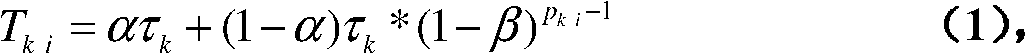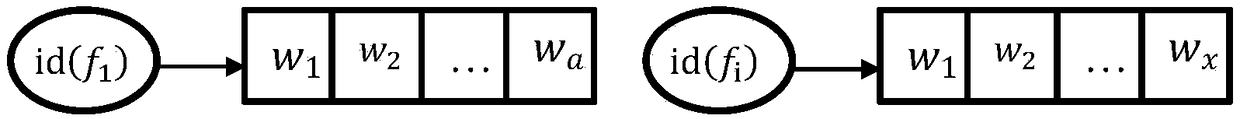Patents
Literature
428results about How to "Control access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Mobile equipment privacy authority control method, mobile equipment privacy authority control device and corresponding mobile phone equipment
InactiveCN105072255ARealize managementEasy to manageDigital data protectionSubstation equipmentInternet privacyData access
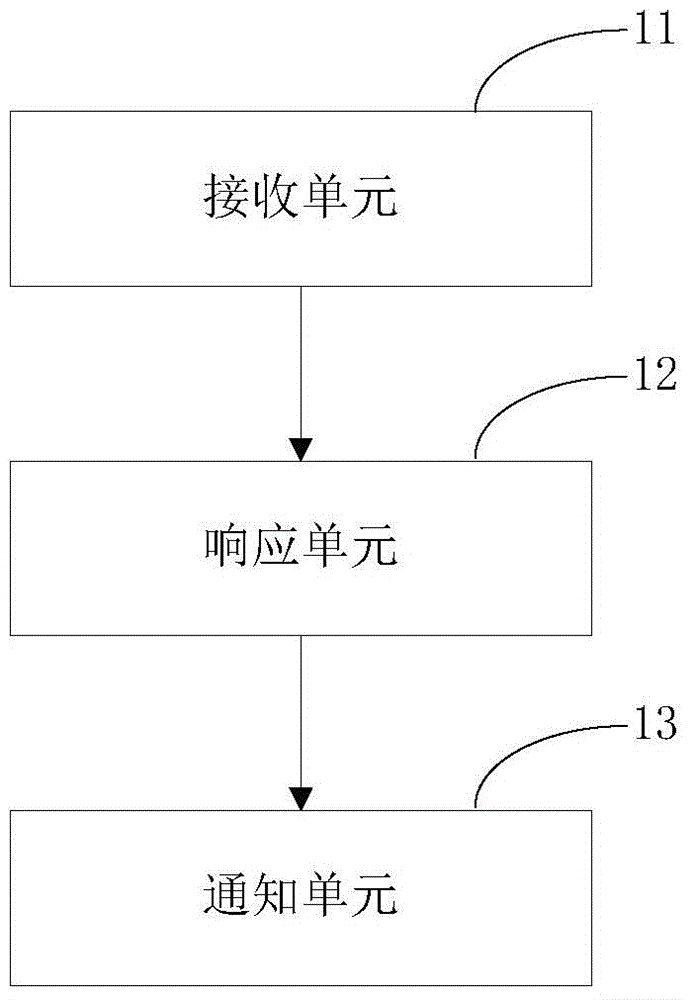
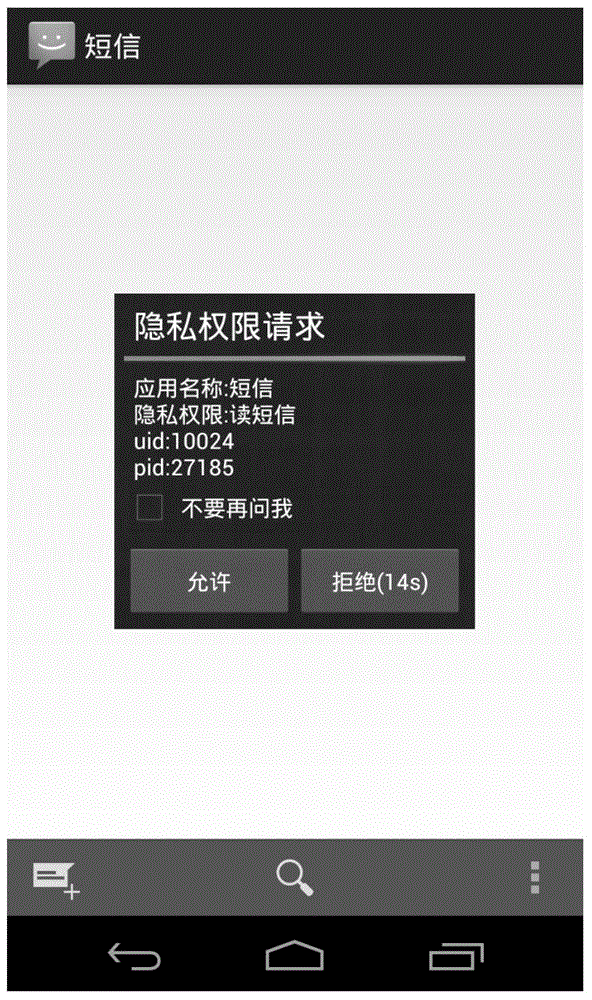
The invention provides a mobile equipment privacy authority control method. The method comprises the steps: receiving a preset event notification, sent by a background service, of privacy data access, wherein the event notification of the privacy data access is generated based on a behavior that the background service intercepts an application program calling a privacy data access interface; in response to the event notification, providing a visual interface to receive a user's authorization instruction for the access privacy data; and, according to the corresponding authorization instruction, notifying the background service to release or prohibit the privacy data access. At the same time, the invention further provides a mobile equipment privacy authority control device and mobile phone equipment. On the condition that an obtaining system root is prevented from causing a system risk, the method and the device can effectively control an access authority of the application program for user privacy data, prevent a leakage of the user privacy data and improve the experience degree.
Owner:BEIJING QIHOO TECH CO LTD +1
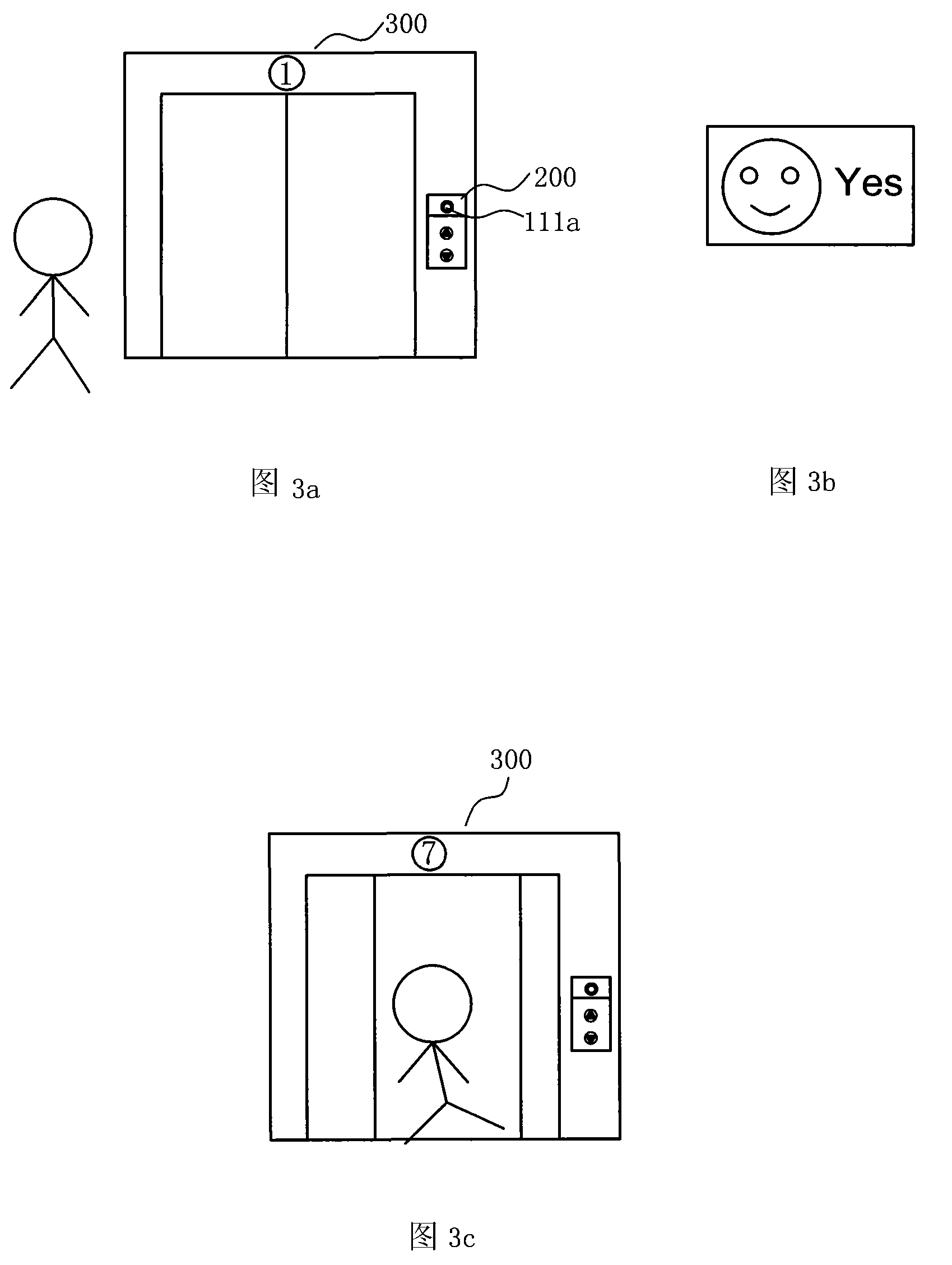
Face recognition elevator reservation system and implementation method thereof
InactiveCN101734527AControl accessShorten the timeCharacter and pattern recognitionElevatorsPattern recognitionElevator control
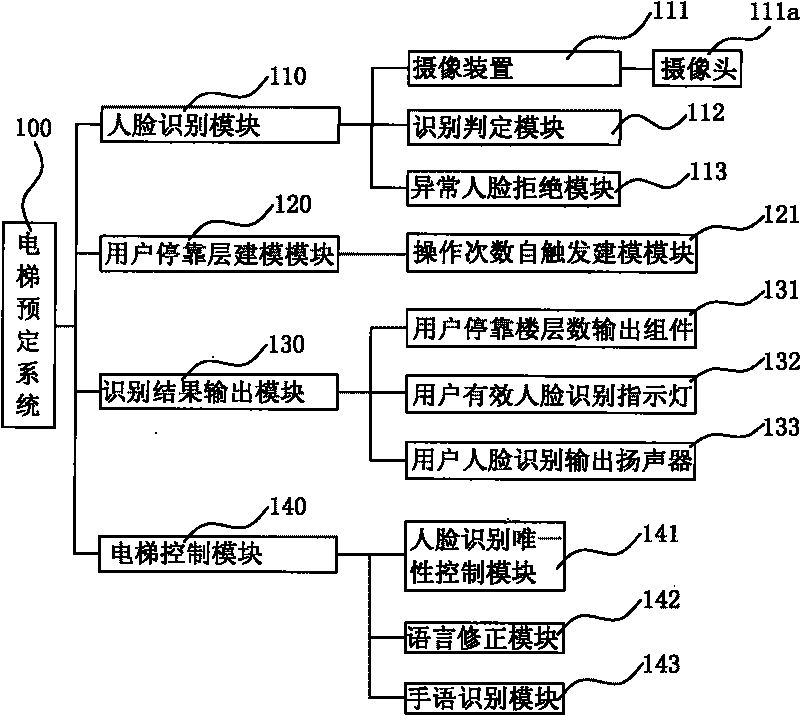
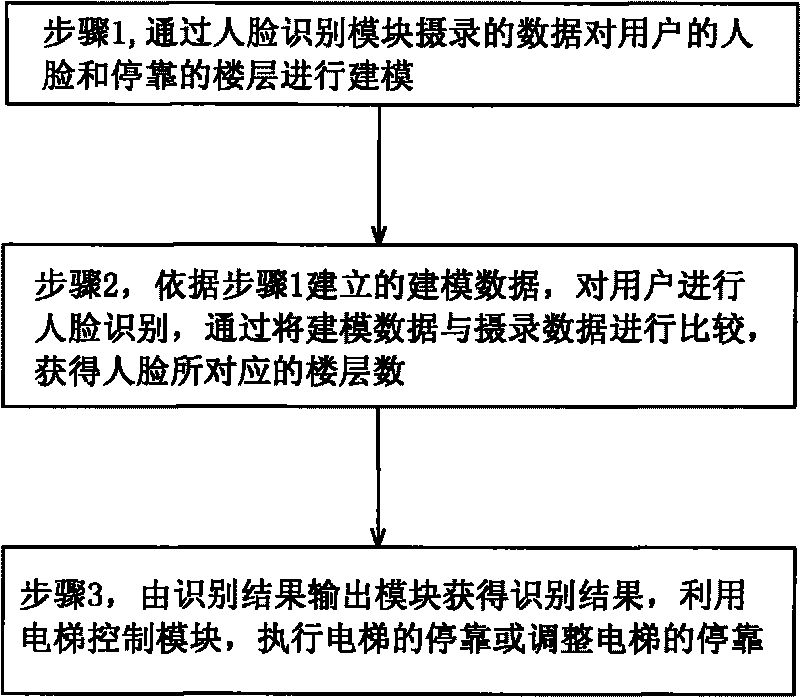
The invention provides a face recognition elevator reservation system and an implementation method thereof, belonging to the technical fields of software and elevator. The face recognition elevator reservation system comprises a face identification module, a user stop-floor modeling module, a recognition result output module and an elevator control module, wherein, the face recognition module is arranged on an elevator lobby or in an elevator car to shoot the face data and taking state of the persons taking the elevator of a calling floor; corresponding relationship between the user face data and the number of the floor to take the elevator is built by setting the user stop-floor modeling module; a recognition result is fed back to a user by the recognition result output module; and a taking task is implemented or taking information is regulated in time by setting the elevator control module. In the invention, not only the elevator use permission is controlled, but also the security of official or living environment is improved, and user time is saved by recognizing and automatically setting a user stop floor.
Owner:上海杰远环保科技有限公司
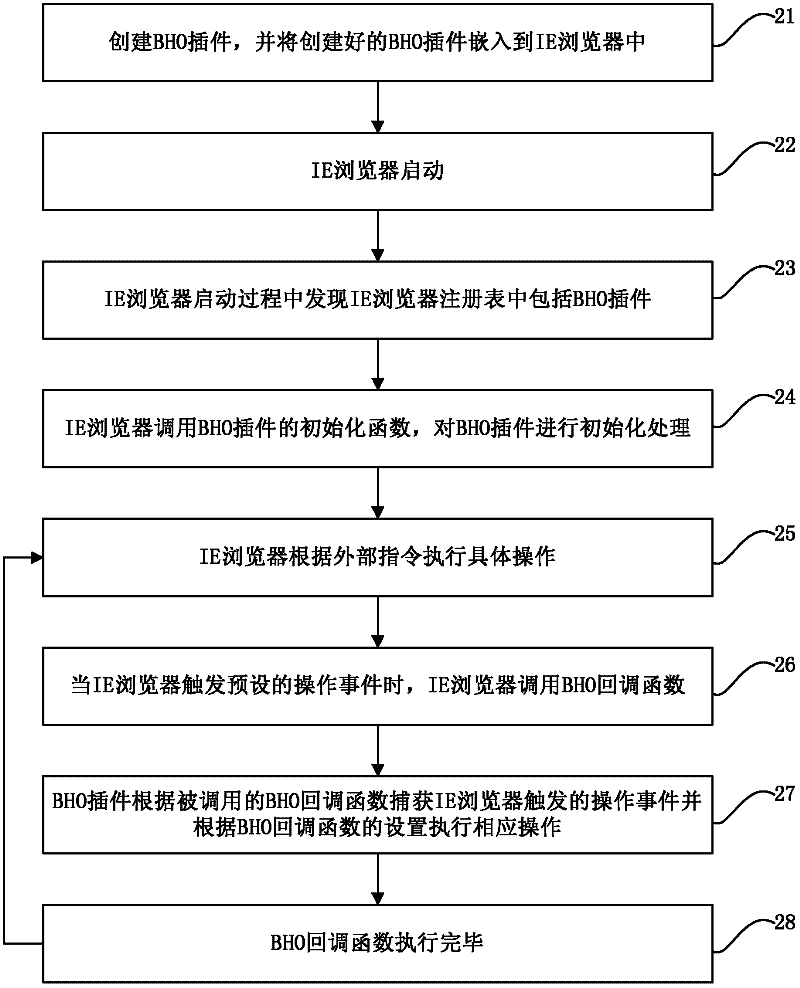
Webpage security detection method and system
ActiveCN102375951AComprehensive security testingLow costPlatform integrity maintainanceSpecial data processing applicationsWeb pagePre embedding
The invention discloses a webpage security detection method and system. The method comprises the following steps of: when switching on a browser, initializing a browser embedment plug-in which is pre-embedded in the browser; controlling the browser to gradually access a webpage, on which addresses of webpage to be detected are centralized, corresponding to each address of the webpage to be detected through the browser embedment plug-in; monitoring a process of accessing the webpage by the browser through an antivirus program, triggering to alarm when the antivirus program captures virus, Trojan virus or malicious feature codes of the present webpage, and recording an alarm logging; and generating a corresponding detection report of the webpage according to the alarm log. According to the webpage security detection method, the cost of the webpage security detection is reduced and the integrity of the webpage security detection is improved.
Owner:北龙中网(北京)科技有限责任公司
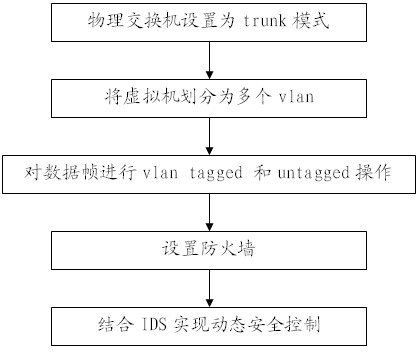
Safety isolation method for virtual network and physical network of cloud computing
InactiveCN102255903AImplement security controlsControl accessTransmissionSafety controlNetwork isolation
The invention provides a safety isolation method for a virtual network and a physical network of cloud computing, wherein the isolation between the both layers of networks is realized by carrying out VLAN (Virtual Local Area Network) tagged and untagged operations on data frames, the access control of three layers is realized by a fire wall, the dynamic safety control is realized with the addition of IDS (Intrusion Detection System) software, so that not only can the communication between different VLANs be controlled, but also the access of other machines in the inner network to the cloud inner network can be controlled. Simultaneously, the network isolation can be performed between virtual machines or between virtual machines and physical machines by employing the VLAN, so that the physical machines and the virtual machines are divided in the different VLANs, namely, the isolation between the physical network and the virtual network can be realized.
Owner:GCI SCI & TECH
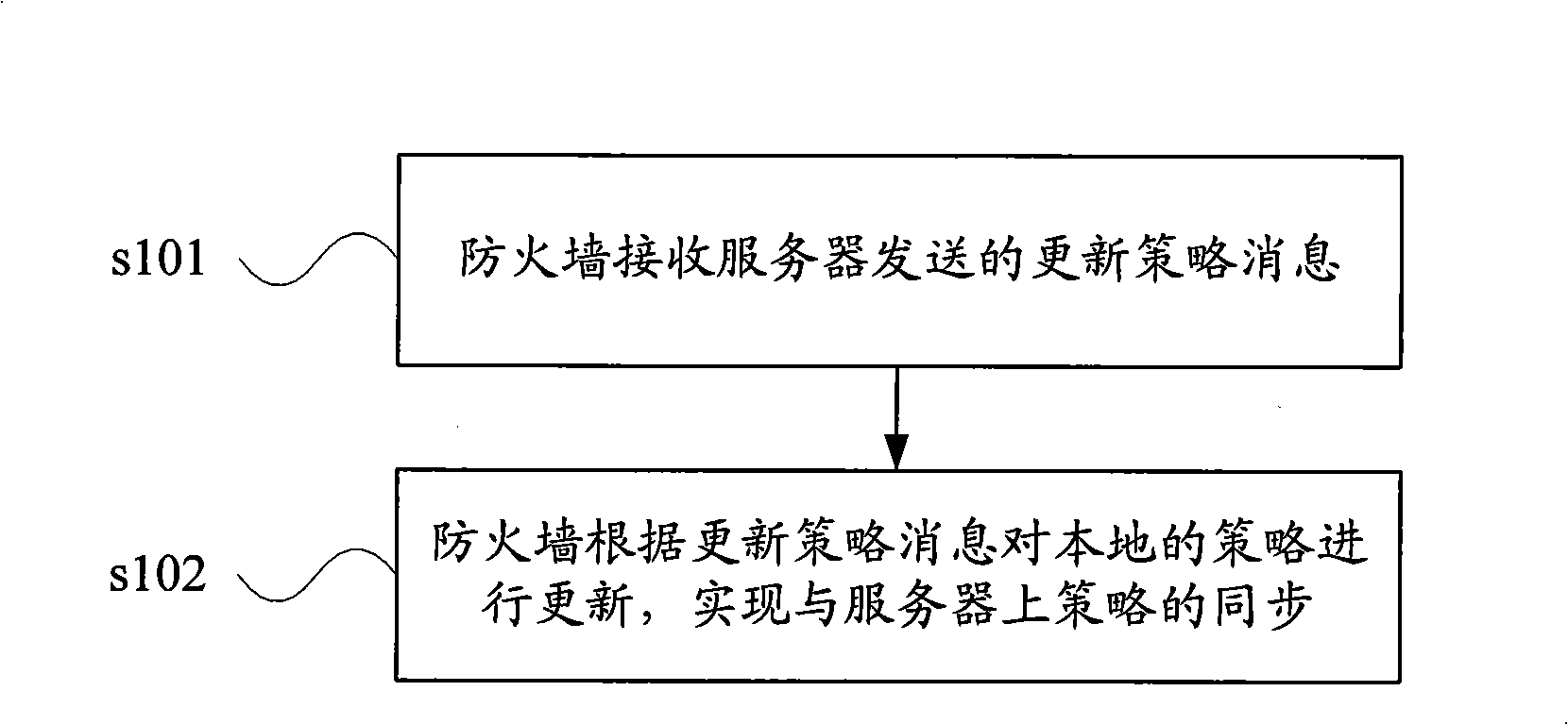
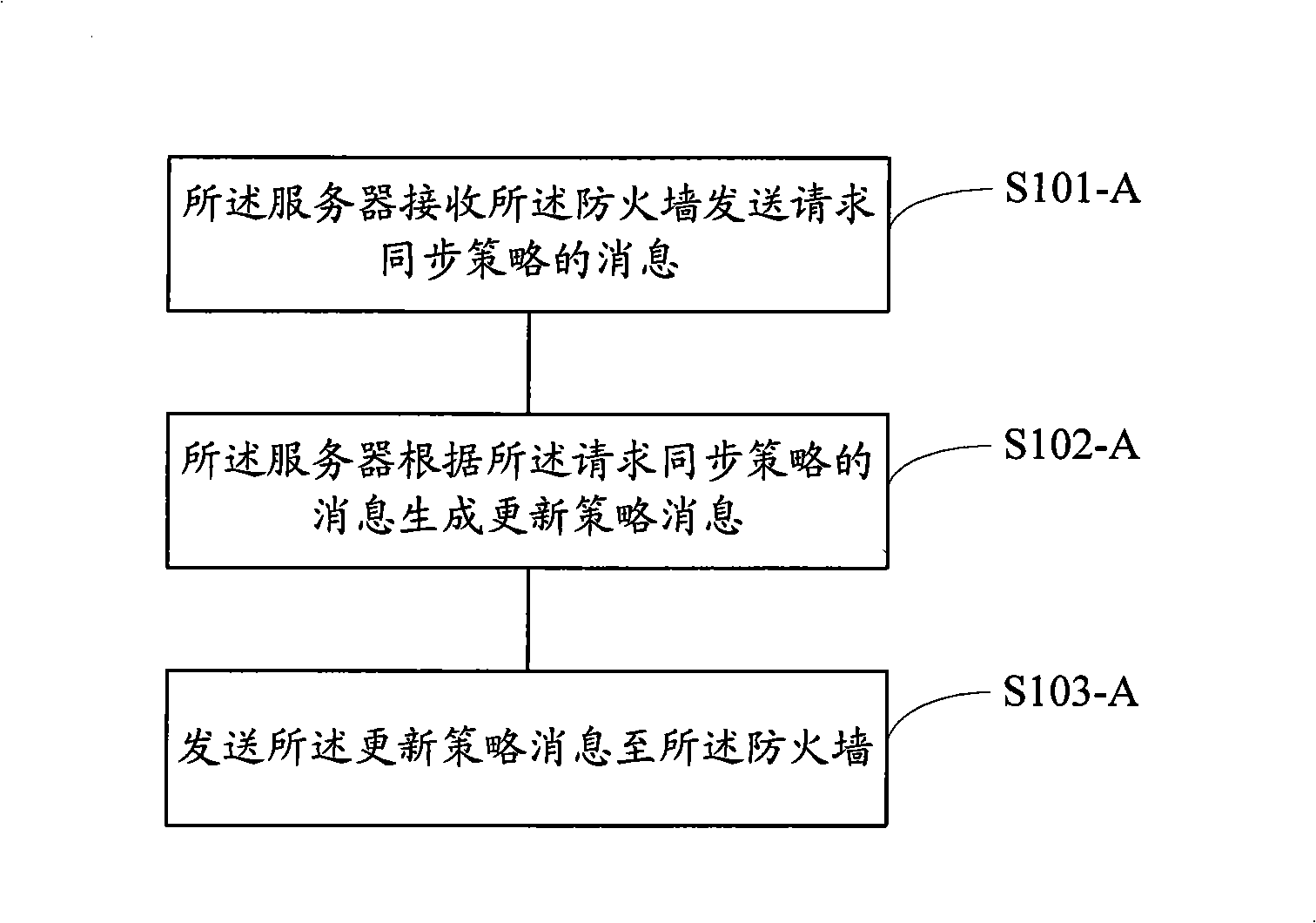
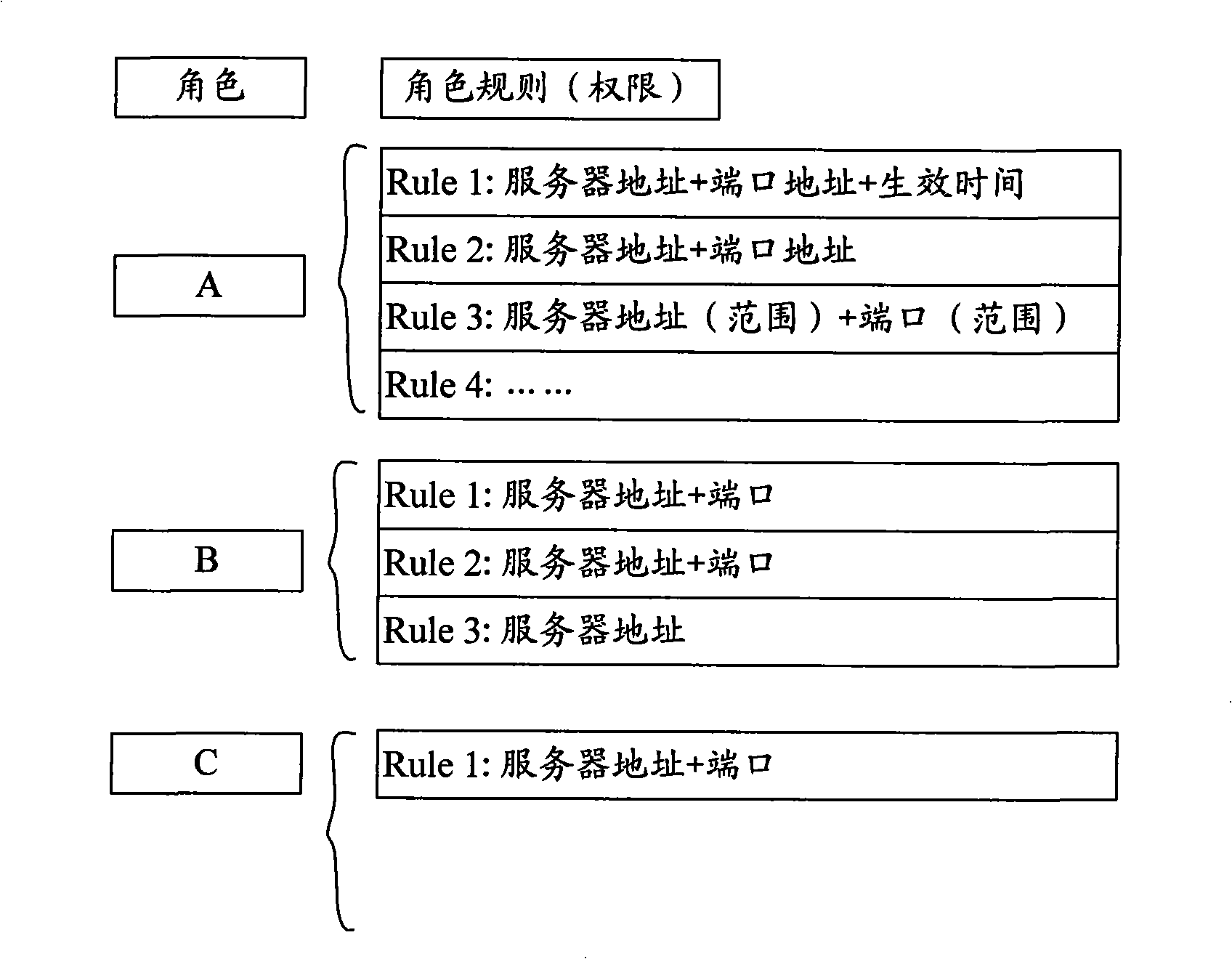
Fireproof wall and server policy synchronization method, system and apparatus
ActiveCN101340444AControl accessAvoid visitingError prevention/detection by using return channelData switching networksDistributed computing
The embodiment of the invention discloses a strategy synchronization method, a system and a device. The method comprises that: a firewall receives an updating strategy message which is sent by a server; the firewall carries out the updating of a local strategy according to the updating strategy message, thereby realizing the strategy synchronization on the server. By adopting the embodiment of the invention, the dynamic synchronized firewall and ACL rules on the server can rapidly update role rules which are bound by a user terminal and the synchronization of more strategies and the switch of authorities of the user terminal can be rapidly realized without the manual configuration on the firewall.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
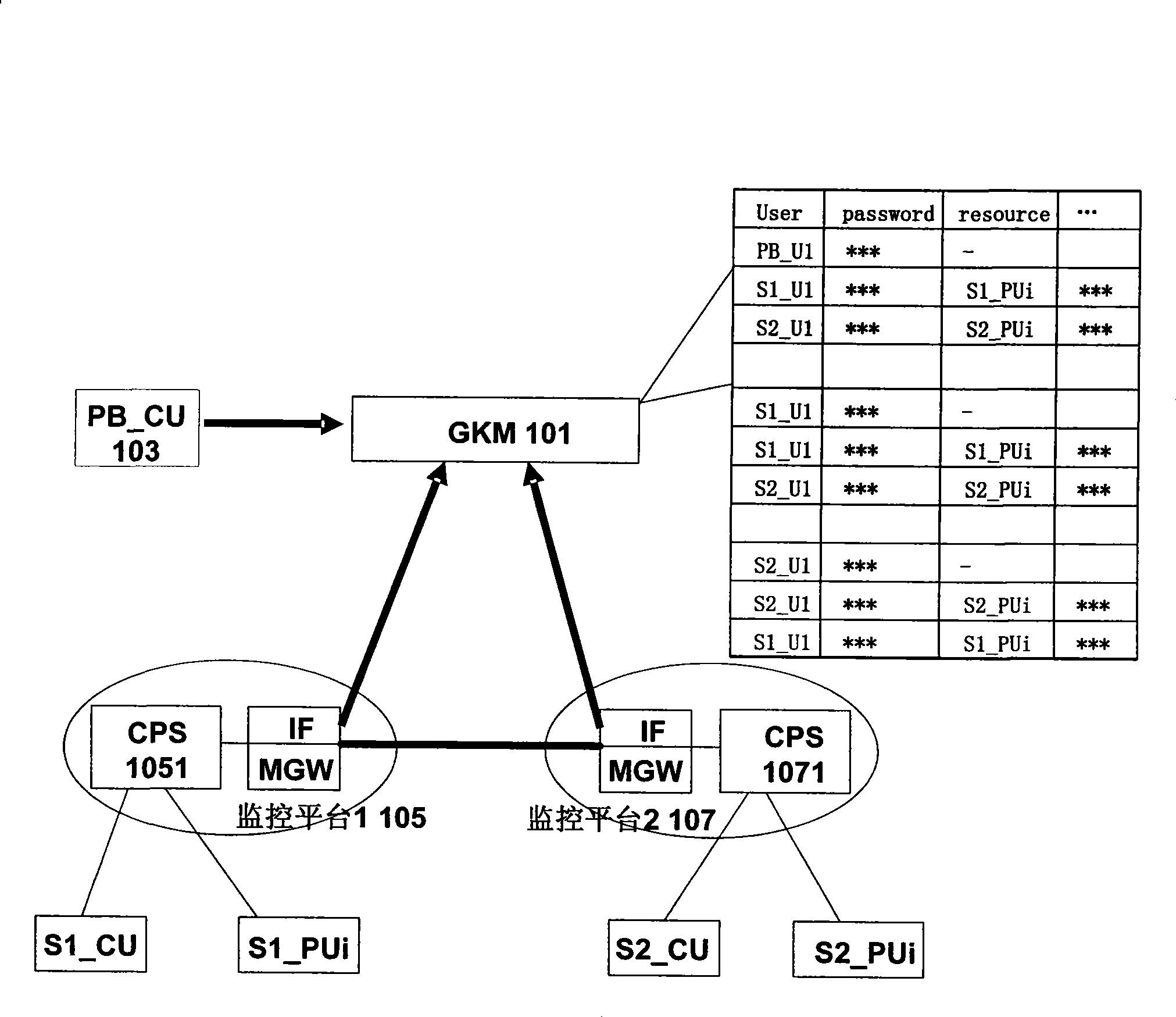
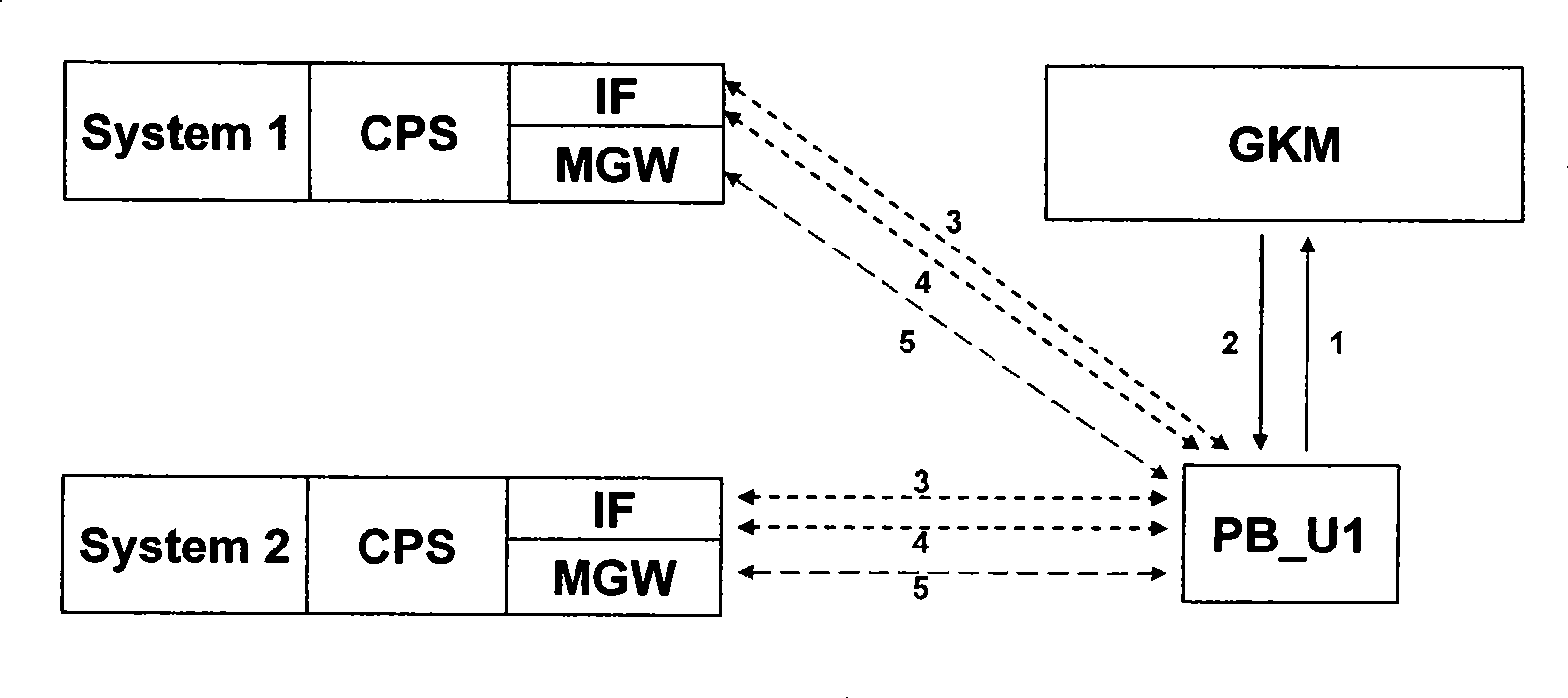
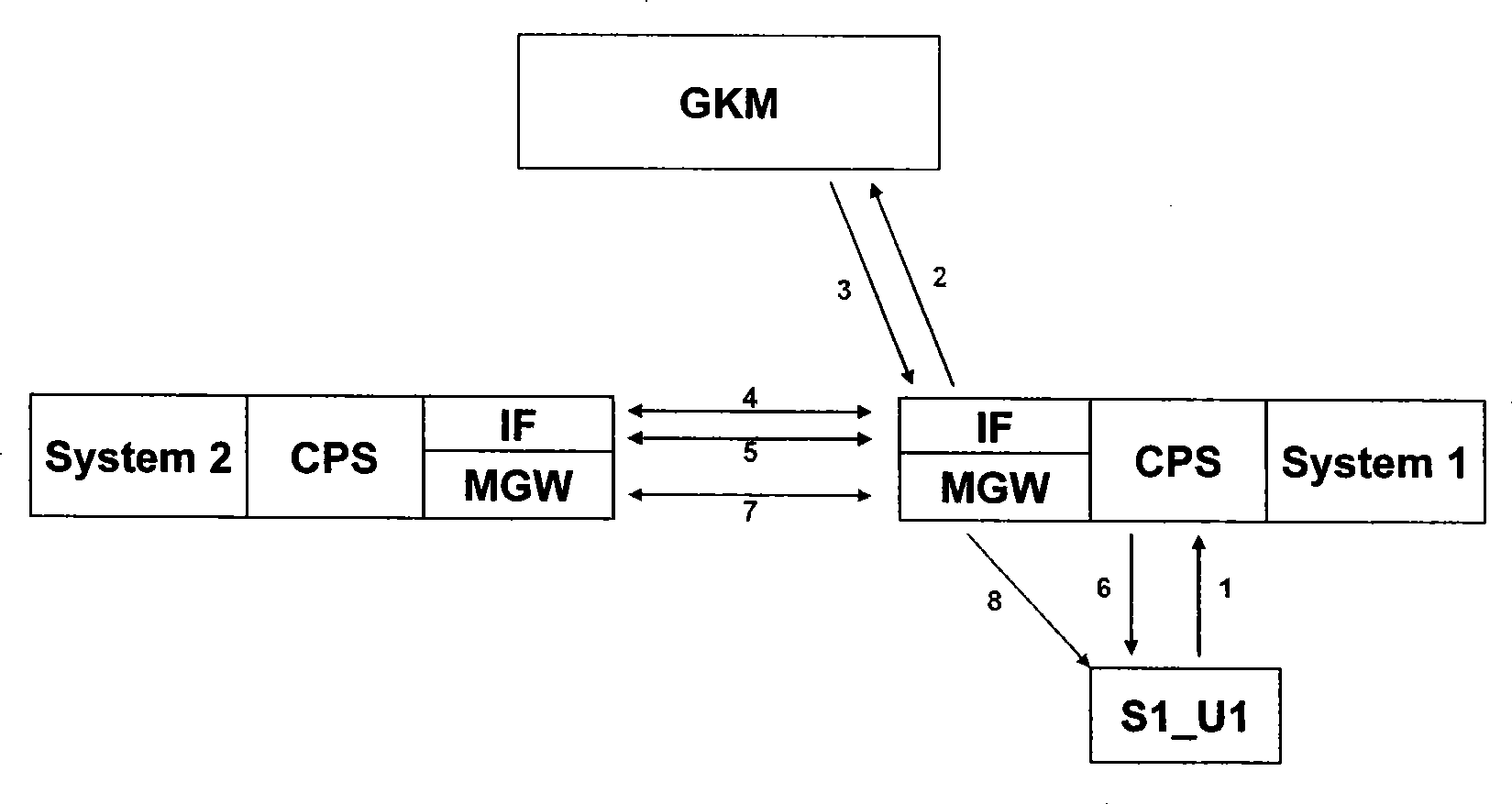
Method and system architecture for realizing service interconnection between multiple video monitoring platforms
ActiveCN101365108AProtect independenceSolve unified managementClosed circuit television systemsTransmissionVideo monitoringInterconnection
The invention relates to a method for achieving service intercommunication between various video monitoring platforms, and system architecture. The method comprises the following steps: a signal interface and a media gateway are added to every video monitoring platform to convert a private signal and video stream transport protocol within the video monitoring platform into a standard signal and video stream transport protocol; an independent gateway custody and management platform and a public client end unit connected with the gateway custody and management platform are added for unified management of signal interaction and the input and output of the video stream between various video monitoring platforms, and for management, authentication, and charging of the intercommunication service, and for the storage of related data of the intercommunication service; and based on a user mapping mode, unified management of the user mapping mode is carried out by the gateway custody and management platform, so as to provide the intercommunication service of the video monitor platform for different kinds of video monitoring platform clients and public clients. The method realizes service intercommunication for the video monitoring platforms.
Owner:CHINA TELECOM CORP LTD
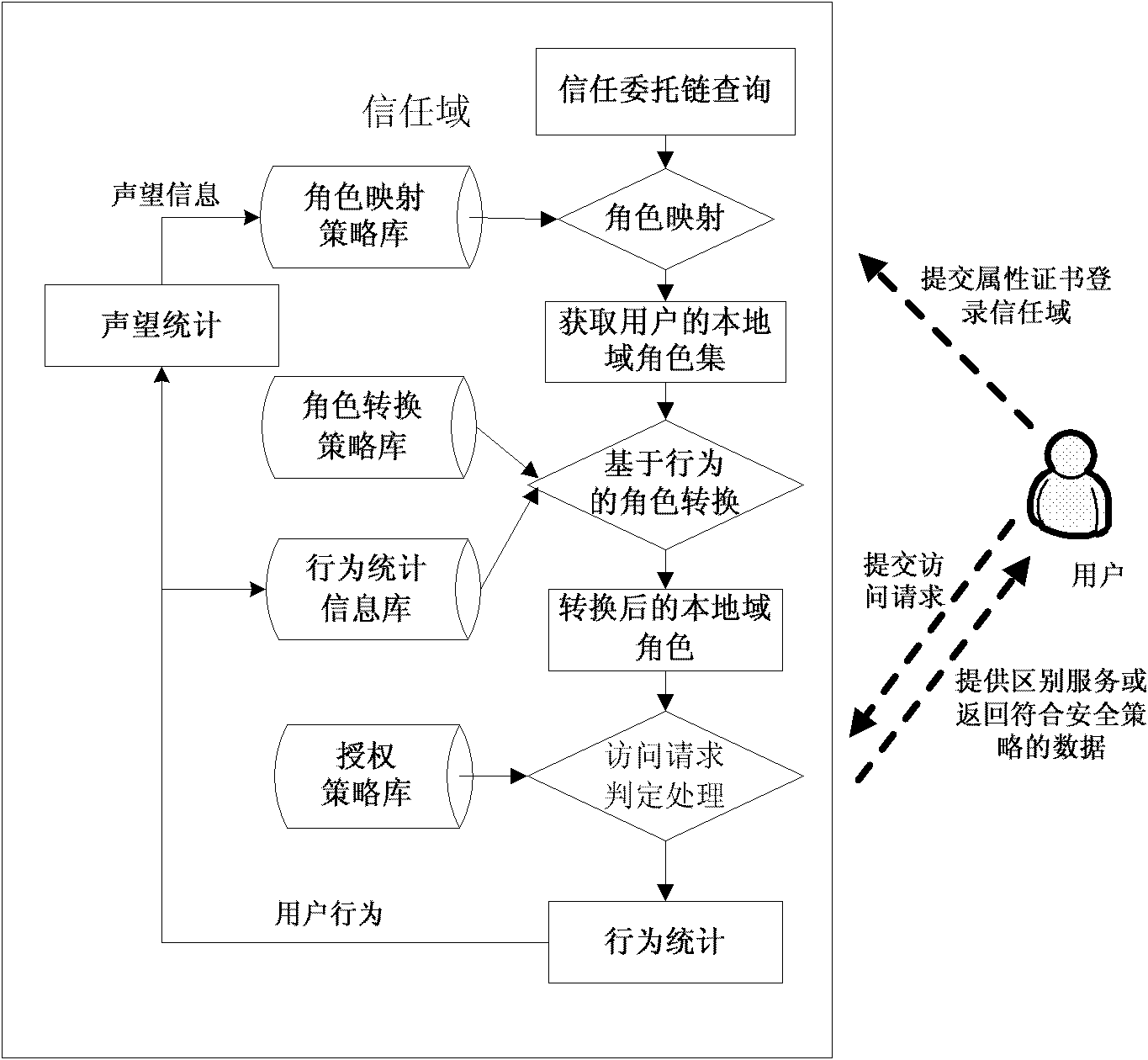
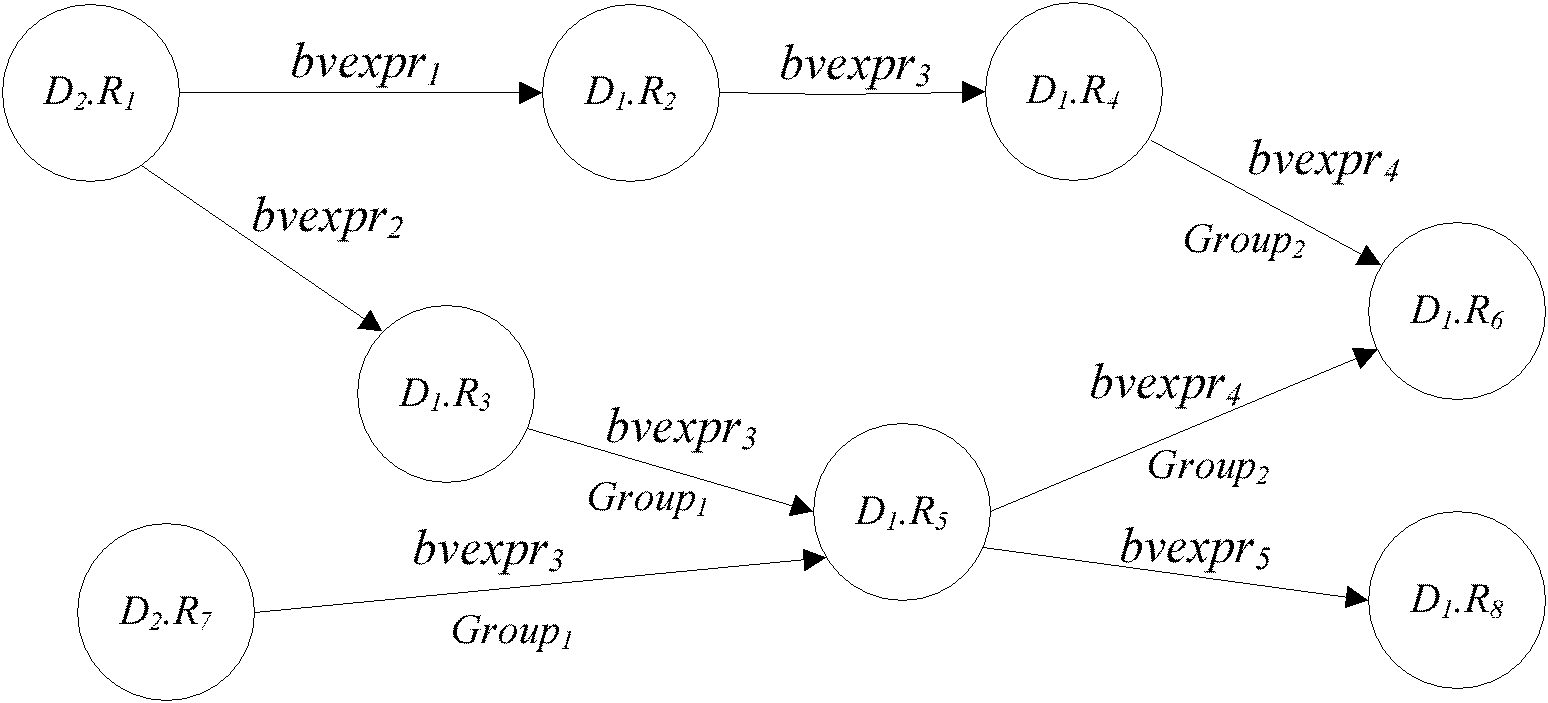
Calculable creditworthiness-based access control method under distributed environment of multiple trusting domains
InactiveCN101888341AIncrease permissionsImprove the trust management mechanismDigital data protectionData switching networksResource informationNetworked system
The invention relates to a calculable creditworthiness-based access control method under the distributed environment of multiple trusting domains in the technical field of network. The method comprises the following steps of: logging in a target trusting domain by a user, and giving the trusting domain a role set of the user by role mapping and role changing; trying acquiring resource informationin the target domain by the user; inquiring a delegated strategy database; updating user behavior variable values in an accumulation behavior library, and updating the times of executing user behaviors corresponding to outland roles in a behavior evaluating library; changing the role on the basis of the behavior; generating behavior evaluation vectors, and calculating a fame value of the role; and regulating a role mapping strategy related to the role. The method realizes dynamic trust management of role mapping, role changing and fame feedback, improves interaction capacity between the trusting domains and the user, improves flexibility, security and reliability of access control in the trusting domains, and effectively solves the problems of user authorization and resource management inservice of network systems by taking the user behavior as trusted evaluation objects.
Owner:SHANGHAI JIAO TONG UNIV
Agriculture and forestry pest and disease monitoring and management system
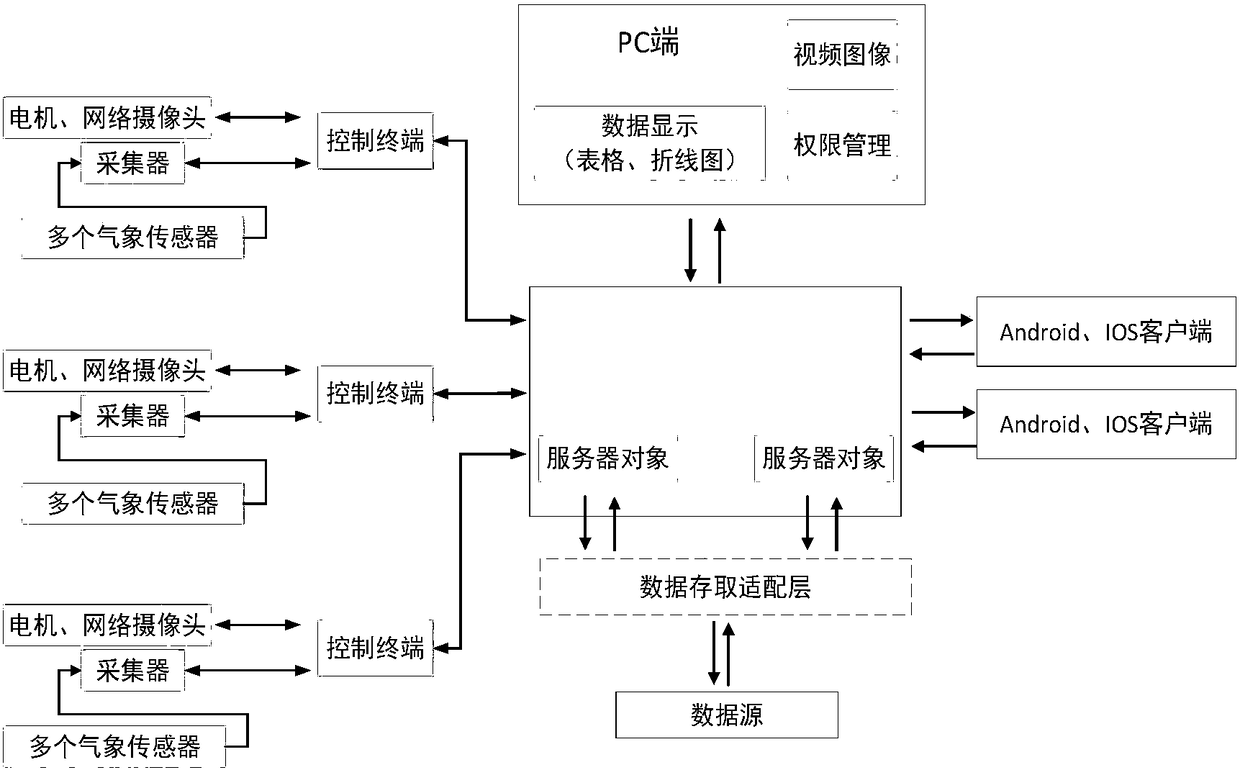
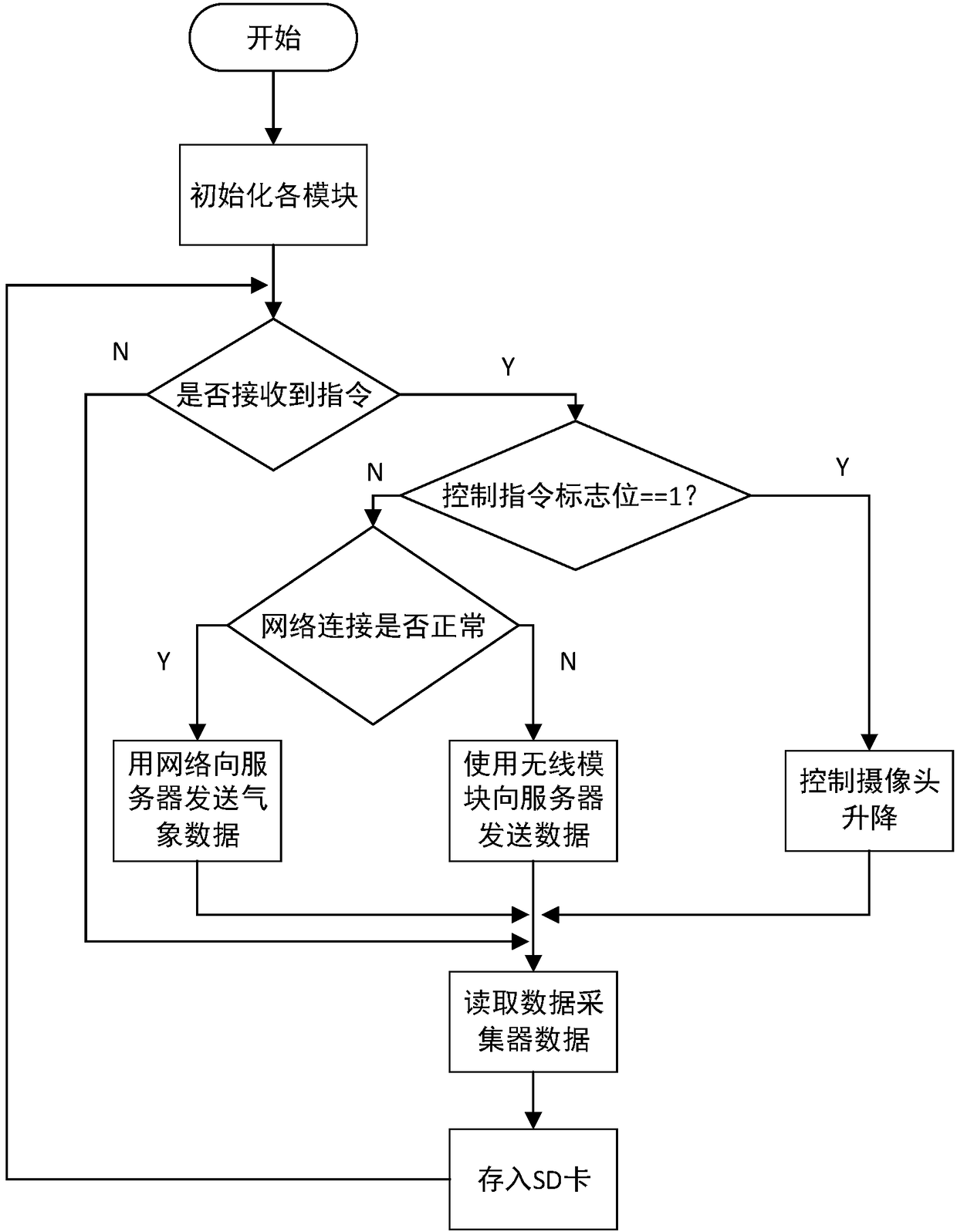
InactiveCN108111614AAvoid confusionRealize the early warning effectIndication of weather conditions using multiple variablesTransmissionDisease monitoringThe Internet
An agriculture and forestry pest and disease monitoring and management system uses the Internet of Things technology, relates to the technical field of system integration and software development, ishighly integrated and excellent in function completeness and forms a relatively complete entirety from a hardware acquisition end to a server receiving end and further to a client side (a remote PC side and a mobile phone APP). The system realizes that the client side can remotely control a camera of the hardware acquisition end through a server to move up and down and acquire meteorological data.The system realizes remote control on a hardware device through the server, controls the camera to go up and down, can take video images in multiple angles, and realizes multi-point monitoring and multi-user access. Intellectualization is reflected fully, a problem that agriculture and forestry experts have to go to farmlands to perform observation is solved, and the experts can check anytime anywhere. An early warning part also reminds people to make corresponding measures. Mass data obtained provide a sufficient data basis for later analysis of crop optimal growth environment, and so on.
Owner:BEIJING UNIV OF TECH
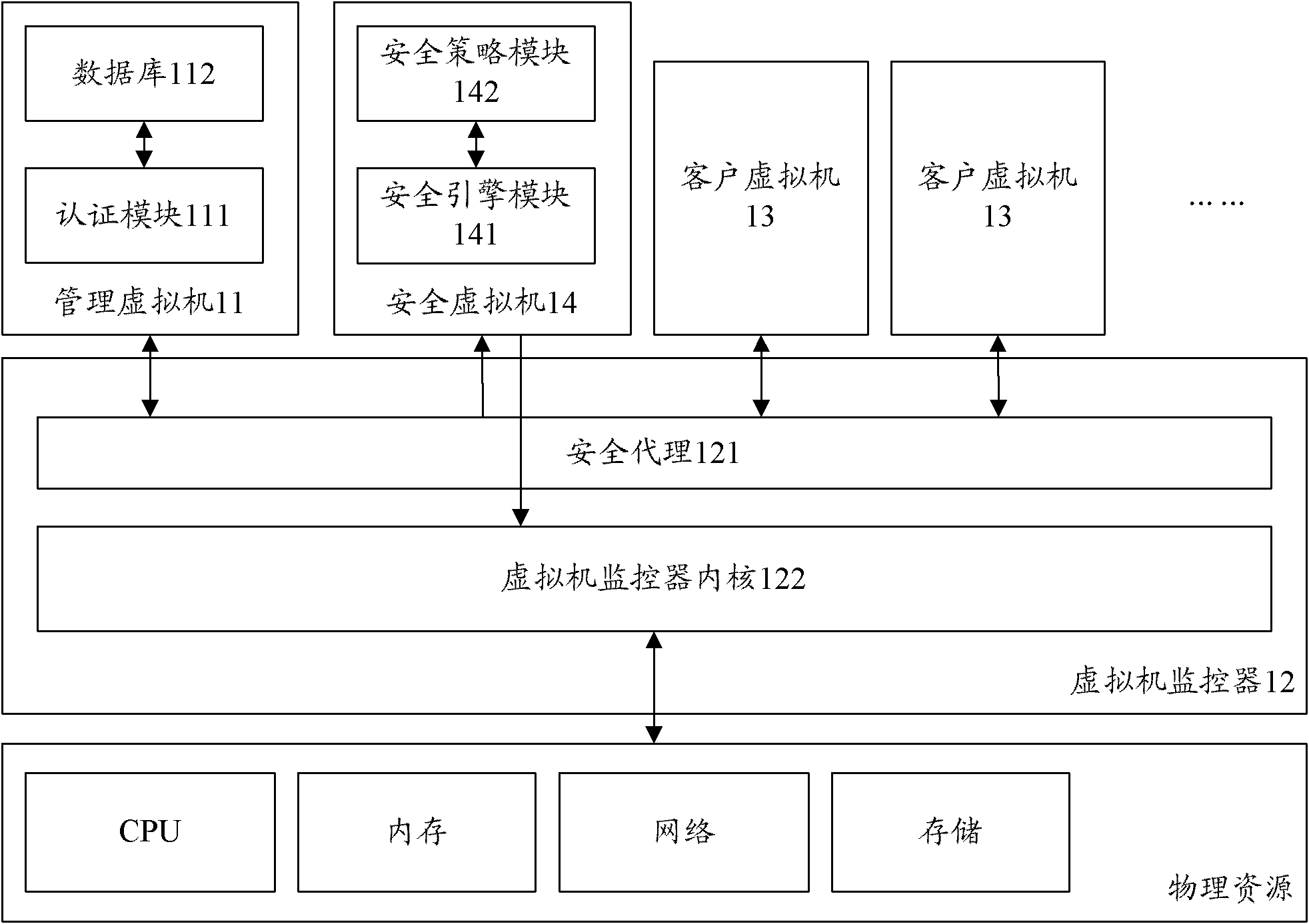
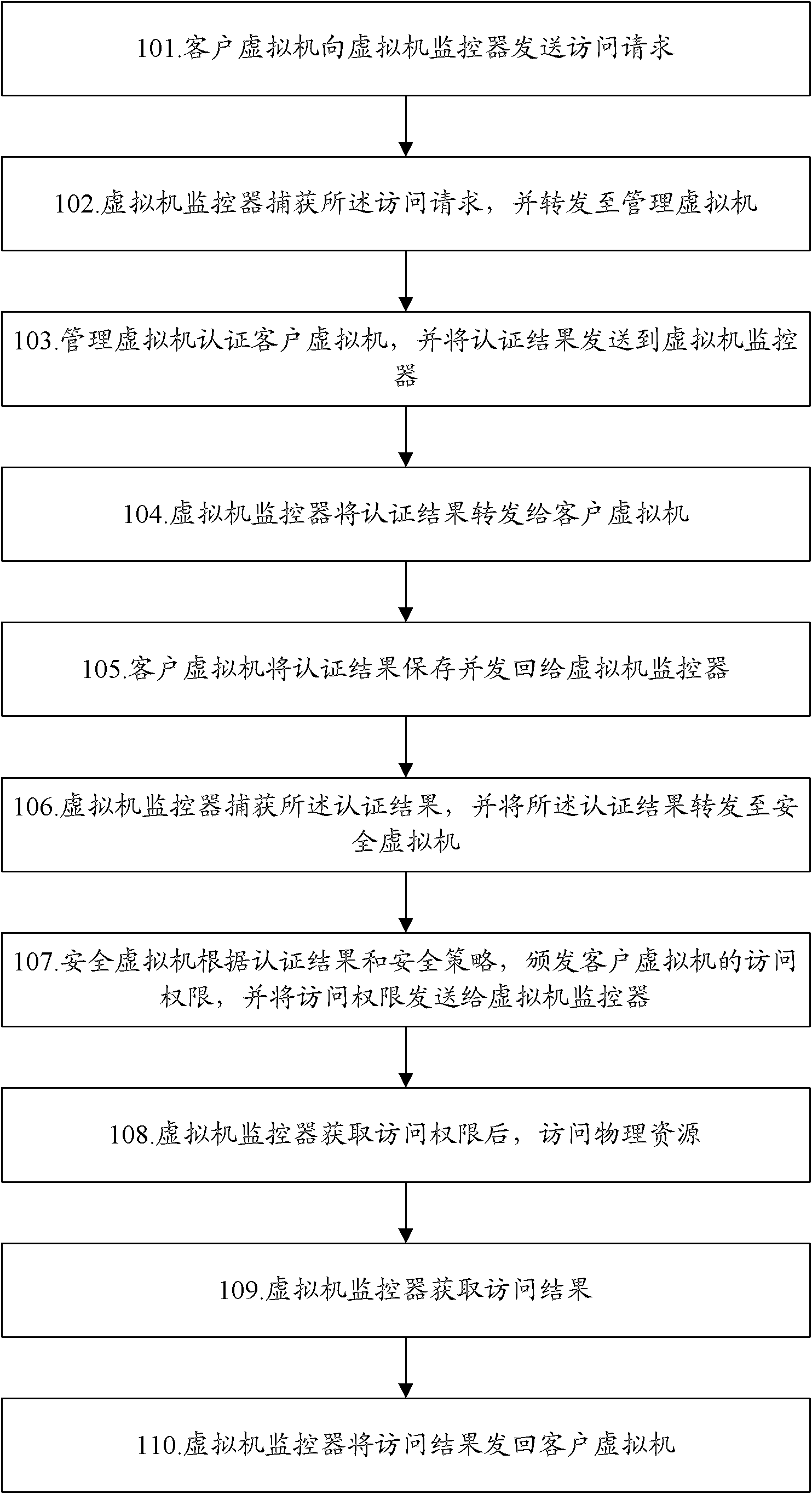
Virtual machine system and safety control method thereof
ActiveCN102811239AAvoid attackAvoid resource hoggingTransmissionSoftware simulation/interpretation/emulationSafety controlWorkload
The invention discloses a virtual machine system which comprises a management virtual machine, a virtual machine monitor, a client virtual machine and a safety virtual machine. The management virtual machine is used for authenticating the client virtual machine and sending an authenticated result to the virtual machine monitor. The virtual machine monitor is used for transmitting an access request sent from the client virtual machine to the management virtual machine. The authenticated result sent from the management virtual machine is transmitted to the client virtual machine. The authenticated result sent from the client virtual machine is transmitted to the safety virtual machine. According to access permission, physical resources are accessed and an access result is returned to the client virtual machine. The client virtual machine is used for sending the access request and the authenticated result to the virtual machine monitor. The safety virtual machine is used for issuing the access permission of the client virtual machine to the virtual machine monitor. The invention further discloses a safety control method of the virtual machine system. With the system and the method, workload of the virtual machine monitor can be lowered, the access permission of the client virtual machine can be flexibly controlled, and the access of the client virtual machine to the physical resources is effectively controlled.
Owner:ZTE CORP
Method for controlling access permissions of electronic document
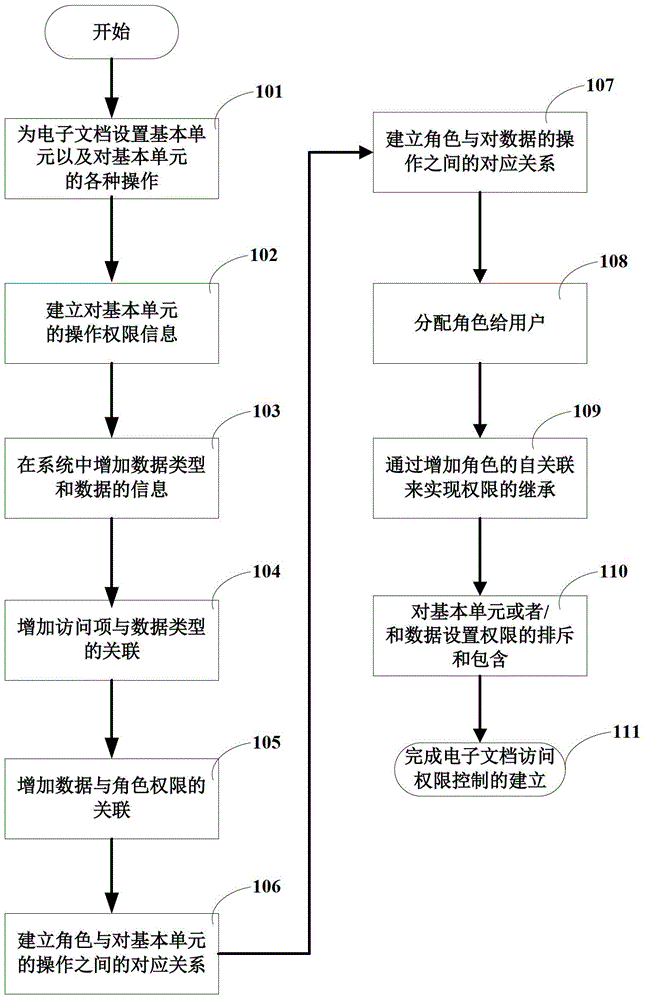
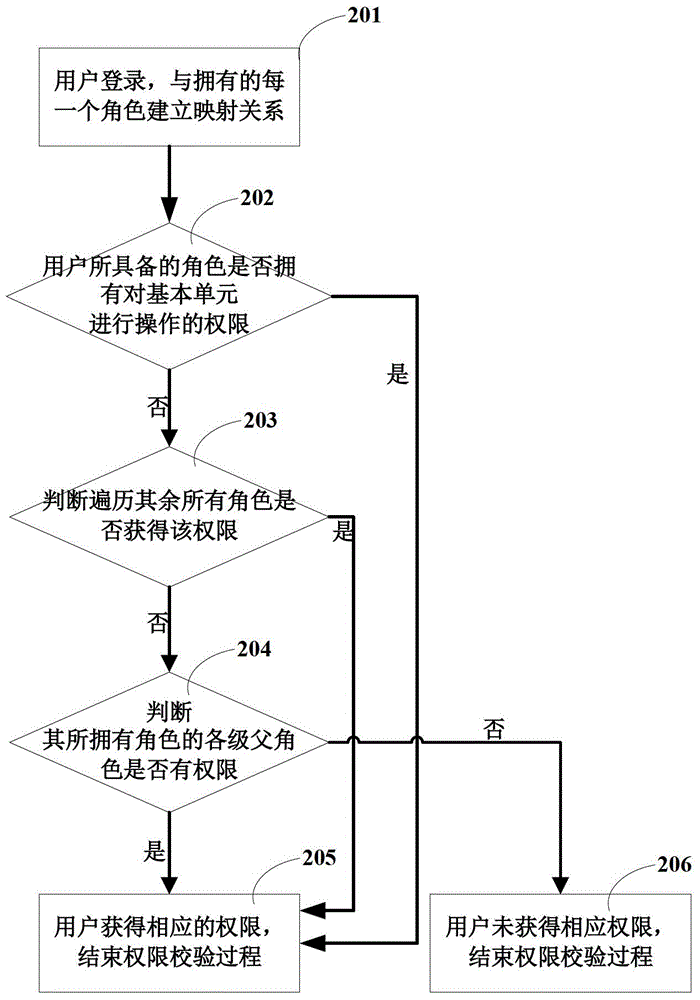
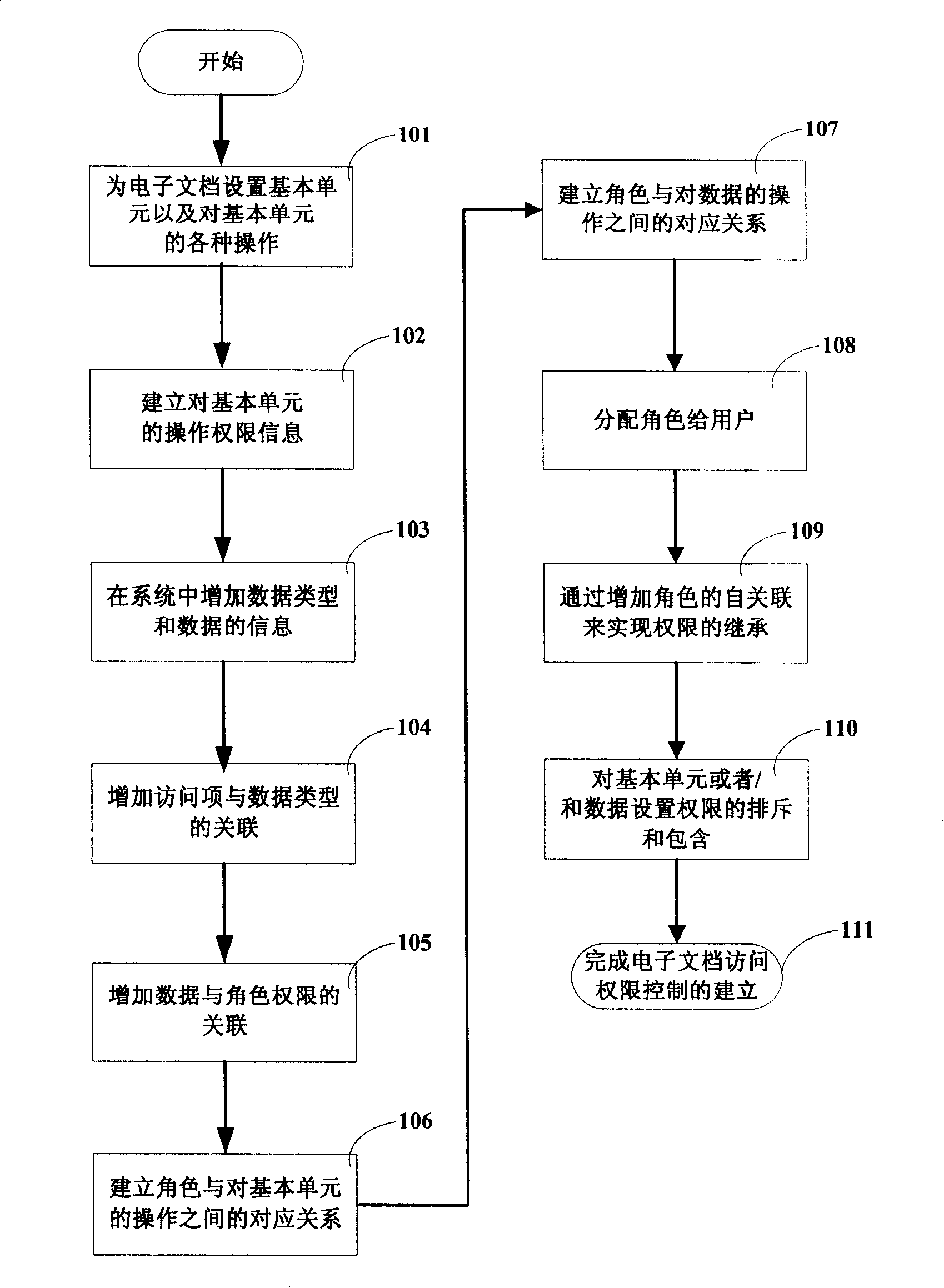
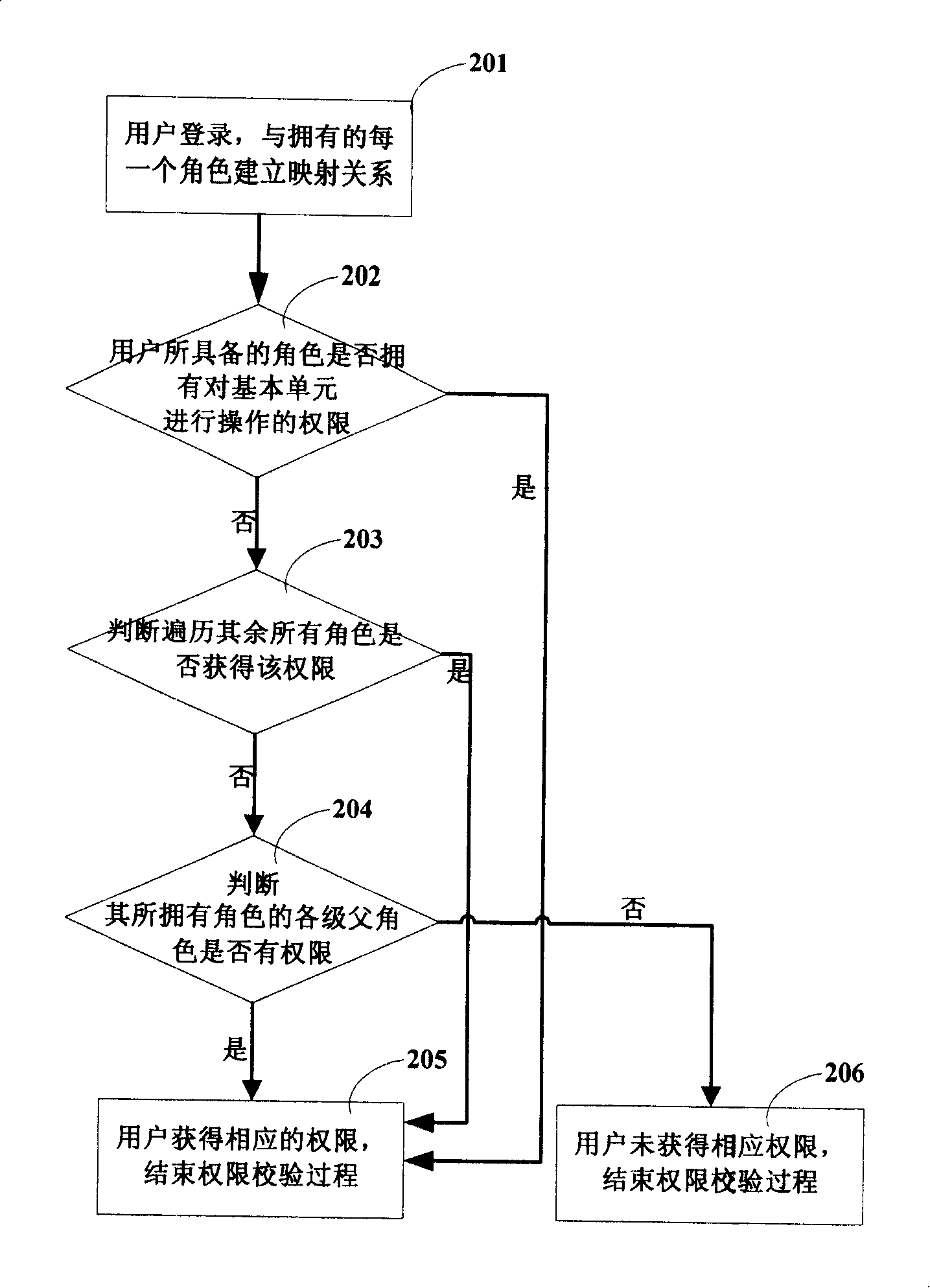
InactiveCN104463005AControl accessEnsure safetyDigital data protectionElectronic documentControl electronics
The invention discloses a method for controlling access permissions of an electronic document. The electronic document is composed of at least two basic units, and the basic units with permissions each have at least one permission. When a user has access to the electronic document, the user has access to the basic units in the electronic document and obtains the permissions corresponding to the basic units. On the basis of the electronic document, the granularity of safety control is decreased to a more detailed basic unit level, and safety of the electronic document is effectively guaranteed by technological means.
Owner:TIANJIN SURSEN INVESTMENT CO LTD
Method for controlling access authority of electric document
InactiveCN101226573AControl accessEnsure safetyDigital data protectionOffice automationElectronic documentControl electronics
The invention discloses a method for control access rights of electronic documents. The electronic document is composed of at least two basic units, and a unit arranged with access right has at least one access right. When accessing the electronic document, users assess the basic unit in the electronic document and acquire an access right corresponding to the basic unit. Electronic documents based on the technique reduces the granularity of safety control to a more detailed basic unit level, and effectively ensures safety of electronic documents by using technical means.
Owner:TIANJIN SURSEN INVESTMENT CO LTD +1
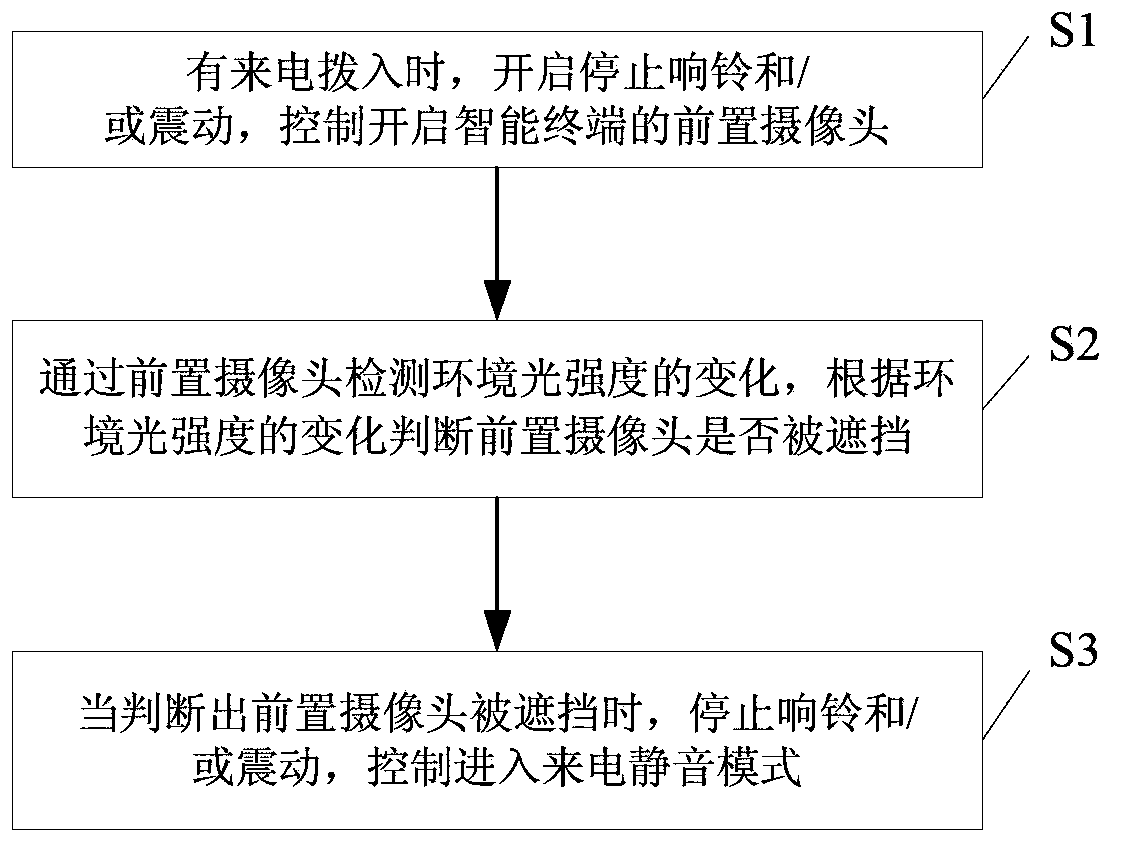
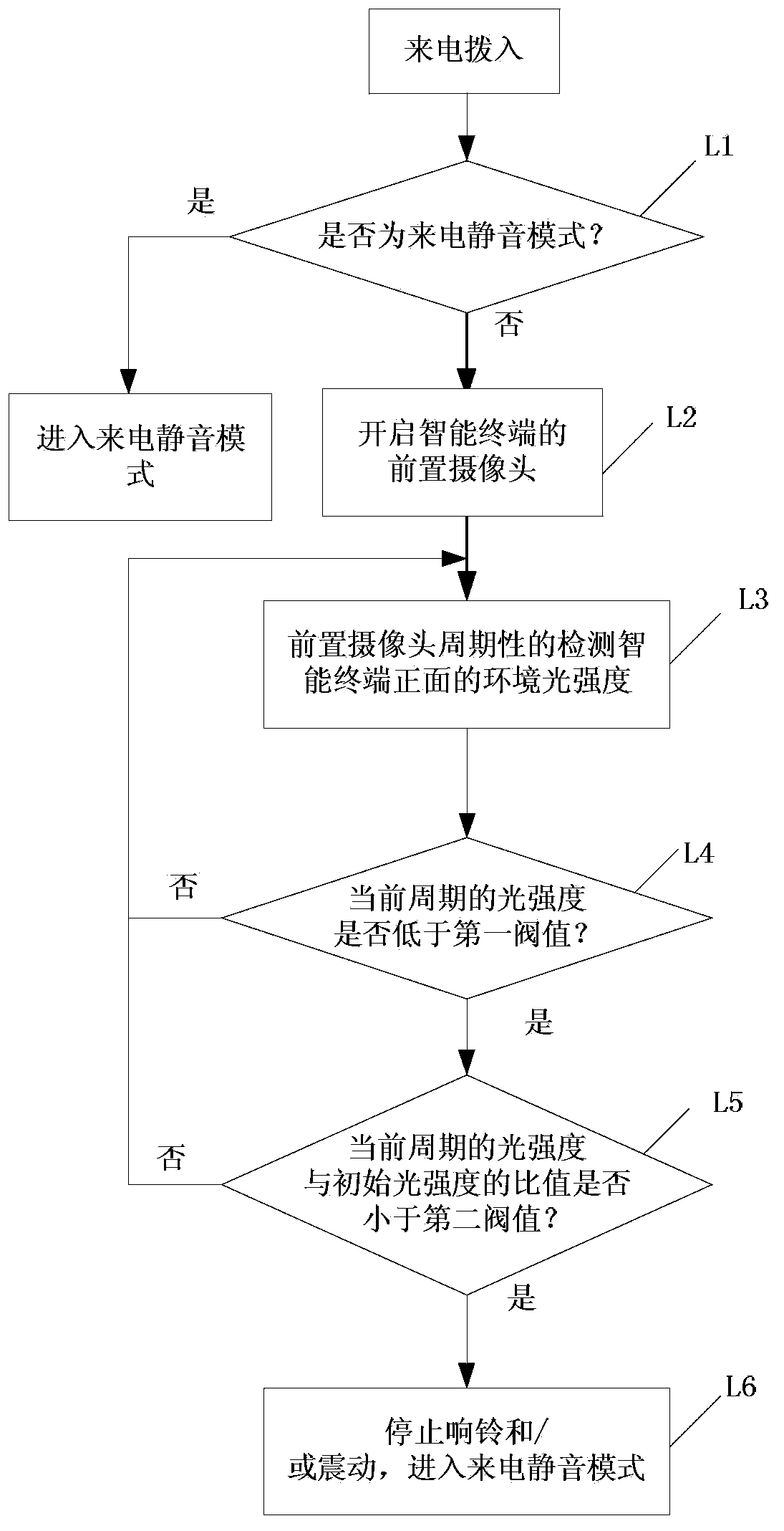
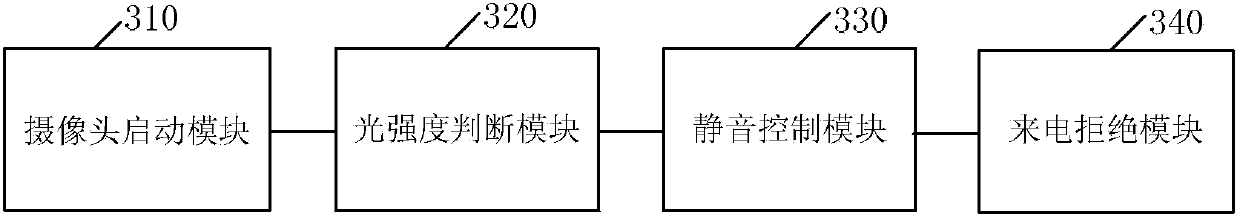
Method and device for realizing silent incoming call of intelligent terminal
The invention discloses a method and a device for realizing a silent incoming call of an intelligent terminal. The method comprises the steps of: controlling to start up a pre-positioned camera of the intelligent terminal when an incoming call exists; detecting the change of environmental light intensity through the pre-positioned camera, judging whether the pre-positioned camera is shielded based on the change of the environmental light intensity; when the pre-positioned camera is judged to be shielded, stopping the ring and / or vibration, and controlling to enter into an incoming call silent mode. If a user turns the screen of the intelligent terminal towards a desktop or shields the pre-positioned camera of the intelligent terminal by using gestures when the intelligent terminal rings and / or vibrates caused by an incoming call, the intelligent terminal can be controlled to stop ringing and / or vibrating through the change of the environmental light intensity which is detected by the pre-positioned camera and enter into the incoming call silent mode so as to provide convenience for the user.
Owner:SHENZHEN HUIYE COMM TECH
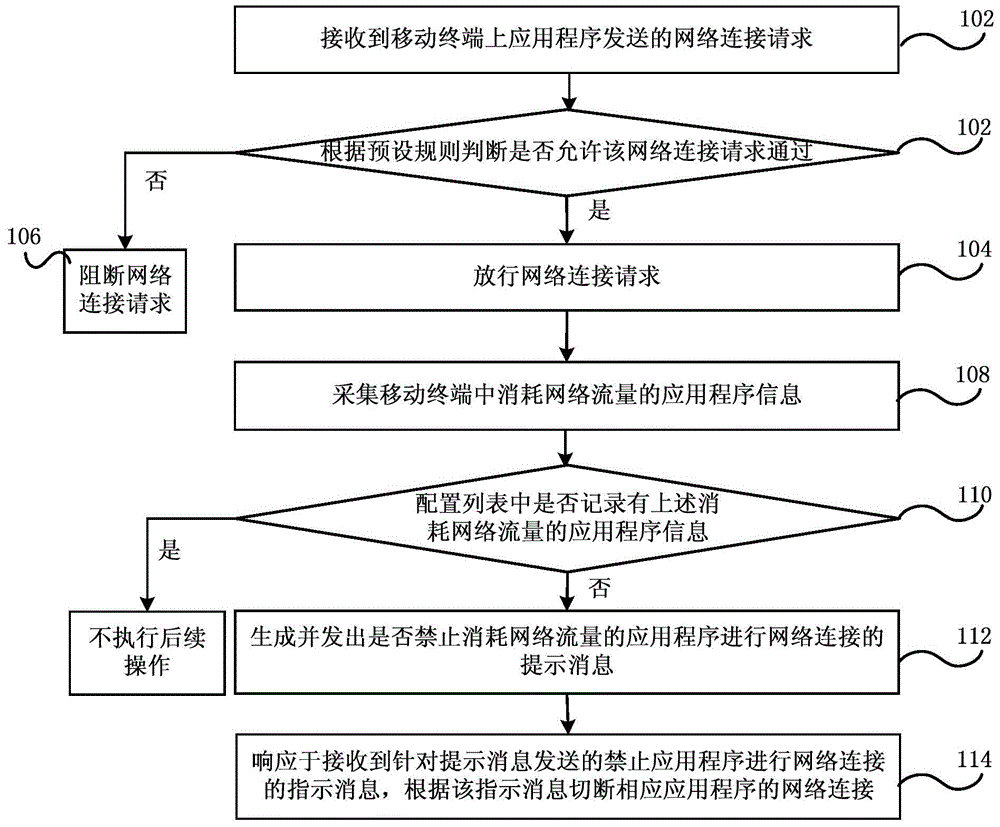
Networking control method, device and system, security gateway and mobile terminal
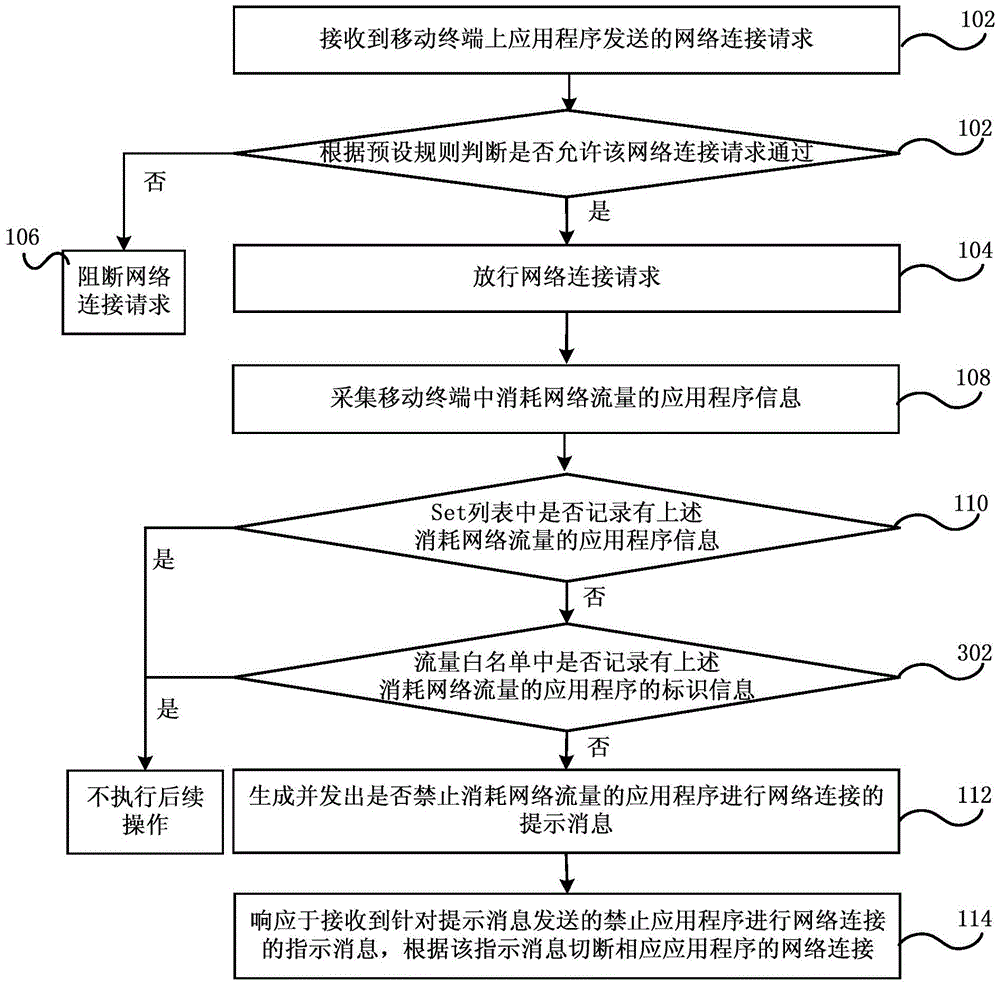
ActiveCN105704066AControl accessEnsure safetyData switching networksTraffic capacityNetwork connection
The embodiment of the present invention discloses a networking control method, device and system, a security gateway and a mobile terminal, wherein the method comprises the steps of using the security gateway to determine whether to allow a network connection request to pass according to a preset rule aiming at the network connection request sent by an application program on the mobile terminal; if not, blocking the network connection request; if yes, passing the network connection request; acquiring the information of the application programs consuming the network flow in the mobile terminal; querying whether the information of the application programs consuming the network flow is recorded in a pre-generated configuration list, wherein the application programs operated at the foreground at different time are recorded in the configuration list; if the information of the application programs consuming the network flow is not recorded in the pre-generated configuration list, generating and sending out a prompting message whether to forbid the application programs consuming the network flow to connect a network, and when the prompting message of forbidding the application programs consuming the network flow to connect the network is received, cutting the network connection of the corresponding application program. According to the embodiment of the present invention, the differentiated management of the flow generated by the application programs can be realized.
Owner:BEIJING QIHOO TECH CO LTD
Access control system and access control method of fine-grained privacy security
ActiveCN104683362AGuarantee data securityMeet fine-grained privacy protection requirementsTransmissionUser privacyMedia access control
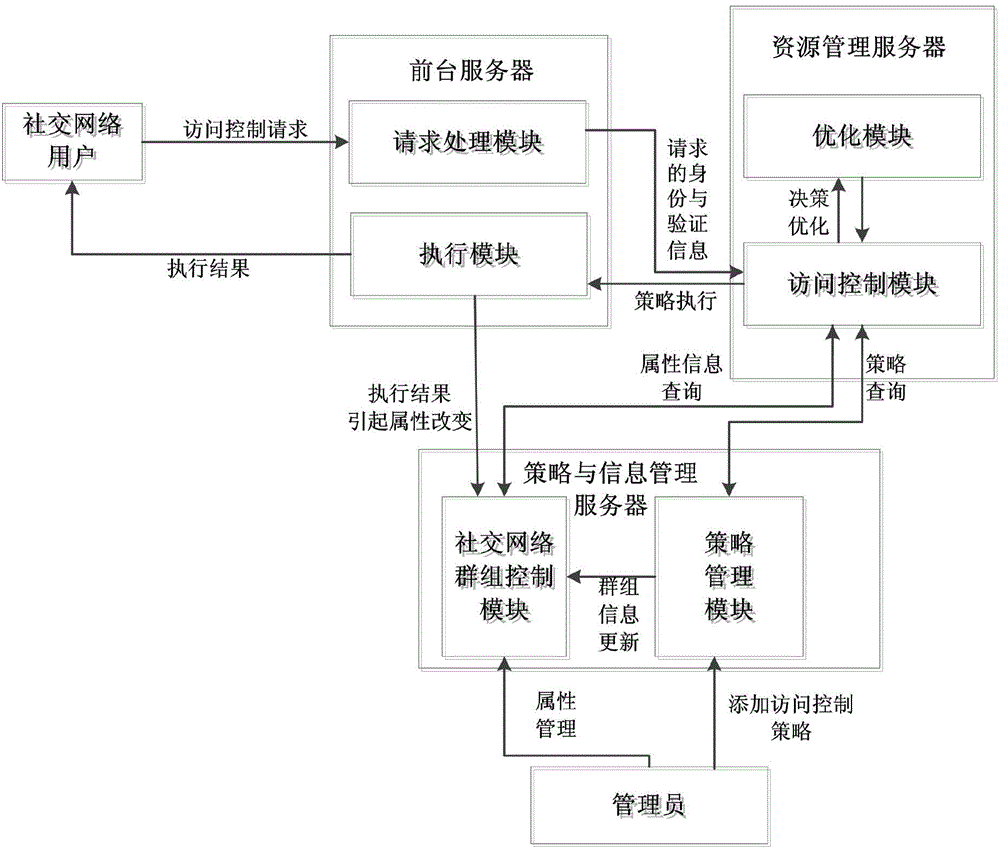
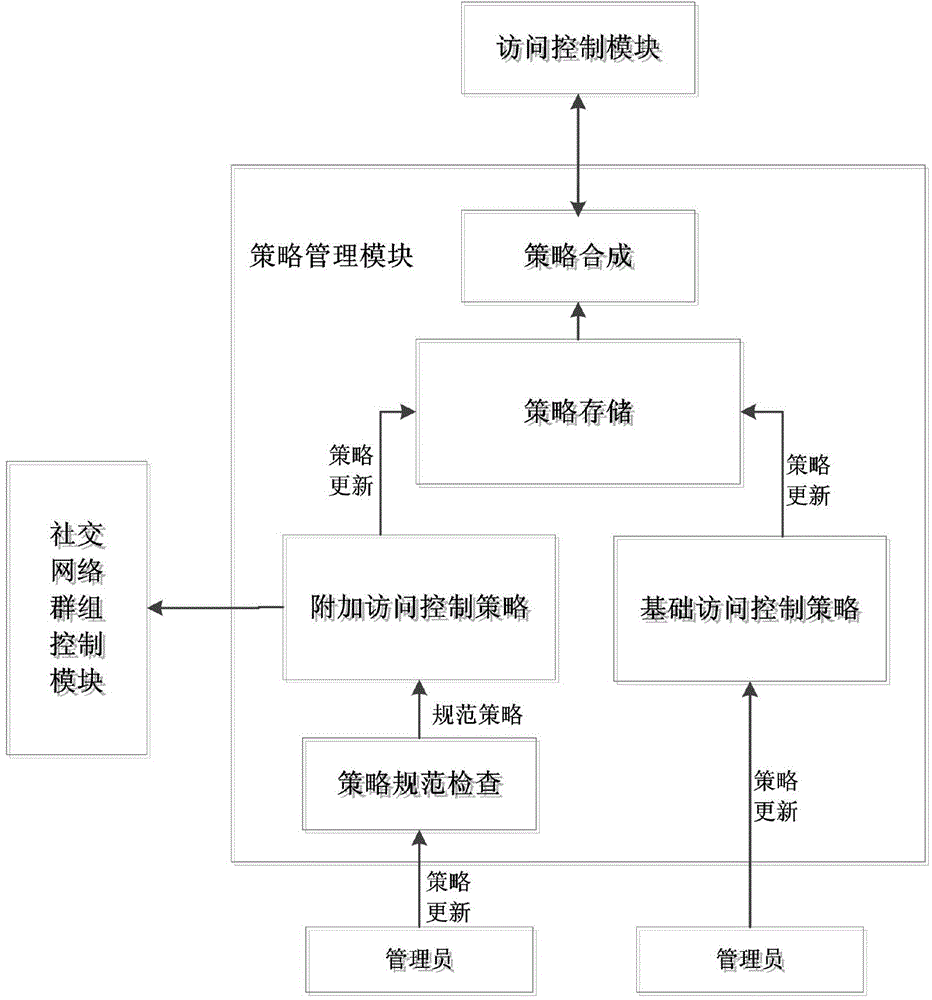
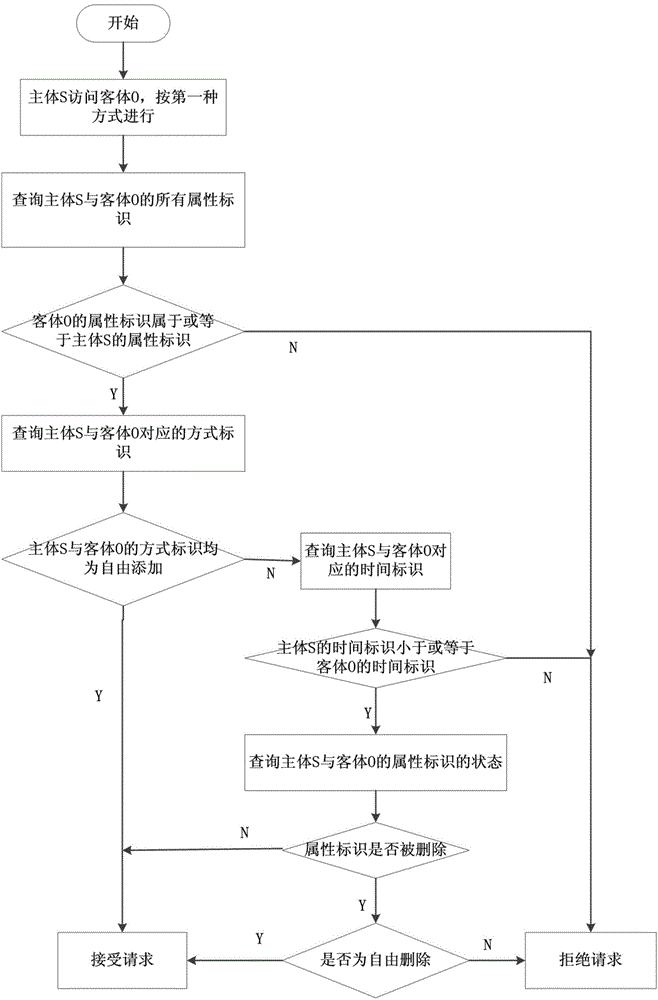
The invention discloses an access control system and an access control method of the fine-grained privacy security. The access control system of the social networking service fine-grained privacy security comprises a strategy management module, a social networking service group control module, a request processing module, an access control module, an optimizing module and an execution module. The strategy management module is used for maintaining and combining access control strategies; the social networking service group control module is used for maintaining all attribute sets; the request processing module is used for verifying identification; the access control module is used for carrying out the decision for the access request to obtain a decision result; the optimizing module is used for carrying out the exclusiveness processing on the decision result; the execution module is used for executing the decision result. The access control system is used for controlling the security of data flow in the social networking service, a more fine-grained access control mechanism is provided for a user, the user privacy can be protected, and the application requirement of the social networking service can be met.
Owner:HEFEI UNIV OF TECH
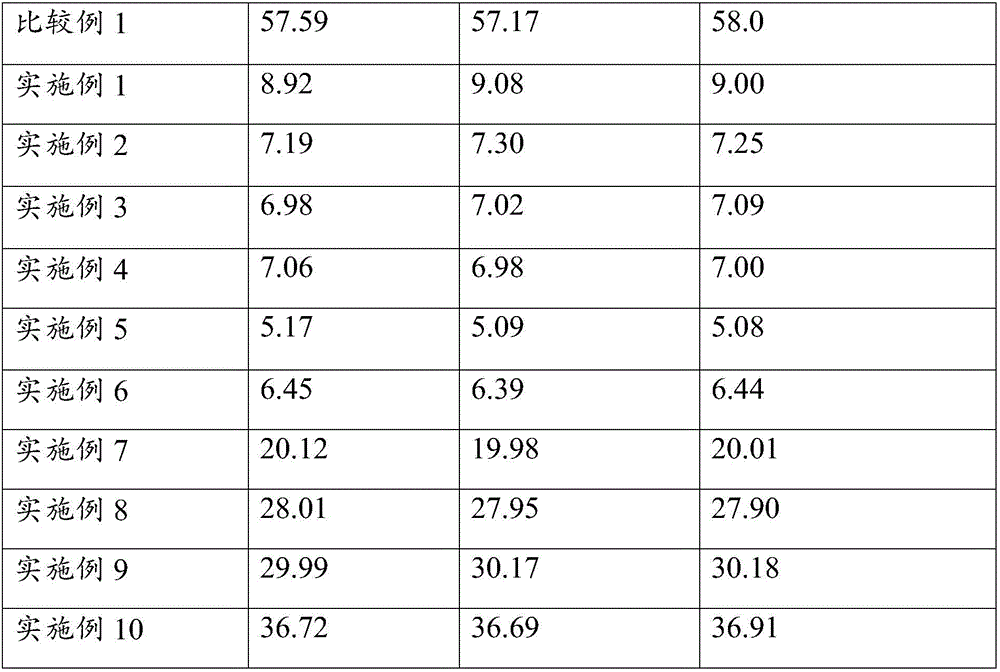
Formation method and lithium-ion secondary battery
ActiveCN106785148AImprove comprehensive electrochemical performanceImprove formation qualitySecondary cells charging/dischargingLithium electrodeEngineering
The invention provides a formation method and a lithium-ion secondary battery, and relates to the technical field of lithium-ion batteries. The invention provides a formation method. The lithium-ion battery is formed through four formation stages which are sequentially carried out. The formation current of the four formation stages is gradually increased, and negative pressure extracted for four times is also linearly increased. According to the formation method, the formation quality of an SEI film can be effectively improved and the bulging rate of the lithium-ion battery is reduced, so that the comprehensive electrochemical properties of the lithium-ion battery are improved. According to the lithium-ion secondary battery, an electrolyte of the lithium-ion secondary battery is a non-aqueous system and formation treatment is carried out by using the formation method. The lithium-ion secondary battery does not easily bulge in the using process and has good comprehensive electrochemical properties.
Owner:深圳一特科技有限公司
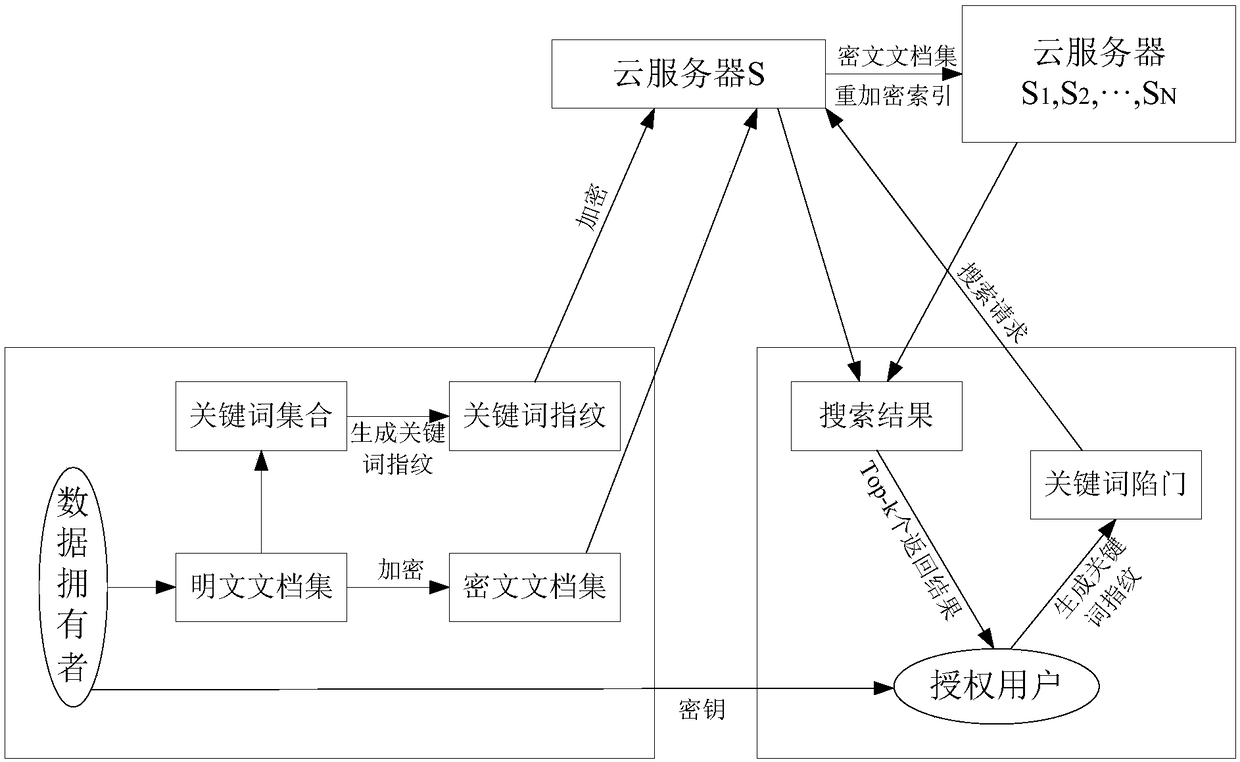
Fuzzy keyword search method oriented to multi-server and multi-user
InactiveCN108062485AImprove processing powerFix security issuesDigital data protectionSpecial data processing applicationsFingerprintTrap door
The invention discloses a fuzzy keyword search method oriented to multi-servers and multi-users. The method comprises the steps: a data owner encrypts a clear-text set into a cipher-text set, extractsa keyword set, generates an index of a clear-text document set based on a MinHash and stores the cipher-text set and the encrypted index in a cloud server S; the cloud server S distributes the cipher-text set and the re-encrypted index to cloud servers S1, S2, ..., SN; an authorized user generates the keyword needing to be searched into a keyword fingerprint based on the Minhash to obtain a keyword trap door; and the cloud server S performs a Jaccard similarity comparison on the keyword trap door and the index and performs sorting, outputs a cipher-text document to the authorized user. According to the fuzzy keyword search method oriented to the multi-servers and the multi-users, through the use of a dimensionality reduction concept of the MinHash, fuzzy keyword search is realized; retrieval files are sorted by use of a Jaccard distance; and multi-user inquiry is realized by use of re-encryption and the efficiency of the fuzzy keyword search can be effectively improved.
Owner:BEIJING UNIV OF TECH
Method and device for improving safety of network ID authentication
ActiveCN101567878AImprove experienceImprove securityUser identity/authority verificationWeb serviceService provision
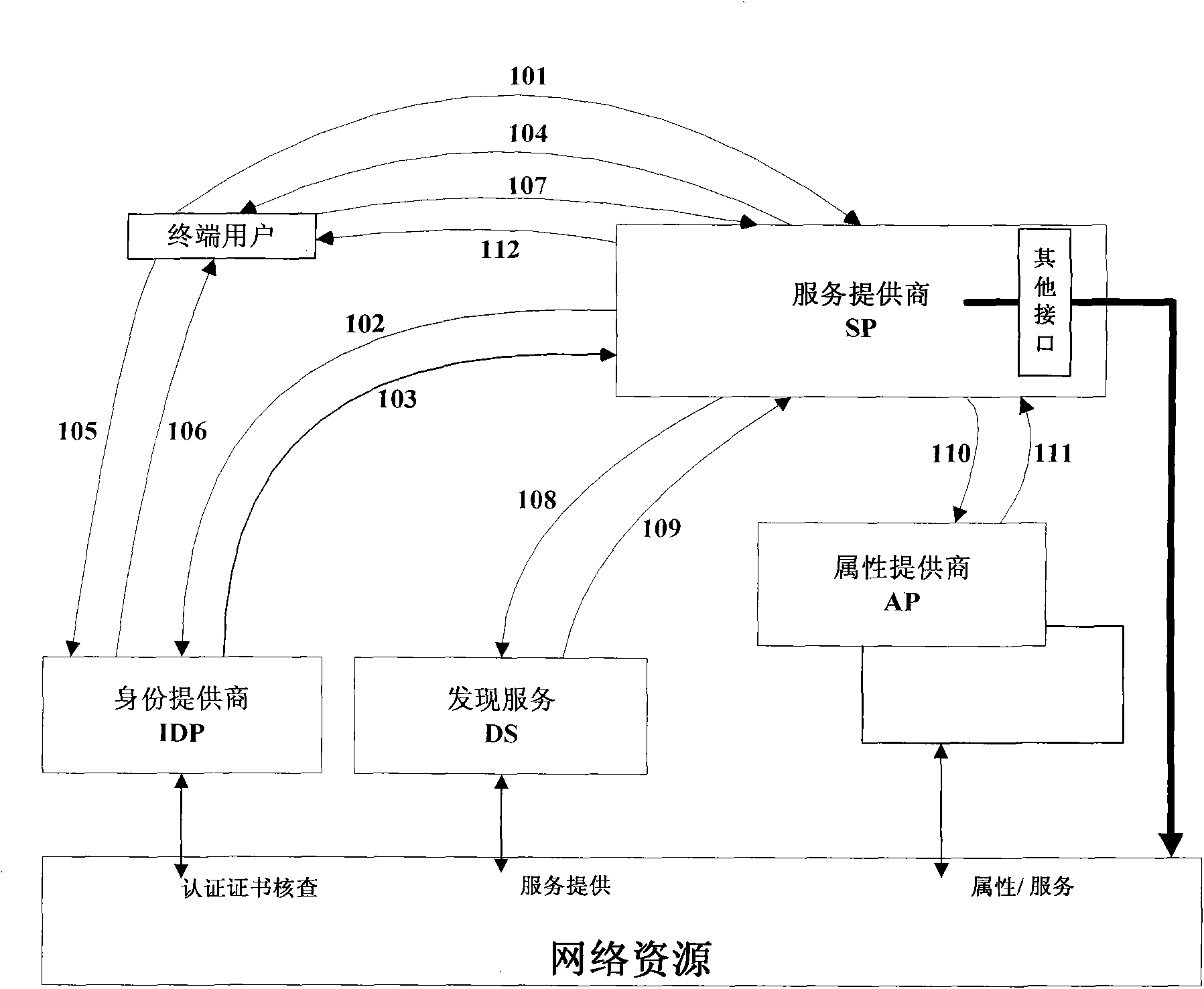
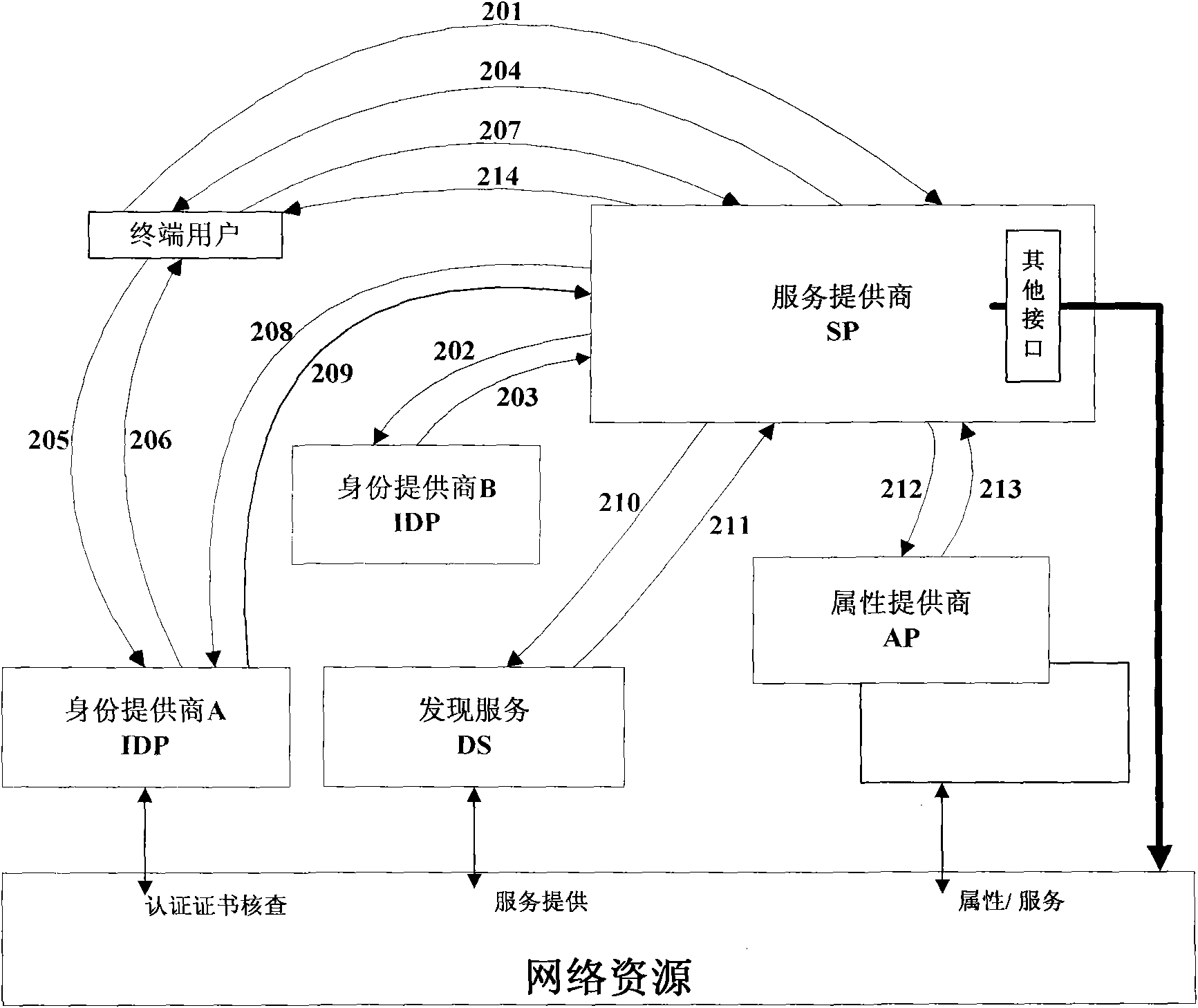
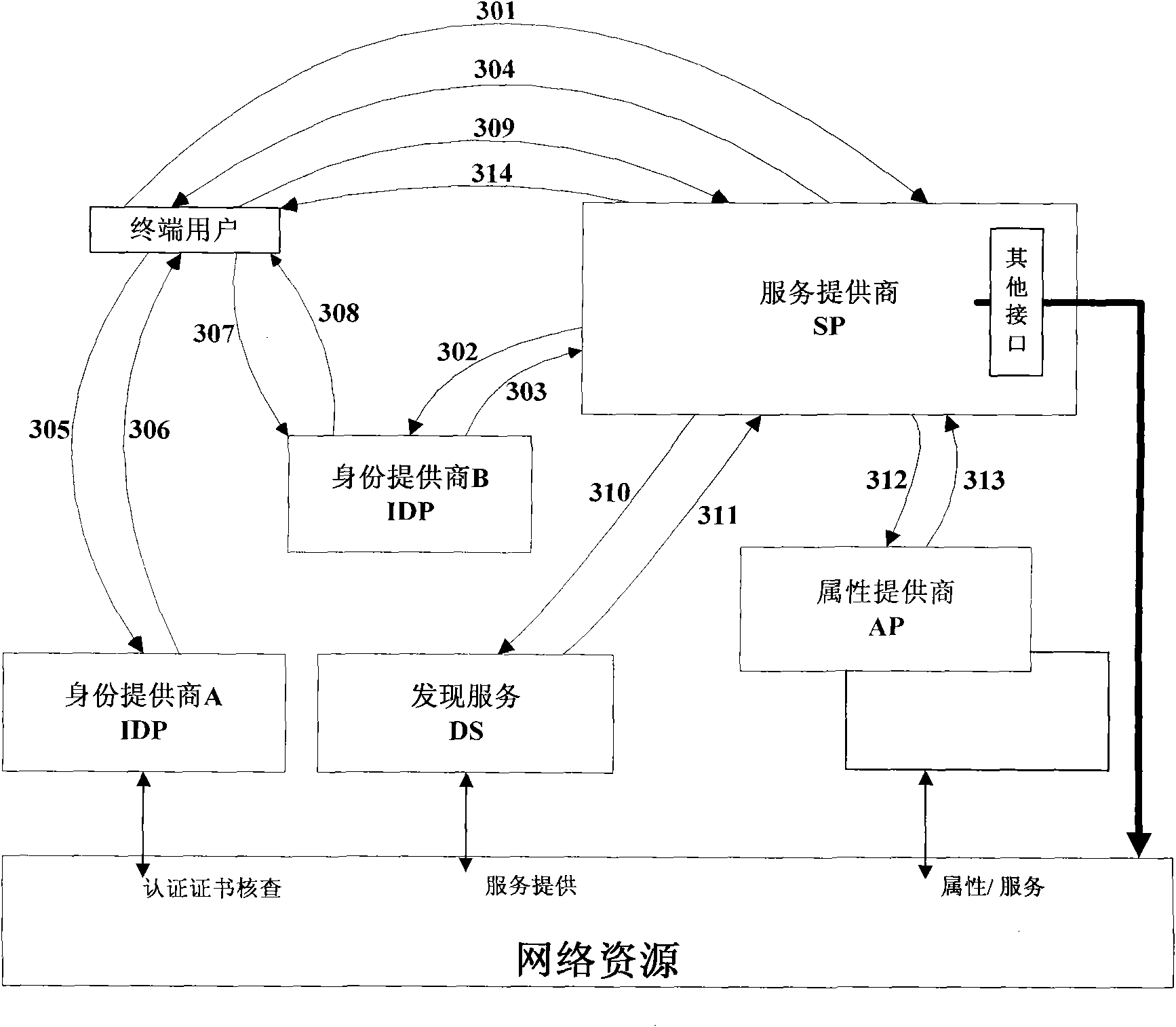
The invention discloses a method and a device for improving the safety of network ID authentication and a method and a device for realizing seamless switching in the single sign-on procedure, which are applied to web services and belong to the field of communication technology. The method for improving the safety of network ID authentication improves the safety of network ID authentication by executing network ID authentication to SP and terminal users or controlling network ID authentication according to the SP access right information, and can control the acquisition of the SP to the attribute information of the terminal users, thus the SP provides different services for the terminal users. The method for realizing seamless switching in the single sign-on procedure realizes the seamless switching in the single sign-on procedure by executing network ID authentication to the terminal users through the IDP to which the SP affiliated or executing authentication to the terminal users through the SP. The devices comprise an ID provider device and a service provider device.
Owner:HUAWEI TECH CO LTD
An identity control method based on credibility platform module and fingerprint identifying
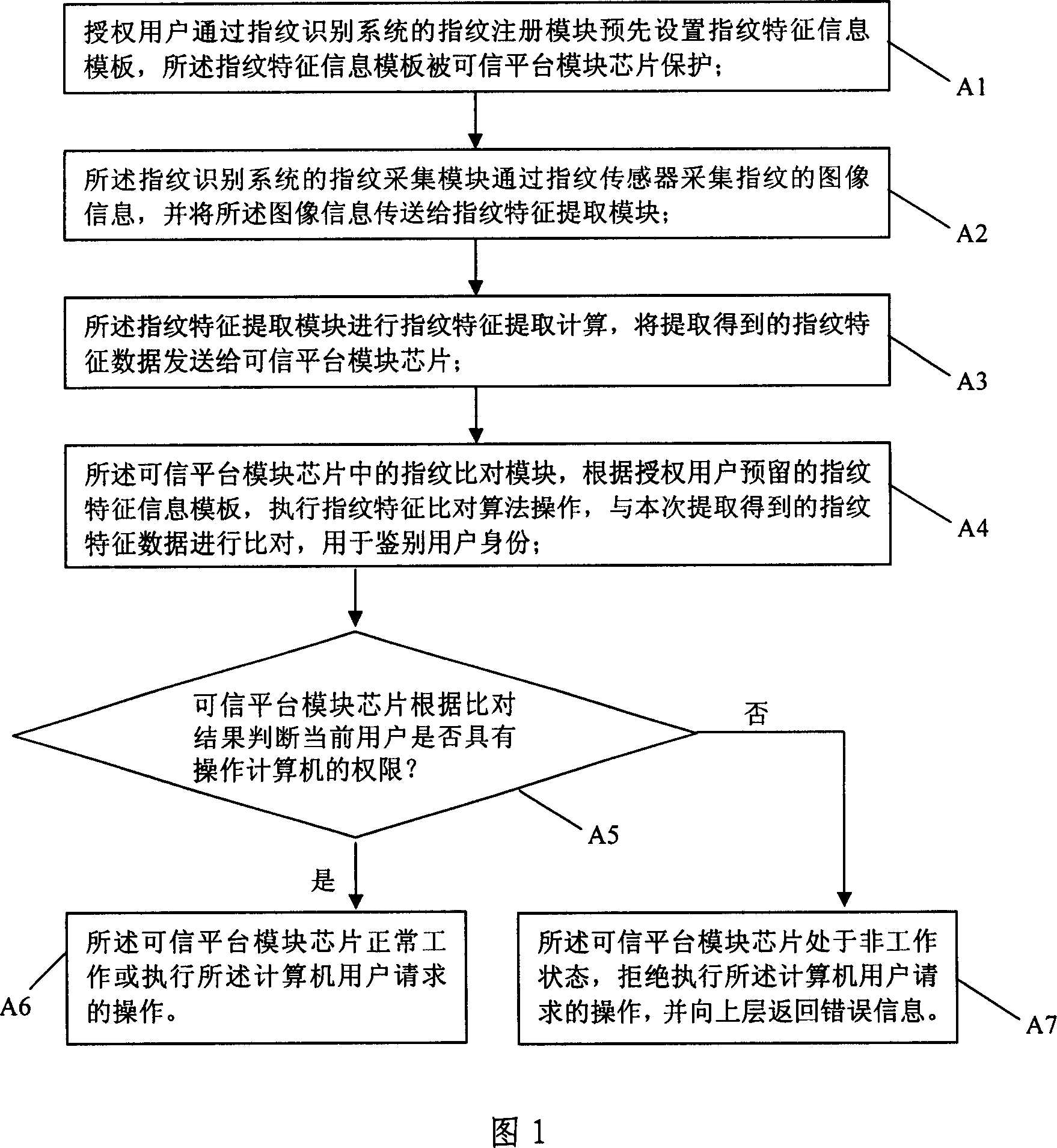
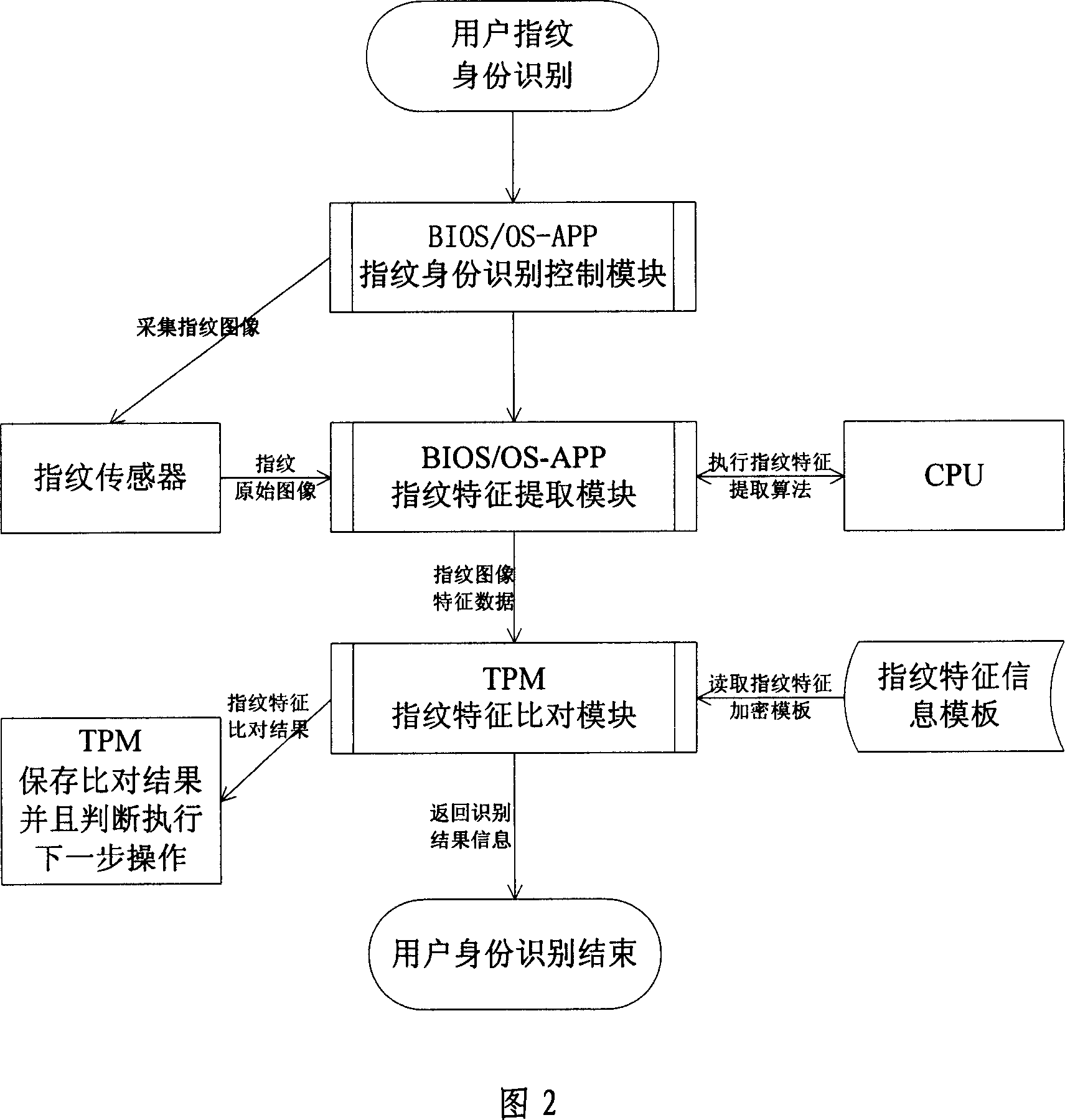
ActiveCN1971575AMake up for lack of computing powerImprove safety and reliabilityCharacter and pattern recognitionInternal/peripheral component protectionFingerprintTrusted Platform Module
The invention provides an identity control method based on TPM and fingerprint identification that includes steps: A1, presetting the fingerprint characteristic information module, the module is protected by the TPM; A2, the fingerprint collecting module collects the image information of present user's fingerprint, and the information is transmitted to the fingerprint extracting module; A3, the fingerprint extracting module extracts and calculates the characteristic of fingerprint, and the results is sent to the TMP chip; A4, The fingerprint comparison module of the TMP chip compares with the fingerprint characteristic data extracted this time according to the fingerprint characteristic module to identify the user's identity; A5, the TPM chip judges that the user has the authority to operate the computer according to the comparing result and to execute the step A6, otherwise execute the step A7; A6, the TPM chip works normally and executes the operation of user's requirement; A7, the TPM chip is in inactive state and rejects the operation of user's requirement, and return the error information for upper layer.
Owner:SHENZHEN SINOSUN TECH
Security reinforcement method and system for Linux system
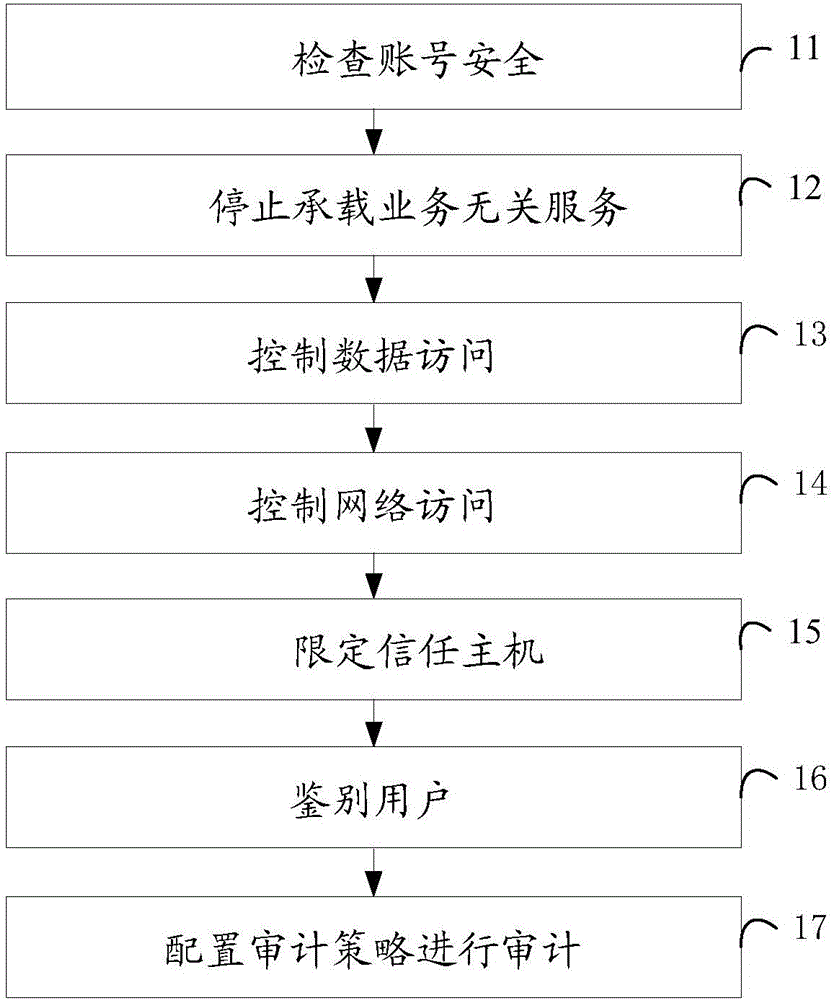
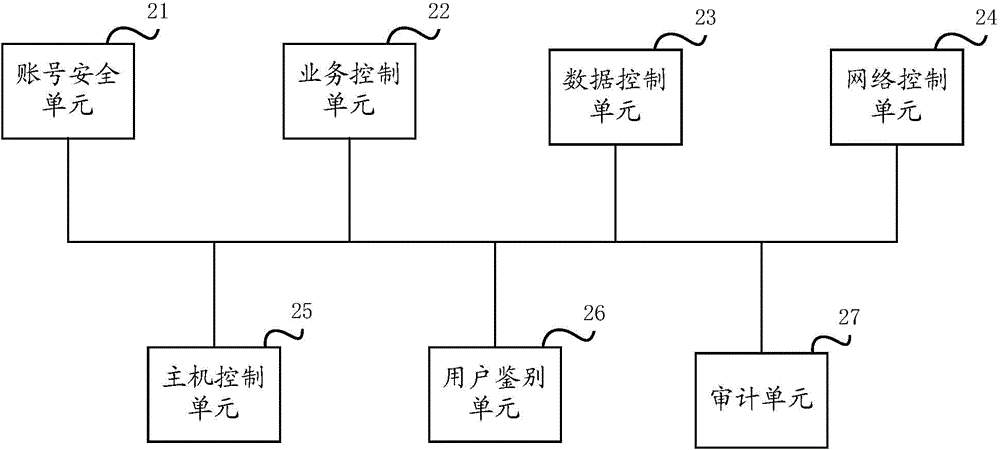
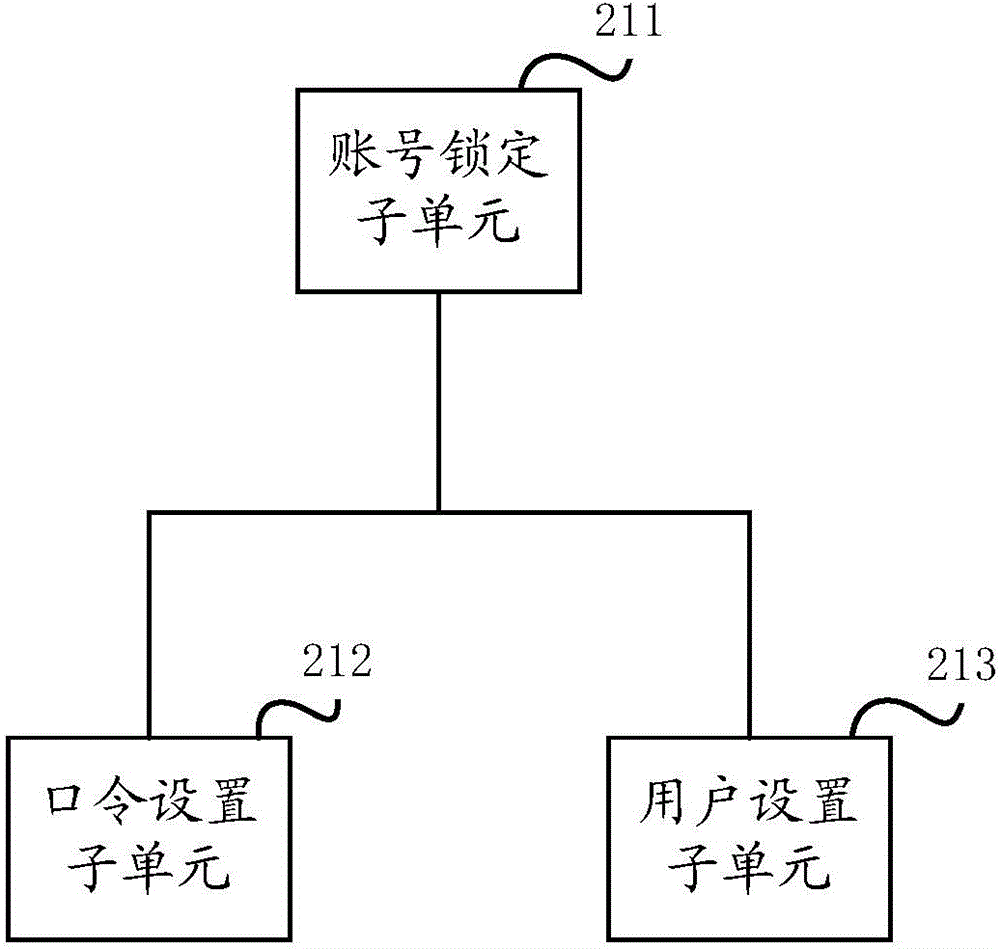
The invention discloses a security reinforcement method and system for a Linux system. The method includes the following steps that: a weak link in the system is automatically detected, and account security is checked; services unrelated to business are stopped; data access is controlled; network access is controlled; a trust host is limited; a user is authenticated; and an audit strategy is configured, and a series of automatic operations are audited. With the method adopted, security reinforcement work for the Linux system can be completed automatically; all processes that need to be executed manually can be executed automatically, so that time can be save; security reinforcement for the Linux system can be realized quickly; efficiency can be improved; and the security of the system can be enhanced.
Owner:上海天脉聚源文化传媒有限公司
IP access method and device of SSL VPN
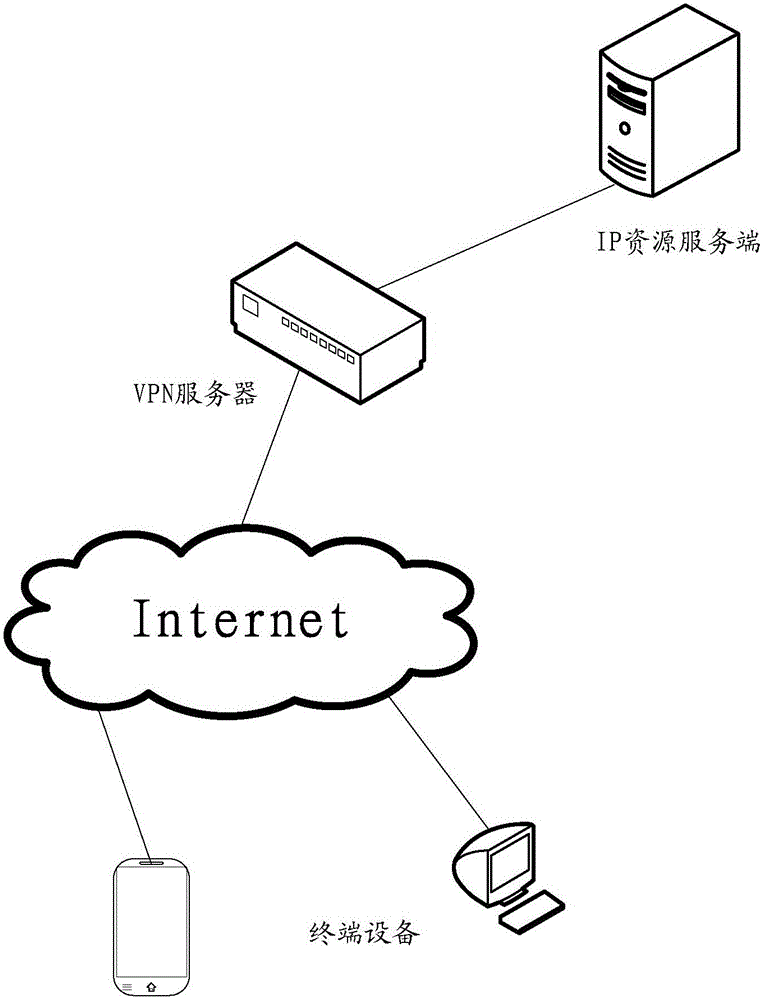
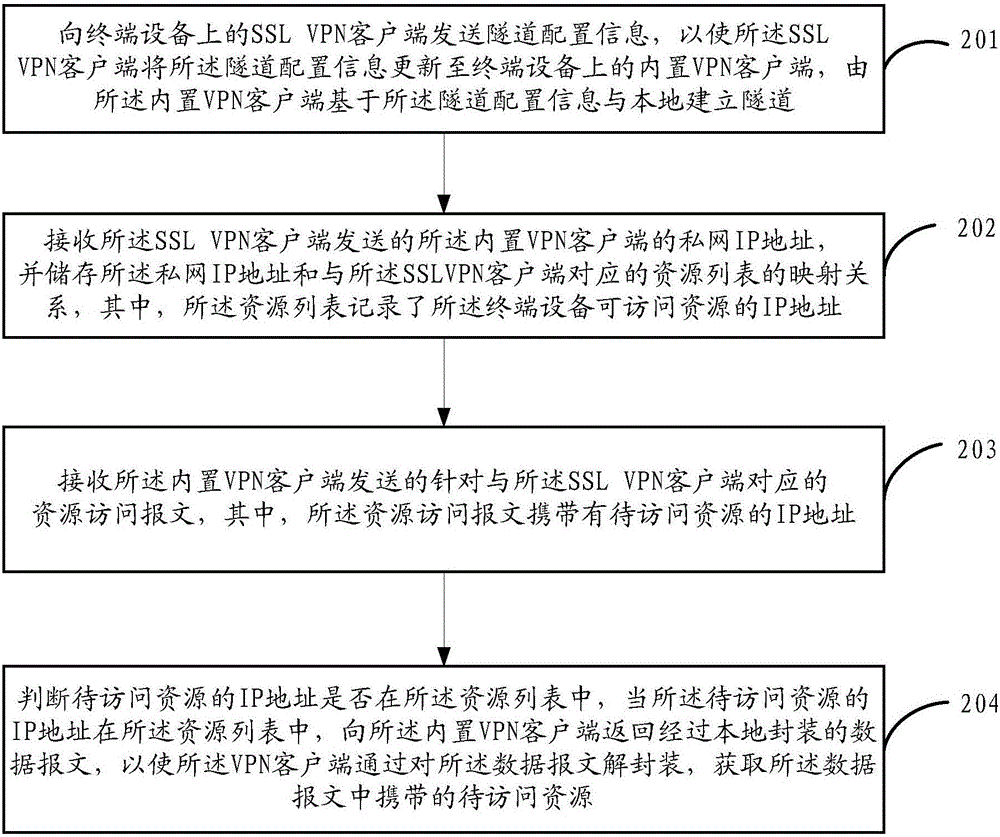
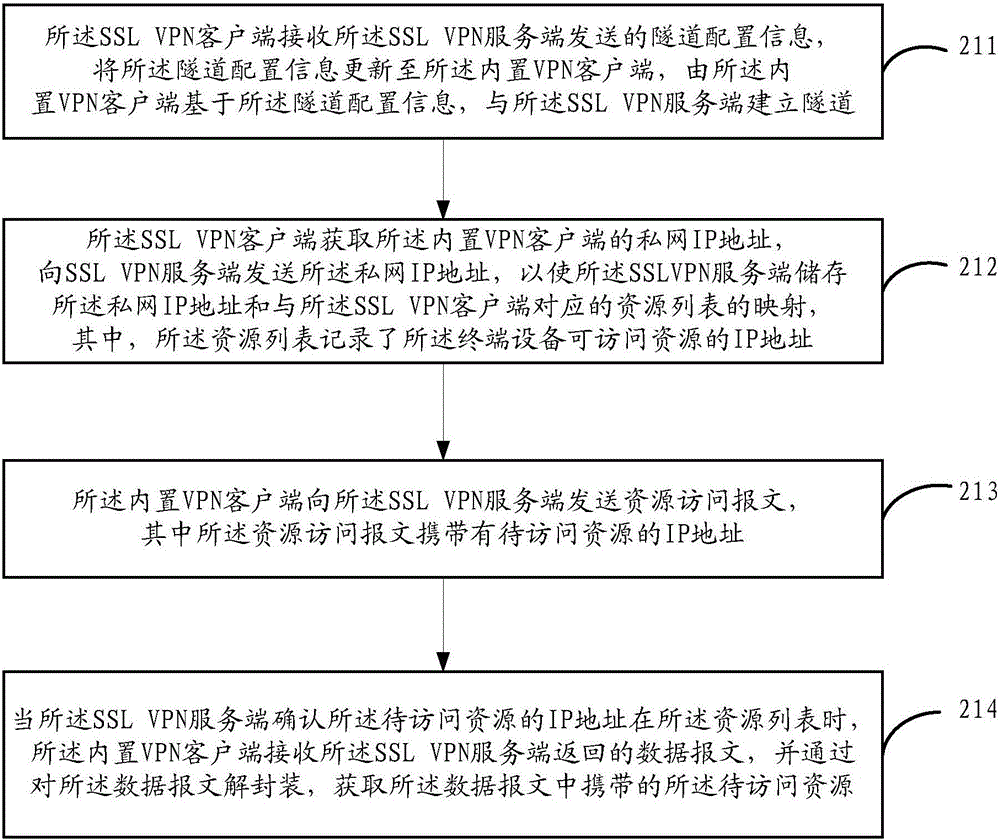
ActiveCN106209838AControl accessImplement add/unpackNetworks interconnectionAccess methodPrivate network
The application provides an IP access method of an SSL VPN. The method comprises the following steps: sending tunnel configuration information to an SSL VPN client on terminal equipment so that the SSL VPN client updates the tunnel configuration information to a built-in client on the terminal equipment; receiving a private network IP address of the built-in VPN client sent by the SSL VPN client, storing the mapping relationship of the private network IP address and a resource list corresponding to the SSL VPN client; receiving a resource access message which is sent by the built-in VPN client and corresponding to the SSL VPN client; judging whether an IP address of a to-be-accessed resource is in the resource list, returning a locally encapsulated data message to the built-in VPN client when the IP address of the to-be-accessed resource in the resource list. Through the adoption of the method provided by the embodiment of the invention, the terminal equipment can access the resource in an IP access mode of the SSL VPN in the system with high security.
Owner:HANGZHOU DPTECH TECH
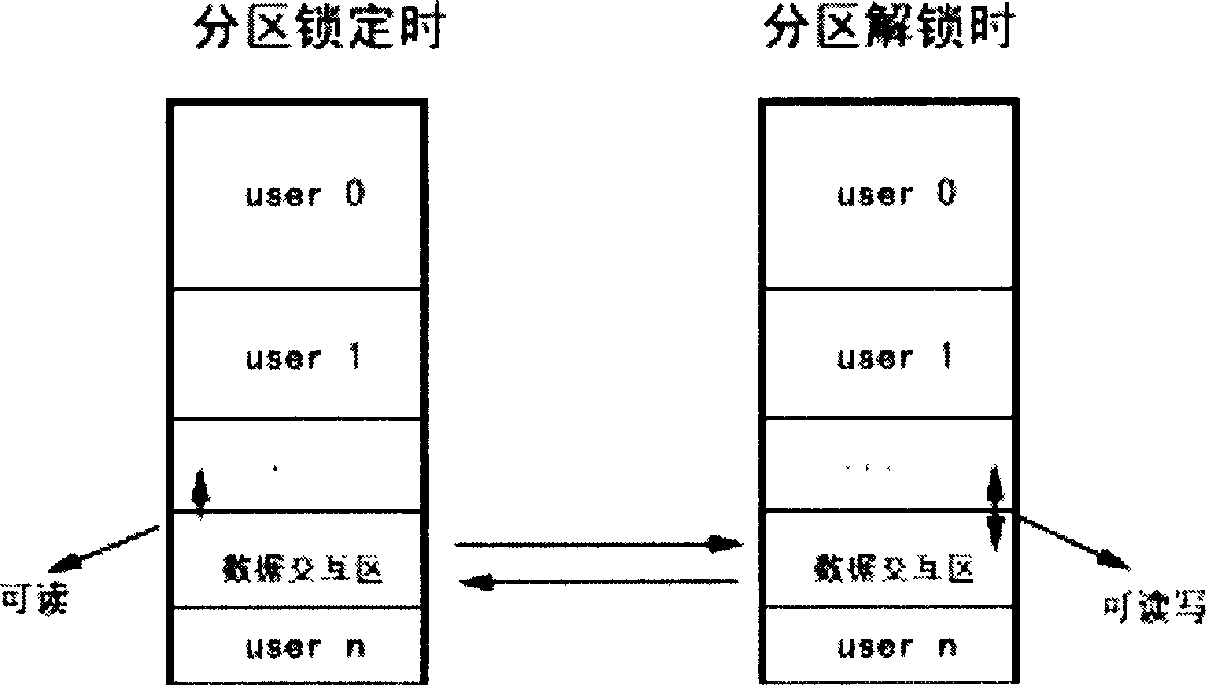
A method for locking hard disk partition safely
InactiveCN1595517AImprove securityLow costUnauthorized memory use protectionDigital recordingComputer compatibilityNetwork isolation
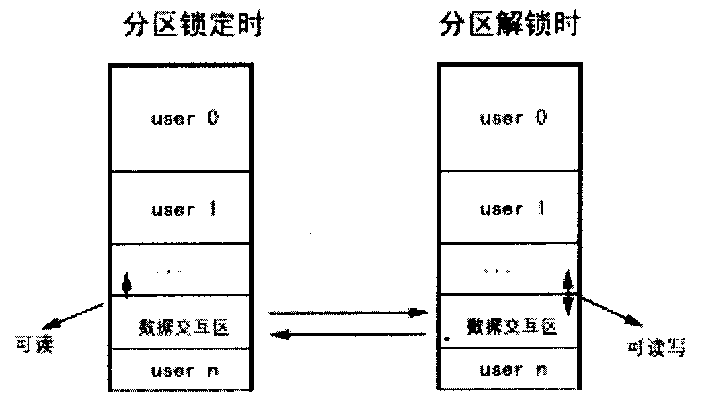
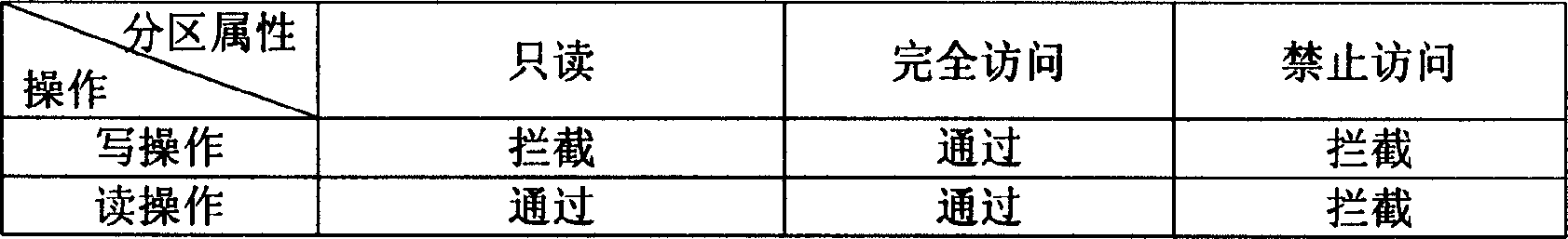
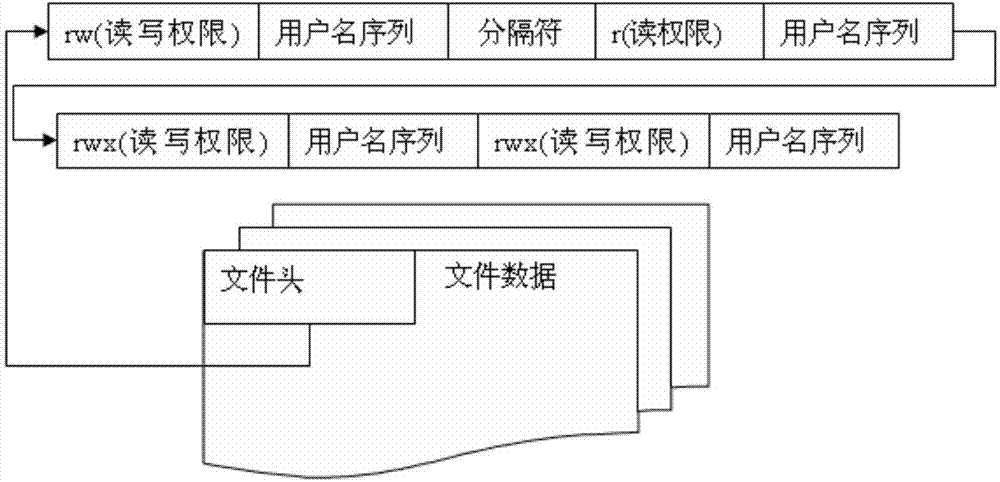
The invention relates to a method, which is used to lock the disc partition safely through BIOS layer and OS layer. The invention separates a disc into many working partitions with self-defining locking through the read-write control technique of the disc magnetic track. Data of different users in these partitions is kept secret on the one hand, but provides good interactivity within a permission range on the other hand. That is to say, many persons may share one computer safely, and one PC is visualized to be many PCs by physical means. Thus the multi-users state of the workstation is realized, and the network isolation card function is implemented with software. Regardless of the disc type, with perfect compatibility, the invention controls the disc partition data effectively, without influence of the reading-writing speed. The locking function is implemented costively.
Owner:西安三茗科技股份有限公司
Method and system for controlling access rights
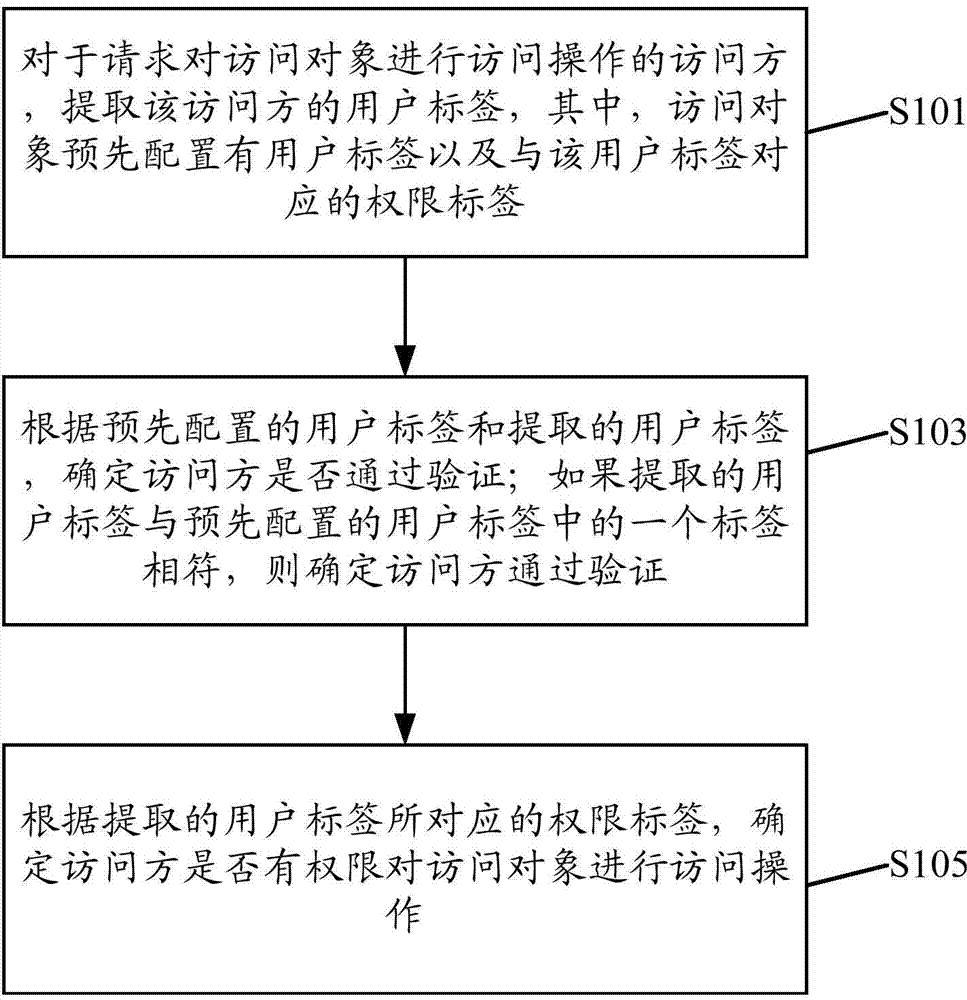
ActiveCN103581187AControl accessAvoid the problem of not being able to restrict superusersTransmissionData miningControl system
The invention discloses a method and system for controlling access rights. The method includes the steps of firstly, extracting a name tag of an access party which requests to conduct access operation on an access object, wherein name tags and right tags corresponding to the name tags are preset in the access object; secondly, determining whether the access party passes validation or not according to the preset name tags and the extracted name tag, and determining that the access party passes the validation if the extracted name tag is consistent with one of the preset name tags; thirdly, determining whether the access party has the access right to conduct access operation on the access object or not according to the right tag corresponding to the extracted name tag. According to the method and system for controlling the access rights, the access rights of all users are effectively controlled, the problem that an existing related technology can not limit super users is solved, and safety and reliability of the system are improved.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Credible computer platform
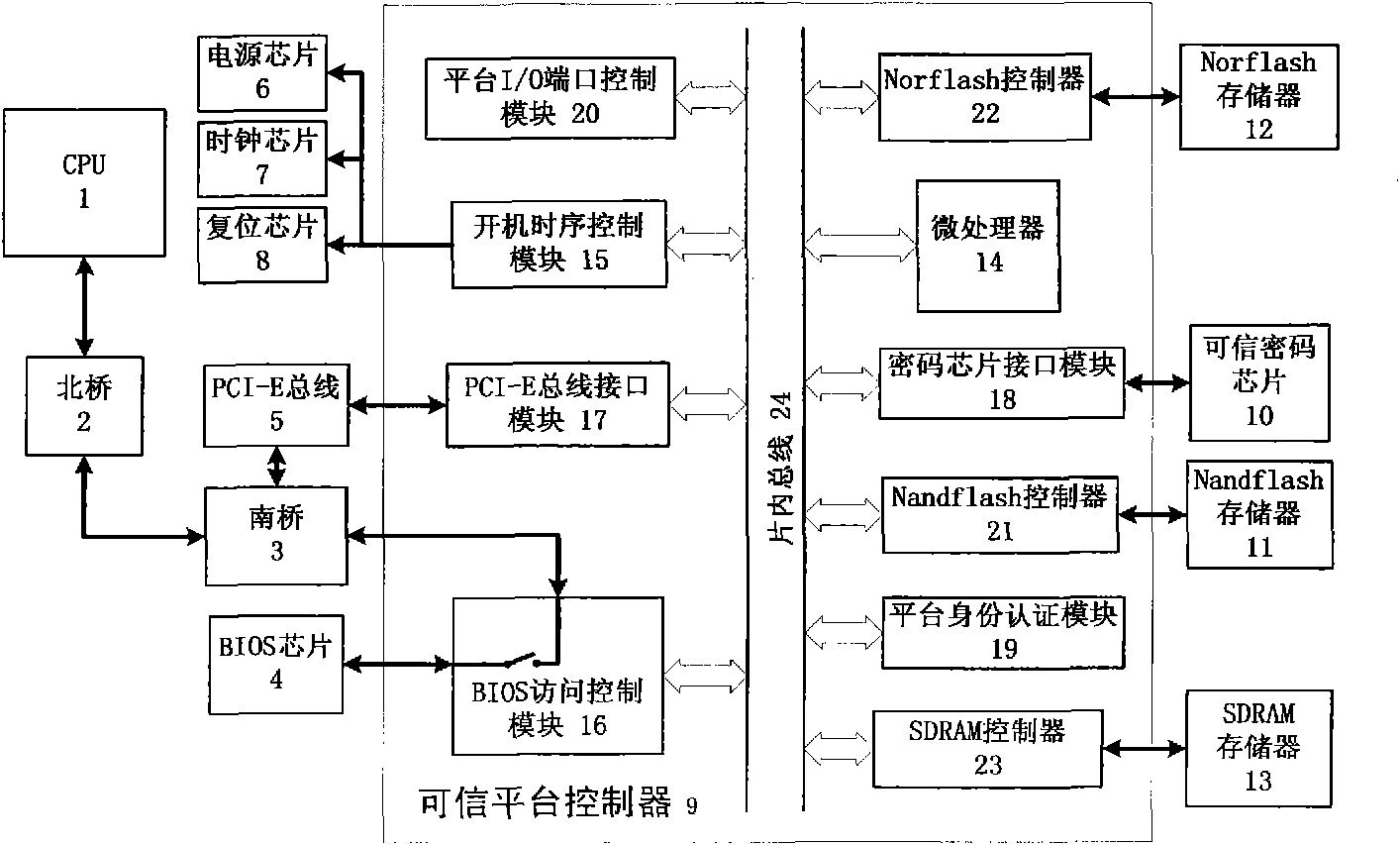
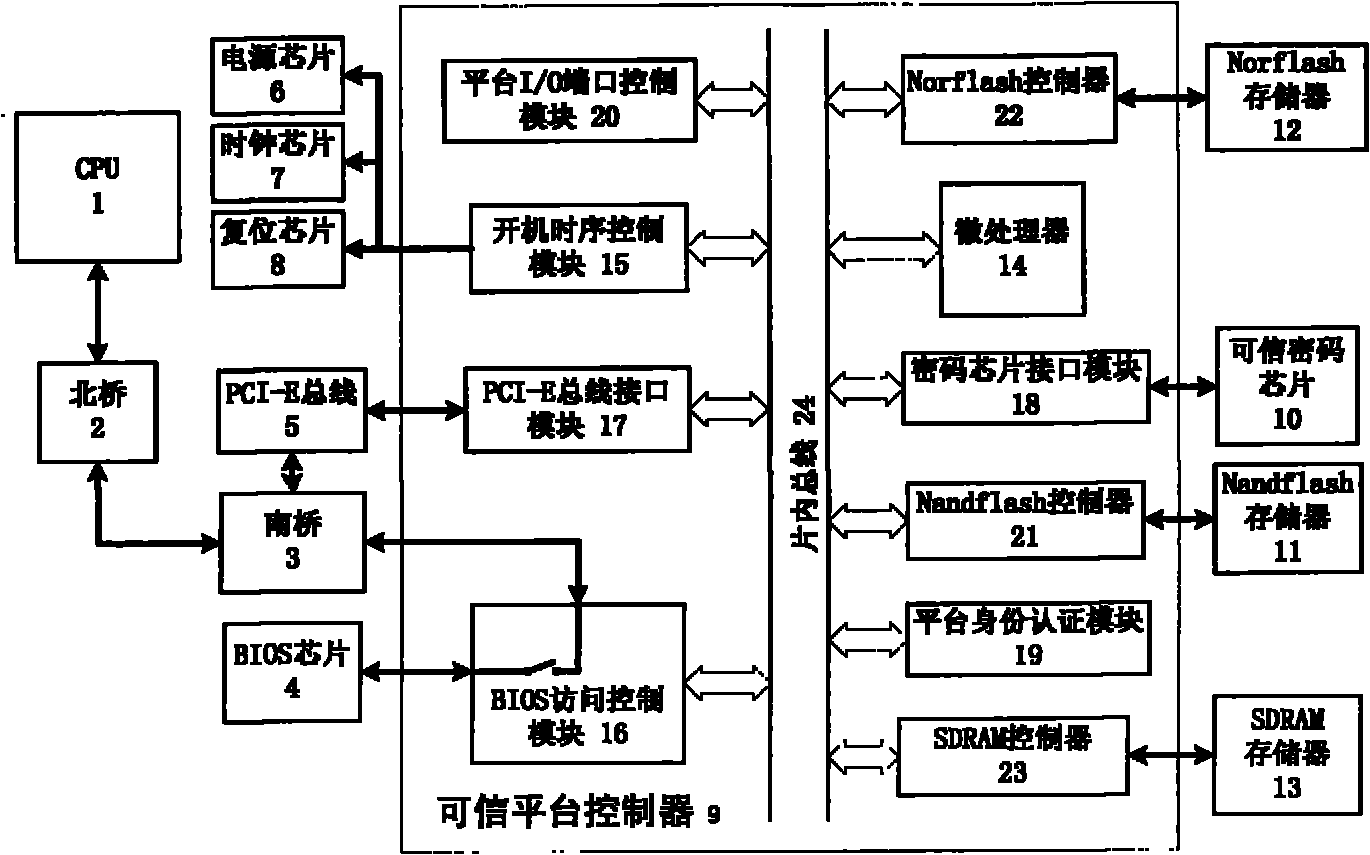
InactiveCN101976320AControl accessPrevent tamperingInternal/peripheral component protectionElectricityTrusted Computing
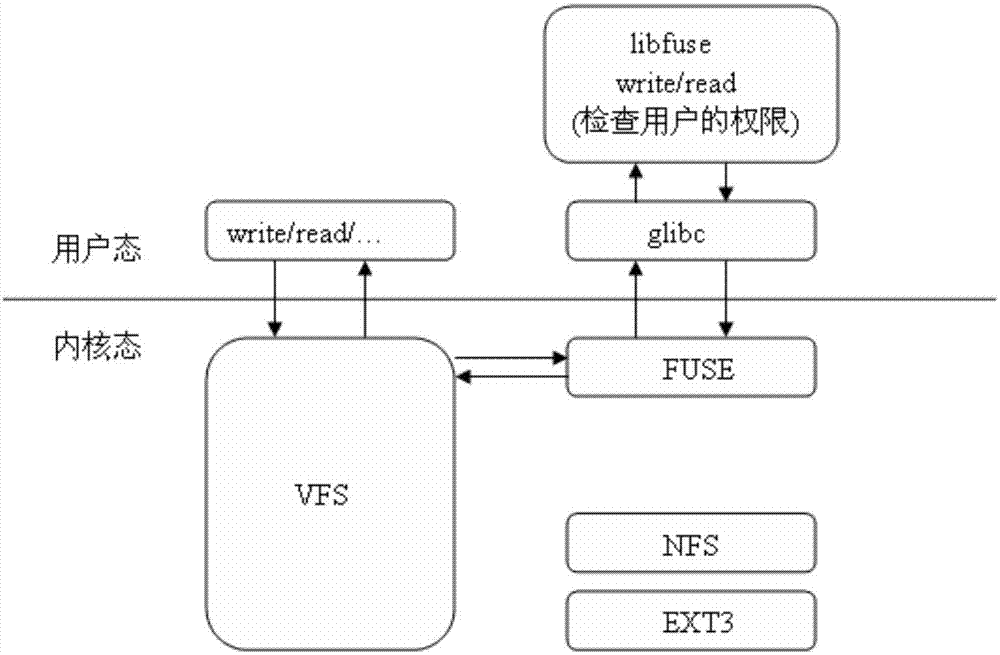
The invention discloses a credible computer platform, comprising a CPU (1), a North bridge (2), a South bridge (3), a credible platform controller (9), a credible crypto chip (10), a Nandflash storage (11), a Norflash storage (12) and a SDRAM (Synchronous Dynamic Random Access Memory) storage (13). The CPU (1) is bidirectionally connected with the North bridge (2), the North bridge (2) is bidirectionally connected with the South bridge (3), and buses are mutually connected inside the credible platform controller (9). The credible platform controller (9) isolates the South bridge (3) and a BIOS (Basic Input / Output System) chip (4) physically, and when being electrified, the credible platform controller (9) can be used for measuring and recovering BIOS completeness, verifying user identity, controlling the opening and closing of an I / O (Input / Output) port, and performing high-speed encryption / decryption on key data. The invention can be used for effectively controlling malicious codes from entering a computer system and preventing BIOS from falsification and illegal users from logging in, and thus, information safety protection capability of the system is improved.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
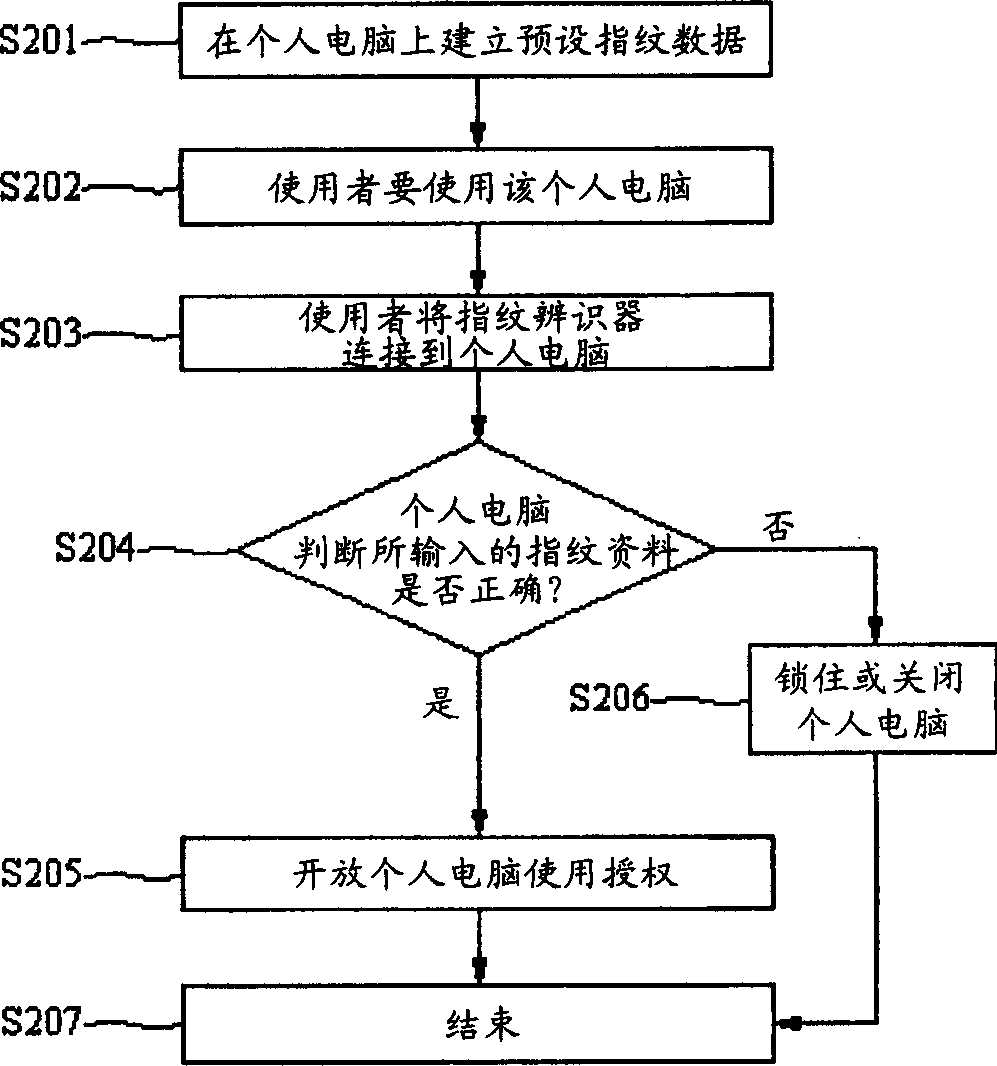
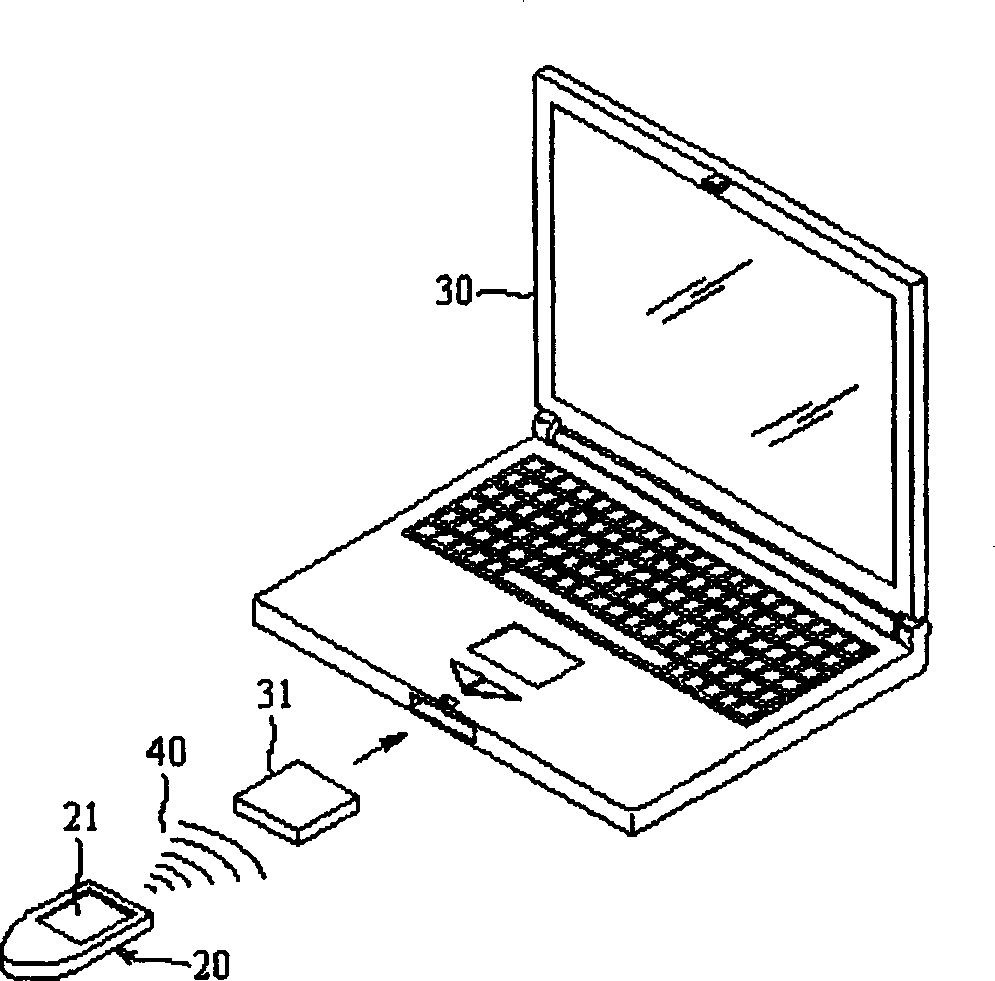
Wireless recognition apparatus for fingerprint and method thereof
InactiveCN1421816AControl accessCharacter and pattern recognitionTransmissionElectronic systemsComputer module
The radio fingerprint recognizing equipment for one electronic system includes one recognizer including fingerprint pick-up module to take the fingerprint data of the user and RF module to transmit fingerprint data based one radio transmission protocol; one to receive the fingerprint data; and one fingerprint identifying module connected to the receiving module and a memory. When the compared fingerprint accords with the preset fingerprint, the user right for the electronic system is opened, or else it is closed.
Owner:WISTRON CORP +1
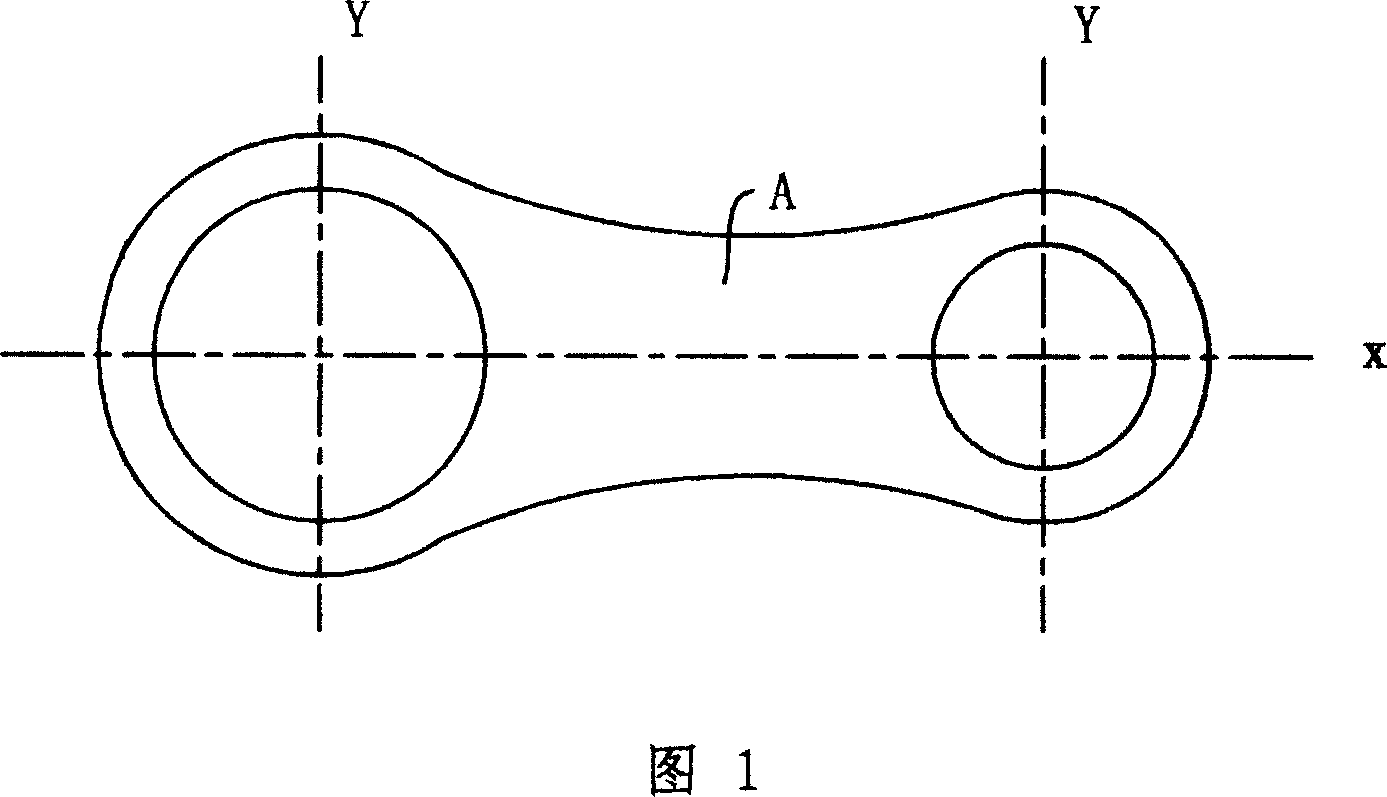
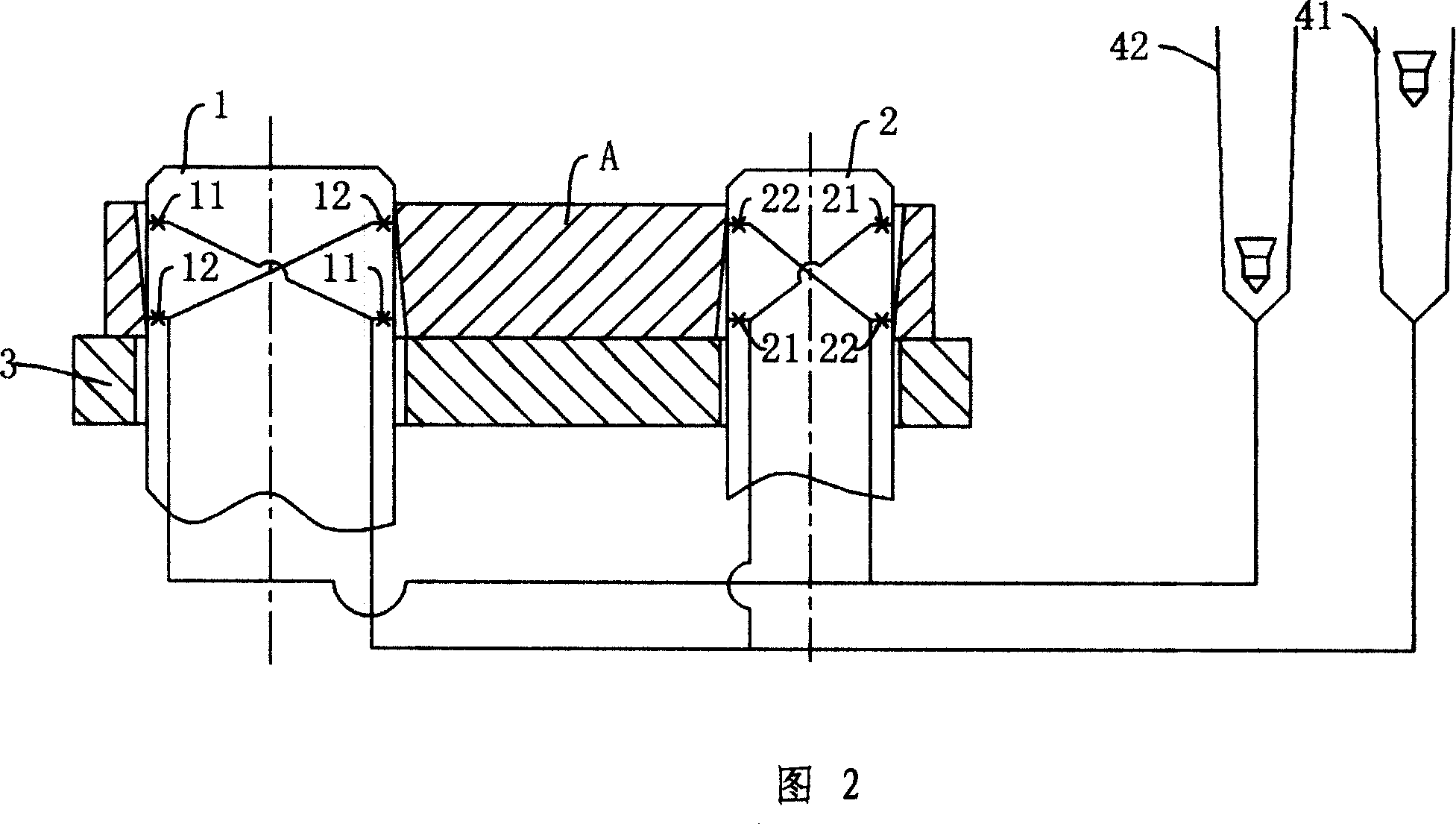
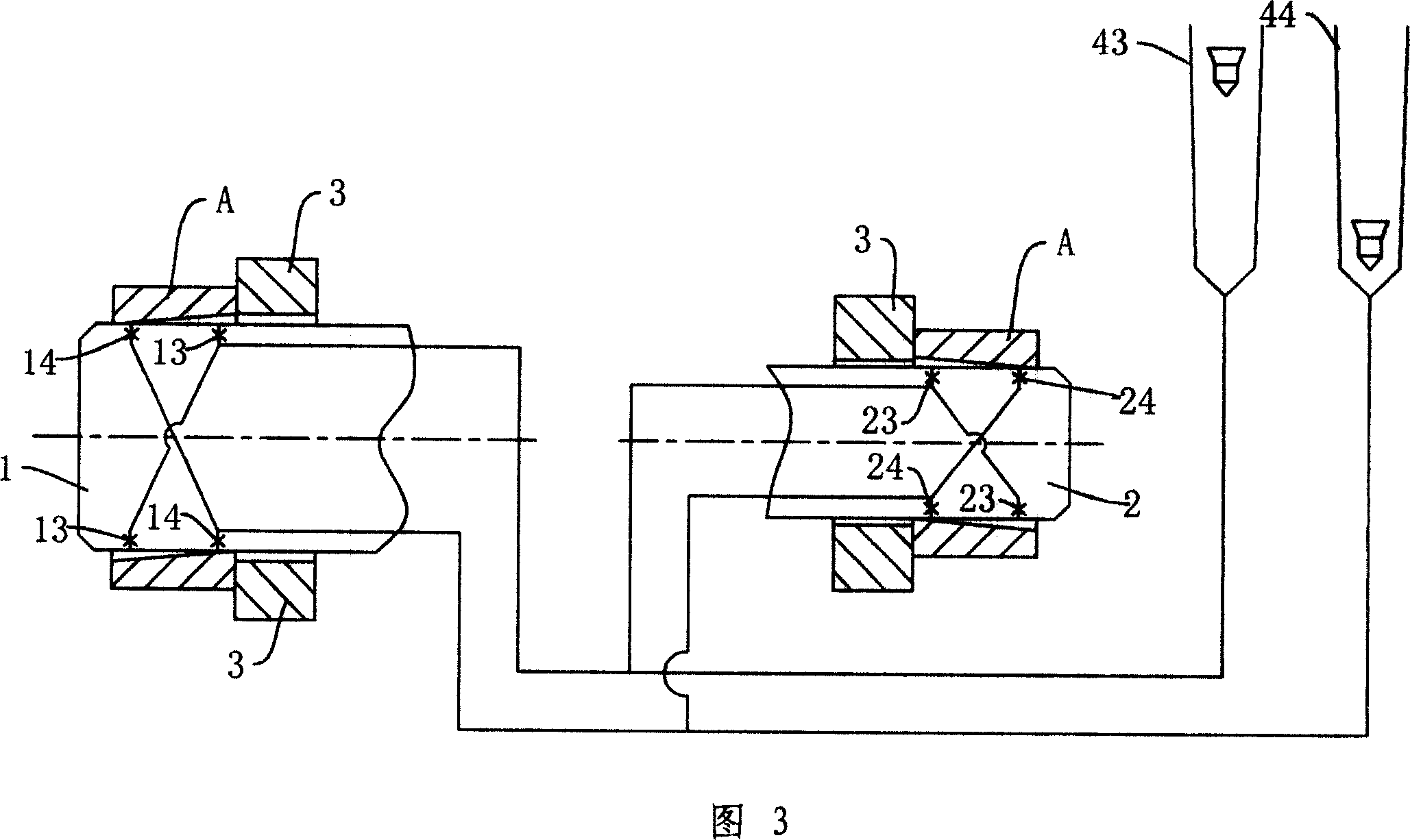
Comprehensive pneumatic measuring device for link rod
InactiveCN101029821APneumatic measurement implementationHigh measurement accuracyUsing fluid meansMeasurement deviceUltimate tensile strength
An integrated pneumatic measurement device used on link is prepared as setting the first measurement branch for measuring x directional parallelism of link two holes axle, the second measurement branch for measuring Y directional parallelism of link two hole axle, the third measurement branch for measuring center distance of link two holes, the fourth measurement branch for measuring the first hole cylindricity of link and the fifth measurement branch for measuring the second hole cylindricity of link separately on the first and the second measurement heads.
Owner:SHENGRUI TRANSMISSION
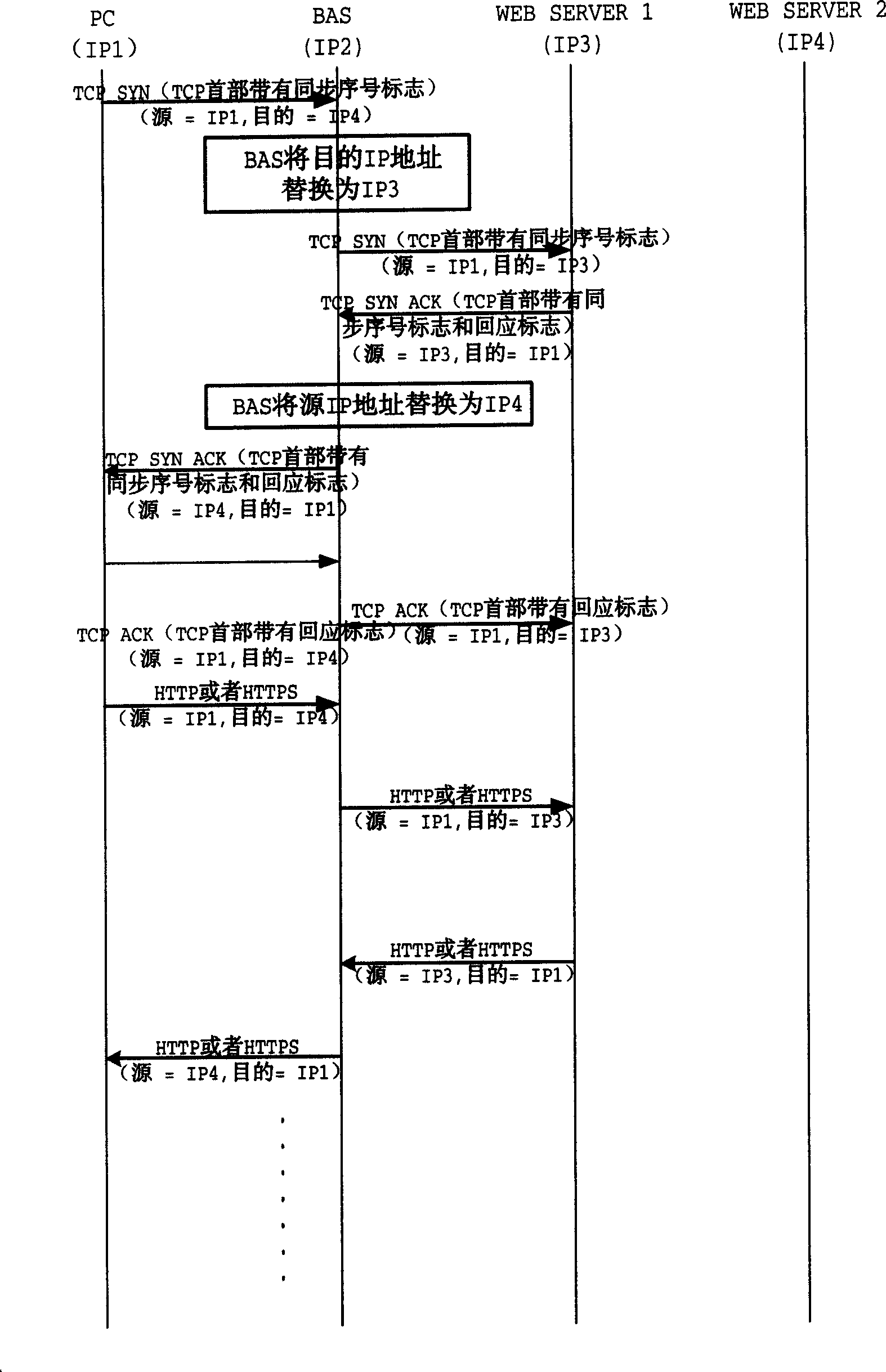
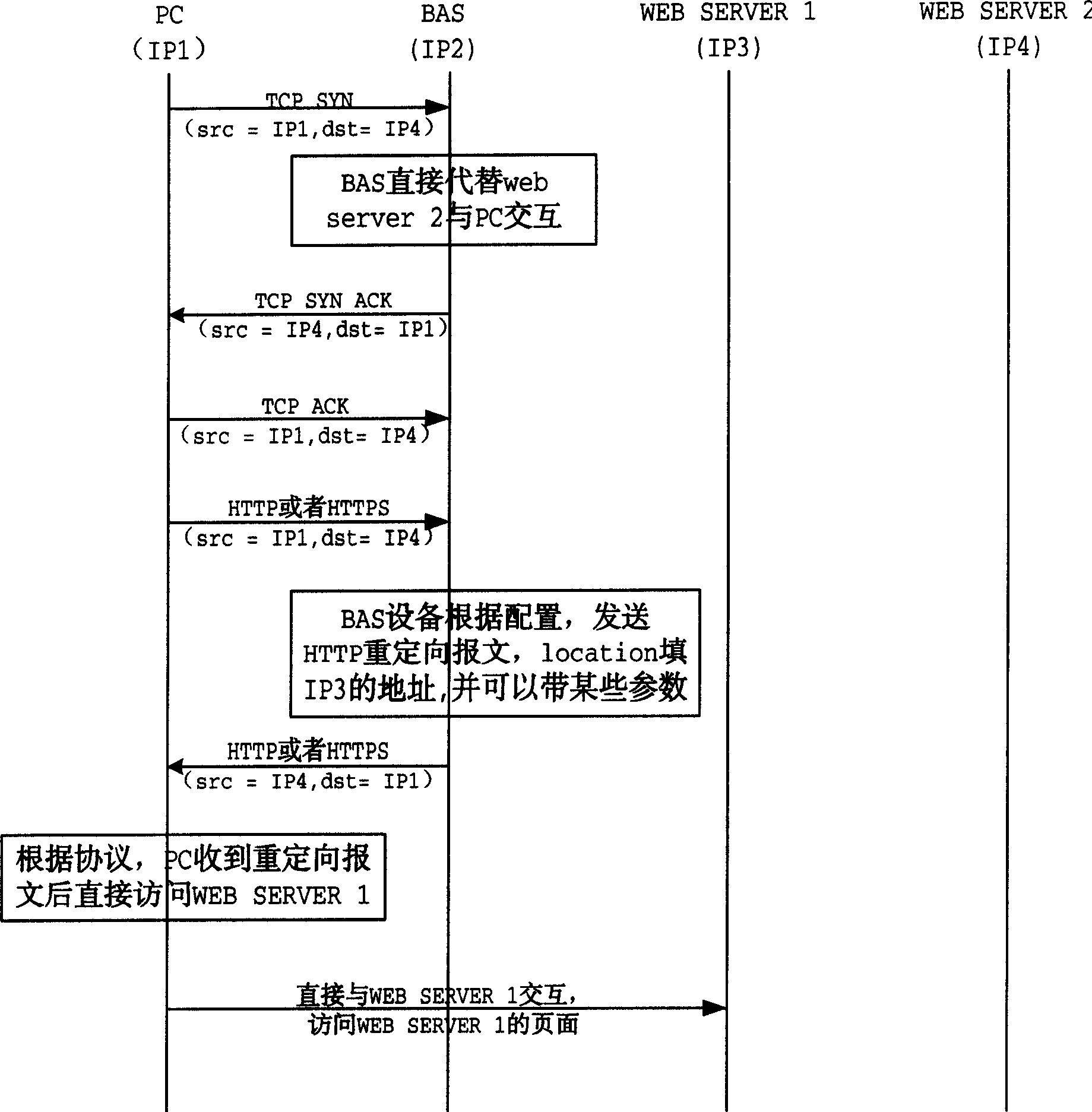
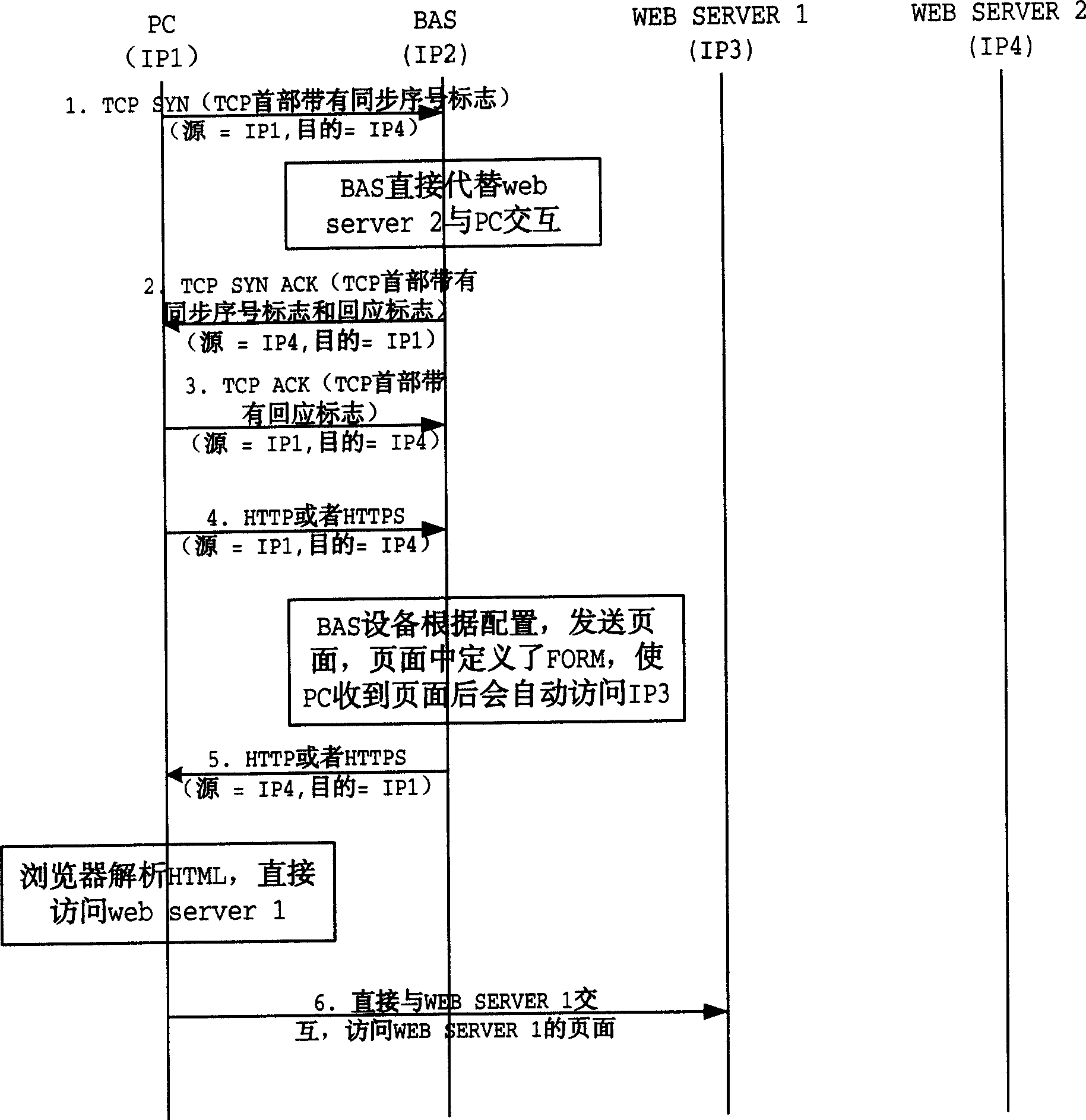
A method for implementing forced door
InactiveCN1571356AControl accessData switching by path configurationSelection arrangementsProtocol for Web Description ResourcesWeb server
The invention provides a forced portal realizing method, including the steps: a user builds a connection with a web server to be accessed through wideband access server (BAS); then, the user sends HTTP or HTTPS request message; the BAS receives the message and then configures web page containing forced portal information and sends the web page to the user; the user receives the web page and then automatically connect to forced portal website. The invention can make BAS easily realize forced portal and can appoint concrete web page of forced portal and can carry parameters to web server, flexibly setting if it displays parameters in address column and can make BAS flexibly control the mode of user accessing web page by HTML and network programming technique.
Owner:HUAWEI TECH CO LTD
File usage authority management method, device and system
InactiveCN104537315AImprove efficiencyControl accessDigital data protectionService informationDocument security
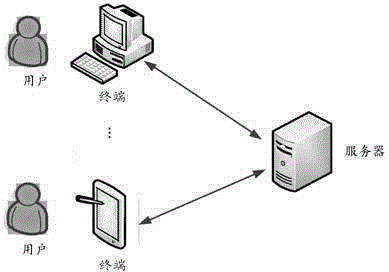
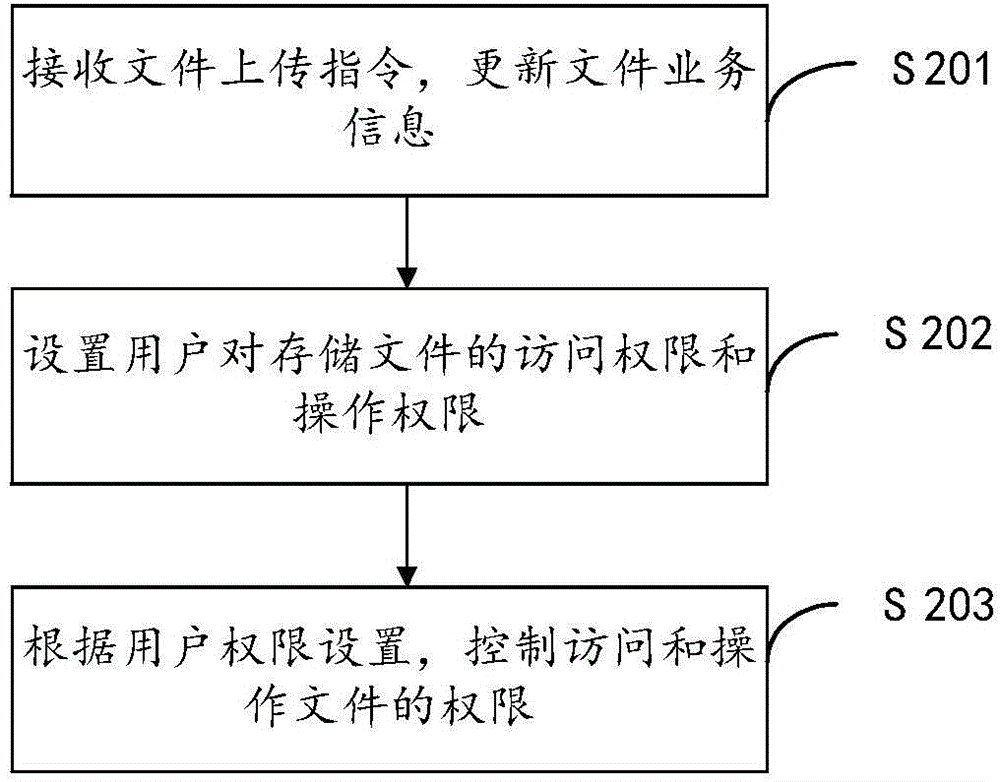
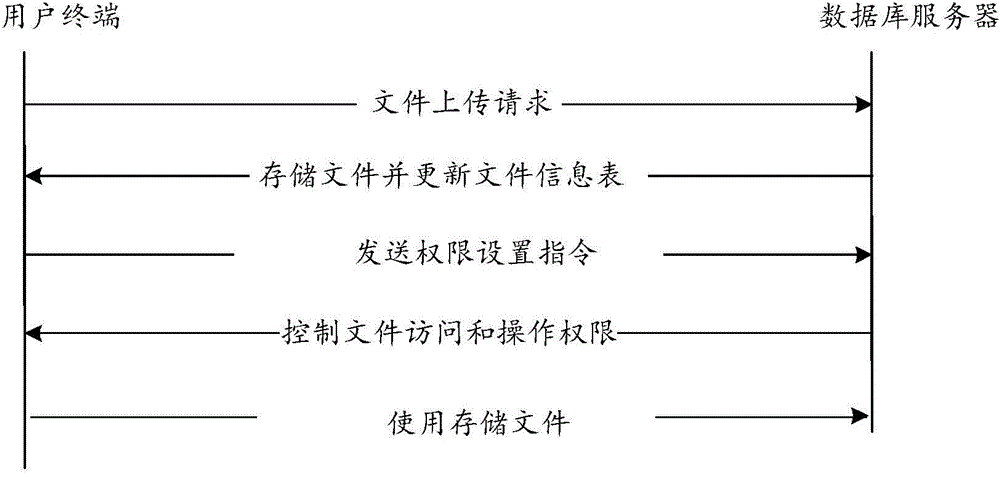
The invention belongs to the field of computers and provides a file usage authority management method. The file usage authority management comprises the following steps that a request of a user for uploading a file is received, the uploaded file is stored, and the file service information of the uploaded file is recorded in a file information data list; an authority setting order is received, and according to the file service information in the file information data list and the authority setting order, the authorities of the user to access and process the stored files in a data base server are set; according to information of a user account and the set user authorities, the authorities of the user to access and process the stored files in the data base server are controlled. According to the file usage authority management method, files are managed in a classified mode, the authorities of different users to access and process the stored files are set, the usage authorities of the users on the files are controlled, uniform management of the file authorities is achieved according to file levels and user levels, and the file security management efficiency is improved.
Owner:NINGBO JIANGDONG HENGGUAN INFORMATION TECH
Media access control method for a bus system and communication apparatus
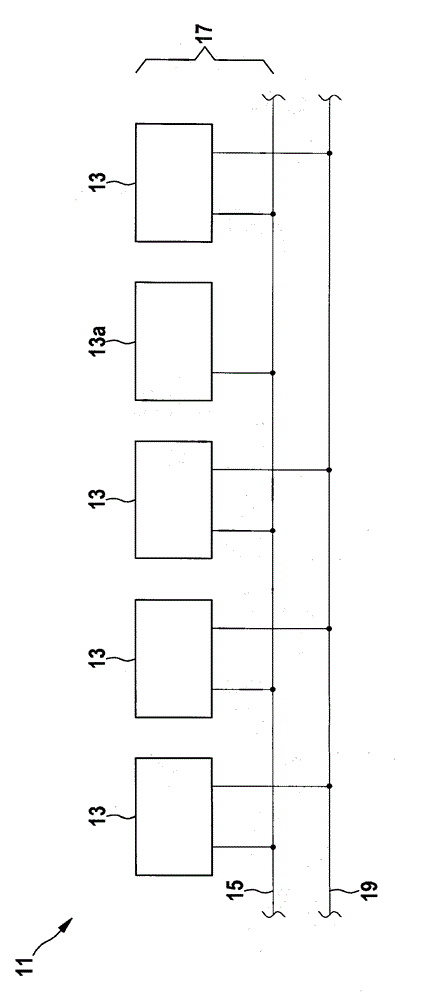
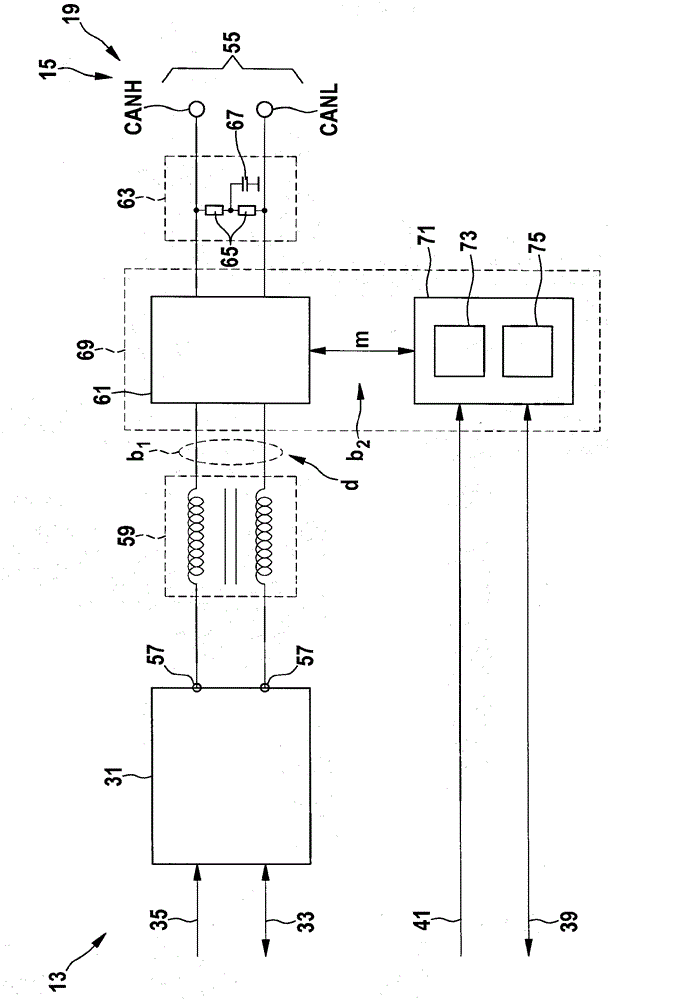
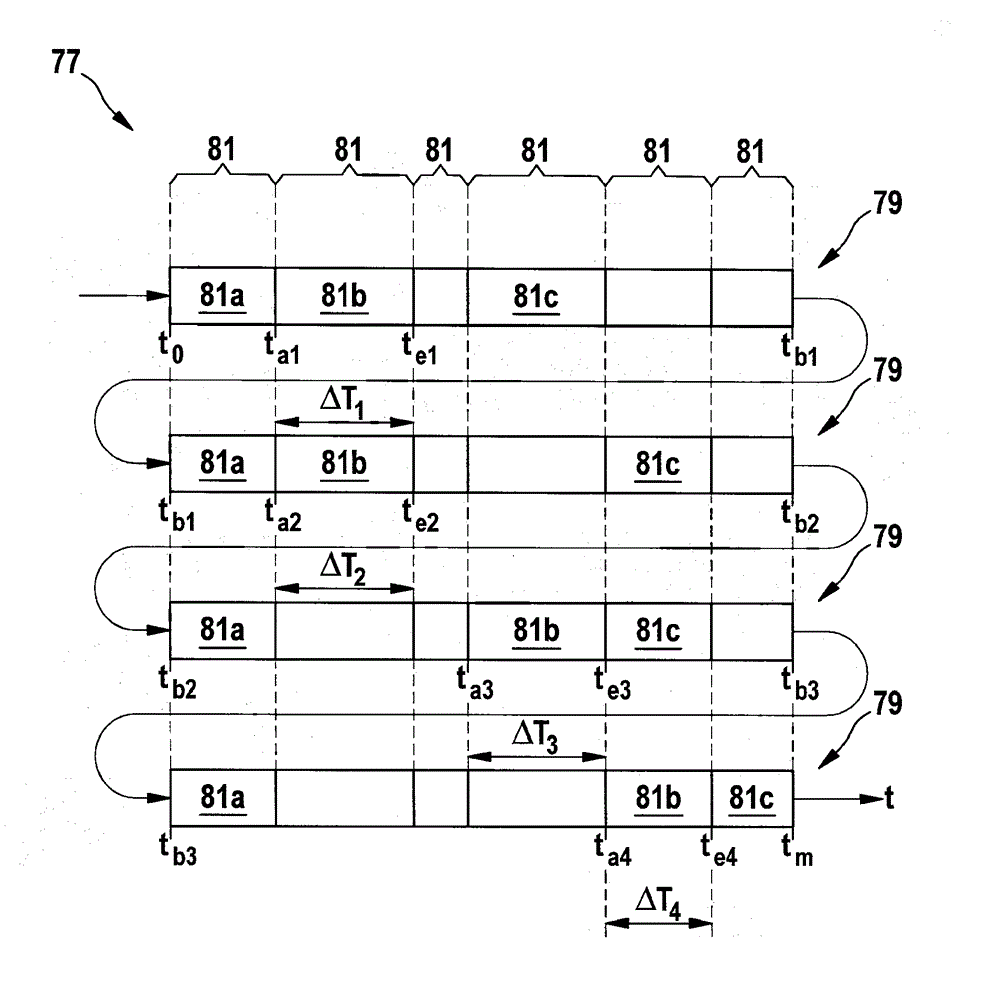
ActiveCN102804697AGuaranteed average bitrateControl accessElectric digital data processingBus networksTelecommunicationsStation
The invention relates to a media access control method for controlling the access of a subscriber station (13) of a bus system (11) to a first channel (15) of the bus system (11) jointly used by several subscriber stations (13), wherein in the method at least one enabling interval ([delta]T1, [delta]T2, [delta]T3, [delta]T4, [delta]T5) is specified for the subscriber station (13), within which enabling interval the subscriber station (13) has exclusive access to the first channel (15). In order to specify a media access control method, wherein large amounts of data can be transmitted relatively quickly and real-time conditions can be maintained when messages are transmitted by means of the bus system (11), it is proposed that the access to a second channel (19) used by several subscriber stations (13) be controlled using the method, wherein the second channel (19) is enabled only within the enabling interval ([delta]T1, [delta]T2, [delta]T3, [delta]T4, [delta]T5) during which access by the subscriber station (13) is enabled.
Owner:ROBERT BOSCH GMBH
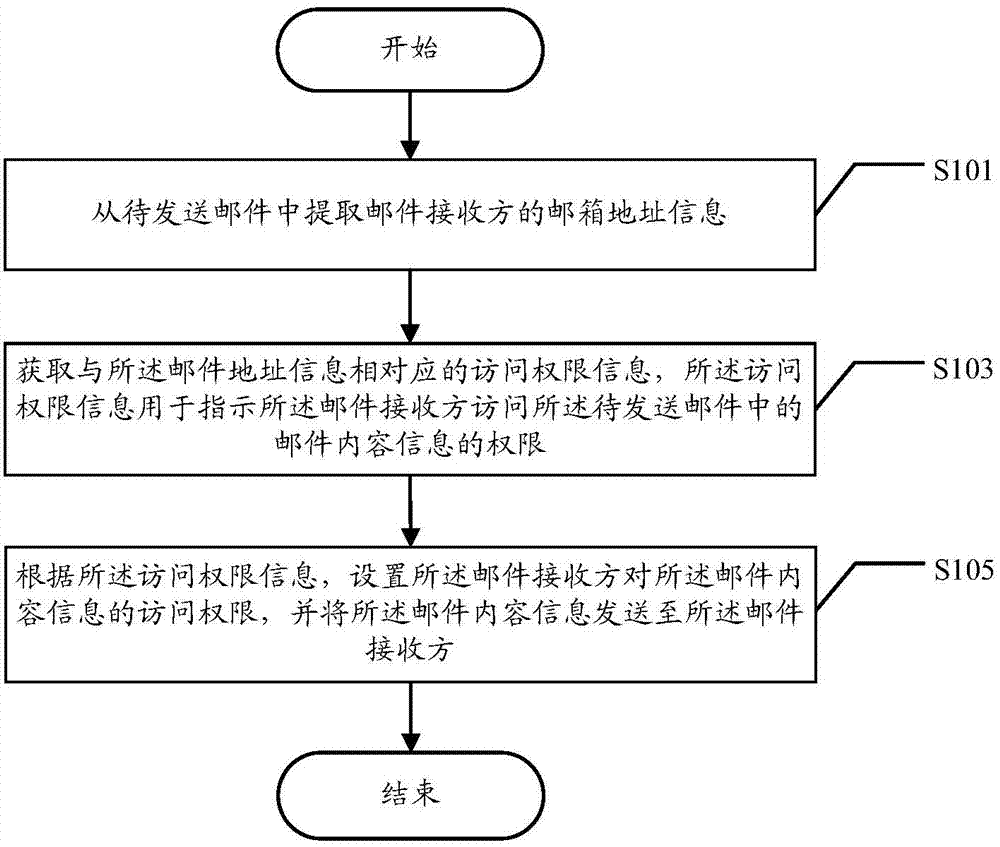
Mail processing method and terminal
An embodiment of the invention discloses a mail processing method and a terminal. The mail processing method can include: extracting mailbox address information of a mail receiver from a to-be-sent mail; acquiring access right information corresponding to the mailbox address information, wherein the access right information is used for indicating access right, to mail content information in the to-be-sent mail, of the mail receiver; according to the access right information, setting access right, to the mail content information, of the mail receiver, and sending the mail content information to the mail receiver. By the main processing method and the terminal, sharing of mail content by multiple mail receivers in one mail can be realized while access right, to the mail content, of each mail receiver is controlled.
Owner:MEIZU TECH CO LTD
Sucking pig early weaning-post-weaning two-week compound feed and preparation method thereof
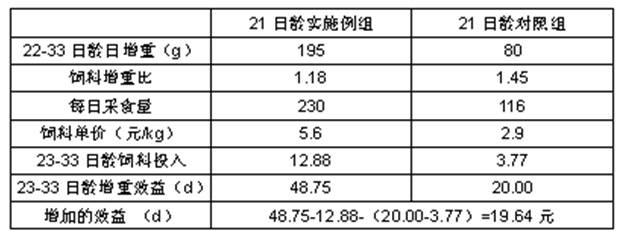
The invention provides a sucking pig early weaning-post-weaning two-week compound feed and a preparation method thereof, wherein the compound feed consists of the following raw materials in percentage by weight: 58-61% of corn, 19-22% bean pulp, 7.8-9.3% of whey powder, 1-3% of fish meal, 2-4% of cane sugar, 0.4-0.6% of mountain flour, 1.1-1.5% of calcium hydrophosphate, 0.15-0.35% of trace element mineral substance premix compound, 0.15-0.35% of vitamine premix compound, 0.3-0.5% of salt, 0.1-0.3% of acidulant, 0.02-0.05% of micro zoology, 0.07-0.09% of complex enzyme premix compound, 0.01-0.03% of phytase, 0.12-0.25% of oligosaccharide, 0.5-0.8% of amino acid and 0.05-0.08% of choline chloride. The raw materials are micro-crushed so that 100% of the raw materials pass through a standardsieve of 0.8mm, and granulation is carried out at 60-70 DEG C. The invention can improve the survival rate of the sucking pigs, the problems that the sucking pigs have diarrhea, loss condition and the like after the weaning are avoided, the sucking pig slaughter period and disease infectant opportunity are reduced, and the breeding efficiency of a sow is improved.
Owner:SHANDONG NEW HOPE LIUHE GROUP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com