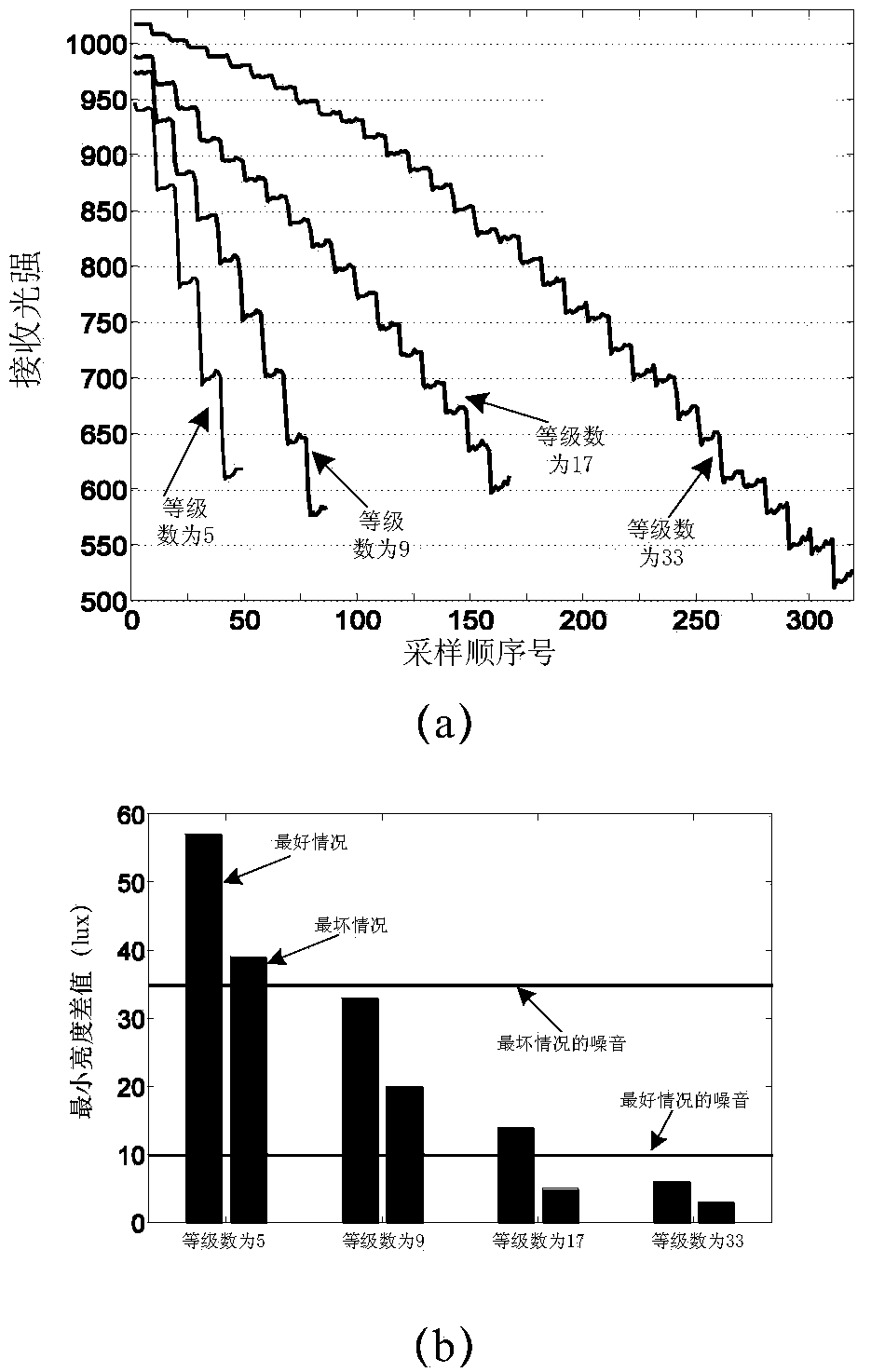
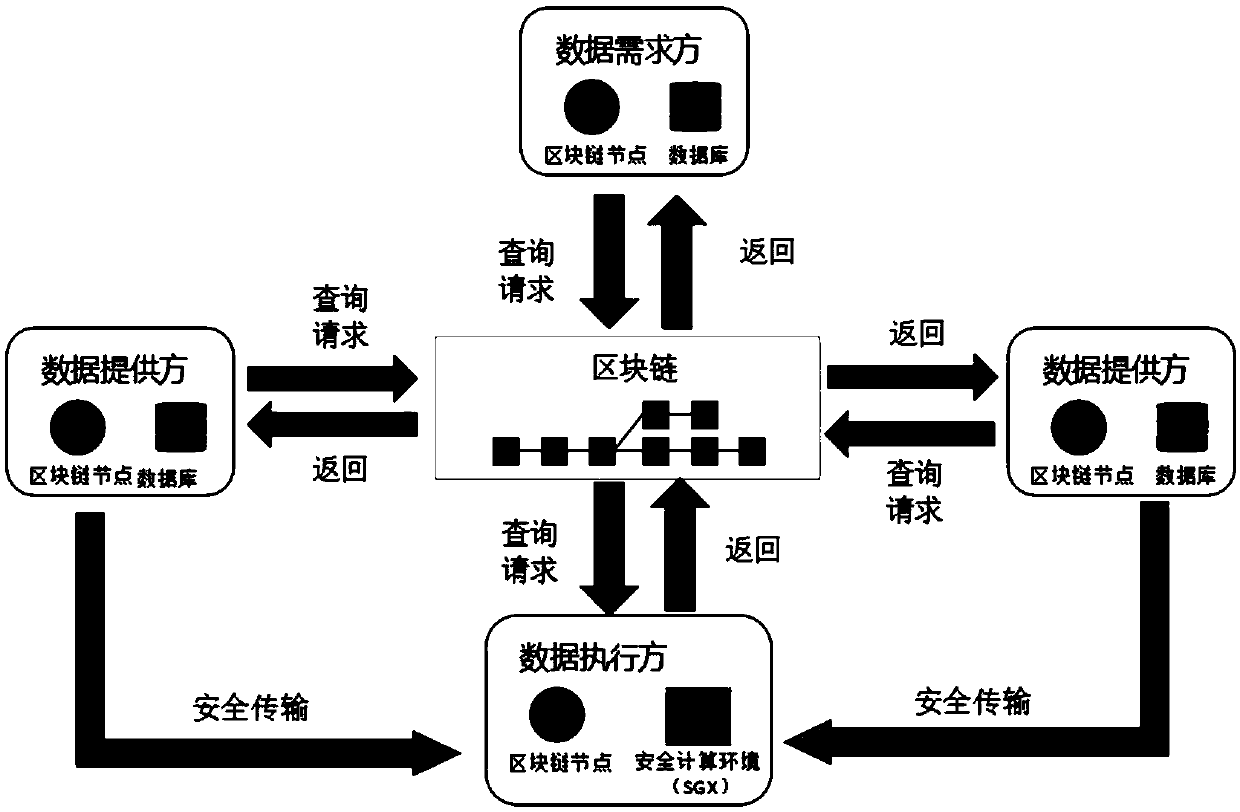
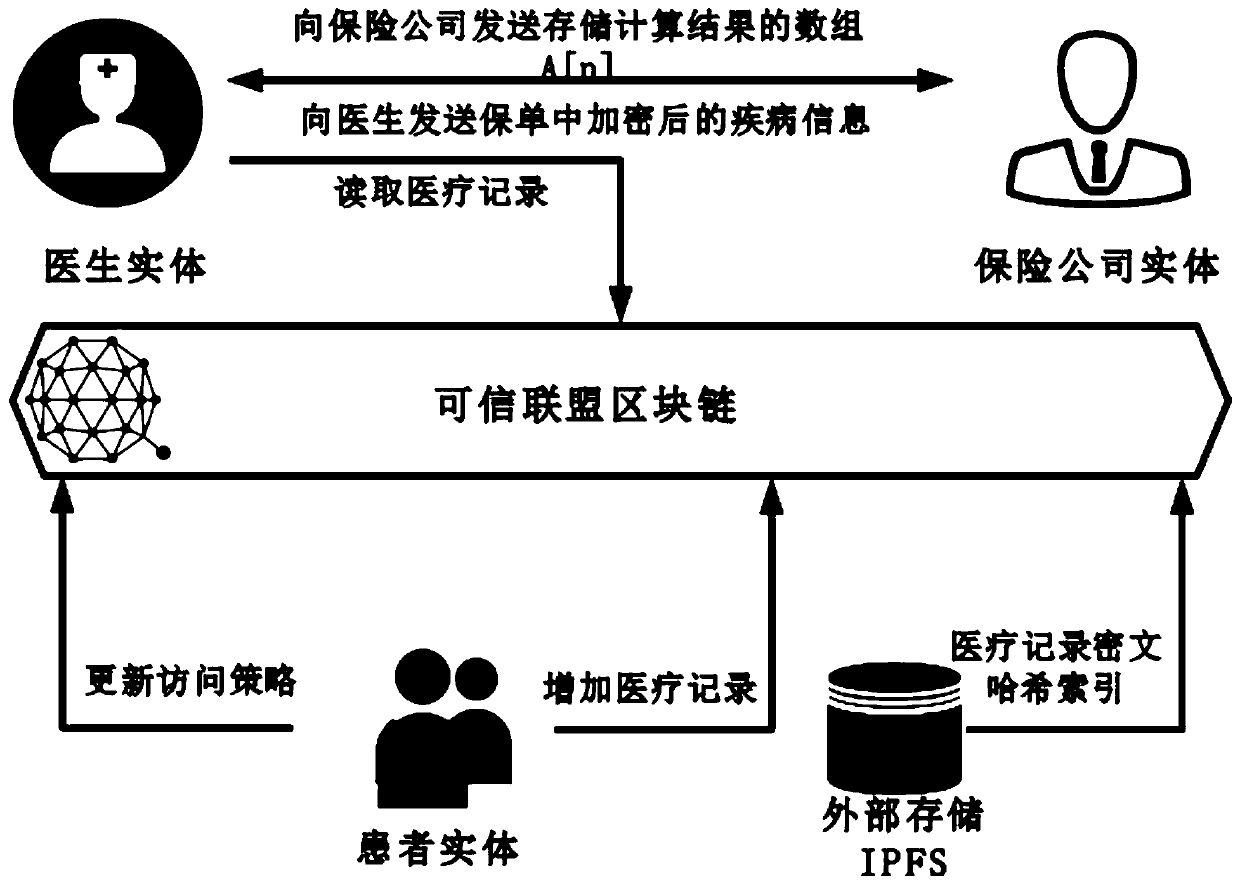
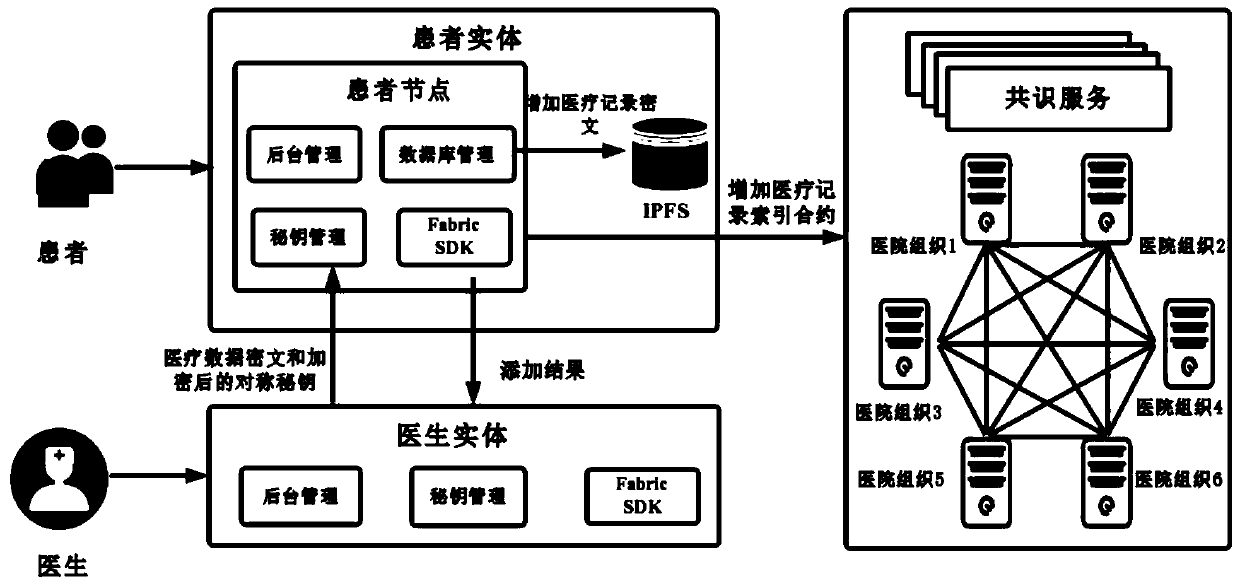
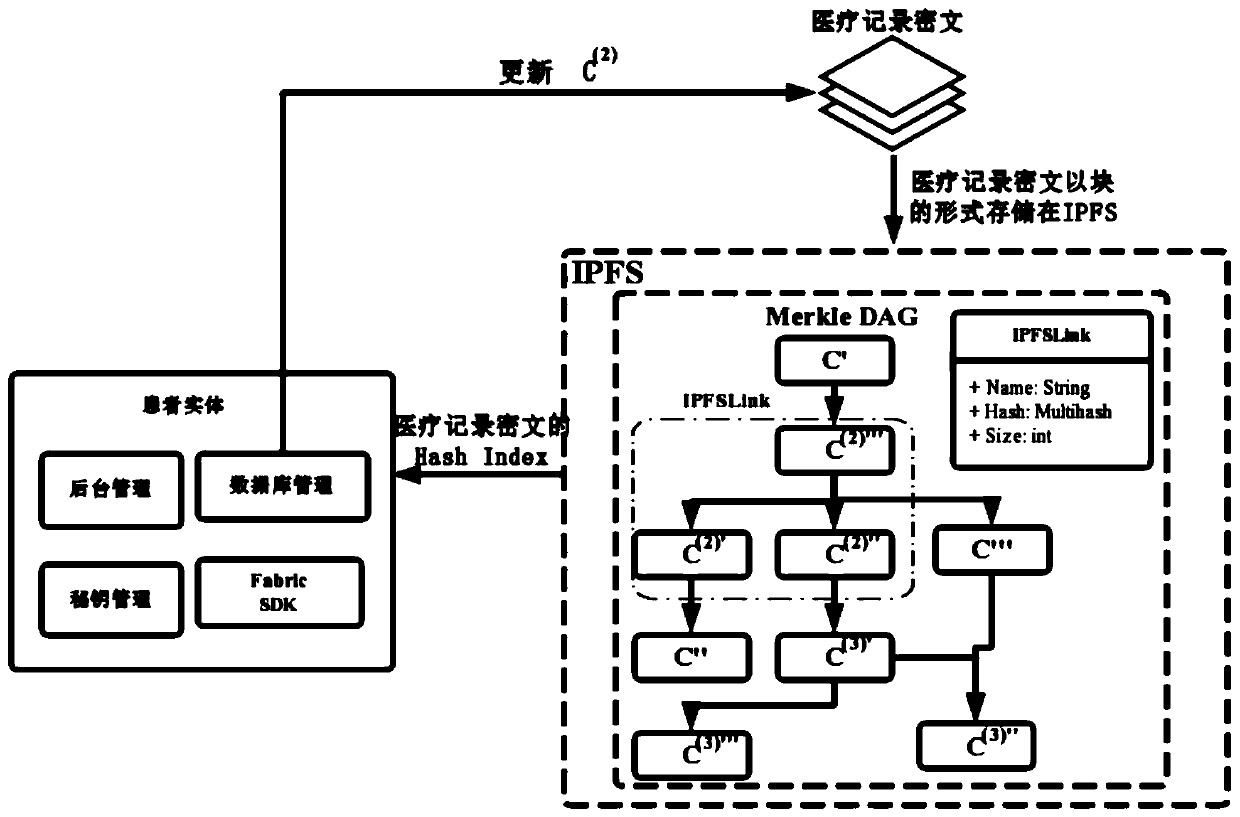
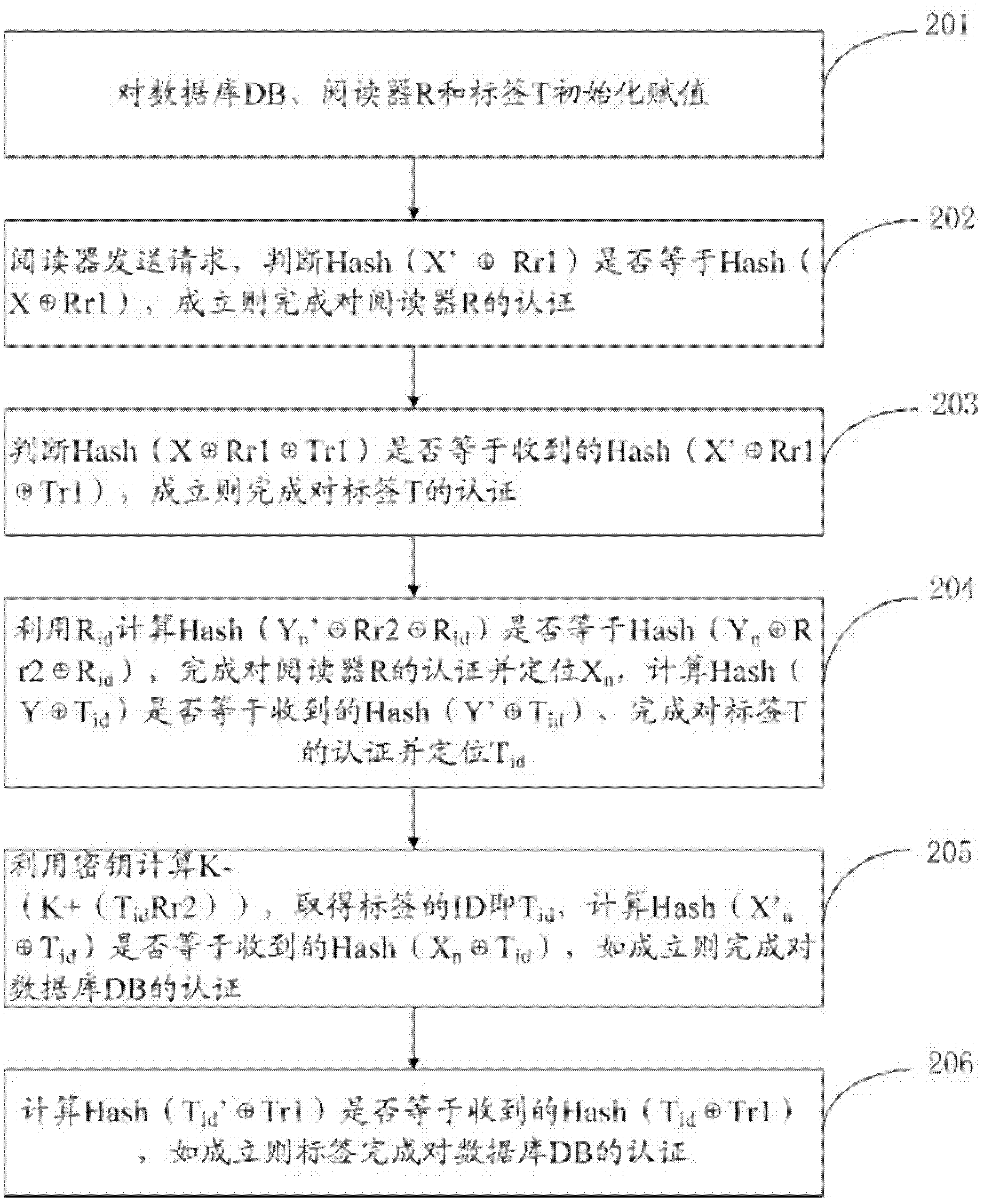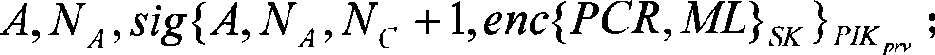Patents
Literature
1913results about How to "Guaranteed privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
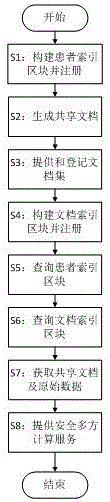
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
Anonymous transfer method and system based on block chain, and storage medium
ActiveCN108764874AGuaranteed privacyRealize anonymous transferFinancePayment protocolsTransfer systemChain network
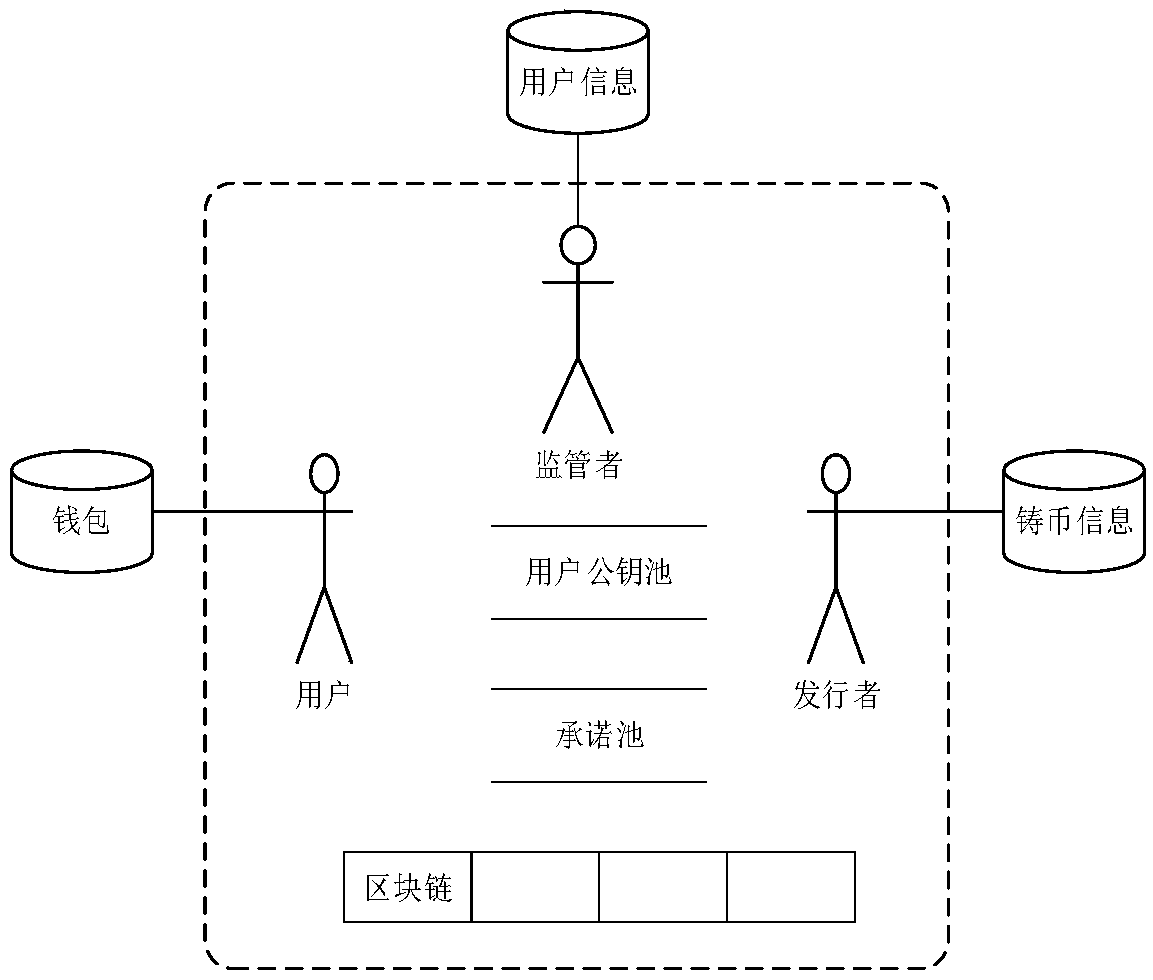
The invention discloses an anonymous transfer method based on a block chain. The method comprises the steps that a first node initiates a transfer transaction request to a second node, and receives public key information returned by the second node; the first node generates transaction information of a current transaction and sends the transaction information to the second node, wherein the transaction information comprises a new currency commitment generated based on the public key information, a transaction amount encrypted based on the public key information, and a zero knowledge proof; thesecond node verifies the transaction amount encrypted based on the public key information, and if the verification is passed, the transaction information is published in a block chain network, so that a miner node can perform verification and bookkeeping on the current transaction; and the miner node verifies proof contents in the zero knowledge proof, and if the verification is passed, the transaction is determined to be valid and the transaction information is recorded in the block chain. The invention furthermore discloses an anonymous transfer system based on the block chain and a computer readable storage medium. According to the method and the system, anonymous transfer is realized, so that the privacy of information of two transaction parties of block chain-based transfer is guaranteed.
Owner:WEBANK (CHINA)
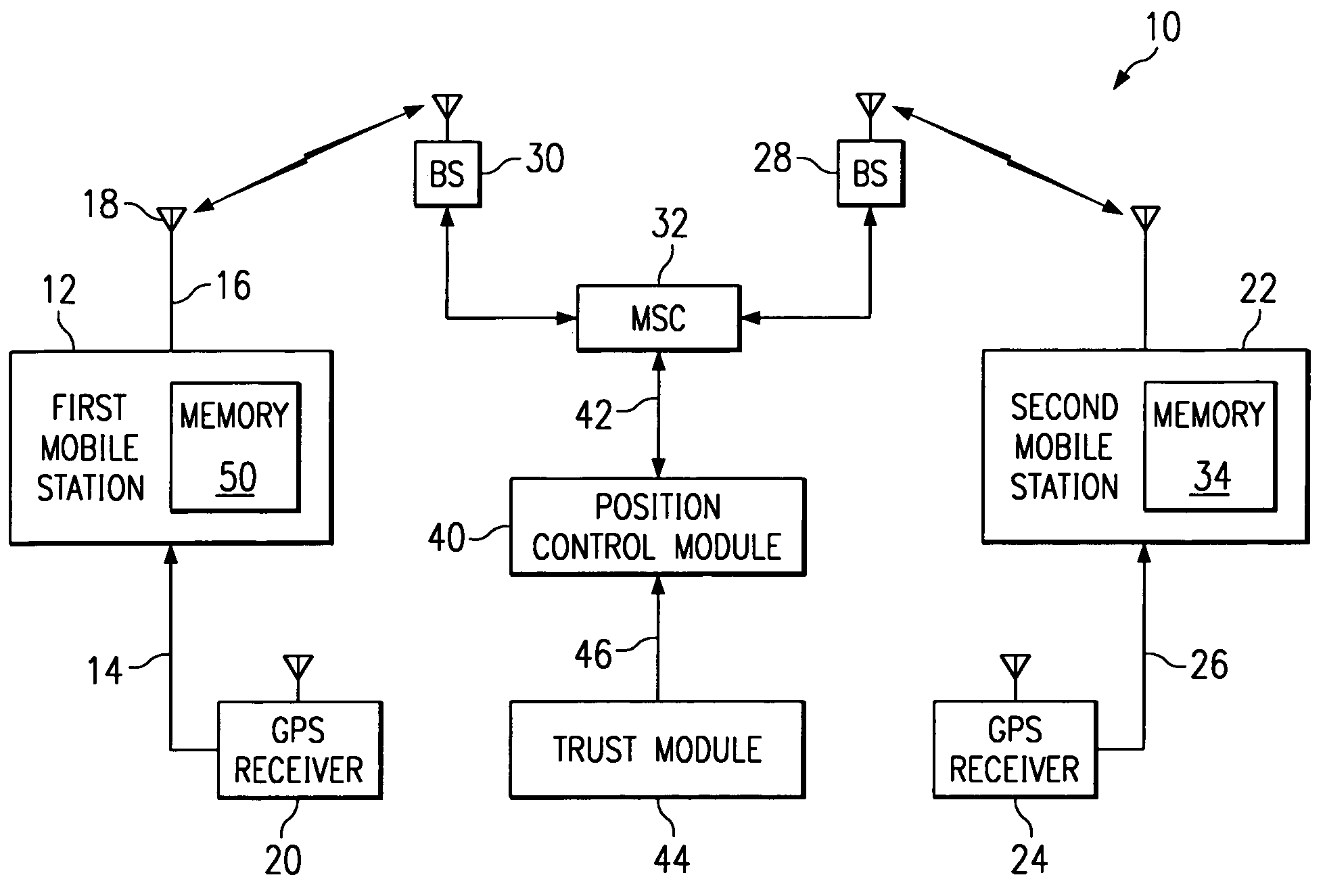
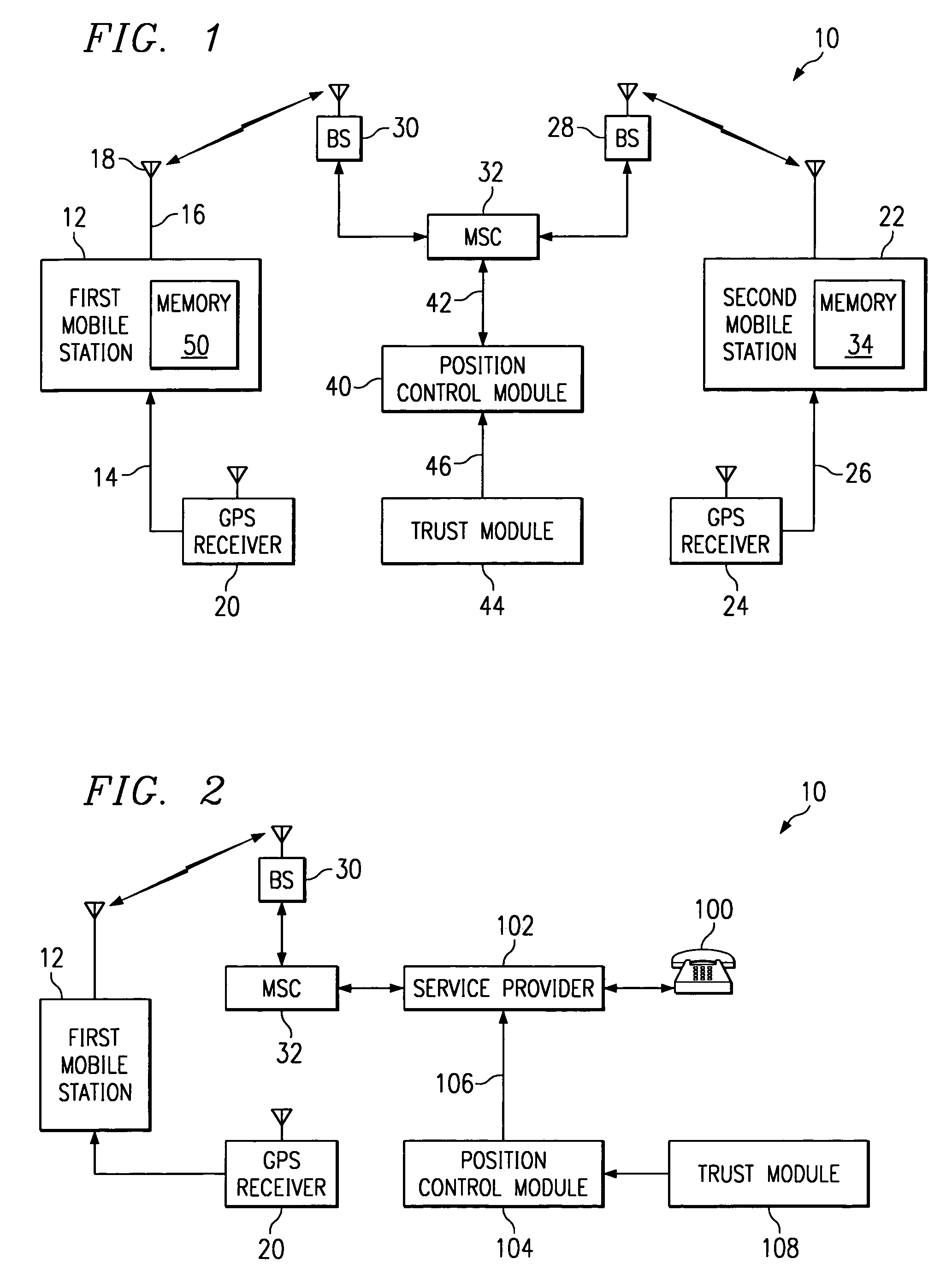
System and method for the exchange of location information in a telephone network
InactiveUS7177651B1Guaranteed privacyRoad vehicles traffic controlSpecial service for subscribersCommunications systemService provision
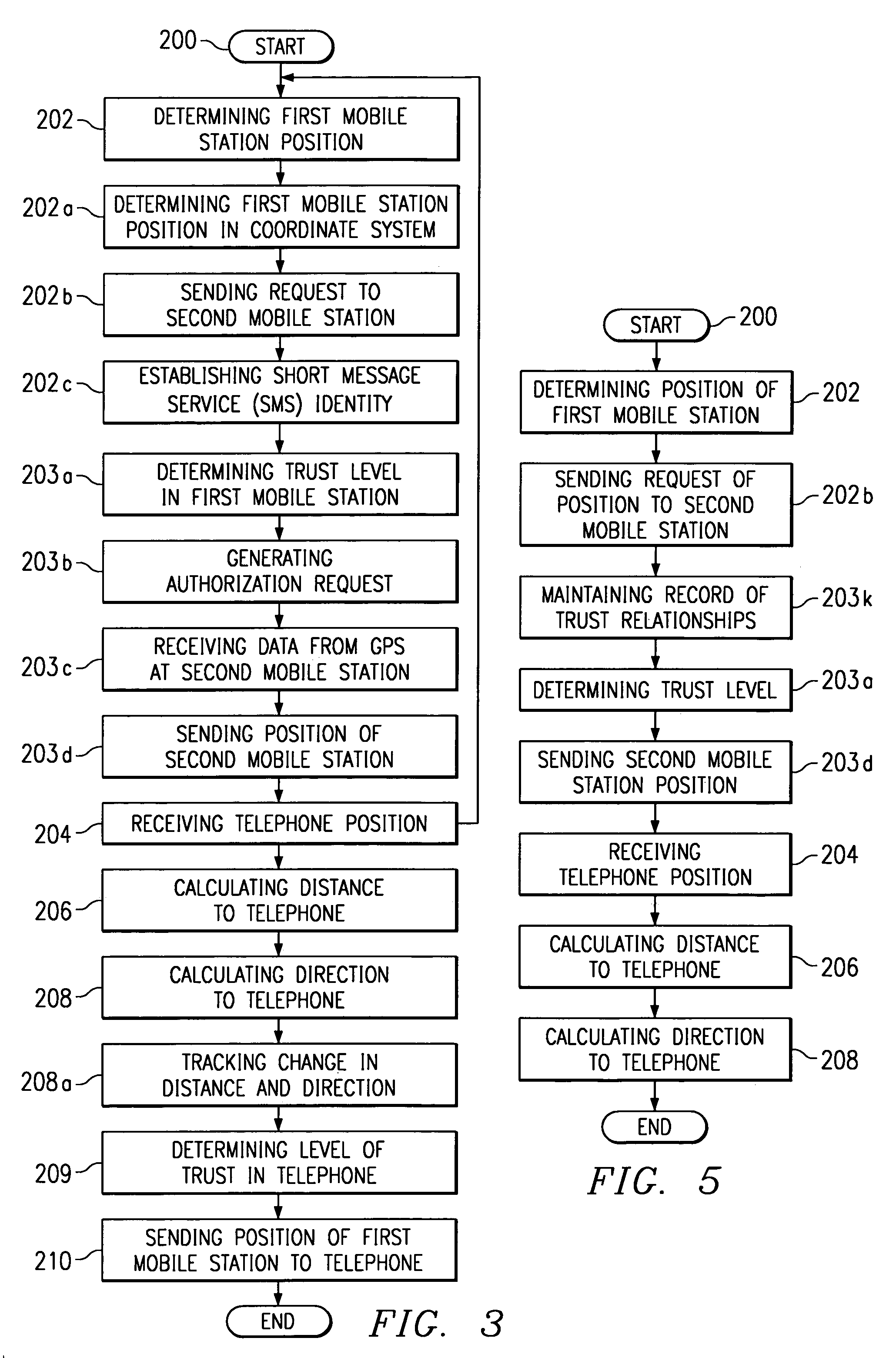
A wireless communications system is presented where a mobile station is able to automatically determine its proximity to a second mobile station or landline telephone. Once the proximity determination command has been given, no further actions are required by the users of either telephone. A GPS receiver connected to the first mobile station is able to provide that mobile with its position and direction. The first mobile station makes a request to the other telephone for its position, through SMS messaging for example. A GPS receiver connected to the second mobile station is able to provide the second mobile station with data to enable the position request. Trust determinations can be enabled so that position data is sent to a restricted list of requesting telephone numbers. Likewise, the second mobile station can request position data from the first mobile station. When position information is requested from a landline telephone, the request can be fulfilled by the landline telephone service provider. A method for automatically exchanging position information is also provided.
Owner:TEXAS INSTR INC
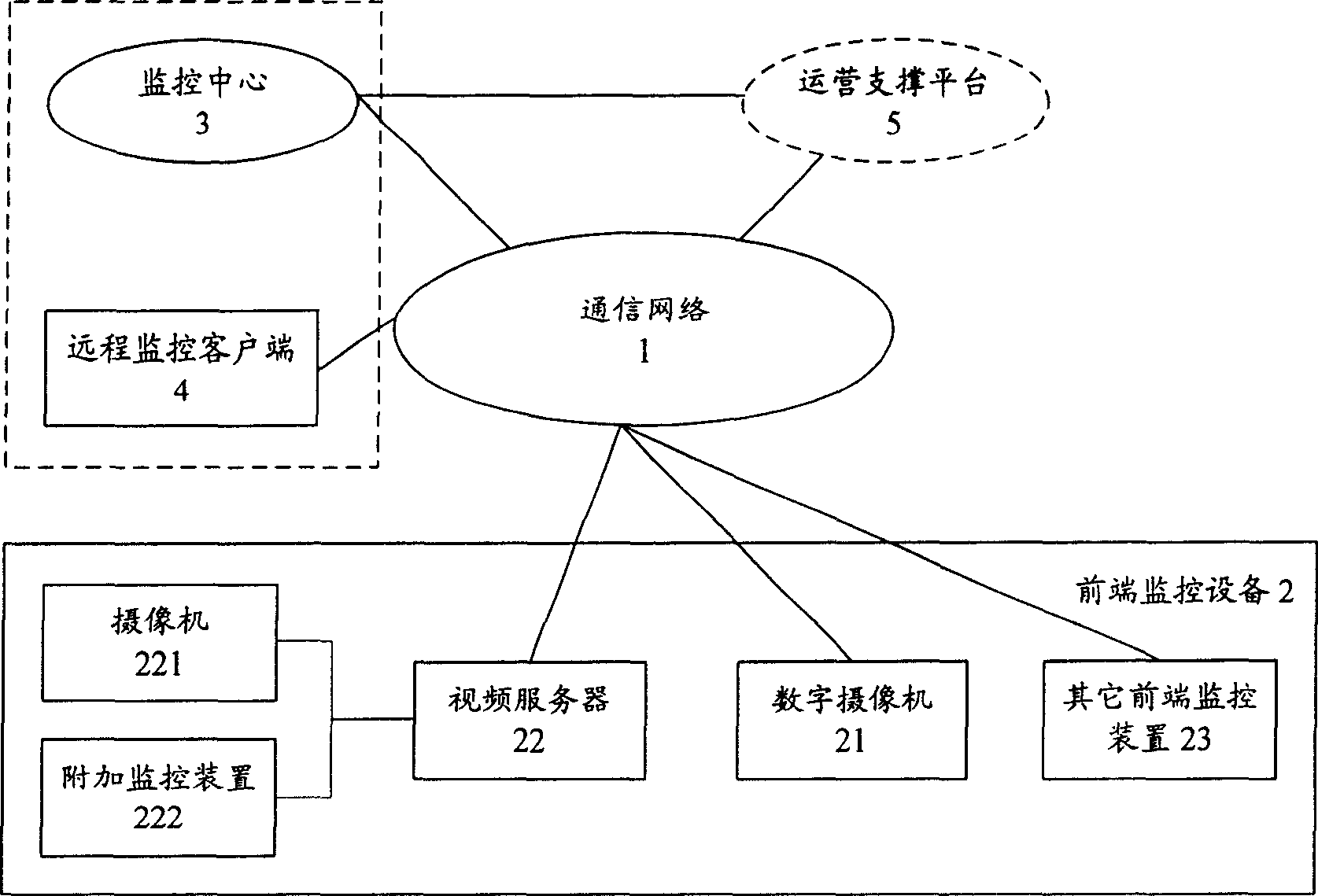
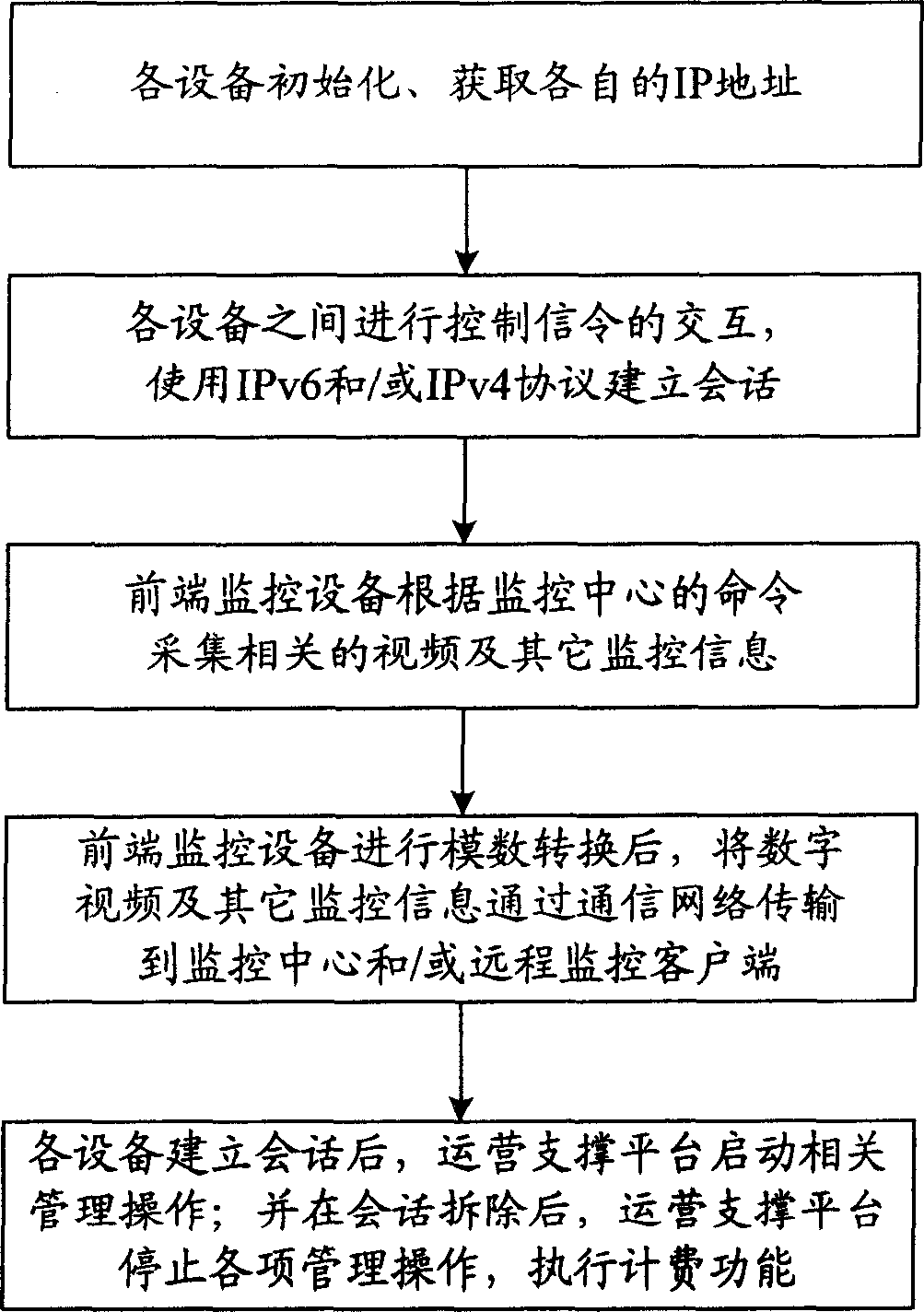
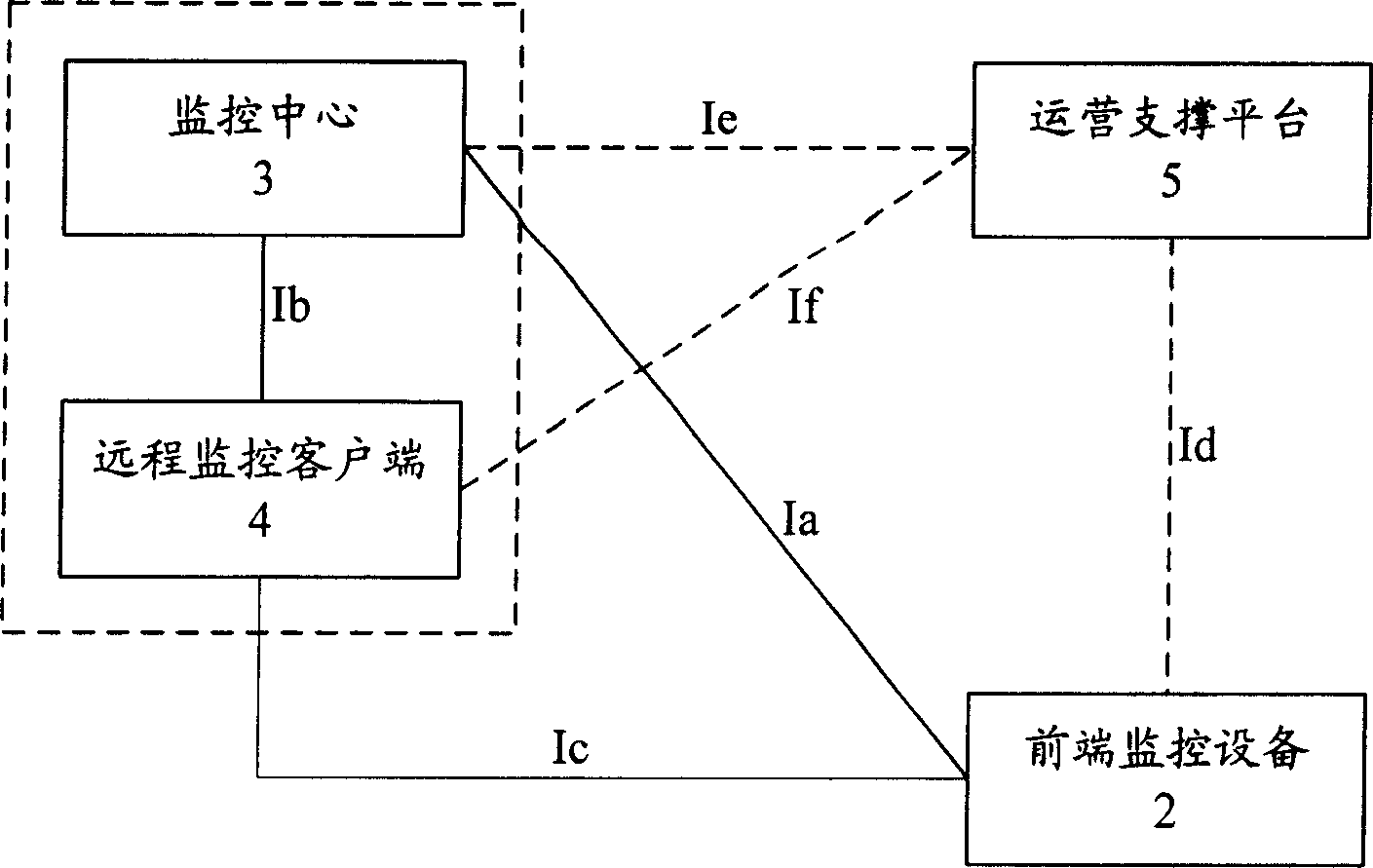
Remote vedio monitoring system based on next generation interconnection network and its implementing method
InactiveCN1913461ASimple structureComplete structureClosed circuit television systemsTransmission monitoringVideo monitoringDigital video
This invention relates to a remote video monitor system and a realization method based on the next generation, in which, said system is composed of a communication network, a front monitor device, a monitor center and a remote monitor customer end and a business supporting platform, provides business level remote video monitor service to the public by applying a multi-stage regional structure network topological and digital video compression coding technology, supporting two kinds of network protocols of IPv6 and IPv4 at the same time and using the IPv6 transmission data first, in which, coding addresses of the monitor nodes are ruled and unified and the monitor terminal is set with the only IP address in the world suitable for being accessed and applied at any time and any place.
Owner:BEIJING INTERNET INST
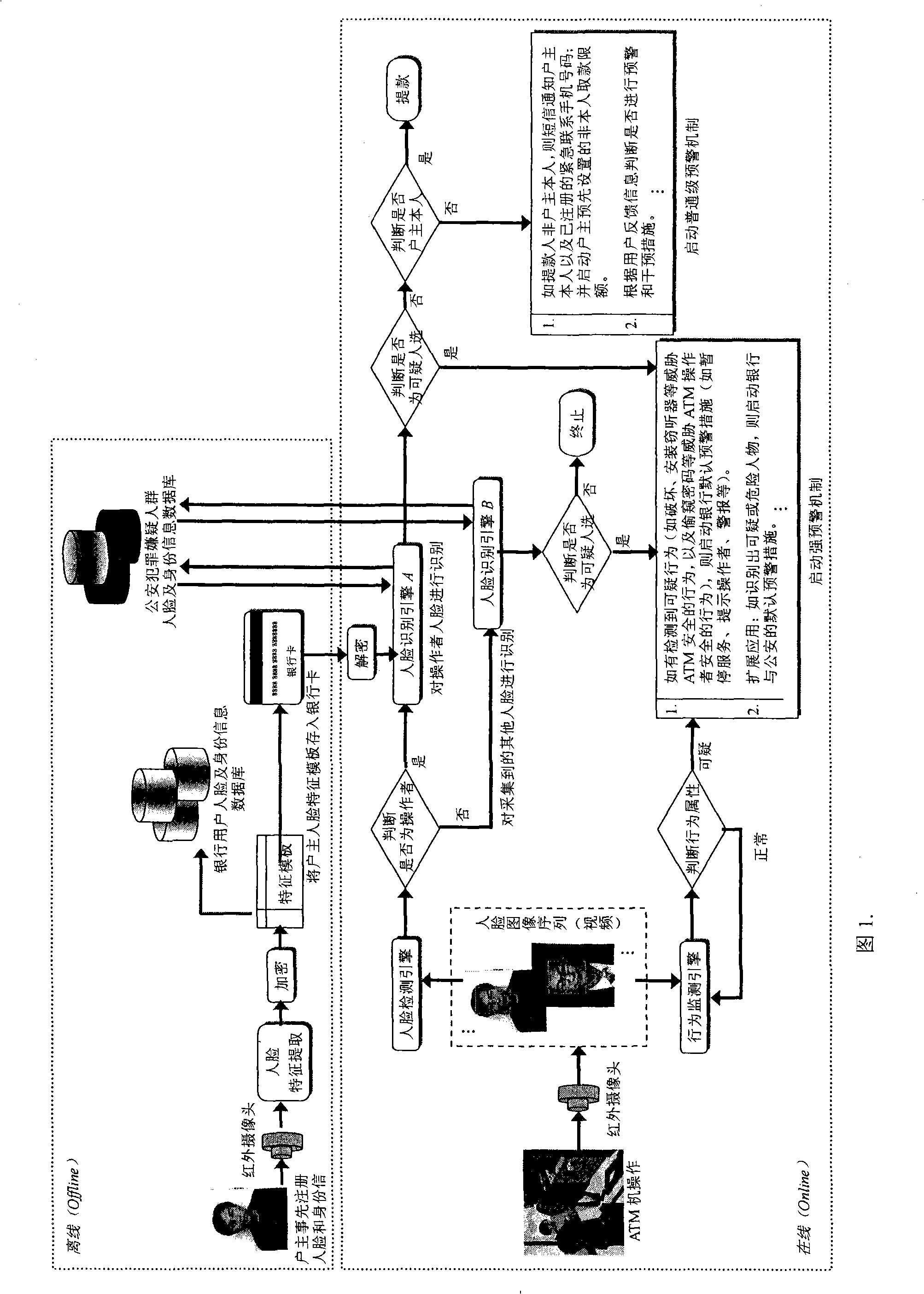
ATM secure authentication and pre-alarming method based on face recognition
ActiveCN101266704AEnsure safetyGuaranteed privacyCharacter and pattern recognitionAlarmsComputer networkAcquisition apparatus
The invention discloses an ATM security certificate and a pre-warning method based on face recognition. The invention introduces face recognition and video detection into the applications of ATM and bank card business for the first time, which can obviously improve the security of ATM financial system, effectively reduce and overawe various ATM fraud and criminal activities. The complete system operation process in the method of the invention is: firstly, registering the face information of a holder at a service window which arranges an infrared face acquisition equipment or with the registration by the users themselves on ATM in bank, and saving the encrypted face information to a bank database and a bank card. Then, determining whether the ATM operator to be recognized is the holder of the bank card or not through verifying the user's identity by a face recognition engine; determining and recognizing whether existing behaviors that threaten ATM and the users though a behavior monitoring engine; and determining whether to trigger corresponding pre-warning mechanism or not according to the recognition result. The invention can extend to the applications of bank book business, public security monitoring and pursuing escaped criminals, etc.
Owner:哈尔滨维科智能系统有限公司
Right control method, apparatus, system and node device of block chain
ActiveCN106796688AEnsure safetyGuaranteed privacySecuring communicationProtocol authorisationChain networkBlockchain
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
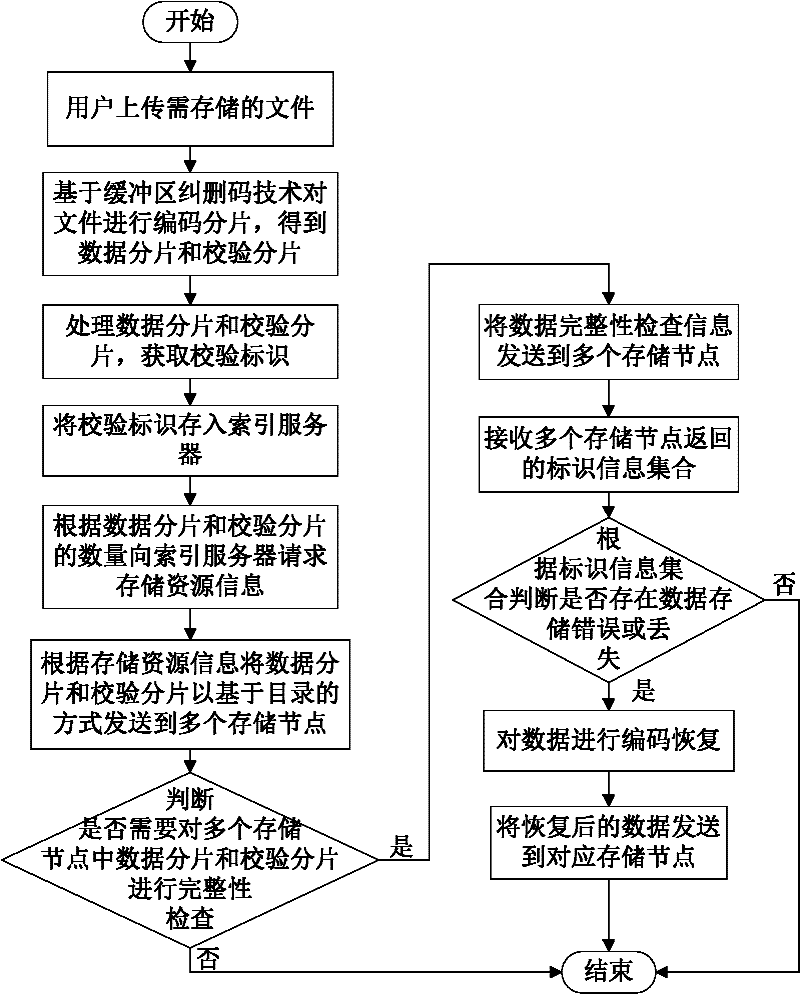
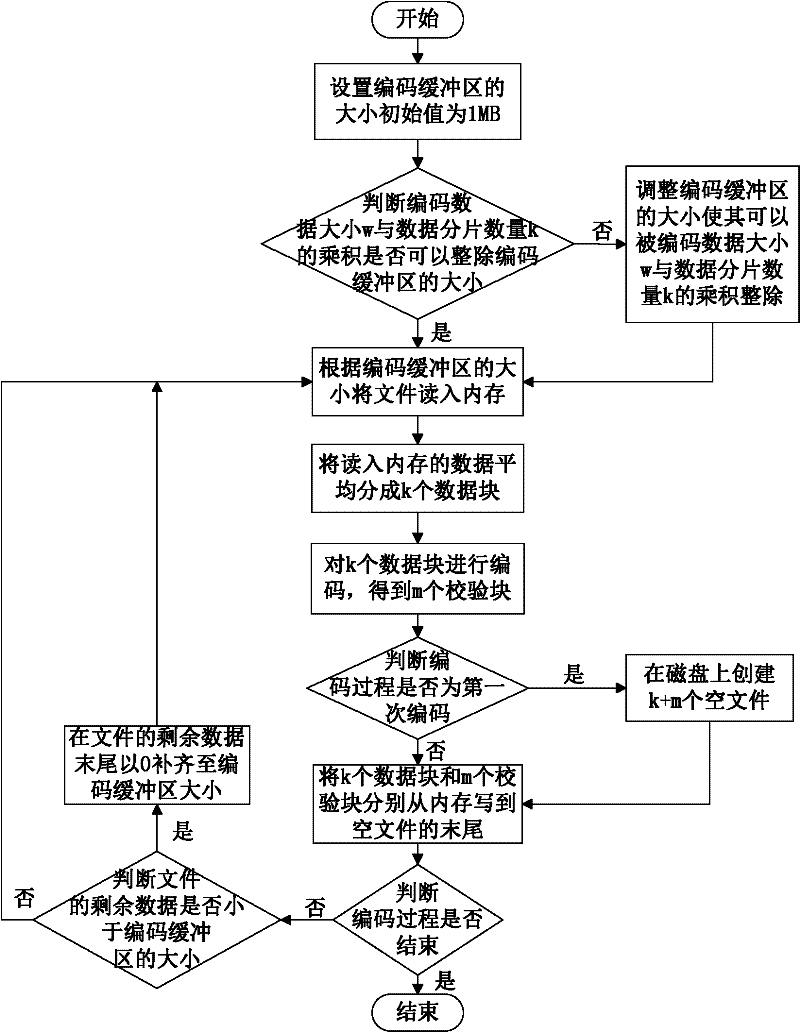
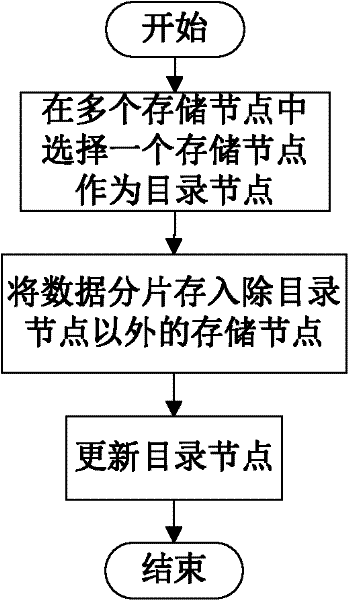
Data storage method of cloud storage system
InactiveCN102546755ADoes not affect recoveryImprove data availabilityTransmissionSpecial data processing applicationsComputer hardwareData integrity
The invention discloses a data storage method of a cloud storage system, which comprises the steps of: carrying out coding fragmentation on a file on the basis of a buffer zone erasure code technology to obtain data fragments and check fragments; processing the data fragments and the check fragments to obtain a check identification; storing the check identification in an index server; requesting storage resource information to the index server according to the quantity of the data fragments and the check fragments; sending the data fragments and the check fragments to a plurality of storage nodes according to the storage resource information; judging whether needing to carry out integrity check on the data fragments and the check fragments in the storage nodes; if needing to carry out integrity check on the data fragments and the check fragments in the storage nodes, sending the data integrity check information to the storage nodes, receiving an identification information set returned by the storage nodes, and judging whether data storage errors or data losses exist according to the identification information set, if yes, coding for recovering the data, and sending the recovered data to the corresponding storage nodes.
Owner:HUAZHONG UNIV OF SCI & TECH
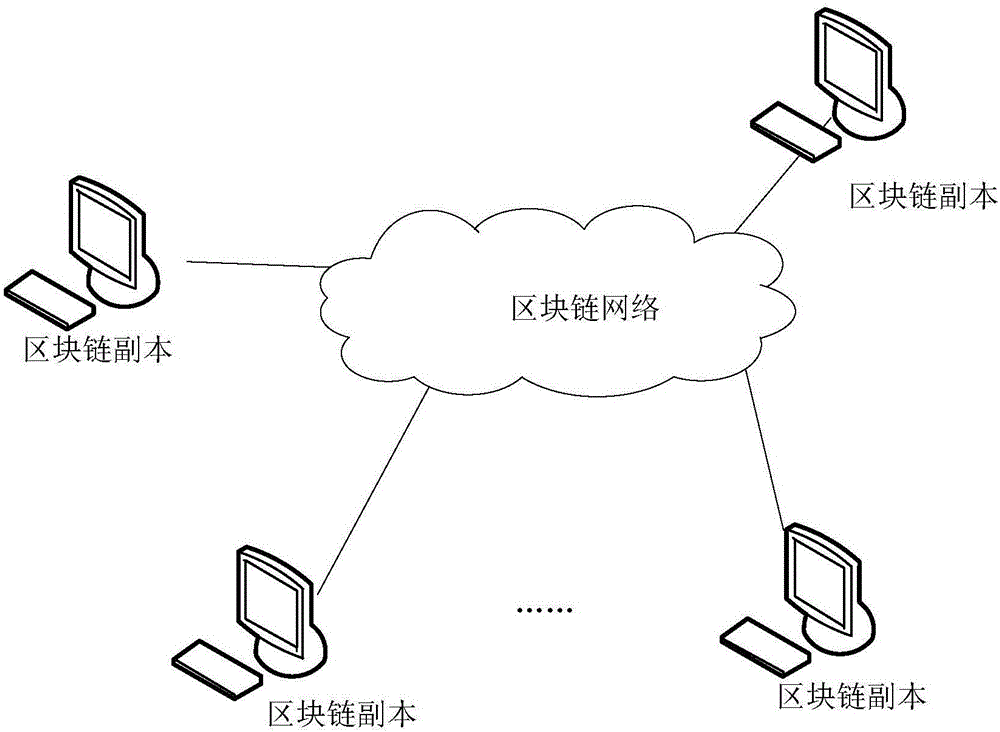
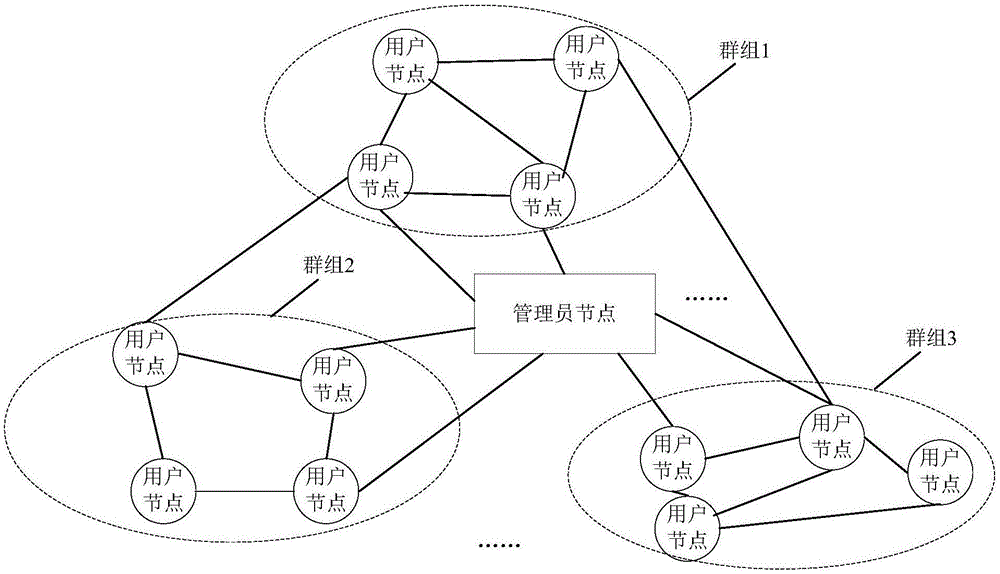
Block chain storage system
InactiveCN107122477APrevent data privacy breachesReach the consensus of the whole networkDigital data protectionTransmissionCloud computingBlockchain
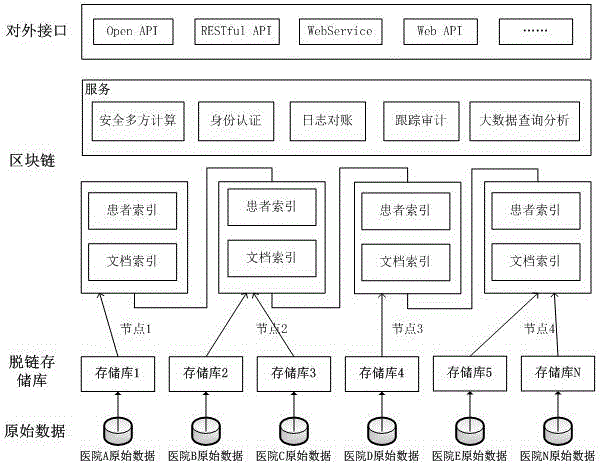
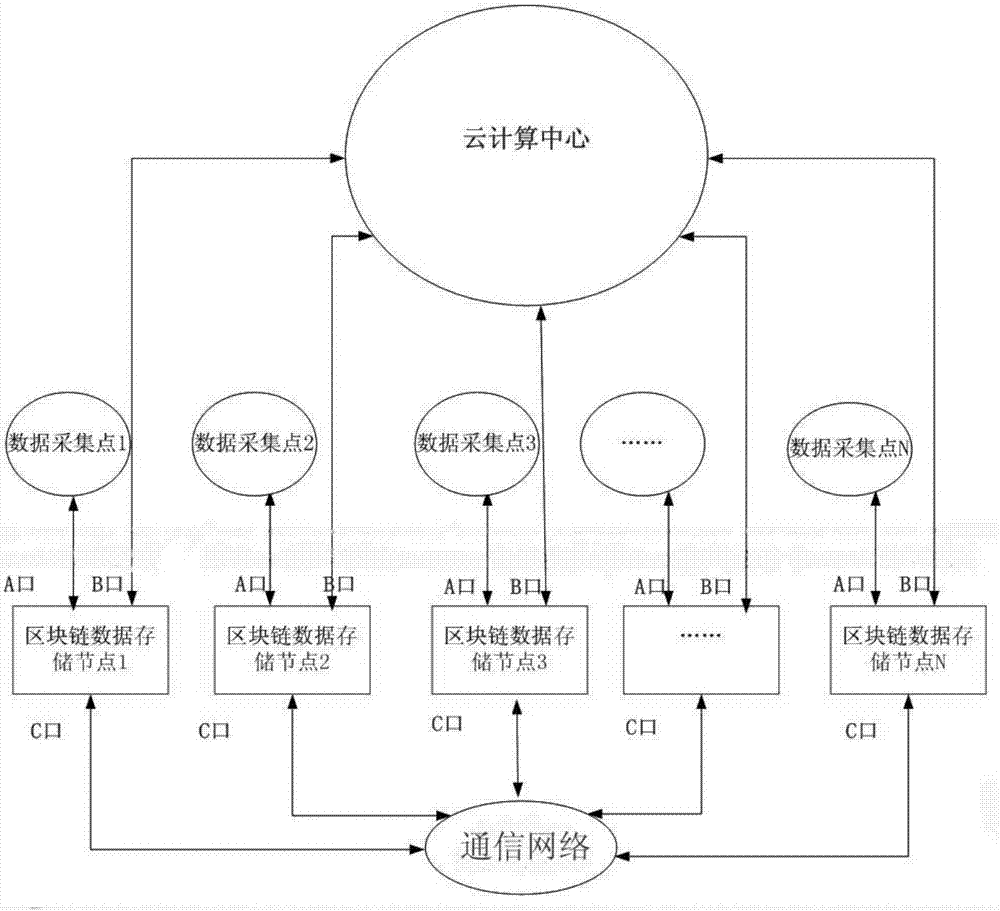
The invention discloses a block chain storage system. The system comprises a plurality of data collection modules and block chain data storage nodes corresponding to the data collection modules, wherein the data collection modules send collected data into the block chain data storage nodes, and all the block chain data storage nodes are connected with a communication network through a wired interface, a wireless interface, an optical interface, a Bluetooth interface or other technical interfaces and can complete synchronization and data communication. The system also comprises a cloud computing center, wherein the cloud computing center can call the data in the block chain data storage nodes, and a user can check the data from the cloud computing center through terminal equipment. The block chain storage system is composed of N block chain data storage nodes, and all the block chain data storage nodes are connected with the communication network through the wired interface, the wireless interface, the optical interface, the Bluetooth interface or other technical interfaces and can complete synchronization and data communication between themselves.
Owner:CHENGDU ZHONGYUANXIN ELECTRONICS TECH
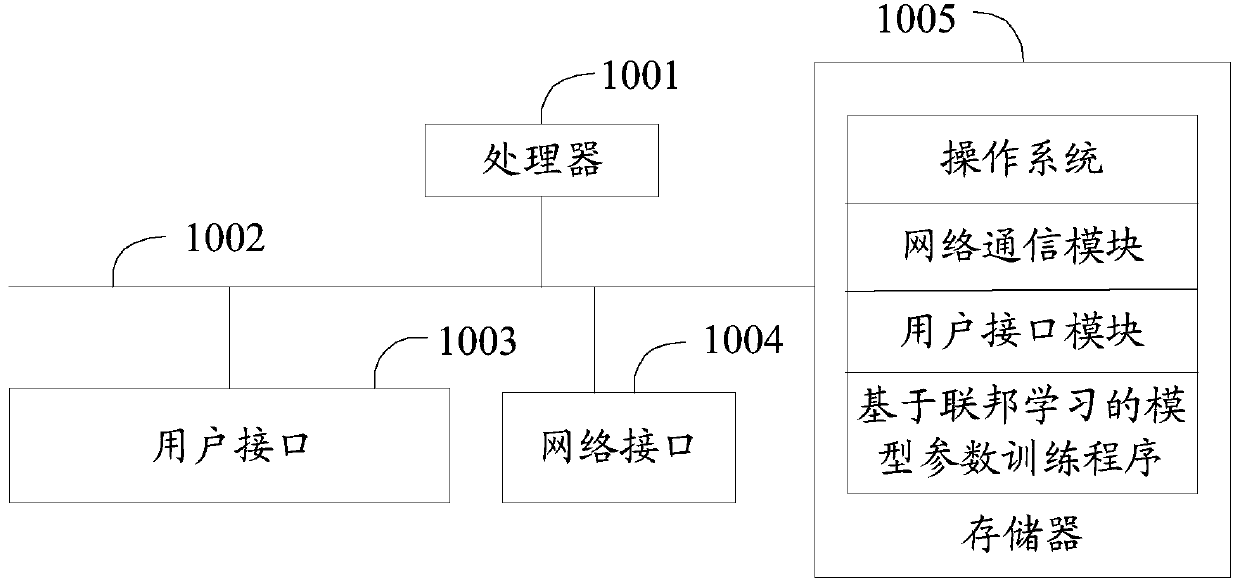
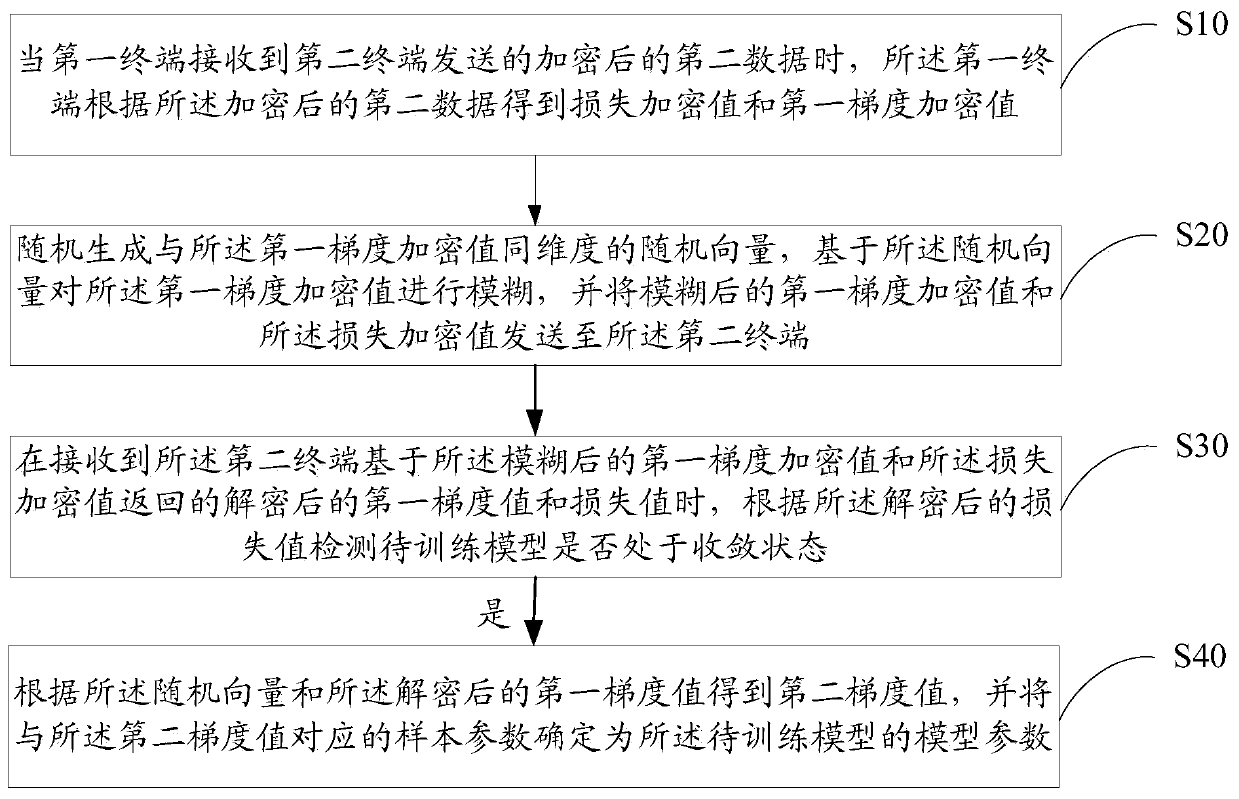
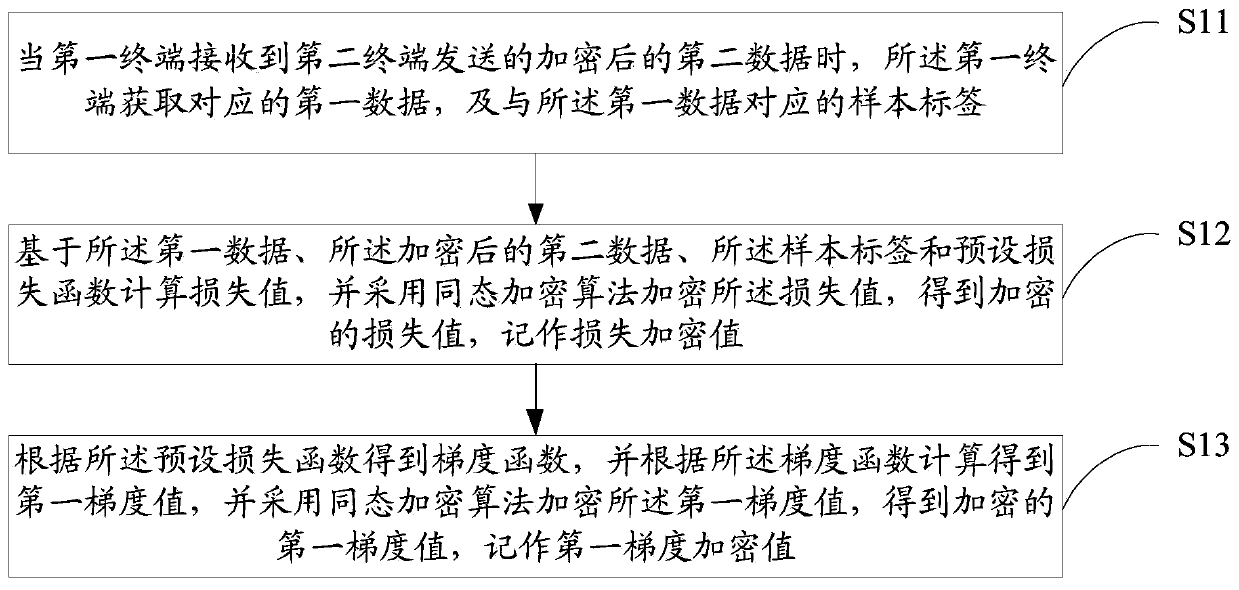
Model parameter training method and device based on federated learning, equipment and medium
PendingCN109886417ASolve application limitationsWon't leakPublic key for secure communicationDigital data protectionTrusted third partyModel parameters
The invention discloses a model parameter training method and device based on federal learning, equipment and a medium. The method comprises the following steps: when a first terminal receives encrypted second data sent by a second terminal, obtaining a corresponding loss encryption value and a first gradient encryption value; randomly generating a random vector with the same dimension as the first gradient encryption value, performing fuzzy on the first gradient encryption value based on the random vector, and sending the fuzzy first gradient encryption value and the loss encryption value toa second terminal; when the decrypted first gradient value and the loss value returned by the second terminal are received, detecting whether the model to be trained is in a convergence state or not according to the decrypted loss value; and if yes, obtaining a second gradient value according to the random vector and the decrypted first gradient value, and determining the sample parameter corresponding to the second gradient value as the model parameter. According to the method, model training can be carried out only by using data of two federated parties without a trusted third party, so thatapplication limitation is avoided.
Owner:WEBANK (CHINA)
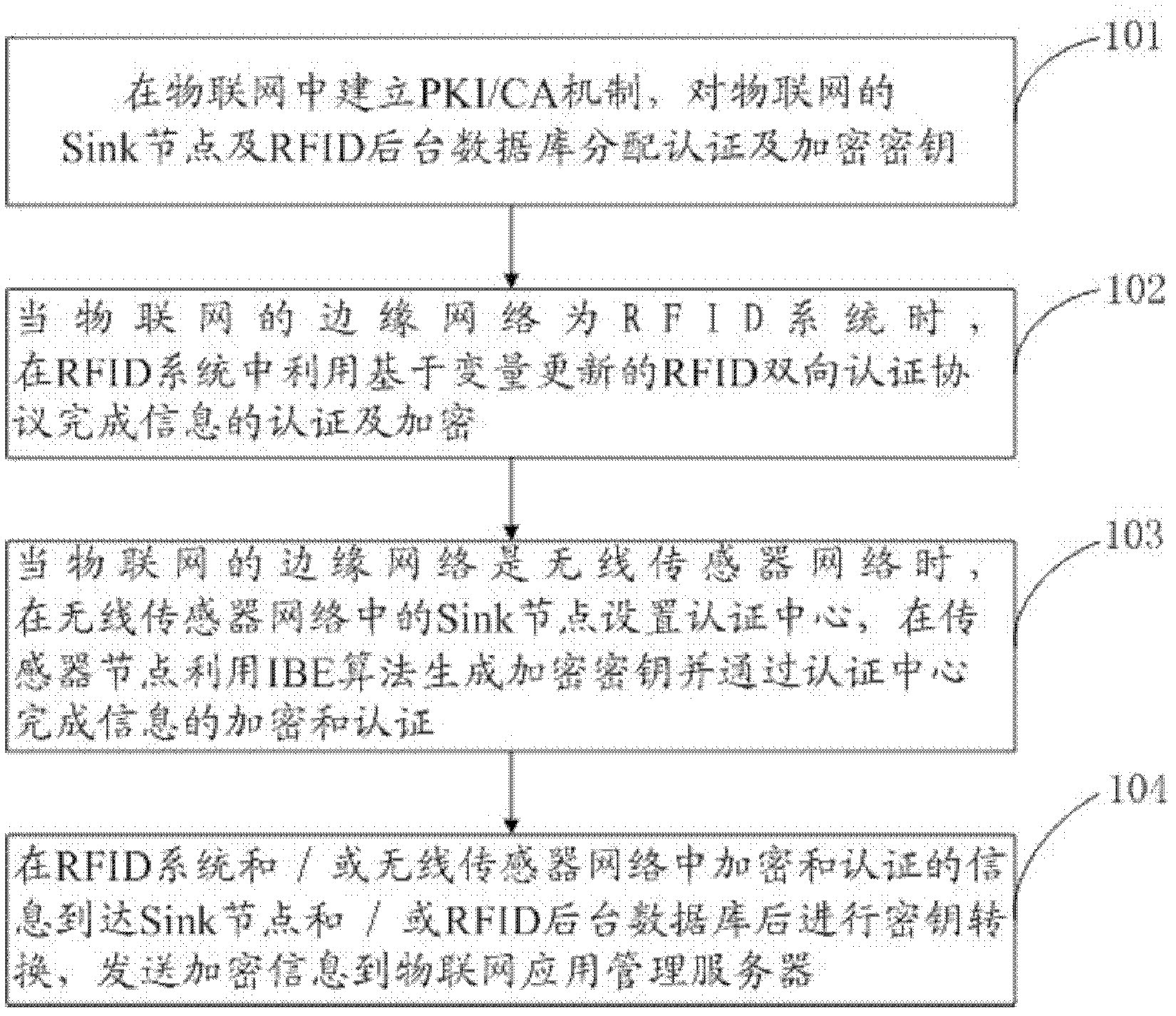
Method and system for internet of things information transmission
ActiveCN103166919AImprove securityGuaranteed privacyUser identity/authority verificationInformation transmissionThe Internet
The invention discloses a method and a system for internet of things information transmission. Firstly, a public key infrastructure / certificate authority (PKI / CA) mechanism is established in the internet of things and an authentication key and an encryption key are distributed to an aggregation node of the internet of things; transmitted information is encrypted and authorized in an edge network of the internet of things; and key conversion is conducted after the encrypted and authorized information reaches the aggregation node of the internet of things and the information encrypted again is sent to an application management server of the internet of things. According to the method and the system for the internet of things information transmission, the internet of things can effectively resist interior attack, information safety transmission level is improved and complexity of encryption and safety authentication calculation in the edge network of the internet of things is reduced.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
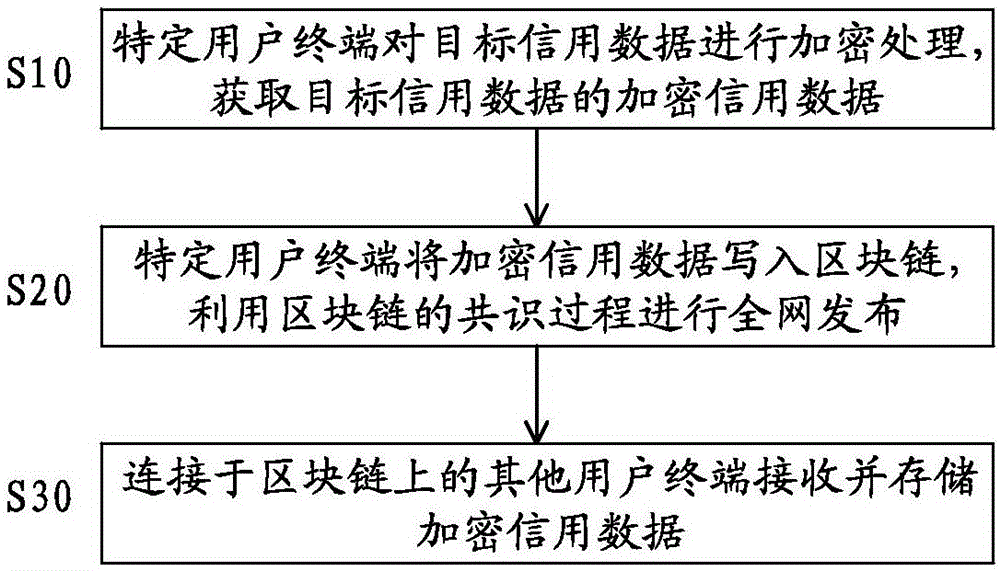
Credit recording system and method based on block chain
ActiveCN106485167AWide variety of sourcesReduce complexityDigital data protectionExtensibilityComputer terminal
The invention discloses a credit recording system and method based on a block chain. The credit recording system comprises a plurality of user terminals which are connected to the block chain and used for acquiring and verifying credit data, wherein each user terminal is installed with an encryption module for encrypting target credit data to be transmitted to form encrypted credit data, a communication module for transmitting the encrypted credit data together with the block chain, and a storage module for storing the target credit data of the user terminal and other encrypted credit data transmitted by the block chain. The credit data are wide in sources, independent, reliable and real; the cleaning and sieving complexity of the credit data are lowered greatly; and the credit recording system and method have flexible and diverse application scenes and high extensibility.
Owner:CENTRIN DATA SYST
Mobile phone near field communication system and method based on visible light
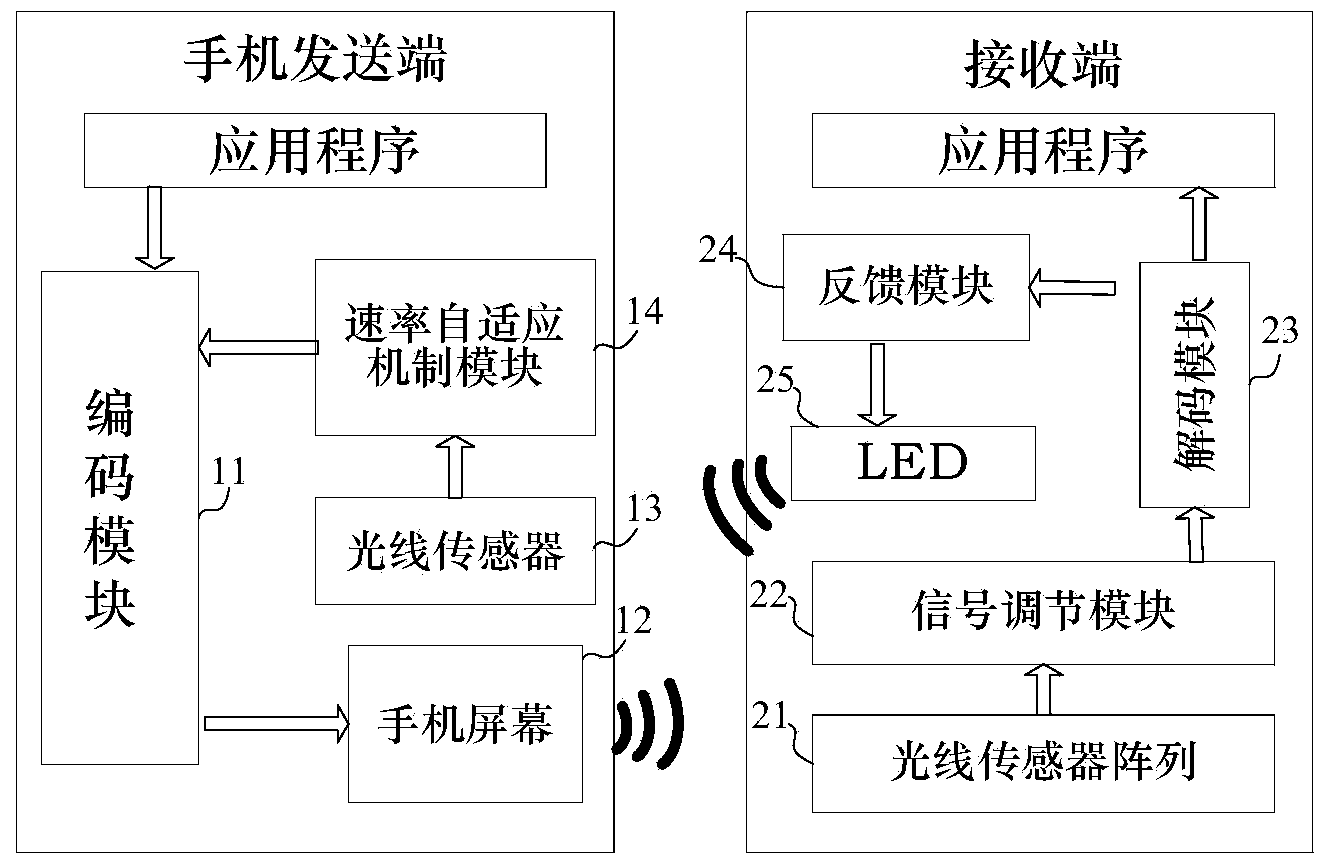
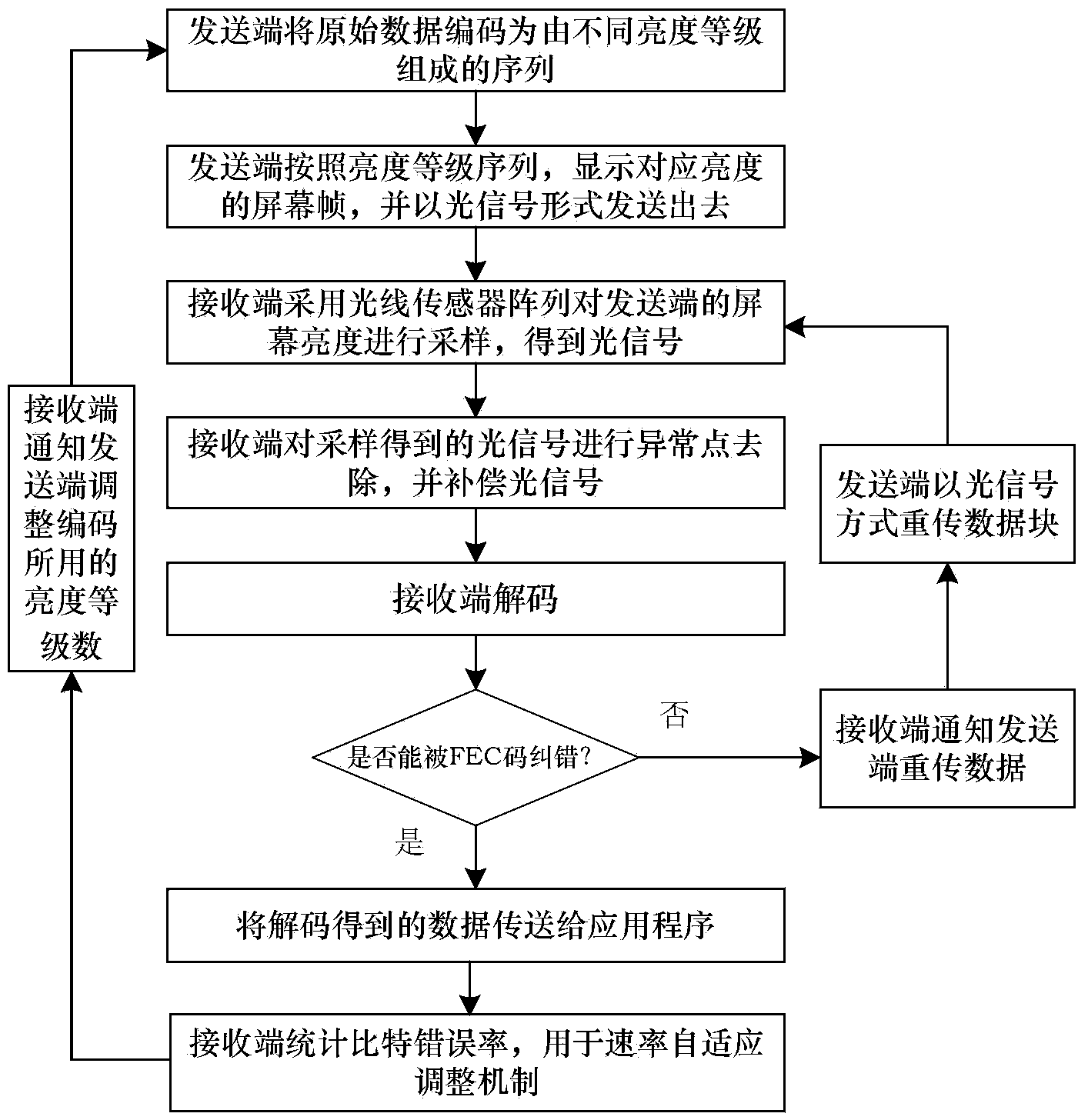
ActiveCN103490812AGuaranteed privacyEnsure safetyClose-range type systemsLine sensorComputer hardware
The invention provides a mobile phone near field communication system and method based on visible light. The mobile phone near field communication system and method based on the visible light are used for short distance wireless communication. According to the mobile phone near field communication system, a transmitting terminal is arranged on a mobile device provided with a light-emitting screen and a light sensor, and comprises an encoding module and a rate adaptive mechanism module; a receiving terminal is provided with an LED and comprises a light sensor array, a signal conditioning module, a decoding module and a feedback module. The encoding module encodes data into a brightness level sequence and sends the brightness level sequence out through light signals; the receiving terminal collects the light signals to conduct signal conditioning and decoding so as to obtain decoded data; the feedback module is used for feeding back a signal of data blocks which need retransmission and a signal of adjustment of brightness level numbers to the transmitting terminal; the transmitting terminal controls the retransmission of the data blocks and the adjustment of the brightness level numbers through the rate adaptive mechanism module. The mobile phone near field communication system and method based on the visible light are low in cost, easy to use, safer, free of addition of extra hardware, and capable of achieving the near field communication functions such as mobile payment, equipment matching and data exchange between mobile phones.
Owner:BEIHANG UNIV
Block chain authority control method, device and node device
PendingCN106796685AEnsure safetyGuaranteed privacyCryptography processingPublic key for secure communicationComputer networkEngineering
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
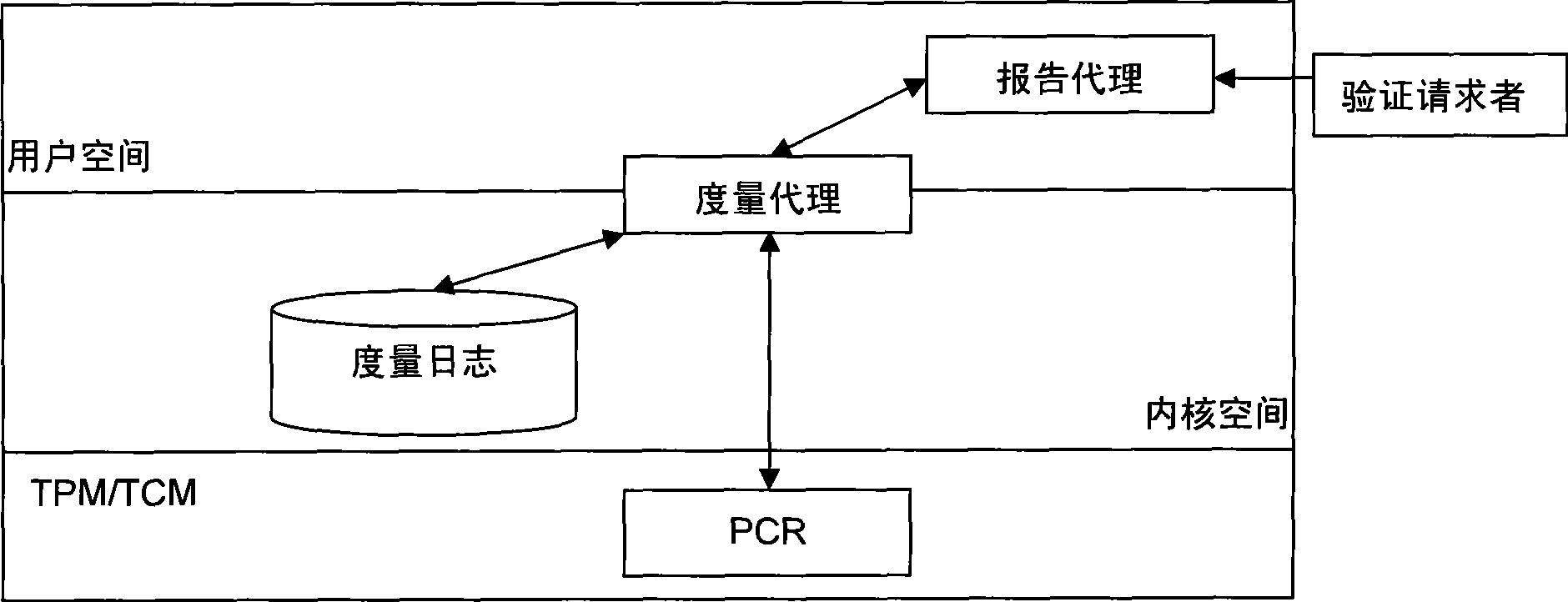
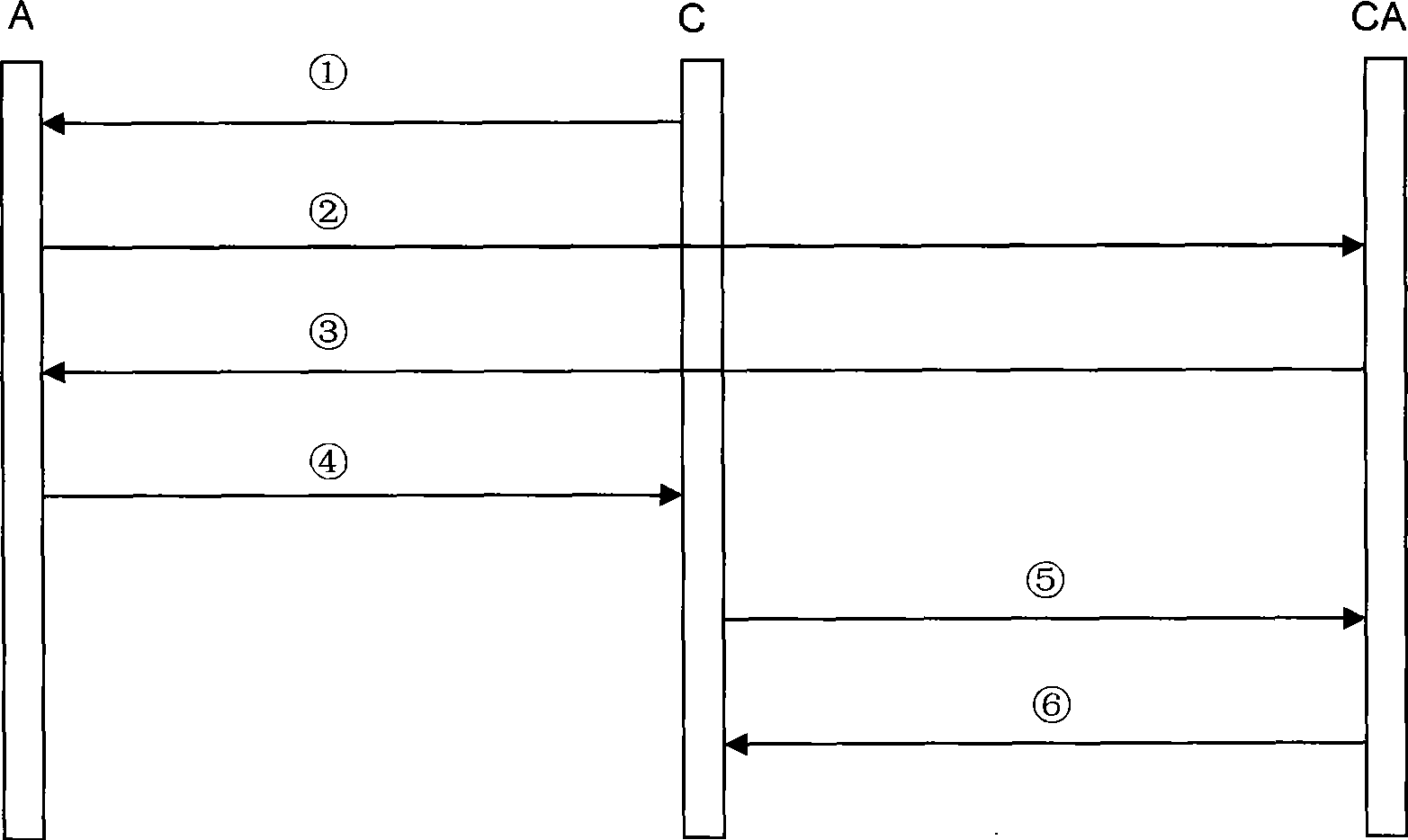
Remote proving method in trusted computation environment
InactiveCN101477602AGuarantee authenticityGuaranteed privacyInternal/peripheral component protectionTransmissionMan-in-the-middle attackDigital signature
The invention provides a method for remote attestation in a trusted computing environment. The method is characterized in that secure session key is adopted for encrypting the metric value and the metric log of trusted platform to be verified, and signs for encryption result data. The method is based on a security chip TPM / TCM; the adopted remote attestation framework comprises three parts: an integrity measuring mechanism, a reporting mechanism and a validation mechanism, which are achieved by an integrity measuring agency, a report agency and a verification requestor, wherein, the measuring agency, the report agency and the verification requestor are installed in the trusted platform to be verified. The method ensures that the authenticity of the integrity measuring value and the measuring log and the privacy of the platform are kept; the replay attack, impersonation attack and man-in-the-middle attack are effectively prevented; the method is used for proving to the verification requestor that the running environment of the platform is credible, or used for self-test of the platform running environment; the method can be used for not only proving to the requestor that the platform running environment is credible, but also the self-test of the platform running environment; and the method is more suitable for a fair and open network environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
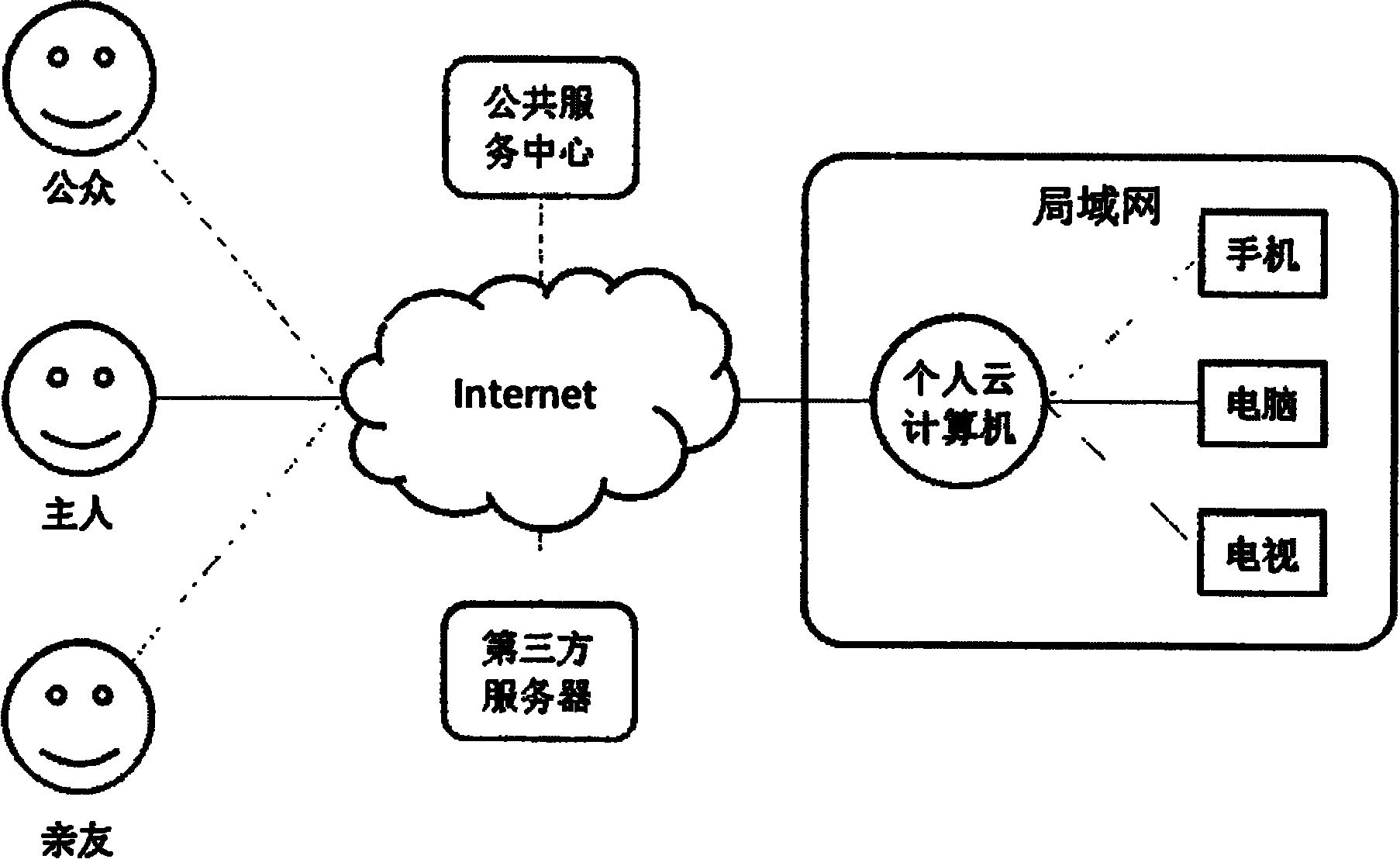
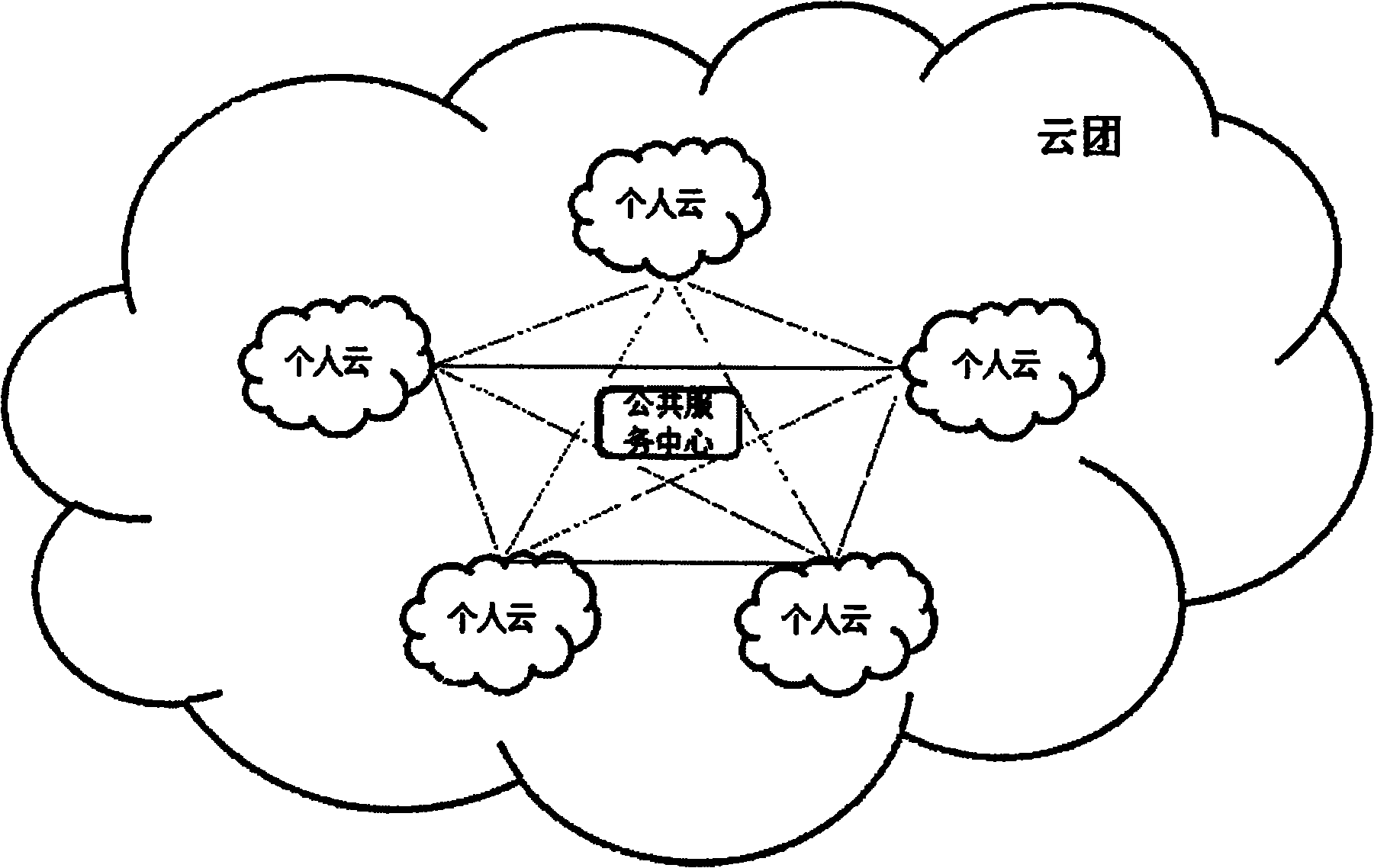
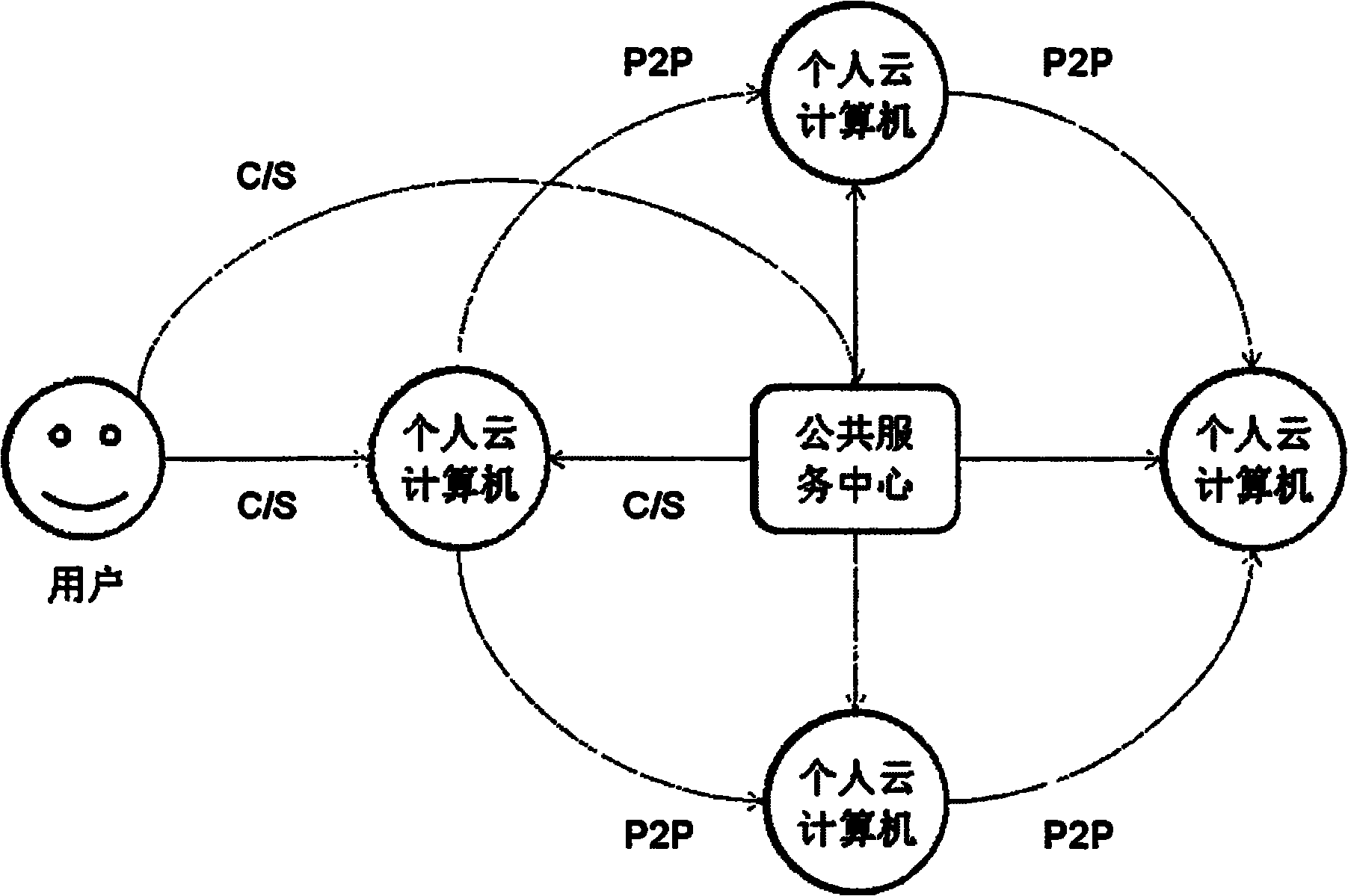
System and equipment for realizing personal cloud computing
The invention relates to a system, a method and equipment of cloud computing, particularly to a system, a method and equipment for realizing personal cloud computing. The system for realizing the personal cloud computing is composed of one or more personal cloud computing computers and clients thereof; each personal cloud computing computer is possessed and managed by different users, is placed in a own local area network of the user, and is on line 24*7; the personal cloud computing system is composed of a personal cloud computing system, a public service center system and / or a third-party server; huge number of personal cloud computers form a completely distributed large-scale parallel computing network; and the personal cloud computing system provides the network servers, such as files, database and equipment and the like, for the clients through a WEB service manner. The personal cloud computing system in the invention comprises a distributed computing module, a multi-stage buffermodule, a storage exchanging module, an equipment virtual module, a neighbor discovery module, a peer-to-peer access module, a network address translation (NAT) traversal module and a dedicated client module.
Owner:李斌
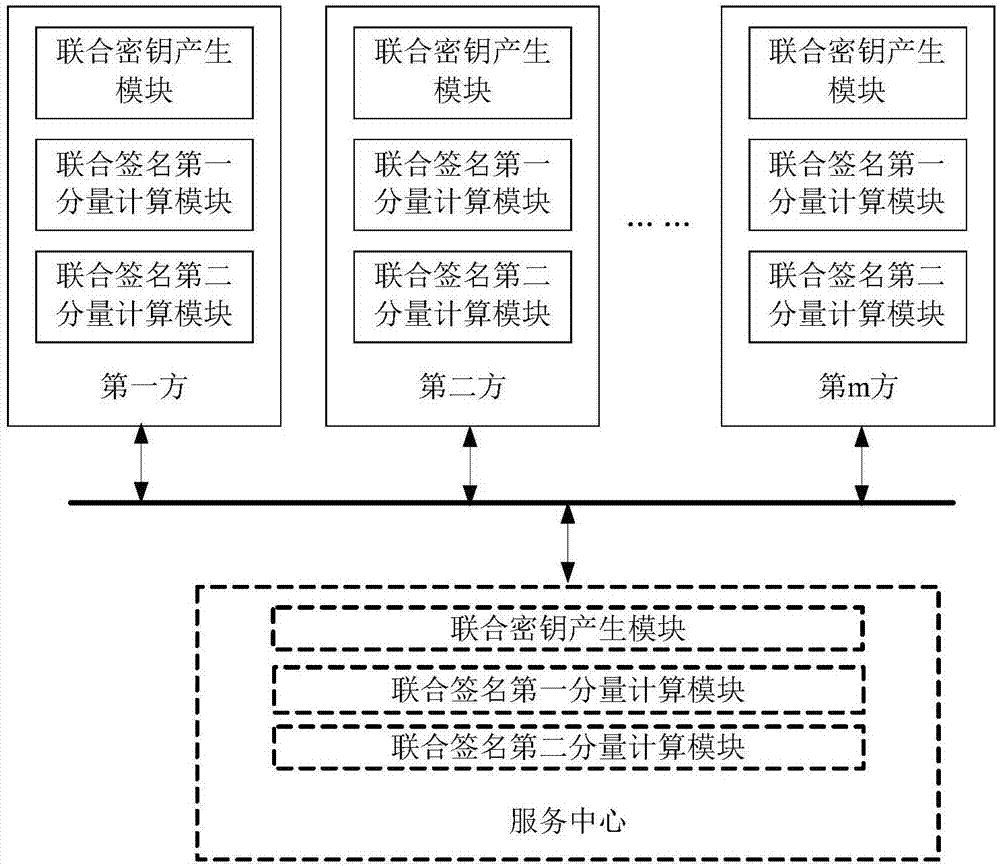
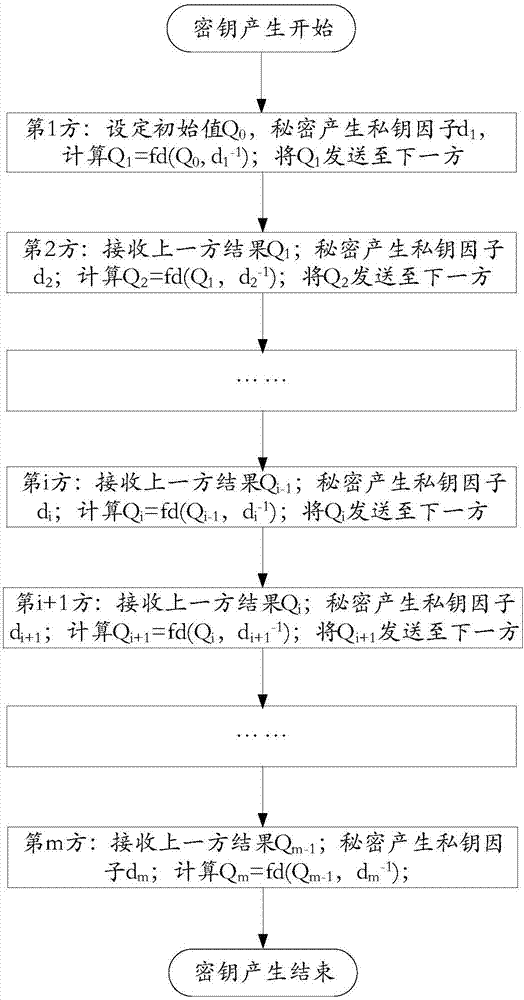
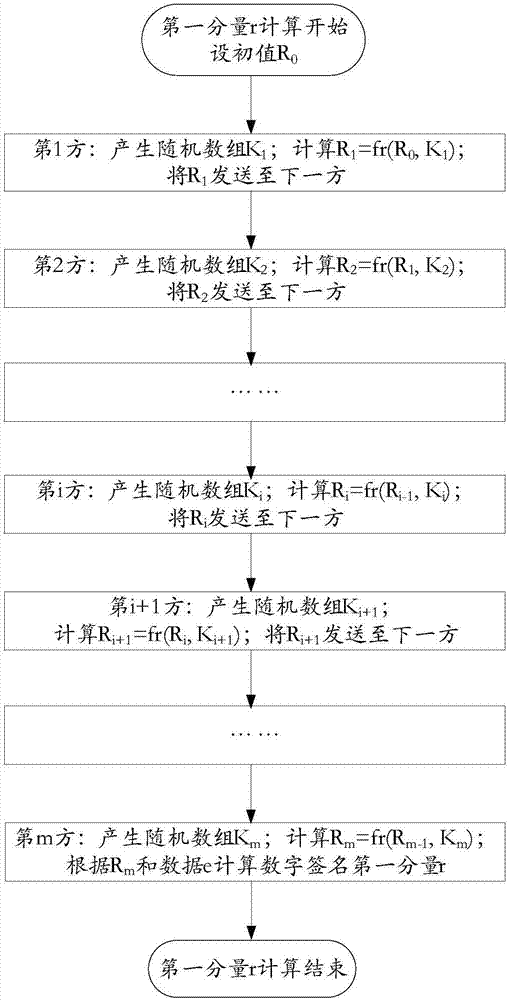
Multiparty joint key production and digital sign method and system
ActiveCN107017993AImprove protectionPrevention and control measures are effectiveKey distribution for secure communicationPublic key for secure communicationDigital signatureEngineering
The invention provides a multiparty joint key production and digital sign method and system. A joint sign private key d is composed of m private key factors di. The i is equal to [1, m]. The m is greater than or equal to 3. The m private key factors di are produced by the joint parties independently and secretly when the private key is produced and are stored in own devices secretly. The joint digital sign is finished by the parties according to a certain sequence and is finished jointly through utilization of the secretly stored key factors di based on calculation. The system comprises m joint parties. Each joint party has an independent subsystem. Each subsystem is composed of three parts: a joint key production module, a joint sign first component calculation module and a joint sign second component calculation module. According to the method and the system, the multiparty joint key production and digital sign method of an SM2 cryptographic algorithm and various formed systems: acentric and centered systems are realized. The digital sign is no longer finished by a single individual and is finished by multiple parities jointly.
Owner:BEIJING JN TASS TECH
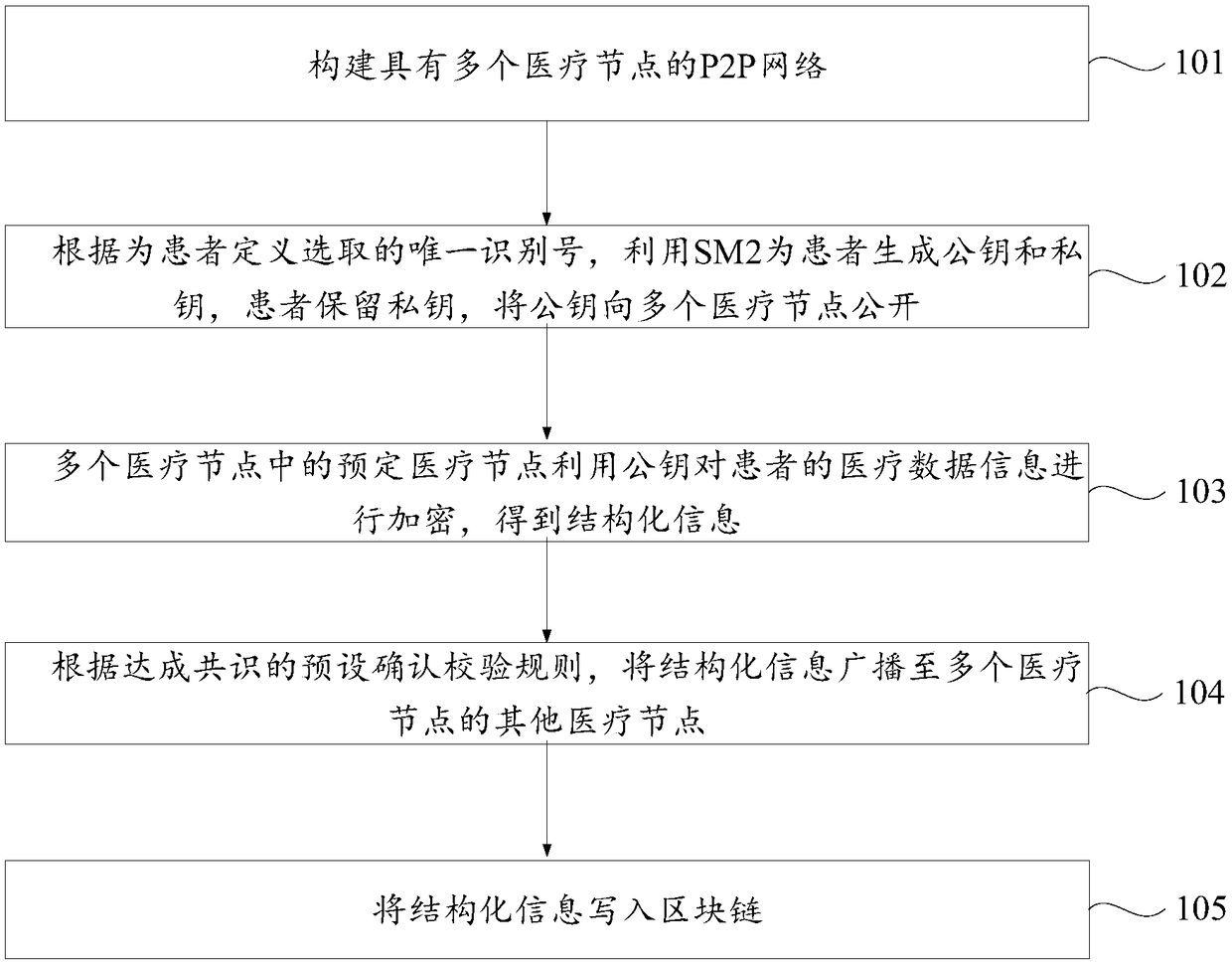
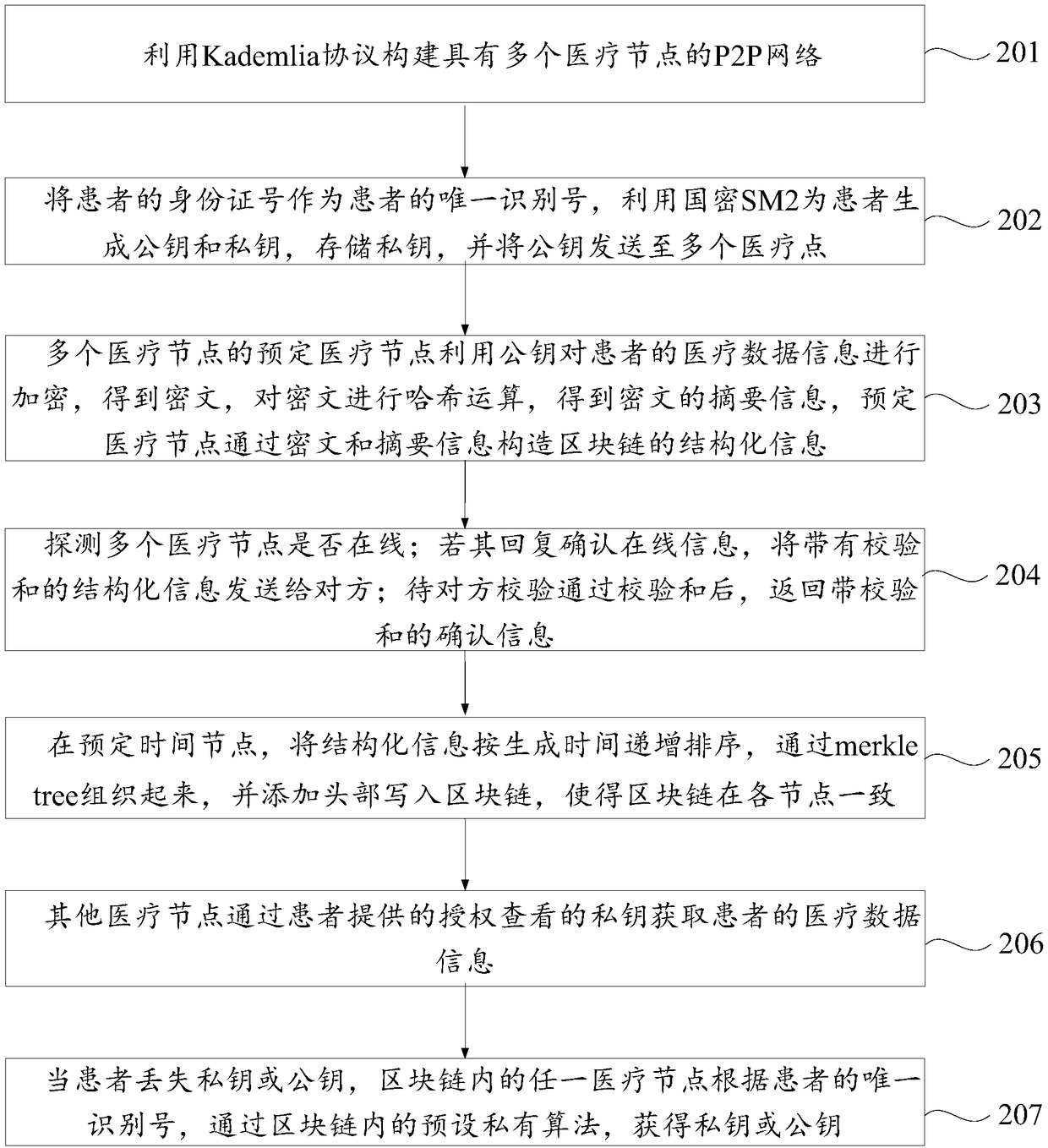
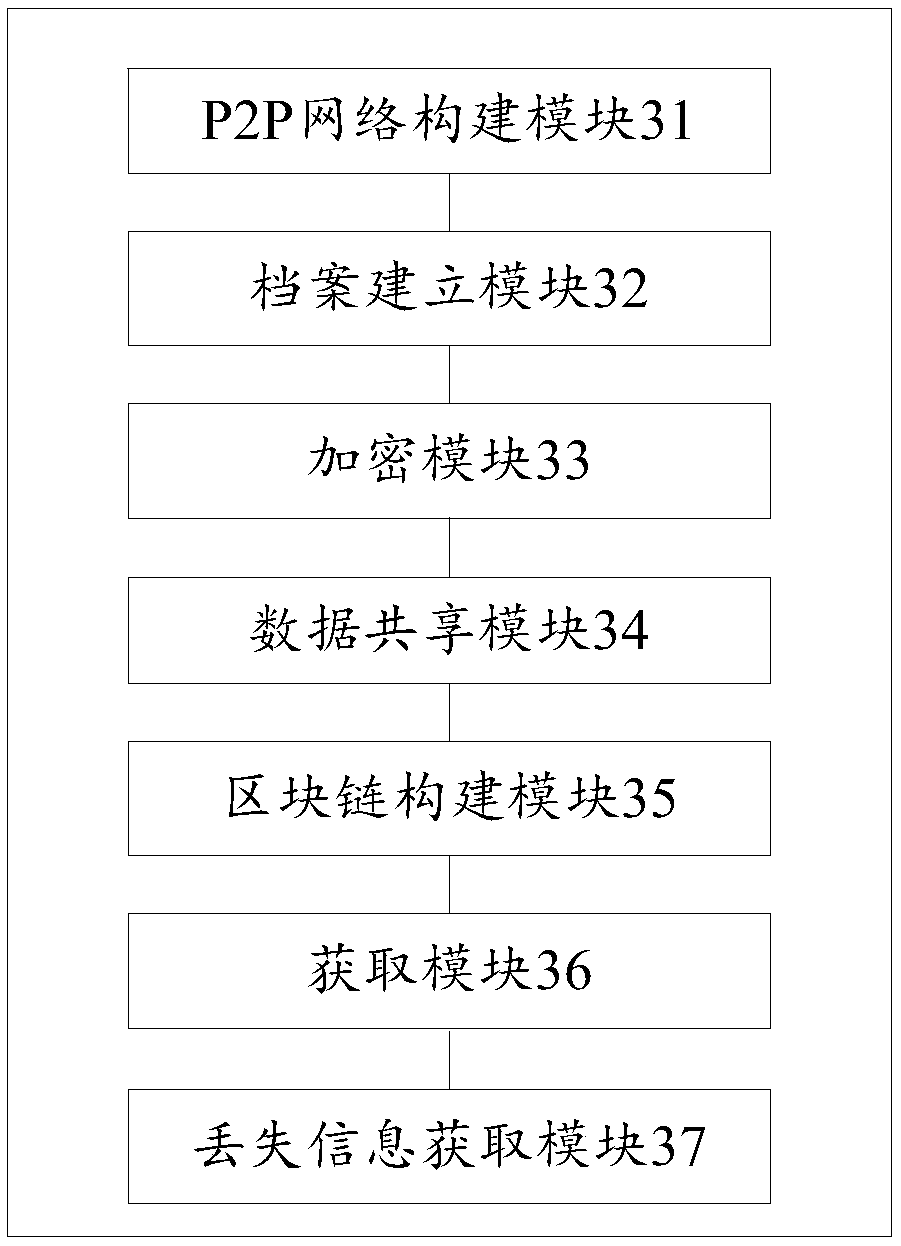
Medical data sharing method and device based on block chain
ActiveCN108600227AImprove data sharing efficiencyGuaranteed security and privacyPayment protocolsTransmissionBlockchainData sharing
The invention discloses a medical data sharing method and device based on a block chain, and belongs to the technical field of the block chain. The method comprises the following steps: constructing aP2P network with multiple medical nodes; generating a public key and a private key for the patient by using SM2 according to a unique identification number defined and selected for the patient, wherein the patient reserves the private key and opens the private key to multiple medical nodes, and a predetermined medical node in multiple medical nodes encrypts the medical data information of the patient by using the public key so as to construct structural information of the block chain through the ciphertext; broadcasting the structural information to other medical nodes of multiple medical nodes according to mutually agreed preset confirming checking rule; and writing the structural information into the block chain. Through the medical data sharing method disclosed by the invention, the data sharing efficiency between the hospitals can be improved, and the privacy and the security of the information can be guaranteed from the technology, and the method is suitable for extensively popularizing and applying in the medical field.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD +1
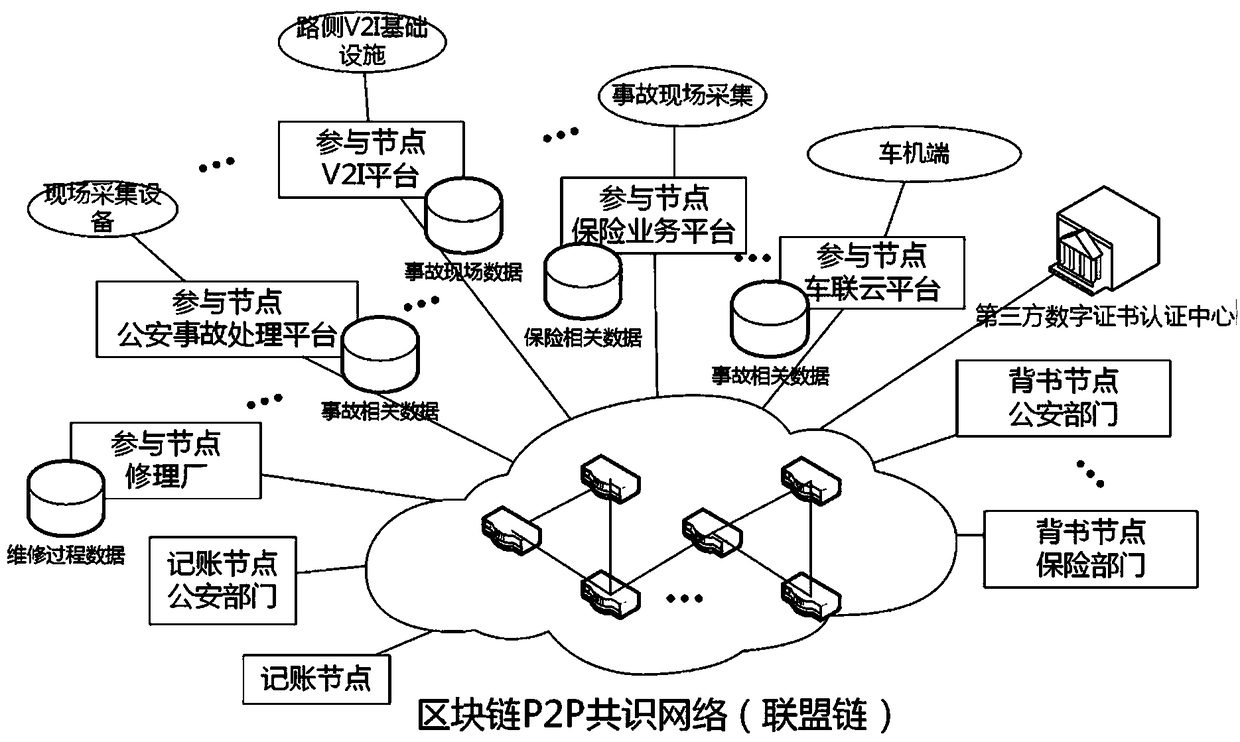
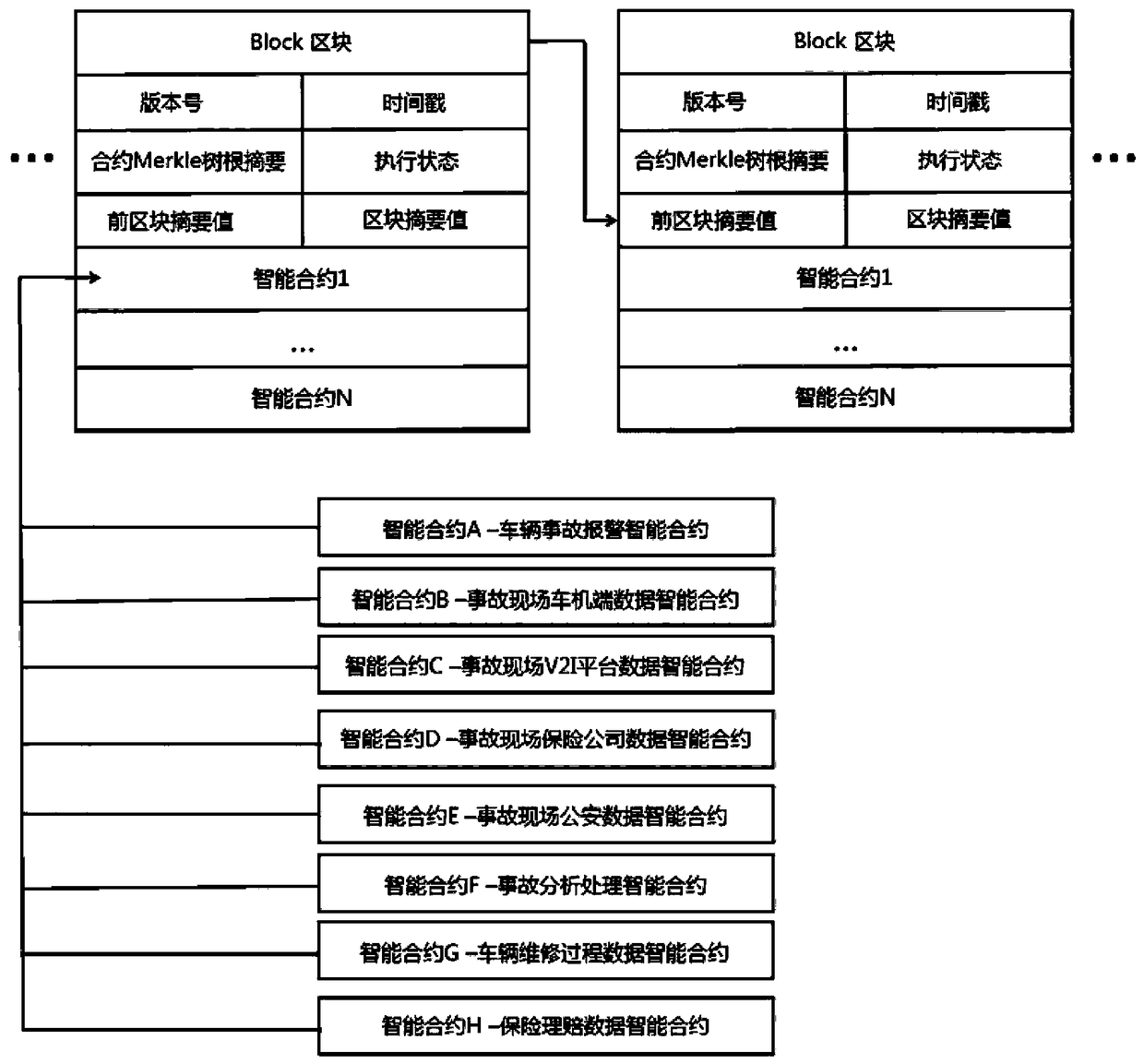
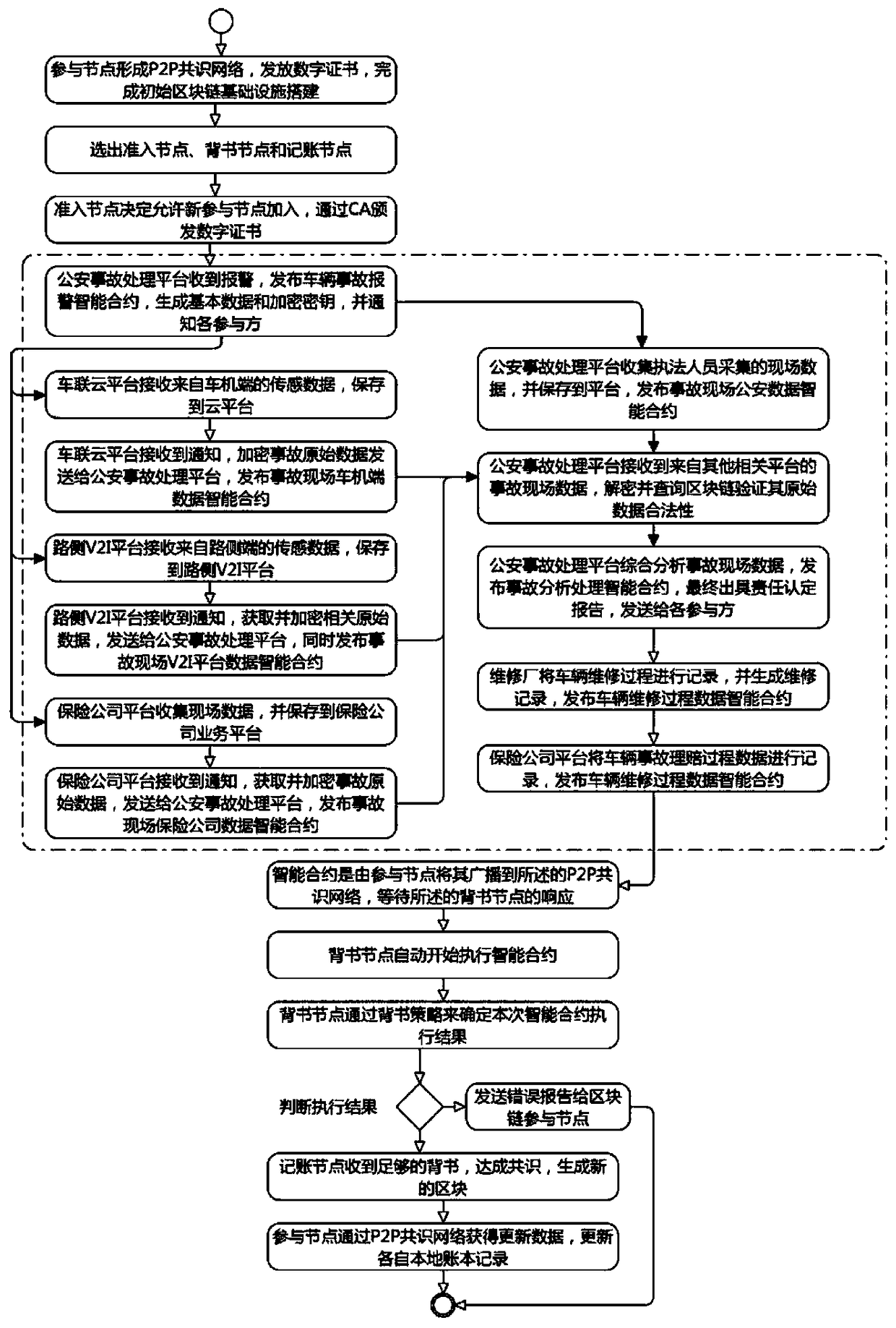
Network connected vehicle accurate accident handling method based on block chain
InactiveCN108446992AImprove accuracyImprove processing speedFinanceUser identity/authority verificationReal-time computingBlockchain
The invention discloses a network connected vehicle accurate accident handling method based on block chain. The implementation process of the method comprises: 1, firstly, through a block chain technology, connecting all participated joints which are associated with accident handling, based on a P2P consensus network, establishing an alliance chain, putting life cycle of accident handling in the block chain to record; through an intelligent terminal on a vehicle accident site, acquiring on-site data and uploading, the participated joints which are associated with accident handling completing accident handling. Compared with the prior art, the network connected vehicle accurate accident handling method based on block chain effectively solves a mutual trust problem of involve parties throughan unified and decentralized method, improves accident responsibility confirmation accuracy rate and handling speed, and provides an accident retroactive function, improves transparency of accident handling process, shortens accident handling time, and saves vehicle accident handling cost.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
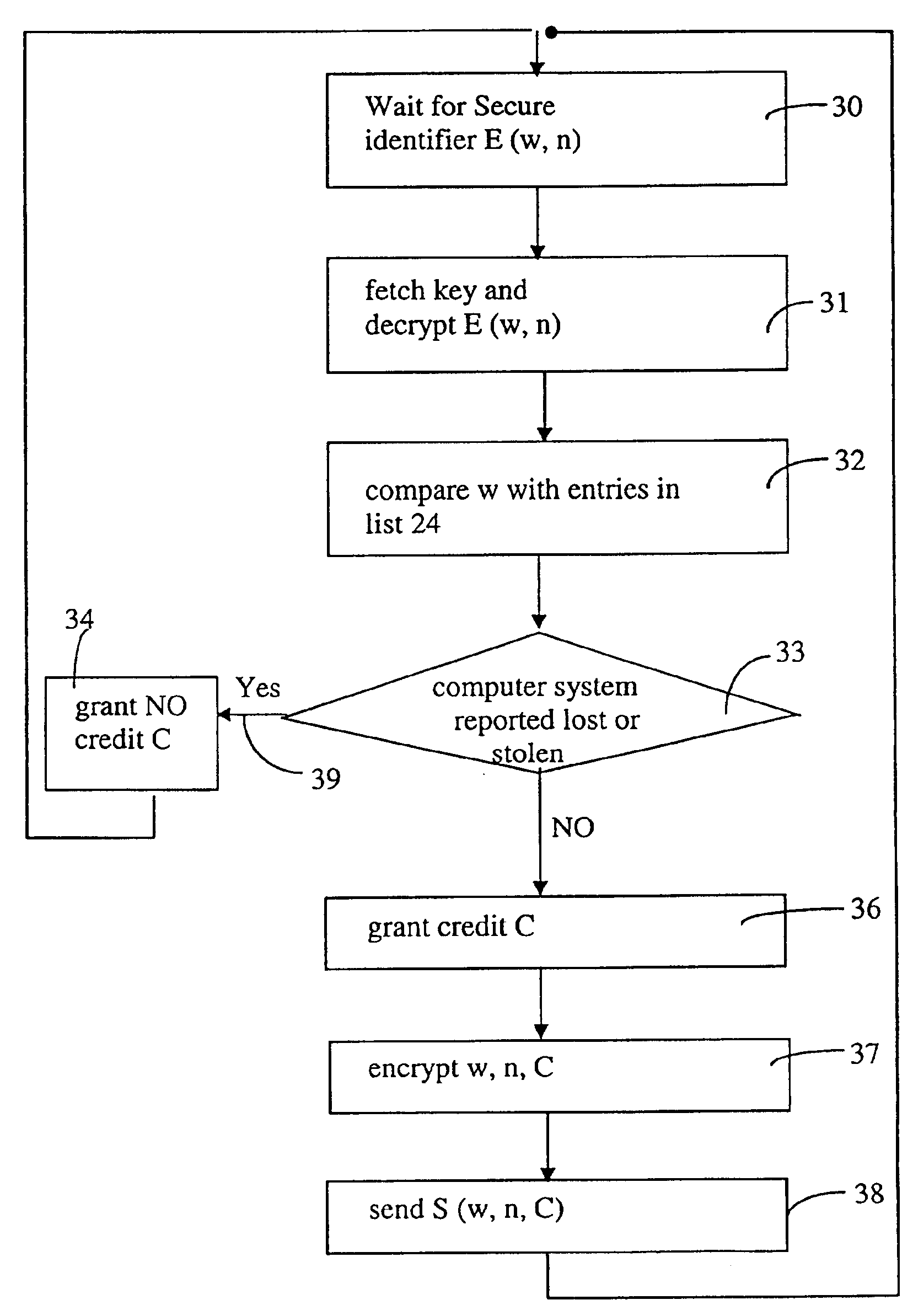
Scheme for blocking the use of lost or stolen network-connectable computer systems
ActiveUS6925562B2Easy to tamper withMaximum flexibilityDigital data processing detailsUser identity/authority verificationCommunication interfaceTrusted hardware
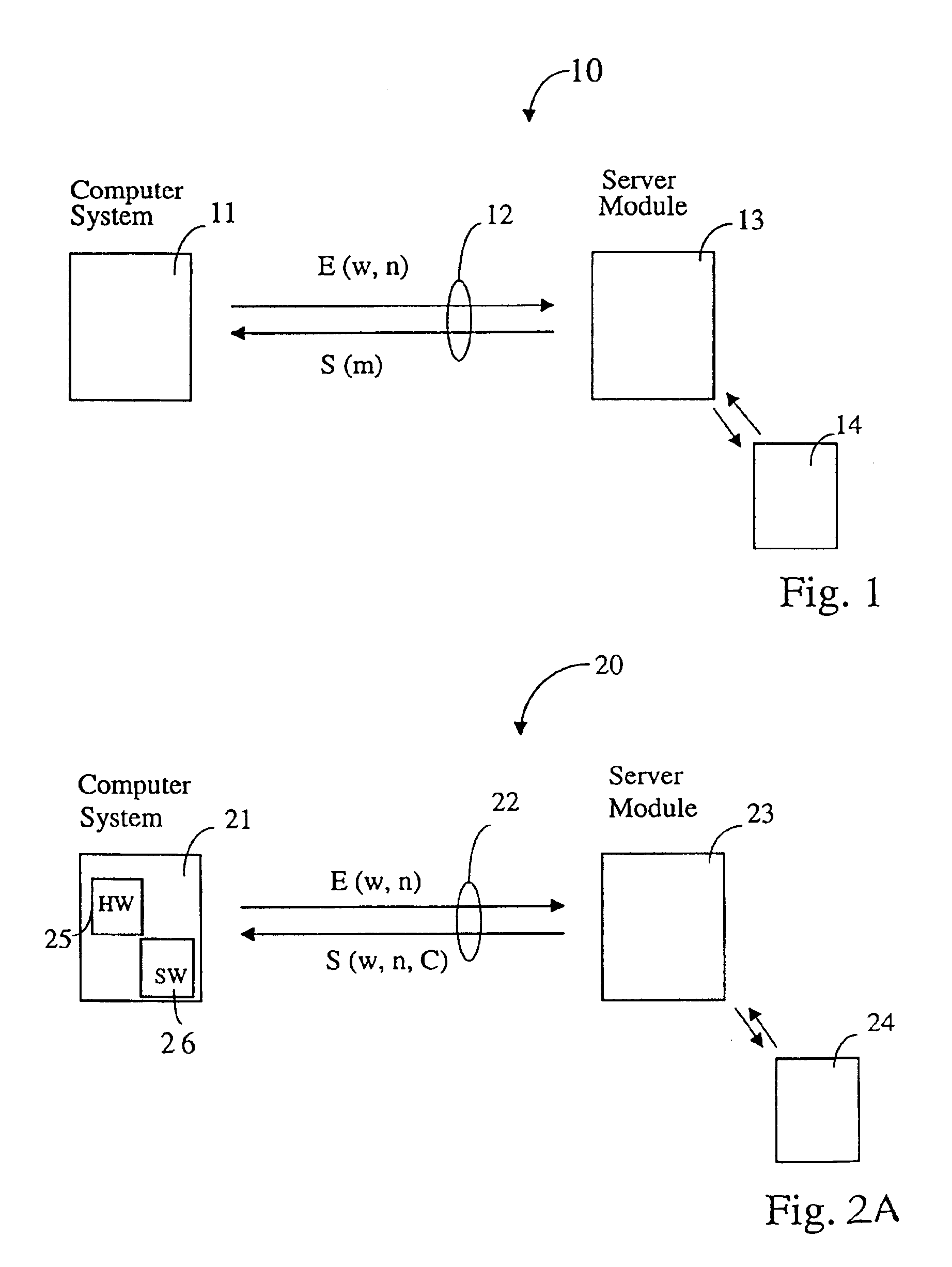
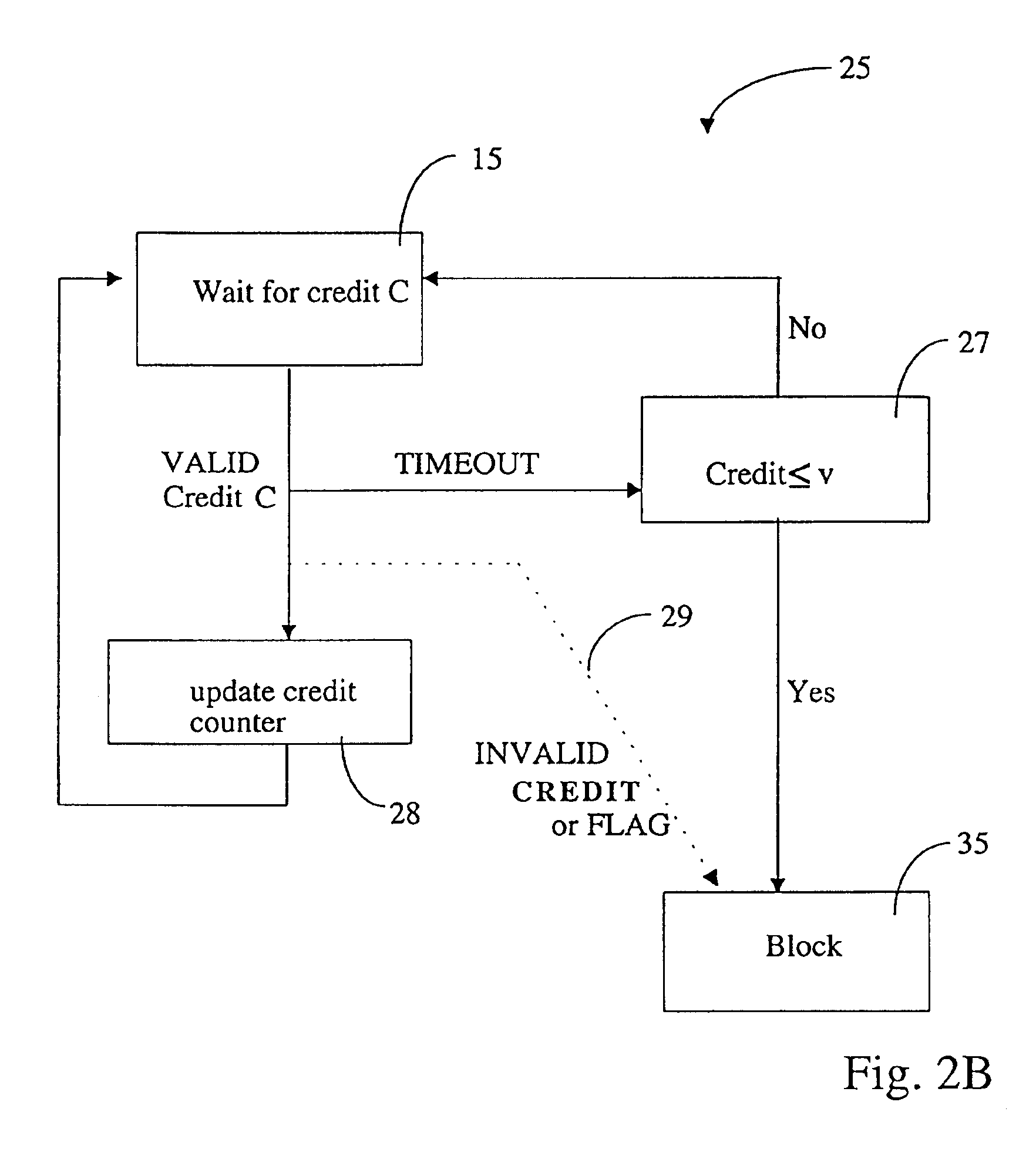
Scheme for switching a computer system (21), which is connectable via a communication interface and a network (22) to a server module (23), into a special mode of operation. The computer system (21) comprises a software component (26) for sending an identifier (w) assigned to the computer system (21) via the communication interface and the network (22) to the server module (23). In response, the software component (26) receives a token (S), issued by the server module (23), whereby the token (S) comprises a credit (C). In addition, the computer system (21) comprises a trusted hardware component (25) storing the identifier (w) and comprising a credit counter (44) with a credit which is automatically exhaustible step-by-step, and which is updateable with the credit (C) received from the server module (23). The computer system (21) has a trigger unit for switching the computer system (21) into the special mode of operation, e.g. a mode where the computer system (21) is of limited use to a user, if the credit of the credit counter is exhausted.
Owner:TREND MICRO INC
Mutual authentication method between terminal and server
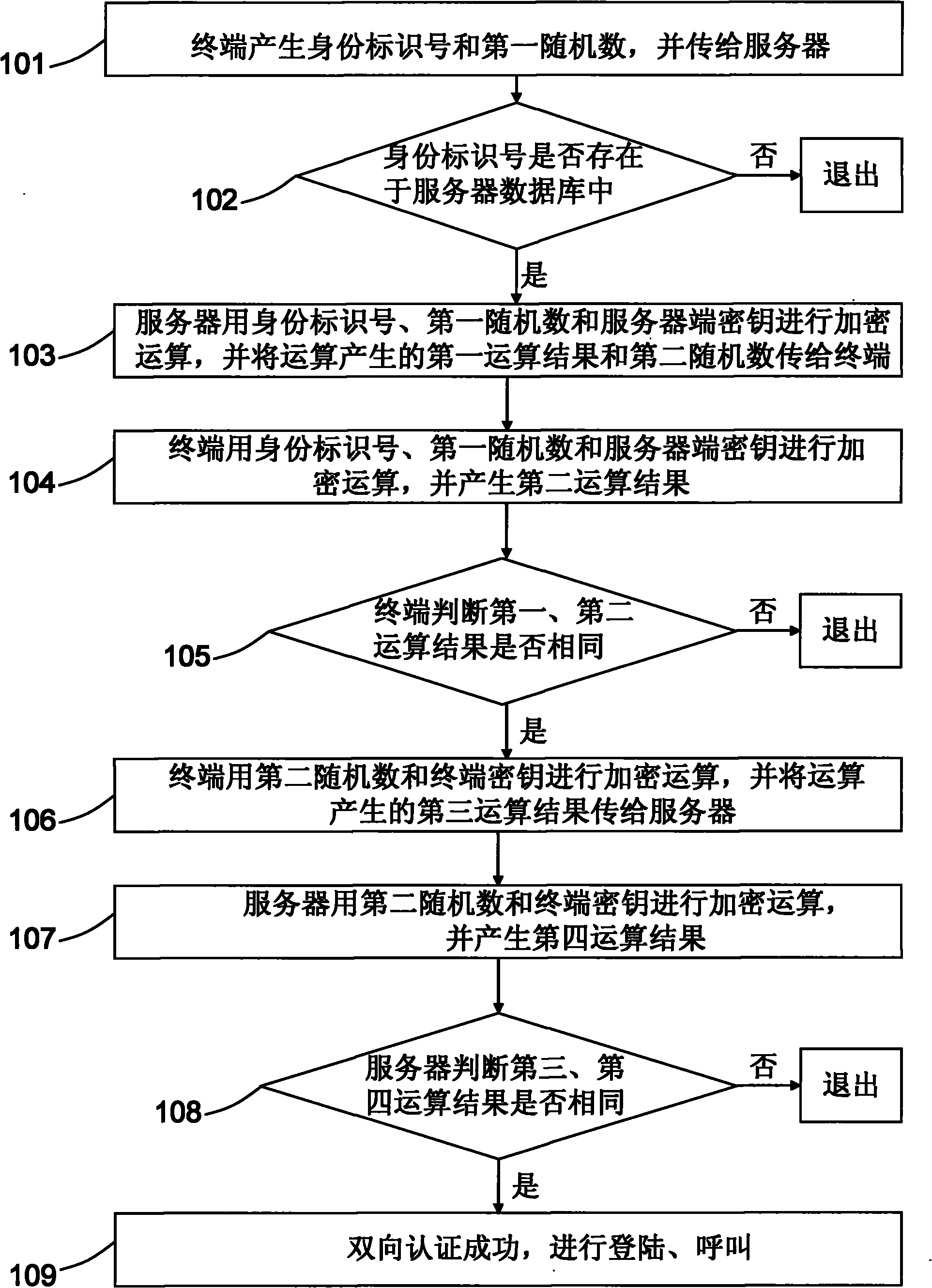
InactiveCN101771535AEnsure safetyGuaranteed privacyKey distribution for secure communicationUser identity/authority verificationMutual authentication
The invention relates to a mutual authentication method between a terminal and a server. The method comprises that: the terminal generates an identity number and a first random number and sends the identity number and the first random number to the server; the server verifies whether the identity number exists in a database of the server; the server generates a first operation result according to the identity number, the first random number and a server secret key, and the first operation result and a second random number are transmitted to the terminal; the terminal generates a second operation result according to the identity number, the first random number and the server secret key and carries out authentication on the server according to the first and second operation results; the terminal generates a third operation result according to the second random number and a terminal secret key and sends the third operation result to the server; and the server generates a fourth operation result according to the second random number and the terminal secret key and carries out authentication on the terminal according to the third and fourth operation results.
Owner:上海茂碧信息科技有限公司
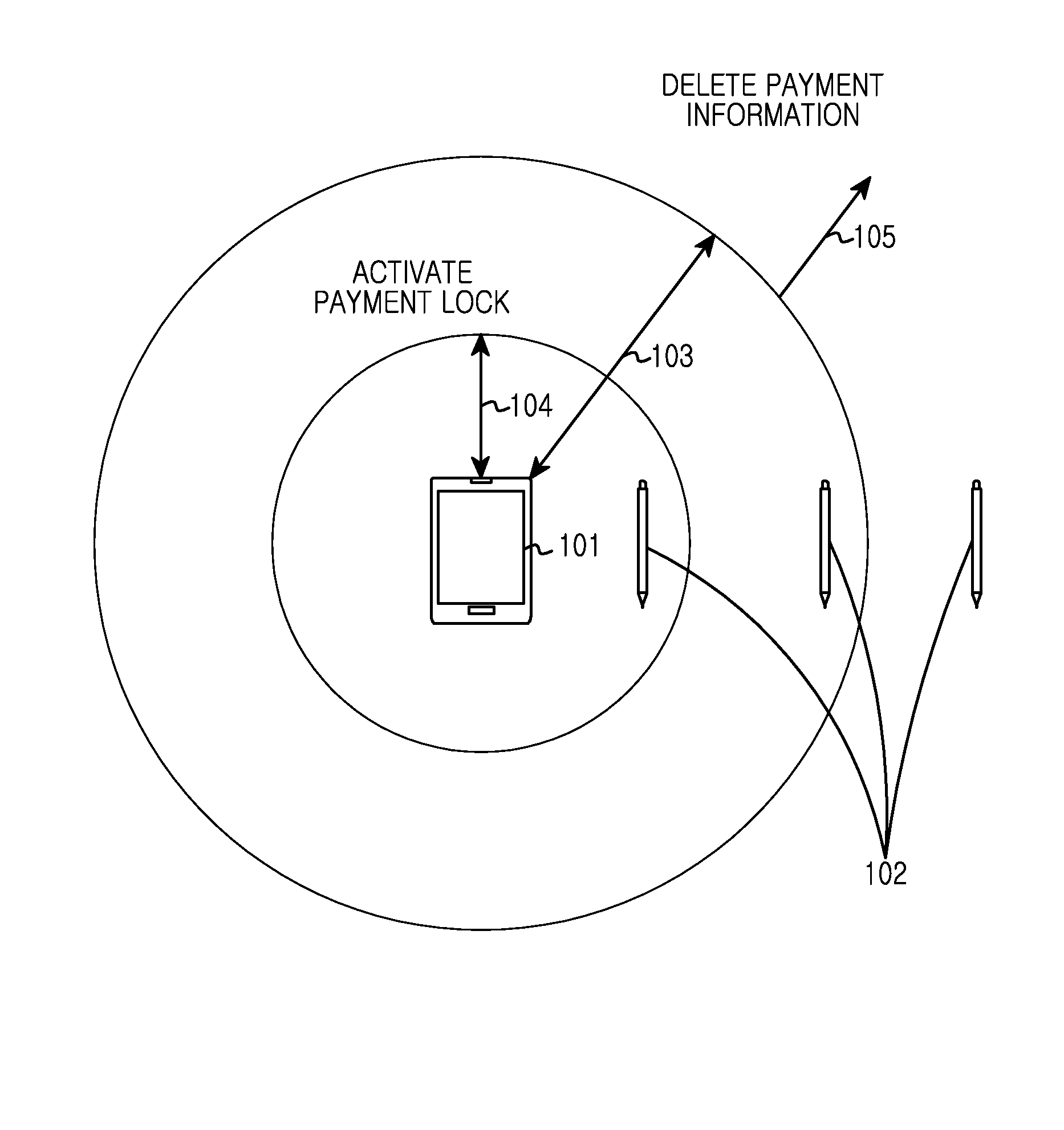
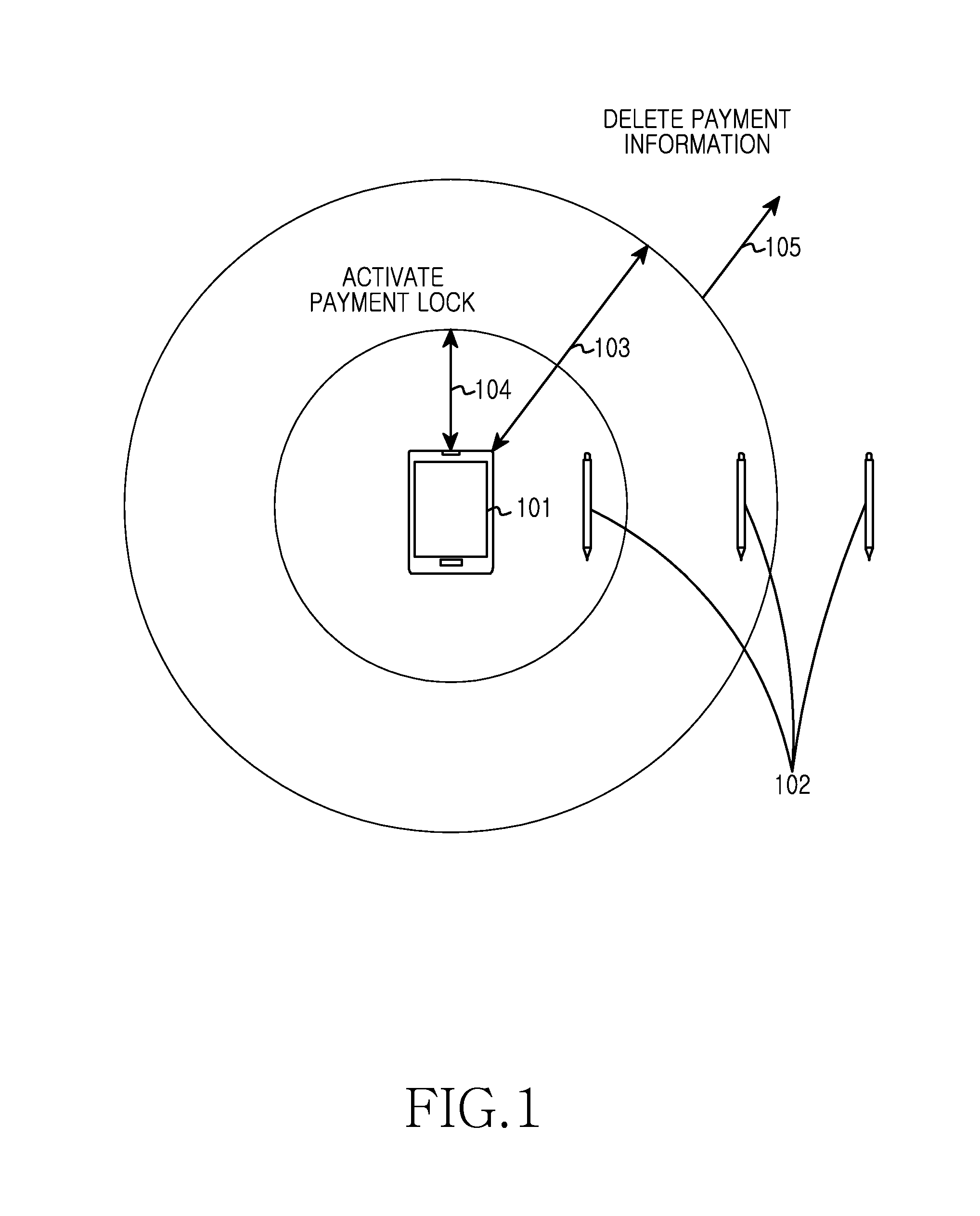
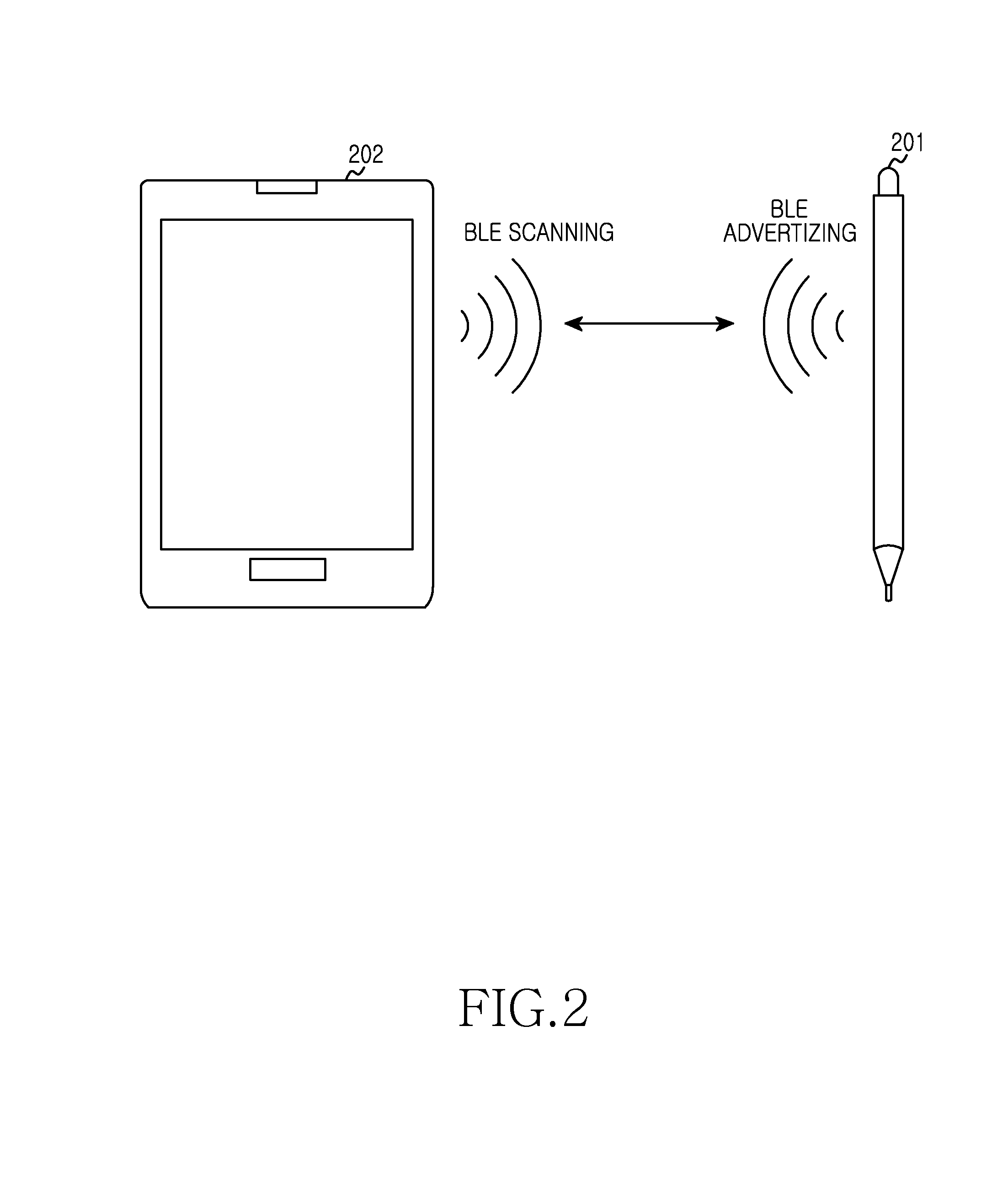
Electronic device and method for controlling payment function of input means
InactiveUS20140136411A1Improve user convenienceGuaranteed privacyFinancePayment architectureComputer hardwarePayment
An electronic device and a method for controlling a payment function of an input means are provided. The operating method of the electronic device includes receiving a packet periodically transmitted from an input means, determining a distance from the electronic device to the input means based on determining a signal reception strength of the packet, extracting a distance value from storage associated with a matching reception strength and sending to the input means a signal according to the extracted distance value of the input means and the received packet.
Owner:SAMSUNG ELECTRONICS CO LTD
Cloud computation treating system and method
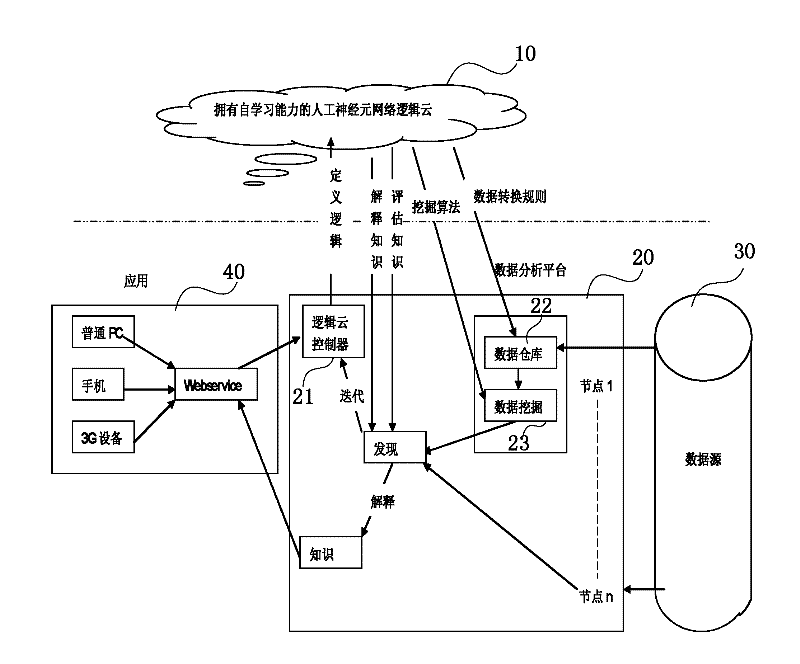
InactiveCN102523246AProtection securitySolve practical problemsTransmissionInformatizationData profiling
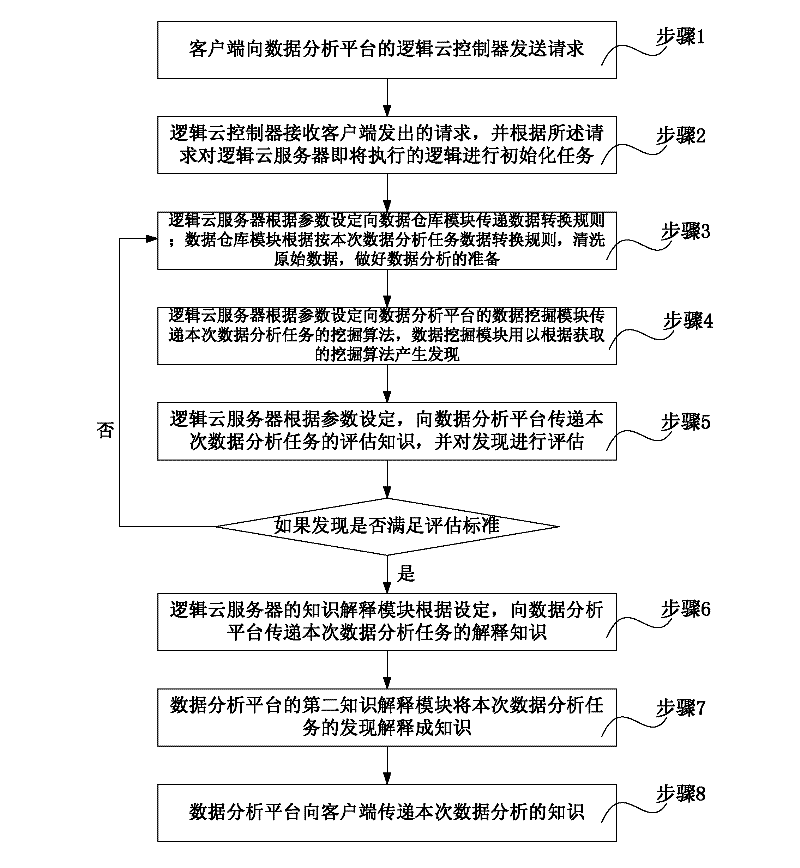
The invention discloses a cloud computation treating system and a method. The system comprises a client end, a database, a logical cloud server and a data analyzing platform, wherein the client end is used for sending out a request to the data analyzing platform; the database is used for storing data; the logical cloud server is used for setting a plurality of logics and providing the specific logics to the data analyzing platform according to different conditions; and the data analyzing platform is connected with the client end, the database and the logical cloud server and is used for receiving the request which is sent out by the client end, obtaining the logics of the logical cloud server according to the parameter of the request, also carrying out operational treatment by the logics through combining the data in the database and returning a treating result to the client end. According to the cloud computation treating system and the method which are provided by the invention, the data safety of an enterprise is effectively protected; and meanwhile, cloud computation service is provided, and the predicament of SaaS confronted in China is solved. Meanwhile, the obstruction on a data excavation technology, which is caused by structurized data or incomplete and non-standard informatization to which a traditional data excavation company faces, is also solved.
Owner:陈刚 +1
Digital asset transaction method and device, medium and equipment
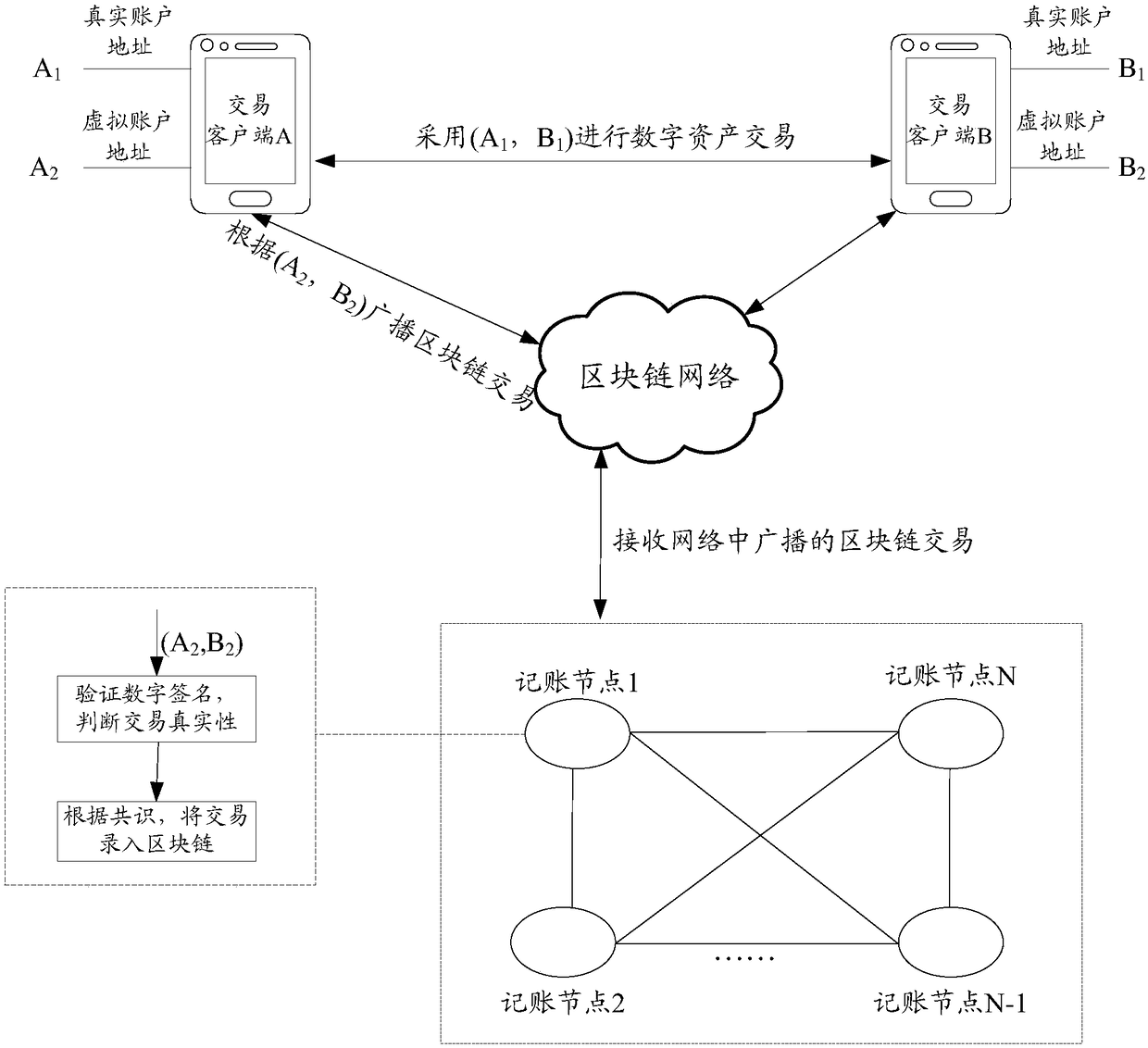
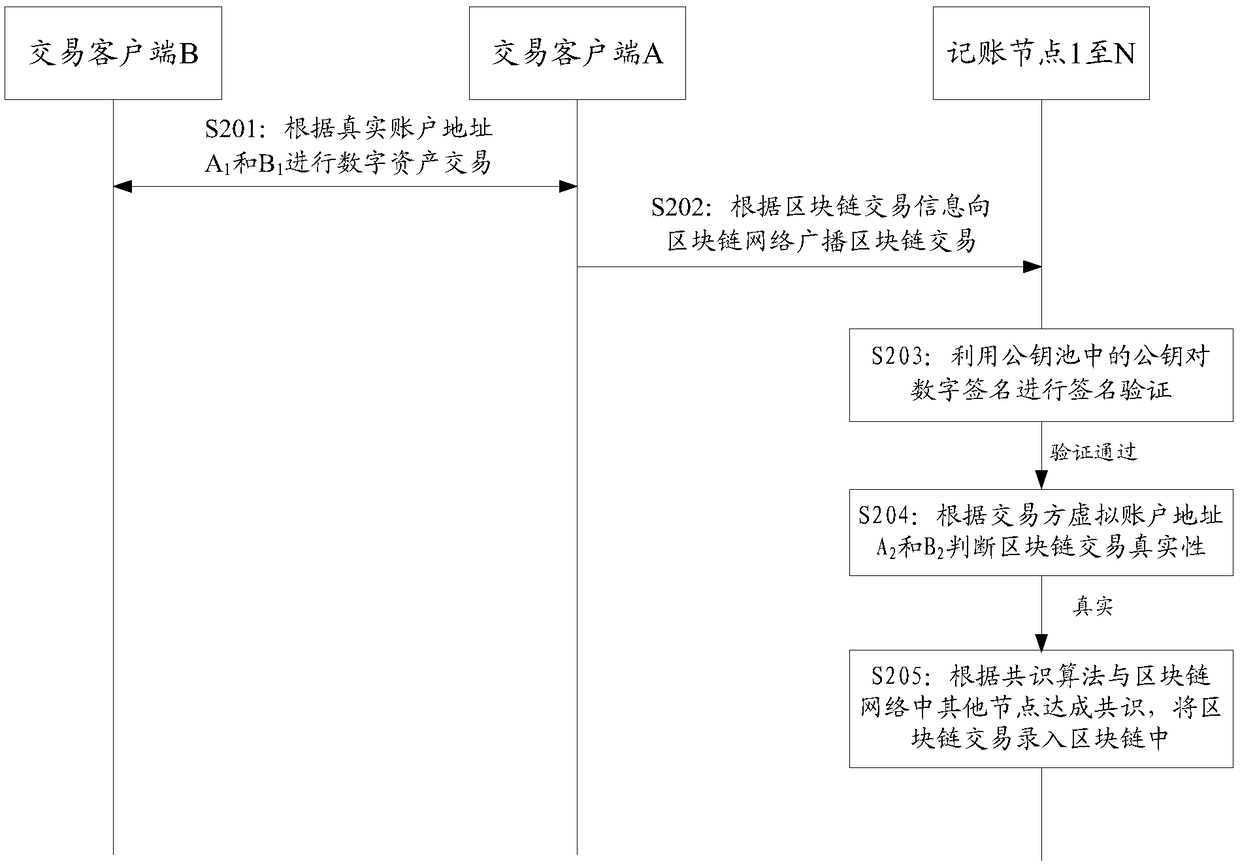
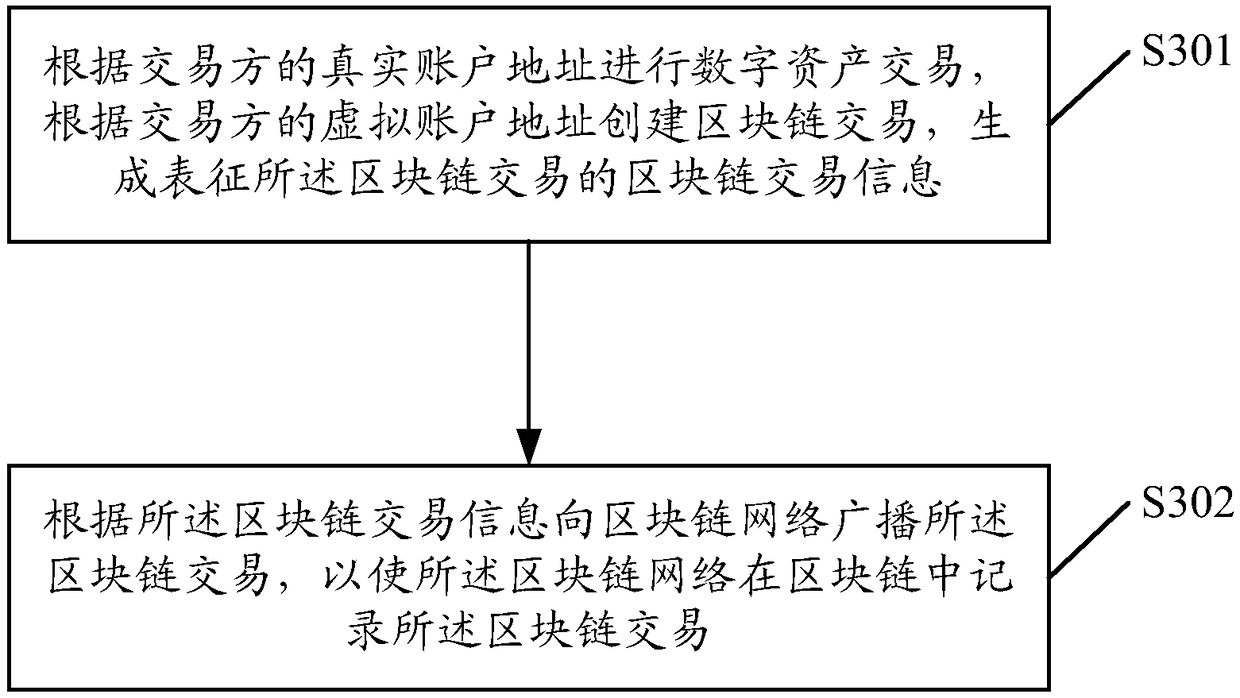
ActiveCN108694668AGuaranteed privacyGuarantee authenticityFinancePayment protocolsTerminal equipmentChain network
The embodiment of the invention discloses a digital asset transaction method. The method comprises the steps that when a digital asset transaction is performed, both transaction parties perform the transaction by the adoption of real account addresses to guarantee normal and orderly progress of the transaction; but when the transaction is published into a block chain network, virtual account addresses of the transaction parties are used as public addresses for publishing, wherein the virtual account addresses are irreversible and unique virtual addresses generated according to the real accountaddresses of the transaction parties and an irreversible algorithm to guarantee that bookkeeping nodes in the block chain network can recognize the authenticity of the transaction according to the virtual account addresses of the transaction parties. Therefore, it is guaranteed that the transaction is normally processed in the block chain network, meanwhile, it can be guaranteed that the real account addresses of the transaction parties in the transaction are not published, and the privacy of the transaction addresses in the transaction process is guaranteed. The embodiment of the invention furthermore discloses a digital asset transaction device, terminal equipment, computing equipment, a storage medium and other relevant products.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data circulation method based on block chain and enclave
ActiveCN109660358AGuaranteed privacyWon't leakUser identity/authority verificationData transmissionTransfer procedure
The invention provides a data circulation method based on a block chain and an enclave. Privacy of a data processing process is ensured through utilization of a trusted computation environment provided by SGX (Software Guard Extensions), and moreover, the privacy of a data transmission process is ensured through utilization of an encrypted channel, so private data is prevented from being leaked ina whole process. According to the method, data integrity and legality are ensured through utilization of the block chain, a participant cannot fabricate data on the chain and moreover, and moreover,data quality is verifiable. According to the method, correct execution of a computation task is ensured through utilization of a smart contract, and rights and interests are rationally allocated. Traceability and auditability of a computation process are ensured through recording of operation logs on the chain.
Owner:余炀
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
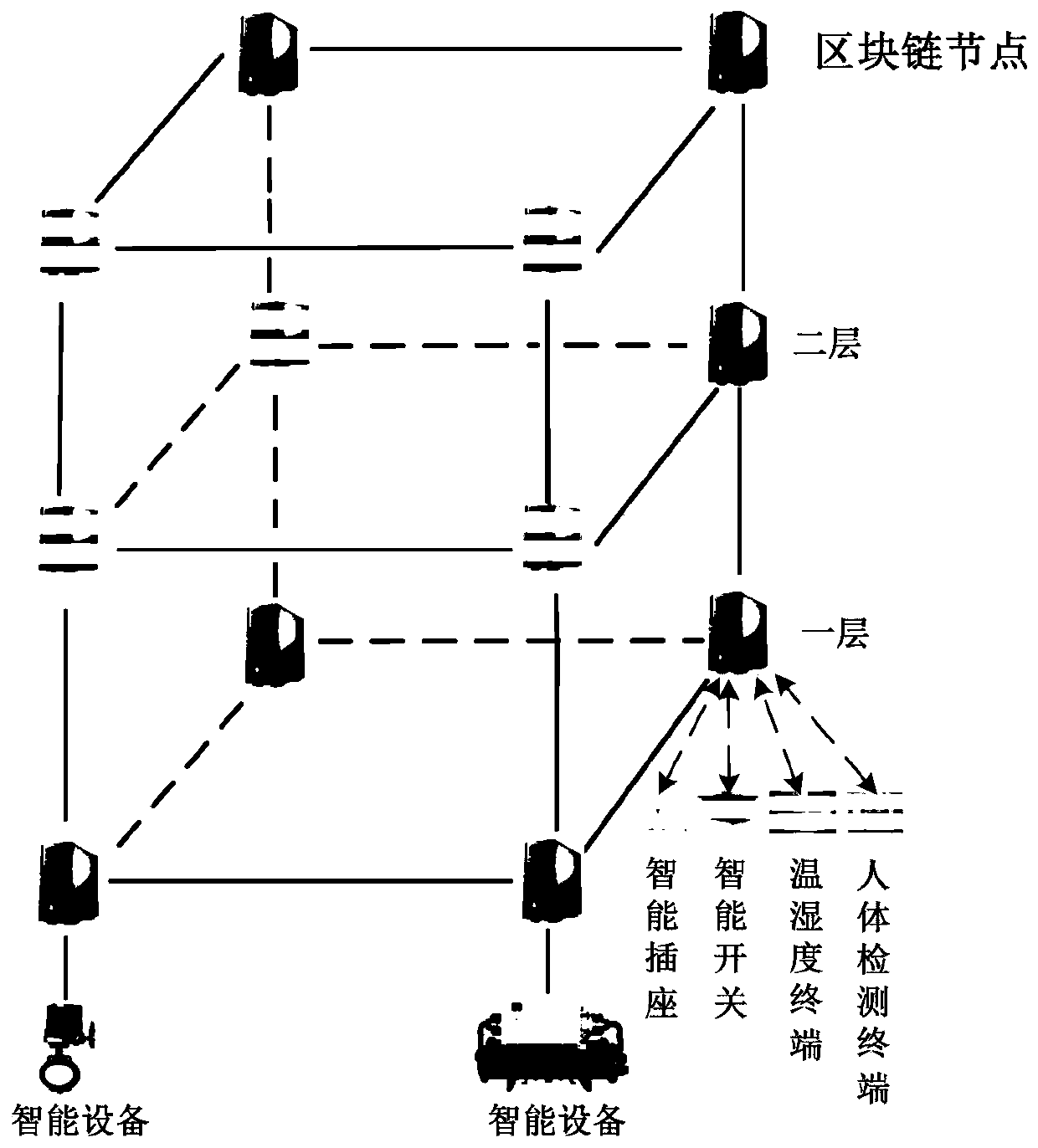
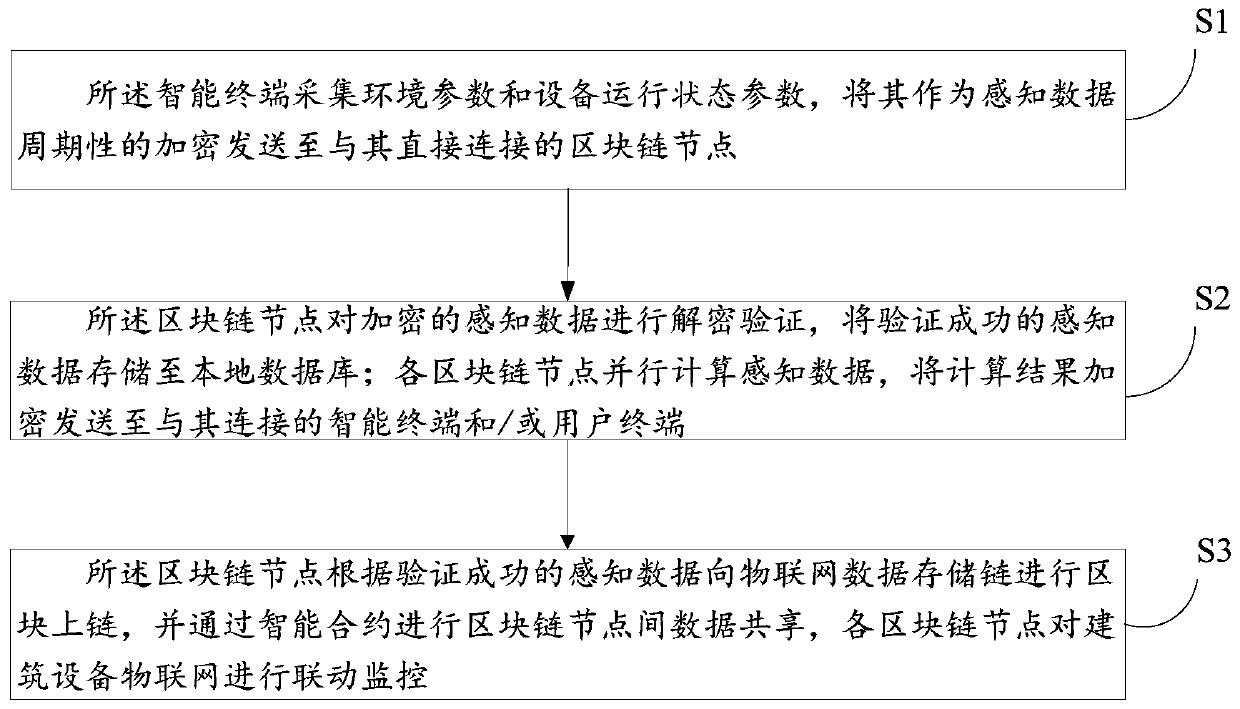
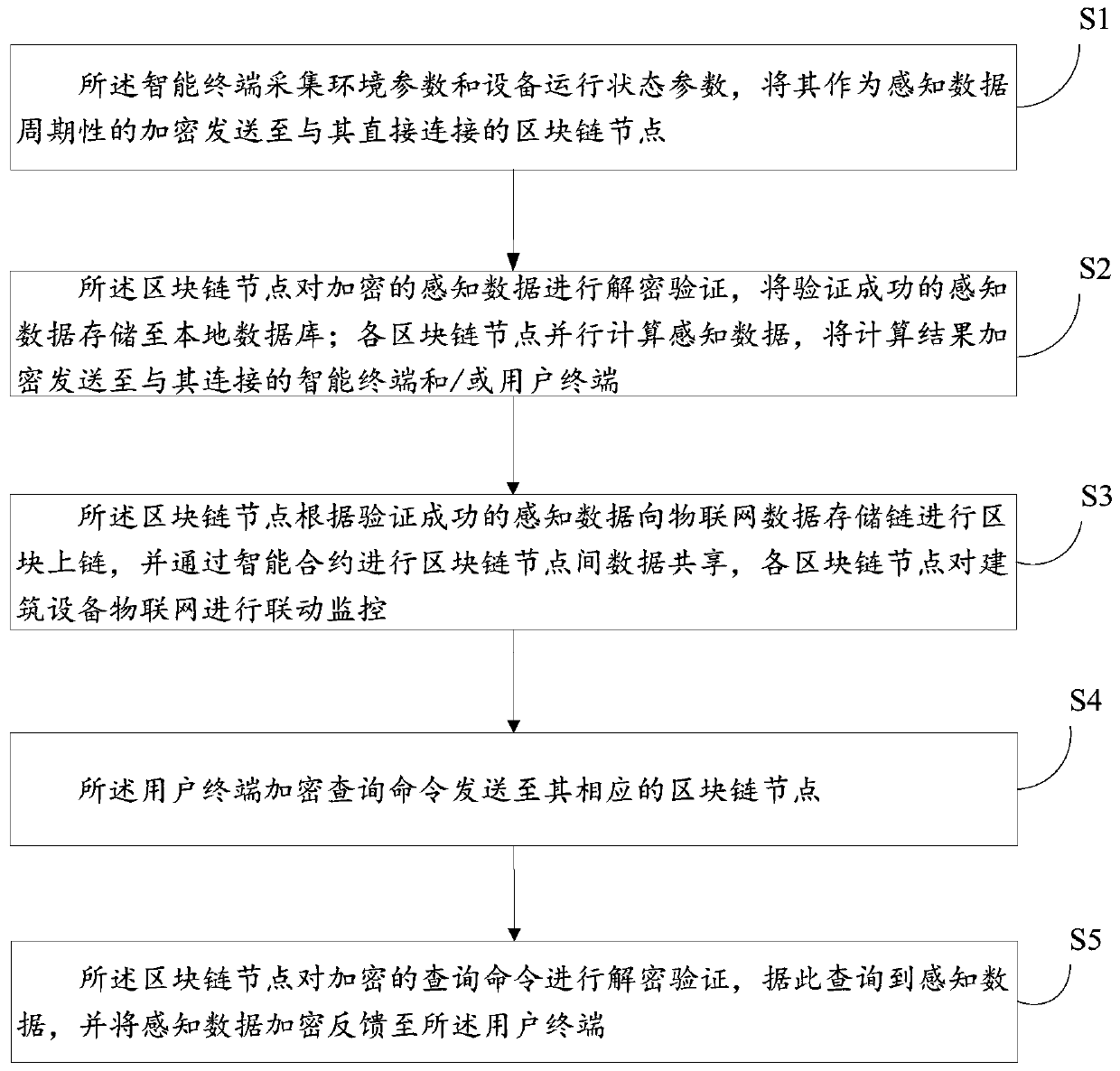
A flattened building equipment Internet of Things monitoring system and method based on a block chain
The invention discloses a flat building equipment Internet of Things monitoring system and method based on a block chain. The system comprises a plurality of block chain nodes, a plurality of intelligent terminals and a plurality of user terminals, the block chain nodes are deployed in a building subspace. wherein the blockchain nodes are respectively connected with a user terminal and intelligentterminals arranged in the building subspace, are in one-to-one correspondence with the building subspaces, and are configured to authenticate the intelligent terminals, decrypt the received intelligent terminal data, store and carry out parallel computing, and carry out data sharing among the blockchain nodes through an intelligent contract; the intelligent terminal is configured to collect environment parameters and equipment operation state parameters, and periodically encrypt and send the environment parameters and the equipment operation state parameters as sensing data to the blockchainnode directly connected with the intelligent terminal; and the user terminal is configured to perform data interaction with the block chain node.
Owner:SHANDONG JIANZHU UNIV
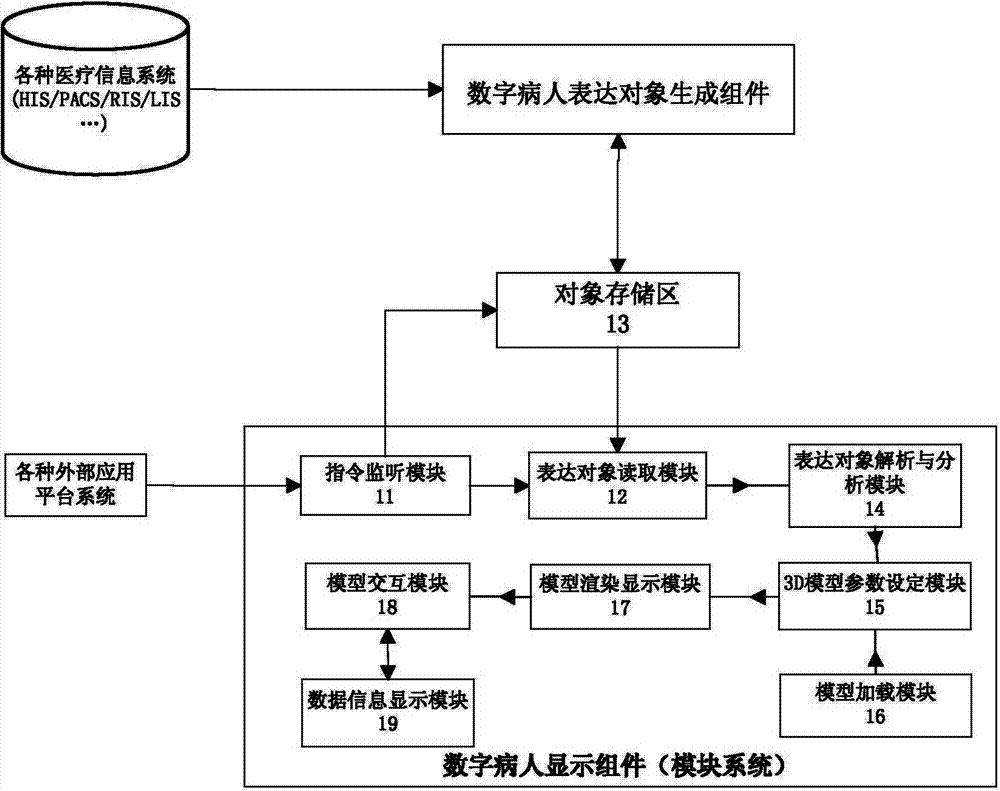
Medical information visualization method and device
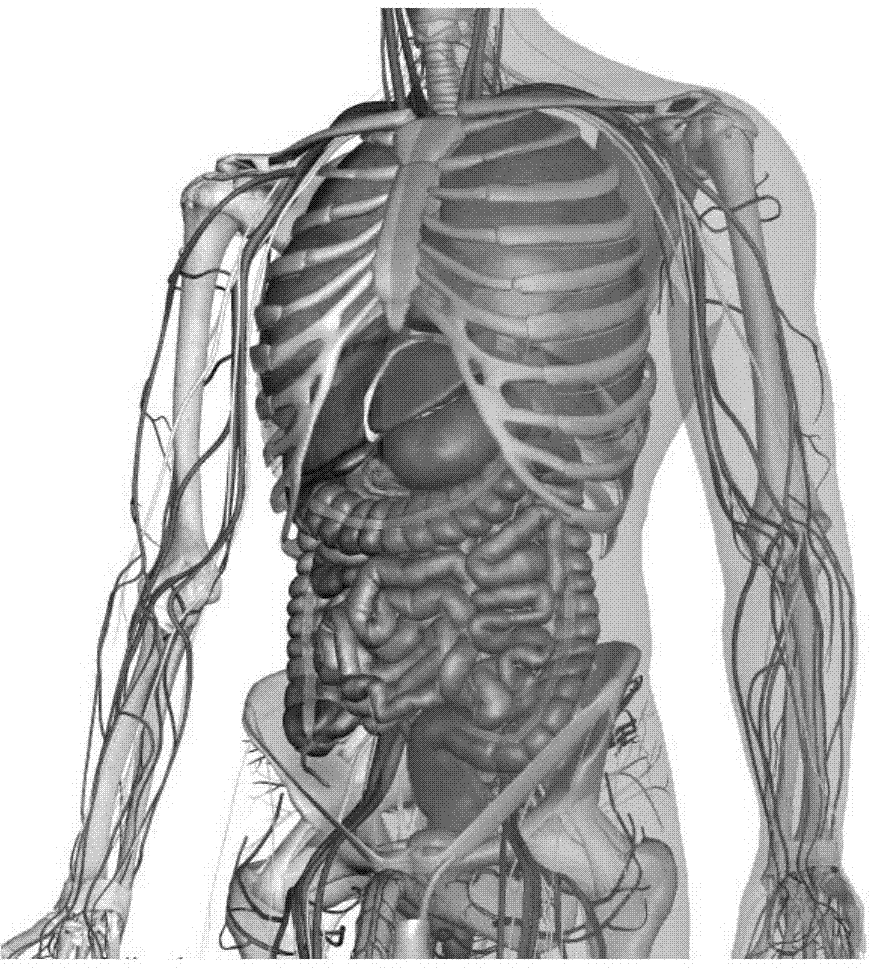
ActiveCN103793611AEasy accessObtain intuitivelySpecial data processing applicationsPersonalizationUsability
The invention relates to a medical information visualization method and device. The method includes the steps of loading a human model through 3D drawing software, converting patient information stored in a medical information system to structured medical information, and finally loading the medical information onto the human model. The medical information visualization device receives an instruction of a user and selects a displayed organ, a subclinical organ and / or the corresponding medical information according to the instruction of the user so that integration expression and visualized display of various types of digital medical information of patients can be achieved. The medical information visualization device can be integrated with various types of medical application platform systems. According to the medical information visualization method and device, materials such as clinical medical data, images and medical examination reports of the patients can be fully utilized; because of the visualization function, the recognition degree of non-medical staff on the health conditions of the patients can be improved, the intellectualization and personalization of user interfaces can be improved, the usability of the medical information of the patients can be improved, and the value chain and use efficiency of the medical information can be prolonged.
Owner:SHANGHAI INST OF TECHNICAL PHYSICS - CHINESE ACAD OF SCI
Efficient cryptograph image retrieval method capable of supporting privacy protection under cloud environment
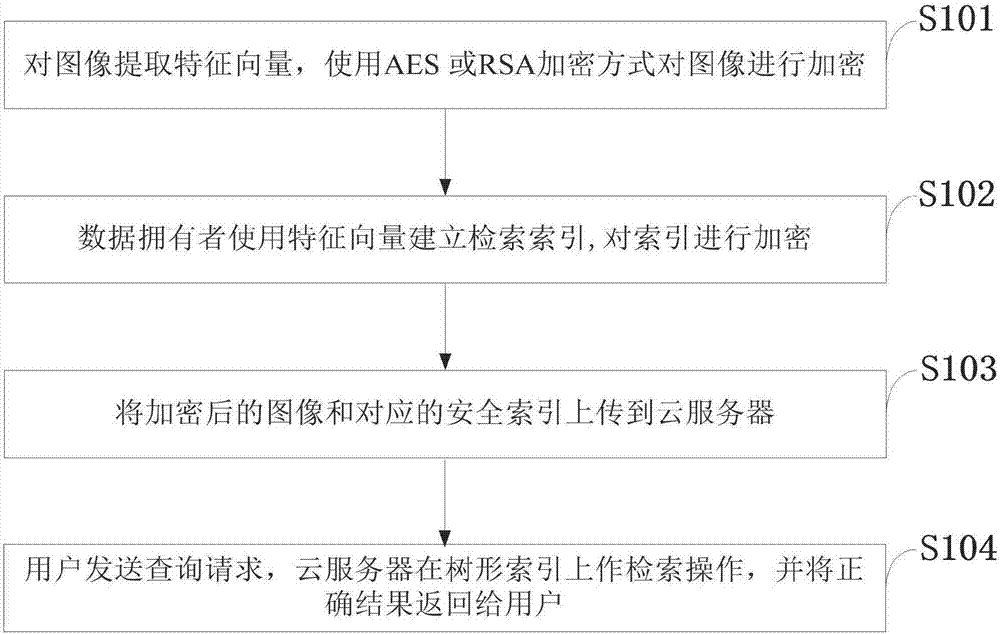
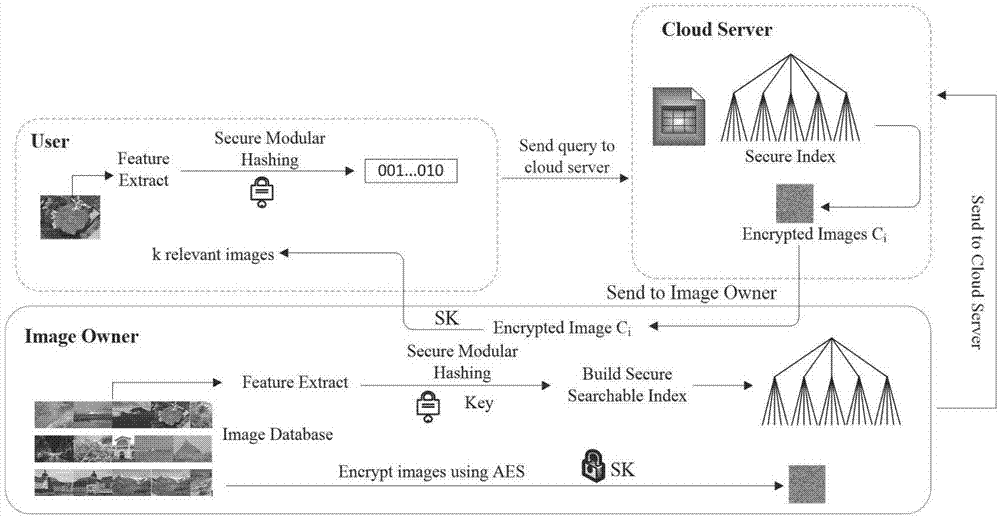
ActiveCN107480163AGuaranteed privacyReduce computational overheadImage data processing detailsTransmissionImage extractionPlaintext
The invention belongs to the technical field of image retrieval and discloses an efficient cryptograph image retrieval method capable of supporting privacy protection under a cloud environment. The efficient cryptograph image retrieval method capable of supporting the privacy protection under the cloud environment comprises the steps that an image owner firstly extracts characteristic vectors of an image in a database and encrypts the image by an AES or RSA encryption manner; the owner establishes indexes using a hierarchical K-means algorithm based on the characteristic vectors and uses a safe mode Hash technology to encrypt the indexes; and the encrypted image and indexes are uploaded to a cloud server, and a retrieval operation is executed. According to the invention, the privacy protection of the cryptograph image retrieval can be achieved, and retrieval accuracy equivalent with public image retrieval can be reached. In addition, detailed safety analysis of the disclosed method is conducted, and experimental assessment of efficiency and accuracy is conducted in different datasets. Results indicate that the method disclosed by the invention can reach expected safety targets, and can increase retrieval efficiency on the premise of ensuring retrieval accuracy.
Owner:XIDIAN UNIV
Ciphertext data query method, device and ciphertext query server
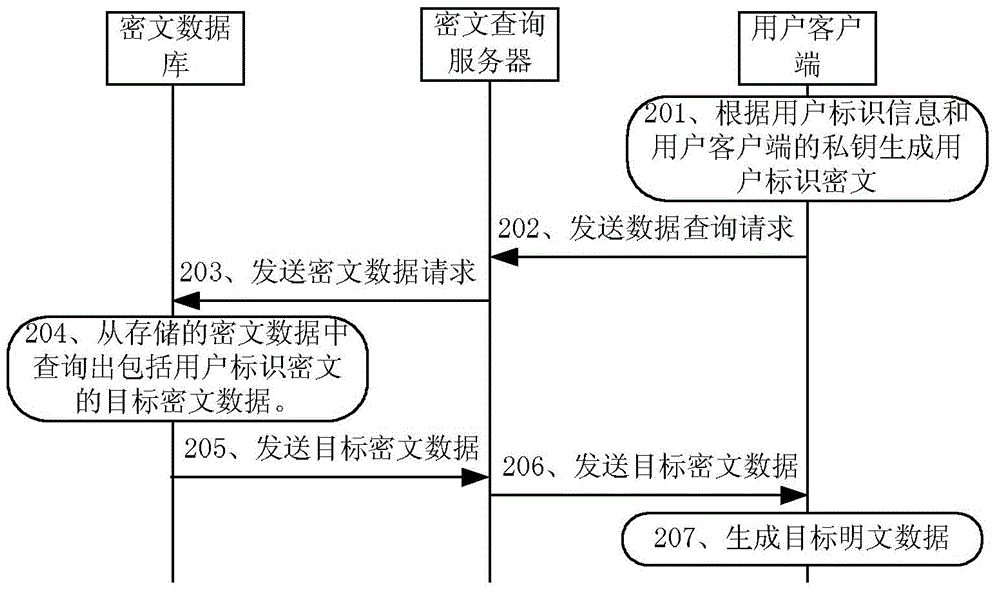
ActiveCN105471826APrevent leakageGuaranteed privacyUser identity/authority verificationSpecial data processing applicationsClient-sideData query
The invention discloses a ciphertext data query method, a ciphertext data query device and a ciphertext query server. The ciphertext data query method comprises the steps of: receiving a data query request sent by a user client, wherein the data query request comprises a user identifier ciphertext; sending a ciphertext data request to a ciphertext database, wherein the ciphertext data request comprises the user identifier ciphertext, so that target ciphertext data comprising the user identifier ciphertext can be queried from stored ciphertext data in the ciphertext database; receiving the target ciphertext data sent by the ciphertext database, wherein the target ciphertext data comprises a target data identifier ciphertext, a target user identifier ciphertext and a target data content ciphertext; and sending the target ciphertext data to the user client. The ciphertext data query method, the ciphertext data query device and the ciphertext query server provided by the invention ensure the privacy and security of user data.
Owner:CEC CYBERSPACE GREAT WALL
Outsourcing encrypted data-orientated verifiable intersection operation method and system
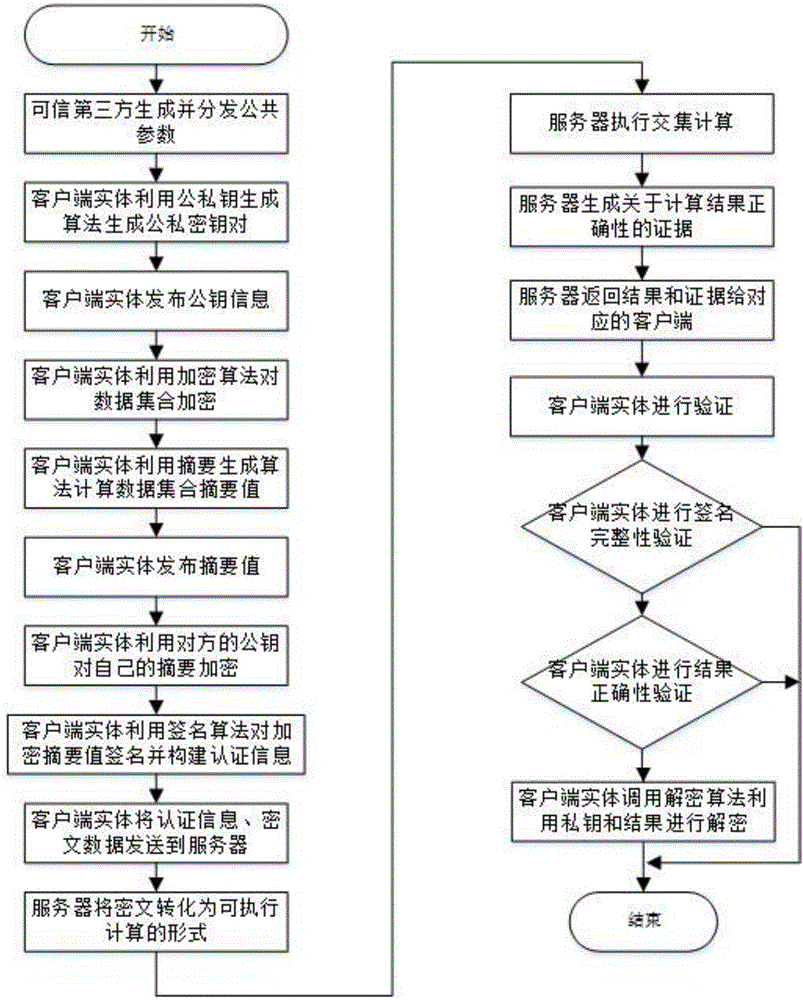
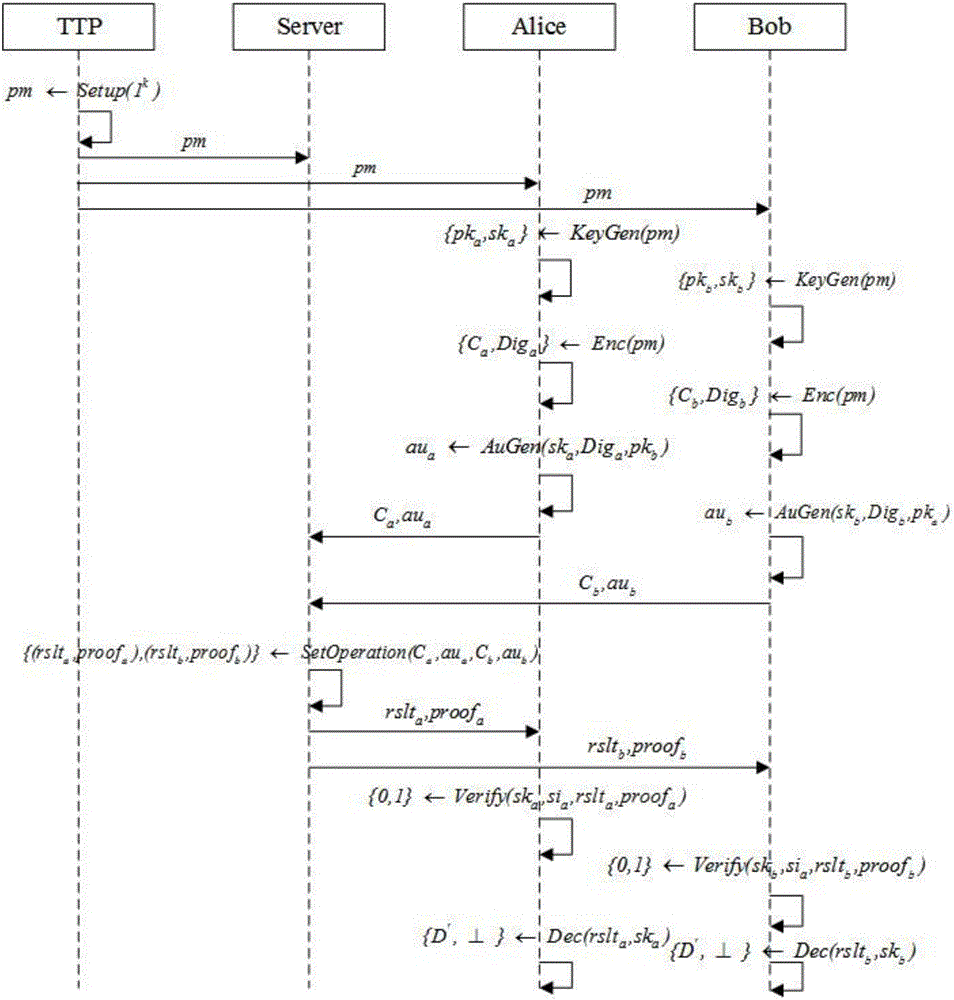
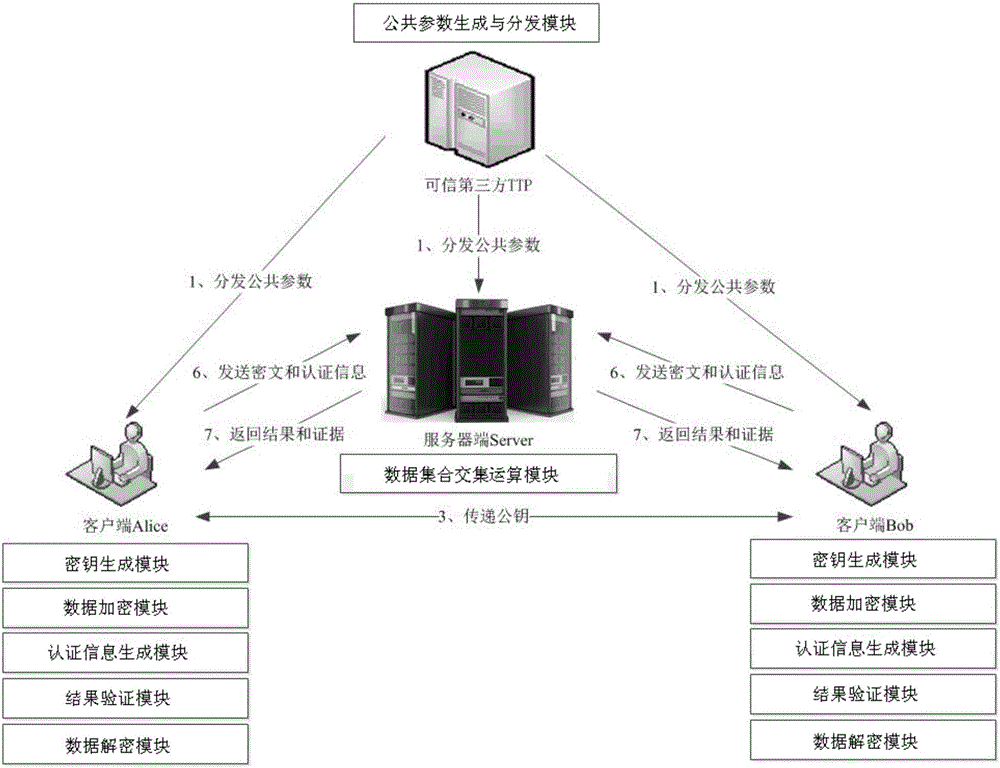
ActiveCN105812141AGuaranteed privacyReduce the number of interactionsUser identity/authority verificationPlaintextThird party
The invention relates to an outsourcing encrypted data-orientated verifiable intersection operation method and system and belongs to the verifiable outsourcing computation field. The method is carried out among a third-party trusted entity, at least two client entities and an outsourcing server side; the client entities are holders of data sets and requesters of data set intersection operation; the third-party entity is mainly responsible for the initialization and distribution of common parameters; the two client entities are mainly responsible for generating keys, encrypting data sets, calculating authentication information, verifying results and proofs returned by the outsourcing server side and decrypting an ciphertext data set returned by the outsourcing server side; the outsourcing server side is mainly responsible for performing data set intersection operation; and a plaintext data set is not required to be obtained through decryption when the outsourcing server side performs intersection operation, and the outsourcing server performs operation on a ciphertext, and therefore, the privacy of user data can be ensured. The method and system have the advantages of low frequency of interaction among the entities, low communication cost and efficient correctness verification of operation results.
Owner:NORTHEASTERN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com