A data encryption/decryption method and encryption/decryption apparatus
A data encryption and data technology, which is applied in secure communication devices, digital transmission systems, usage of multiple keys/algorithms, etc., can solve the problems of increasing the amount of calculation, outweighing the losses, and being vulnerable to threats, and achieves the effect of protecting confidentiality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
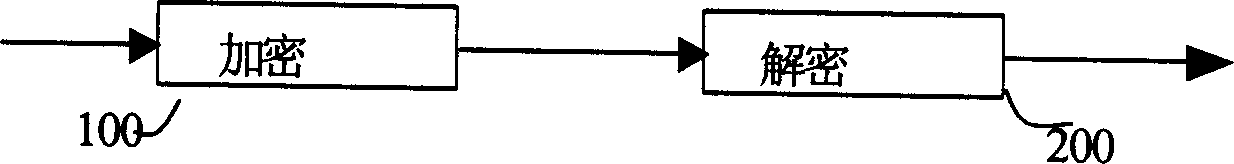
[0042] A data encryption method for encrypting plaintext data. The method includes the following processes: the process of digitizing the user key K, converting the user key K from a character expression to a digital expression through a character number code table, the user The key K is used to encrypt plaintext data; the process of constructing a plaintext data block, where the length of the plaintext data block is less than or equal to the length of the user key K, and the corresponding plaintext data vector X and the plaintext data are constructed from the plaintext data block in the form of a digital stream Position vector WX; there is a permutation function f, the random key vector D is constructed by the inverse function f'of the permutation function f and the plaintext data position vector WX, and the secret key vector D is constructed by the permutation function f, the data position vector WX and the random key vector D The process of text data location vector WY; the pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com