Patents
Literature
198results about How to "Performance of was minimized" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Finger-mapped character entry systems
ActiveUS20140298266A1Fast inputMove quicklyInput/output processes for data processingPhysical medicine and rehabilitationComputer graphics (images)
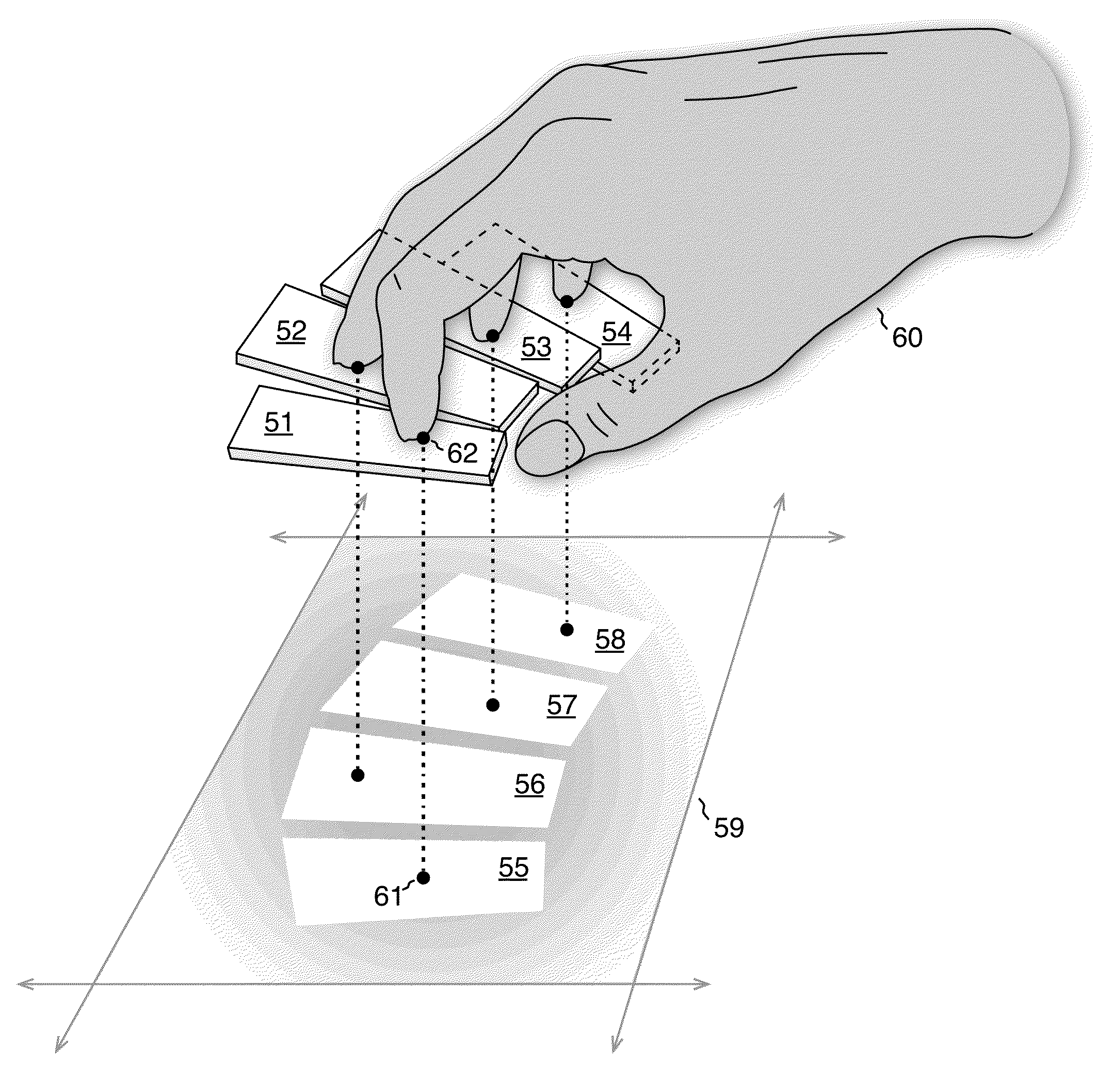
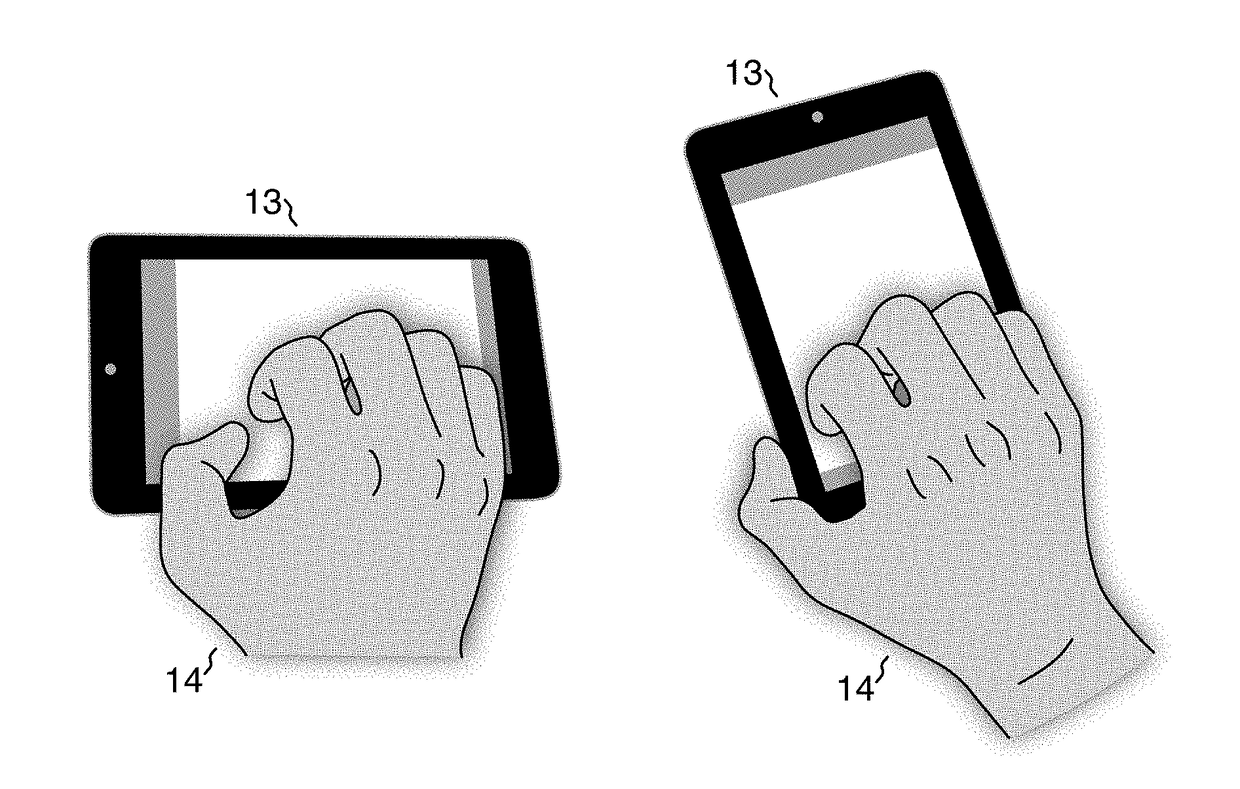
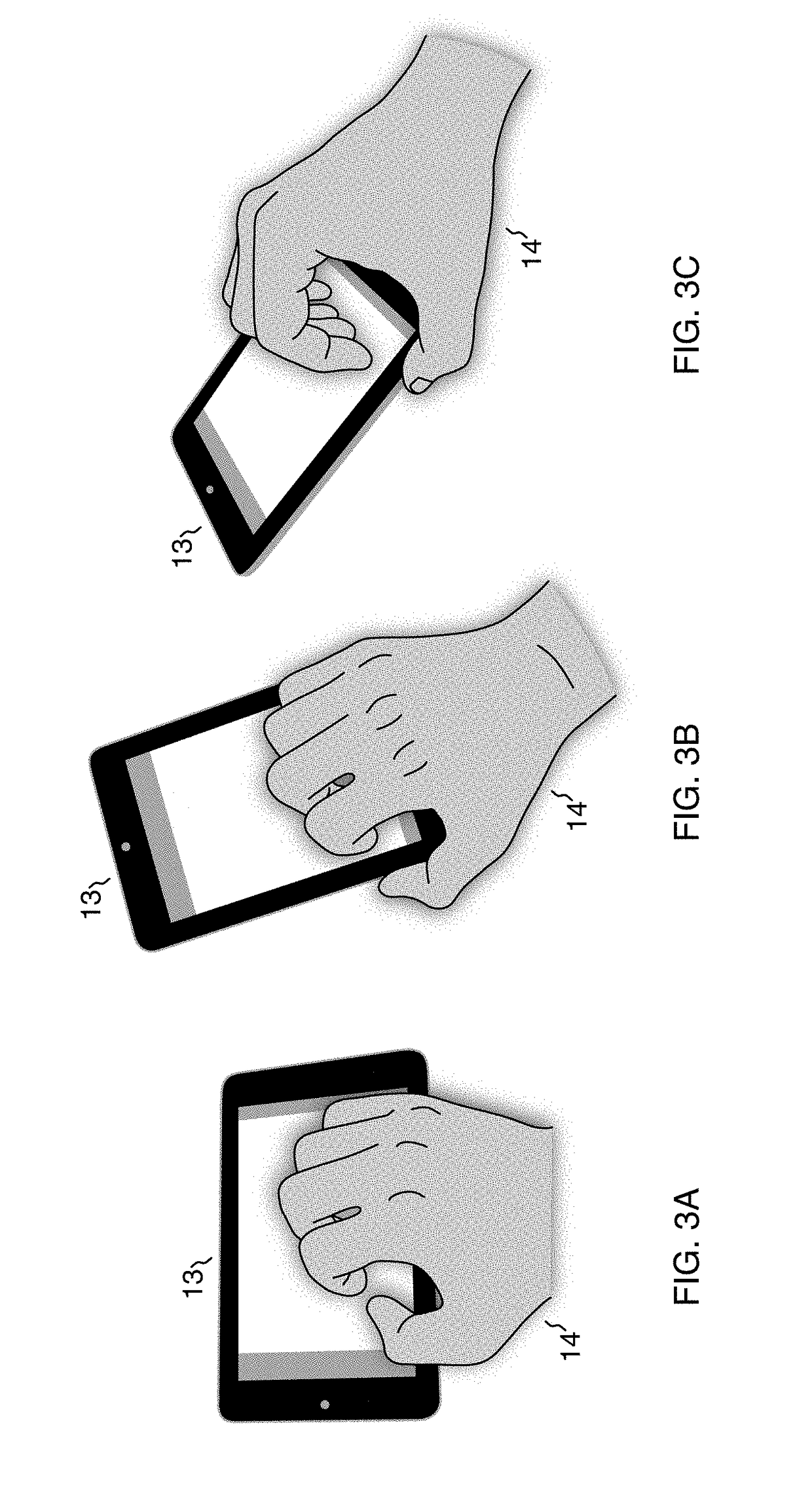
A finger-mapped gesture system is a user interface method and apparatus for rapid data input on a touch-sensitive surface. The user gestures by holding the hand stationary relative to the surface and moving the fingers primarily by extension and flexion on the surface. Each finger gestures on a gesturing area instead of selecting among keys. Individual gestures are constructed from finger actions that each independently parameterize the gesture. In combination, the particular fingers gesturing and the parameters that the fingers gesture indicate the input that the user intends. On devices that do not directly identify fingers, fingers are identified via a finger map that, after calibration to a person's hand, associates each finger with a gesturing area. Gestures are otherwise independent of where they are performed, freeing users from having to look at their fingers to target visual elements. The system is optimized for rapid character data entry.
Owner:LAPP JOSEPH T
Learning stochastic apparatus and methods
InactiveUS20130325774A1Shorten the timeNot alleviating taskDigital computer detailsDigital dataModularitySelf adaptive
Generalized learning rules may be implemented. A framework may be used to enable adaptive signal processing system to flexibly combine different learning rules (supervised, unsupervised, reinforcement learning) with different methods (online or batch learning). The generalized learning framework may employ non-associative transform of time-averaged performance function as the learning measure, thereby enabling modular architecture where learning tasks are separated from control tasks, so that changes in one of the modules do not necessitate changes within the other. The use of non-associative transformations, when employed in conjunction with gradient optimization methods, does not bias the performance function gradient, on a long-term averaging scale and may advantageously enable stochastic drift thereby facilitating exploration leading to faster convergence of learning process. When applied to spiking learning networks, transforming the performance function using a constant term, may lead to non-associative increase of synaptic connection efficacy thereby providing additional exploration mechanisms.
Owner:BRAIN CORP
Light efficient packaging configurations for LED lamps using high refractive index encapsulants
InactiveUS20060255353A1High refractive indexImprove optical efficiencyMechanical apparatusPoint-like light sourceSurface mountingRefractive index
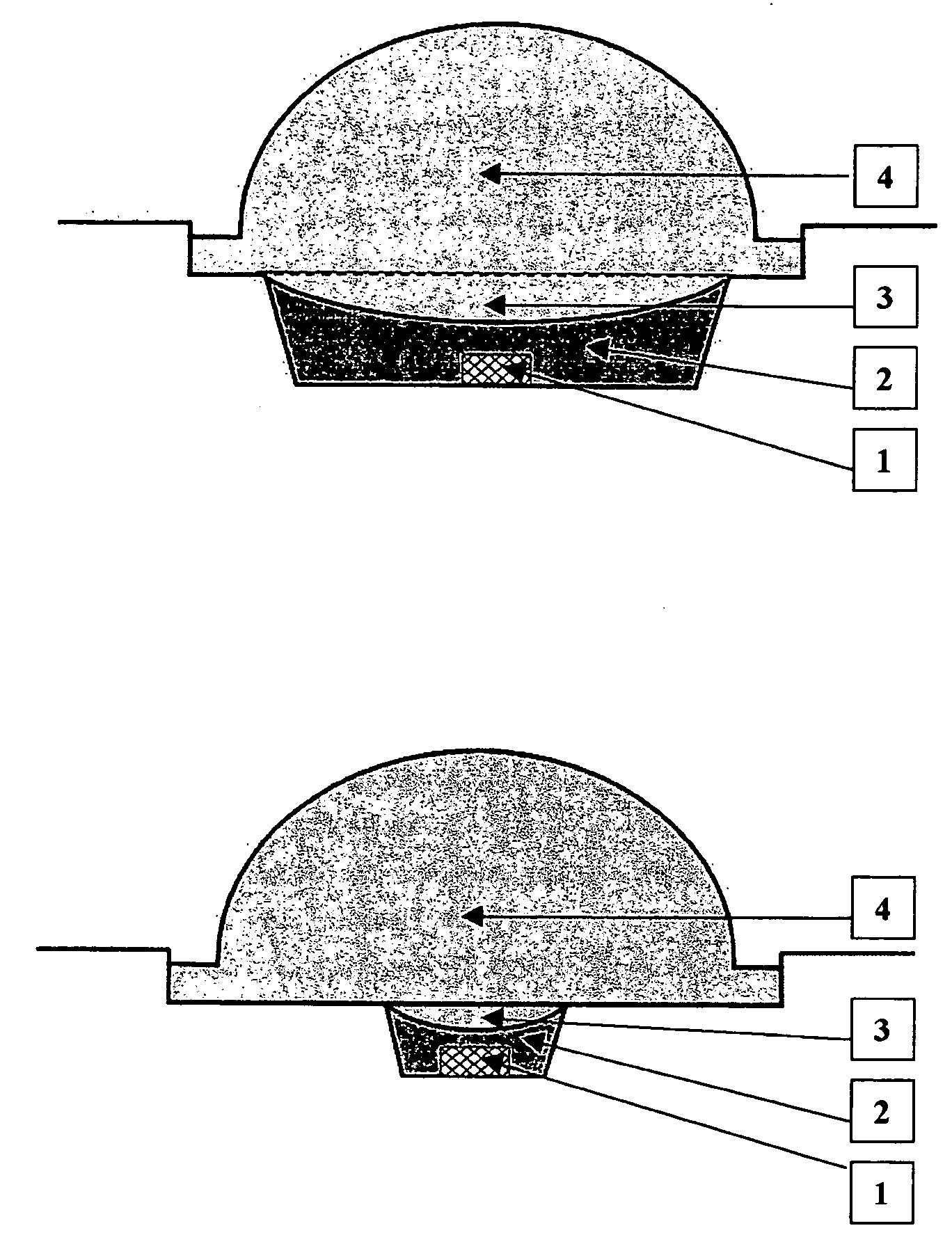
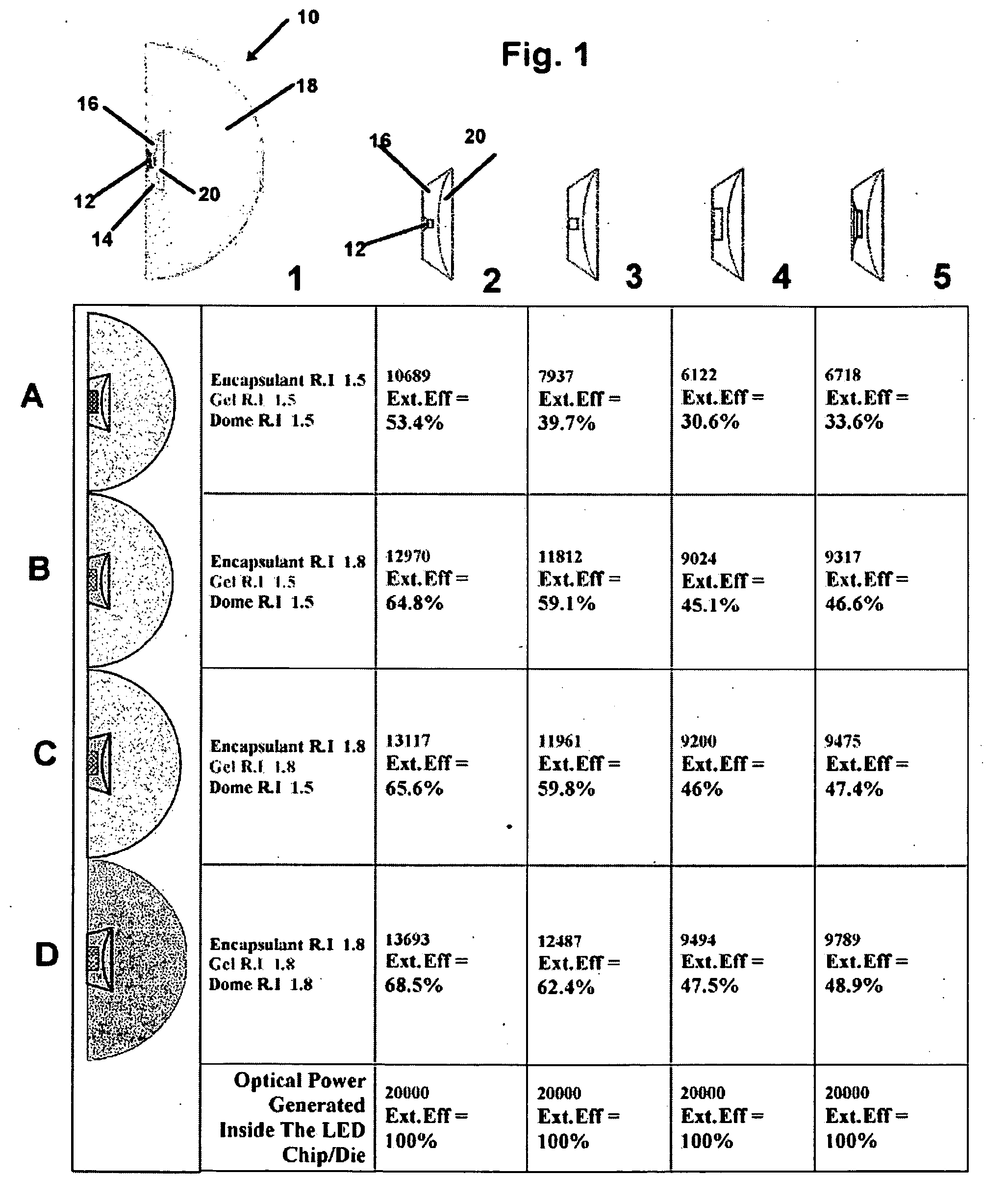
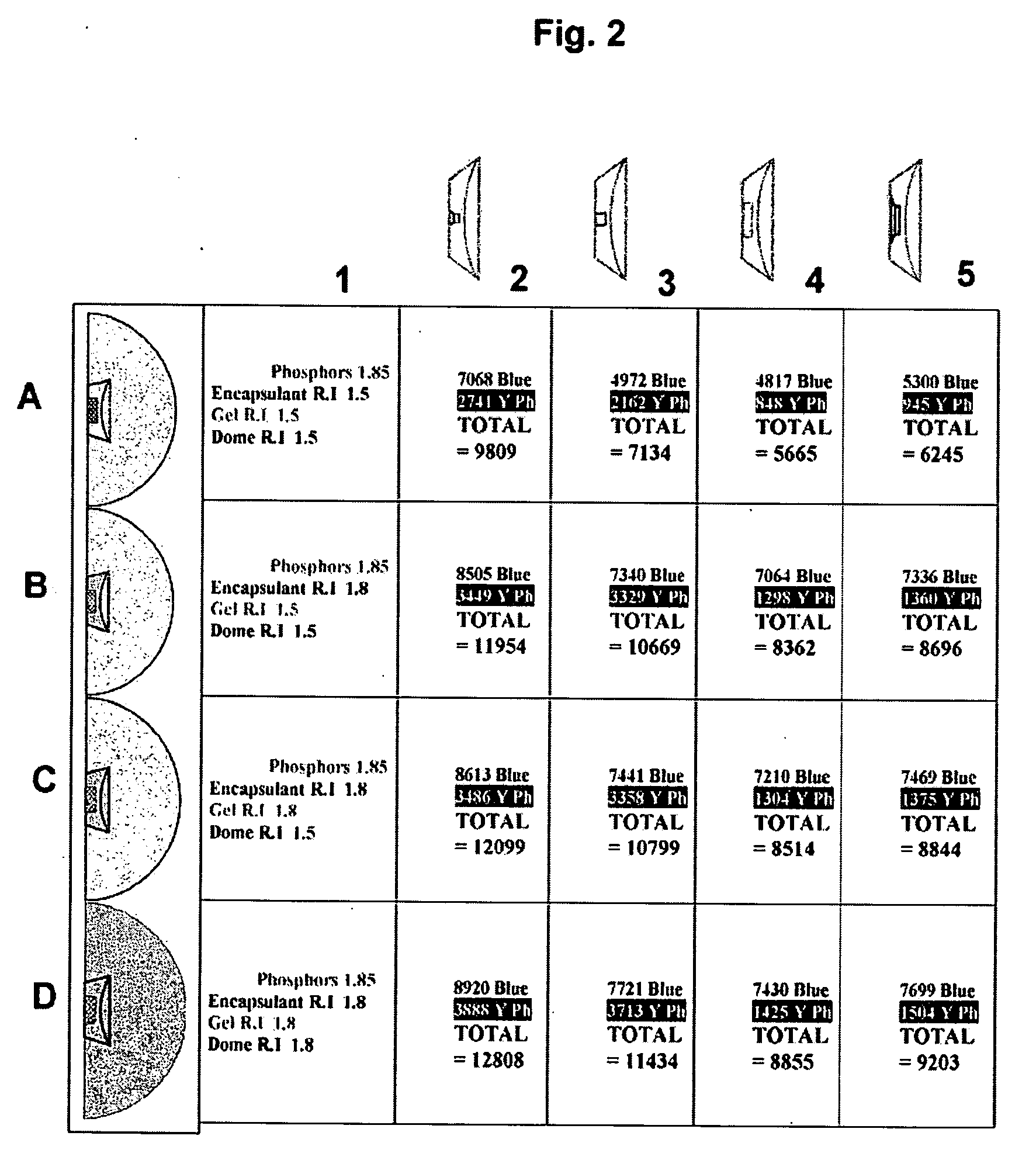
Light efficient packaging configurations for LED lamps using high refractive index encapsulants. The packaging configurations including dome (bullet) shaped LED's, SMD (surface mount device) LED's and a hybrid LED type, including a dome mounted within a SMD package. In another embodiment used with SMD LED devices a relatively small semi-hemispherical “blob” of HRI encapsulant surrounds the LED chip with the remainder of the SMD cavity filled with conventional encapsulant. The packaging configurations increase the LED's light emission efficiency at a reasonable cost and in a commercially viable manner, by maximizing the light efficiency while minimizing the amount of high refractive index encapsulant used.
Owner:TASKAR NIKHIL R +3
Network function virtualization method and apparatus using the same
InactiveUS20140376555A1Performance of was minimizedMinimize delayData switching by path configurationVirtualizationDistributed computing
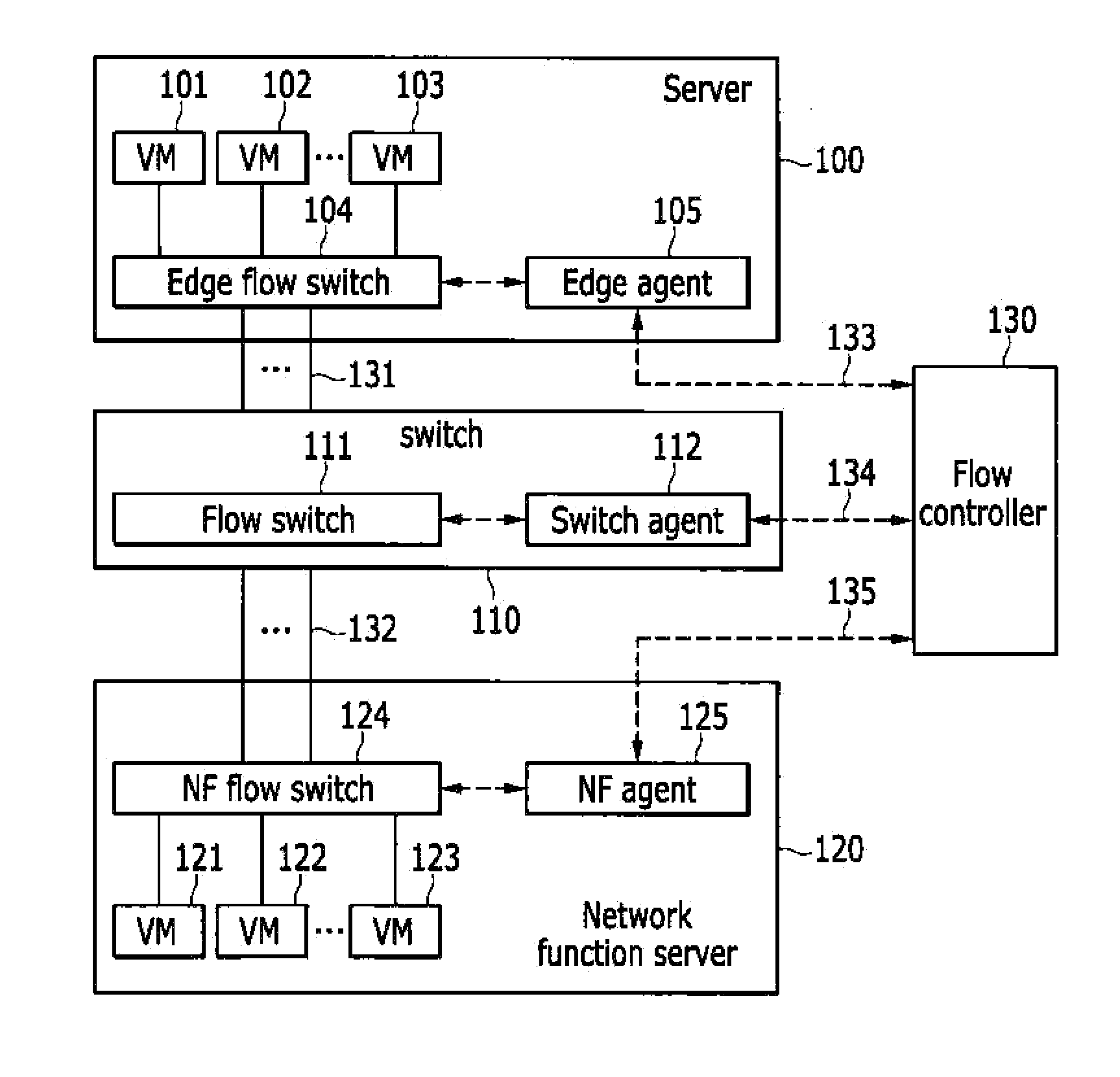
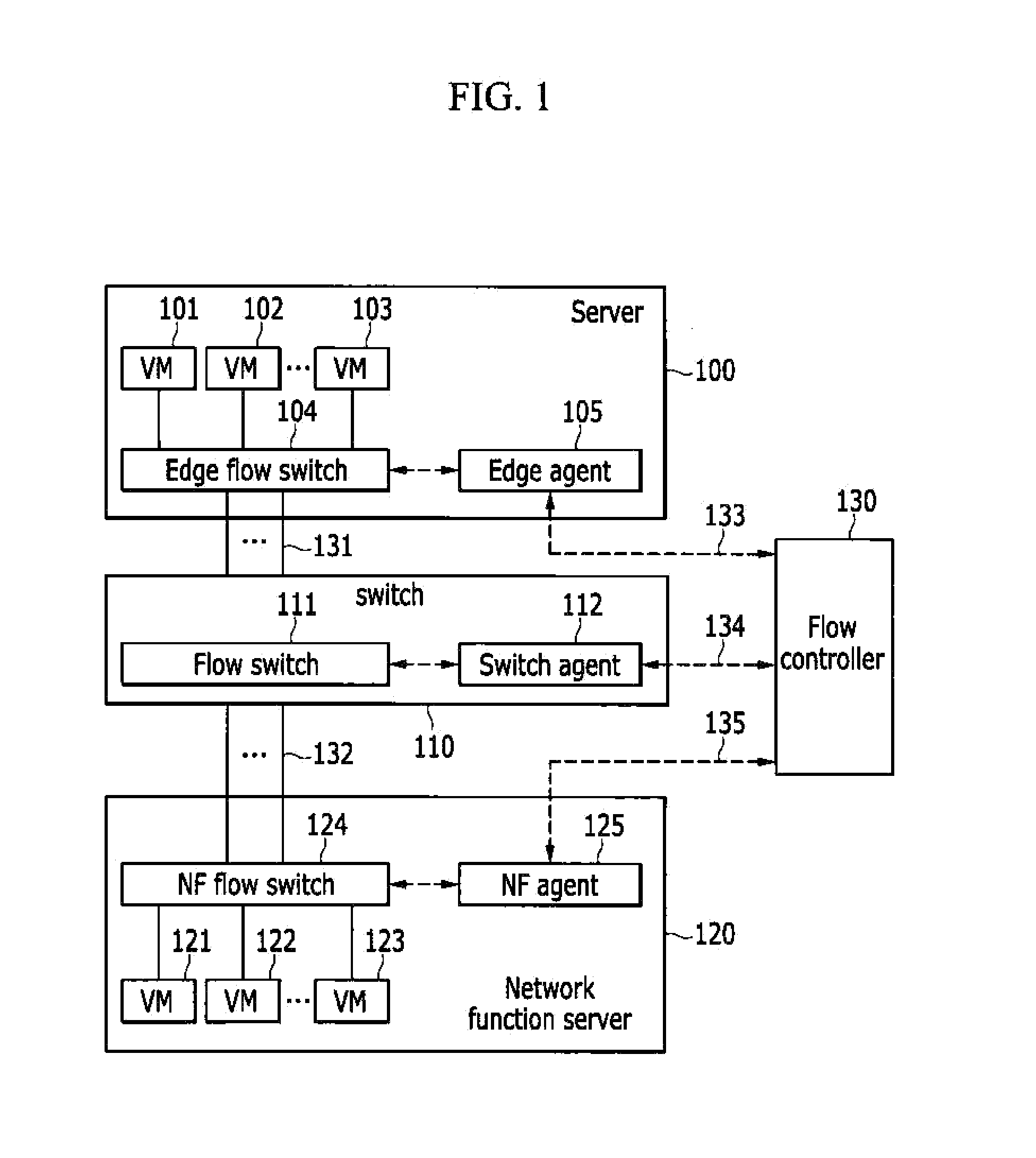
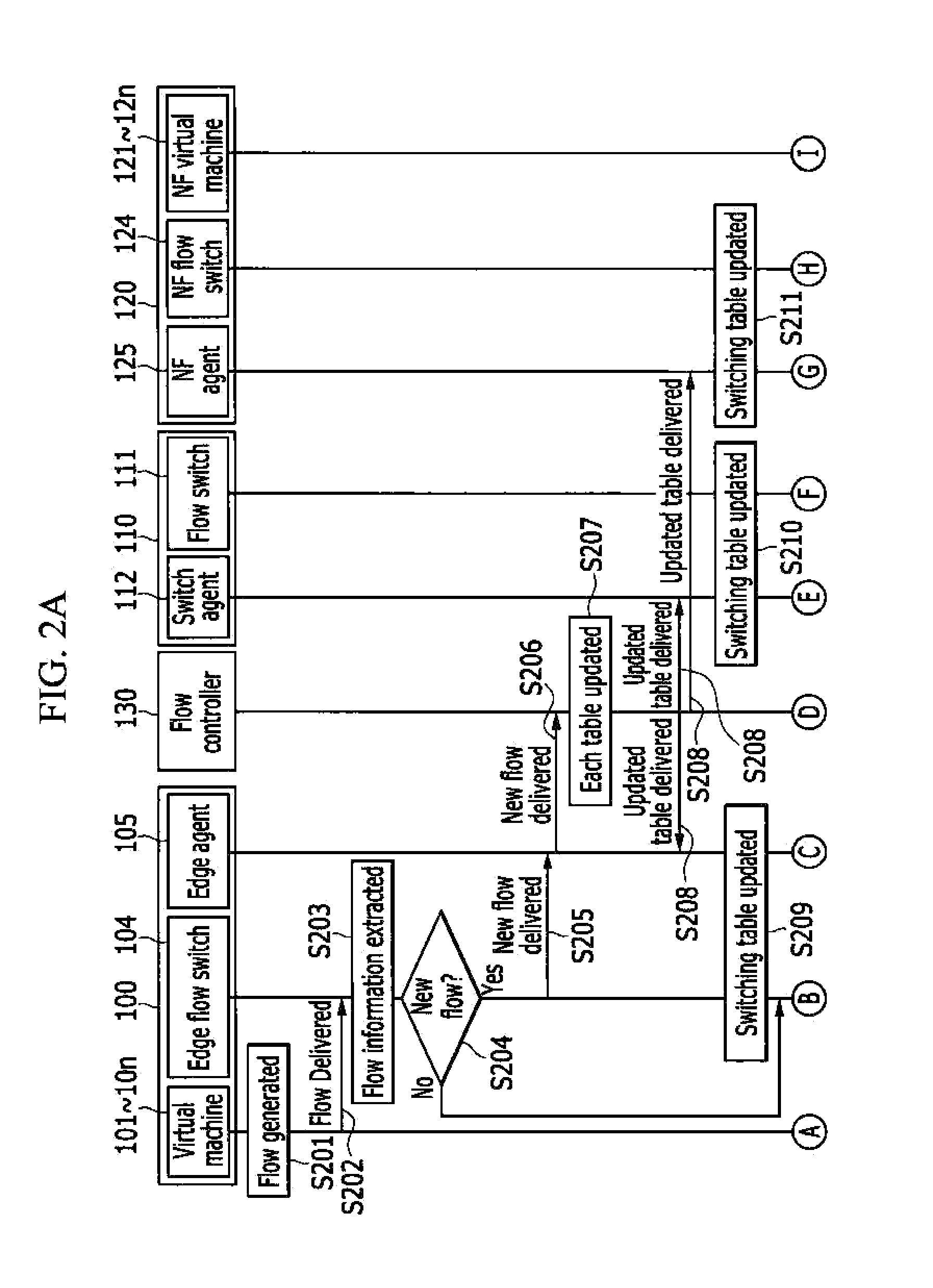
A network function virtualization device includes at least one network function virtual machine; and a network function flow switch configured to receive flows and to switch the flows to the at least one network function virtual machine, and a network functions virtualization method for applying the virtualized network function to the flows.
Owner:ELECTRONICS & TELECOMM RES INST
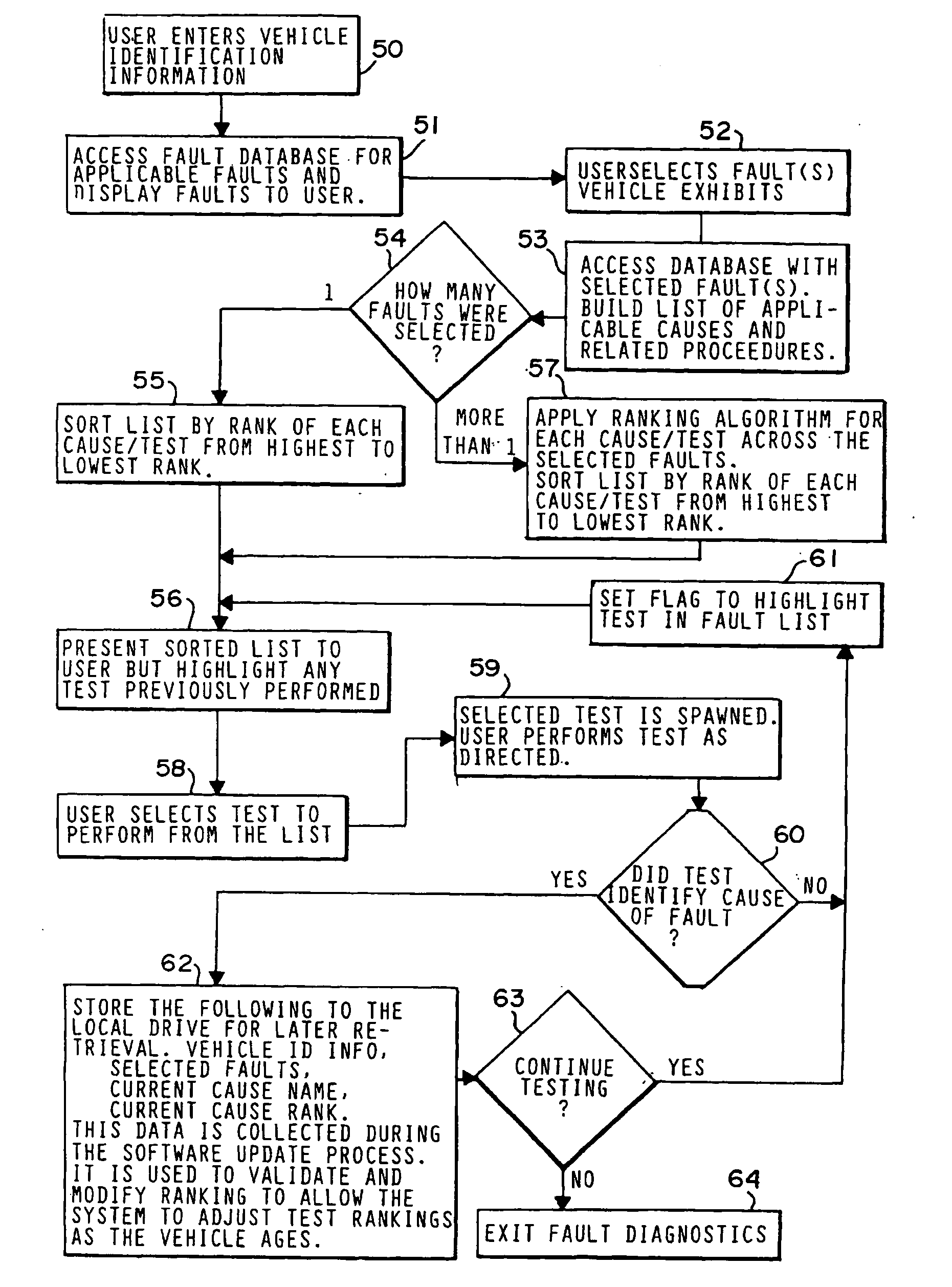
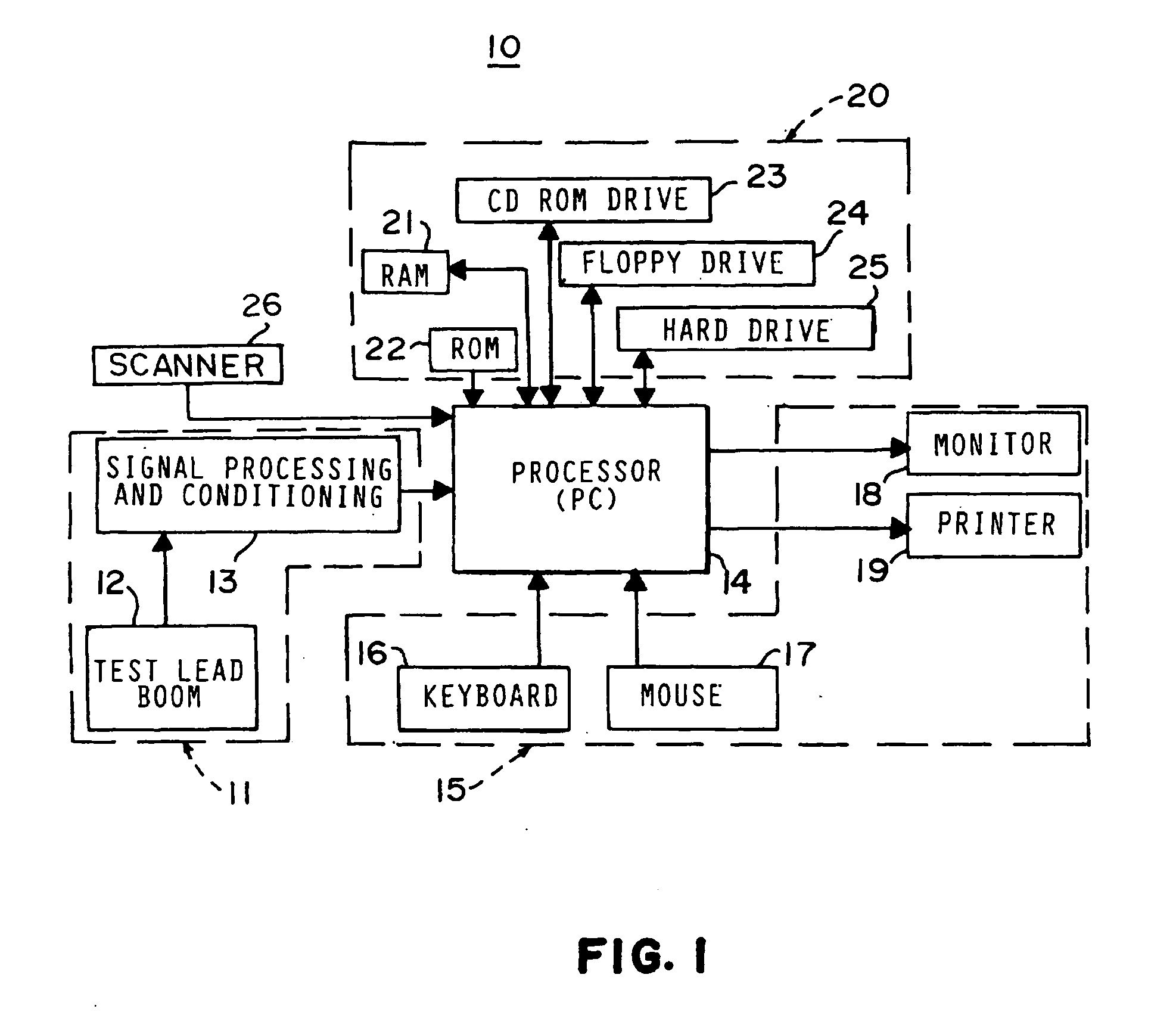
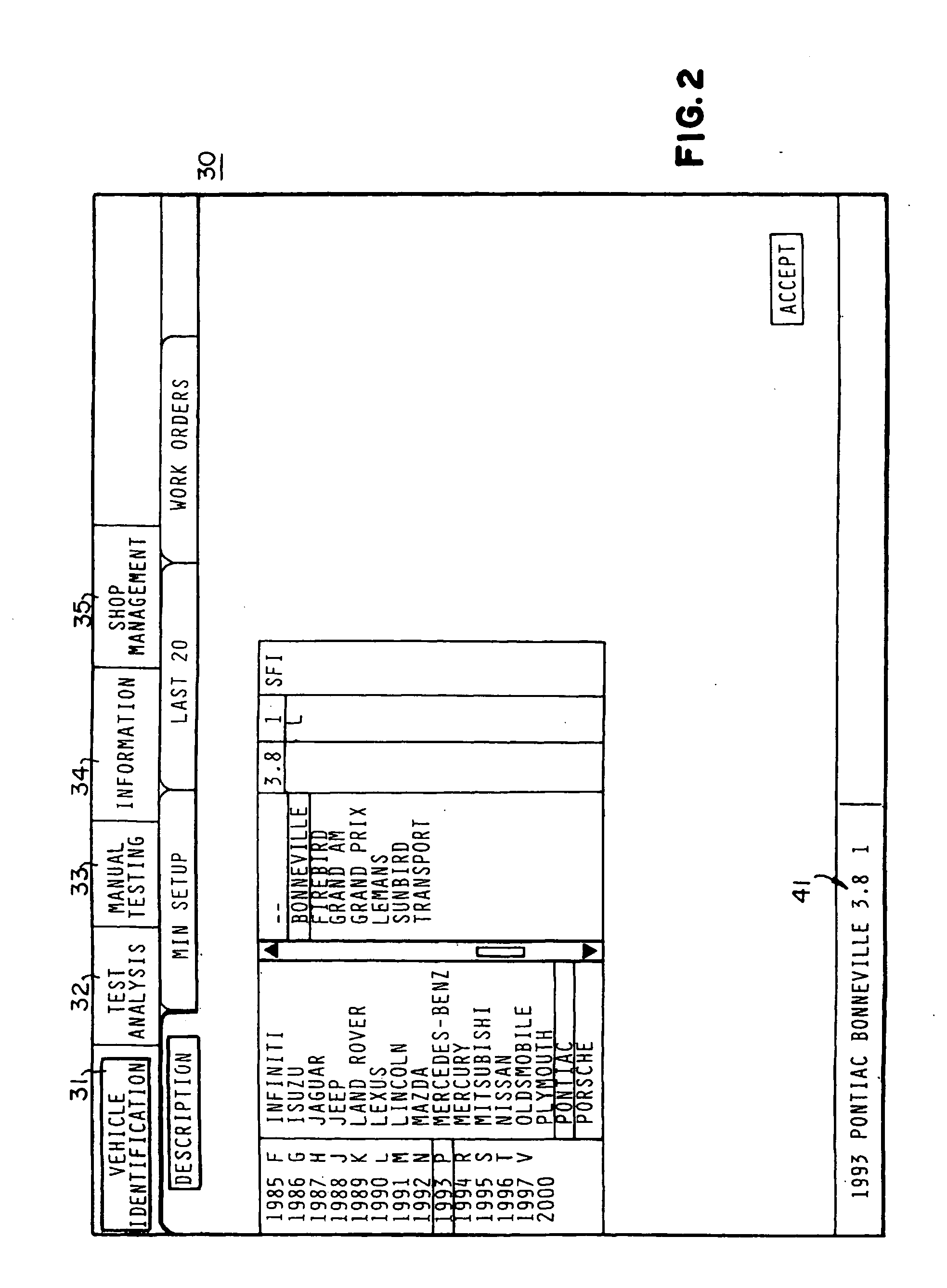
System for dynamic diagnosis of apparatus operating conditions
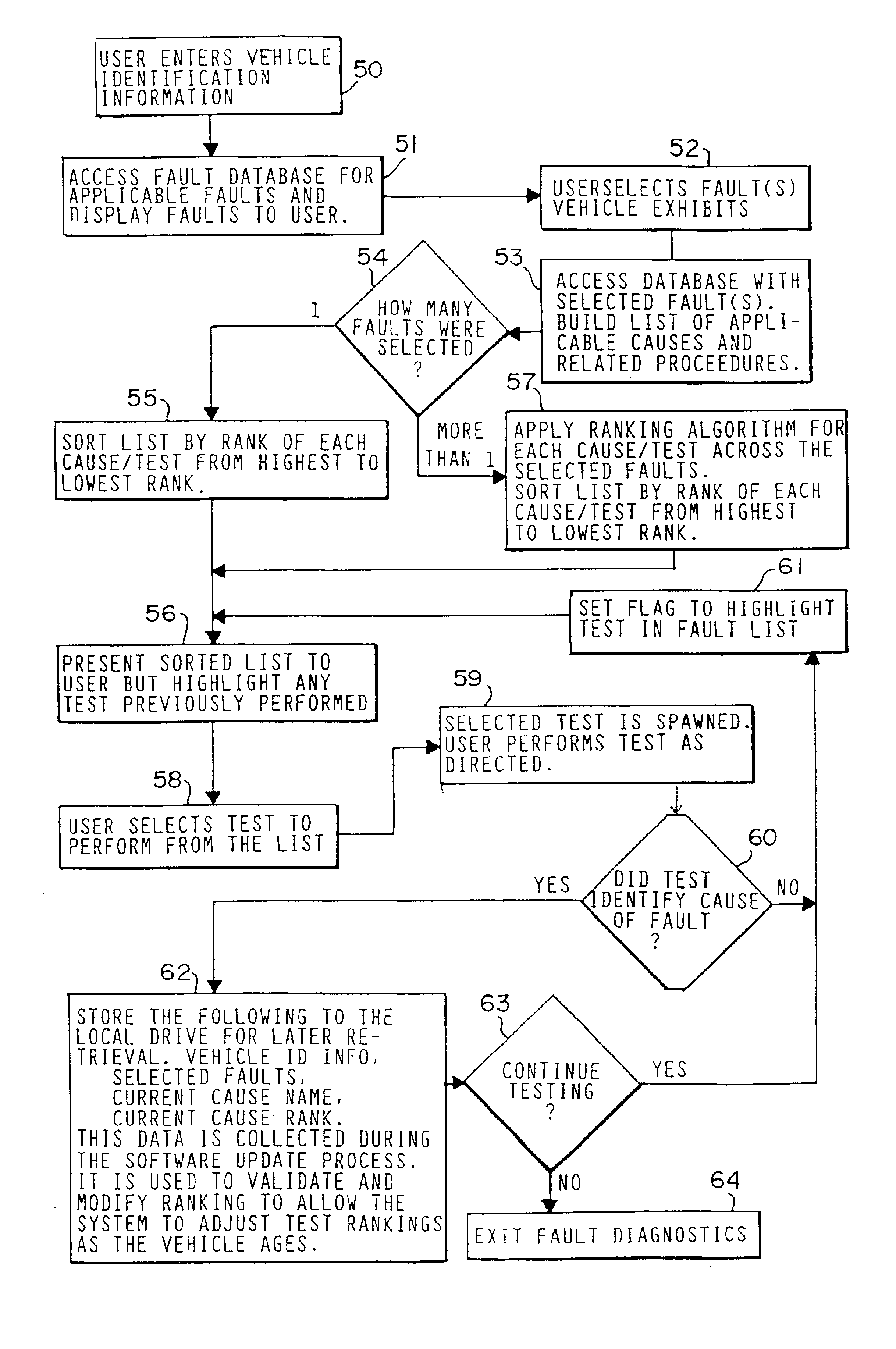
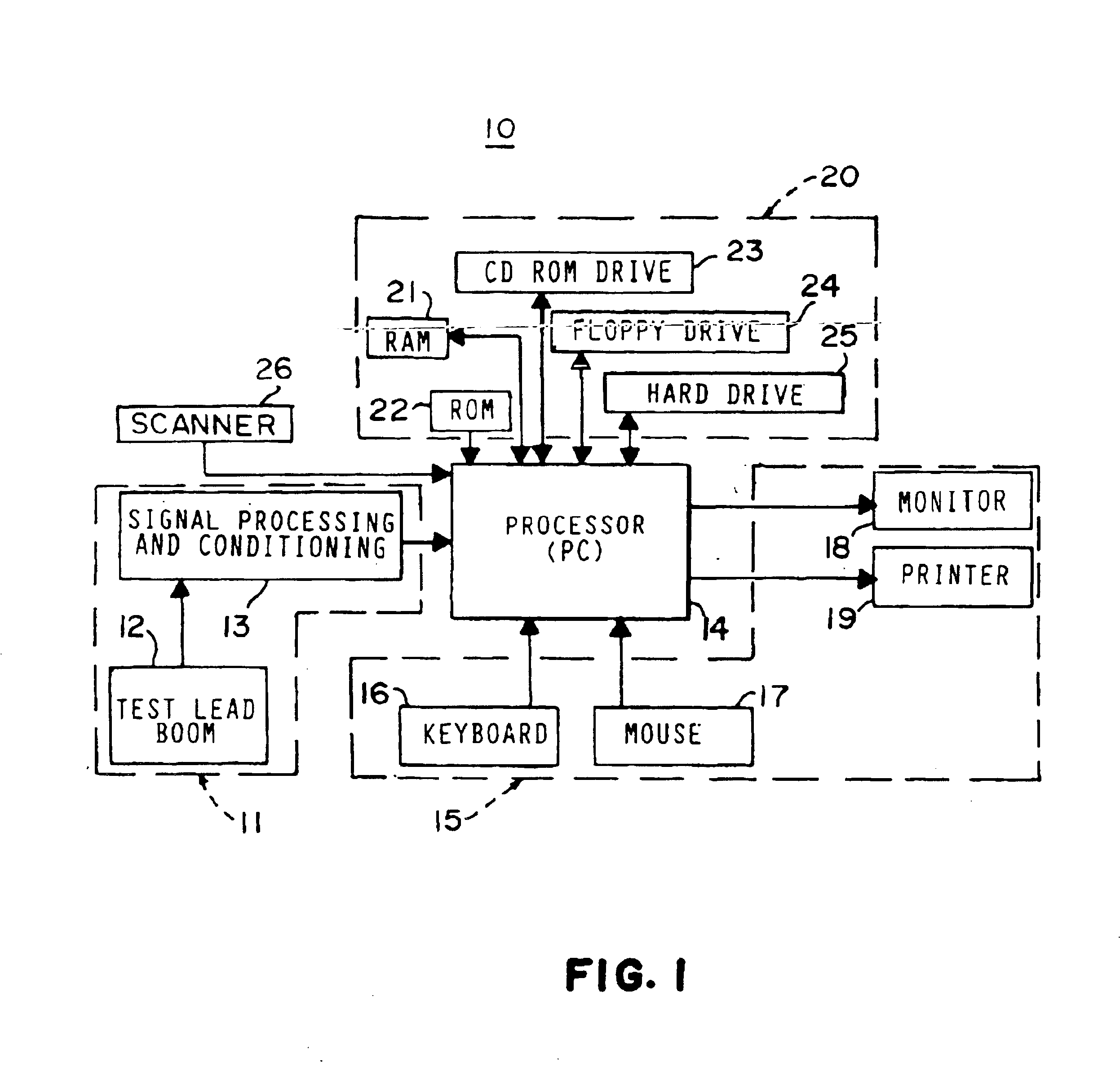
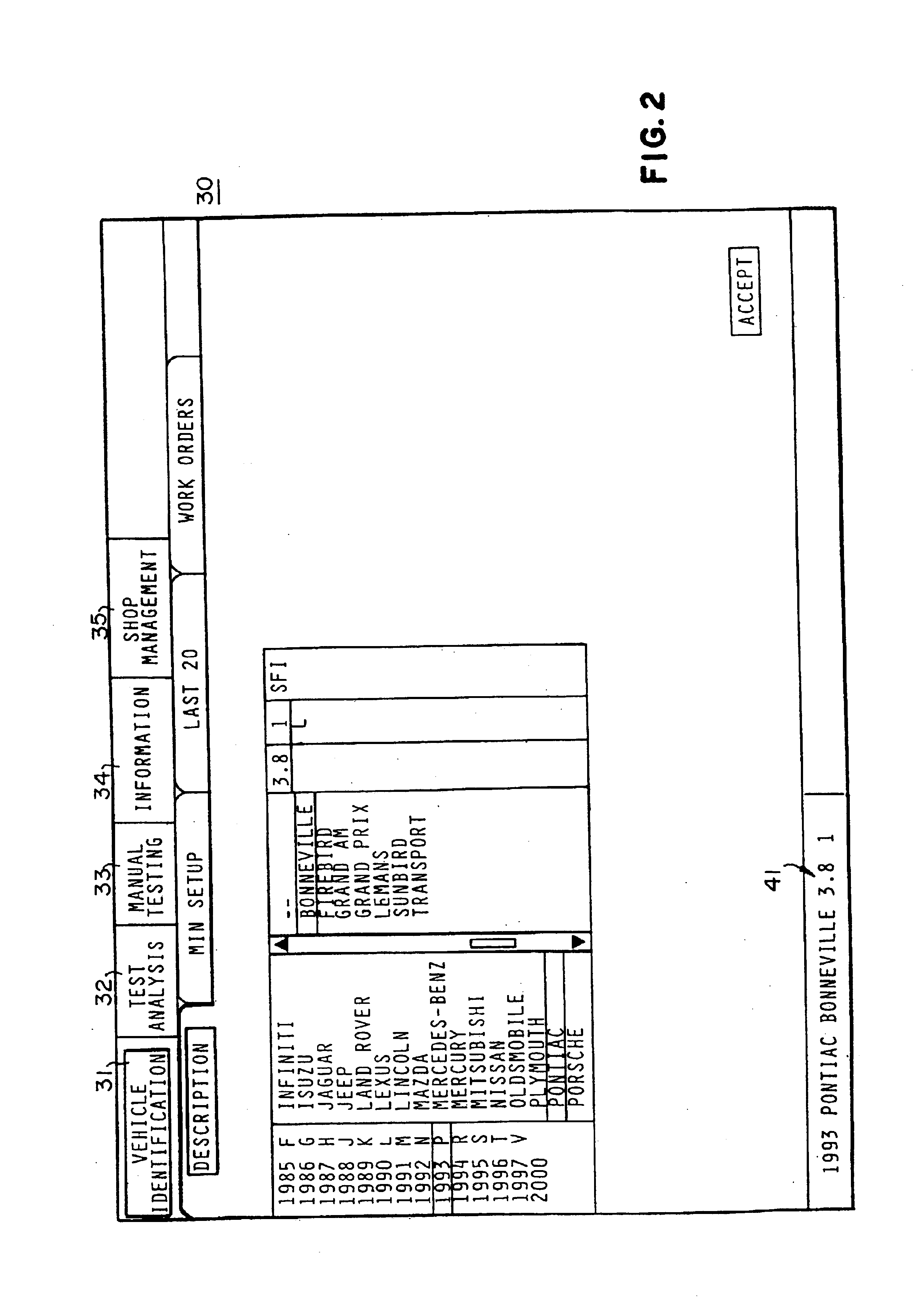
InactiveUS6845307B2Enhanced advantageAvoid disadvantagesVehicle testingRegistering/indicating working of vehiclesInformation repositoryOn board
A diagnostic platform includes a processor, storage media and user interfaces, including a display screen, the processor being coupled to engine analyzer hardware and adapted to be coupled to a scanner for downloading data from vehicle on-board computers. The system stores libraries of information regarding vehicle identifications, drivability symptoms exhibited by vehicles, vehicle system and component tests and service codes which can be registered by the vehicle on-board computer. System software permits the user to input an identification of the vehicle under test and, in one mode of operation, displays a library of faults, such as symptoms or service codes, from which the user can select those exhibited by the vehicle, whereupon the system selects from the test library those tests pertinent to diagnosis of the causes of the selected faults and displays them in a hierarchically ranked order based on likelihood of successful diagnosis of the faults. The user can then select and initiate any displayed test. In other modes, the system initially displays one of the libraries of system or component tests, from which the user selects those deemed appropriate, whereupon the system highlights icons which can be selected for initiating pertinent test procedures. Selected test procedures may include links to the engine analyzer or scanner hardware or other appropriate test modules.
Owner:SNAP ON INC
User selection method in a zero-forcing beamforming algorithm
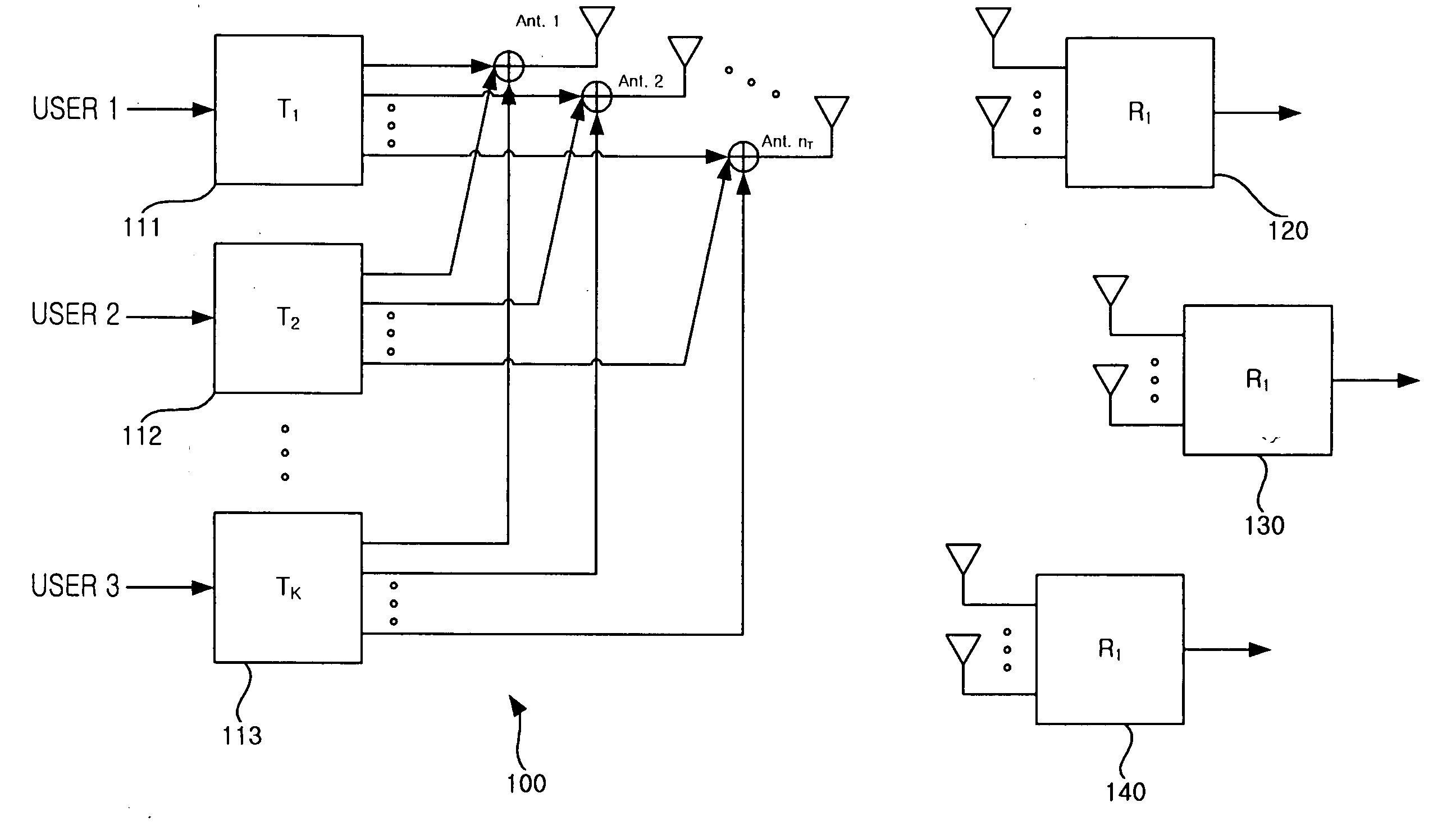
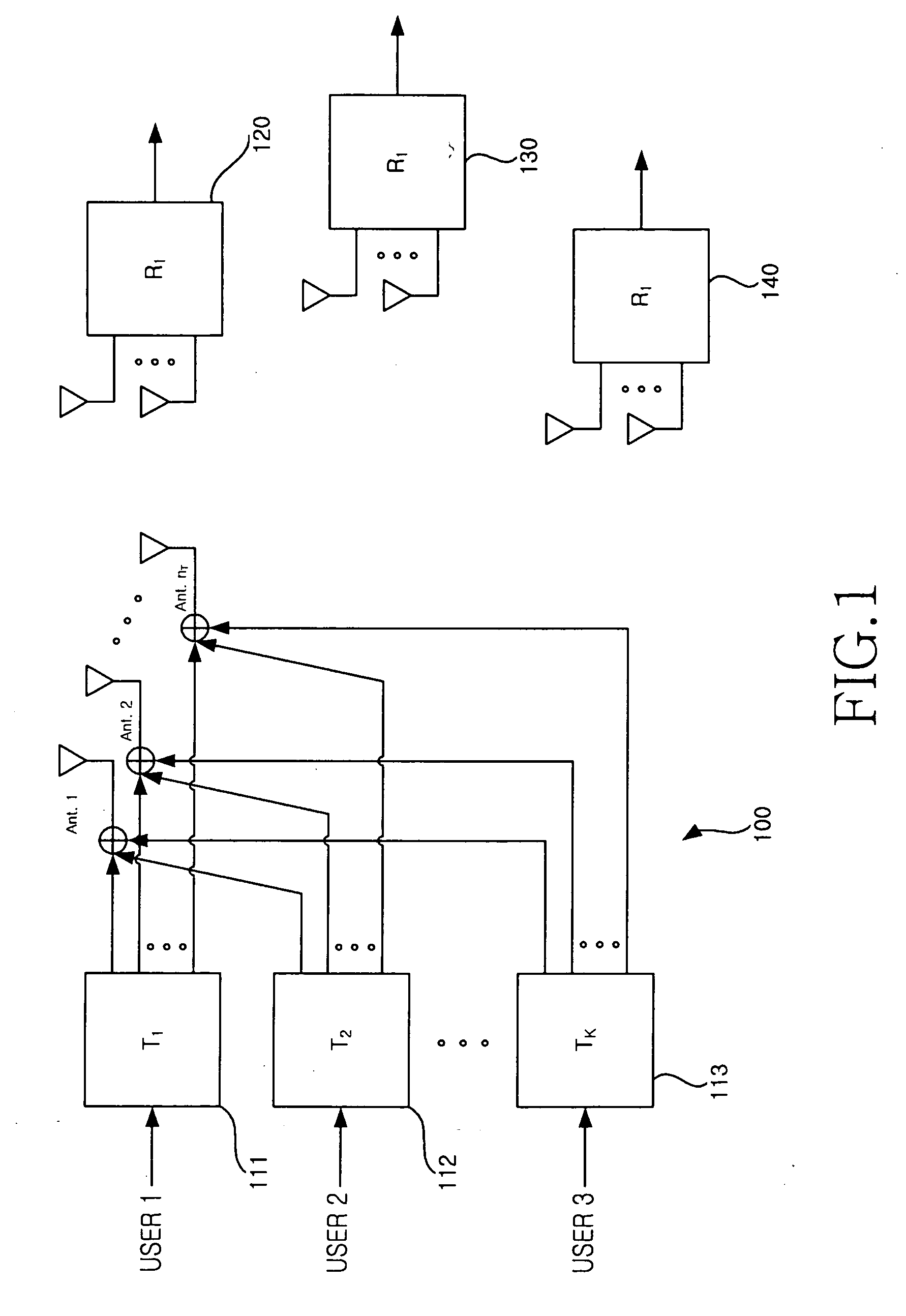
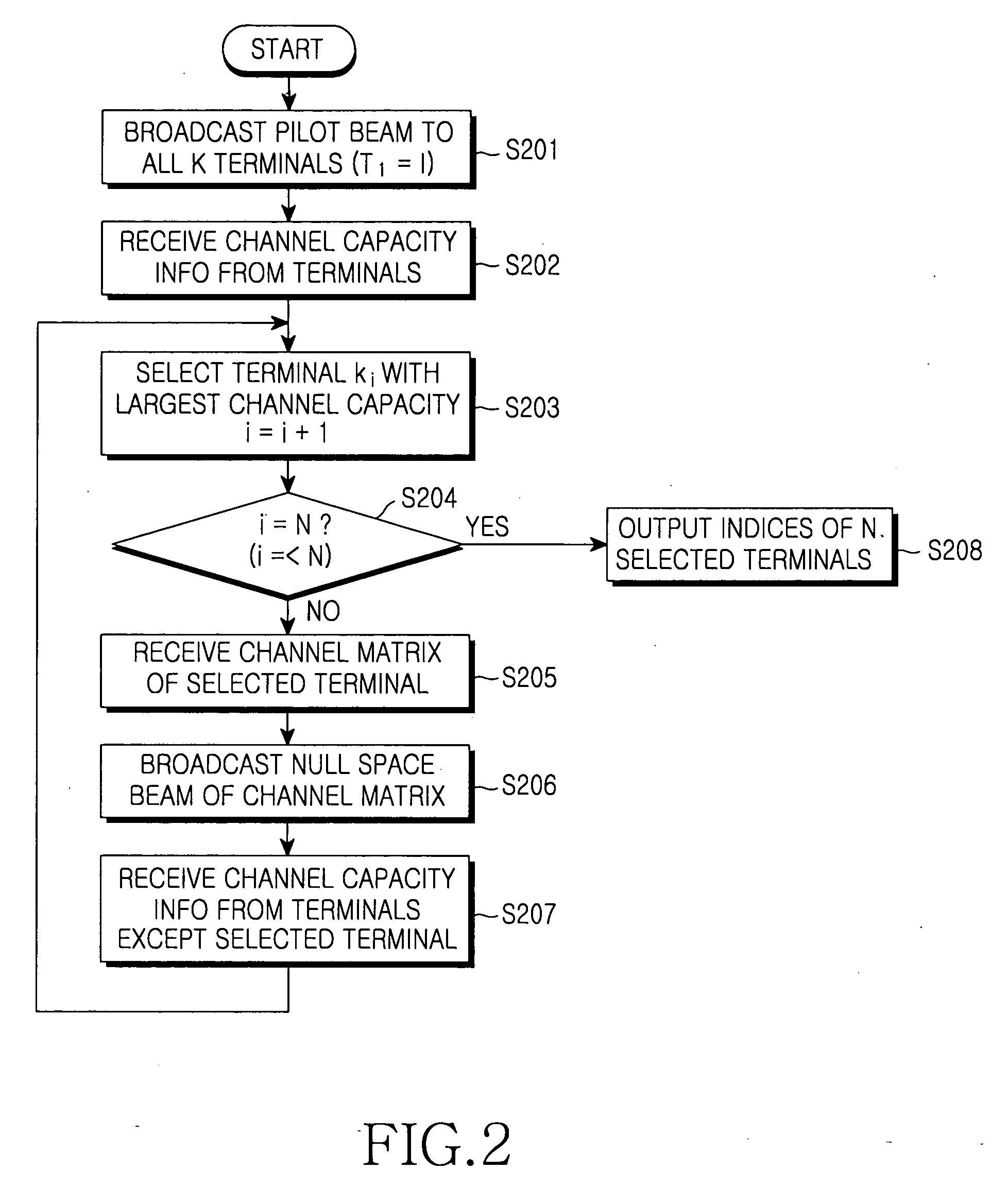
InactiveUS20070058590A1Improve performanceIncrease throughputDiversity/multi-antenna systemsSubstation equipmentChannel capacityEngineering
In a method for selecting a transmission target terminal in a zero-forcing beamforming algorithm, information about a channel capacity of each terminal is received from all K terminals. A terminal with a largest channel capacity is selected as an initial transmission target terminal. A determination is made as to whether the number of currently selected terminals, i, is equal to the predefined number N. If the number of currently selected terminals, i, is different from the predefined number N, information about channel capacities of remaining terminals except previously selected transmission target terminals is received until i is equal to N and a terminal with a largest channel capacity is selected as a transmission target terminal.
Owner:SAMSUNG ELECTRONICS CO LTD +1
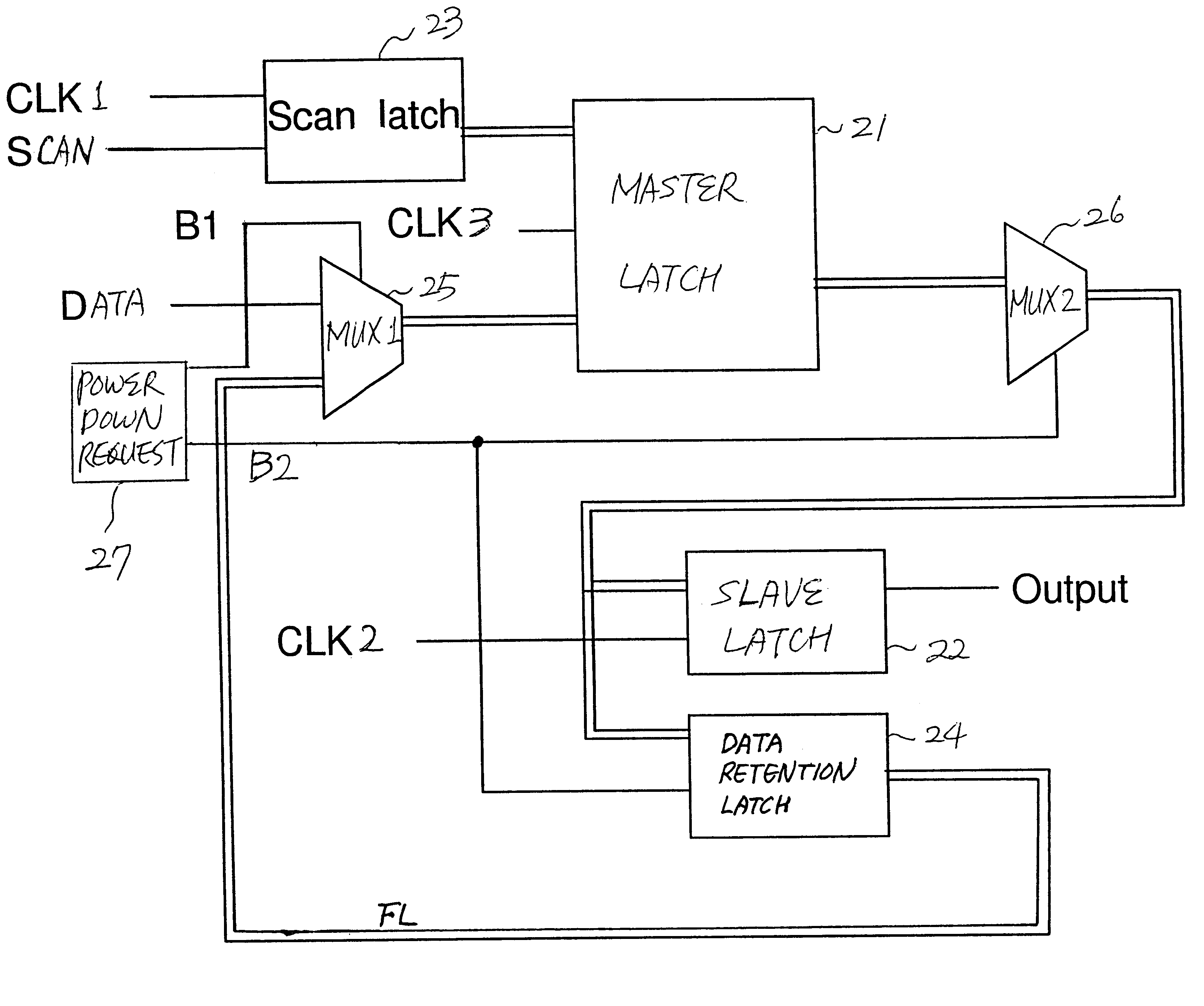
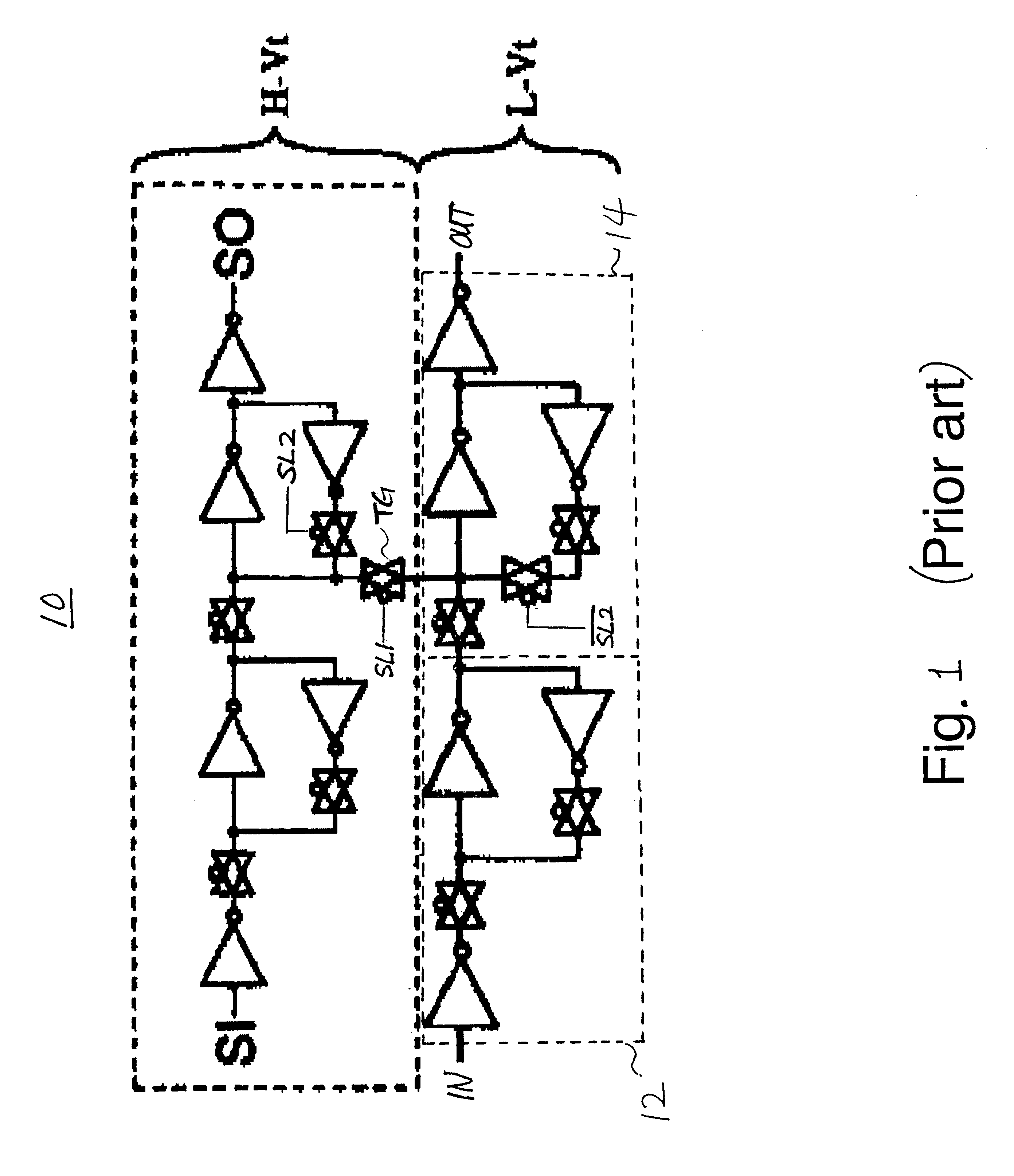
Data retention registers
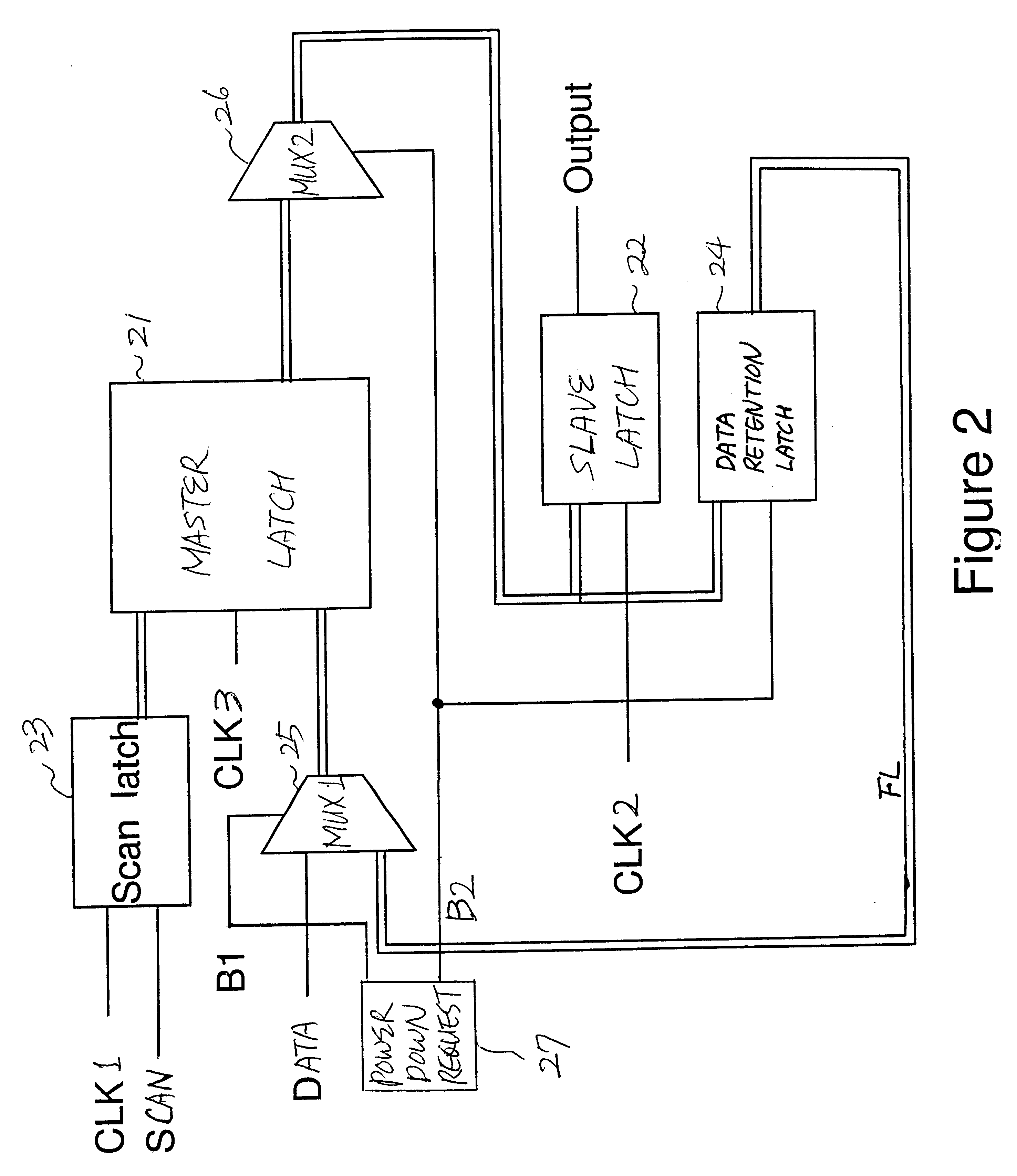
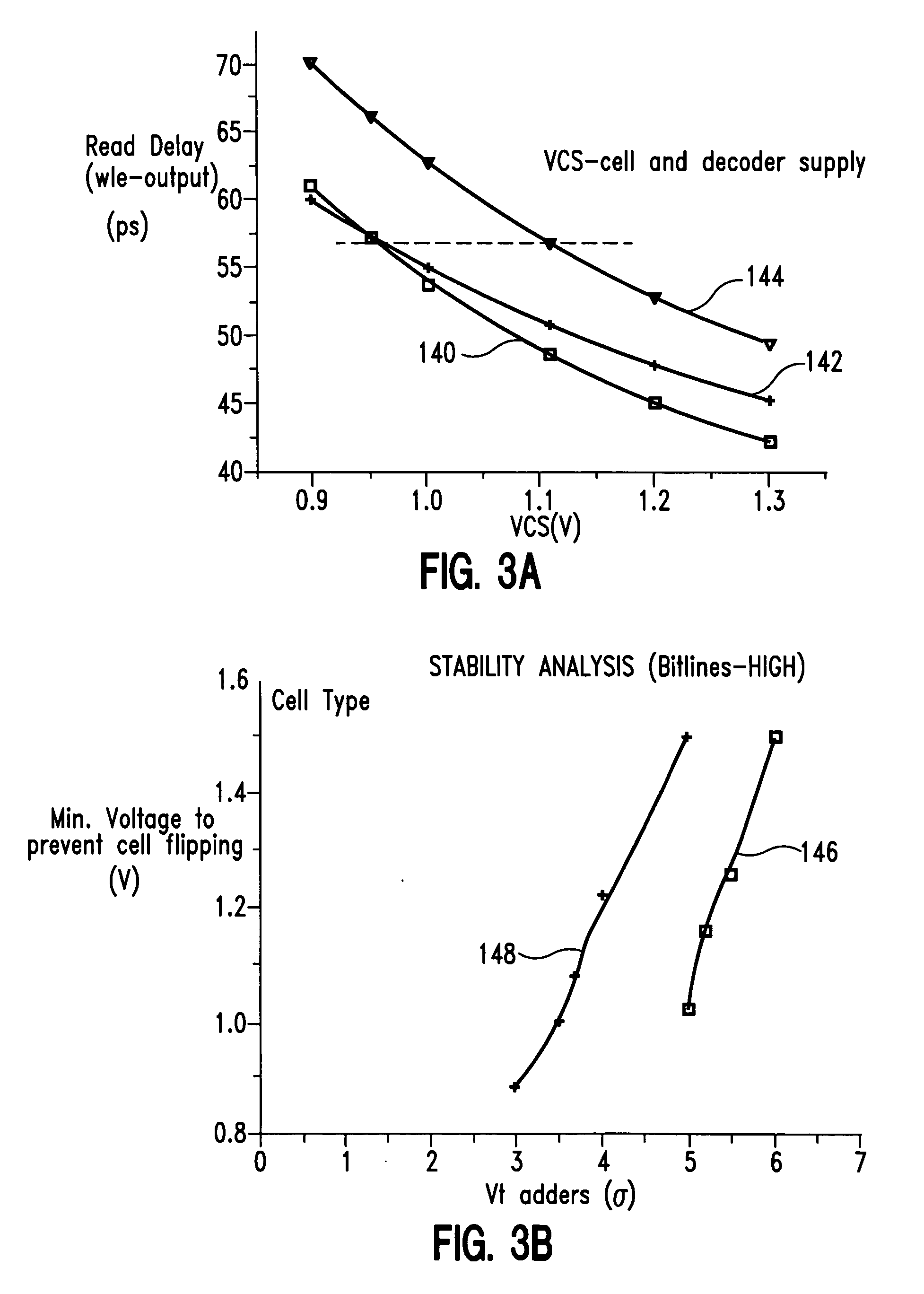
InactiveUS6437623B1Performance of was minimizedSimple designDigital circuit testingElectric pulse generatorControl signalProcessor register
A data retention system has master-slave latches for holding data in an active mode; a data retention latch for preserving data read from the master latch in a sleep mode, which is connected to the master latch in parallel with the slave latch; a first multiplexer for receiving data externally provided and feedback data from the data retention latch, and selectively outputting either the data externally provided or the feedback data to the master latch in response to a first control signal; and a second multiplexer for transferring output data of the master latch to the slave latch and the data retention latch in response to a second control signal, wherein power for the data retention latch remains turned on in the sleep mode, while power for the data retention system except for the data retention latch is turned off. The data retention latch may include gate transistors controlled by the second control signal and a data holding unit having transistors for holding data transferred through the gate transistors, wherein the gate transistors and the transistors in the data holding unit have a high-threshold voltage.
Owner:IBM CORP
Computer apparatus, storage apparatus, system management apparatus, and hard disk unit power supply controlling method
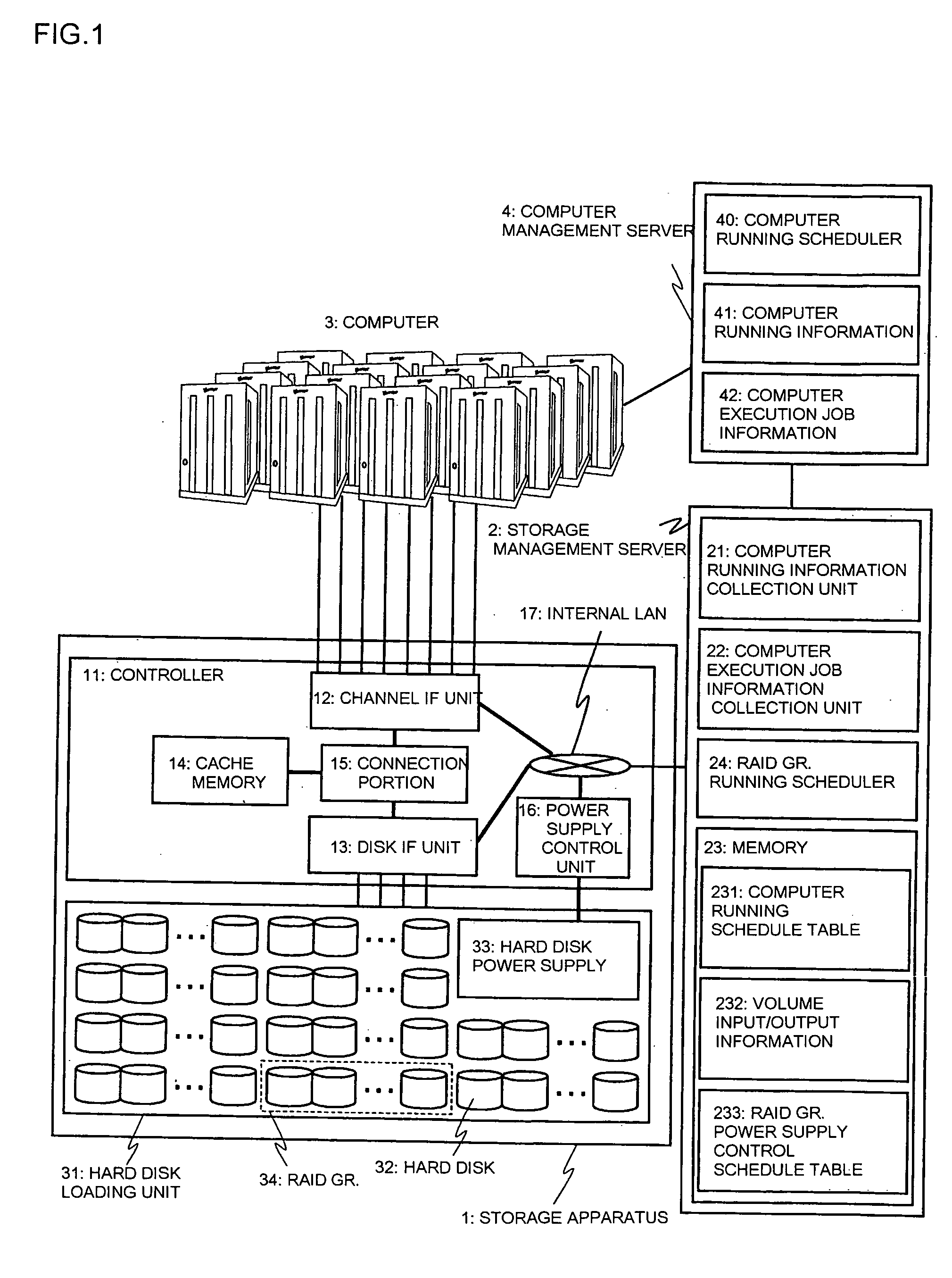
InactiveUS20070079156A1Performance of was minimizedSave powerEnergy efficient ICTVolume/mass flow measurementSystems managementStorage management
To provide a storage system capable of minimizing a performance deterioration, saving power consumption, and realizing a high reliability. A storage system according to the present invention includes a computer, a storage apparatus 1 connected with the computer, and a storage management apparatus connected to the storage apparatus, the storage apparatus including a hard disk unit to control a data write operation and a data read operation between the computer and the hard disk unit, and control on / off states of power supply of the hard disk unit on a group basis, and the system management apparatus collecting running information about the computer and computer execution job information for each computer, and determining an on / off time of the power supply of the hard disk unit on the group basis to record the collected information and the on / off time of the power supply on the group basis.
Owner:HITACHI LTD
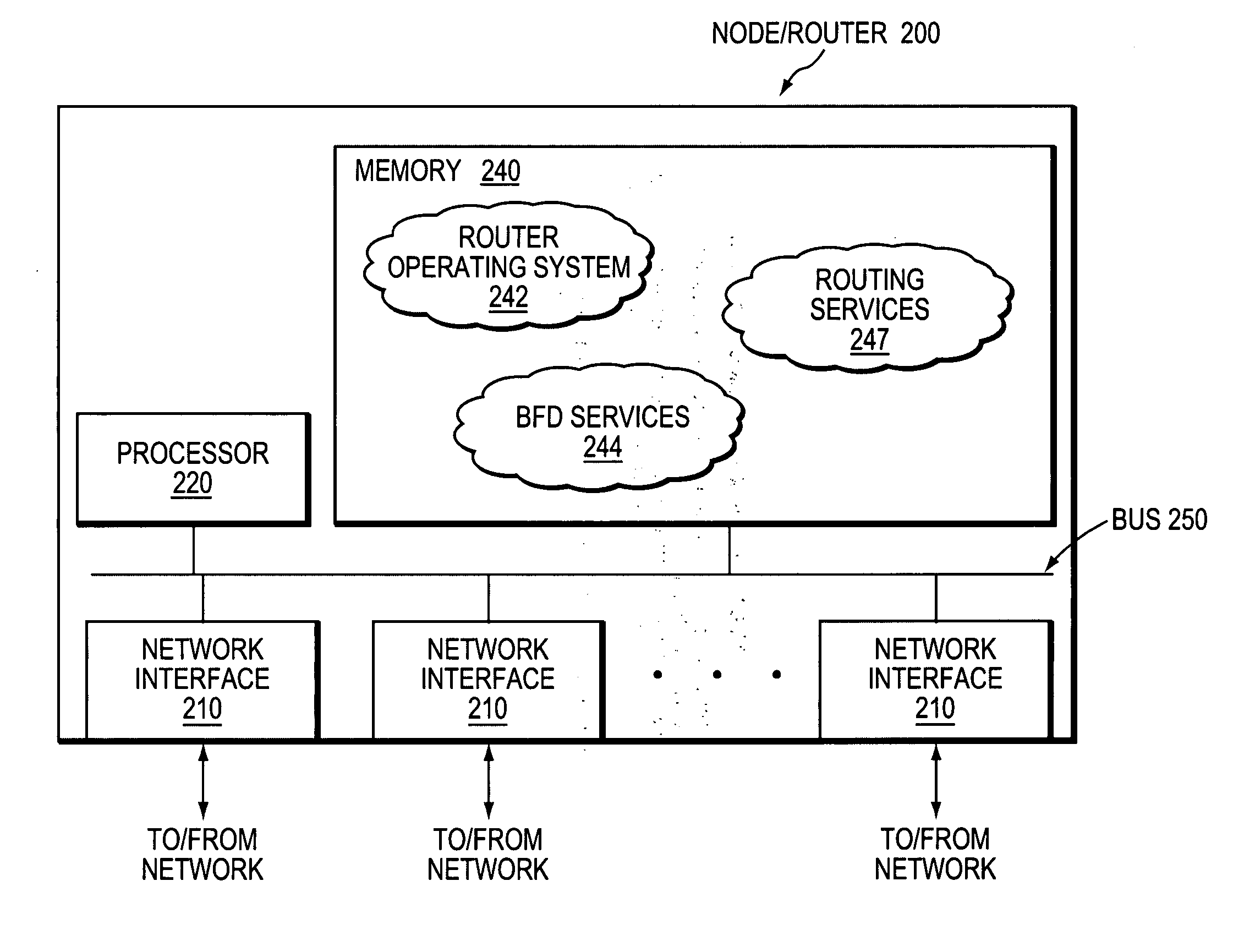
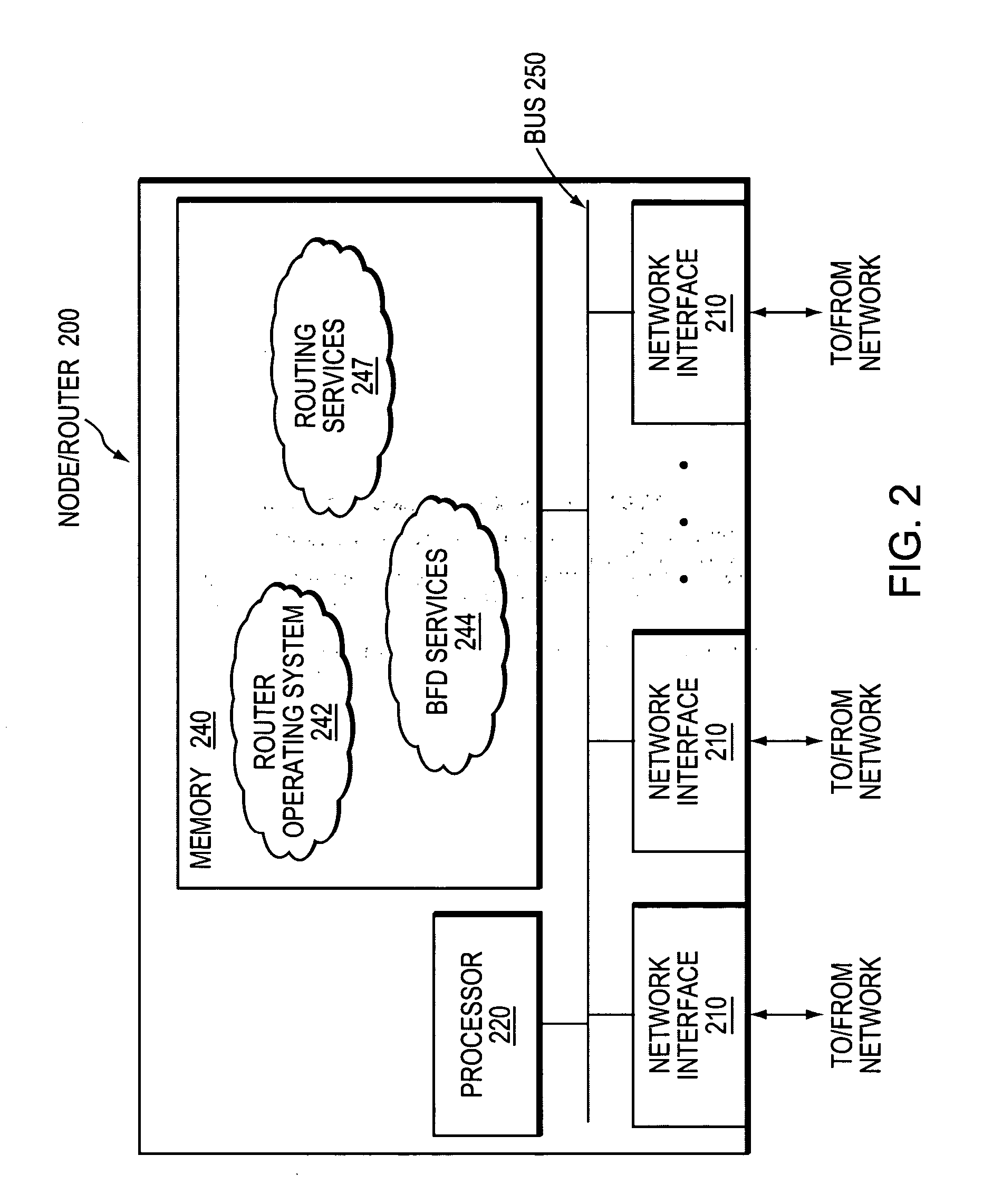
Technique for distinguishing between link and node failure using bidirectional forwarding detection (BFD)
ActiveUS20070180105A1False detection of failedPerformance of was minimizedDigital computer detailsElectric digital data processingBidirectional Forwarding DetectionLine card
A technique distinguishes between link and node failure using bidirectional forwarding detection (BFD) in a computer network. According to the novel technique, a BFD session is established over a first link between a monitoring node and a first interface of a monitored node. In addition, one or more novel unidirectional BFD (uBFD) sessions from one or more corresponding other interfaces of the monitored node to the monitoring node (e.g., as configured by the monitored node to detect its failure), the one or more uBFD sessions traversing links other than the first link (e.g., “not-via” the monitored node) are established, the one or more uBFD sessions traversing links other than the first link (e.g., “not-via” the monitored node). For instance, the one or more uBFD sessions correspond to one or more line cards of the monitored node. In response to detecting a lack of connectivity resulting from, e.g., failure of the BFD session, the monitoring node determines that the first link has failed if at least one uBFD session is operational. Moreover, in response to detecting failure of the BFD session and all of the one or more uBFD sessions, the monitoring node determines that the monitored node has failed.
Owner:CISCO TECH INC
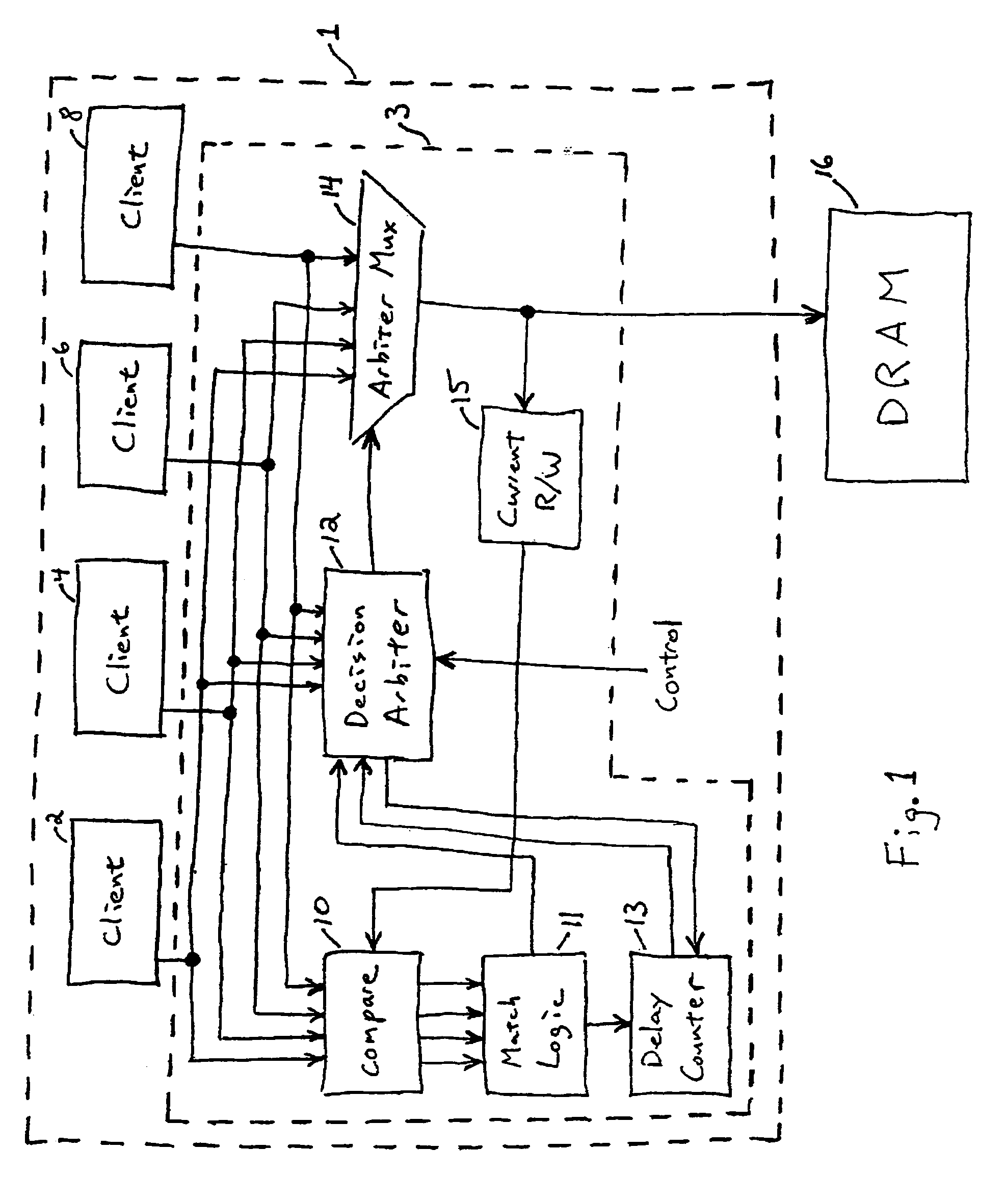
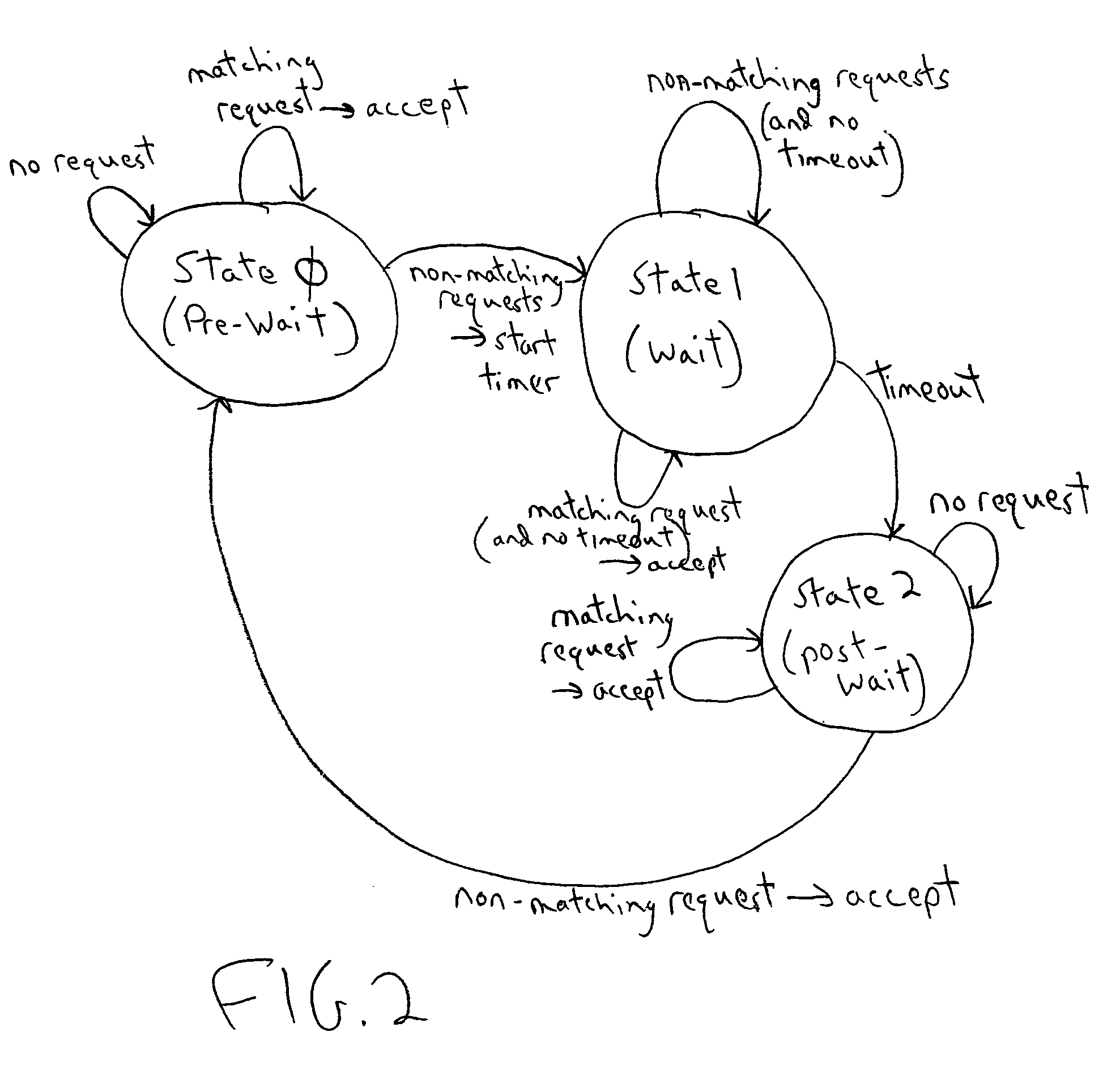
Method and system for memory access arbitration for minimizing read/write turnaround penalties
InactiveUS7080194B1Minimize performance penalty associatePerformance of was minimizedMemory adressing/allocation/relocationUnauthorized memory use protectionEmbedded systemClient-side
A method and system for arbitrating among memory access commands from clients seeking access to a DRAM or other memory, and an arbiter for use in implementing such method or system. When arbitrating among competing commands that include at least one command of the same read / write type as the current command, the arbiter selects a command of the same read / write type as the current command. In a wait mode, when arbitrating among a set of the commands that includes no command of the same read / write type as the current command, the arbiter prevents each command in the set from reaching the memory. Preferably, after operating in the wait mode for a limited time, the arbiter enters another arbitration mode in which it can select a command of the opposite read / write type as the current command. Preferably, the arbiter is implemented to be operable in any of multiple operating modes. For example, it can have separately programmable wait times for “read to write” and “write to read” situations. Preferably, the arbiter monitors for occurrence of potential page fault conditions.
Owner:NVIDIA CORP
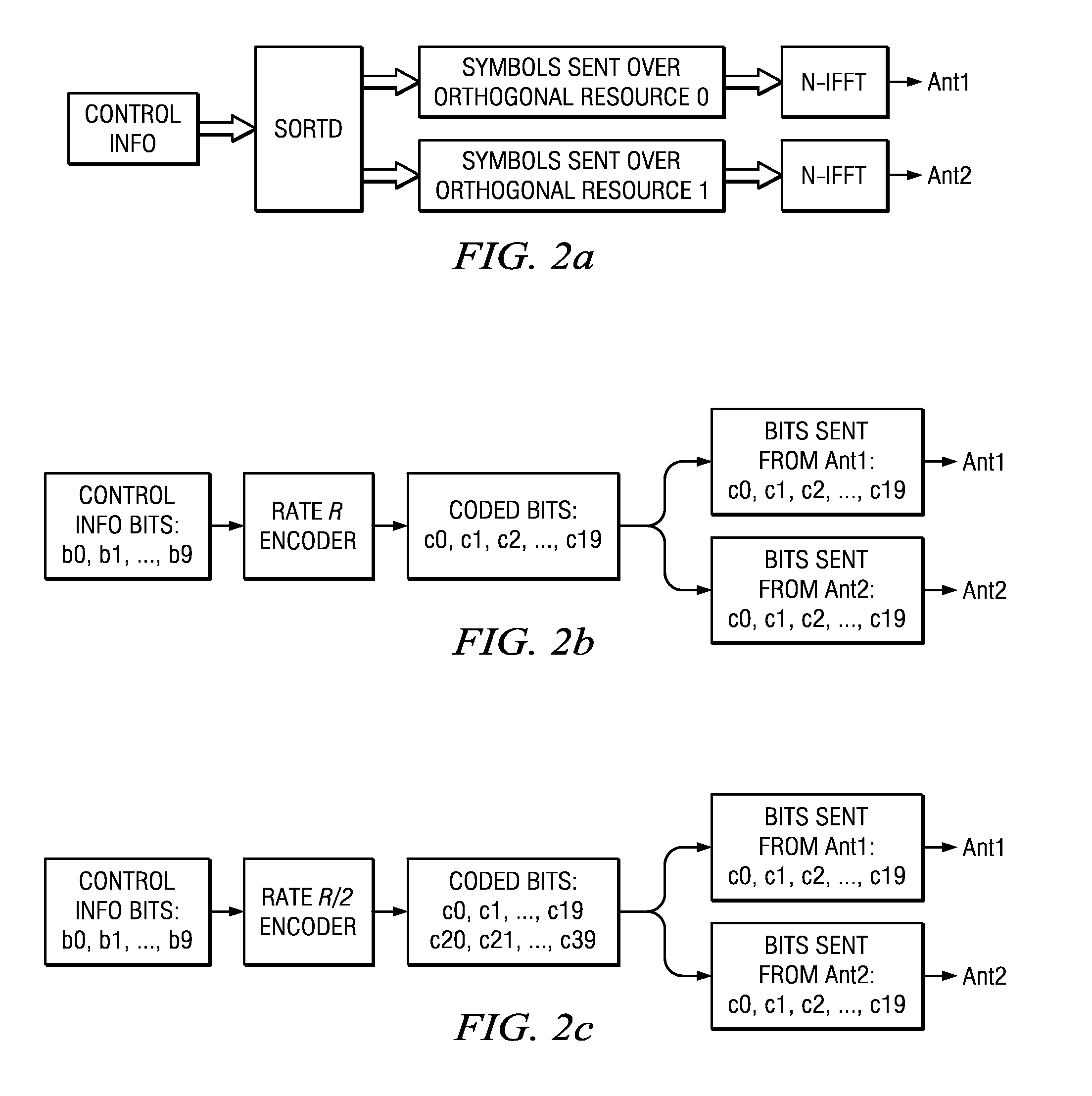
Orthogonal Resource Selection Transmit Diversity
InactiveUS20120082263A1Maximum diversity gainPerformance of was minimizedError preventionModulated-carrier systemsDiversity schemeComputer science
Owner:MALIKIE INNOVATIONS LTD
Finger-mapped character entry systems
ActiveUS10082950B2Maximizing numberReduce in quantityInput/output processes for data processingKey pressingHuman–computer interaction
A finger-mapped gesture system is a user interface method and apparatus for rapid data input on a touch-sensitive surface. The user gestures by holding the hand stationary relative to the surface and moving the fingers primarily by extension and flexion on the surface. Each finger gestures on a gesturing area instead of selecting among keys. Individual gestures are constructed from finger actions that each independently parameterize the gesture. In combination, the particular fingers gesturing and the parameters that the fingers gesture indicate the input that the user intends. On devices that do not directly identify fingers, fingers are identified via a finger map that, after calibration to a person's hand, associates each finger with a gesturing area. Gestures are otherwise independent of where they are performed, freeing users from having to look at their fingers to target visual elements. The system is optimized for rapid character data entry.
Owner:LAPP JOSEPH T
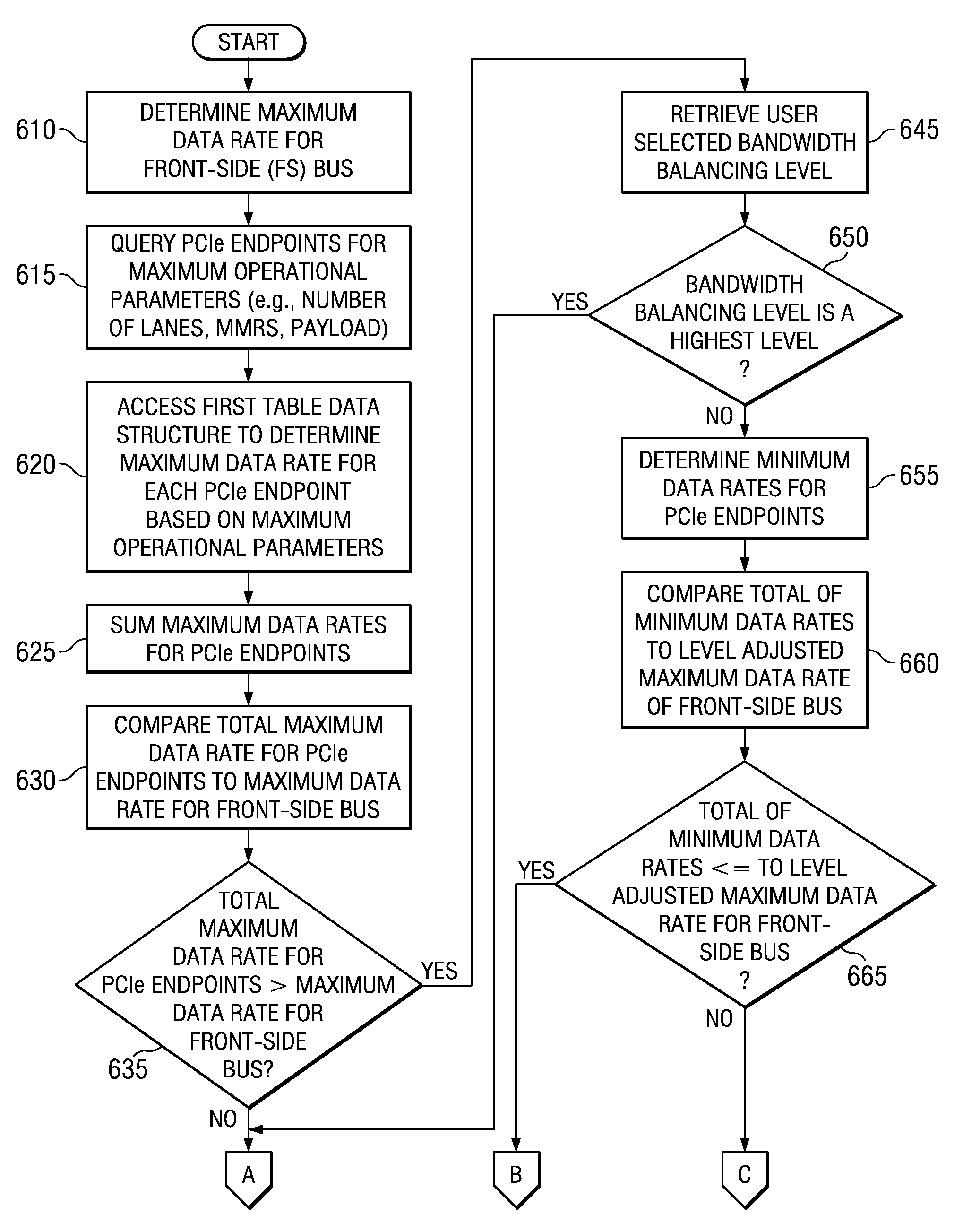
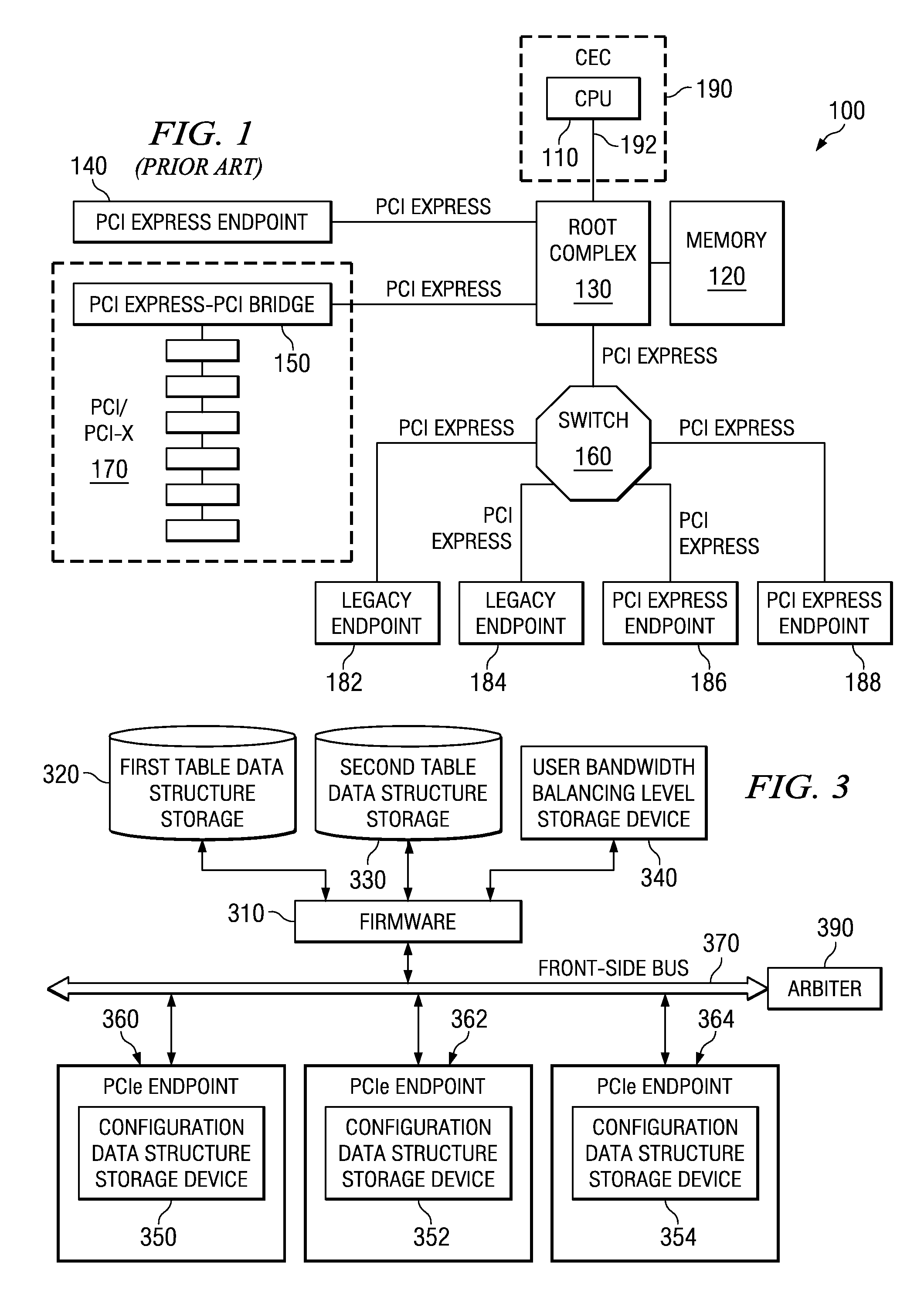
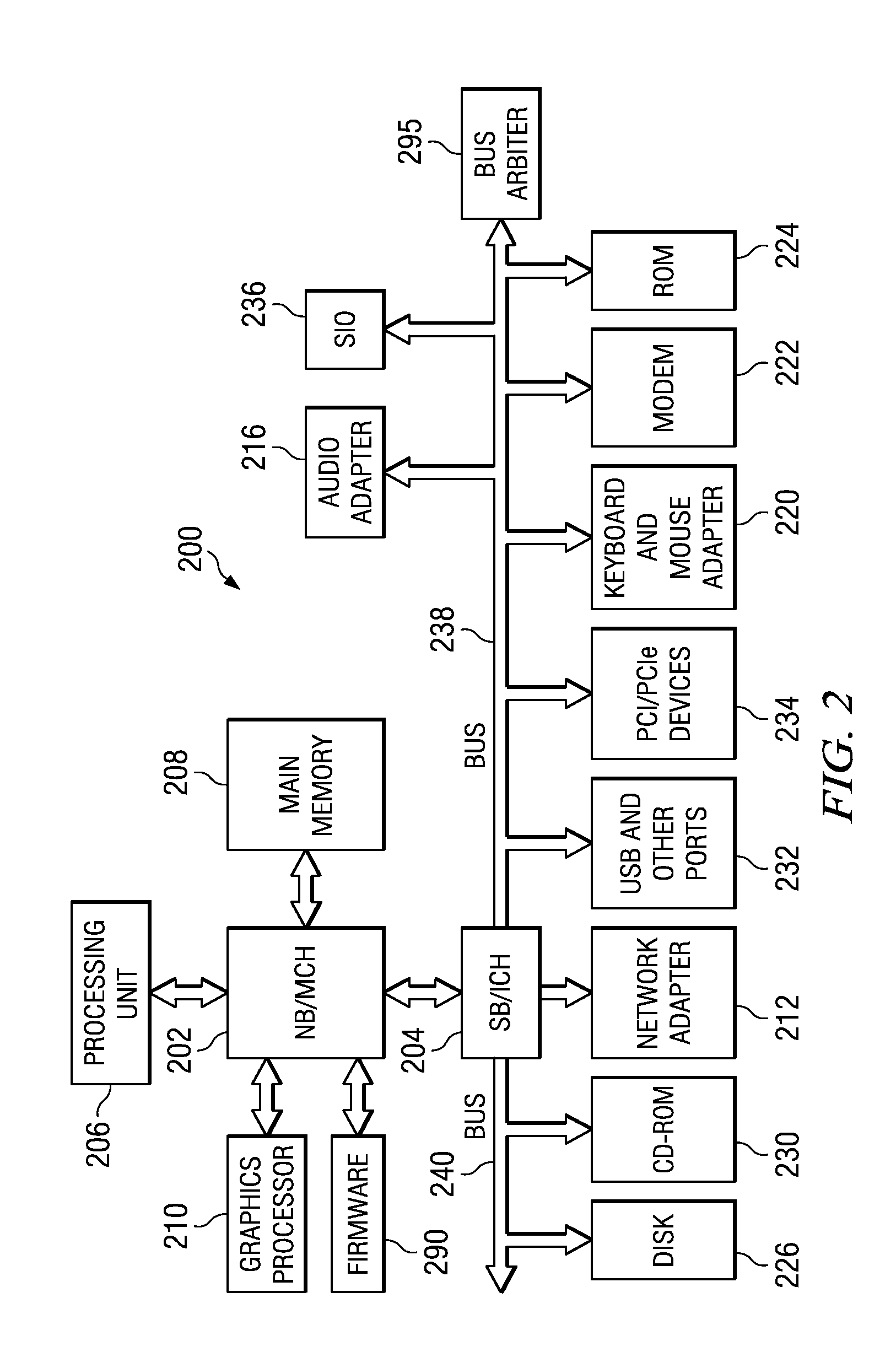
System and Method for Balancing PCI-Express Bandwidth
InactiveUS20080263246A1Maximize useMinimize the possibilityElectric digital data processingData processing systemControl data
A system and method for balancing bus bandwidth across a plurality of PCI-Express (PCIe) endpoints are provided. Firmware automatically operates in concert with established data structures to set operational parameters of the PCIe endpoints so as to maximize usage of the available bandwidth of a front-side bus while minimizing isochronous issues and the likelihood that the performance of the PCIe endpoints cannot be guaranteed. A first table data structure comprises various combinations of operational parameter settings for controlling bandwidth usage of each of the endpoints of the data processing system. A second table data structure contains a listing of the endpoints that the data processing system supports with their associated minimum data rates, priorities, and whether the endpoints have isochronous requirements. A setting of the desired bandwidth balancing level is used along with these data structures to determine how to adjust the operating parameters of the PCIe endpoints.
Owner:IBM CORP
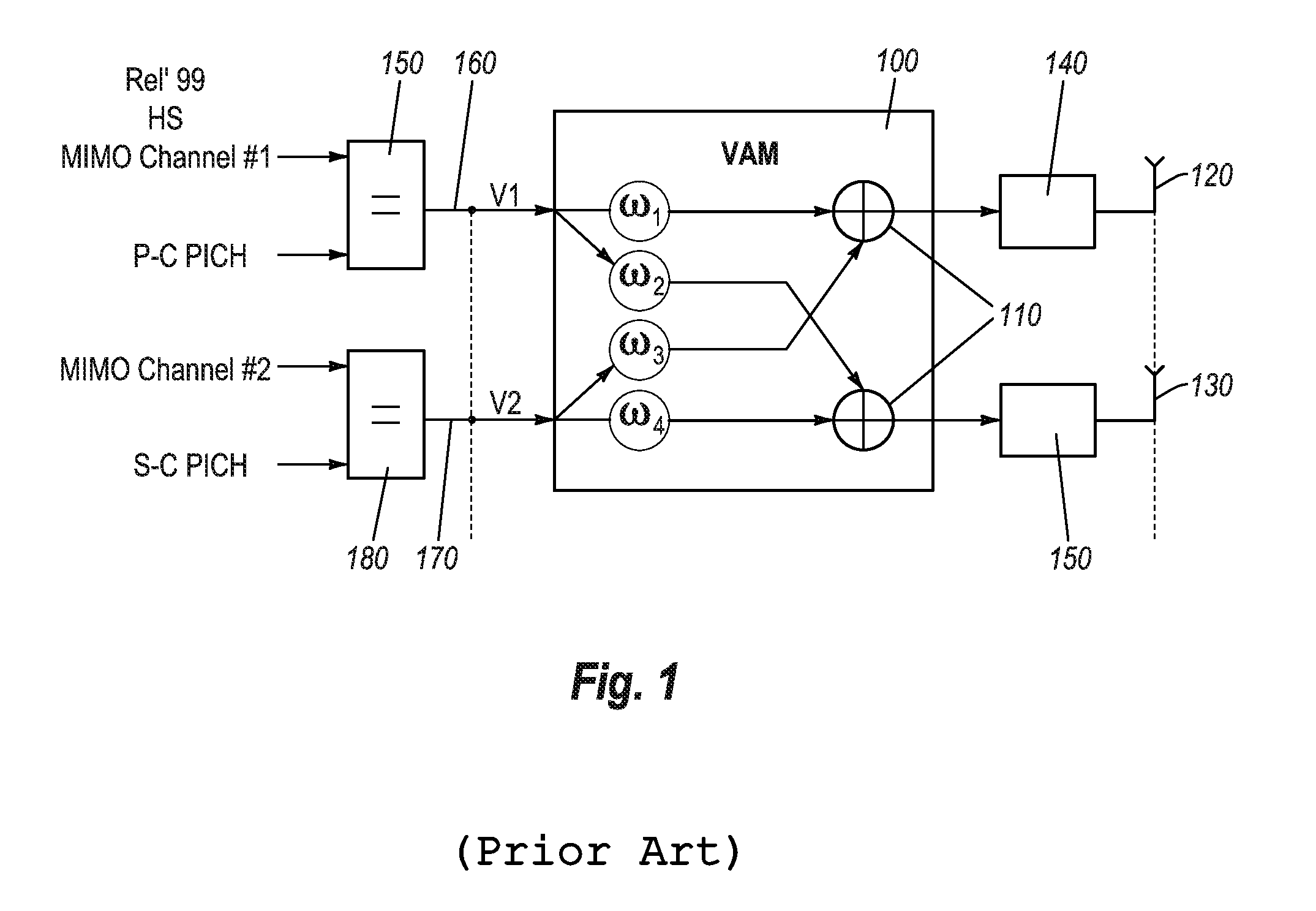
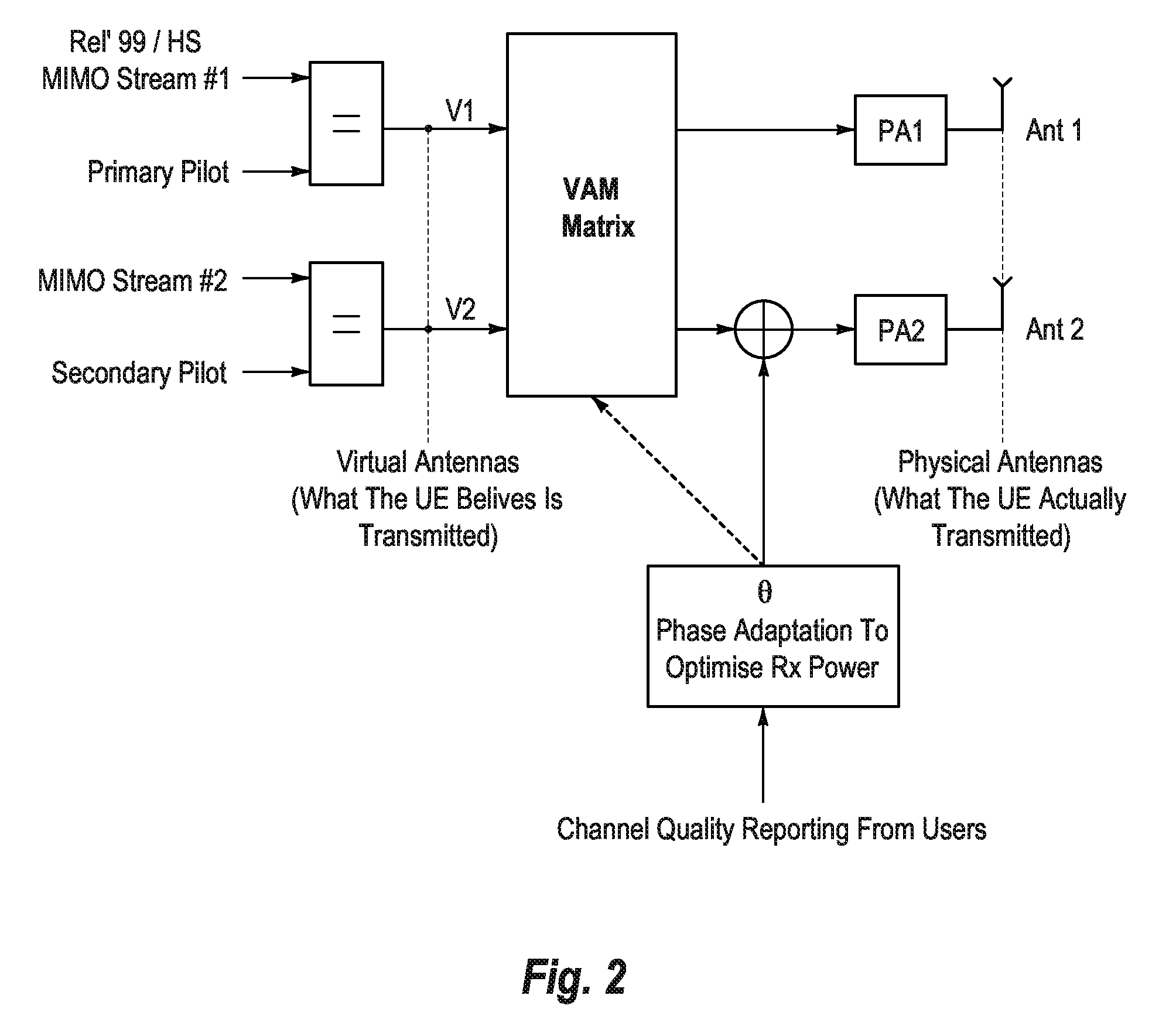
Method and system for enhanced transmission in mobile communication networks
ActiveUS9065515B2Maximize throughputMaximize energySpatial transmit diversityError preventionUser equipmentComputer science
Method and system for improving the performance of mobile communication networks. The method and system employs the additional functionality whereby an additional phase offset can be applied to one of the physical paths (one physical antenna) in order to modify and adapt the transmit polarization. In the preferred embodiment, the criterion for selecting the additional phase offset will be to maximize the energy received from the HSPA serving cell by the legacy HSDPA user equipments.
Owner:VODAFONE IP LICENSING
System for dynamic diagnosis of apparatus operating conditions
InactiveUS20050137762A1Enhanced advantageAvoid disadvantagesVehicle testingRegistering/indicating working of vehiclesInformation repositoryOn board
A diagnostic platform includes a processor, storage media and user interfaces, including a display screen, the processor being coupled to engine analyzer hardware and adapted to be coupled to a scanner for downloading data from vehicle on-board computers. The system stores libraries of information regarding vehicle identifications, drivability symptoms exhibited by vehicles, vehicle system and component tests and service codes which can be registered by the vehicle on-board computer. System software permits the user to input an identification of the vehicle under test and, in one mode of operation, displays a library of faults, such as symptoms or service codes, from which the user can select those exhibited by the vehicle, whereupon the system selects from the test library those tests pertinent to diagnosis of the causes of the selected faults and displays them in a hierarchically ranked order based on likelihood of successful diagnosis of the faults. The user can then select and initiate any displayed test. In other modes, the system initially displays one of the libraries of system or component tests, from which the user selects those deemed appropriate, whereupon the system highlights icons which can be selected for initiating pertinent test procedures. Selected test procedures may include links to the engine analyzer or scanner hardware or other appropriate test modules.
Owner:SNAP ON INC
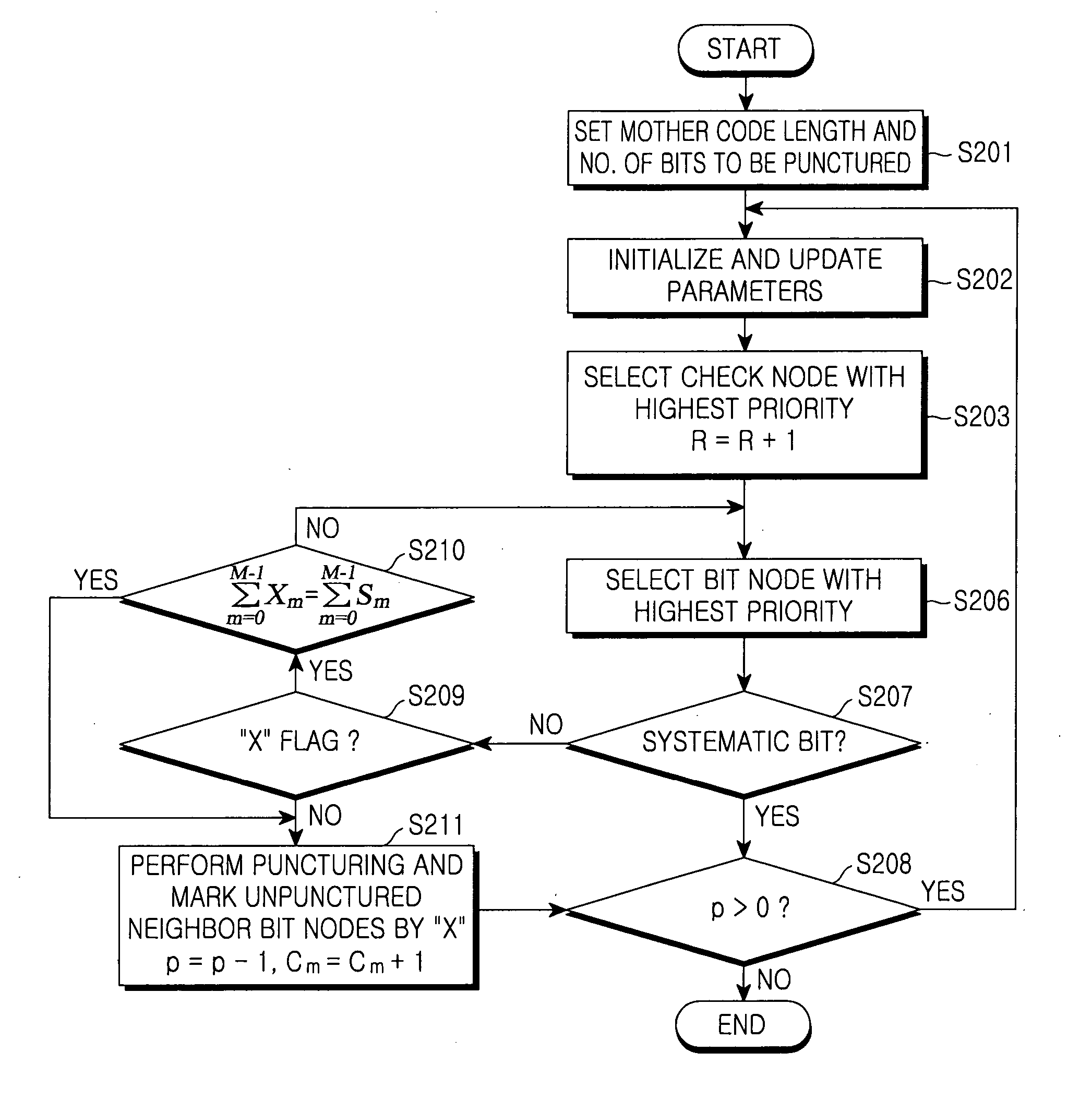
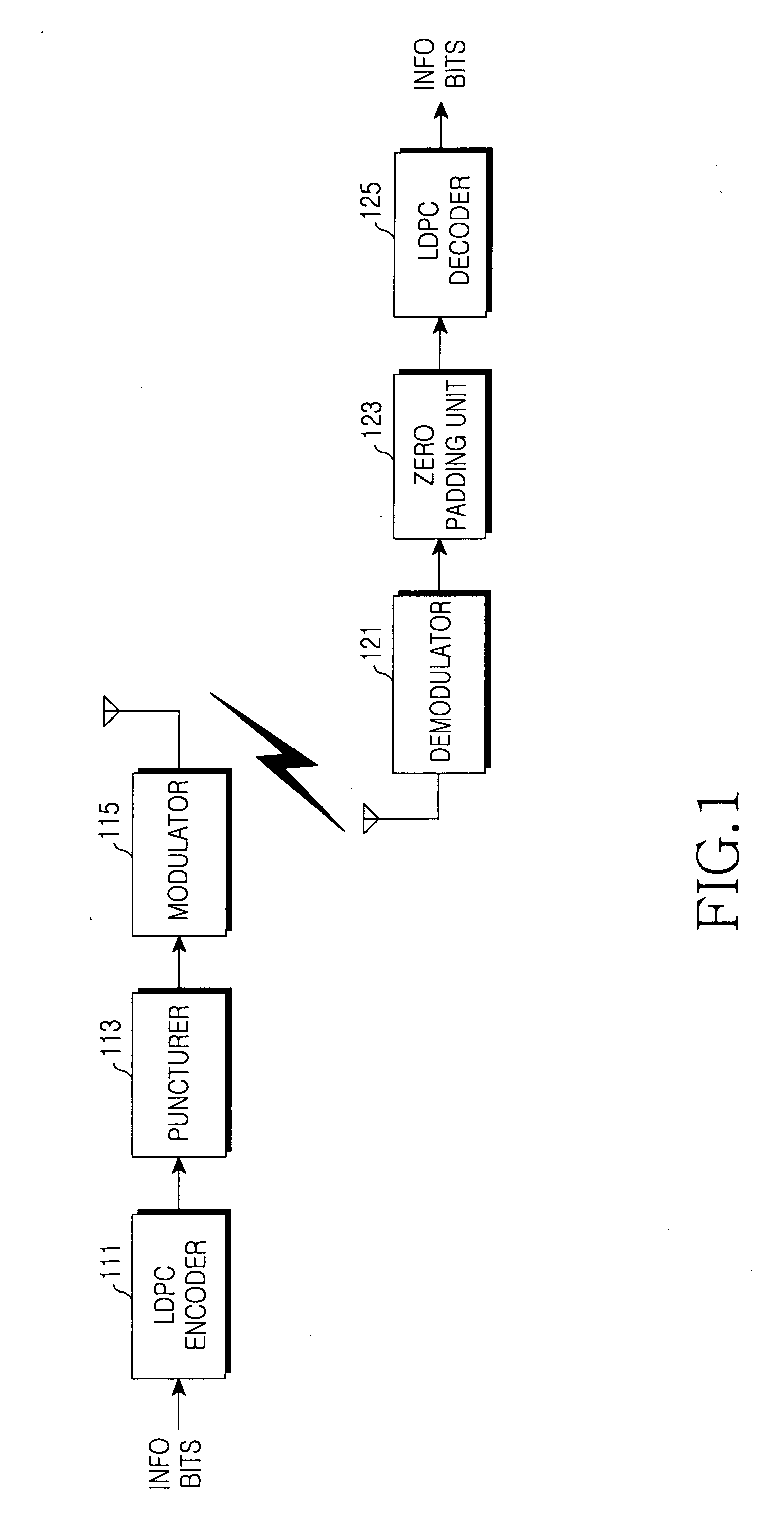
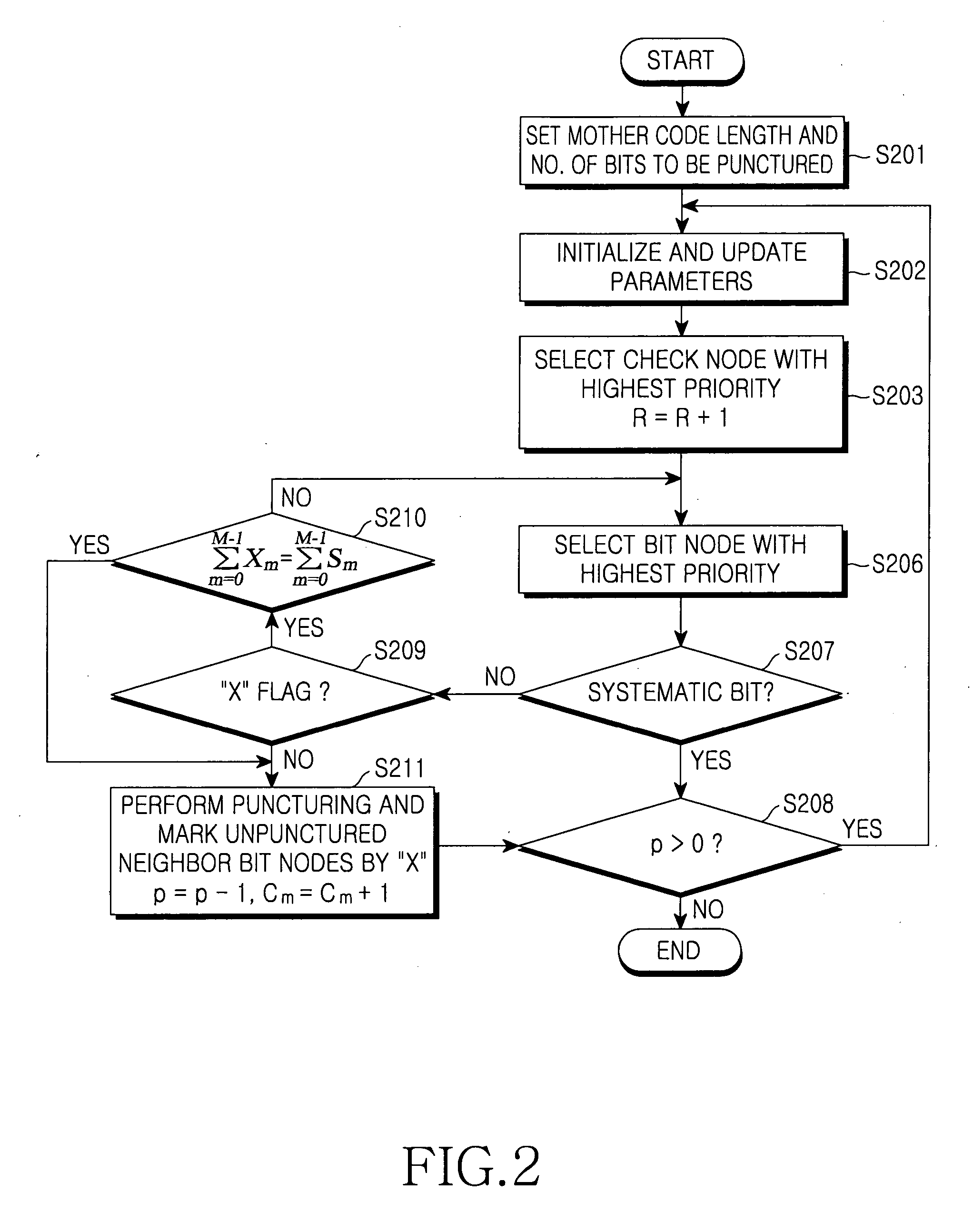
Method for puncturing a low density parity check code
ActiveUS20070101243A1Performance degradation can be minimizedPerformance of was minimizedError correction/detection using multiple parity bitsCode conversionLow-density parity-check codeLow density
A method for puncturing a Low Density Parity Check (LDPC). The method includes a) setting a codeword length and the total number of bit nodes to be punctured; b) selecting a check node (or check nodes) with highest priority excluding check nodes completely checked in a current round; c) selecting a bit node (or bit nodes) with a highest priority excluding bit nodes completely checked among bit nodes connected to the selected check node (or check nodes); d) determining whether the selected bit node is a bit node to be punctured, that is, it is not systematic, not set by a puncturing prohibition flag; e) puncturing an associated bit node if the selected bit node is the bit node to be punctured, setting unpunctured bit nodes connected to the selected check node by a puncturing prohibition flag, decreasing the number of remained bit nodes to be punctured by 1 and increasing the number of connected punctured node of associated check node by 1; f) determining whether the number of remaining bits to be punctured is greater than 0; and g) returning to step b) if the number of remaining bits to be punctured is greater than 0, and ending a puncturing process if the number of remaining bits to be punctured is not greater than 0.
Owner:SAMSUNG ELECTRONICS CO LTD +1
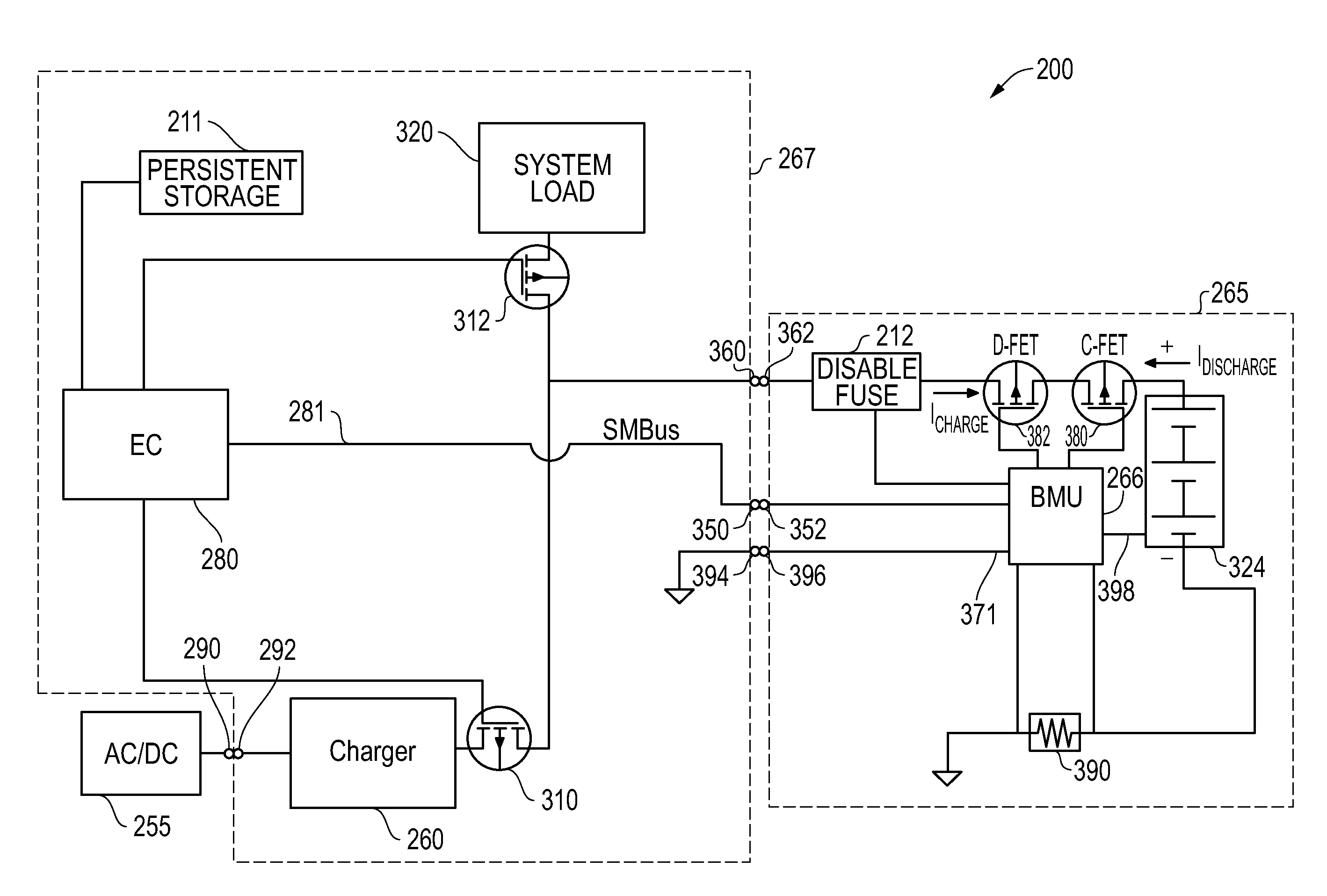
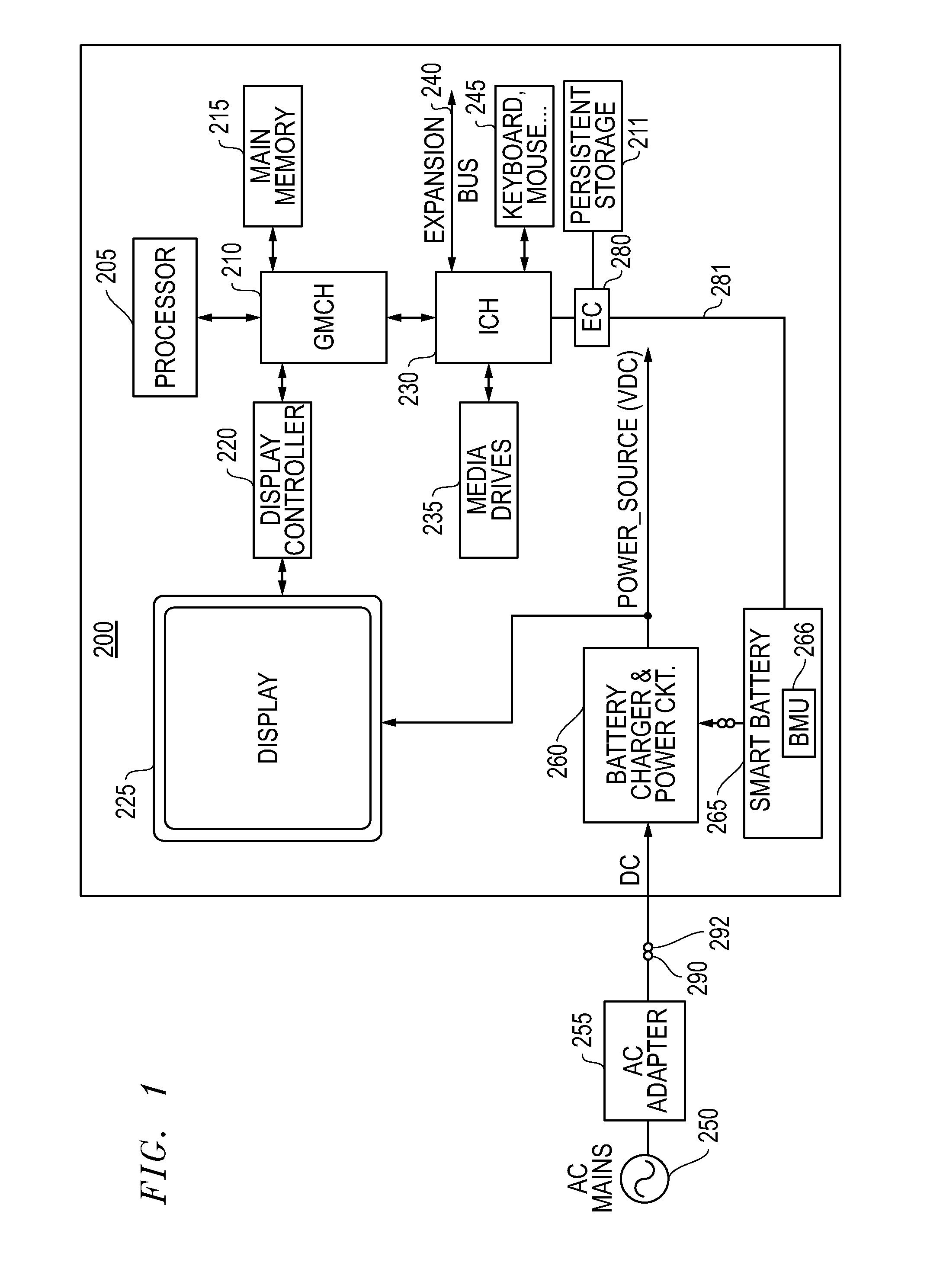
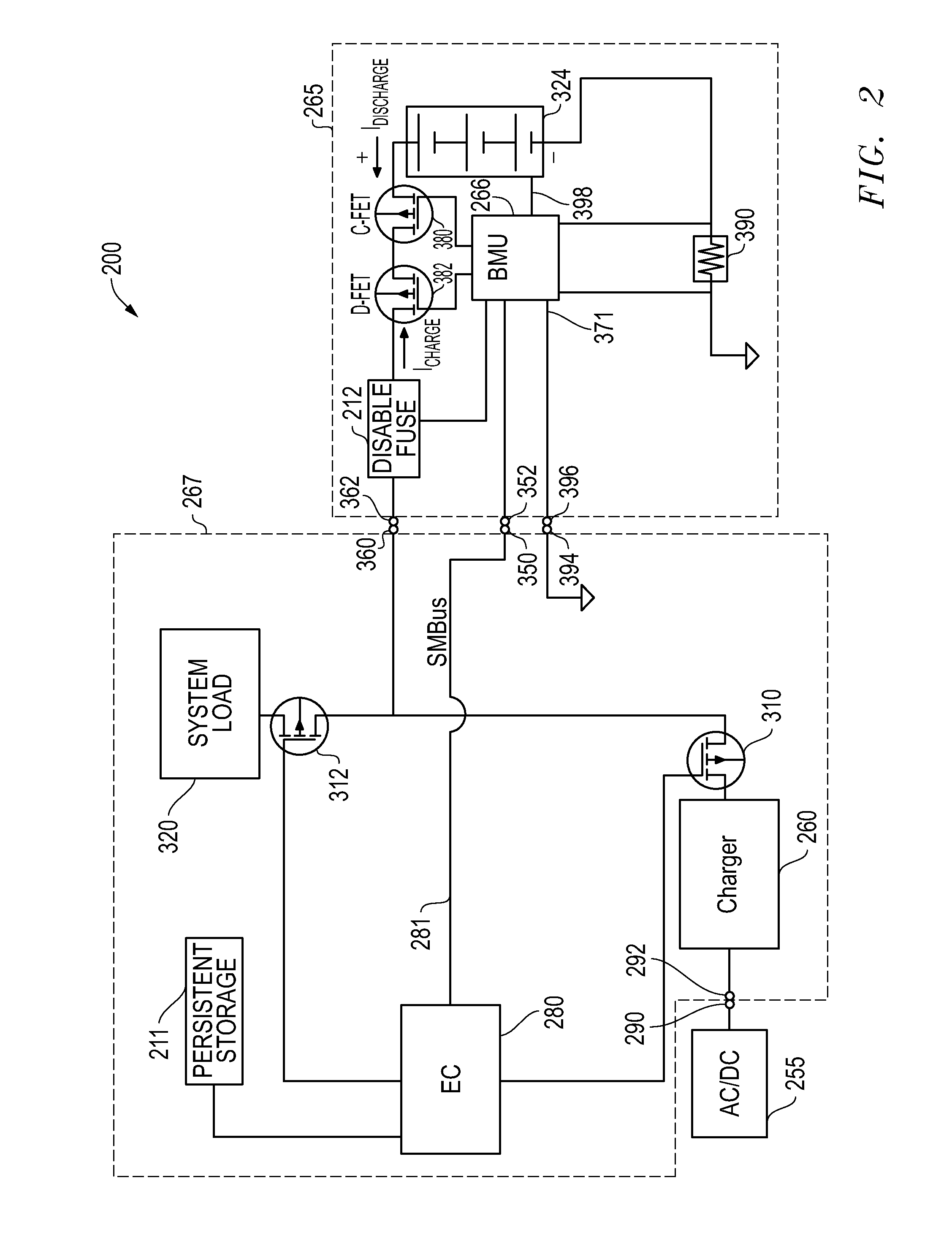
Systems and methods for implementing persistent battery shutdown for information handling systems
ActiveUS20140068310A1Not allowShorten the timeHardware monitoringPower supply for data processingElectrical batteryHandling system
Systems and methods are provided for implementing a persistent battery system shutdown condition when a battery pack voltage level drops below a predetermined minimum acceptable operating voltage threshold that is above a pre-determined permanent failure operating voltage threshold at which the battery pack is permanently disabled. The disclosed systems and methods may be implemented such that shutdown portion of the power-consuming components of the information handling system are not allowed to be restarted until external power has been first provided and applied to at least partially recharge the battery cells of the battery pack to a battery voltage level that is above the minimum acceptable operating voltage threshold and / or when sufficient external power is applied to power the information handling system and at the same time charge the battery cells of the battery pack.
Owner:DELL PROD LP
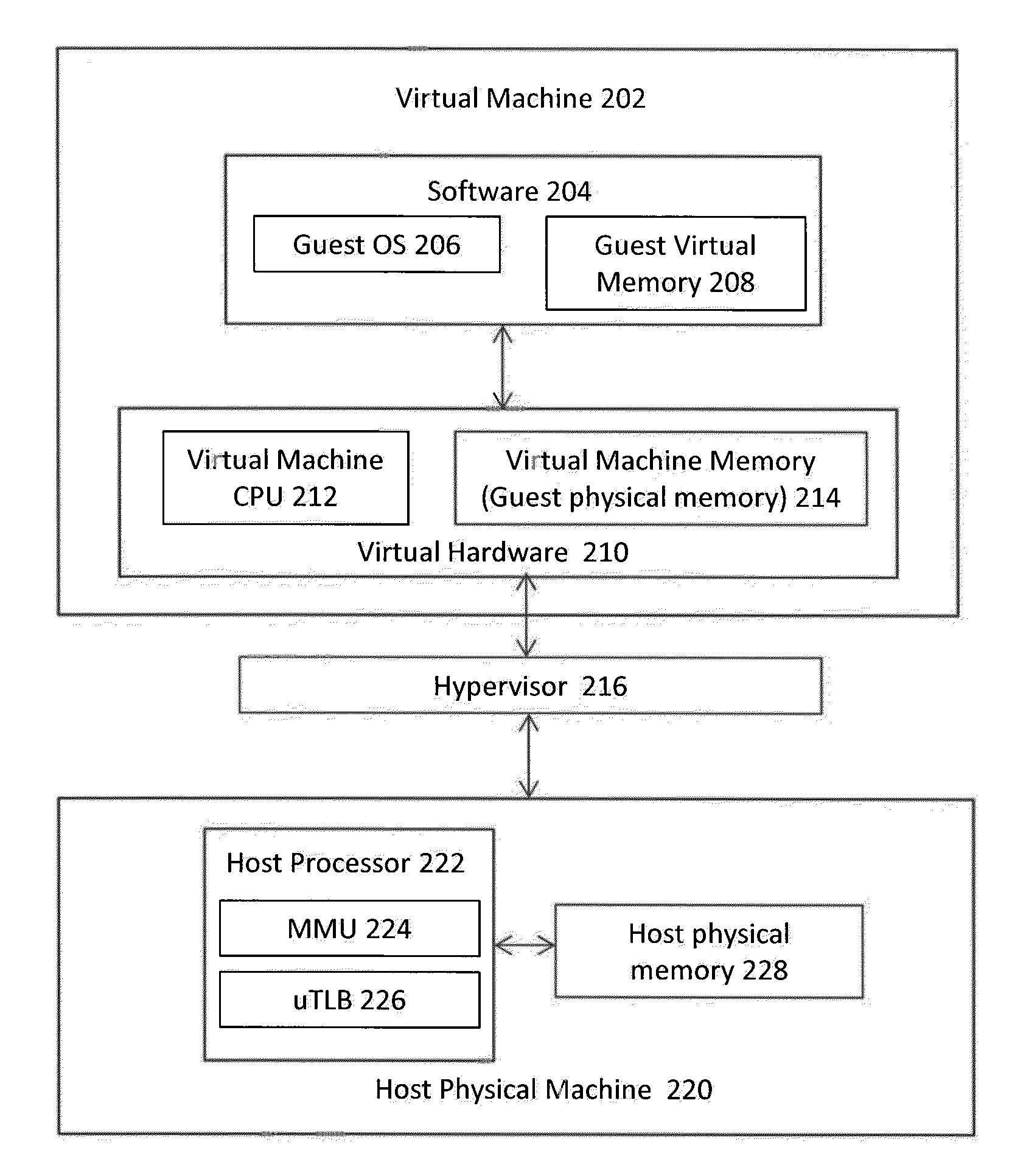
Memory management in a virtualization environment
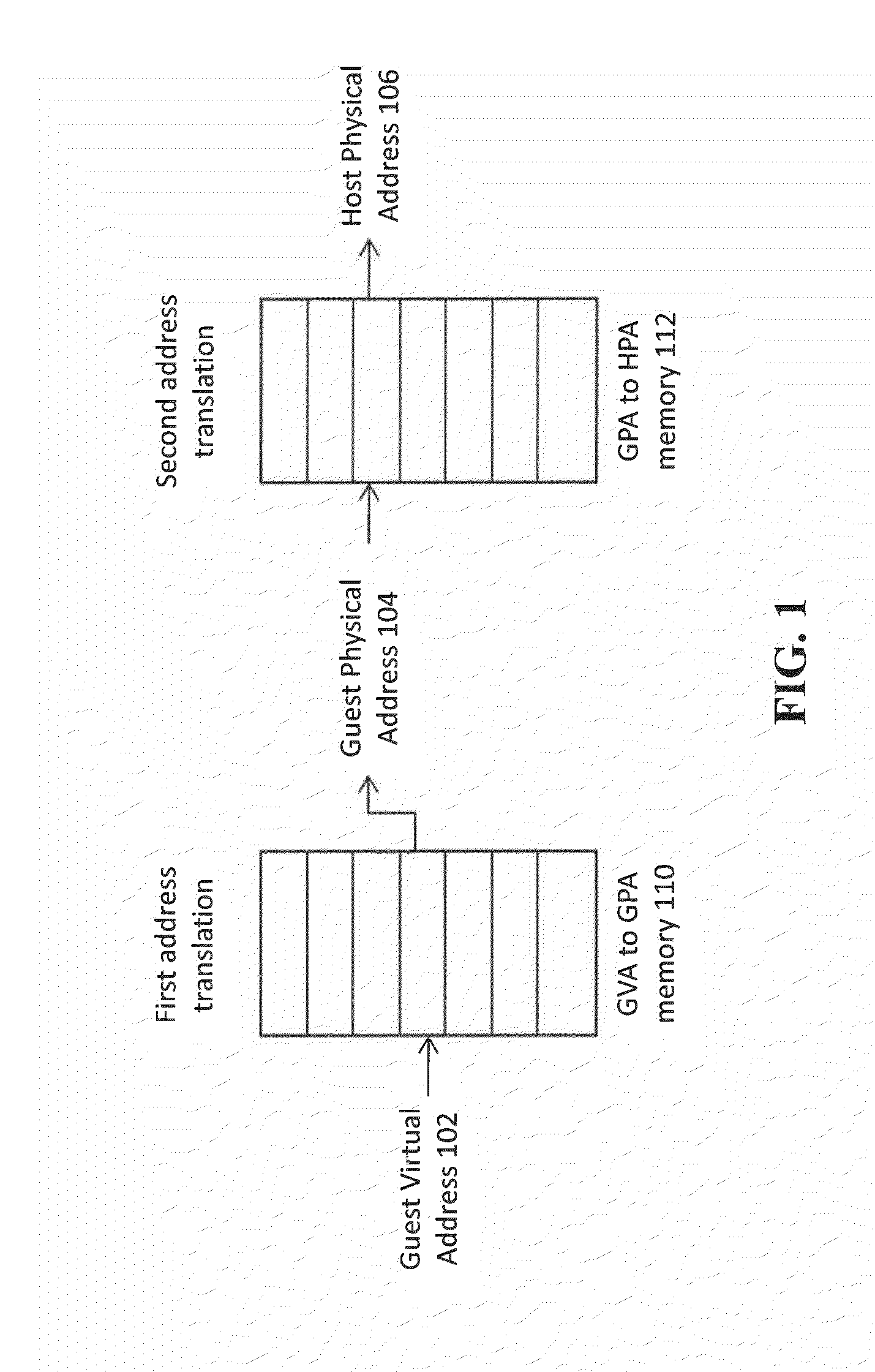
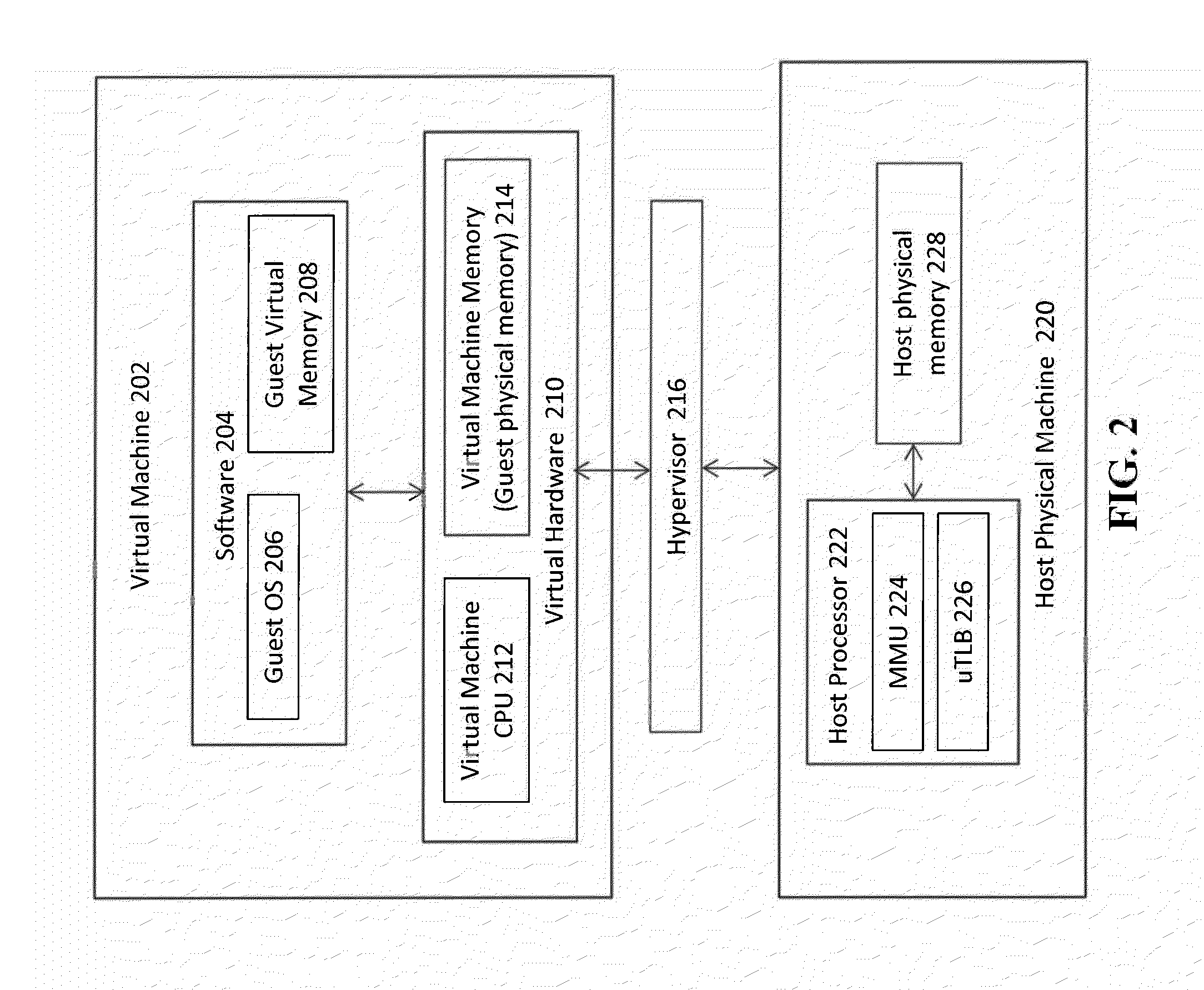
InactiveUS20140006681A1Avoids multiple address translationPerformance of was minimizedMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtualizationMemory management unit
An architecture is described for performing memory management in a virtualization environment. Multiple levels of caches are provided to perform address translations, where at least one of the caches contains a mapping between a guest virtual address and a host physical address. This type of caching implementation serves to minimize the need to perform costly multi-stage translations in a virtualization environment.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
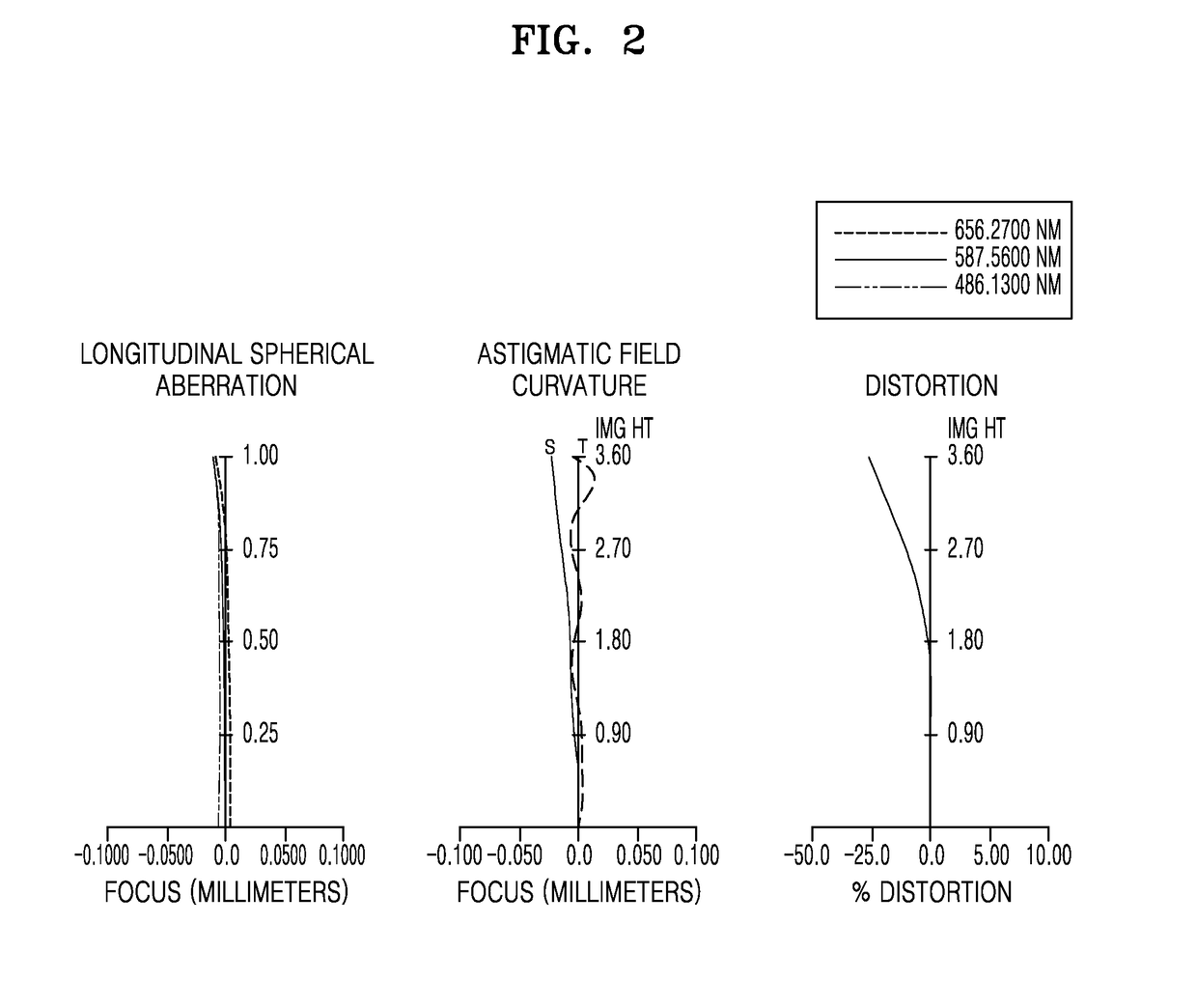
Optical lens assembly and electronic apparatus including the same
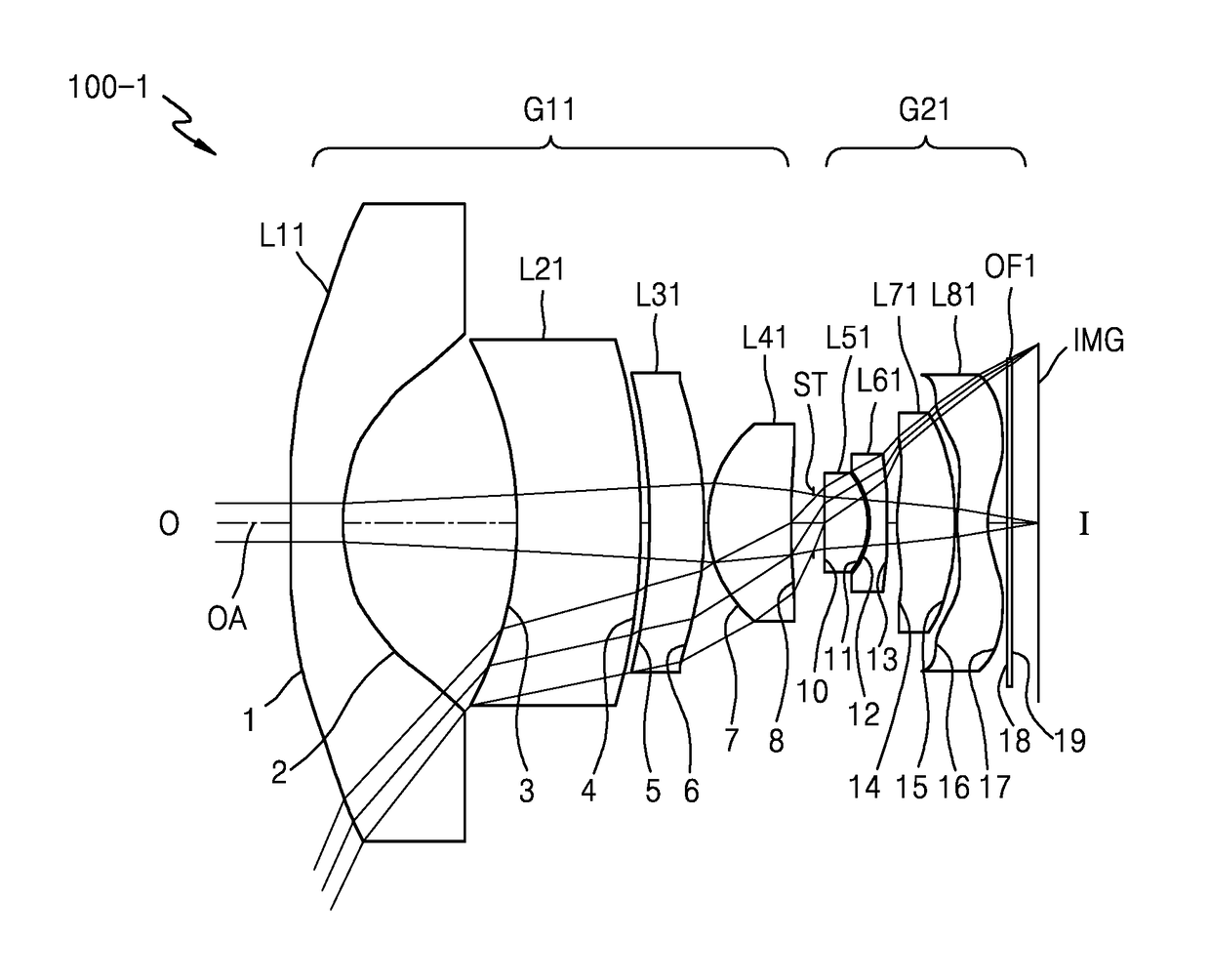
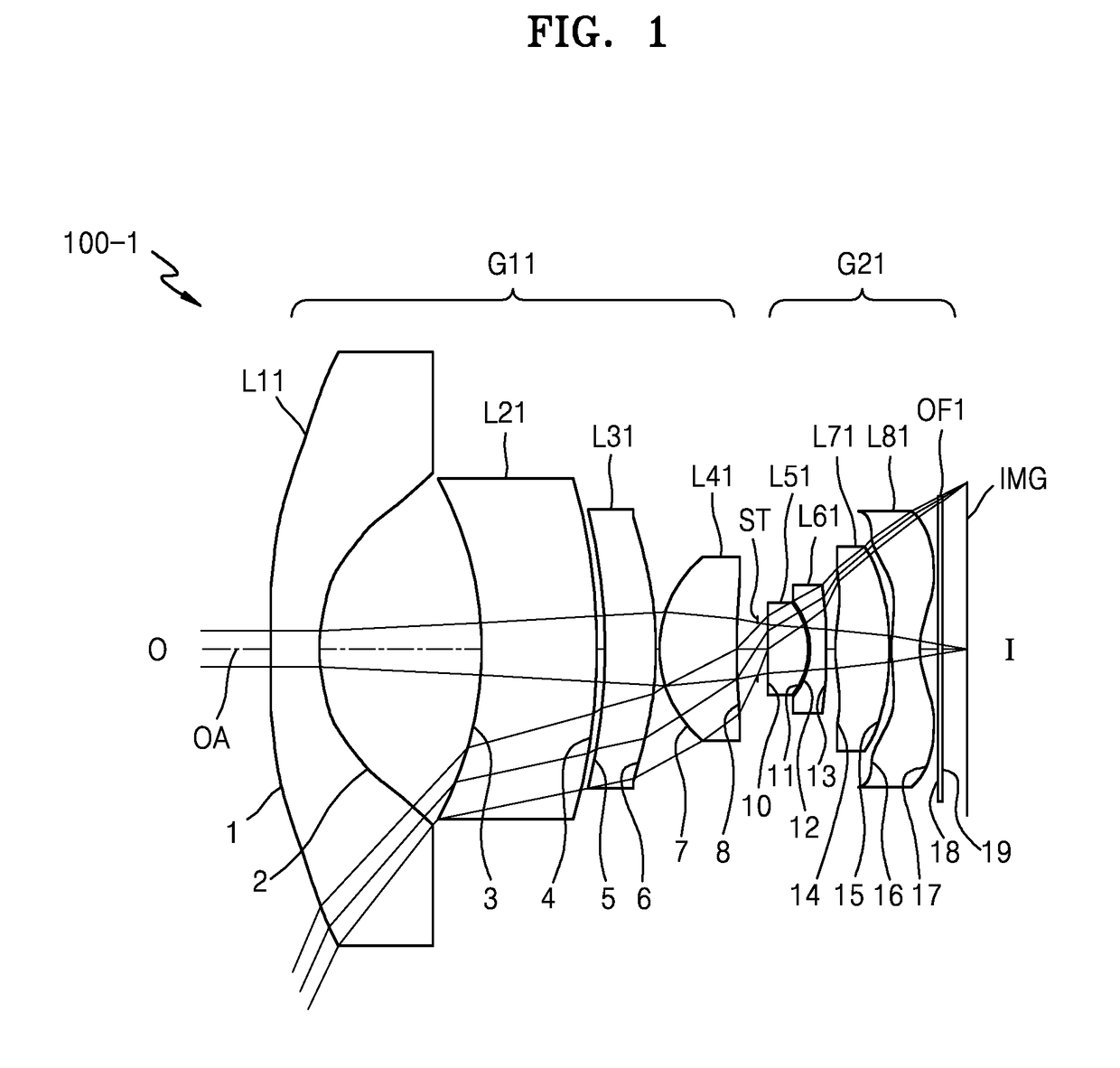
Provided are an optical lens assembly and an electronic apparatus including the same. The optical lens assembly implements a wide-angle lens system by including a first lens group having positive refractive power, an iris diaphragm, and a second lens group having positive refractive power, where the first lens group, the iris diaphragm, and the second lens group are arranged from an object side to an image side, and the first lens group includes at least one negative lens and two positive lenses.
Owner:SAMSUNG ELECTRONICS CO LTD
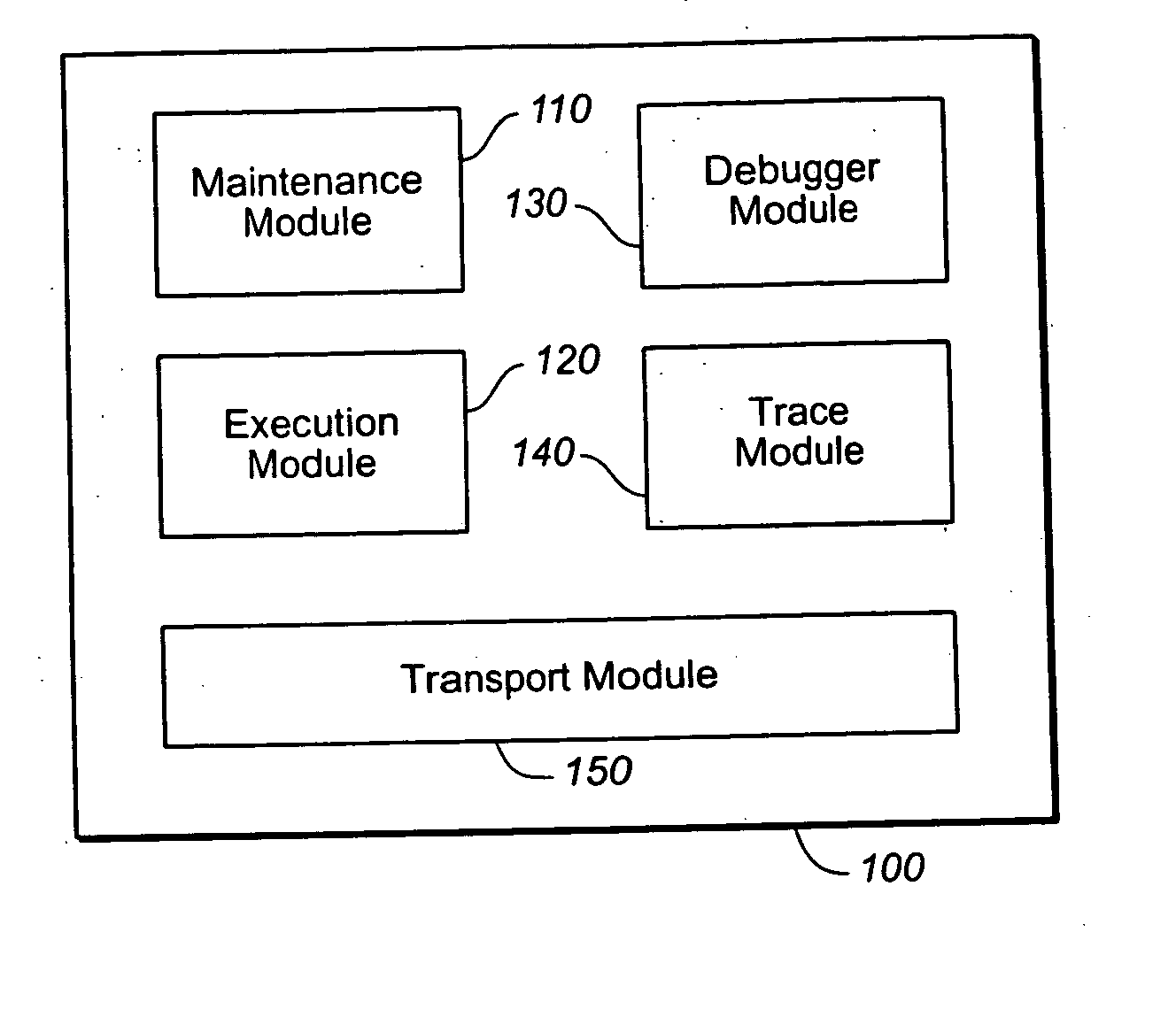
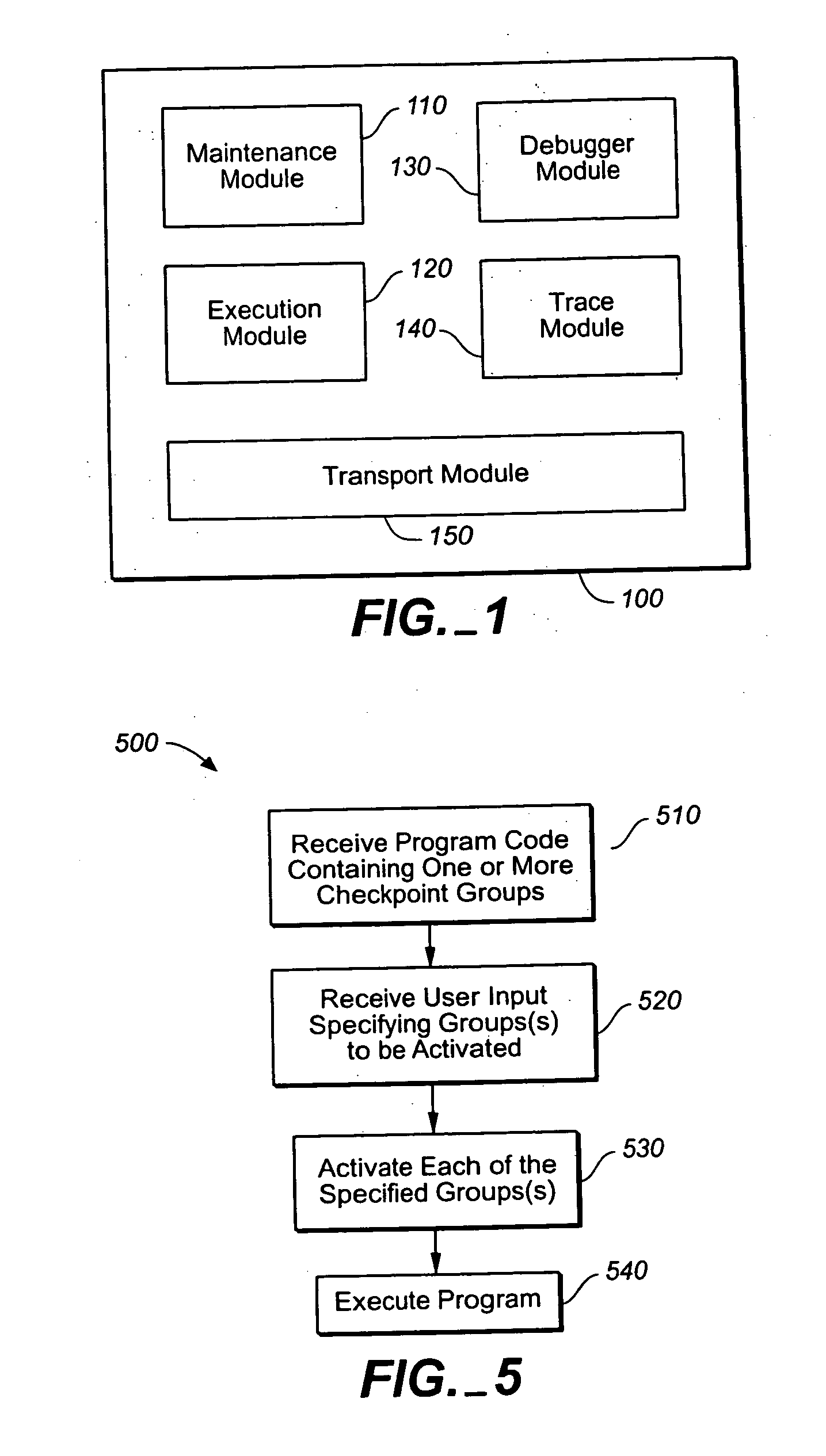
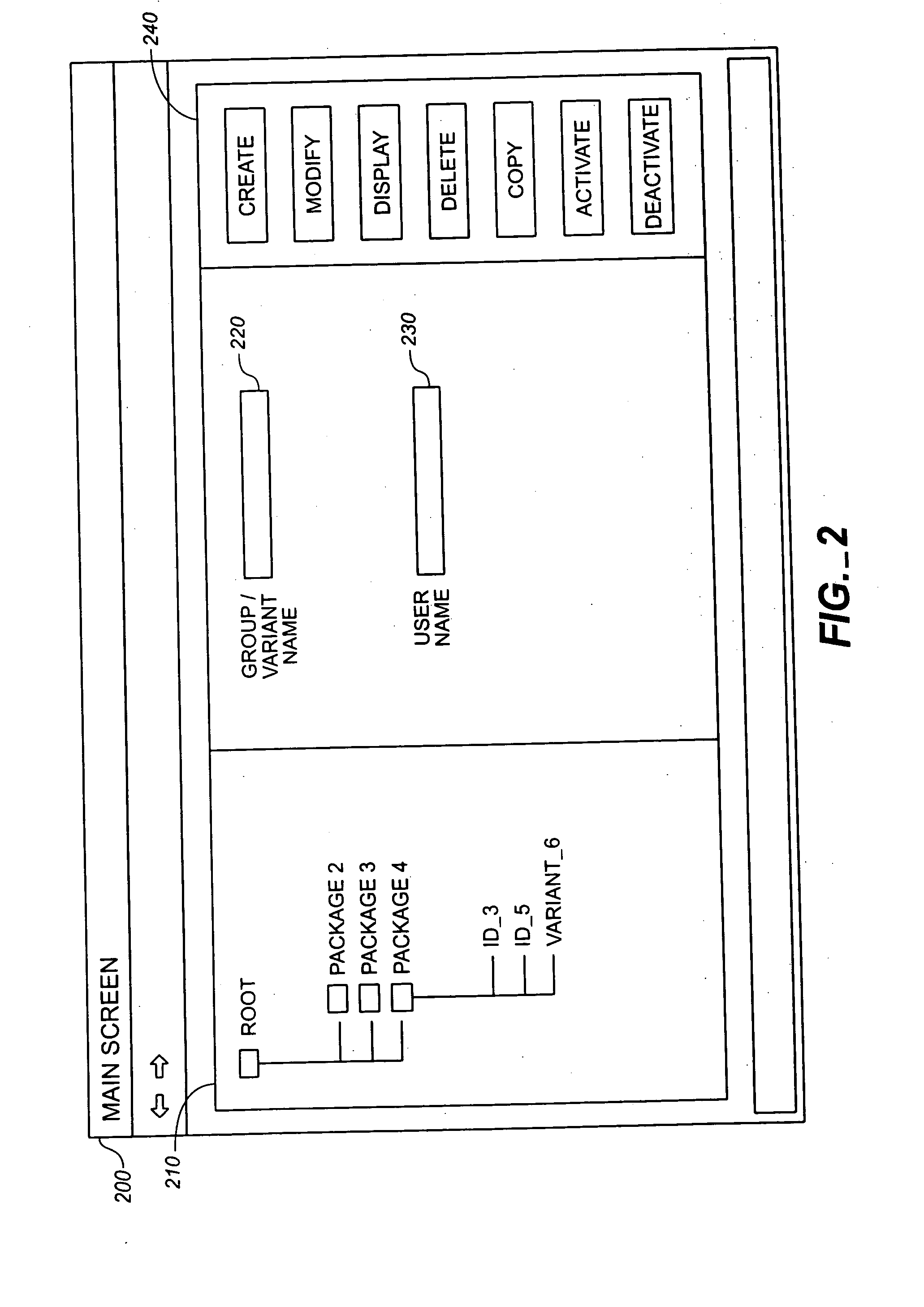
Activating assertions and breakpoints
ActiveUS20050055605A1Performance of was minimizedError detection/correctionSpecific program execution arrangementsBiological activationComputer program
Methods and apparatus, including computer program products, for activating assertions and breakpoints. The techniques include establishing any number of checkpoints in a first computer program; and including each checkpoint in a checkpoint group, wherein each checkpoint group can include any number of the checkpoints regardless of where the checkpoints are in the first computer program. The checkpoints can include assertion statements and breakpoint statements. Activation variants enable checkpoint groups or compilation units or both to be managed jointly.
Owner:SAP AG
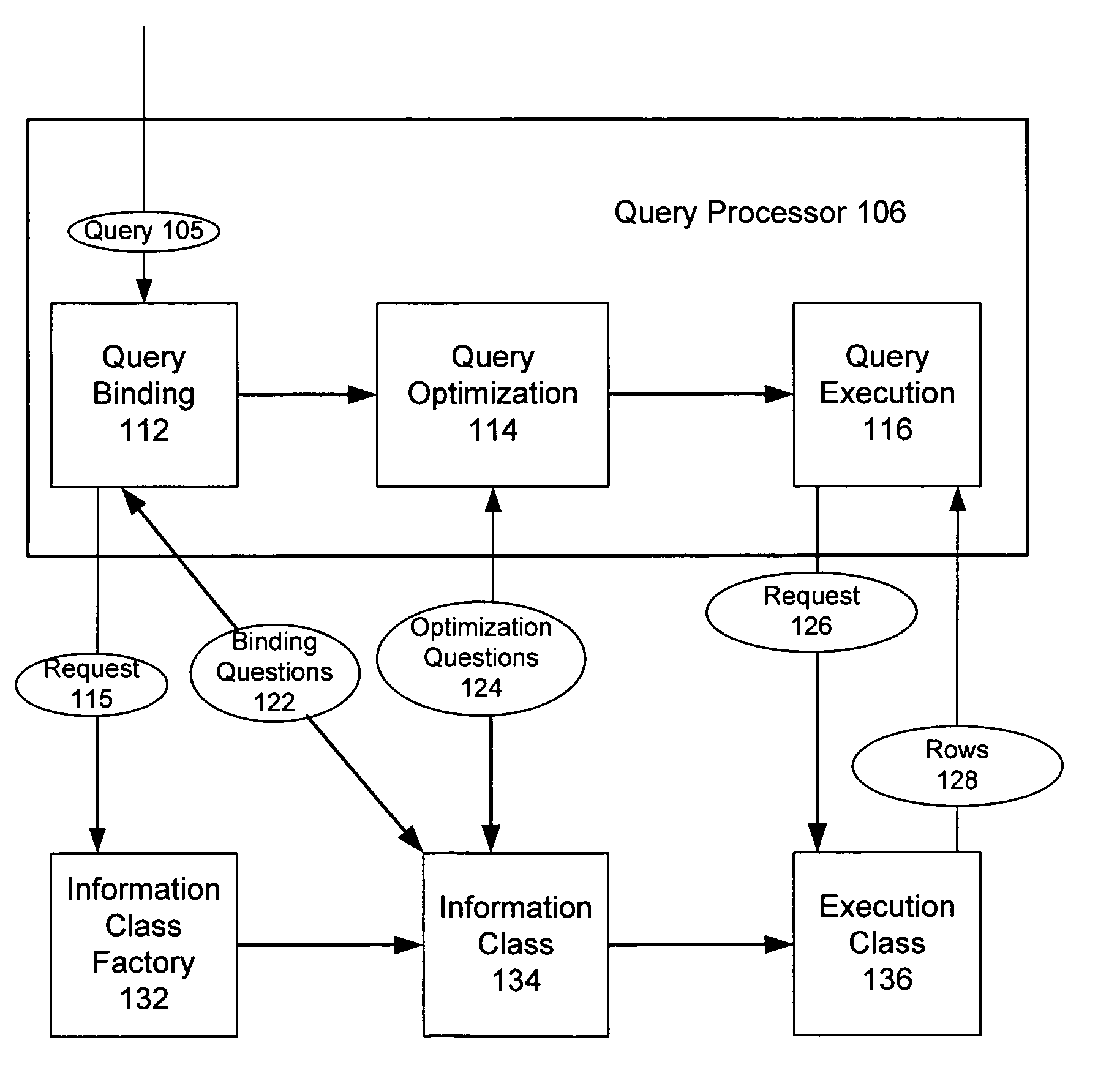
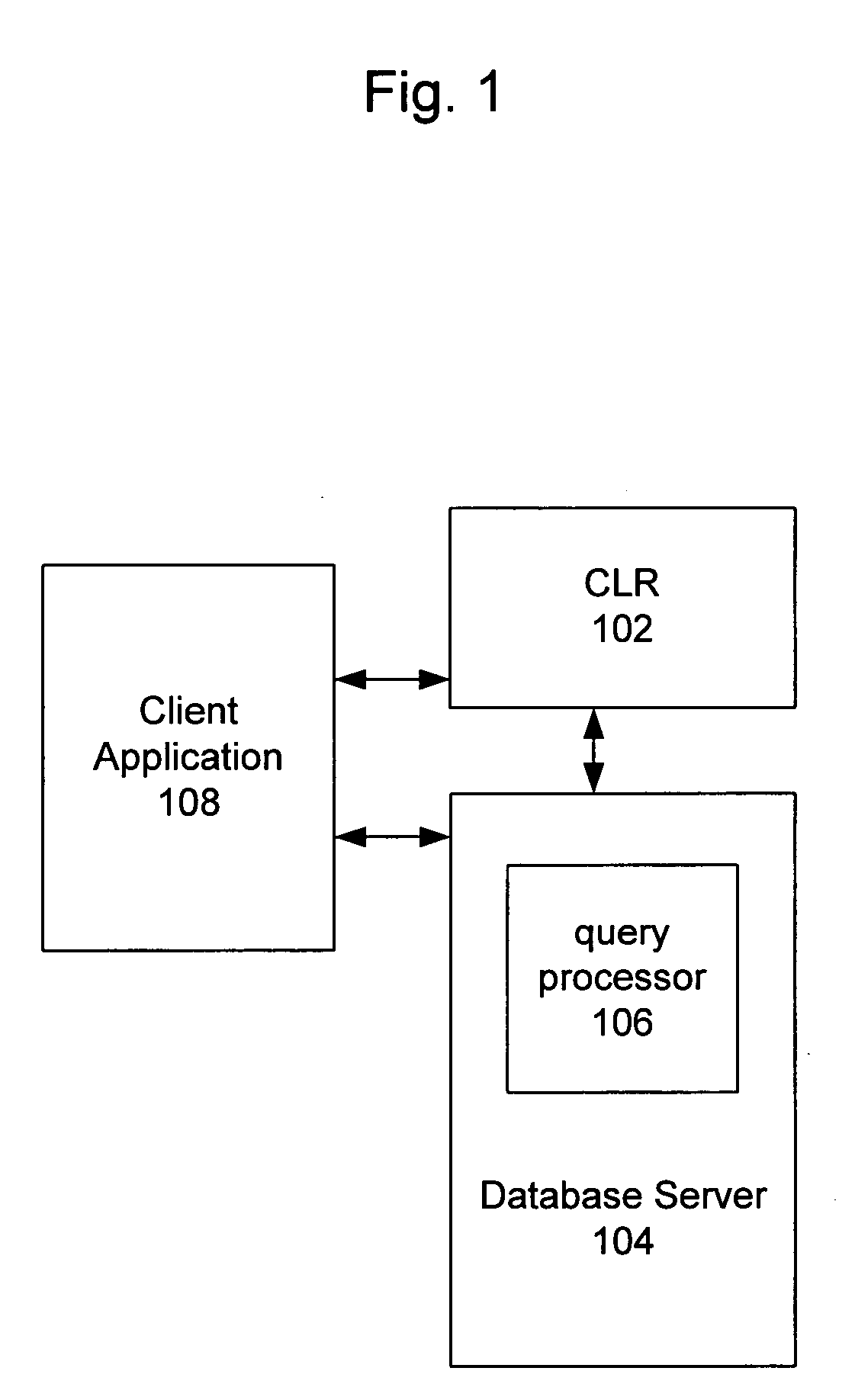
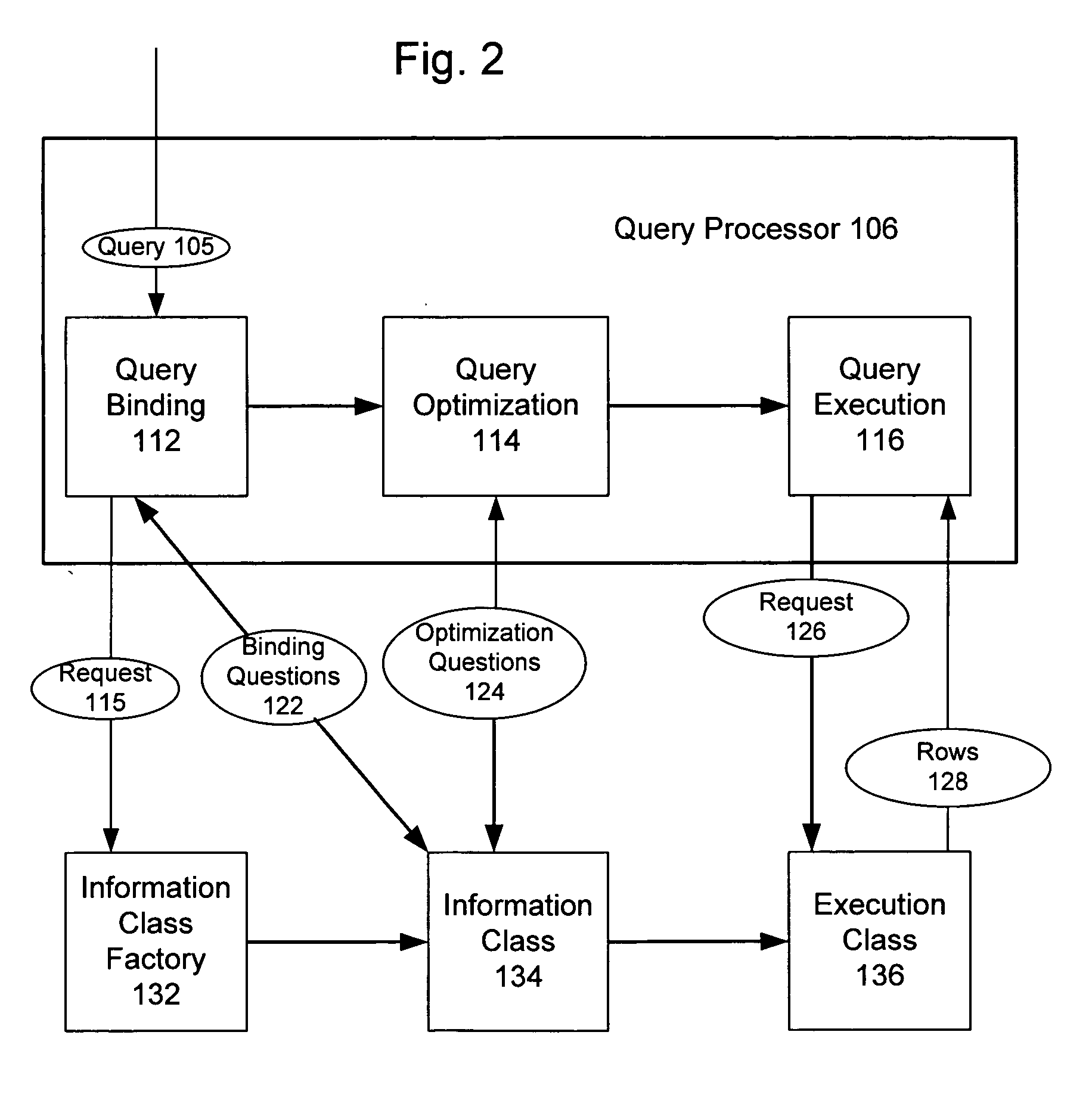
System and method for efficient evaluation of a query that invokes a table valued function
InactiveUS20050209988A1Performance degradation can be minimizedEfficiently and dynamically extendData processing applicationsDigital data information retrievalExtensibilityRelational database
The present invention describes an efficient and fast framework for implementing table-valued functions (TVF's) in a relational database server. The framework provides desirable extensibility properties and has the ability to minimize performance degradations by integrating tightly with the optimization infrastructure in a query processor. The present invention also enables a managed execution environment (MEE) such as the Common-Language-Runtime (CLR), to efficiently and dynamically extend the logic of the database engine with user-supplied code.
Owner:MICROSOFT TECH LICENSING LLC
System for Dynamically Balancing PCI-Express Bandwidth
ActiveUS20090094401A1Maximize useMinimize the possibilityEnergy efficient ICTTransmissionData ratePCI Express
In a dynamic mode, firmware sets a threshold of errors that may occur within a predetermined period of time. If the threshold is exceeded, the firmware queries the front-side bus performance counters to determine whether the front-side bus is operating at its maximum data rate. If the front-side bus is not running at the maximum data rate, then the firmware bumps the data rate settings for the endpoint that exceeds the threshold by one step. If the front-side bus is running at its maximum data rate, then the firmware queries all the endpoints to determine which endpoints are active. The firmware then determines whether there are any active endpoints that are lower priority than the complaining endpoint. The mechanism drops the lower priority endpoints by one step and raises the complaining endpoint by one step.
Owner:IBM CORP
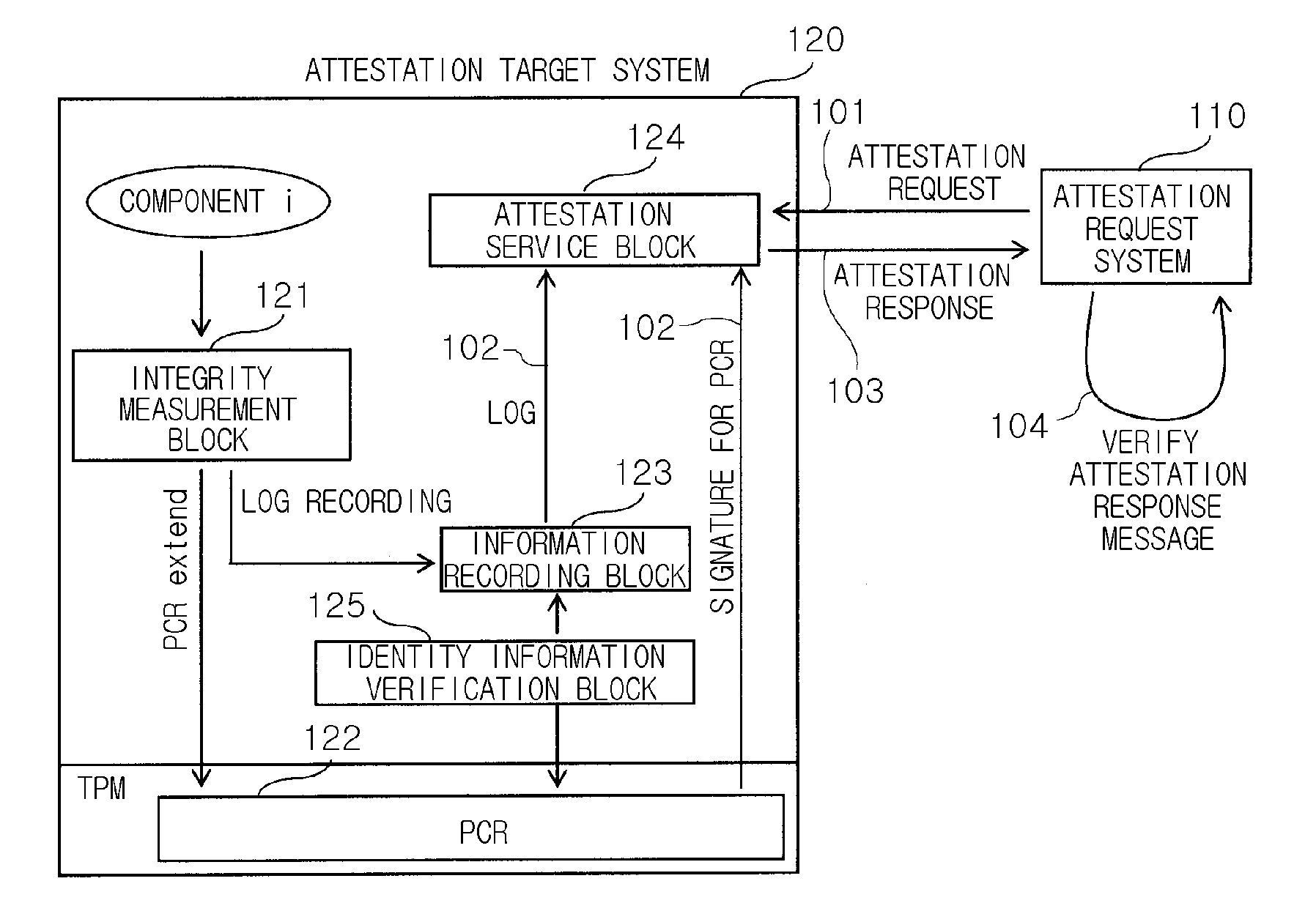
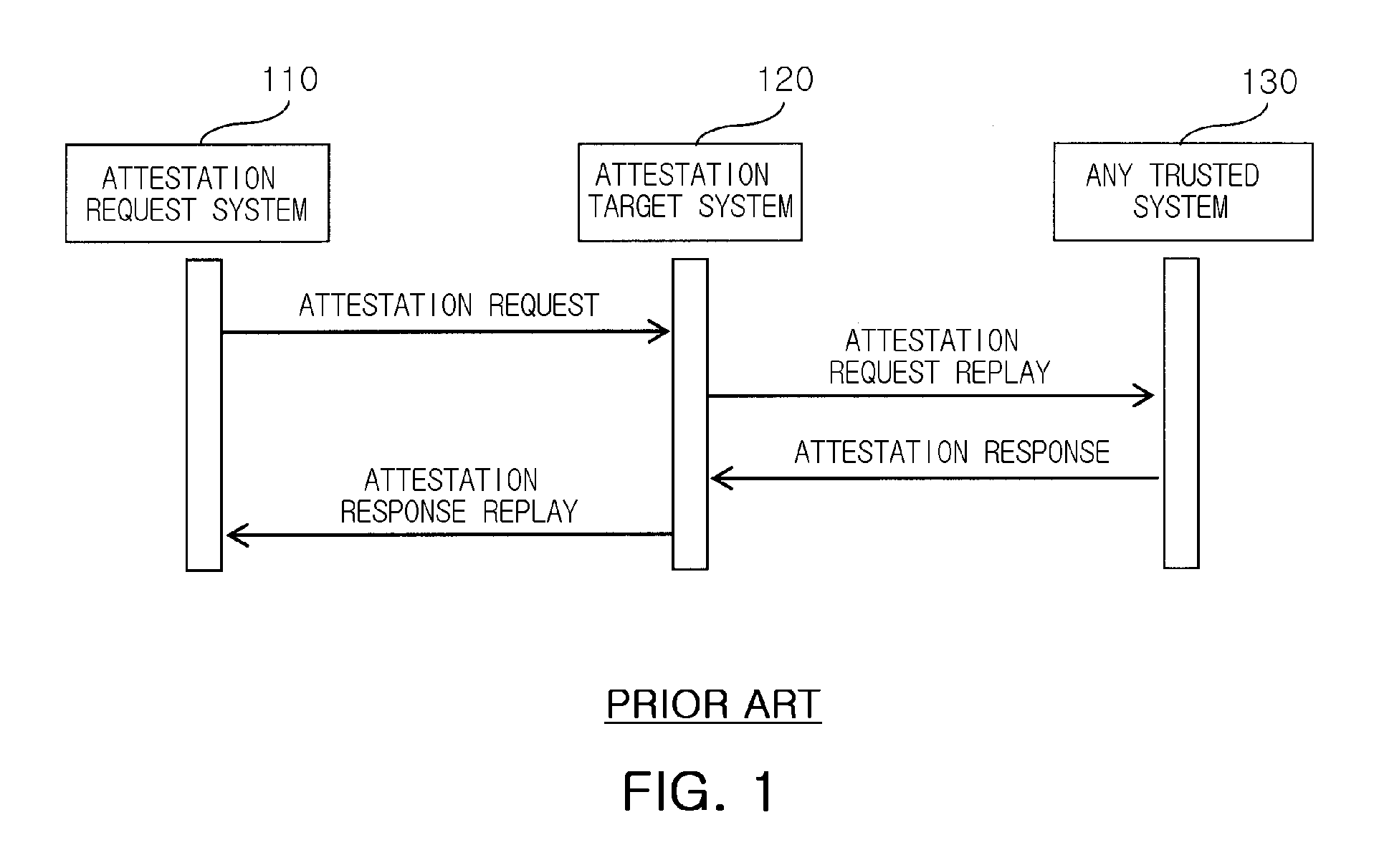
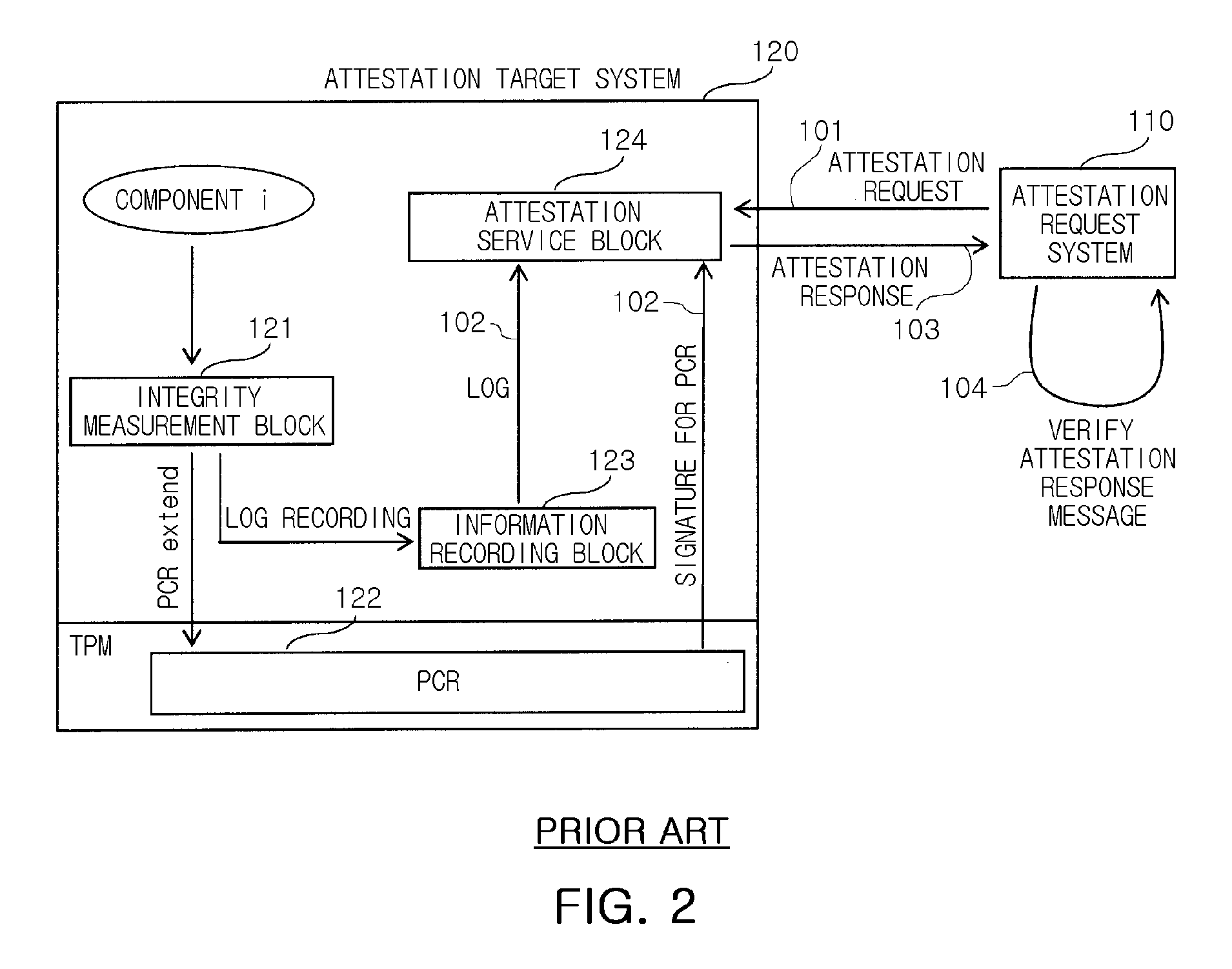
Method and attestation system for preventing attestation replay attack
InactiveUS20090013181A1Prevent attackPerformance of was minimizedUser identity/authority verificationDigital computer detailsComputer networkReplay attack
Provided are a method and an attestation system for preventing an attestation replay attack. The method for preventing an attestation replay attack in an attestation system including an attestation target system and an attestation request system, the method including: measuring associated components when an event that affects the integrity of the attestation target system occurs; perceiving own identity information and verifying the perceived identity information; extending the measured component and the identity information into a register and logging the measured component and the identity information; generating an attestation response message including values of the log and the register when an attestation request message is received from the attestation request system; and transmitting the generated attestation response message to the attestation request system. Therefore, the method and an attestation system may be useful to provide an additional simple mathematical operation in verifying an attestation message by preventing an attestation replay attack, and thus to minimize performance degradation in the attestation system, compared to the conventional attestation processing mechanisms.
Owner:ELECTRONICS & TELECOMM RES INST
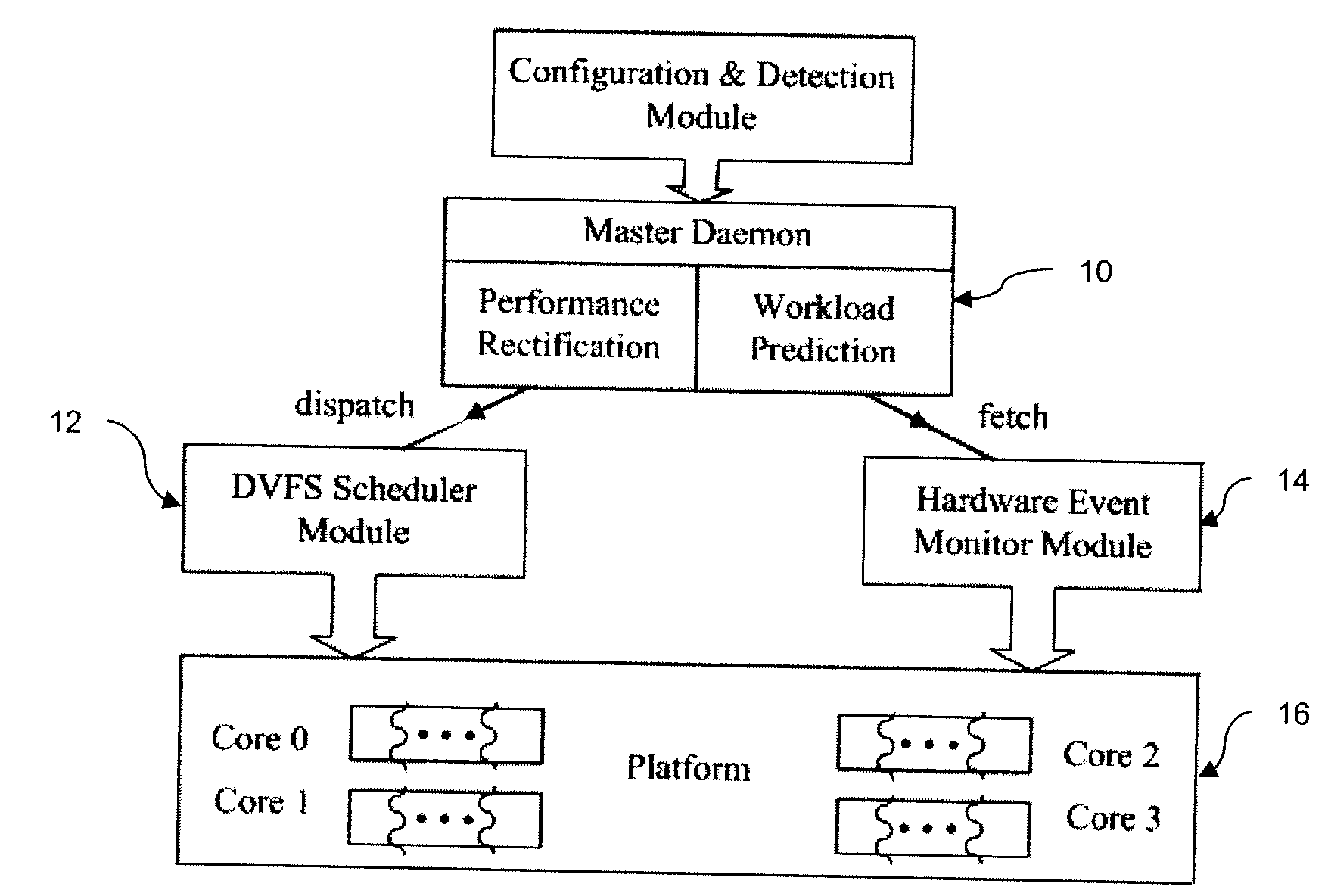
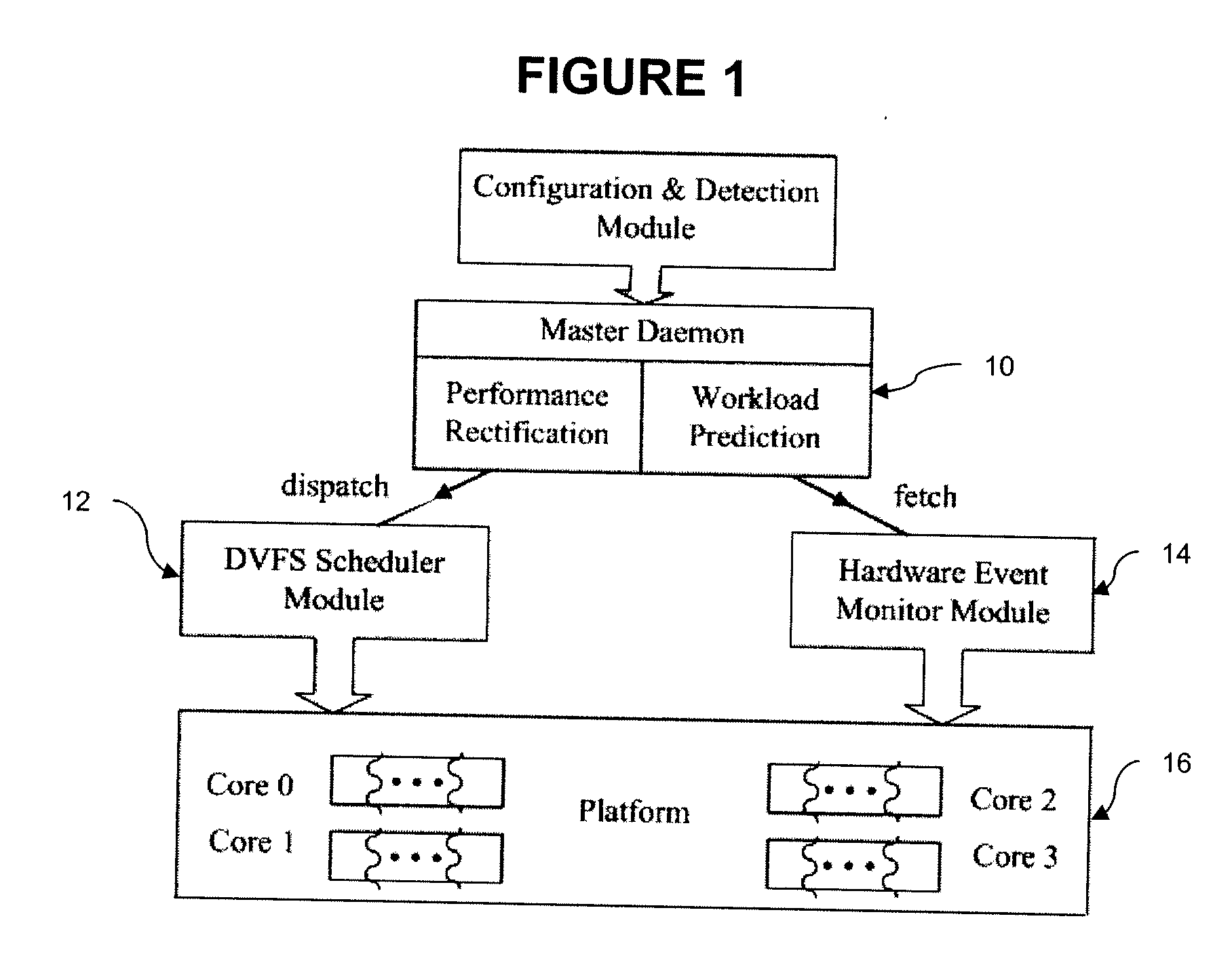
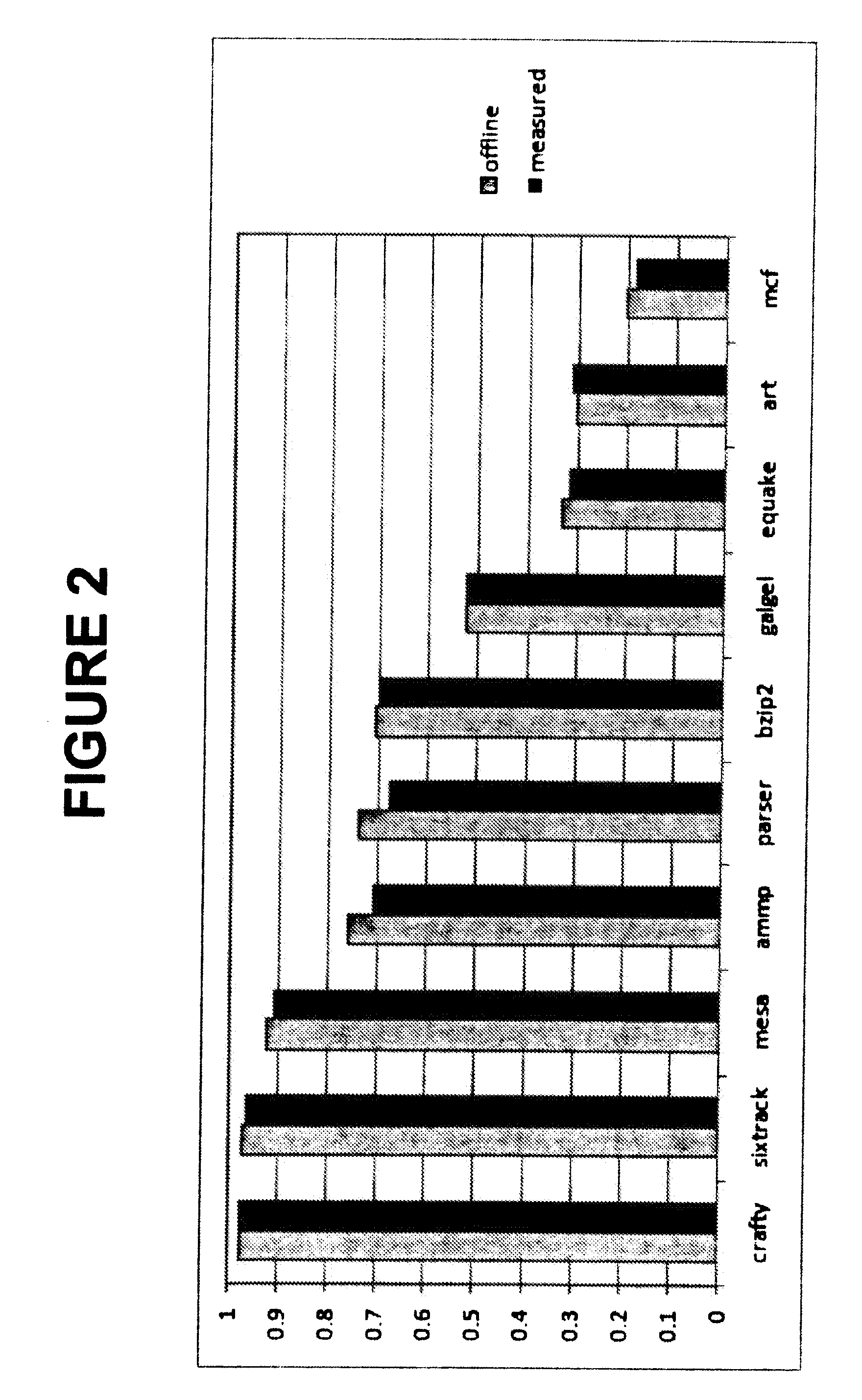
Off-chip access workload characterization methodology for optimizing computing efficiency
InactiveUS20090210740A1Reduce power consumptionMaintain performanceEnergy efficient ICTGenerating/distributing signalsEnergy expenditureWorkload
A system, apparatus, and method are provided which allows for reducing power consumption in dynamic voltage and frequency scaled processors while maintaining performance within specified limits. The method includes determining the off-chip stall cycle in a processor for a specified interval in order to characterize a frequency independent application workload in the processor. This current application workload is then used to predict the application workload in the next interval which is in turn used, in conjunction with a specified performance bound, to compute and schedule a desired frequency and voltage to minimize energy consumption within the performance bound. The apparatus combines the aforementioned method within a larger-scale context that reduces the energy consumption of any given computing system that exports a dynamic voltage and frequency scaling interface. The combination of the apparatus and method form the overall system.
Owner:VIRGINIA TECH INTPROP INC
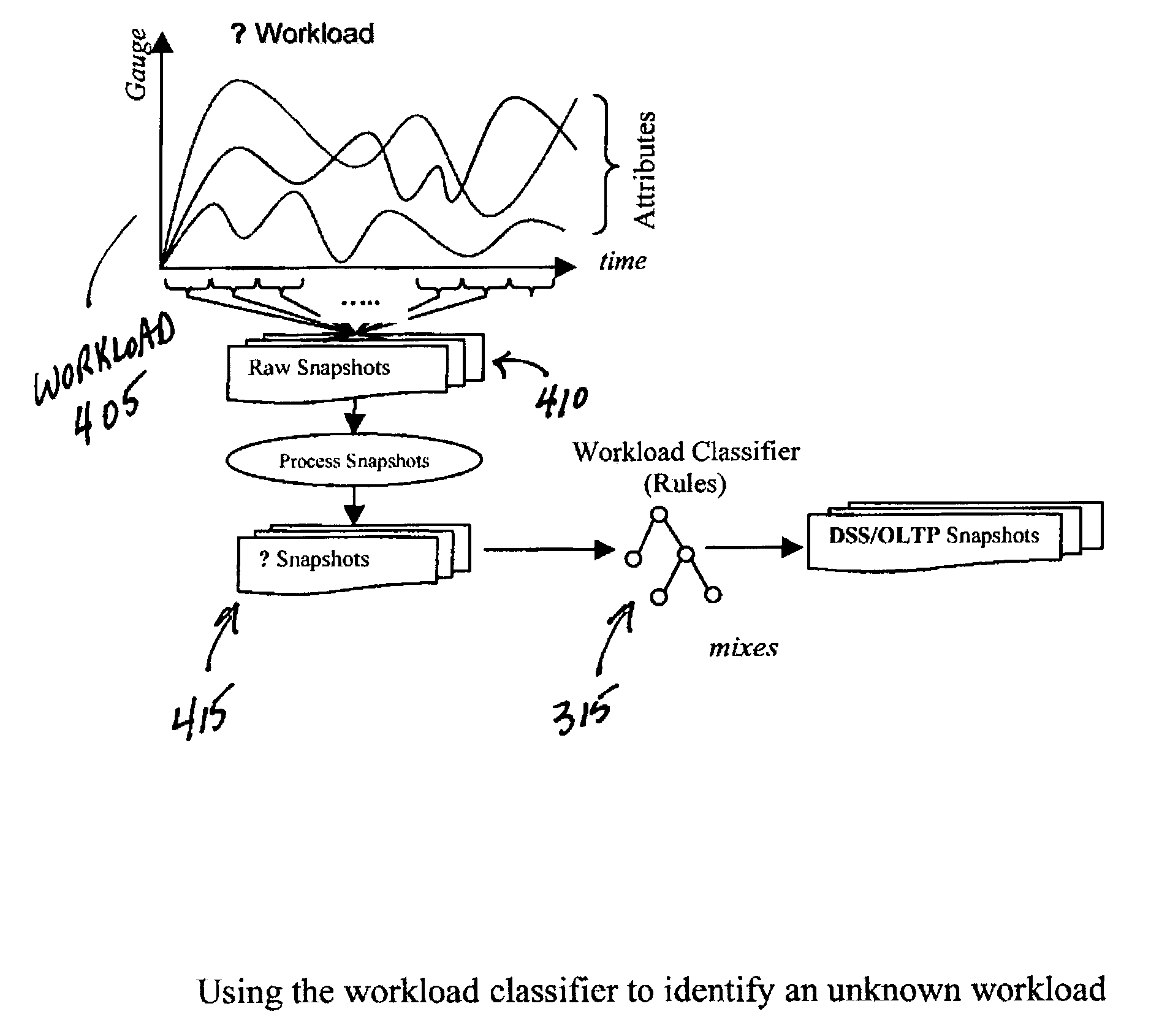
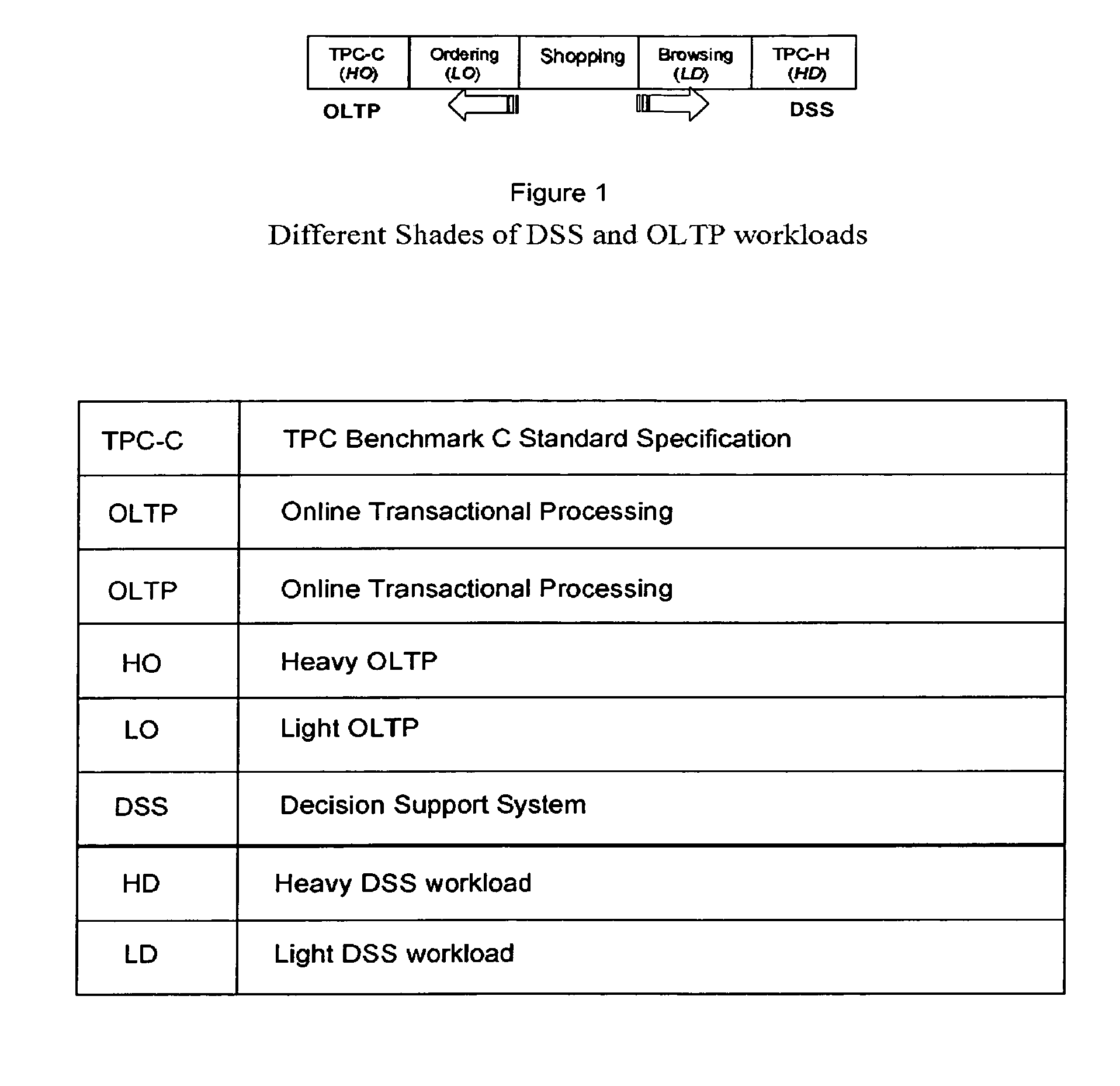
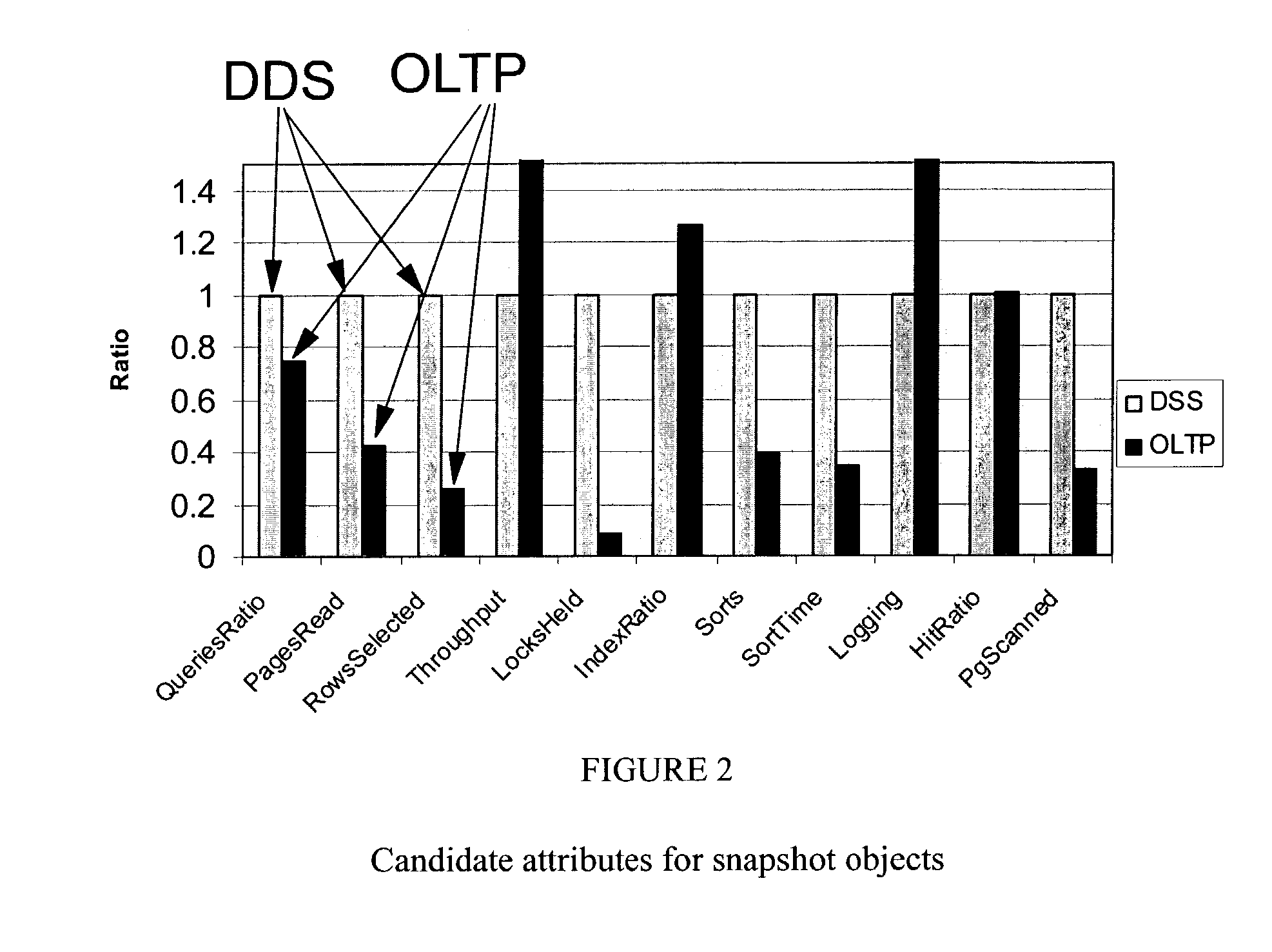
Method for identifying a workload type for a given workload of database requests
InactiveUS7499908B2Easy to operateEfficiently process workloadData processing applicationsResource allocationDecision takingWorkload
Workload type to be managed by a database management system (DBMS) is a key consideration in tuning the DBMS. Allocations for resources, such as main memory, can be very different depending on whether the workload type is Online Transaction Processing (OLTP) or Decision Support System (DSS). The DBMS also experiences changes in workload type during the normal processing cycle of the DBMS. It would be preferable for the database administrators to recognize the significant shifts of workload type that demand reconfiguring the DBMS to maintain acceptable levels of performance. Disclosed is a workload type classifier module, used by a DBMS, for recognizing workload types so that the DBMS may then manage or adjust its performance and reconfigure its resources accordingly. The classifier may be constructed based on the most significant workload characteristics that differentiate OLTP from DSS. The classifier is then used for identifying changes in workload types contained in a workload.
Owner:IBM CORP
Integrated circuit chip with improved array stability
InactiveUS20050063232A1Improve static random access memory (SRAM) cell stabilityReduce SRAM cell leakageDigital storageCMOSStatic random-access memory
A multi-threshold integrated circuit (IC) that may be supplied by multiple supplies, with an array of latches such as an array static random access memory (SRAM) cells and a CMOS SRAM with improved stability and reduced subthreshold leakage. Selected devices (NFETs and / or PFETs) in array cells and support logic, e.g., in the data path and in non-critical logic, are tailored for lower gate and subthreshold leakage. Normal base FETs have a base threshold and tailored FETs have a threshold above. In a multi-supply chip, circuits with tailored FETs are powered by an increased supply voltage.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for in situ depositon and regeneration of high efficiency target materials for long life nuclear reaction devices
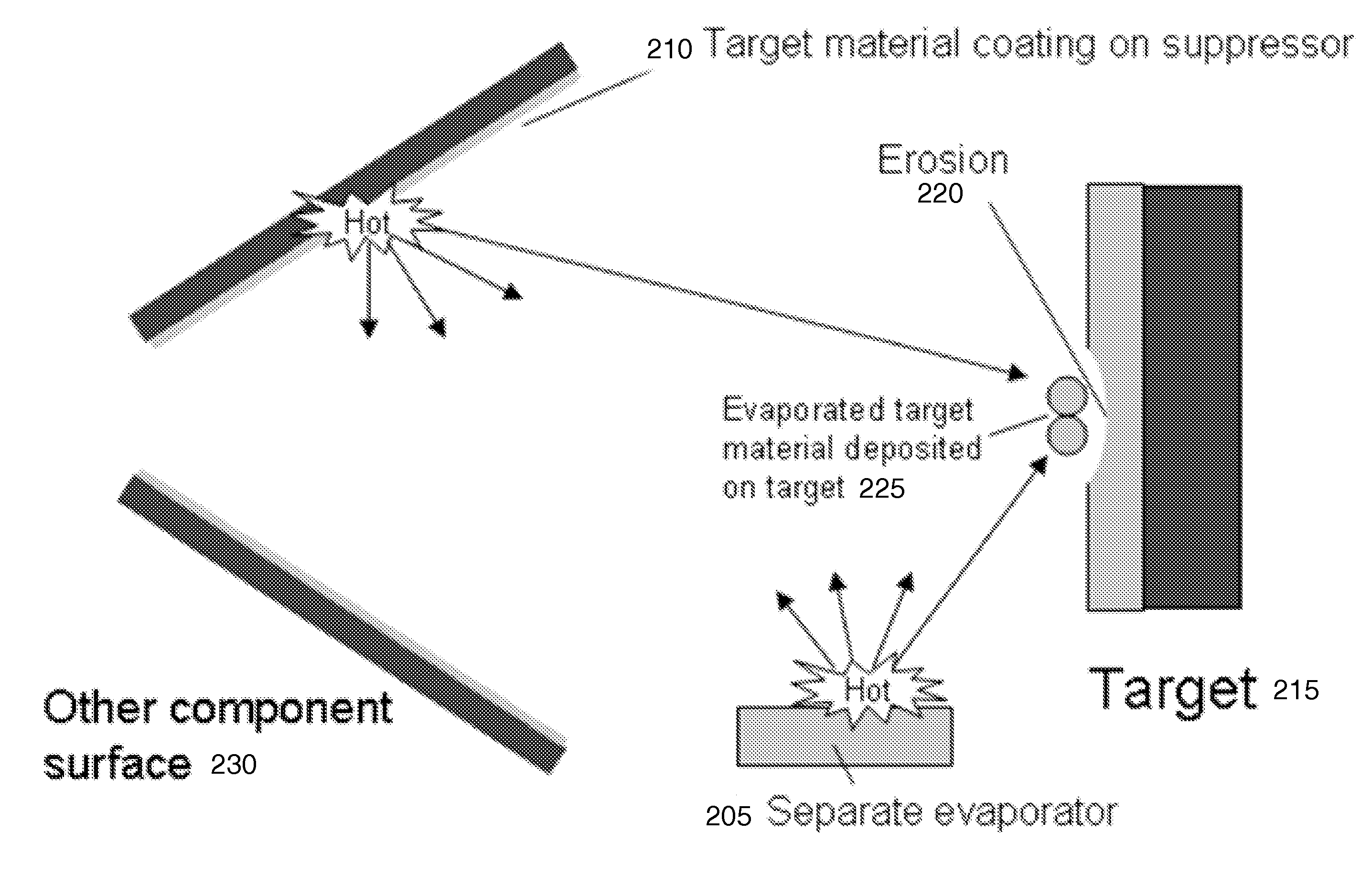
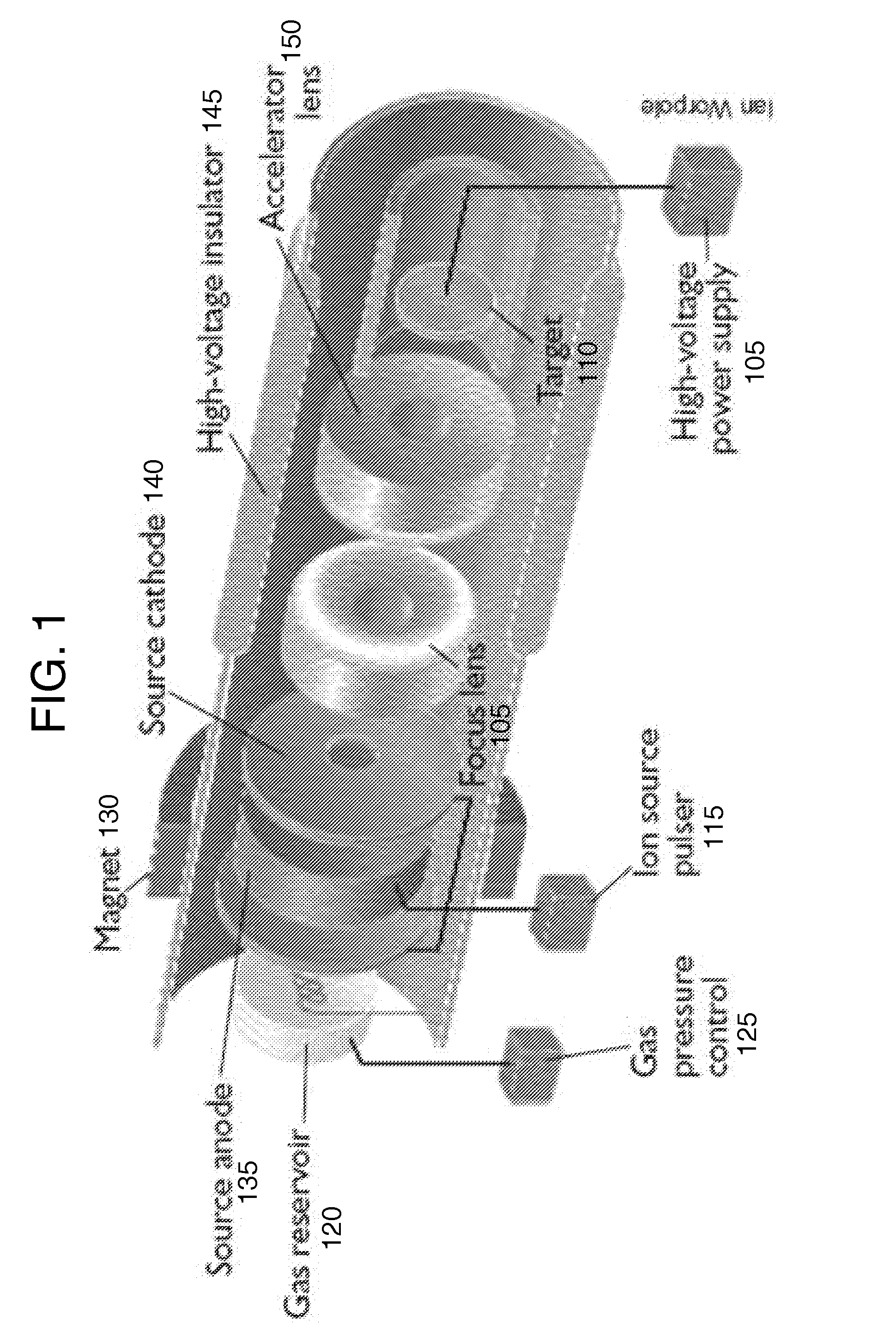
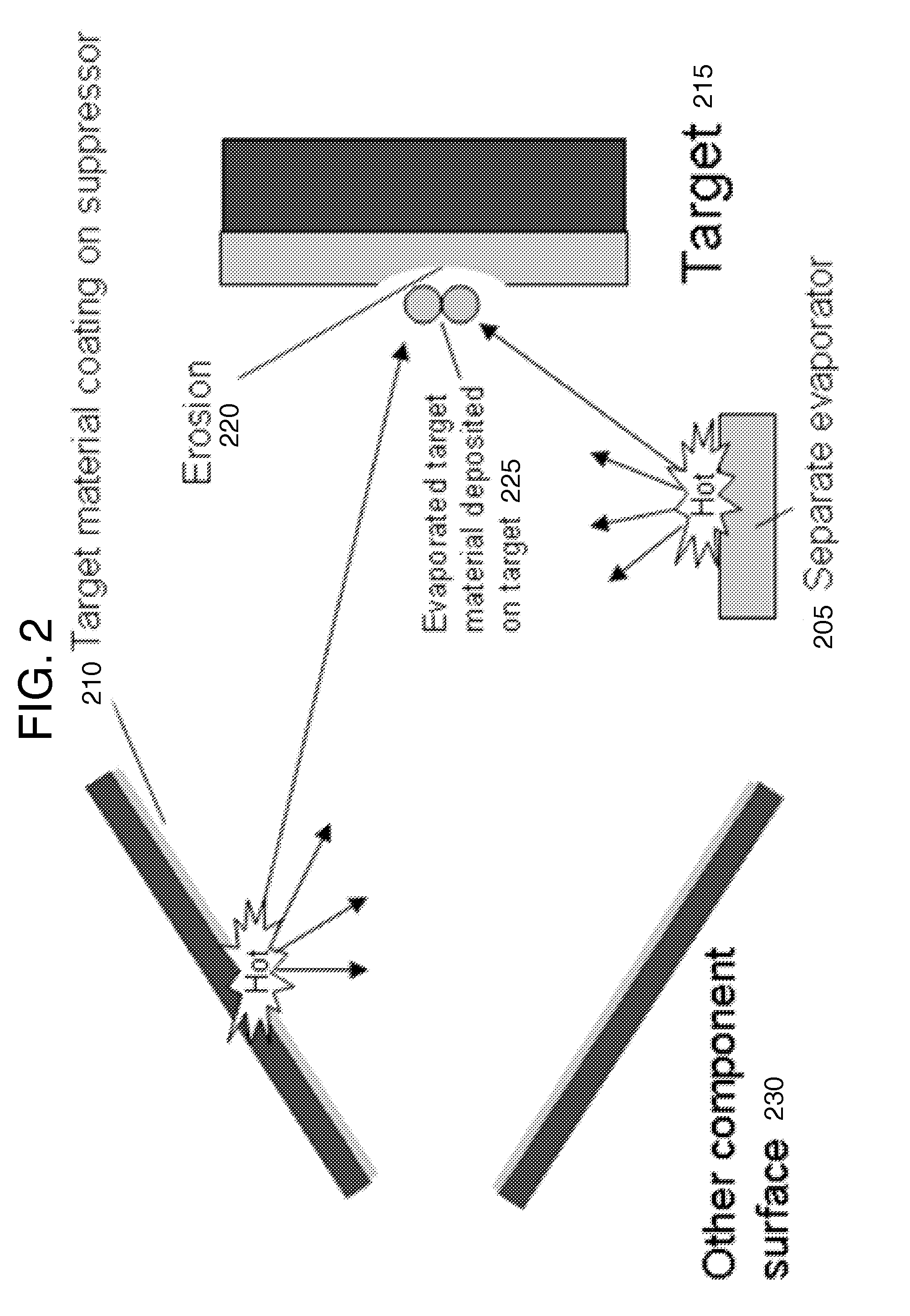
ActiveUS20110091000A1Maintain purityMinimize the numberNuclear energy generationDirect voltage acceleratorsNeutron energy spectrumNuclear reaction
Aspects of the invention relate to several methods to deposit and regenerate target materials in neutron generators and similar nuclear reaction devices. In situ deposition and regeneration of a target material reduces tube degradation of the nuclear reaction device and covers impurities on the surface of the target material at the target location. Further aspects of the invention include a method of designing a target to generate neutrons at a high efficiency rate and at a selected neutron energy from a neutron energy spectrum.
Owner:STARFIRE IND LLC
Highly-available application operation method and system, and method and system of changing application version on line
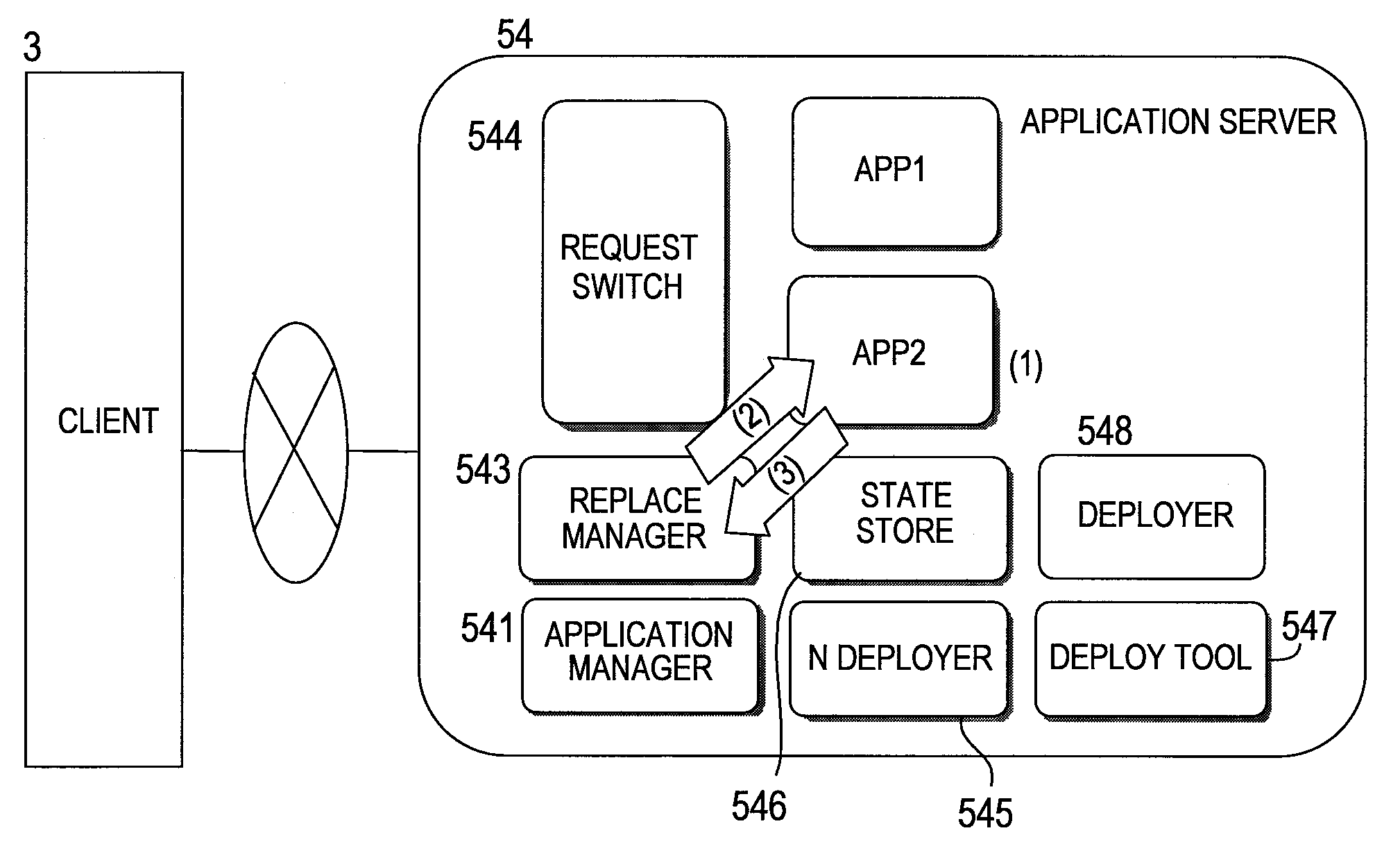
InactiveUS20080282255A1Minimizes lowering of cache hit ratePerformance degradation can be preventedError detection/correctionApplication softwareOperating system
By releasing a part of execution environment that contains a leaked resource, a failure is avoided while the remaining part of execution environment in a memory and the like prevents performance degradation that results from a cold cache. This invention provides a highly available application operation method for replacing a first application (App1) which receives a processing request with a second application (App2). The method includes the steps of: invoking the first application (App1) and forwarding the processing request to the first application (App1); when a given condition is met, invoking the second application (App2) and forwarding a new processing request to the second application (App2); and, when the first application (App1) completes the processing request after the second application (App2) is invoked, stopping the first application (App1).
Owner:HITACHI LTD
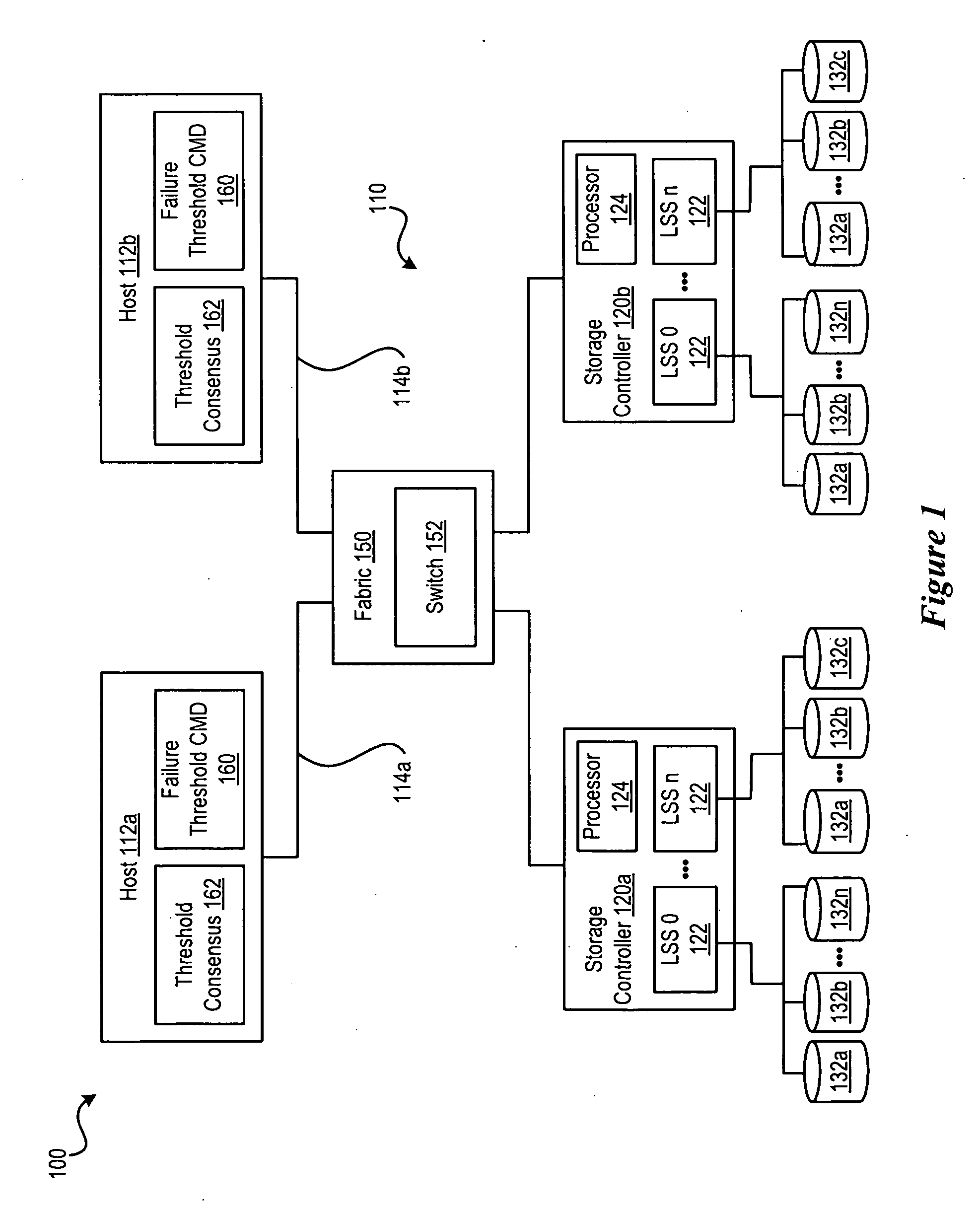
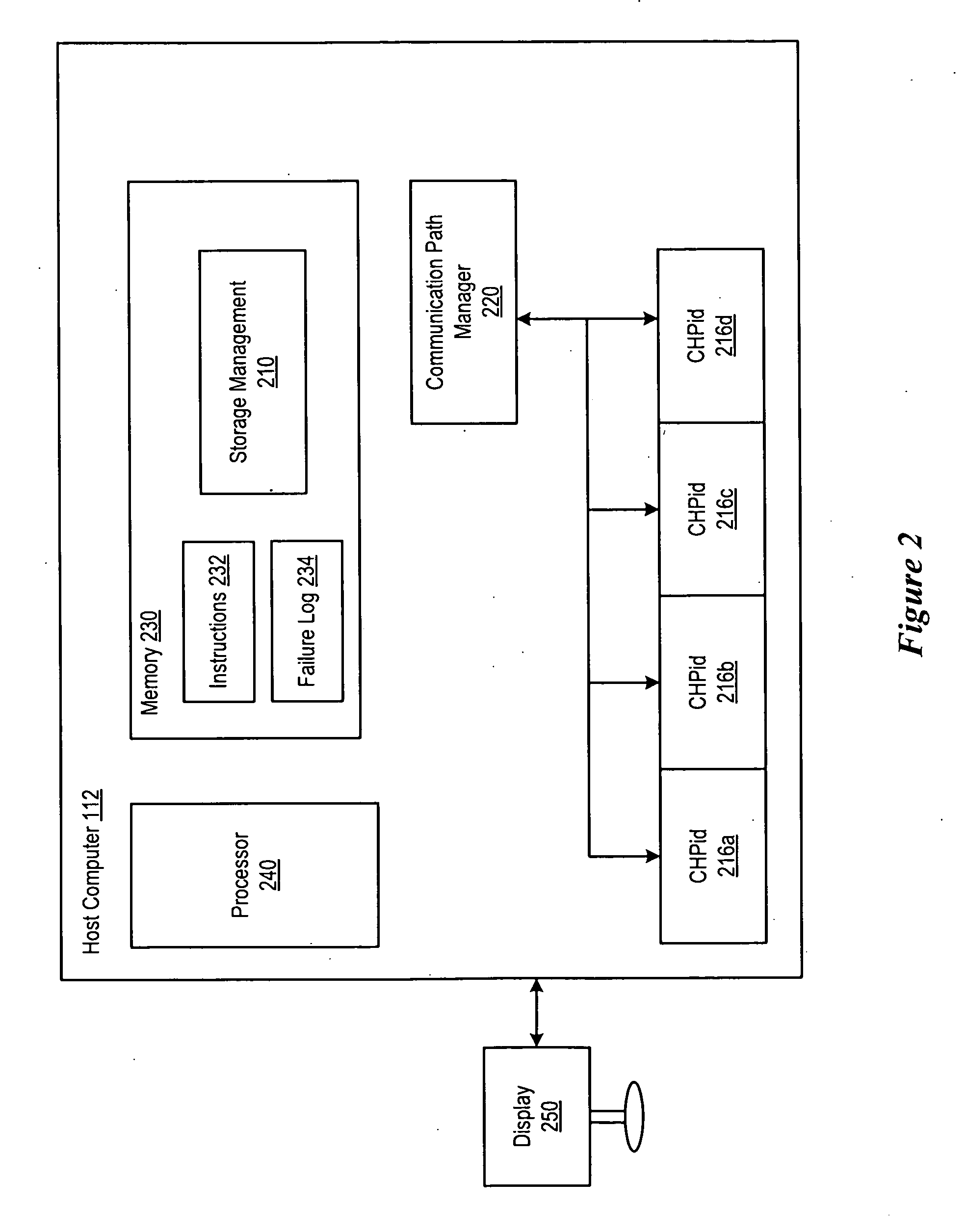
Method to Manage Path Failure Threshold Consensus
InactiveUS20100080117A1Performance degradation can be preventedPerformance degradation can be minimizedError preventionTransmission systemsControl storeDistributed computing
A system for providing hosts with a capability to determine which threshold rule of a plurality of threshold rules to use based upon threshold consensus. For example, the system would address a configuration case of several hosts sharing an output port of a fabric via zoning and that port being connected to a single port of a storage controller. If one host is executing lower priority jobs and its threshold is much higher than another host with higher priority jobs and a lower threshold, and the storage controller recognizes that several hosts are sharing the same storage controller port, the consensus will be to ignore the threshold of the first host and to use the threshold of the second host to prevent performance degradation in the system.
Owner:IBM CORP
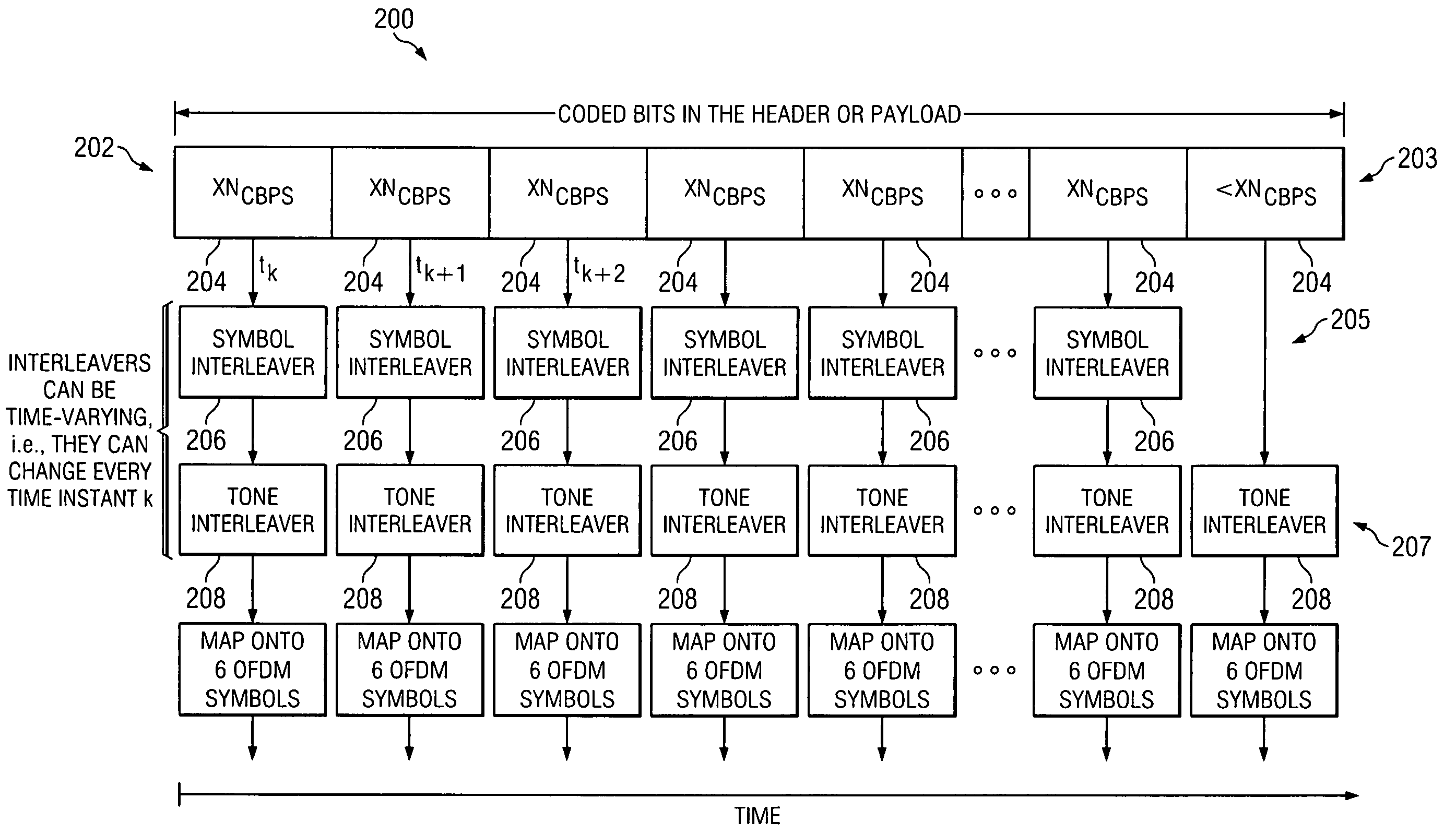
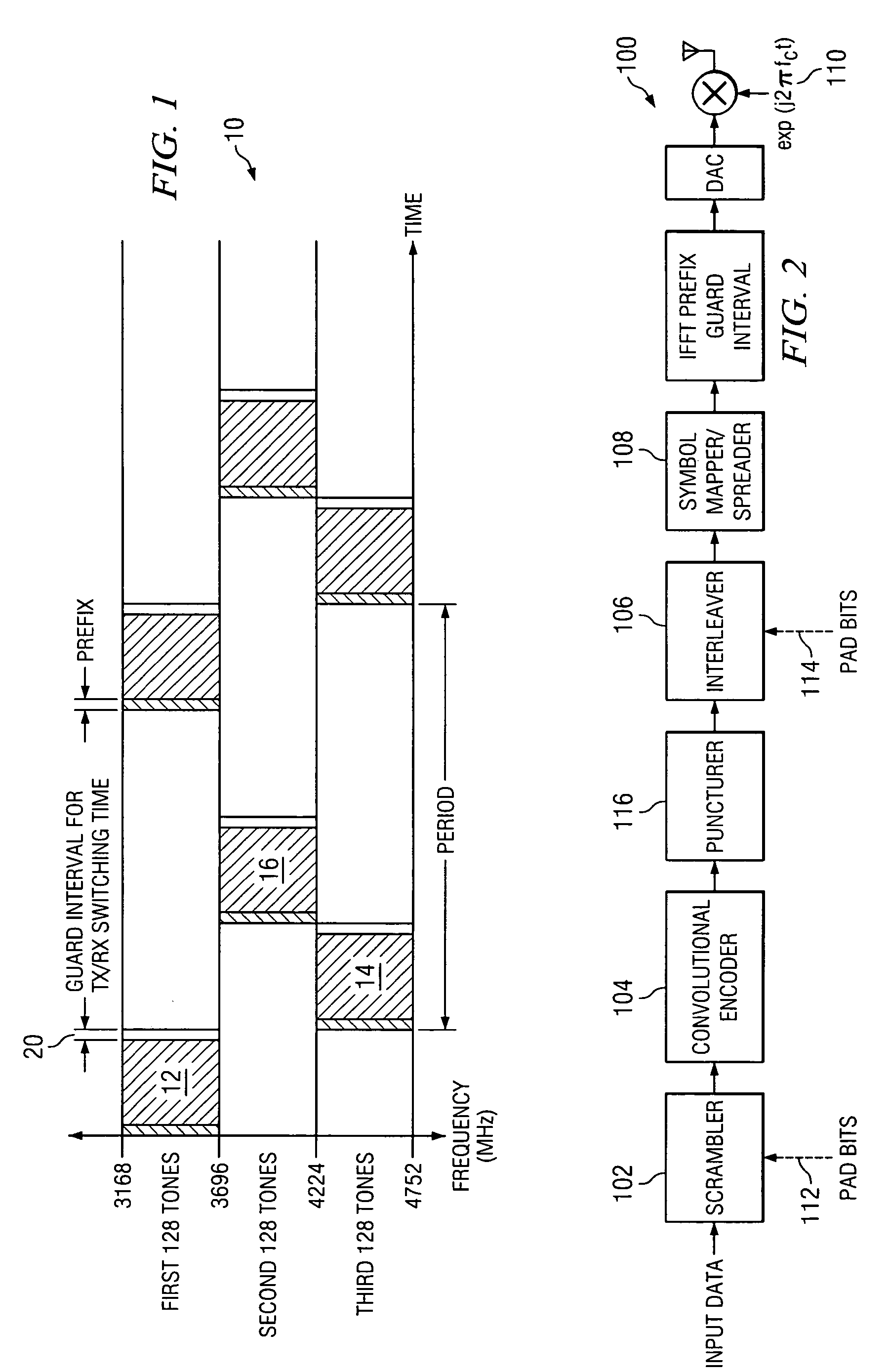
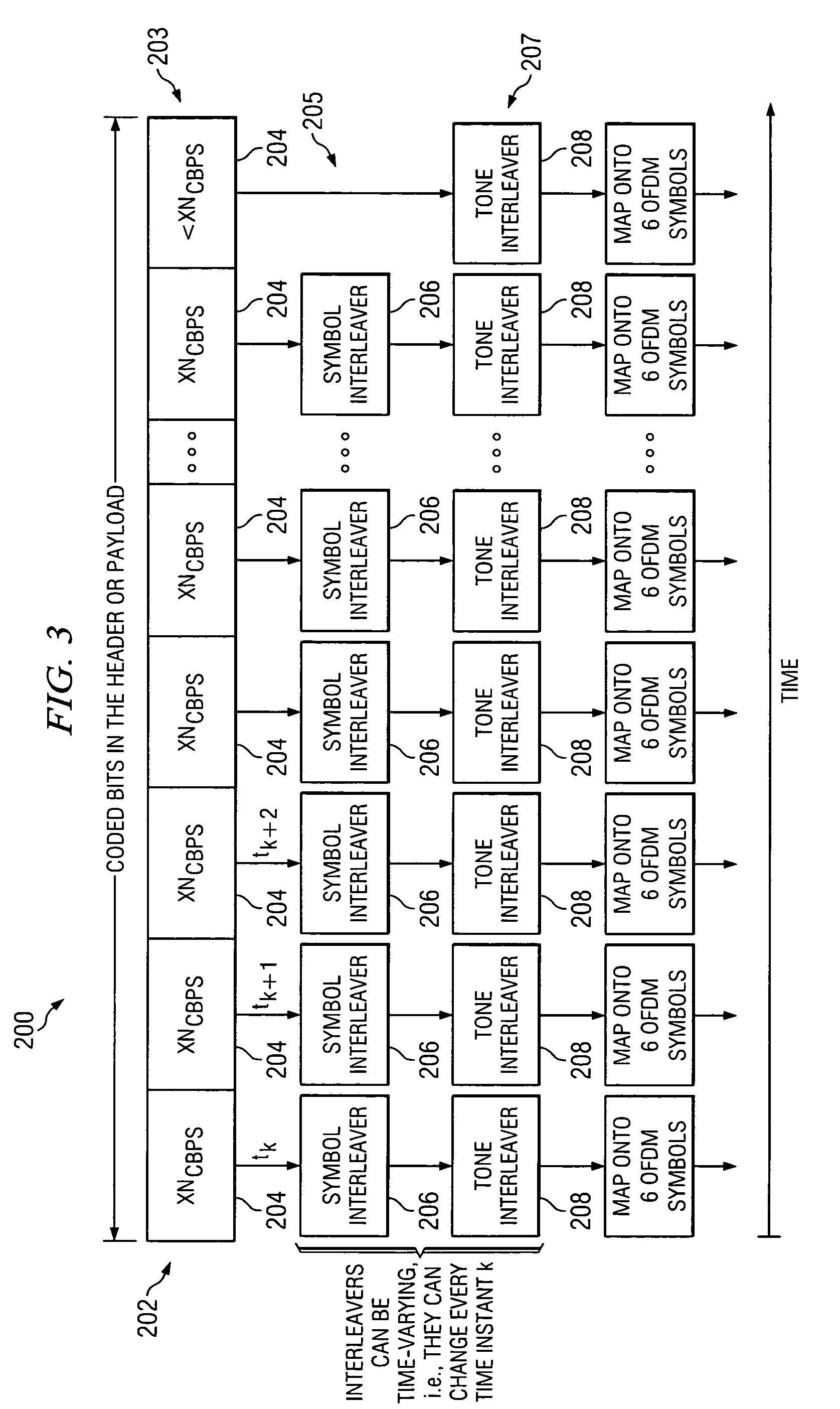
Efficient bit interleaver for a multi-band OFDM ultra-wideband system
ActiveUS7313190B2Performance degradation can be minimizedPerformance of was minimizedData representation error detection/correctionTransmission path divisionMulti bandUltra-wideband
An efficient bit interleaving scheme for a multi-band OFDM ultra-wideband (UWB) system. The encoded bits of the multi-band OFDM system are interleaved within each OFDM symbol and across OFDM symbols. The bit interleaving scheme minimizes performance degradation due to groups of contiguous OFDM tones experiencing a poor SNR caused by the frequency selective channel, exploits the frequency diversity across sub-bands, randomizes the effect of co-channel interference from simultaneously operating un-coordinated piconets, and randomizes the impact of generic narrow-band interferers present within the UWB spectrum.
Owner:TEXAS INSTR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com