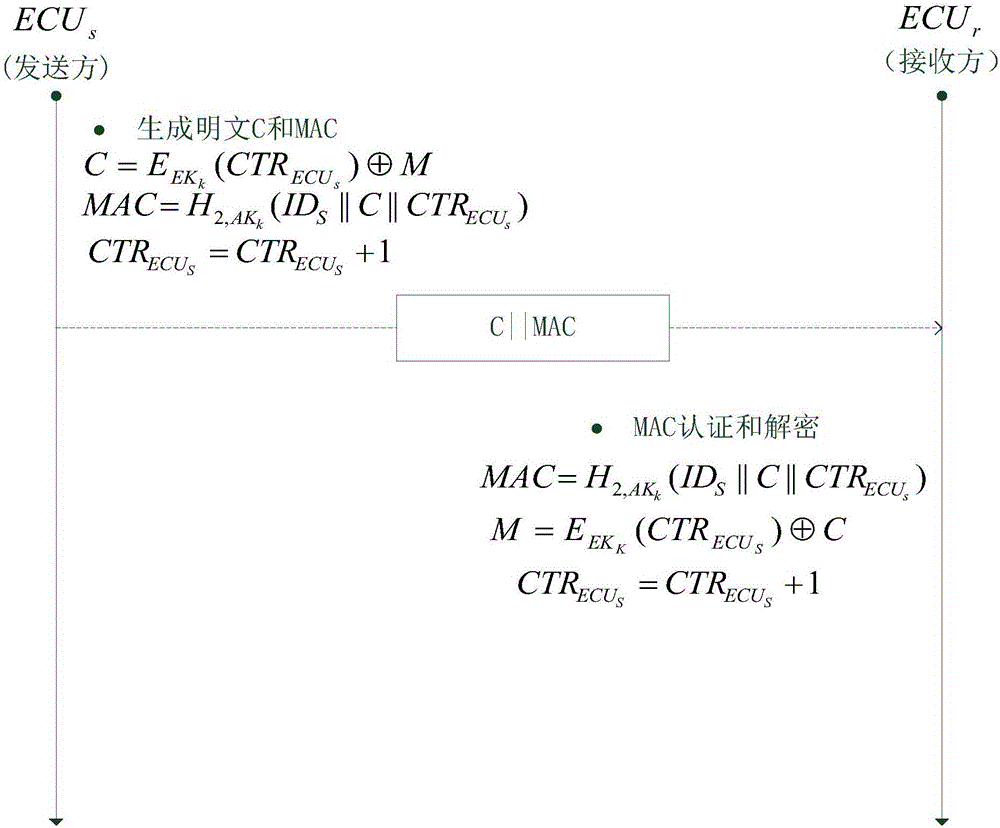Patents
Literature
425results about How to "Prevent replay attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
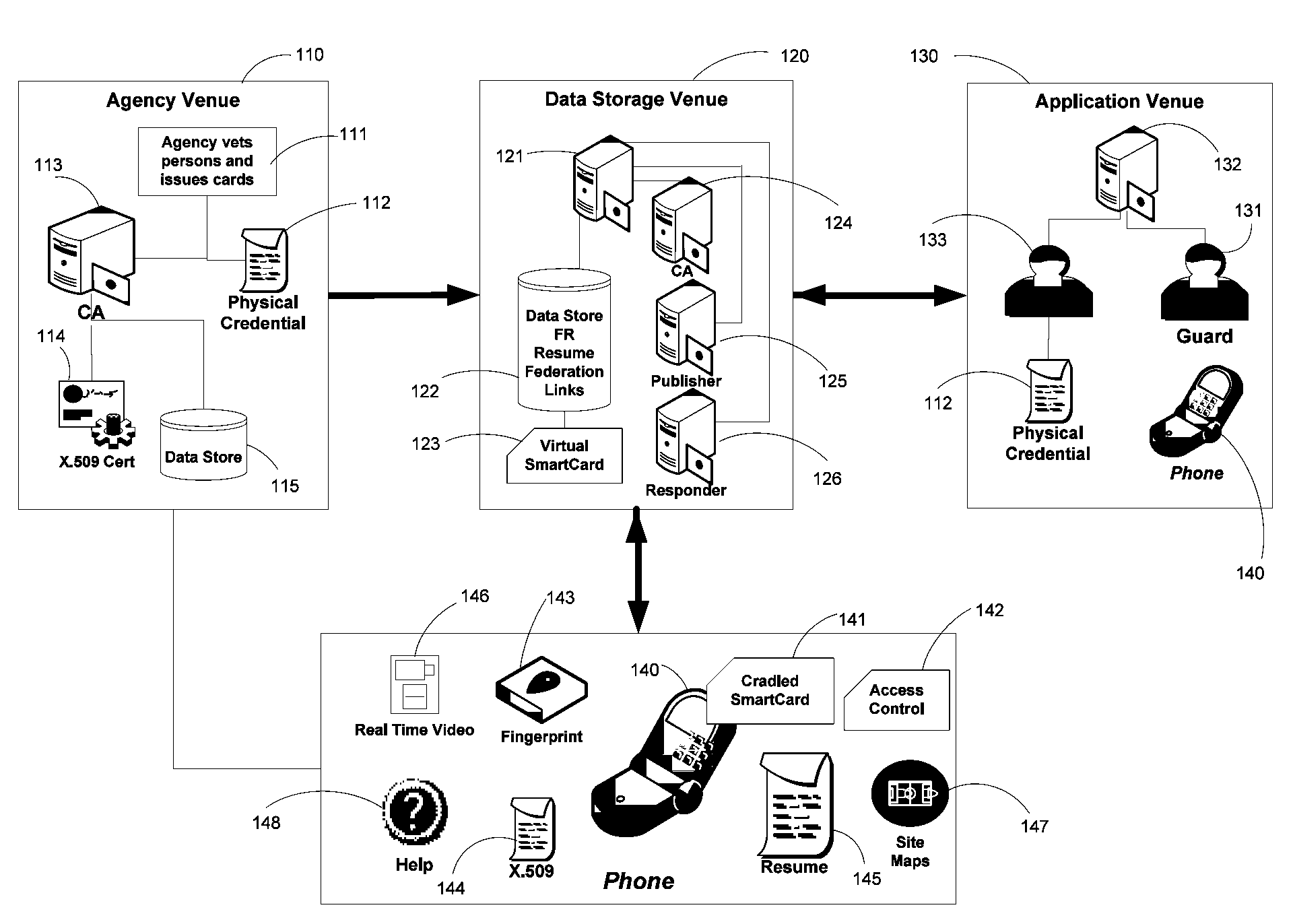
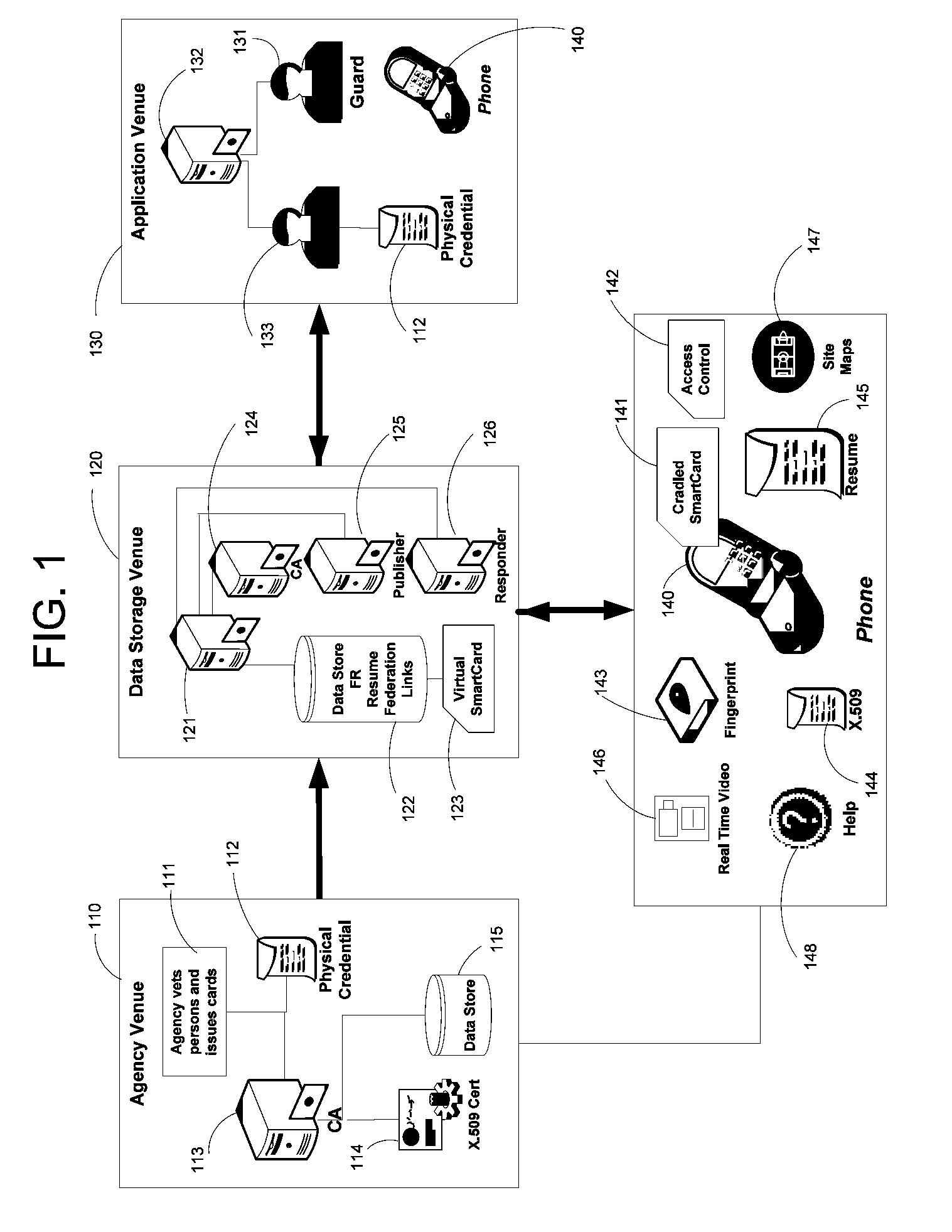
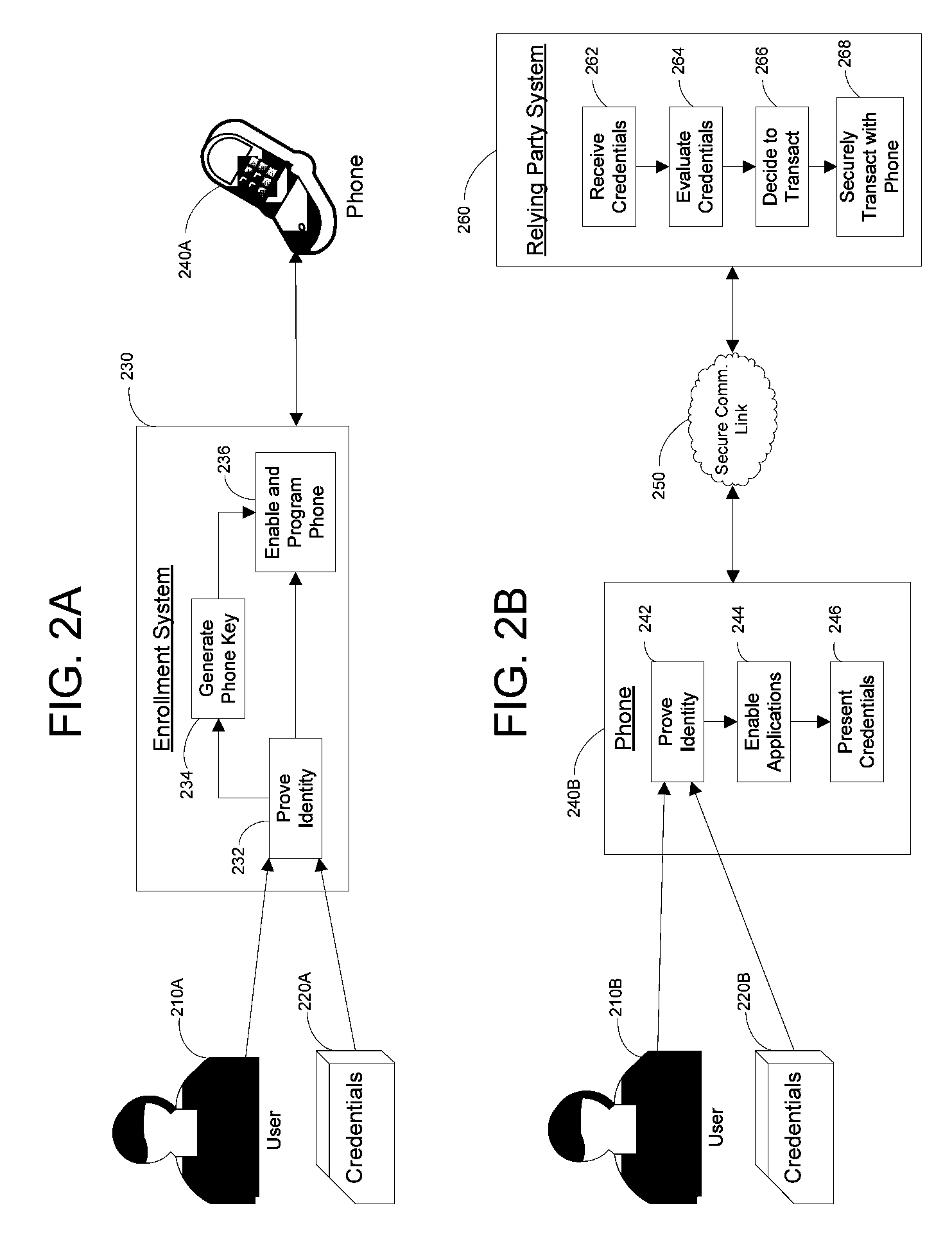
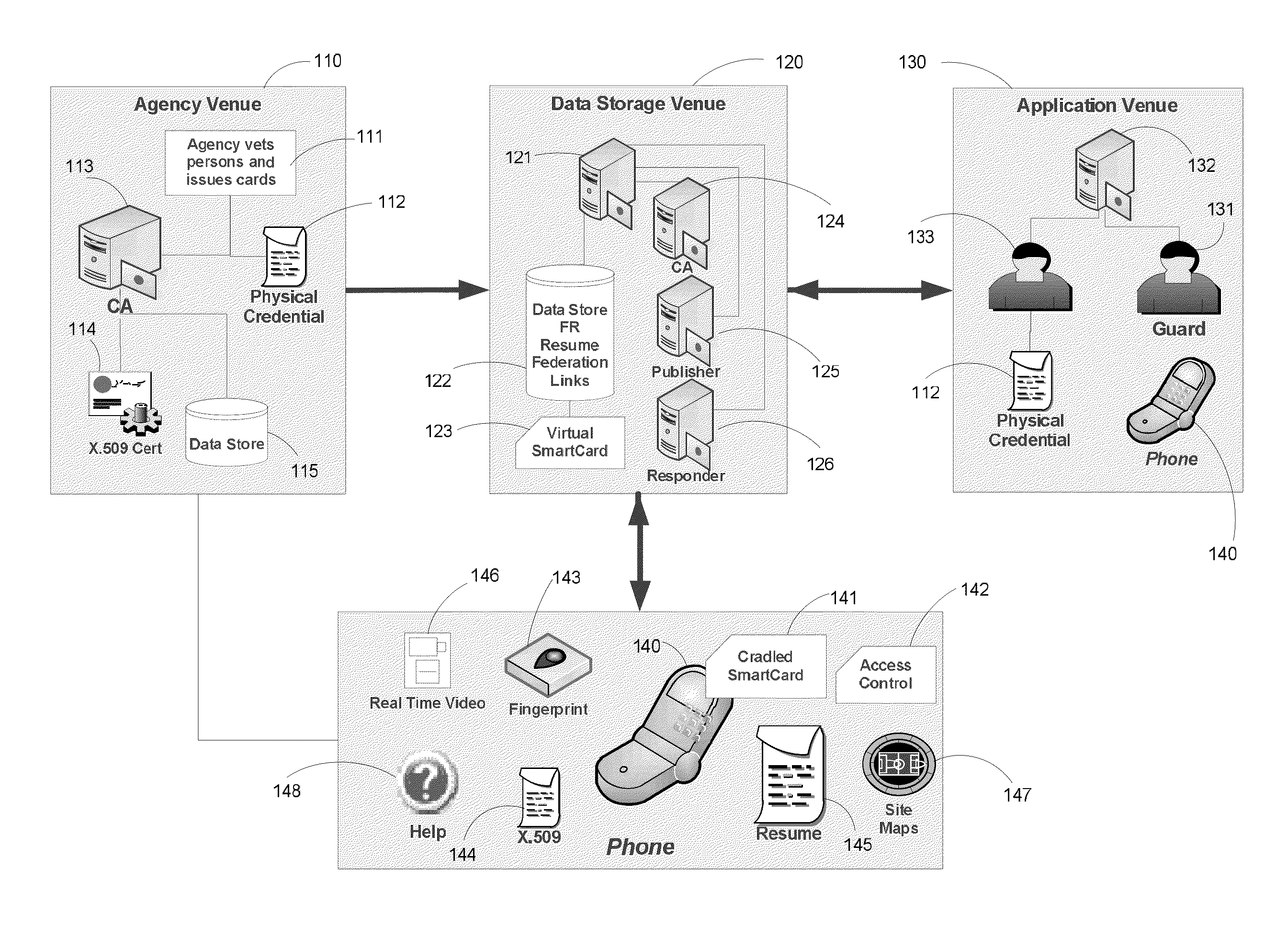
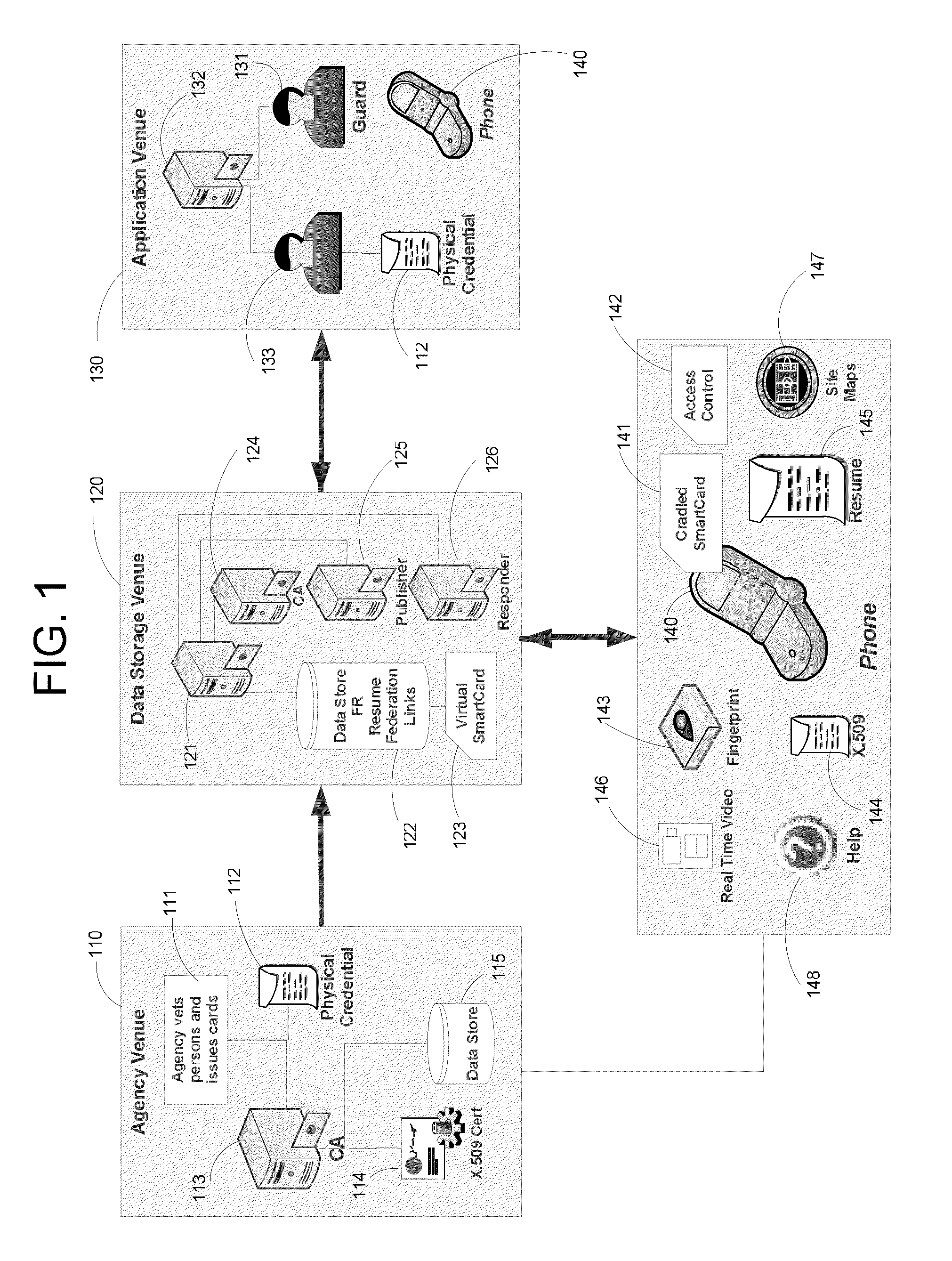
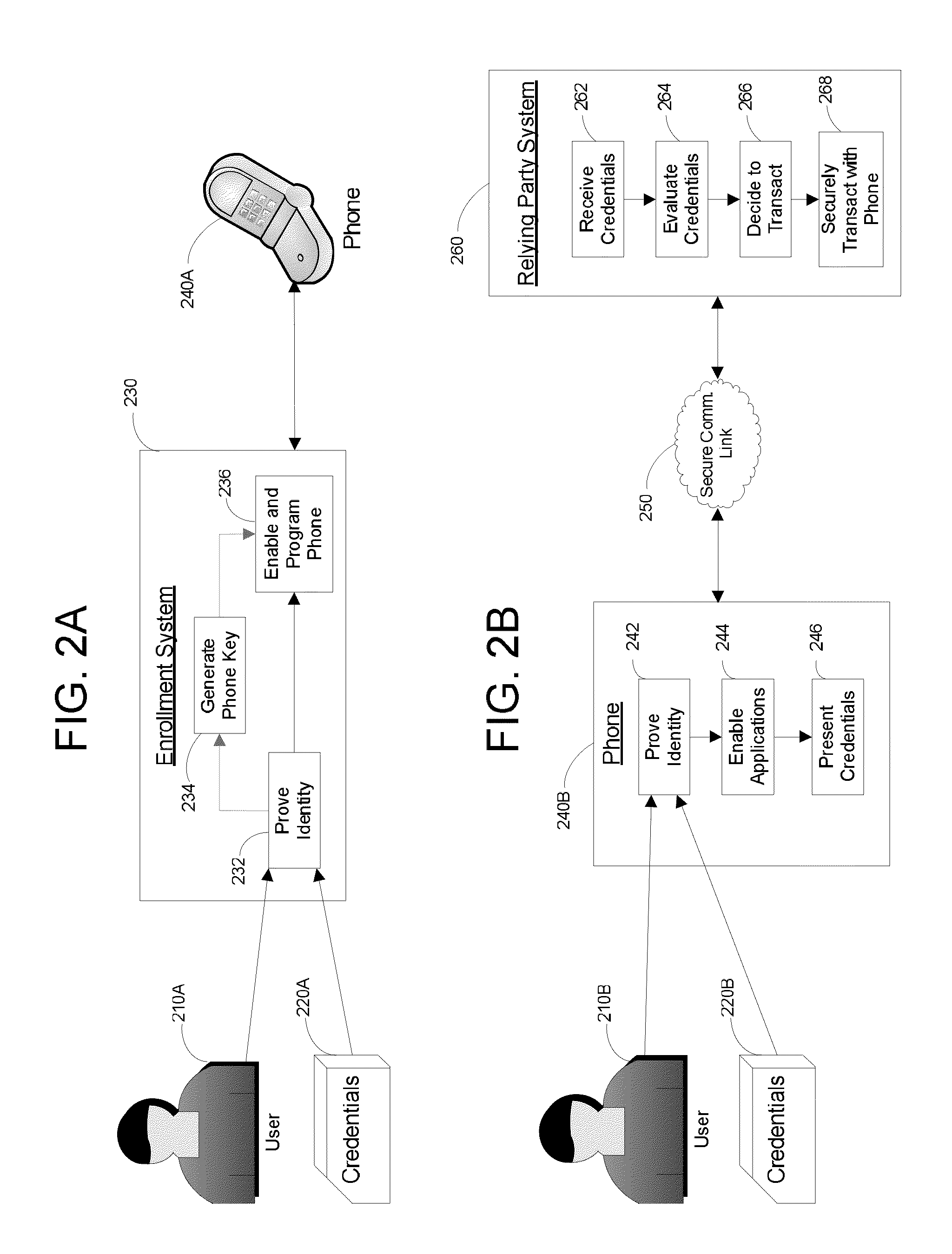
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
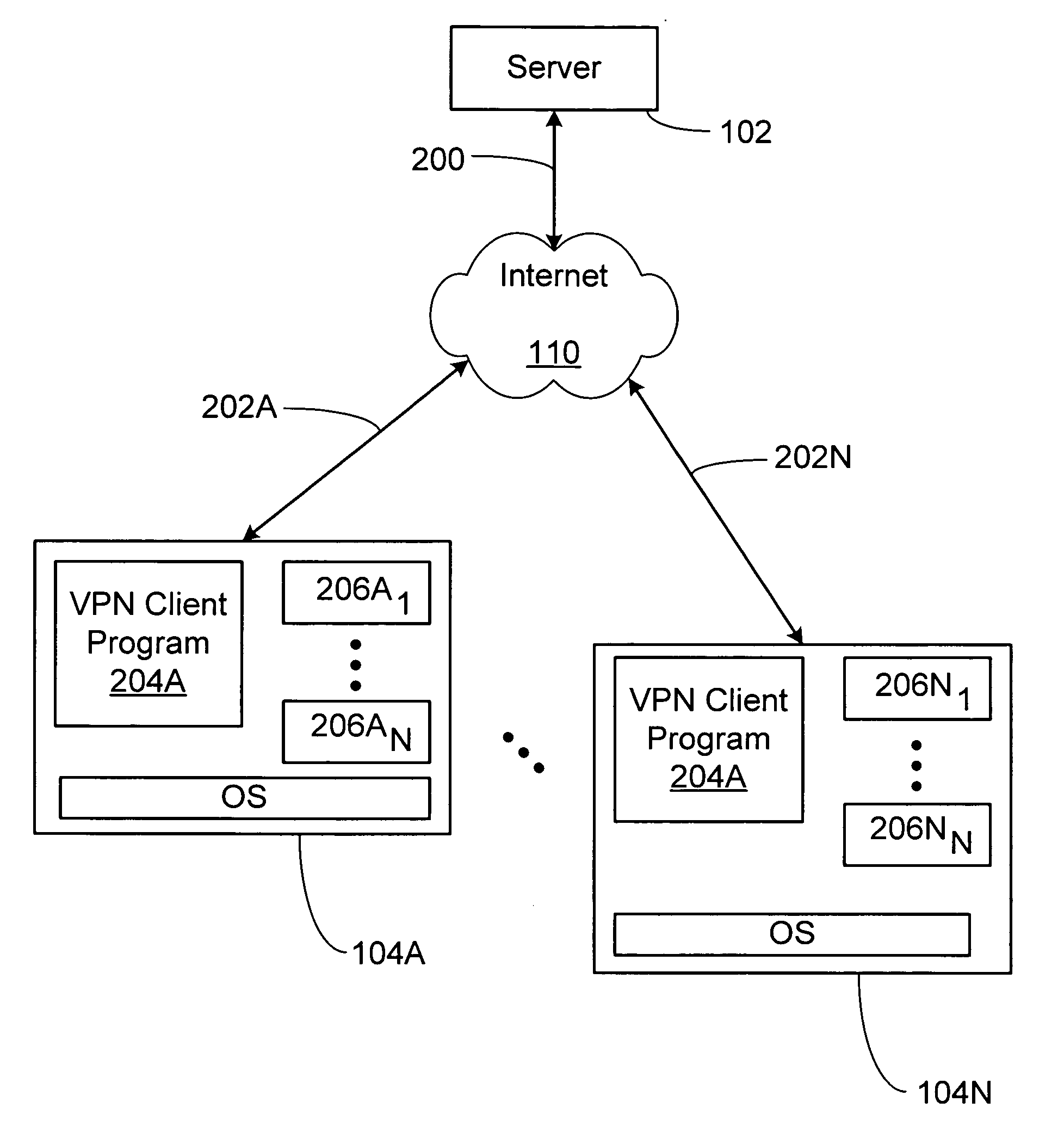
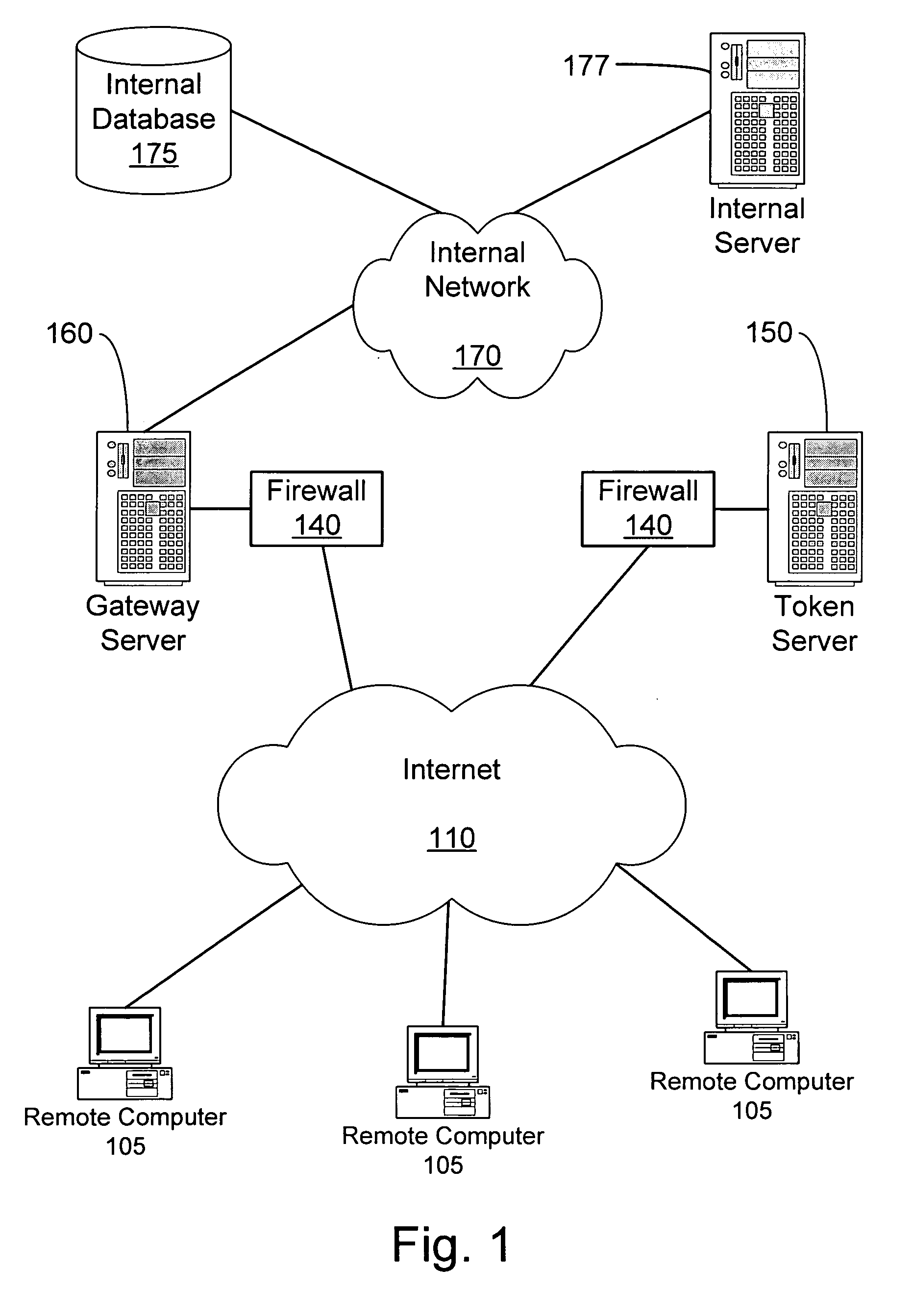
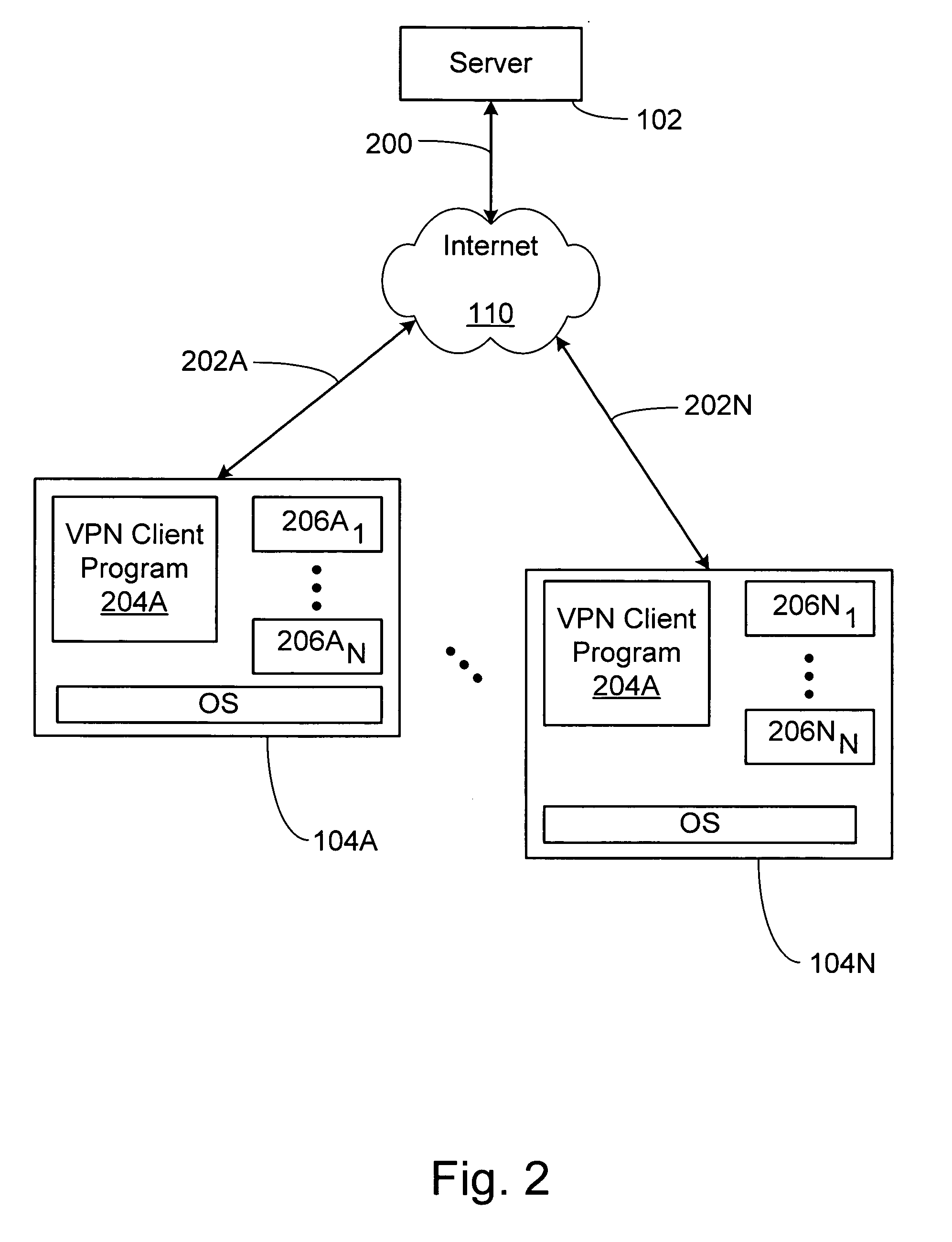
System and method for secure network connectivity
InactiveUS20070101405A1Accurate protectionConnection securityRandom number generatorsMemory loss protectionSecurity checkRemote computer
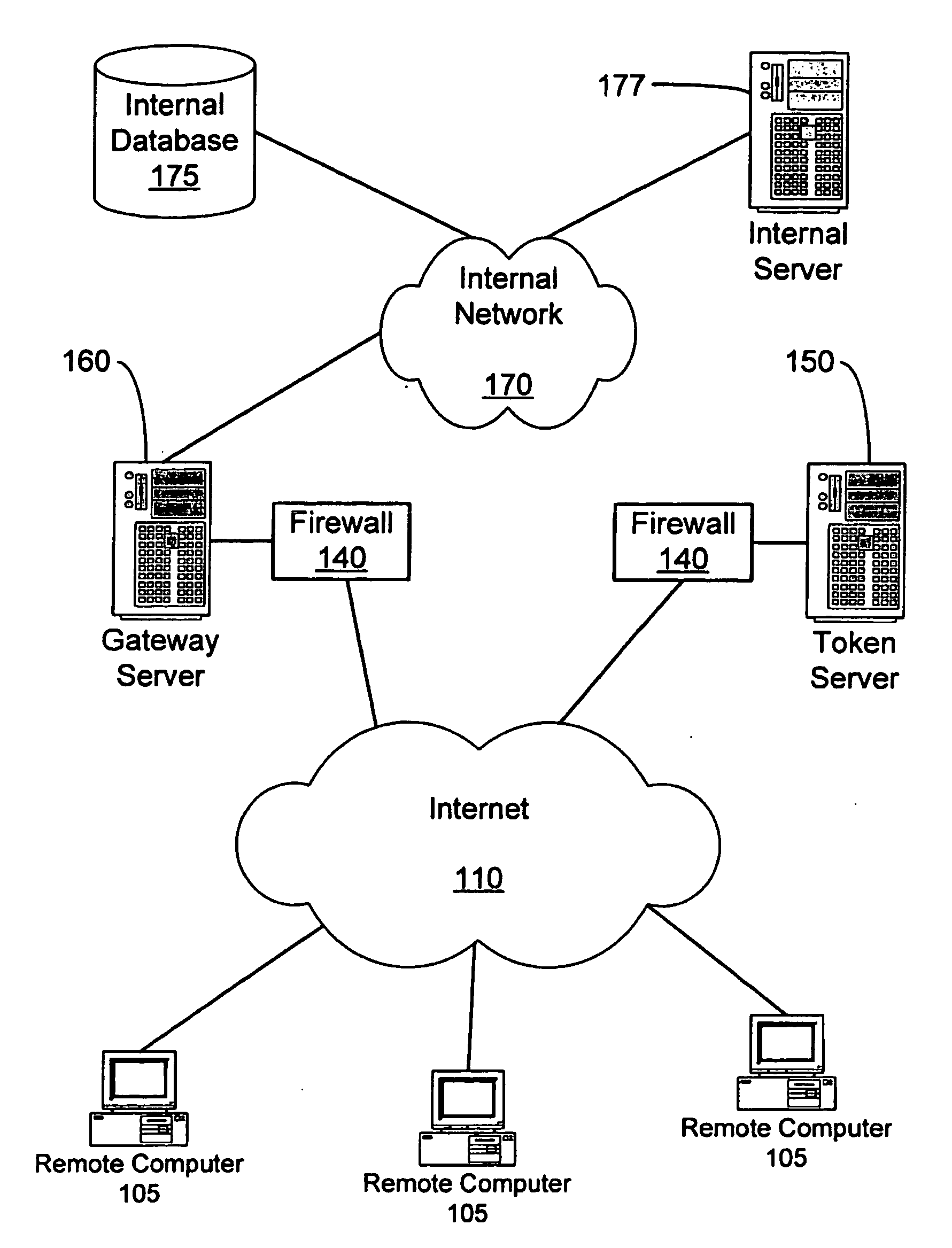
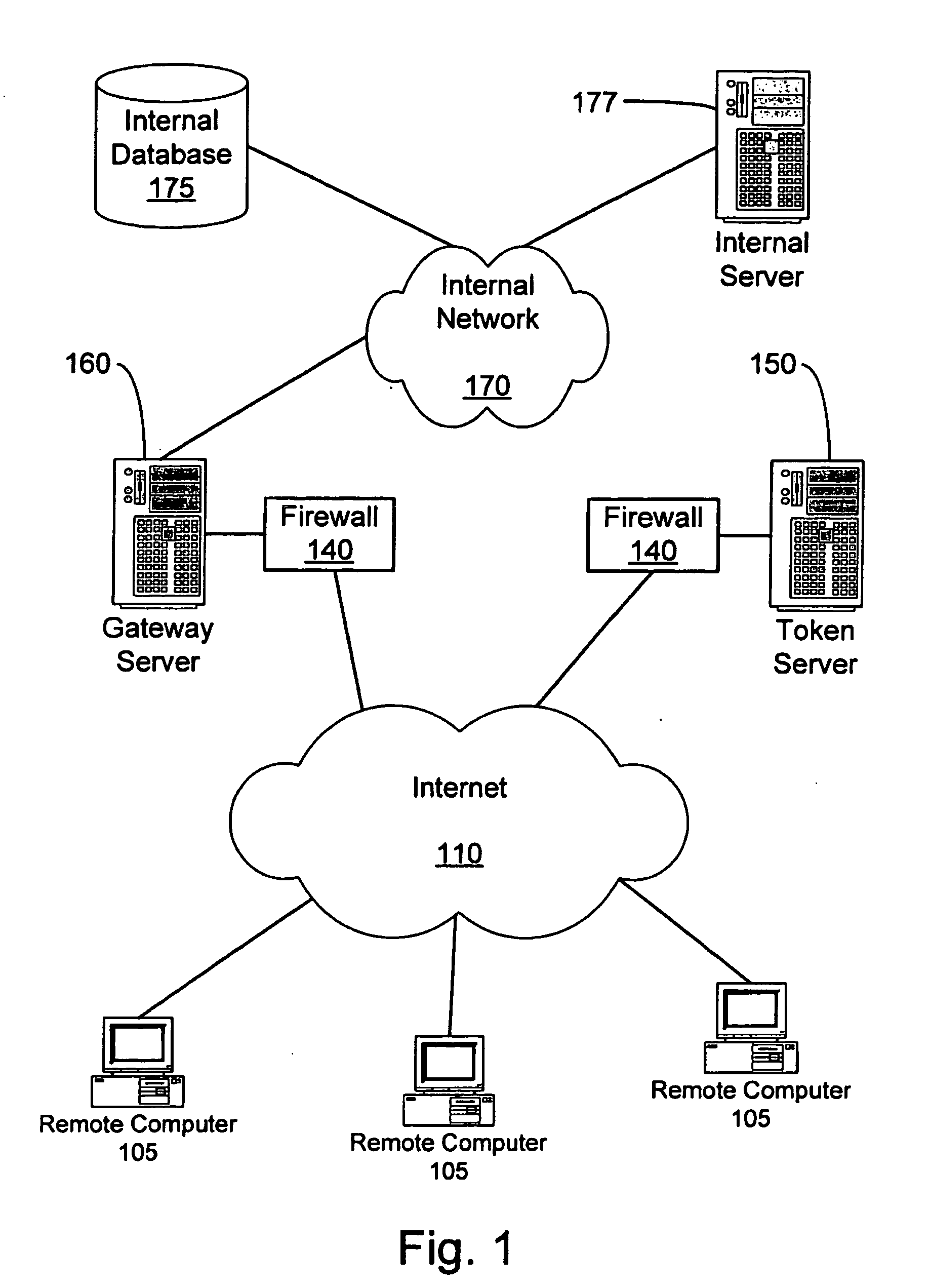
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server-driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20130061055A1Reduce computing power requirementsIncrease the number ofDigital data processing detailsUser identity/authority verificationCredit cardHardware security module
A virtual smartcard and methods for creating the same are provided. A virtual smartcard is a set of computer-implemented processes, associated with an individual, which simulate the behavior of a physical smartcard or other authentication token containing a hardware security module. In one embodiment, a computer receives credential data derived from the physical credential and authentication data pertinent to the individual such as a biometric imprint, and creates a virtual smartcard by storing the credential data in association with the authentication data in a network storage. The credential data may later be used for identification and encryption purposes upon the individual providing the authentication data to the network storage, even if the physical credential itself has been lost. Thus, the virtual smartcard provides a network-based method for backing up a passport, driver's license, credit card, public transportation card, or other such identification card or device.
Owner:INFERSPECT
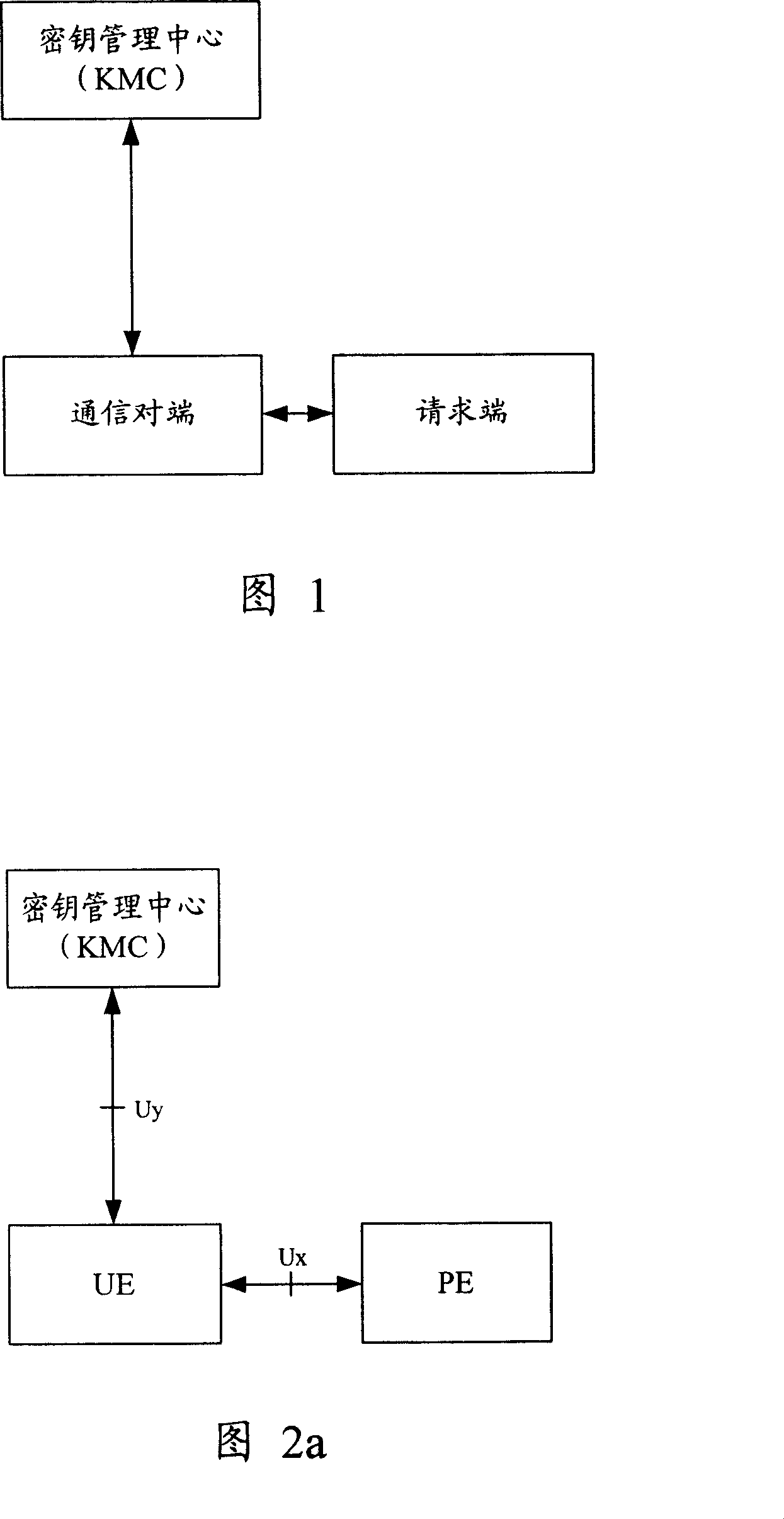
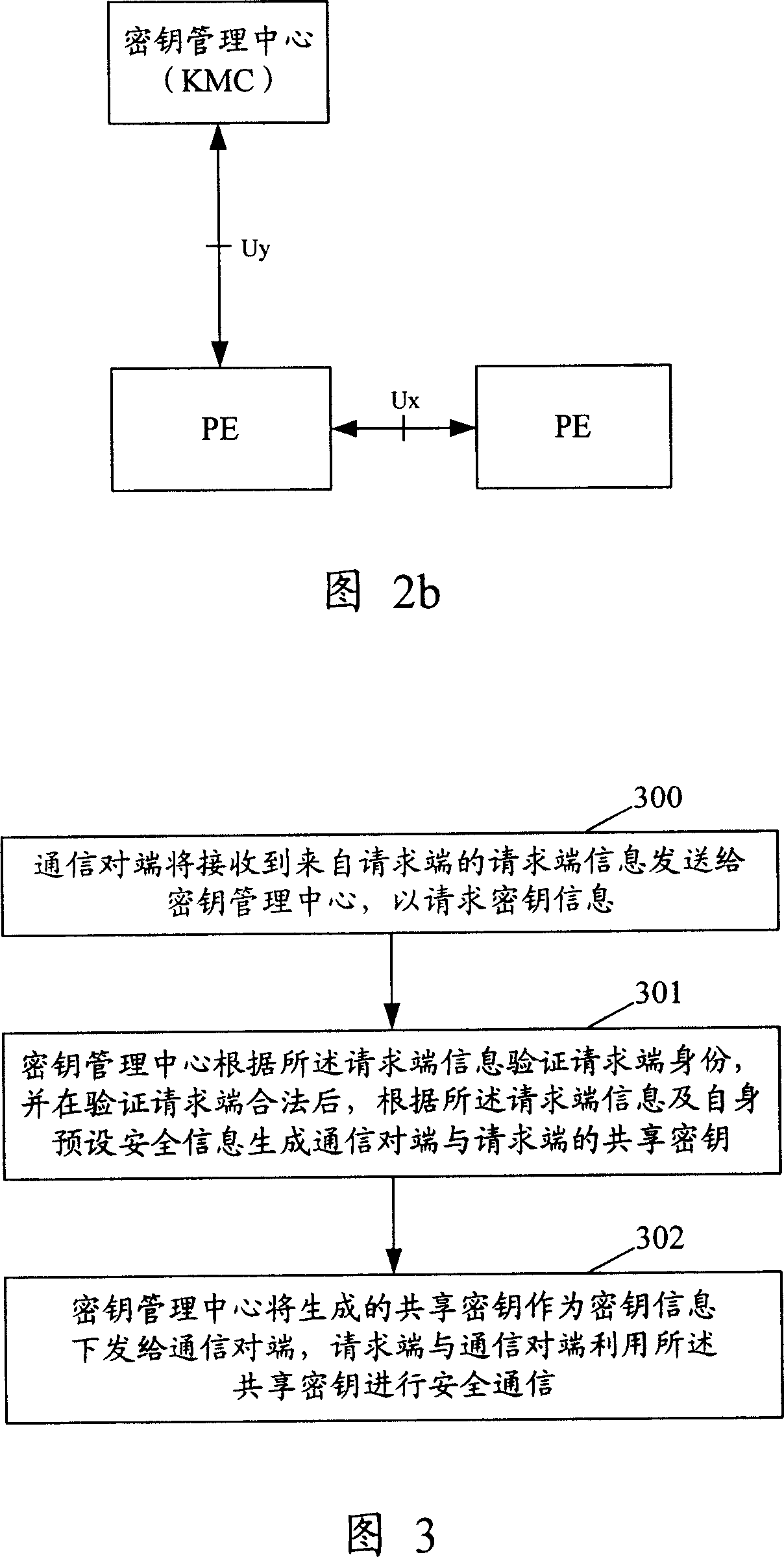
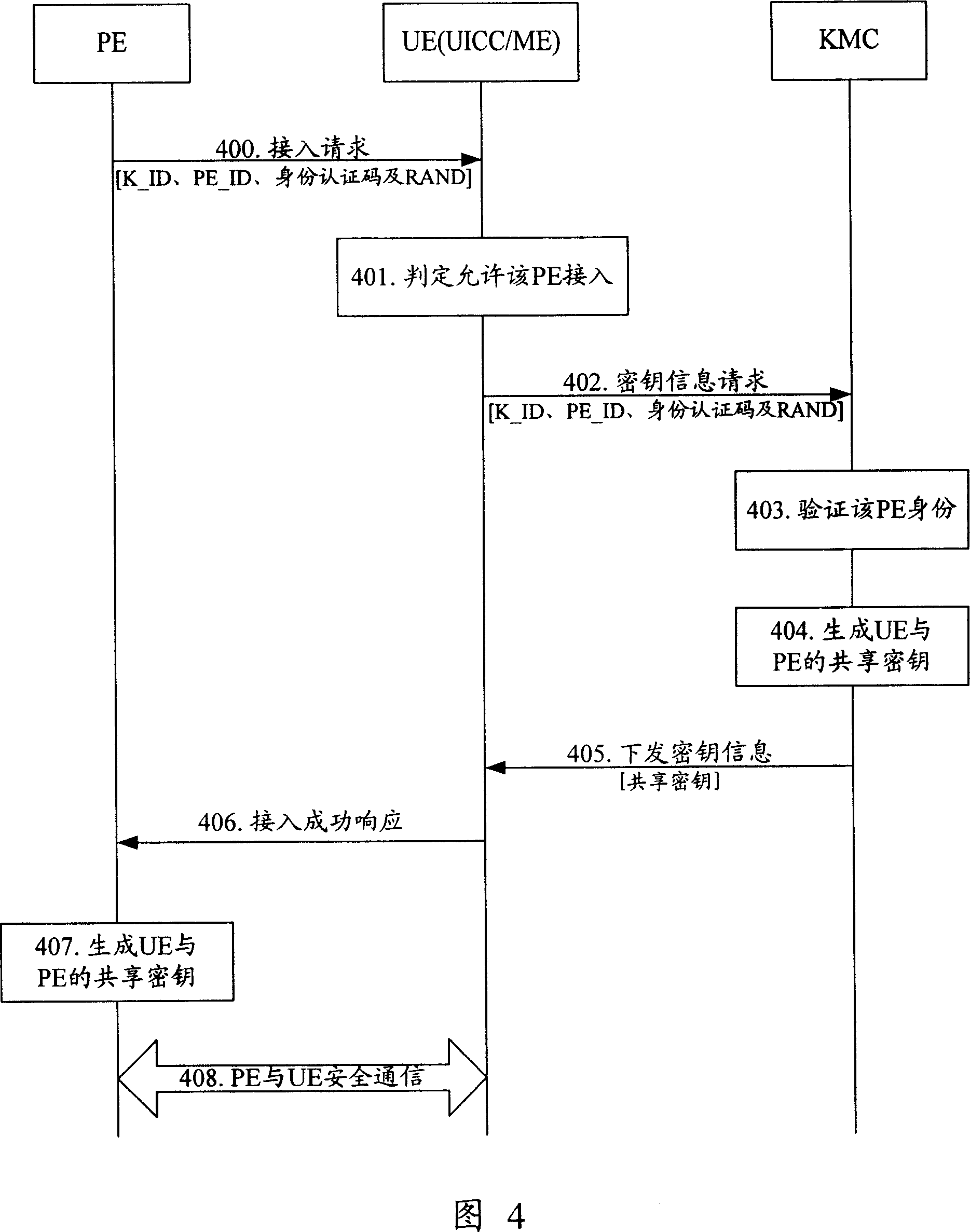
Method and device for realizing safety communication between terminal devices
ActiveCN101005359AEnsure secure communicationStable deliveryKey distribution for secure communicationUser identity/authority verificationSecure communicationTerminal equipment
The method includes steps: communication opposite terminal (COT) sends the request end information received from the request end to the key management center (KMC); based on the request end information, KMC validates ID of the request end; after validating validity of the request end, KMC creates shared cipher key for COT and the request end based on the request end information, and self prearranged security information; KMC down sends the created shared cipher key as information of cipher key to COT; using the said shared cipher key, the request end and COT carry out security communication. The invention also discloses device for security communication between terminal devices. Guaranteeing security communication between terminal devices, the invention especially guarantees security communication between ME / UICC / PE and PE.
Owner:HUAWEI TECH CO LTD
Bidirectional identification method and system
InactiveCN101119196AEffective calculationImprove security strengthUser identity/authority verificationHand shakesNetwork communication
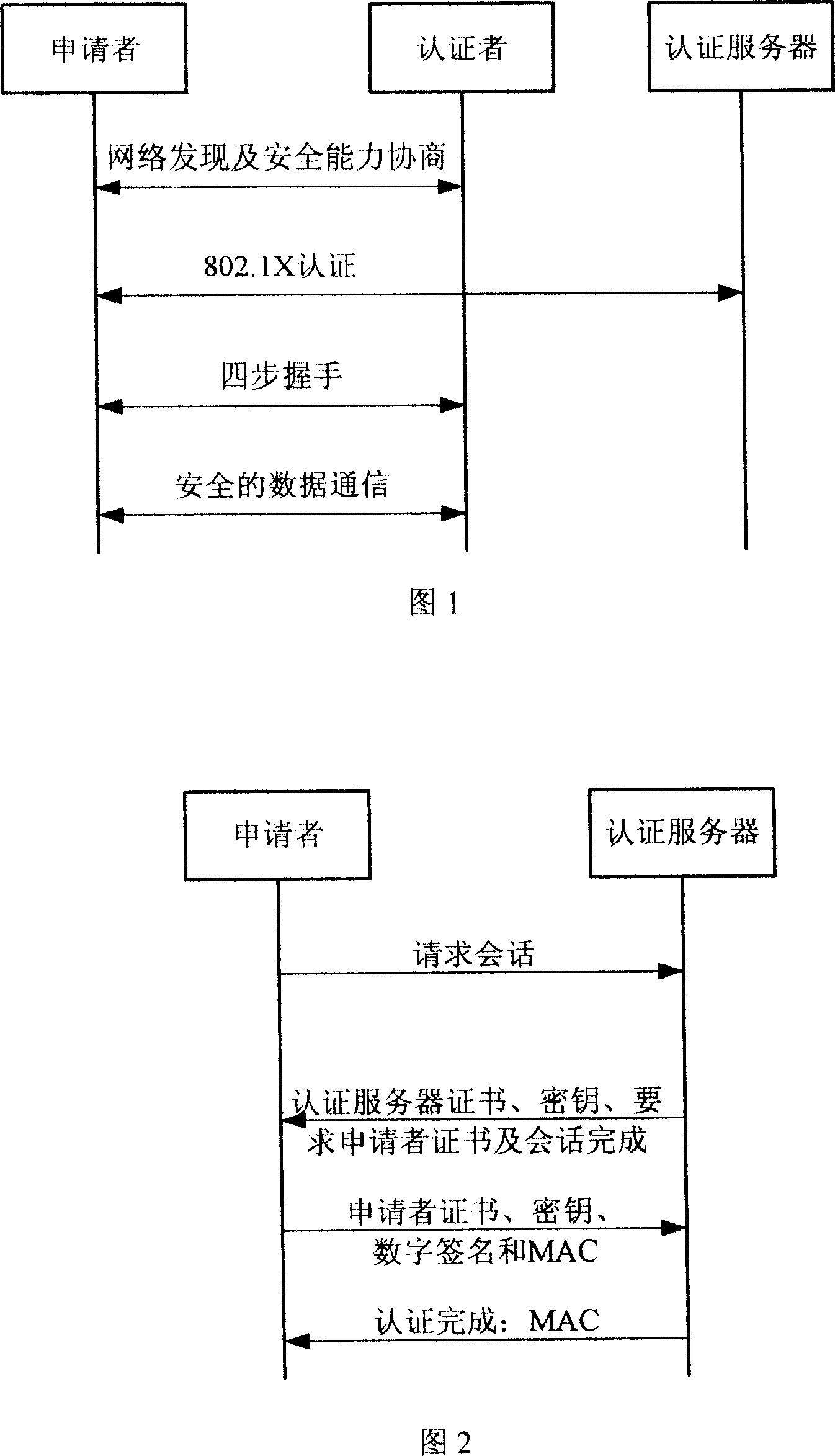
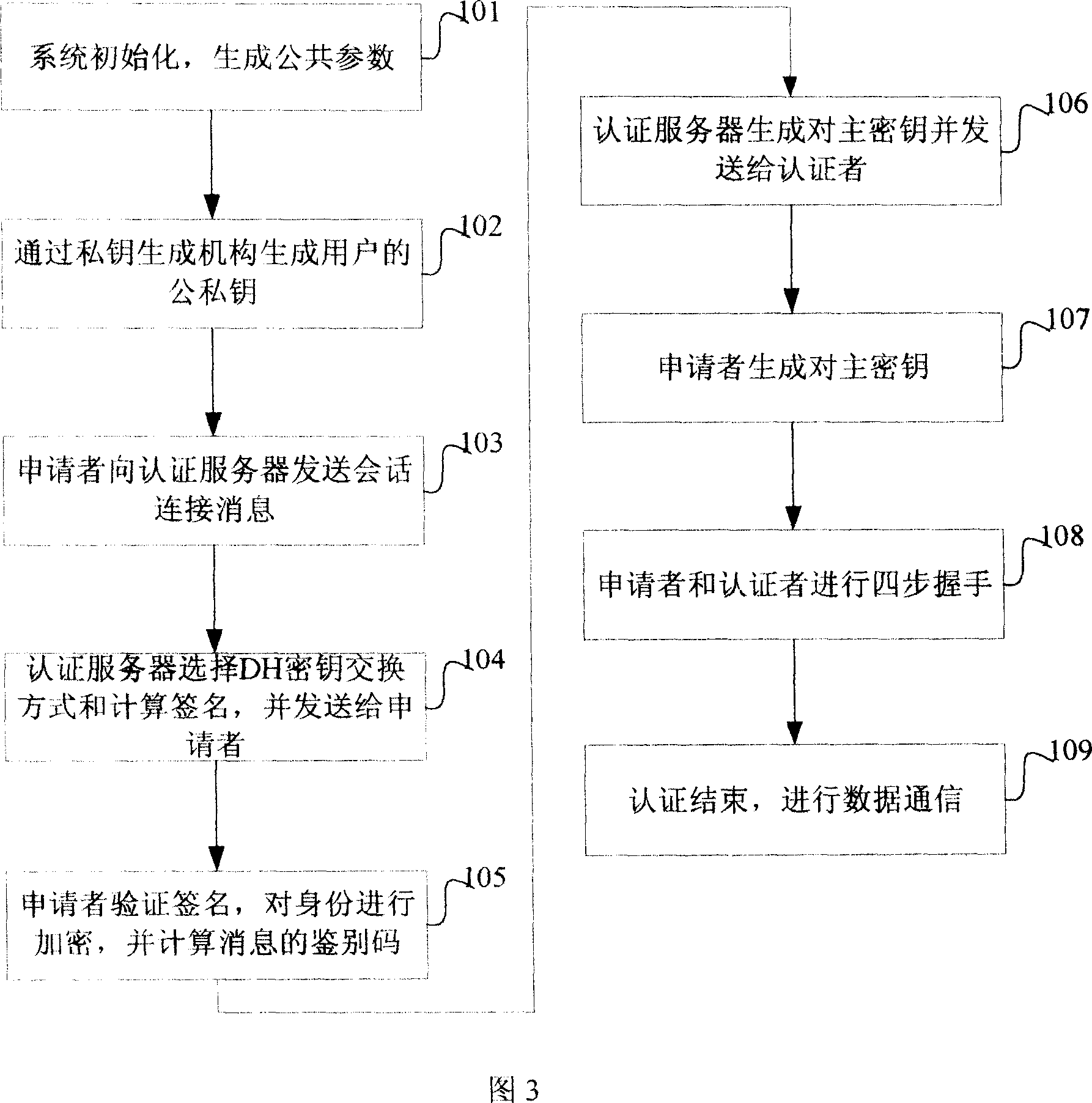
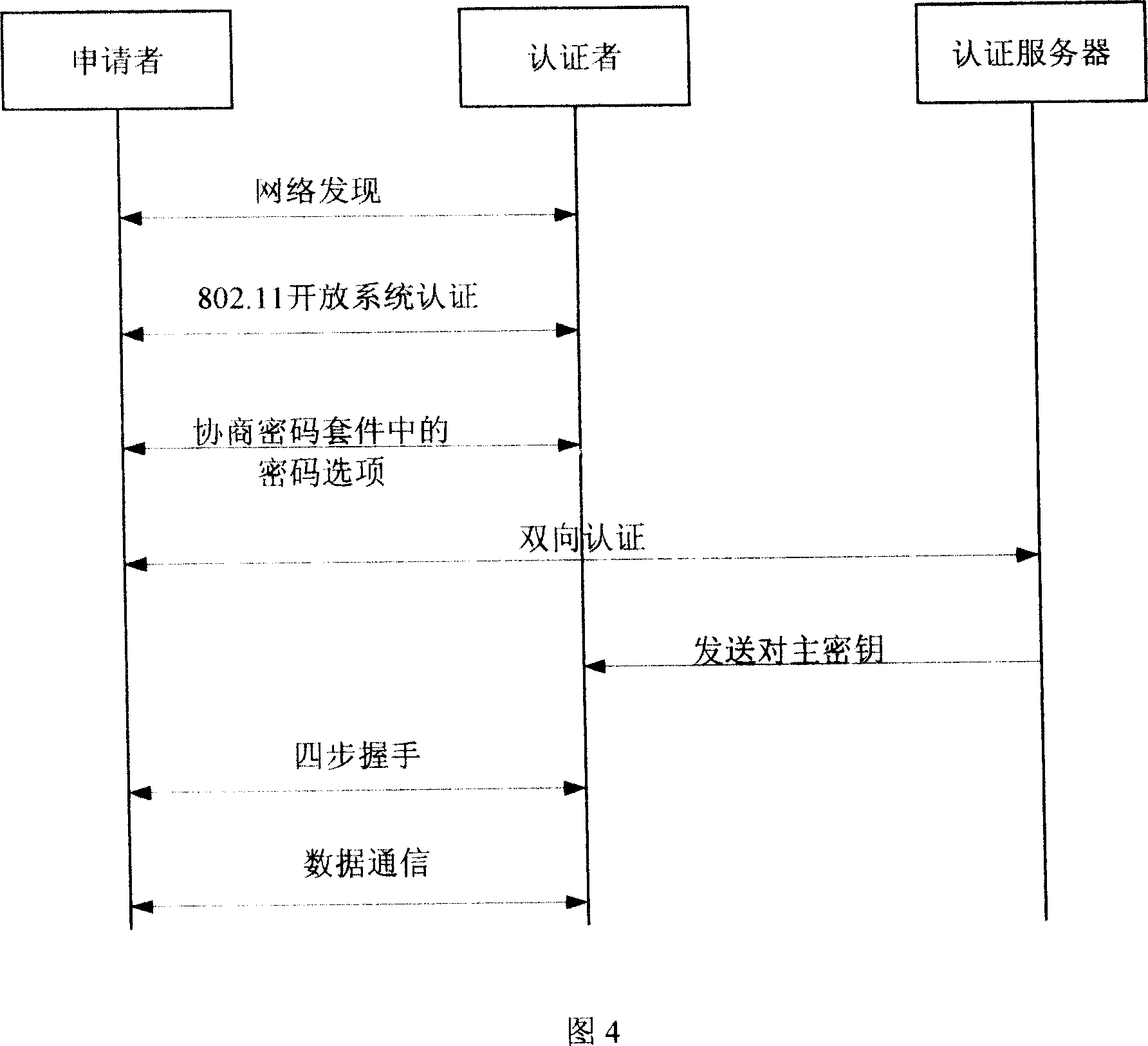
The present invention provides a bi-direction authentication method and system which belongs to the field of network communication. The present invention aims at solving the problems that certificate management in present private key authority technology is complex and the certificate management can not protect the identity of the users. The present invention provides a bi-direction authority method. The present invention includes the procedures of the system initialization and generating system parameters, an applicant initializing a dialogue request to establish connection with an authorization server, the applicant and the authorization server mutually check identity and generate a pair of main key which is used for the four-procedure-hand-shaking. The present invention also provides a bi-direction authorization system. The system includes a parameter initialization module, an establishing dialogue connecting module, a server identity verification module and an applicant identify verification. Applications of the technical proposal of the present invention can reduce the establishing and maintenance cost of the system, to enhance the running efficiency of the system, and to realize the target of protecting applicants.
Owner:XIDIAN UNIV +1
Integrity check in a communication system
InactiveUS20020044552A1Improve user securityPrevent replay attacksError preventionTransmission systemsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECHNOLOGLES OY
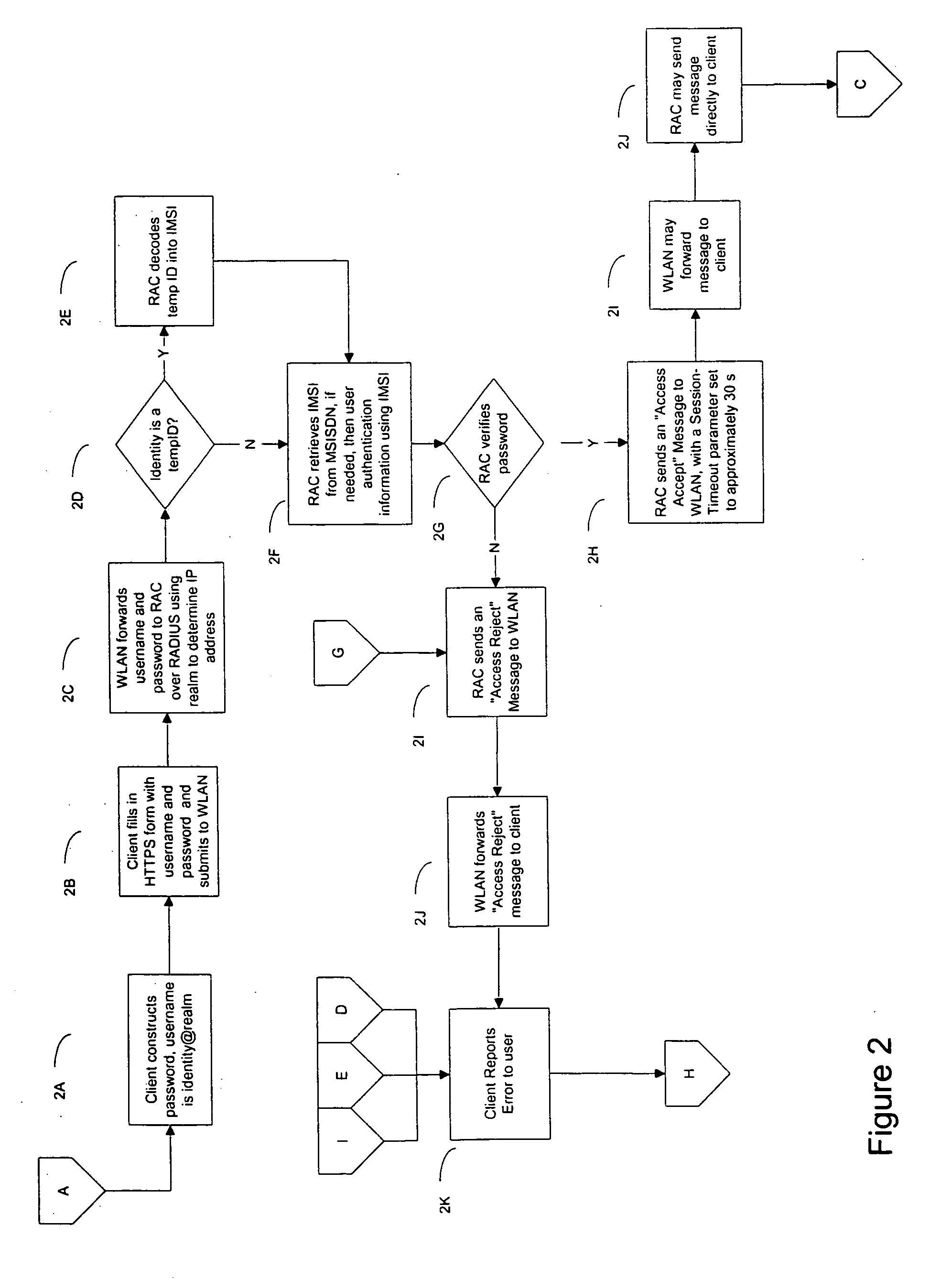
Method and system for providing SIM-based roaming over existing WLAN public access infrastructure
InactiveUS20050114680A1Prevent replay attacksUser identity/authority verificationNetwork topologiesWeb authenticationAccess method
A method and apparatus for performing SIM-based authentication and authorization in a WLAN Internet Service Provider (WISP) network supporting the universal access method (UAM) of authentication and authorization enabling roaming for customers of mobile service providers onto said networks. In addition, the invention provides a secure way of authenticating the customer's client device to the mobile service provider's network by employing temporary credentials for authentication that provide privacy of the user's identity and prevent replay attacks. Finally, if the WISP network supports the ‘pass-through’ facility, the authentication can be done more securely and quickly.
Owner:AZAIRE NETWORKS
Authentication and cryptographic key negotiation method, authentication method, system and equipment
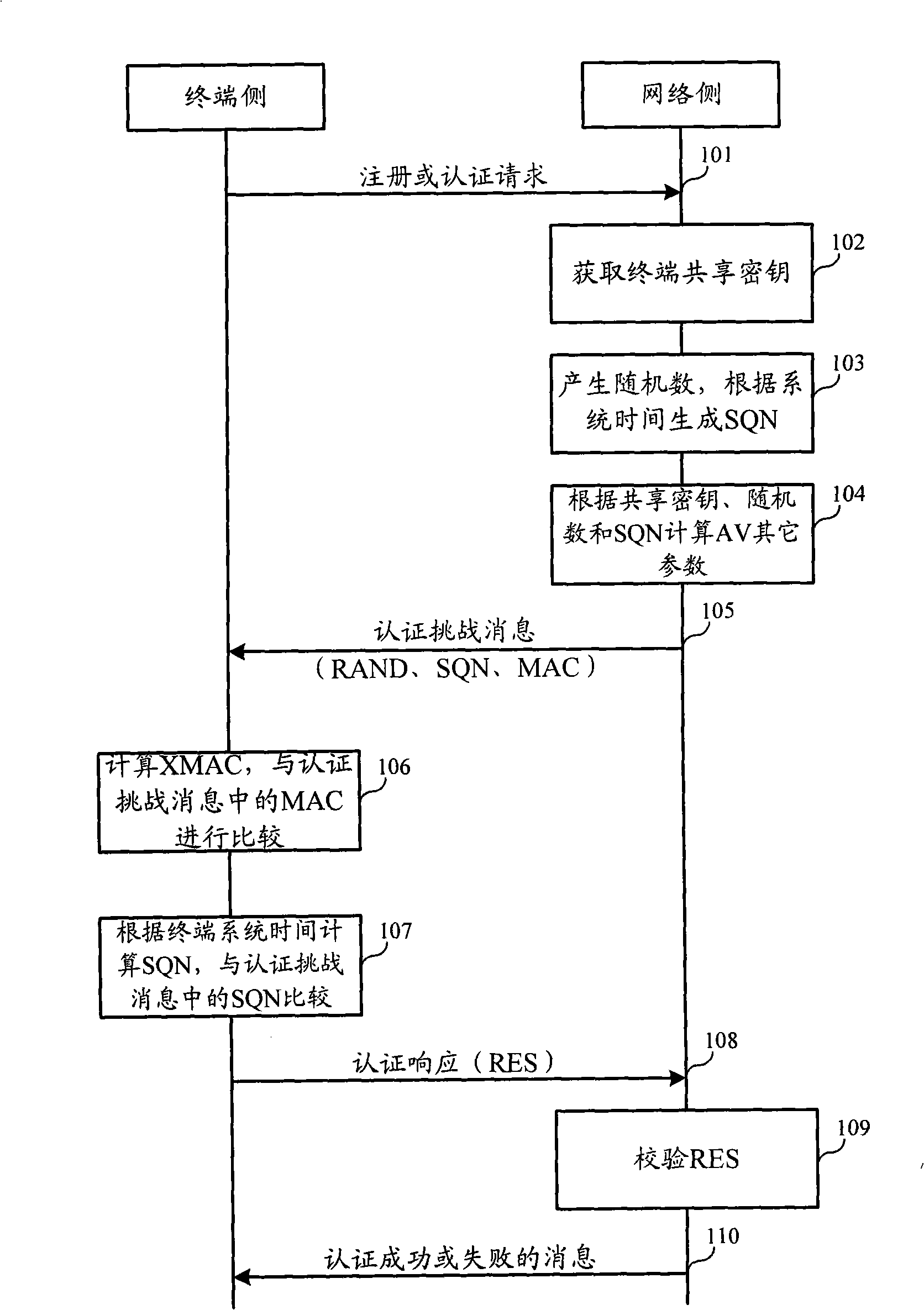
ActiveCN101272251AReplay is unique and accurateNo securitySynchronising transmission/receiving encryption devicesUser identity/authority verificationSystem timeReplay attack
The invention relates to the field of commutation and discloses an authentication and key negotiation method, an authentication method, a system and a device, which leads a user card to be capable of resisting the playback attack during the process of an AKA under the situation of not supporting SQN storing. In the invention, when a network side receives the authentication request of a terminal, a random number, a first sequence number SQN1 and a first authentication code MAC are sent to the terminal according to the shared key, the random number and the first authentication code MAC generated by the first sequence number SQN1, the first authentication code MAC represents the current system time at the network side; if a second authentication code XMAC is the same as the first authentication code MAC, and the difference value of a second sequence number SQN2 representing the current system time at the terminal side and the first sequence number SQN1 meet a preset condition, the terminal determines the network side legal according to the key shared with the network side, the received random number and the first authentication code MAC generated by the first sequence number SQN1.
Owner:HUAWEI TECH CO LTD
Integrity check in a communication system
InactiveUS7009940B2Improve user securityPrevent replay attacksError preventionFrequency-division multiplex detailsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
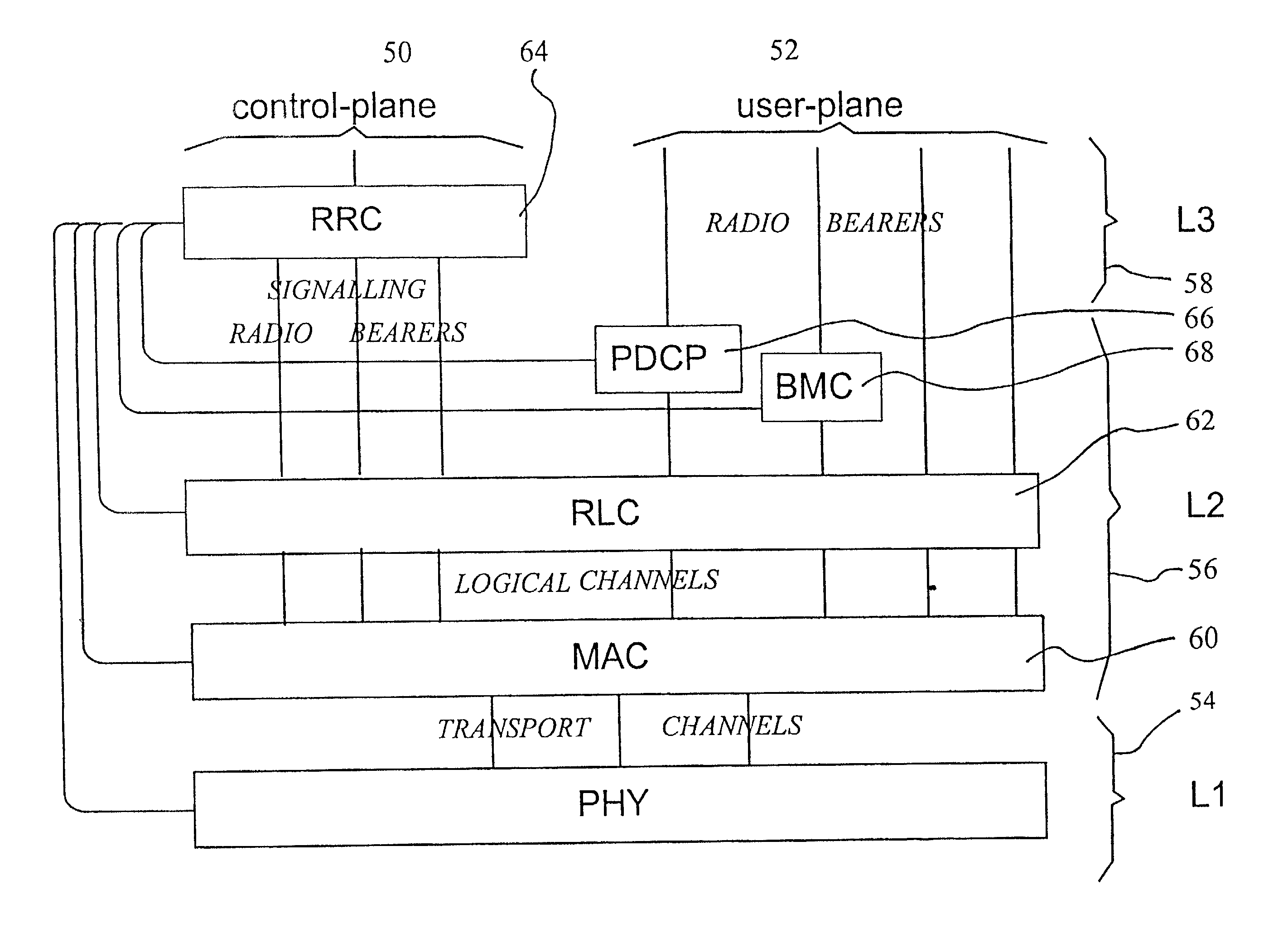
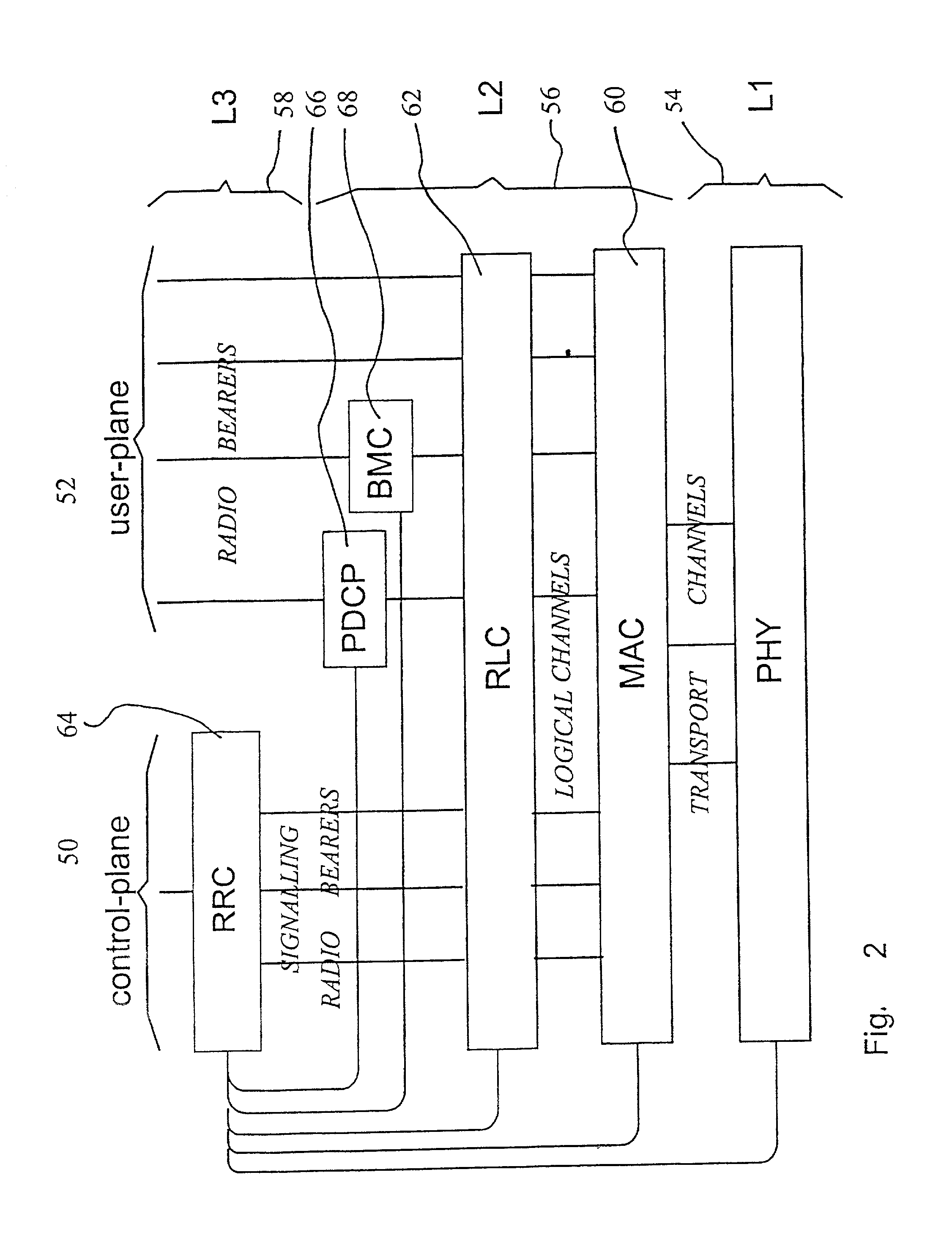
Owner:NOKIA TECHNOLOGLES OY
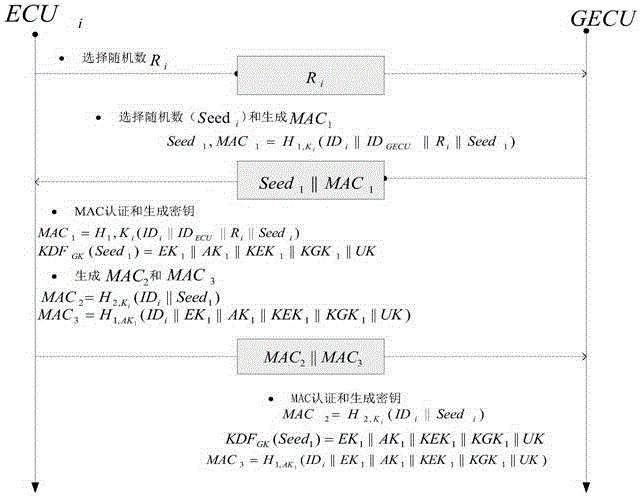
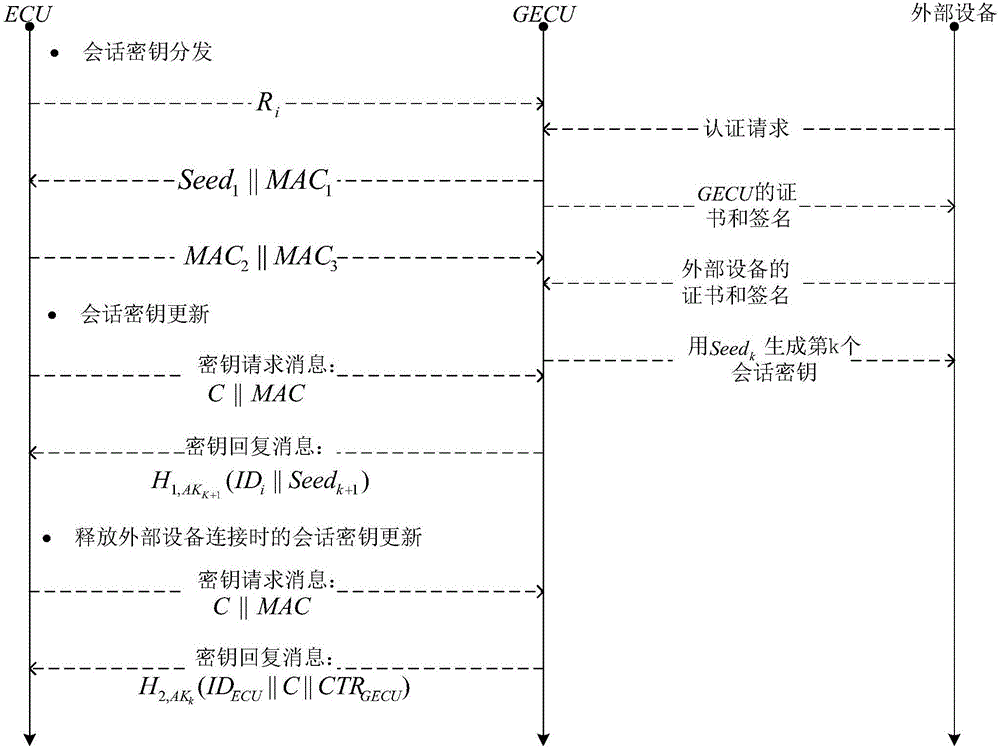
Method for safety communication of ECUs (Electronic Control Unit) in CAN (controller area network) bus
ActiveCN106790053AReduce computing costImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesArea networkKey generation
The invention discloses a method for safety communication of ECUs (Electronic Control Unit) in a CAN (controller area network) bus, which comprises the steps that: 1, a system model is established; 2, an GECU (Gateway Electronic Control Unit) loads a session key into a safety storage of the GECU; 3, the GECU carries out session key distribution on each ECU in the CAN bus; 4, a receiver ECUr carries out authentication on an encrypted data frame sent by a sender ECUs; 5, the GECU updates an encryption key and an authentication key which are used for communication, wherein update is mainly divided into two stages of in-vehicle ECU key update and key update when a connection of external equipment is released; and 6, when a vehicle is connected with the external equipment, designing an additional authentication and key distribution method so as to ensure legality of the accessed external equipment. According to the method disclosed by the invention, calculation cost can be obviously reduced, and a load of the CAN bus is reduced; and optimization is carried out for a key distribution protocol in the in-vehicle CAN bus, a key update problem generated when the external equipment is connected and released is considered, a counter is used for generating a random number to change a parameter for key generation, and a relay attack is effectively prevented.
Owner:JIANGSU UNIV
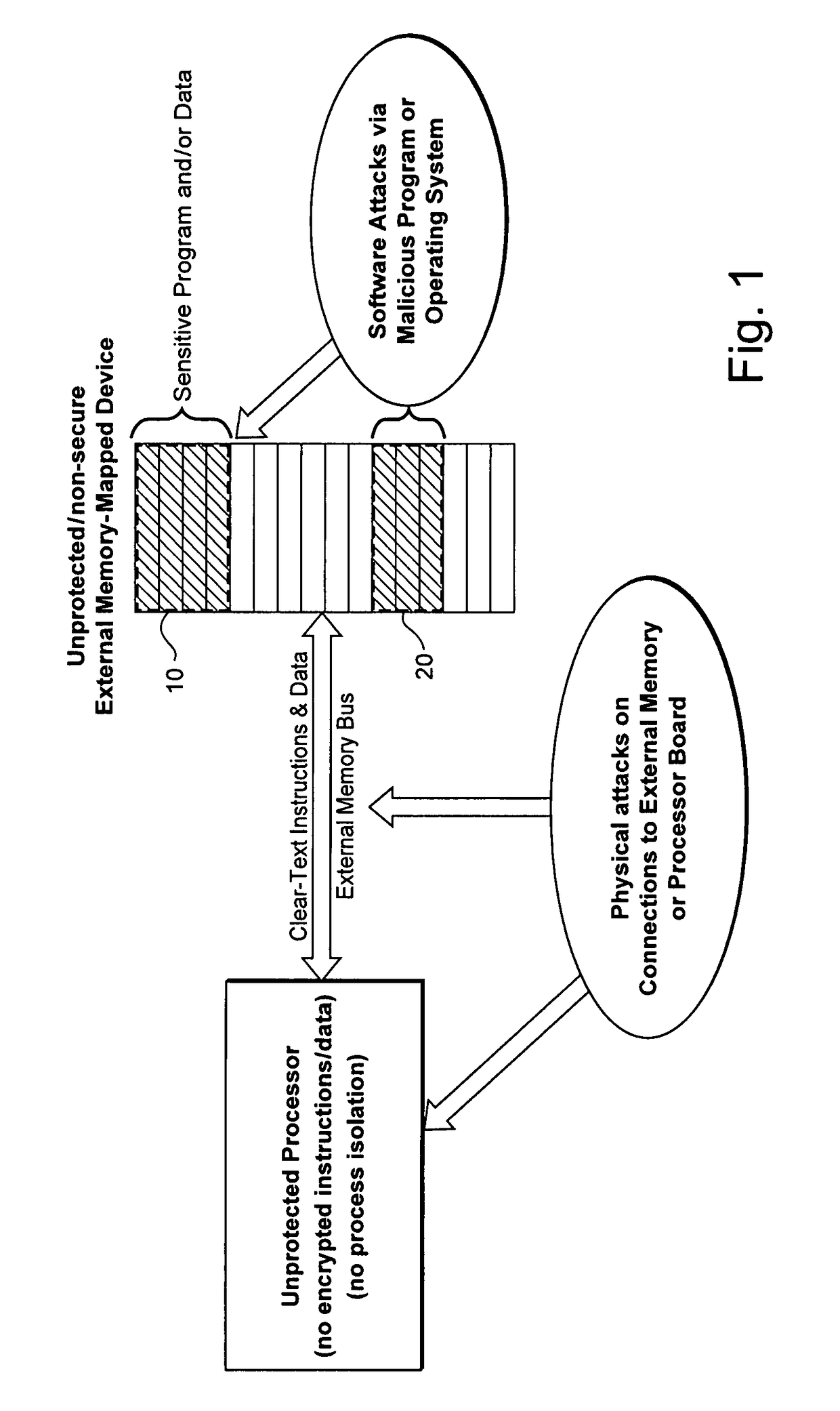
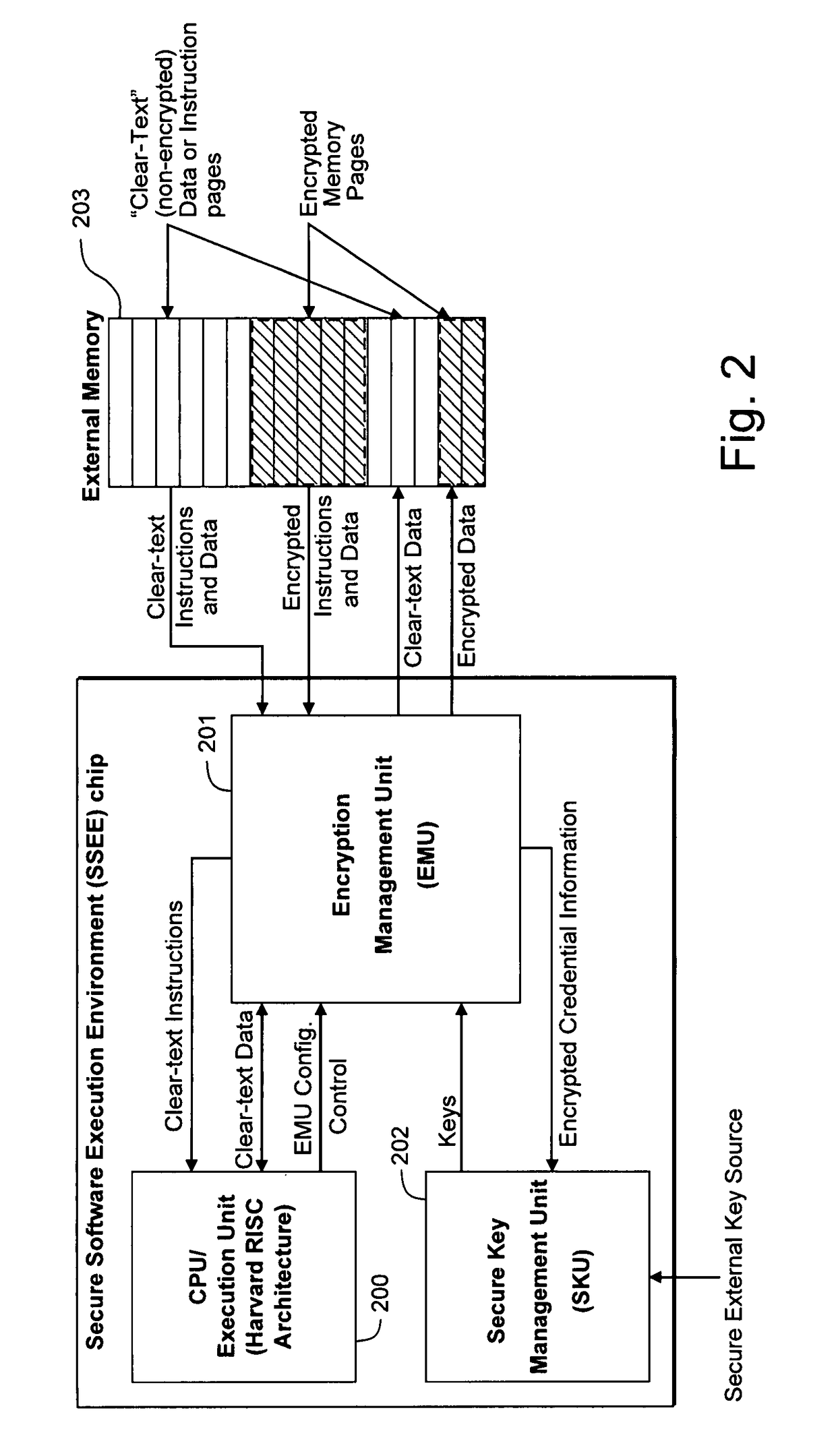
Hardware-facilitated secure software execution environment
InactiveUS8473754B2Avoid unwanted disclosureProvide confidentialityUser identity/authority verificationUnauthorized memory use protectionConfidentialityKey management
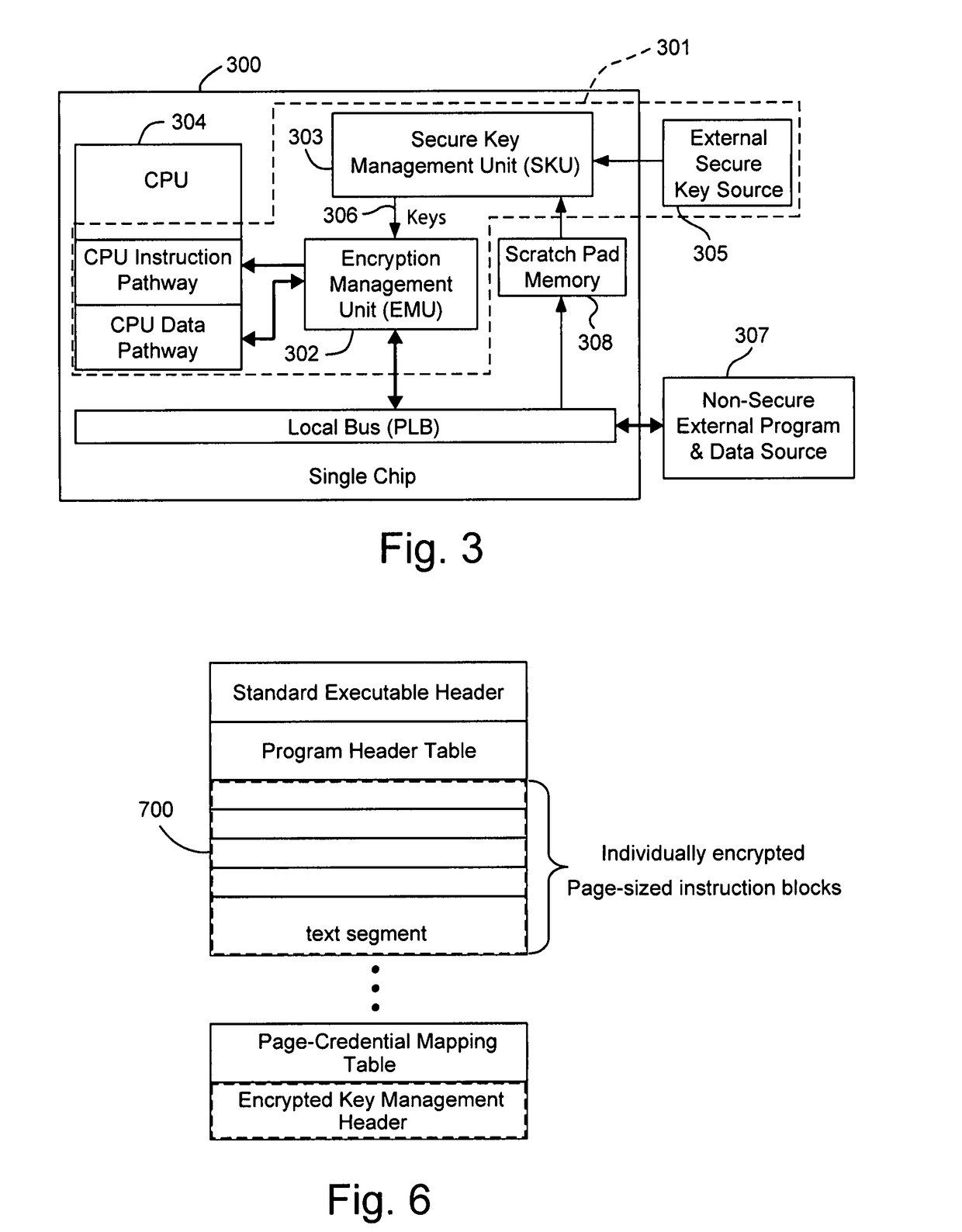
A hardware-facilitated secure software execution environment provides protection of both program instructions and data against unauthorized access and / or execution to maintain confidentiality and integrity of the software or the data during distribution, in external memories, and during execution. The secure computing environment is achieved by using a hardware-based security method and apparatus to provide protection against software privacy and tampering. A Harvard architecture CPU core is instantiated on the same silicon chip along with encryption management unit (EMU) circuitry and secure key management unit (SKU) circuitry. Credential information acquired from one or more sources is combined by the SKU circuitry to generate one or more security keys provided to the EMU for use in decrypting encrypted program instructions and / or data that is obtained from a non-secure, off-chip source such as an external RAM, an information storage device or other network source. In a non-limiting illustrative example implementation, the EMU decrypts a single memory page of encrypted instructions or data per a corresponding encryption key provided by the SKU. Although instantiated on the same chip, the CPU core does not have direct access to the SKU circuitry or to encryption key information generated by the SKU.
Owner:MACAULAY BROWN +1
Data transmission method, server side and client
ActiveCN104023013ASecure transmissionSecure one-way transmissionUser identity/authority verificationKey exchangeClient-side
The invention discloses a data transmission method, a server side and a client. The data transmission method comprises the following steps that: the server side and the client carry out information interaction through an authentication protocol, and perform identity authentication with each other; a session key is generated by the server side and the client through a key exchange protocol; a data packet to be transmitted is encrypted by the client through adopting an encryption algorithm and the session key, and the encrypted data packet is transmitted to the server side; and the received encrypted data packet is decrypted by the server side through utilizing the session key and the encryption algorithm, and the corresponding operation is executed. According to the scheme, unidirectional transmission of the transmitted data packet from the client to the server side can be implemented, establishing process is simple, and the computing resource is effectively saved, so that the data transmission is safer and more reliable.
Owner:SHANGHAI DNION INFORMATION & TECH
Mobile terminal digital certificate electronic signature method
ActiveCN105323062AIngenious ideaReasonable ideaUser identity/authority verificationIssuing bankInternet privacy
The invention relates to a mobile terminal digital certificate electronic signature method. According to the method, based on the characteristics of public keys and private keys and on the premise of not violating the rules prescribed by the electronic signature law, for example, a private key should be generated in a user terminal and should not leave the user terminal, a private key should not be transmitted via the network, and the like, a private key is discarded and locally and discretely stored after encryption, and the cloud uses strategies such as storing the public key and certificate to ensure that the private key is not locally cracked. In the transport layer, strategies such as double key and one-time pad are adopted to ensure that important information is not intercepted and decoded in network transmission. The identity of a certificate applicant is verified through the interface of an issuing bank, the user identity verification result of the bank counter is inherited, and therefore, remote online certificate issuing is realized in the system. The method not only can ensure that all the links of certificate applying, certificate issuing, certificate storing and certificate using are safe, but also can prevent hackers and Trojans from stealing certificate files, prevent network package-capture parsing, prevent password intercepting through screen capture and prevent an algorithm from being known through software decompiling.
Owner:BANKEYS TECH
Disordered transaction control method based on block chain account model
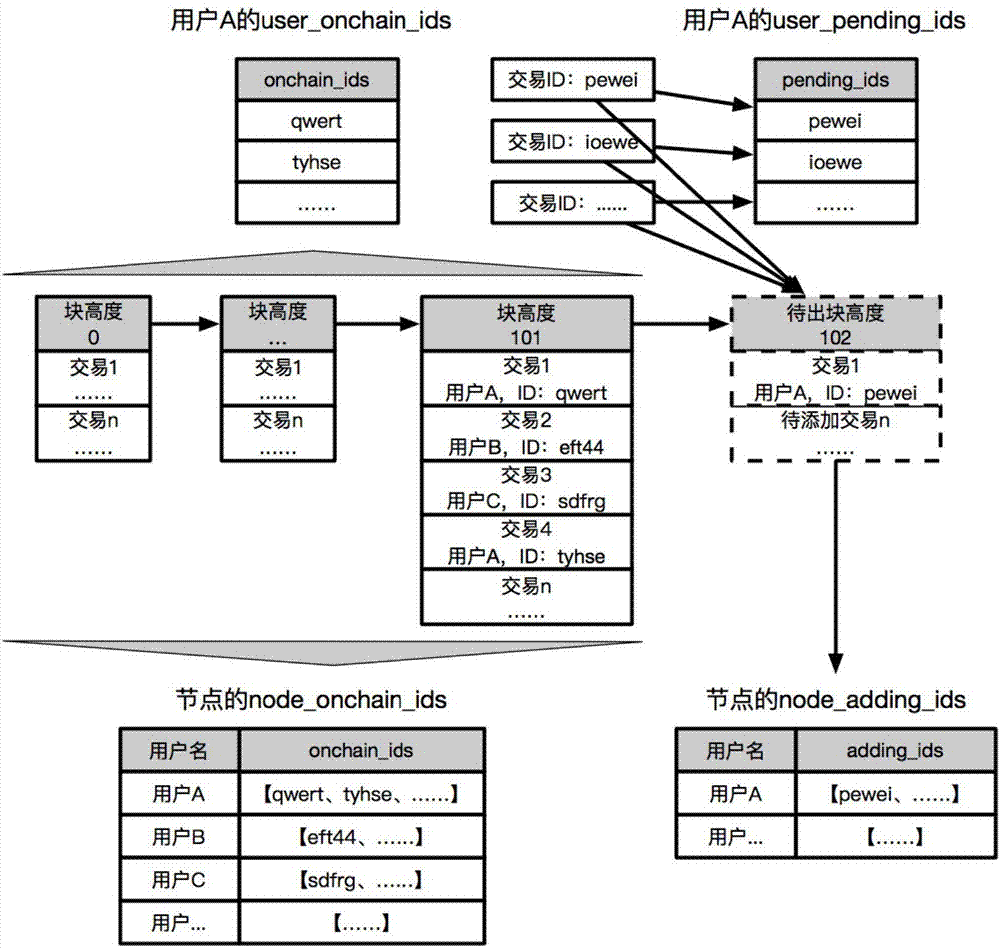
ActiveCN106991607AMeet the scenario requirements of high concurrent transactionsPrevent double spendingFinanceDigital numberUnique identifier
The invention discloses a disordered transaction control method based on a block chain account model. The disordered transaction control method based on a block chain account model is characterized in that based on an account model, a user utilizes a unique ID (such as UUID) taken from an increment digital number as the unique identifier for transaction; a node determines whether the behavior of double expenditure exists by determining whether a new transaction ID exists in a historical transaction ID list of the user; an order dependence relationship does not exist between the transaction IDs; an accounting node can packing the transactions into blocks in any order; and the successive dependence relationship of the service layer between the transactions can be guaranteed when a client issues a transaction without influencing disordered packing of the accounting node. The disordered transaction control method based on a block chain account model utilizes the unique ID to prevent double expenditure and playback attack, enables the transaction to not depend on the fixed order, and can use a disordered mode to directly enters the chain, thus satisfying the scene requirement for single-account high concurrent transaction of the client, and avoiding the situation that other transactions are postponed after the transactions are lost in the past.
Owner:HANGZHOU RIVTOWER TECH CO LTD
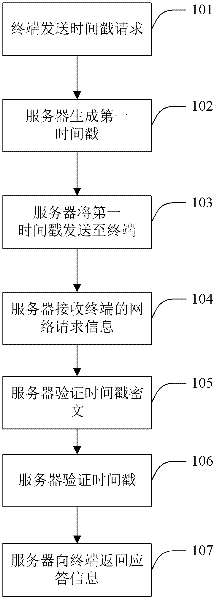
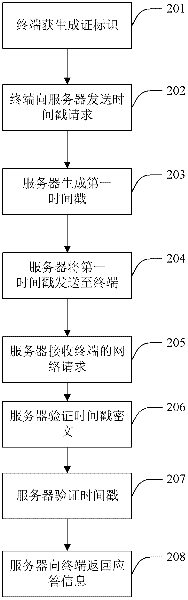
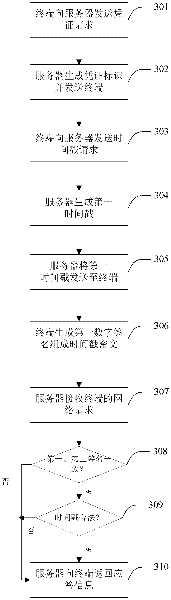
Communication method, server and terminal based on HTTP (Hypertext Transfer Protocol)
The application provides a network communication method, a system, a server and a terminal based on HTTP (Hypertext Transfer Protocol), aiming at resisting replay attack in HTTP network communication. The network communication method comprises the steps of sending a first time stamp to the terminal according to a terminal request; receiving network request information sent by the terminal, wherein the network request information includes the first time stamp and corresponding time stamp ciphertext, and the time stamp ciphertext is generated by encrypting algorithm factor containing the first time stamp according to a preset encryption algorithm at the terminal; and verifying whether the time stamp ciphertext is in effect or not according to the preset encryption algorithm, if no, judging the network request information is an invalid request. By verifying the validity and effectiveness of the time stamp ciphertext containing time stamp information, the possibility that the time stamp information in the network request is tampered can be further prevented, and occurrence of network replay attack can be avoided.
Owner:BEIJING QIHOO TECH CO LTD
Block chain identity system
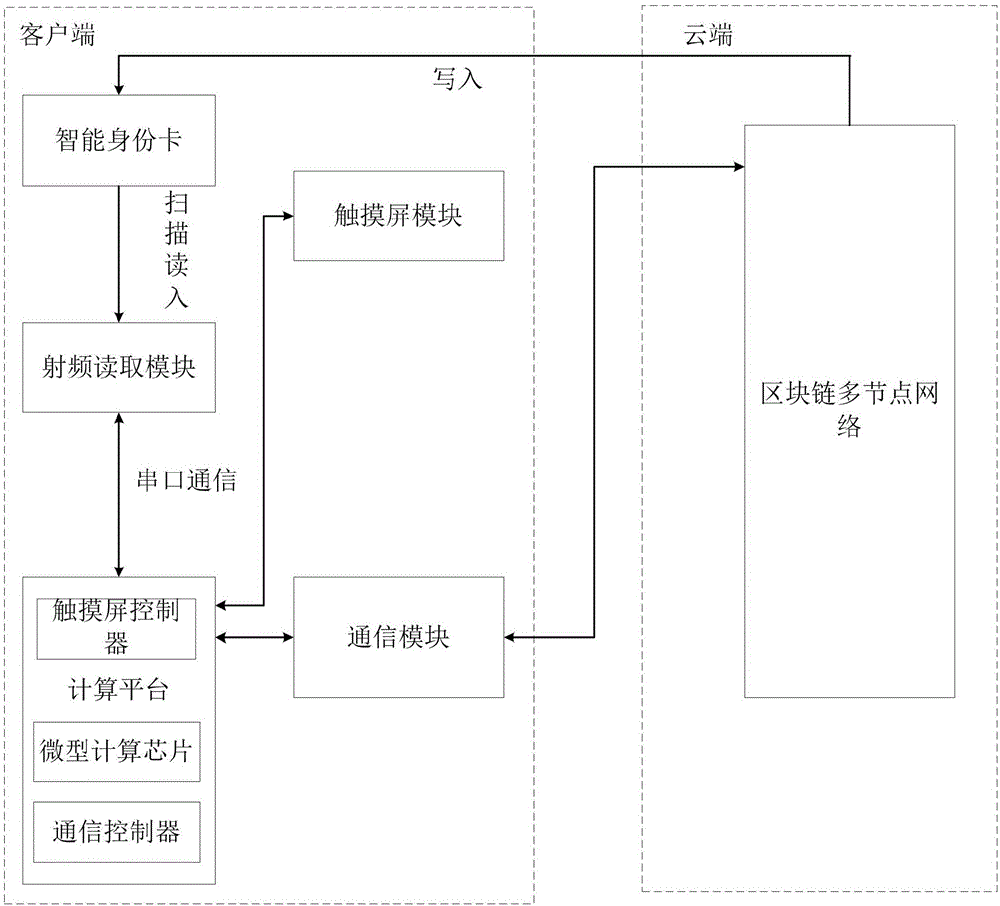
ActiveCN106789047ANo need to worry about leaksPrevent replay attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesGeneration processRadio frequency
A block chain identity system comprises a client and a cloud, wherein the client consists of a radio frequency reading module, a computing platform, a touch screen module, a communication module and an intelligent identity card, the cloud consists of a block chain multi-node network which comprises a data block chain and a multi-node network, and the multi-node network takes charge of coordination with the client to complete an identity generation process and an identity authentication process. The authentication system uses an intelligent identity card to guarantee safety of a user identity, transmitted information is transmitted after being encrypted and cannot be leaked in the transmission process, the validity of two times of authentication is guaranteed, and unnecessary attacks in the authentication process are avoided.
Owner:SHANGHAI WEILIAN INFORMATION TECH CO LTD
System and method for secure network connectivity
InactiveUS20070107061A1Accurate protectionEasy to useRandom number generatorsMemory loss protectionSecurity checkRemote computer
A system and method to ensure that a remote computer making a VPN connection complies with network security policies. Server driven security checks may be configured to verify compliance with each access level before access is granted at that level. The security checks may be selected based at least according to the information received from the remote computer. After the server determines that the remote computer complies with the security policy for the requested access level, the server may pass a token to the remote computer, or may grant VPN access to the remote computer. If the remote computer does not comply with the security policy associated with the requested access level but is in compliance with a security policy corresponding to a lower access level, the server may grant the remote computer access to the lower access level.
Owner:BARCLAYS CAPITAL INC
Bidirectional identity authentication method for wireless sensor network node
InactiveCN102325131APrevent replay attacksPublic key for secure communicationUser identity/authority verificationWireless sensor networkingWireless sensor network
The invention discloses a bidirectional identity authentication method for a wireless sensor network node. Double authentication parties in the identity authentication process need to generate the corresponding physical un-duplicated function (PUF) response according to the challenge provided by the opposite party, and the PUF can not be partitioned with a chip in the node and can not be duplicated, so the node can not be duplicated and attacked; a disposable random number is set in a packet sent by the node during applying for authentication every time, and a signature message is related with the random number, so replay attack of an attacker is avoided; and meanwhile, triple information related with the authentication in the node and the PUF are positioned in the same chip, so even if the attacker acquires the information, other nodes in the network can not be threatened because the PUF property is destroyed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
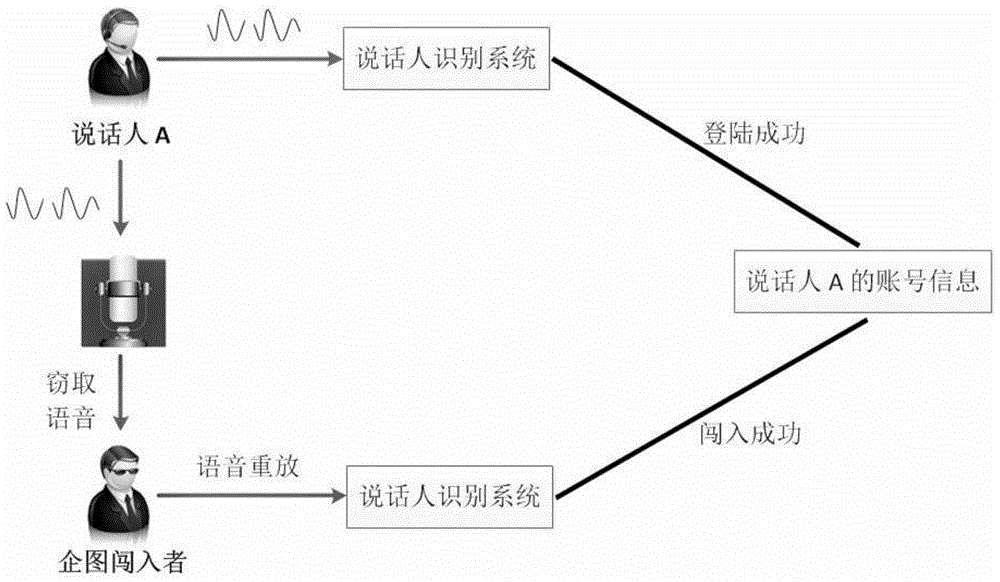
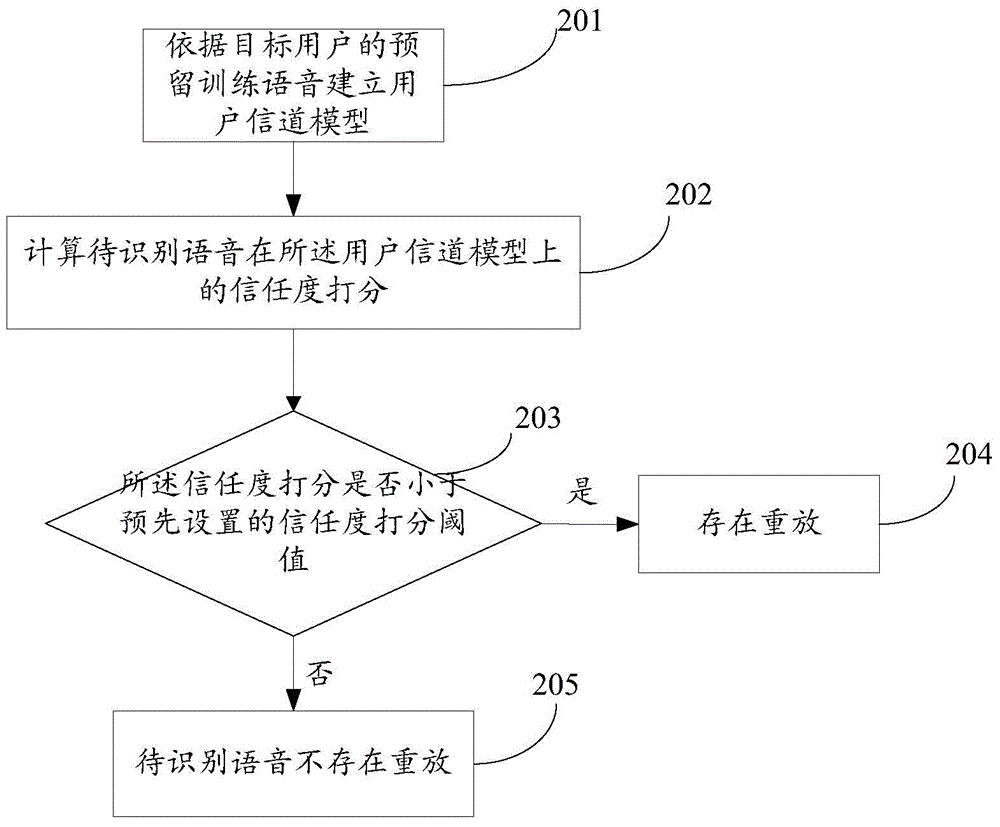
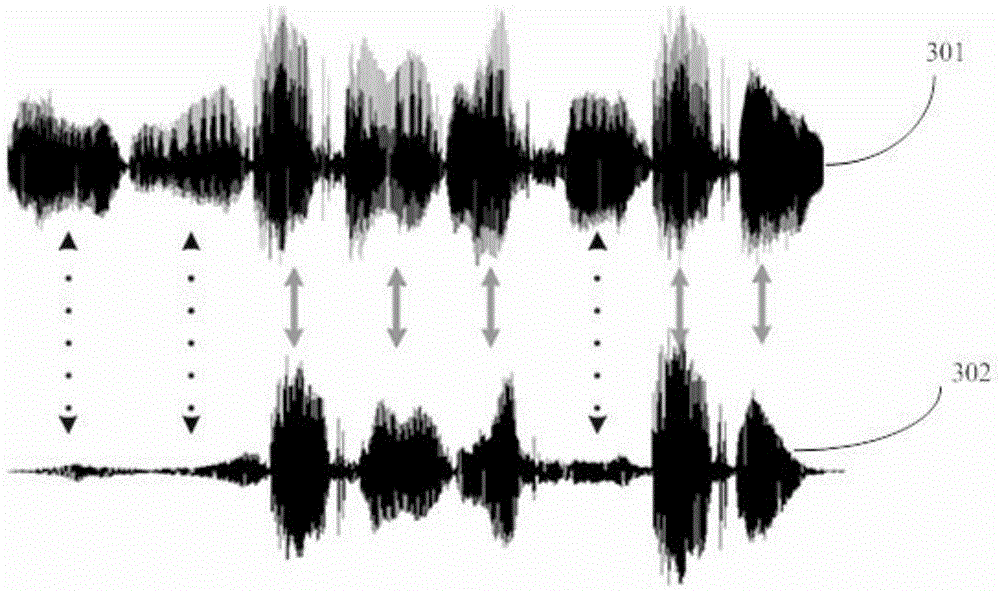
Voice playback detection method and device
The application discloses a voice playback detection method and device. The method comprises the steps of establishing a user channel model according to the reserved training voice of a target user; calculating the trust degree score of the to-be-recognized voice on the user channel model; if the trust degree score is less than a set threshold value, determining that the to-be-recognized voice needs to play back, and the return authentication is unsuccessful; on the contrary, passing the playback detection, thereby solving the voice playback attack problem in a current voiceprint recognition technology.
Owner:TSINGHUA UNIV +1
Identity authentication server and identity authentication token
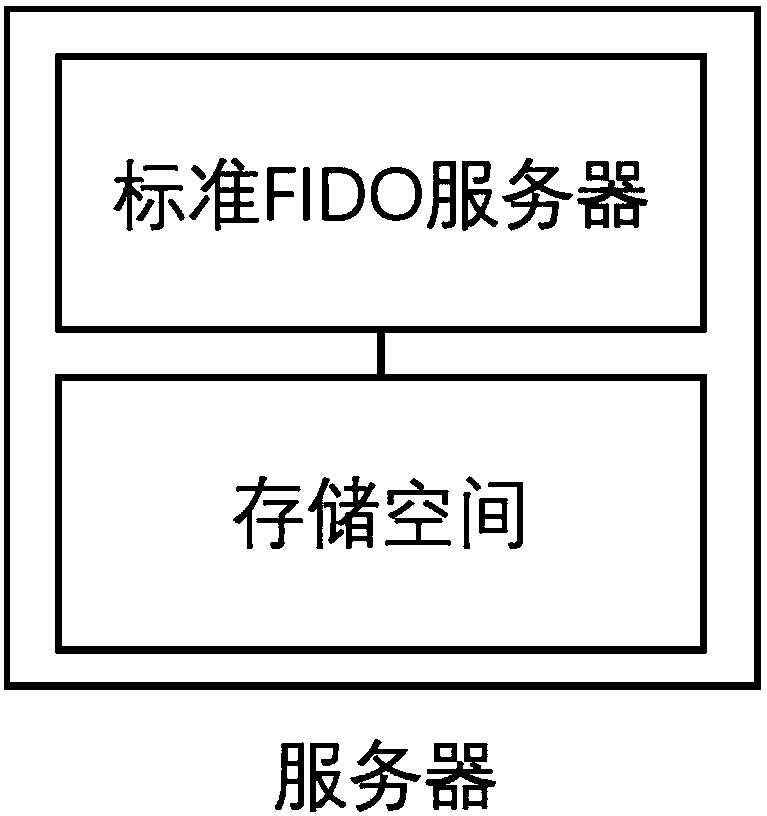
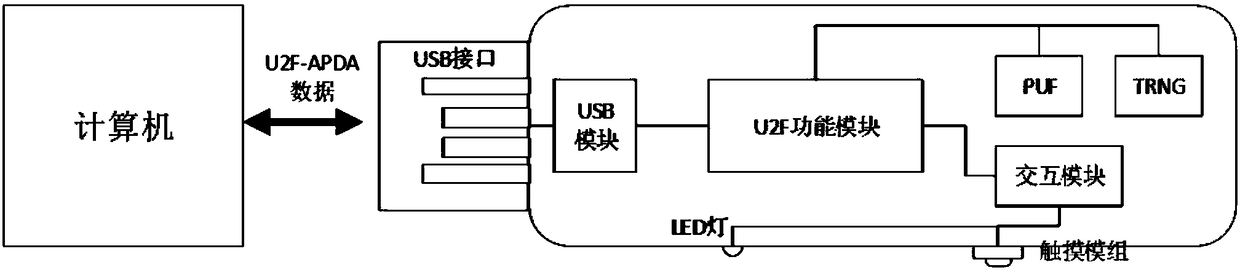
ActiveCN108092776APrevent replay attacksAddressing leaked passwordsUser identity/authority verificationClient-sideNon-repudiation
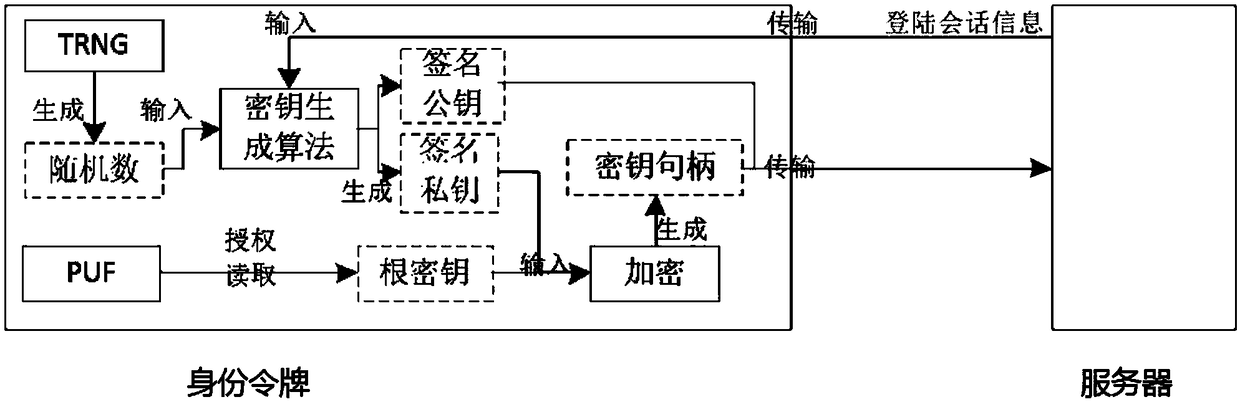
The invention discloses an identity authentication server and an identity authentication token, wherein the identity authentication server comprises a standard FIDO server and a storage space for storing keys, namely, a database, which are connected with each other; the identity authentication token is based on physical unclonable and the FIDO U2F protocol and comprises a U2F module, and a PUF module,a TRNG module, a USB module and an interaction module, which are connected with the U2F module, and a touch module connected with the interaction module; and an identity token interacts with a client browser, and the client browser in turn interacts with an FIDO server in the authentication server. According to the identity authentication server disclosed by the invention, the physical unclonable function is combined with the FIDO, the uniqueness and non-replicability of the token are ensured by the physical unclonable function, and the accuracy of the user identity and the non-defective modification and non-repudiation of the operation are ensured by the FIDO.
Owner:NARI INFORMATION & COMM TECH
Terminal authentication method and device based on single sign-on
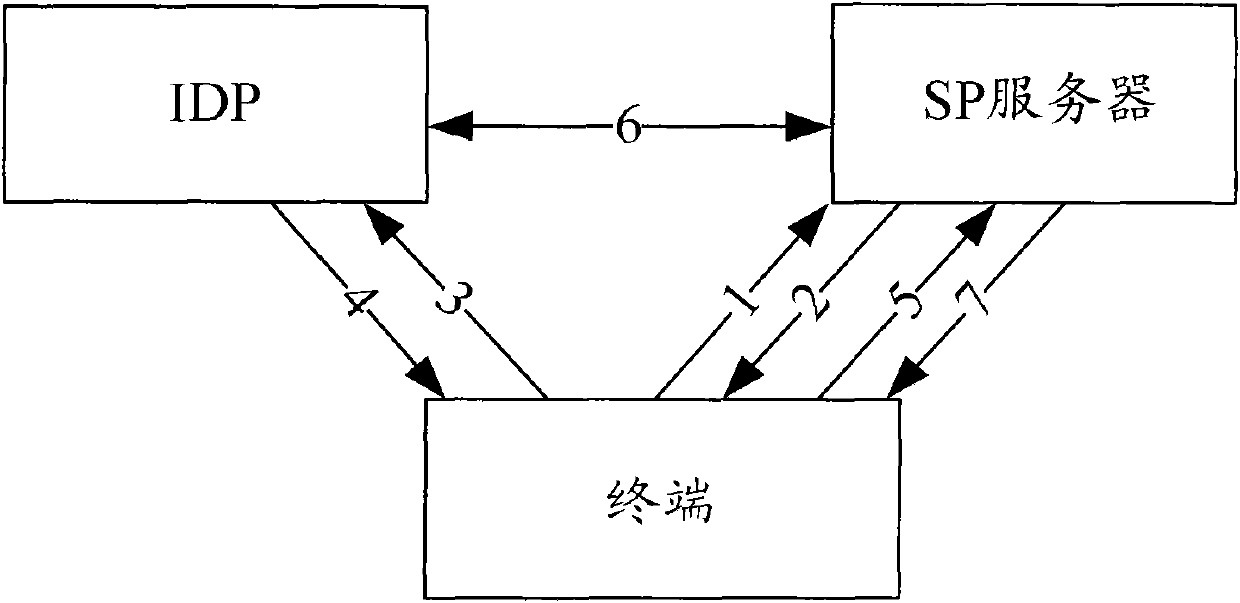
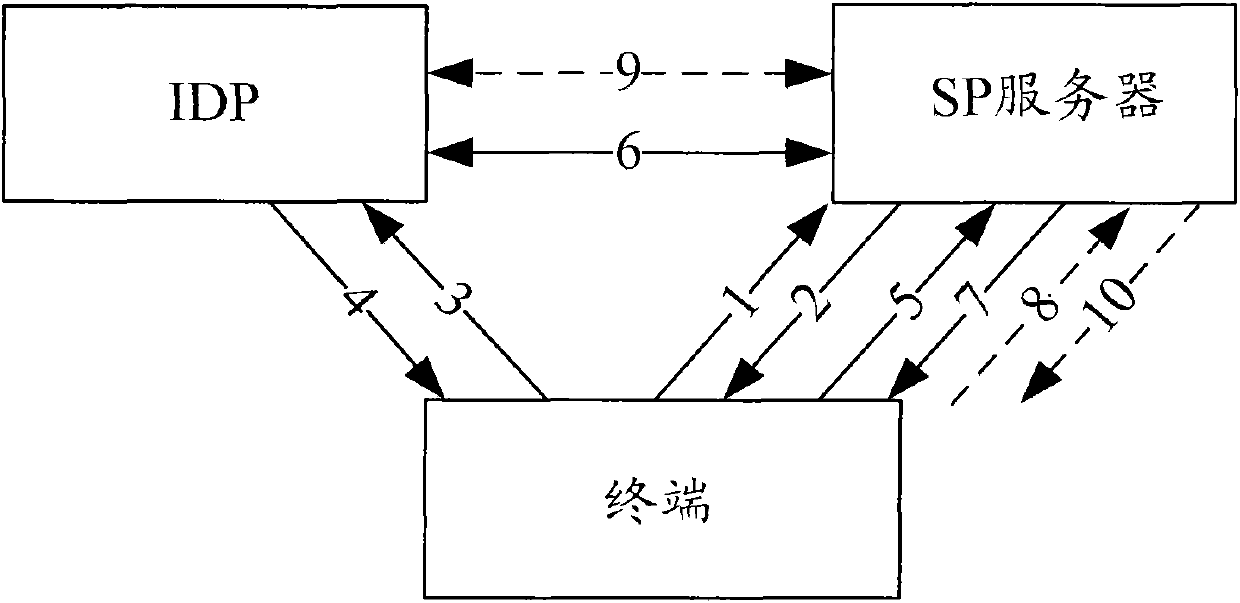
ActiveCN102201915AImprove login efficiencyPrevent replay attacksUser identity/authority verificationComputer terminalKey generation
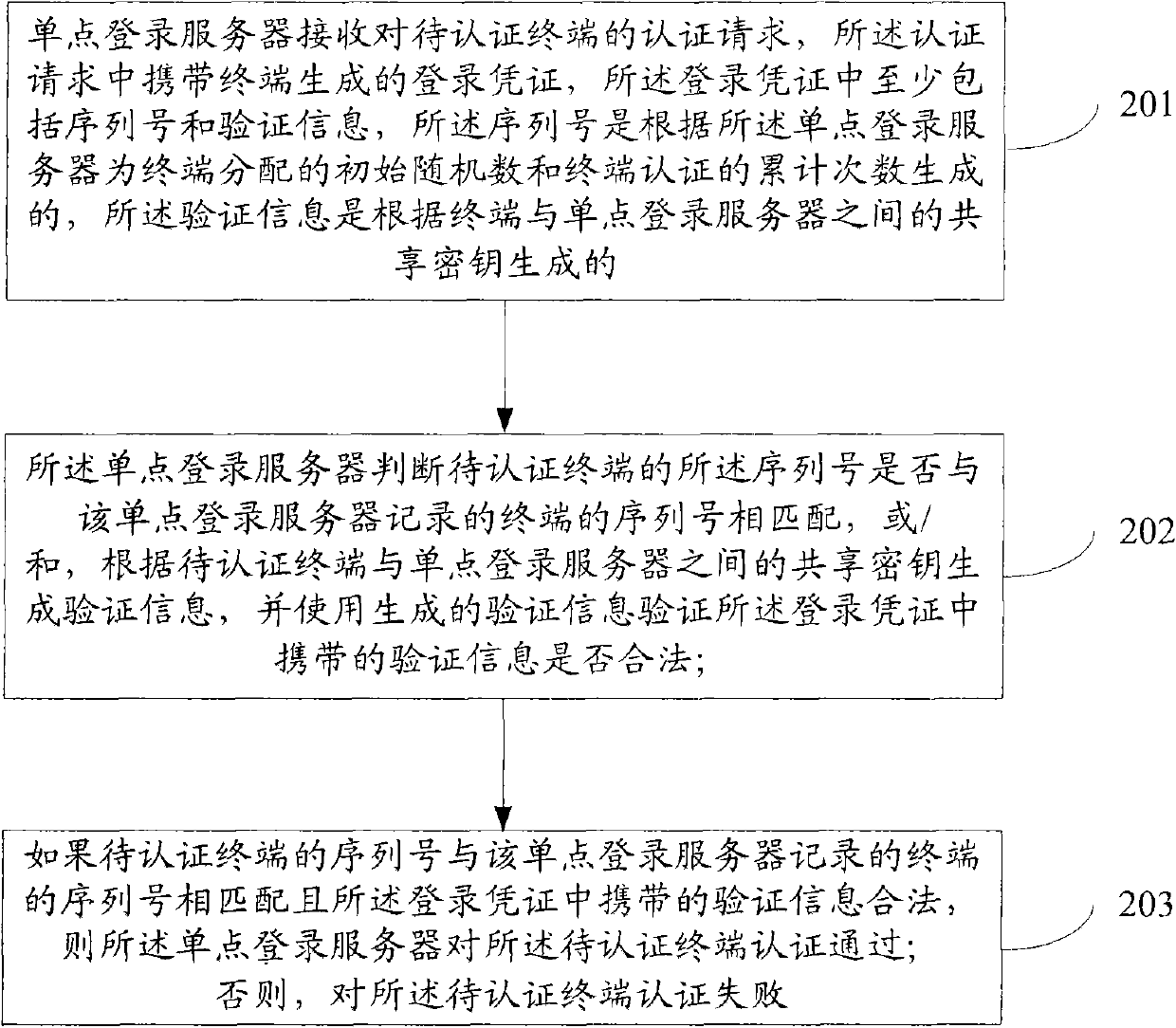
The embodiment of the invention discloses a terminal authentication method and device based on single sign-on. The method comprises the following steps: a single sign-on server receives log-on evidence generated by a terminal to be authenticated carried in an authentication request of the terminal, wherein the log-on evidence at least comprises a serial number and verification information, the serial number is generated according to an initial random number distributed for the terminal by the single sign-on server and the cumulative number of terminal authentication, and the verification information is generated according to a shared key between the terminal and the single sign-on server; the single sign-on server judges that the terminal to be authenticated passes authentication if the serial number of the terminal to be authenticated is matched with the serial number of a terminal recorded by the single sign-on server; and otherwise, the authentication of the terminal to be authenticated fails. By adopting the method and the device, replay attack is prevented, and the singe log-on efficiency is increased.
Owner:CHINA MOBILE COMM GRP CO LTD
Bidirectional identity authentication method based on dynamic password and biologic features under cloud environment
ActiveCN103124269AImprove securityImprove stabilityUser identity/authority verificationPasswordDependability
The invention discloses a bidirectional identity authentication method based on dynamic password and biologic features under cloud environment, wherein a plurality of authentication methods and encryption technologies are comprehensively used, a one-time random key is obtained by receiving messages, the bidirectional authentication is realized, a user can login anywhere, finish registration process on net, and has no need to register information at designated location. According to the bidirectional identity authentication method based on dynamic password and biologic features under cloud environment, the one-time dynamic password is combined with the biological features, secret key is transmitted to GSM (Global System for Mobile Communication), and accordingly, security and reliability of authentication process are enhanced.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Efficient anonymous identity authentication method in Internet of Vehicles environment
ActiveCN111372248AImprove authentication efficiencyEnhanced anonymityPublic key for secure communicationParticular environment based servicesInternet privacyAttack
The invention provides an efficient anonymous identity authentication method in an Internet of Vehicles environment, and belongs to the technical field of Internet of Vehicles security. According to the technical scheme, the method comprises the following steps of vehicle offline registration, online registration and rapid identity authentication. The method has the beneficial effects that a temporary identity certificate Token mechanism is set, so that the authentication efficiency is improved while the vehicle anonymous two-way communication is realized; a block chain distributed account book mode is utilized, so that data traceability and tamper resistance are guaranteed, and the problems of relatively low identity authentication efficiency, easiness in attack and the like caused by traditional PKI authentication centralization of the Internet of Vehicles are solved; the combination of the blockchain PBFT consensus mechanism and the smart contract greatly reduces the authenticationtime delay of the traditional method.
Owner:NANTONG UNIVERSITY
Method and device for verifying integrity of security critical data of program in process of running
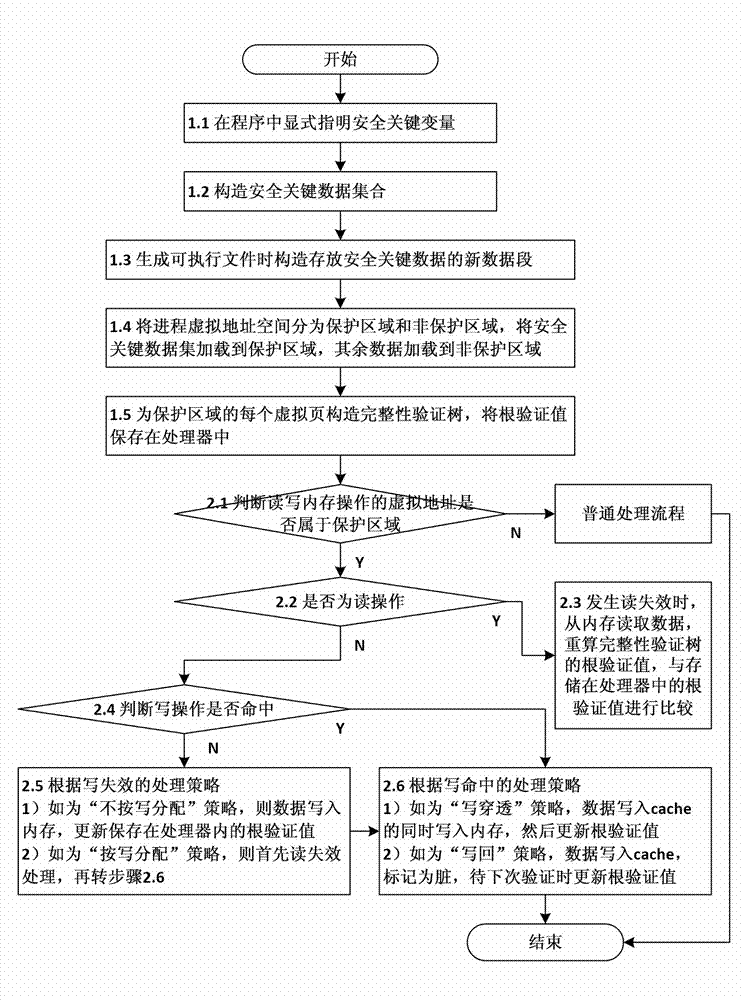
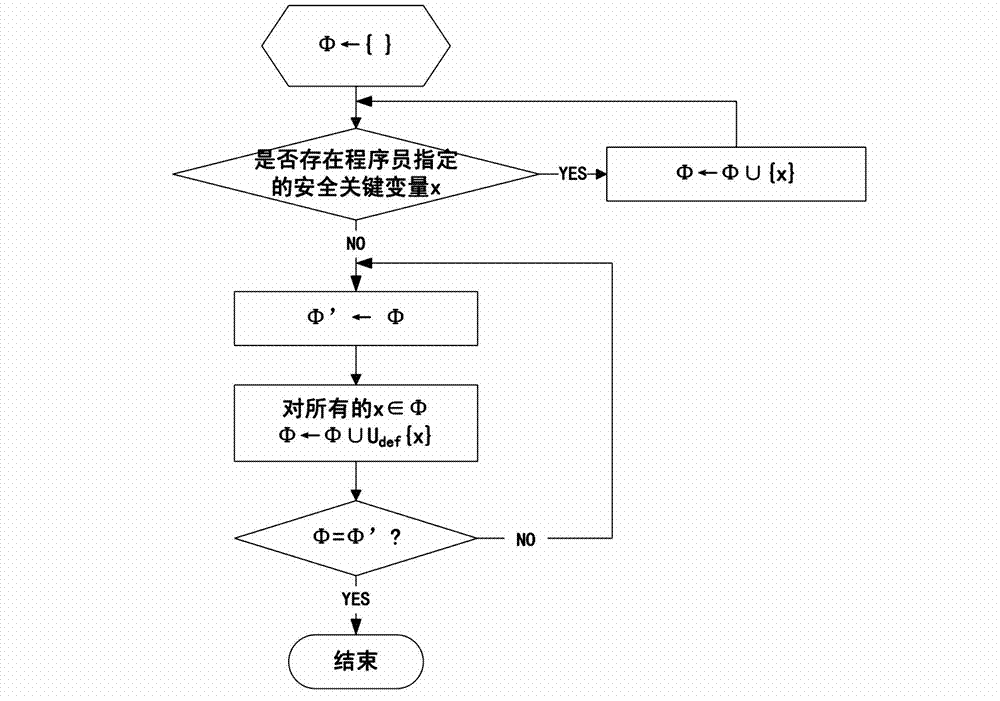
ActiveCN102930185AAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
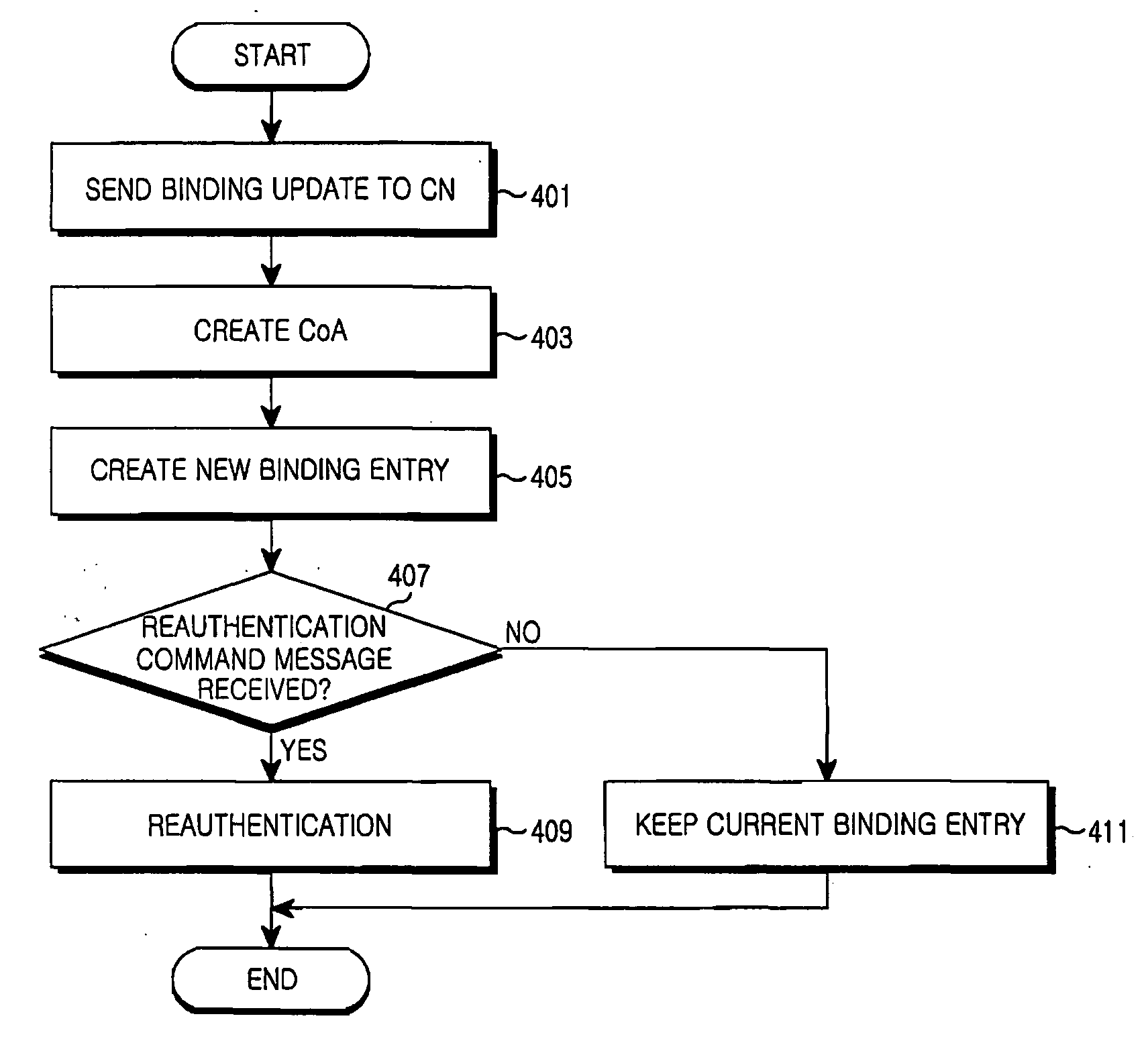
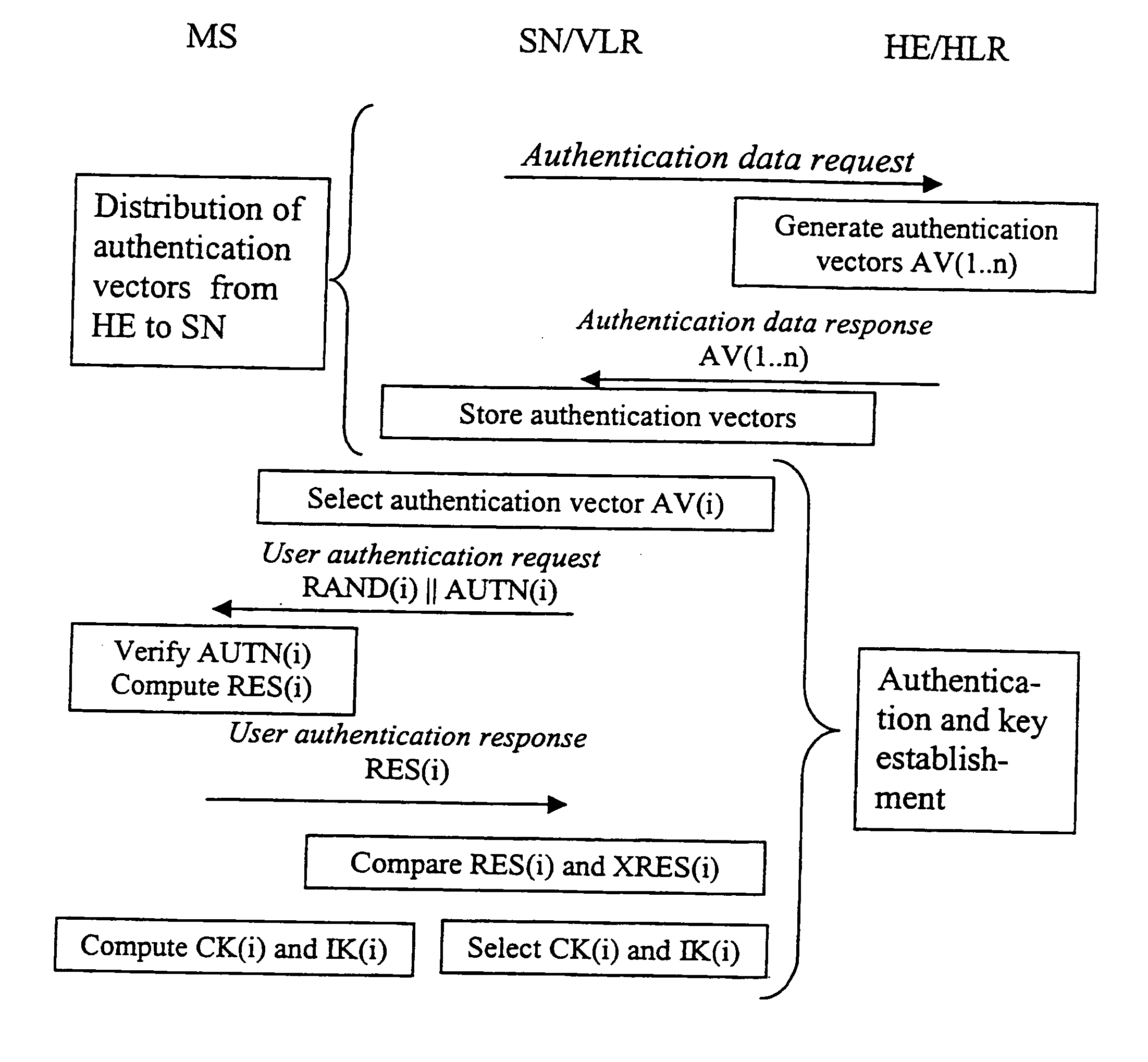
Method of preventing replay attack in mobile IPv6
ActiveUS20060259969A1Prevent replay attackPrevent replay attacksUnauthorised/fraudulent call preventionData taking preventionReceiptCare-of address
Disclosed is a method of preventing a replay attack during a handoff in a communication system using a Mobile IPv6 protocol. A mobile node creates a CoA (Care of Address) by handoff and sends the CoA to a correspondent node, thereby creating a binding entry. Upon receipt of a binding update message including a HoA and a CoA from the mobile node or an attacker, the correspondent node searches a binding cache for a binding entry having the same HoA (Home Address) and CoA as included in the binding update message. If it is determined that the binding entry has the same respective HoA and CoA as contained in the binding update message, the correspondent node checks a Used field of the binding entry. If it is determined that the Used field of the binding entry is equal to a predetermined value, the correspondent node sends a reauthentication command message to the mobile node.
Owner:SAMSUNG ELECTRONICS CO LTD
Secure registration
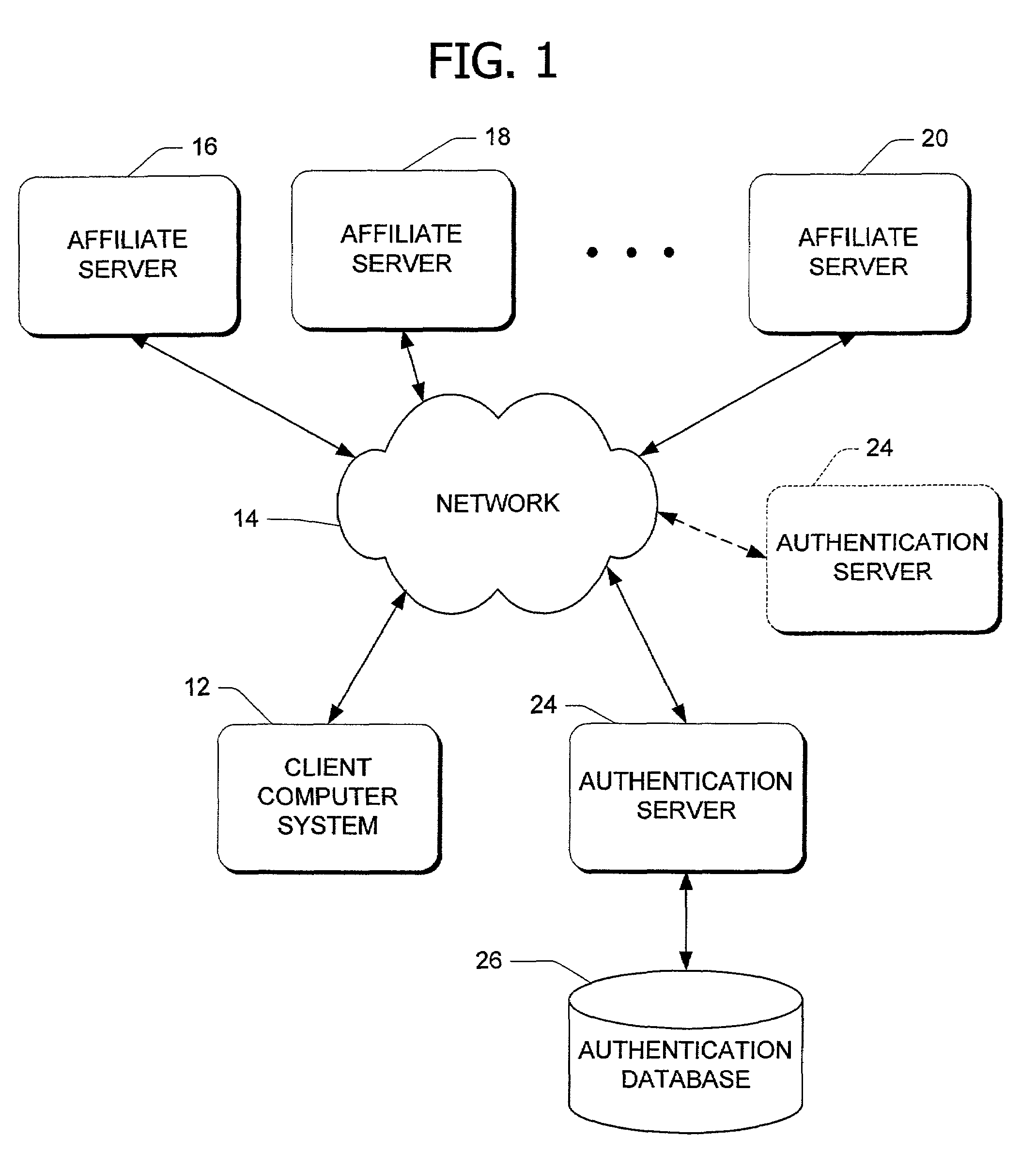
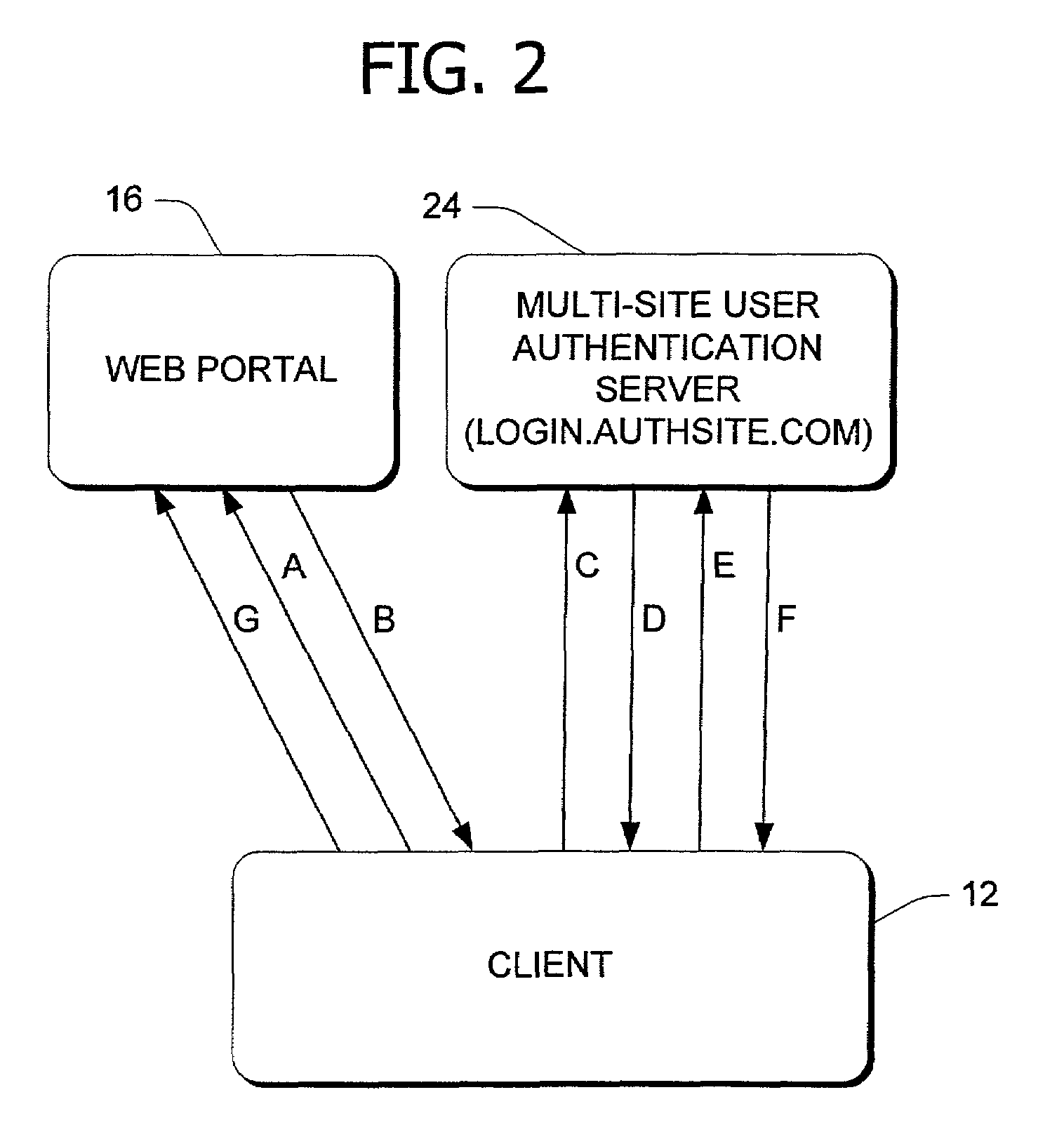
InactiveUS7356711B1Prevent tamperingReduce riskRandom number generatorsUser identity/authority verificationMulti siteQuery string
Secure site-to-site transactional communication between at least two network servers coupled to a data communication network, including secure registration by an authentication server associated with a multi-site user authentication system. A network server receives a request via a browser f of a client computer. In response, the network server initiates a transaction with the authentication server and defines a data structure, such as a query string, associated with the transaction. The network server also generates a digital signature of the data structure and then adds it to the data structure before directing the client computer from the network server to the authentication server with the data structure and the added digital signature. The network server also adds an index to the data structure. The index is associated with the transaction and unique, per transaction, to the network server initiating the transaction.
Owner:MICROSOFT TECH LICENSING LLC
Integrity check in a communication system
InactiveUS20060159031A1Improve user securityPrevent replay attacksError prevention/detection by using return channelTransmission systemsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECH OY
Identification authentication method between peer-to-peer user nodes in P2P network
InactiveCN101442411ARelieve pressureGuaranteed freshnessPublic key for secure communicationUser identity/authority verificationEncryptionPeer-to-peer
The invention provides a method for authenticating identification among peer-to-peer nodes in a P2P network. Each peer-to-peer node in the P2P network has a certificate which is acquired when a user node logs on the network through a certificate server, and the certificate comprises an encryption result of a private key of the certificate server to a public key of the user node. The method comprises the following steps: a first user node transmits an identification authentication message to a second user node in the network, wherein the identification authentication message comprises a certificate of the first user node and the public key of the first user node; a second user node authenticates identification of the first user node by the identification authentication message, after authentication succeeds, the identification authentication message is returned to the first user node, wherein the identification authentication message comprises a certificate of the second user node and the public key of the second user node; and the first user node authenticates the identification of the second user node by the identification authentication message returned by the second user node, and if the authentication succeeds, identification authentication between two user nodes succeeds.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and attestation system for preventing attestation replay attack
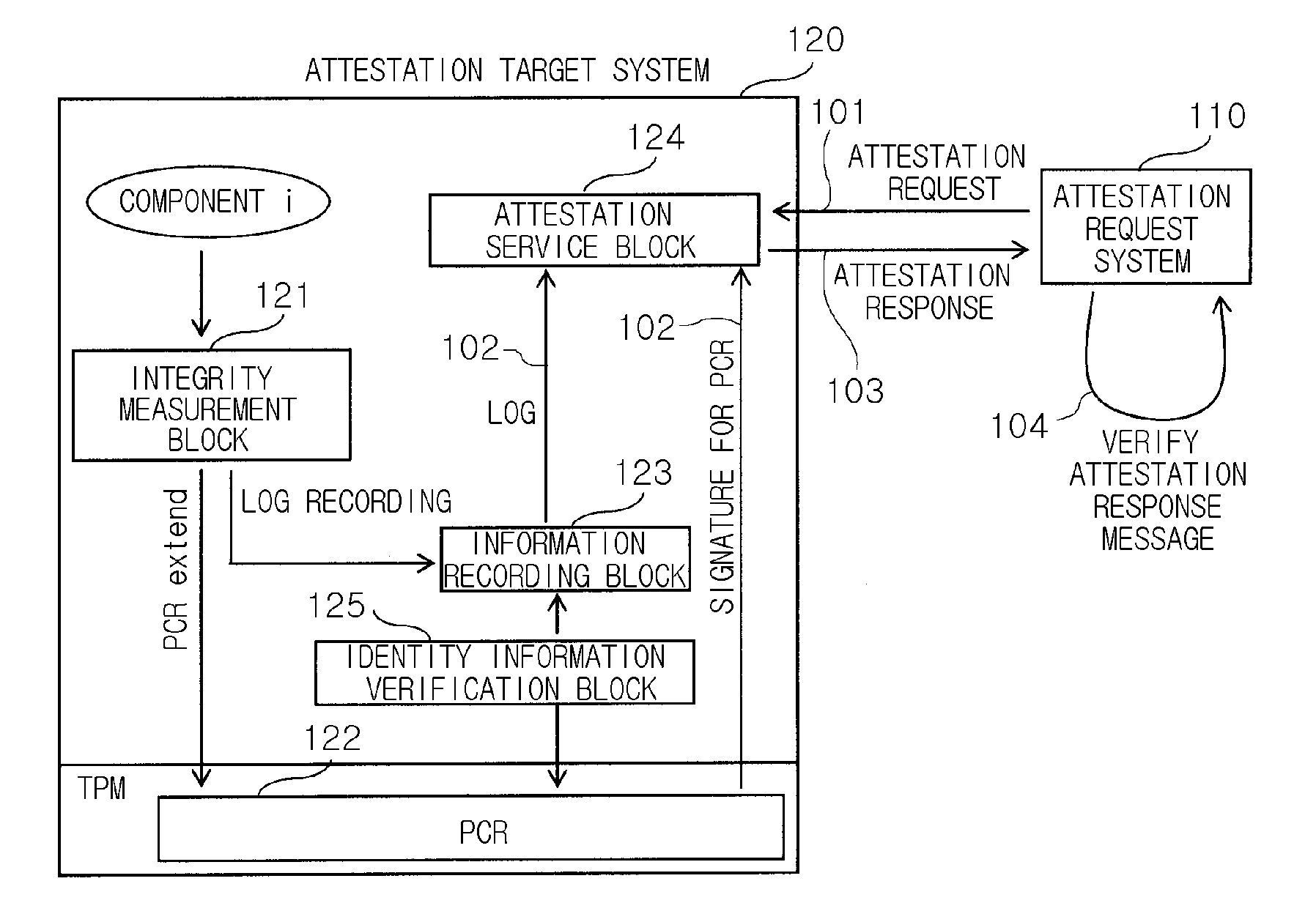
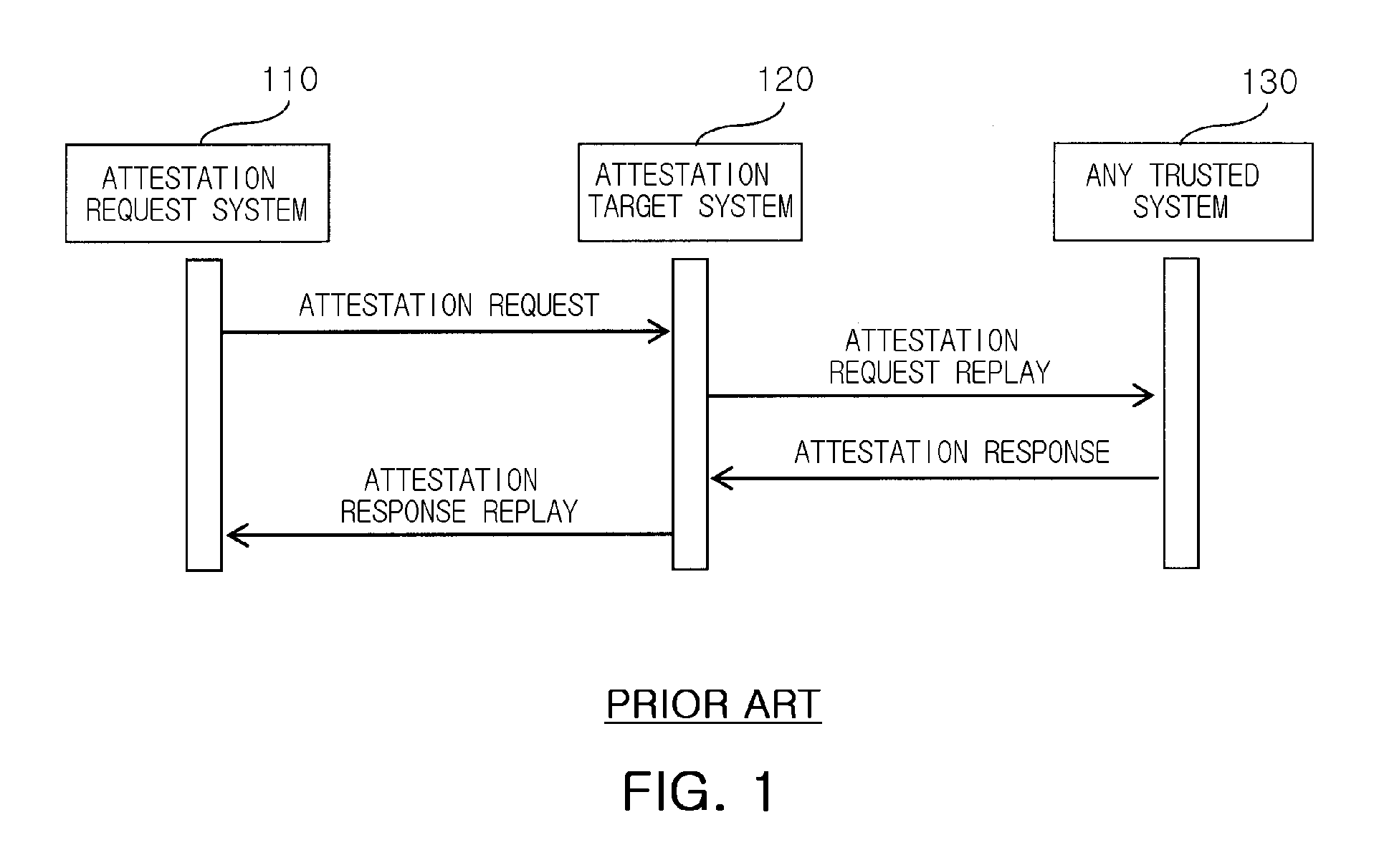
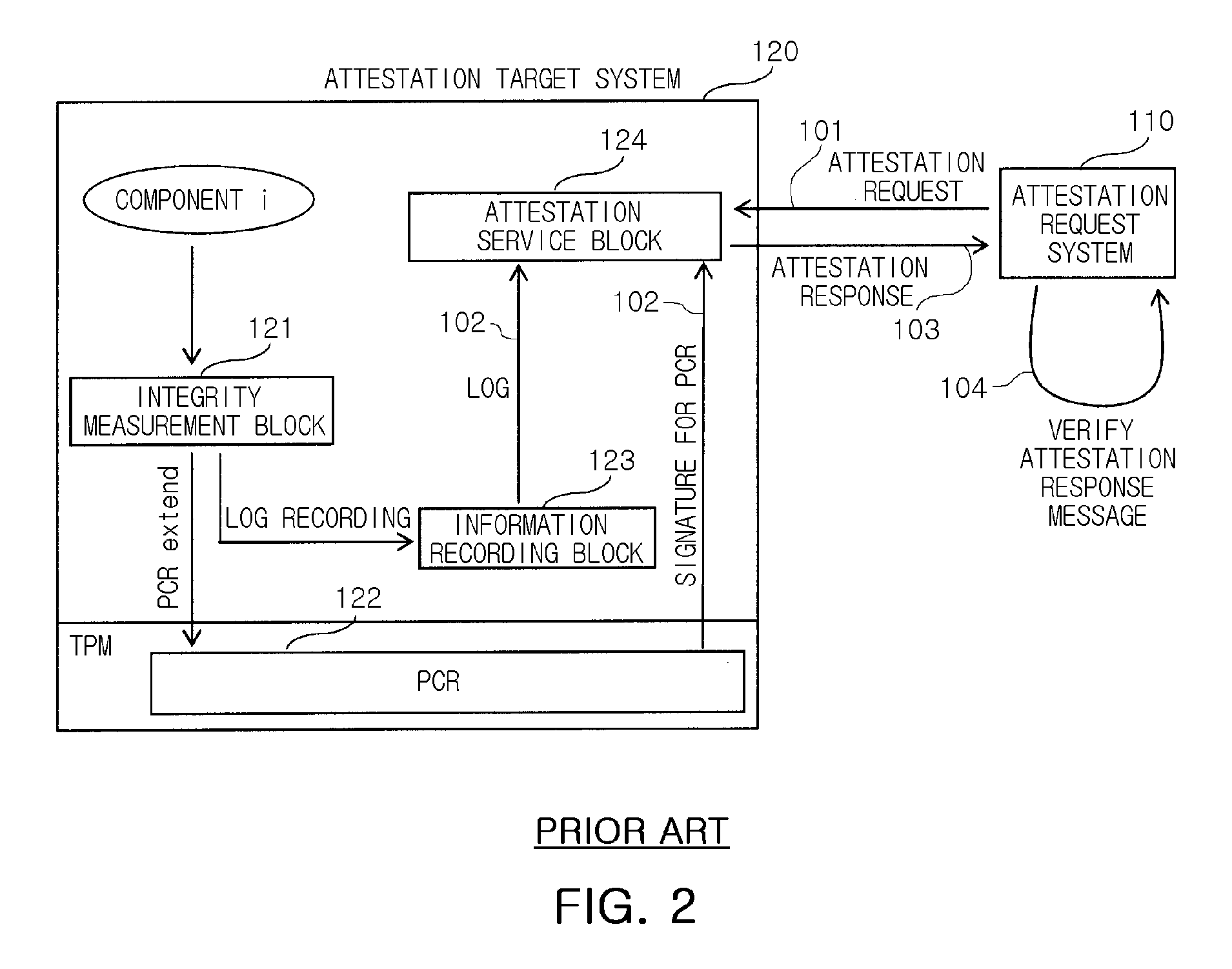
InactiveUS20090013181A1Prevent attackPerformance of was minimizedUser identity/authority verificationDigital computer detailsComputer networkReplay attack
Provided are a method and an attestation system for preventing an attestation replay attack. The method for preventing an attestation replay attack in an attestation system including an attestation target system and an attestation request system, the method including: measuring associated components when an event that affects the integrity of the attestation target system occurs; perceiving own identity information and verifying the perceived identity information; extending the measured component and the identity information into a register and logging the measured component and the identity information; generating an attestation response message including values of the log and the register when an attestation request message is received from the attestation request system; and transmitting the generated attestation response message to the attestation request system. Therefore, the method and an attestation system may be useful to provide an additional simple mathematical operation in verifying an attestation message by preventing an attestation replay attack, and thus to minimize performance degradation in the attestation system, compared to the conventional attestation processing mechanisms.
Owner:ELECTRONICS & TELECOMM RES INST
Secure transmission system for broadcast automatic monitoring information
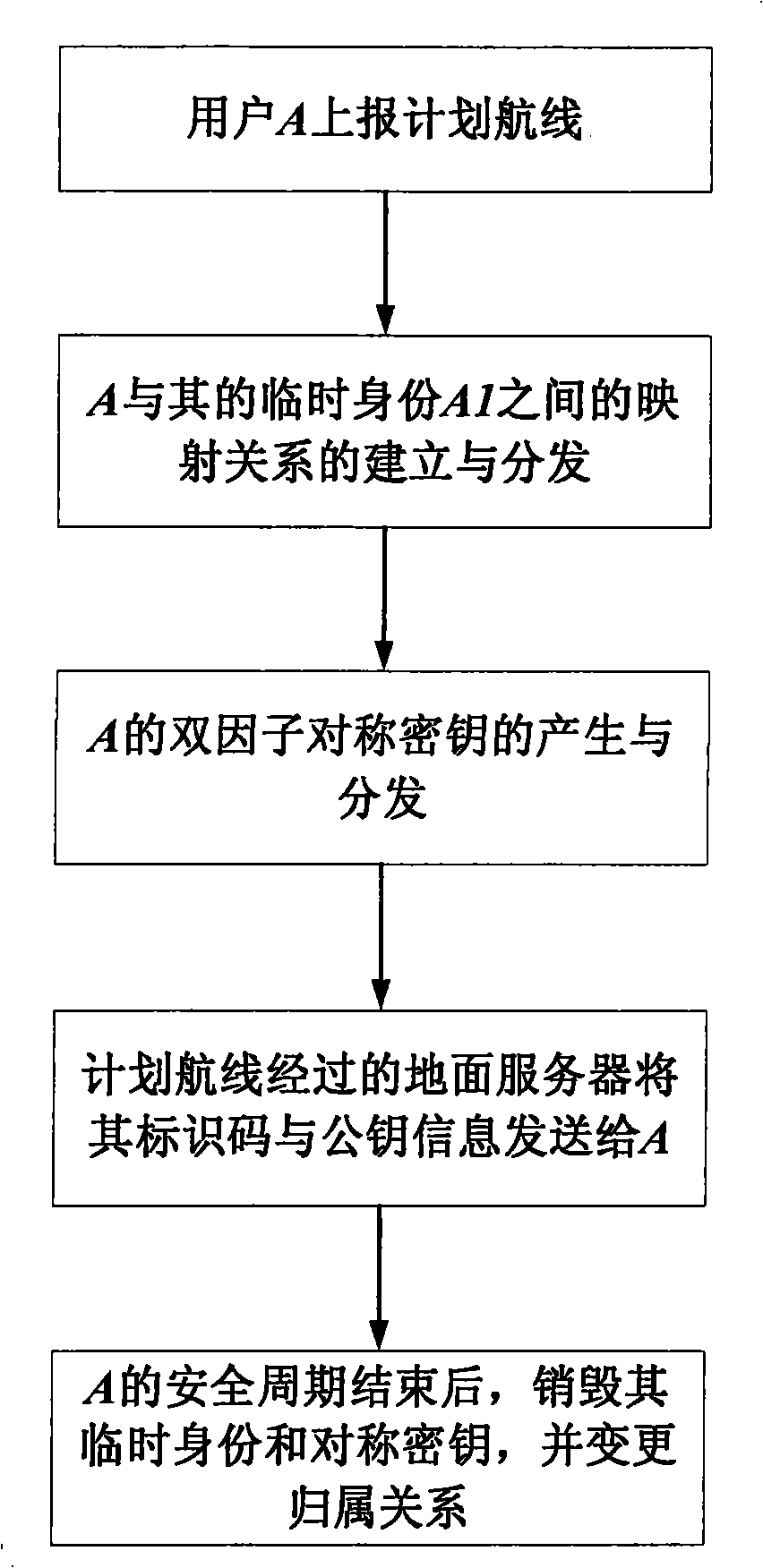
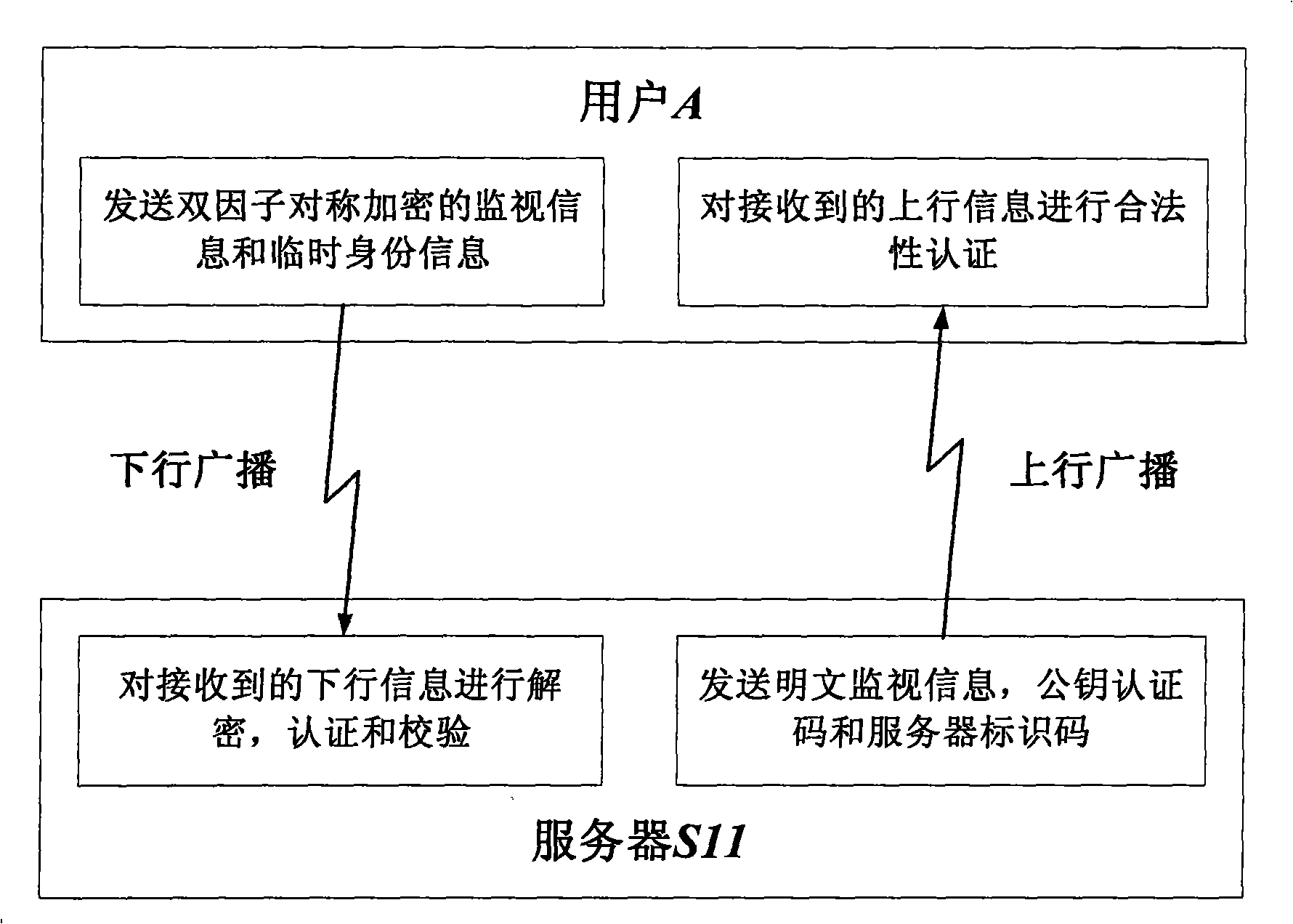
InactiveCN101261772ASecure transmissionGuaranteed normal transmissionTransmissionAircraft traffic controlThree levelInformation transmission
The method for realizing secure transmission of an Automatic Dependent Surveillance Broadcast Information includes: (1) a three-level vertical management system is constructed according to the Aviation Management & Controlling Center, the flight information region and the control area subordinated to the flight information center; the lowest level is ADS-B user belonging to each control area, and the ADS-B user communicates with the control area server that ADS-B user belongs to by means of independent mutual certification mode; (2) at the beginning stage of the planning air line safety period, the Aviation Management & Controlling Center allots a temporary identity for the ADS-B user, establishes a mapping relationship from the temporary identity to a true identity and send the mapping relationship to the administration of the flight information region which the ADS-B user planning air line passes through; before the ADS-B user takes off, the administration of the control area that the ADS-B user belongs to secretly provides the ADS-B user with the temporary user identity and double factor symmetric-key in the server, and public key information of the server identification and the server message authentication code of the ground server near the planning air line. The invention can effectively resist a plurality of active attacks, realize security certification and ensure the safety of ADS-B information transmission.
Owner:AVIATION DATA COMM +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com