Patents
Literature
2027results about "Checking apparatus" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
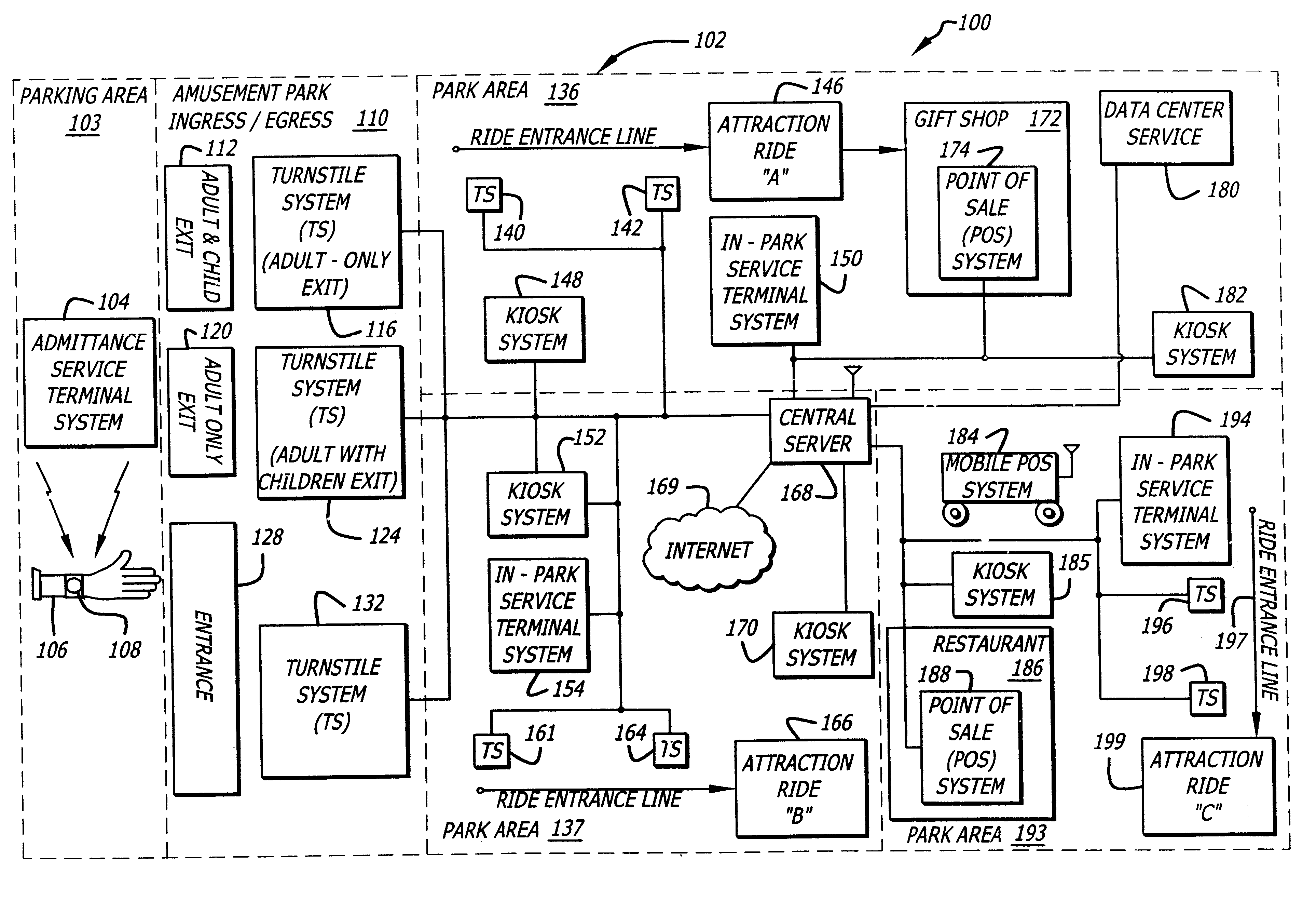
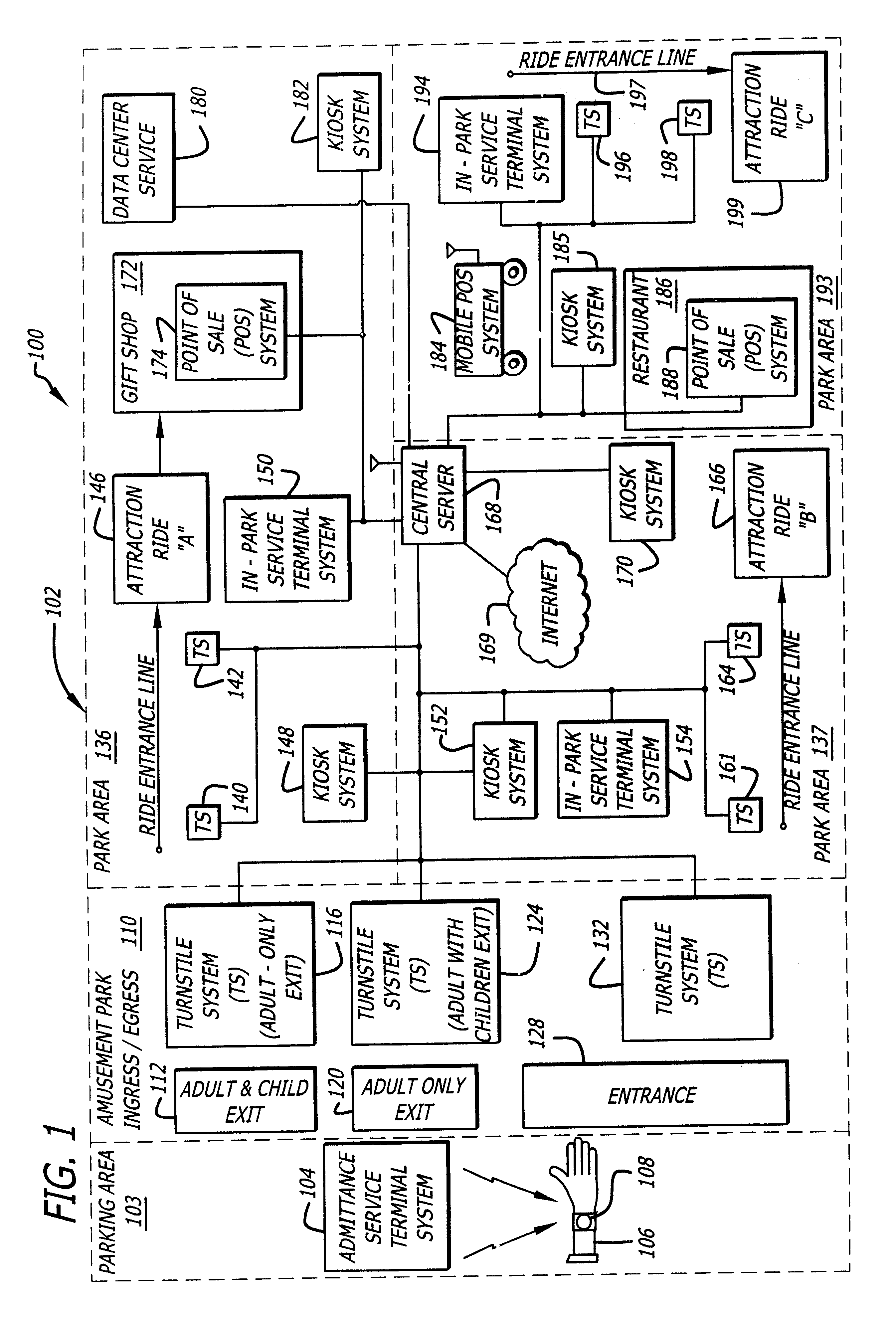
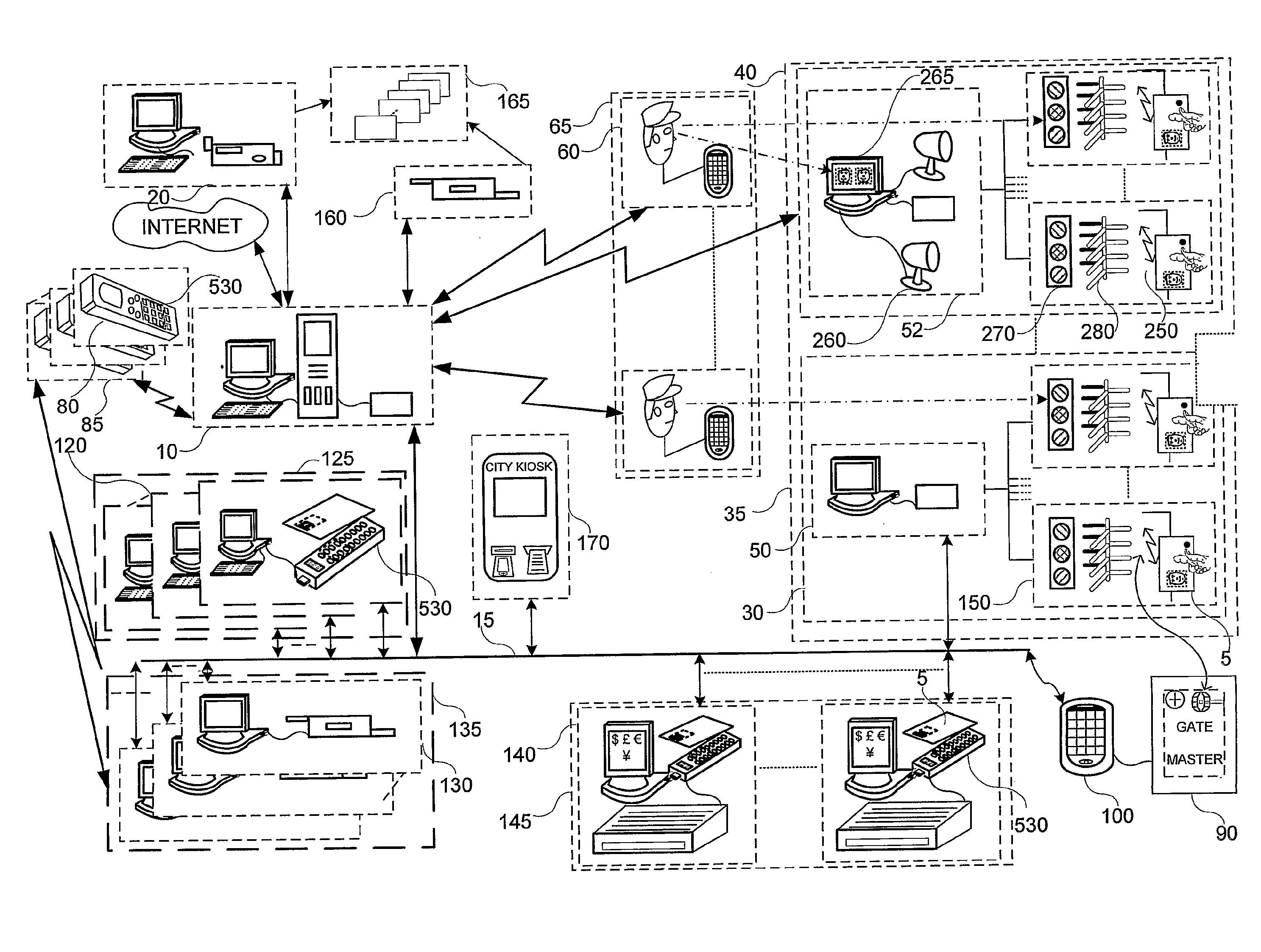
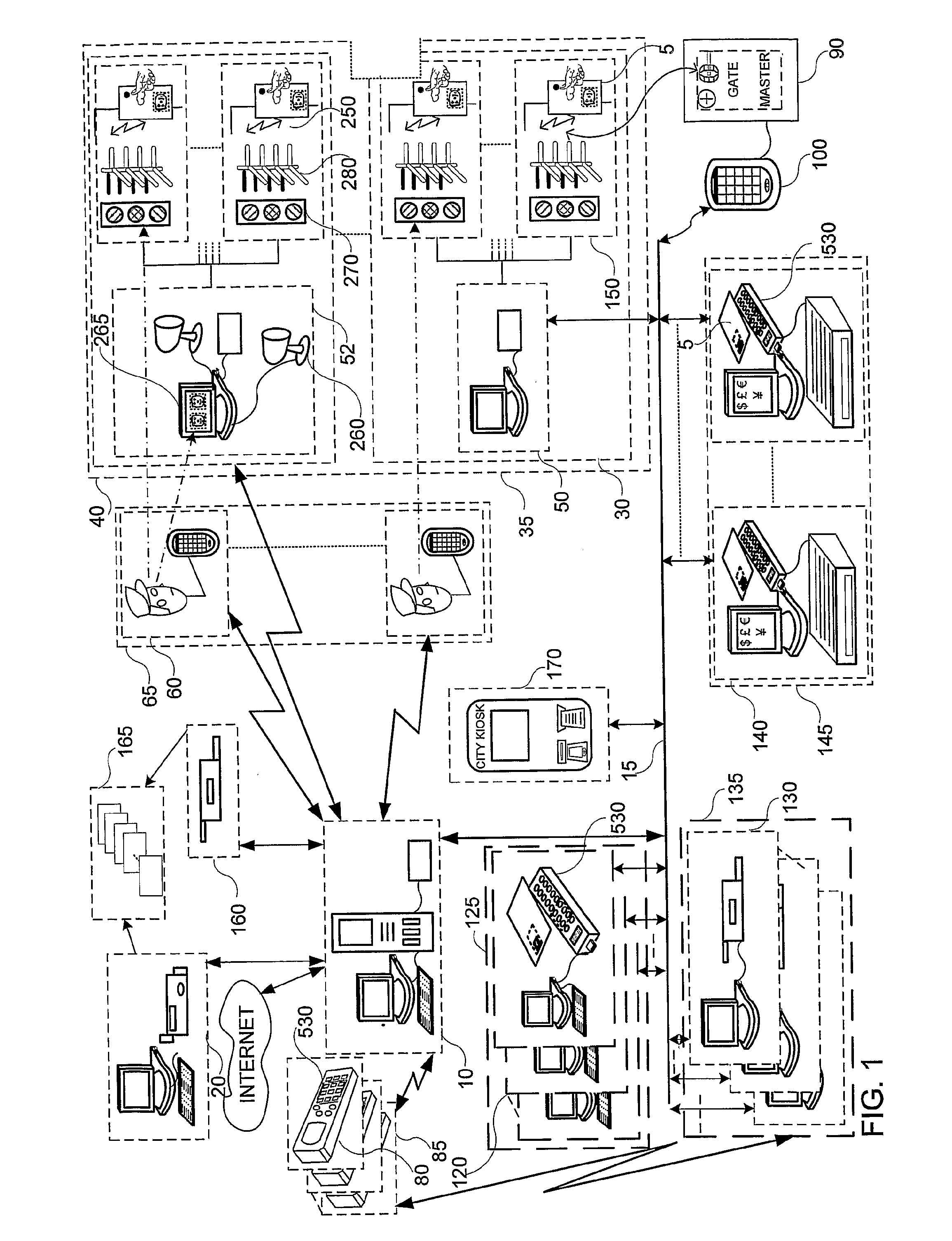
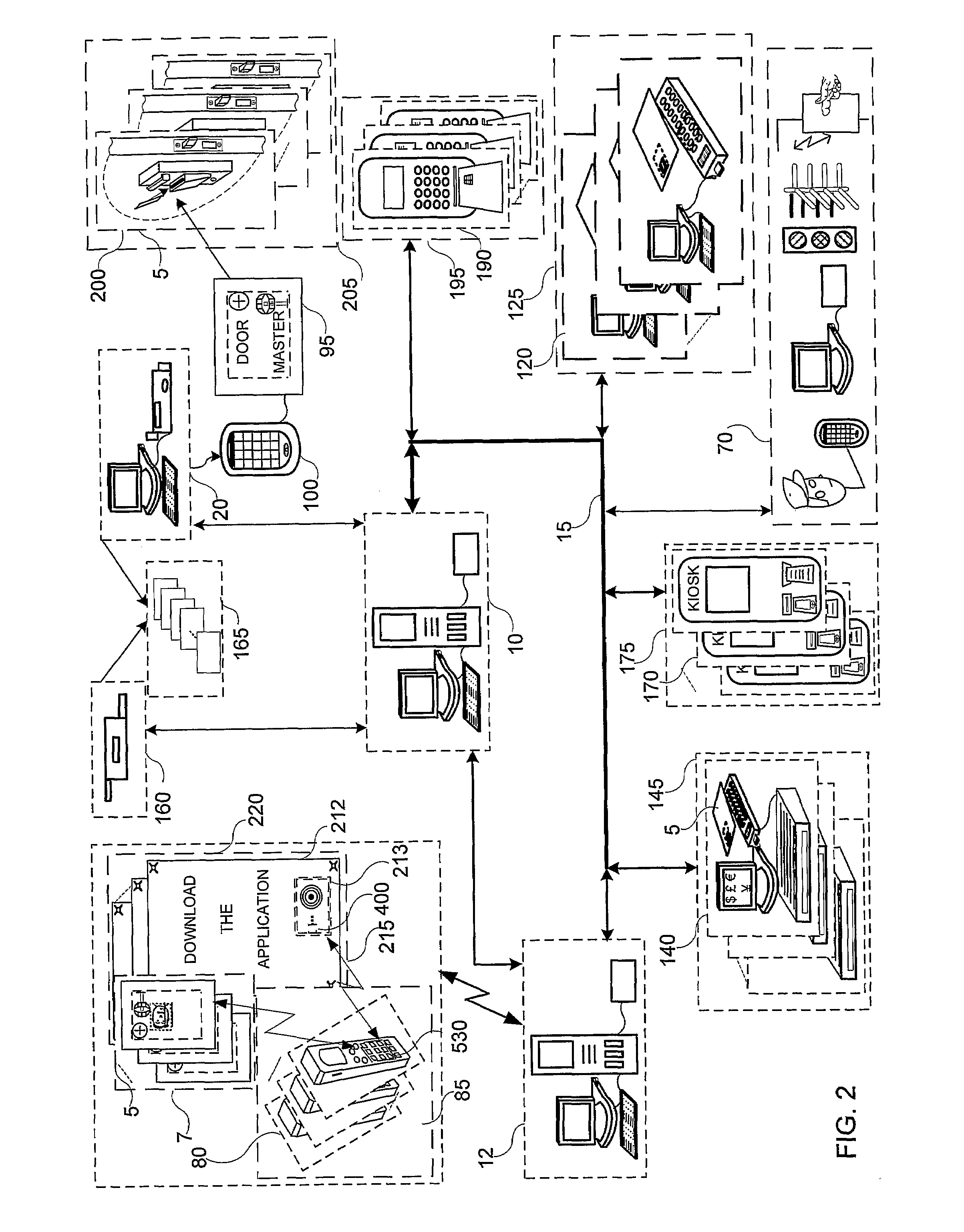
System and method for selectively allowing the passage of a guest through a region within a coverage area
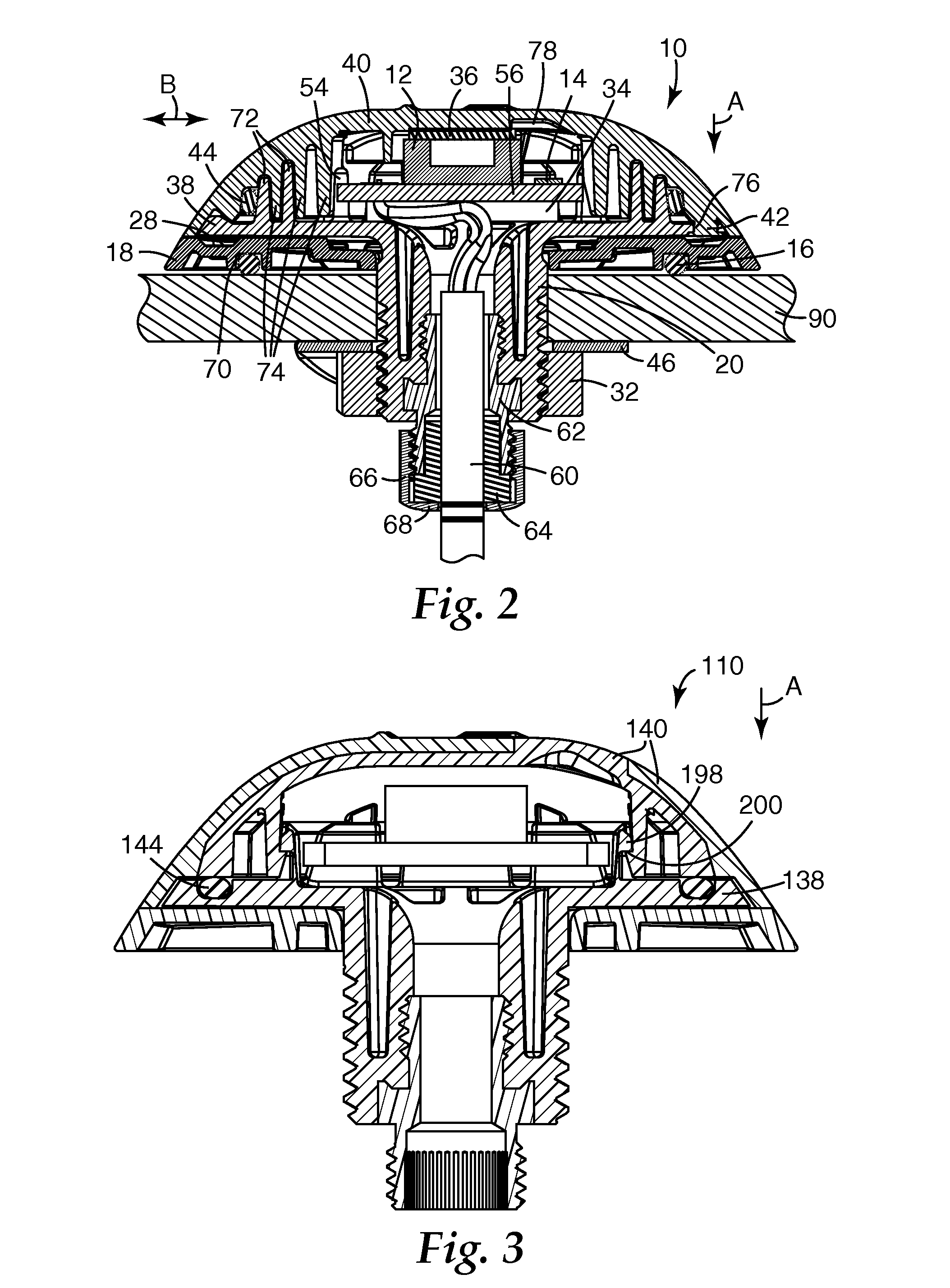
InactiveUS6873260B2Electric signal transmission systemsMultiple keys/algorithms usageControl signalData field
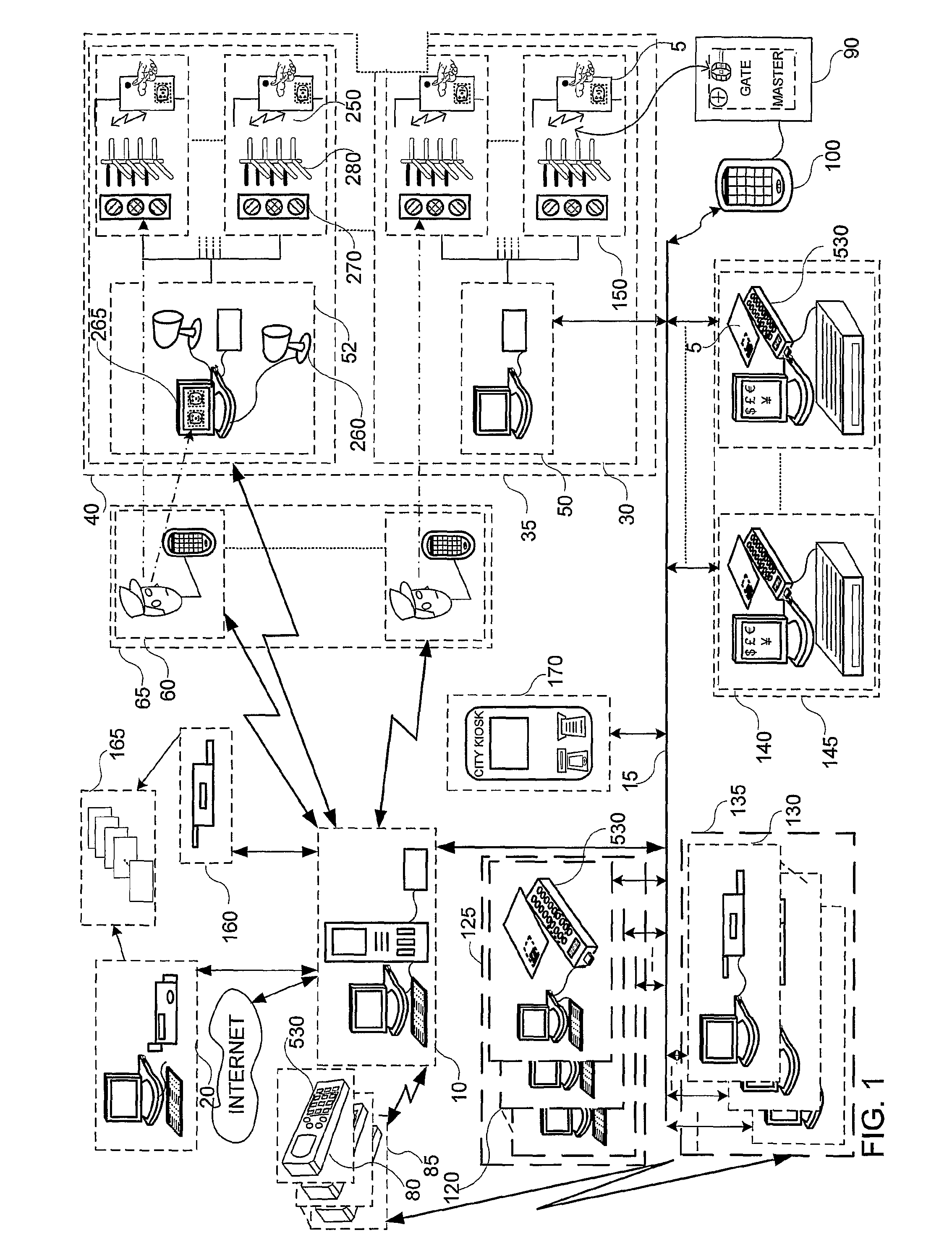
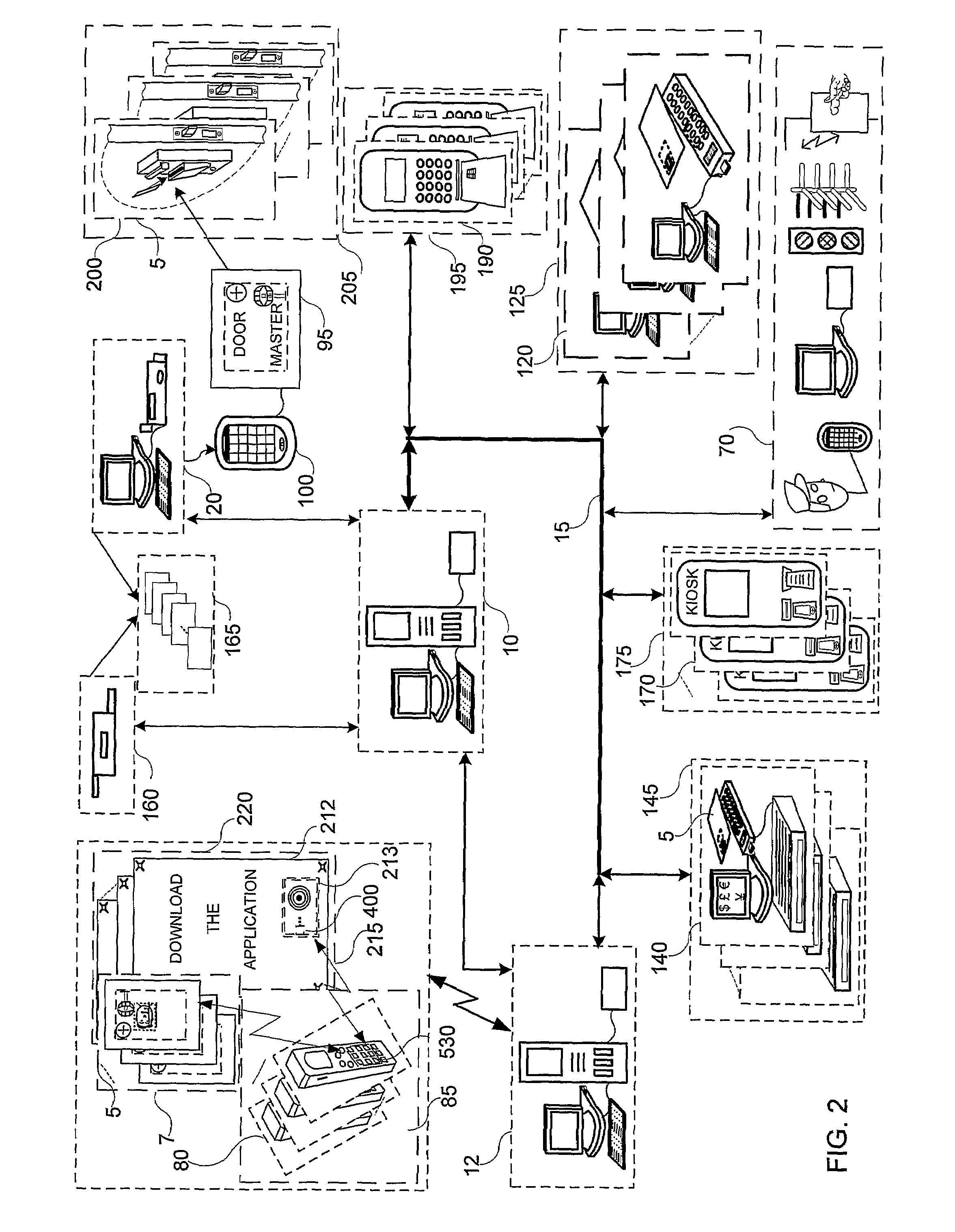
A system and method for selectively allowing the passage of a guest through a region within at a coverage area. The system includes a turnstile system having an RFID reader, a network interface, an entry mechanism and a processor, and a central server having a network interface, a non-volatile memory, and a processor. An RFID reader reads a tag identifier from an RFID tag worn by a guest. The tag identifier is transmitted from the turnstile system to the central server. The central server processor access a guest data object using the tag identifier and reads a data field containing information related to the guest. Based on this information, the central server transmits a control signal to the turnstile system to activate its entry mechanism, thereby allowing the guest to pass through. The information may relate to monetary credits of the guest, statistical information of the guest, and restrictions, disabilities, health conditions and special access of the guest.
Owner:NOBLE LINDA +1
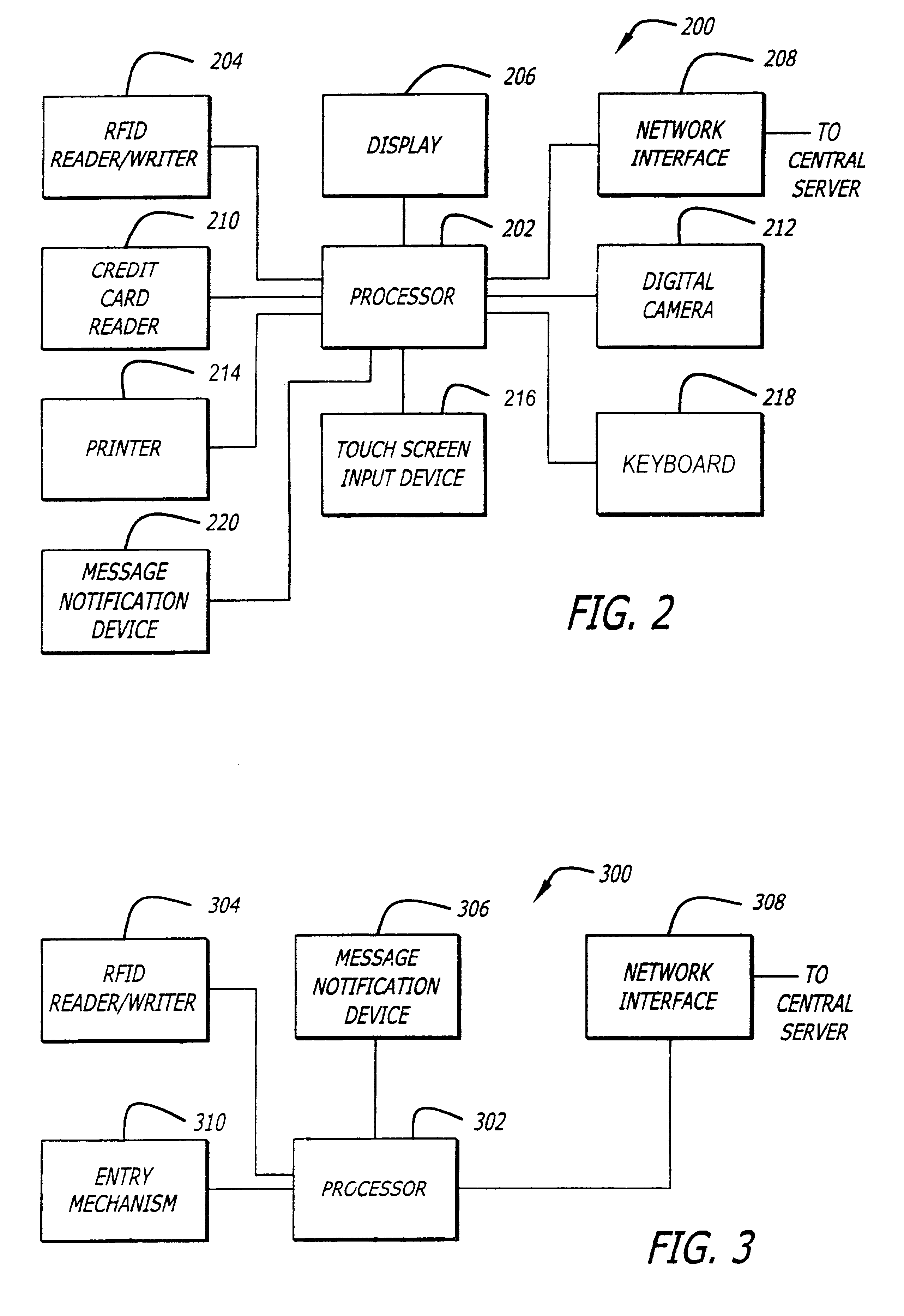
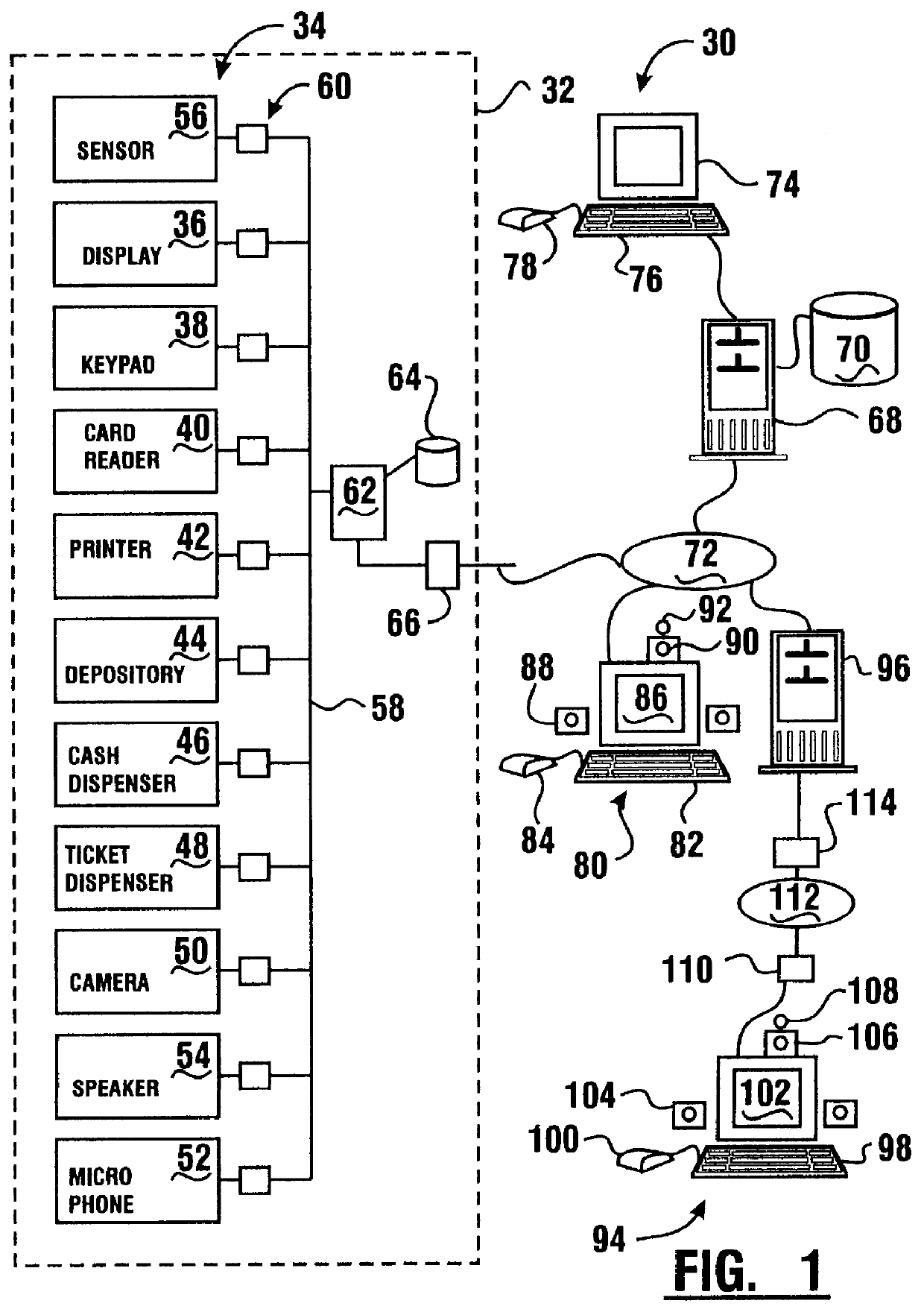
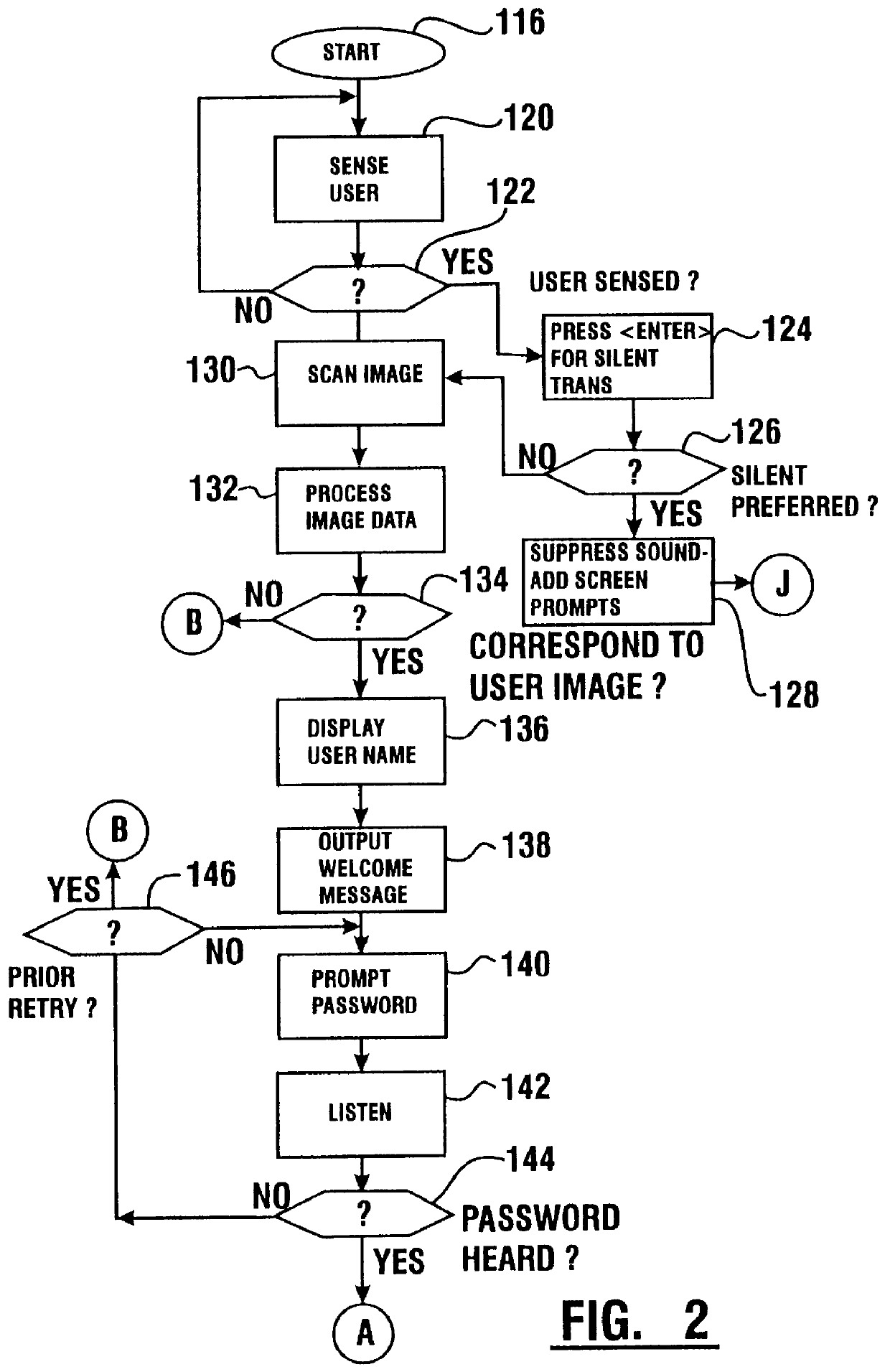
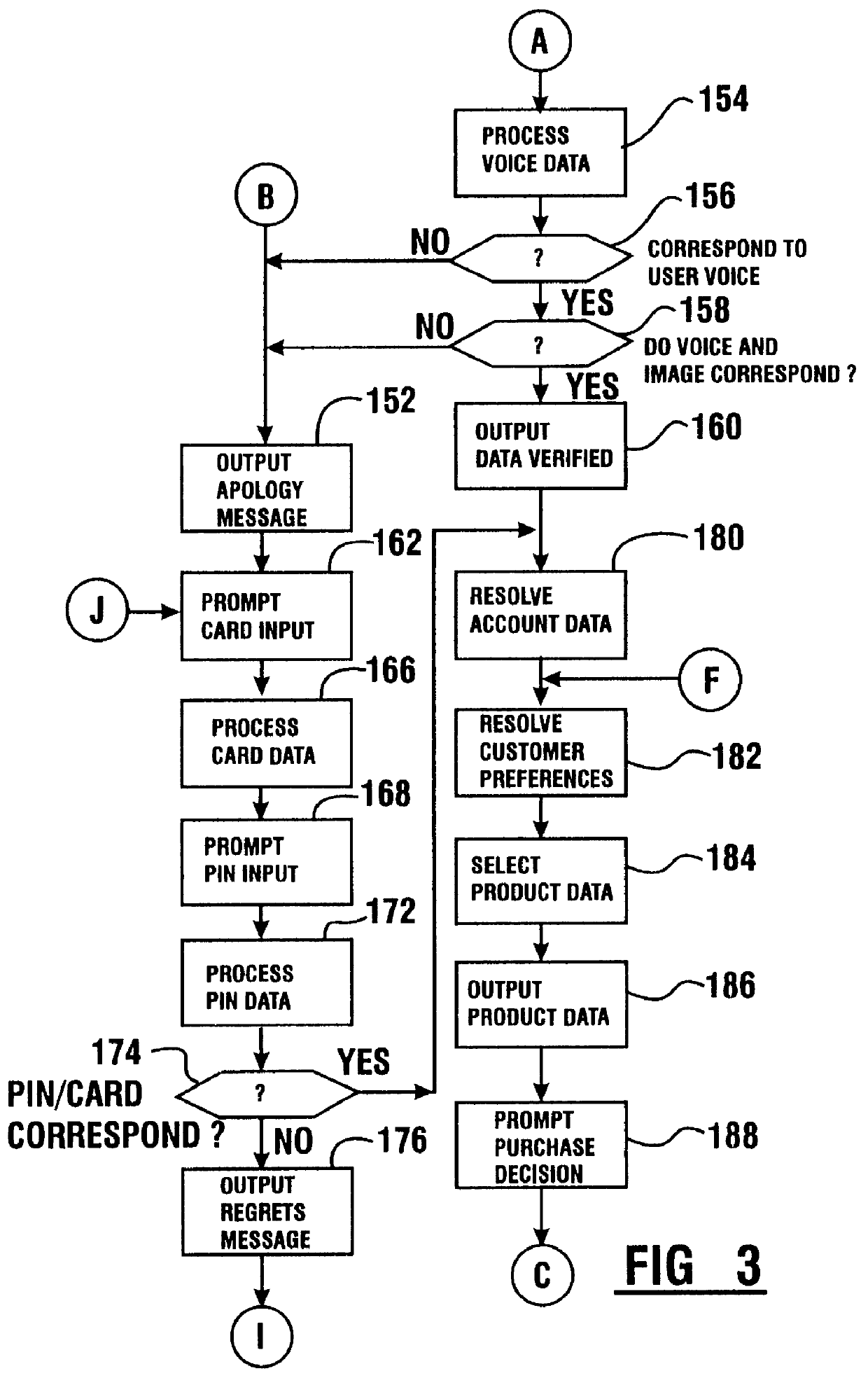
Transaction apparatus and method that identifies an authorized user by appearance and voice
A financial transaction apparatus (30) includes a financial transaction machine (32). The machine includes devices (34) including transaction function devices (42, 44, 46, 48) for carrying out operations associated with financial transactions. The terminal also includes an imaging device (50) and an audio input device (52), as well as a visual output device (36) and an audio output device (54). Terminal (32) is connected to a computer (68) which has an associated data store (70). The data store includes user data including image data and voice data corresponding to authorized users. The identity of a customer operating the machine is determined by resolving first identity data based on image signals from the imaging device which correspond to a user's appearance. Second identity data is resolved by the processor from voice signals from the audio input device corresponding to the user's voice. The computer enables operation of the transaction function devices if the level of correlation between the first and second identity data is sufficient to establish that the image and voice signals originate from a single authorized user.
Owner:DIEBOLD NIXDORF
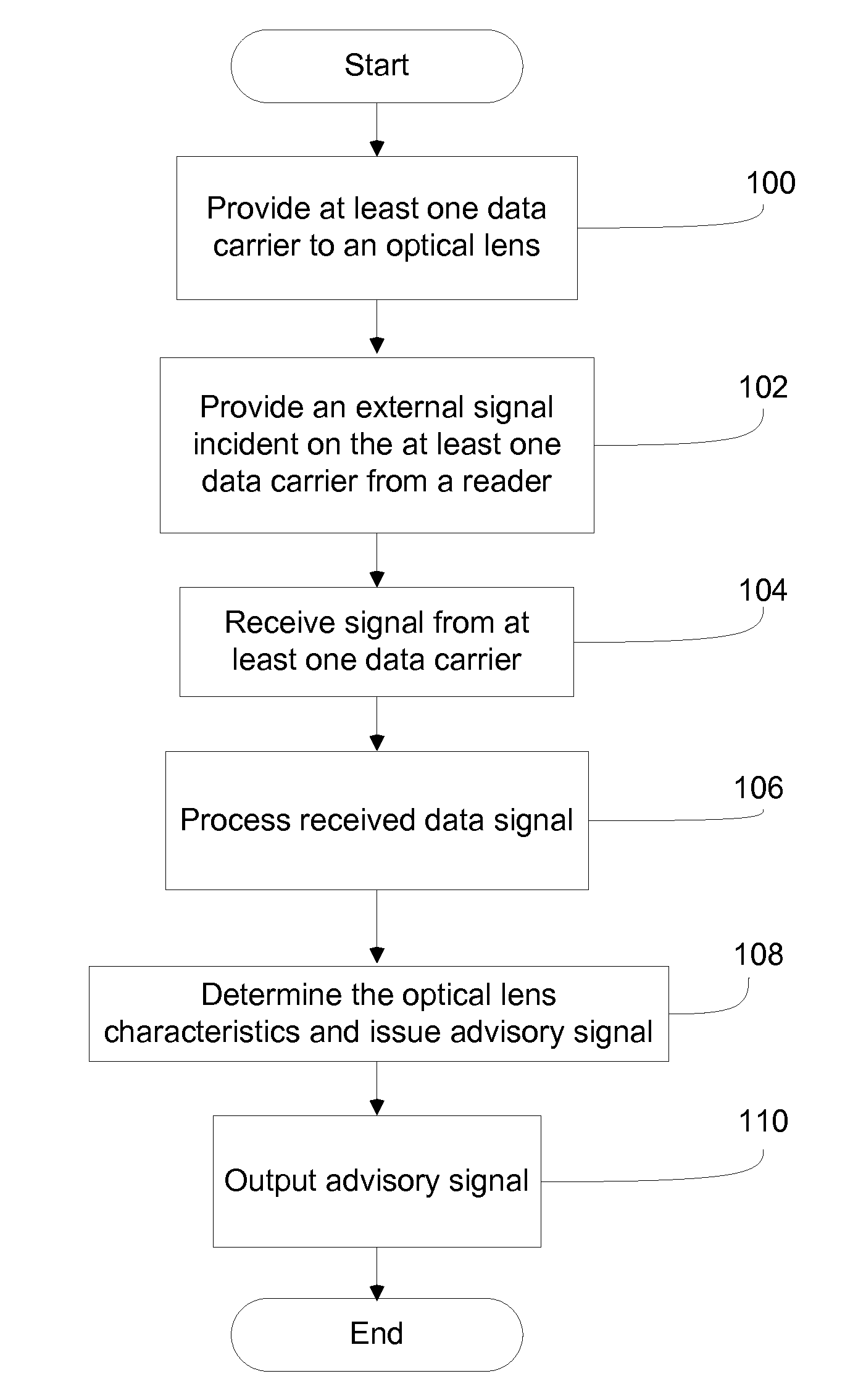
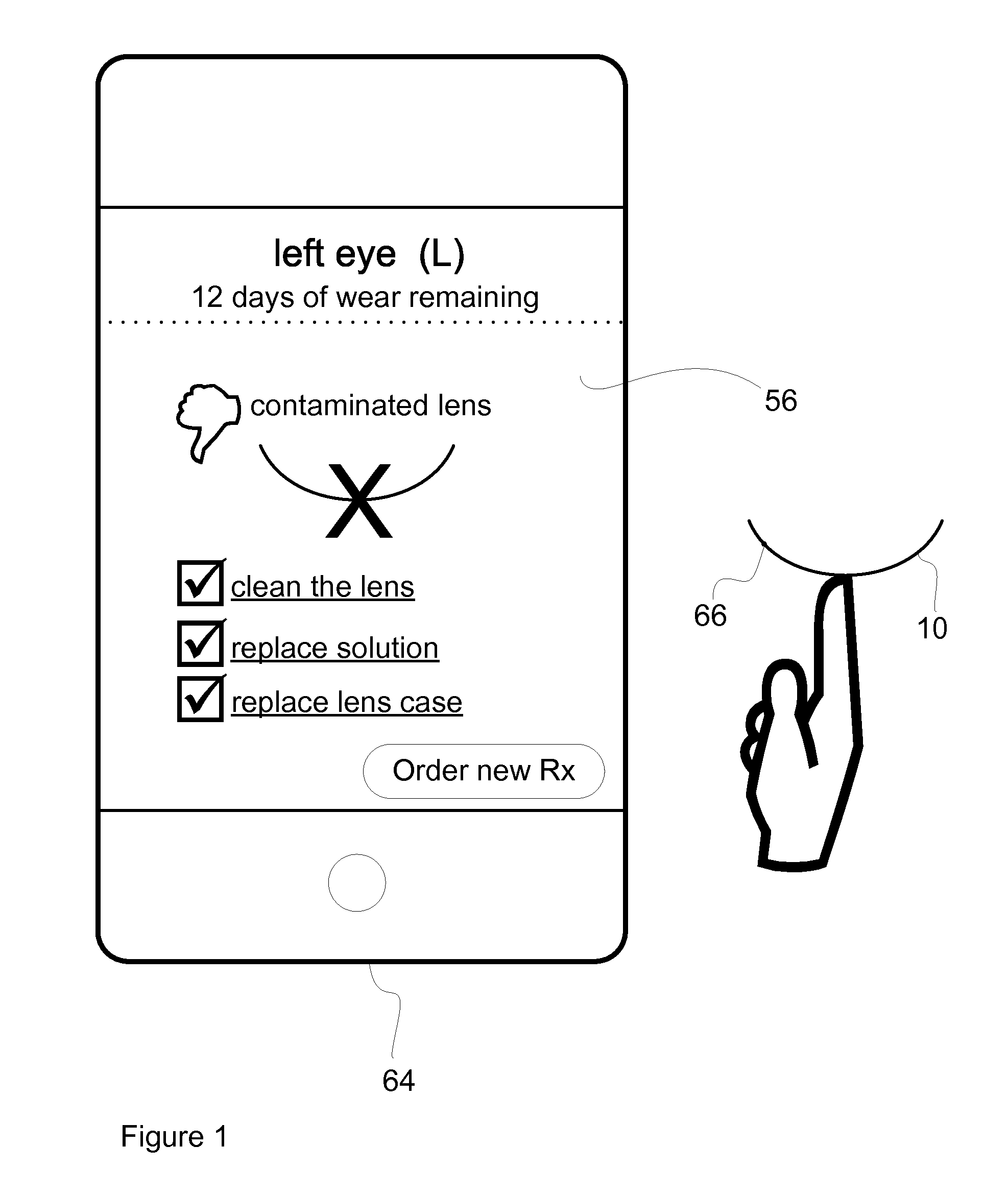
Method and System for Contact Lens Care and Compliance
InactiveUS20110084834A1Reduce complicationsFacilitate complianceChecking apparatusOther accessoriesOphthalmic ProductComputer science
A method for tracking ophthalmic lens care compliance, said method comprising the steps of: including at least one sensor with said ophthalmic product for monitoring at least one ambient condition and for logging and recording at least one reading associated said at least one ambient condition, following a predetermined event; determining whether said at least one reading exceeds at least one predetermined threshold, and issuing an alert when said at least one reading exceeds at least one predetermined threshold.
Owner:SABETA ANTON
Child protection system
InactiveUS7164354B1Ticket-issuing apparatusElectric/electromagnetic visible signallingMonitoring systemEngineering
A child monitoring system is provided for facilities and areas where parents and children generally enter and exit together, but are likely to become separated while in the facility or area. Using devices on a child's person coupled with monitoring devices on exit and entry ways, parents may be alerted in the event that a child wanders off or is the subject of an abduction attempt. Upon crossing a monitoring point, an alarm is triggered to alert parents and public safety officials of an unauthorized exit attempt. Thus with this system, a monitored child can not leave a monitored location (e.g., store, museum, etc) alone nor without the child's parent or guardian.
Owner:PANZER JUSTIN
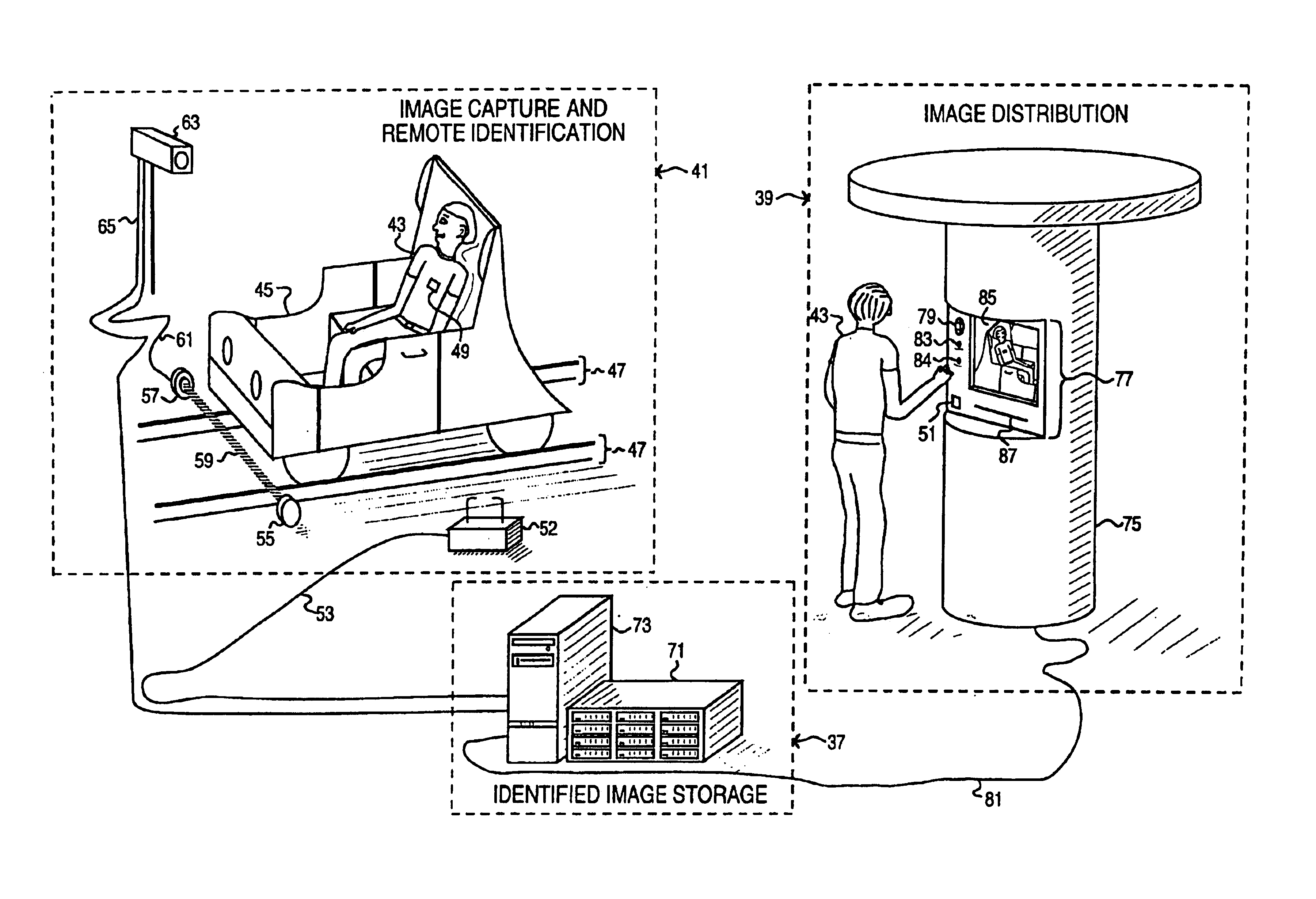
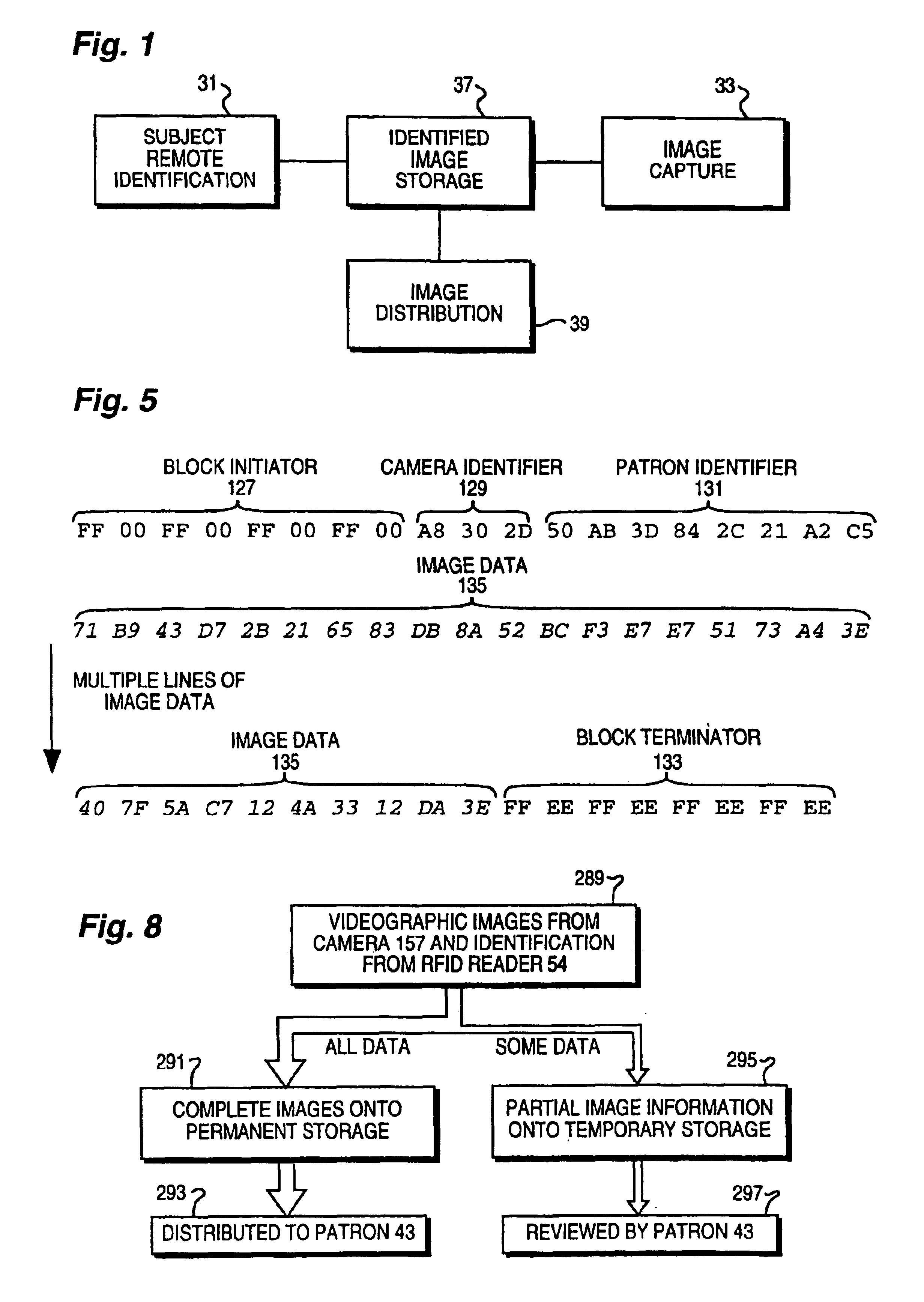
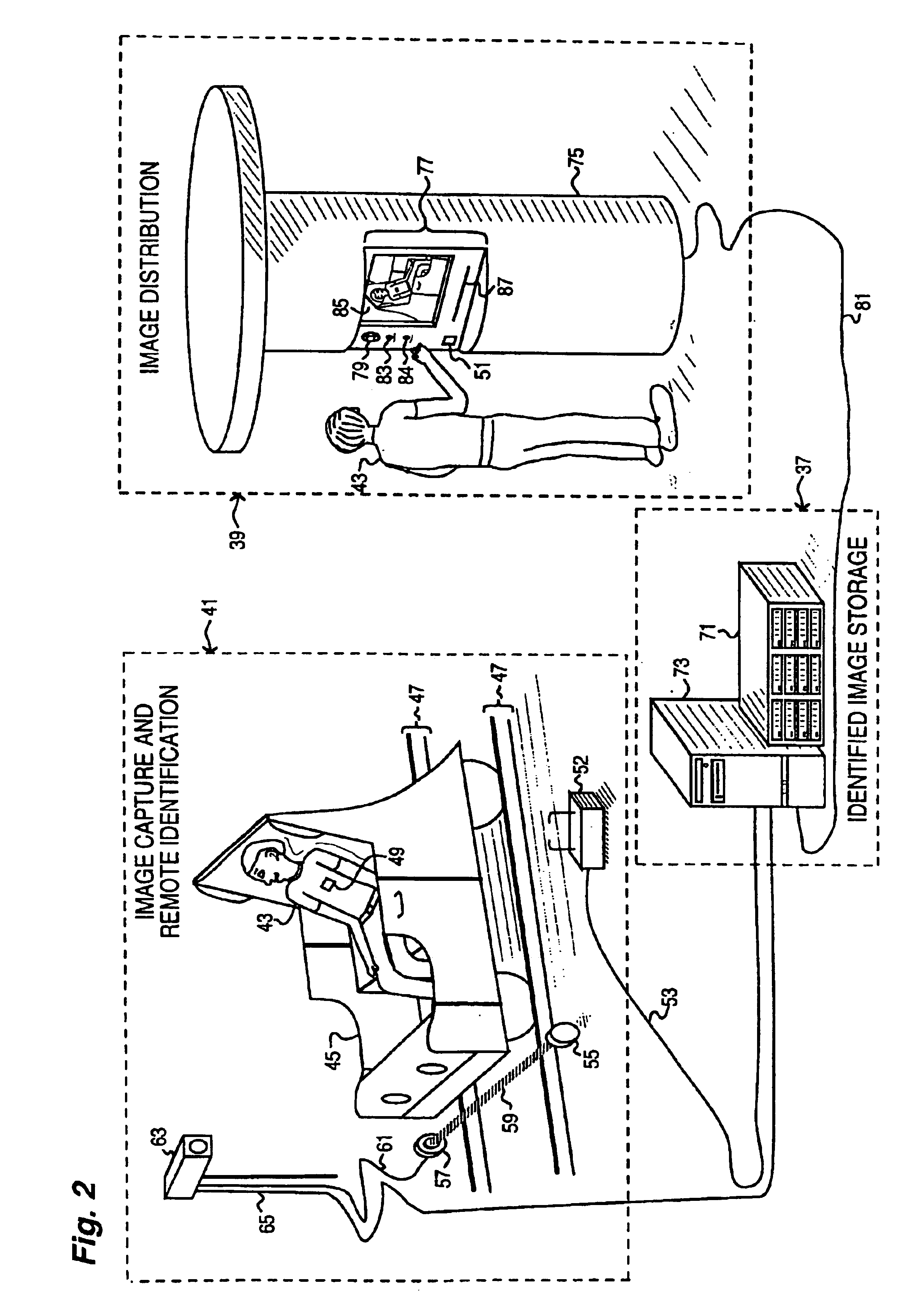
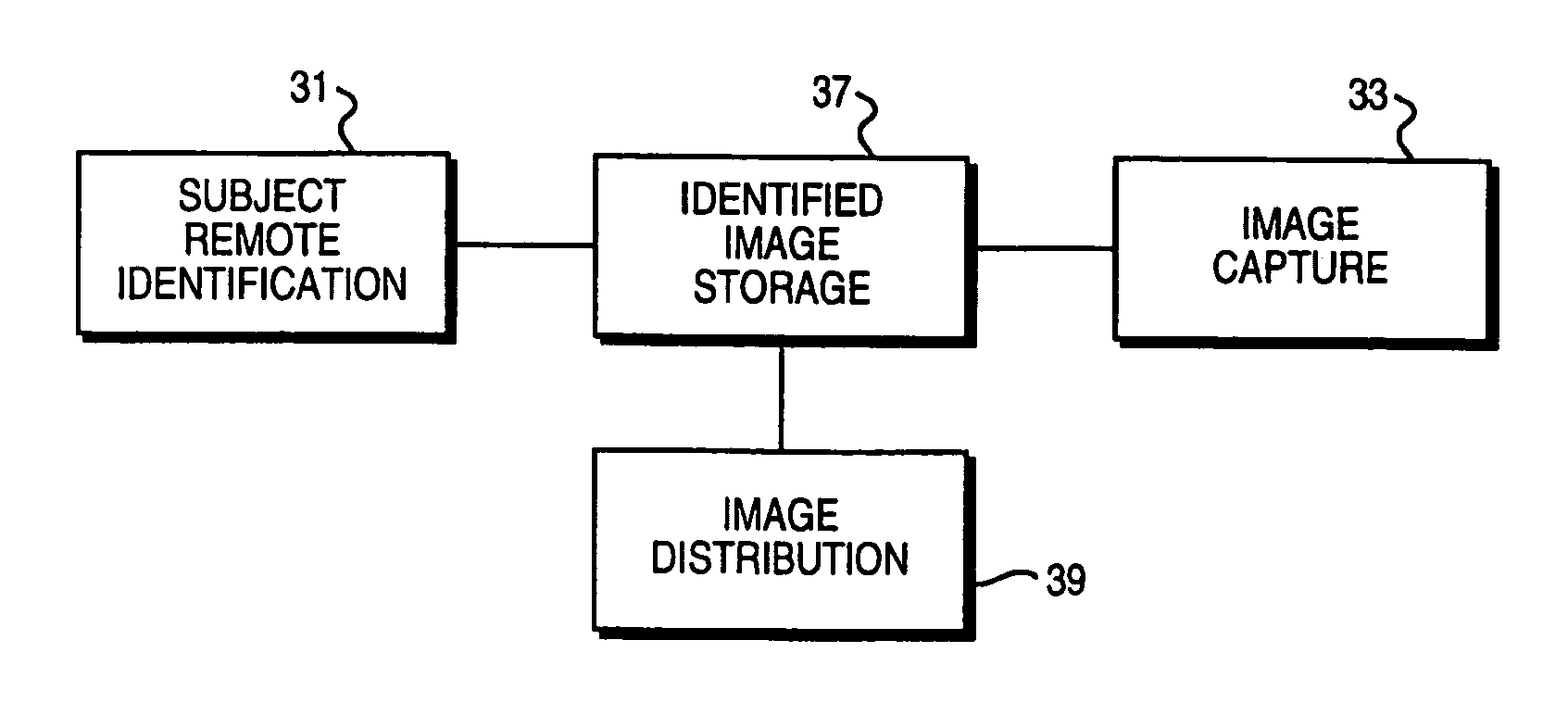
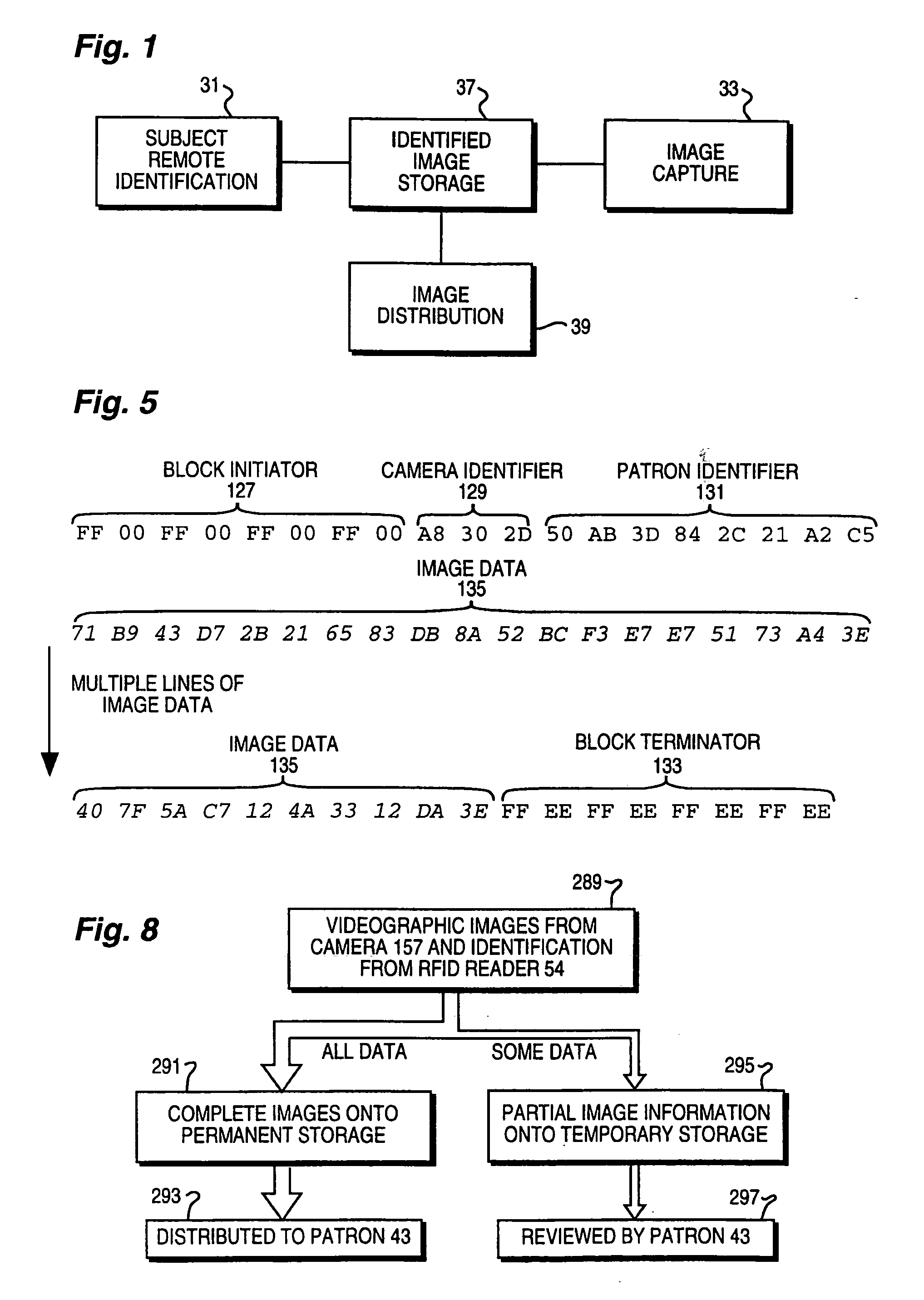
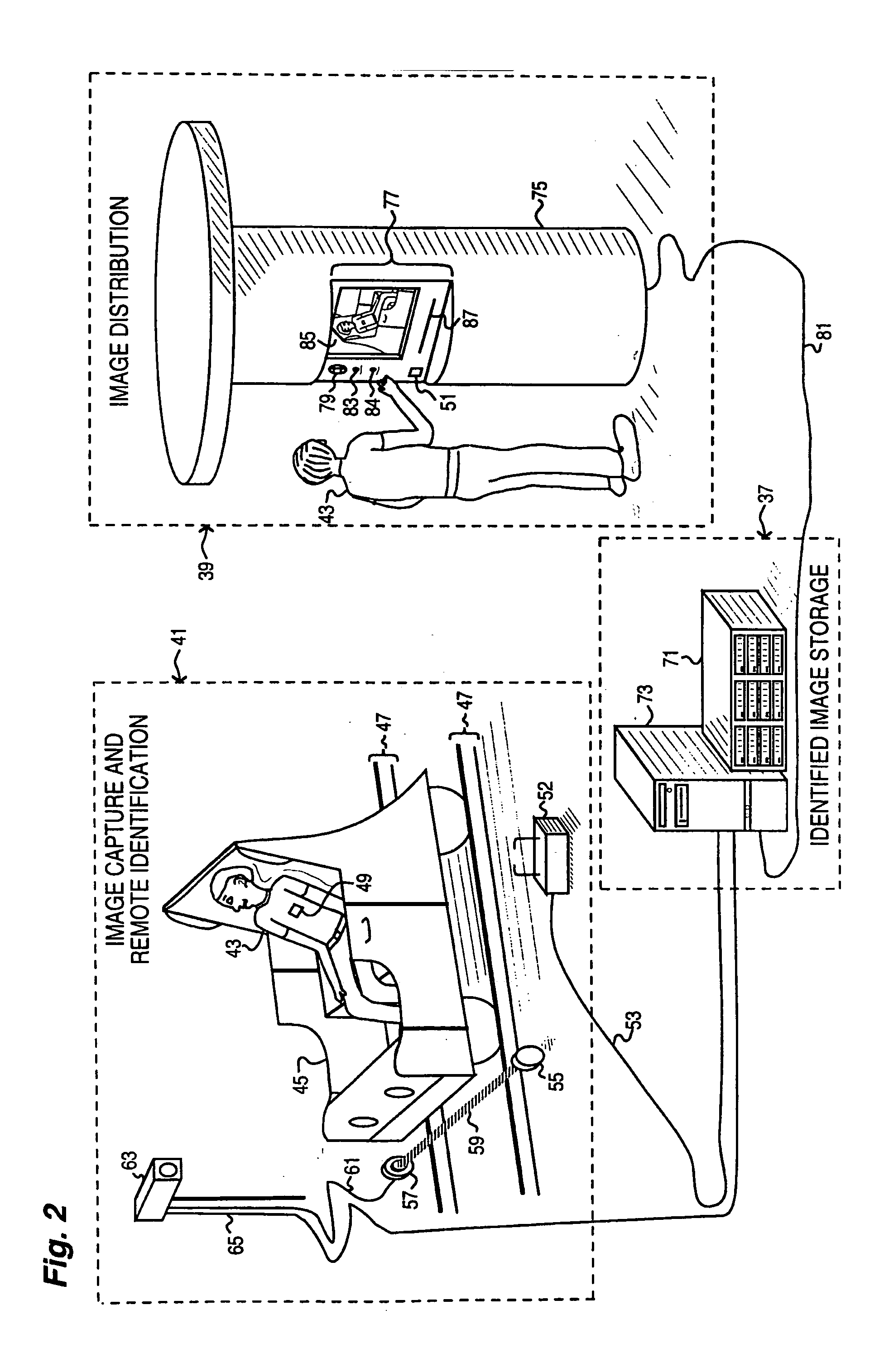
Obtaining person-specific images in a public venue
InactiveUS6819783B2Improve accuracyFewer false positivesProcessed material treatmentRecord information storagePublic placeEyewear
Collecting images of a patron in an entertainment venue is performed by facial recognition of the patron's face within the images, simplifying the storage and distribution of the images for a patron. In order to enhance the reliability of the facial recognition system, information about the patron that is not directly related to most facial recognition systems, including clothes, height, other associated people, use of glasses and jewelry, disposition of facial hair, and more, can be used. Some of the characteristics used can be specific to a particular date or event, and which will not be more generally characteristic of the patron. The facial recognition system can also be used to identify the patron requesting images to be collected. The present invention also relates to the use of facial recognition in sorting and collecting images from an electronically-stored image collection, enabling the easy retrieval of images that are related to a particular person or set of people.
Owner:HYSTERICAL SUNSET
Methods and systems for gathering market research data inside and outside commercial establishments
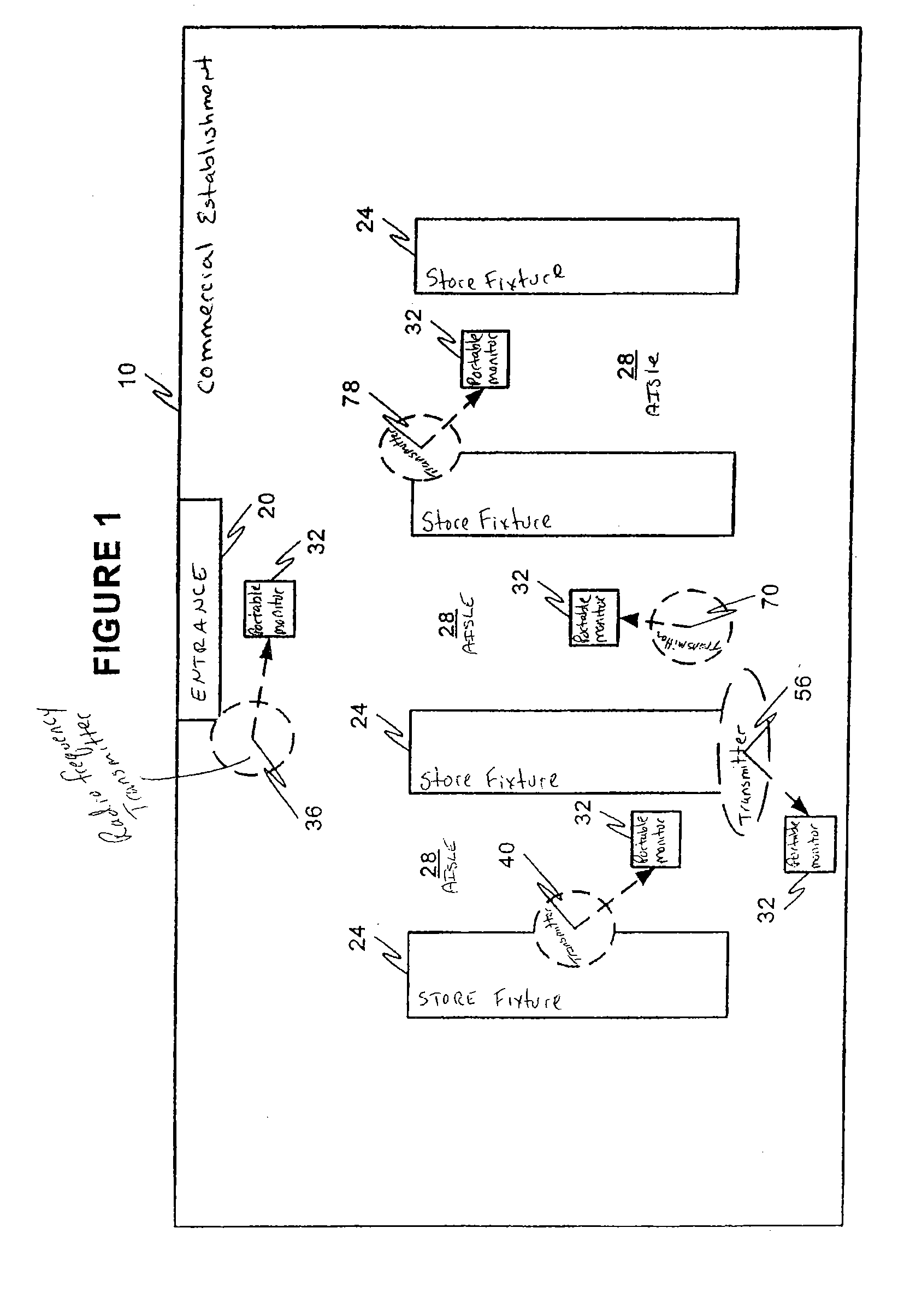
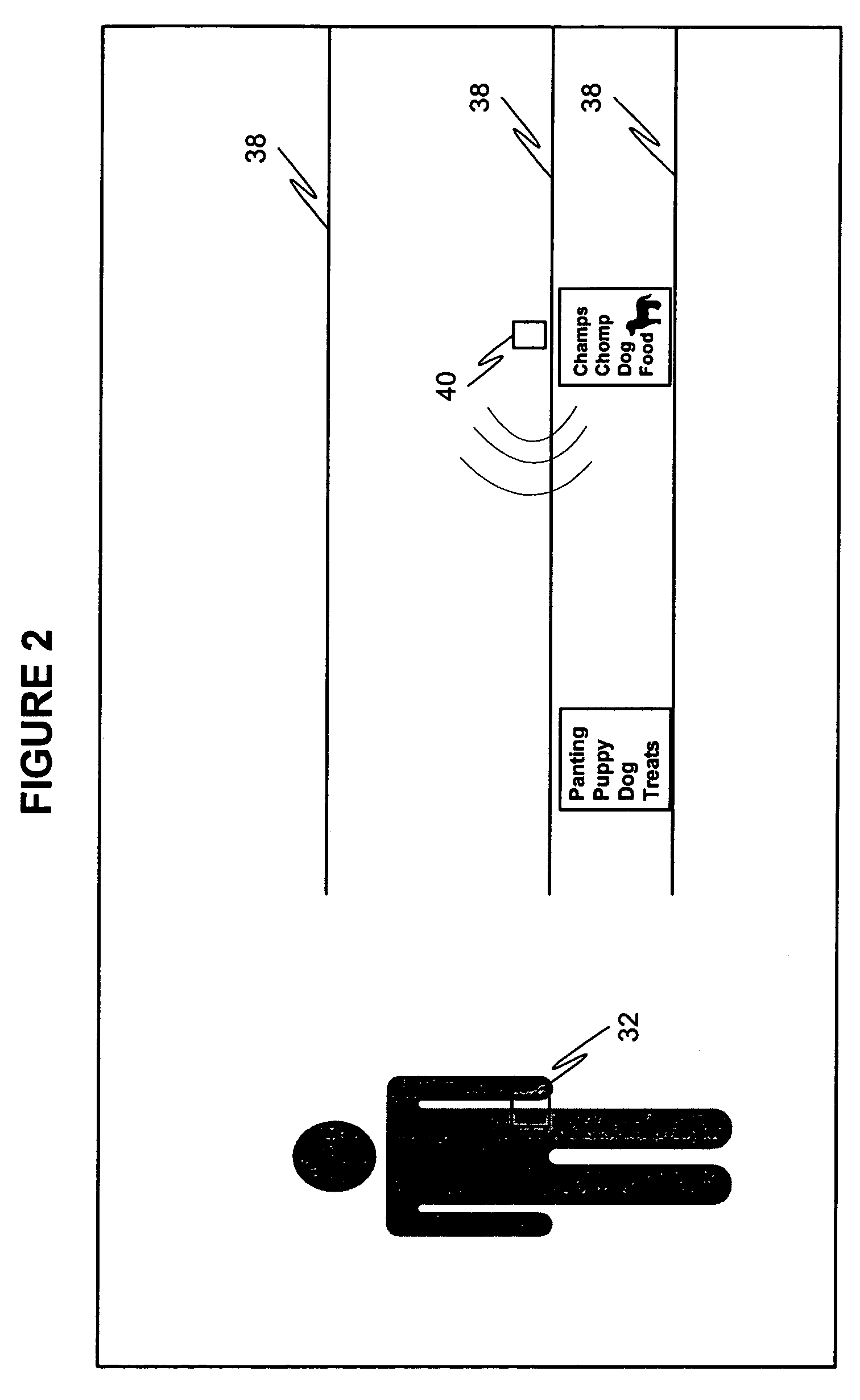
ActiveUS7420464B2Beacon systems using radio wavesElectric/electromagnetic visible signallingResearch dataLocation data
Methods and systems for tracking movements of participants in a market research study, for example, outside retail establishments, are provided. The methods and systems employ portable monitors carried on the persons of the participants to gather location data.
Owner:THE NIELSEN CO (US) LLC +1
Identification tag for real-time location of people
InactiveUS6747562B2Programme controlElectric signal transmission systemsUser identifierComputer science
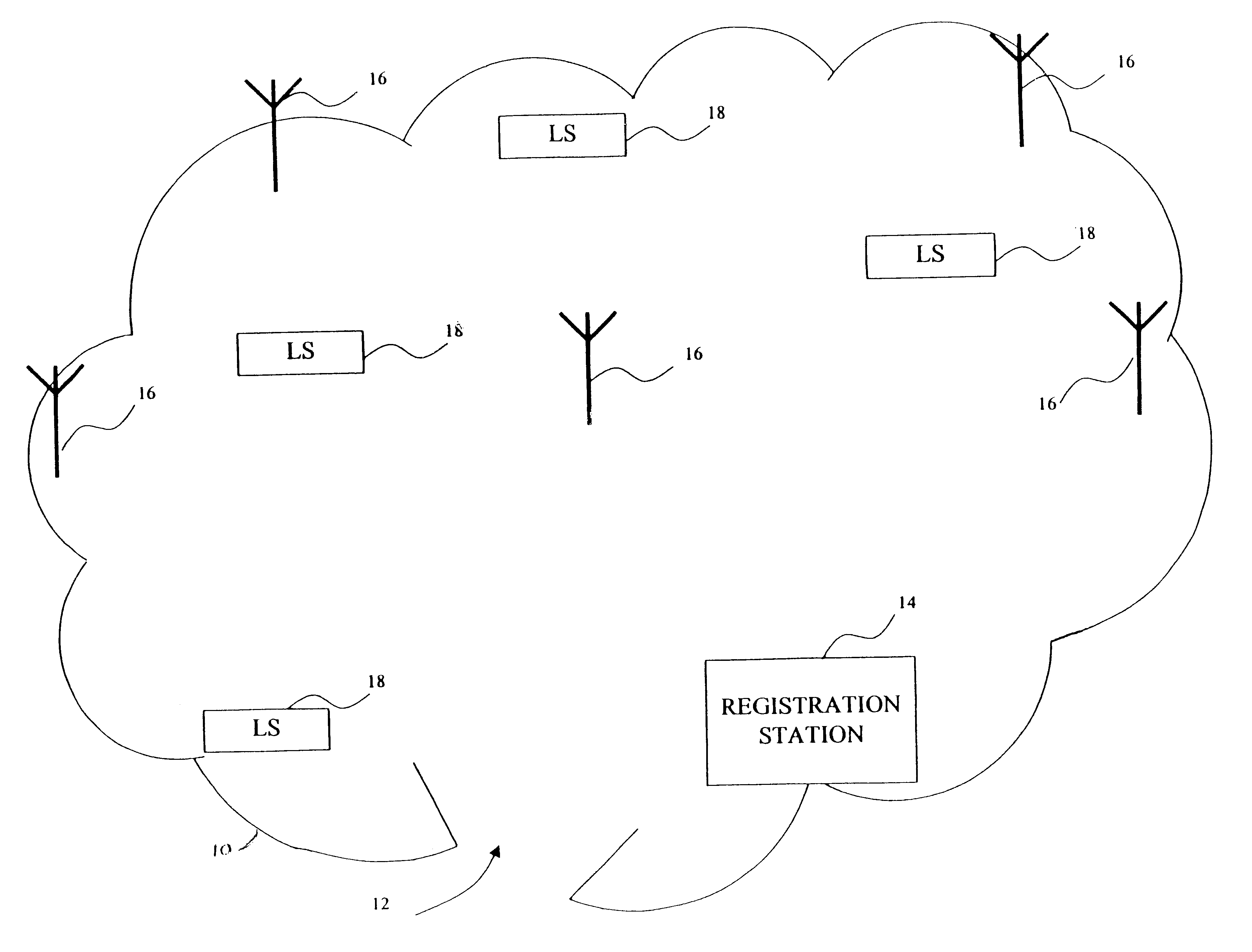
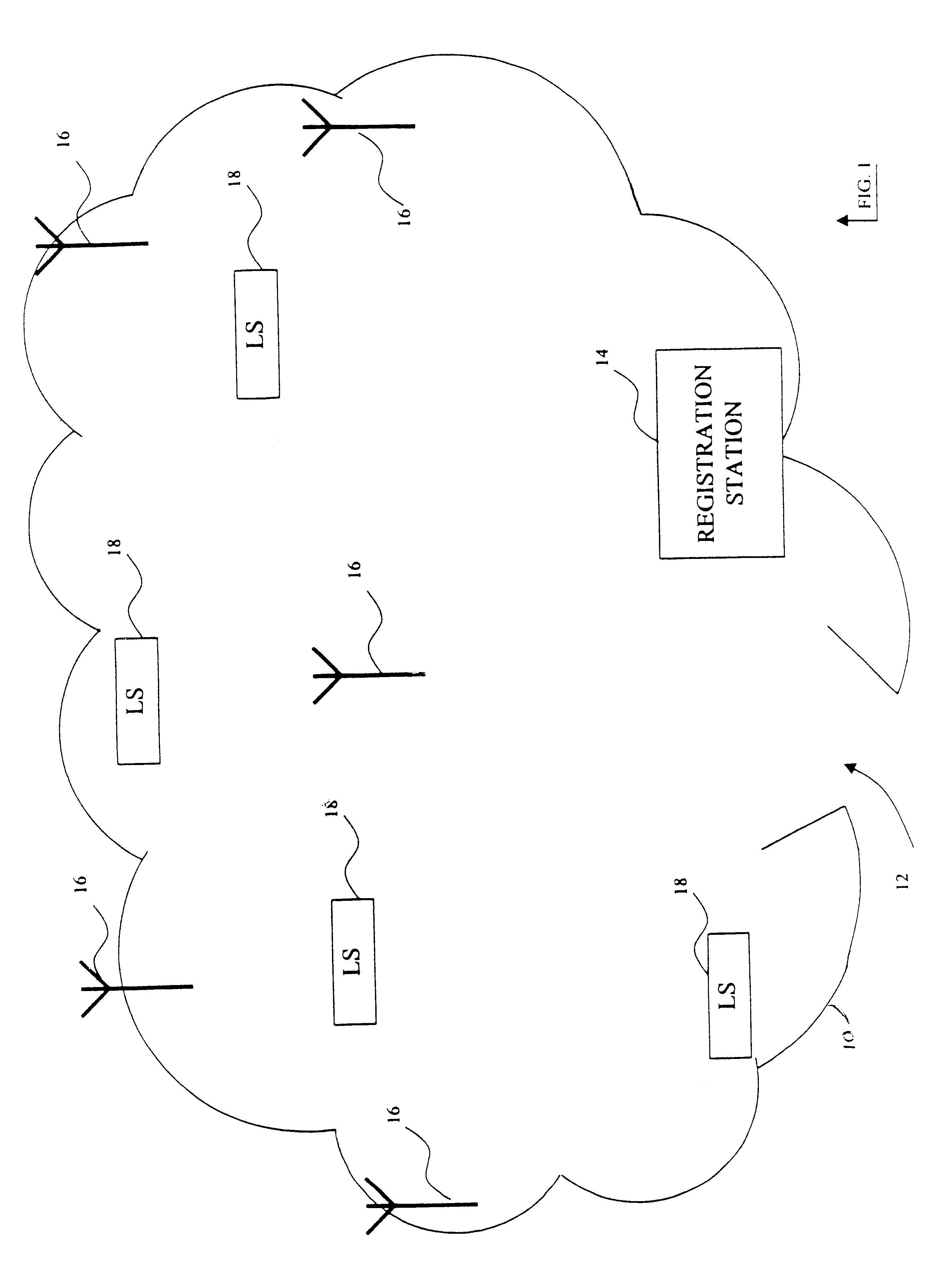
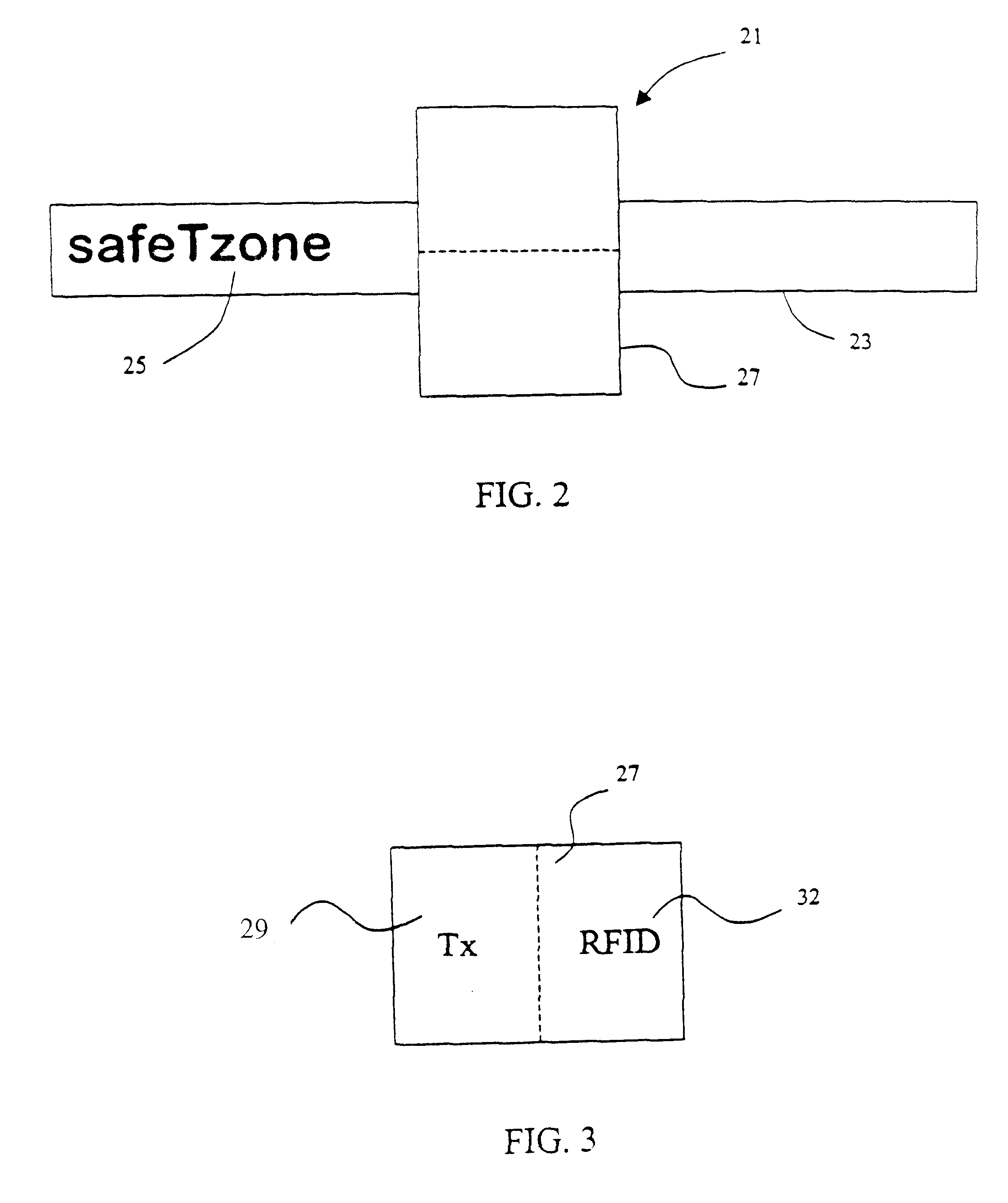
A locator system for tracking the location of individuals in a defined environment is disclosed. The system comprises at least one user identifier, at least one reader, at least one locator station and an identification server. The user identifier includes a long-range transmitter adapted to transmit an identification signal and a short-range passive component having identification information. The reader is adapted to receive the identification signal from the long-range transmitter. The locator station is adapted to read the identification information from the short-range passive component. The identification server is adapted to communicate with the reader and the locator, and has a database associating the identification signal of the long-range transmitter and the identification information of the short-range passive component with a particular user. The identification signal from the long-range transmitter may be an intermittent chirp. The long-range transmitter and the short-range passive component may be mounted on an identification tag, which may be attached to a wrist strap for securing the identification tag to a user's wrist.
Owner:SAFETZONE TECH
Method and apparatus for associating the movement of goods with the identity of an individual moving the goods
InactiveUS6909356B2Electric signal transmission systemsMultiple keys/algorithms usageEngineeringHuman–computer interaction
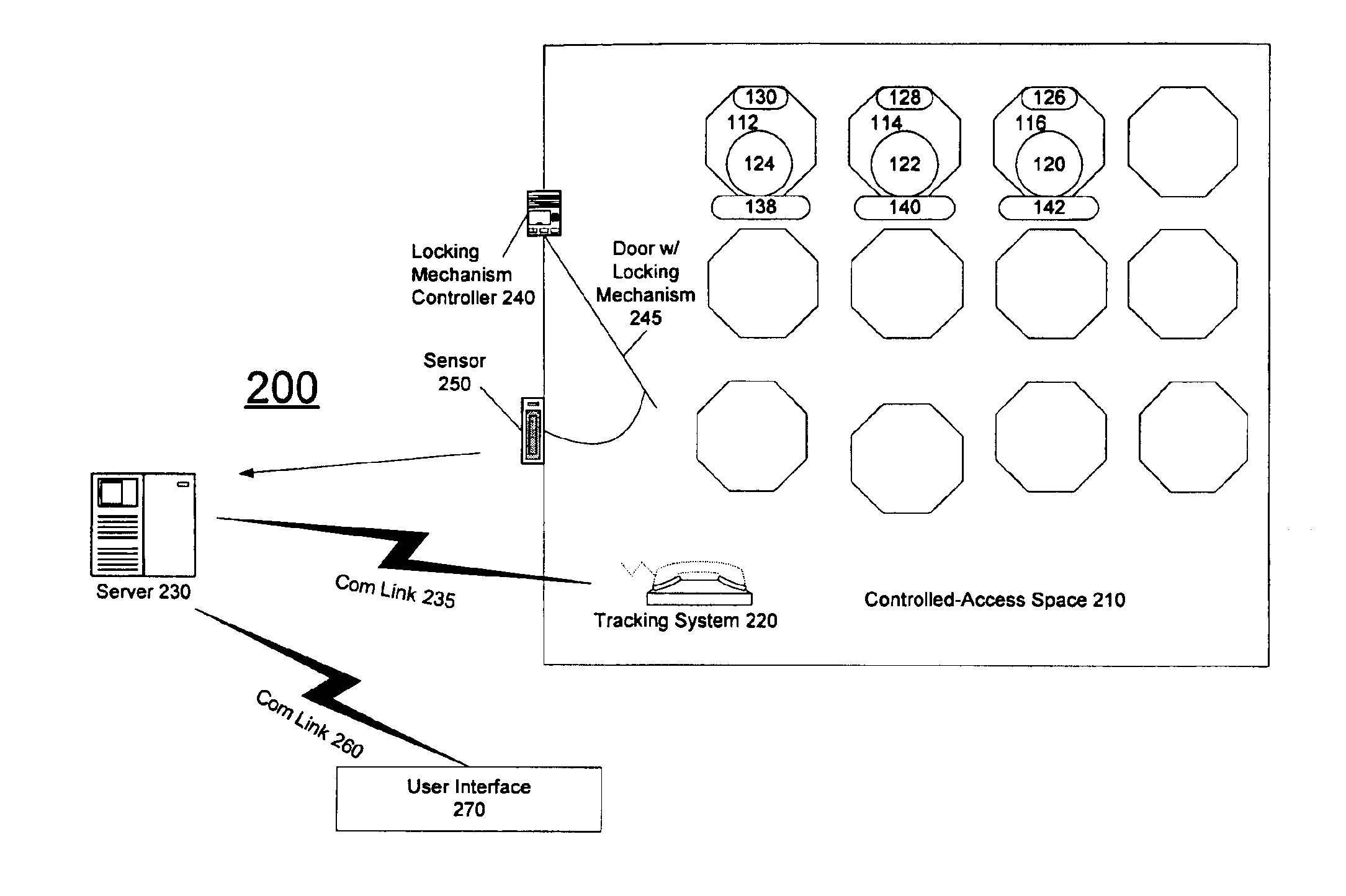
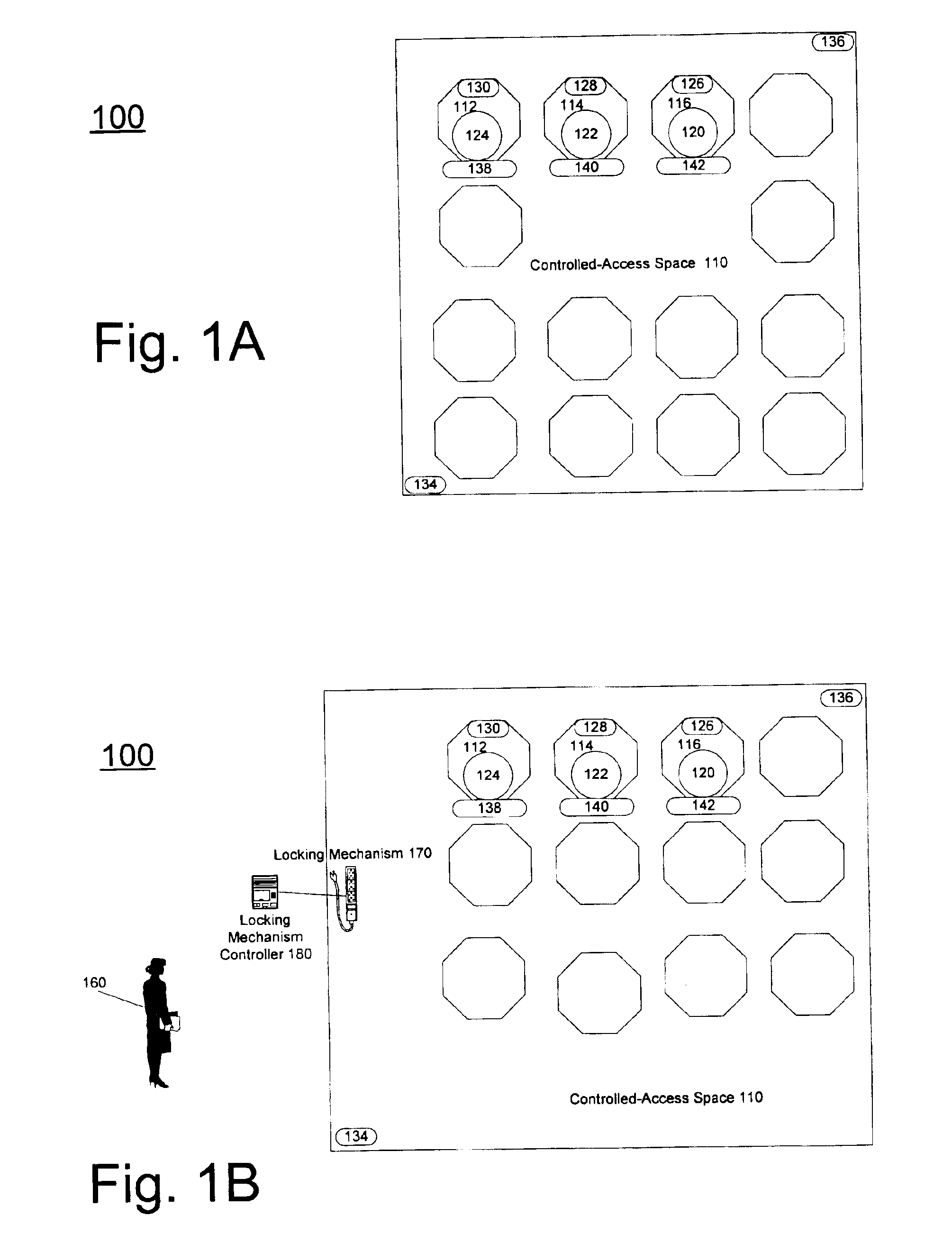
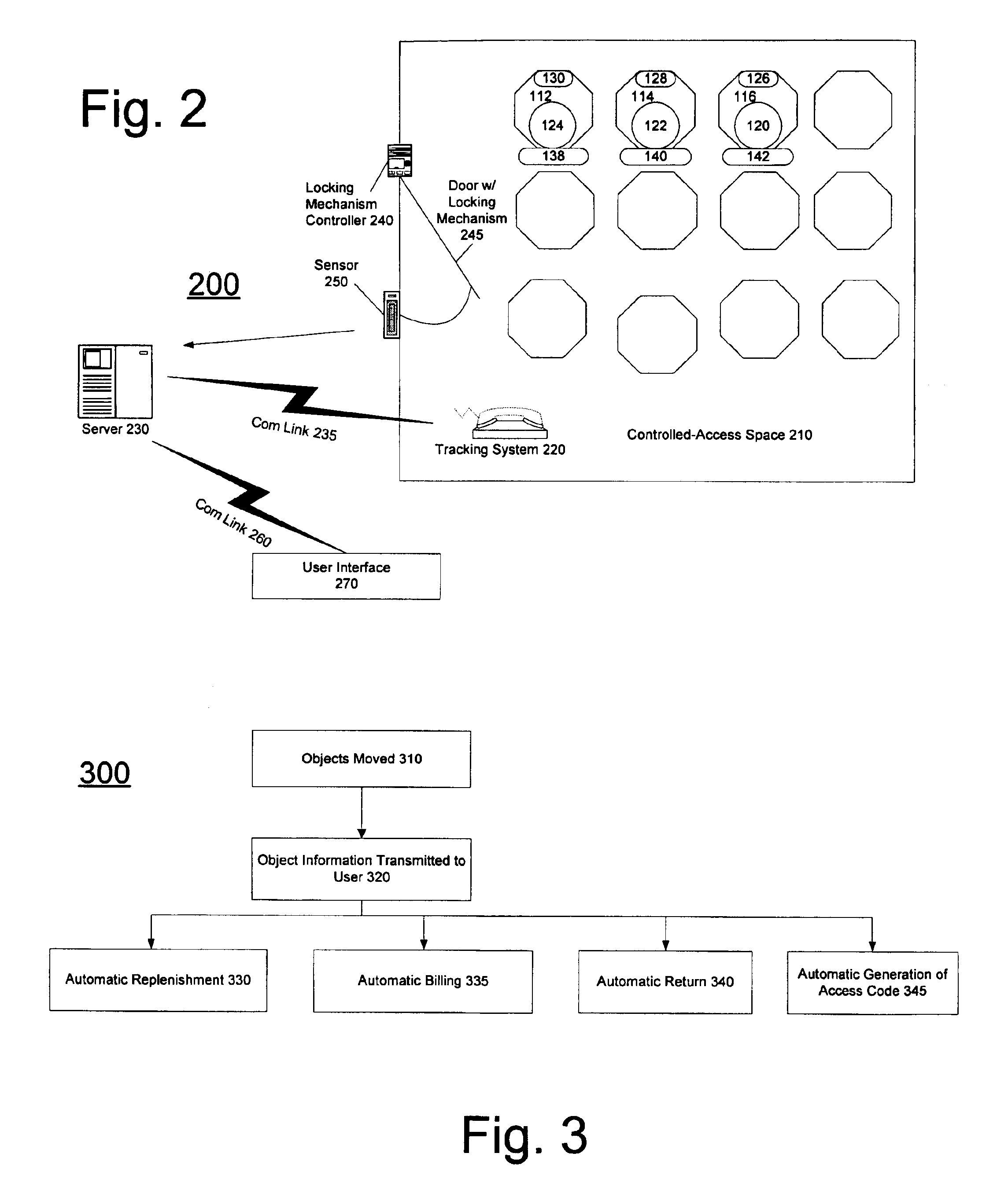
A tracking system monitors an entity that enters a controlled space and the addition, removal, or other movement or status changes of objects in the controlled space. A computer system, coupled to the tracking system, automatically associates the addition, removal or other movement or status changes of the objects with the identity of the entity and transmits this information to a server computer system. A user may subsequently access this information through one or more client computers coupled to the server computer system. The server computer system may also automatically notify a user or other computer systems, e.g., through a network interface, wireless interface, or telephone interface, when objects in the controlled space have been moved or the status has been changed and / or whether such movement or status change is authorized or not.
Owner:THINKLOGIX LLC
Portable device-interoperable home network system
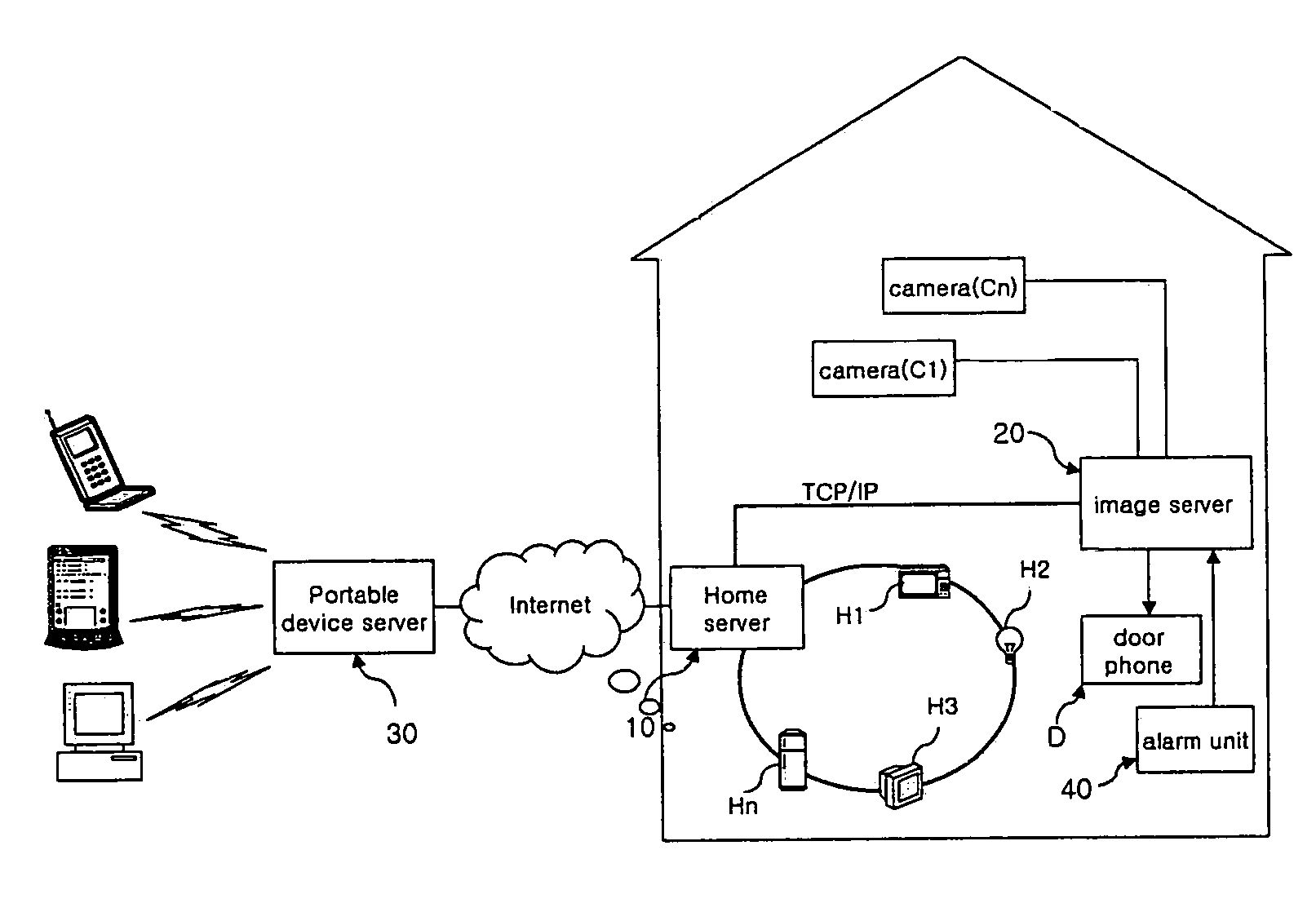
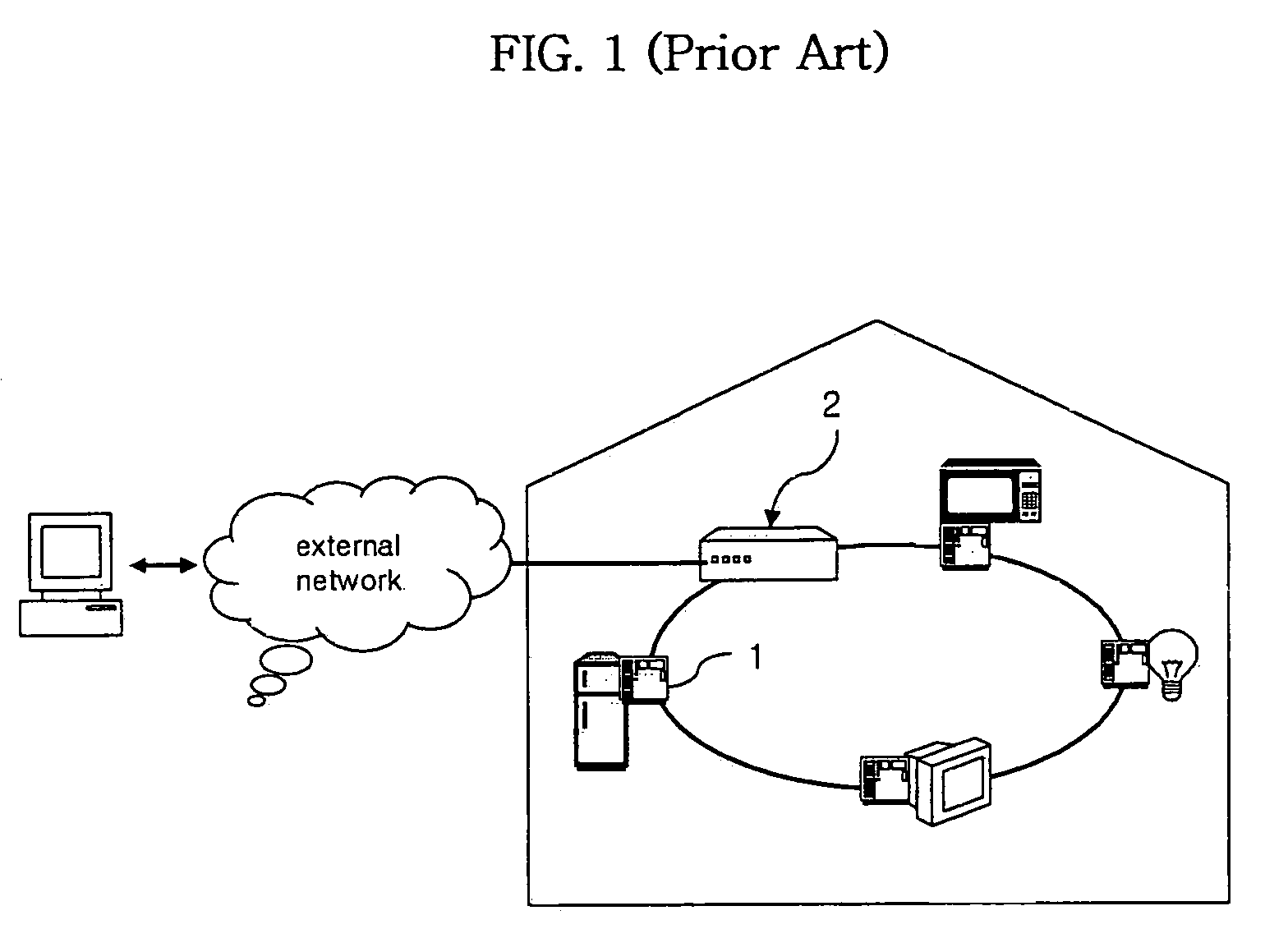
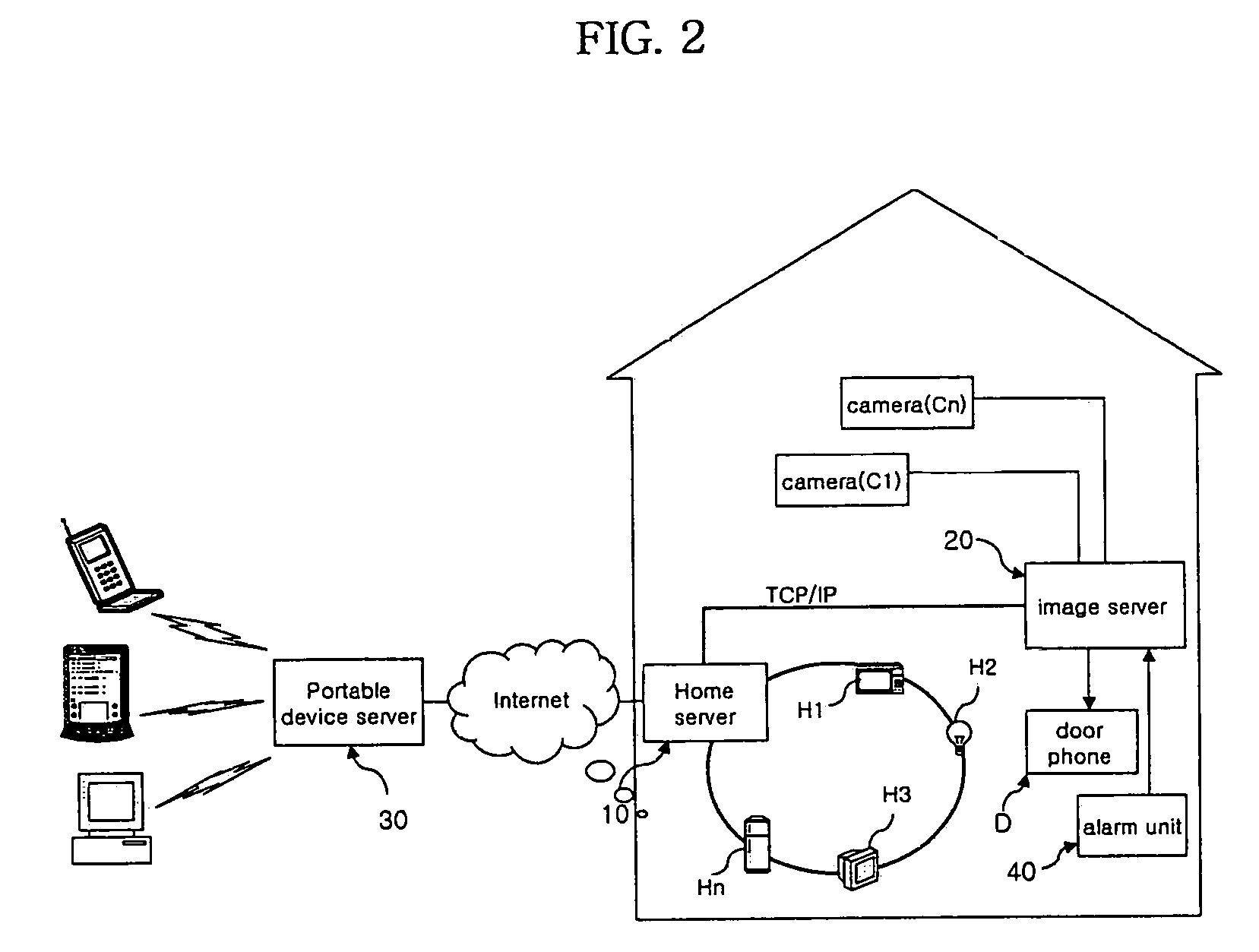
InactiveUS7106176B2Reducing the user's anxietyFrequency-division multiplex detailsTime-division multiplexImage serverHome appliance
A portable device-interoperable home network system includes a home server controls data transmission and reception of an internal network to which a plurality of home appliances are connected in a home. An image server outputs information regarding at least one image in the home to the home server. A portable device server receives the image information from the image server via the home server and transfers it to a portable electronic device. Therefore, a user can recognize a situation in the home through the portable electronic device from anywhere outside of the home, resulting in an increase in convenience of use.
Owner:LG ELECTRONICS INC
Mobile key using read/write RFID tag
ActiveUS20050242921A1Lessening and even eliminating needEasy to updateElectric signal transmission systemsMultiple keys/algorithms usageBiometric dataAuthorization
A mobile key includes an RFID tag associated with a memory. The memory holds a secure access code. An authorization status for a person or item associated with the mobile key is determined by interrogating the mobile key using an RFID interrogation field. Security information, such as a secure identifier or access code, physical measurement data, or biometric data may be provided by the mobile key. The key may also comprise a wireless communication device, such as a cellular telephone. Security information, such as an access code, may be provided to the key using the wireless communication device or other communications network.
Owner:INTERMEC IP
Telecommunication enclosure monitoring system
ActiveUS8135352B2Interconnection arrangementsFrequency-division multiplex detailsElectricityTransceiver
A remote monitoring system for telecommunication enclosures includes a low profile or flush mounted sealed transceiver or antenna unit, an electronic module inside of the enclosure electrically connected to the transceiver and a communication device to send signals to the electronic module through the transceiver. The sealed housing generally comprises a portion extending through the exterior surface of the enclosure. In some embodiments, the transceiver may include a radio frequency antenna, a photoelectric cell, a light sensor or an infrared sensor, and the communication device may be a handheld device, a transponder, or a networked computer.
Owner:3M INNOVATIVE PROPERTIES CO
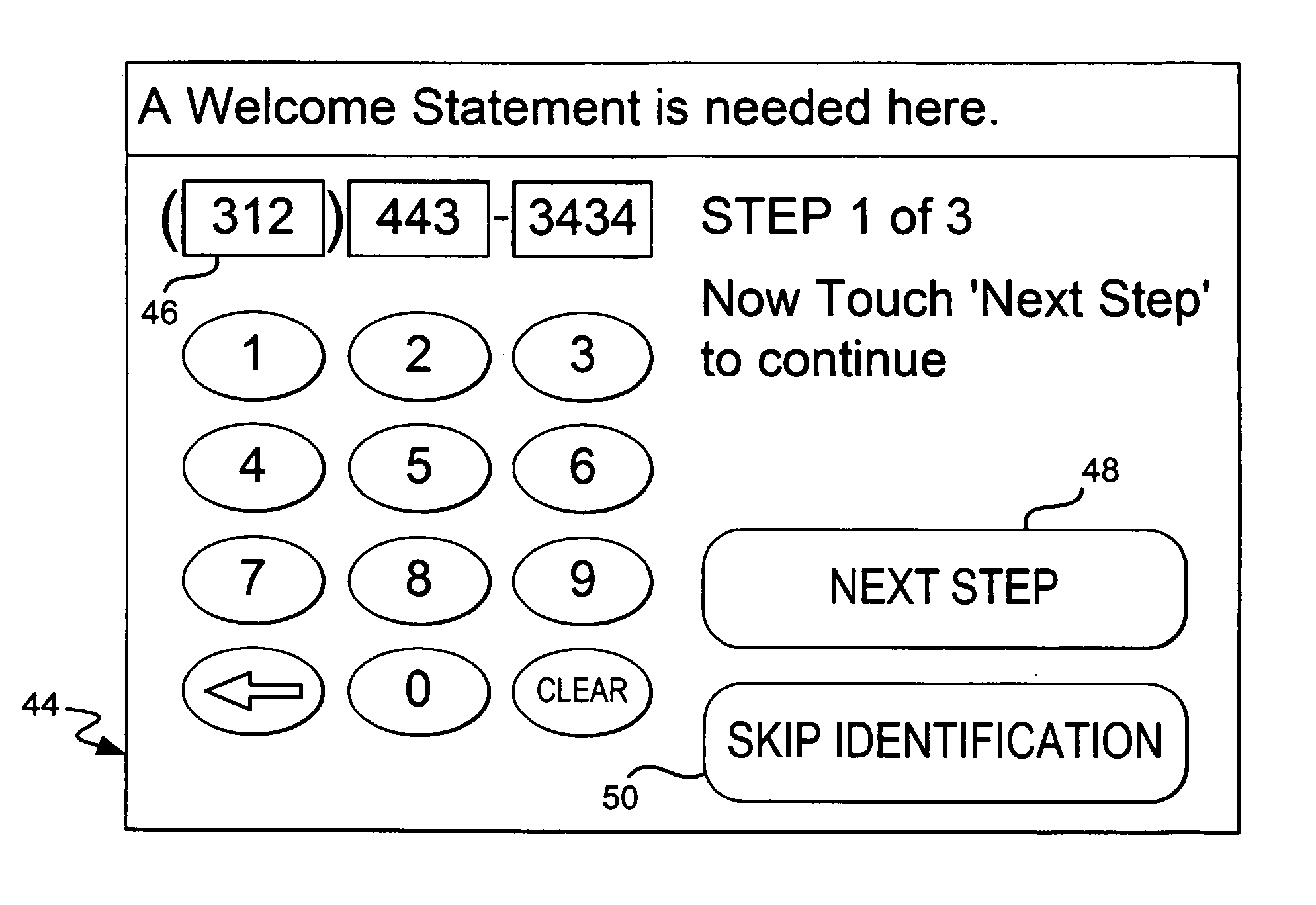
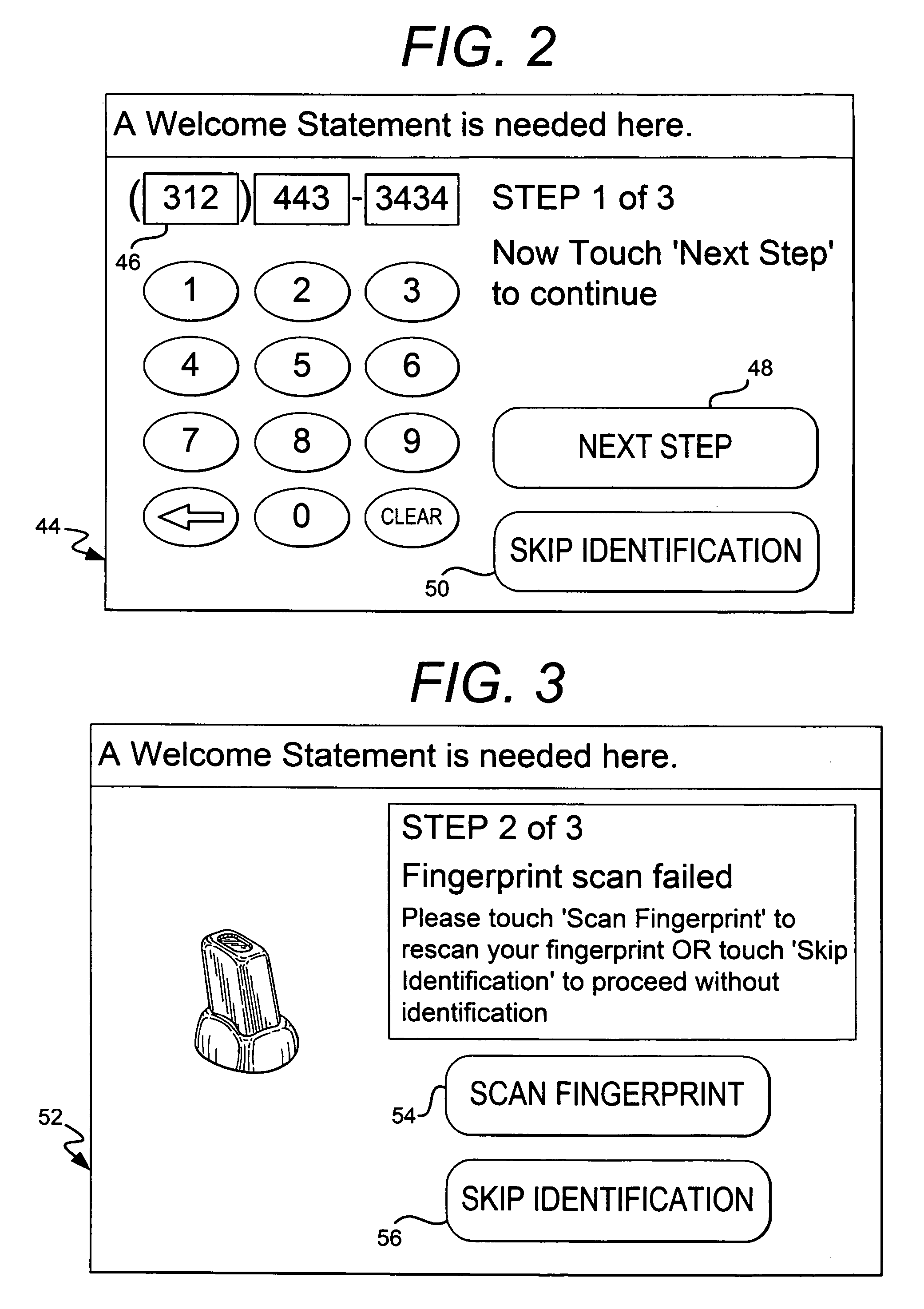
System and method for identifying and managing customers in a financial institution
InactiveUS20060253358A1Preventing account fraudAccurate identificationFinanceChecking apparatusCustomer informationLibrary science
A system and method for managing a customer in a banking institution. The system includes a customer kiosk with biometric device for identifying the customer. The system places the customer in a virtual queue to see a service provider.
Owner:US BIOMETRICS CORP
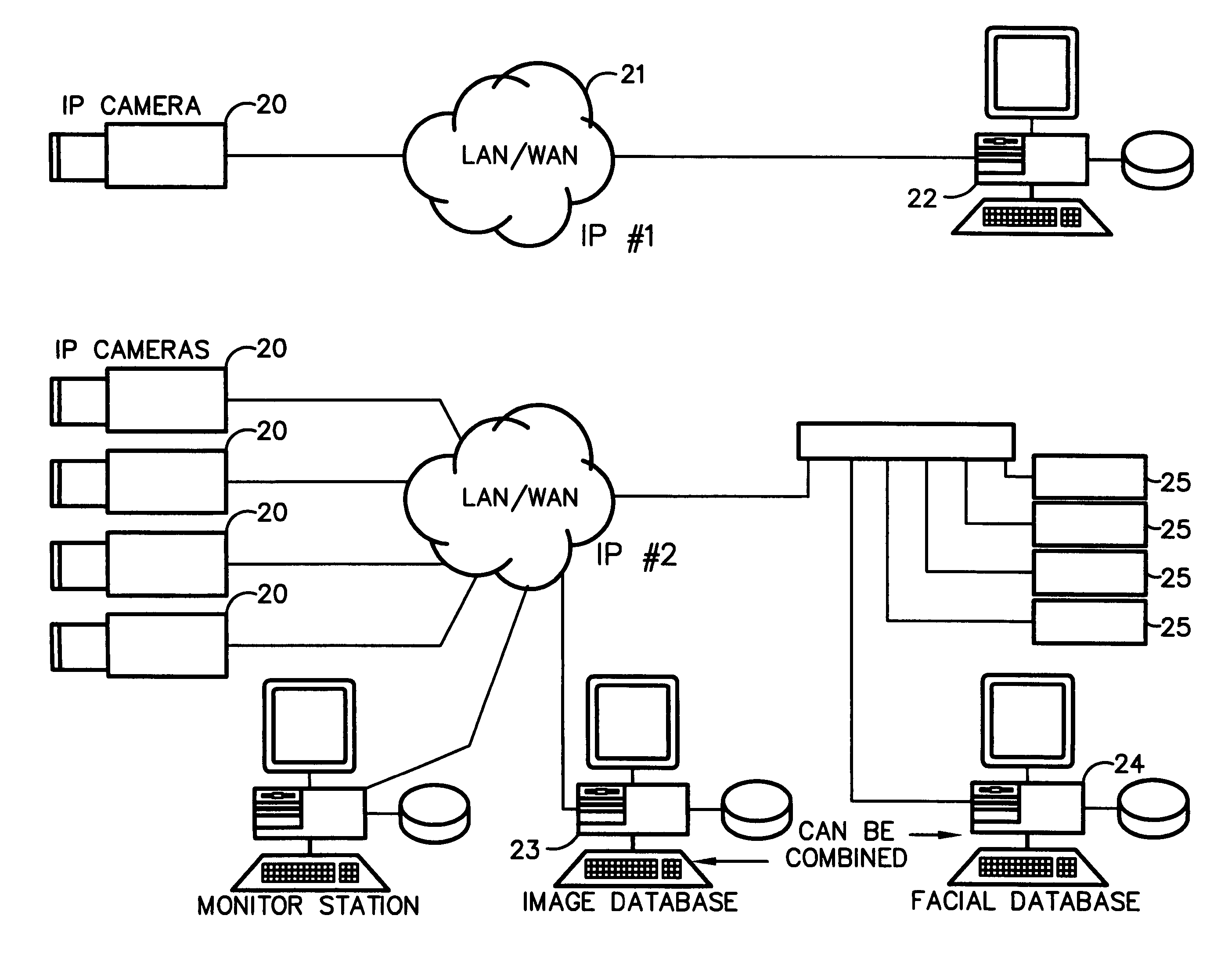
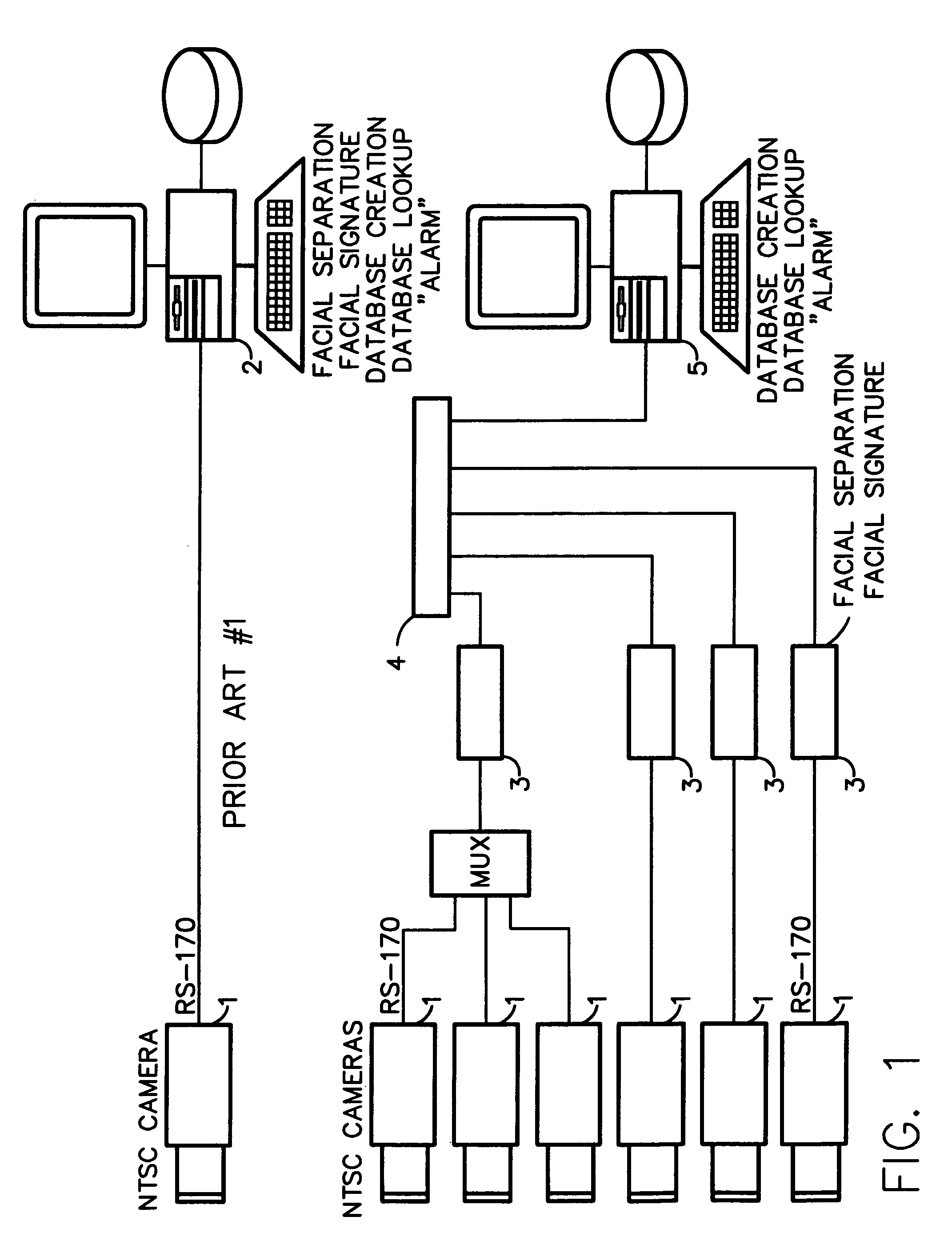
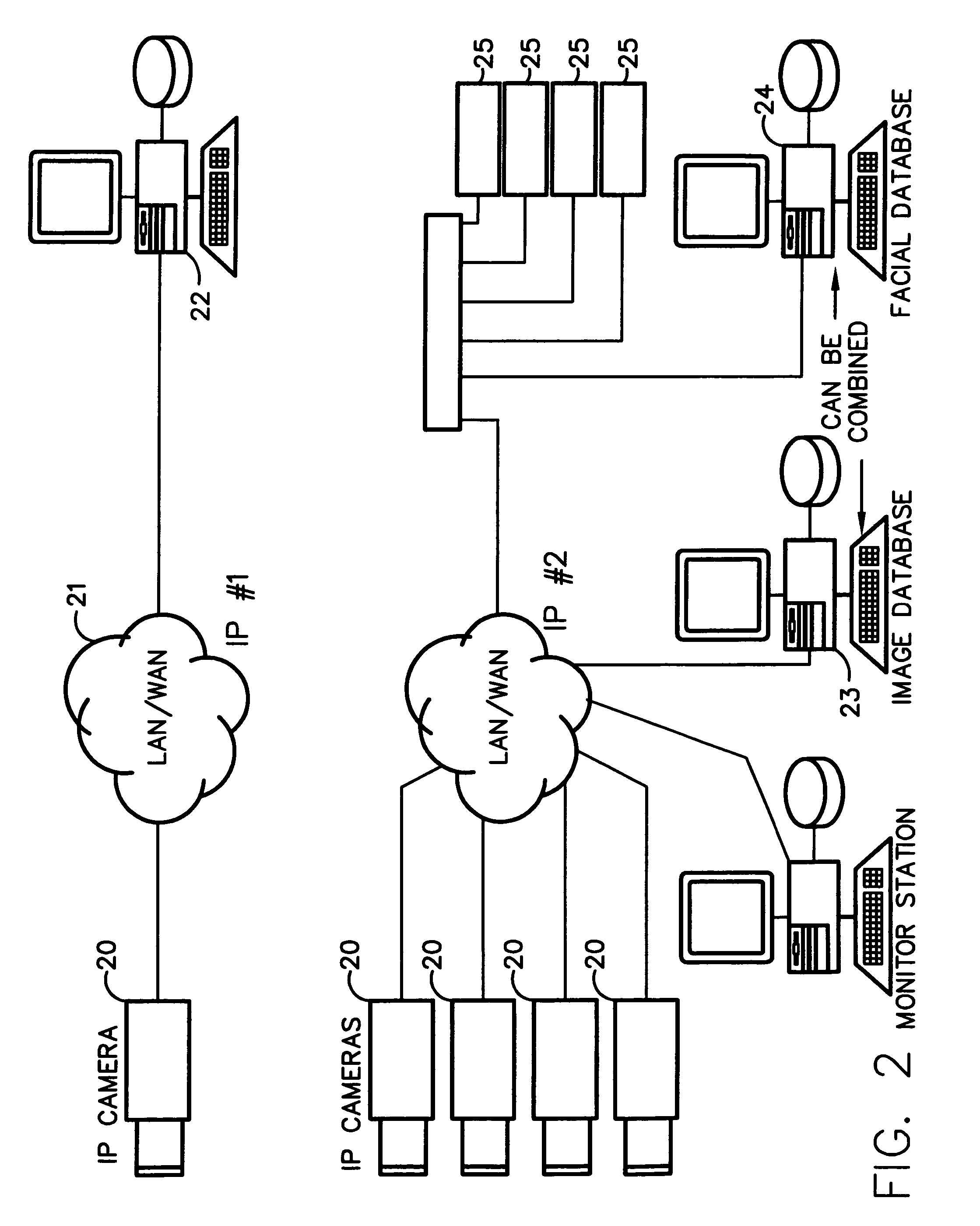
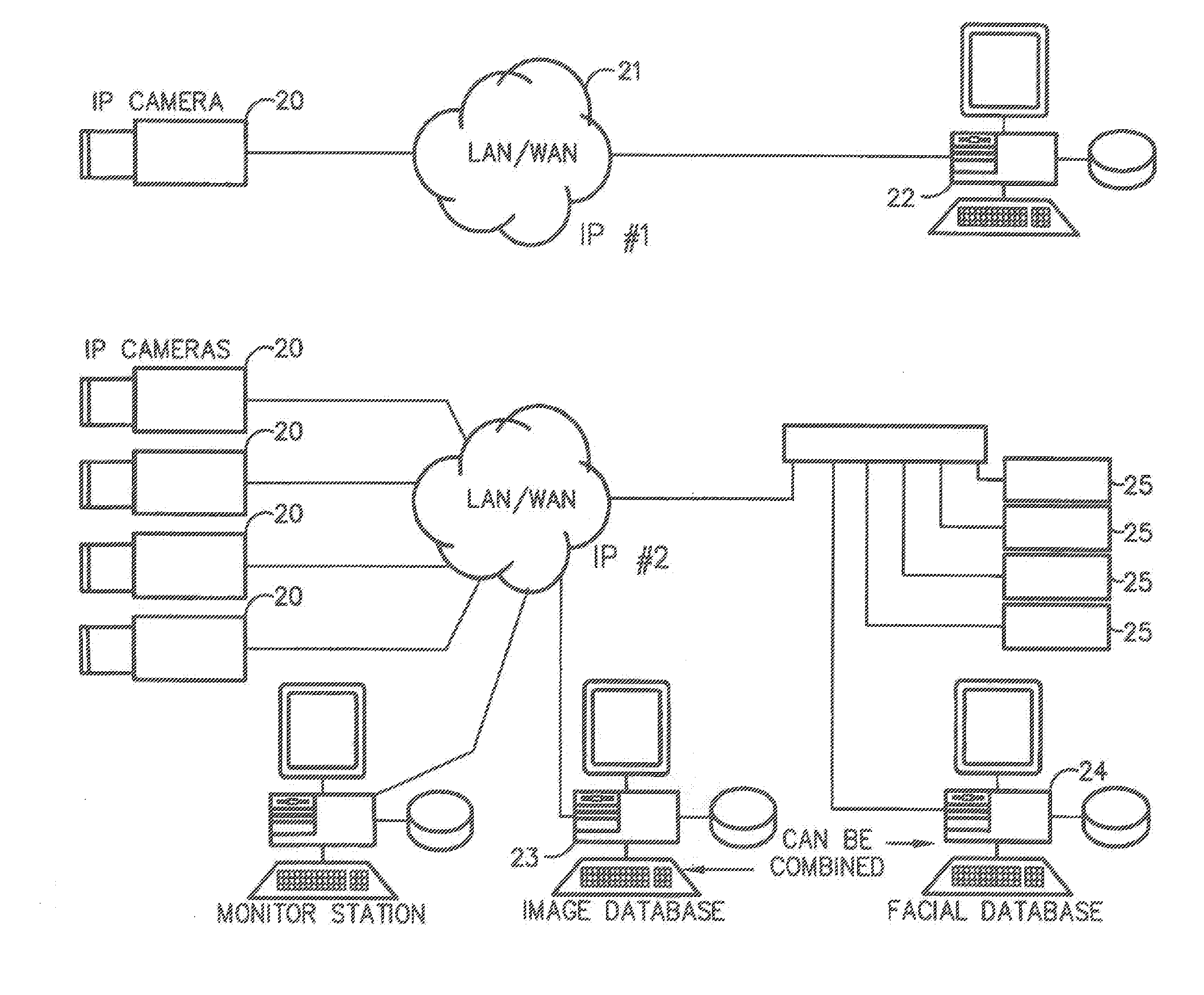
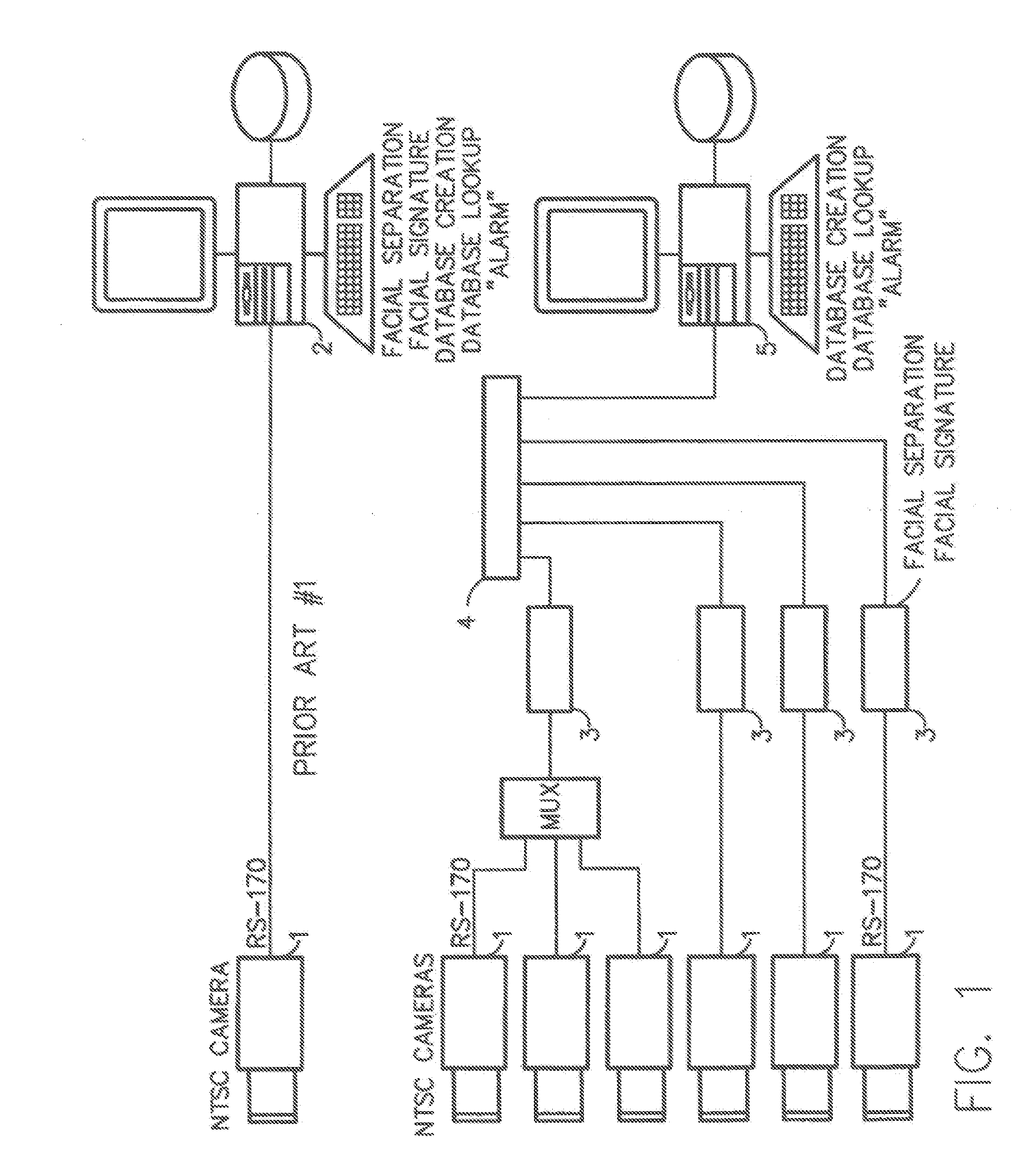
Method for incorporating facial recognition technology in a multimedia surveillance system
InactiveUS7634662B2Function increaseImprove economyChecking time patrolsCharacter and pattern recognitionSurveillance cameraRecognition algorithm
Embodiment provide a surveillance camera adapted to be connected to an internet protocol network, the surveillance camera including at least one facial processor, at least one facial recognition algorithm embodied in suitable media, at least one facial recognition algorithm executable with digital format image data by at least one facial processor detecting faces, execution of at least one facial recognition algorithm producing unique facial image data, execution of at least one facial separation algorithm producing facial separation data, at least one facial processor in communication with at least one facial signature database to obtain reference data, execution of at least one facial signature algorithm comparing facial separation data and reference data to identify correlations, at least one compression algorithm producing compressed image data, and a network stack configured to transmit to the network unique facial image data for each detected face and compressed image data.
Owner:PR NEWSWIRE
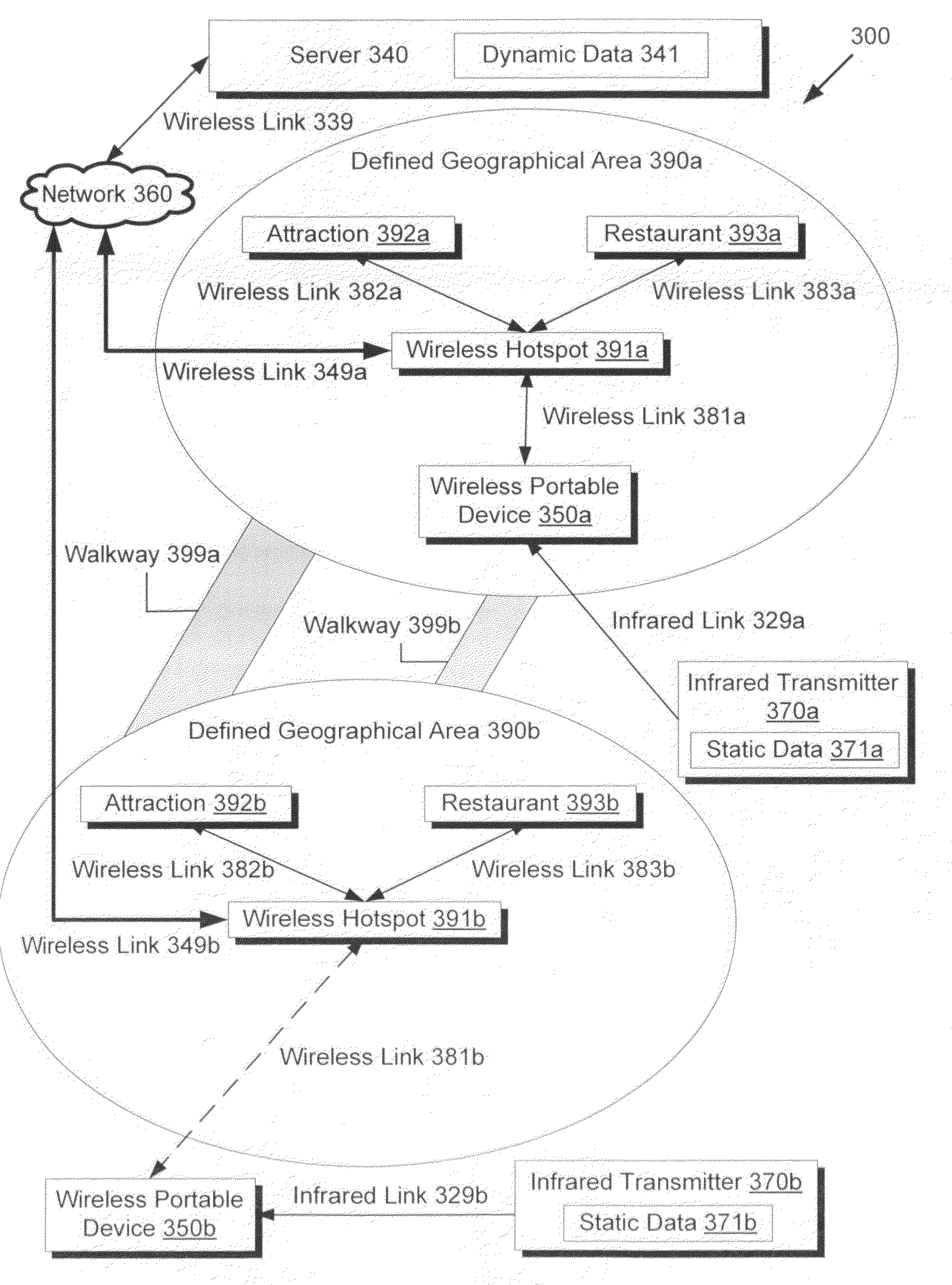
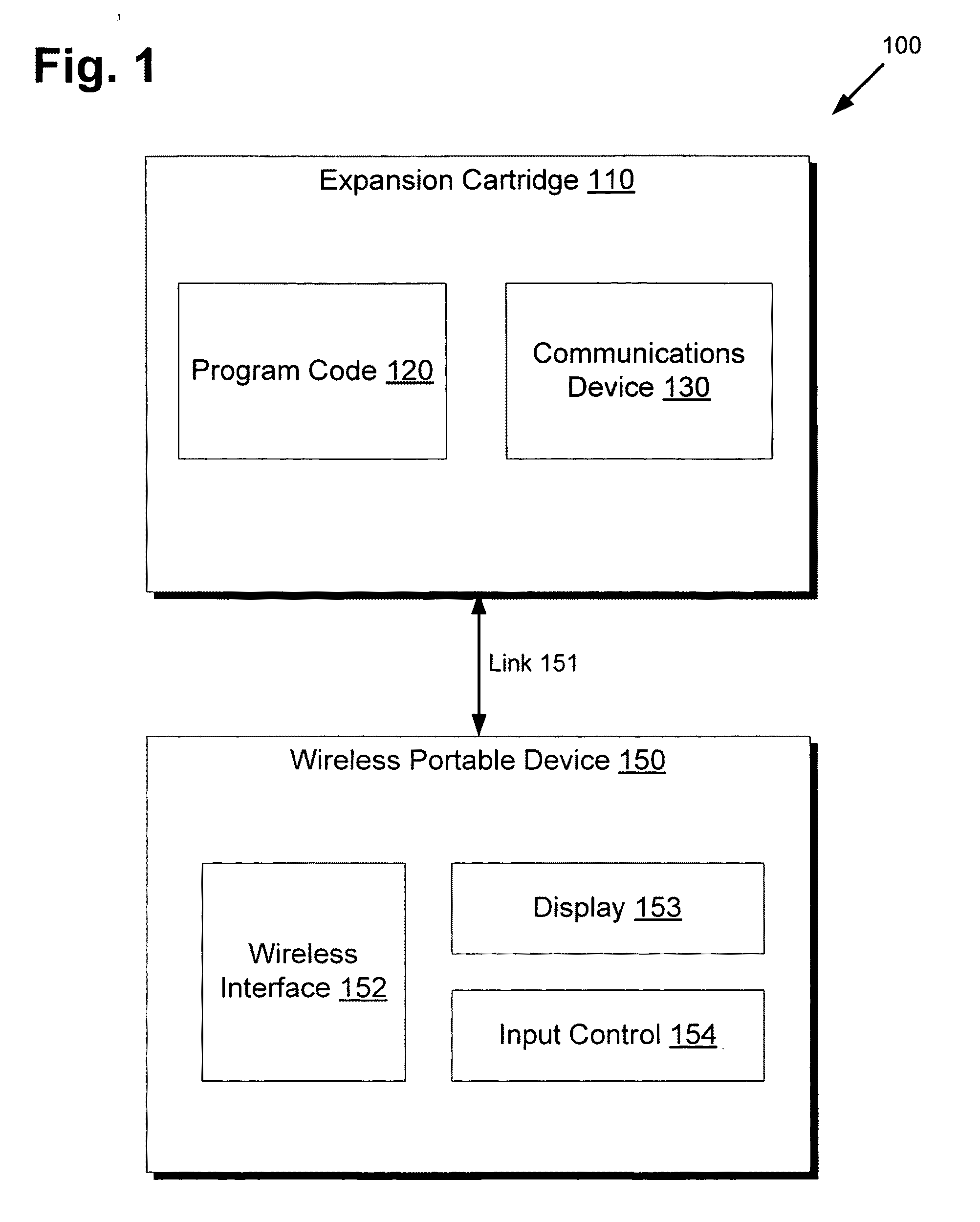
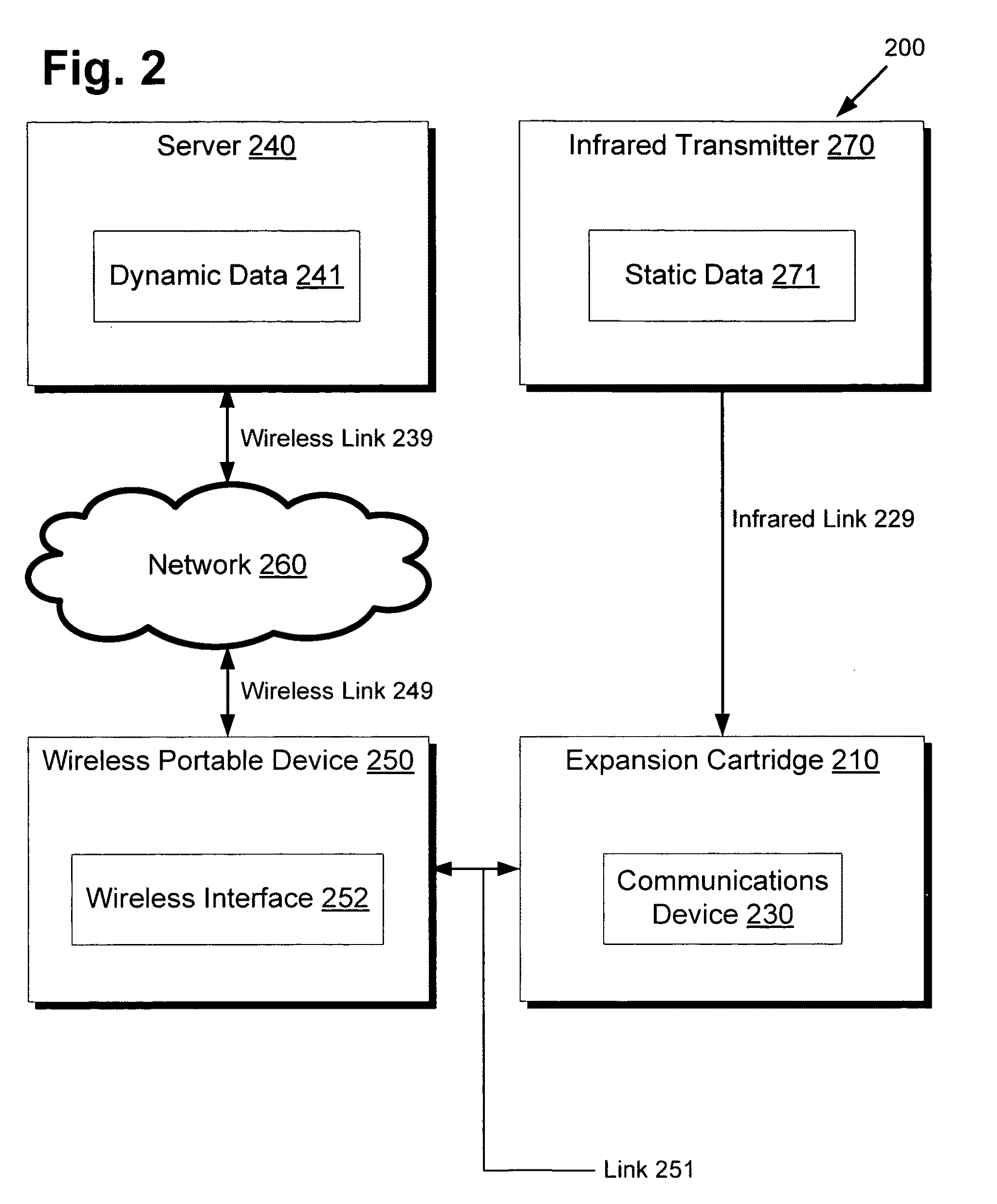
System and method for providing location-based data on a wireless portable device
There is provided a wireless portable device for providing location-based data to a user in a defined geographical area including a plurality of points of interest, the wireless portable device comprising a wireless transmitter, a wireless receiver, and a display. The wireless transmitter can transmit location information to a wireless server over a wireless network. The wireless receiver can receive location-based data relating to a point of interest from the wireless server periodically and automatically, based on the location of the wireless portable device. By optimizing map routes and schedules using the location-based data and user preferences including wish lists, the wireless portable device can provide helpful recommendations via the display, enabling the user to plan an efficient schedule of activities in the defined geographical area optimized by walking distance, queue wait times, booking and arriving at reserved events, and / or by other user preferences.
Owner:DISNEY ENTERPRISES INC
Obtaining person-specific images in a public venue
InactiveUS20040156535A1Improve accuracyFewer false positivesProcessed material treatmentRecord information storagePublic placeEyewear
Collecting images of a patron in an entertainment venue is performed by facial recognition of the patron's face within the images, simplifying the storage and distribution of the images for a patron. In order to enhance the reliability of the facial recognition system, information about the patron that is not directly related to most facial recognition systems, including clothes, height, other associated people, use of glasses and jewelry, disposition of facial hair, and more, can be used. Some of the characteristics used can be specific to a particular date or event, and which will not be more generally characteristic of the patron. The facial recognition system can also be used to identify the patron requesting images to be collected. The present invention also relates to the use of facial recognition in sorting and collecting images from an electronically-stored image collection, enabling the easy retrieval of images that are related to a particular person or set of people.
Owner:HYSTERICAL SUNSET
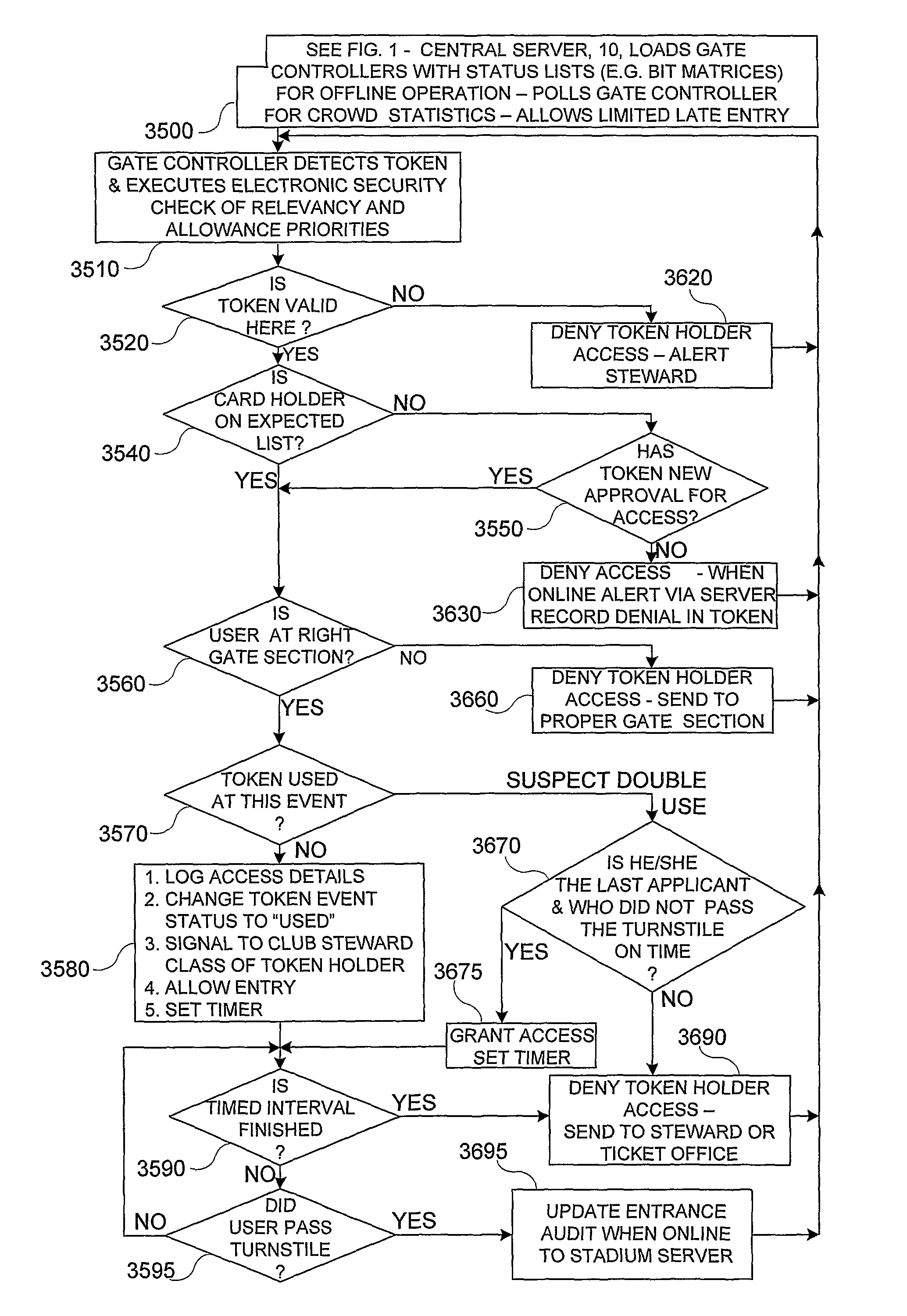
System and Methods for Accelerated Recognition and Processing of Personal Privilege Operative for Controlling Large Closed Group Environments
ActiveUS20080191009A1Process is accelerated and simplifiedAvoid practicalTicket-issuing apparatusDigital data processing detailsCrowd controlCrowds
Methods (3500-3695) and apparatus (10, 20) for controlling physical (30, 40) and virtual (12) access for accelerated recognition and processing of privileges, benefits, value transfers, crowd control, community membership and status, in particular for institutions, arenas and other large venues.
Owner:FORTRESS GB
Method and apparatus for facilitating personal attention via wireless networks
InactiveUS20030043042A1Electric signal transmission systemsDigital data processing detailsDisplay deviceBackground information
A method and system for identifying individuals, accessing and updating background information regarding such individuals and directing appropriate personal interaction with the individuals. Presence of the individual may be detected by recognition of a biometric feature or by use of an automatically readable tag, such as an RFID tag. Information regarding the individual, such as a unique code corresponding to that individual, may be communicated to a computer system that has a database in connection with which the code is used as a key to retrieve relevant background information, which is then communicated over a wireless link to a portable display device. The system may also automatically capture an image of an individual being identified and may then transmit that image over a wireless link to the portable display device. Various systems may employ multiple RFID scanners, facial recognition, various image capture devices, and multiple portable display devices, such as PDA's.
Owner:TABULA RASA
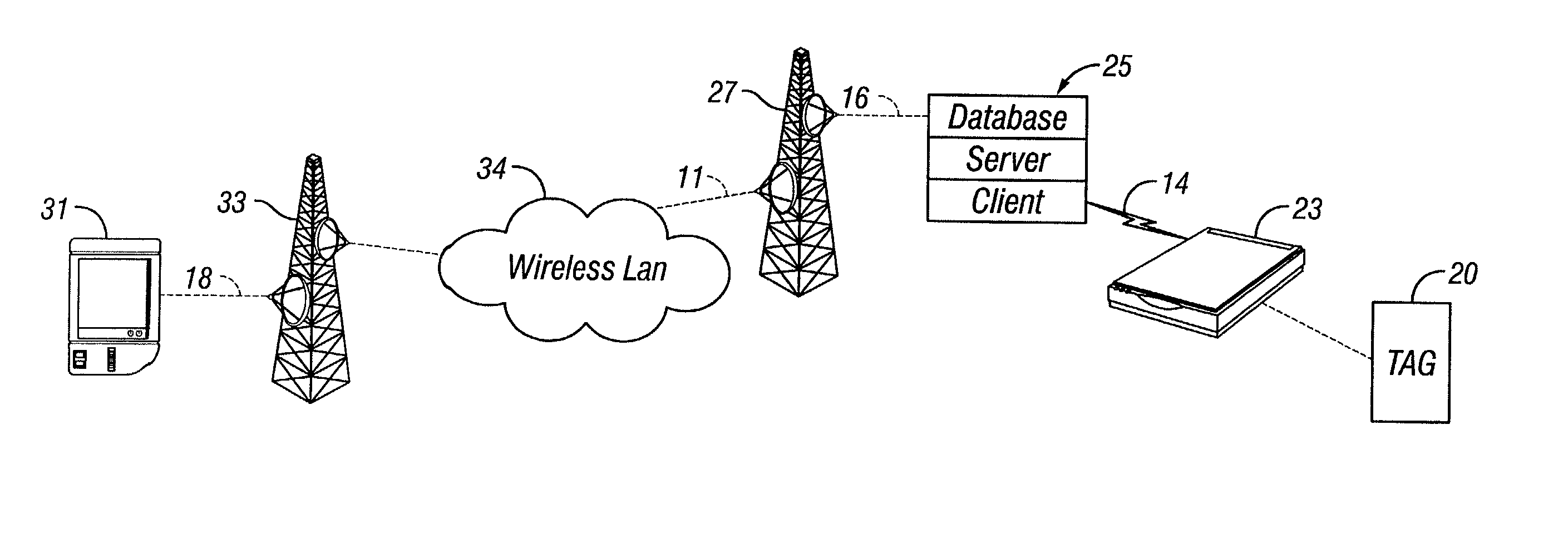
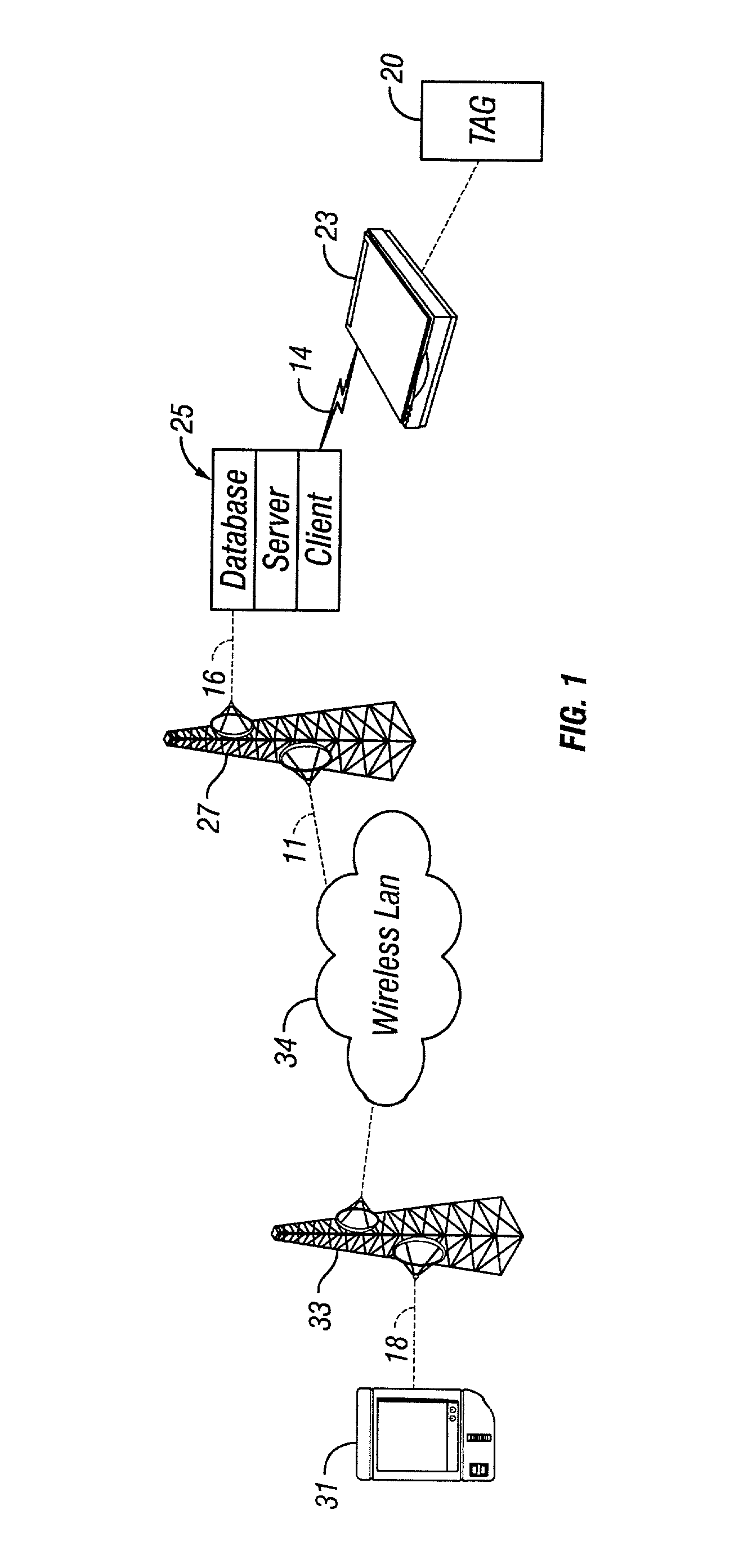
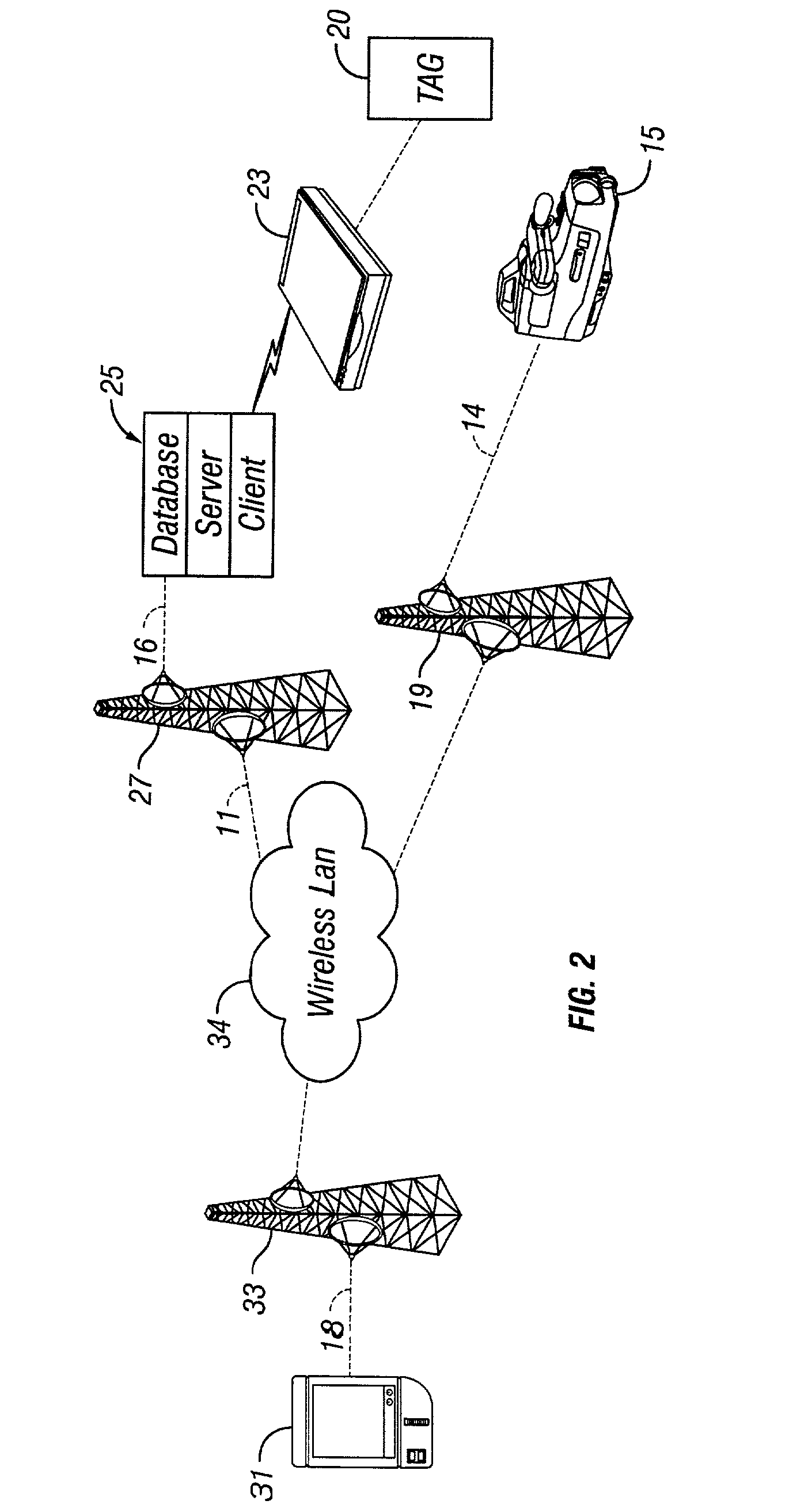
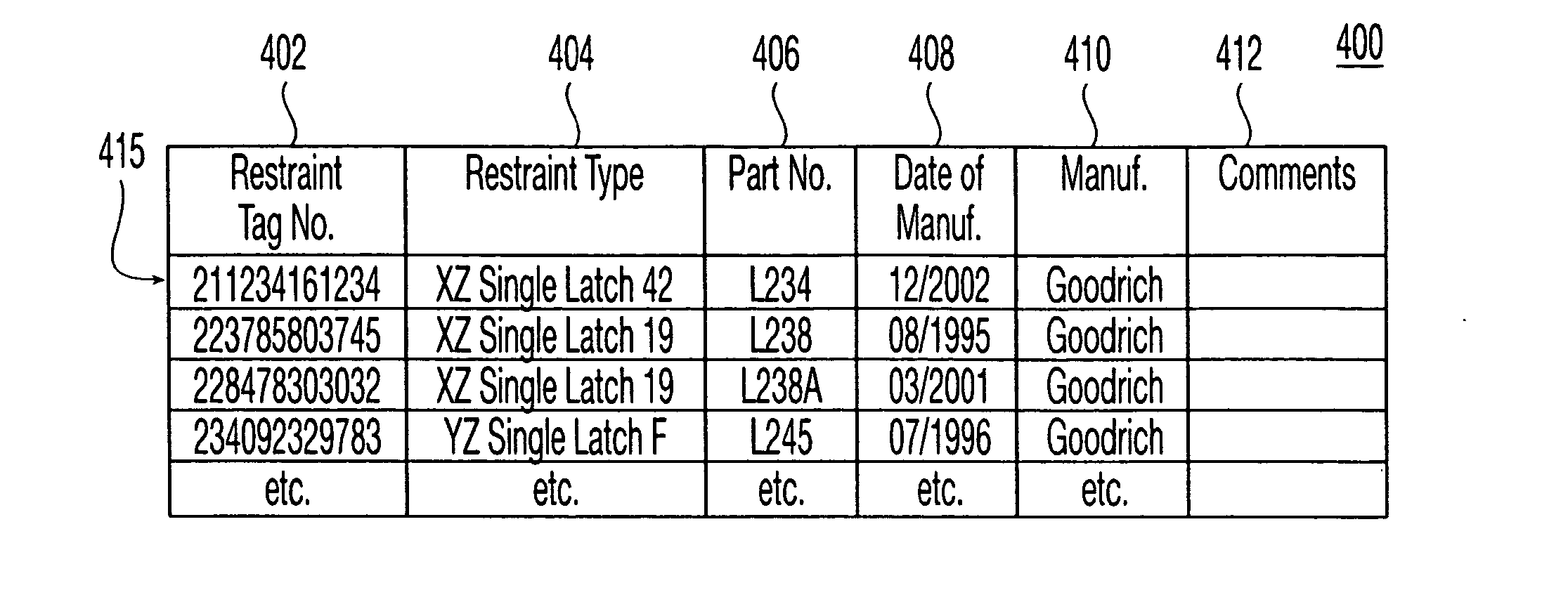
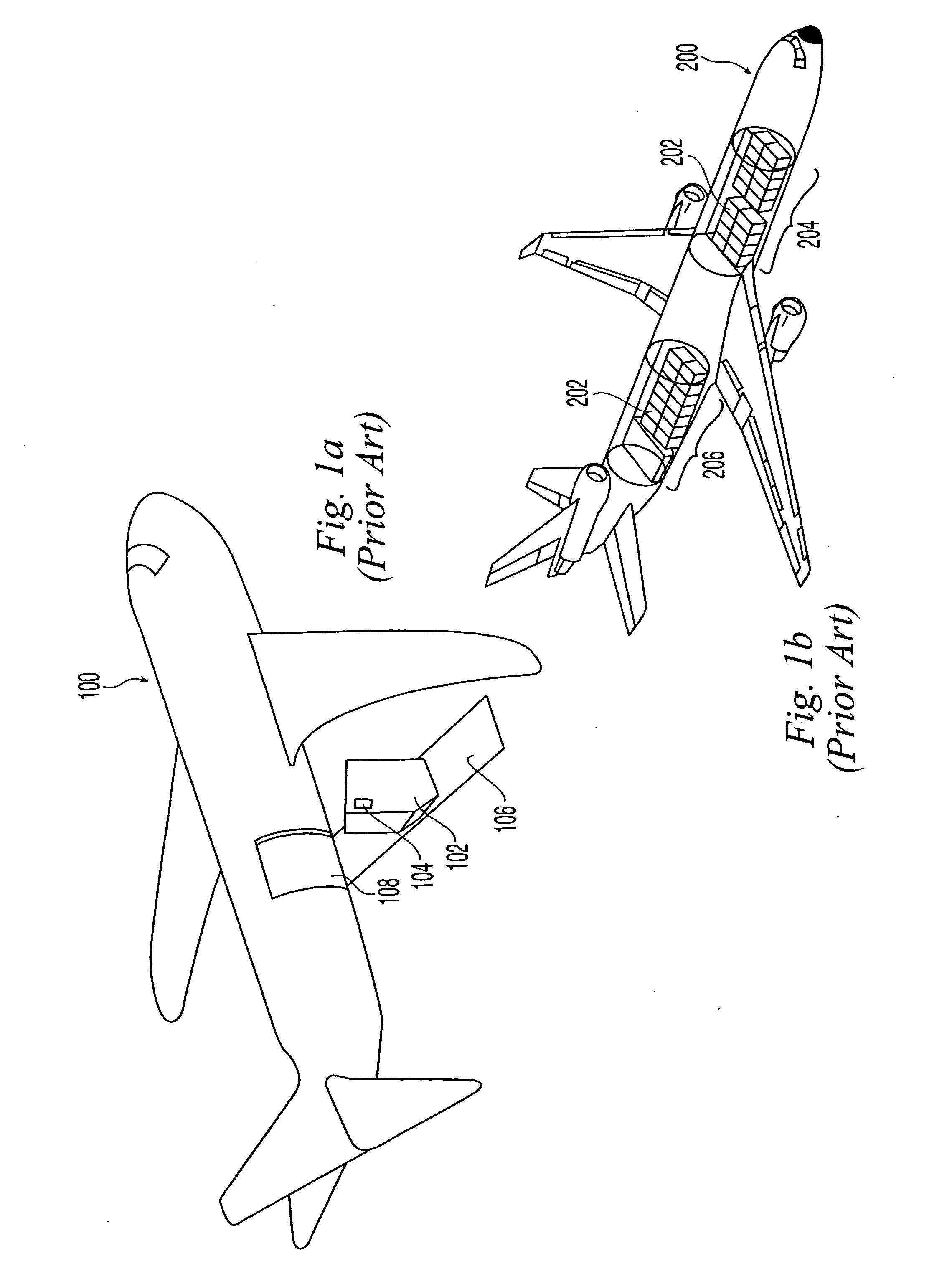
Aircraft cargo loading logistics system
A cargo loading logistics system for verifying cargo loaded on an aircraft receives a desired restraint configuration from a database and determines an actual restraint configuration on the aircraft by receiving data from a plurality of machine readable identifiers corresponding to a plurality of install points and data from a plurality of machine readable identifiers corresponding to a plurality of restraints. The cargo loading logistics system then compares the desired restraint configuration with the actual restraint configuration and determines if the aircraft is properly configured to be loaded for an upcoming flight.
Owner:THE BF GOODRICH CO
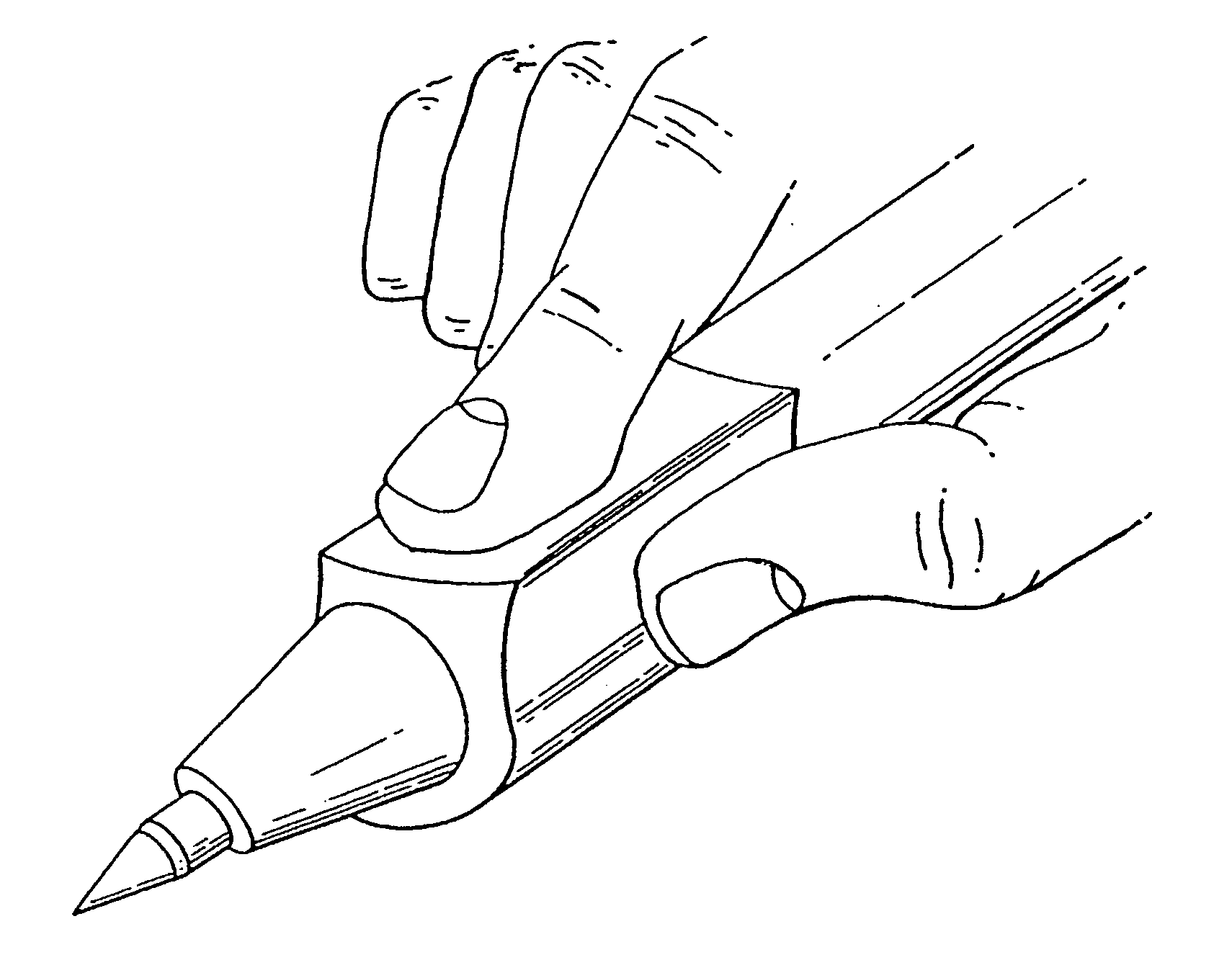
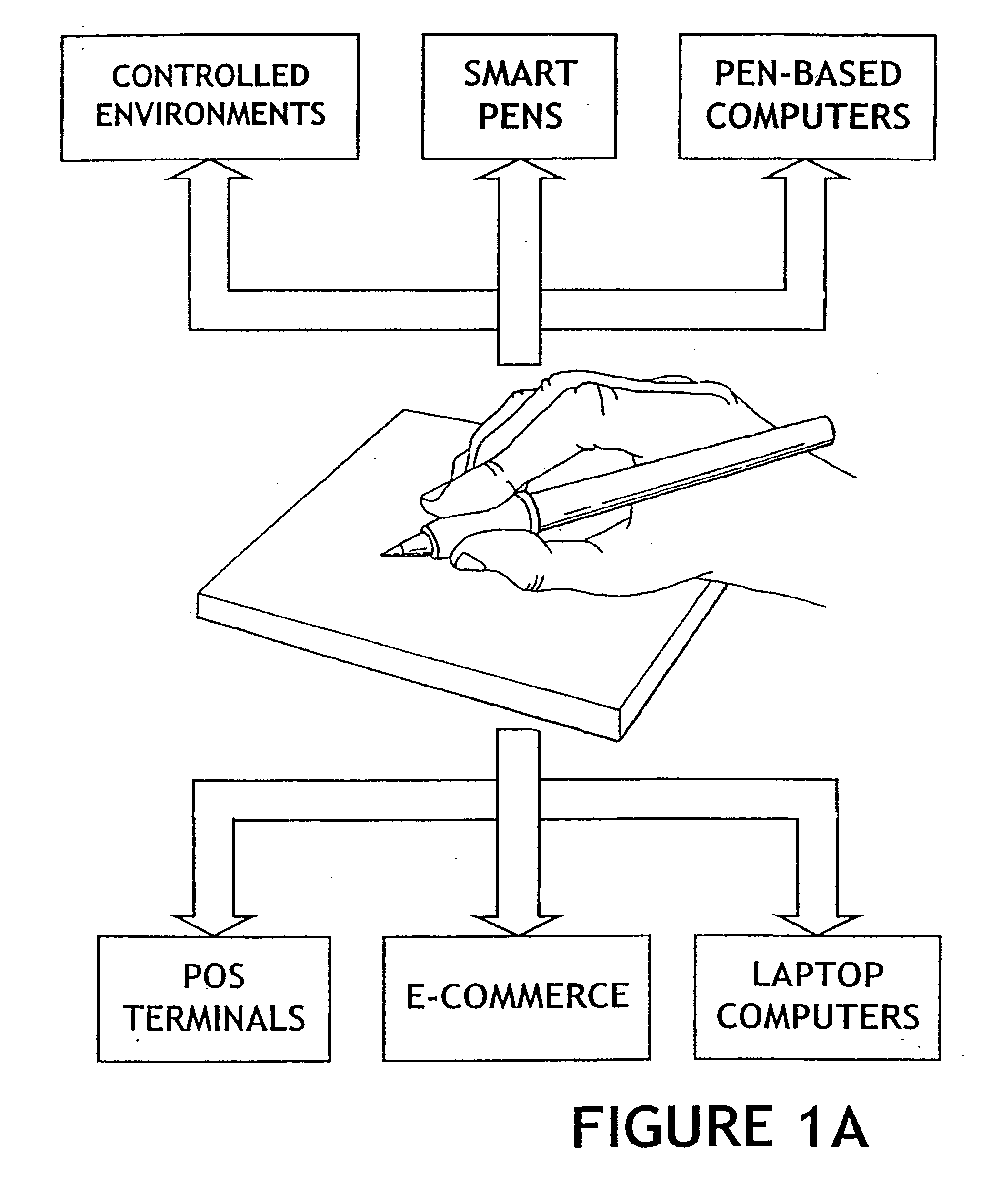
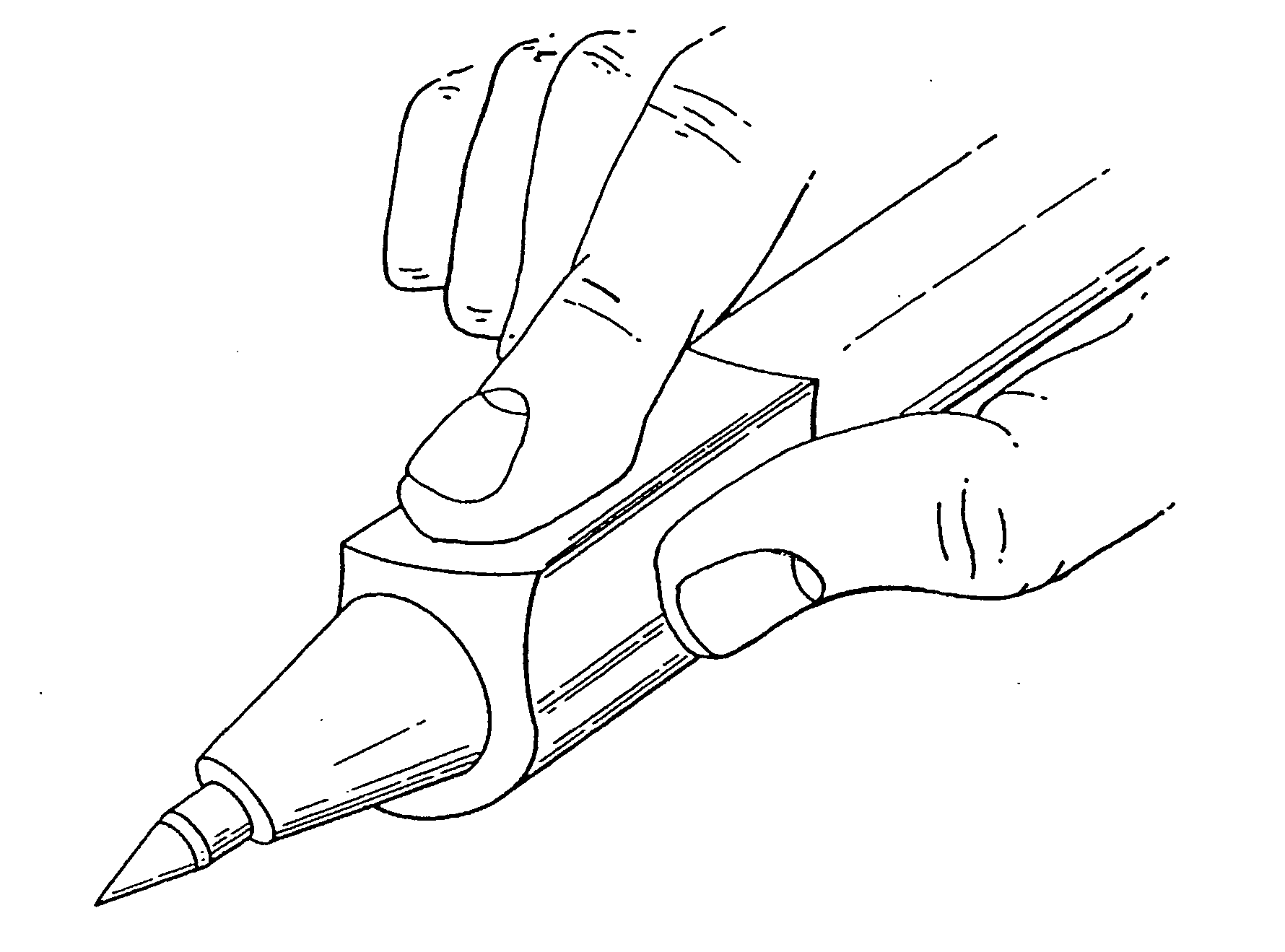
Method for identity verification
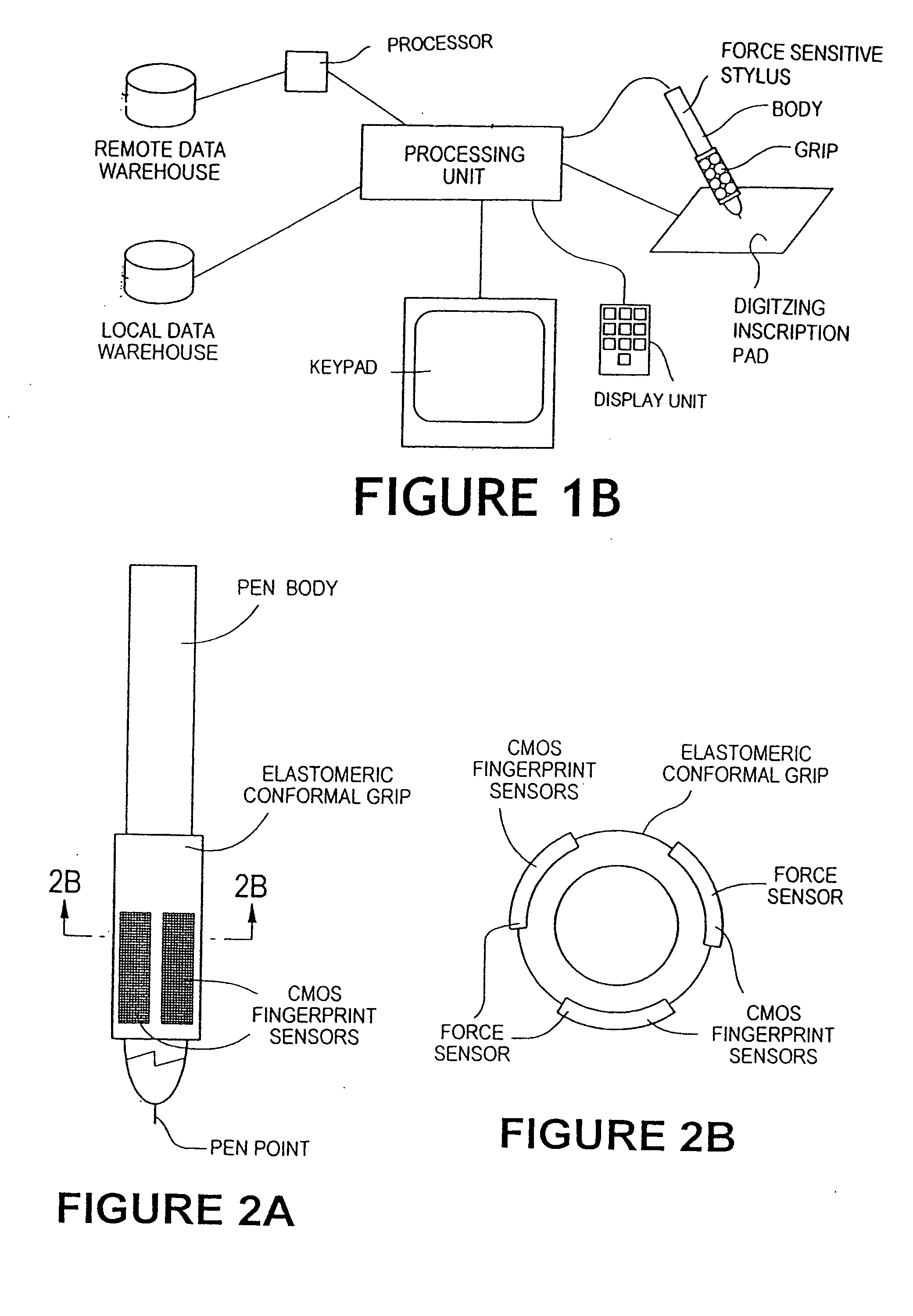
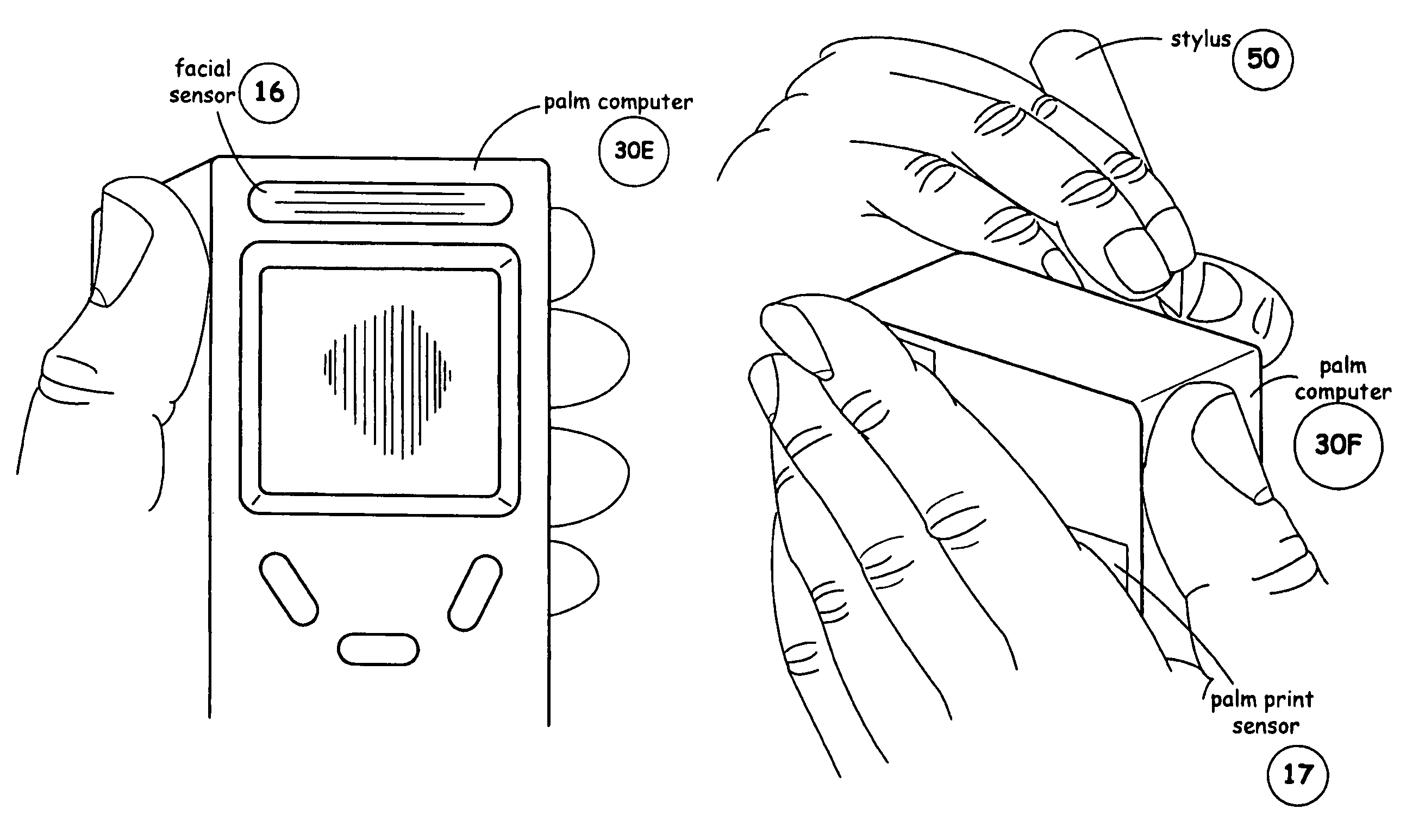
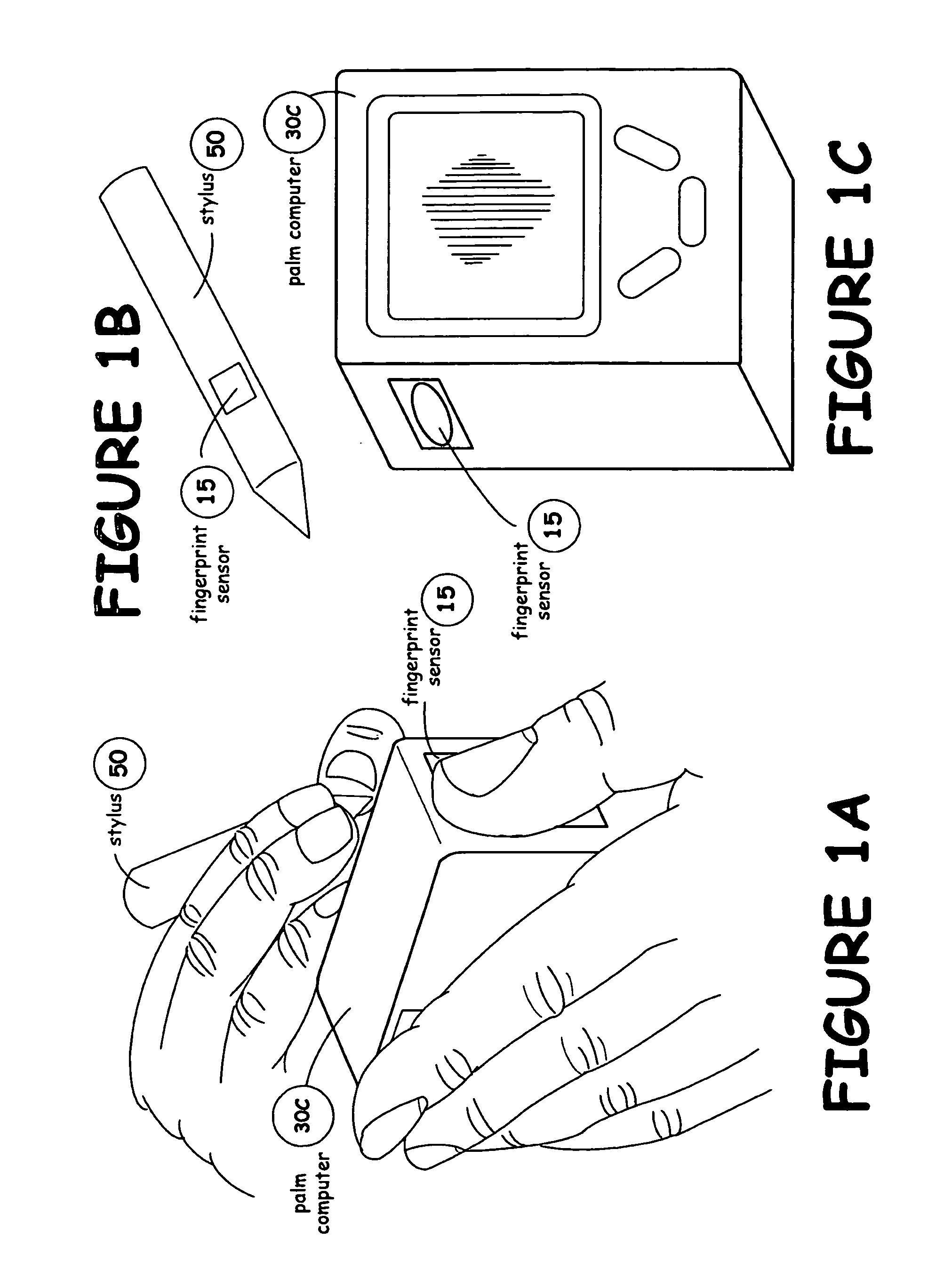
InactiveUS20050180618A1Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusInternet privacyIndex finger
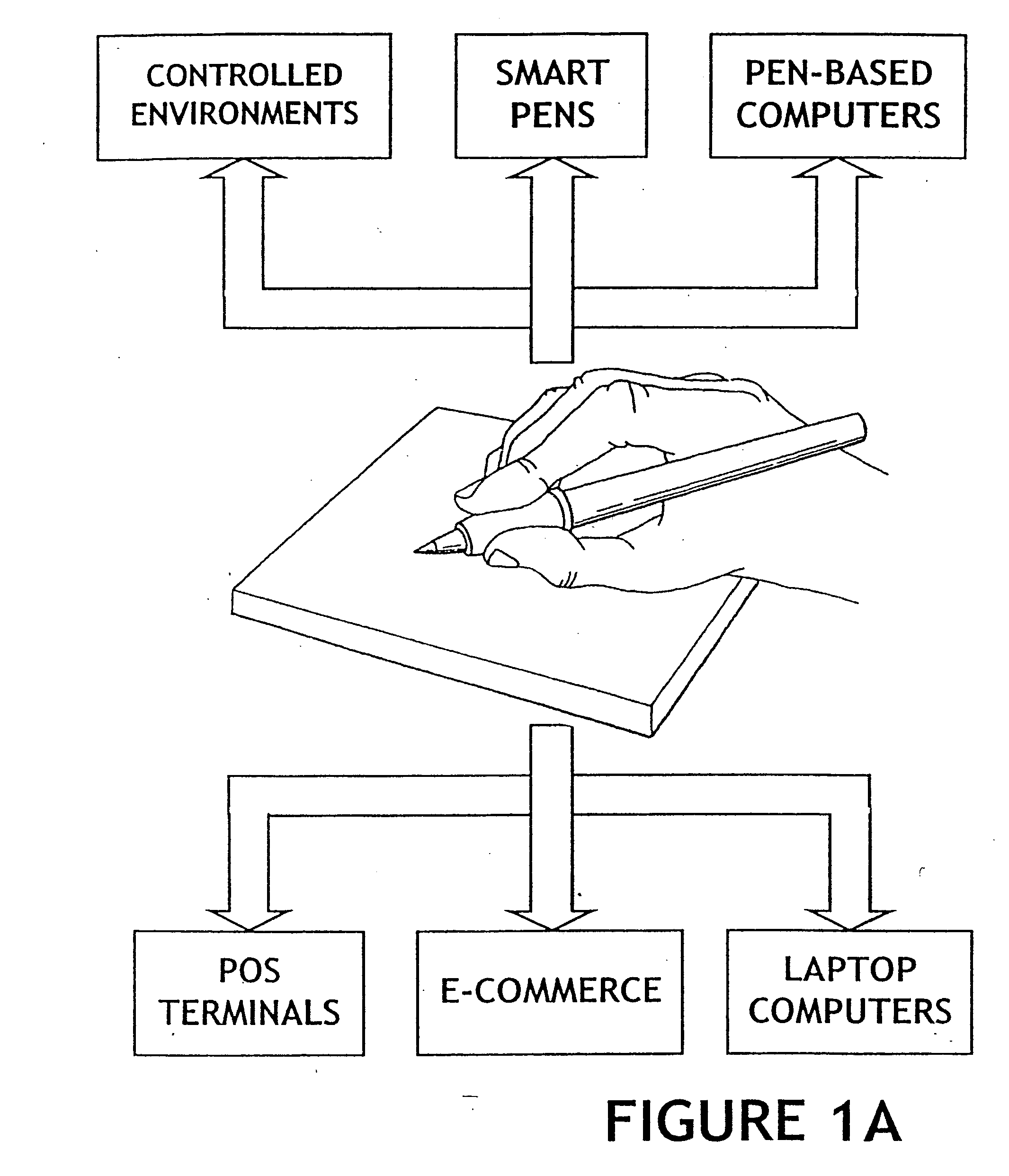
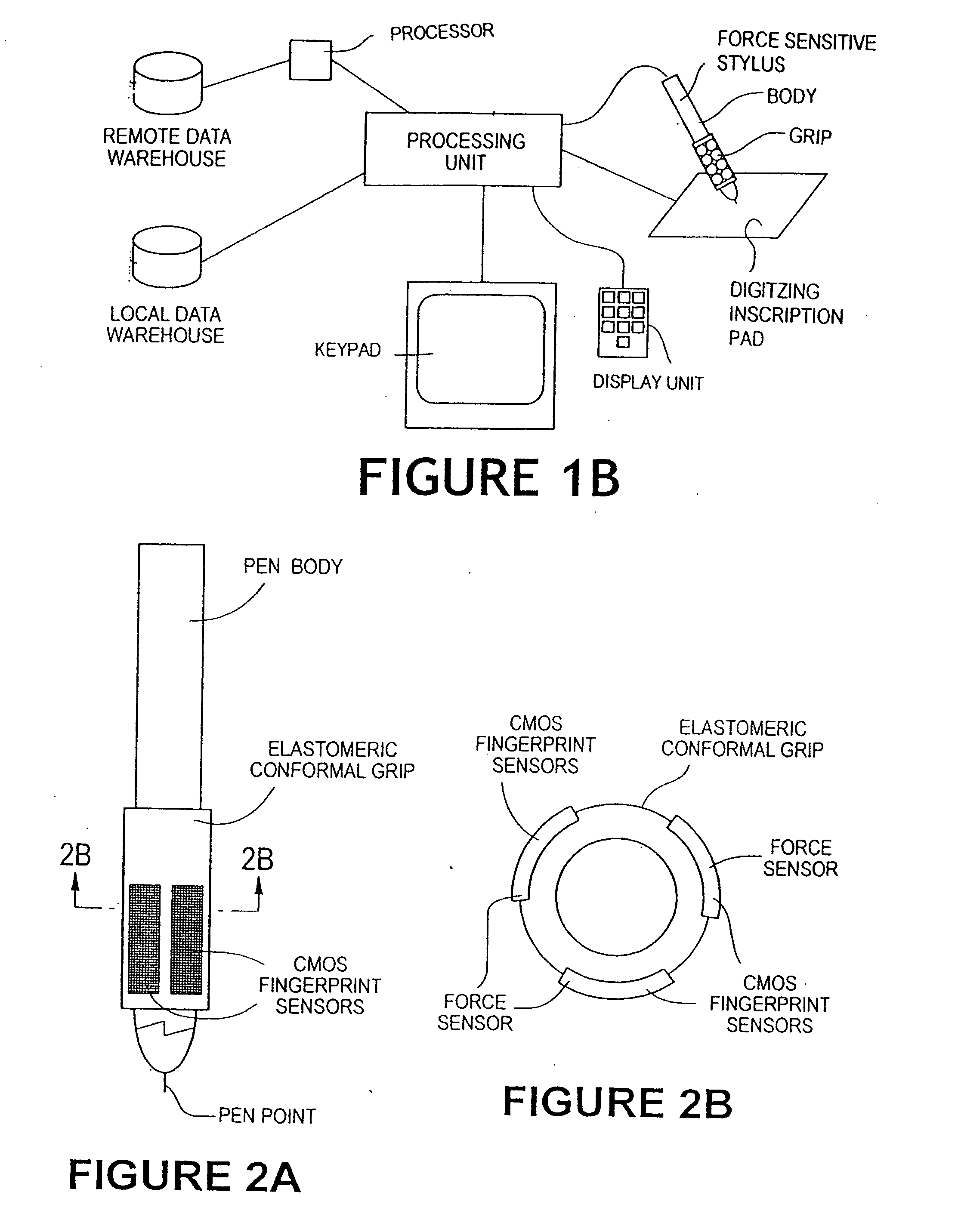
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:UNITED STATES CP LLC
Data security system
InactiveUS7047419B2Easy accessNeed can be addressedDigital data processing detailsInternal/peripheral component protectionComputer usageData access
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
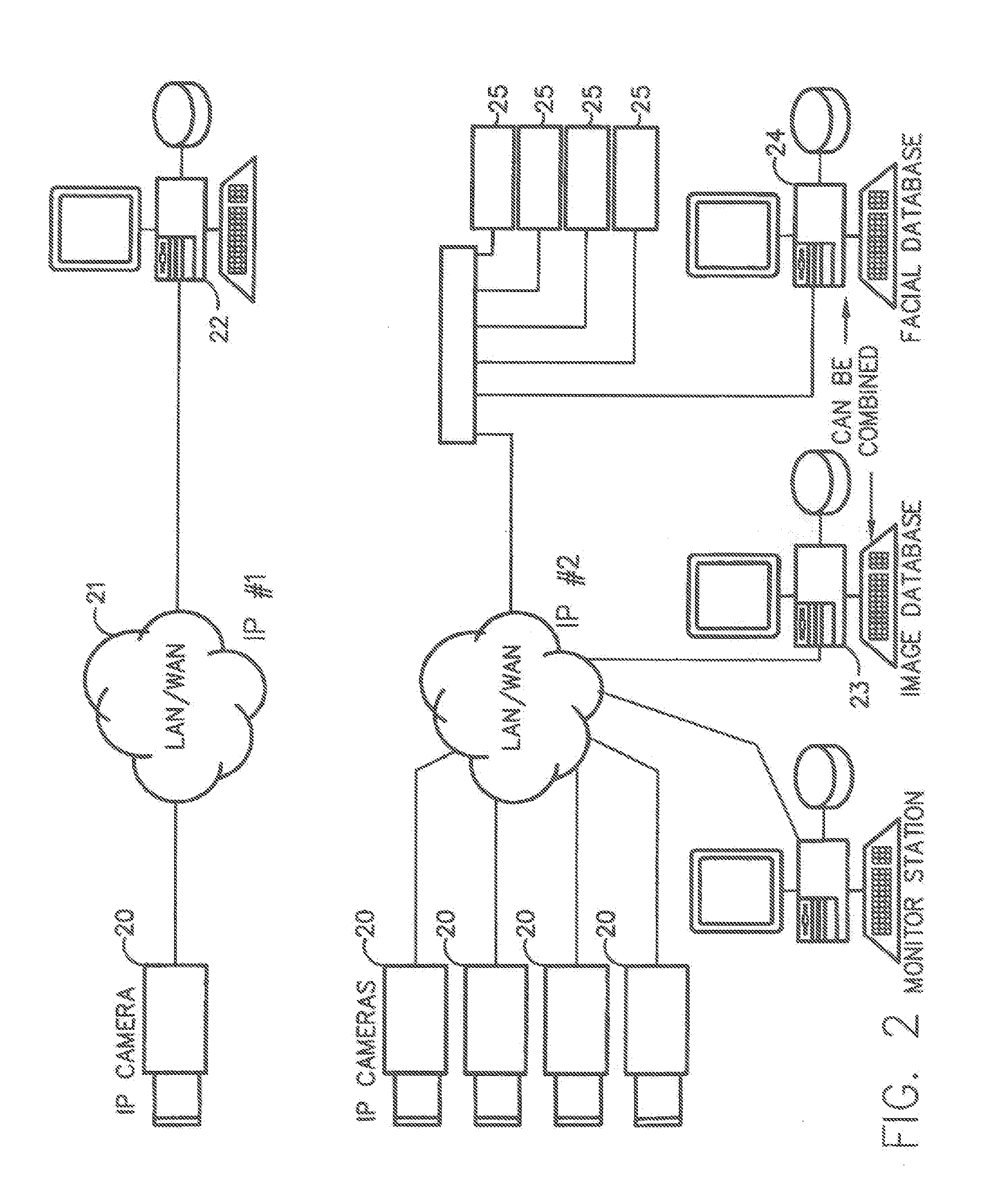
Method for Incorporating Facial Recognition Technology in a Multimedia Surveillance System
InactiveUS20100111377A1Function increaseImprove economyChecking time patrolsChecking apparatusMonitoring systemRecognition algorithm
Embodiments provide a surveillance system having at least one camera adapted to produce an IP signal, the at least one camera having an image collection device configured for collecting image data, the at least one camera having at least one facial processor configured to execute with digital format image data at least one facial recognition algorithm, execution of the at least one facial recognition algorithm with the digital format image data detecting faces when present in the digital format image data, execution of the at least onefacial recognition algorithm providing for each detected face at least one set of unique facial image data.
Owner:MONROE DAVID A
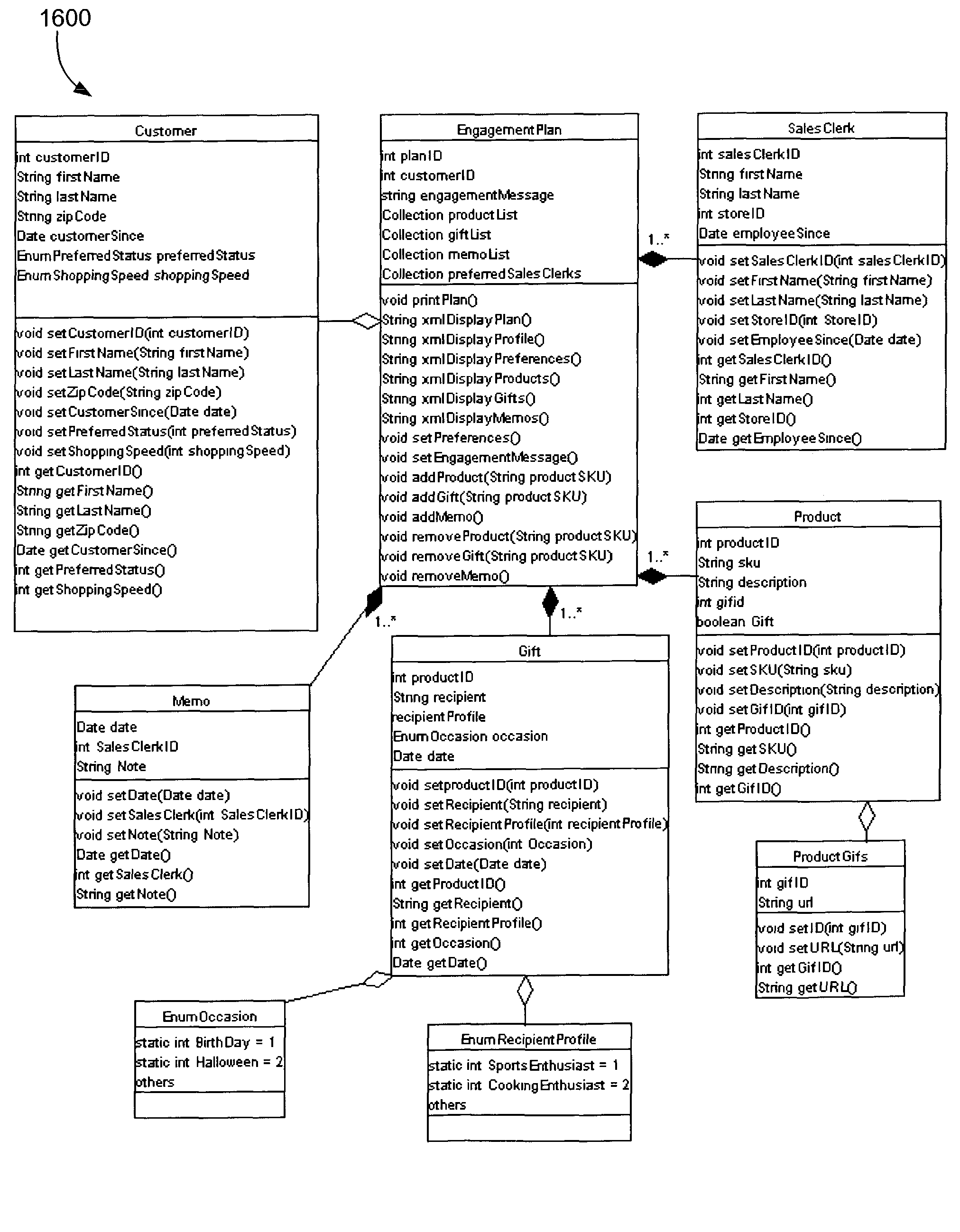
Customer relationship management system for physical locations
ActiveUS7962361B2Improve customer experienceImprove concentrationAdvertisementsChecking apparatusCustomer relationship managementProgram planning
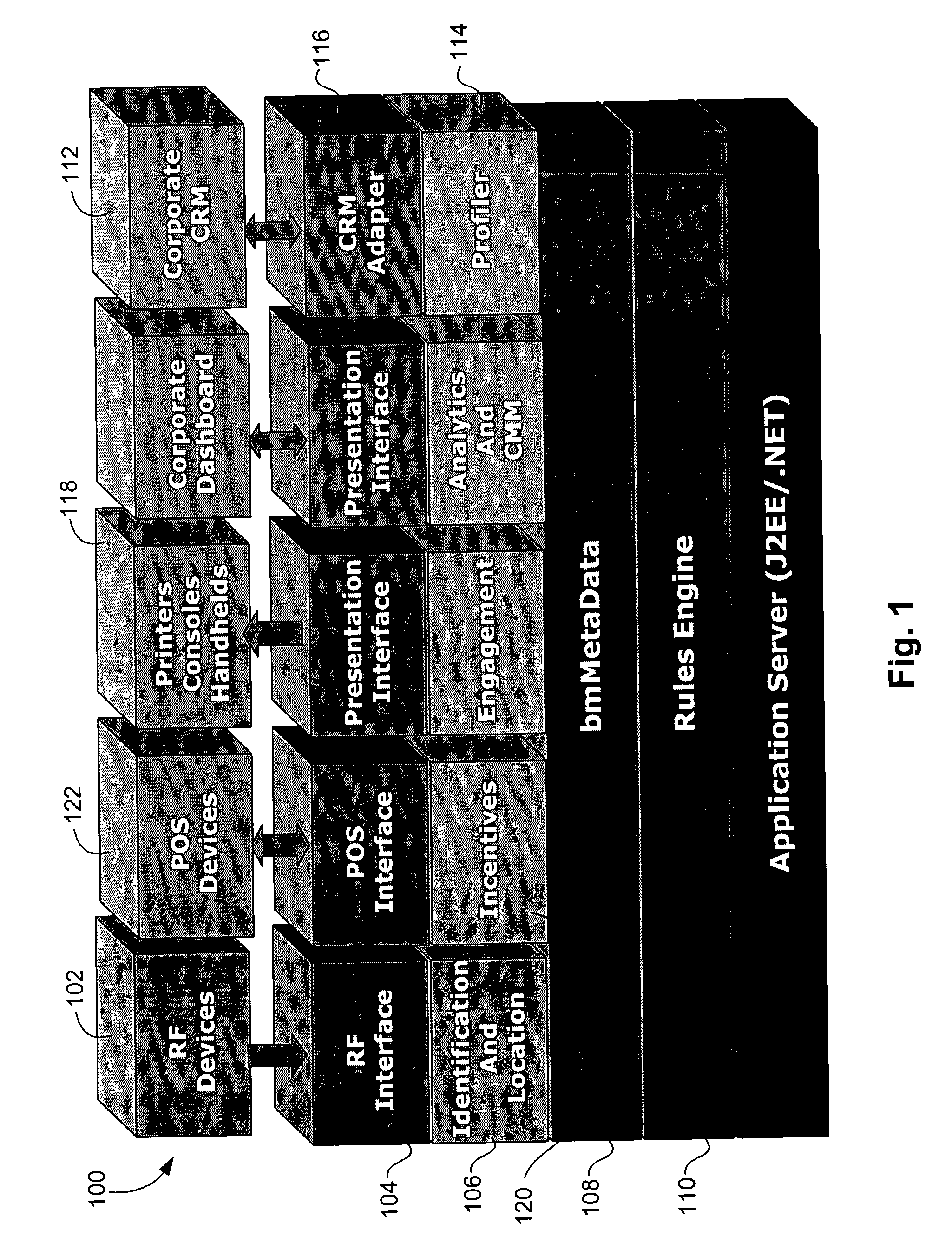
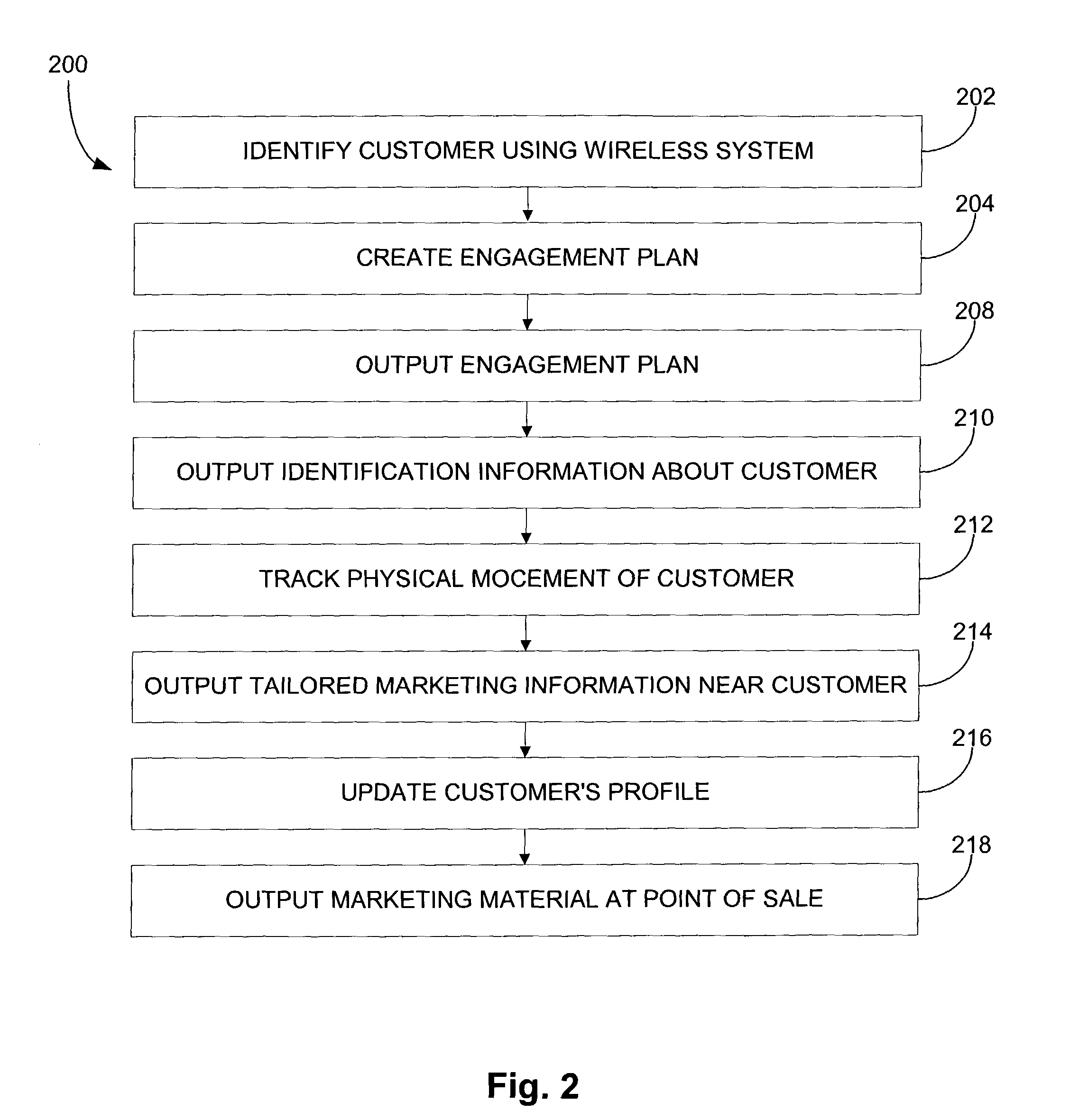
A method for outputting information about a person includes identifying the person utilizing a wireless system upon entry into a physical location, and also includes locating the person within the physical structure. An engagement plan is retrieved based on the identification of the person and output. The engagement plan has information useful for interacting with the person. The engagement plan is created based at least in part on personal information of the person, the preferences of the person, and the past transactions of the person. A system for outputting information about a person, such as a customer, includes an object carried by the person, which is capable of being identified by a wireless system. A wireless interface communicates with the object. A computing device correlates the identification of the object with the person. An output device outputs information relating to the person.
Owner:MAPLEBEAR INC DBA INSTACART
Video acquisition and compilation system and method of assembling and distributing a composite video
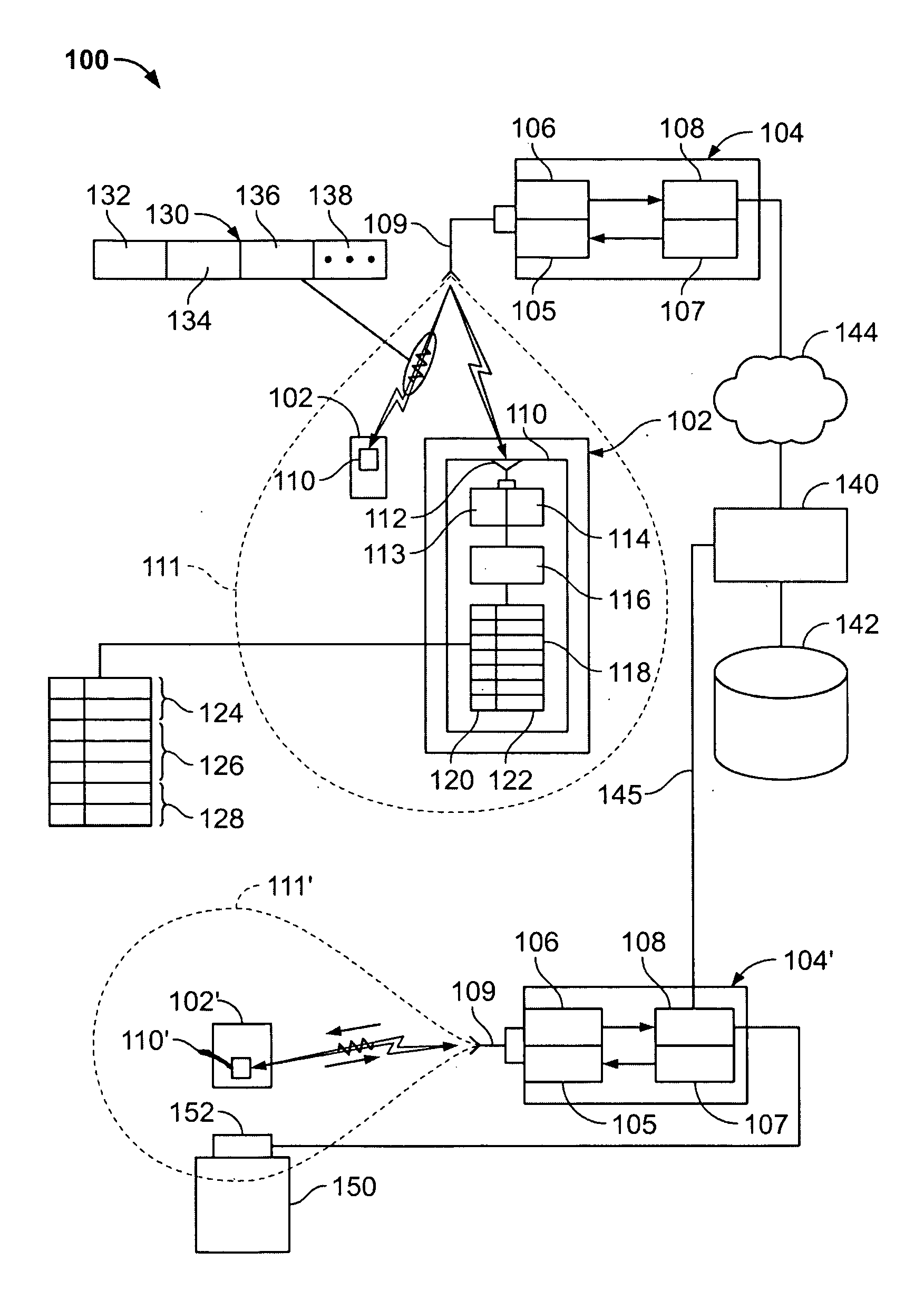
InactiveUS20120162436A1Loss of timeTelevision system detailsRegistering/indicating time of eventsComputer graphics (images)Image capture
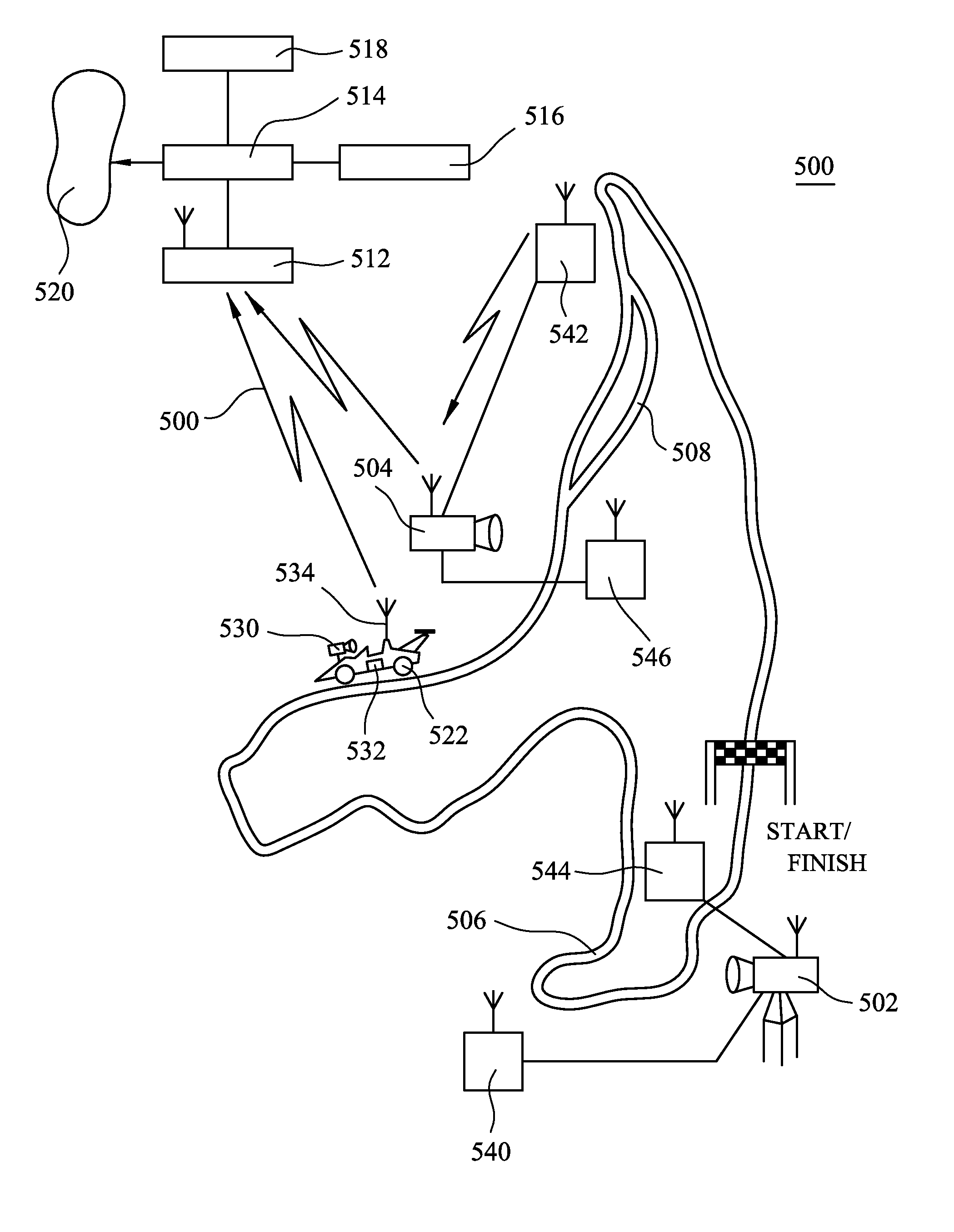
FIG. 7 shows a camera system (700) that operates to time-stamp video content captured from multiple cameras (740) relative to a recorded and time-synchronized location of a portable tracking unit (722). The position of the cameras (740) is known to the system. Based on the time and position data for each uniquely identifiable tracking unit, an editing suite (770) automatically compiles a composite video made up from time-spliced video segments from the various cameras. Video or still images captured by the cameras (740)are cross-referenced against the client address stored in database (760) and related to the assigned, uniquely identifiable tracking unit (722). A server (750) is arranged to use the client address to send reminder messages, which reminder messages may include selected images taken by the composite video. Alternatively, a client (720) can use the client address to access the database and view the composite video. In the event that the client (720) wants to receive a fair copy of the composite video, the server (750) is arranged to process the request and send the composite video to the client. Streaming of multiple video feeds from different cameras that each encode synchronized time allows cross-referencing of stored client-specific data and, ultimately, the assembly of the resultant composite video that reflects a timely succession of events having direct relevant to the client (720).
Owner:E PLATE
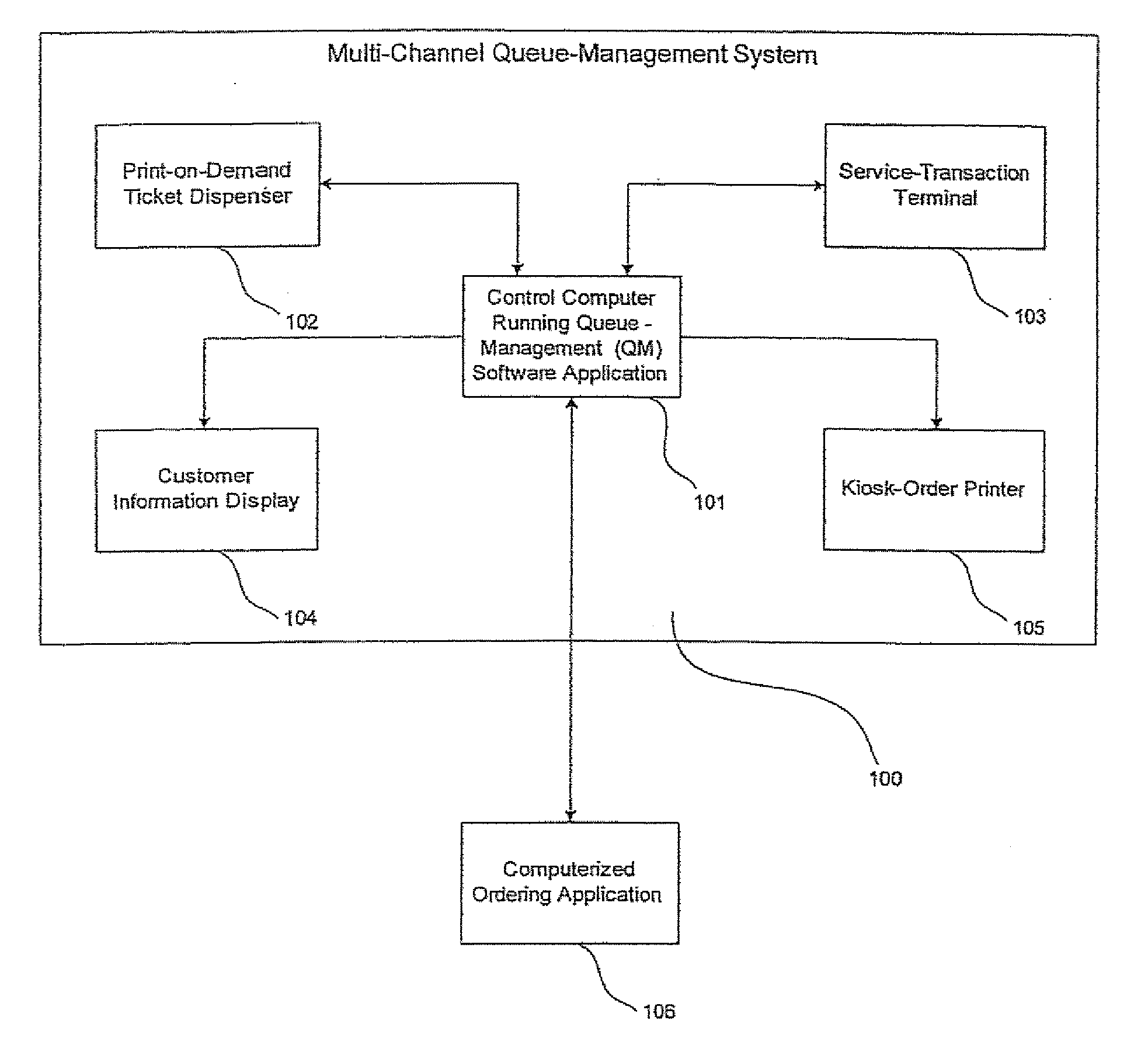
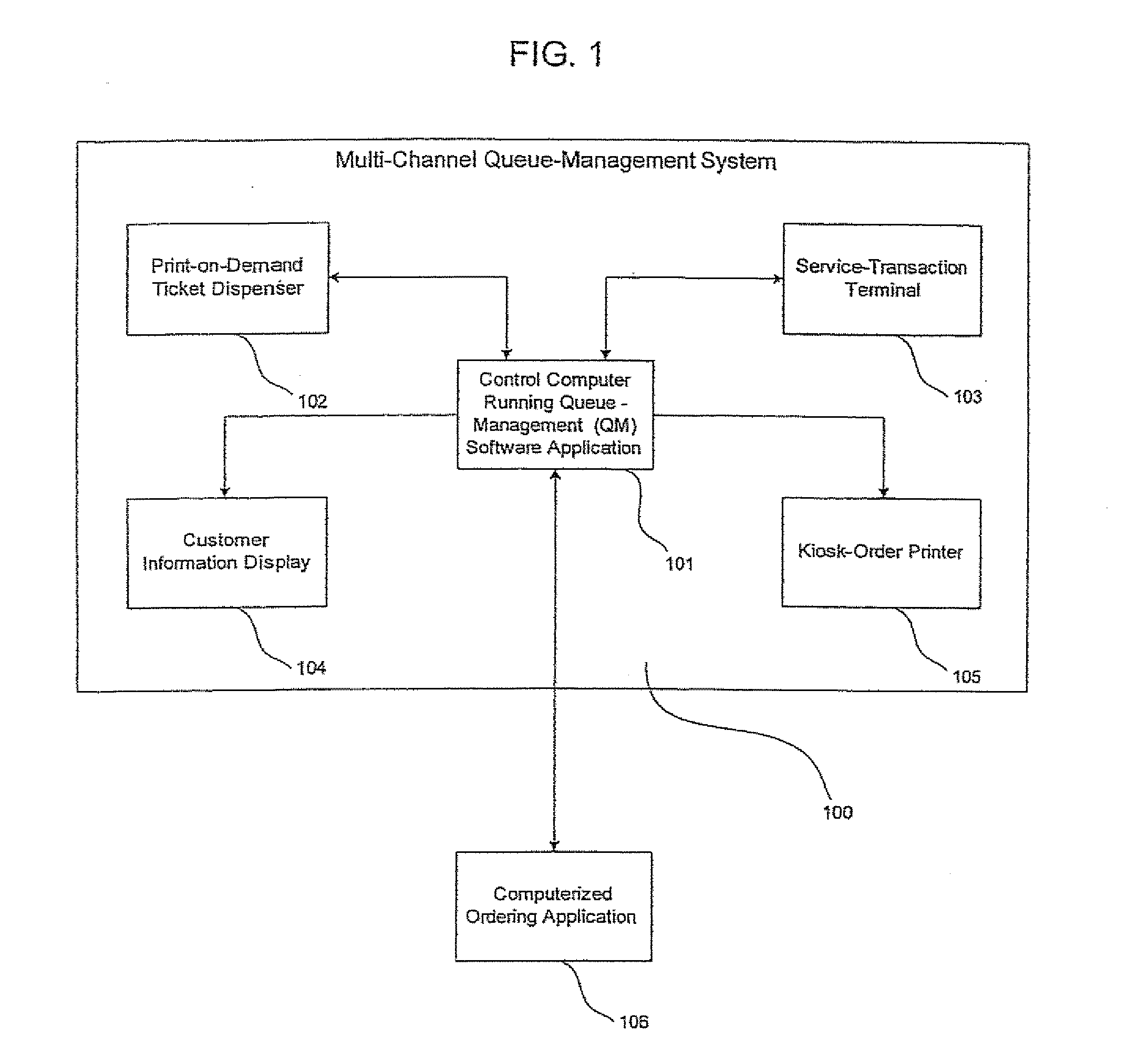
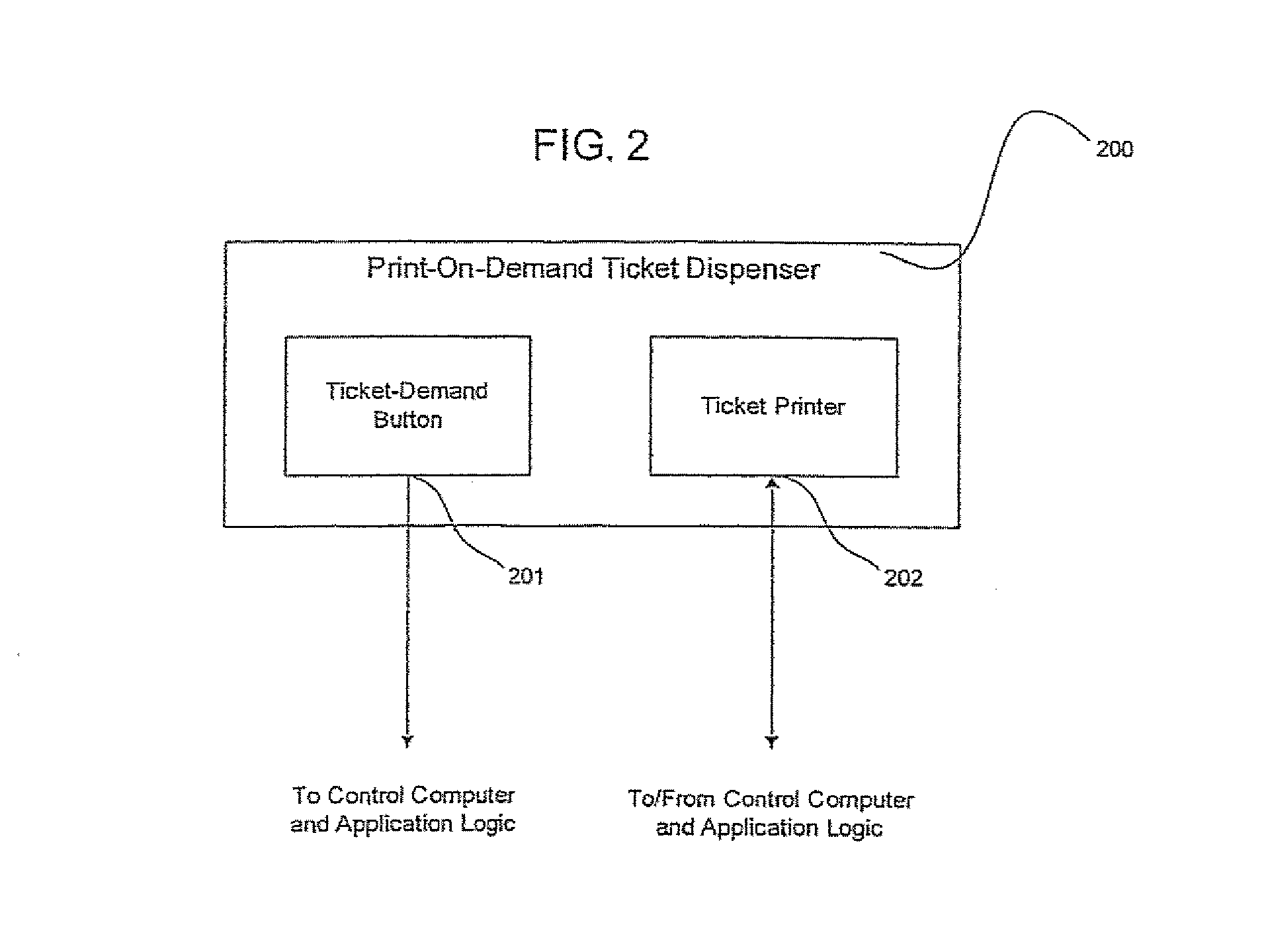
System for queue and service management
A system for service queue management is disclosed including a terminal controlled by the system having a processing platform to generate service queue information for a user, and a mechanism for the user to request or receive the service queue information. The processing platform preferably transmits promotions related to goods and services associated with the service queue information to a user. The mechanism for the user to request or receive service queue information may preferably include a user's mobile communications device or a manually-activated device located on the terminal. Service queue information may include a queue number, next queue number to be issued, estimated wait time for service, a predicted time of service, time of issuance of ticket, predicted queue-waiting time, marketing messages, instructions for use of said ticket dispenser, and average queue-waiting time.
Owner:AHOLD DELHAIZE LICENSING SARL
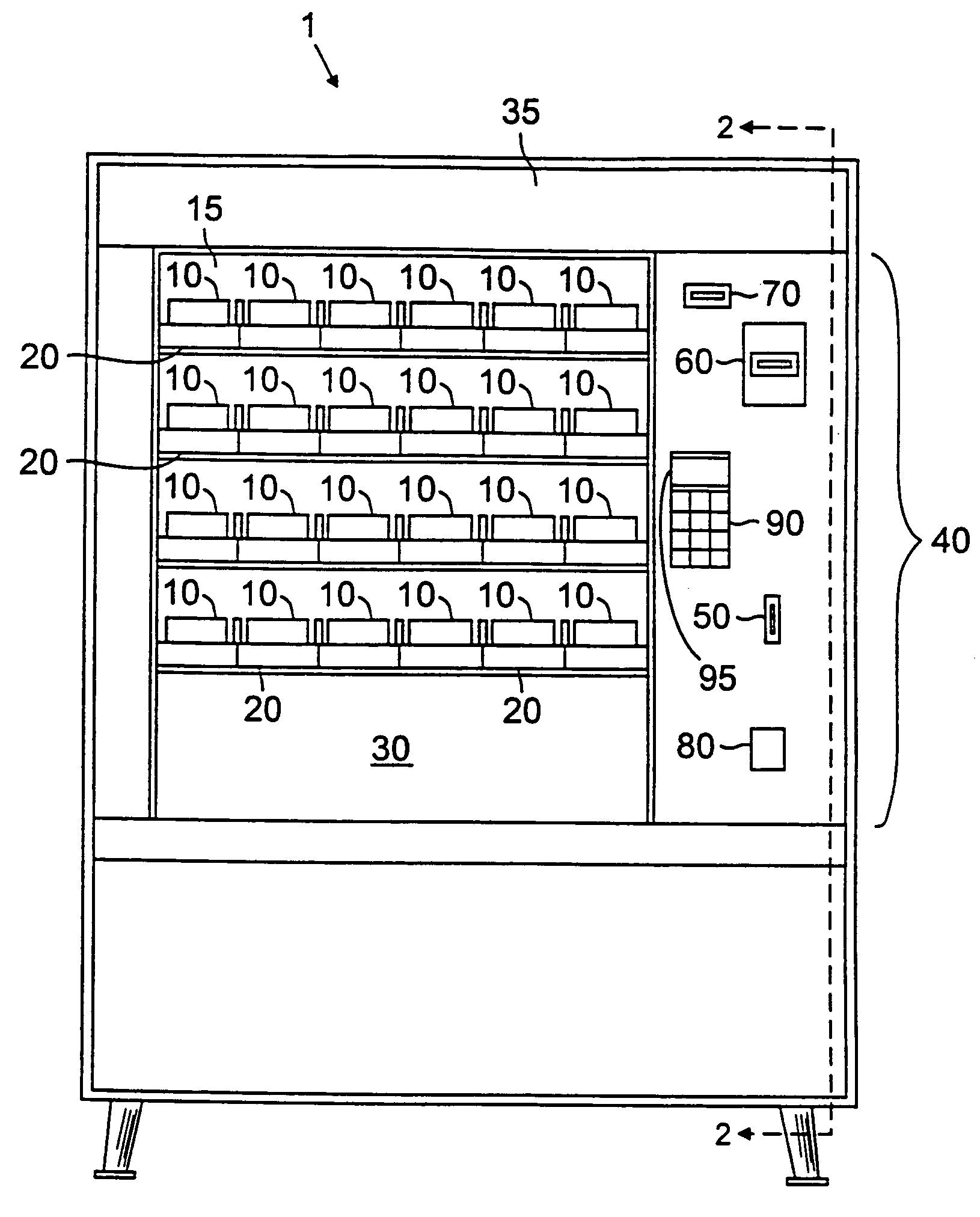
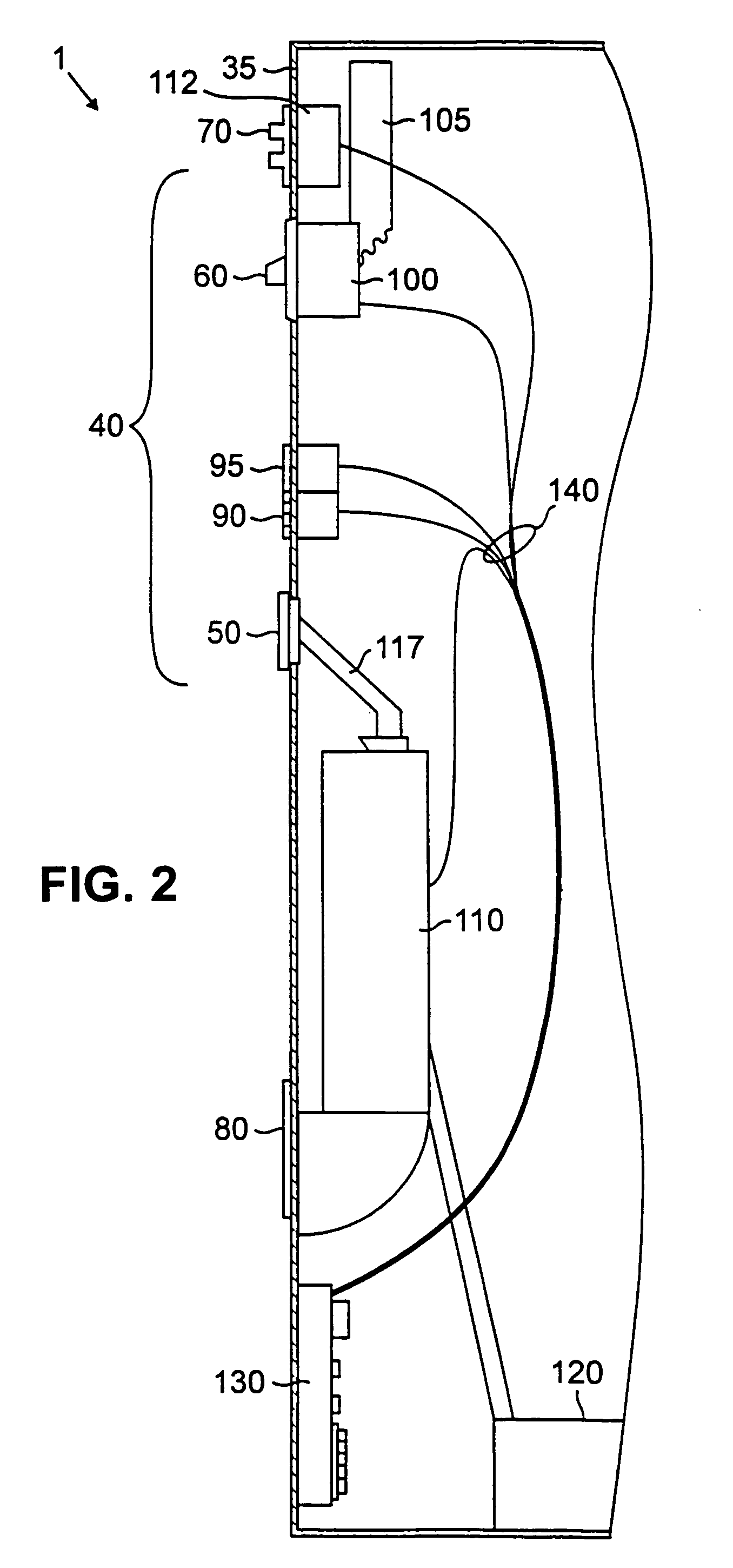
Vending audit system
InactiveUS7053773B2Electric signal transmission systemsControlling coin-freed apparatusControl circuitEngineering
A vend audit system and methods are described. In an implementation, the system includes vend items with packaging having tags, at least one tag sensor, and a control circuit capable of receiving data from the tag sensor. A method for tracking inventory in a vending machine is also described. In an implementation, the technique includes loading vend items having tags into a vending machine, sensing the tags, and transferring information to a control circuit. The tags may be RF tags, and the tag sensor may be an RF antenna sensor.
Owner:CRANE PAYMENT INNOVATIONS INC
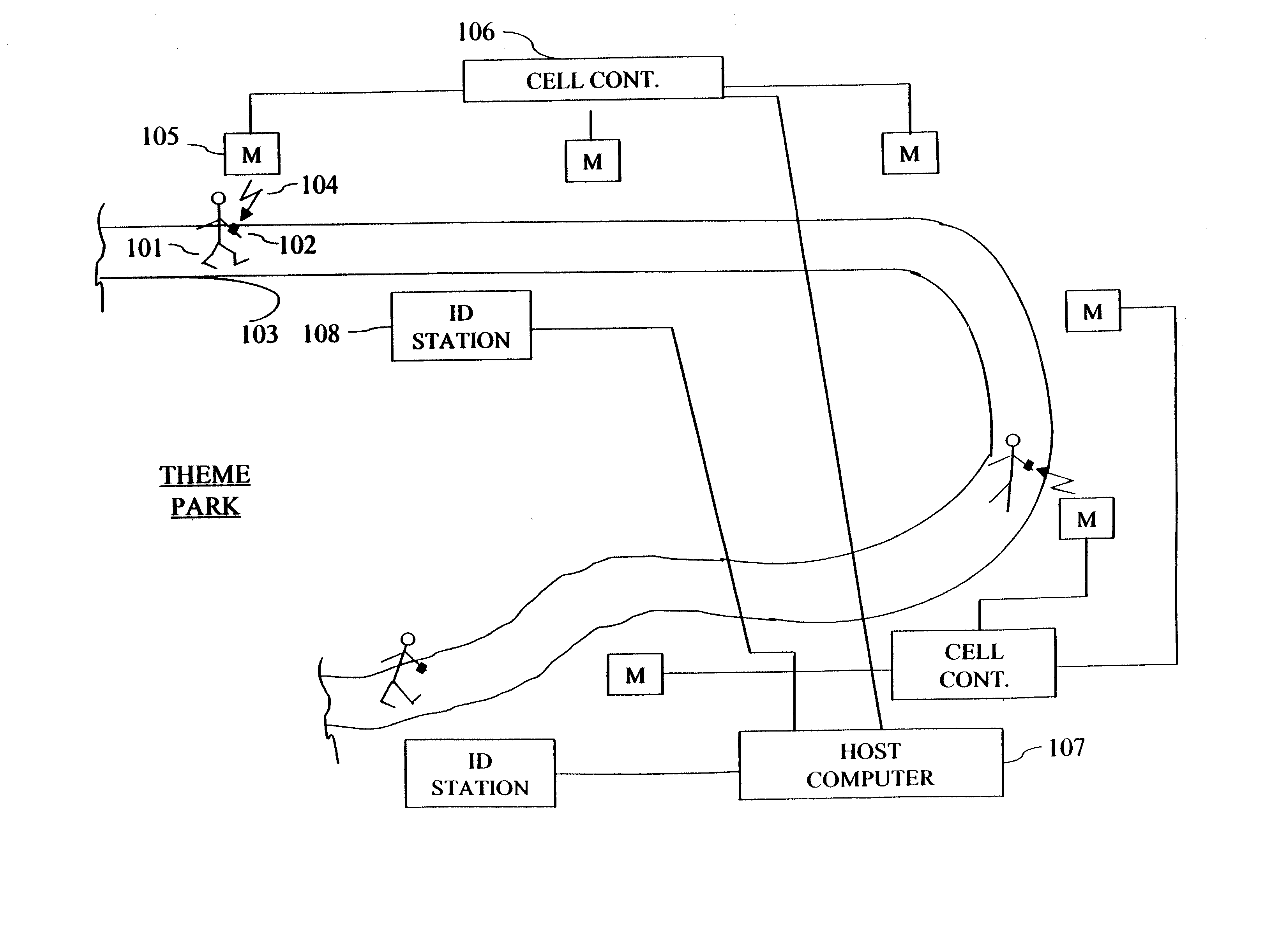
System for real-time location of people in a fixed environment
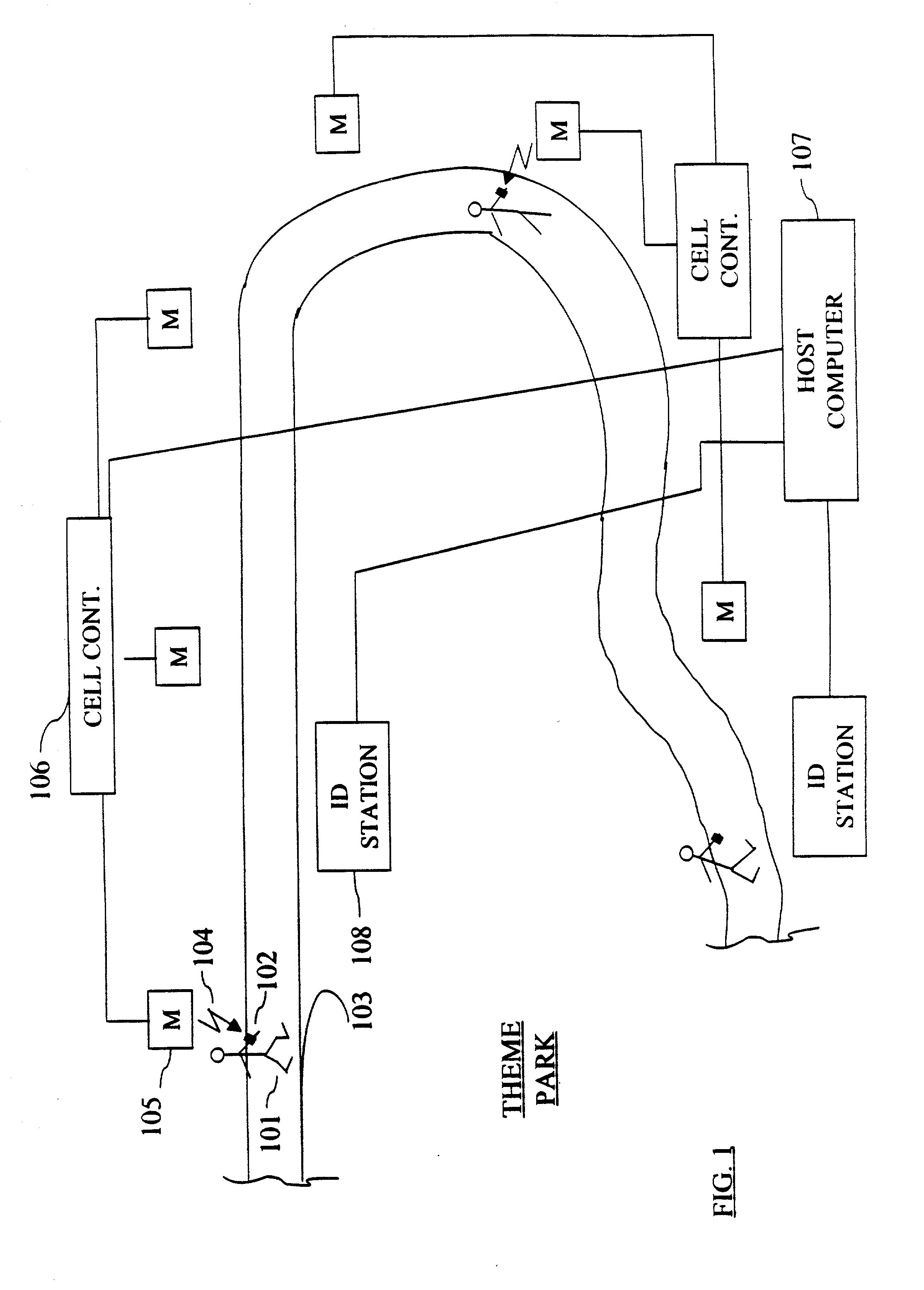
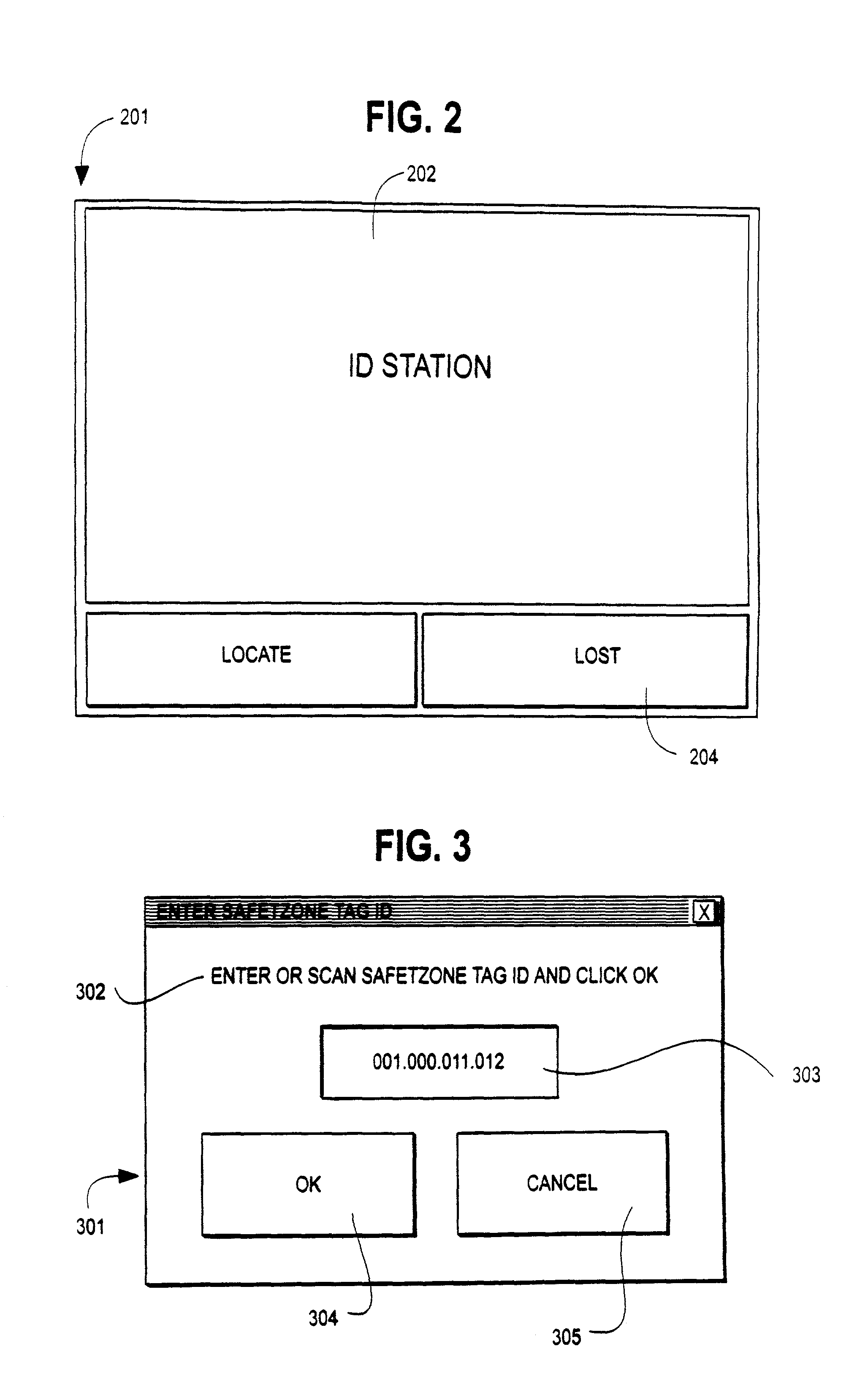
A system is provided for tracking in real-time the location of a group of individuals within a defined environment, for providing information to an individual user about the location of any other individuals of the group and for gaining assistance to locate and reunite lost individuals. The system uses an identification tag with a serial number worn by each individual of the group, has means for communicating with each tag as it moves with the individual through the environment and means for using the communication to determine the position of the tag in the environment. The system also uses strategically placed identification stations distributed within the environment for users to activate a request that the system locate members and for displaying a map indicating the location of members of the group.
Owner:SAFETZONE TECH
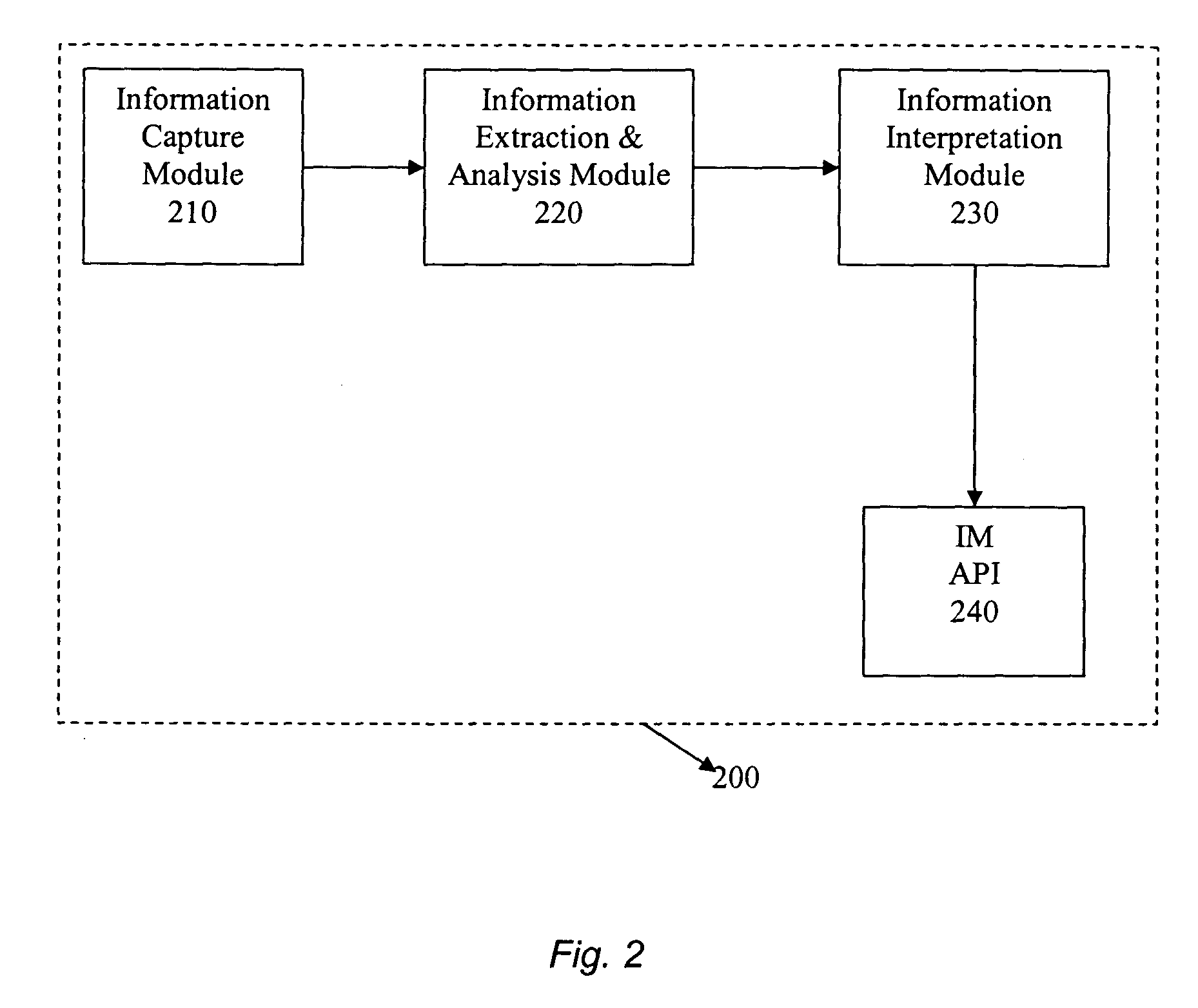
Instant messenger presence and identity management
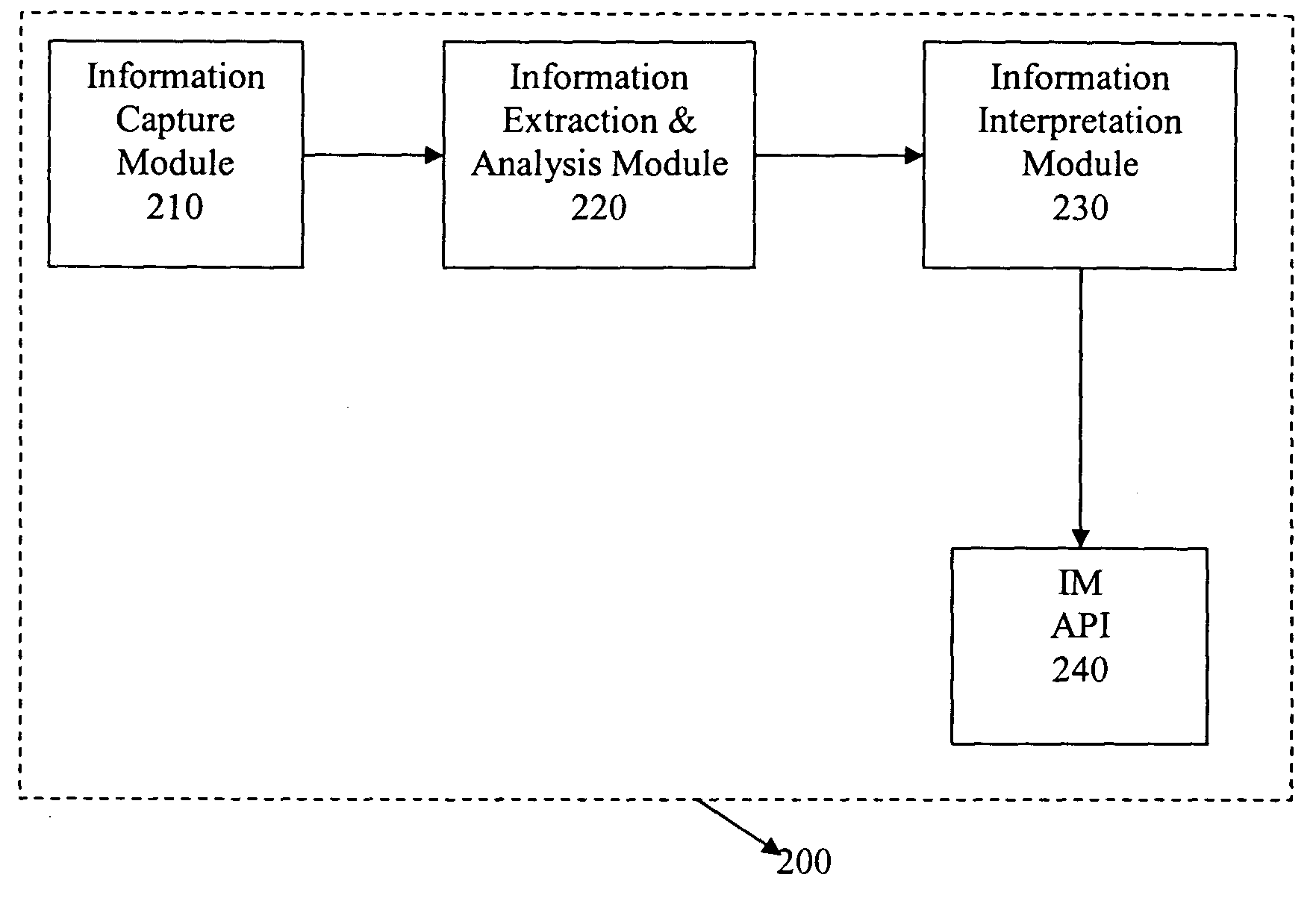
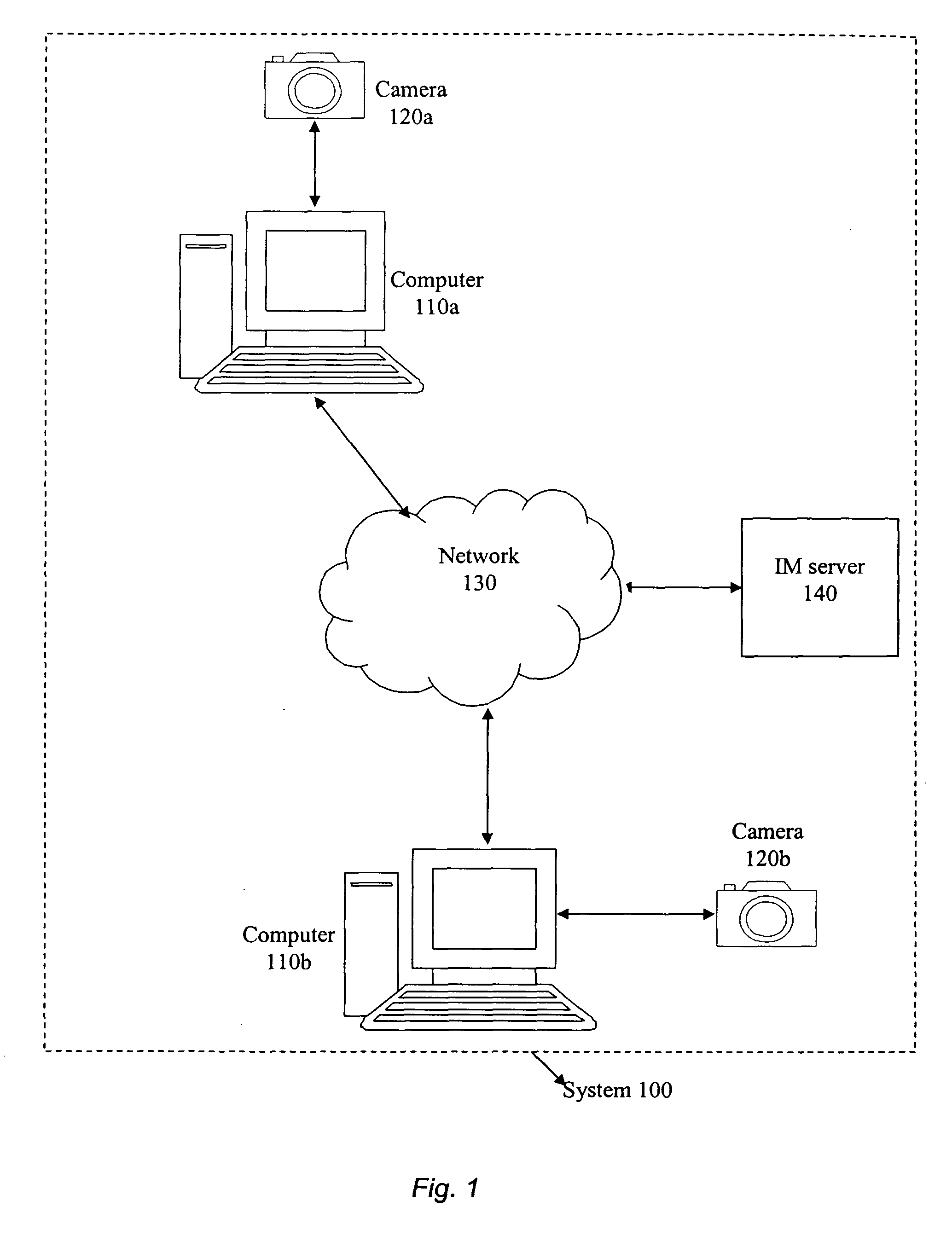
InactiveUS20050044143A1Accurate and reliable detectionCharacter and pattern recognitionChecking apparatusRelevant informationAnalysis data
The present invention provides a method and system for reliable and accurate presence / status management and identity detection in Instant Messaging (IM) applications by using video, still image, and / or audio information. In one embodiment, a device such as a camera captures still image, video, and / or audio data. Relevant information is then extracted from the captured data and analyzed. Known techniques such as face recognition, face tracking, and motion detection, can be sued for extracting and analyzing data. This information is then interpreted for the IM application, and provided to an Application Programs Interface (API) for the IM application. The API can use the information for various purposes, including updating the status of the user (e.g., available, busy, on the phone, away from desk, etc.) and updating the identity of the user.
Owner:LOGITECH EURO SA
System and methods for accelerated recognition and processing of personal privilege operative for controlling large closed group environments
ActiveUS8056802B2Process is accelerated and simplifiedAvoid practicalTicket-issuing apparatusPayment architectureCrowd controlMedicine
Methods (3500-3695) and apparatus (10, 20) for controlling physical (30, 40) and virtual (12) access for accelerated recognition and processing of privileges, benefits, value transfers, crowd control, community membership and status, in particular for institutions, arenas and other large venues.
Owner:FORTRESS GB
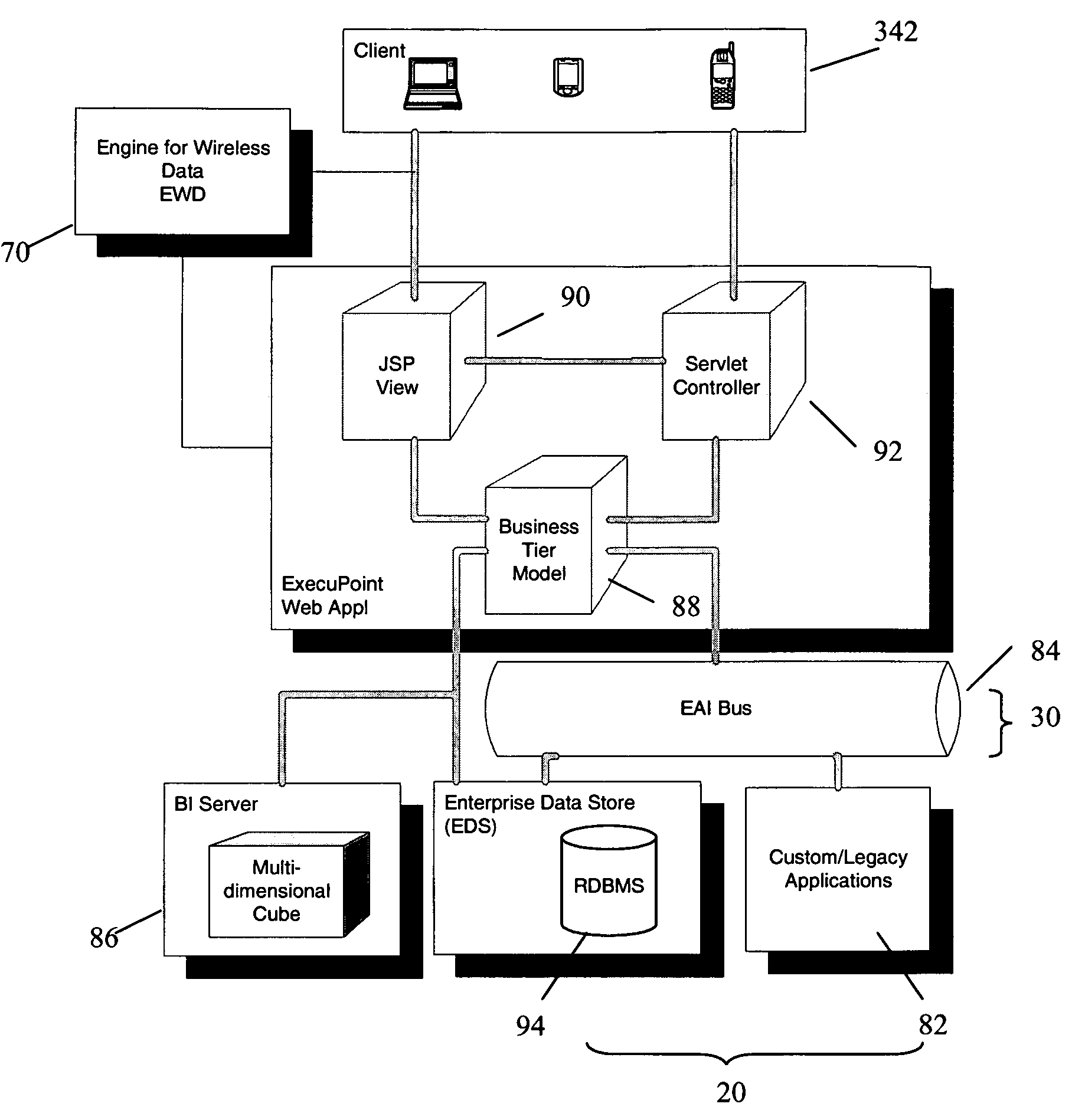
System and wireless device for providing real-time alerts in response to changes in business operational data
InactiveUS7151438B1Extension of timeImprove efficiencyChecking apparatusOffice automationEnterprise application integrationBusiness enterprise
A system for providing in response to changes within current operational data of a business enterprise, alert information including an alert to a wireless device in real-time. The system architecture includes an enterprise application integration services component for accessing and conditioning the current operational data and other business intelligence information. An analytics services component monitors for changes within the current operational data from a predetermined target level and communicates an alert and alert information if a change occurs. The analytics services component also extracts contextually-related first and second sets of critical business information, and converts the operational data, alert and alert information, and the first and second sets of critical business information into a device-independent, web-enabled format, which is then recoded by a delivery services component in accordance with the data delivery requirements of the wireless device. The alert and alert information will be displayed in the context of the current operational data and first and second sets of critical business information.
Owner:UNISYS CORP
Method for identity verification
InactiveUS20050169504A1Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusInternet privacyIndex finger
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:PEN ONE INC
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com