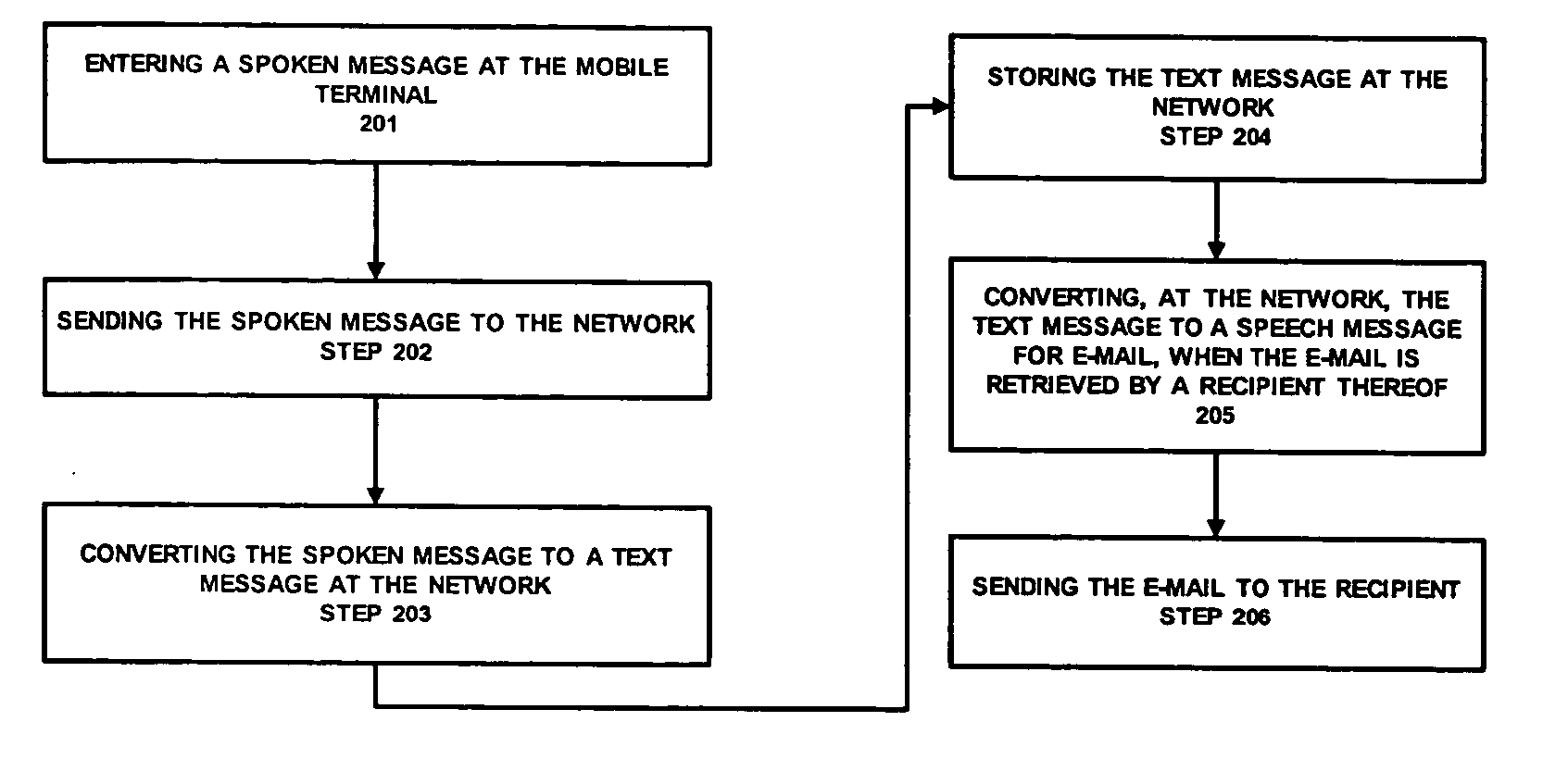
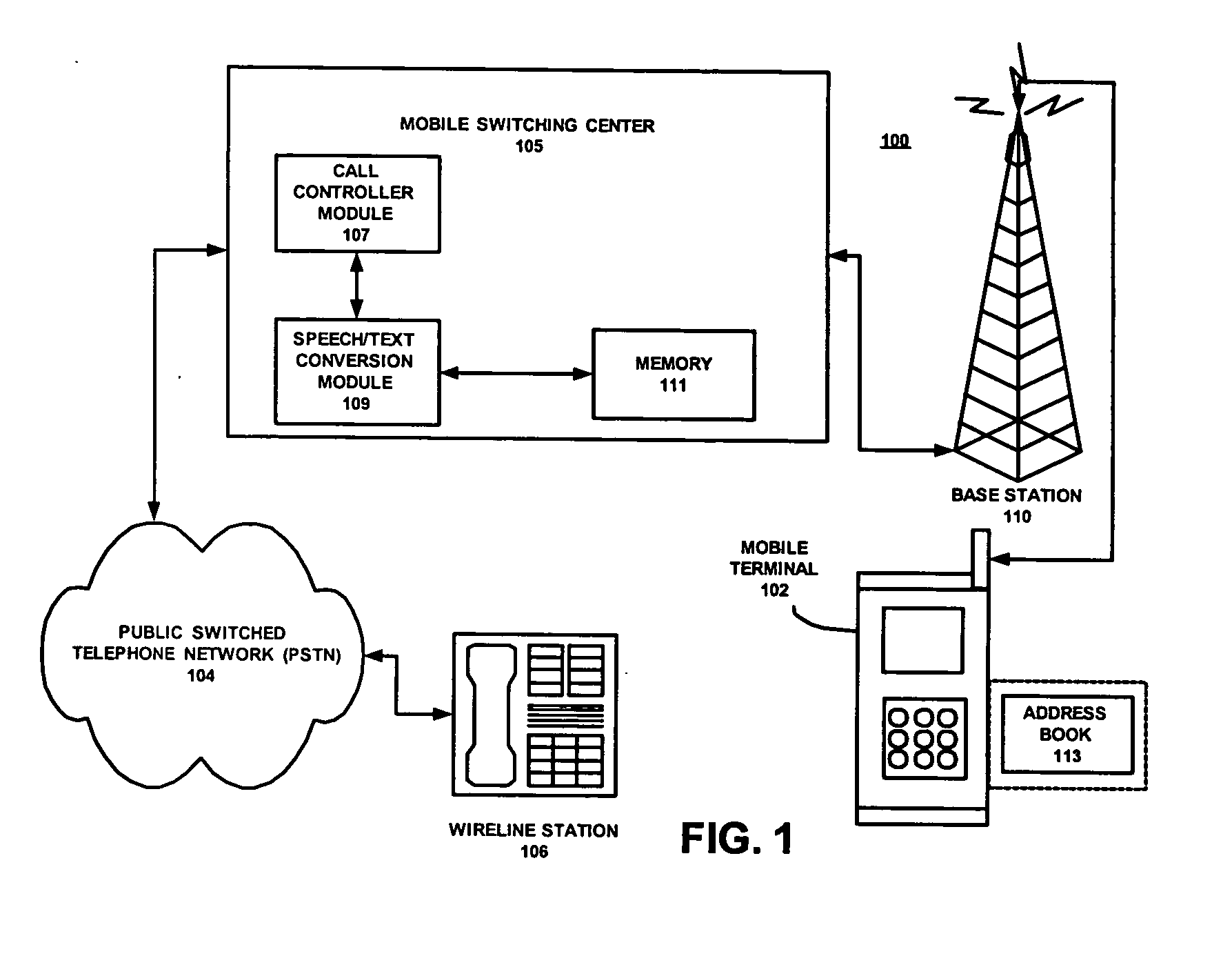
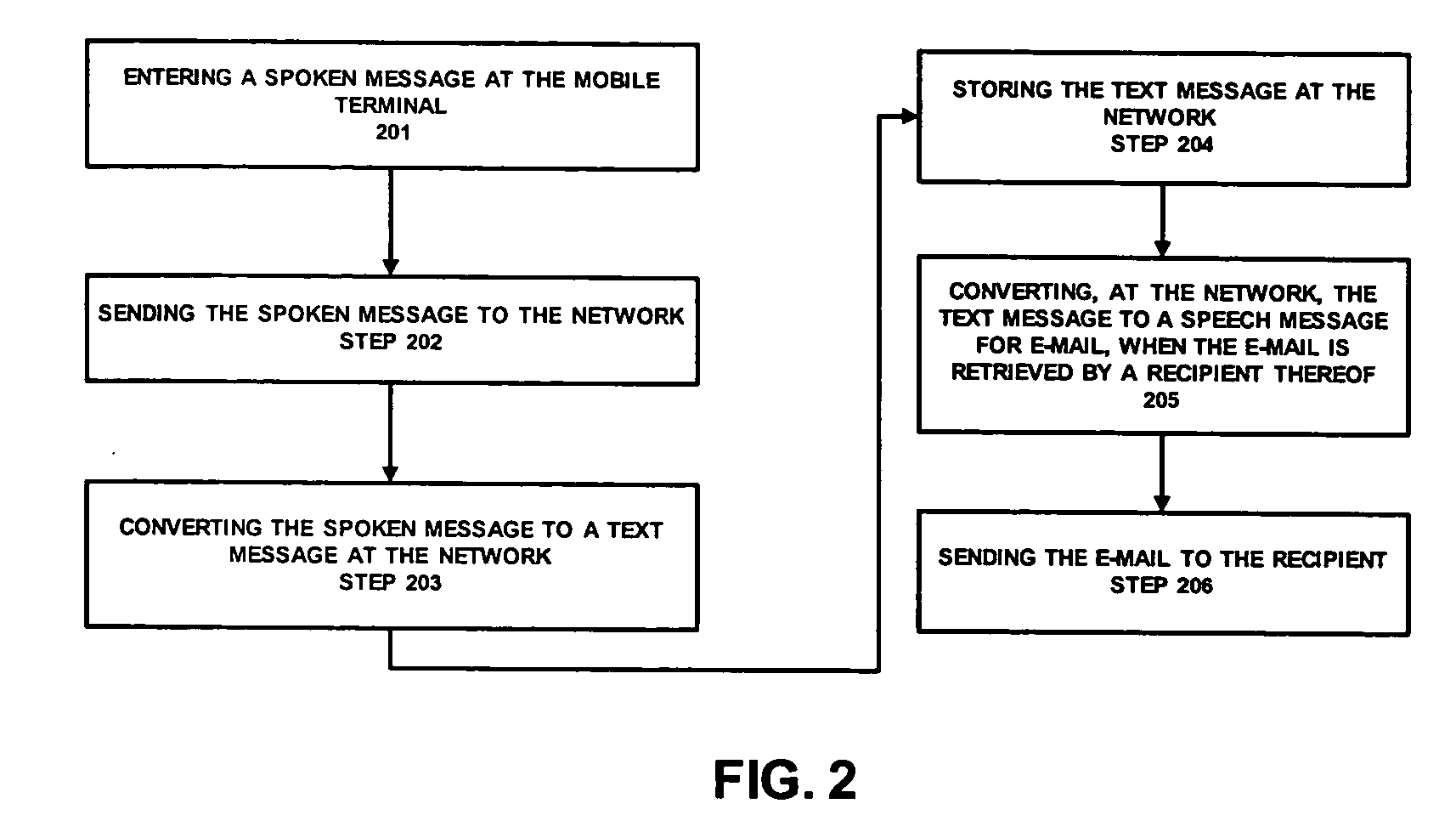
Network support for wireless e-mail using speech-to-text conversion
Embodiments of the system, and method provide for network support for wireless e-mail using speech-to-text conversion. One embodiment of the method may have the steps of: entering a spoken message at the mobile terminal; sending the spoken message to the network; and converting, at the network, the spoken message to an e-mail message that is sendable to any e-mail address.
Owner:LUCENT TECH INC
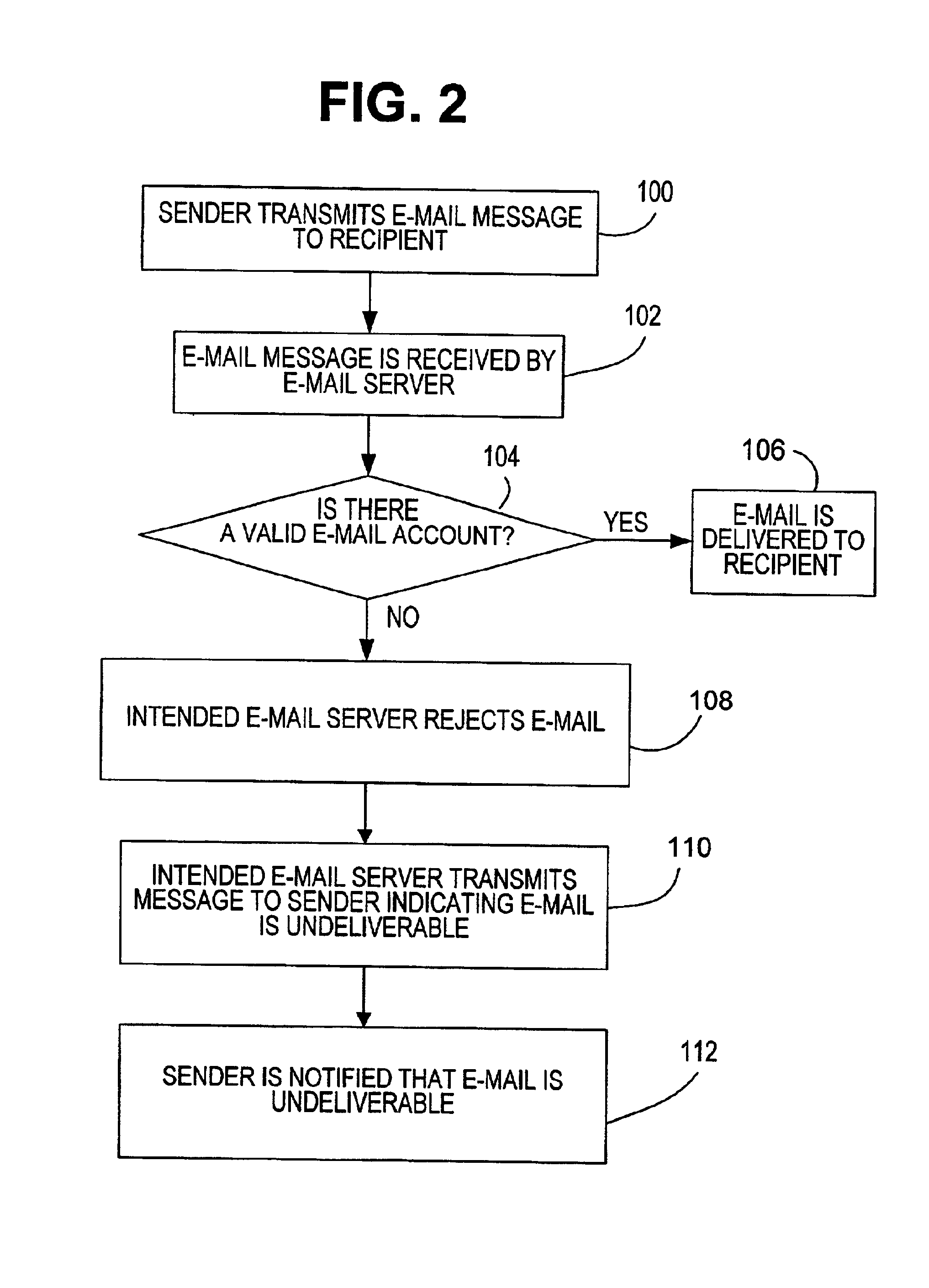
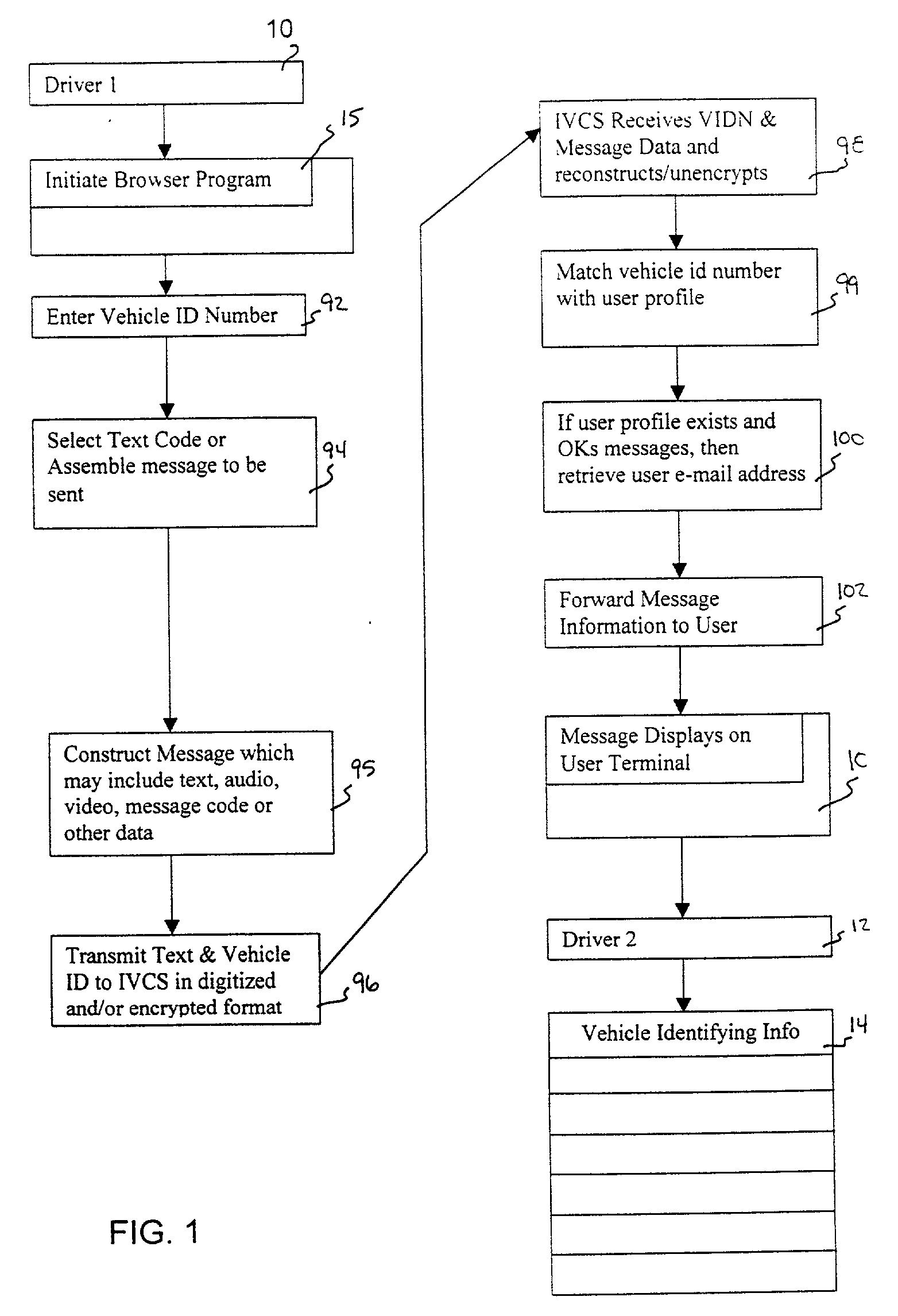
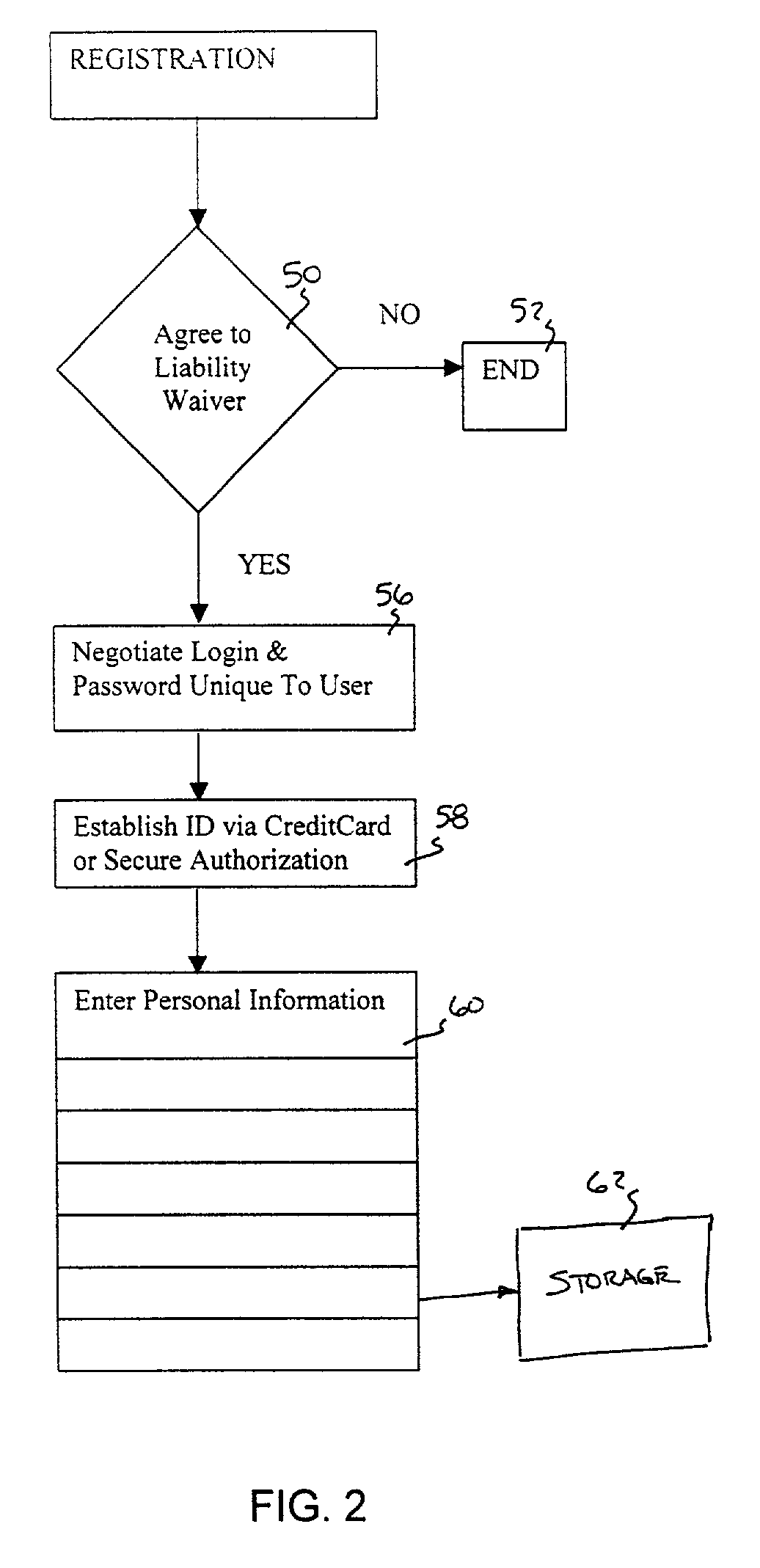
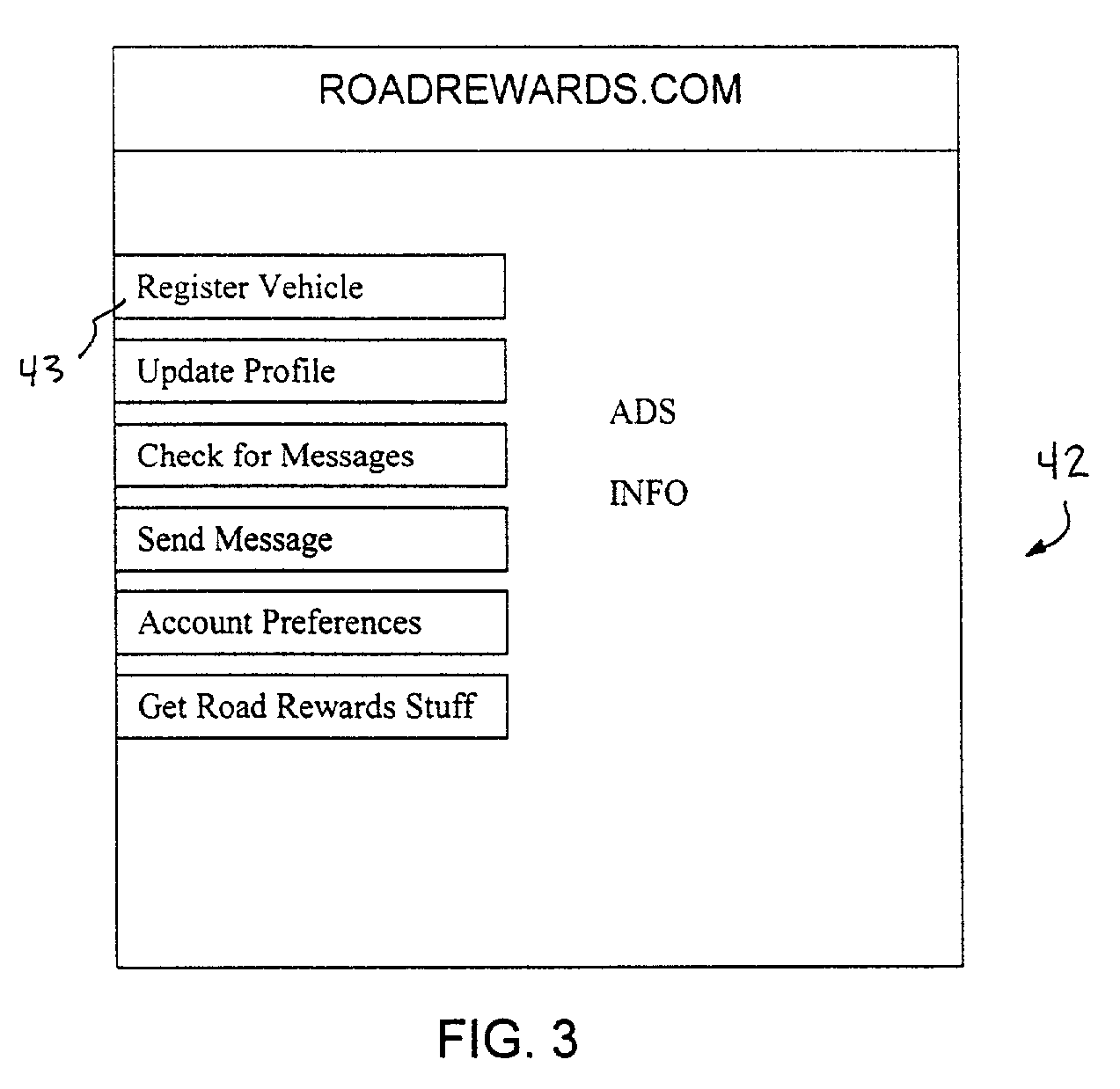
Inter vehicle communication system
InactiveUS20010034768A1Instruments for road network navigationDigital data processing detailsEmail addressInter-process communication
A method and network for transmitting a message from a sender to a recipient wherein the sender has no previous knowledge of the recipient's address. A network is provided for registering a user with an internet service by providing correlating data on the user's e-mail address and vehicle license plate number and other vehicle identifying information. A sender observing a recipient's can send a message to the recipient by logging onto the service and sending a message including the license plate number of the vehicle or other vehicle identifying information. The service will forward the message to the recipient by looking up the vehicle information and providing the corresponding e-mail address to the message and sending to the recipient.
Owner:BUMP NETWORK
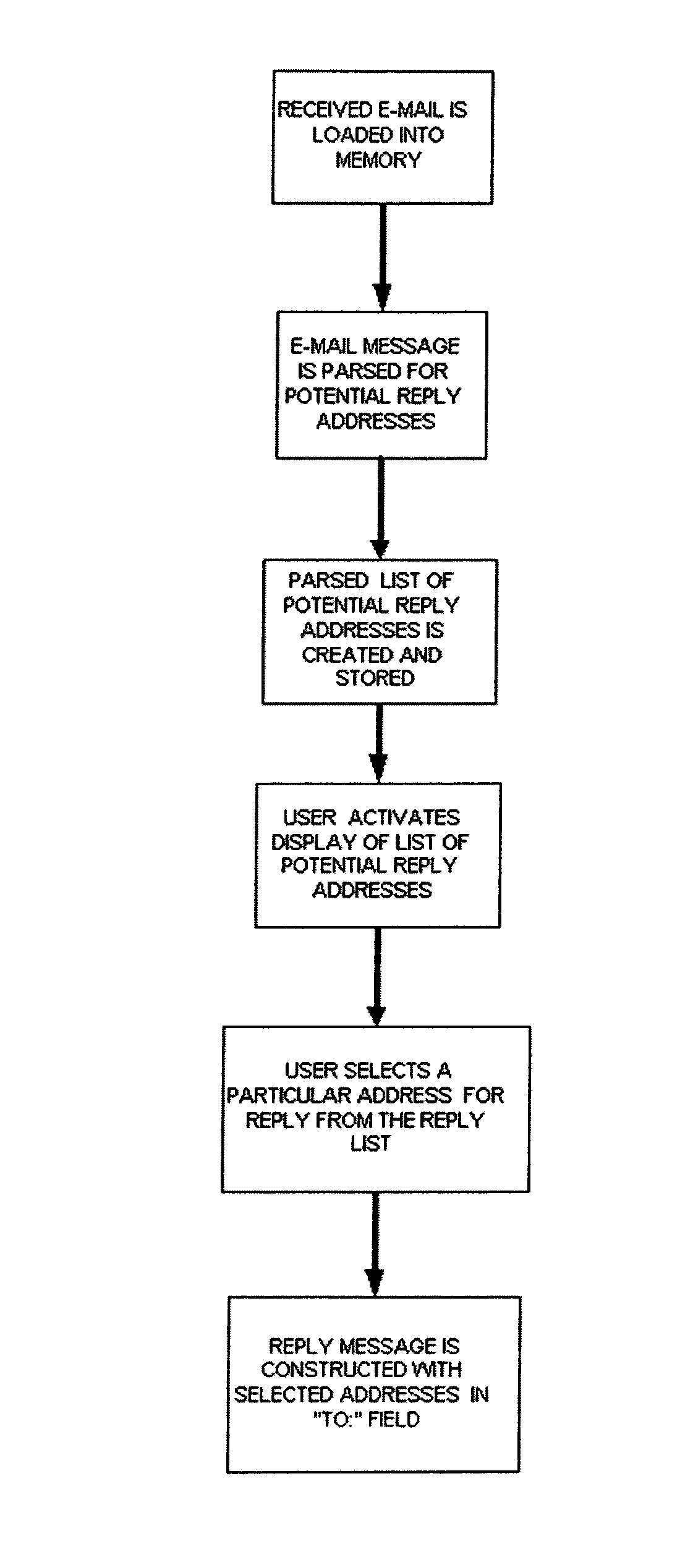
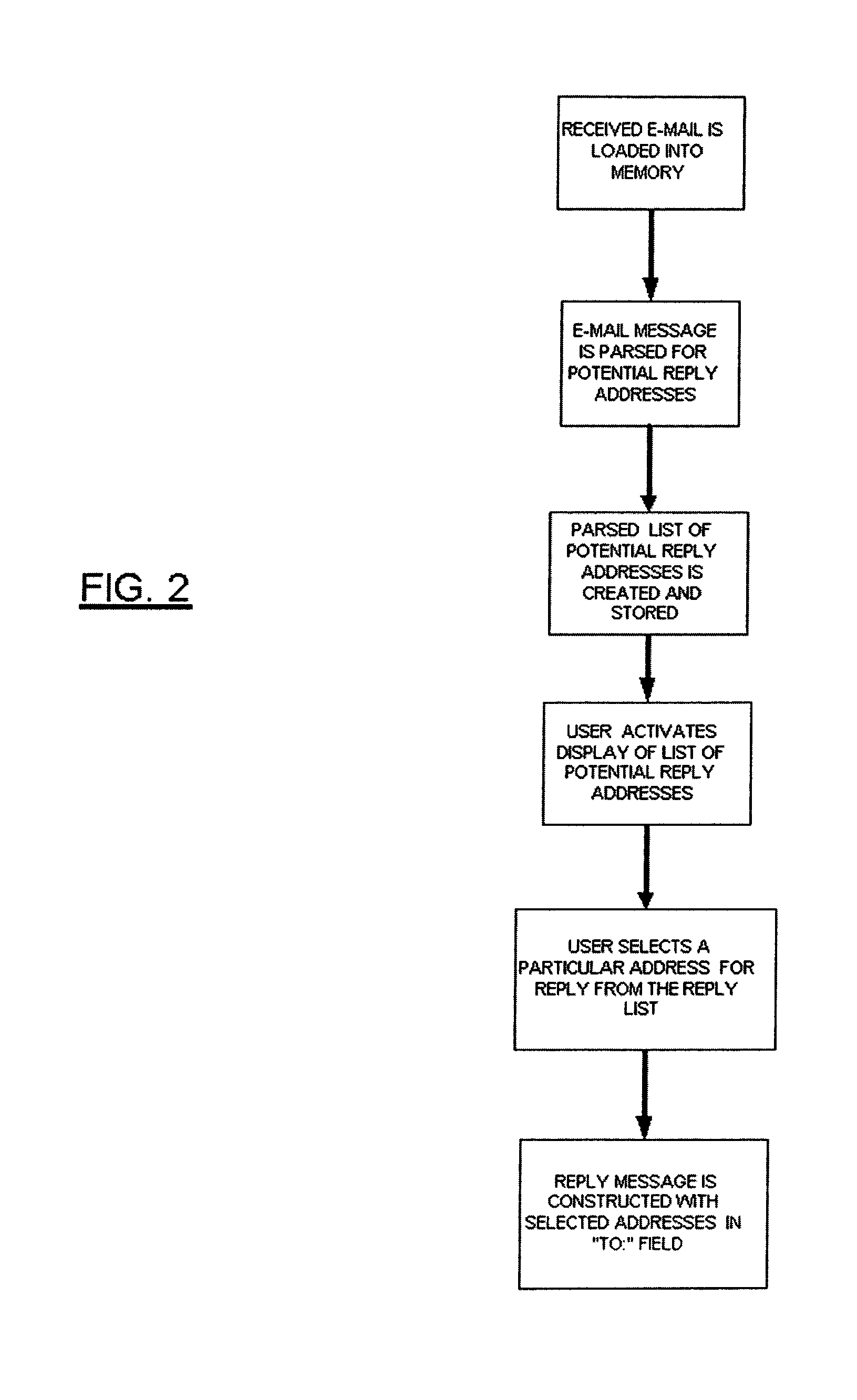
Method and computer product for identifying and selecting potential e-mail reply recipients from a multi-party e-mail
InactiveUS20040078488A1Multiple digital computer combinationsData switching networksEmail addressEngineering
Currently, e-mail systems automatically compose reply e-mail messages by entering the previous sender's address as the reply recipient address. The present invention provides a method to permit a recipient of a multi-party e-mail message to select recipients of a reply message by parsing the received message for e-mail addresses and forming a list from which the user can select reply recipients.
Owner:IBM CORP
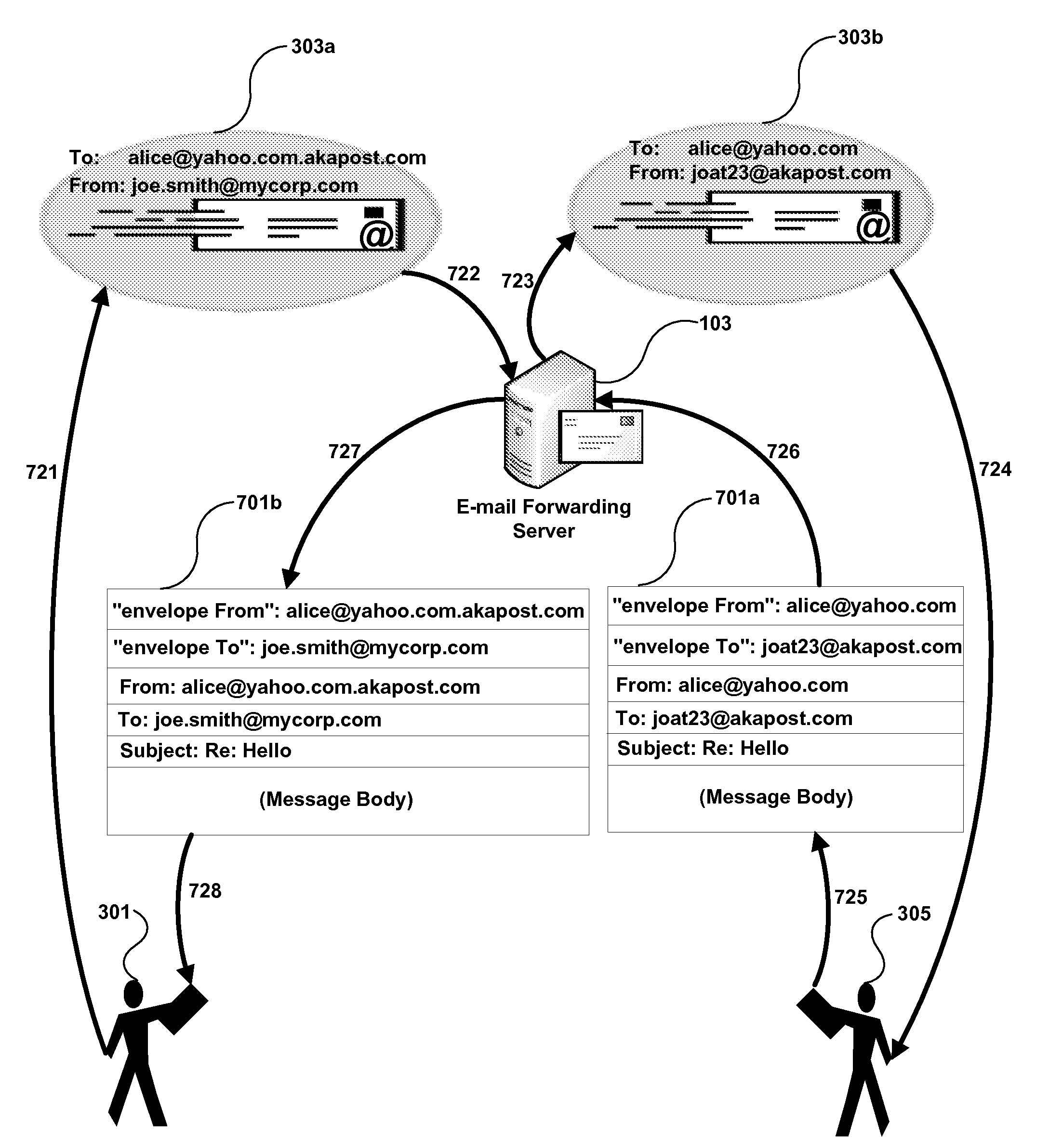
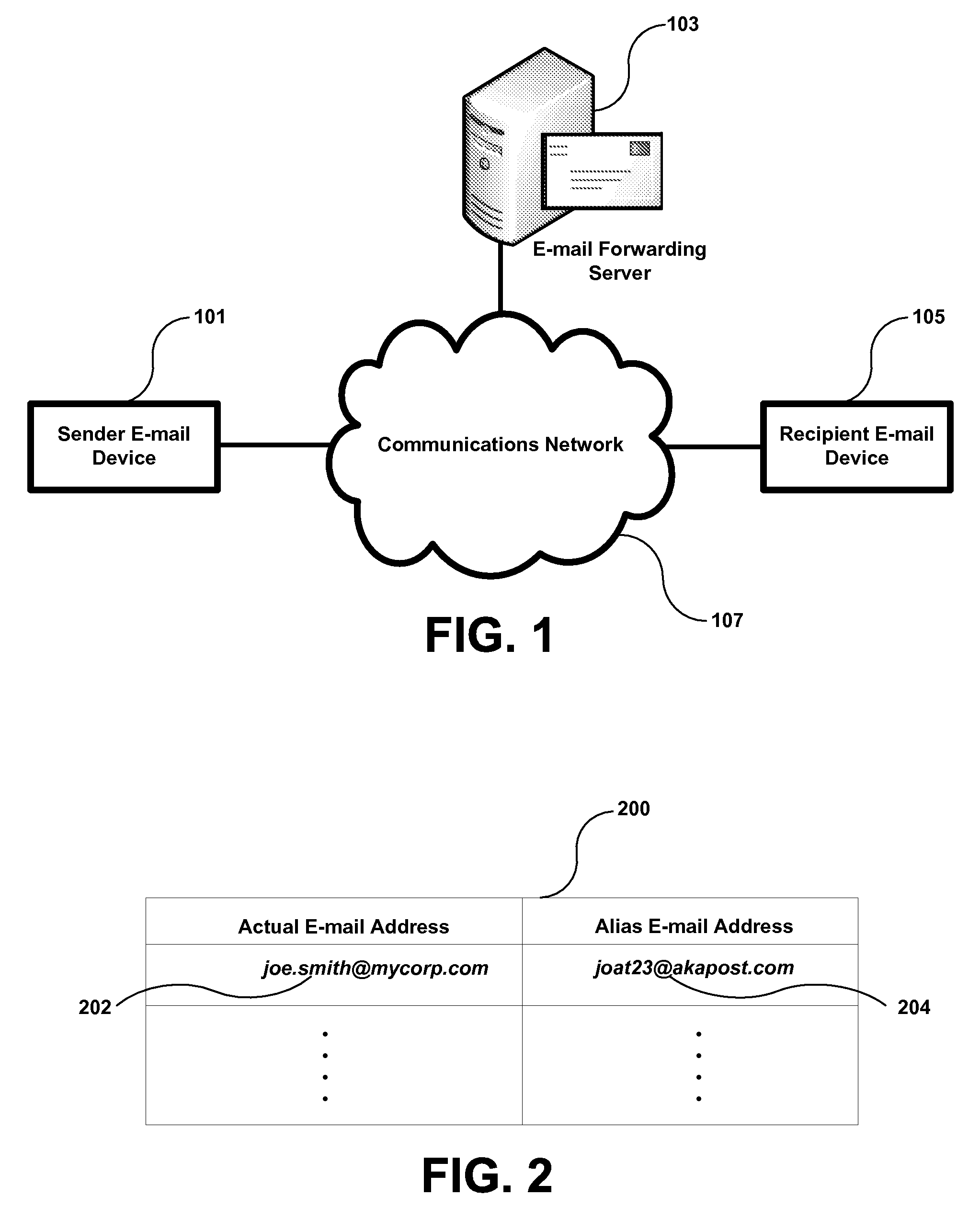
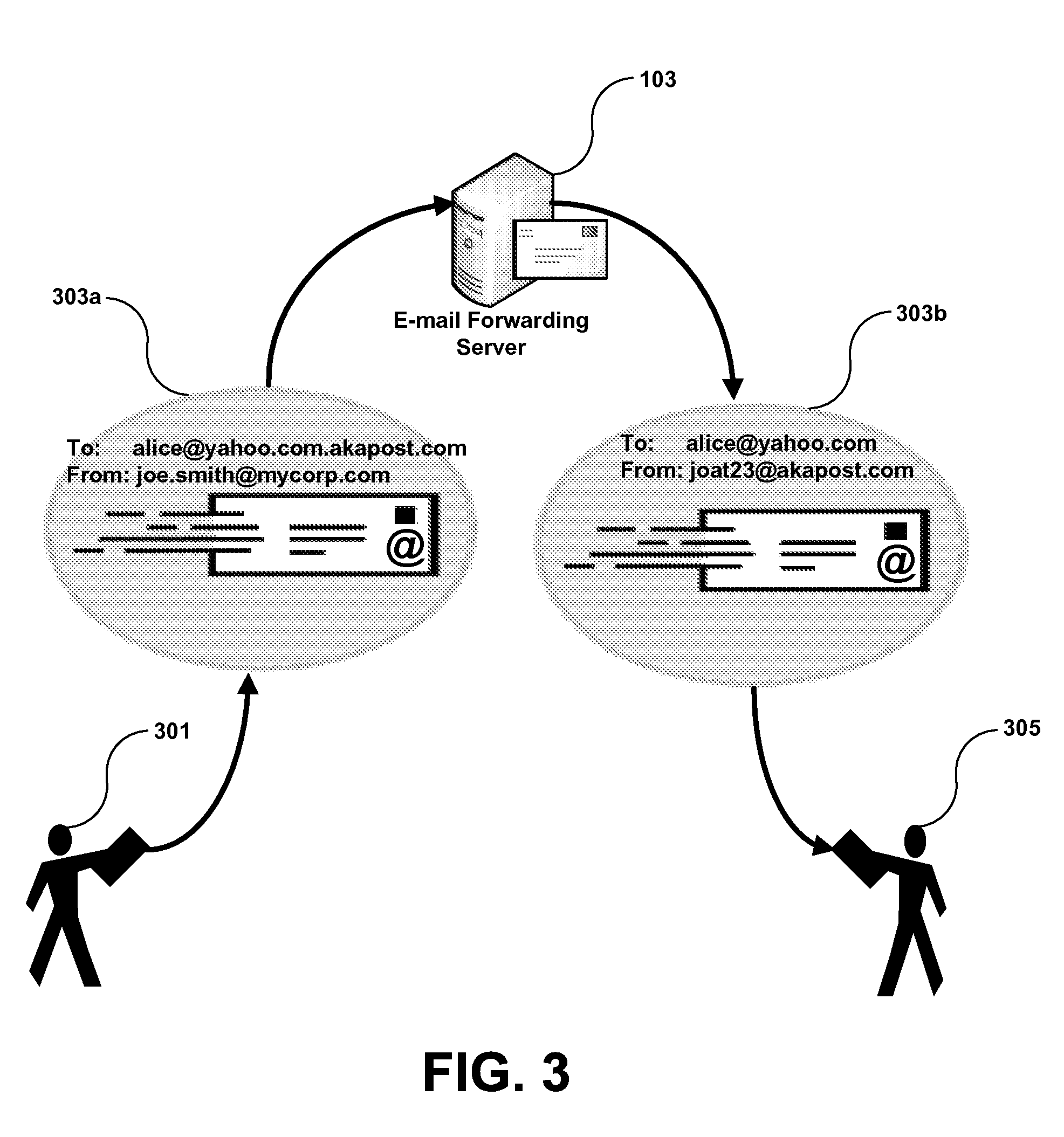
System and method for protecting e-mail sender identity via use of customized recipient e-mail addresses
InactiveUS20080052364A1Good choiceMultiple digital computer combinationsTransmissionEmail addressInternet privacy
A system and method are disclosed for protecting e-mail sender identity by redirecting e-mail messages to an e-mail forwarding server via use of customized recipient e-mail addresses. An e-mail message is sent from a user's actual e-mail account to a customized recipient e-mail address. Because an e-mail forwarding server of the present invention is the Mail Exchange (MX) authority for the domain of the customized recipient e-mail address, the e-mail message is sent to the e-mail forwarding server. The e-mail forwarding server contains a database that stores users' actual e-mail addresses and their associated alias e-mail addresses. When the message is received by the e-mail forwarding server, it parses the message recipient's e-mail address to obtain the intended recipient's e-mail address, replaces the message sender's actual e-mail address with its associated alias e-mail address, and delivers the message to the original intended recipient. To the recipient the message appears to be sent directly from the sender's alias e-mail address. Therefore the sender's actual e-mail identity is not exposed to the recipient. When the e-mail forwarding server receives an e-mail message sent or replied to the user's alias e-mail address, it automatically forwards the message to the user's actual e-mail address.
Owner:ZHOU XIANG
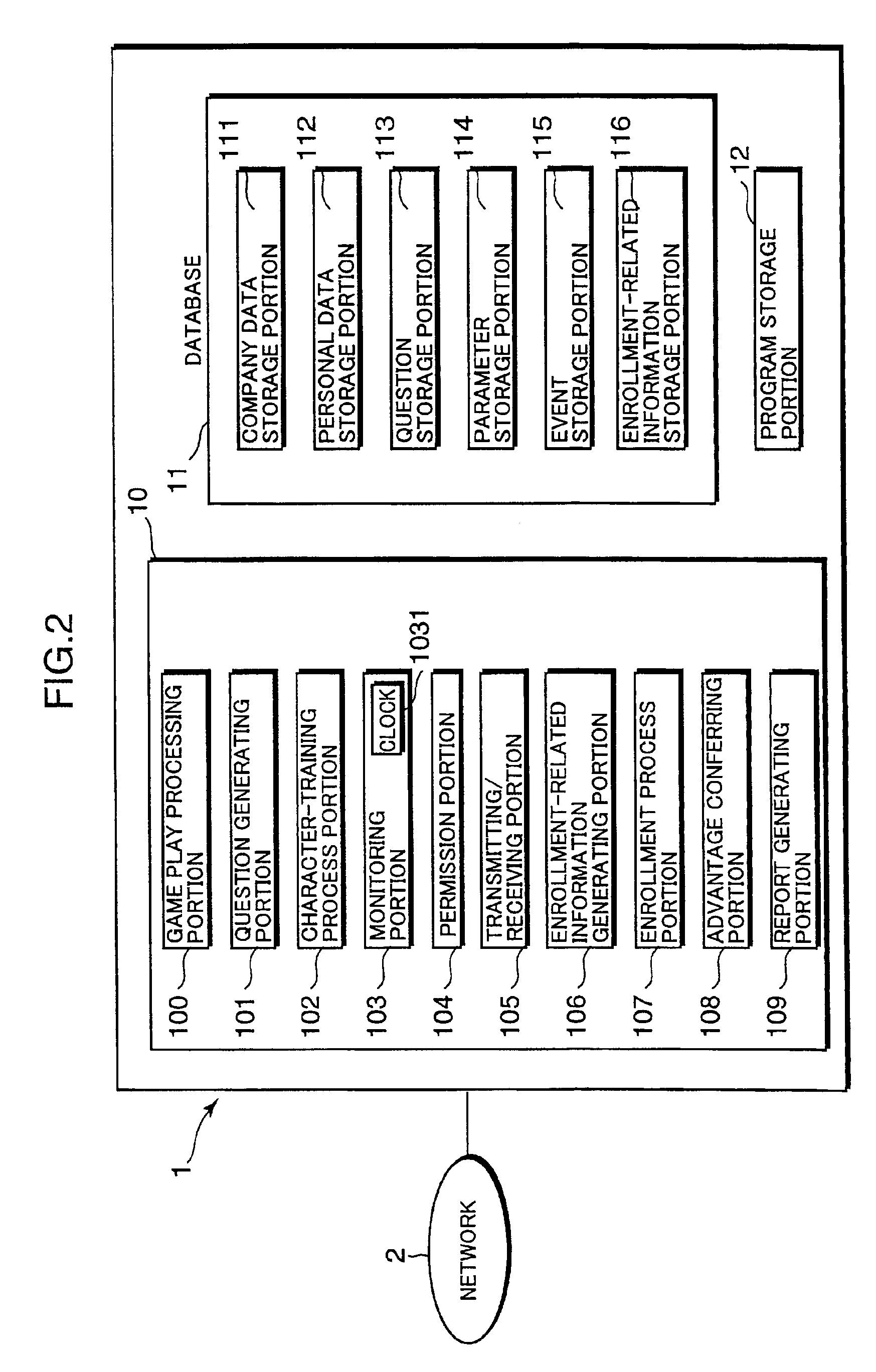
Net game system, processing method for playing net game, and computer-readable storage medium for storing program for playing net game
InactiveUS6881148B2Increase the number ofBuying/selling/leasing transactionsVideo gamesData terminalComputer terminal
Network game system for playing a game with the aim of a achieving a predetermined goal. The game is played, via data terminals operated by member players, in a game space provided on a game server, while communicating with the game server on the network. The game server includes a recruiting information generating section for generating, upon receipt from a member player of referral information specifying the mail address of the data terminal of a non-member player, recruiting information including information specifying the member player, an enrollment processing section for performing enrollment processing upon receiving application information in response to recruiting information sent to the mail address of the non-member, and an advantage conferring section for conferring to the referring member player advantages useful in achieving the goal of the game.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
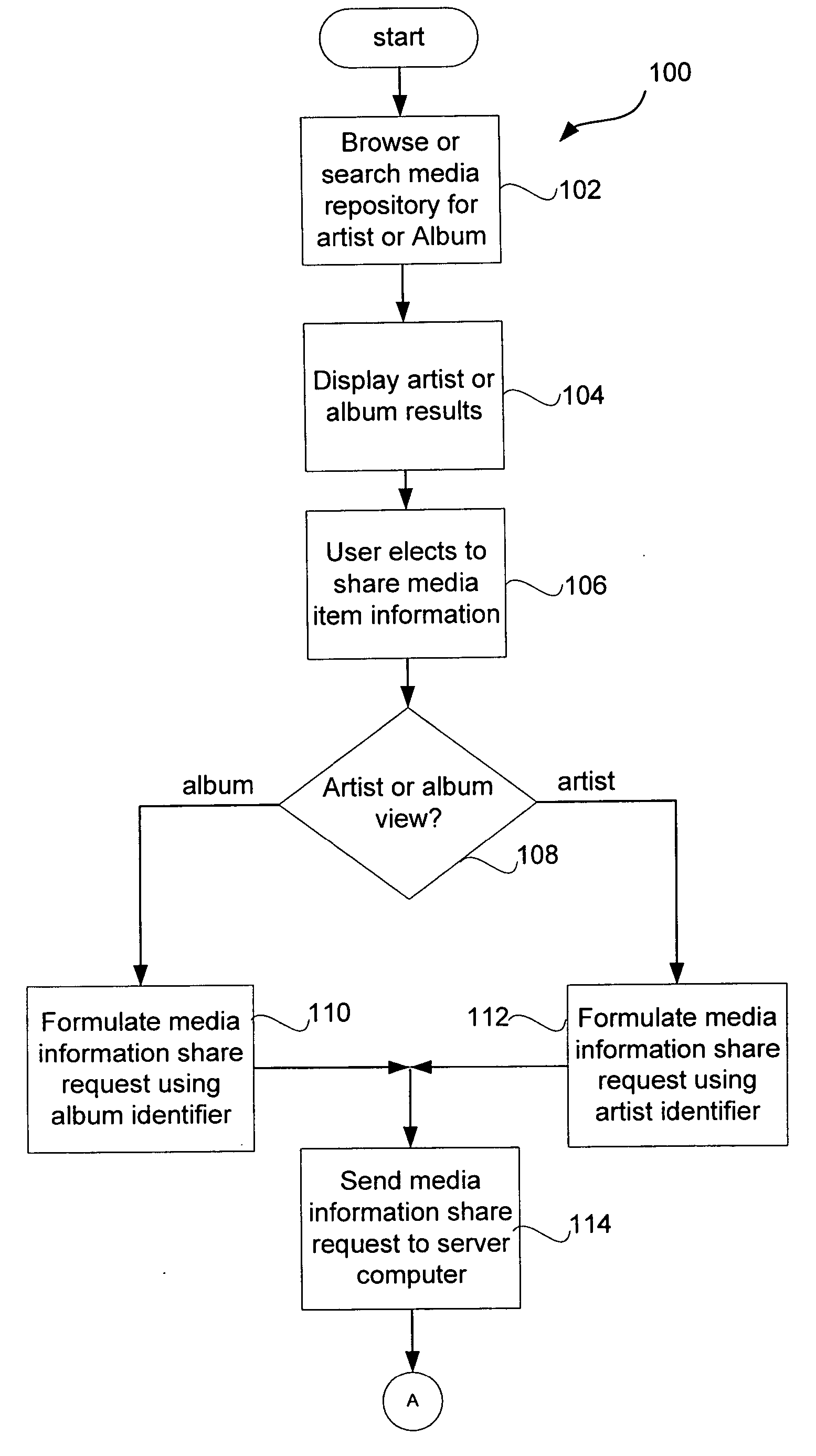
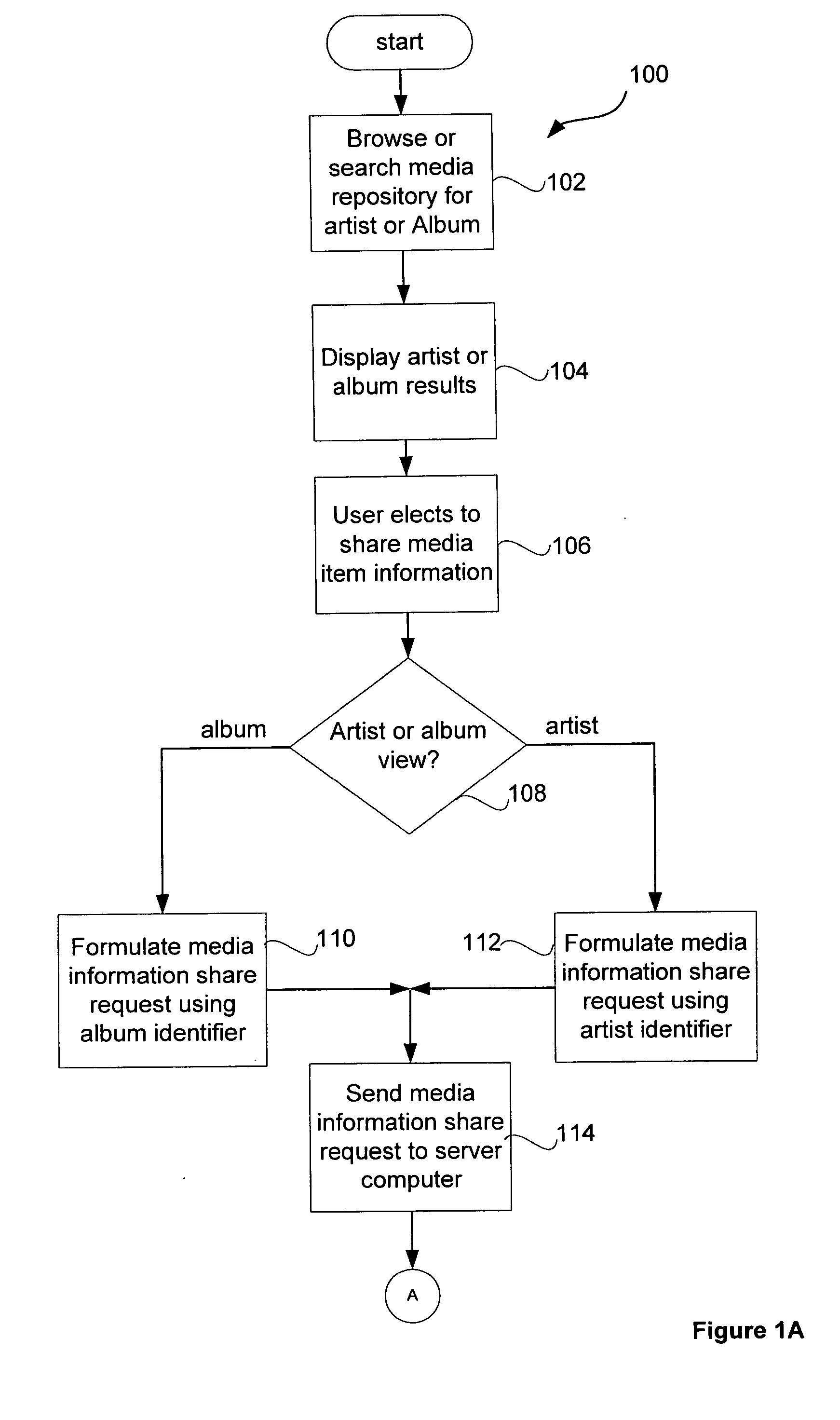
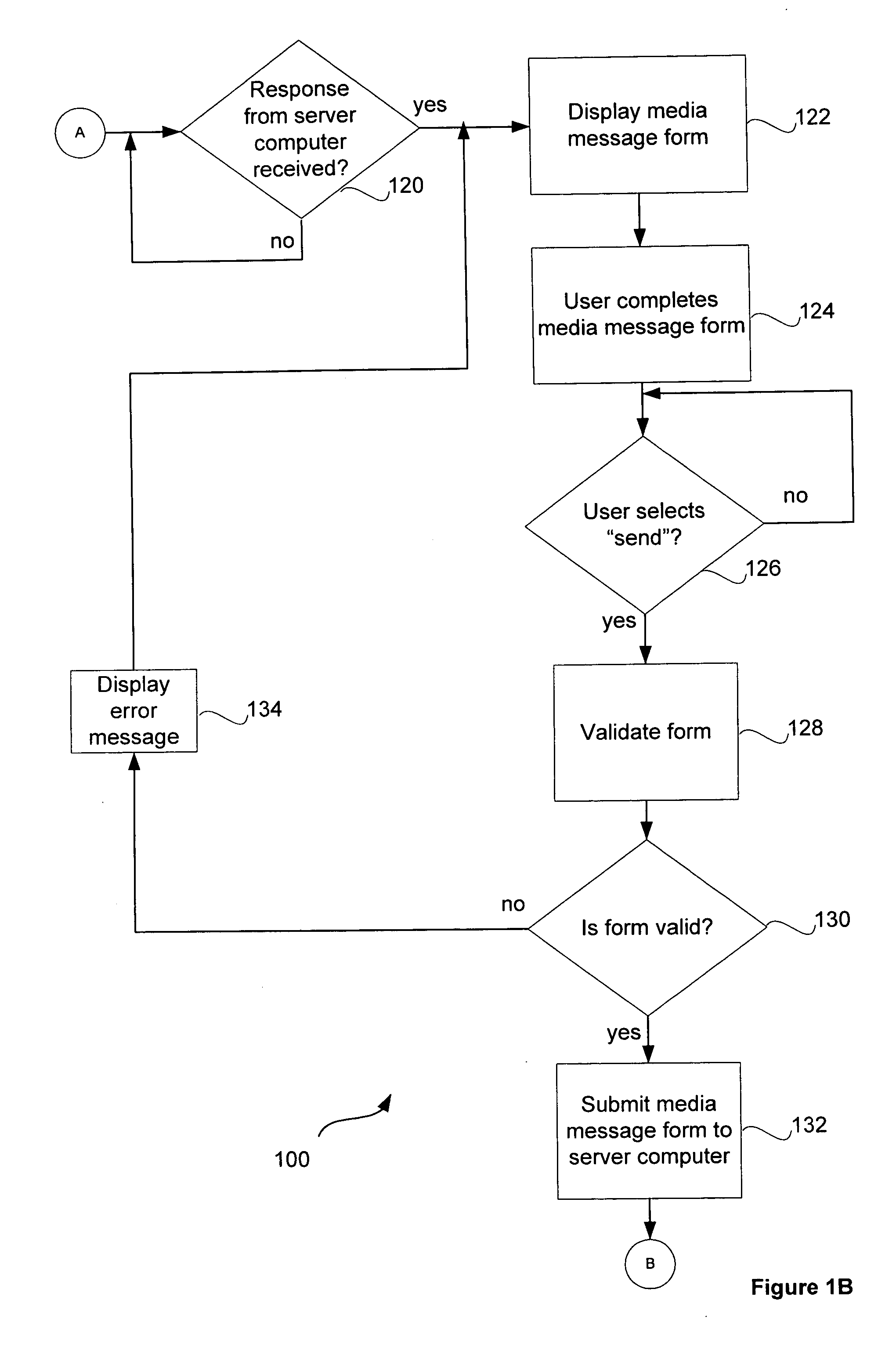
Method and system for sharing information about media items
InactiveUS20060026119A1Metadata audio data retrievalMetadata multimedia retrievalEmail addressClient-side
A method for sharing information between users of a media management application is disclosed. In one embodiment, a server computer receives a media information share request, retrieves artist or album information according to the media information share request, constructs a media message form containing artist or album information according to the media information share request and blanks boxes for the user to enter a plurality of recipient e-mail addresses, the user's name and e-mail address, and a message to the recipients, and sends the completed media message form to the client computer. The server computer then receives a completed media message form from a client computer, constructs a media message containing artist or album information according to the media message form, extracts a list of e-mail addresses from the media message form, selects an e-mail address from the list of e-mail addresses and sends a media message to each e-mail address in the list of e-mail addresses.
Owner:APPLE INC
Technique for assisting a user with information services at an information/call center
InactiveUS20060018441A1Easy to replyInstruments for road network navigationArrangements for variable traffic instructionsEmail addressPersonal details
A service providing information assistance may maintain for a subscriber contacts folders comprising private directories of the subscriber, and a personal profile containing the subscriber's preferences. When a user calls the service to attempt to communicate with a desired party through the service, the service can ascertain whether the desired party has a personal profile and / or a contacts folder associated with him / her. If so, the caller is allowed to communicate with the desired party on the terms and conditions defined by the desired party in his / her personal profile and / or contacts folder. For instance, the desired party may have defined therein who should be allowed to contact him / her, when he / she should be contacted, by what communication means, and whether the caller can be told any of the desired party's communication addresses (e.g., telephone number, email address, etc.).
Owner:GRAPE TECH GROUP
Methods and systems for protection of identity
InactiveUS20070078786A1Reduce harmImprove identityFinanceCharacter and pattern recognitionCredit cardEmail address
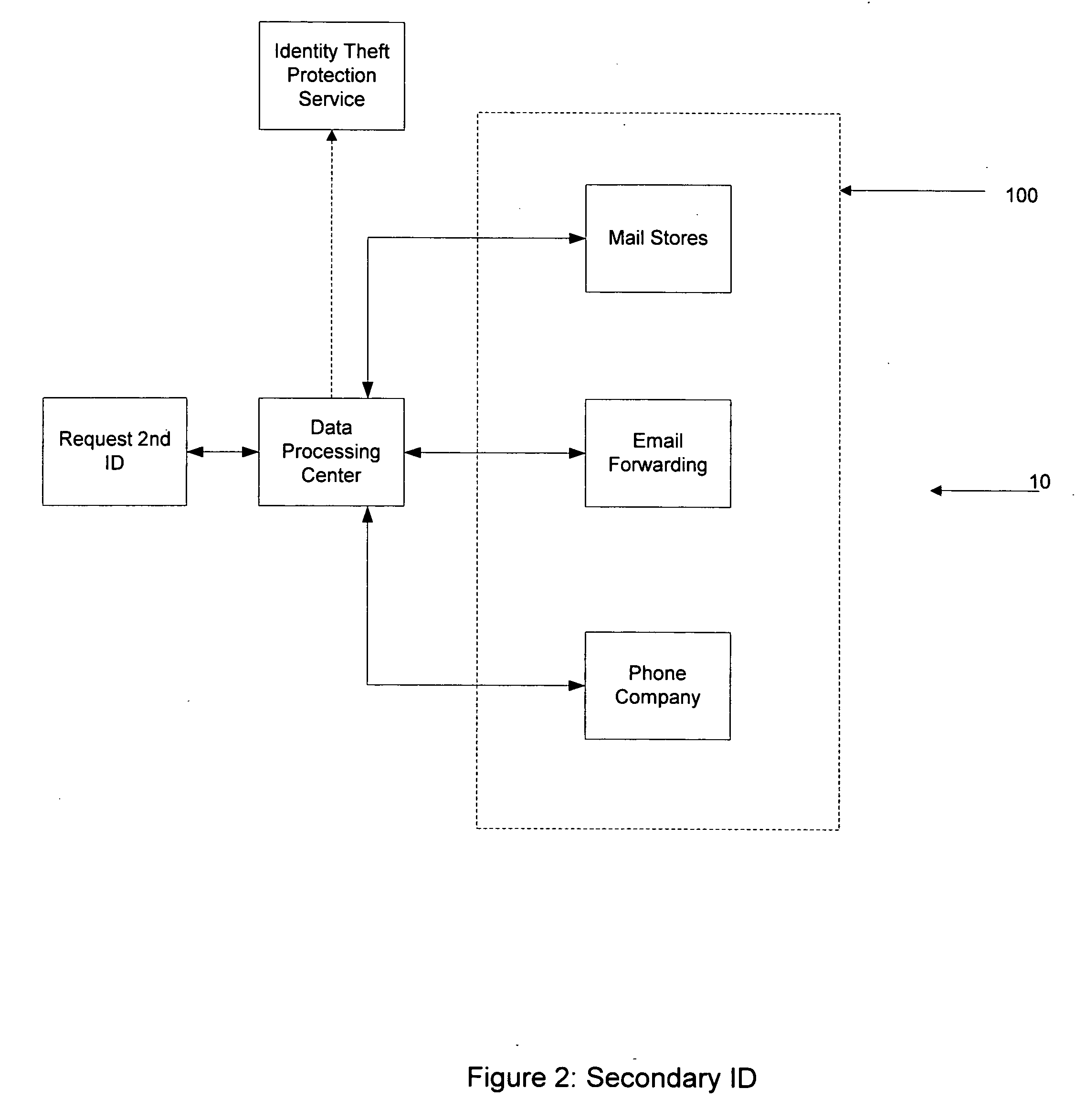
The present invention relates to a method to the creation and management of a secondary identification to avoid identify theft. Identity theft may occur over the internet, the purchase of goods and services by credit, and many other forms not yet known. The present invention creates a secondary identification for a person by creating one or more of the following secondary identifications which include a secondary email address, a secondary postal address, a secondary phone number, and any other identifying secondary information. The present invention describes methods and systems to create a secondary identification. Further, the present invention may be used to create a credit card containing the requestor's secondary identification.
Owner:SEAGATE TECH LLC
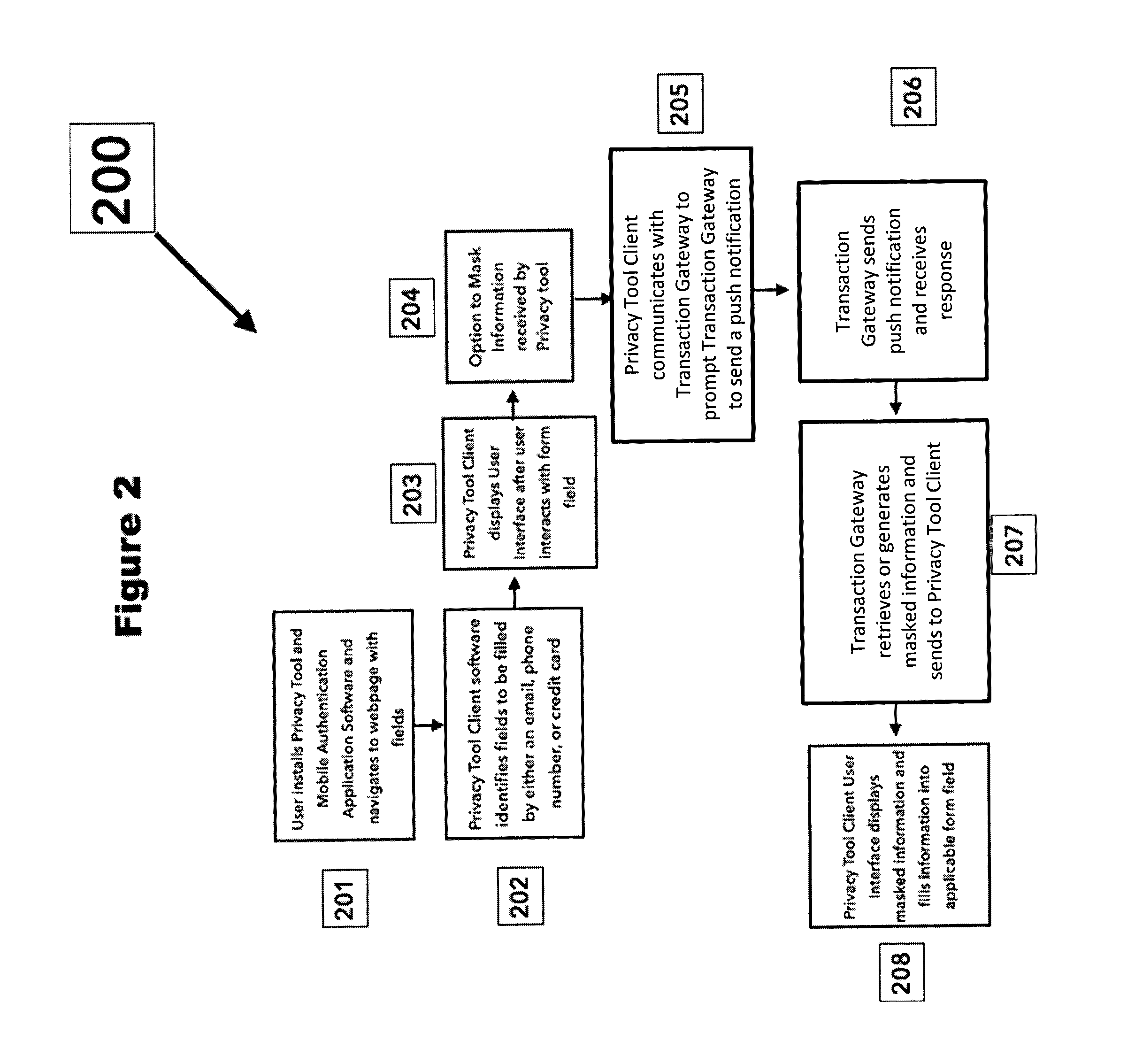
Push notification authentication platform for secured form filling
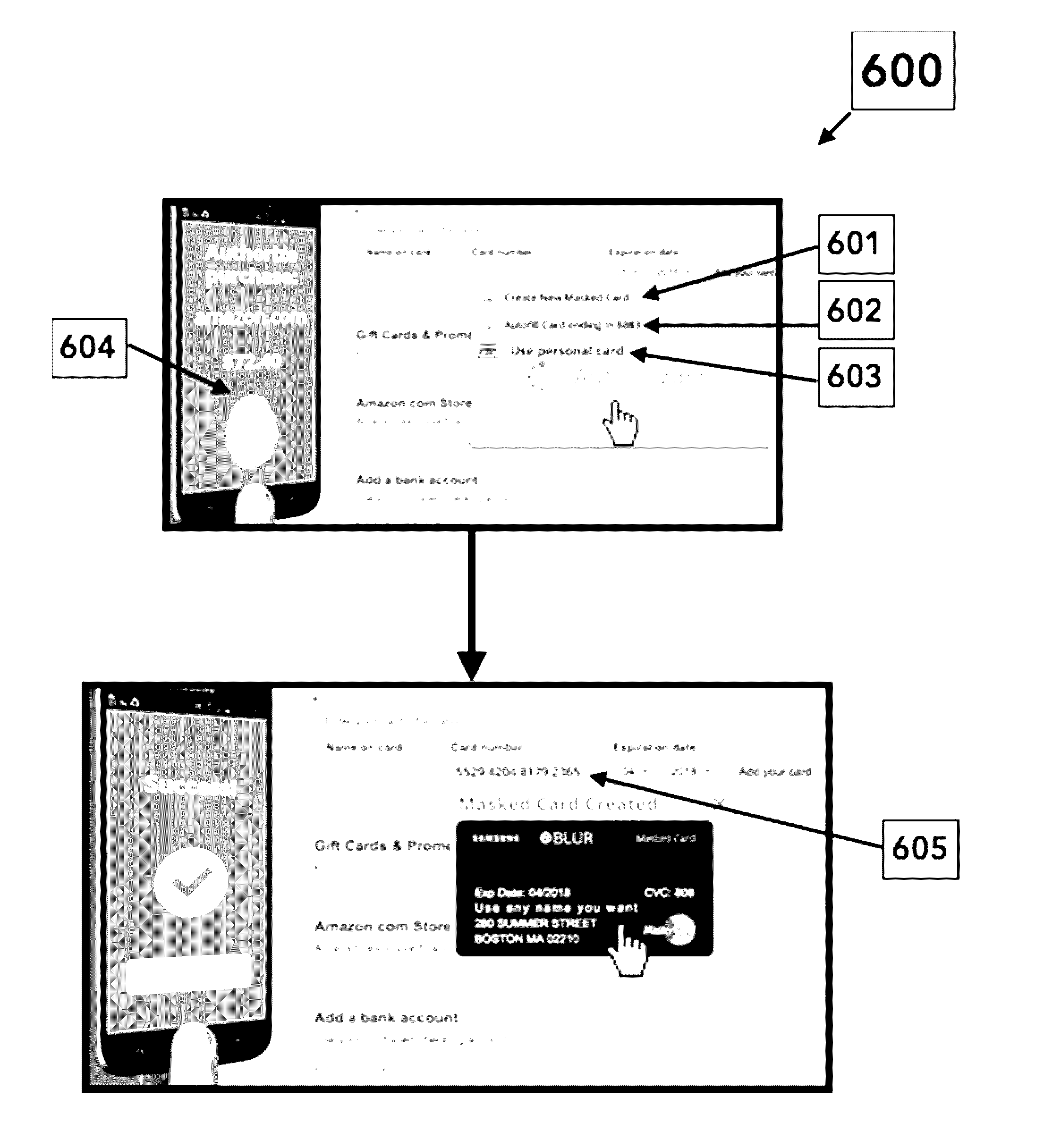
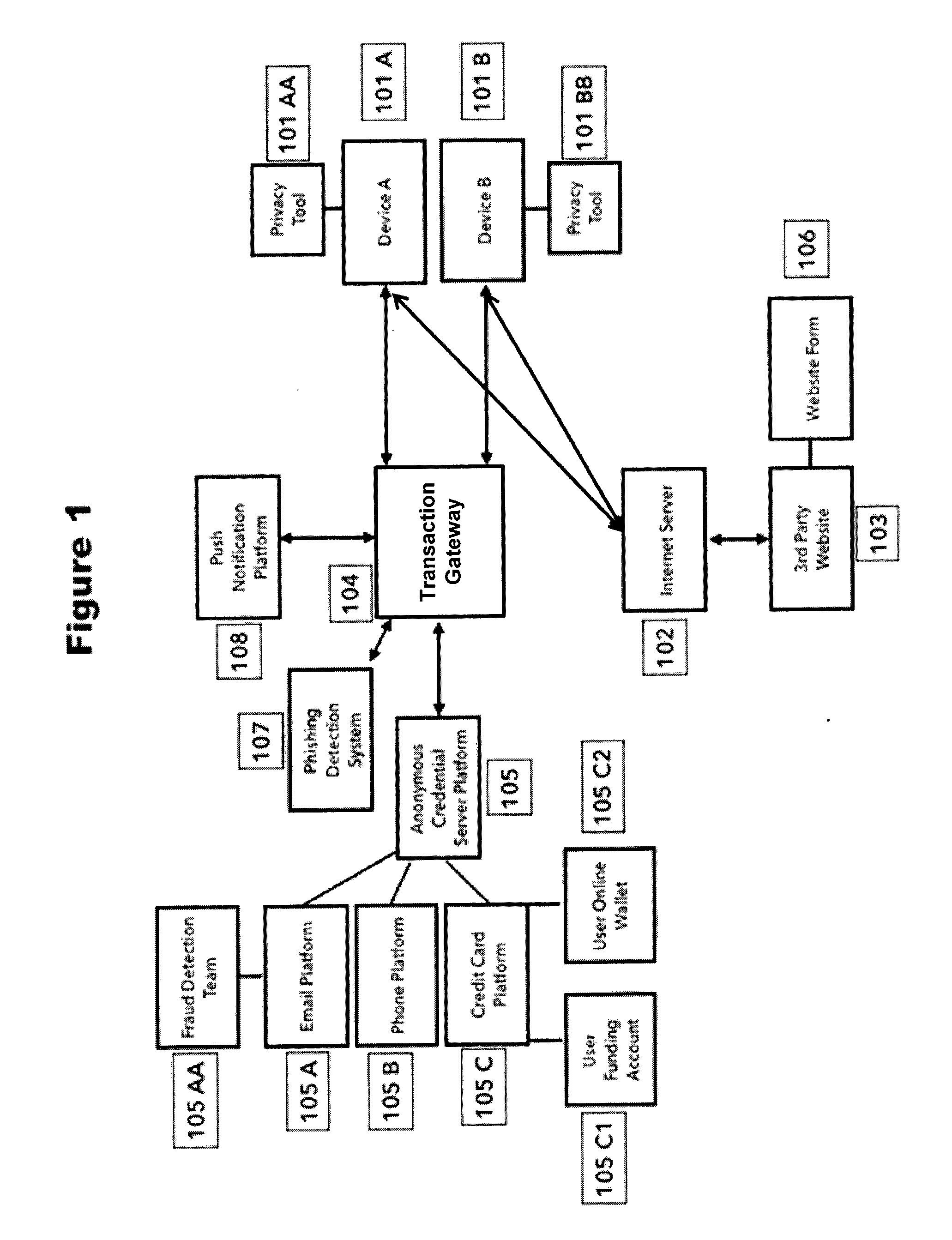
The present disclosure relates to systems and methods for notifying a user of attempts to provide masked credentials associated with the user to a third party, and for providing the user with an opportunity to approve or deny the attempt. The third party can be a website having a form field that receives the masked credential. The masked credential can include a telephone number, an email address, a mail address, a user name, a password, and funding account information (e.g., credit card or bank account numbers). Attempts to provide the masked credential using a device can be detected by an application installed on the device, and the notification can be implemented through a push notification sent to one or more devices registered with the user. Users can respond to the push notification by indicating whether the attempt to provide the masked credential is approved or denied.
Owner:IRONVEST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com