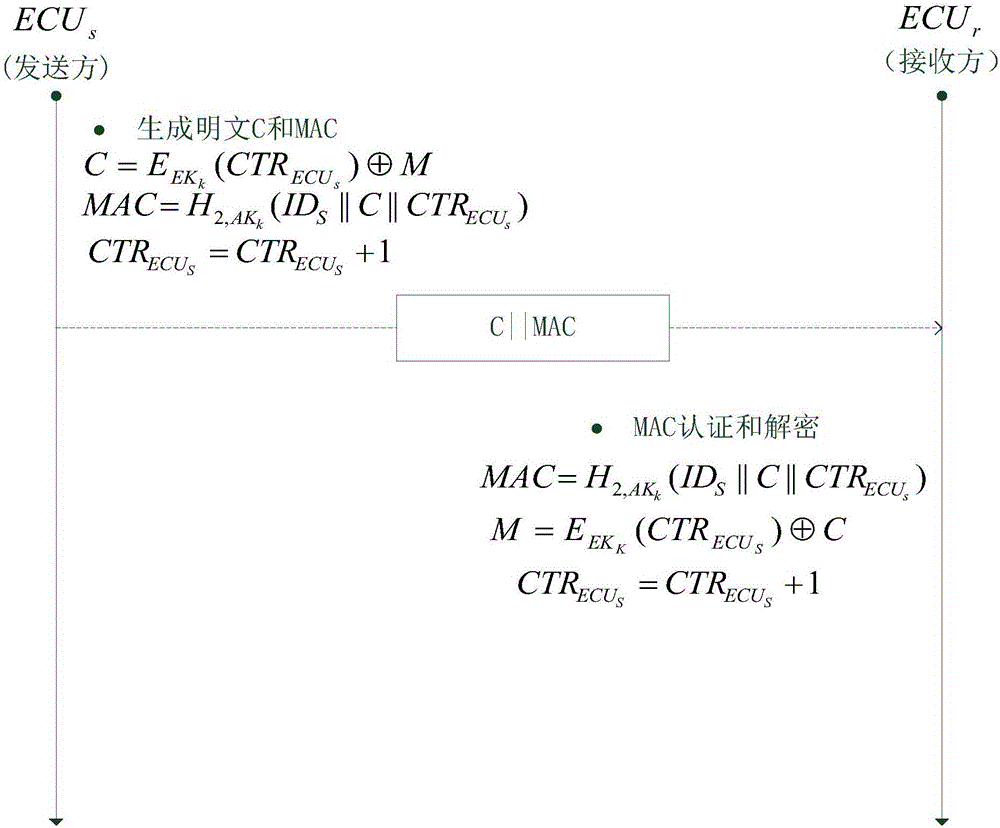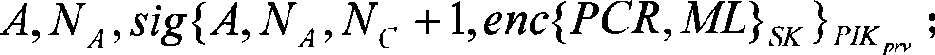Patents
Literature
685 results about "Replay attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A replay attack (also known as playback attack) is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and re-transmits it, possibly as part of a masquerade attack by IP packet substitution. This is one of the lower tier versions of a "Man-in-the-middle attack".
Detecting and preventing replay in authentication systems
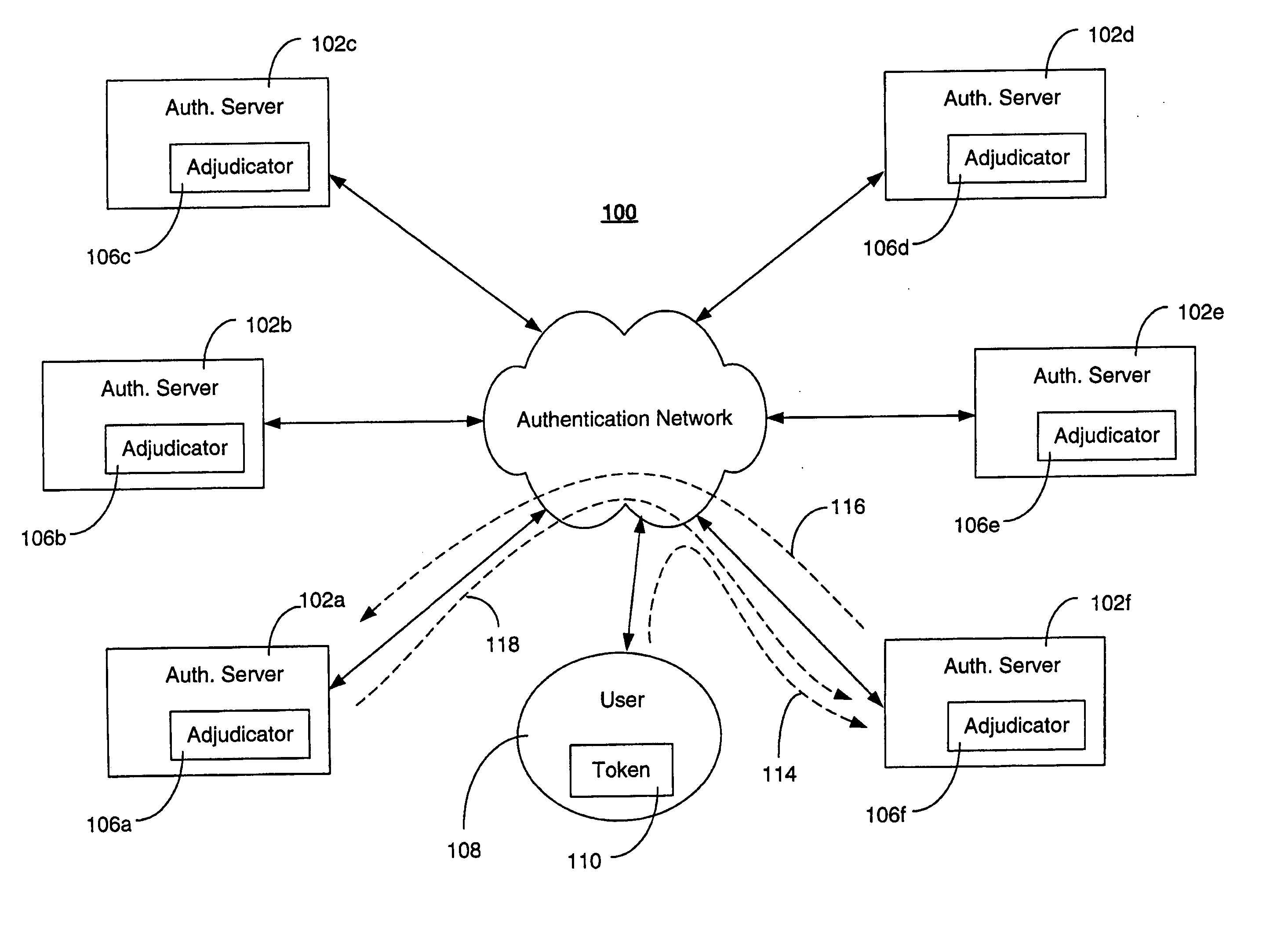
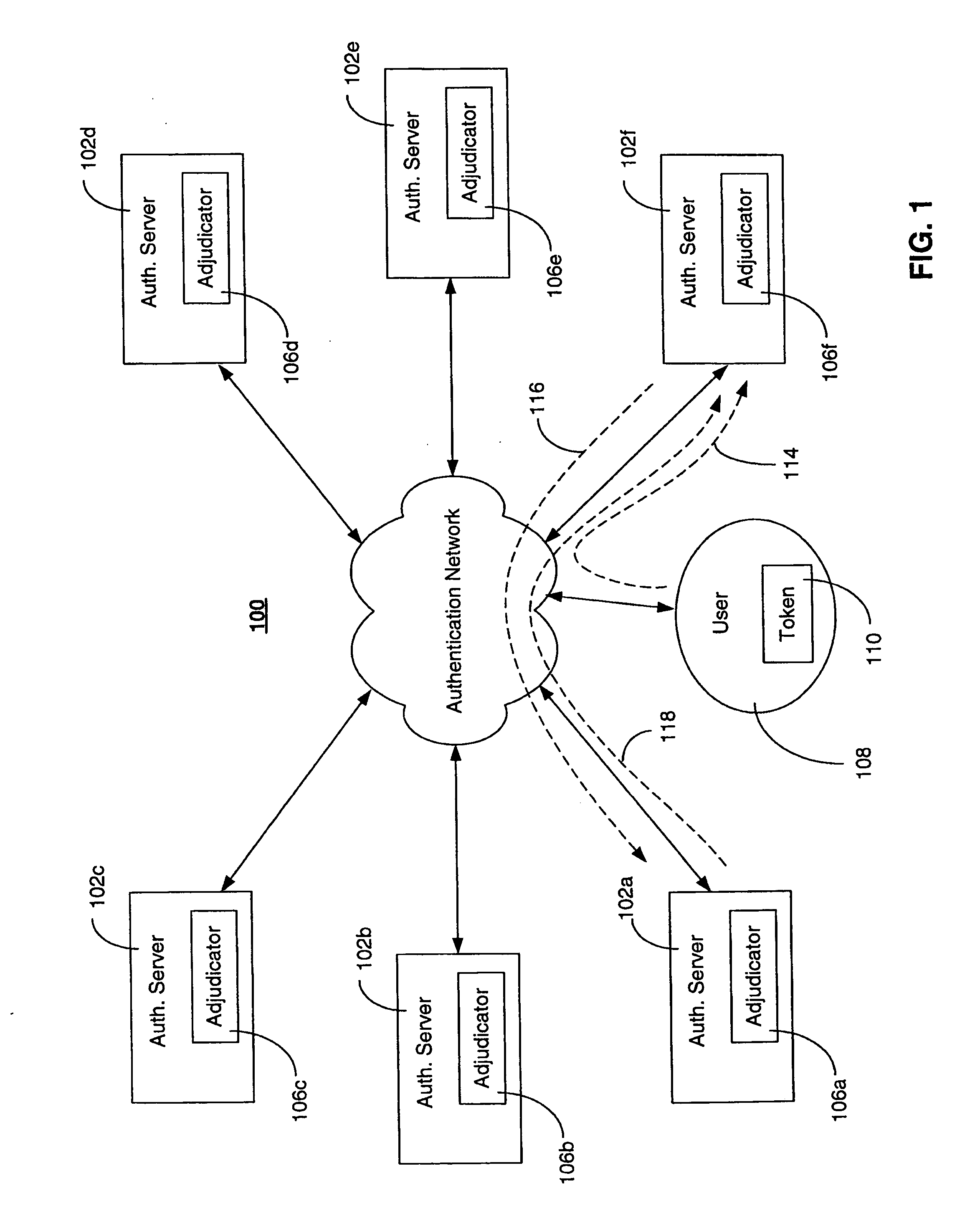
ActiveUS20070256123A1Detecting and preventing replay attackAvoid authenticationDigital data processing detailsUser identity/authority verificationAuthentication serverOne-time password
A system for detecting and preventing replay attacks includes a plurality of interconnected authentication servers, and one or more tokens for generating a one-time passcode and providing the one-time passcode to one of the authentication servers for authentication. The system includes an adjudicator function associated with each authentication server. The adjudicator evaluates a high water mark value associated with a token seeking authentication, allows authentication to proceed for the token if the high water mark evaluation indicates that the one-time passcode was not used in a previous authentication, and prevents authentication if the high water mark evaluation indicates that the one-time passcode was used in a previous authentication. The token is associated with a home authentication server that maintains a current high water mark of the token. The home authentication server validates the current high water mark on behalf of the adjudicator function evaluating the token for authentication.
Owner:RSA
Authentication in a packet data network
InactiveUS7107620B2Strong authenticationKey distribution for secure communicationUnauthorised/fraudulent call preventionTelecommunications networkComputer science
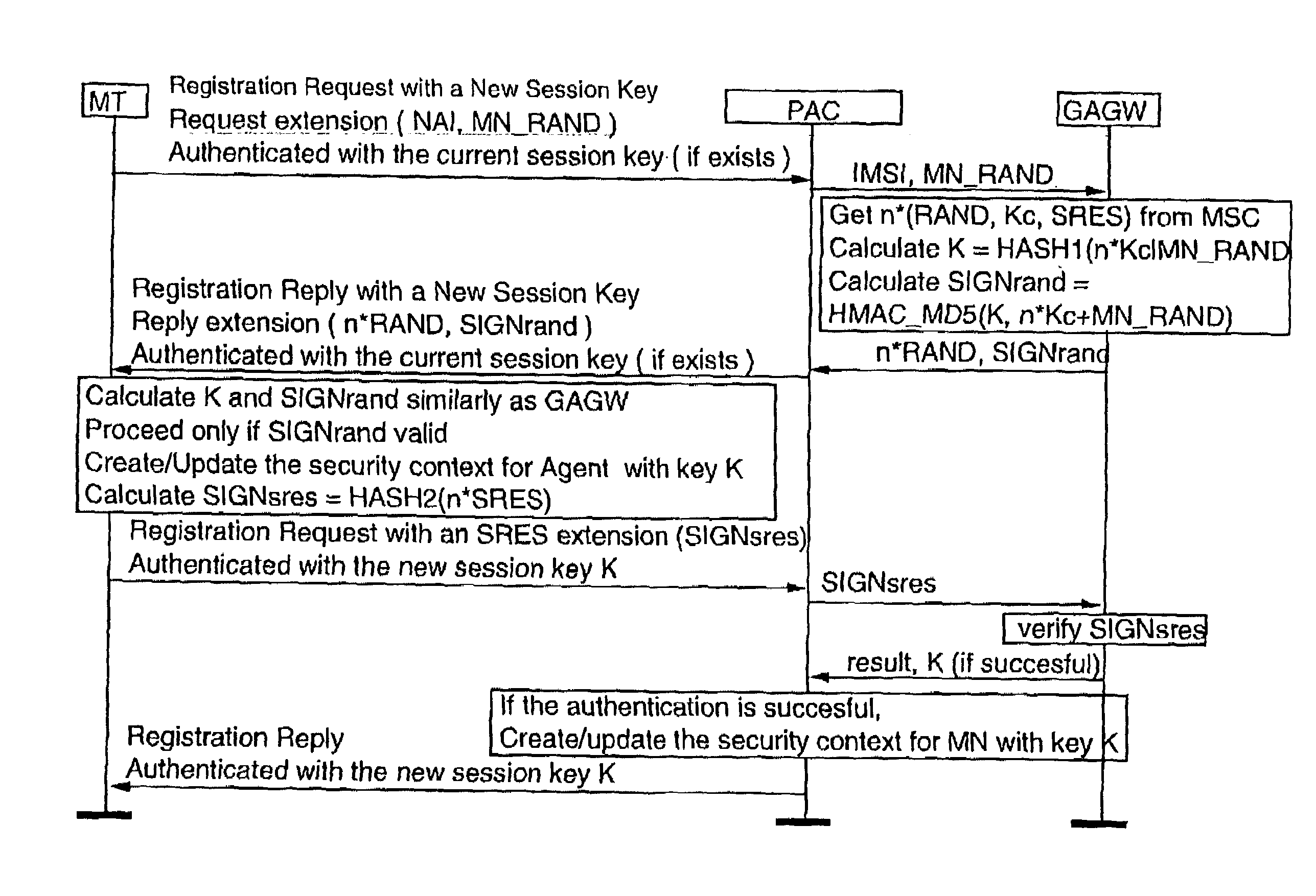
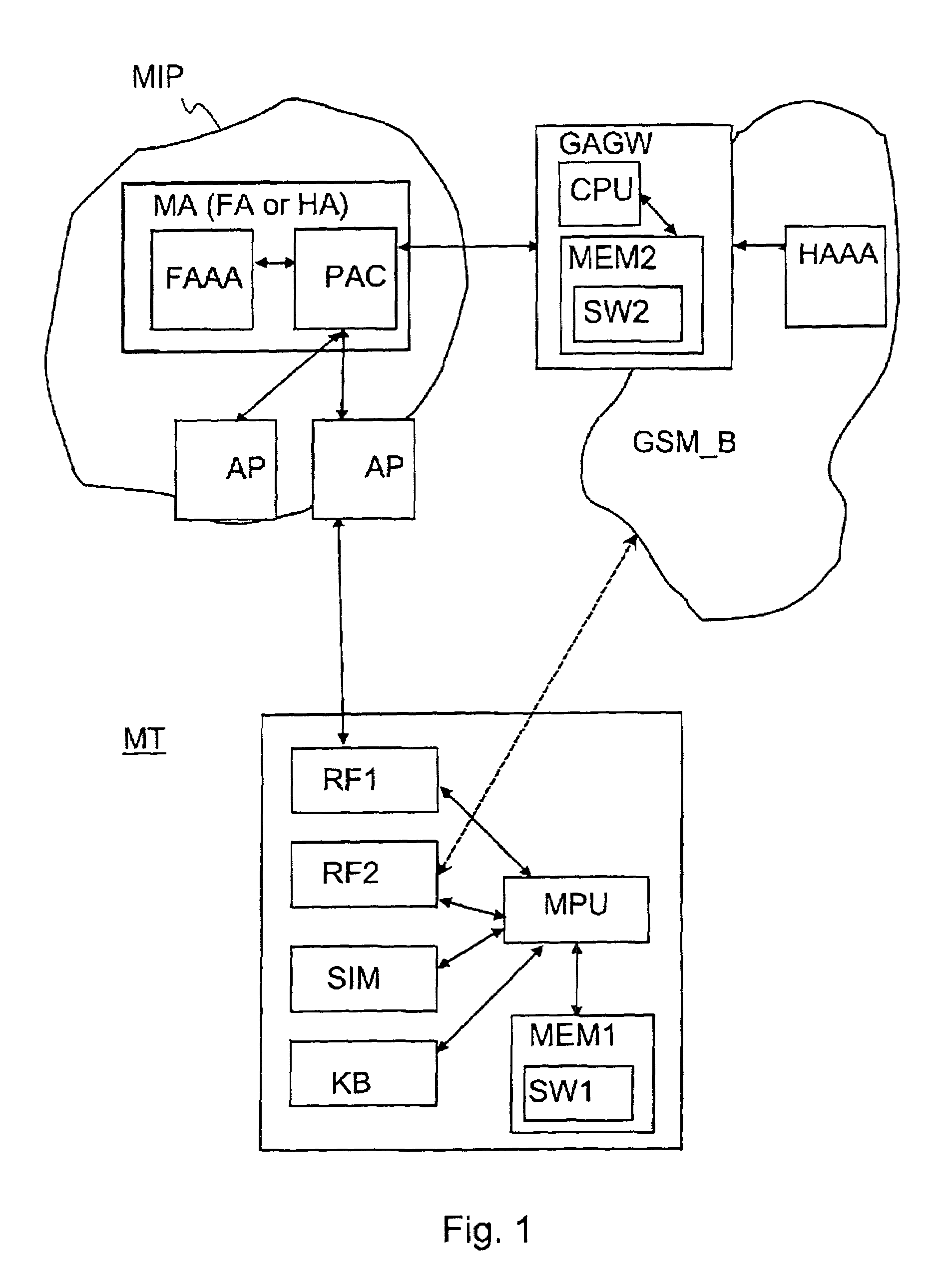
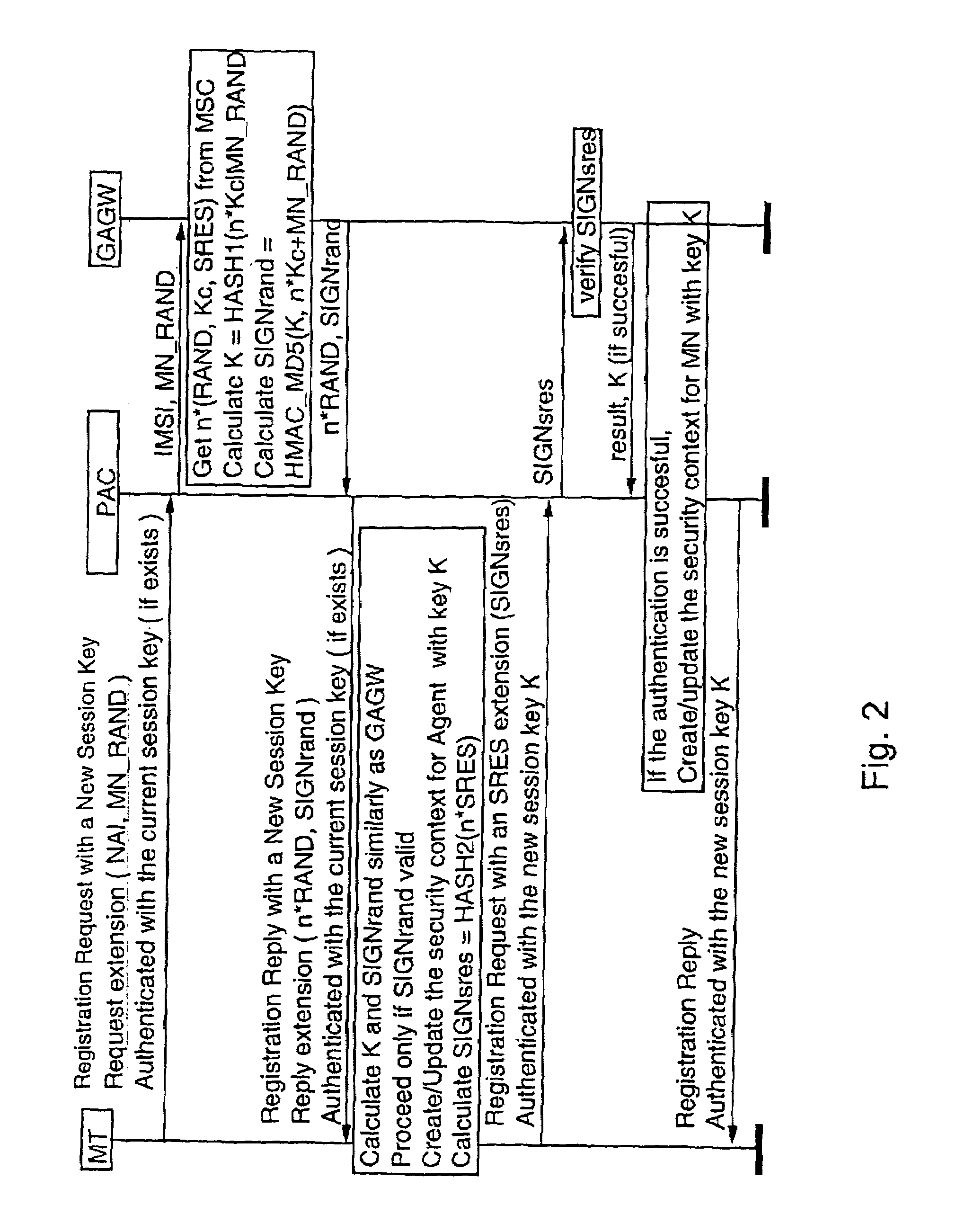
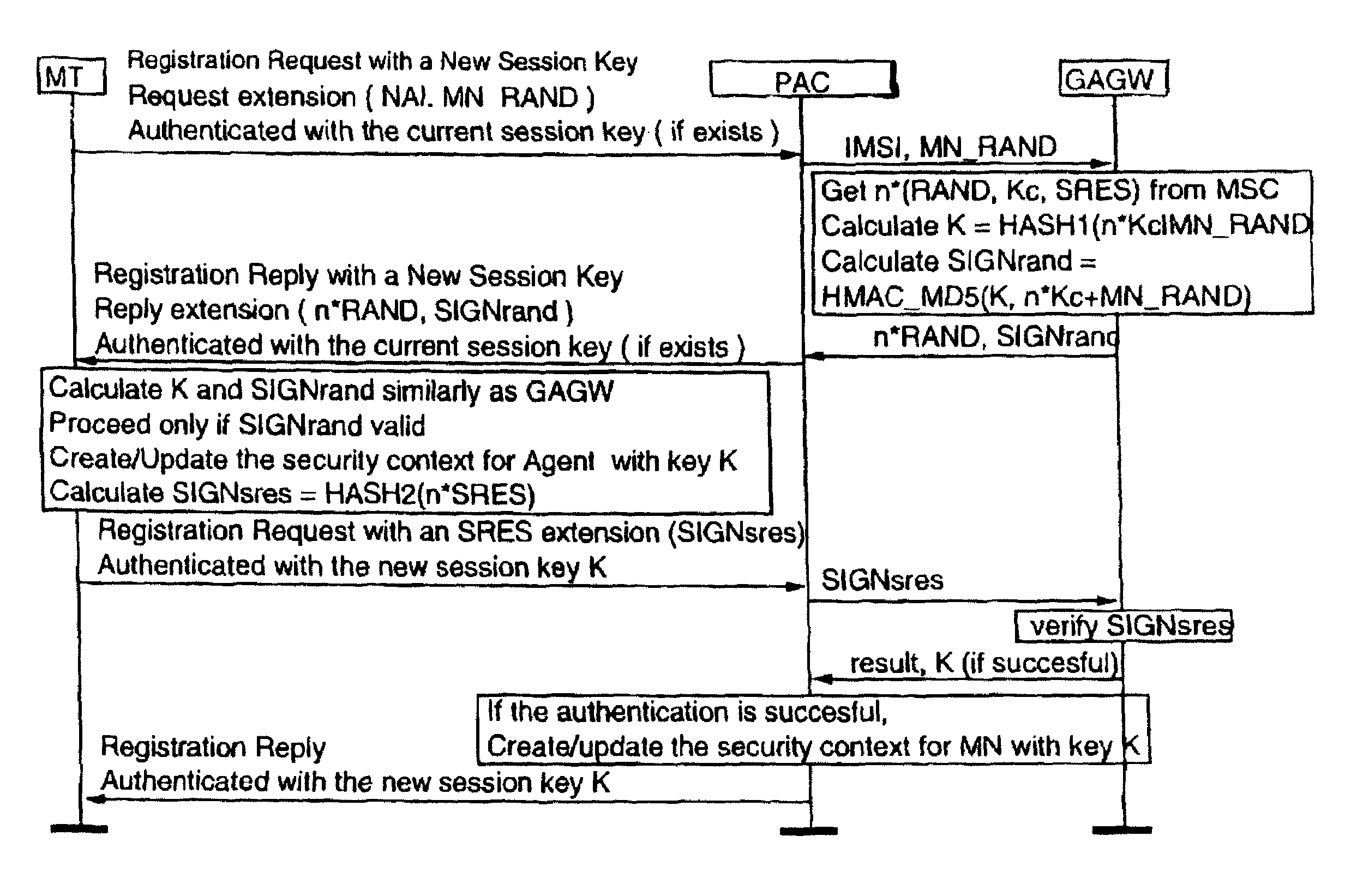
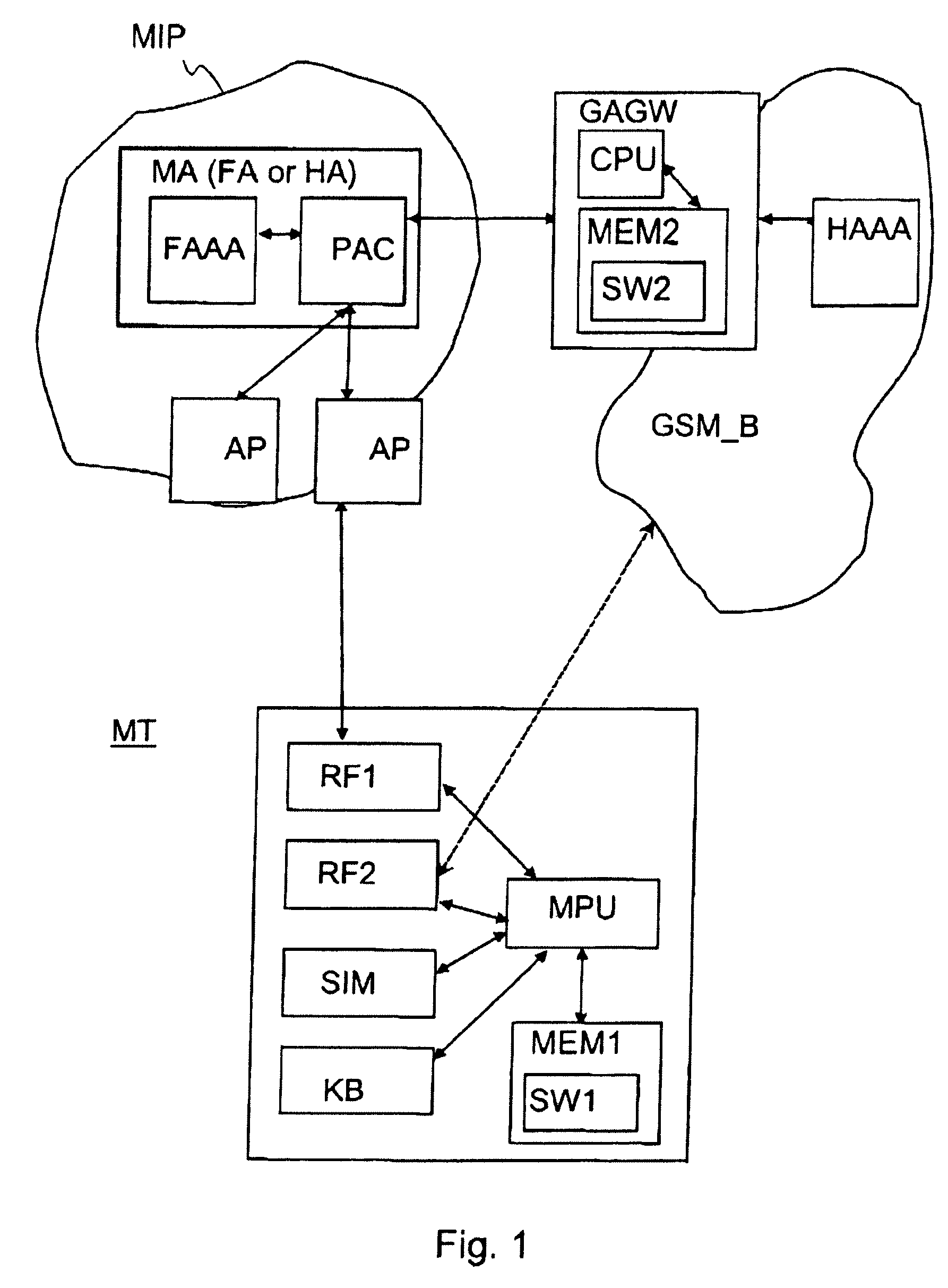
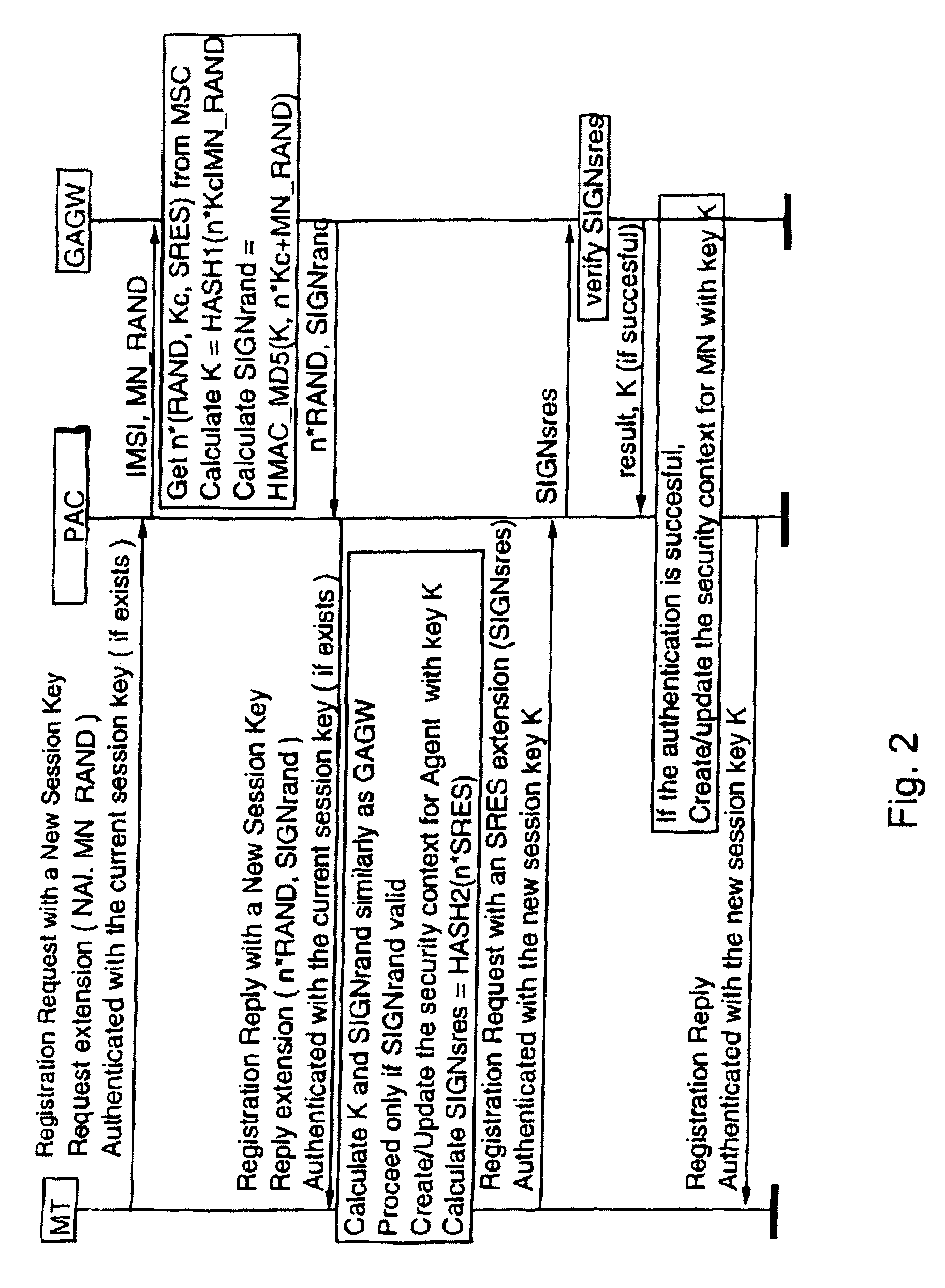
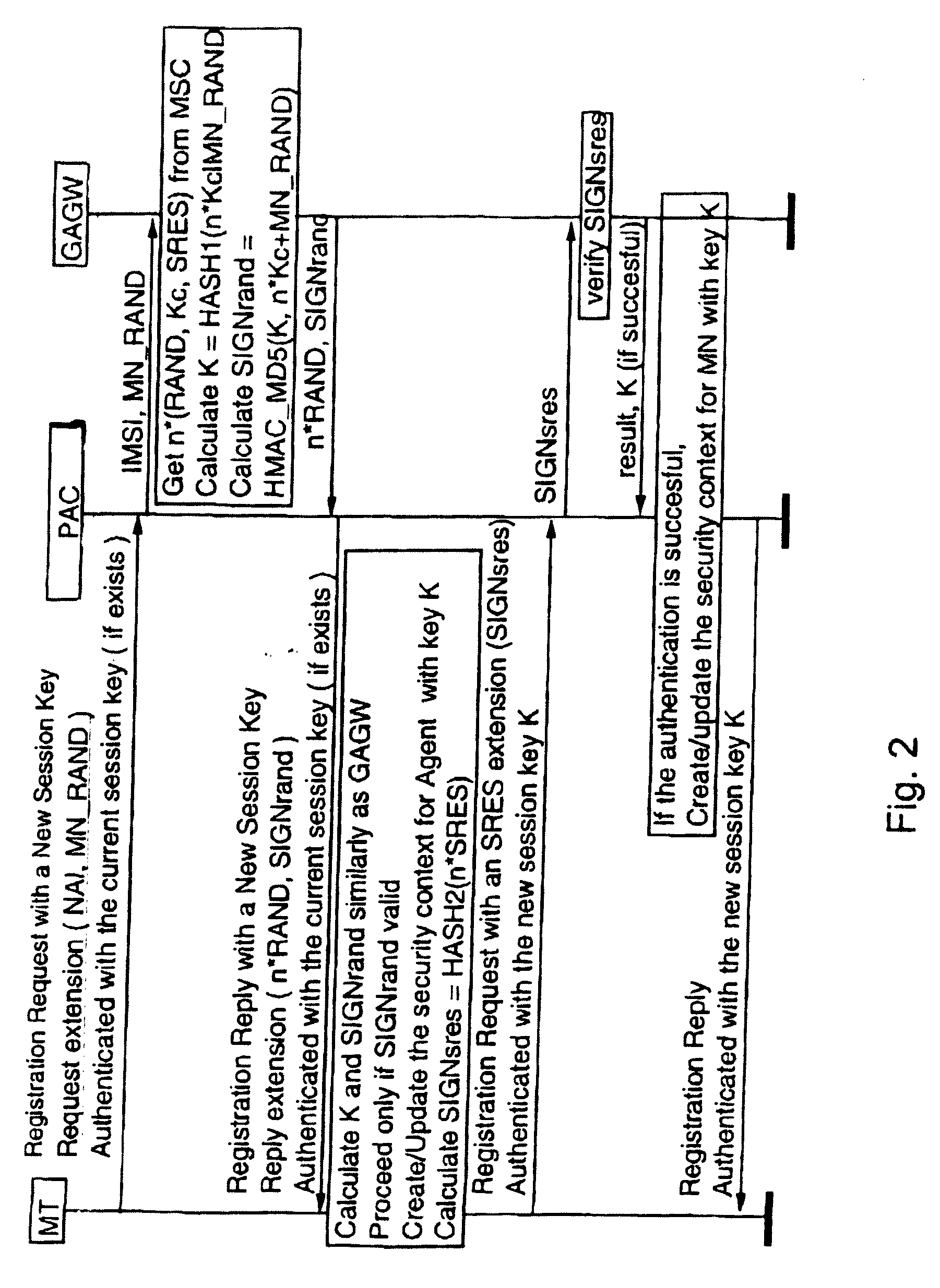
Authentication method for authenticating a mobile node to a packet data network, in which a shared secret for both the mobile node and the packet data network is arranged by using a shared secret of the mobile node and a telecommunications network authentication center. In the method, the mobile node sends its subscriber identity to the packet data network together with a replay attack protector. The packet data network obtains authentication triplets, forms a session key using them, and sends back to the mobile node challenges and a cryptographic authenticator made by using the session key. The mobile node can then form the rest of the authentication triplets using the challenges and then form the session key. With the session key, the mobile node can check the validity of the cryptographic authenticator. If the authenticator is correct, the mobile node sends a cryptographic response formed using the session key to the packet data network for authenticating itself to the packet data network.
Owner:NOKIA TECHNOLOGLES OY
Prevention of unauthorized scripts
ActiveUS7606915B1Improved script preventionEasy to solveDigital data processing detailsMultiple digital computer combinationsComputer hardwareCorrect response
Methods and system of preventing unauthorized scripting. The invention includes providing one or more tests to a user for distinguishing the user from a machine when the user requests access to the server. By storing information on a correct solution to the test in a block of data and sending the block of data together with the test, the invention provides stateless operation. Moreover, maintaining a database of previously used correct responses prevents replay attacks. The invention also includes providing combinations of alternative tests, such as visually altered textual character strings, audible character strings, and computational puzzles. Other aspects of the invention are directed to computer-readable media for use with the methods and system.
Owner:MICROSOFT TECH LICENSING LLC
Single sign on method and system based on Cookie and application server thereof
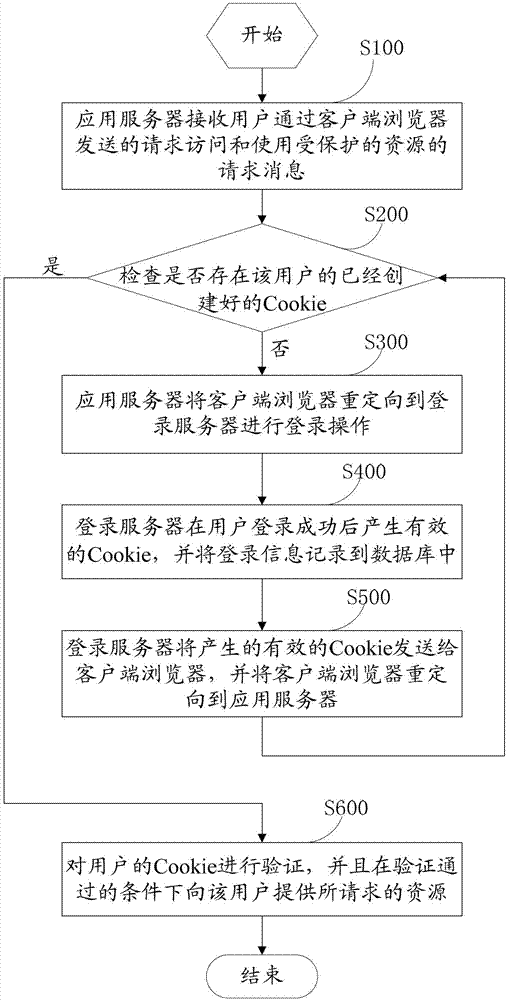
The invention discloses a single sign on method and system based on Cookie and an application server thereof. The technical problems of replay attack and frequent access of the database are solved through the following operations: receiving request a message transmitted by a client browser by an application server; B, checking whether Cookie of a user exists in the client browser; if so, directly returning a failure result and entering a step C, otherwise entering the step F; C, redirecting the client browser to a login server for performing login operation; D, generating effective Cookie through the login server after the user login is successful; E, transmitting the generated effective Cookie to the client browser, redirecting to the application server, and turning to the step B; and F, verifying the Cookie of the user, comprising judging whether the authentication information value of the Cookie of the user is matched with Session value of the server, whether the ID value of the Cookie is unique, whether the timestamp of the Cookie is repeated and overtime, and providing the requested resources to the user under the verification condition.
Owner:CHINA CONSTRUCTION BANK
Method and system for online security trading
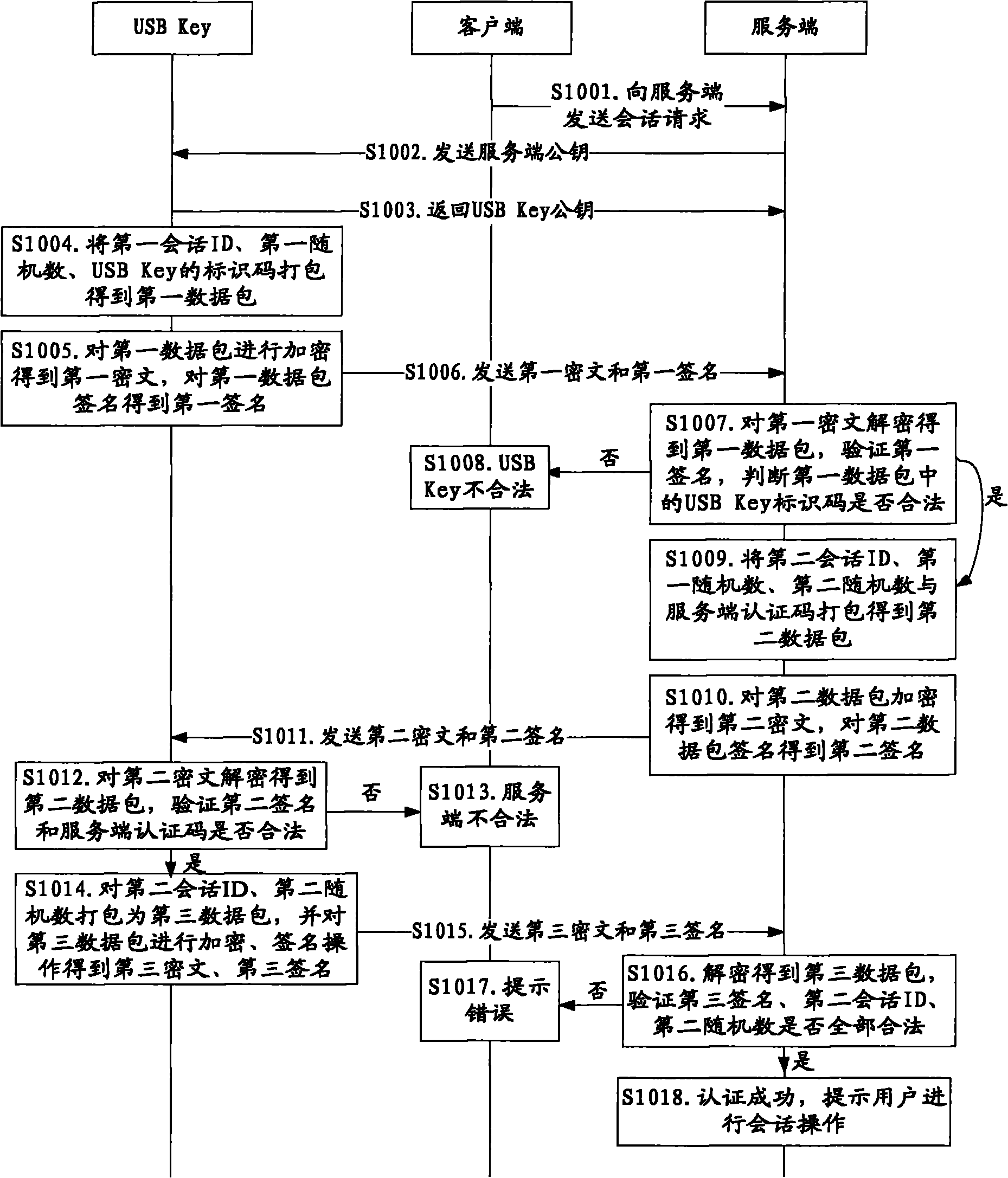
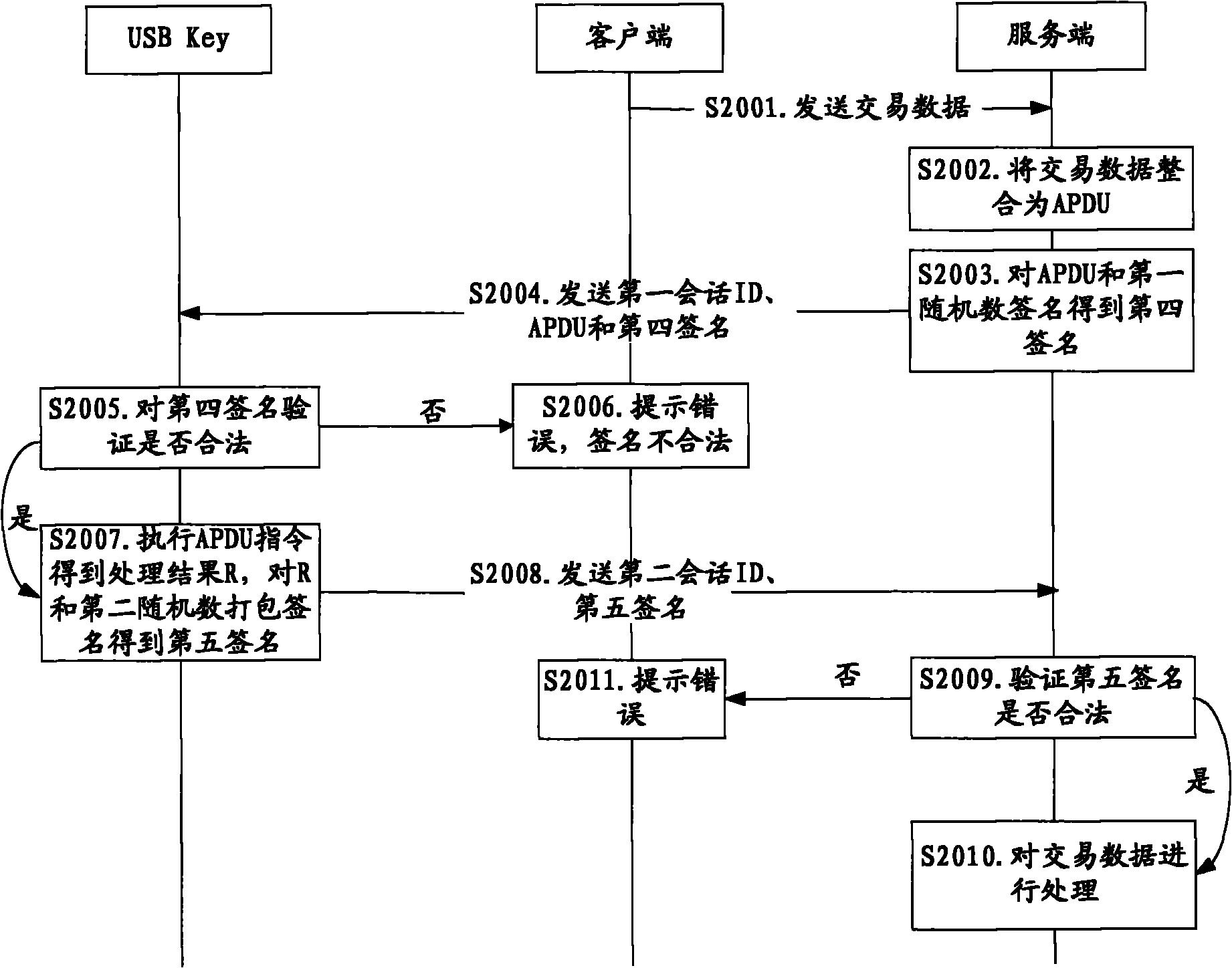
ActiveCN101789934ASolve the replay attack problemPrevent replay attacksKey distribution for secure communicationFinanceProtection systemOnline security
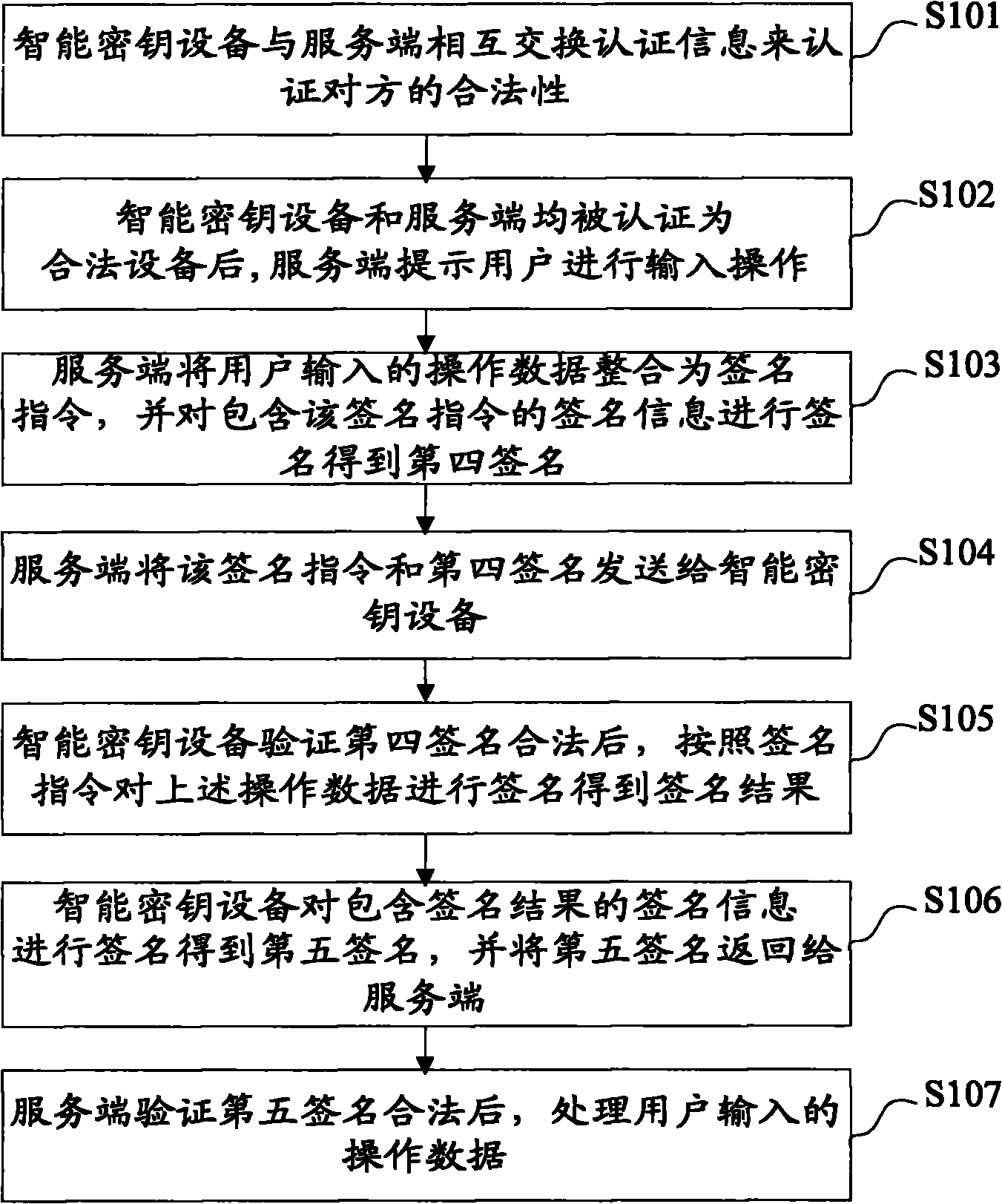
The invention discloses a method and a system for online security trading, wherein the method for the online security trading comprises the following steps that: intelligent key equipment and a server verify the validities of each other by mutually exchanging authentication information; after both sides are verified be valid by each other, the server integrates the operational data of the user into a signature command, and transfers the signature command and signature information to the intelligent key equipment by a client; after the intelligent key equipment verifies the validity of the signature information, the intelligent key equipment executes the signature command and returns the signature result to the server; and the server processes the operational data of the user according to the signature result. By the mutual authentication of the server and the intelligent key equipment and operations such as verification on the data in a session, the system can effectively judge whether the received data are valid and further prevent the replay attach of the hackers and protect the security operation of the system.
Owner:FEITIAN TECHNOLOGIES
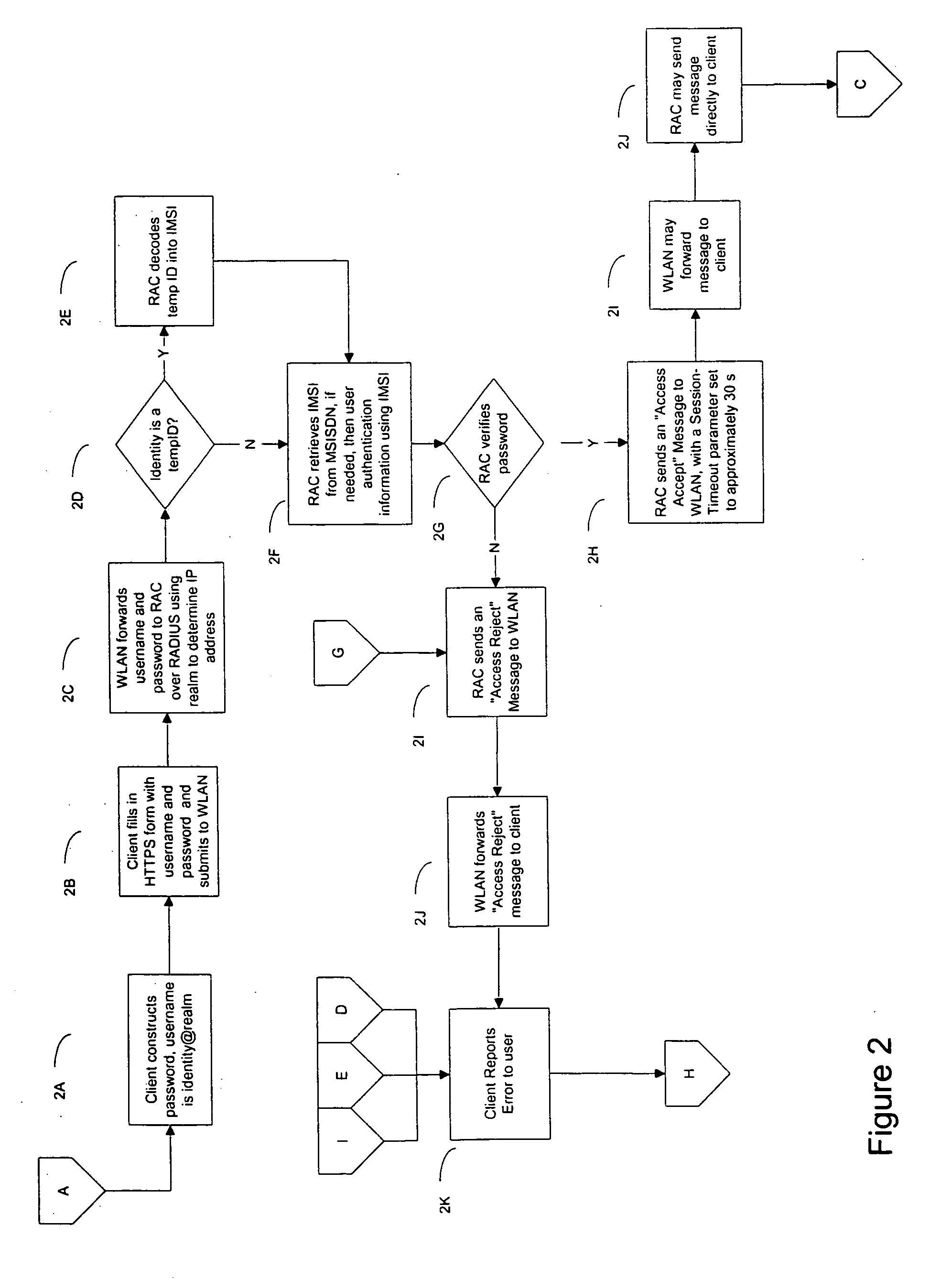
Method and system for providing SIM-based roaming over existing WLAN public access infrastructure
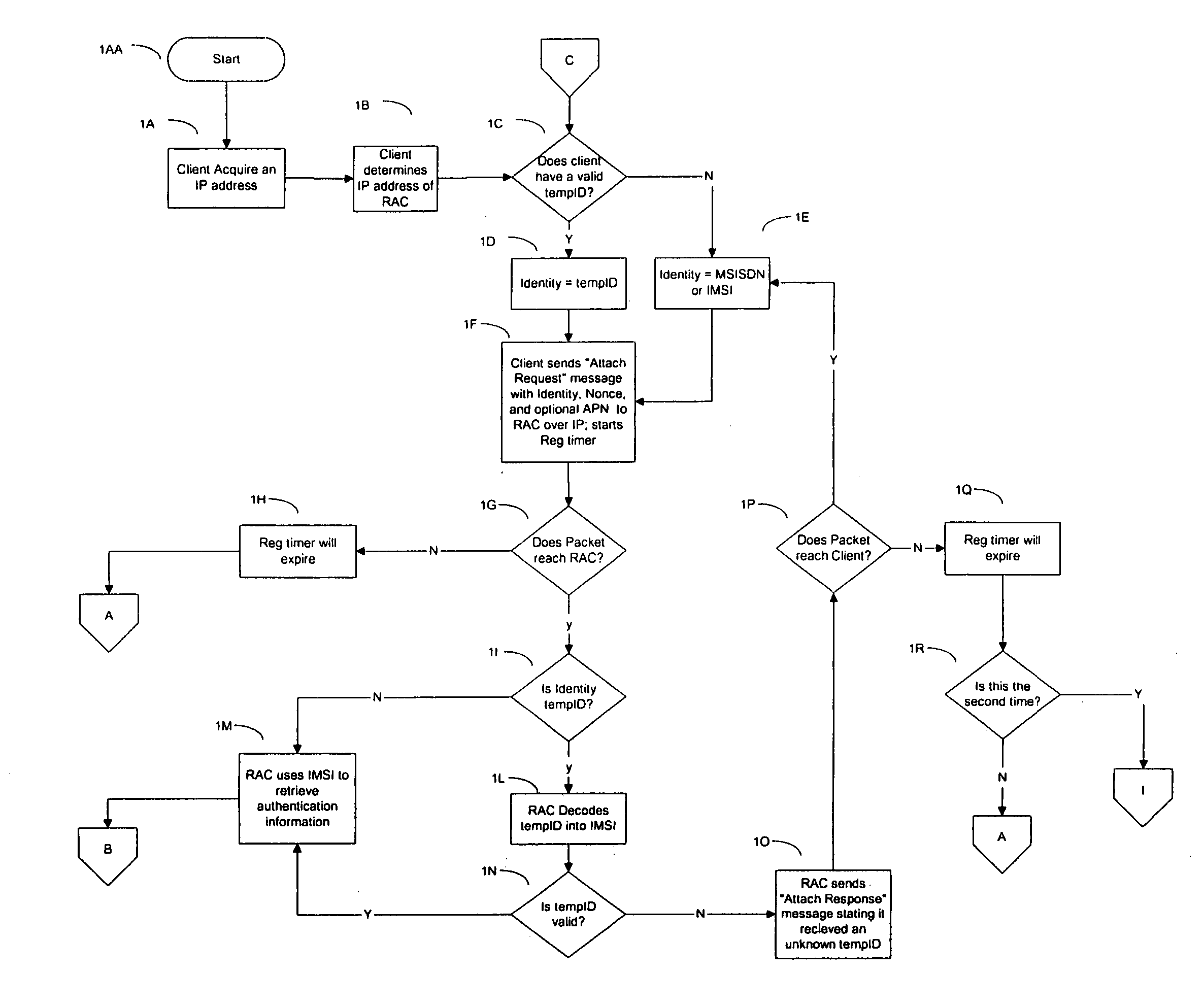
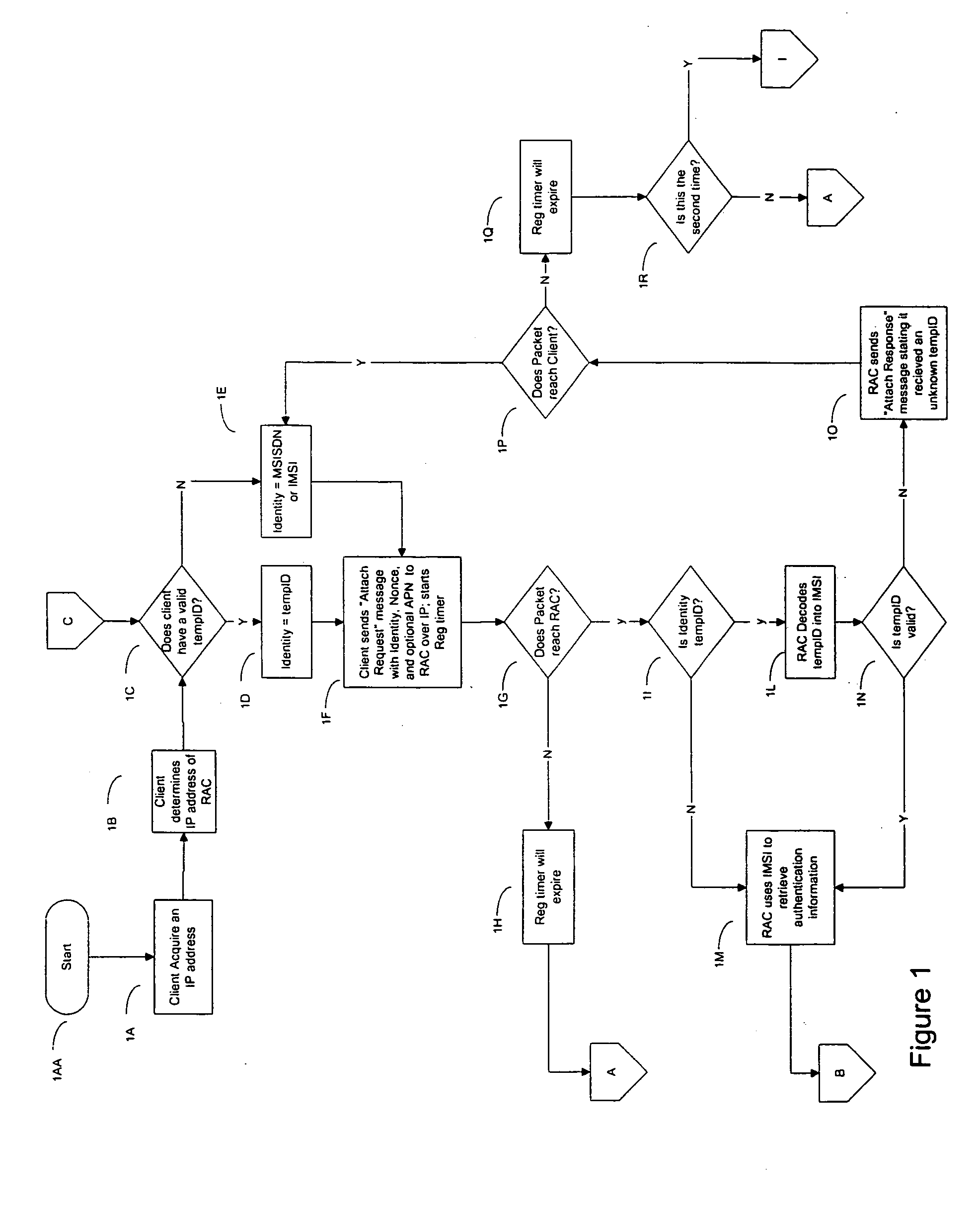
InactiveUS20050114680A1Prevent replay attacksUser identity/authority verificationNetwork topologiesWeb authenticationAccess method
A method and apparatus for performing SIM-based authentication and authorization in a WLAN Internet Service Provider (WISP) network supporting the universal access method (UAM) of authentication and authorization enabling roaming for customers of mobile service providers onto said networks. In addition, the invention provides a secure way of authenticating the customer's client device to the mobile service provider's network by employing temporary credentials for authentication that provide privacy of the user's identity and prevent replay attacks. Finally, if the WISP network supports the ‘pass-through’ facility, the authentication can be done more securely and quickly.
Owner:AZAIRE NETWORKS
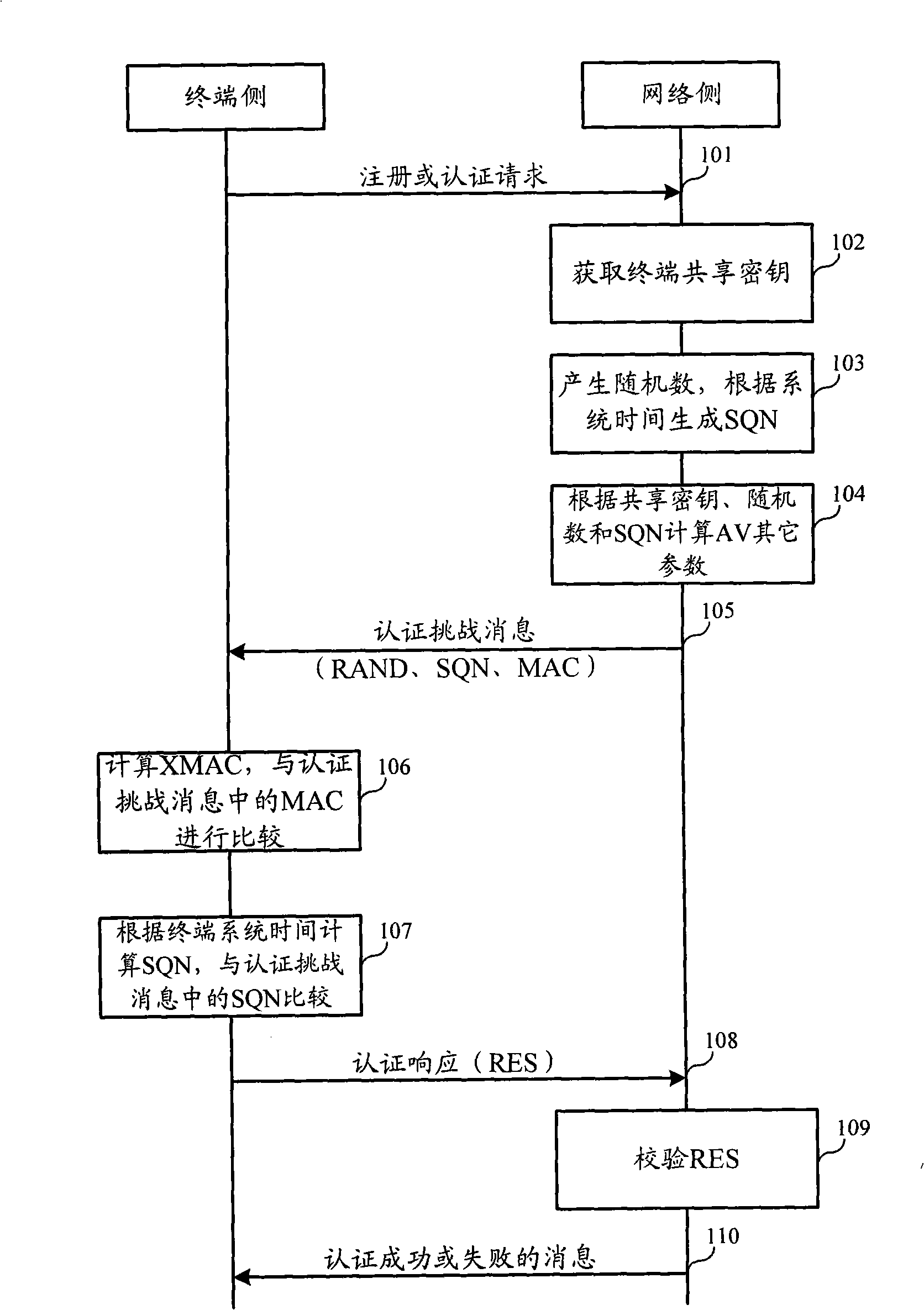
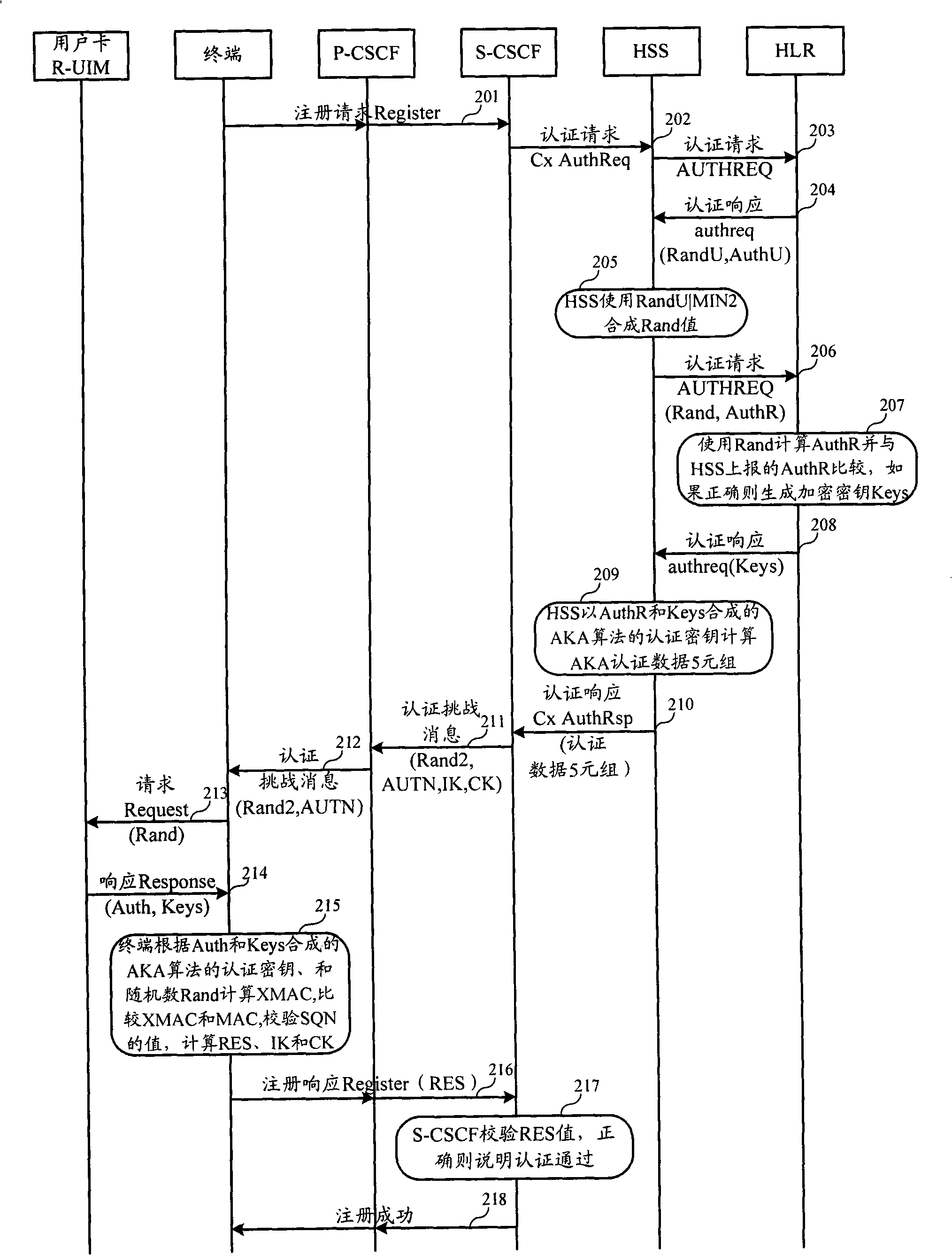
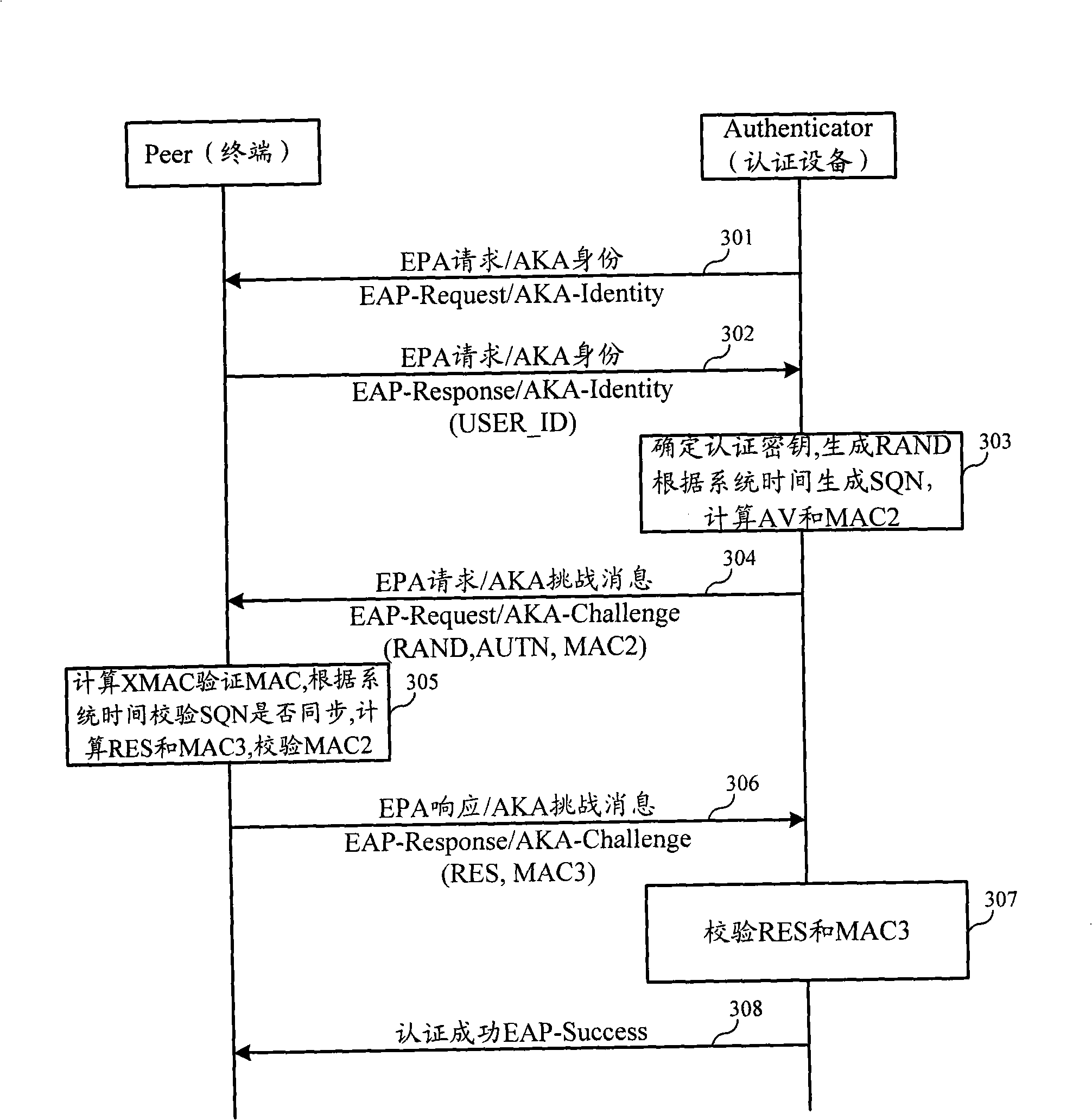
Authentication and cryptographic key negotiation method, authentication method, system and equipment
ActiveCN101272251AReplay is unique and accurateNo securitySynchronising transmission/receiving encryption devicesUser identity/authority verificationSystem timeReplay attack
The invention relates to the field of commutation and discloses an authentication and key negotiation method, an authentication method, a system and a device, which leads a user card to be capable of resisting the playback attack during the process of an AKA under the situation of not supporting SQN storing. In the invention, when a network side receives the authentication request of a terminal, a random number, a first sequence number SQN1 and a first authentication code MAC are sent to the terminal according to the shared key, the random number and the first authentication code MAC generated by the first sequence number SQN1, the first authentication code MAC represents the current system time at the network side; if a second authentication code XMAC is the same as the first authentication code MAC, and the difference value of a second sequence number SQN2 representing the current system time at the terminal side and the first sequence number SQN1 meet a preset condition, the terminal determines the network side legal according to the key shared with the network side, the received random number and the first authentication code MAC generated by the first sequence number SQN1.
Owner:HUAWEI TECH CO LTD
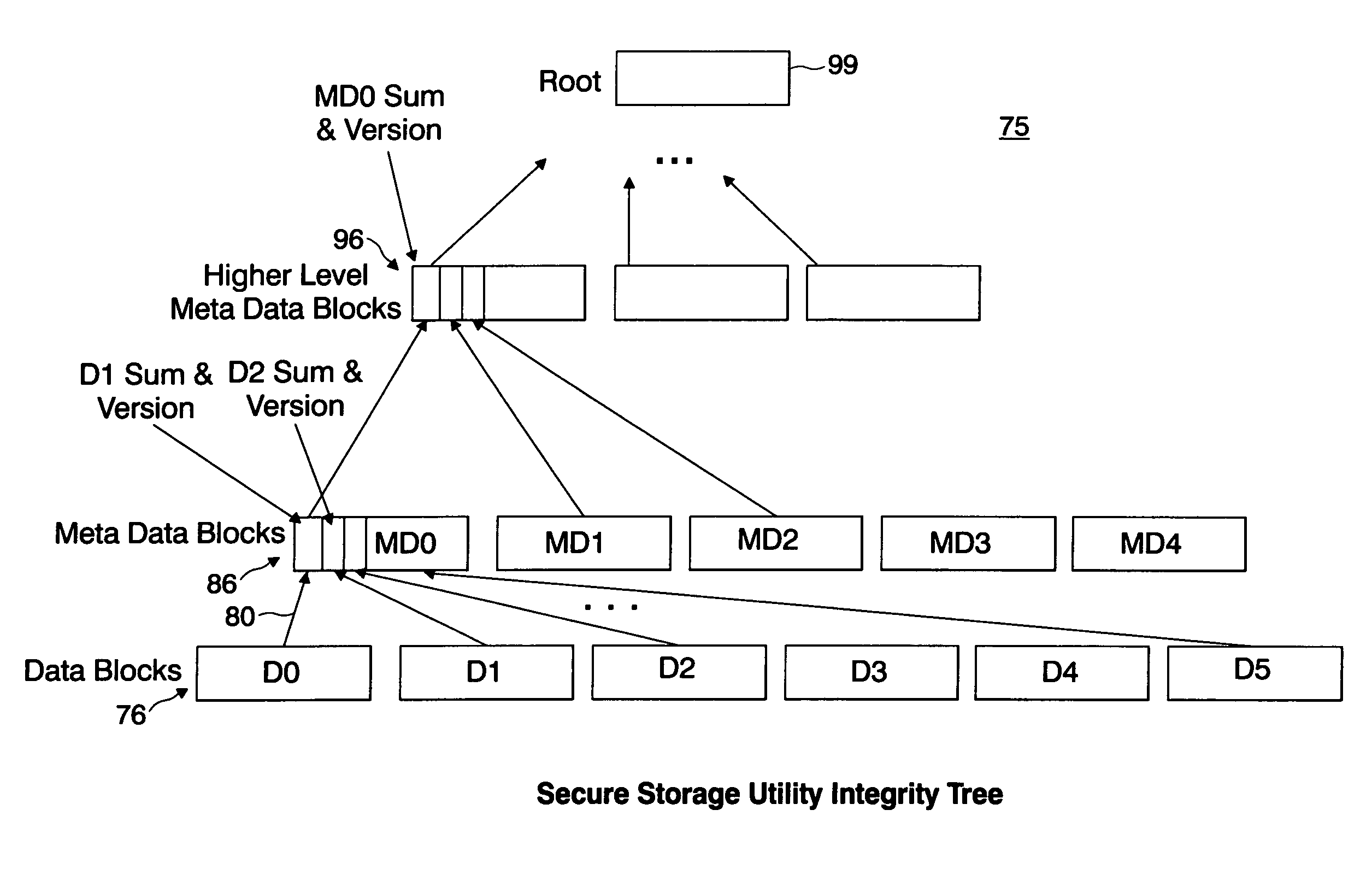
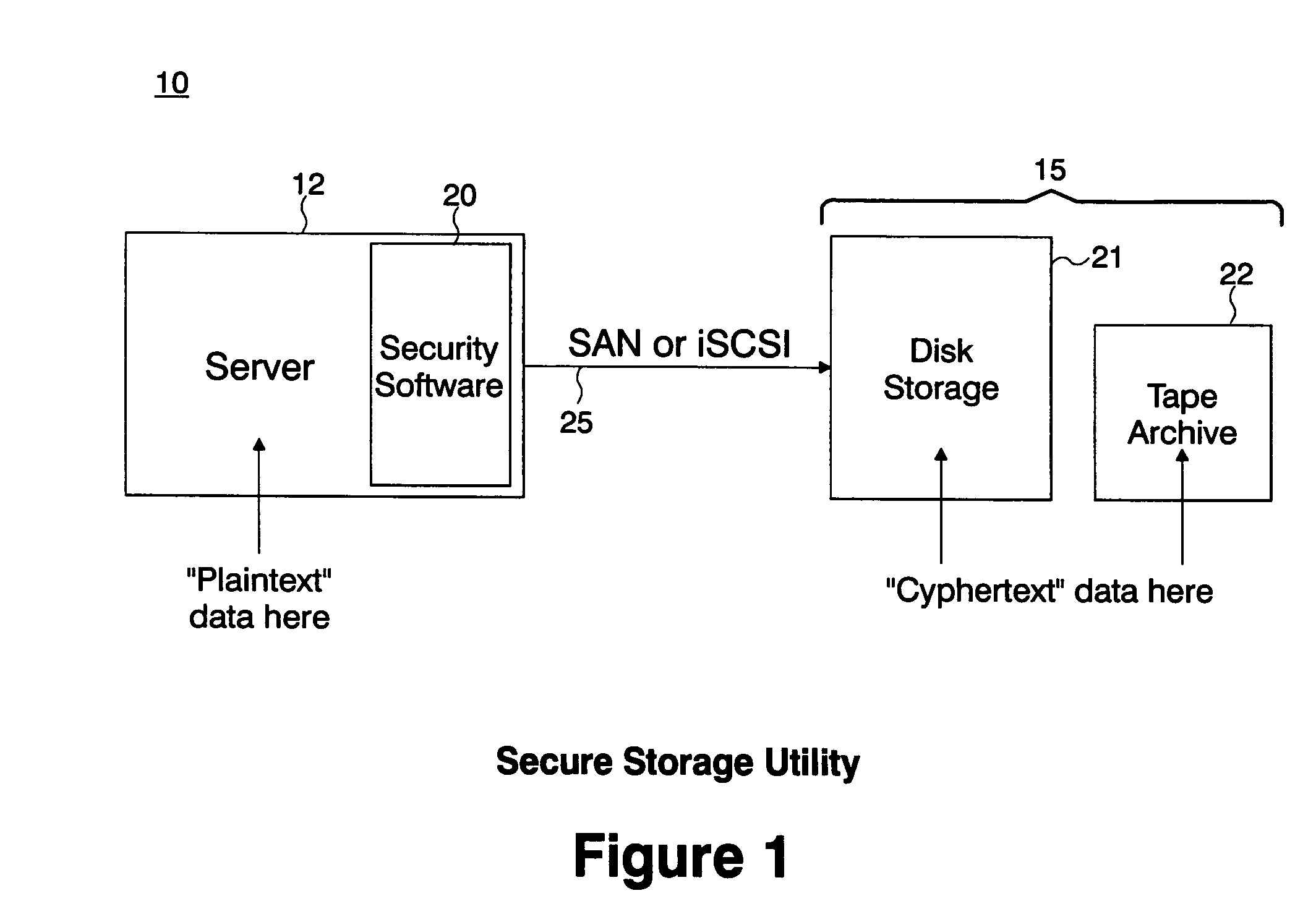
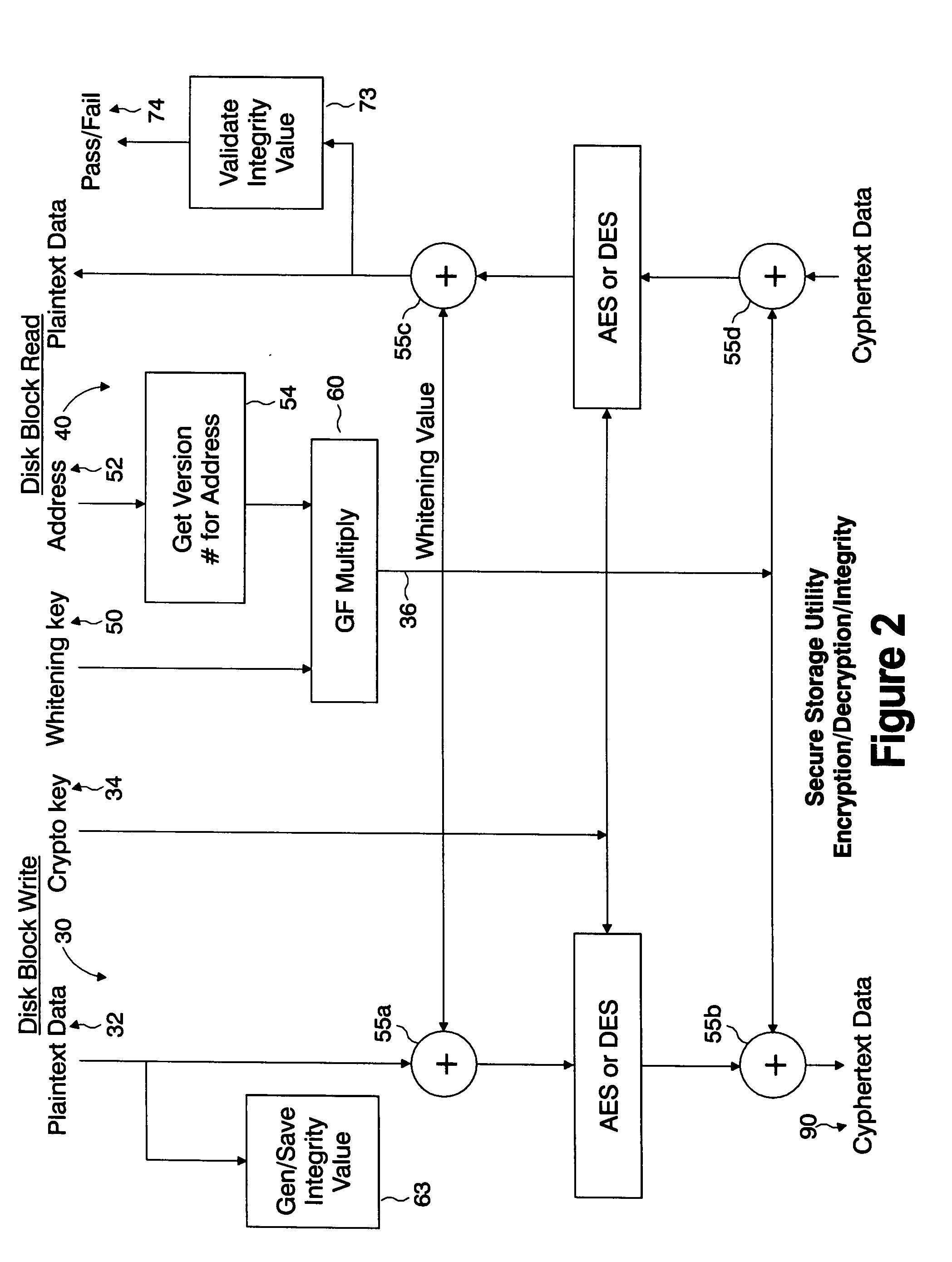
Secure storage utility
InactiveUS20050050342A1Improve efficiencyImprove integrityUser identity/authority verificationUnauthorized memory use protectionComputer hardwarePlaintext
A system and method implementing advanced cryptographic techniques to protect both the confidentiality and integrity of data sent to and received from a storage system or storage utility. Particularly, the system and method provides for the privacy and integrity of stored data. The integrity protection scheme employed defends against modification of data as well as “replay” and “relocation” of data since cryptographic integrity values are not only a function of the plaintext data and a cryptographic key, but also a function of the “address” of the disk block and a “whitening” value that defends against “replay attacks”. The integrity scheme protects the integrity of an entire virtual disk while allowing incremental, random access updates to the blocks on the virtual disk.
Owner:IBM CORP
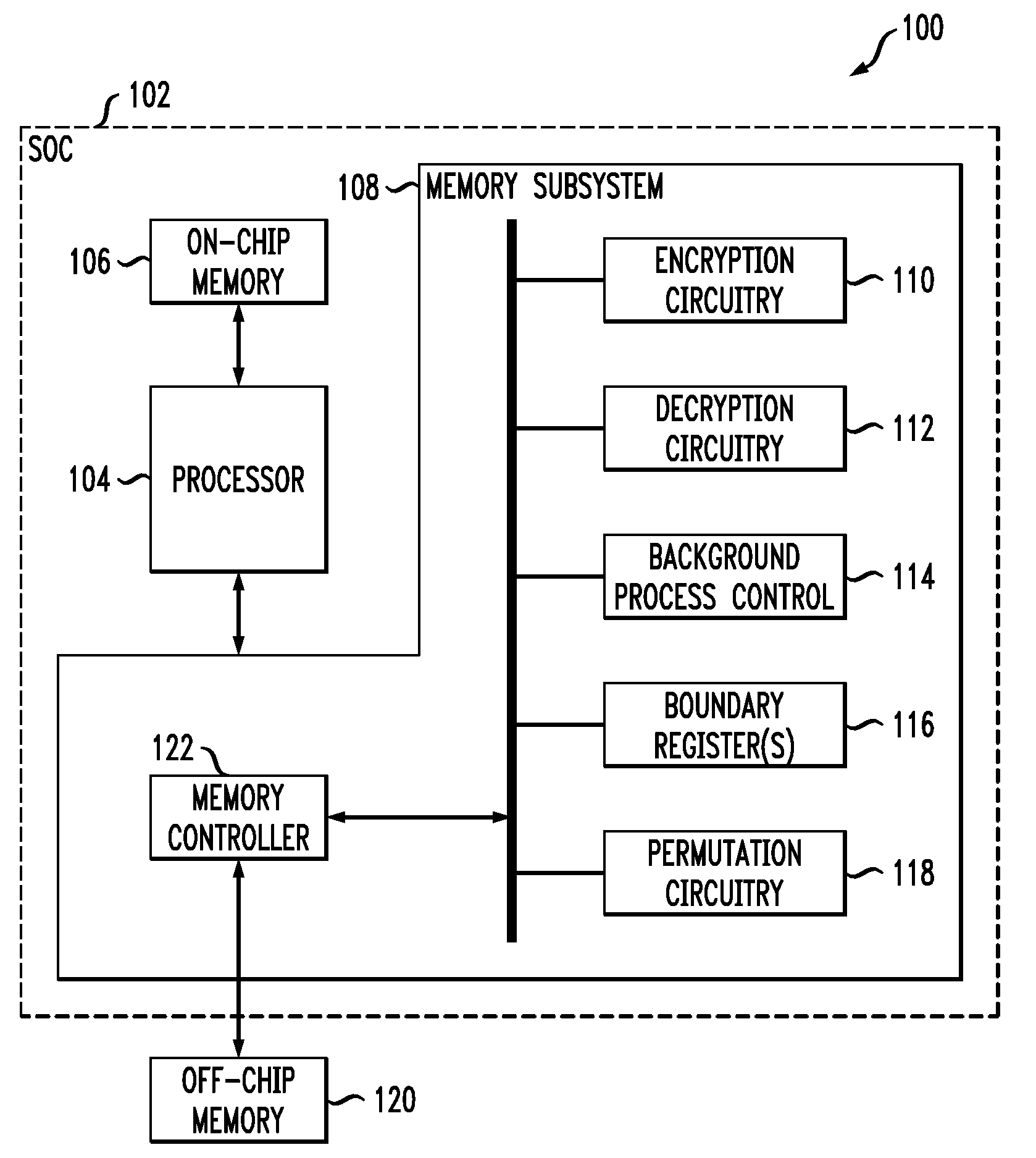
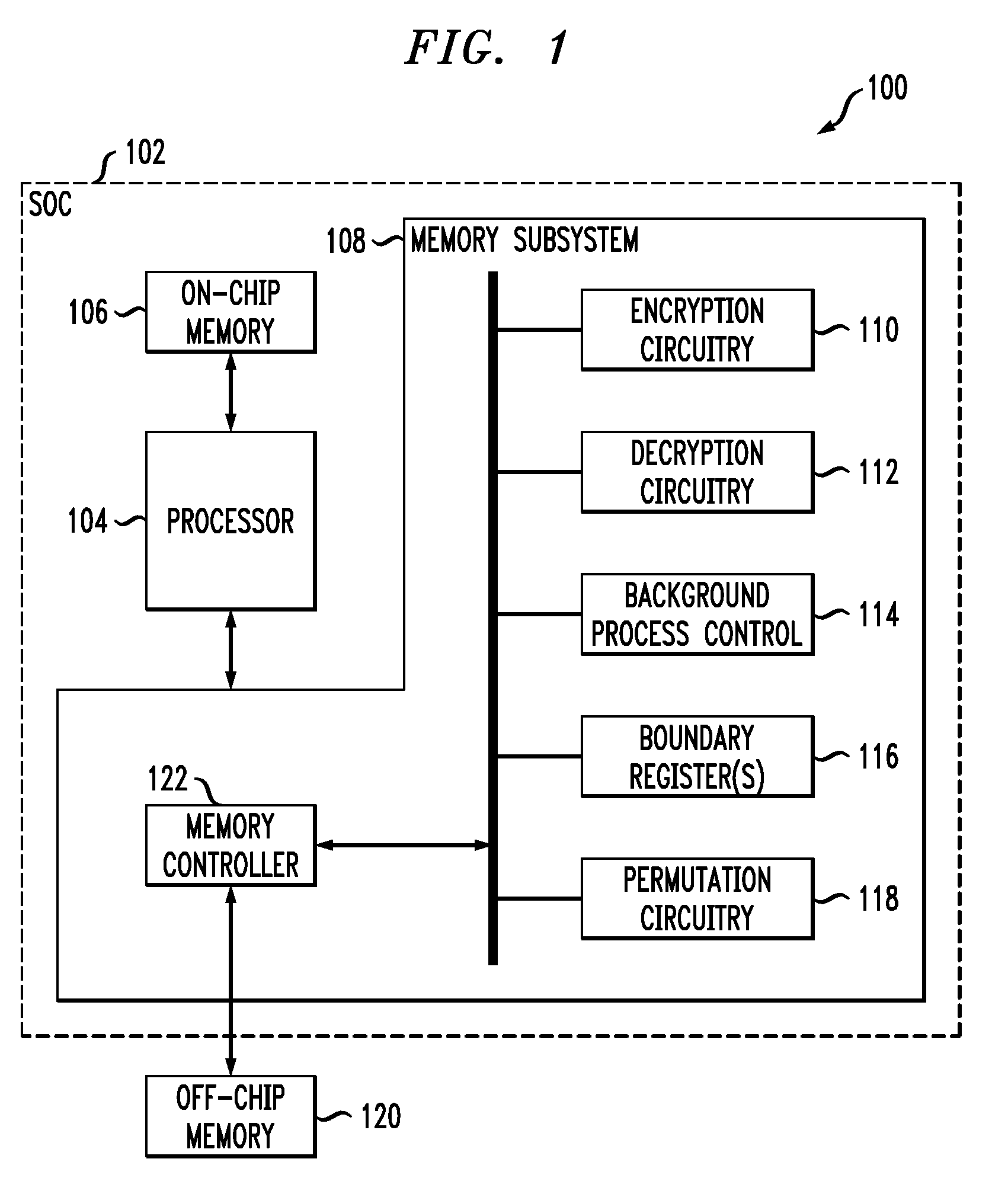
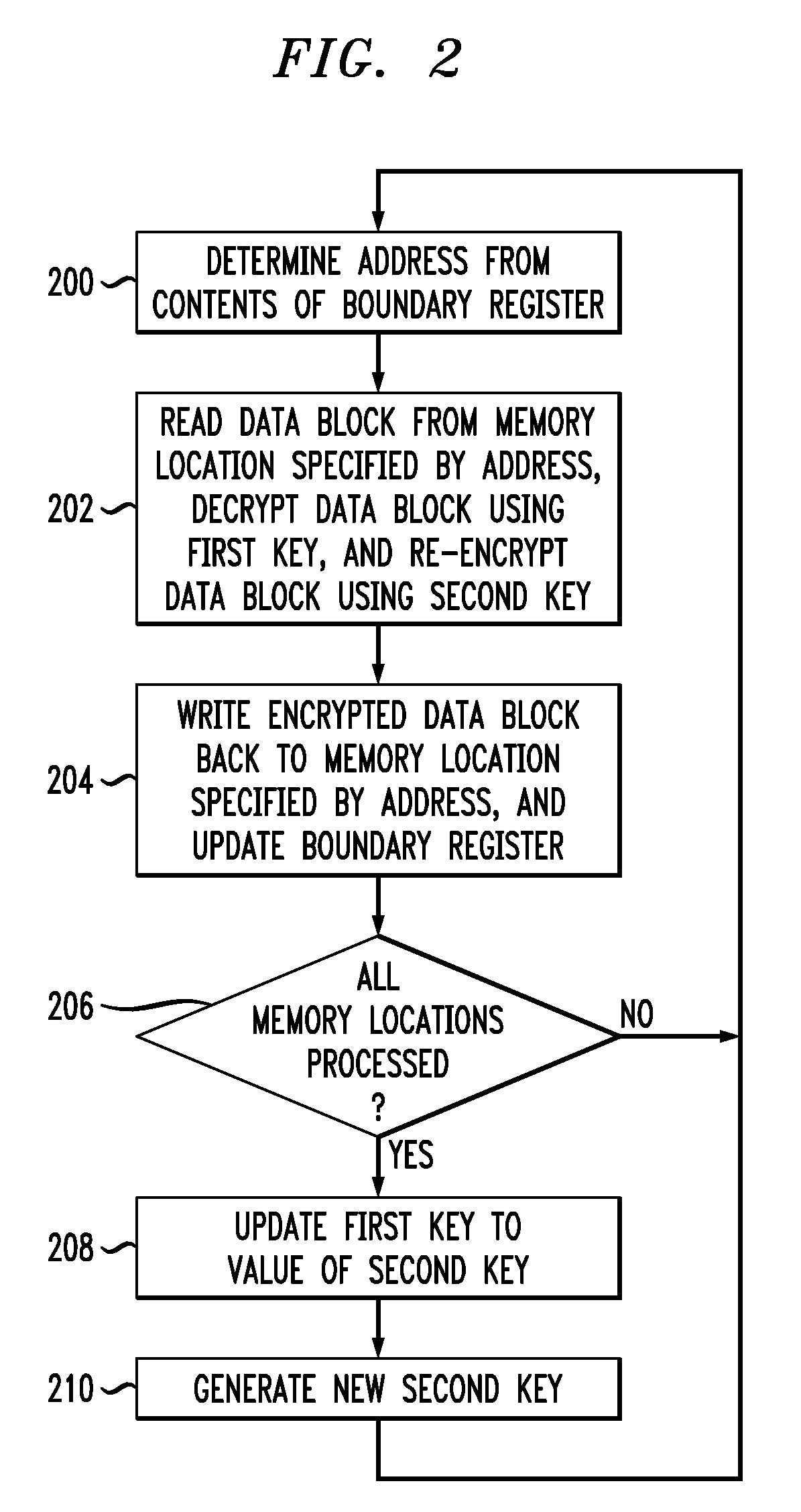
Secure data storage with key update to prevent replay attacks
InactiveUS20090187771A1Undermines effectivenessAvoid problemsEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionProcessor registerComputer data storage
A key update process applied to encrypted memory in a processing system determines an address from contents of a boundary register, reads an encrypted data block from a memory location specified by the address, decrypts the encrypted data block using a first key, re-encrypts the decrypted data block using a second key, writes the re-encrypted data block back to the memory location specified by the address, and updates the boundary register. These operations are repeated for one or more additional addresses. The boundary register contents are also used to determine appropriate keys for use in other read and write transactions to the memory. The key update process can be run as a background process, separate from the other read and write transactions to the memory, so as to incur minimal processing overhead.
Owner:LUCENT TECH INC
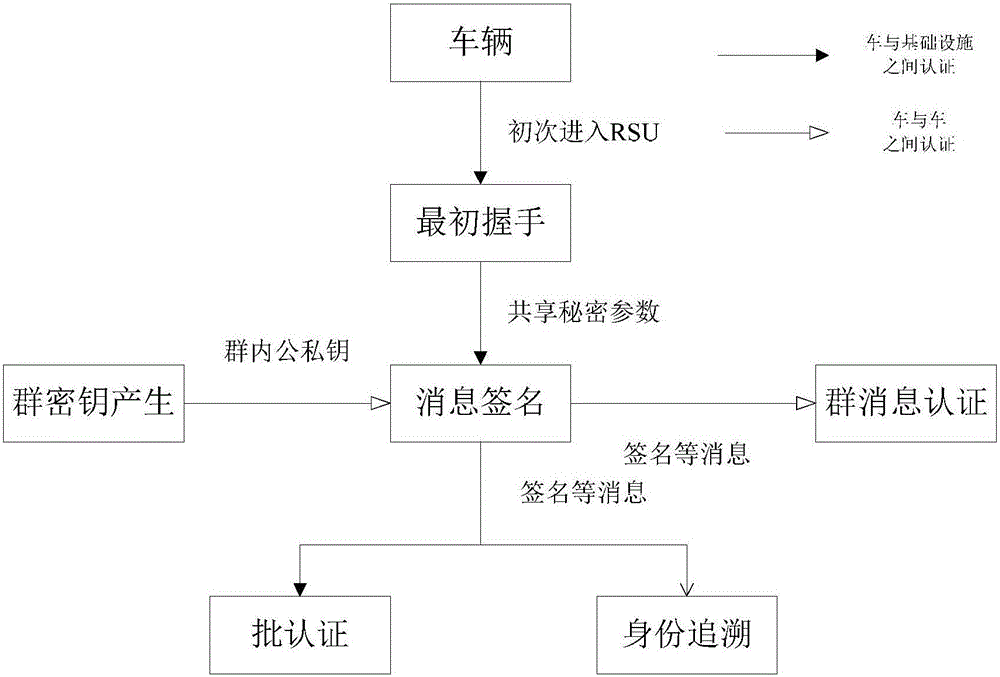
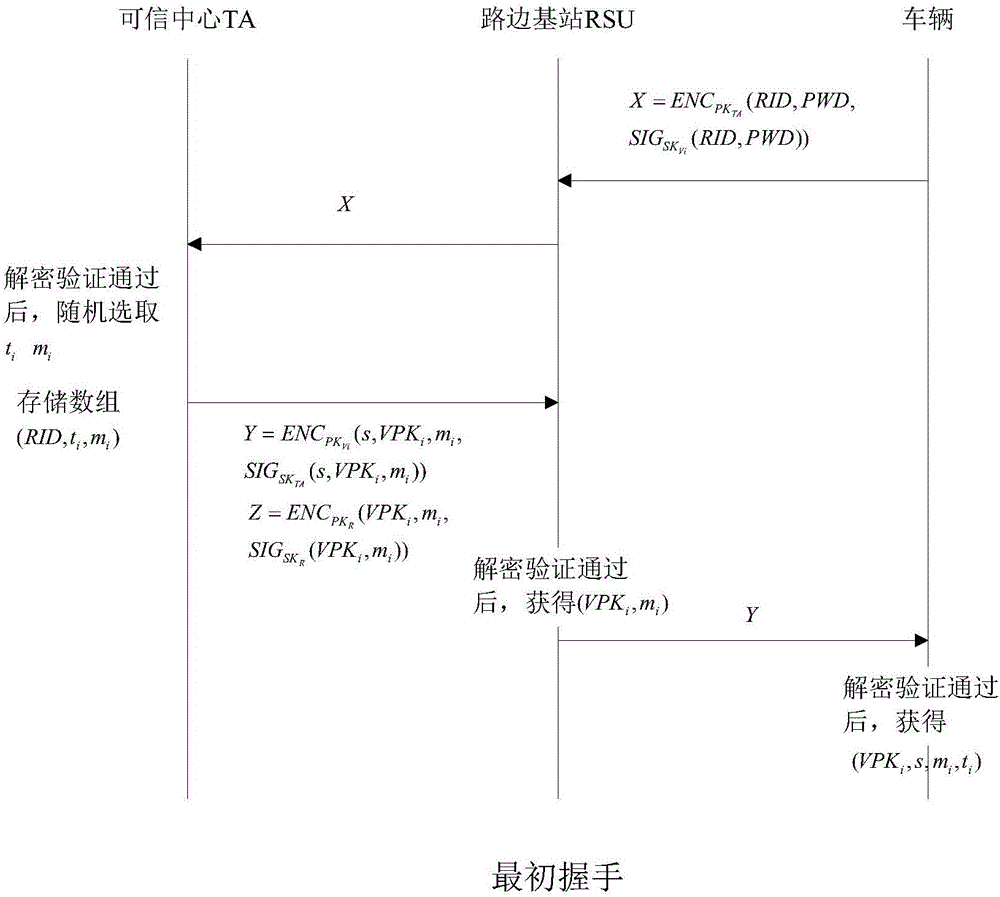
Identity based efficient anonymous batch authentication method in IOV (Internet of Vehicles) environment
ActiveCN105847235AAchieve authenticationImprove securityUser identity/authority verificationTrusted authorityTamper resistance
The invention discloses an identity based efficient anonymous batch authentication method in an IOV (Internet of Vehicles) environment. The identity based efficient anonymous batch authentication method in the IOV environment comprises an initial handshake module, a message signature module, a batch authentication module, an identity tracing module, a group key generation module and a group message signature and authentication module. According to the identity based efficient anonymous batch authentication method in the IOV environment, authentication between vehicles and infrastructures and authentication between vehicles can be realized, no tamper-proofing device is depended, privacy protection is realized by utilizing a pseudonymous name, conditional privacy protection is realized as a TA (Trusted Authority) can trace the real identity of each vehicle if necessary, the efficiency is improved as batch authentication is adopted, and the authentication process is simple and efficient. The message signature process and the group message signature process are same, the operating cost is low, and a replay attack can be borne as a time stamp is added.
Owner:南京秉蔚信息科技有限公司
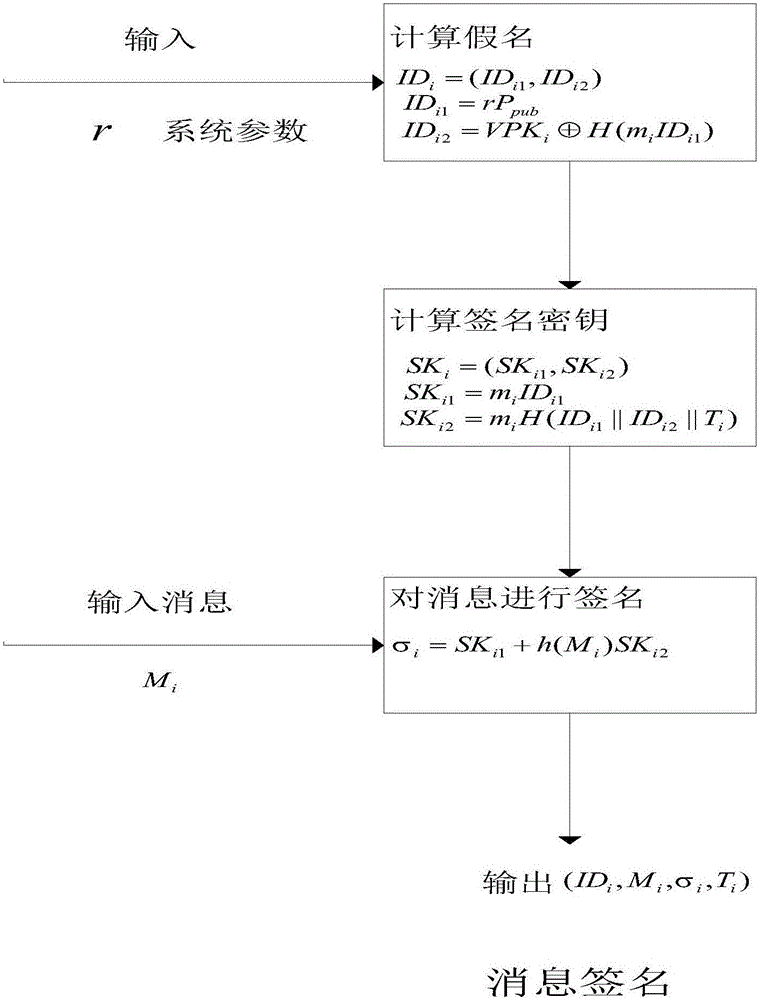
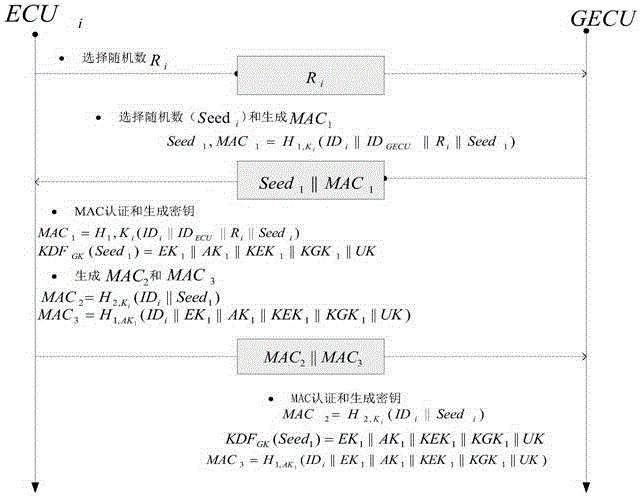
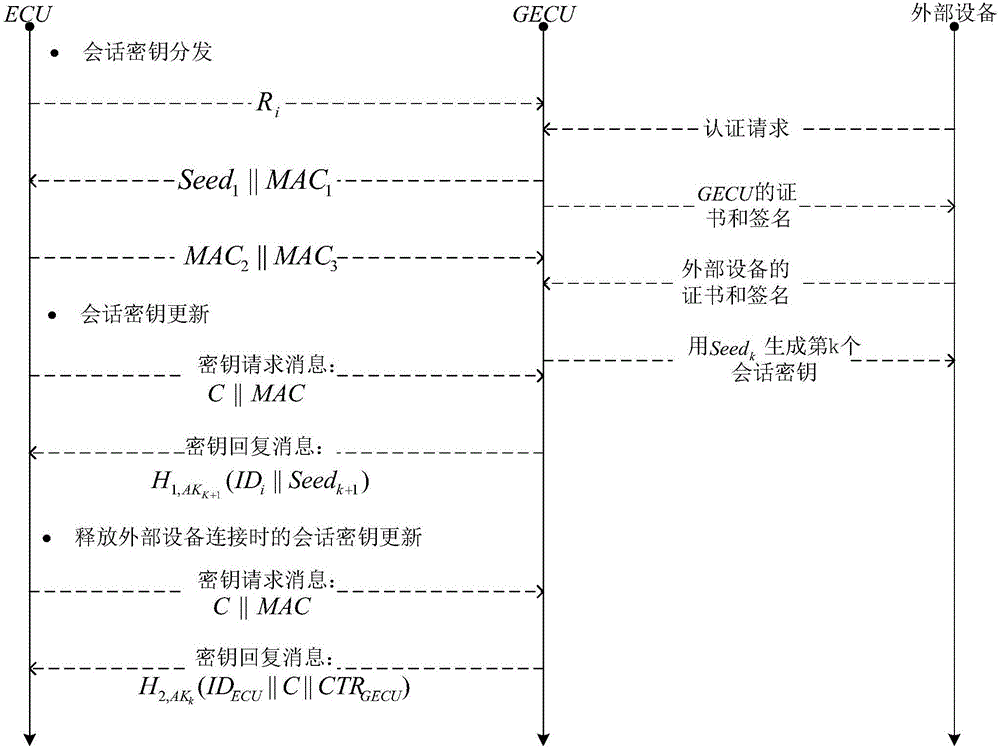
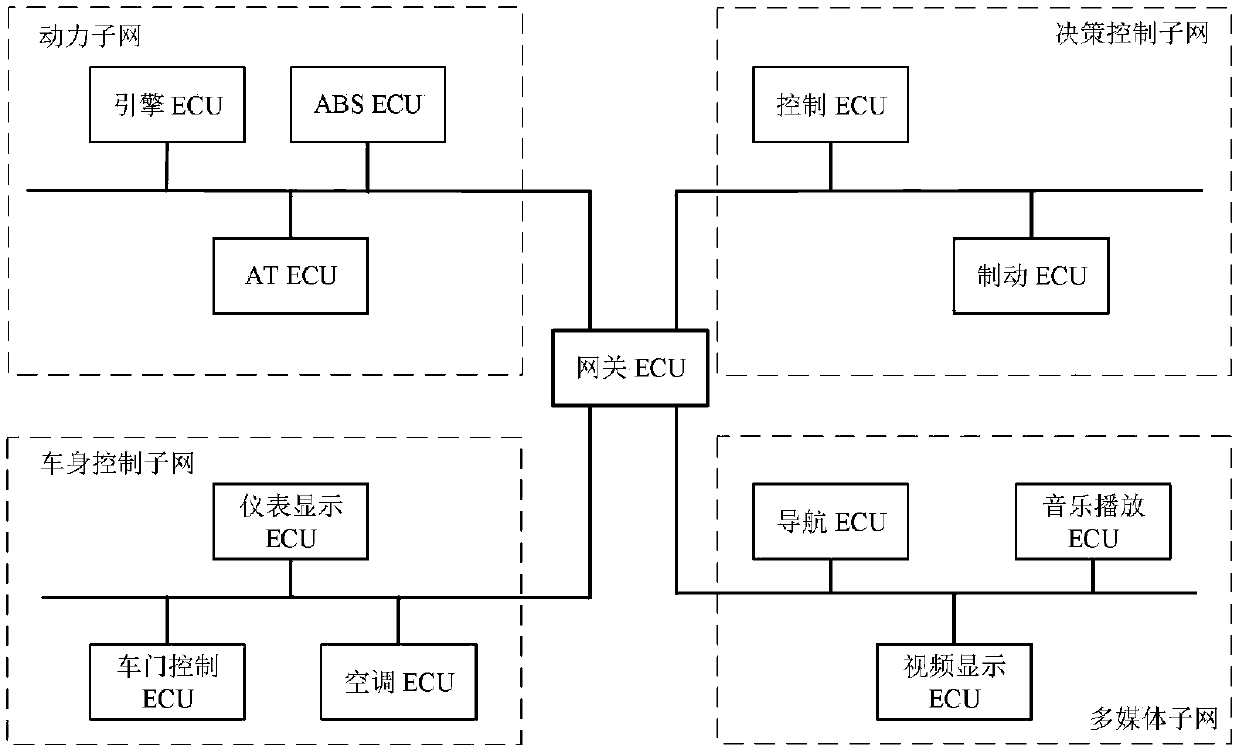
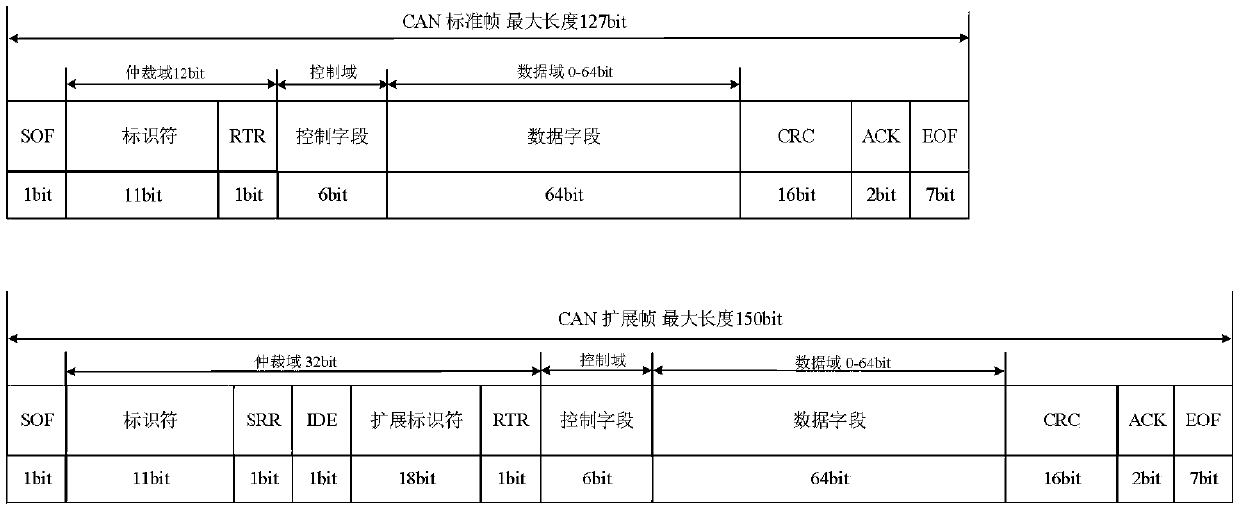
Method for safety communication of ECUs (Electronic Control Unit) in CAN (controller area network) bus
ActiveCN106790053AReduce computing costImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesArea networkKey generation
The invention discloses a method for safety communication of ECUs (Electronic Control Unit) in a CAN (controller area network) bus, which comprises the steps that: 1, a system model is established; 2, an GECU (Gateway Electronic Control Unit) loads a session key into a safety storage of the GECU; 3, the GECU carries out session key distribution on each ECU in the CAN bus; 4, a receiver ECUr carries out authentication on an encrypted data frame sent by a sender ECUs; 5, the GECU updates an encryption key and an authentication key which are used for communication, wherein update is mainly divided into two stages of in-vehicle ECU key update and key update when a connection of external equipment is released; and 6, when a vehicle is connected with the external equipment, designing an additional authentication and key distribution method so as to ensure legality of the accessed external equipment. According to the method disclosed by the invention, calculation cost can be obviously reduced, and a load of the CAN bus is reduced; and optimization is carried out for a key distribution protocol in the in-vehicle CAN bus, a key update problem generated when the external equipment is connected and released is considered, a counter is used for generating a random number to change a parameter for key generation, and a relay attack is effectively prevented.
Owner:JIANGSU UNIV
Remote proving method in trusted computation environment
InactiveCN101477602AGuarantee authenticityGuaranteed privacyInternal/peripheral component protectionTransmissionMan-in-the-middle attackDigital signature
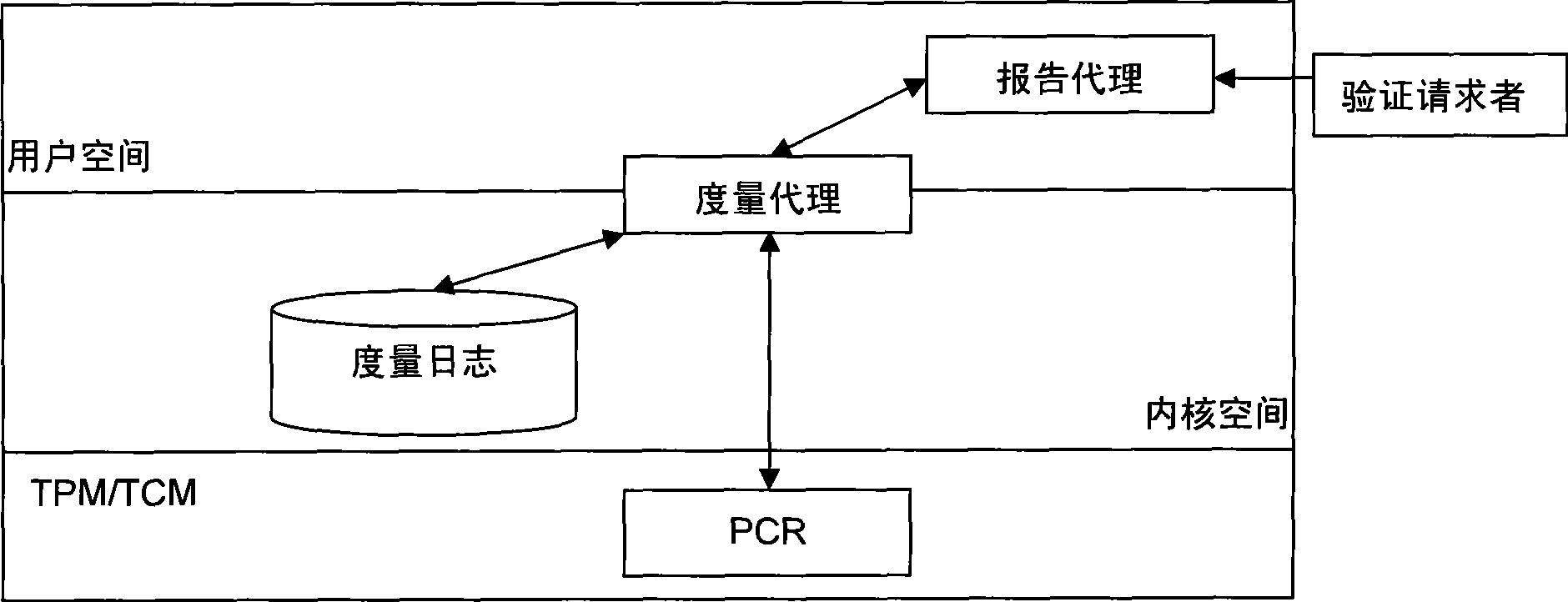
The invention provides a method for remote attestation in a trusted computing environment. The method is characterized in that secure session key is adopted for encrypting the metric value and the metric log of trusted platform to be verified, and signs for encryption result data. The method is based on a security chip TPM / TCM; the adopted remote attestation framework comprises three parts: an integrity measuring mechanism, a reporting mechanism and a validation mechanism, which are achieved by an integrity measuring agency, a report agency and a verification requestor, wherein, the measuring agency, the report agency and the verification requestor are installed in the trusted platform to be verified. The method ensures that the authenticity of the integrity measuring value and the measuring log and the privacy of the platform are kept; the replay attack, impersonation attack and man-in-the-middle attack are effectively prevented; the method is used for proving to the verification requestor that the running environment of the platform is credible, or used for self-test of the platform running environment; the method can be used for not only proving to the requestor that the platform running environment is credible, but also the self-test of the platform running environment; and the method is more suitable for a fair and open network environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
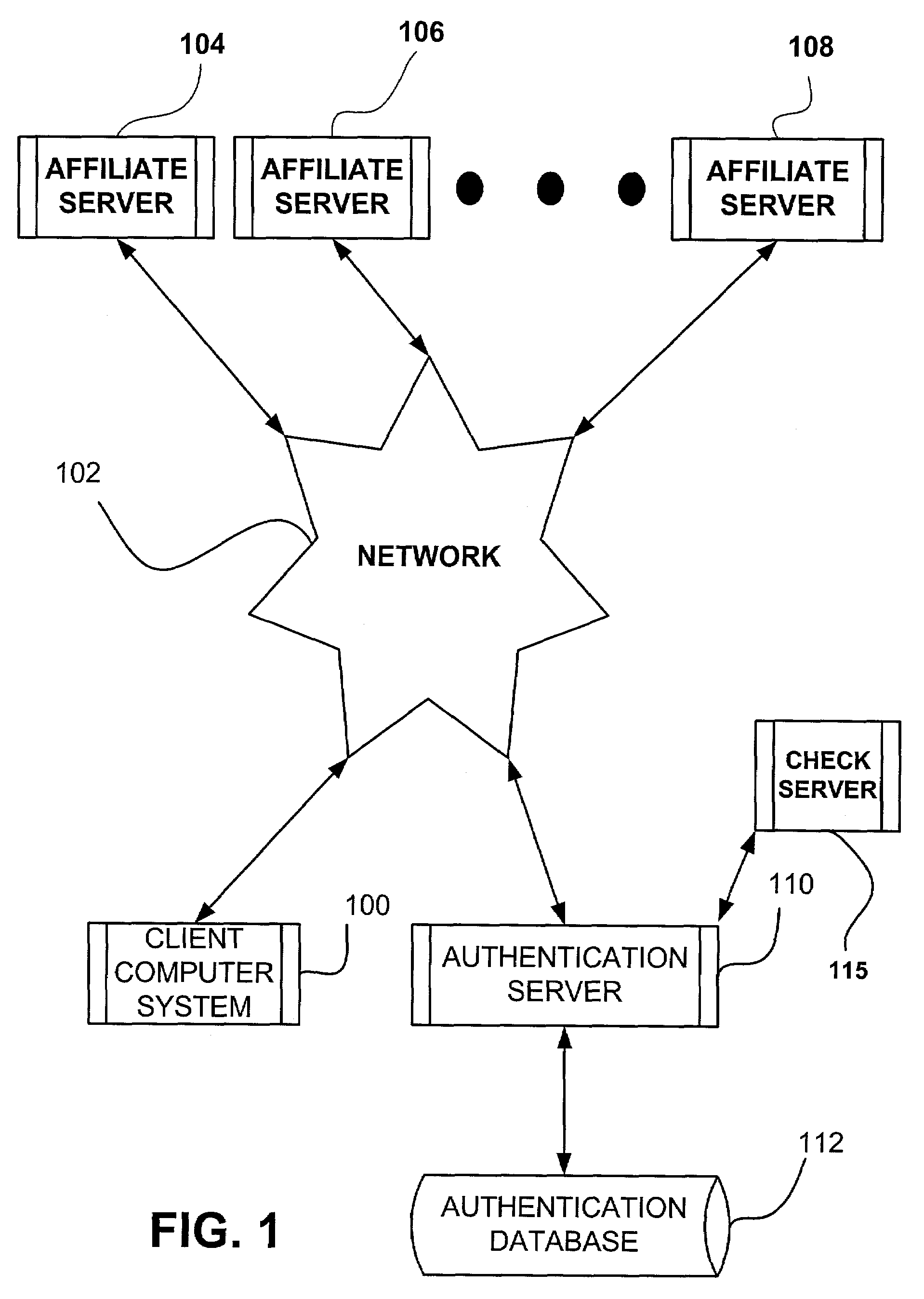
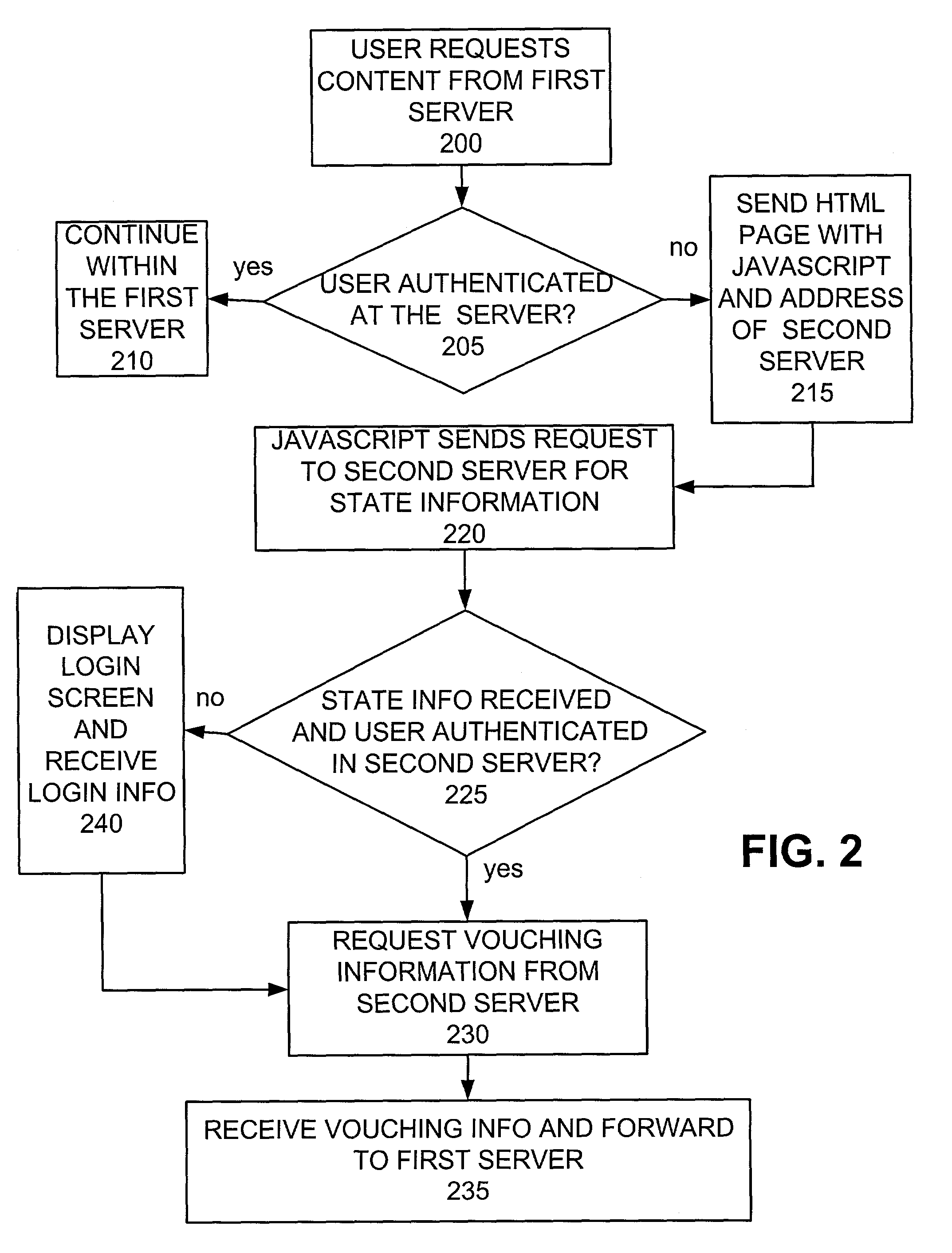
In-line sign in
InactiveUS7251827B1Random number generatorsMultiple digital computer combinationsUser needsInternet privacy
A method of in-line sign in that allows a user to sign into a first server based on a sign-in methodology of a second server is disclosed. The method uses, among other things, a nonce and approved URL list to prevent spoofing and replay attack. Additionally, the method allows error messages that occur during the authentication process to be displayed to the user having the look and feel of the first server, despite using the authentication process of the second server. A method of dual or distributed authentication is also disclosed wherein the user need only to input the login id and password once and wherein the two authentication processes need not exchange the user's password.
Owner:MICROSOFT TECH LICENSING LLC
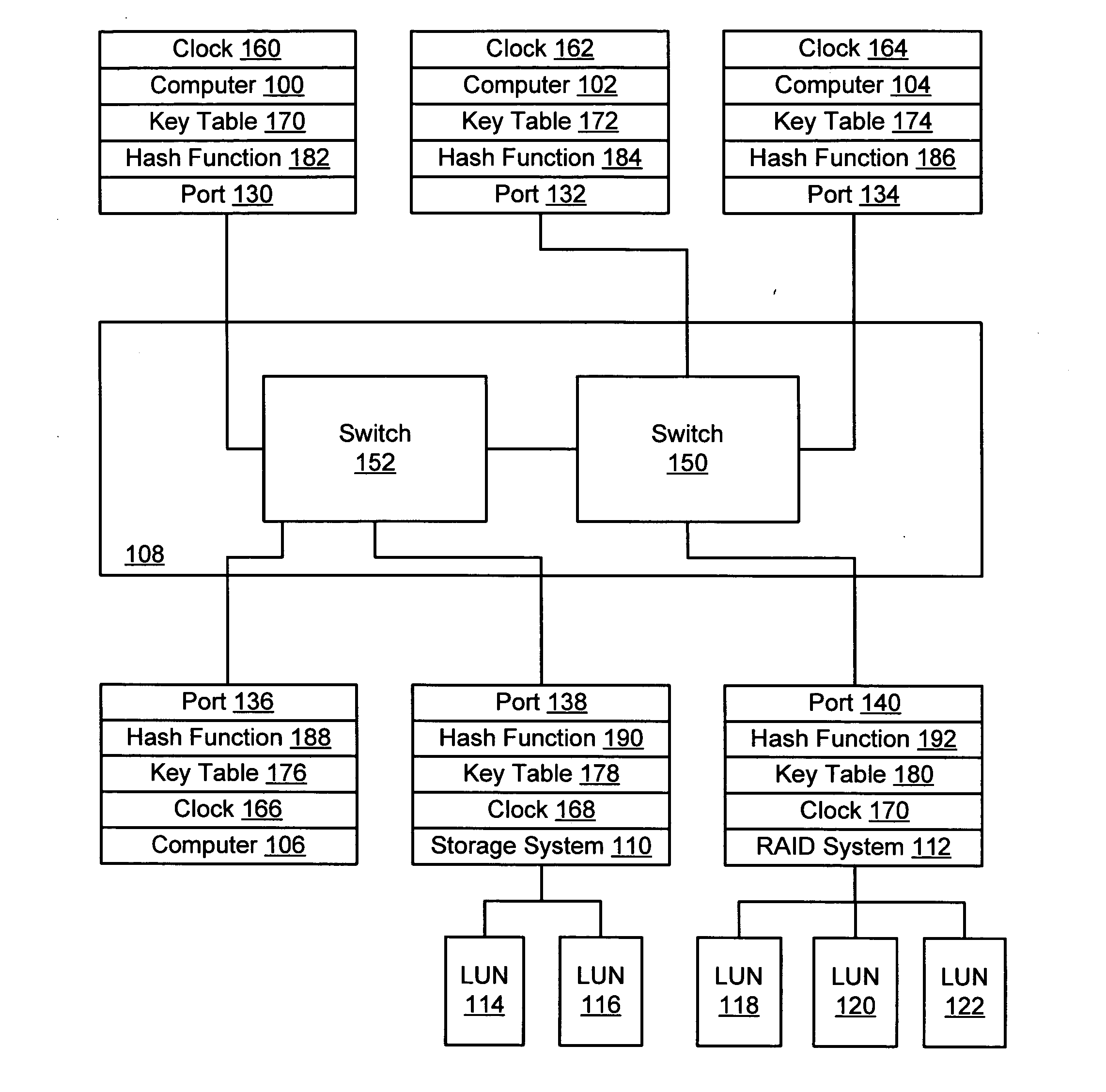
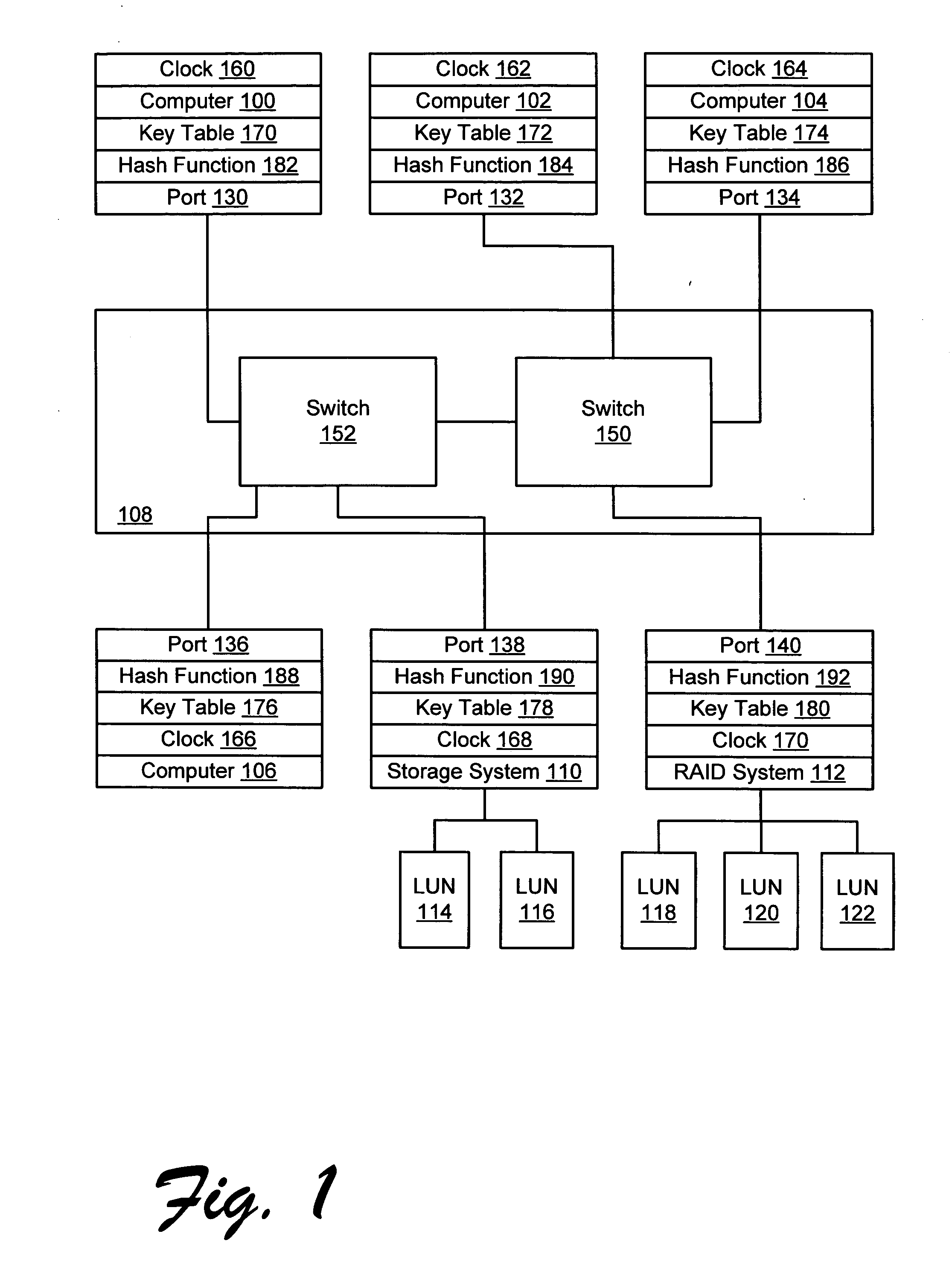
Apparatus and method for implementing spoofing-and replay-attack-resistant virtual zones on storage area networks
InactiveUS20050044354A1Digital data processing detailsUser identity/authority verificationHash functionStorage area network
A storage area network resistant to spoofing attack has several nodes each having a port, and storage area network interconnect interconnecting the ports. Each port is provided with a hash function generator for providing and verifying an authentication code for frames transmitted over the storage area network, and a key table for providing a key to the hash function generator. The authentication code is generated by applying a hash function to the key and to at least an address portion of each frame. In each node, the key is selected from that node's key table according to address information of the frame.
Owner:GOOGLE LLC
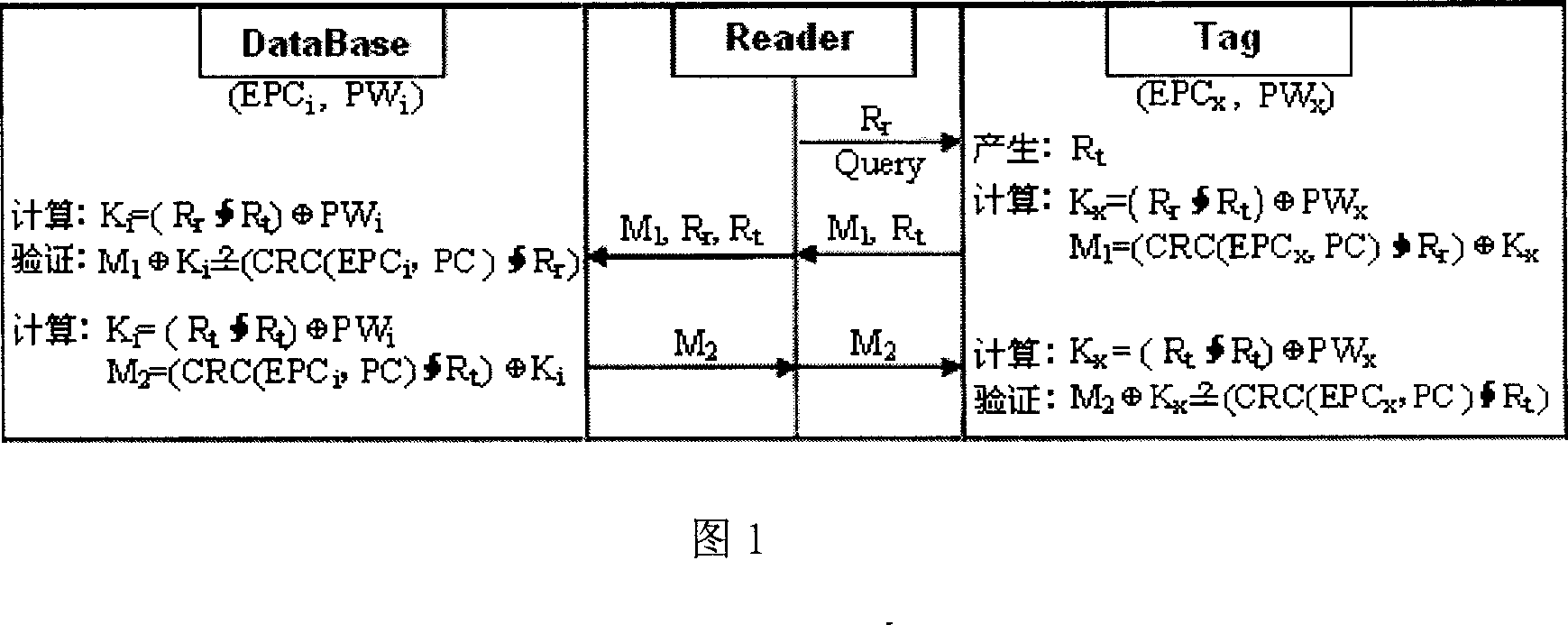
RFID random key two-way certifying method accord with EPC C1G2 standard
InactiveCN101051903AComputationally intensiveLong calculation timeUser identity/authority verificationRecord carriers used with machinesReplay attackRadio-frequency identification
The method satisfies security requirement of wireless communication between tagging reader and tag in radio frequency identification technique according to EPC C1G2 standard. The disclosed security mechanism can prevent masquerading attack, replay attack, and denial of service successfully so as to solve main security problems including privacy, trackability and personal privacy existed in RFID system effectively.
Owner:SUN YAT SEN UNIV
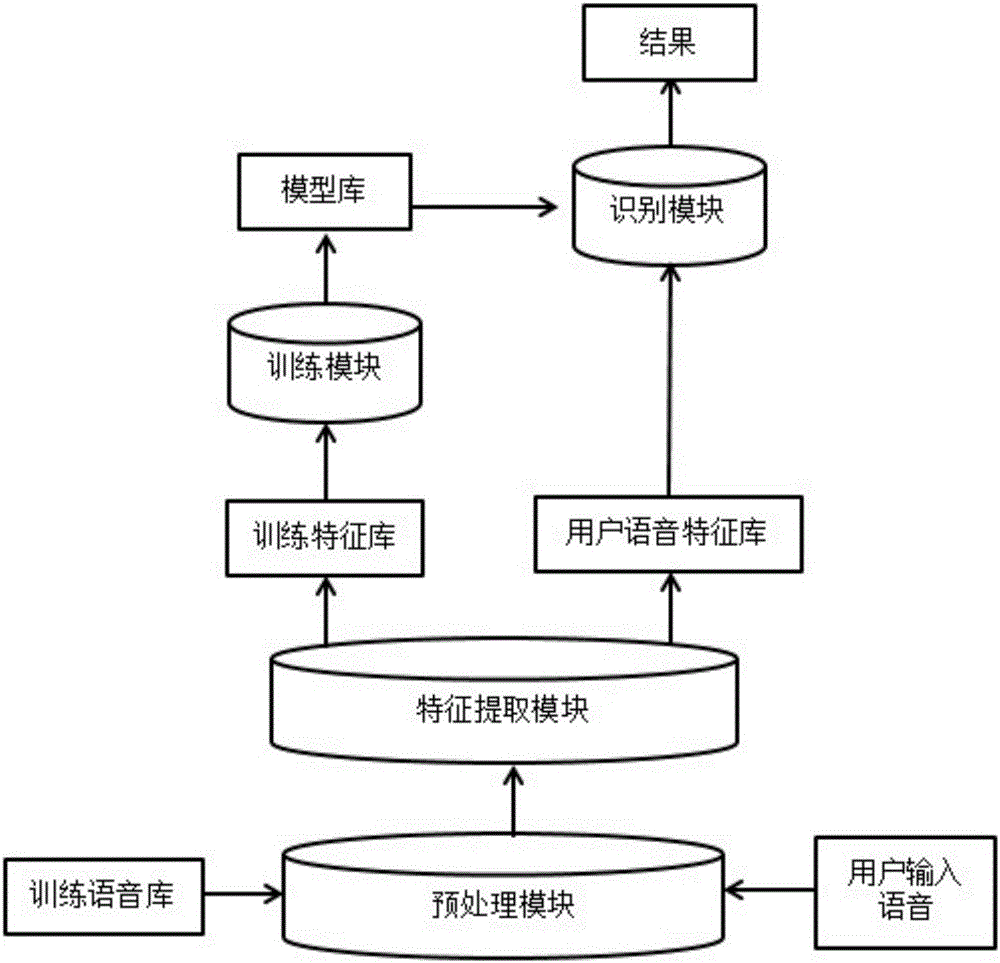
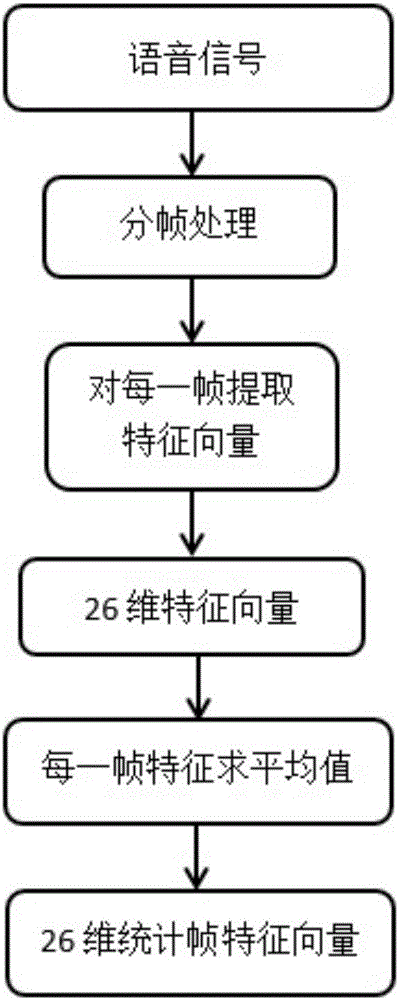
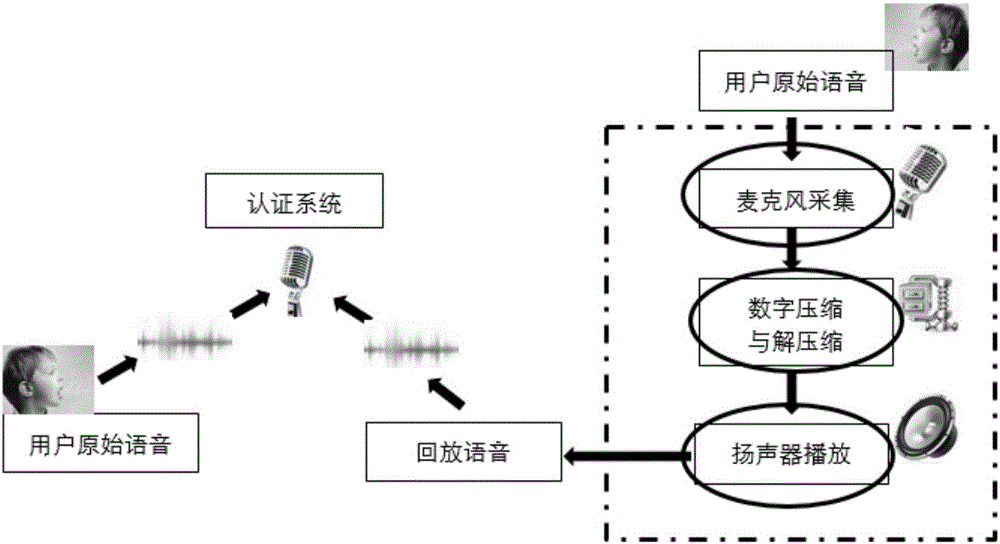
Replay attack detection method based on distortion features of speech signals introduced by loudspeaker
InactiveCN106297772AEfficient detectionSpeech recognitionTransmissionNonlinear distortionFeature vector
The invention discloses a replay attack detection method based on the distortion features of speech signals introduced by a loudspeaker. The method includes the following steps that: speech signals to be detected are pre-processed, and noised speech frames in the speech signals to be detected are reserved; feature extraction is carried out on each noised speech frame in the pre-processed speech signals, so that speech signal linear distortion and nonlinear distortion feature-based feature vectors can be obtained; the average value of the feature vectors of all the noised speech frames is obtained, and statistical feature vectors can be obtained, and the feature model of the speech signals to be detected is obtained; the feature vectors of a training speech sample are extracted, so that a training speech feature model can be obtained, the training speech feature model is utilized to train an SVM (Support Vector Machine model), so that a speech model library can be obtained; and SVM mode matching is performed on the feature model of the speech signals to be detected and the trained speech model library, and a decision result can be outputted. With the replay attack detection method of the invention adopted, real-time and effective detection of replayed speech can be realized.
Owner:WUHAN UNIV
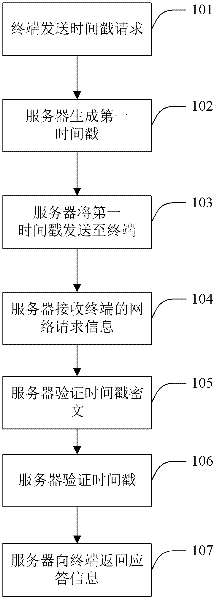
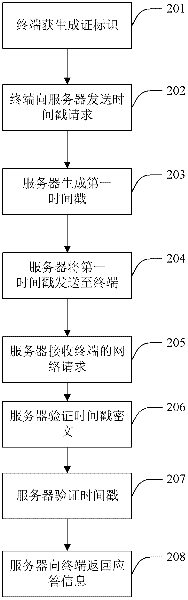
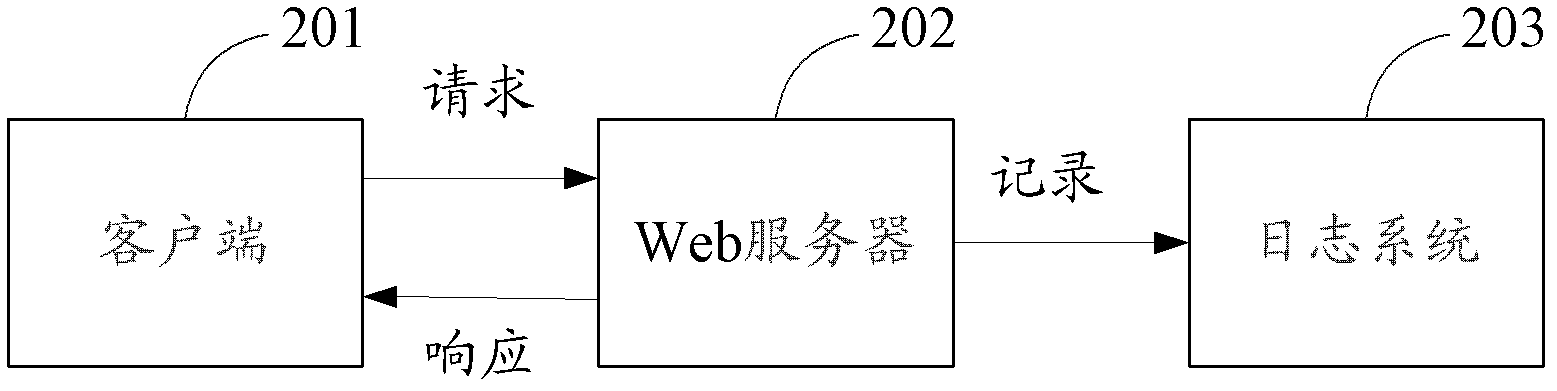
Communication method, server and terminal based on HTTP (Hypertext Transfer Protocol)
The application provides a network communication method, a system, a server and a terminal based on HTTP (Hypertext Transfer Protocol), aiming at resisting replay attack in HTTP network communication. The network communication method comprises the steps of sending a first time stamp to the terminal according to a terminal request; receiving network request information sent by the terminal, wherein the network request information includes the first time stamp and corresponding time stamp ciphertext, and the time stamp ciphertext is generated by encrypting algorithm factor containing the first time stamp according to a preset encryption algorithm at the terminal; and verifying whether the time stamp ciphertext is in effect or not according to the preset encryption algorithm, if no, judging the network request information is an invalid request. By verifying the validity and effectiveness of the time stamp ciphertext containing time stamp information, the possibility that the time stamp information in the network request is tampered can be further prevented, and occurrence of network replay attack can be avoided.
Owner:BEIJING QIHOO TECH CO LTD
Authentication in a packet data network
InactiveUS7512796B2Key distribution for secure communicationUnauthorised/fraudulent call preventionTelecommunications networkSession key
Owner:NOKIA CORP
Safety test system and method
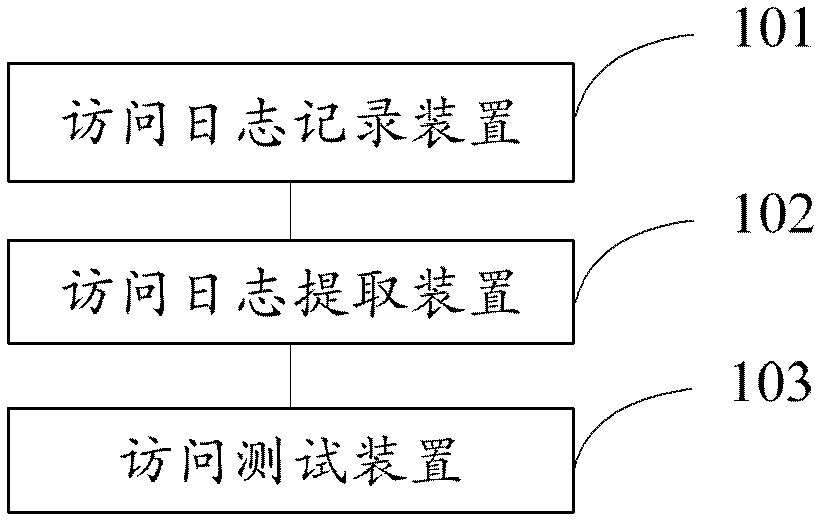
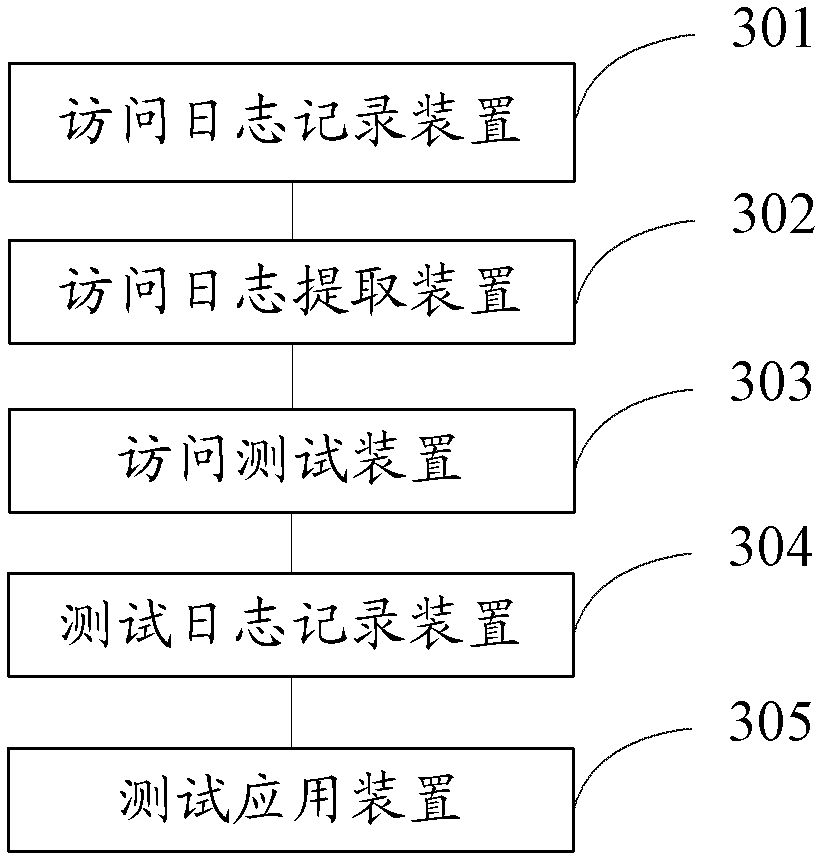
ActiveCN103023710ASave human resourcesImprove logic coveragePlatform integrity maintainanceData switching networksTest scriptLogbook
The application provides a safety test system and method. The system specifically comprises a visiting log recording device, a visiting log extraction device and a visiting test device, wherein the visiting log recording device aims at an on-line application program, the characteristic data of a user visiting request is preserved in a visiting log record, and the user visiting request comprises a normal visiting request and an abnormal request; the visiting log extraction device is used for extracting a visiting log record corresponding to the abnormal visiting request from the visiting log record of the on-line application program; and the visiting test device is used for using an obscuring test script to replay and attack the abnormal visit request and cam judge whether a loop hole exists according to the returned respondence. The safety test system and the method provided by the application can reduce the consumed substantive machine resources and manpower resources by safety test, and business logic coverage rate of the safety test is improved.
Owner:ALIBABA GRP HLDG LTD
Authentication in a packet data network
InactiveUS20070060106A1Key distribution for secure communicationUnauthorised/fraudulent call preventionTelecommunications networkSession key
Owner:NOKIA CORP
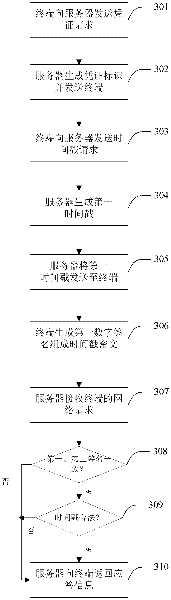
Authentication method for preventing replay attack
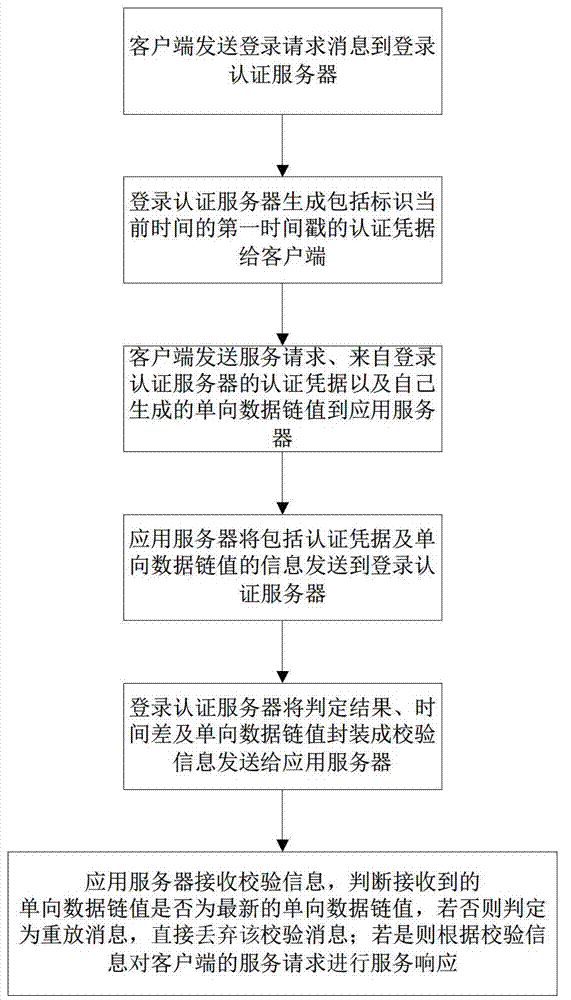
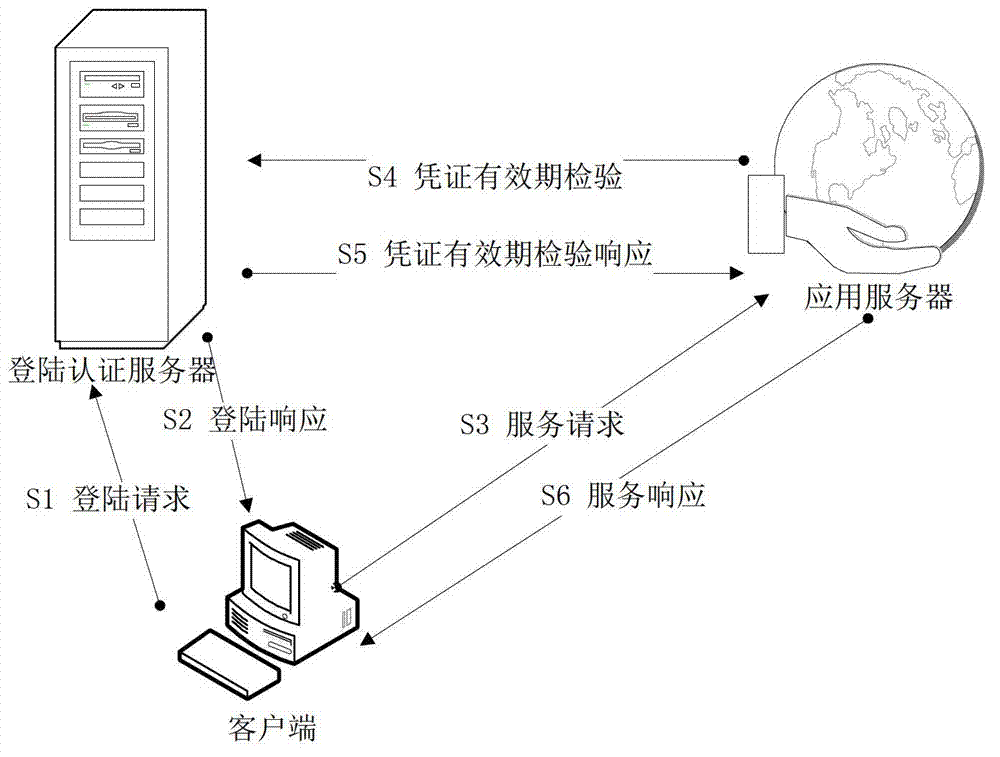
ActiveCN102739659ALegitimate service requests are immune to replay attacksGuaranteed accuracyTransmissionApplication serverAuthentication server
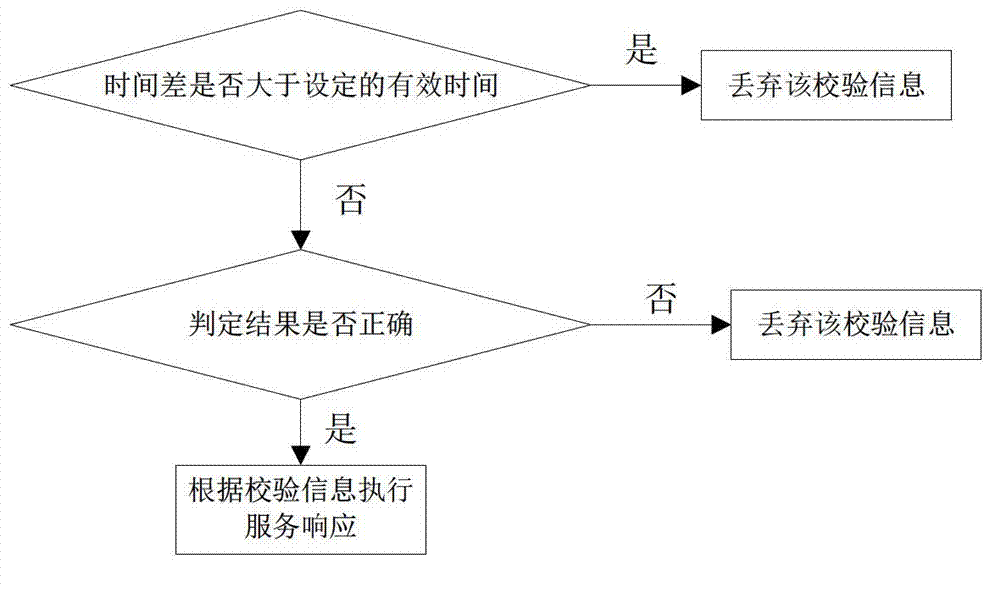
The invention discloses an authentication method for preventing a replay attack. The method comprises the following steps of transmitting an authentication evidence and service requests to an application server, wherein the authentication evidence is acquired from a login authentication server by a client side and is provided with a first time stamp; identifying the sequence of the user requests by using a unidirectional data chain; calculating the time difference between the current time and the first time stamp at the login authentication server end; packaging a judging result, the time difference and a unidirectional data chain value into verification information; and transmitting the verification information to the application server, wherein the application server judges whether the verification information is replay information or not according to the received unidirectional data chain value, and furthermore, whether the service requests are authenticated within effective time or not can be judged according to the time difference and the judging result. Time is not required to be synchronous, so that the complexity of the system or a protocol is avoided, and the delay caused by synchronization of time is also avoided. The probability that the user requests undergo the replay attack is avoided through the application of the unidirectional data chain.
Owner:SOUTH CHINA NORMAL UNIVERSITY +1
Method and system for pre-authentication
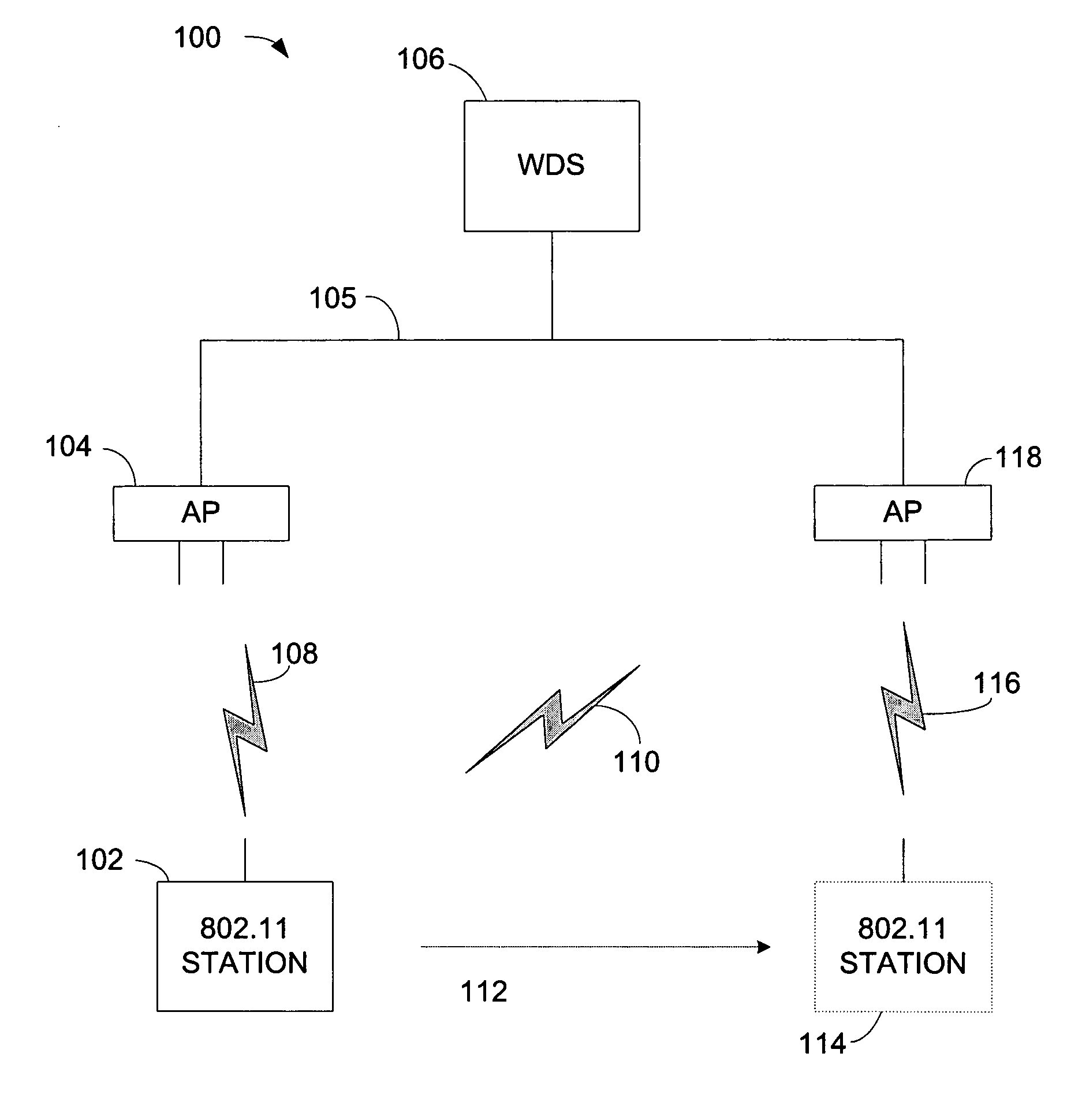
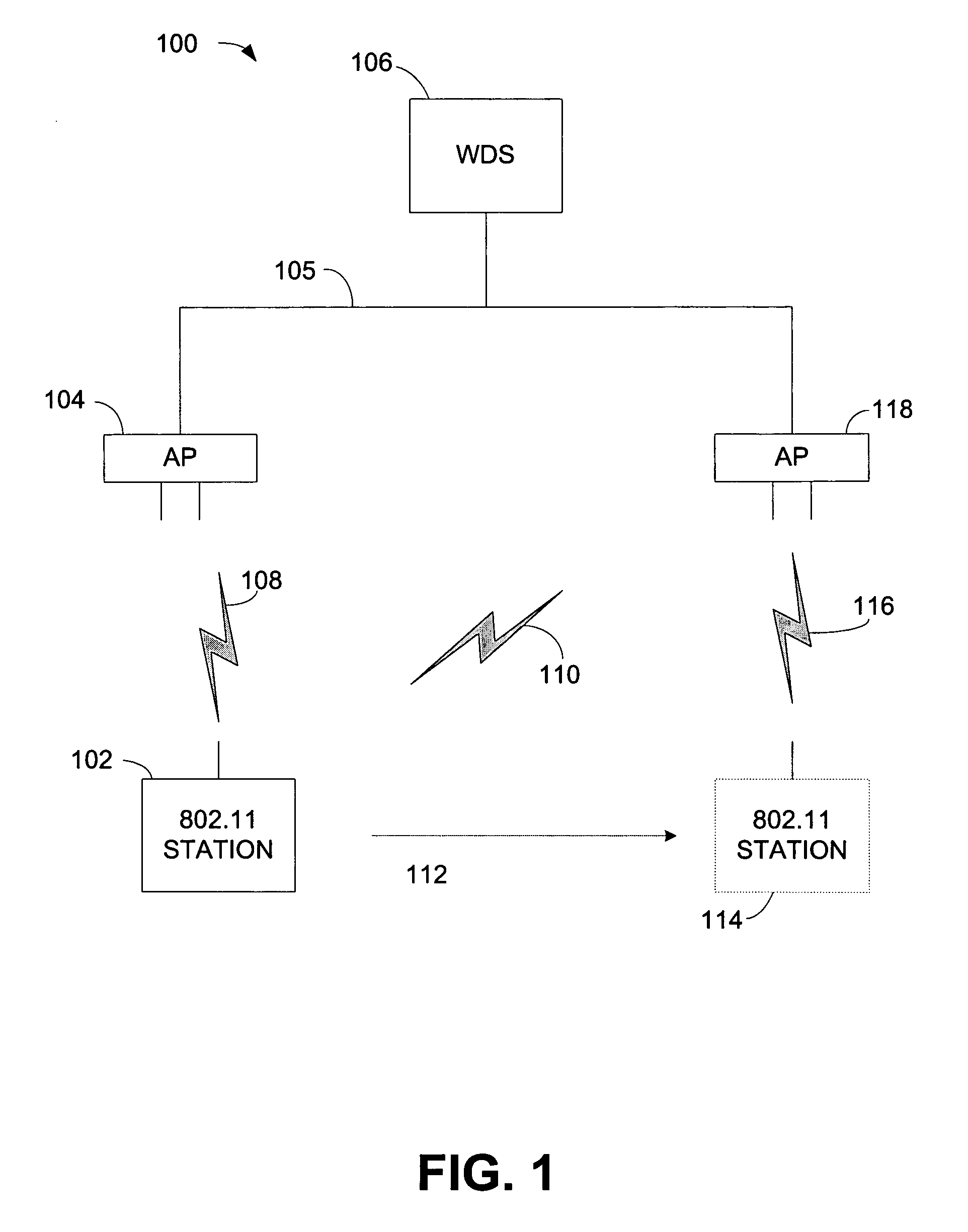
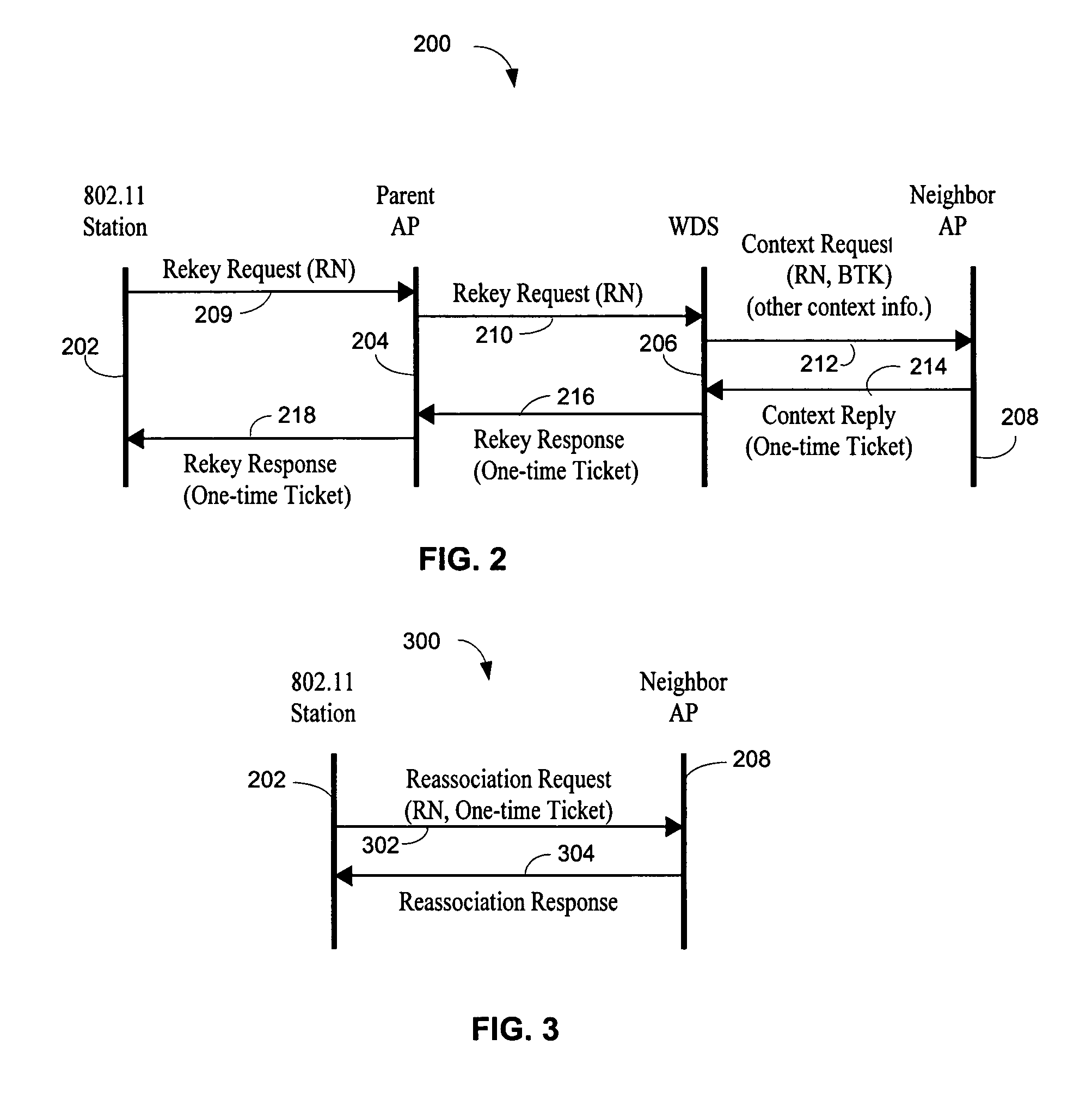
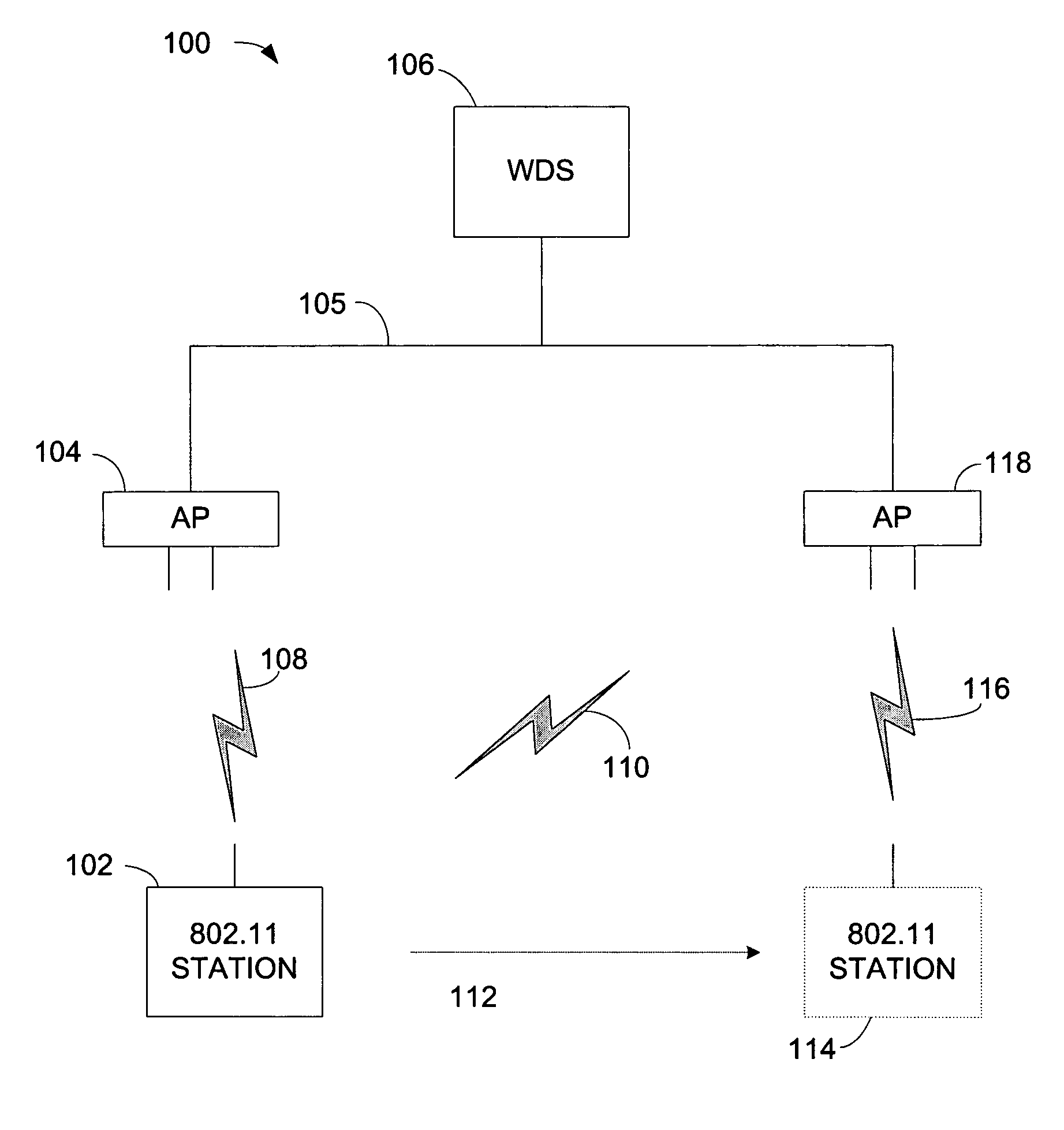
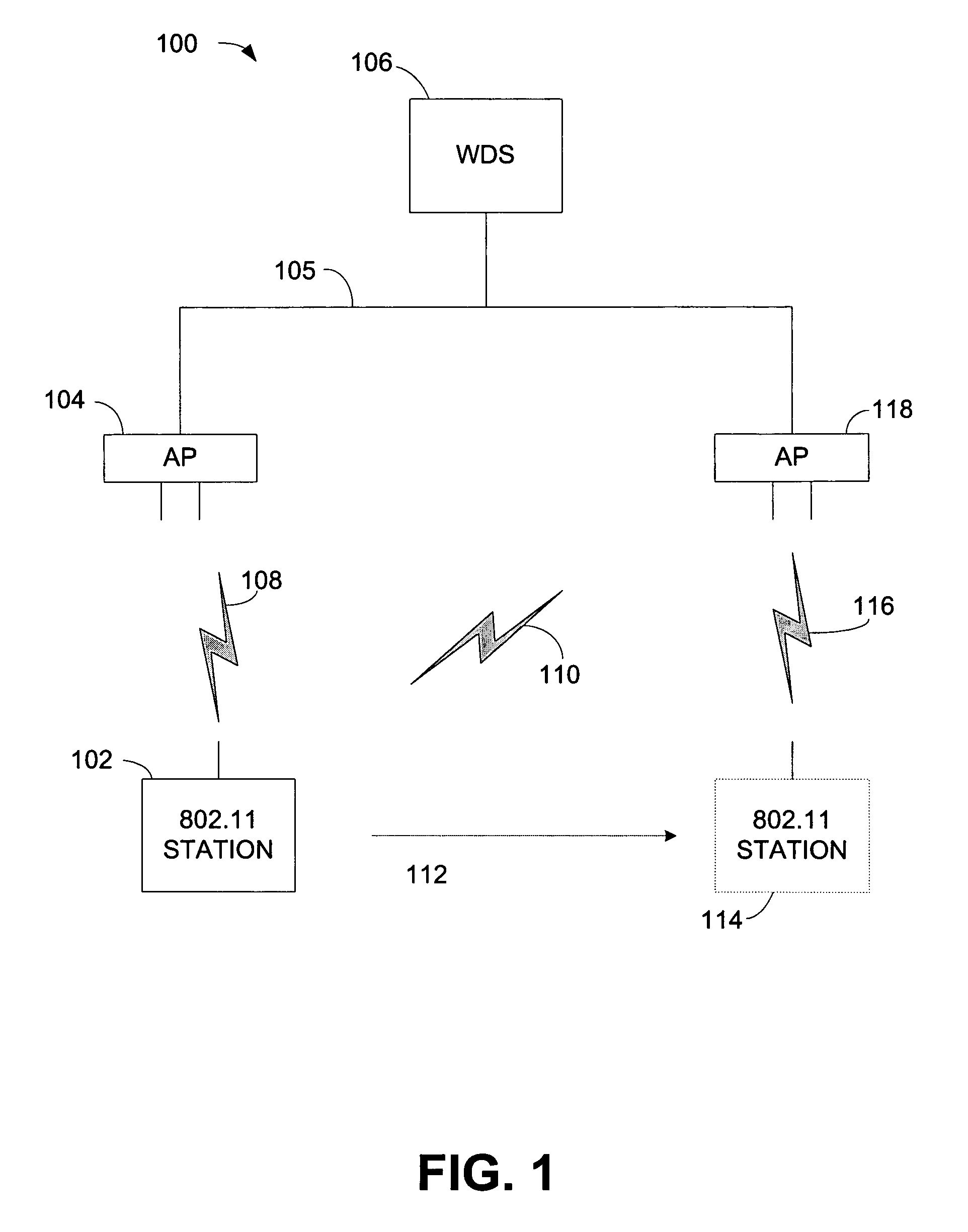
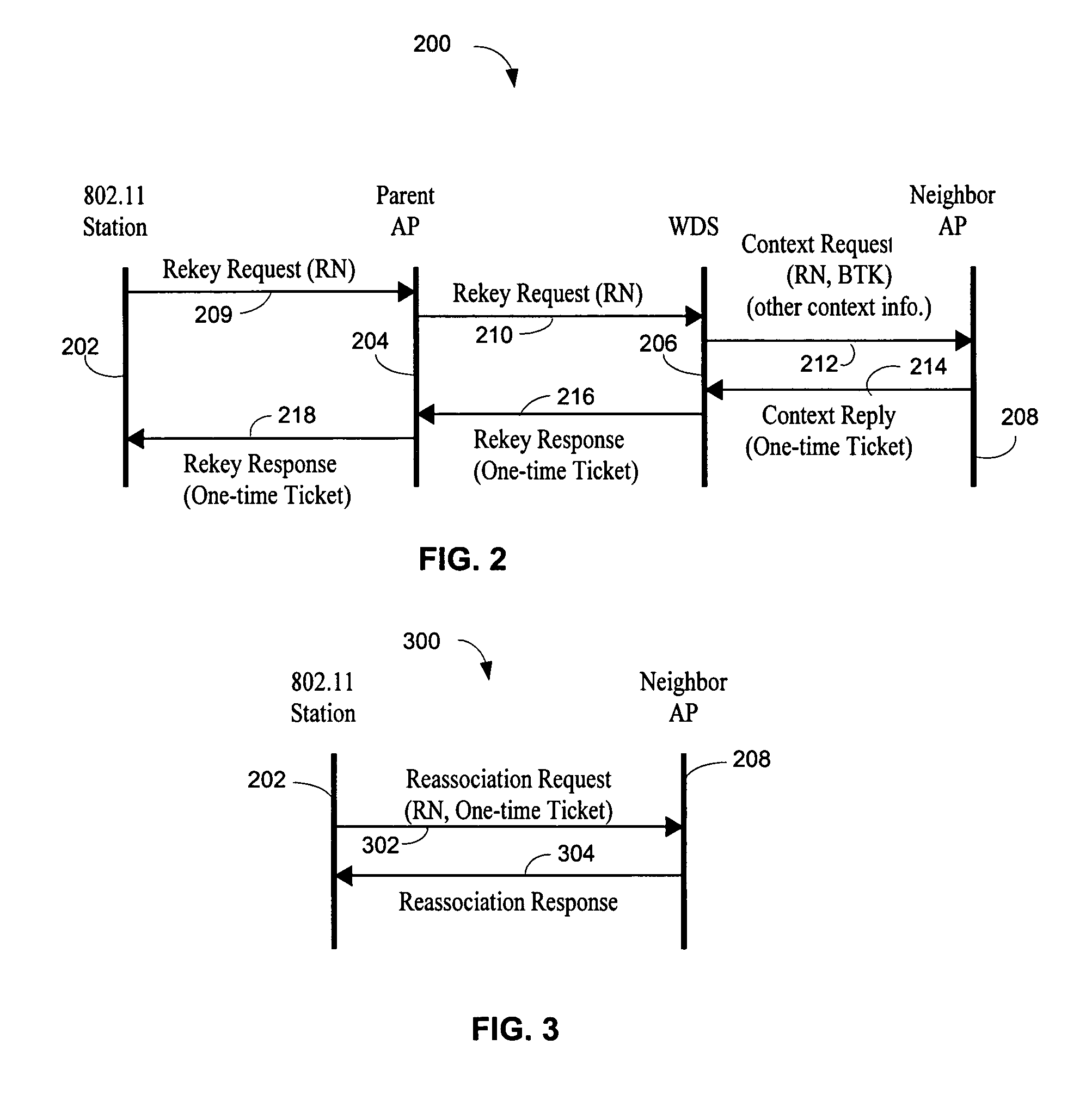
ActiveUS20060013398A1Quick buildReduce in quantityUser identity/authority verificationNetwork topologiesSecure communicationTelecommunications
A wireless station prepares to roam by pre-authenticating itself with a neighboring access point. The wireless station sends a rekey request, which can include an incremented rekey number. The wireless station receives a rekey response. The rekey response can include the incremented rekey number. Because the wireless station is pre-authenticated, after it roams it only needs to perform a two-way handshake with a new access point to establish secure communications with the new access point. The two-way handshake starts by the wireless station sending a reassociation request to the neighboring access point, the reassociation request comprising the incremented rekey number established during pre-authentication. The wireless station receives a reassociation response from the neighboring access point. To protect against replay attacks, the neighboring access point can verify the rekey number sent in the reassociation request matches the rekey number sent in the rekey response.
Owner:CISCO TECH INC
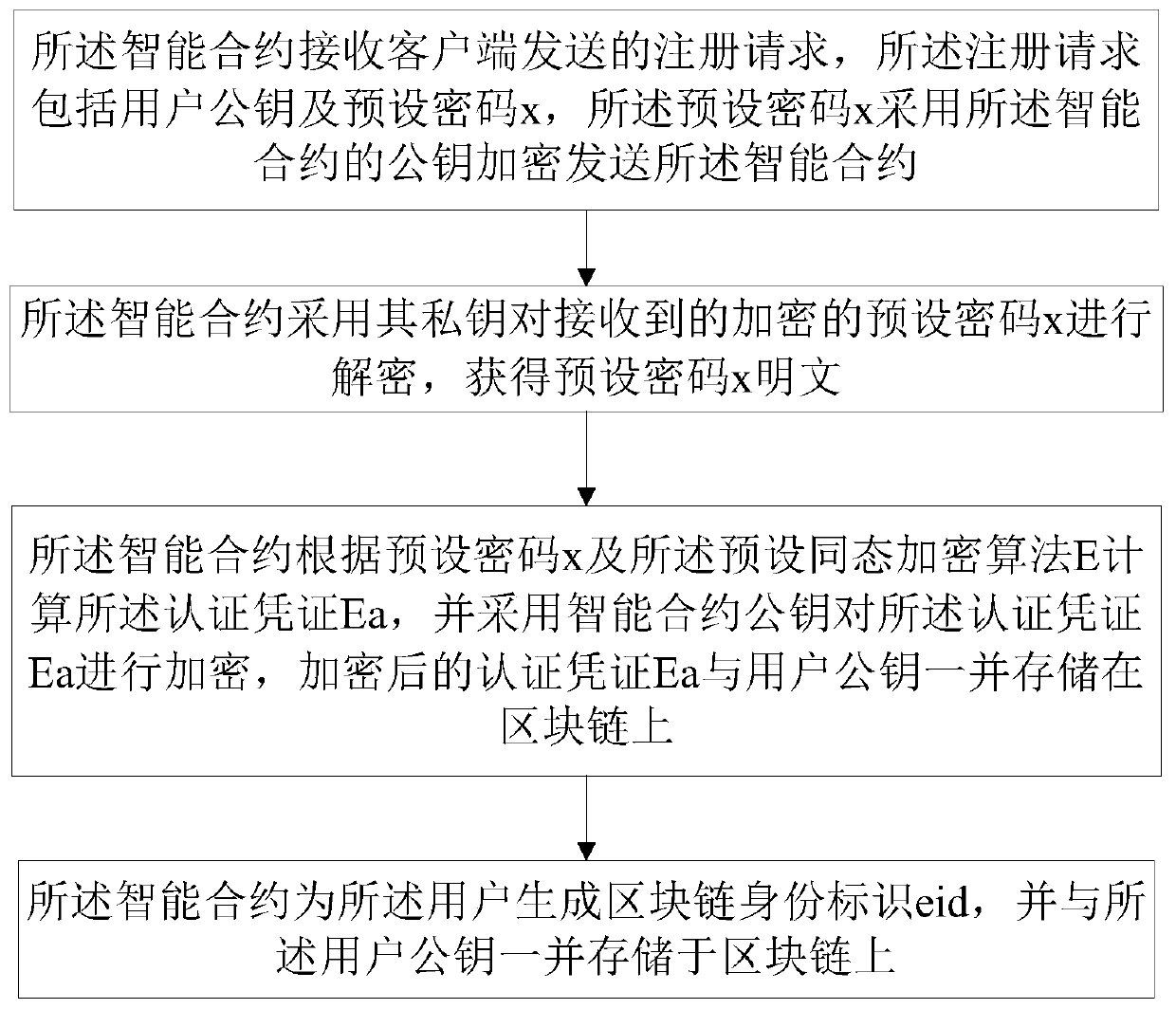
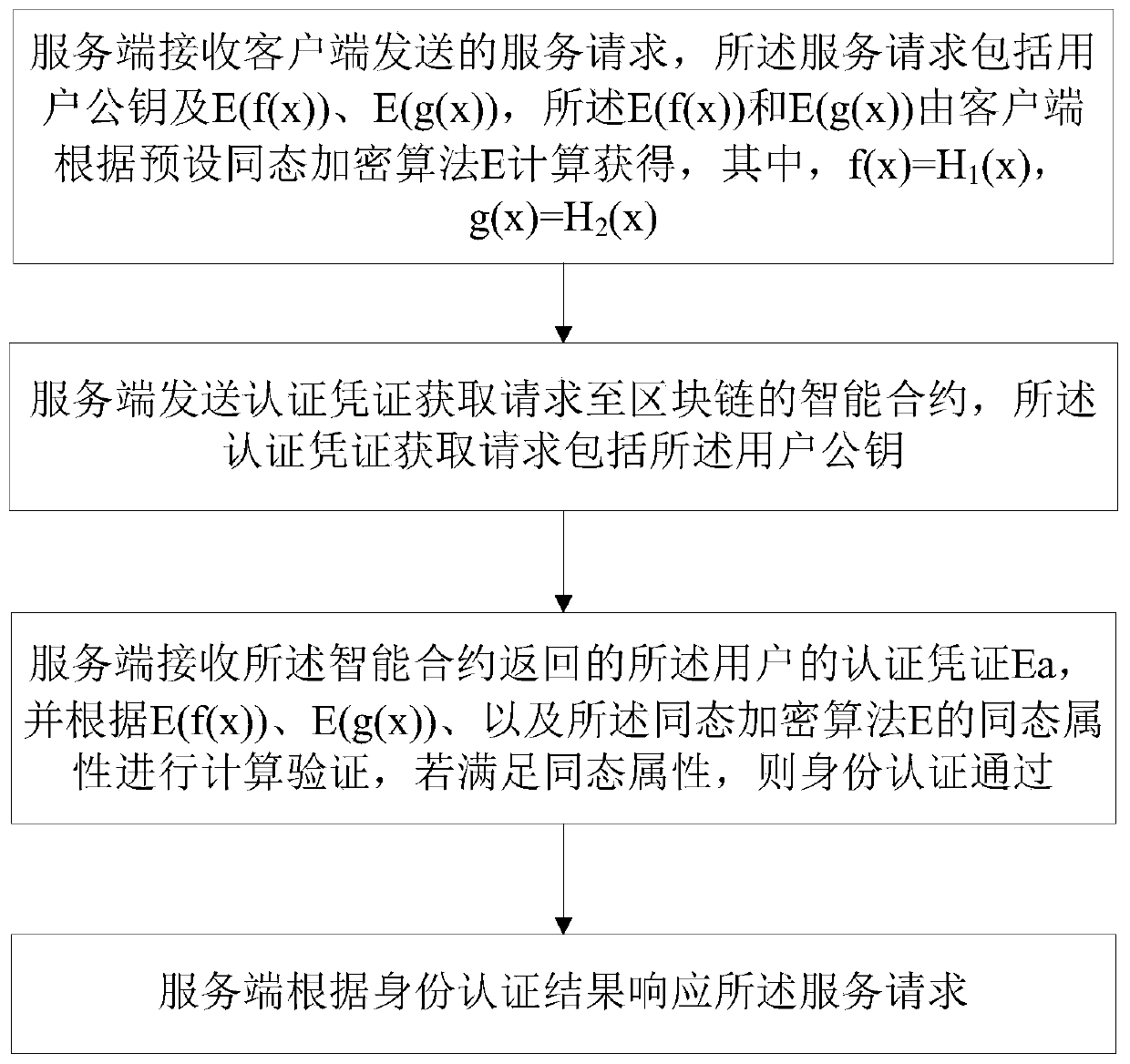
A blockchain-based identity authentication method and a blockchain-based identity authentication system
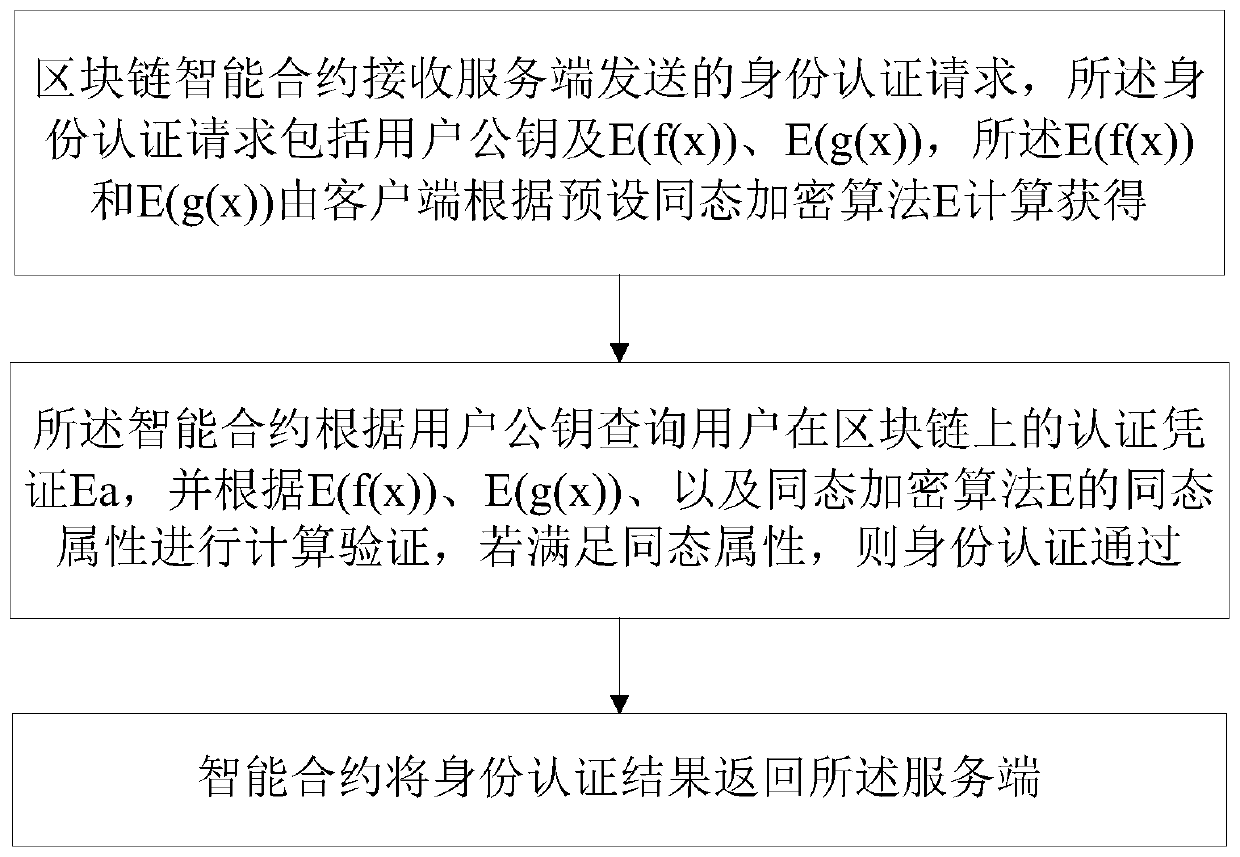
ActiveCN109922077AGuaranteed not to movePrevent leakageSecuring communicationSmart contractClient-side
The invention relates to a blockchain-based identity authentication method and a blockchain-based identity authentication system. The identity authentication method based on the block chain comprisesthe following steps that an intelligent contract of the block chain receives an identity authentication request sent by a server side, the identity authentication request comprises a user public key and E(f (x)), and the E(g (x)), the E(f (x)) and the E(g (x)) are obtained through calculation by a client side according to a preset homomorphic encryption algorithm E; the intelligent contract inquires an authentication certificate Ea of the user on the block chain according to the public key of the user, carries out calculation and verification according to E (f (x)) , E (g (x)) and the homomorphic attribute of a homomorphic encryption algorithm E, and passes identity authentication if the homomorphic attribute is met; and the smart contract returns the identity authentication result to theserver. The method has the beneficial effects that based on the characteristics of the block chain, the threats of replay attacks and violent cracking can be resisted, so that the attack cost is increased. By utilizing a homomorphic encryption attribute equation, the nizk can be constructed, and under the condition that an original credential for user identity authentication is not leaked, the user is proved to have the credential, so that the identity of the user is proved.
Owner:朗新数据科技有限公司
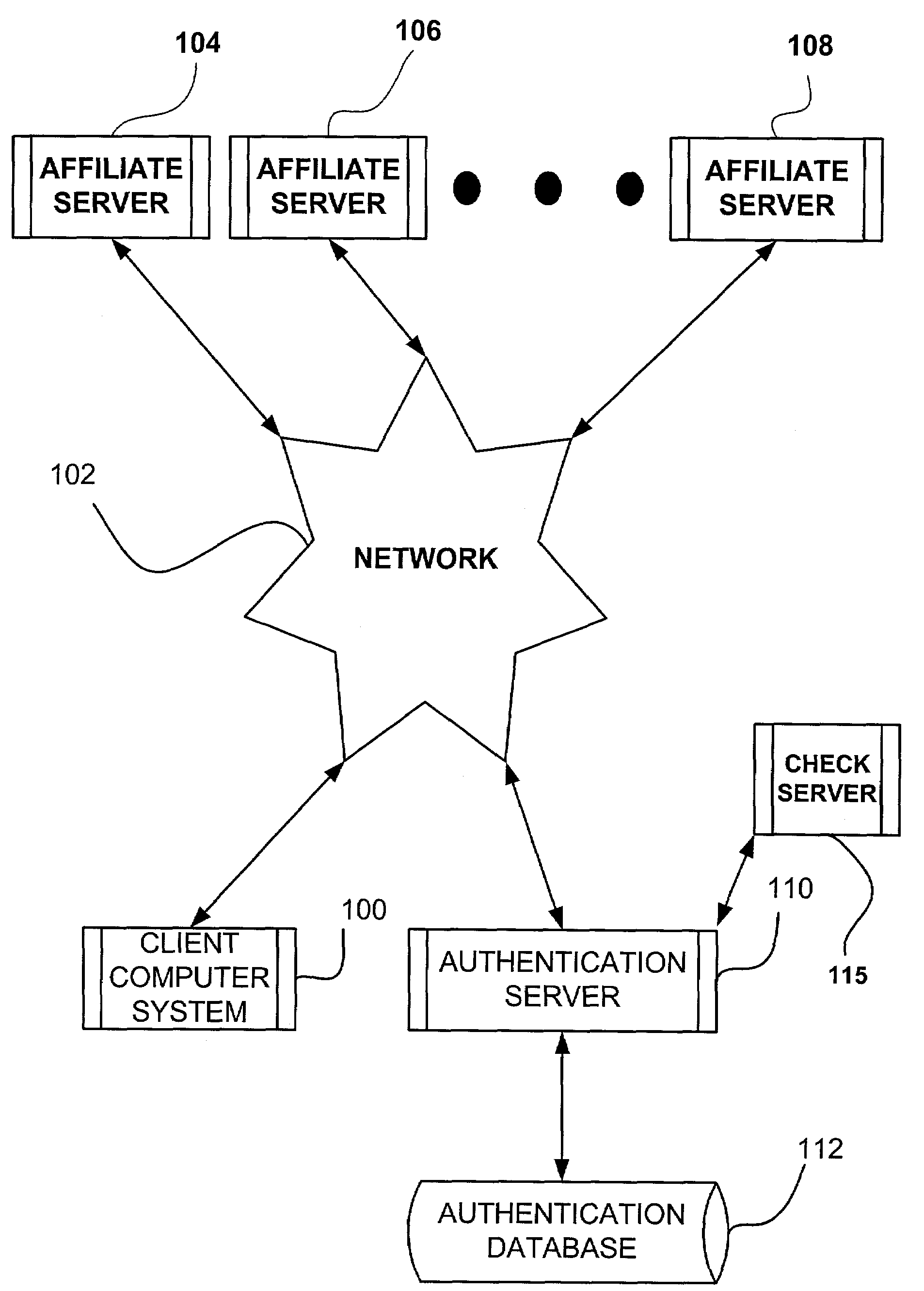
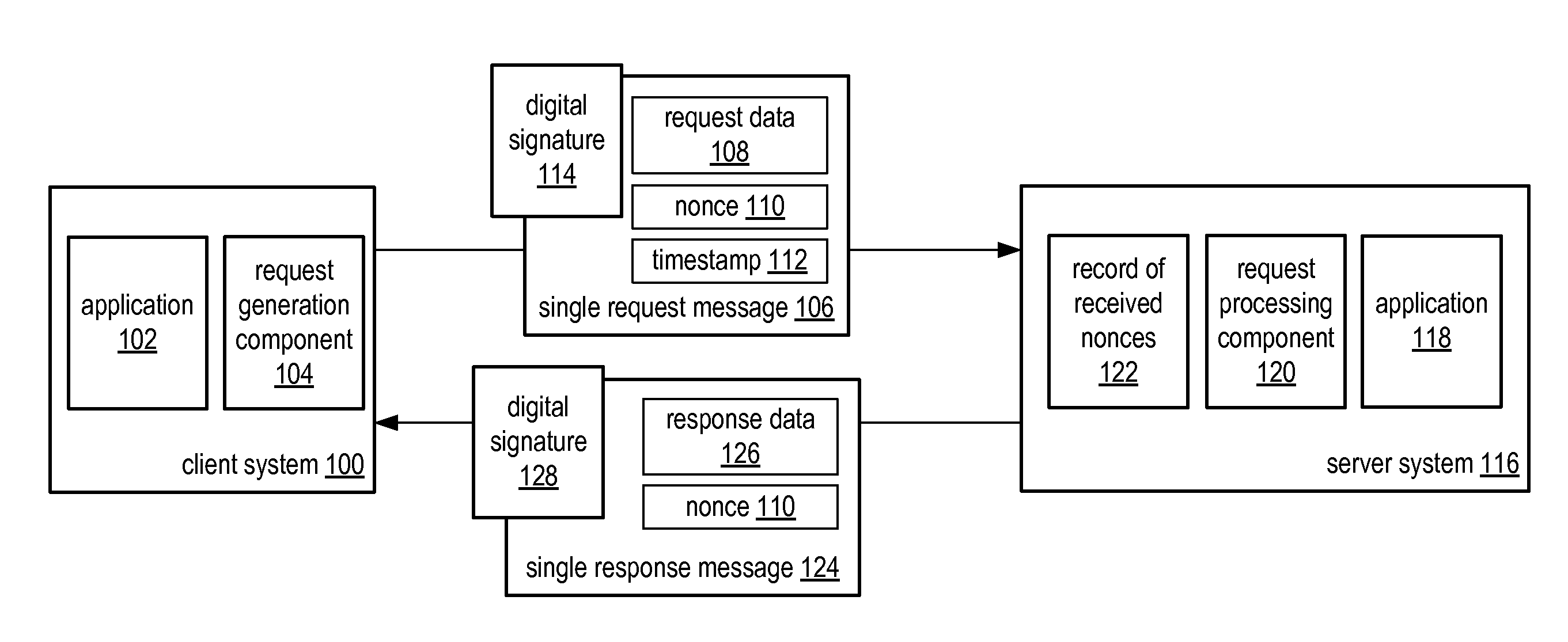
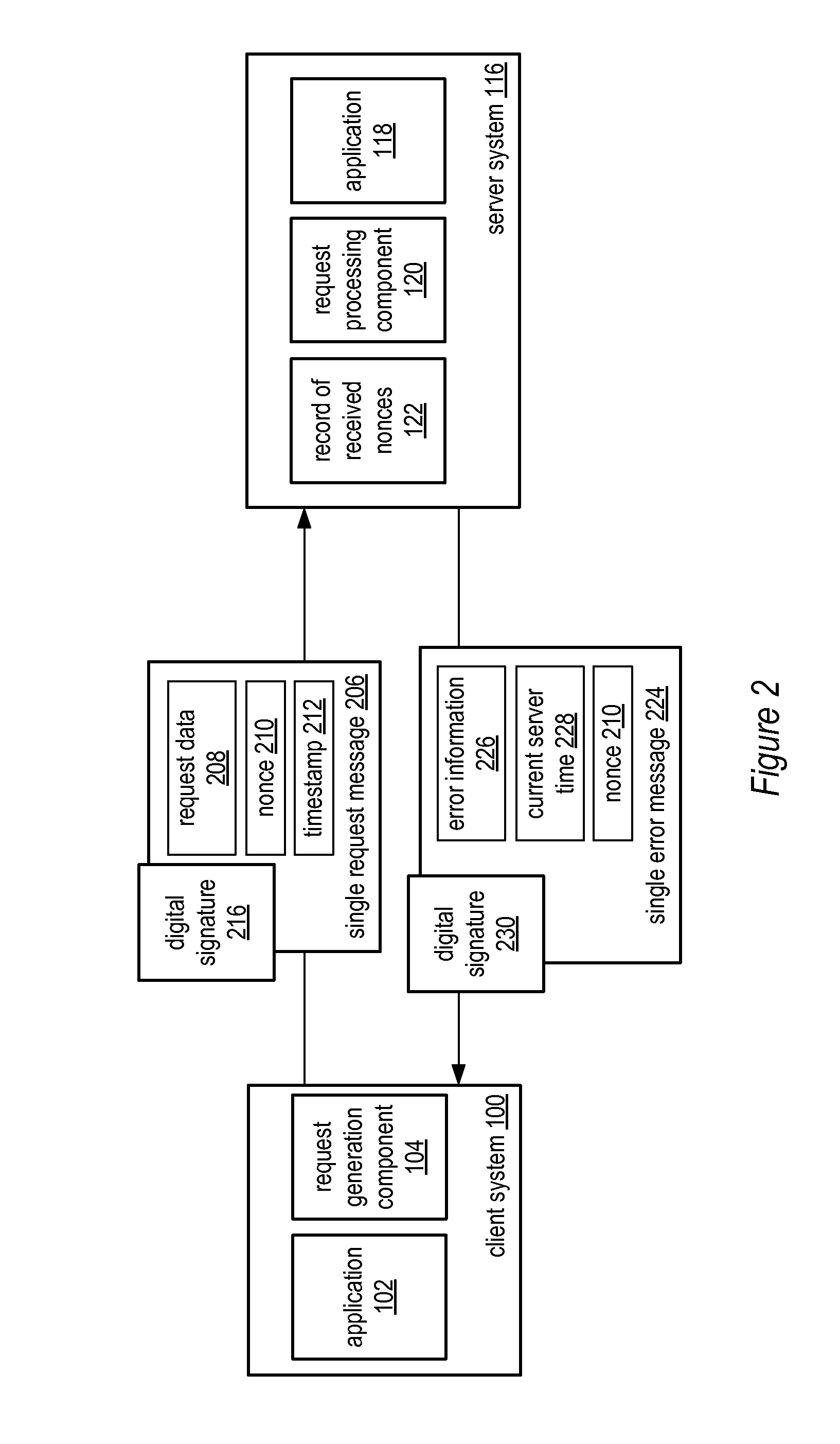
System and method for a single request—single response protocol with mutual replay attack protection
Various embodiments of a system and method for a single request—single response protocol with mutual replay attack protection are described. Embodiments may include a system that receives multiple single request messages, each of which may include a respective nonce, timestamp, and digital signature. The system may create a record of previously received nonces that, at any given time, may include multiple message nonces received within a valid period of time prior to that given time. To validate a given single request message the system may verify the digital signature of the that message, determine that the timestamp of that message indicates a time within the valid period of time prior to the current time, and determine the nonce of the that message is not present within the record of previously received nonces. The system may send a single response message that includes the same nonce as the validated message.
Owner:ADOBE SYST INC
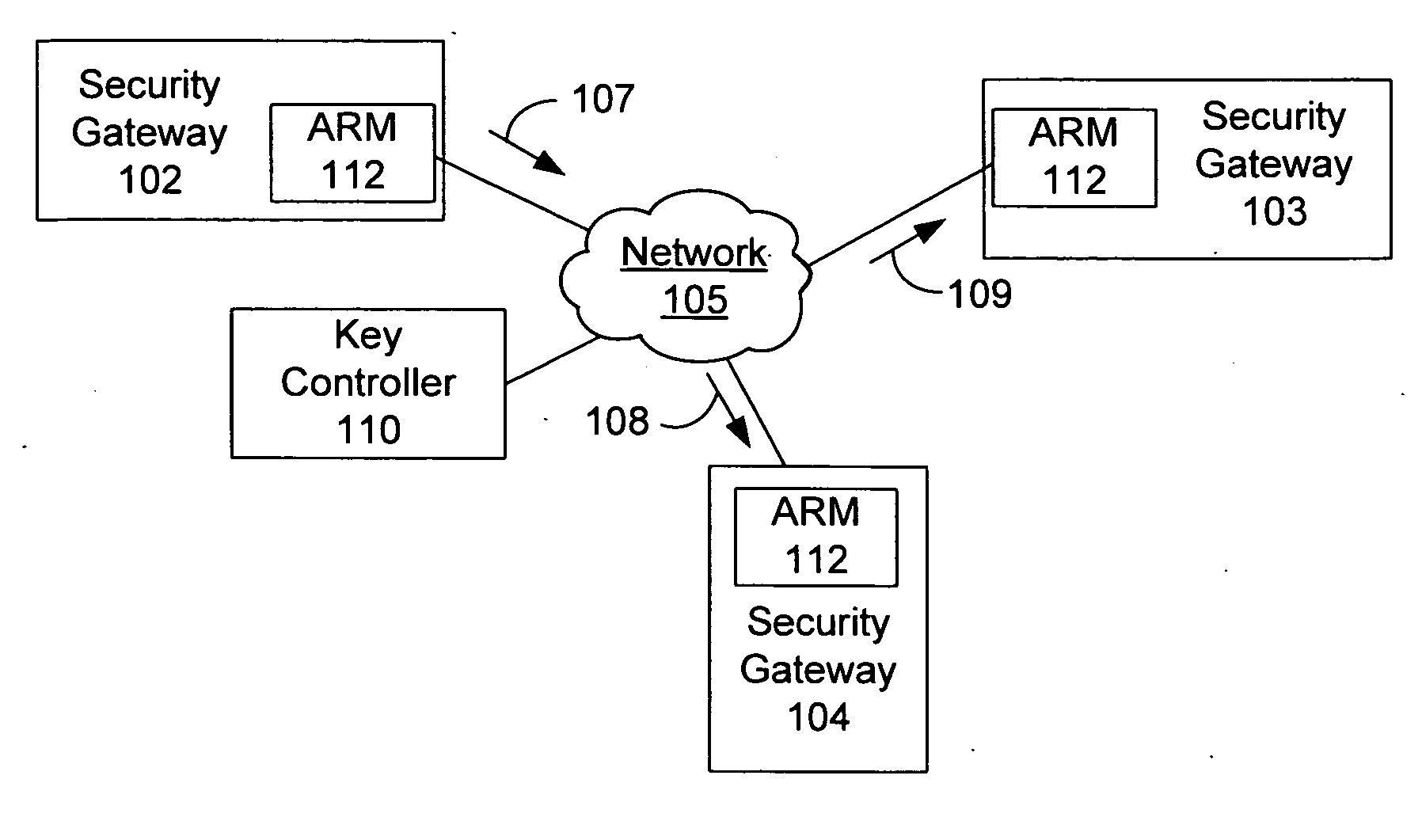
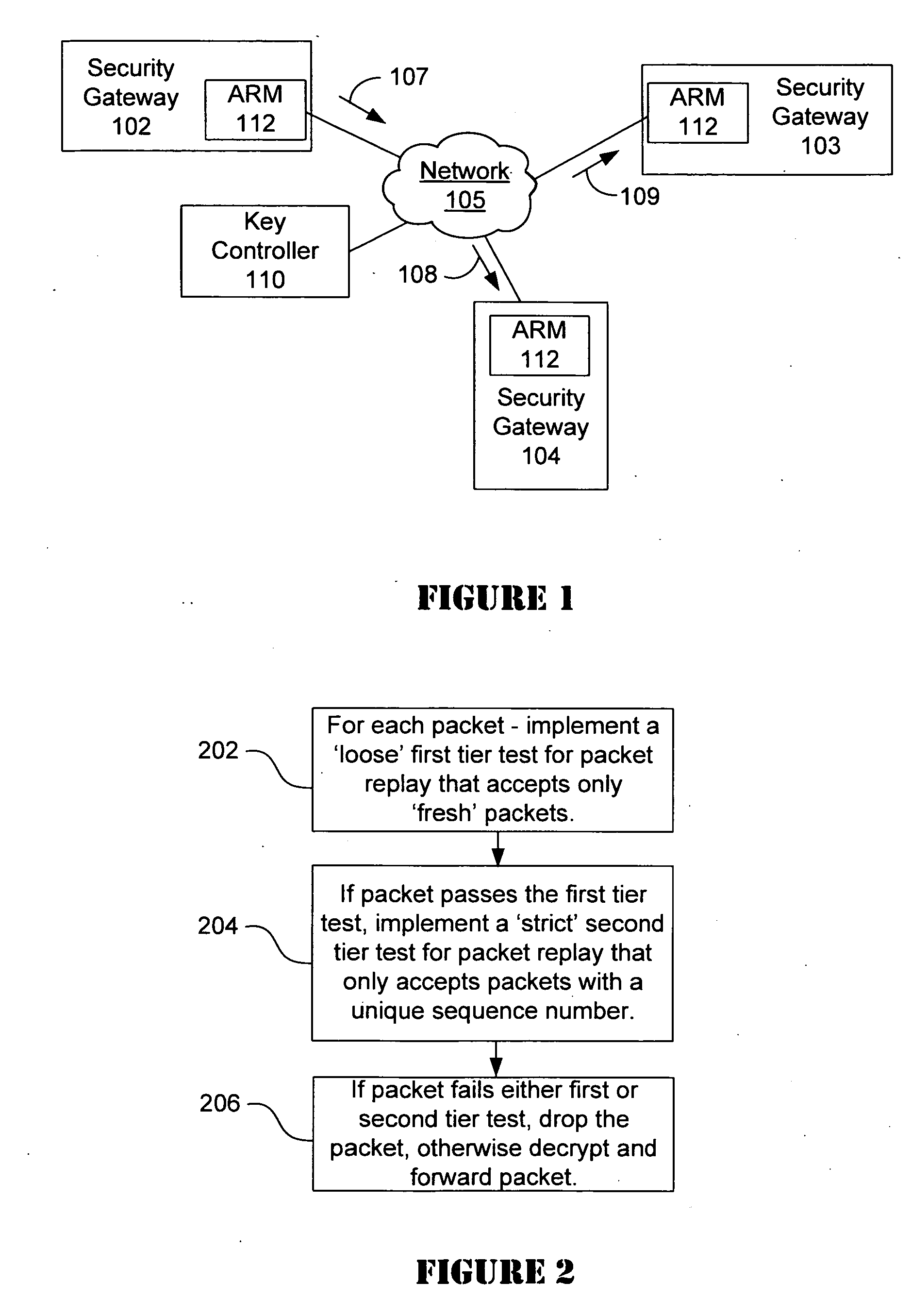
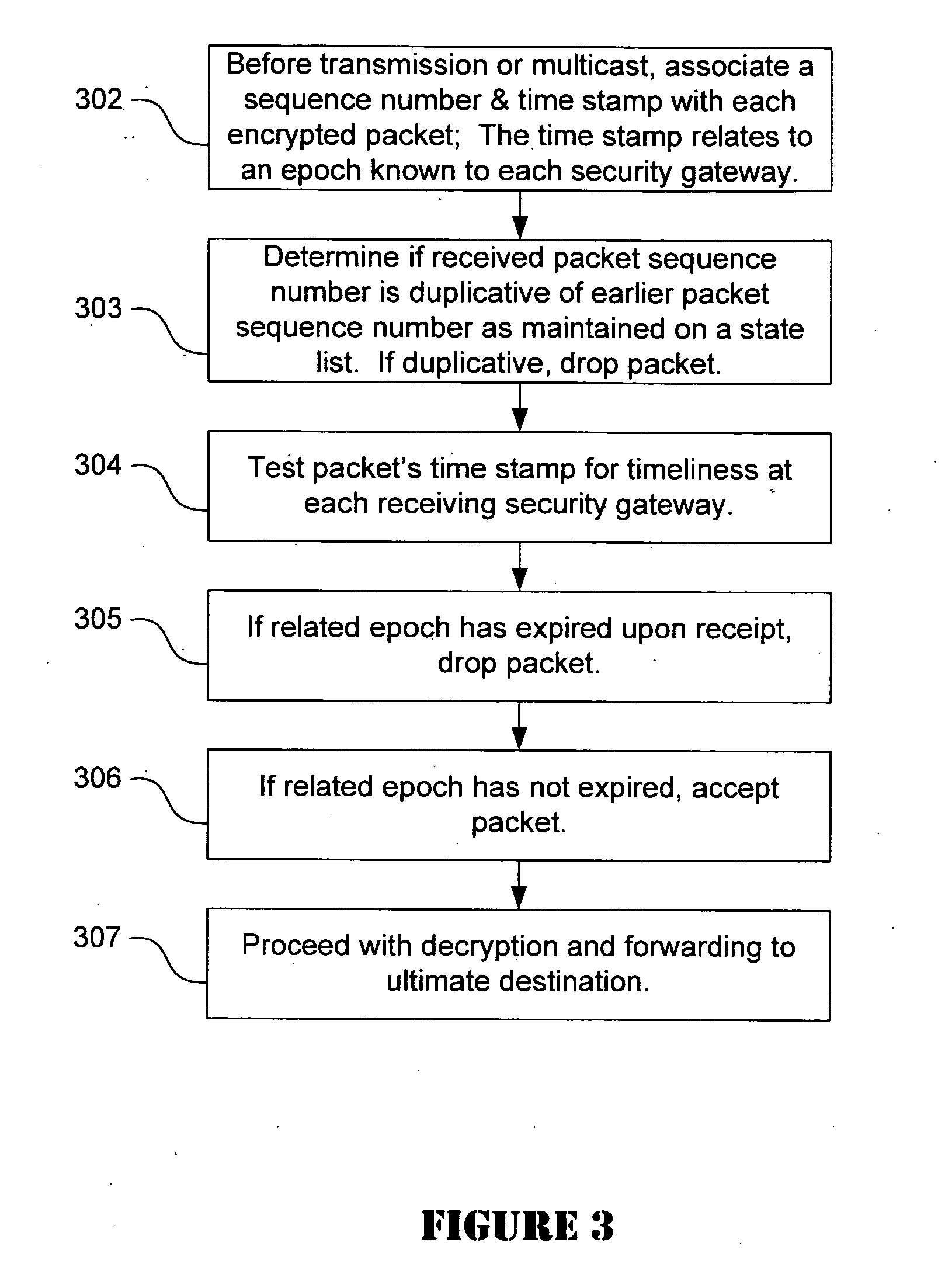
Strong anti-replay protection for IP traffic sent point to point or multi-cast to large groups
Owner:CISCO TECH INC
Method and system for pre-authentication
ActiveUS7451316B2Reduce in quantityAdd any extra messaging overheadUser identity/authority verificationNetwork topologiesSecure communicationTelecommunications
A wireless station prepares to roam by pre-authenticating itself with a neighboring access point. The wireless station sends a rekey request, which can include an incremented rekey number. The wireless station receives a rekey response. The rekey response can include the incremented rekey number. Because the wireless station is pre-authenticated, after it roams it only needs to perform a two-way handshake with a new access point to establish secure communications with the new access point. The two-way handshake starts by the wireless station sending a reassociation request to the neighboring access point, the reassociation request comprising the incremented rekey number established during pre-authentication. The wireless station receives a reassociation response from the neighboring access point. To protect against replay attacks, the neighboring access point can verify the rekey number sent in the reassociation request matches the rekey number sent in the rekey response.
Owner:CISCO TECH INC
Method and user equipment (UE) for reconnecting rrc connection with radio access network (RAN) node
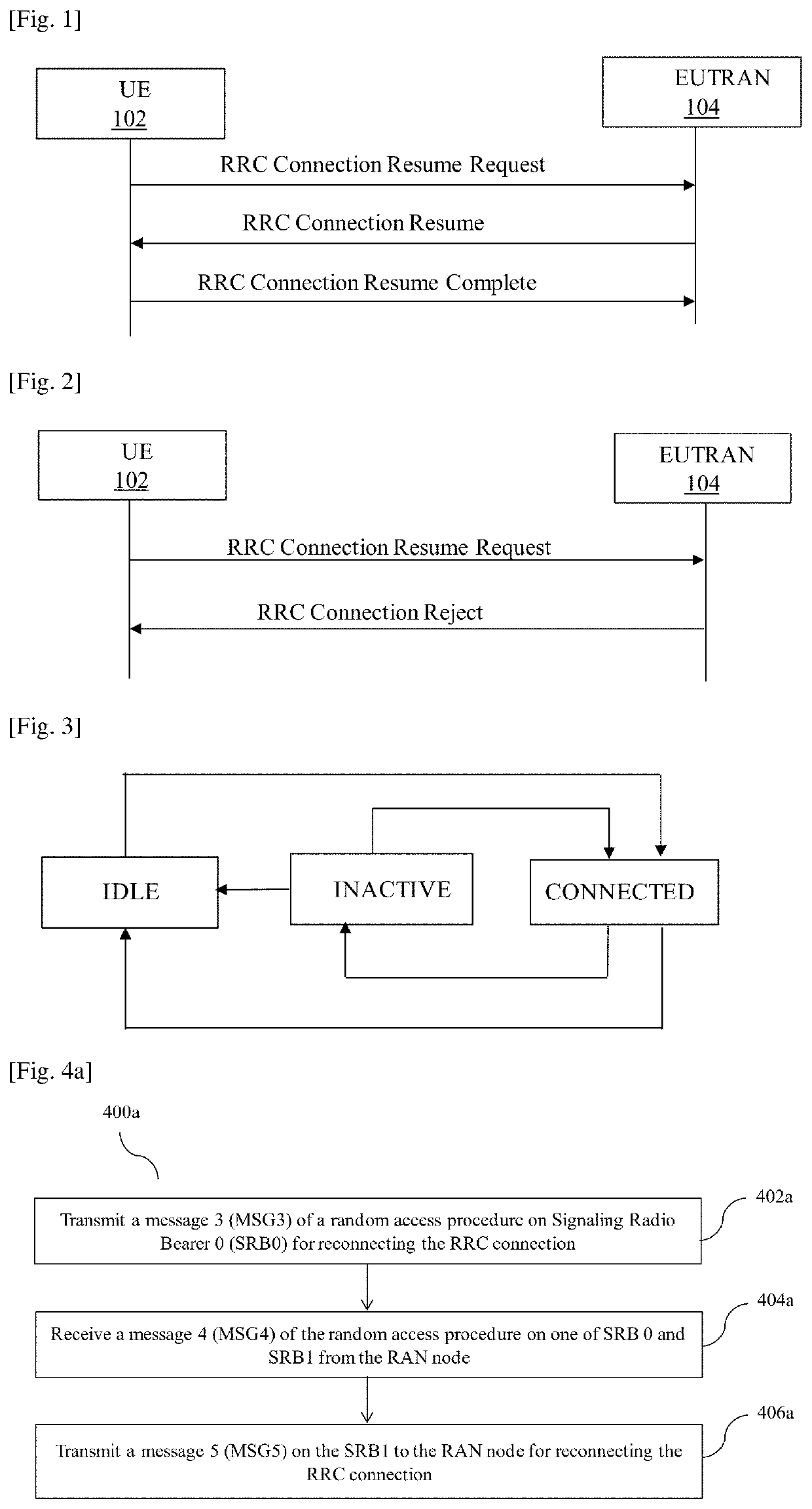
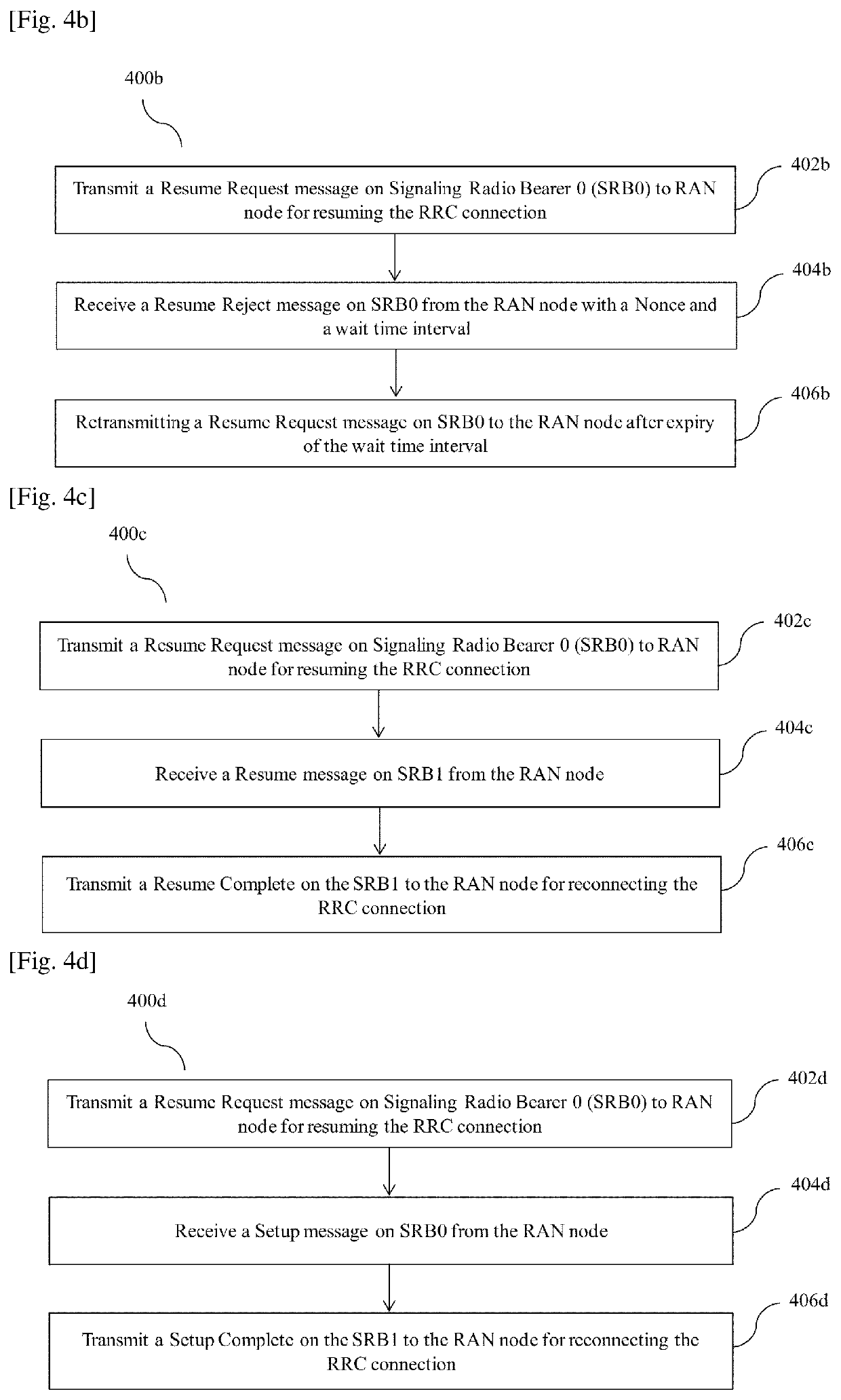
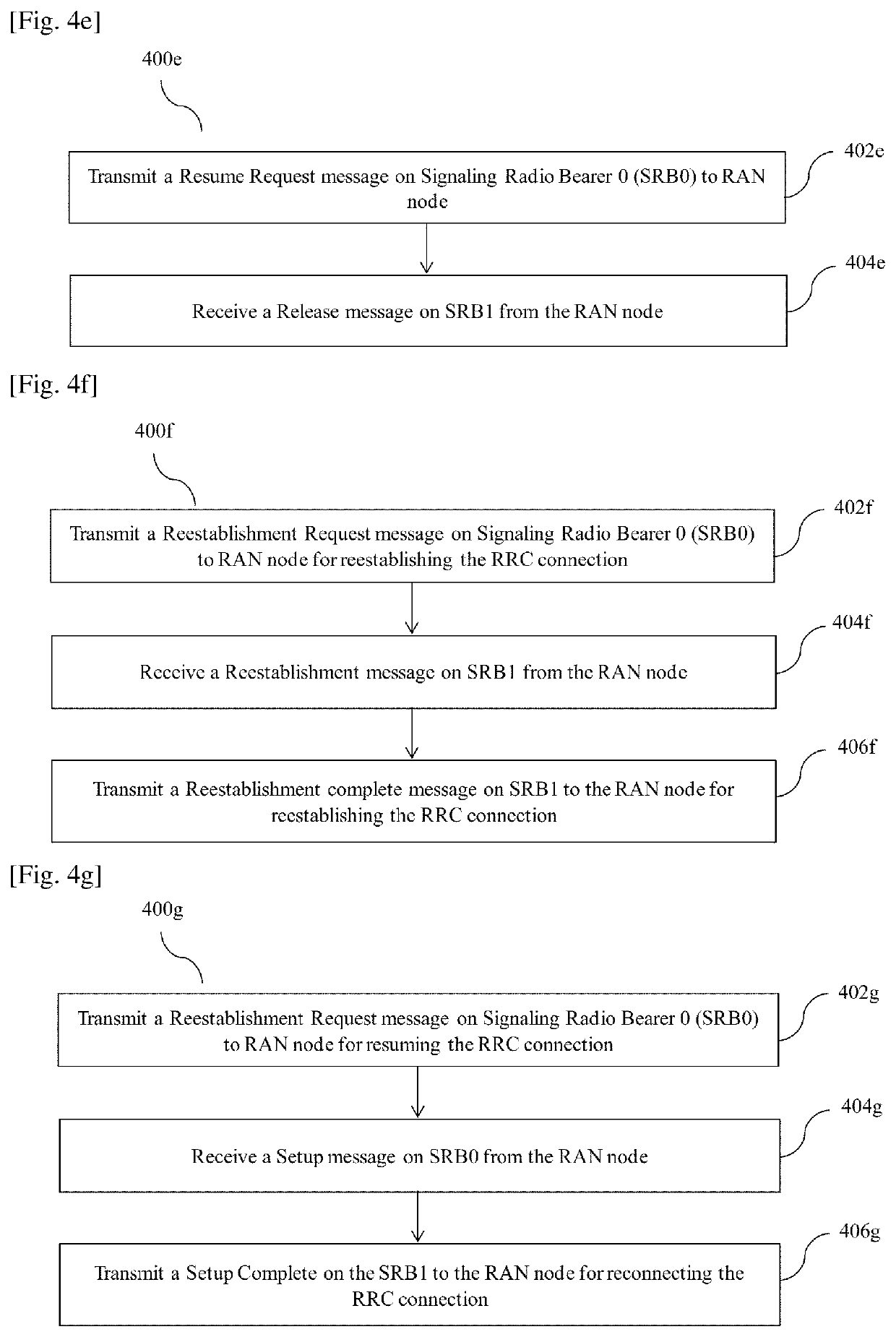
InactiveUS20200214070A1Reduce attackConnection managementSecurity arrangementAccess networkCommunications system
Accordingly the embodiments herein provide a method for reconnecting a Radio Resource Control (RRC) connection with a Radio Access Network (RAN) node by a User Equipment (UE) in a wireless communication system. The method includes transmitting a message 3 (MSG3) of a random access procedure on Signaling Radio Bearer 0 (SRB0) for reconnecting the RRC connection. The MSG3 is a request message to the RAN node with set of connection parameters. Further, the method includes receiving a message 4 (MSG4) of the random access procedure from the RAN node. The MSG4 is received on a SRB0 or a Signaling Radio Bearer 1 (SRB1). Furthermore, the method includes transmitting a message 5 (MSG5) on the SRB1 to RAN node for reconnecting RRC connection. The proposed method can be used to mitigate a replay attack on the UE in a inactive state using a nonce and a wait time interval.
Owner:SAMSUNG ELECTRONICS CO LTD
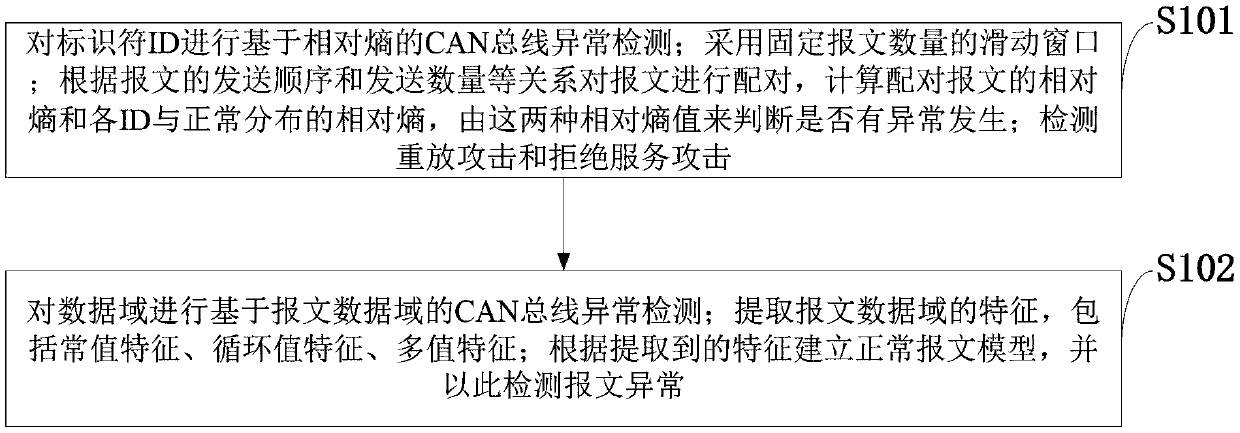
Vehicle-mounted CAN bus network abnormity detection method and system
ActiveCN110275508ANo need to change the structureAvoid the influence of relative entropyProgramme controlElectric testing/monitoringAnomaly detectionSlide window
The invention, which belongs to the technical field of vehicle-mounted network, discloses a vehicle-mounted CAN bus network abnormity detection method and system. CAN bus abnormity detection based on a relative entropy is performed on an identifier ID; a sliding window with a fixed message number is employed; messages are paired based on a relationship between a message sensing sequence and a sending number, relative entropies of the paired messages and relative entropies of all IDs and normal distribution are calculated, and whether abnormity occurs is determined based on the two kinds of relative entropies; a replay attack and a denial of service attack are detected; CAN bus network abnormity detection based on a message data domain is performed on a data domain; features, including a constant value feature, a cyclic value feature, and a multi-value feature, of the message data domain are extracted; and a normal message model is established based on the extracted features and the message abnormity is detected. Therefore, the replay attack, the denial of service attack, the tampering attack and the forgery attack can be detected effectively and efficiently; more abnormal information is provided; and thus subsequent protection can be performed well.
Owner:XIDIAN UNIV
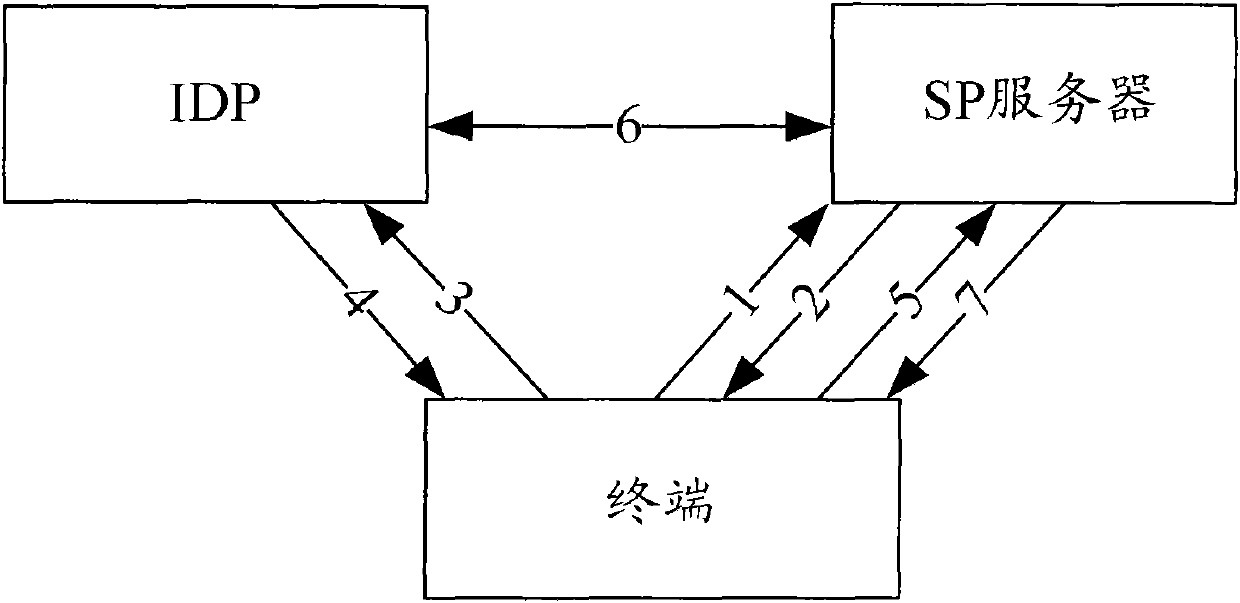
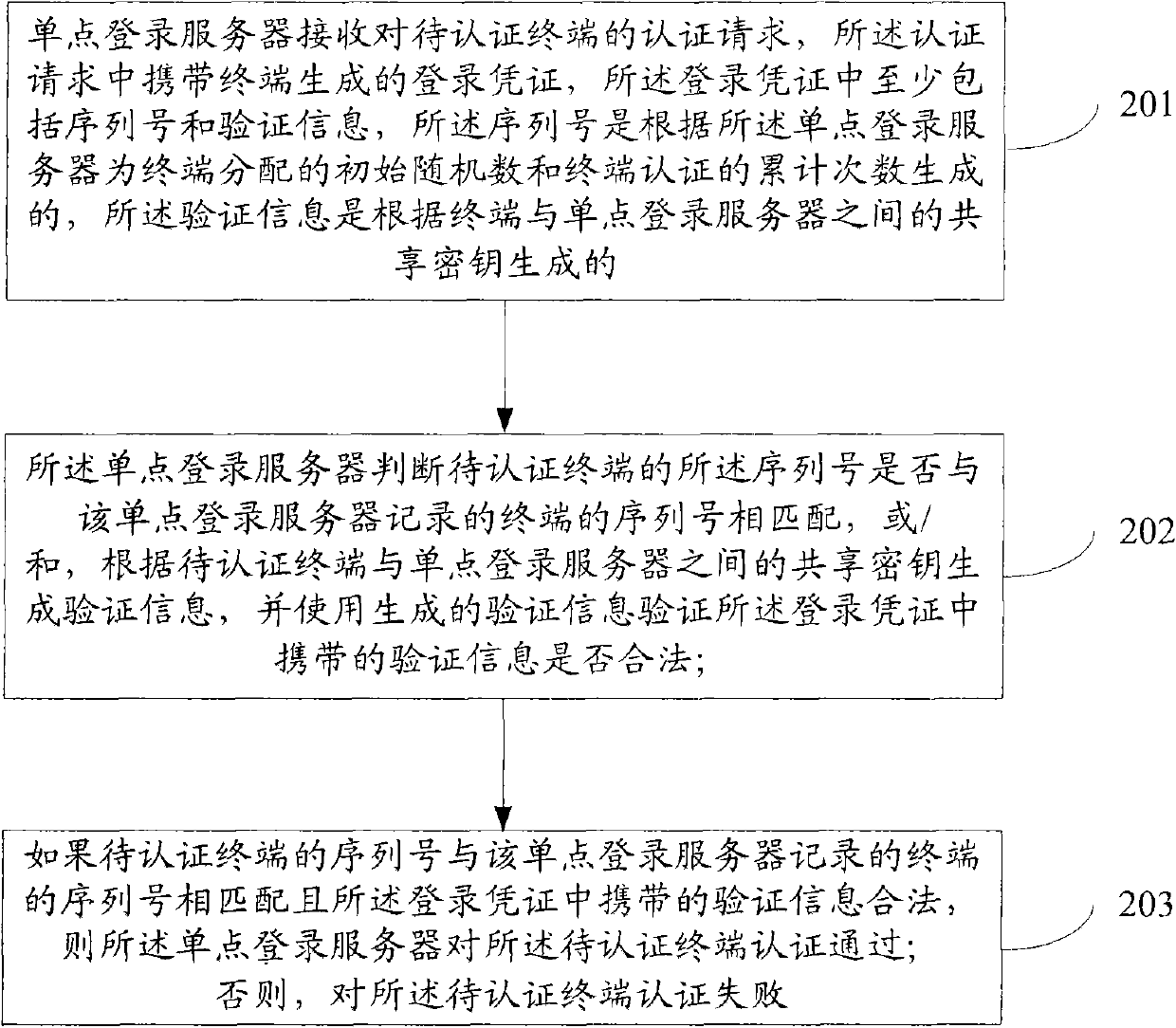
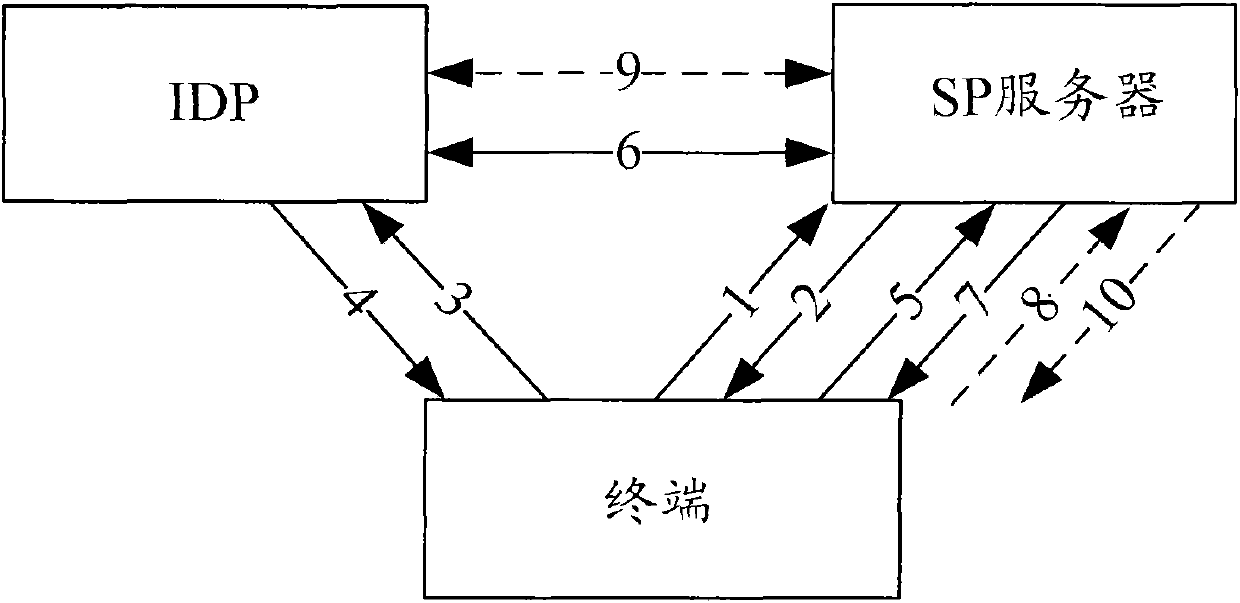
Terminal authentication method and device based on single sign-on
ActiveCN102201915AImprove login efficiencyPrevent replay attacksUser identity/authority verificationComputer terminalKey generation
The embodiment of the invention discloses a terminal authentication method and device based on single sign-on. The method comprises the following steps: a single sign-on server receives log-on evidence generated by a terminal to be authenticated carried in an authentication request of the terminal, wherein the log-on evidence at least comprises a serial number and verification information, the serial number is generated according to an initial random number distributed for the terminal by the single sign-on server and the cumulative number of terminal authentication, and the verification information is generated according to a shared key between the terminal and the single sign-on server; the single sign-on server judges that the terminal to be authenticated passes authentication if the serial number of the terminal to be authenticated is matched with the serial number of a terminal recorded by the single sign-on server; and otherwise, the authentication of the terminal to be authenticated fails. By adopting the method and the device, replay attack is prevented, and the singe log-on efficiency is increased.
Owner:CHINA MOBILE COMM GRP CO LTD
Mobile phone door lock system based on asymmetric secret key and realization method thereof
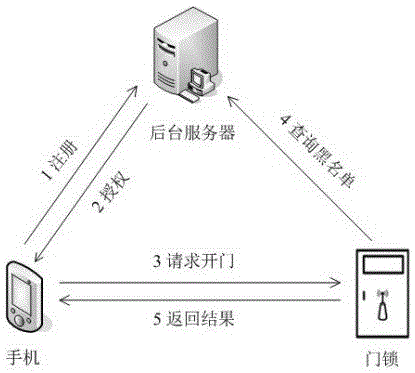
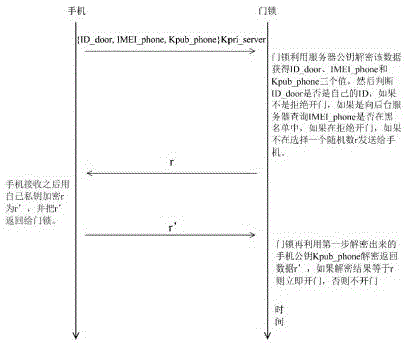
InactiveCN105139499AImprove securitySimple structureIndividual entry/exit registersMultiple encryptionBlack list
The invention discloses a mobile phone door lock system based on an asymmetric secret key and a realization method thereof, and belongs to a mobile phone door lock. The system comprises an intelligent mobile phone, a door lock and a server; data transmission among the intelligent mobile phone, the door lock and the server is carried by network; the server is used for storing a mobile phone identification number blacklist, and encrypting door opening permission serial data after the verification is valid and sending the serial data to the mobile phone; the intelligent mobile phone is used for sending the door opening permission serial data of the mobile phone to the door lock, and the door opening authority serial data at least comprises a door lock ID, a mobile phone identification number, etc.; the encrypted permission serial data and black list verification and multiple encryption and decryption verifications are carried out between the mobile phone, the door lock and the server, thereby solving the technology problem that the prior mobile phone door lock product cannot withstand replay attack and the invalid unlocking risk is high, providing a complete permission distribution, authentication and cancel process, greatly improving safety performance of the mobile phone door lock product, and promoting the development of the mobile phone door lock industry.
Owner:蔡炜
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com