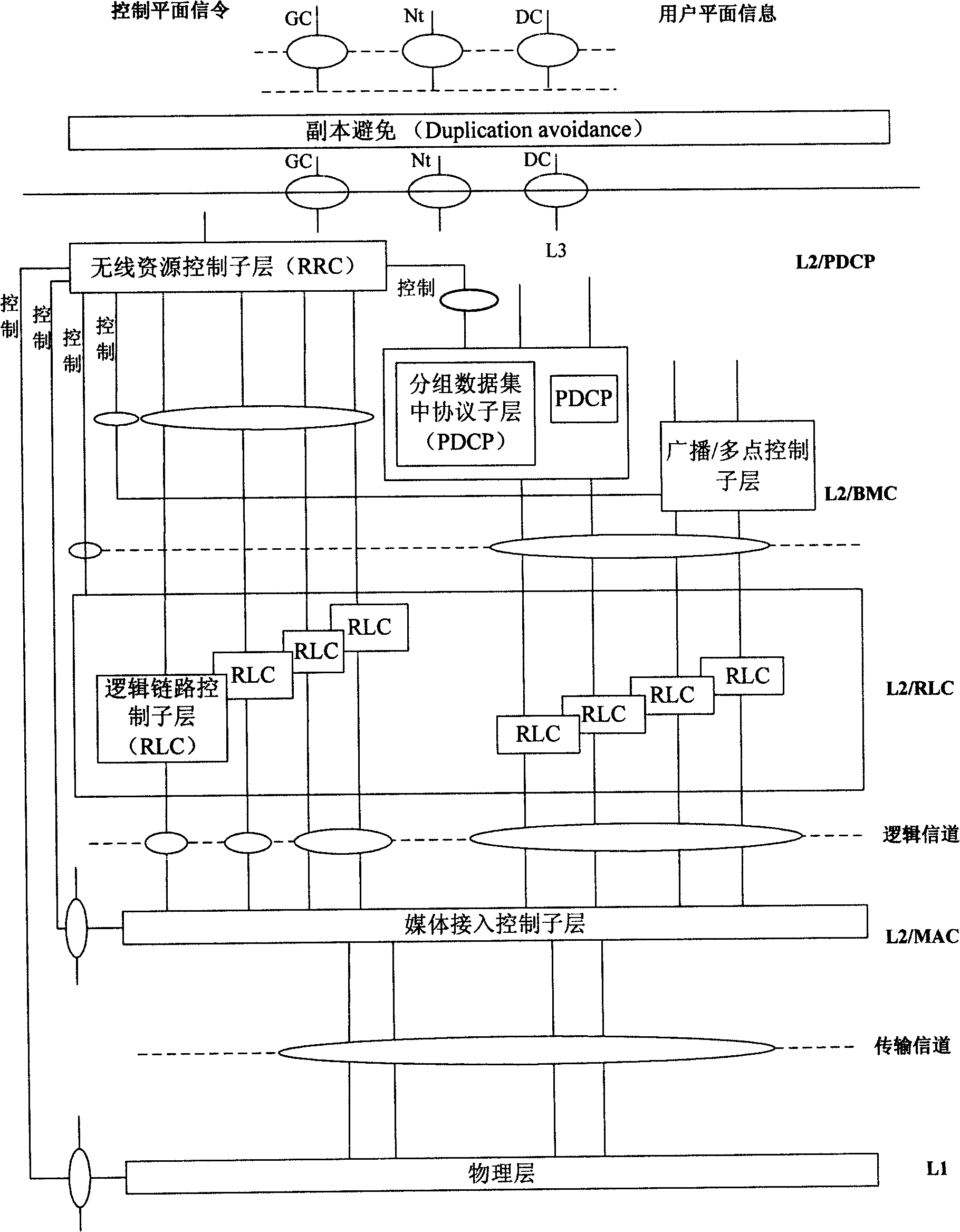
Patents
Literature
62results about How to "Avoid resource hogging" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
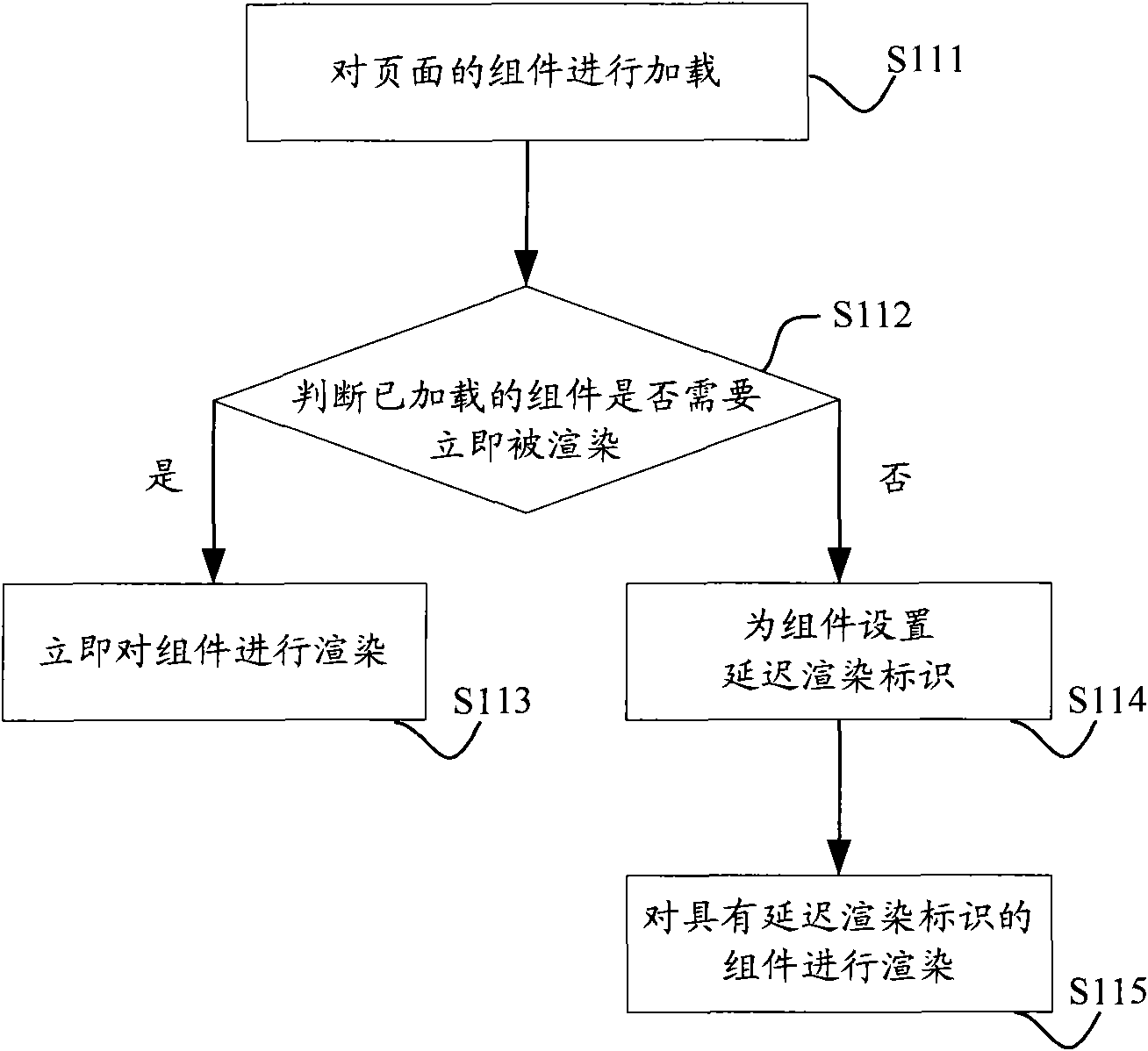
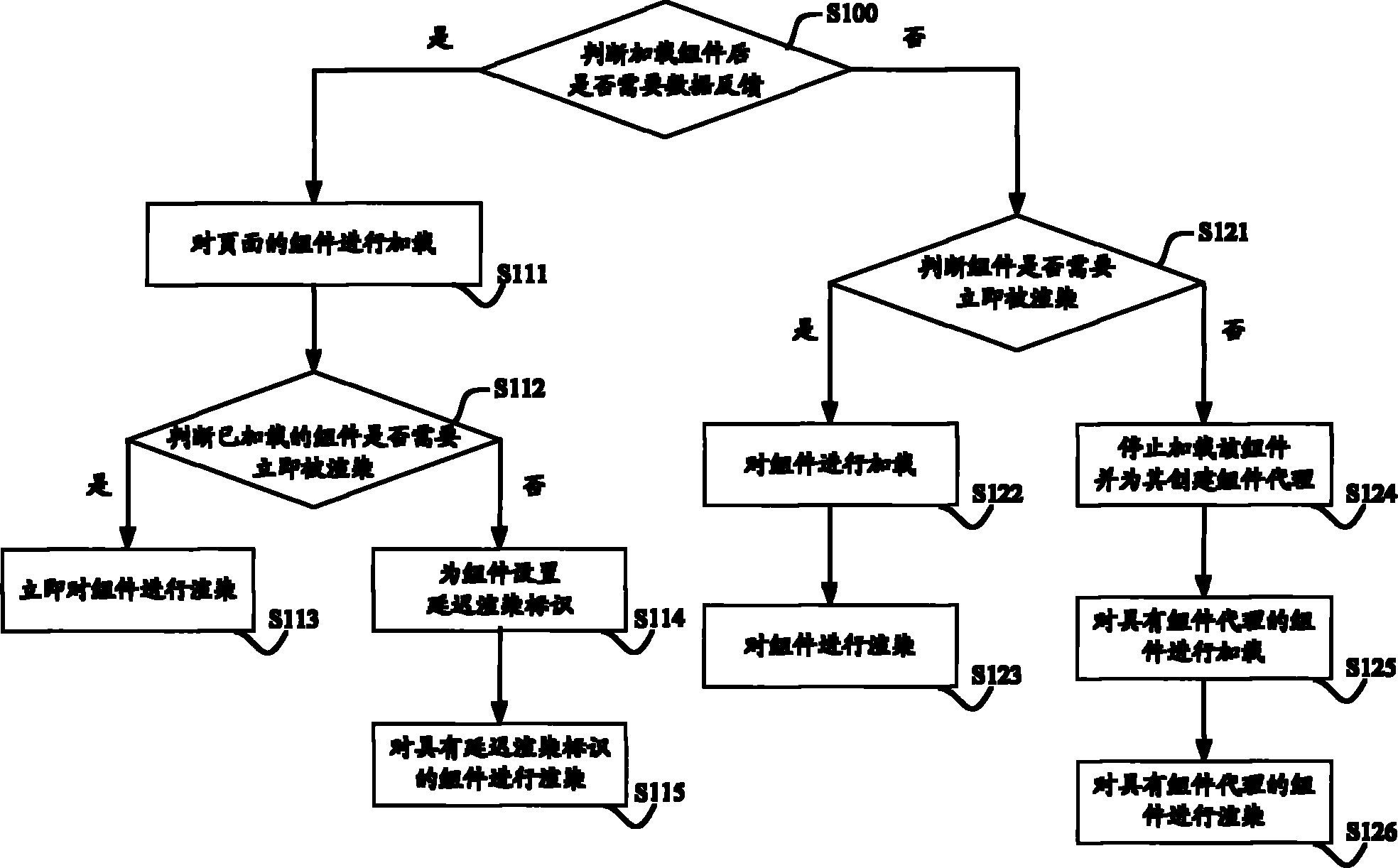
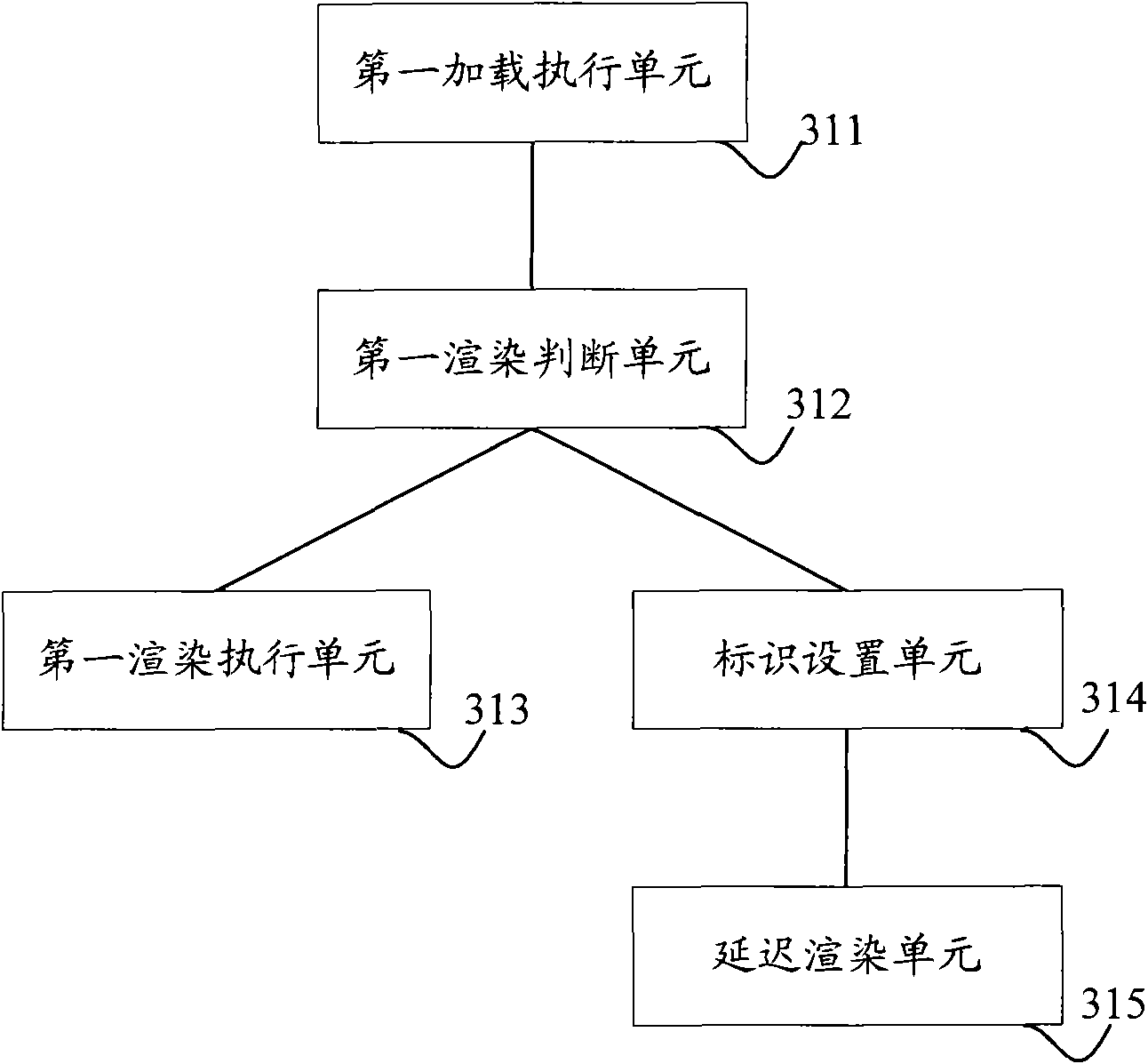
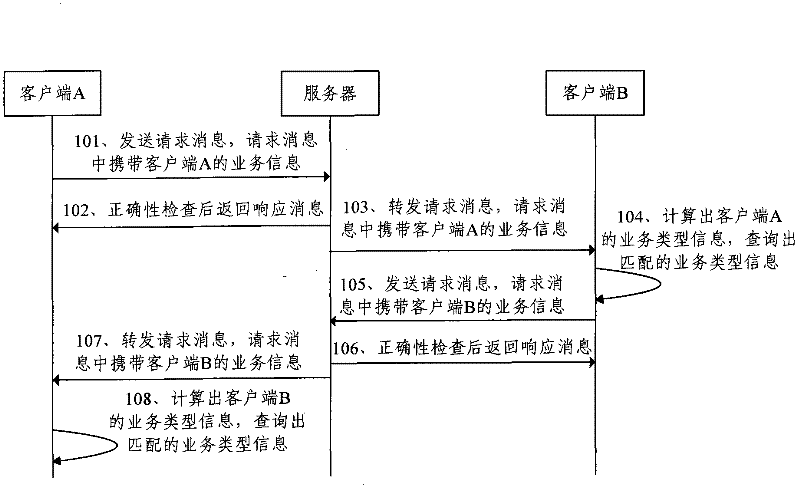
Component rendering method and device
ActiveCN101996073AAvoid rendering operationsAvoid resource hoggingProgram loading/initiatingComputer graphics (images)Proper time
The invention discloses component rendering method and device. The component rendering method comprises the steps of: initializing page data and then loading components of a page according to the page data; judging whether the loaded components are in need of immediate rendering or not according to content to be displayed and output currently; if so, immediately rendering the components; and or else, setting deferred rendering identifications for the components. By applying the technical scheme provided by the invention, on one hand, meaningless rendering operations can be avoided so as to save system resources, and on the other hand, the loaded components without being rendered immediately can be set with the deferred rendering identifications so as to render the components at a proper time and avoid the problem of system resource occupation caused by rendering a mass of components in a short time.
Owner:ALIBABA GRP HLDG LTD
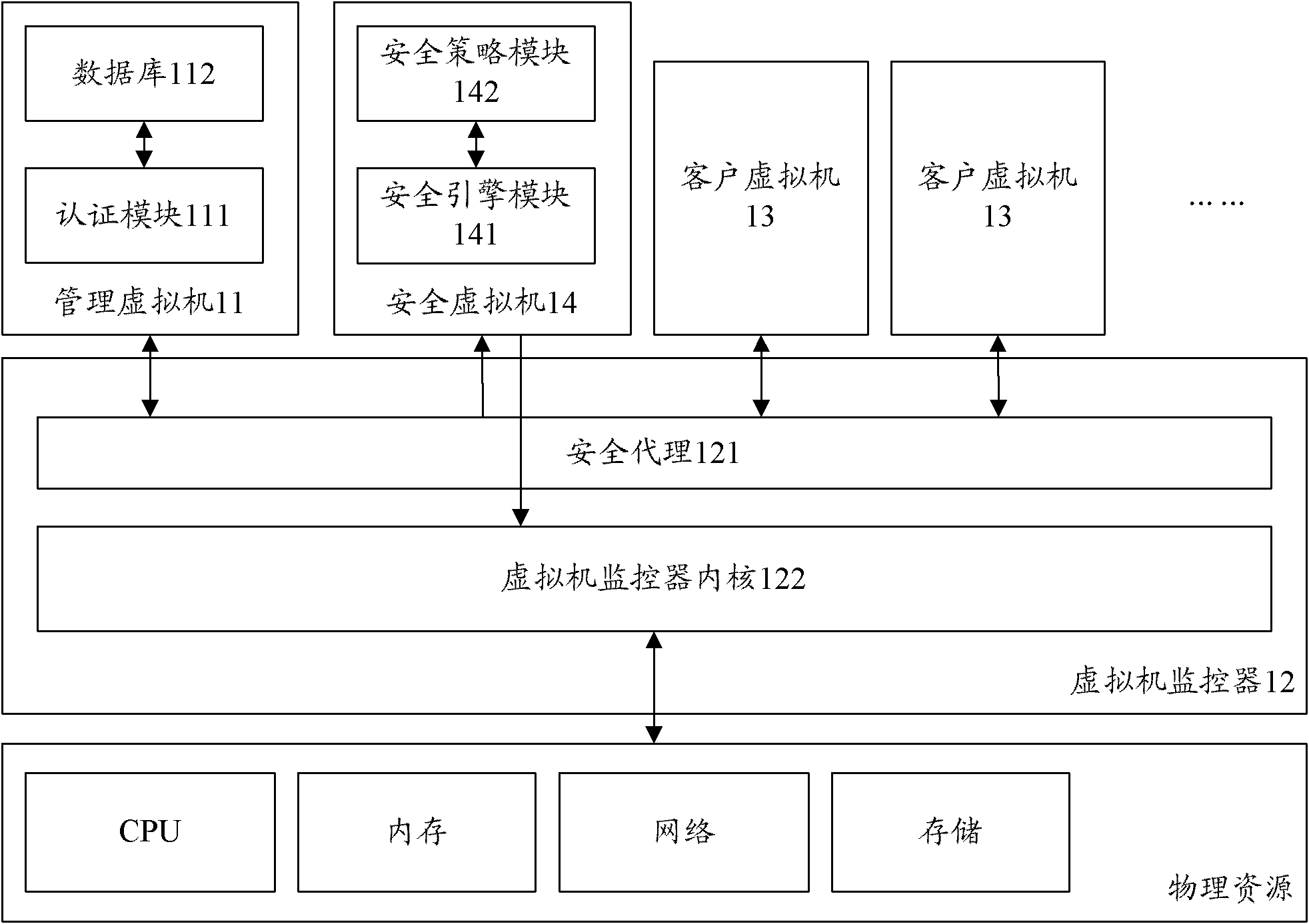
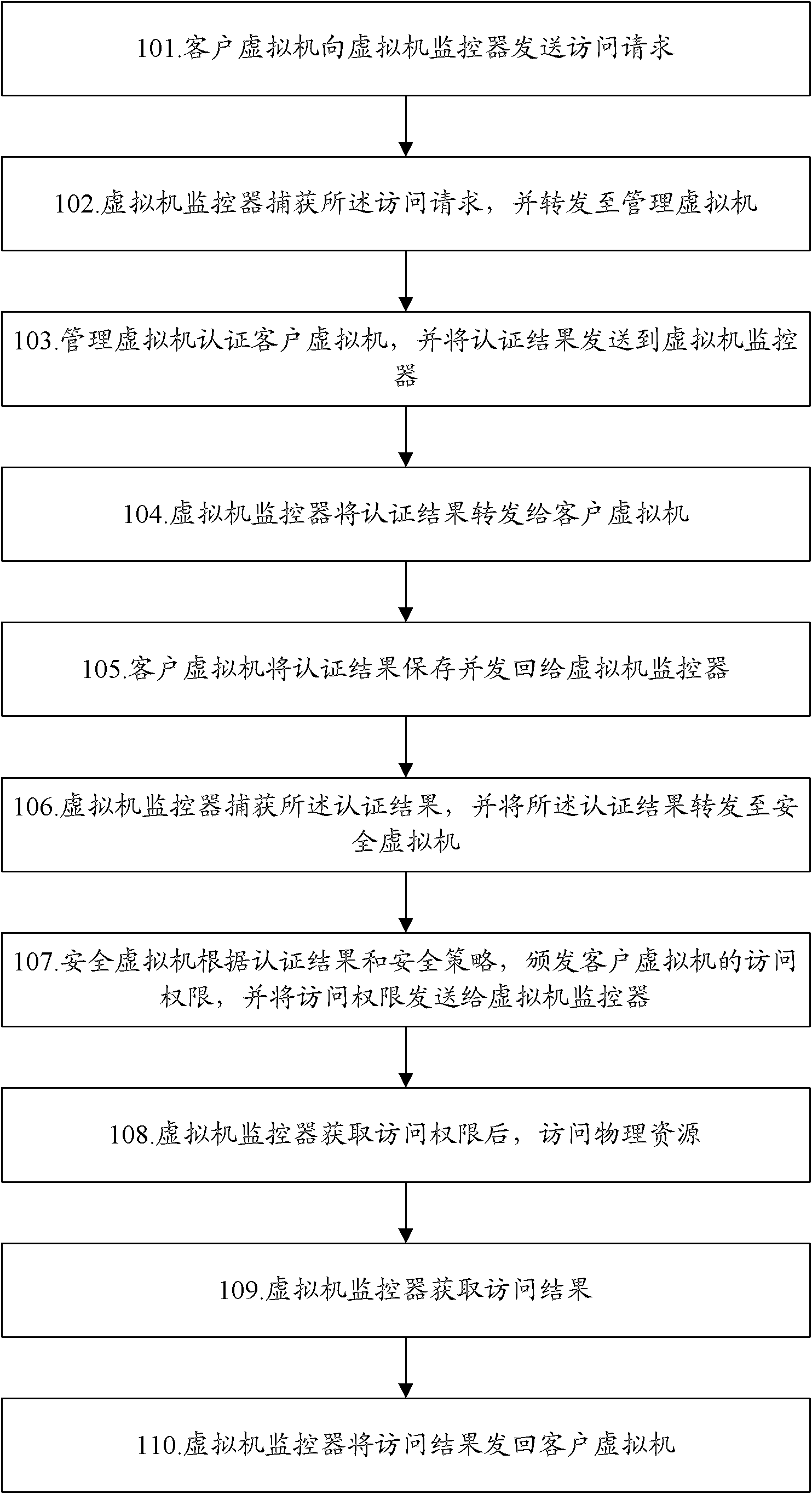
Virtual machine system and safety control method thereof
ActiveCN102811239AAvoid attackAvoid resource hoggingTransmissionSoftware simulation/interpretation/emulationSafety controlWorkload
The invention discloses a virtual machine system which comprises a management virtual machine, a virtual machine monitor, a client virtual machine and a safety virtual machine. The management virtual machine is used for authenticating the client virtual machine and sending an authenticated result to the virtual machine monitor. The virtual machine monitor is used for transmitting an access request sent from the client virtual machine to the management virtual machine. The authenticated result sent from the management virtual machine is transmitted to the client virtual machine. The authenticated result sent from the client virtual machine is transmitted to the safety virtual machine. According to access permission, physical resources are accessed and an access result is returned to the client virtual machine. The client virtual machine is used for sending the access request and the authenticated result to the virtual machine monitor. The safety virtual machine is used for issuing the access permission of the client virtual machine to the virtual machine monitor. The invention further discloses a safety control method of the virtual machine system. With the system and the method, workload of the virtual machine monitor can be lowered, the access permission of the client virtual machine can be flexibly controlled, and the access of the client virtual machine to the physical resources is effectively controlled.
Owner:ZTE CORP
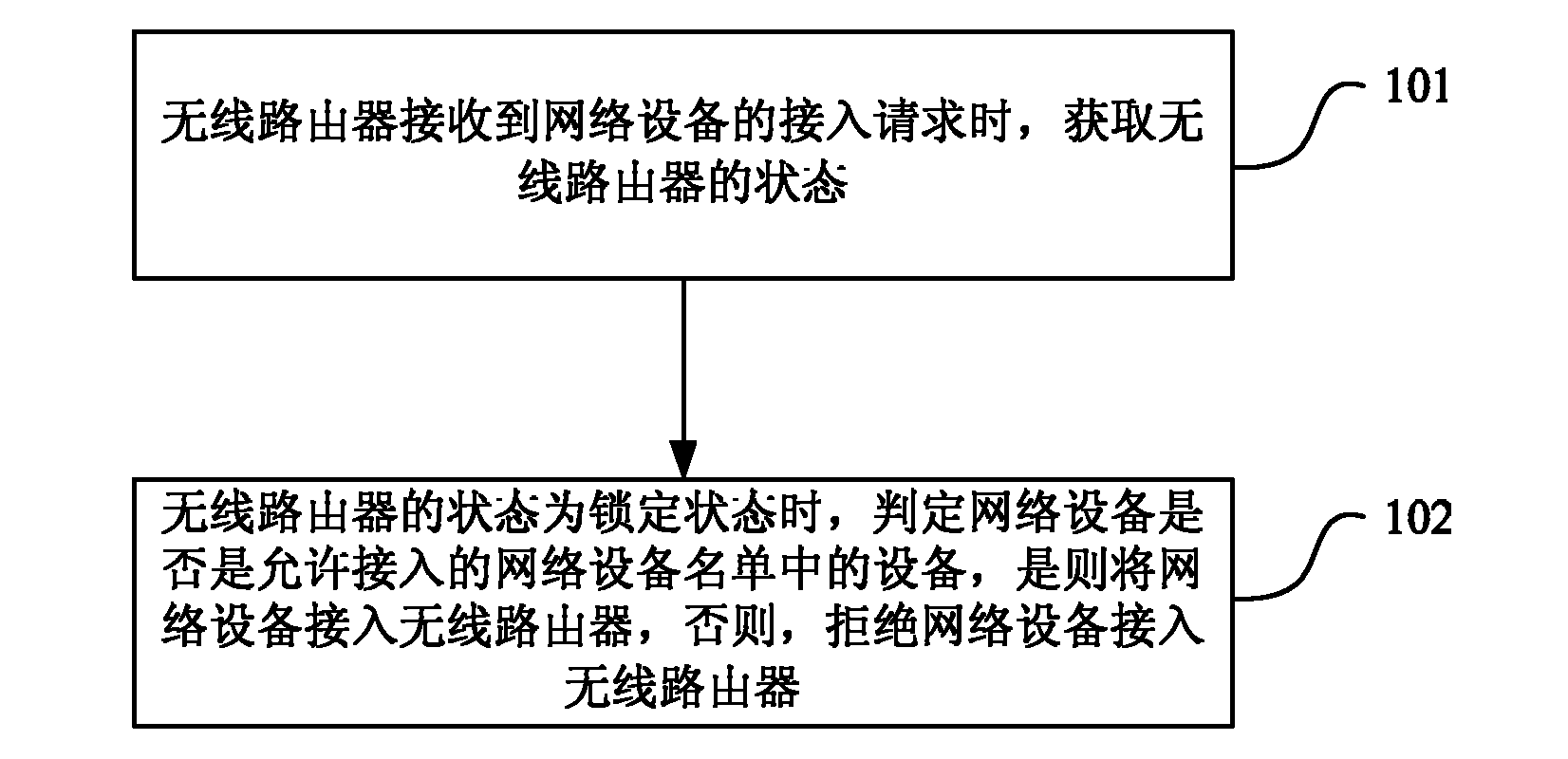
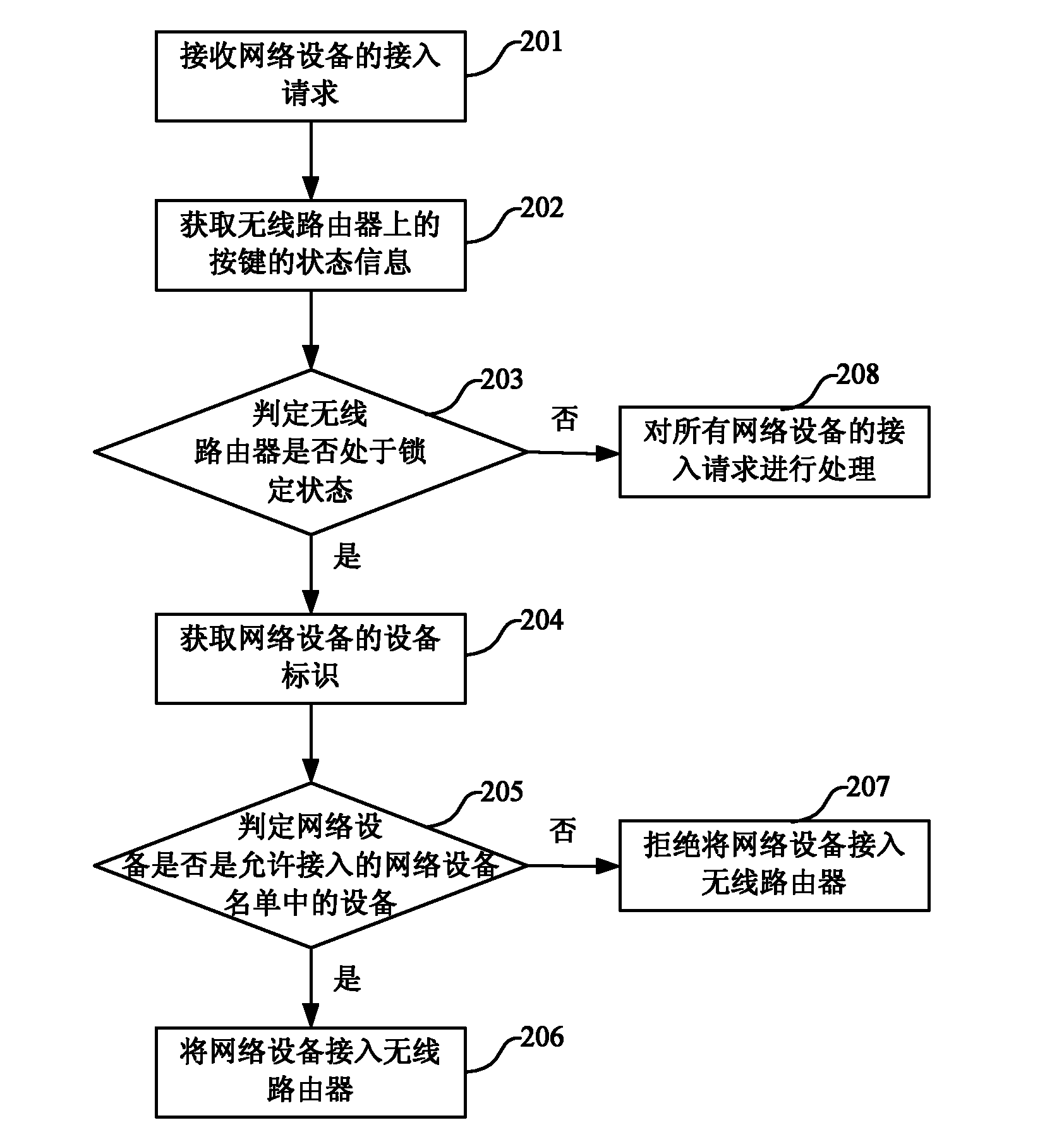
Wireless router and access method thereof
InactiveCN102149162AEnsure safetyGuaranteed reliabilityAssess restrictionWireless routerAccess method
The invention discloses a wireless router and an access method thereof. The method comprises the steps of obtaining a state of the wireless router while receiving an access request of a network device, wherein the state of the wireless router comprises a locking state and an opening state; judging whether the network device is a device in a network device list allowed to be accessed while the state of the wireless router is the locking state; and if so, accessing the network device into the wireless router; and otherwise, refusing the network device to be accessed into the wireless router. In a technical scheme of the invention, the network device can be effectively accessed into the wireless router to increase the safety and reliability of the wireless router access.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Home network security management method and device and system
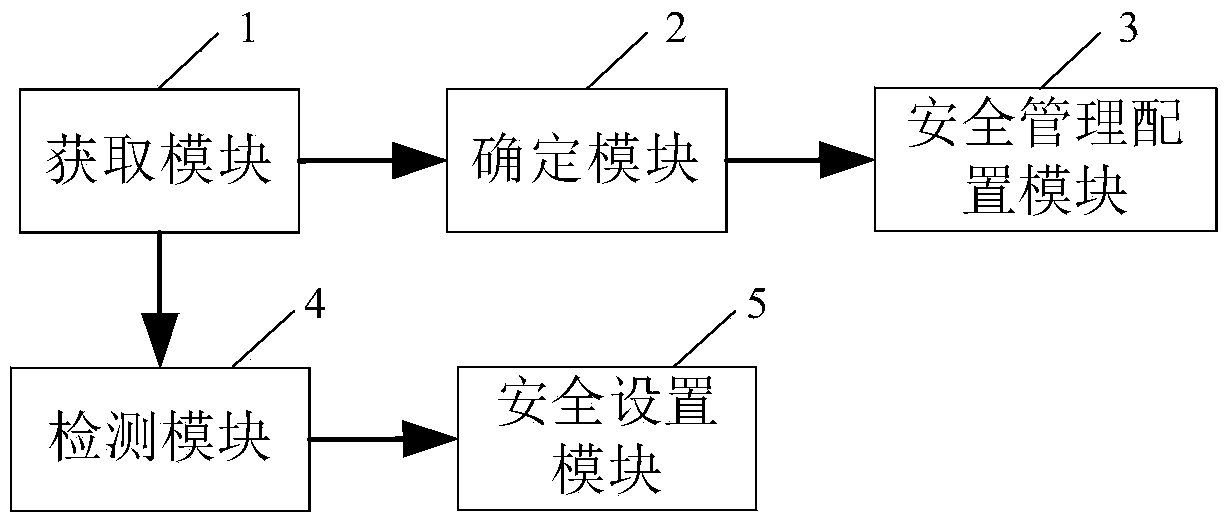
InactiveCN104079575AStrengthen security managementRealize a comprehensive physical examinationData switching by path configurationNetwork connectionComputer terminal
The invention relates to a home network security management method and device and a system. The method includes the steps of conducting security scanning on a home network so as to obtain network connection information of all terminals in the home network and network configuration information of gateway devices, confirming whether unknown terminals have access to the home network or no according to the network connection information of all the terminals, conducting security management configuration on the unknown terminals if the unknown terminals have access to the home network so that the unknown terminals can be allowed or refused to have access to the home network, detecting the network configuration information to obtain a detection result, and conducting security set operation on the gateway devices according to the detection result. According to the technical scheme, security vulnerabilities can be effectively checked, resource occupancy and / or security threats caused when unknown devices have access to the network can be effectively avoided, and the security defense capacity of the home network is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
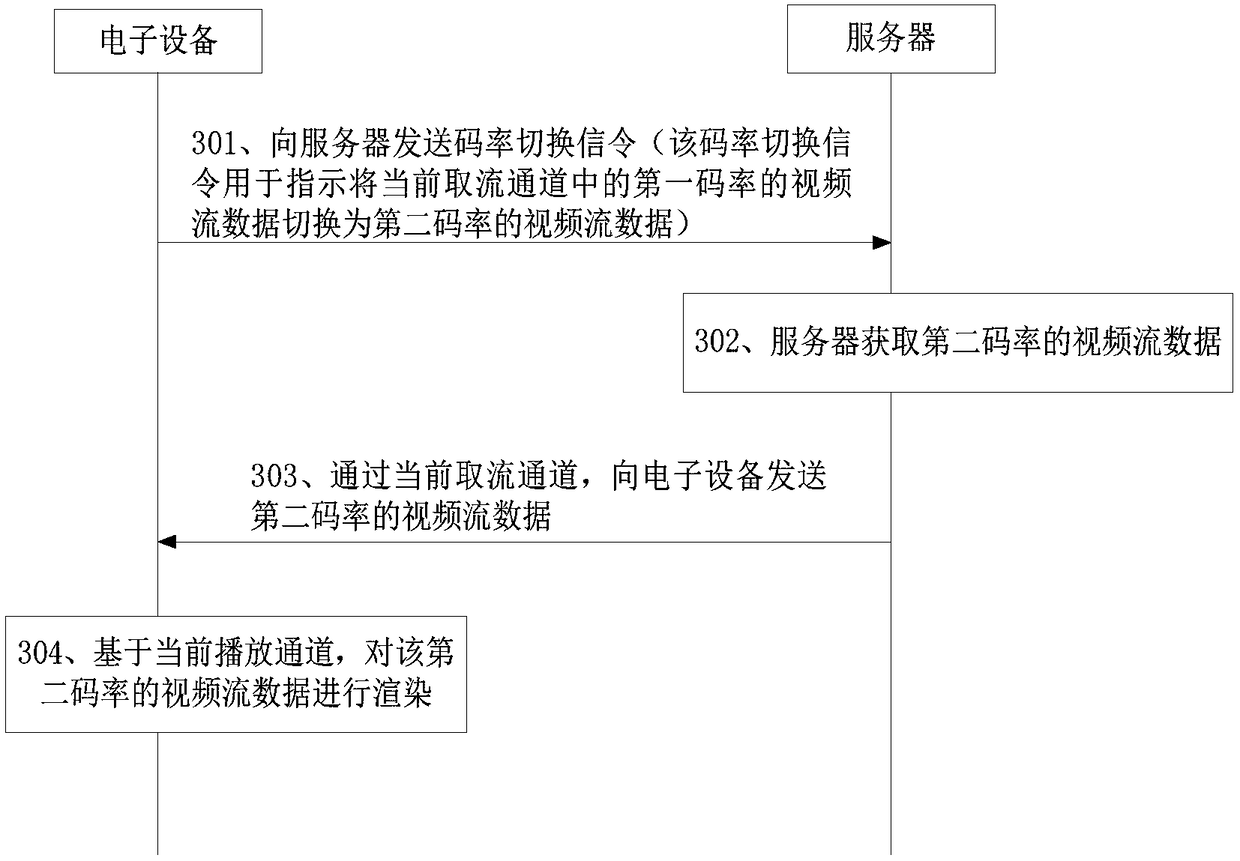
Video switching method and device
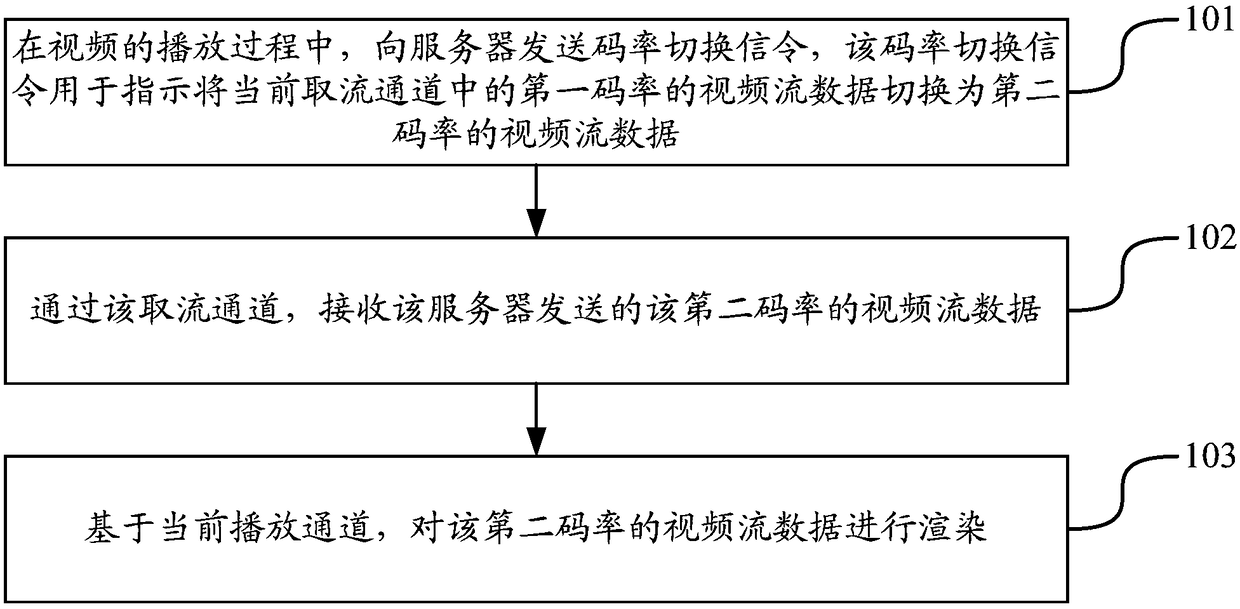
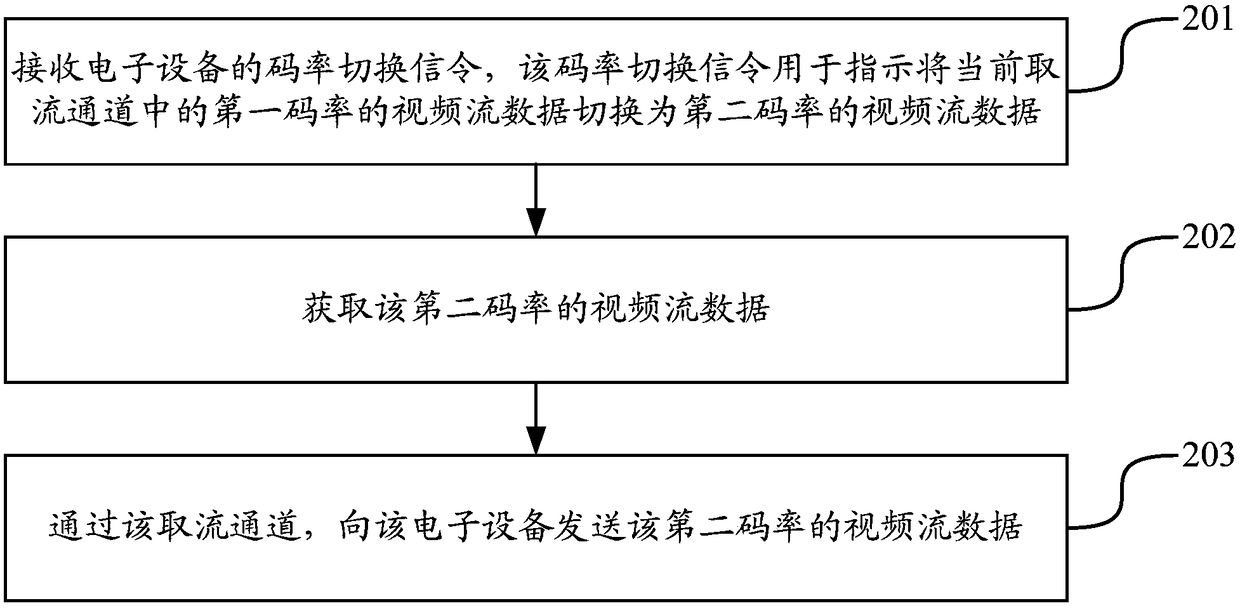
InactiveCN109495761AFast switching speedAvoid resource hoggingSelective content distributionStreaming dataSwitching signal
The invention discloses a video switching method and device, and belongs to the field of multimedia. The method comprises the steps that in a video playing process, a code rate switching signaling issent to a server, wherein the code rate switching signaling is used for instructing video stream data with a first code rate in a current stream acquisition channel to be switched to video stream datawith a second code rate; receiving the video stream data with the second code rate, sent by the server through the stream acquisition channel; and rendering the video stream data with the second coderate on the basis of a current playing channel. According to the method, one code rate switching signaling instructs the server to obtain the video stream data with different code rates, and the video stream data subjected to code rate switching is transmitted on the existing stream acquisition channel; an electronic device renders the switched video stream data based on the existing playing channel; and a new channel is not required to be established, so that the problems of resource occupation and time consumption caused by establishing the new channel are solved, the resources saved, and the switching speed of videos is improved.
Owner:HANGZHOU HIKVISION SYST TECH
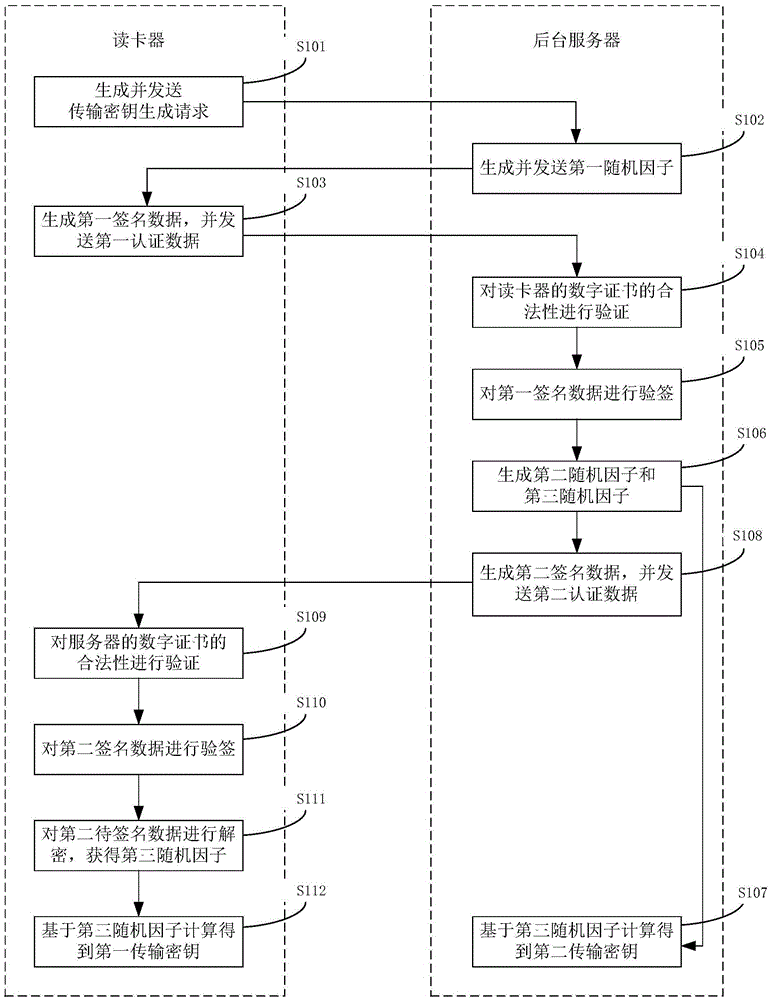
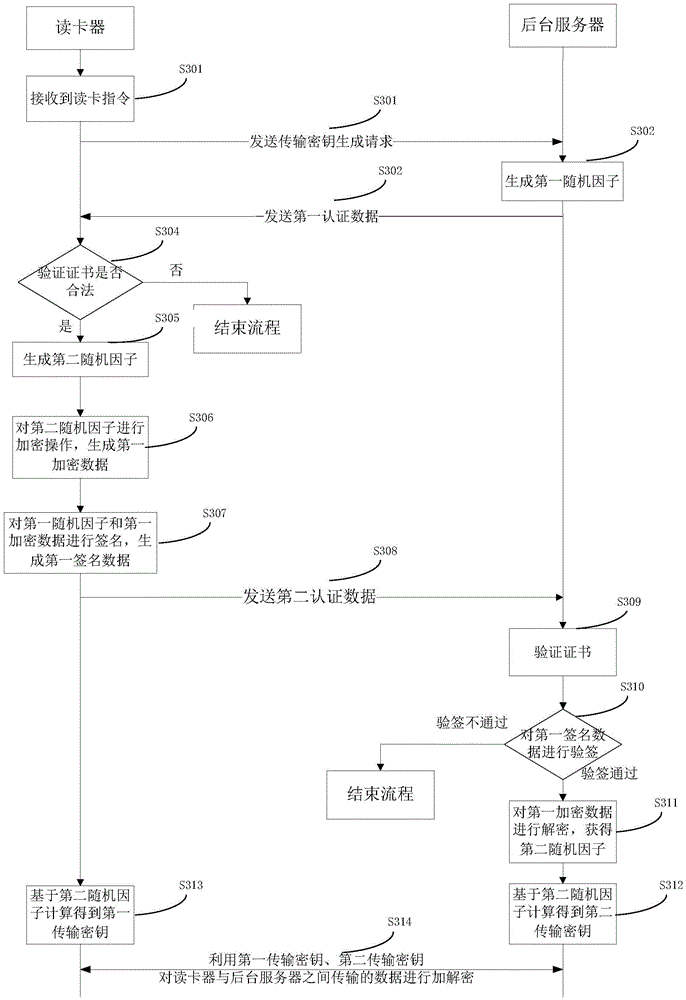
Identity card information safety transmission method and system
ActiveCN106027250AImprove authentication efficiencyAvoid resource hoggingKey distribution for secure communicationUser identity/authority verificationCard readerInformation security
The invention provides an identity card information safety transmission method and system. The method comprises the steps that a card reader receives a card reading instruction and then transmits a transmission secret key generation request to a background server; the background server generates and transmits a first random factor; the card reader carries out the signing of first to-be-signed data, generates first signature data, and transmits first authentication data; the background server carries out the verification of the validity of a digital certificate of the card reader; and the flow is ended if the verification is not passed. After the card reader receives the first random factor, a private key is used at once to sign the first random factor, and the first random factor is transmitted to the server, thereby enabling the background server to receive and verify the first authentication data in shortest time, improving the authentication efficiency of the background server for the card reader. Therefore, the background server instantly determines whether the card reader is legal at the initial stage of the mutual authentication of the card reader and the background server or not. The flow is ended if the card reader is illegal, thereby preventing illegal transaction from occupying resources of the background server.
Owner:TENDYRON CORP
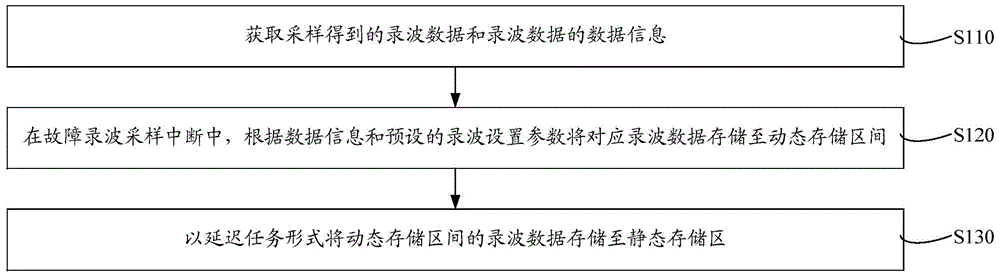
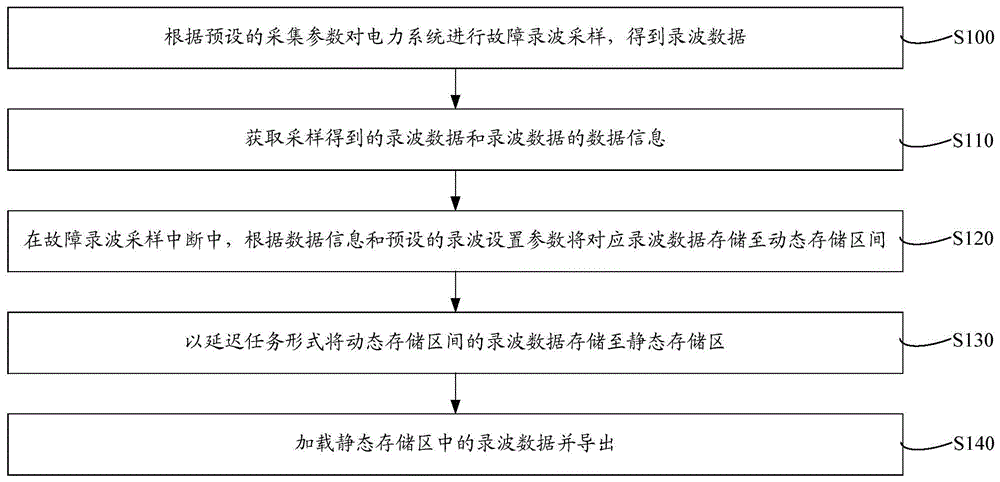
Recording method and system of fault recording data
ActiveCN105676023AAchieve recordGuaranteed real-time storageElectrical testingReal-time dataData information
The invention relates to a recording method and system of fault recording data. The recording method includes the steps: acquiring recording data obtained through sampling and the data information of the recording data; during the process for interruption of sampling of fault recording, according to the data information and the preset recording setting parameters, storing the corresponding recording data in a dynamic storage interval; and in the mode for delaying tasks, storing the recording data in the dynamic storage interval in a static storage zone. As the real time data is stored during the process for interruption of sampling and the original data is transferred from a designated recording file to a static memory by delaying the tasks, the recording method and system of fault recording data can guarantee the real-time for data storage and can avoid that file storage time occupies the resource of the main task of the system, and can realize real-time recording of the fault recording data under smaller software and hardware resource so that the applicability is improved.
Owner:HNAC TECH
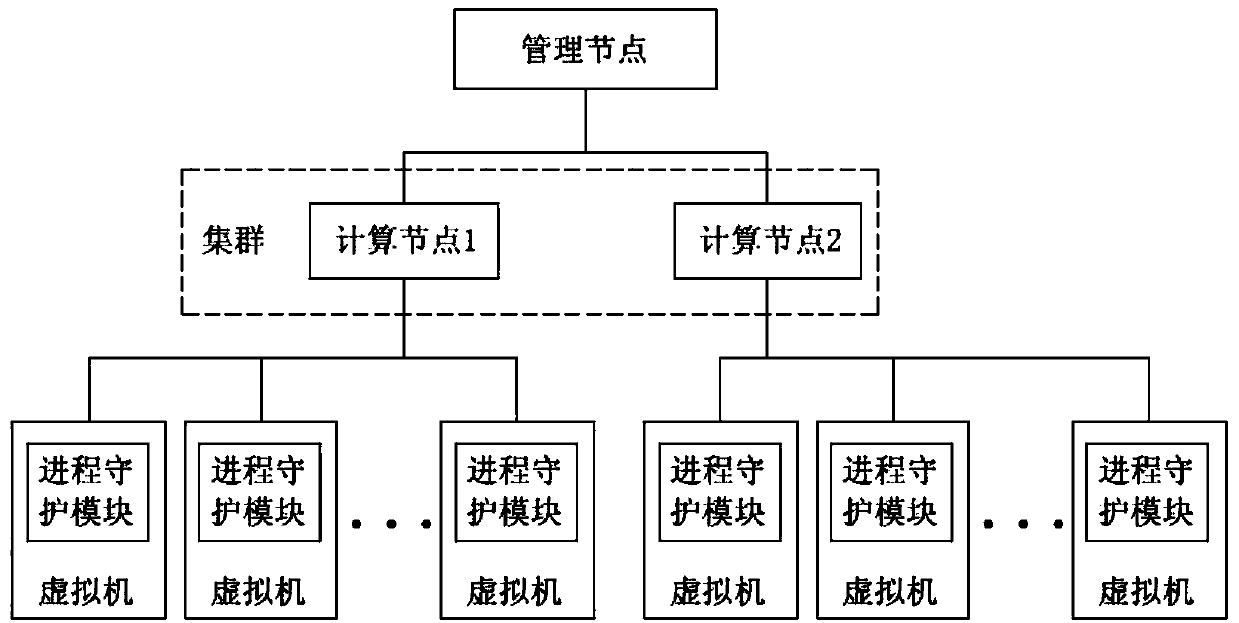
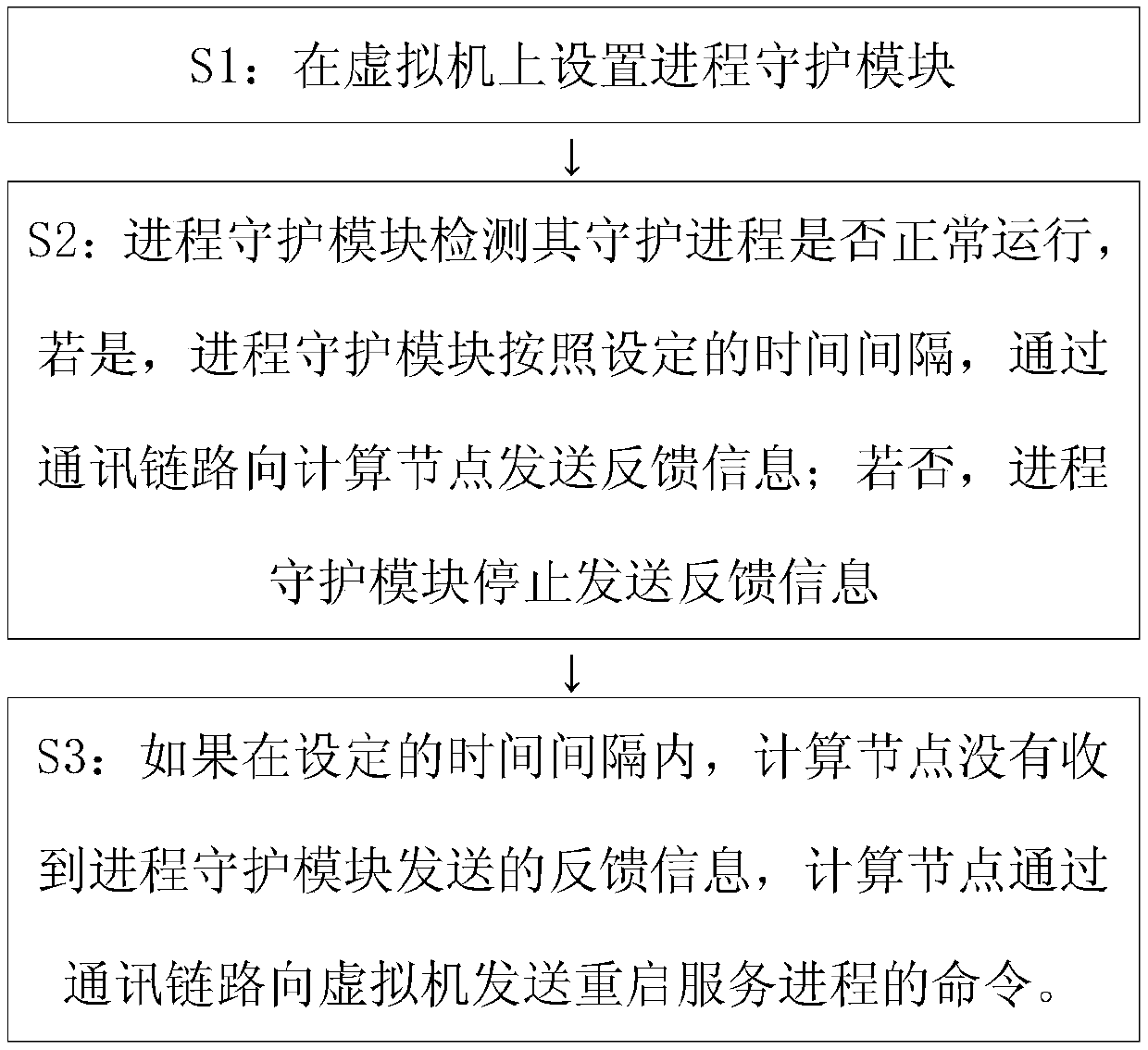
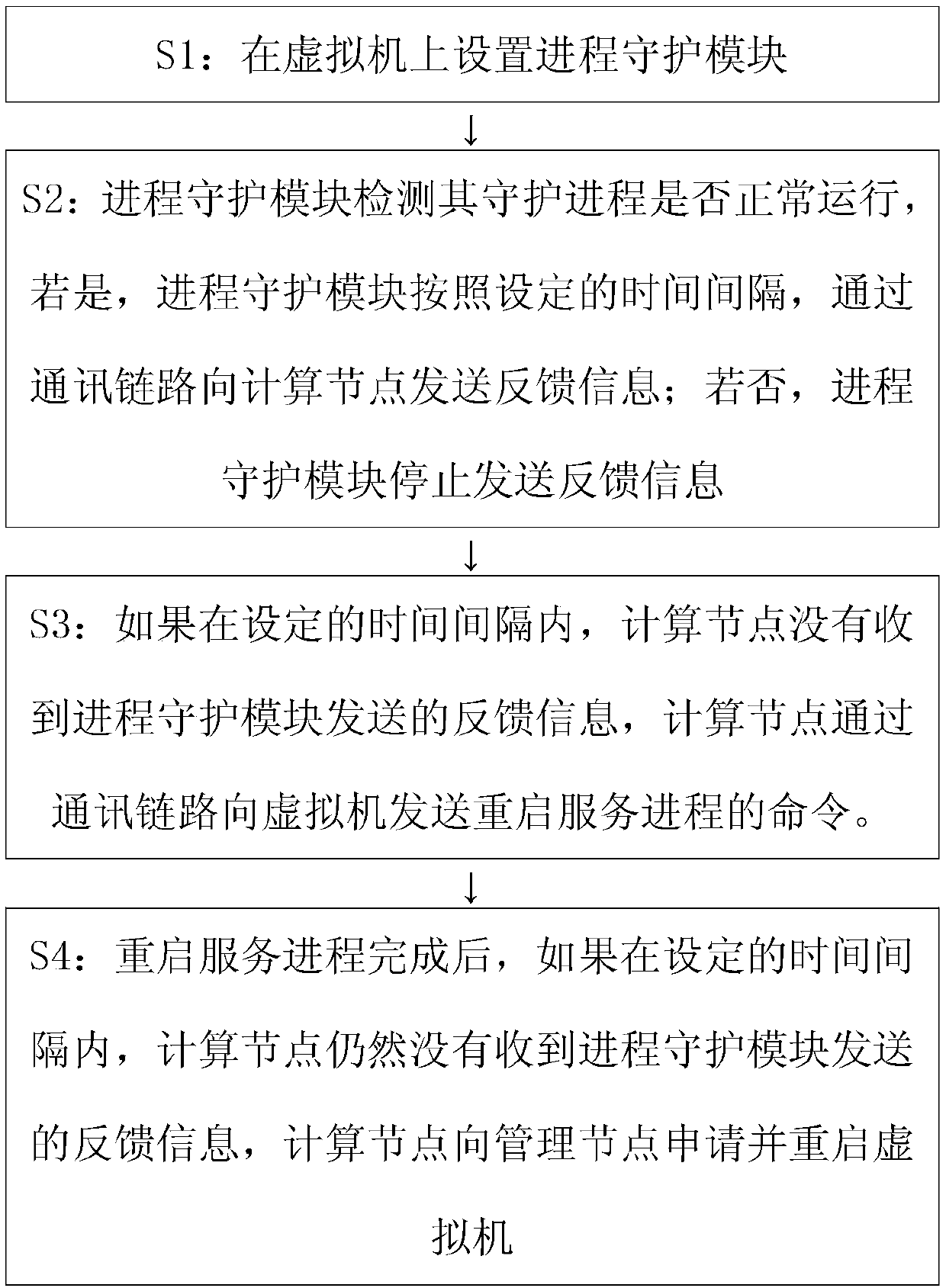
Virtual machine process monitoring system and method
InactiveCN107741876AAccurate judgmentGuaranteed uptimeSoftware simulation/interpretation/emulationData informationHigh availability
The invention provides a virtual machine process monitoring system and method. The system comprises management nodes, computing nodes and virtual machines, wherein the management nodes are used for receiving data information sent by all the computing nodes under a same cluster and issuing corresponding management instructions, the computing nodes are used for receiving and forwarding data information of all the virtual machines under the computing nodes and sending the instructions issued by the management nodes to the corresponding virtual machines, and the virtual machines are used for running all processes and sending the process states to the computing nodes corresponding to the virtual machines. The method comprises the steps that 1, process daemon modules are set on the virtual machines; 2, the process daemon modules send the process states to the computing nodes corresponding to the virtual machines; 3, the computing nodes receive the process states of the virtual machines and issue the management instructions according to the process states. One daemon process is added to each virtual machine so that it can be ensured that services of a user on the corresponding virtual machine run normally, and the reliability and high availability of the services are improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Method of realizing heartbeat mechanism, apparatus and system thereof
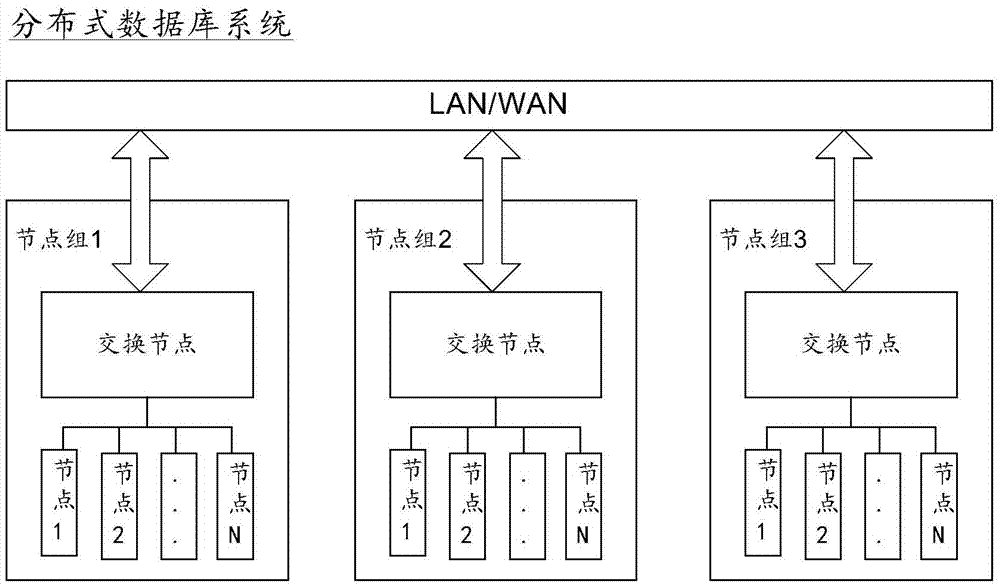
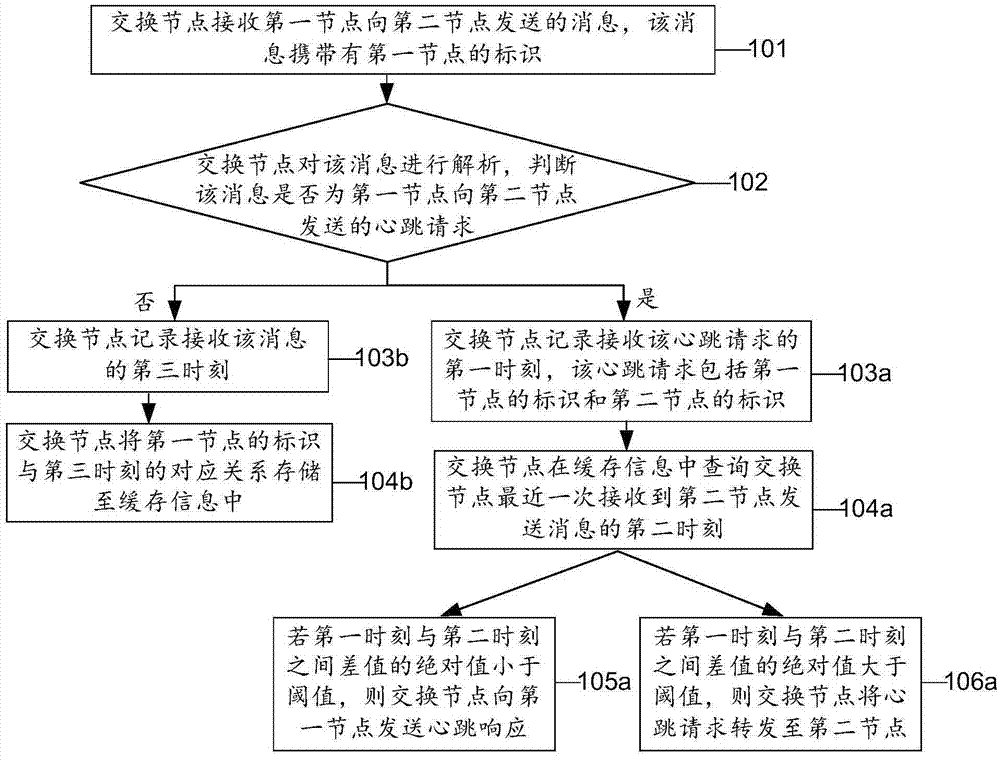
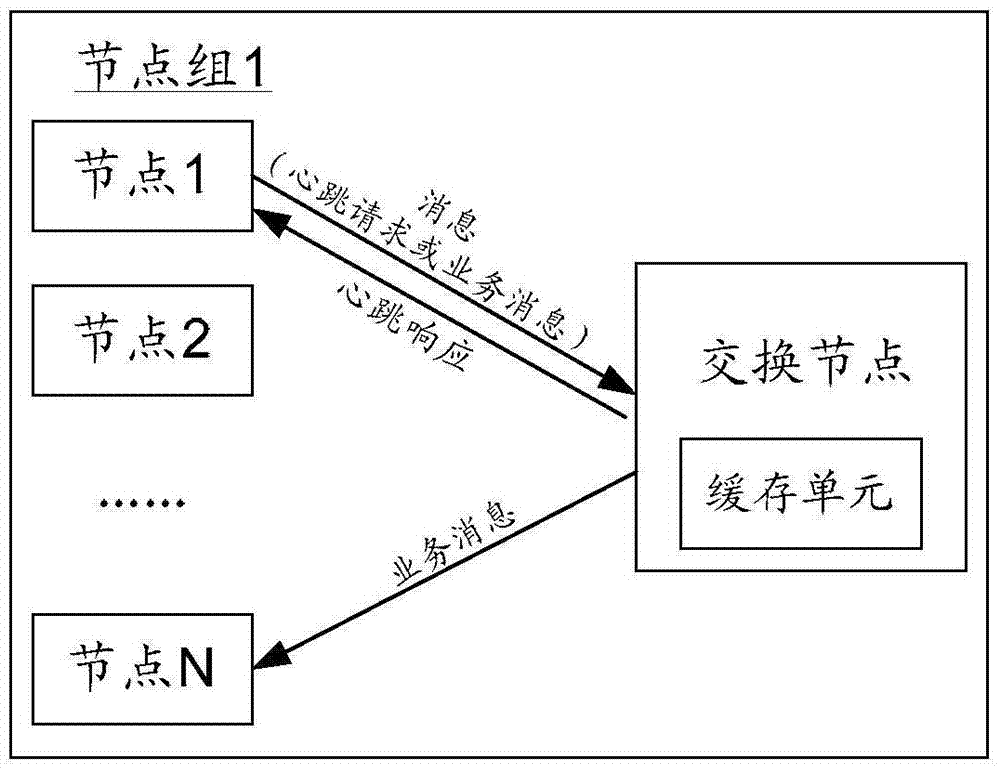
ActiveCN106936662ALower latencyReduce fault detection timeData switching networksDistributed databaseComputer science
An embodiment of the invention provides a method of realizing a heartbeat mechanism, an apparatus and a system thereof. A quantity of heartbeat responses sent by a node can be reduced so that unnecessary resource occupation cost in a distributed database system can be decreased. The scheme comprises the following steps that an exchange node acquires a heartbeat request sent by a first node to a second node, wherein the heartbeat request includes an identification of the first node and an identification of the second node; the exchange node records and receives a first moment of the heartbeat request; the exchange node inquires a second moment of receiving a second node sending message most recently by the exchange node in buffer memory information according to the identification of the second node, wherein the buffer memory information stores a corresponding relation of a moment for any one node to send a message and the identification of the node and the moment is received by the exchange node; and if an absolute value of a difference value between the first moment and the second moment is less than a threshold, the exchange node sends the heartbeat responses to the first node.
Owner:HUAWEI TECH CO LTD
Implementation method of SM4-GCM network encryption transmission system based on FPGA
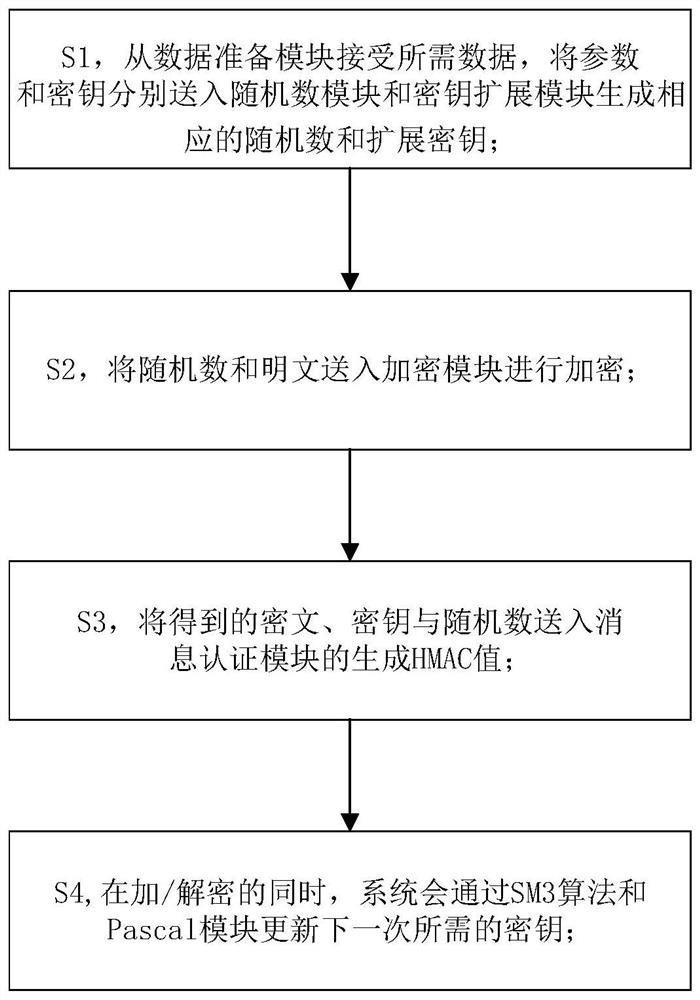
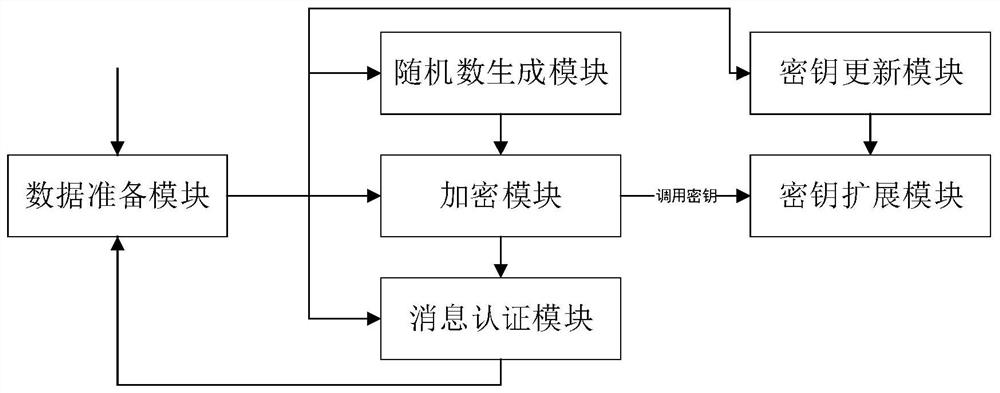
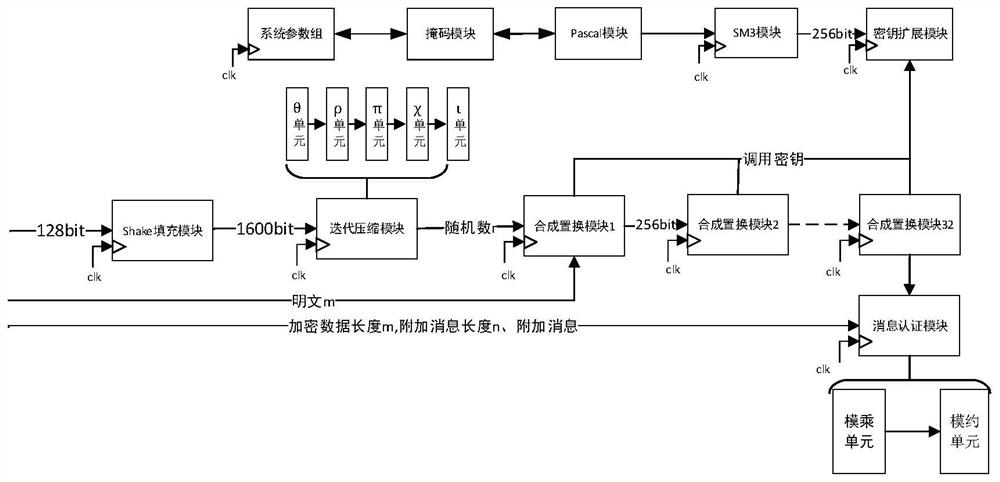
ActiveCN112769551AEnsure safetyImplement revisionKey distribution for secure communicationSecurity arrangementData preparationTransmission system
The invention relates to an SM4-GCM network encryption transmission system implementation method based on an FPGA, and the method comprises the following steps: S1, receiving required data from a data preparation module, and respectively sending a parameter and a secret key into a random number module and a secret key extension module to generate a corresponding random number and an extension secret key; S2, sending the random number and the plaintext into an encryption module for encryption; S3, sending the obtained ciphertext, key and random number to a message authentication module to generate an HMAC value; S4, during encryption / decryption, enabling the system to update a key required for the next time through an SM3 algorithm and a Pascal algorithm. According to the invention, the shake-128 algorithm in the Keccak is utilized to realize the generation of the random number, the security of the random number is improved, and the resource utilization rate and the working frequency of the random number are improved by optimizing the nonlinear transformation operation and the message authentication operation, so the method is more suitable for the environment of a high-speed network; the SM3 algorithm and the Pascal algorithm are utilized to realize the safe change of the secret key, and the GMAC module is combined to ensure the correctness of the system secret key update.
Owner:HANGZHOU DIANZI UNIV
Traffic guidance system constructing method suitable for large-screen high-definition display
InactiveCN104933880AAvoid resource hoggingImprove access efficiencyArrangements for variable traffic instructionsVehicle position indicationGuidance systemSplit window
The invention provides a traffic guidance system constructing method suitable for large-screen high-definition display. The method includes the steps of: (1) obtaining a large-screen base map host environment and various system interfaces; (2) determining a realization effect, large-screen split windows and display content; (3) determining an operational process, and adjusting a software interface according to screen resolution; (4) performing map cutting operation on a map according to the resolution of a display area, optimizing map display according to the resolution of the display area after determining a system interface, accessing the map in a B / S mode, and performing high-definition large-picture display while avoiding resource occupation and improving access efficiency; and (5) adjusting various map icons according to a display area effect after mapping cutting is performed on the map, optimizing system display efficiency, and enabling a picture effect to be clear and the sizes of the icons to be suitable for watching.
Owner:CHINA CHANGFENG SCI TECH IND GROUPCORP
Cross-domain computing task scheduling method and system based on intelligent perception
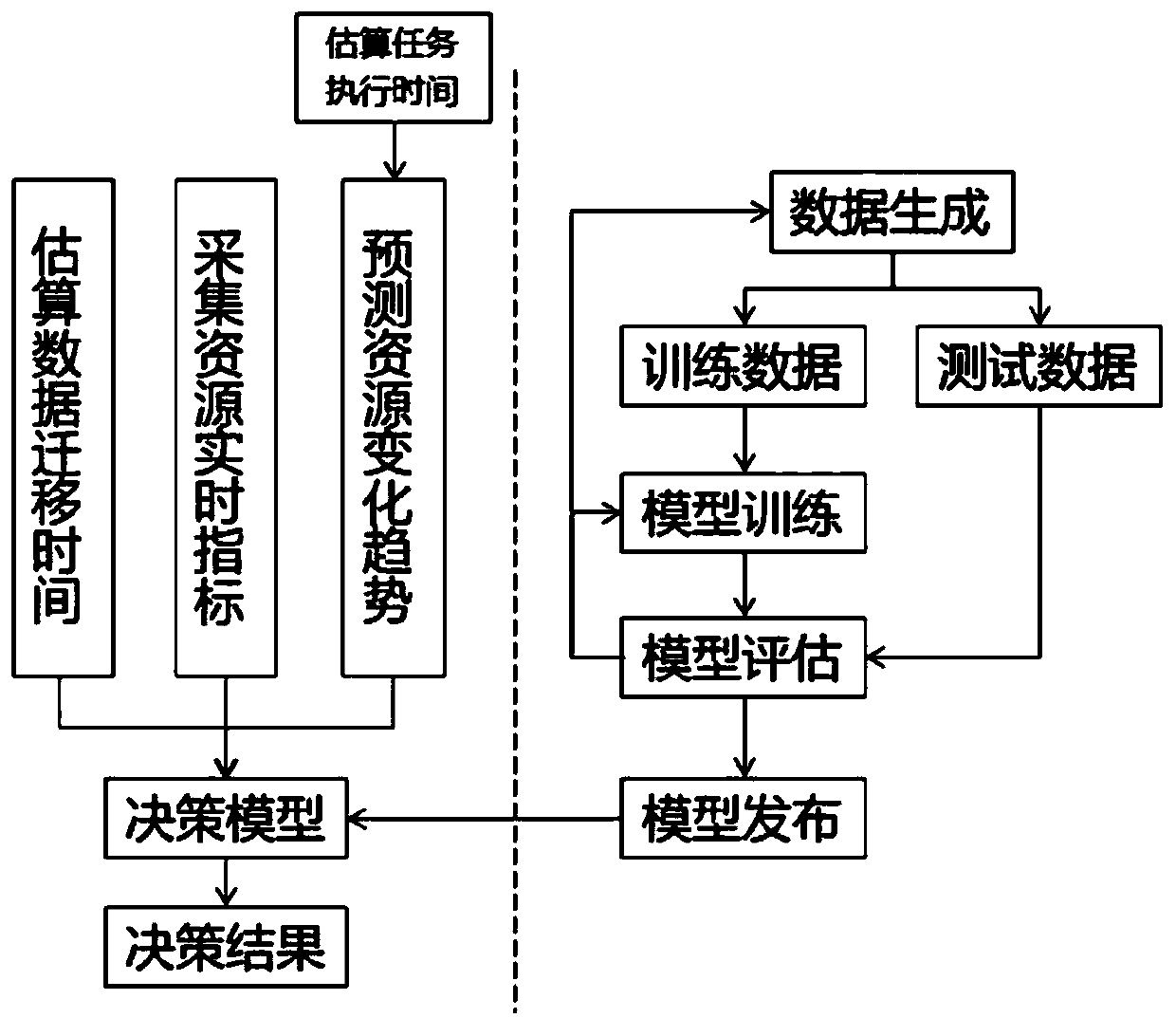
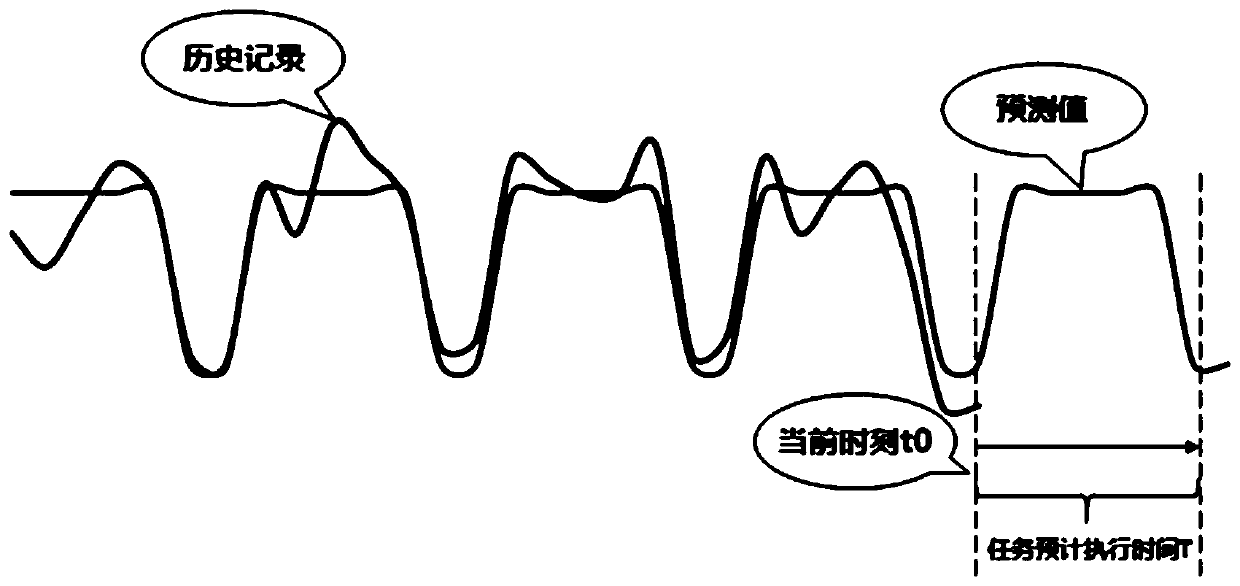
ActiveCN109960573AAvoid preemptionSolve the problem of low accuracy of scheduling decisionsProgram initiation/switchingResource allocationPattern perceptionTime complexity
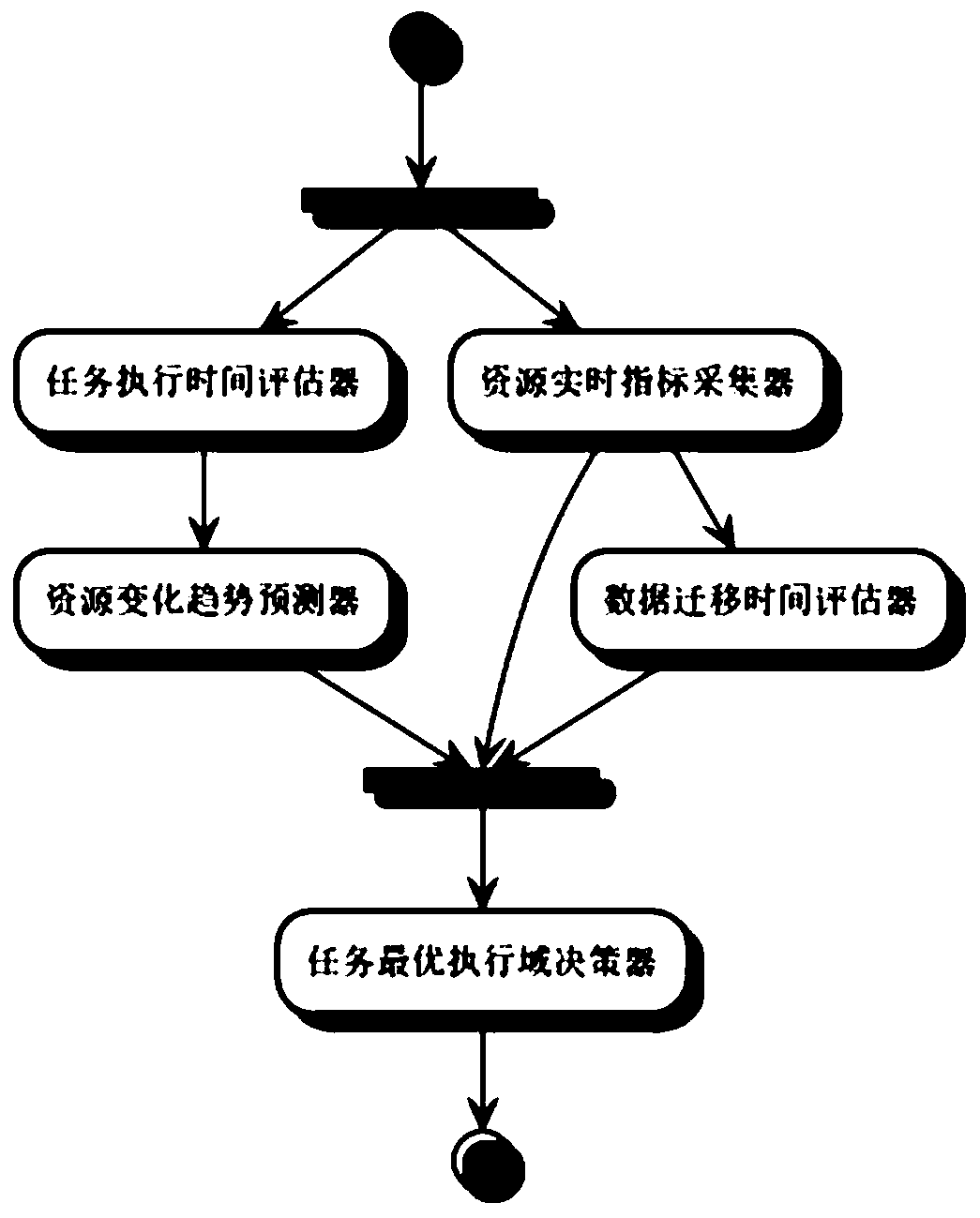
The invention provides a cross-domain computing task scheduling method and system based on intelligent perception. The cross-domain computing task scheduling method comprises the steps of step 1, training a decision tree model based on label data; step 2, estimating and calculating the execution time of the task based on the relative time complexity; step 3, predicting a resource change trend index of each domain based on the resource historical record and an ARIMA algorithm; step 4, obtaining resource real-time state indexes of each domain by using a resource state interface; step 5, estimating migration time of the data migrated to each domain based on the available bandwidth; and step 6, deciding the task optimal execution domain based on the decision tree model and the comprehensive index. The trend prediction algorithm and the decision tree algorithm are creatively and comprehensively applied to the cross-domain computing task scheduling scene, the task resource preemption phenomenon is avoided, and the problem that the scheduling decision accuracy is low is solved; through the flow type machine learning technology, the performance problems of a trend prediction algorithm anda decision tree algorithm are solved, and the overall time of cross-domain computing task scheduling is greatly shortened.
Owner:TIANJIN NANKAI UNIV GENERAL DATA TECH
Top layer design platform for electronic system
InactiveCN101436964AReduce duplication of workImprove effectivenessData switching networksSpecial data processing applicationsLevel designReal-time computing
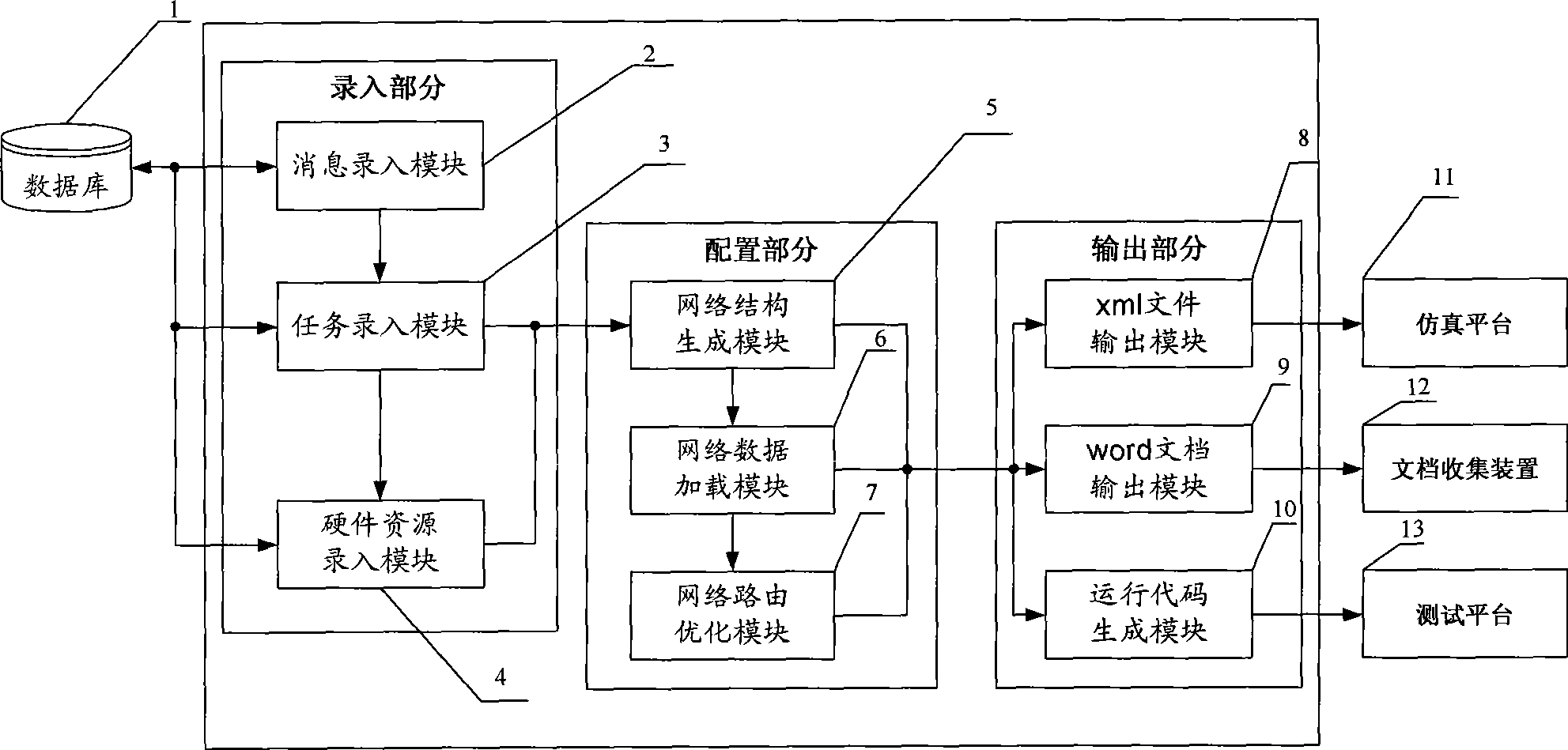
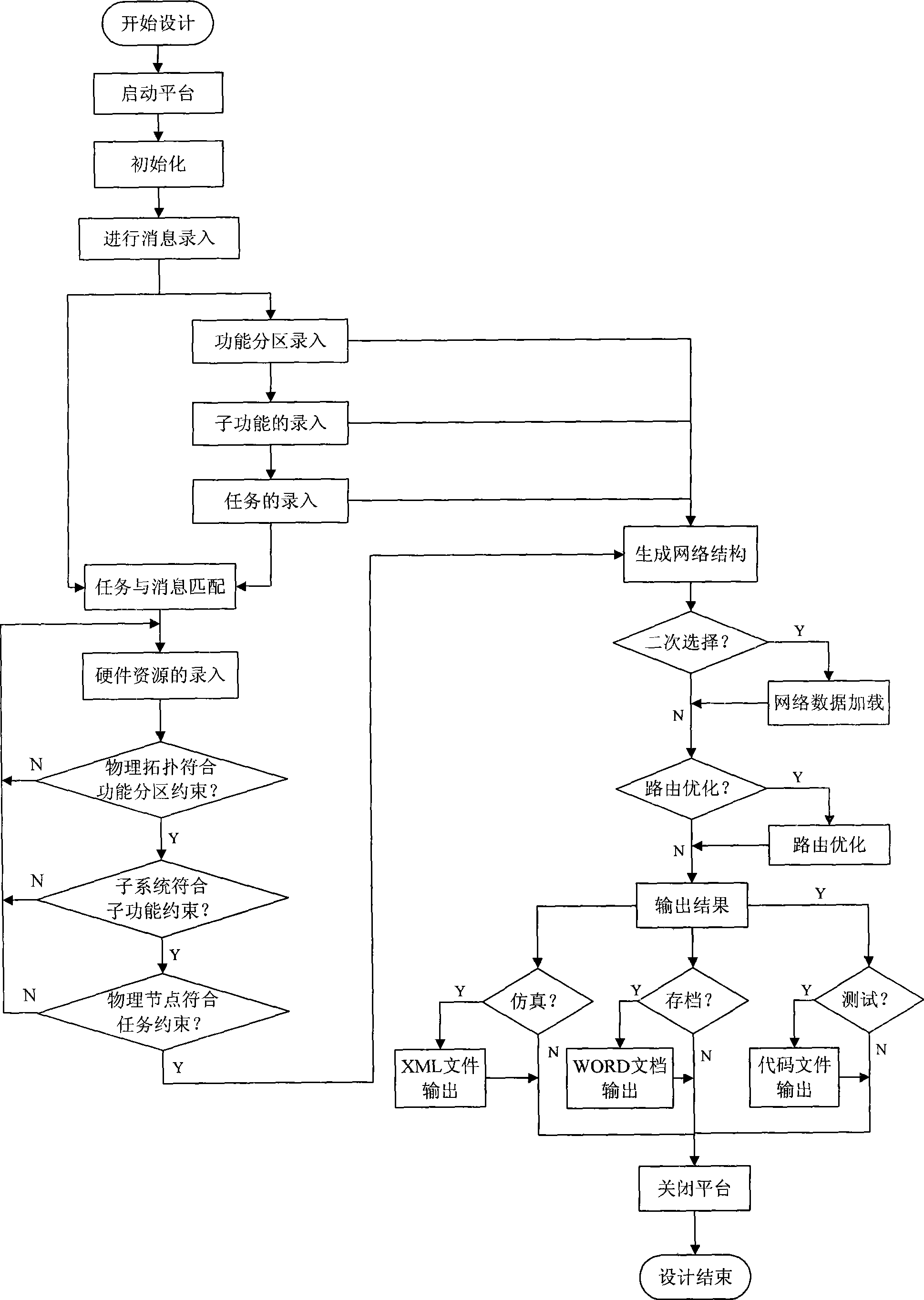
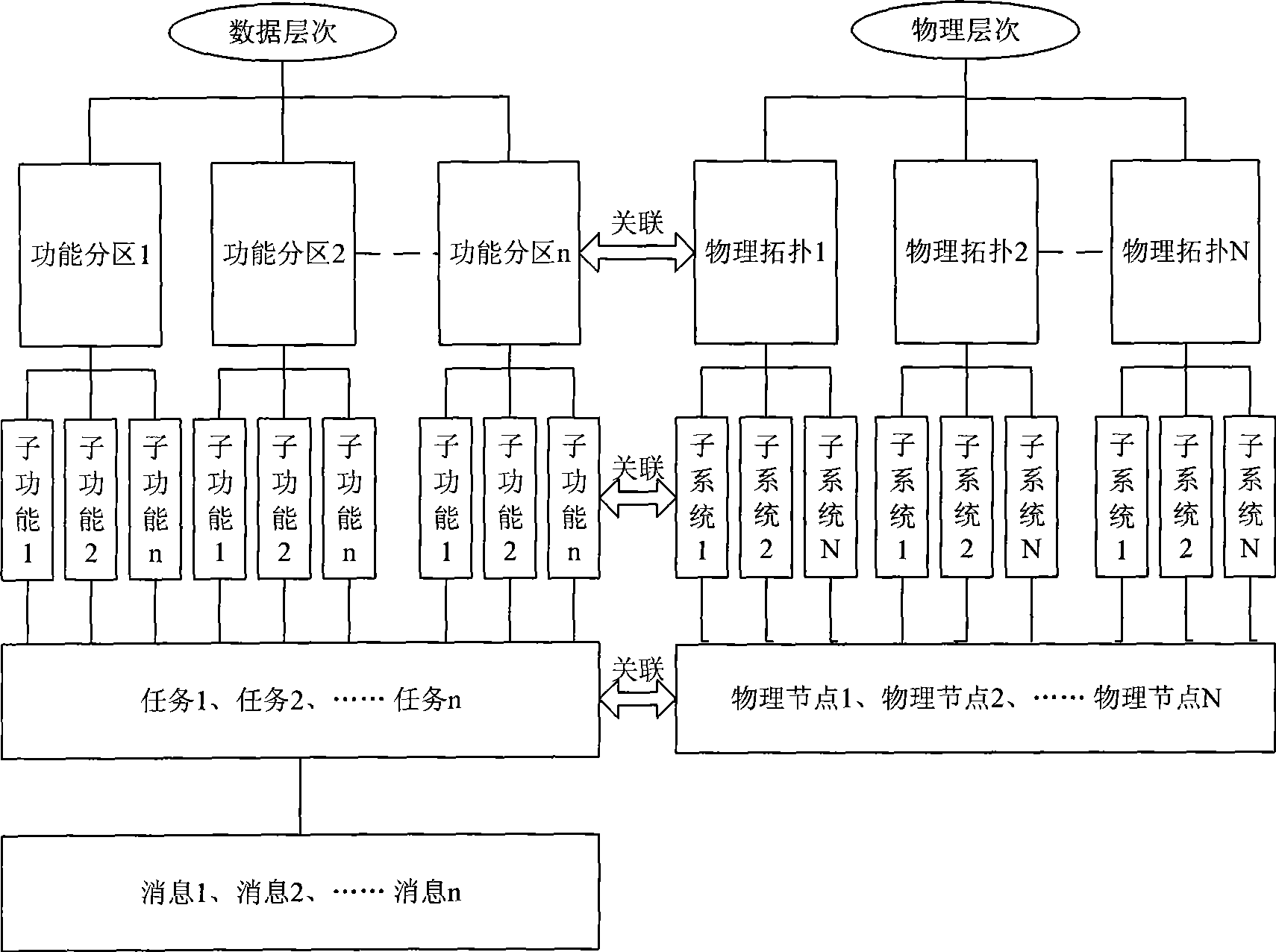
The invention provides a top level design platform of an electronic system, which comprises an output part, an entry part and a configuration part. The entry part transforms inputted data information to a communication data message and physical resource information to be outputted to the configuration part; after the communication data message and the physical resource information are subjected to network configuration in the configuration part, the communication data message and the physical resource information are transformed into configuration information to be transmitted to the output part; and the output part transforms the configuration information into corresponding output information in a template mode, and outputs the output information to an simulation platform, a document collecting device and a test platform. The device is the top level design platform of the electronic system which dynamically generates a final proposal, and uniformly manages simulating, filing and testing, effectively prevents occupancy of invalid information to resource in a real-time communication network, fundamentally reduces network delay of communication, shortens designing time, and improves designing efficiency.
Owner:BEIHANG UNIV
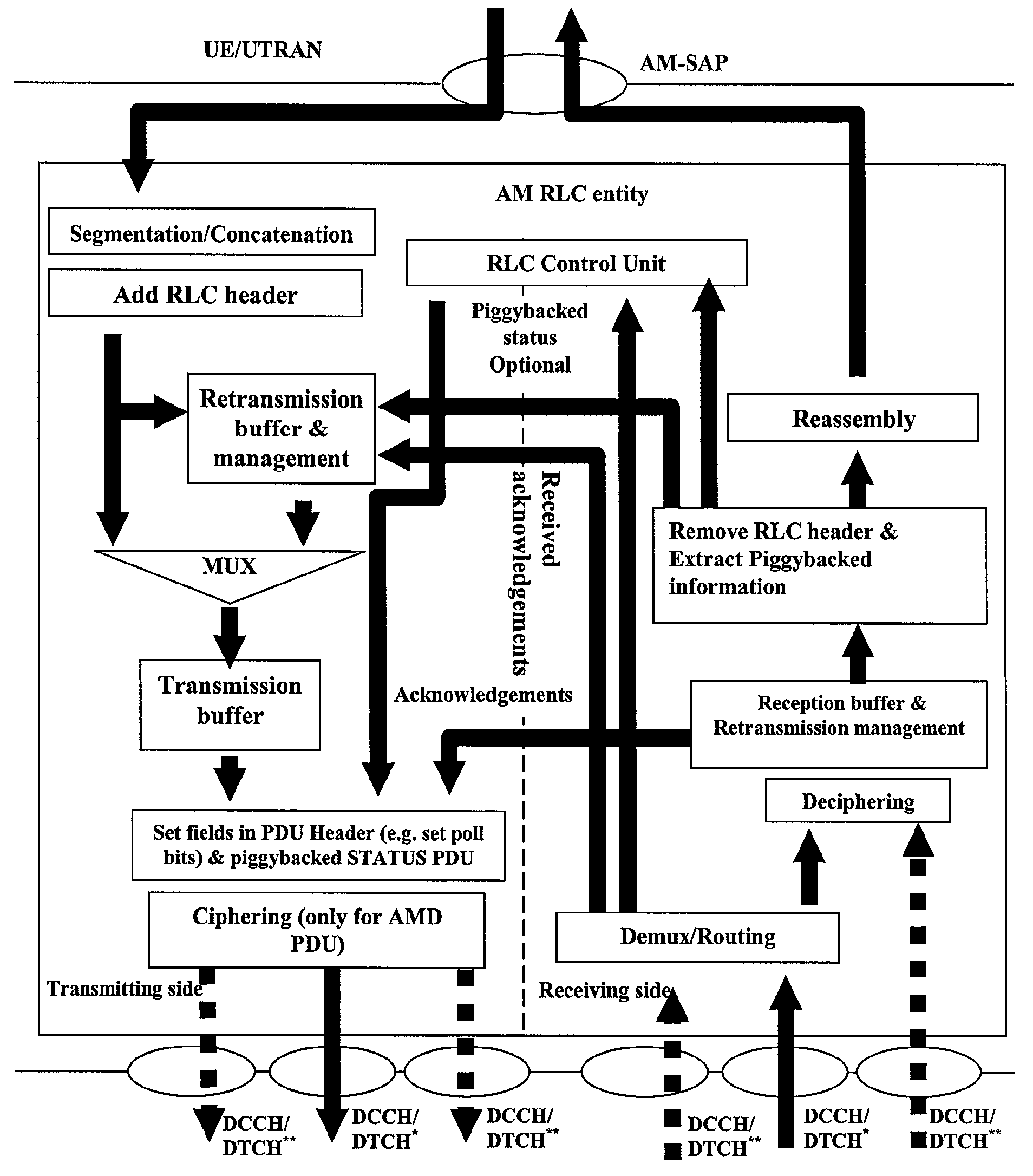
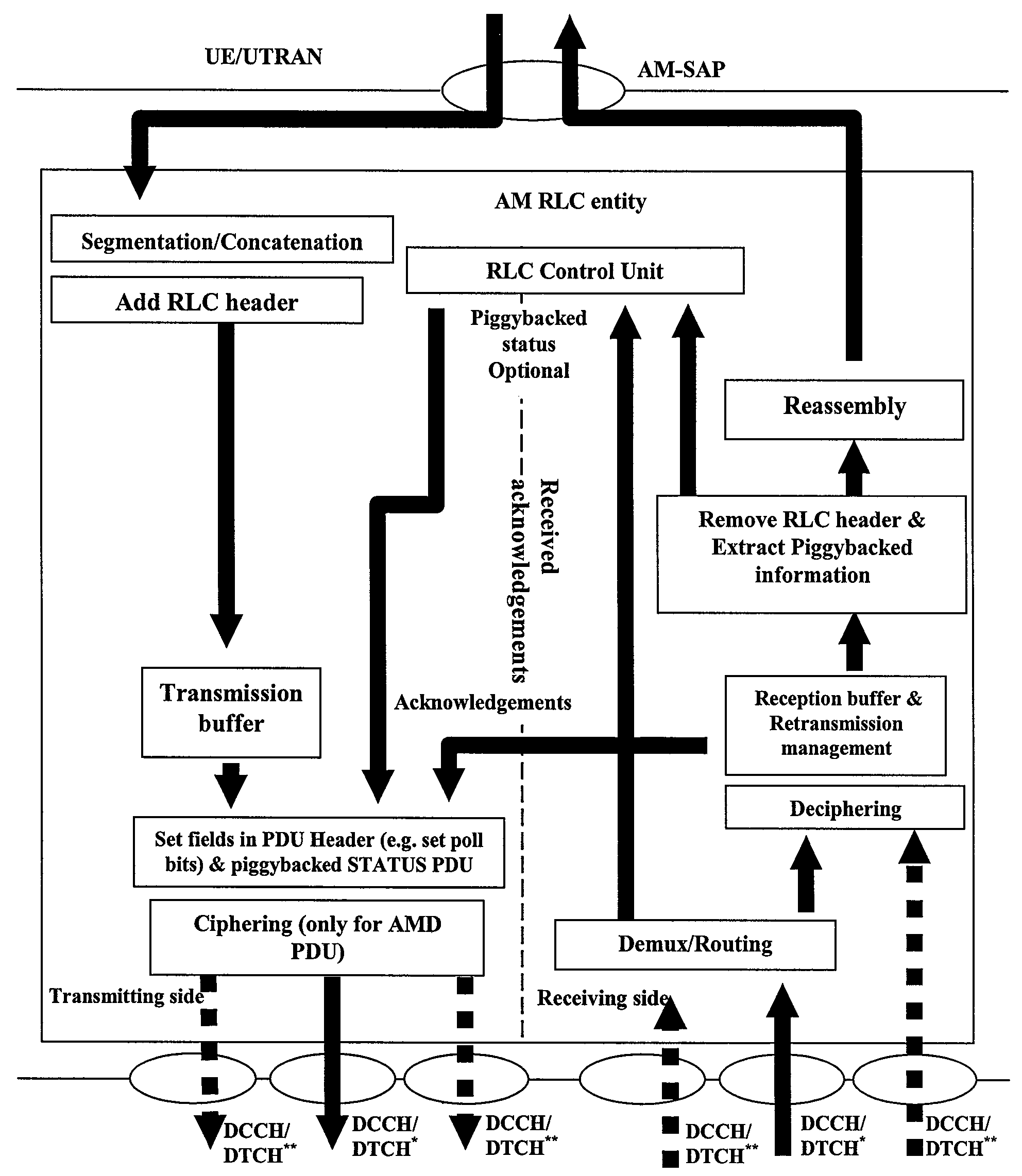
Radio link control retransmission processing method and device
InactiveCN101557282ASimplified data retransmission functionAvoid resource hoggingError prevention/detection by transmission repeatTransfer modeReal-time computing
This inventive embodiment discloses a radio link control retransmission processing method, comprising the step of stopping the RLC retransmission on a data link layer L2 when the radio link control RLC uses an answering transmission mode. The other embodiment of the invention further discloses a radio link control retransmission processing device, comprising a judging module and a control module, wherein the judging module is used for judging whether the radio link control RLC layer uses the answering transmission mode, and the control module is used for stopping the RLC retransmission on the data link layer L2 when the judging result of the judging module is that the radio link control RLC layer uses the answering transmission mode. The embodiment of the invention simplifies the L2 RLC data retransmission function at the AM mode in a HSDPA downlink system and avoids the RLC retransmission function occupying the source.
Owner:HUAWEI TECH CO LTD
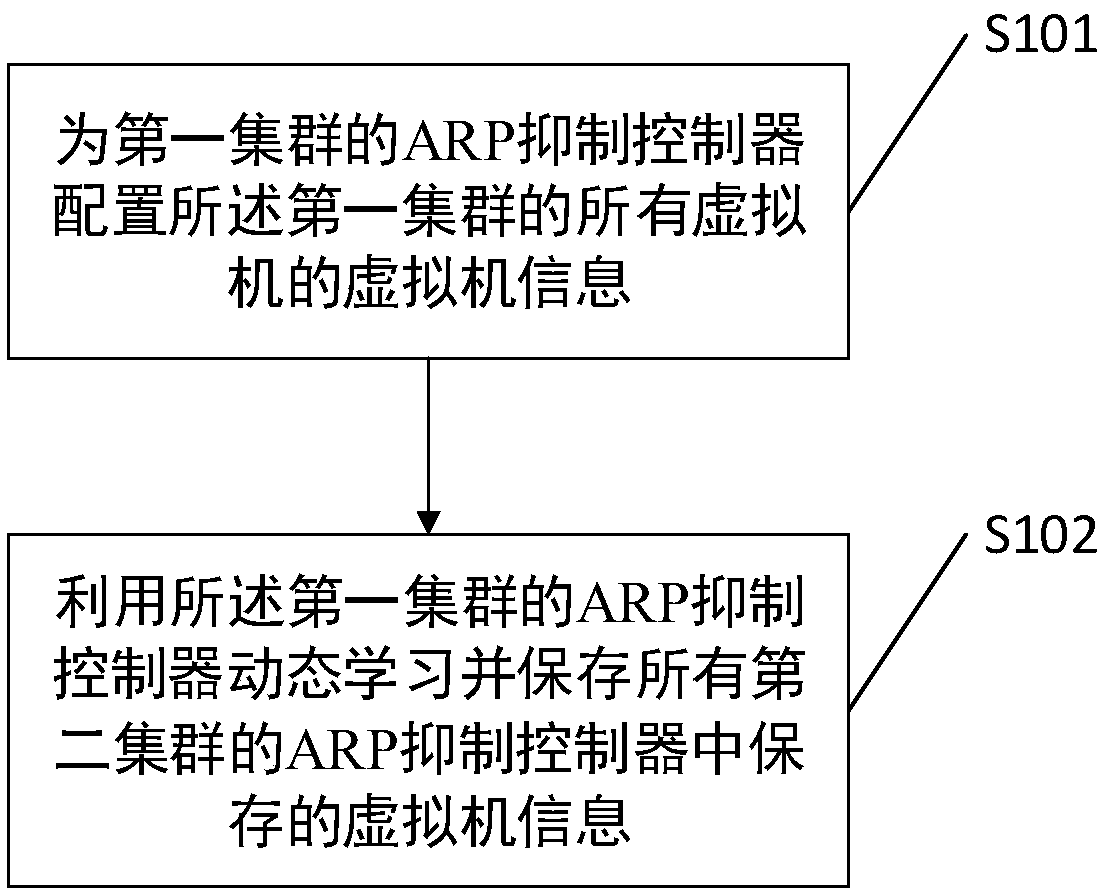
A method and relate device for communicating between clusters
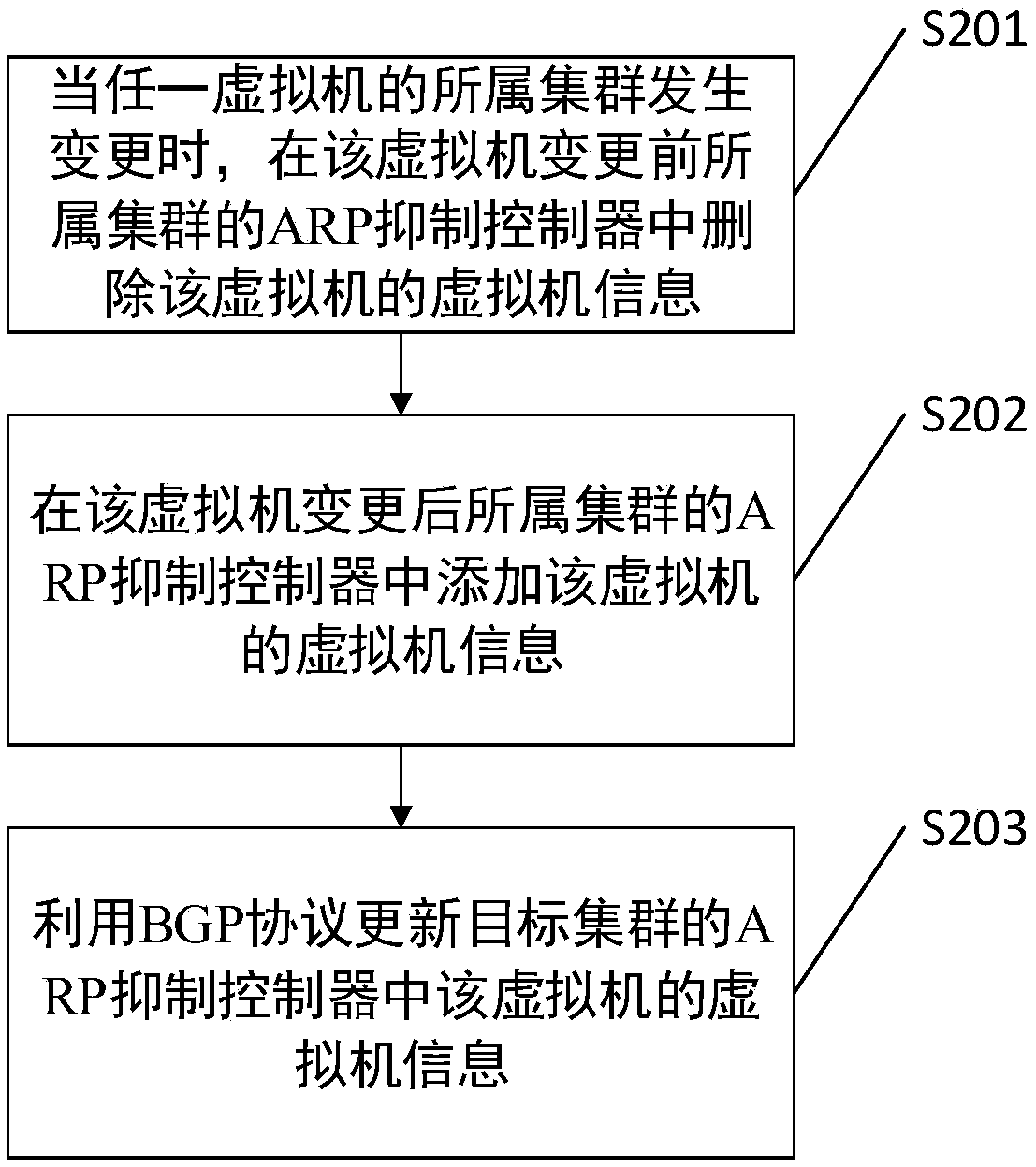
InactiveCN109039790AAvoid resource hoggingAvoid occupyingData switching networksDynamic learningBroadcasting
A method, a system, apparatus and compute readable storage medium for communicating between clusters. The method comprises: first configuring information of all virtual machines of the first cluster for the ARP suppression controller of the first cluster, and configuring the information of all virtual machines of all the second clusters for the ARP suppression controllers of the first cluster in adynamic learning manner instead of configuring the information of all virtual machines of all the clusters for the ARP suppression controllers of each cluster in a static configuration method. By dynamically learning the virtual machine information of other clusters, the effect of automatically synchronizing the virtual machine information of other clusters can be realized, thus saving the configuration process. Also, it is not necessary to broadcast the request information when the virtual node initiates the connection establishment request, so the problem of link resource occupancy can be avoided.
Owner:SANGFOR TECH INC
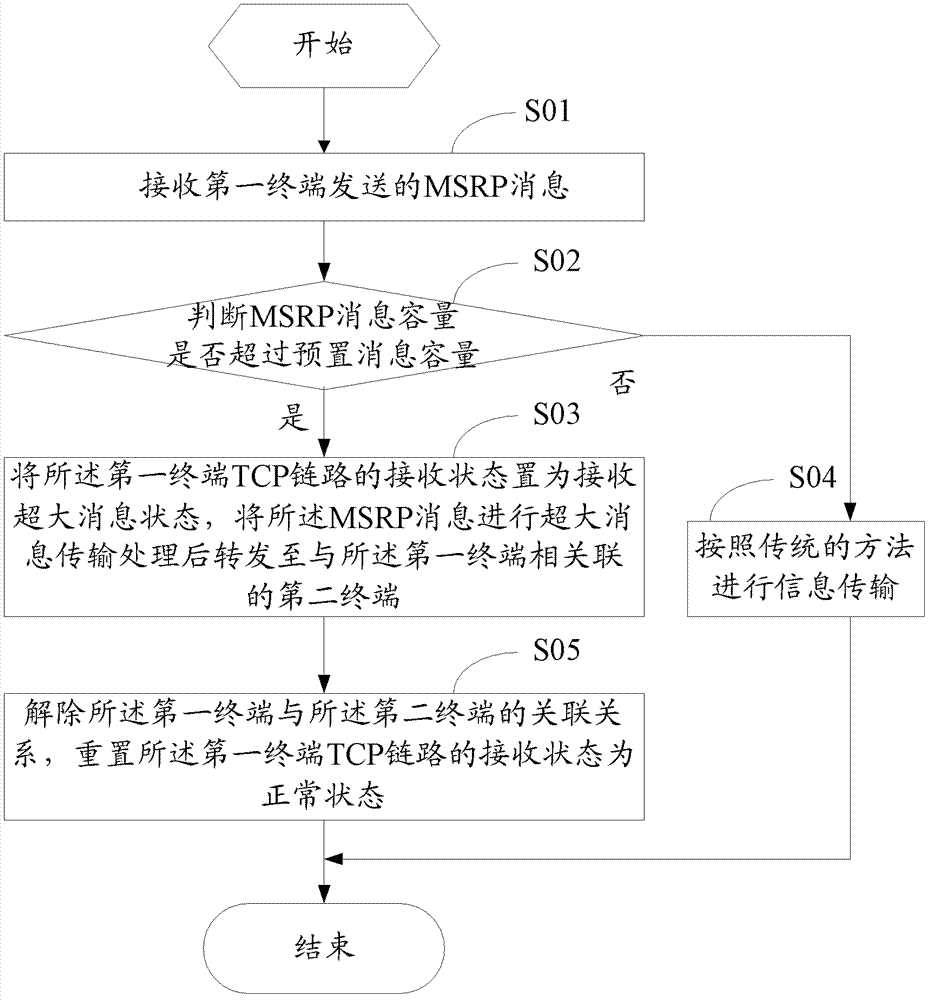
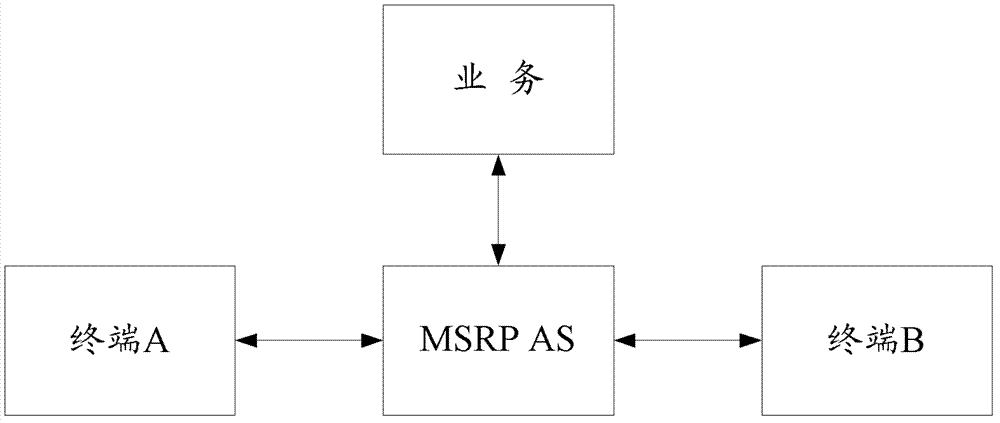
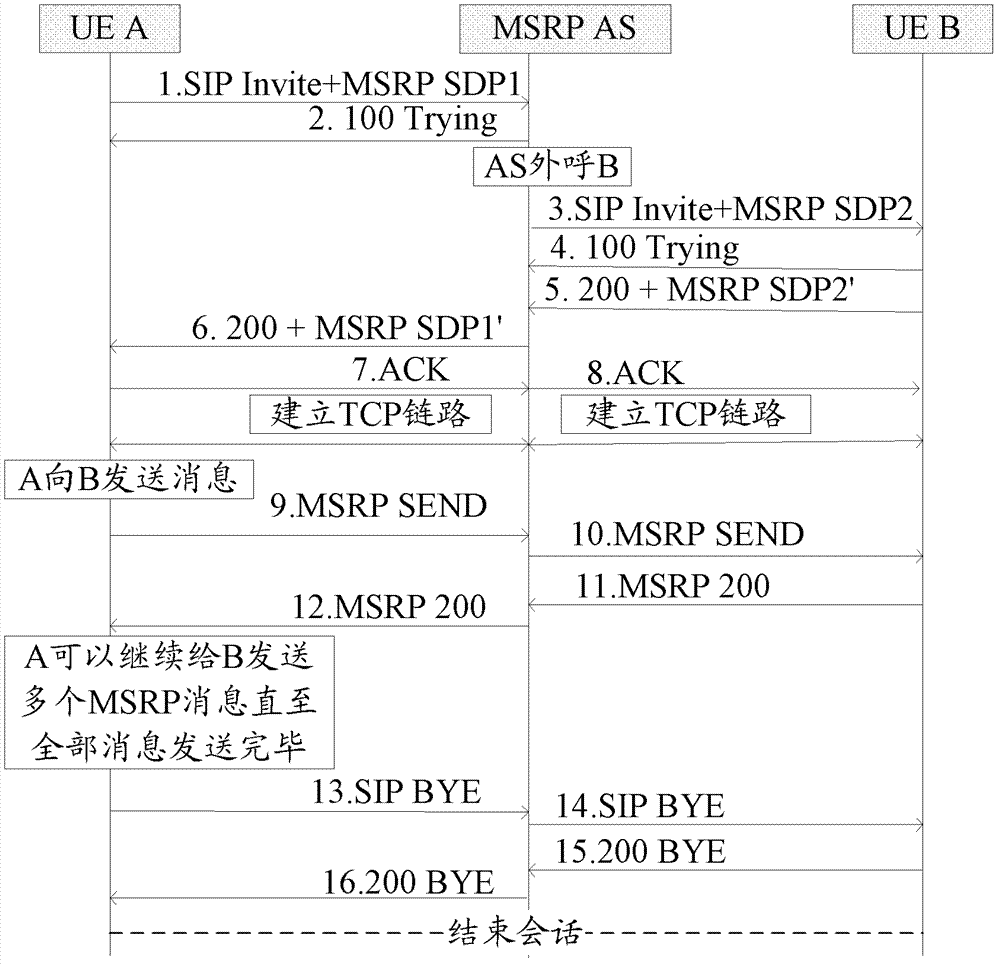
Message transmission and processing method and device
The invention discloses a message transmission and processing method and device. The method includes the following steps: receiving an MSRP message sent by a first terminal; judging whether a capacity of the MSRP message exceeds a preset message capacity; if so, setting a receiving state of a TCP link of the first terminal as a large-message receiving state, carrying out large-message transmission processing on the MSRP message which is then forwarded to a second terminal associated with the first terminal; ending an association relationship between two parties of a session; and resetting the receiving state of the TCP link of the first terminal as a normal state. Through the method of identification that the capacity of the MSRP message exceeds the preset message capacity and establishment of a session association link between two session parties and real-time processing of abnormal situations in a forwarding process, an beneficial effect of rapid processing and forwarding is realized when an AS transmits the MSRP message.
Owner:ZTE CORP
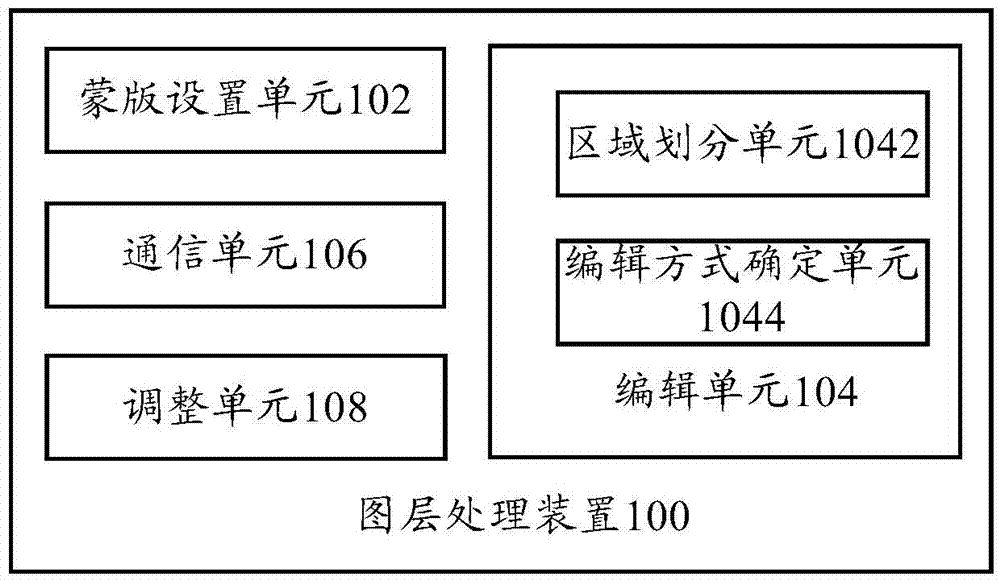
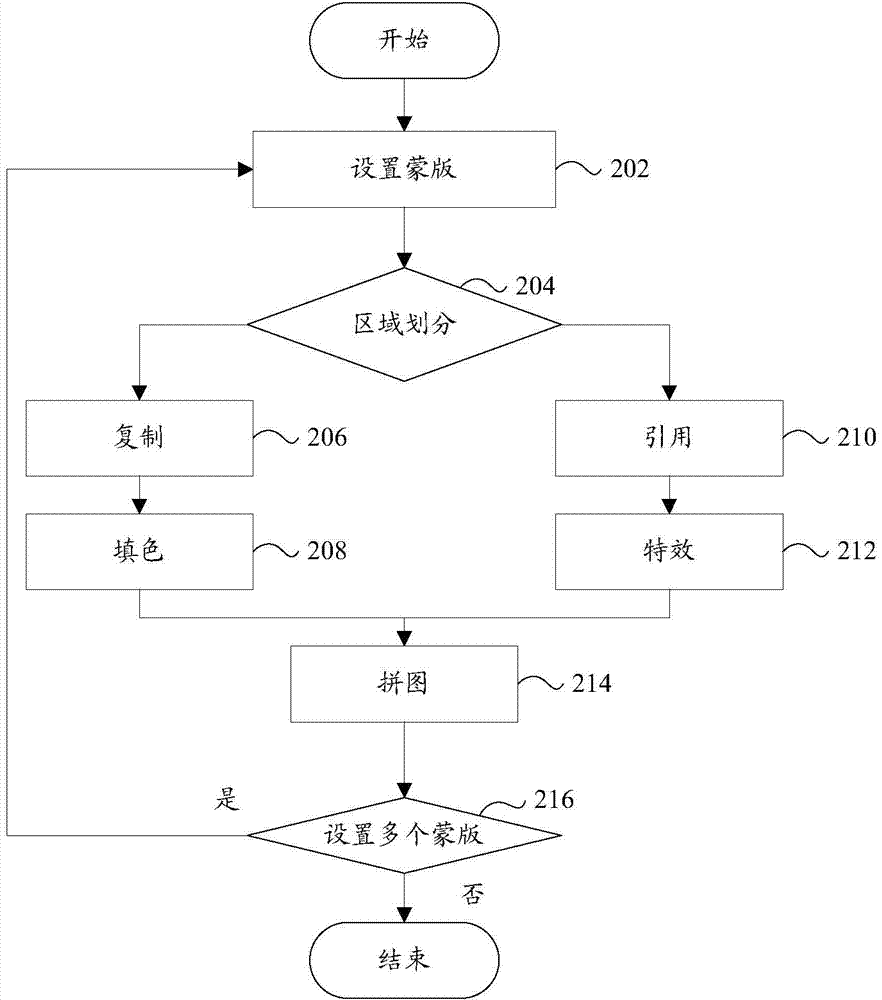
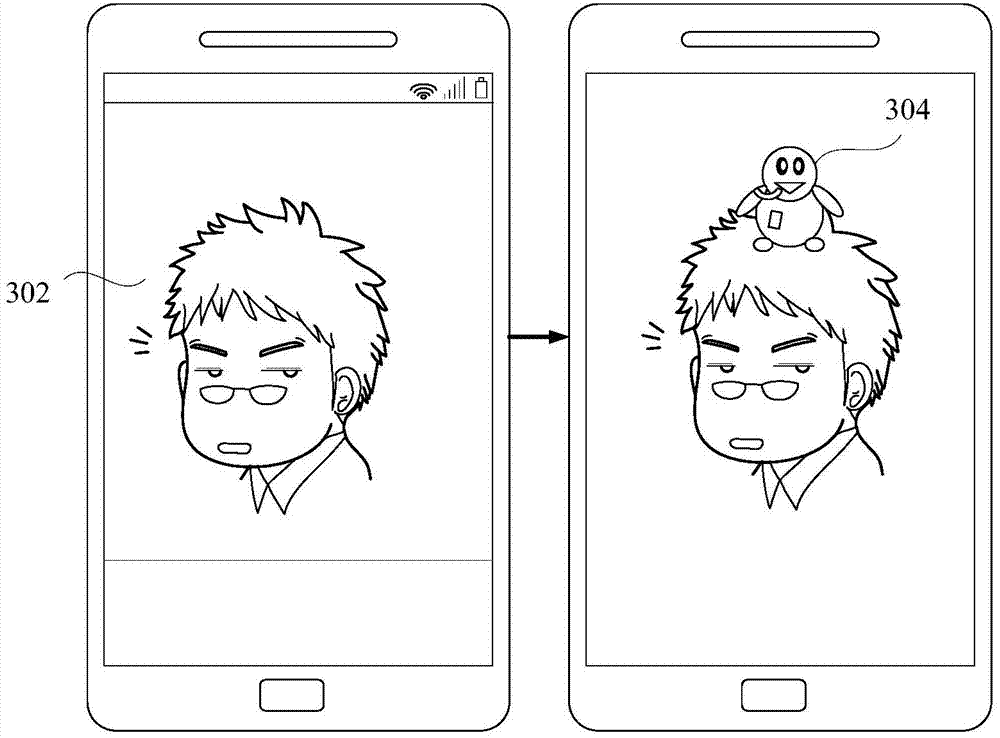
Layer processing device and layer processing method
InactiveCN104751503ARich editing effectsAvoid resource hoggingEditing/combining figures or textCommunication unitComputer science
The invention provides a layer processing device and a layer processing method. The layer processing device comprises a mask setting unit, an editing unit and a communication unit, wherein the mask setting unit is used for setting at least one mask layer on a selected cartoon picture according to a received operation instruction when the cartoon is displayed; the editing unit is used for calling an editing interface to carry out editing processing on the at least one mask layer to obtain a new cartoon picture; and the communication unit is used for uploading the new cartoon picture to a server. According to the device and the method of the invention, multiple cartoon pictures can be combined together in a layer mode, the cartoon showing mode can be flexibly controlled, customization of personalized information of the cartoon can be realized, interaction between a user and the cartoon is enhanced, and occupation of system resources is reduced.
Owner:PEKING UNIV +2
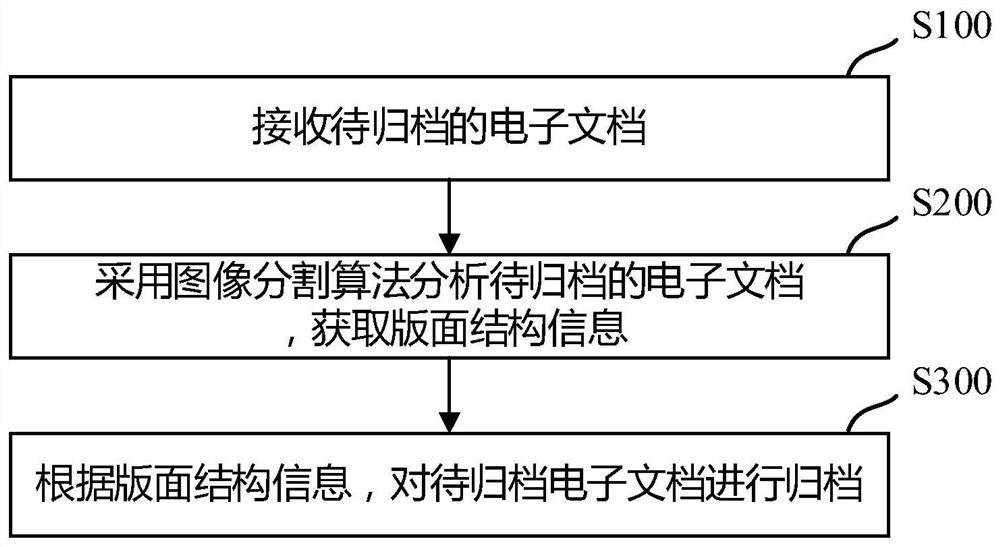
Electronic document filing method and device
ActiveCN112733658AImplement classificationHigh precisionImage enhancementImage analysisElectronic documentImage segmentation algorithm
Owner:BEIJING THUNISOFT INFORMATION TECH
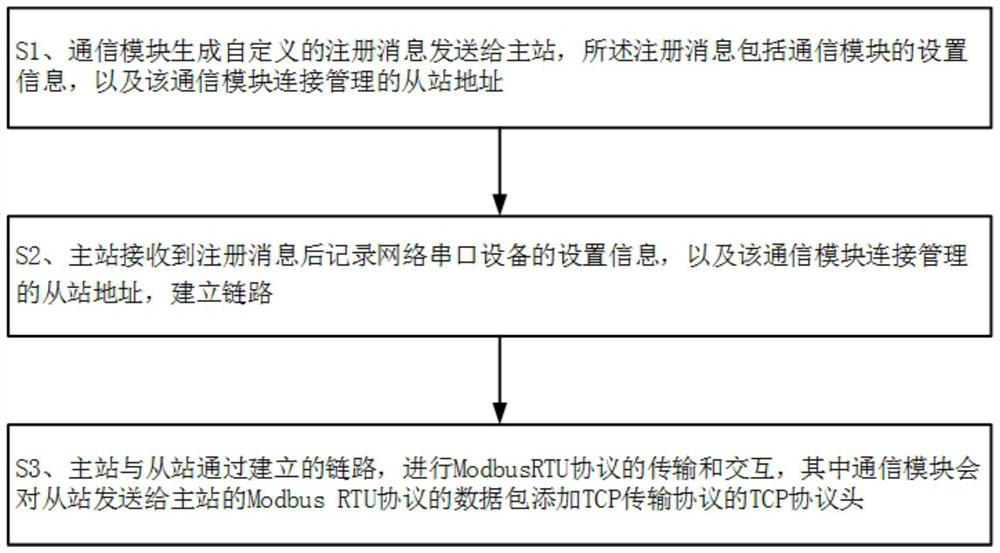
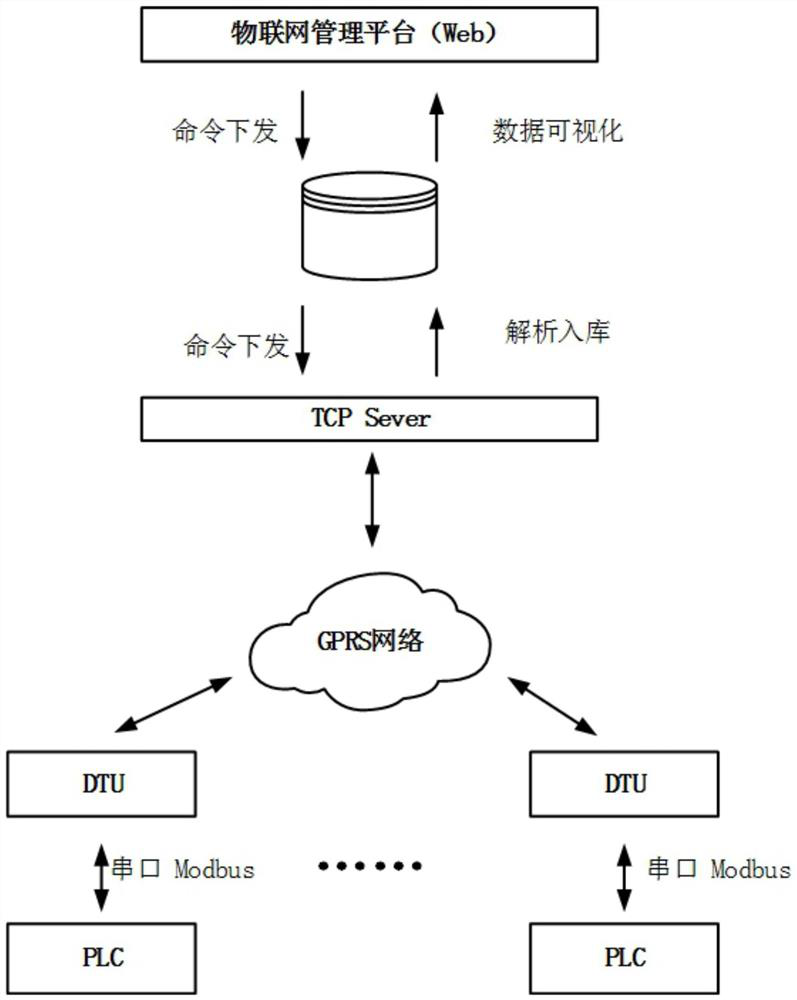
Method for transmitting Modbus RTU protocol in wide area network
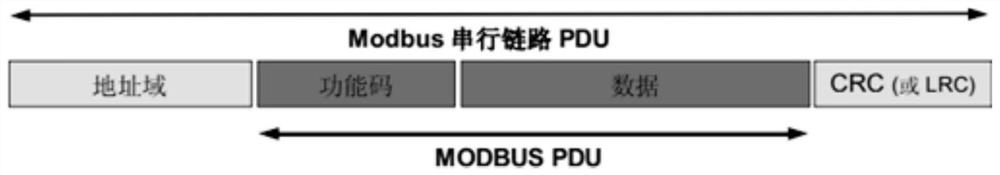
ActiveCN113162931ARealize centralized monitoringGuaranteed accuracyError preventionTotal factory controlTransmission protocolModbus
The invention relates to the technical field of Internet of Things sensing equipment communication, in particular to a method for transmitting a Modbus RTU protocol in a wide area network, which is applied to a network in which a slave station is connected with a master station through a communication module, and comprises the steps that the communication module generates a self-defined registration message and sends the registration message to the master station, and the registration message comprises setting information of the communication module; the communication module is connected with a managed slave station address; after receiving the registration message, the master station records the setting information of the communication module and the address of the slave station connected and managed by the communication module, and establishes a link; and the master station and the slave station carry out transmission and interaction of the Modbus RTU protocol through the established link. According to the method, the Modbus RTU protocol is transmitted in the wide area network, the whole process is not limited by the fact that the slave station must have a fixed IP address, the protocol conversion process and a conversion module are omitted, the monitoring function cost of the Internet of Things sensing equipment is reduced, and the monitoring efficiency is improved.
Owner:CHINA COAL TECH & ENG GRP CHONGQING RES INST CO LTD +1
Information system based on vehicle-mounted terminal information, vehicle-mounted terminal and information processing method thereof
ActiveCN103188315AImprove interactivityAvoid feedbackTransmissionInformation processingInformation feedback
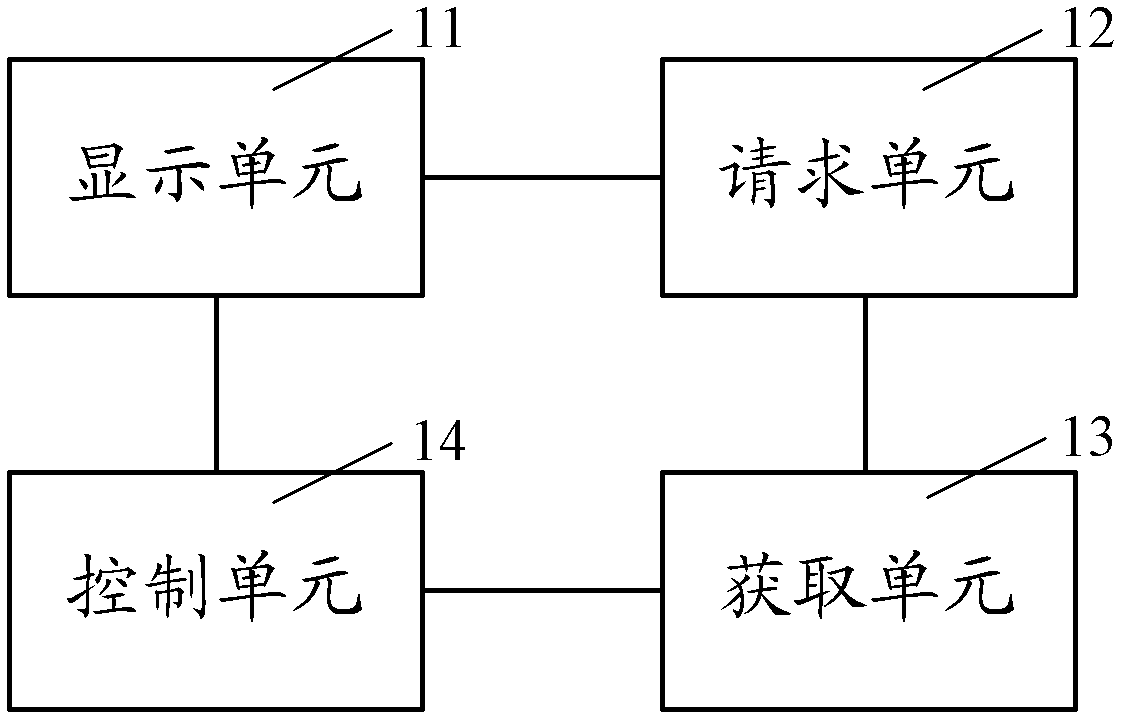
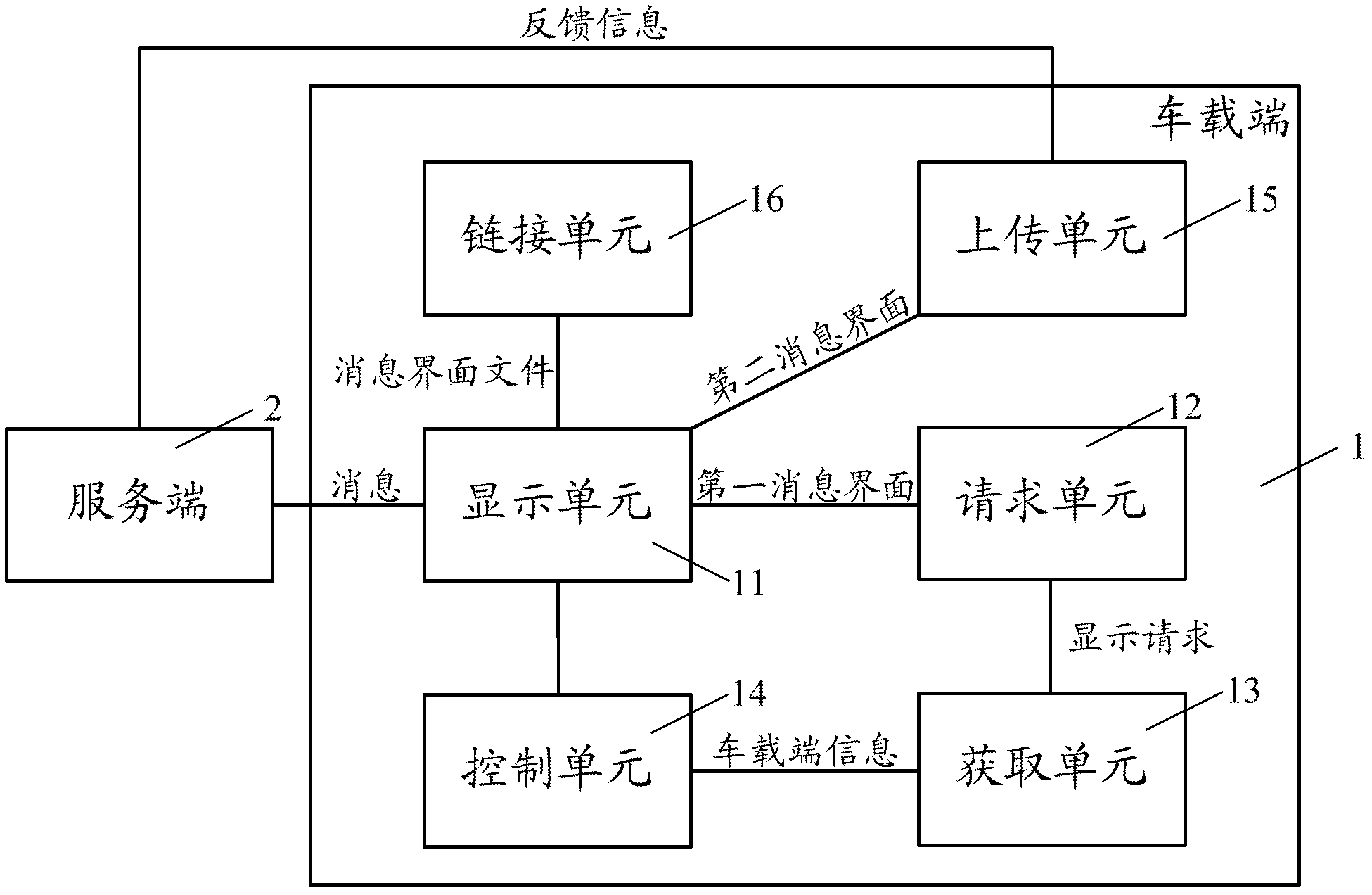
Provided are an information system based on vehicle-mounted terminal information, a vehicle-mounted terminal and an information processing method thereof. The vehicle-mounted terminal comprises a display unit suitable for displaying a first information interface based on information sent by a server, a request unit suitable for generating a display request requesting displaying of a second information interface based on the first information interface, an obtaining unit suitable for obtaining vehicle-mounted information comprising device information of vehicle-mounted devices and / or user information based on the display request and a control unit suitable for controlling the display unit to display the second information interface based on the vehicle-mounted information obtained by the obtaining unit, wherein the second information interface is used for generating feedback information for the information sent by the service terminal. According to the technical scheme, the problem that resources are occupied due to the fact that the vehicle-mounted terminal conducts feedback to the information sent by the service terminal repeatedly for a plurality of times is avoided. Accuracy of information feedback, to the service terminal, of the vehicle terminal is improved. Interactivity among the service terminal, the vehicle-mounted terminal and a user is also improved.
Owner:SHANGHAI PATEO ELECTRONIC EQUIPMENT MANUFACTURING CO LTD
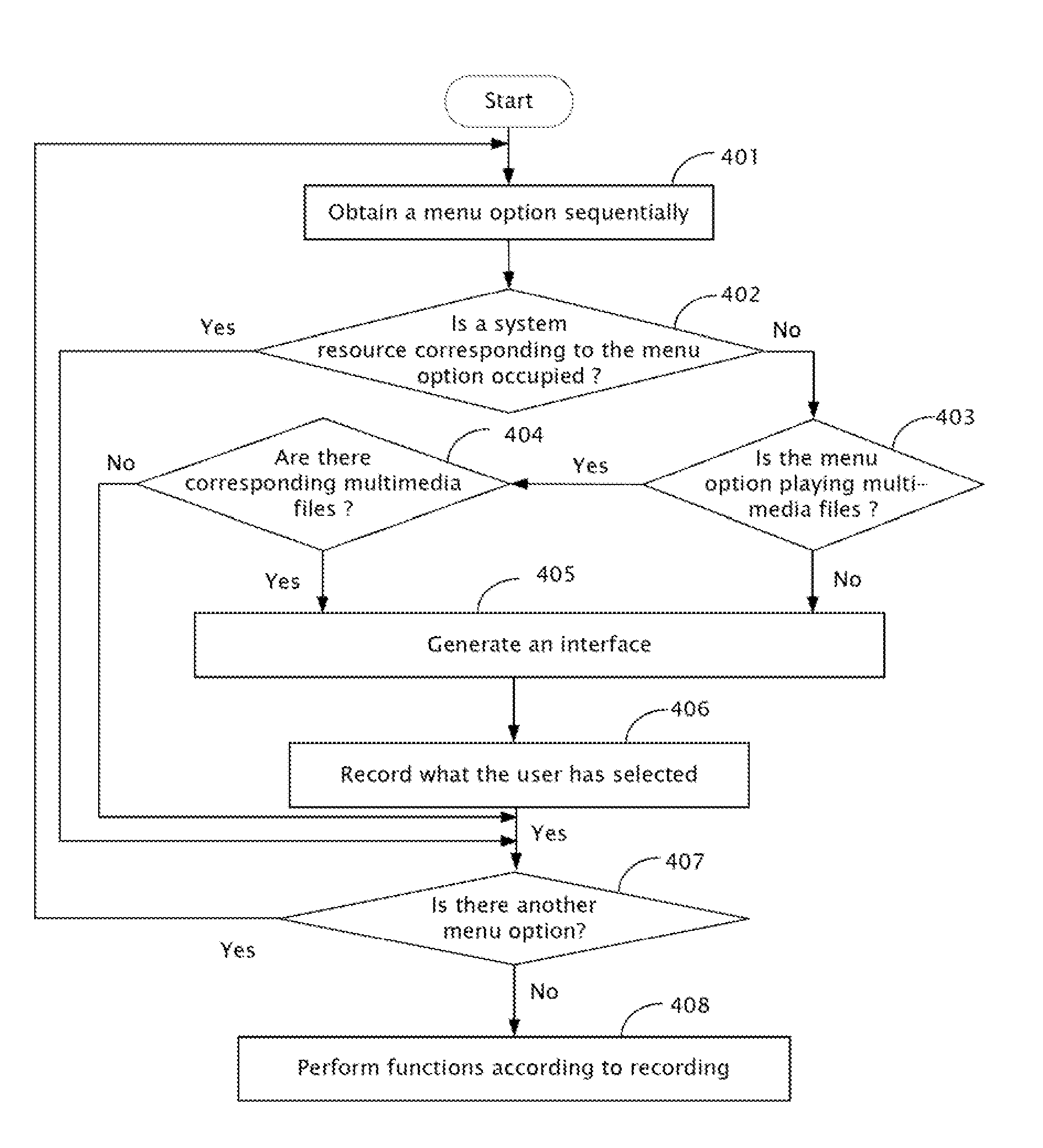
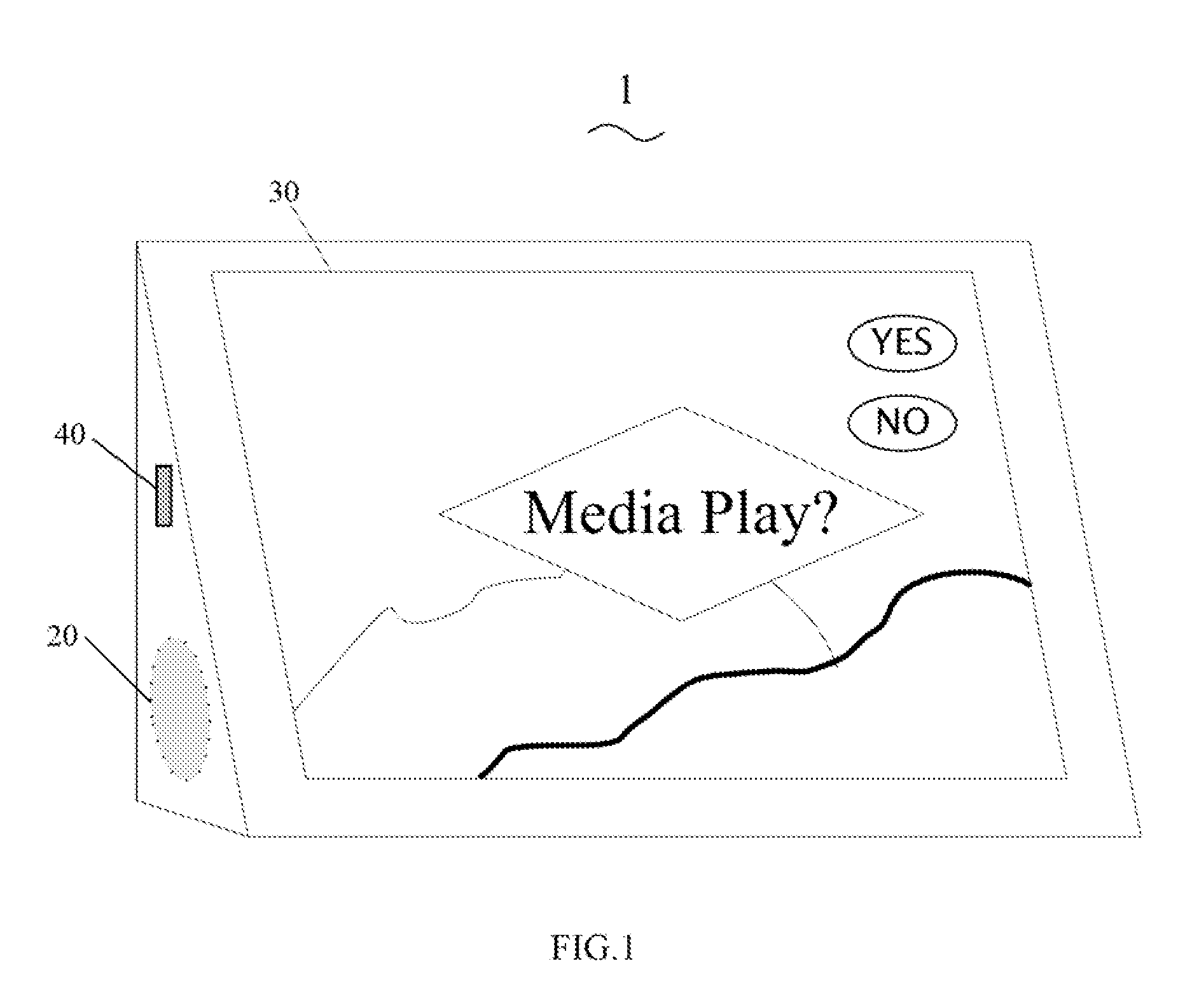
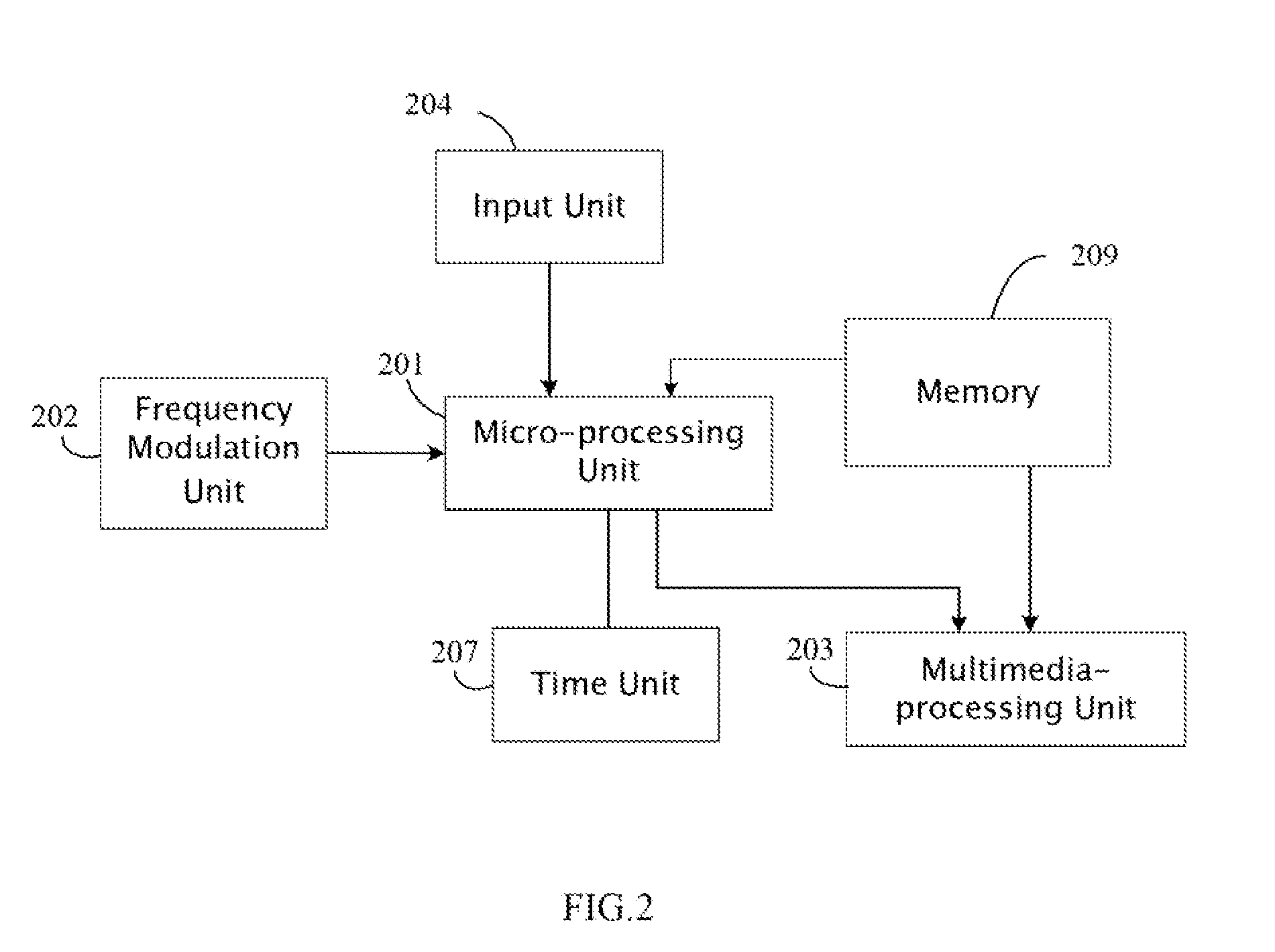
Digital photo frame with menu options setting function and method of setting the menu options
InactiveUS20090162023A1Avoid resource hoggingTelevision system detailsColor television signals processingDigital photo frame
A method for setting menu options for a digital photo frame includes a memory configured for storing a plurality of multimedia files. The method further includes outputting a menu of at least one of a plurality of menu options, receiving inputs, determining current available system resources and available menu options associated with multimedia file in response to a selected operation, and generating a different menu on the menu to prevent system resource occupation. A digital photo frame with menu options setting function is also provided.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
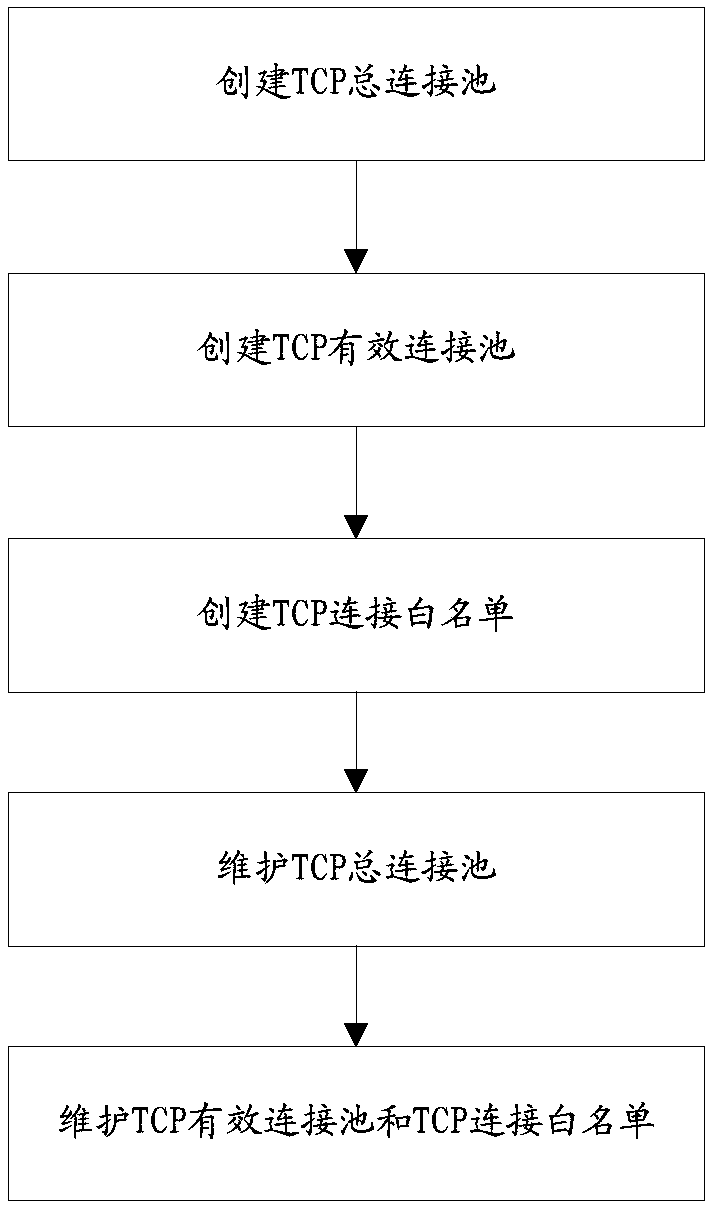
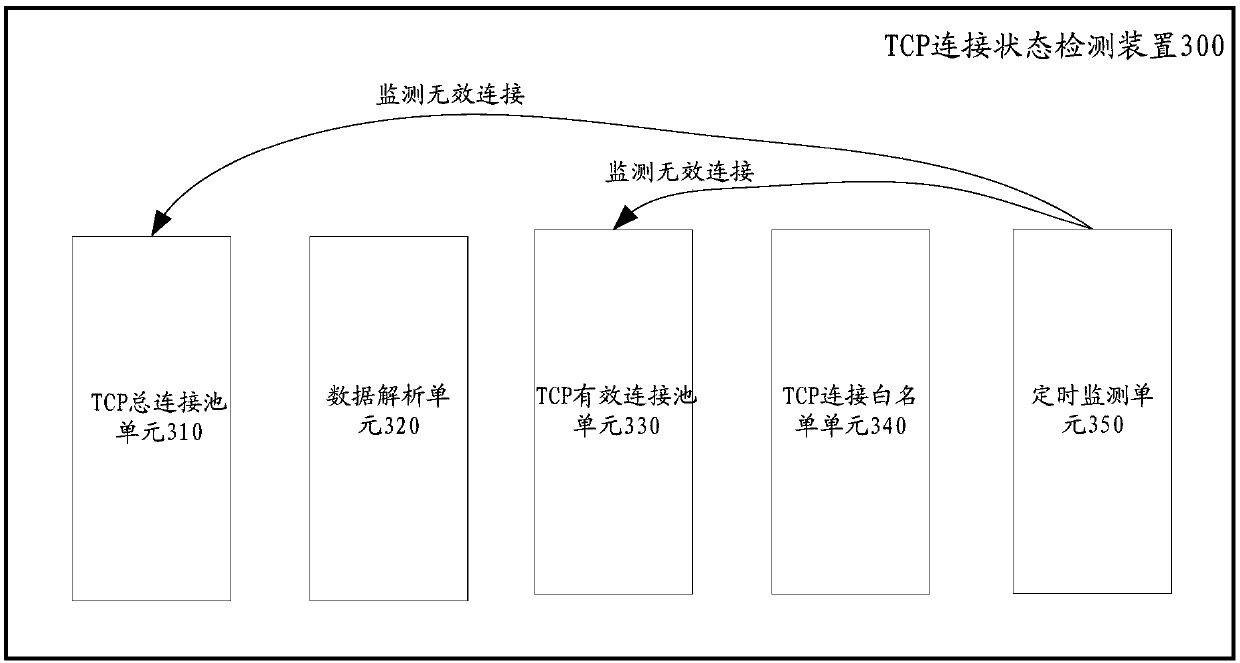
Method for detecting TCP connection state
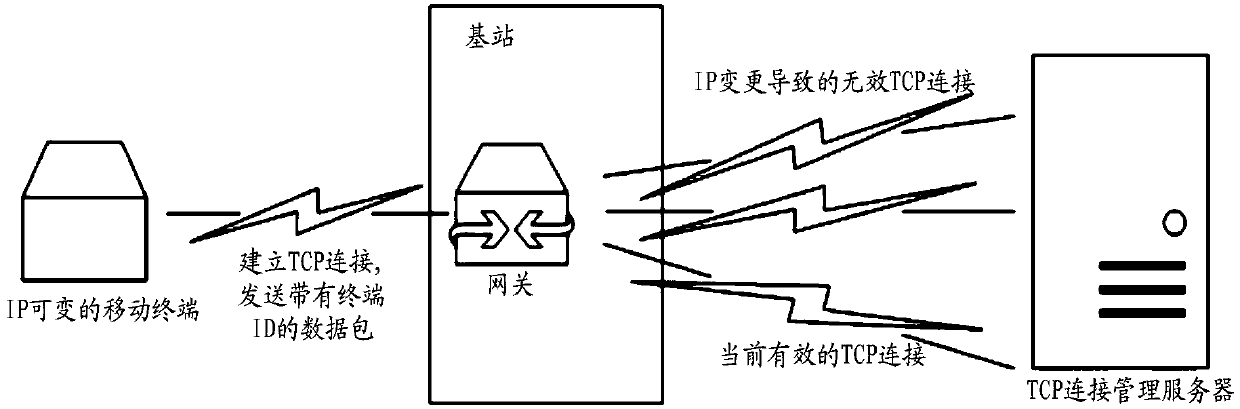
InactiveCN109996250AImprove reliabilityAvoid resource hoggingData switching networksWireless communicationResource utilizationIp address
The invention provides a method for detecting a TCP (Transmission Control Protocol) connection state at a network side, the network side stores a TCP connection white list, and the TCP connection white list is used for storing a corresponding relation between an identity identifier of equipment and an equipment IP (Internet Protocol) address. The method comprises the following steps: obtaining anidentity and an IP address of equipment which currently initiates TCP connection; and judging whether the IP address of the equipment is changed relative to the historical TCP initiated by the equipment based on the TCP connection white list, and determining the TCP connection state of the equipment. According to the method provided by the invention, the TCP connection in an invalid state can be effectively and actively detected, so that the resource utilization rate is improved, and the method is particularly suitable for the TCP connection initiated by an IP variable terminal.
Owner:洛阳中科晶上智能装备科技有限公司
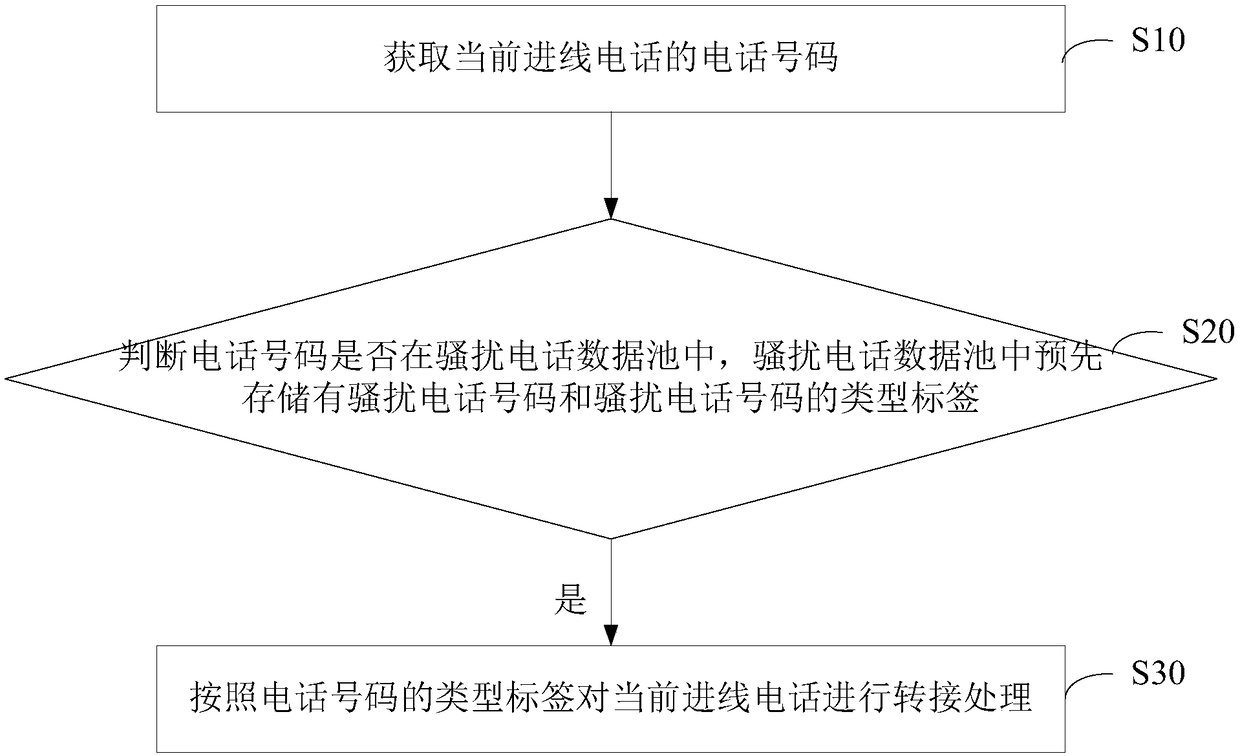
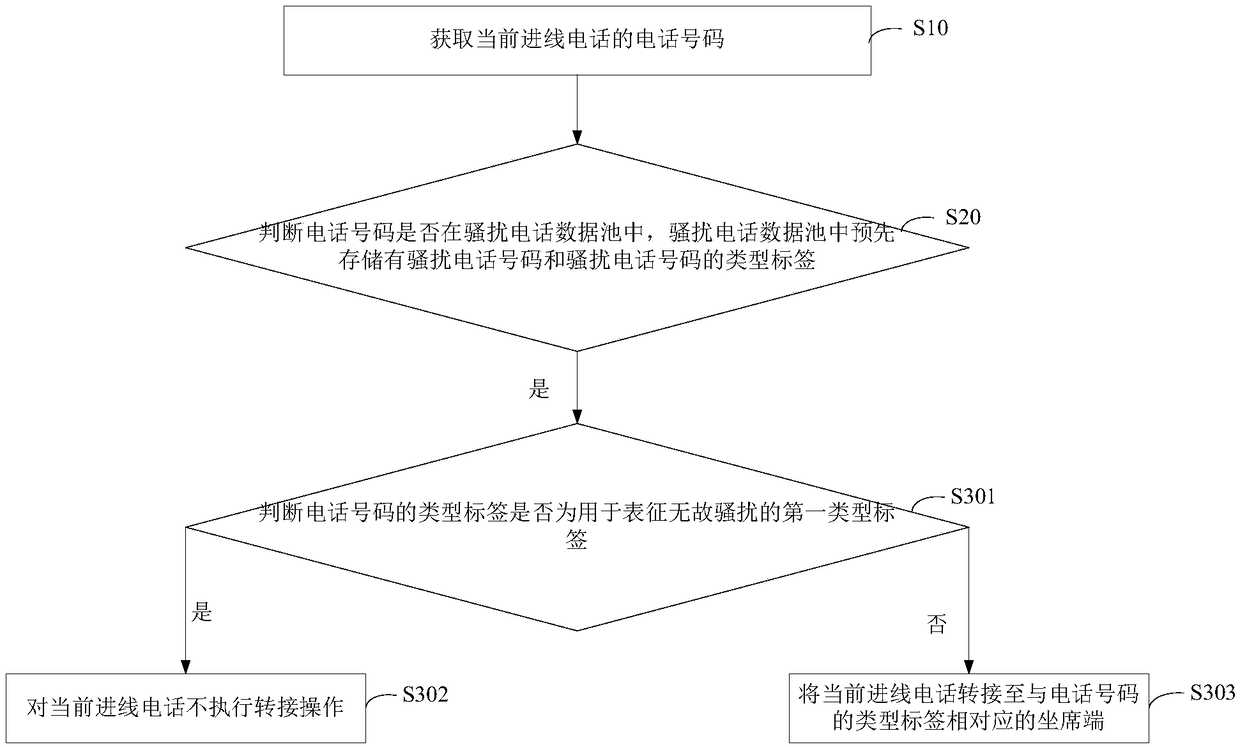
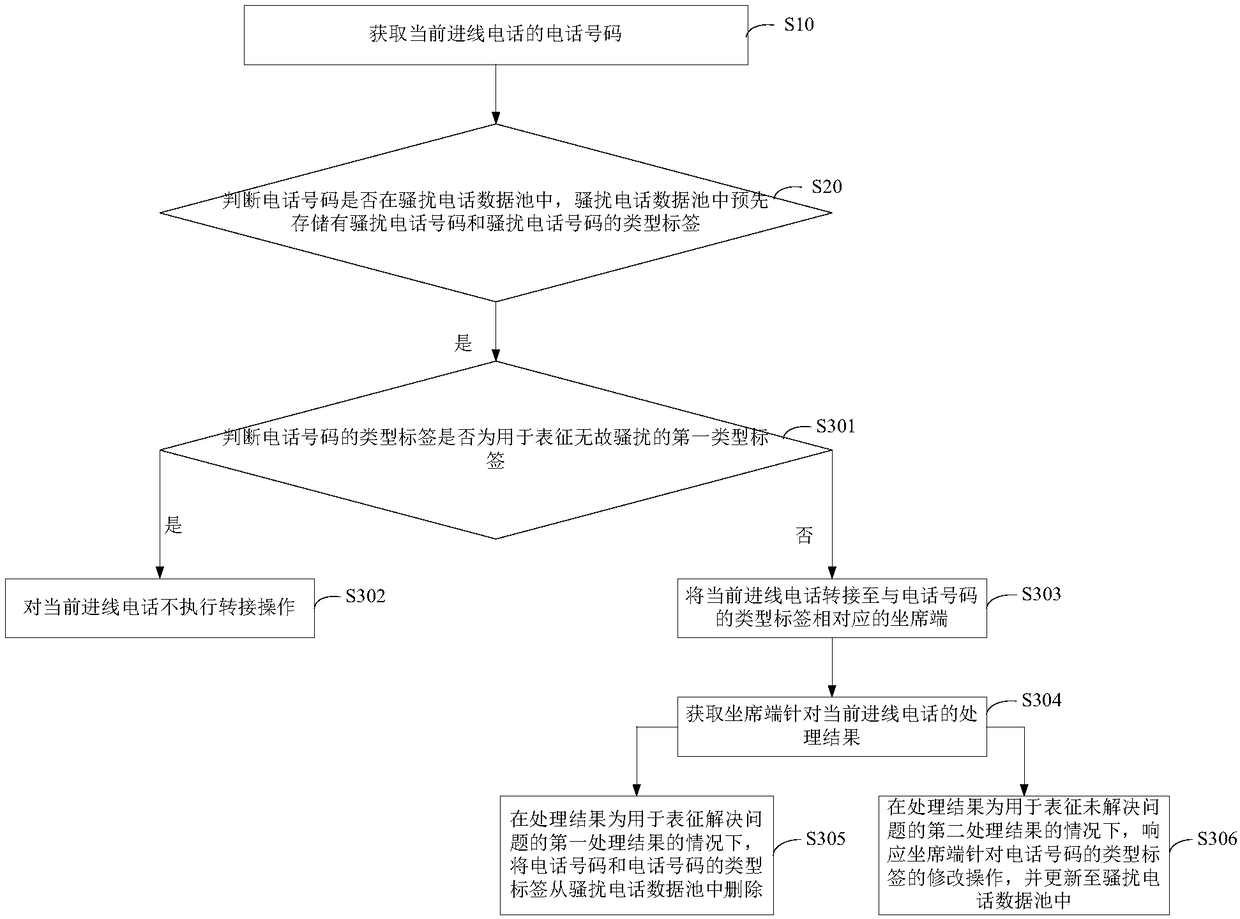
Processing method and apparatus
ActiveCN109474758AAvoid resource hoggingSupervisory/monitoring/testing arrangementsTelephonyData Pooling
The present invention provides a processing method and apparatus. The method includes: obtaining a phone number of a current incoming call; determining whether the phone number is in a nuisance call data pool, where nuisance call numbers and type labels of the nuisance call numbers are stored in the nuisance call data pool; if the telephone number is in the nuisance call data pool, forwarding thecurrent incoming call according to a type label of the telephone number. Based on the present invention, the nuisance call can be intelligently processed according to the type label, so that unnecessary resource occupation for an agent system and an agent is avoided.
Owner:BANK OF CHINA
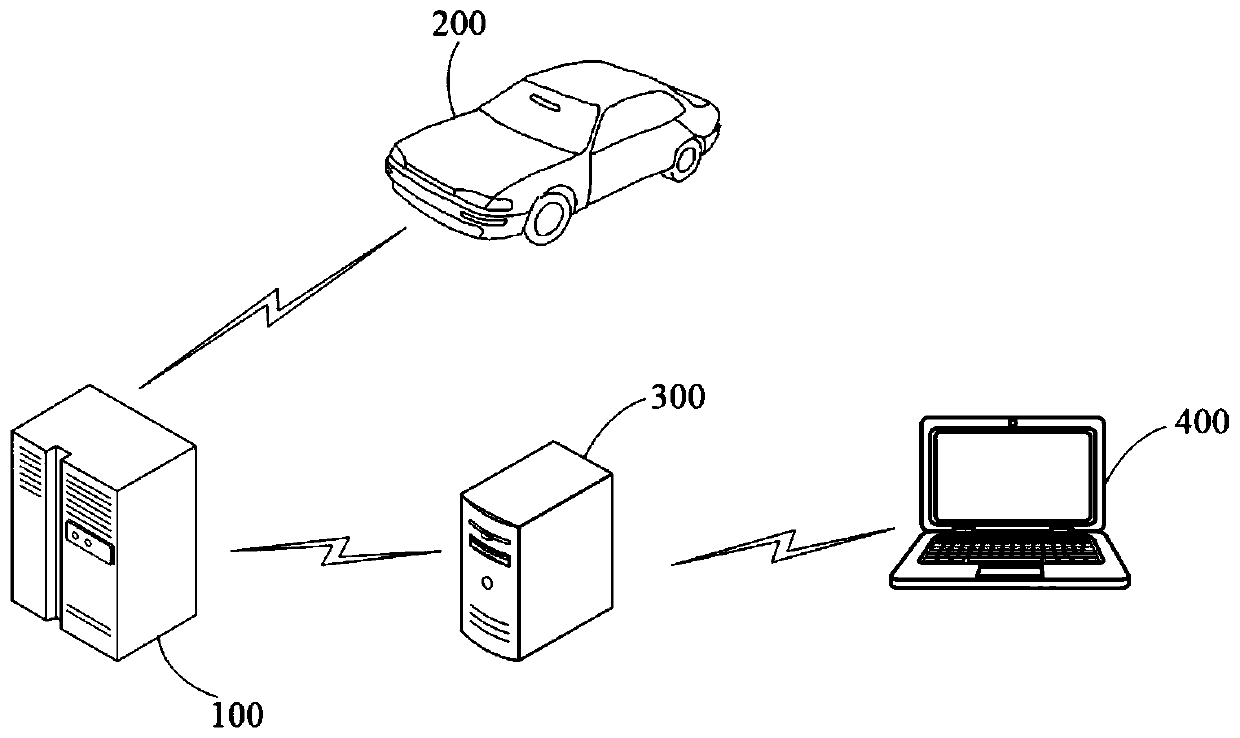
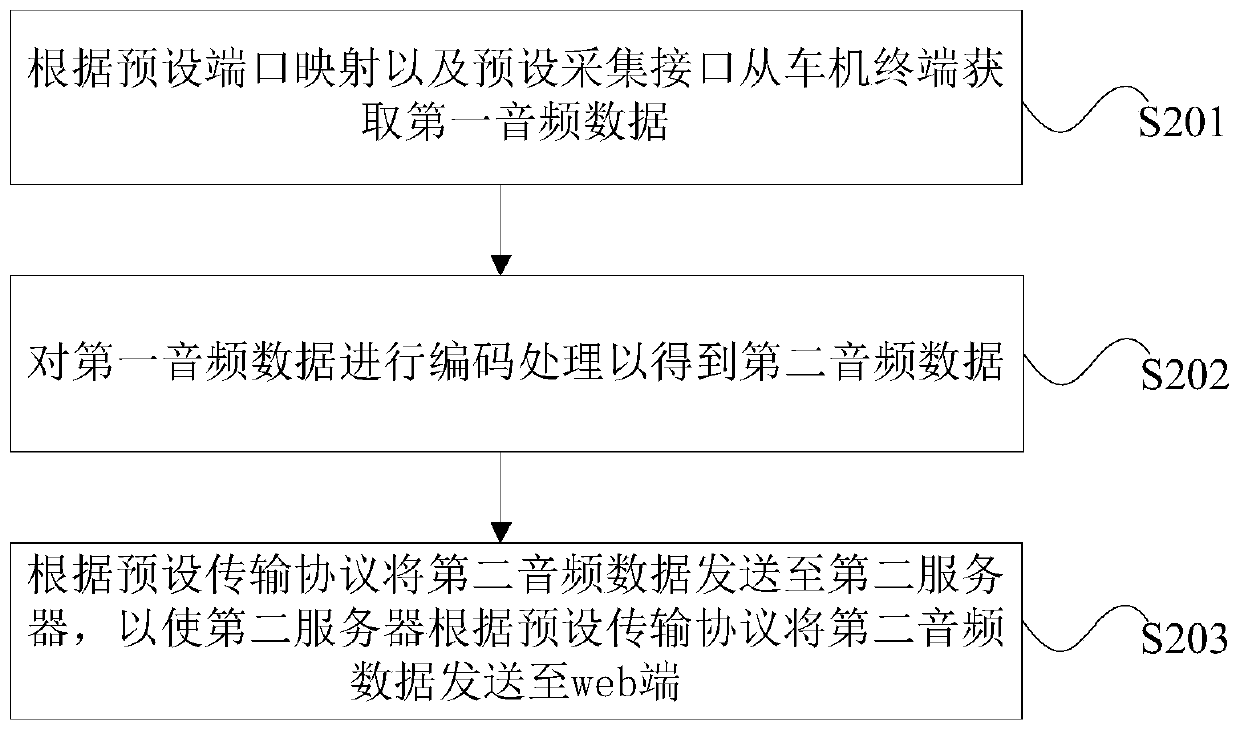
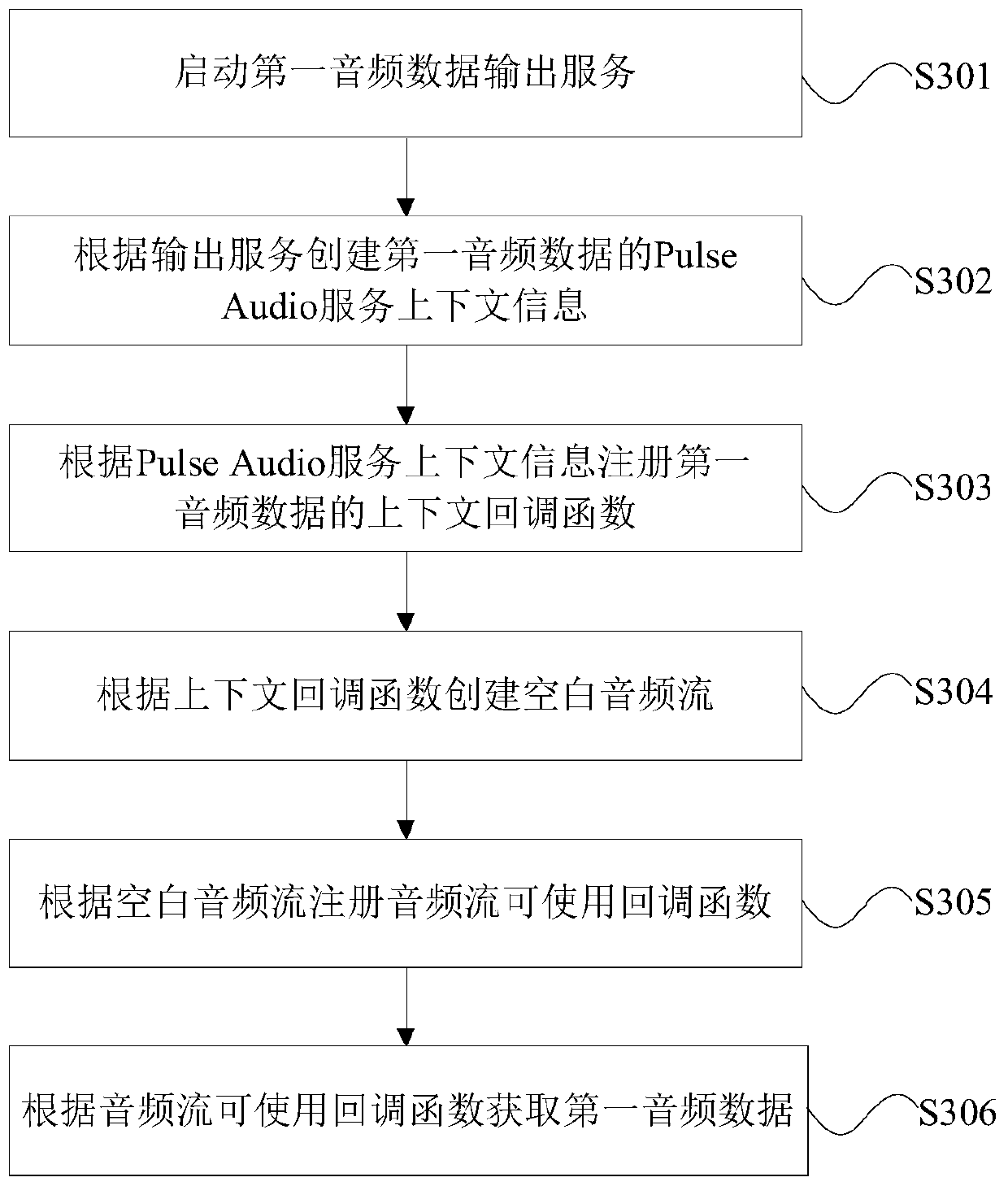
Audio remote transmission method and device, server and storage medium
ActiveCN110944015ARealize remote transmissionImprove experienceTransmissionTransmission protocolMachine control
The invention provides an audio remote transmission method and device, a server and a storage medium. The audio remote transmission method provided by the invention is applied to a first server, the first server belongs to a vehicle machine control system, and the vehicle machine control system further comprises a vehicle machine terminal, a second server and a web terminal. The first server acquires the first audio data from the vehicle terminal according to the preset port mapping and the preset acquisition interface, and then encoding the first audio data to obtain second audio data, sending the second audio data to a second server according to a preset transmission protocol, and enabling the second server to send the second audio data to the web terminal so as to enable the web terminal to play the second audio data. Therefore, the remote transmission of the audio data is realized through a non-intrusive method, the resource occupation of the vehicle-mounted terminal and the generated influence are avoided, the time delay is reduced, the audio quality is ensured, and the user experience is improved.
Owner:ZEBRED NETWORK TECH CO LTD
Interaction method and interaction system for implementing energy conservation of network client sides
ActiveCN102546539AAvoid resource hoggingReduce power consumptionTransmissionClient-sideInternal logic
The invention discloses an interaction method for implementing energy conservation of network client sides. The method includes operating a request message sent by a request client side according to the internal logic by the aid of a server, and then adding operating results into the request message and transmitting the operating results to a response client side by the aid of the server. The invention further discloses an interaction system for implementing energy conservation of the network client sides, the server in the system is used for operating the request message sent by the request client side according to the internal logic of the server, and then adding the operating results into the request message and transmitting the operating results to the response client side. By the aid of the method and the system, a large number of resources can be prevented from being occupied, power consumption of the client sides is reduced, and energy conservation of the client sides is benefited.
Owner:TENCENT TECH (SHENZHEN) CO LTD
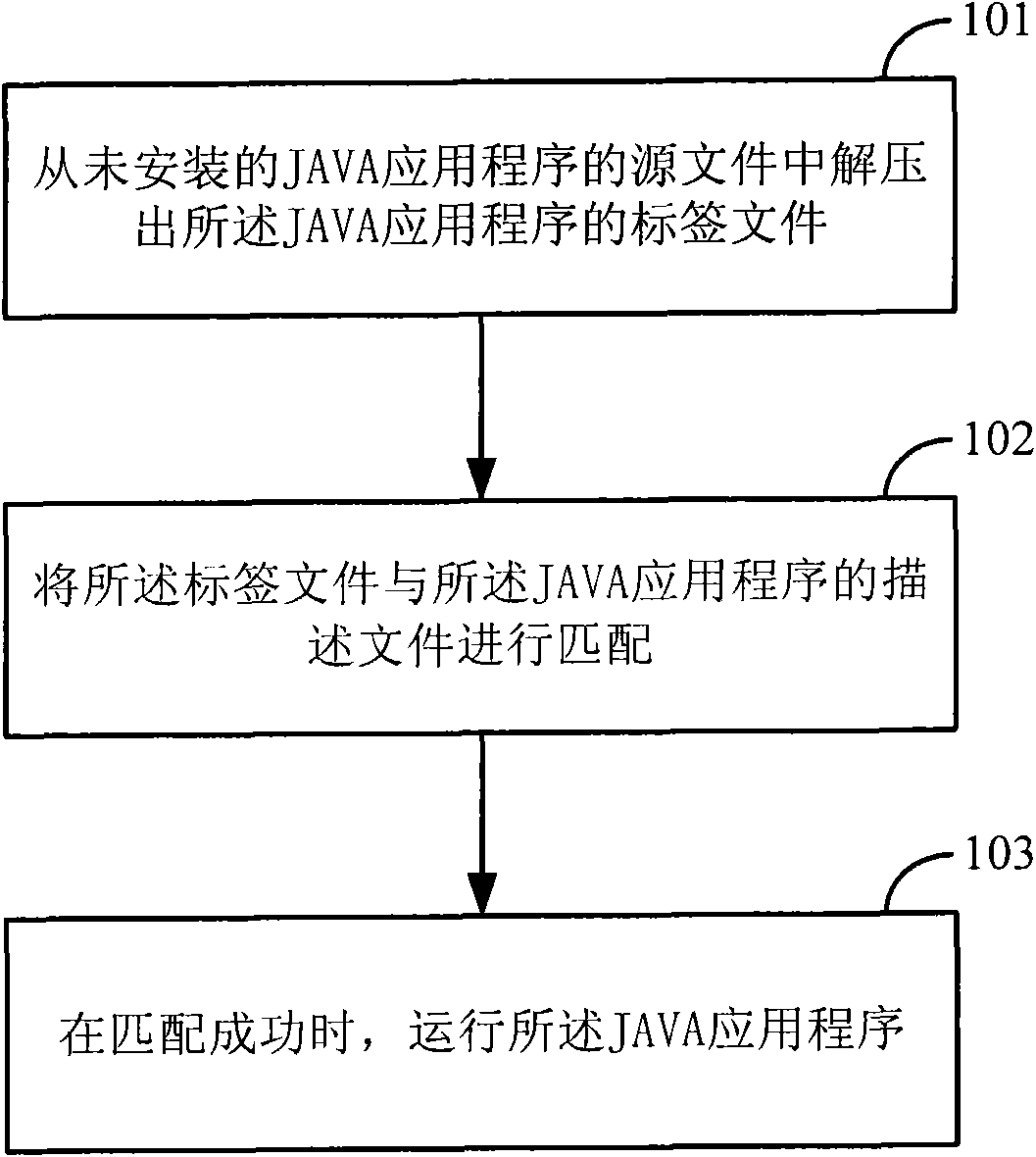
Method and device for running JAVA application
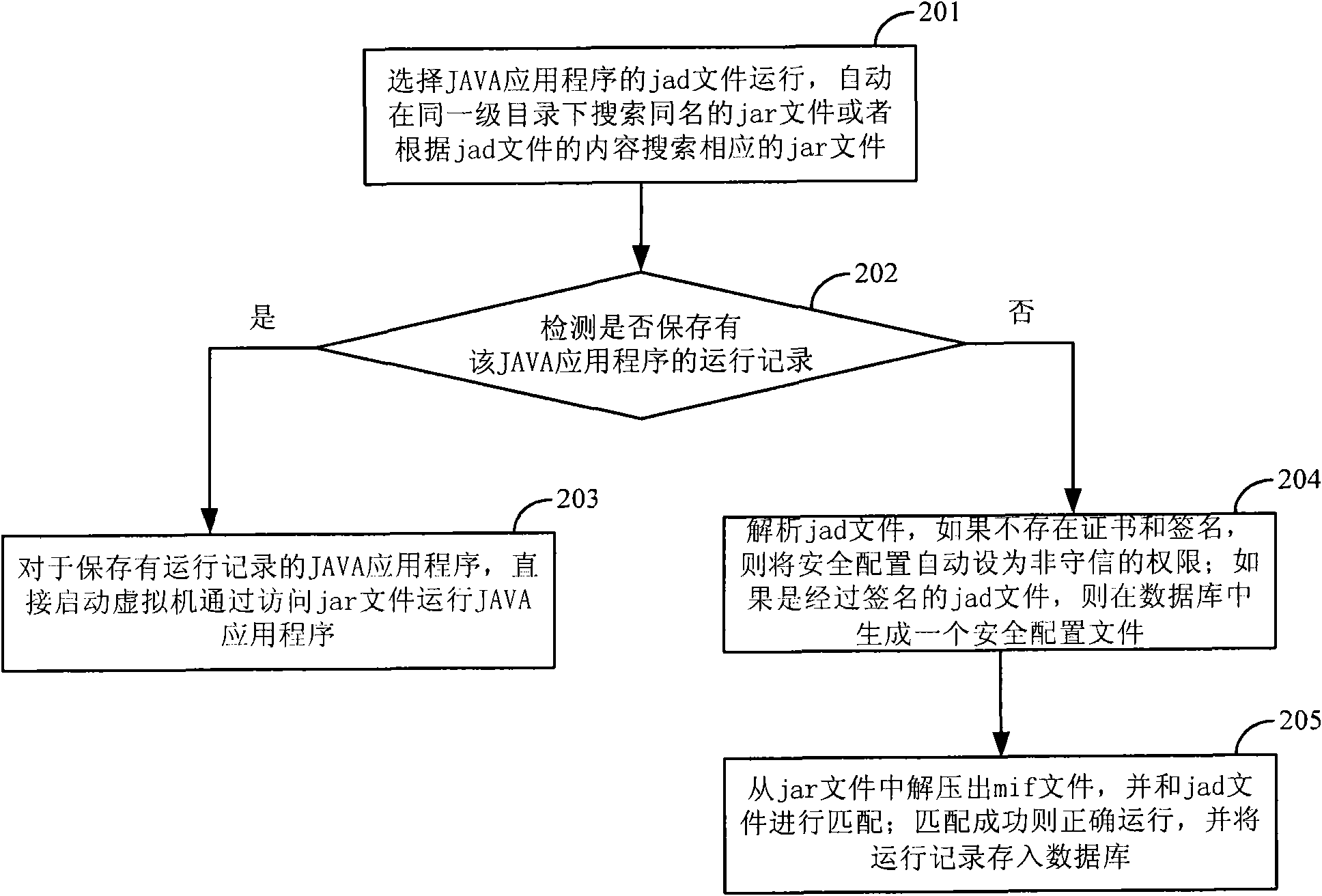
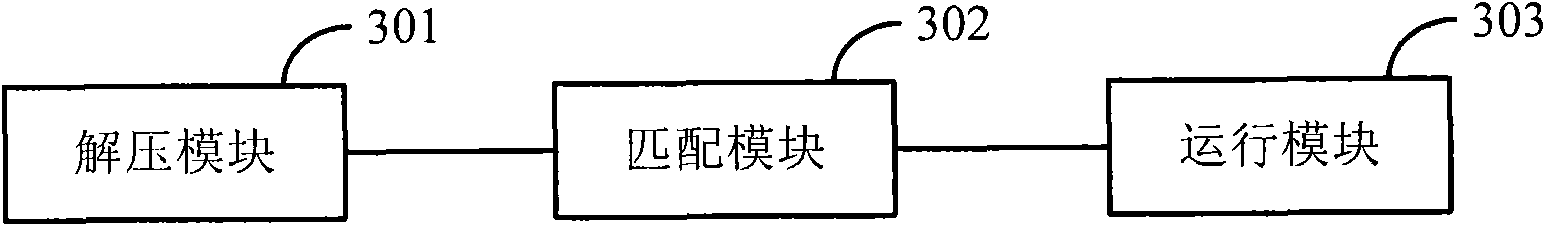
InactiveCN101847103AAchieve normal operationEasy to useProgram loading/initiatingJavaSoftware engineering
The invention discloses a method for running the JAVA application, which comprises the following steps of: extracting tagged files of the JAVA application from the source file of uninstalled JAVA application; matching the tagged files with description files of the JAVA application; and if the matching succeeds, running the JAVA application. Meanwhile, the invention also discloses a device for running JAVA application. By adopting the method and the device for running JAVA application, the running of the JAVA application can be realized under the condition of not installing the JAVA application in advance, which facilitates the use of the user, and avoids the phenomenon of resources occupation and long elapsed time caused by the installation of the JAVA application.
Owner:HUAWEI DEVICE CO LTD
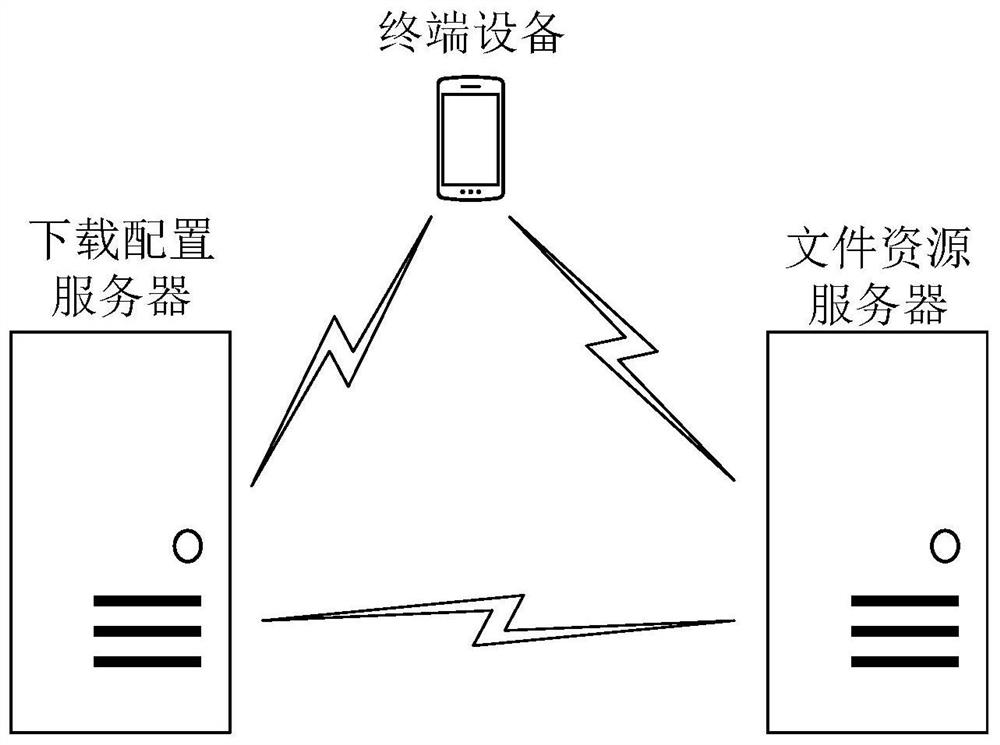
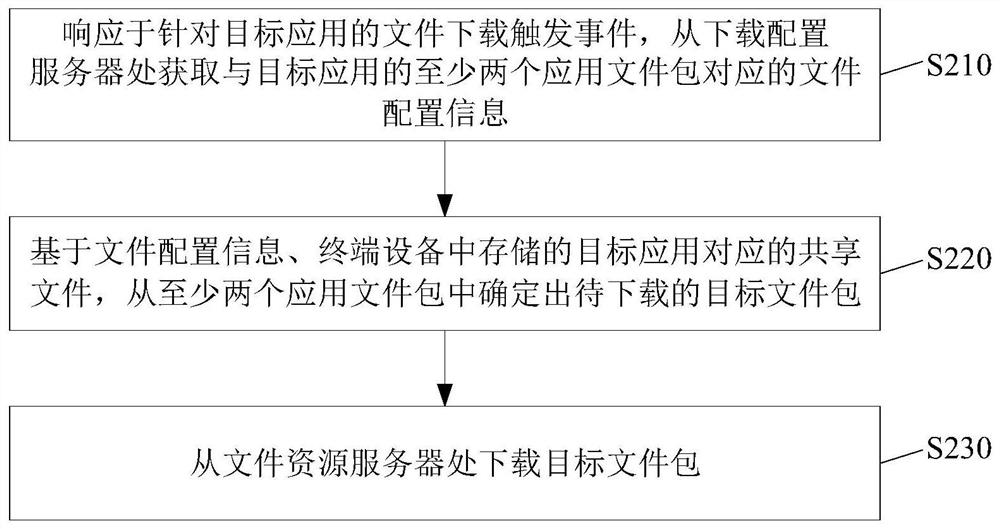
Application downloading method, terminal, server, computer equipment and storage medium
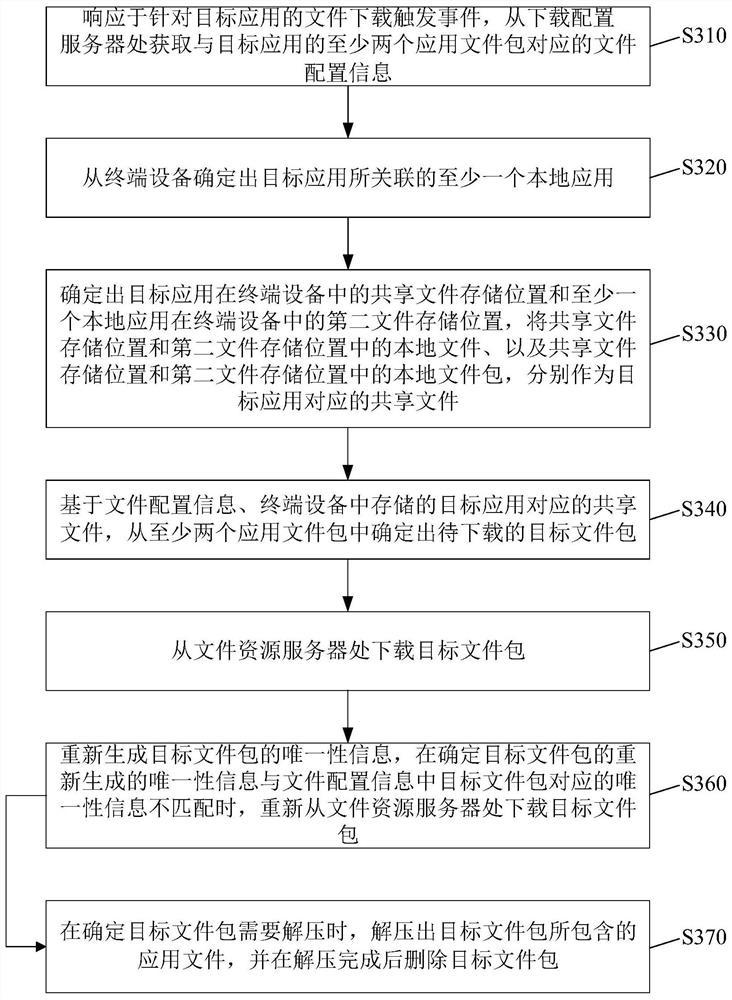
PendingCN113535226AAvoid resource hoggingImprove download speedVersion controlTransmissionTerminal serverTerminal equipment
The invention provides an application downloading method, a terminal, a server, computer equipment and a storage medium, and the method comprises the steps: obtaining file configuration information corresponding to at least two application file packages of a target application from a downloading configuration server in response to a file downloading trigger event for the target application; determining a to-be-downloaded target file package from the at least two application file packages based on the file configuration information and a shared file corresponding to a target application stored in the terminal equipment; downloading the target file package from the file resource server, wherein the at least two application file packages are obtained by performing file clustering on a plurality of application files of the target application according to a preset clustering condition. According to the application file downloading mode, the probability that the device downloads repeated files can be effectively reduced, the downloading speed can be increased, the downloading flow can be saved, the storage space of the device is effectively prevented from being occupied by repeated resources, and the running speed of the device can be increased.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Management data synchronization method and device, storage equipment and readable storage medium
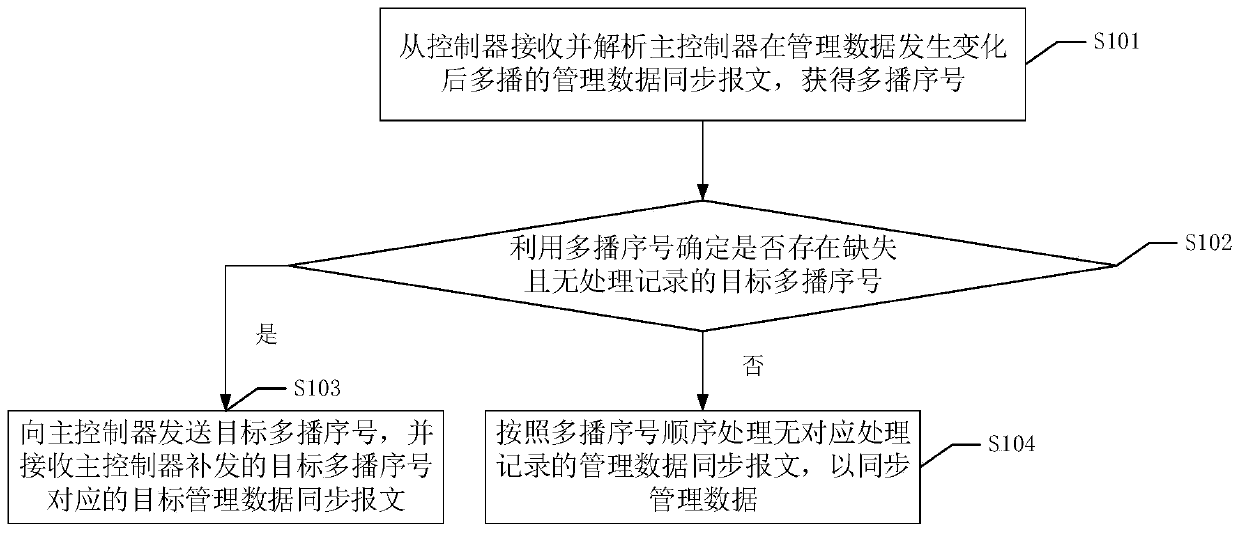
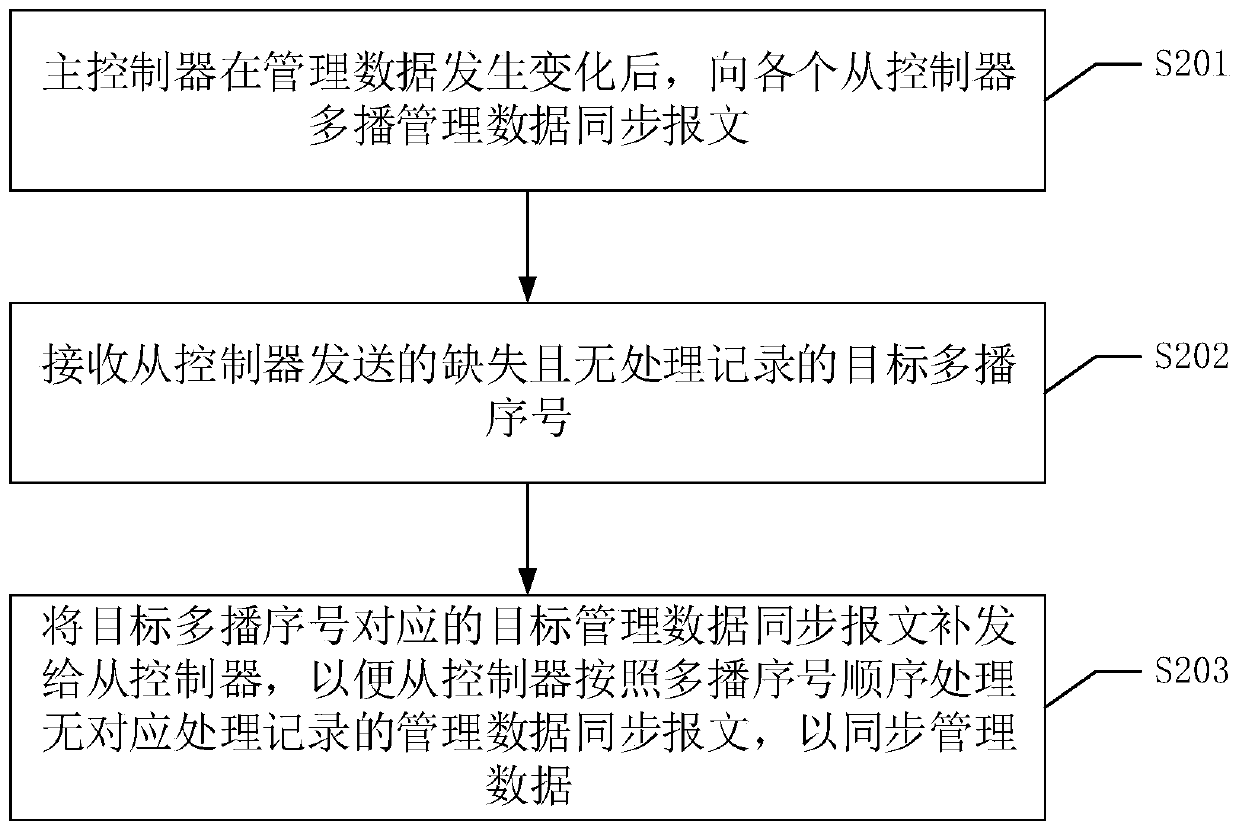
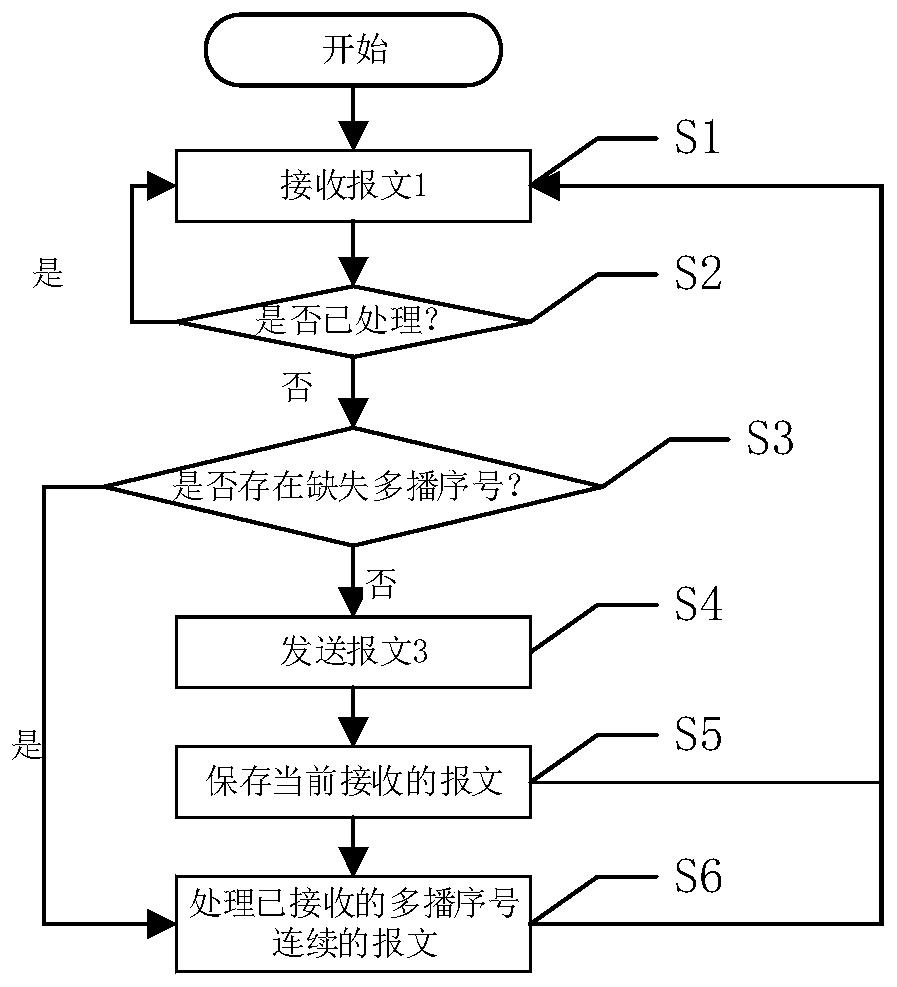
InactiveCN110557399AGuaranteed stabilityAvoid occupyingTransmissionData synchronizationSystem stability
The invention discloses a management data synchronization method and device applied to a master controller, a management data synchronization method and device applied to a slave controller, storage equipment and a readable storage medium. According to the technical scheme, a multicast technology is utilized, increasing multicast serial numbers are designed, multicast messages are sequentially processed, whether messages are missing or not is determined by a slave controller through the multicast serial numbers, and the missing messages are actively pulled from a master controller under the condition that the messages are missing, so that management data synchronization is realized. According to the technical scheme, under the condition that the synchronization workload of the master controller is reduced, the consistency of management data in the slave controller and the master controller is ensured, and the system stability of the multi-controller storage array can be further ensured.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
A distributed data processing method and a server based on multithreading
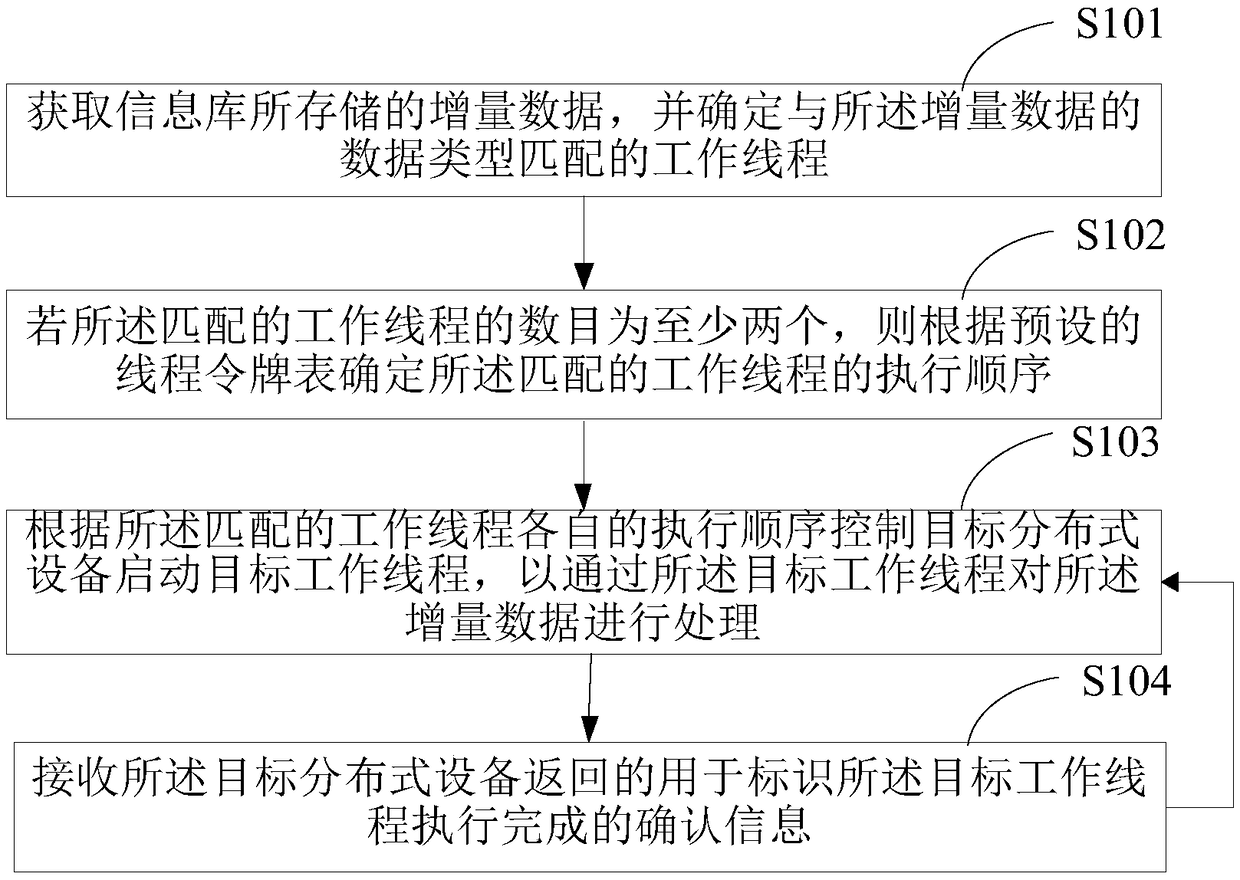
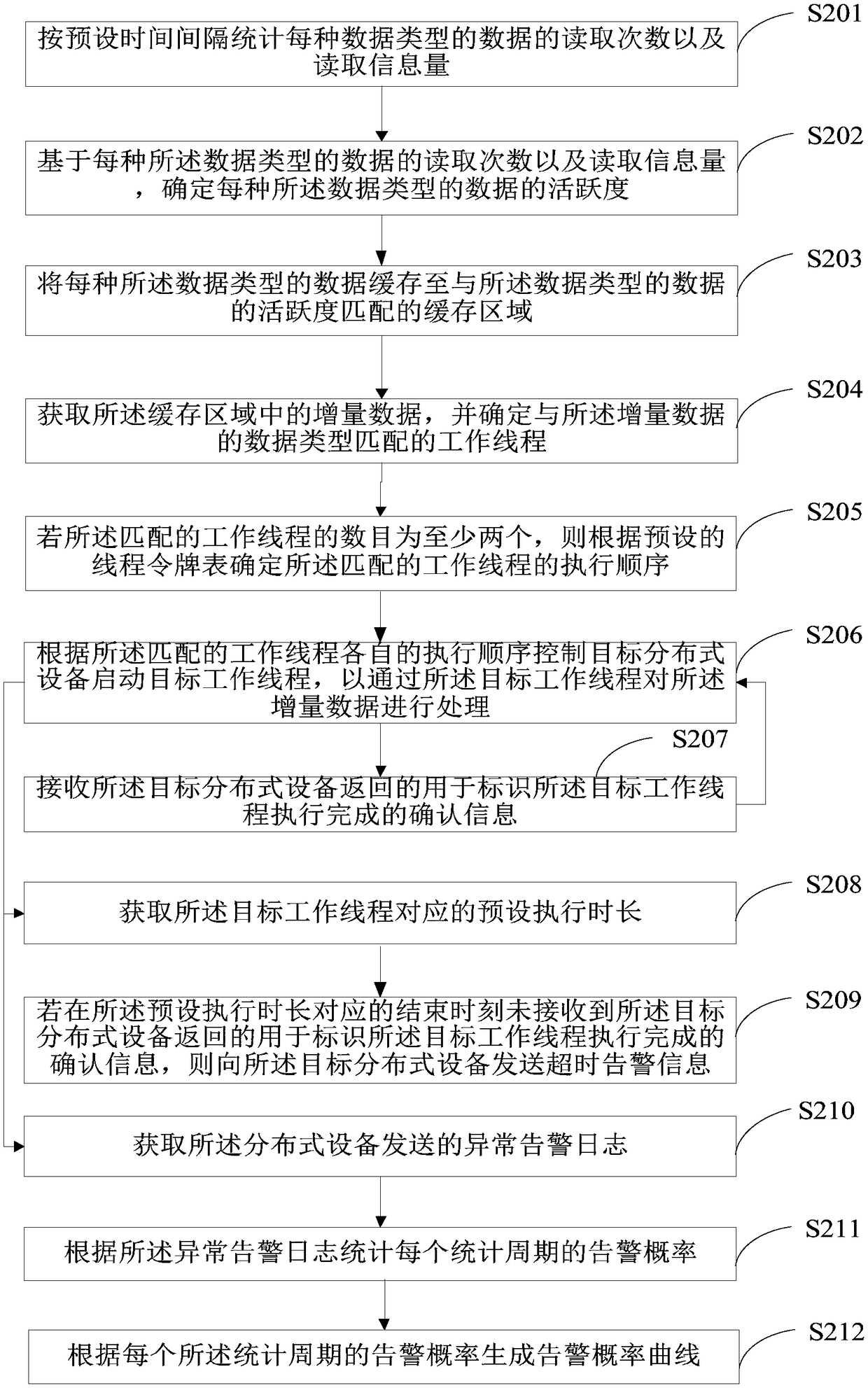
ActiveCN109284193AMaintain integrityAvoid resource hoggingProgram synchronisationData storingData type
The invention is applicable to the computer technical field, and provides a distributed data processing method and a server based on multi-threading. The method comprises the following steps: acquiring incremental data stored in an information base, and determining a work thread matching with the data type of the incremental data. If the number of matching worker threads is at least two, determining the execution order of the matching worker threads according to a preset thread token table; controlling the target distributed device to start the target worker thread according to the execution order of the matching worker threads, so as to process the incremental data through the target worker thread; receiving confirmation information returned by the target distributed device identifying completion of execution of the target worker thread; the confirmation information is used to redefine the target worker thread and to start the redefined target worker thread. The embodiment of the invention can avoid the working thread to preempt the resources, save the system resources, and also avoid the same thread to repeatedly execute disturbing the certificate preparation operation flow, andcan improve the certificate preparation efficiency.
Owner:PING AN TECH (SHENZHEN) CO LTD
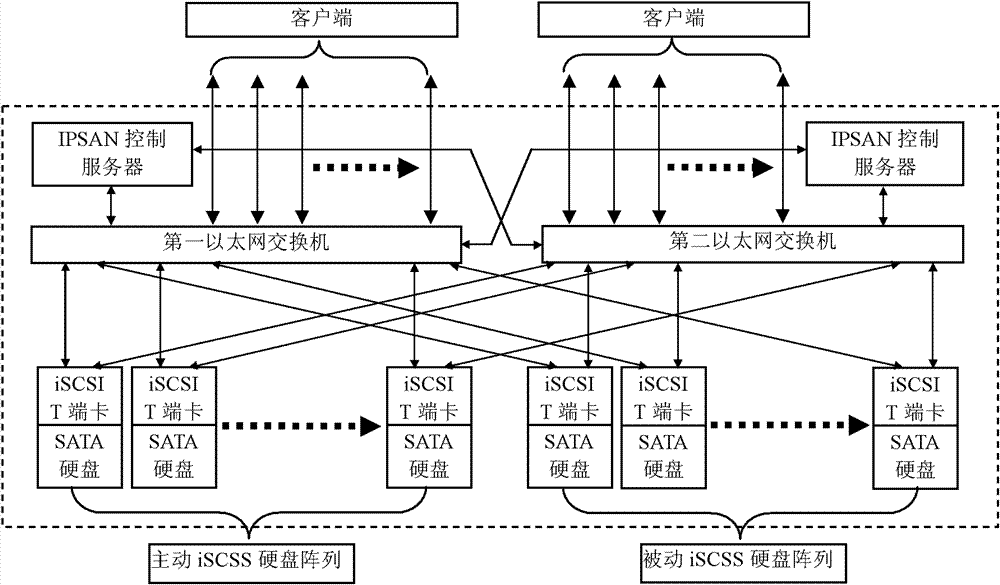
Whole-disk copying method based on ISCSI (Internet Small Computer System Interface) and storage system
ActiveCN102902683AAvoid resource hoggingSpecial data processing applicationsStorage area networkDisk array
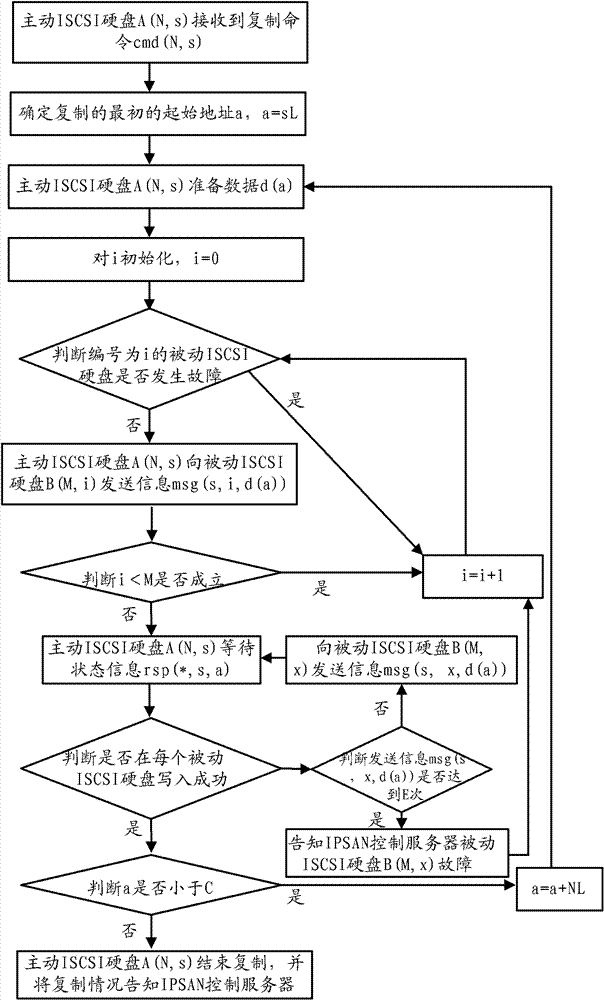
The invention provides a whole-disk copying method based on an ISCSI (Internet Small Computer System Interface) and a storage system. The whole-disk copying method comprises the following steps of: step S100: controlling a server to generate a whole-disk copying command cmd (N) by an IPSAN (Internet Protocol Storage Area Network), and sending the copying command cmd (N,s) to each driving ISCSI hard disk A (N,s) in an initiative ISCSI hard disk array A (N); and step 200: copying a set region to M driven ISCSI hard disks in a driven ISCSI hard disk array B (M) by each driving ISCSI hard disk A (N,s) according to the copying command cmd (N,s), wherein the setting regions of each driving ISCSI hard disk are different, and the setting regions of the N driving ISCSI hard disks A (N,s) are gathered into a whole disk. Each ISCSI hard disk is interconnected through an Ethernet switch and the adopted ISCIS hard disk has a data transmission and logic function so that the ISCIS hard disks can carry out port-to-port block-free communication through the Ethernet switch; the whole-disk copying of the data is realized under an instruction of an IPSAN control server; and the copying delaying and the resource occupation, which are caused by that the data is stored and transmitted by the IPSAN control server, are avoided.
Owner:BEIJING FORTUNET INFORMATION & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com