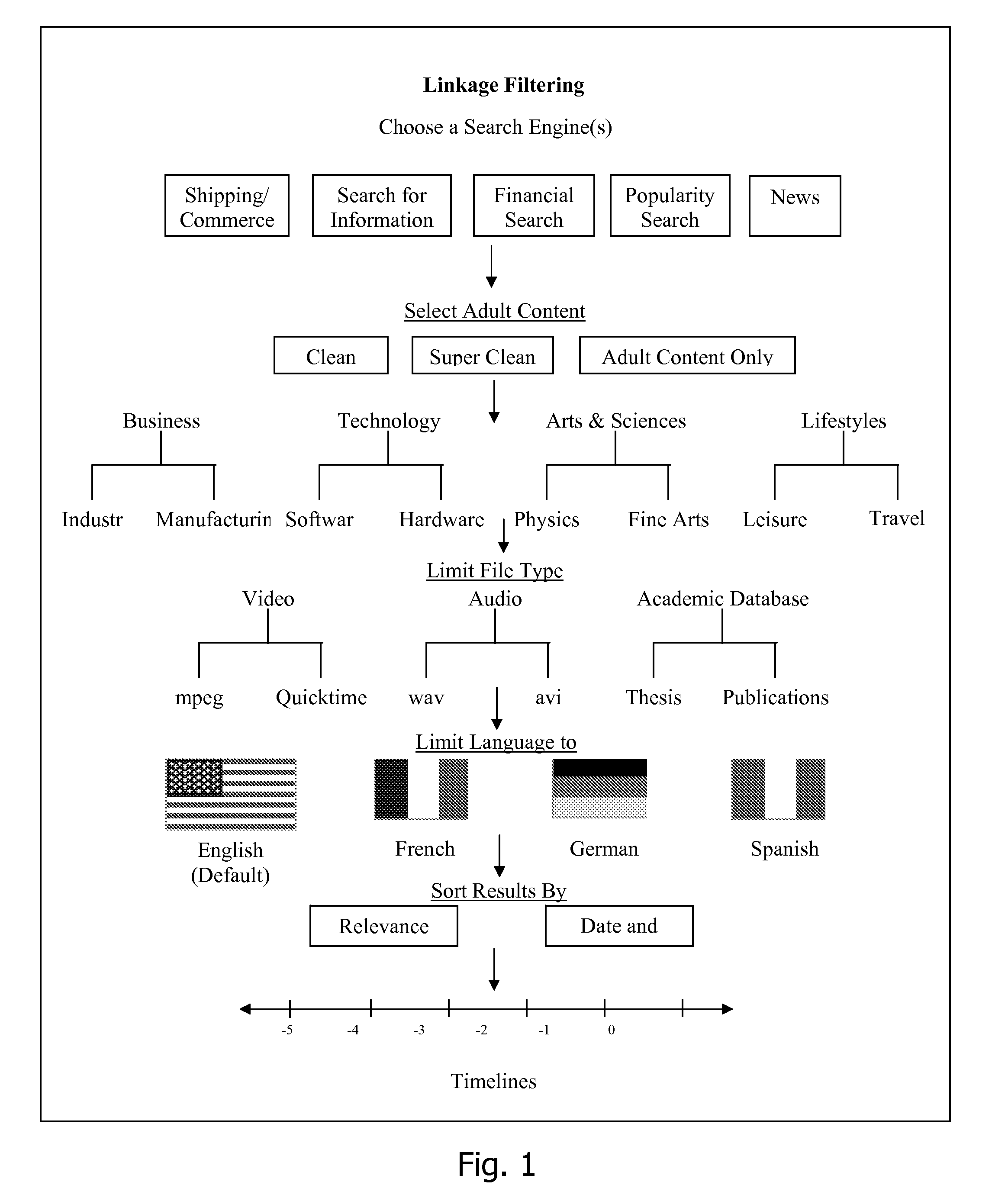
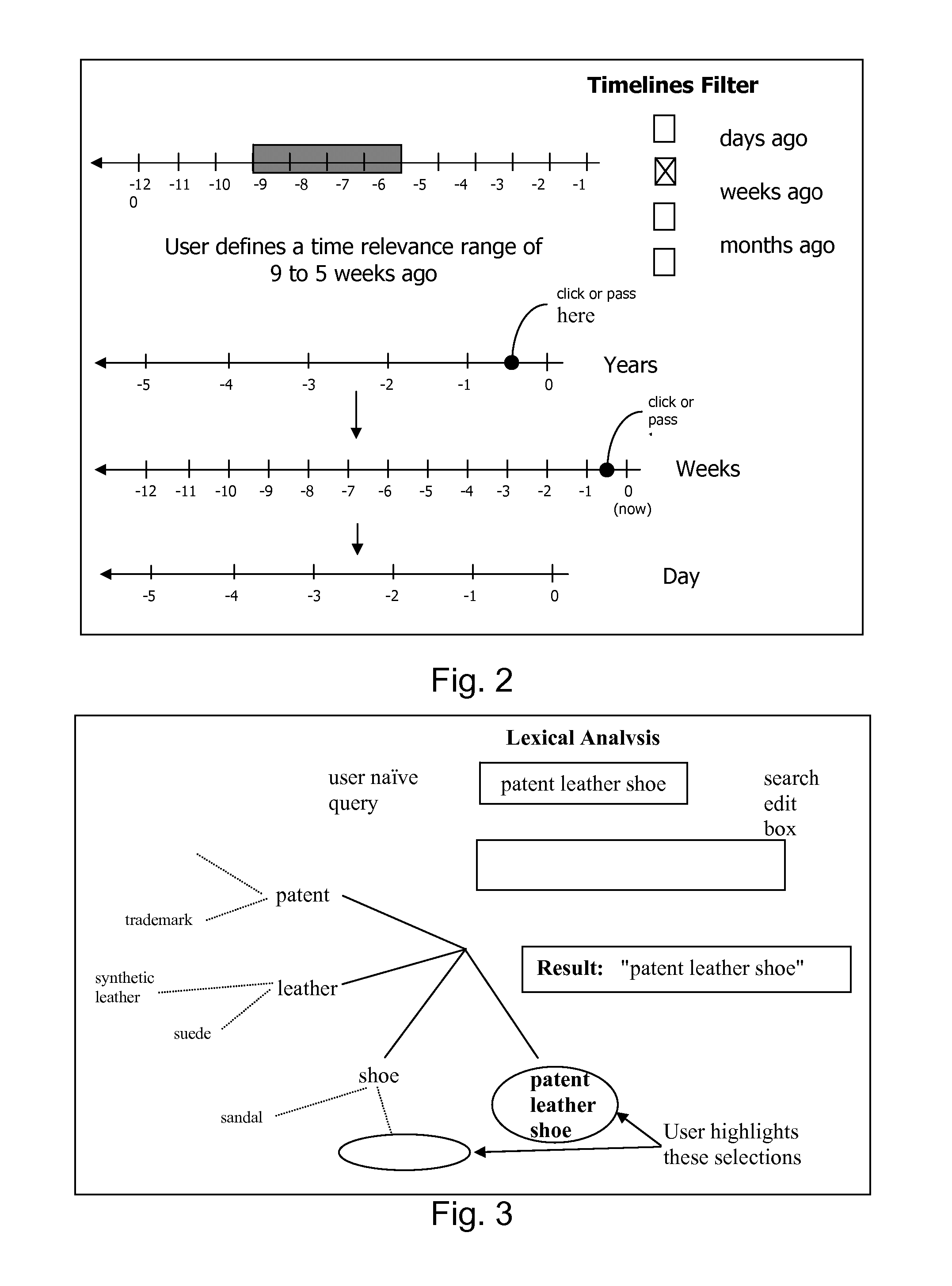
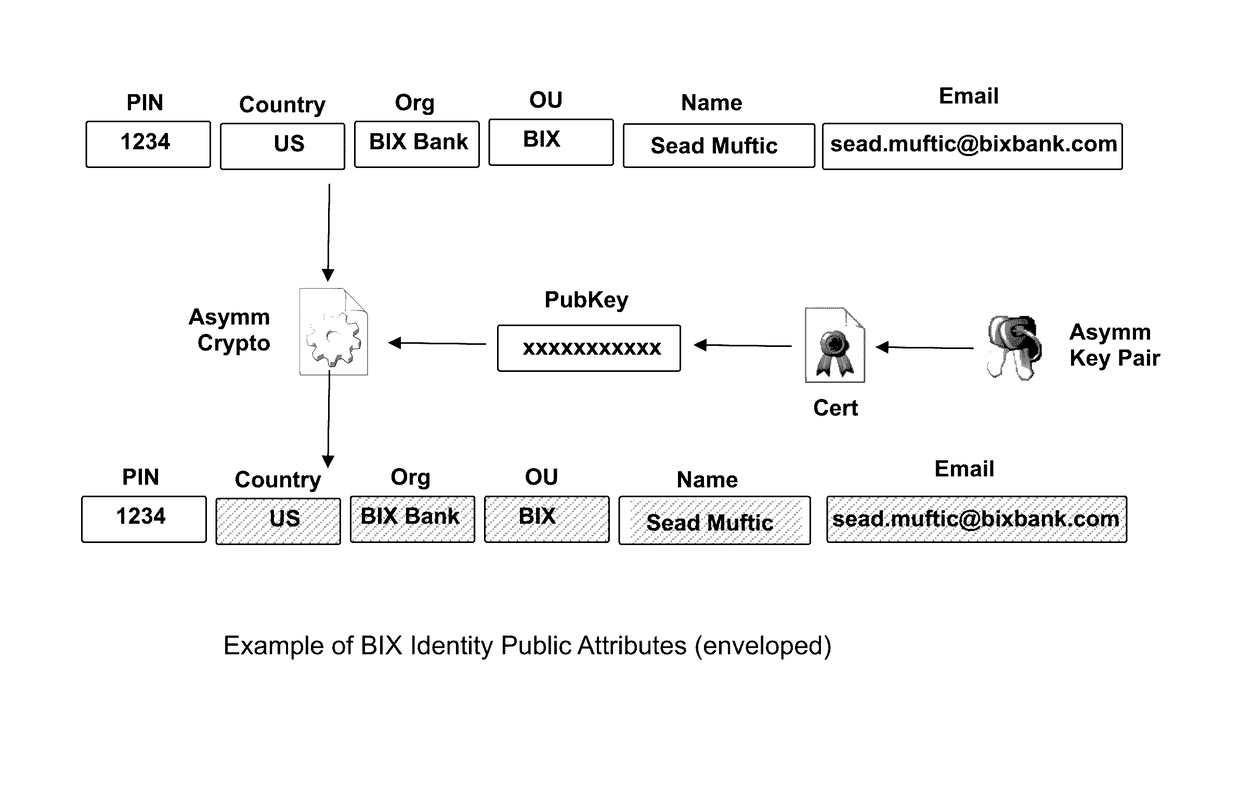
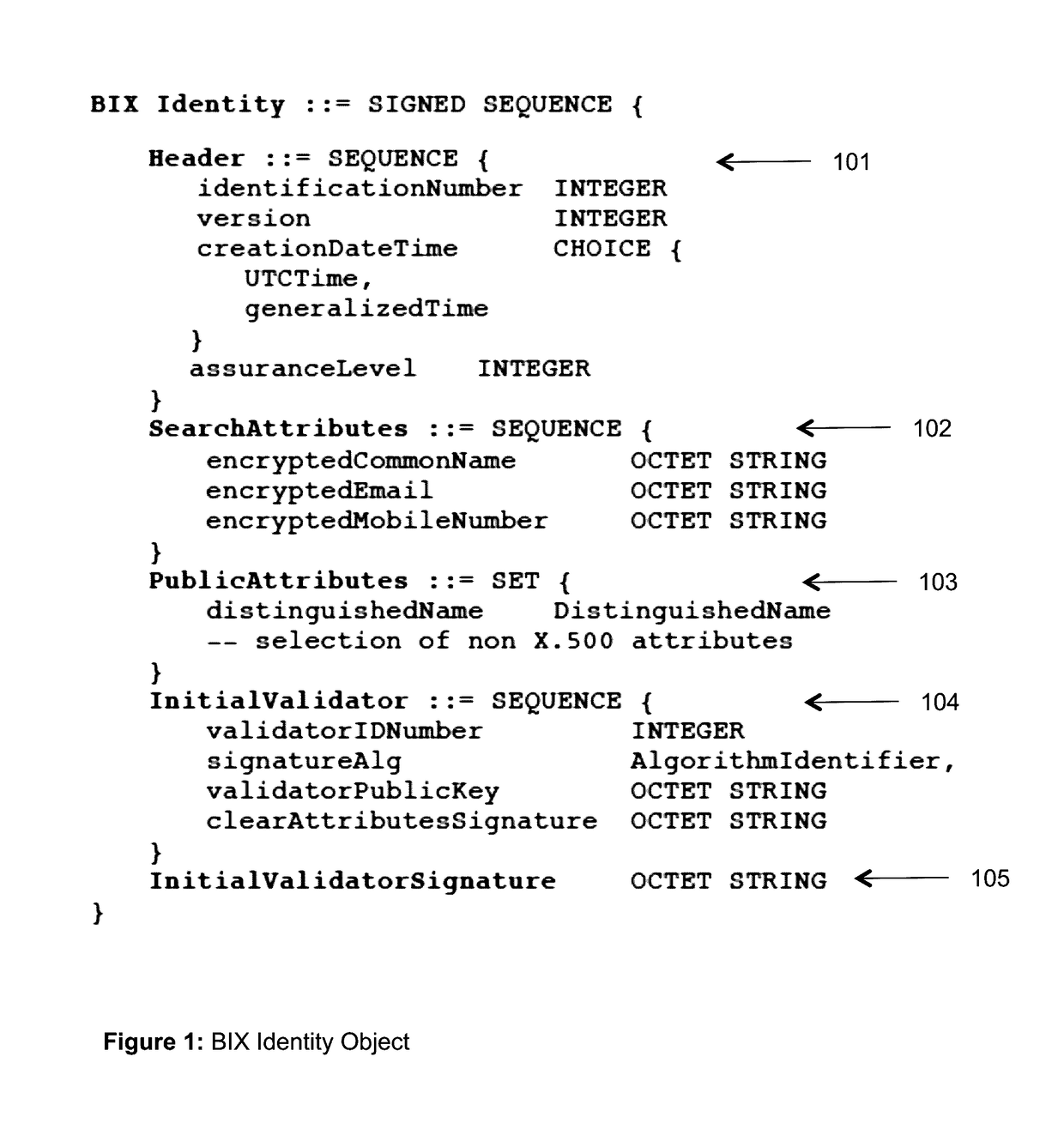
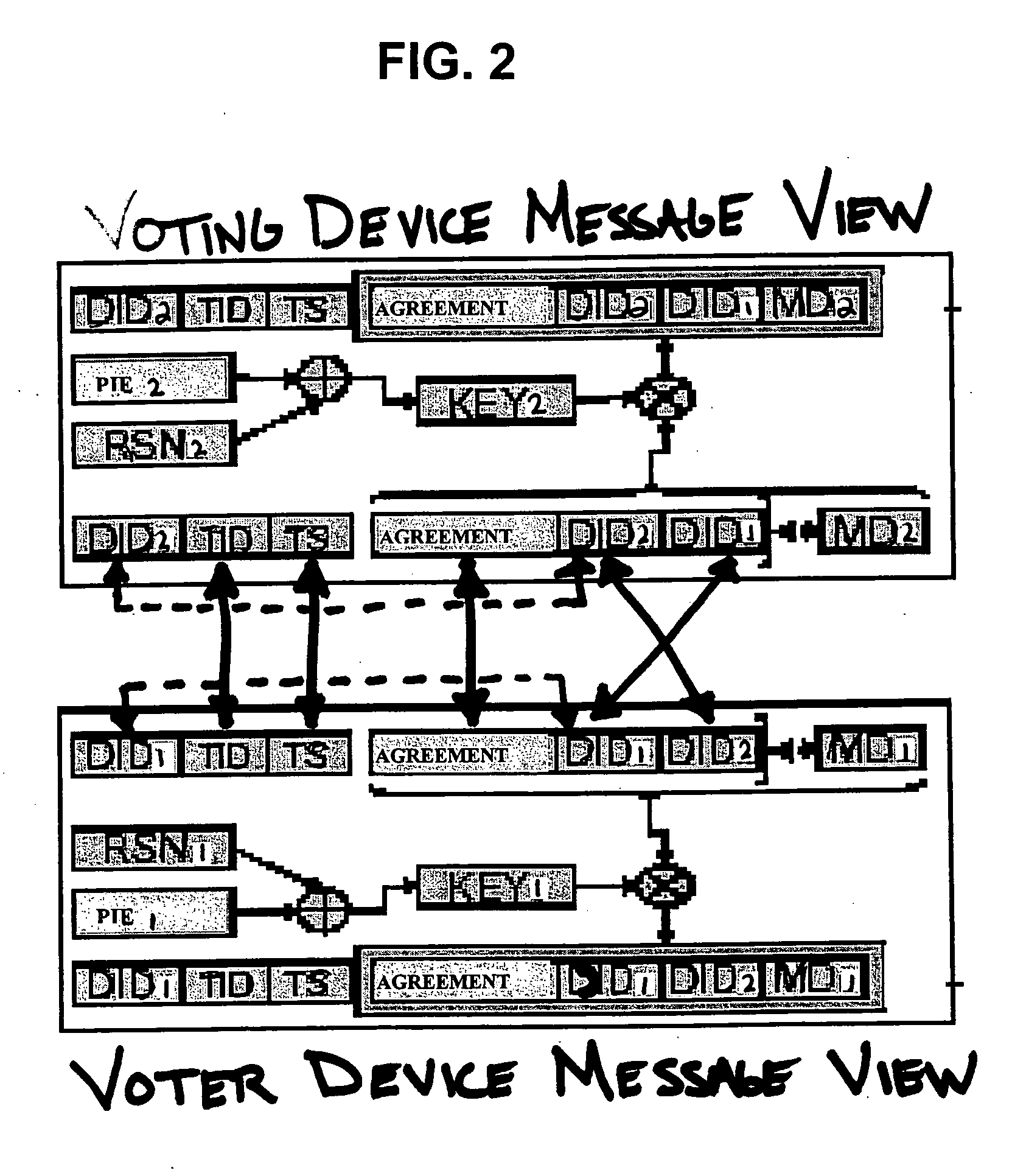
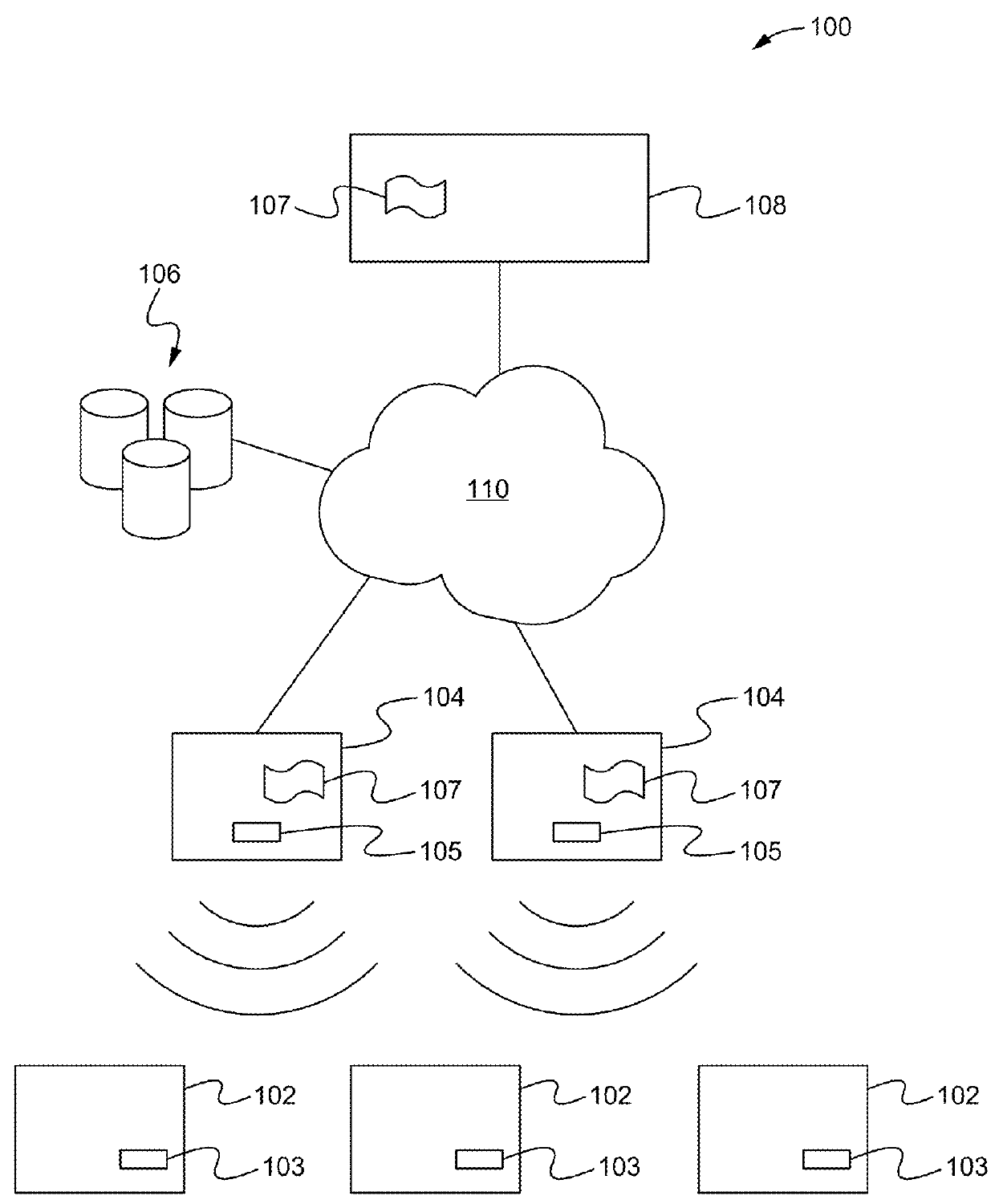
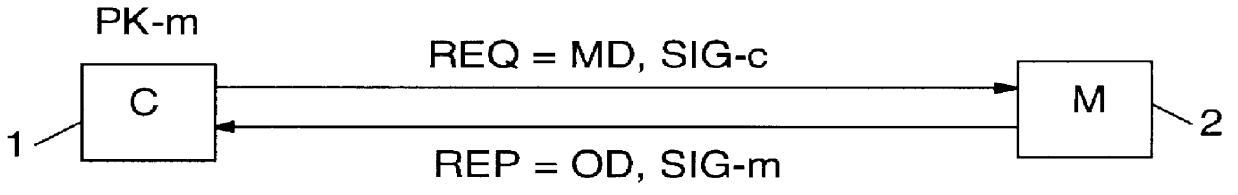Patents
Literature
904 results about "Anonymity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Anonymity, adjective "anonymous", is derived from the Greek word ἀνωνυμία, anonymia, meaning "without a name" or "namelessness". In colloquial use, "anonymous" is used to describe situations where the acting person's name is unknown. Some writers have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is that a person be non-identifiable, unreachable, or untrackable. Anonymity is seen as a technique, or a way of realizing, a certain other values, such as privacy, or liberty.
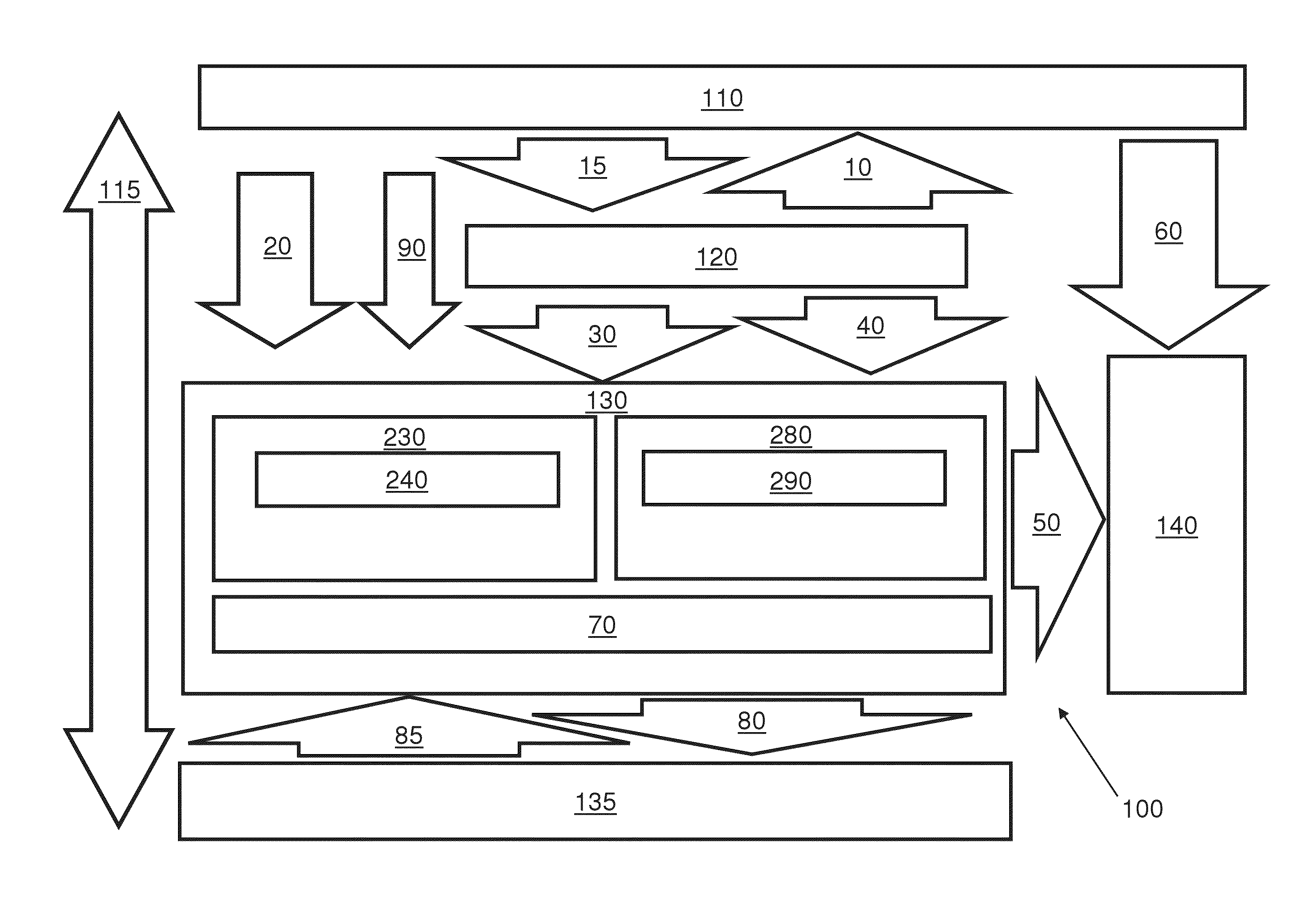
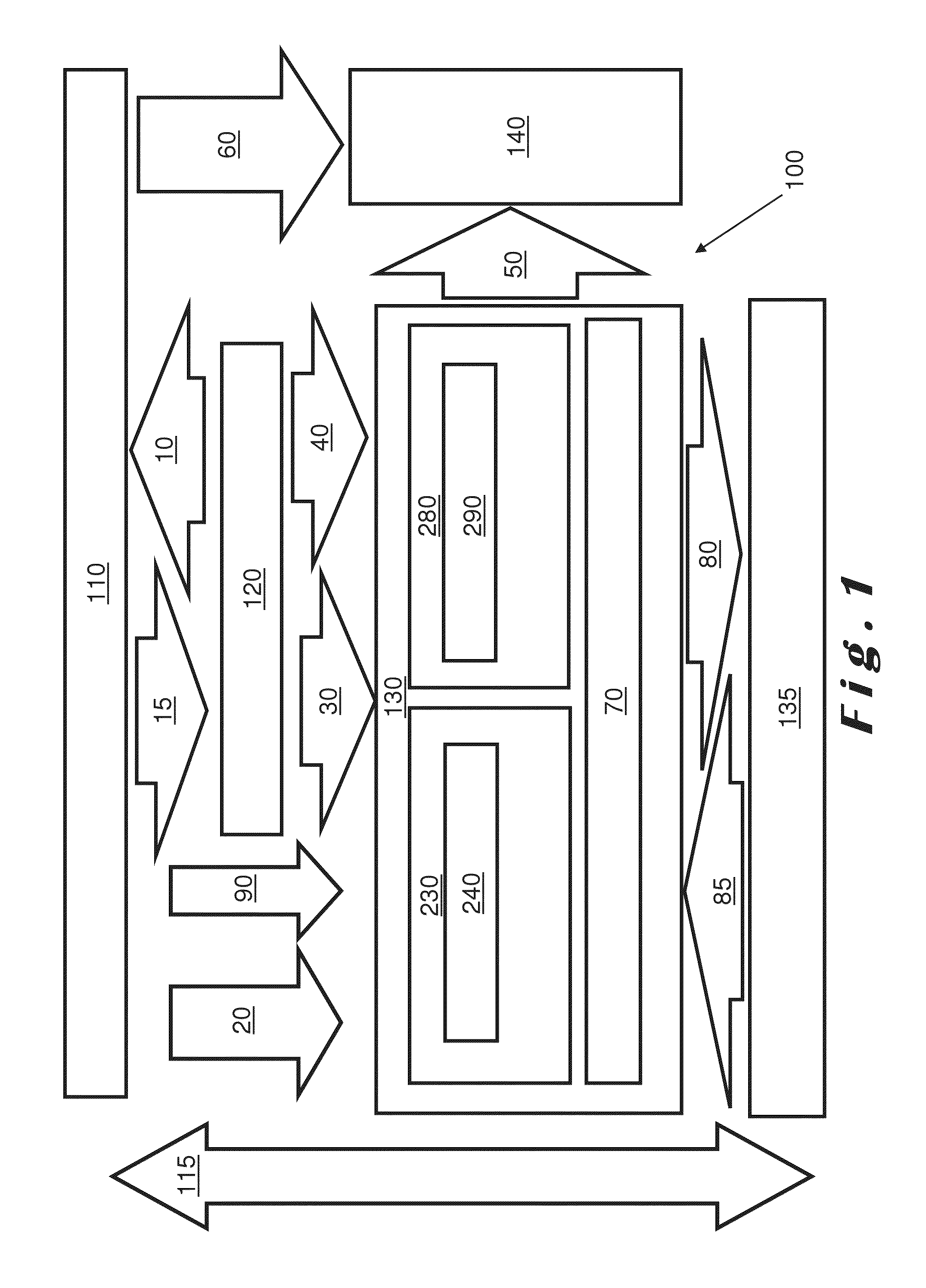
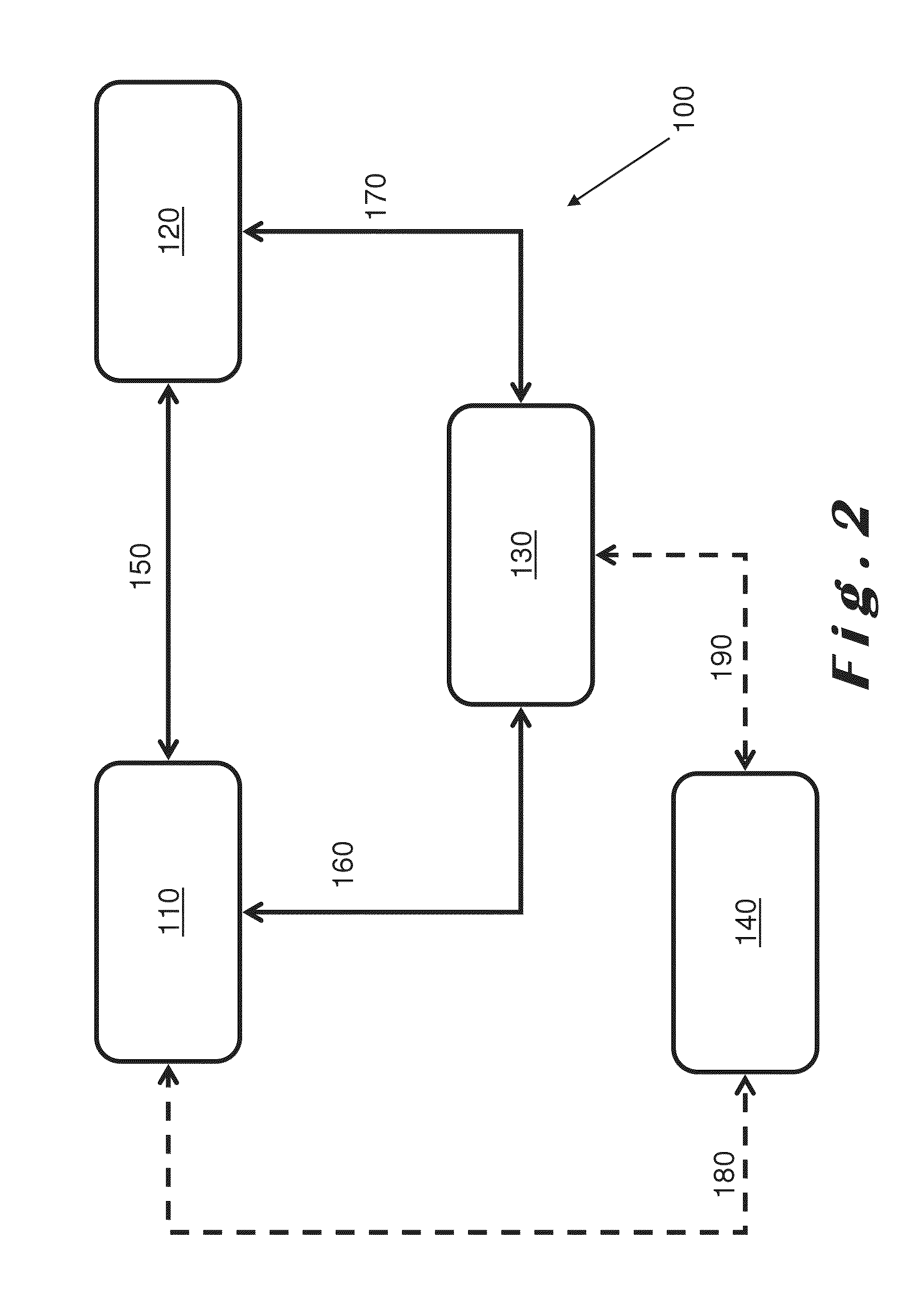
Database access system
ActiveUS7181438B1Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Database access system
InactiveUS20070156677A1Increased formationGood user interfaceDigital data information retrievalAdvertisementsPersonal detailsAnonymity
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
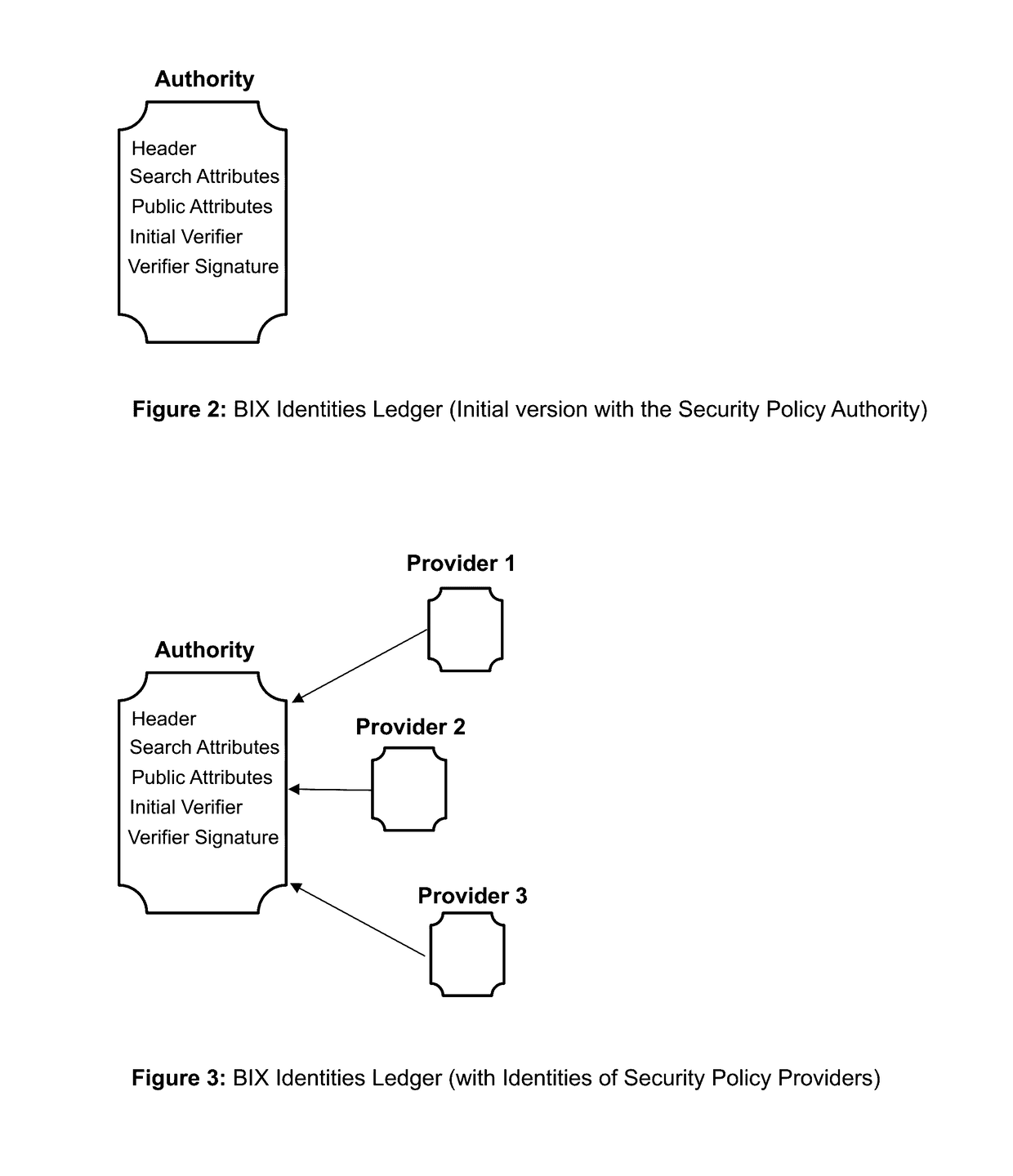
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
Mobile data processing system moving interest radius
InactiveUS20100131584A1Automatically determinePosition fixationConnection managementData processing systemWeb service
Owner:APPLE INC
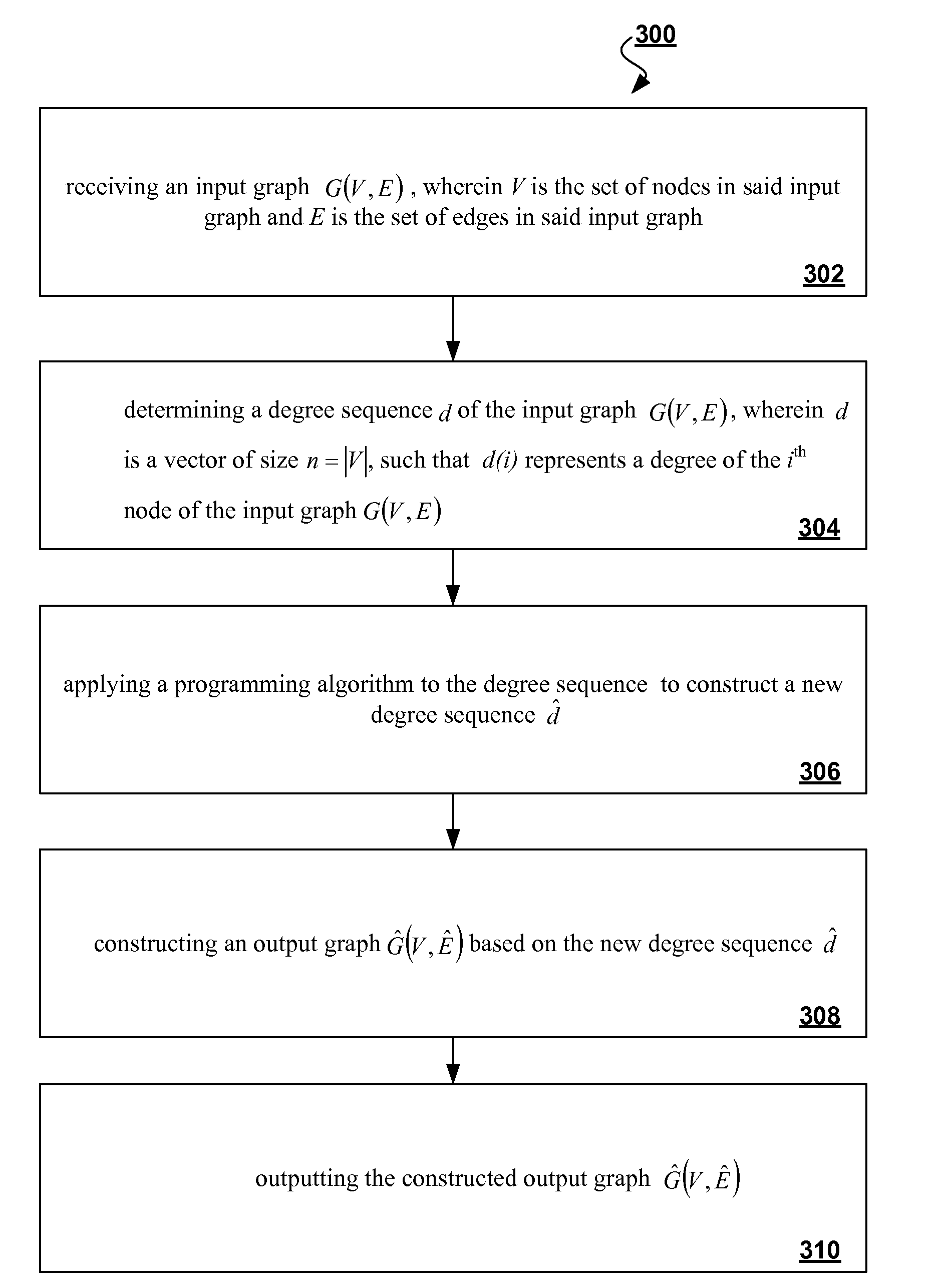
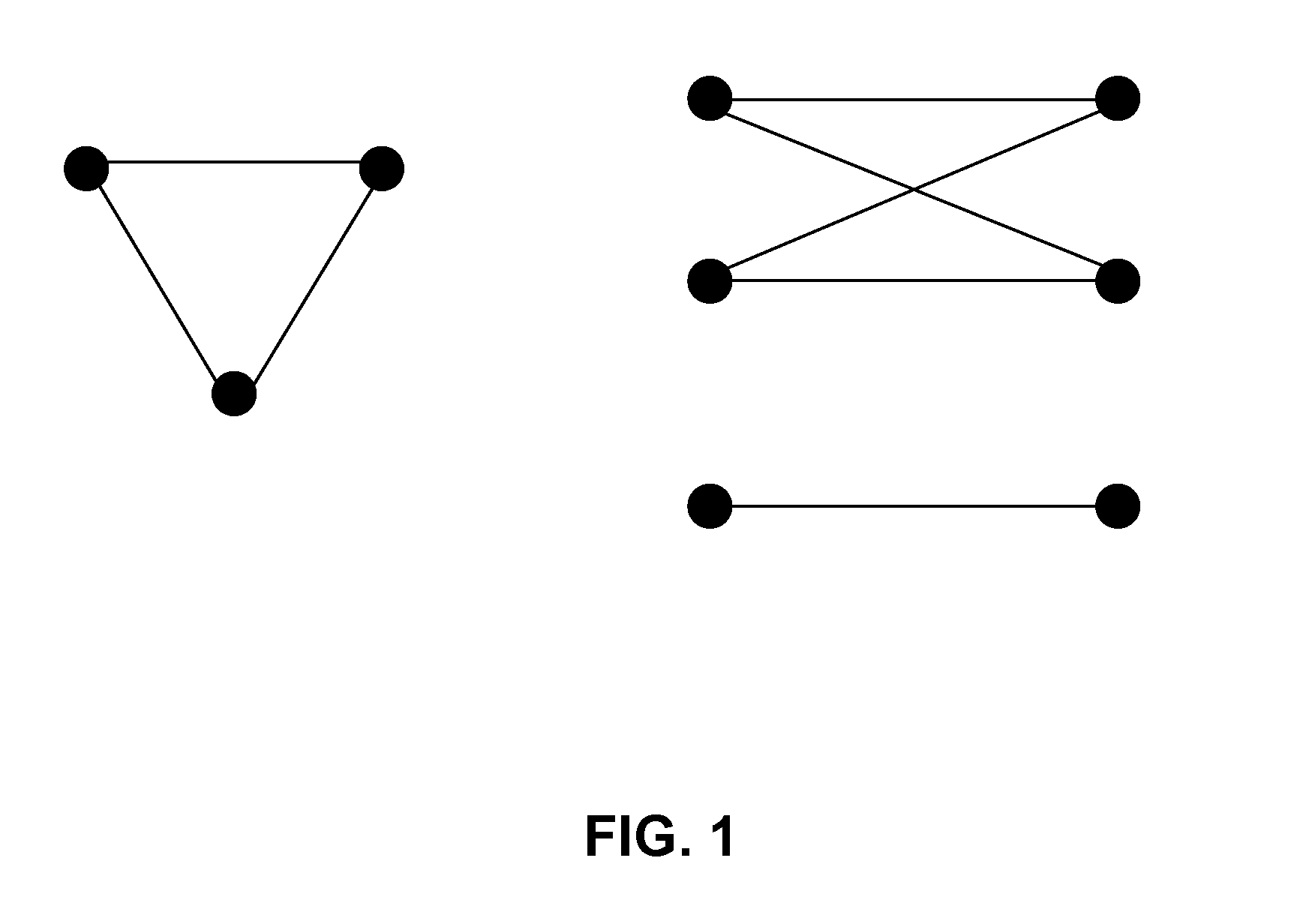
Algorithms for identity anonymization on graphs
InactiveUS20090303237A1Preserving individual privacy and basic structure of networkDrawing from basic elementsTransmissionGraphicsRe identification
The proliferation of network data in various application domains has raised privacy concerns for the individuals involved. Recent studies show that simply removing the identities of the nodes before publishing the graph / social network data does not guarantee privacy. The structure of the graph itself, and in is basic form the degree of the nodes, can be revealing the identities of individuals. To address this issue, a specific graph-anonymization framework is proposed. A graph is called k-degree anonymous if for every node v, there exist at least k−1 other nodes in the graph with the same degree as v. This definition of anonymity prevents the re-identification of individuals by adversaries with a priori knowledge of the degree of certain nodes. Given a graph G, the proposed graph-anonymization problem asks for the k-degree anonymous graph that stems from G with the minimum number of graph-modification operations. Simple and efficient algorithms are devised for solving this problem, wherein these algorithms are based on principles related to the realizability of degree sequences.
Owner:IBM CORP
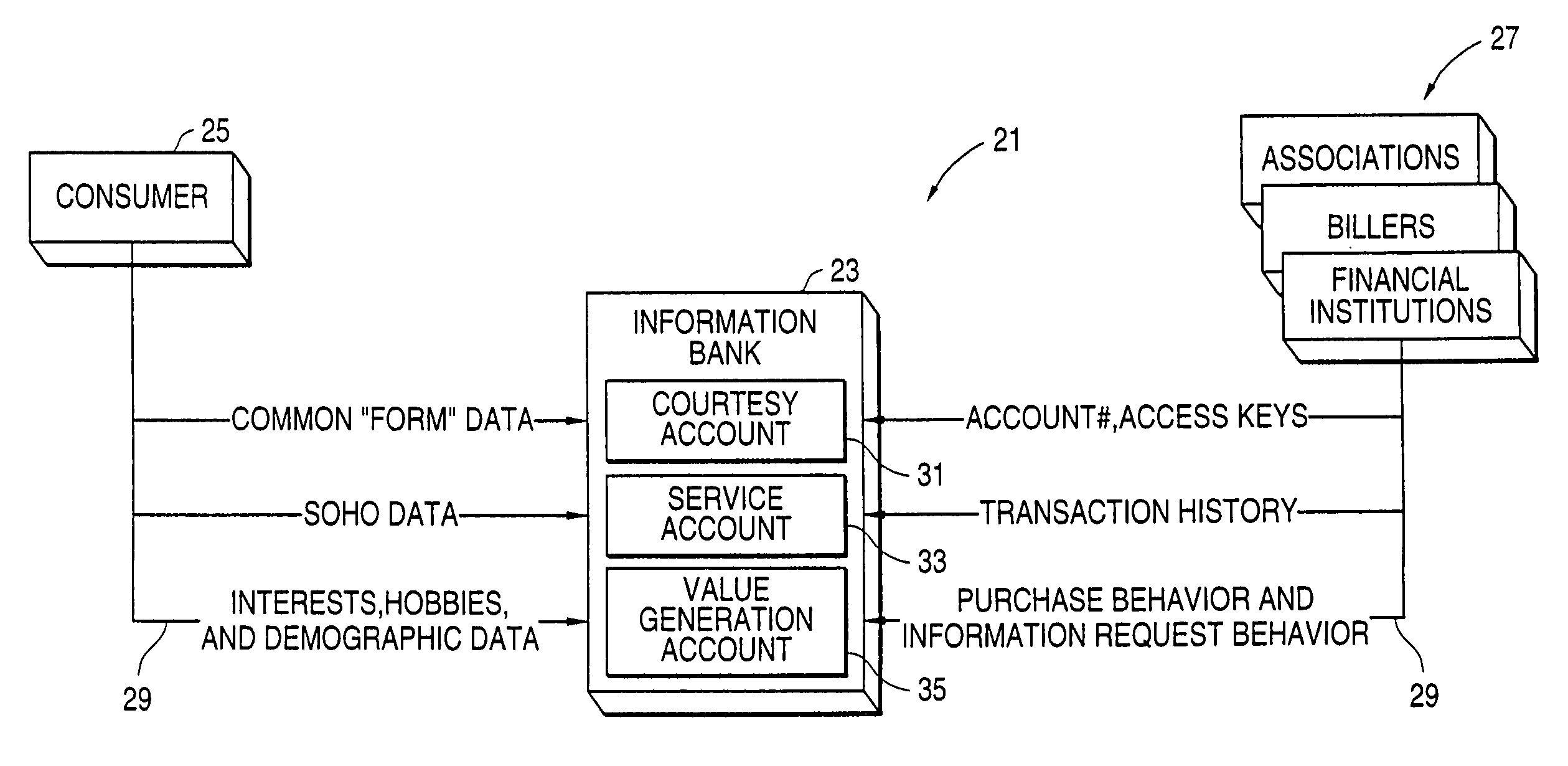
Method and system for anonymizing purchase data
InactiveUS7200578B2Easy accessEliminate needComplete banking machinesFinanceInternet privacyData storing
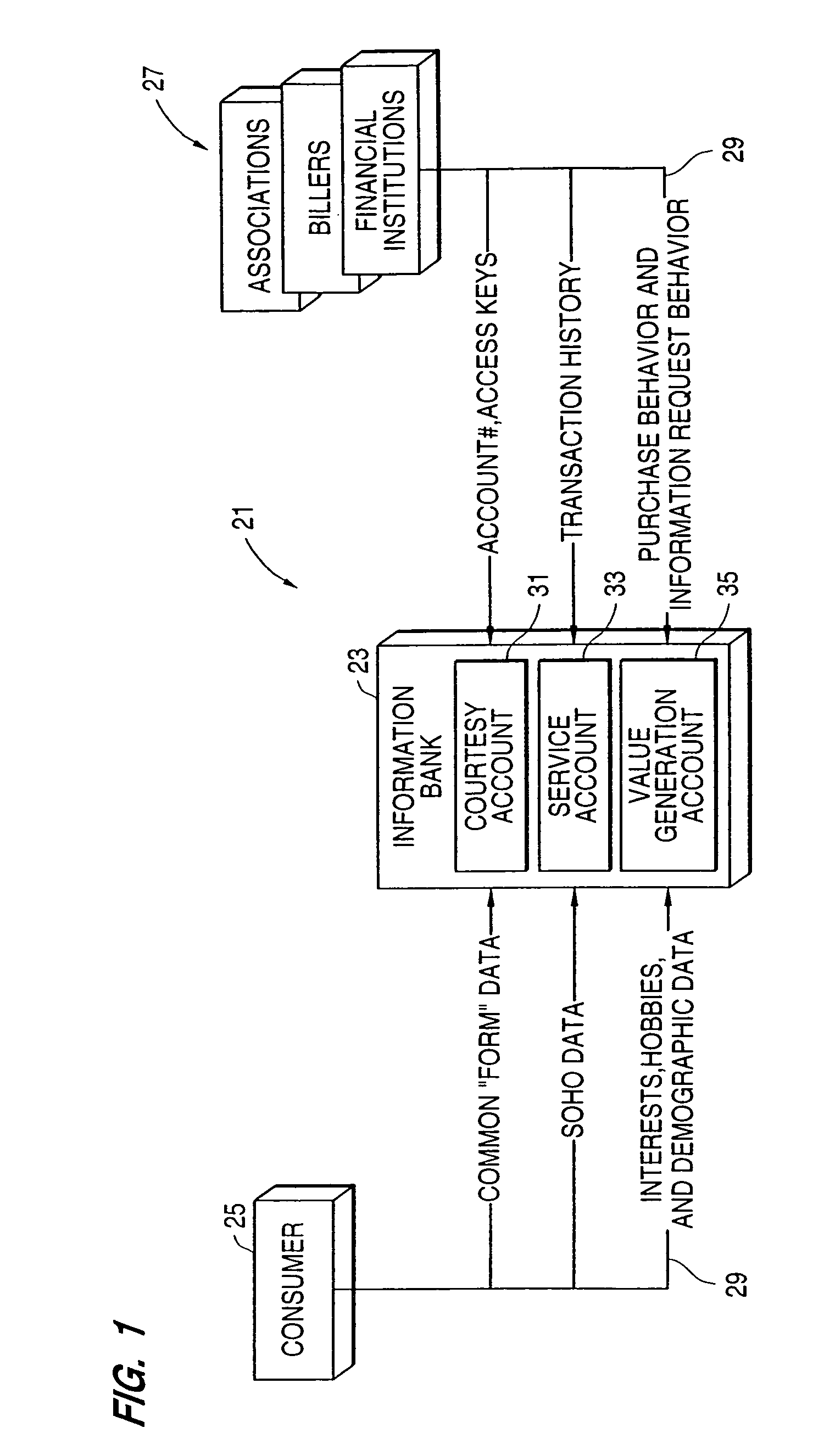
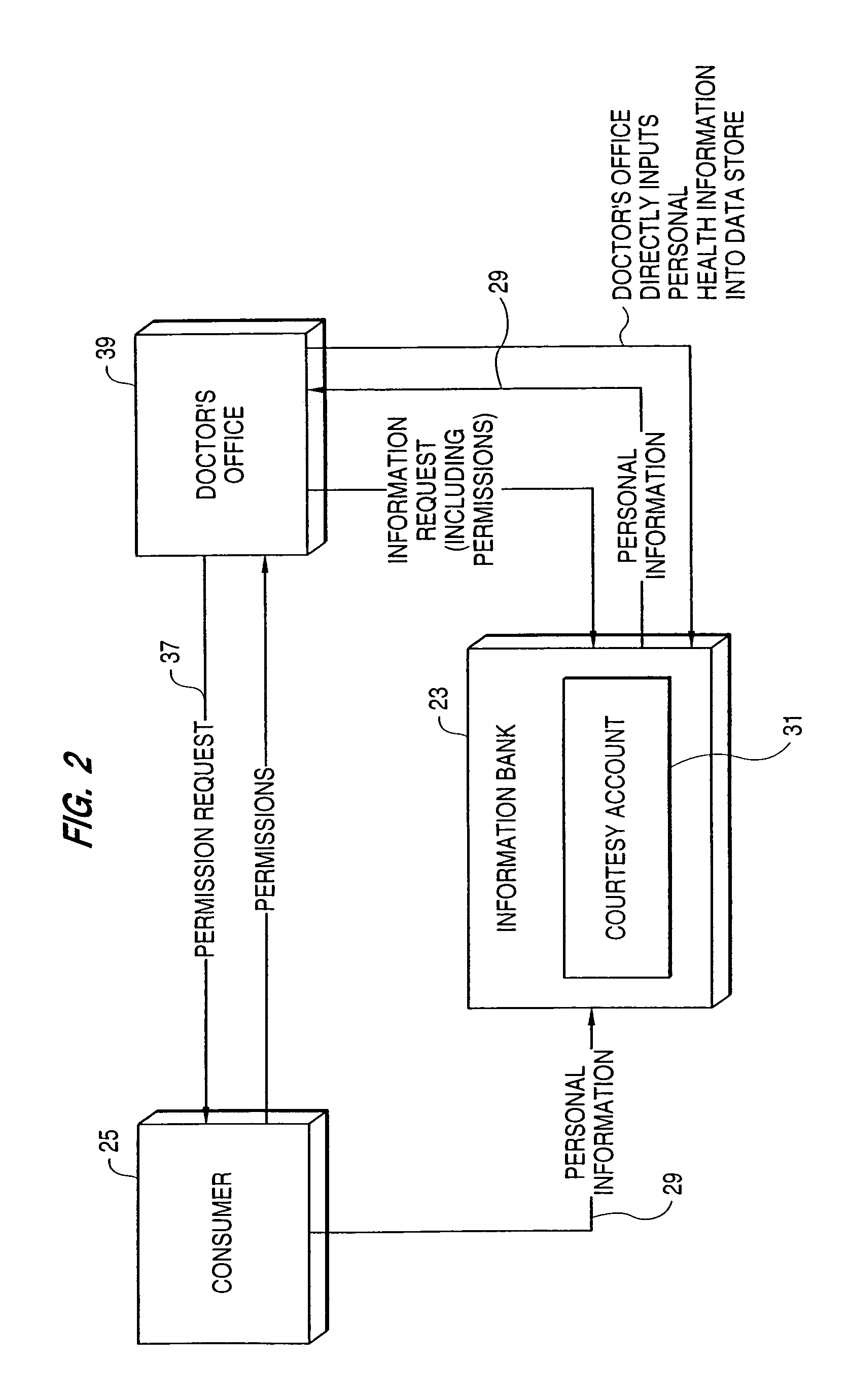
A system, in which information is the primary asset and in which investments may be made in information, includes multiple data stores for storing different types of a user's information. The safe, secure and properly authorized transfer of information while preserving individual privacy is provided. The system also provides for secure backup and storage, as well as for ubiquitous and nomadic access to information while maintaining the privacy of such information. A first data store includes static identification data about a user. A second data store includes moderately dynamic personal data about the user. A third data store includes dynamic demographic information data about the user. An electronic wallet can be used with the system to download selected portions of the data for use by the user. A method of use of the data includes using the data for billing out forms, providing services to the user and allowing merchants to selectively target users for sales while maintaining user anonymity.
Owner:CITICORP CREDIT SERVICES INC (USA)
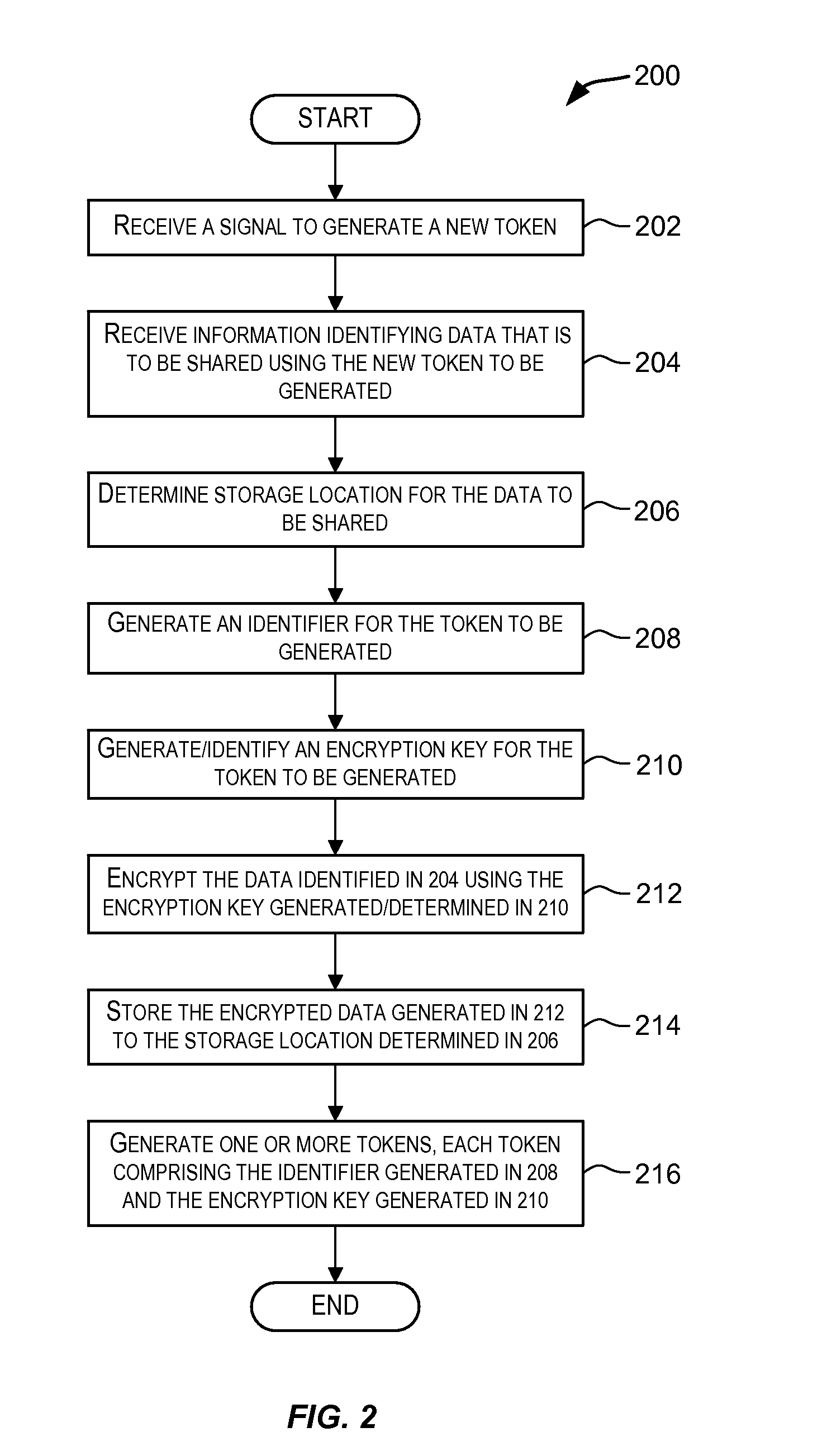
Tokens Usable in Value-Based Transactions
InactiveUS20080243702A1Maintaining anonymitySufficient informationUser identity/authority verificationPayment architectureThird partyInternet privacy
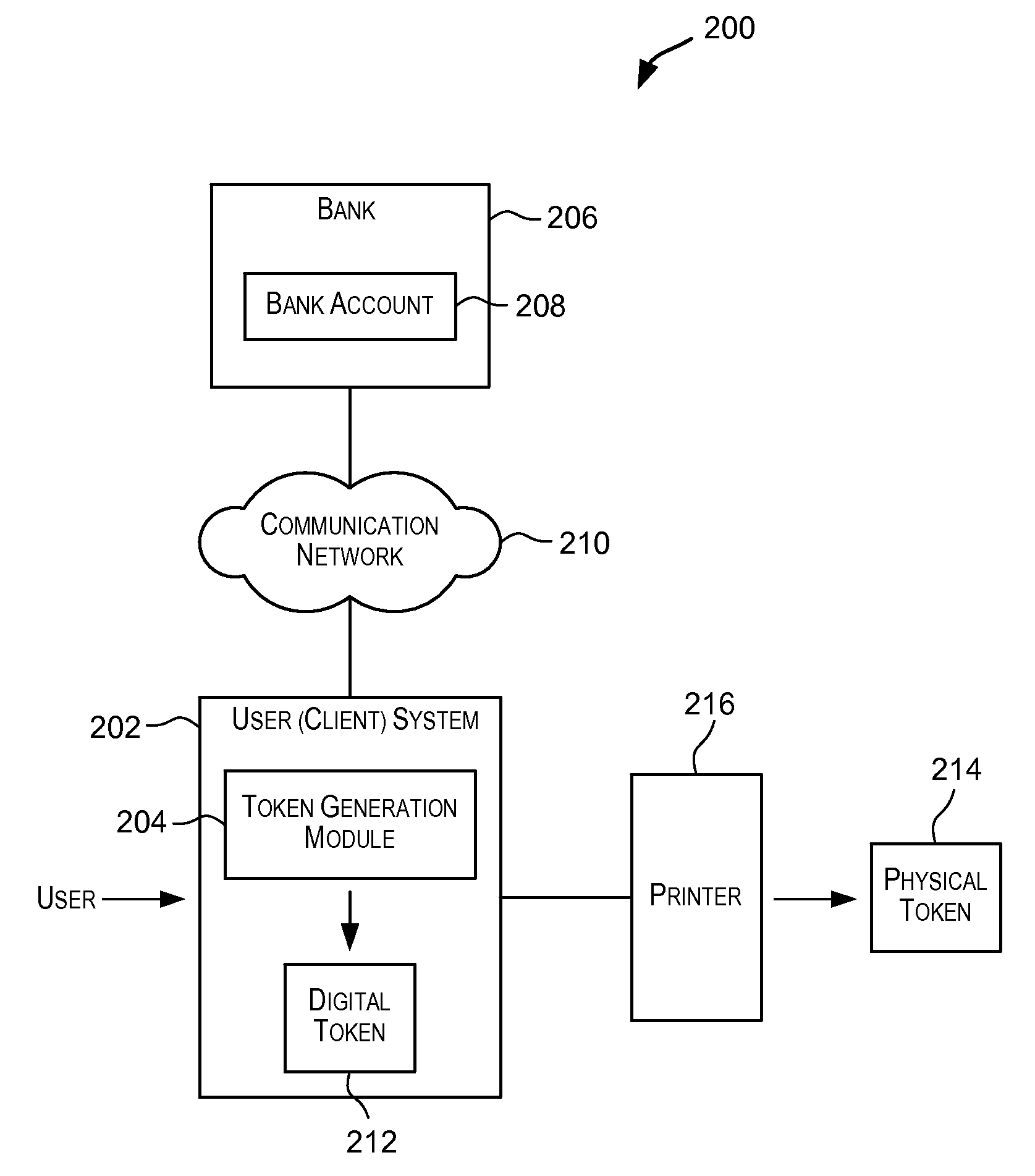
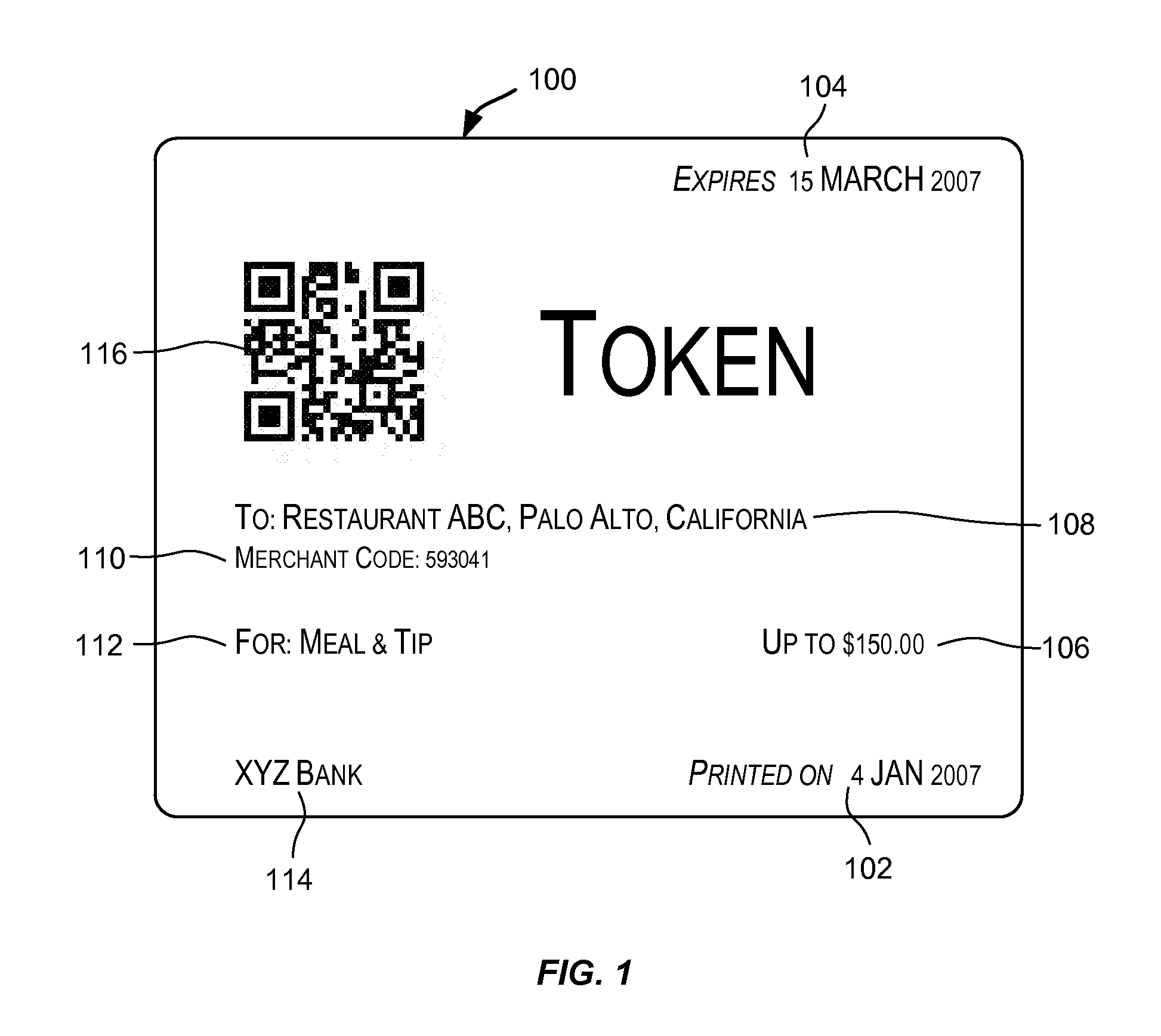
Techniques for generating a token that can be used to transfer value. The token may be used to transfer value in a value-based transaction with a vendor in a way that is secure and safe and maintains anonymity of the source of the value and preserves secrecy of information that should preferably not be disclosed to an untrusted third party such as a vendor. The token comprises sufficient information that enables value to be transferred from an account associated with the token to a vendor during a value-based transaction. Such a token may be presented by a user to a vendor in a value-based transaction with the purpose of transferring value involved in the transaction to the vendor in order to complete the transaction.
Owner:RICOH KK
Process for making a payment using an account manager
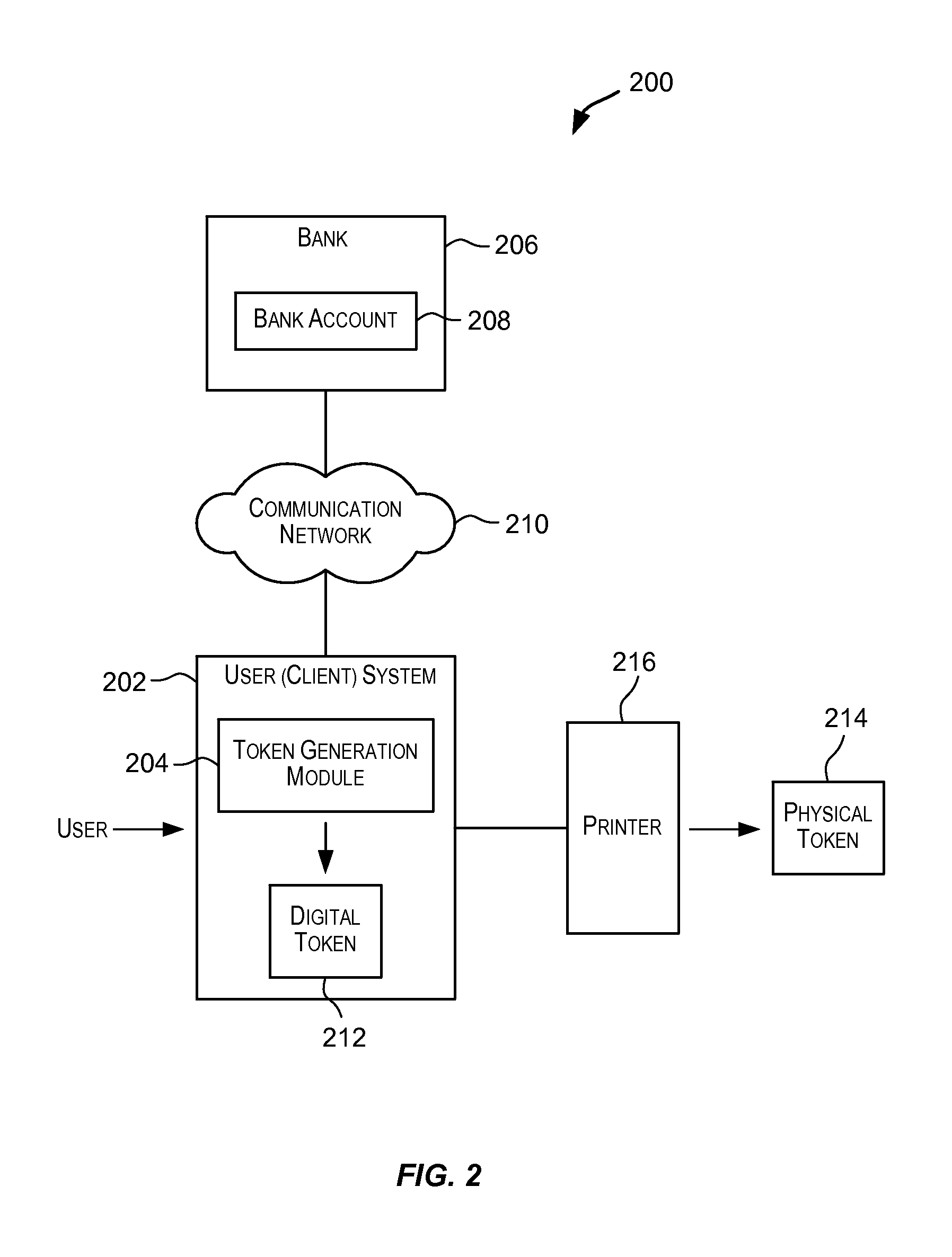
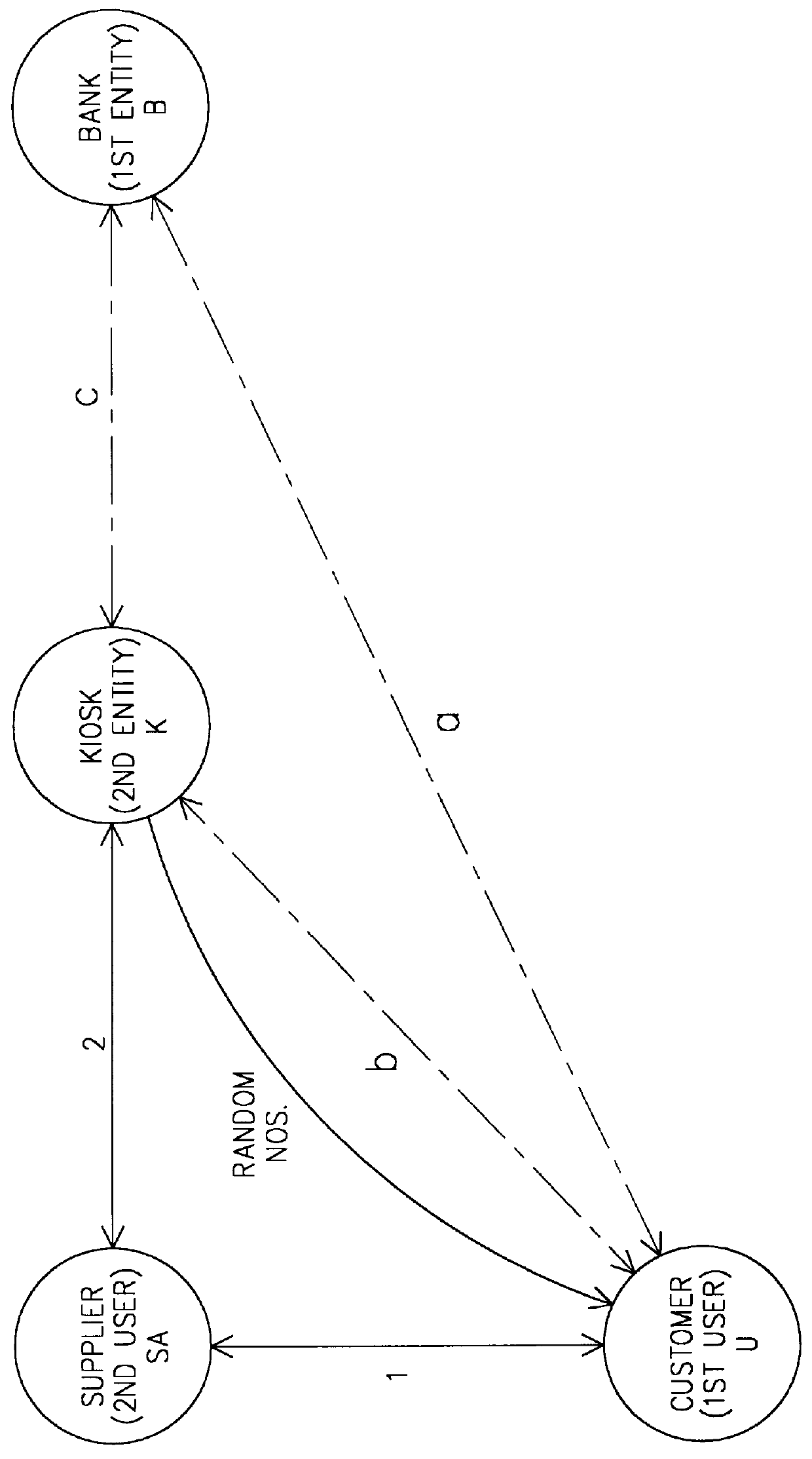
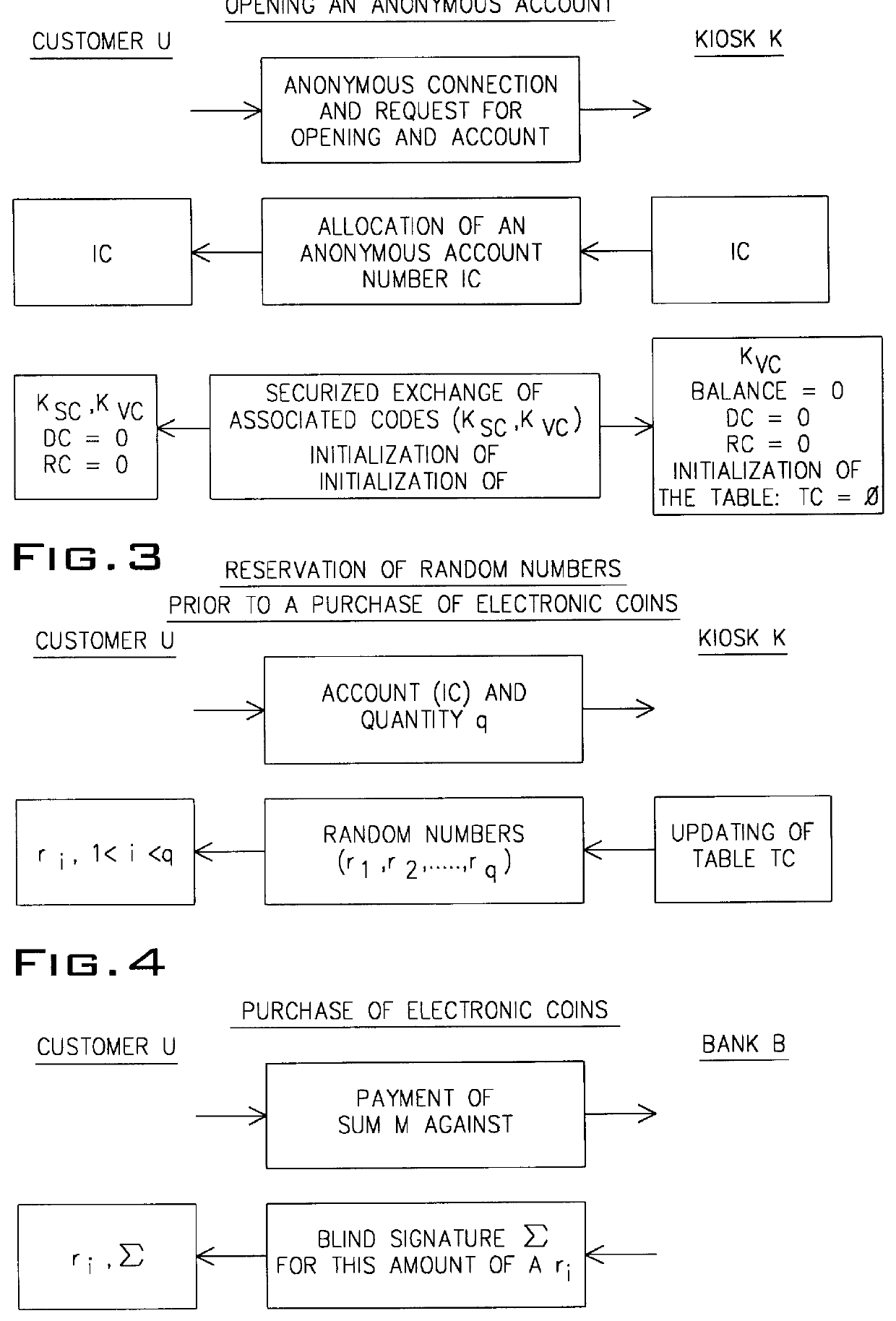
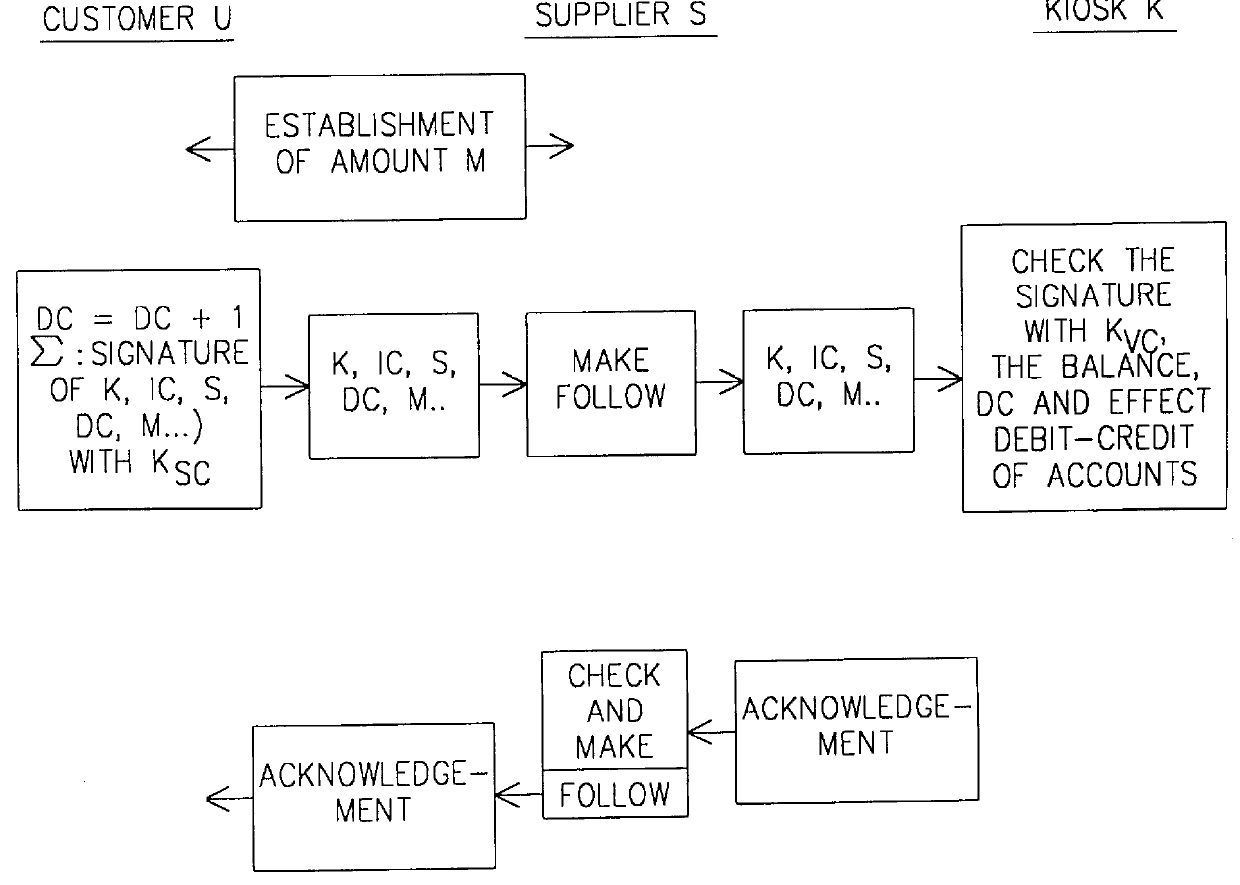
The present invention relates to a process for making a payment using an account manager or kiosk, the process guaranteeing the payment of the supplier and the anonymity of the customer. A customer (U) withdraws from his bank (B) a sum in the form of "blind" electronic coins or cash, deposits the latter in one or more anonymous accounts in a kiosk (K) and finally uses said account or accounts for paying suppliers of goods or services (SA). The invention has application to streamline and voice telepayment.
Owner:FRANCE TELECOM SA
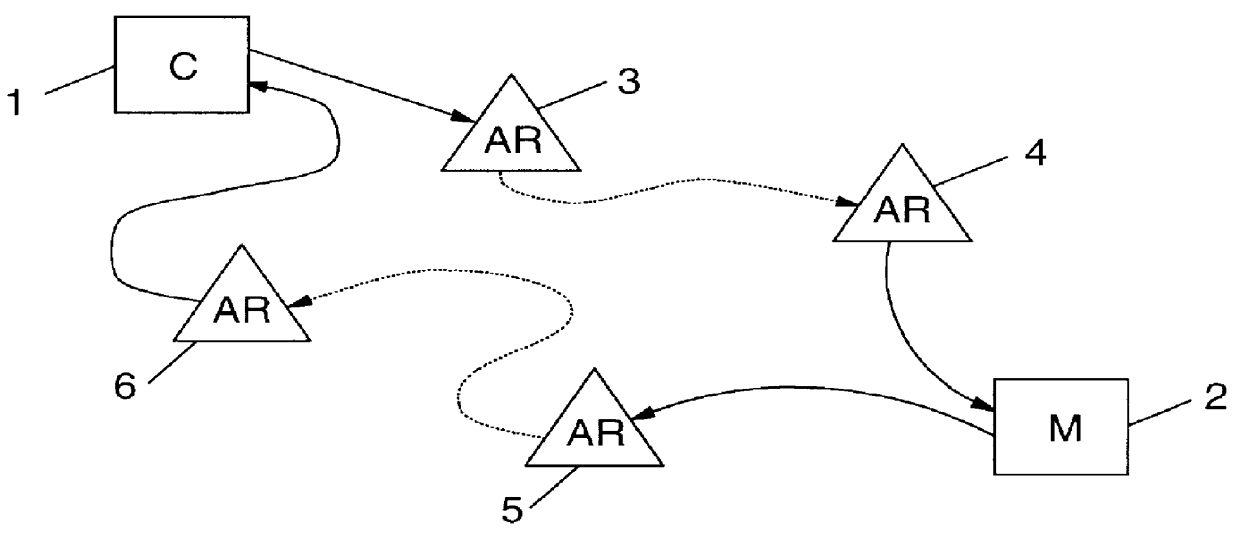
Authentication & authorization of transactions using an external alias
Described herein is a transaction system (100) in which a transaction is authenticated using an external alias. When procuring an item from a supplier (120), a customer (110) needs to provide payment in some form or the other. Profiles relating to both the customer (110) and the supplier (120) are stored in an environment managed by a broker (130) and payment is effected by transfer of within that environment from a customer wallet to a supplier wallet. The customer (120) is represented as an alias as far as the supplier (120) is concerned, whereby the alias is provided by an external identity provider (140) such as a social network with which the customer (120) is associated. The anonymity of the customer (120) is maintained with respect to the supplier (120).
Owner:DUBOIS PIETER
Secure anonymous information exchange in a network
InactiveUS6061789AMinimize additional effort and expenditureUser identity/authority verificationDigital data protectionSystems designData set
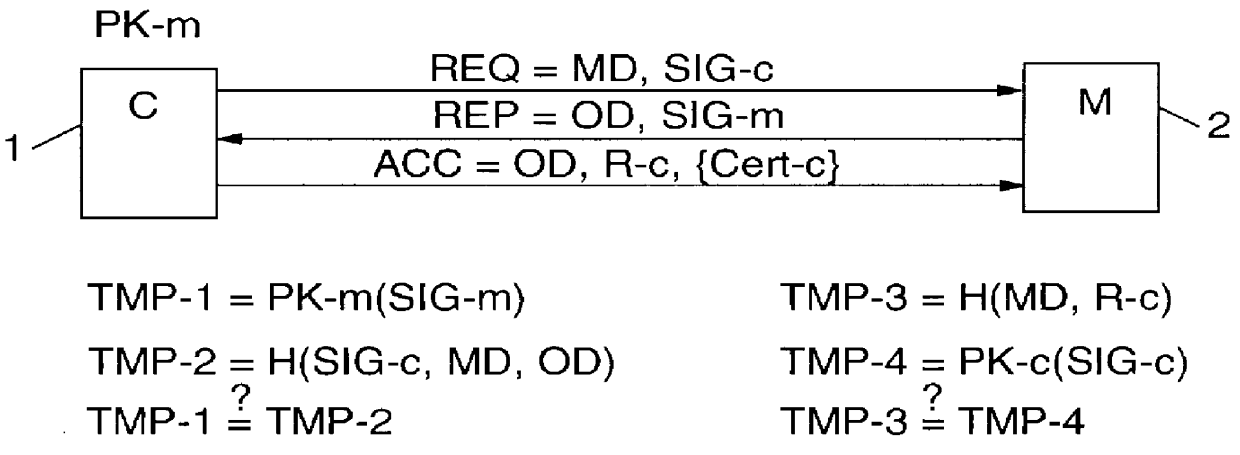
PCT No. PCT / IB96 / 00025 Sec. 371 Date Jul. 2, 1998 Sec. 102(e) Date Jul. 2, 1998 PCT Filed Jan. 12, 1996 PCT Pub. No. WO97 / 25801 PCT Pub. Date Jul. 17, 1997Computer network management for electronic commerce requires technical implementations of business processes. The process addressed here is a technical method for a communication in which two or more parties legitimately want to communicate anonymously, often before discussing a deal or closing a business, e.g. for anonymous bidding or auctioning in electronic commerce. Essentially, the invention is a method, described by a protocol, for safely exchanging data in a network that provides a public key infrastructure and an anonymous communication possibility between network users. It consists of a sequence of steps in which both sender (e.g. customer) and addressee (e.g. merchant) compose data sets (i.e., requests and replies) that are based on received data and / or prior knowledge. The data sets are enciphered to provide anonymity, and digitally signed to provide proof of the partner. The invention is also a system designed to implement the invented method.
Owner:GOOGLE LLC
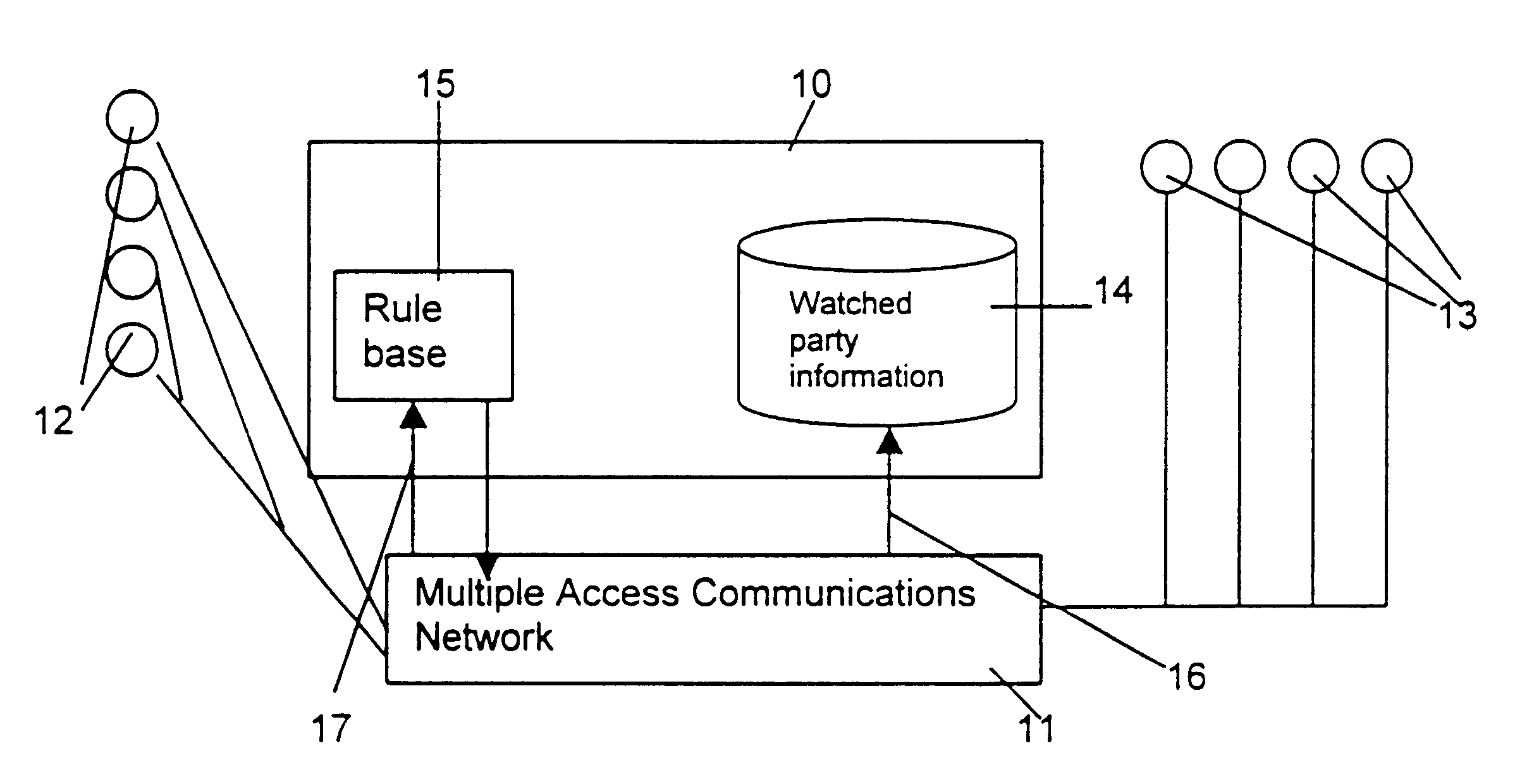
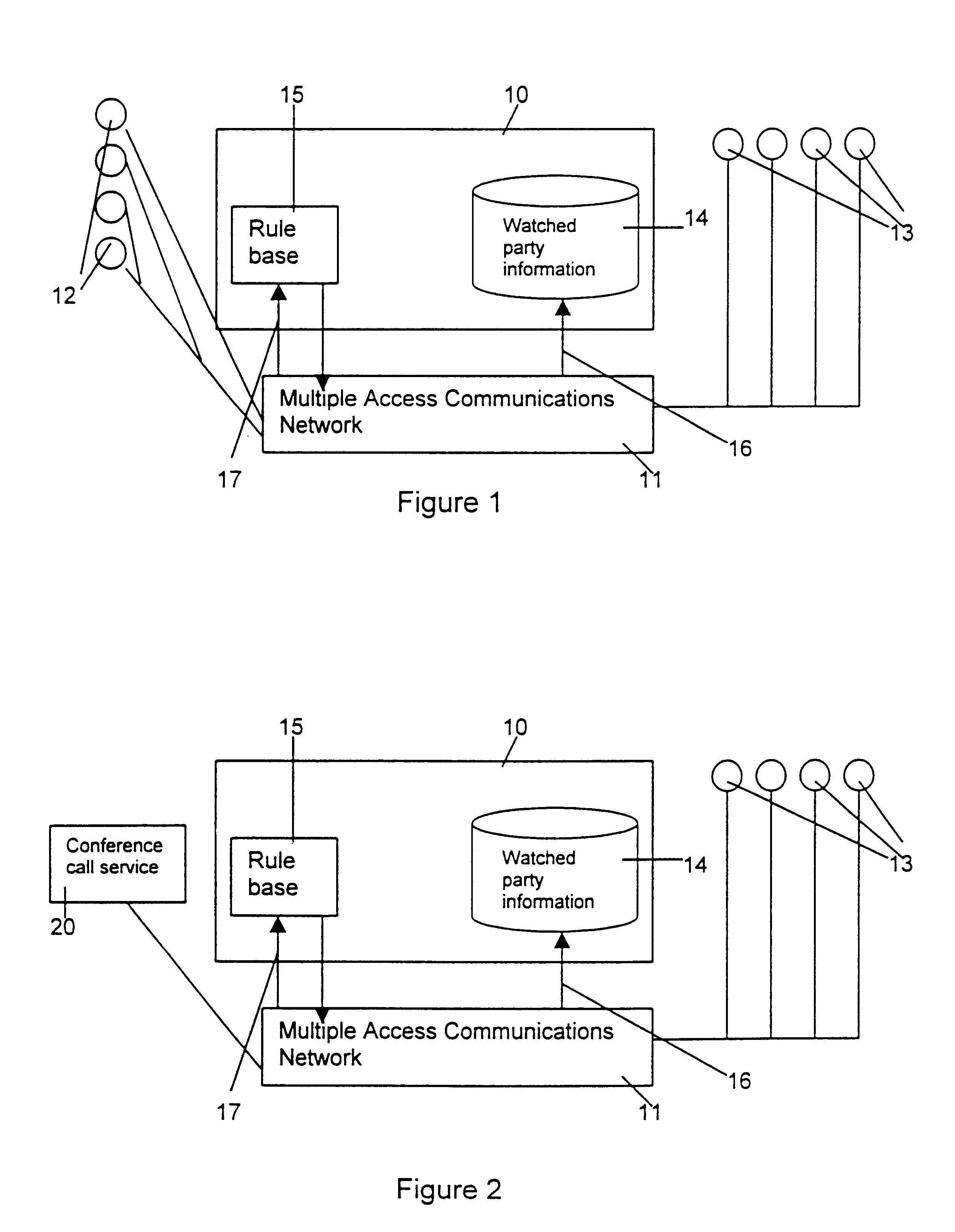
Anonymity in a presence management system
InactiveUS6853634B1Limited abilitySpecial service provision for substationSpecial service for subscribersComputer networkComputer science
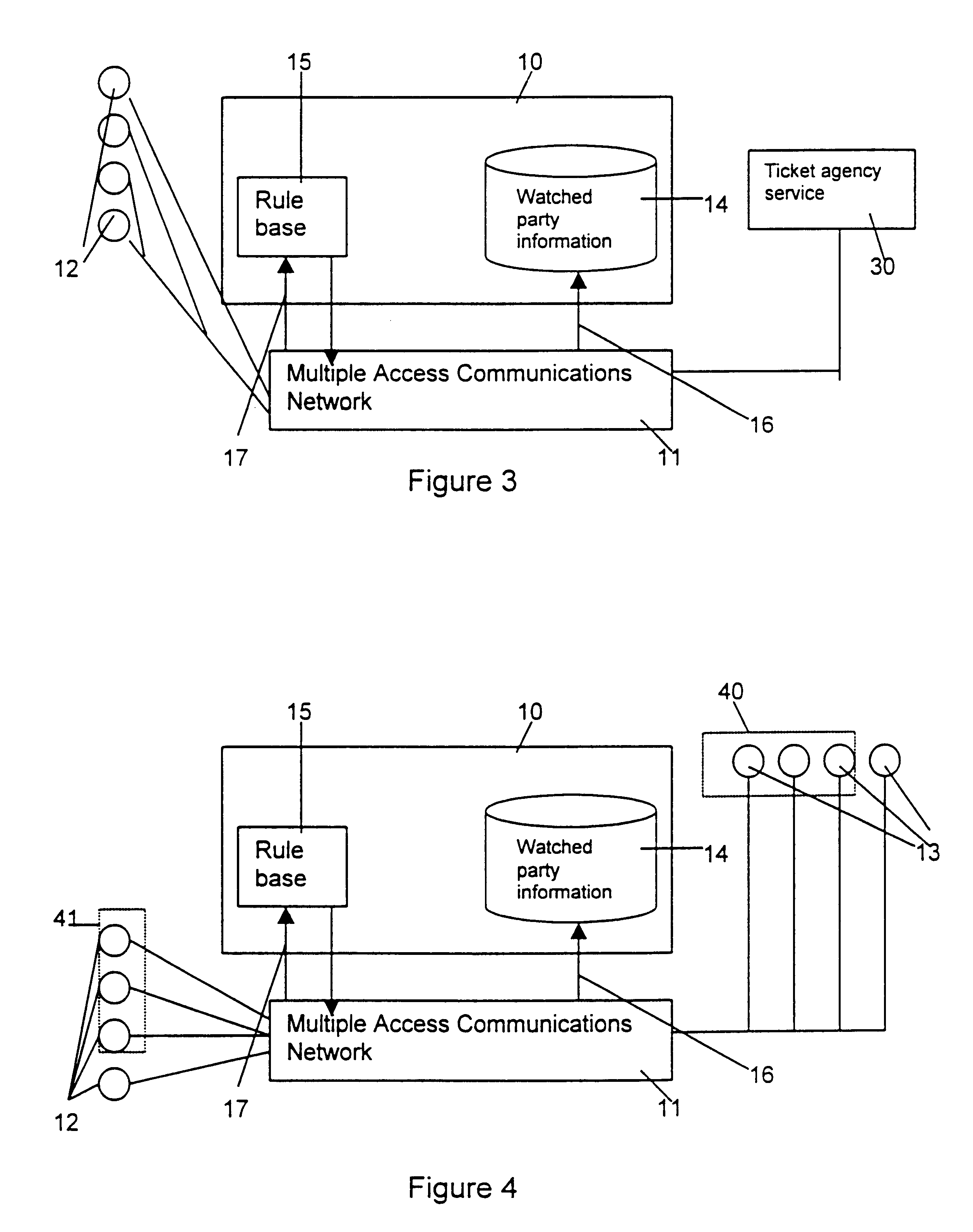
A presence management system allows connections between watching parties and watched parties in a multiple access communications network to be managed. When the presence management system receives a contact request from a watching party it determines whether the required watched party is available for contact. The system then provides information about this to the watching party who made the request. The presence management system chooses the best mode of communication (e.g. email or fax) taking into account the watched parties preferences and details about the facilities available to the watching party.
Owner:RPX CLEARINGHOUSE
Database access system
InactiveUS7801896B2Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
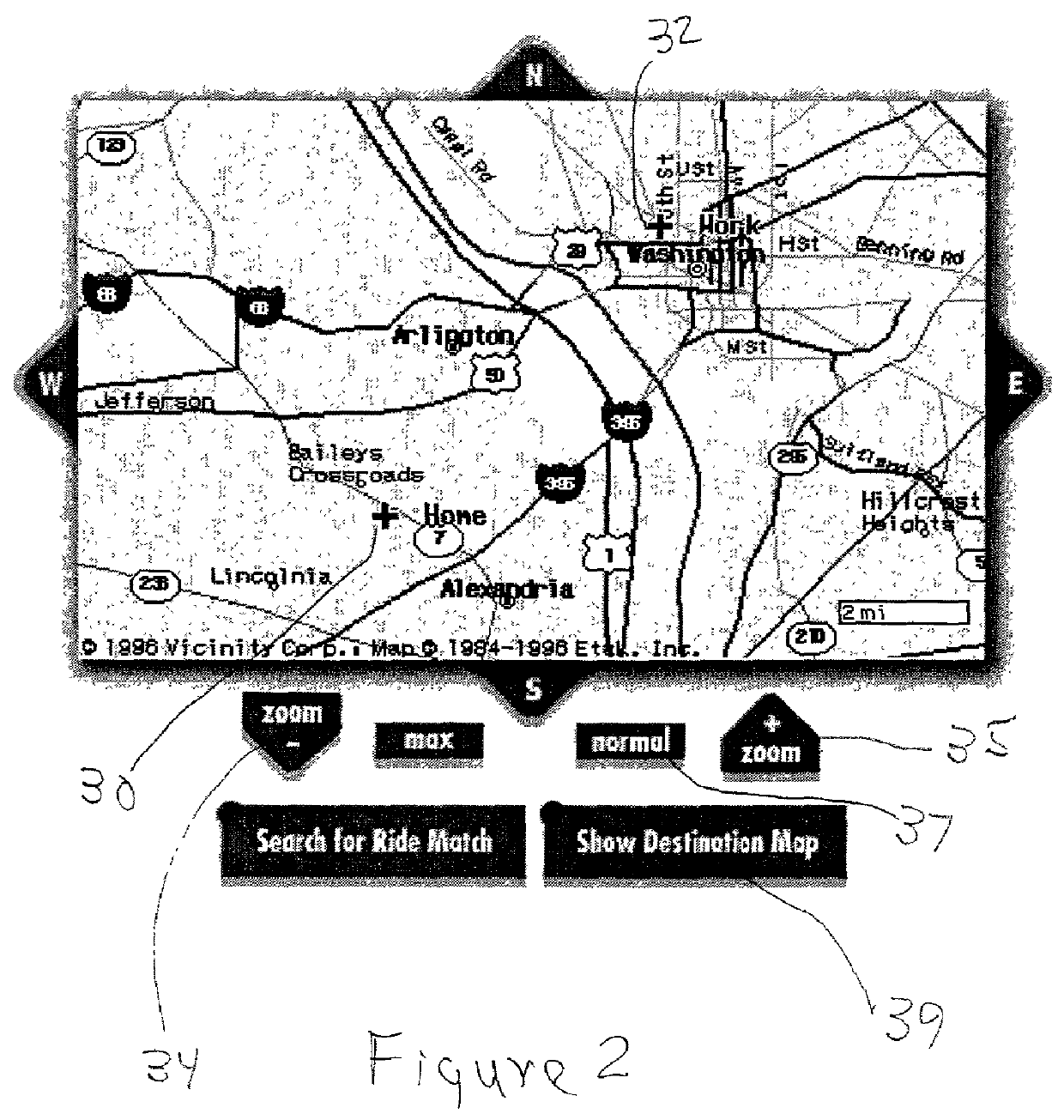
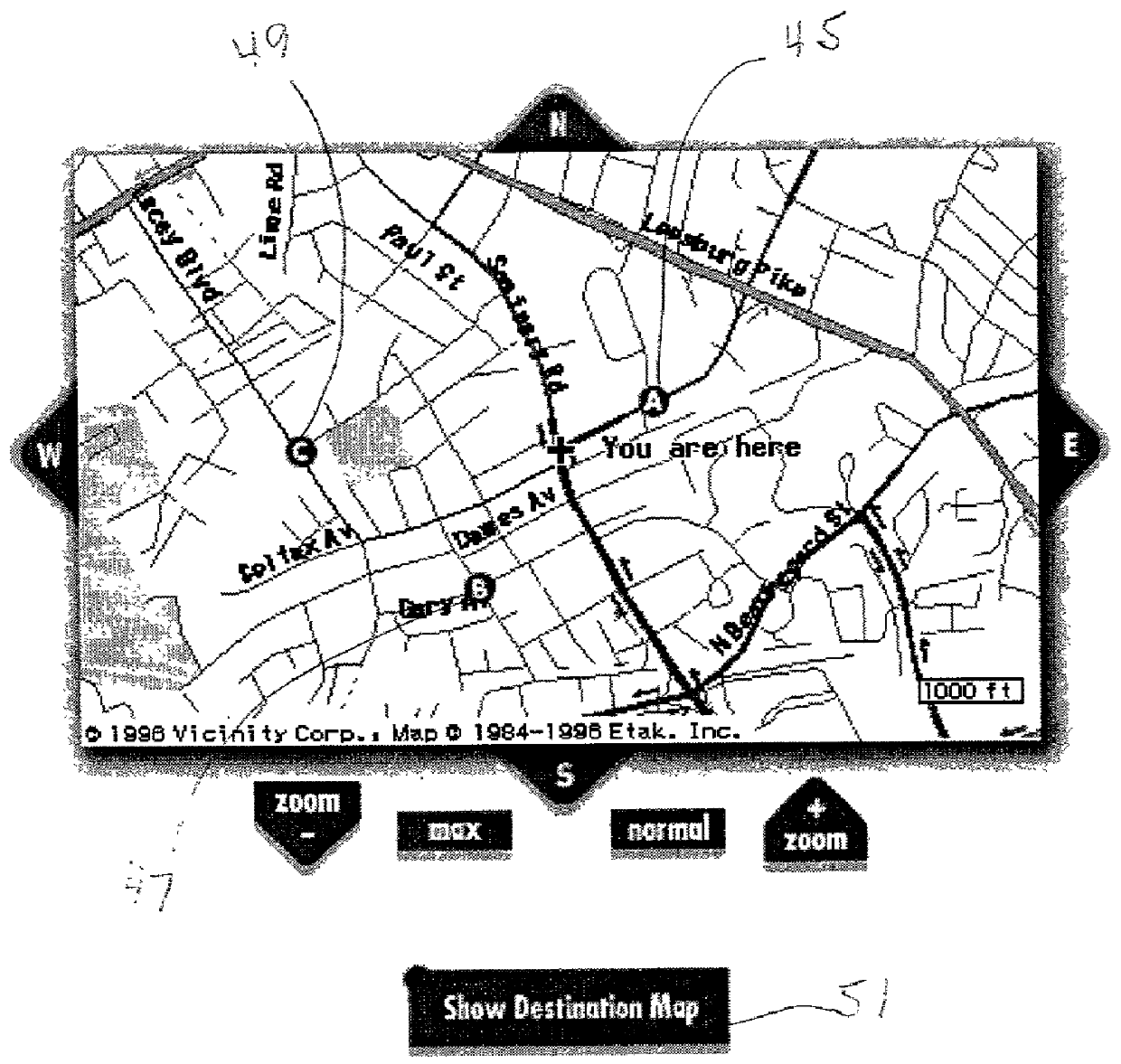
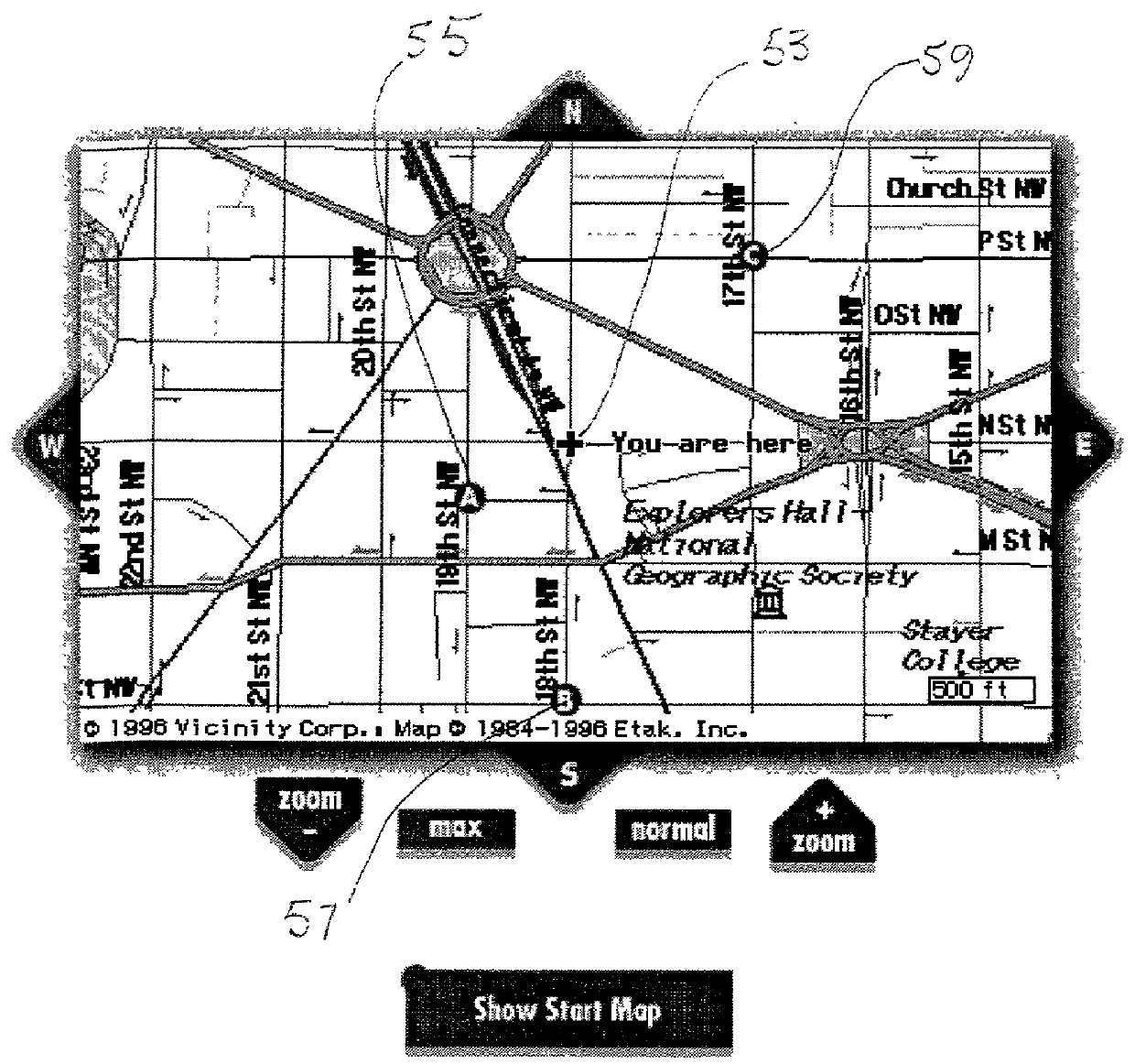
System for providing ride matching services using e-mail and the internet
An on-line ride sharing system employs a dynamic database of geographical information in map form together with information that is input into the system by individual users and potential users of the system. An analysis program is integrated with the database to evaluate applications filed by users, and to present a user with a map display of origin and destination locations of potential ride sharing partners. A communication route is provided by the system between the user and potential partners to allow the parties to maintain anonymity and privacy so long as is desired.
Owner:GANTZ DONALD T +1
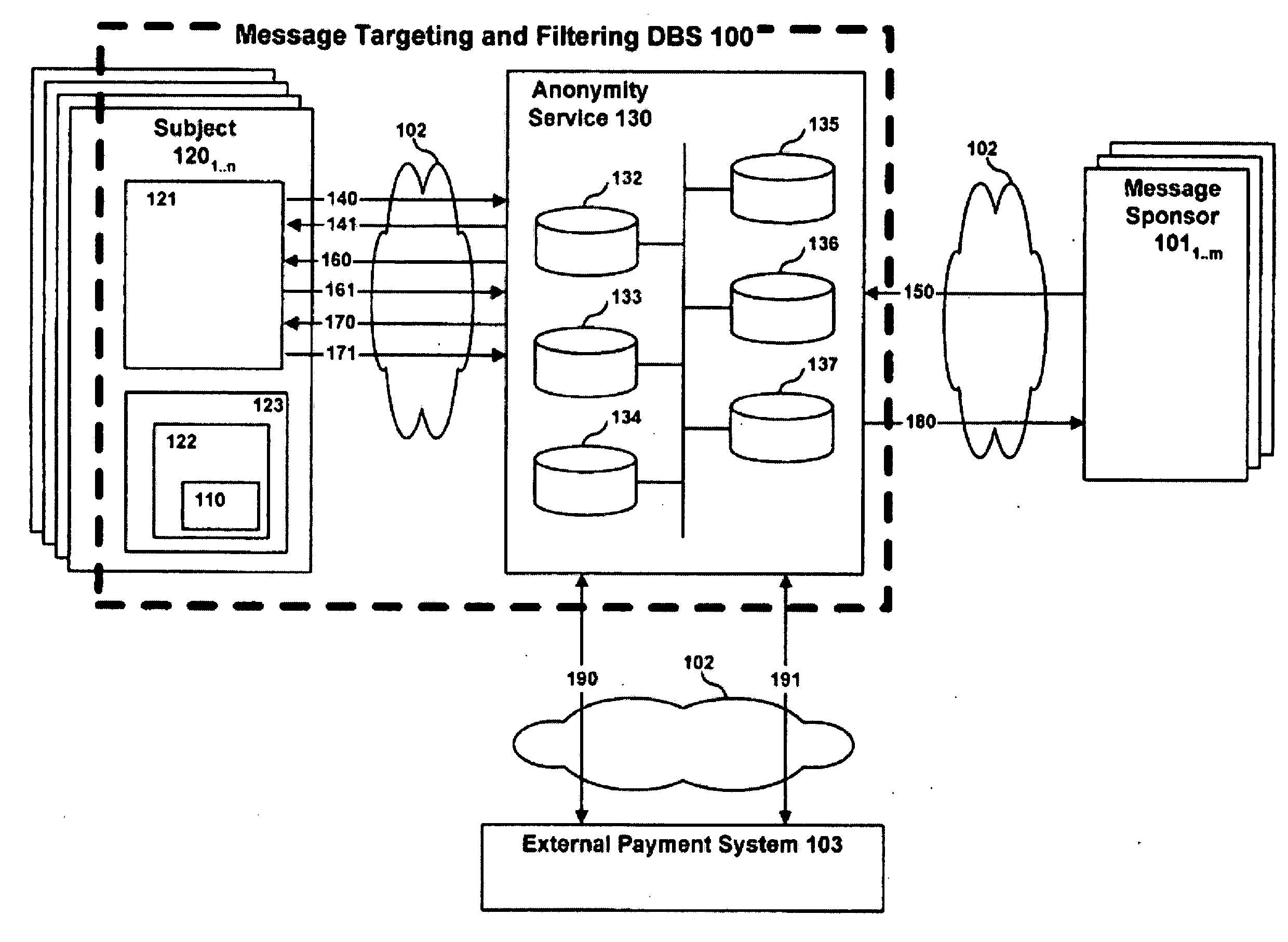
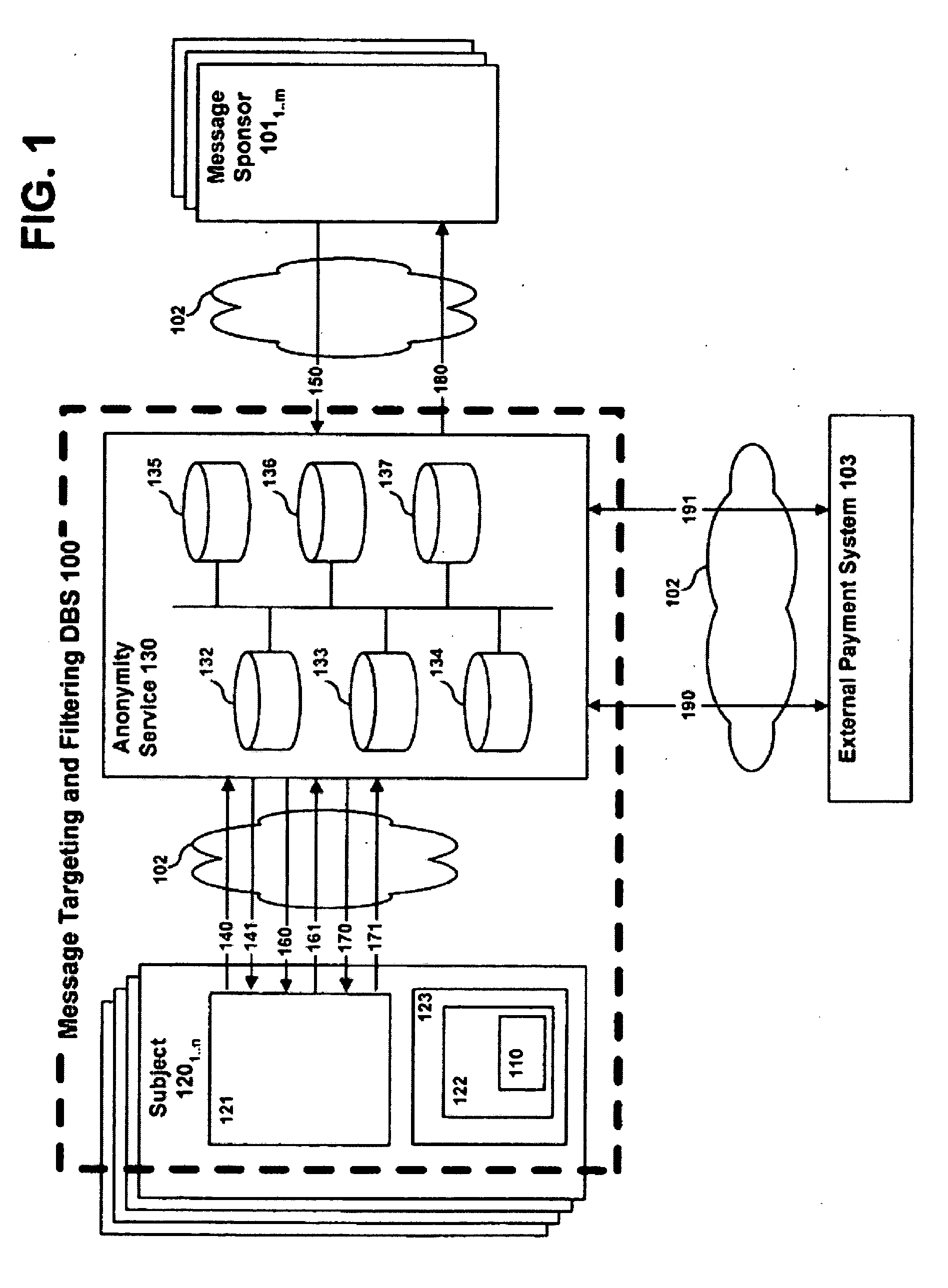
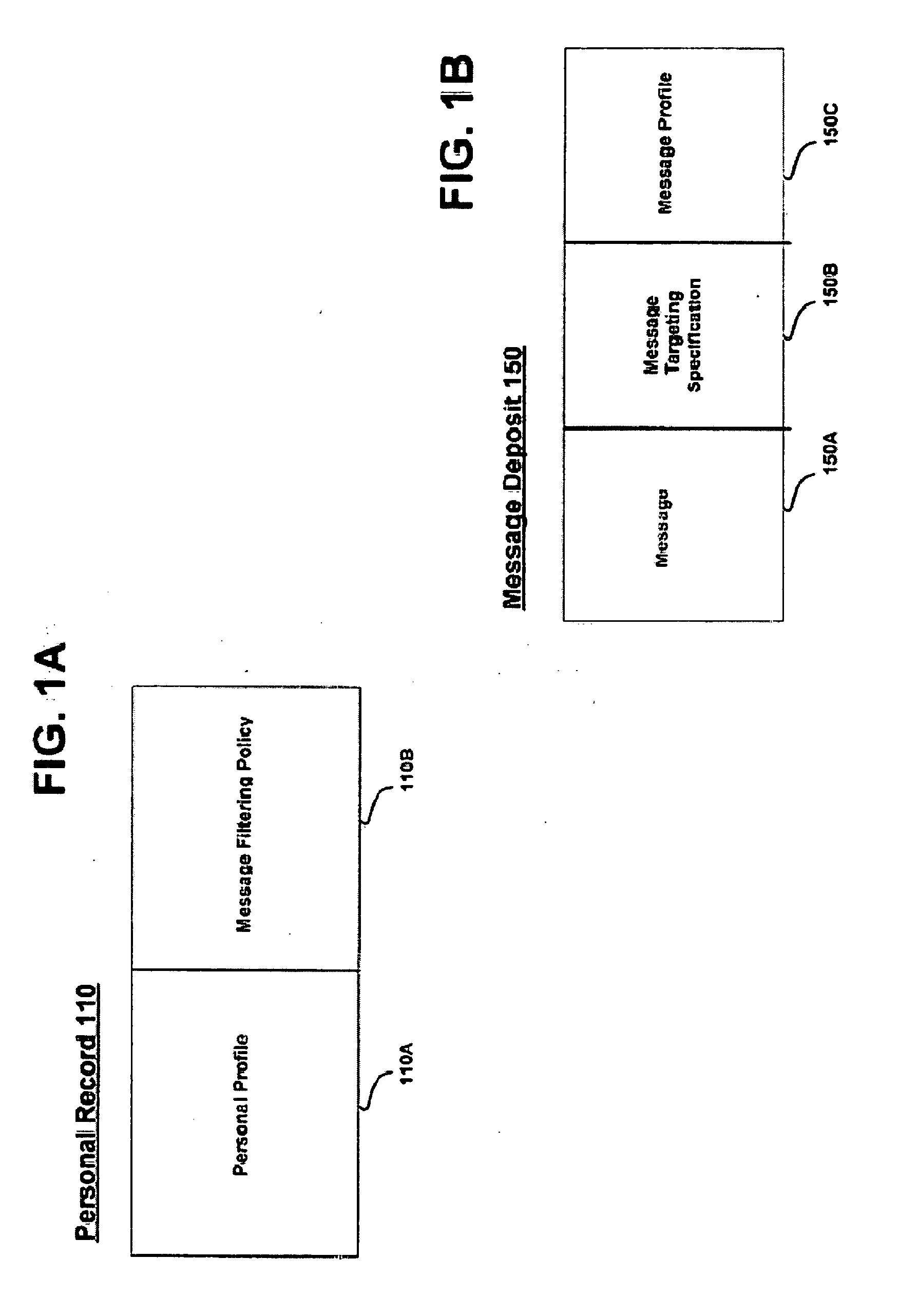
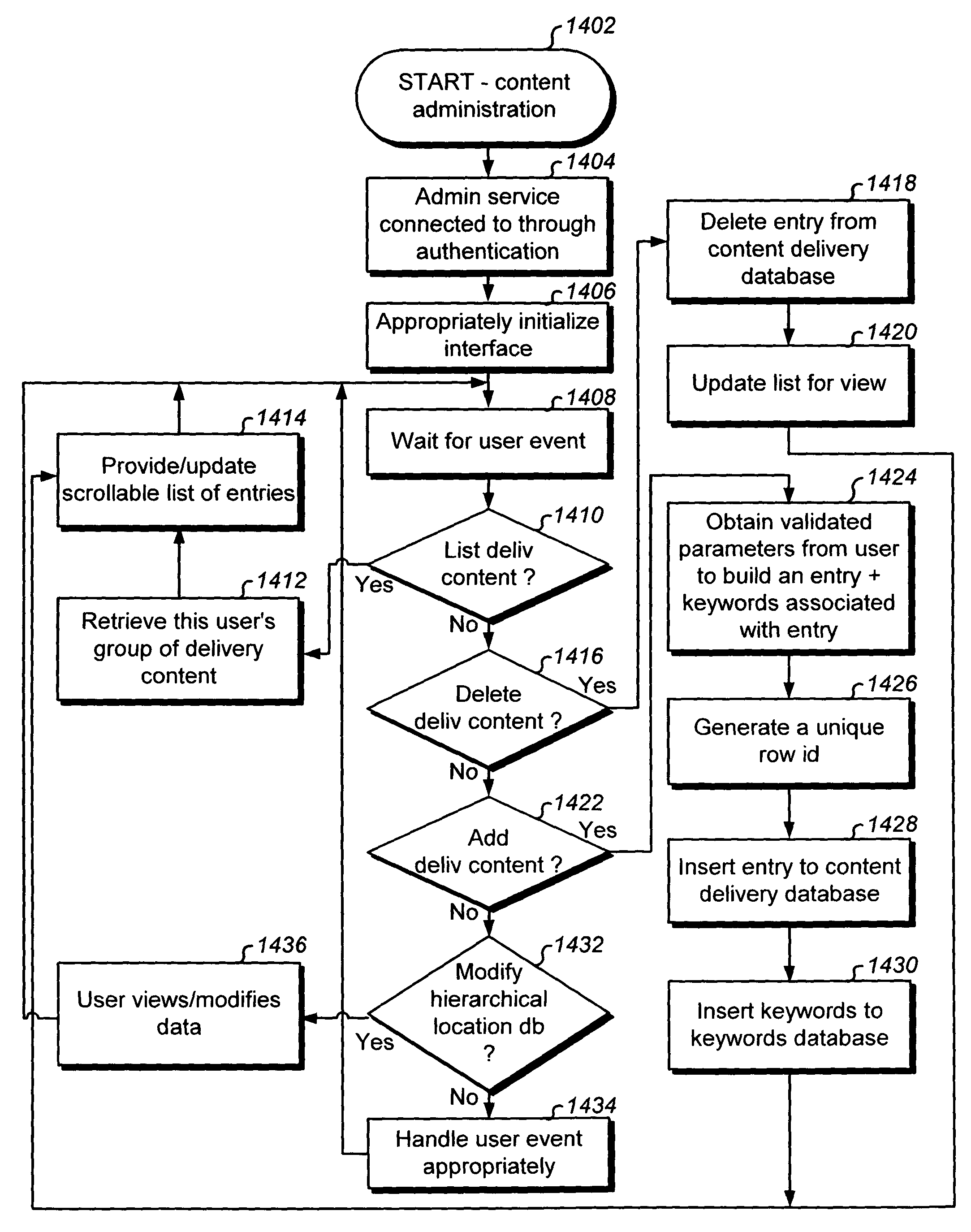
System, method and apparatus for message targeting and filtering
InactiveUS20100223349A1Digital data processing detailsUser identity/authority verificationClient-sideAnonymity
A system, method and apparatus for message targeting and filtering are provided to deliver bulk messages to demographically selected audiences of willing recipients while preserving each recipient's anonymity and control over his private personal data, accomplished by means of a radically distributed database technique in which all operations requiring unencrypted data access are distributed to individual client devices.
Owner:THORSON JOEL
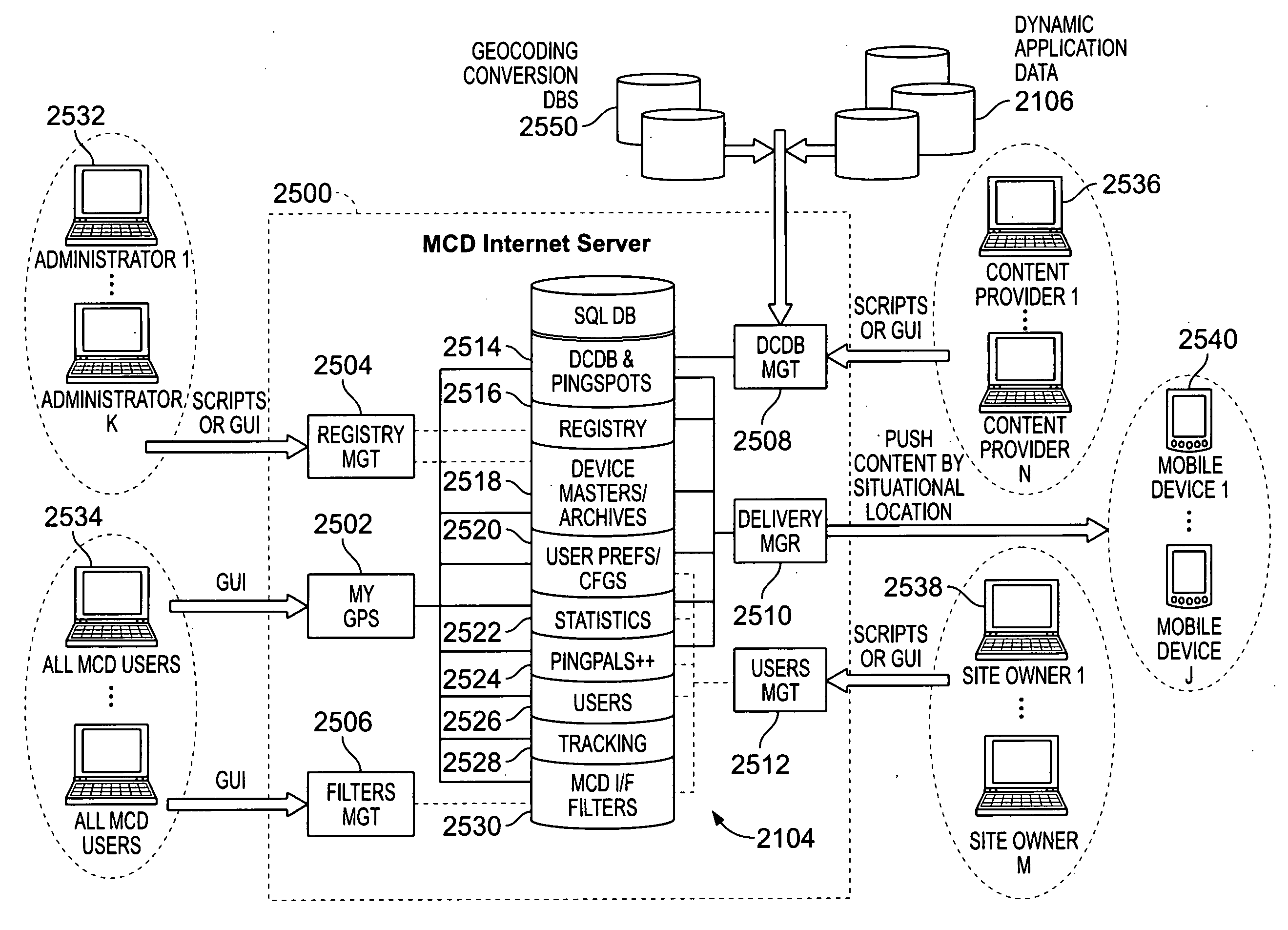
System and method for anonymous location based services
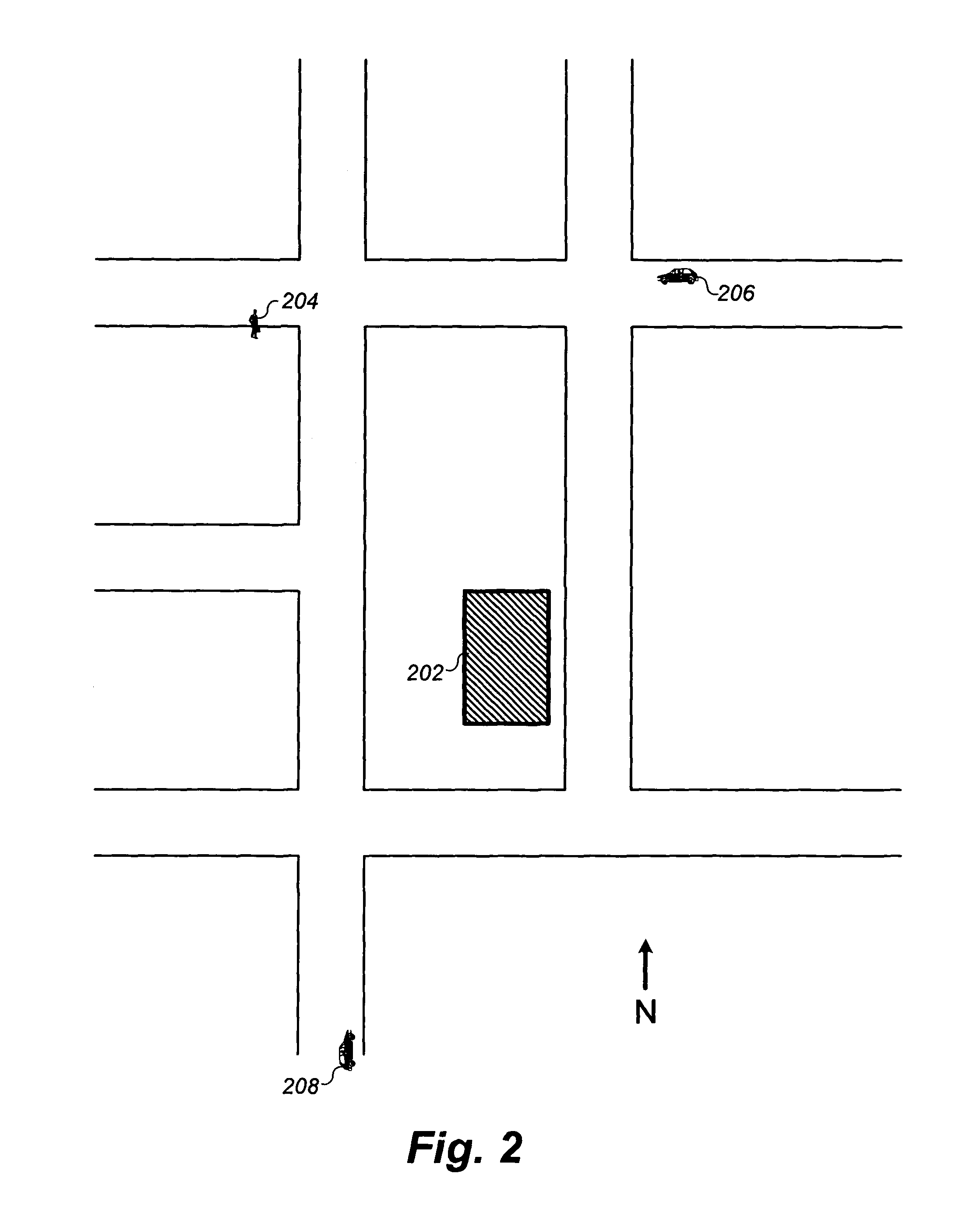
Provided is a fully automated web service with location based services generally involved in transmission of situational location dependent information to automatically located mobile receiving data processing systems. The web service communicates with a receiving data processing system in a manner by delivering information to the device when appropriate without the device requesting it at the time of delivery. There are varieties of configurations made by different user types of the web service for configuring information to be delivered, and for receiving the information. The web service maximizes anonymity of users, provides granular privacy control with a default of complete privacy, and supports user configurable privileges and features for desired web service behavior and interoperability. The web service is fully automated to eliminate human resources required to operate services. Integrated with the web service are enhanced location based services providing map solutions, alerts, sharing of novel services between users, and complete user control for managing heterogeneous device interoperability through the web service.
Owner:APPLE INC
Systems and methods to consolidate and communicate user profiles and modality preferences information for content delivery or interaction experiences
ActiveUS20120109882A1Digital data processing detailsOffice automationHuman–computer interactionUser profile
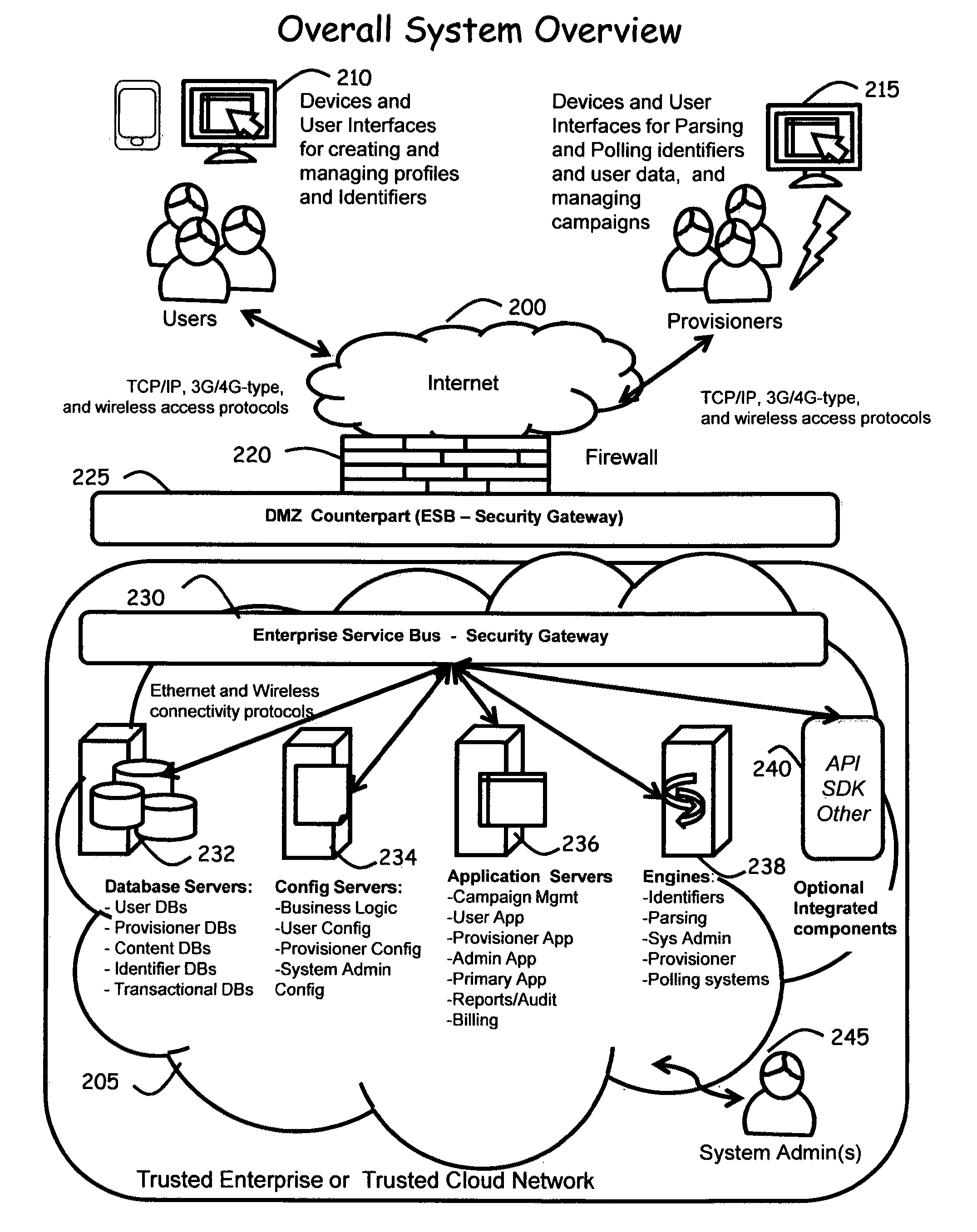
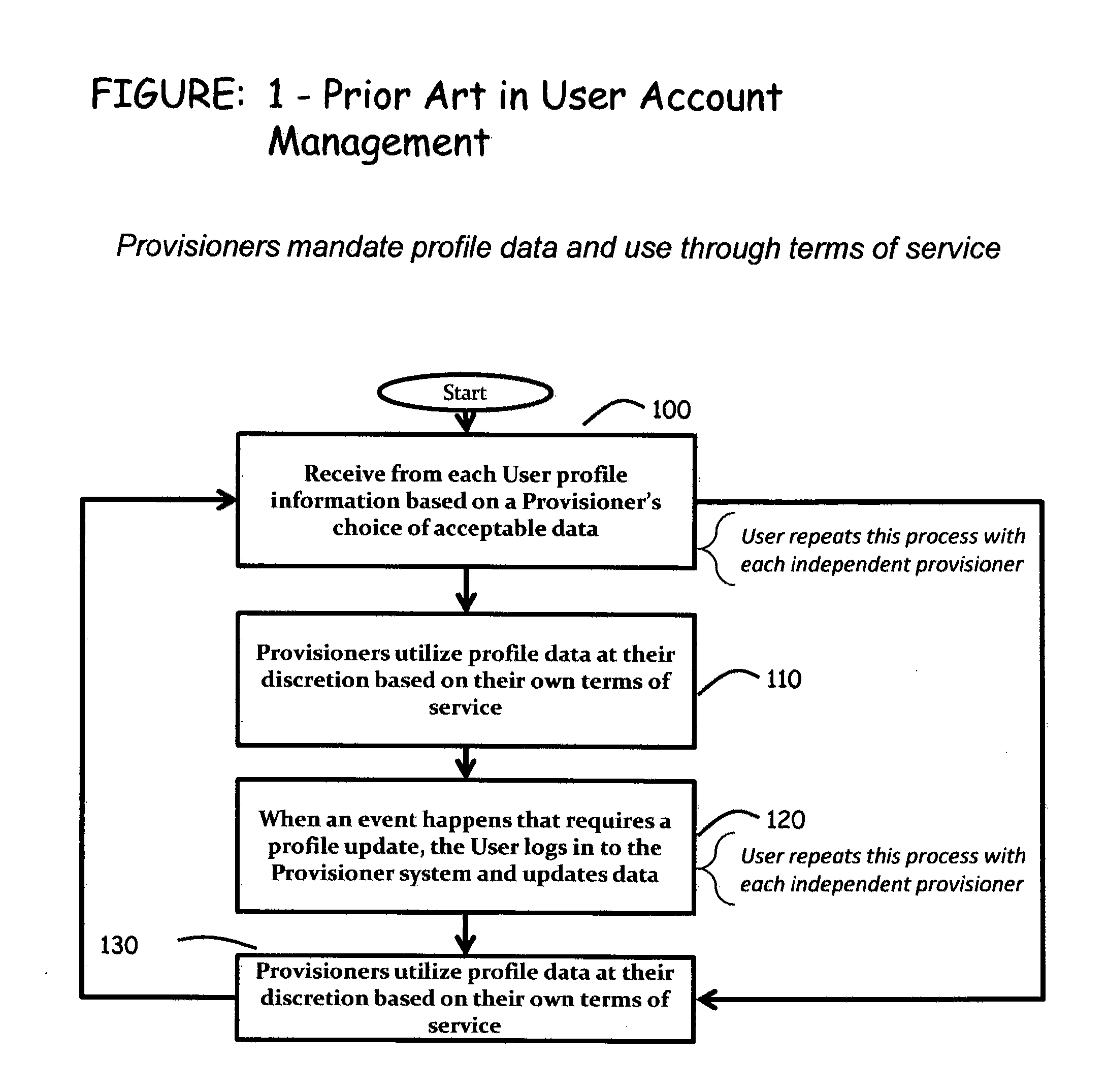
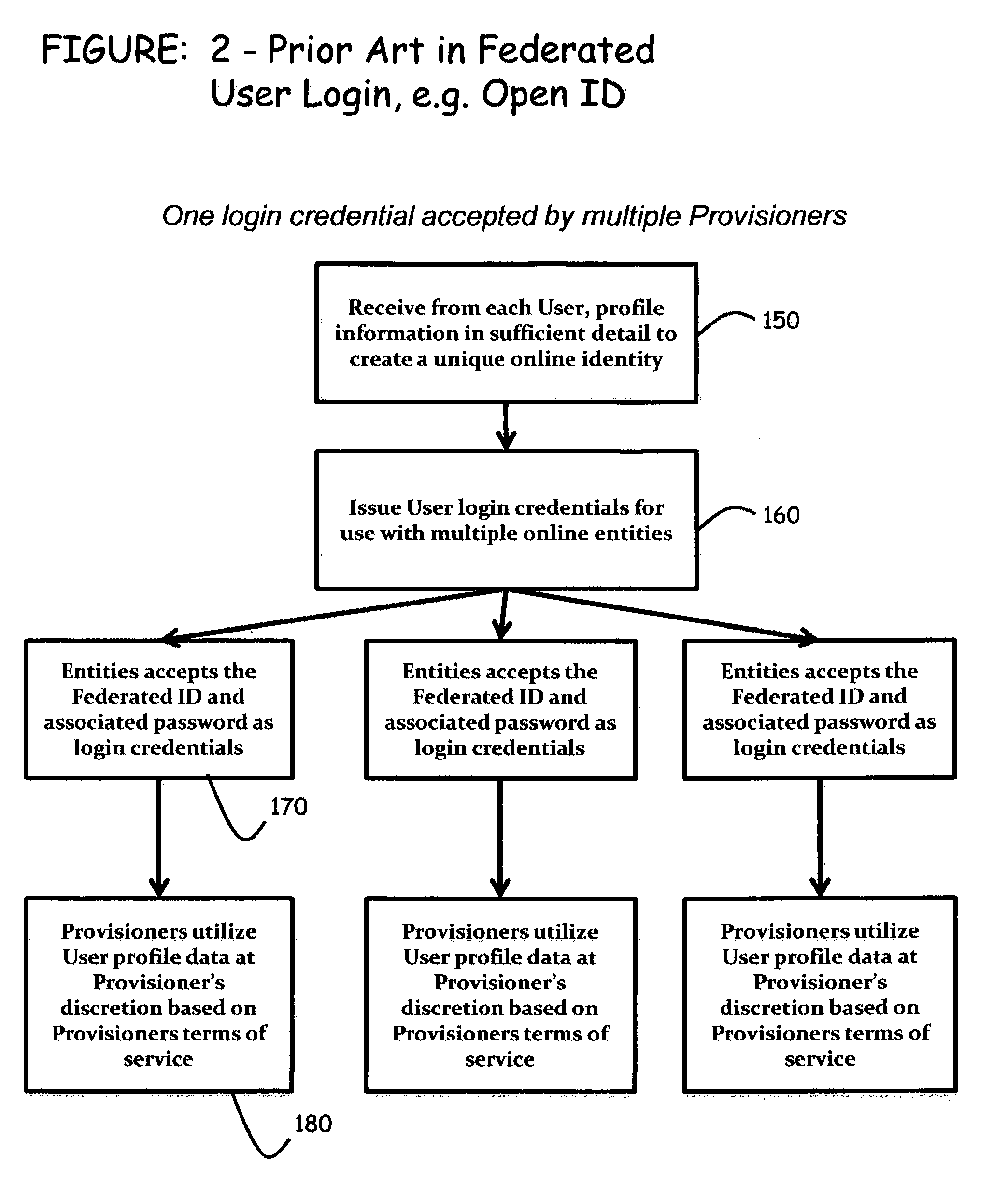
Computer-implemented systems and methods are provided whereby Users can dynamically configure and control the use of their preferences for both types and modality of interactions with multiple Provisioners. These inventive systems and methods also enable Provisioners to gain access to User preferences to establish or affect interactions and transactions with Users. Advantageously, these inventive systems and methods provide User control of the receipt of content, matter / substance, experiences and interactions, to enable consolidating management of the User's “interaction profile” into a unified system, while increasing the quality and depth of the relationship between the User and the Provisioner, including but not limited to the creation of emotional / affinity ties to the Provisioner. Furthermore, multiple instances of User profile data can be shared amongst multiple Provisioners in a way that creates affinity between Users and Provisioners and improves User experience, while maintaining User anonymity.
Owner:BOUSE RUSSELL KENT +1
Data anonymization based on guessing anonymity
ActiveUS8627483B2Maximizes guessing anonymityMinimize distortionDigital data processing detailsPublic key for secure communicationGame basedOptimization problem
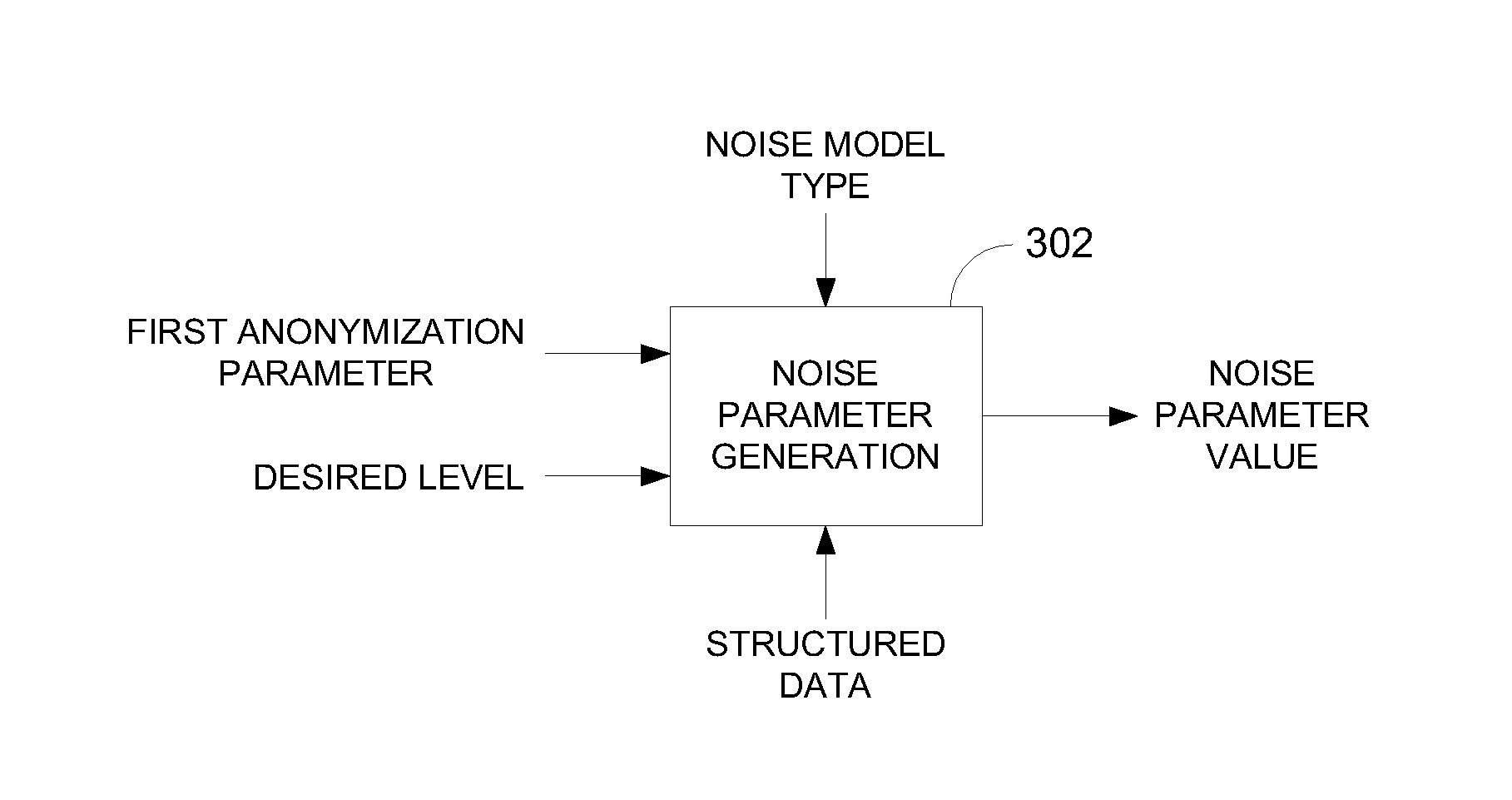
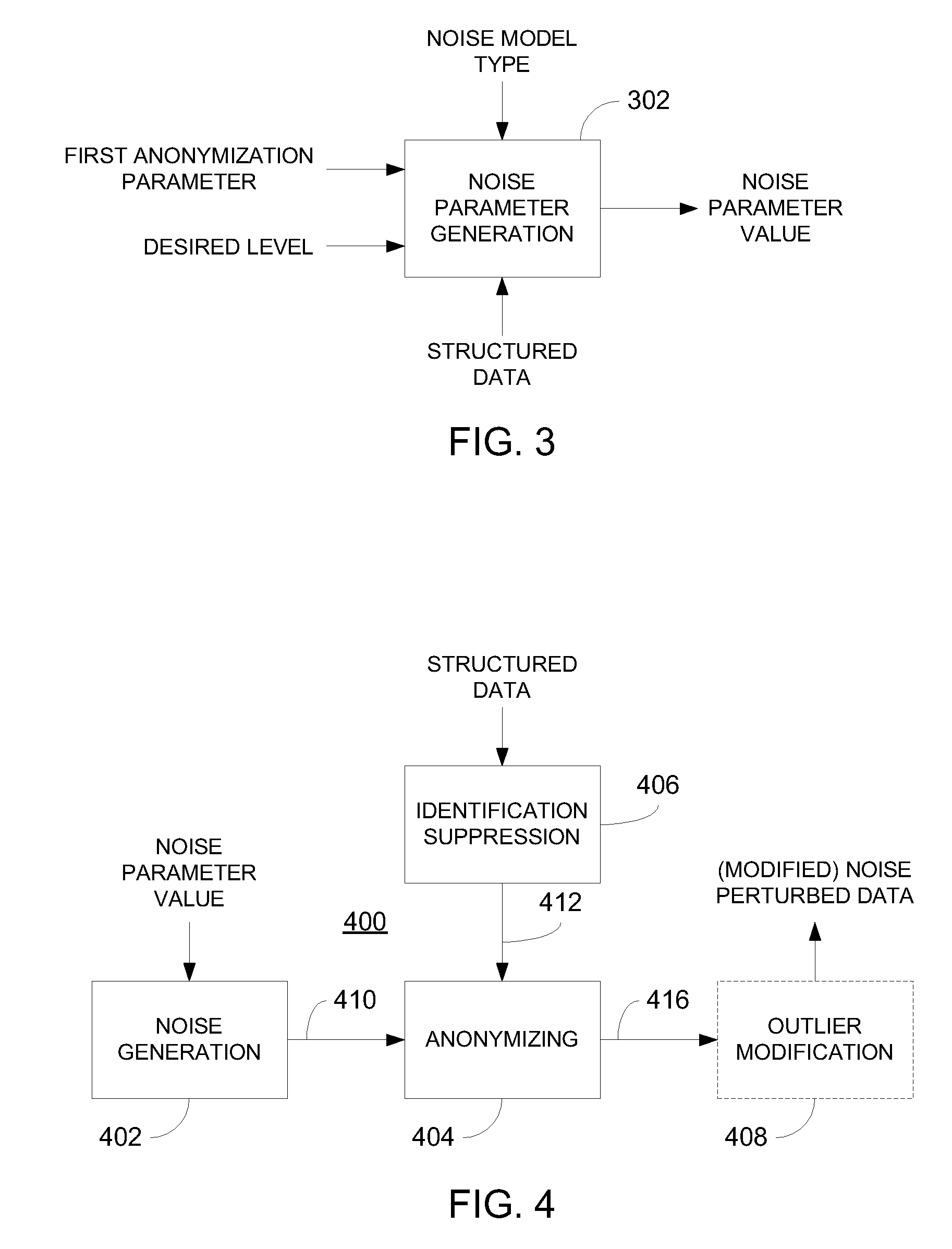
Privacy is defined in the context of a guessing game based on the so-called guessing inequality. The privacy of a sanitized record, i.e., guessing anonymity, is defined by the number of guesses an attacker needs to correctly guess an original record used to generate a sanitized record. Using this definition, optimization problems are formulated that optimize a second anonymization parameter (privacy or data distortion) given constraints on a first anonymization parameter (data distortion or privacy, respectively). Optimization is performed across a spectrum of possible values for at least one noise parameter within a noise model. Noise is then generated based on the noise parameter value(s) and applied to the data, which may comprise real and / or categorical data. Prior to anonymization, the data may have identifiers suppressed, whereas outlier data values in the noise perturbed data may be likewise modified to further ensure privacy.
Owner:ACCENTURE GLOBAL SERVICES LTD
Systems and methods for monitoring caregiver and patient protocol compliance
ActiveUS20120212582A1Improve abilitiesSimple processAlarmsHealthcare resources and facilitiesCaregiver personPatient compliance
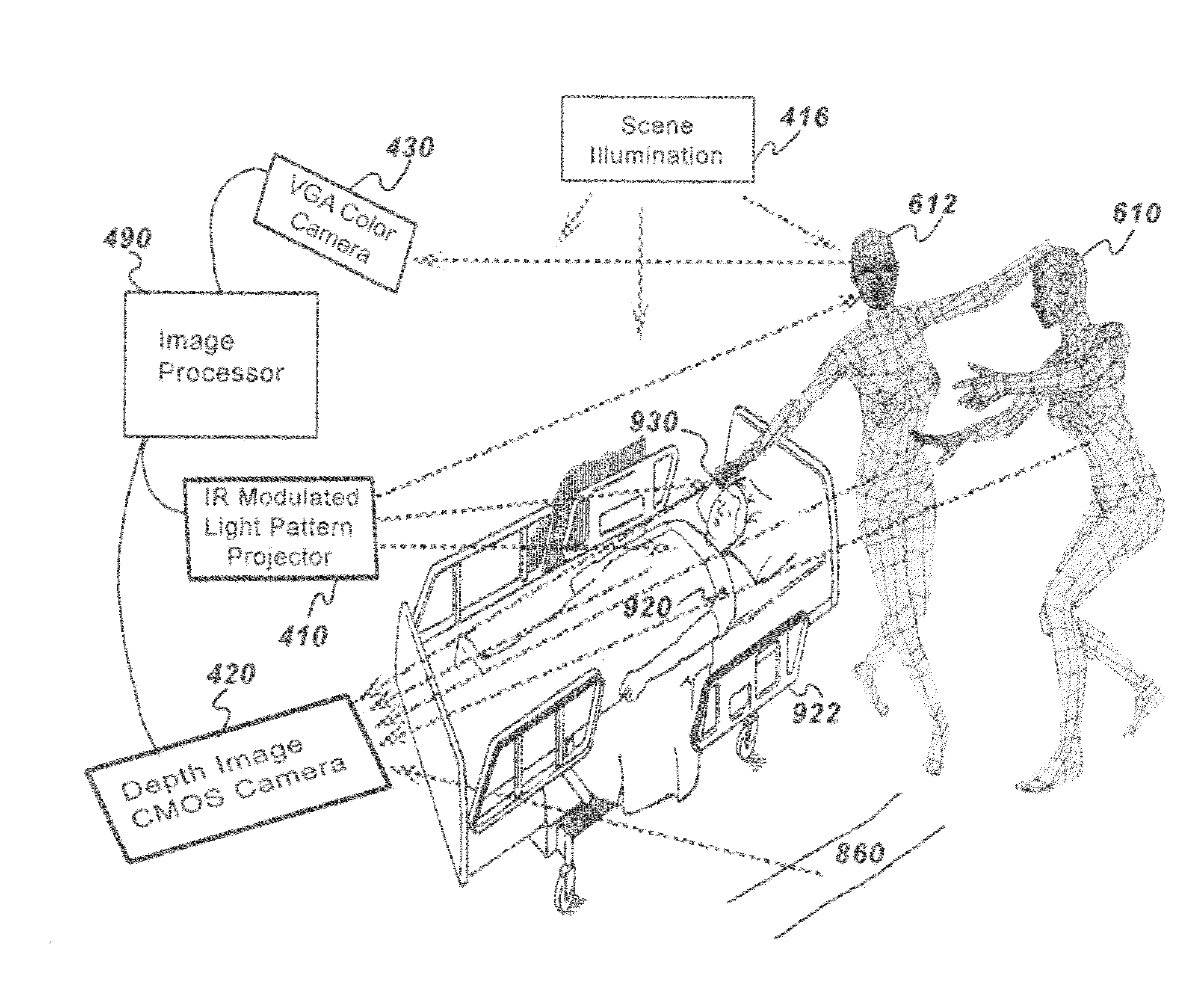
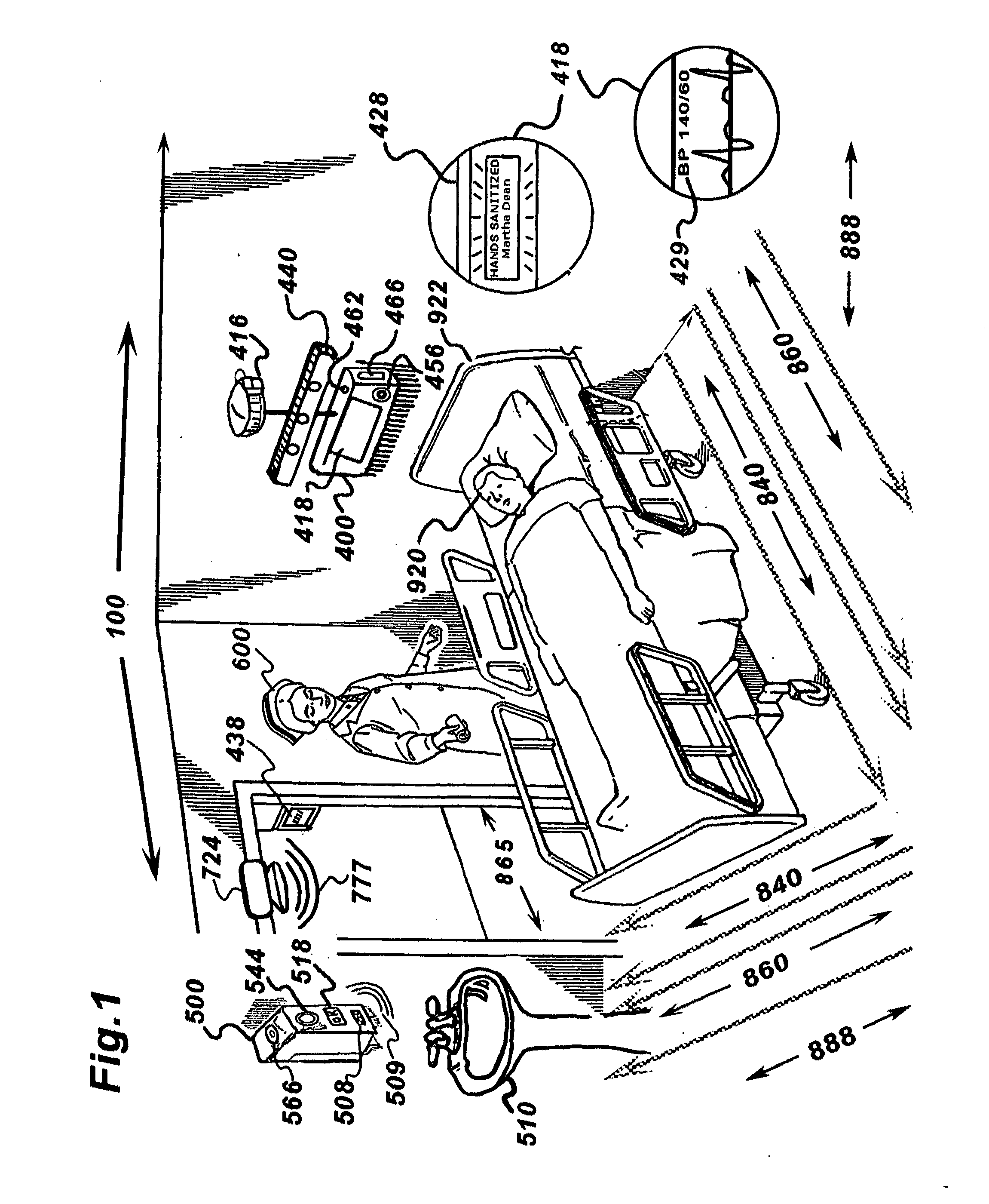
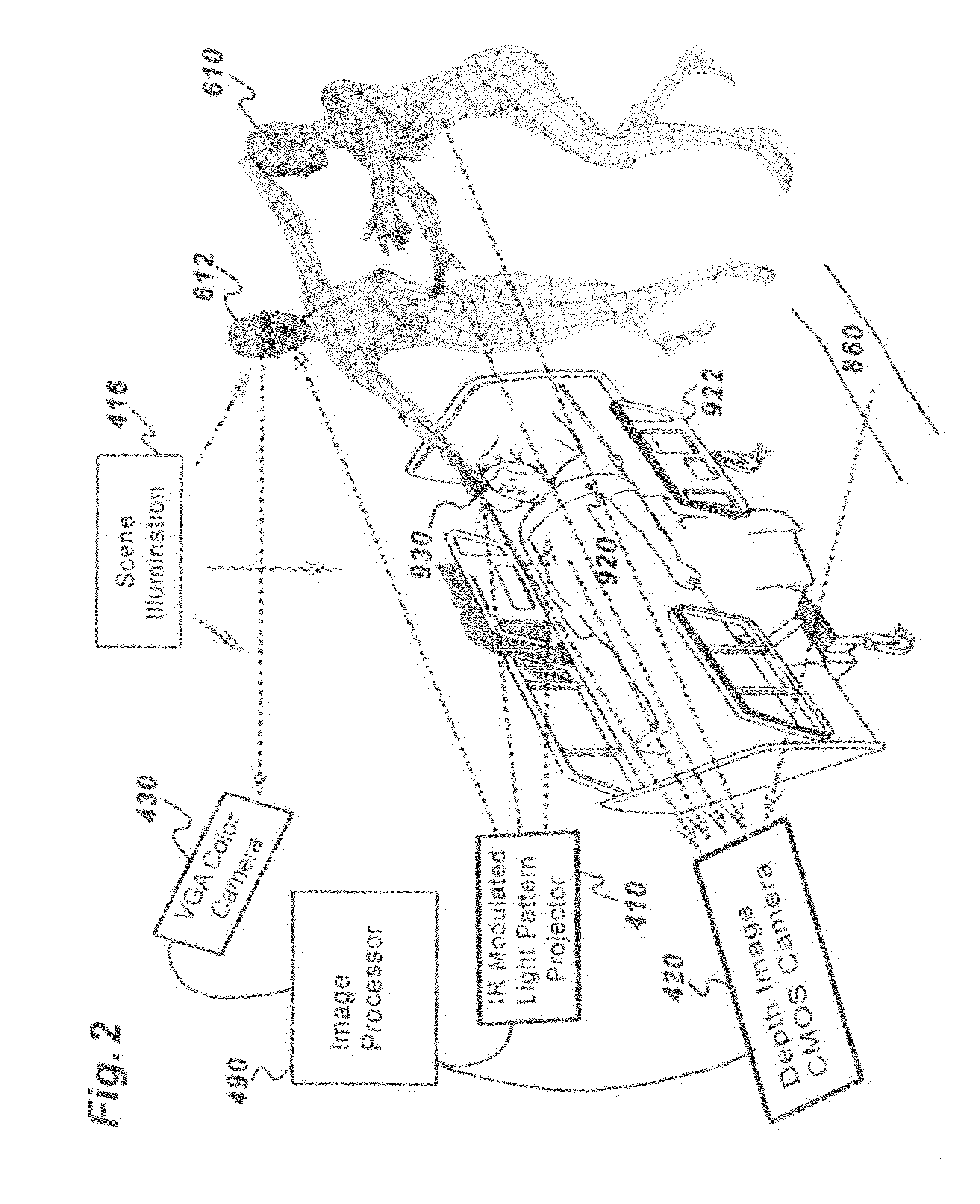
A system and methods is provided for facilitating, monitoring and recording caregiver and patient compliance with established hospital hand hygiene protocols. The system comprises a 3-D imaging and monitoring assembly and an optional intelligent programmable monitor / sanitizer. Three dimensional imagery tracks a caregiver's movements and location while generating a representative image value. Information acquired by the imaging system determines the proximity of a caregiver to the patient and / or contamination source and determines if the sanitizers provided have been utilized and if so, at an appropriate time and distance from the patient per hospital protocol. While being monitored, a representative Avatar based on physical characteristics derived from three dimensional images of the caregiver and patient may be generated so as to maintain anonymity of both unless a violation of institutional protocol occurs which may be forensically recorded in real-time for analysis.
Owner:DEUT RICHARD
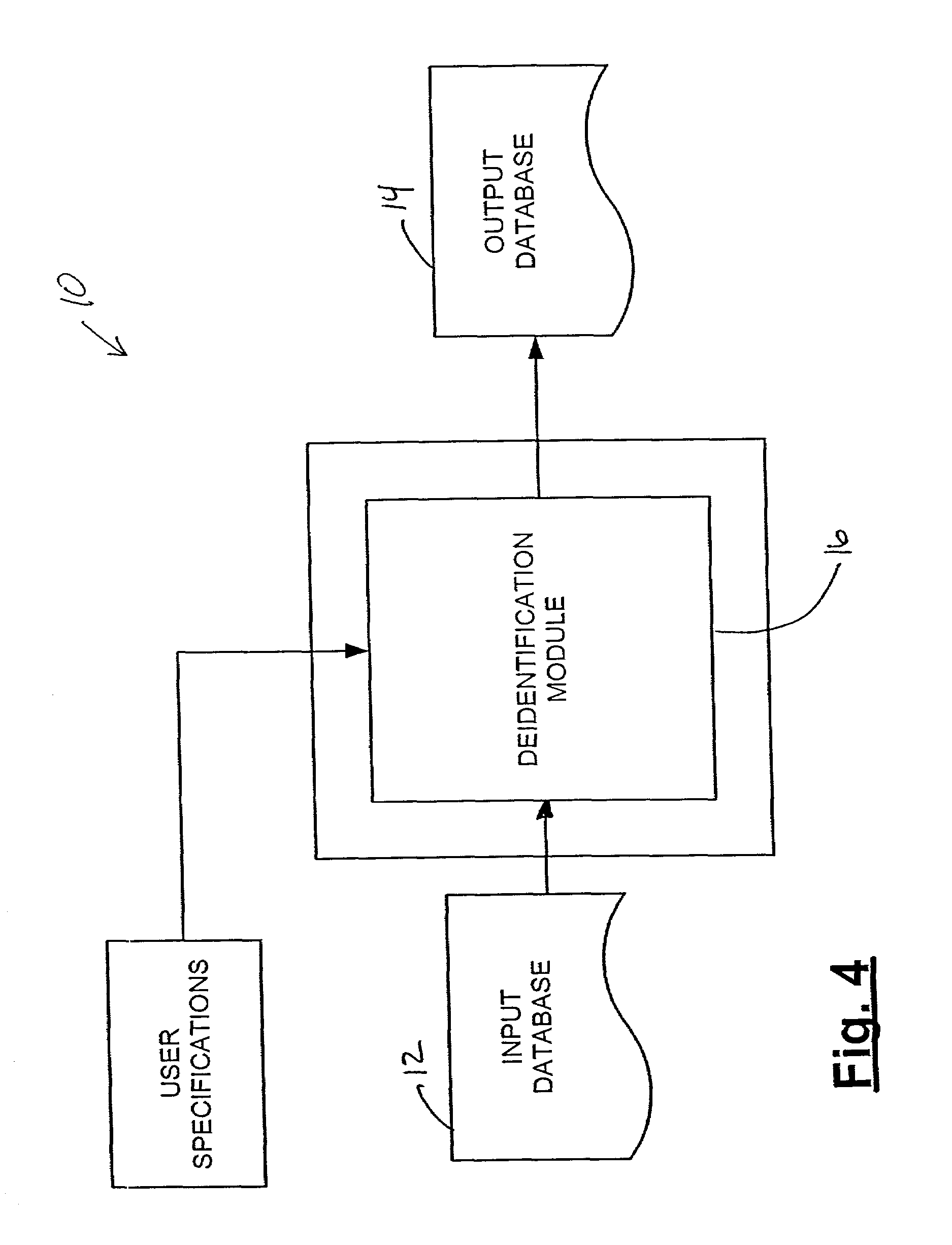
Systems and methods for deidentifying entries in a data source
InactiveUS7269578B2Digital data information retrievalComputer security arrangementsData sourceAnonymity
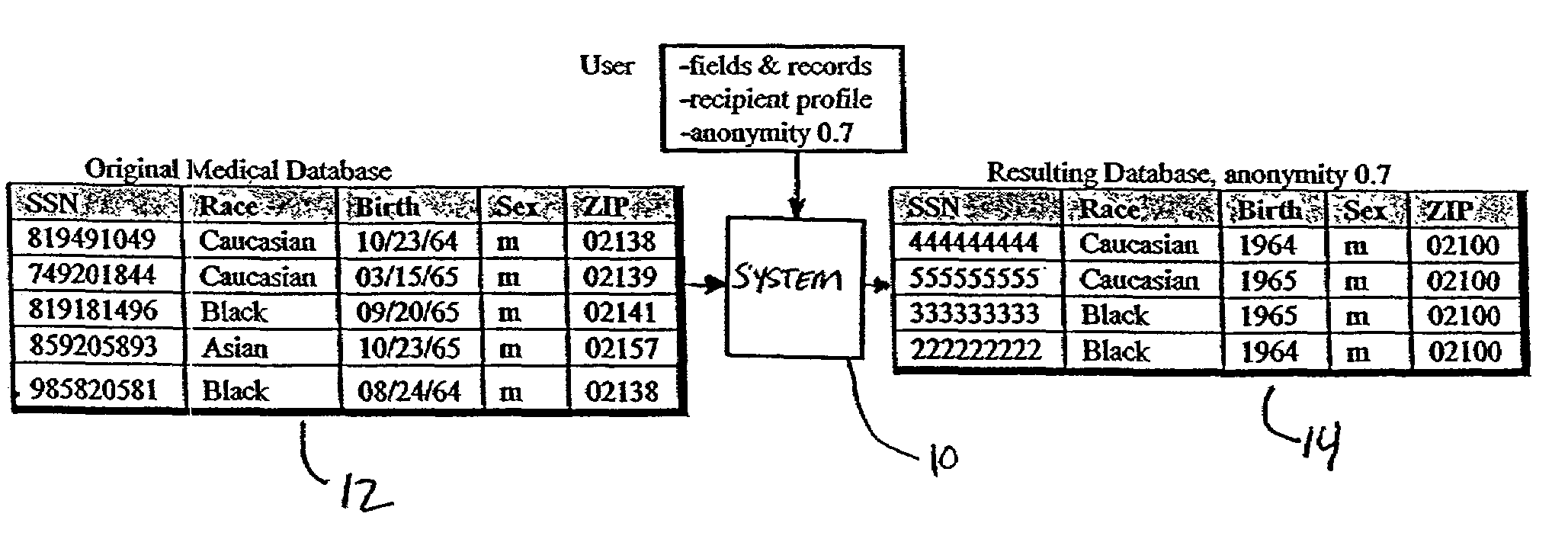
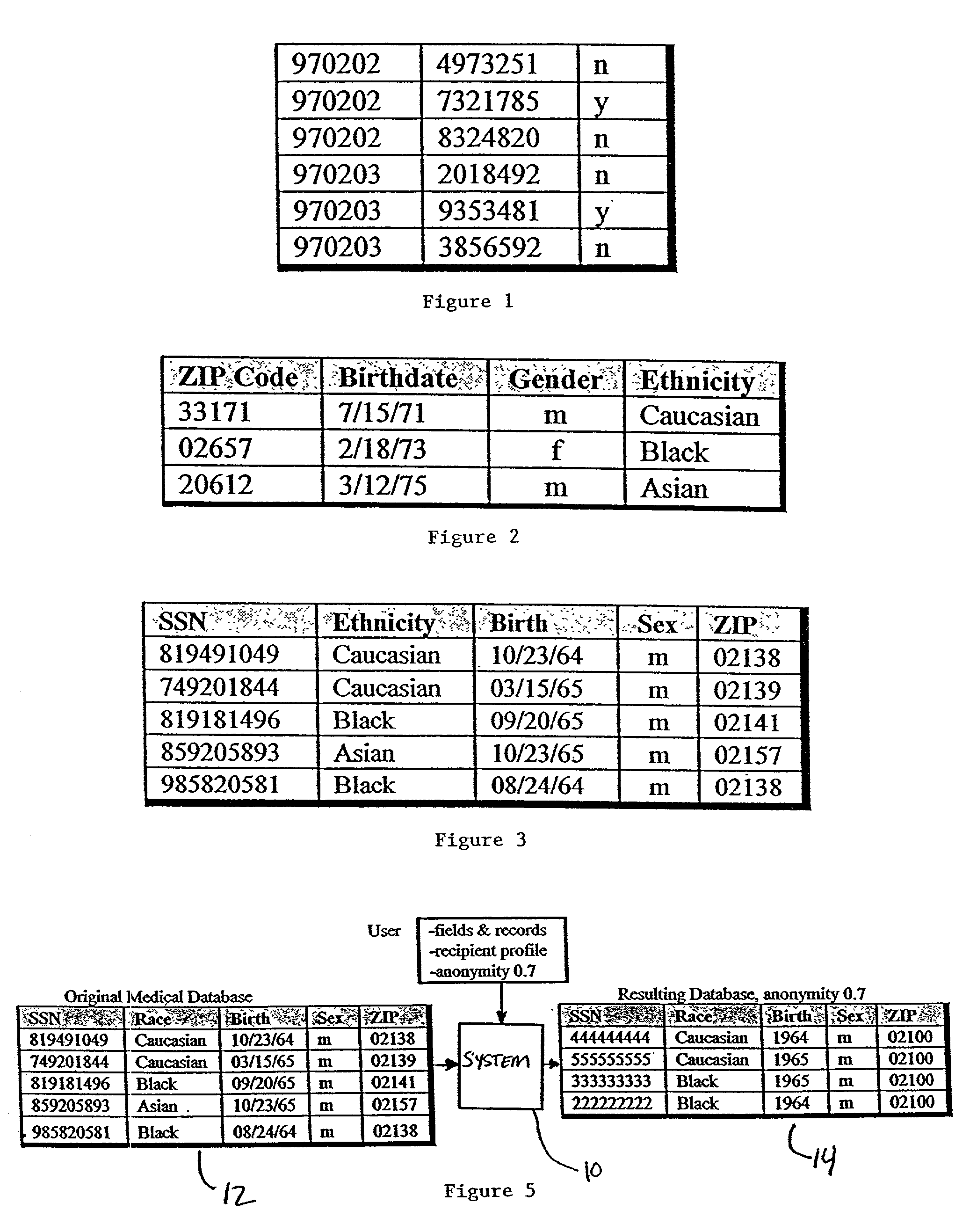
Systems and methods for deidentifying, or anonymizing, entries in an input data source are presented. According to one embodiment, the system includes a deidentification module for modifying entries in a version of the input data source to yield an output data source such that the entries of the output data source match a specified anonymity requirement. According to one embodiment, the resulting output data source may match the specified anonymity requirement with respect to a recipient profile that is input to the system. The deidentification module may further modify the entries in the version of the input data source such that the entries in the output data source are minimally distorted given the specified anonymity requirement.
Owner:SWEENEY DESIGN LABS
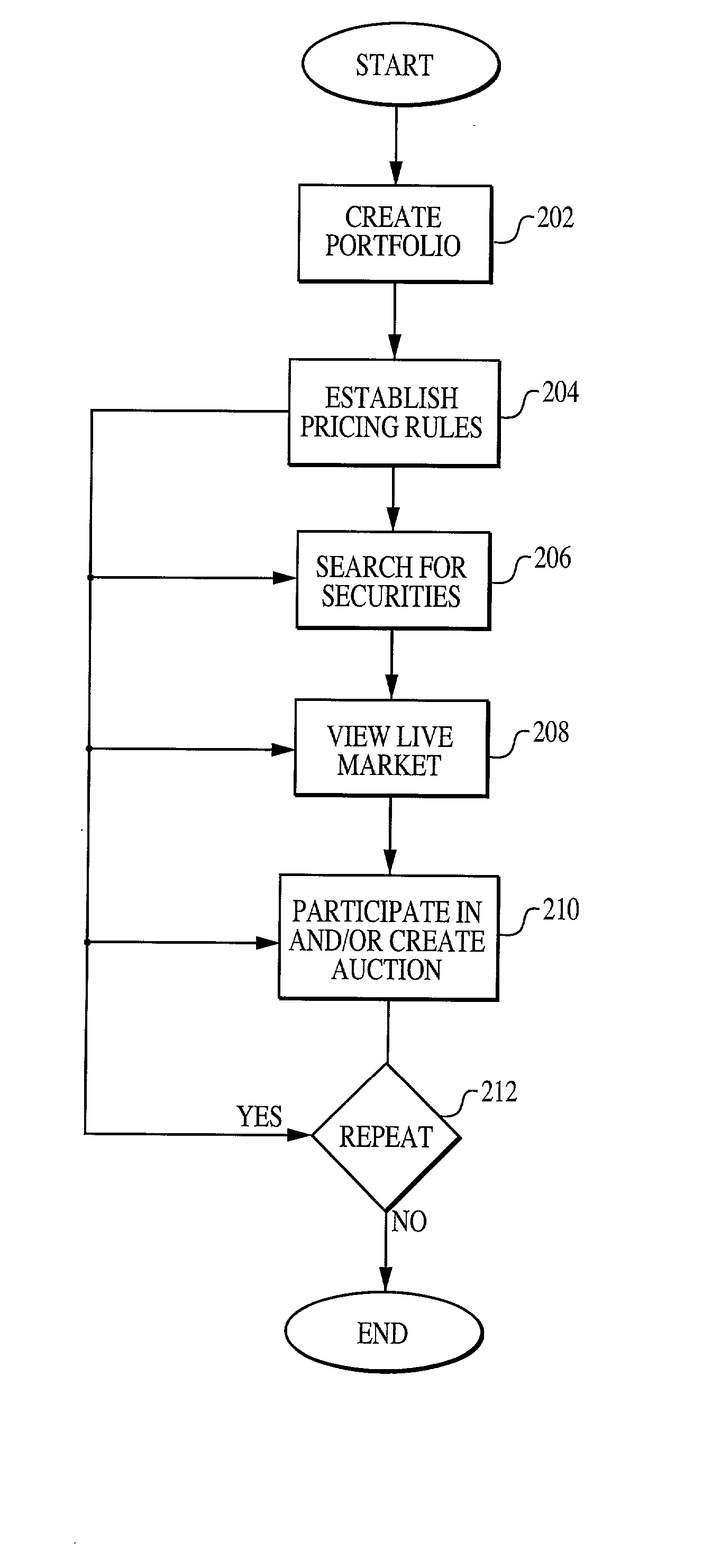
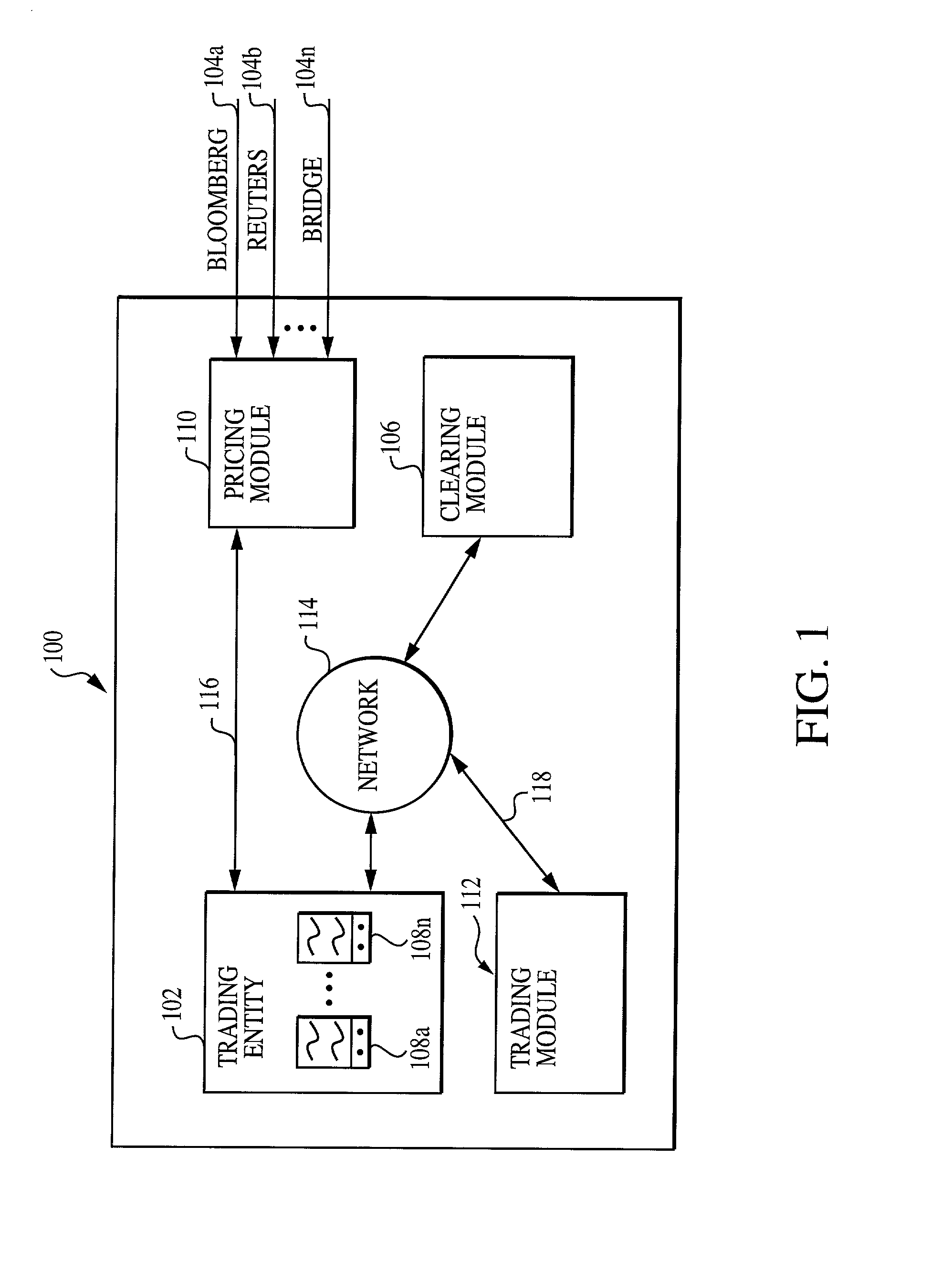
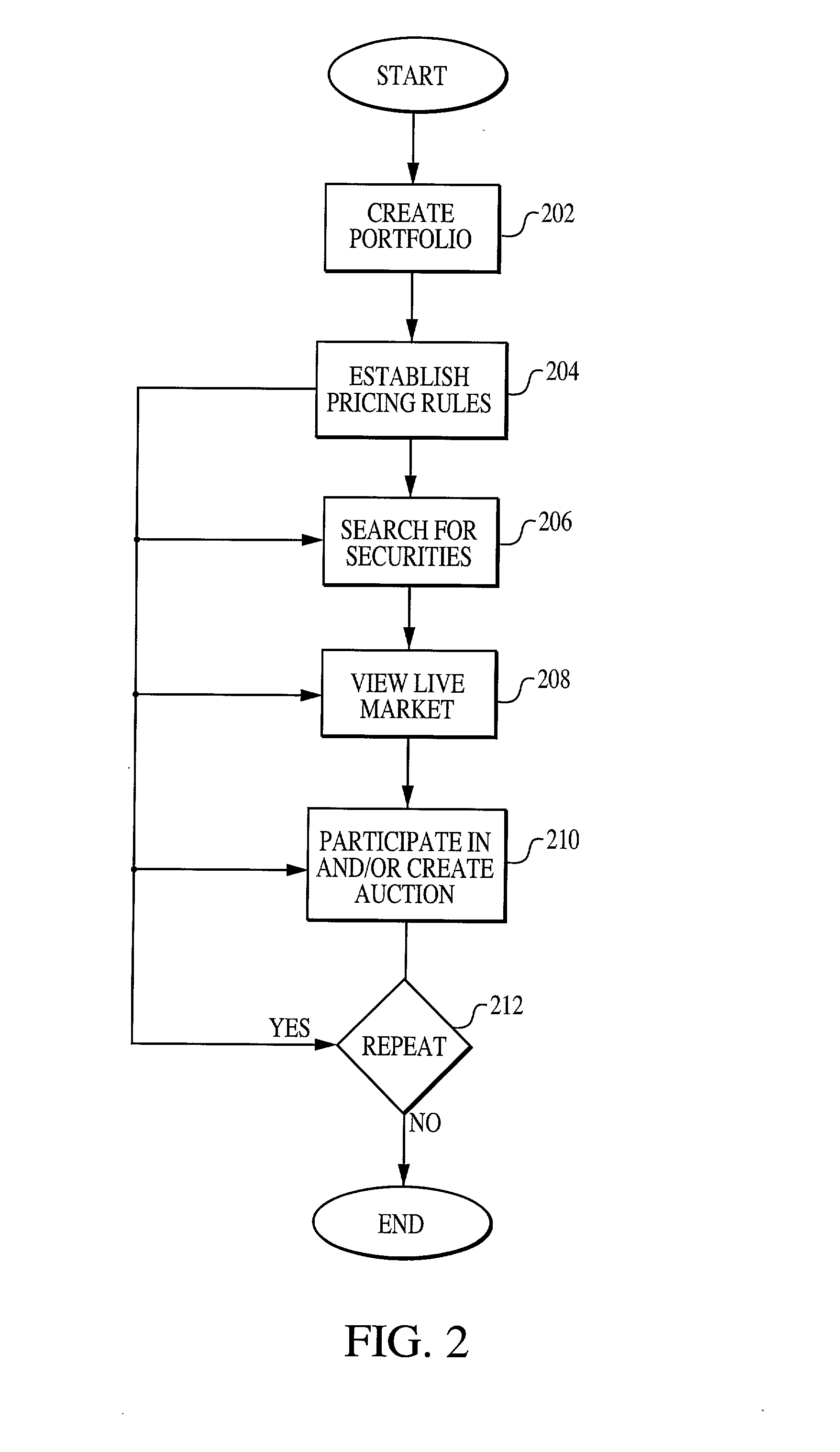
System, medium and method for trading fixed income securities
A system, method and medium for performing electronic fixed income trading that allows users to specify and / or control price and / or time limits associated with potential trades while preserving buyer and seller anonymity. According to at least some of the embodiments of the present invention, a pricing module receives financial information from at least one financial data provider, and transmits the data to one or more trading entities. Purchase and / or sell offers are transmitted to a trading module, and can be defined according to any of a plurality of pricing methods. Depending on the user specified parameters that comprise the offer, the system can automatically place the user into the market, or automatically take the user out of the market. Once a trade is executed, a clearing module monitors and records the transactions executed in clearing the trade.
Owner:TRUMARKETS
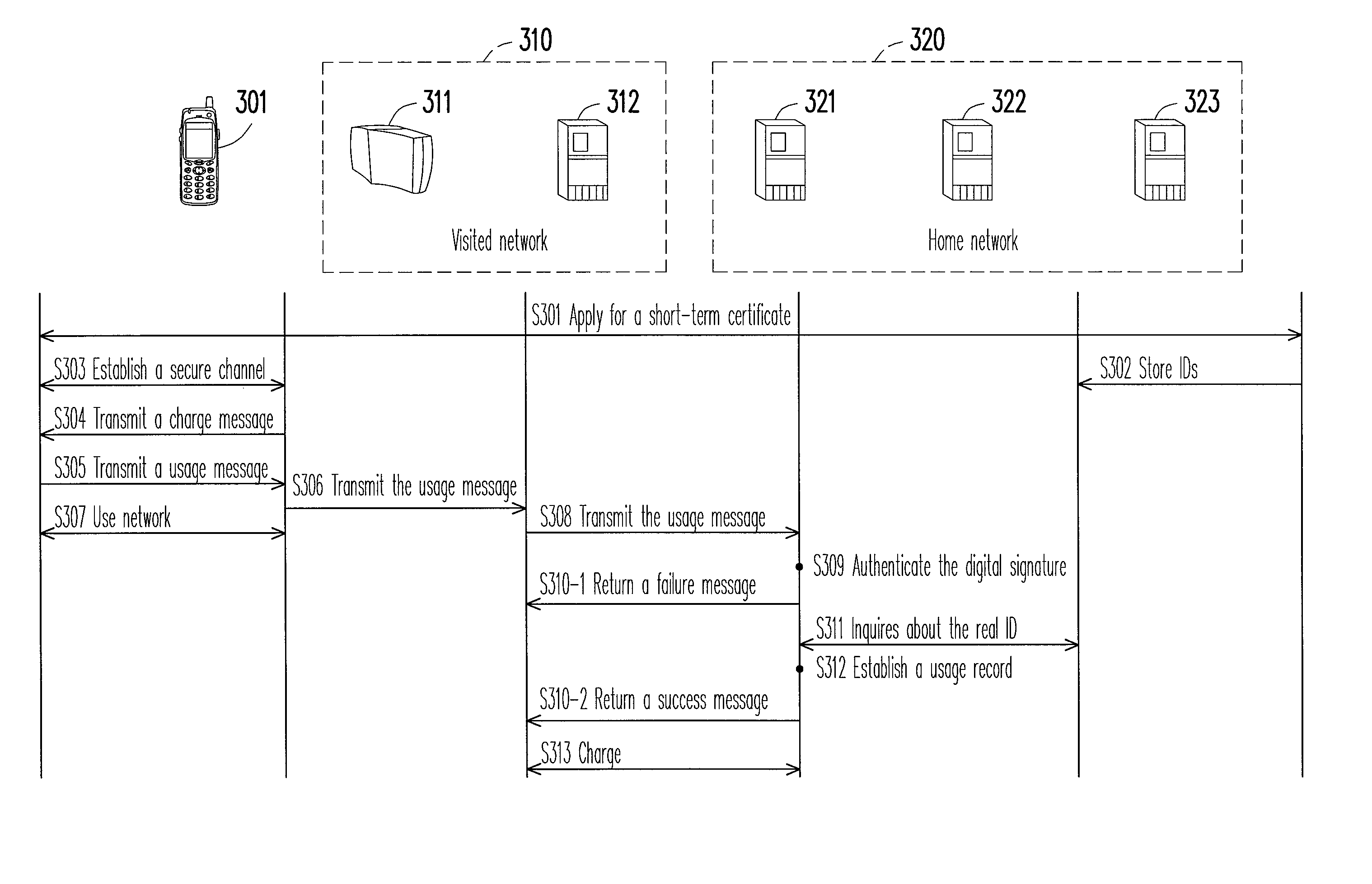
Method and system for managing network identity
A method and a system for managing network identity are provided. The method and the system realize a management mechanism of temporary identification (ID) and real ID, which simultaneously achieves functionalities such as anonymity, accounting, and authorization. A short-term certificate and a corresponding public / private key pair are used to protect a temporary ID usable for accounting. This protection prevents the temporary ID from theft. The user generates a digital signature in the reply to a charge schedule statement from the visited network. This procedure is incorporated into an existing authentication framework based on Transport Layer Security (TLS) in order to provide an undeniable payment mechanism. The payment mechanism is applicable in an environment of multiple network operators and reduces the difficulty of integrating network operators. The method and the system do not have to consult a certificate revocation list (CRL) for authentication and thus are able to shorten authentication time.
Owner:IND TECH RES INST
System and method for alerting a first mobile data processing system nearby a second mobile data processing system
InactiveUS8073565B2Automatically determineRoad vehicles traffic controlPosition fixationData processing systemWeb service
Provided is a fully automated web service with location based services generally involved in transmission of situational location dependent information to automatically located mobile receiving data processing systems. The web service communicates with a receiving data processing system in a manner by delivering information to the device when appropriate without the device requesting it at the time of delivery. There are varieties of configurations made by different user types of the web service for configuring information to be delivered, and for receiving the information. The web service maximizes anonymity of users, provides granular privacy control with a default of complete privacy, and supports user configurable privileges and features for desired web service behavior and interoperability. The web service is fully automated to eliminate human resources required to operate services. Integrated with the web service are enhanced location based services providing map solutions, alerts, sharing of novel services between users, and complete user control for managing heterogeneous device interoperability through the web service.
Owner:APPLE INC
Techniques for Sharing Data
ActiveUS20080244721A1Maintaining anonymityMultiple keys/algorithms usageDigital data processing detailsInternet privacyAnonymity
Techniques for sharing data between users in a manner that maintains anonymity of the users. Tokens are generated and provided to users for sharing data. A token comprises information encoding an identifier and an encryption key. A user may use a token to upload data that is to be shared. The data to be shared is encrypted using the encryption key associated with the token and the encrypted data is stored such that it can be accessed using the identifier associated with the token. A user may then use a token to access the shared data. The identifier associated with the token being used to access the shared data is used to access the data and the encryption key associated with the token is used to decrypt the data. Data is shared anonymously without revealing the identity of the users using the tokens.
Owner:RICOH KK
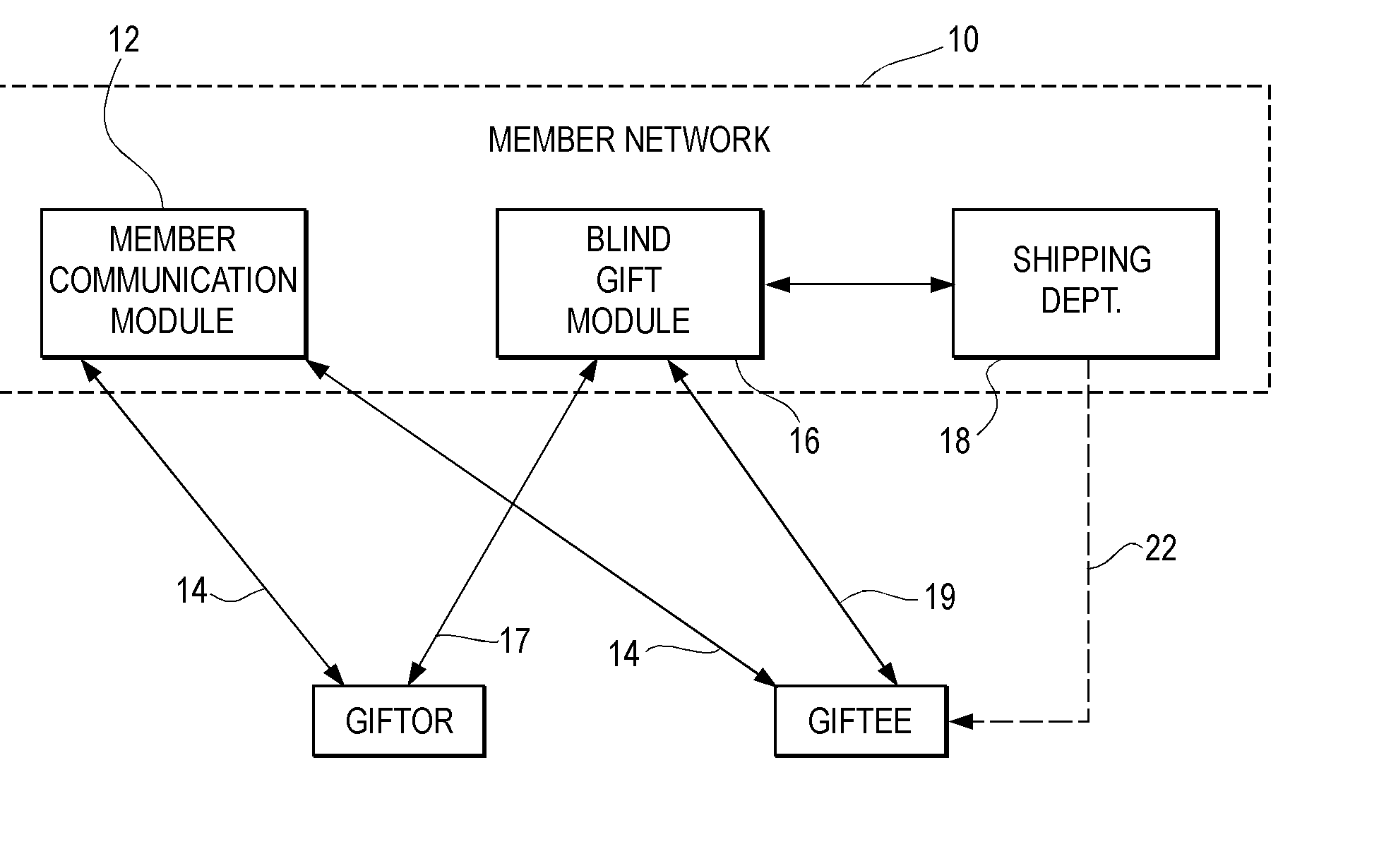
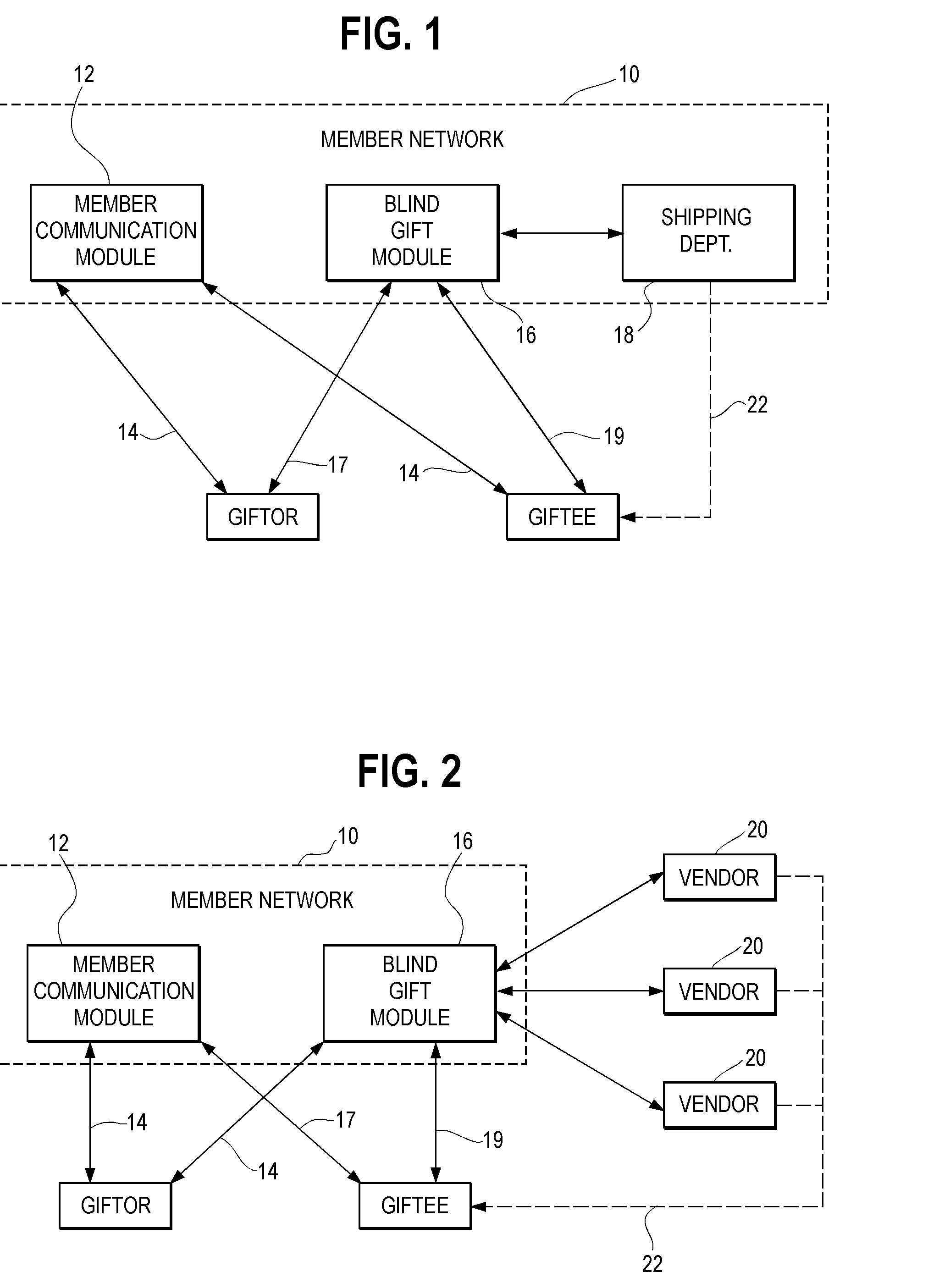
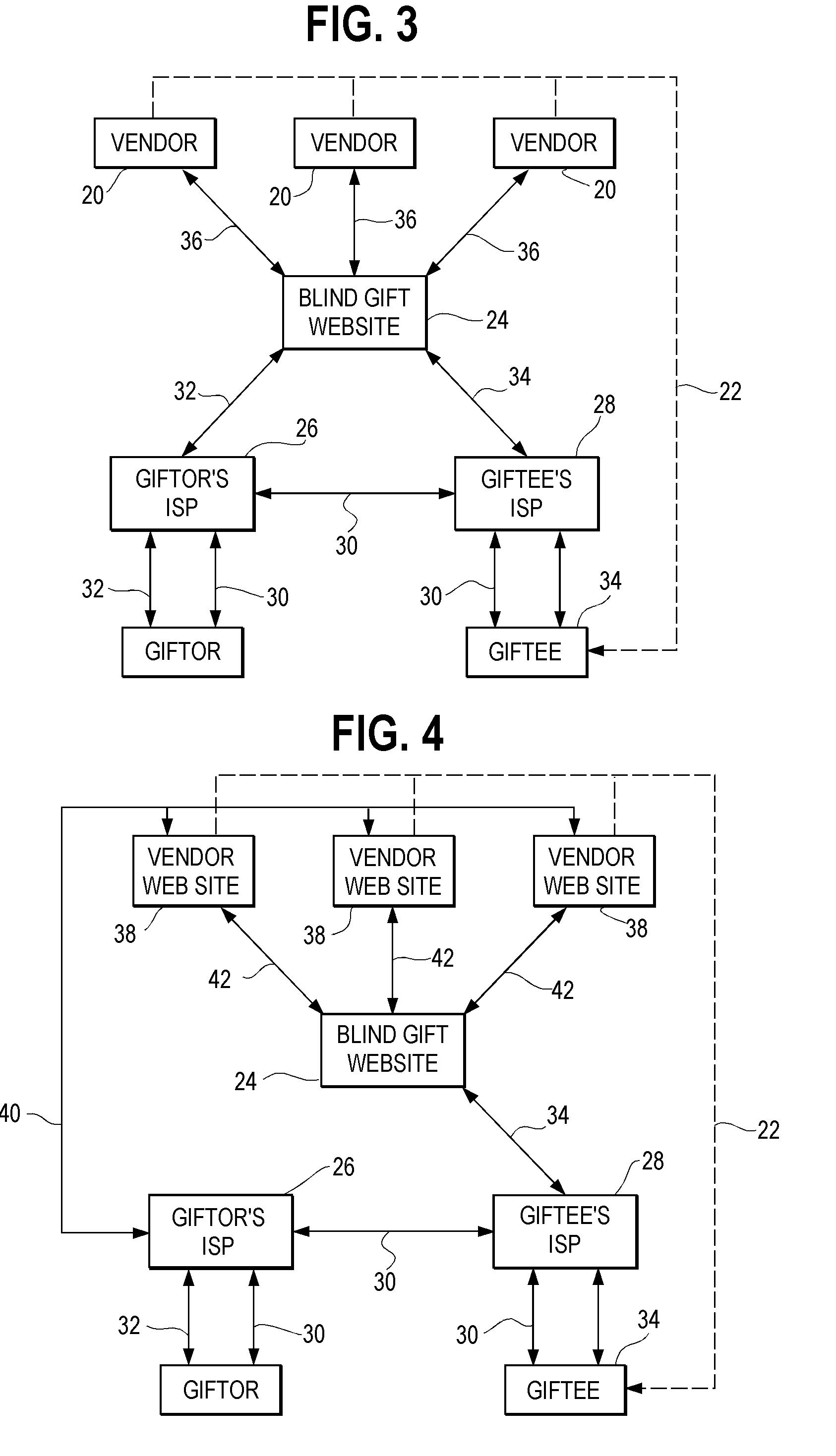
Blind Gift Method and System
InactiveUS20020095298A1Overcomes shortcomingAvoid disadvantagesBuying/selling/leasing transactionsMarketingThe InternetComputer science
<heading lvl="0">Abstract of Disclosure< / heading> This is a method and system whereby parties who know each other only by pseudonyms, such as by Internet e-mail addresses, may send and receive gifts while maintaining anonymity behind their pseudonyms. Steps of the method include receiving a request from a first pseudonymous party to take an order for a gift to be sent to a second party; obtaining from the first party an identification of the intended gift, and the pseudonym of the second party; and, looking up a non-pseudonymous name and address associated with the second in a database. Alternatively, the second party may be contacted and asked to confidentially reveal his or her name and mailing address for gift delivery purposes. While the second party's information is kept confidential from the first party, the second party has various choices including accepting the gift, accepting it upon certain conditions, or refusing it. The system of the invention includes components for permitting the first party to enter the second party's pseudonym; for determining the second party's true name and mailing address from his or her pseudonym; and, for sending the gift to the second party's true name and mailing address.
Owner:JOVIAN HLDG
System and method for representation of multiple-identities of a user in a social networking environment
InactiveUS20090125521A1Facilitate web-based communicationFacilitate communicationComputer security arrangementsSpecial data processing applicationsInternet privacySocial web
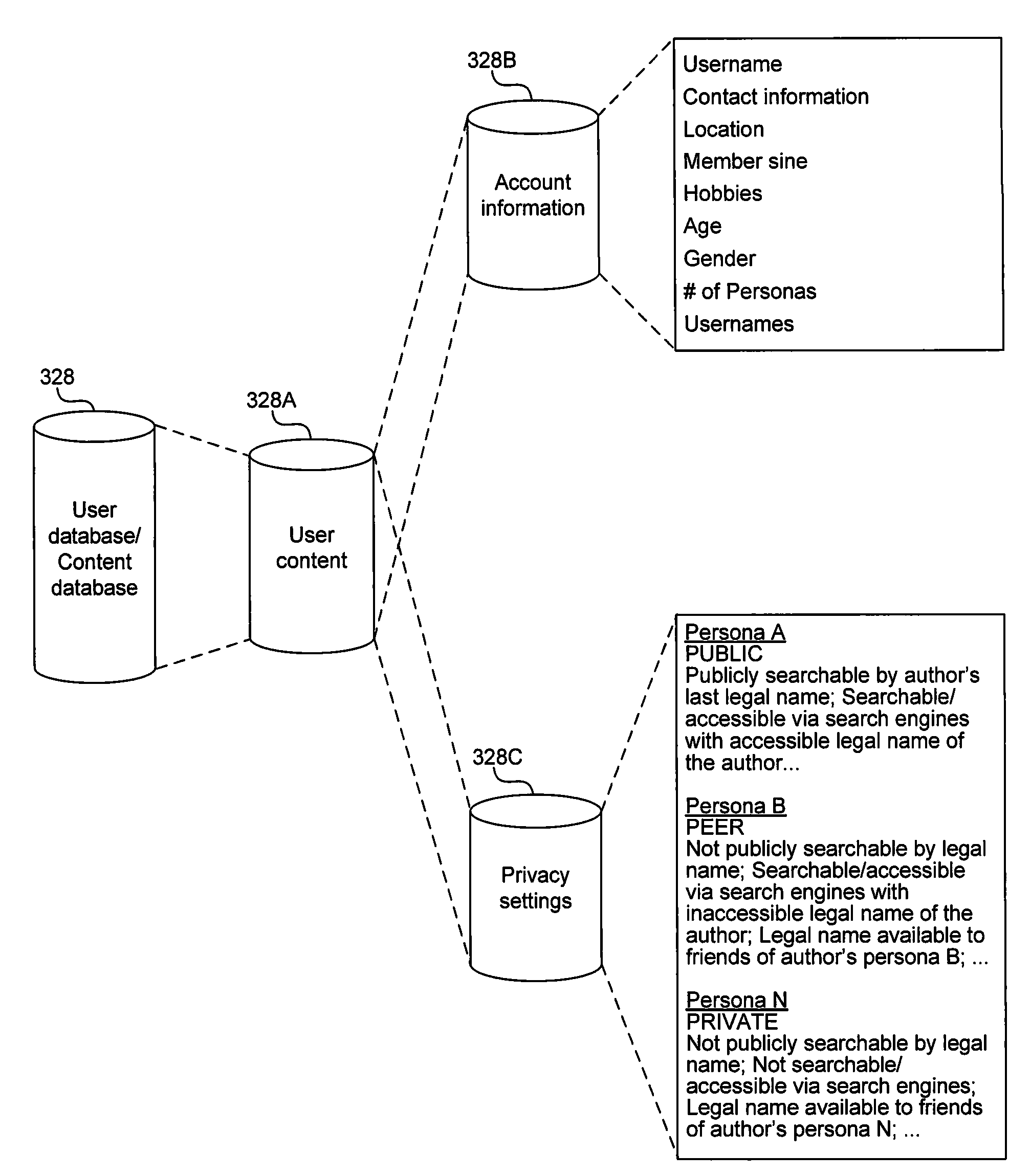
Systems and methods for representation of a user in a social networking environment are disclosed. In one aspect of the present disclosure, a method of a social networking environment includes managing anonymity levels of a set of user content provided by a user to the social networking environment. The set of user content includes a first content subset having a first anonymity level corresponding to a privacy setting of a public status, a second content subset having a second anonymity level corresponding to a privacy setting of a peer status, and / or a third content subset having a third anonymity level corresponding to a privacy setting of a private status.
Owner:FIELD REPORT
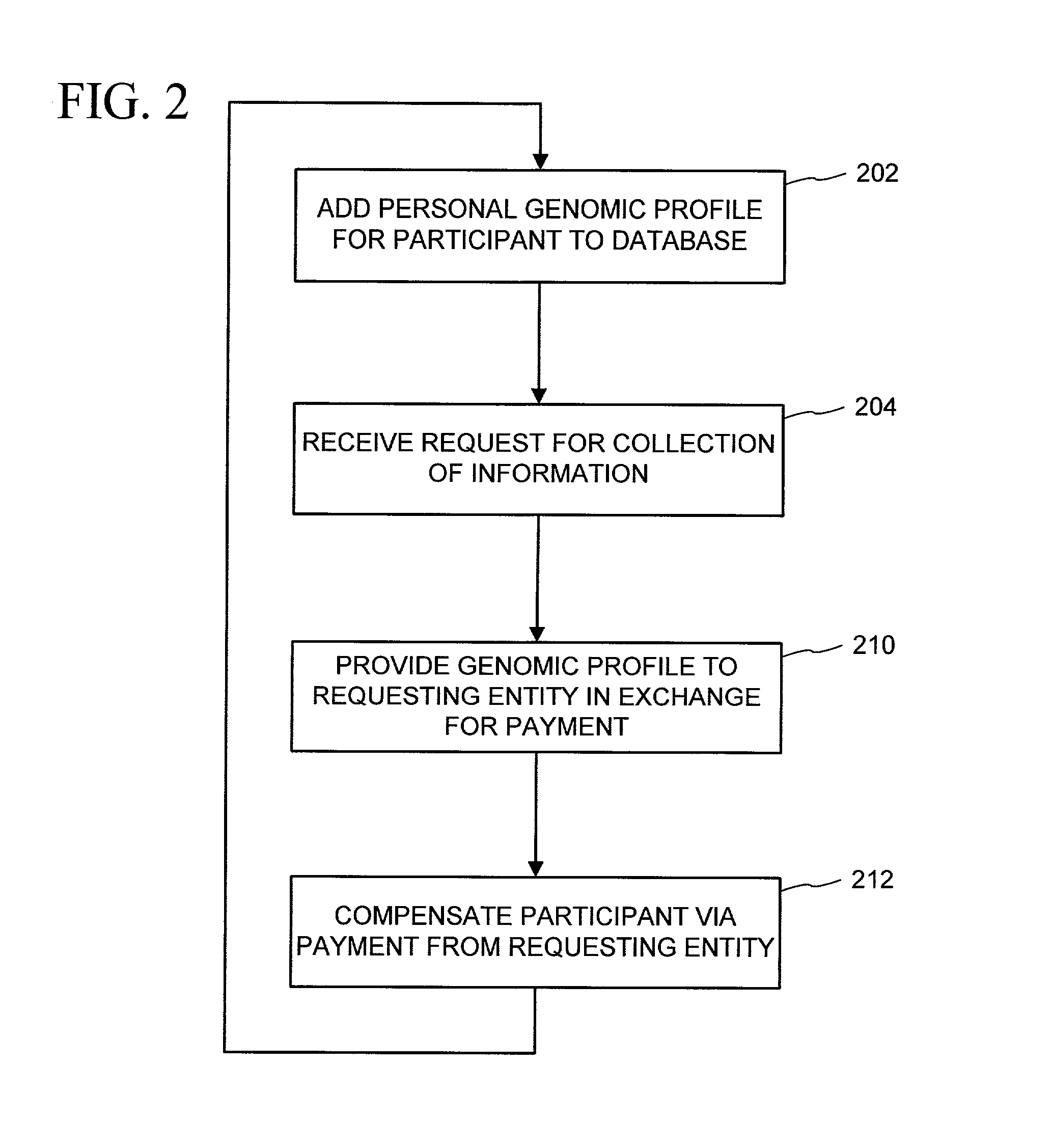
Genomic profile information systems and methods
InactiveUS20020095585A1Increase valueSignificant compensationComputer security arrangementsProteomicsInformation networksAnonymity
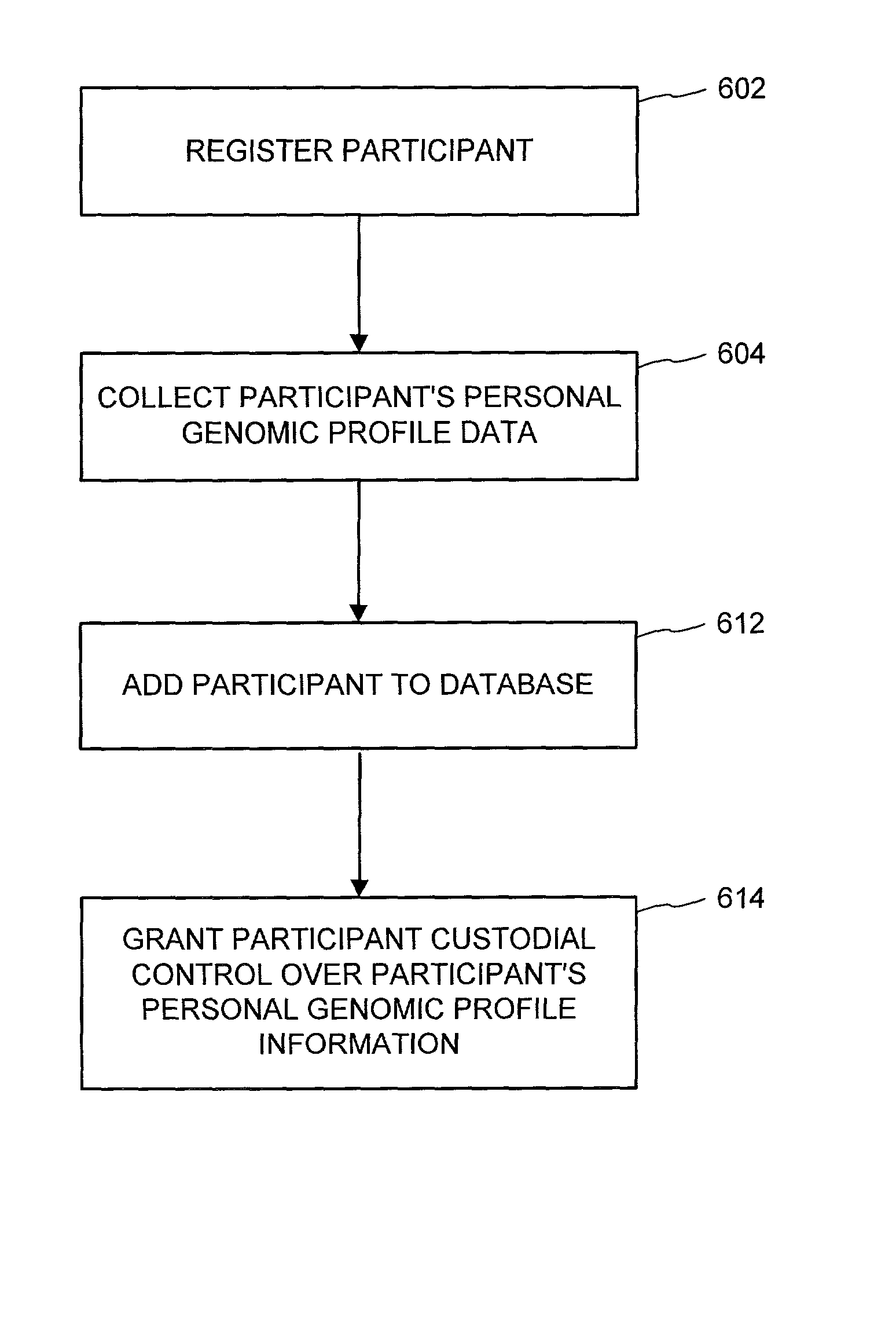
A variety of methods and systems related to genomic profile information and related participants are described. Participants can be encouraged to allow access to their genomic profile information in a variety of ways. A peer-to-peer genomic profile information network can be implemented. A collection of genomic profile information for a large number of participants can be built, and anonymity of the participants can be maintained. Participants can maintain custodial control over their genomic profile information. Comparative tools and groups can help participants identify and communicate with other participants having similar information.
Owner:GENOMIC HEALTH INC
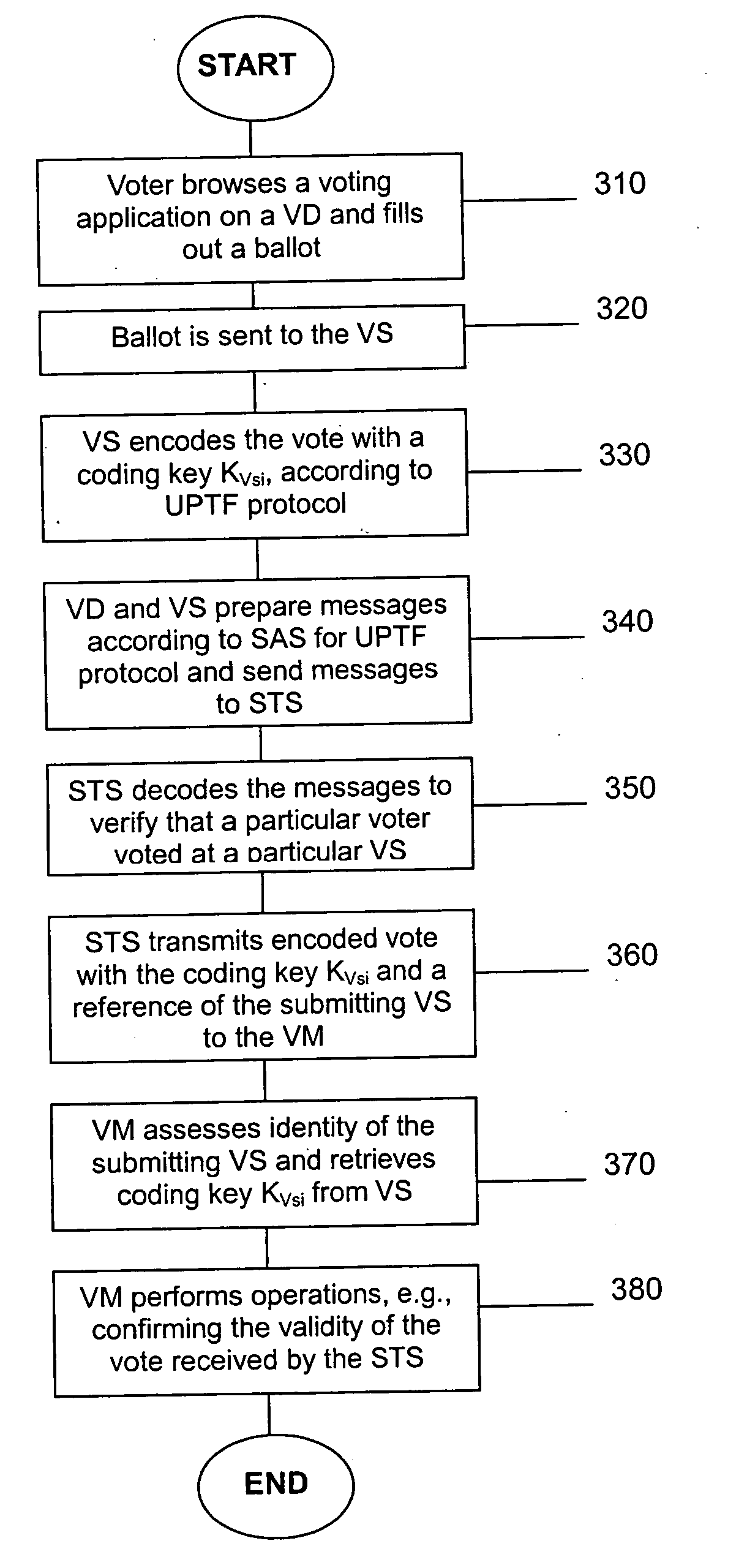
Opinion registering application for a universal pervasive transaction framework
InactiveUS20050203966A1Digital data processing detailsUser identity/authority verificationUser inputAnonymity
A computer-based system securely transmitting and authenticating a transaction input by a user while retaining the anonymity of the user with respect to content of the transaction, including a device encoding the content of the transaction input by the user with a key known only to another device, encoding other portions of the transaction with another key known only to a secure transaction server, and sending the encoded content of the transaction and the encoded other portions of the transaction to the secure transaction server to authenticate an identity of the user of the device, wherein the secure transaction server decodes the other portions of the transaction and sends the encoded content of the transaction to the another device to be finally decoded.
Owner:PCMS HOLDINGS INC
Open registry for provenance and tracking of goods in the supply chain
InactiveUS20180108024A1Avoid flowEncryption apparatus with shift registers/memoriesCryptography processingThird partyThe Internet
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with items / goods without relying on a third-party-controlled authentication service. The system includes tags having alphanumeric values and coupled to items / goods and an open registry database and ledger where digital records associated with the items / goods is able to be stored. The open registry enables public access to the items / goods and data combined with item registration anonymity.
Owner:CHRONICLED INC
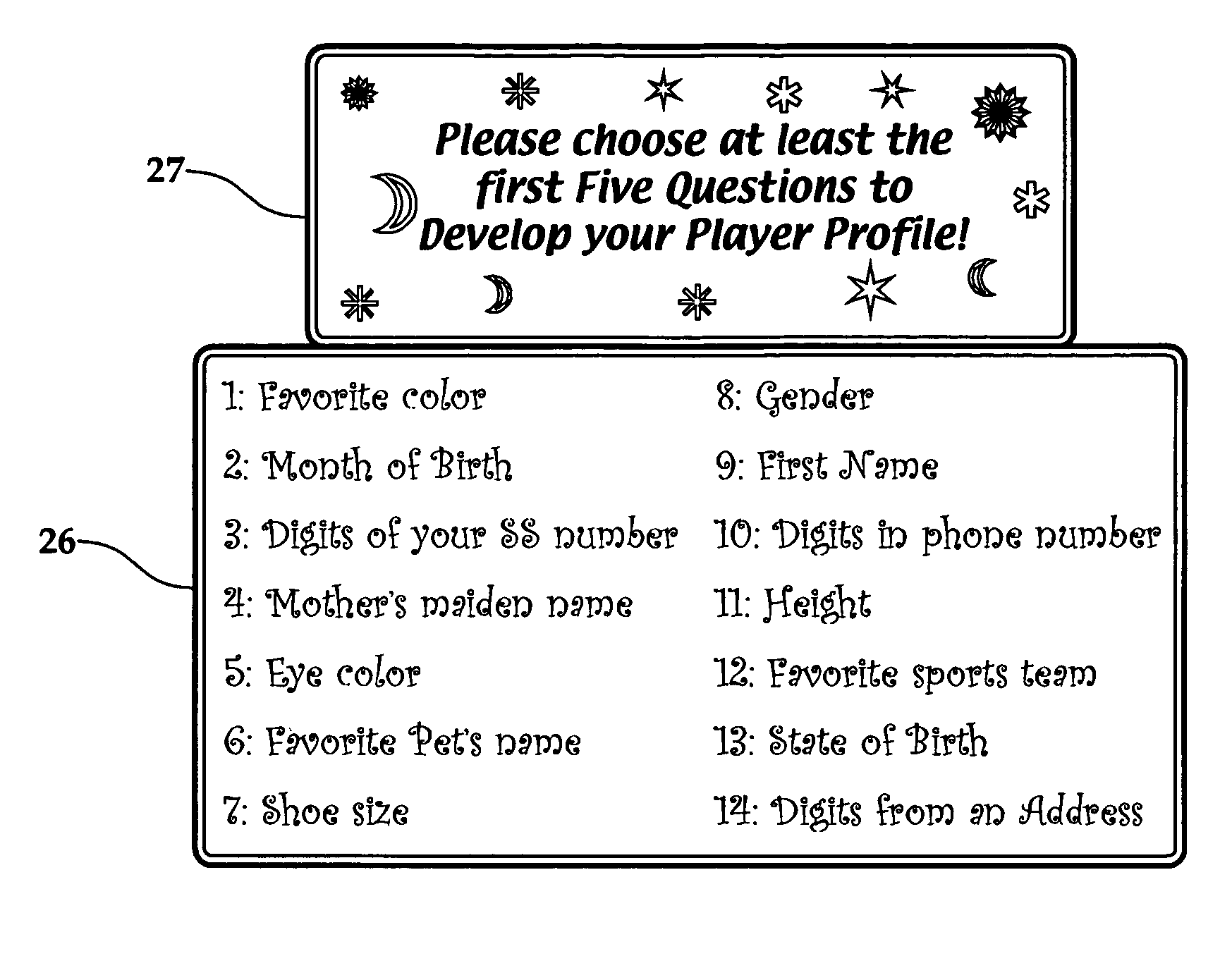
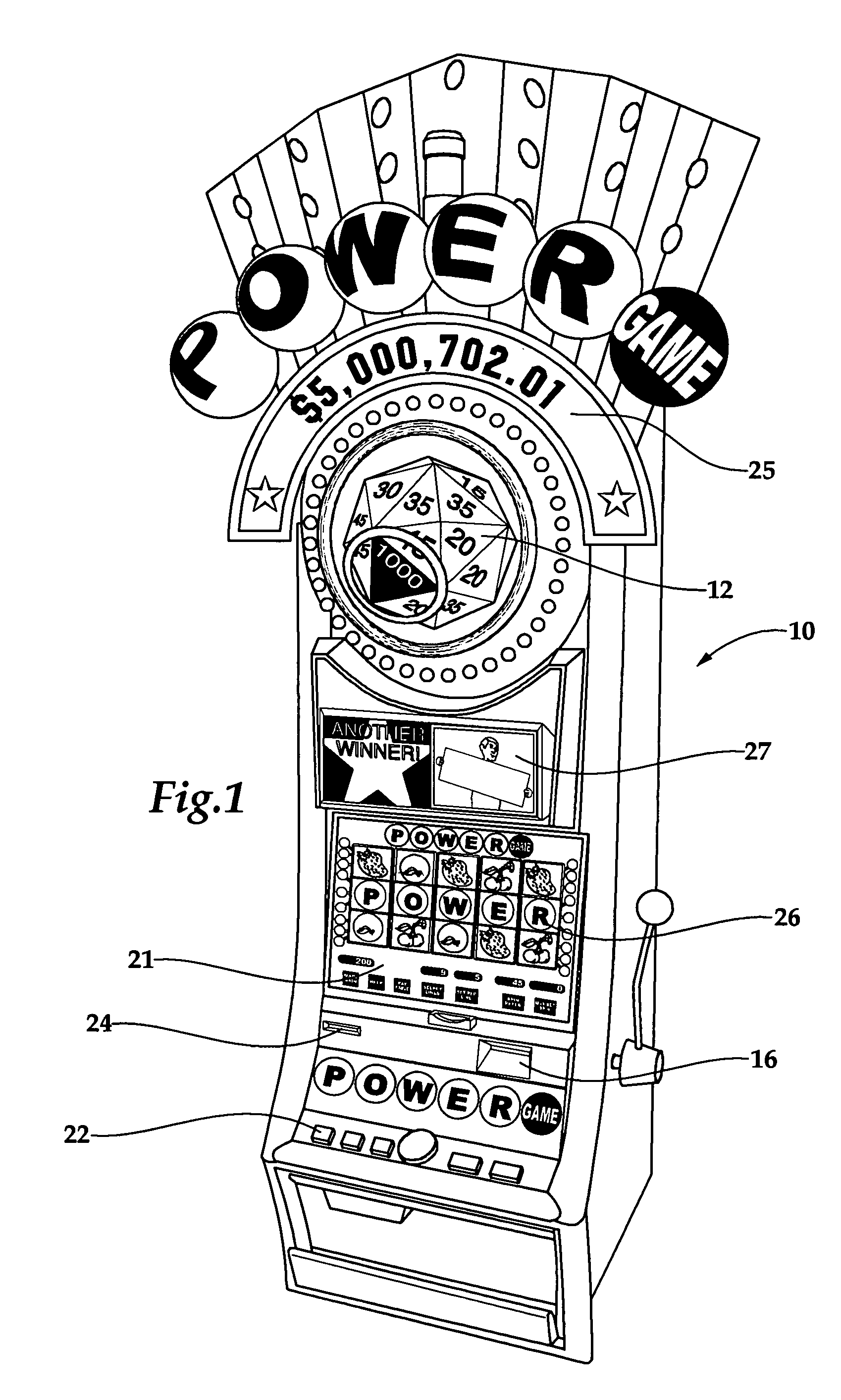
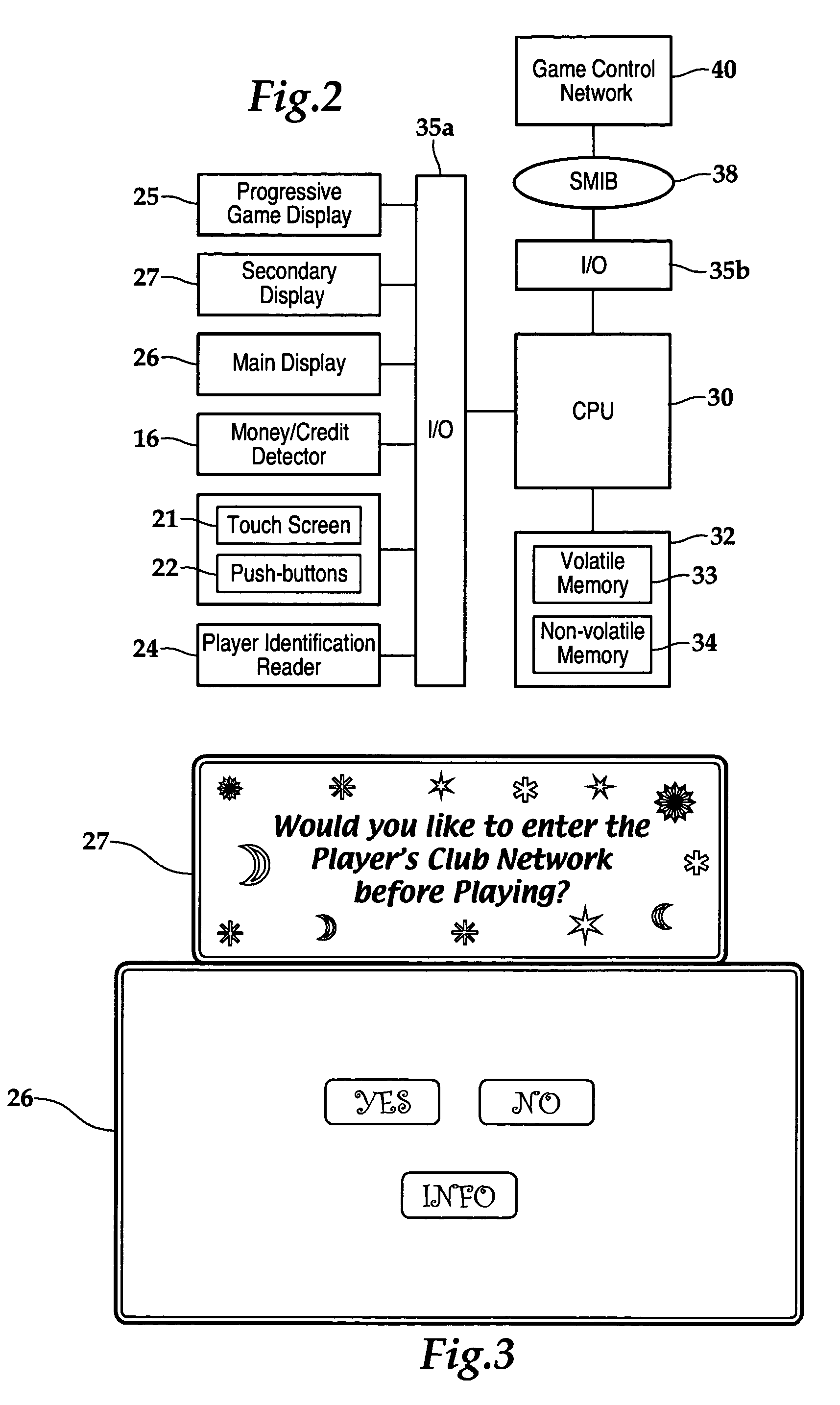
Gaming system having player-profile input feature for maintaining player anonymity
A method of operating a wagering game includes conducting a wagering game at a gaming terminal, and receiving inputs from a player that relate to a profile of the player. The inputs exclude a player's true identity. The method includes comparing the player inputs with a plurality of player-profile data sets to match the player inputs with a particular player-profile data set. In response to this comparison yielding a matched player-profile data set, the method includes activating one or more personalized attributes at the gaming terminal associated with the matched player-profile data set. The method can be practiced within a gaming system comprising a database, a controller, and at least one gaming terminal. The database stores the player-profile data sets. Each data set is associated with and maintains anonymity of a respective player. An input device at the gaming terminal receives player-profile inputs for comparison to the player-profile data sets.
Owner:BALLY GAMING INC
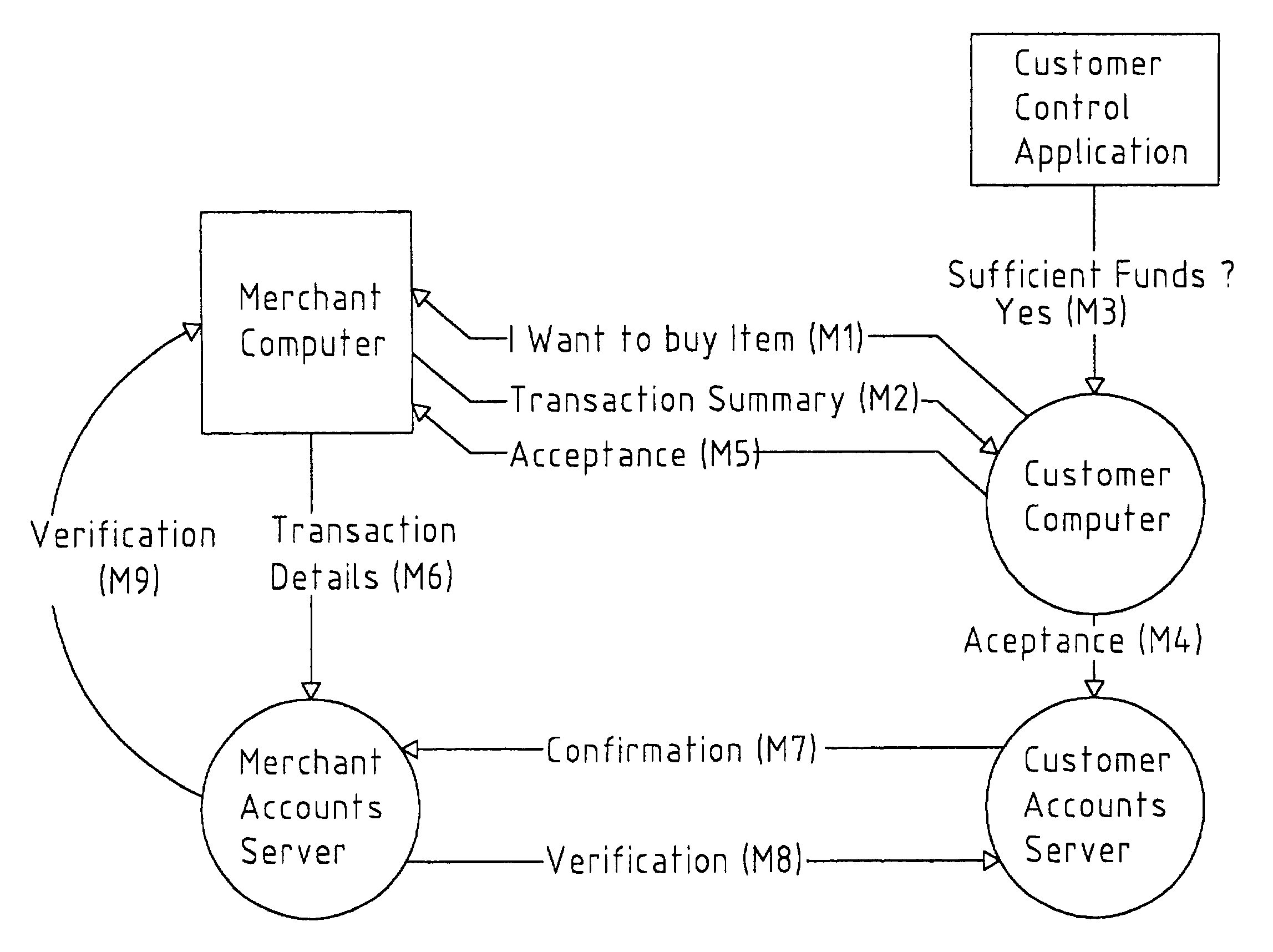
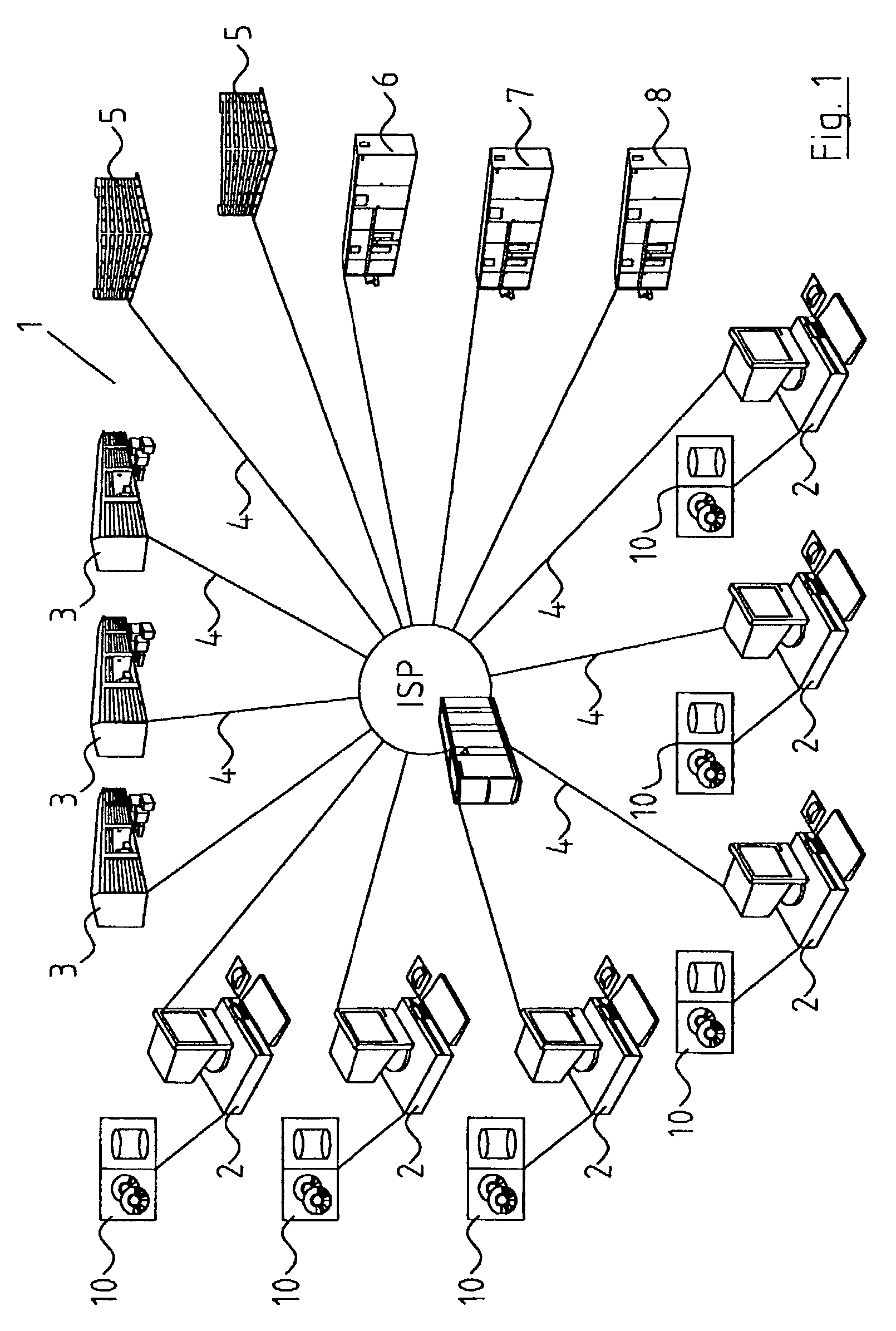
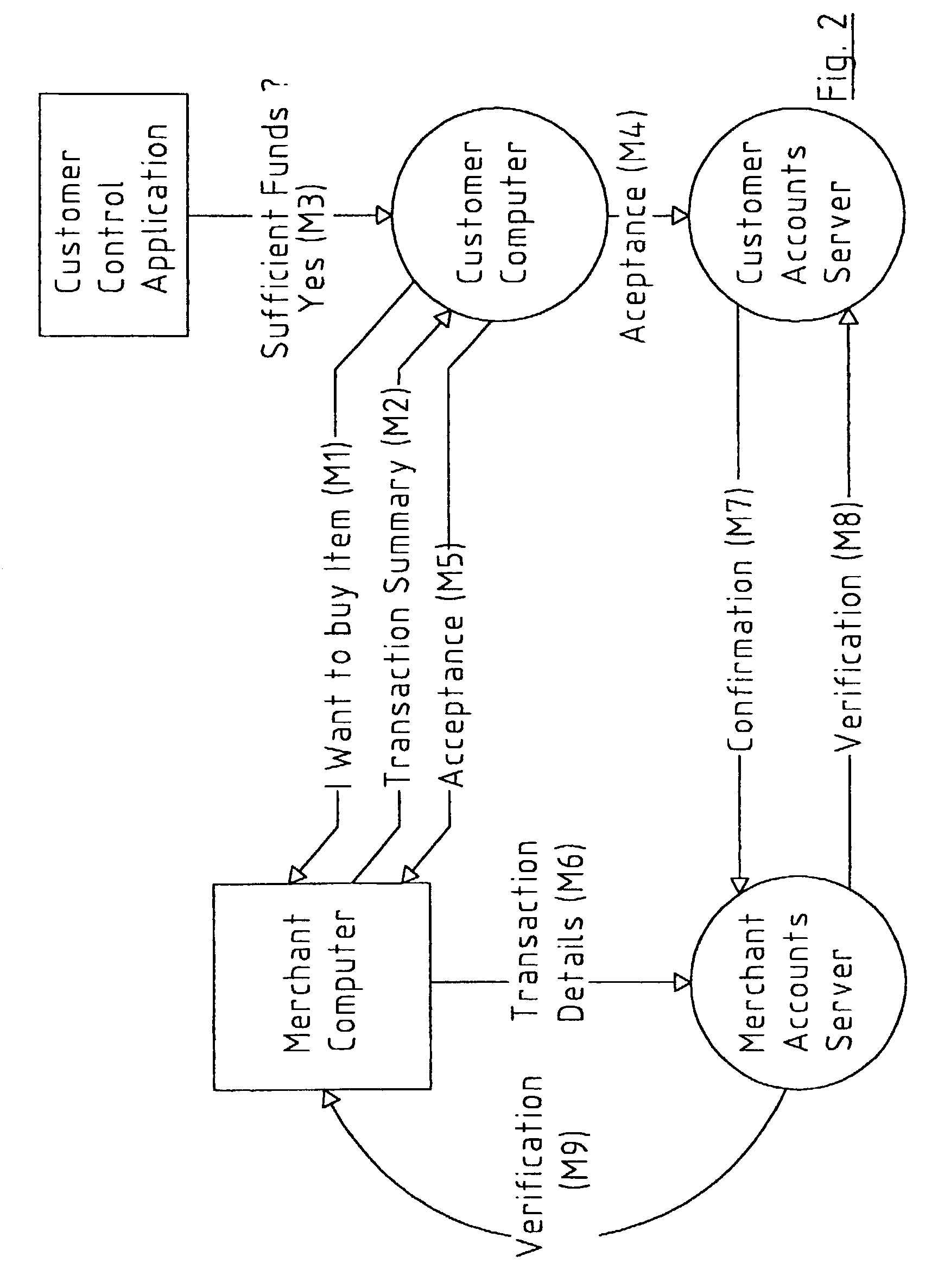
Network-based system
A transaction settlement system and method for internet and other trading over a telecommunications network. Customer computers and merchant computers are connected to customer account servers and merchant account servers respectively, the former maintains a customer account and conducts the financial aspects of the transaction with the merchant server without revealing the customers identity. The sequence of the messages are such that once in message M4, the customer computer instructs the customer accounts server to accept the transaction and the customer accounts server accepts it, the customer accounts server deals with the merchant accounts server to settle the account in accordance with agreed procedures. The merchant can have surely of payment. There is also provided methods to deliver coupons, e.g. discount coupons and to ship goods with anonymity.
Owner:INTERNET PAYMENTS PATENTS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com