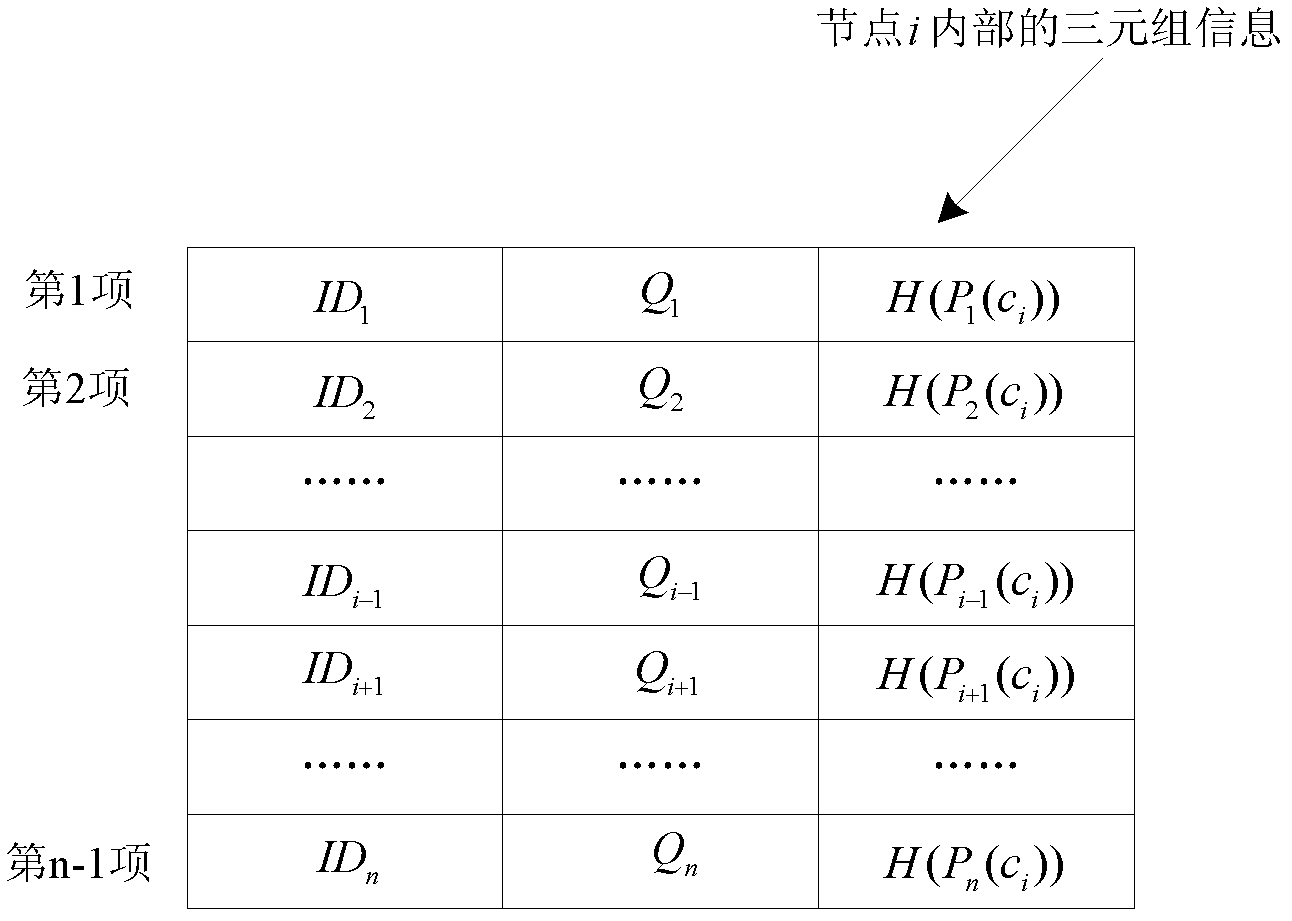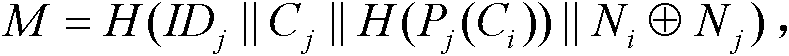Bidirectional identity authentication method for wireless sensor network node
A two-way identity authentication, wireless sensor technology, applied in the field of two-way identity authentication of wireless sensor network nodes, can solve the problems of getting rid of database dependence, unpredictable response, and inability to equipment, and achieve the effect of avoiding replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0030] The following are descriptions of nouns and symbols used in the examples.
[0031]
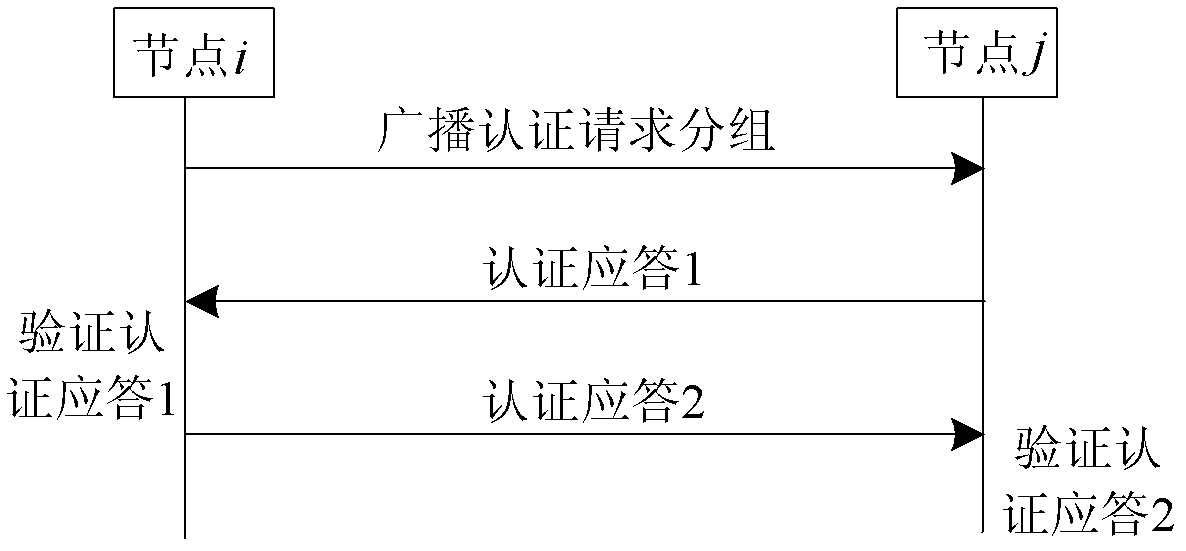
[0032] Referring to the accompanying drawings, the node two-way identity authentication method of the present invention is divided into two stages: an initialization stage and an authentication stage. The stages and their specific steps are as follows:
[0033] 1. Initialization phase
[0034] The initialization phase needs to be completed with the assistance of a trusted third party. Assume that there are n nodes in the sensor network, the node numbers are from 1 to n, and the identities are ID 1 , ID 2 , ID 3 .....ID n , the specific steps of the initialization phase are as follows:
[0035] 1) A trusted third party randomly generates a challenge for each node in the network. For example, generate a challenge C for node i i .
[0036] 2) The trusted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com