Patents
Literature
3228results about How to "Won't leak" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
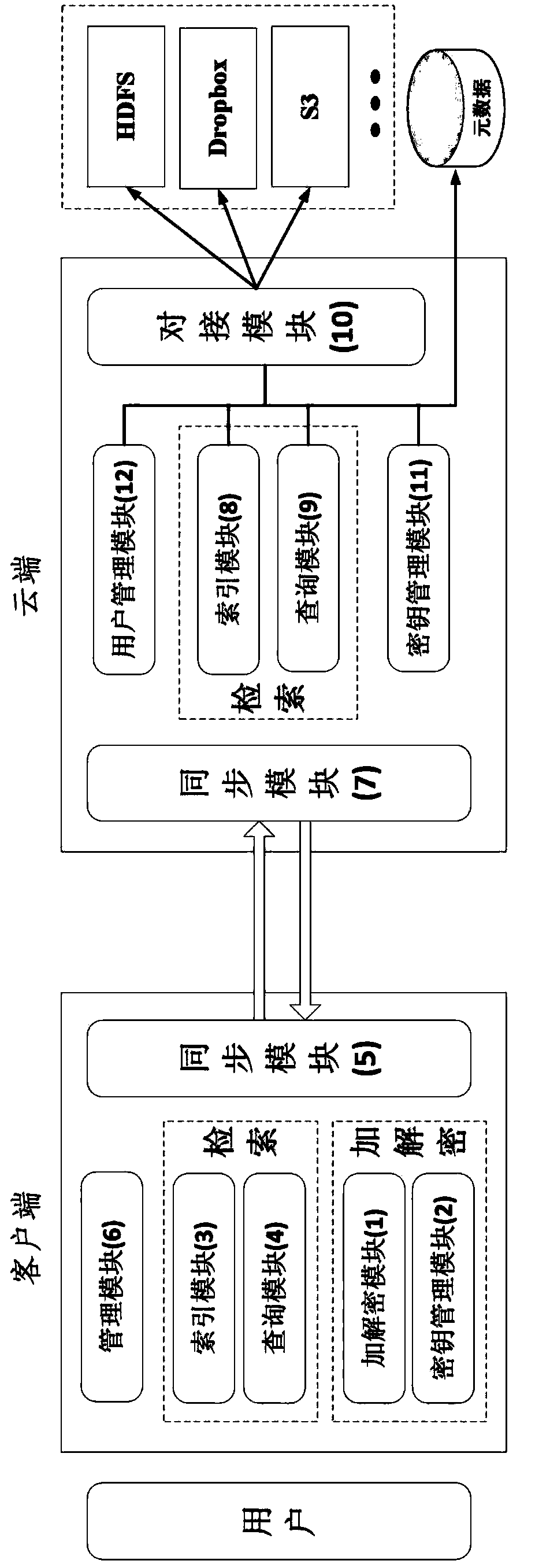
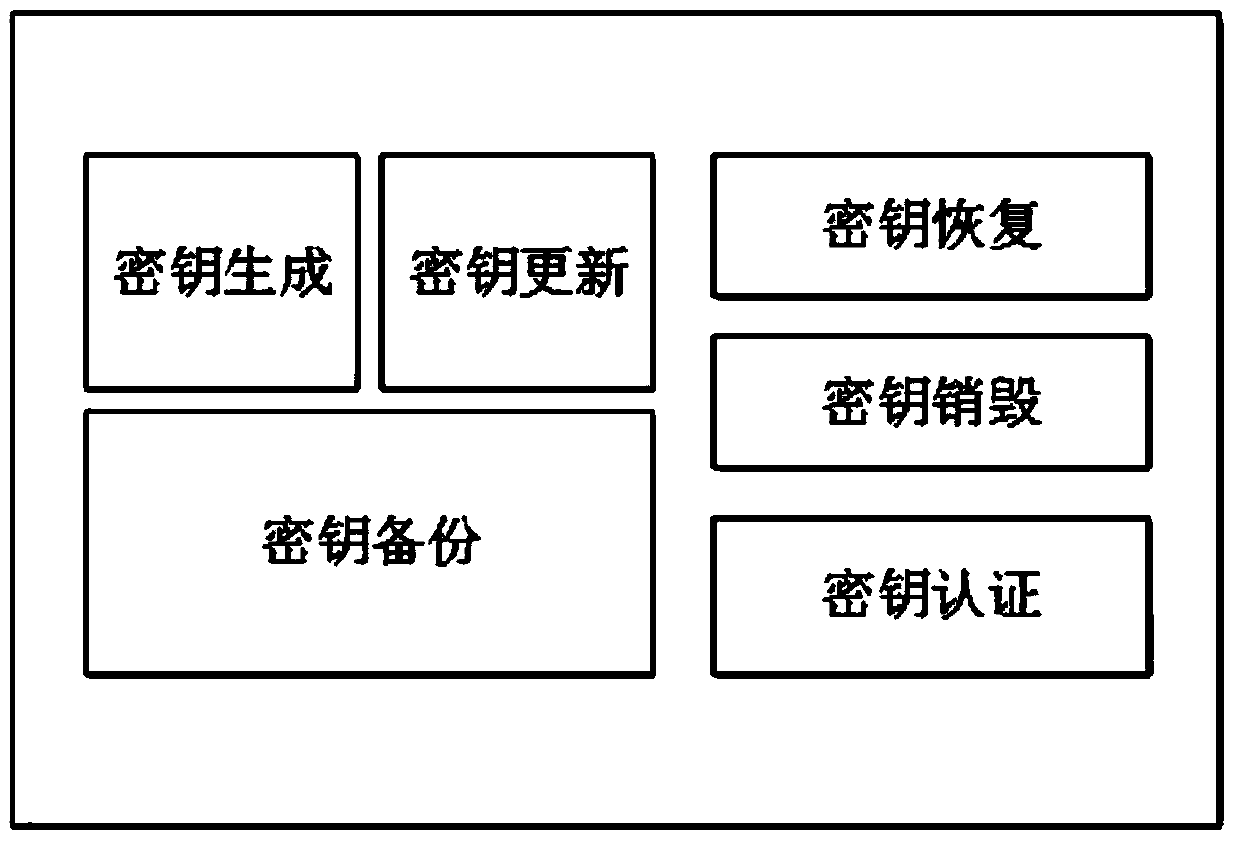
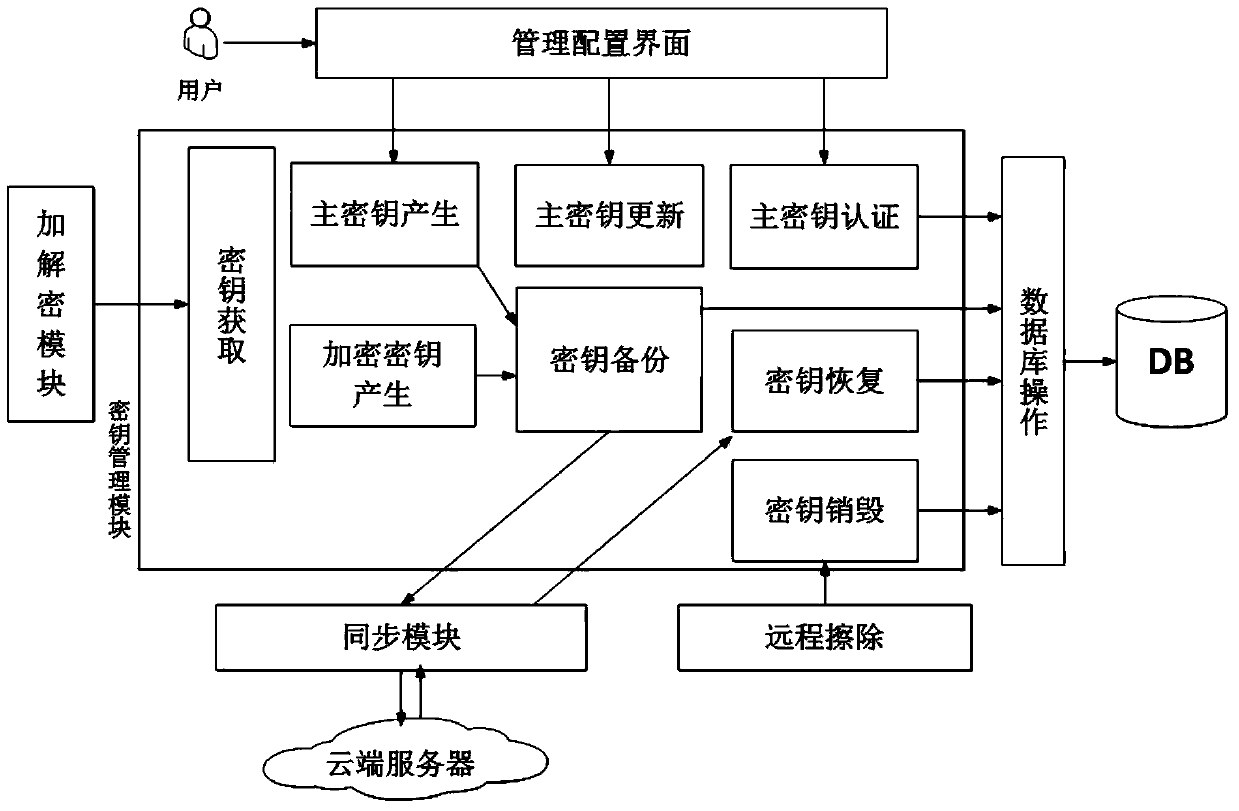
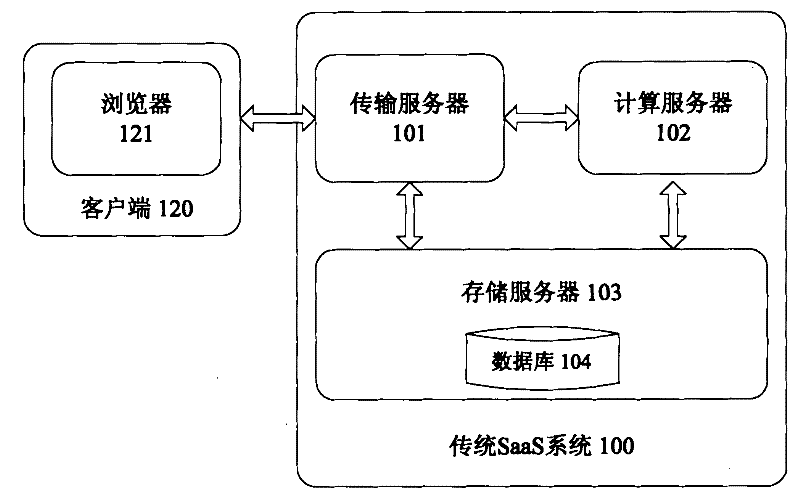
Ciphertext cloud storage method and system
InactiveCN103595730AWon't leakDoes not affect survivalTransmissionComputer hardwareData synchronization
The invention relates to a ciphertext cloud storage method and system. In the ciphertext cloud storage method system composed of at least one client terminal and a cloud terminal server, the ciphertext cloud storage method comprises the steps that (1) a user adopts a ciphertext and / or a plaintext to conduct data synchronism on the client terminal in the process of data storage and selects an encryption algorithm for the ciphertext; (2) authentication parameters provided based on the identity of the user is used for generating a master key, synchronous data of the ciphertext are encrypted on the client terminal through two-level keys comprising the master key and an encryption and decryption key, and the master key is backed up; (3) the ciphertext and a ciphertext index are synchronized on the client terminal and a cloud terminal, or a plaintext index is established after synchronous data of the plaintext are synchronized on the cloud terminal and the client terminal; (4) the plaintext and / or ciphertext is / are stored in a local private cloud storage server or in a storage server of a cloud storage provider according to a mount point requested by the user. By the adoption of the ciphertext cloud storage method and system, the data cannot be lost when the terminal is lost, if protection is inappropriate, only the ciphertext form of a file is damaged, and the ciphertext cloud storage system can dock with multiple cloud server providers.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
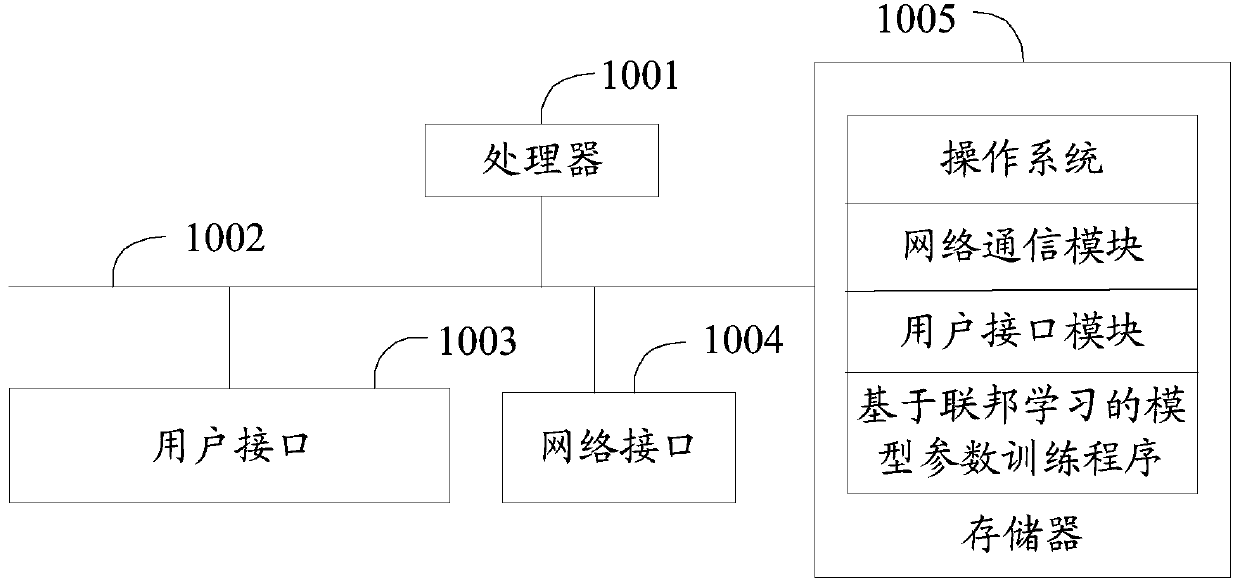
Model parameter training method and device based on federated learning, equipment and medium
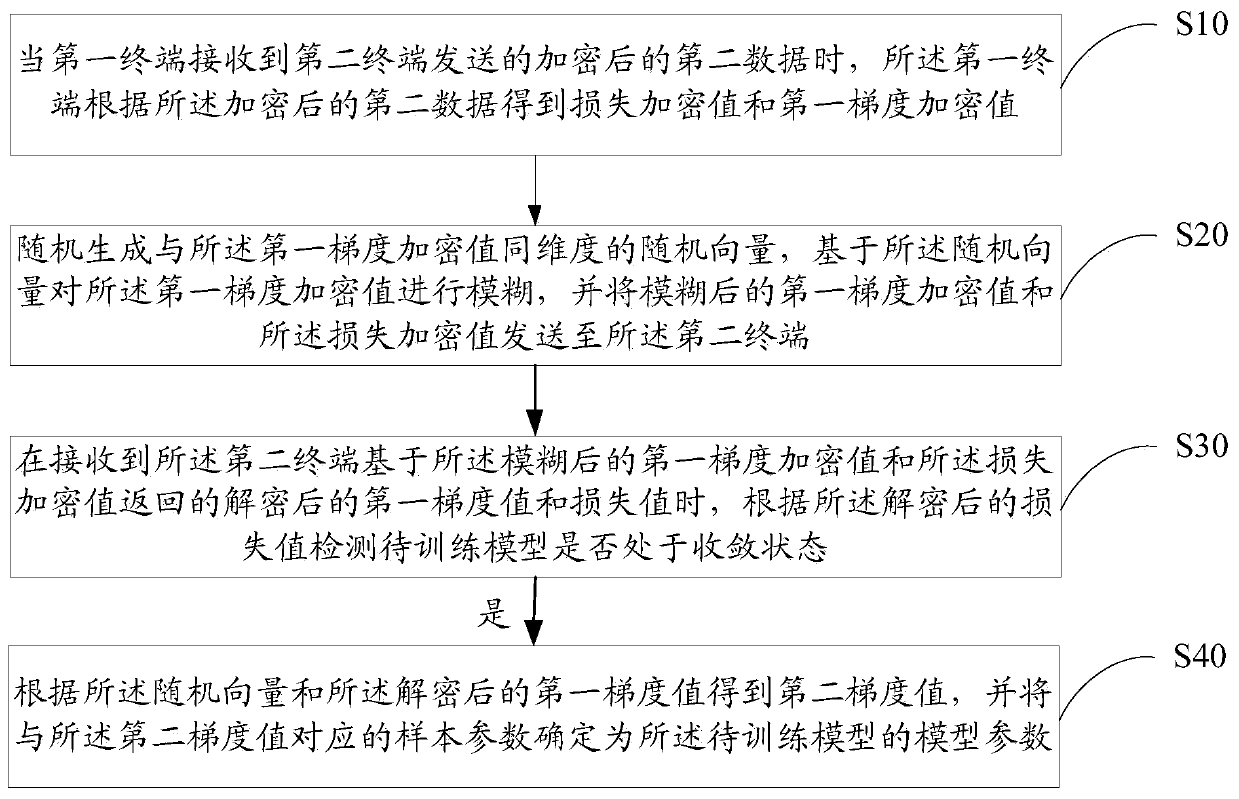
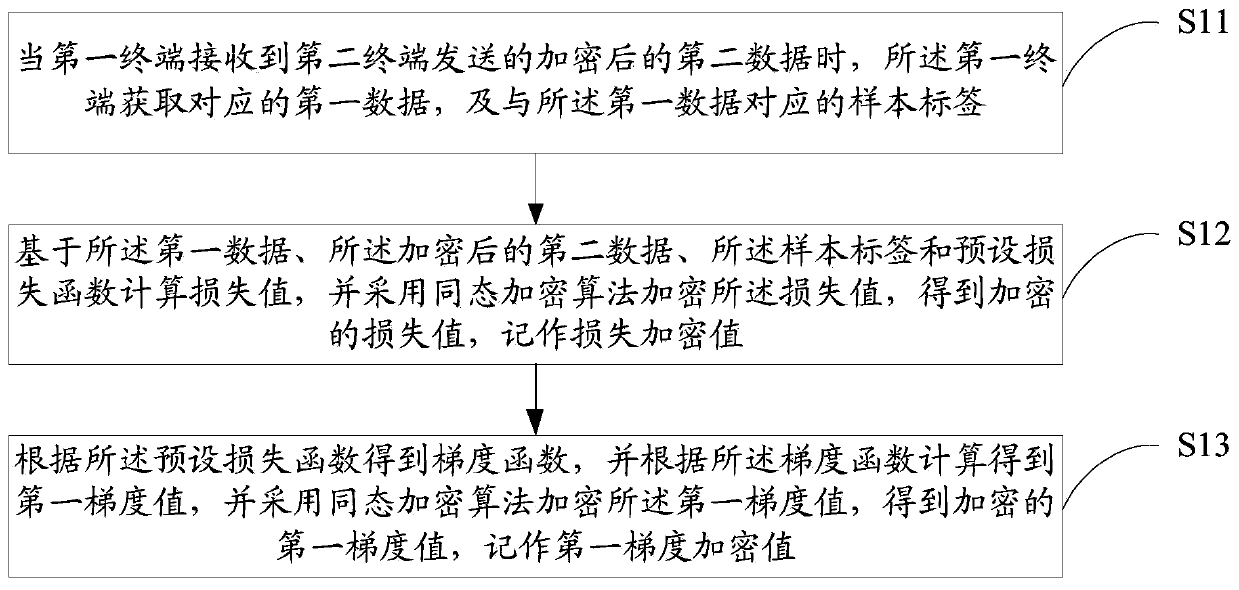
PendingCN109886417ASolve application limitationsWon't leakPublic key for secure communicationDigital data protectionTrusted third partyModel parameters
The invention discloses a model parameter training method and device based on federal learning, equipment and a medium. The method comprises the following steps: when a first terminal receives encrypted second data sent by a second terminal, obtaining a corresponding loss encryption value and a first gradient encryption value; randomly generating a random vector with the same dimension as the first gradient encryption value, performing fuzzy on the first gradient encryption value based on the random vector, and sending the fuzzy first gradient encryption value and the loss encryption value toa second terminal; when the decrypted first gradient value and the loss value returned by the second terminal are received, detecting whether the model to be trained is in a convergence state or not according to the decrypted loss value; and if yes, obtaining a second gradient value according to the random vector and the decrypted first gradient value, and determining the sample parameter corresponding to the second gradient value as the model parameter. According to the method, model training can be carried out only by using data of two federated parties without a trusted third party, so thatapplication limitation is avoided.
Owner:WEBANK (CHINA)
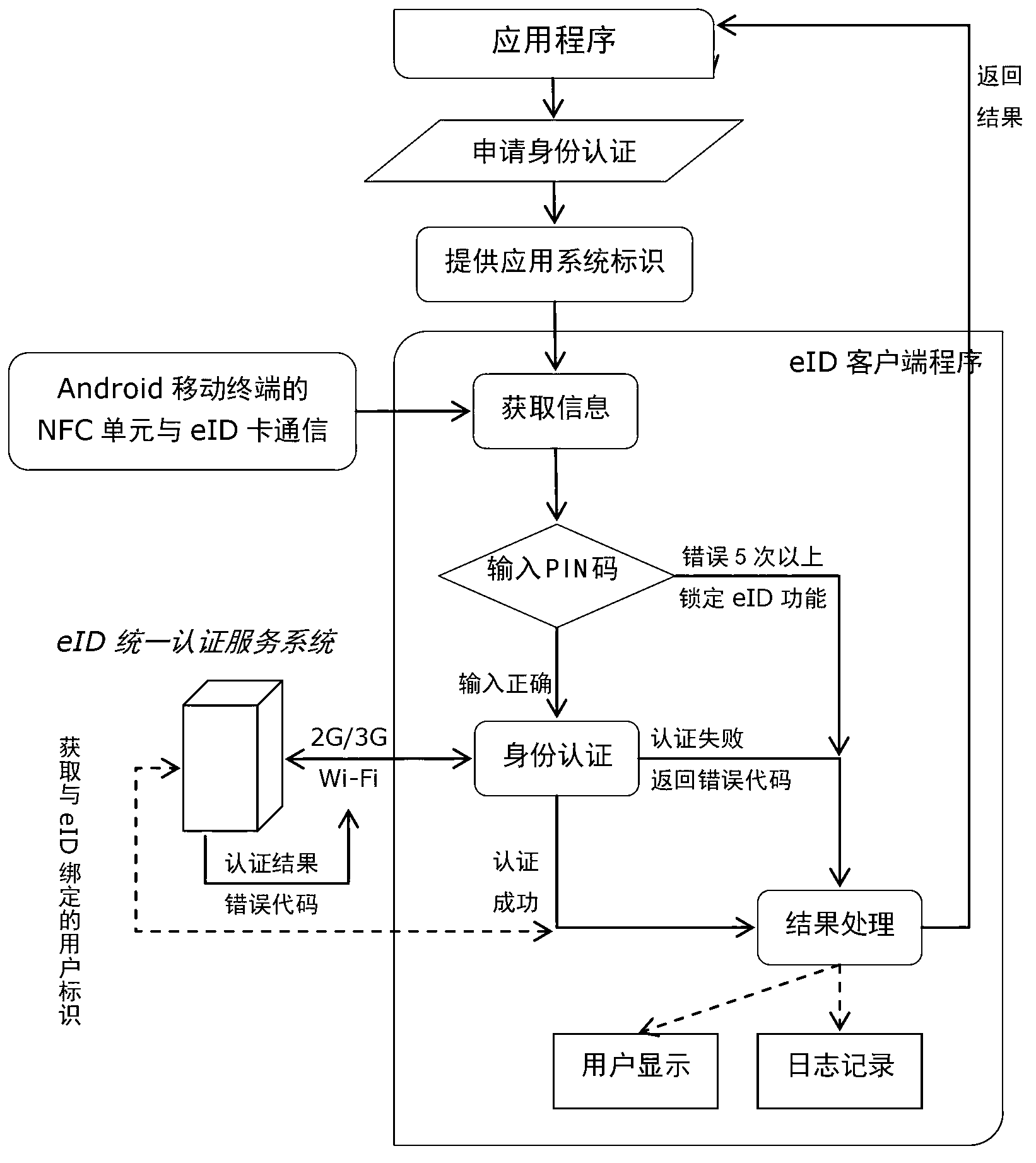
Method and system for eID authentication on mobile terminal
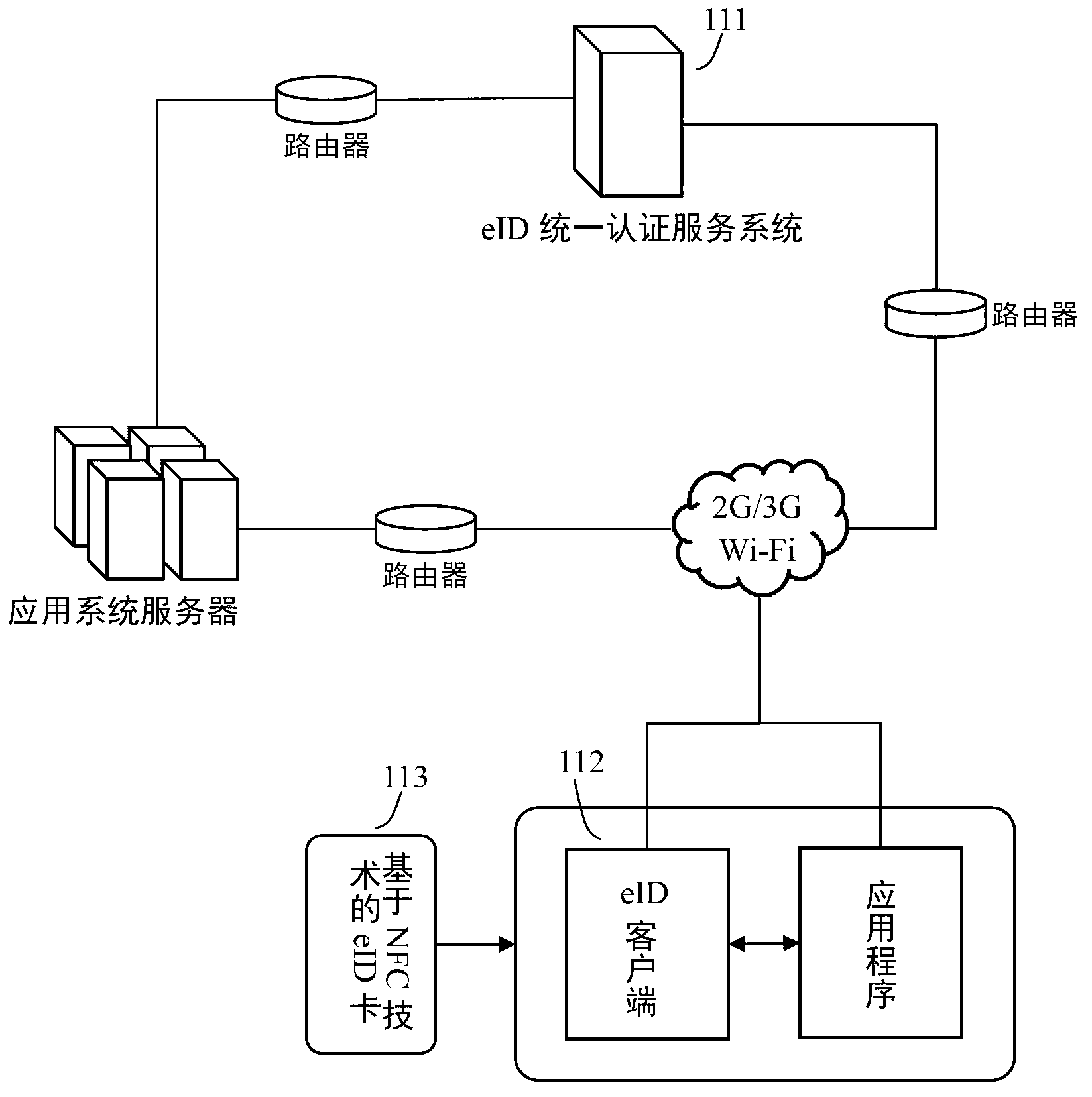
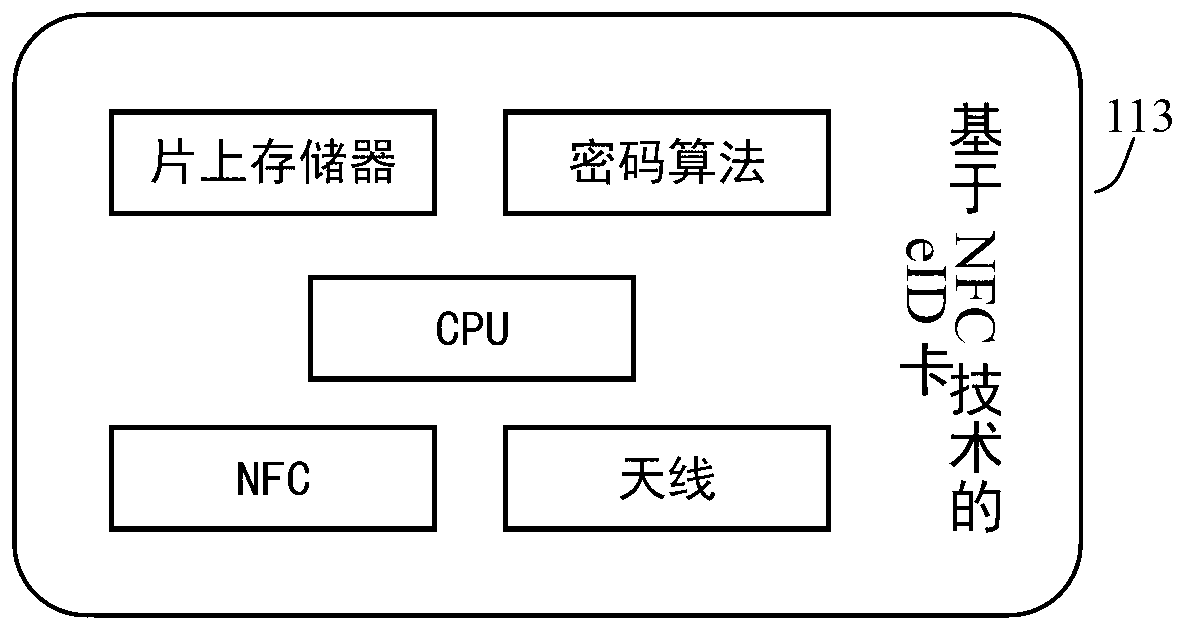
InactiveCN103259667AWon't leakPrevent the risk caused by cookies being stolen and used by othersNear-field transmissionUser identity/authority verificationComputer terminalUser authentication
The invention relates to the technical field of wireless communication, and provides a method and a system for eID (electronic identity) authentication on a mobile terminal. The system comprises an eID terminal carrier, an eID client and an eID unified authentication service system, wherein the eID client acquires relevant eID information from the eID terminal carrier; and the eID client and the eID unified authentication service system perform information exchange and user identity verification. The information transferred by the system does not contain personal information, and leakage of the personal information cannot be caused; With the adoption of an NFC (Near Field Communication) technology, an applicable occasion of the eID authentication is expanded; and the eID unified authentication service system is required to be accessed twice in the whole authentication process, so that the security of the system is improved, and a risk due to the fact that a browser cookies is stolen and utilized by others is prevented.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Bidirectional authentication method
InactiveCN101431415AImprove encryption efficiencyShort ciphertext lengthKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The present invention discloses a method of mutual authentication which is suitable for digital right management domain of interactive network TV. The invention comprises the following procedures: registering in an authentication server by a user terminal; executing key agreement between user terminal and authentication server; executing mutual authentication between user terminal and authentication server; obtaining license certificate for content broadcasting by user terminal. Mutual authentication is established between server of IPTVDRM and client taking advantage of high encryption efficiency of ECC and short length of cipher text by adopting the technical scheme described in the invention; obtaining session key from key protocol agreement before mutual authentication, authenticating ID of mutual parties through certificate mutually, and preventing certificate from tampering attack in transmitting process; making authentication valid and encryption and decryption efficiency higher than RSA mutual authentication by adopting mutual authentication of the certificate, and obtaining information of counterpart in plaintext by both parties for mutual confirmation without leaking plaintext simultaneously.
Owner:天柏宽带网络技术(北京)有限公司
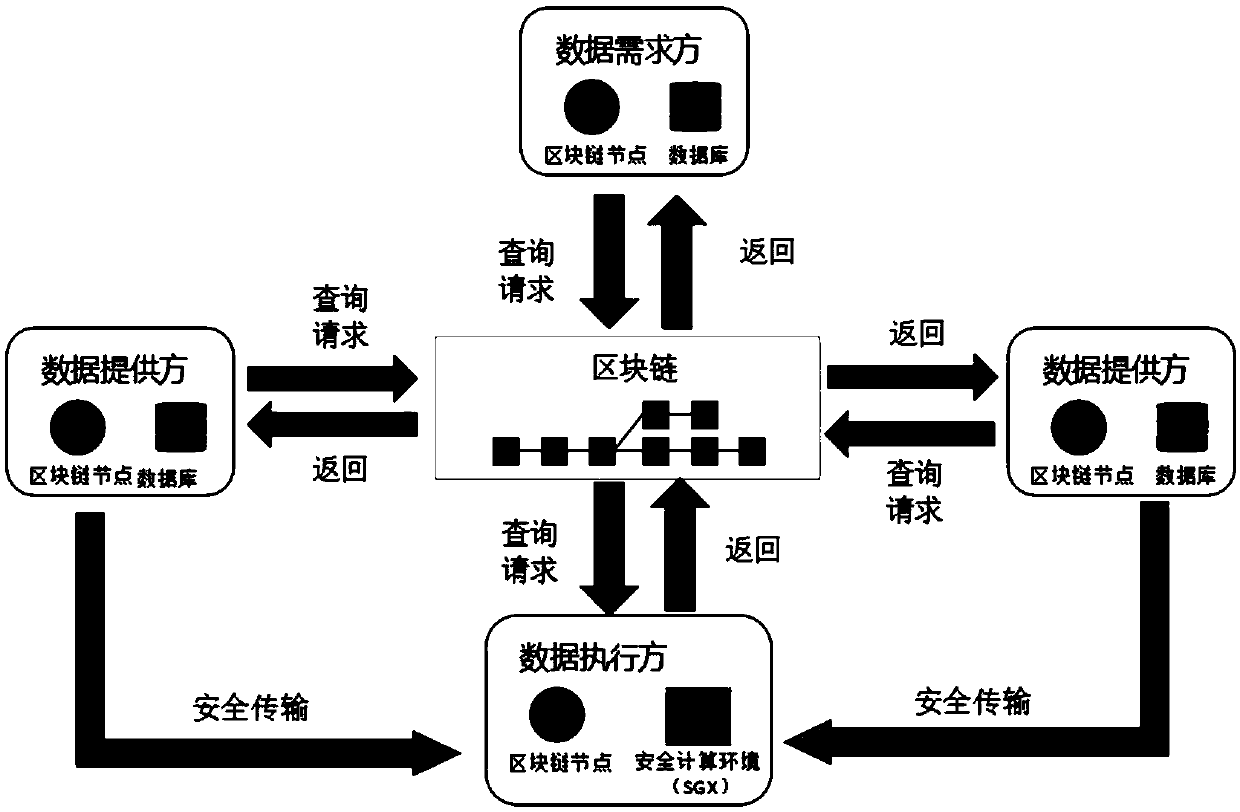
Data circulation method based on block chain and enclave
ActiveCN109660358AGuaranteed privacyWon't leakUser identity/authority verificationData transmissionTransfer procedure
The invention provides a data circulation method based on a block chain and an enclave. Privacy of a data processing process is ensured through utilization of a trusted computation environment provided by SGX (Software Guard Extensions), and moreover, the privacy of a data transmission process is ensured through utilization of an encrypted channel, so private data is prevented from being leaked ina whole process. According to the method, data integrity and legality are ensured through utilization of the block chain, a participant cannot fabricate data on the chain and moreover, and moreover,data quality is verifiable. According to the method, correct execution of a computation task is ensured through utilization of a smart contract, and rights and interests are rationally allocated. Traceability and auditability of a computation process are ensured through recording of operation logs on the chain.
Owner:余炀
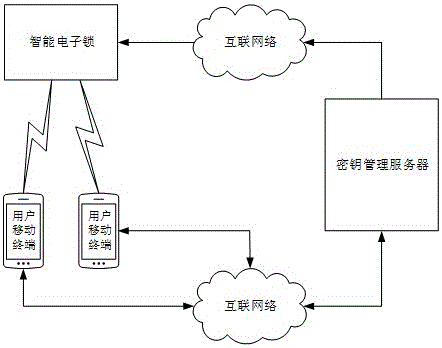
Electronic key sharing service system for house renting
ActiveCN105915344AMeet the needs of useRealize identification verificationKey distribution for secure communicationPublic key for secure communicationUser - individualKey sharing
The invention provides an electronic key sharing service system for house renting. Asymmetric encryption operation is carried out by using user identification information to generate a uniquely corresponding public renting key and a uniquely corresponding private renting key, wherein the private renting key is used for generating an electronic private key with an established unique corresponding relationship between an individual user and an intelligent electronic lock in an encrypted mode and the public renting key is used for executing delocking identification verification with user individual variation for decryption of the electronic key by the smart electronic lock. The private renting key is kept by a private key management server to guarantee security of the distribution and delocking process of the electronic key. Possible different using requirements for randomness, individual variation, and security in house renting sharing can be met well; convenience of the system in house renting sharing application is improved; the convenience degree of housing renting is enhanced; and development of the intelligent door lock industry can be promoted. Therefore, the system has the broad market promotion and application prospects.
Owner:CHONGQING JINOU SCI & TECH DEV
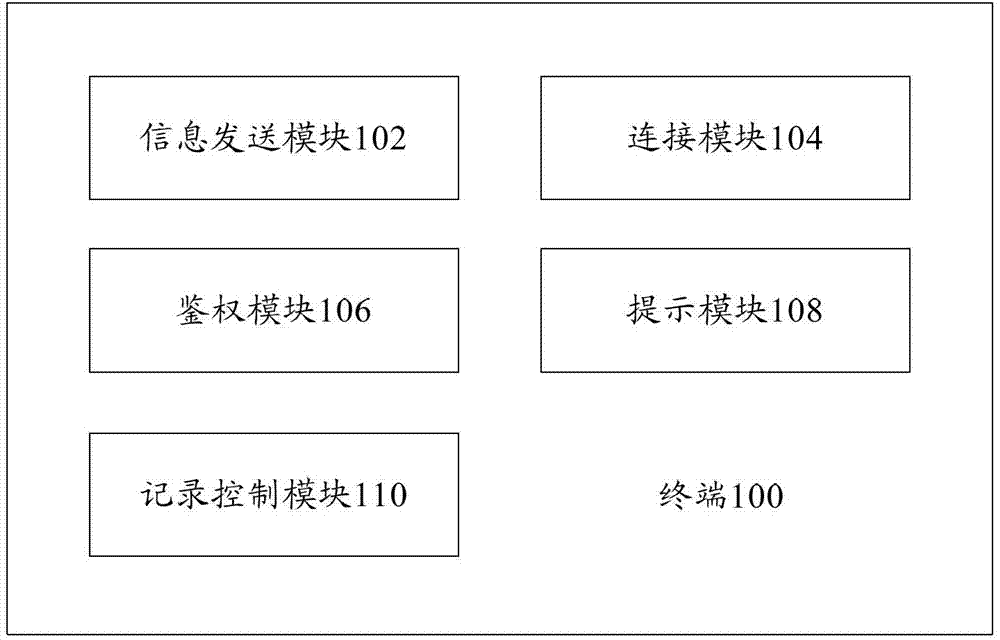
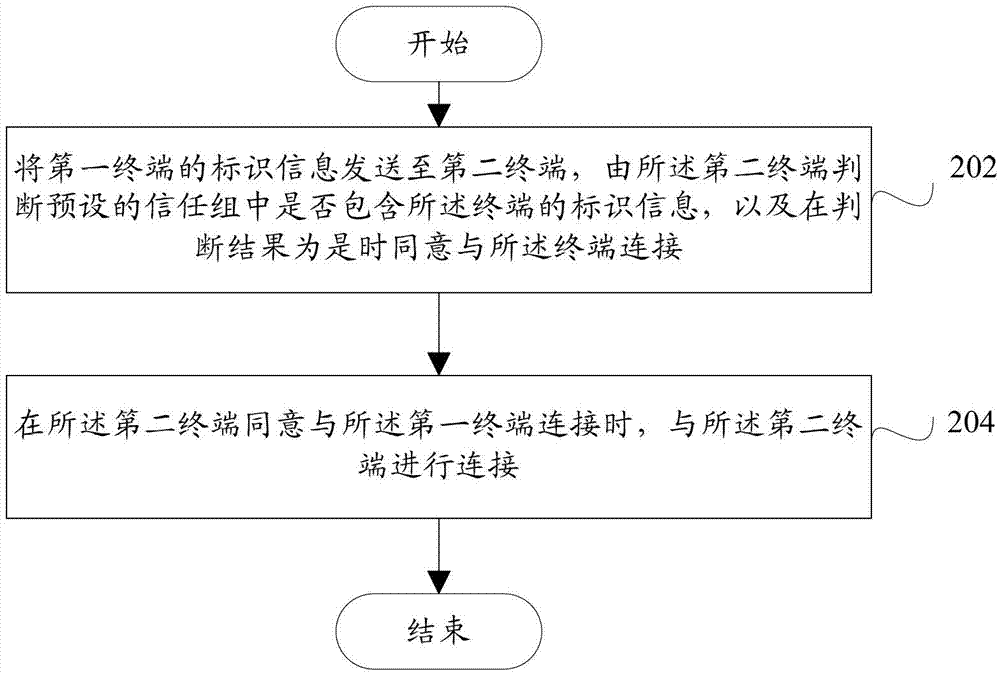
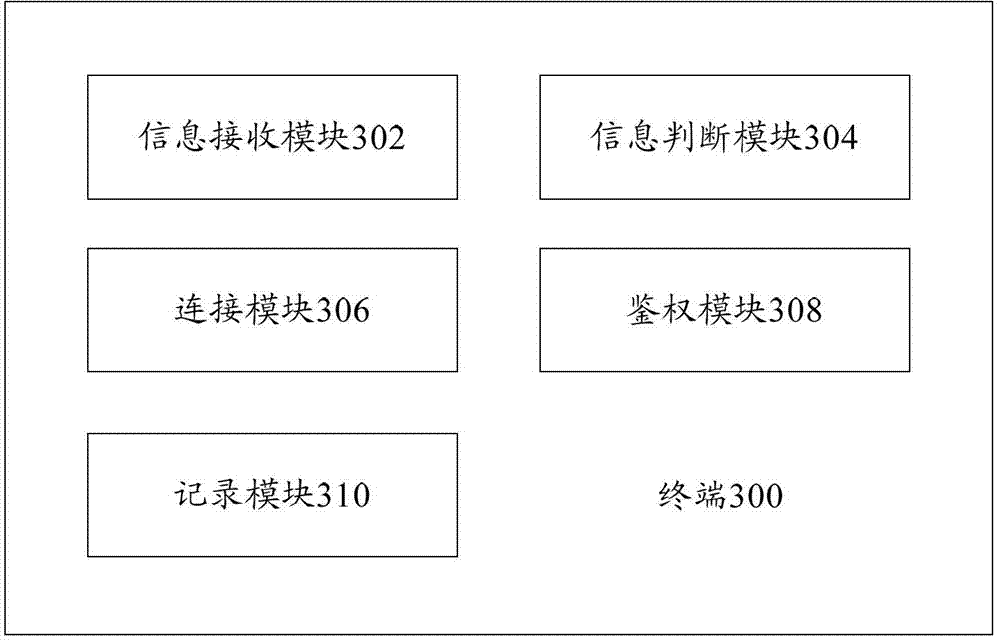
Terminal and data communication method
The invention provides a terminal and a data communication method. The terminal comprises an information sending module and a connection module, wherein the information sending module is used for sending identification information of the terminal to a second terminal, which is used for judging whether a preset trusted group includes the identification information of the terminal or not, and agrees to the connection with the terminal when a positive judgment result is achieved; and the connection module is connected with the second terminal when the second terminal agrees the connection with the terminal. By means of the technical scheme disclosed by the invention, when one mobile terminal access to another terminal serving as a Soft AP (Access Point) in a Wifi (Wireless Fidelity) manner, passwords do not needs to be input all the time for authentication, so that not only is a user prevented from complex operation but also the password safety of the user can be guaranteed.
Owner:DONGGUAN YULONG COMM TECH +1
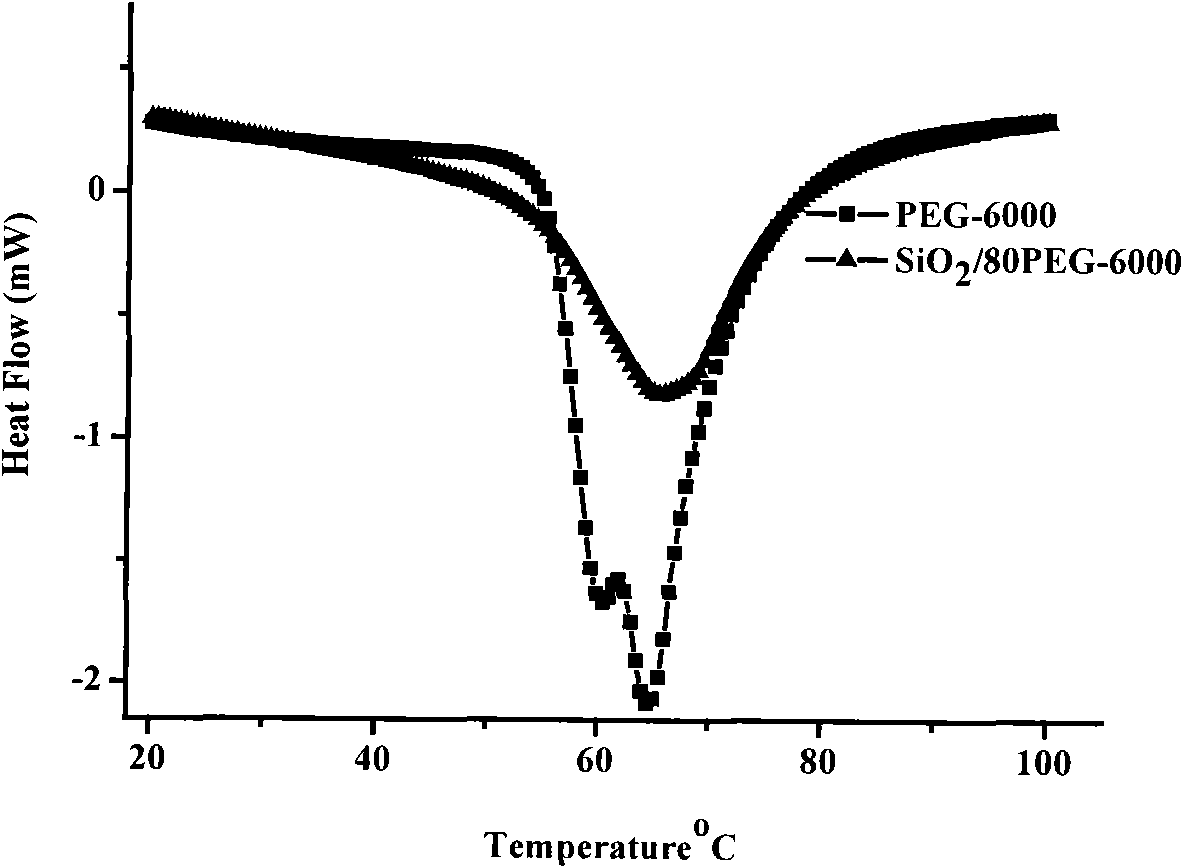
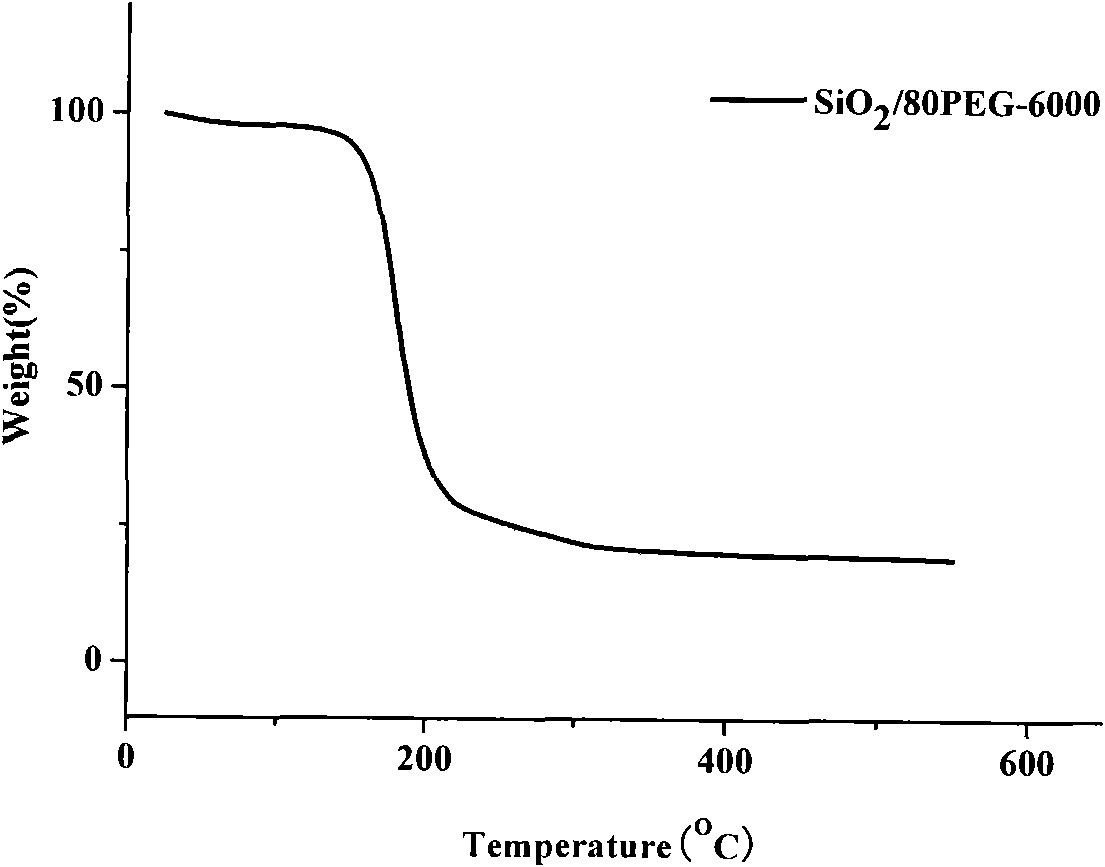
Method for preparing polyethylene glycol/silicon dioxide composite shape-stabilized phase change energy storage material and product thereof
InactiveCN101942290AEase of industrial productionReduce manufacturing costHeat-exchange elementsPolyethylene glycolHydrolysis
The invention discloses a method for preparing a polyethylene glycol / silicon dioxide composite shape-stabilized phase change energy storage material and a product thereof. The method comprises the following steps of: dissolving polyethylene glycol serving as a work substance into water in an amount of between 0.2 and 1.0g / ml to obtain water solution of the polyethylene glycol; dripping a side product SiCl4 of polycrystalline silicon into the obtained water solution of the polyethylene glycol for a hydrolysis and sol-gel reaction to form gel with a three-dimensional network structure; drying the gel to prepare powder, removing water and hydrogen chloride from the powder; and dripping a modifier for modifying the surface of the powder hydrophobically in an amount which accounts for 0.1 to 1.5 weight percent of the powder at the temperature of 80 DEG C under the protection of nitrogen for surface modification to obtain the polyethylene glycol / silicon dioxide composite shape-stabilized phase change energy storage material. The method can change wastes into valuables and reduce the manufacturing cost of the product by using the side product SiCl4 of the polycrystalline as a silicon source, and is favorable for the industrial production and wide popularization and application of the SiO2 shape-stabilized phase change energy storage material.
Owner:SOUTHWEST JIAOTONG UNIV +1
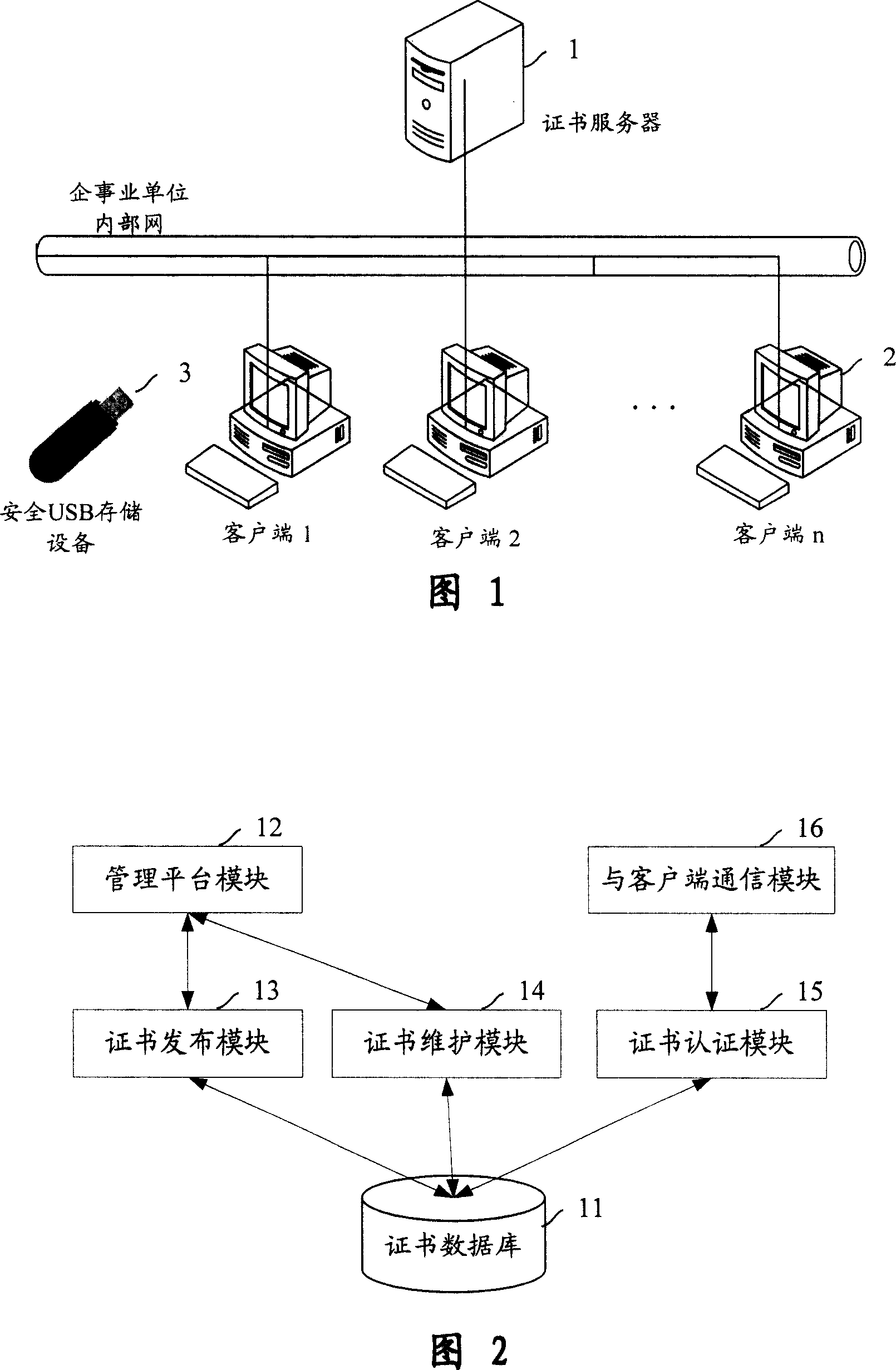
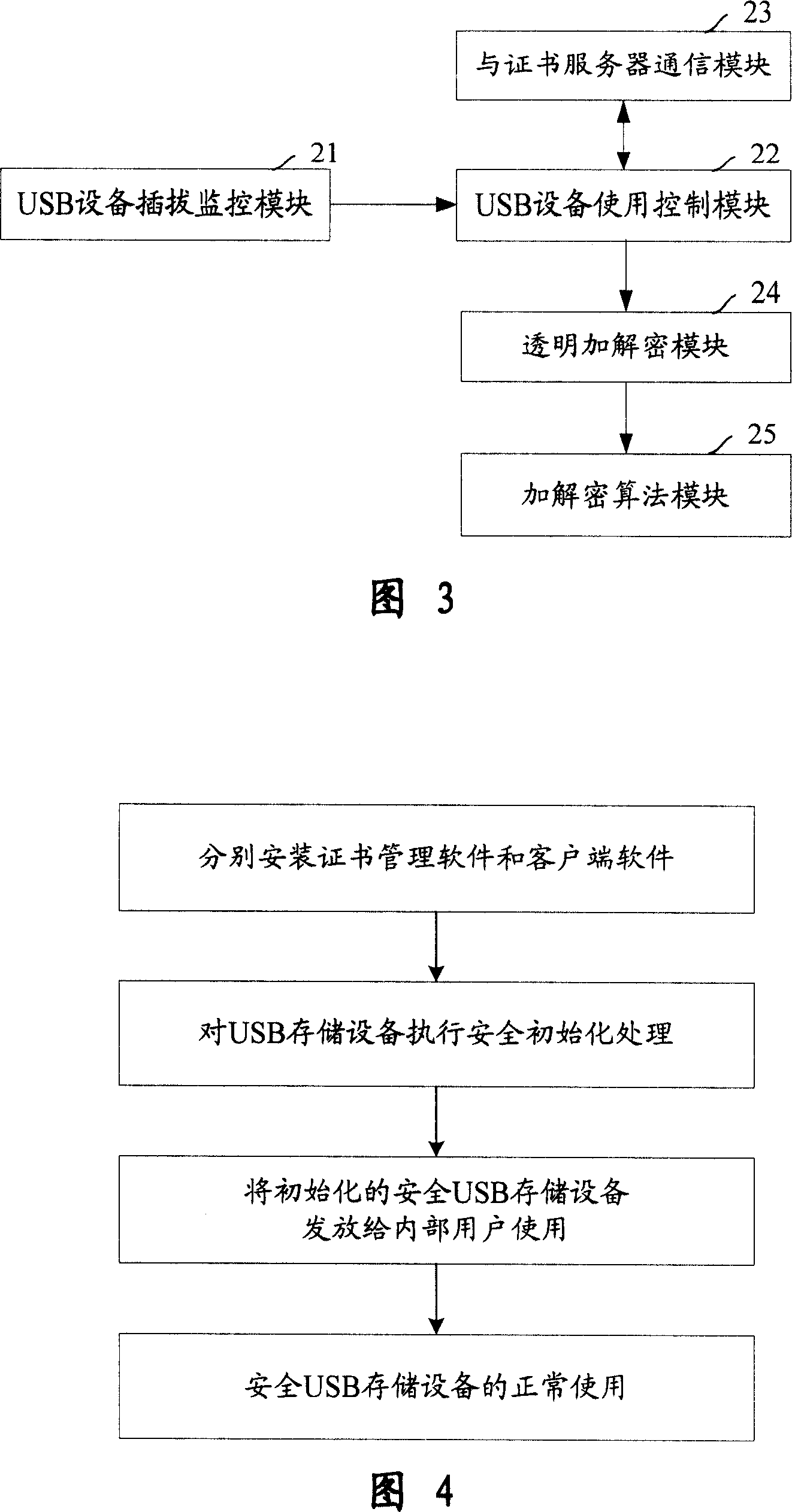
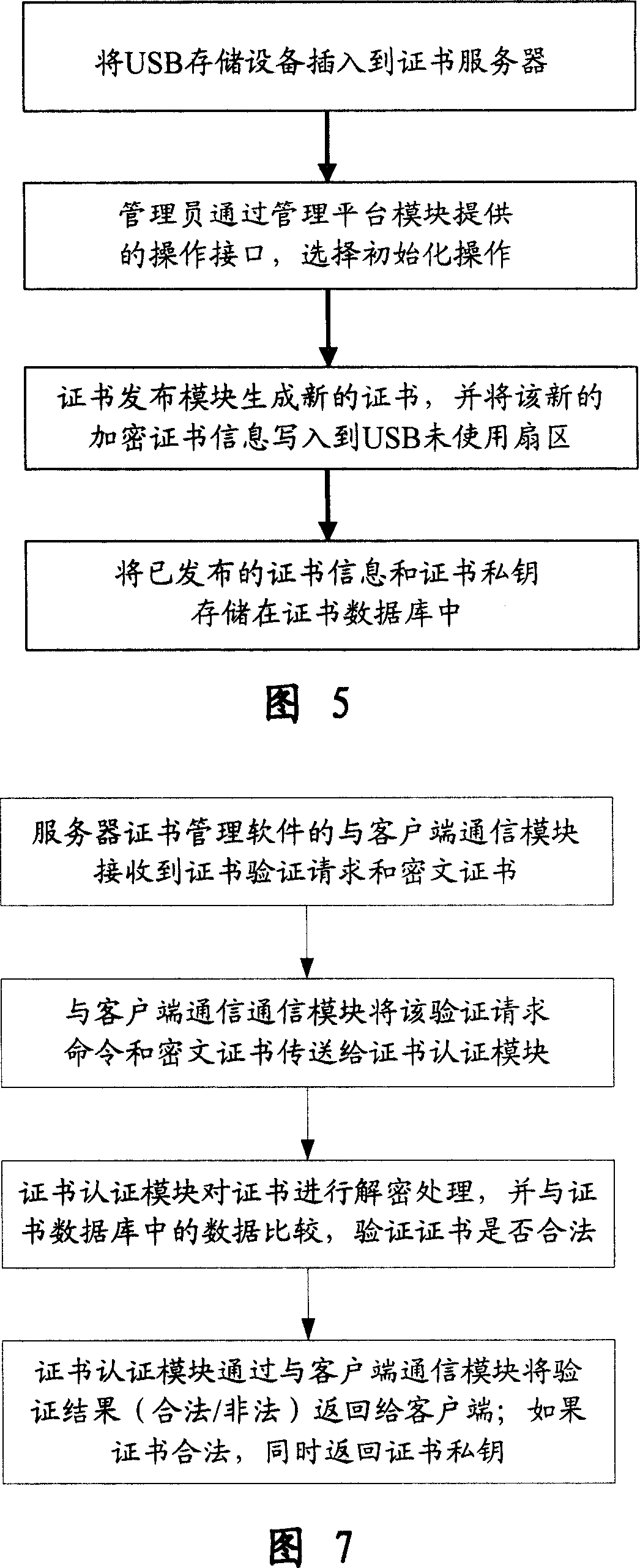
Divulging secrets prevention system of USB storage device date based on certificate and transparent encryption technology
InactiveCN101017525APrevent leak riskReduce the Risk of ConfidentialityUser identity/authority verificationUnauthorized memory use protectionClient-sideUSB
This invention relates to one USB memory data anti-leakage system based on certificate and transparent coding technique, which comprises the following parts: one certificate management software; certificate servo with physical isolation and network protection actions, inner network host to customer end with customer end software; safety USB memory device by multiple common USB devices through the servo. The method comprises the following steps: a, separately fixing certificate management software and customer end software in network servo and each host; b, executing safety initial process in certificate servo on USB memory device; c, sending the memory device to inside user; d, safety USB memory device is for normal use.
Owner:BEIJING UNIV OF POSTS & TELECOMM
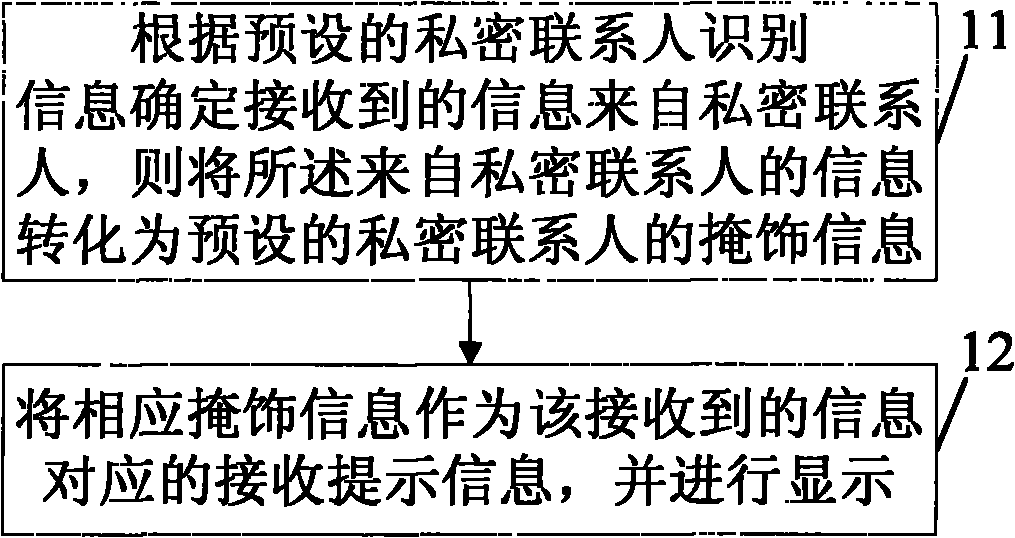
Method and terminal for protecting user privacy information
InactiveCN101895607AFlexible and safe to useWon't leakCalling susbscriber number recording/indicationInternet privacyUser privacy
The invention relates to a method and a terminal for protecting user privacy information. The method comprises the following steps: according to the identifying information of a preset privacy contact person, determining that the received information comes from a privacy contact person, then converting the information from the privacy contact person into concealing information of the preset privacy contact person; and taking the concealing information as the receiving prompt information corresponding to the received information and displaying. The embodiment of the invention enables a user to receive the information sent by the privacy contact person timely and safely under any phone profile and to flexibly and safely use the communication terminal in various phone profiles.
Owner:HUAWEI DEVICE CO LTD
Encrypted data file storage and retrieval system and method
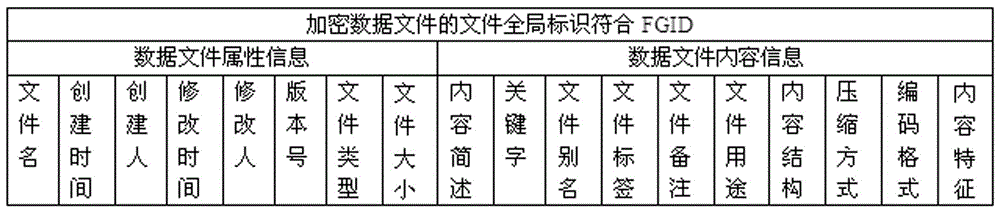
ActiveCN105678189ASearch guaranteeEnsure safetyDigital data protectionSpecial data processing applicationsData fileCloud storage system
The invention discloses an encrypted data file storage and retrieval method. The method comprises the steps that after content metadata is extracted from a data file, the data file is encrypted to generate an encrypted data file to be stored in storage equipment of a cloud storage system; the content metadata is added with a file global identifier of the data file in an encrypted state and then stored in a content metadatabase of the cloud storage system; when the encrypted data file stored in the cloud storage system is retrieved, the content metadatabase is retrieved through an inverted index method to acquire the file global identifier matched with a retrieval keyword, and attribute information and content information of the encrypted data file corresponding to the file global identifier are listed to serve as a retrieval result. According to the method, the content metadata is extracted before the data file is encrypted, the file global identifier of the file in the encrypted state is added into the content metadata, the encrypted data file stored in the cloud storage system is retrieved through the file global identifier, and the retrieval convenience of the data file is guaranteed while the safety and the privacy of the data file in a cloud storage environment are guaranteed.
Owner:SHANGHAI MARITIME UNIVERSITY
Role based dynamic database desensitization service method and system
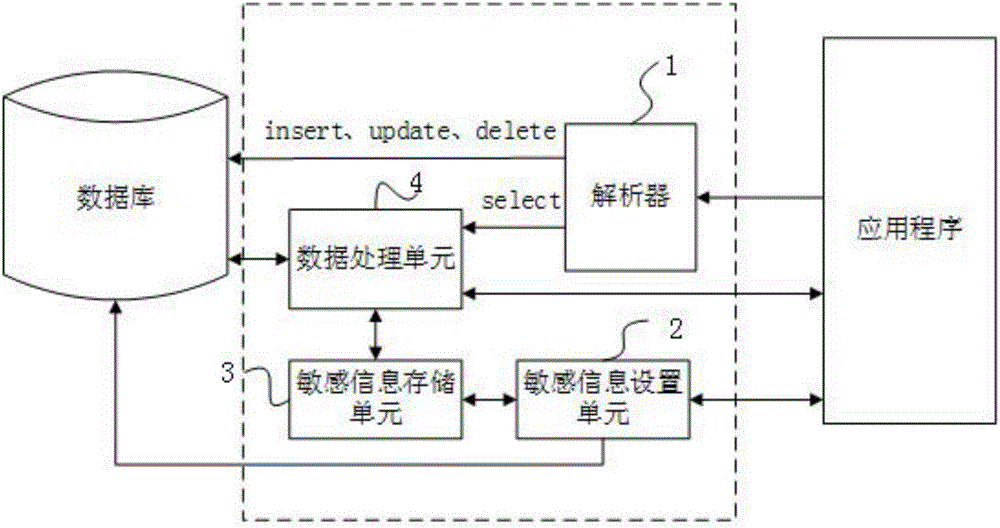
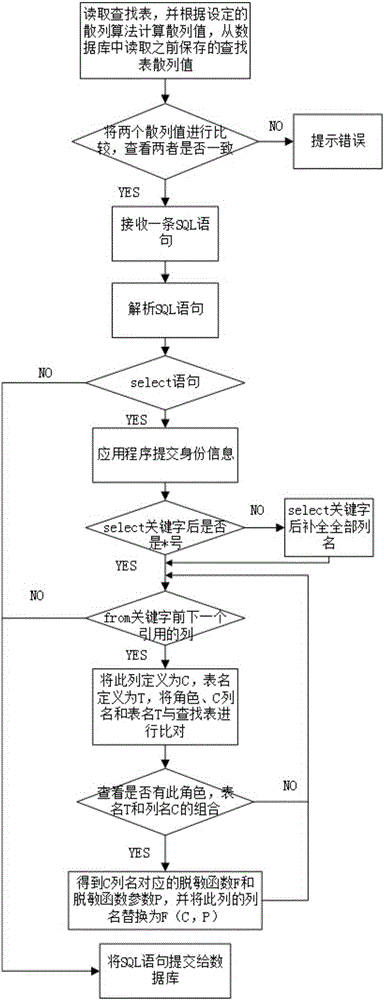
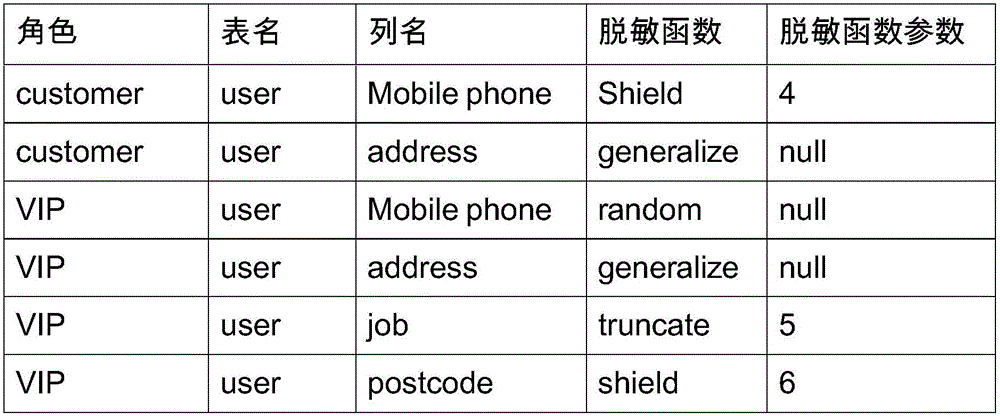
InactiveCN106203170AMeet different service level requirementsWon't leakDigital data protectionSpecial data processing applicationsLookup tableInformation security
The invention belongs to the field of information safety and provides a role based dynamic database desensitization service method and system. The system comprises a parser for parsing SQL statements, a sensitive information setting unit for setting sensitive fields, desensitization functions and parameters for users of different roles, a sensitive information storage unit for storing a lookup table, a data processing unit for generating the desensitization functions in a database, obtaining user roles, verifying the integrity of the lookup table and modifying SELECT statements according to the requirements in the lookup table. In addition, the invention discloses the method, the method comprises the steps that the SQL statements are parsed through the parser, if the SQL statements are SELECT statements, the statements are submitted to the data processing unit for processing; if not, the statements are submitted to the database. Different sensitive fields and desensitization functions are set for the users of different roles, different desensitization functions can be also set for the same sensitive fields, the requirement for different sensitive data protection degrees of the users of different roles are met, and the diversification demand during provision of data service is met.
Owner:北京同余科技有限公司
Mean-temperature method of cylindrical battery
InactiveCN104993187AImprove thermal conductivityWon't leakBattery isolationSecondary cellsEngineeringSealant
The invention discloses a mean-temperature method of a cylindrical battery. The mean-temperature method of the cylindrical battery has the technical scheme that 1, the arrangement mode is determined according to the battery pack forming requirements, and a casing module is designed; 2, a cylindrical battery cell is assembled in the casing module, and sealant is coated for sealing; 3, liquid phase change material composite glue is prepared; 4, the phase change material composite glue is poured into the casing module, and a battery pack with good temperature consistency is obtained after curing and forming. The phase change material composite glue is prepared by phase change materials and organic silicon filling and sealing glue according to a certain ratio, wherein the phase change materials use paraffin and graphite as major components; the organic silicon filling and sealing glue uses vinyl silicone oil and modified aluminum oxide powder as major components. Through the structure features of the mean-temperature method, the mean-temperature method has the beneficial effects that the battery core has good temperature consistency; the module structure is good in intensity and can pass by the battery pack-relevant vibration, falling and collision tests. The phase change material composite glue is encapsulated in the casing; no loss occurs after the long-time cyclic use; the permanent service life is realized.
Owner:广东万锦科技股份有限公司
Fermenting and drying treatment device for organic wastes
InactiveCN102030569AAirtightWon't leakBioreactor/fermenter combinationsBiological substance pretreatmentsEngineeringMechanical engineering
The invention discloses a fermenting and drying treatment device capable of reliably and effectively fermenting and drying organic wastes with simple structure for avoiding cost increment. The device is provided with an airtight container, a hollow cylindrical rotating shaft rotating freely and vertically arranged in the container, a plurality of stirring blades extending to the horizontal direction from multiple upper and lower positions of the rotating shaft, a driving mechanism for driving the rotating shaft to rotate, an air supply mechanism for supplying air to the container, and an exhaust port for exhausting the air in the container. The plurality of stirring blades comprises stirring blades which have hollow interiors and are provided with through holes communicating the outside from the hollow space, the air supply mechanism is connected at the axial end of the rotating shaft, and the hollow space of the rotating shaft is mutually communicated with the hollow space of the stirring blades. Therefore, the air supplied by using the air supply mechanism is exhausted from the through holes of the stirring blades through the rotating shaft. The organic wastes are put into the container, the air is introduced into the container, the organic wastes are stirred, and the organic wastes are subjected to fermenting treatment and drying treatment based on the action of aerobic microbes.
Owner:CHUBU ECOTEC
Automatic fruit preprocessing device for canned fruit production
ActiveCN108634341ASave human effortKeep the tasteFruit and vegetables preservationFruit stoningMotor shaftIntegrated devices
The invention discloses an automatic fruit preprocessing device for canned fruit production. The automatic fruit preprocessing device comprises a base, wherein a fruit peeling and dicing integrated device is mounted on the base; the fruit peeling and dicing integrated device comprises a U-shaped frame; a peeling device is mounted at the top end of the U-shaped frame; a pushing and conveying deviceis mounted at the bottom end of the U-shaped frame through a support plate; a second horizontal oil cylinder and a low-speed motor are separately mounted on the left side and right side of the U-shaped frame; a pushing and extruding rod is connected with the right end of the second horizontal oil cylinder through a piston rod; an annular pushing block and a pushing and pressing block are separately mounted on the outer side and right end of the pushing and extruding rod; an annular pit cutting knife is connected with the left end of the low-speed motor through a motor shaft; a plurality of slicing knives are mounted on the outer side of the annular pit cutting knife at equal intervals; a second miniature oil cylinder is fixed to the inner side of the annular pit cutting knife; and a compressing block is connected with the left end of the second miniature oil cylinder through a piston rod. The automatic fruit preprocessing device can perform peeling, dicing and pit removing on fruits and automatically convey diced fruits onto the pushing and conveying device, thereby improving the production efficiency of canned fruits.
Owner:重庆稳稳科技有限公司
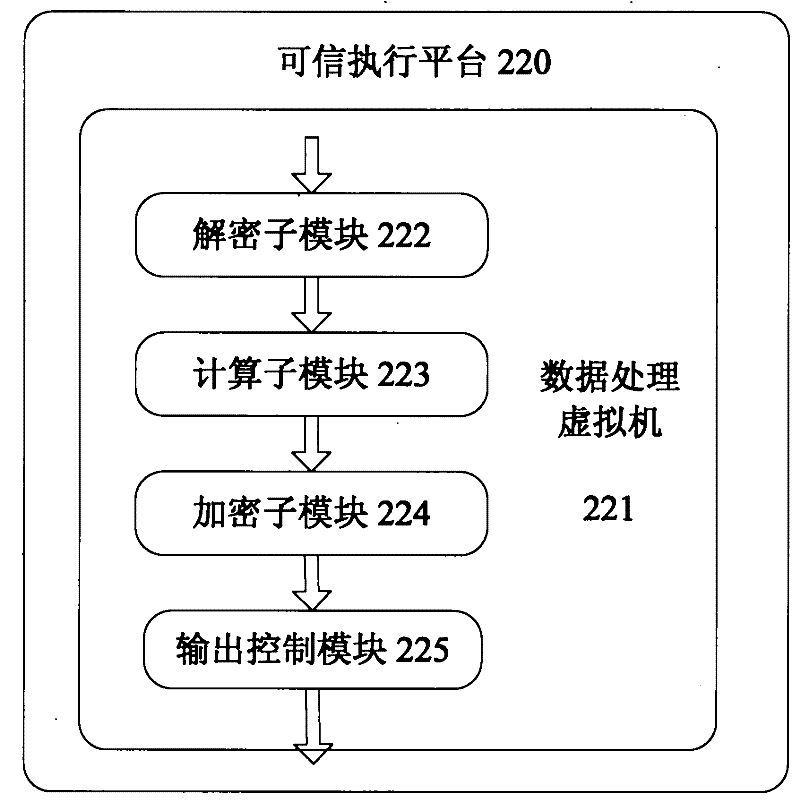
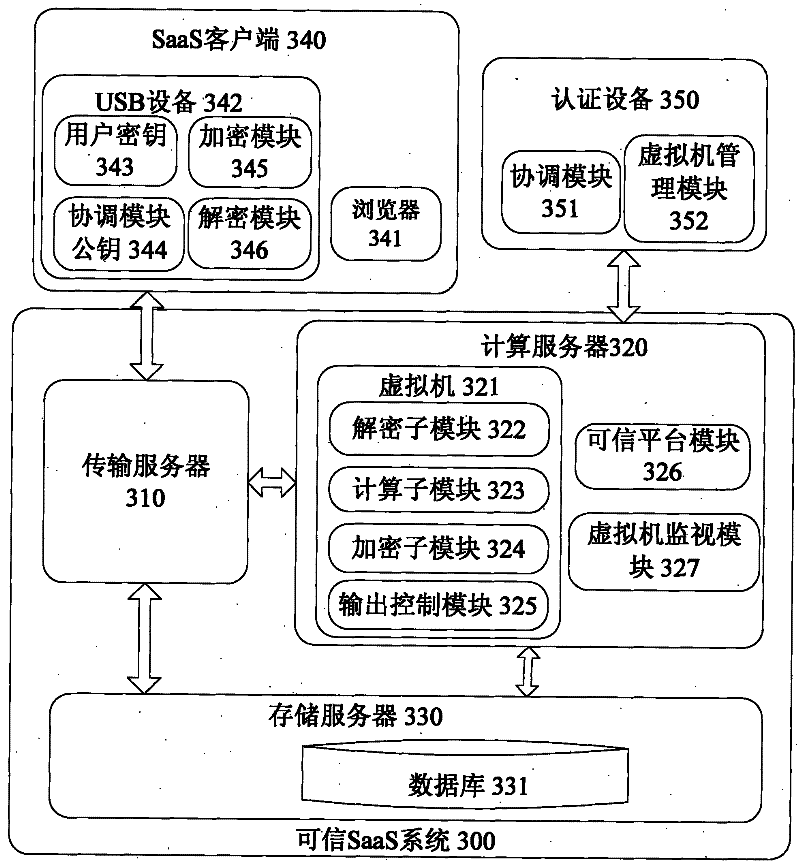
Data processing device and data processing method
The invention relates to data processing equipment and a data processing method. The data processing equipment comprises a trusted-computing-technology-based trusted execution platform. The platform comprises a data processing virtual machine. The data processing virtual machine is used for processing data transmitted by a client and returns a data processing result to the client, and comprises a decryption sub-module, a computing sub-module, an encryption sub-module and an output control module, wherein the decryption sub-module is used for decrypting encrypted data to be processed from the client and providing the decrypted data for the computing sub-module by a first interface; the computing sub-module is used for processing the decrypted data from the decryption sub-module and providing the data processing result for the encryption sub-module by a second interface; the encryption sub-module is used for encrypting the data processing result from the computing sub-module by the second interface; and the output control module is used for all the output of the data processing virtual machine, so that only the encrypted data output by the encryption sub-module serves as the output of the data processing virtual machine to the client. The data processing equipment can ensure data processing security.
Owner:FUJITSU LTD
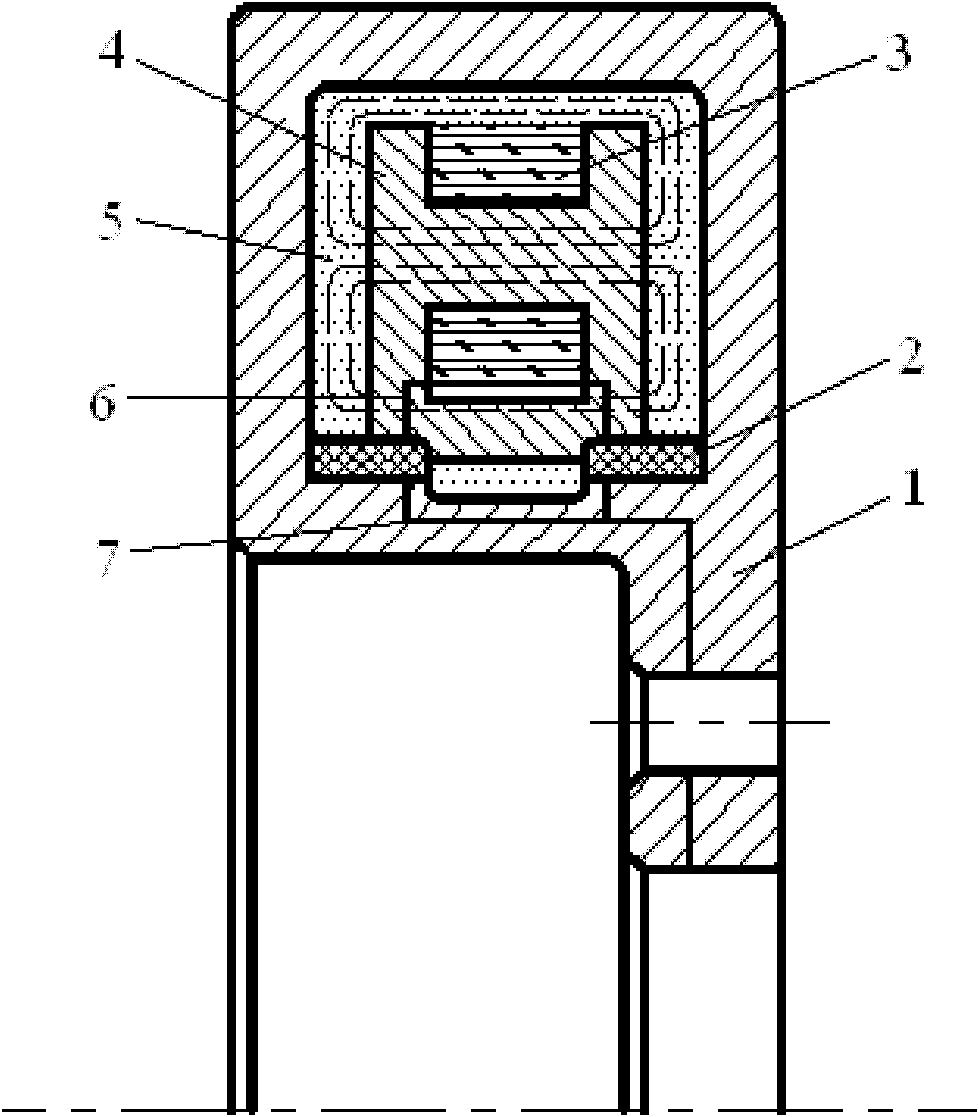
Magnetorheological torsional vibration damper for engine
InactiveCN102168736AWon't leakImprove sealingNon-rotating vibration suppressionDamping factorPower flow
The invention discloses a magnetorheological torsional vibration damper for an engine. The damper is characterized in that: an inertia disc is arranged in an annular shell; an antifriction lining is arranged at the outer end of the inner circumference of the annular shell, and the inertia disc can rotate freely around the antifriction lining in the annular shell; a conductive coil is arranged in the inertia disc; magnetorheological fluid is filled in a gap between the annular shell and the inertia disc; a lead wire is connected with the antifriction lining; and the lead wire is exported from the center of the damper through an insulating conduit of the annular shell. By utilizing the characteristic that the conductive coil is electrified and generates a magnetic field to control flowing of the magnetorheological fluid, the rotation damping force of the damper can be adjusted, so that the defect that the damping coefficient of the traditional silicone oil torsional vibration damper can only be a single damping coefficient is overcome. The external magnetic force is changed by changing the volume of current, so that the damping characteristic of the magnetorheological fluid is changed. Therefore, the magnetorheological torsional vibration damper has excellent damping effect when a crankshaft is resonant, and has better damping effect than that of the silicone oil damper under other frequencies.
Owner:TIANJIN UNIV
Two-component epoxy decorating sealant and preparation method thereof
ActiveCN105802451ANo saggingWon't flowAntifouling/underwater paintsPaints with biocidesGlycidyl ethersColloid
The invention provides a two-component epoxy decorating sealant, comprising component A and component B. The component A comprises, by weight: 70-90 parts of first epoxy resin, 0-7 parts of glycidyl ether type diluent, 1-5 parts of a coupling agent, 3-7 parts of a first thixotropic agent, 0.1-0.3 part of a yellowing aid, and 0.1-0.3 part of a defoaming agent; the component B comprises 20-25 parts of an alicyclic curing agent, 20-30 parts of second epoxy resin, 25-30 parts of benzyl alcohol diluent, 3-6 parts of an accelerant, 3-7 parts of a second thixotropic agent, and 5-10 parts of a pigment. After being constructed and cured, the two-component epoxy decorating sealant attaches tightly to ceramic tiles, and water and dust never enter a gap to cause mold or leakage. In addition, colloid of the decorating sealant of the invention never flows or sags during construction, construction is facilitated, and construction efficiency is improved. The invention also provides a preparation method of the two-component epoxy decorating sealant.
Owner:HUNAN KOSEN NEW MATERIAL
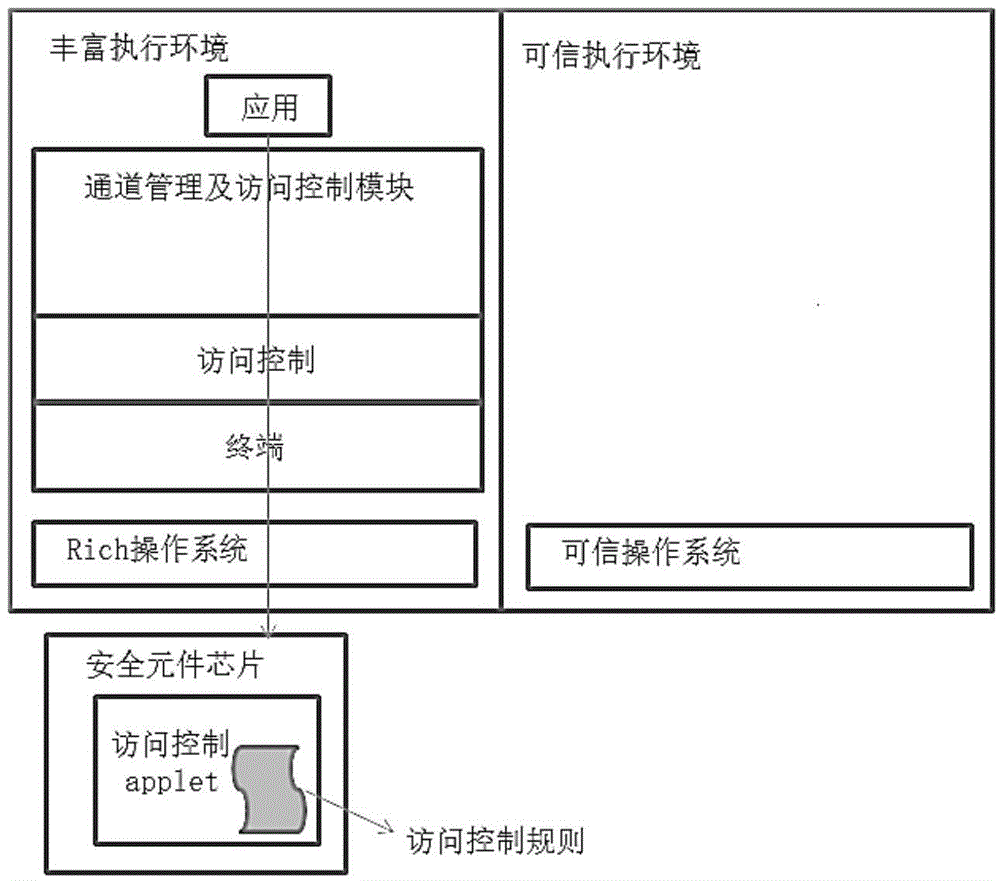
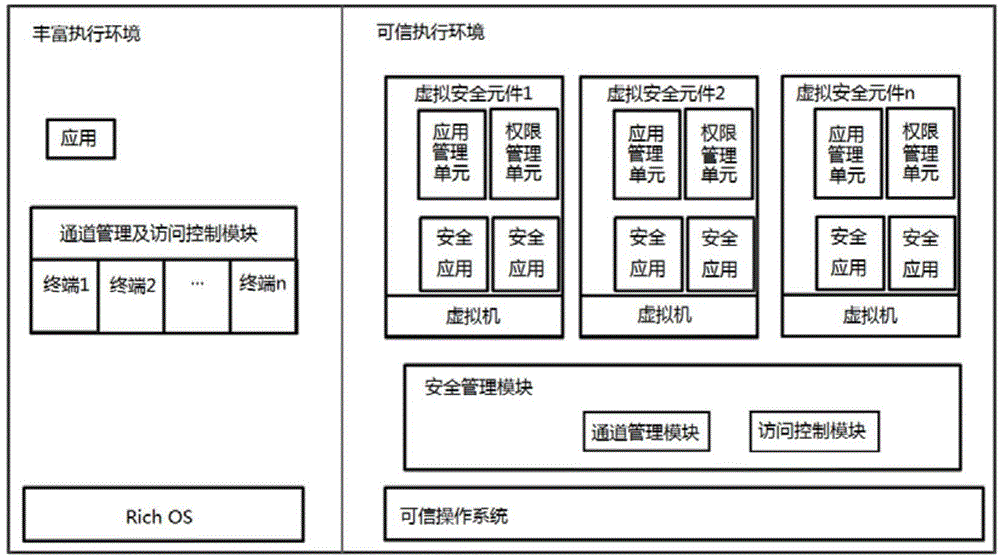
Security system implementation method based on virtual security element in trusted execution environment
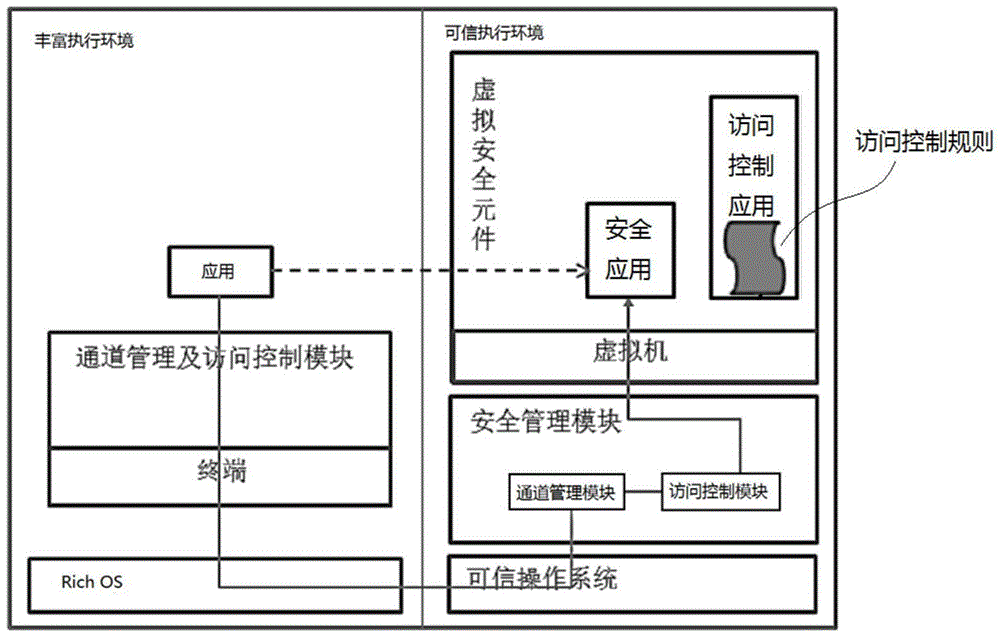
ActiveCN104899506ASimple designImprove efficiencyDigital data protectionInternal/peripheral component protectionUsabilitySystem structure
A security system implementation method based on a virtual security element in a trusted execution environment is provided by the invention and belongs to the field of information security. The method comprises: adding a terminal that accesses a trusted execution environment to a channel management and access control module built in a Rich OS; removing access control processing that is for accessing the trusted execution environment; then, setting a security management module that provides a uniform access interface for applications in the Rich OS and at least one virtual security element in the trusted execution environment; and receiving all access requests from the applications in the Rich OS by using the security management module, thus improving system security. The method provided by the invention simplifies the existing system structure, and significantly improves system security. A virtual machine is set in each virtual security element, thereby significantly improving usability and portability.
Owner:SHENZHEN XUEQIU SCI & TECH
Small perturbance stratified substrate sludge in-situ sampler and sampling method thereof
InactiveCN101620037ADoes not disturb the distributionAccurate layeringWater resource protectionWithdrawing sample devicesEngineeringSludge
The invention relates to a small perturbance stratified substrate sludge in-situ sampler used for collecting deposits in water and a sampling method thereof. The sampler consists of a C-shaped inner tube, a C-shaped outer tube, an outer tube conical head, an inner tube handle, an outer tube handle and an inflatable plug, wherein the outer tube and the inner tube are sleeved together and are respectively formed by fixedly connecting a plurality of sections; the inner tube can be rotated by the inner tube handle at the top so as to superpose or close C-shaped openings of the inner tube and the outer tube. The inner tube is firstly rotated so as to close the C-shaped opening when substrate sludge is fetched; the inner tube is rotated so as to open the C-shaped opening after being inserted by a predetermined depth, and then the inner tube and the outer tube are rotated after being inclined by a small angle together so as to rotate the substrate sludge into the inner tube. Then the inflatable plug is put on the sludge surface and is inflated; the inner tube is rotated to close the C-shaped opening; finally, the inner tube and the outer tube are lifted from the water and laid on the ground for stratified sampling. The invention has small perturbance to the substrate sludge, does not change stratified and physical properties of the substrate sludge, has light weight, portability, convenient operation and wide generalization and application values and , is suitable for sampling work of substrate sludge of hydraulic reclamation yards of river and lake.
Owner:HOHAI UNIV
Federation learning model training method and device and federation learning system
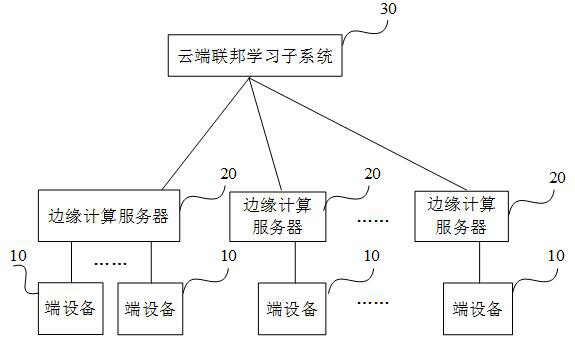
ActiveCN112232528AReduce movementWon't leakEnsemble learningDigital data protectionEdge computingEngineering
The invention discloses a federated learning model training method and device and a federated learning system. An edge computing server and end equipment receive global machine learning model information formed by a cloud federated learning subsystem; one edge computing server and more than one end device form an area by utilizing the advantage of network locality, and the end device completes model local training by depending on local data and adopting a truncation mode. The edge computing server is responsible for multiple rounds of updating of end equipment in a jurisdiction area and sending updated model information to the cloud federated learning subsystem; the edge computing servers also complete model local training in a truncation mode, and the cloud federated learning subsystem isresponsible for gradient updating of the edge computing servers; and when the training reaches a convergence period, performing truncation node compensation on the inner-end equipment of the region under the jurisdiction of the edge computing server and a plurality of edge computing servers in charge of the cloud federated learning subsystem to form global machine learning model information.
Owner:ZHEJIANG LAB
Method and system for backing up mobile phone short messages
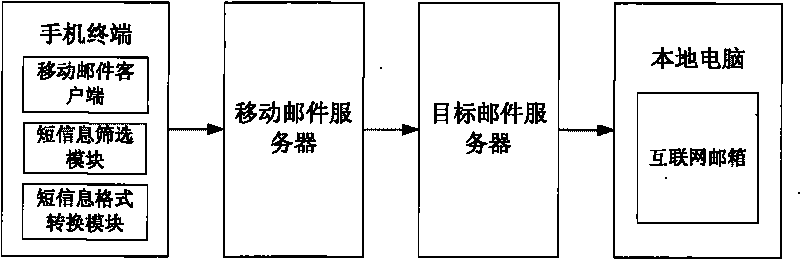
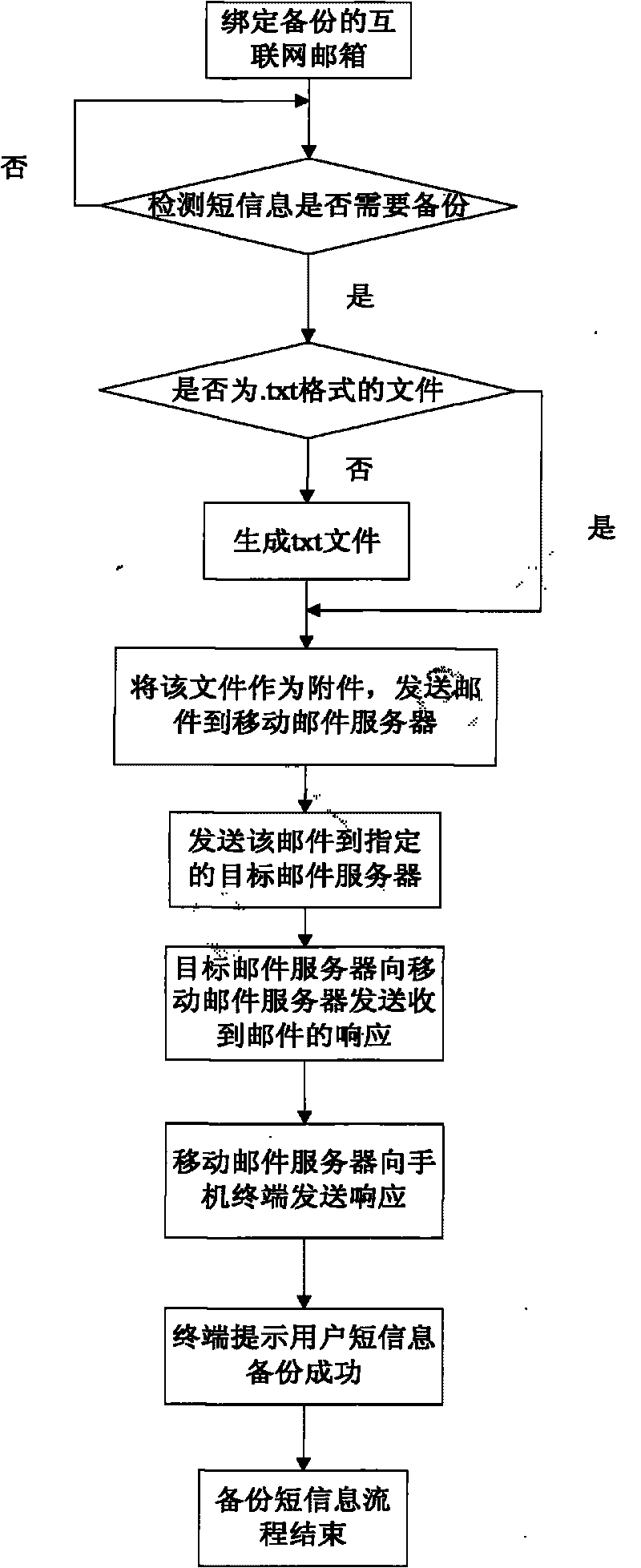
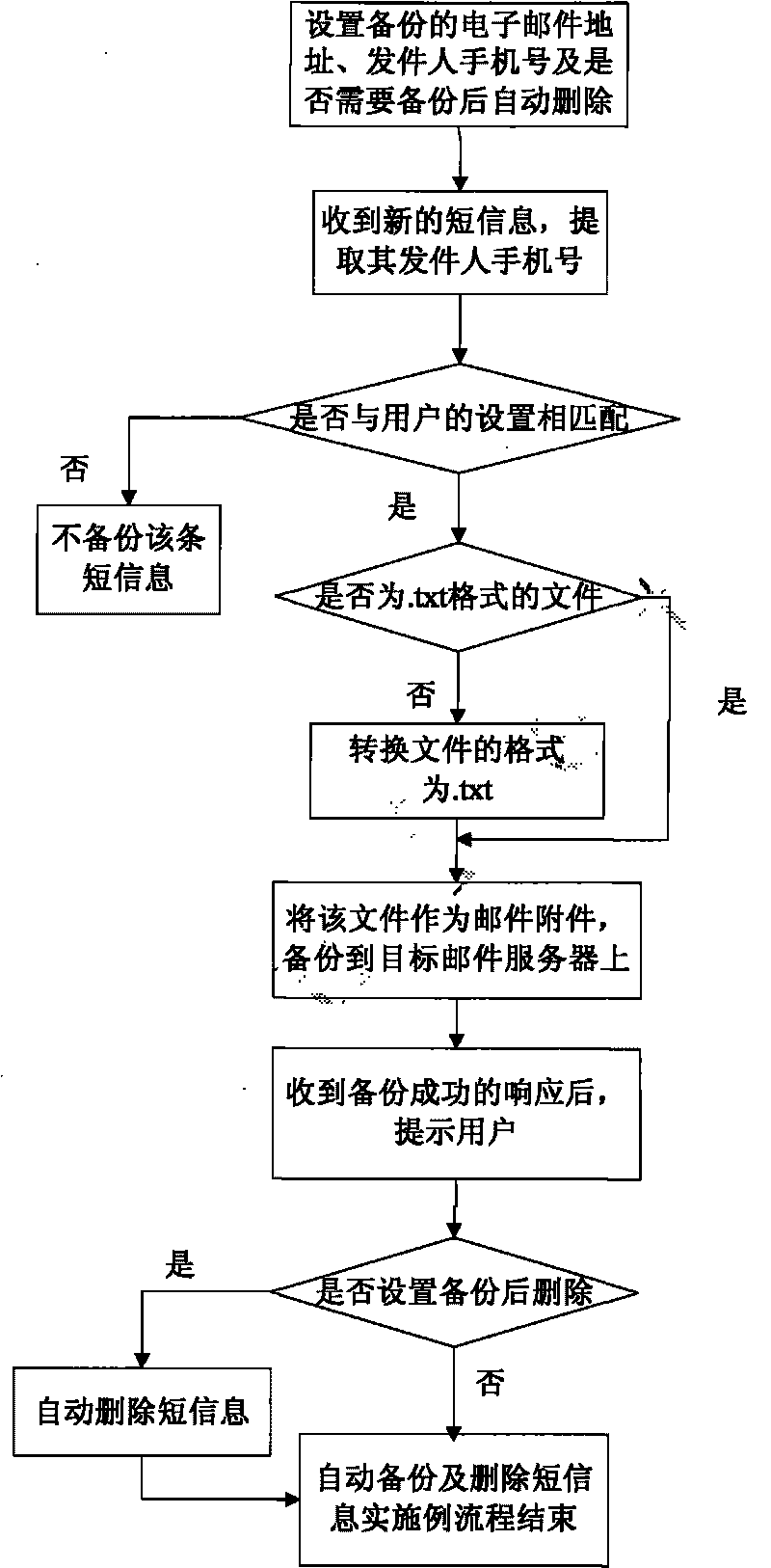
InactiveCN101765068ANot lostWon't leakInformation formatContent conversionShort Message ServiceThe Internet
The invention relates to a method and a system for backing up mobile phone short messages. The method comprises the following steps that: a user selects the short messages needing to be backed up; a mobile phone converts the short messages needing to be backed up into files of formats suitable for multimedia service transmission; and the files of the converted formats serving as an email are sent to a specified Internet mailbox by using a mobile multimedia email service. The system comprises the mobile phone, mobile email client software, a short message filtering module, a short message format converting module, a mobile email server, a target email server and a terminal computer capable of logging in the Internet mailbox, wherein the short message filtering module is used for screening the short messages needing to be backed up according to the setting of the user; and the short message format converting module is used for uniformly converting short message files of different formats into the formats suitable for the multimedia service transmission.
Owner:ZTE CORP
Water cooling balance
ActiveCN104180966AEliminate the effects of aerodynamic measurementsExtended service lifeAerodynamic testingLeaking waterCooling effect
The invention discloses a water cooling balance which comprises a rod-type balance and a water-cooled jacket. Two water flow pipelines are arranged in the rod-type balance. The two ends of each water flow pipeline are arranged on the two end faces of the rod-type balance respectively. A switching joint is arranged between the water-cooled jacket and the rod-type balance and fixed to one end face of the rod-type balance through a screw. A water inlet switching pipeline and a water outlet switching pipeline are arranged on the switching joint. One end of the water inlet switching pipeline and one end of the water outlet switching pipeline correspond to openings of the two water flow pipelines on the end faces of the rod-type balance in position and the other end of the water inlet switching pipeline and the other end of the water outlet switching pipeline correspond to a water inlet and a water outlet of the water-cooled jacket in position. The defects that a corrugated pipe type water cooling balance is large in drag measurement error and inconvenient to install and use and a corrugated pipe is prone to being damaged and leaking water are overcome. In addition, due to the fact that corrugated pipe related devices are omitted, the length of the balance is reduced, the diameter of the balance is increased, the rigidity and the cooling effect of the balance are greatly improved, the temperature effect is reduced, and measurement uncertainty is obviously reduced.
Owner:INST OF HIGH SPEED AERODYNAMICS OF CHINA AERODYNAMICS RES & DEV CENT
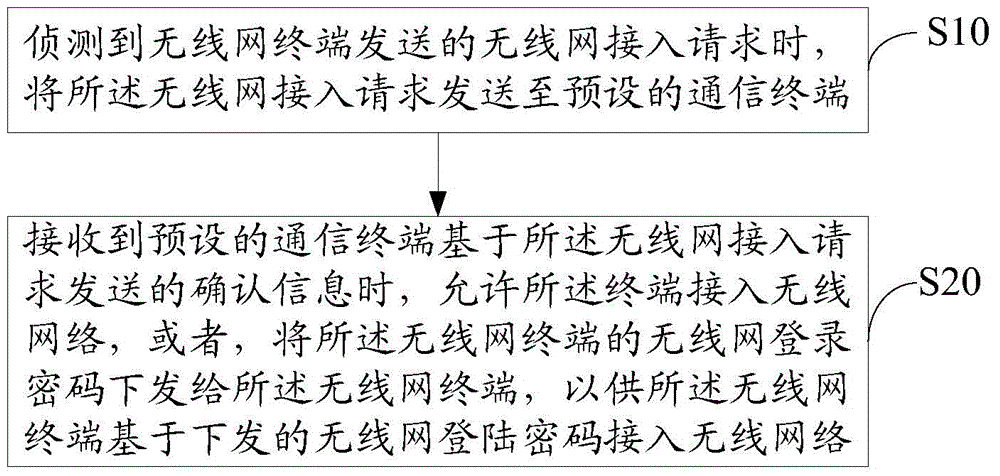
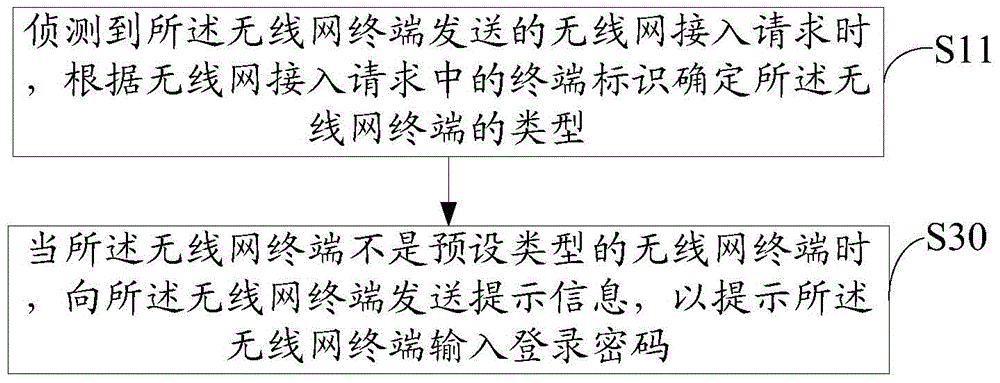
Access method and device for wireless network
The invention relates to an access method and device for a wireless network. When a wireless network access request sent by a terminal is received, the wireless network access request is forwarded to a preset communication terminal for confirmation by a user of the communication terminal. When determination instructions sent by the communication are received, the terminal is permitted to access the wireless network or a login password is sent to the terminal, so that the terminal can access the wireless network according to the received login password. The user does not need to input the login password, so that login is convenient. The method and device are suitable for a terminal without an input device to log in the wireless network, are high in login safety, and cannot cause leakage of passwords due to password inputting by the user.
Owner:SHENZHEN TCL NEW-TECH CO LTD
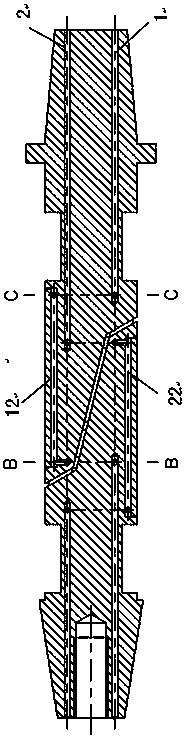
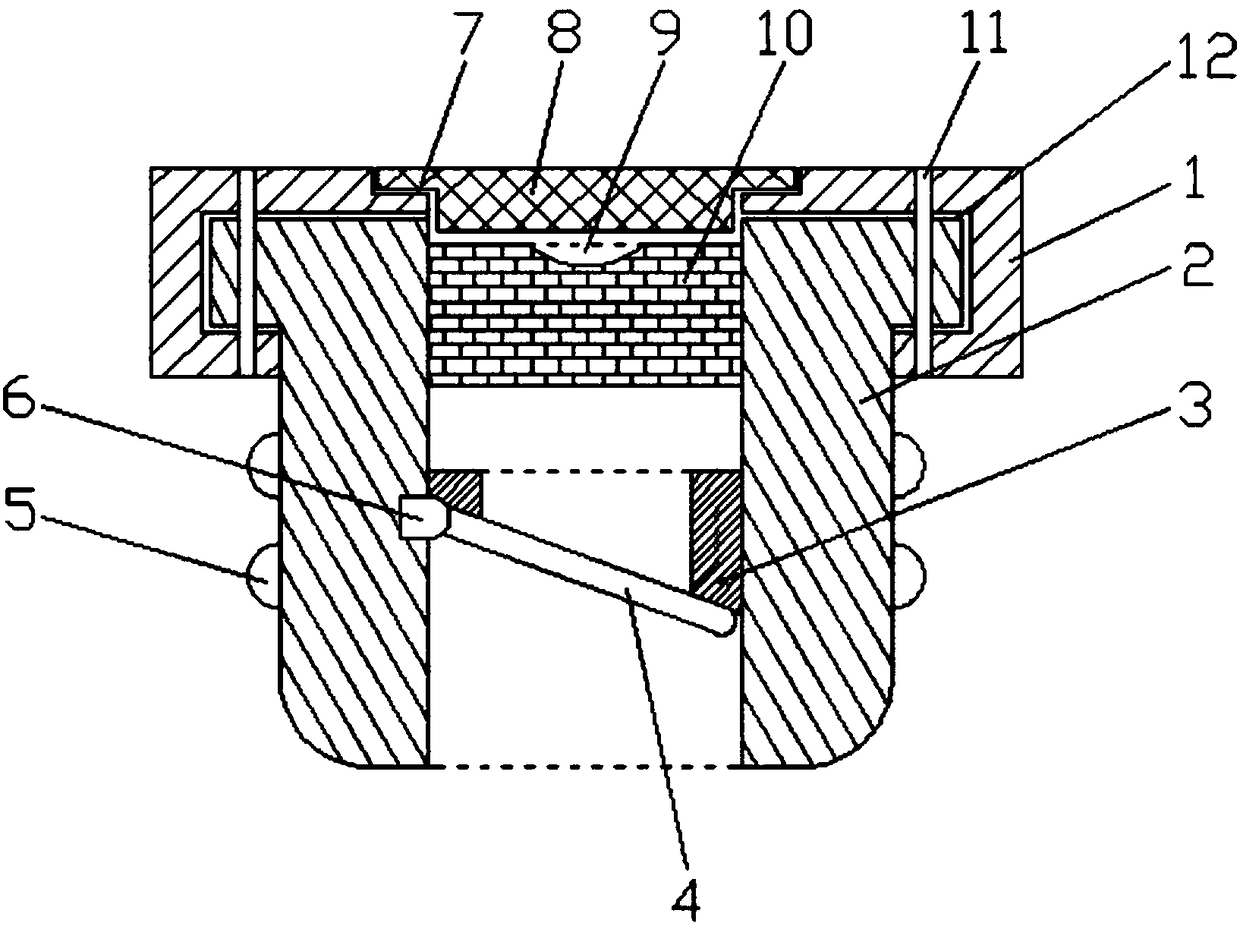
Rubber stopper for medical injection
The invention discloses a rubber stopper for medical injection. The rubber stopper for medical injection includes a rubber stopper top lid, a rubber stopper, a valve plate seat, a valve plate, a rubber stopper hatch cover, sealing rubber and a connection rivet. A mounting groove provided with the rubber stopper is formed in the rubber stopper top lid, the rubber stopper is installed in the mounting groove, and the bottom of the rubber stopper extends out of the rubber stopper top lid; the connection rivets are arranged on the two sides of the rubber stopper top lid, wherein the connection rivets sequentially penetrate through the upper surface of the rubber stopper top lid, the top upper surface of the rubber stopper, the top lower surface of the rubber stopper and the top lower surface ofthe rubber stopper top lid to achieve connection. When a syringe needle is pulled out, a valve plate of the rubber stopper for the medical injection can rotate back and finally covers the bottom surface of the valve plate seat under the elastic action of a rubber connecting seat, so that a communicating hole inside the rubber connecting seat is closed; through the structure, the rubber stopper for medical injection can ensure that the medicine liquid inside an infusion bottle does not leak when the syringe needle is pulled out under the condition of unused medicine liquid still in the infusion bottle.
Owner:杨倩倩
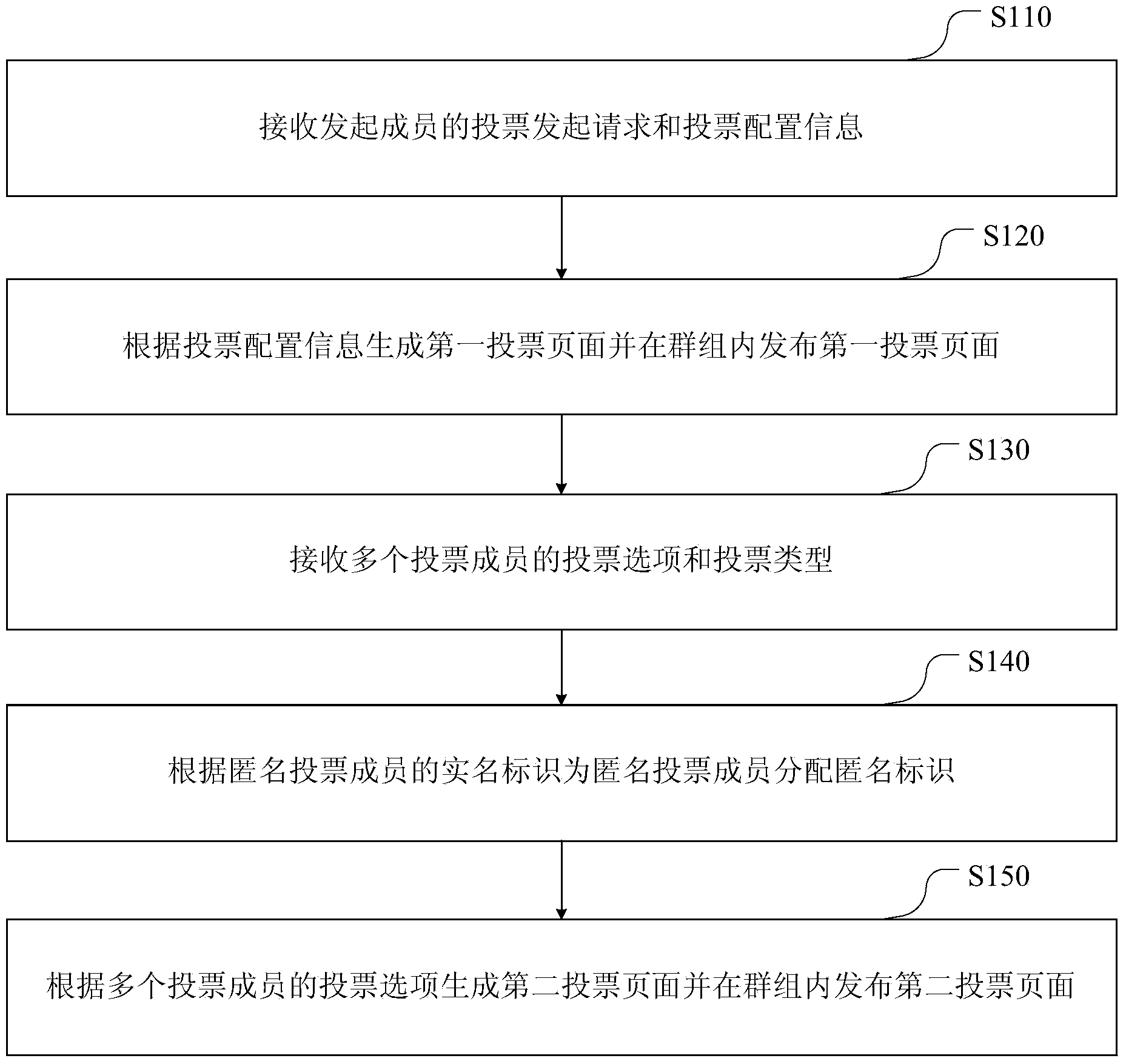
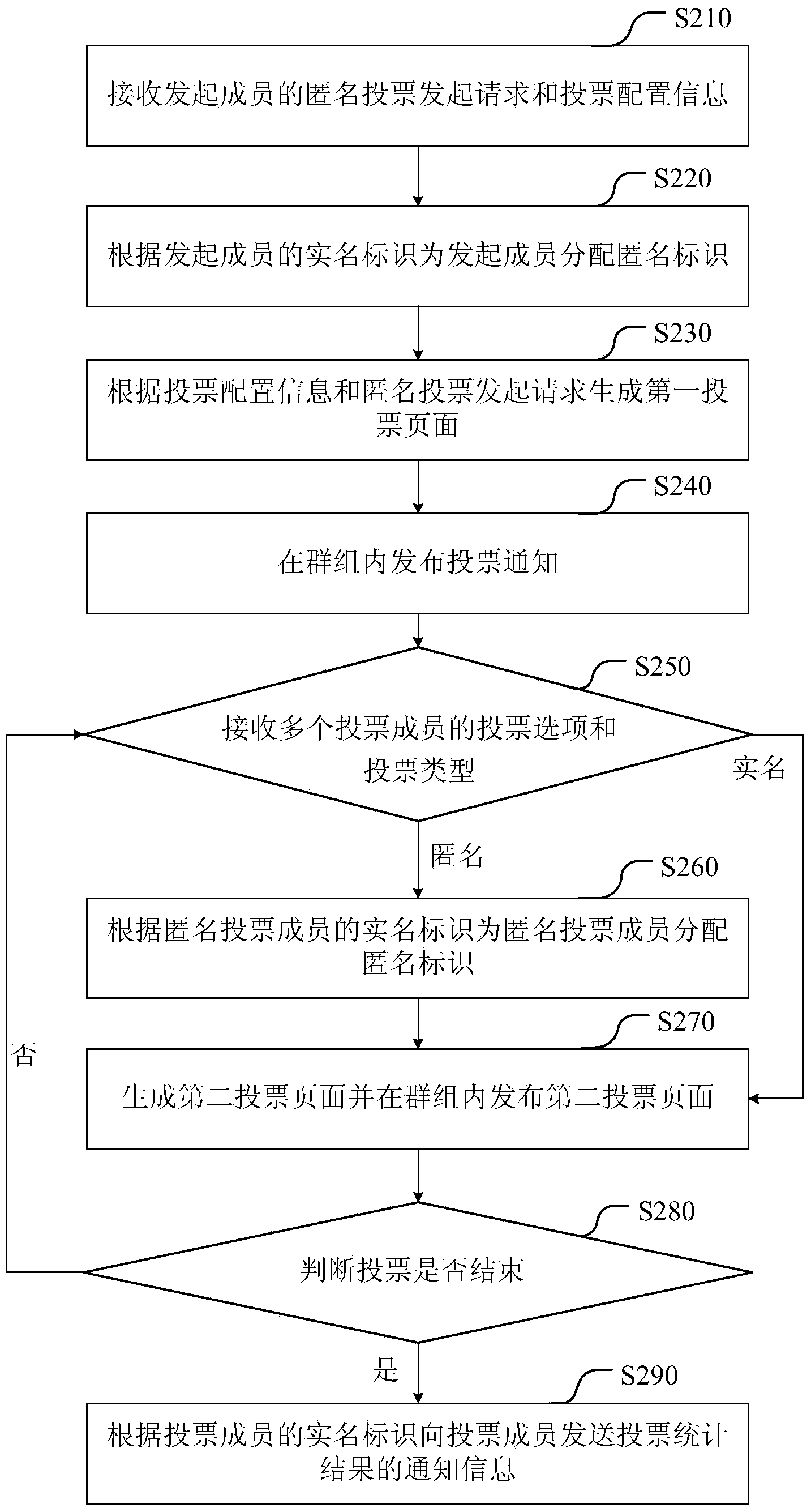
Method and device for voting in group
The invention discloses a method and a device for voting in a group. The group has more than one member, and each member has a real name identifier. The method comprises the following steps: receiving a voting initiation request and voting configuration information of an initiation member to generate a first voting page and releasing in the group; receiving the voting options and voting type of the more than one voting member, wherein the voting type is real name voting or anonymity voting; distributing anonymity identifiers to anonymity voting members according to the real name identifiers of the anonymity voting members; generating a second voting page according to the voting options of the more than one member and releasing in the group, wherein the second voting page comprises the voting results of the anonymity voting members, displayed by the anonymity identifiers. According to the scheme, the displaying of the voting results is relatively diversified; moreover, the real identifies of the voting members cannot be revealed when the voting members express intention to certain sensitive topics, so that the information can be accurately collected.
Owner:BEIJING QIHOO TECH CO LTD
Enhanced MASK code method for resisting DES (data encryption standard) power consumption attack
ActiveCN102752103AWon't leakSmall design areaEncryption apparatus with shift registers/memoriesLogical operationsOperation mode
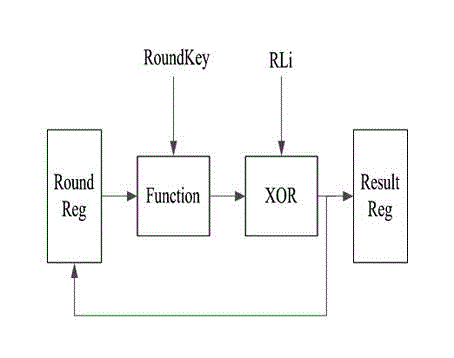
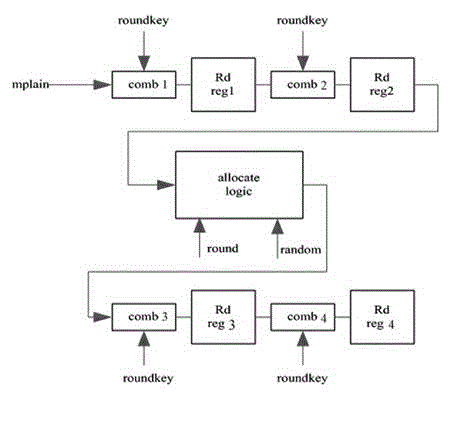
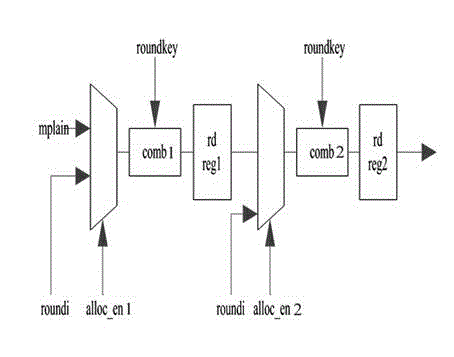
The invention relates to an enhanced MASK code method for resisting DES (data encryption standard) power consumption attack, comprising the steps as follows: step 1, realizing two rounds of DES (data encryption standard) calculations with a pipeline operation mode, realizing a calculating circuit by means of a first calculating circuit and a second calculating circuit which are mutually independent and isolated; step 2, realizing the DES (data encryption standard) calculation processes from the third round to the fourteenth round by means of a random positioning logical operation mode; step 3, realizing the last two rounds of DES (data encryption standard) calculations by means of a pipeline operation mode, and realizing the calculating circuit by means of a third calculating circuit and a fourth calculating circuit which are mutually independent and isolated, wherein each round of the DES (data encryption standard) calculations in step 1 to 3 is calculated with a MASK code method. The method provided by the invention not only reduces the design area of the chip, but also completely solves the problem in the prior art in which the two adjacent rounds of the MASK code solutions have a Hamming distance leakage, and keeps the sensitive information between wheels from leakage, and simultaneously keeps the Hamming distance and other sensitive information between two adjacentwheels from leakage, and effectively resists the power consumption attack.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
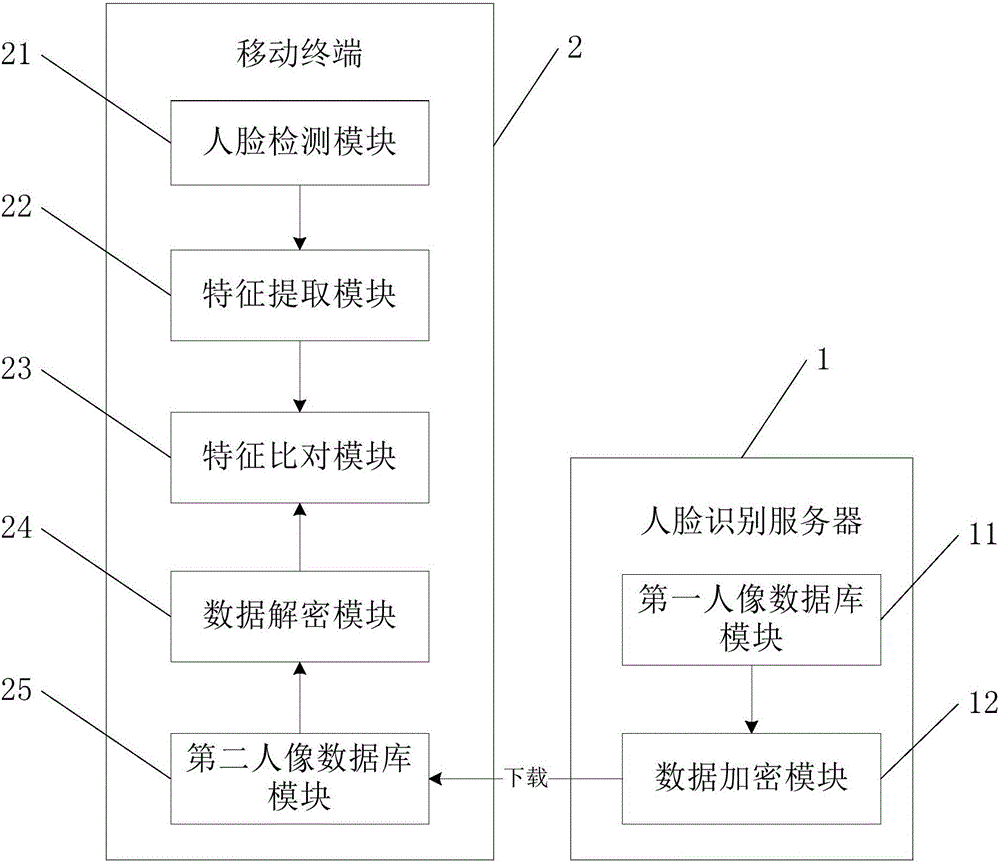
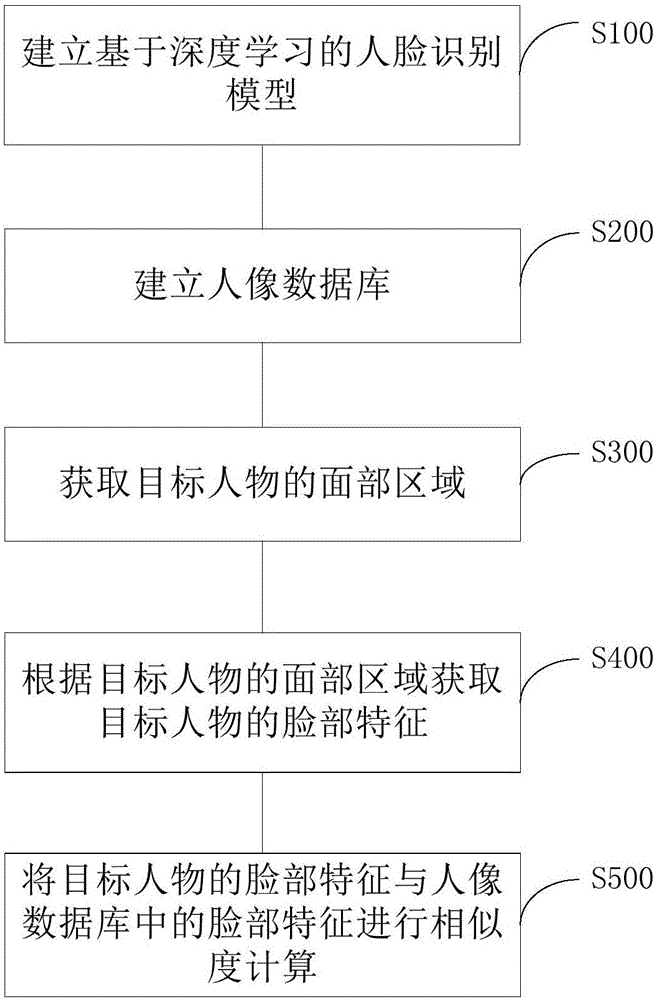
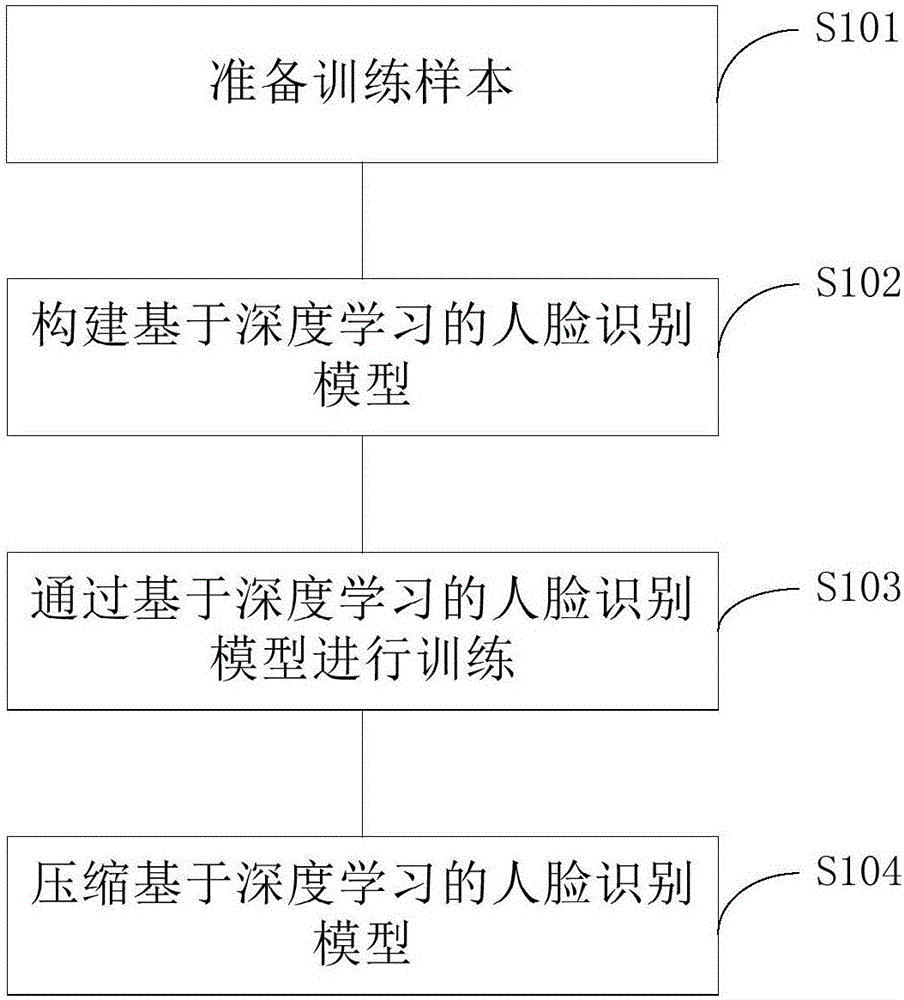
Mobile terminal face recognition method and system based on technology of embedded deep learning
InactiveCN106682650AQuick judgmentAccurate judgmentCharacter and pattern recognitionDigital data protectionState of artFace detection
The invention belongs to the field of image recognition, and specifically provides a mobile terminal face recognition method and system based on the technology of embedded deep learning. The invention aims at solving problems in the prior art that a human face recognition program is complex, an occupied memory is large, the recognition speed is small, the recognition precision is low and a hand-held mobile terminal for human face recognition is limited by a network signal. In order to solve the above problems, the system comprises a human face detection module for obtaining a face region of a target person; a feature extraction module which is used for obtaining the face features of the target person according to the obtained face region; and a feature comparison module which is used for calculating the similarity between the obtained face features of the target person and preset face features, wherein the human face detection module, the feature extraction module and the feature comparison module are disposed on a mobile terminal. Therefore, the system enables the mobile terminal to be able to judge the identity of the target person quickly and accurately under the condition that there is no network signal.
Owner:北京中科神探科技有限公司
Composite fixing phase change material of 79-83 deg.c and its preparing method
InactiveCN1782018AReduce weight lossStable material performanceHeat-exchange elementsParaffin waxComposite phase change material
The composite fixed 76-83 deg C phase change material and its preparation belongs to the field of phase change heat accumulating material technology. The present invention has SEBS of smelting point 76-81.6 deg C as the packing and oil absorbing material and paraffin of phase change latent heat 200-220 kJ / kg as main energy storing material, and consists of paraffin in 66-80 wt%, high density polyethylene in 11-15 wt%, SEBS in 4-12 wt% and expanded graphite in 3-7 wt%. The composite phase change material is prepared through smelting paraffin in a reactor, adding and smelting high density polyethylene and SEBS, adding expanded graphite and mixing homogeneously, molding at 200-300 KPa pressure to form plate, cooling and demoulding. The material may be set directly inside boiler to contact water as heat transferring medium, and after soaking in hot water in temperature above the smelting point for 200 hr, it has weight loss less than 2 % and phase change latent heat change less than 10 %.
Owner:BEIJING UNIV OF TECH
Photonic crystal optical fiber methane sensing device based on modular interference
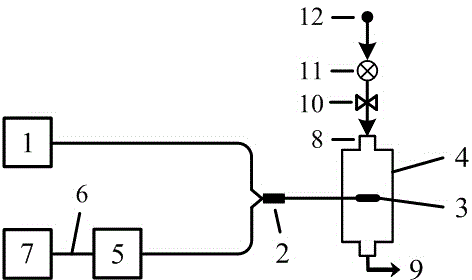
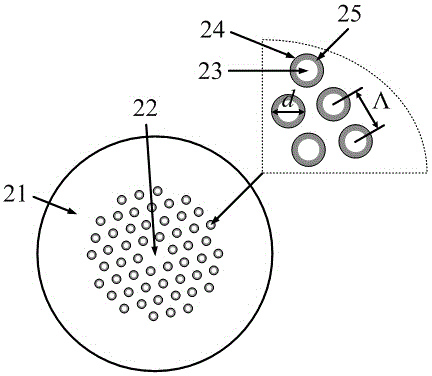
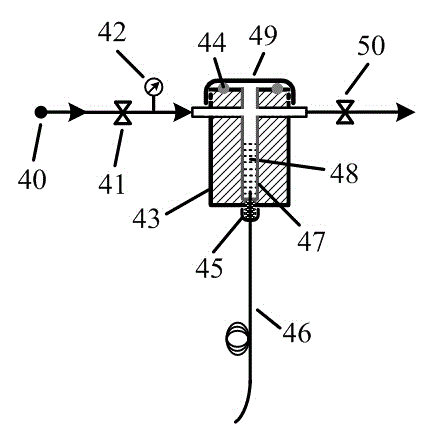
ActiveCN104568841AUndisturbed by background lightAmbient temperature insensitiveCladded optical fibrePhase-affecting property measurementsSpectrum analyzerRefractive index
The invention discloses a photonic crystal optical fiber methane sensing device based on modular interference. The device is composed of a broadband light source, an optical circulator, a photonic crystal optical fiber methane sensor cladding an air hole coated polymer sensitive film, a testing air chamber, a switching valve, a quality flow controller, a spectrum analyzer and a computer, wherein the optical fiber methane sensor consists of a single mode fiber, a photonic crystal optical fiber and a welding area of the two fibers; the adopted photonic crystal optical fiber refers to an endless single mode solid core photonic crystal optical fiber; the polymer sensitive film refers to a polycarbonate resin methane sensitive film containing a cage molecule E-(OC2H5)6, and the inner wall of the cladding air hole of the photonic crystal optical fiber is coated with the film by virtue of an air pressure driving device; when the to-be-tested methane gas acts with the sensitive film on the inner wall of the cladding air hole of the photonic crystal optical fiber, the refractive index of the sensitive film changes, the reflection interference spectrum characteristic wavelength of the sensor is moved, the average movement amount shown in the description of the reflection interference spectrum characteristic wavelength before and after contacting the sensor with the methane gas is analyzed, so that the concentration of the to-be-tested methane gas can be obtained. The device disclosed by the invention has the characteristics of high sensitivity, high stability, high selectivity and the like.
Owner:重庆科知源科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com