Patents
Literature
139results about How to "High encryption strength" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
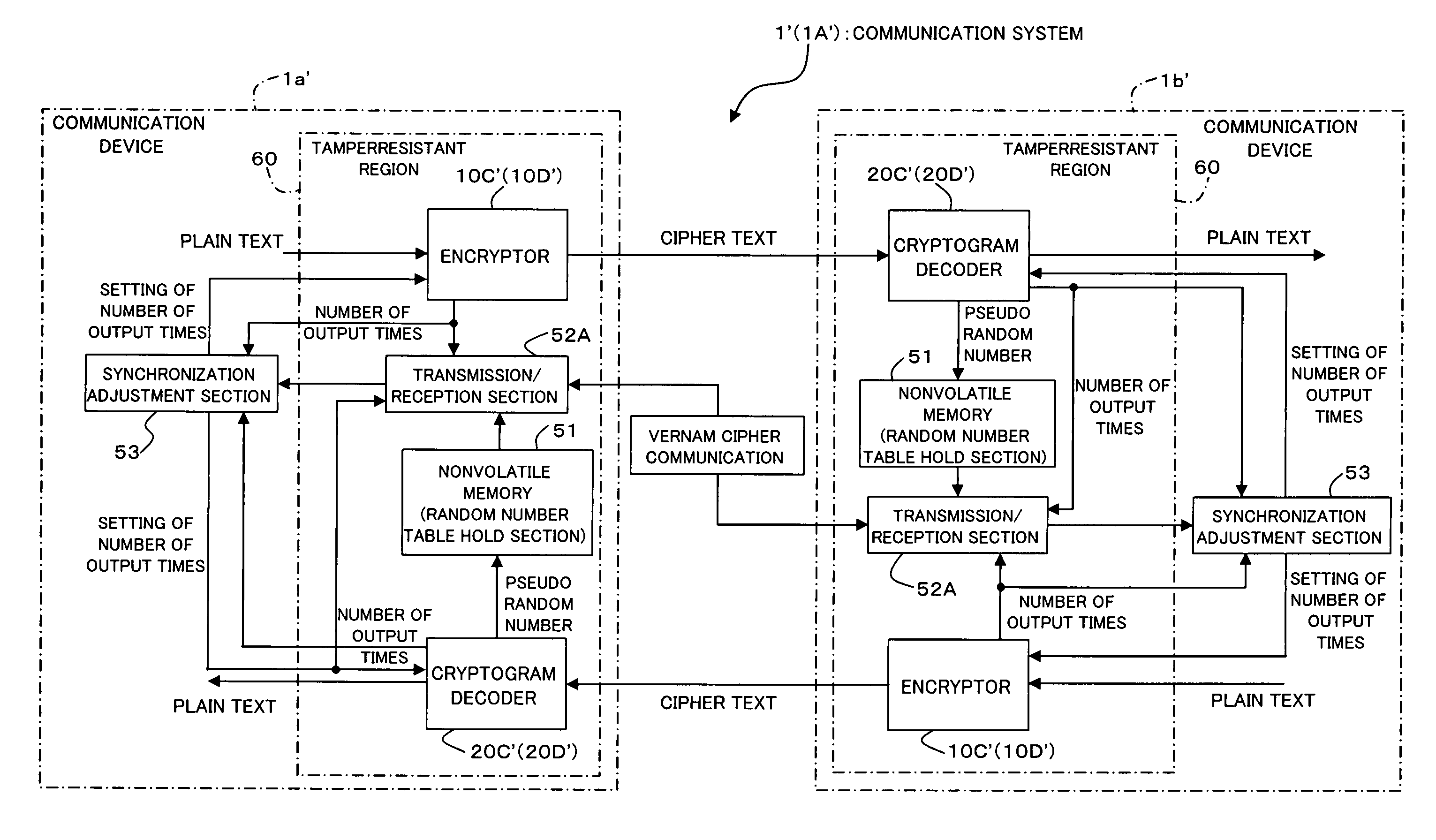
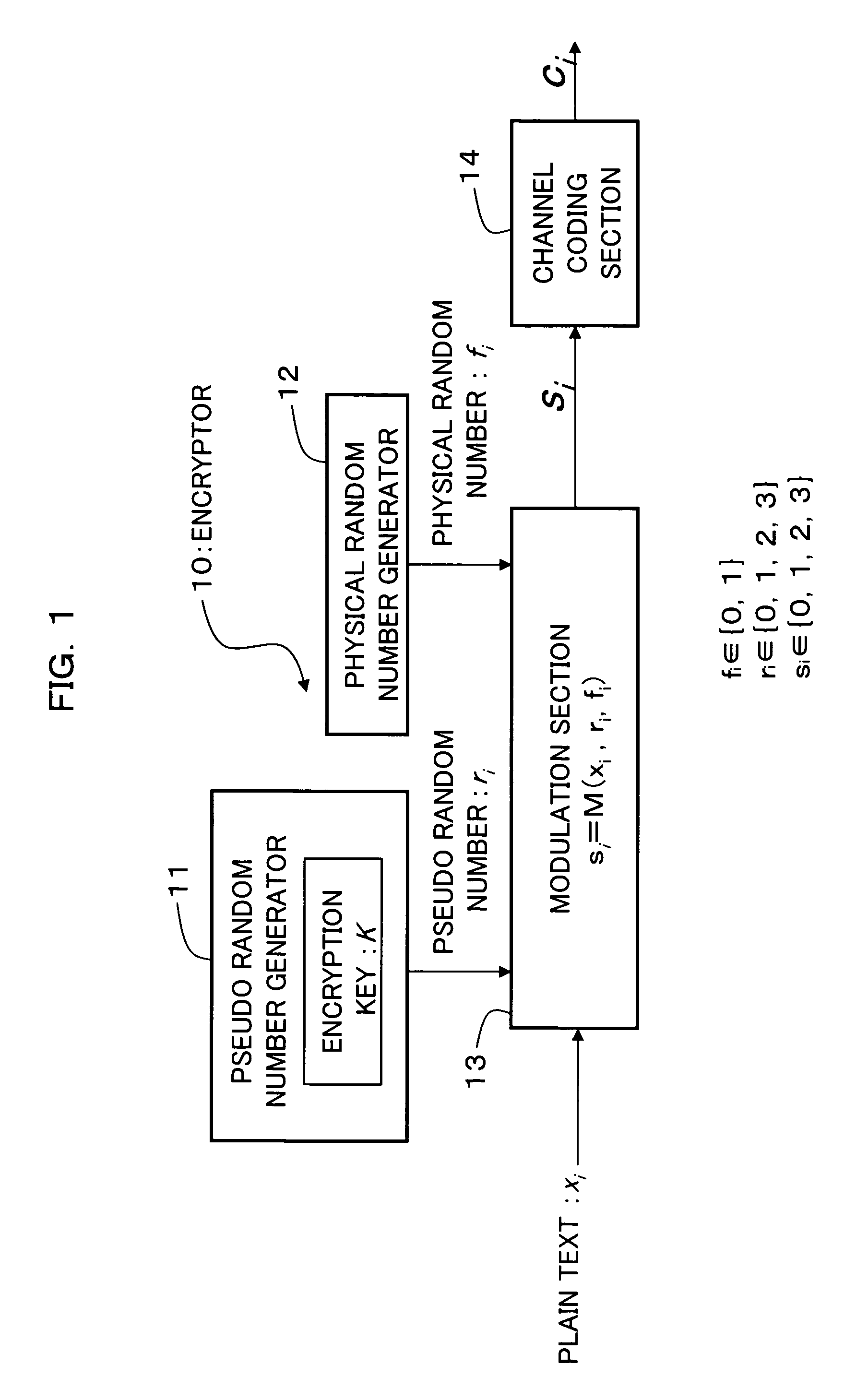
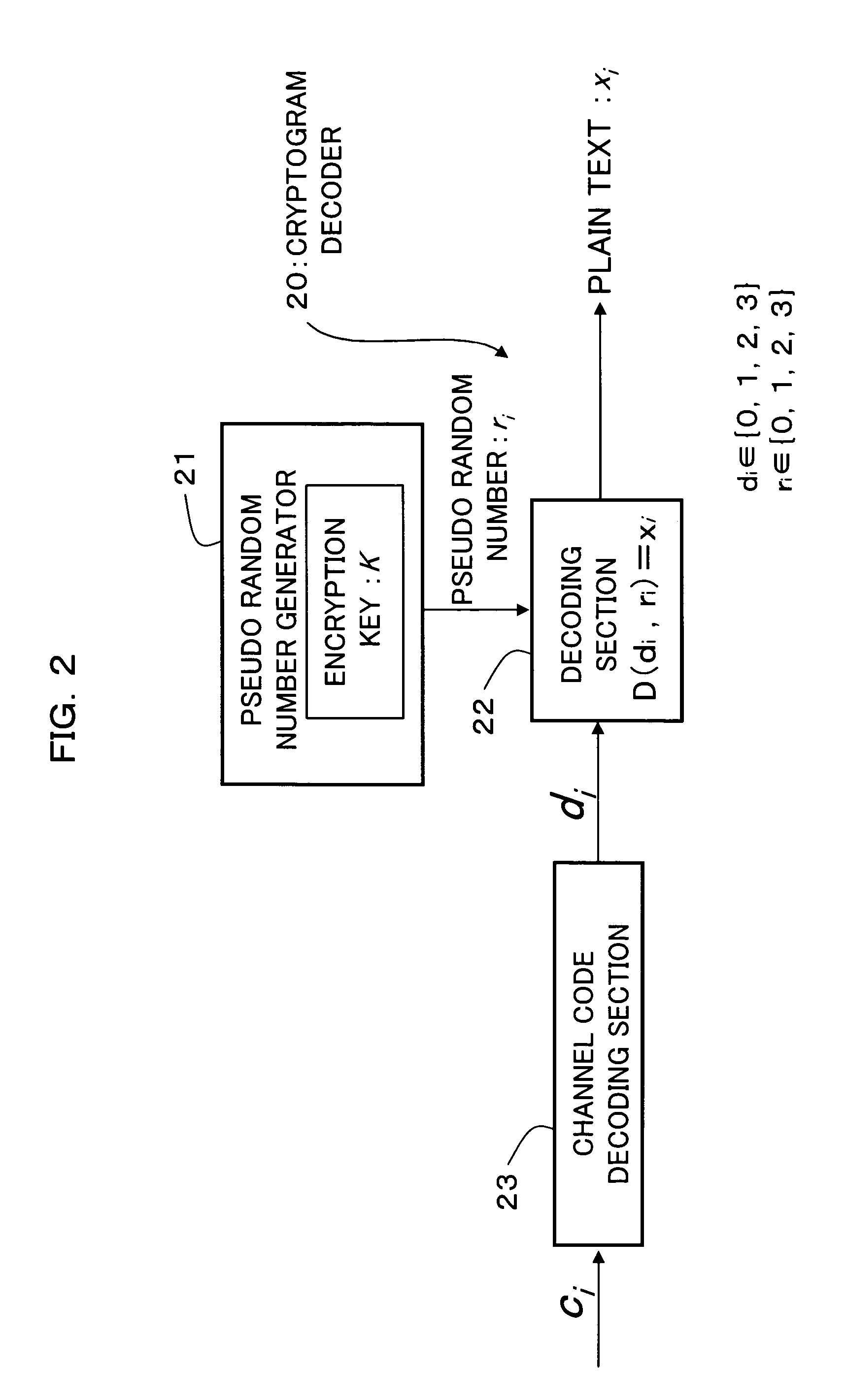
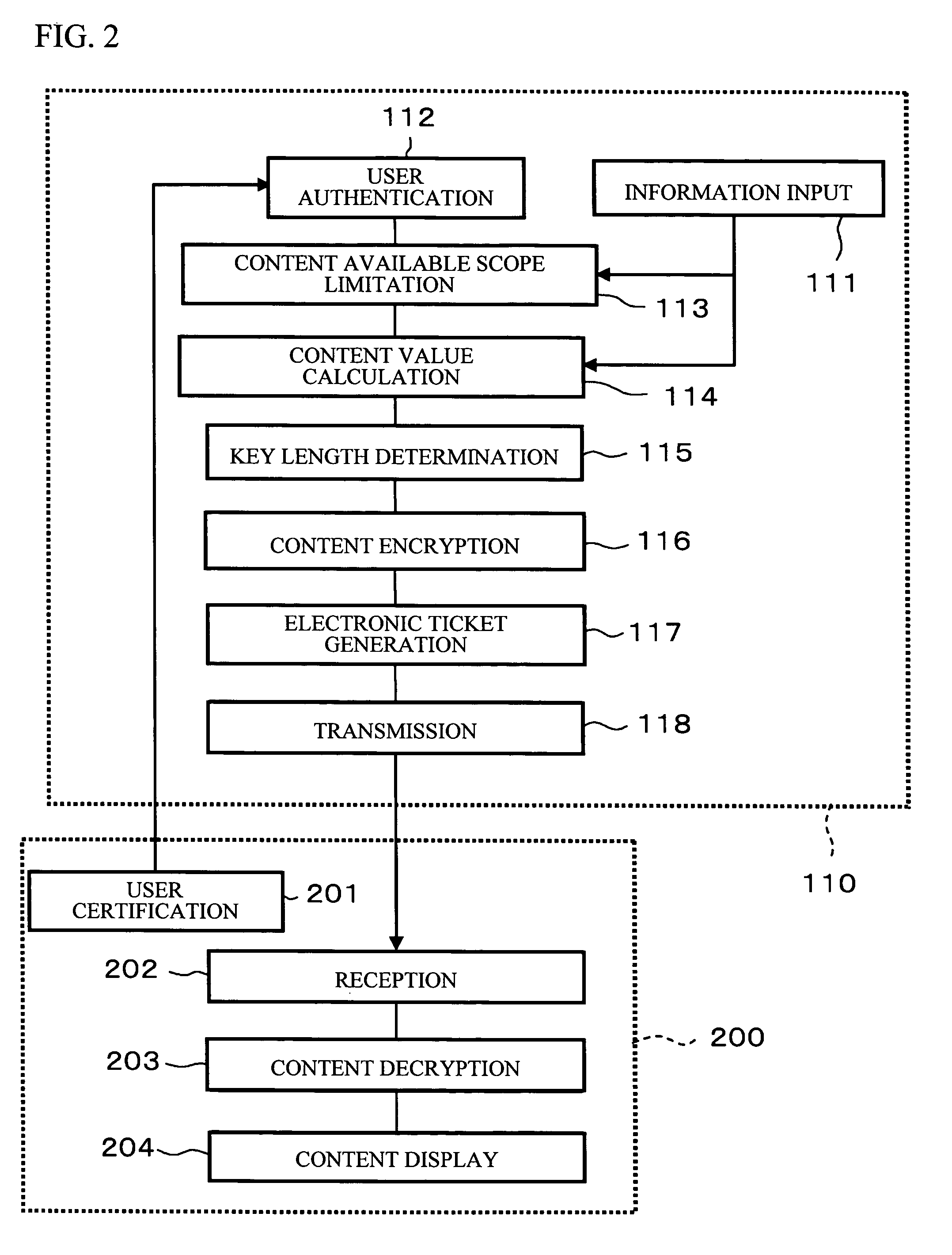
Encryption method, cryptogram decoding method, encryptor, cryptogram decoder, transmission/reception system, and communication system
ActiveUS20080044011A1High encryption strengthMinimize impactSynchronising transmission/receiving encryption devicesError preventionComputer hardwareCommunications system
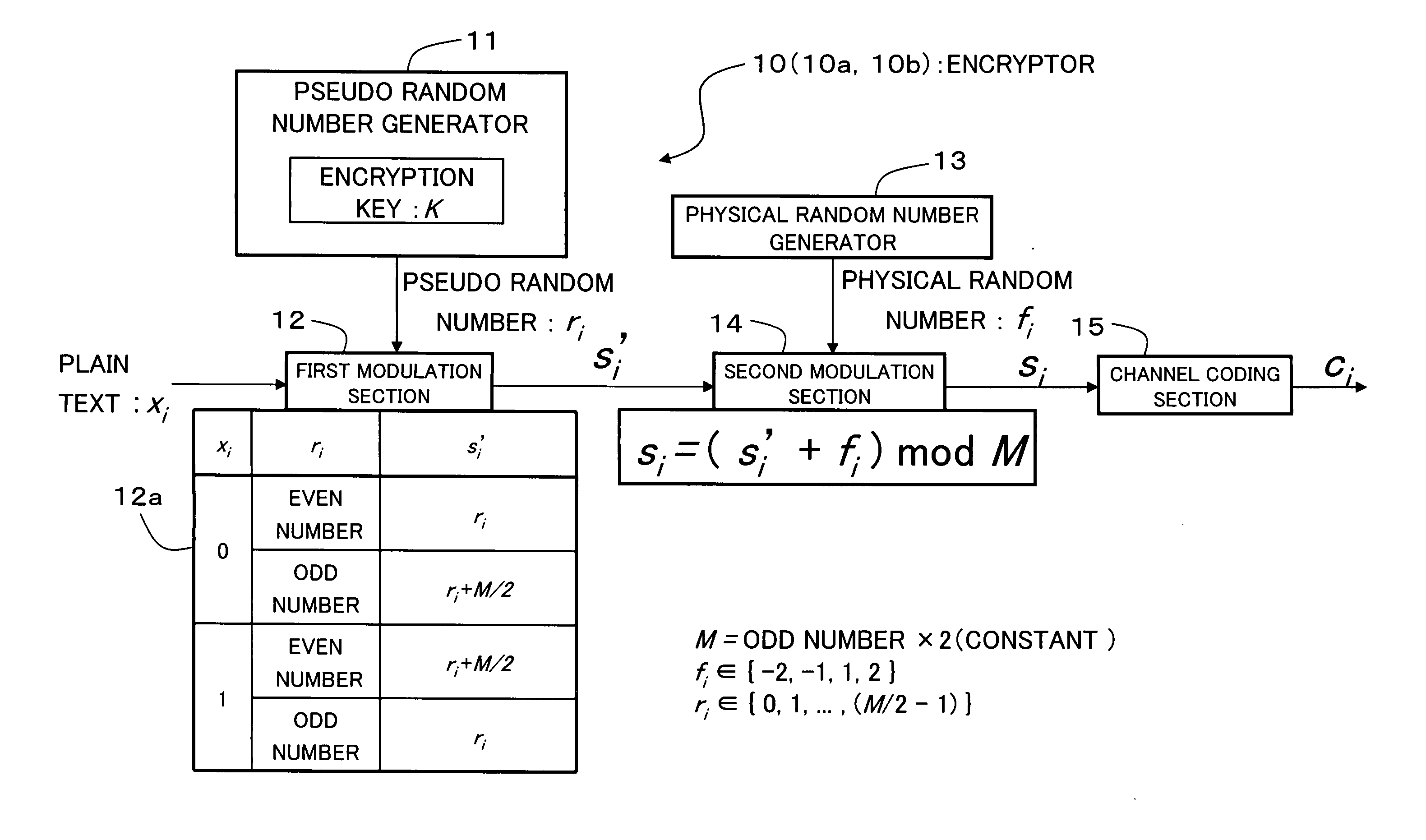
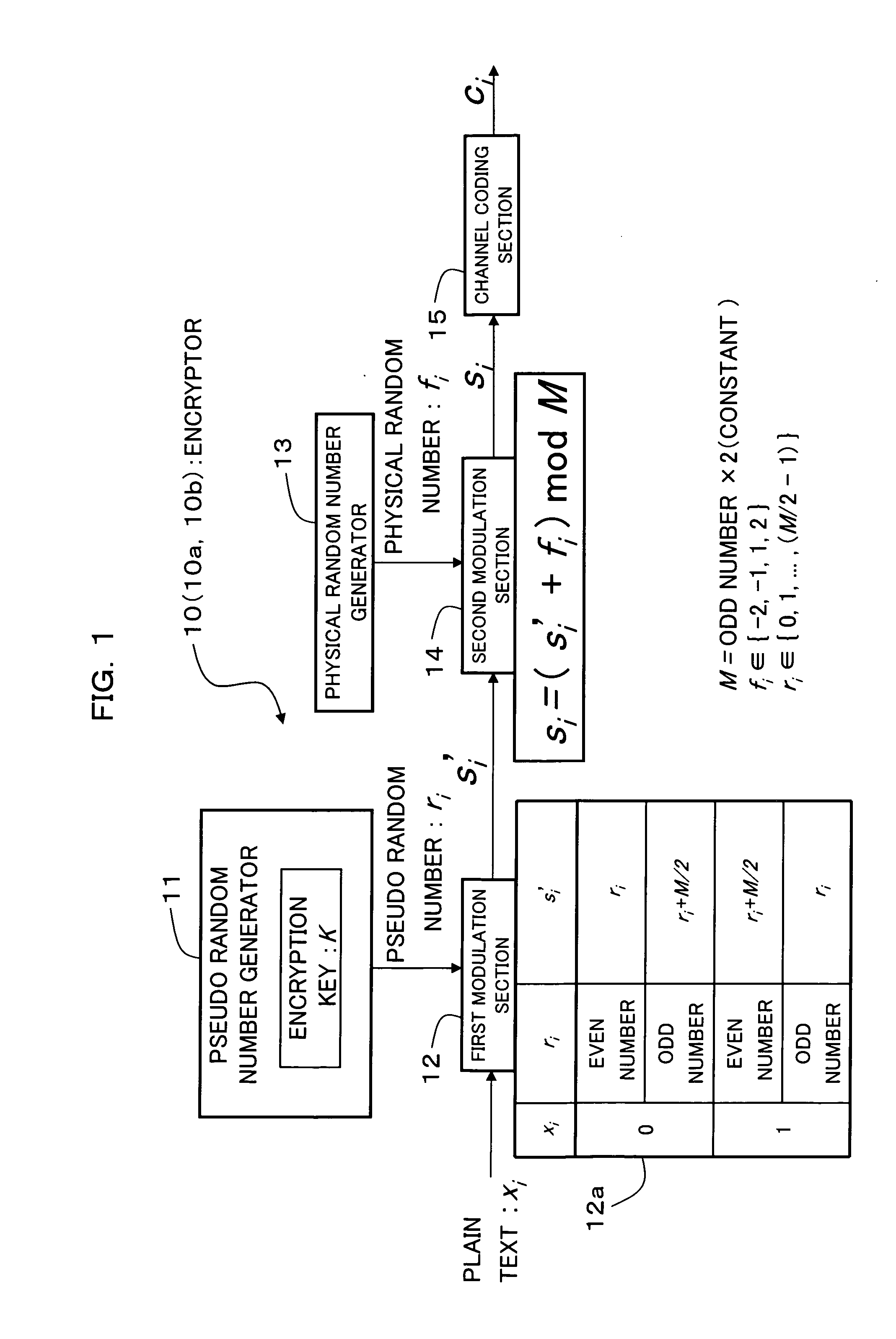
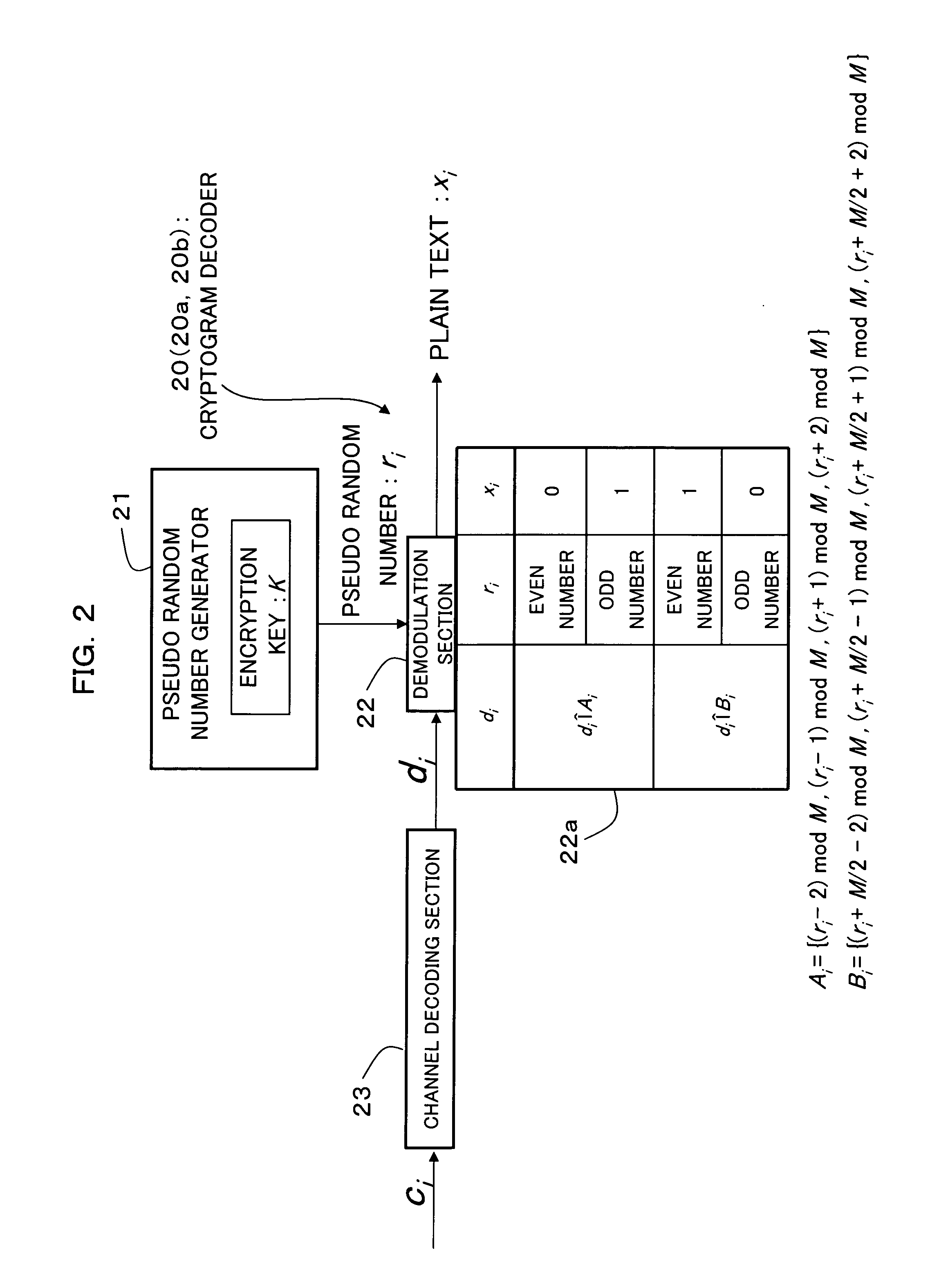
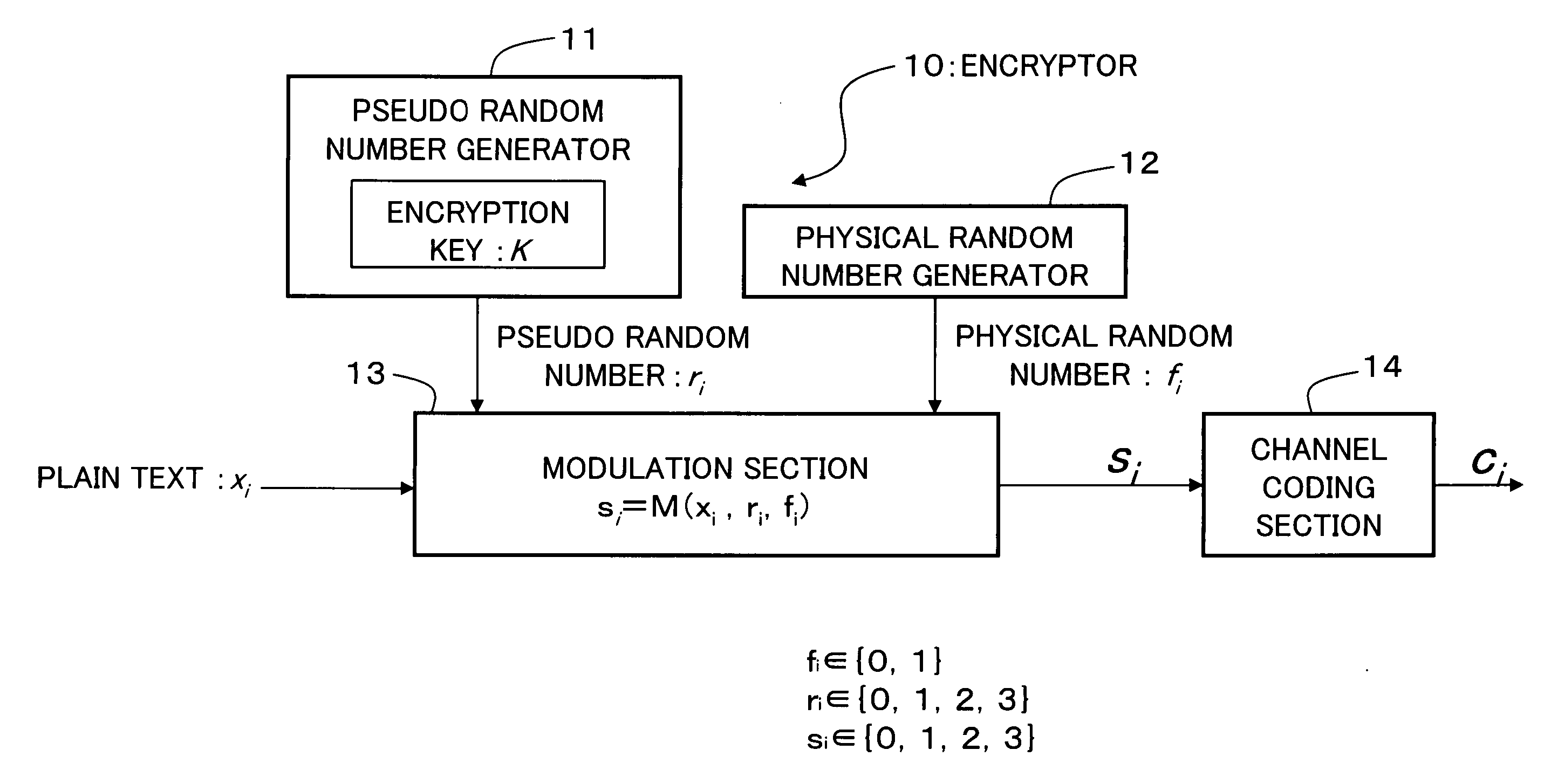
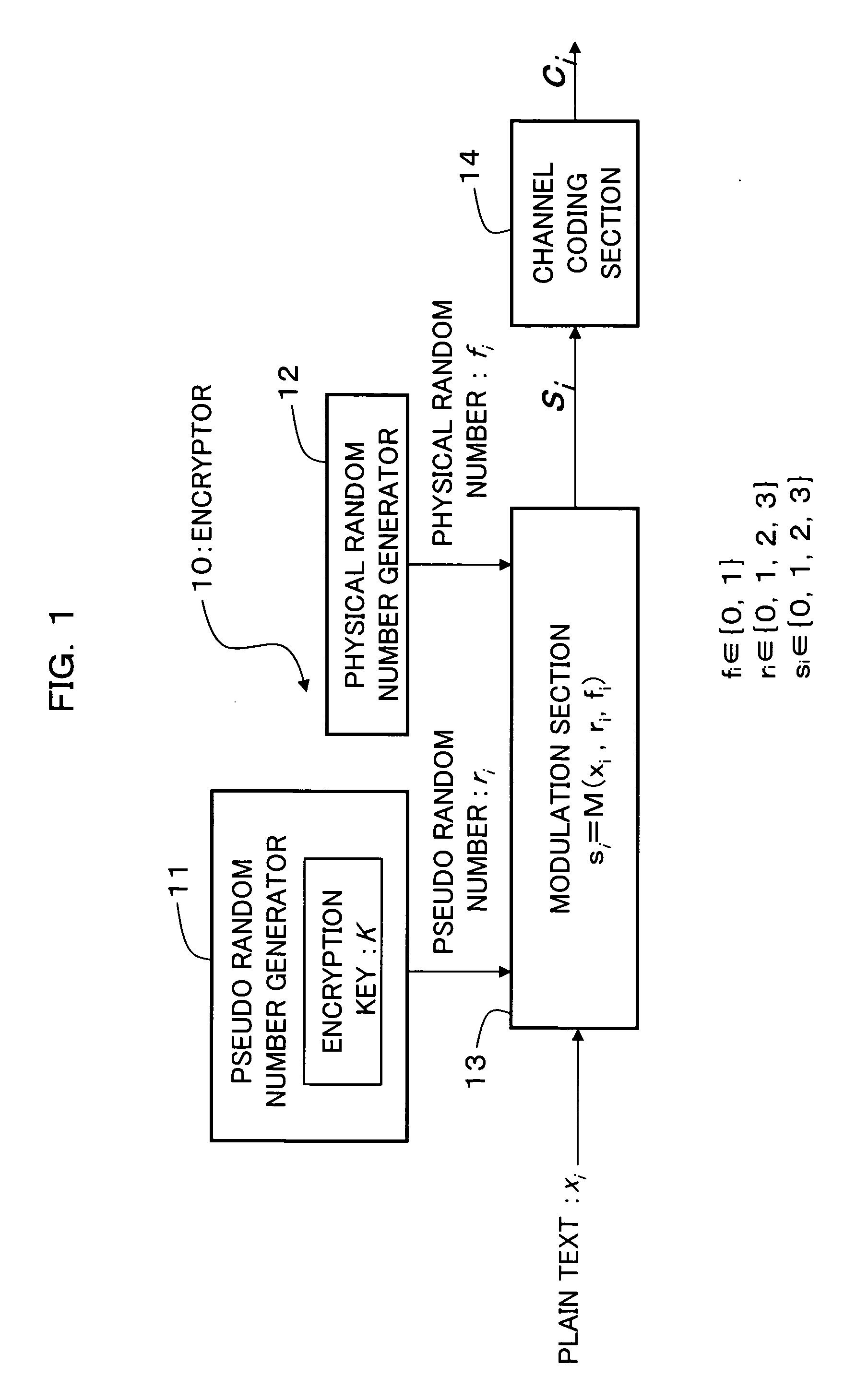
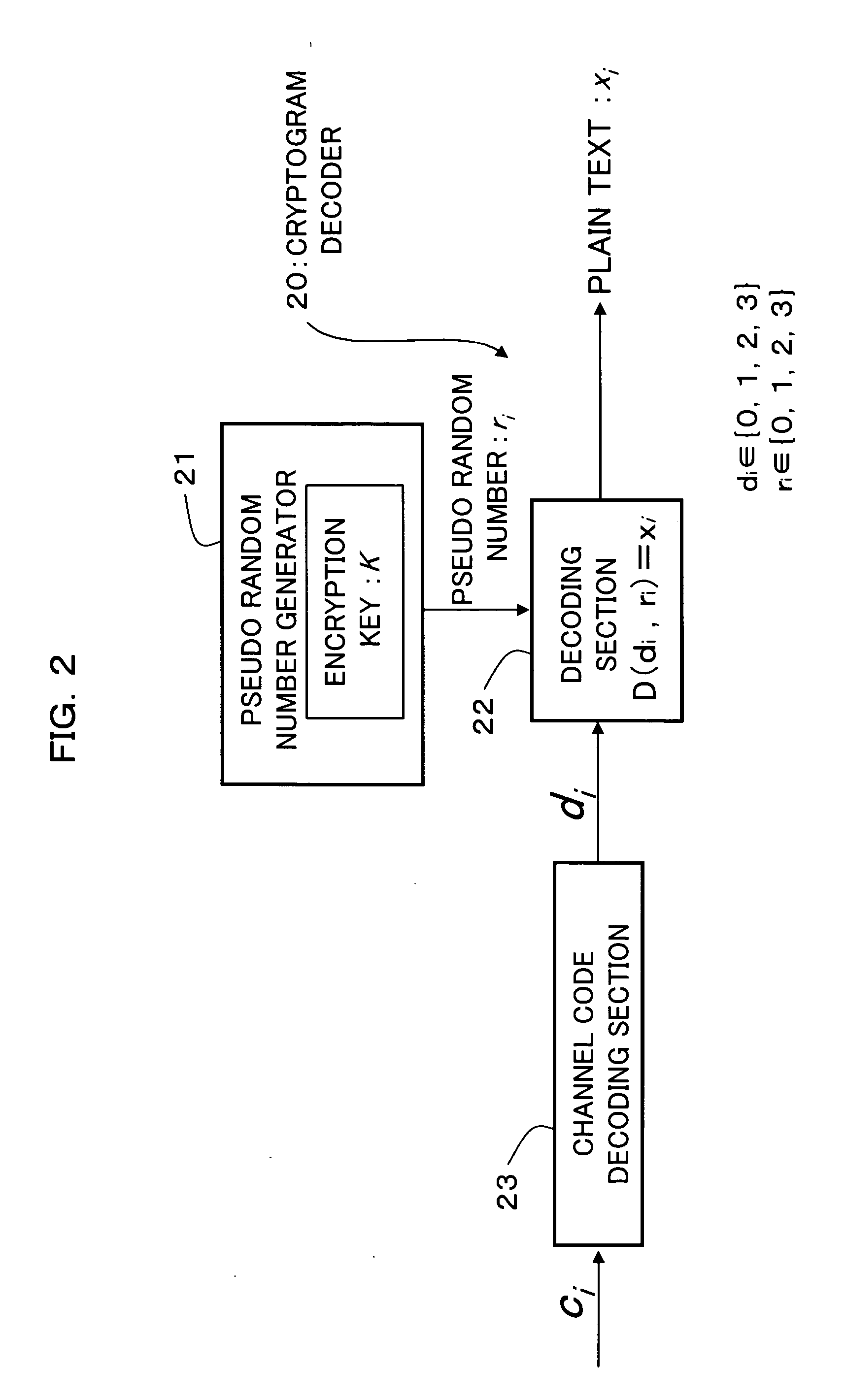
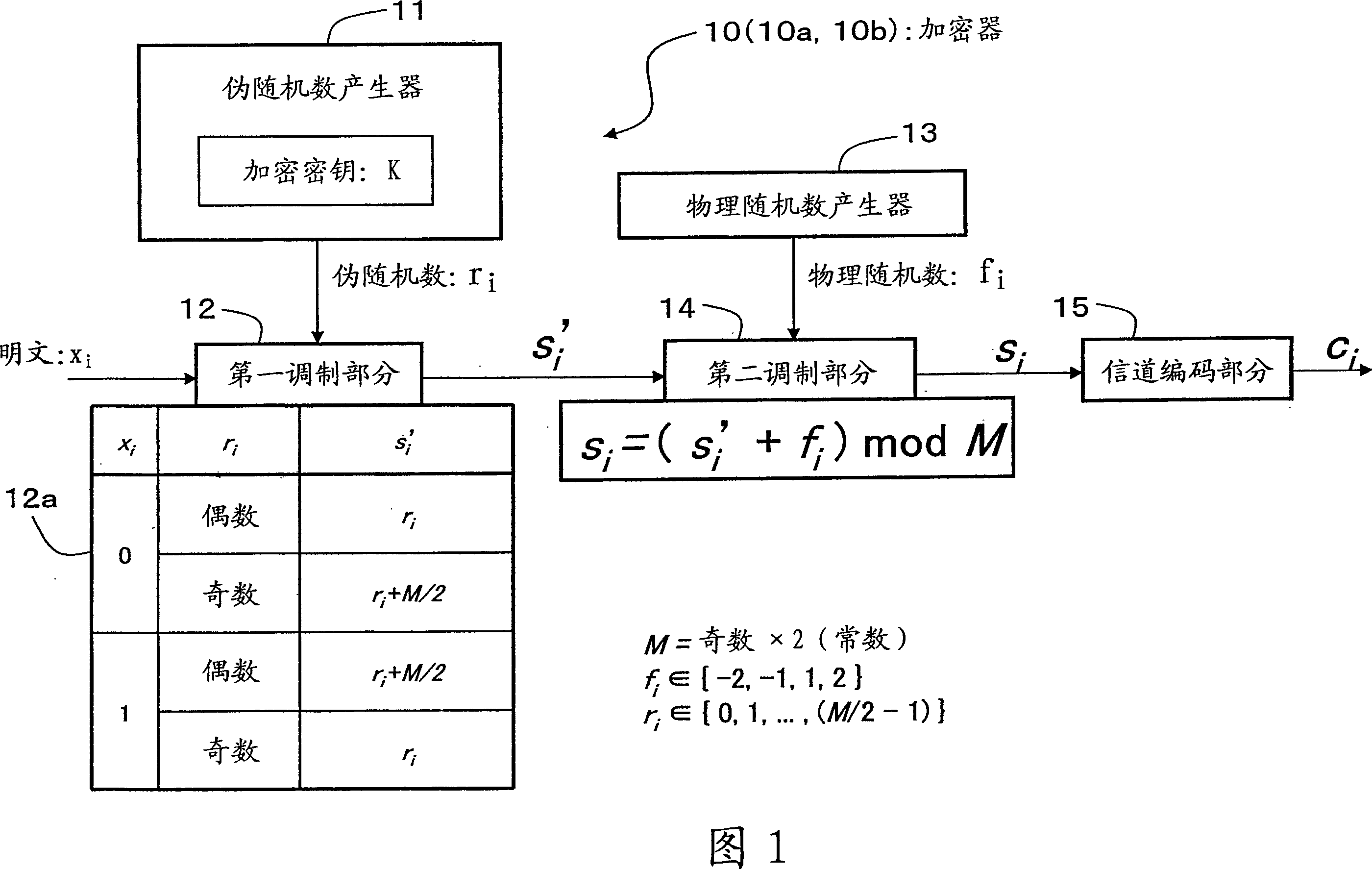
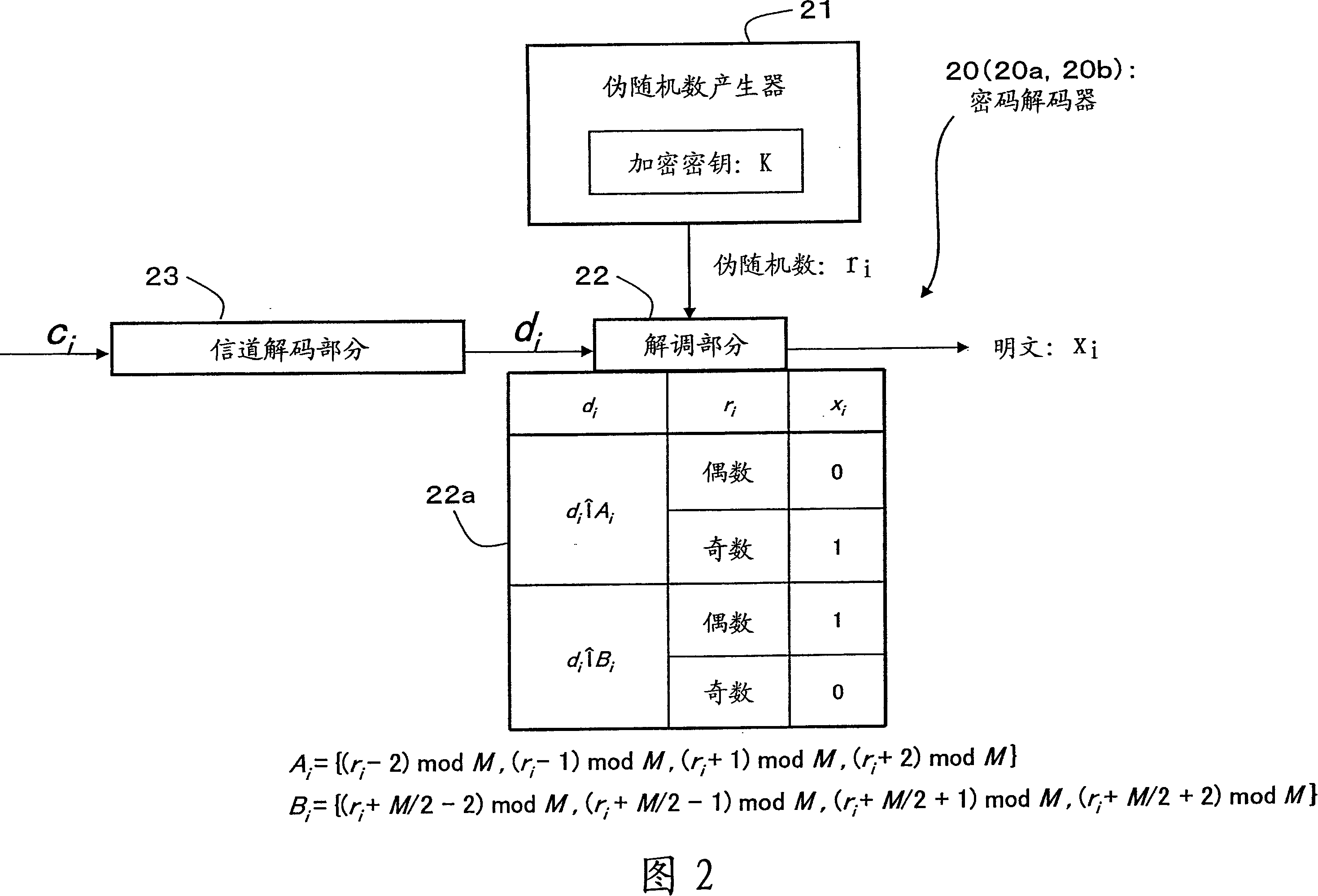
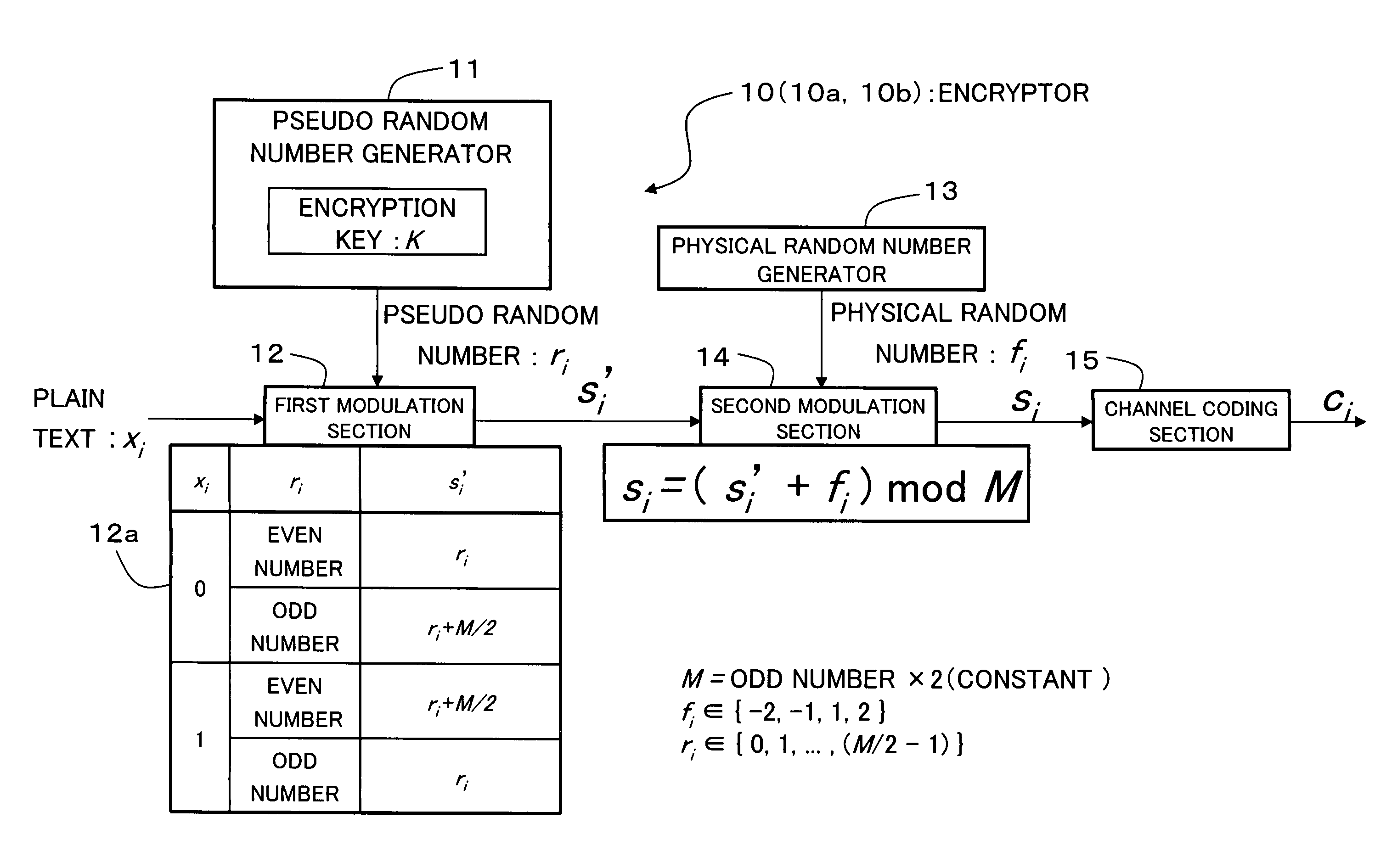
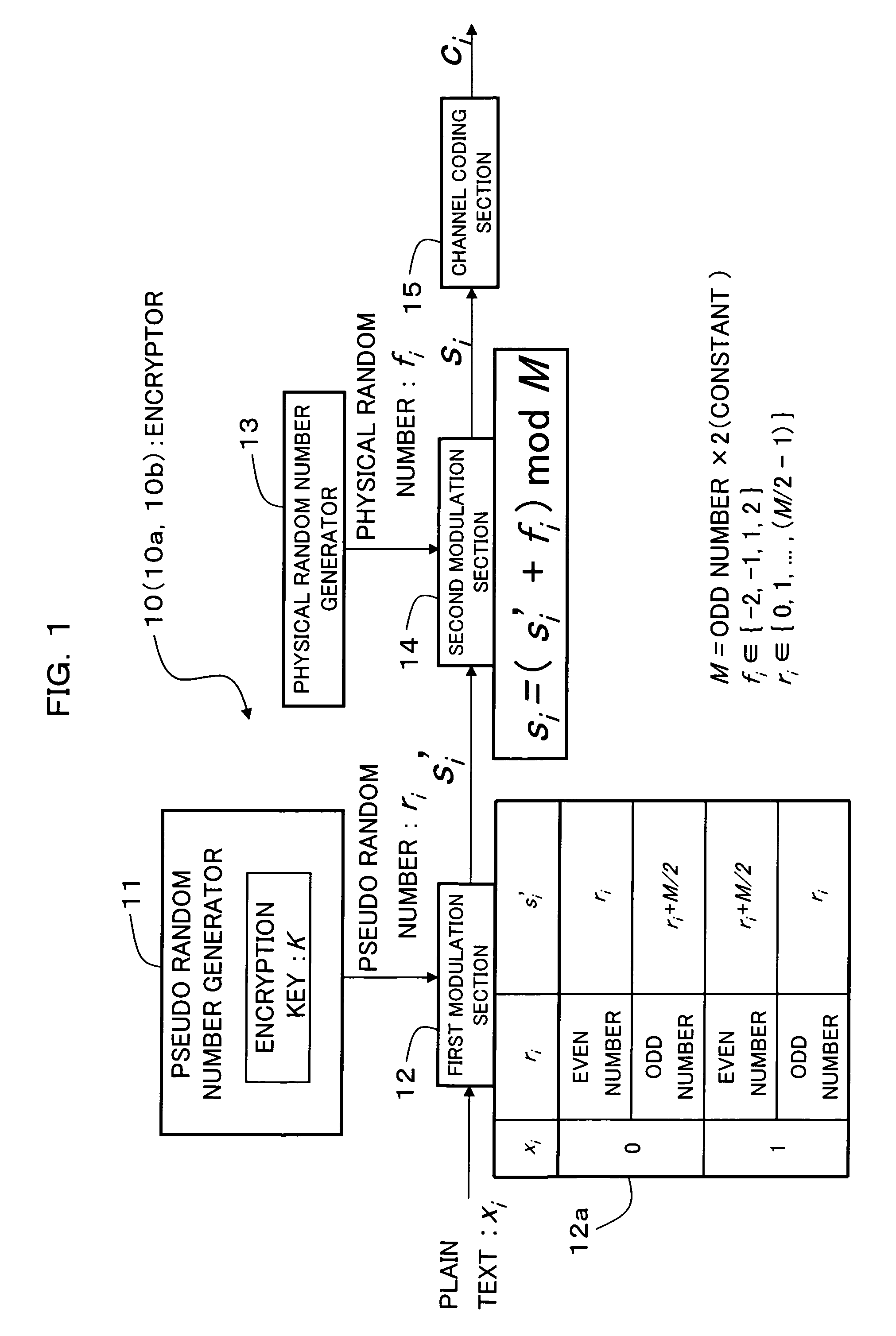
An encryption technique allowing use of classic Y-00 scheme performed using classic physical random numbers instead of quantum fluctuation in electrical communication and data storage in recording media, including a first modulation step for multilevel-modulating input data by associating with specific state pairs determined by physical random numbers, a second modulation step for outputting the output of the first step by irregularly associating with another signal by physical random numbers, and a channel coding step for channel-coding the output of the second step into desired codeword and outputting it as encrypted data, wherein the decoded signal obtained by channel-decoding the encrypted data can be discriminated which of specific state pairs the signal corresponds to and demodulated into the input data, and output by the first modulation by state pairs other than the specific state pairs and the second modulation by a physical random number different from the physical random number.
Owner:FUJITSU LTD +1
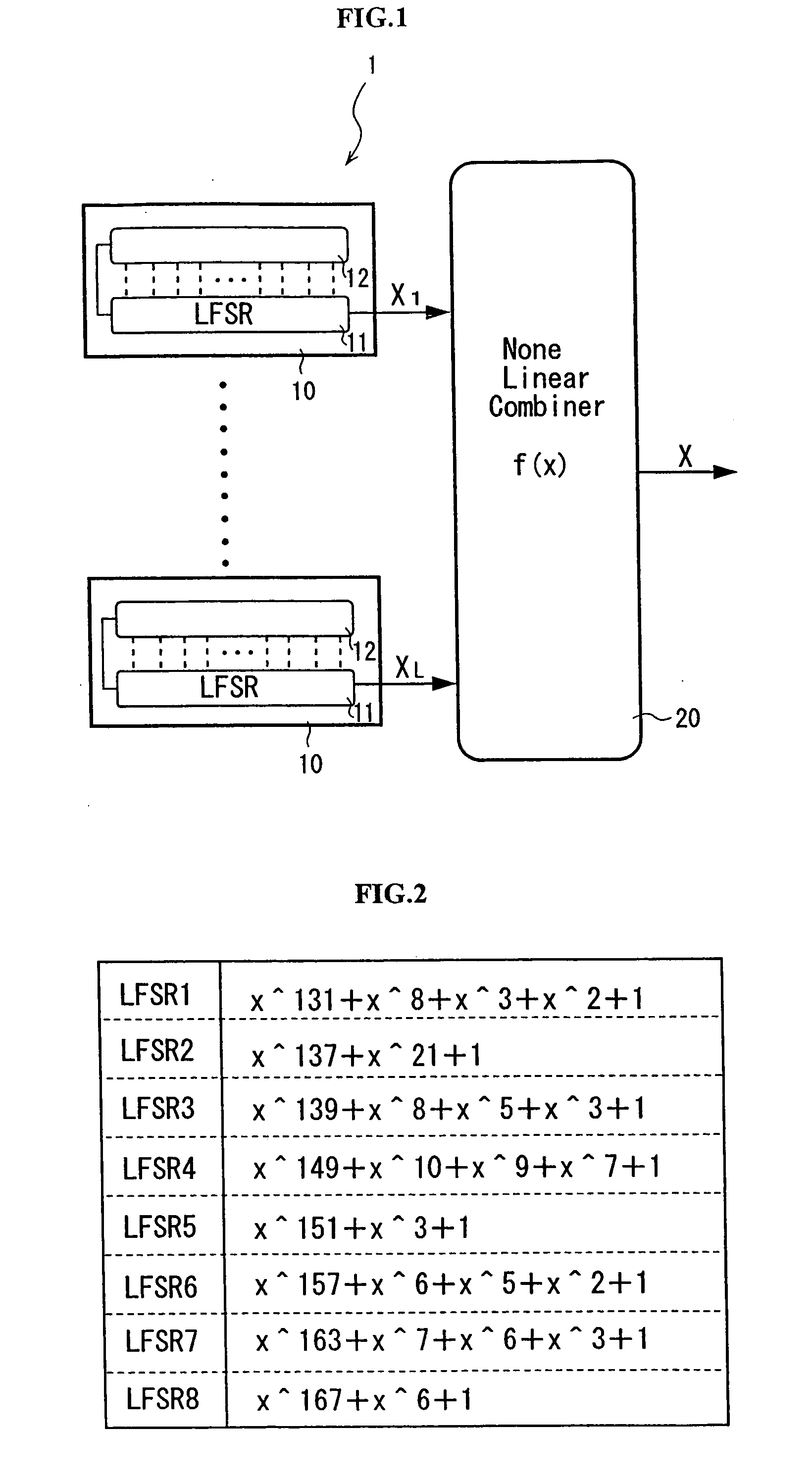
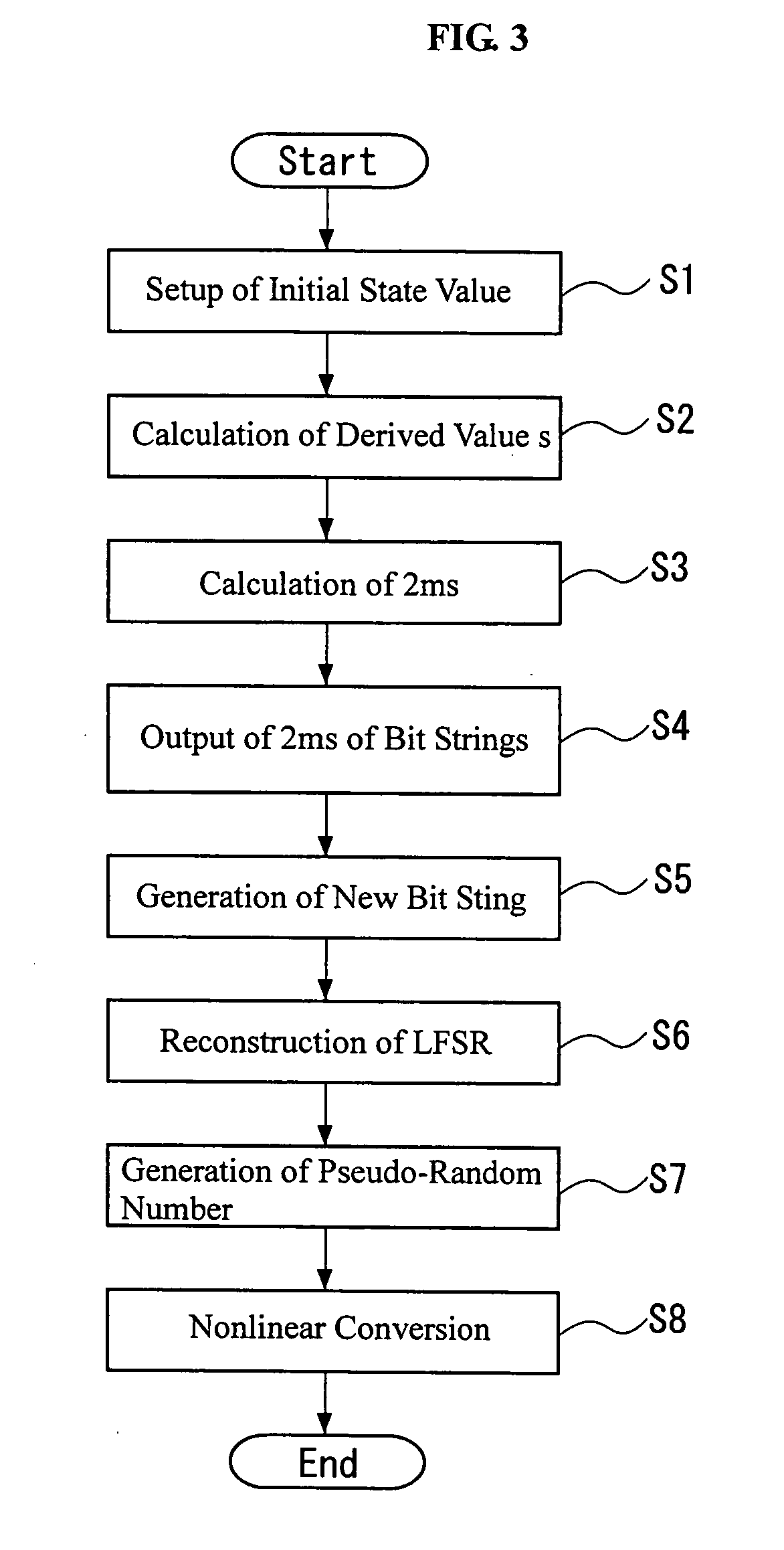
Pseudo-random number generation method and pseudo-random number generator
InactiveUS20060039558A1Easy to changeHigh encryption strengthRandom number generatorsCoding/ciphering apparatusLinearityNumber generator
A bit string obtained by sampling, every the number s, bits of a bit string whose output sequence is M sequence, when the bit number per one cycle of the M sequence is prime to the derived value, constitutes M sequence of a linear feedback shift register having other construction. Further, the linear feedback shift register can be determined from bits corresponding to at least two cycles by Berlekamp-Massay algorithm, whereby the linear feedback shift register 11 can be easily and dynamically reconstructed based on the initial state value.
Owner:KOBAYASHI AKIRA +1
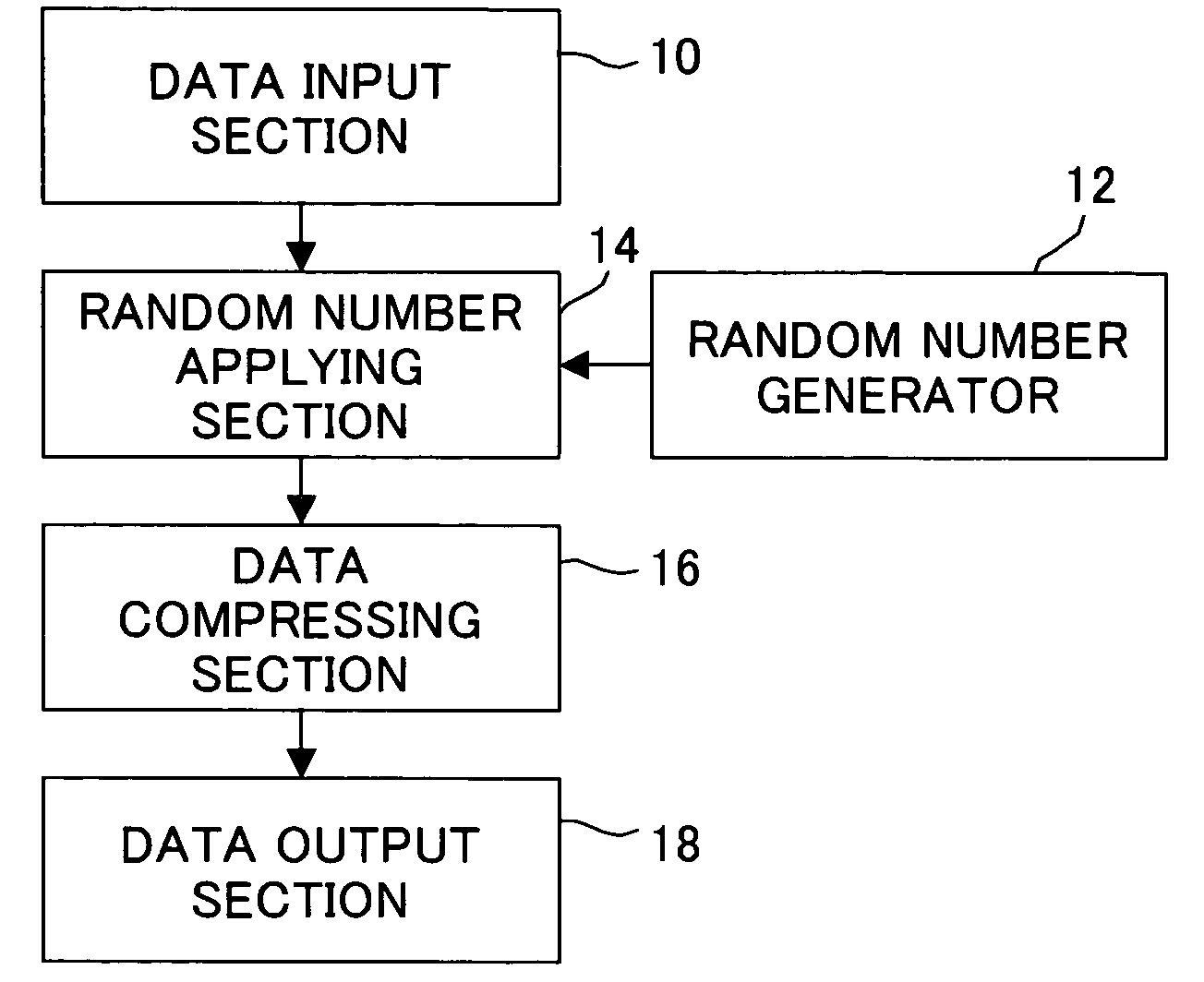
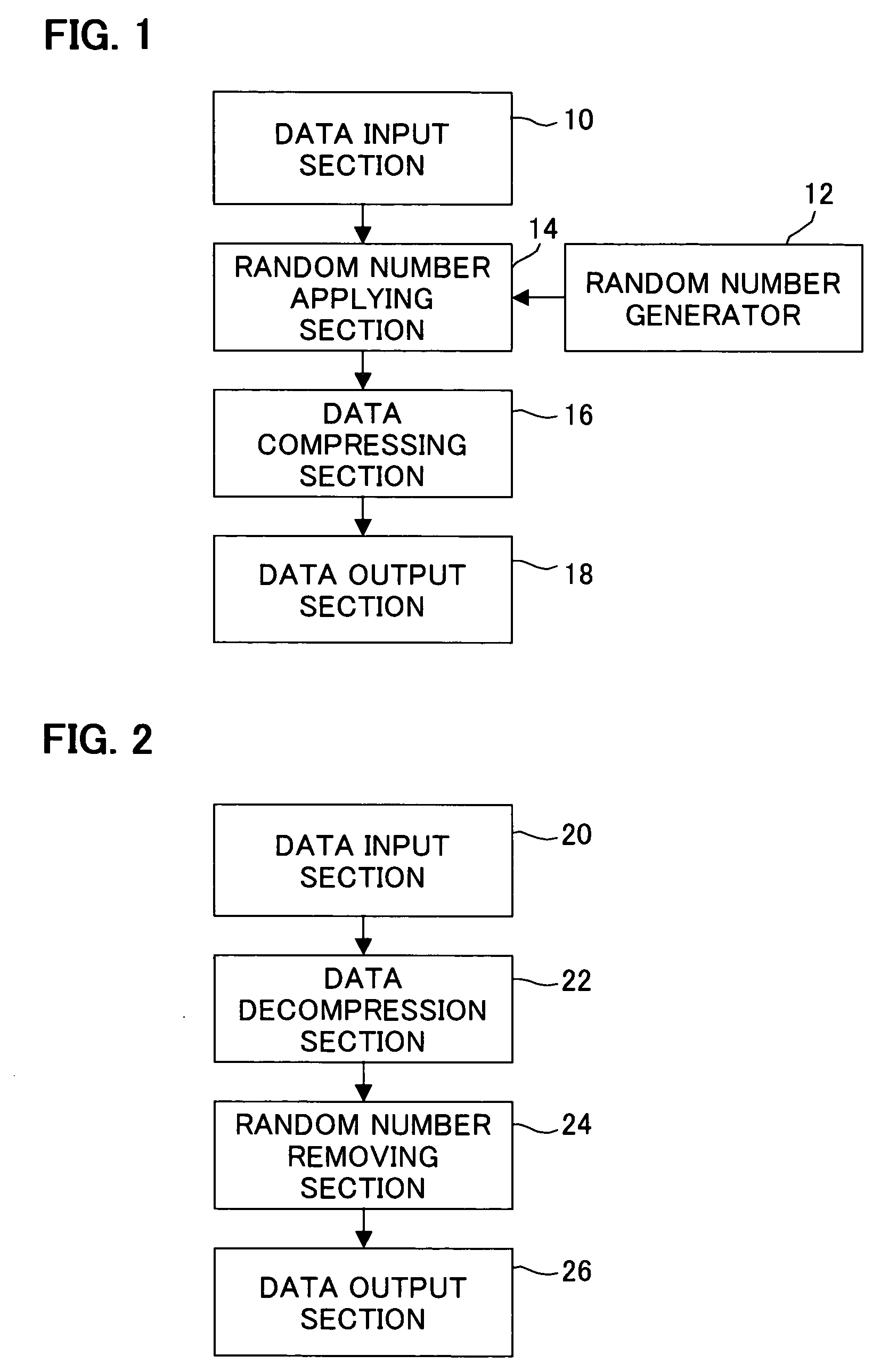
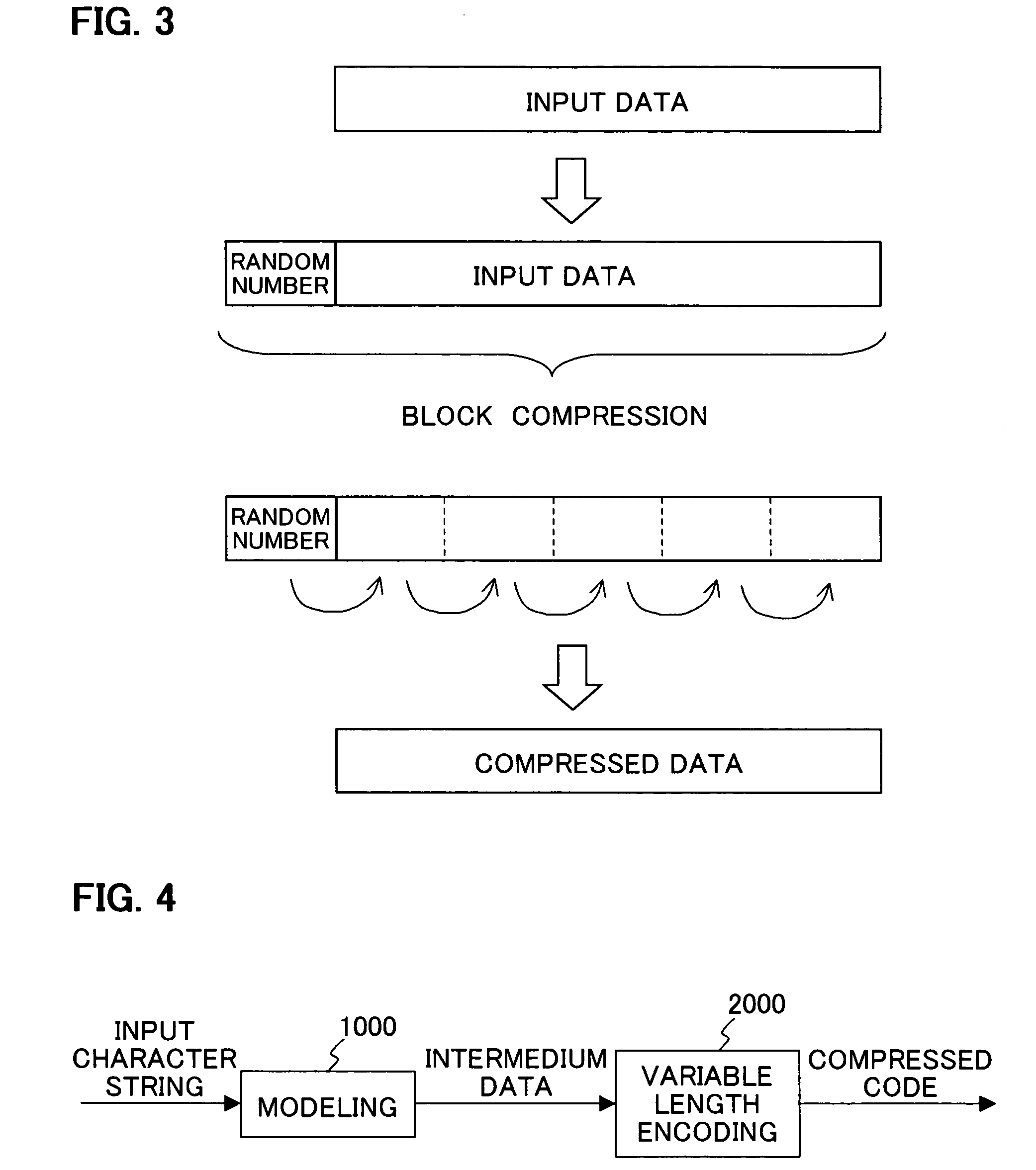
Data compression method, data decompression method, data conversion method and program for same
InactiveUS20050169465A1Increase randomnessReduce processing timeEncryption apparatus with shift registers/memoriesCode conversionData compressionData stream
A data compression method, to generate a compressed data stream from an uncompressed data stream, enhances the secrecy of data compression. A scramble value is appended to the beginning of the uncompressed data stream, and a dynamic variable-length encoding method is used to perform data compression. Compressed data with high randomness can be generated, and data for processing can easily be randomized. That is, there is no need to share a common initial value on the generating side and on the restoring side, processing is simple, and the processing time can be shortened.
Owner:FUJITSU LTD
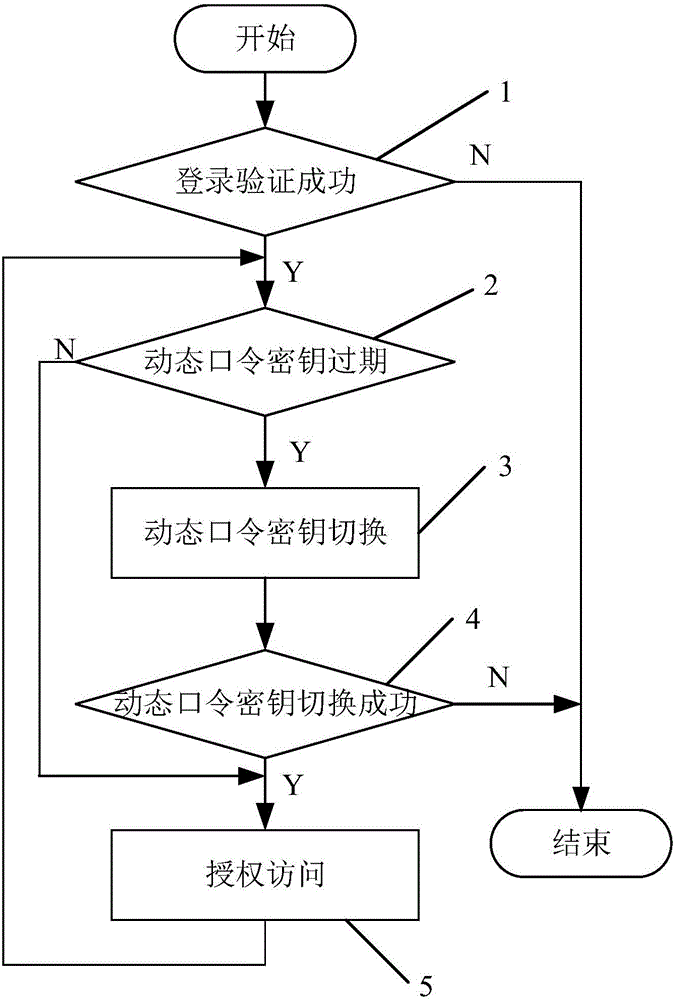
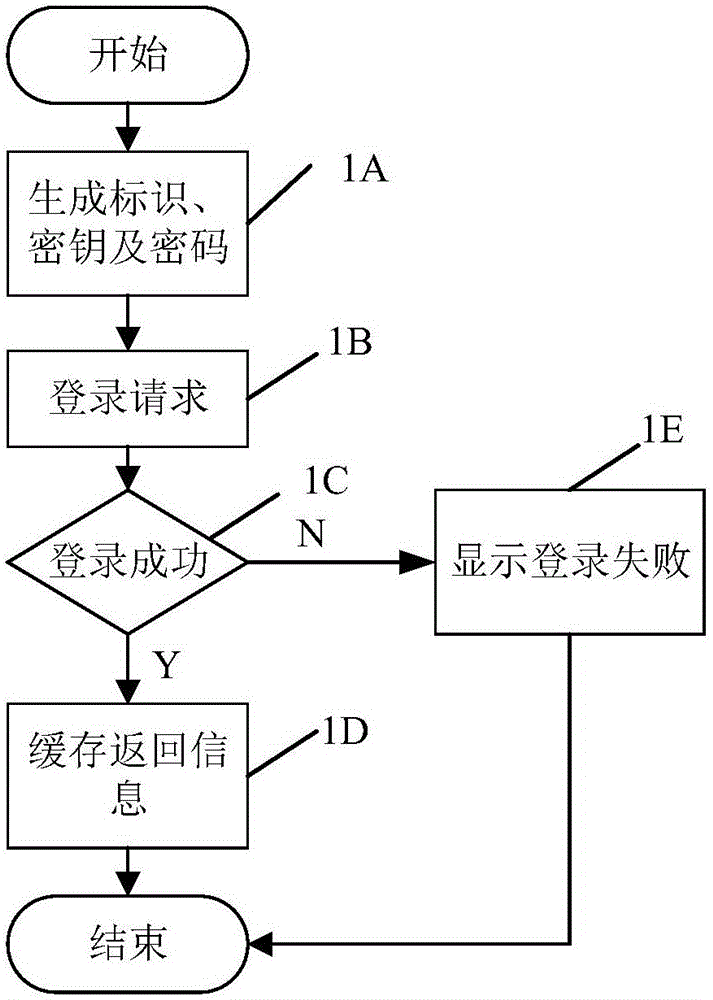
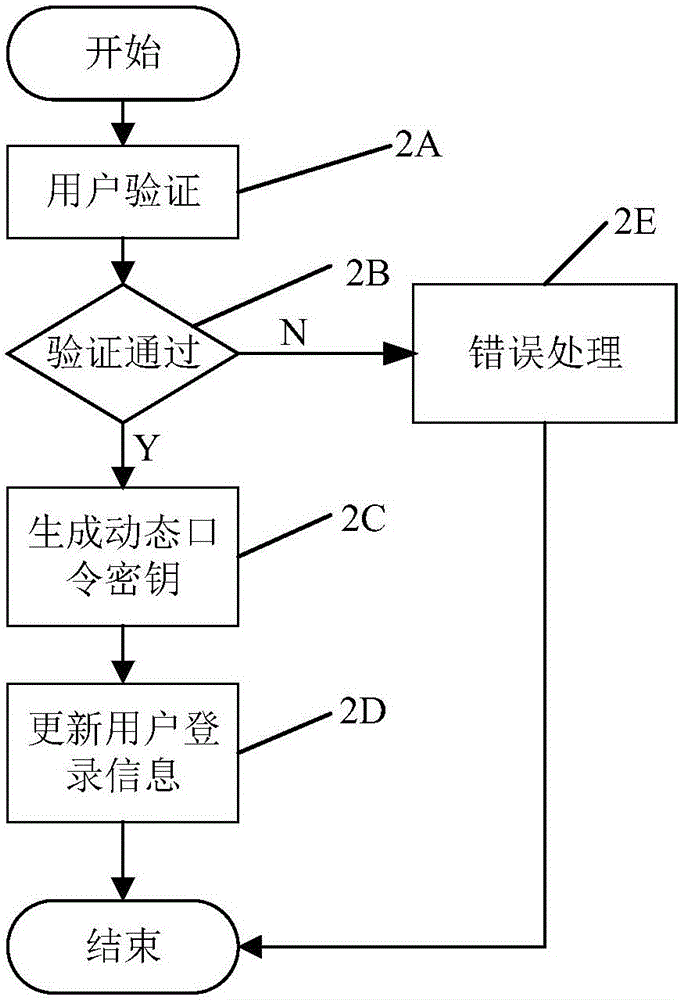
Authorized access method for browser client and server
ActiveCN105721502AAvoid crackingPlay the role of identity verificationTransmissionClient-sideExpiration Time
The invention relates to an authorized access method for a browser client and a server. The method comprises following steps of (1), login verification; generating a dynamic password secret key, server time and dynamic password secret key expiration time by a server if the login verification is successful; storing in client cache; executing a step (2); otherwise, finishing; (2) judging whether the dynamic password secret key expiration time in the client cache arrives or not, if the expiration time arrives, executing a step (3); otherwise, executing a step (4); (3), switching the dynamic password secret key; obtaining new dynamic password secret key, server time and dynamic password secret key expiration time if the dynamic password secret key is switched successfully; correspondingly updating the client cache; executing the step (4); otherwise, finishing; (4), generating a dynamic password through adoption of the dynamic password secret key and the server time in the client cache of a browser; carrying out authorized access to the server; and returning to the step (2). Compared with the prior art, the method has the advantages that the authorized access process is safe and reliable and is not liable to be cracked.
Owner:SHANGHAI SIIC LONGCHUANG SMARTER ENERGY TECH CO LTD
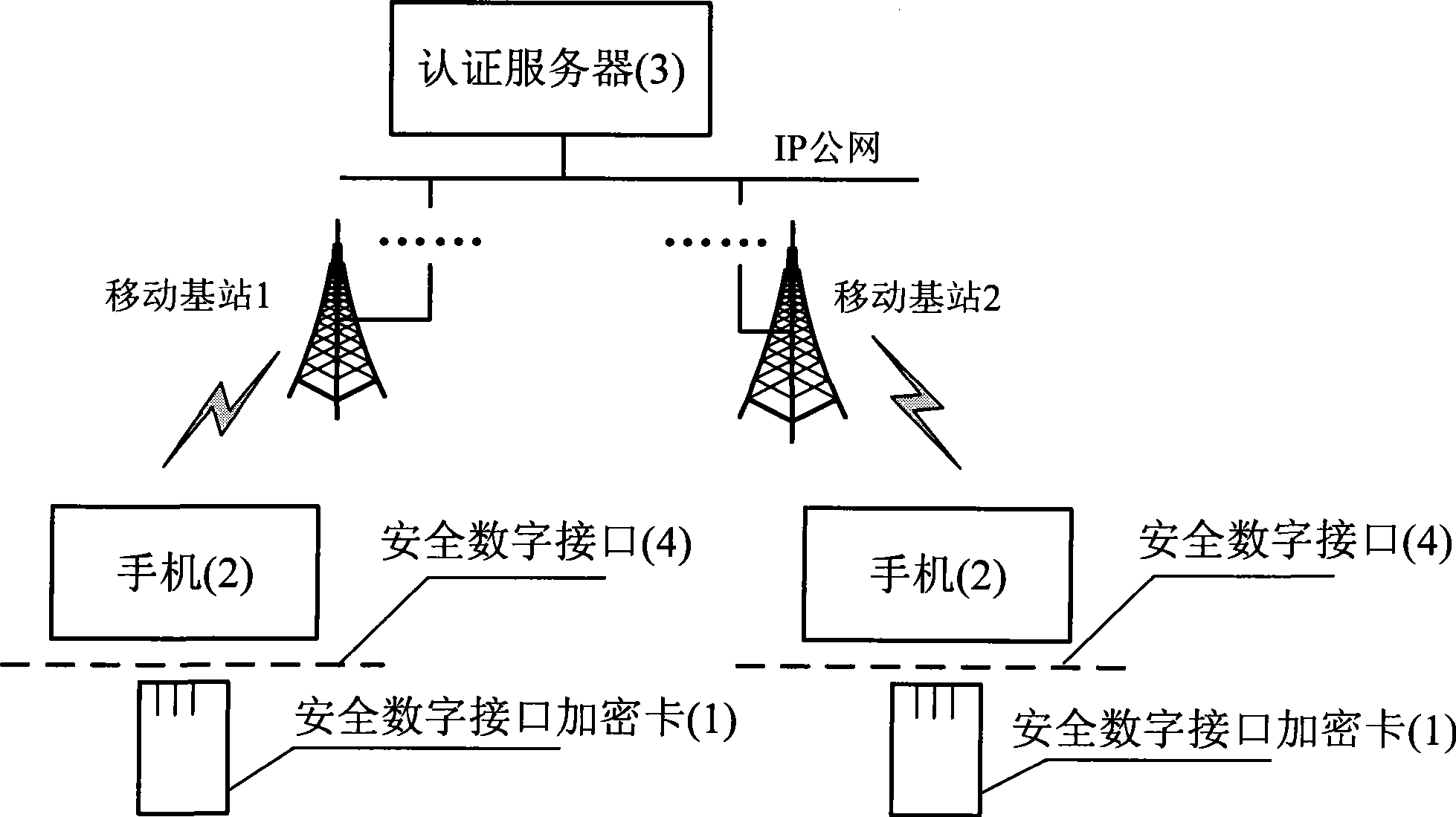
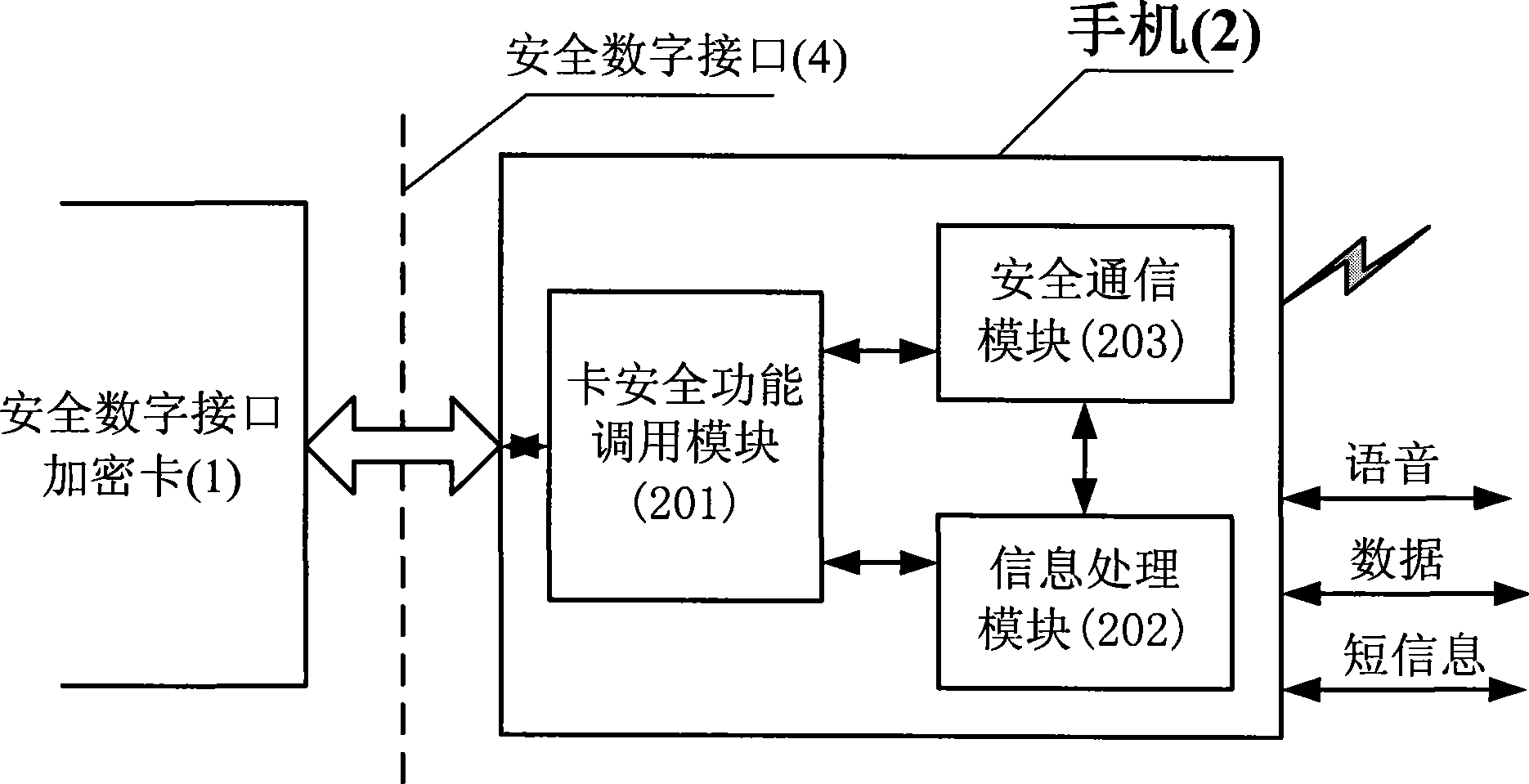
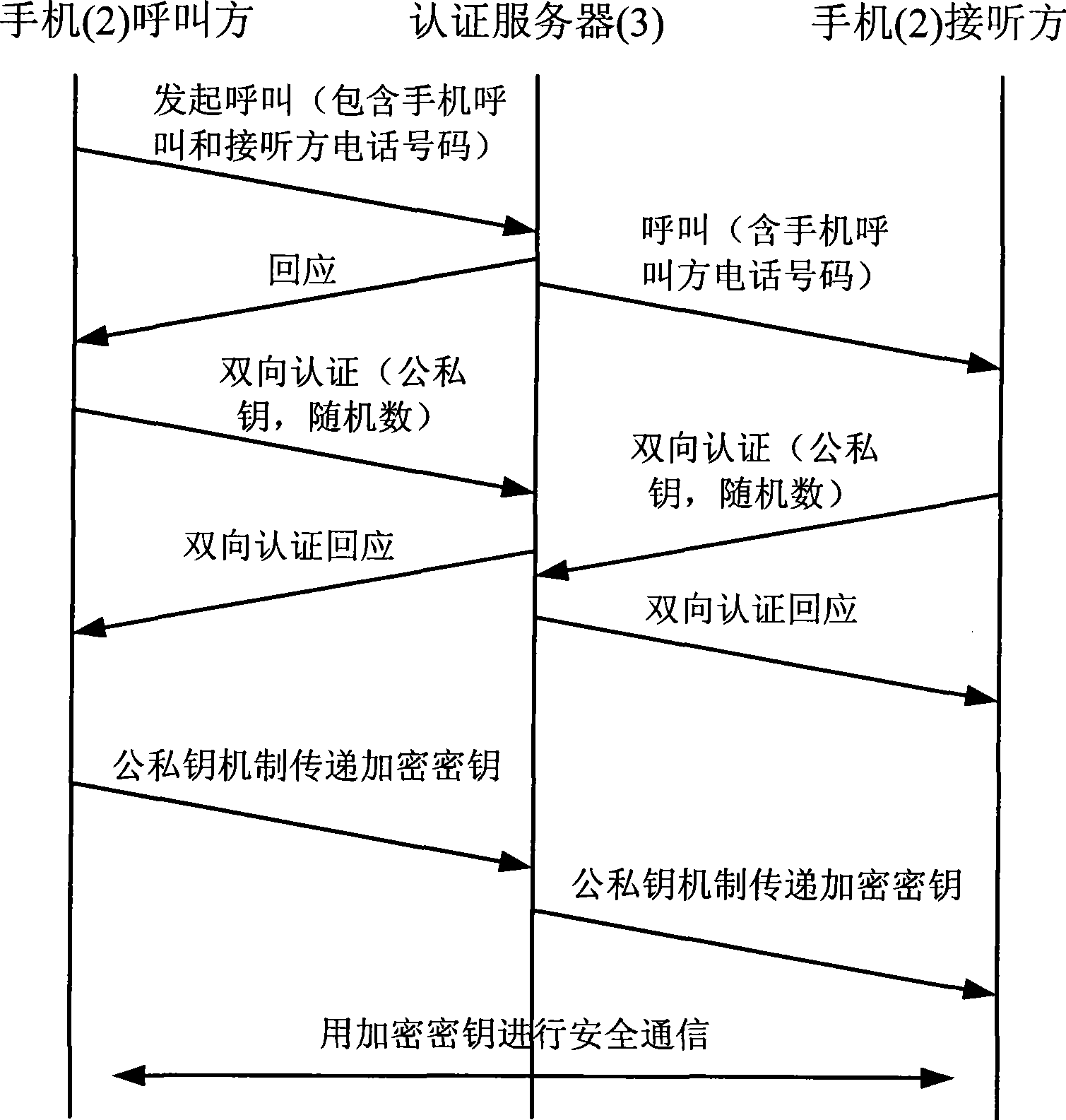
Mobile phone ciphering method based on safe digital interface ciphering card
InactiveCN101384042AAchieve safe distributionHigh encryption strengthRadio/inductive link selection arrangementsTransmissionEnd-to-end encryptionDigital interface
The invention discloses a handset encryption method based on a safety digital interface encryption card, which can realize end-to-end encryption data transmission on the basis of unchanging the prior handset hardware facilities through inserting the safety digital interface encryption card in a handset with a safety digital interface slot. The invention is mainly based on three safety main bodies including the safety digital interface encryption card, the handset (2) and a certificate server (3). The connection and communication of the safety digital interface encryption card and the handset are finished in accordance with the mechanical feature, the electrical character and the communication protocol of a safety digital interface (4). After the encryption process of the safety digital interface encryption card, voice, data and the data of messages on one handset are transmitted to the other handset through a mobile communication network, and the encryption of the data is finished by another safety digital interface encryption card. Before the encryption data is transmitted, the certificate server, a handset calling party and a handset called party which are set up need to finish the mutual certificate and secret negotiation together.
Owner:SOUTHEAST UNIV
A data encryption/decryption method and encryption/decryption apparatus
InactiveCN1633070AConfidentiality is not compromised by unauthorizedSimple thinkingMultiple keys/algorithms usagePlaintextCiphertext
This invention discloses a data ciphering and deciphering method which randomly selects a random cryptographic key to replace positions to clear-text data, then dispatches a user cryptographic key to cipher the random cryptographic keys and the data layer by layer and outputs the cipher-text. Deciphering method: the random cryptographic key is recovered first, then the clear-text data position replaced vector is got and clear-text data are recovered by dispatching suitable user cryptographic key to output the clear-text finally. A device includes a cipher / decipher processor, clear-text cipher-text buffer memory for storing the clear-text cipher-text input data and inputting them to a processor, a memory for staring various data and inputting them to a processor, an output device for outputting the cipher-text.
Owner:徐子杰
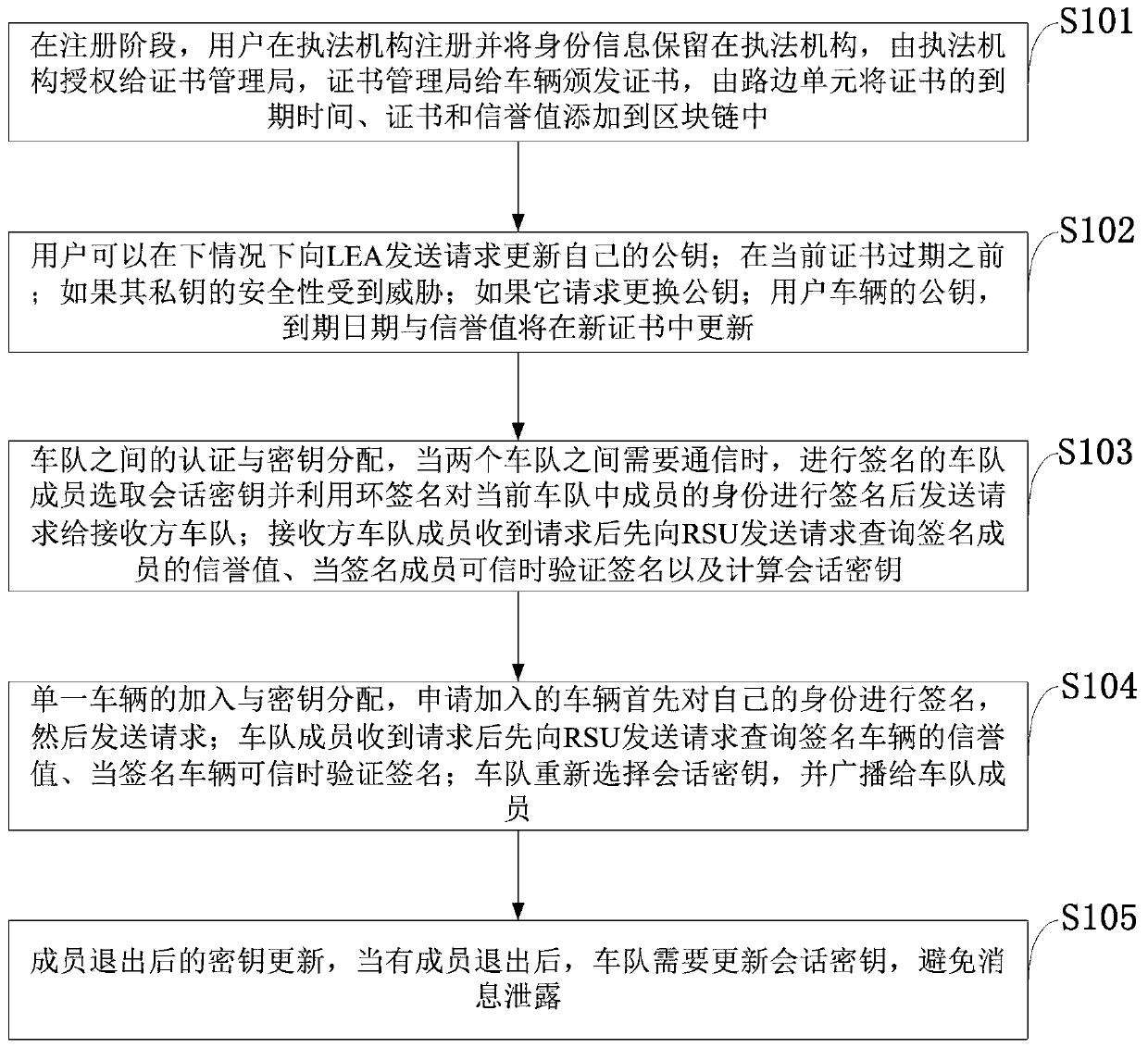
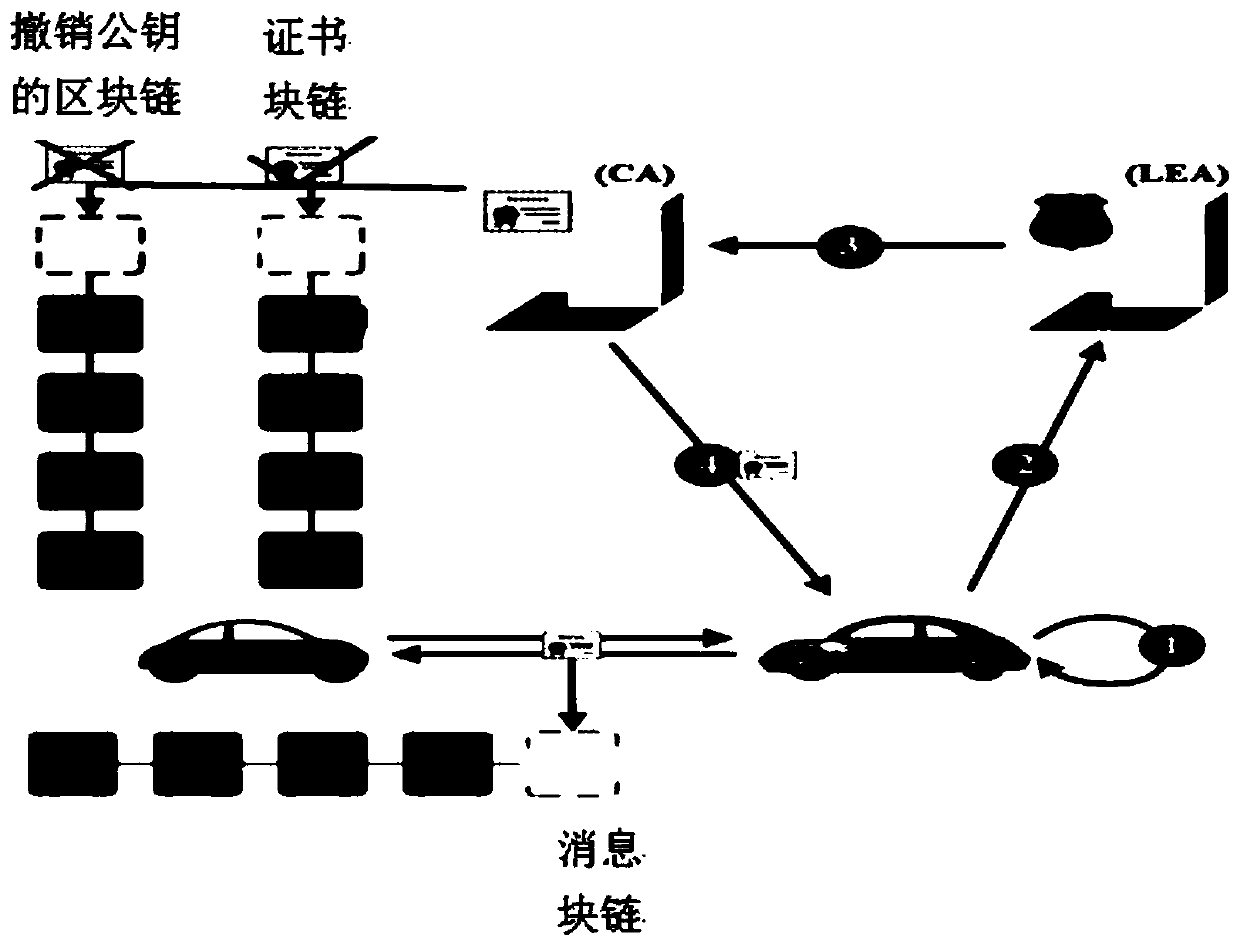
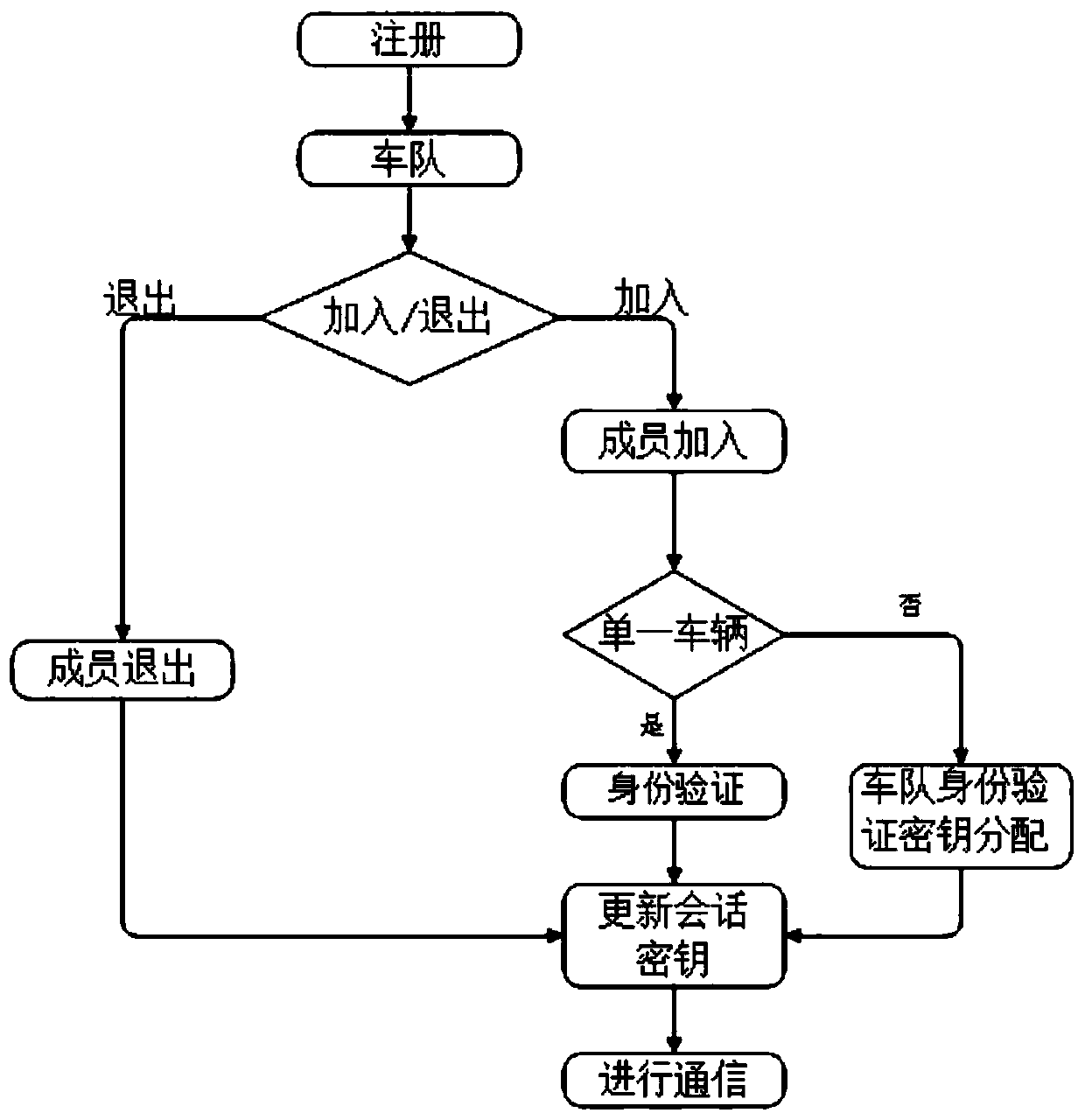
Motorcade safety management system and method based on ring signature and vehicle management platform
ActiveCN109698754AEnsure safetyPrevent leakageKey distribution for secure communicationPublic key for secure communicationSafety management systemsRing signature
The invention belongs to the technical field of Internet of Vehicles, and discloses a motorcade safety management system and method based on ring signatures, and a vehicle management platform. identity-based ring signatures are performed on the identities of motorcade members on the basis of an elliptic curve. Hiding and public key updating are conducted on identities of motorcade members throughthe elliptic curve, the block chain and the ring signatures, the identities of the message senders are authenticated, and session keys are updated; the block chain is utilized to publish a public keycertificate and a reputation value of the vehicle; The vehicle inquires the public key, the public key validity and the current reputation value of the surrounding vehicles through the roadside unit,so that the addition of malicious vehicles is avoided; Updating of the public key can prevent information from being intercepted and tampered by malicious vehicles when the private key of the user issubjected to security threats. The privacy of registered users and the privacy of motorcade members are effectively prevented from being leaked, and the communication safety of the members in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
Random ciphering method which needs to be deciphered by exhaust algorithm
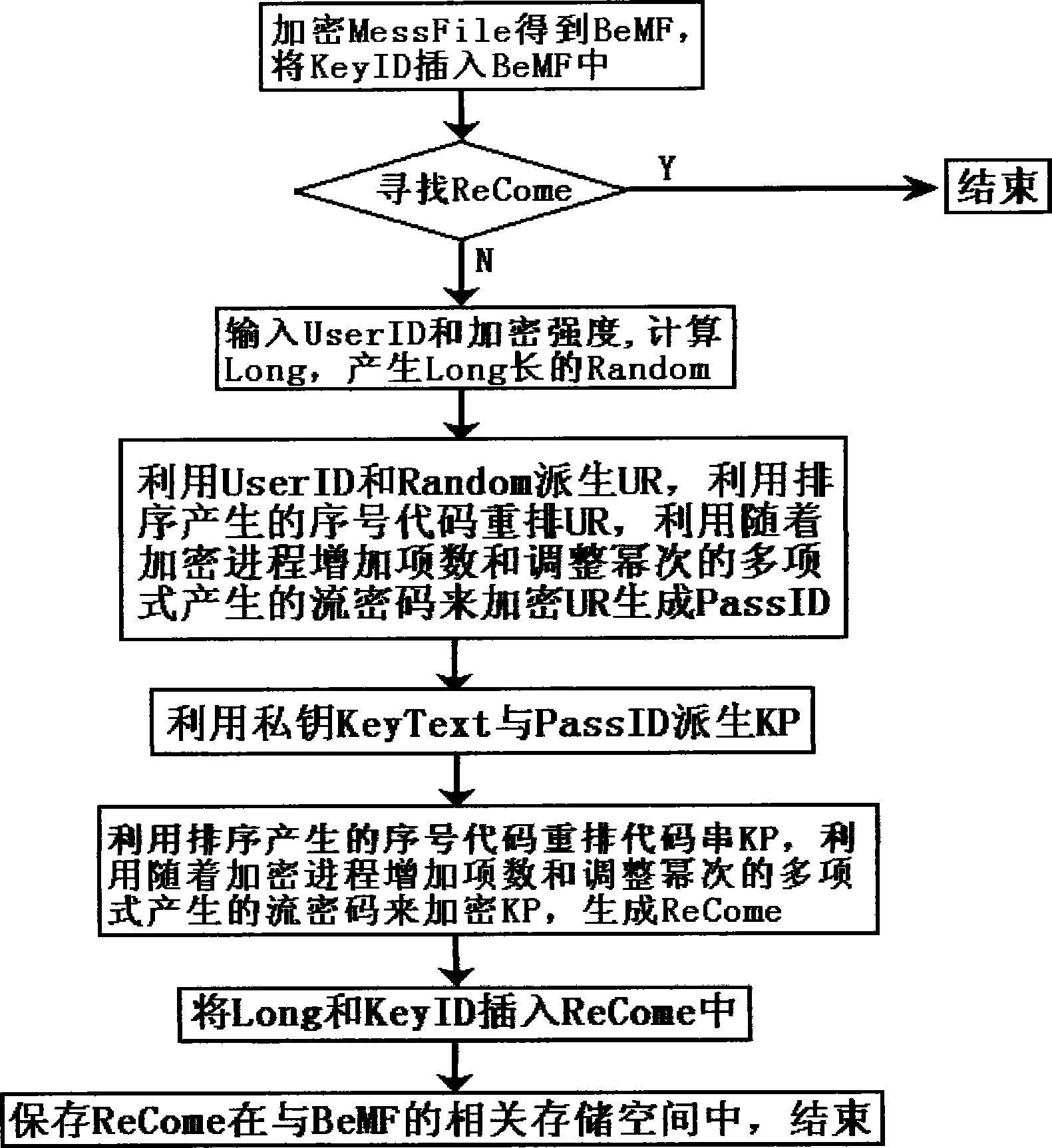
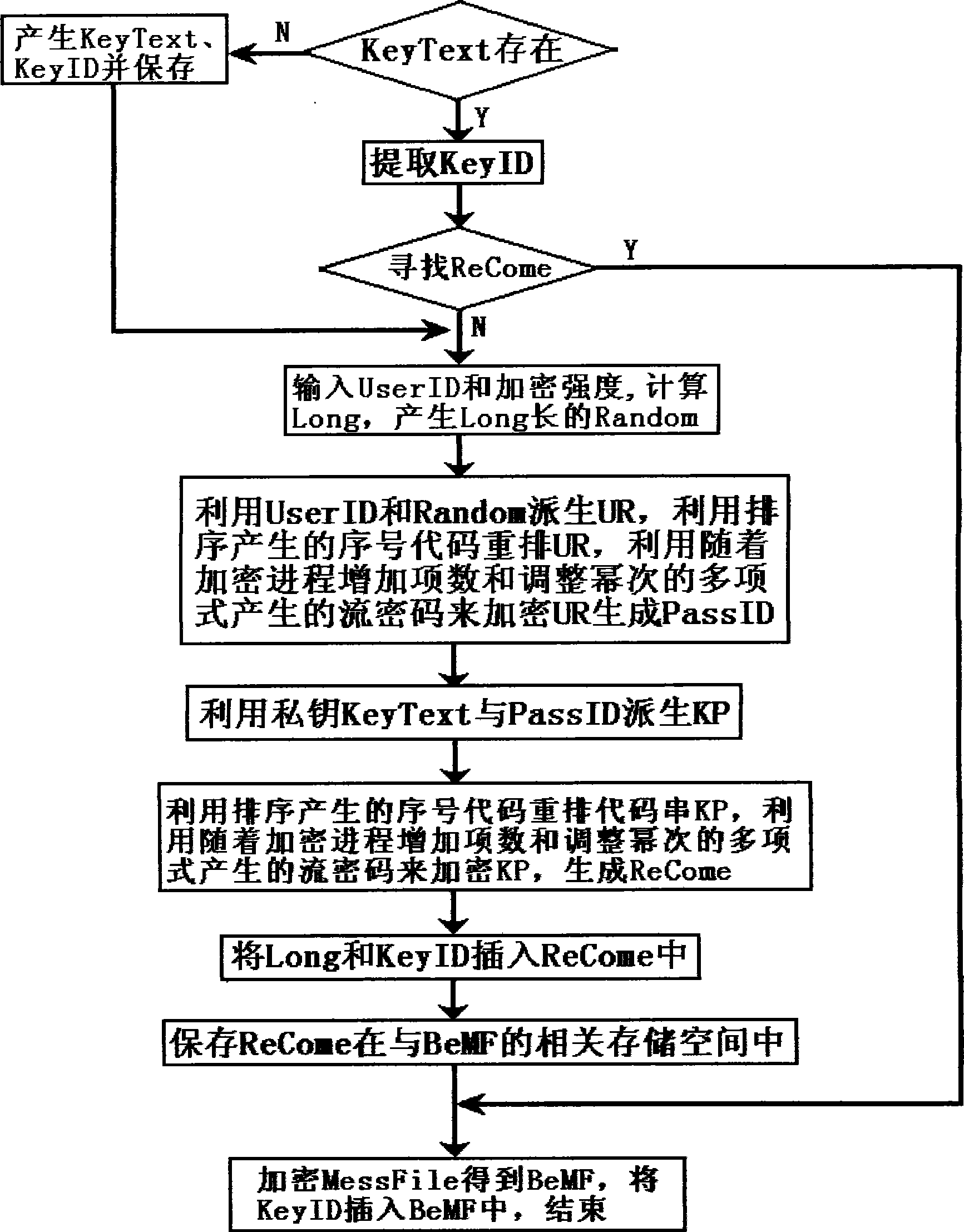
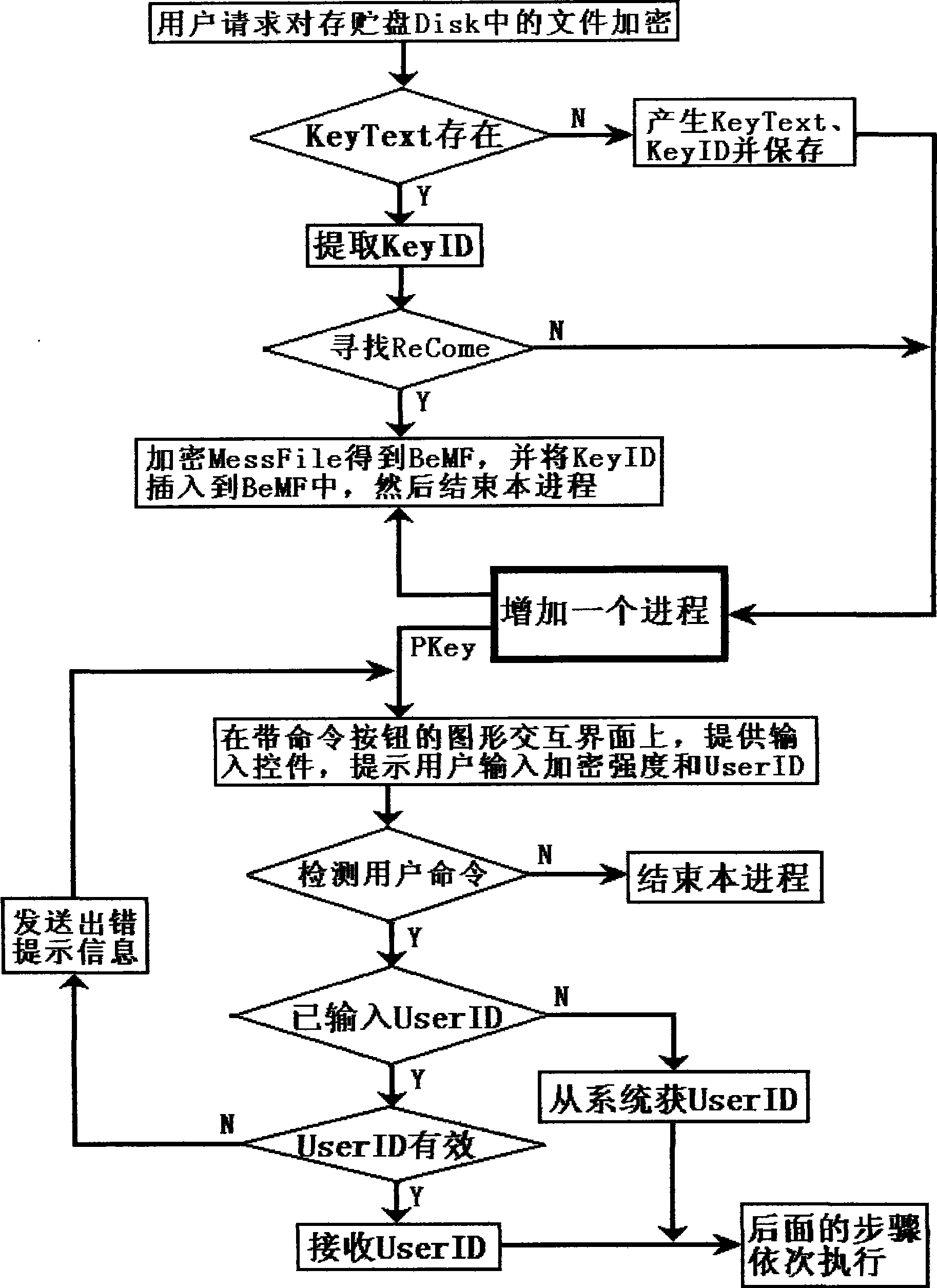
InactiveCN101488858AEnsure safetyHigh encryption strengthUser identity/authority verificationInformation needsReliability engineering
The invention provides an accidental ciphering method by using an exhaustion method to decipher, the method is designed based on increasing the ciphering strength for the user identification information and the accidental cipher key, the method is mainly used for ciphering a backup private key, a certificate and important files. The ciphering process flow comprises: inputting the user identification information and the ciphering strength; calculating the length of the accidental cipher key according to the relationships among the length of the accidental cipher key, the ciphering strength and the preset deciphering program speed and generating the accidental cipher key of the length; ciphering the private key and the certificate to obtain the backups of the ciphered private key and the ciphered certificate by using the user identification information and the accidental cipher key according to the ciphering algorithm determined by the program, and locking the user identification information and the accidental cipher key in the cipher recognition information by the ciphering algorithm determined by the program. The backup generated by the ciphering method, however, the writing of the deciphering program, even inputting the correct user identification information, the exhaustion method is also used for deciphering, and not only the user identification information needs to be compared, but also the accidental cipher keys need to be compared.
Owner:刘海云
Encryption method, cryptogram decoding method, encryptor, cryptogram decoder, and communication system
ActiveUS20070183593A1High encryption strengthMinimize impactSecret communicationSecuring communicationCommunications systemCryptogram
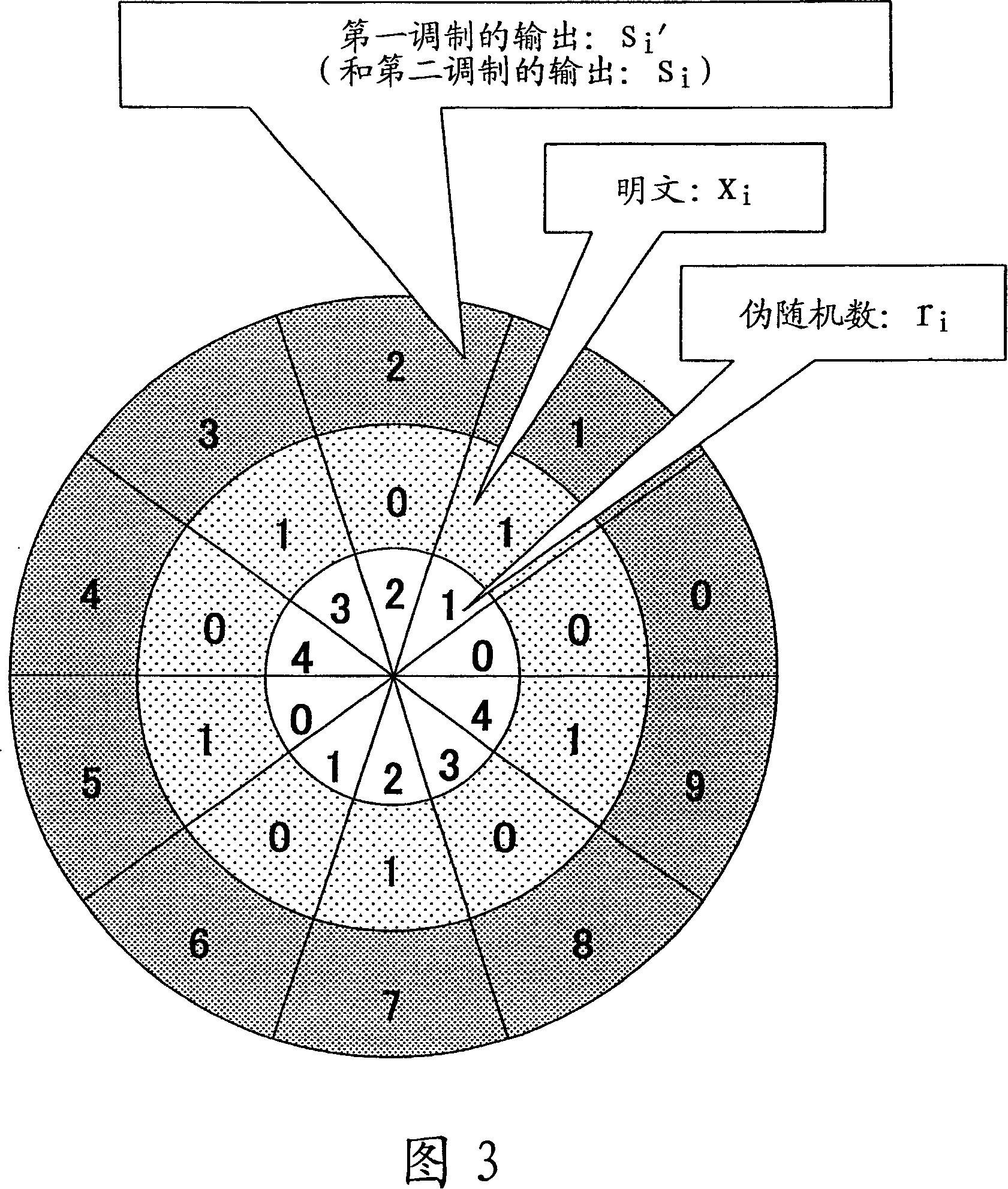
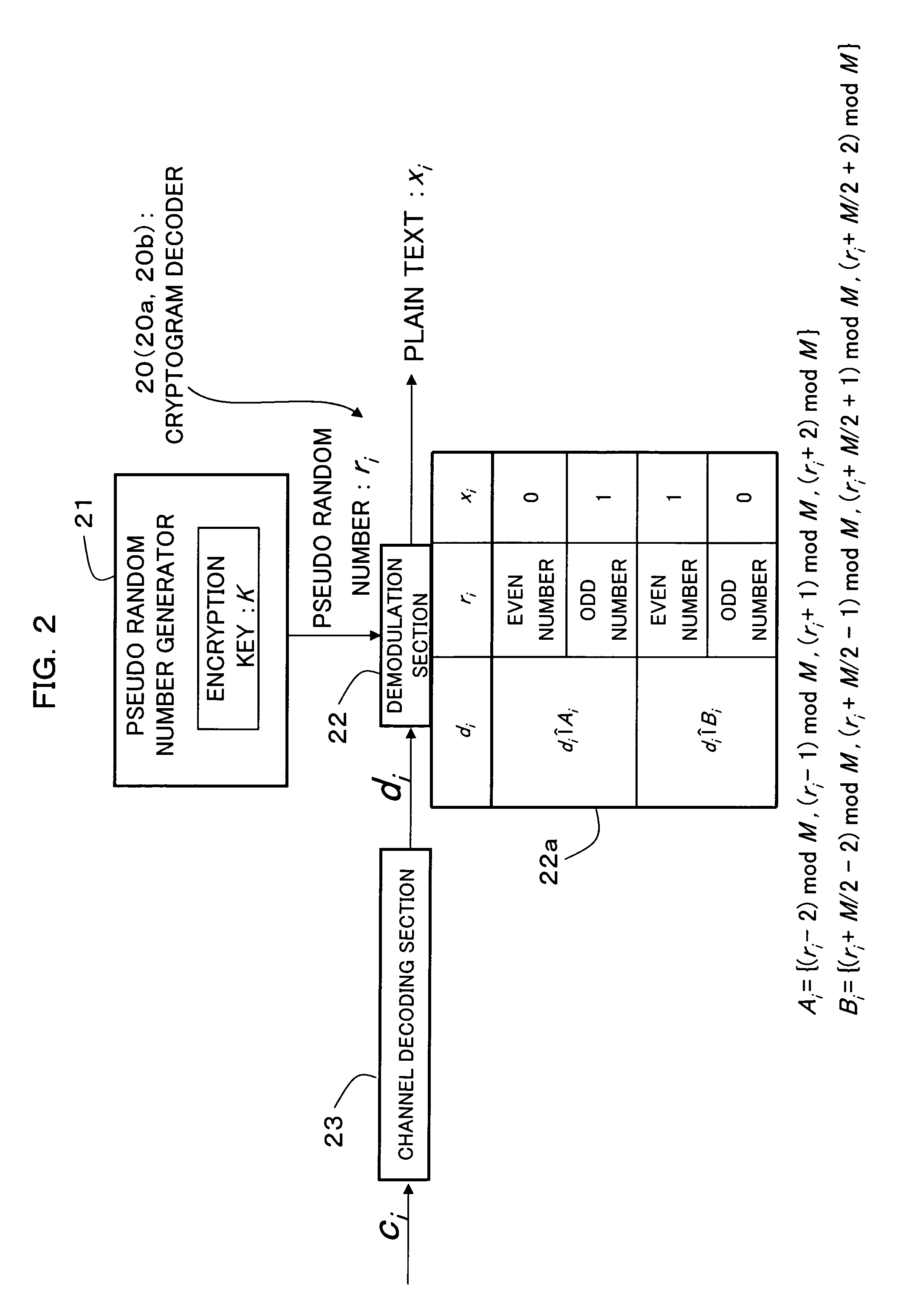
An encryption technique having a greater encryption strength than conventional mathematical encryption by using classic physical random numbers etc., including a step for modulating one-bit input data into a coded signal by associating it with a discrete value of at least two bits determined by pseudo random numbers and physical random numbers and a step for channel-coding and outputting the coded signal, wherein 1) the coded signal can be demodulated into the input data by the pseudo random number, 2) the number of sets of input data, pseudo random number, and physical random number corresponding to a particular discrete value is equal for two values of the input data, and 3) the number of sets of pseudo random number and physical random number corresponding to respective values of the input data and respective values of the discrete value is equally associated also with any set of them.
Owner:FUJITSU LTD +1
Encryption method, cryptogram decoding method, encryptor, cryptogram decoder, transmission/reception system, and communication system
ActiveCN1937008AHigh encryption strengthThe impact of communication speed is minimizedCoding/ciphering apparatusComputer hardwareCommunications system
Encryption method, cryptogram decoding method, encryptor, cryptogram decoder, transmission / reception system, and communication system are provided in the invention. The encryption technique includes a first modulation step for multilevel-modulating input data by associating with specific state pairs determined by physical random numbers, a second modulation step for outputting the output of the first step by irregularly associating with another signal by physical random numbers, and a channel coding step for channel-coding the output of the second step into desired codeword and outputting it as encrypted data, wherein the decoded signal obtained by channel-decoding the encrypted data can be discriminated which of specific state pairs the signal corresponds to and demodulated into the input data, and output by the first modulation by state pairs other than the specific state pairs and the second modulation by a physical random number different from the physical random number.
Owner:FUJITSU LTD +1
Data encryption method
ActiveCN104022872AEncrypted fitTransmission fitPublic key for secure communicationPlaintextCiphertext
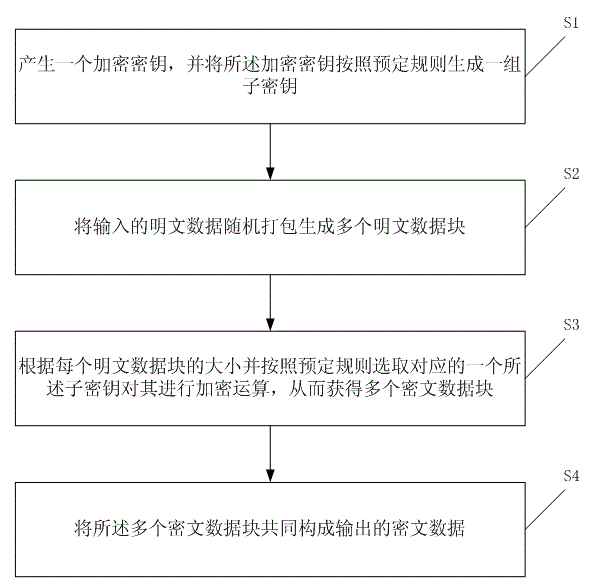
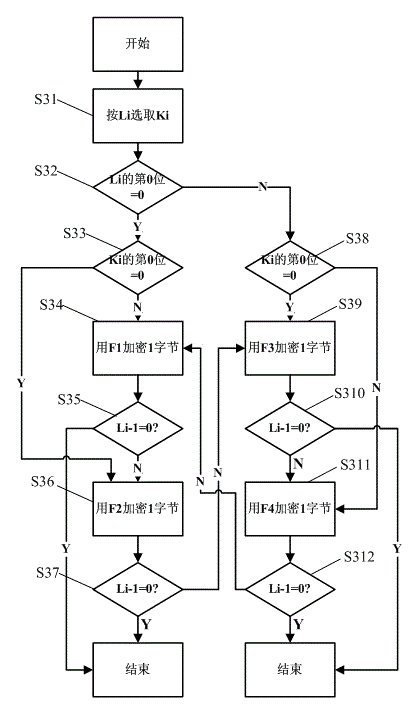
The invention discloses a data encryption method which comprises the following steps of generating an encryption key, and generating a group of sub-keys by the encryption key according to a predetermined rule; B. packing input plain text data randomly to generate a plurality of plain text data blocks; C. selecting a corresponding sub-key and carrying out encryption operation on the sub-key according to size of each plain text data block and the predetermined rule to obtain a plurality of encrypted data blocks; and D. forming output encrypted data by the plurality of the encrypted data blocks. The data encryption method disclosed by the invention has the advantages of being high in encryption strength, quick in operation speed, low in operation system expense, capable of being expanded and optimized, and the like, and is suitable for storage and transmission encryption of mobile equipment.
Owner:GUANGZHOU SIE CONSULTING CO LTD
Encryption method, cryptogram decoding method, encryptor, cryptogram decoder, transmission/reception system, and communication system
ActiveUS7822204B2High encryption strengthSynchronising transmission/receiving encryption devicesError preventionComputer hardwareCommunications system
An encryption technique allowing use of classic Y-00 scheme performed using classic physical random numbers instead of quantum fluctuation in electrical communication and data storage in recording media, including a first modulation step for multilevel-modulating input data by associating with specific state pairs determined by physical random numbers, a second modulation step for outputting the output of the first step by irregularly associating with another signal by physical random numbers, and a channel coding step for channel-coding the output of the second step into desired codeword and outputting it as encrypted data, wherein the decoded signal obtained by channel-decoding the encrypted data can be discriminated which of specific state pairs the signal corresponds to and demodulated into the input data, and output by the first modulation by state pairs other than the specific state pairs and the second modulation by a physical random number different from the physical random number.
Owner:FUJITSU LTD +1
Encryption method, cryptogram decoding method, encryptor, cryptogram decoder, and communication system
ActiveUS7471790B2High encryption strengthSecret communicationSecuring communicationCommunications systemCryptogram
An encryption technique having a greater encryption strength than conventional mathematical encryption by using classic physical random numbers etc., including a step for modulating one-bit input data into a coded signal by associating it with a discrete value of at least two bits determined by pseudo random numbers and physical random numbers and a step for channel-coding and outputting the coded signal, wherein 1) the coded signal can be demodulated into the input data by the pseudo random number, 2) the number of sets of input data, pseudo random number, and physical random number corresponding to a particular discrete value is equal for two values of the input data, and 3) the number of sets of pseudo random number and physical random number corresponding to respective values of the input data and respective values of the discrete value is equally associated also with any set of them.
Owner:FUJITSU LTD +1
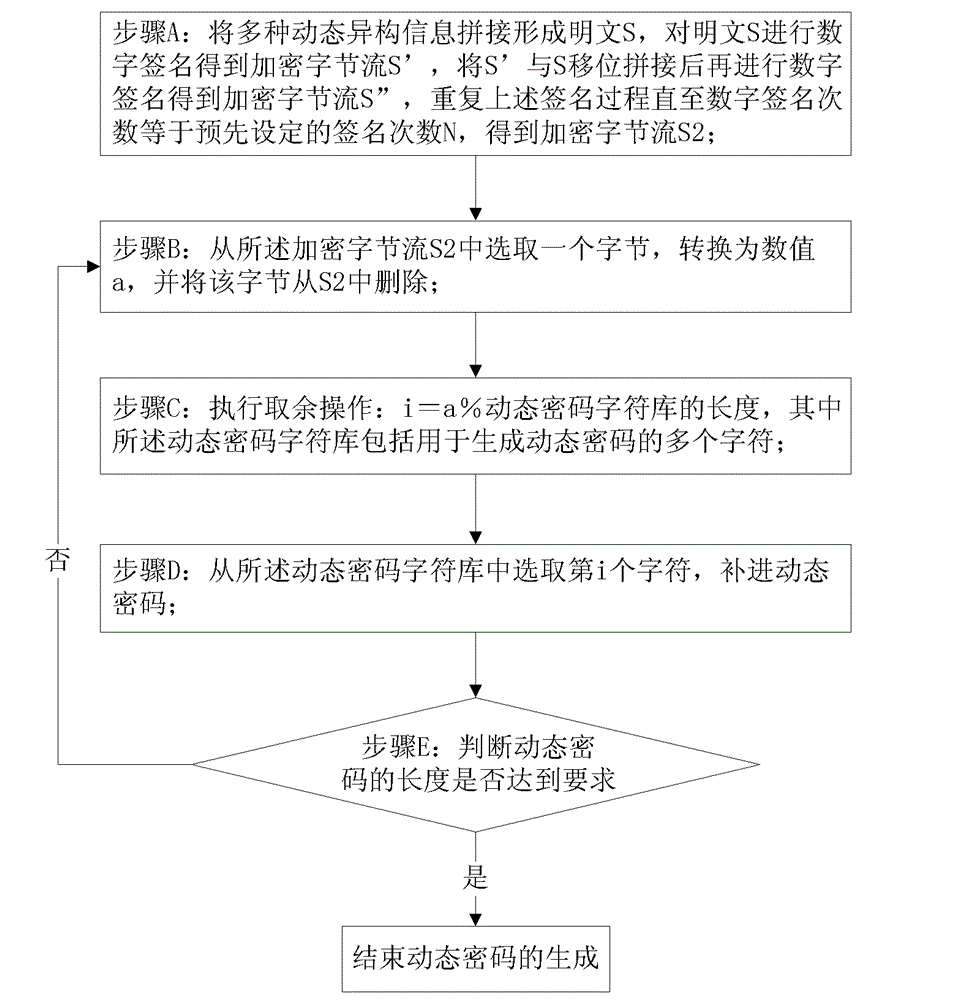
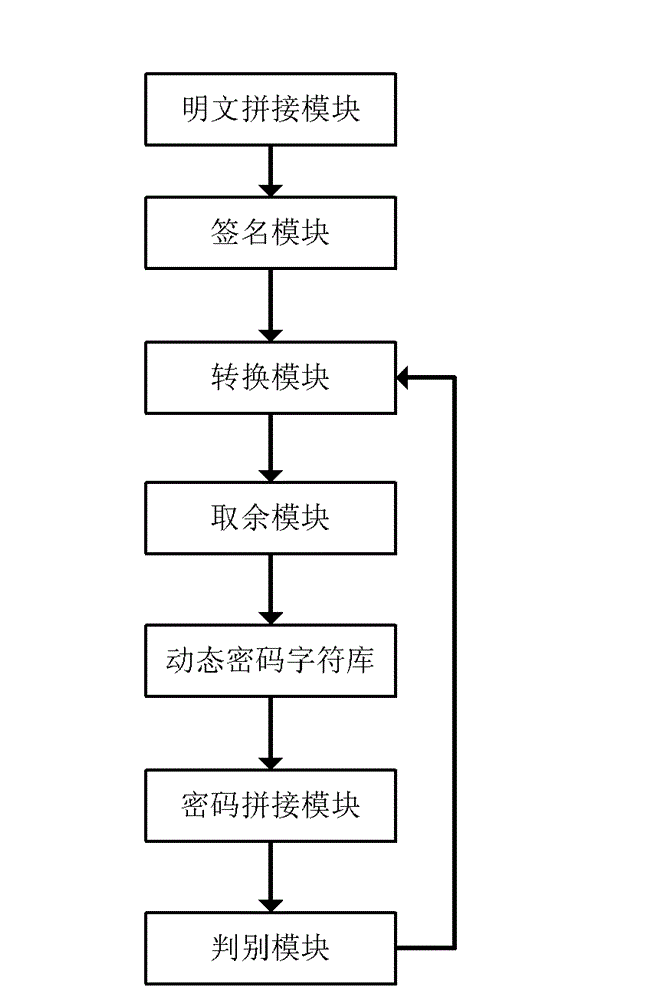
Dynamic password generating method and system
ActiveCN102752110AReduce repetition rateImprove securityUser identity/authority verificationPasswordDigital Signature Algorithm
The invention discloses a dynamic password generating method and system. The method comprises the steps that various dynamic heterogeneous messages are spliced to form a clear text S, and the clear text S is digitally signed for N times to obtain an encrypted byte stream S2; one byte is selected from the S2 and is converted into a numerical value a; remainder operation is executed: i=a%*length of dynamic password character library; the ith character is selected from the dynamic password character library, and the position of a dynamic password is covered; and the dynamic password generating process is repeated until the length of the dynamic password meets the requirement. The system comprises a clear text splicing module, a signing module, a converting module, a dynamic password character library, a remainder module, a password splicing module and a distinguishing module. The dynamic password generating method provided by the invention integrates the advantages of a random number algorithm and a digital signature algorithm, so that the dynamic passwords obtained in the same transaction by the same operator in different time are definitely different; and the dynamic password is generated only in use, the recurrence rate is very low, and the security is higher.
Owner:BANK OF CHINA
Method for directly and arbitrary separating code to encryption lock from software to implement protection of software protection
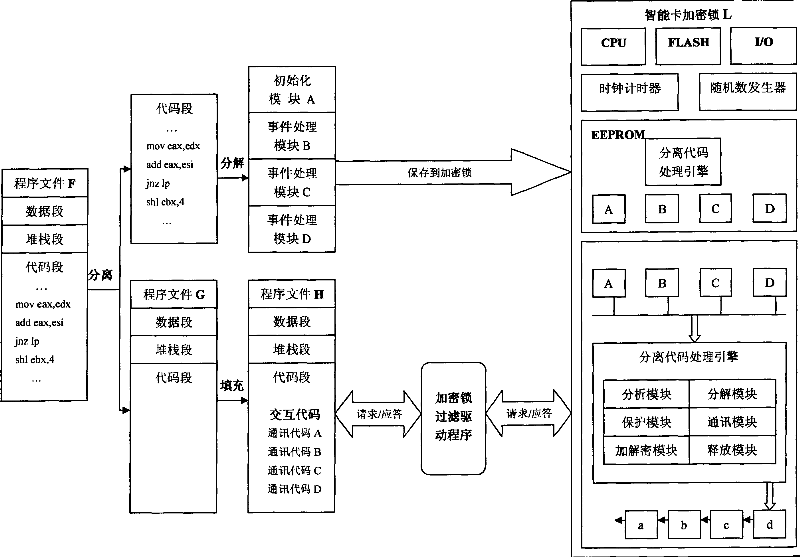
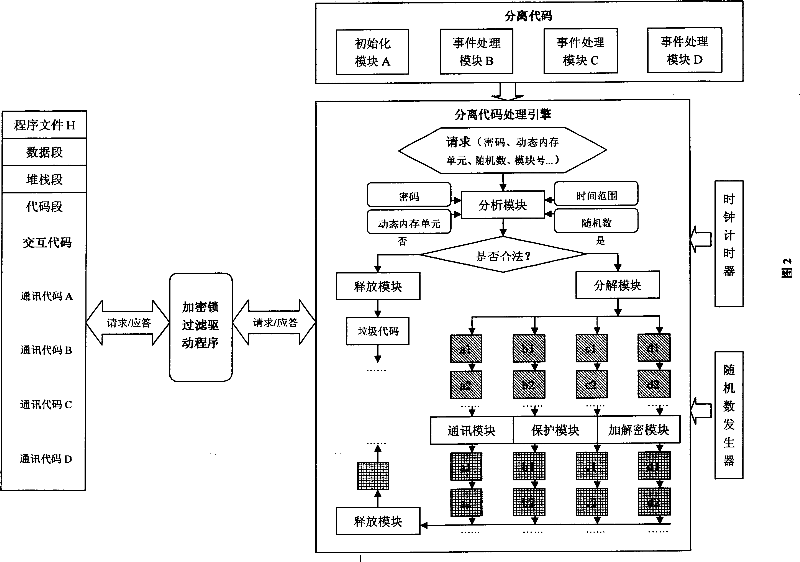
InactiveCN101038615AHigh encryption strengthImprove anti-cracking performanceProgram/content distribution protectionTime rangeCommunication link
The invention provides a method for separating code to an encryption lock from an executable file directly comprising separating code to an encryption lock from an executable file directly, setting a clock timer and a random number generator in the intelligent card encryption lock, filling an interactive code for communication with the encryption lock in the vacancy of the executable file after the code is separated, the encryption lock dynamically decomposing, encrypting and protecting the code that is separated into the lock and needed to be executed continuously by using a specific protocol and algorithm, wherein a plurality of blocks are generated and the release of the block is determined by the normal executed time of the previous block, if the request for demanding the next block sent from the interactive code arrives in the encryption lock in the normal time period, an effective information will be released from the encryption lock, if not, an ineffective information is released. Moreover, a layer of encryption lock filter drive program is added to the encryption lock and the interactive code. Thereby, the illegal monitor and interception of the communication data in the communication link and system are prevented.
Owner:吴晓栋
Ciphering method for generating cipher code recognition information
InactiveCN101488848AEnsure safetyHigh encryption strengthKey distribution for secure communicationUser identity/authority verificationAlgorithmTheoretical computer science
The invention provide a ciphering method for generating cipher recognition information, the ciphering method is designed based on increasing the user identification information and ciphering strength of the random cipher key, the ciphering method is mainly used for adjusting the ciphering strength of the cipher recognition information composed of the user identification information and the random cipher key after being ciphered. The ciphering process flow comprises: inputting the user identification information and the ciphering strength; calculating the length of the random cipher key and generating the random cipher key of the length, according to the relationships among the length of the random cipher key, the ciphering strength and the prescribed deciphering program speed; obtaining the cipher recognition information composed of the user identification information and the random cipher key after being ciphered according to the ciphering algorithm user identification information and the random cipher key determined by the program by utilizing the user identification information and the random cipher key. According to the backup generated by the ciphering method, anyhow the deciphering program is written, even the user identification information is inputted correctly, the deciphering is performed by using the exhaustion method, not only the identification information are compared, but also the random cipher keys are also compared.
Owner:刘海云
Automobile key system with configurable safety strategy and realizing method thereof
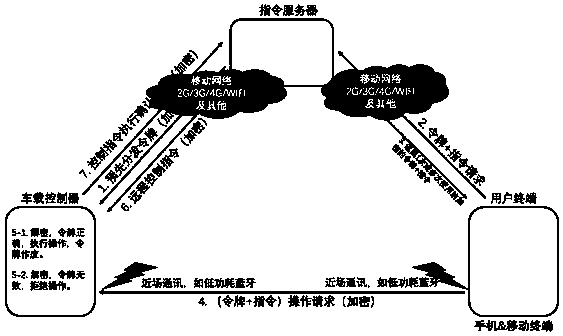
ActiveCN108696476AAuthorization is easy to useHigh encryption strengthKey distribution for secure communicationIndividual entry/exit registersComputer terminalSecurity policy
The invention discloses a realizing method of an automobile key system with a configurable safety strategy. The realizing method comprises the following steps that a vehicle-mounted controller sends aconnecting request to an instruction server through a preset encryption key; the instruction server verifies the identity of the vehicle-mounted controller and sends an effective encryption key to replace the preset encryption key; the instruction server communicates with the vehicle-mounted controller through the effective encryption key; the safety strategy is configured to trigger updating andreplacing of the effective encryption key; and a user terminal obtains authorization through the instruction server and builds connection with the vehicle-mounted controller through near field communication. The identity of the vehicle-mounted controller is authenticated by multiple factors, a dynamic secret key algorithm is adopted, a secret key is replaced regularly, and the encryption strengthis high; the instruction server is used for distributing encrypted control instructions, and through the near field communication technology, a mobile phone and other types of digital mobile terminals can be a carrier of an automobile key, a solid physical automobile key does not need to be carried along for driving an automobile, and automobile authorization and use are more convenient.
Owner:上海航迹数据信息科技有限公司
Parallel encryption method and decryption method supporting big data
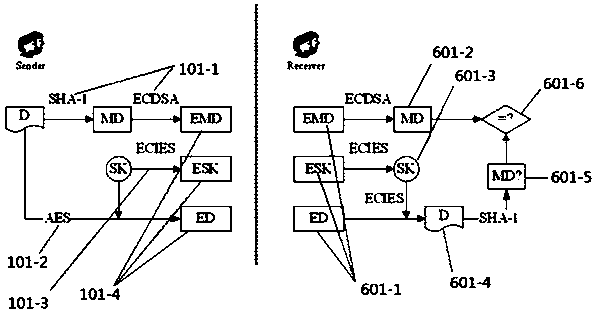
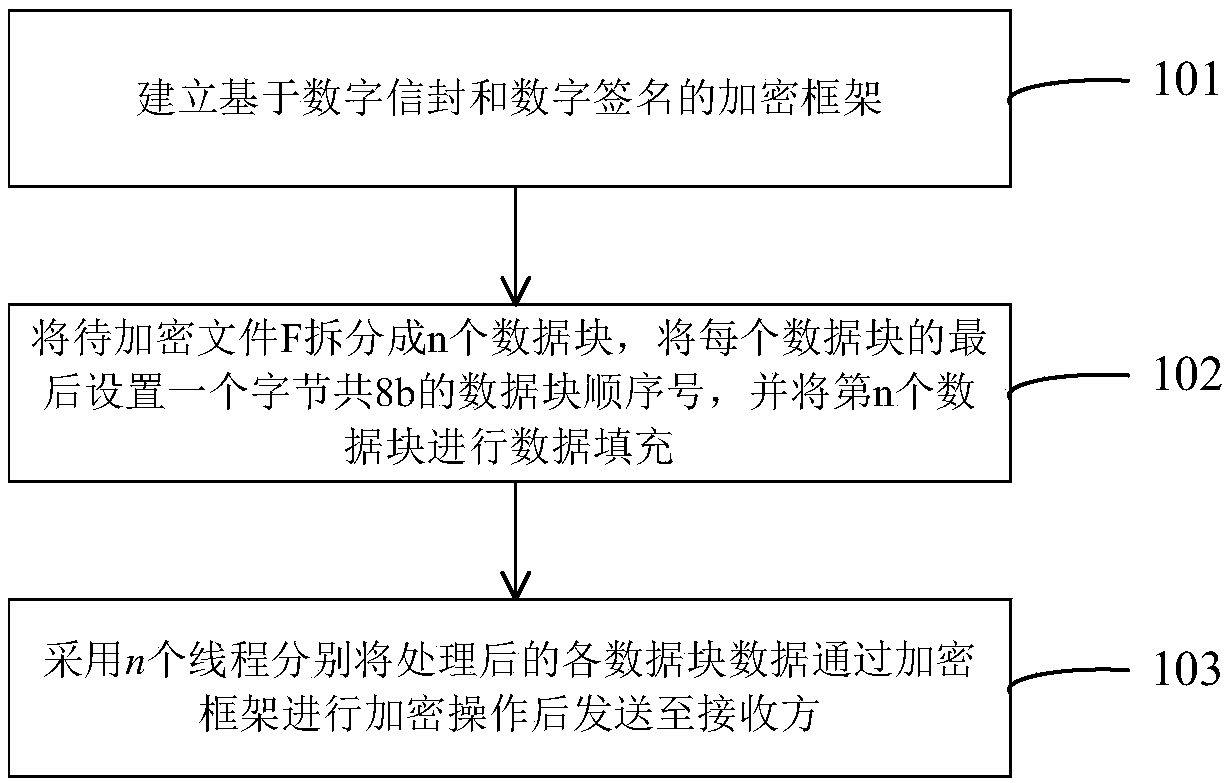
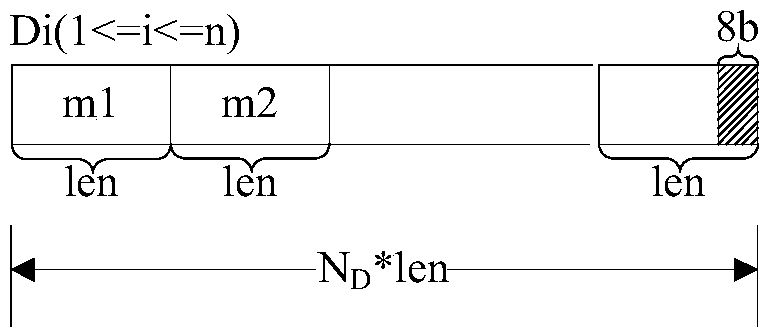
InactiveCN108833343AHigh encryption strengthAdapt to application requirementsEncryption apparatus with shift registers/memoriesUser identity/authority verificationConfidentialityDigital signature
The invention provides a parallel encryption method and decryption method supporting big data. The invention integrates symmetric key encryption and public key encryption organically, and constructs aparallel encryption framework by using digital envelope technology and digital signature technology, so that the confidentiality, the integrity and the non-repudiation of data are guaranteed. Aimingat big data, especially large files, a multithreaded parallel processing method is adopted, which splits a document to be encrypted into several data blocks and encrypts the data blocks separately. Areceiving party does not have to wait for the completion of transmission of the entire document before decryption, verification or even request for retransmission, and only needs to verify whether thereceived data blocks are correct, so that the efficiency of the entire transmission process is improved. On the other hand, blockwise transmission of the documents also ensures the security to a certain extent. Therefore, application requirements of safe data transmission under the background of big data can be met.
Owner:南京搜文信息技术有限公司
Enciphered mobile storage apparatus and its data access method
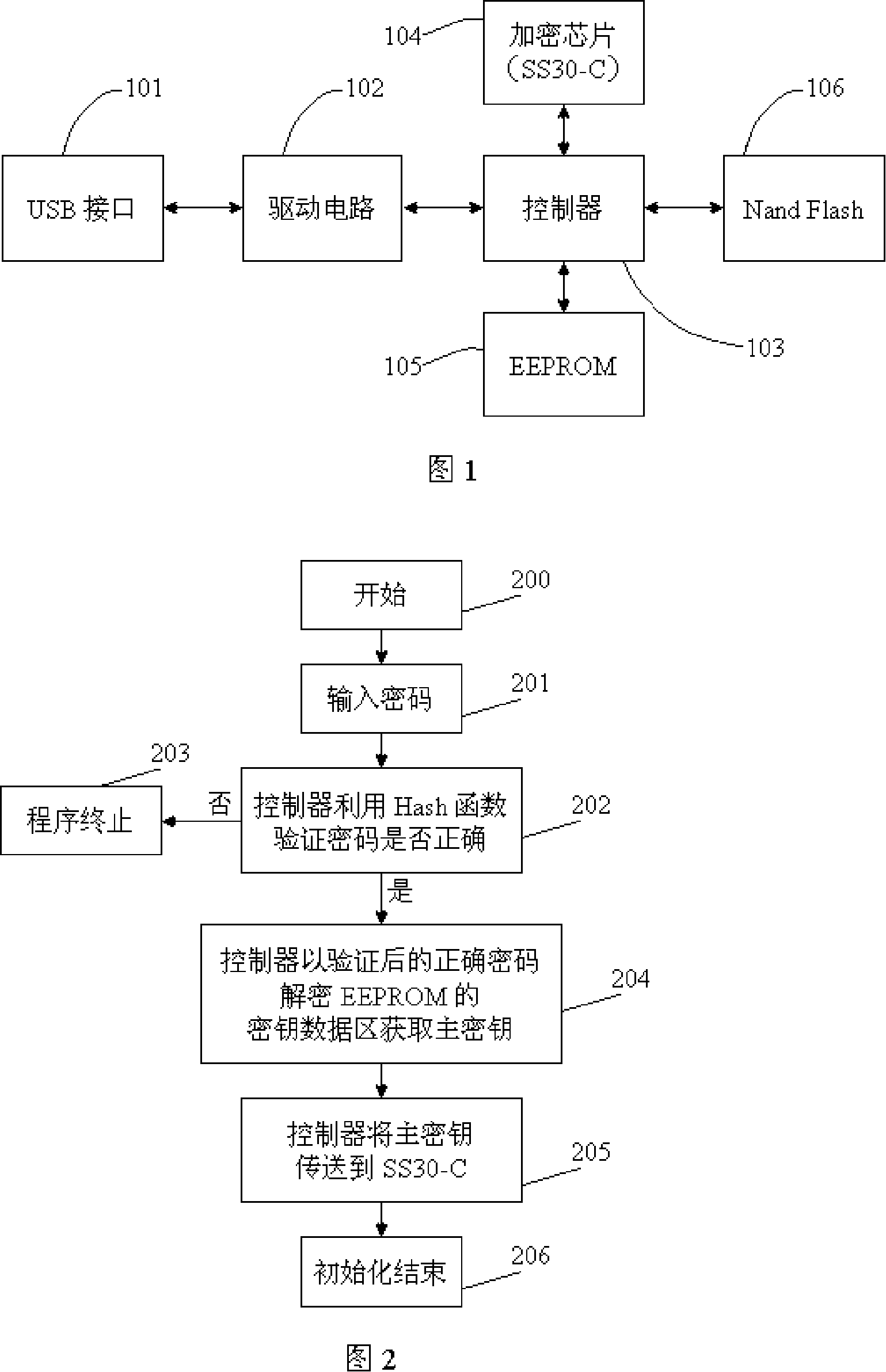
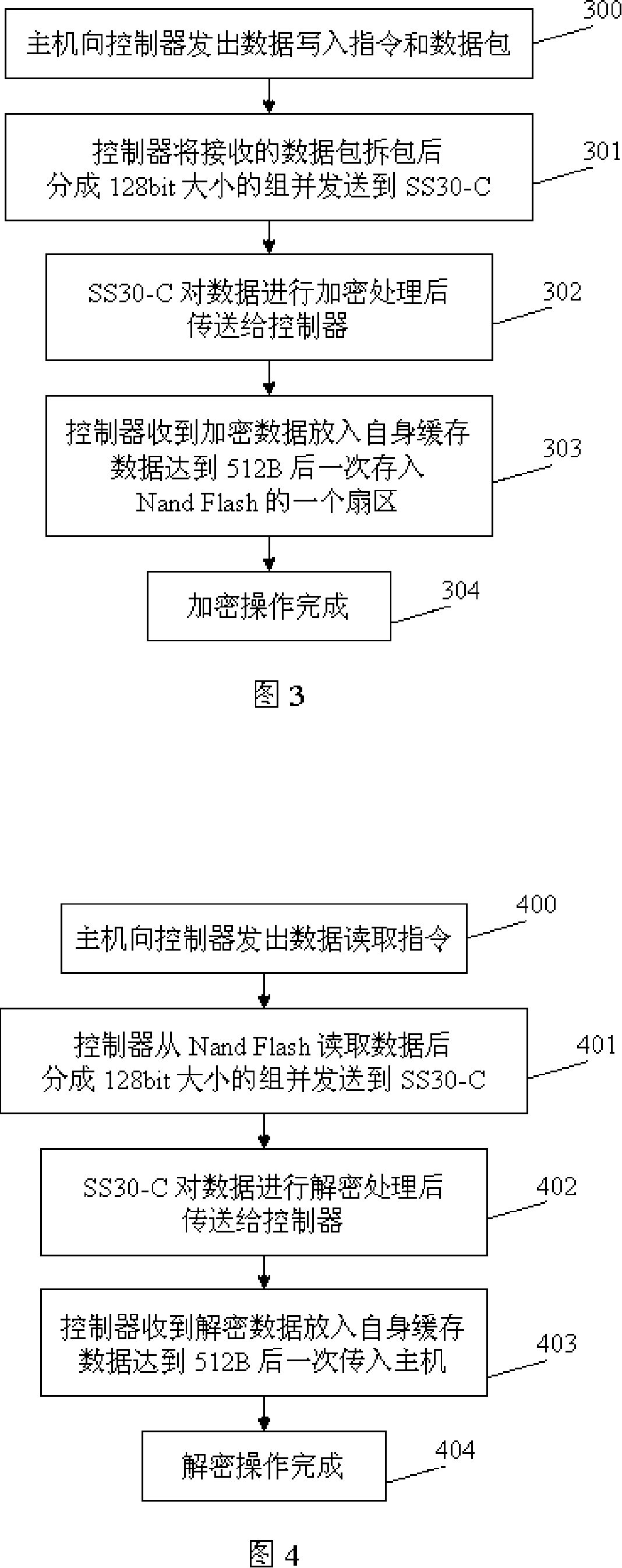
InactiveCN101127013AAuthoritativeReliableUnauthorized memory use protectionInternal/peripheral component protectionAccess methodData access
The utility model relates to data encryption technology, in particular to an encrypted mobile memory device and the data access method. The utility model discloses a mobile memory device that adopts hardware encryption and the data access method to strengthen the security of storing data of mobile memory devices. The technical proposal of the utility model is that: the encrypted mobile memory device comprises a USB interface, a drive circuit, a controller, a memory and an encryption chip; the USB interface, the drive circuit, the controller and the memory are connected sequentially; the encryption chip is connected with the controller; the encryption chip is used for the encryption of stored data and the decryption of read data. The utility model also discloses the data access method of the device. The utility model has the advantages that: special chip hardware encryption is adopted; the encryption algorithm is authentic and reliable; the encryption intensity is high and the secrecy is strong. Decryption data cannot be gotten even the mobile memory device is taken apart and the memory is taken out if the device is not decrypted by the encryption chip.
Owner:CHENGDU SANTAI ELECTRONICS INDUSTRY CO LTD
Method for enciphering and deciphering code of packet, and encipherer and decipherer
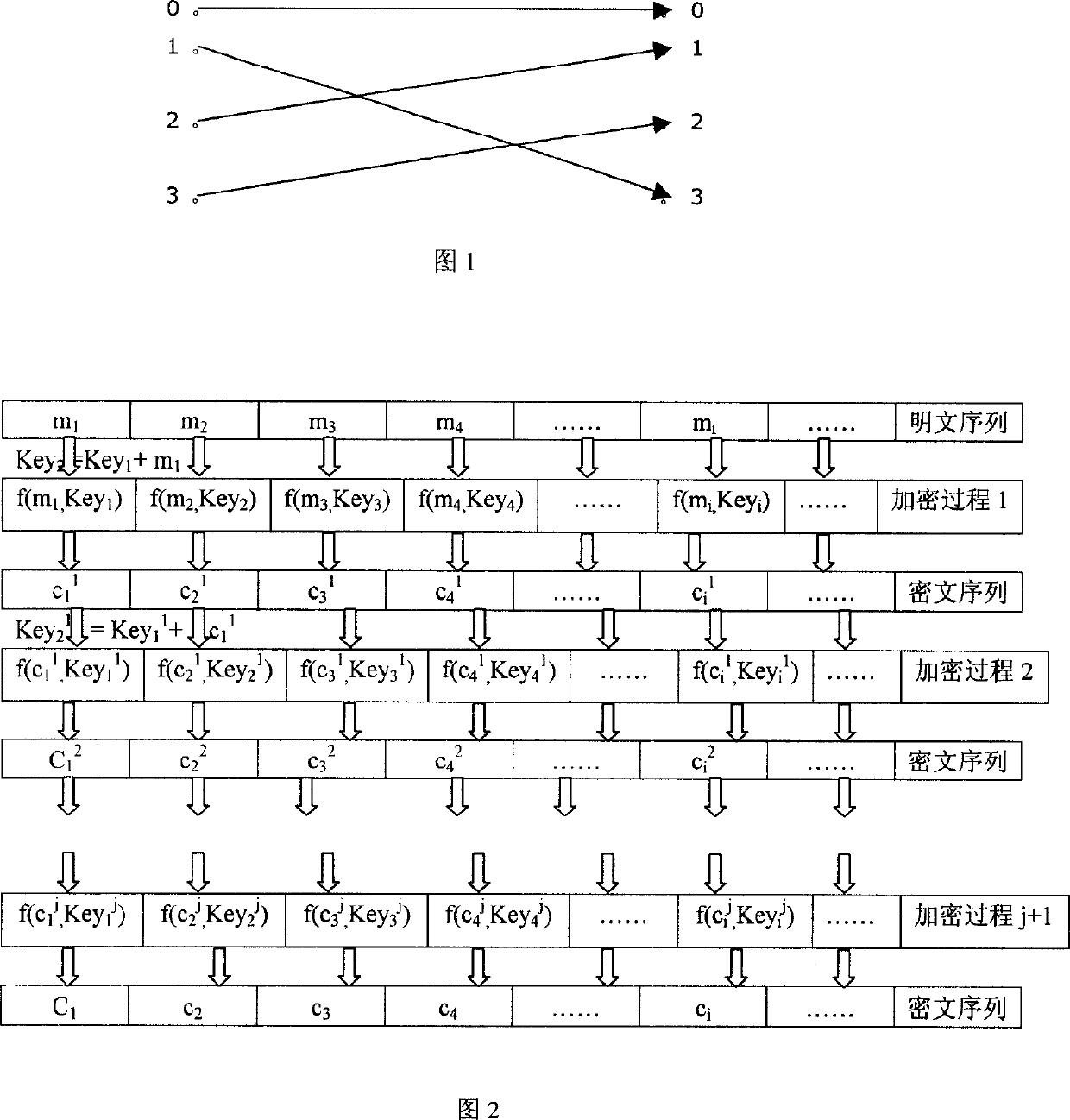
InactiveCN1697369AHigh encryption strengthLarge block length n to improve encryption strengthEncryption apparatus with shift registers/memoriesPlaintextCiphertext
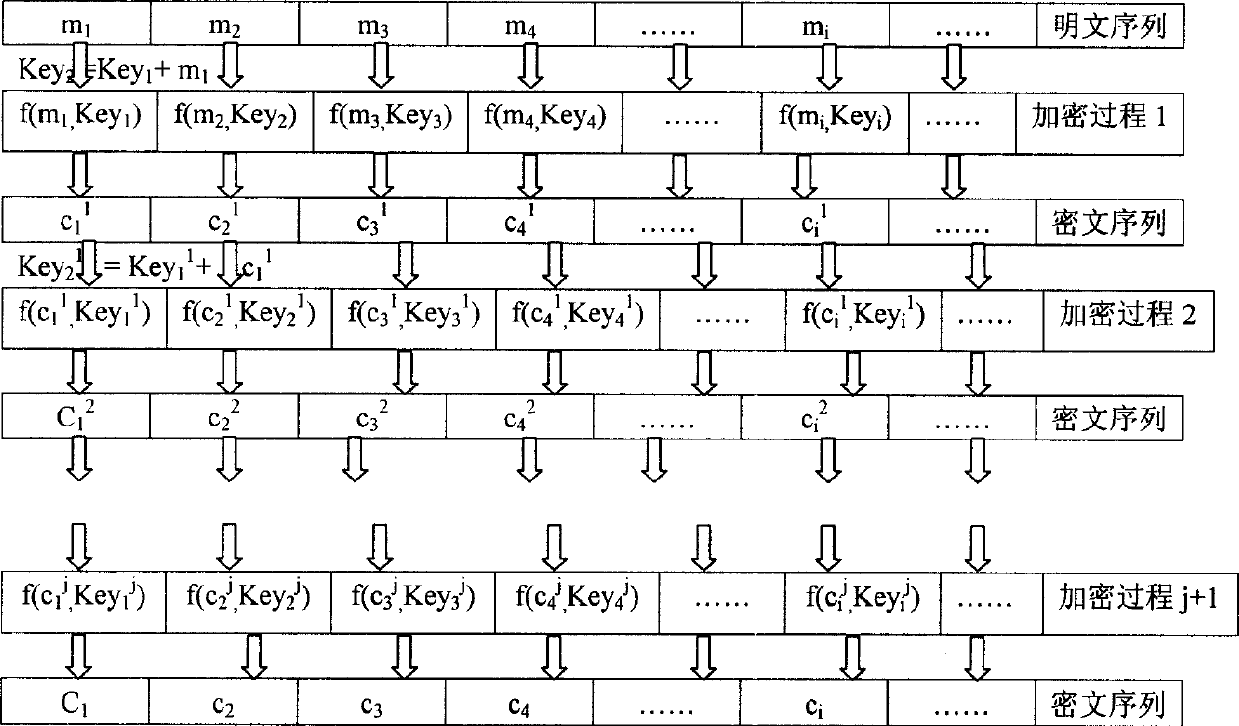
Different Keys including Key1, Key2, Key3... are utilized for each packet or each several packets. Encrypted cryptograph is encrypted again by using a changed cipher key. Or, arranged in groups, cryptograph is encrypted repeatedly for multiple times that is to say: encrypting each packet for multiple times, then encrypting next packet and whole plaintext, after completion, changing a Key and carrying out encryption once again, thus, repeating the above procedure for multiple times. The invention raises encryption intensity, and makes encryption device simple. Encryption method with encryption intensity being higher than 2n can be designed by using the invention. The disclosed method is suitable to all case of encryption by using grouped ciphers, including encryptions for stored digital quantity, transmitted digital signals, or real-time system.
Owner:HEBEI UNIV OF TECH
Instantaneous consumption application processing method and system for intelligent card
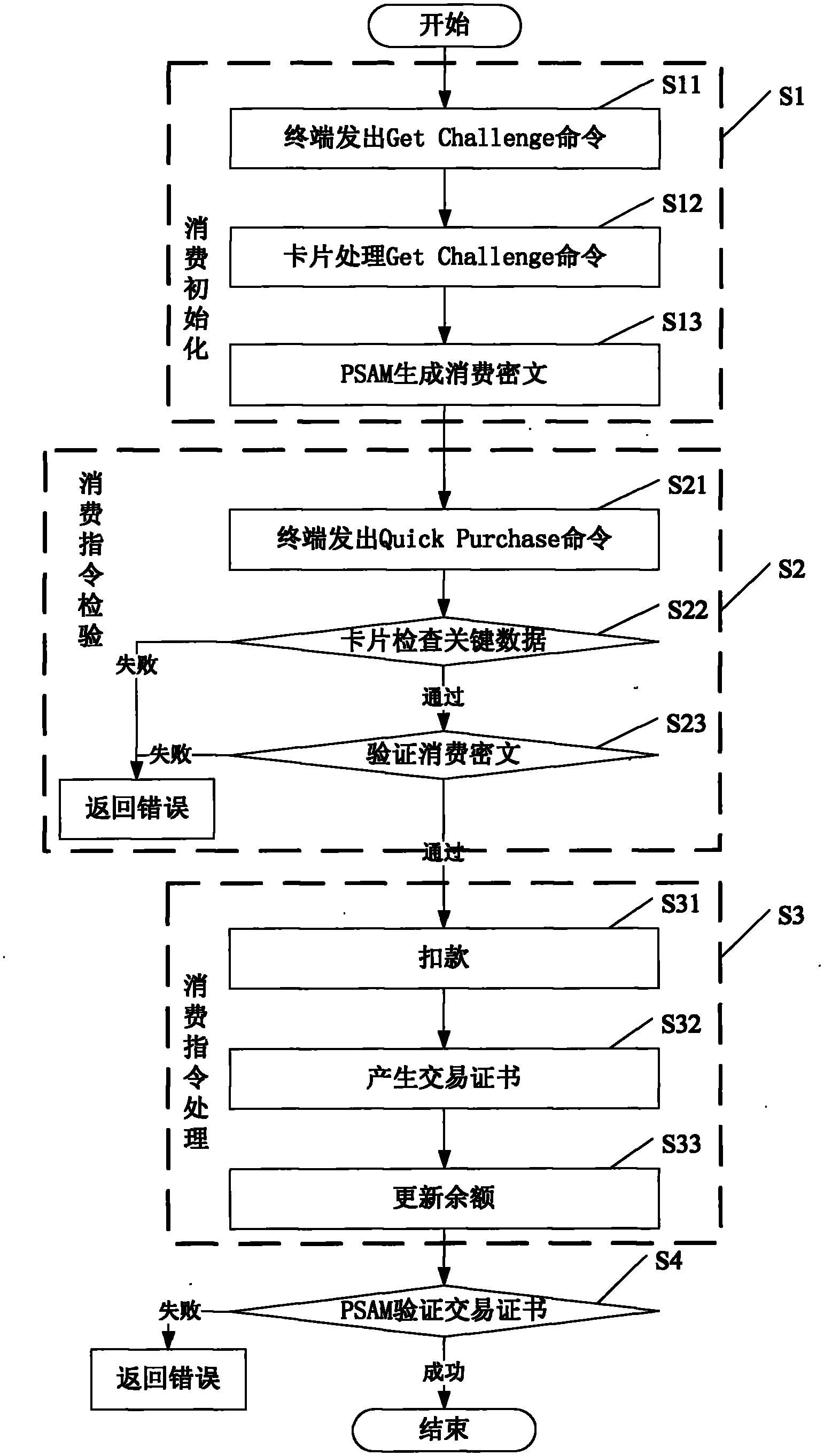
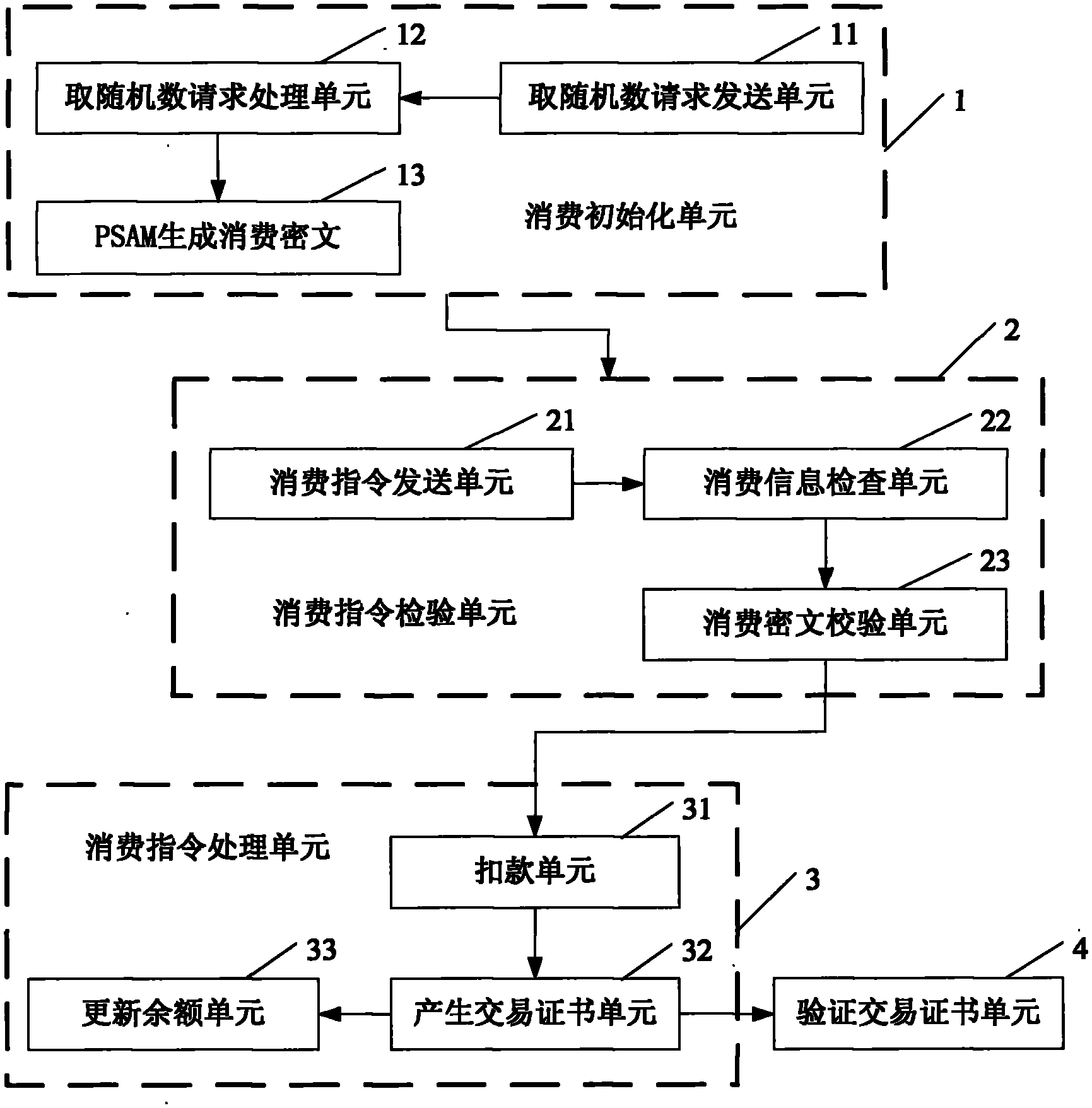
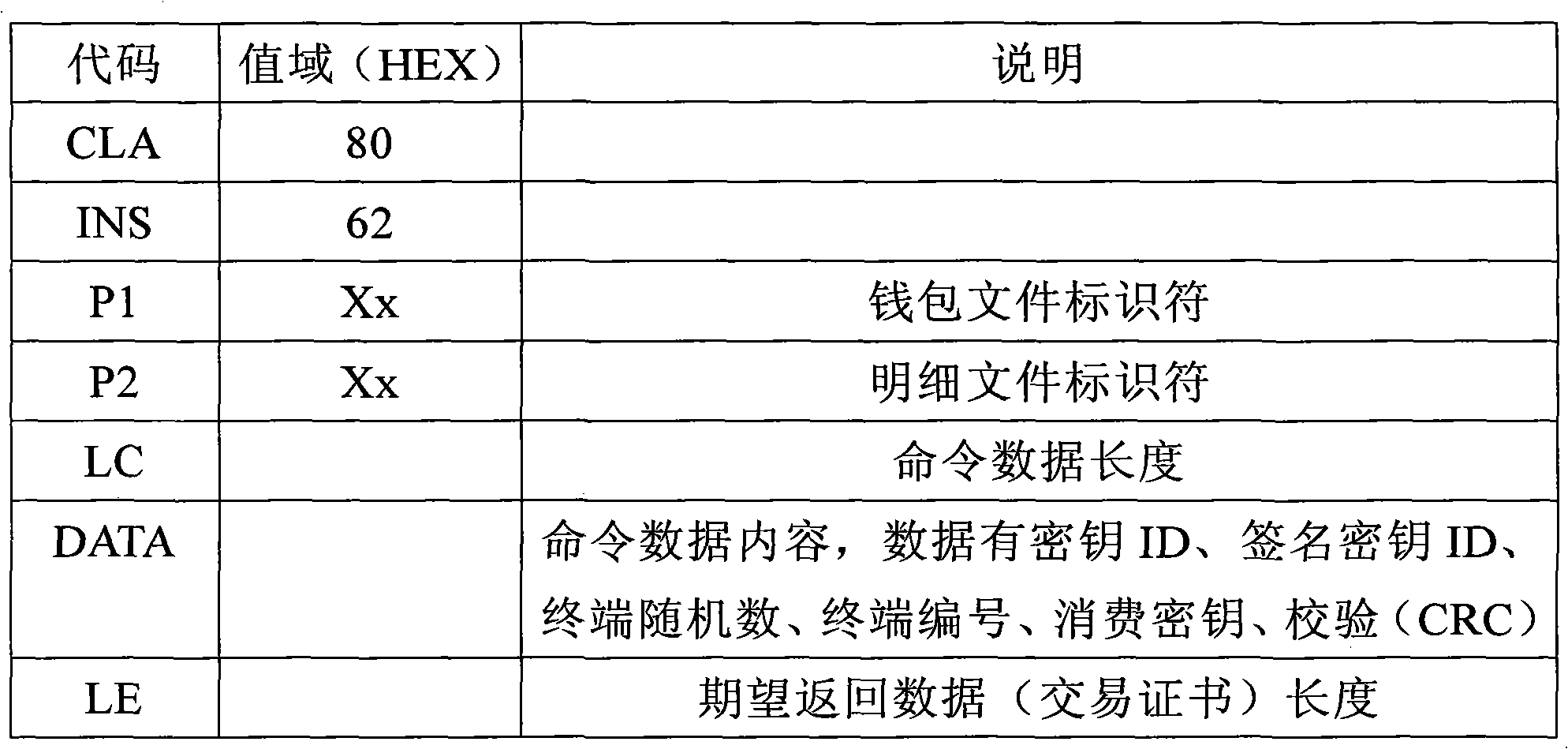
InactiveCN102254261AShorten transaction timeHigh encryption strengthPayment architectureCiphertextSession key
The invention discloses an instantaneous consumption application processing method for an intelligent card. The instantaneous consumption application processing method comprises the steps of: consumption initialization: a terminal safety control module is used for calculating a temporary session key and a consumption ciphertext according to the random number taking response data obtained by a terminal from a card and a preset encryption rule; consumption instruction checking: the card receives the instantaneous consumption instruction sent from the terminal, and then checks the trading key data of the instantaneous consumption instruction and verifying the consumption ciphertext; and consumption instruction processing: after the trading key data checking and consumption ciphertext validation are passed, the consumption is processed. The invention also discloses a corresponding instantaneous consumption processing system for the intelligent card. The instantaneous consumption application processing method and system for the intelligent card can be used for increasing the instantaneous trading speed and ensuring the safety, reliability and stability of trading simultaneously, and meet the requirements of various high-speed consumption occasions.
Owner:WUHAN TIANYU INFORMATION IND
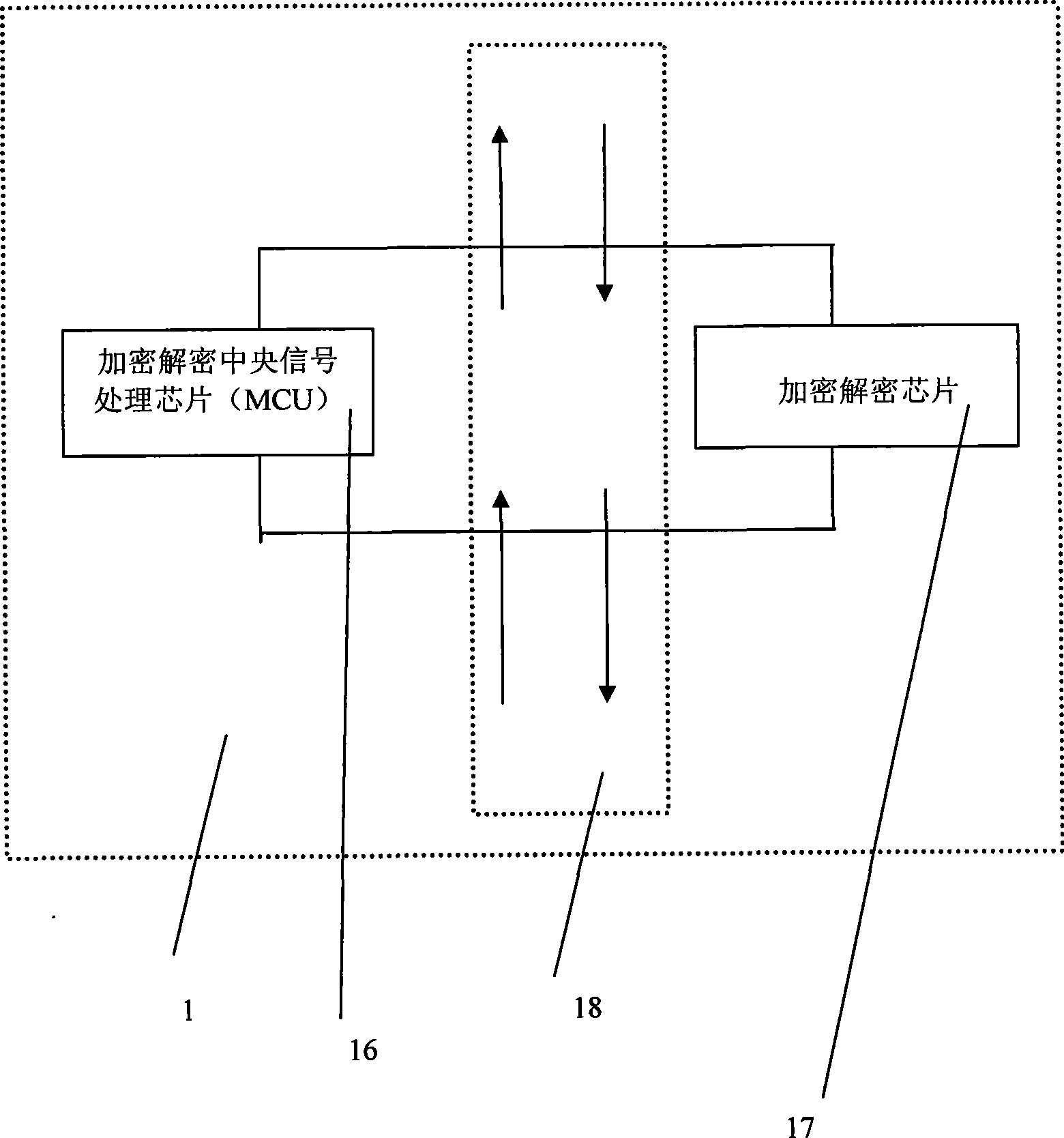
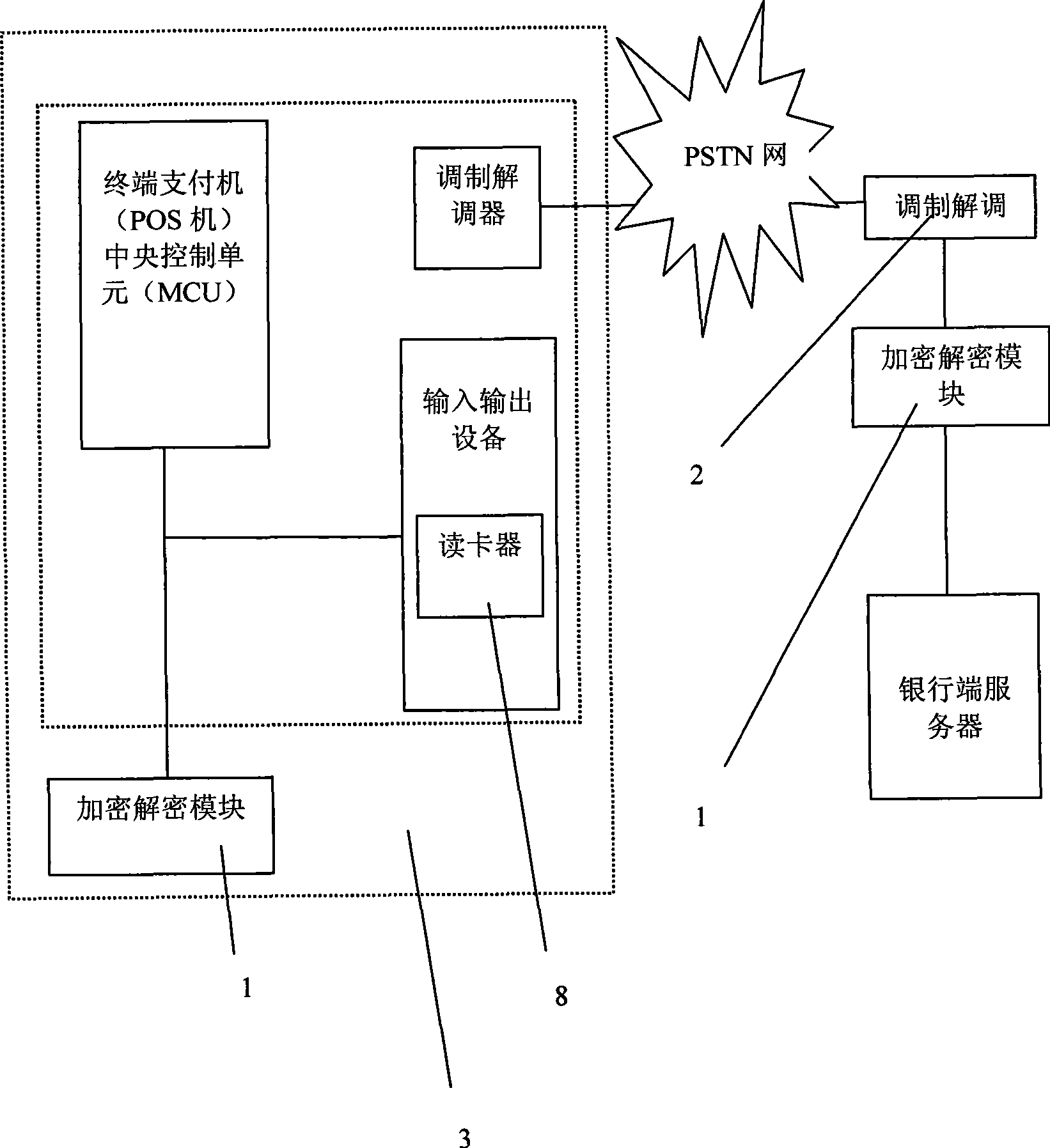
Data ciphering and deciphering module and use thereof
InactiveCN101388766AFunctionalCapable of data format processingSecuring communicationModem deviceChipset
The invention discloses a data encrypting and decrypting module, which is characterized by comprising a central signal processing unit (MCU) and a secrecy chip which applies the reconfigurable logic technique, encrypting data which is inputted into the module by a communication local end, and transmitting the encrypted data to any specific communication device. The data encrypting and decrypting module at least comprises an interface for transmitting data, the data encrypting and decrypting module can decrypt the date which is received through a communication channel and has been encrypted by the other party, the data encrypting and decrypting module can widely used for paying for communication transmission devices, such as a payment device (POS machine), a fax machine, a fixed telephone, a mobile phone, Bluetooth and the like, and the module can allocate with corresponding structures, such as a modulator-demodulator and the like, according to different communication transmission devices, and can realize the encrypting and decrypting transmission of various data which need maintaining secrecy.
Owner:北京大秦兴宇电子有限公司
Processing method of image latent writing based on auxiliary pixel
InactiveCN101452569AIncrease embedding capacityMaintain Embedding EfficiencyImage data processing detailsMethod of imagesNumber generator
The invention relates to an auxiliary pixel-based image steganographic processing method, which embeds two pieces of secret information into one pixel of a carrier image at the same time. The method comprises: using integer pseudo random number between 0 and 255 generated a pseudo random number generator as a gray value of an auxiliary pixel; embedding the two pieces of secret information into the gray value of the carrier image and an auxiliary pixel value; and transferring the information of the auxiliary pixel value to a pixel value of the carrier image. The invention has the advantages of greatly improving embedment capacity due to the embedment of two pieces secret information into one pixel, improving the utilization rate while keeping a certain embedment rate, improving the encryption capacity of the algorithm due to the adoption of a pseudo random sequence for scrambling steganographic information and generating the auxiliary pixel, increasing the difficulty in the extraction of the secret information from the a steganographic image and improving the anti-attack ability of the algorithm.
Owner:WUXI HUASAI INFORMATION TECH
Encryption device, encryption processing method and program, and information protection system employing the encryption device
InactiveUS7839999B2Reduce the amount of calculationHigh encryption strengthMultiple keys/algorithms usageDigital data processing detailsComputer hardwareProtection system
Owner:FUJIFILM BUSINESS INNOVATION CORP
Effective image compression and encryption amalgamation method
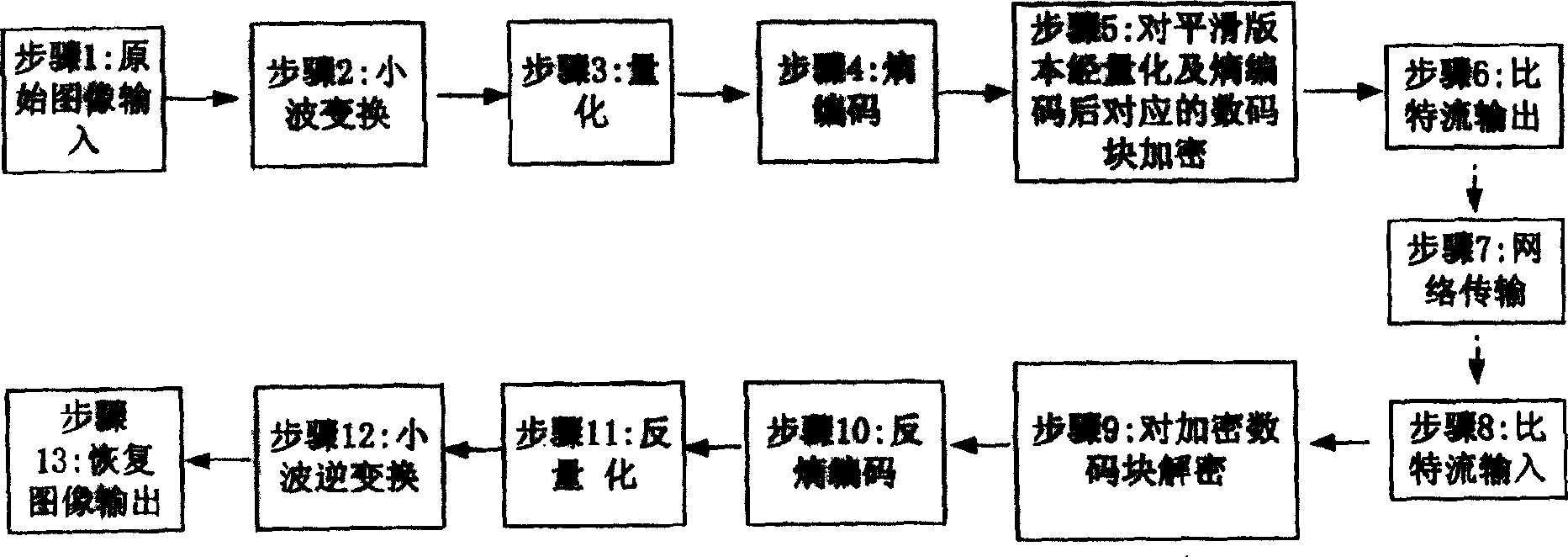
InactiveCN1536532AGuaranteed performanceQuality assuranceImage codingComplex mathematical operationsComputer hardwareImage compression
The invention relates to a network image communication, specially an image-compressing and encryption blending method which can reduce operating amount of image encrypting and deciphering. It adopts triple-DES algorithm to encrypt and decipher the digits corresponding to the smooth part instead of the whole image through quantization coding and entropy coding. Its main steps: wavelet transformation, entropy coding, encrypting digit block through quantization coding and entropy coding, deciphering, reverse entropy coding, reverse quantizing, and wavelet reverse transforming. On the condition of not affecting image compressing effect, it achieves the higher-strength encrypting effect and remarkably reduces the operating amount of encrypting and deciphering.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Encryption method in data transfer of electric power system
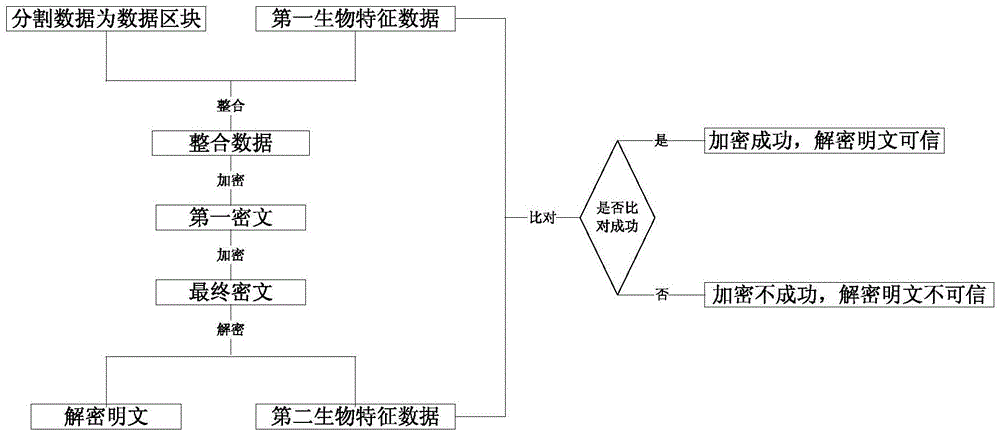
ActiveCN104821879AImprove securityHigh encryption strengthCircuit arrangementsUser identity/authority verificationPlaintextBiometric data
The invention discloses an encryption method in data transfer of an electric power system, which comprises the following steps: when a transmitting end transmits data to an opposite side, dividing the data for generating a plurality of data blocks; acquiring the voiceprint characteristic and other biological characteristic of a transmitter and quantifying to first biological characteristic data, dividing the first biological characteristic data for generating a plurality of first biological characteristic data blocks; integrating the first biological characteristic data with the data blocks and encrypting for obtaining a first cryptograph, wherein a plurality of intermediate detectors are arranged between the transmitting end and the receiving end, the intermediate detectors are used for performing different number of times of encryption according to different transmission speeds of the first cryptograph, thereby finally obtaining a plurality of different final cryptographs for received by the receiving end, wherein related data are recorded in encryption for providing reference data for decryption; performing decryption by the receiving end for obtaining second biological characteristic data and a decrypted plaintext; and comparing the second biological characteristic data with preset biological characteristic data for determining whether the plaintext is reliable.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Method and system for improving encryption/decryption speed of passive optical network
InactiveCN101902664AFast encryption and decryptionHigh encryption strengthMultiplex system selection arrangementsSecuring communicationPlaintextOptical network unit
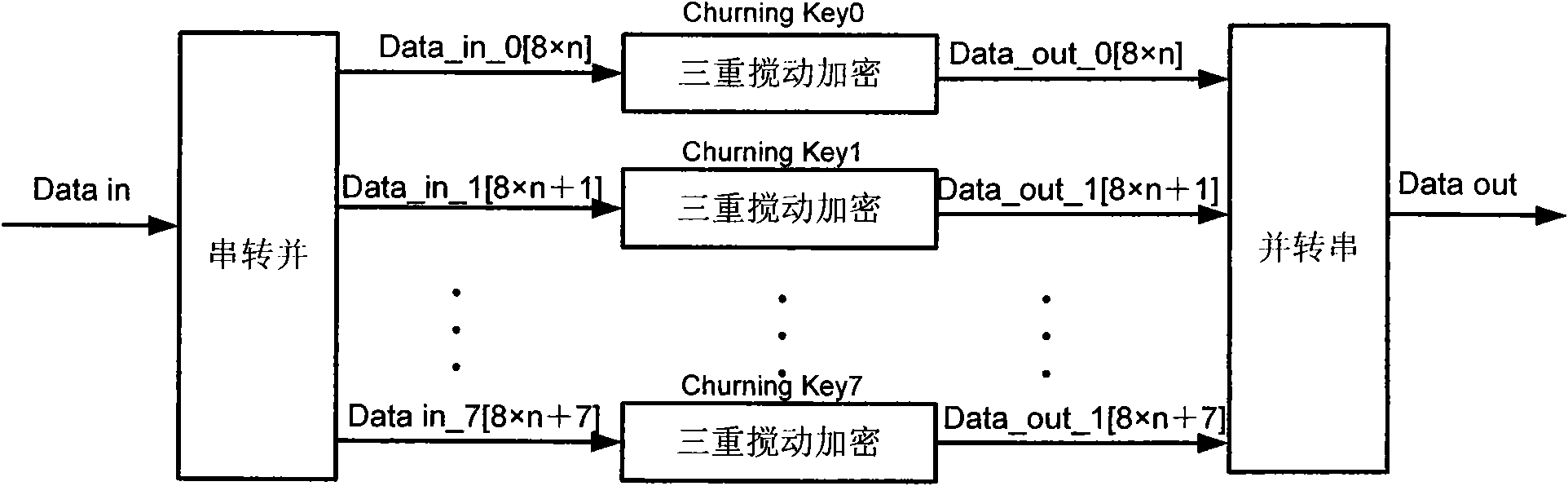
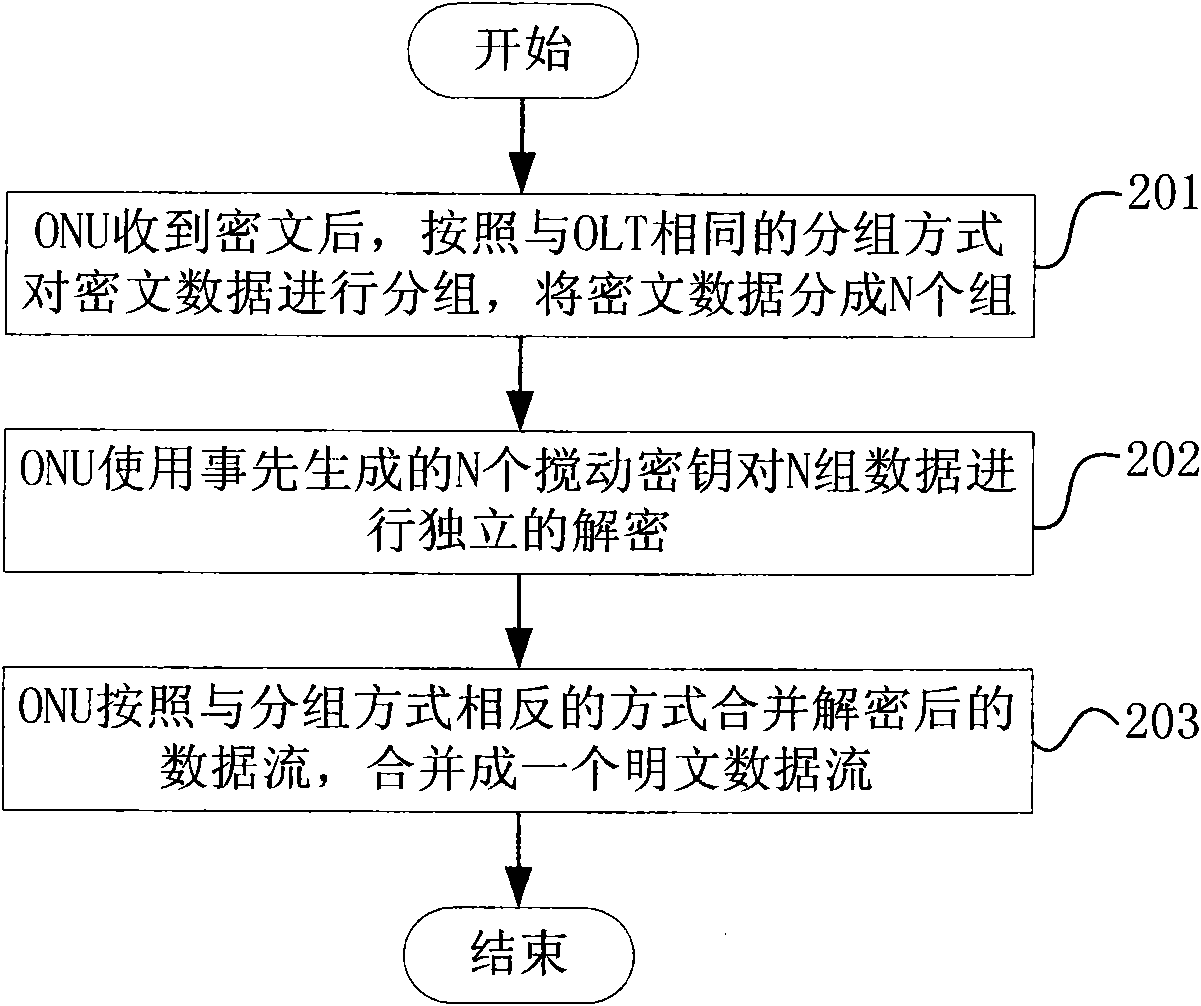
The invention discloses a method and a system for improving the encryption / decryption speed of a passive optical network, which can accelerate an encryption treatment speed and improve encryption effects at the same time. The method comprises the following steps of: dividing cleartext data to be encrypted into N groups by an optimal line terminal (OLT), wherein N is more than 1; encrypting the N groups of data to be encrypted by using N different secrete keys; combining the encrypted N groups of data into a ciphertext stream for output after the encryption is completed, wherein the N different secrete keys are determined by a plurality of seed keys sent by an optical network unit (ONU) or the ONT.
Owner:ZTE CORP
Method for generating anti-counterfeiting code information
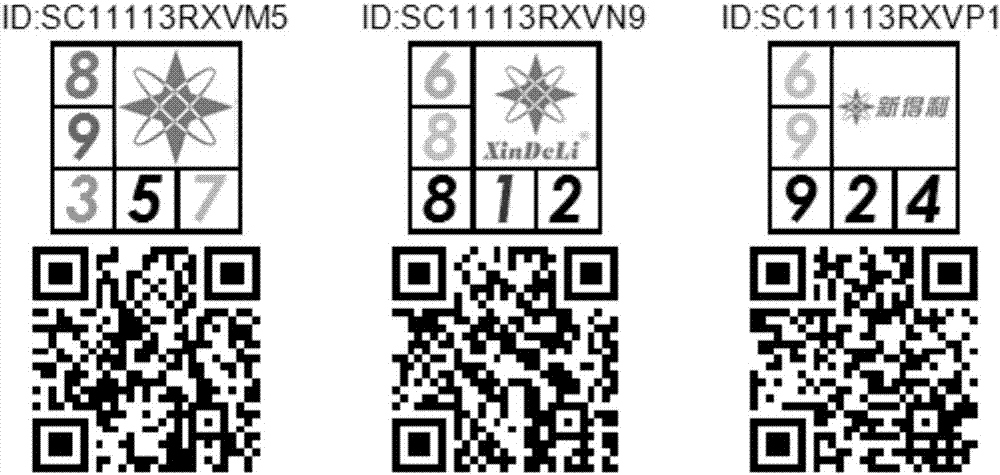
ActiveCN107423797AReduce storage pressureHigh encryption strengthRecord carriers used with machinesSpecial data processing applicationsProgramming languageGeneration process
The invention discloses a method for generating anti-counterfeiting code information. The method comprises the following steps: step one, creating a value color table and an image library; step two, carrying out invoking by an external system by parameters including an internal code, Url and a prefix and starting an anti-counterfeiting information generation process; step three, combining the Url, prefix and internal code, calculating a check code, combining the Url, prefix and internal code with the check code, and forming a two-dimensional code; step four, generating an anti-counterfeiting numerical value information list; step five, in the two-dimensional code obtained in the step three, carrying out image index calculation, carrying out delivery processing on the total number of anti-counterfeiting images in the image library based on the calculation result to obtain an image index, and acquiring a corresponding anti-counterfeiting image from the image library; and step six, combining the two-dimensional code obtained in the step three, the anti-counterfeiting numerical value information list obtained in the step four and the anti-counterfeiting image obtained in the step five to generate anti-counterfeiting code information. With the method disclosed by the invention, invoking becomes simple; and the data storage pressure is low.
Owner:CHENGDU XINDELI ELECTRONICS CO LTD
Anti-counterfeit code generating device
InactiveCN103824197AHigh encryption strengthAvoid crackingUser identity/authority verificationCommerceAdvanced Encryption StandardSerial code
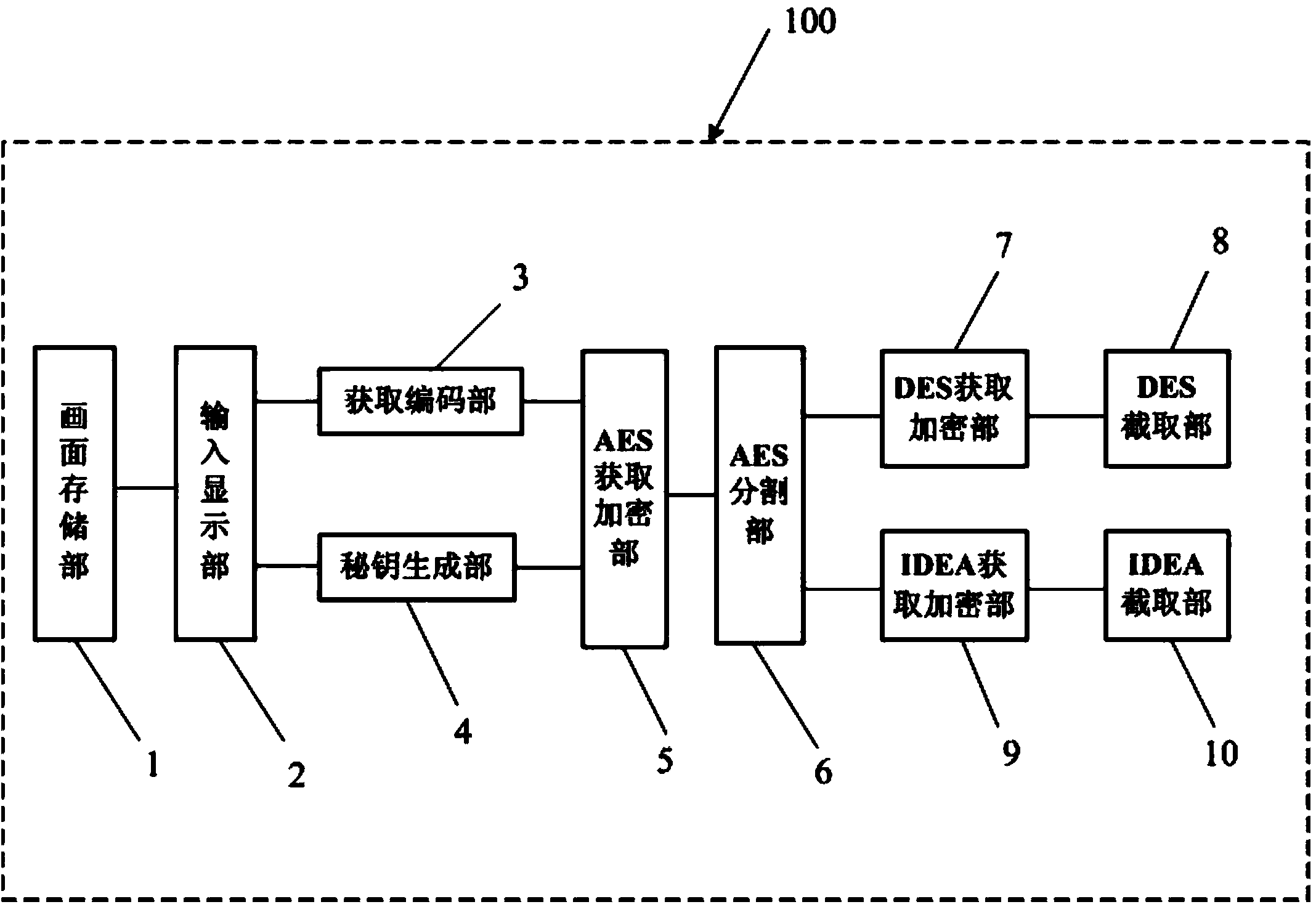
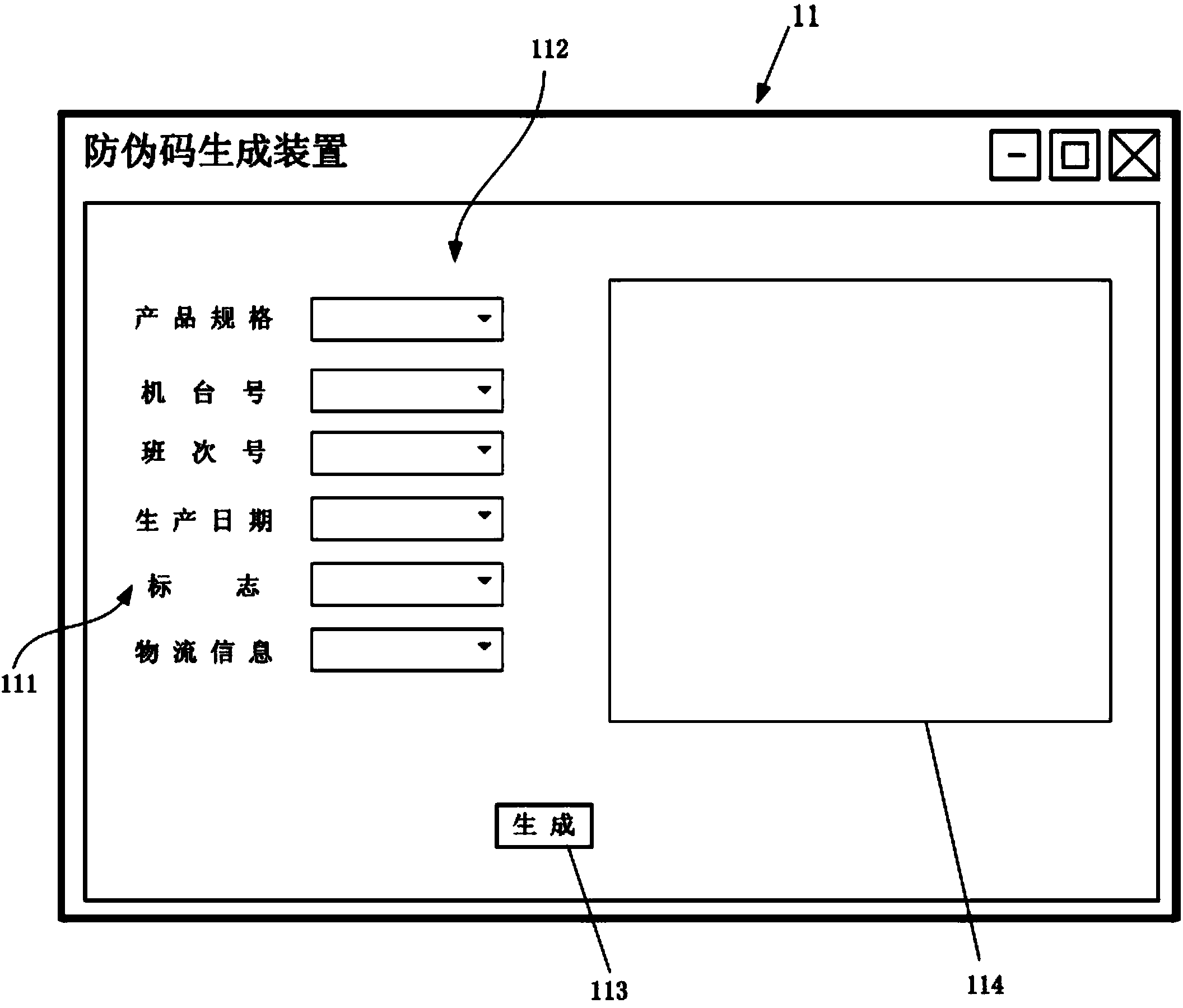
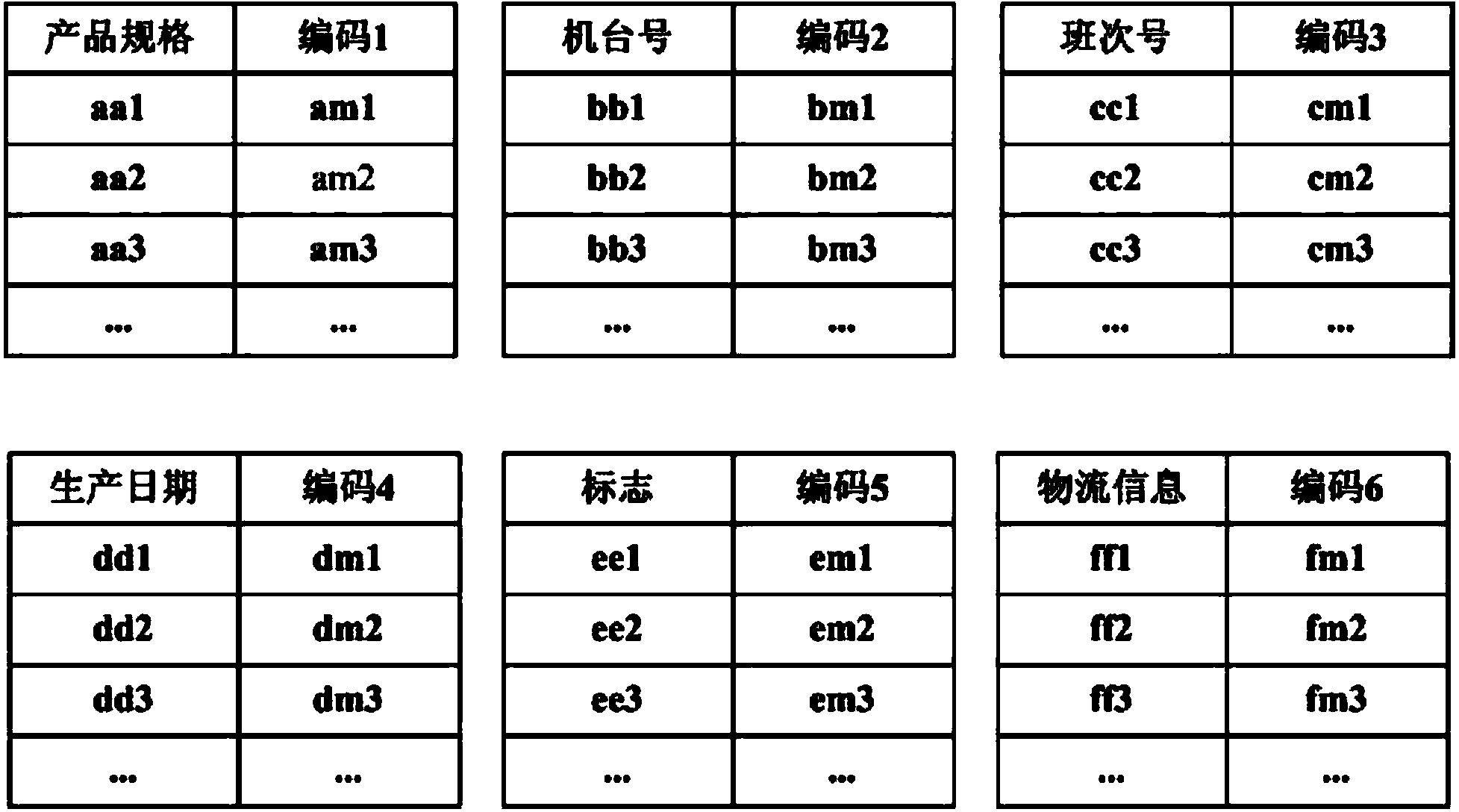
The invention provides an anti-counterfeit code generating device. The anti-counterfeit code generating device is characterized by comprising a picture storage part, an input display part, a code acquiring part, a secret key generating part, an AES (advanced encryption standard) acquiring and encrypting part, an AES cutting part, a DES (data encryption standard) acquiring and encrypting part, a DES cutting part, an IDEA (international data encryption algorithm) acquiring and encrypting part and an IDEA intercepting part, wherein the code acquiring part is used for acquiring input product information, and encoding according to a certain predetermined rule so as to generate corresponding product serial numbers. The anti-counterfeit code generating device provided by the invention firstly encrypts a product serial number by an AES algorithm, and then divides the encrypted result obtained by the AES algorithm into two parts, wherein one part is encrypted by a DES algorithm so as to obtain a logistic anti-counterfeit complete code, and a logistic anti-counterfeit application code is intercepted from the logistic anti-counterfeit complete code; the other part is encrypted by an IDEA algorithm so as to obtain a product anti-counterfeit complete code, and a product anti-counterfeit application code is intercepted from the product anti-counterfeit complete code, so that compared with the prior art, the anti-counterfeit code generating device has the characteristics of high encryption intensity and difficulty in code cracking.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
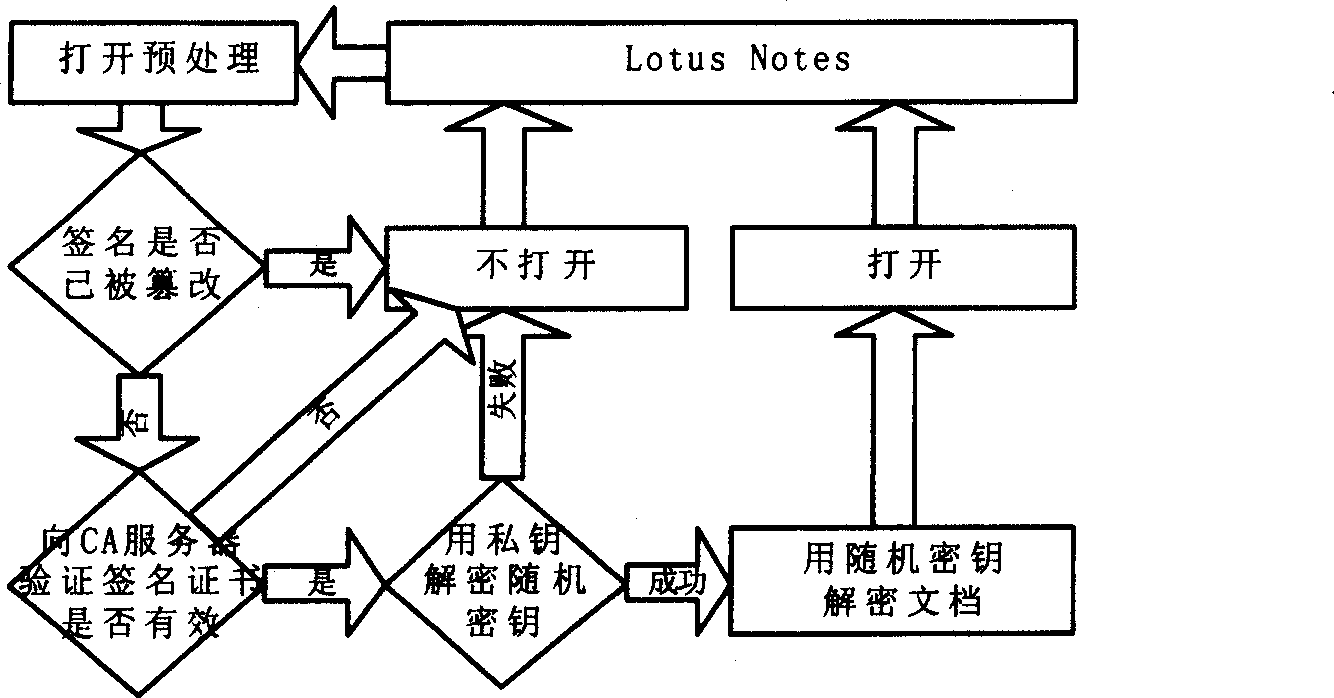
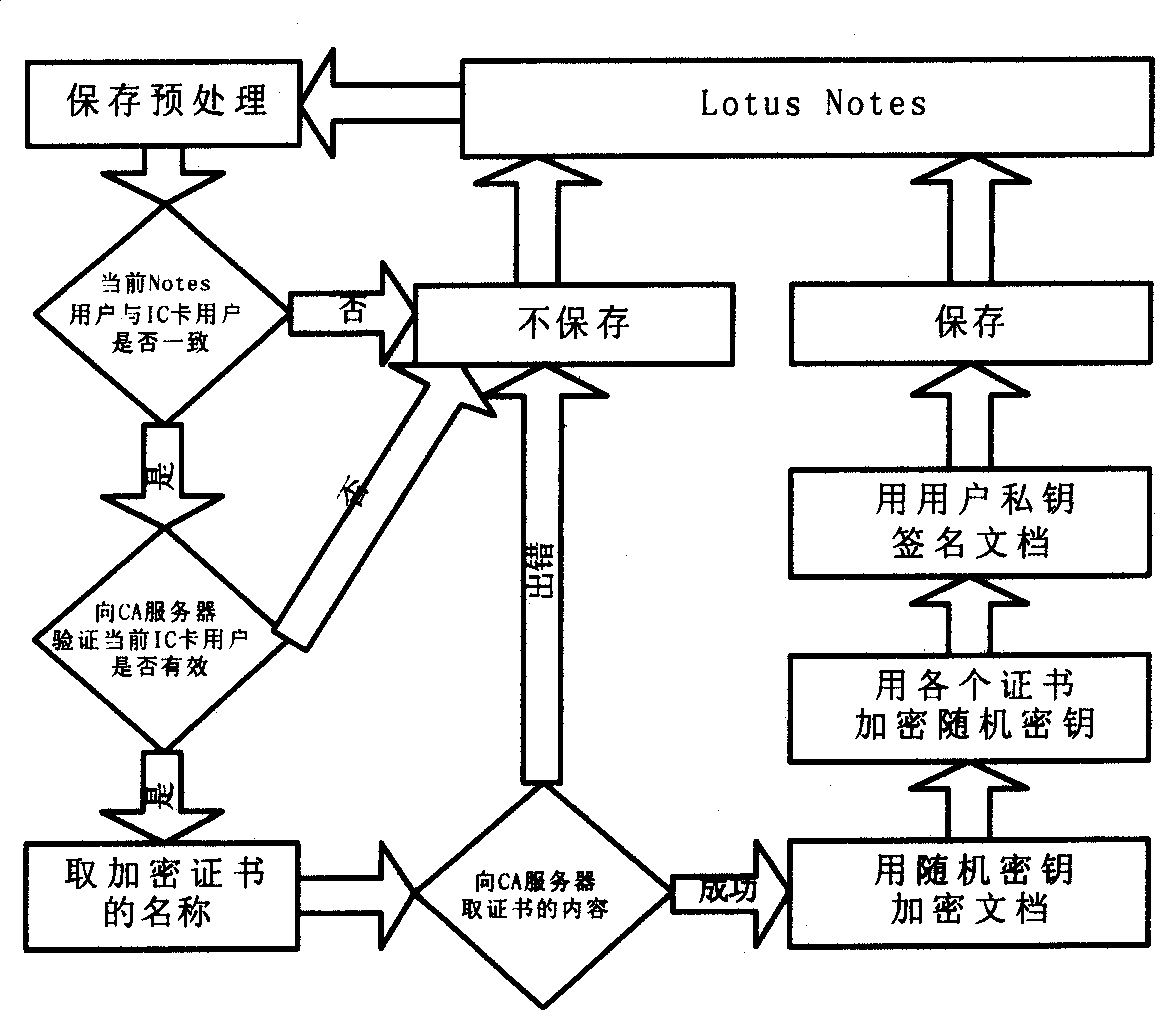
Method for integrating safety E-mail and Lotus Notes
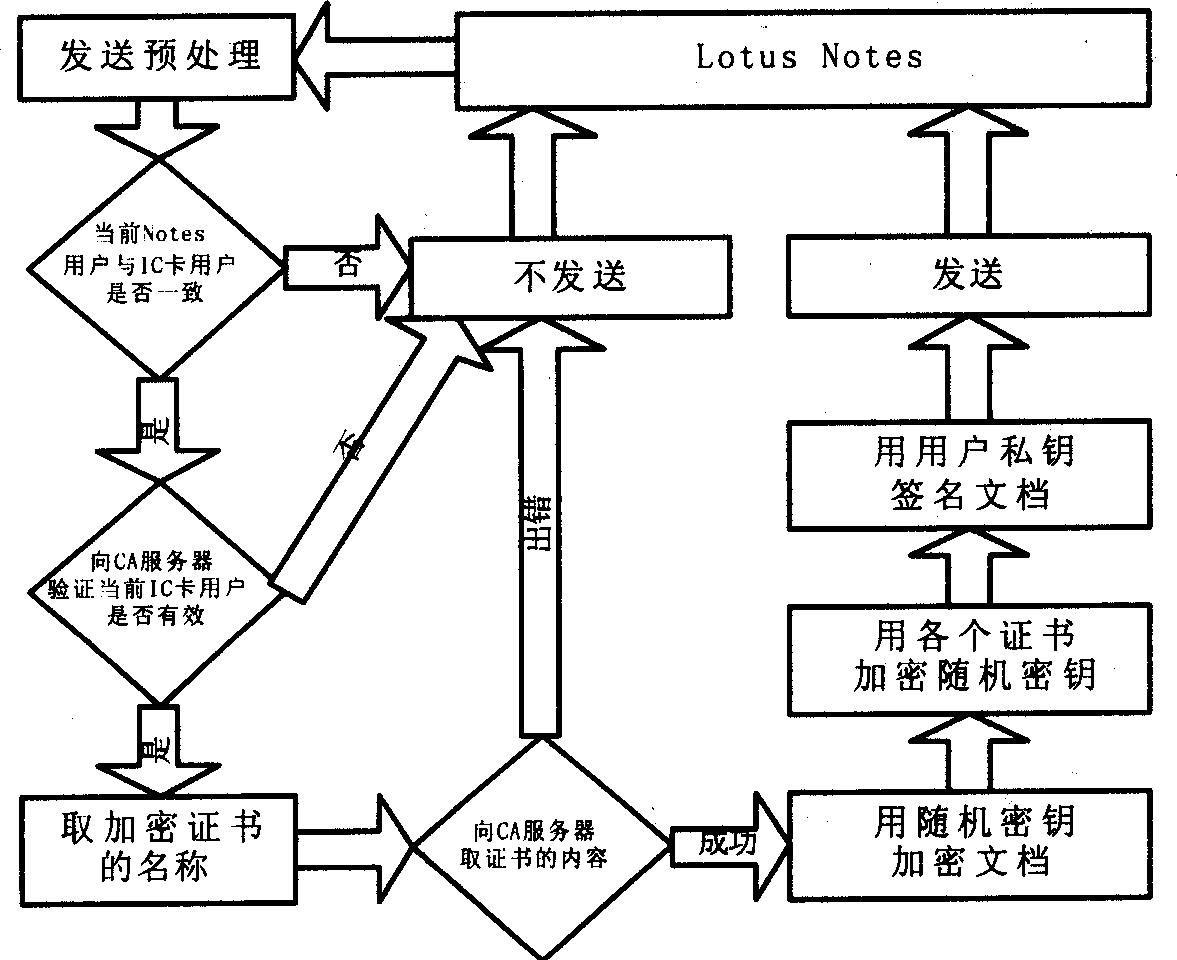
InactiveCN1352433AReduce stepsEasy to operateTransmissionSpecial data processing applicationsComputer scienceElectronic mail
The invention discloses a method for integrating safety E-mail with Lotus Notes. In the process of sending and receiving E-mail, the operating interface is customized and the functions are extended in Lotus Notes by using its safety extension module so as to realize encryption / signature and decryption / validation of signature. The invented method possesses merits of convenient for operation, easy to operate and safety to use.
Owner:KOAL SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com