Authentication and cryptographic key negotiation method, authentication method, system and equipment
A technology of key negotiation and authentication, applied in the field of authentication technology, which can solve the problem of inability to resist replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
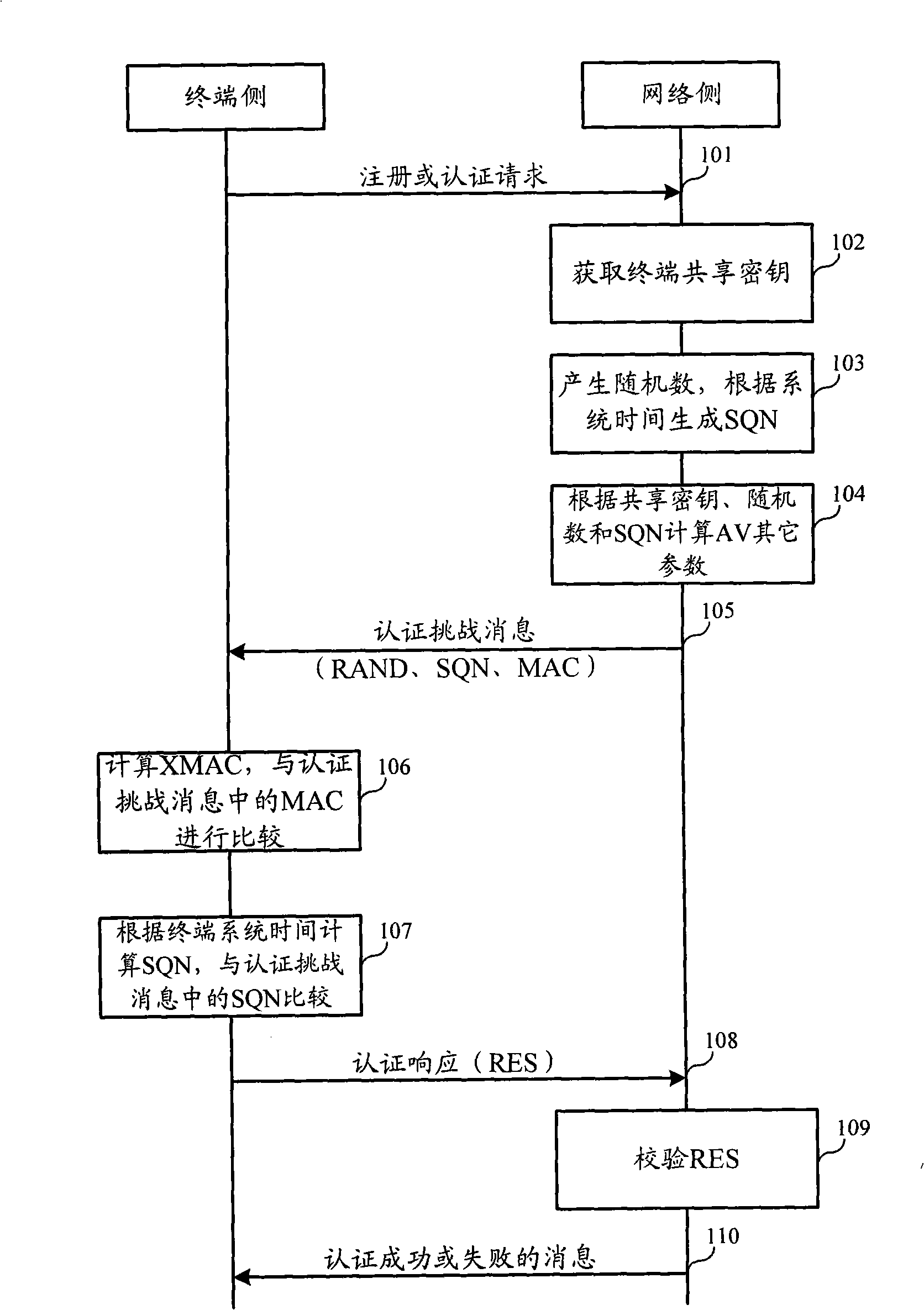
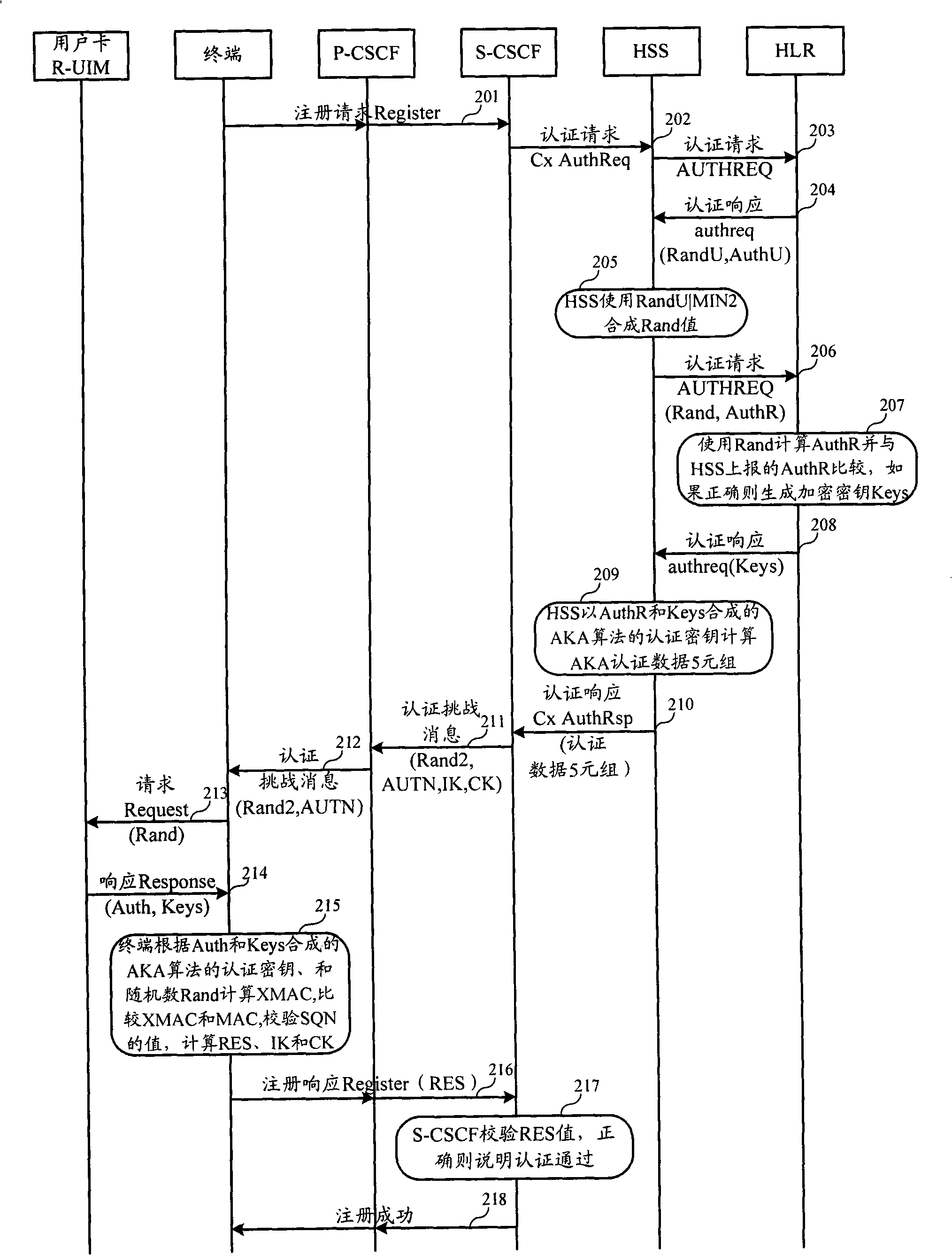
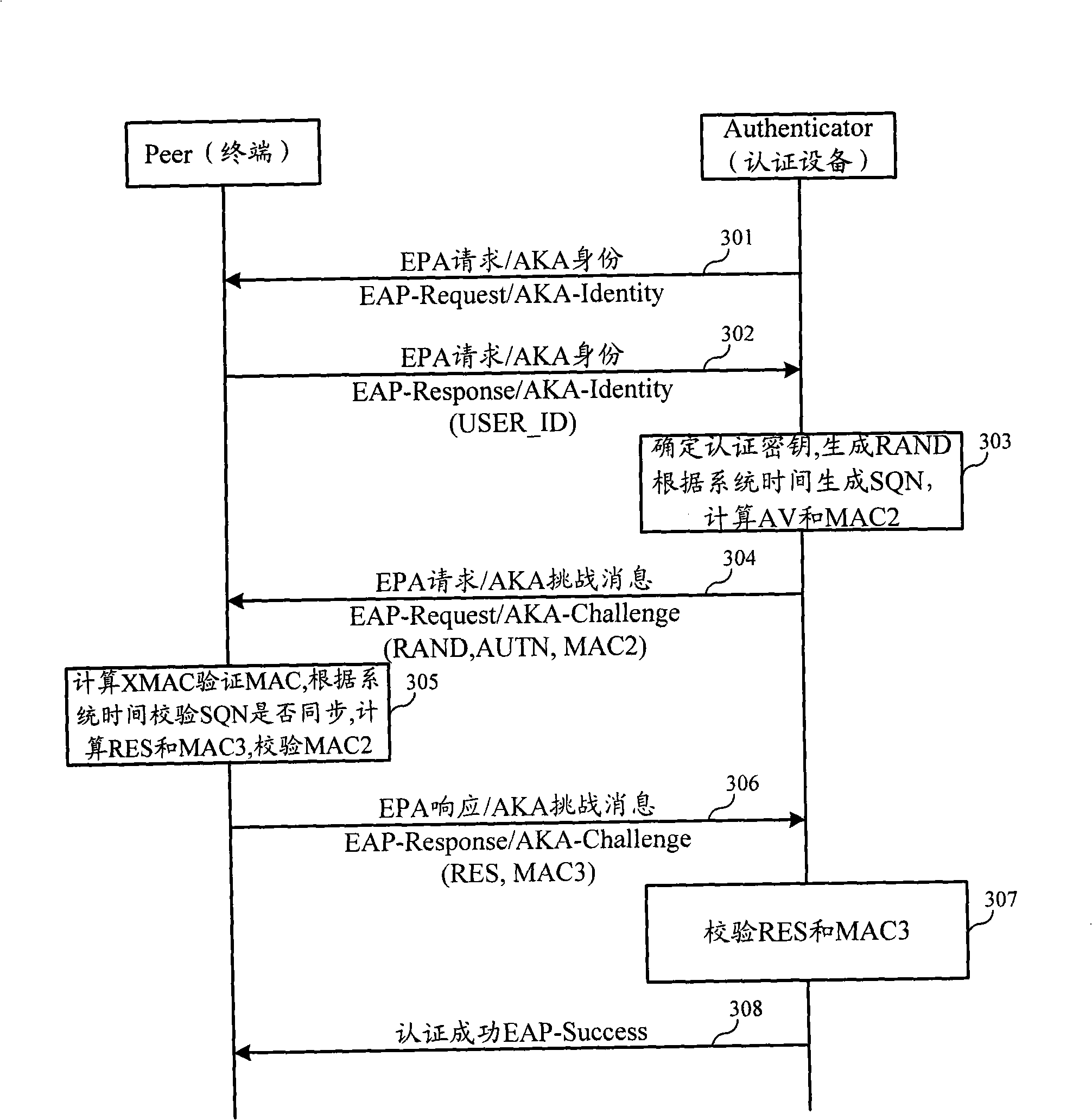
[0057] In order to make the purpose, technical solution and advantages of the present invention clearer, the following will further describe the implementation of the present invention in detail in conjunction with the accompanying drawings.
[0058] The first embodiment of the present invention relates to an authentication and key agreement AKA method. Compared with the existing AKA, the biggest difference between the two lies in the different SQN parameter setting methods. In the existing AKA, SQN is a counter concept. Both the user side and the network side maintain a counter and ensure synchronization. The user terminal can send the counter value (ie SQN) from the network side and the locally maintained counter value ( SQN) is consistent to determine whether the network device sending the SQN is legal. This method requires a user to uniformly maintain a SQN. When the SQN is stored on the user card, no matter how many terminals the user changes, the SQN can be maintained u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com