An identity control method based on credibility platform module and fingerprint identifying
A platform module and fingerprint recognition technology, applied in character and pattern recognition, instruments, digital data authentication, etc., can solve problems such as incompetence for large-scale and complex computing tasks, and achieve the goal of making up for insufficient computing power, high reliability and security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] Preferred embodiments of the present invention are described in detail below.
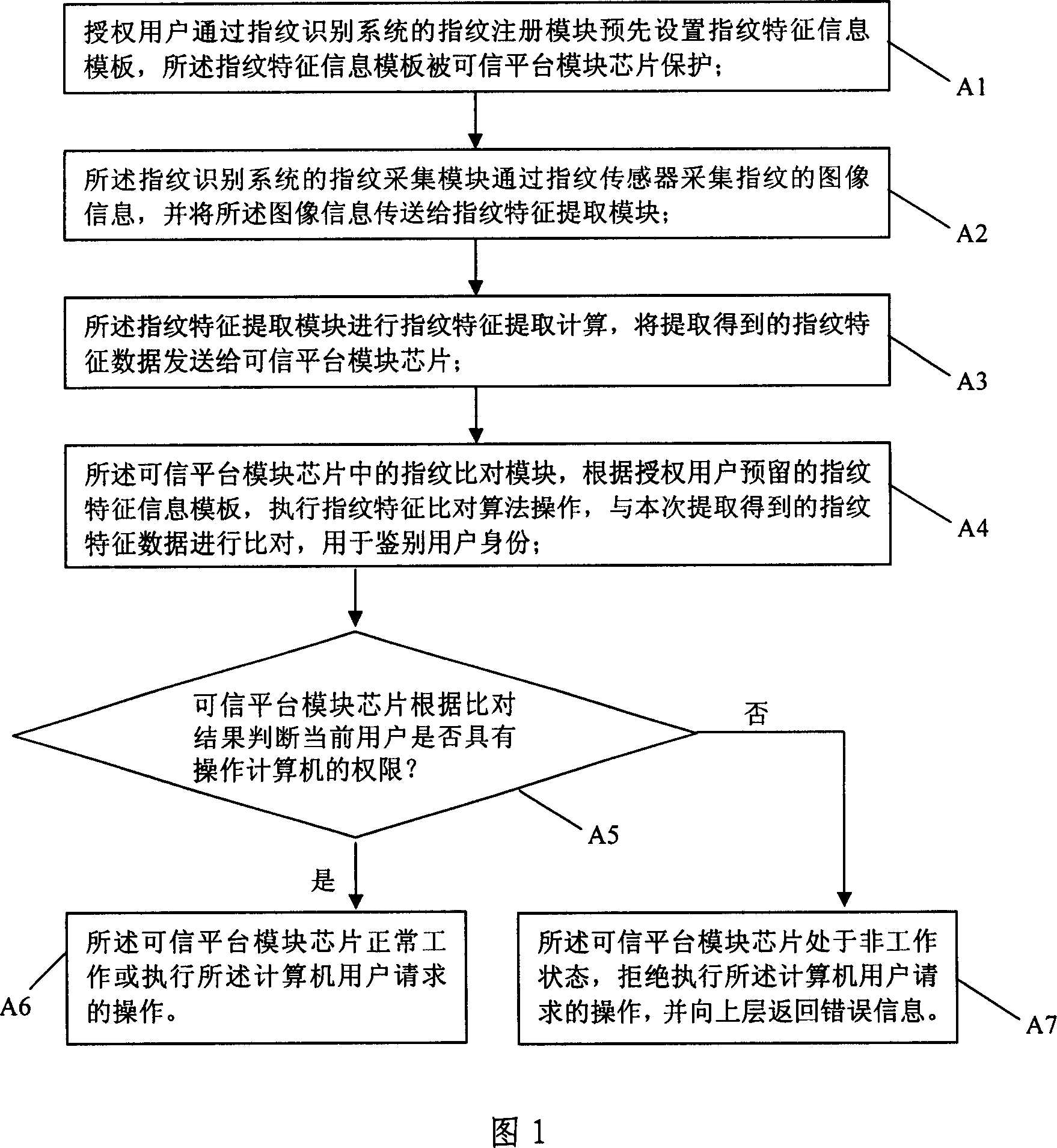
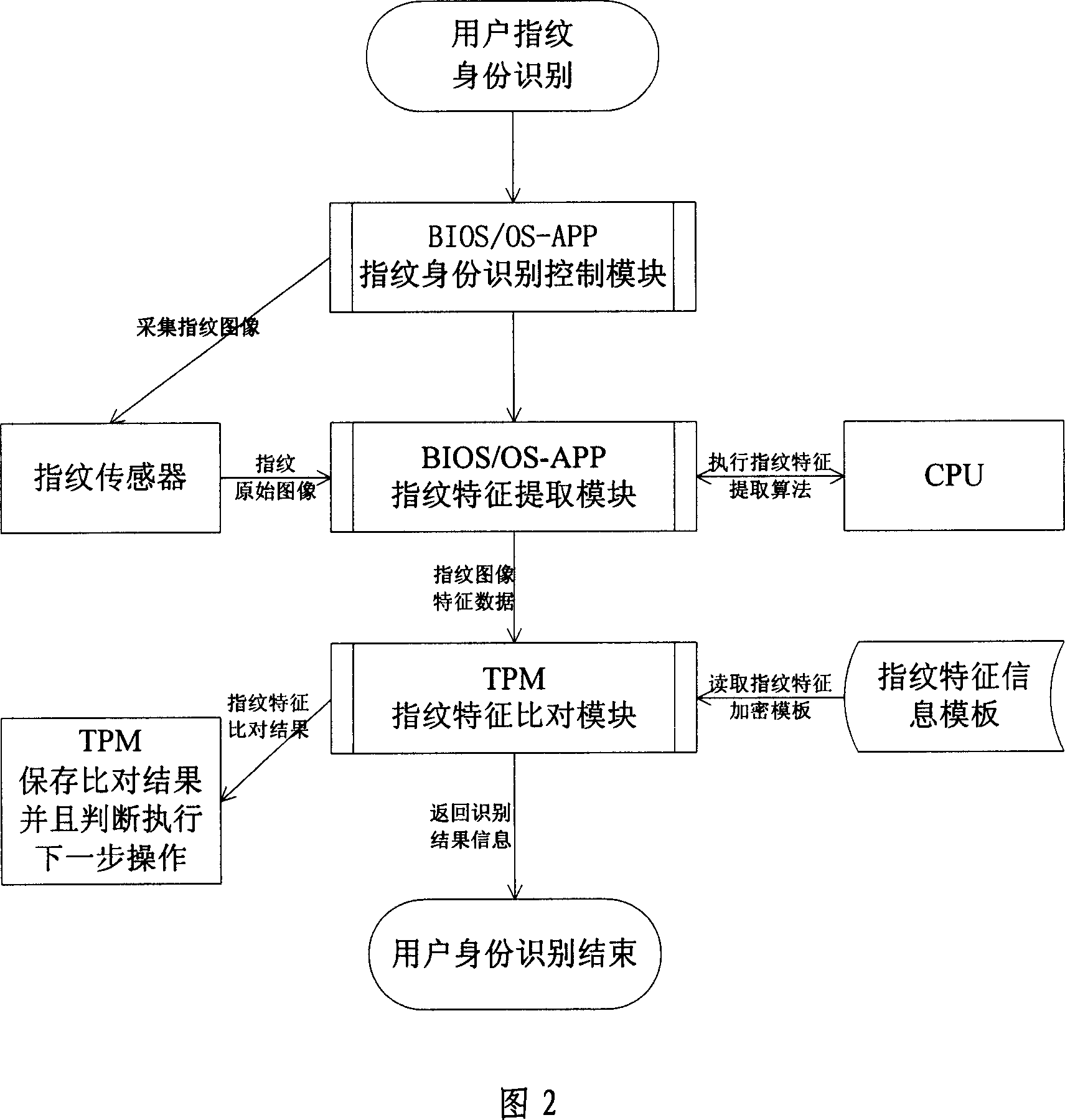
[0027] The invention provides an identity control method based on a trusted platform module and fingerprint identification, which is applied to a trusted computer system, and the system includes: a standard computer motherboard and chipset, a CPU central processing unit chip, RAM memory, and external storage such as a hard disk , as well as TPM chip and fingerprint sensor. The system also needs to have a software operating environment, including: trusted basic input and output system BIOS, trusted operating system OS, TPM chip firmware (Firmware) program and TPM initialization application software, and BIOS and OS drivers related to fingerprint sensors program, user fingerprint registration management and other application software.
[0028] The identity control method based on trusted platform module and fingerprint identification of the present invention is shown in Fig. 1, which includes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com