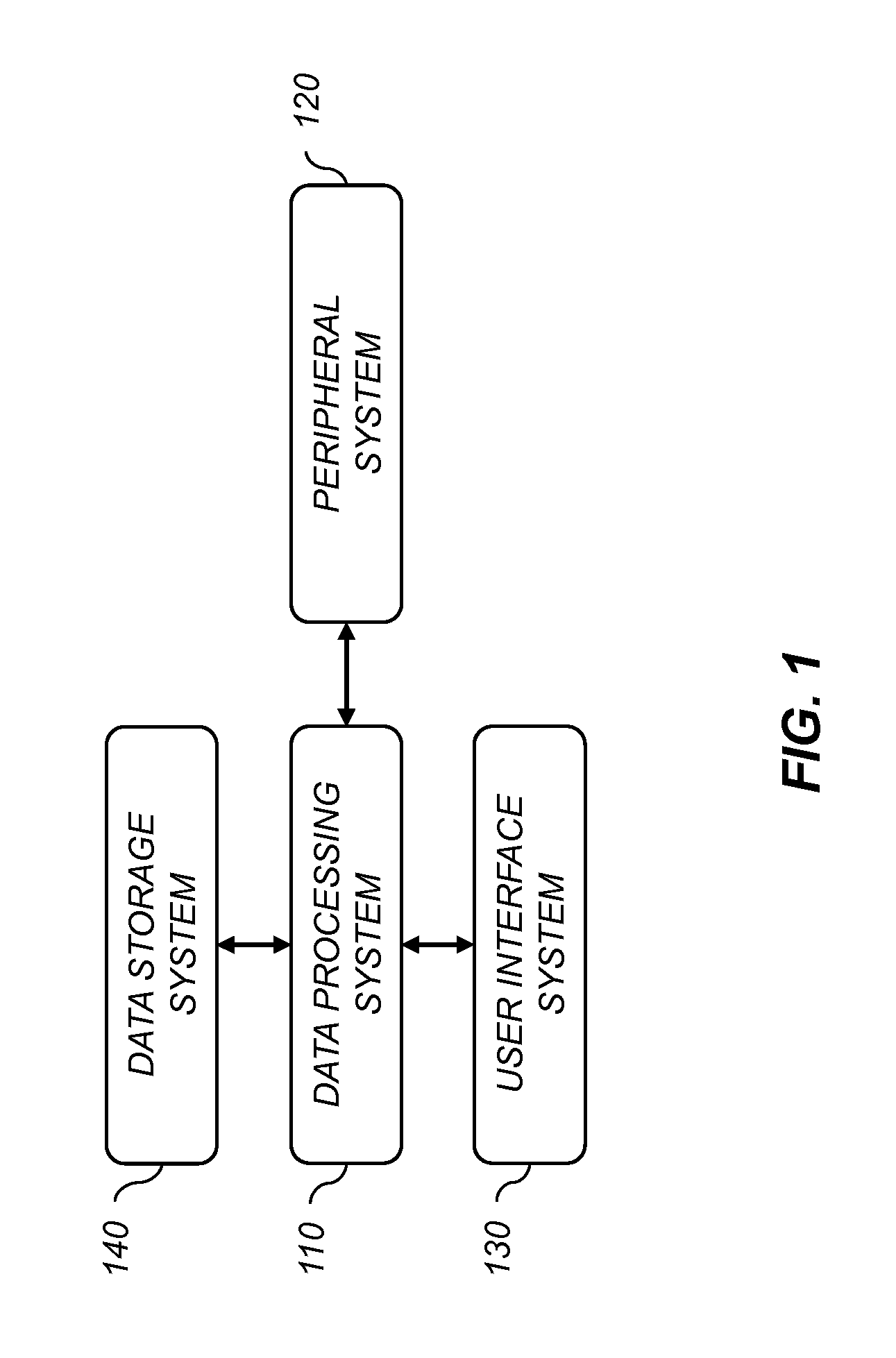
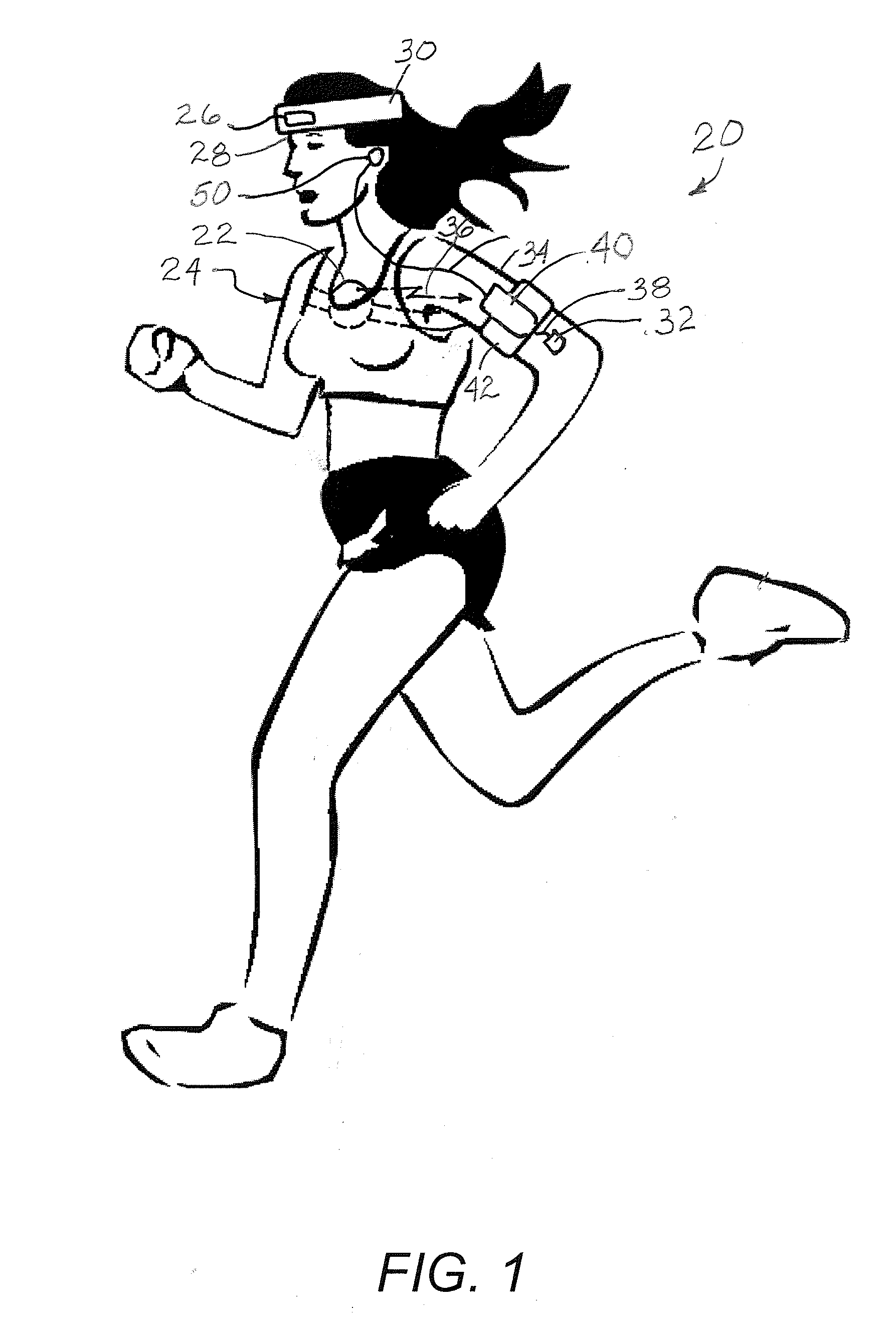Patents
Literature
564 results about "Target level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Target Levels (also referred to as QLI “Qualified List Item”) are used in the Marketing module of Oracle BI to identify and count the members of a segment that should be contacted within a marketing campaign.
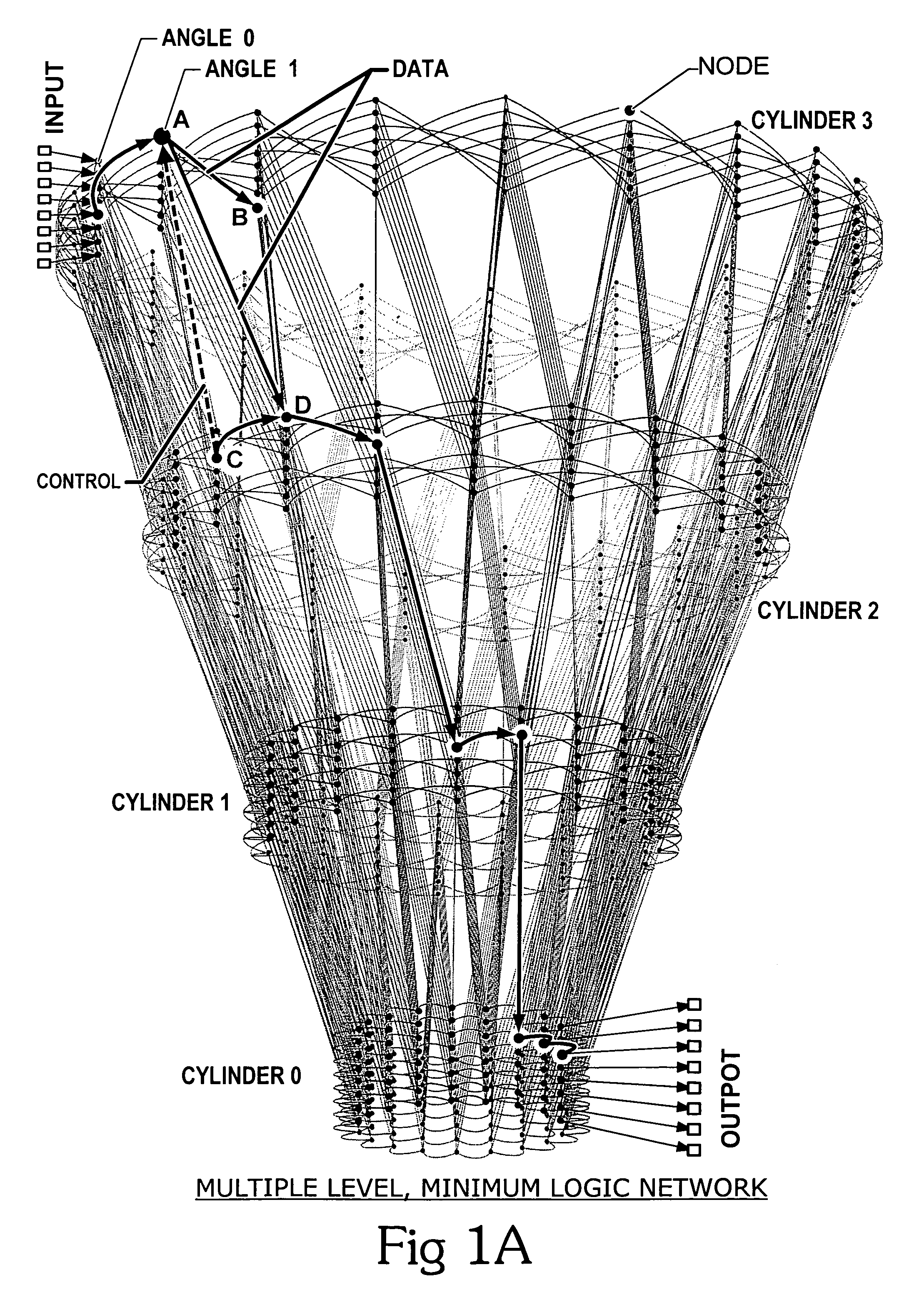
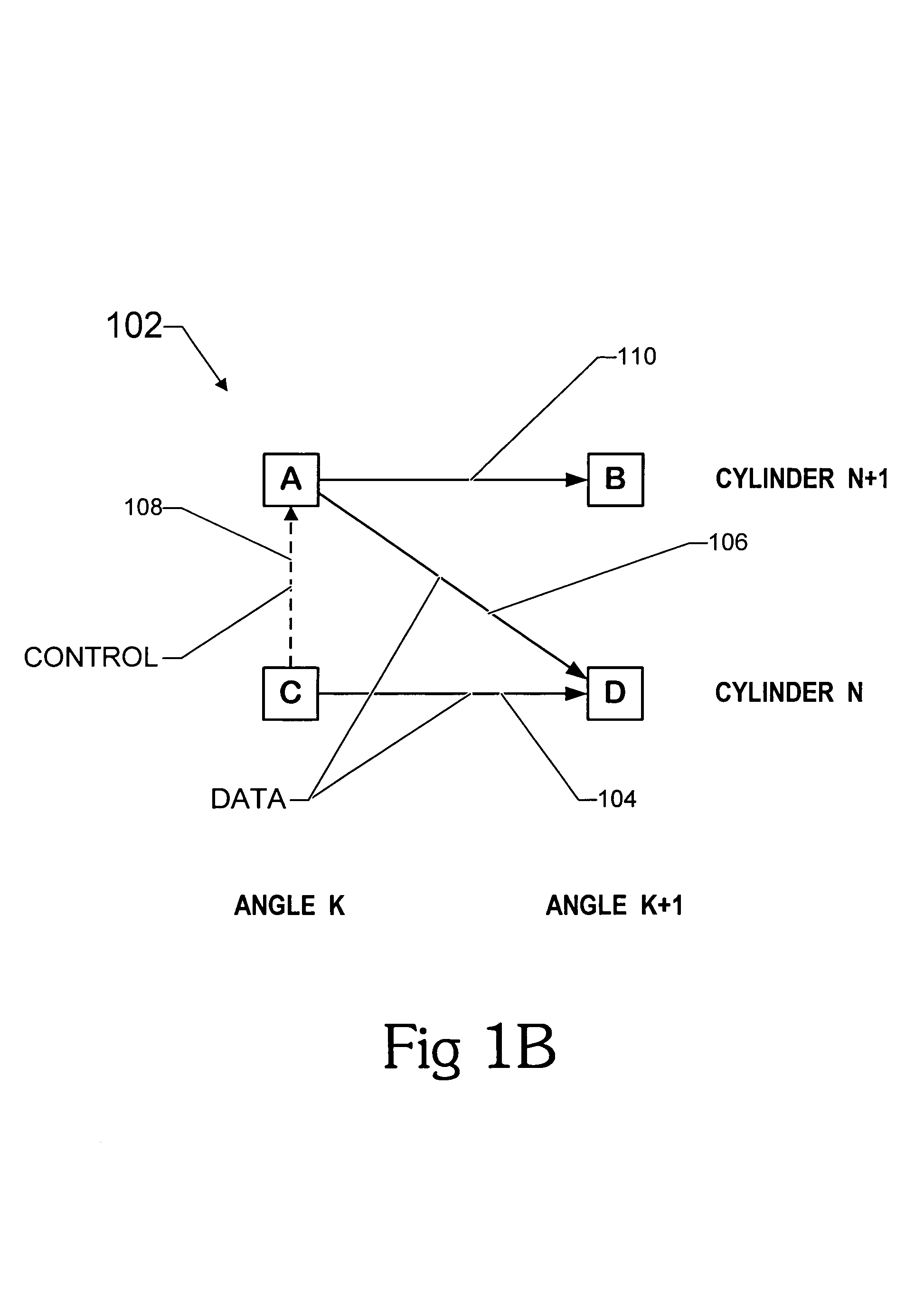
Daylight control system device and method
ActiveUS7190126B1Simple and reliable processEasy to useElectrical apparatusElectric light circuit arrangementElectricityTransceiver
A system and device for and a method of programming and controlling light fixtures is disclosed. A system in accordance with the present invention includes a stationary controller unit that is electrically coupled to the light fixtures. The stationary controller unit is configured to be remotely programmed with a portable commissioning device to automatically control the lights fixtures. The stationary controller unit and the portable commissioning device include light sensors, micro-computers and transceivers for measuring light levels, running programs, storing data and transmitting data between the stationary controller unit and the portable commissioning device. In operation, target light levels selected with the portable commissioning device and the controller unit is remotely programmed to automatically maintain the target level.
Owner:THE WATT STOPPER
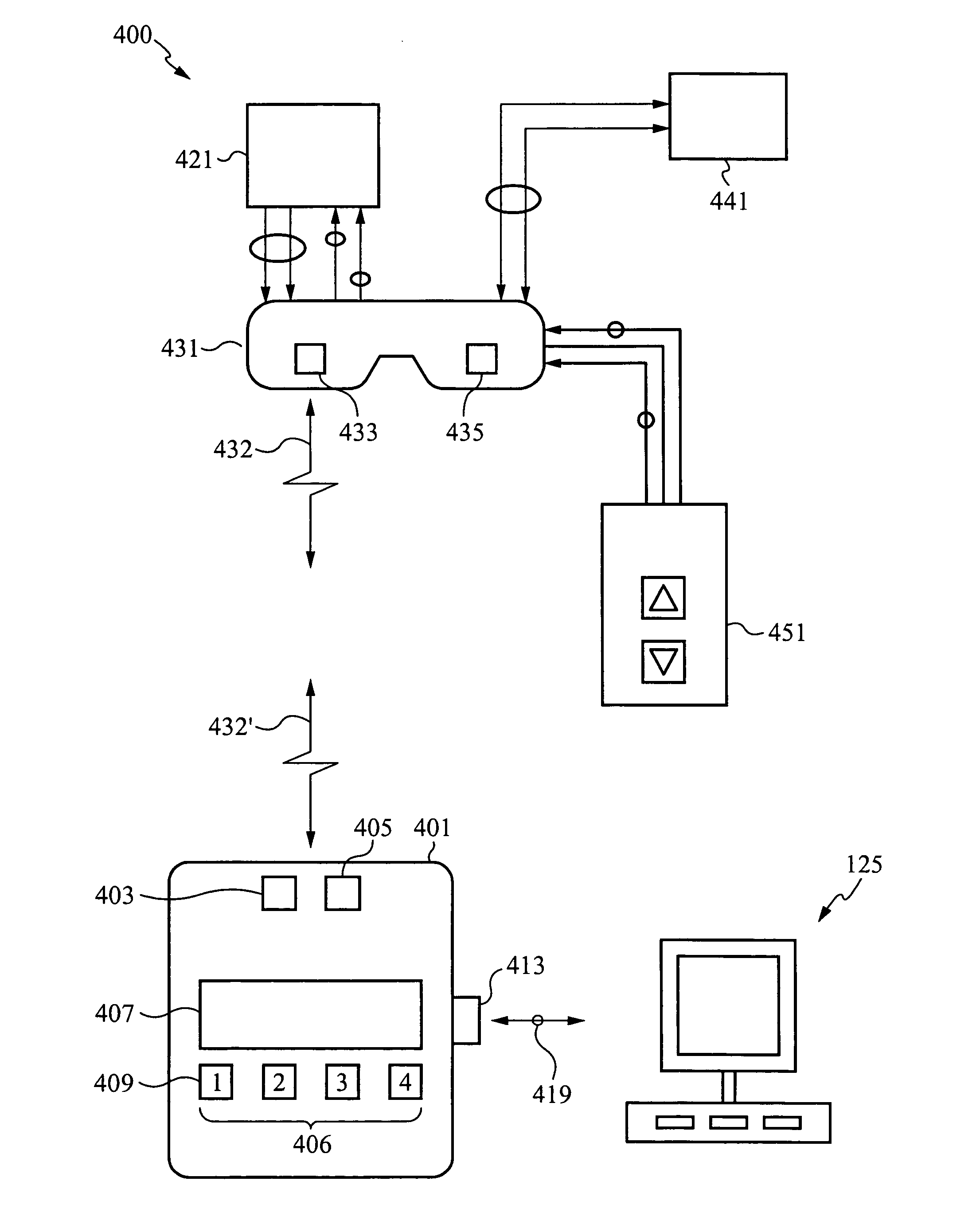
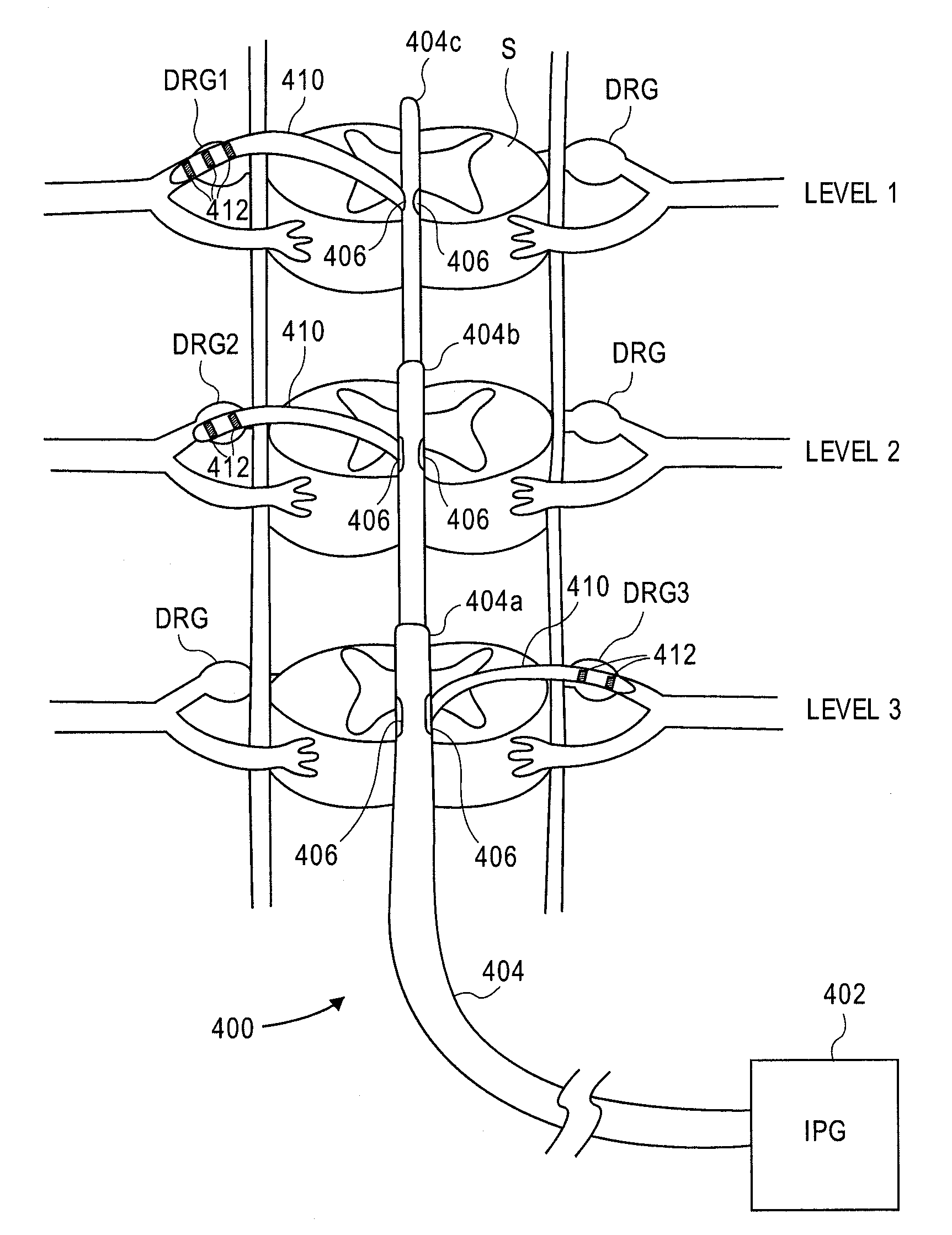
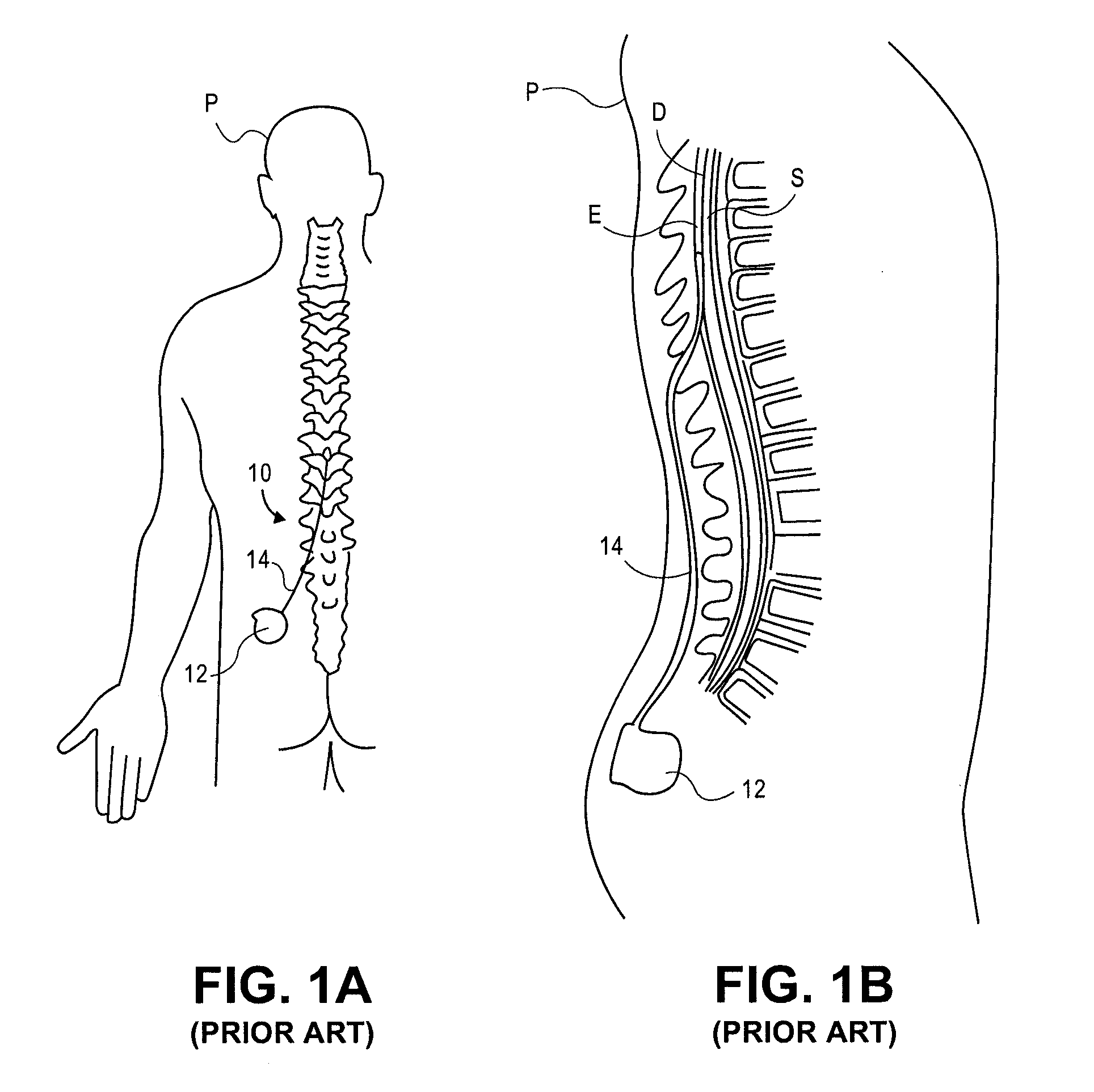
Delivery devices, systems and methods for stimulating nerve tissue on multiple spinal levels
ActiveUS20080140169A1Effectively treat pain symptomReduce deleterious side effectSpinal electrodesImplantable neurostimulatorsSpinal columnSpinal anatomy
Devices, systems and methods are provided for simultaneously stimulating the spinal anatomy at various locations, such as spinal levels, along the spinal cord. By stimulating multiple levels of the spinal column with the use of a single device, a single access path is created to an implantable pulse generator (IPG) rather than individual access paths for each lead at each spinal level to an IPG. By reducing the number of pathways, the procedure complexity, time and recovery are reduced. In addition, some embodiments provide additional specificity within each targeted level, such as selective stimulation of specific tissue, such as the dorsal root ganglion.
Owner:ST JUDE MEDICAL LUXEMBOURG HLDG SMI S A R L SJM LUX SMI
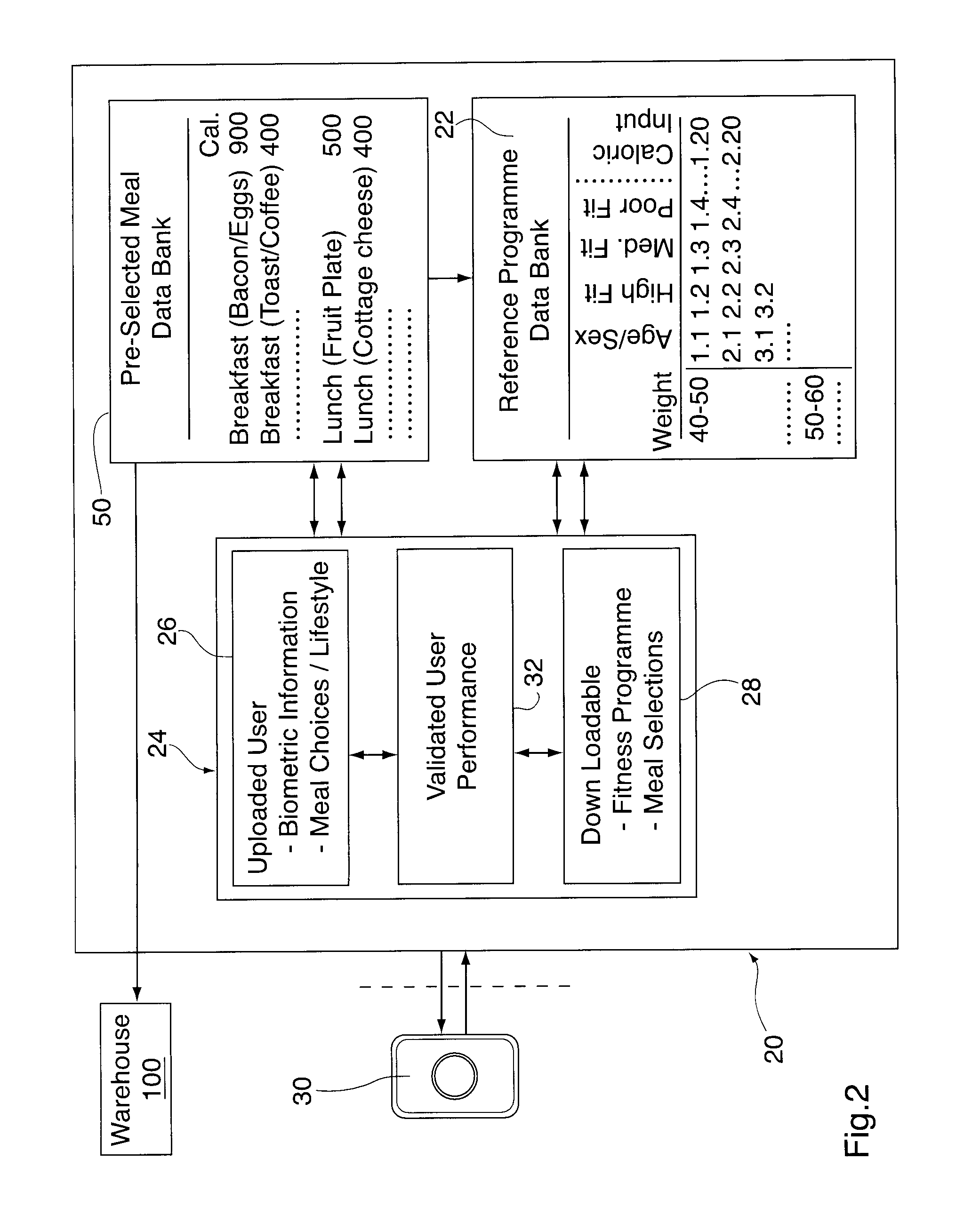
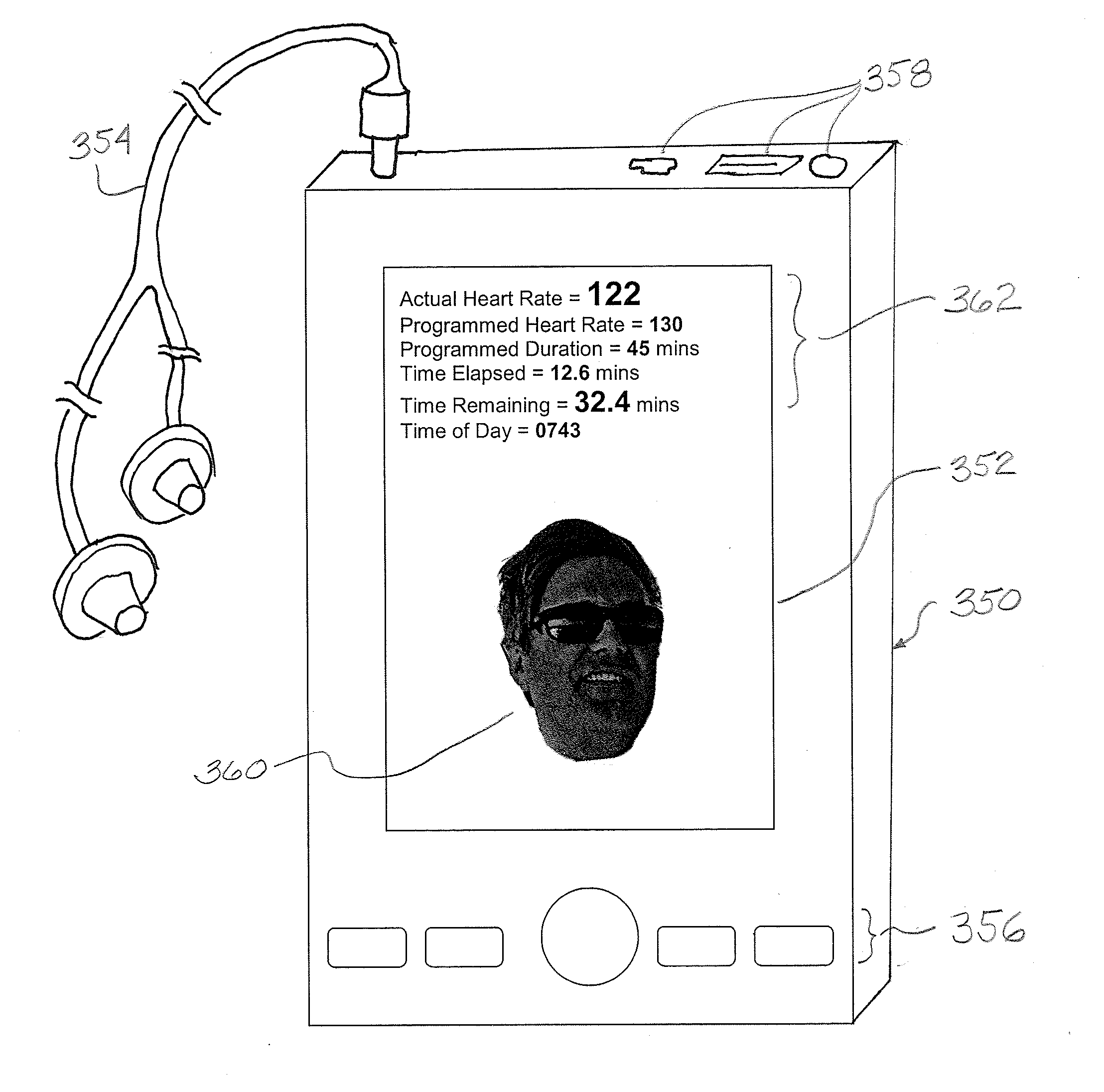
Mobile fitness and personal caloric management system
InactiveUS20110087137A1Continuous monitoringPhysical therapies and activitiesCosmonautic condition simulationsJob descriptionAccelerometer
A user's personal biometric information such as age, sex, weight, height as well as the user's lifestyle information, such as daily caloric input, job description, smoker status and physical fitness, is uploaded onto a host computer. Target heart rate, energy and / or caloric consumption levels related to desired fitness and weight loss goals for a particular individual are then selected having regard to fitness levels for an individual of comparable age, and consuming similar calories are then downloaded to a caloric monitoring unit. The caloric monitoring unit is provided for measuring the user's heart rate and dynamic energy and / or caloric expenditure over one to four weeks. The caloric monitoring unit includes a heart rate monitor, a unit accelerometer, a global positioning system (GPS), and an audio and / or video output. The audio / video output is operable to provide information and / or motivational prompts to the user in the event the heart rate, energy expenditure and / or caloric expenditure falls below or exceeds pre-selected target expenditures over a particular time segment of the selected time period having regard to the calories which are consumed. A display provides a continuously updated visual indication of whether or not the use has achieved the pre-selected optimum caloric burn or energy expenditure for that particular time segment. An internal calendar / clock, a processor and / or memory in the caloric monitoring unit compares measured heart rate and energy expenditures for multiple time segments against target levels stored as the user-specific fitness programme tailored to achieve the desired weight loss. The comparison is then used to generate compliance output data to either the user and / or a nutritionist.
Owner:SALIENT IMAGING
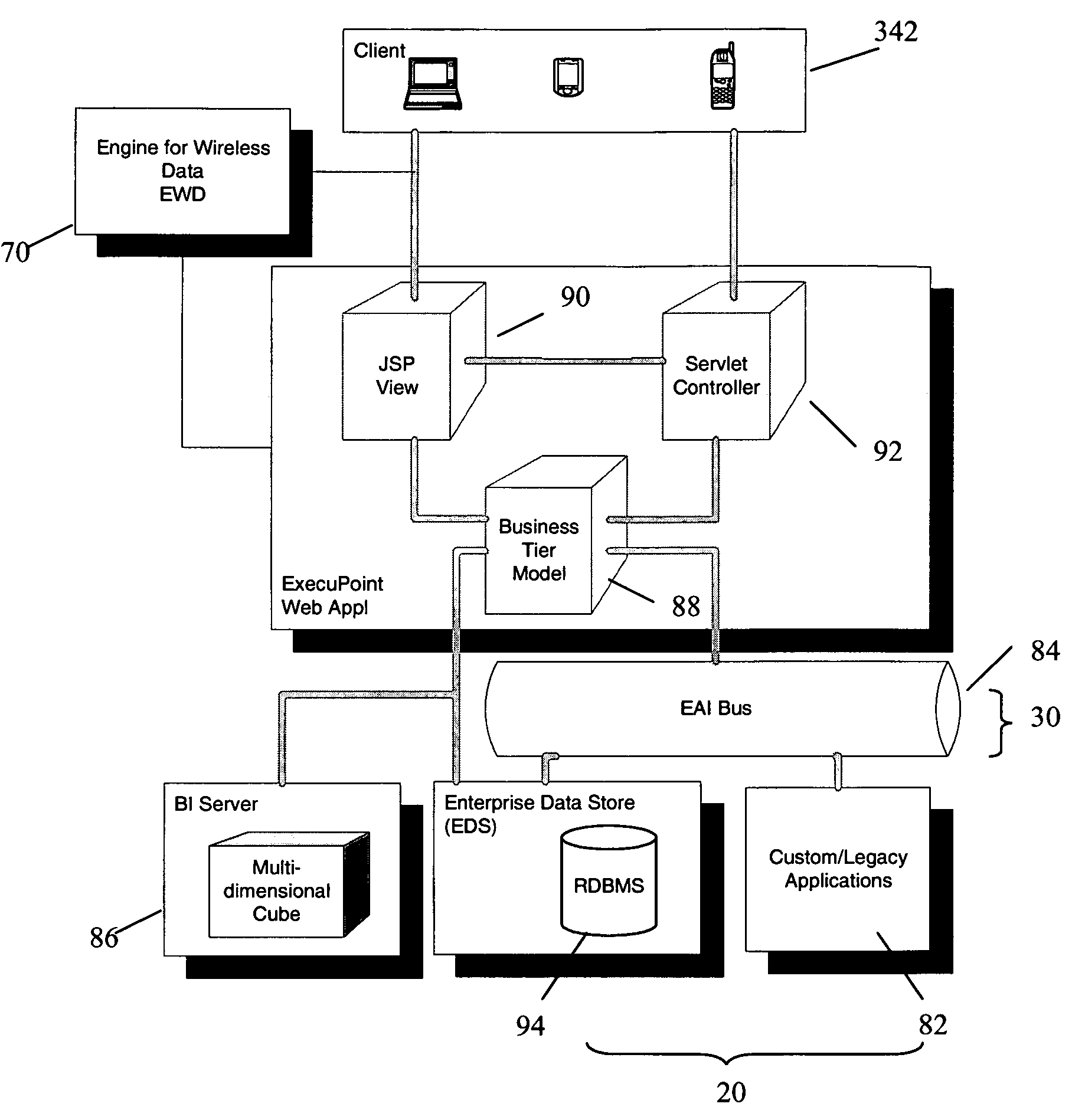
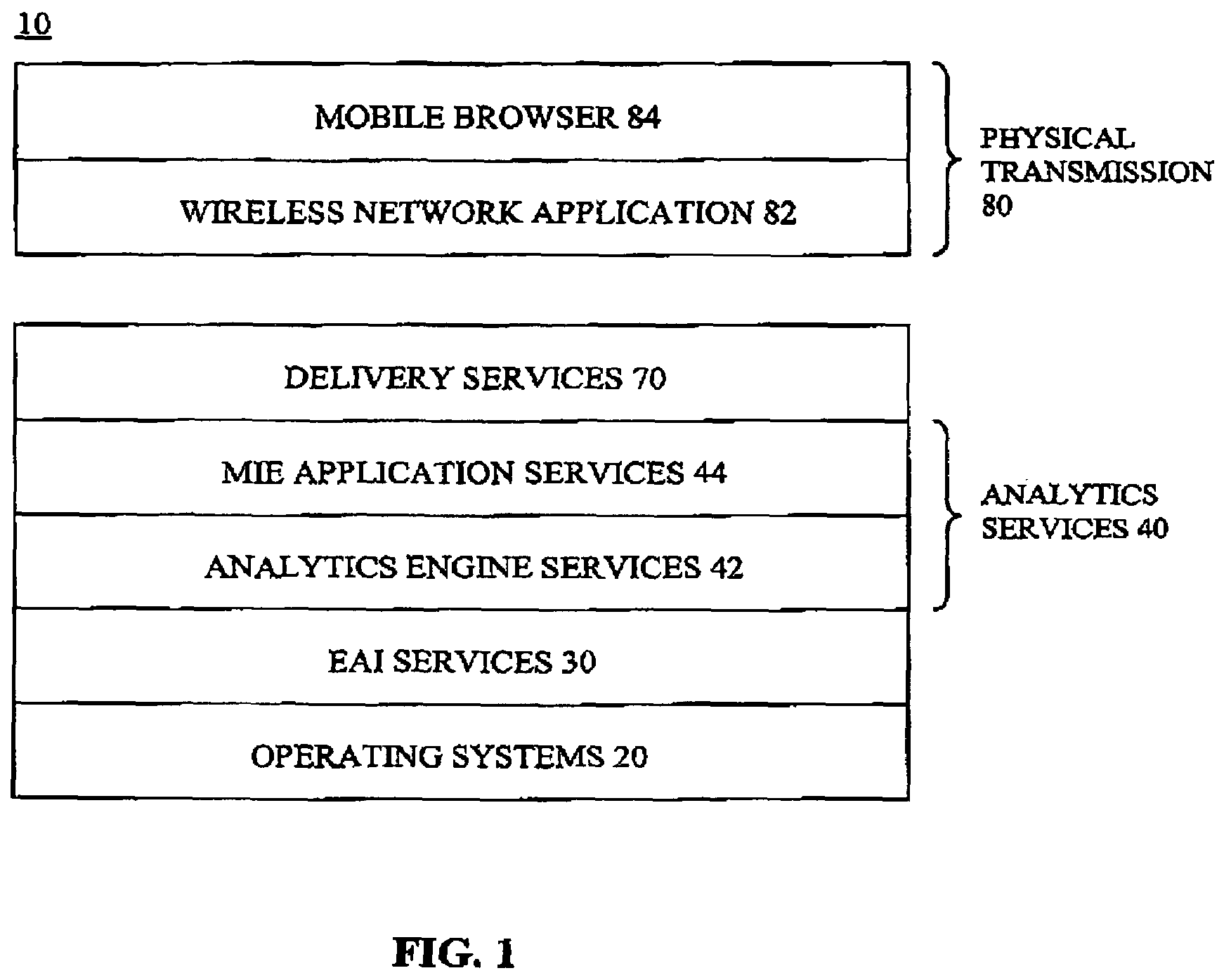
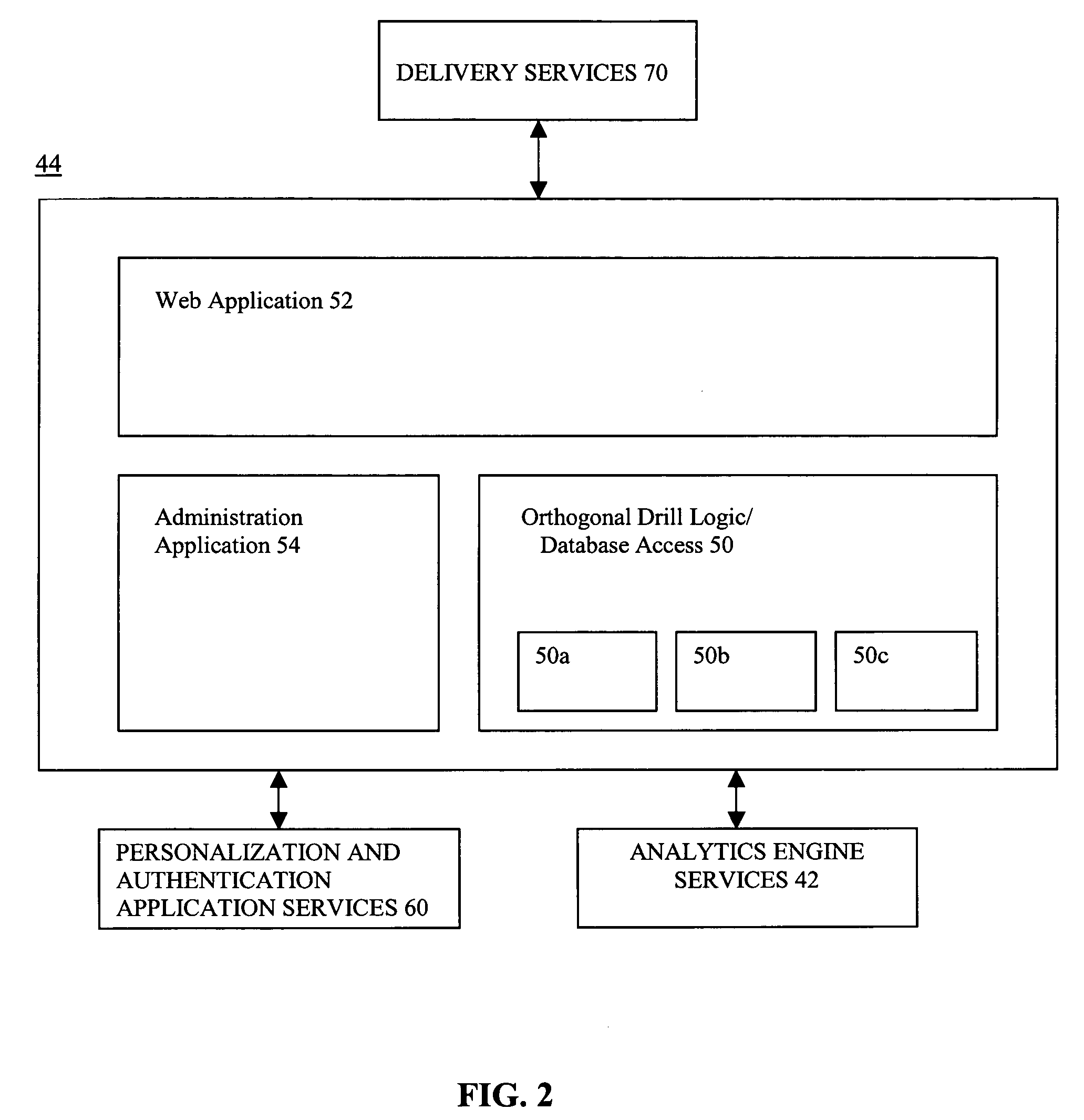
System and wireless device for providing real-time alerts in response to changes in business operational data
InactiveUS7151438B1Extension of timeImprove efficiencyChecking apparatusOffice automationEnterprise application integrationBusiness enterprise
A system for providing in response to changes within current operational data of a business enterprise, alert information including an alert to a wireless device in real-time. The system architecture includes an enterprise application integration services component for accessing and conditioning the current operational data and other business intelligence information. An analytics services component monitors for changes within the current operational data from a predetermined target level and communicates an alert and alert information if a change occurs. The analytics services component also extracts contextually-related first and second sets of critical business information, and converts the operational data, alert and alert information, and the first and second sets of critical business information into a device-independent, web-enabled format, which is then recoded by a delivery services component in accordance with the data delivery requirements of the wireless device. The alert and alert information will be displayed in the context of the current operational data and first and second sets of critical business information.
Owner:UNISYS CORP
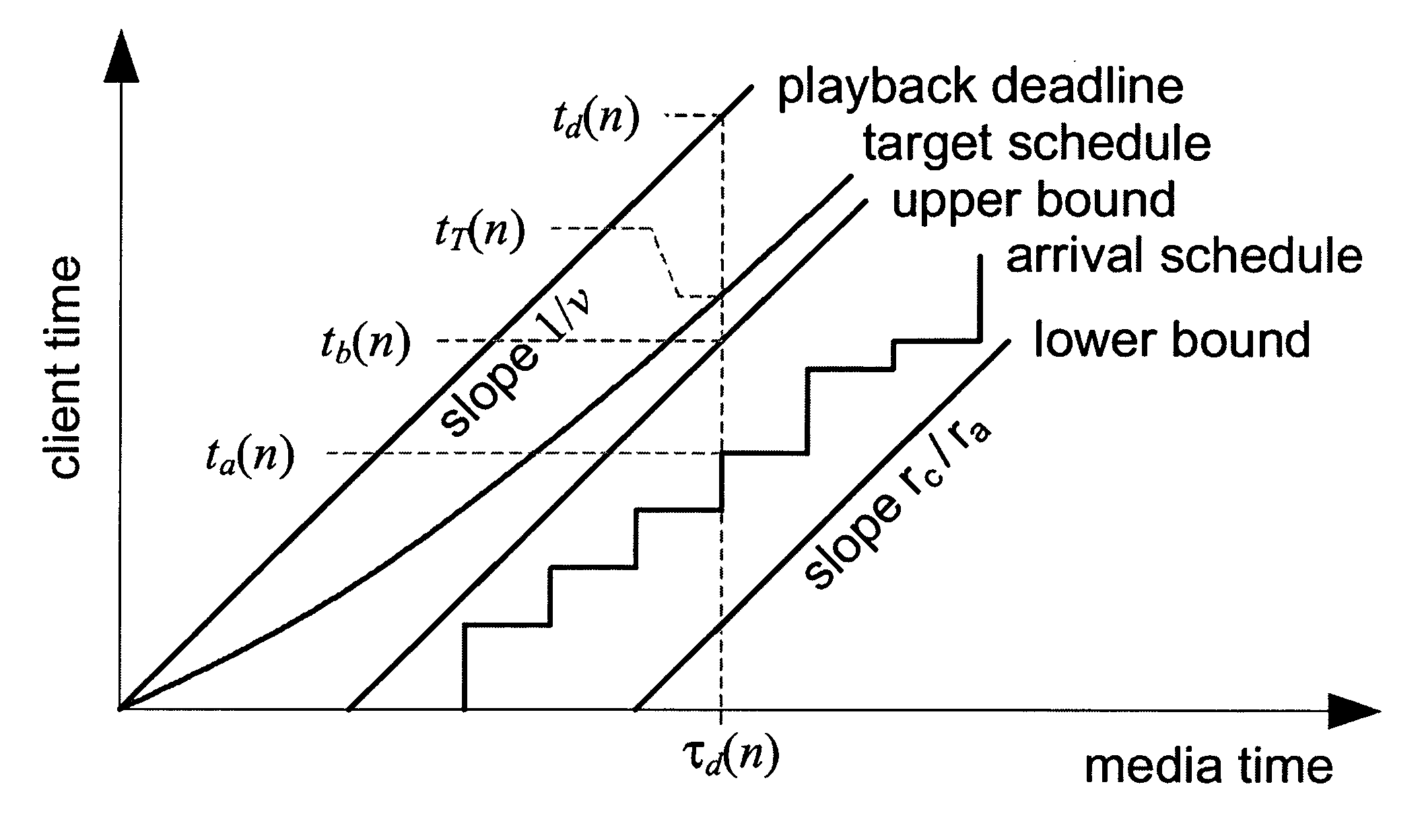
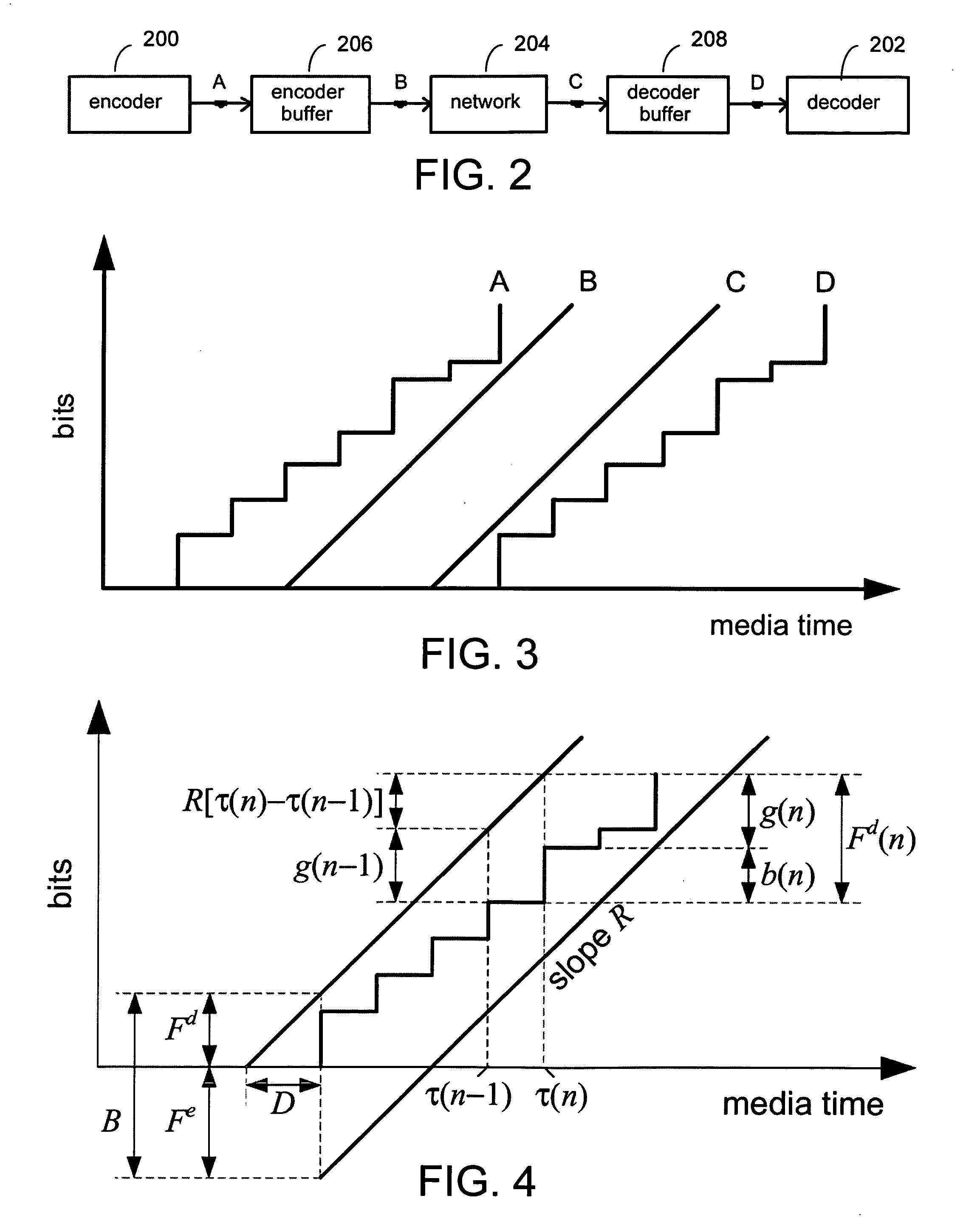
System and process for controlling the coding bit rate of streaming media data employing a linear quadratic control technique and leaky bucket model
InactiveUS20060143678A1Maximize qualitySmoothness of the average coding bit rate over consecutiveTwo-way working systemsDigital video signal modificationModel controlClient buffer
A system and process for controlling the coding bit rate of streaming media data is presented. This coding bit rate control involves dynamically adjusting the coding bit rate to control client buffer duration to prevent the buffer from underflowing, while keeping the average coding bit rate close to the average transmission bit rate of the network (an thus maximizing the quality of the data playback). Using the theory of optimal linear quadratic control, the client buffer duration is kept as close as possible to a target level while still keeping the coding bit rate (and hence the quality) as constant as possible. In addition, a leaky bucket model is incorporated into the control loop so that the changes in buffer duration due to natural variation in the instantaneous coding bit rate are not mistaken for changes in buffer duration due to network congestion.
Owner:MICROSOFT TECH LICENSING LLC
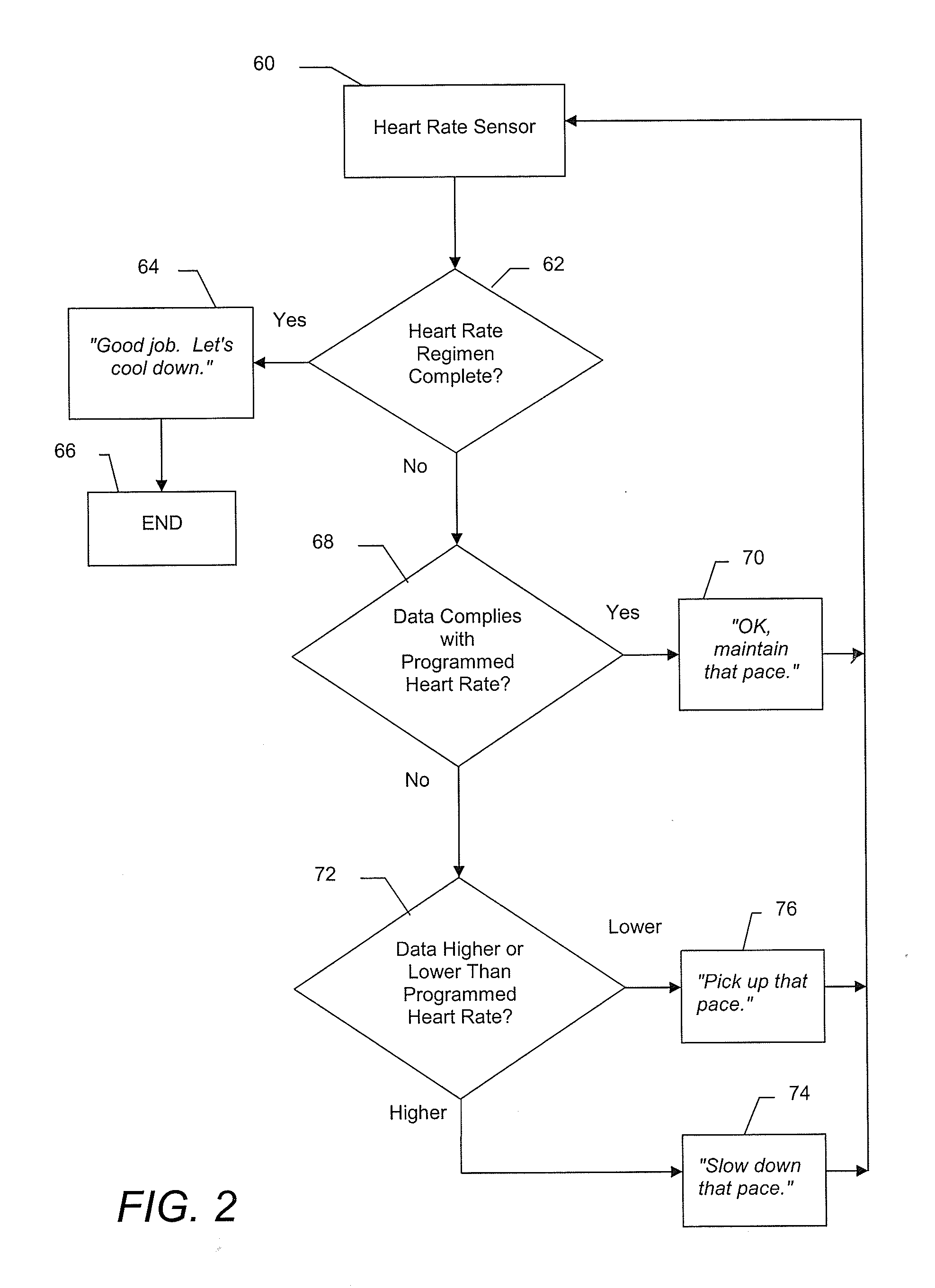
Audible biofeedback heart rate monitor with virtual coach
InactiveUS20110152696A1Physical therapies and activitiesCosmonautic condition simulationsMedicinePulse rate
A system and associated method that provides a virtual coach to a person during an exercise routine includes a sensor used to sense the level of a physiological parameter of the exerciser, such as heart rate, a processor programmed to compare the sensed physiological parameter to a target level of the physiological parameter, and, depending on the comparison, provide coaching prompts to the exerciser. Coaching prompts include audible and visual prompts. In another feature, a visual image of a virtual coach may be made available for display to the exerciser, and in yet another feature, a video of the virtual coach saying the audio prompt may be displayed. The system allows for selection from a plurality of virtual coaches. The audio and video of virtual coaches are recordings of real people and may be produced or obtained from other sources. In one embodiment, audio, visual, and video of the virtual coach may be downloaded from the Internet.
Owner:HALL RYAN LAB
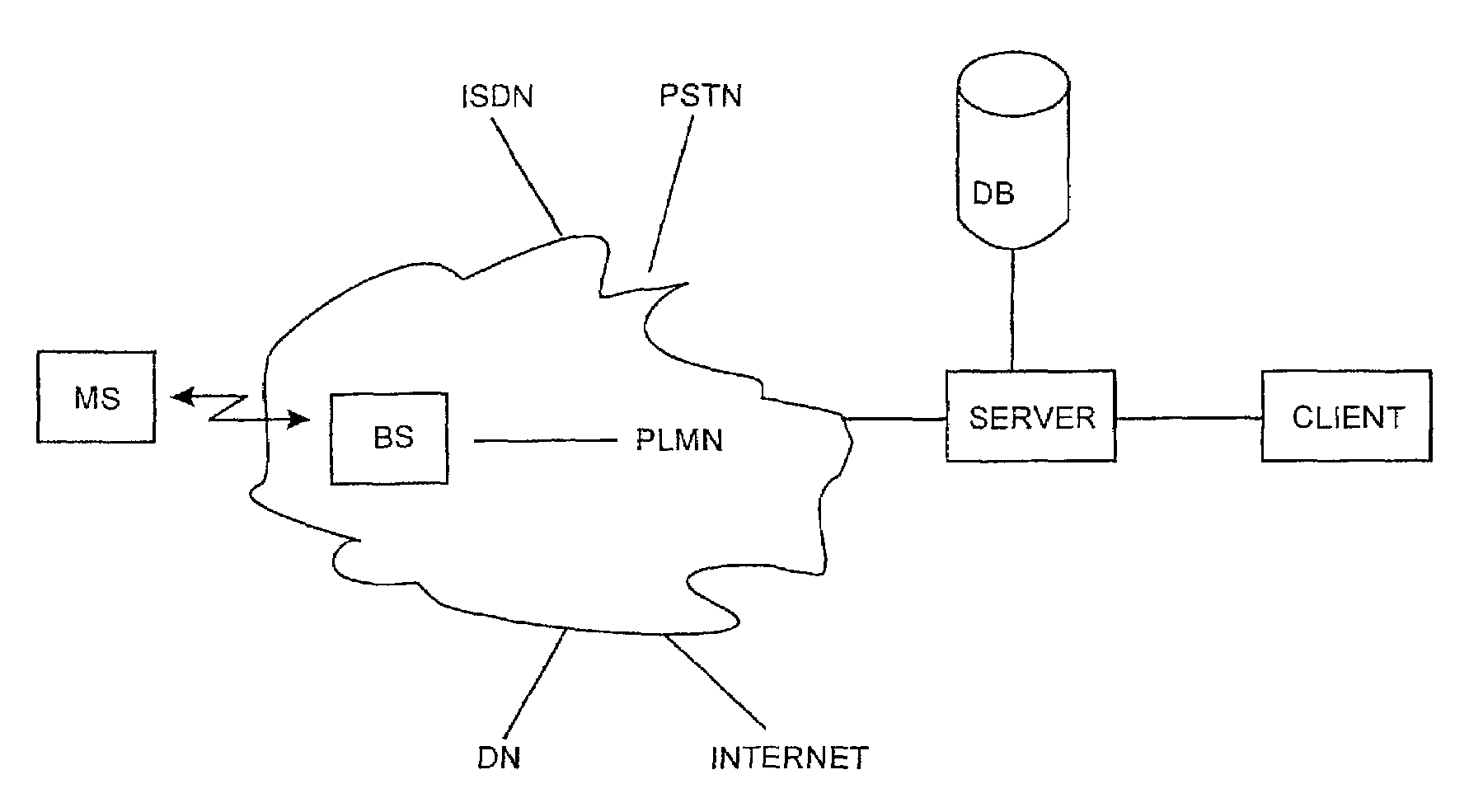
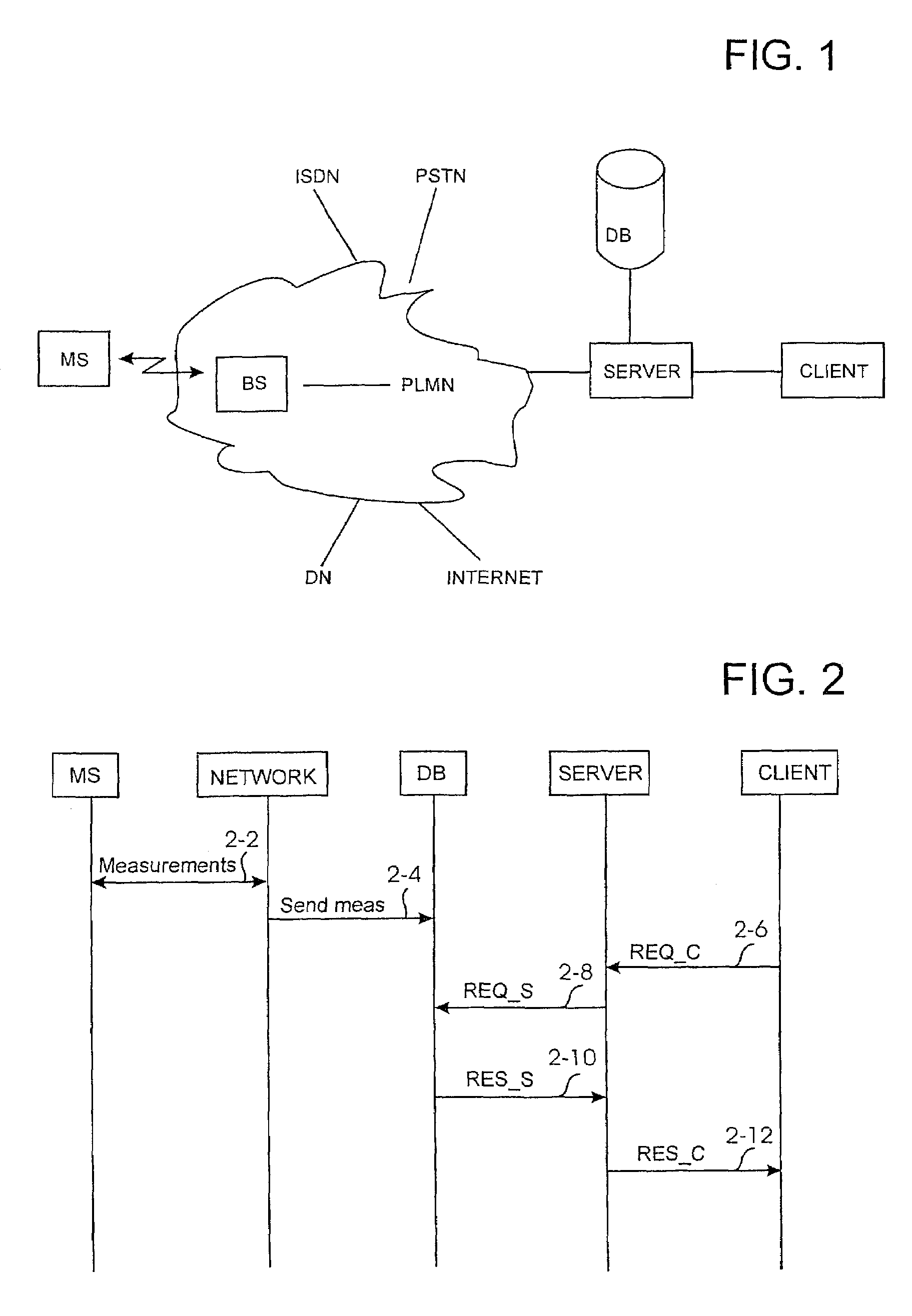
Location determination in telecommunication network
InactiveUS7120449B1Reliable determinationPosition fixationRadio/inductive link selection arrangementsTelecommunications networkMobile station
The invention relates to a method for supporting location determination of a mobile station, in which method location data are stored in and deleted from a memory, each location data item describing the location of the mobile station measured at a given measuring moment. Furthermore, in the method, a distance parameter and / or a target level corresponding to the distance parameter is determined at least for some of the stored location data; and deletion of the location data is at least partly based on the distance parameter and target level.
Owner:NOKIA TECHNOLOGLES OY
Proportional pressure assist ventilation controlled by a diaphragm electromyographic signal
InactiveUS6920878B2RespiratorsOperating means/releasing devices for valvesAssisted ventilationInspiratory Capacity
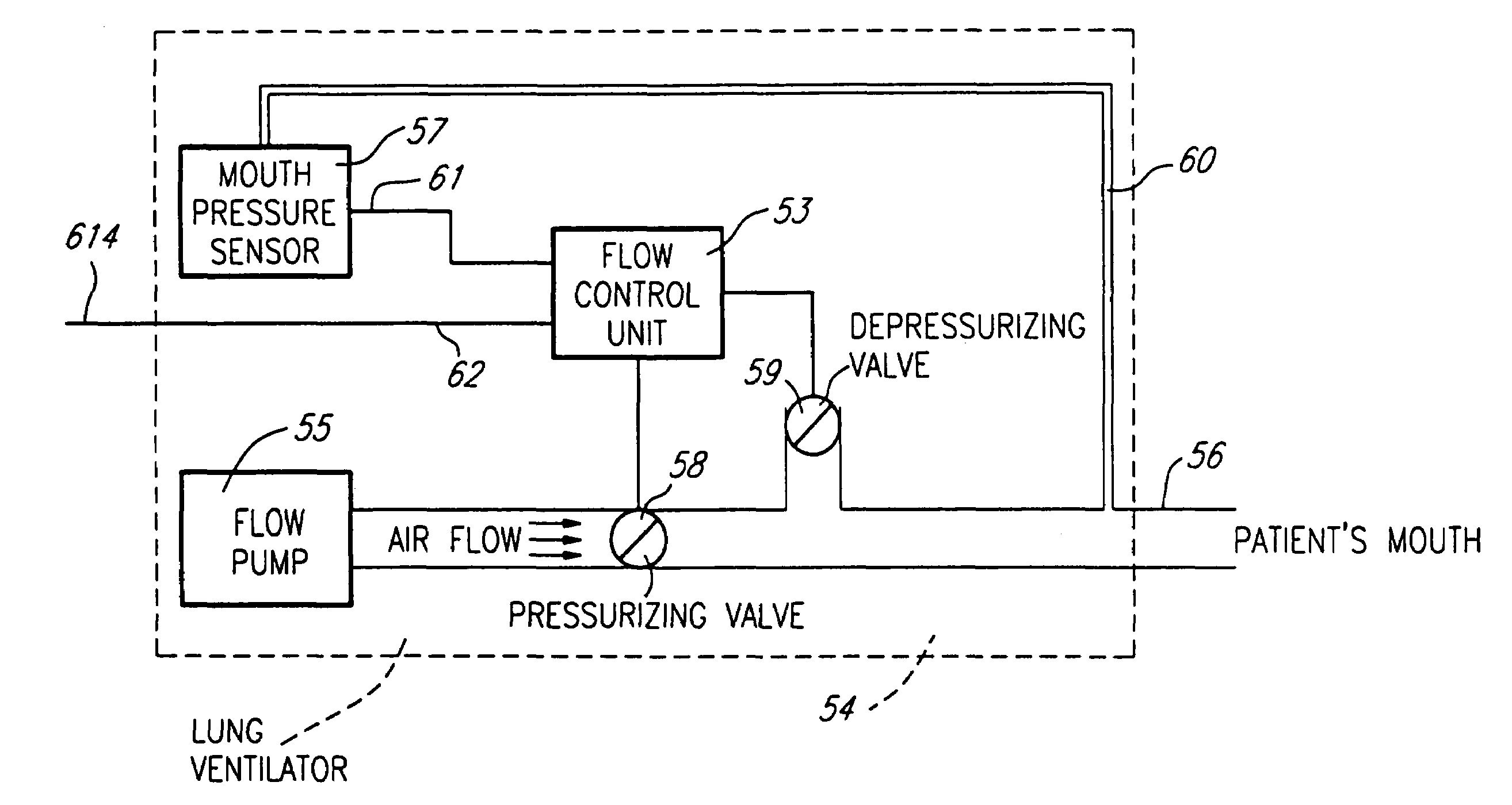
A closed loop system uses (a) the intensity of the diaphragm electromyogram (EMG) for a given inspiratory volume; (b) the inspiratory volume for a given EMG intensity; or (c) a combination of (a) and (b); in view of controlling the level of gas flow, gas volume or gas pressure delivered by a mechanical (lung) ventilator. The closed loop ventilator system enables for automatic or manual adjustment of the level of inspiratory support in proportion to changes in the neuro-ventilatory efficiency such that the neural drive remains stable at a desired target level. An alarm can also be used to detect changes in neuroventilatory efficiency in view of performing manual adjustments.
Owner:UNIV DE MONTREAL
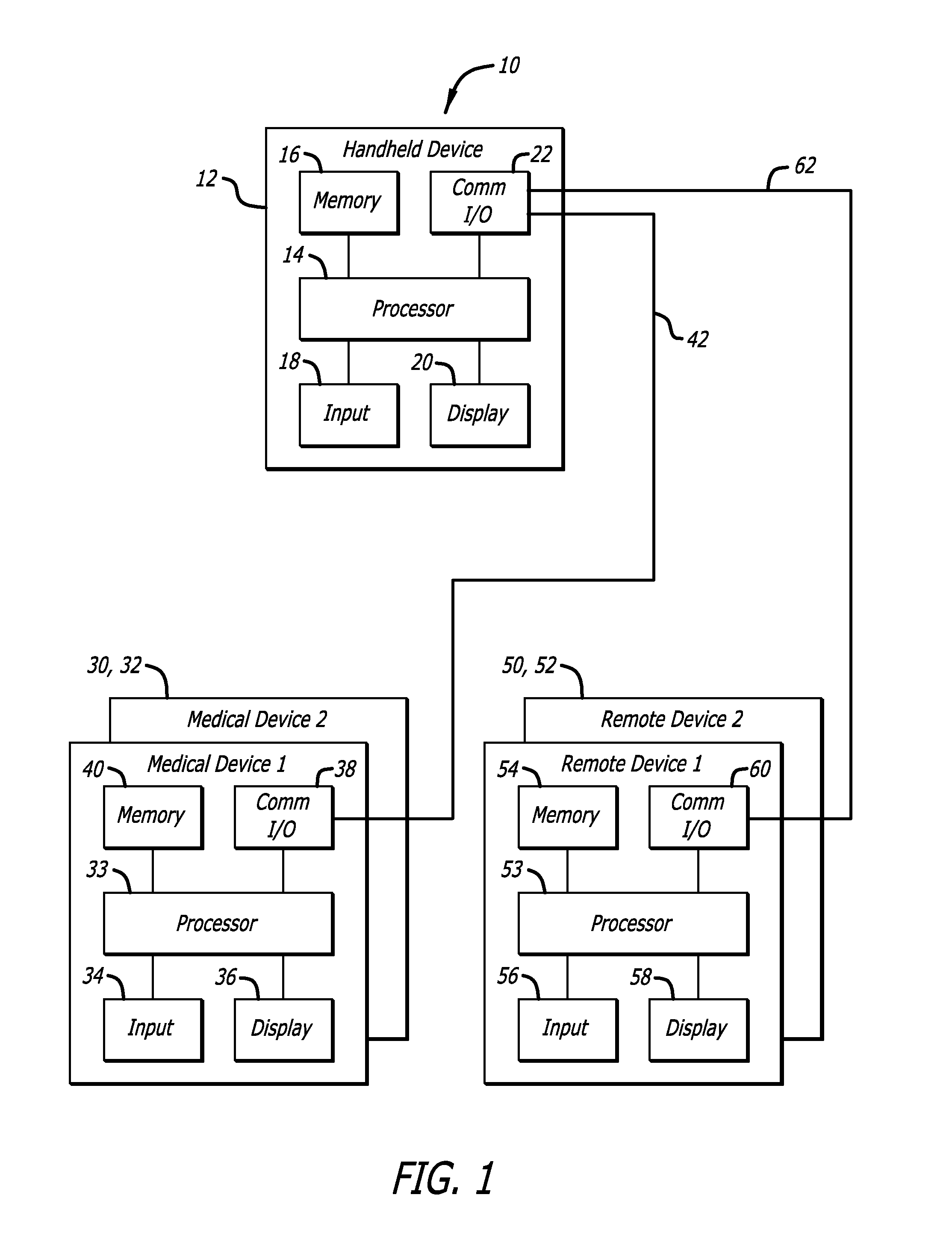
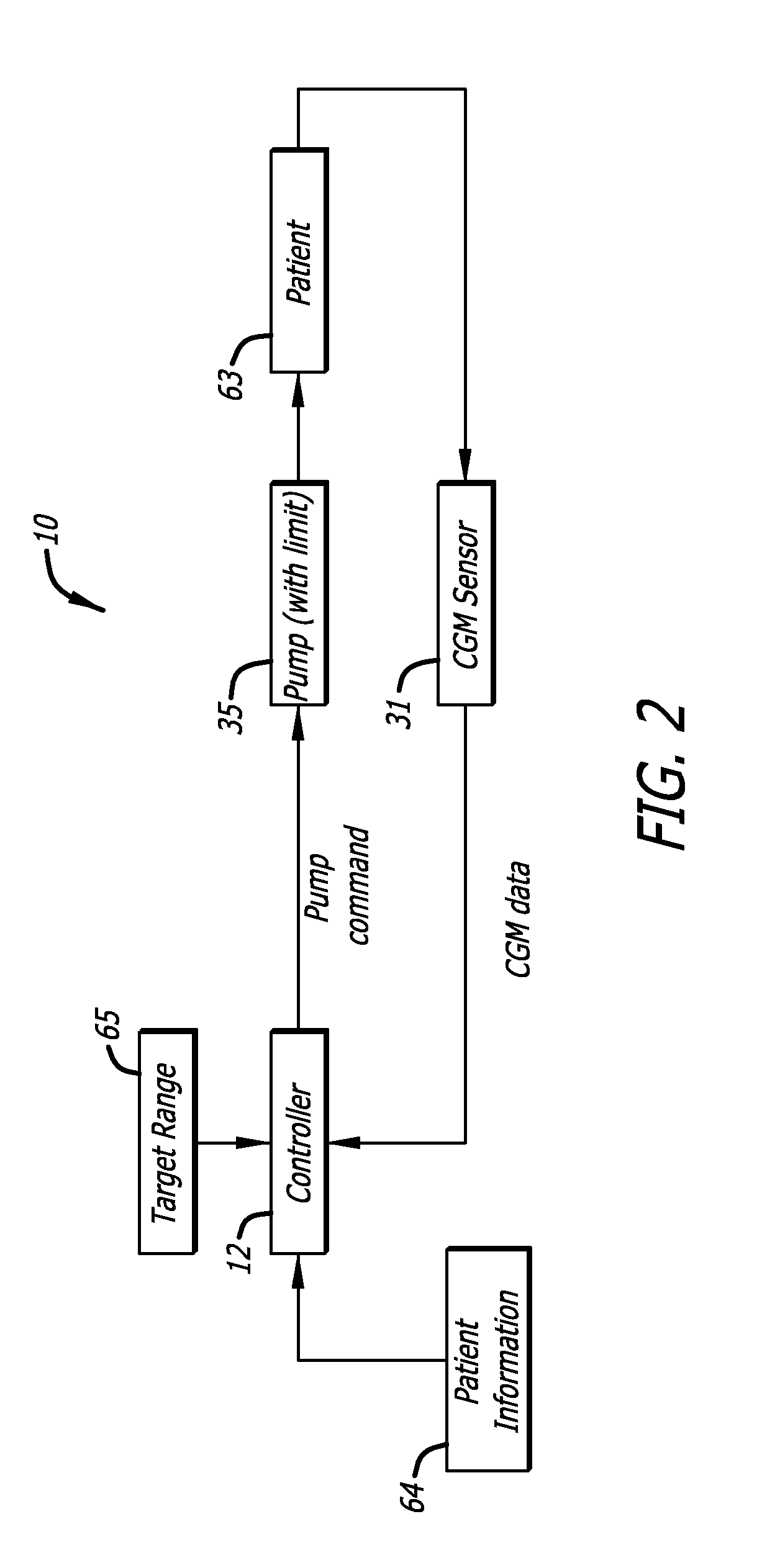
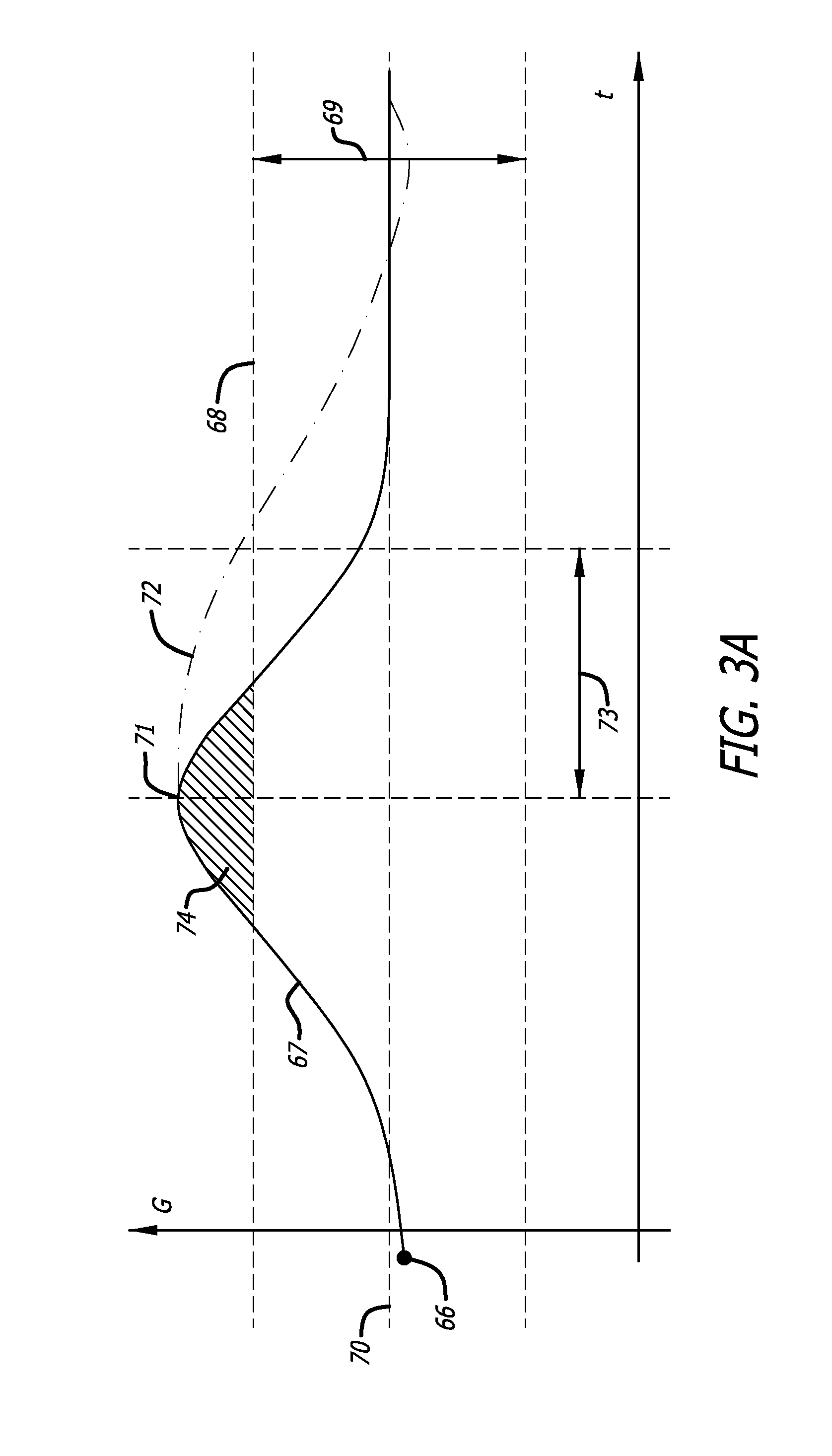
Adaptive insulin delivery system
A proactive system and method in which levels of glucose are monitored after a meal signal and compared to a safe range. If a monitored glucose level is outside the safe range, a post-prandial vertex of the glucose level is identified and an action is provided to more rapidly return the glucose level to a target level within the safe range than if no action was provided. In another aspect a control parameter in an IDM system is adjusted by determining a performance metric of the system as a function of the levels of glucose and a medication administration signal over a first window of time; and, if the performance metric is outside an expected range, adjusting the control parameter to adjust an amount of medication and to bring the performance metric inside the expected range.
Owner:ABBOTT DIABETES CARE INC
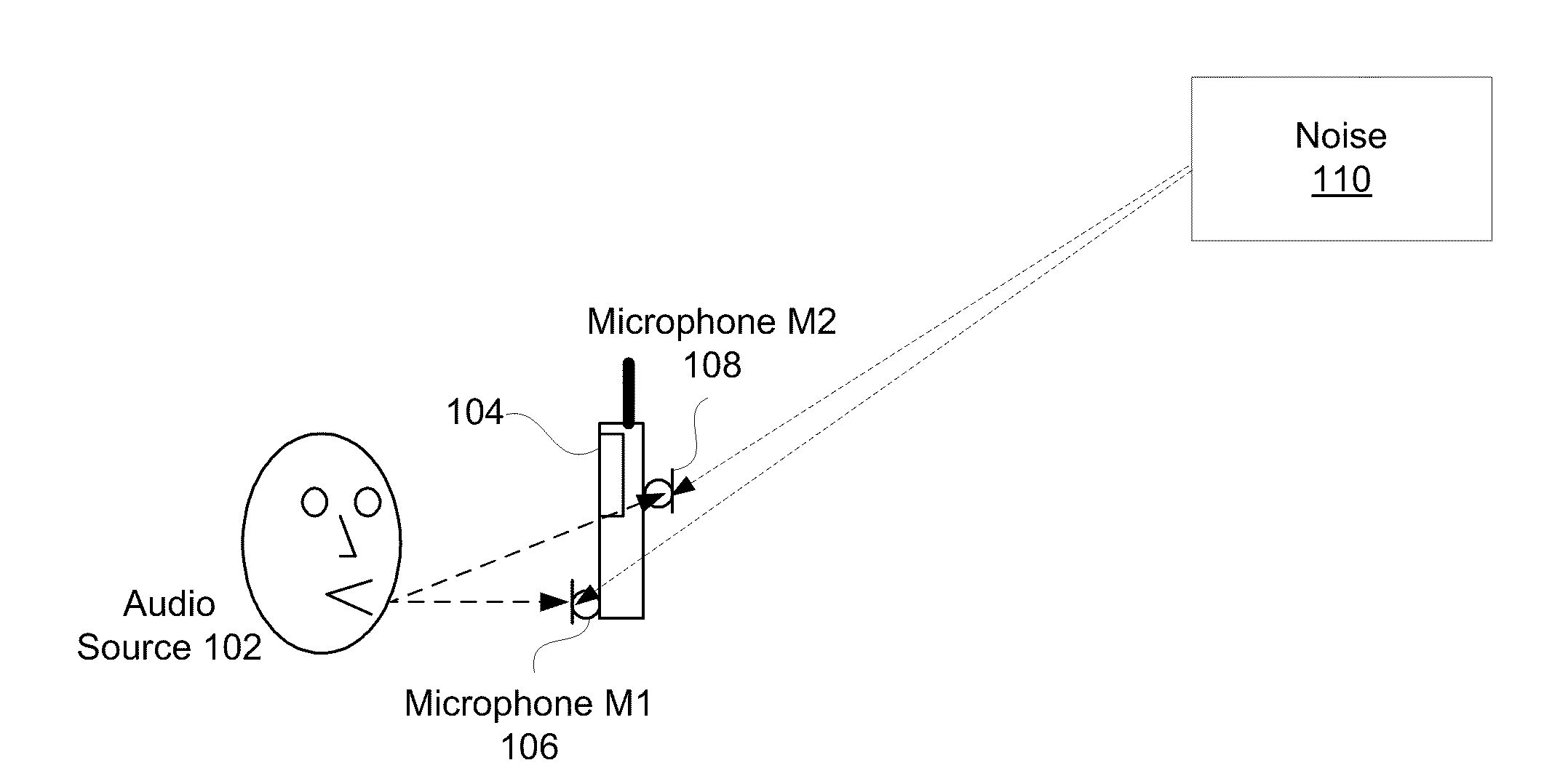
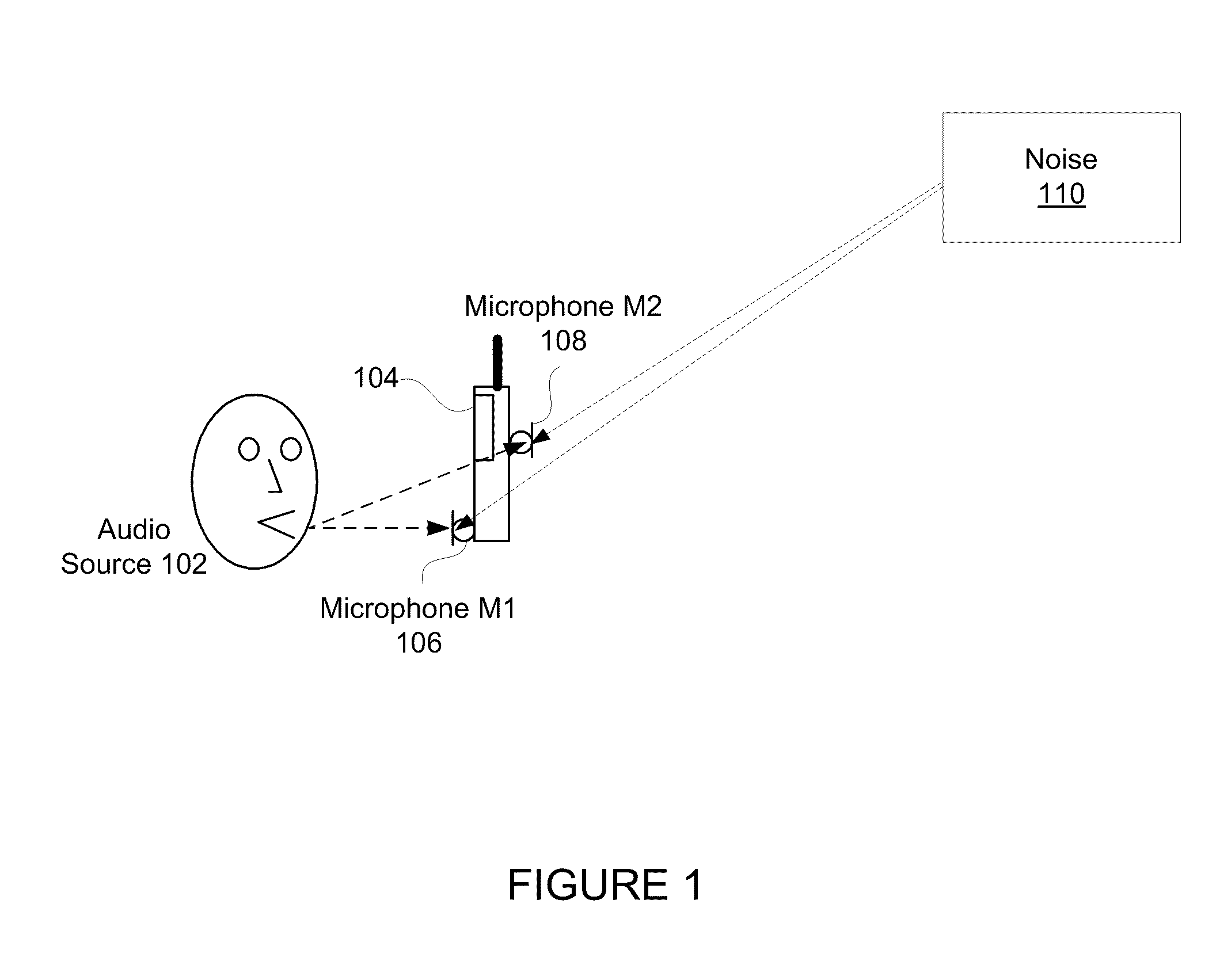
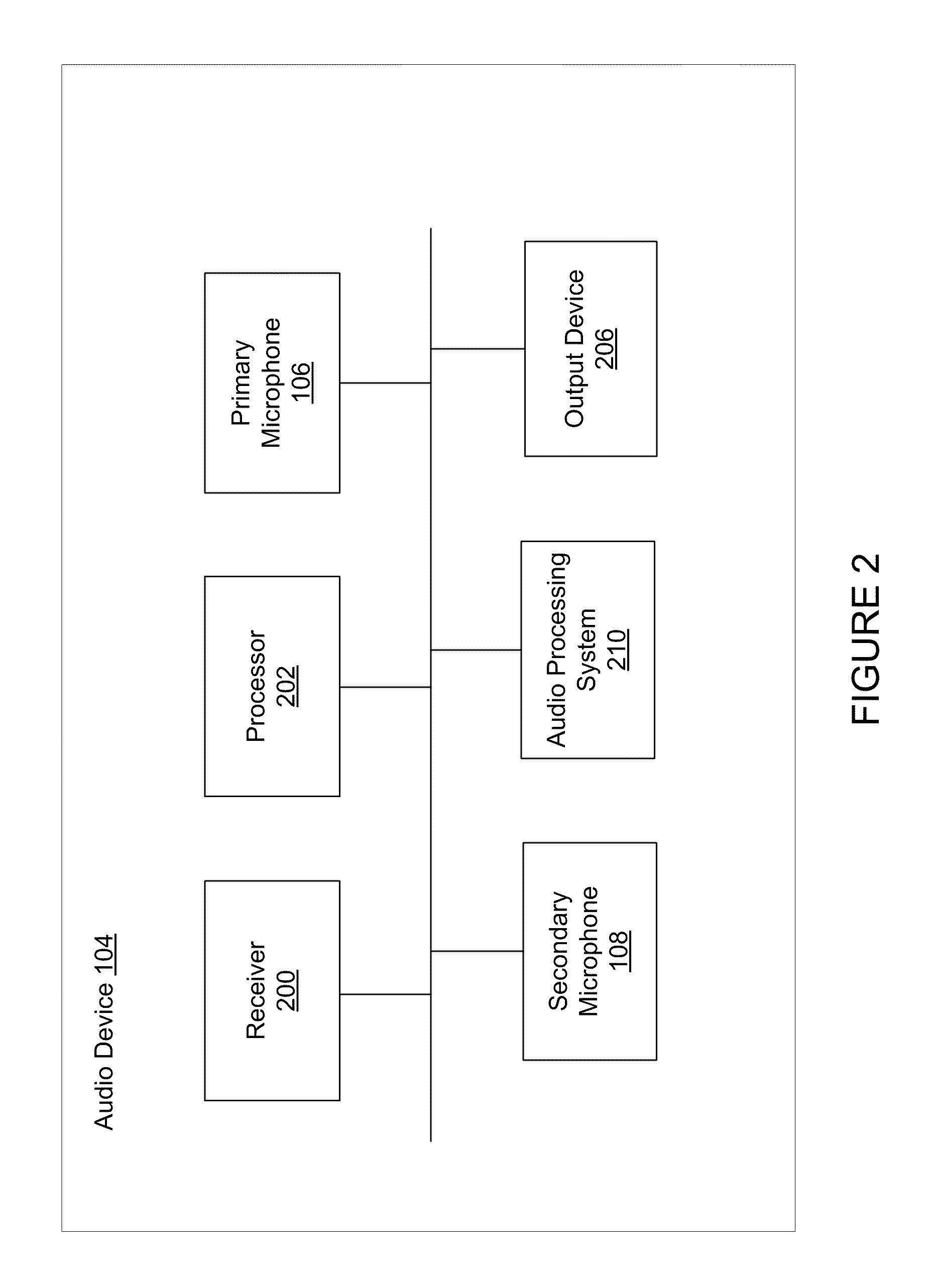
Method for Jointly Optimizing Noise Reduction and Voice Quality in a Mono or Multi-Microphone System
ActiveUS20110257967A1Reduce noiseDecreased energy levelSpeech analysisTransducer circuit dampingAdaptive denoisingEngineering
The present technology provides adaptive noise reduction of an acoustic signal using a sophisticated level of control to balance the tradeoff between speech loss distortion and noise reduction. The energy level of a noise component in a sub-band signal of the acoustic signal is reduced based on an estimated signal-to-noise ratio of the sub-band signal, and further on an estimated threshold level of speech distortion in the sub-band signal. In embodiments, the energy level of the noise component in the sub-band signal may be reduced to no less than a residual noise target level. Such a target level may be defined as a level at which the noise component ceases to be perceptible.
Owner:KNOWLES ELECTRONICS INC
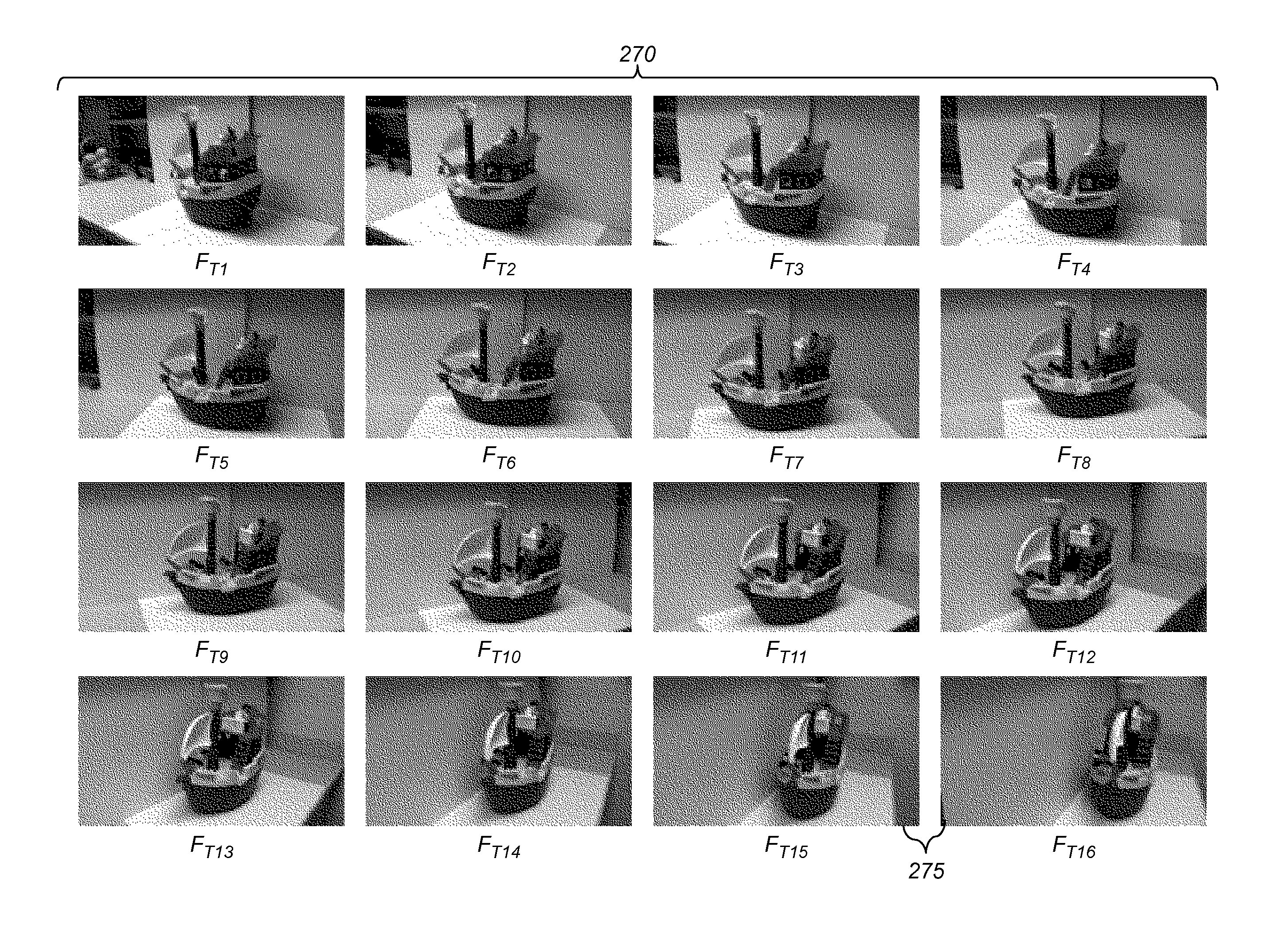
3D scene model from video
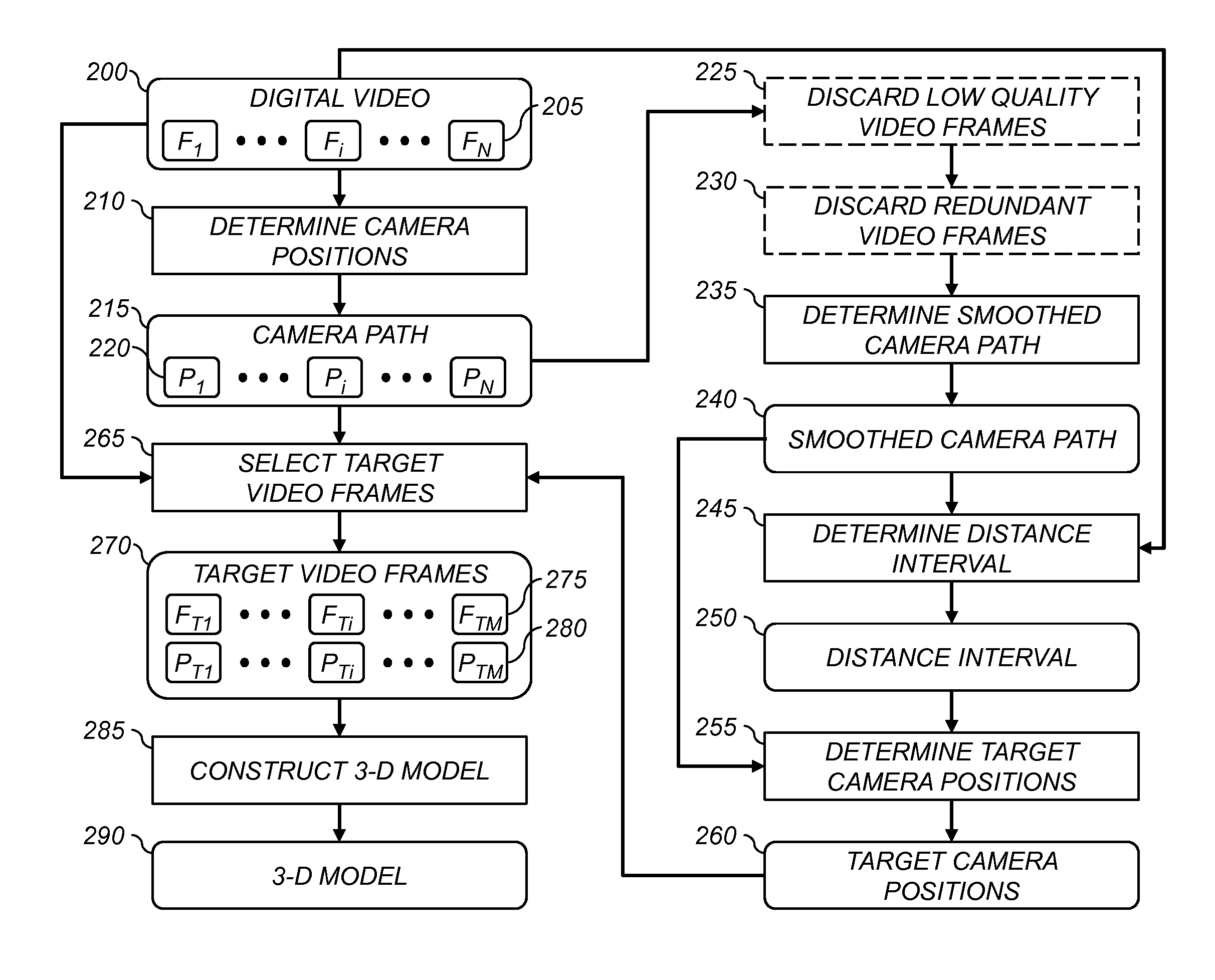
InactiveUS20130215239A1Reduce in quantityImprove efficiencyImage enhancementImage analysisDigital videoThree dimensional model
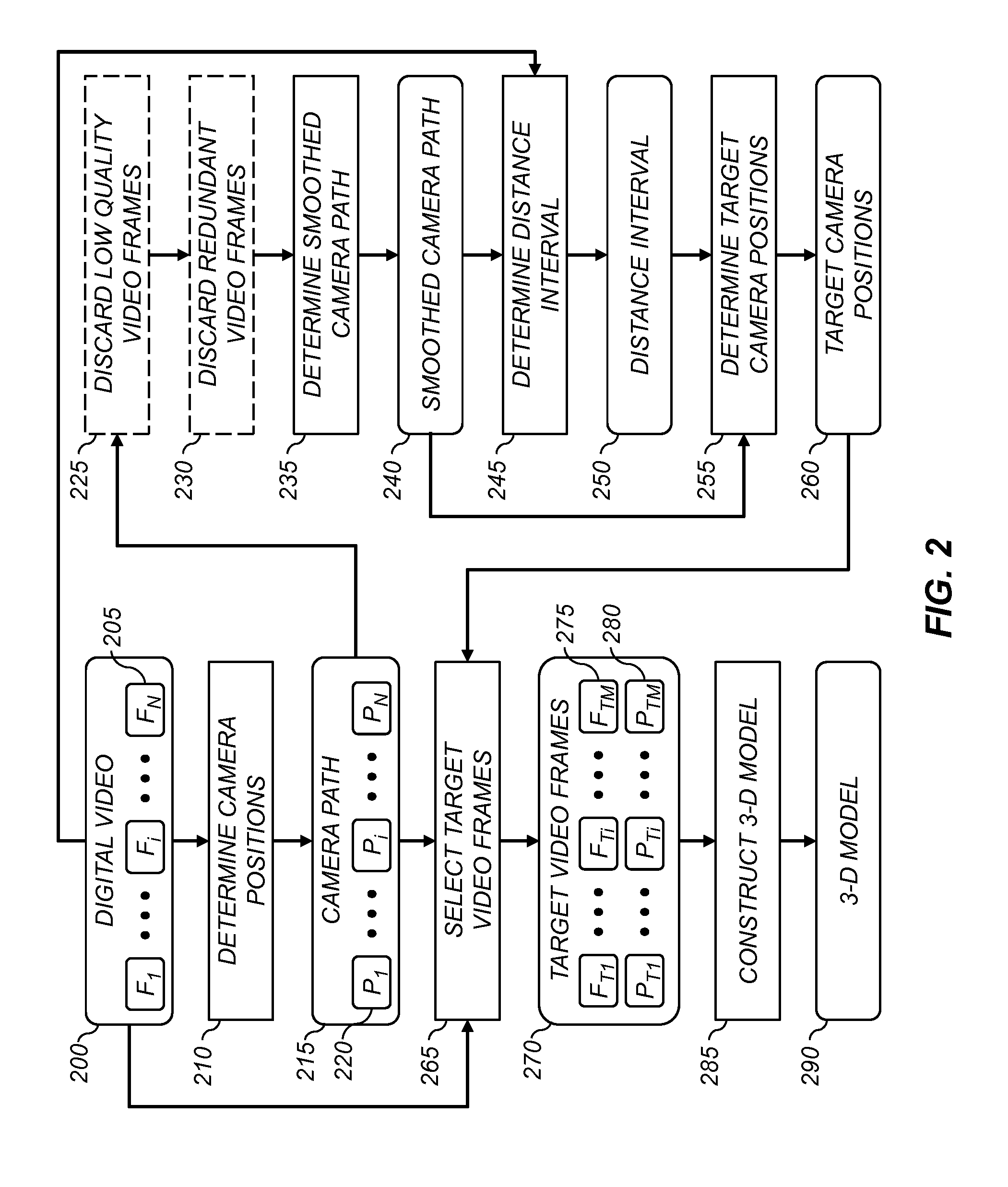
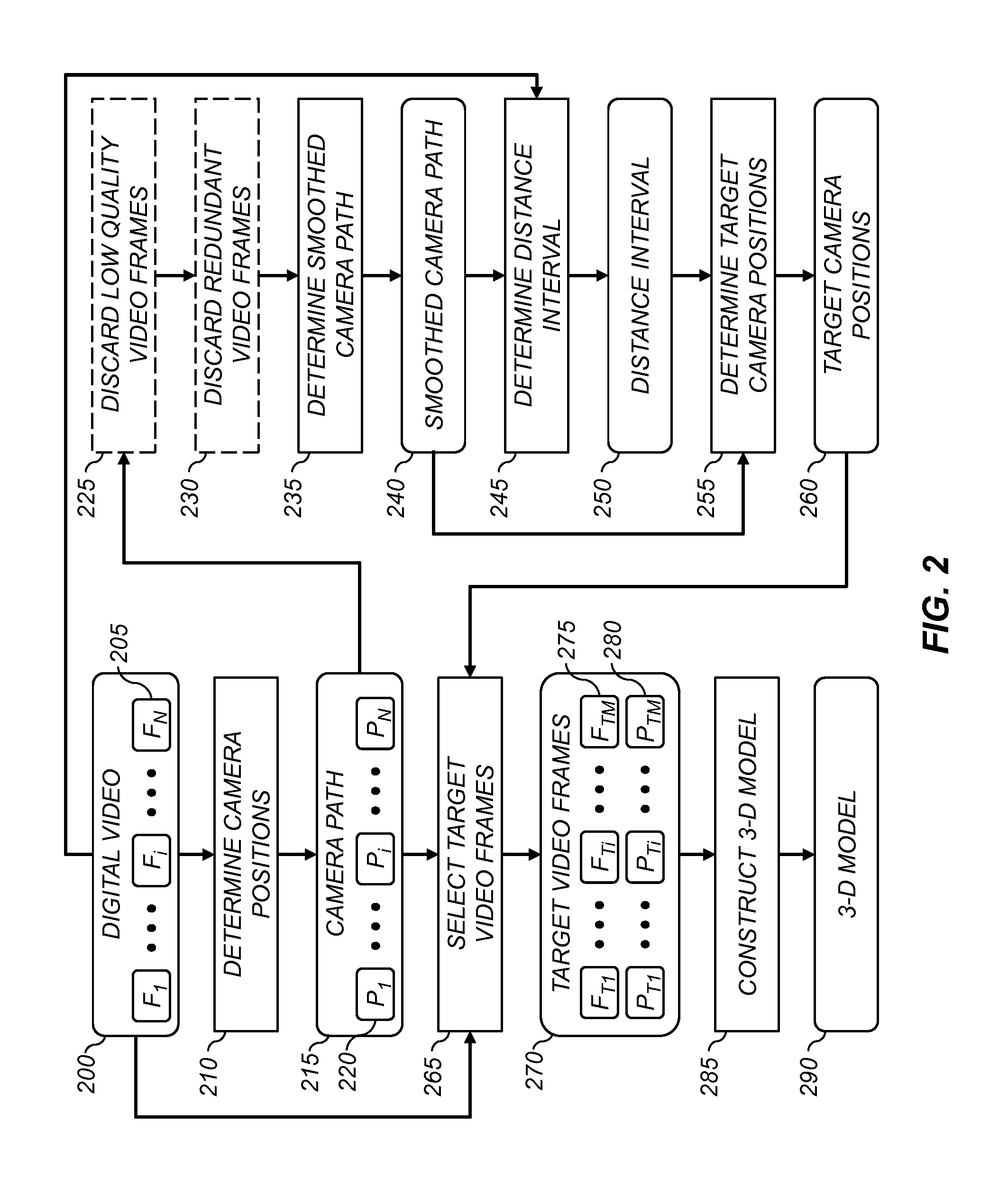
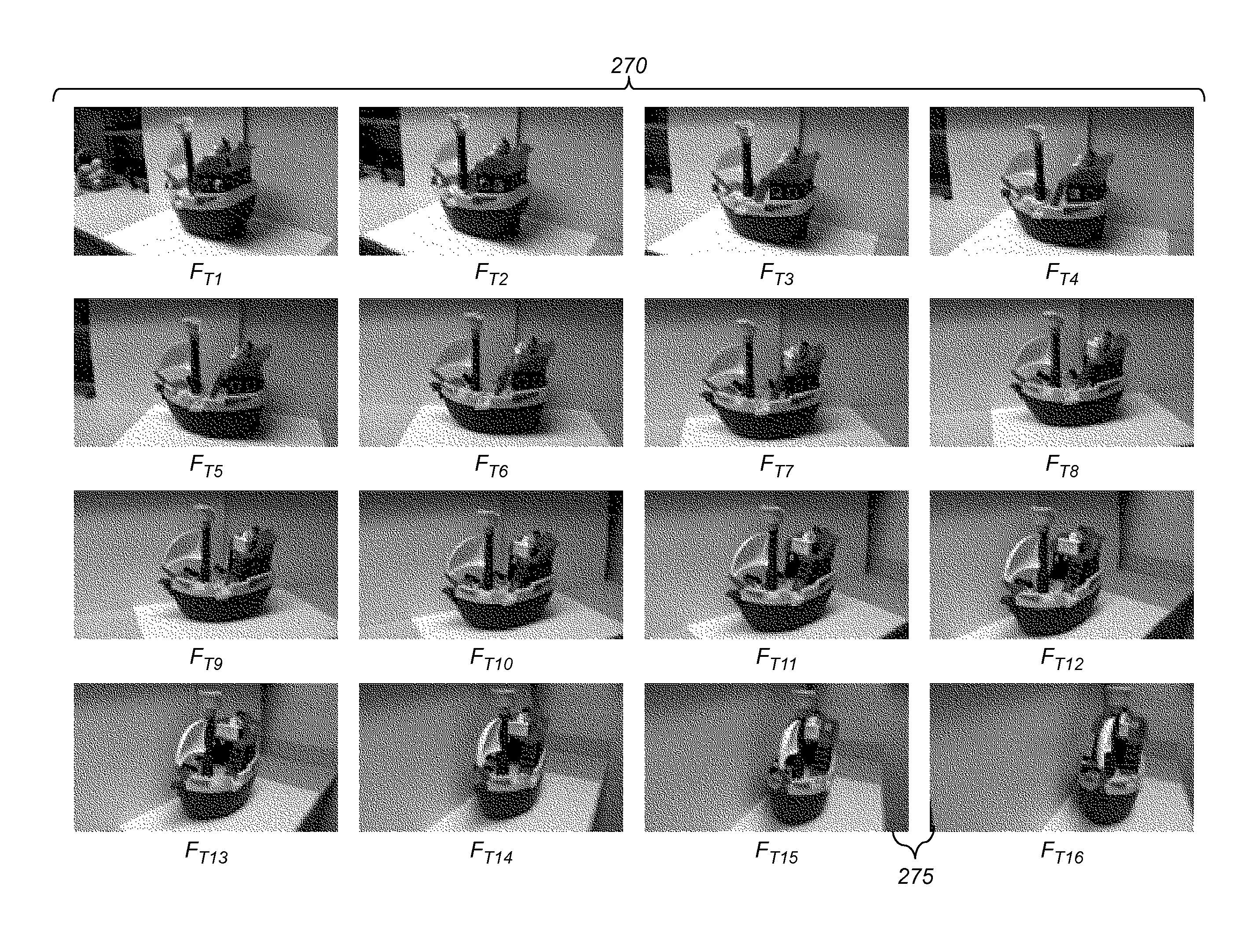
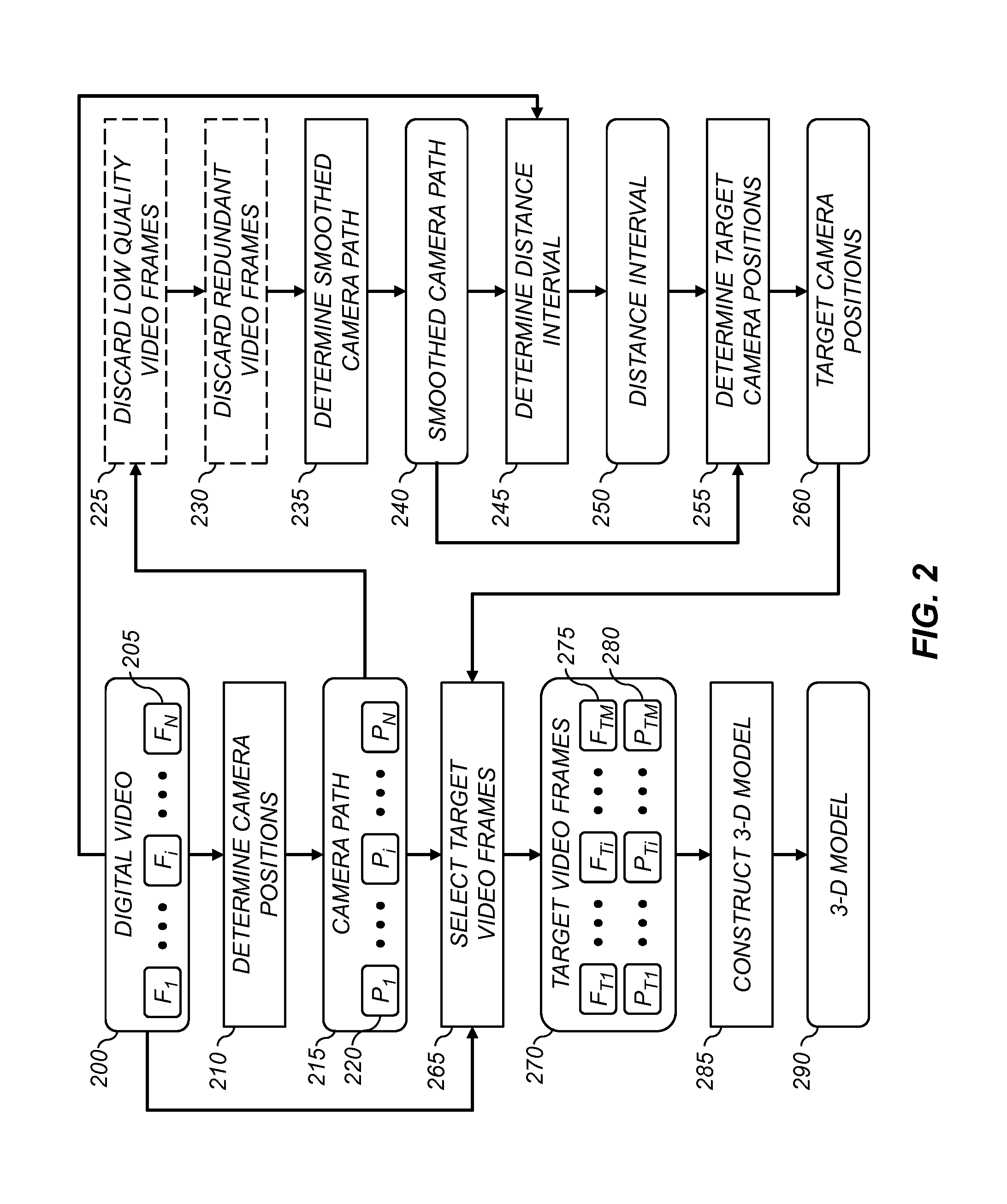
A method for determining a three-dimensional model of a scene from a digital video captured using a digital video camera, the digital video including a temporal sequence of video frames. The method includes determining a camera position of the digital video camera for each video frame, and fitting a smoothed camera path to the camera positions. A sequence of target camera positions spaced out along the smoothed camera path is determined such that a corresponding set of target video frames has at least a target level of overlapping scene content. The target video frames are analyzed using a three-dimensional reconstruction process to determine a three-dimensional model of the scene.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
Circuit and method for soft start from a residual voltage
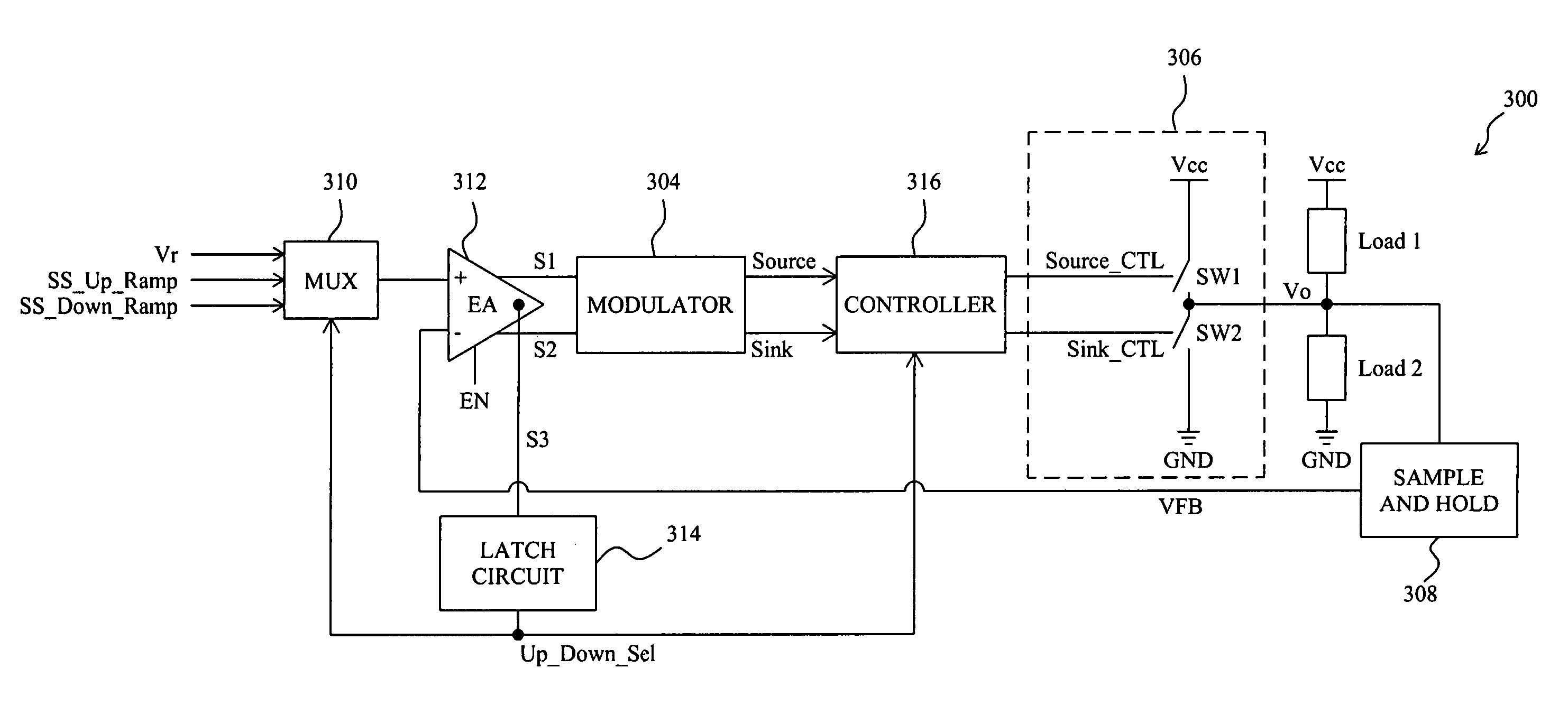
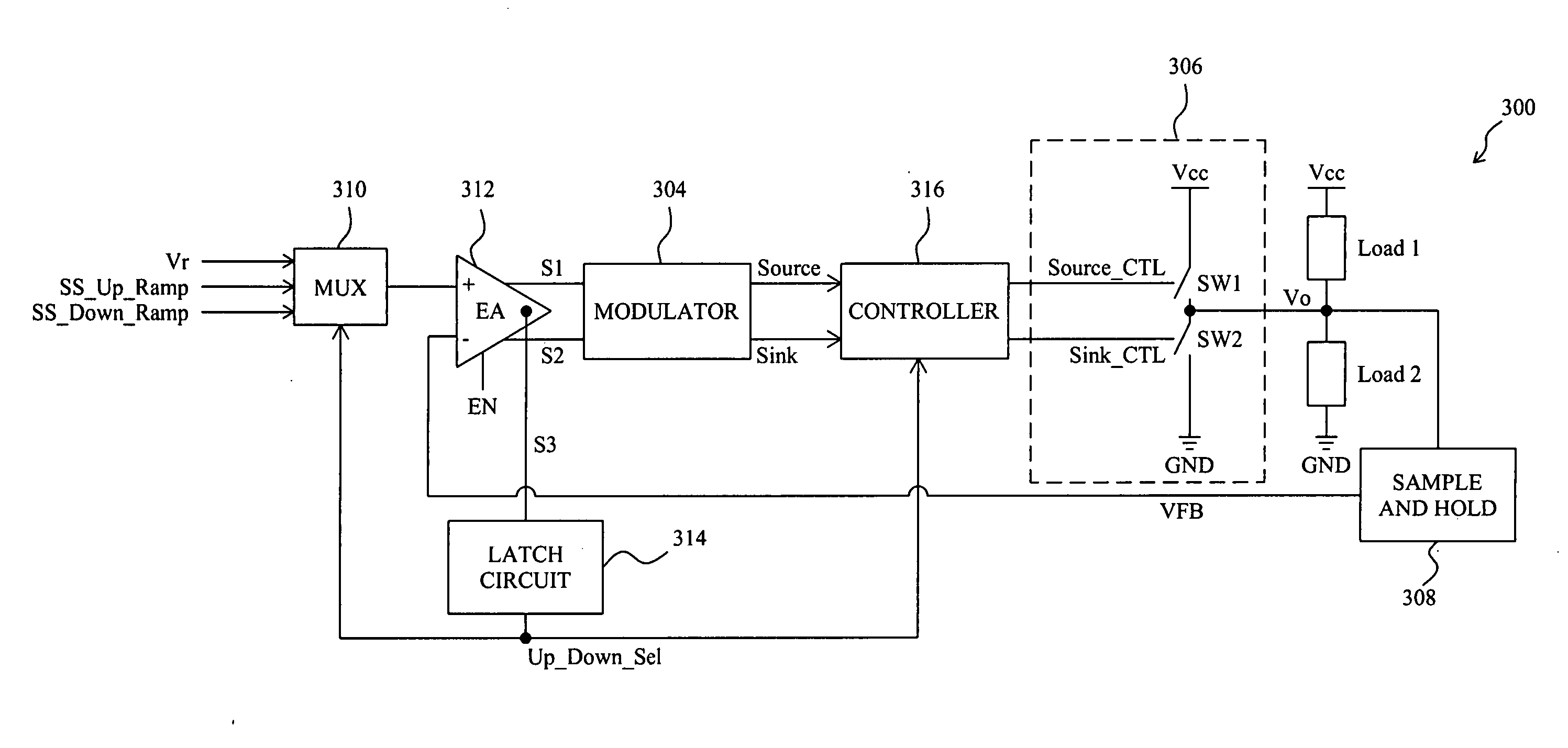
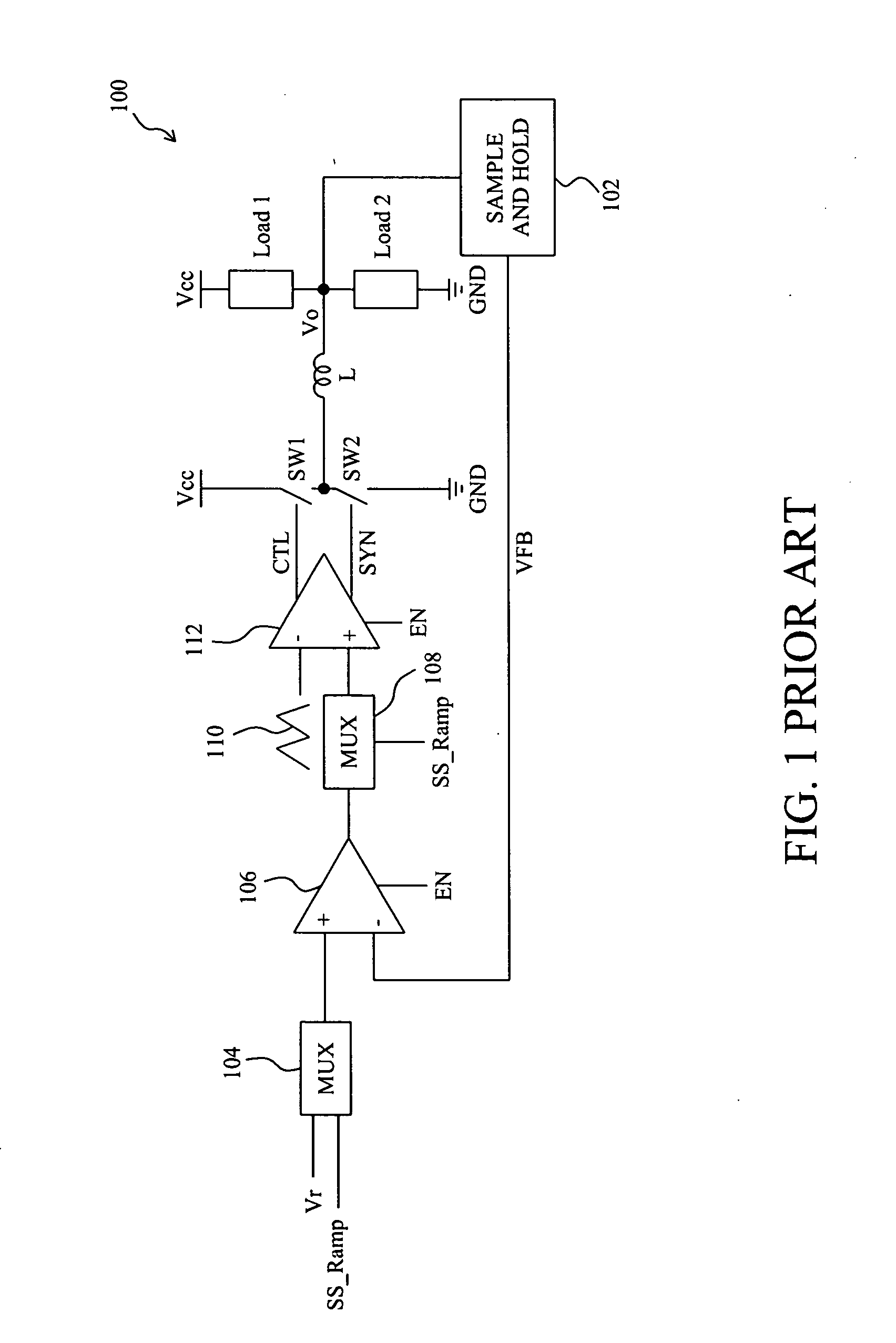
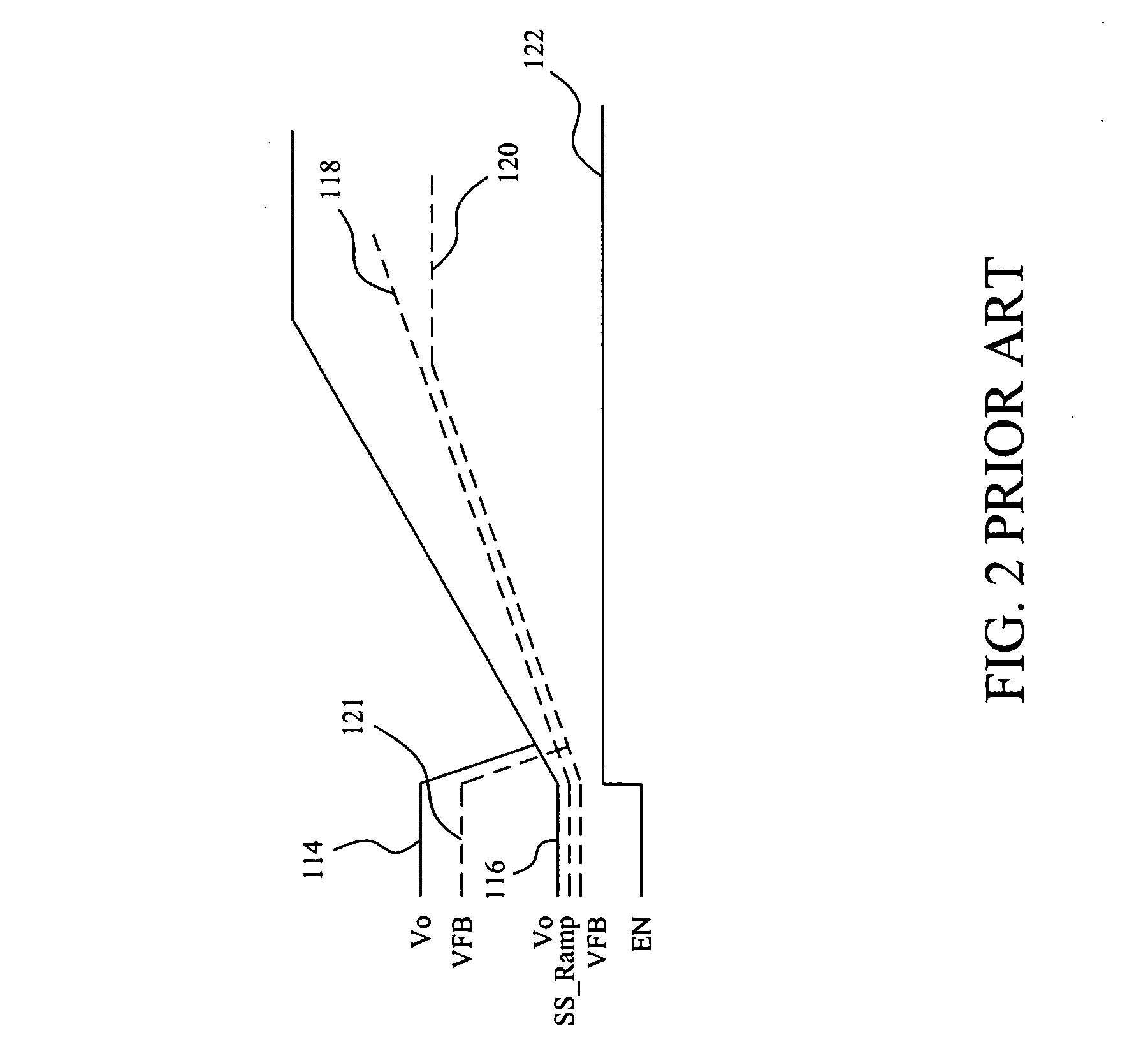
A circuit and method for soft start of a system compare a feedback signal produced from an output voltage of the system with a ramp signal to generate a comparison signal, and enables the system once the comparison signal indicating the ramp signal reaches the feedback signal, such that the output voltage becomes active from a residual voltage toward a target level.
Owner:RICHTEK TECH
Network configuration manager
InactiveUS7150037B2Fast executionDigital data processing detailsUnauthorized memory use protectionPasswordEngineering
Owner:INT BUSINESS MASCH CORP
Target drive ventilation gain controller and method
InactiveUS6962155B1Extreme support levelCompensation changesRespiratorsOperating means/releasing devices for valvesLine tubingPhysiologic States
A gain controller and method for controlling the value of a gain is used in conjunction with an electrode array for detecting a signal representative of respiratory drive output of a patient during inspiration, and a lung ventilator for assisting inspiration of the patient. The gain controller comprises an input for receiving the signal representative of respiratory drive output; a comparator for determining whether the signal representative of respiratory drive output is higher or lower than a target drive signal; and a gain adjustment unit for increasing the value of a gain when the amplitude of the signal representative of respiratory drive output is higher than the amplitude of the target drive signal and for decreasing the value of this gain when the amplitude of the signal representative of respiratory drive output is lower than the amplitude of the target drive signal. The gain is applied to the signal representative of respiratory drive output to produce an amplified respiratory drive output representative signal used for controlling the lung ventilator. The advantage of target drive ventilation is that this mode of ventilation does not depend on pressure, flow or volume measurements. A leaky ventilatory line will introduce a change in respiratory drive which will change the ventilatory assist in order to return the respiratory drive to its target level. Also, changes in the patient's metabolic or patho-physiological status which result in altered respiratory drive will be compensated.
Owner:UNIV DE MONTREAL
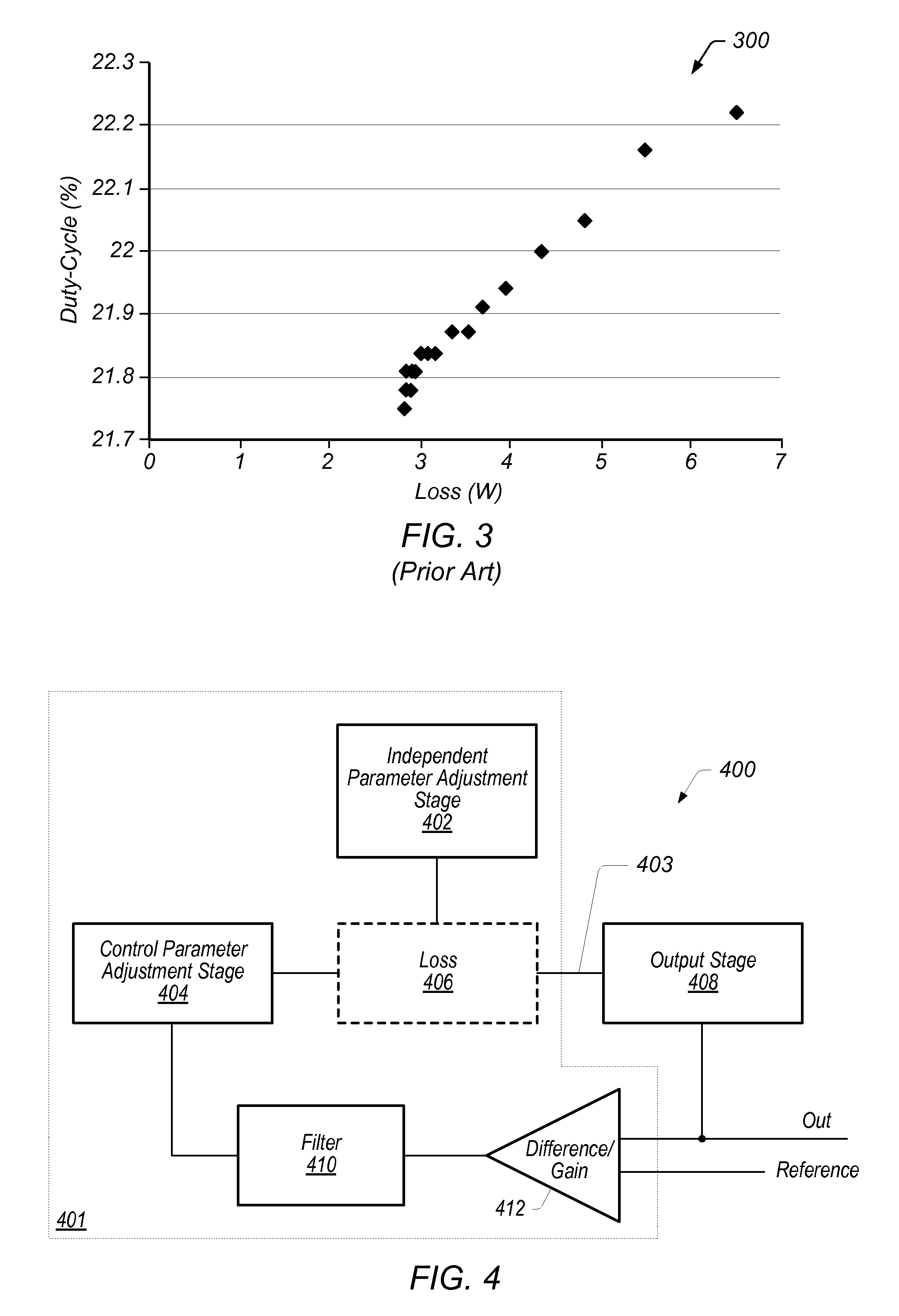
Control system optimization via independent parameter adjustment
InactiveUS7825642B1Improve power efficiencyAdversely affecting regulationDc-dc conversionElectric variable regulationControl signalControl system
A method for optimizing operation of a feedback system may include generating a control signal according to a control parameter, regulating an output of the feedback system via the control signal, and monitoring the control parameter. In response to the monitoring indicating that the present value of the control parameter is outside a specific range of values, a first parameter that impacts an operating characteristic of the feedback system may be adjusted until the present value of the control parameter is within the specific range of values. The specific range of values of the control parameter may correspond to a target level of the operating characteristic of the feedback system with respect to the first parameter. One or more additional independent parameters also impacting the operating characteristic of the system may be similarly adjusted to obtain a minimum present value of the control parameter at which the output of the feedback system would be regulated, with the minimum value of the control parameter corresponding to the target level of the operating characteristic of the feedback system with respect to, collectively, the first parameter and the one or more additional independent parameters.
Owner:INTERSIL INC
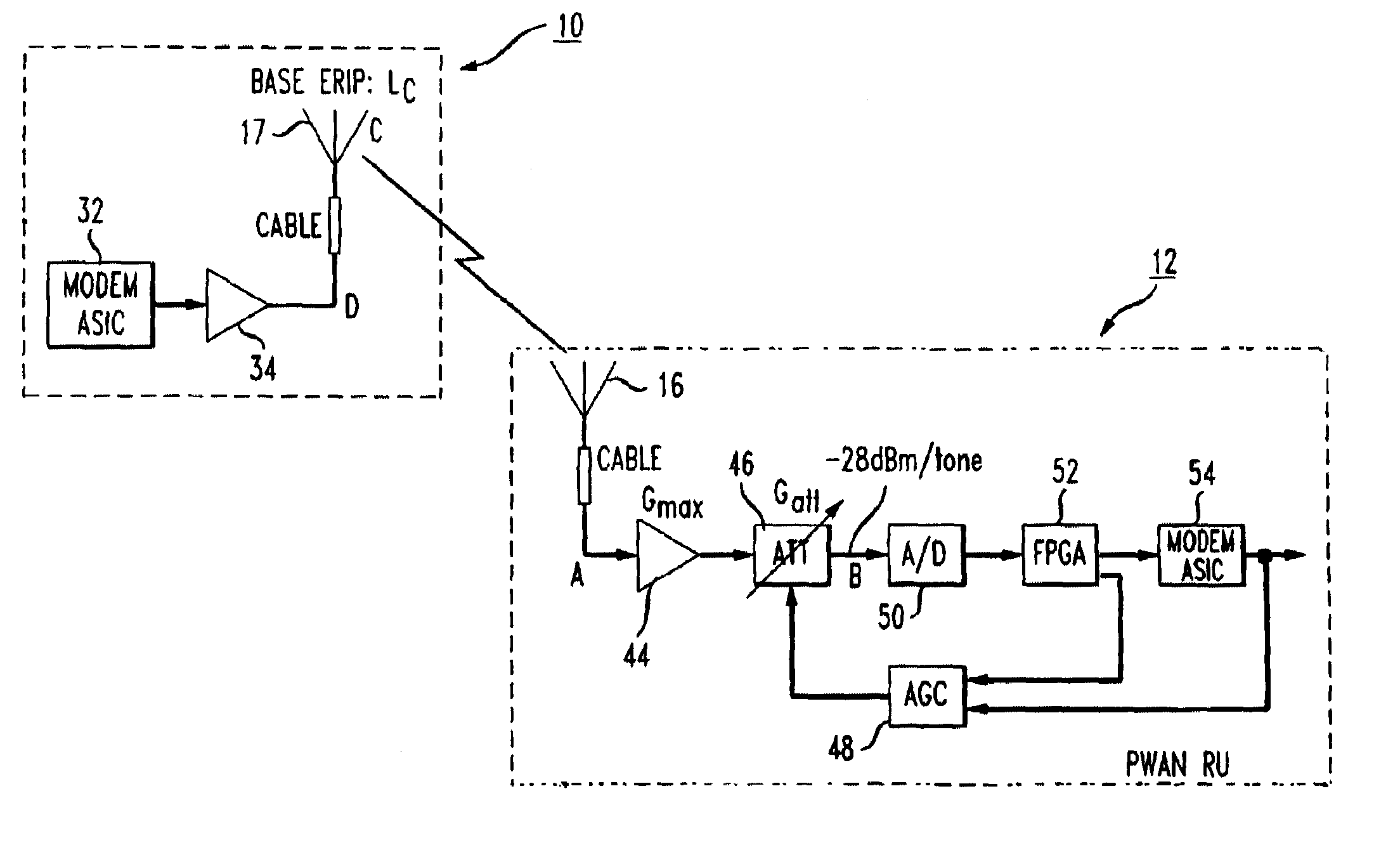
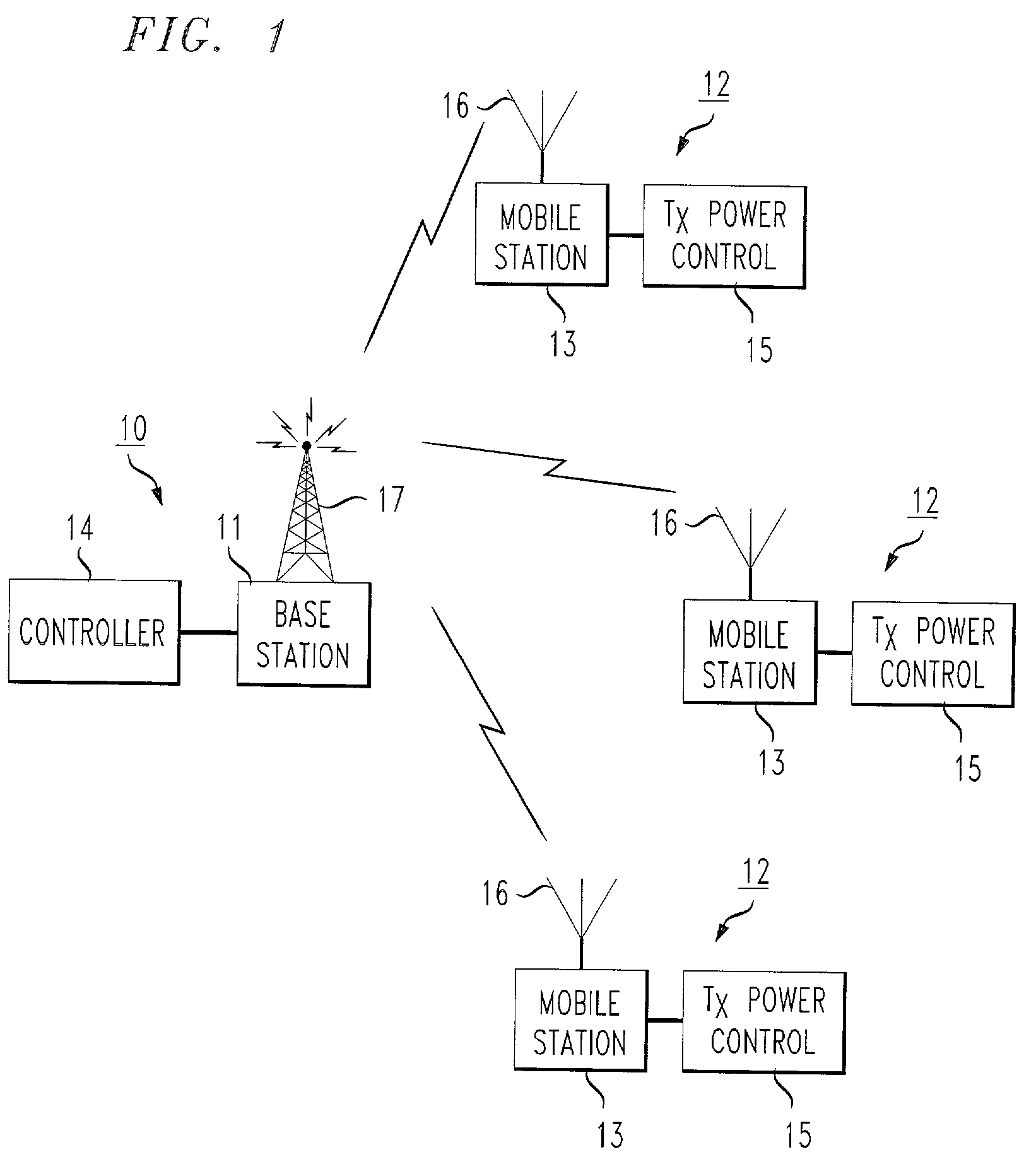
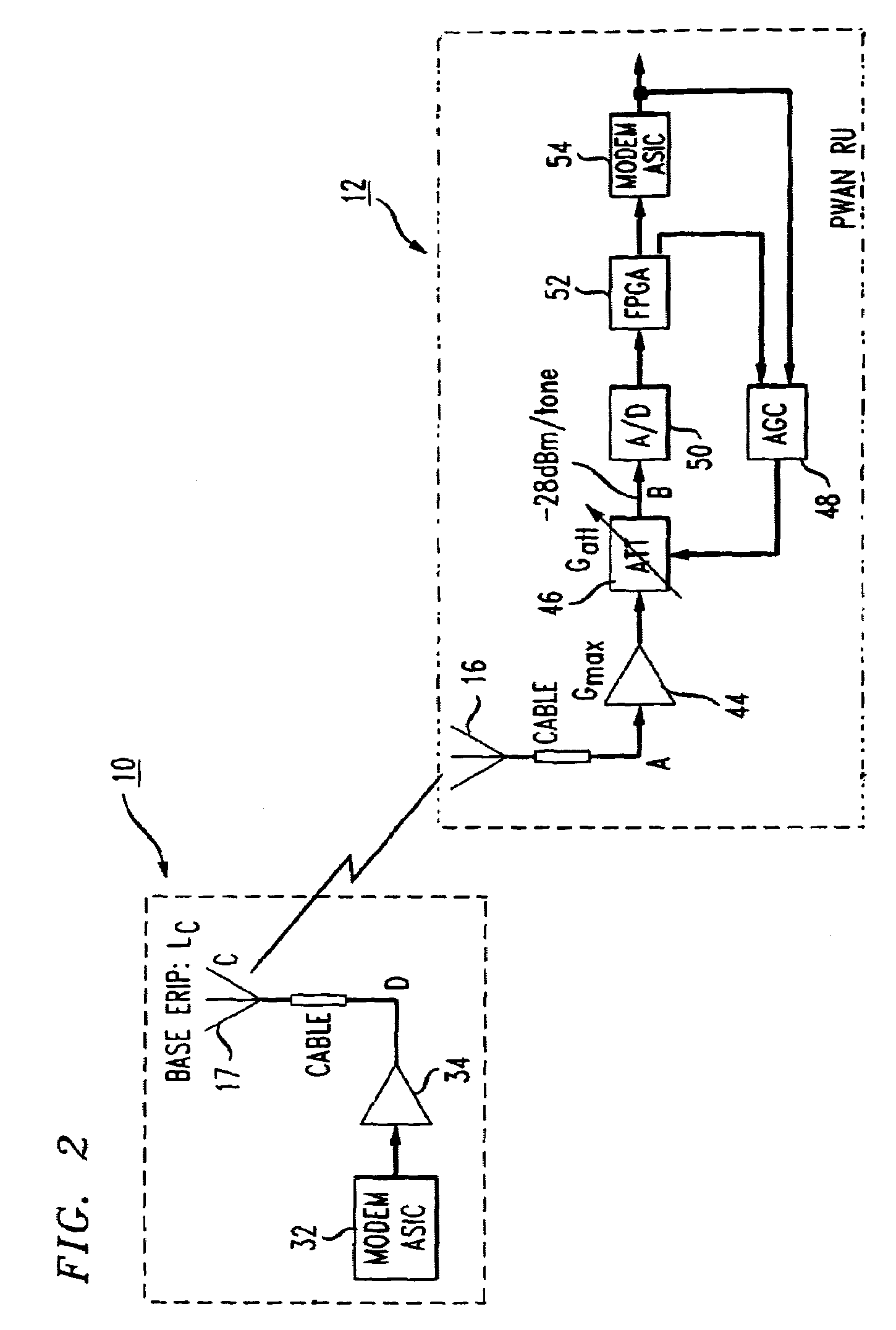
Transmit power control for an OFDM-based wireless communication system
InactiveUS7151740B2Increase and decrease transmitting power levelEnergy efficient ICTError preventionBroadcast channelsTransmitted power
An open loop power control system for an orthogonal frequency division modulation (OFDM)-based fixed / mobile wireless system. A preferred system and method comprise measuring signal strength of received interference-free pilot tones transmitted by a base station; determining pathloss according to received power level of pilot tones; and controlling transmit power level of the remote unit by adjusting transmitting channel attenuation according to the pathloss determined in the preceding step. The method may further comprise monitoring at the base station the received signal level of uplink pilot tones; checking if received signal level of uplink pilot tones is outside pre-set limits around the target level at the start of each call; and sending a command to the mobile station over the broadcast channel to increase or decrease the transmitting power level.
Owner:AT&T WIRELESS SERVICES
Training system and method for improving user knowledge and skills
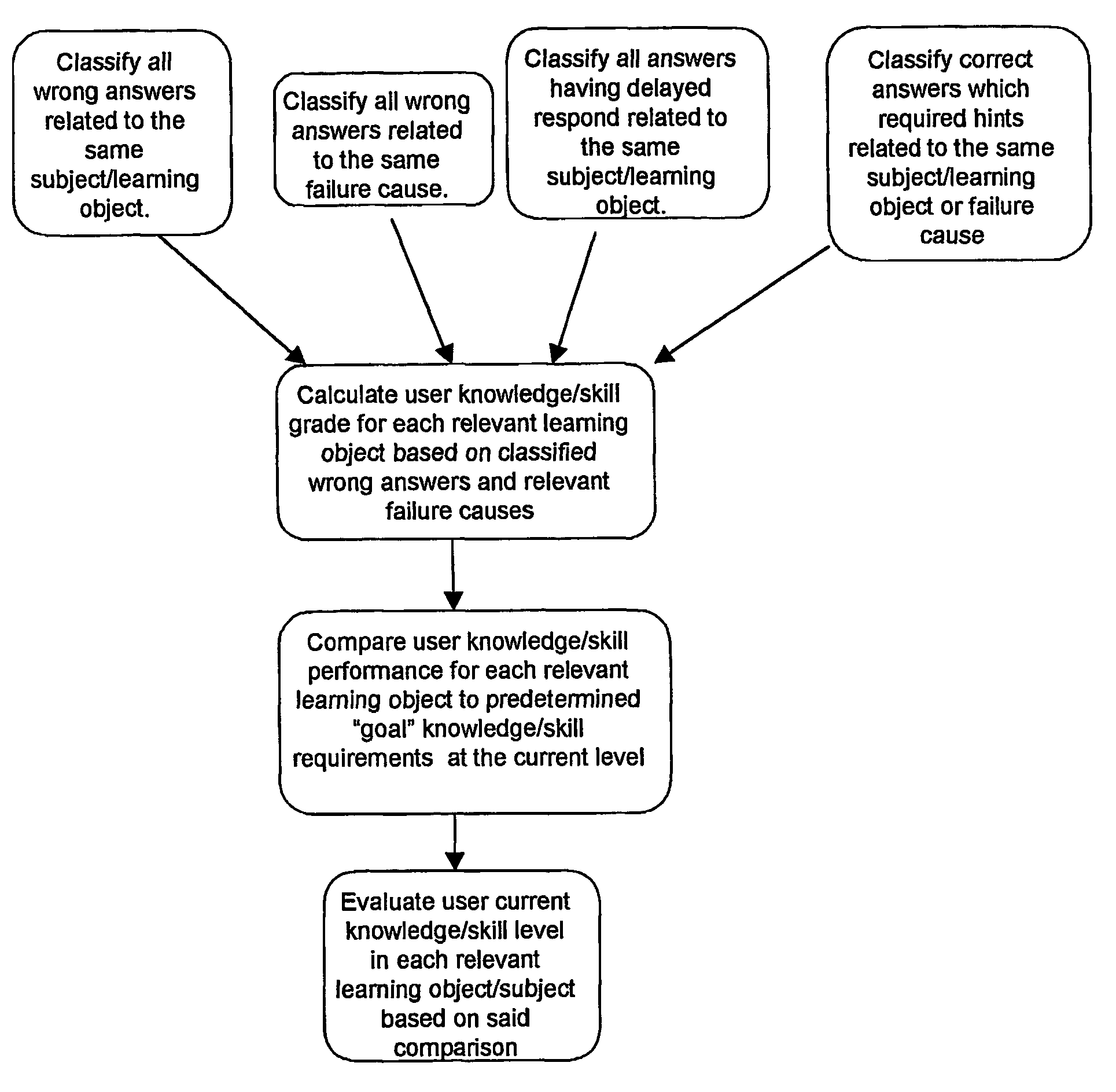
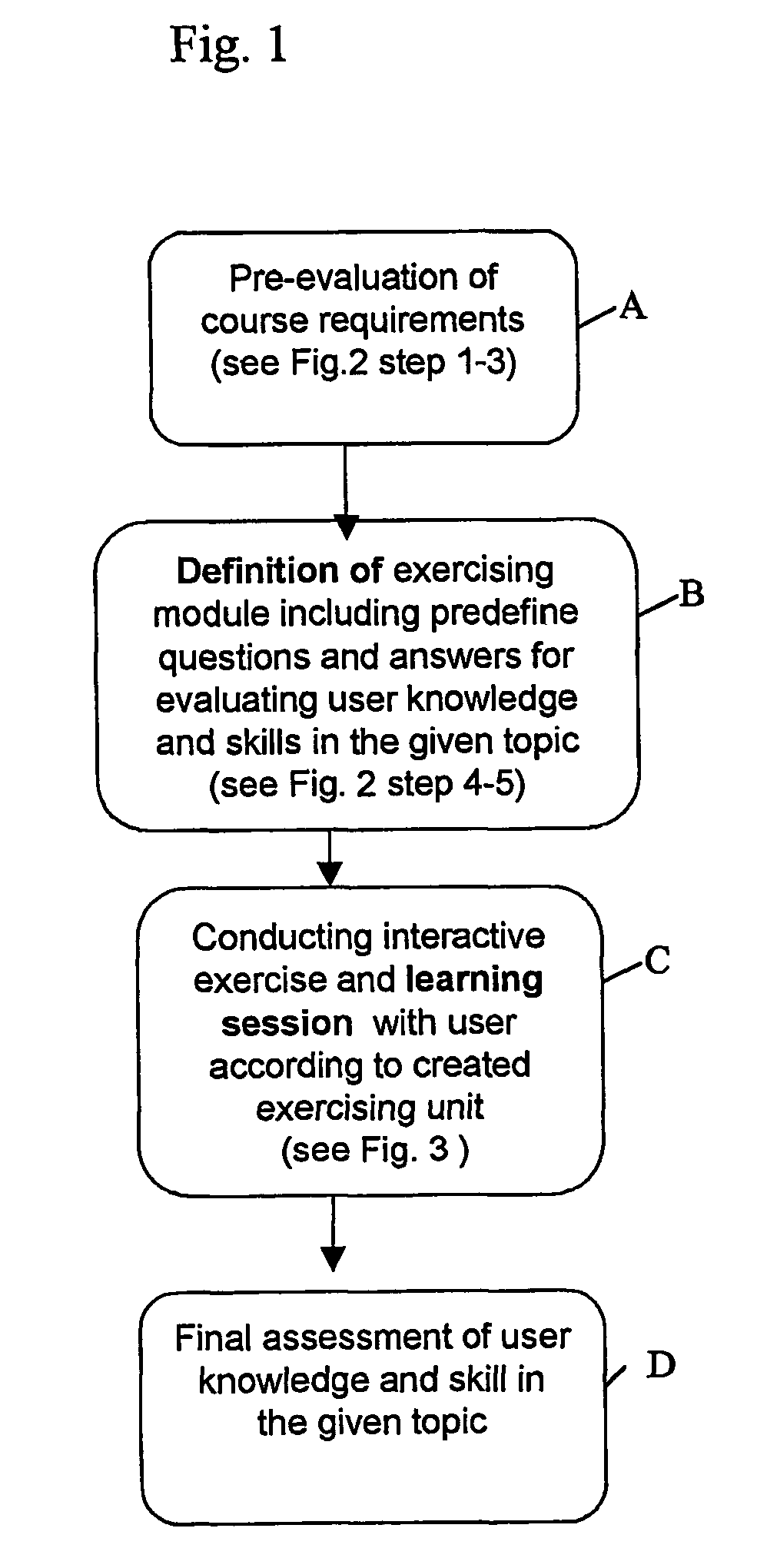
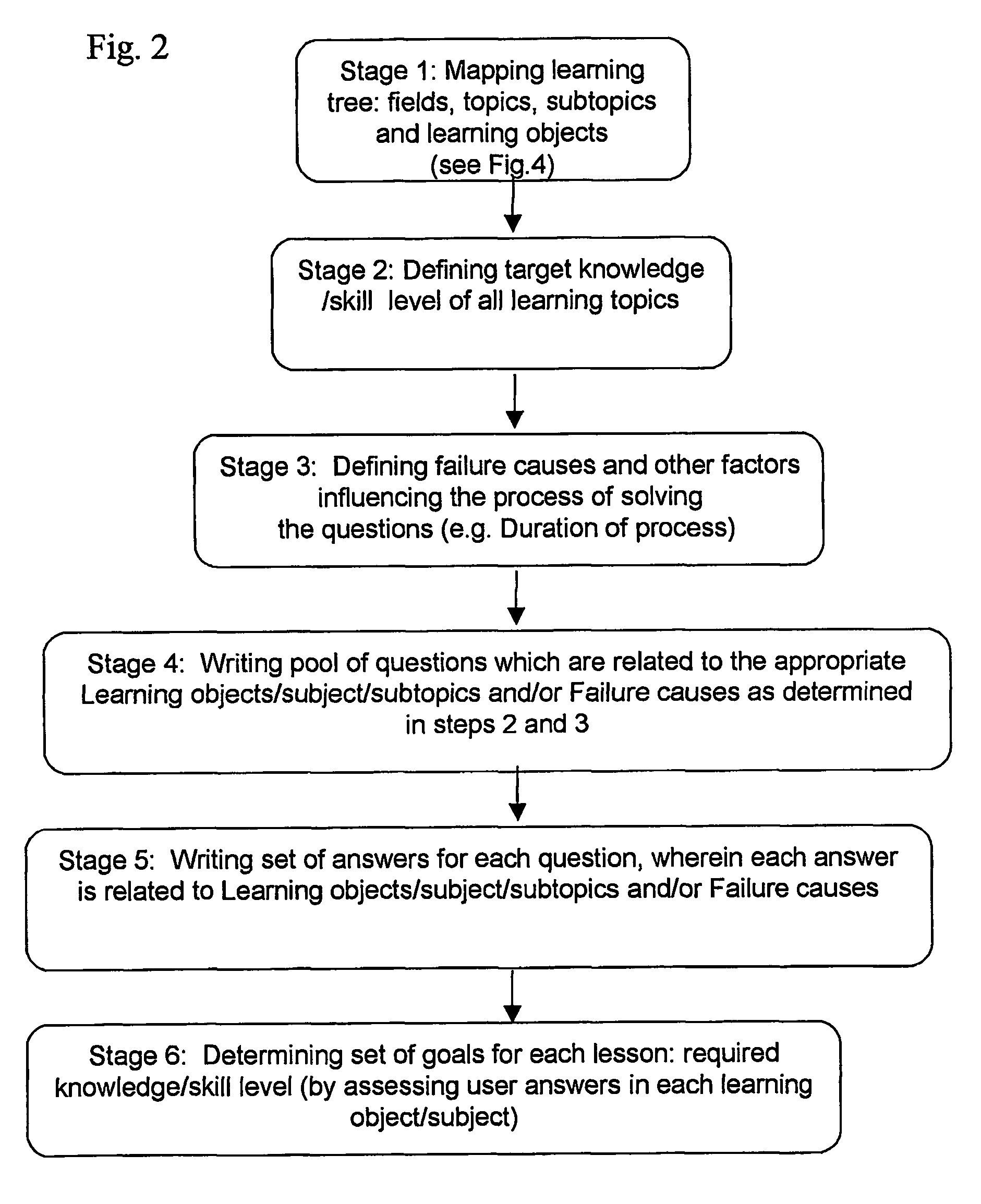
A method for creating training systems including analyzing / mapping course requirements for evaluating required knowledge / skills according to mapped subjects and defining possible failure causes, wherein each failure cause represents knowledge / skill weakness relating a certain subject or general weakness, defining knowledge / skills target level correct / wrong answers in each subject as function of the number of users, preparing a question pool, wherein each question relates to a subject knowledge / skill and / or failure cause, preparing correct and wrong answers for each question, wherein each wrong answer is related to a specific sub-subject / subject and / or to a failure cause, defining an evaluation module for assessing user knowledge / skills level based on user's success in giving correct answers in comparison to predefined target levels and type of failure causes related to the user's wrong answers, and defining exercise module for selecting sequence of questions from predefined question set based on evaluations of user knowledge / skills level and detected failure causes.
Owner:PREP4
Key video frame selection method
InactiveUS20130215221A1Improve efficiencyEfficient selectionImage enhancementImage analysisDigital videoFrame based
A method for selecting key video frames from a digital video captured using a digital video camera, the digital video including a temporal sequence of video frames. The method includes determining a camera position of the digital video camera for each video frame, and fitting a smoothed camera path to the camera positions. A sequence of target camera positions spaced out along the smoothed camera path is determined such that a corresponding set of target video frames has at least a target level of overlapping scene content. A set of key video frames are selected from the temporal sequence of video frames based on the target camera positions;
Owner:INTELLECTUAL VENTURES FUND 83 LLC
Proportional pressure assist ventilation controlled by a diaphragm electromyographic signal
InactiveUS7021310B1RespiratorsOperating means/releasing devices for valvesAssisted ventilationInspiratory Capacity
A closed loop system uses (a) the intensity of the diaphragm electromyogram (EMG) for a given inspiratory volume; (b) the inspiratory volume for a given EMG intensity; or (c) a combination of (a) and (b); in view of controlling the level of gas flow, gas volume or gas pressure delivered by a mechanical (lung) ventilator. The closed loop ventilator system enables for automatic or manual adjustment of the level of inspiratory support in proportion to changes in the neuro-ventilatory efficiency such that the neural drive remains stable at a desired target level. An alarm can also be used to detect changes in neuroventilatory efficiency in view of performing manual adjustments.
Owner:UNIV DE MONTREAL
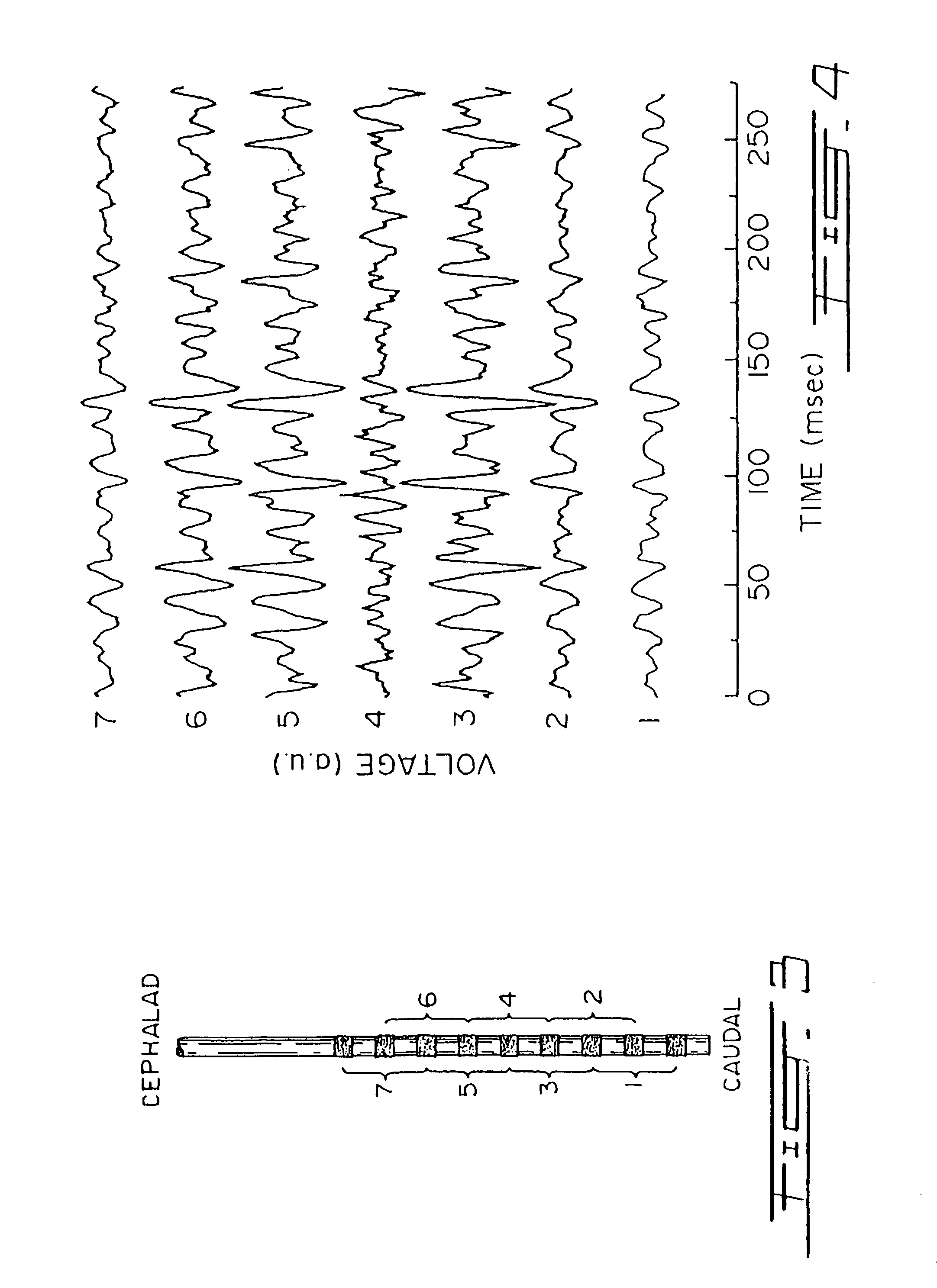
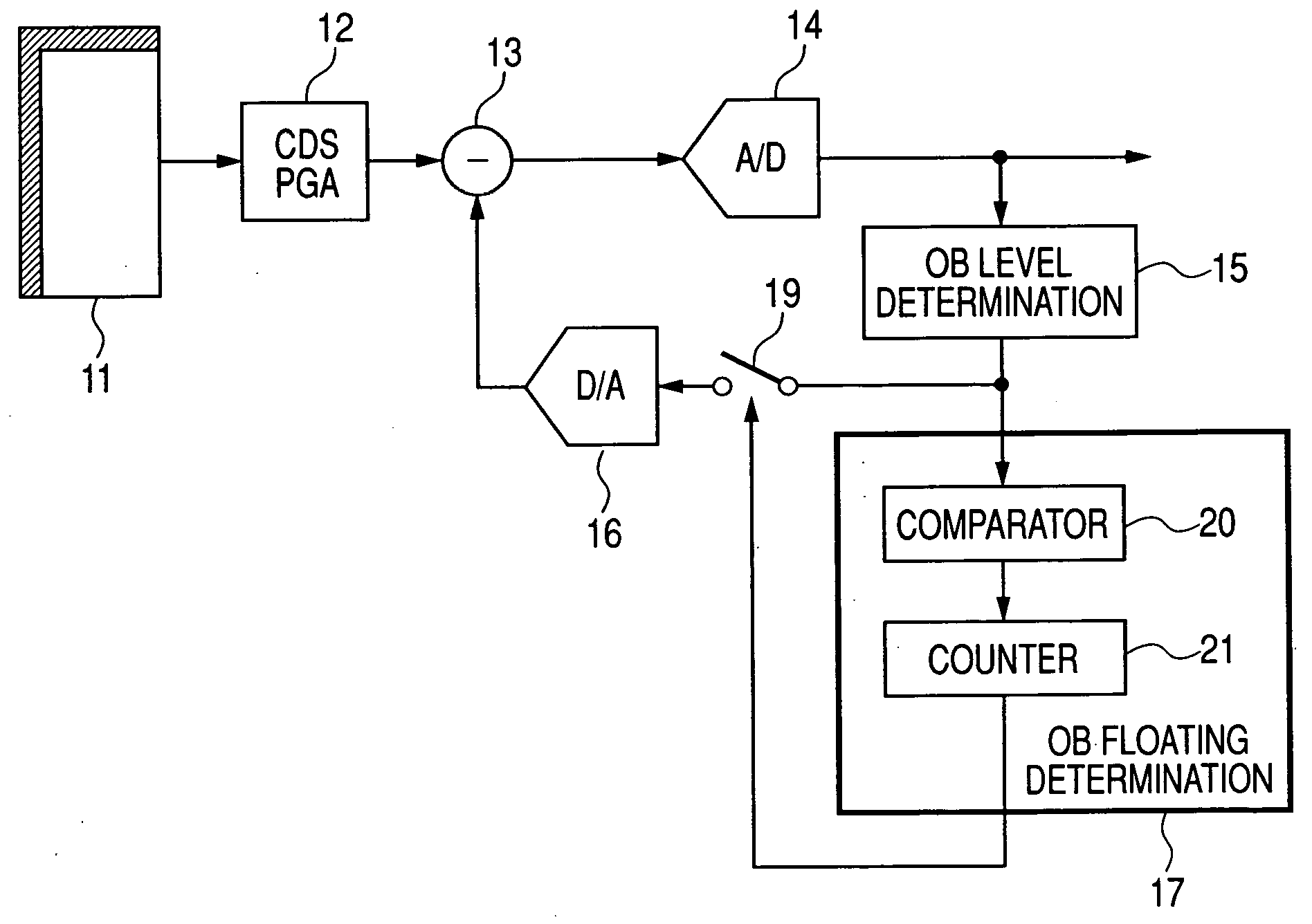
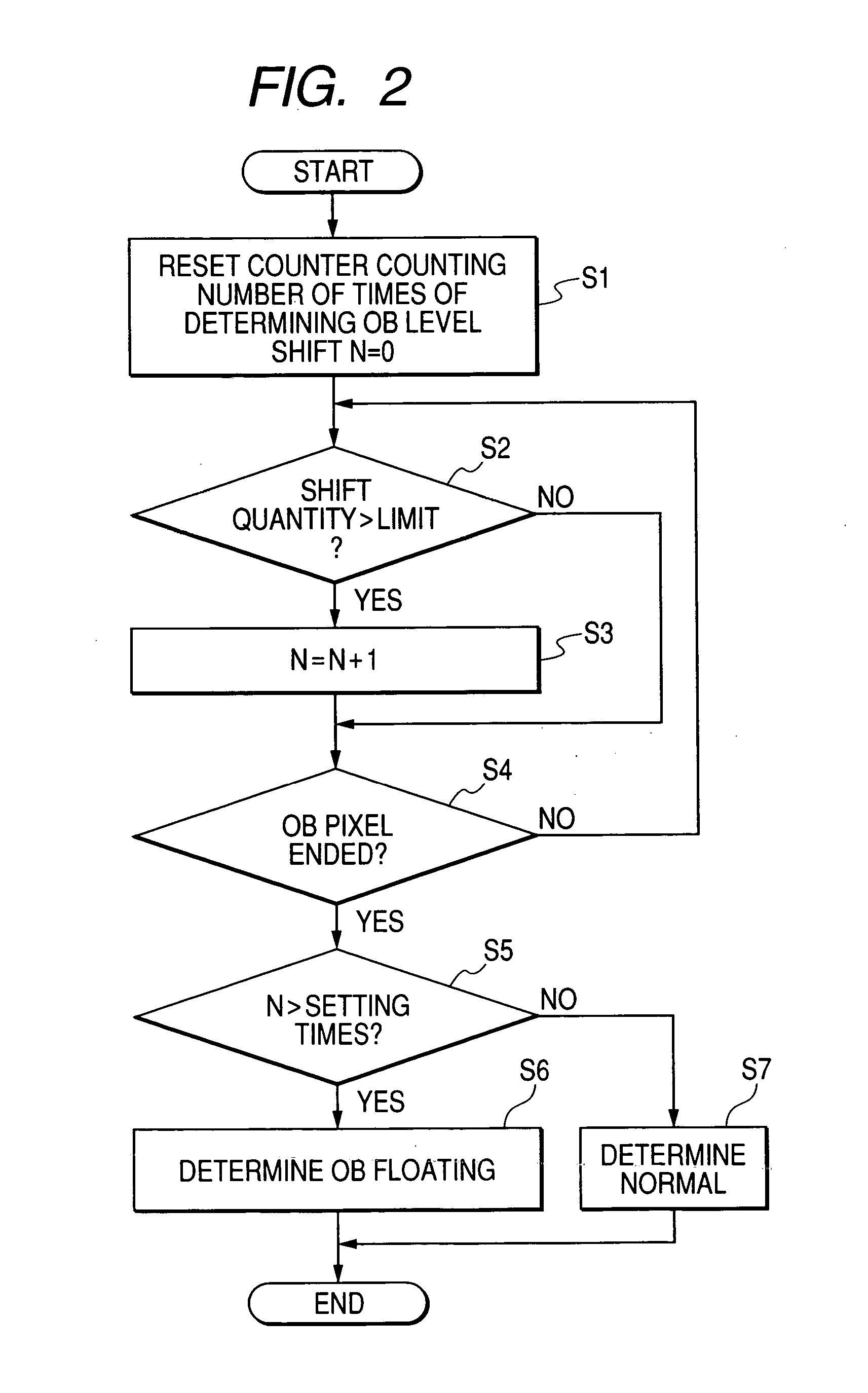
Image signal processing apparatus, image signal processing method and camera using the image signal processing apparatus
InactiveUS20060044424A1High-quality image signalEasy to adjustTelevision system detailsColor signal processing circuitsComputer scienceImage signal
When clamping a signal from a solid state image sensor, float of an optical black pixel output due to incoming of infrared light avoids a malfunction of a clamp from occurring. When clamping a signal from the solid state image sensor, the difference between the optical black pixel output and a clamp target level is output as a difference output, the difference output is compared with a comparison level to integrate the number of times larger than the comparison level every horizontal line. When the number of times is equal to or more than a certain rate (⅔) from the number of optical black pixels on the horizontal line, an optical black float state is determined and clamping operation is performed in accordance with a held value immediately before.
Owner:CANON KK
Height adjusting system for automotive vehicle
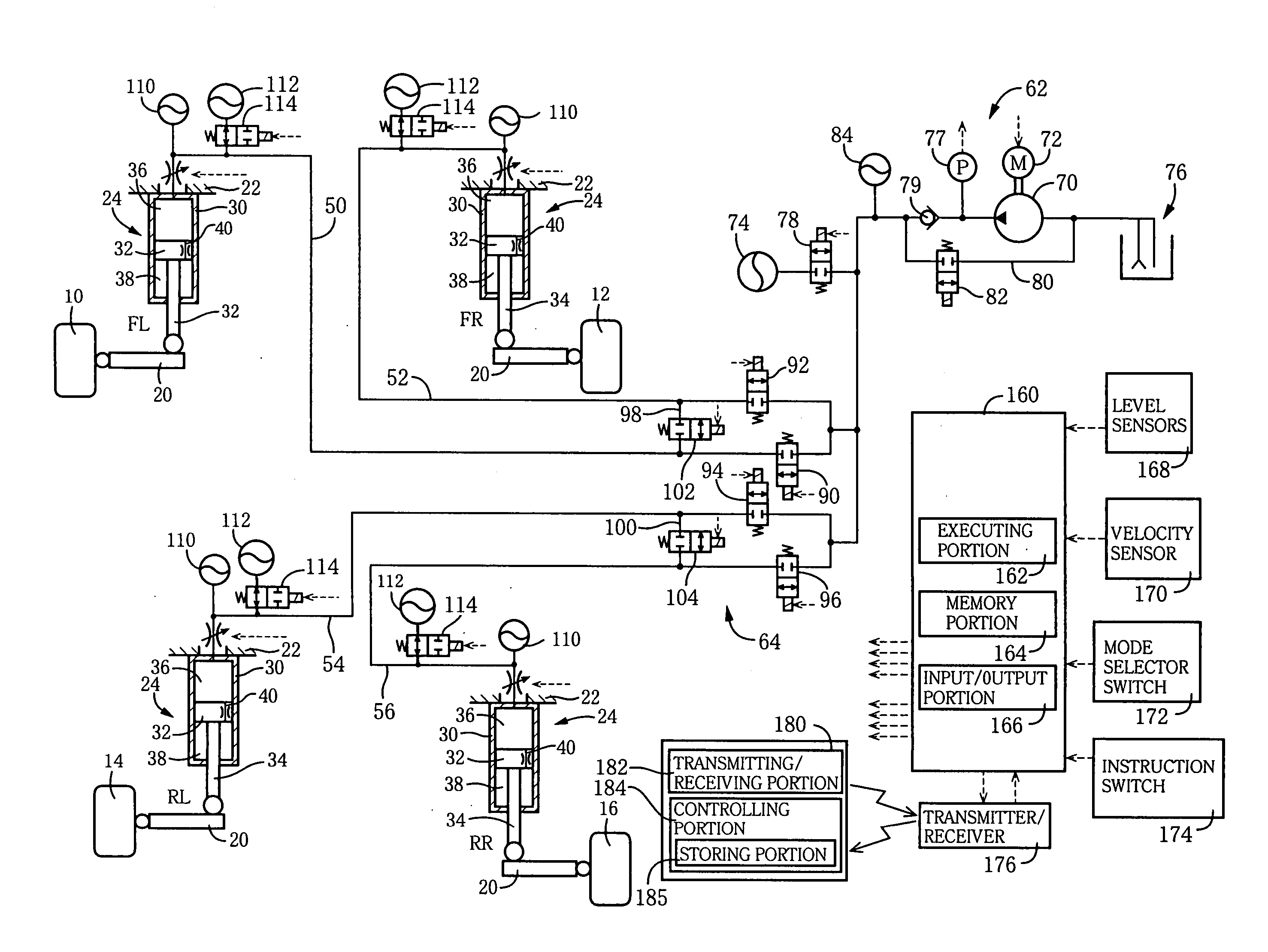
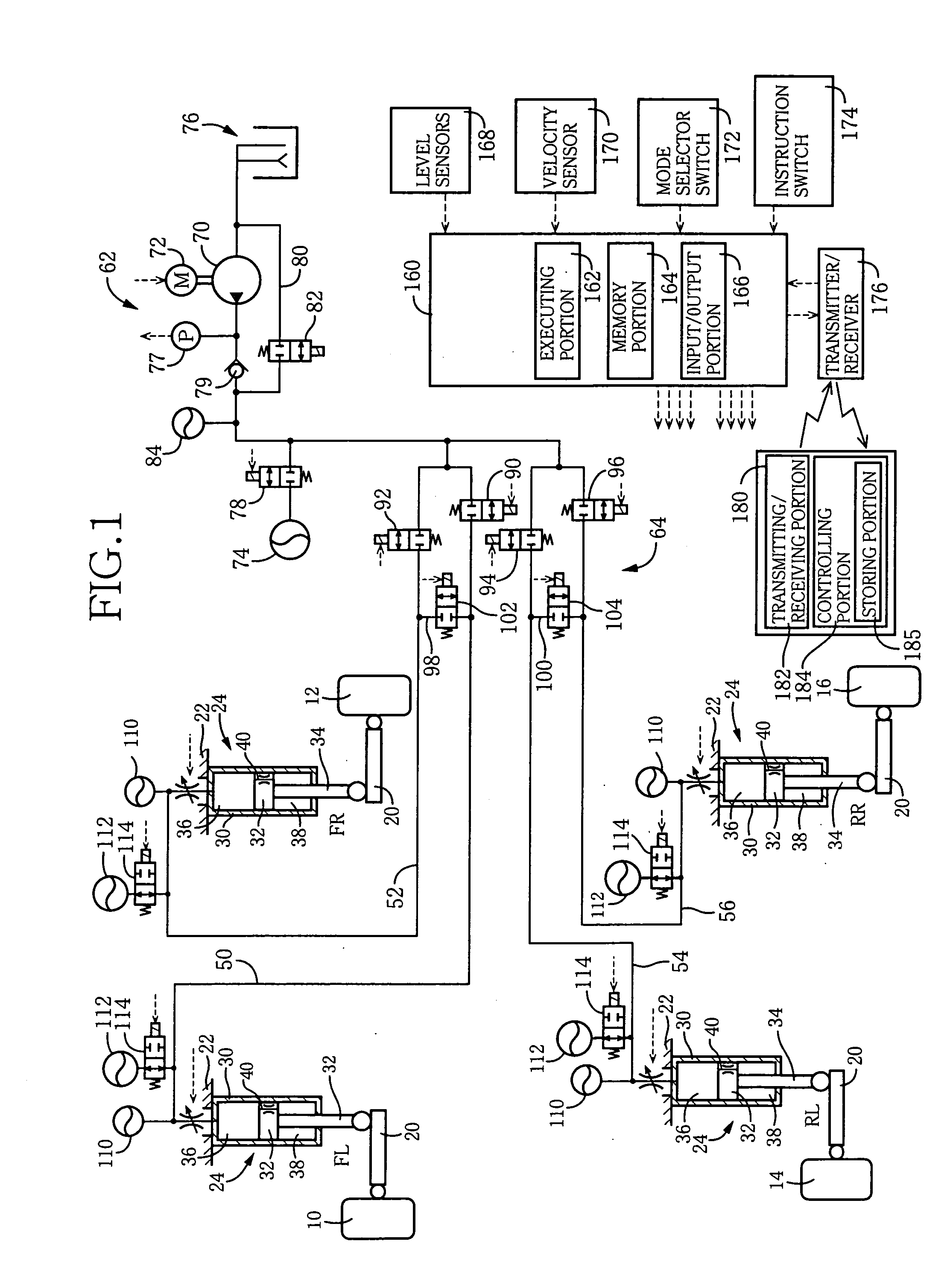
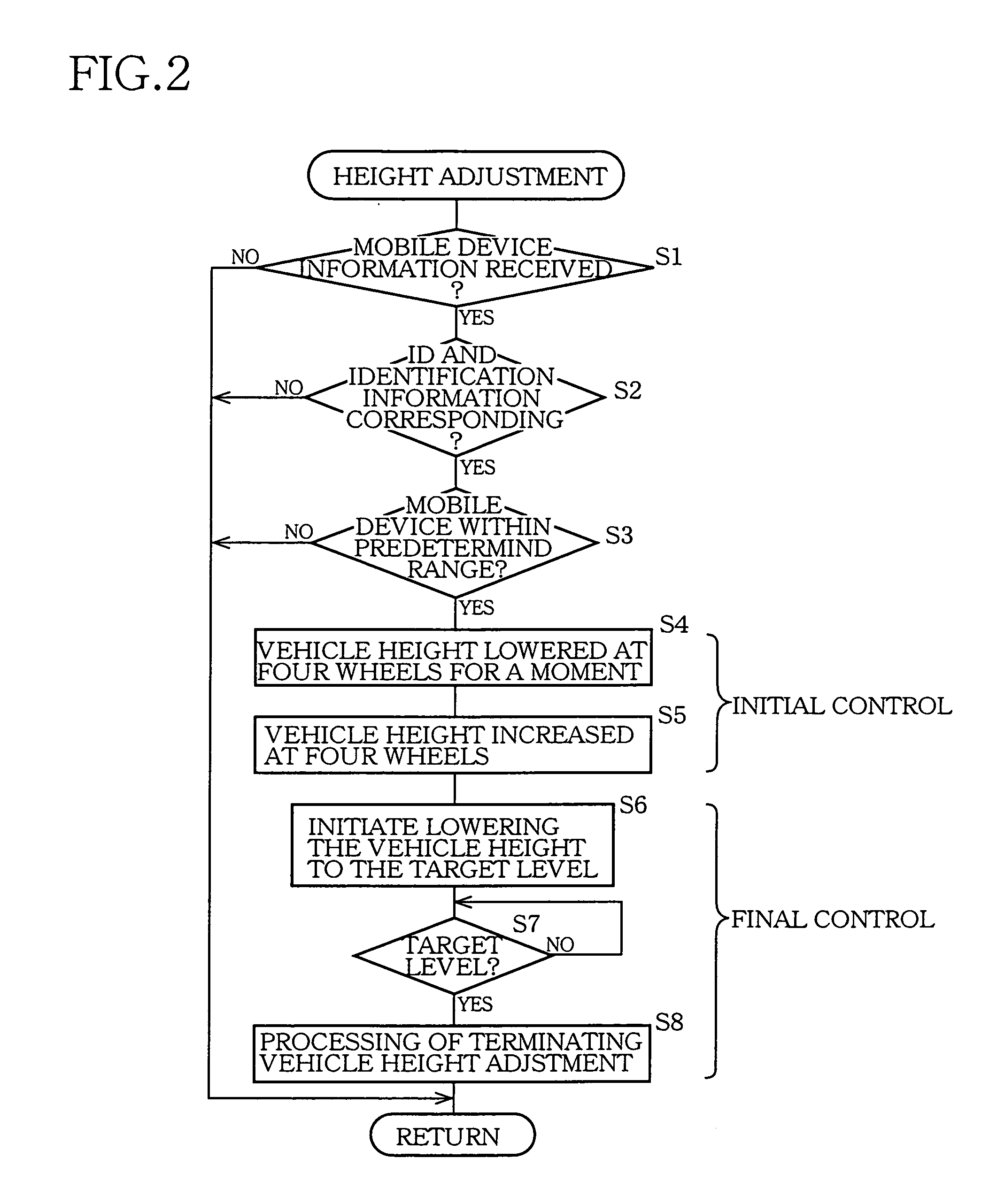
InactiveUS20060055129A1Improve reliabilityReduce component countResilient suspensionsAutomotive engineeringTarget level
A system for adjusting a height of an automotive vehicle having four wheels, the system comprising: four height adjusters provided for the respective wheels; and a controller controlling an operation of each height adjuster so as to adjust the vehicle height at each of four positions corresponding to the wheels, the controller including: an initial control portion controlling the operation of at least one of the height adjusters such that the vehicle height is initially changed at at least two of the four positions, in a first direction which is one of an upward direction and a downward direction, and then in a second direction which is the other direction; and a final control portion controlling the operation of all the height adjusters after the control by the initial control portion, such that the vehicle height is changed at all the four positions to respective target levels.
Owner:TOYOTA JIDOSHA KK
Data communication method and device
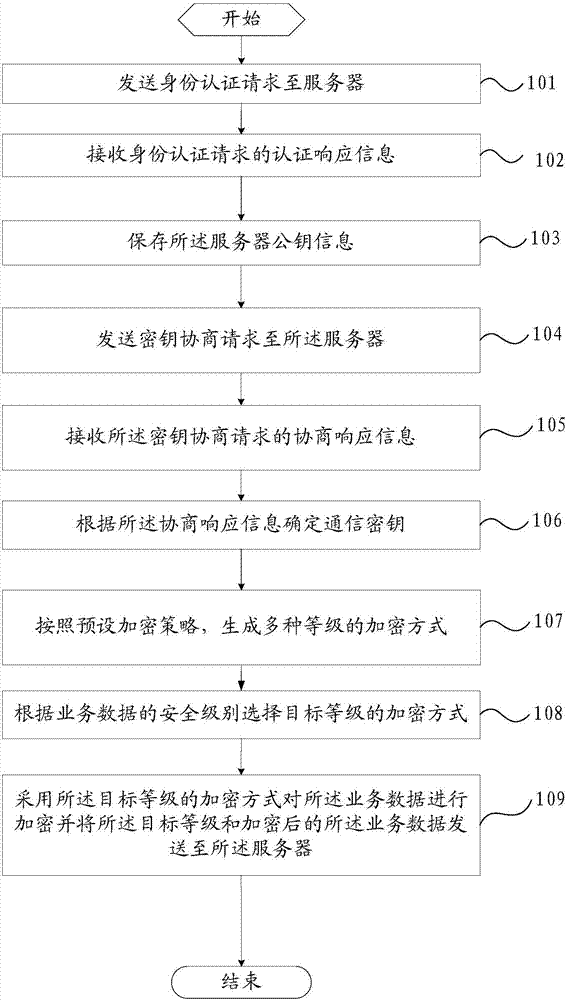
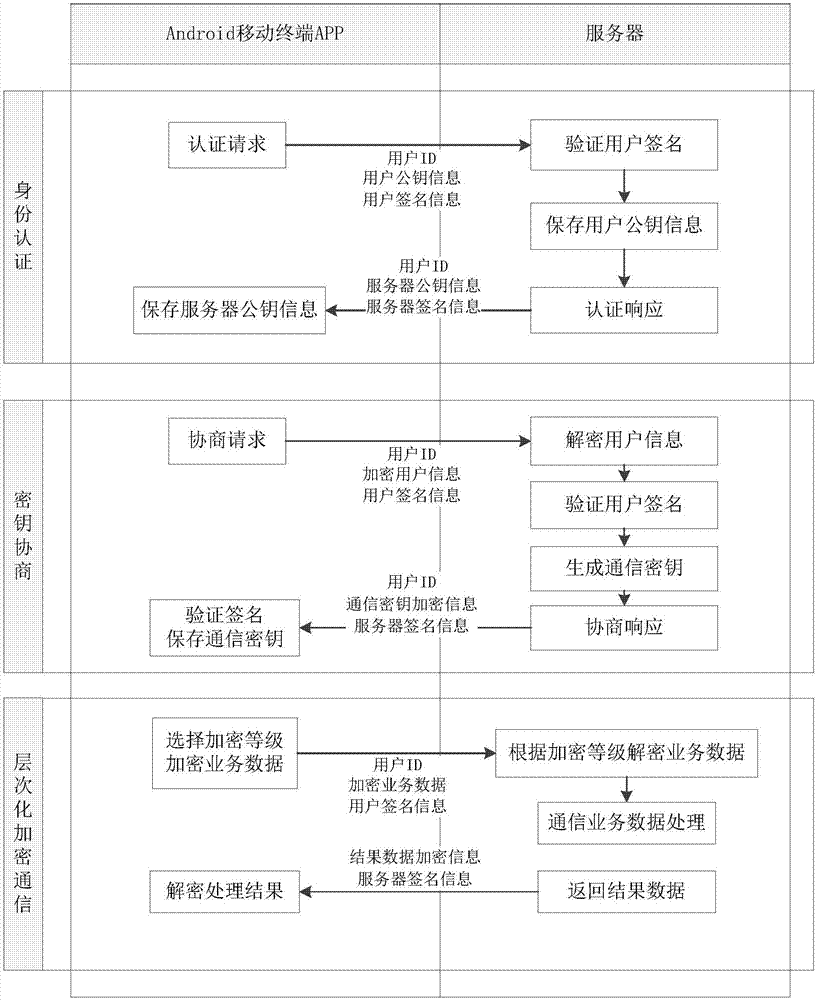
ActiveCN107508796AHigh encryption strengthEnhanced encryption flexibilityKey distribution for secure communicationUser identity/authority verificationBusiness dataSecurity level
Owner:北京明朝万达科技股份有限公司
Circuit and method for soft start from a residual voltage
A circuit and method for soft start of a system compare a feedback signal produced from an output voltage of the system with a ramp signal to generate a comparison signal, and enables the system once the comparison signal indicating the ramp signal reaches the feedback signal, such that the output voltage becomes active from a residual voltage toward a target level.
Owner:RICHTEK TECH
Power factor improving converter and control method thereof
InactiveUS6980445B2Improve efficiencyLower Level RequirementsEfficient power electronics conversionDc-dc conversionSwitched currentAudio power amplifier
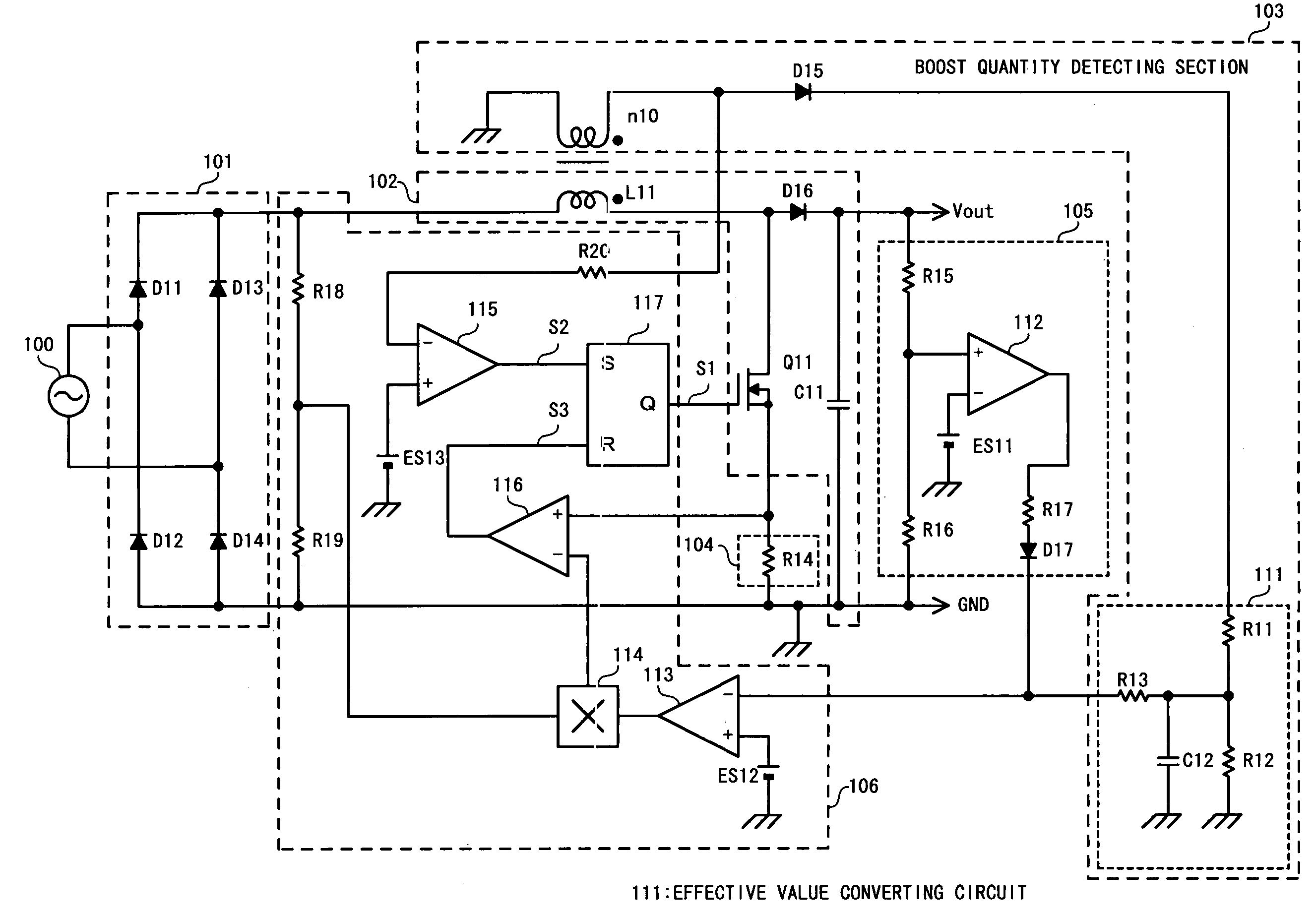
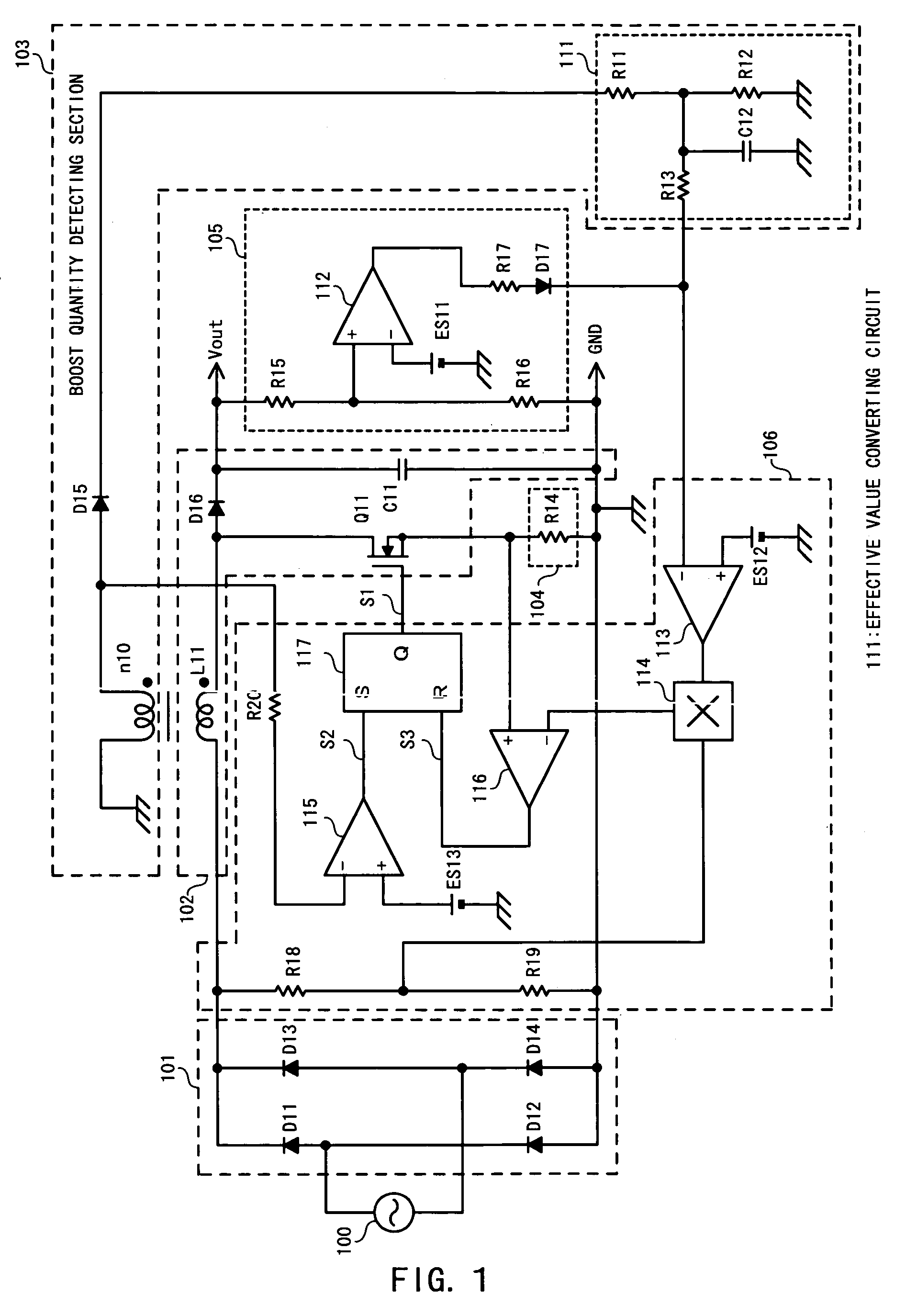
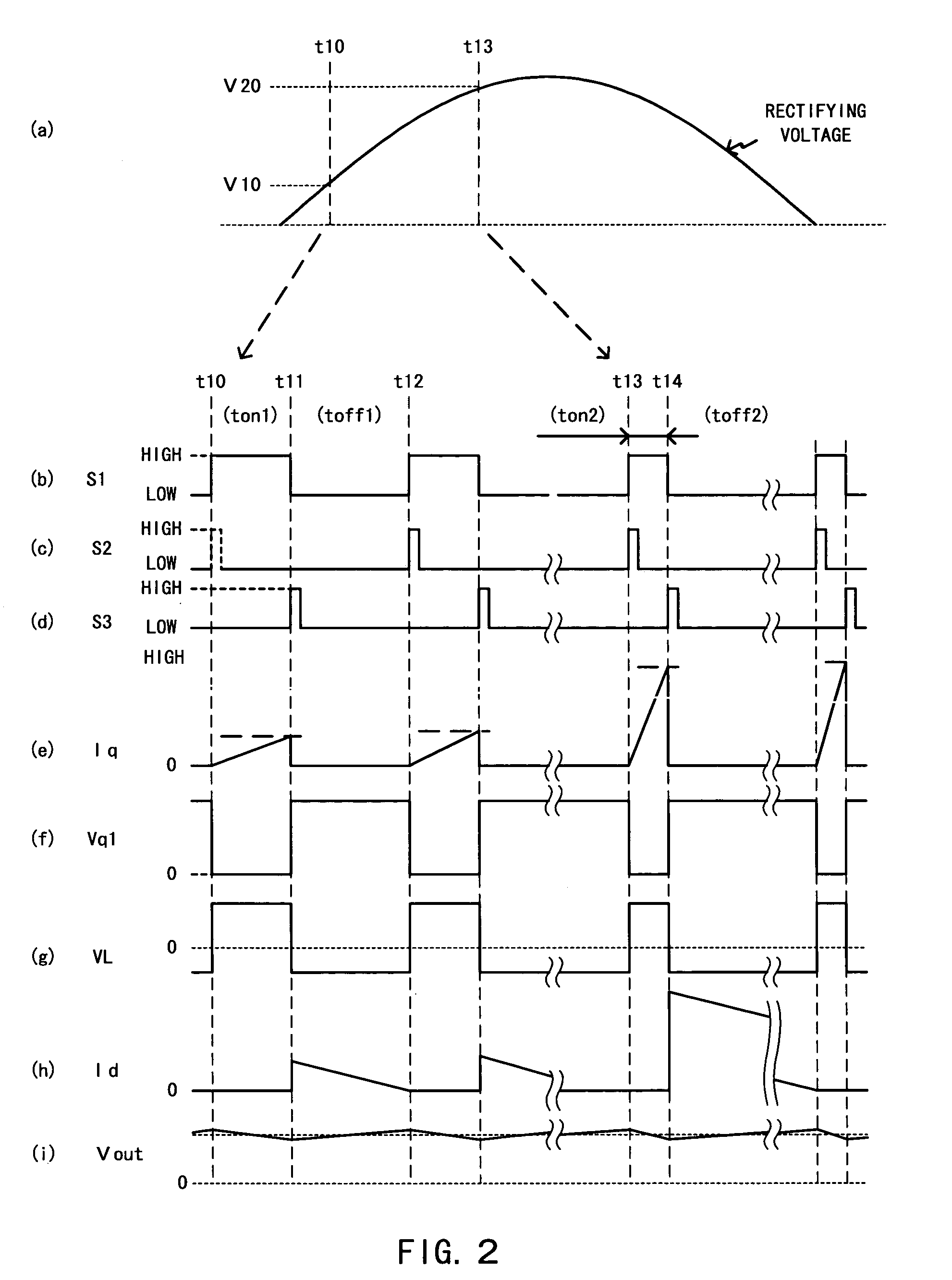
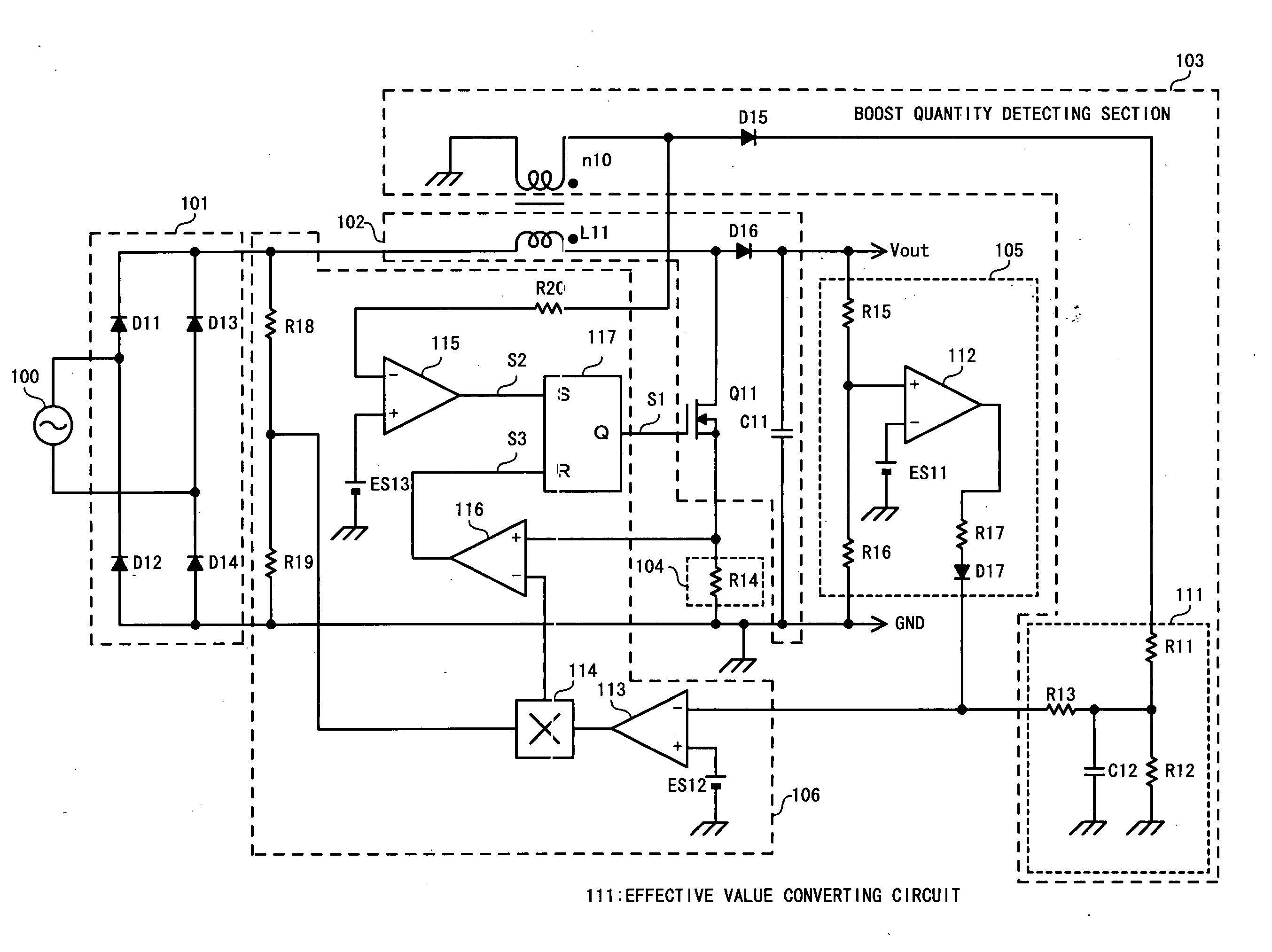
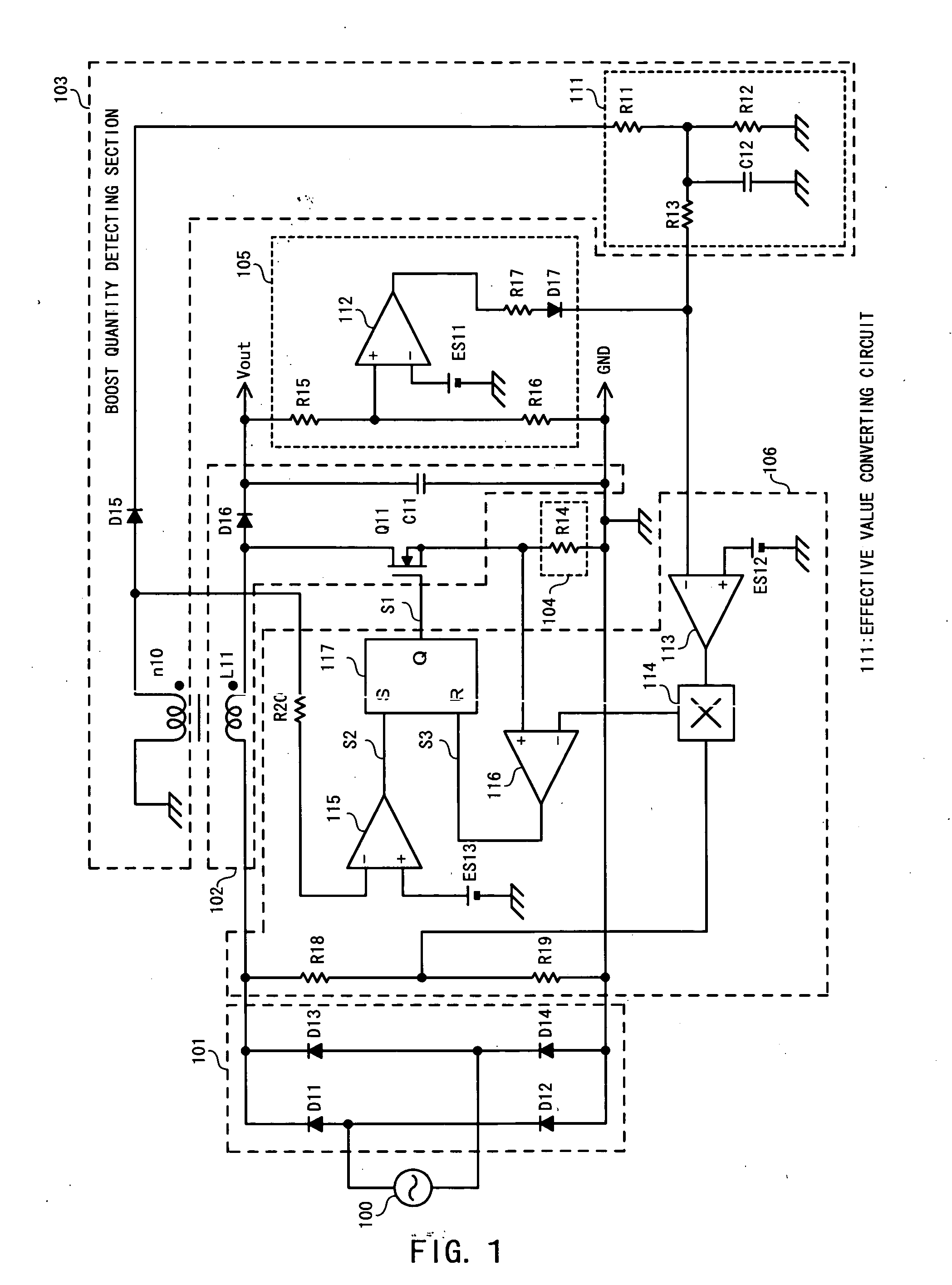
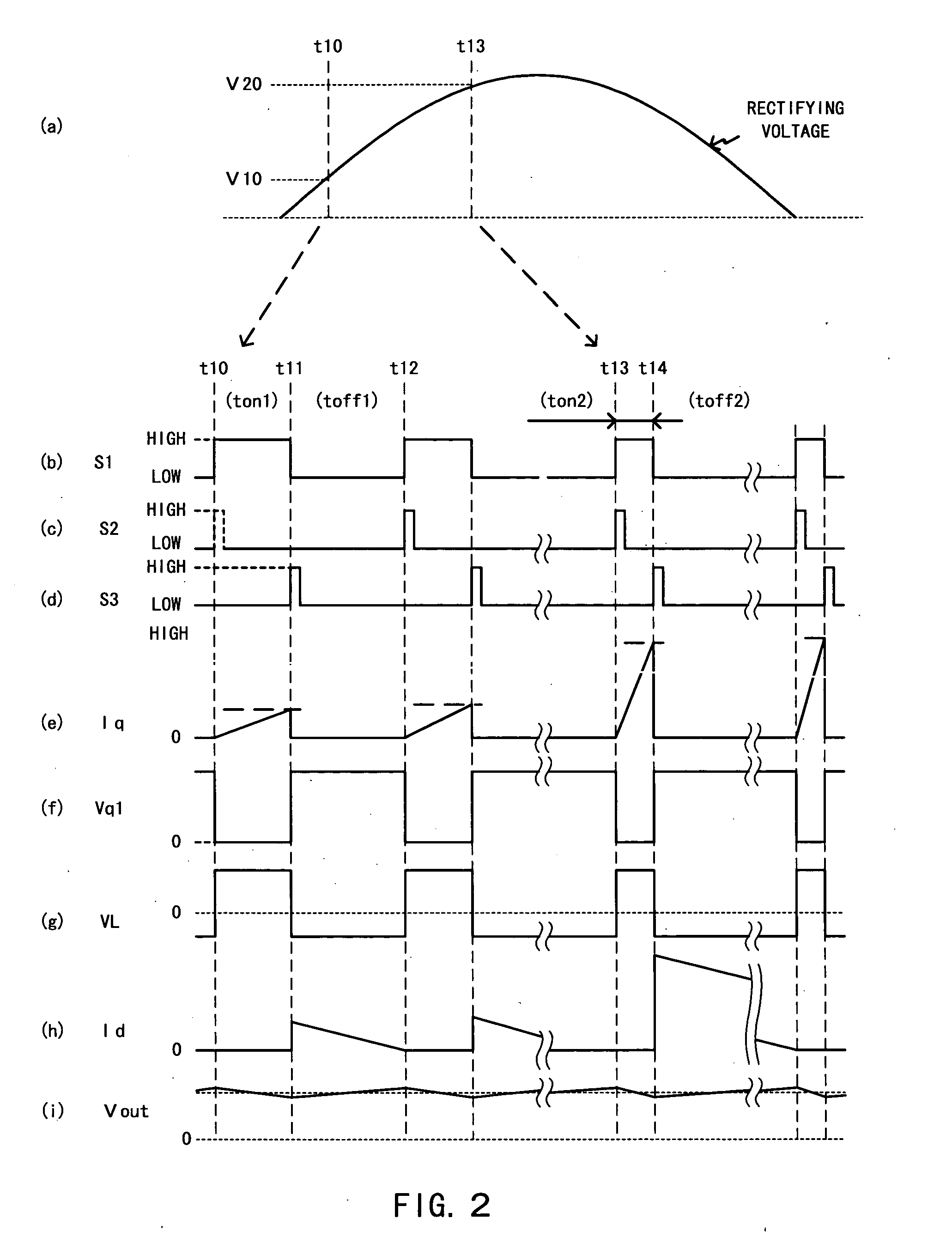
A boost quantity detecting section (103) detects a boost quantity of an inductor (L11). An operational amplifier (113) of a control section (106) compares the boost quantity detected by the boost quantity detecting section (103) with a reference voltage (ES12). When a supply voltage supplied from an AC power source (100) reduces and an output voltage is unchanged, the boost quantity detected by the boost quantity detecting section (103) increases. When a signal level of a boost quantity detection signal is higher than the reference voltage (ES12), a control section (106) reduces a target level of a switching current. The target level of the switching current decreases, so that the output voltage decreases and energy loss due to boosting reduces.
Owner:SANKEN ELECTRIC CO LTD
Network configuration manager
InactiveUS20060242690A1Fast executionDigital data processing detailsUser identity/authority verificationPasswordProgram planning
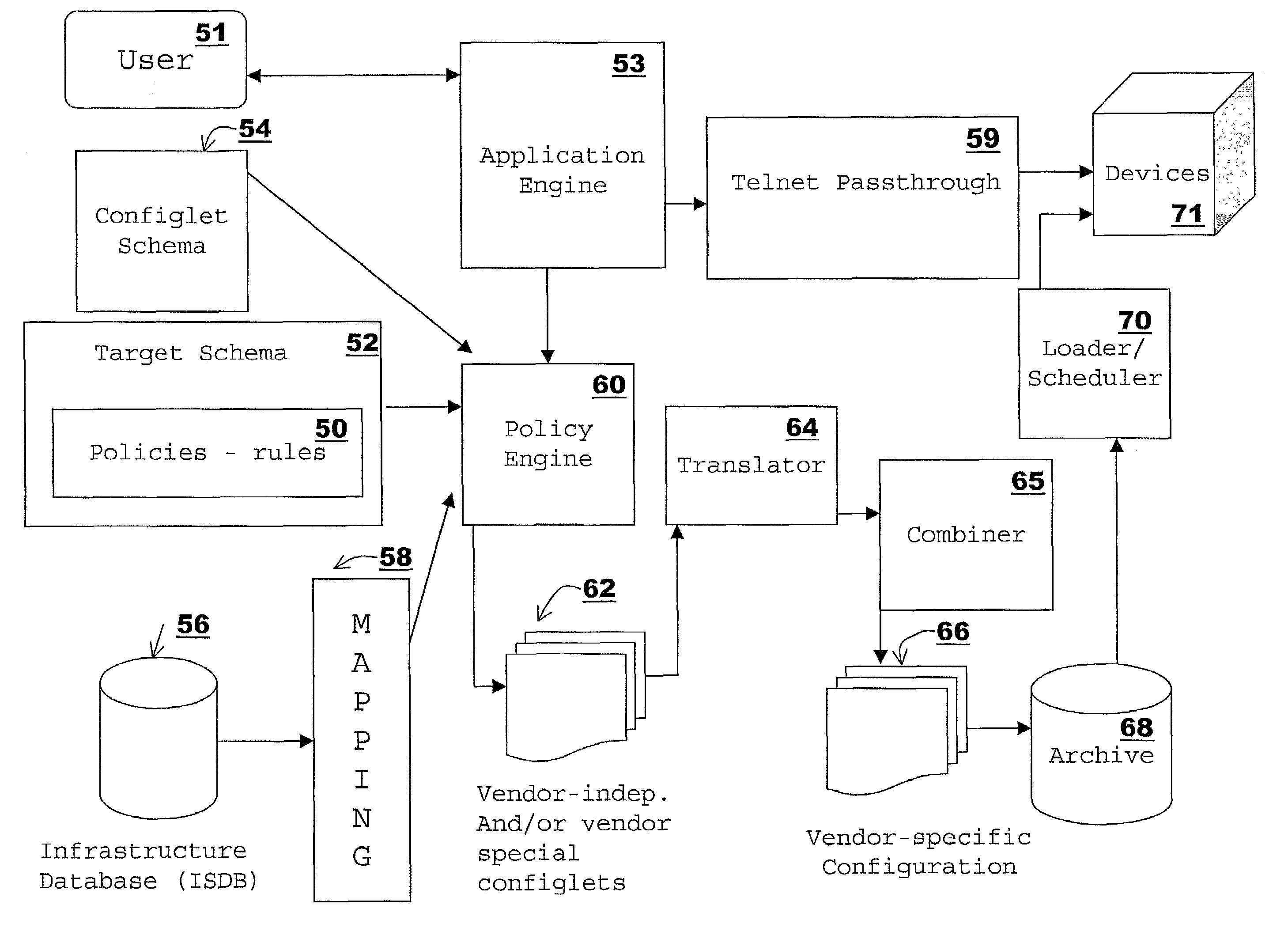
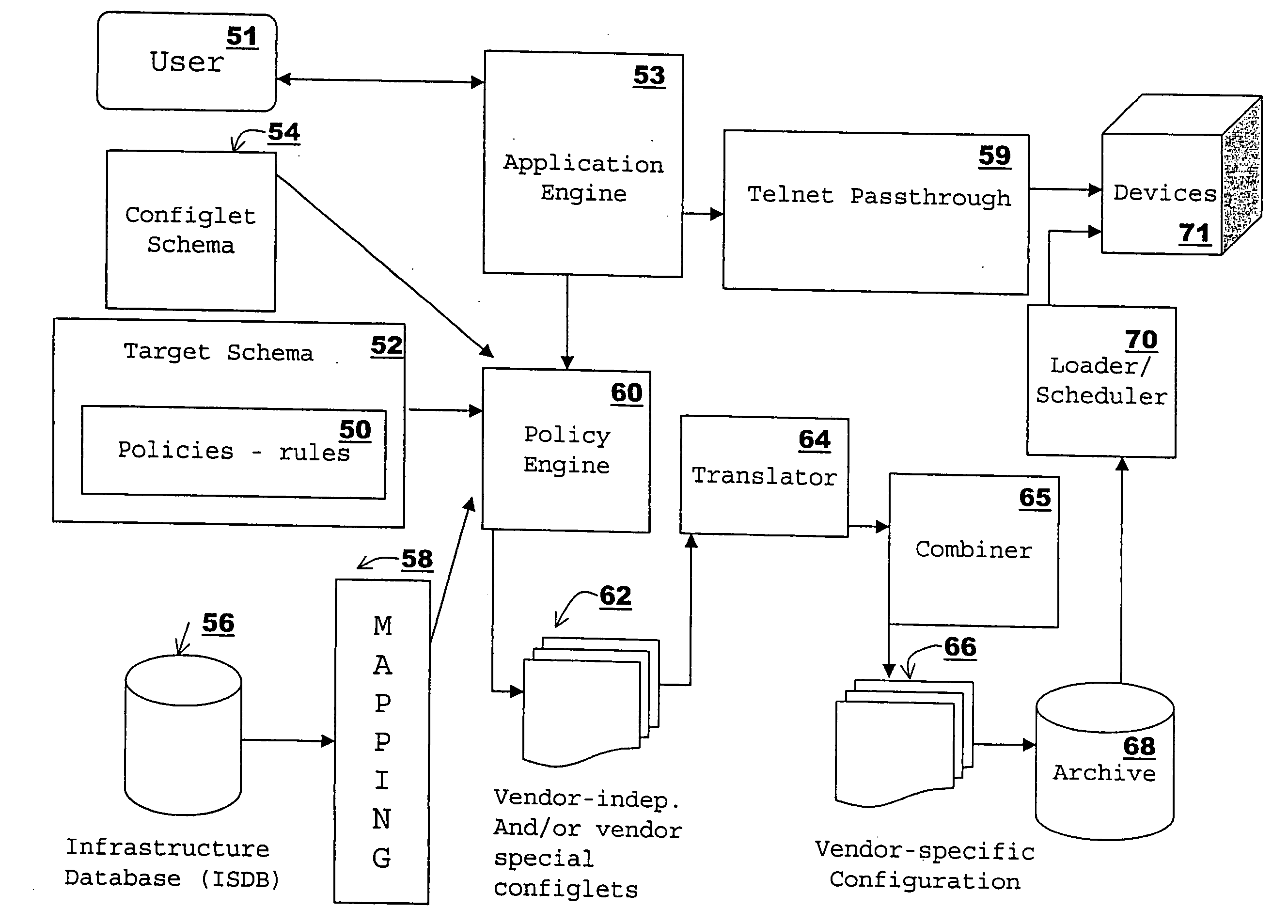
A policy engine generates configlets that are vendor-neutral, vendor-specific or both, based on a selected target level and a selected device / device group. A translator translates and combines the configlets to form vendor-dependent configuration files. The policy engine generates the configlets using policies associated with the selected target level and its sub-target levels, as defined by a target level hierarchy. A policy includes at least a condition, and an action which the policy engine performs if the condition is true. In performing the action, the policy engine typically writes to at least a partial configlet. A policy may further include a verification clause, which is used to verify a running configuration. Policy dependencies may also be defined such that where a second policy is dependent on a first policy, the second policy must be evaluated after the first policy. This is necessary, where, for example, the first policy generates and stores a value to be used by the second policy. Policies are small programs written as small programs. A configlet hierarchy is defined, such that a child configlet inherits properties which it does not define from its parent. A mapping function maps infrastructure data in a first format to a second format, so that the second format is recognizable by the policy engine. A loader batches, schedules and loads a configuration file to its intended device. Upon replacing a first device using a first configuration format with a second device using a second configuration format, the first device's configuration is read in or uploaded and reverse-translated into configlets. The configlets are then translated into a configuration formatted for the second device. The system retains device logins and passwords in encrypted format. A user desiring to connect to a device must log in to the system instead. The system in turn logs in or connects to the device and passes information back and forth between the user and the device, as if the user were logged directly into the device.
Owner:IBM CORP
Scaleable interconnect structure utilizing quality-of-service handling
InactiveUS7016363B1Quality improvementData switching by path configurationTime-division multiplexing selectionQuality of serviceLevel structure
An interconnect structure and method of communicating messages on the interconnect structure assists high priority messages to travel through the interconnect structure at a faster rate than normal or low priority messages. An interconnect structure includes a plurality of nodes with a plurality of interconnect lines selectively coupling the nodes in a hierarchical multiple-level structure. Data moves from an uppermost source level to a lowermost destination level. Nodes in the structure are arranged in columns and levels. Data wormholes through the structure and, in a given time-step, data always moves from one column to an adjacent column and while remaining on the same level or moving down to a lower level. When data moves down a level, an additional bit of the target output is fixed so data exiting from the bottom of the structure arrives at the proper target output port.
Owner:INTERACTIC HLDG LLC
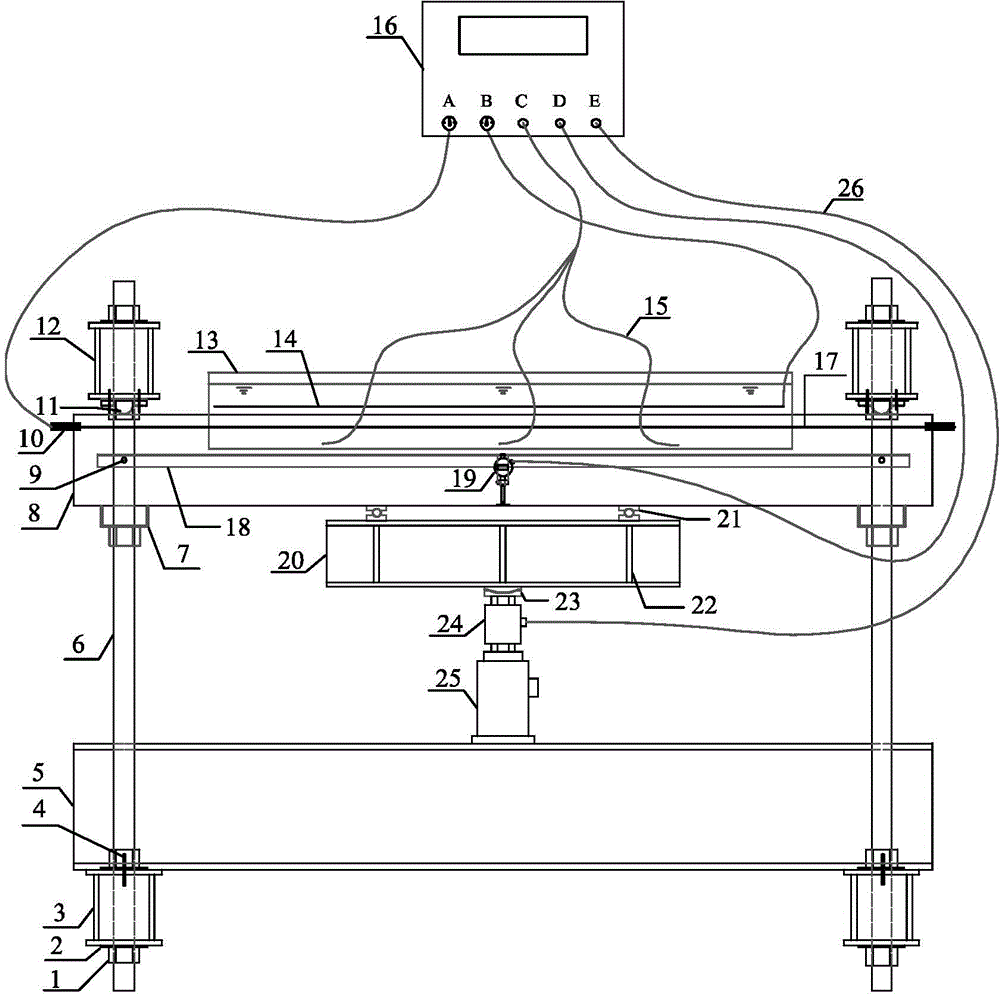
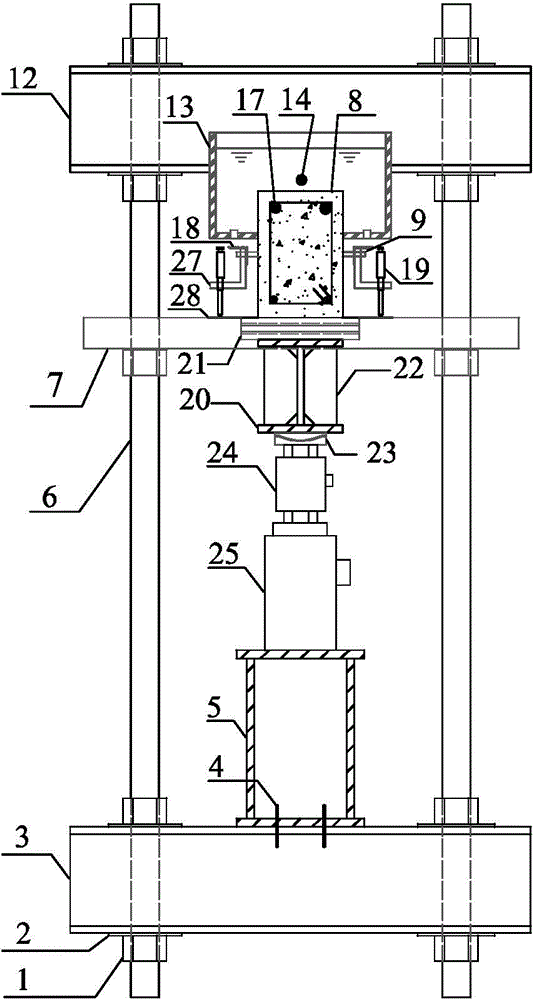
Device and method for testing chloride corrosion of reinforced concrete member under continuous load
ActiveCN104132847ATroubleshoot test setup issuesSolve the real problemMaterial strength using tensile/compressive forcesMicrocontrollerData acquisition
The invention provides a device and method for testing chloride corrosion of a reinforced concrete member under a continuous load. The device comprises a continuous load loading device, a rapid chloride corrosion device and a measurement and control device. A continuous load is applied by a loading frame and a drive device, a frame body is filled with a chloride solution and is fixed at the upper-middle part of a test beam in a sealing manner, air is continuously injected in the chloride solution by adopting an air pump, and direct current is introduced into reinforced steel bars of the test beam to implement the rapid corrosion. Relevant data acquirers, electrochemical testers and output equipment which are controlled through a single chip microcomputer in a unified manner are integrated in the main control box, the continuous load is measured in real time, and periodically corrected to a target level, corrosion behaviors of a corroded member are periodically tested, and data are acquired, displayed, stored, printed and output in real time. The device is capable of effectively simulating an actual corrosion working condition of the on-active service reinforced concrete structure member under the coupling effect of a chloride environment and the load, and provides a scientific basis for evaluating the durability of engineering structures under chloride environments such as sea and salt lakes.
Owner:HOHAI UNIV
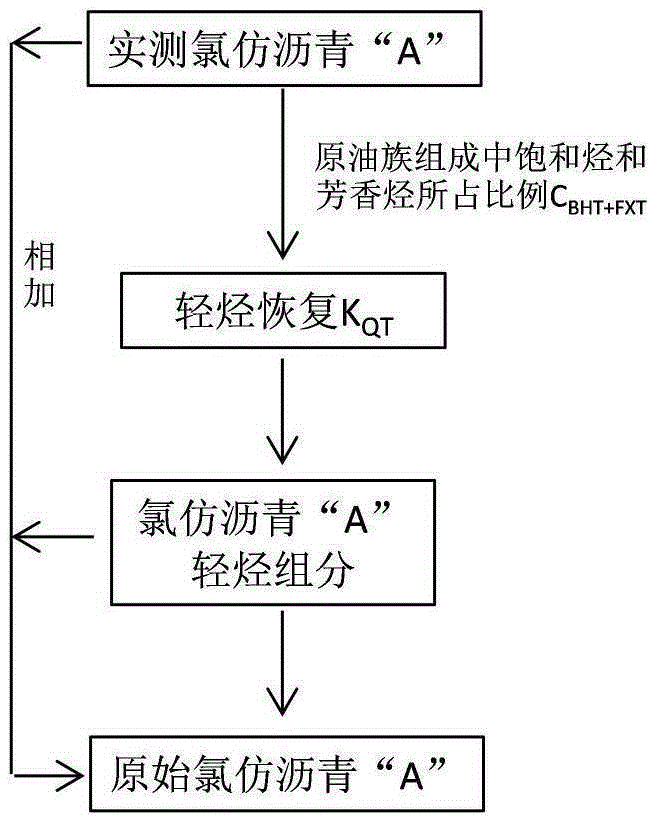
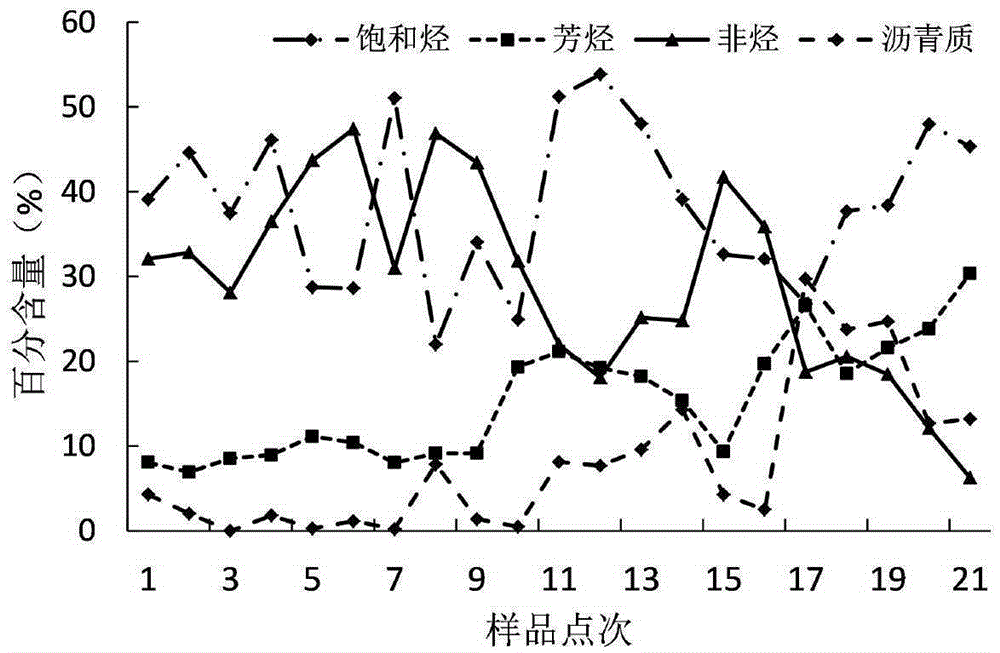
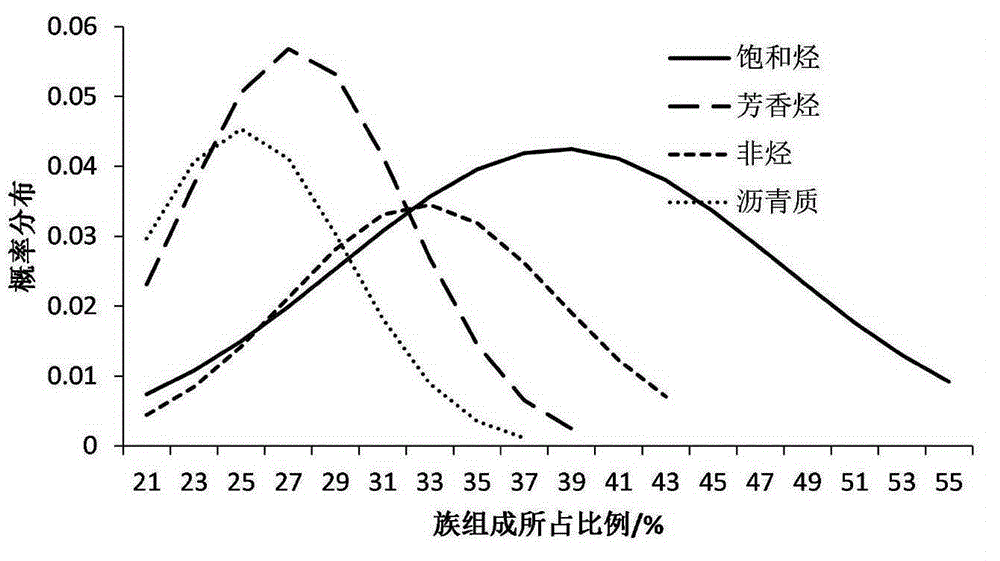
Method for evaluating hydrocarbon potential key parameters of high-quality hydrocarbon-source rock
The invention discloses a method for evaluating hydrocarbon potential key parameters of high-quality hydrocarbon-source rock, and belongs to the technical field of oil and gas resource evaluation. The method includes the key steps of firstly, determining an immature and low-mature oil hydrocarbon expelling threshold, a normal hydrocarbon threshold and a normal hydrocarbon expelling threshold of high-quality hydrocarbon-source rock according to geochemistry data of hydrocarbon-source rock; secondly, establishing the hydrocarbon-source rock hydrocarbon amount and a hydrocarbon rate evaluating model; thirdly, establishing the hydrocarbon-source rock hydrocarbon expelling amount and a hydrocarbon expelling evaluating model, and evaluating the target level hydrocarbon-source rock hydrocarbon expelling amount and hydrocarbon expelling rate key parameters; fourthly, establishing a high-quality hydrocarbon-source rock organic carbon recovery coefficient evaluating model, and evaluating a target level hydrocarbon-source rock organic carbon recovery coefficient; fifthly, evaluating a research area target level high-quality hydrocarbon-source rock hydrocarbon potential plane graph, and analyzing the relation between the plane graph and tight oil hydrocarbon contribution. Immature and low-mature stage hydrocarbon potential key parameters of high-quality hydrocarbon-source rock are subjectively and accurately evaluated, and the blank, weakened by people in the past, of immature and low-mature stage hydrocarbon of high-quality hydrocarbon-source rock is filled in.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
3D scene model from collection of images
ActiveUS20130215233A1Efficiently determinedReduce in quantityDetails involving processing stepsImage analysisComputer graphics (images)Digital image
A method for determining a three-dimensional model of a scene from a collection of digital images, wherein the collection includes a plurality of digital images captured from a variety of camera positions. A set of the digital images from the collection are selected, wherein each digital image contains overlapping scene content with at least one other digital image in the set of digital images, and wherein the set of digital images overlap to cover a contiguous portion of the scene. Pairs of digital images from the set of digital images to determine a camera position for each digital image. A set of target camera positions is determined to provide a set of target digital images having at least a target level of overlapping scene content. The target digital images are analyzed using a three-dimensional reconstruction process to determine a three-dimensional model of the scene.
Owner:MONUMENT PEAK VENTURES LLC
Power factor improving converter and control method thereof
InactiveUS20050162143A1Improve efficiencyLower Level RequirementsEfficient power electronics conversionDc-dc conversionSwitched currentAudio power amplifier
A boost quantity detecting section (103) detects a boost quantity of an inductor (L11). An operational amplifier (113) of a control section (106) compares the boost quantity detected by the boost quantity detecting section (103) with a reference voltage (ES12). When a supply voltage supplied from an AC power source (100) reduces and an output voltage is unchanged, the boost quantity detected by the boost quantity detecting section (103) increases. When a signal level of a boost quantity detection signal is higher than the reference voltage (ES12), a control section (106) reduces a target level of a switching current. The target level of the switching current decreases, so that the output voltage decreases and energy loss due to boosting reduces.
Owner:SANKEN ELECTRIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com