Patents
Literature
618 results about "Identity management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
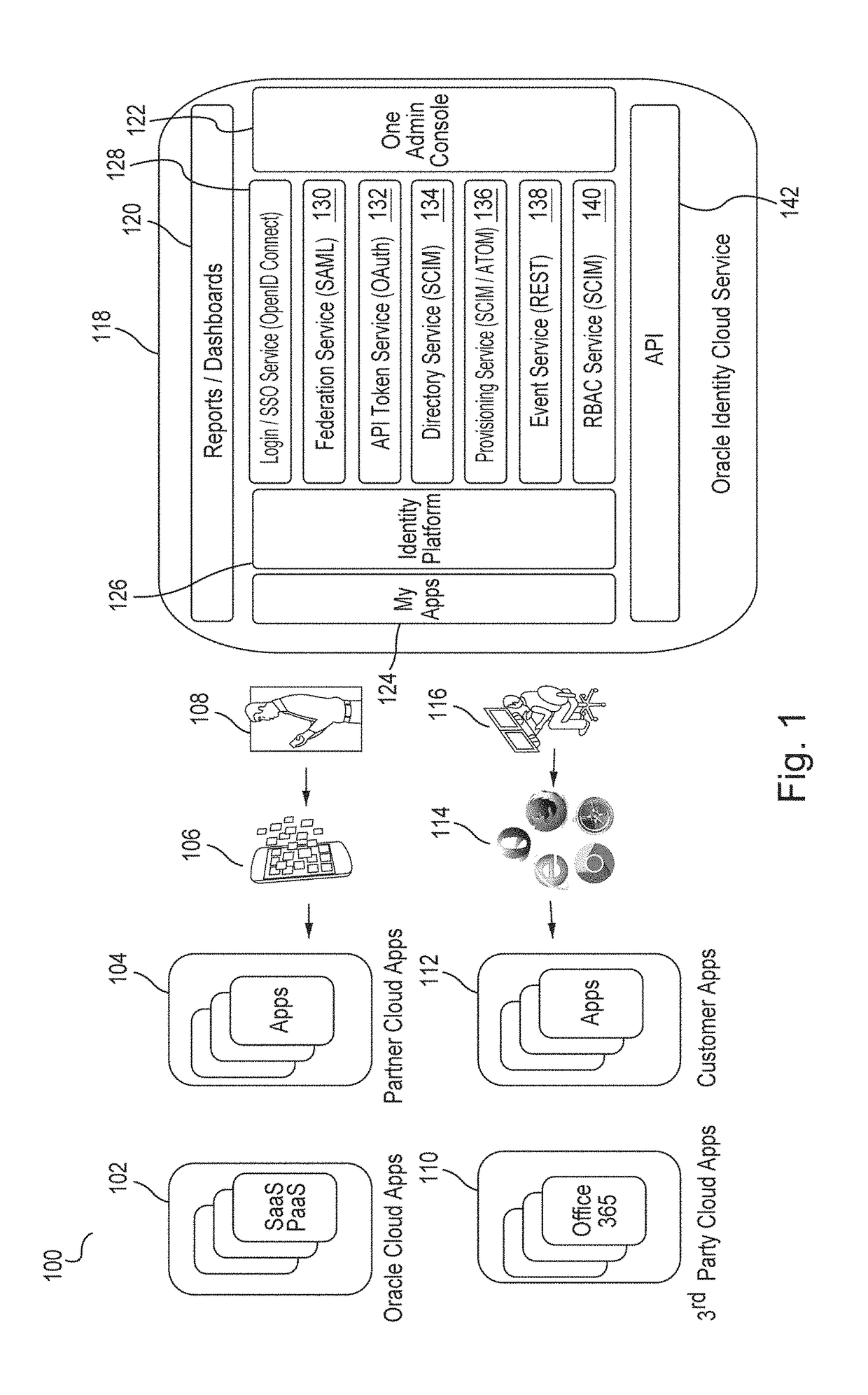
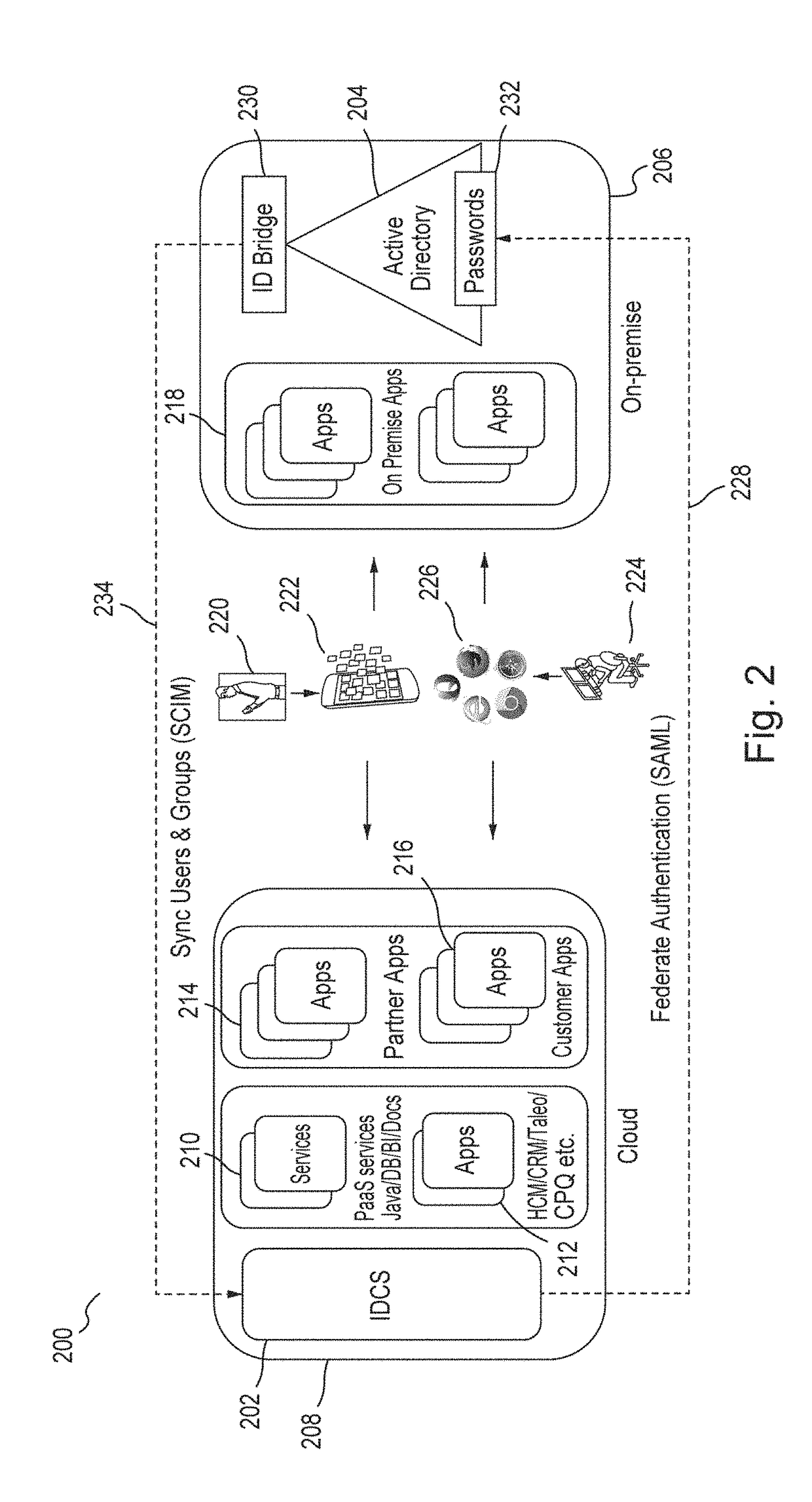
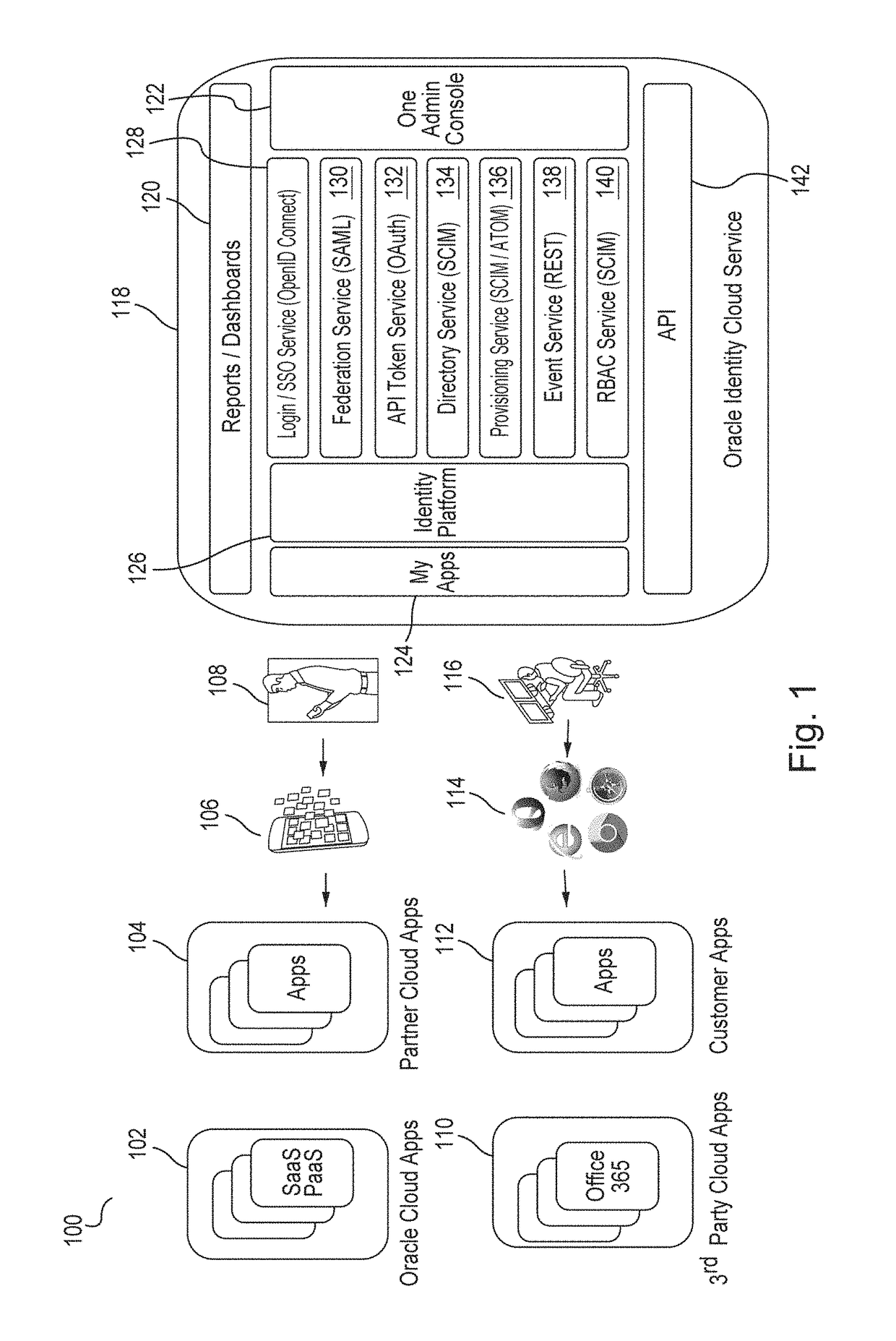
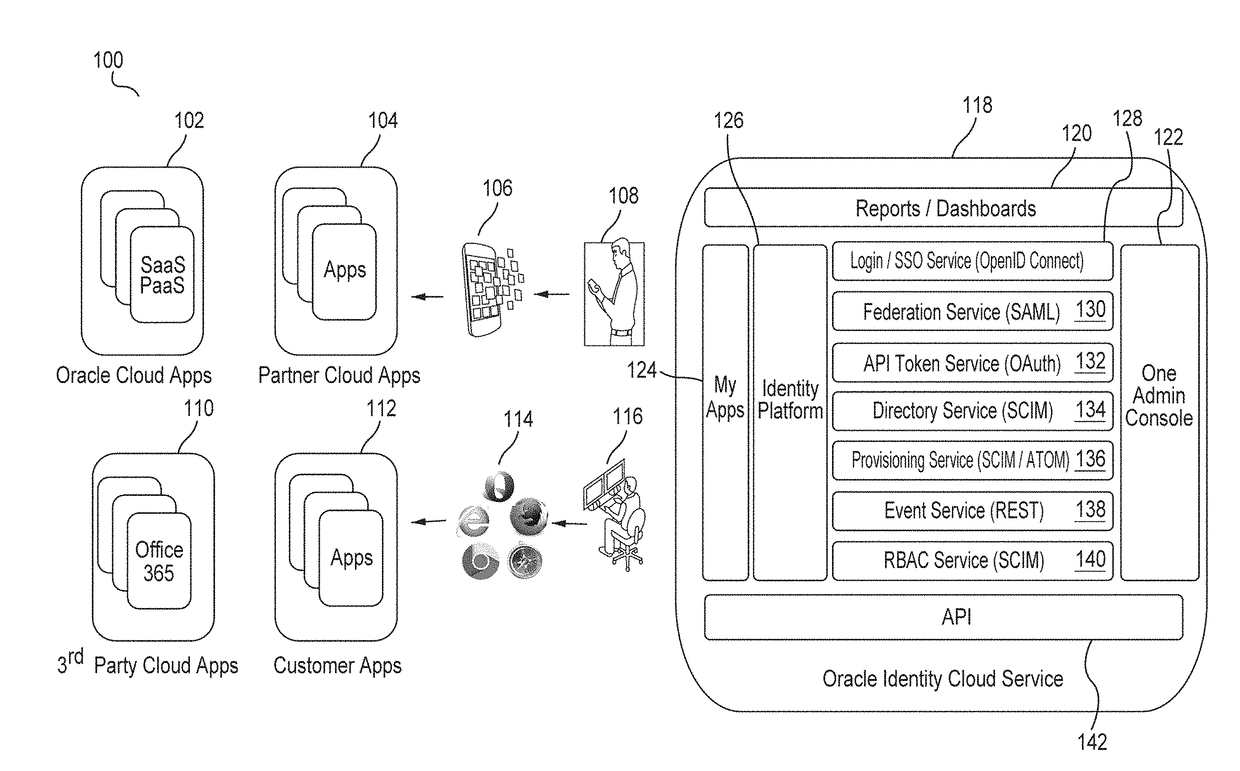
Identity management (IdM), also known as identity and access management (IAM or IdAM), is a framework of policies and technologies for ensuring that the proper people in an enterprise have the appropriate access to technology resources. IdM systems fall under the overarching umbrella of IT security and Data Management . Identity and access management systems not only identify, authenticate and authorize individuals who will be utilizing IT resources, but also the hardware and applications employees need to access. Identity and Access Management solutions have become more prevalent and critical in recent years as regulatory compliance requirements have become increasingly more rigorous and complex. It addresses the need to ensure appropriate access to resources across increasingly heterogeneous technology environments and to meet increasingly rigorous compliance requirements.
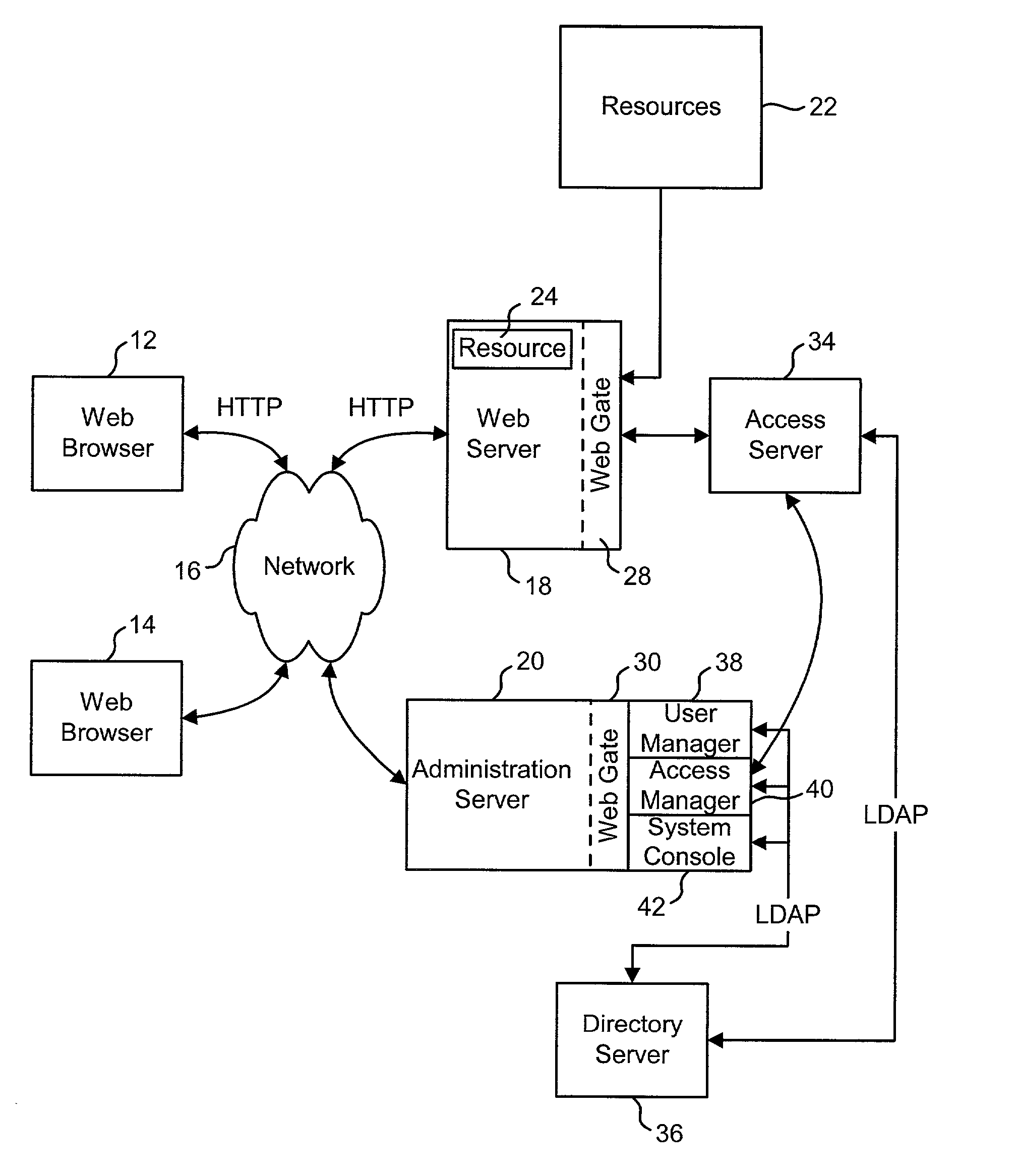
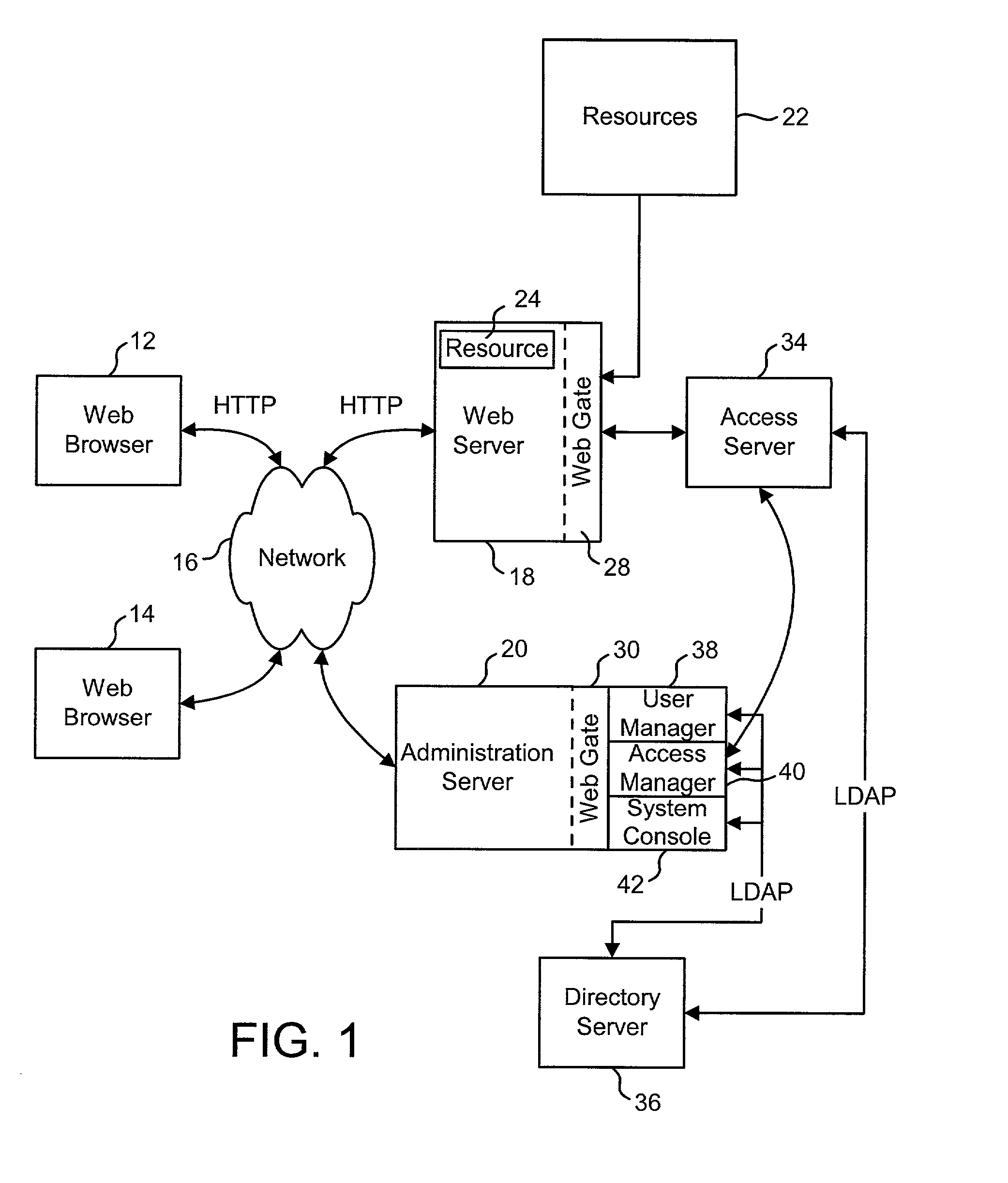
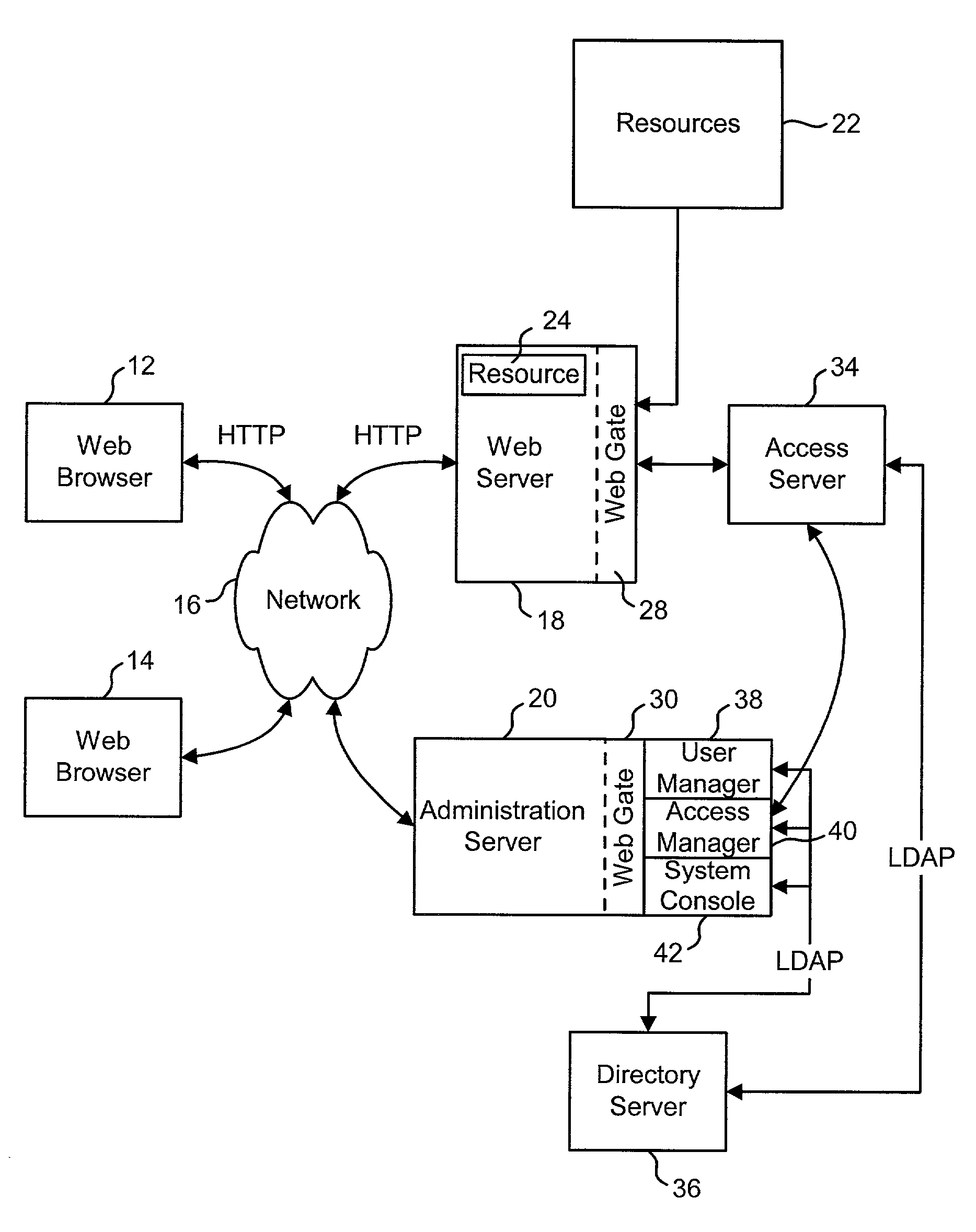
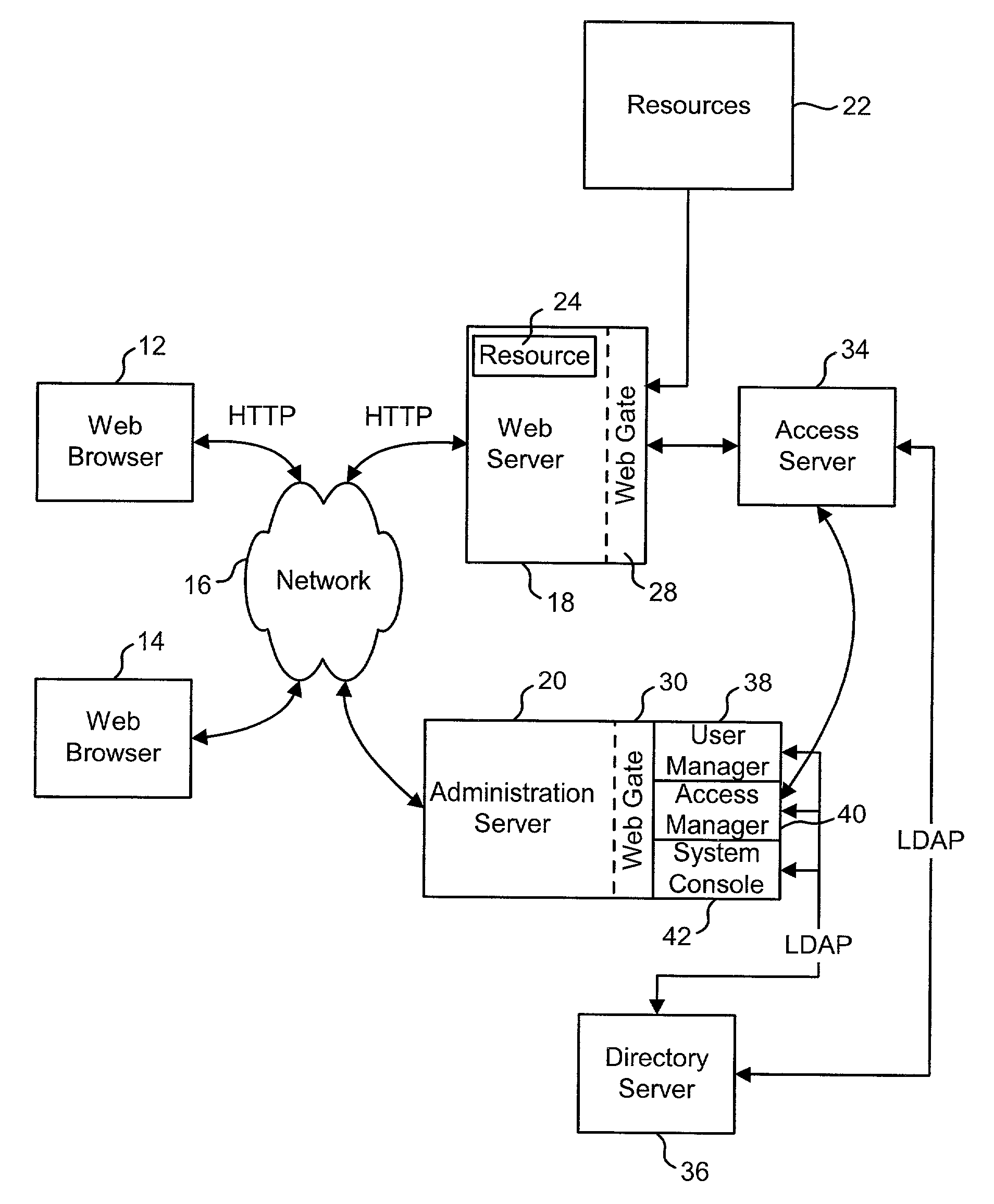
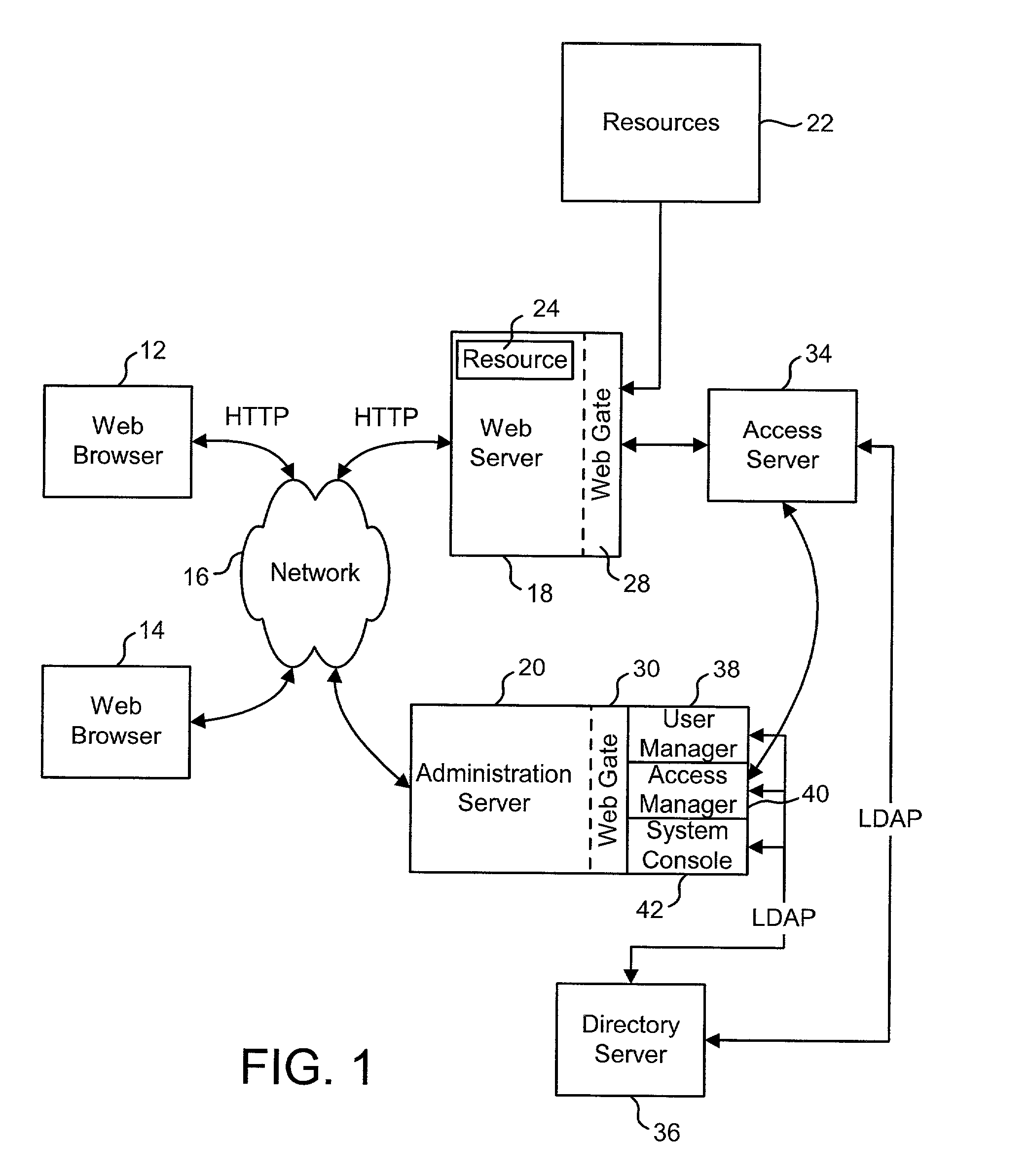
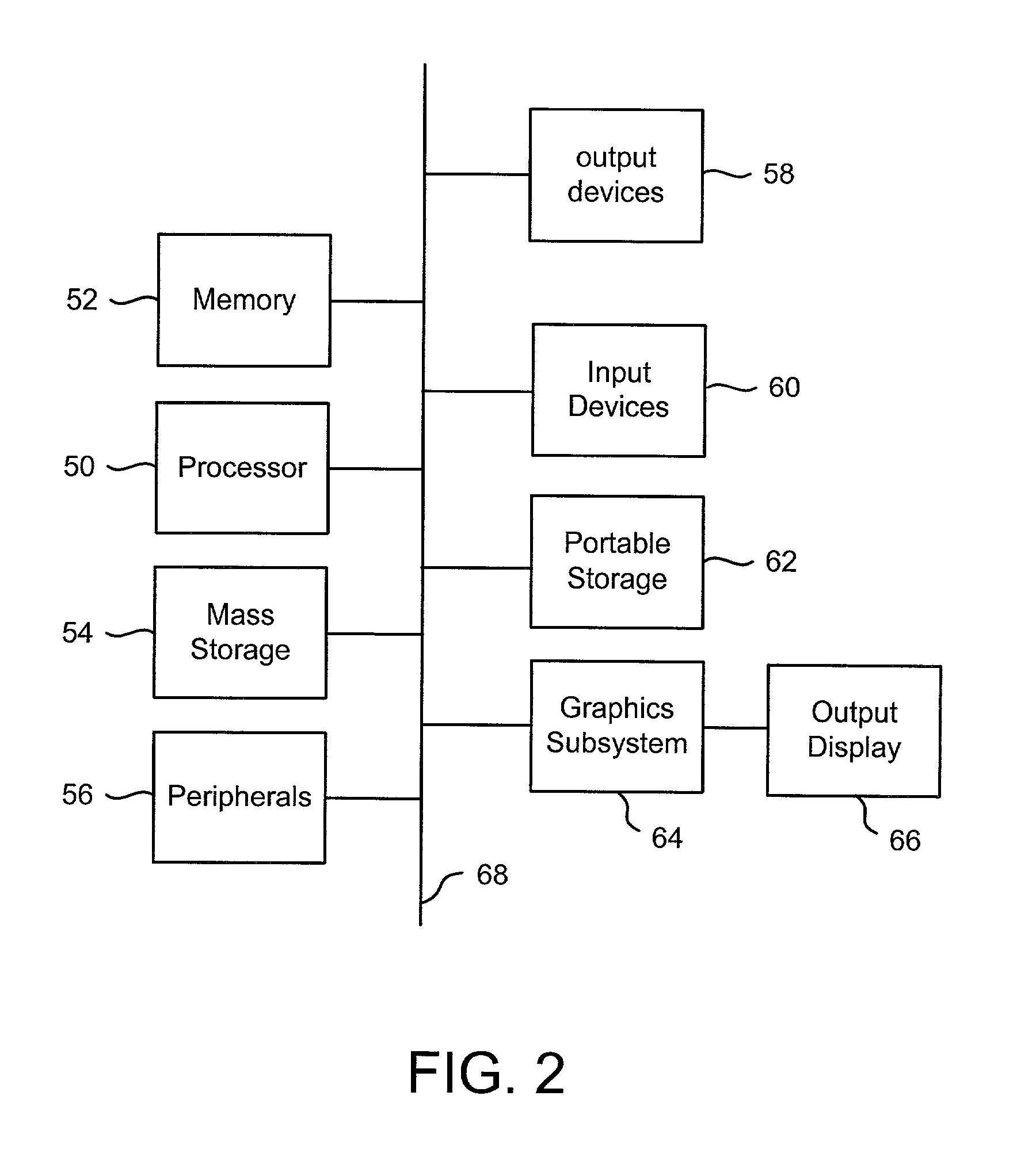
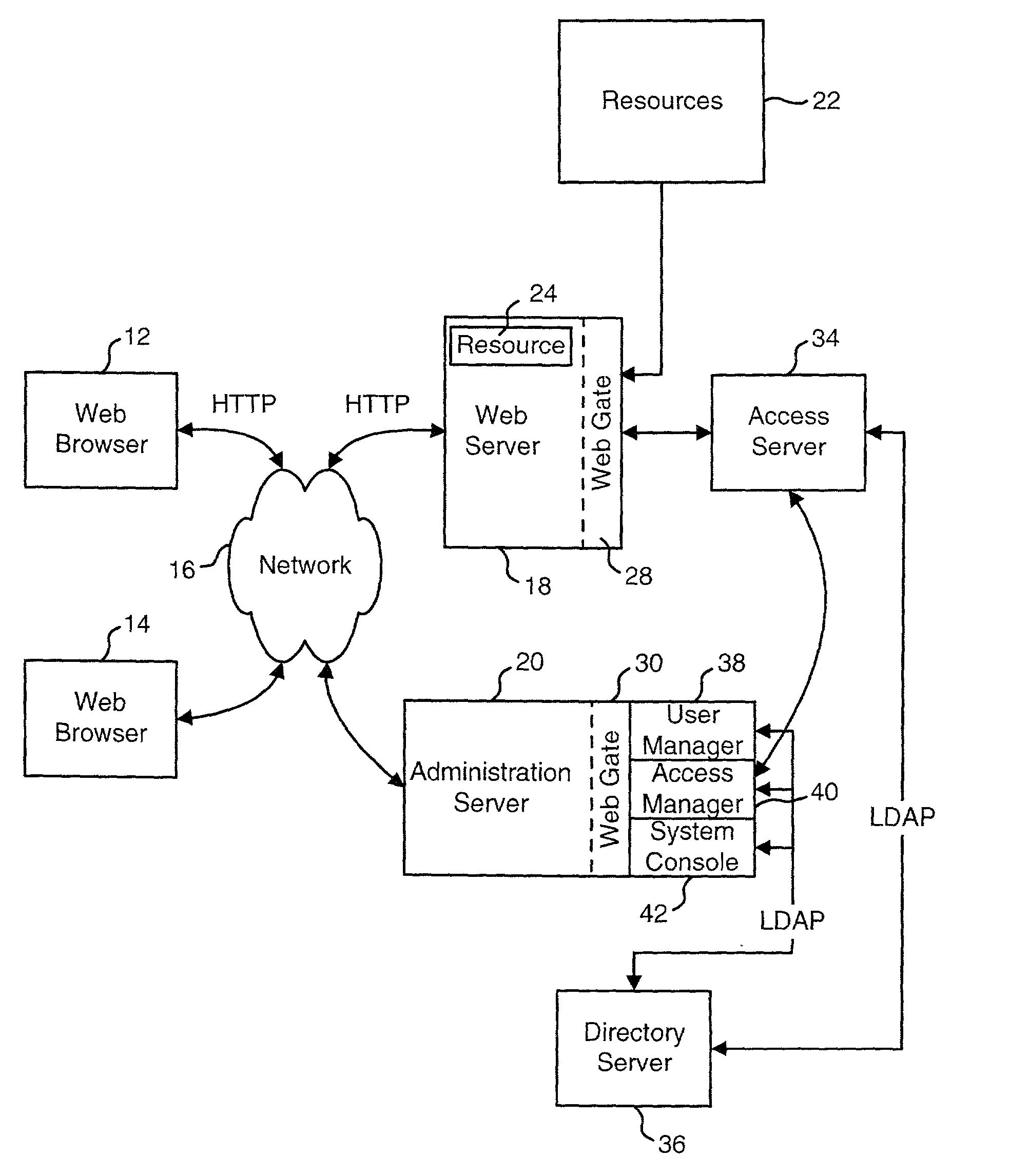
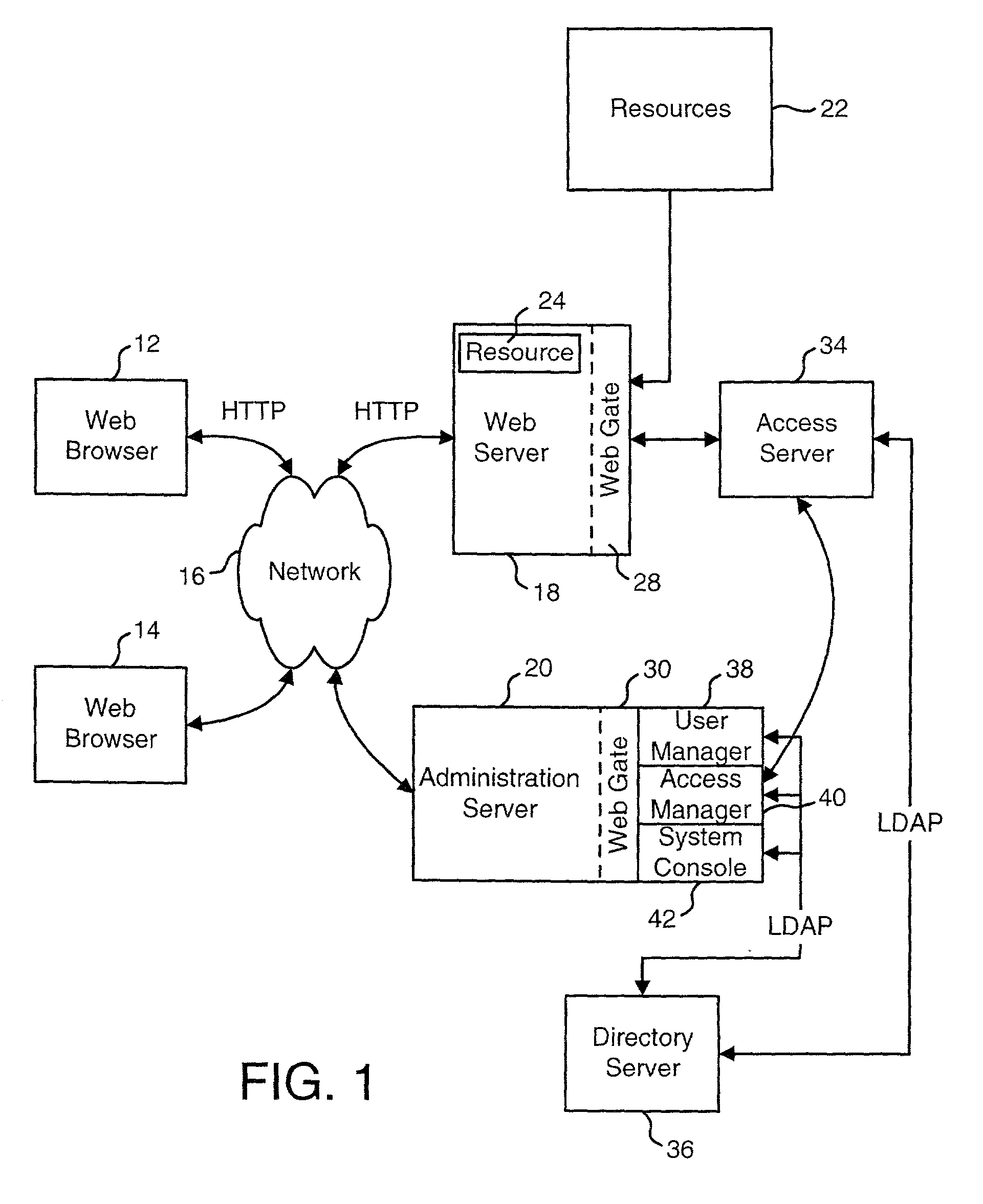
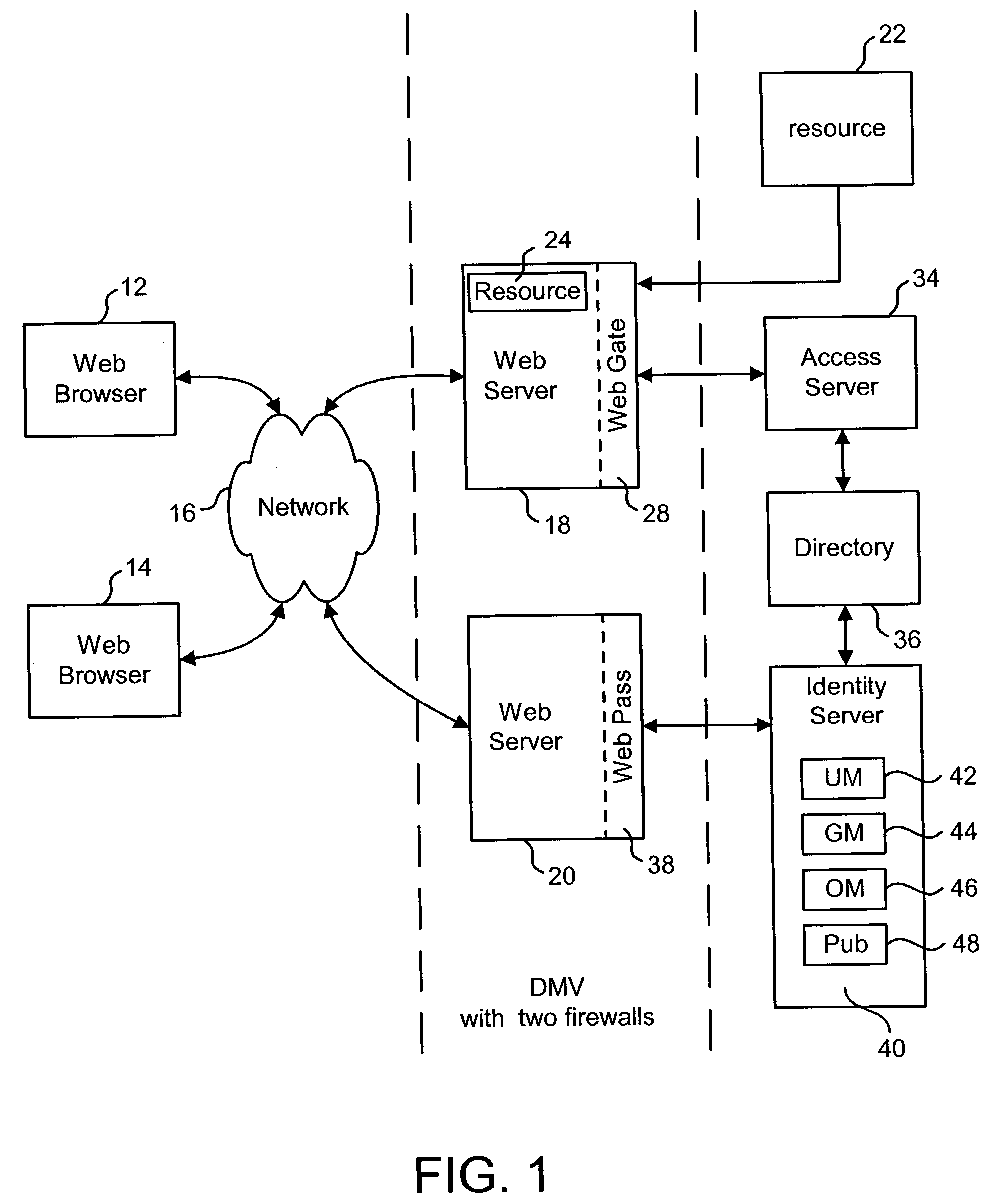
Access system interface
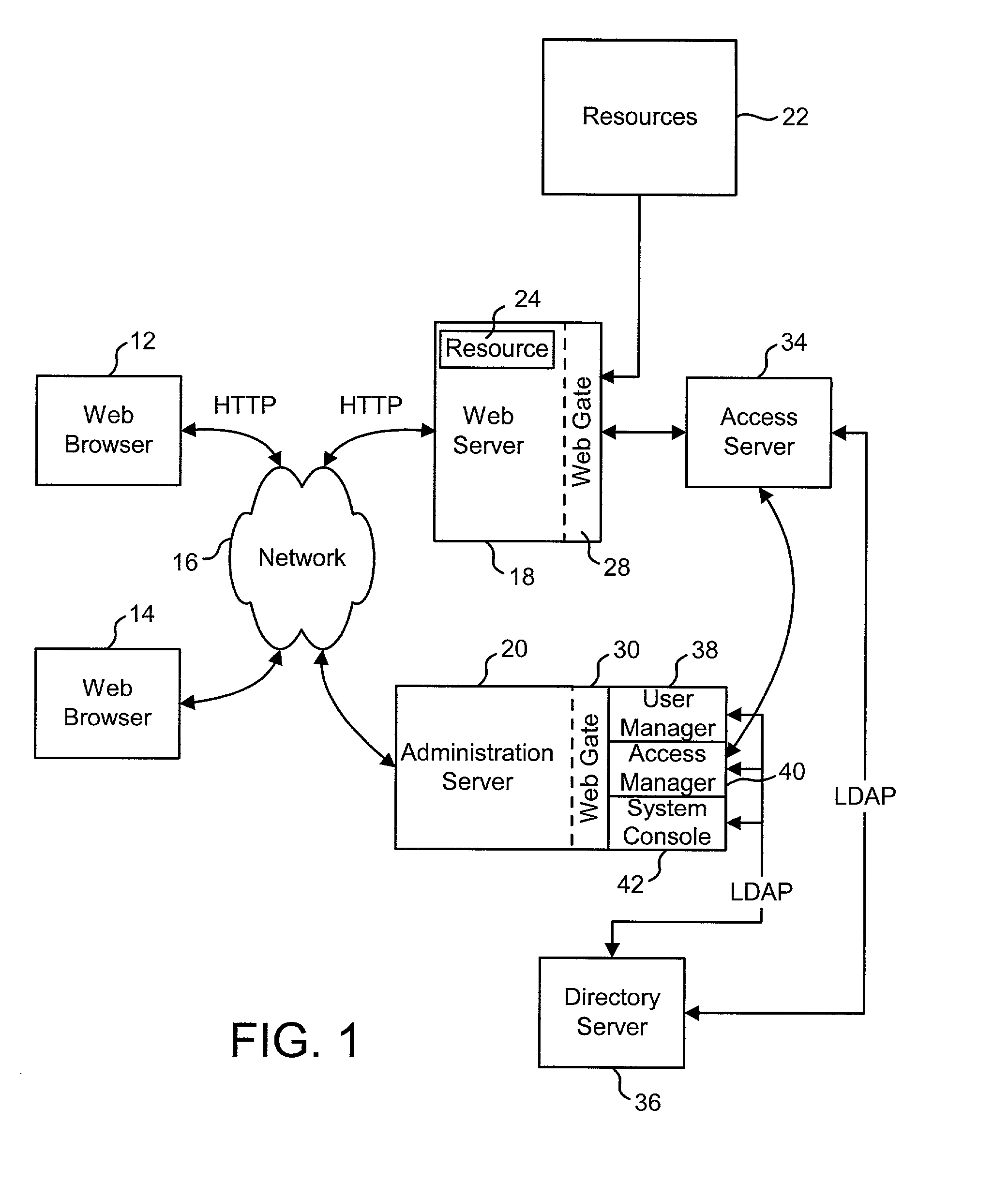
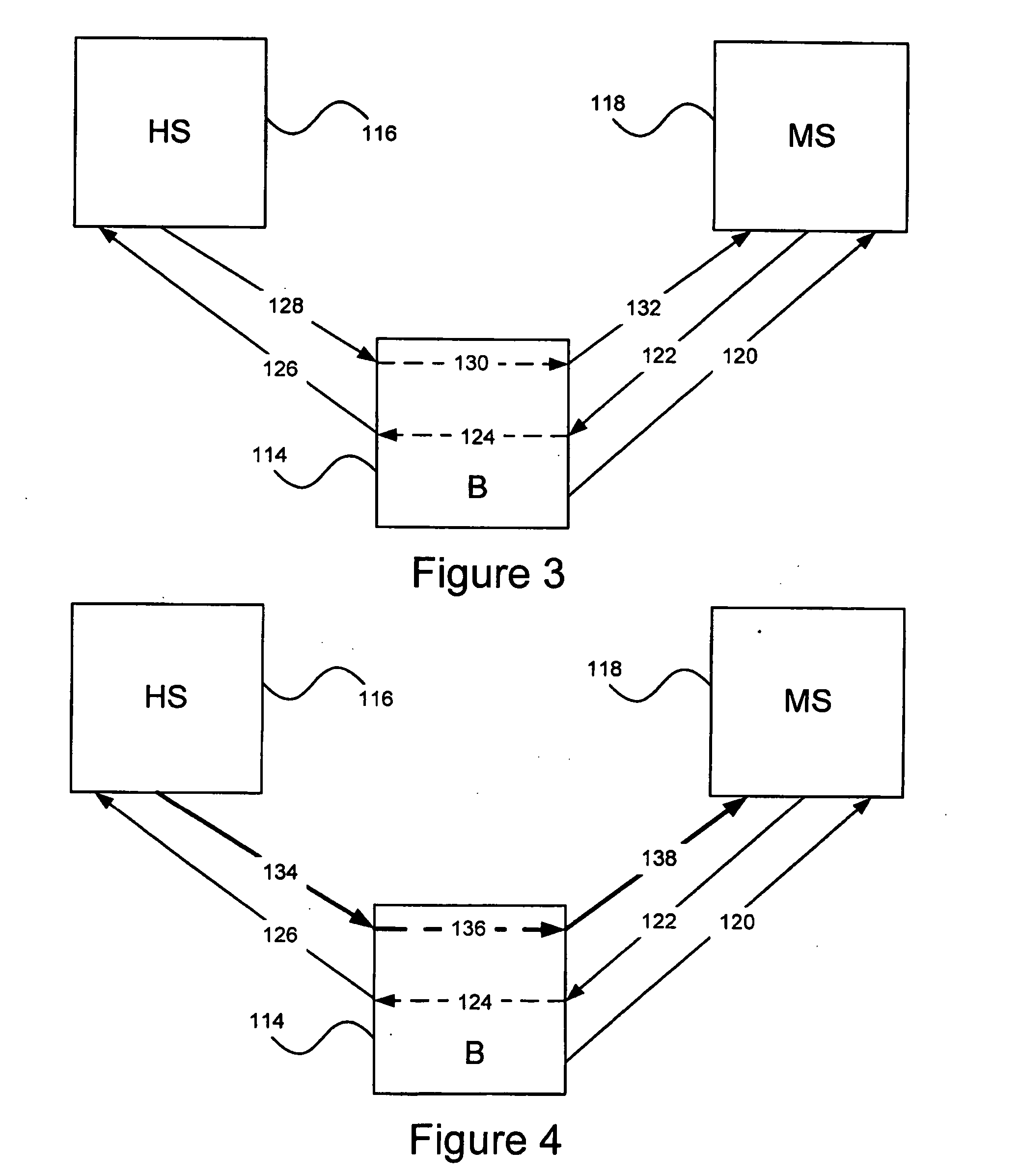
InactiveUS20030074580A1Easy mappingEasy to useDigital data processing detailsUser identity/authority verificationWeb serviceApplication software
An access system provides identity management and / or access management services for a network An application program interface for the access system enables an application without a web agent front end to read and use contents of an existing encrypted cookie to bypass authentication and proceed to authorization. A web agent is a component (usually software, but can be hardware or a combination of hardware and software) that plugs into (or otherwise integrates with) a web server (or equivalent) in order to participate in providing access services.
Owner:ORACLE INT CORP
Access system interface
InactiveUS7185364B2Digital data processing detailsUser identity/authority verificationWeb serviceApplication software
An access system provides identity management and / or access management services for a network. An application program interface for the access system enables an application without a web agent front end to read and use contents of an existing encrypted cookie to bypass authentication and proceed to authorization. A web agent is a component (usually software, but can be hardware or a combination of hardware and software) that plugs into (or otherwise integrates with) a web server (or equivalent) in order to participate in providing access services.
Owner:ORACLE INT CORP
System and method for socially aware identity manager
InactiveUS20100063993A1Multiple digital computer combinationsOffice automationWeb siteSelection criterion
A system and method for a Socially Aware Identity Manager. A request is received over a network from a first user for data relating to a second user, wherein the request comprises an identification of the second user. Spatial, temporal, topical, and social data available to the network relating to the second user is retrieved using a global index of data available to the network, wherein such data comprises at least one website comprising data relating to the second user, which can include social networking sites. The data relating to the second user is filtered using at least one filter criteria. A subset of the filtered data relating to the second user is selected using at least one selection criteria. The filtered subset of data relating to the second user is transmitted over the network to the first user.
Owner:YAHOO INC
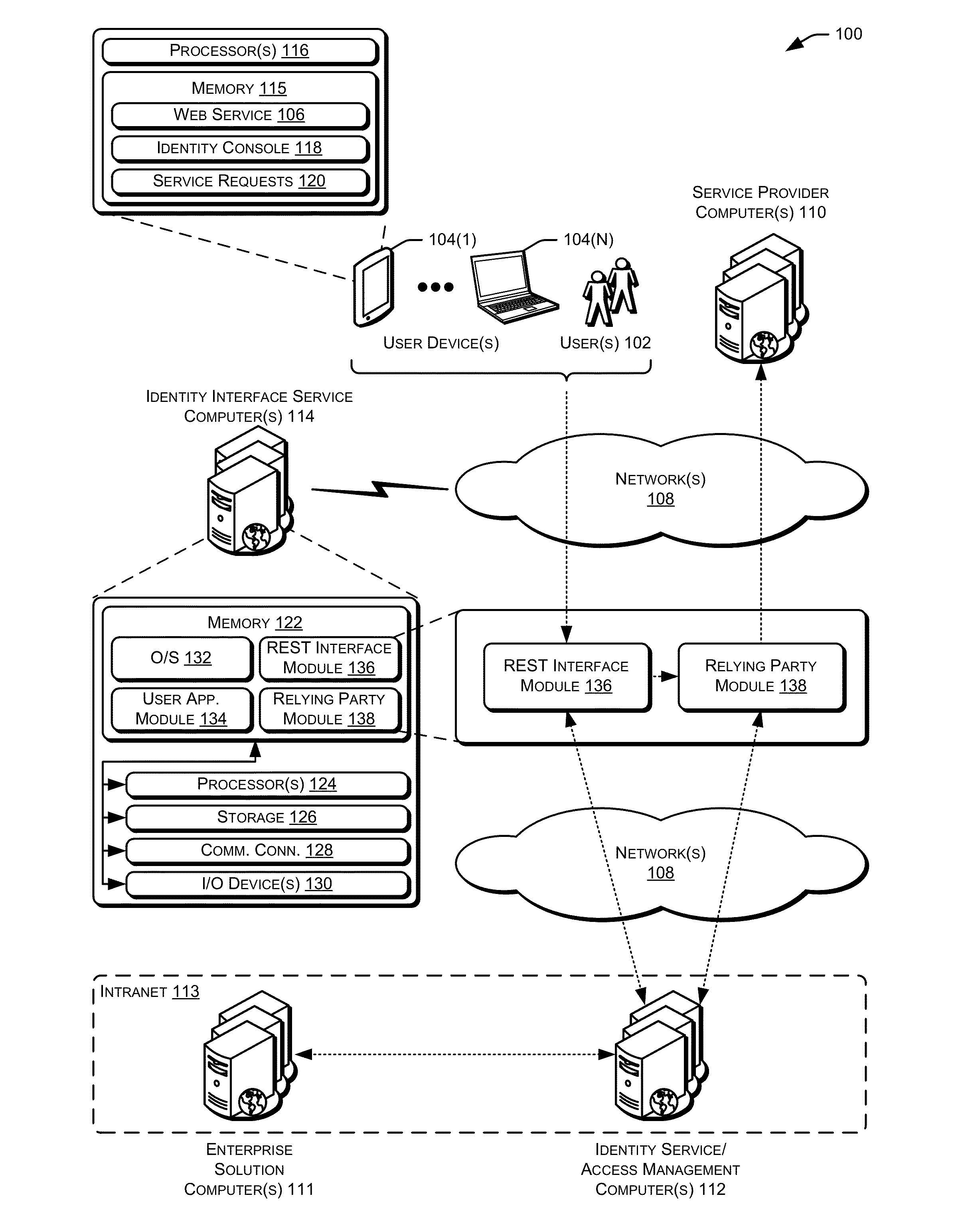
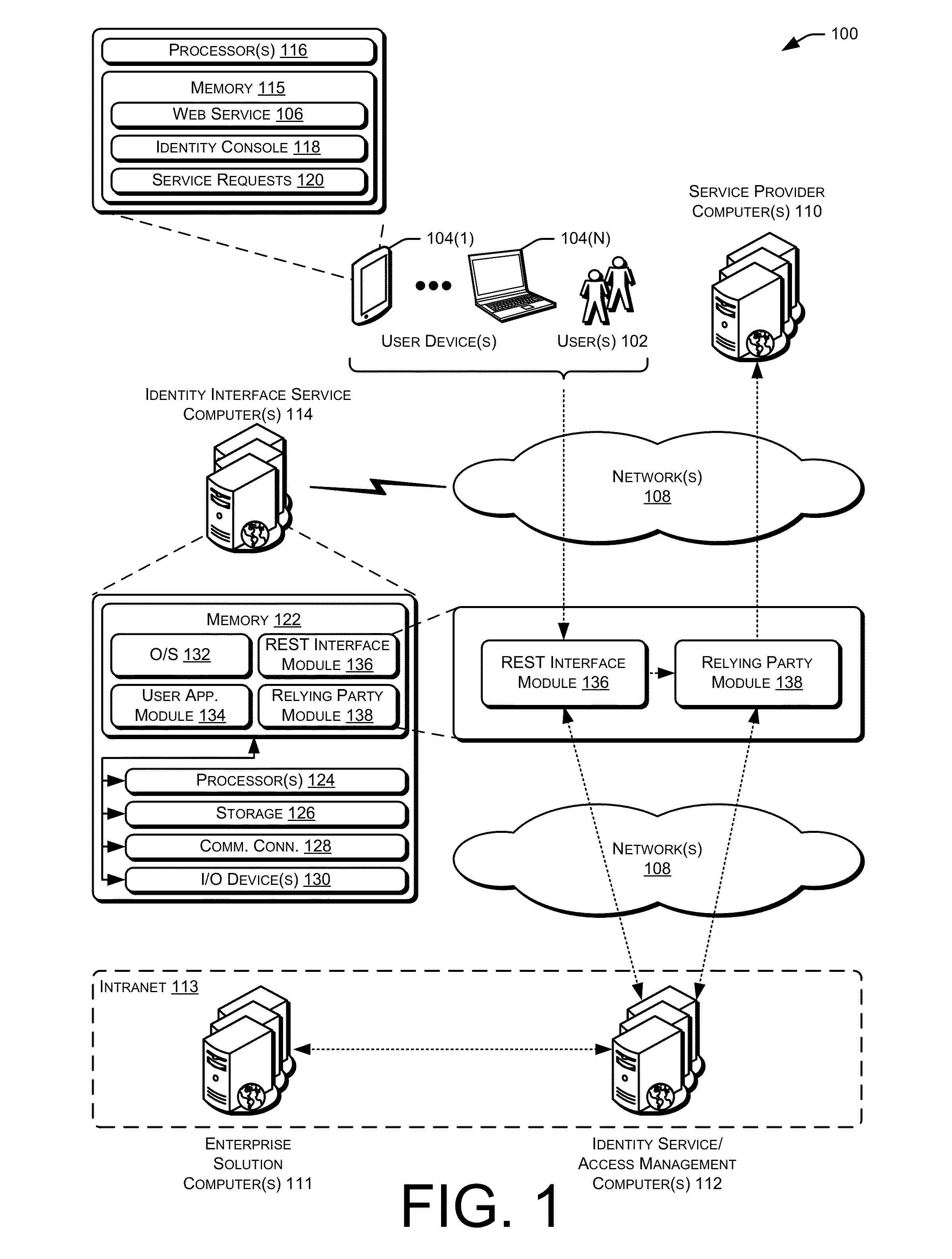
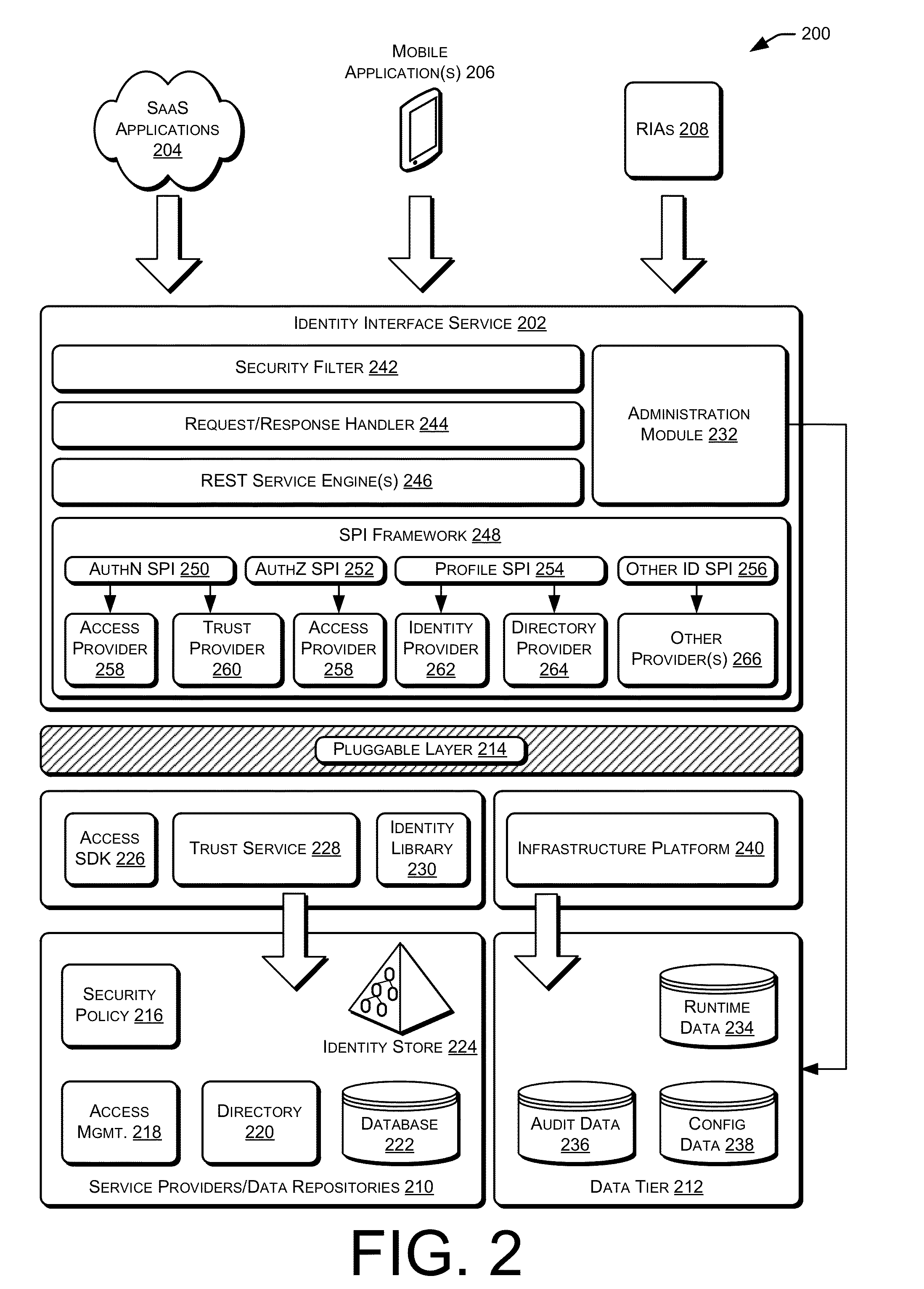
Mobile application, identity interface
ActiveUS20130086639A1Digital data processing detailsMultiple digital computer combinationsApplication programming interfaceApplication software
Techniques for managing identities are provided. In some examples, identity management, authentication, authorization, and token exchange frameworks may be provided for use with mobile devices, mobile applications, cloud applications, and / or other web-based applications. For example a mobile client may request to perform one or more identity management operations associated with an account of a service provider. Based at least in part on the requested operation and / or the particular service provider, an application programming interface (API) may be utilized to generate and / or perform one or more instructions and / or method calls for managing identity information of the service provider.
Owner:ORACLE INT CORP
Systems and methods for managing identity information
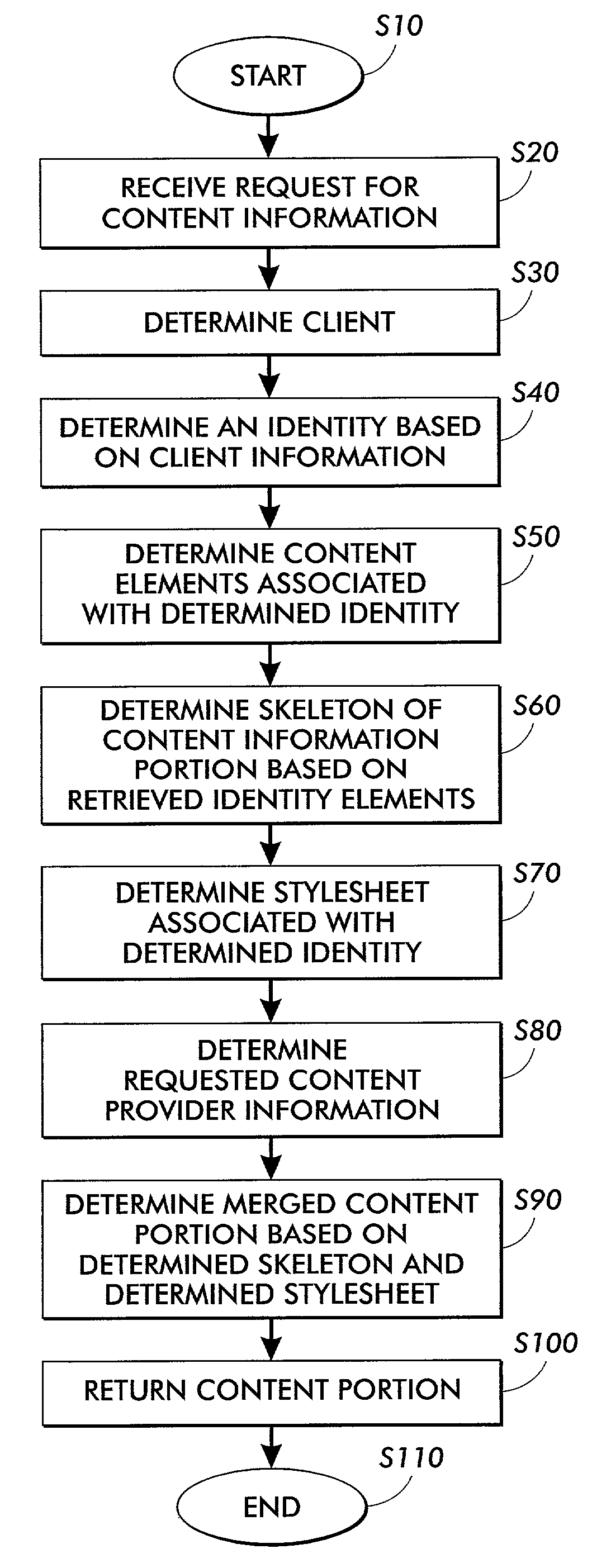
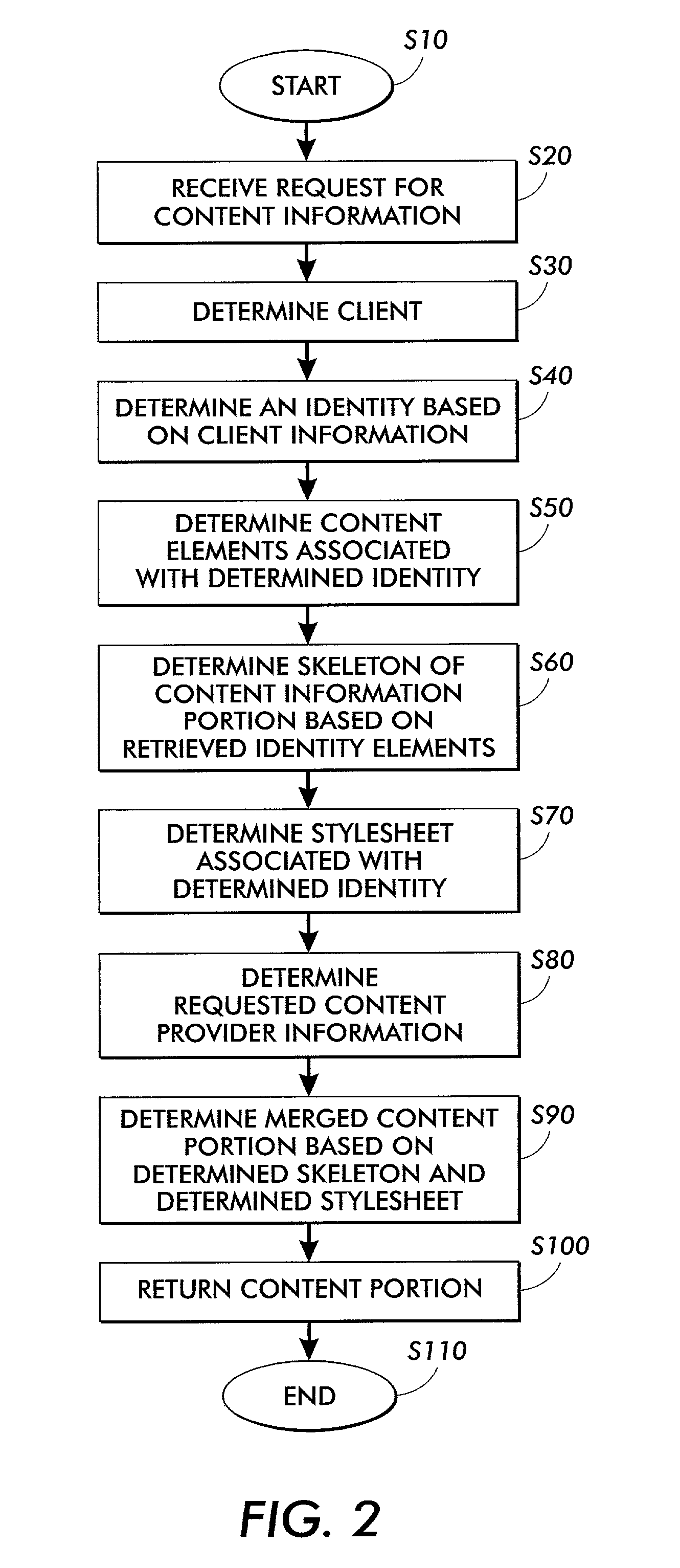
InactiveUS7146560B2Easy to useReduce needNatural language data processingMultiple digital computer combinationsInternet privacyLook and feel
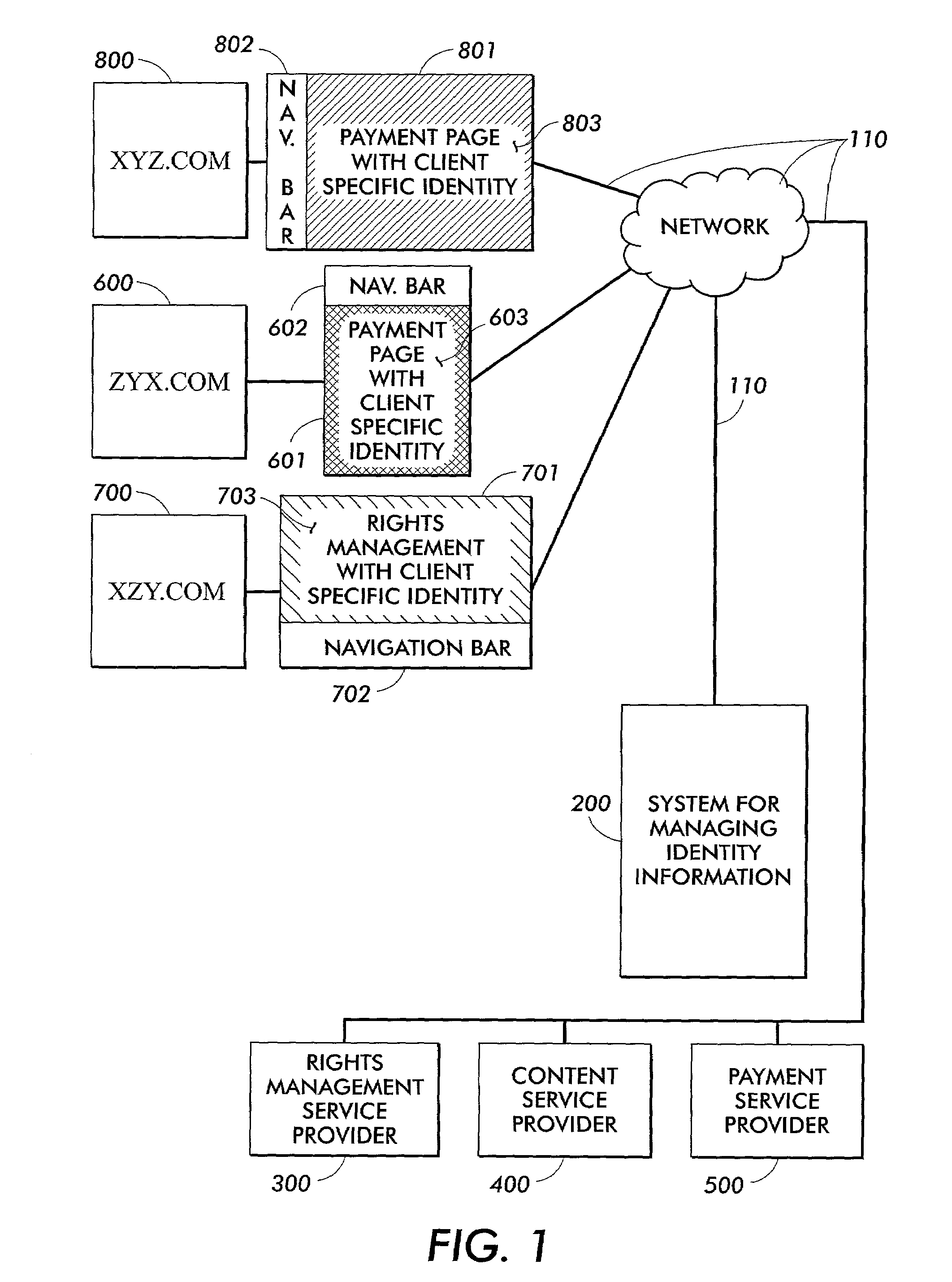
Consistent identity information is provided for content information through the use of an identity manager. The identity manager stores styles and style elements and presentation information associated with a specific client identity. The styles and presentation information for each identity are stored based on client information. When a request for content is received, the information is retrieved. The styles and presentation information associated with the specific client identity are retrieved and merged with the content. The content and the client or user identity or look and feel information are integrated without expensive custom programming.
Owner:XEROX CORP
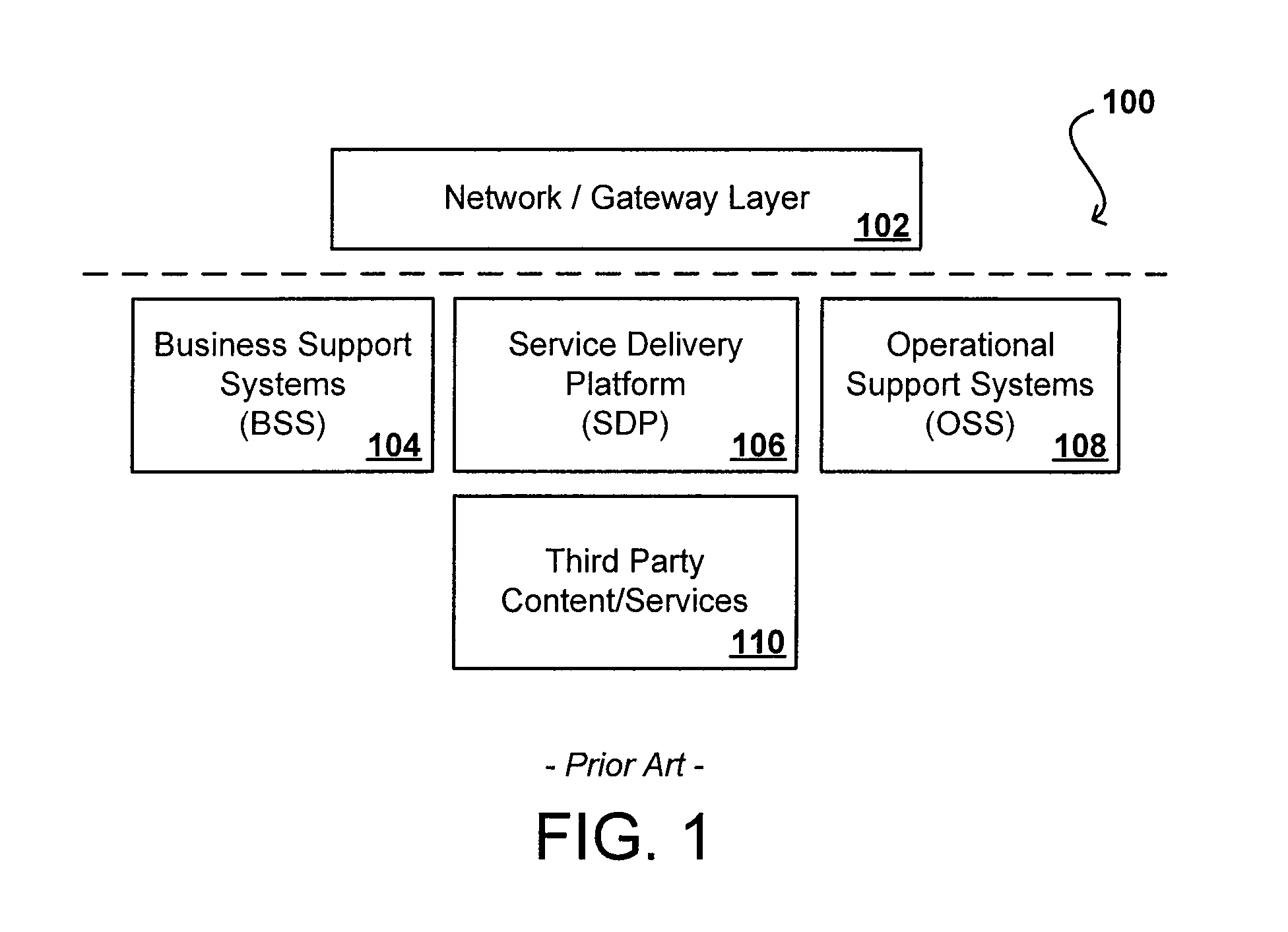
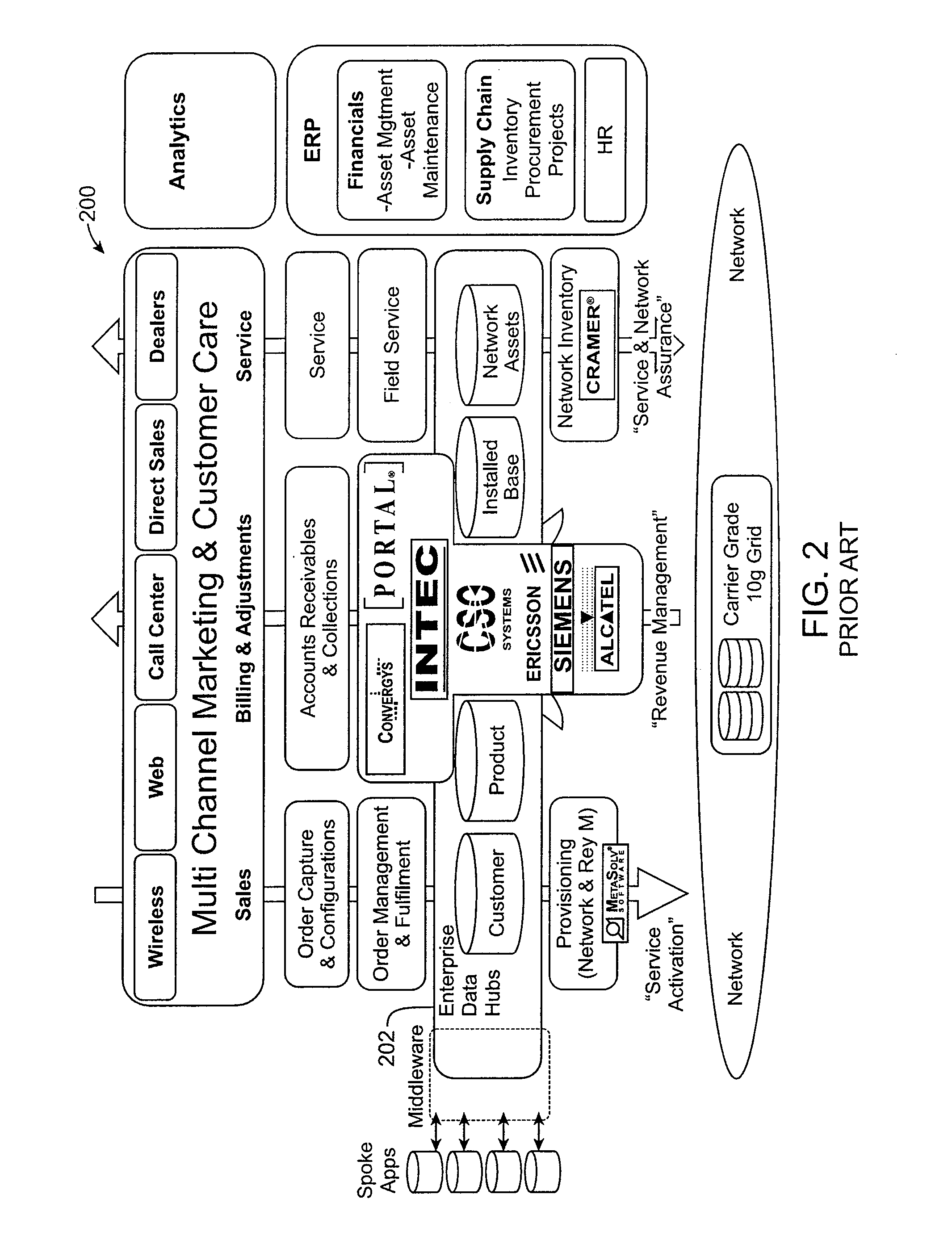
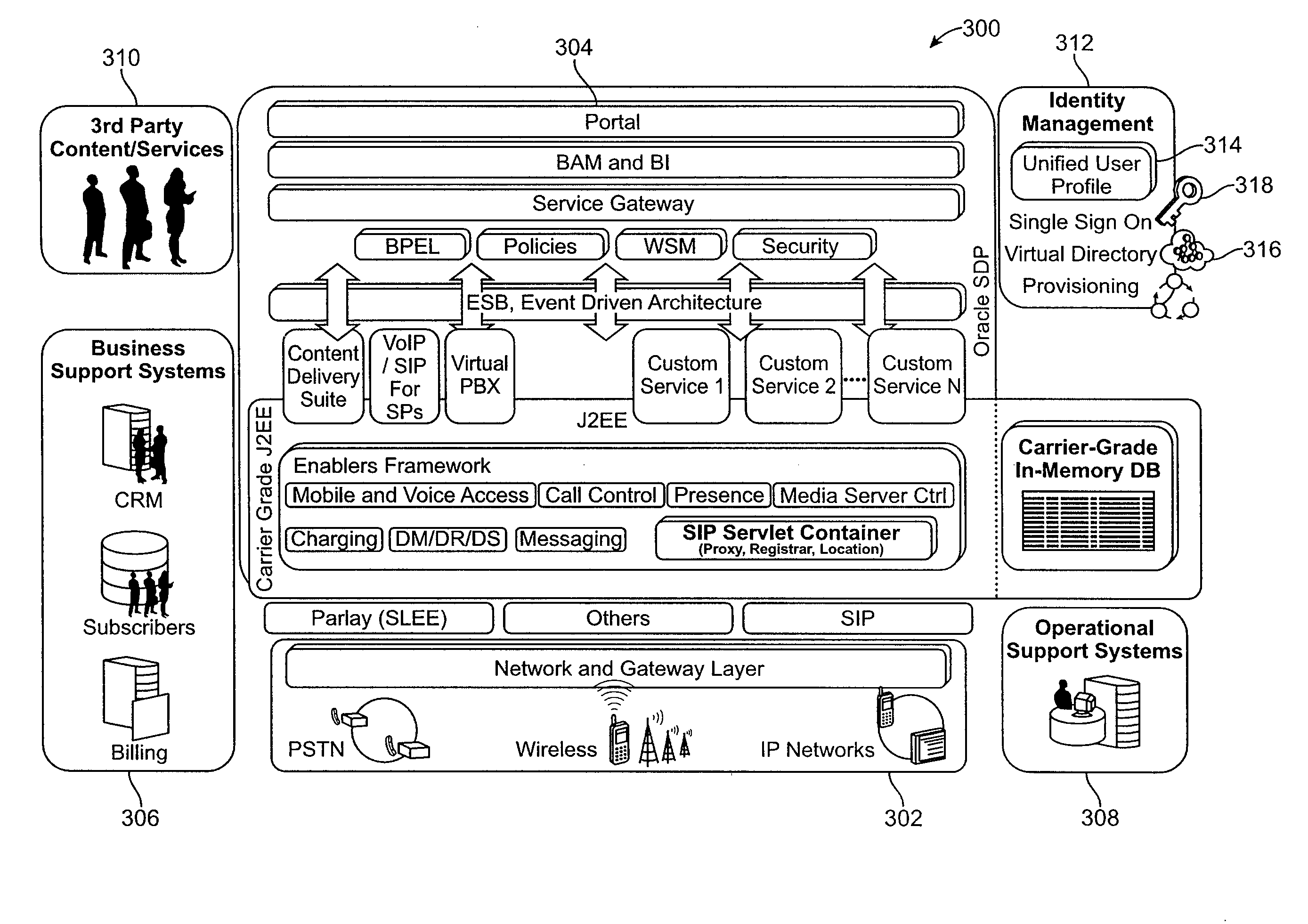
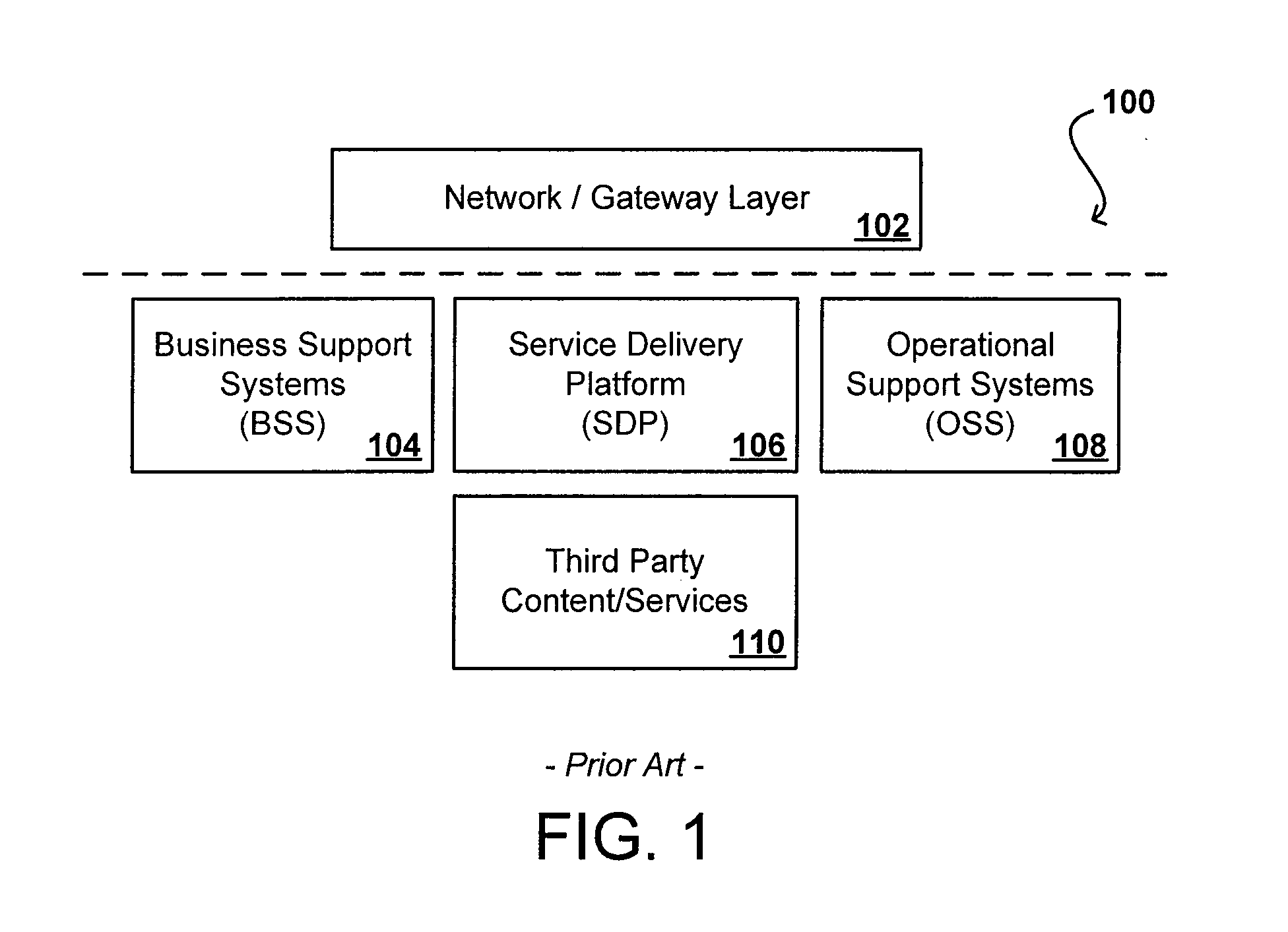
Shared view of customers across business support systems (BSS) and a service delivery platform (SDP)
ActiveUS8073810B2Overcome deficienciesDigital data processing detailsDatabase distribution/replicationData aggregatorCustomer information
Owner:ORACLE INT CORP
Authorization services with external authentication
InactiveUS7231661B1Digital data processing detailsUser identity/authority verificationInternet Authentication ServiceIdentity management
An Access System can provide identity management and / or access management services. Examples of access management services include authentication and authorization services. In some implementations, users of an Access System want to use the authorization services of the Access System but do not want to use the authentication services of the Access System. The present invention allows some or all of the resources protected by the Access System to use the authentication services of the Access System and some or all of the resources protected by the Access System to use external authentication services.
Owner:ORACLE INT CORP
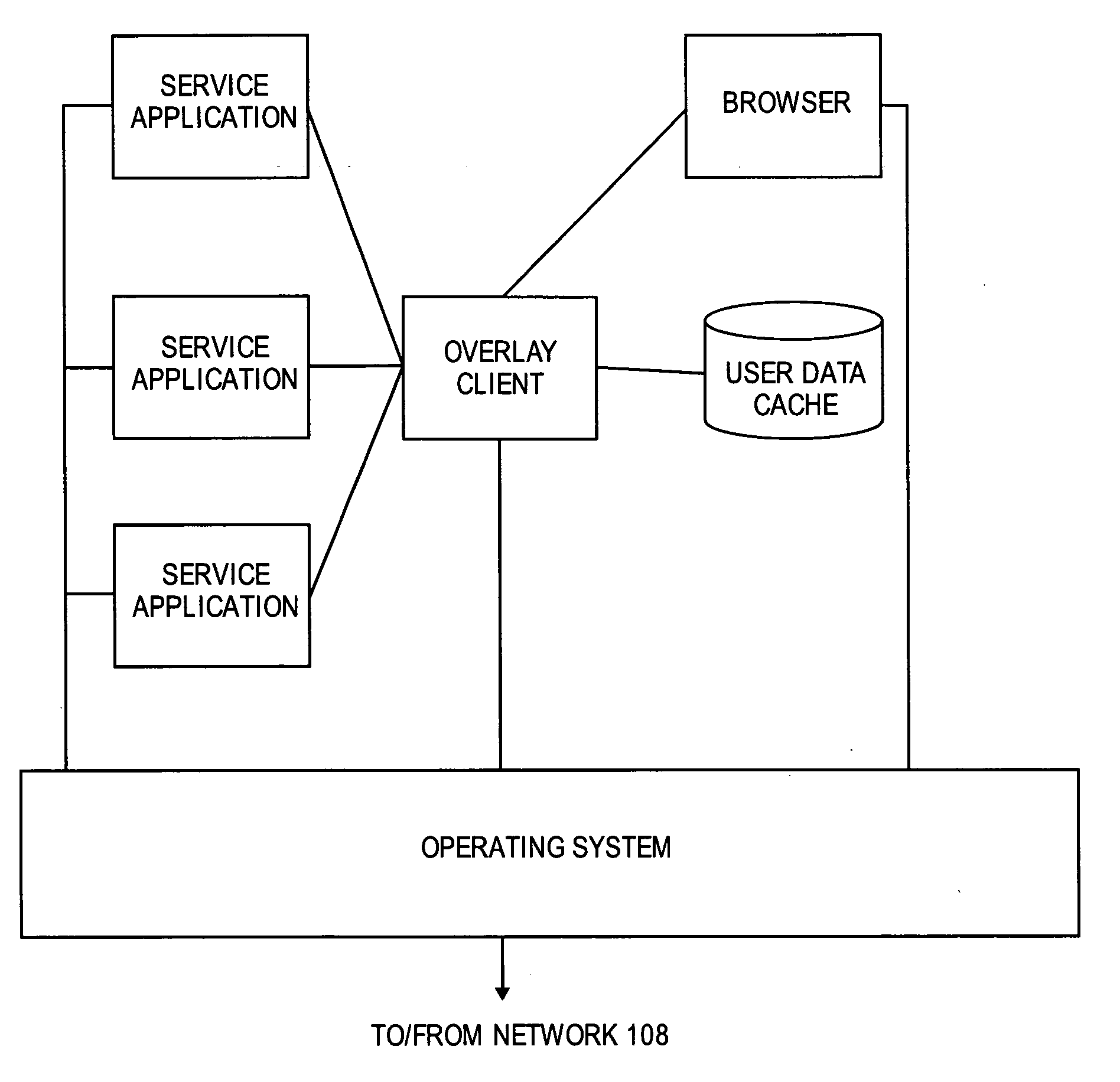
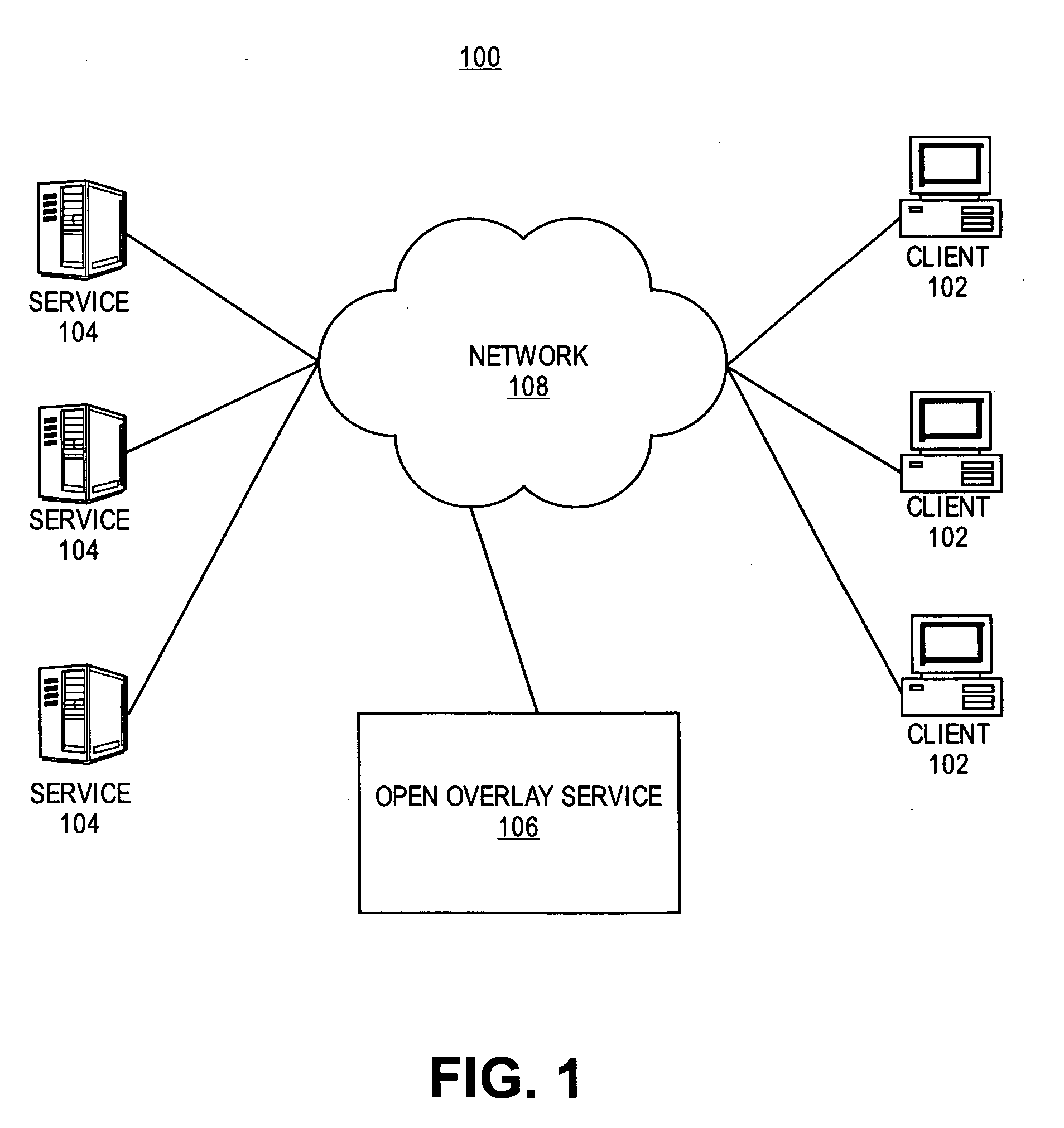
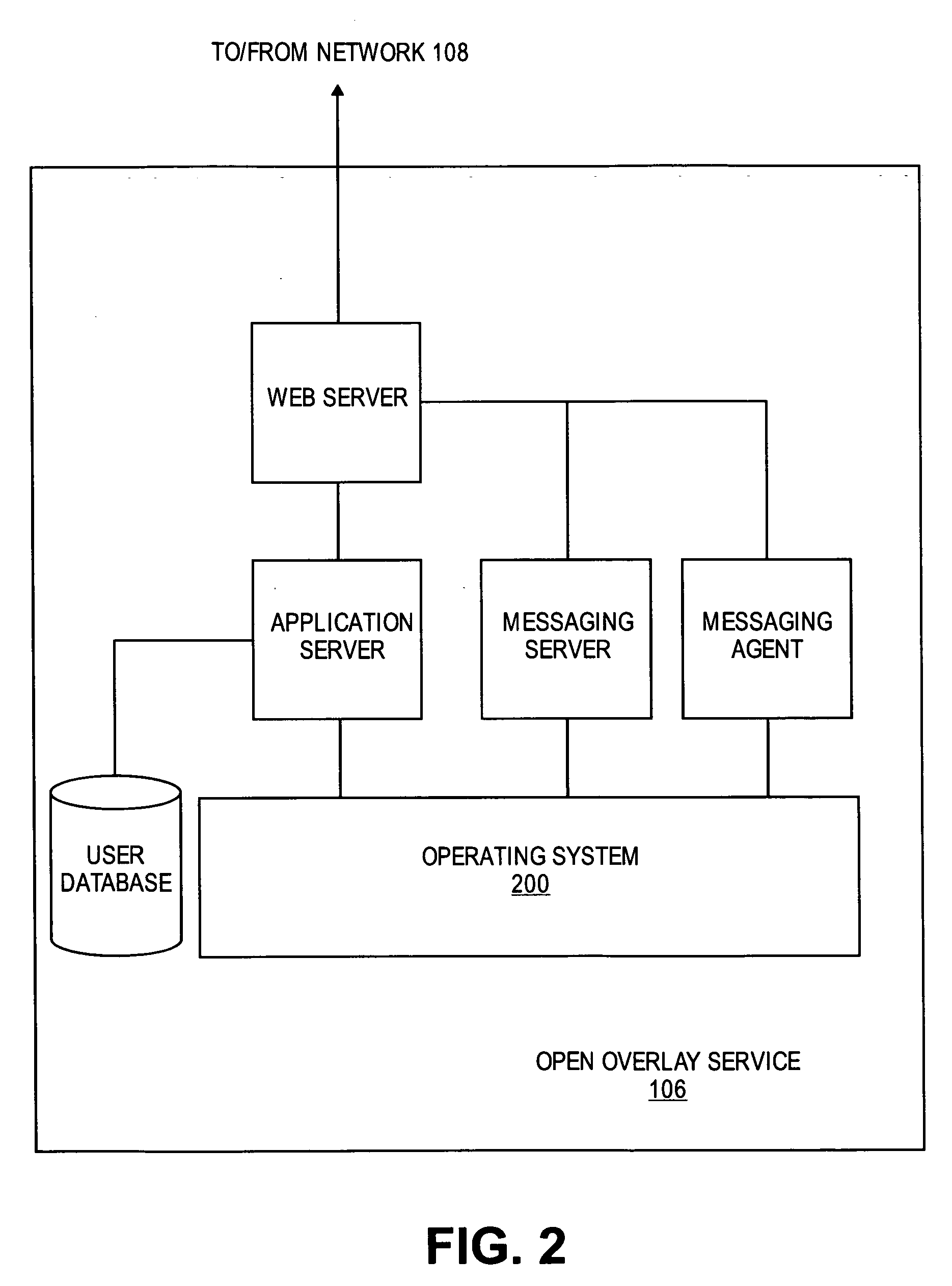
Identity management for open overlay for social networks and online services
Embodiments of the present invention provide methods and systems for managing the multiple identities used by a user. The user's existing contact lists, website accounts, buddy lists, and the like are analyzed to determine the identities used by the user. A graph is then constructed in order to track and integrate the multiple identities of the user in a social network. The social network graph may then be used by a social network overlay so that the user can share information across their different identities with different users that only know some of the user's multiple identities.
Owner:RED HAT
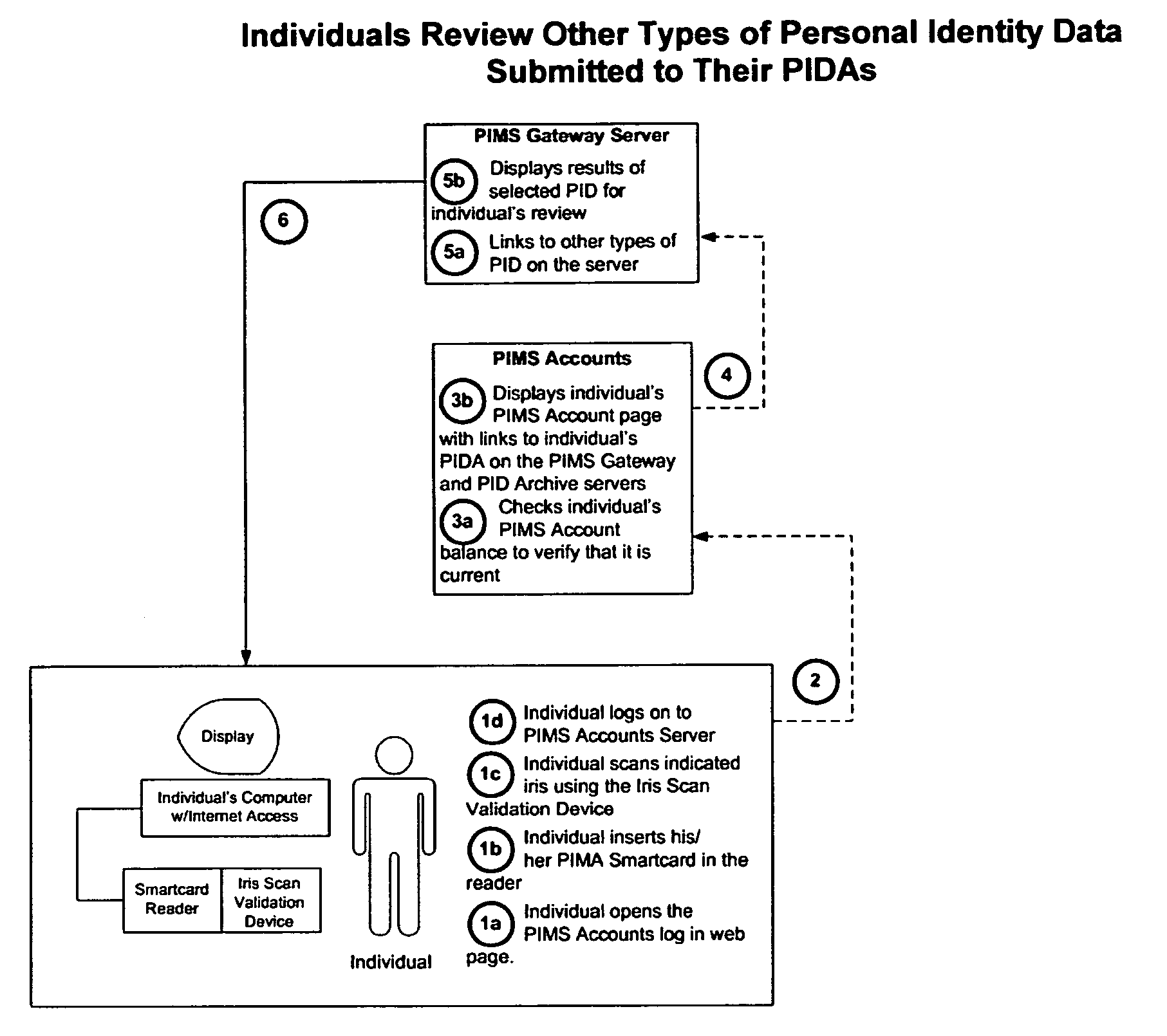
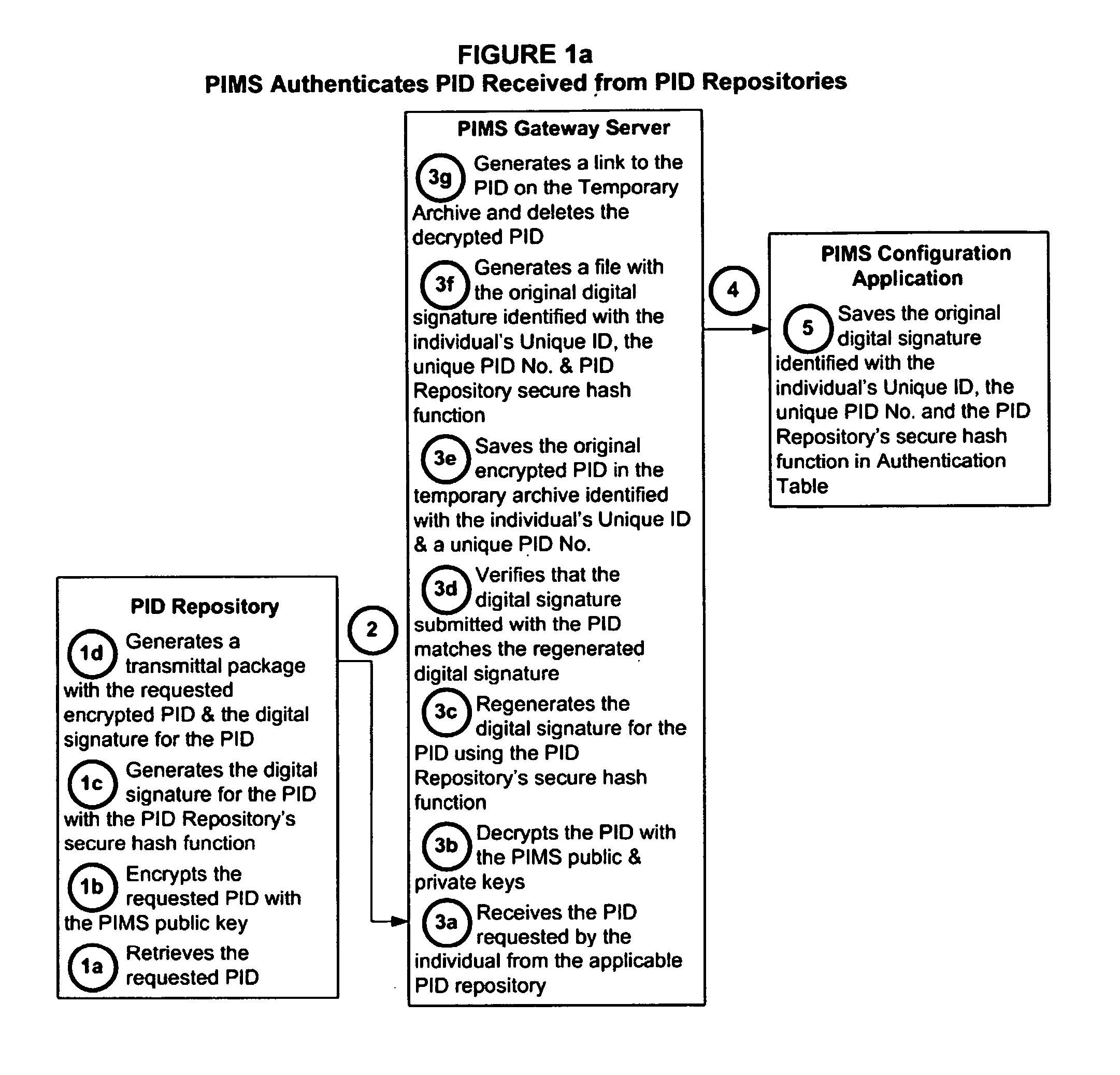
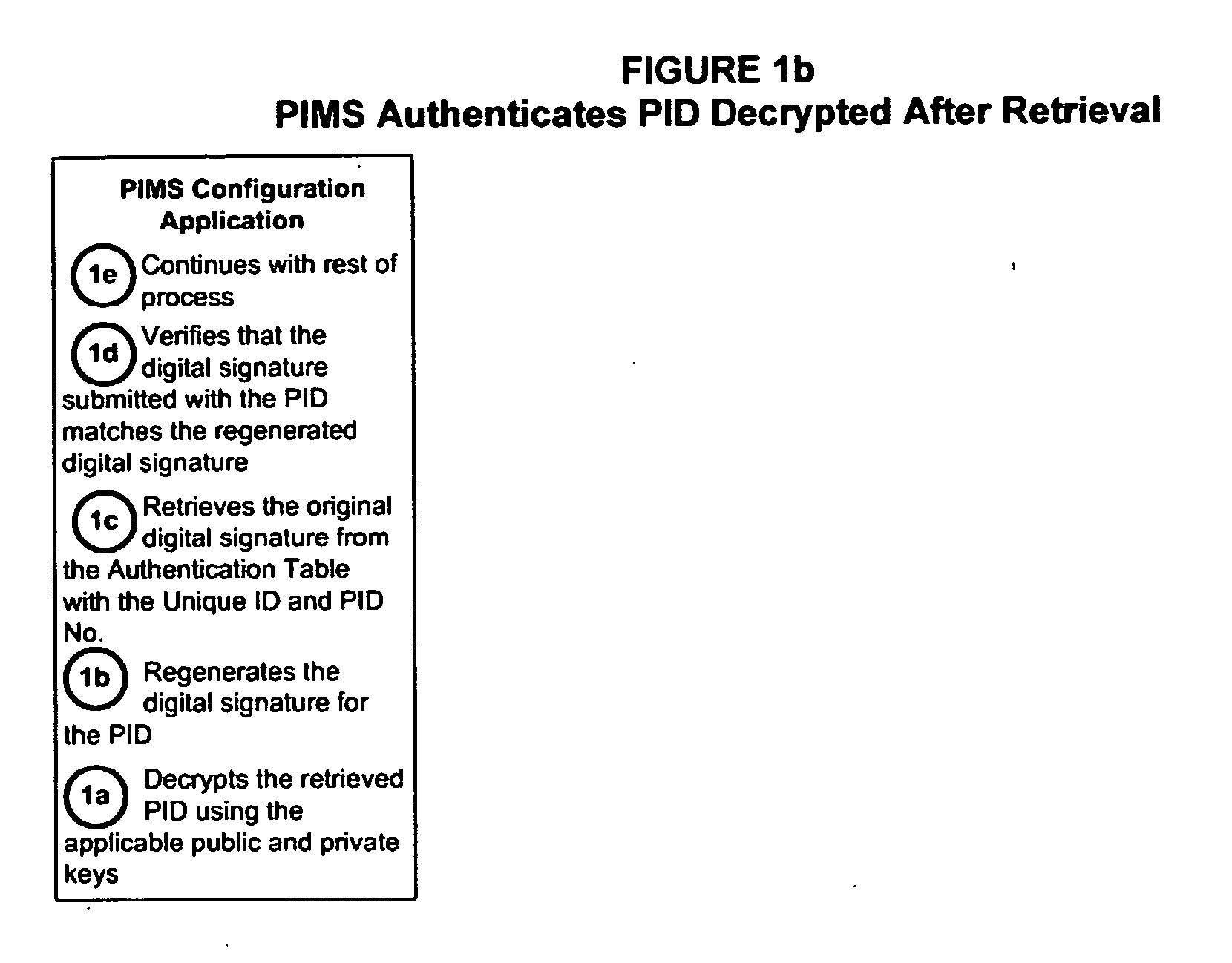
Personal identity data management
InactiveUS20060034494A1Public key for secure communicationUser identity/authority verificationSocial Security numberSmart card
Systems, methods and apparatus for personal identity data management permit individuals to manage their criminal background, credit history, employment, demographic and educational information, for example, to establish their credentials and to help protect their good names. All access to this personal identity data, including the biometrics that uniquely establish the individuals' identity, is under the personal control of the individuals, with access limited to others only with their specific authorization. The subject systems, methods and apparatus include at least two separate archives that store encrypted data about individuals that can be accessed only via the individuals' biometrics specific to the archives and unique Identification Numbers. The Identification Numbers are encrypted when they are associated with the individuals' demographic data, which includes their names, Social Security Numbers and the Unique Identifiers assigned by the system to each of the individuals. Public / private key encryption is used to encrypt the Personal Identity Data maintained in the archives and the Identification Numbers maintained in a Personal Identity Management Service configuration application server that links the rest of the system to the archives. To permit the private keys to be securely retained for use in regenerating a. Smartcard in case of loss or damage, separate segments of the private key are stored on different servers each of which requires submittal of a different biometric, which must match the biometric associated with the private key segment.
Owner:NAT BACKGROUND DATA
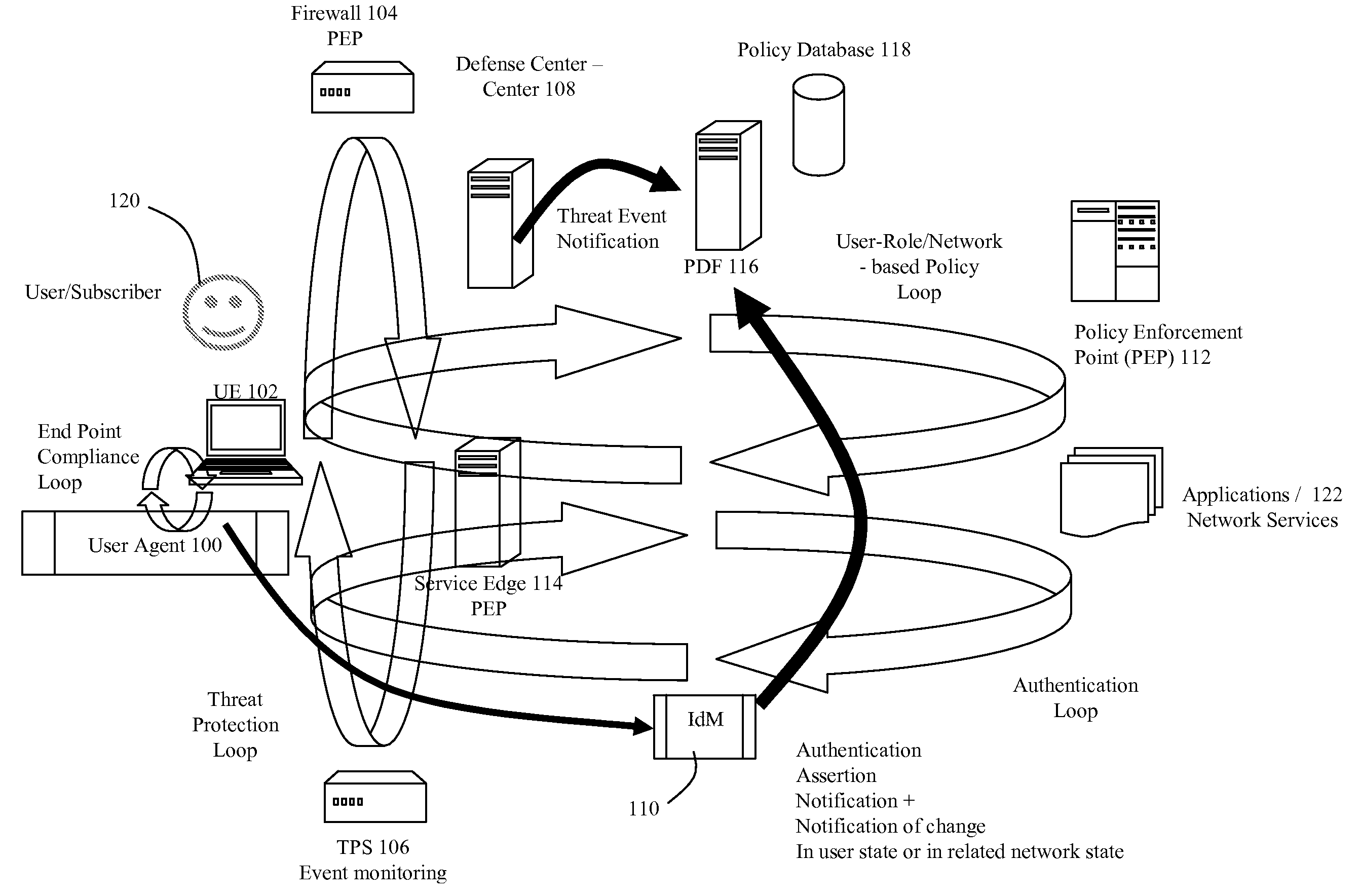
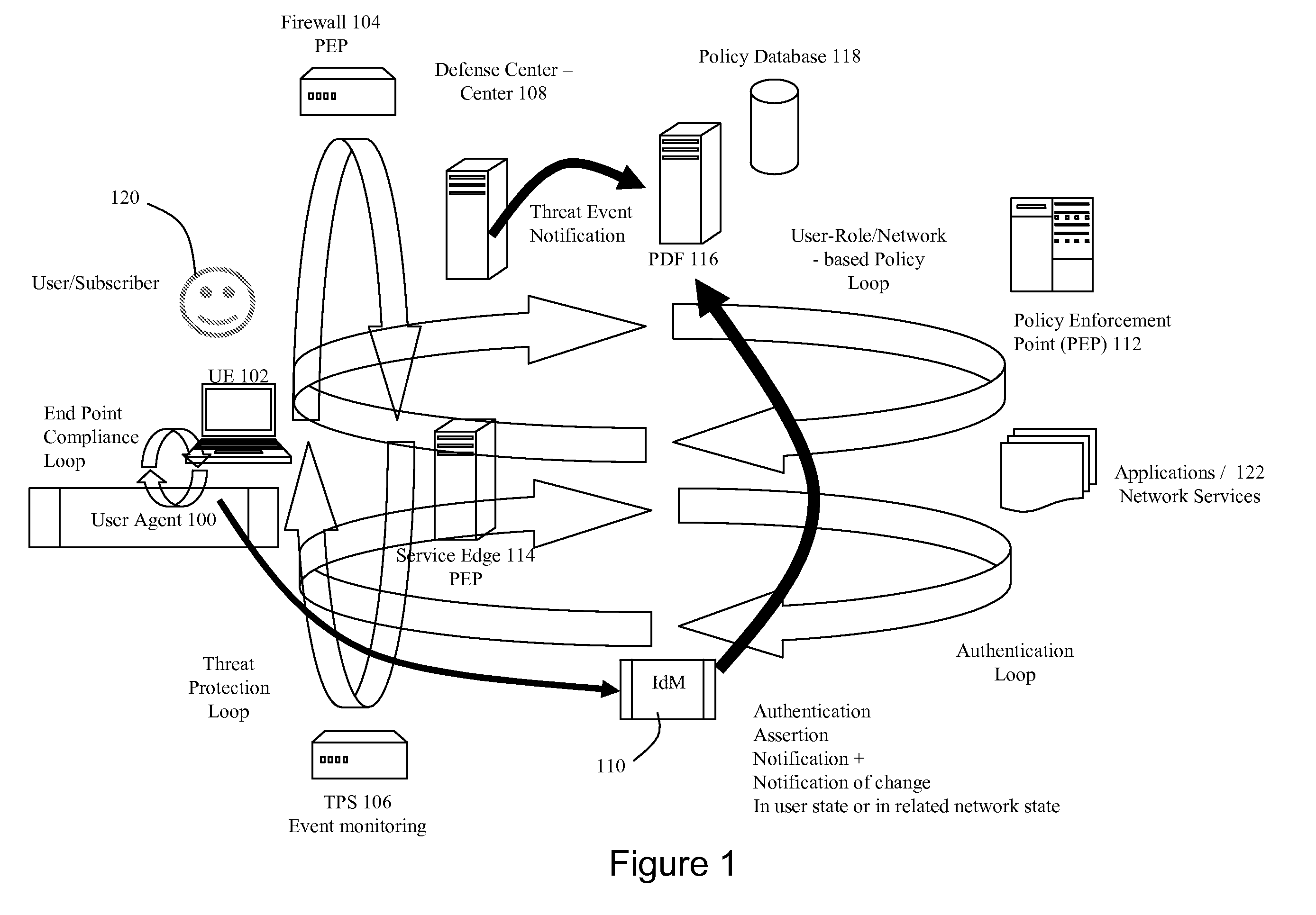
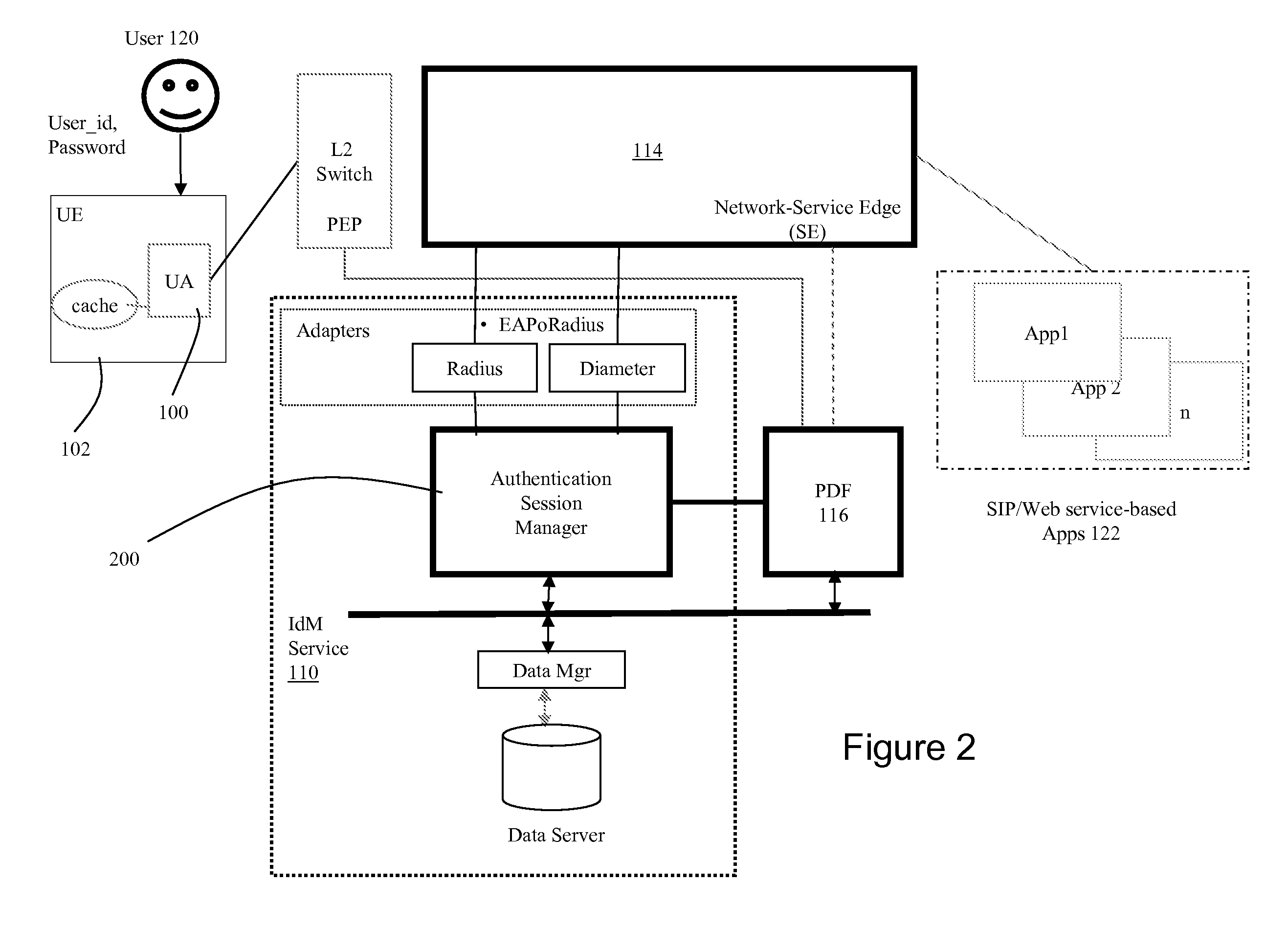
Dynamic Network Identity and Policy management
InactiveUS20070150934A1Network resource is limitedSpecial data processing applicationsSecurity arrangementTarget ResponsePassword
Network policies are managed based at least in-part on user / entity identity information with: a state monitor operable to monitor for state change events in user / entity state and related, network state or in traffic pattern and traffic flow state; an identity manager operable to obtain and validate user credentials; and a policy manager operable in response to a state change event detected by the state monitor (either the identity manager or a defense center) to select a policy based in-part on the user identity obtained by the identity manager or security context obtained by the defense center, and to prompt application of the selected policy. The policies are indicative of user / device authorization entitlements and restrictions to utilization of certain network resources, network services or applications. Dynamic policy selection and targeted responses can be used, for example, against a user who gains network access with stolen user ID and password, and subsequently attempts malicious behavior. In particular, the malicious behavior is detected and identified, and the malicious user can then be restricted from abusing network resources without adversely affecting other users, groups, network devices, and other network services.
Owner:NORTEL NETWORKS LTD
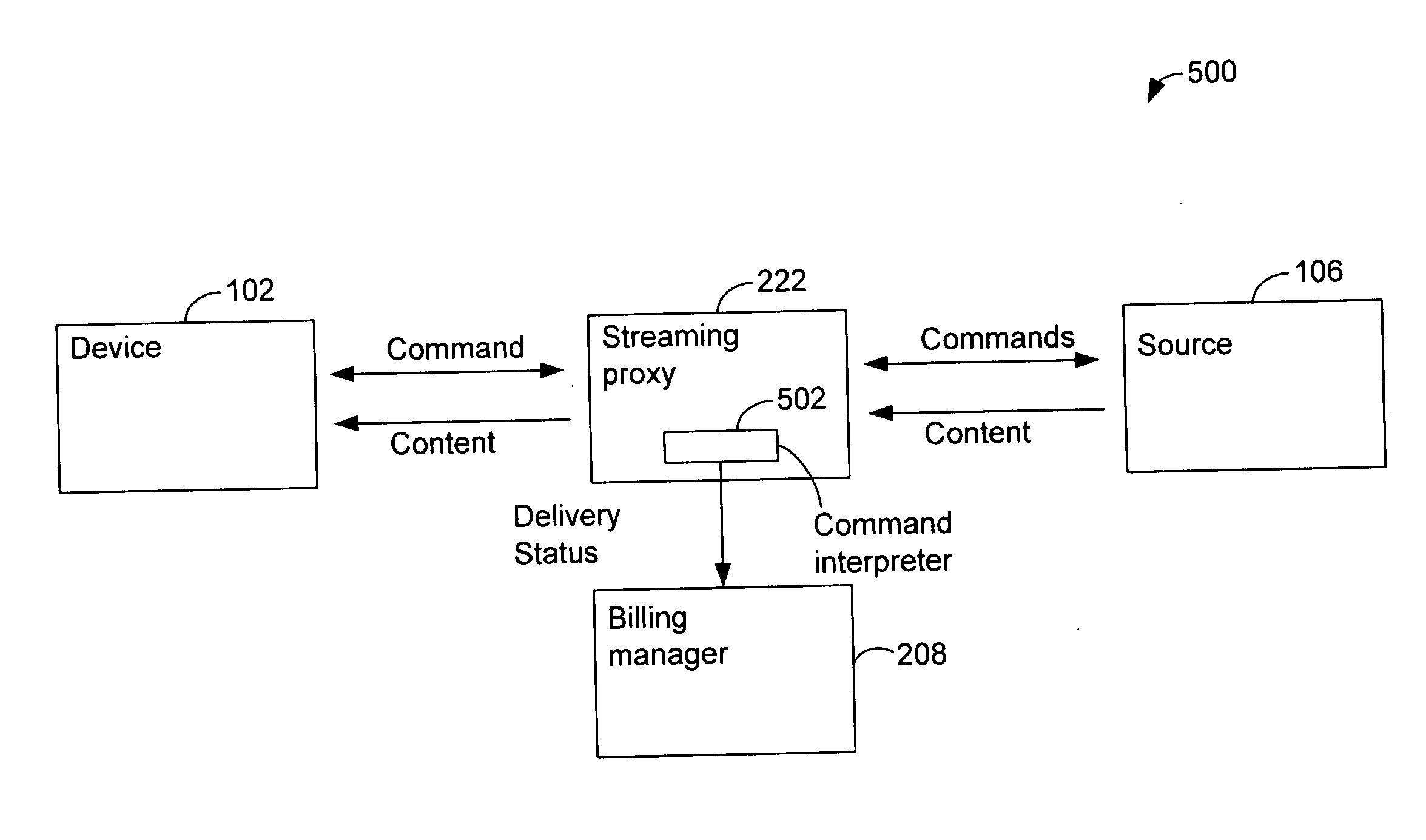
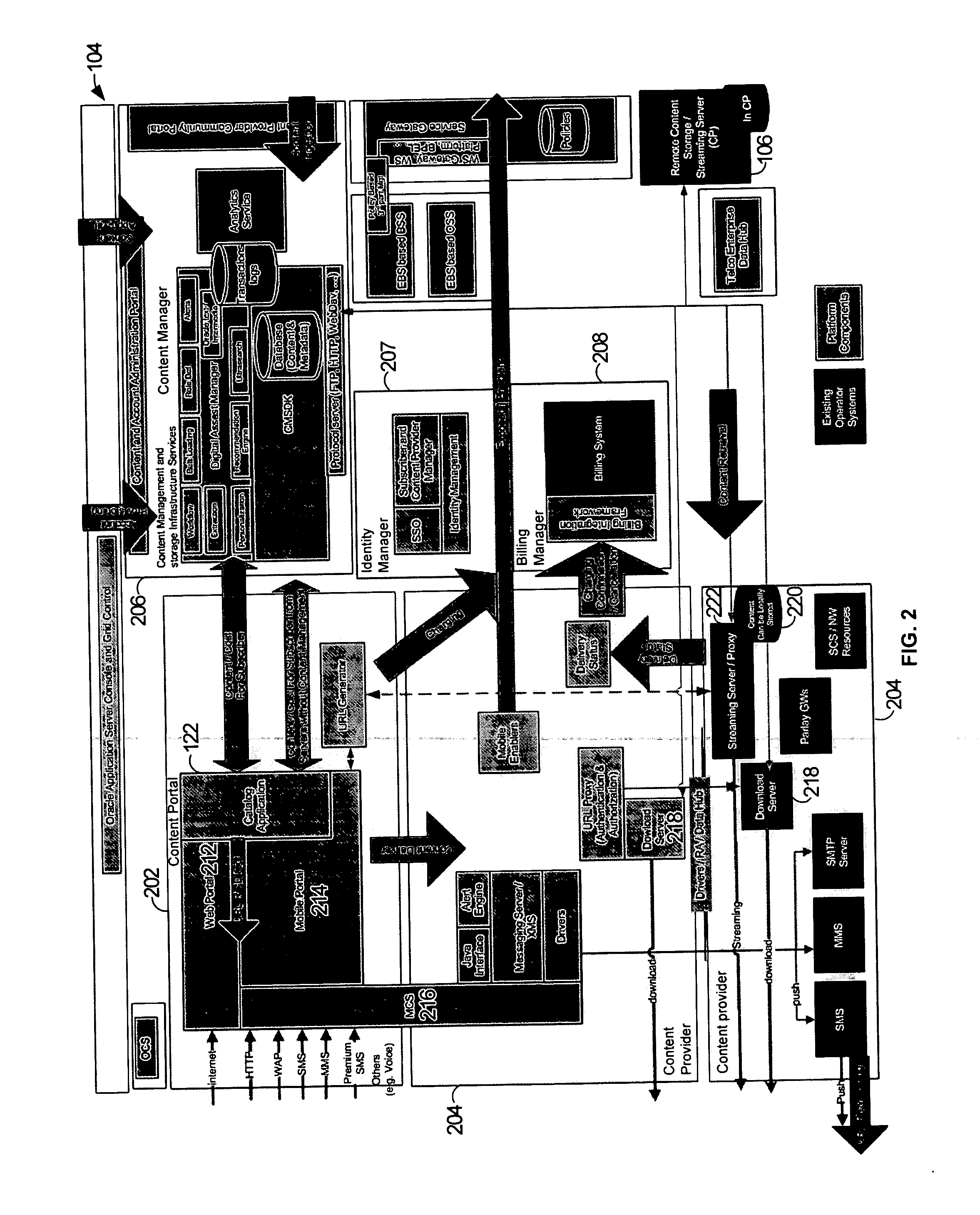
Platform and service for management and multi-channel delivery of multi-types of contents
ActiveUS20060272028A1Random number generatorsUser identity/authority verificationIdentity managementContent management
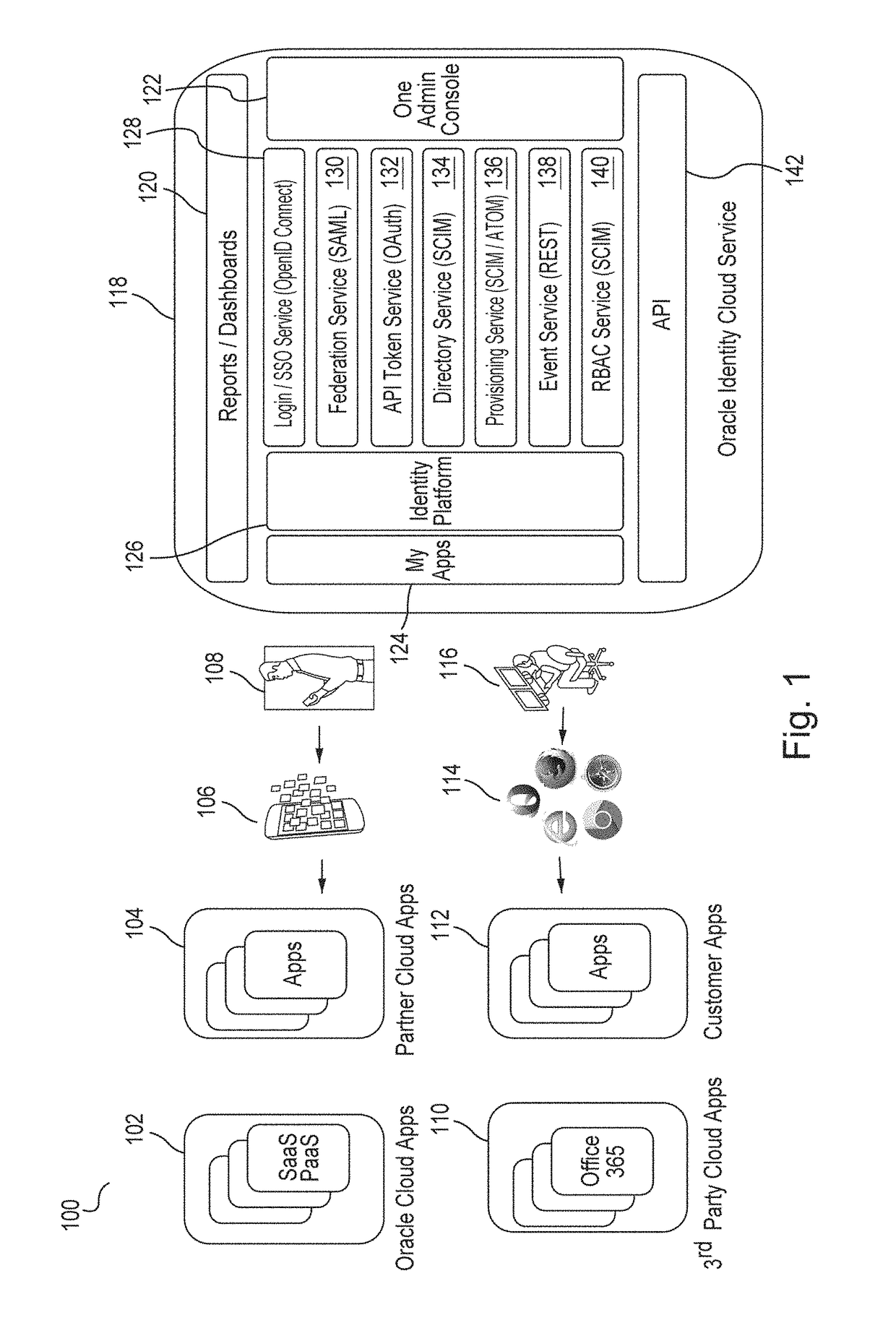
A platform for managing delivery of content originating from one or more content providers to users is provided. The platform includes a portal that is configured to support access through a plurality of access channels configured to receive requests through one or more access channels. A request for content is received from an access device through an access channel. An identity management module is configured to determine a user associated with the message. A content manager is configured to manage content for delivery through the plurality of access channels and configured to determine eligible content for the user. A billing module is configured to process billing for the user and content provider based on the content provided to the user. The content manager is then configured to deliver the requested content to the user's access device through the access channel.
Owner:ORACLE INT CORP
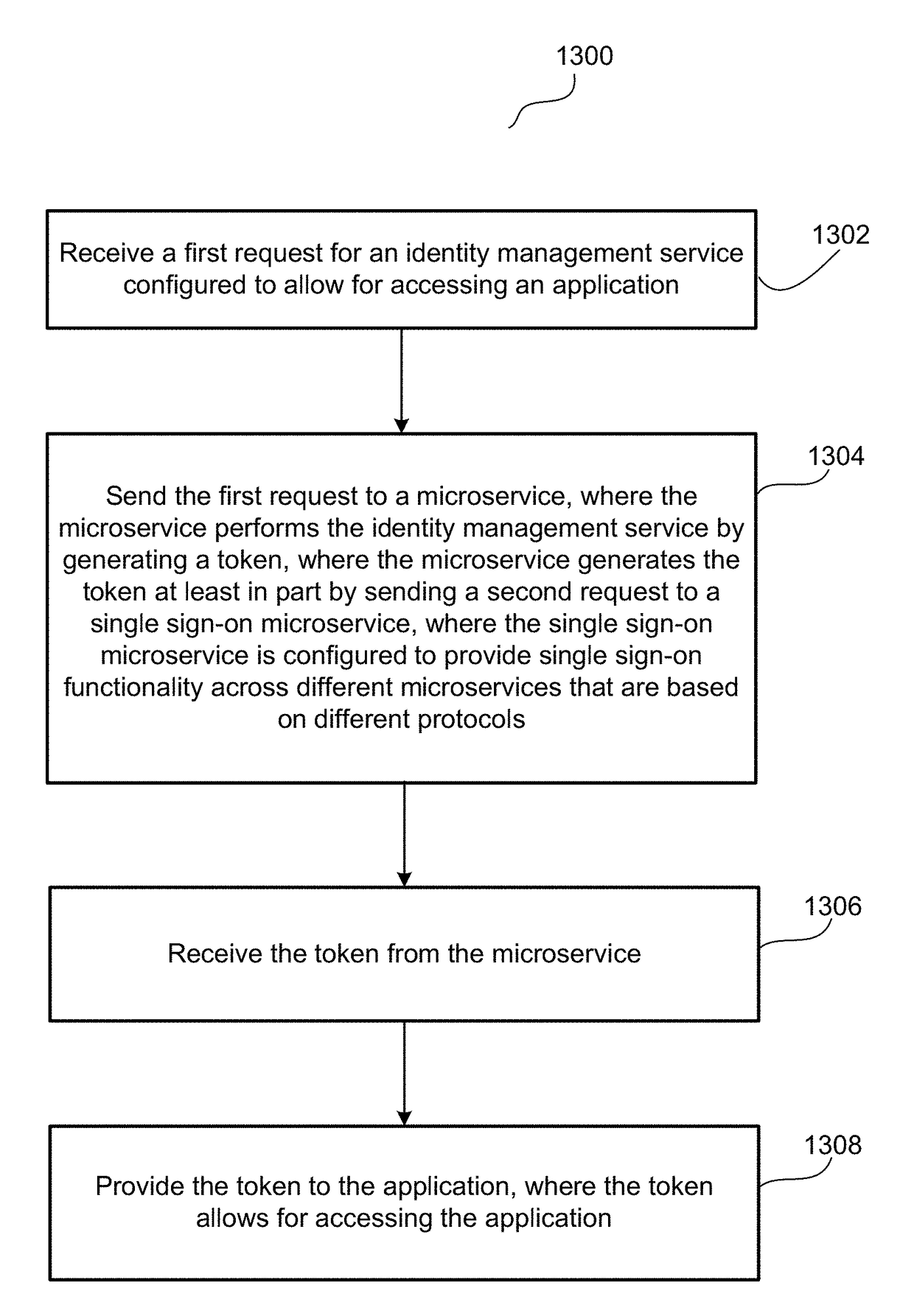
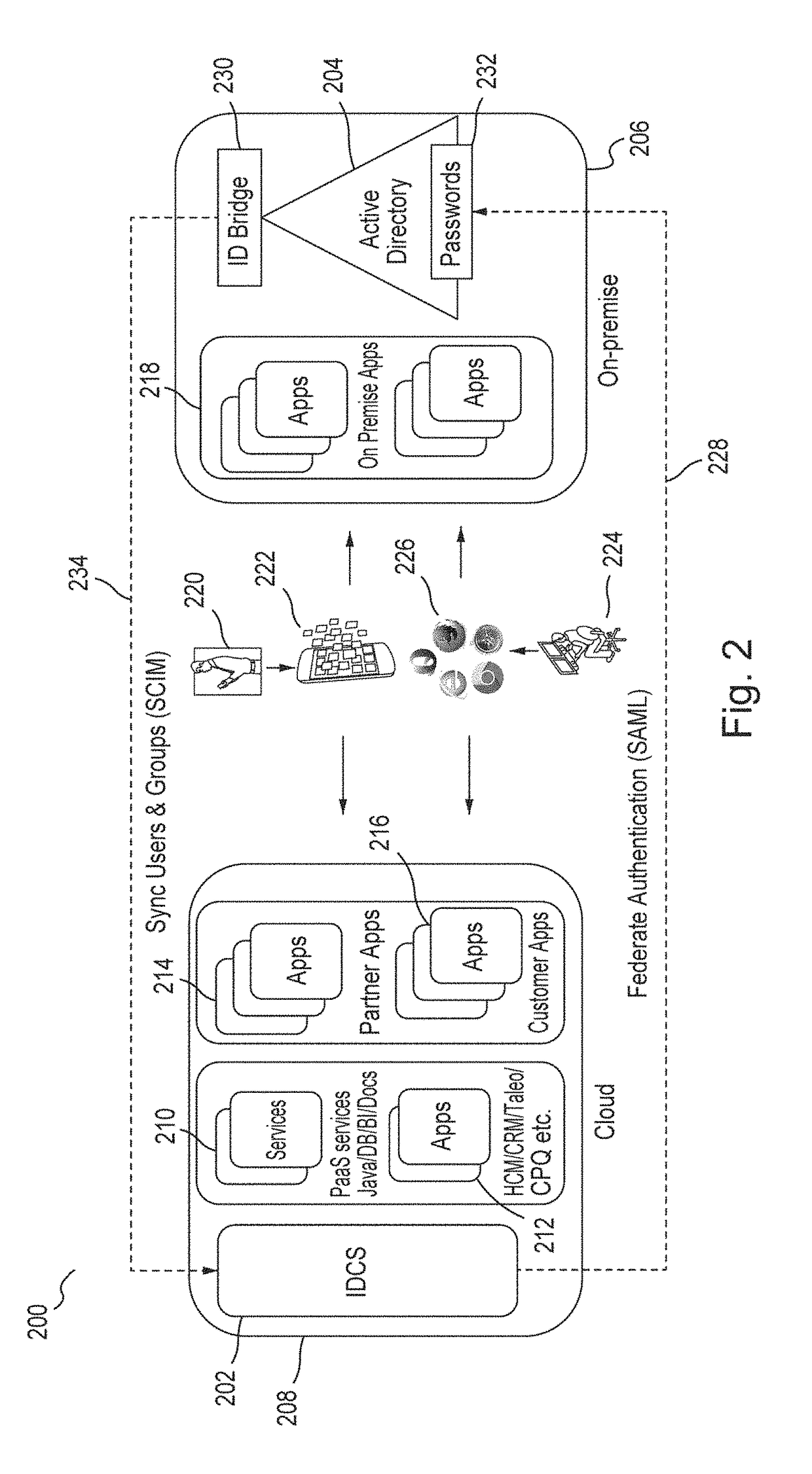
Single sign-on functionality for a multi-tenant identity and data security management cloud service
ActiveUS20180075231A1Digital data information retrievalDigital data authenticationInternet privacyCloud base
A cloud-based identity and access management system that implements single sign-on (“SSO”) receives a first request for an identity management service configured to allow for accessing an application. Embodiments send the first request to a first microservice which performs the identity management service by generating a token. The first microservice generates the token at least in part by sending a second request to a SSO microservice that is configured to provide SSO functionality across different microservices that are based on different protocols. Embodiments then receive the token from the first microservice and provide the token to the application, where the token allows for accessing the application.
Owner:ORACLE INT CORP
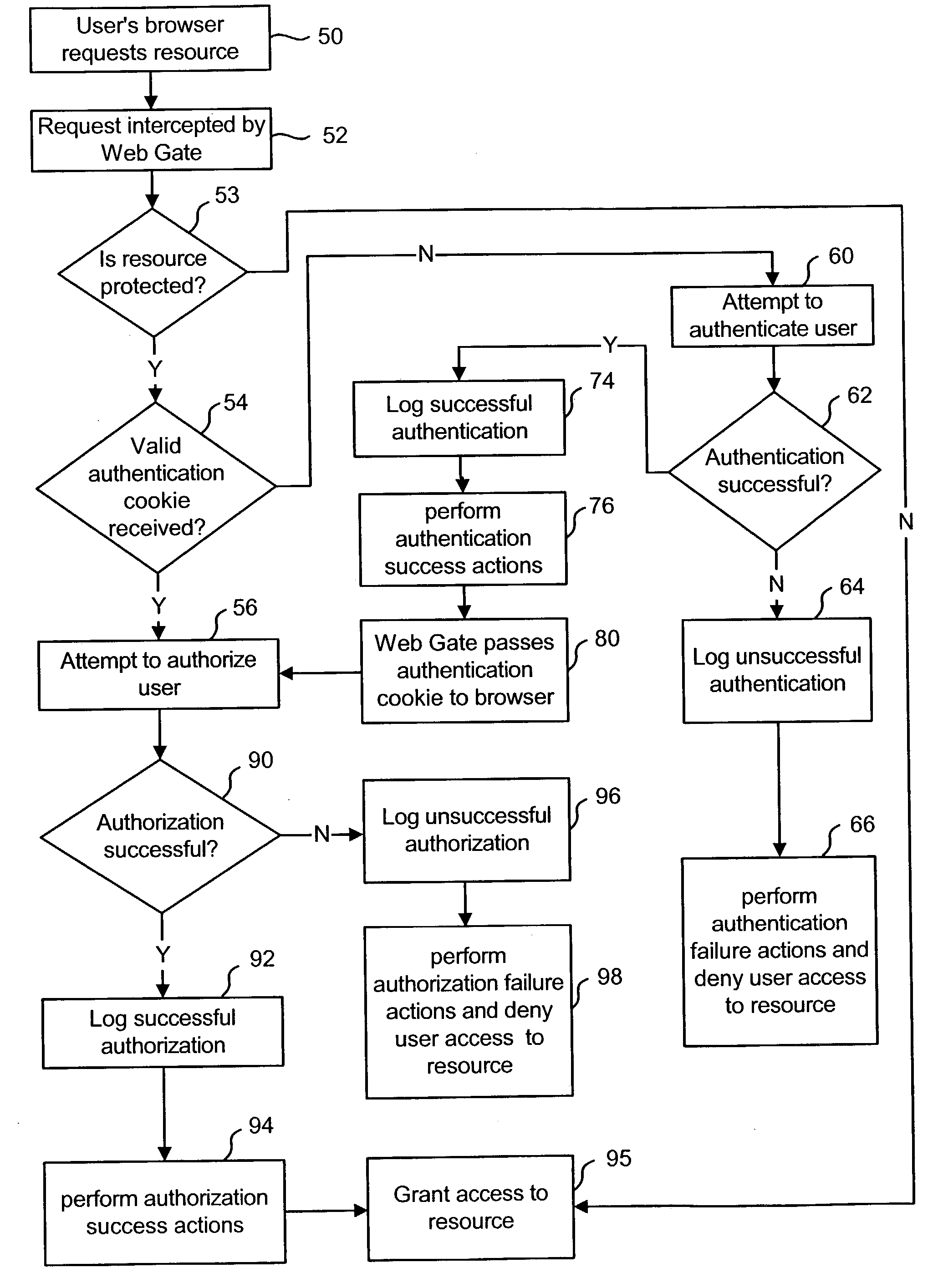
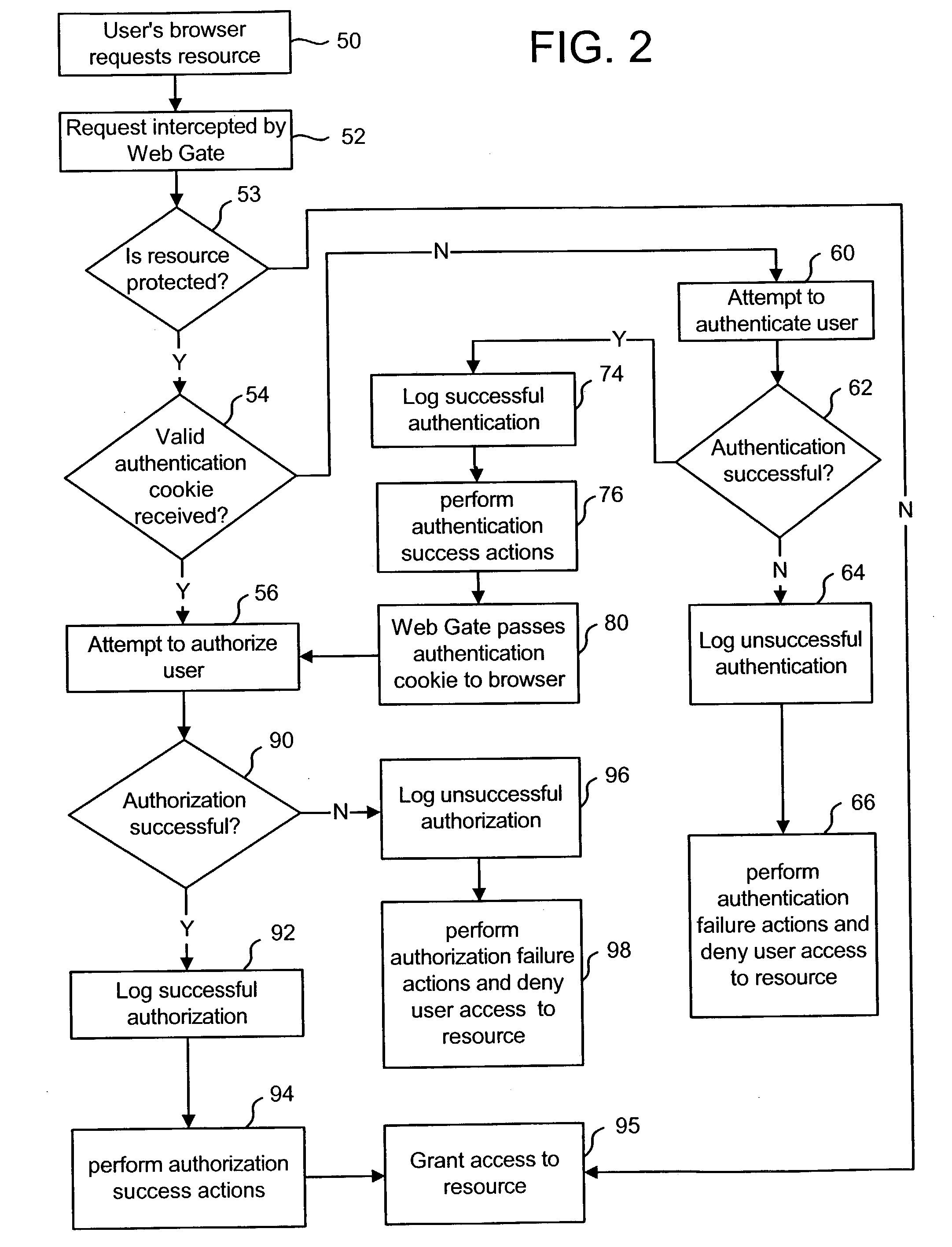
Logging access system events
ActiveUS20020116642A1Easy mappingDigital data protectionSpecial data processing applicationsLibrary scienceAccess management
A system is disclosed that logs access system events. When an access system event occurs, a log entry is created for the access system event. Information from an identity profile is stored in the log entry. The identity profile pertains to a first user. The first user is the entity who caused or was involved with the access system event. In one embodiment, the access system includes identity management and access management functionality.
Owner:ORACLE INT CORP
Method and system for enterprise network access control and management for government and corporate entities
InactiveUS20090254392A1Data processing applicationsComputer security arrangementsNetwork Access ControlIdentity management
A method, system, computer program product, and devices for enterprise network access control and management for Government and Corporate entities, including interagency identity management; connectors and controls; an interagency directory services transformation service; a user / duty position resolving service; role-based encryption key management; role-based business process modeling; and proximity-based access control enabled by user-role-track association.
Owner:ZANDER VAN S
Mobile application, identity relationship management
ActiveUS20130086210A1Multiple digital computer combinationsDigital data authenticationApplication softwareIdentity management
Techniques for managing identities are provided. In some examples, identity management, authentication, authorization, and token exchange frameworks may be provided for use with mobile devices, mobile applications, cloud applications, and / or other web-based applications. For example a mobile client may request to perform one or more identity management operations associated with an account of a service provider. Based at least in part on the requested operation and / or the particular service provider, an application programming interface (API) may be utilized to generate and / or perform one or more instructions and / or method calls for managing identity information of the service provider.
Owner:ORACLE INT CORP
Identity management for open overlay for social networks and online services
ActiveUS7792903B2Multiple digital computer combinationsOffice automationSocial graphIdentity management
Embodiments of the present invention provide methods and systems for managing the multiple identities used by a user. The user's existing contact lists, website accounts, buddy lists, and the like are analyzed to determine the identities used by the user. A graph is then constructed in order to track and integrate the multiple identities of the user in a social network. The social network graph may then be used by a social network overlay so that the user can share information across their different identities with different users that only know some of the user's multiple identities.
Owner:RED HAT
Networked identity framework
ActiveUS20070143860A1Digital data processing detailsUser identity/authority verificationData setInternet privacy
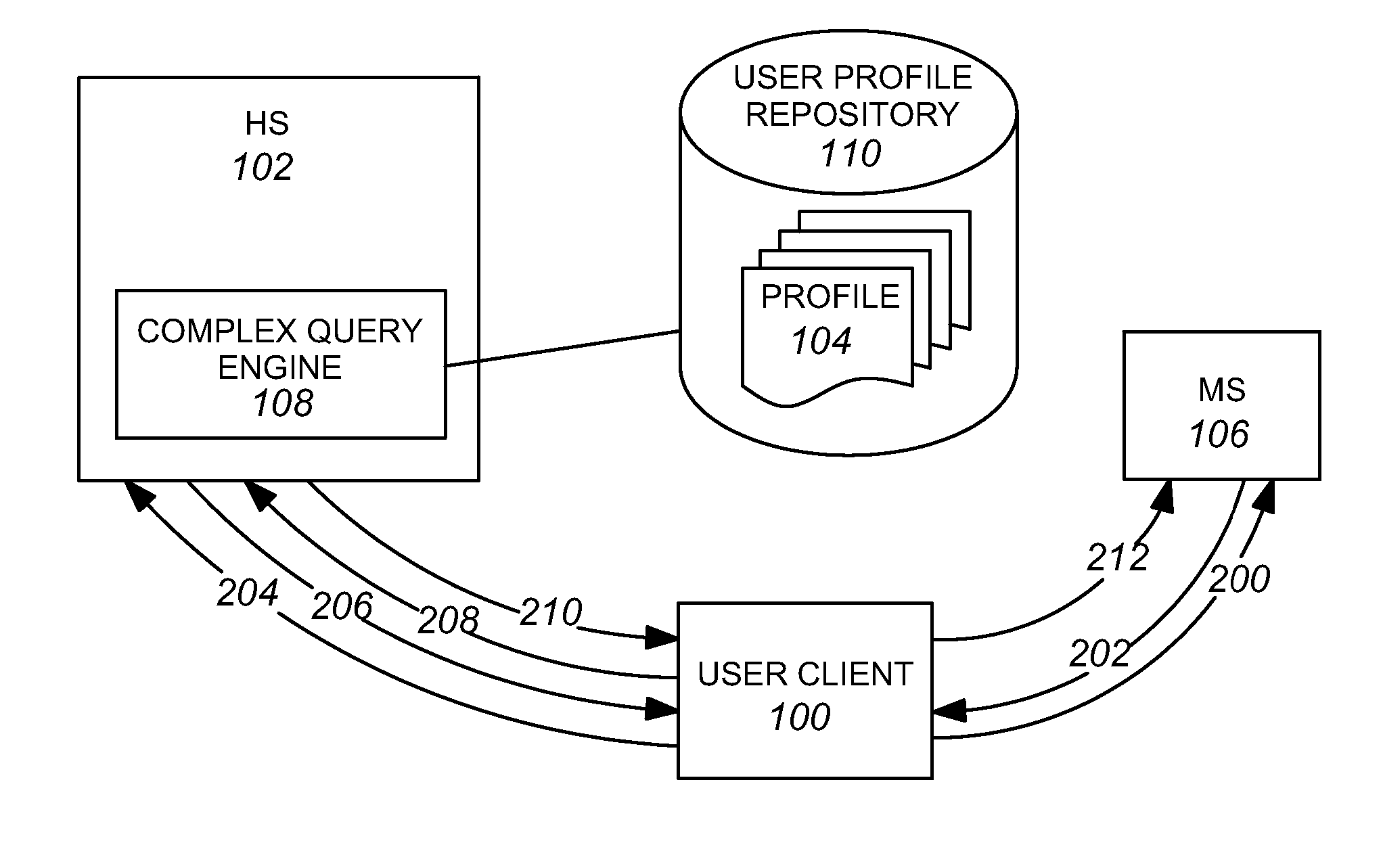
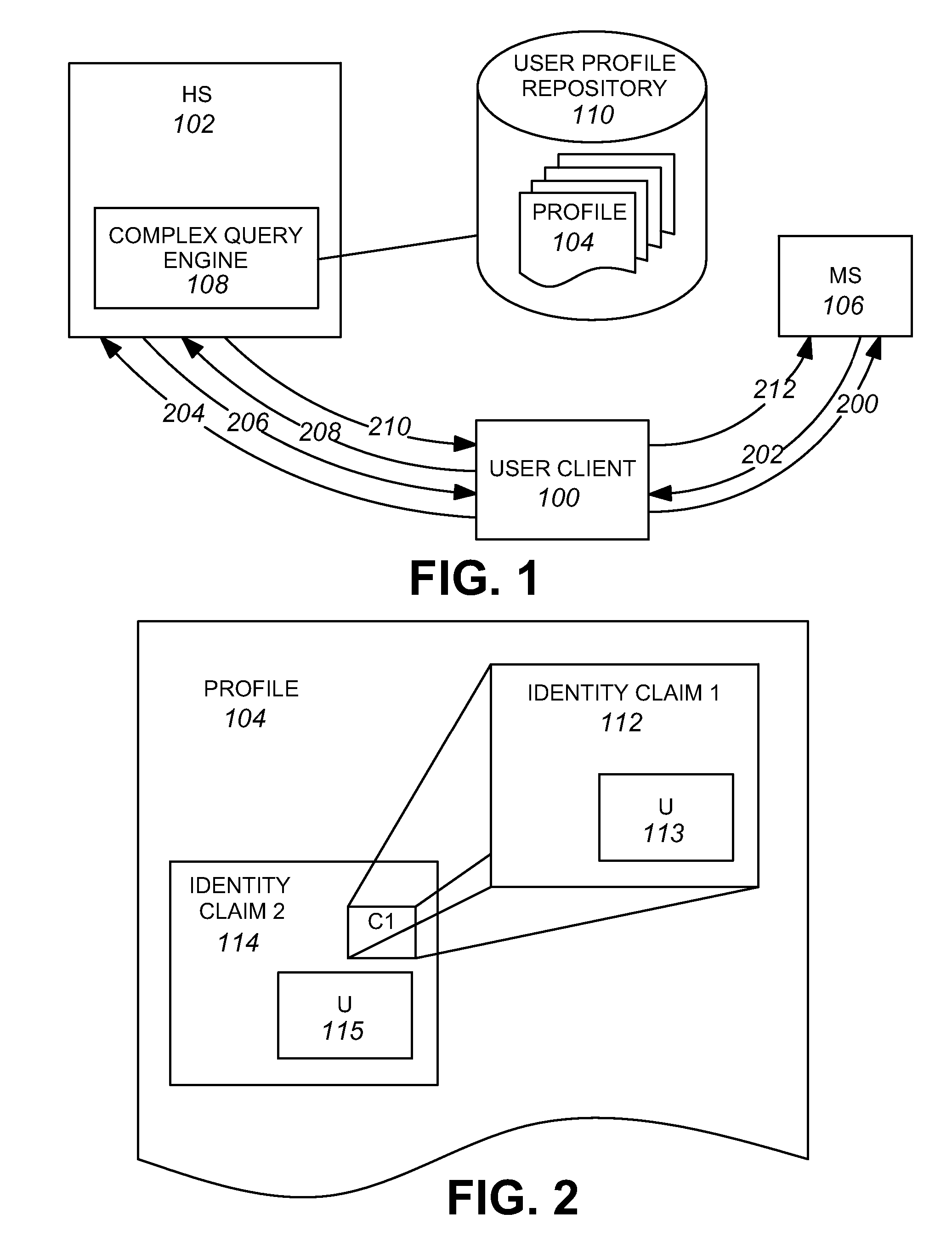
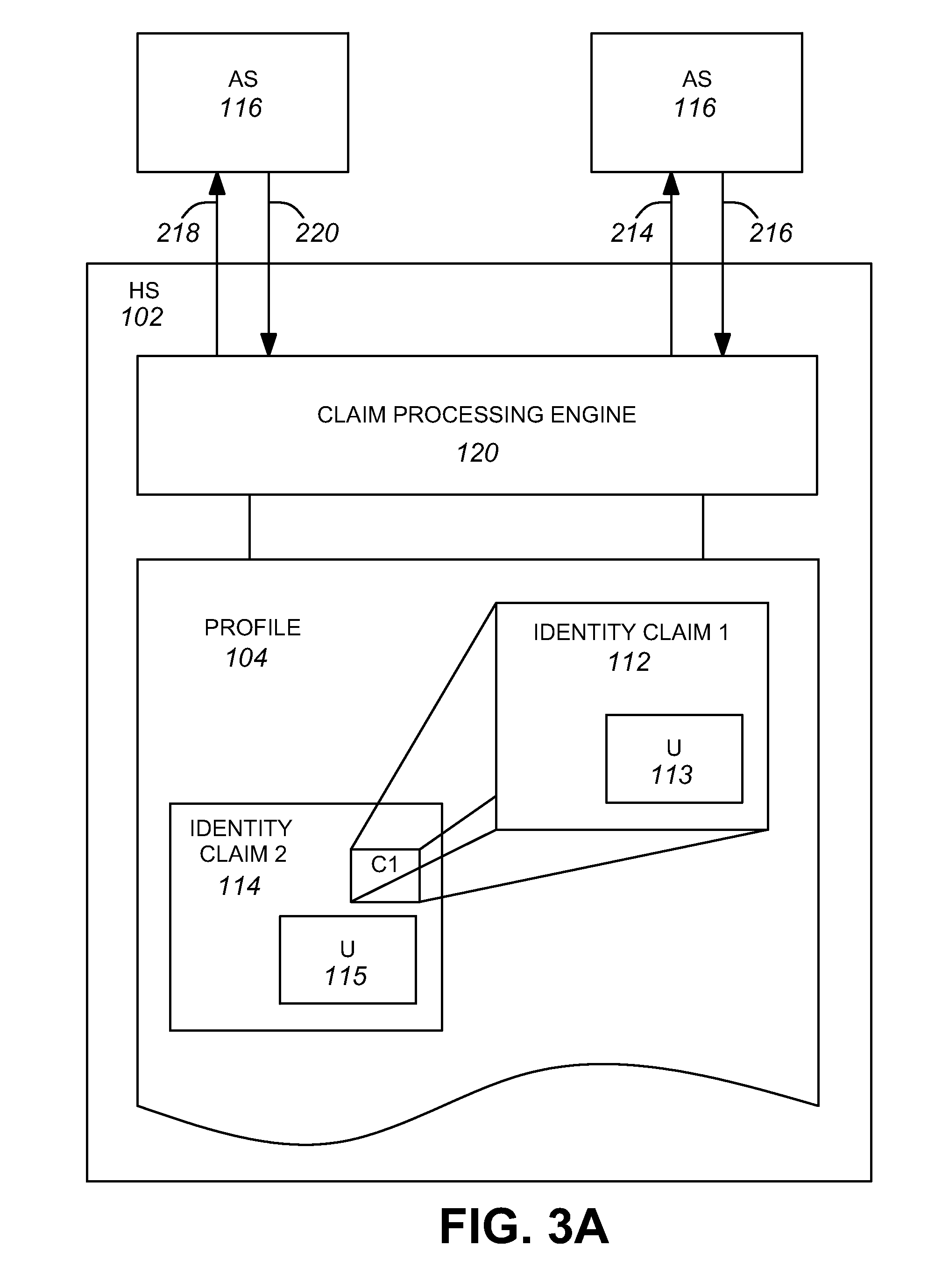
A system and method provide a framework for networked identity management in a user-centric model by providing the ability for a user to delegate permissions to release identity information, by enabling a mechanism for releasing one of a requested plurality of data sets and by providing facilities for the retrieval of identity information from an external server. Anonymization of identity data is enabled through the use of an anonymizer system that can optionally be integrated with an identity store such as a homesite.
Owner:CALLAHAN CELLULAR L L C +1
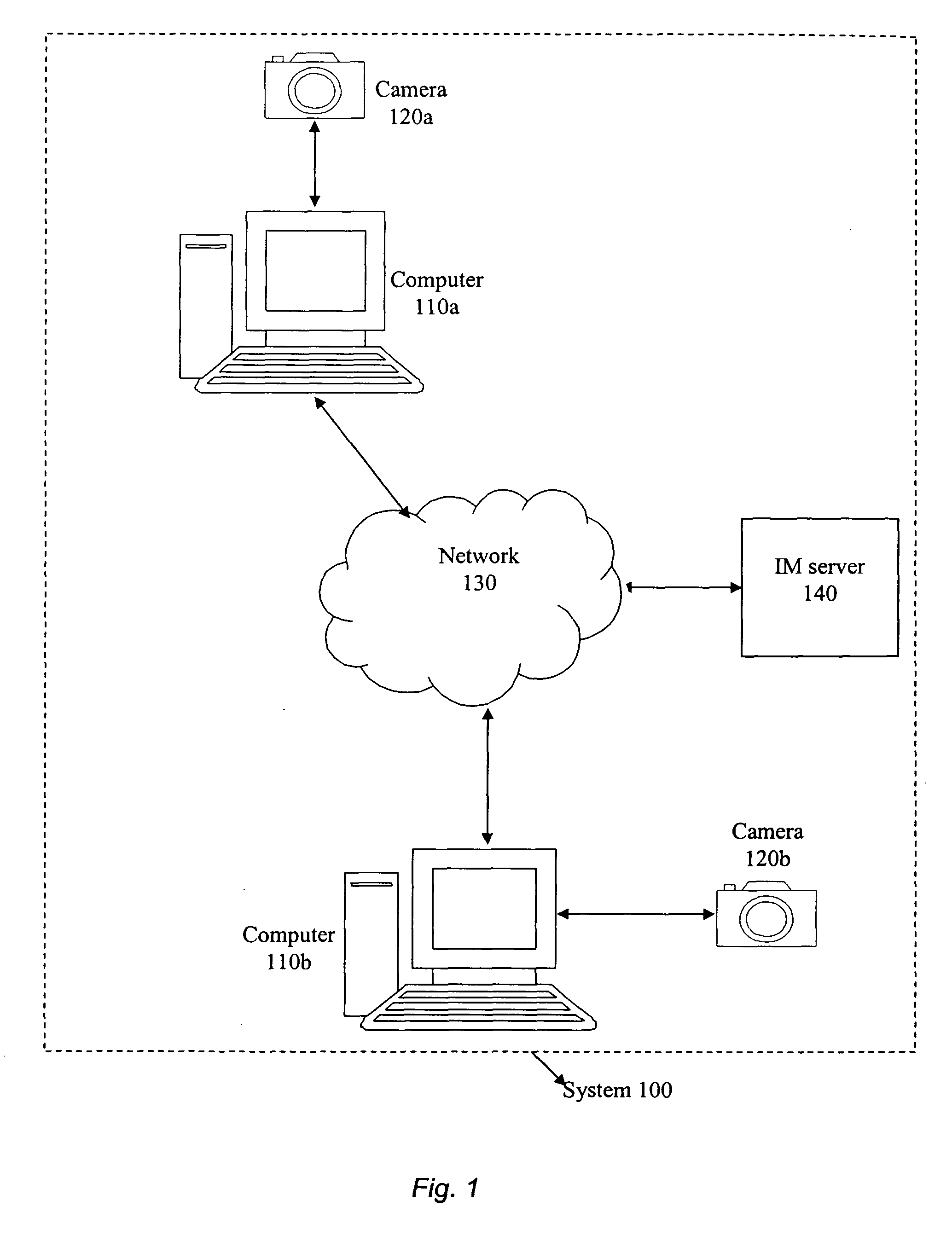
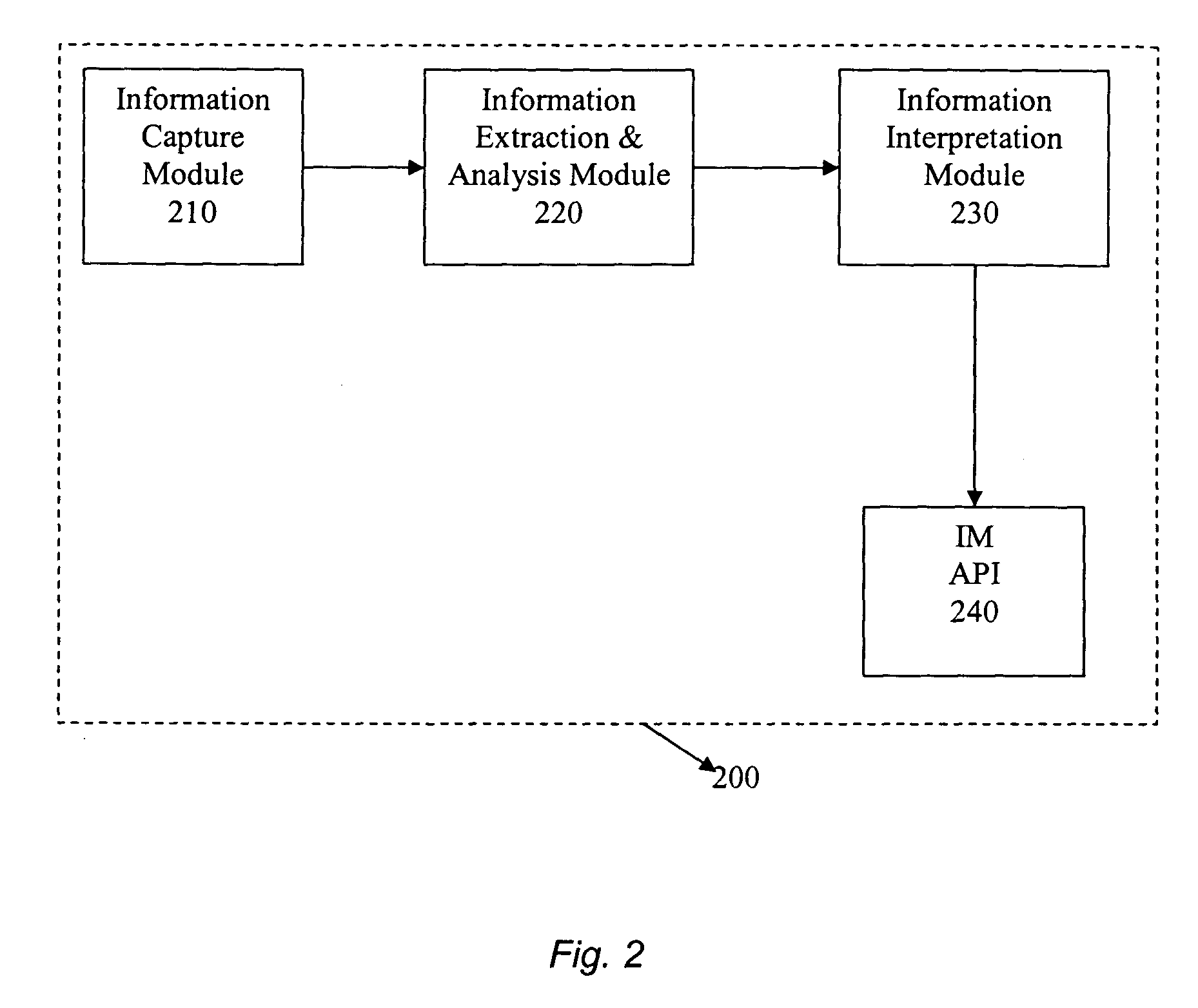
Instant messenger presence and identity management
InactiveUS20050044143A1Accurate and reliable detectionCharacter and pattern recognitionChecking apparatusRelevant informationAnalysis data
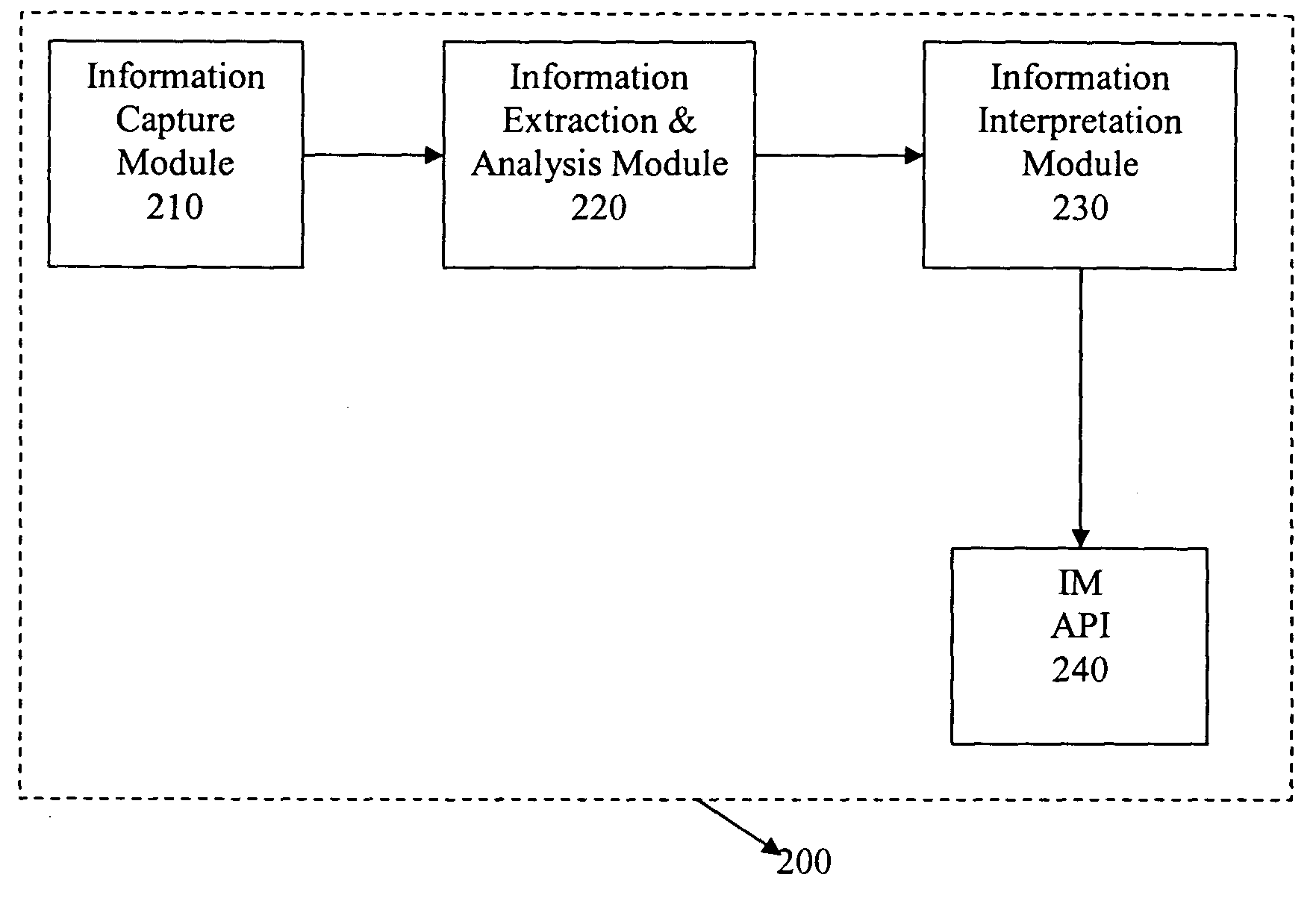
The present invention provides a method and system for reliable and accurate presence / status management and identity detection in Instant Messaging (IM) applications by using video, still image, and / or audio information. In one embodiment, a device such as a camera captures still image, video, and / or audio data. Relevant information is then extracted from the captured data and analyzed. Known techniques such as face recognition, face tracking, and motion detection, can be sued for extracting and analyzing data. This information is then interpreted for the IM application, and provided to an Application Programs Interface (API) for the IM application. The API can use the information for various purposes, including updating the status of the user (e.g., available, busy, on the phone, away from desk, etc.) and updating the identity of the user.
Owner:LOGITECH EURO SA
Shared view of customers across business support systems (BSS) and a service delivery platform (SDP)
ActiveUS20090112875A1Overcome deficienciesDigital data processing detailsDatabase distribution/replicationData aggregatorCustomer information
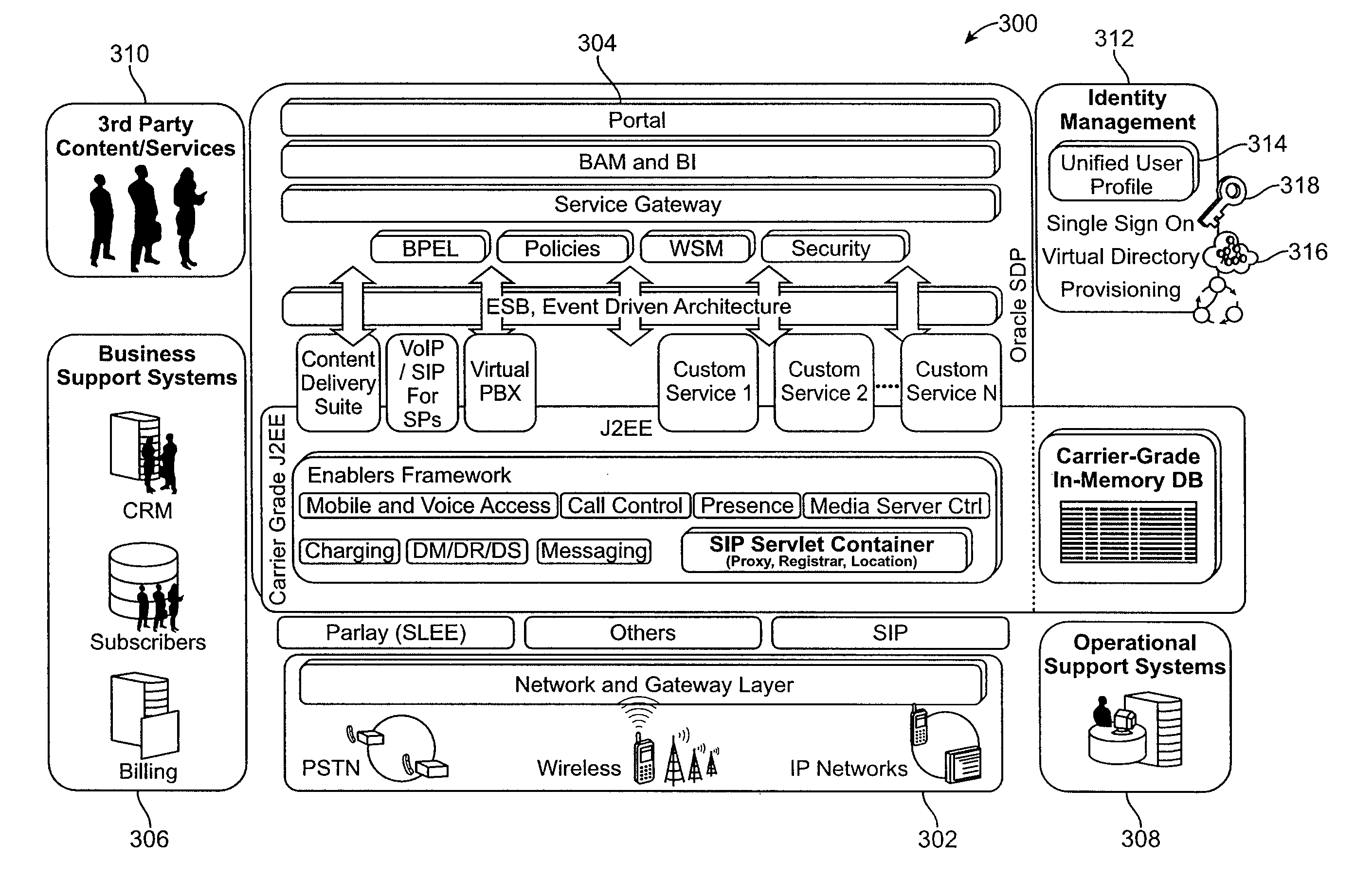
An identity management tool provides identity management across multiple domains, providing a single access point not only for information for runtime, network, and service layer information, but also for systems such as business support systems (BSS), operational support systems (OSS), and third party systems. The identity management tool creates a unified user profile that maps customer identities across the various domains, and presents the information in a virtual directory wherein the information appears to come from a single source, creating a central data hub for the various systems. This aggregation provides for the same experience and service across various access networks and using various channels. Such an architecture allows billing and service information to be shared with subscription and customer information, even though the data is substantially unrelated data from disparate data sources, without the need to combine schemas or aggregate the data into a single data store.
Owner:ORACLE INT CORP
Identity management user experience
InactiveUS20060224611A1Digital data processing detailsComputer security arrangementsInternet privacyIdentity management
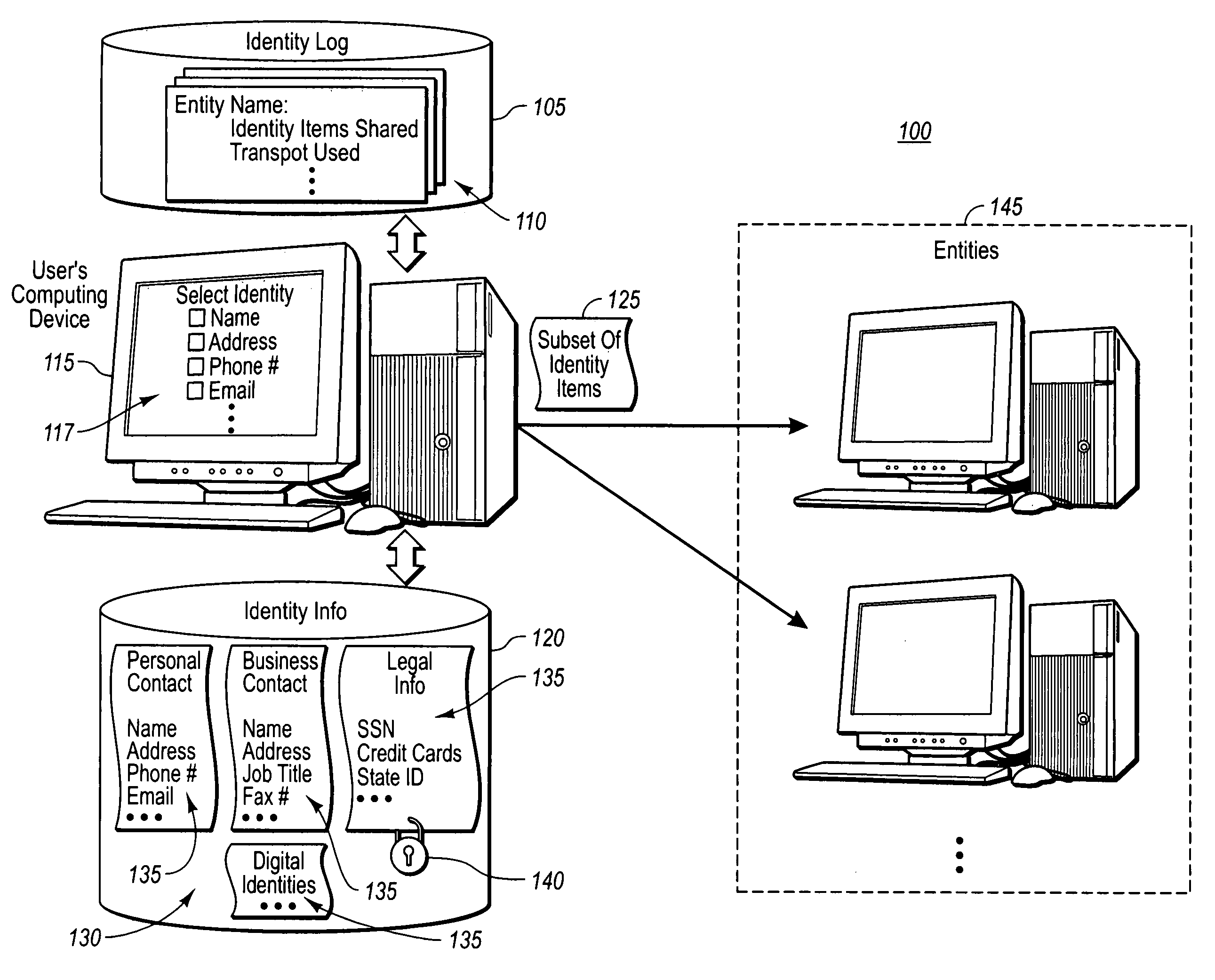
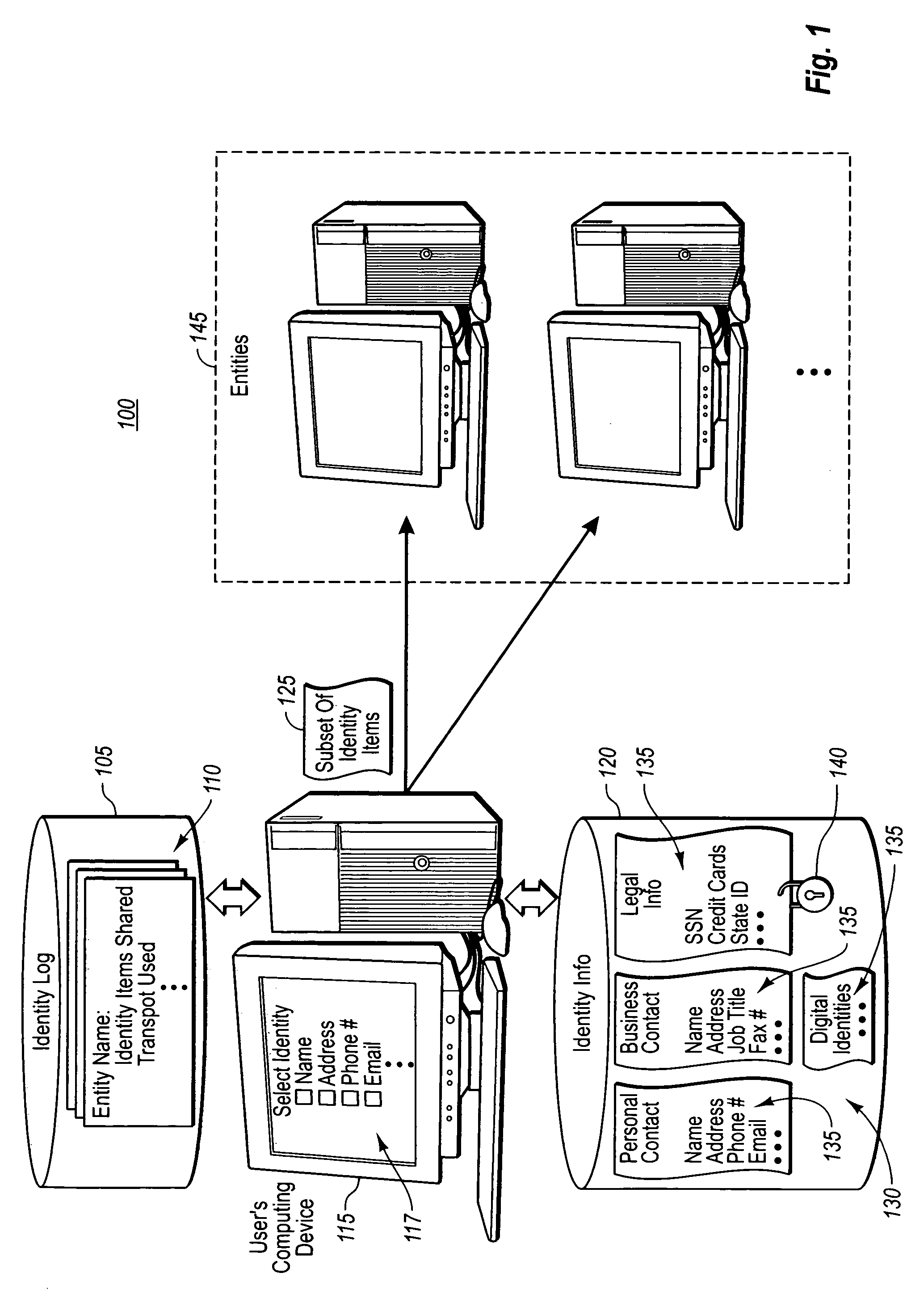
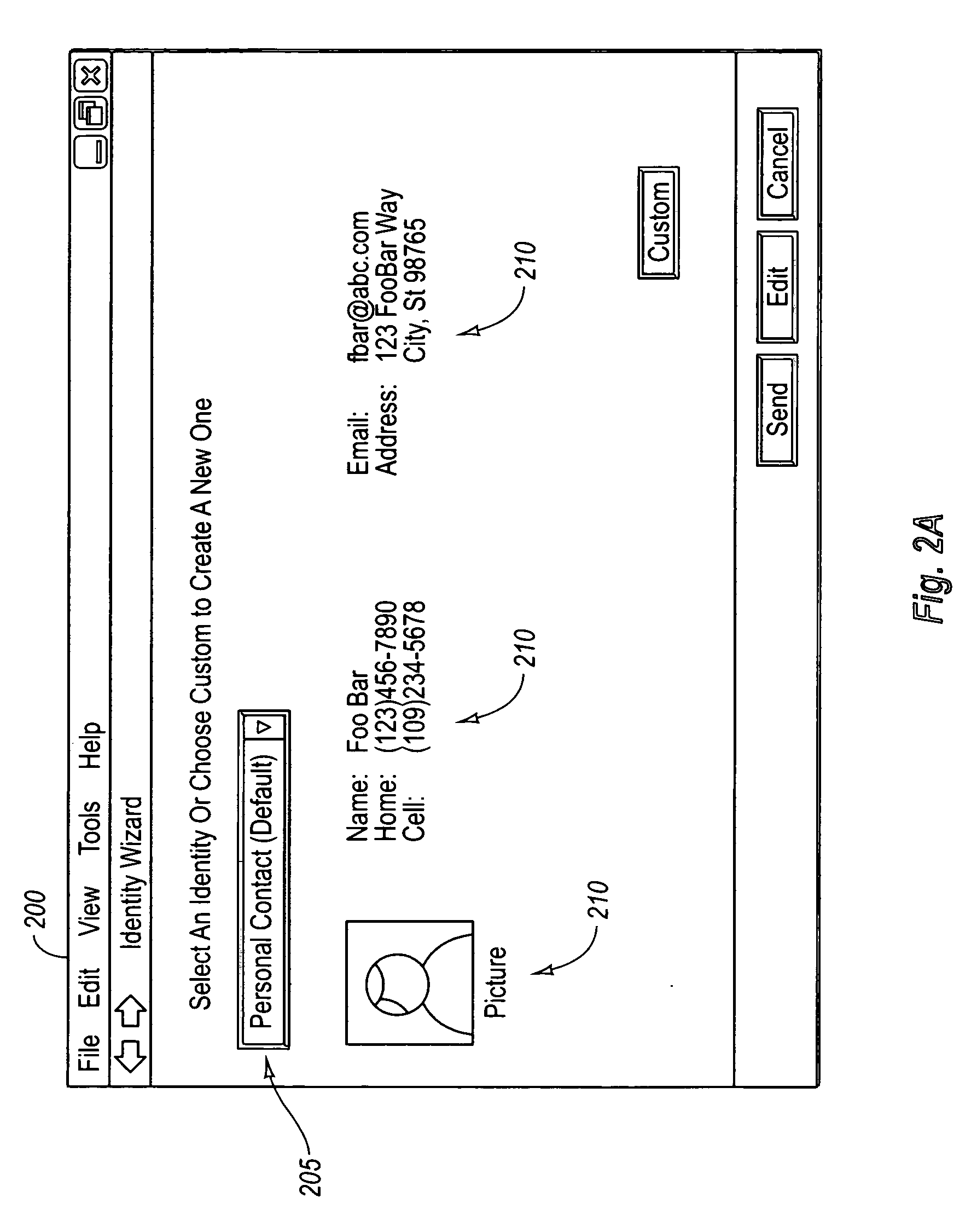
Example embodiment of the present invention provide for assisting a user in managing the user's shared persona on a request-by-request basis. Upon requesting to share one or more types of identity information, the user is automatically presented with an interface through which the user can interact in selecting an amount of identity items to share. A subset of the total identity items selected may then be shared with specified entities. In another embodiment, the present invention assists a user in managing identity information that has been shared with others by providing the user with a visual list of entities for which the user has shared specified identity information. Other embodiments of the present invention use shared information about an entity to automatically provide the user with the ability to update identity information that has subsequently been edited.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for providing identity template management as a part of a marketing and sales program for universal life stage decision support
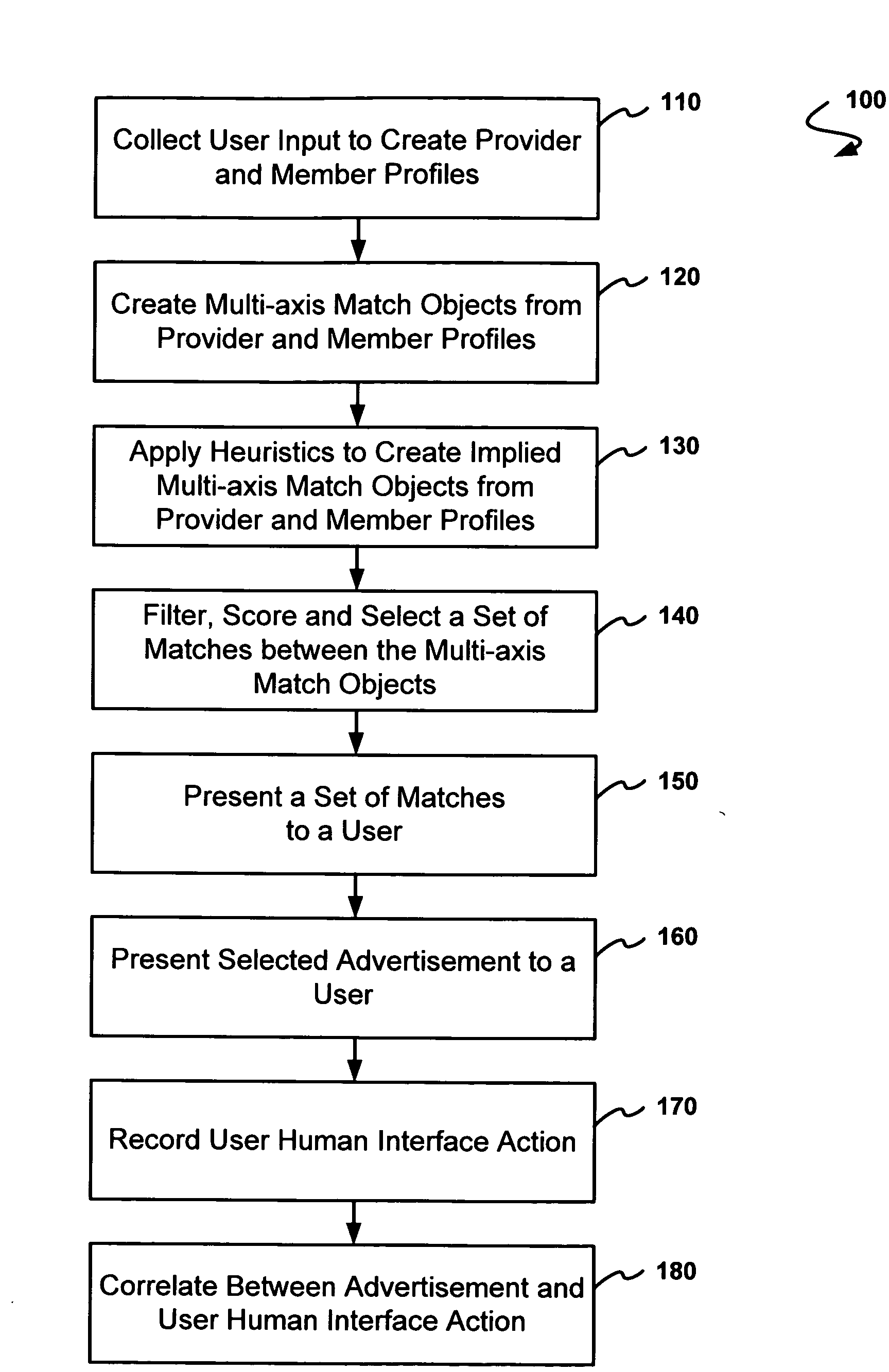
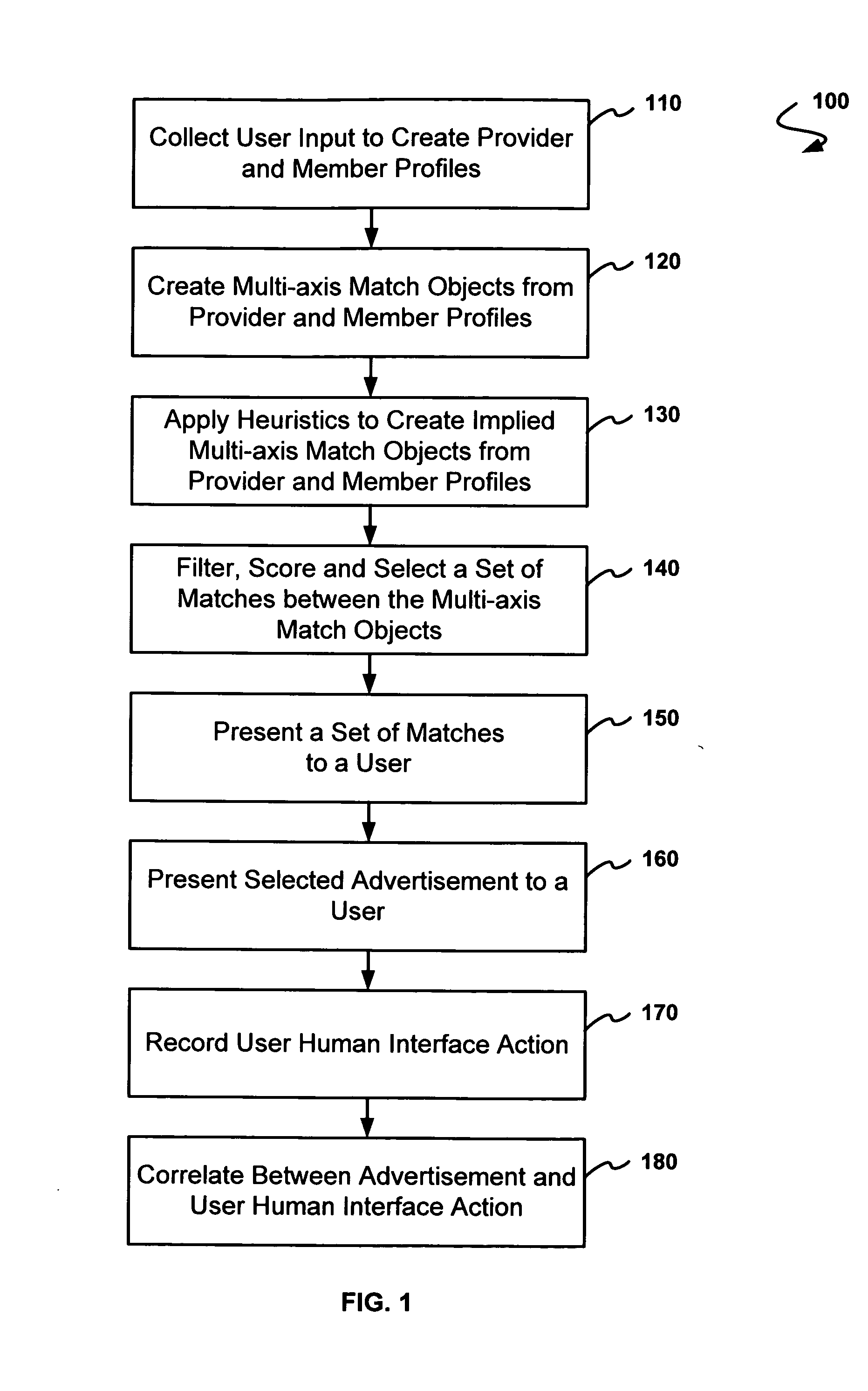
A method for dynamic identity template management as a part of a marketing and sales program for universal life stage decision support. A user-defined template can be shared (pushed) to other networks, and template fields can be dynamically populated (pulled) from other networks; thus a template can grow in extensible dimensions, as well as become automatically updated. Also disclosed are techniques for be-friending based on identity template field matching, and for matching user's needs to service providers by collecting user input in profiles, creating multi-axis match objects from the profiles, and applying heuristics to create scored matches between profiles. Techniques for dynamic management of the identity profiles include defining extensible profile fields, launching automated agents corresponding to the extensible fields, and recording reported action from the automated agents. Users may create and manage permissions to permit other users or third party agents to populate information in a user-defined identity profile.
Owner:UNIVERSAL PASSAGE
Method and system for managing user identities on a network
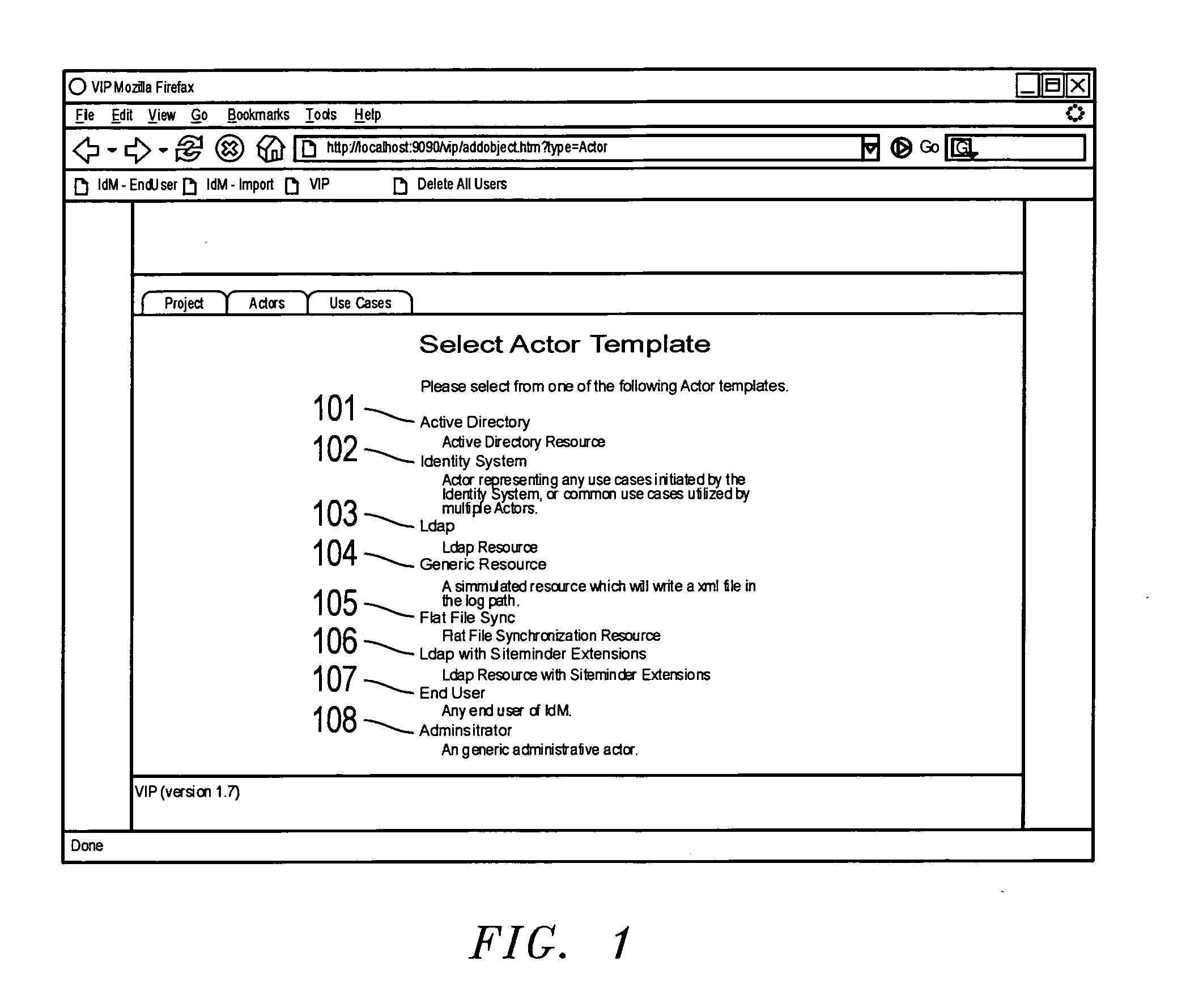
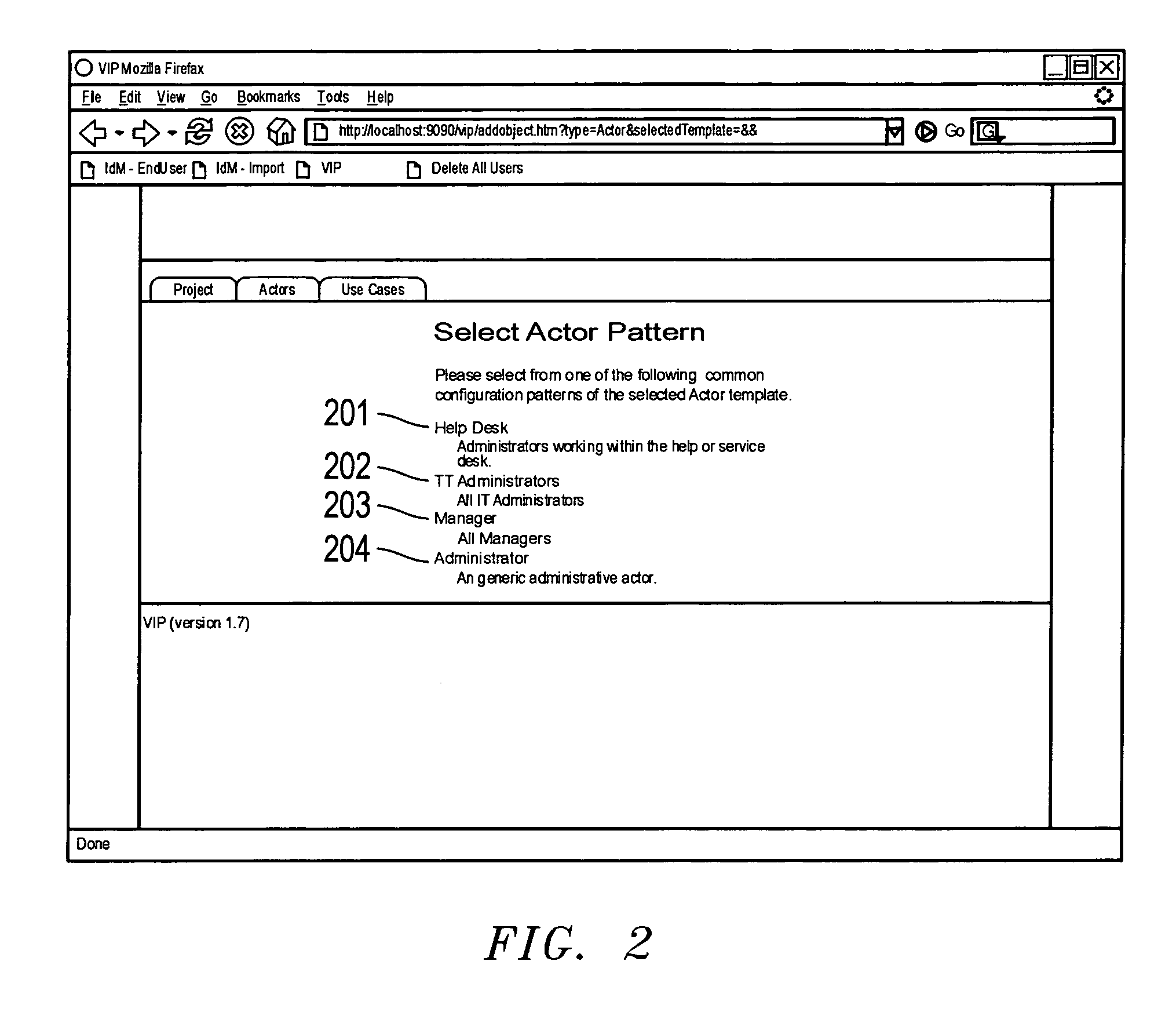
InactiveUS20070174903A1Low costImprove efficiencyDigital data processing detailsUser identity/authority verificationSkill setsIdentity management
A method and system for managing user identities on a network is disclosed. form independent model for managing user identities on a network is disclosed which translated to one or more platform-specific models for the actual implementation. An trator is provided with the ability to add, modify and delete actors on the network. or, such as a help desk, is ascribed use cases, such as enabling passwords, resetting s, and disenabling passwords, that are appropriate for that actor. The administrator modify each use case, such as by unlocking a user's account before resetting the d or providing an email notification to a user prior to resetting a password, to the desired by the administrator. As a result, an actor with no or little programming skills form sophisticated identity management functions resulting in improved efficiency and lower cost to the company.
Owner:SUN MICROSYSTEMS INC
Distributed contact information management
ActiveUS20060005263A1Data taking preventionDigital data processing detailsInternet privacyWeb service
A method and system for interaction with webservices and for performing distributed contact management use standard interfaces to communicate with other entities in an identity management network. The use of homesites as user data stores allows for homesite to homesite communication to allow for distributed contact management, and the generic interface allows for homesite to webservice interaction.
Owner:BLAME CANADA HLDG
Rule based data management
ActiveUS20040010519A1Digital data information retrievalData processing applicationsDynamic populationFiltering rules
Data is acquired for an Identity System based on a one or more rules. The data can be from the same Identity System Component, another Identity System Component or a component external to the Identity System. The acquired data can be used to populate an Identity Profile, configure a workflow, or provide information to any other object, process, component, etc. of the Identity System. In one embodiment, the present invention combines dynamic identity value substitution and directory filter rules to enable rule based identity management. It enables dynamic population of identity data and real-time routing for identity management workflows. In other embodiments, the present invention can be applied to systems other than Identity Systems.
Owner:ORACLE INT CORP
Methods and apparatus for optimizing identity management
InactiveUS20060174350A1Easy accessDigital data processing detailsUser identity/authority verificationIdentity managementComputer science
Owner:NAVIO SYST
Zero down time upgrade for a multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request for performing an identity management service. The request identifies the service and a current version of a microservice. The current version of the microservice is in a first stateless middle tier in a first topology that includes a first web tier. The system performs the identity management service by the current version of the microservice using tenant data stored in a database. The system then determines an upgrade to be applied to the microservice, and deploys a second topology that implements the upgrade. The second topology includes a second web tier and a second stateless middle tier including a new version of the microservice. The system tests the new version of the microservice in the second topology using test data stored in the database, promotes the second topology, and drains and shuts down the first topology.
Owner:ORACLE INT CORP
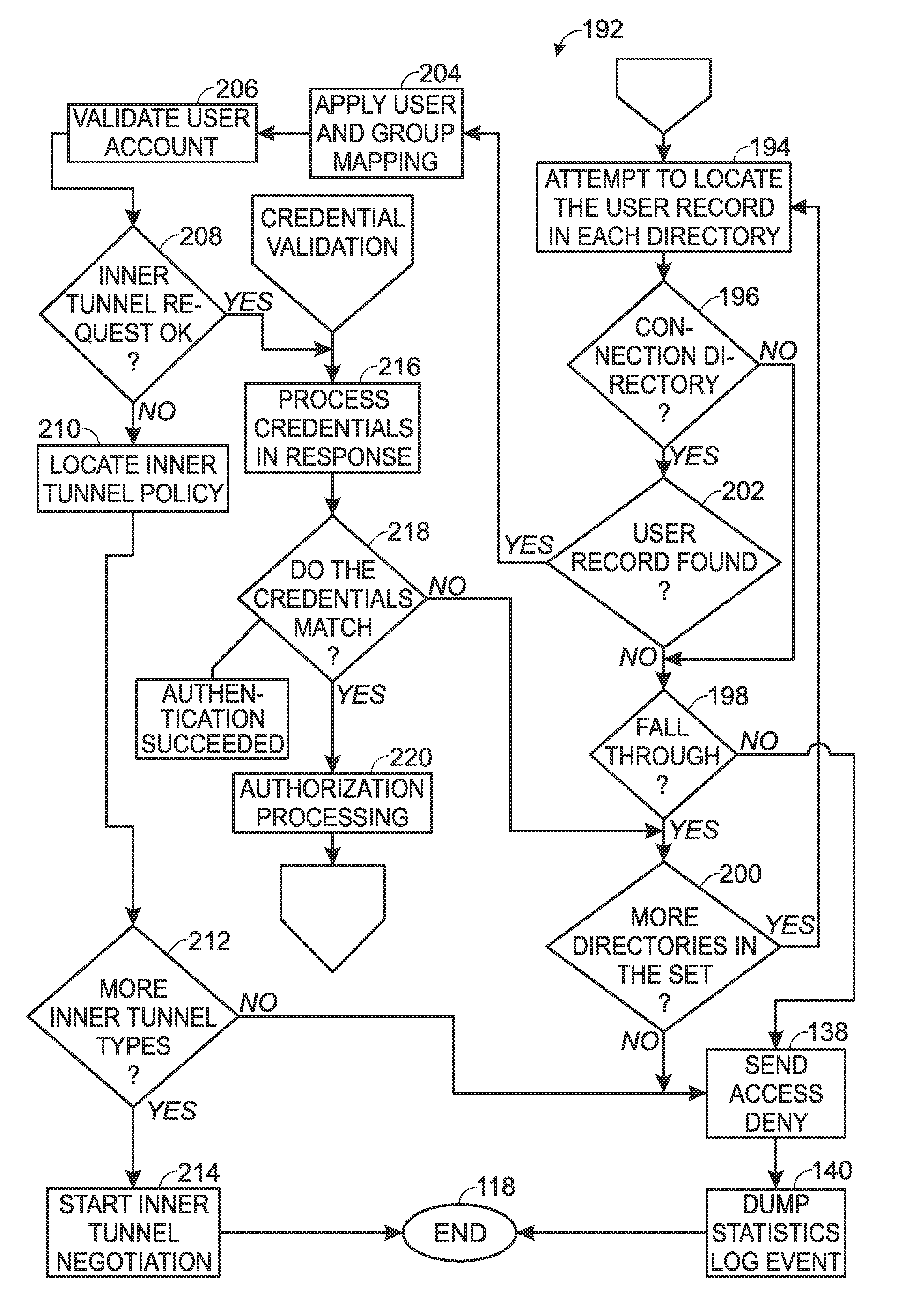
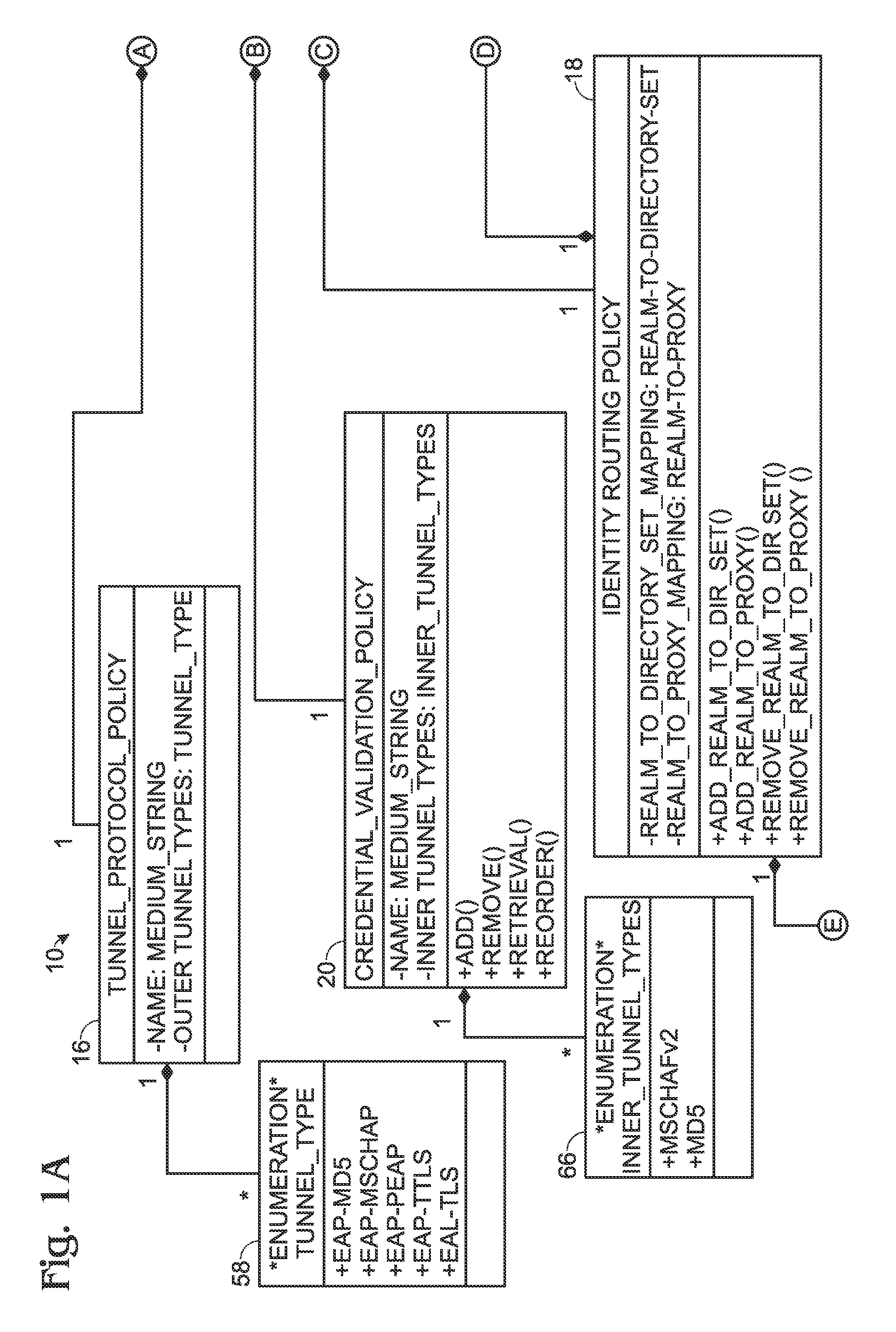
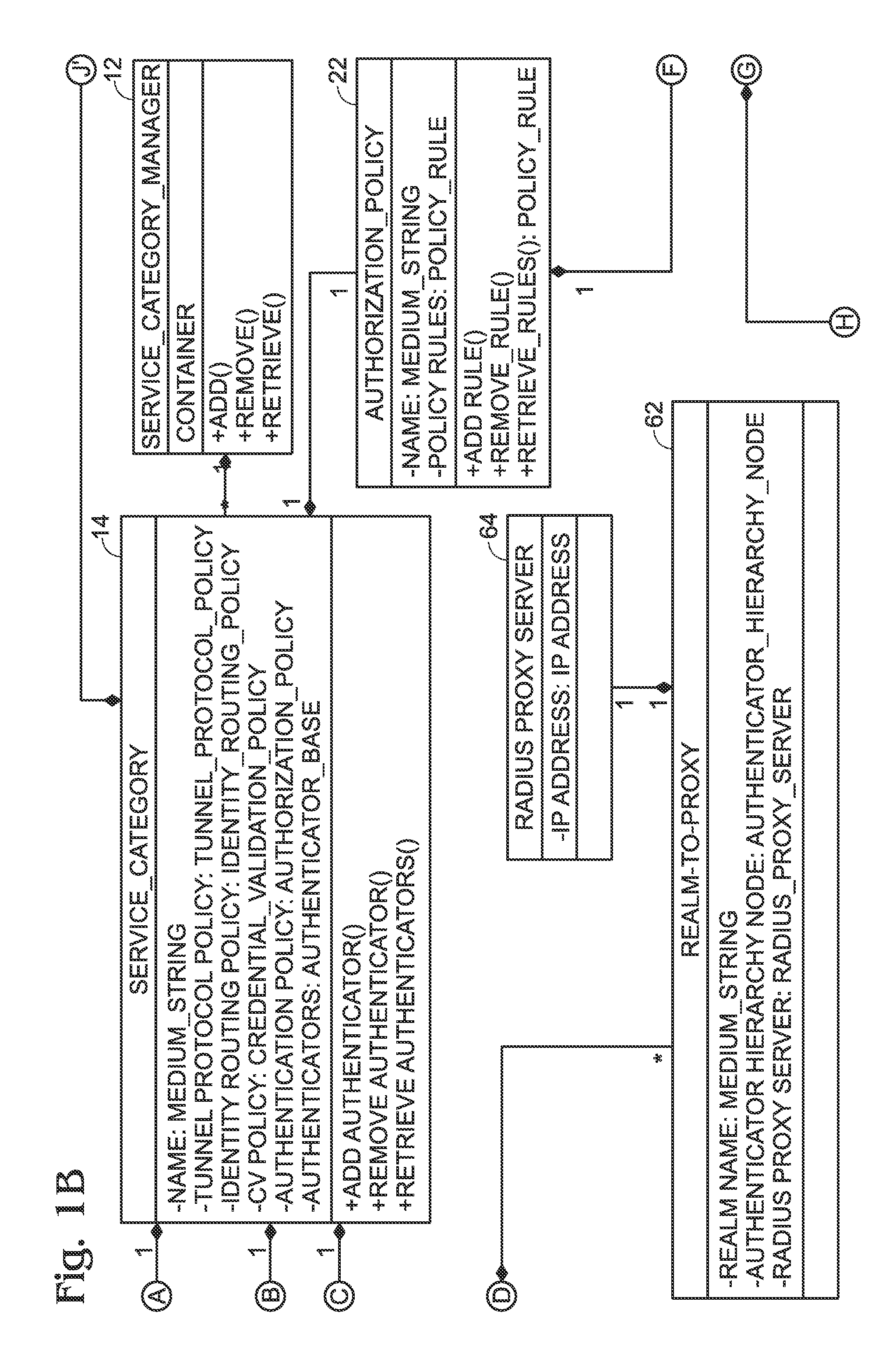
Segmented Network Identity Management
A service category associates a set of authenticators and a set of authentication and authorization policies. When an authenticator attempts to connect the network, the service category for such authenticator determined and the authentication and authorization policies applied. A feature of the present invention is that these policies are segmented into several sub-policies to support multiple services and apply different authentication and authorization policies for each type of service. These sub-policies are a tunnel policy, a credential validation policy, in inner tunnel policy and an authorization policy. Successful negotiation of each policy allows the authenticator to connect a network.
Owner:RPX CLEARINGHOUSE +2
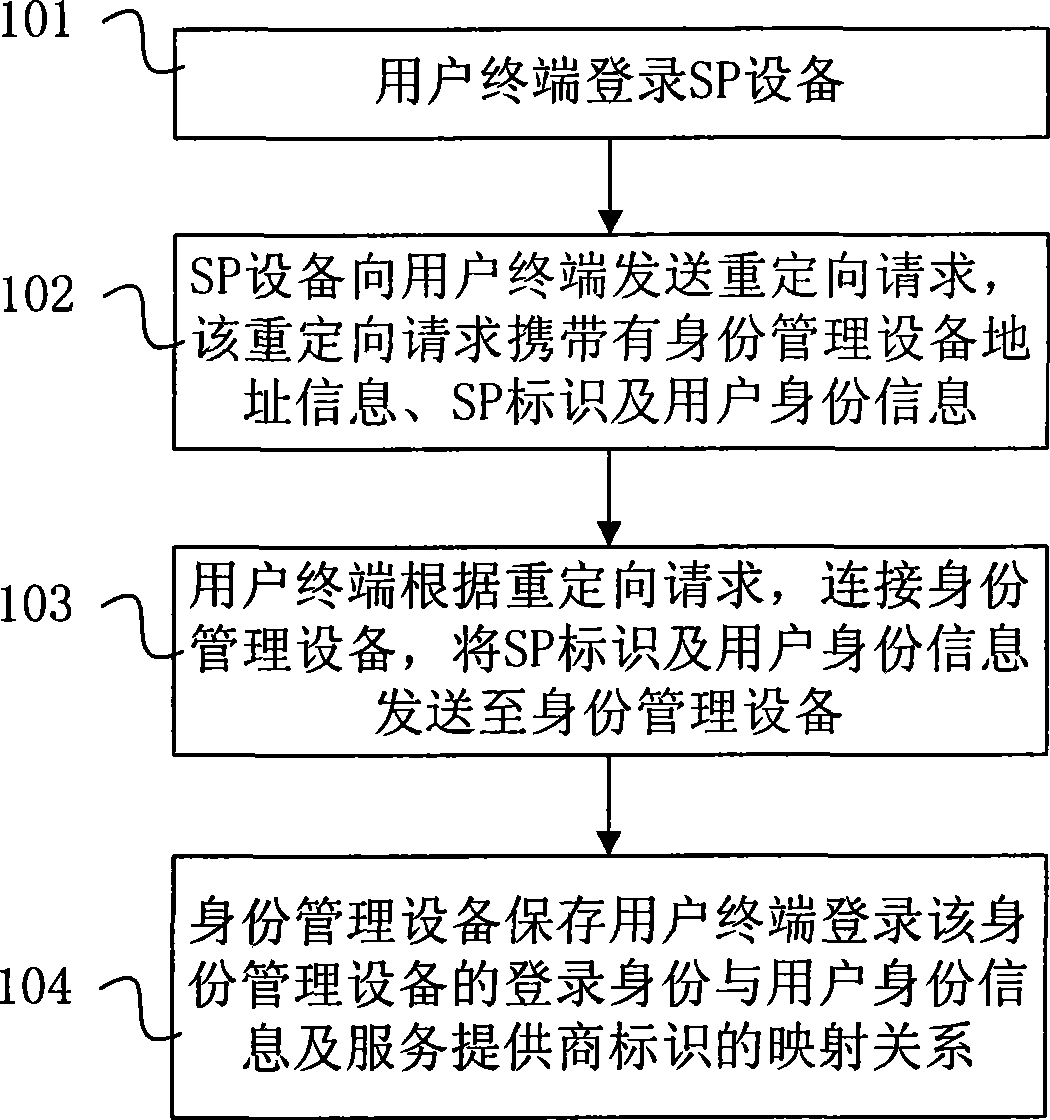
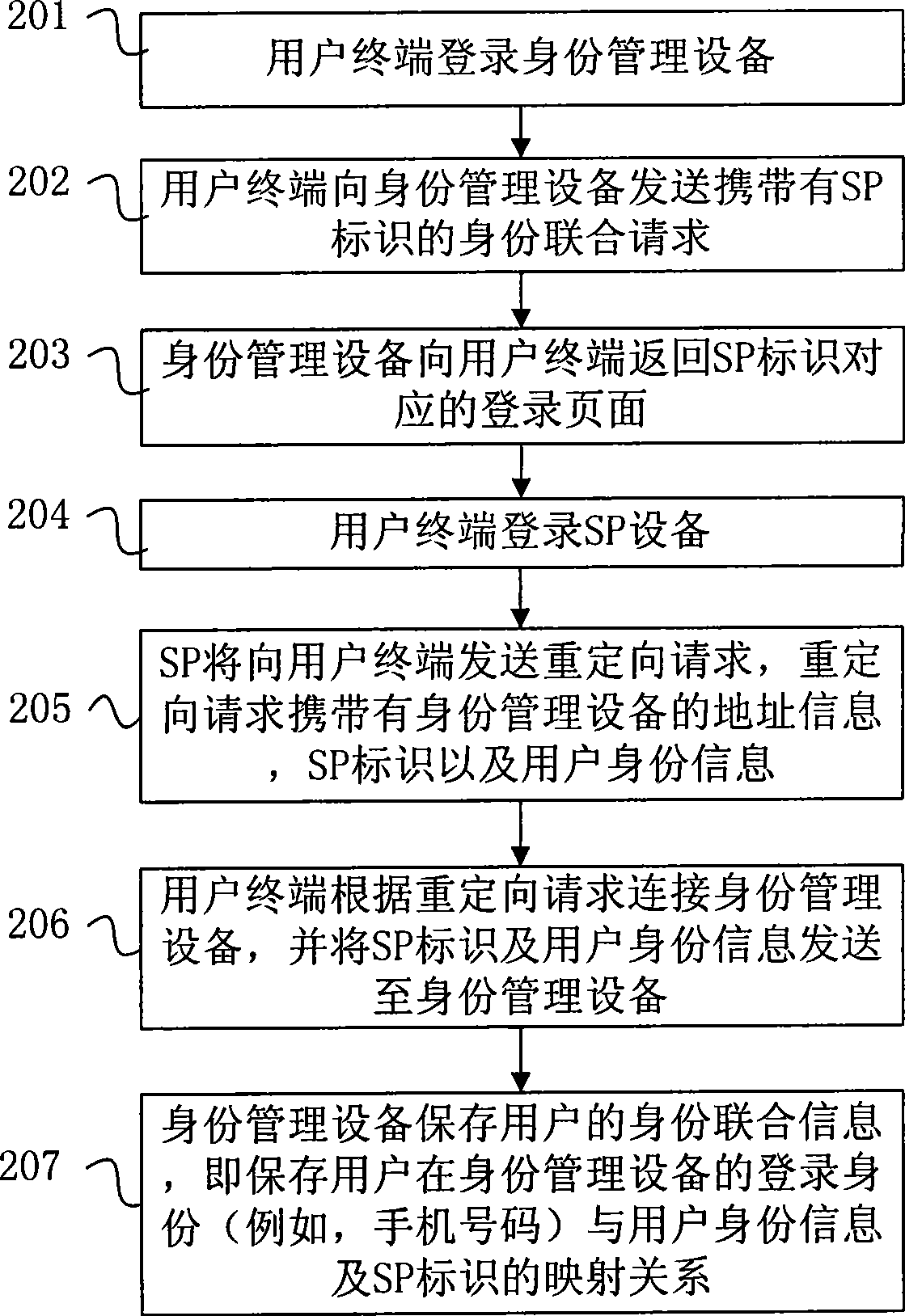
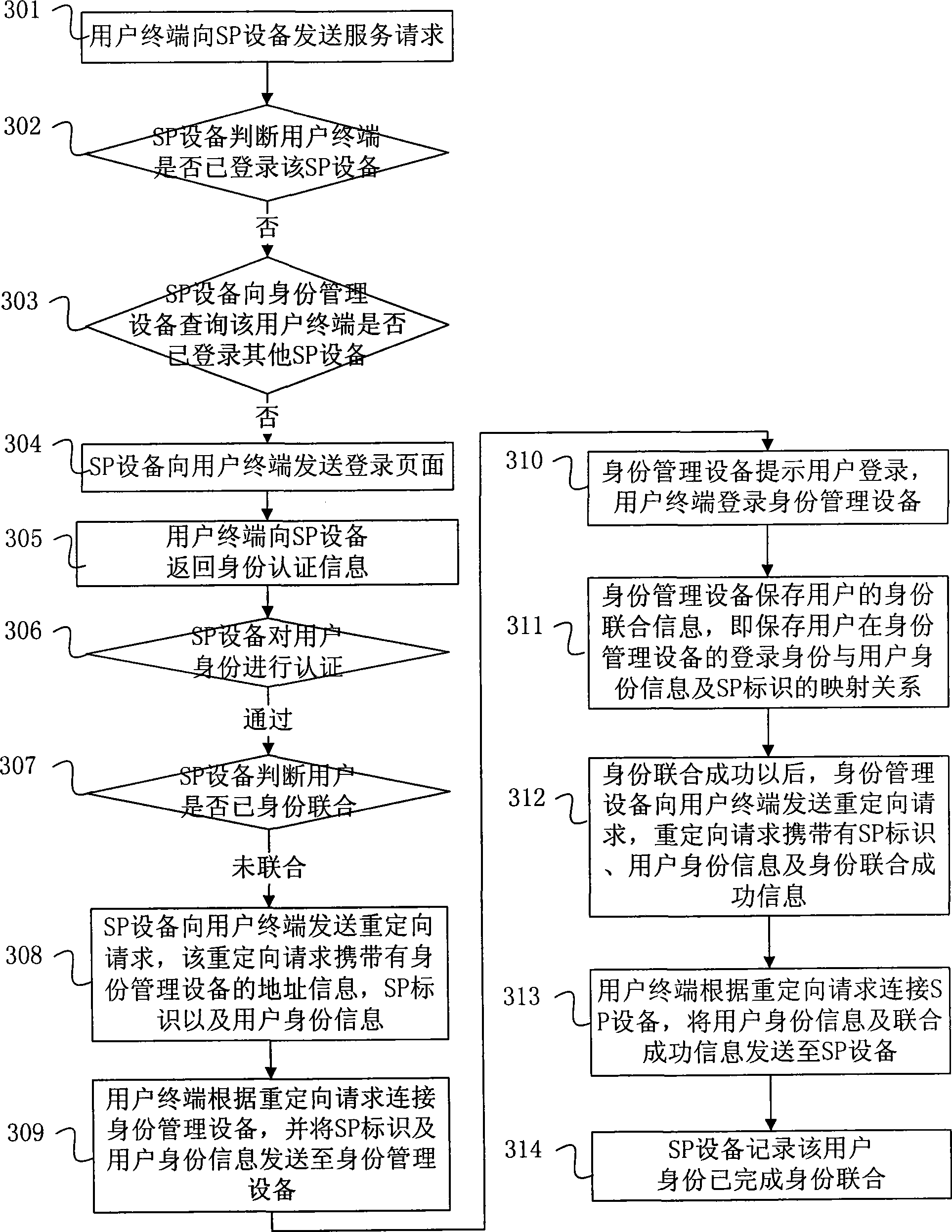
Identity combination method
ActiveCN101399813ARealize unified loginTransmissionSpecial data processing applicationsSoftware engineeringIdentity management
The invention relates to an identification joint method and comprises user terminal login service provider equipment which sends a redirection request to the user terminal, wherein, the redirection request carries identification management equipment address information, a service provider mark and user identification information; the user terminal connects the identification management equipment and sends the service provider mark and the user identification information to the identification management equipment according to the redirection request; and the identification management equipment preserves the mapping relationship among the login identification of the user terminal login identification management equipment, the user identification information and the service provider mark. The invention realizes the establishment of the mapping relationship between the user identification on a plurality of SPs and the identification on the identification management equipment; by using the mapping relationship, when the user logins the identification management equipment or a SP and then accesses other SPs, the identification management equipment can inquire and obtain the identification information of the user on other SPs, thereby realizing united login.
Owner:CHINA MOBILE COMM GRP CO LTD +1
Generating derived credentials for a multi-tenant identity cloud service
A multi-tenant system that provides cloud-based identity management receives a request to execute a job, where the job has a scheduled start time, or a timeframe to complete, that exceeds the validity time of a request access token. The system generates the request access token corresponding to the job, where the request access token has access privileges. The system schedules the job and persists the request access token. The system triggers the job at the scheduled start time and generates a derived access token based on the request access token, where the derived access token includes the access privileges. The system then injects the derived access token during runtime of the job and calls a microservice using the derived access token to execute the job.
Owner:ORACLE INT CORP
System and method for providing user authentication and identity management
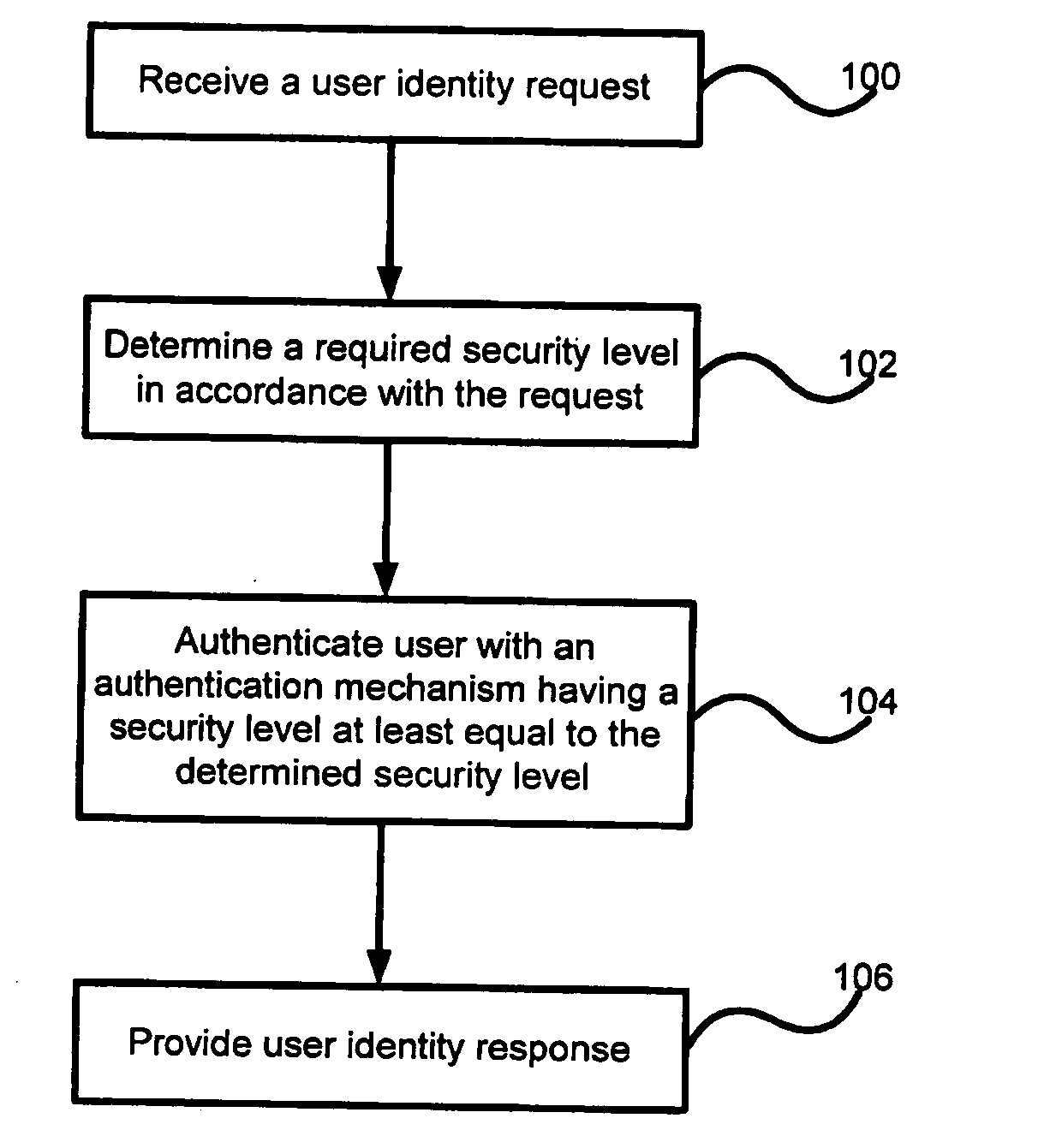
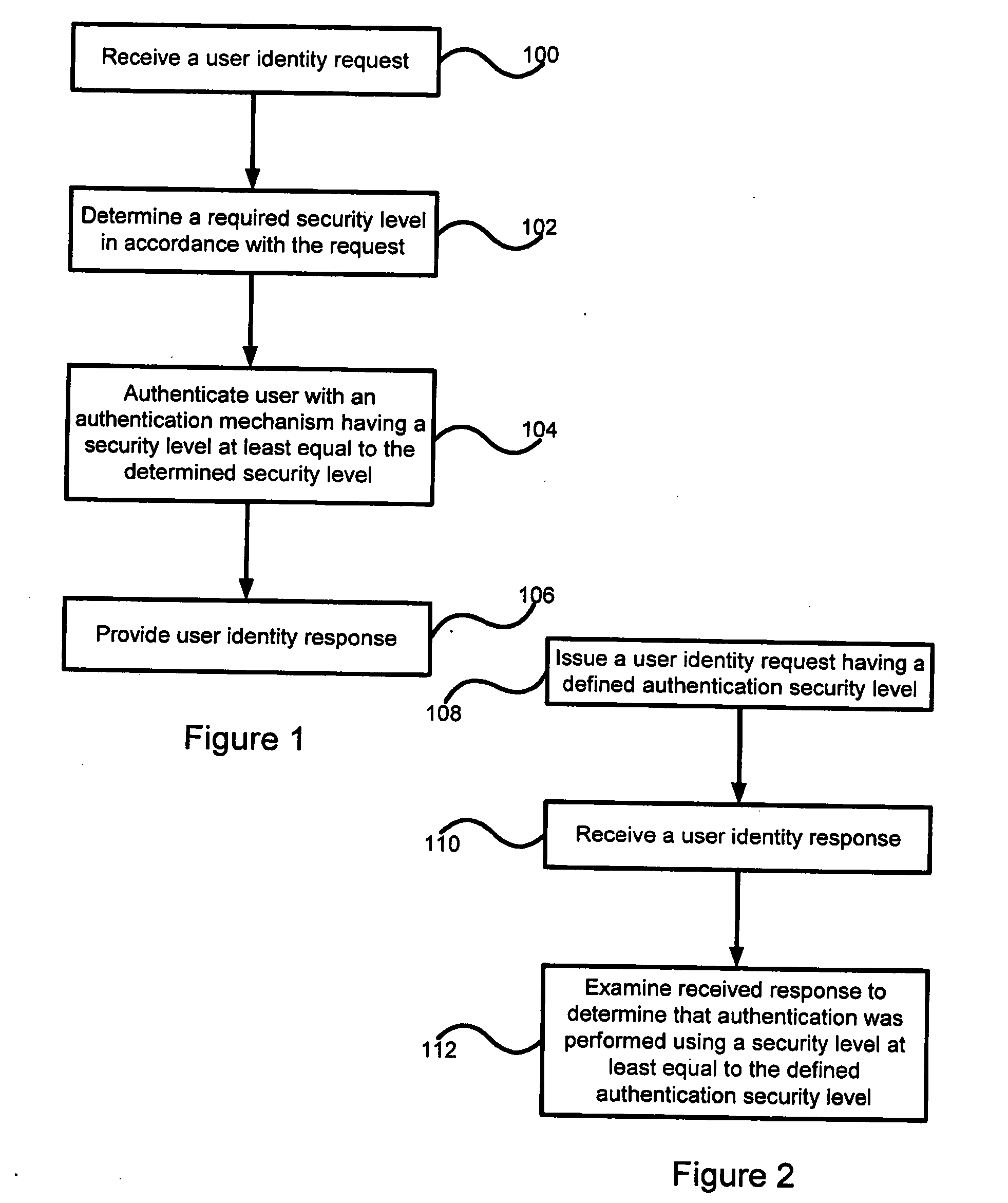
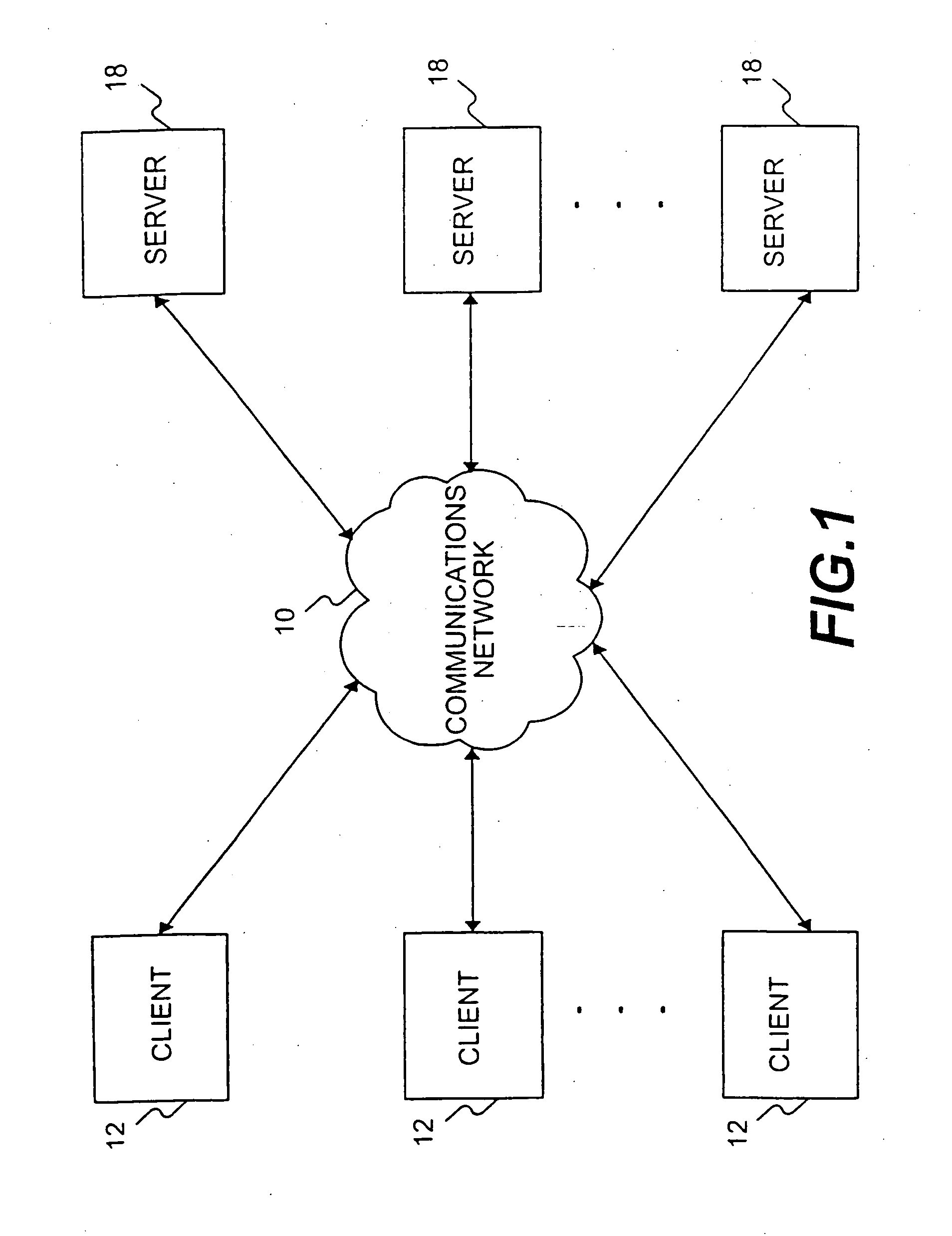
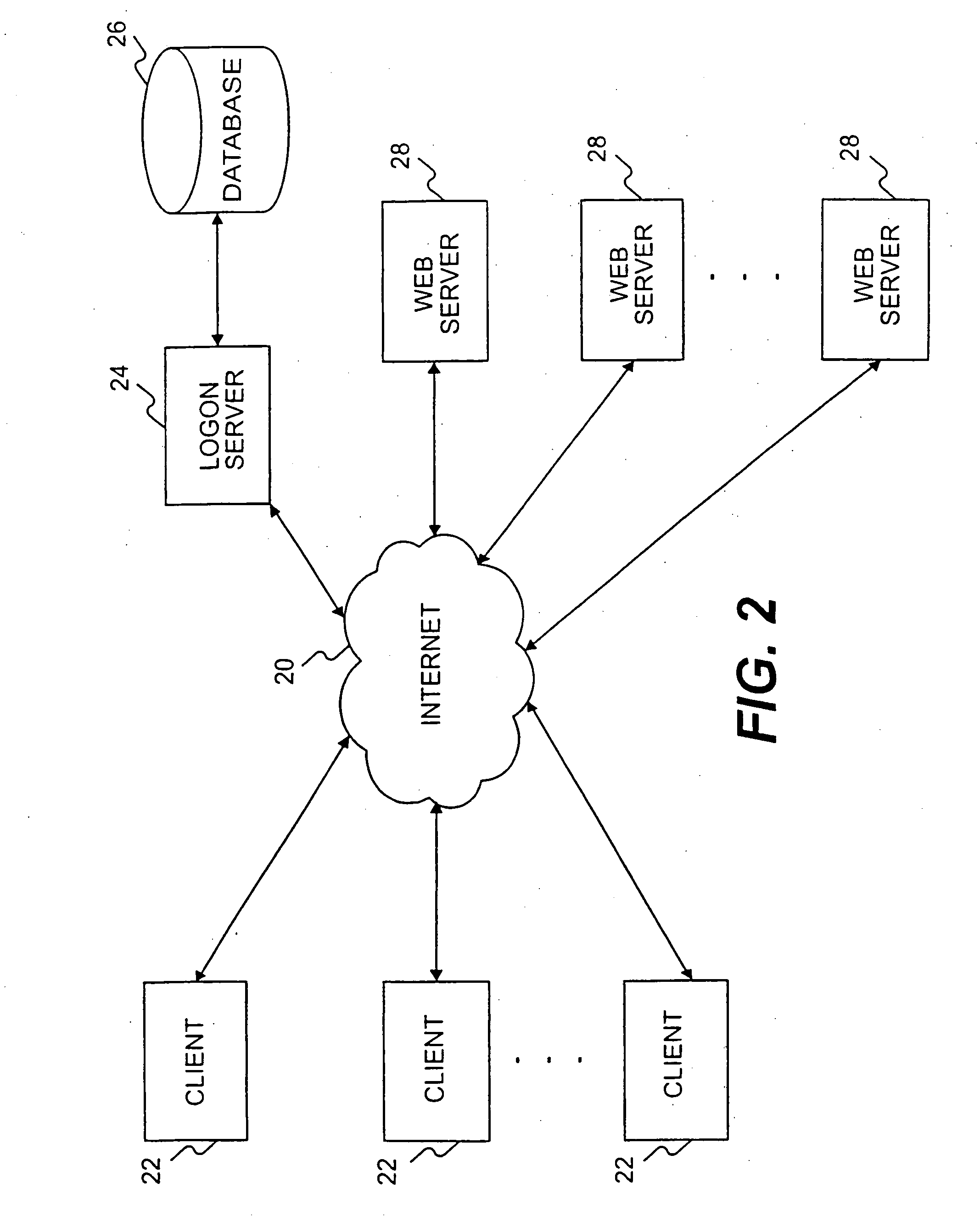
InactiveUS20070277235A1Improve mobilityMore automatedUser identity/authority verificationMultiple digital computer combinationsEngineeringUser authentication
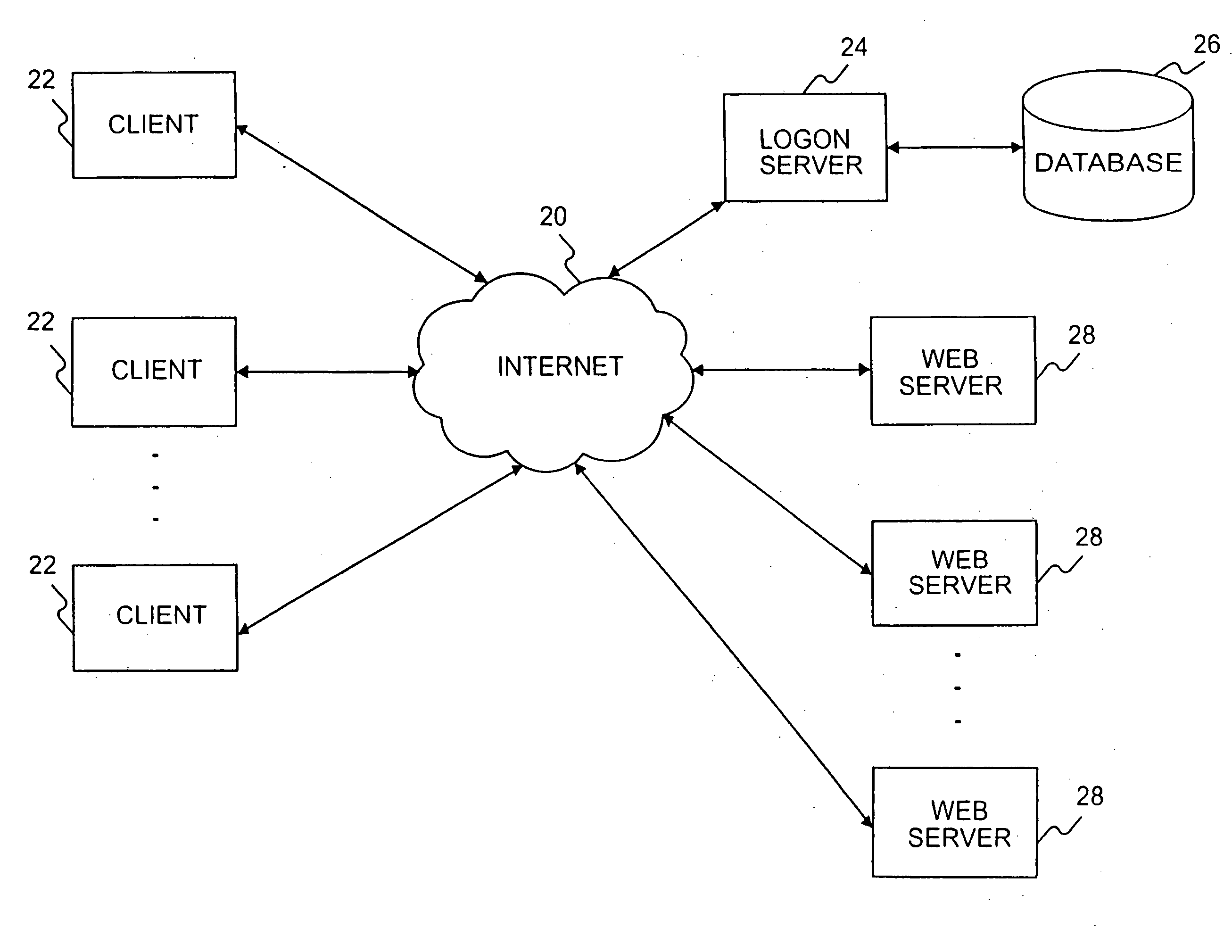
A distributed client / server system comprises a network of servers and clients, such as the Internet, in which user access to certain restricted resources is controlled by a logon procedure that identifies an authorized user to the respective administering server. The disclosed system and method includes a logon server that comprises a user authentication procedure by which a user can logon to the logon server from any client in the network and uniquely identify itself to the logon server. The logon server also includes a library of usernames and passwords for the restricted resources chosen by each user and the ability to automatically log the users on to any of the restricted resources when selected by the user through a personal catalog maintained by the logon server. The disclosed system and method also includes various other features for providing user authentication and identity management in a network environment, such as the Internet.
Owner:BARRETT PAUL D +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com