Patents
Literature
1377 results about "Data retention" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data retention defines the policies of persistent data and records management for meeting legal and business data archival requirements; although sometimes interchangeable, not to be confused with the Data Protection Act 1998.
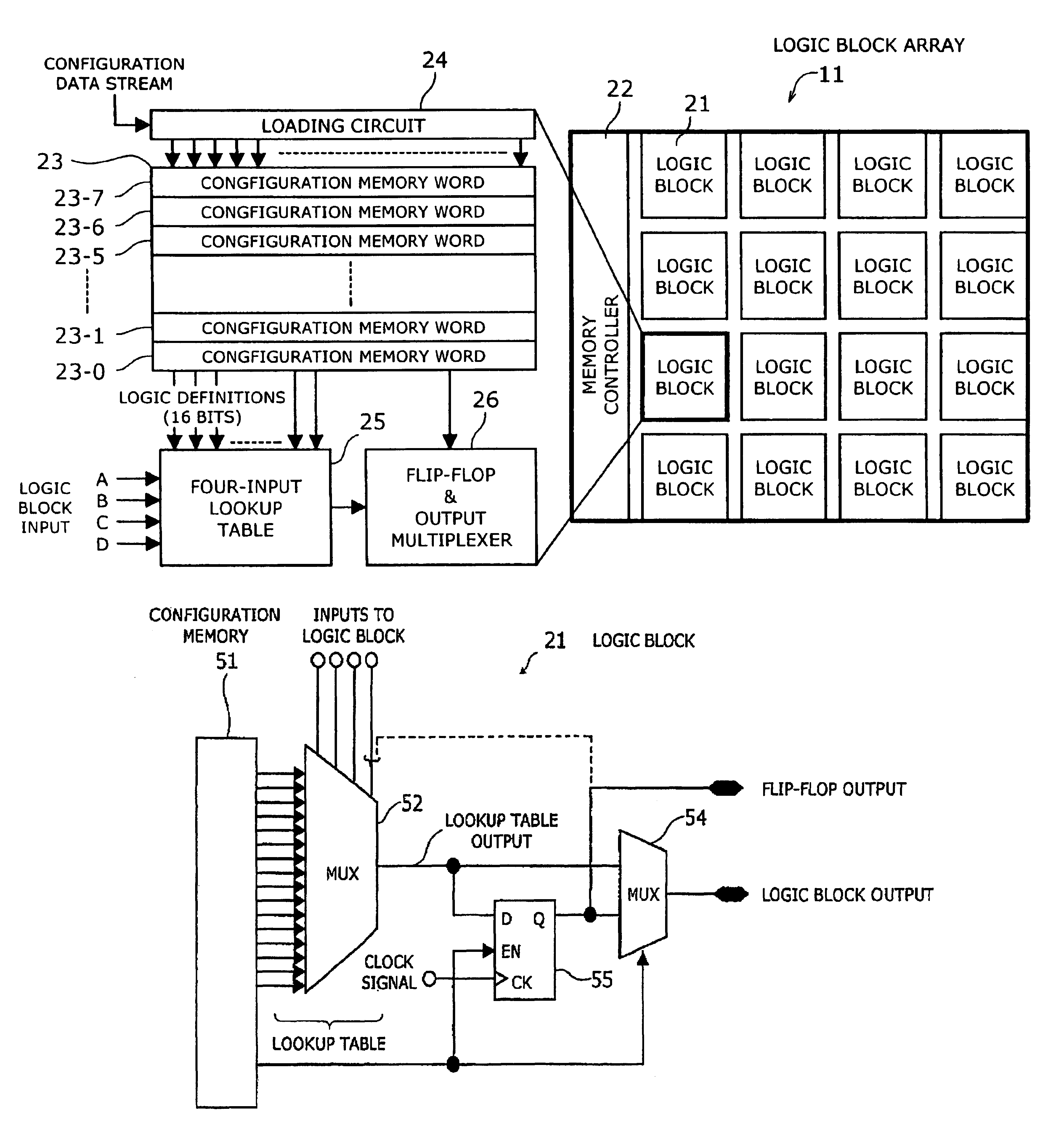
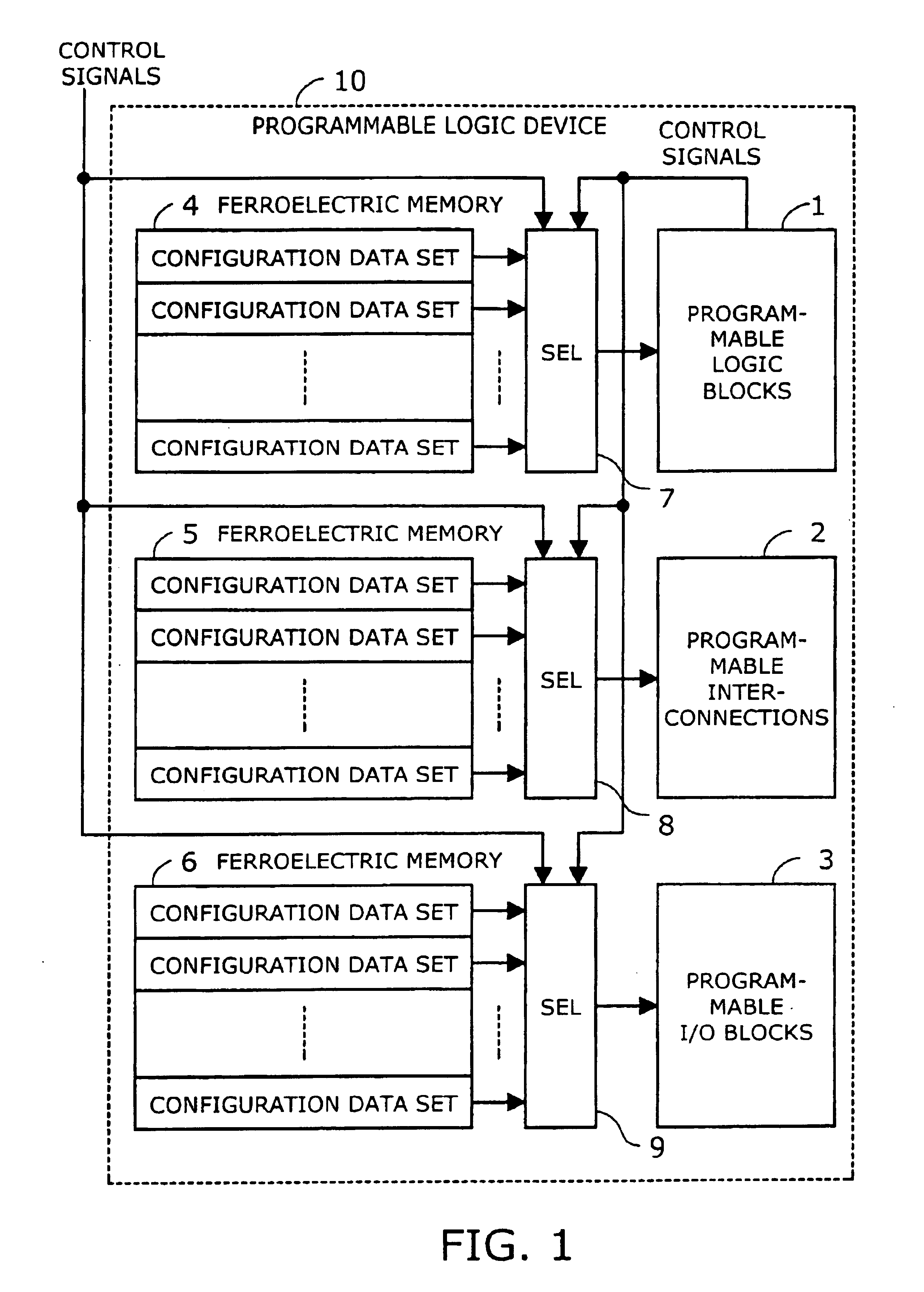
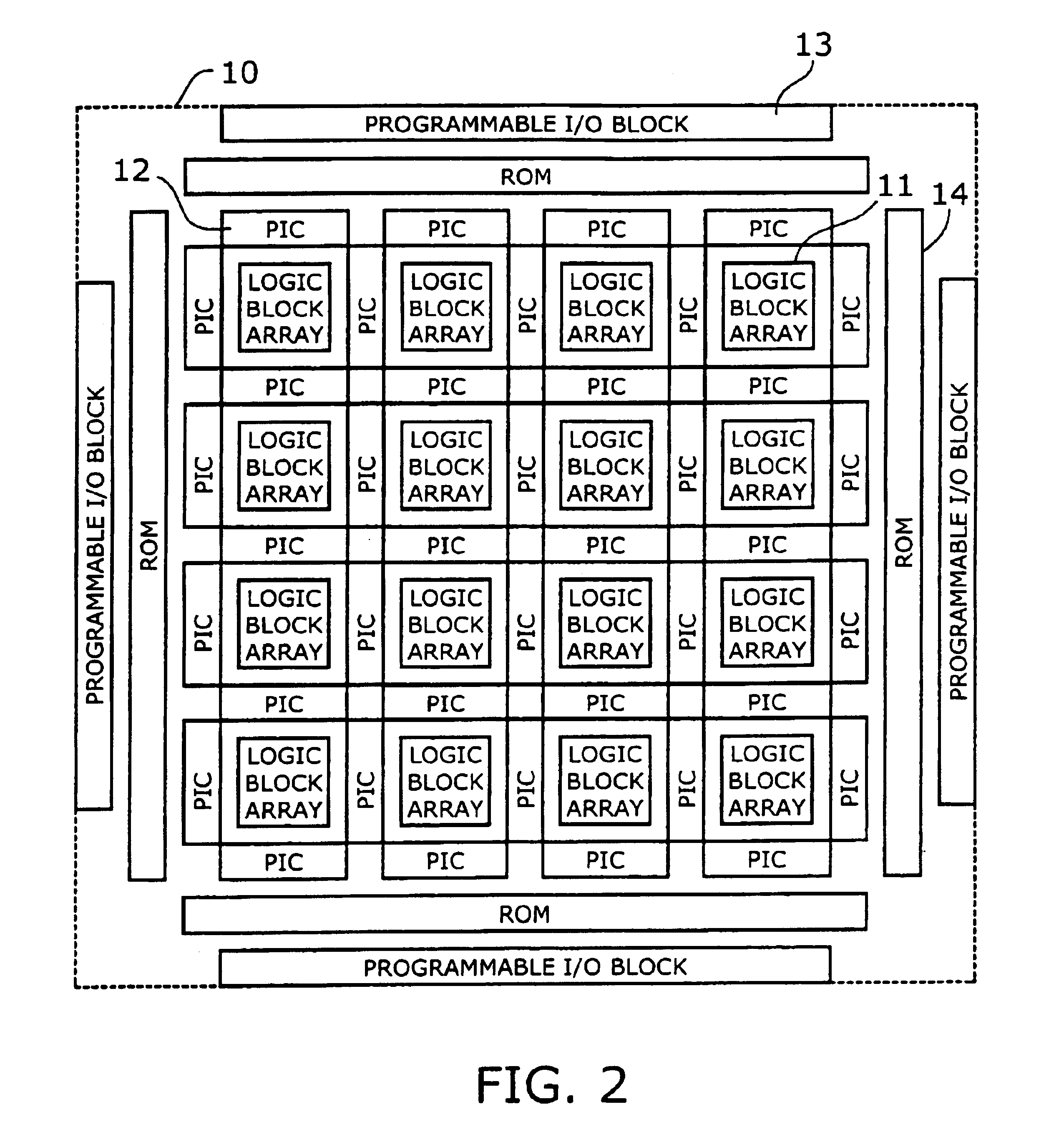
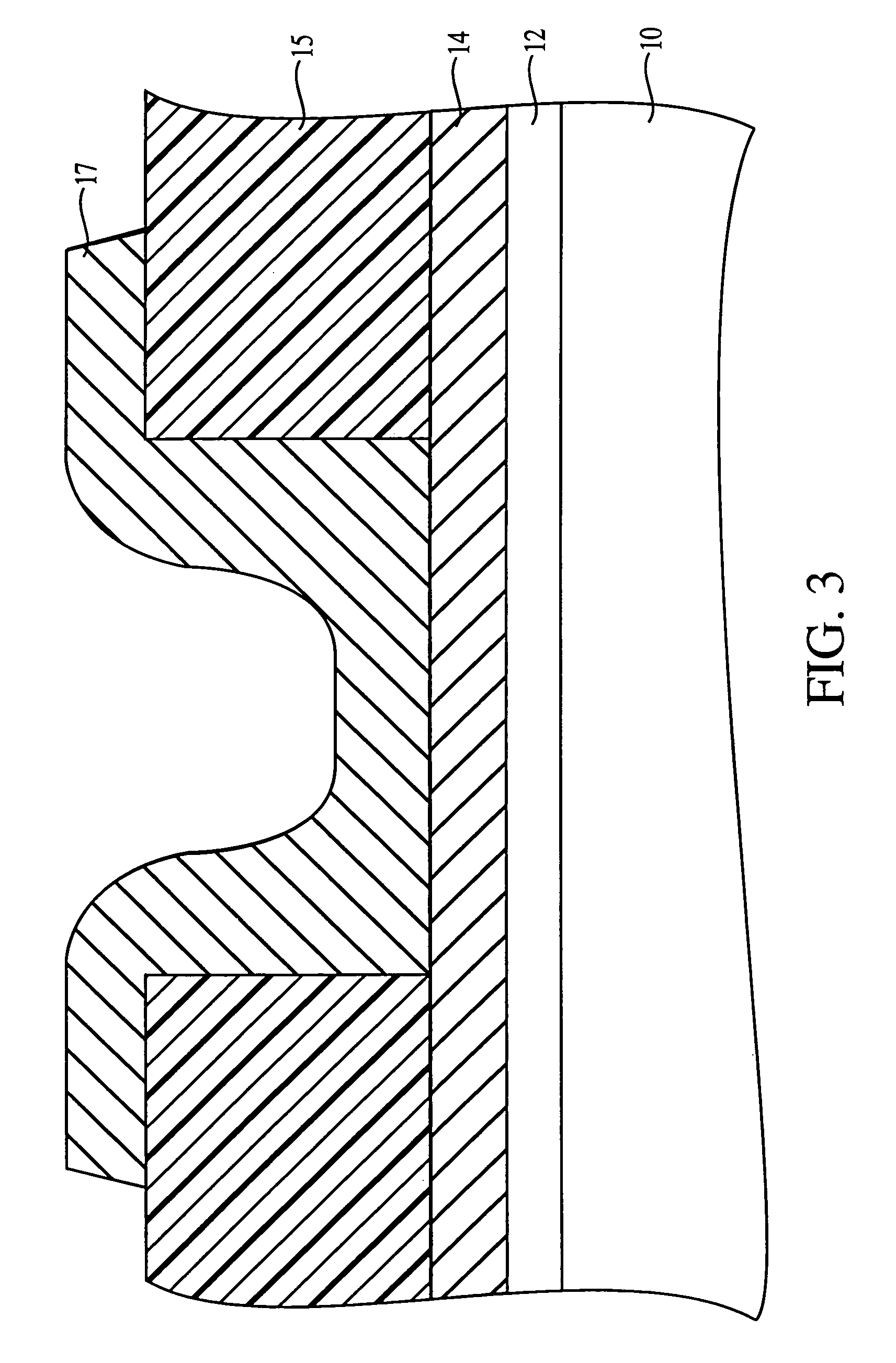
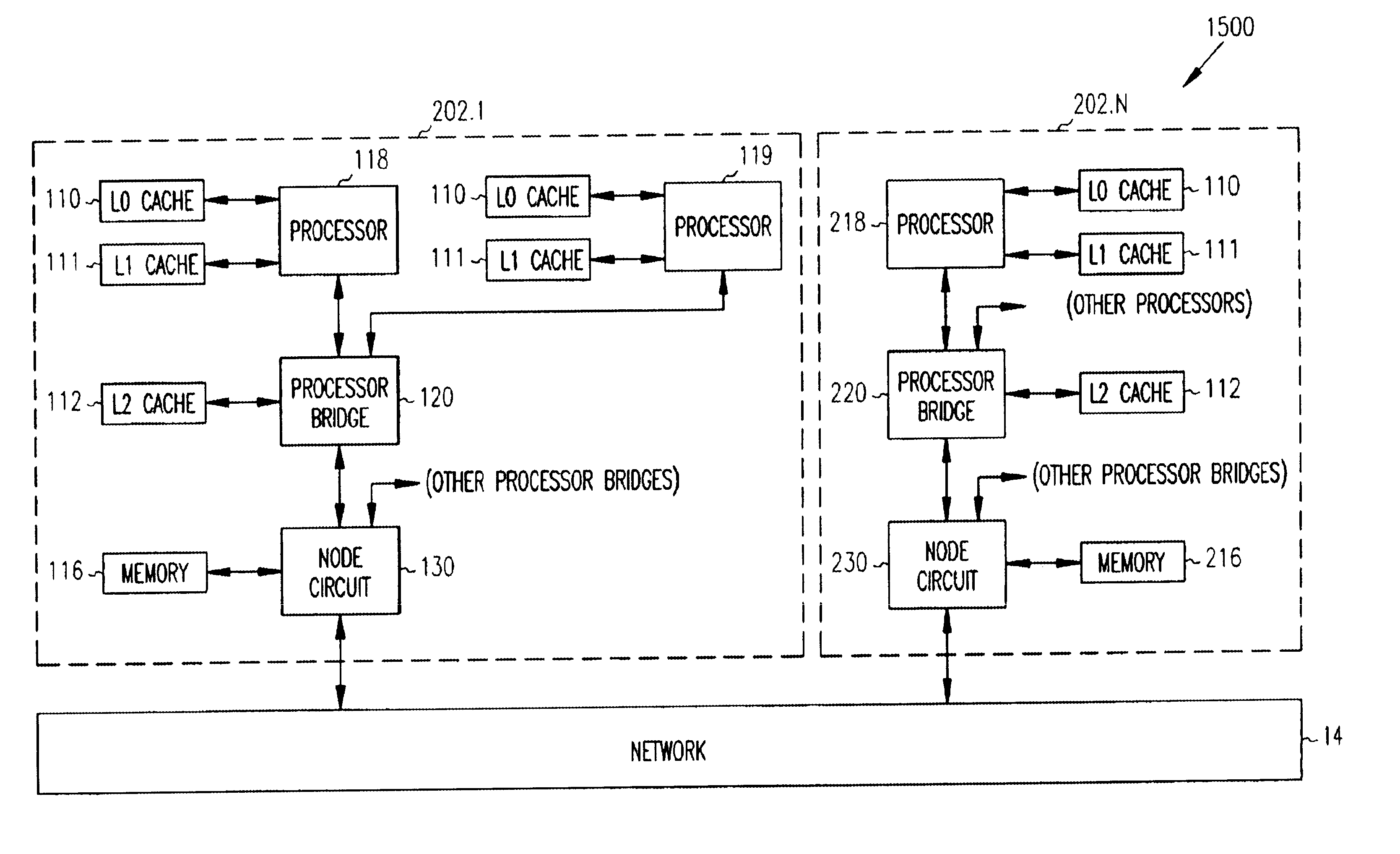
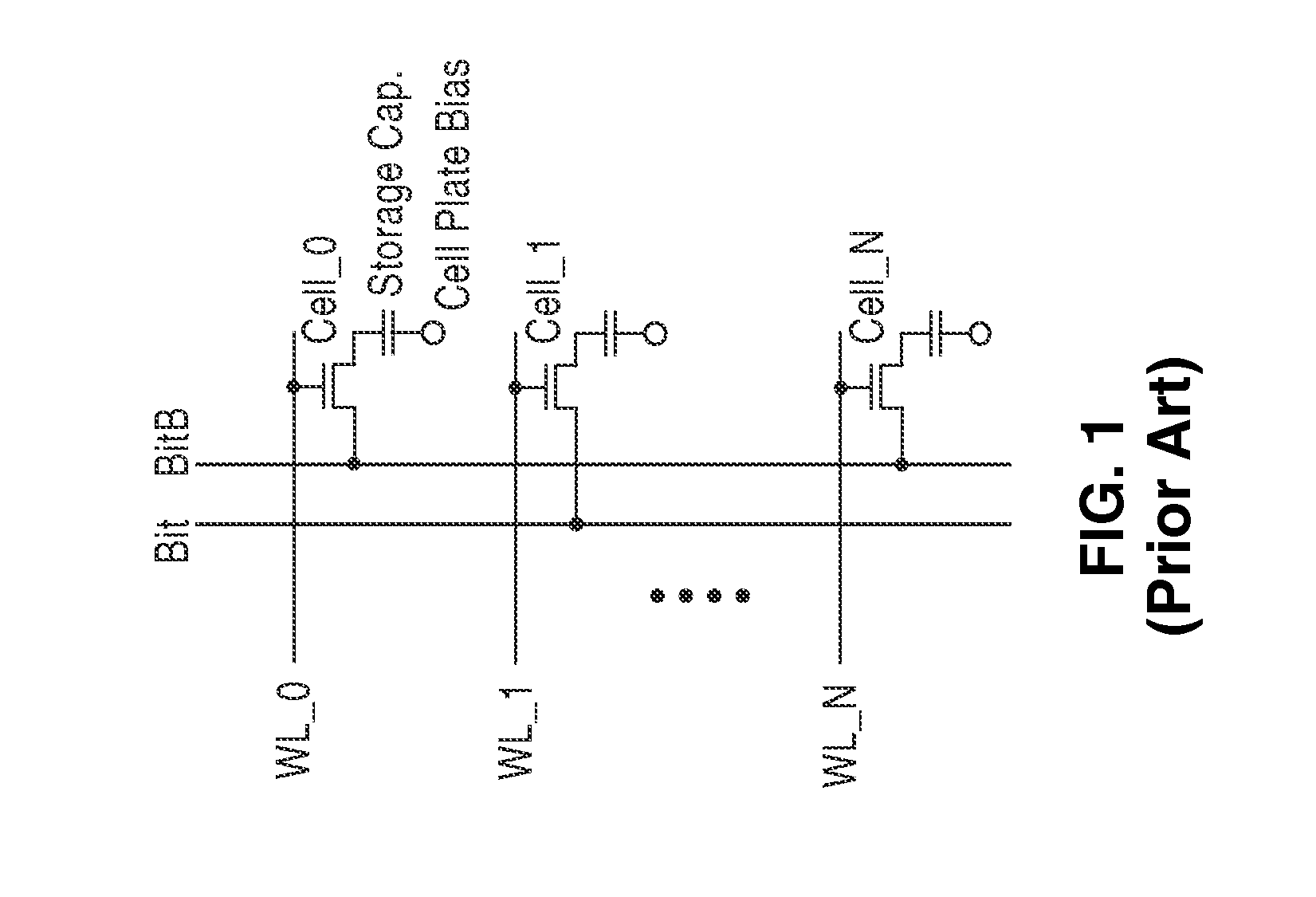
Programmable logic device with ferroelectric configuration memories
InactiveUS6924663B2Increase the effective amountEfficient architectureDigital storageInternal/peripheral component protectionElectricityData stream
A programmable logic device with ferroelectric configuration memories storing multiple configuration data sets. The device has programmable logic blocks, interconnections, and I / O blocks to provide desired logic functions. Those building blocks can be dynamically reconfigured by changing the selection of configuration data stored in the device's integral configuration memories. The configuration memories are divided into groups, so that they can be loaded concurrently with multiple configuration data streams. To protect the content of configuration memories from unauthorized access, the device employs an authentication mechanism that uses security IDs stored in the configuration memories. The device has a memory controller to provide an appropriate power supply sequence for ferroelectric memory cells to ensure the reliable data retention when the device is powered up or shut down.
Owner:FUJITSU SEMICON LTD
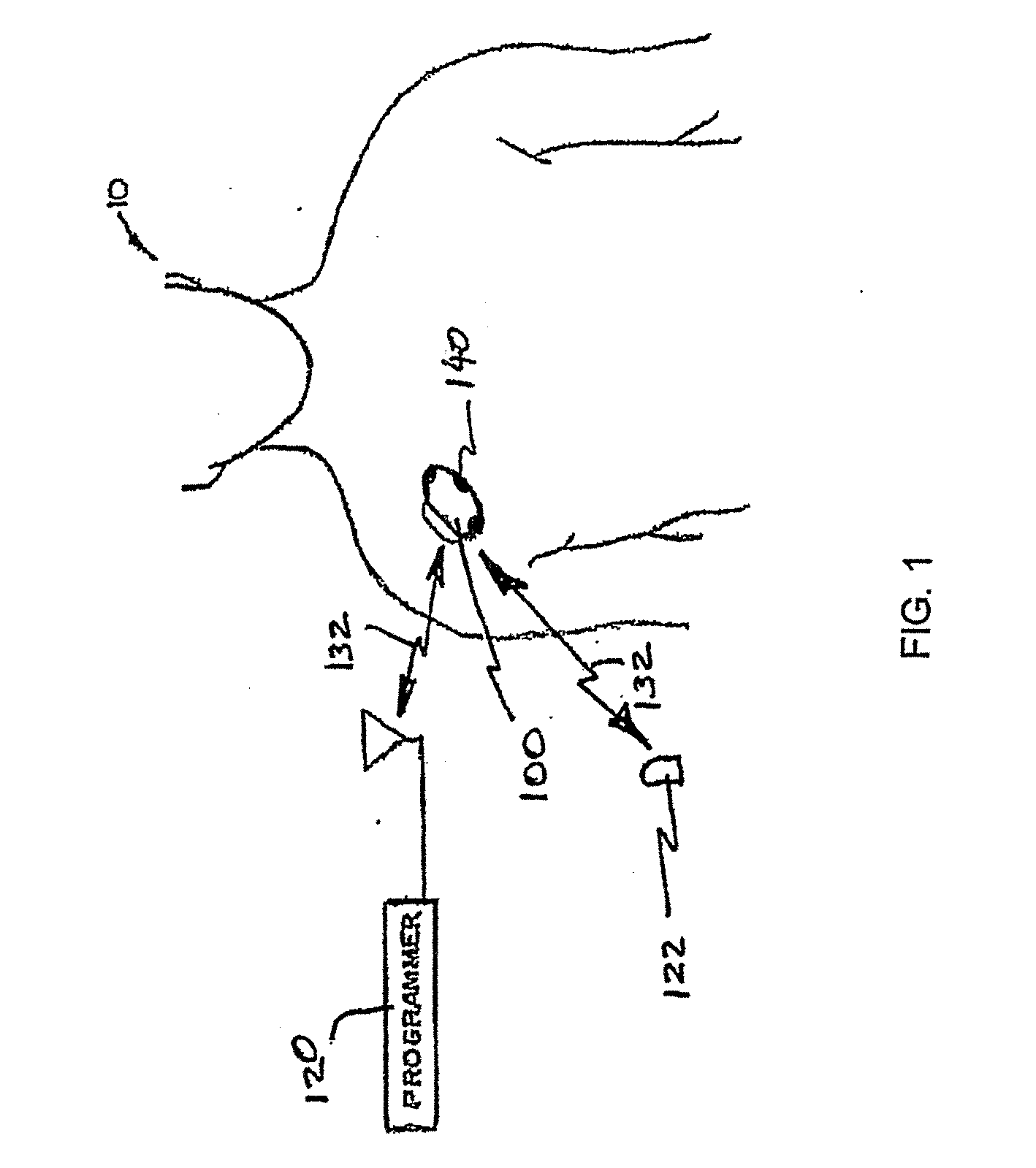
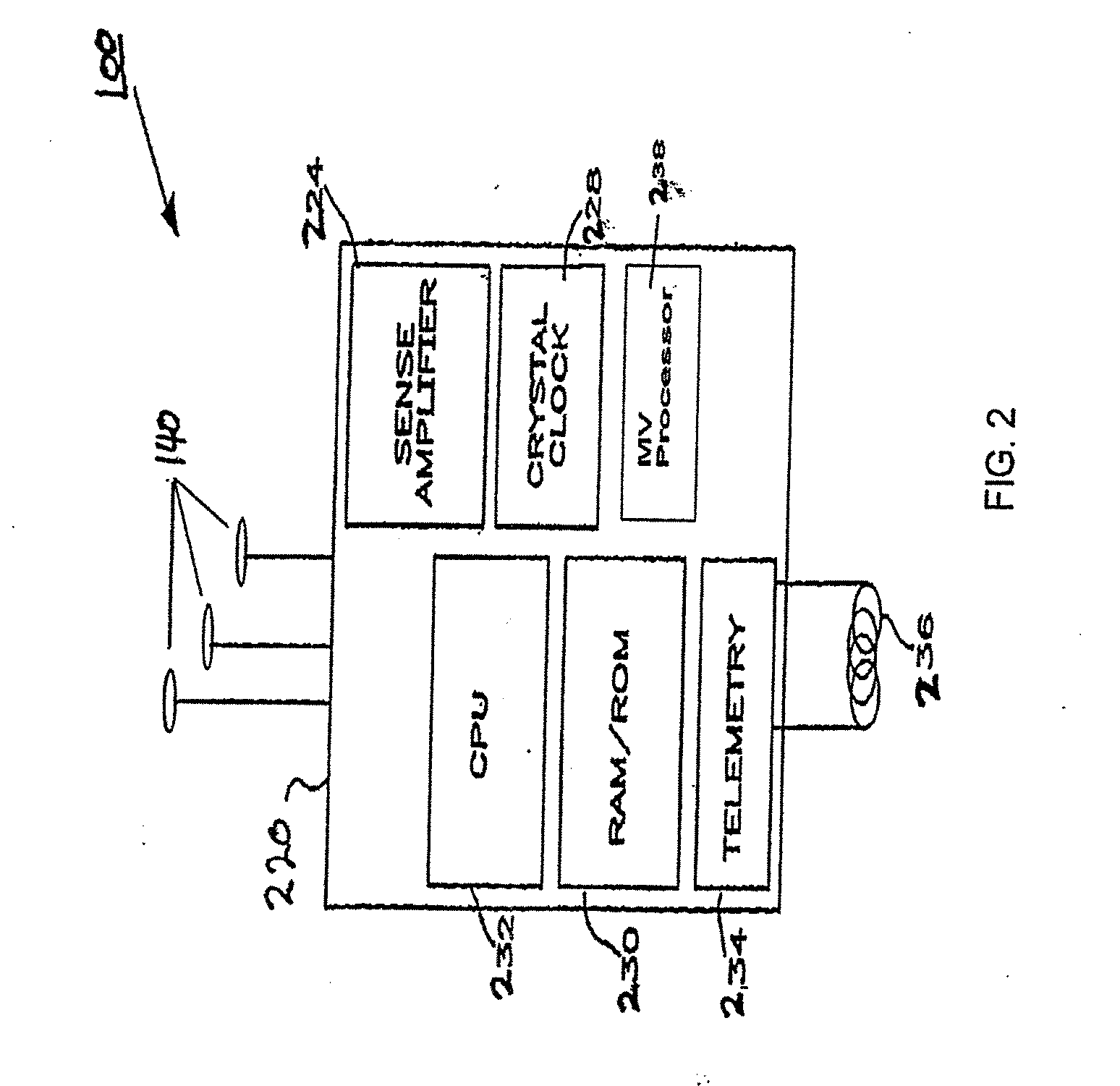
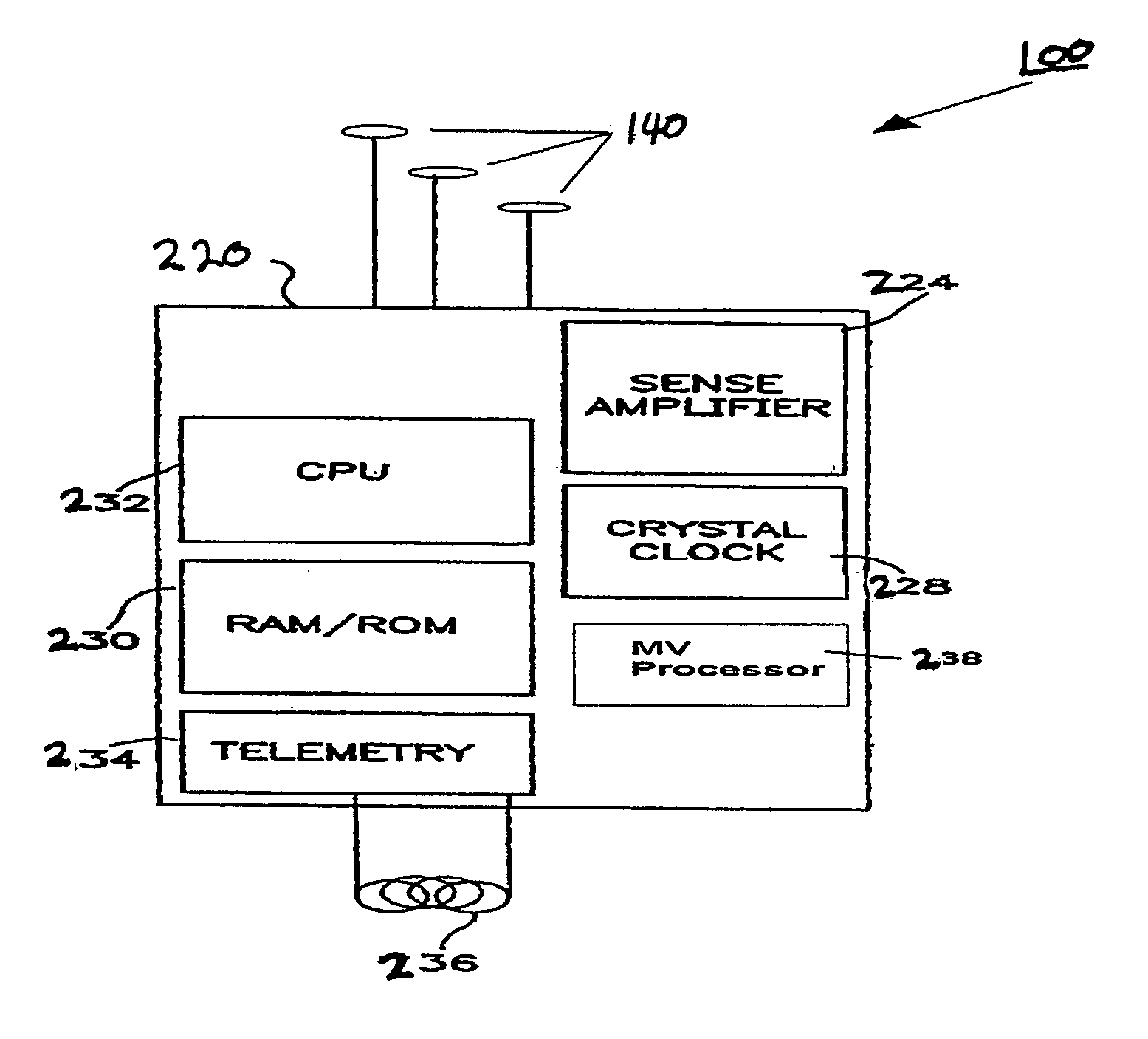
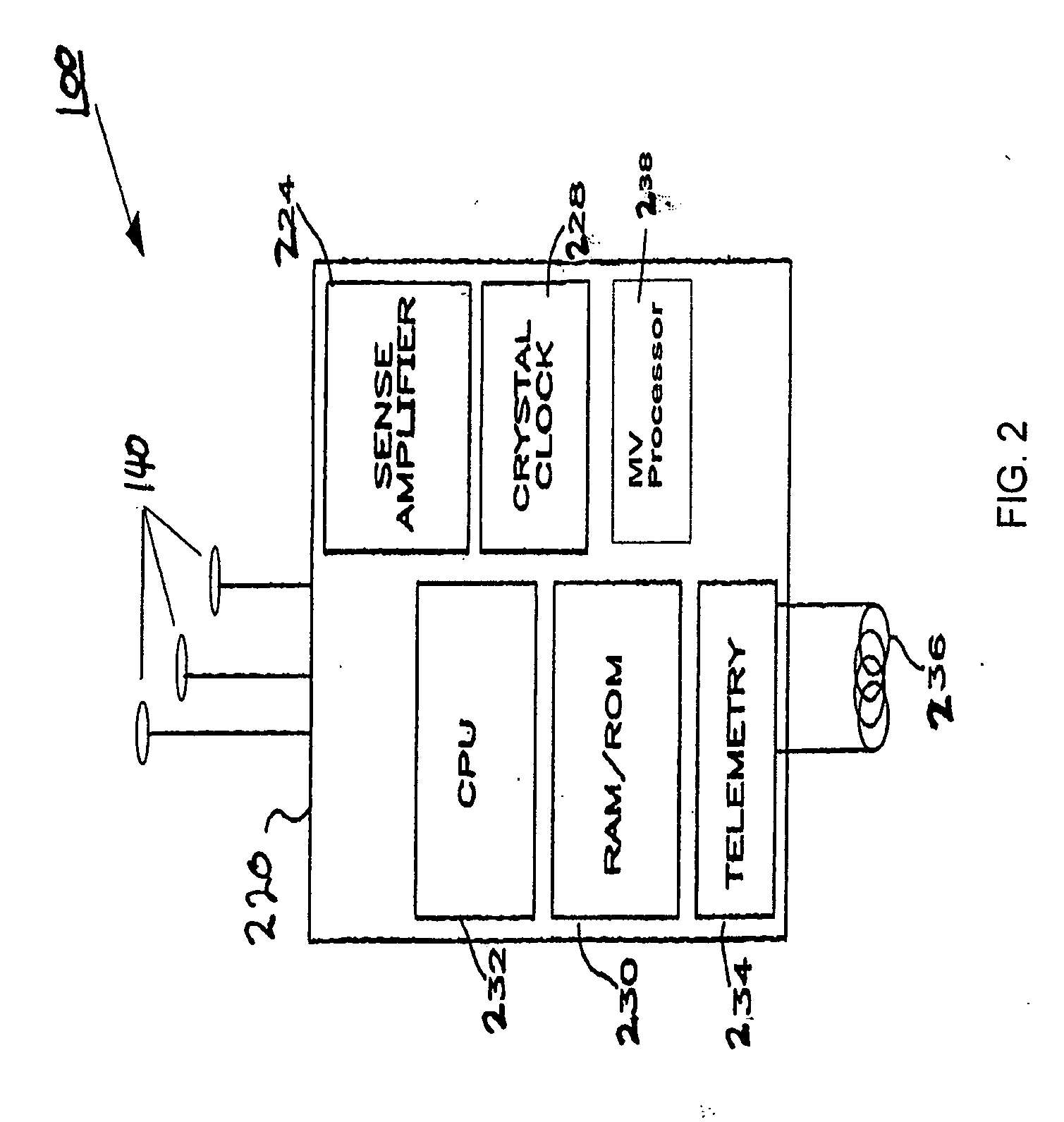
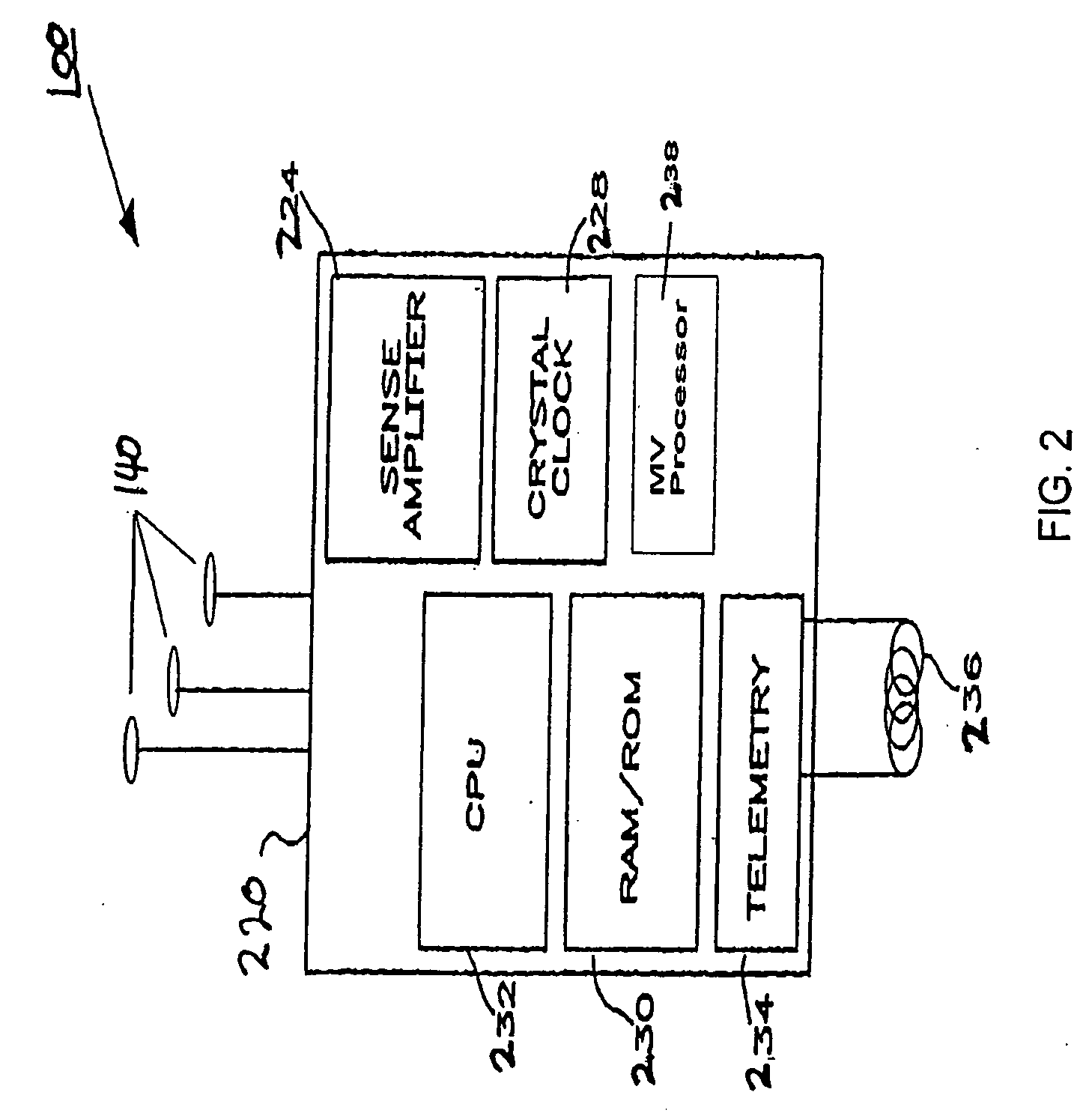
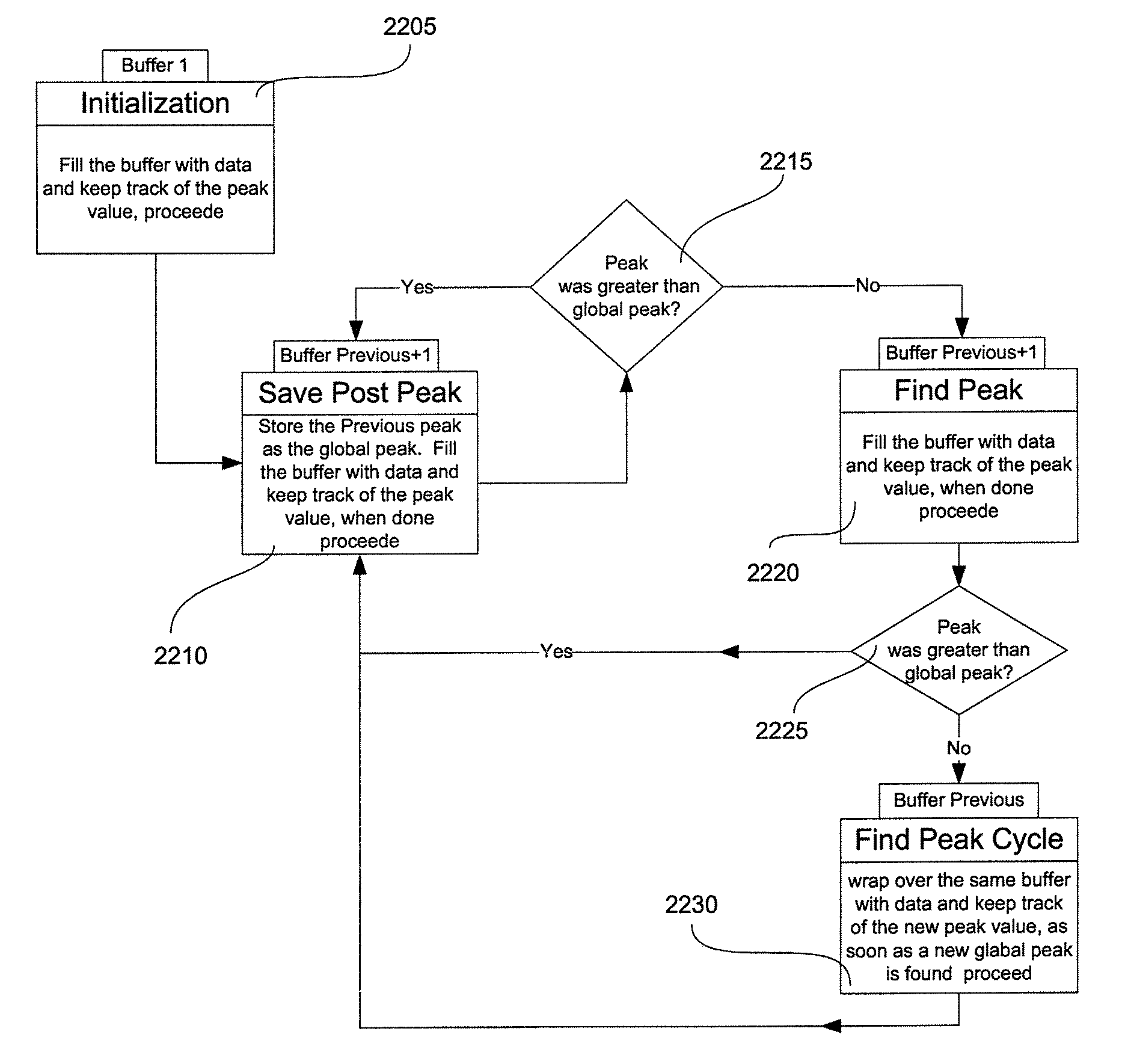
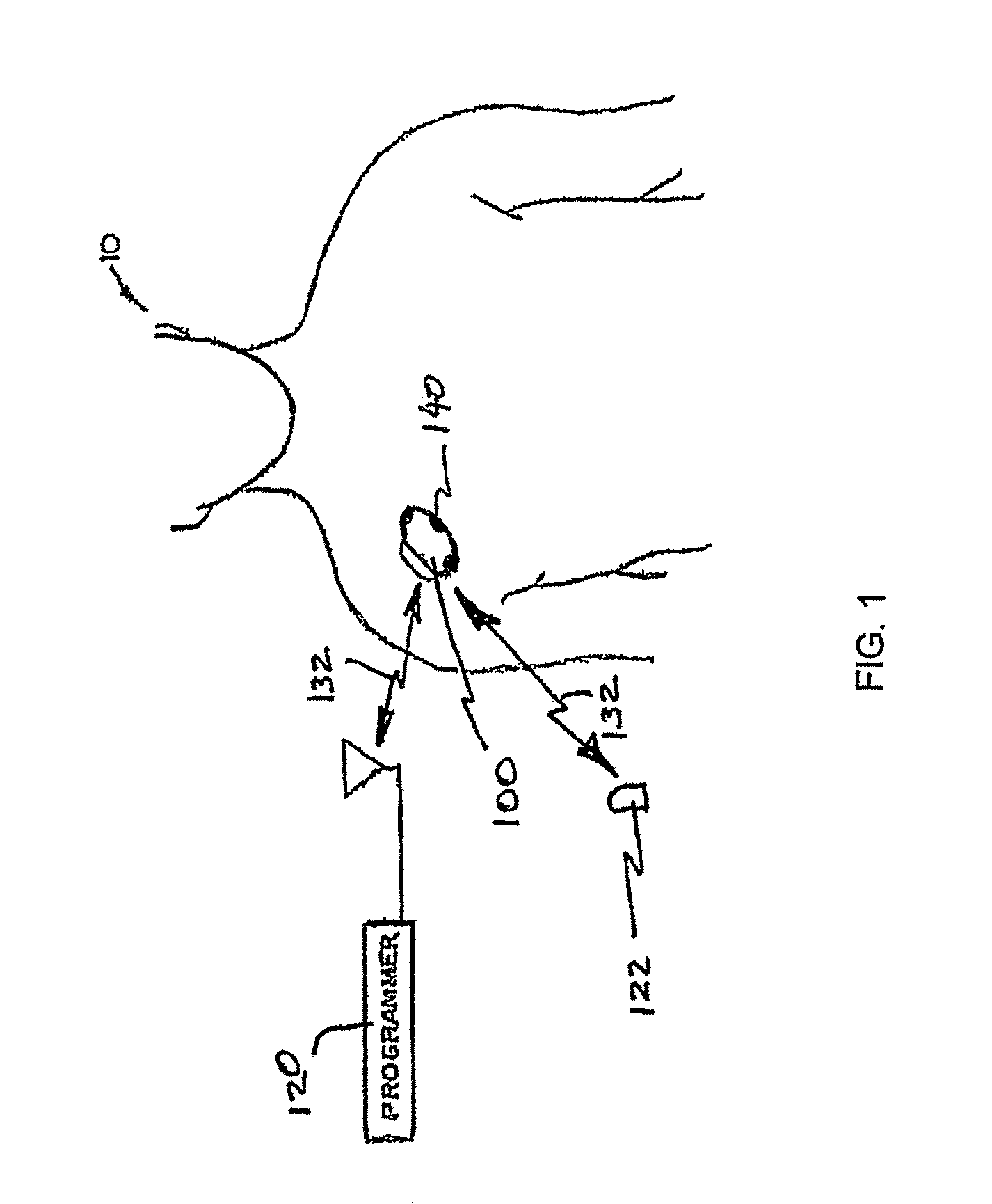
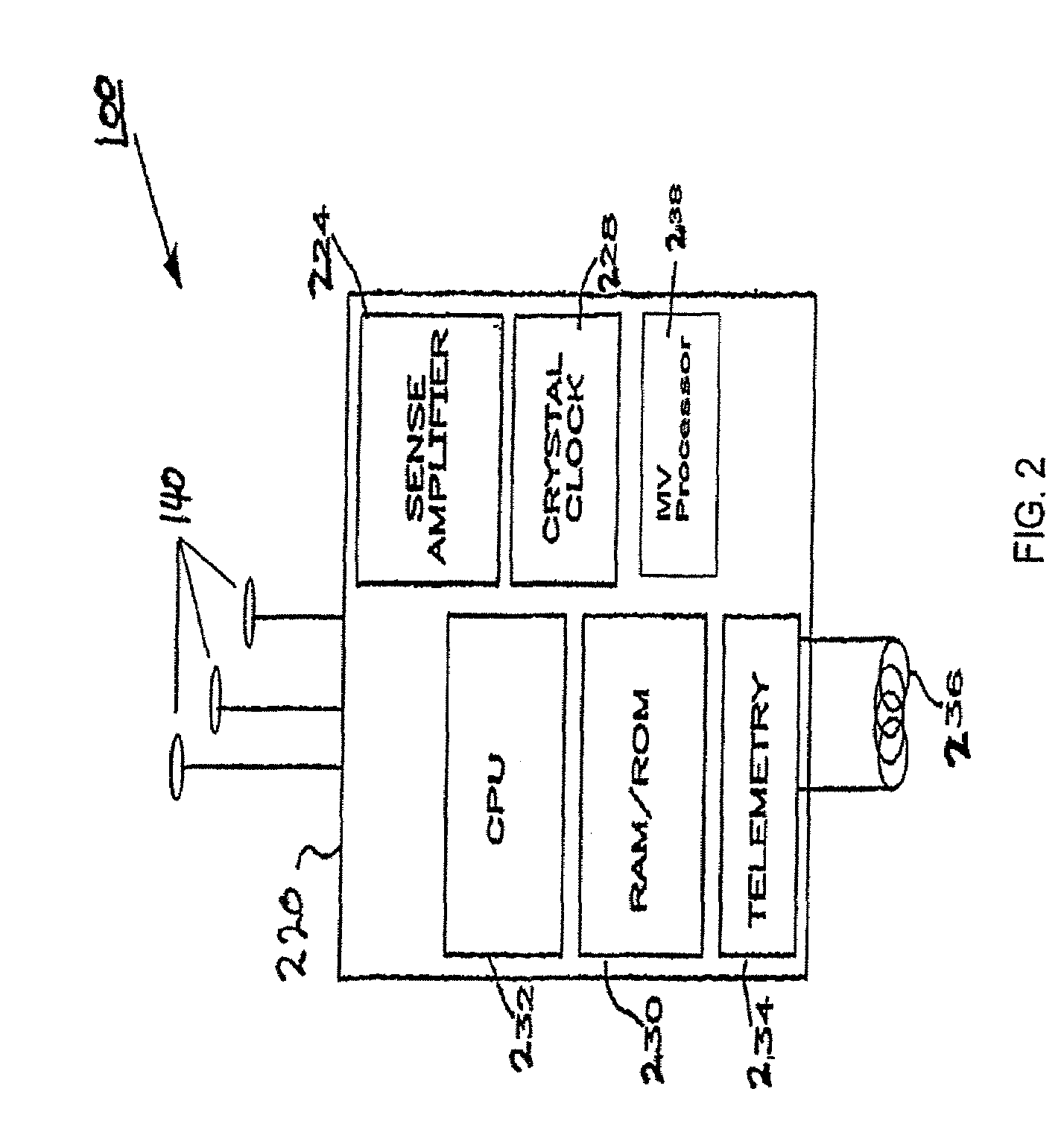
Peak data retention of signal data in an implantable medical device
InactiveUS20070255531A1ElectrotherapyAmplifier modifications to reduce noise influencePeak valueData recording
Methods and apparatus for storing data records associated with an extreme value are disclosed. Signal data is stored in a first buffer of a set of buffers. If a local extreme value for the first buffer exceeds a global extreme value, signal data is stored in a second buffer of the set of buffers. This process is repeated, wrapping around and overwriting buffers until the signal data in a current buffer does not have a local extreme value that exceeds the global extreme value. When this happens, signal data may be stored in a subsequent buffer and if a local extreme value of the subsequent buffer does not exceed the global extreme value, further signal data may be stored in the subsequent buffer in a circular manner until either an instantaneous extreme value exceeds the global extreme value or the recording period ends. In an embodiment, the extreme value may be a peak value.
Owner:MEDTRONIC INC
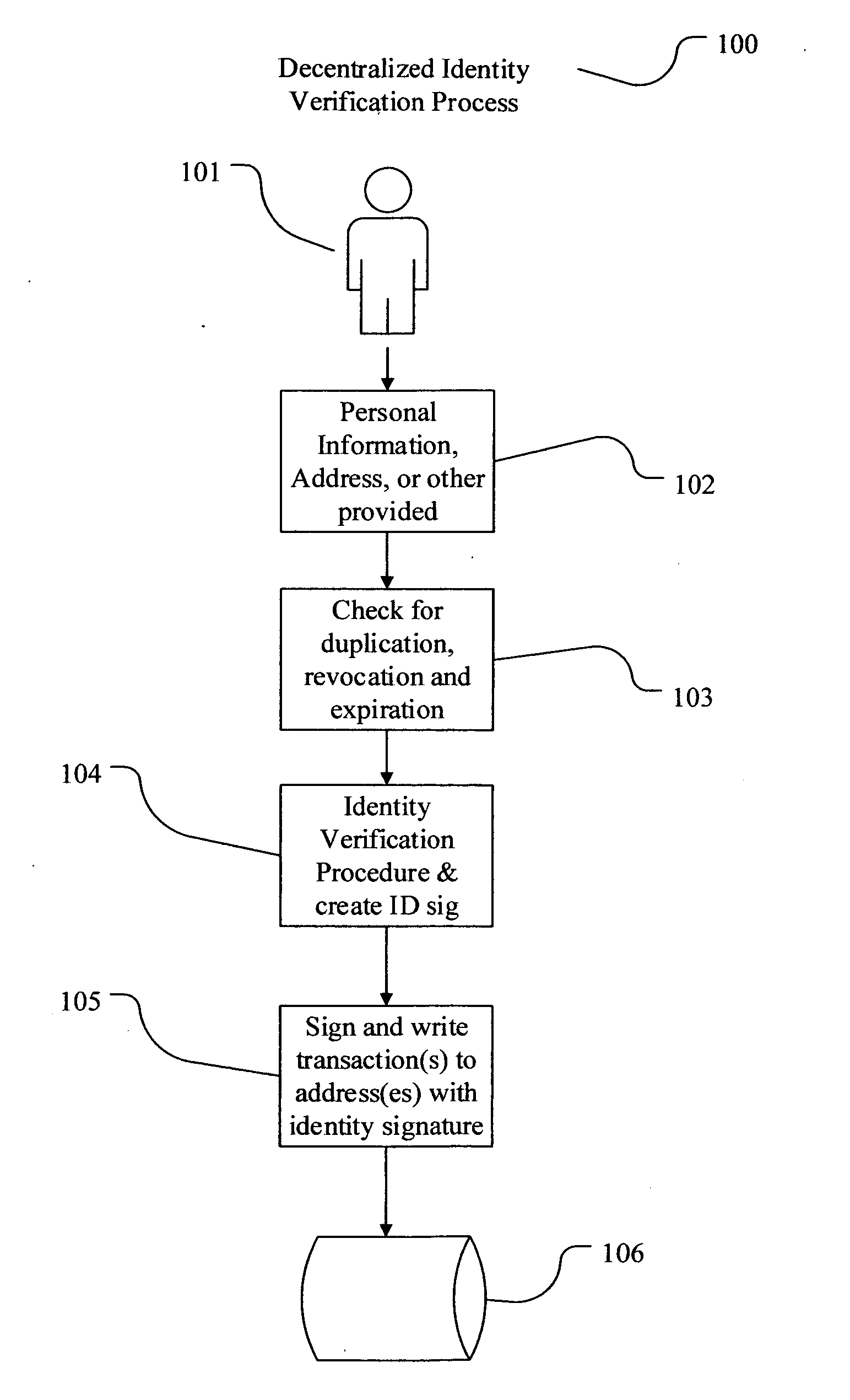
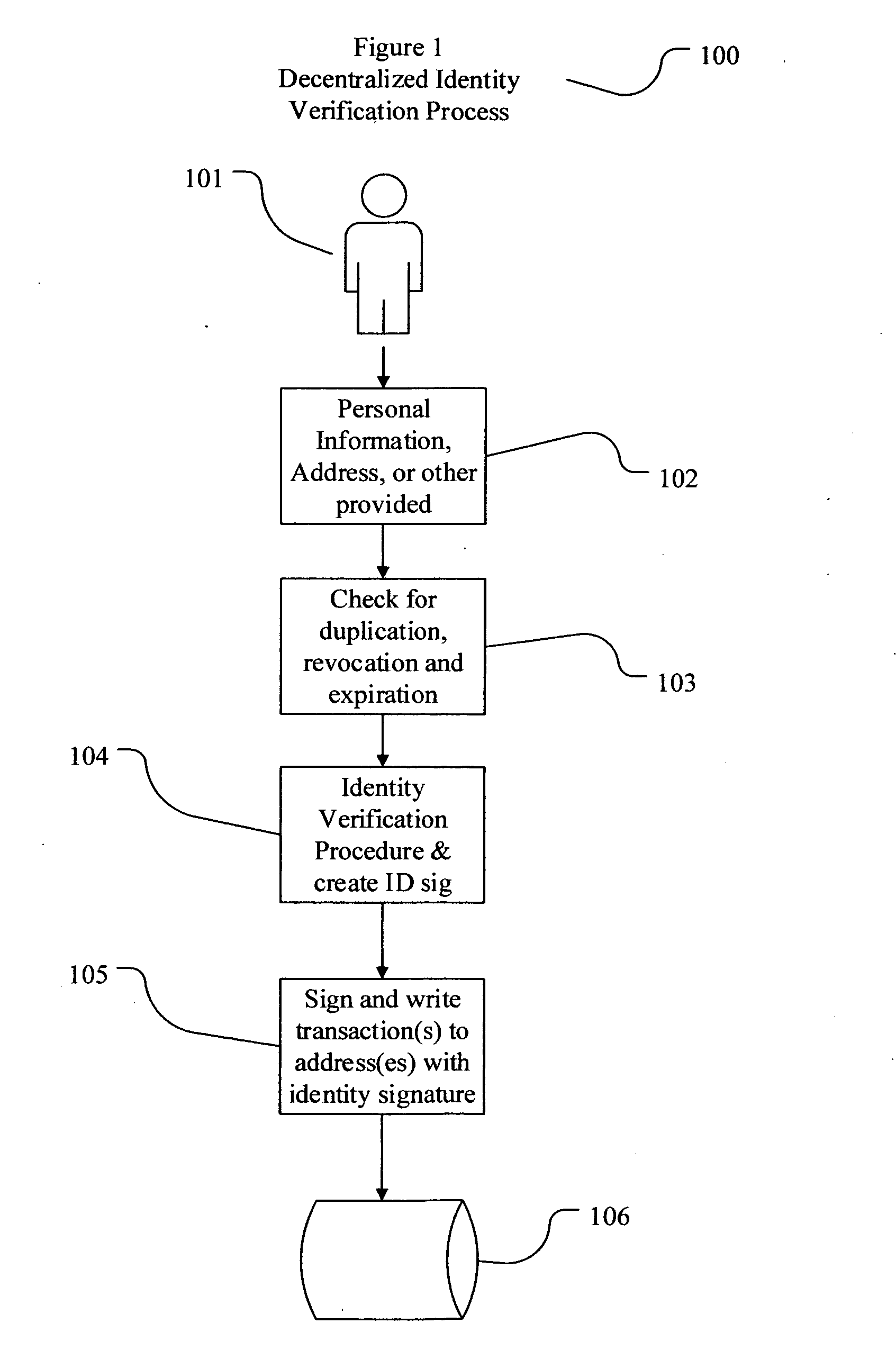
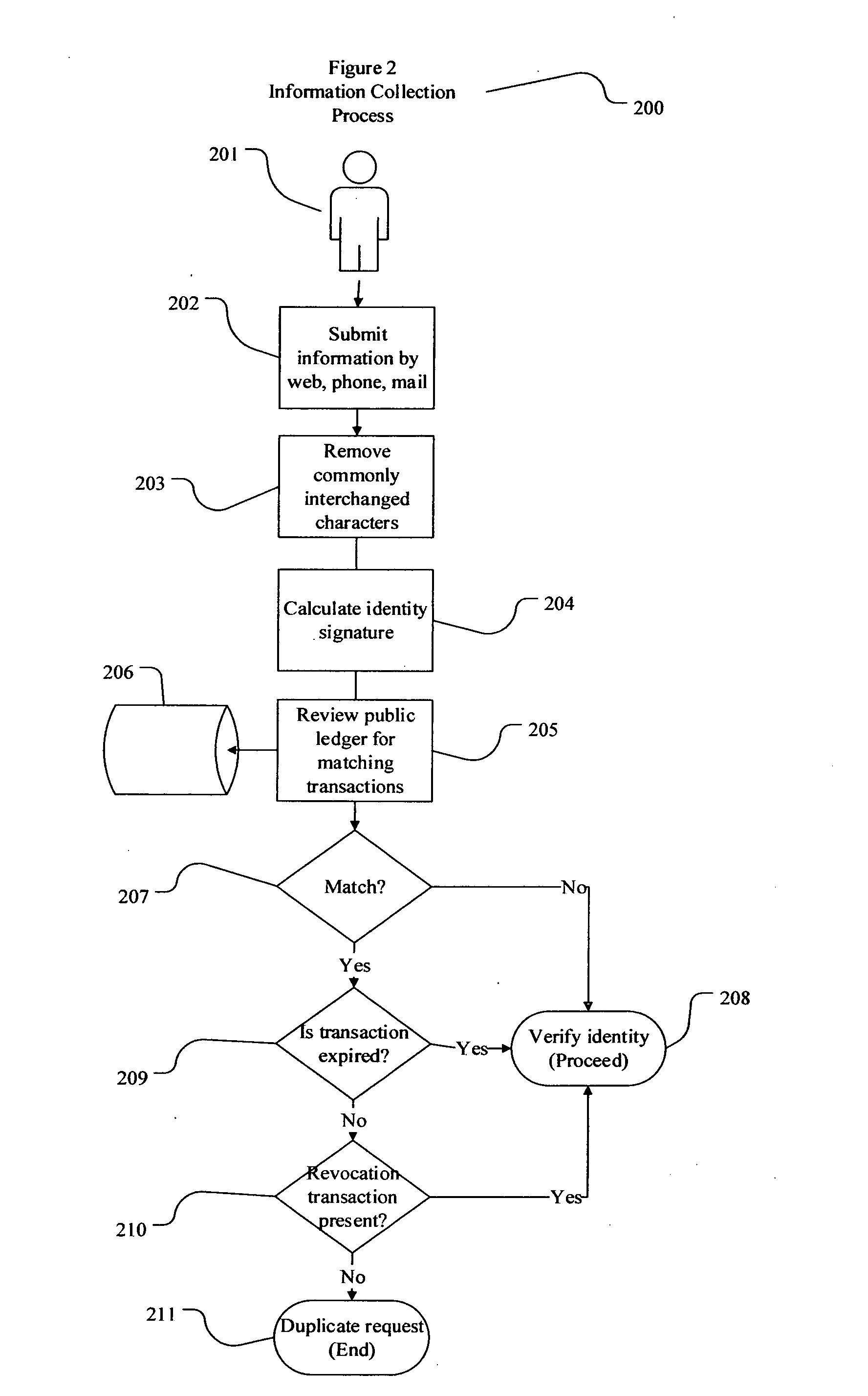
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
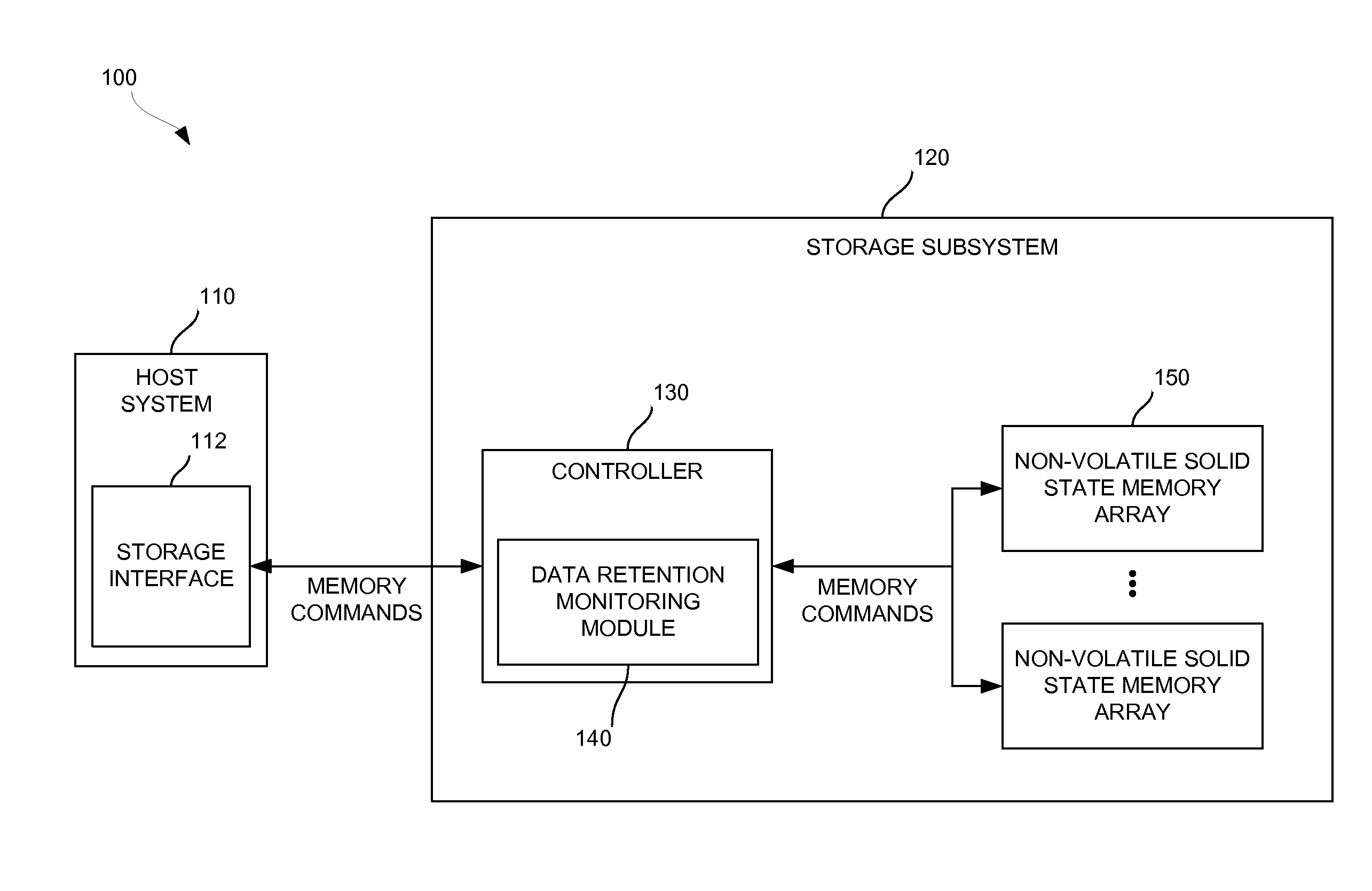
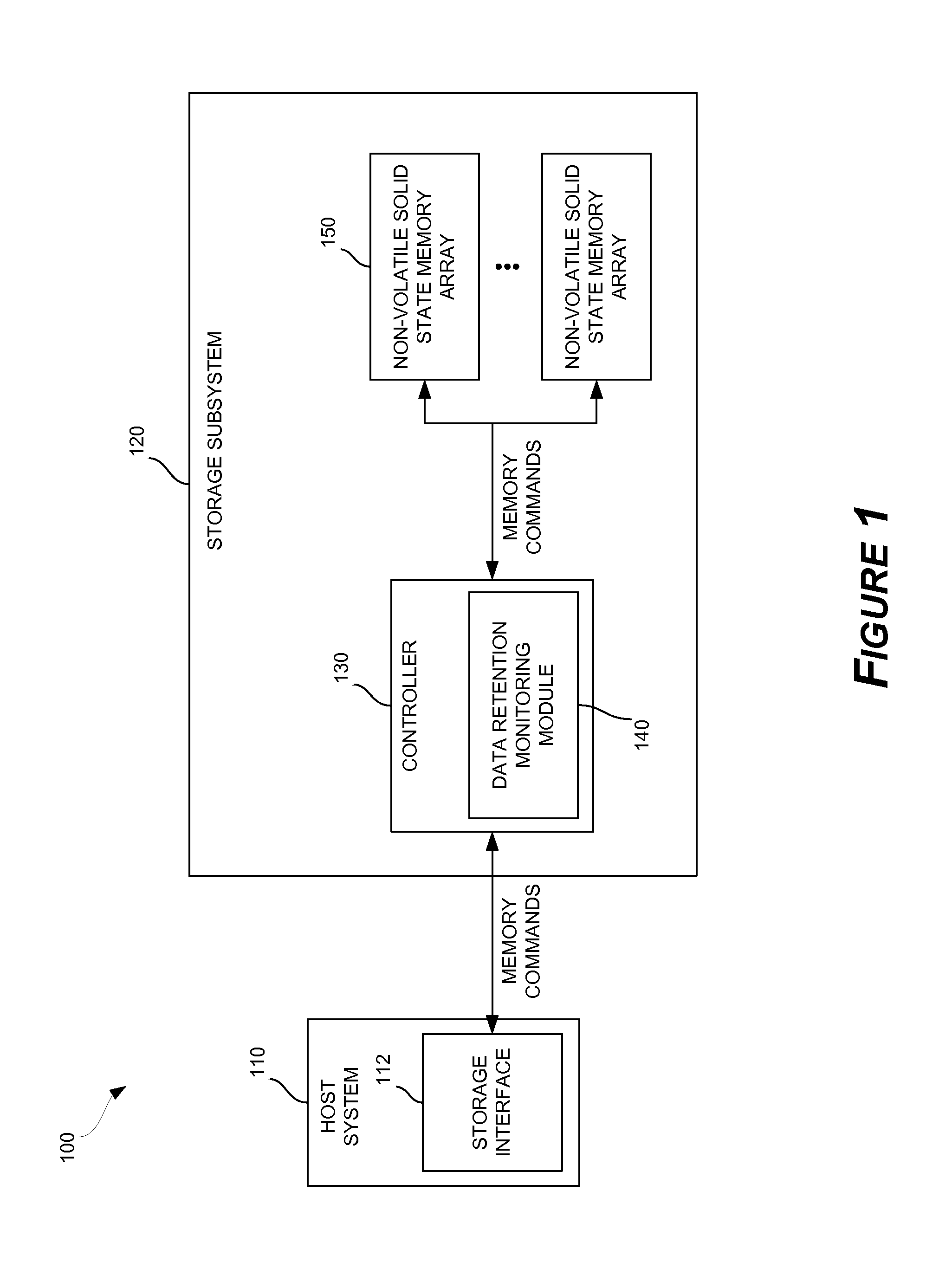
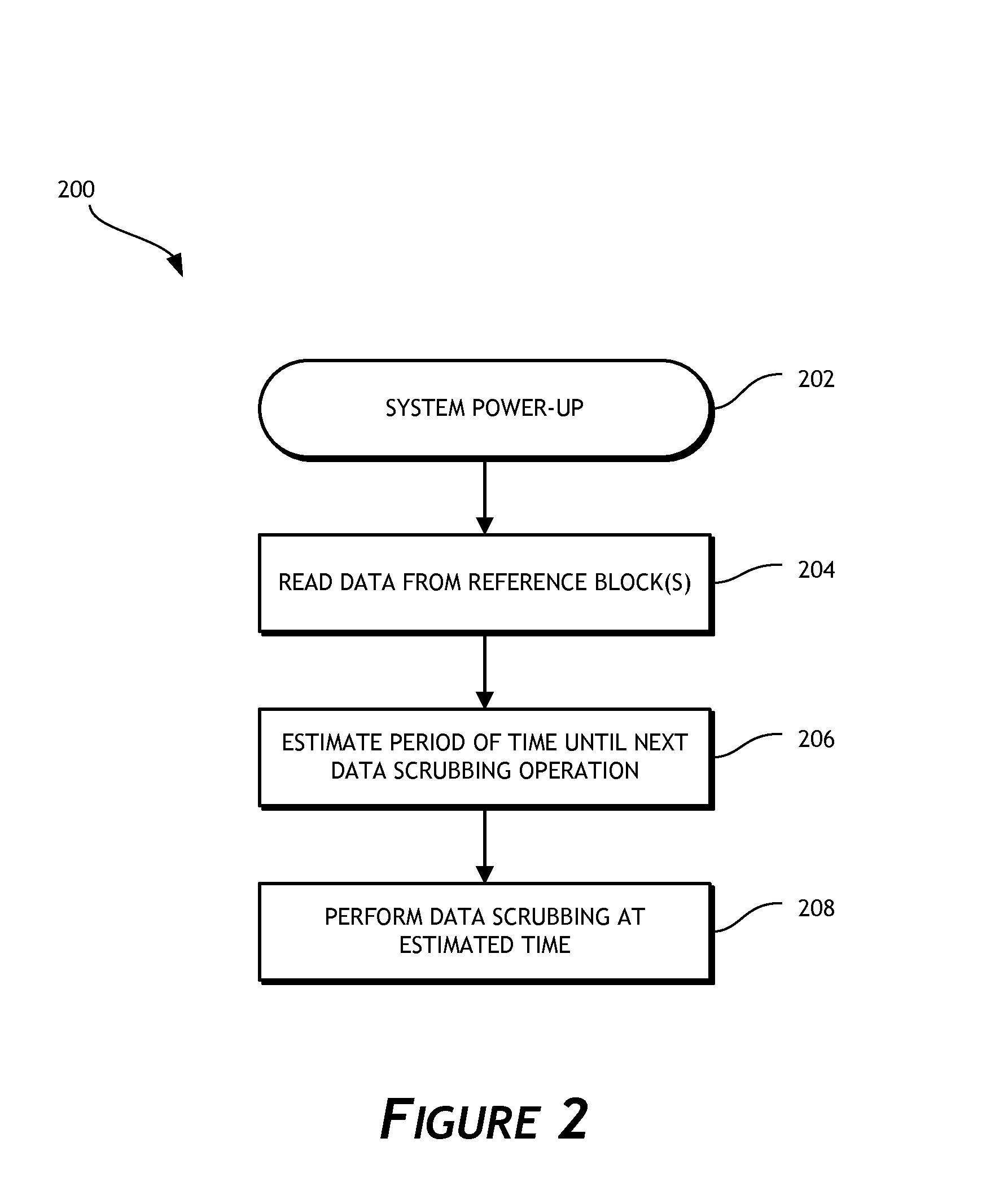
Solid-state drive retention monitor using reference blocks
A solid-state storage retention monitor determines whether user data in a solid-state device is in need of a scrubbing operation. One or more reference blocks may be programmed with a known data pattern, wherein the reference block(s) experiences substantially similar P / E cycling, storage temperature, storage time, and other conditions as the user blocks. The reference blocks may therefore effectively represent data retention properties of the user blocks and provide information regarding whether / when a data refreshing operation is needed.
Owner:WESTERN DIGITAL TECH INC
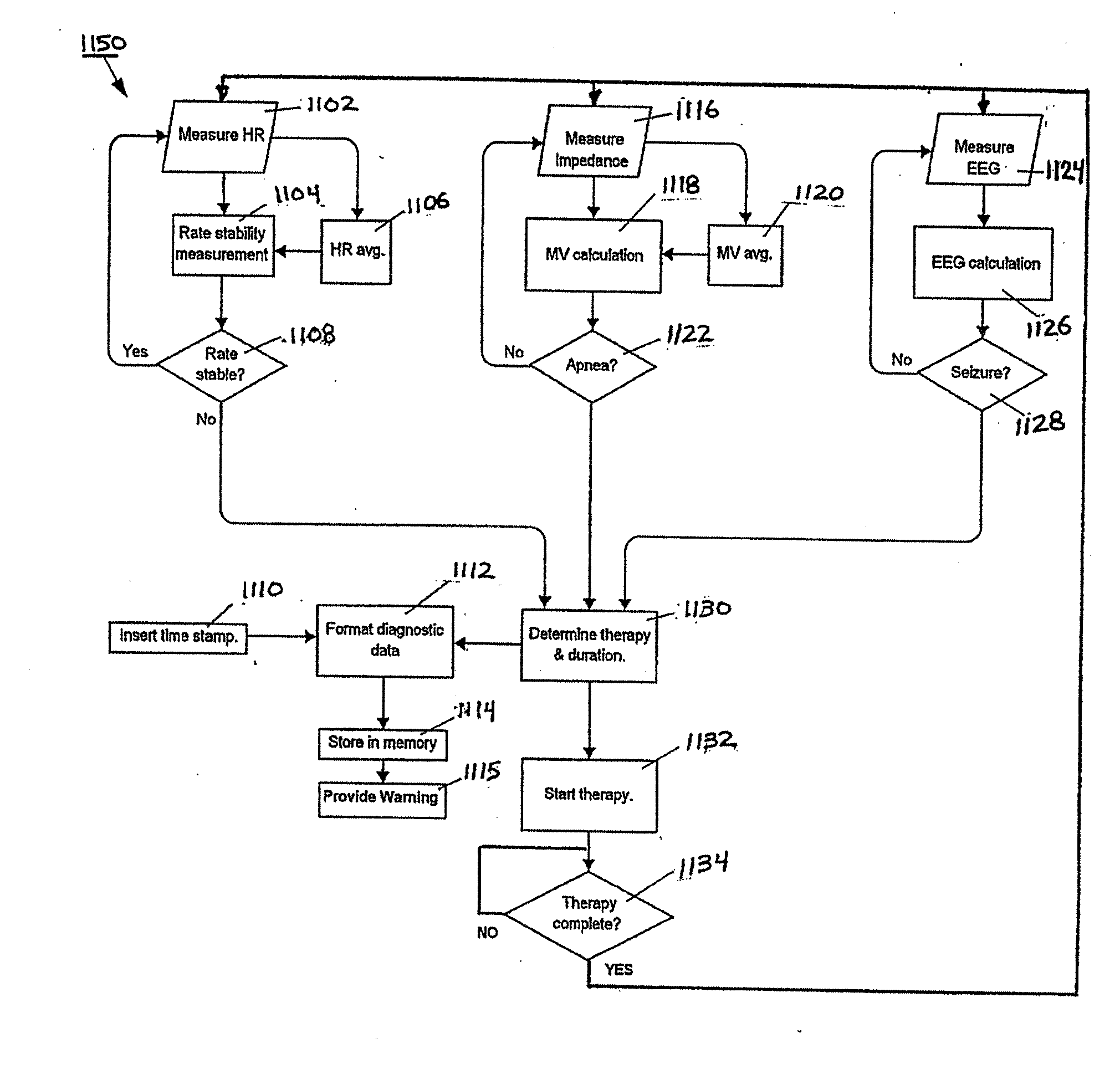
Methods for data retention in an implantable medical device
ActiveUS20060287691A1Physical therapies and activitiesHeart stimulatorsImplanted deviceSeverity level
Methods for storing data records associated with a medical monitoring event in a data structure. An implanted device obtains data and stores the data in the data record in a first data structure that is age-based. Before an oldest data record is lost, the oldest data record may be stored in a second data structure that is priority index-based. The priority index may be determined by a severity level and may be further determined by associated factors. The implanted device may organize, off-load, report, and / or display a plurality of data records based on an associated priority index. Additionally, the implanted device may select a subset or composite of physiologic channels from the available physiologic channels based on a selection criterion.
Owner:MEDTRONIC INC
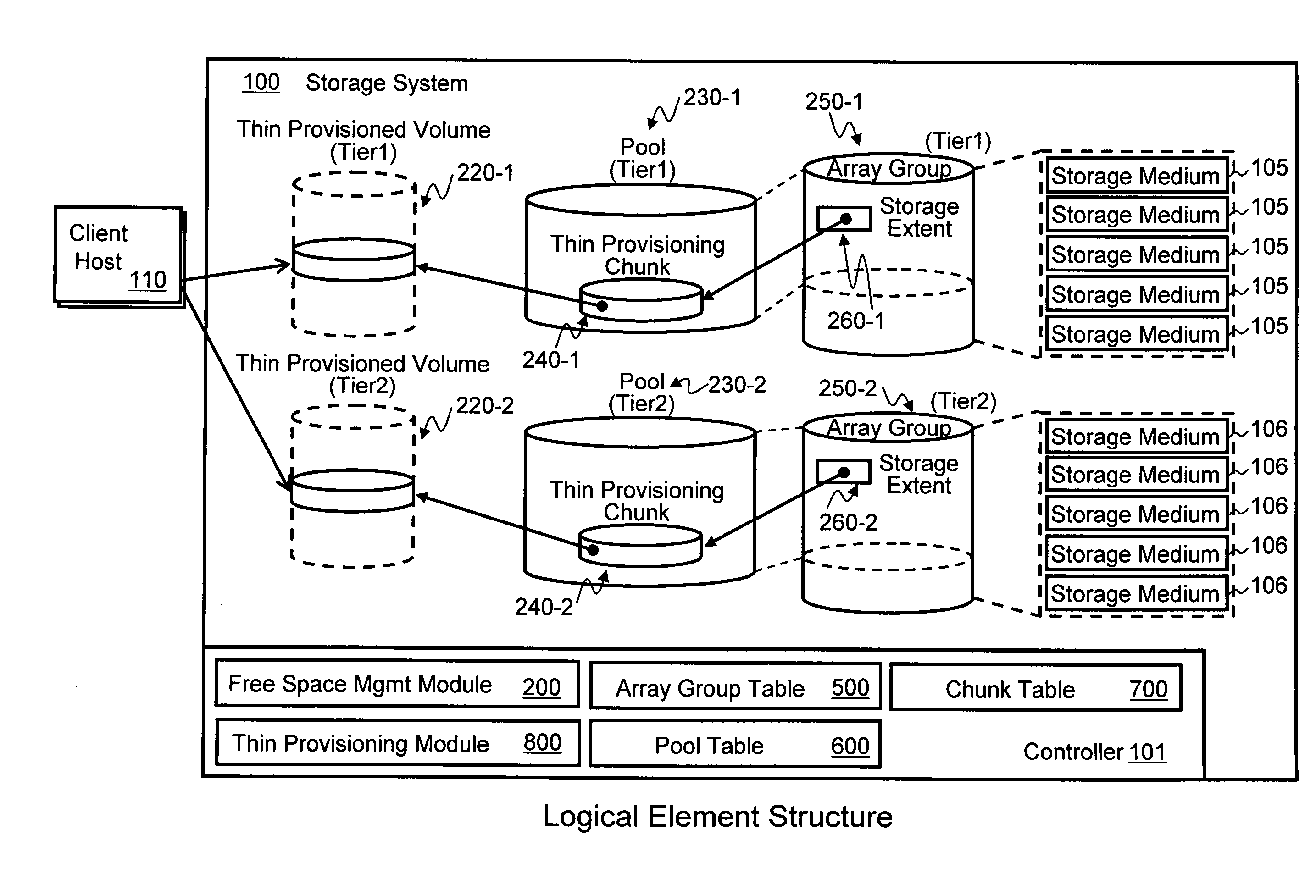
Free space utilization in tiered storage systems
ActiveUS20090276588A1Low costEliminate redundancyMemory adressing/allocation/relocationInput/output processes for data processingHybrid storage systemThin provisioning
Embodiments of the invention include first storage mediums having first storage characteristics for making up a first pool of capacity of a first tier of storage, and second storage mediums having second storage characteristics for making up a second pool of capacity of a second tier of storage. Free capacity of the first and second pools is shared between the first and second tiers of storage. When the first pool has an amount of free capacity available over a reserved amount of free capacity reserved for first tier data, a first quantity of second tier data is moved from the second tier to the first tier. In exemplary embodiments of the invention, the first and second storage mediums are contained within one or more thin provisioning storage systems, and data is moved between the first and second tiers by allocating thin provisioning chunks to the data being moved.
Owner:HITACHI LTD
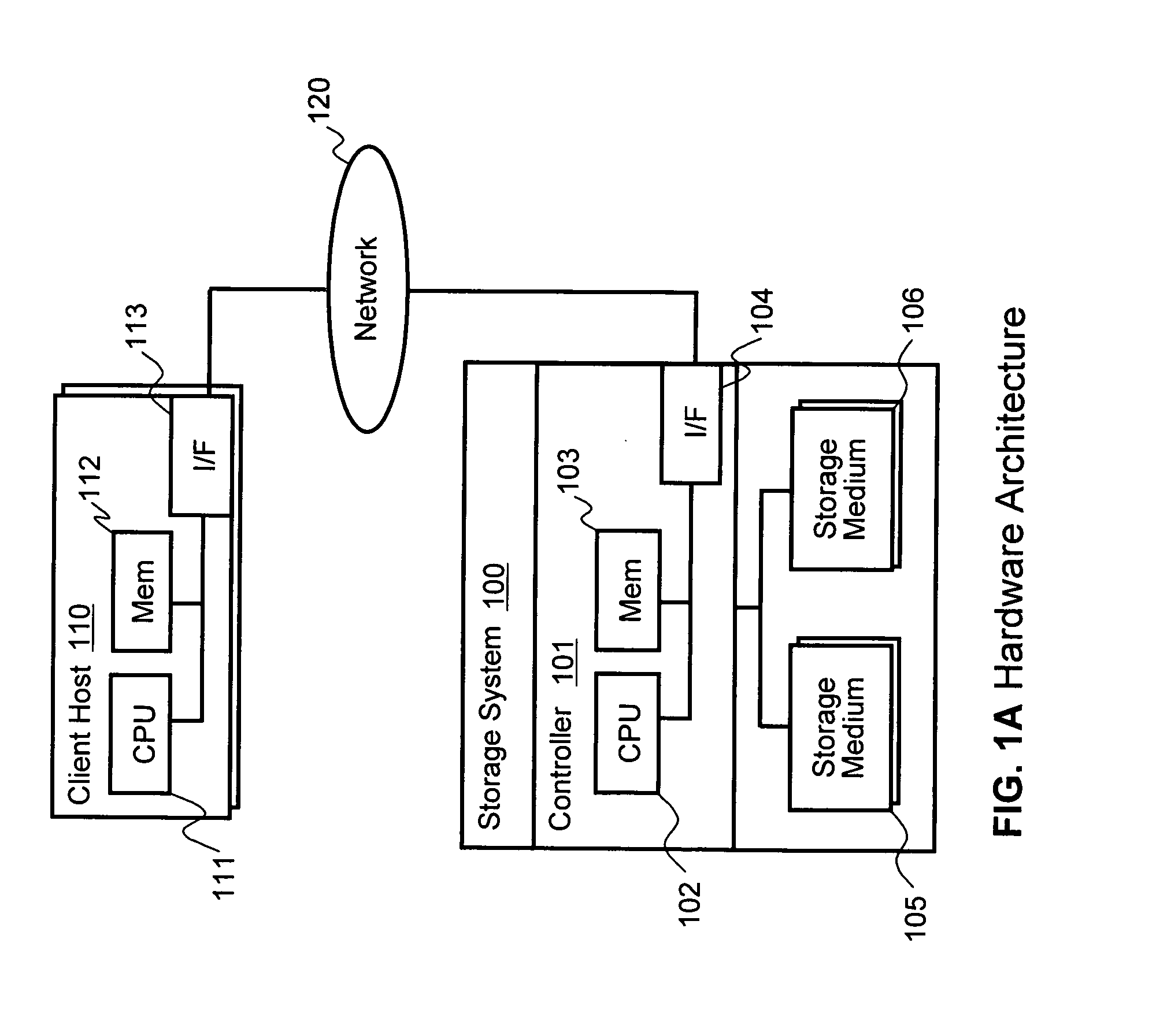
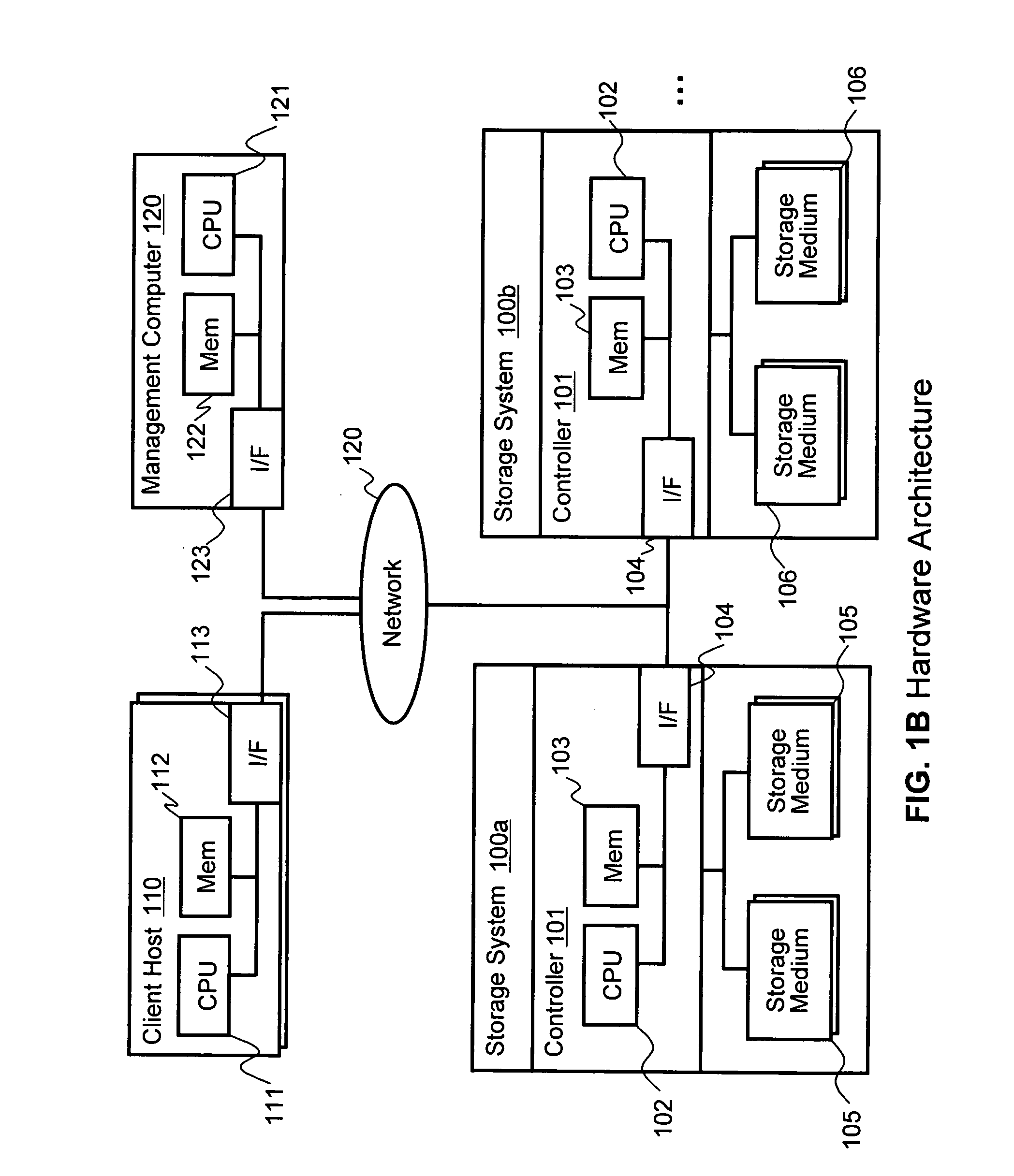
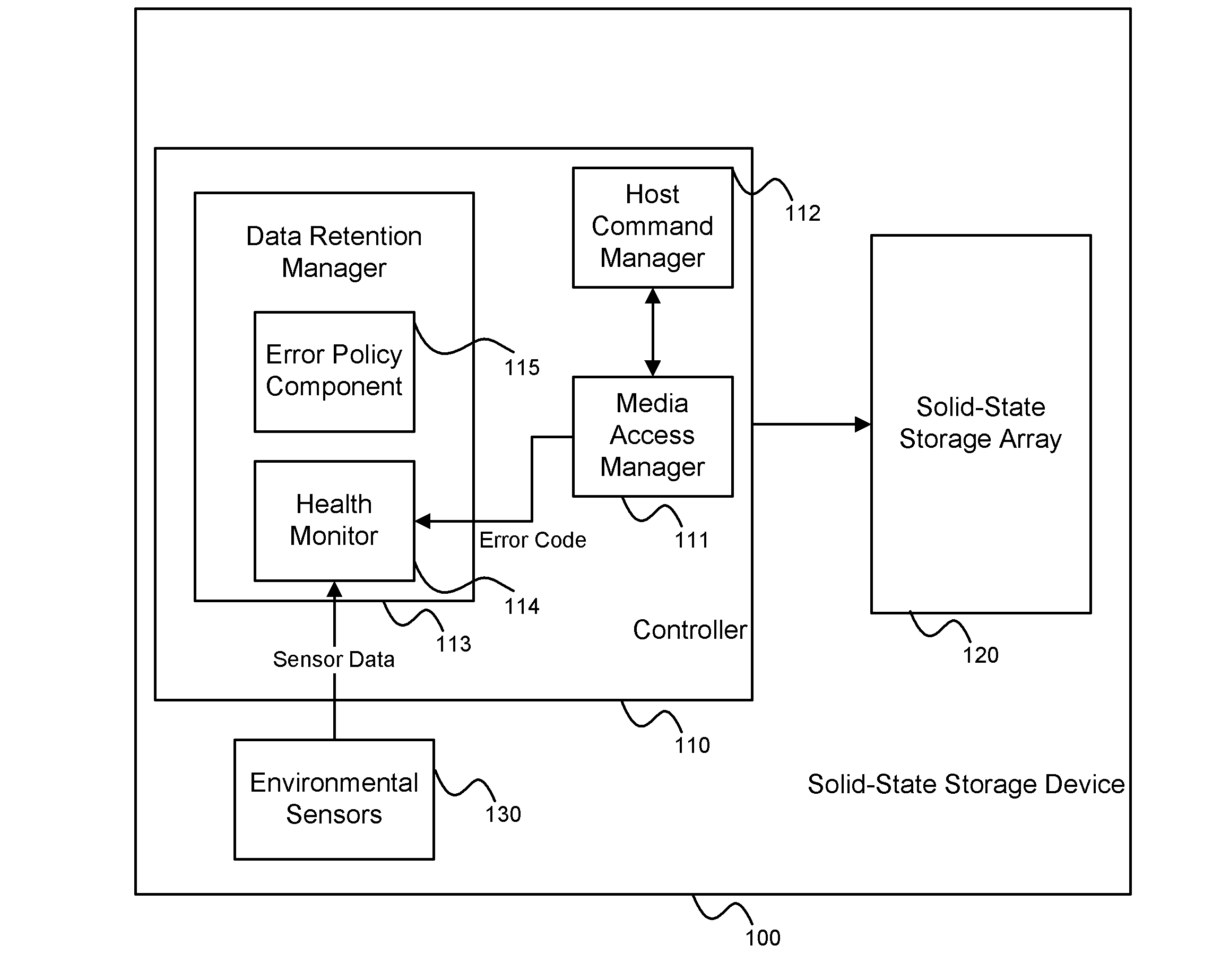
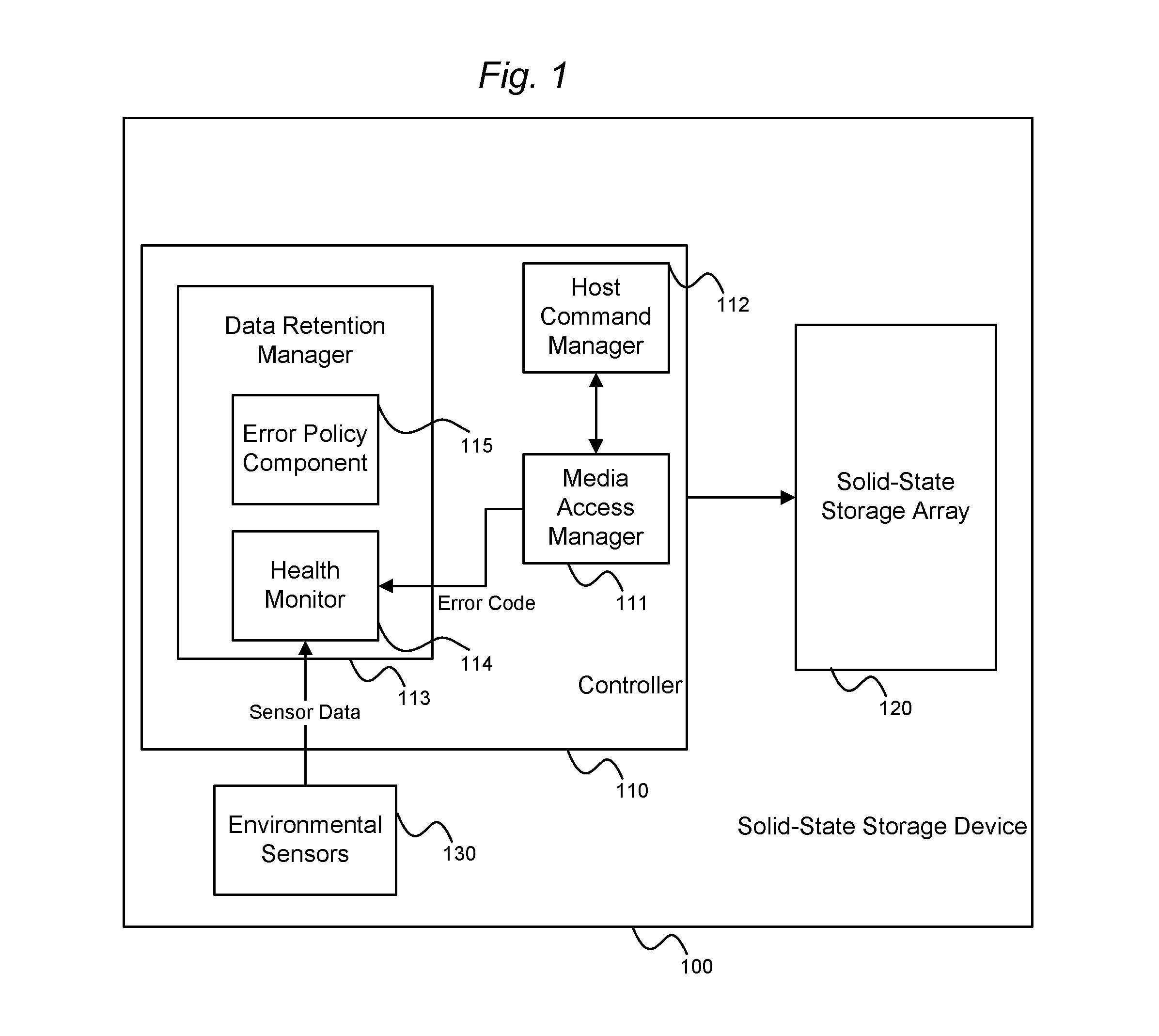
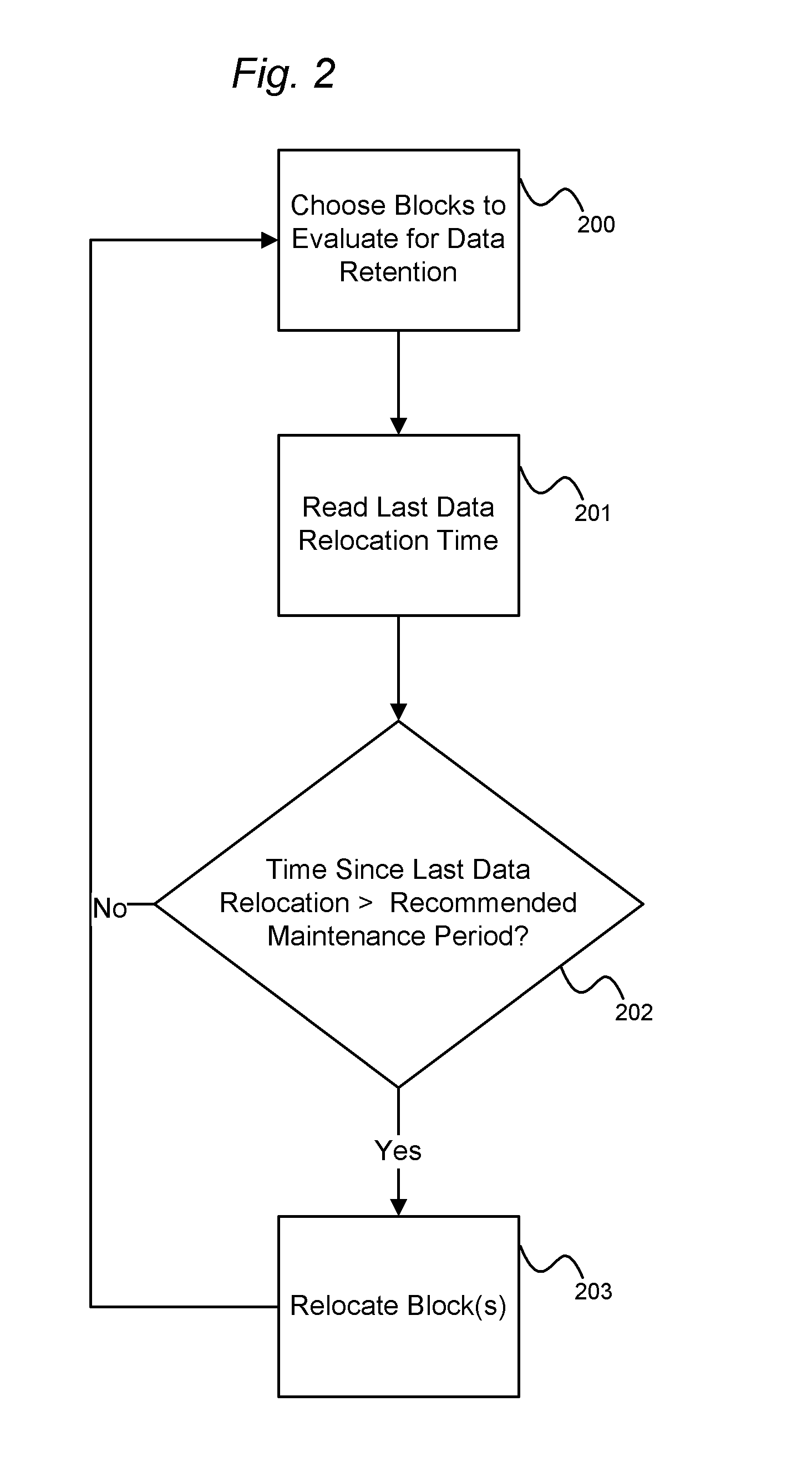
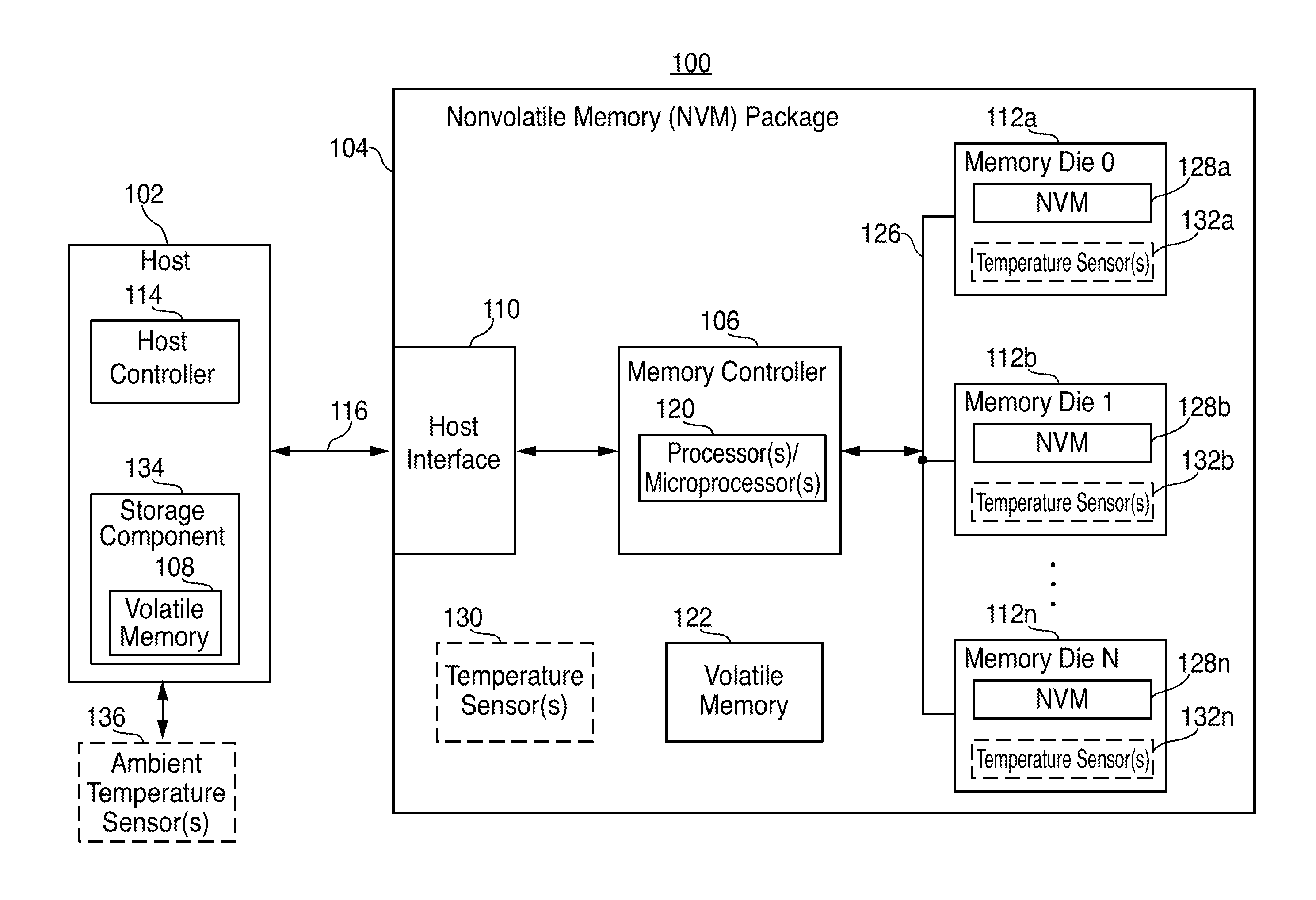
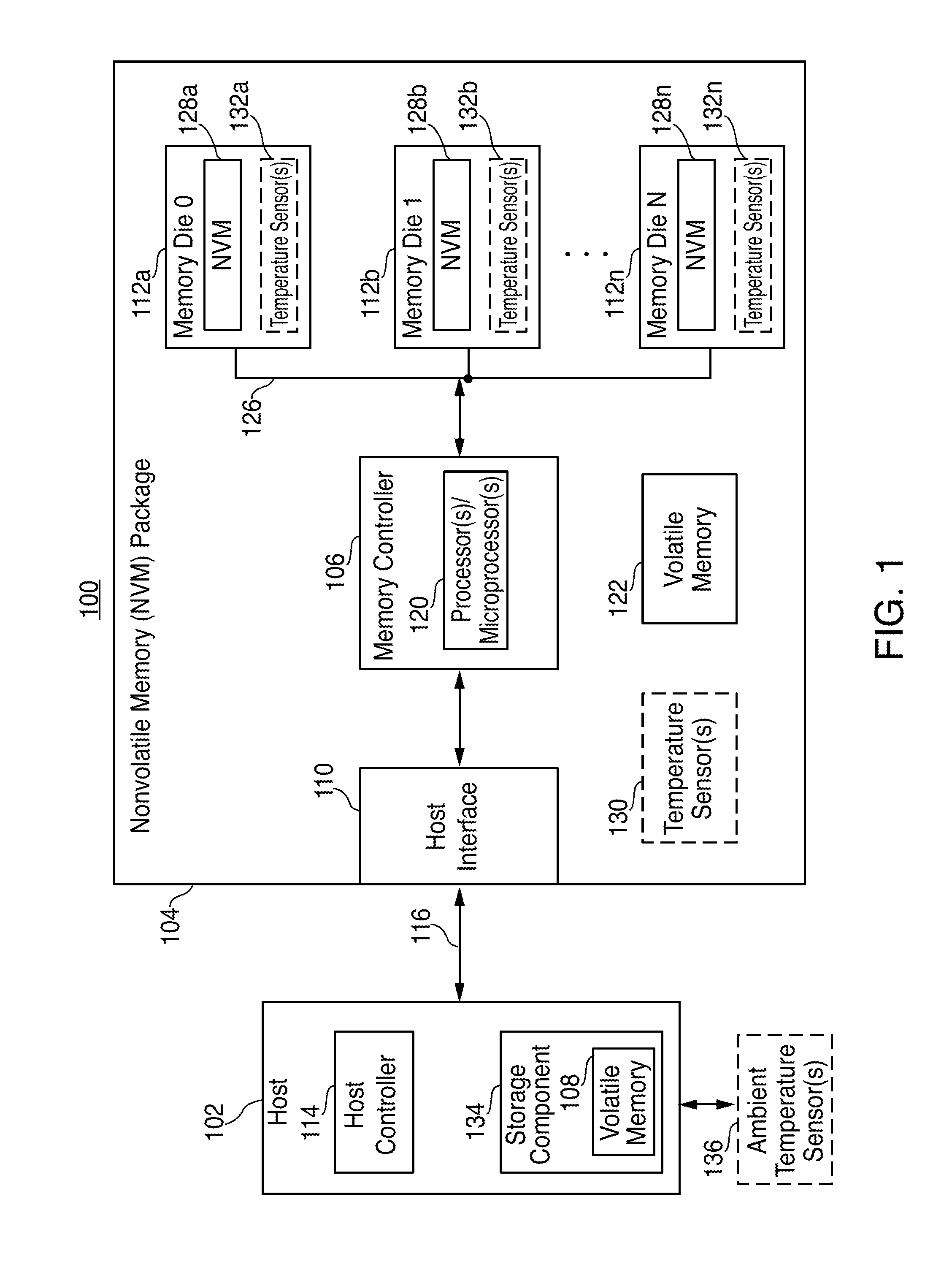
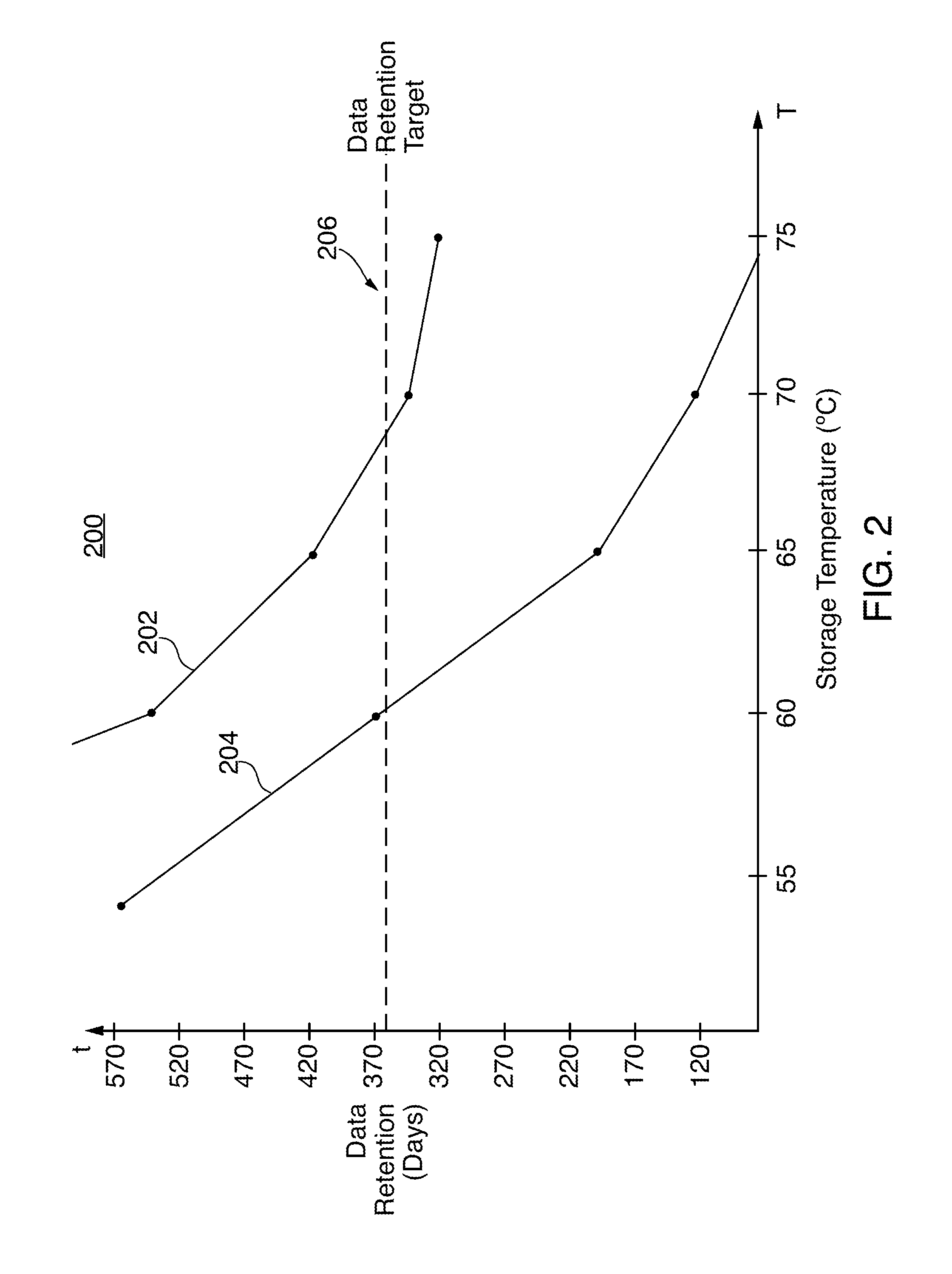
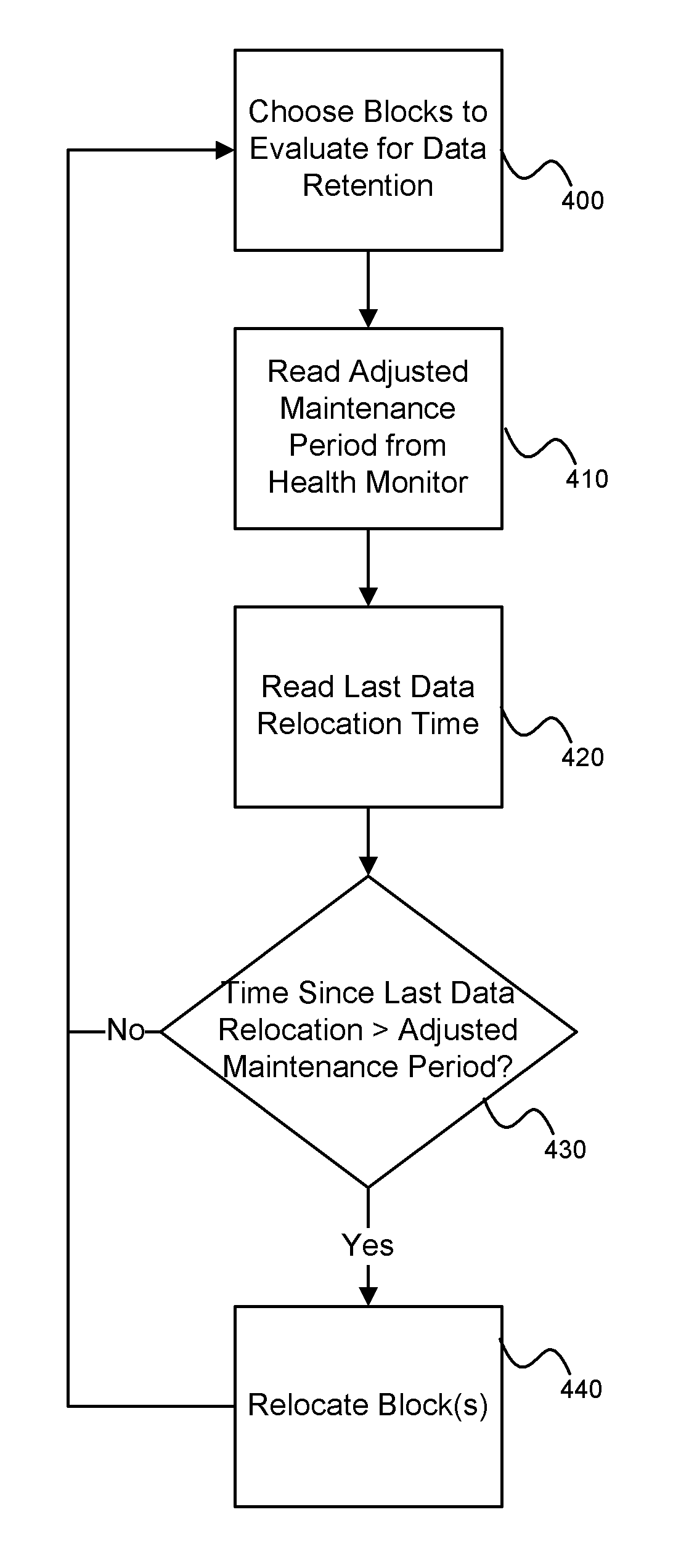
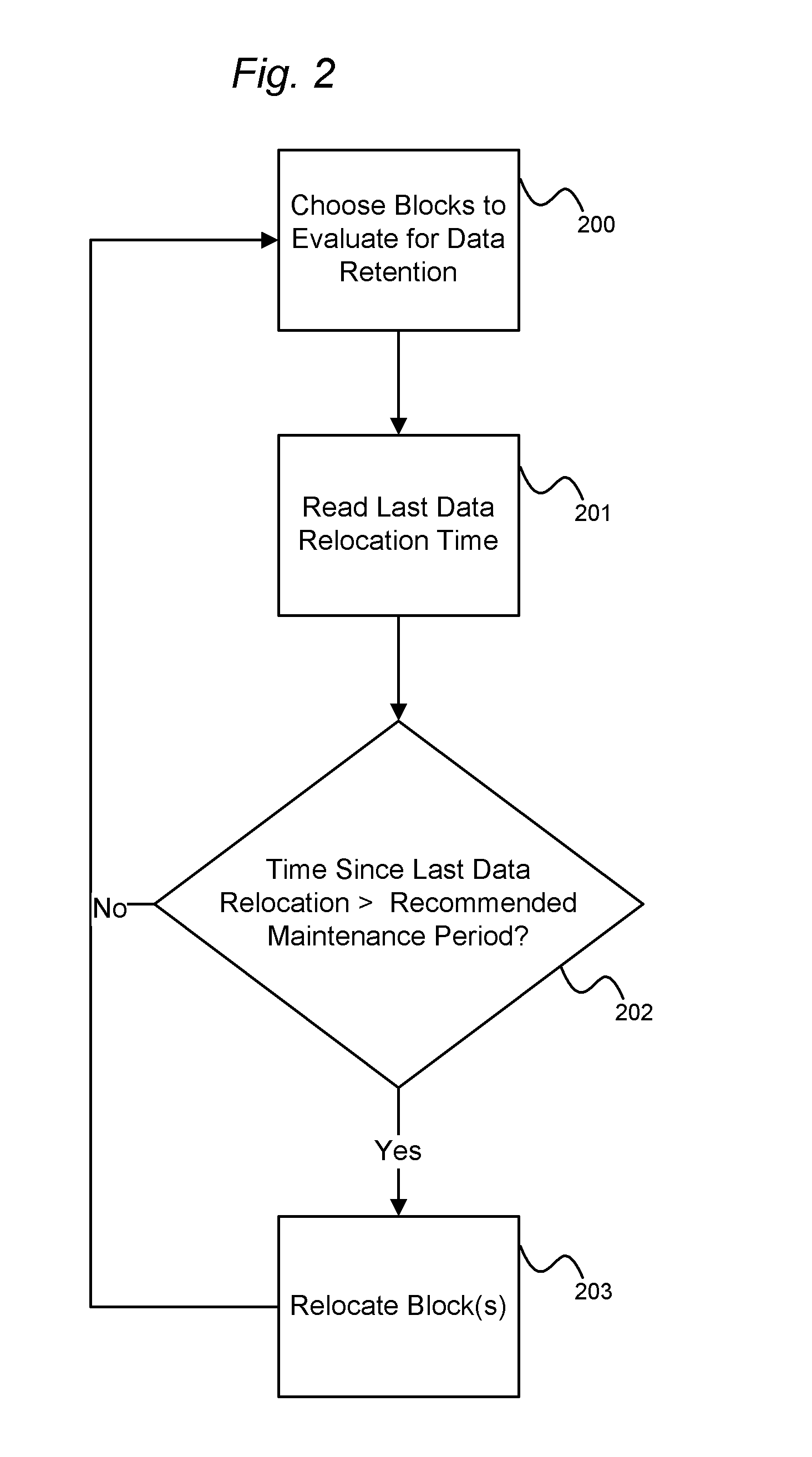
System and method for performing data retention that incorporates environmental conditions
ActiveUS20120324191A1Memory adressing/allocation/relocationReliability/availability analysisSolid-state storageIncreased risk
A solid-state storage system is described with a method for adjusting the frequency of data retention operations. The data retention operation frequency can be increased or decreased according to a variety of environmental factors such as error code frequency, system temperature, altitude, and other operating conditions. These factors can indicate an increased or decreased risk of failure and accordingly provide increased or decreased rates of data retention operations.
Owner:WESTERN DIGITAL TECH INC
Drift compensation in a flash memory
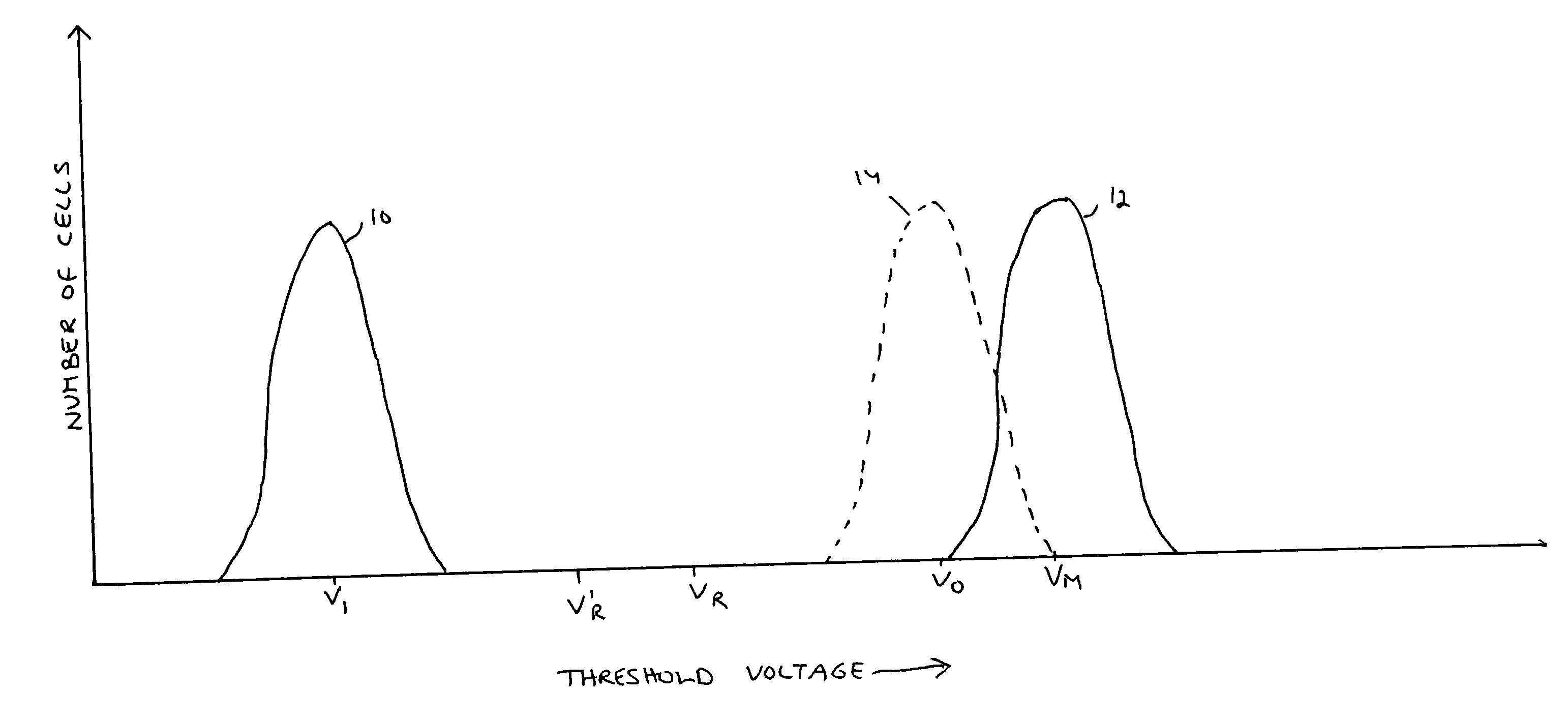
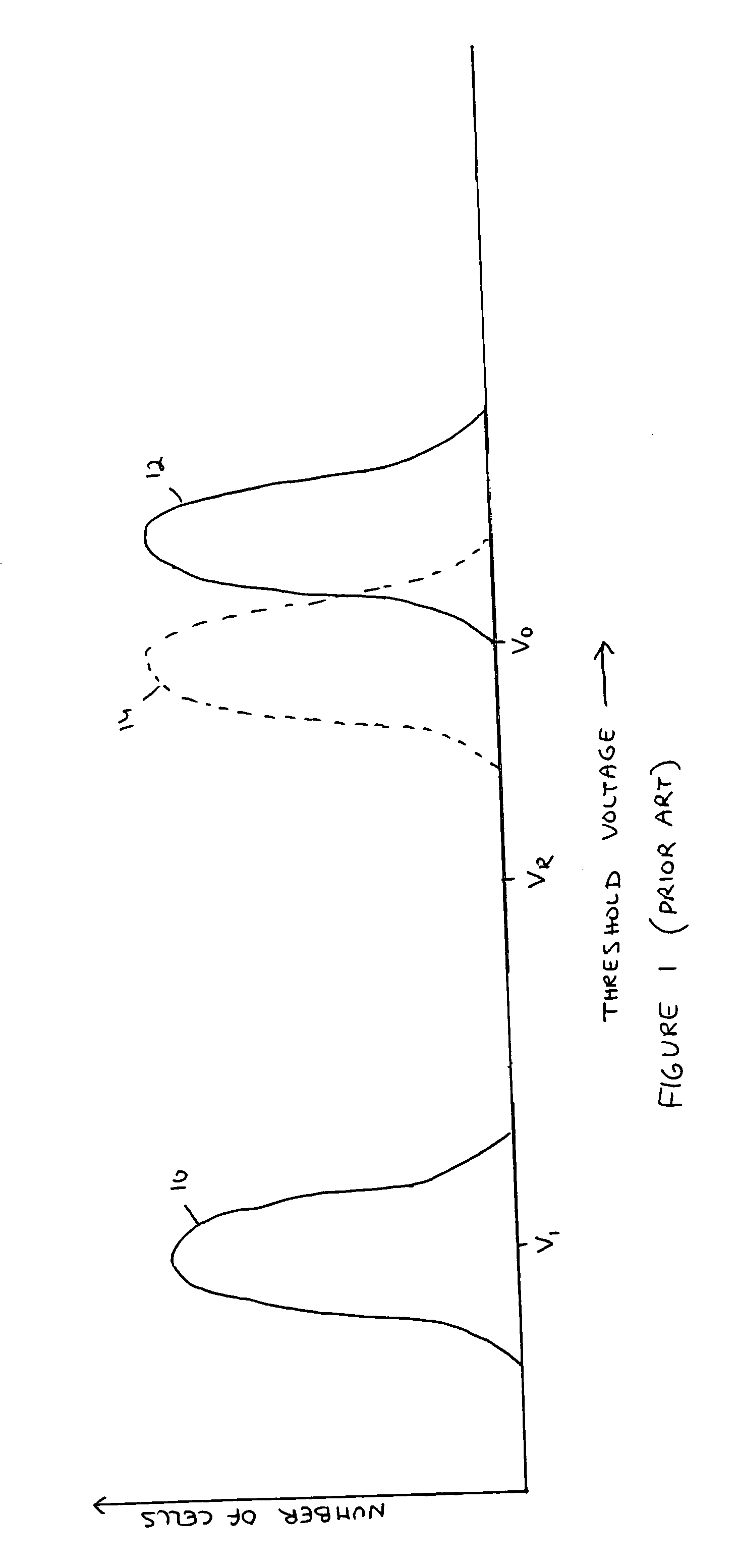
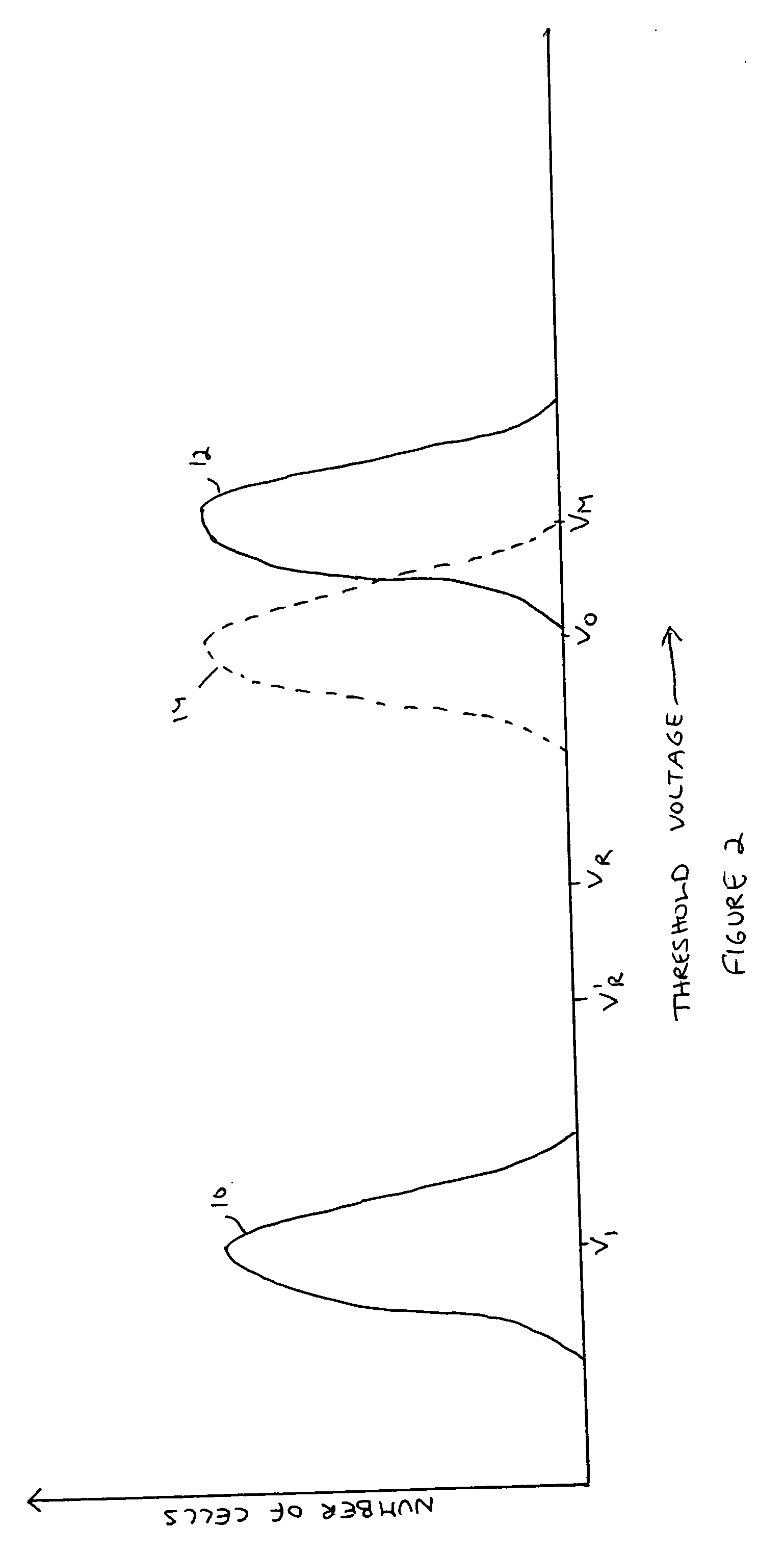
A plurality of memory cells are managed by obtaining values of one or more environmental parameters of the cells and adjusting values of one or more reference voltages of the cells accordingly. Alternatively, a statistic of at least some of the cells, relative to a single reference parameter that corresponds to a control parameter of the cells, is measured, and the value of the reference voltage is adjusted accordingly. Examples of environmental parameters include program-erase cycle count, data retention time and temperature. Examples of reference voltages include read reference voltages and program verify reference voltages. Examples of statistics include the fraction of cells whose threshold voltages exceed initial lower bounds or initial medians.
Owner:WESTERN DIGITAL ISRAEL LTD
Memory system and method having selective ECC during low power refresh
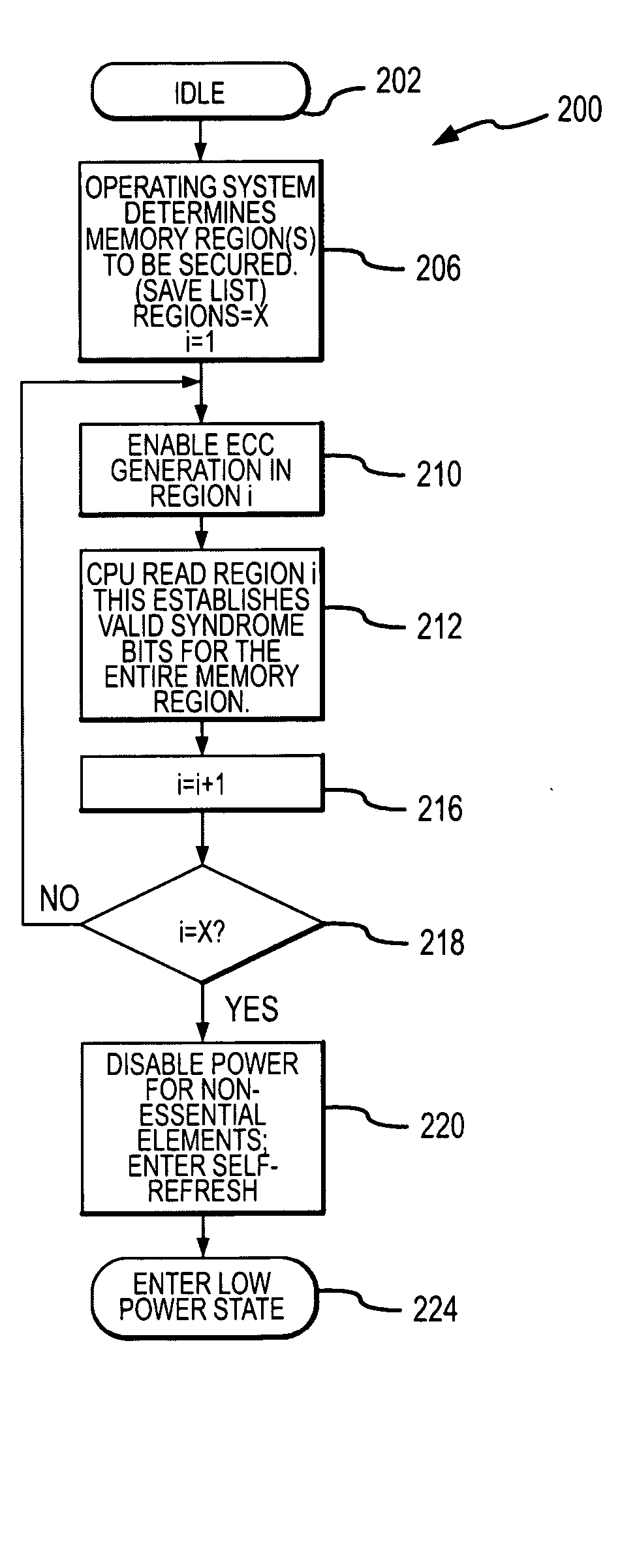
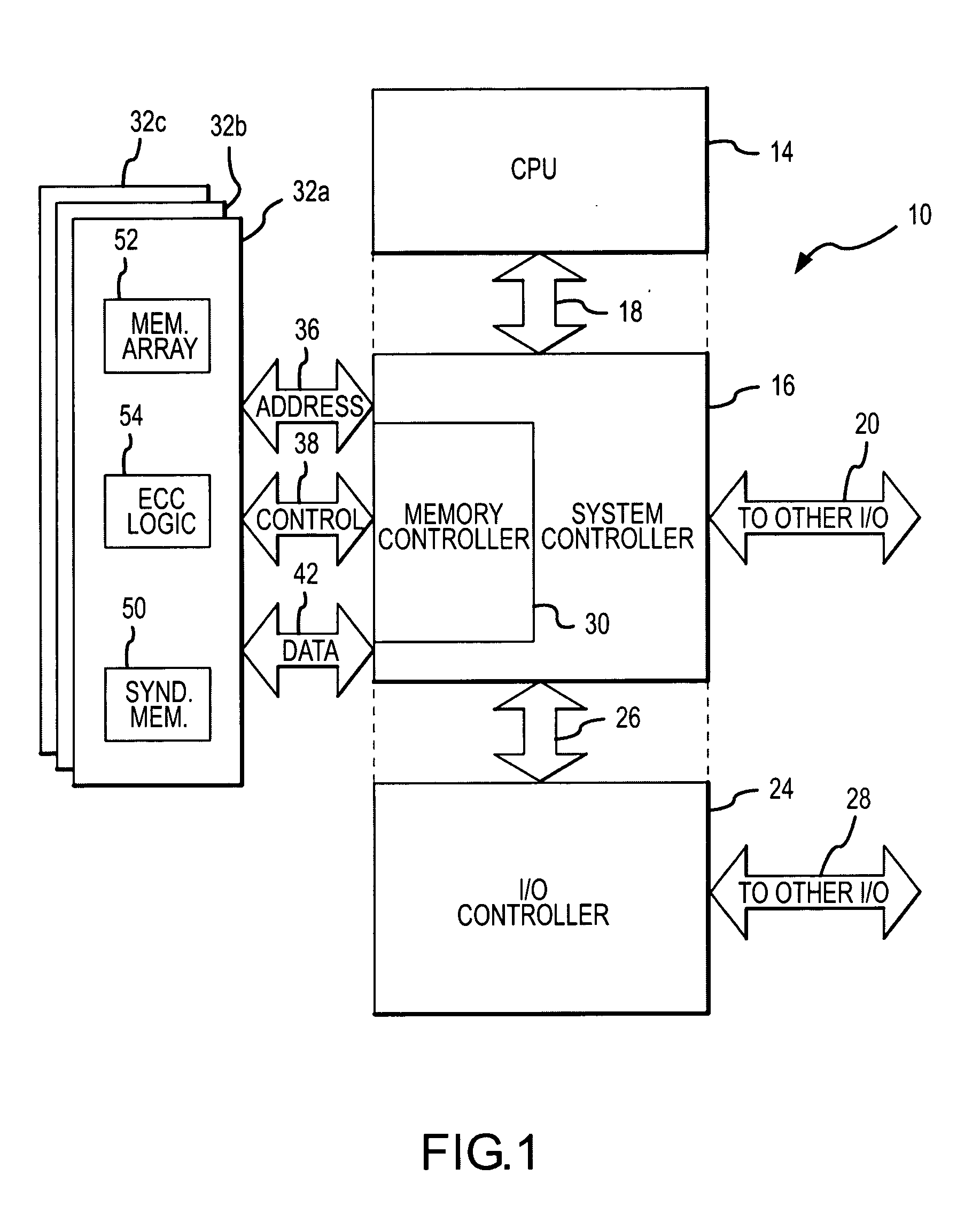
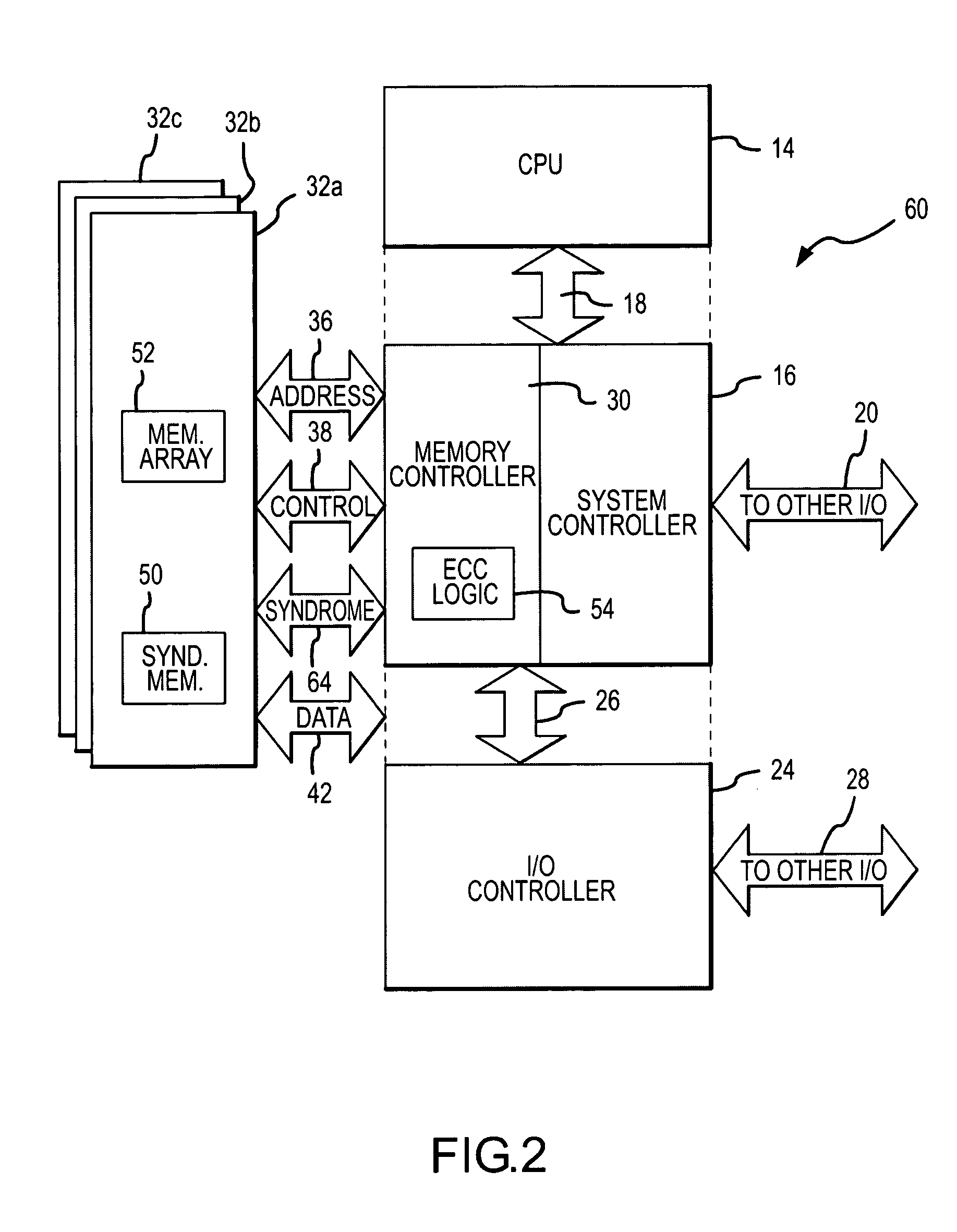
InactiveUS20060010339A1Reduced power ratingMemory loss protectionError avoidanceError checkingMemory controller
A computer system includes a processor coupled to a DRAM through a memory controller. The processor switches the DRAM to a low power refresh mode in which DRAM cells are refreshed at a sufficiently low rate that data retention errors may occur. Prior to switching the DRAM to the low power refresh mode, the processor identifies a region of an array of DRAM cells that contains essential data that needs to be protected from such data retention errors. The processor then reads data from the identified region, and either the DRAM or the memory controller generates error checking and correcting syndromes from the read data. The syndromes are stored in the DRAM, and the low power refresh mode is then entered. Upon exiting the low power refresh mode, the processor again reads the data from the identified region, and the read data is checked and corrected using the syndromes.
Owner:MICRON TECH INC
Systems and methods for nonvolatile memory performance throttling
ActiveUS20140101371A1Safe storageMemory architecture accessing/allocationError detection/correctionComputer scienceMemory performance
Systems and methods for nonvolatile memory (“NVM”) performance throttling are disclosed. Performance of an NVM system may be throttled to achieve particular data retention requirements. In particular, because higher storage temperatures tend to reduce the amount of time that data may be reliably stored in an NVM system, performance of the NVM system may be throttled to reduce system temperatures and increase data retention time.
Owner:APPLE INC
Apparatus for data retention in an implantable medical device
ActiveUS20060095091A1Physical therapies and activitiesHeart stimulatorsDevice implantImplanted device
An apparatus for storing data records associated with a medical monitoring event in a data structure. An implanted device obtains data and stores the data in the data record in a first data structure that is age-based. Before an oldest data record is lost, the oldest data record may be stored in a second data structure that is priority index-based. The priority index may be determined by a severity level and may be further determined by associated factors. The implanted device may organize, off-load, report, and / or display a plurality of data records based on an associated priority index. Additionally, the implanted device may select a subset or composite of physiologic channels from the available physiologic channels based on a selection criterion.
Owner:MEDTRONIC INC
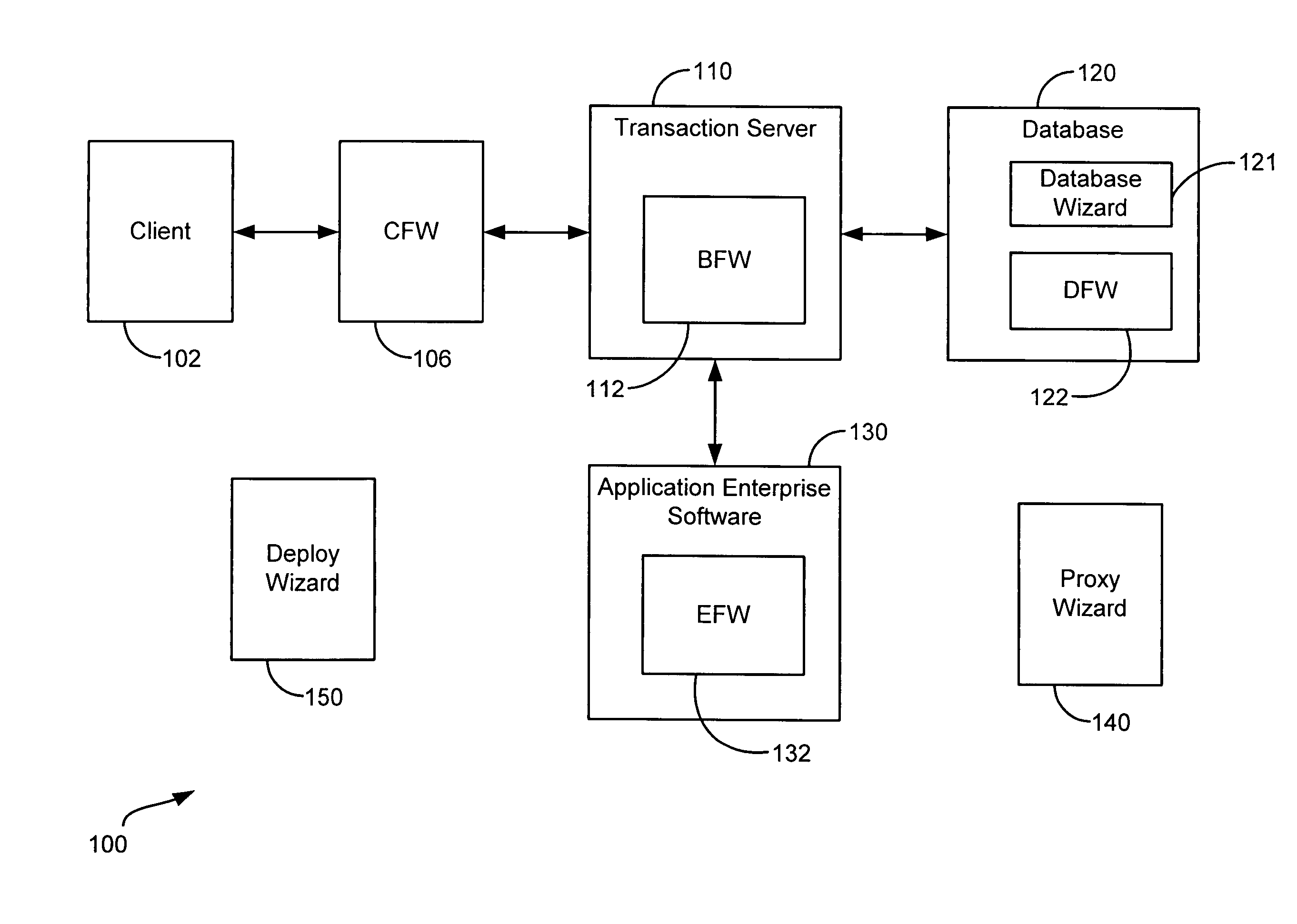
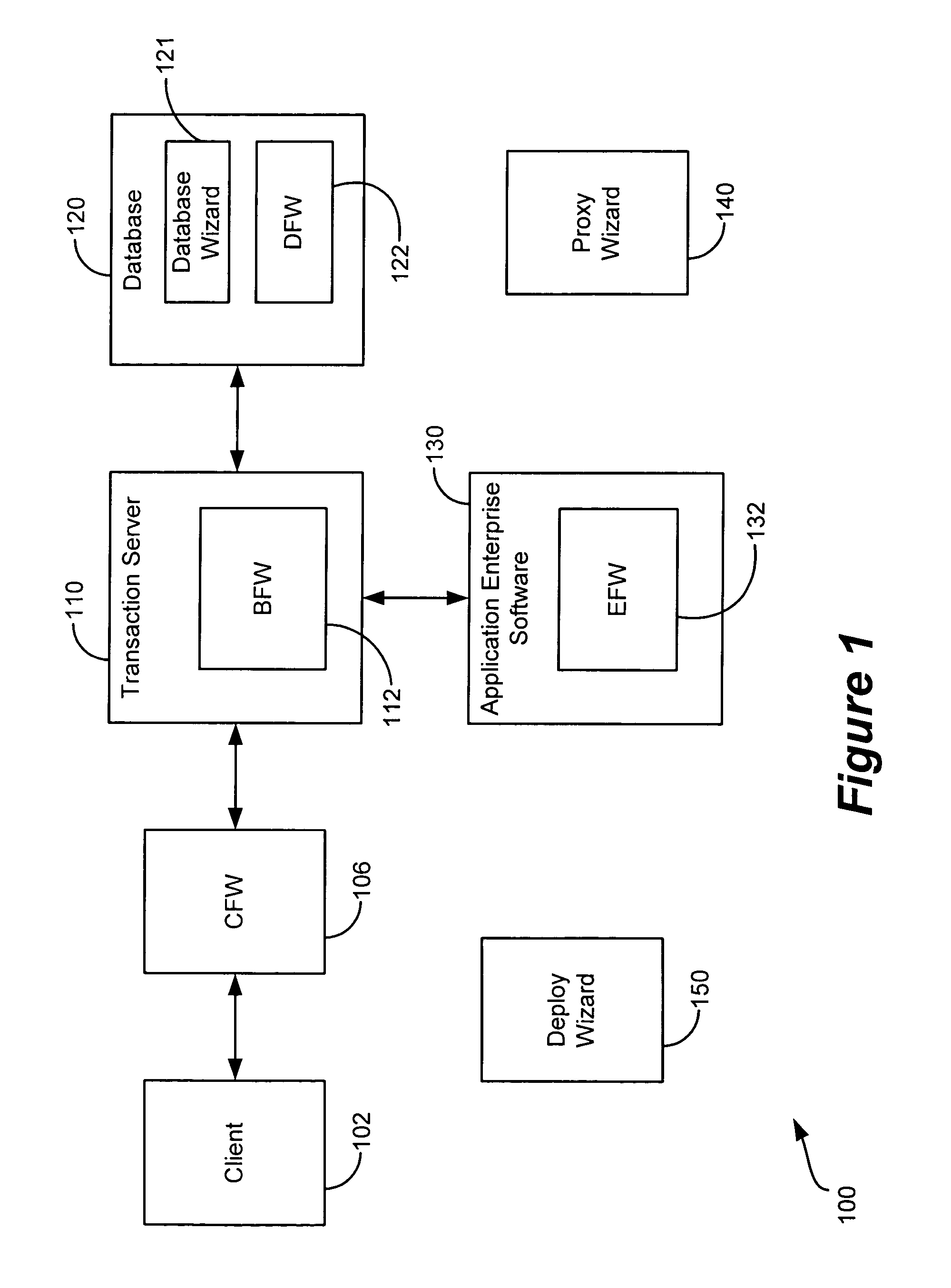
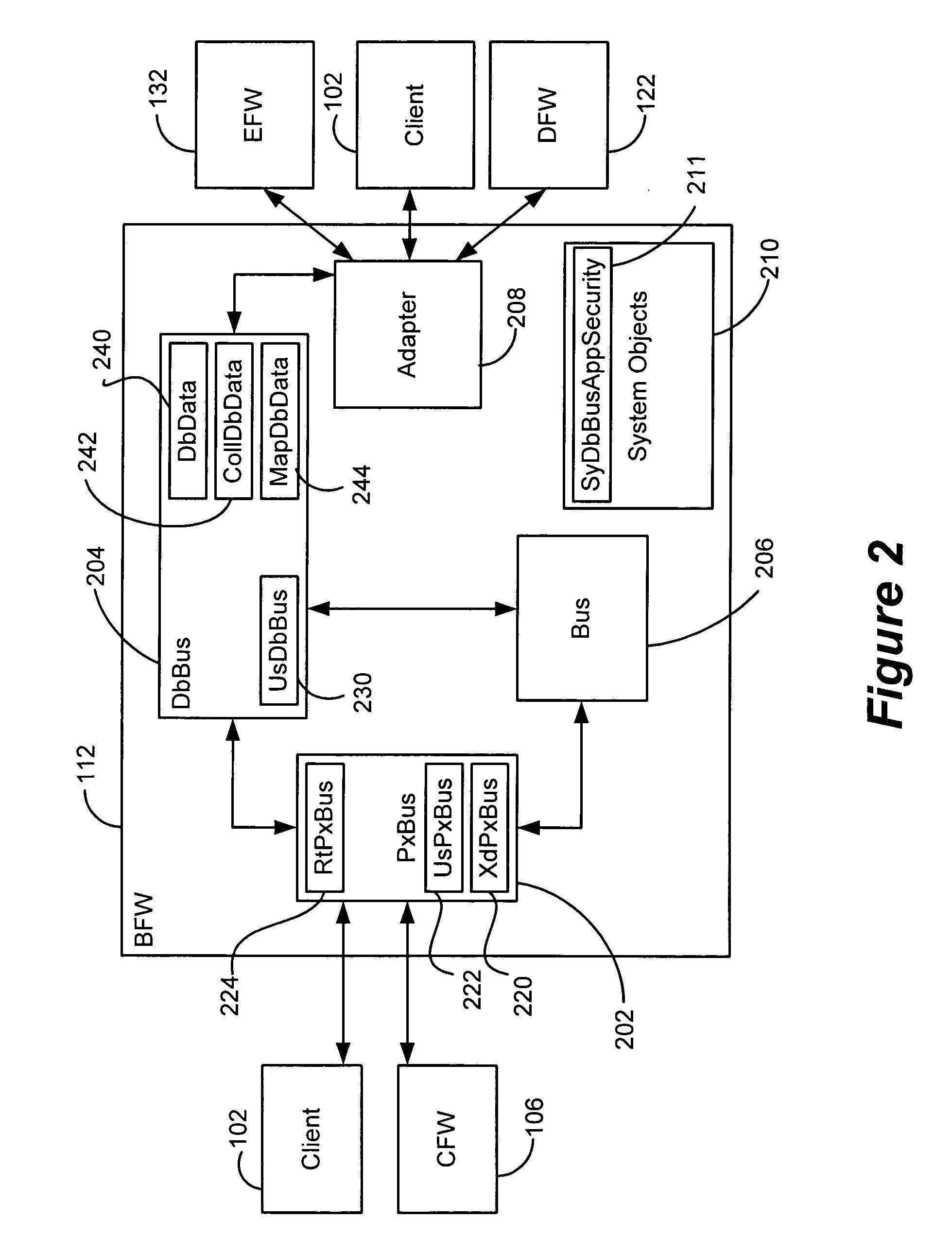
Generic framework for applying object-oriented models to multi-tiered enterprise applications
A system and method are provided for the structured, rapid development and deployment of software components that together, would constitute a robust multi-tiered enterprise software application. Four sub-components are provided for handling various aspects of the business objects. A client framework is used to interact with client users and client software processes. A database framework is used to handle data retention and search functions. An external framework is used to interact with software processes that are outside the gambit of the present system. Finally, a business framework is used to operate the business objects themselves. The business framework can be configured under the services of a transaction server.
Owner:MARATHON PETROLEUM
System and method for performing data retention that incorporates environmental conditions
A solid-state storage system is described with a method for adjusting the frequency of data retention operations. The data retention operation frequency can be increased or decreased according to a variety of environmental factors such as error code frequency, system temperature, altitude, and other operating conditions. These factors can indicate an increased or decreased risk of failure and accordingly provide increased or decreased rates of data retention operations.
Owner:WESTERN DIGITAL TECH INC
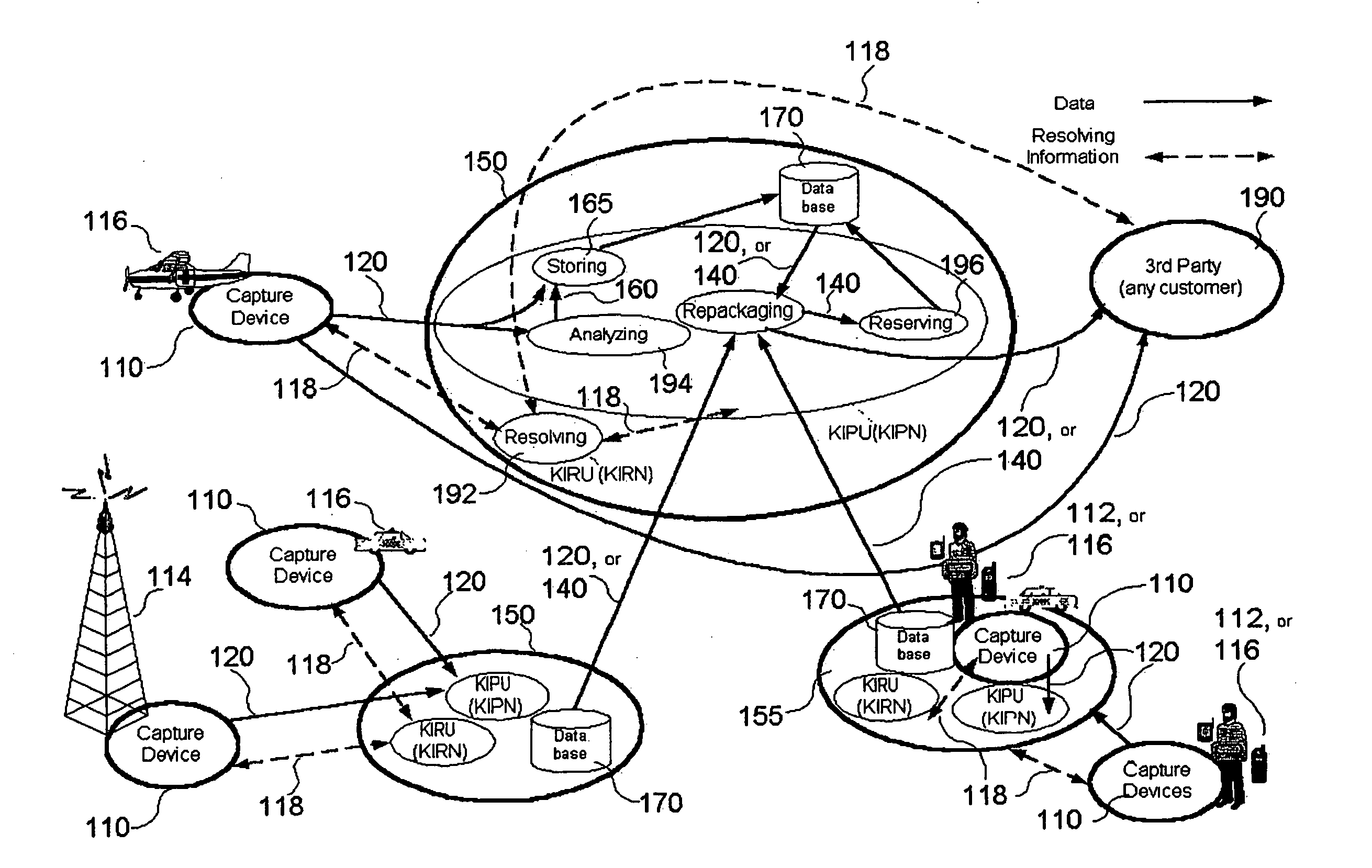
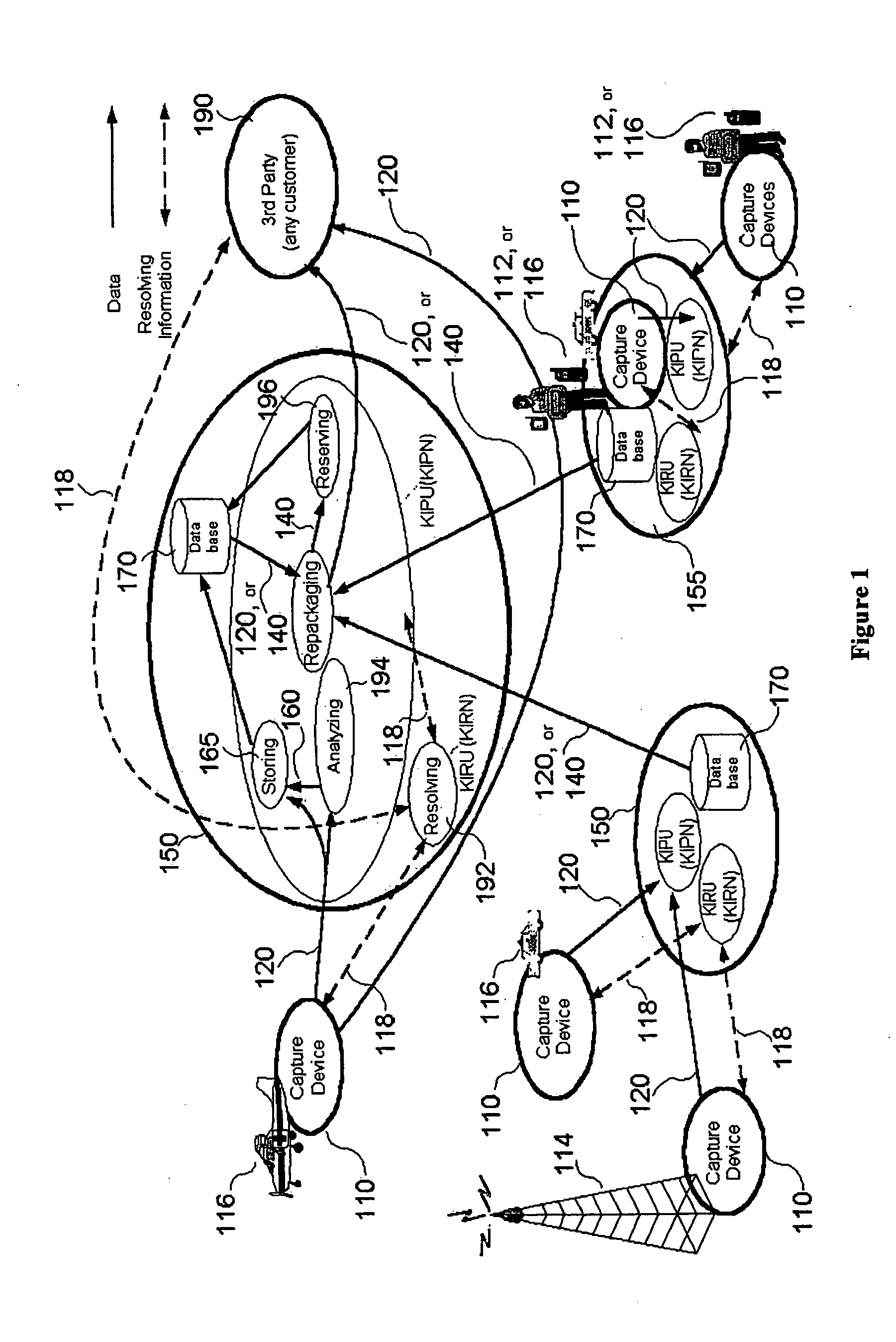
Collecting, analyzing, consolidating, delivering and utilizing data relating to a current event
InactiveUS20060168185A1Road vehicles traffic controlDigital computer detailsThird partyAffected site
Arrangements for collecting, analyzing, consolidating and delivering consolidated and enhanced data from a plurality of sources relating to a current event, to a third party, and reserving the consolidated and enhanced data for internal use so as to create a commercial proactive emergency management and disaster response information system that can also be used for emergent commercial purposes. A data capture device associated with an individual or a location captures data related to a current event or affected site. Incoming data may include raw data, repackaged data, or value-added data from source inputs. Captured data is sent to a centralized command center or distributed command centers where it is analyzed, resolved, correlated and repackaged for use by other parties.
Owner:KOYO MUSEN CORP
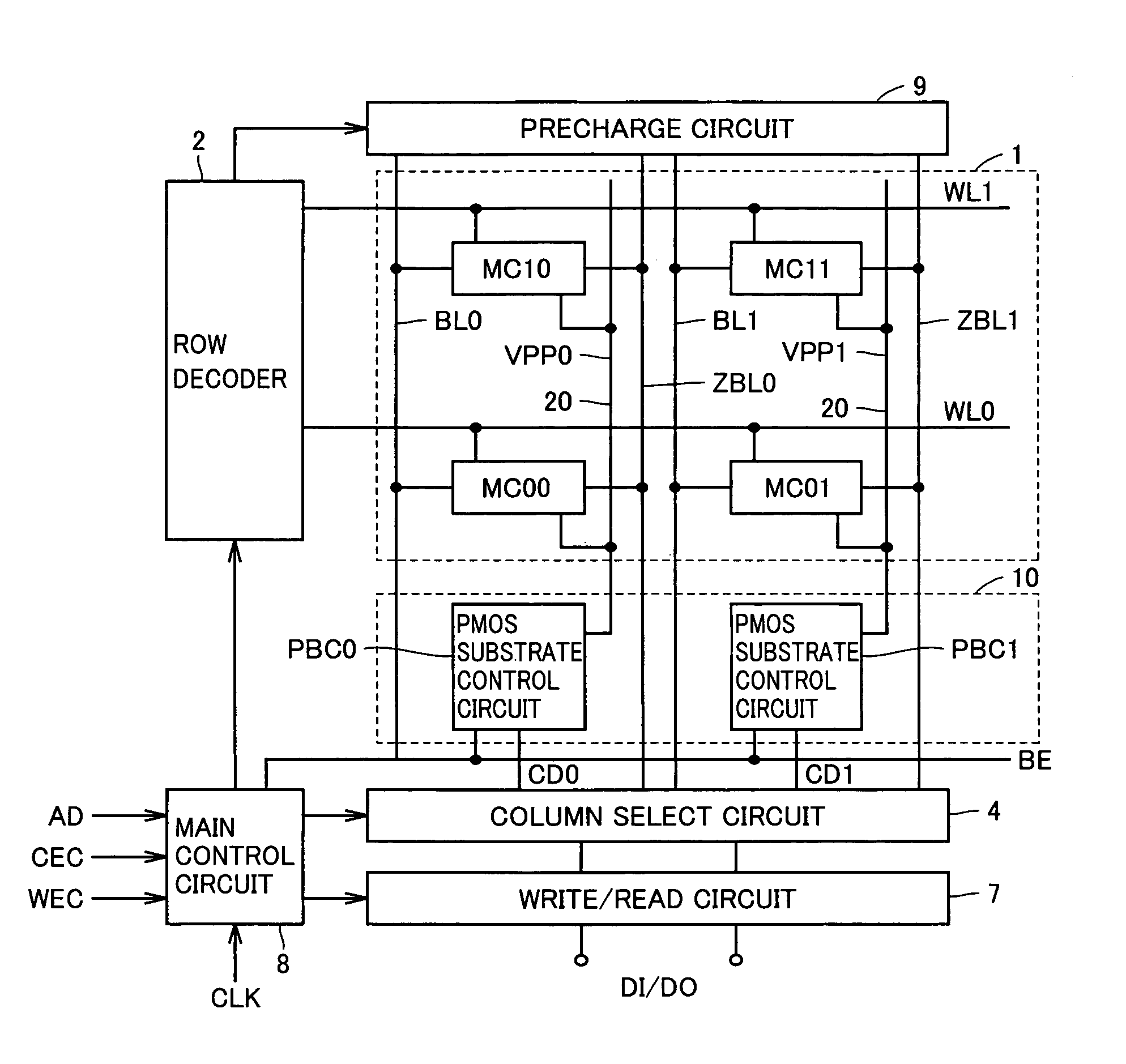
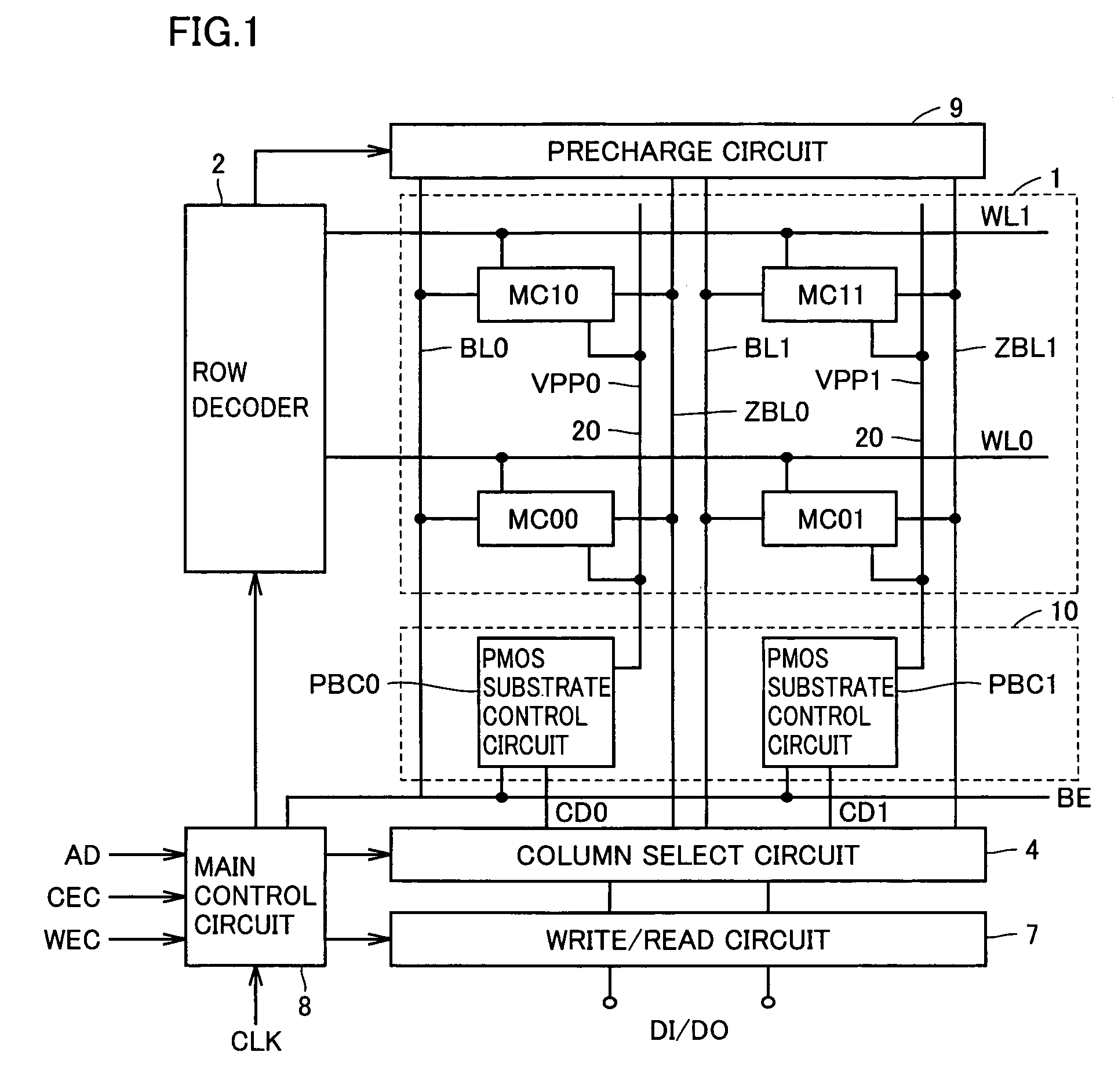
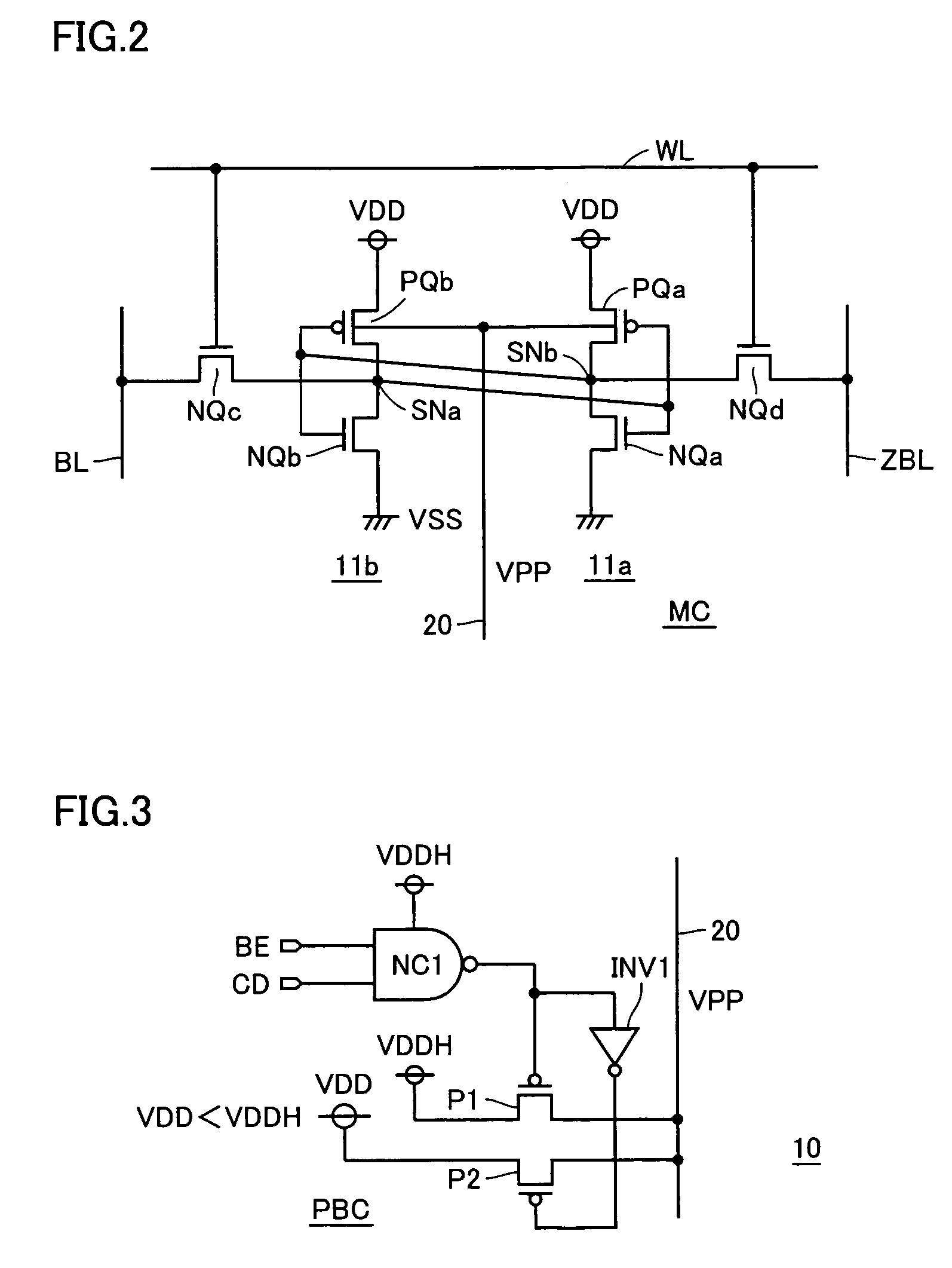
Semiconductor memory device with back gate potential control circuit for transistor in memory cell
ActiveUS7079413B2High-speed and stable data readingHigh-speed and stable and writingTransistorSolid-state devicesEngineeringStatic noise margin
A substrate potential setting circuits are provided which control substrate potentials in units of columns of a memory cell array at least in data writing. Upon data writing, the potential of the substrate region of memory cell transistors on a selected column is changed to reduce the data holding characteristics (static noise margin) to ensure high-speed data writing to the memory cells. Data writing is performed at high speed without impairing stability of data retention.
Owner:RENESAS ELECTRONICS CORP
System and Method for Improving Performance of Data Container Backups
ActiveUS20110208928A1Improve performanceImprove efficiencyMemory loss protectionError detection/correctionComputer scienceData retention
Owner:CA TECH INC
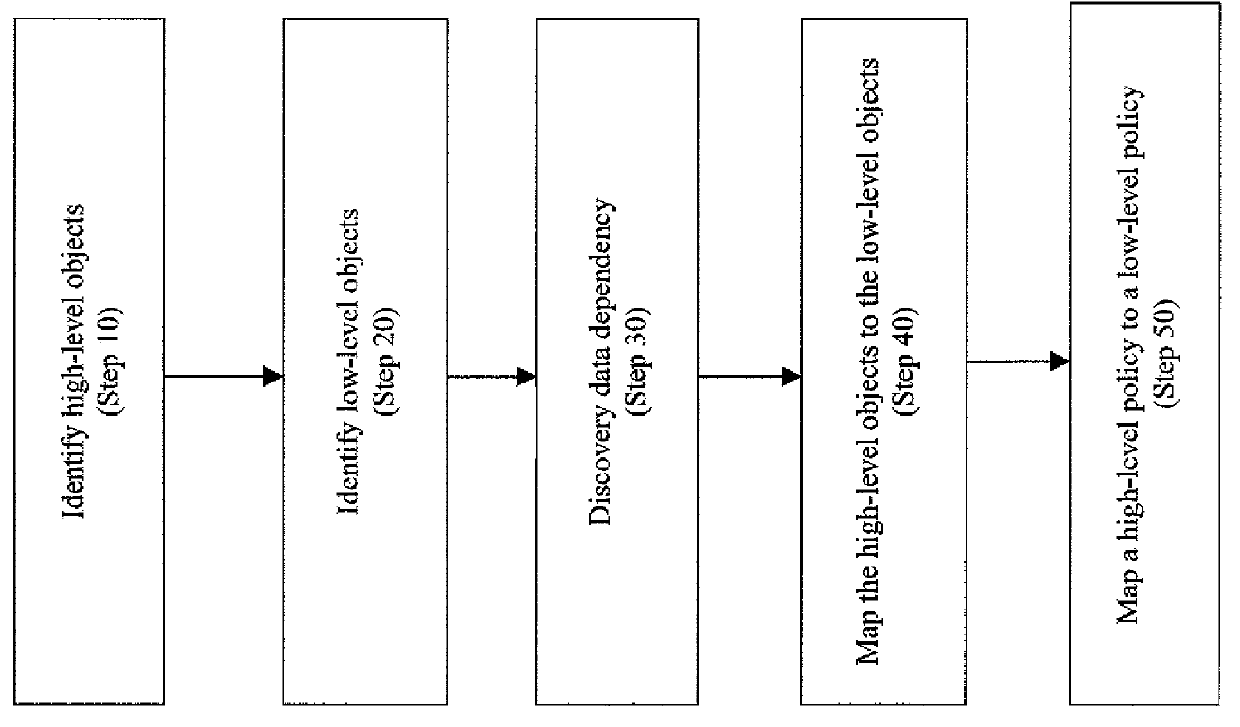
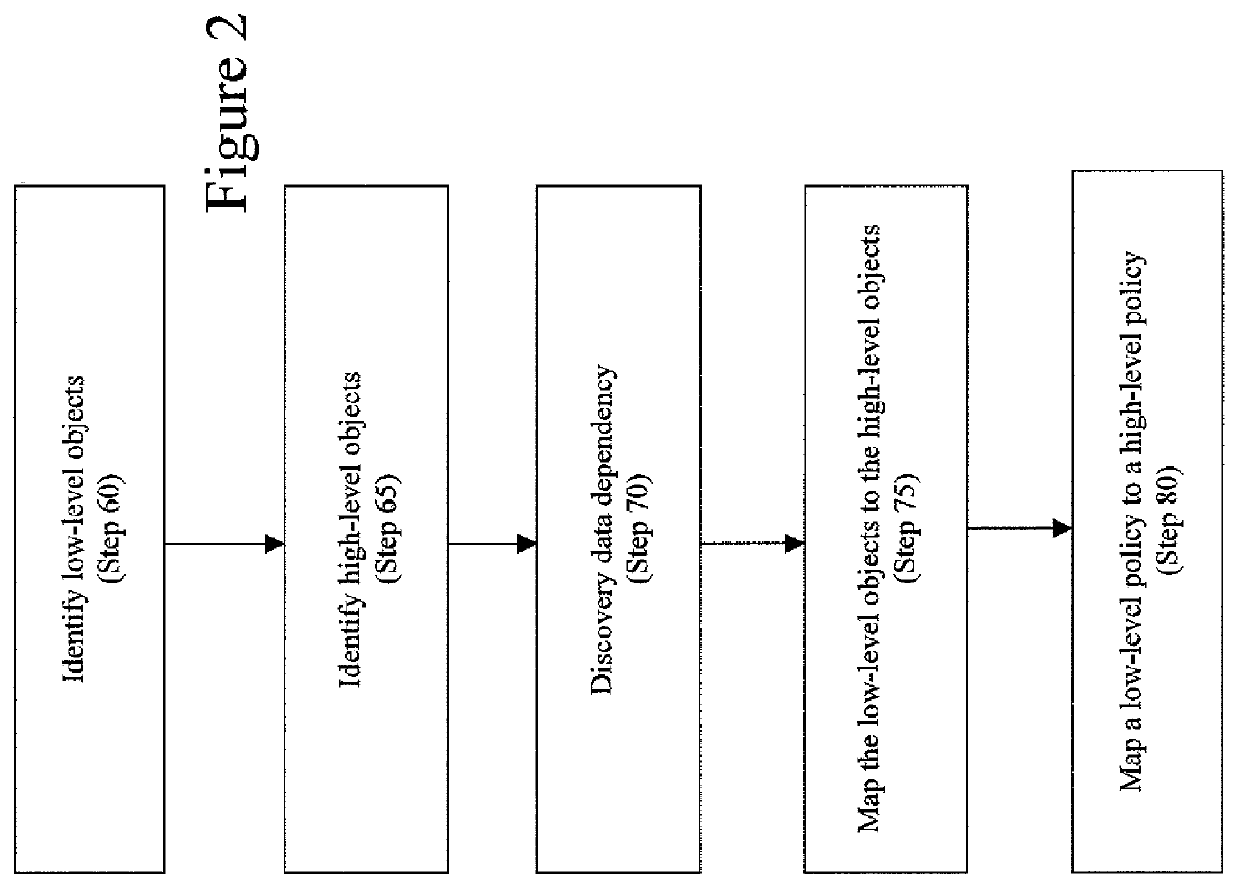
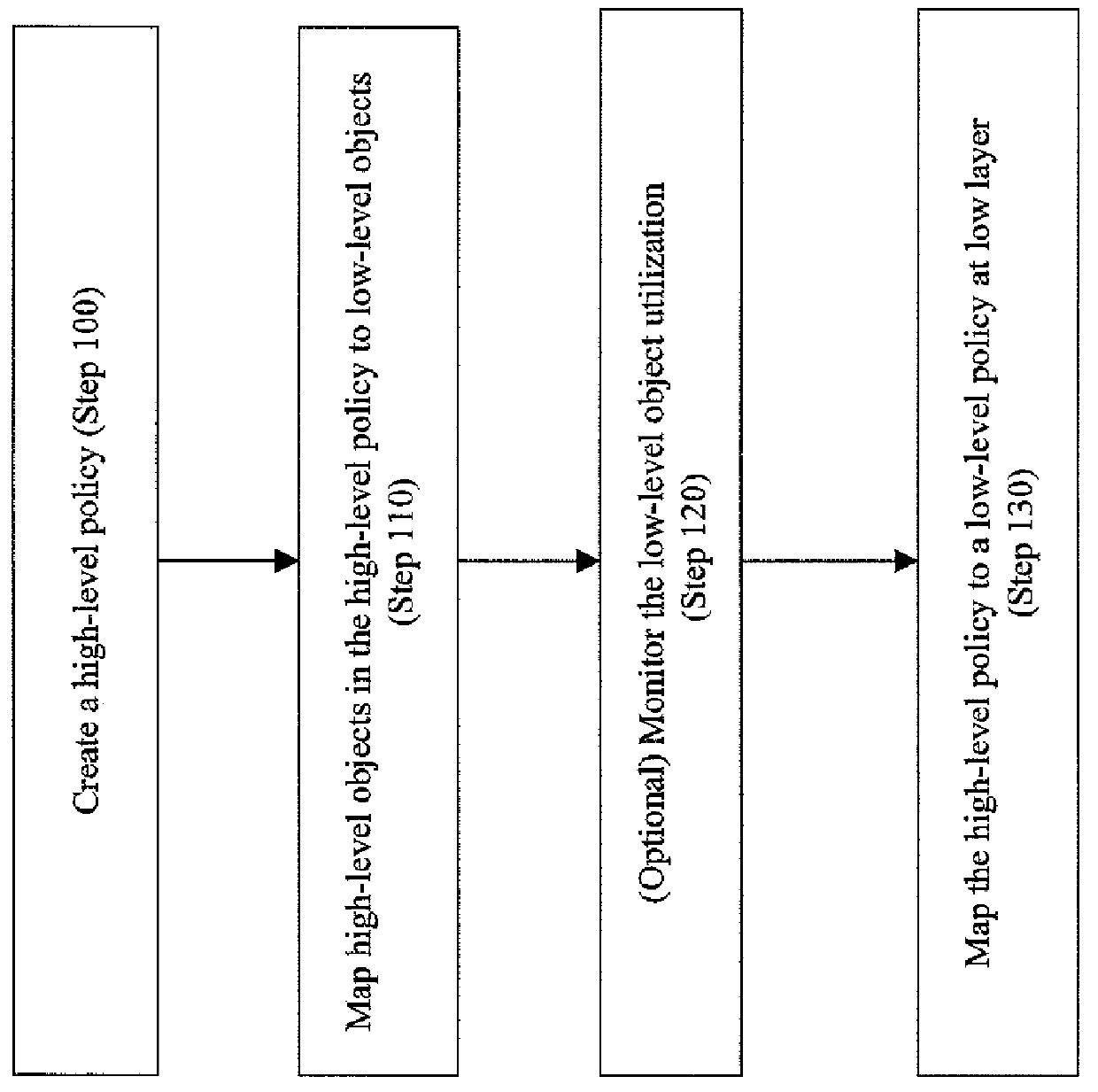
Method to automatically map business function level policies to it management policies
A method, system, computer program product, and computer program storage device for transforming a high-level policy associated with a high layer to a low-level policy associated with a low layer. Mapping between high-level objects in a high layer and low-level objects in a low layer is derived by an automated discovery tool. The high-level policy is mapped to the low-level policy according to the mapping (e.g., by substituting the high-level objects with the low-level objects and by performing a syntax transformation). In one embodiment, a low-level policy is transformed to a high-level policy according to the mapping. As exemplary embodiments, policy transformations in traffic shaping and data retention are disclosed.
Owner:INT BUSINESS MASCH CORP
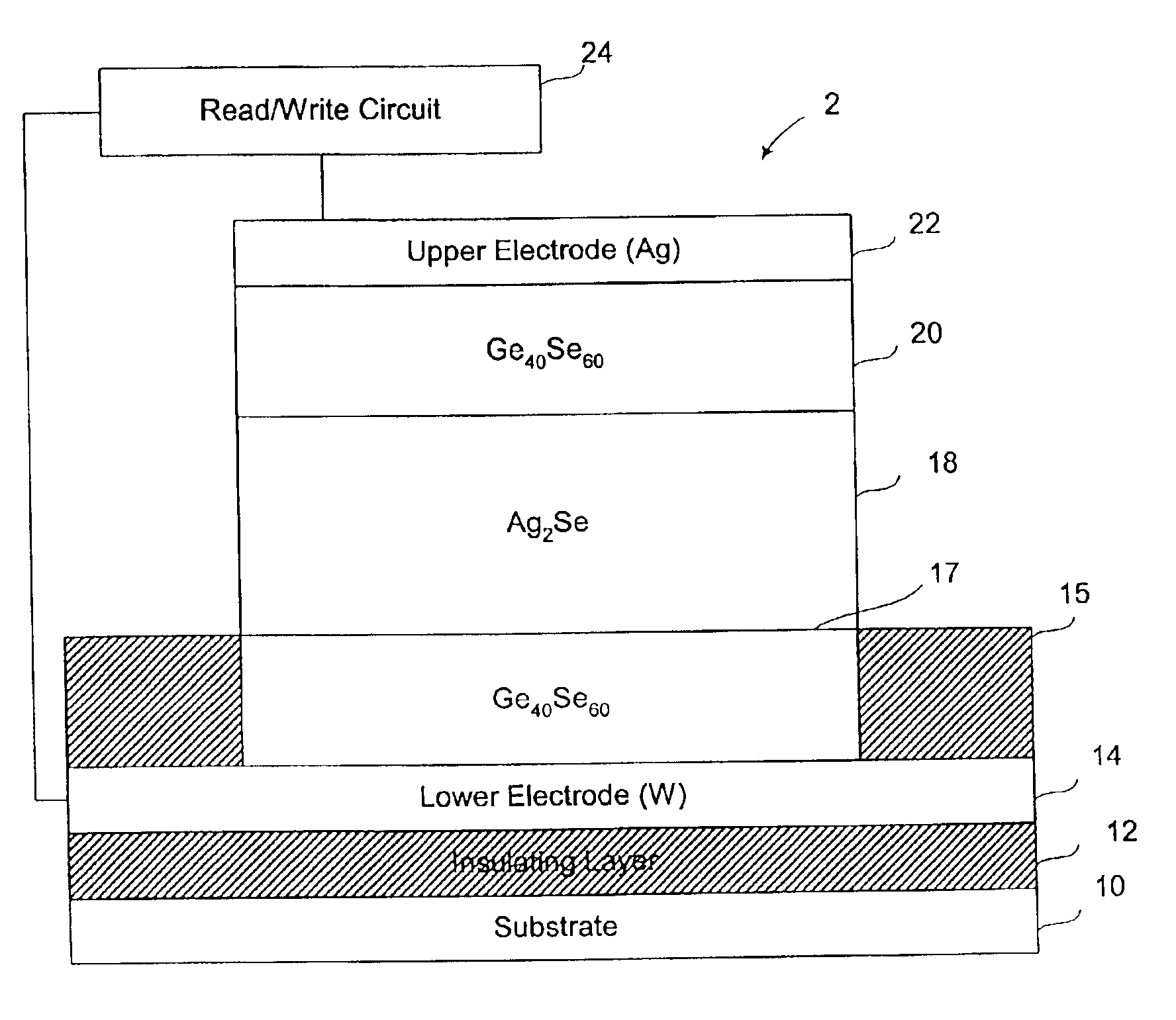
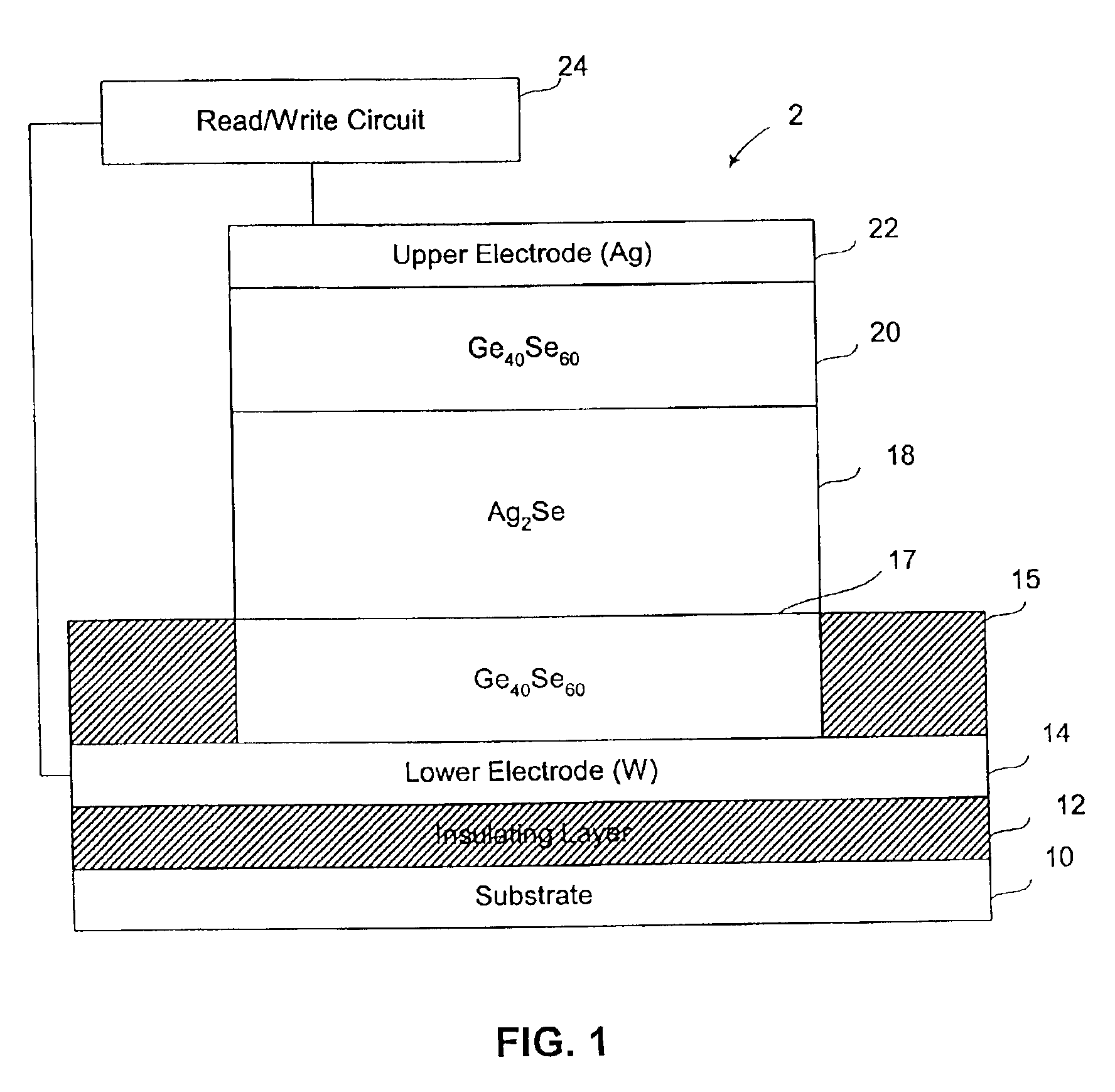
Silver-selenide/chalcogenide glass stack for resistance variable memory
InactiveUS7151273B2Solid-state devicesSemiconductor/solid-state device manufacturingComputer hardwareSulfur
The invention is related to methods and apparatus for providing a resistance variable memory element with improved data retention and switching characteristics. According to an embodiment of the invention a resistance variable memory element is provided having at least one silver-selenide layer in between glass layers, wherein at least one of the glass layers is a chalcogenide glass, preferably having a GexSe100−x composition.
Owner:MICRON TECH INC
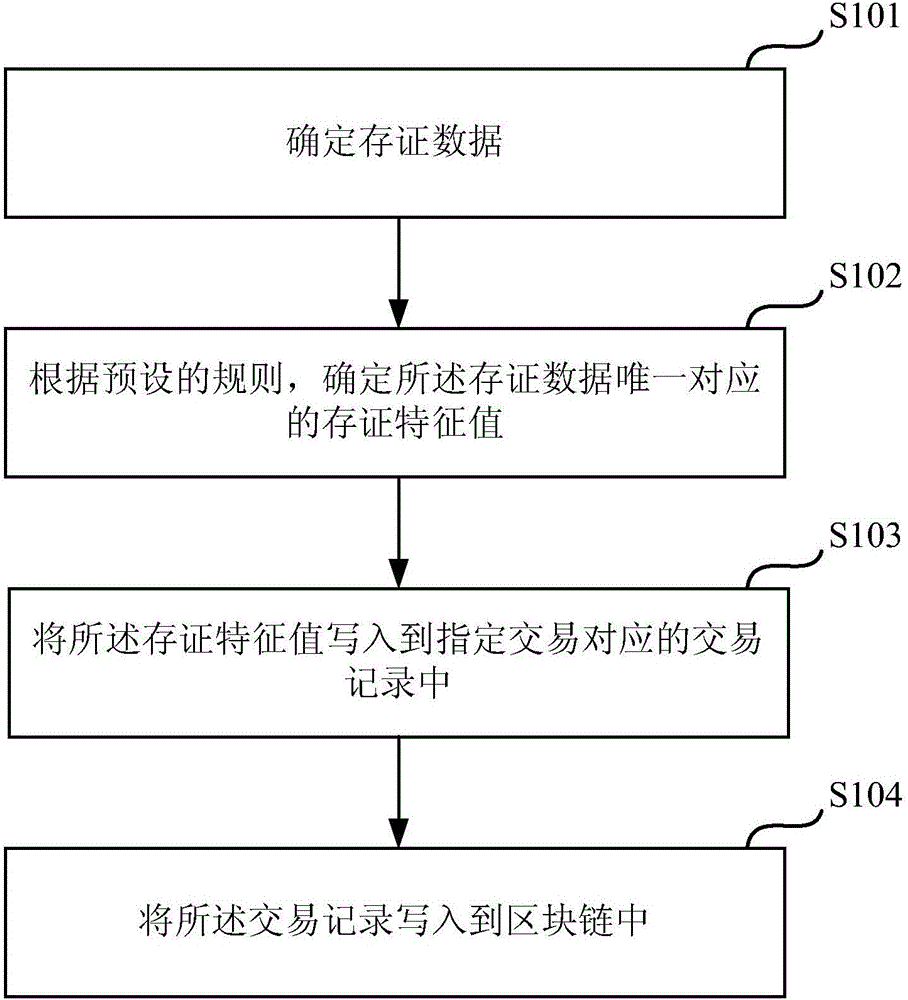
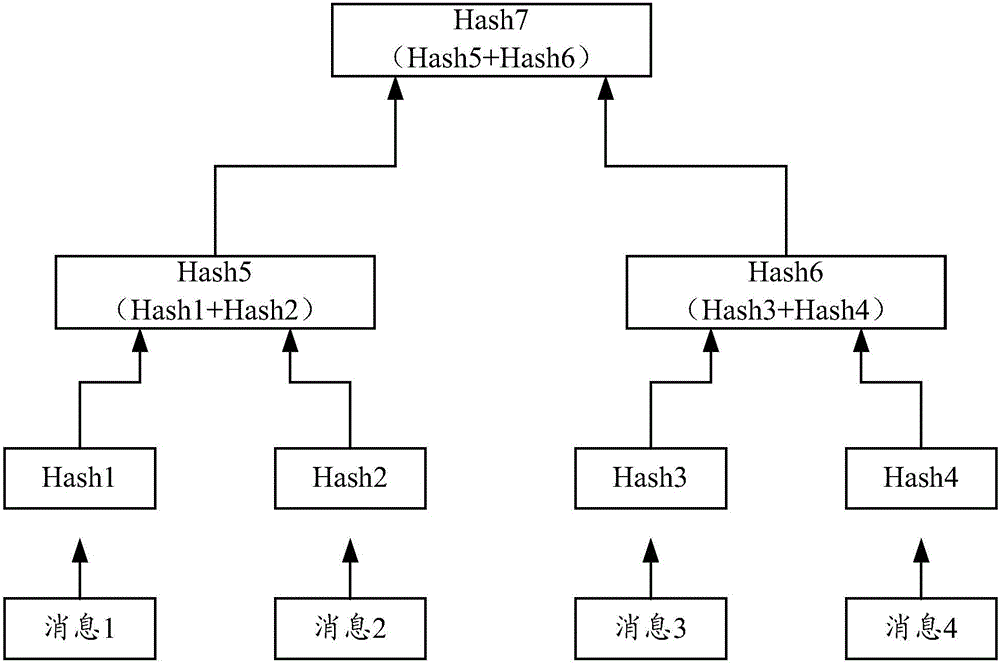
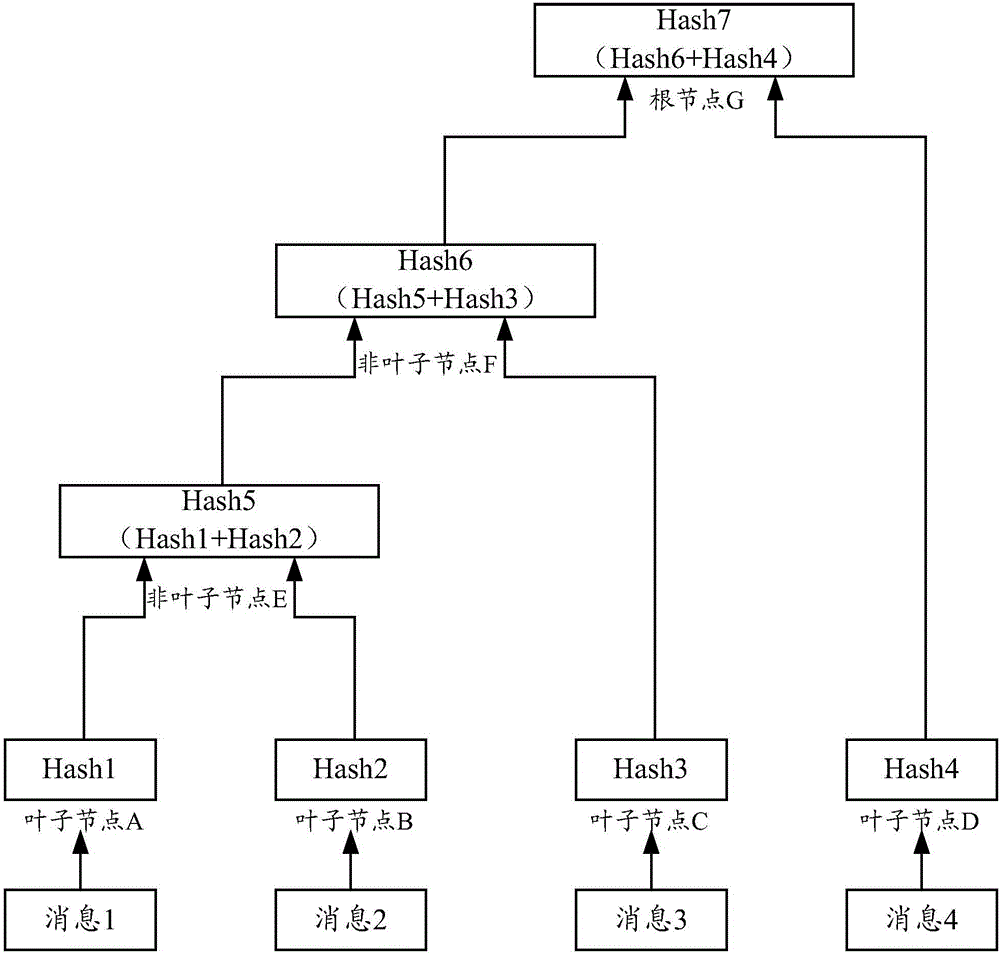
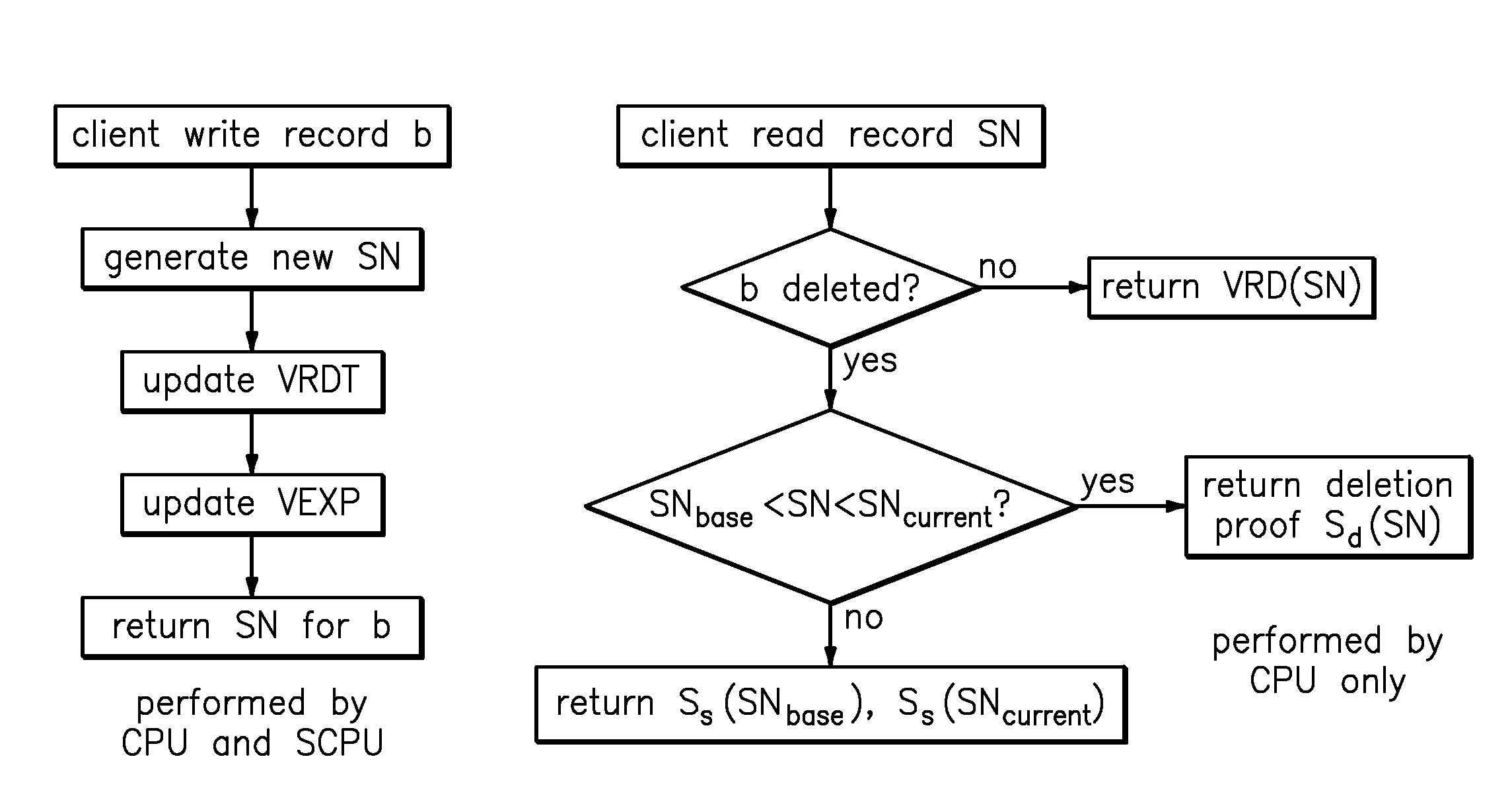
Data retention and verification method and device
InactiveCN106548091AGuaranteed reliabilityRealization of certificate depositDigital data protectionIndividual entry/exit registersData validationSource Data Verification
Embodiments of the invention provide a data retention and verification method and device. The method comprises the following steps of: determining a retention characteristic value uniquely corresponding to retention data by a server according to a preset rule, writing the retention characteristic value into a transaction record of an appointed transaction, and writing the transaction record into a block chain to be stored; when the server verifies verification data, determining a to-be-verified characteristic value uniquely corresponding to the verification data according to the previously adopted manner, and comparing the to-be-verified characteristic value with the retention characteristic value stored in the transaction record of the block chain so as to verify the verification data. Through the method, the data stored in the block chain is unchangeable, and the server can attach the retention characteristic value uniquely corresponding to the retention data into the transaction record to be stored in the block chain, so that the reliability of the retention characteristic value is ensured, and the reliability of carrying out data verification on the verification data by the server through the retention characteristic value is further ensured.
Owner:北京爱接力科技发展有限公司
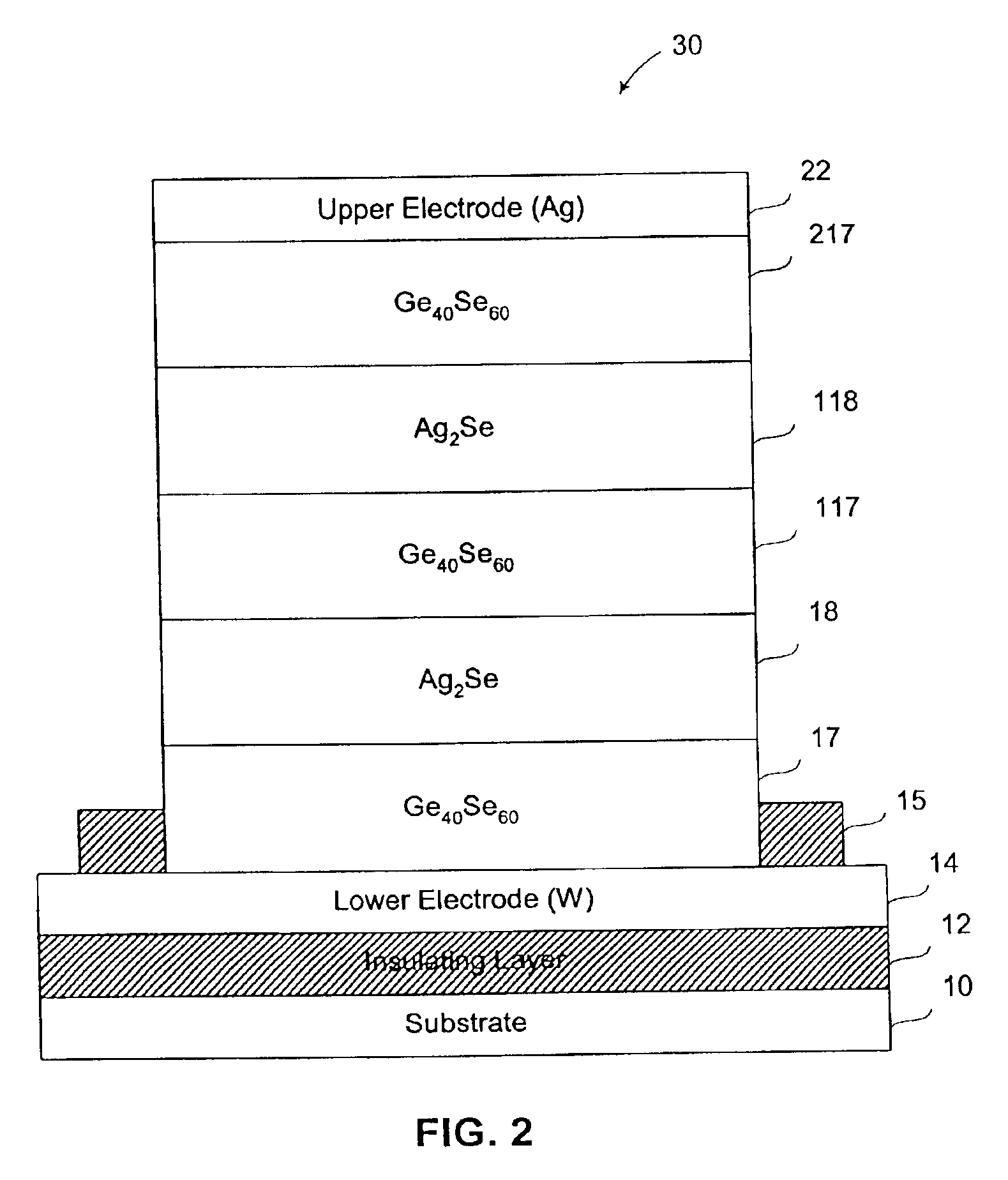
Single-polarity programmable resistance-variable memory element
A resistance variable memory element with improved data retention and switching characteristics switched between resistance memory states upon the application of write pulses having the same polarity. The resistance variable memory element can be provided having at least one silver-selenide layer in between glass layers, the glass layers are a chalcogenide glass having a GexSe100−x composition.
Owner:OVONYX MEMORY TECH LLC
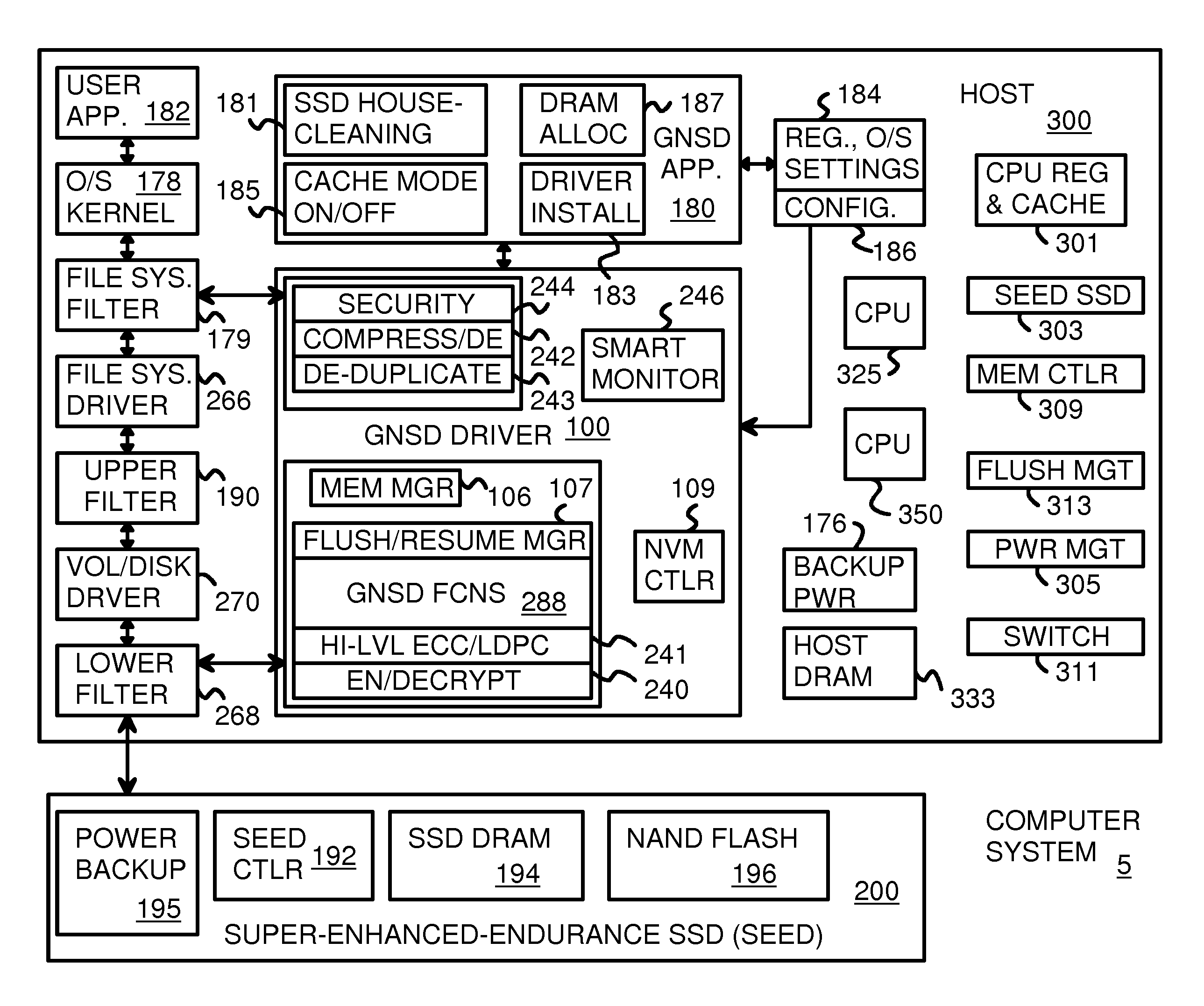
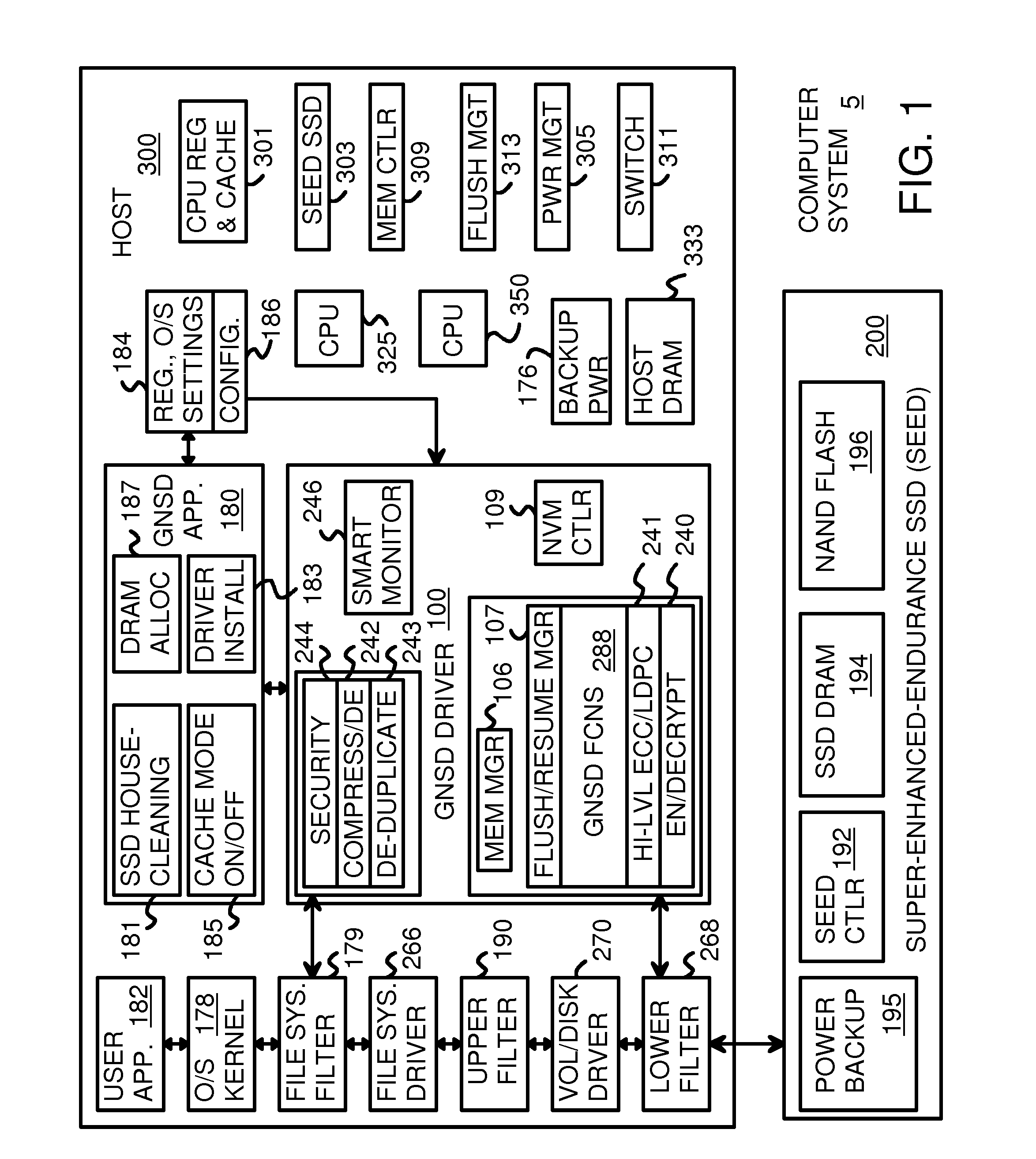
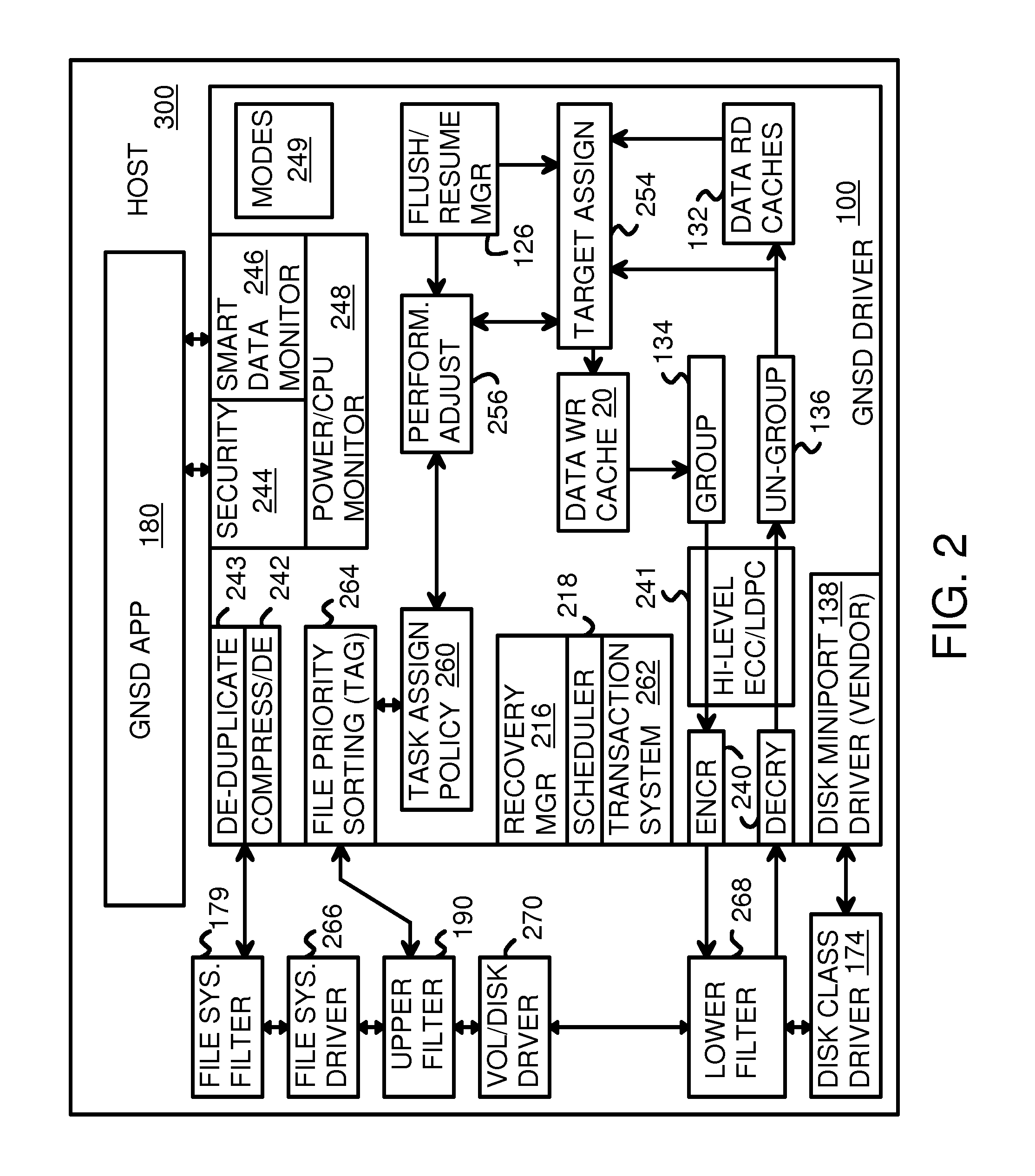
Data-Retention Controller/Driver for Stand-Alone or Hosted Card Reader, Solid-State-Drive (SSD), or Super-Enhanced-Endurance SSD (SEED)
ActiveUS20160070474A1Memory architecture accessing/allocationInput/output to record carriersSolid-state driveCard reader
A Green NAND SSD Driver (GNSD) driver executes on a host to increase data-retention of flash memory attached to a Super Enhanced Endurance Device (SEED) or Solid-State Drive (SSD). Host accesses to flash are intercepted by the GNSD driver using upper and lower-level filter drivers. A retention-check timer causes a retention routine to be periodically executed. The routine sends high-level commands to the SEED that causes the SEED to refresh either all data or just data blocks with older write dates. Data is refreshed by moving to a new physical block. The retention routine can track write dates of logical blocks and command a SSD to move logical blocks with older write dates. A retention card has a controller that performs the retention routine when not connected to a host, while a SEED power card allows the SEED to refresh data when no host is attached to the SEED.
Owner:SUPER TALENT TECH CORP
Low-power band-gap reference and temperature sensor circuit
InactiveUS6876250B2Short refresh cycle timeIncrease temperatureSemiconductor/solid-state device detailsThermometers using electric/magnetic elementsLow voltageMicroprocessor
A combined low-voltage, low-power band-gap reference and temperature sensor circuit is provided for providing a band-gap reference parameter and for sensing the temperature of a chip, such as an eDRAM memory unit or CPU chip, using the band-gap reference parameter. The combined sensor circuit is insensitive to supply voltage and a variation in the chip temperature. The power consumption of both circuits, i.e., the band-gap reference and the temperature sensor circuits, encompassing the combined sensor circuit is less than one μW. The combined sensor circuit can be used to monitor local or global chip temperature. The result can be used to (1) regulate DRAM array refresh cycle time, e.g., the higher the temperature, the shorter the refresh cycle time, (2) to activate an on-chip or off-chip cooling or heating device to regulate the chip temperature, (3) to adjust internally generated voltage level, and (4) to adjust the CPU (or microprocessor) clock rate, i.e., frequency, so that the chip will not overheat. The combined band-gap reference and temperature sensor circuit of the present invention can be implemented within battery-operated devices having at least one memory unit. The low-power circuits of the sensor circuit extend battery lifetime and data retention time of the cells of the at least one memory unit.
Owner:GLOBALFOUNDRIES INC
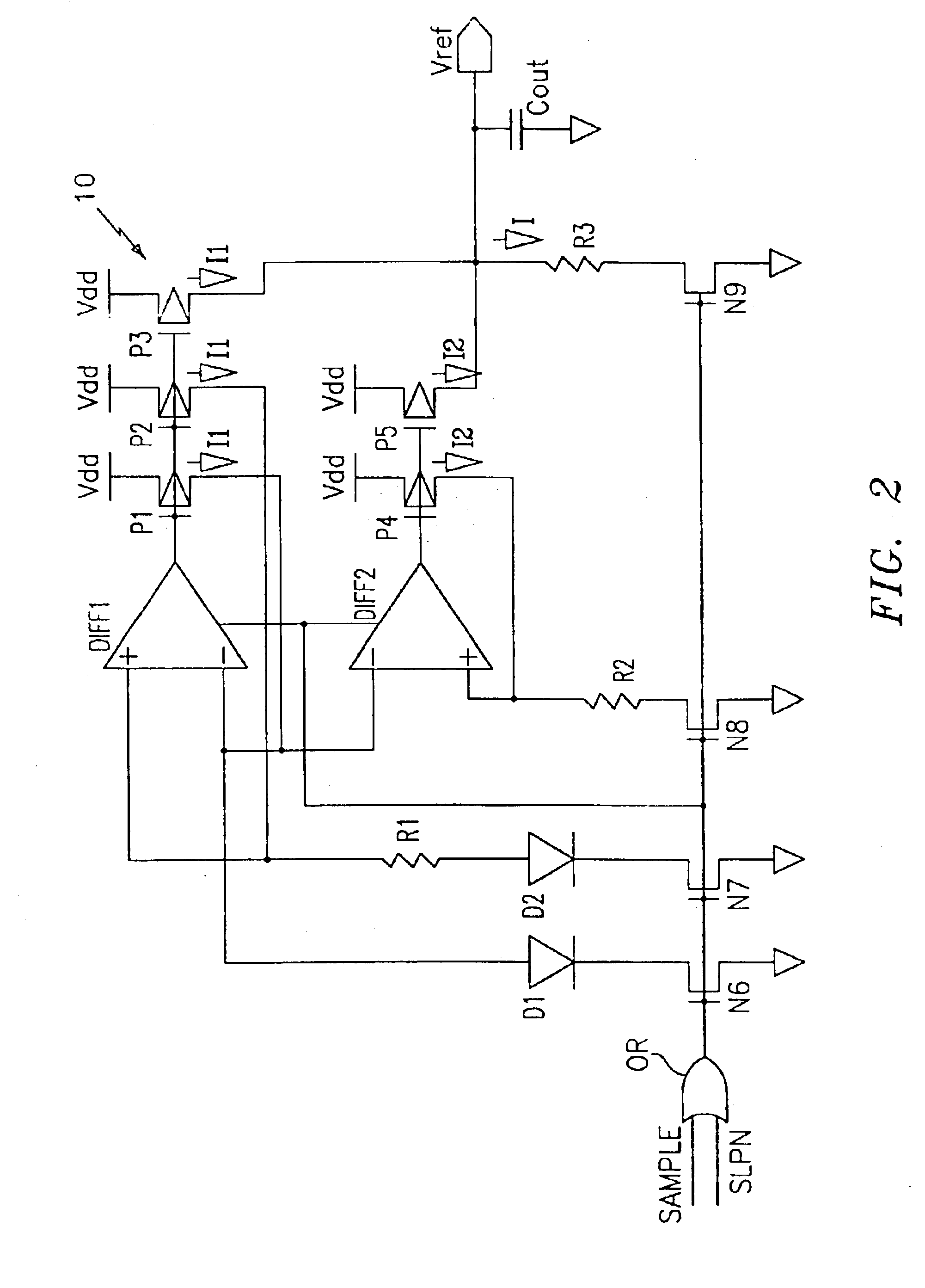
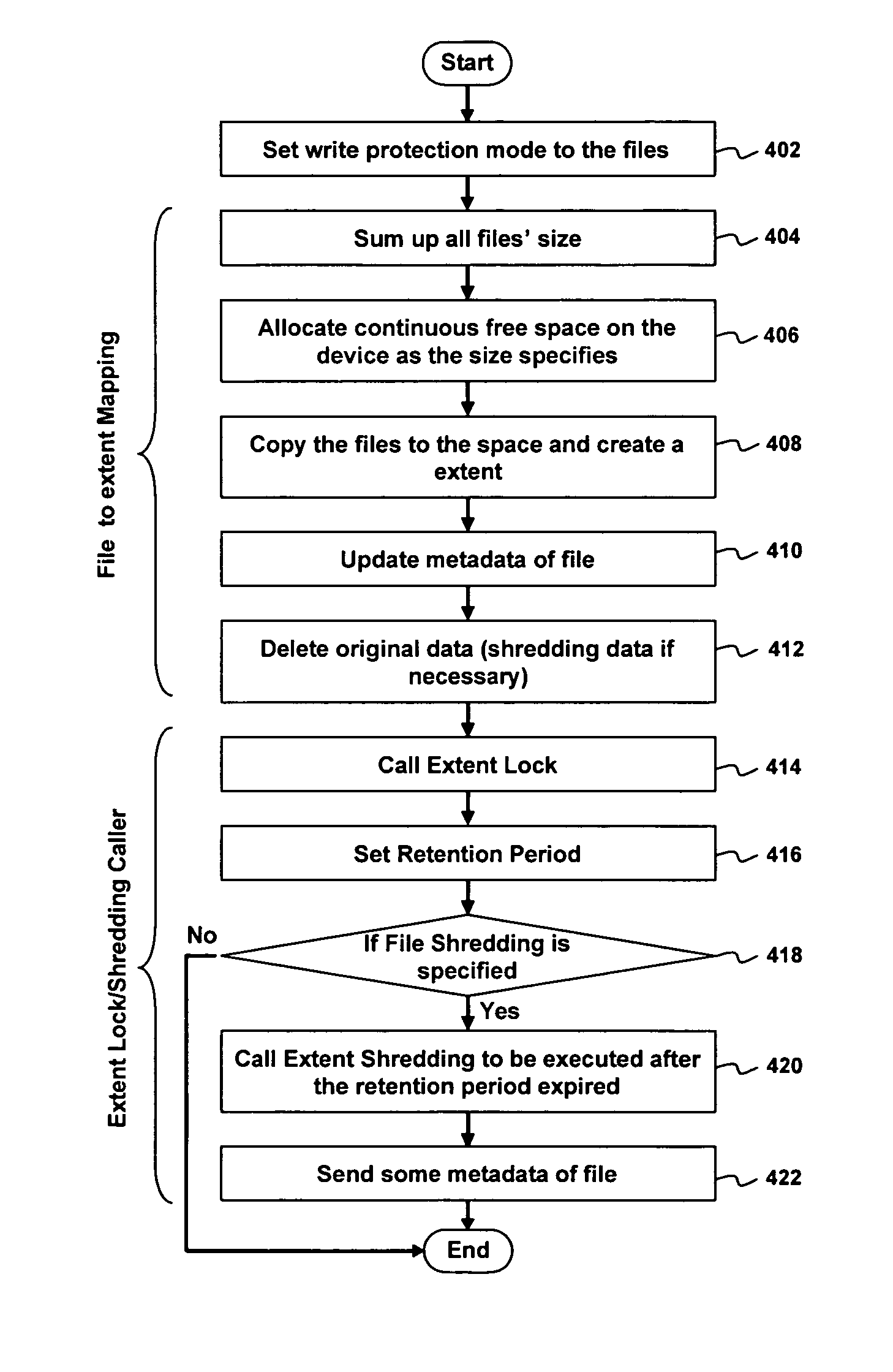
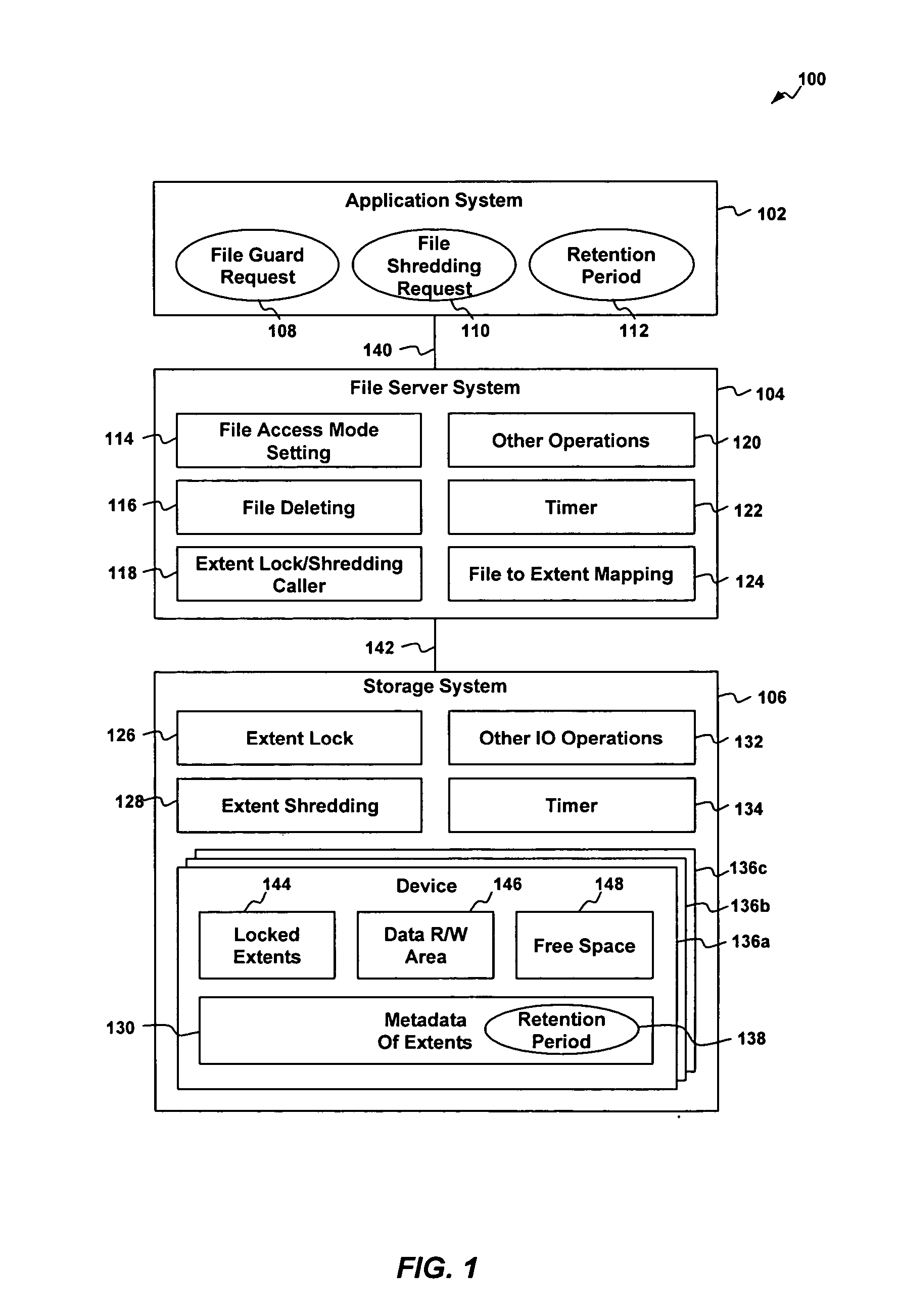
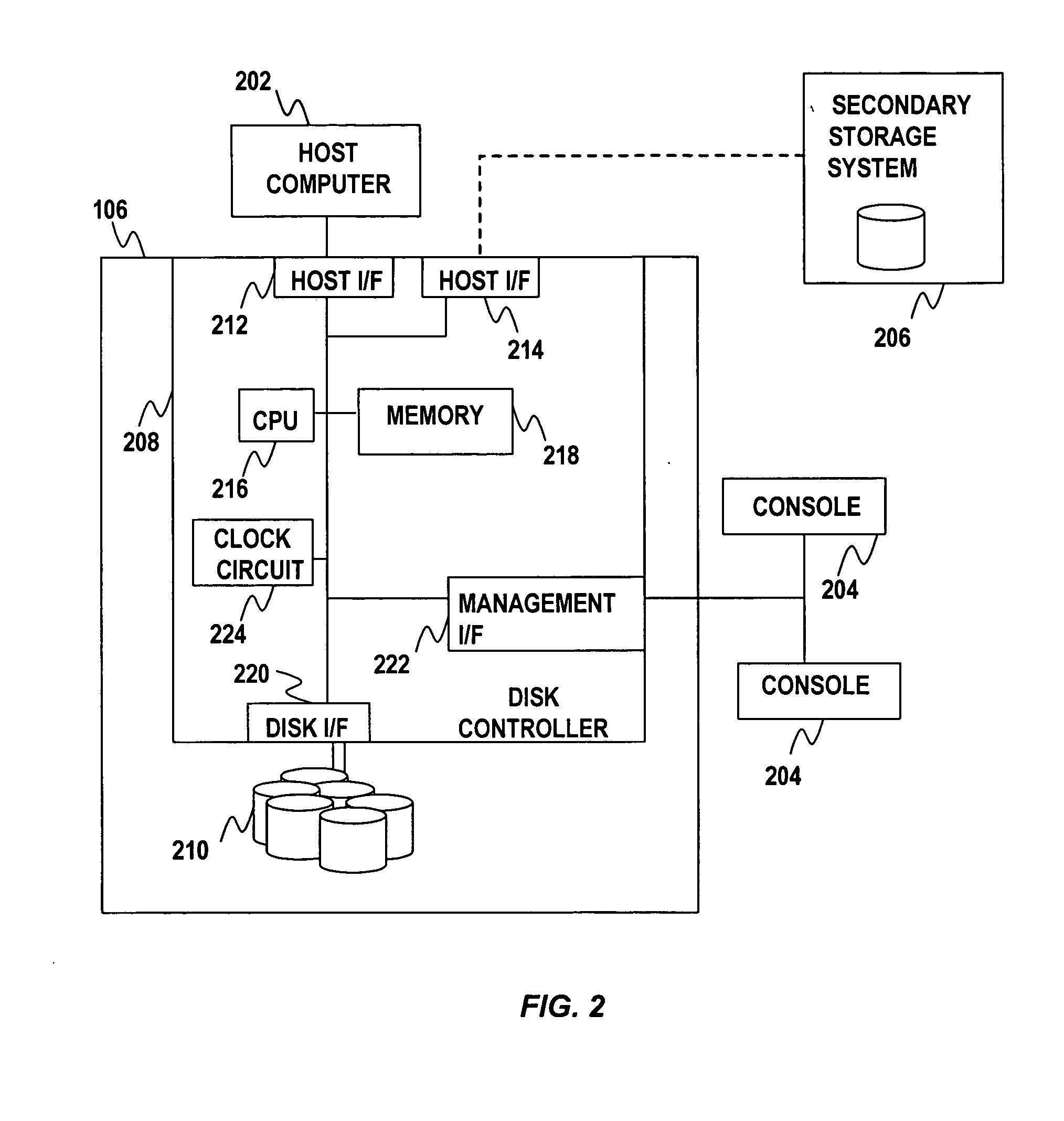
Method and apparatus for file guard and file shredding
InactiveUS20060010301A1Digital data information retrievalUnauthorized memory use protectionData fileData storing
Techniques to assure genuineness of data stored on a data retention system are provided. The data retention system includes a file server system and a storage system. The file server system is configure to map a data file to contiguous memory blocks of the storage system in one embodiment. The storage system is configured to store a write protect attribute associated with the contiguous memory blocks. The storage system denies write access to the contiguous memory blocks depending on the write protect attribute.
Owner:HITACHI LTD
Method and cache-coherence system allowing purging of mid-level cache entries without purging lower-level cache entries
A method and apparatus for purging data from a middle cache level without purging the corresponding data from a lower cache level (i.e., a cache level closer to the processor using the data), and replacing the purged first data with other data of a different memory address than the purged first data, while leaving the data of the first cache line in the lower cache level. In some embodiments, in order to allow such mid-level purging, the first cache line must be in the "shared state" that allows reading of the data, but does not permit modifications to the data (i.e., modifications that would have to be written back to memory). If it is desired to modify the data, a directory facility will issue a purge to all caches of the shared-state data for that cache line, and then the processor that wants to modify the data will request an exclusive-state copy to be fetched to its lower-level cache and to all intervening levels of cache. Later, when the data in the lower cache level is modified, the modified data can be moved back to the original memory from the caches. In some embodiments, a purge of all shared-state copies of the first cache-line data from any and all caches having copies thereof is performed as a prerequisite to doing this exclusive-state fetch.
Owner:RPX CORP +1
Peak data retention of signal data in an implantable medical device
InactiveUS7359837B2ElectrotherapyAmplifier modifications to reduce noise influencePeak valueMedical device
Methods and apparatus for storing data records associated with an extreme value are disclosed. Signal data is stored in a first buffer of a set of buffers. If a local extreme value for the first buffer exceeds a global extreme value, signal data is stored in a second buffer of the set of buffers. This process is repeated, wrapping around and overwriting buffers until the signal data in a current buffer does not have a local extreme value that exceeds the global extreme value. When this happens, signal data may be stored in a subsequent buffer and if a local extreme value of the subsequent buffer does not exceed the global extreme value, further signal data may be stored in the subsequent buffer in a circular manner until either an instantaneous extreme value exceeds the global extreme value or the recording period ends. In an embodiment, the extreme value may be a peak value.
Owner:MEDTRONIC INC
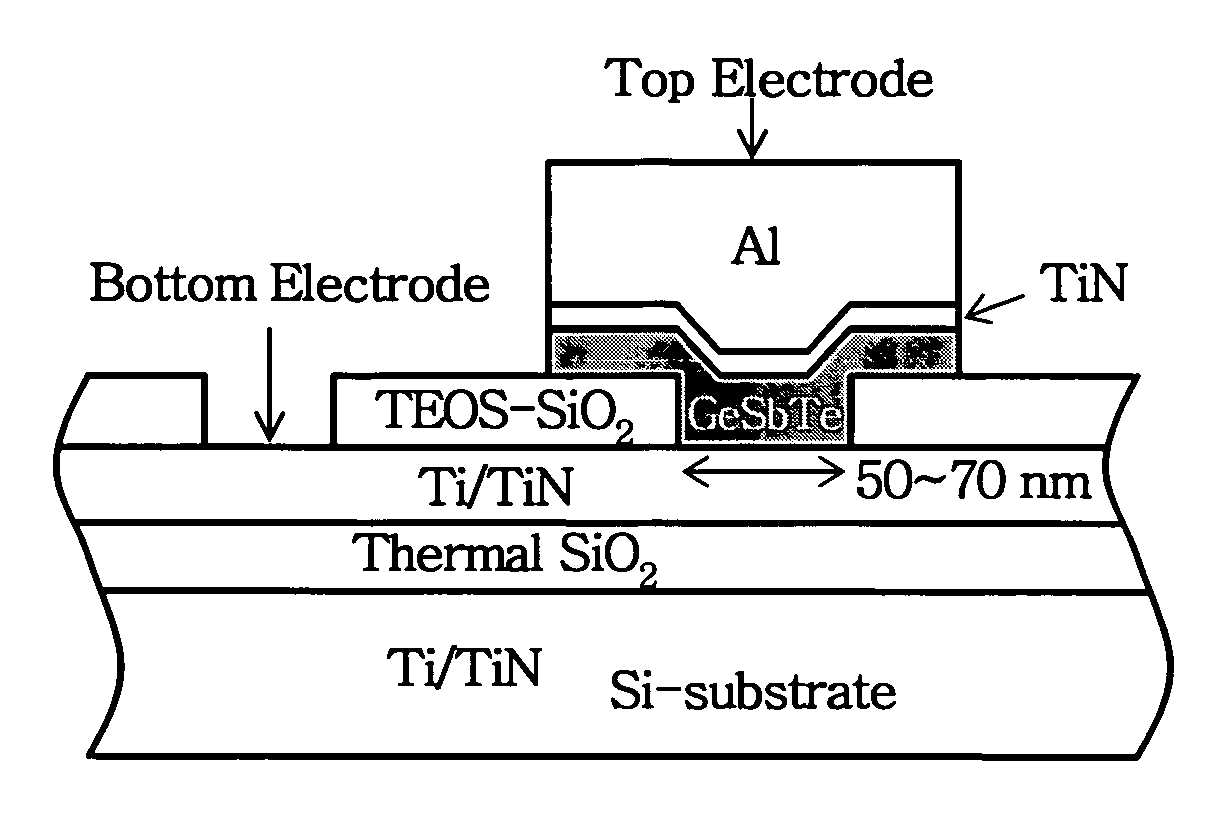
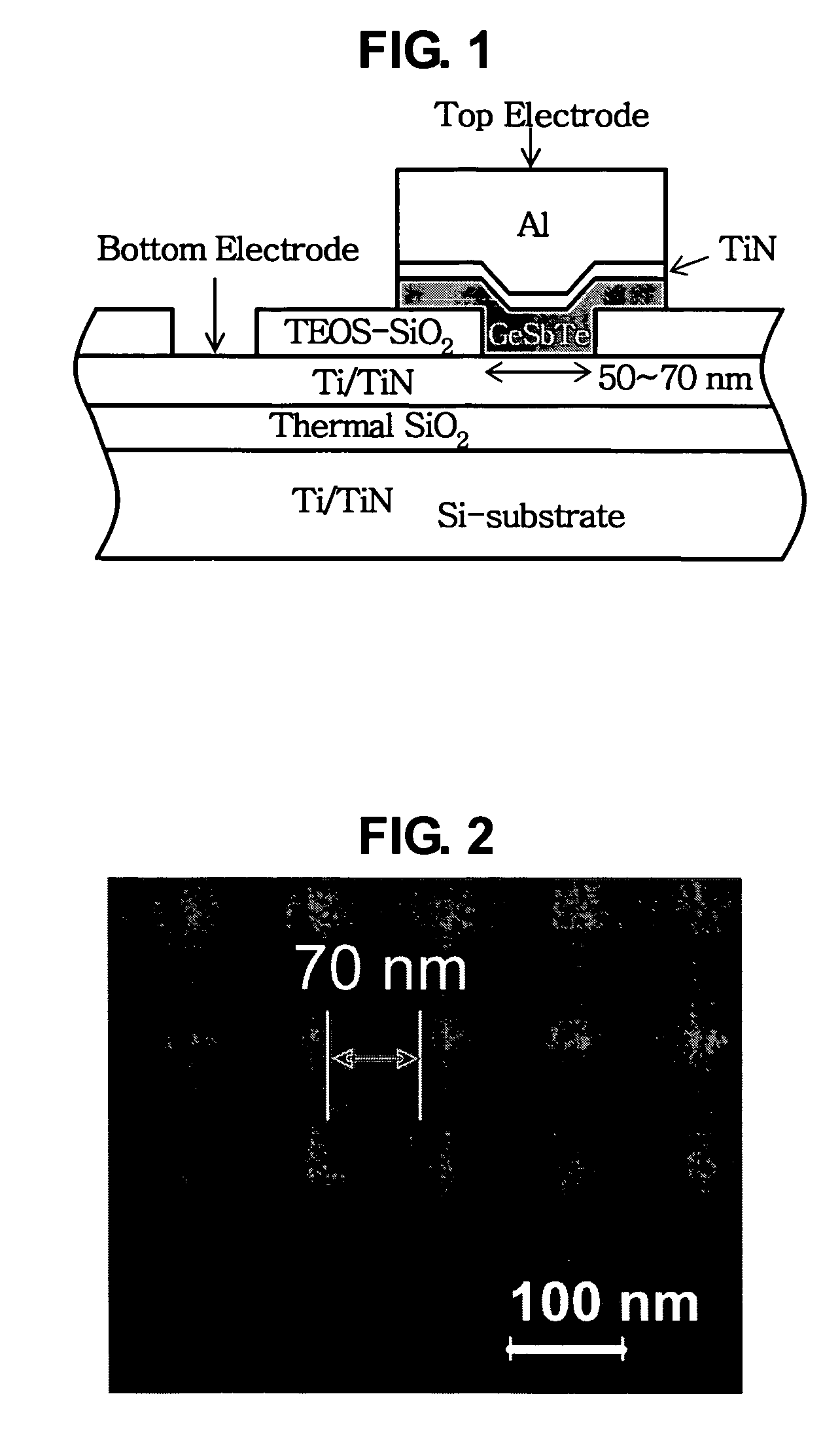
Phase change material and non-volatile memory device using the same
ActiveUS20070120104A1Large atomic numberSmall diatomic bond strengthBulk negative resistance effect devicesSemiconductor devicesPhase-change memoryMetal alloy
The present invention provides a phase change memory cell comprising (GeASbBTeC)1−x(RaSbTeC)x solid solution, the solid solution being formed from a Ge—Sb—Te based alloy and a ternary metal alloy R—S—Te sharing same crystal structure as the Ge—Sb—Te based alloy. A nonvolatile phase change memory cell in accordance with the present invention provides many advantages such as high speed, high data retention, and multi-bit operation.
Owner:SK HYNIX INC
Semiconductor memory and method for operating the same
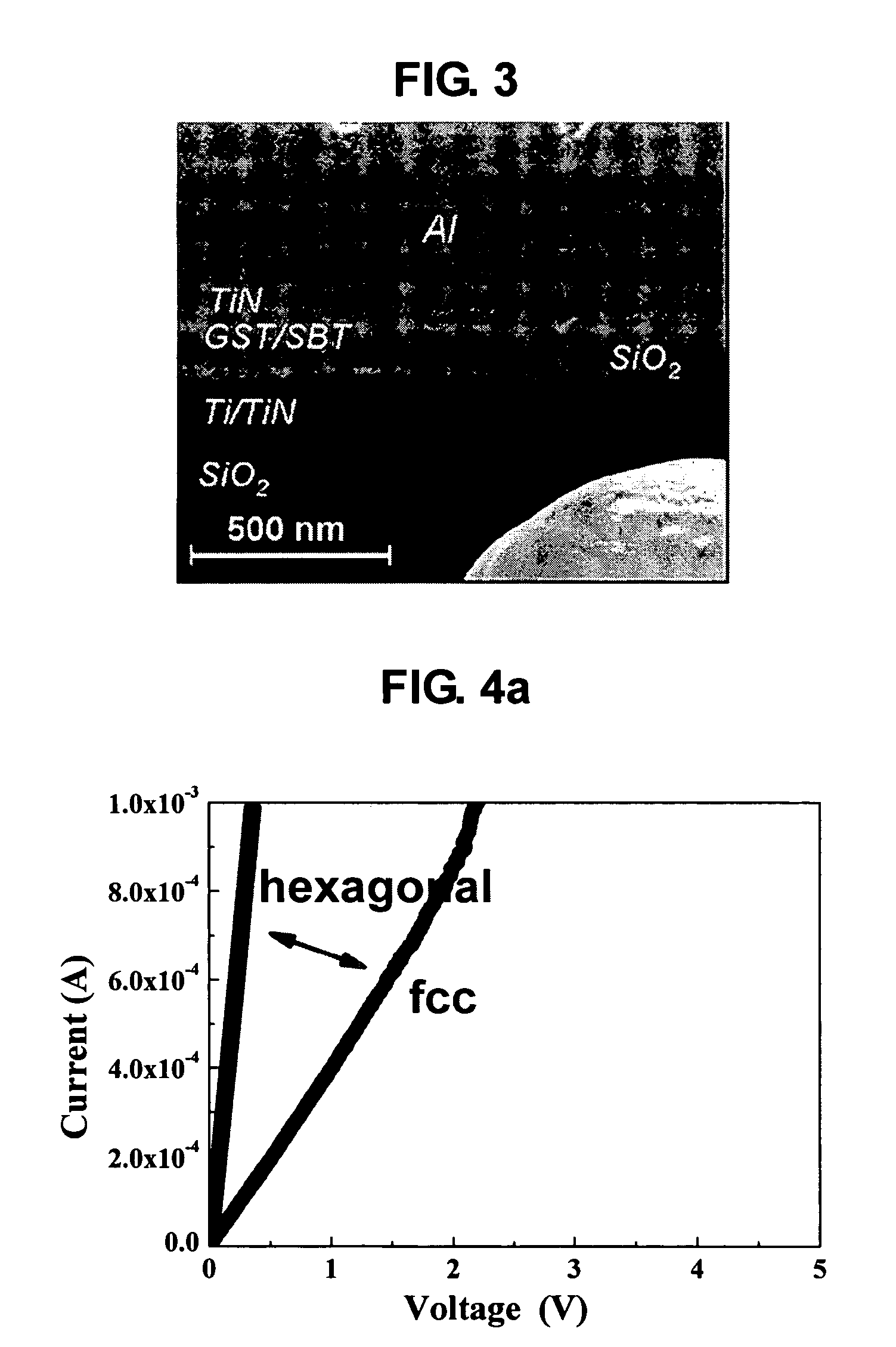
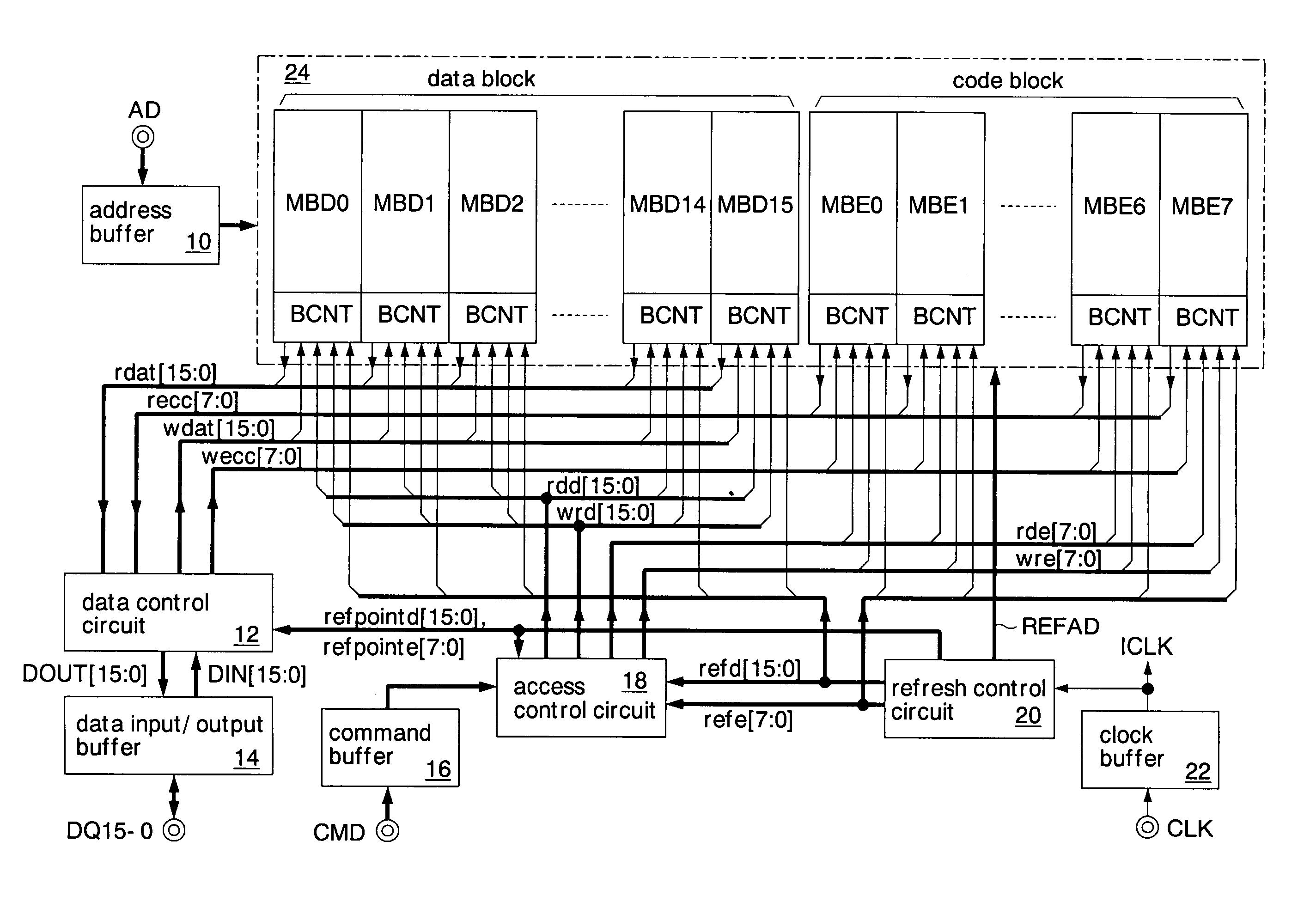
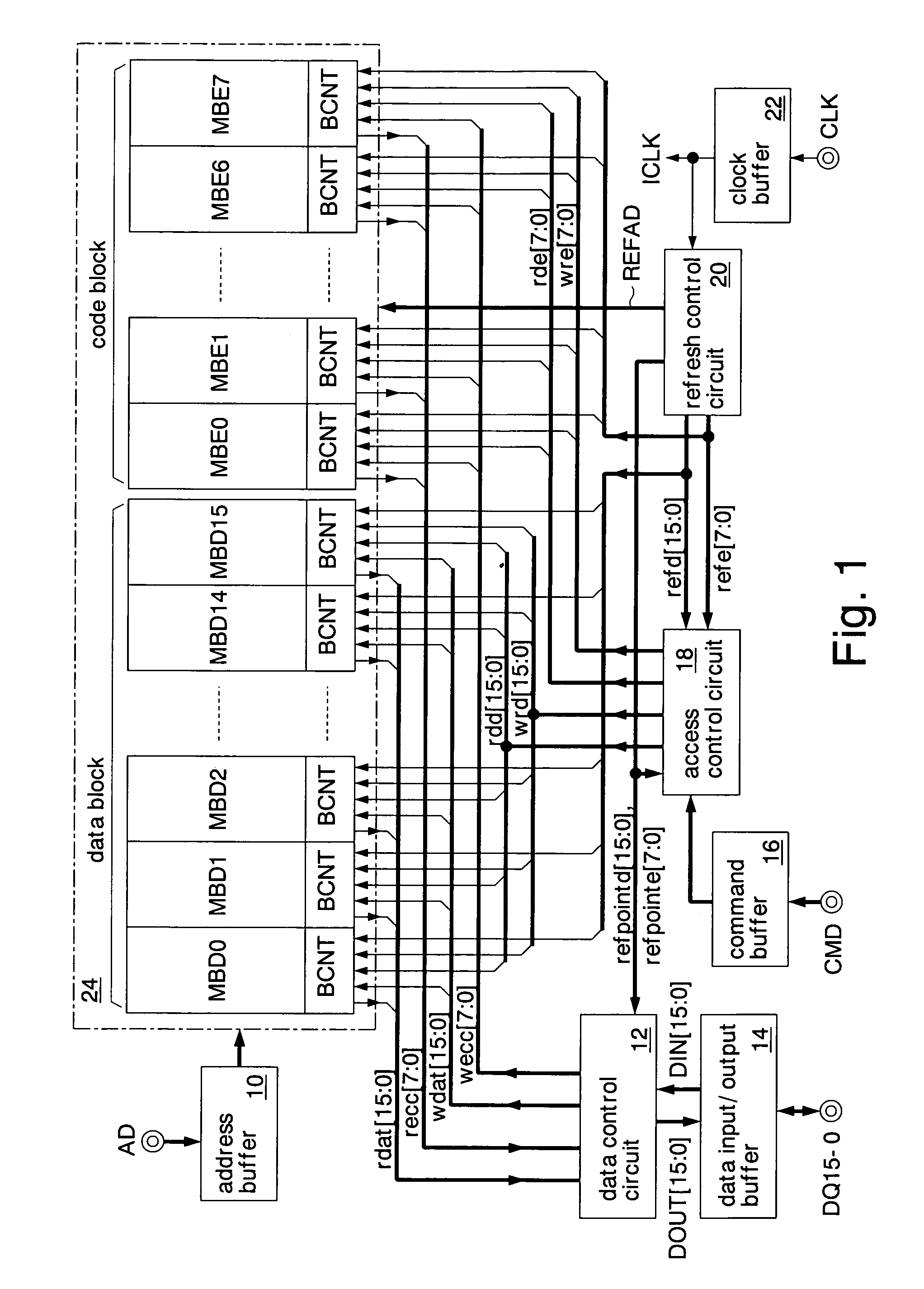
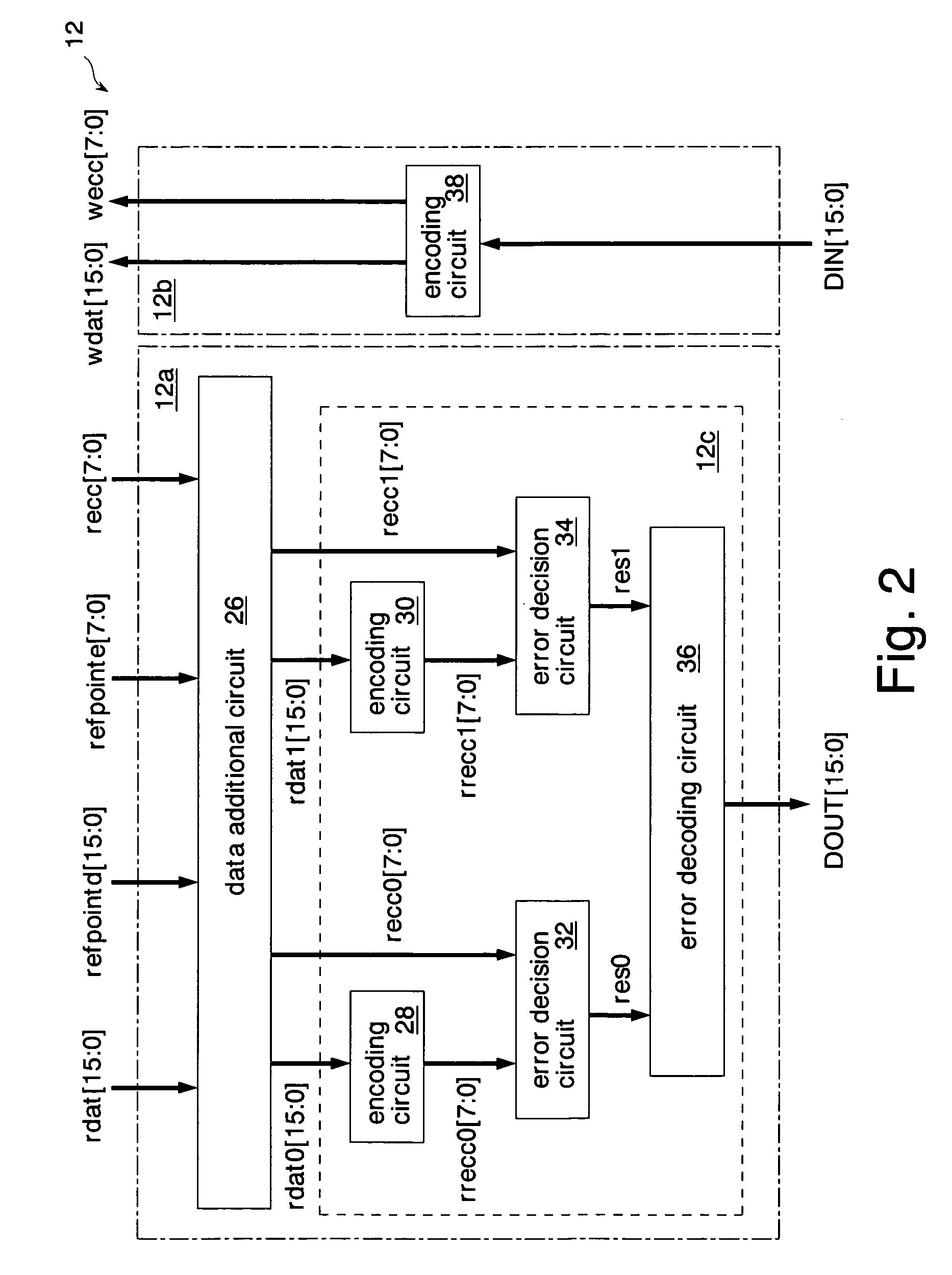
A data additional circuit adds plural types of expectation data to be read from a refresh block to data read from other blocks, respectively, to generate plural read data strings. An error correction circuit detects errors for each read data string, and sets the most reliable result of the error detection results to be true. The error correction circuit decodes data to be read from the refresh block based on a true error detection result. Moreover, the error correction circuit corrects the error of the read data string corresponding to the true error detection result. Consequently, without extending the read cycle time, a refresh operation can be hid, and errors can be corrected simultaneously. By correcting a data error read from a bad memory cell of data retention characteristics, a refresh request interval can be extended, and power consumption during a standby period can be reduced.
Owner:SOCIONEXT INC
Dynamic memory refresh configurations and leakage control methods
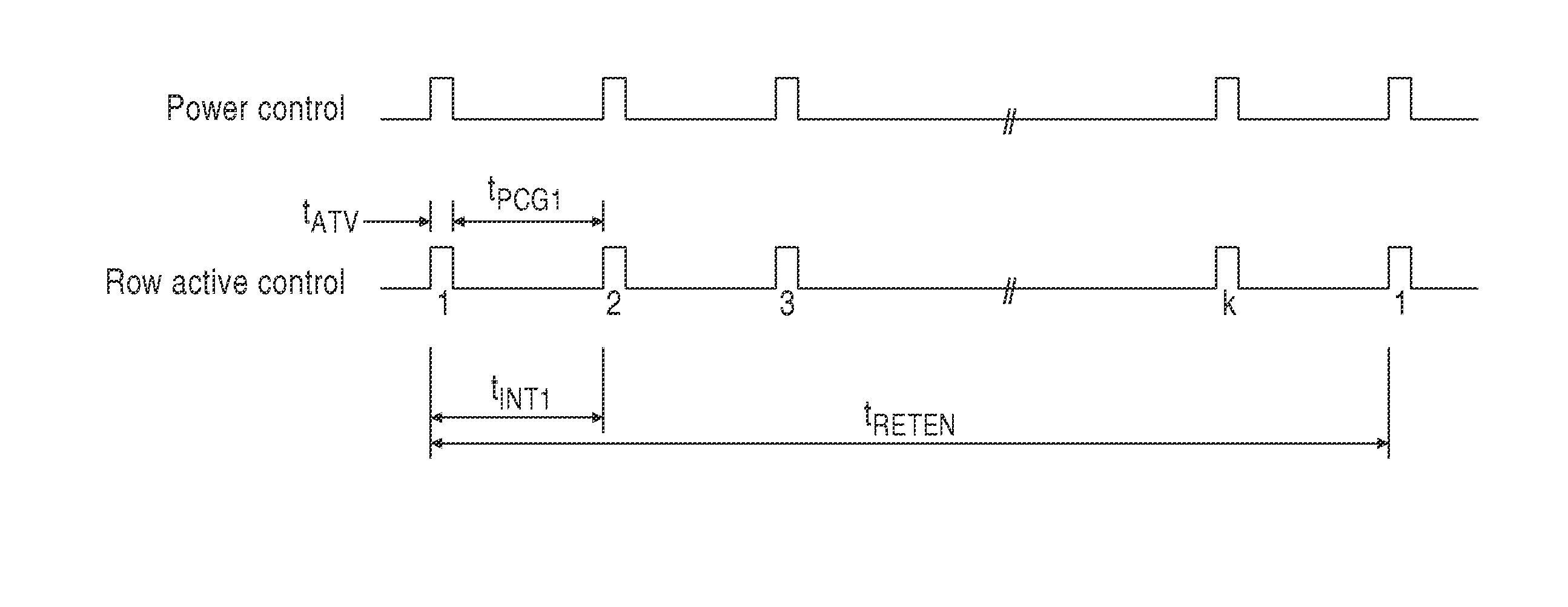
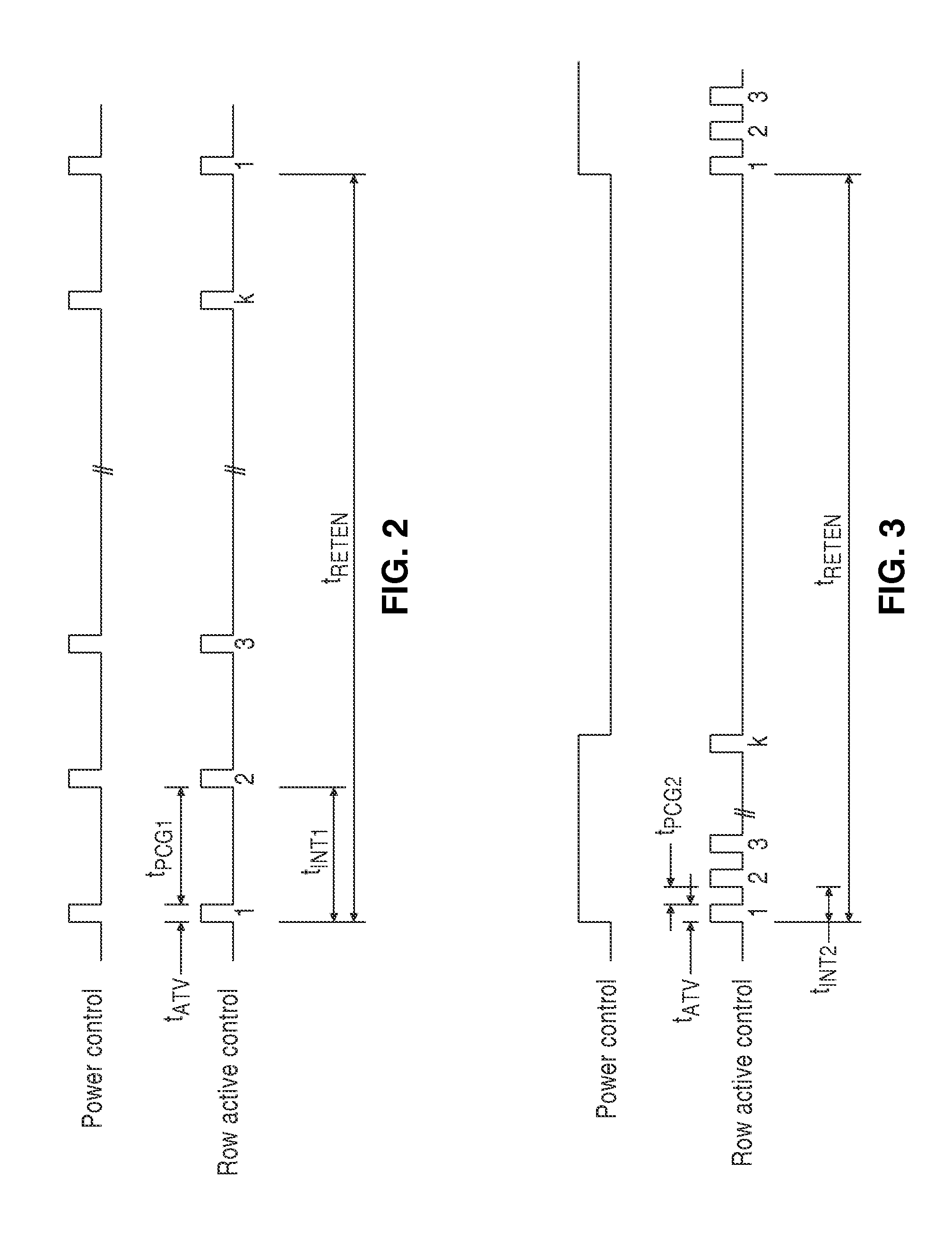
Dynamic Random Access Memory (DRAM) circuits and methods are described for reducing leakage and increasing repaired yield. These objects are accomplished according to the invention by grouping refresh cycles within a single activation of power control, the use of limiting circuits or fuses to mitigate power losses associated with micro-bridging of bit-lines and word-lines, modulating the bit-line voltage at the end of precharge cycles, configuring refresh control circuits to use redundant word-lines in generating additional refresh cycles for redundant rows of memory cells, and combinations thereof. In one aspect, word-line fuses indicate modes of use as: unused, replacement, additional refresh, and replacement with additional refresh. The refresh control circuit utilizes these modes in combination with the X-address stored in the word-line fuses for controlling the generation of additional refresh cycles toward overcoming insufficient data retention intervals in select memory cell rows.
Owner:ZMOS TECH
Method and apparatus for tamper-proof wirte-once-read-many computer storage
InactiveUS20100088528A1Minimize overheadAvoids malicious actDigital data information retrievalUnauthorized memory use protectionTamper resistanceTrusted hardware
Disclosed is a method for storing digital information for storage in an adversarial setting in which trusted hardware enforces digital information compliance with data storage mandates. Secure storage overhead is minimized by identifying sparsely accessing the trusted hardware based on data retention cycles. Data retention assurances are provided for information stored by a Write-Once Read-Many (WORM) storage system.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Data storage system with non-volatile memory and method of operation thereof
InactiveUS20120254519A1Maximizing a data retention period of the target blockMaximize a data retention period of the target blockMemory architecture accessing/allocationEnergy efficient ICTData storeData retention
A method of operation of a data storage system includes: identifying a target block; configuring a command setting for maximizing a data retention period of the target block for refreshing the target block; writing a pre-archived memory block to the target block based on the command setting; and updating an archive status for sending to a host device.
Owner:SANDISK TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com