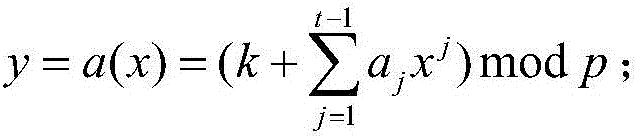Patents
Literature
657results about How to "Without compromising security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
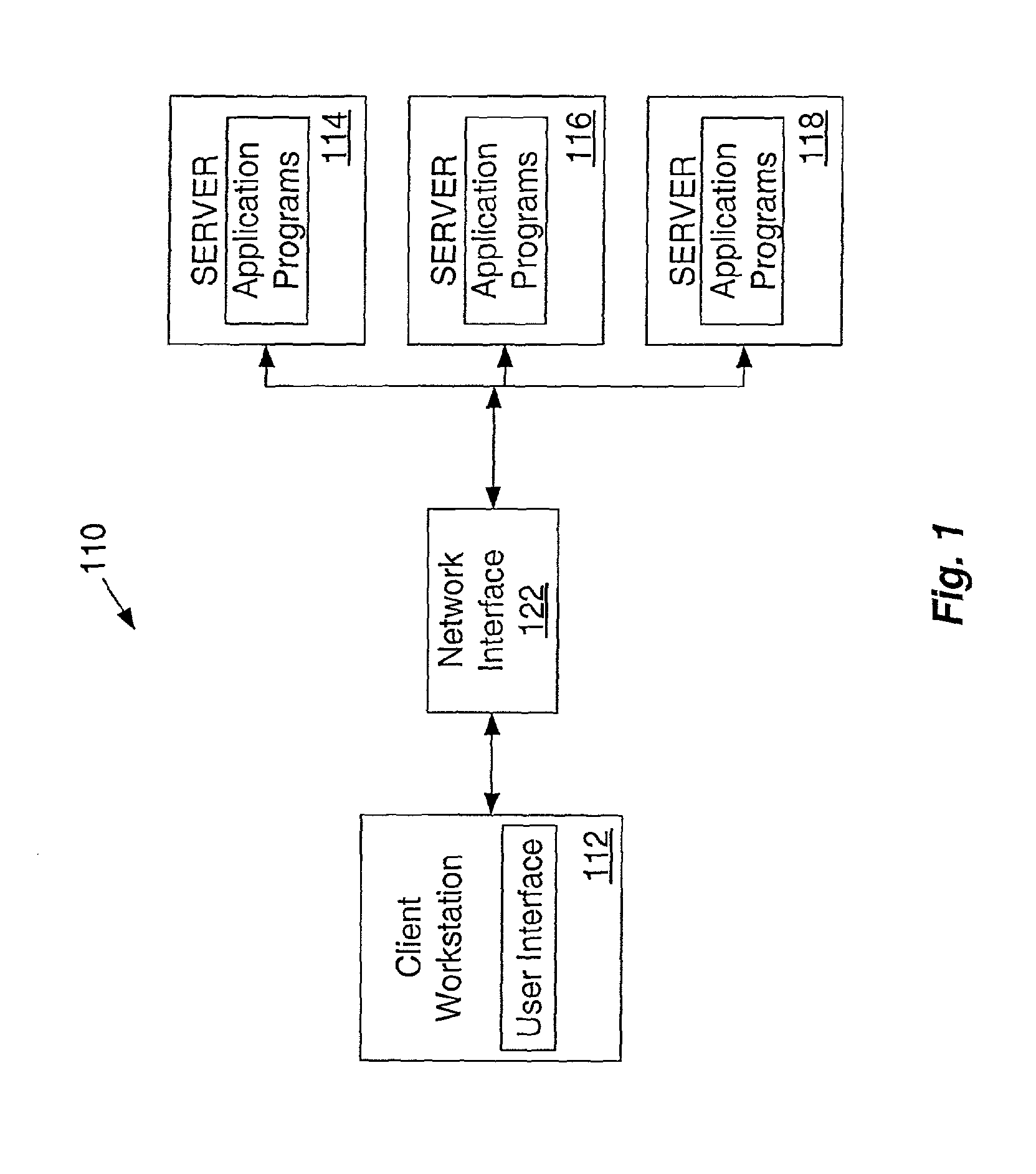
Electronic system for provision of banking services
ActiveUS20060136334A1Increased positional freedomWithout compromising securityComplete banking machinesFinanceElectronic systemsMobile telephony
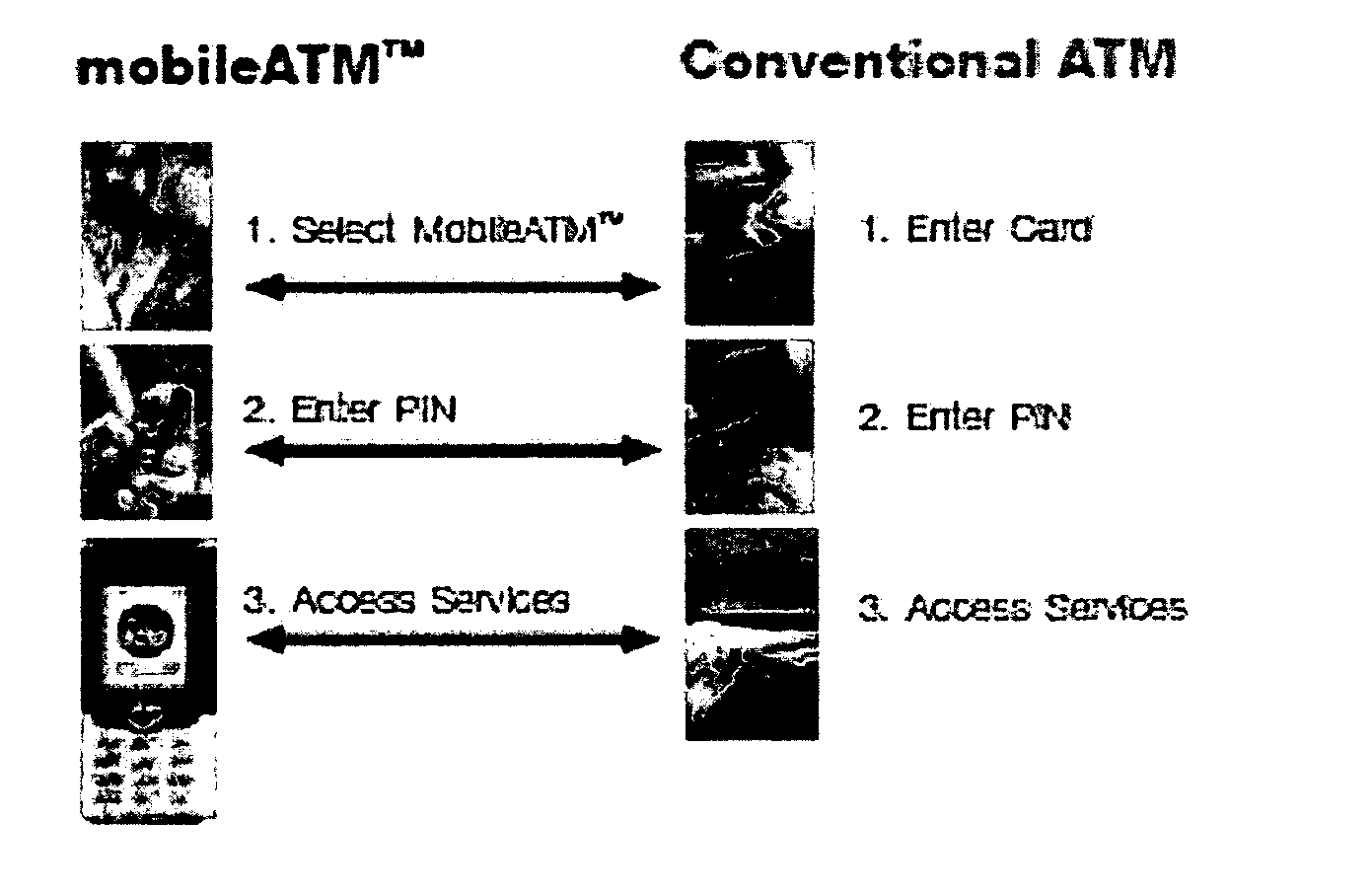
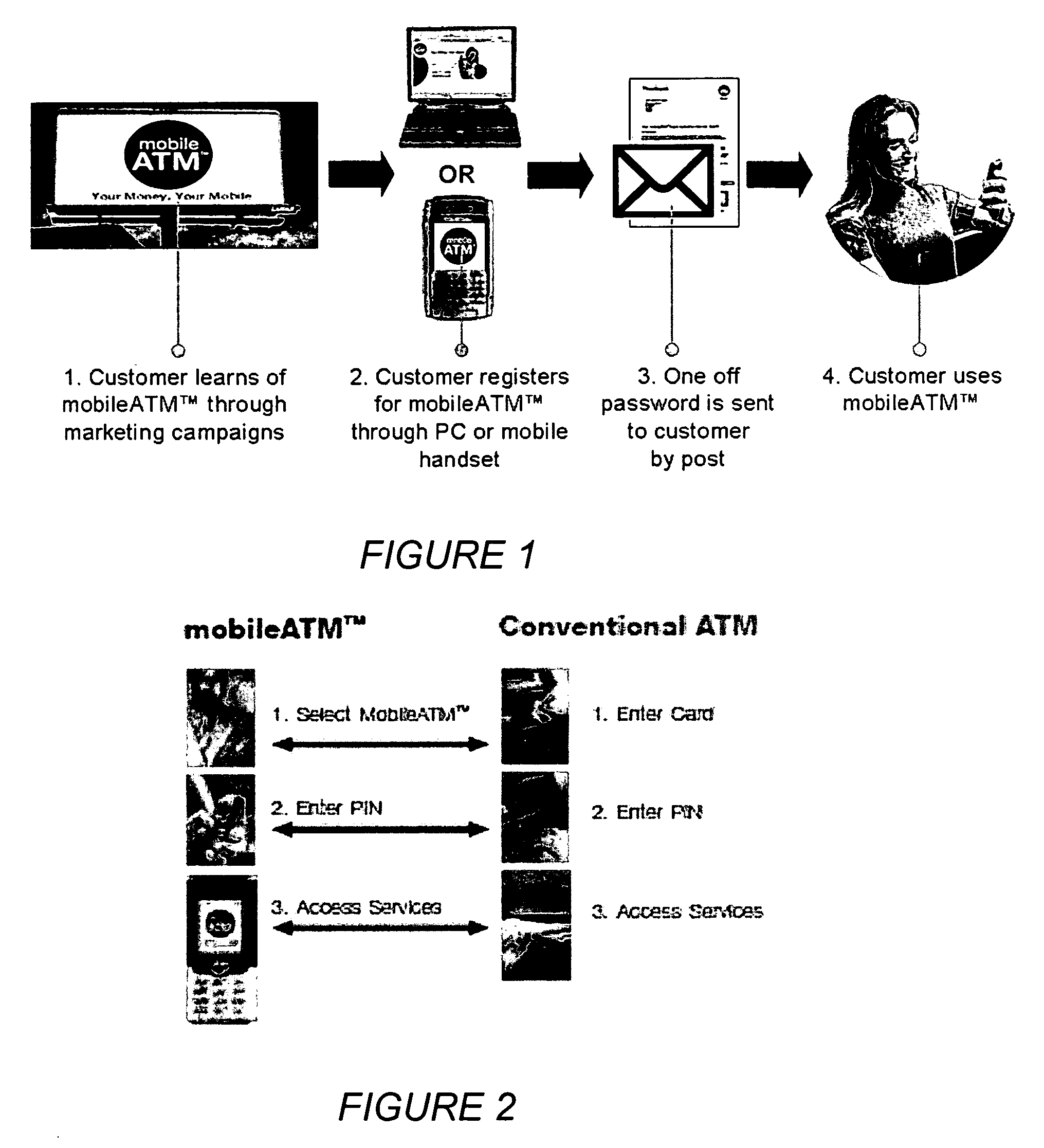
An electronic system providing banking services, comprises a server having a first interface for communication with user mobile telephony devices over a mobile telephone network; and a second interface for communication with an intermediary acting as a gateway to banking records of multiple banking organisations. The first interface is adapted to allow at least balance enquiry requests to be submitted to one of the multiple banking organisations by means of the intermediary and to provide at least balance enquiry replies for display on the user mobile telephony device. The invention provides the functions of the high street ATM using the mobile phone environment.
Owner:FISERV
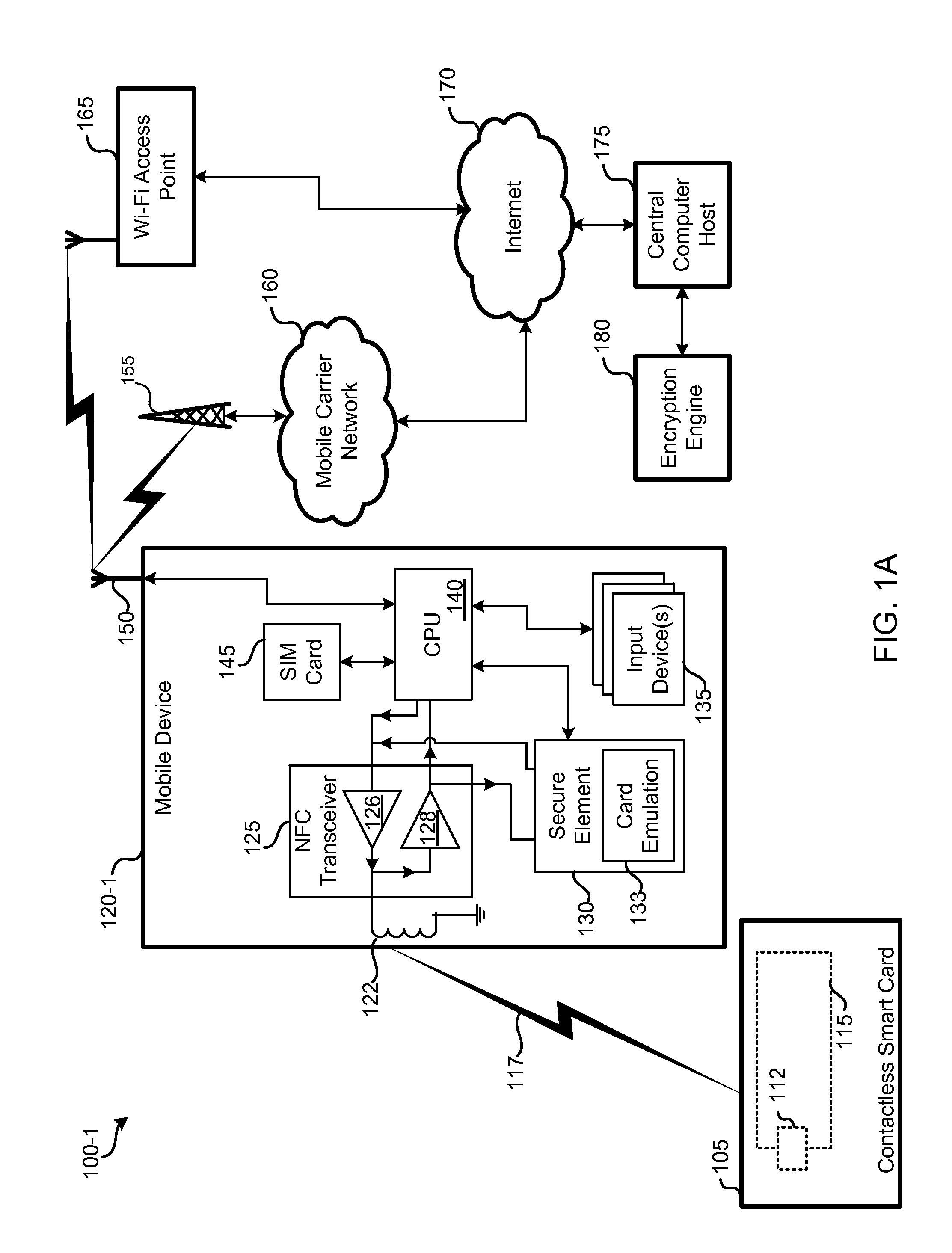
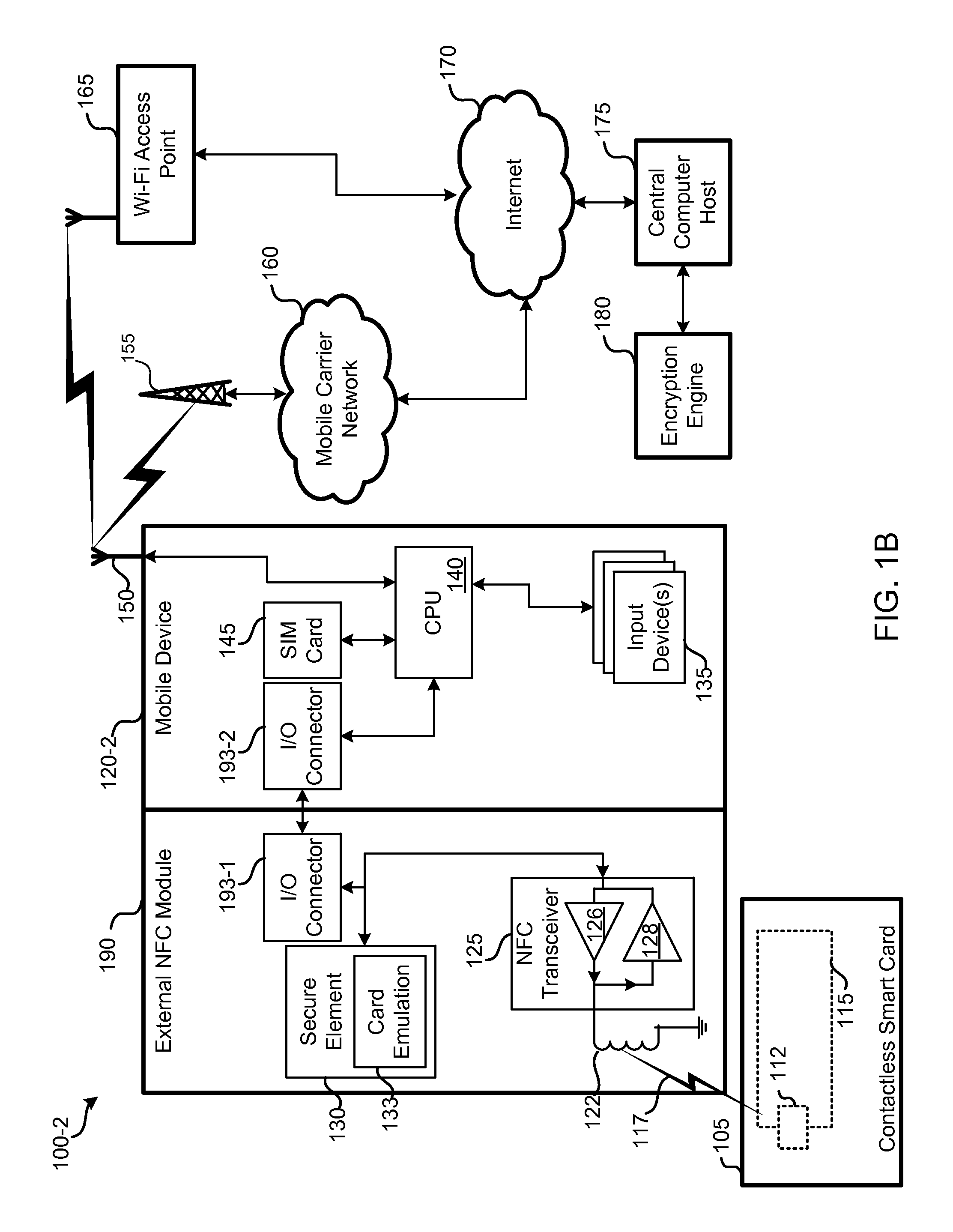
Personal point of sale
InactiveUS20130086375A1Low costNo costAcutation objectsNear-field transmissionRemote computerMobile device
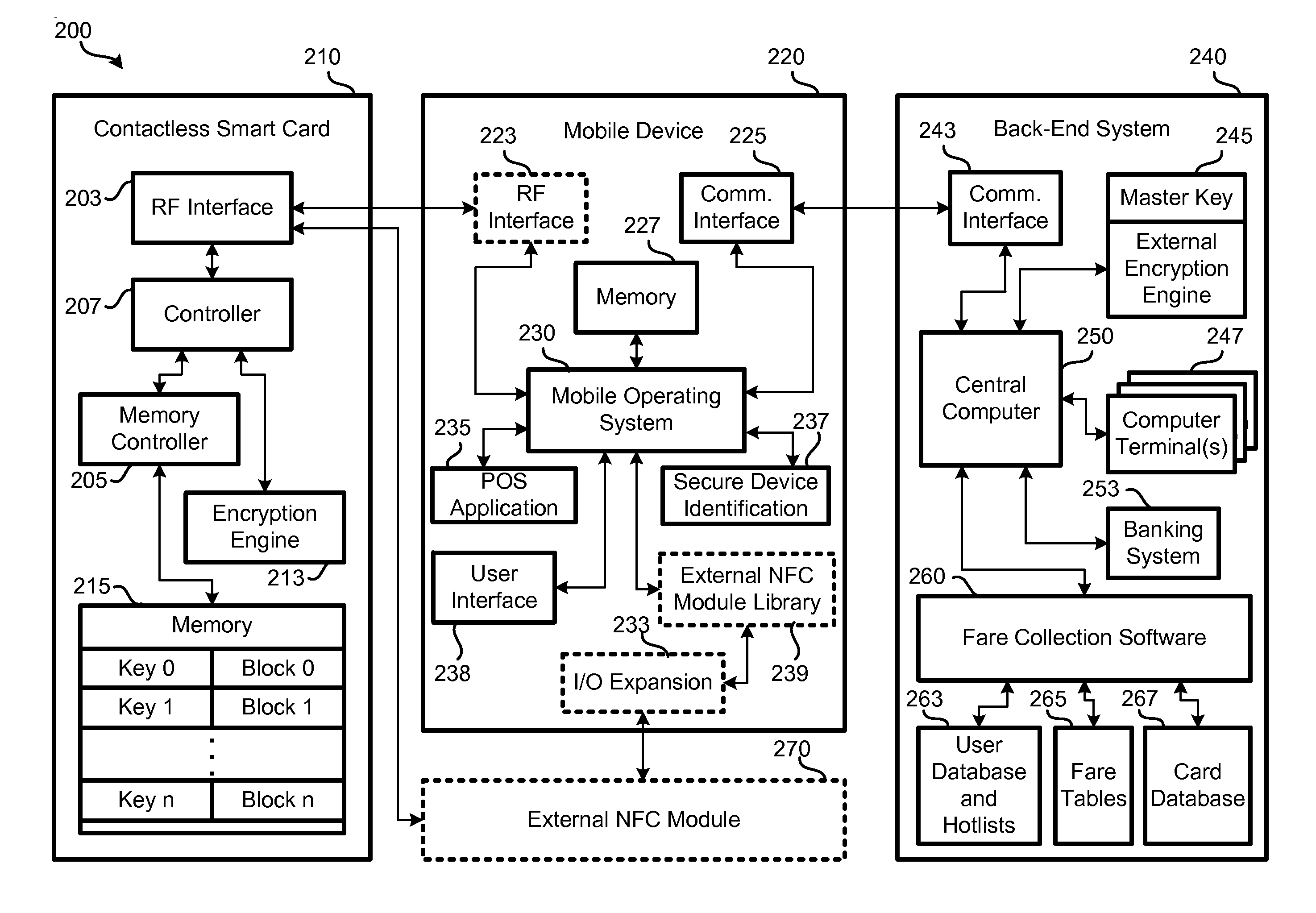
Embodiments provided herein include techniques for enabling a mobile device to communicate with smart media in a manner that can sidestep the secure element of the mobile device—and the costs associated with it. The mobile device can communicate with the smart media using near-field communication (NFC) by creating an encrypted connection with a remote computer while bypassing a secure element of the mobile device. This allows the mobile device to provide point-of-sale (POS) functionality by reading and / or writing to the smart media, without compromising the security of the smart media.
Owner:CUBIC CORPORATION
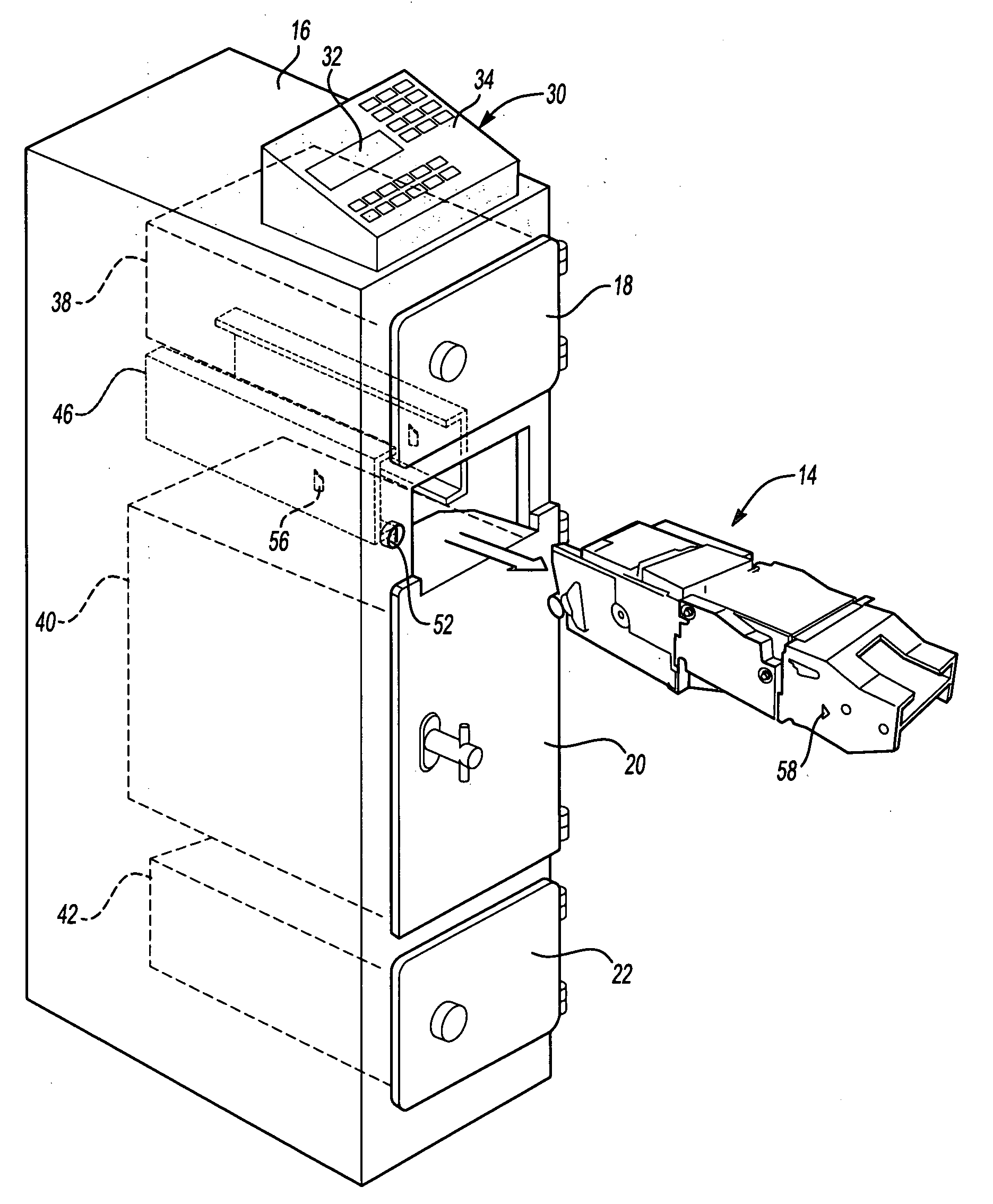
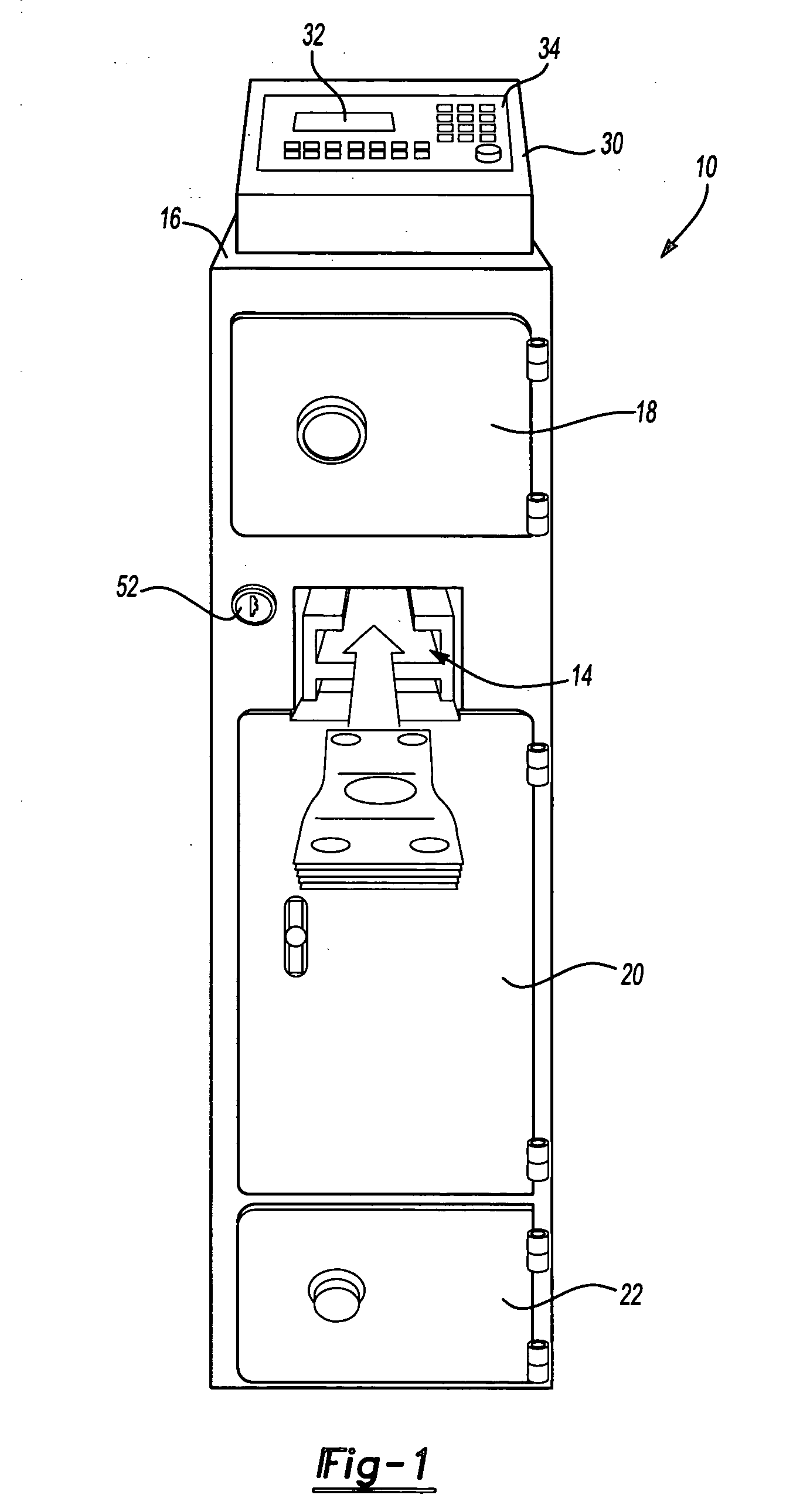
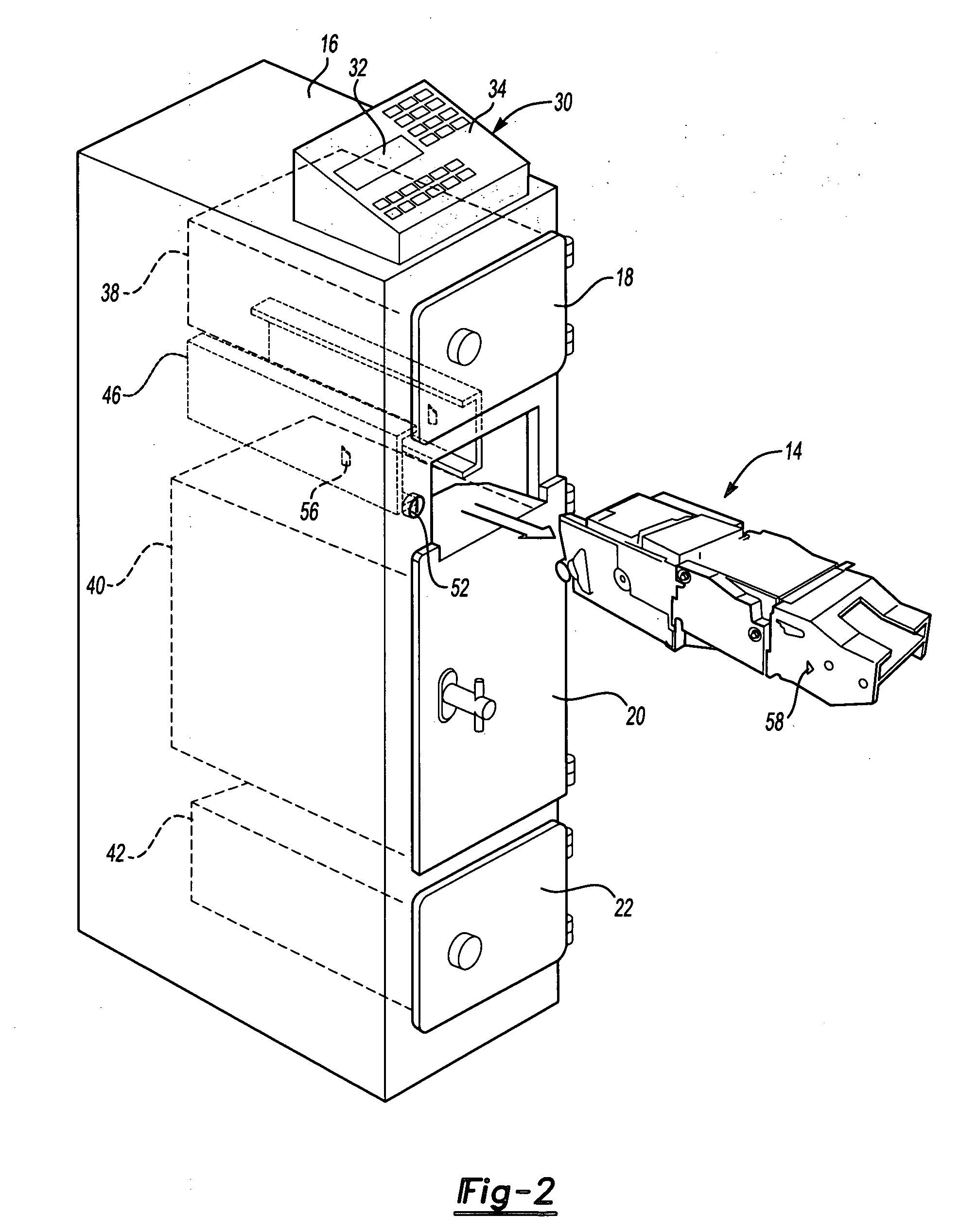
Apparatus having a bill validator and a method of servicing the apparatus
ActiveUS20060021848A1Without compromising securityCoin/currency accepting devicesATM depositingValidatorEngineering
An apparatus having a bill validator. The apparatus having a storage area within a housing. The bill validator operable to input bills into the storage area. The bill validator being removable secured within the housing. The removable bill validator permitting the bill validator to be removed from the housing for servicing without comprising security of the storage area.
Owner:FIRE KING SECURITY PRODS
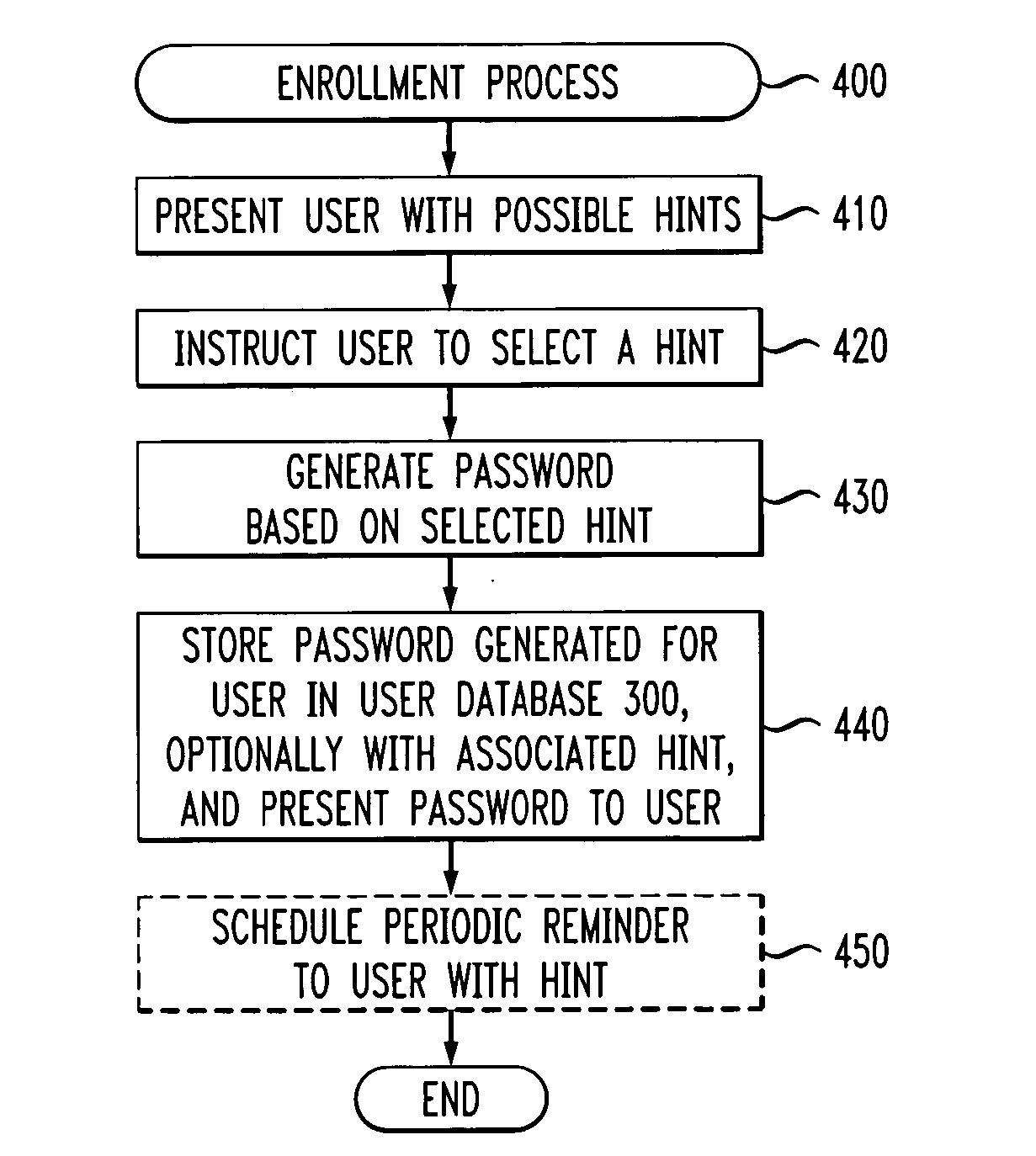
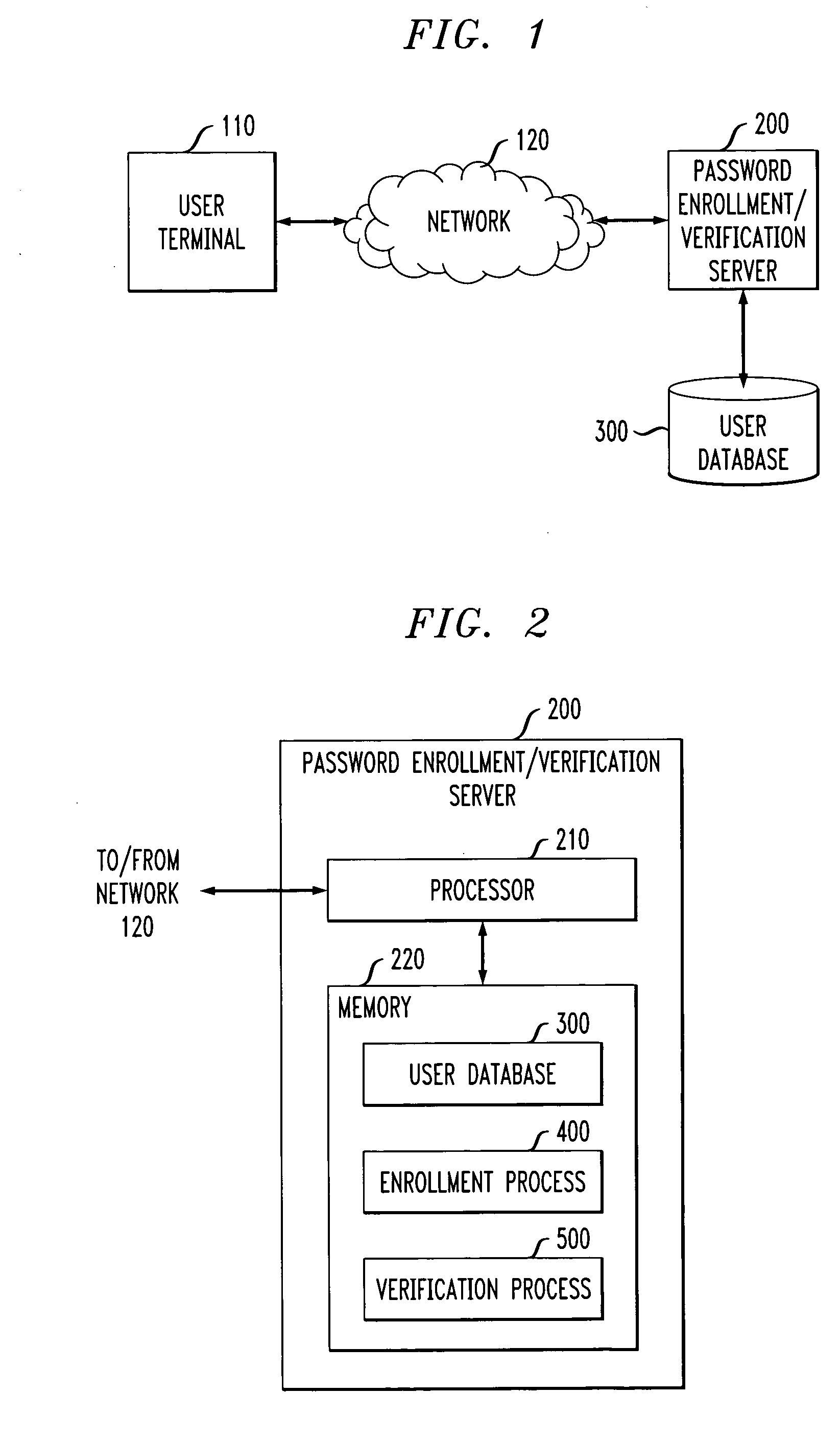
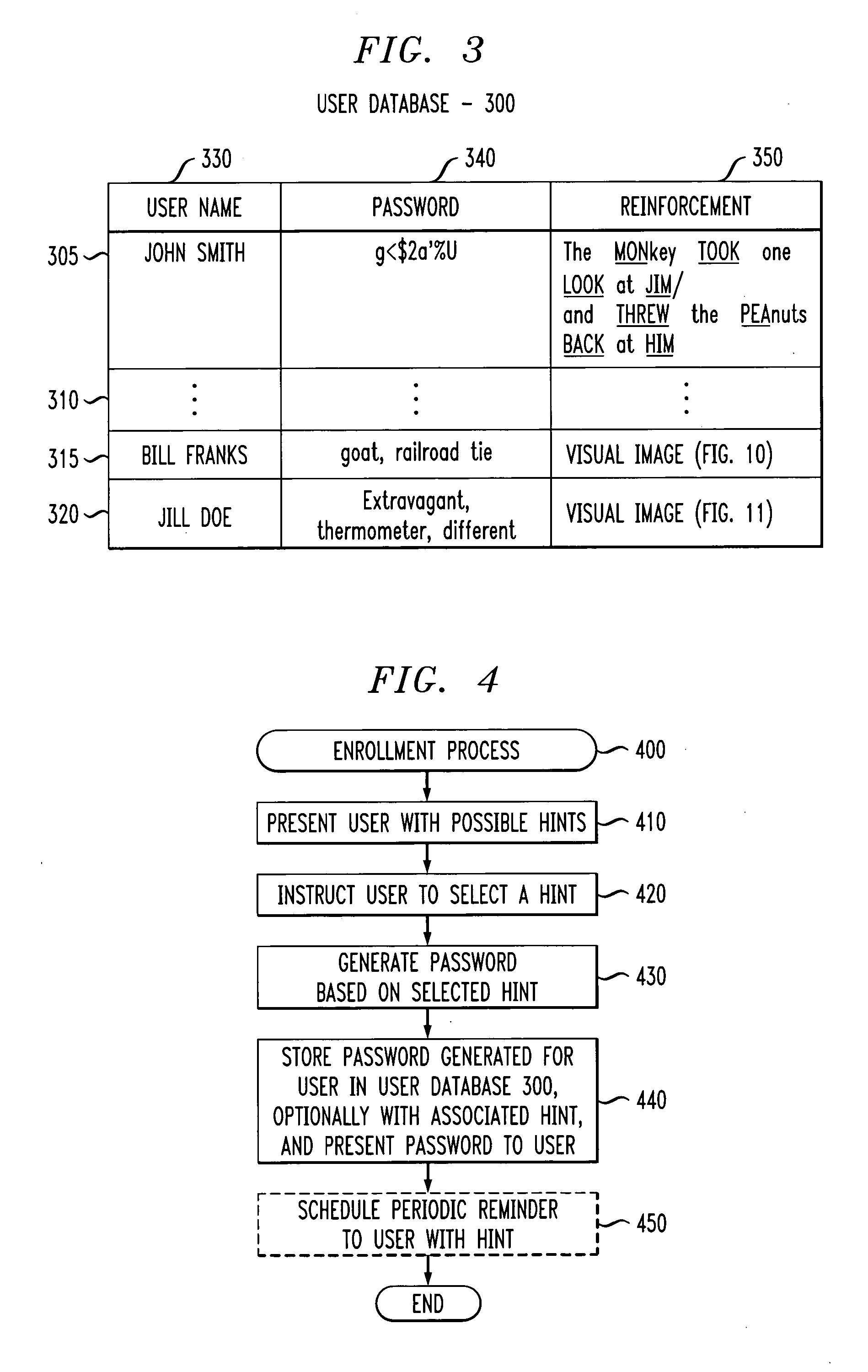
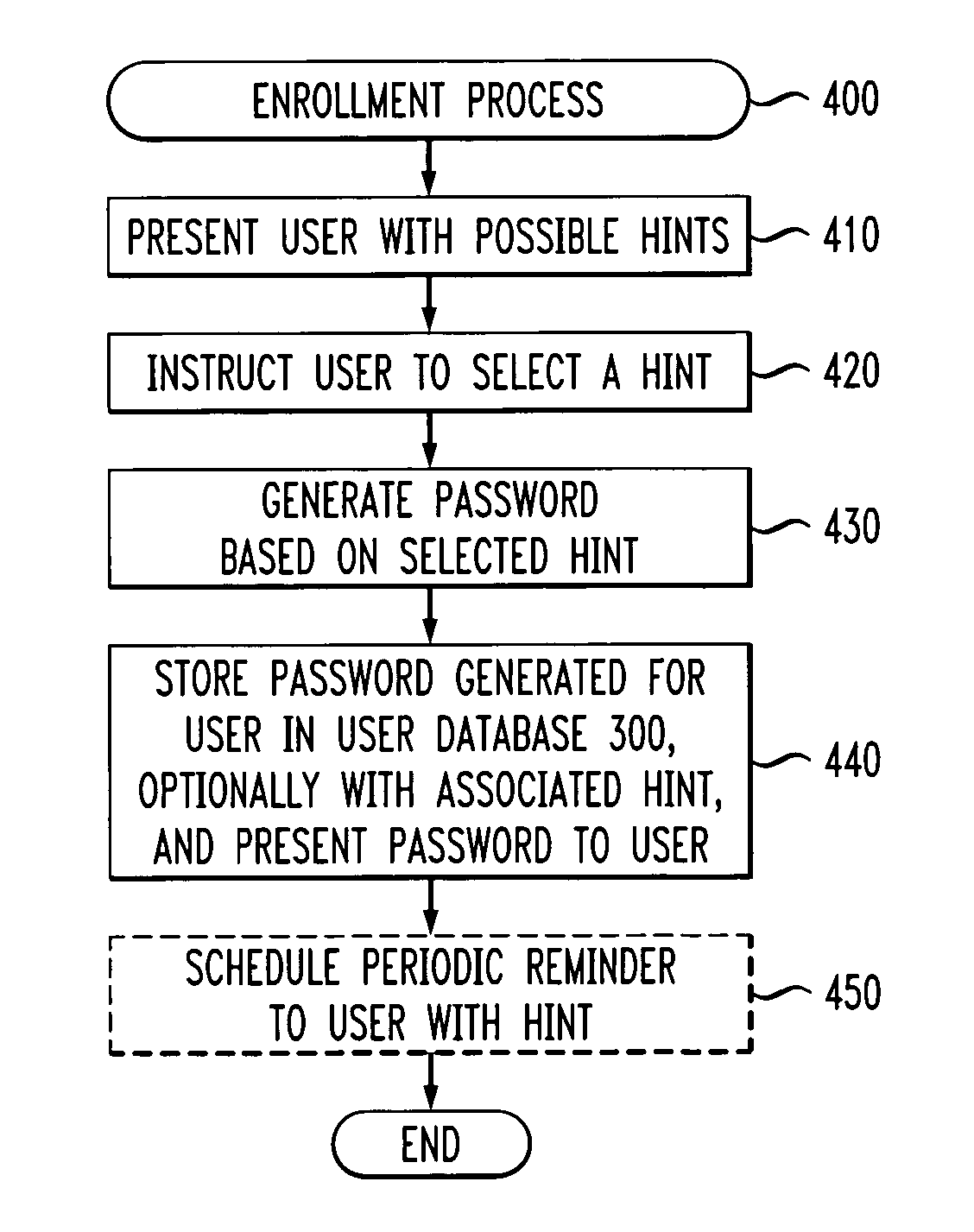
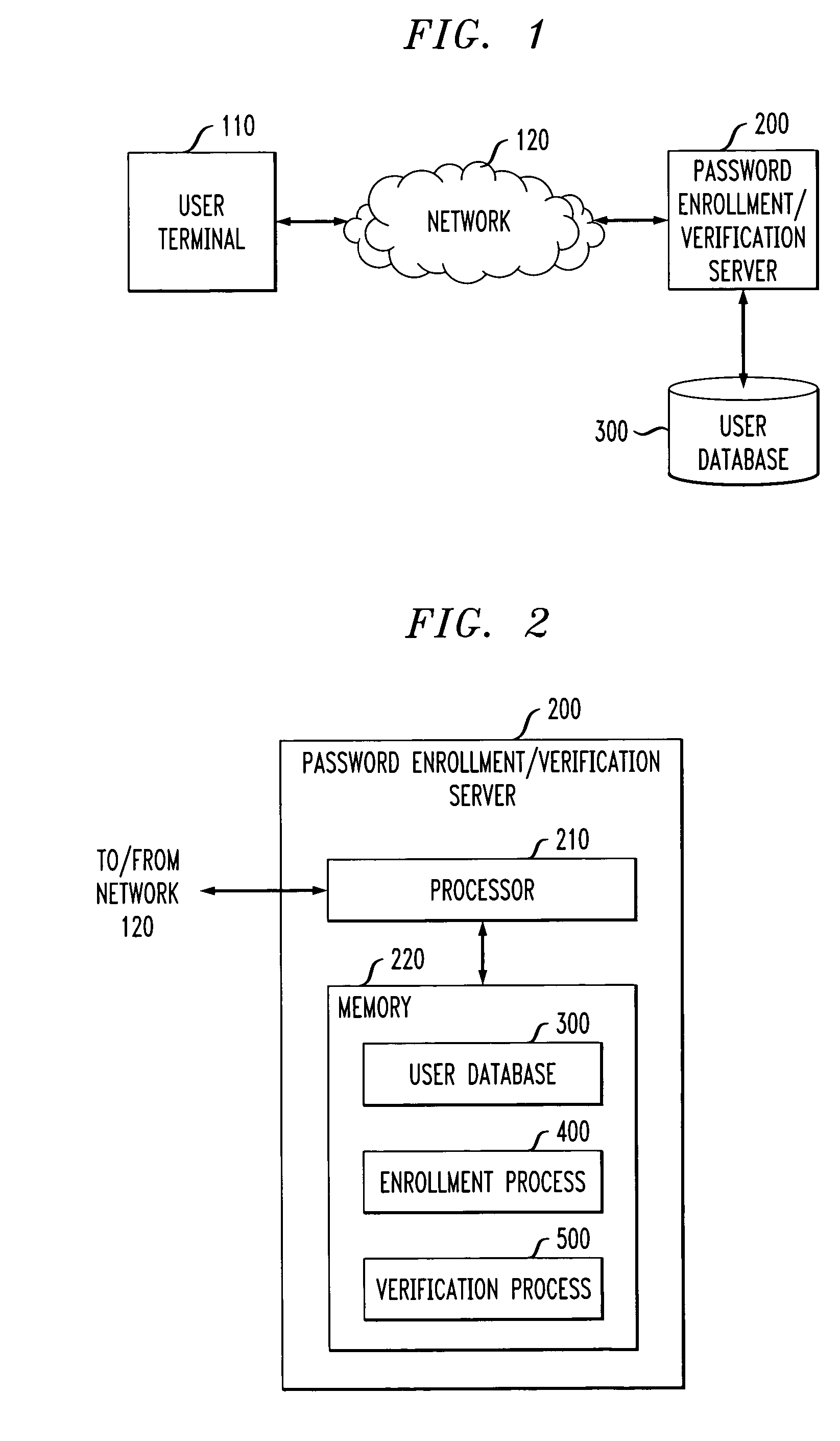
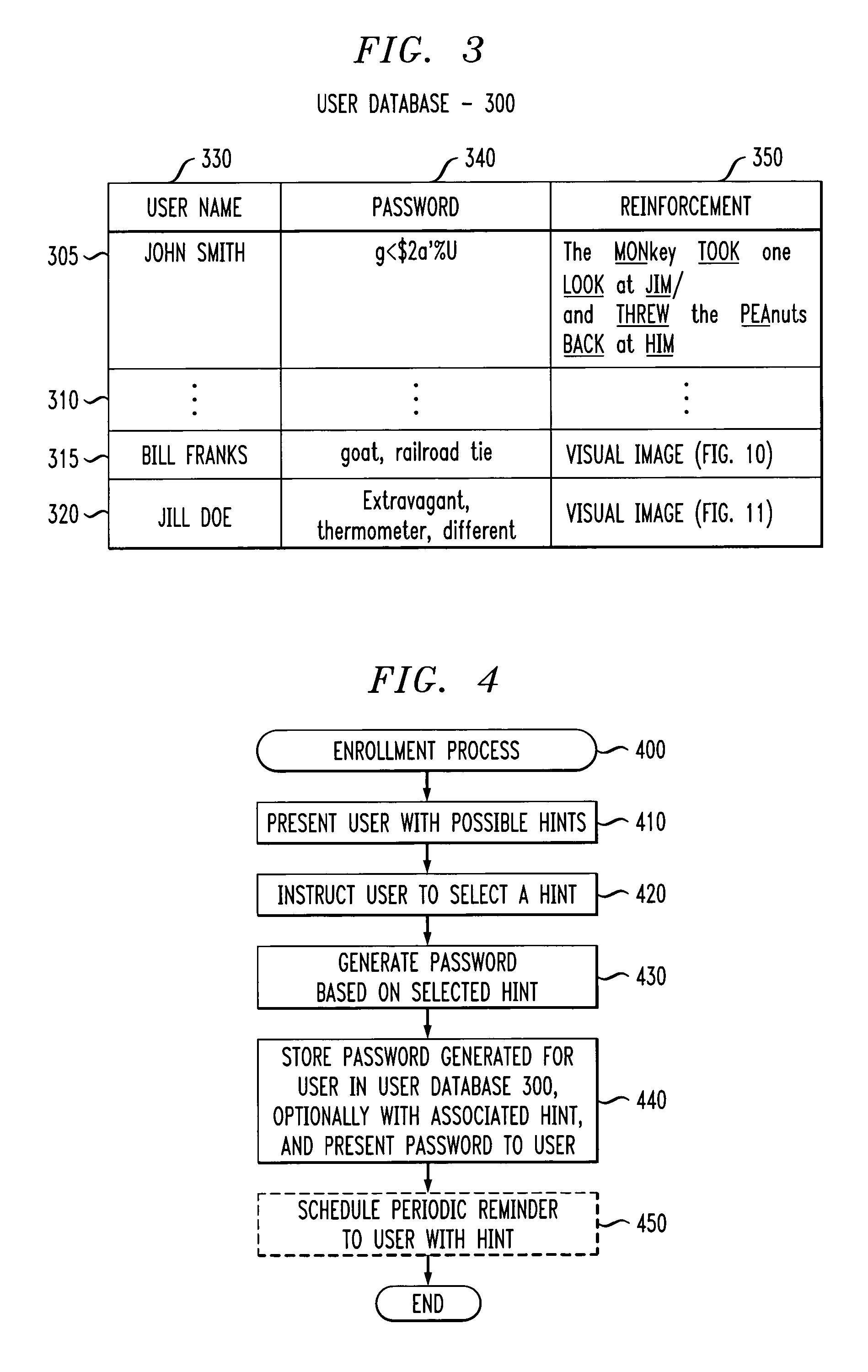
Method and apparatus for generating and reinforcing user passwords
ActiveUS20050071686A1Without compromising securityReinforce the generated passwordDigital data processing detailsUnauthorized memory use protectionPasswordWorld Wide Web
A method and apparatus are provided for generating passwords that may be memorized by a user, yet not easily guessed by an attacker. A user is presented with one or more textual, audio or visual hints. A password is automatically generated based on the selected hint (and possibly further input from the user). The presented hints may include poems, songs, jokes, pictures or words. The generated password and selected hint can be presented to the user during enrollment for further reinforcement and stored in a user database for subsequent reinforcement and verification. The enrollment process may schedule the sending of one or more reminder messages to the user containing the hint to reinforce the password in the user's memory.
Owner:AVAYA INC
Method and apparatus for providing electronic purse
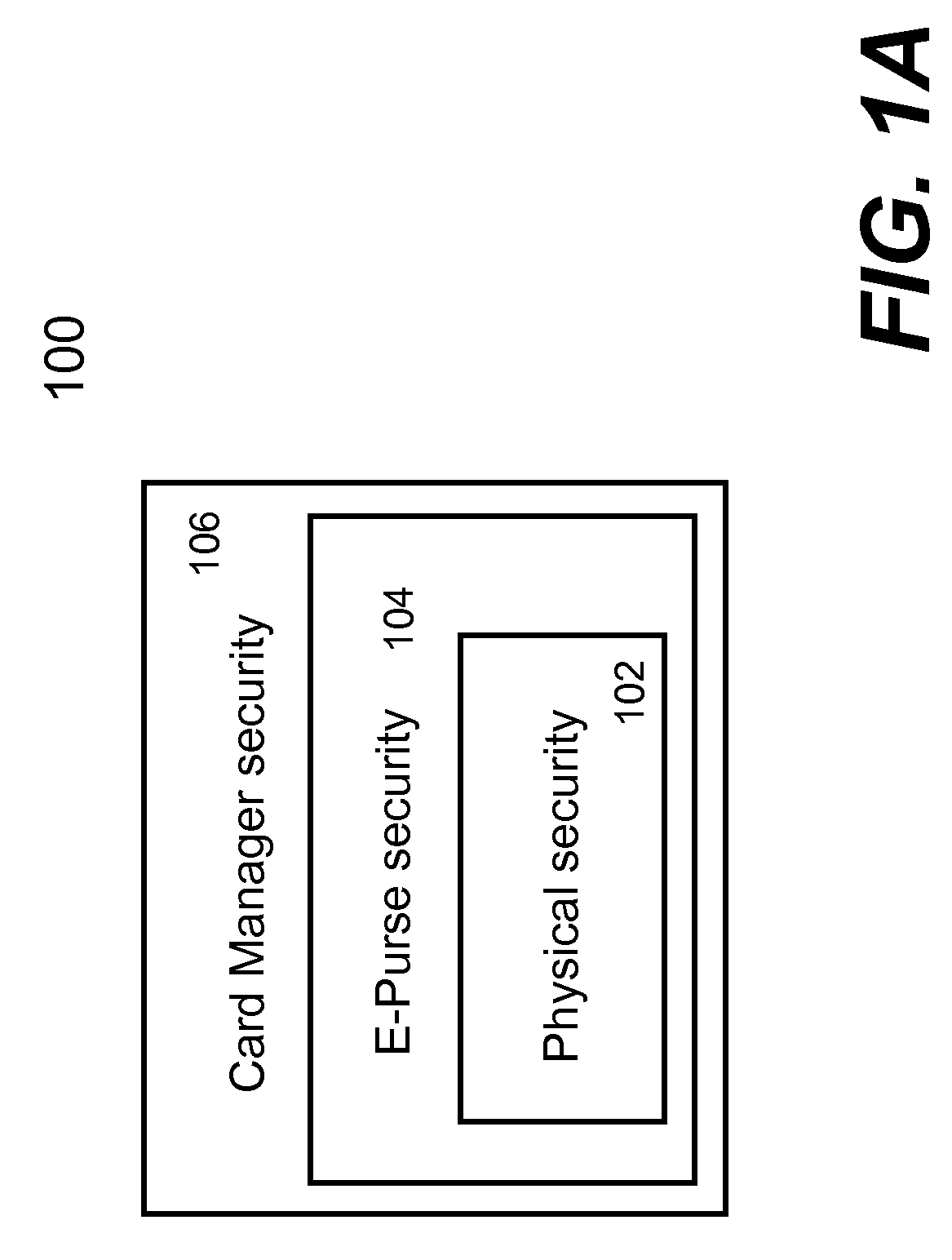
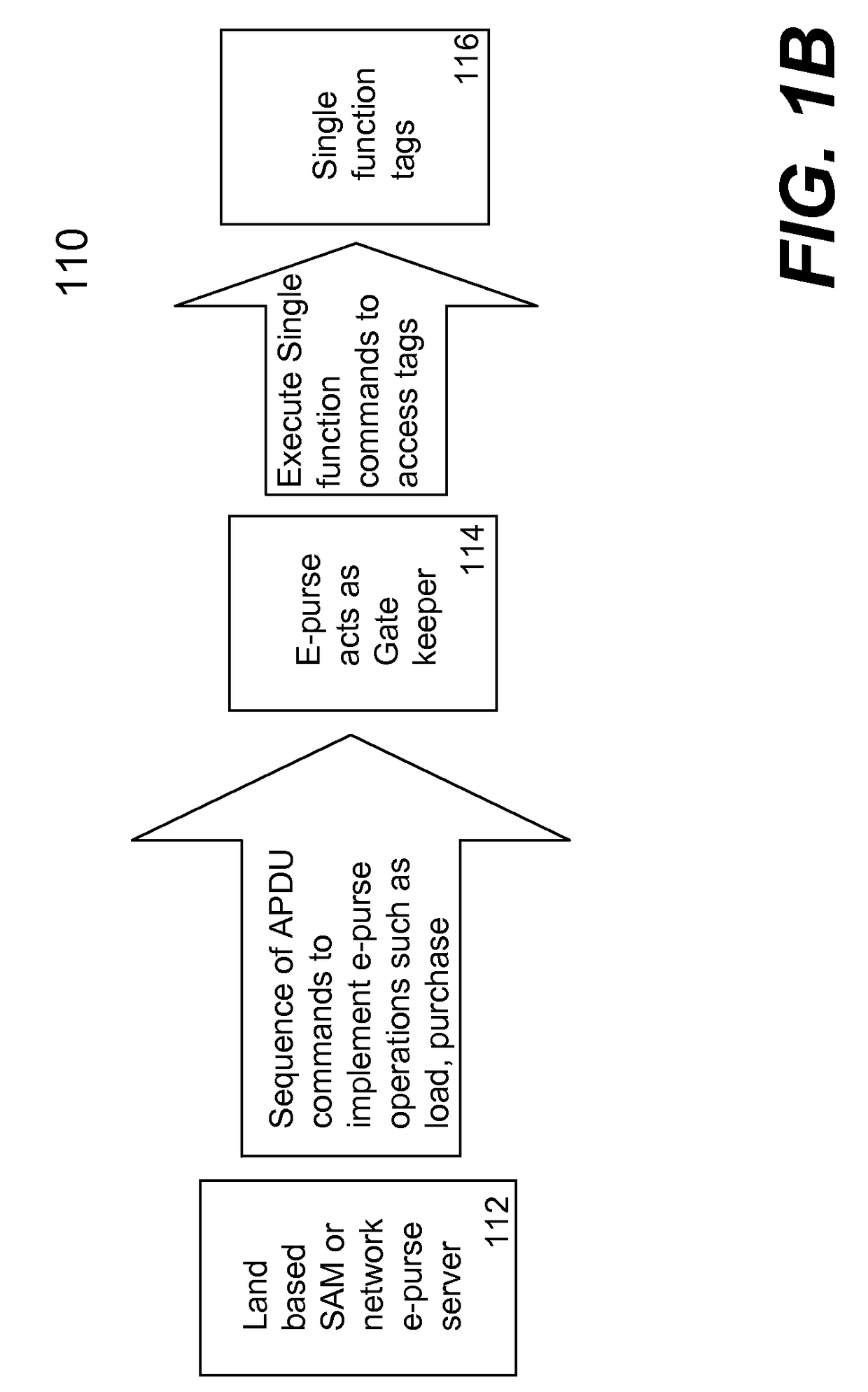
ActiveUS20080073426A1Facilitate communicationWithout compromising securityFinancePayment protocolsPersonalizationPhysical security
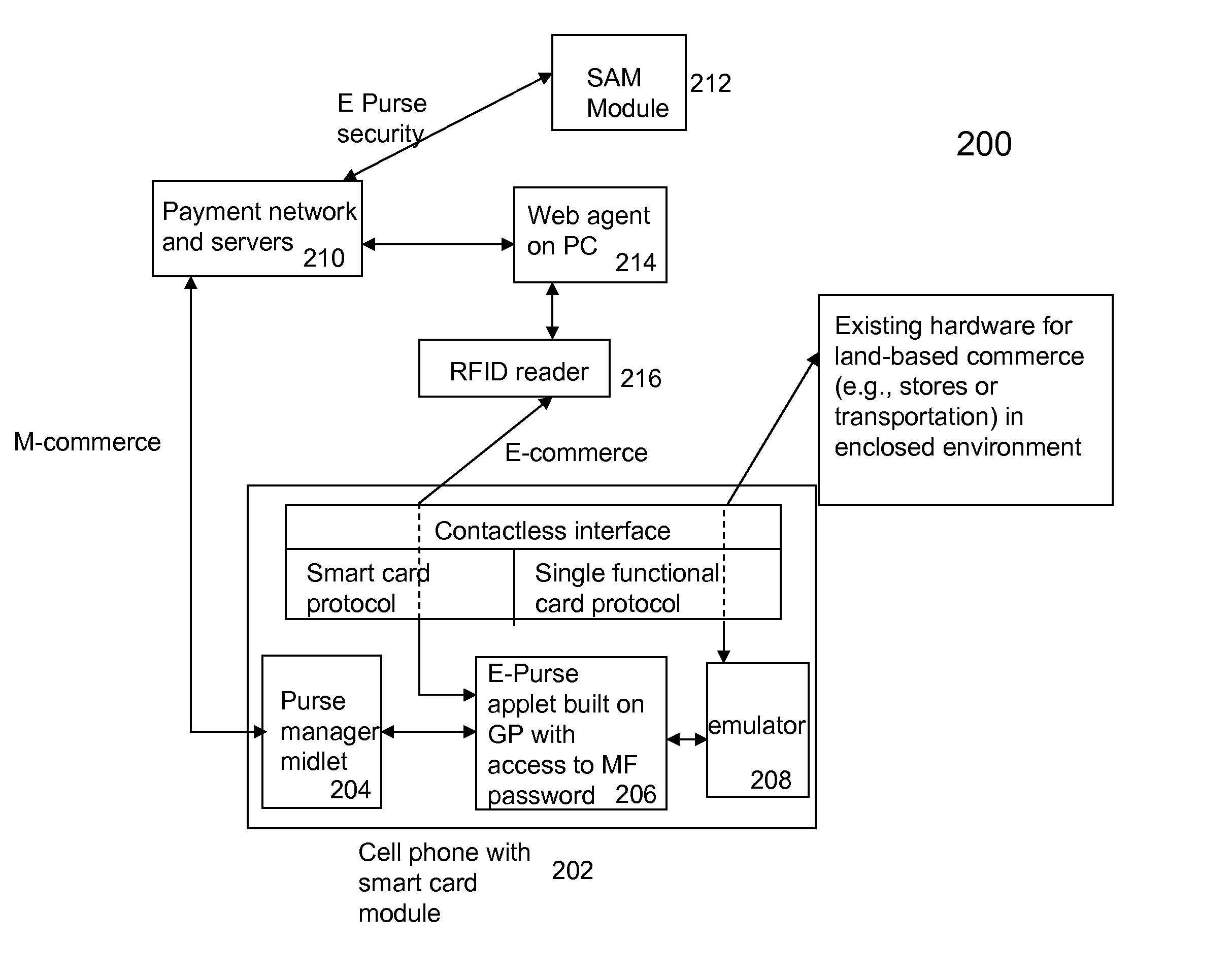
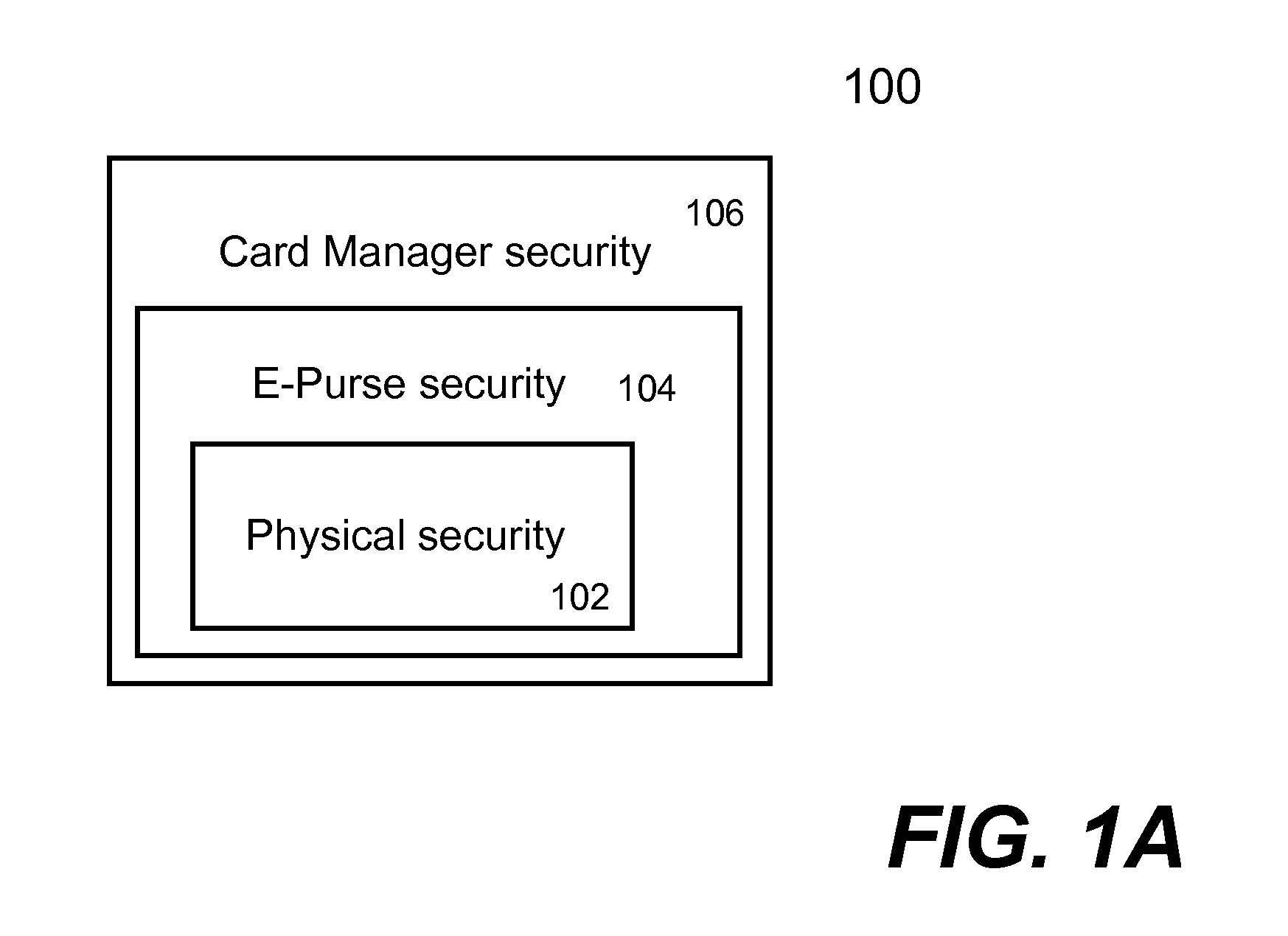
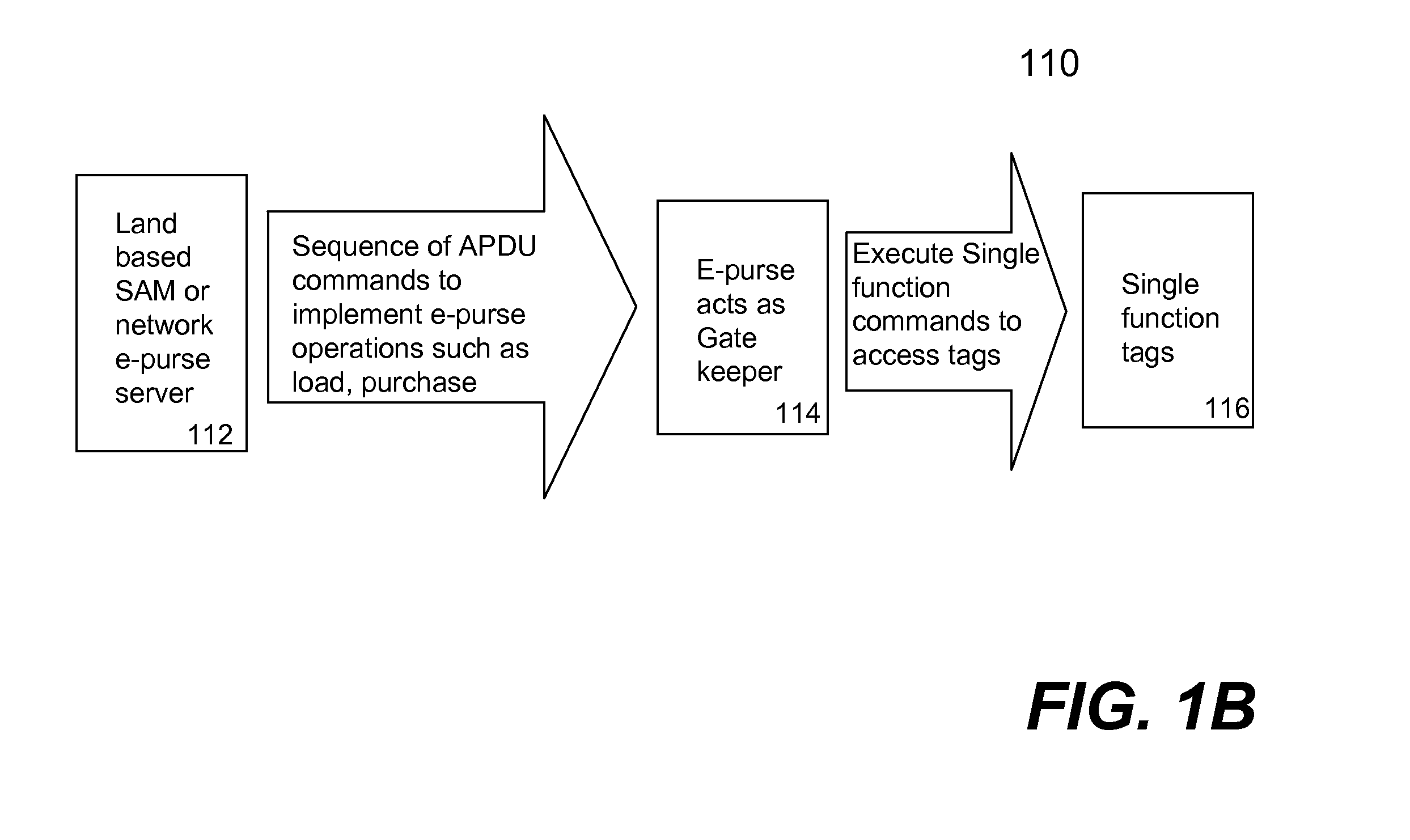
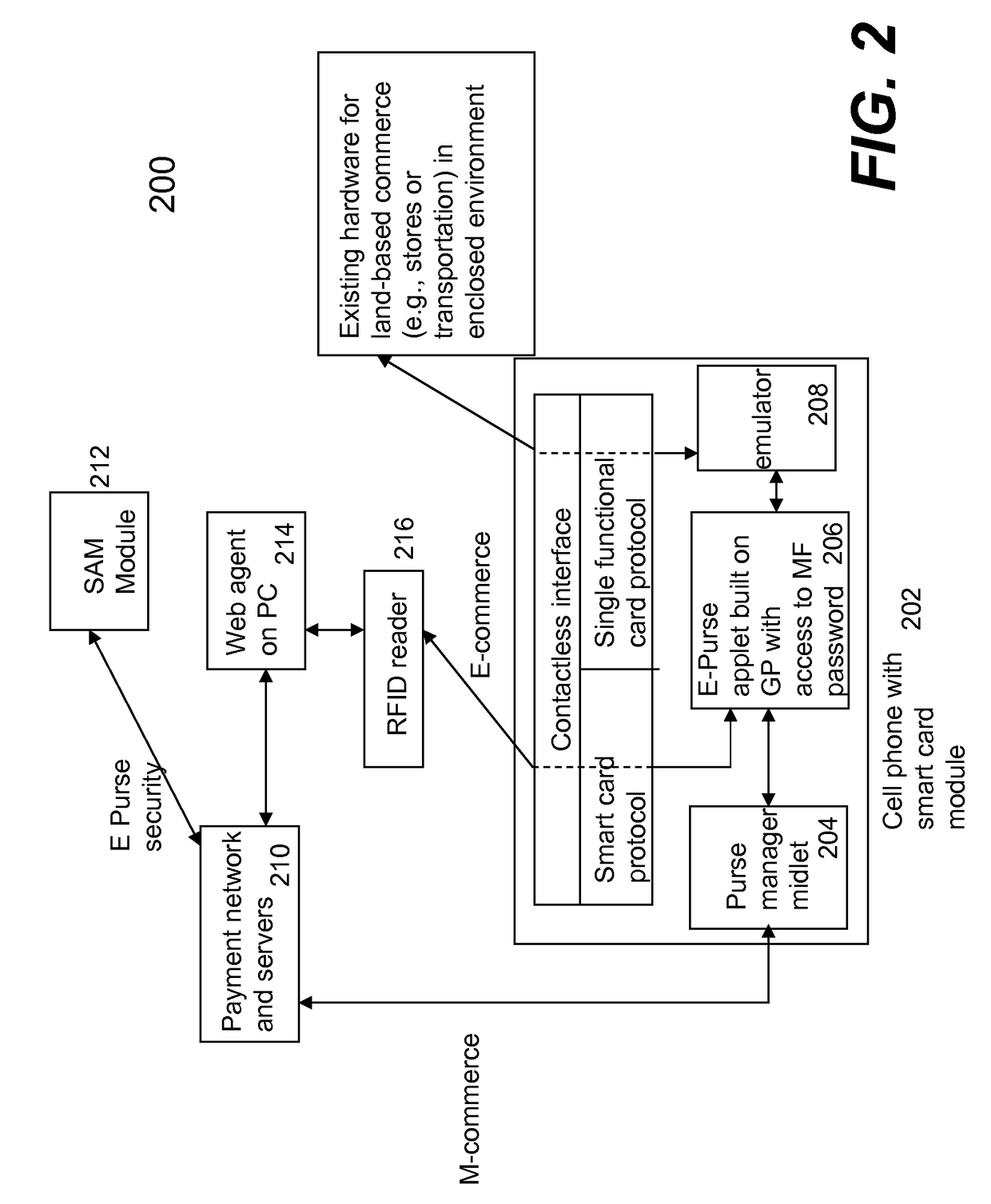
Techniques for portable devices functioning as an electronic purse (e-purse) are disclosed. According to one aspect of the invention, a mechanism is provided to enable a portable device to conduct transactions over an open network with a payment server without compromising security. In one embodiment, a device is loaded with an e-purse manager. The e-purse manager is configured to manage various transactions and functions as a mechanism to access an emulator therein. The transactions may be conducted over a wired network or a wireless network. A three-tier security model is contemplated to support the security of the transactions from the e-purse. The three-tier security model includes a physical security, an e-purse security and a card manager security, concentrically encapsulating one with another. Security keys (either symmetric or asymmetric) are personalized within the three-tier security model.
Owner:SHENZHEN RFCYBER ASSET MANAGEMENT
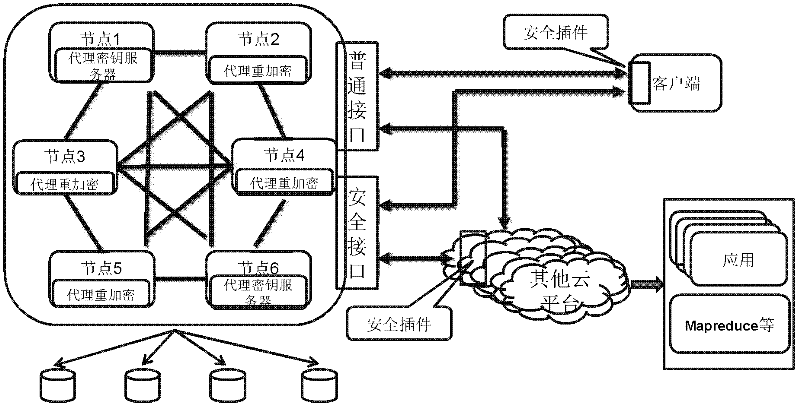
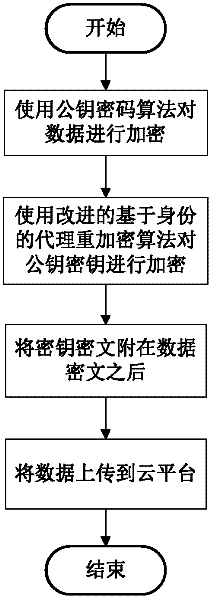
Method for protecting privacy data of users in cloud environment
InactiveCN102655508AWith transparencyReduce overheadEncryption apparatus with shift registers/memoriesPlaintextInternet privacy
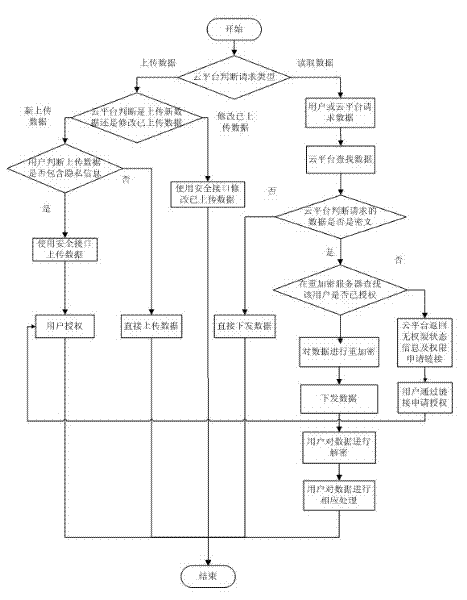
The invention discloses a method for protecting the privacy data of users in a cloud environment. The method comprises the following steps that: a cloud platform receives a user request, and judges whether the user request is a data uploading request or a data reading request; if the user request is a data reading request, the cloud platform searches corresponding data according to an identifier of to-be-read data in the data reading request, and judges whether the data is a ciphertext; if the data is a ciphertext, the cloud platform searches whether the user is authorized in a re-encryption key server; if the user is authorized, the cloud platform re-encrypts the data into a ciphertext (can be decrypted by the user) by using a proxy re-encryption service and a re-encryption key corresponding to the user, and issues the ciphertext to the user; the user decrypts the ciphertext by using a decryption key of the user and a decryption interface of a safety plugin so as to obtain plaintext data; and the user calls a corresponding application program interface to carry out modification on uploaded data by using a client plug-in. According to the invention, the application demands of user data on the cloud platform are not affected while the privacy data of the users is protected,.
Owner:HUAZHONG UNIV OF SCI & TECH
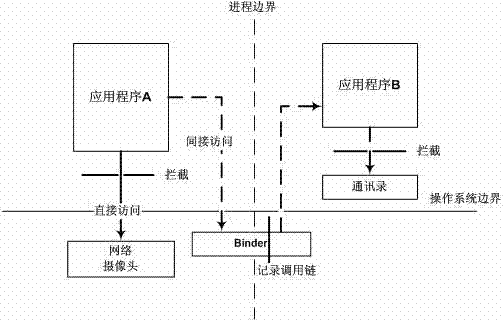
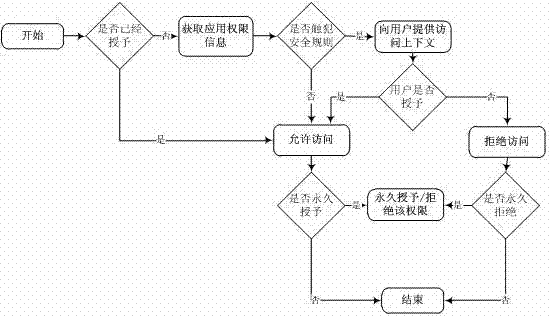
Immediate access conferring method aiming at low interference of mobile platform
InactiveCN103116716APrevent gettingReduce authorization requestsDigital data authenticationPlatform integrity maintainanceSystem callAccess to information
The invention belongs to the technical field of mobile platform access control, and particularly discloses an immediate access conferring method aiming at low interference of a mobile platform. According to the fact that a system call interceptor is designed and achieved on the interior of a mobile platform operating system, direct access of application programs on the mobile platform to sensitive resources can be effectively intercepted. According to the fact that communication information among courses is recorded in operating system nucleus, the fact that the application programs indirectly access the sensitive resources through open interfaces of other application programs can be effectively controlled, and therefore all standing of access of the sensitive resources is achieved. According to the immediate access conferring method aiming at the low interference of the mobile platform, safety is guaranteed, most of harmless access can be filtered at the same time, for tiny minority of access possibly triggering the safe problems, access information can be immediately provided for a user so as to help the user to make correct access conferring.
Owner:FUDAN UNIV
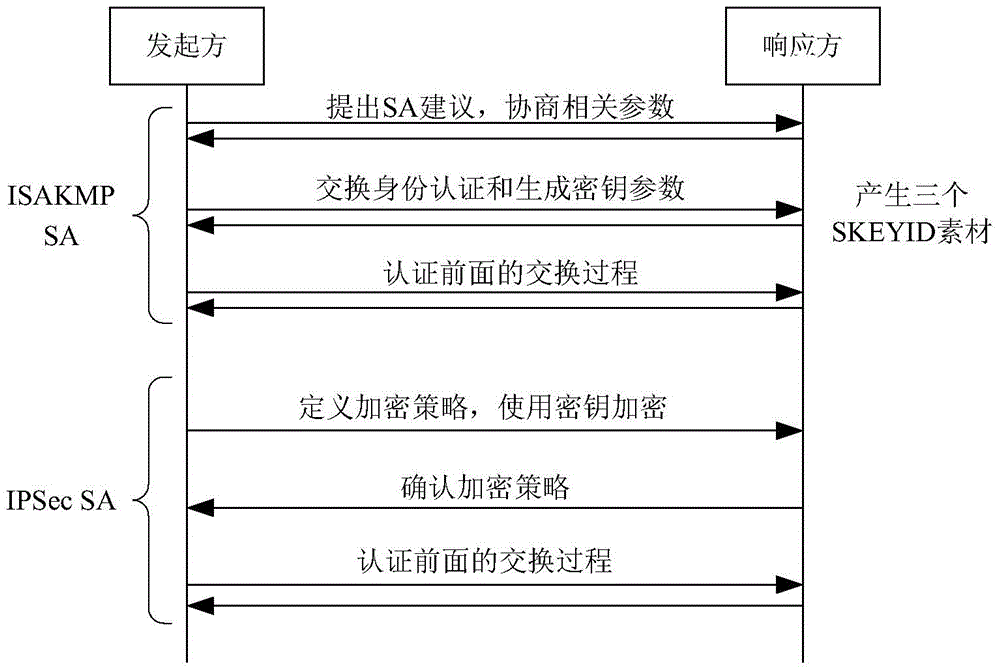
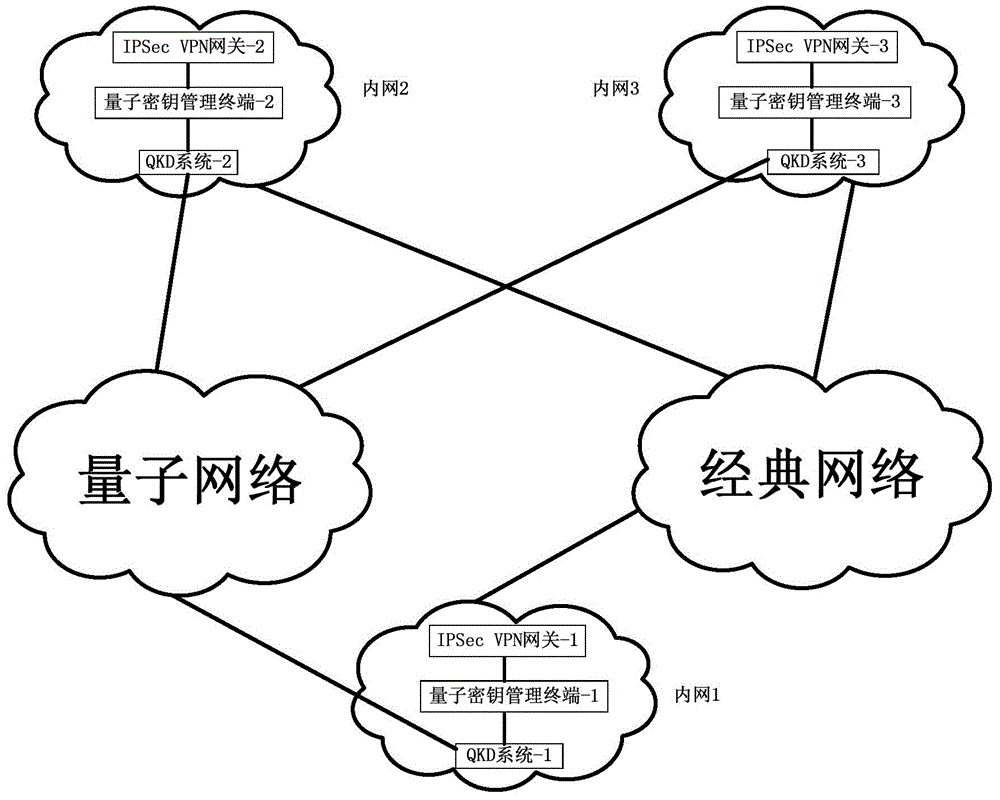
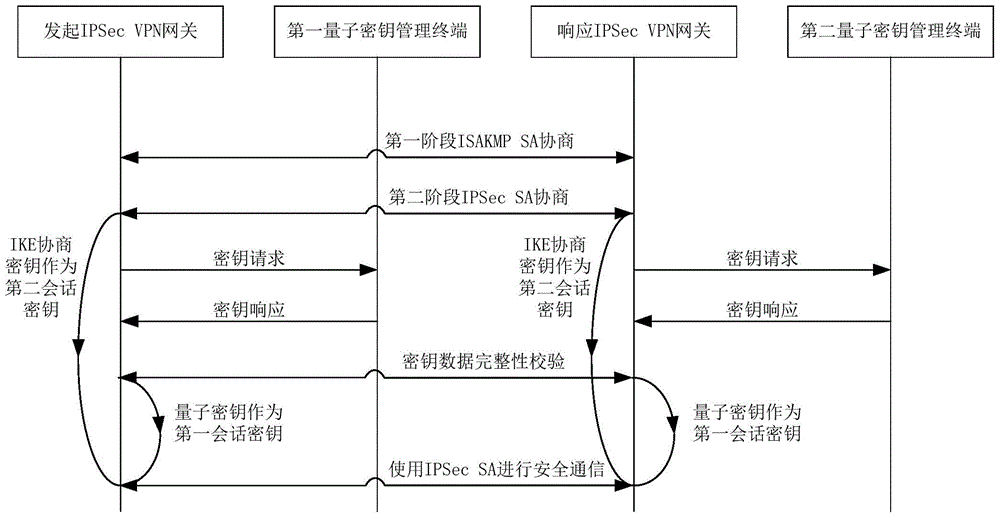
Method and system for extended use of quantum keys in IPSec VPN (internet protocol security-virtual private network)
ActiveCN104660603ANovel structureIncrease update frequencyKey distribution for secure communicationData switching networksSession keyKey management
The invention discloses a method and a system for extended use of quantum keys in an IPSec VPN (internet protocol security-virtual private network) system. The IPSec VPN system comprises at least two IPSec VPN gateways including an initiating IPSec VPN gateway and a responding IPSec VPN gateway as well as corresponding quantum key management terminals. The method comprises steps as follows: through parallel processing of negotiation of the quantum keys and IKE (internet key exchange) negotiated keys, the quantum keys are taken as first session keys for preferential use, and the IKE negotiated keys are taken as second session keys for safety communication. Besides, the invention further provides the corresponding IPSec VPN gateway, the quantum key management terminals and the IPSec VPN system. The quantum keys are taken as the session keys through extended use, so that the session key updating frequency is greatly increased and the safety communication performance of conventional IPSec VPN is guaranteed under the condition that an original IPSec VPN is compatible.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +1
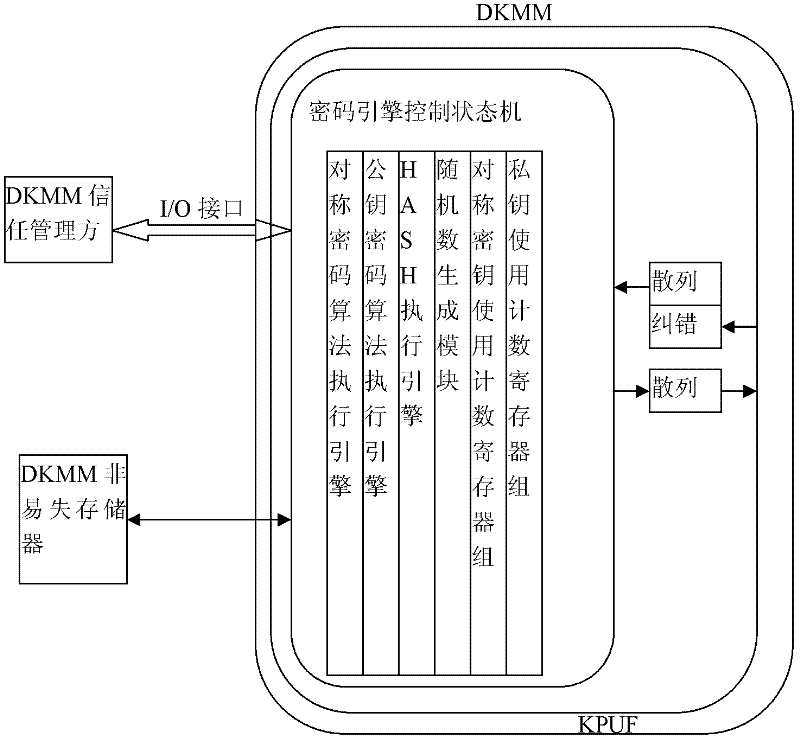
Crypto chip system for resisting physical invasion and side-channel attack and implementation method thereof
InactiveCN102393890AUse lessUnable to break throughPlatform integrity maintainanceKey generationComputer security
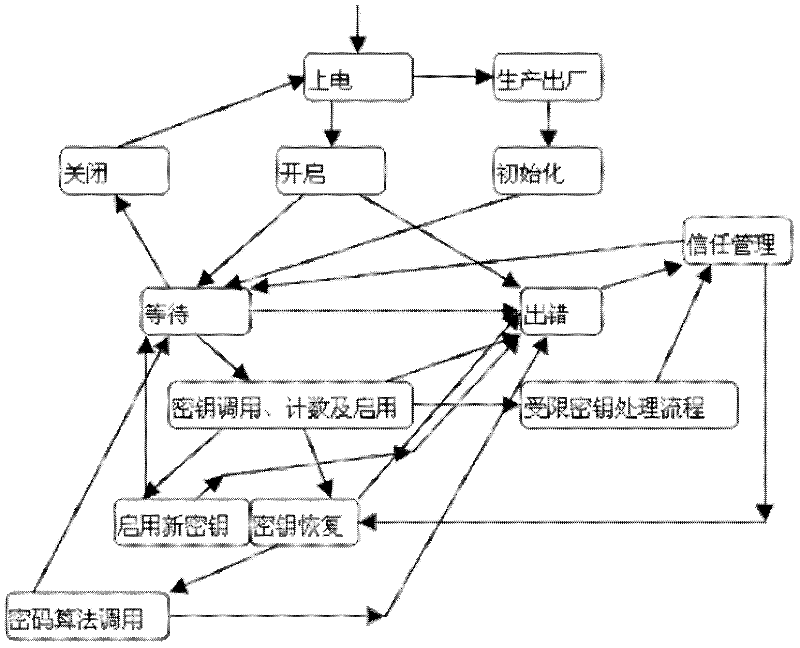
The invention discloses a crypto chip system for resisting physical invasion and side-channel attack and an implementation method thereof. The system comprises a dynamic key management module, a nonvolatile memory module and a trust management end. The invention also discloses an implementation method for the system, which comprises the following steps: (1) initializing, (2) key calling counting and starting; (3) key generation and recovery; (4) closing; and (5) opening. The key is dynamically extracted from a physically no-cloning key module, the trust management end is introduced, and the steps in the implementation method are combined, so that the nonvolatile memory of the chip has the capacity for resisting physical invasion and attack. The application number of times of each key is counted to implement forced updating after reaching the specified value, so that the side-channel attacker can not collect the same key to adequately reveal the sample, and thus, the side-channel attack becomes invalid.
Owner:GUANGZHOU UNIVERSITY +1
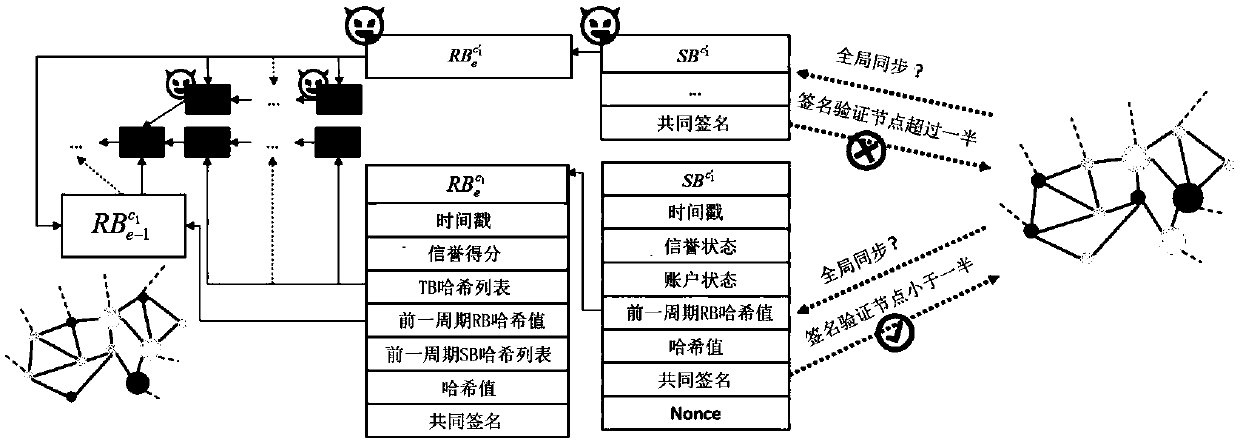
A method for implementing a network scalability block chain
InactiveCN109544334AImprove scalabilityImprove securityFinanceEncryption apparatus with shift registers/memoriesLeader electionChain structure
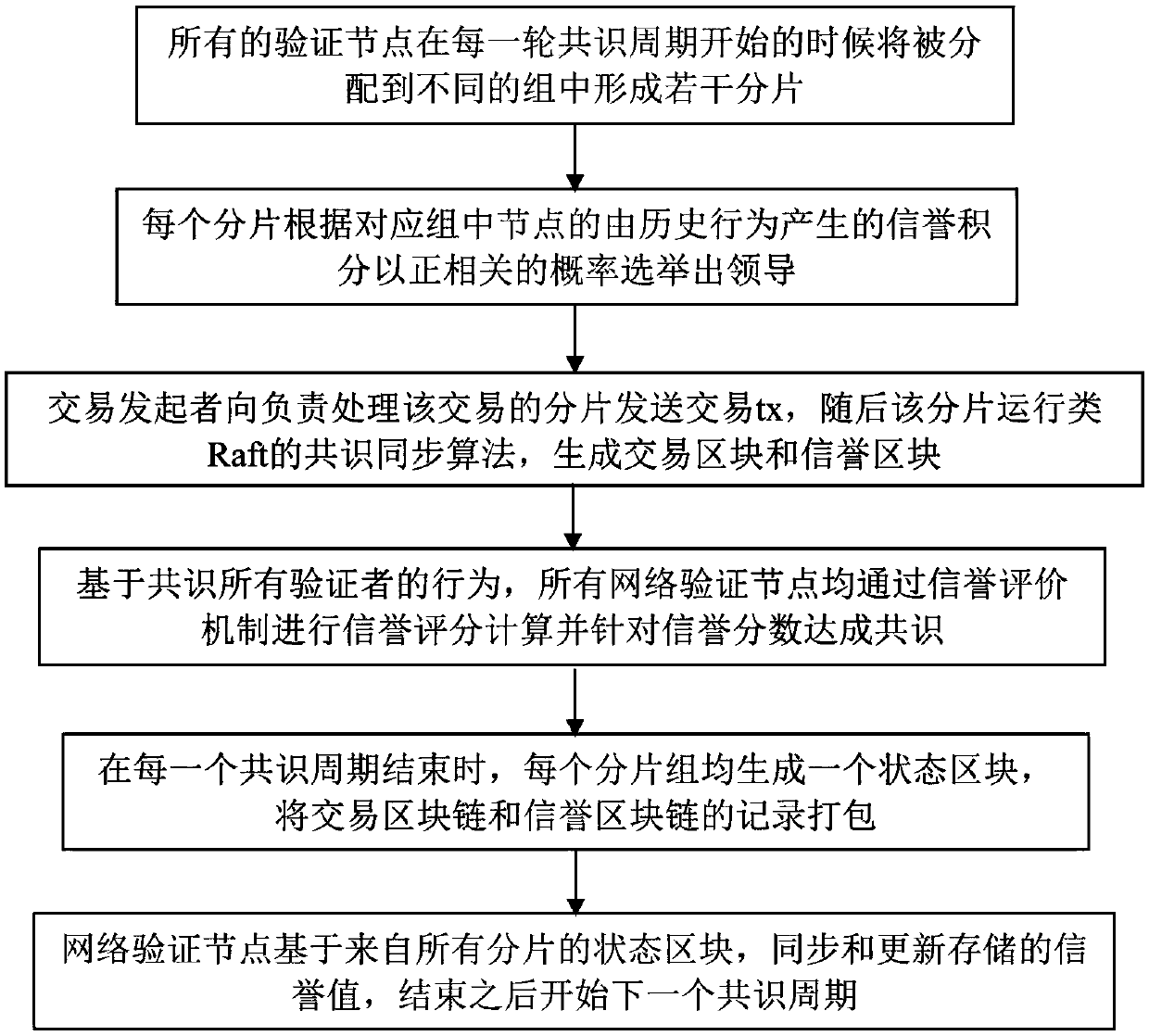
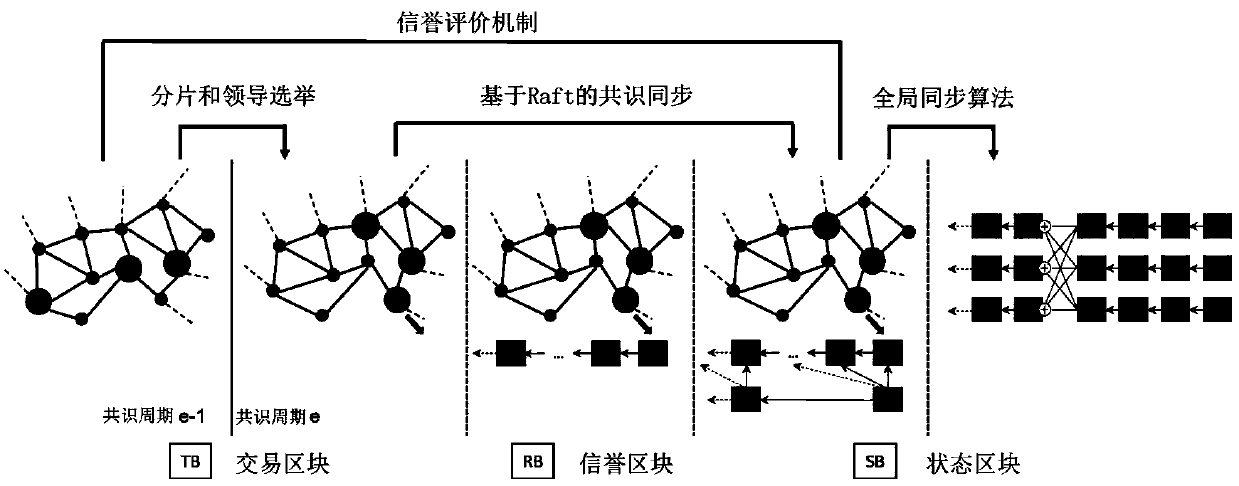
The embodiment of the invention discloses a method for implementing a network scalability block chain, which comprises the following steps: slicing and leadership election, consensus synchronization based on slicing leadership, reputation evaluation mechanism and global synchronization algorithm. The embodiment of the invention proposes a parallel chain structure, which separates the transaction and the consensus into two chains, so as to improve the scalability of the block chain network. The consensus part is carried out in the reputation chain. The network of reputation chain pays attentionto the security and supports the high-speed transaction of the network of transaction chain with proper speed. Based on the advantages of the reputation evaluation mechanism, the embodiment of the invention proposes a network slicing method based on the reputation evaluation mechanism. After the network slicing, the honest and excellent performance node has a greater probability to become the leader of the slicing, so as to realize the high throughput of the network without reducing the safety of the block chain network.
Owner:SHENZHEN HUSHTREE TECH CO LTD
System and method for remotely debugging application programs
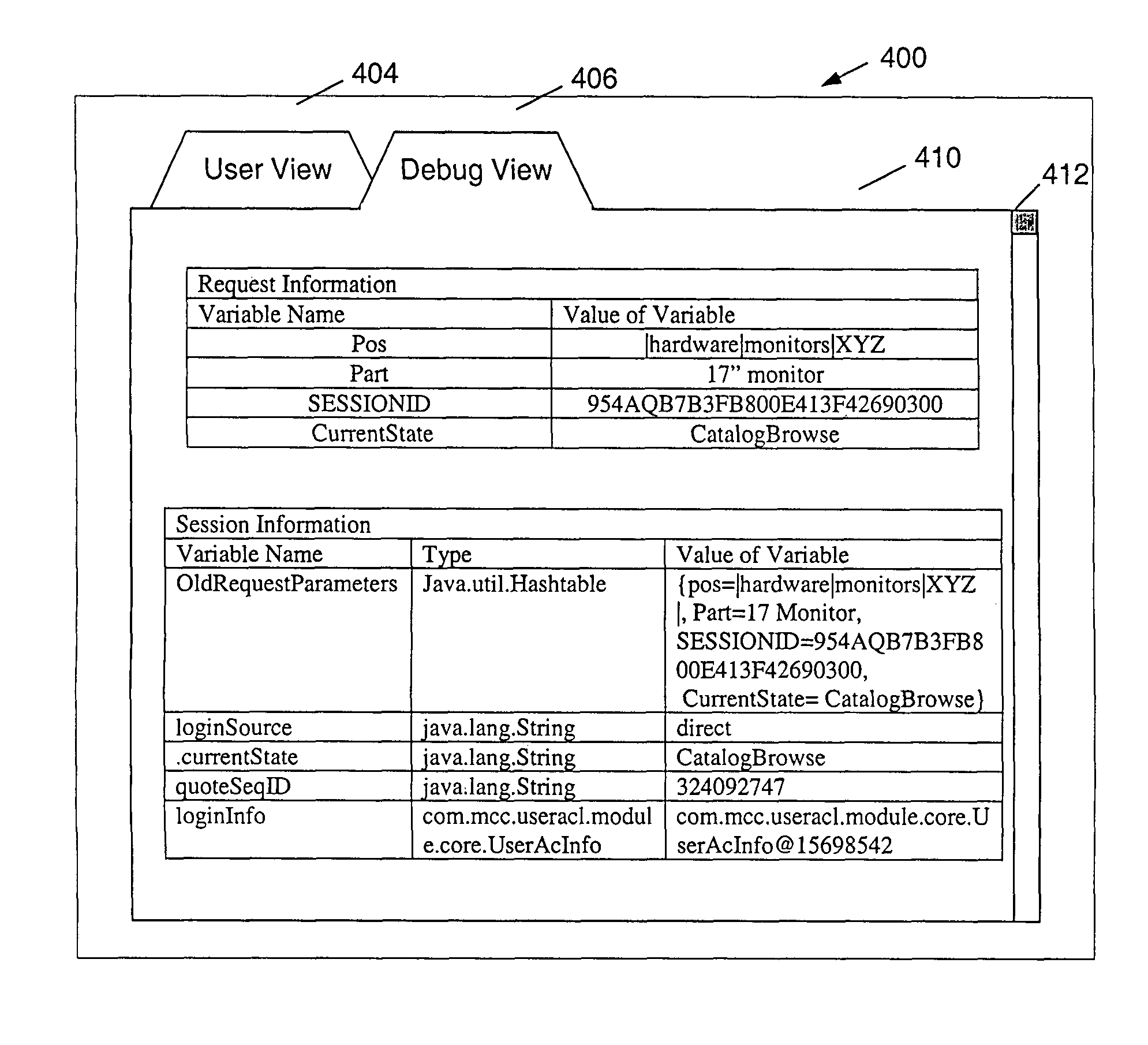
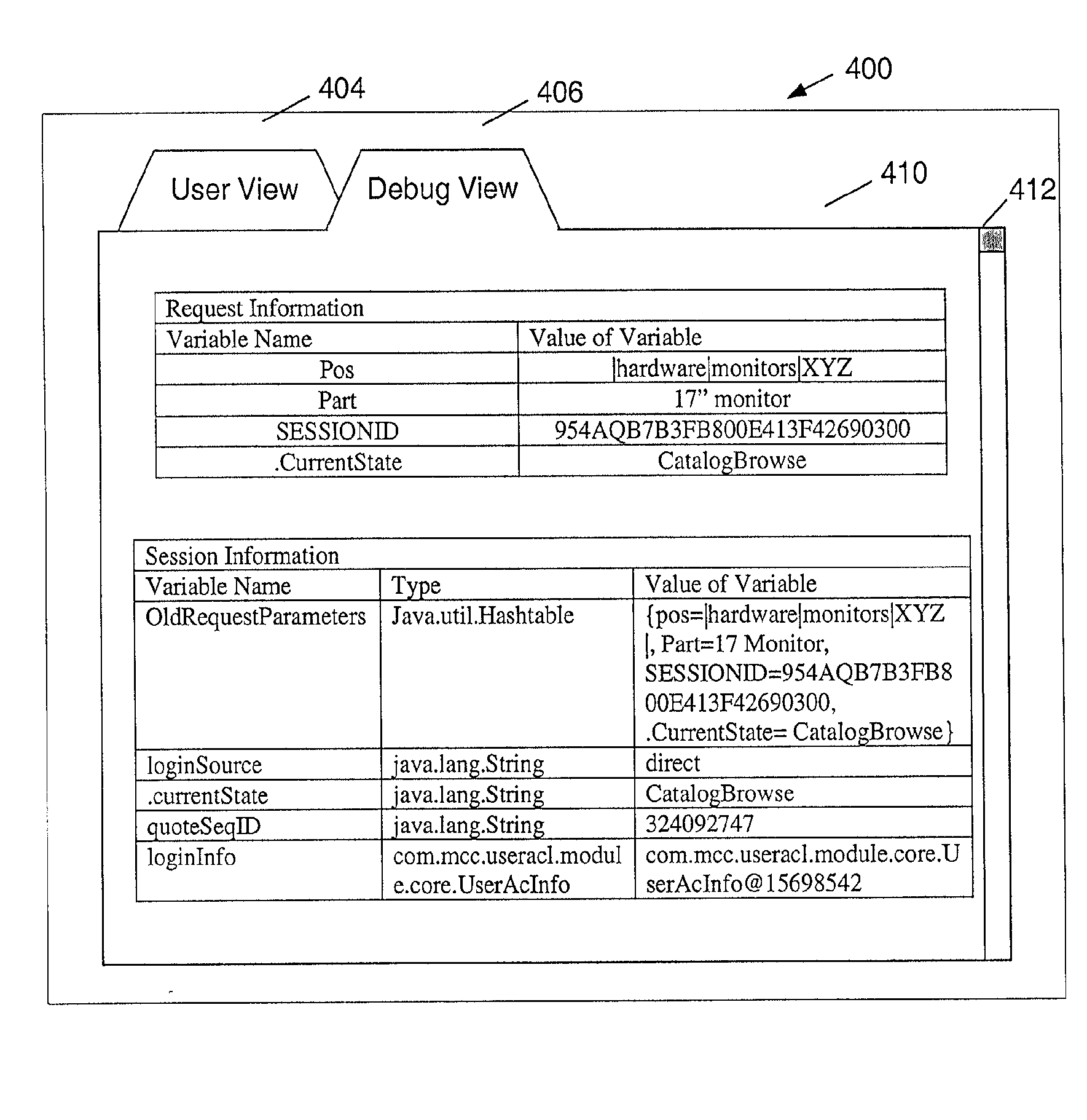
ActiveUS7873872B1Without compromising securityLess attentionError detection/correctionSpecific program execution arrangementsProgramming languageApplication software
A method, system, and apparatus for debugging an application program from a workstation that is remote from a server on which the application program resides includes invoking the application program from the workstation via a network interface; displaying a user frame at the workstation that includes information generated by the application program; providing a debug view option at the workstation for generating a debug frame of the application program; and displaying the debug frame at the workstation when the debug view option is selected. A user can select options to switch between the user frame and the debug frame. The debug frame includes information about one or more components of the application program such as a list of the variables or objects, and the fields, methods, and / or the constructors associated with them. When the debug view option is selected, the information for the user frame is saved, and can be restored to regenerate the information on the user frame when the user view option is selected. The developer can view internal, public, and private code associated with the application program without compromising the security of other application programs on the server. This ability to remotely debug application programs in accordance with the present invention is thus more time and cost efficient than previous methods, and also alleviates concerns about security and unauthorized access to the server.
Owner:VERSATA DEV GROUP
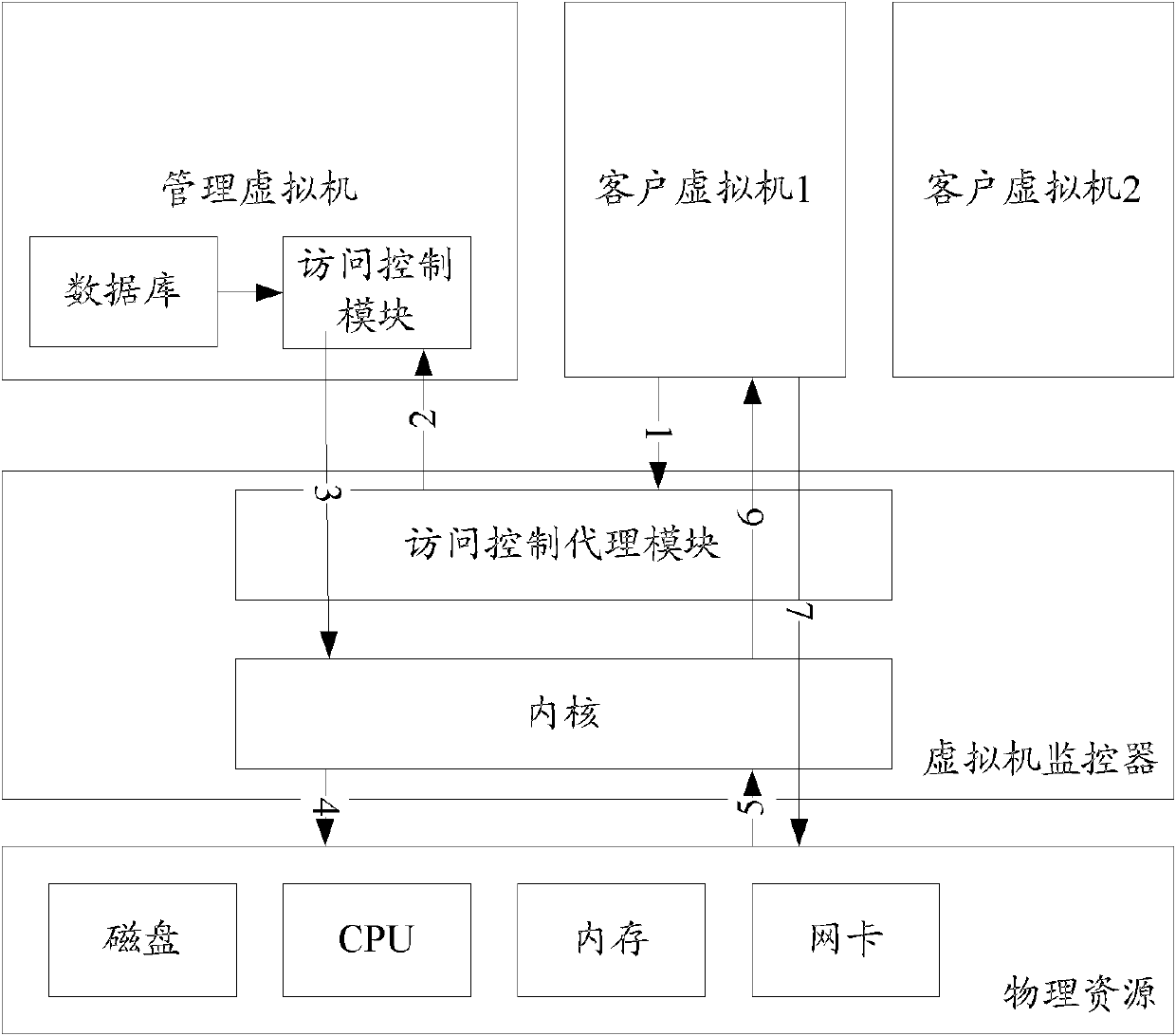
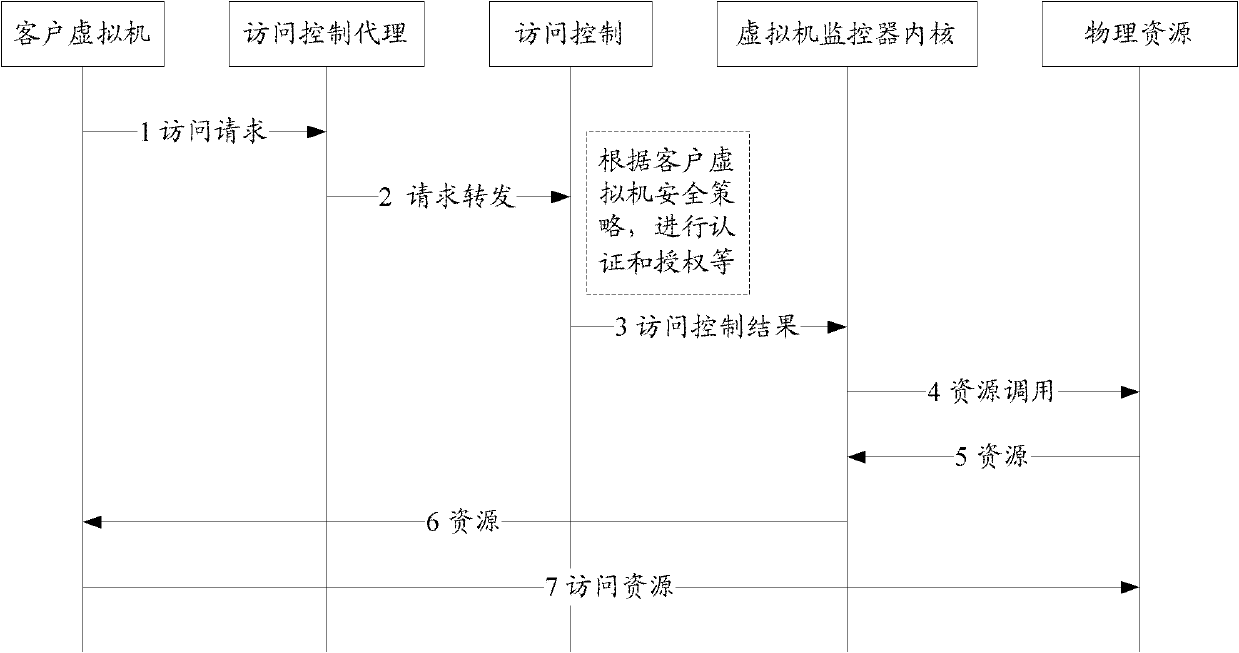
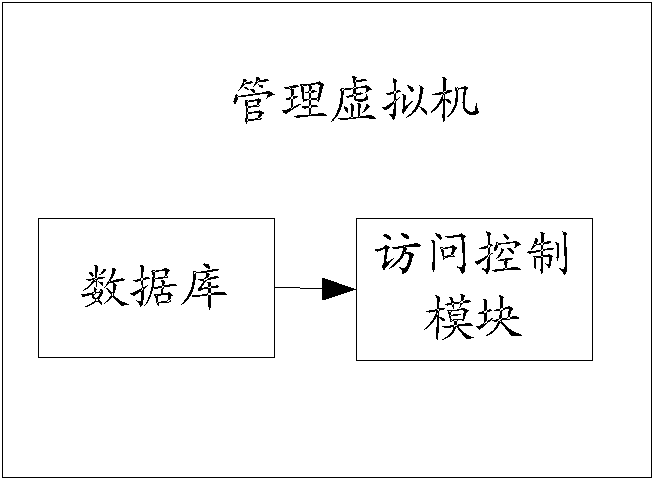
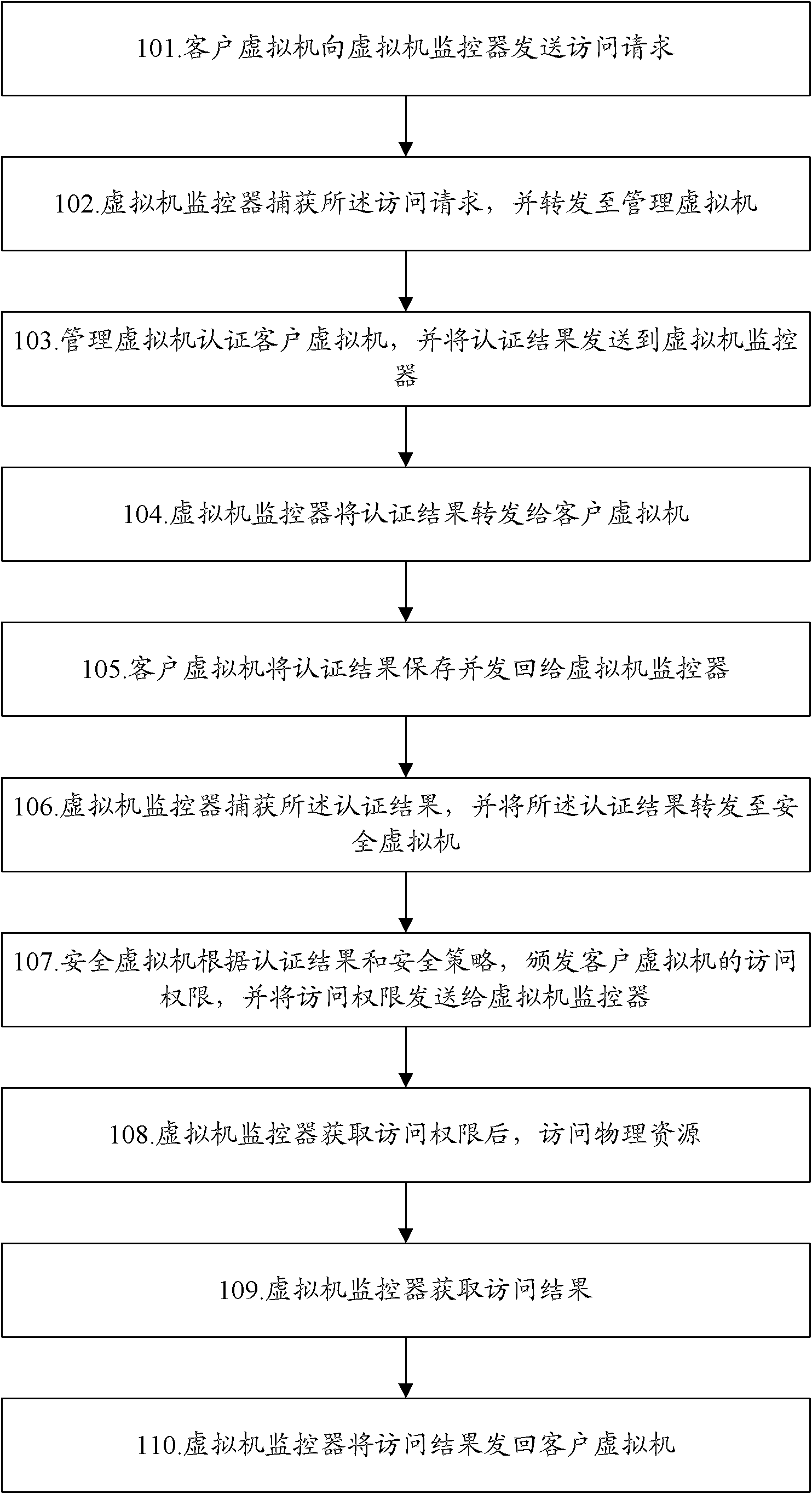
Access control method and system for virtual machine system
InactiveCN102707985AReduce problem sizeImprove securitySpecific access rightsTransmissionComputer moduleVirtual machine
The invention discloses an access control method for a virtual machine system. A virtual machine is arranged in a system to serve as a manager virtual machine, and other virtual machines serve as client virtual machines. An access control module is arranged in the manager virtual machine and used for performing access control over the client virtual machines according to the information of the client virtual machines, and an access control proxy module is arranged in a virtual machine monitor and used for receiving access request information of the client virtual machines and forwarding the access request information to the access control module. By the technical scheme, the scale of the virtual machine monitor is not increased, the safety of the virtual machine monitor is not reduced, the access control over the virtual machines can be performed, the access of the virtual machines to physical resources can be effectively controlled, and safety threat such as attack and communication among the virtual machines and service rejection in the virtual machine system can be avoided.
Owner:ZTE CORP
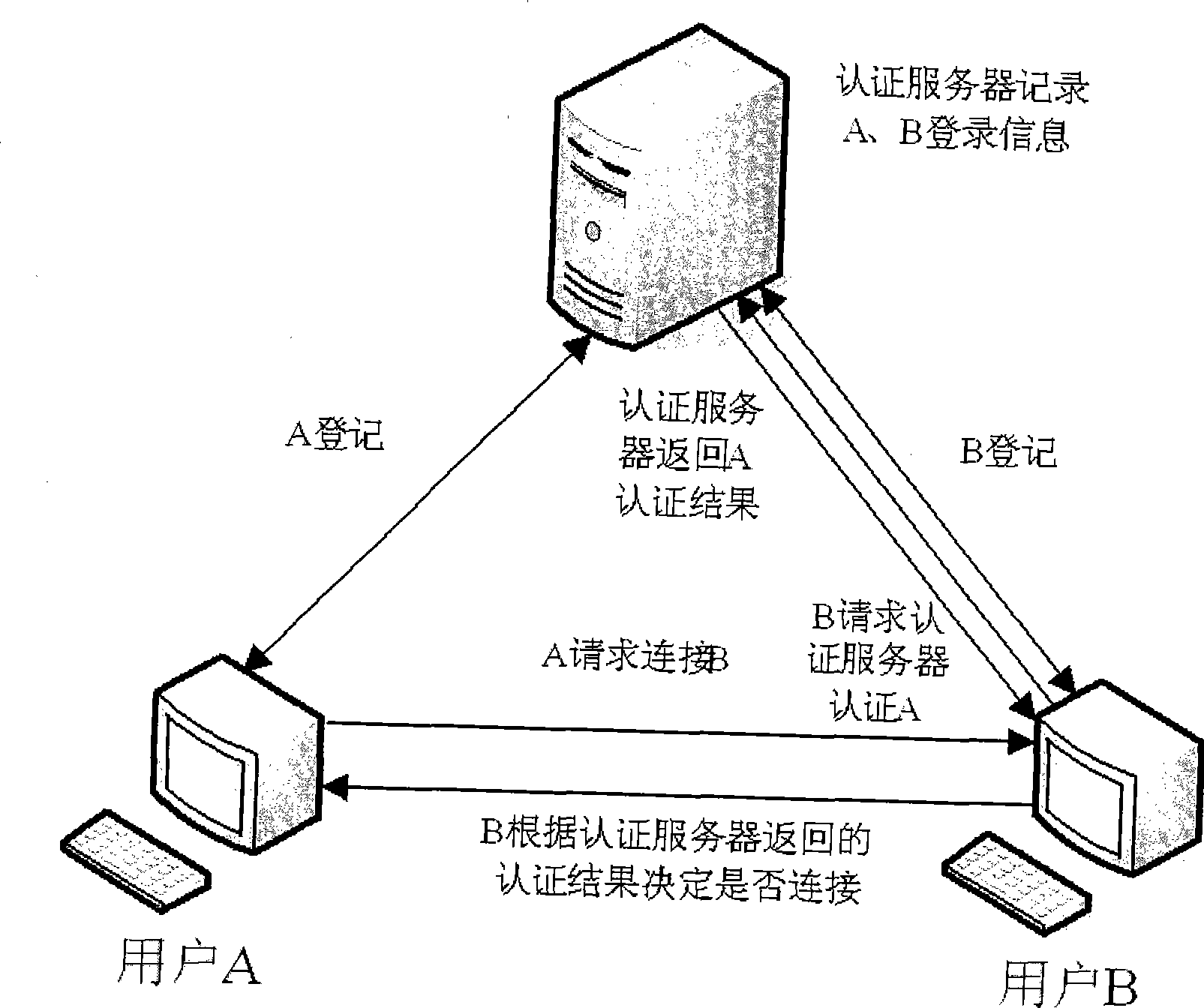
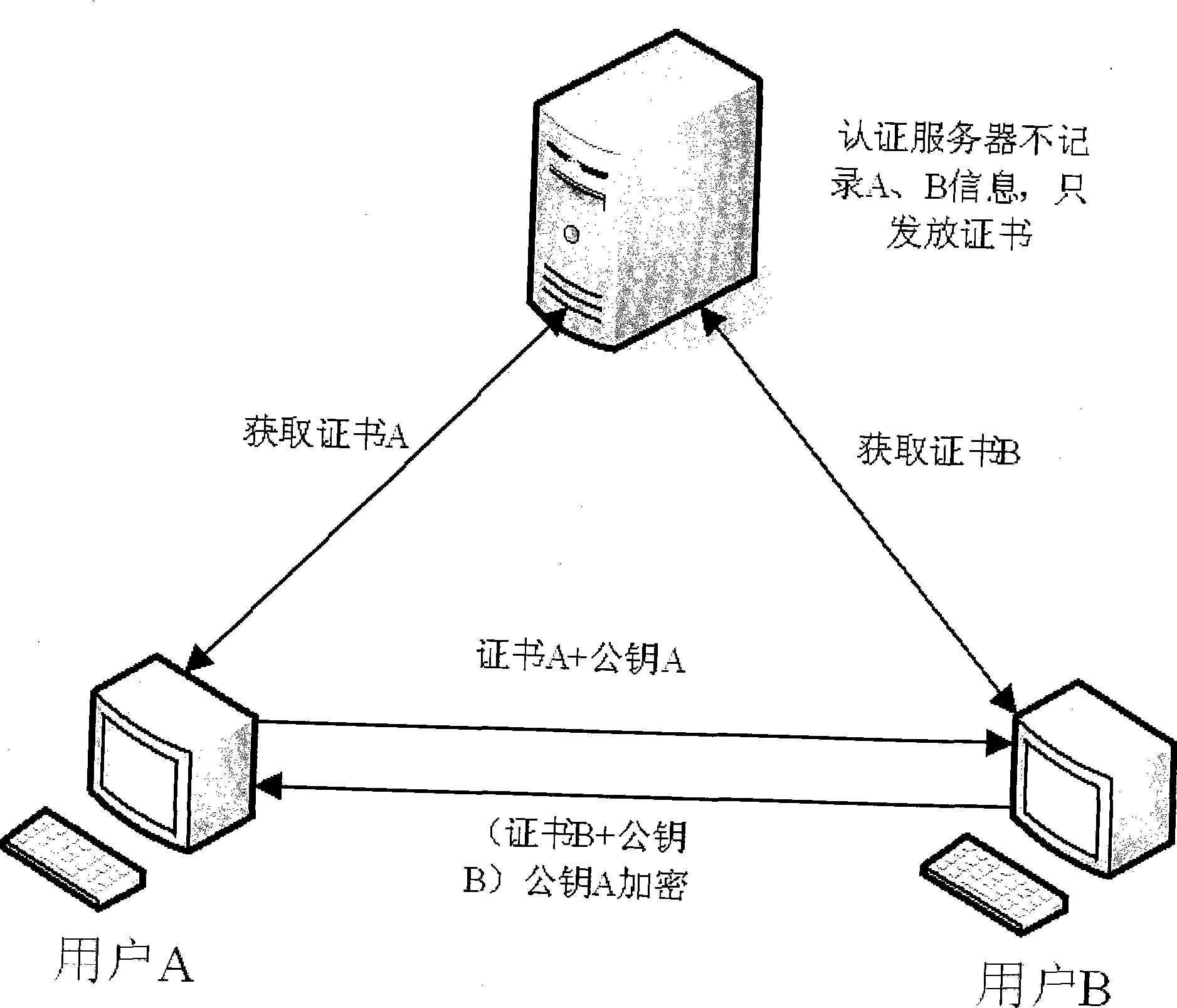
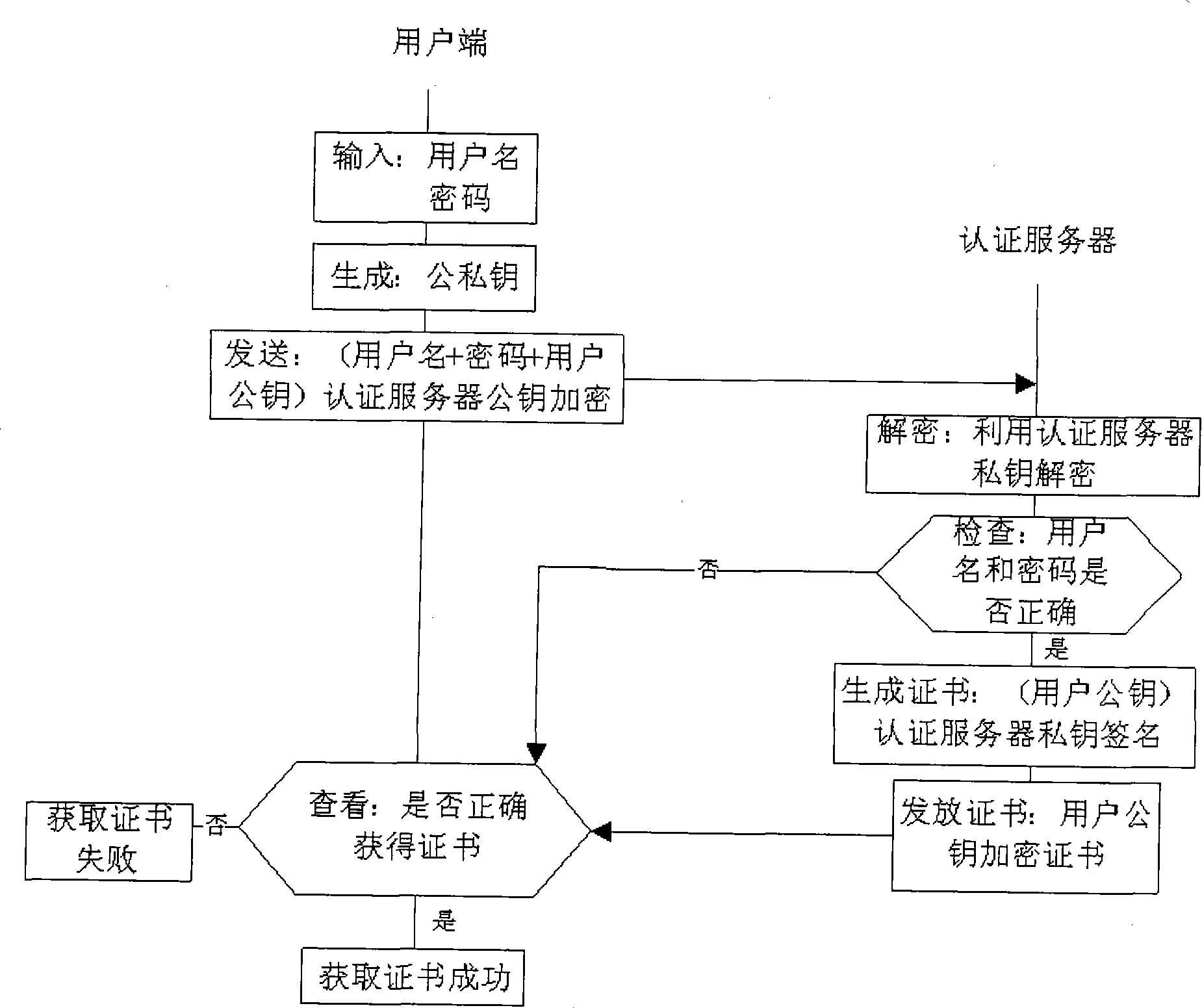
Identification authentication method between peer-to-peer user nodes in P2P network
InactiveCN101442411ARelieve pressureGuaranteed freshnessPublic key for secure communicationUser identity/authority verificationEncryptionPeer-to-peer
The invention provides a method for authenticating identification among peer-to-peer nodes in a P2P network. Each peer-to-peer node in the P2P network has a certificate which is acquired when a user node logs on the network through a certificate server, and the certificate comprises an encryption result of a private key of the certificate server to a public key of the user node. The method comprises the following steps: a first user node transmits an identification authentication message to a second user node in the network, wherein the identification authentication message comprises a certificate of the first user node and the public key of the first user node; a second user node authenticates identification of the first user node by the identification authentication message, after authentication succeeds, the identification authentication message is returned to the first user node, wherein the identification authentication message comprises a certificate of the second user node and the public key of the second user node; and the first user node authenticates the identification of the second user node by the identification authentication message returned by the second user node, and if the authentication succeeds, identification authentication between two user nodes succeeds.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and apparatus for providing electronic purse
ActiveUS8118218B2Facilitate communicationWithout compromising securityFinancePayment protocolsPersonalizationPhysical security
Techniques for portable devices functioning as an electronic purse (e-purse) are disclosed. According to one aspect of the invention, a mechanism is provided to enable a portable device to conduct transactions over an open network with a payment server without compromising security. In one embodiment, a device is loaded with an e-purse manager. The e-purse manager is configured to manage various transactions and functions as a mechanism to access an emulator therein. The transactions may be conducted over a wired network or a wireless network. A three-tier security model is contemplated to support the security of the transactions from the e-purse. The three-tier security model includes a physical security, an e-purse security and a card manager security, concentrically encapsulating one with another. Security keys (either symmetric or asymmetric) are personalized within the three-tier security model.
Owner:SHENZHEN RFCYBER ASSET MANAGEMENT
Dual authentication method, system and device for SSH safe login
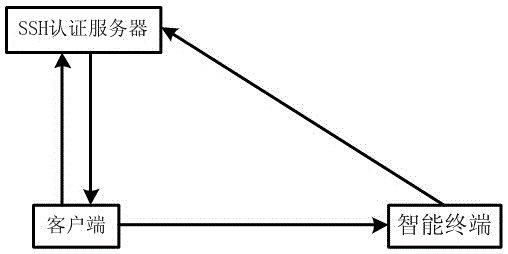
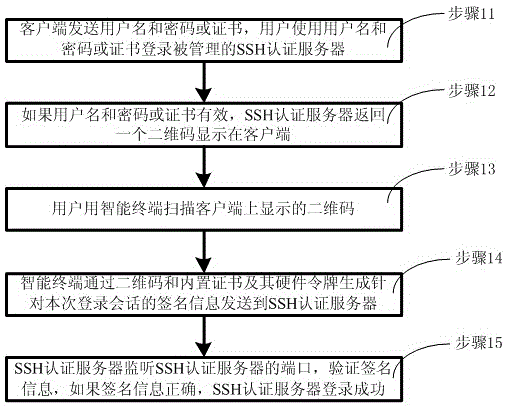
InactiveCN105162764ARealize remote login authenticationWithout compromising securityTransmissionPasswordIdentity theft
The invention discloses a dual authentication method for SSH safe login. The method includes the following steps: a client sends a user name and a password or certificate, and a user uses the user name and the password or certificate to log in a managed SSH authentication server; if the user name and the password or certificate are valid, the SSH authentication server returns a two-dimensional code to be displayed on the client; the user uses an intelligent terminal to scan the two-dimensional code displayed on the client; the intelligent terminal generates signature information for a login session of this time to a two-dimensional verification server or the SSH authentication server through the two-dimensional code, a built-in certificate and a hardware token thereof; and the SSH authentication server verifies whether the signature information is correct, and if the signature information is correct, the SSH authentication server logs in successfully. The dual authentication method for SSH safe login has the beneficial effects that a secondary authentication process based on a two-dimensional code is added, and two-dimensional code information is leaked, is unique and cannot be repetitive, thereby greatly improving security of login verification of the SSH authentication server, and preventing the problem of identity theft caused by user password loss.
Owner:BEIJING STONE SHIELD TECH
Inner temperature estimation method for single cell
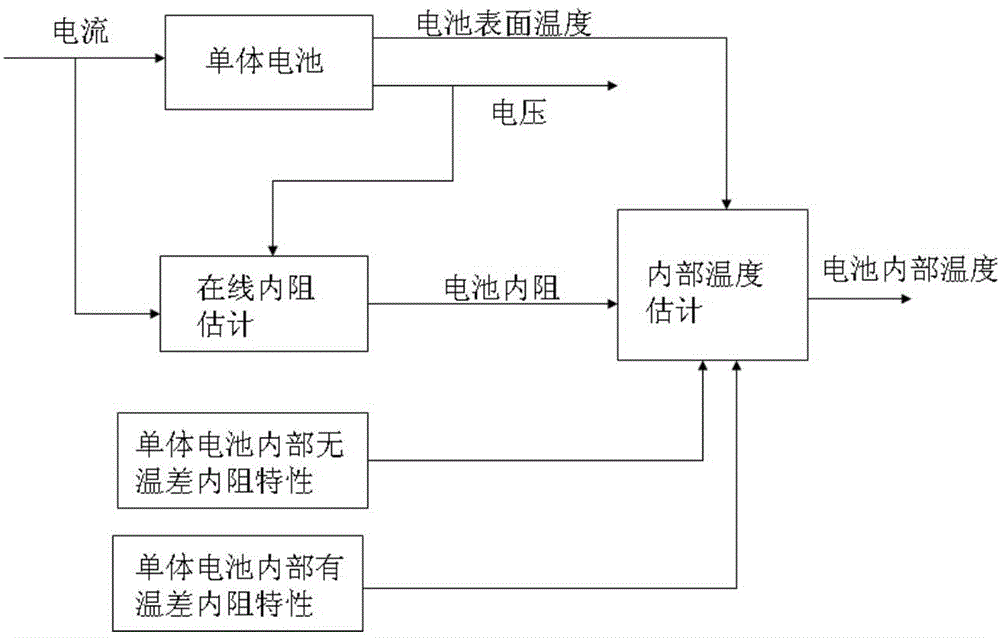
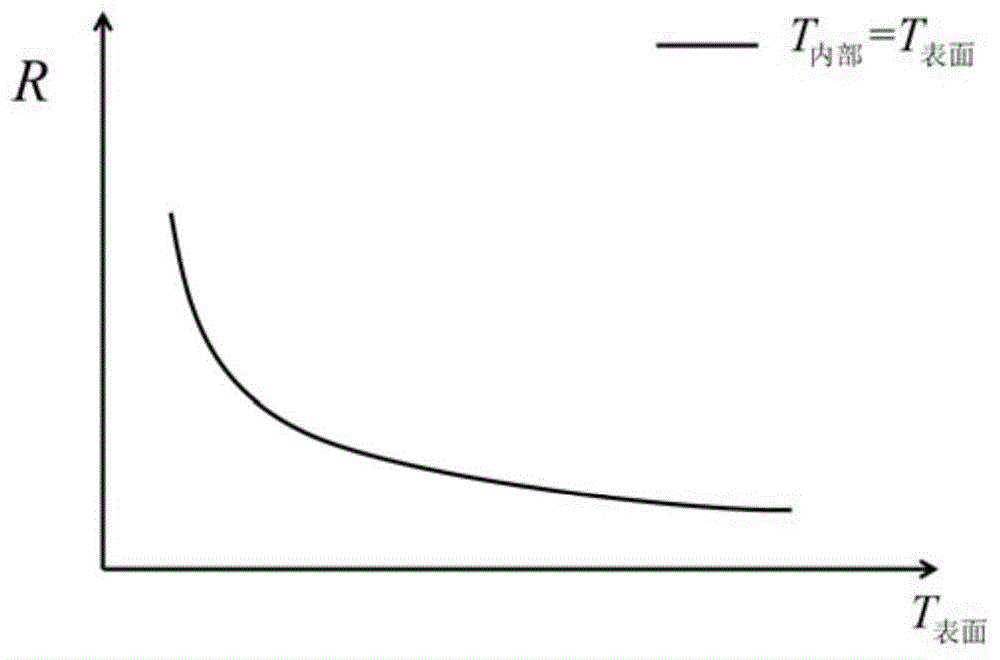
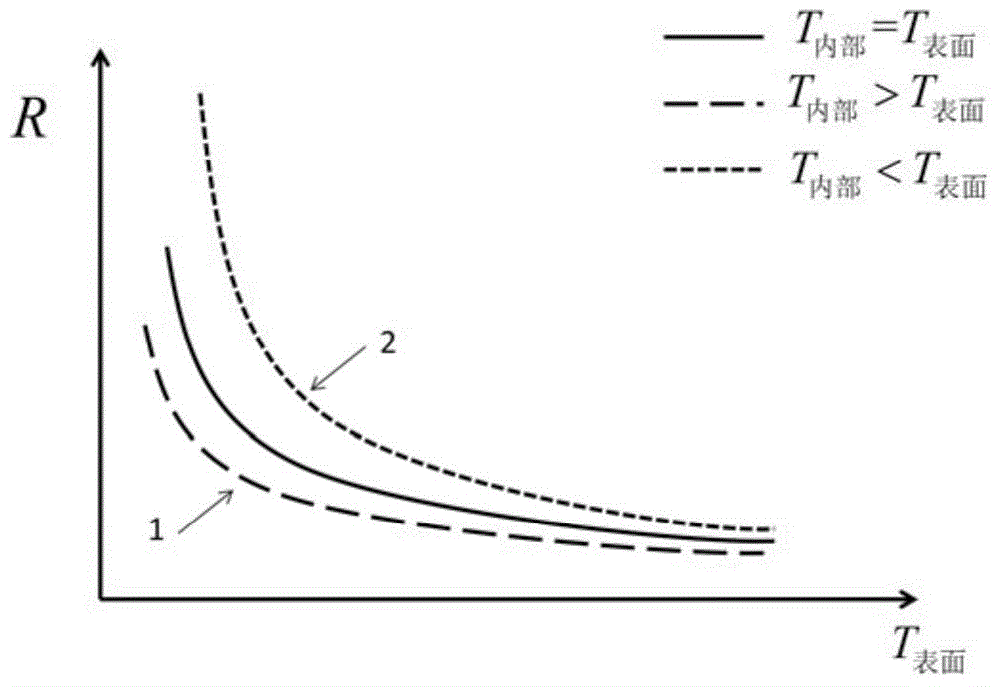
ActiveCN104865534APerformance is not affectedWithout compromising securityElectrical testingInternal resistanceEstimation methods
The invention relates to an inner temperature estimation method for a single cell, which comprises an offline part and an online part. The offline part executes the steps of a1) acquiring the internal resistance characteristic of the single cell at different temperatures; and a2) acquiring a standard relationship between the inner temperature of the cell and the internal resistance of the cell according to the internal resistance characteristic. The online part executes the steps of b1) performing online detection on the current, end voltage and surface temperature of a current working cell; be) performing online estimation for the internal resistance of the current working cell according to the current and the end voltage; and b3) estimating the internal temperature of the current working cell according to the internal resistance acquired in the step b2), the surface temperature acquired in the step b1) and the standard relationship acquired in the step a2). Compared with the prior art, the inner temperature estimation method for the single cell has advantages of effective online estimation for the inner temperature of the single cell, simple operation, effective calculation amount reduction, etc.
Owner:TONGJI UNIV
Modified self-insulating composite external wall material
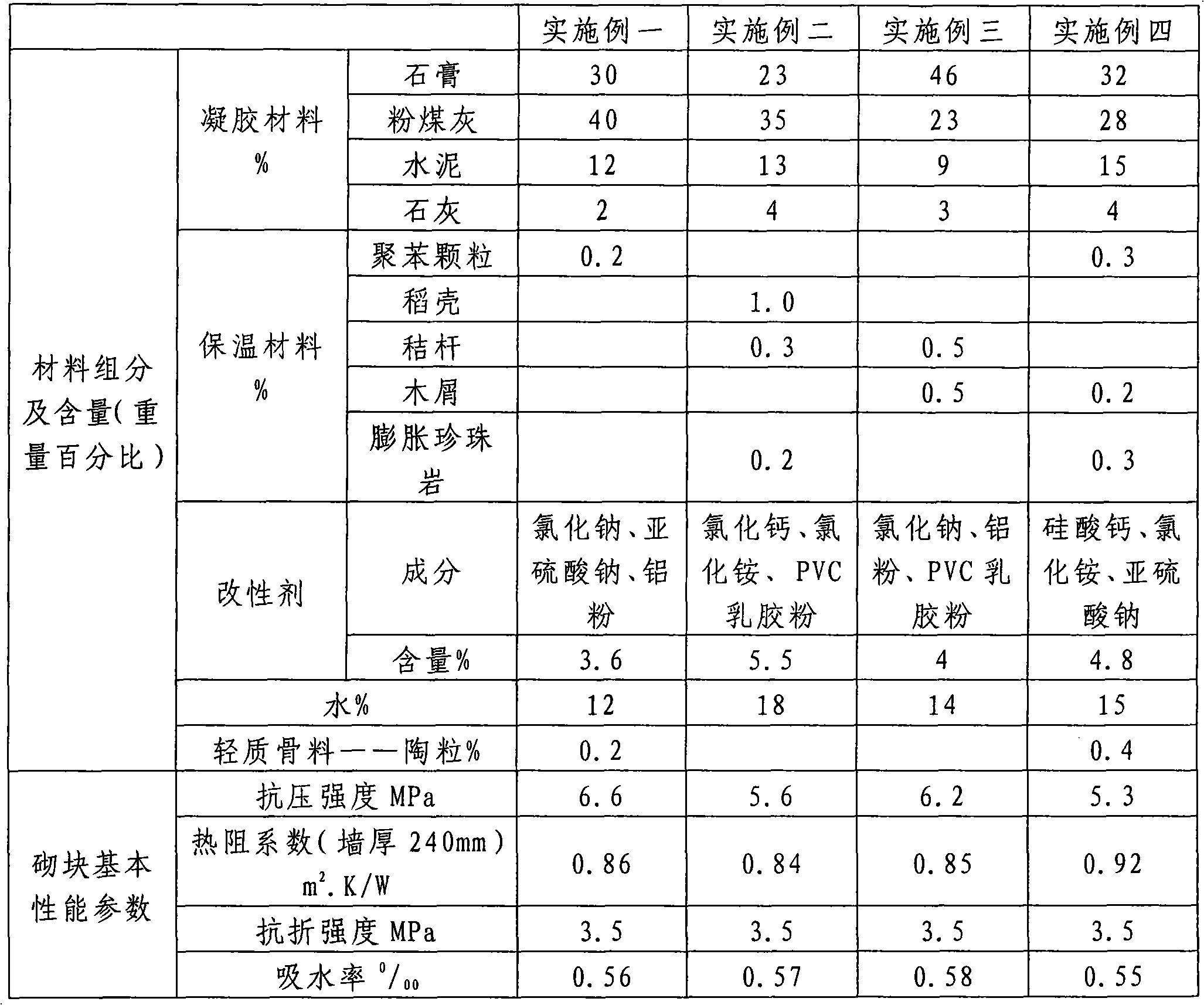
InactiveCN102040361ANo damageMissing edges and cornersSolid waste managementCeramicwarePolyvinyl chlorideShock resistance
The invention discloses a modified self-insulating composite external wall material, and belongs to a gypsum building material. The material comprises the following components in percentage by weight: 75 to 84 percent of gel material, 0.2 to 1.5 percent of heat insulating material, 3 to 6 percent of modifying agent and 12 to 18 percent of water; the gel material consists of gypsum, fly ash, cement and lime, wherein the gypsum and the fly ash are in the majority; the heat insulating material is one or more of polyphenyl granules, rice hulls, straws, saw dust and expanded perlite; and the modifying agent is a common salt compound or a mixture of the common salt compound, aluminum powder and polyvinyl chloride (PVC) latex powder. The external wall material for manufacturing external wall building blocks or external wallboards by optimized proportion and modification treatment remarkably improves the comprehensive performance of water prevention, heat insulation, shock resistance and pressure resistance; and production and construction are convenient, the raw materials are easily obtained, industrial and agricultural byproducts are fully utilized, and environmentally-friendly and energy-saving requirements are met.
Owner:李宁 +1
System and method for remotely debugging application programs
InactiveUS20110088015A1Without compromising securityLess attentionError detection/correctionMultiple digital computer combinationsProgramming languageApplication software
A method, system, and apparatus for debugging an application program from a workstation that is remote from a server on which the application program resides includes invoking the application program from the workstation via a network interface; displaying a user frame at the workstation that includes information generated by the application program; providing a debug view option at the workstation for generating a debug frame of the application program; and displaying the debug frame at the workstation when the debug view option is selected. A user can select options to switch between the user frame and the debug frame. The debug frame includes information about one or more components of the application program such as a list of the variables or objects, and the fields, methods, and / or the constructors associated with them. When the debug view option is selected, the information for the user frame is saved, and can be restored to regenerate the information on the user frame when the user view option is selected. The developer can view internal, public, and private code associated with the application program without compromising the security of other application programs on the server. This ability to remotely debug application programs in accordance with the present invention is thus more time and cost efficient than previous methods, and also alleviates concerns about security and unauthorized access to the server.
Owner:VERSATA DEV GROUP
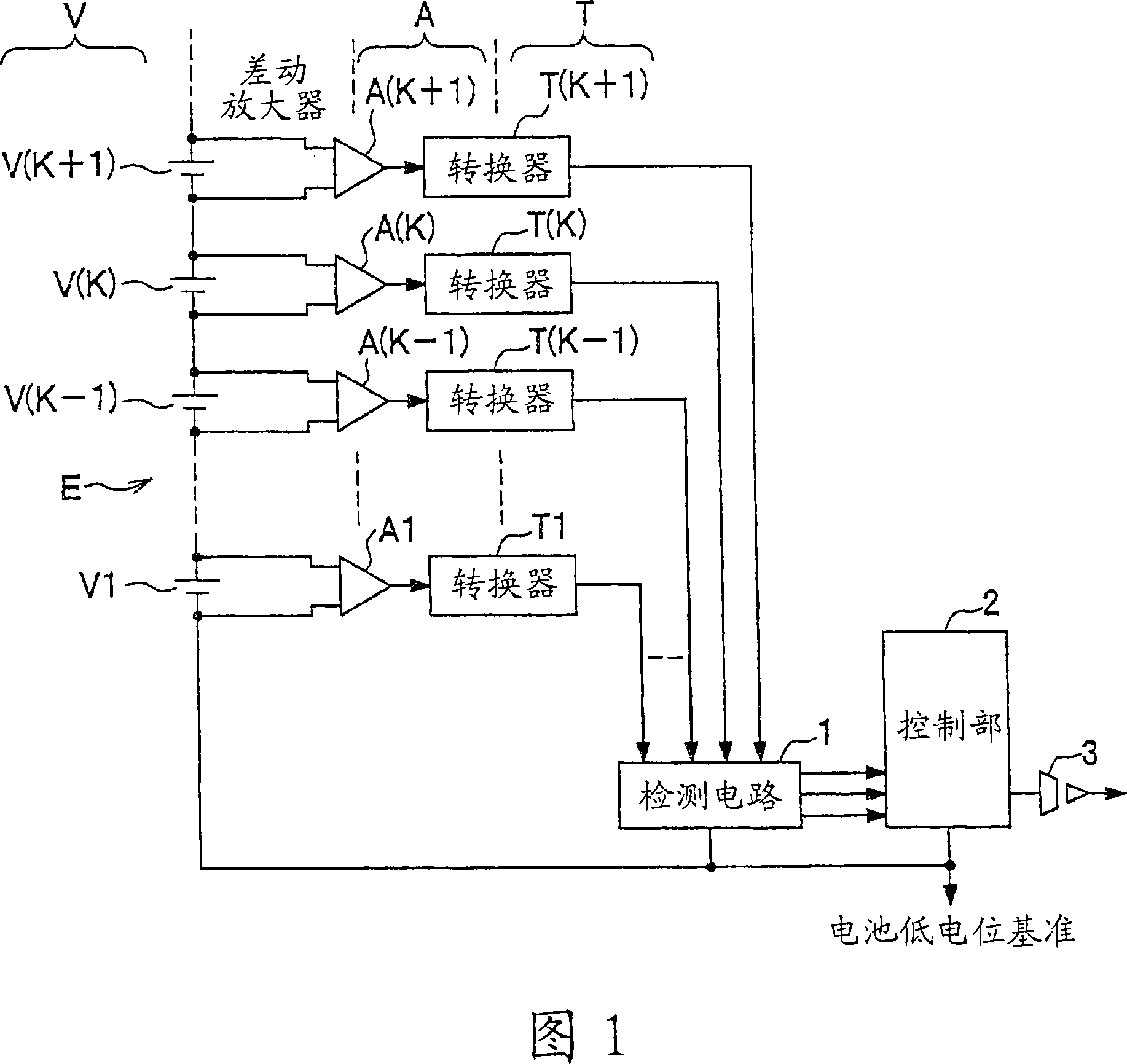
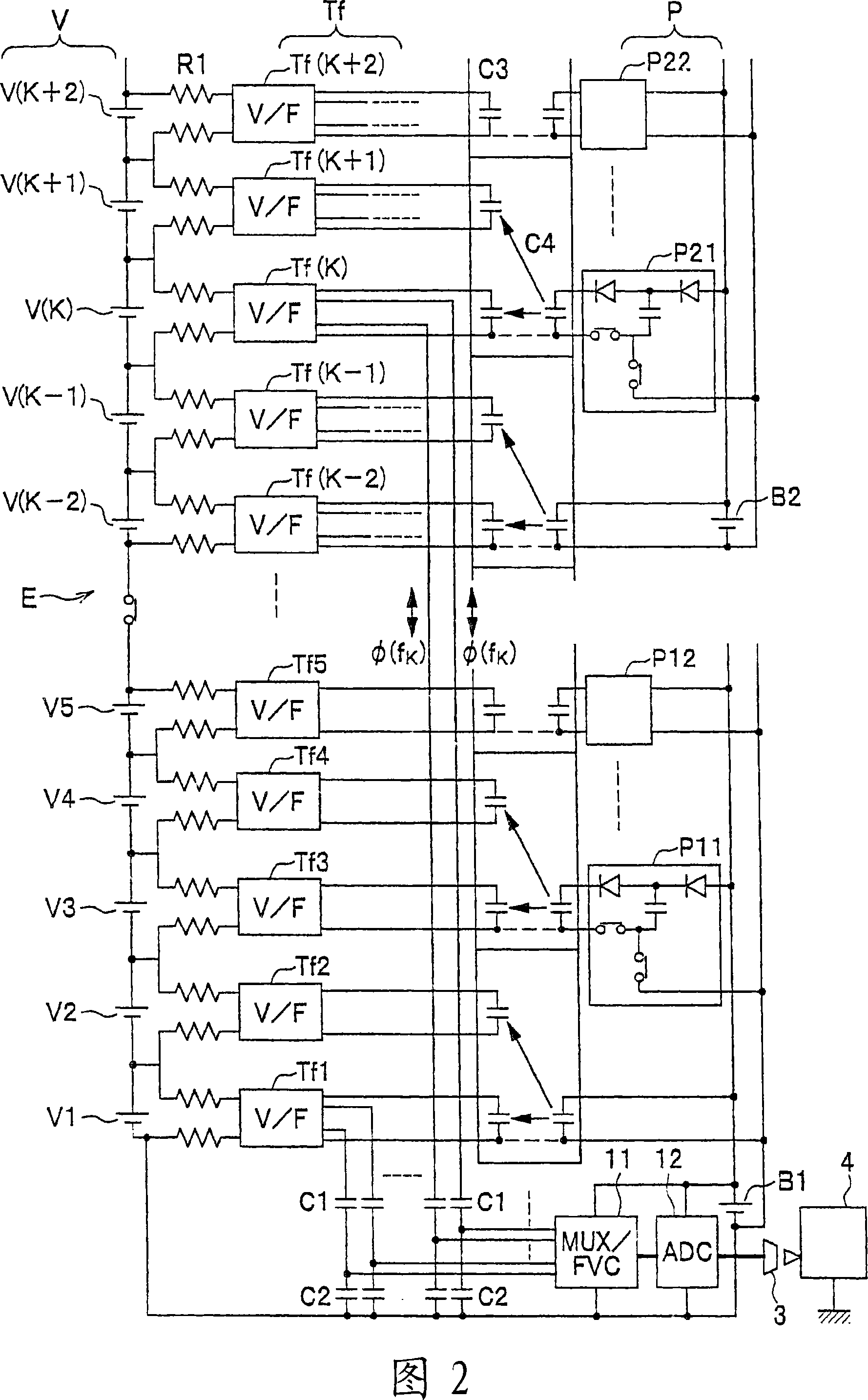
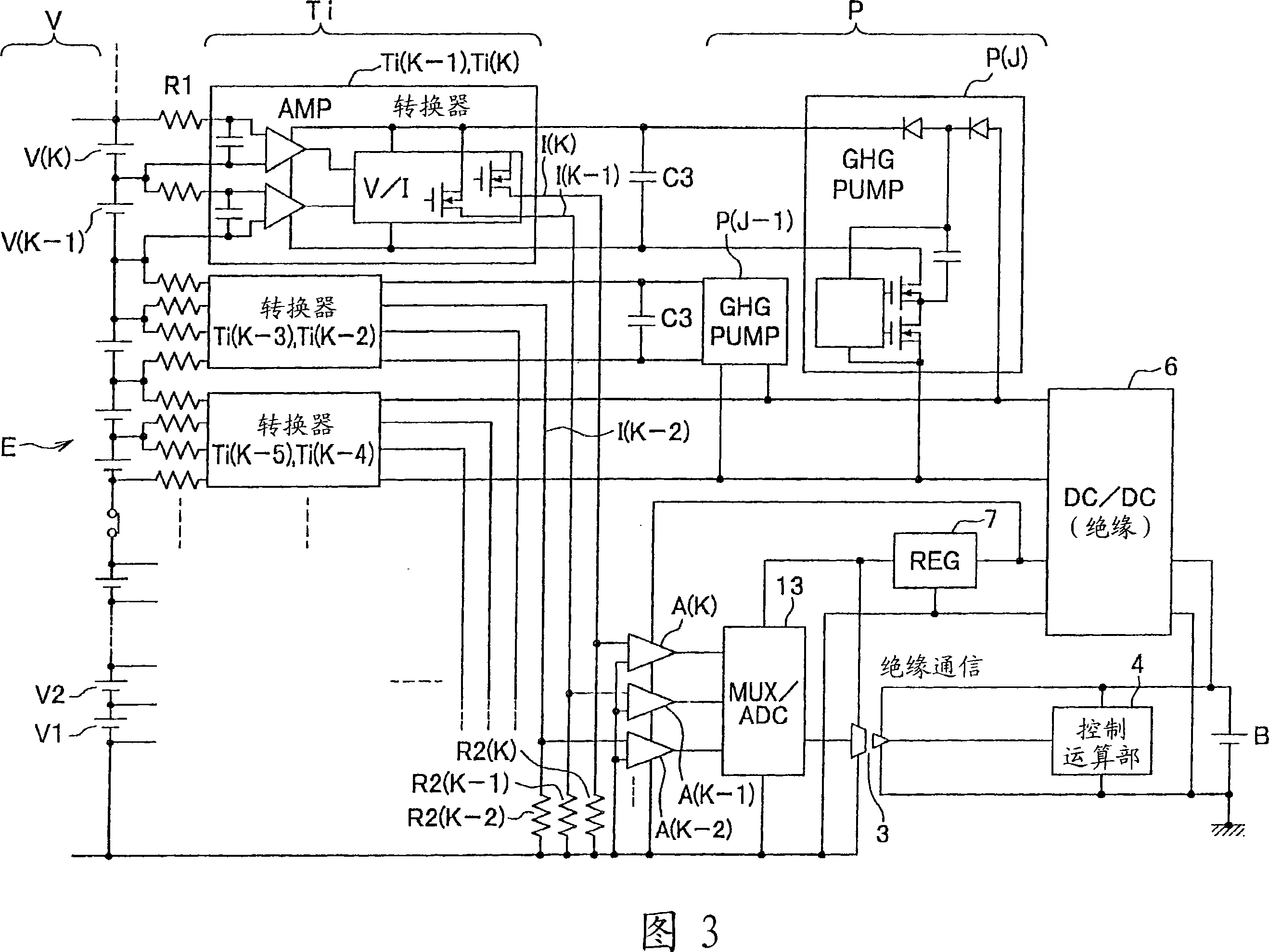
Battery voltage measurement circuit, battery voltage measurement method, and battery electric control unit
InactiveCN101043094AWithout compromising securityCurrent/voltage measurementSecondary cellsElectrical batteryElectric control
The invention provides a battery voltage measurement circuit, a battery voltage measurement method and a battery electronic control device. The object is to precisely measure a battery voltage by a simple and low-cost structure and via a common measurement circuit. As a solving means, voltages at two ends of each unit battery V are amplified by a differential amplifier A, and are converted to special physical quantities corresponding to the voltages at two ends of each unit battery V by a converter T, voltage levels are performed with shift by a detection circuit (1), and are inversely converted into voltages using a lowest level of the battery as a common reference level. In addition, the inversely converted voltages are orderly selected in a multi-path scanner by a control portion (2) to perform an A / D conversion, serial digital signals are transmitted to a control calculation portion (4) via an insulative buffer circuit (3).
Owner:KEIHIN CORP
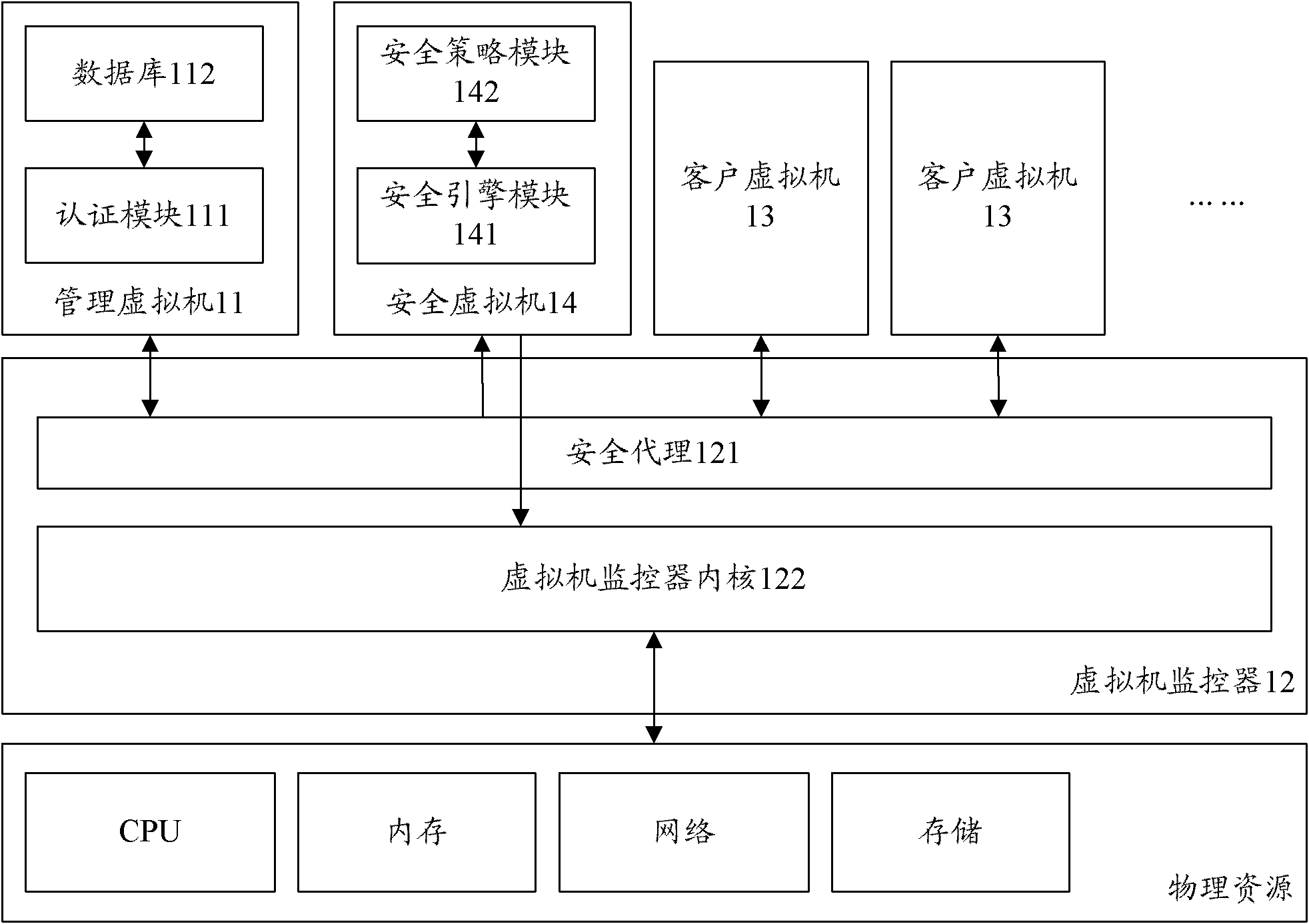
Virtual machine system and safety control method thereof
ActiveCN102811239AAvoid attackAvoid resource hoggingTransmissionSoftware simulation/interpretation/emulationSafety controlWorkload
The invention discloses a virtual machine system which comprises a management virtual machine, a virtual machine monitor, a client virtual machine and a safety virtual machine. The management virtual machine is used for authenticating the client virtual machine and sending an authenticated result to the virtual machine monitor. The virtual machine monitor is used for transmitting an access request sent from the client virtual machine to the management virtual machine. The authenticated result sent from the management virtual machine is transmitted to the client virtual machine. The authenticated result sent from the client virtual machine is transmitted to the safety virtual machine. According to access permission, physical resources are accessed and an access result is returned to the client virtual machine. The client virtual machine is used for sending the access request and the authenticated result to the virtual machine monitor. The safety virtual machine is used for issuing the access permission of the client virtual machine to the virtual machine monitor. The invention further discloses a safety control method of the virtual machine system. With the system and the method, workload of the virtual machine monitor can be lowered, the access permission of the client virtual machine can be flexibly controlled, and the access of the client virtual machine to the physical resources is effectively controlled.
Owner:ZTE CORP
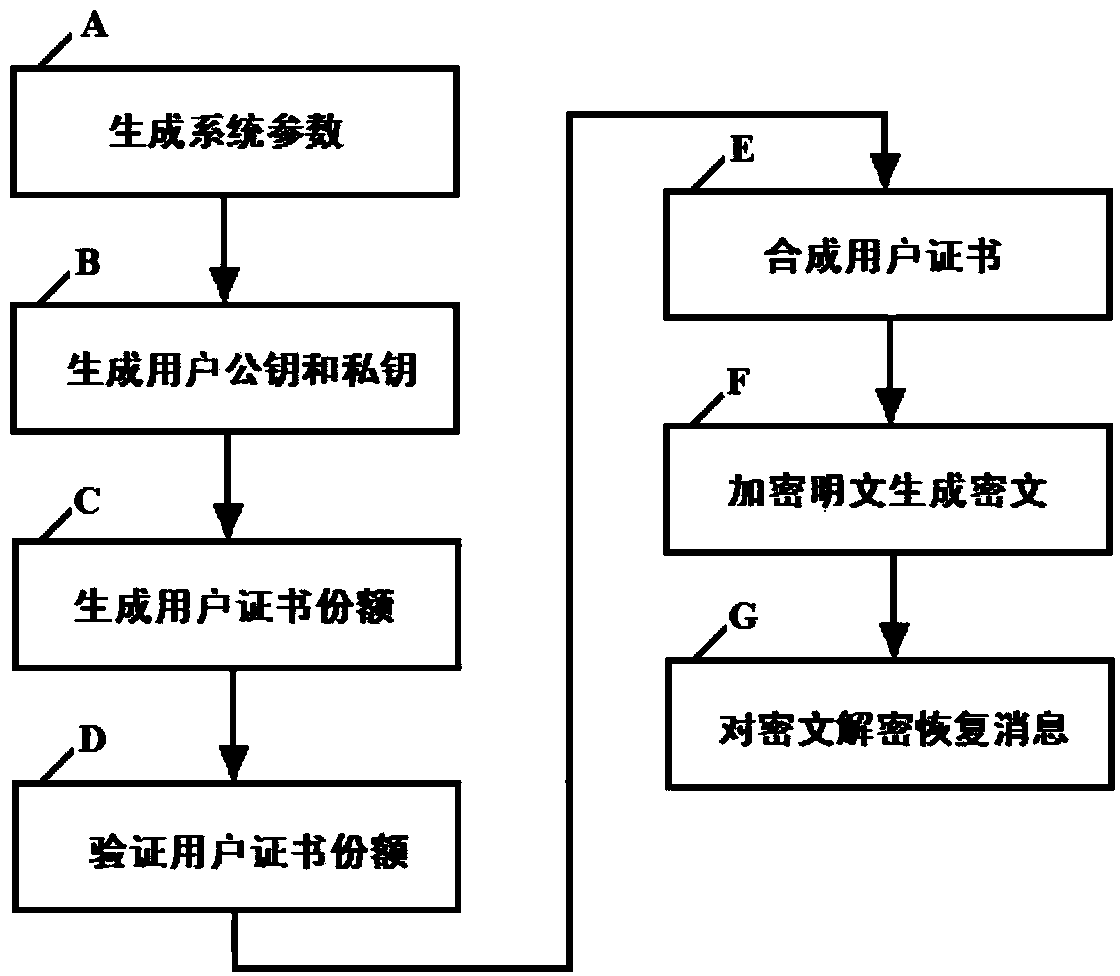
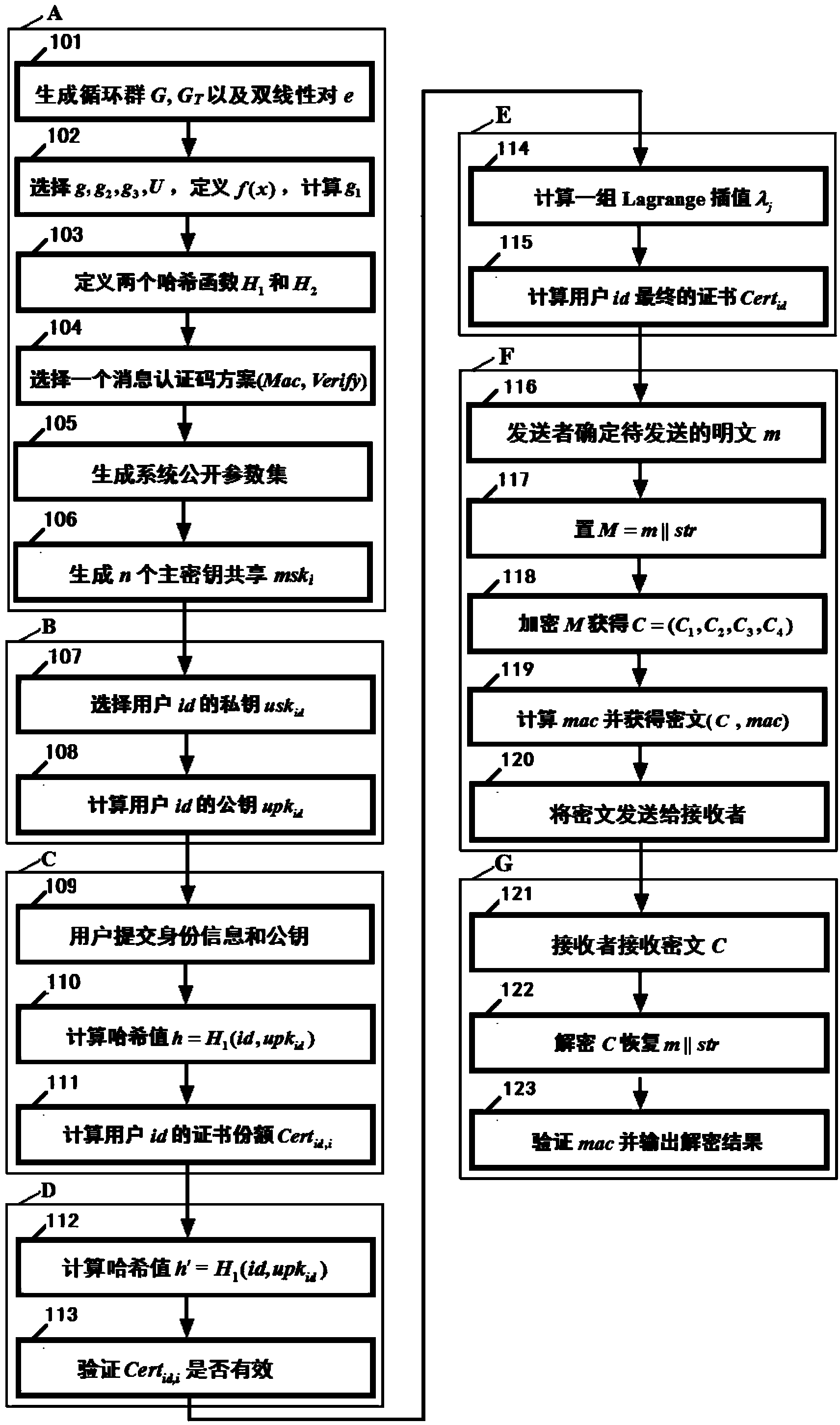
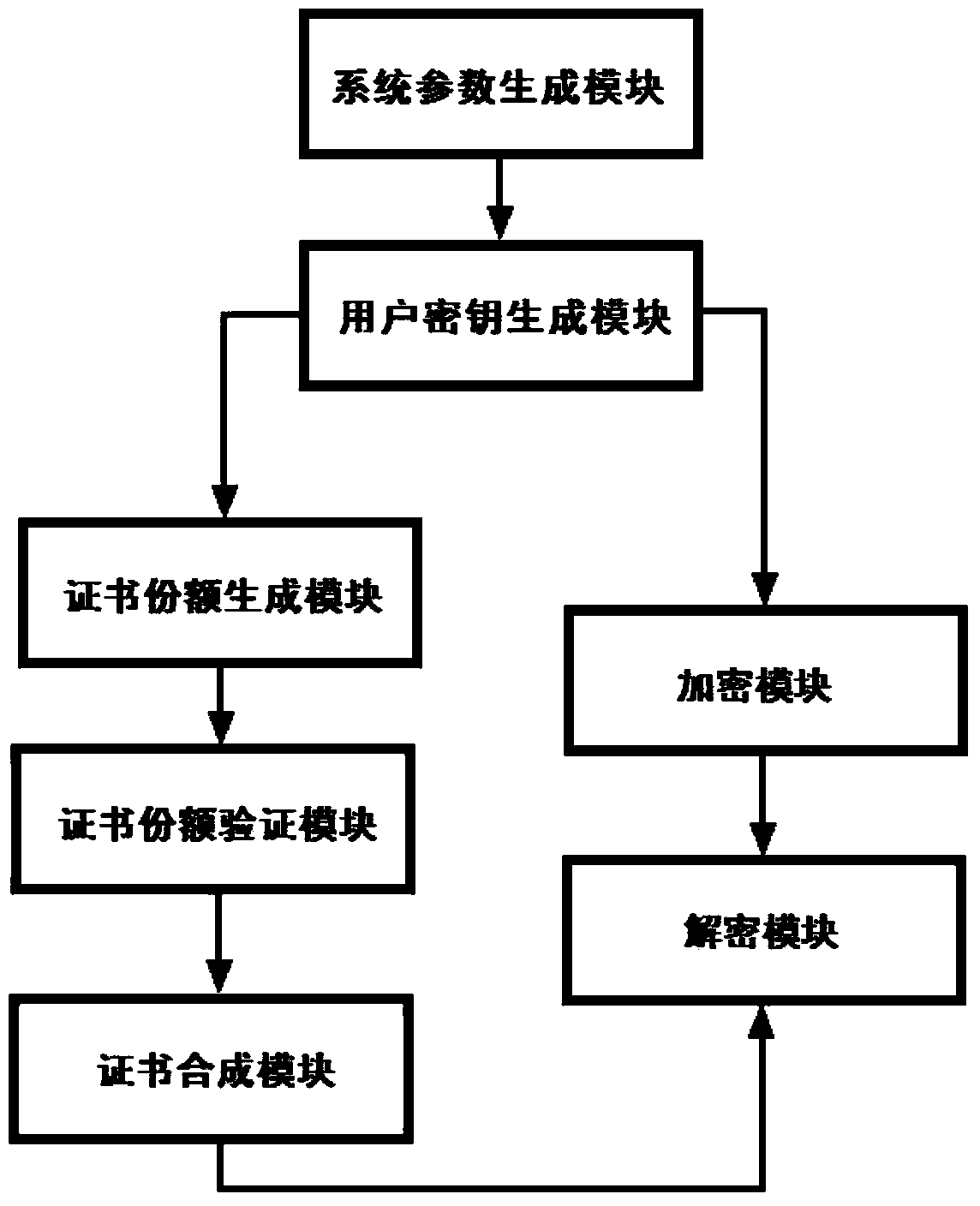
Distributed type (k, n) threshold certificate-based encrypting method and system
InactiveCN104168114ADoes not affect secrecyWithout compromising securityUser identity/authority verificationCryptosystemMaster key
The invention discloses a distributed type (k, n) threshold certificate-based encrypting method and system. The secret sharing technology and certificate-based encrypting are combined. The method comprises the steps of system parameter generating, public user key and private user key generating, user certificate share generating, user certificate share validity verifying, user certificate combining, message encrypting and message decrypting. The system comprises a system parameter generating module, a user key generating module, a certificate share generating module, a certificate share verifying module, a certificate combining module, an encrypting module and a decrypting module. By means of the technical scheme, the capacity of resisting to master key revealing, denial of service attack and certificate server failure of a cryptosystem is greatly enhanced, and the defects of an existing certificate-based encrypting method are effectively overcome.
Owner:HOHAI UNIV
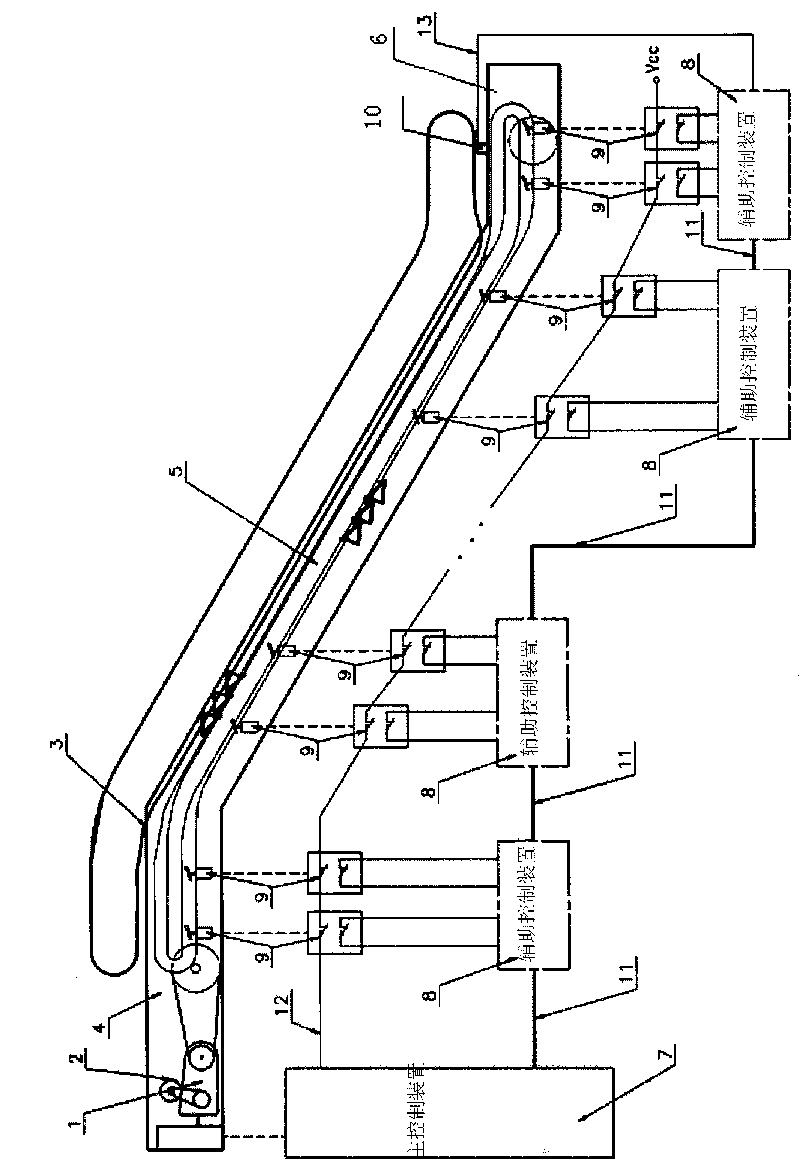
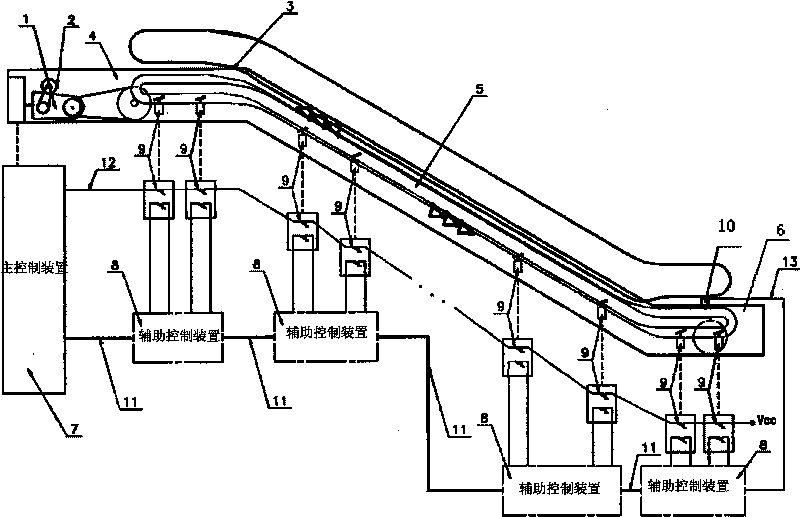
System for escalator and automatic moving pavement
ActiveCN101746662AWithout compromising securityEasy wiringEscalatorsEngineeringElectrical and Electronics engineering
The invention discloses a system for an escalator and an automatic moving pavement, which comprises all safety switches for detecting deletion of steps, chain fracture of chains, strap breakage of hand straps, skirt panels and the like, an escalator main control device, a plurality of auxiliary control devices and communication buses for connecting all the control devices, wherein a group of contacts of all safety switches is connected with the escalator main control device, when any one safety switch is turned off, the power supply of an escalator driving device is cut off so as to ensure safety. Another group of contacts of the safety switches is connected with the auxiliary control devices for detecting the state of the safety switches. Each auxiliary control device is connected with the main control device through the buses for carrying out data communication. The invention is capable of conveniently carrying out failure detection and control, is easy for system expansion and has low manufacturing cost.
Owner:SHANGHAI MITSUBISHI ELEVATOR CO LTD
Train-receiving signal control system of passenger dedicated line railway station
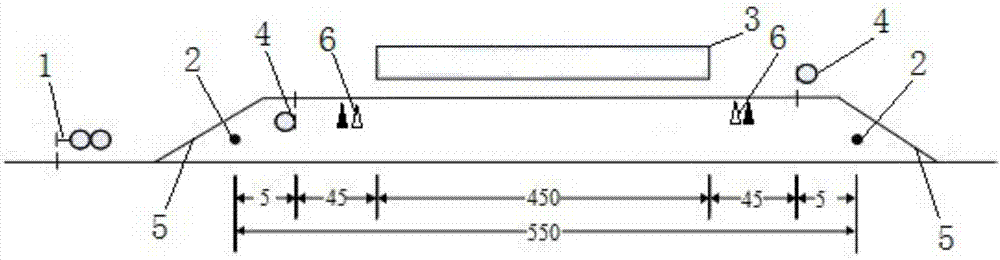
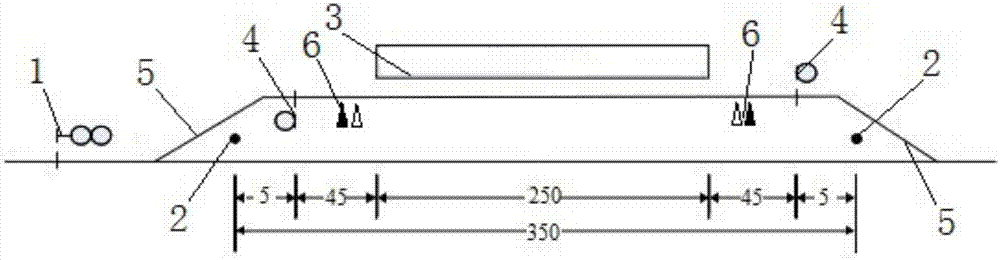
ActiveCN107323485AShorten the lengthImprove securityRailway signalling and safetyRailway stationControl systemEngineering
The invention relates to passenger dedicated lines and provides a train-receiving signal control system of a passenger dedicated line railway station. The train-receiving signal control system comprises two station-entering signal machines and an effective station track. Fouling posts are arranged at the two ends of the effective station track correspondingly. A platform section is arranged in the position, corresponding to a platform, of the effective station track and located between the two fouling posts. A departure signal machine is arranged between each fouling post and the platform section. At least parts of passing protective areas are located on first turnout sections on the inner sides of the departure signal machines in the corresponding directions. Successive routes of train-receiving routes are automatically arranged through interlocking equipment, and the tail ends of the successive routes are located on the first turnout sections on the inner sides of the corresponding departure signal machines. According to the improved train-receiving signal control system of the passenger dedicated line railway station, the original travelling safety is not reduced, and meanwhile at least parts of the passing protective areas are arranged on the inner sides of the departure signal machines, so that the distances between the departure signal machines and the fouling posts are shortened, the length of the station track can be decreased, and land and the construction cost are saved.
Owner:CHINA RAILWAY SIYUAN SURVEY & DESIGN GRP
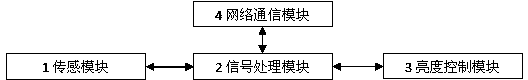
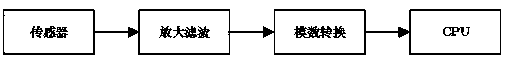
Luminance-controllable roadway illumination control method and system
InactiveCN103561511AImprove securityReduce consumptionElectric light circuit arrangementEnergy efficient lightingEngineeringHigh luminance
The invention discloses a luminance-controllable roadway illumination control method and system. Luminance of illumination lamps is dynamically controlled according to factors such as the danger level of a road, the weather, the environment, and positions, advancing directions and speeds of vehicles and pedestrians. High-luminance continuous illumination is conducted on dangerous road sections where accidents easily occur and critical areas with poor public security and is conducted when the severe weather such as the windy weather and the rainy weather exists. For common road sections and time periods, when the vehicles and the pedestrians pass by, illumination is only conducted on the security area in front of the vehicles and the pedestrians and the security area behind the vehicles and the pedestrians, and the illumination lamps outside the security areas are only kept in the pre-working states of the illumination lamps or turned off. According to the method and the system, the requirement for conducting illumination as required is met by dynamically adjusting the luminance, and therefore energy consumption can be well lowered, illumination efficiency is improved, and cost is reduced.
Owner:SOUTH CHINA UNIV OF TECH
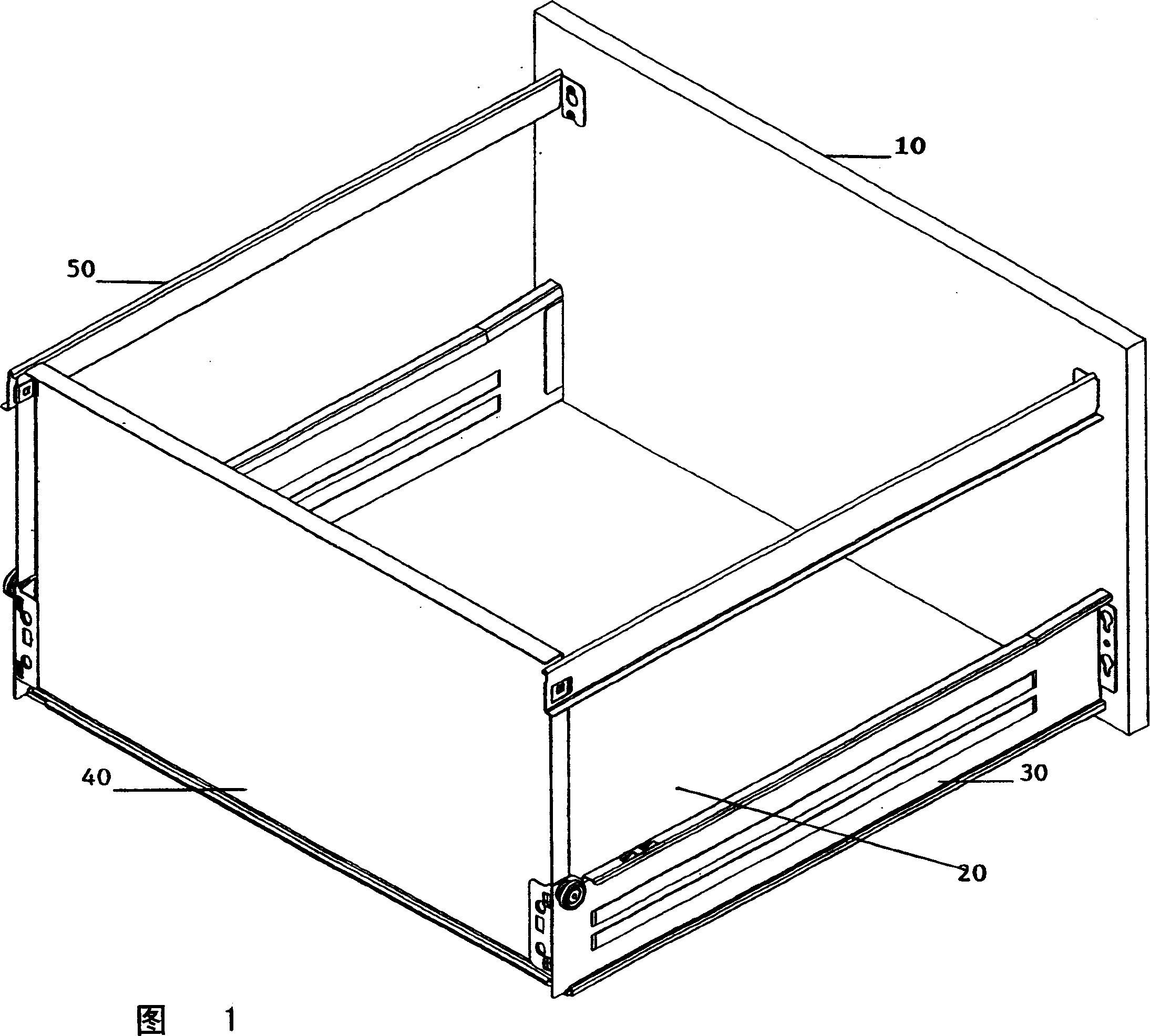
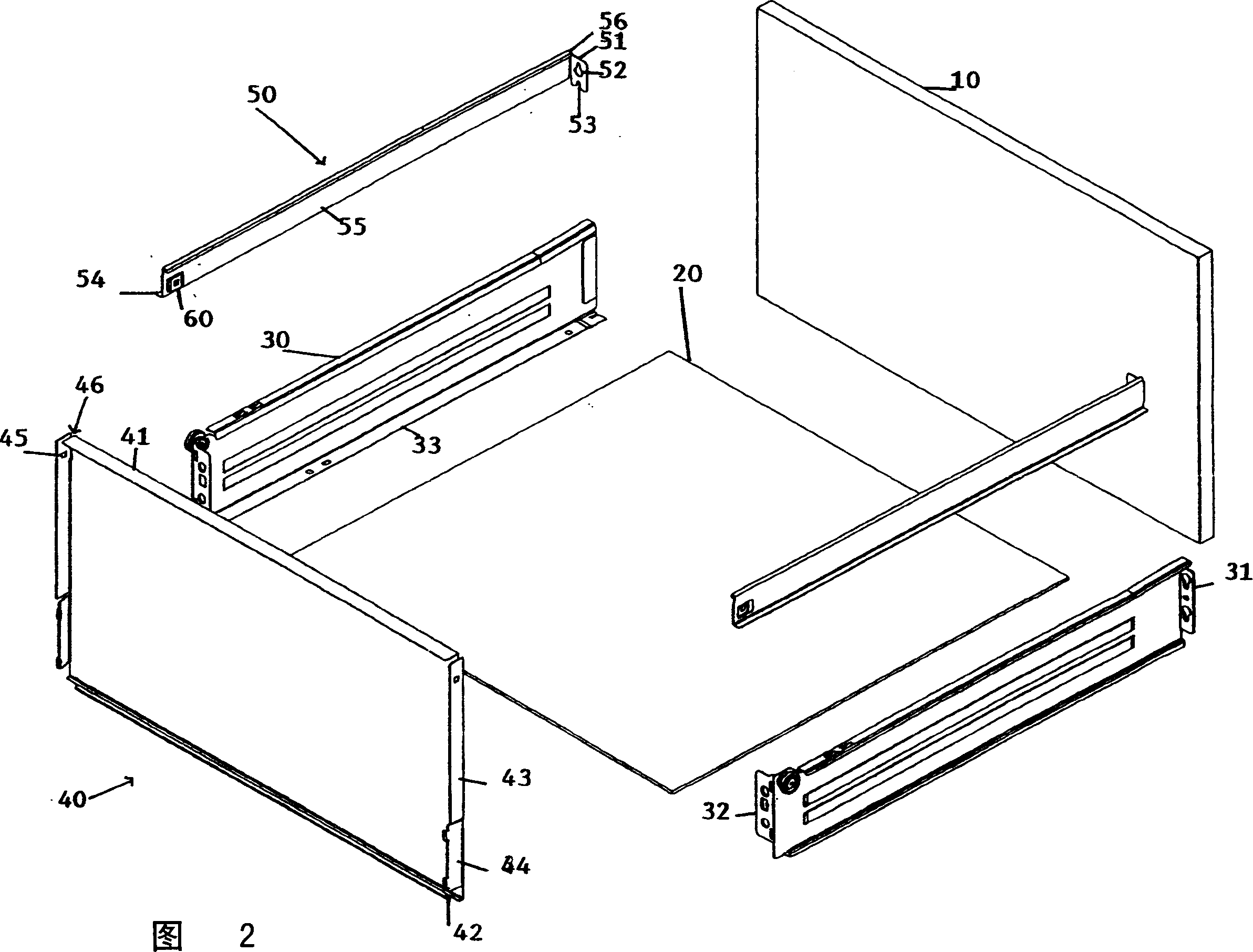
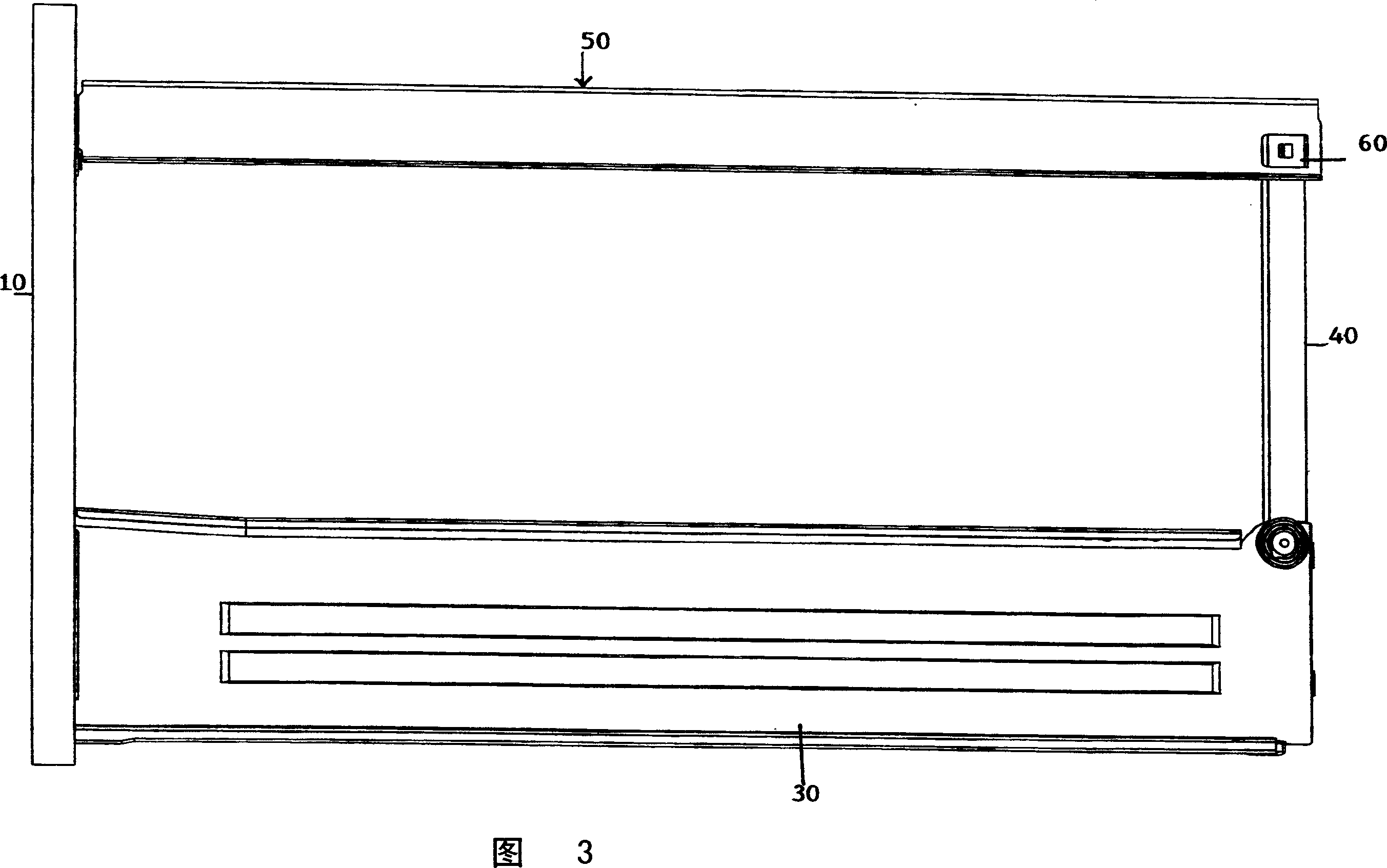
Drawer assembly
The invention discloses a drawer assembly, which comprises a front panel (10), a rear panel (40), a bottom panel (20), two side panels (30) and two side rails (50). Each side panel (30) extends respectively on the side of the drawer assembly between the front panel (10) and the rear panel (40) and has an associated side rail (50) which is upright with the side panel separated. The rear end of the side track (50) is connected to the rear panel (40) by a clip (60) with a locking structure, the clip is located on one of the side track and the rear panel, and the complementary locking structure is located on the side track and the rear panel the other one of the panels. A portion of the other of the side rail or the rear panel having a complementary locking structure is insertable into the clip such that the locking structure and the complementary locking structure are interlocked.
Owner:HARN MARKETING
Key sharing method and device
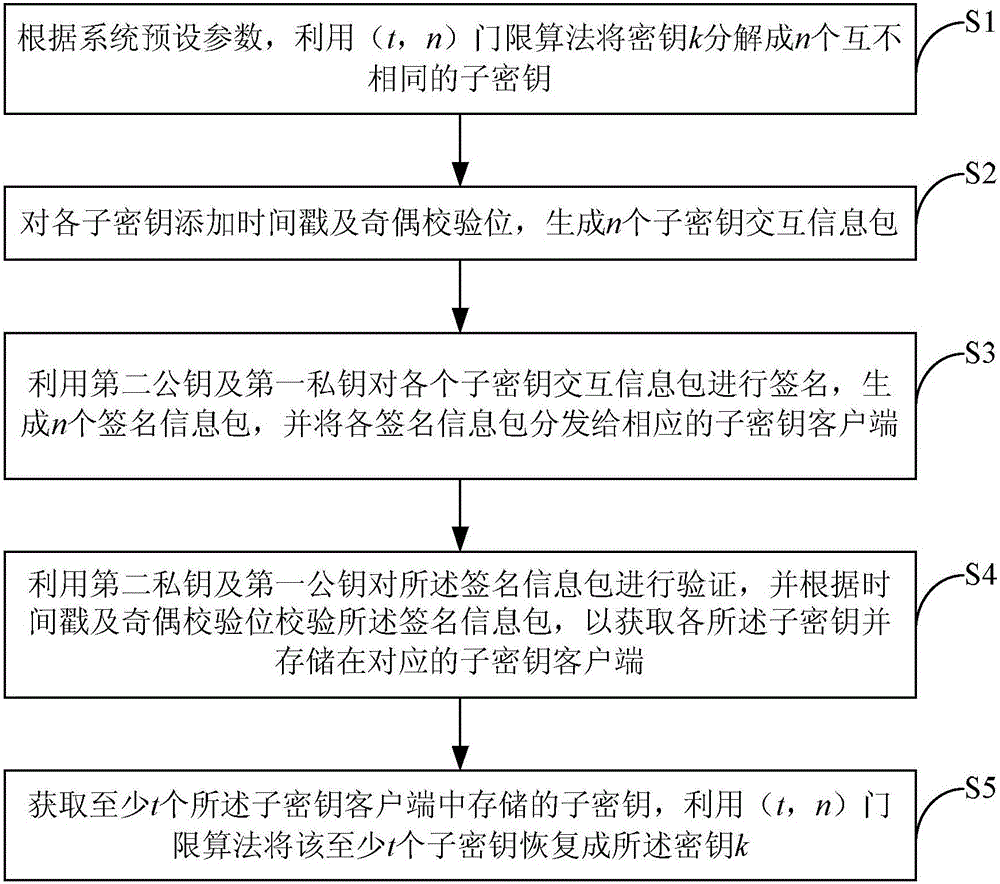
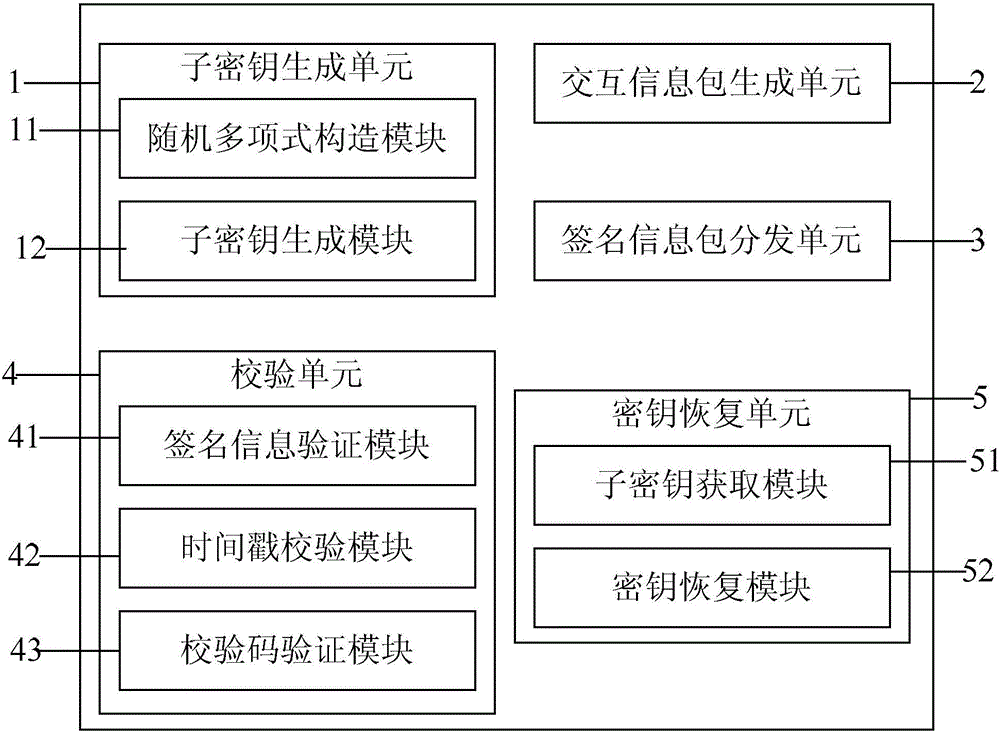
ActiveCN106027245AGuaranteed correctnessEnsure safetyKey distribution for secure communicationKey sharingParity bit
The invention provides a key sharing method and device. The method comprises the steps of decomposing a key k into n mutually different sub-keys by employing a (t, n) threshold algorithm according to preset parameters of a system; adding time stamps and parity check bits to the sub-keys, thereby generating n sub-key interaction information packets; signing the sub-key interaction information packets by employing a second public key and a first private key, thereby generating n signed information packets, and distributing the signed information packets to corresponding sub-key clients; verifying the signed information packets by employing a second private key and a first public key and checking the signed information packets according to the time stamps and the parity check bits, thereby obtaining the sub-keys, and storing the sub-keys in the corresponding sub-key clients; and obtaining the sub-keys stored in at least t sub-key clients, restoring the at least t sub-keys to the key k by employing the (t, n) threshold algorithm, wherein the first private key and the first public key are a mutually matching key pair, and the second private key and the second public key are a mutually matching key pair.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
External internet-of-things smart-phone call-out elevator wireless simulation artificial-triggering device
InactiveCN105110107ABig room for developmentWithout compromising securityElevatorsInternet of ThingsCam
The invention discloses an external internet-of-things smart-phone call-out elevator wireless simulation artificial-triggering device. The device comprises externally arranged button controllers on elevator rooms of all floors, the button controllers comprise button control boxes, the part, on one side of each button control box, of a box body covers corresponding elevator buttons, the part, on the other side of each button control box, of the box body is fixedly installed on a wall, a button touching mechanism is arranged inside the part, on one side of each button control box, of the box body, and a button driving mechanism is arranged inside the part, on the other side of each button control box, of the box body. The button touching mechanisms comprise inner and outer touching buttons, and the outer touching buttons press the elevator buttons through the inner touching buttons in a touching mode. The button driving mechanisms comprise telescopic shafts, transmission rods and cams, wherein the transmission rods are arranged in the left-right direction. Wireless signal receiving and transmitting devices are further arranged inside the box bodies and used for receiving wireless signal instructions and controlling the cams to rotate, and at the maximum eccentric positions of the cams, the telescopic shafts push the inner touching buttons to touch the elevator buttons through the transmission rods. The device is arranged outside the elevator rooms, corresponds to the elevator buttons, is only responsible for controlling the elevator buttons and does not affect safe and normal usage of an elevator.
Owner:冯新州
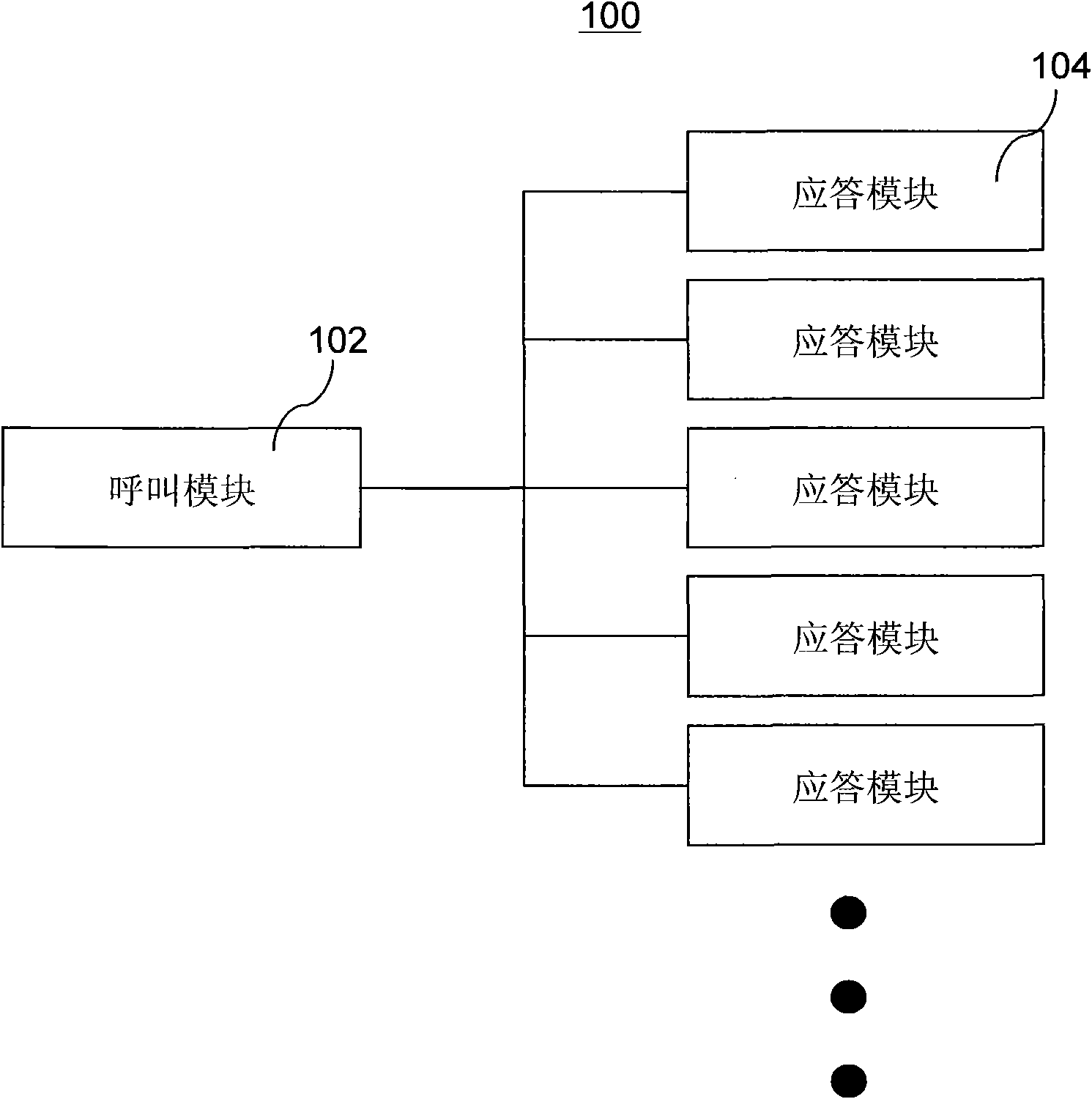
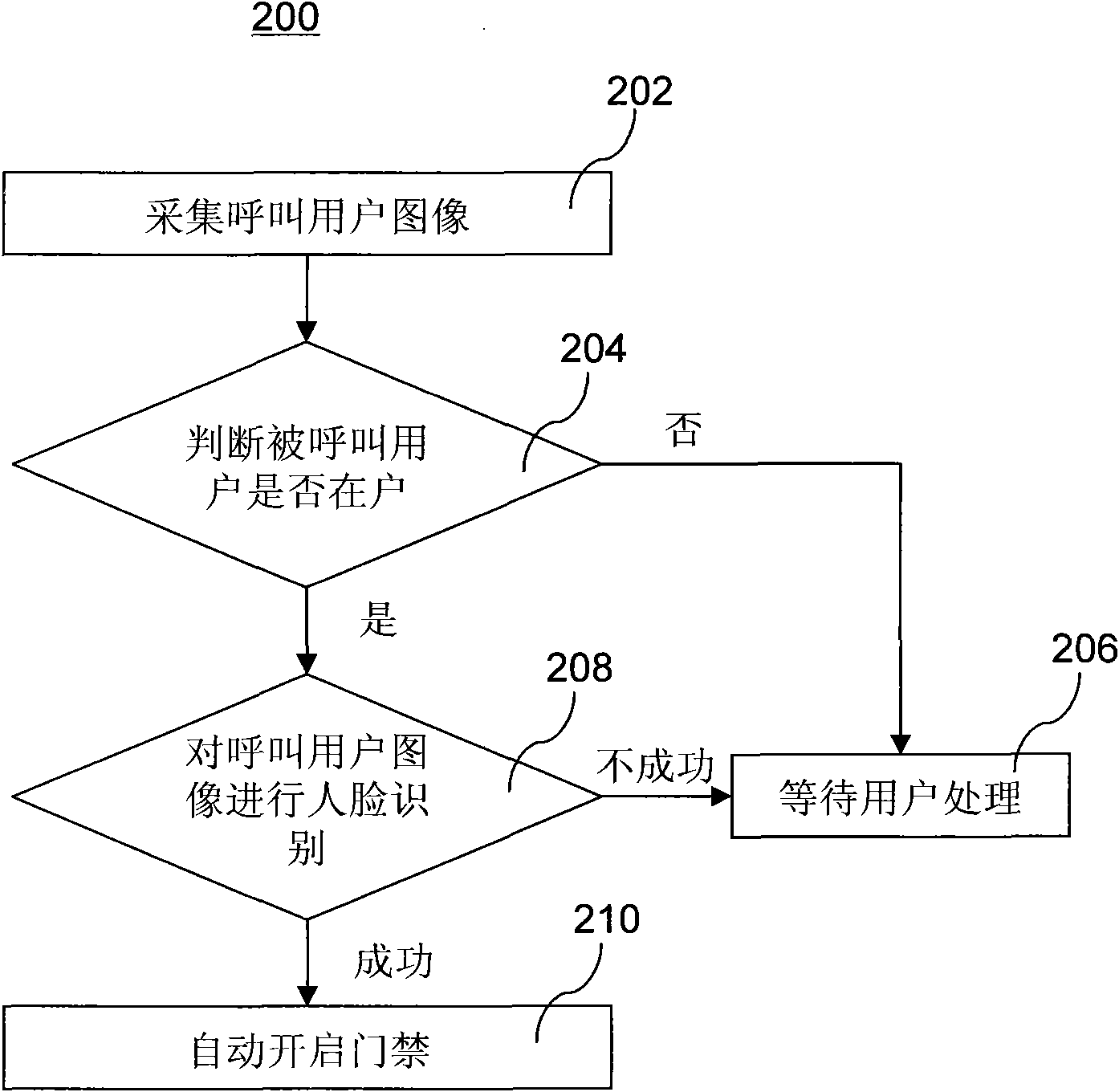
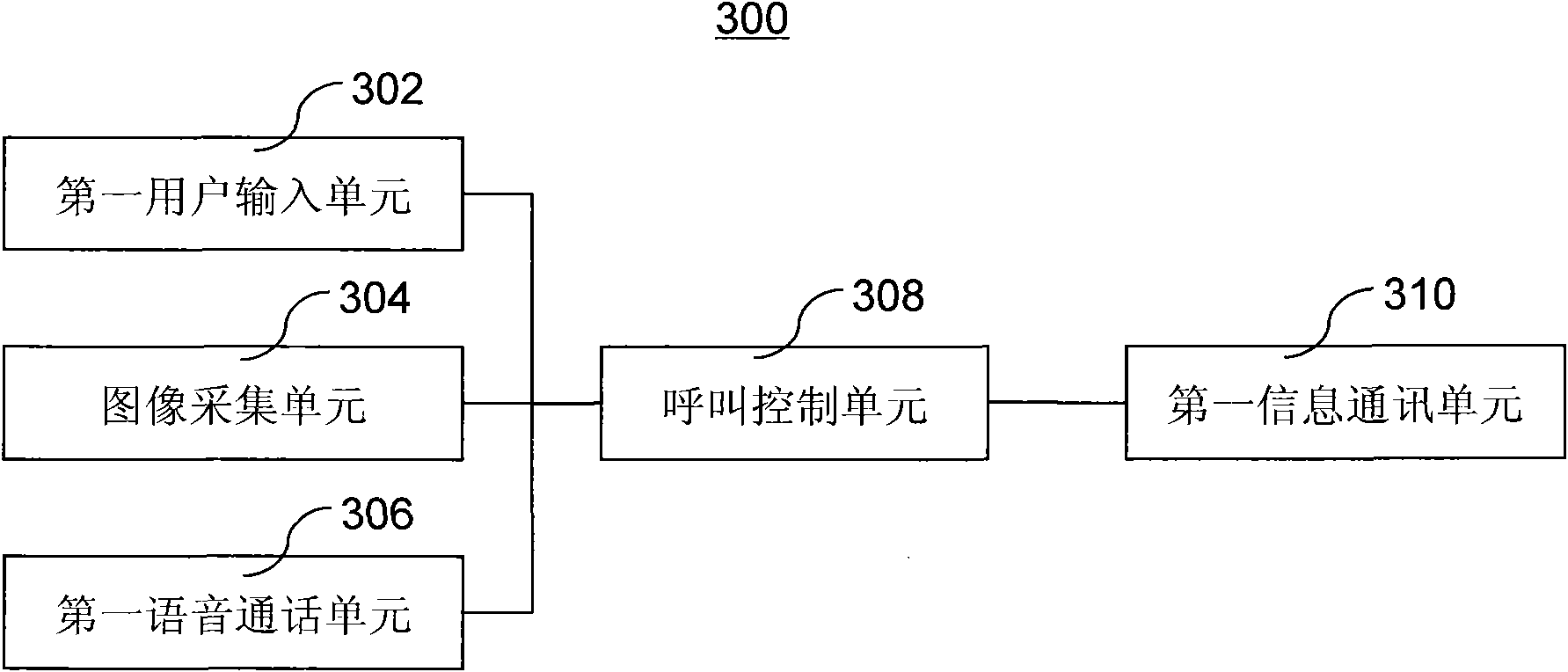
Door control system and door control management method
ActiveCN101853535AImprove experienceEasy to useIndividual entry/exit registersControl systemUser experience design
The invention discloses a door control system and a control management method. The method comprises the following steps of: acquiring a face image of a calling user in advance by using the door control system; identifying the face image of the calling user; and automatically opening the door control after successful identification and when the called user is at home. Compared with the prior art, the door control system adopts different processing modes for an external user who needs to enter the door control system by establishing a personnel association information database and adopting a face identifying technique, so that the external user who needs to access the door control system usually can automatically open the door control when the visited user is at home. The door control system and the control management method have the advantages of improving the user experience of the door control system, facilitating the using of the users and not reducing safety.
Owner:WUXI ZGMICRO ELECTRONICS CO LTD
Method and apparatus for generating and reinforcing user passwords
ActiveUS7873995B2Without compromising securityReinforce the generated passwordDigital data processing detailsUnauthorized memory use protectionPasswordHuman–computer interaction
Owner:AVAYA INC
Small current grounding line selection method based on residual current variable
ActiveCN102279349AReduce ground currentExtinguish the ground arcFault location by conductor typesShort-circuit testingSingle phaseGround current
The invention discloses a low current grounding wire selection method based on residual current variable, and the method comprises the following steps of: (1) correctly identifying whether an electric distribution network has a single-phase ground fault by adopting the neutral point displacement voltage of the electric distribution network as characteristic quantity; (2) after the ground fault happens, compensating the grounding current of a fault point by virtue of an arc-suppression coil to achieve the effects of reducing the grounding current and extinguishing grounding arc light; (3) adjusting the tap position of a first tap arc-suppression coil on the premise of ensuring that the grounding residual current meets the standard request; (4) because the neutral point displacement voltagebefore and after the tap position adjustment of the arc-suppression coil changes, converting the zero-sequence current of each outgoing line subjected to the tap position adjustment to be below the voltage level before the top position adjustment by utilizing a voltage translation method so as to prevent the wire selection characteristic quantity from being influenced by the neutral point displacement voltage; and (5) selecting the line with the single-phase ground fault according to the change values of the zero-sequence current of each outgoing line after voltage translation before and after the tap position adjustment. The low current grounding wire selection method based on residual current variable can be used for improving the accuracy of wire selection.
Owner:STATE GRID ELECTRIC POWER RES INST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com