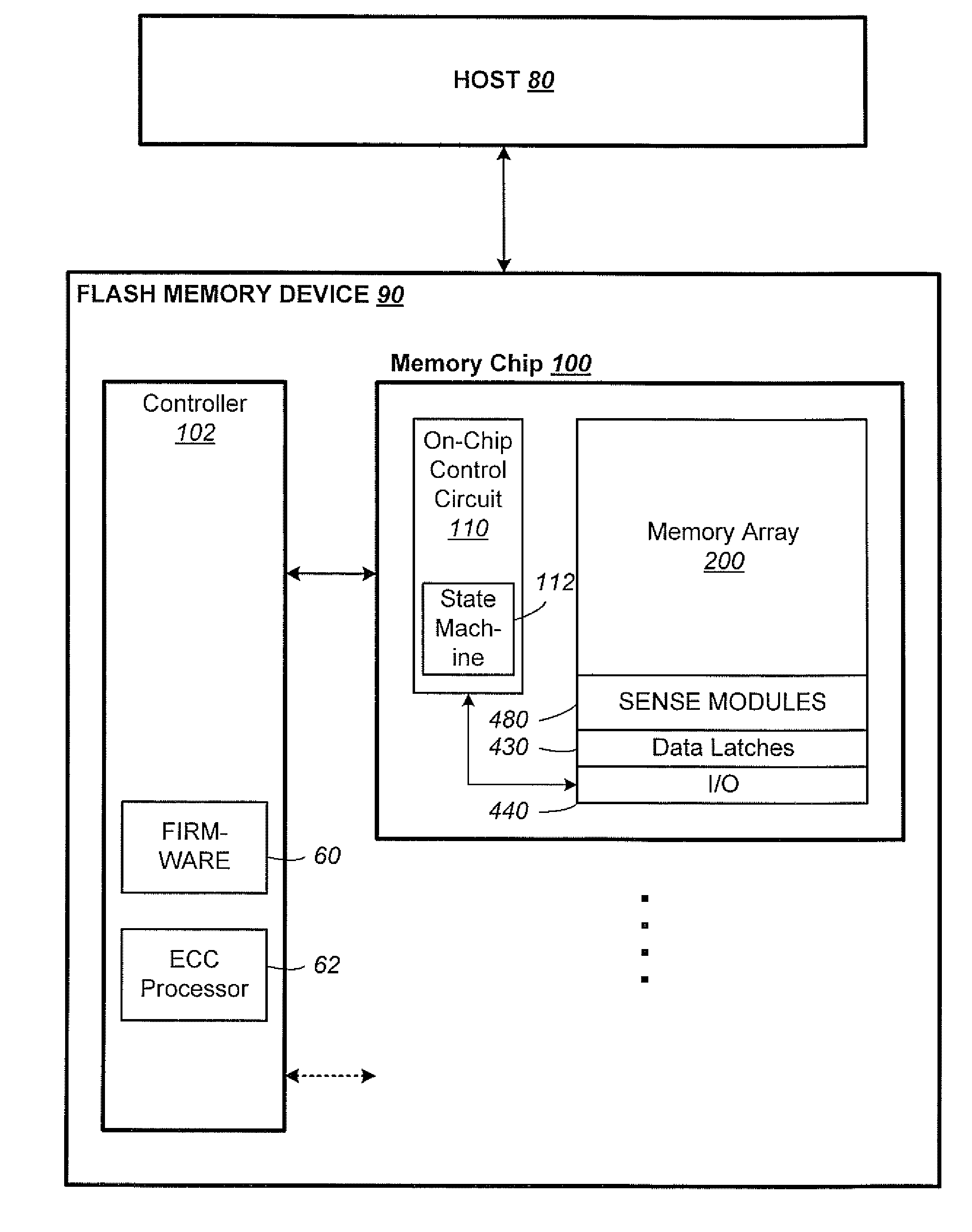
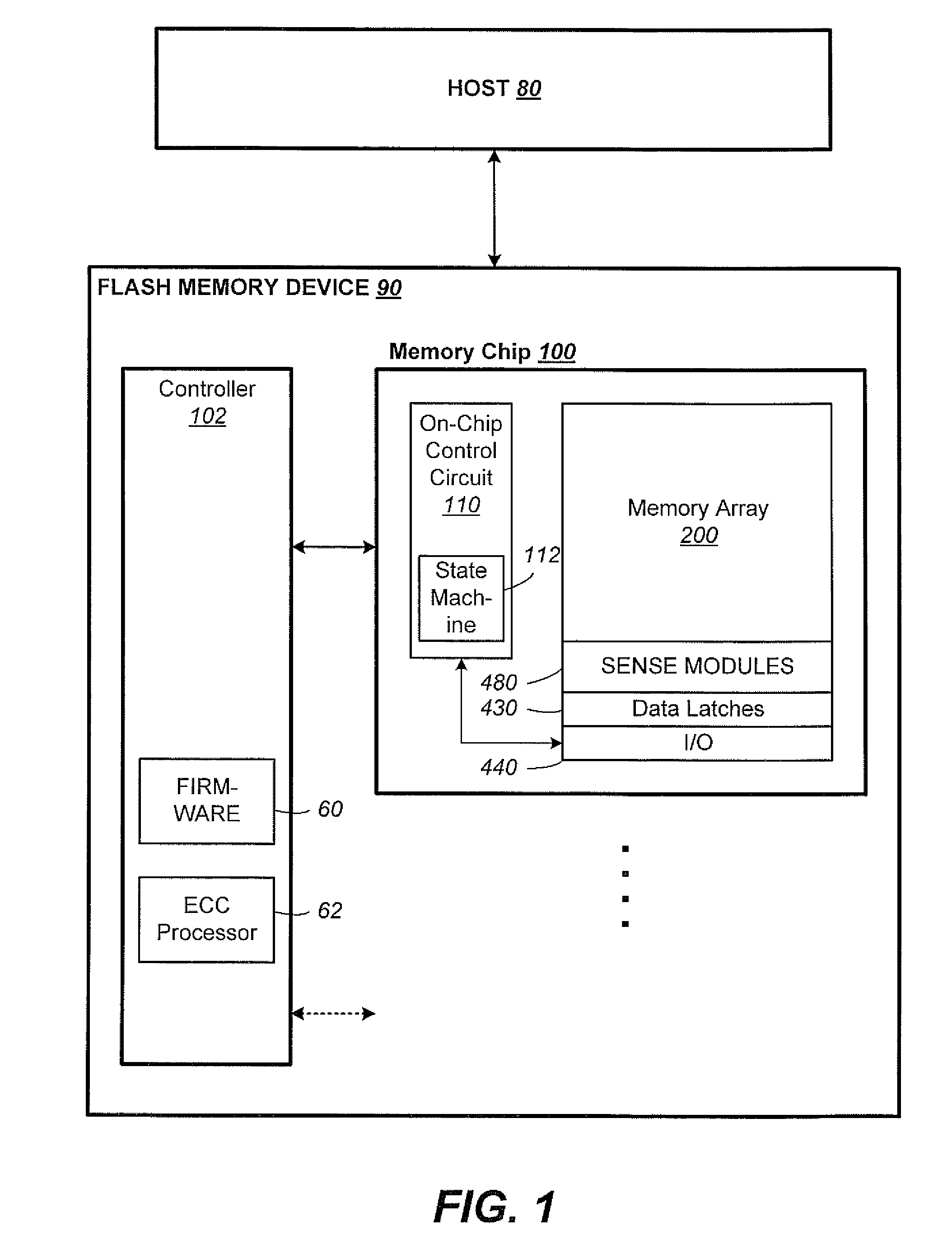
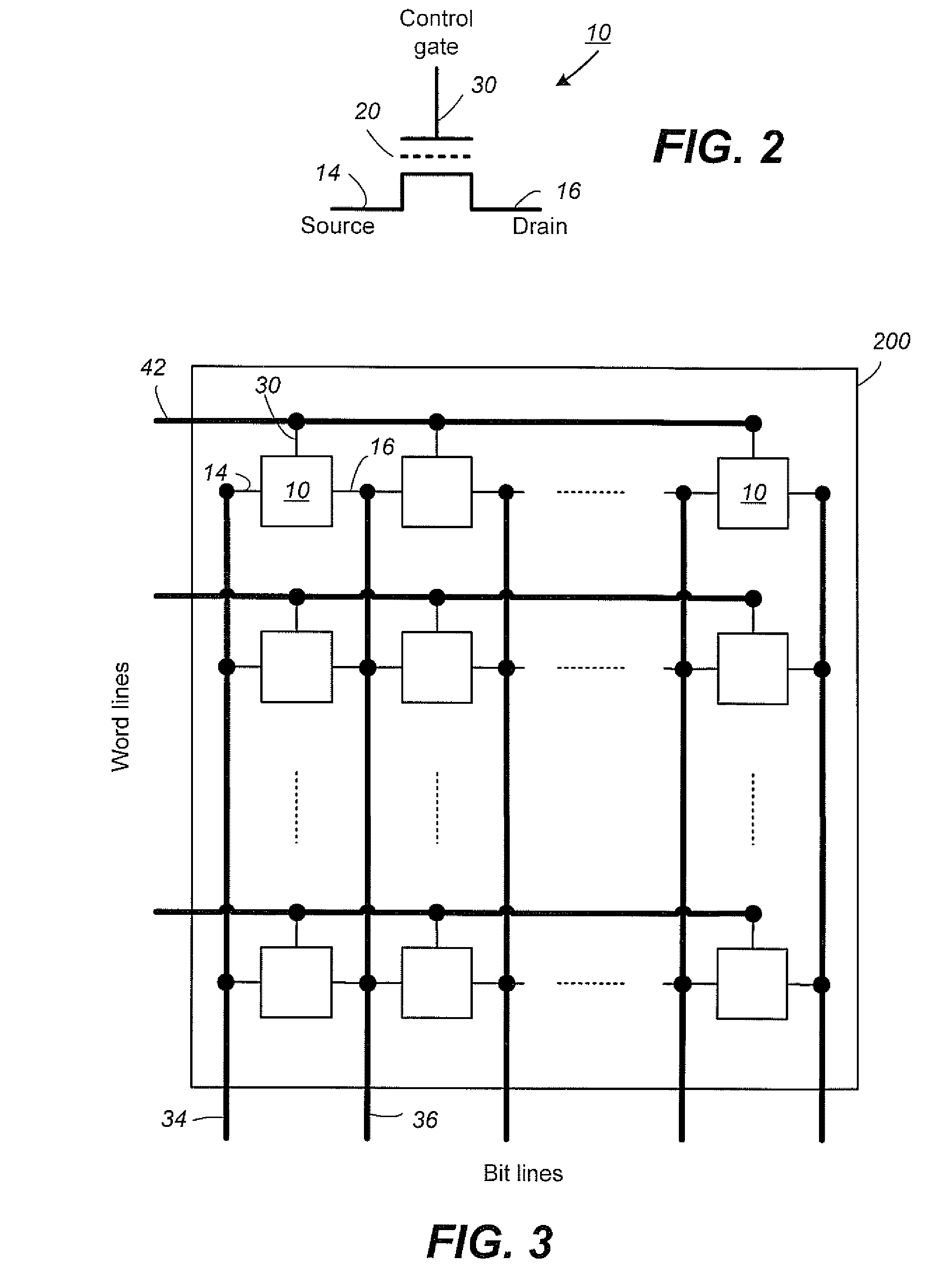
Patents
Literature
2845 results about "Data error" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
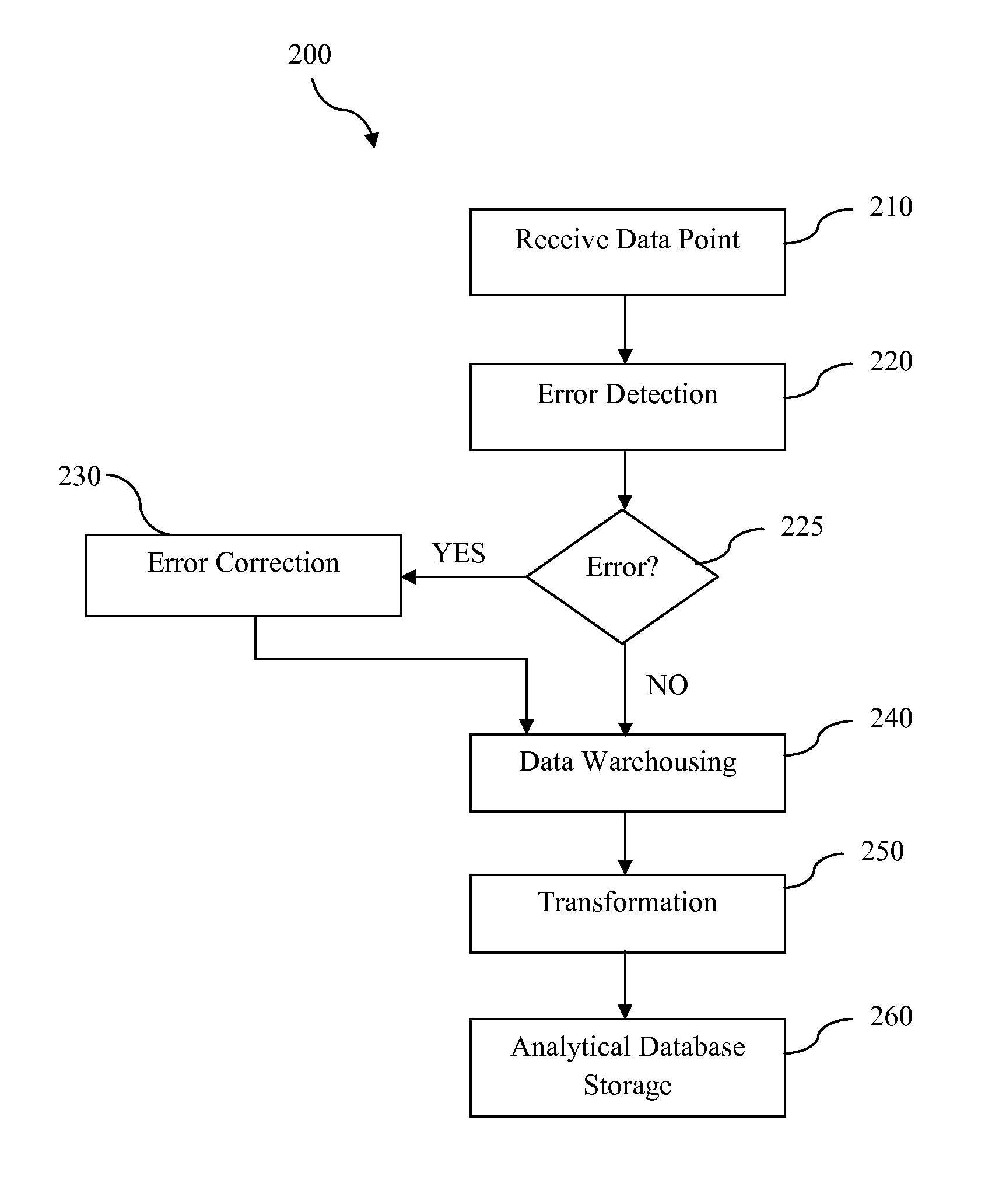
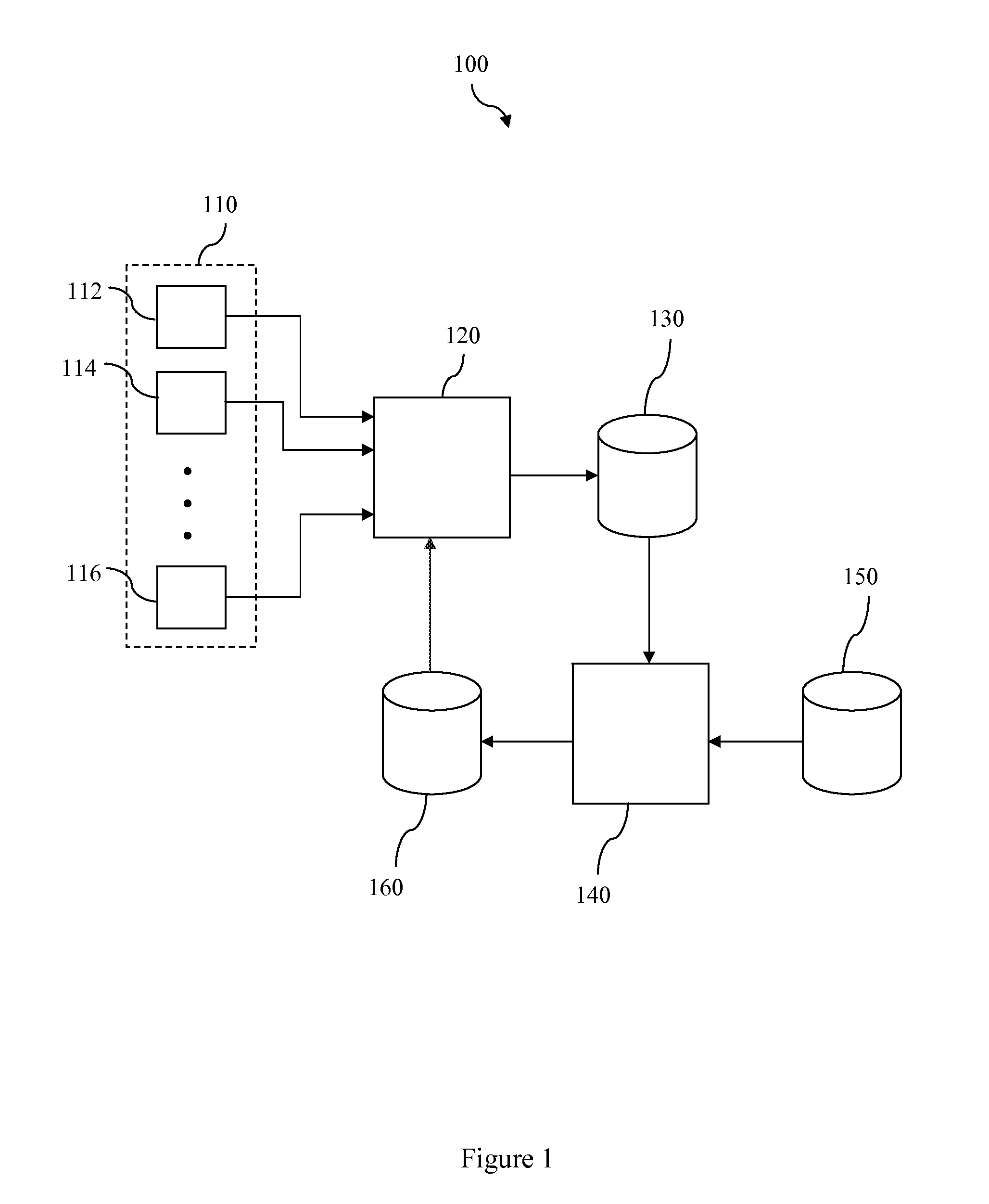
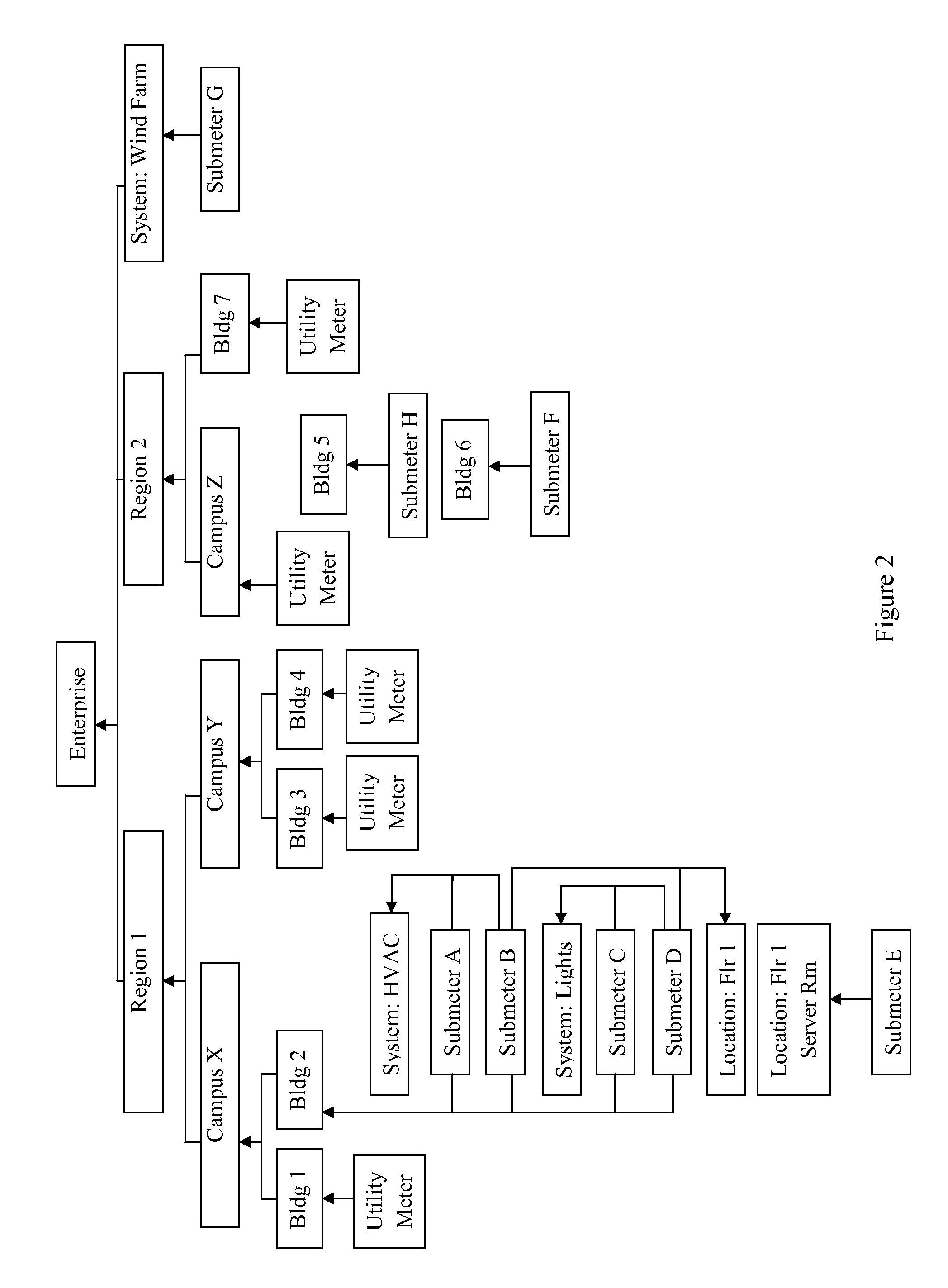
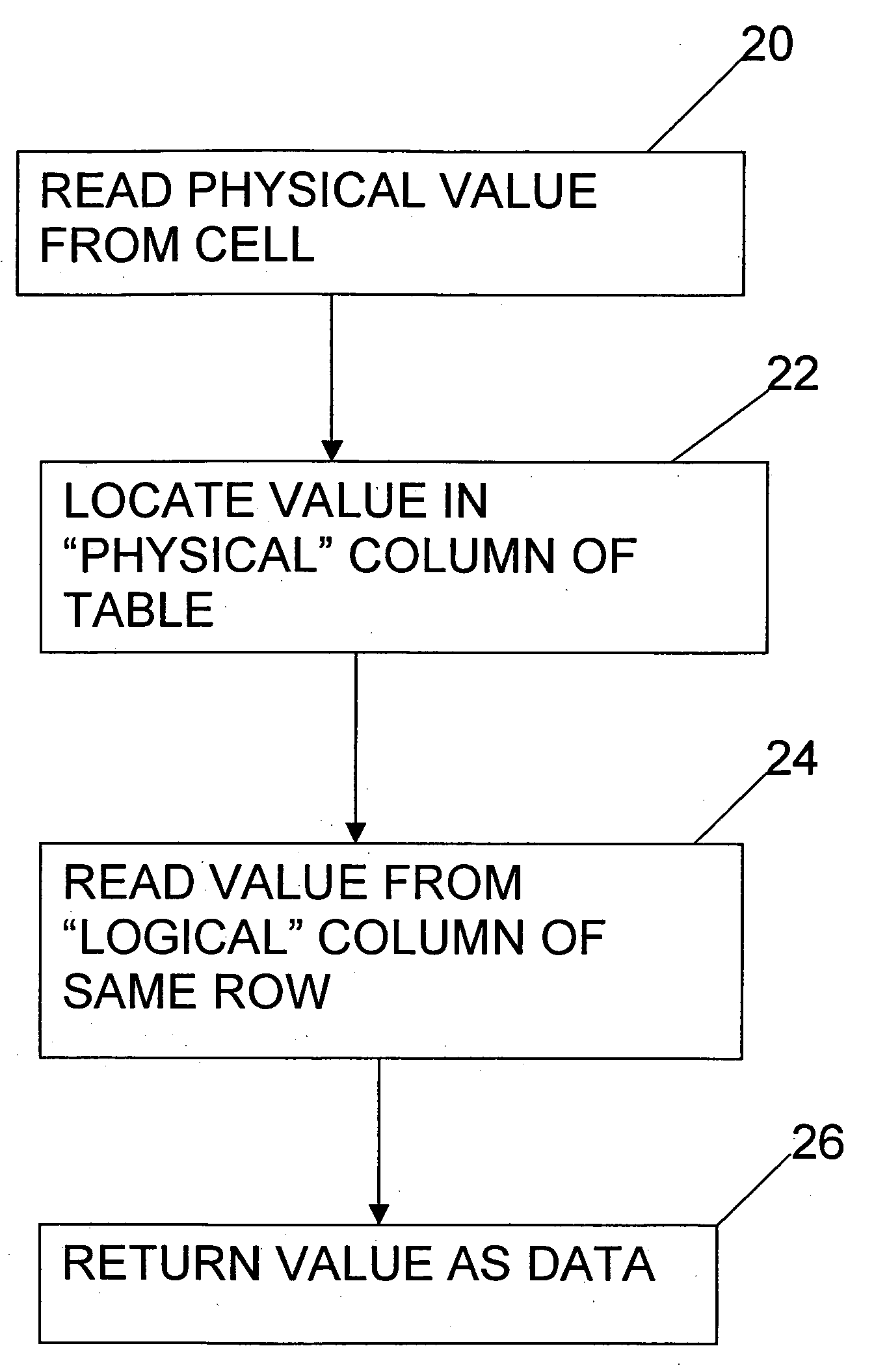
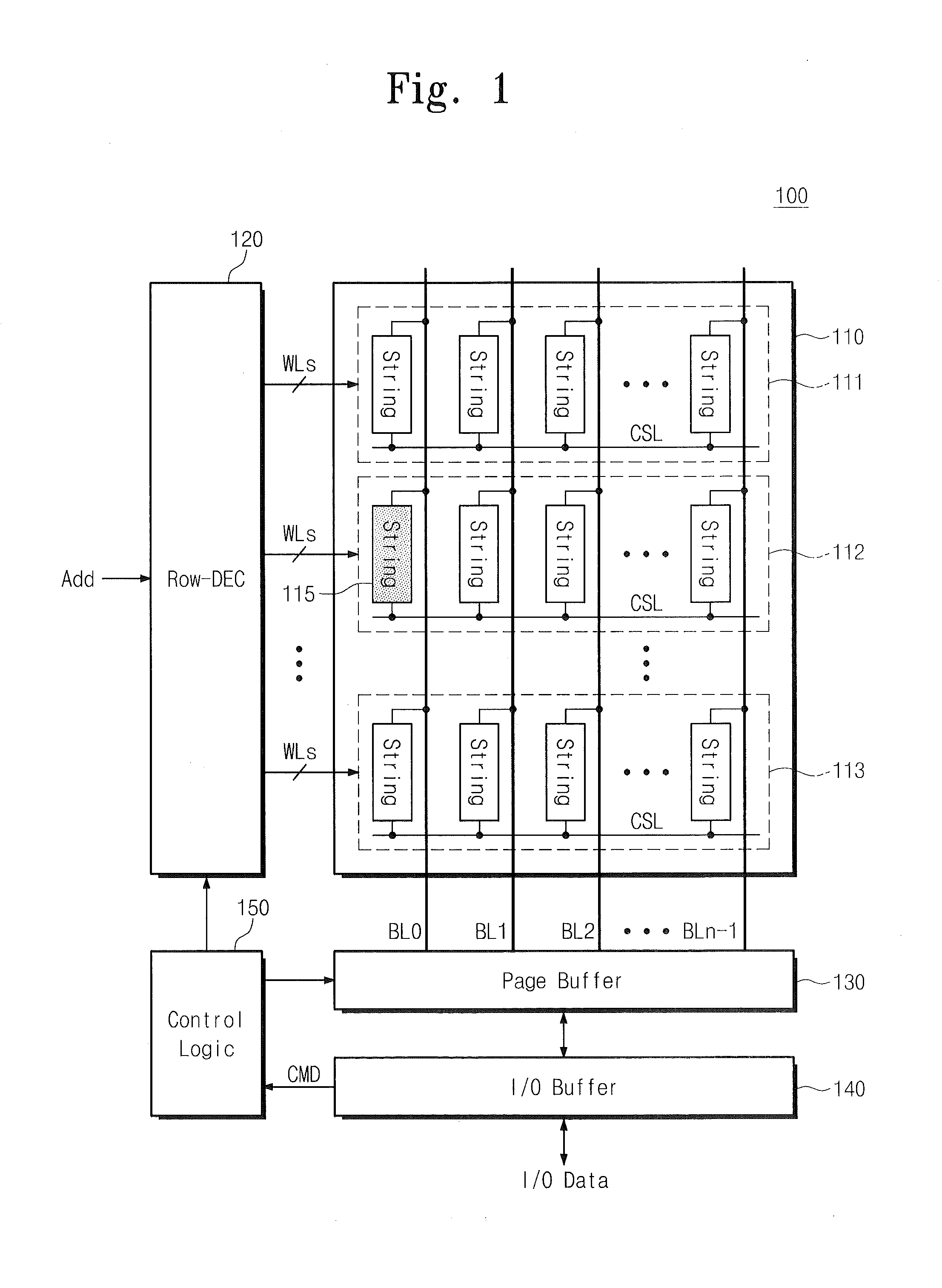
System and methods for real-time detection, correction, and transformation of time series data
InactiveUS20140032506A1Digital data information retrievalDigital data processing detailsAnalysis dataData set
Systems and methods for time series data error detection, correction, and transformation may detect gaps and anomalies in time series data, such as from a meter device, and may correct the gaps and adjust the anomalies prior to long-term record storage. Data forecasting may be used to correct the errors in the time series data. The error corrected data may be regarded as an actual set of time series data and become a base data set against which additional heuristic projections are generated. In addition, the time series data may be transformed into any number of physical and virtual device hierarchies that represent the underlying data source configurations, and may then be stored in an analytical database for further analysis. The hierarchies may be irregular and may change over time.
Owner:SUMITOMO CHEM U K
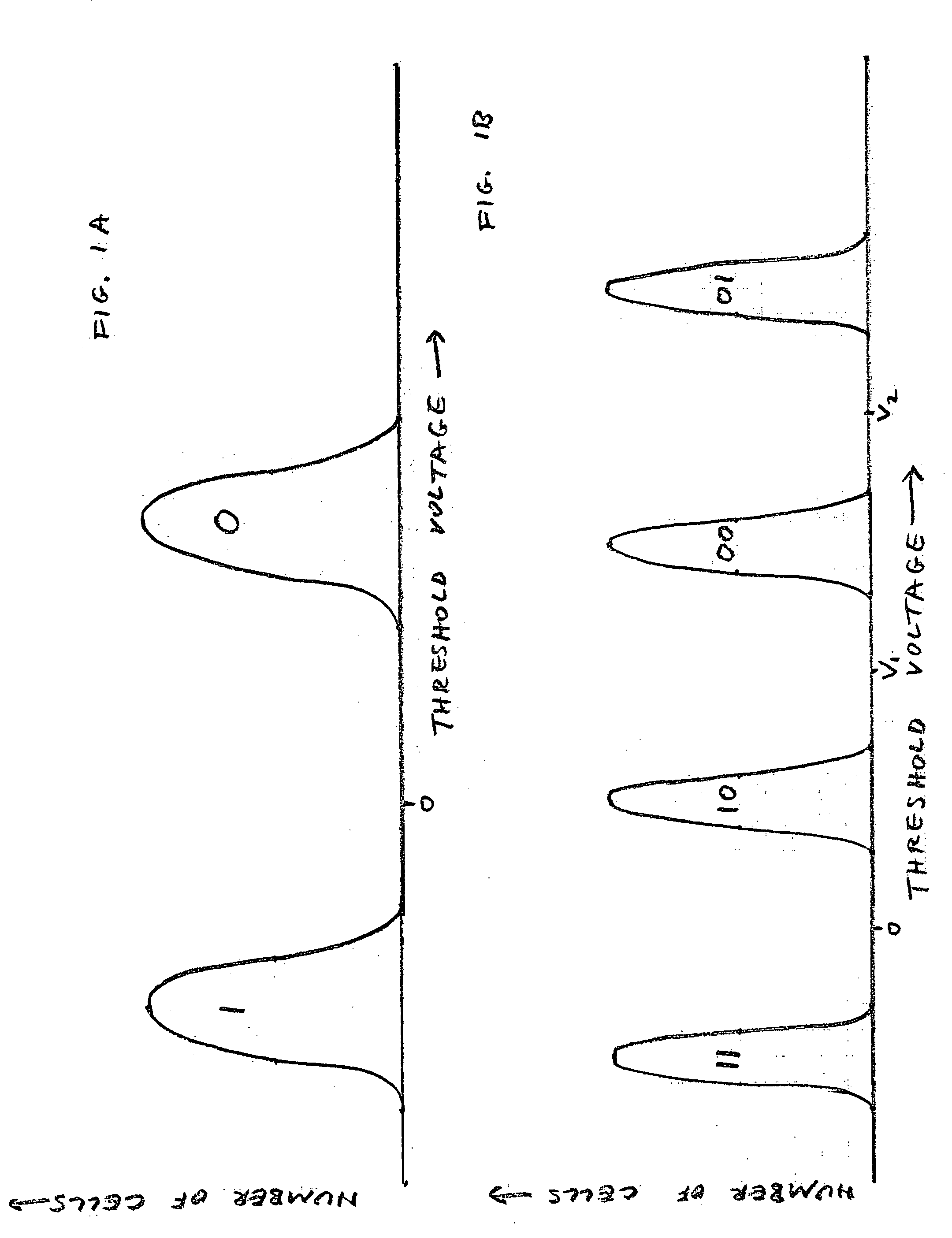
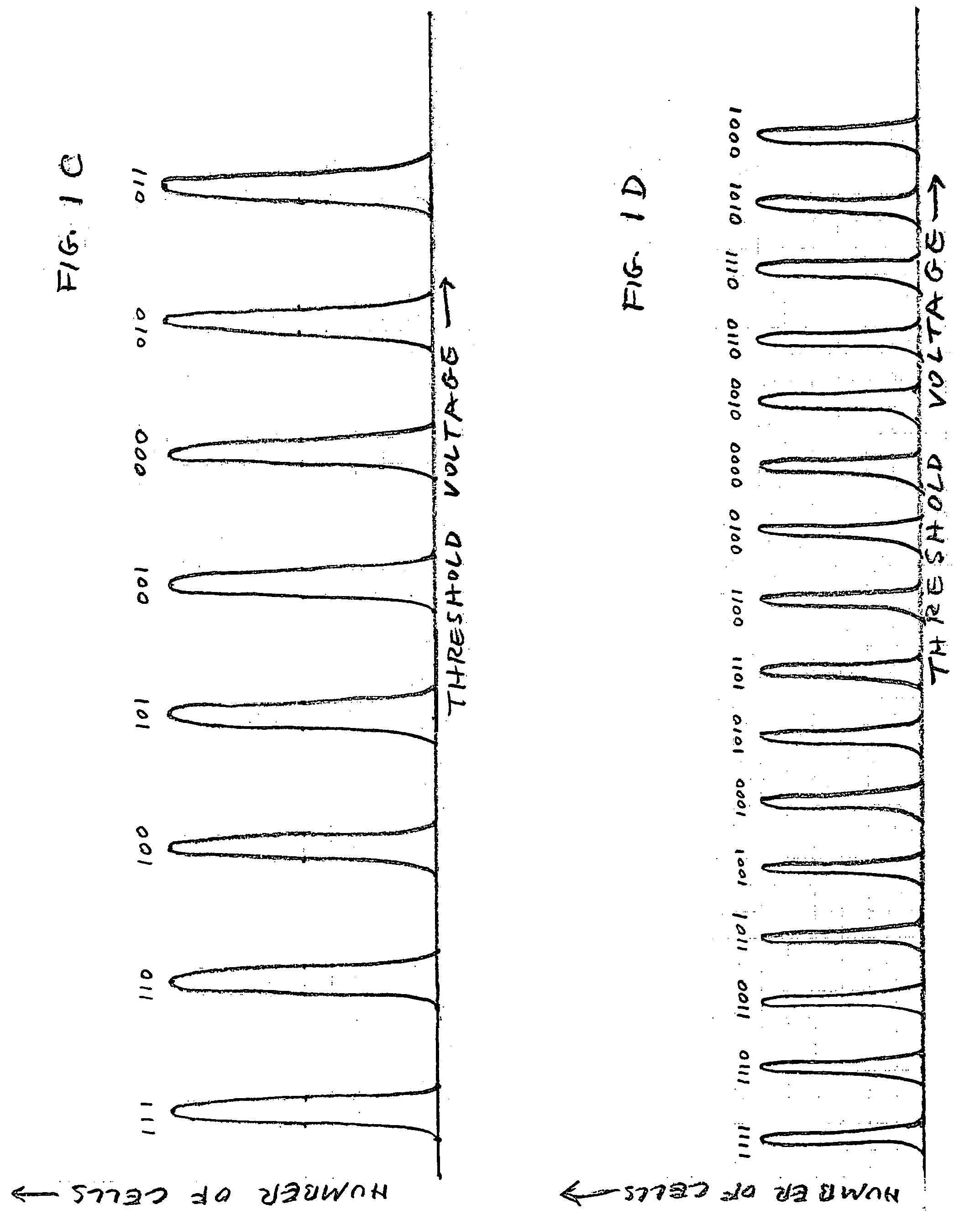
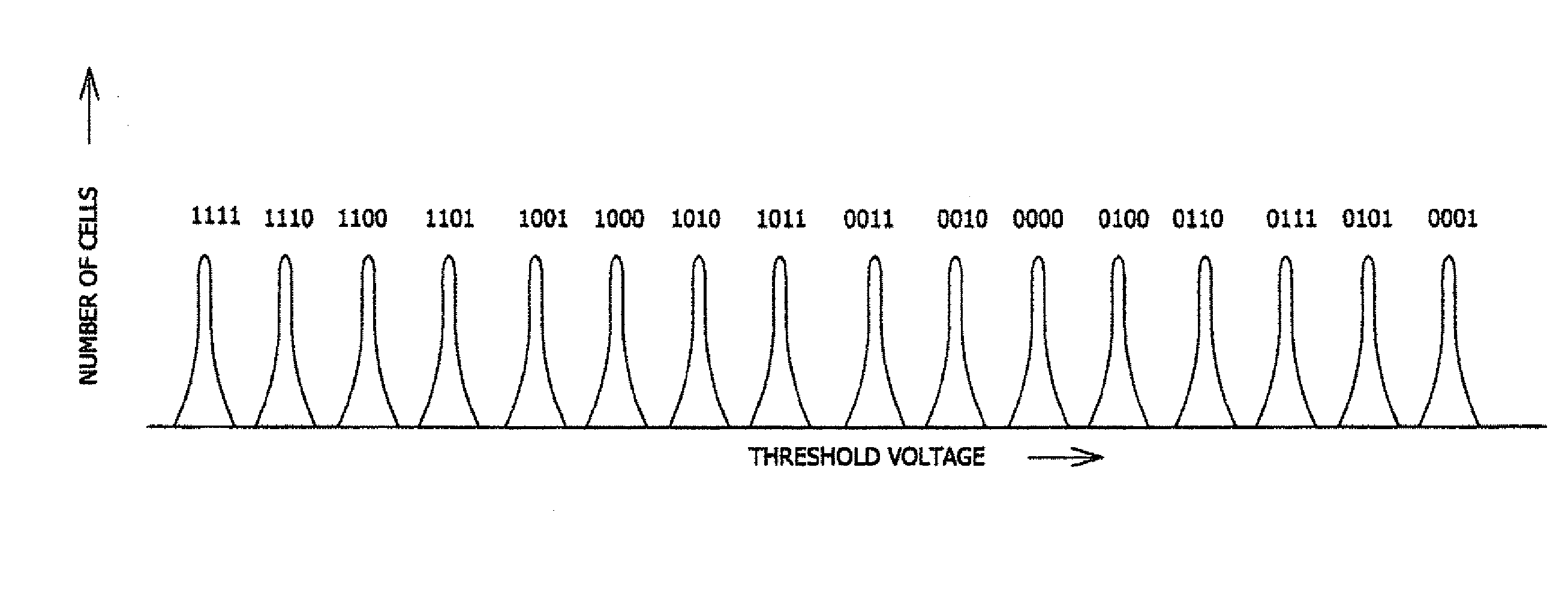
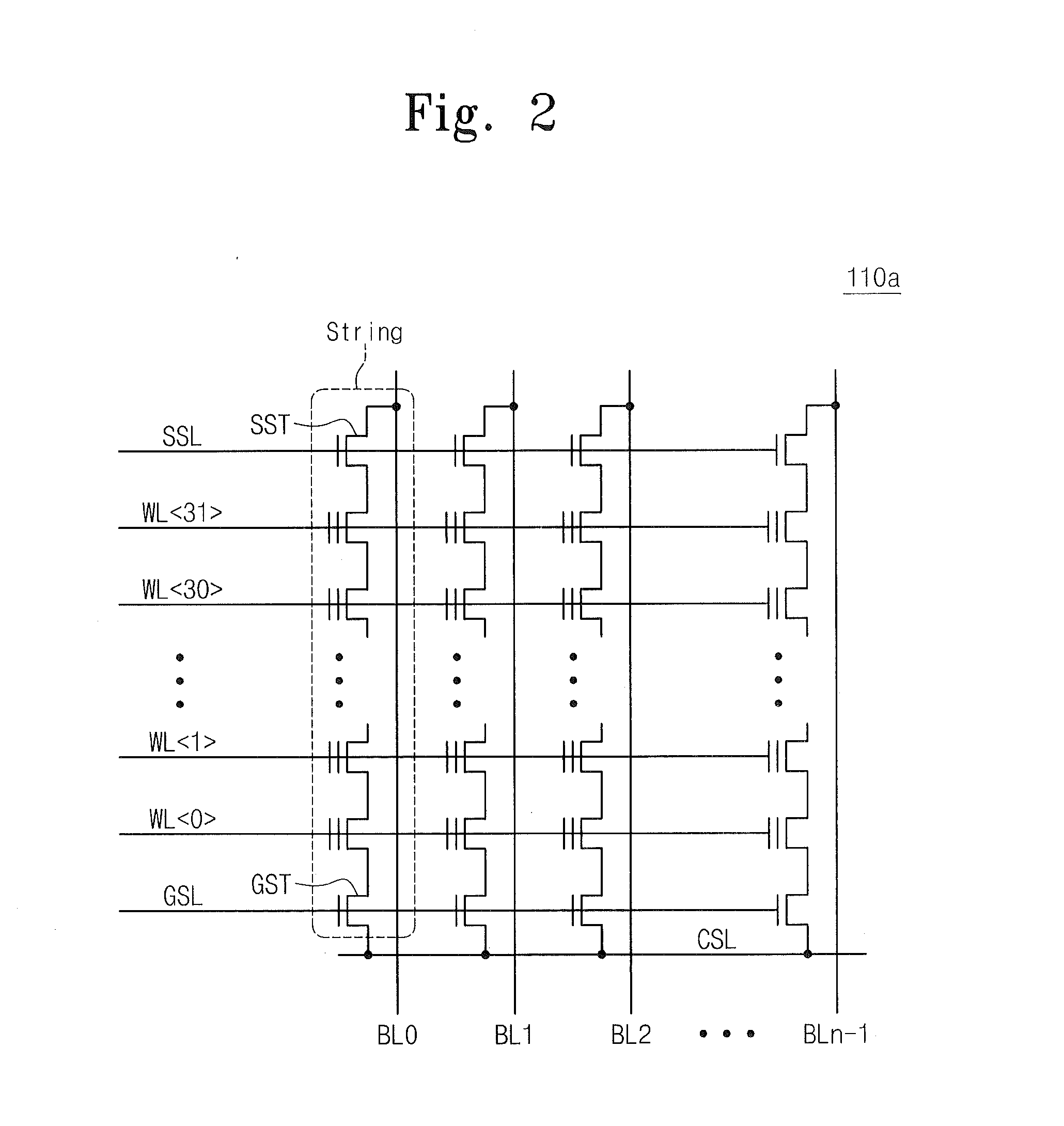
States encoding in multi-bit flash cells for optimizing error rate
InactiveUS20050213393A1Equally distributedRead-only memoriesDigital storageTest error rateData error
Owner:SANDISK IL
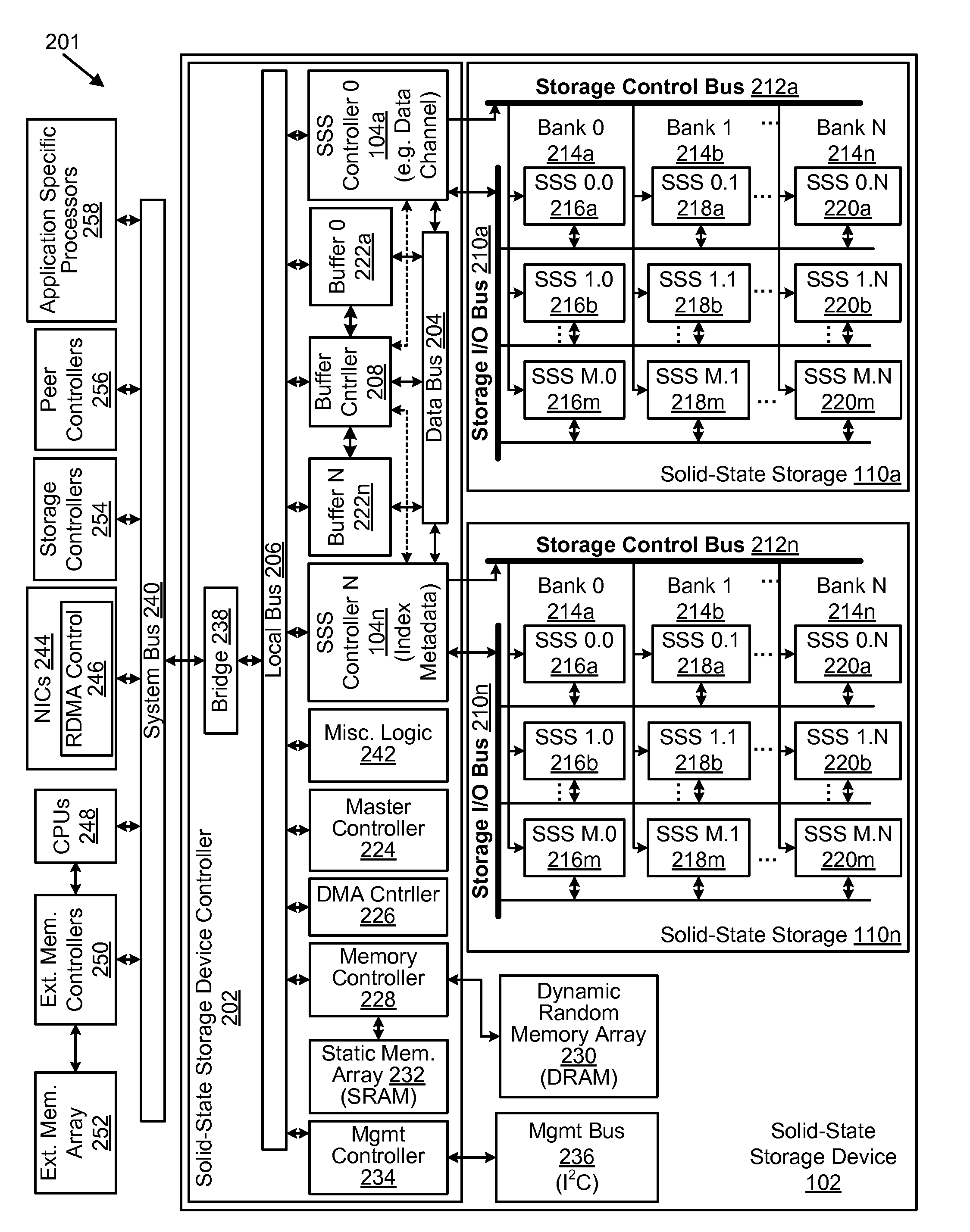
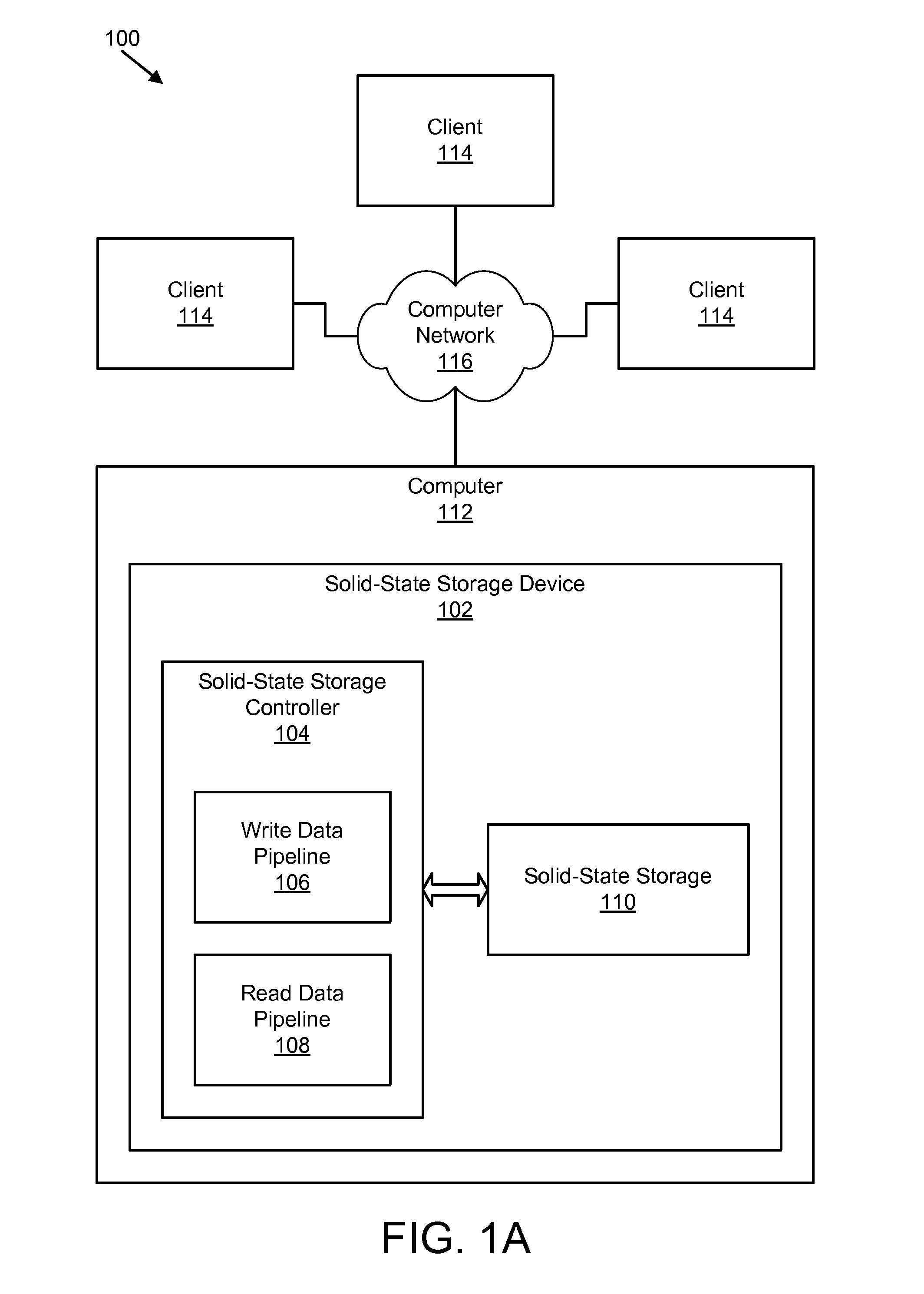
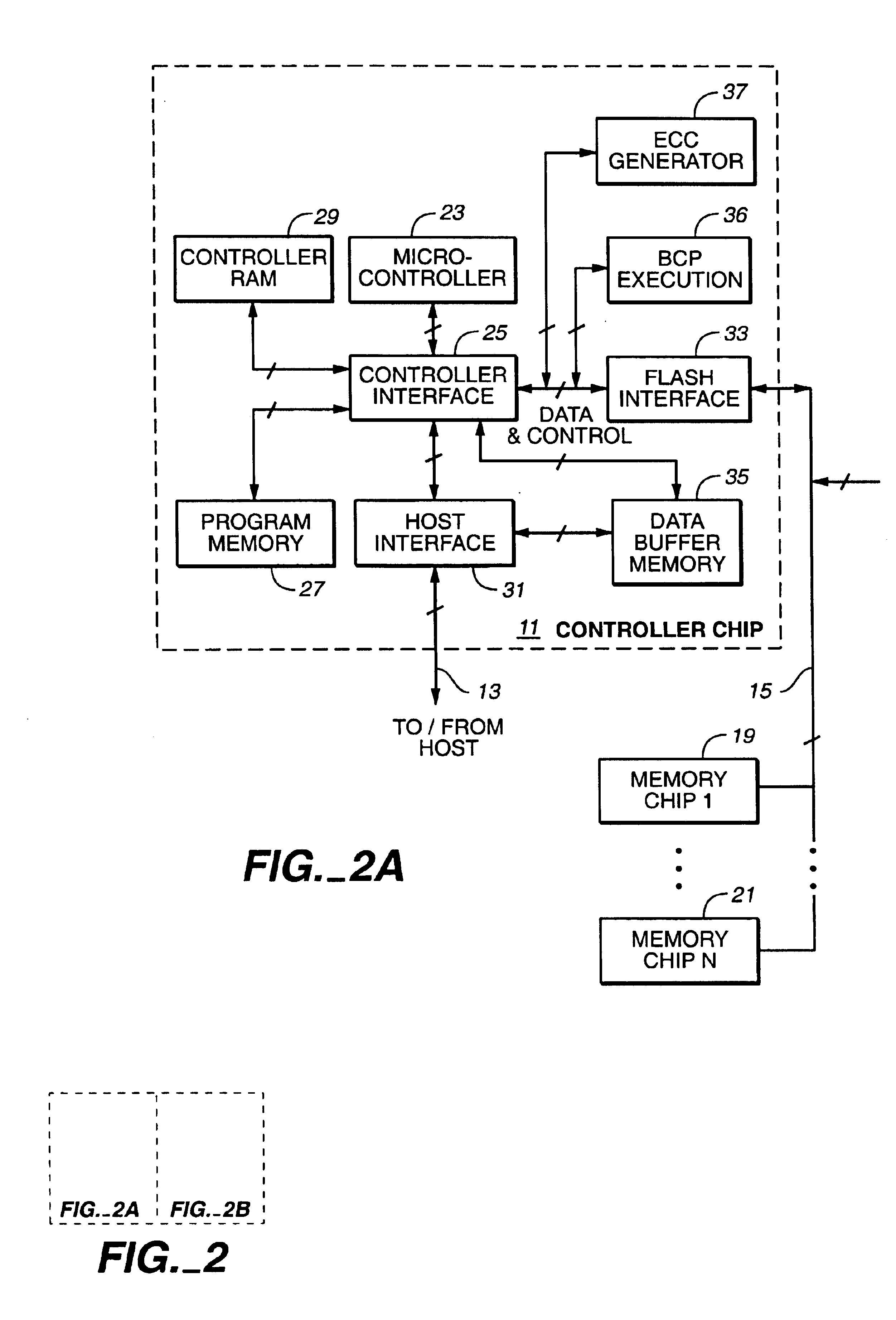
Apparatus, system, and method for managing data using a data pipeline
ActiveUS20080141043A1Energy efficient ICTInput/output to record carriersSolid-state storageData segment
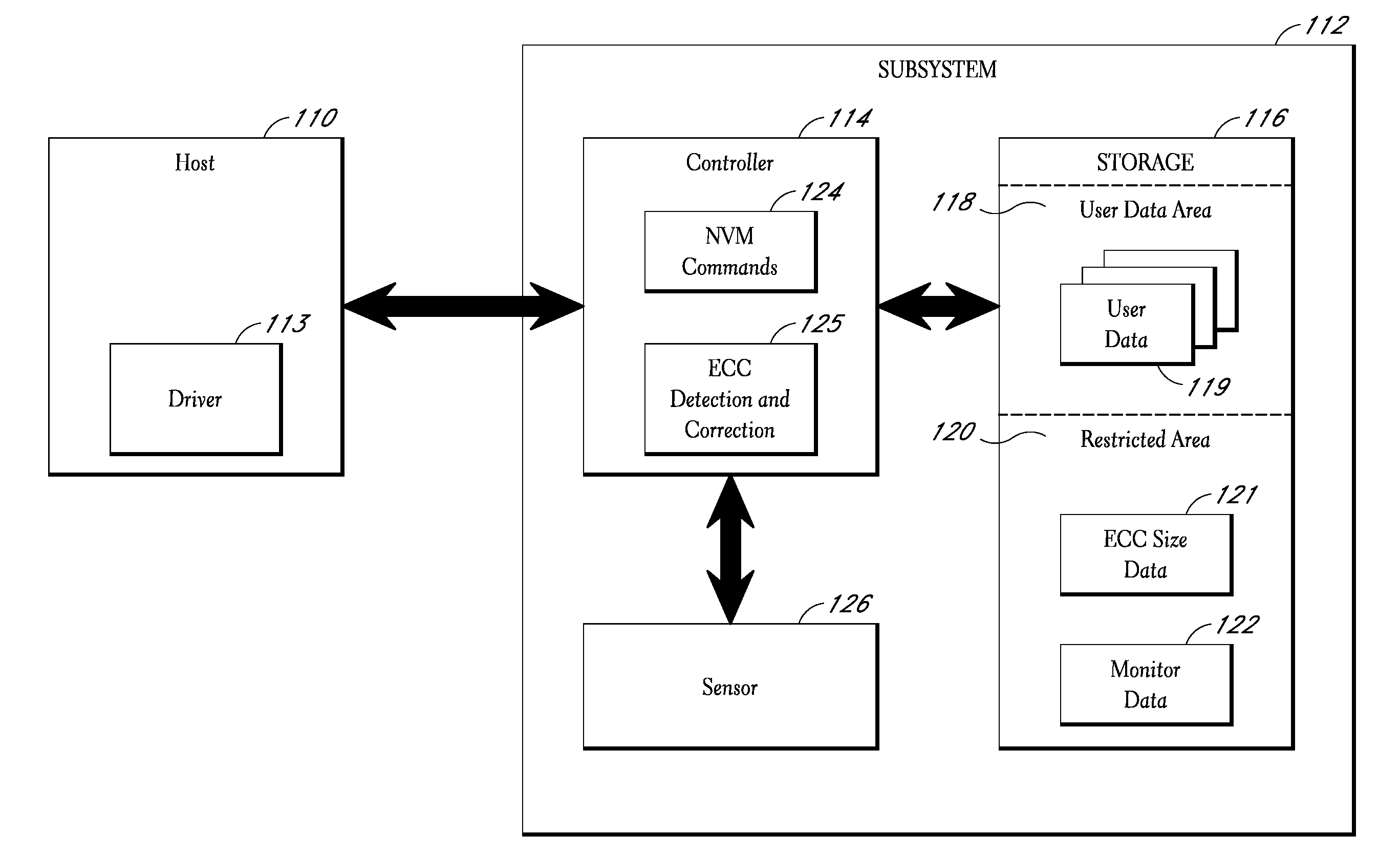
An apparatus, system, and method are disclosed for managing data in a solid-state storage device. A solid-state storage and solid-state controller are included. The solid-state storage controller includes a write data pipeline and a read data pipeline The write data pipeline includes a packetizer and an ECC generator. The packetizer receives a data segment and creates one or more data packets sized for the solid-state storage. The ECC generator generates one or more error-correcting codes (“ECC”) for the data packets received from the packetizer. The read data pipeline includes an ECC correction module, a depacketizer, and an alignment module. The ECC correction module reads a data packet from solid-state storage, determines if a data error exists using corresponding ECC and corrects errors. The depacketizer checks and removes one or more packet headers. The alignment module removes unwanted data, and re-formats the data as data segments of an object.
Owner:UNIFICATION TECH LLC
Non-Volatile Memory And Method With Post-Write Read And Adaptive Re-Write To Manage Errors
ActiveUS20110099460A1Small marginImprove performanceMemory loss protectionRead-only memoriesHigh densityLow density
Data errors in non-volatile memory inevitably increase with usage and with higher density of bits stored per cell. The memory is configured to have a first portion operating with less error but of lower density storage, and a second portion operating with a higher density but less robust storage. Input data is written and staged in the first portion before being copied to the second portion. An error management provides checking the quality of the copied data for excessive error bits. The copying and checking are repeated on a different location in the second portion until either a predetermined quality is satisfied or the number or repeats exceeds a predetermined limit. The error management is not started when a memory is new with little or no errors, but started after the memory has aged to a predetermined amount as determined by the number of erase / program cycling its has experienced.
Owner:SANDISK TECH LLC
Solid state storage subsystem that maintains and provides access to data reflective of a failure risk
Owner:WESTERN DIGITAL TECH INC
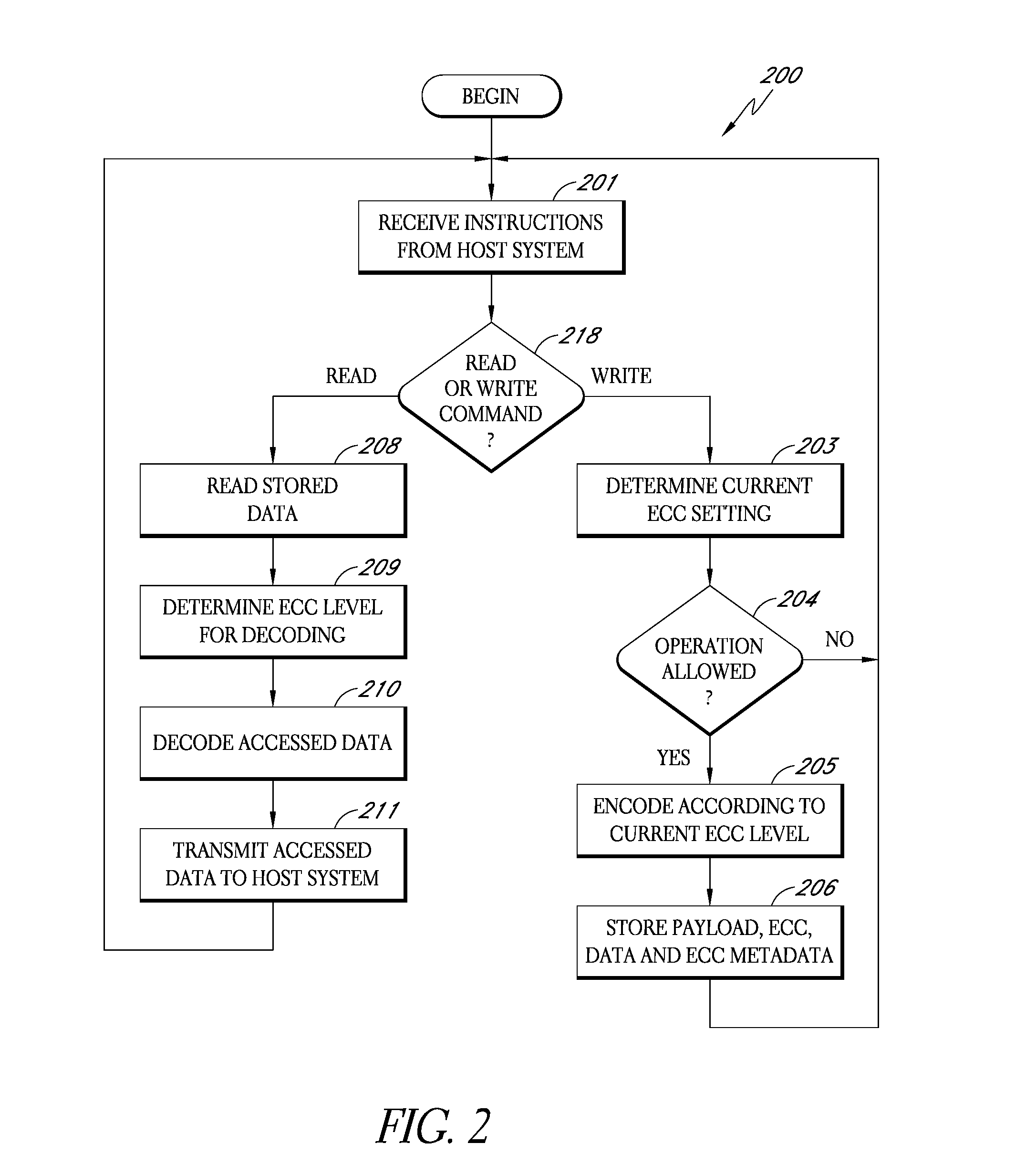
Storage subsystem capable of adjusting ECC settings based on monitored conditions
ActiveUS8095851B2Effective balanceImprove the level ofError detection/correctionCode conversionMultiple criteriaData error
Owner:WESTERN DIGITAL TECH INC
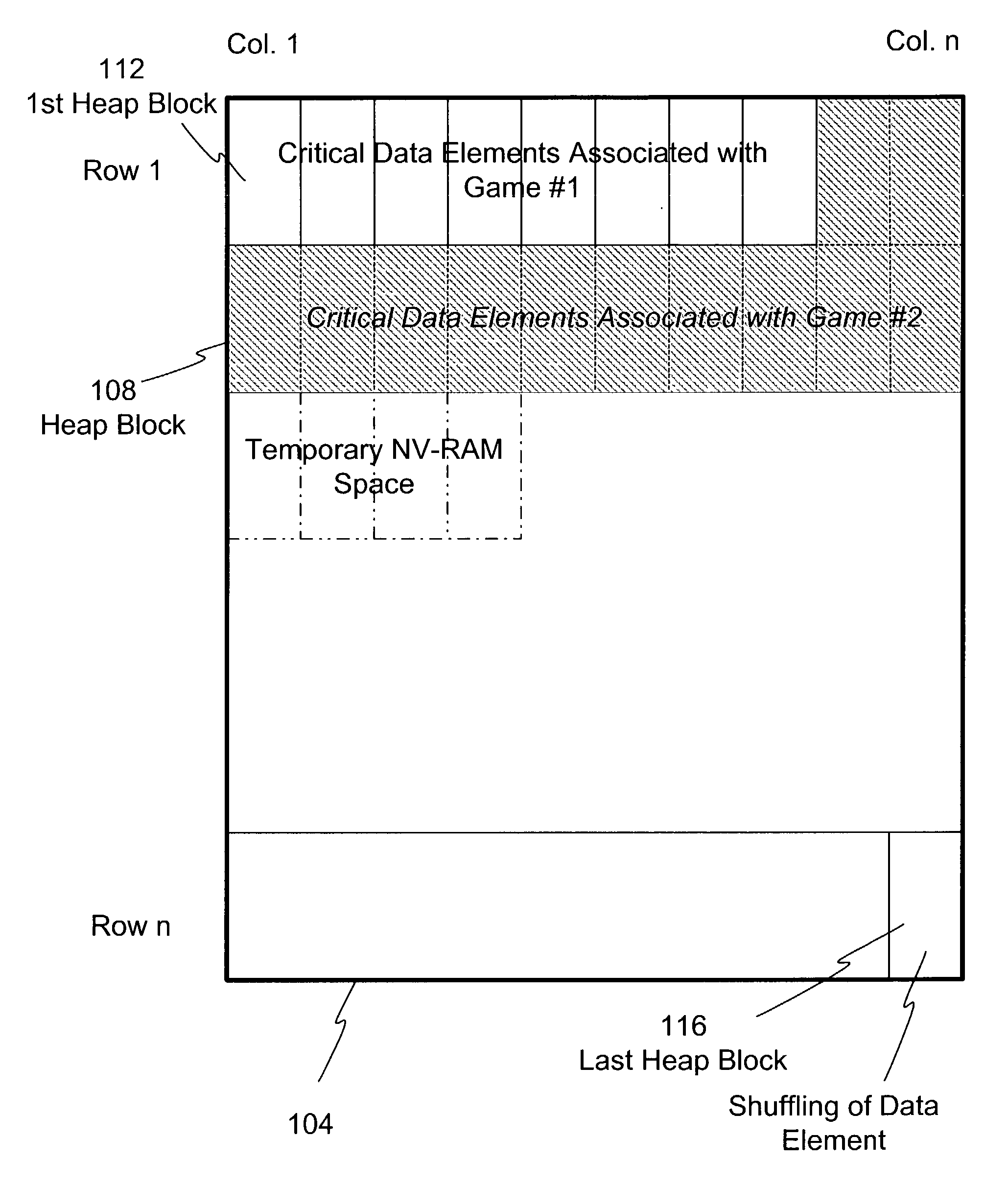
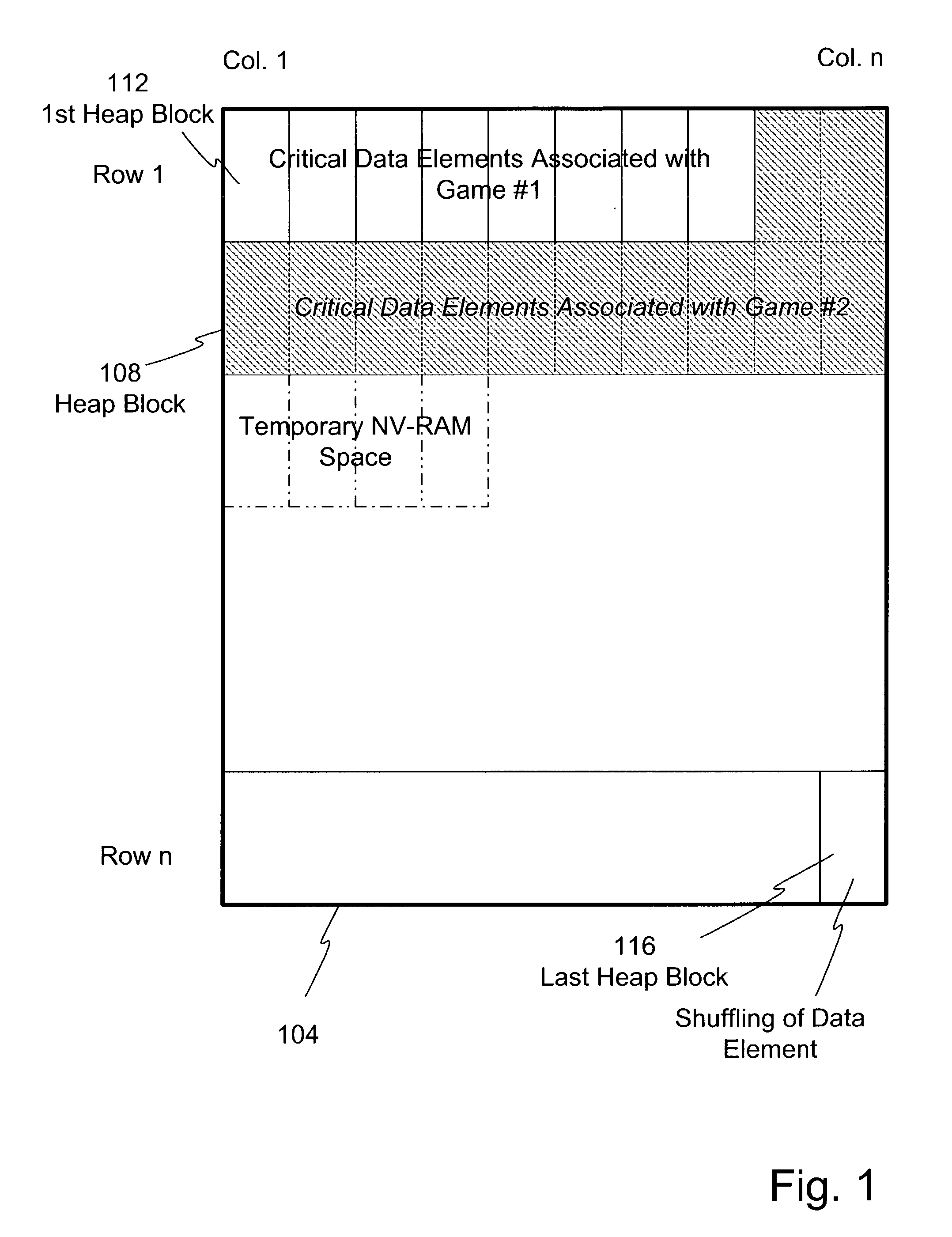
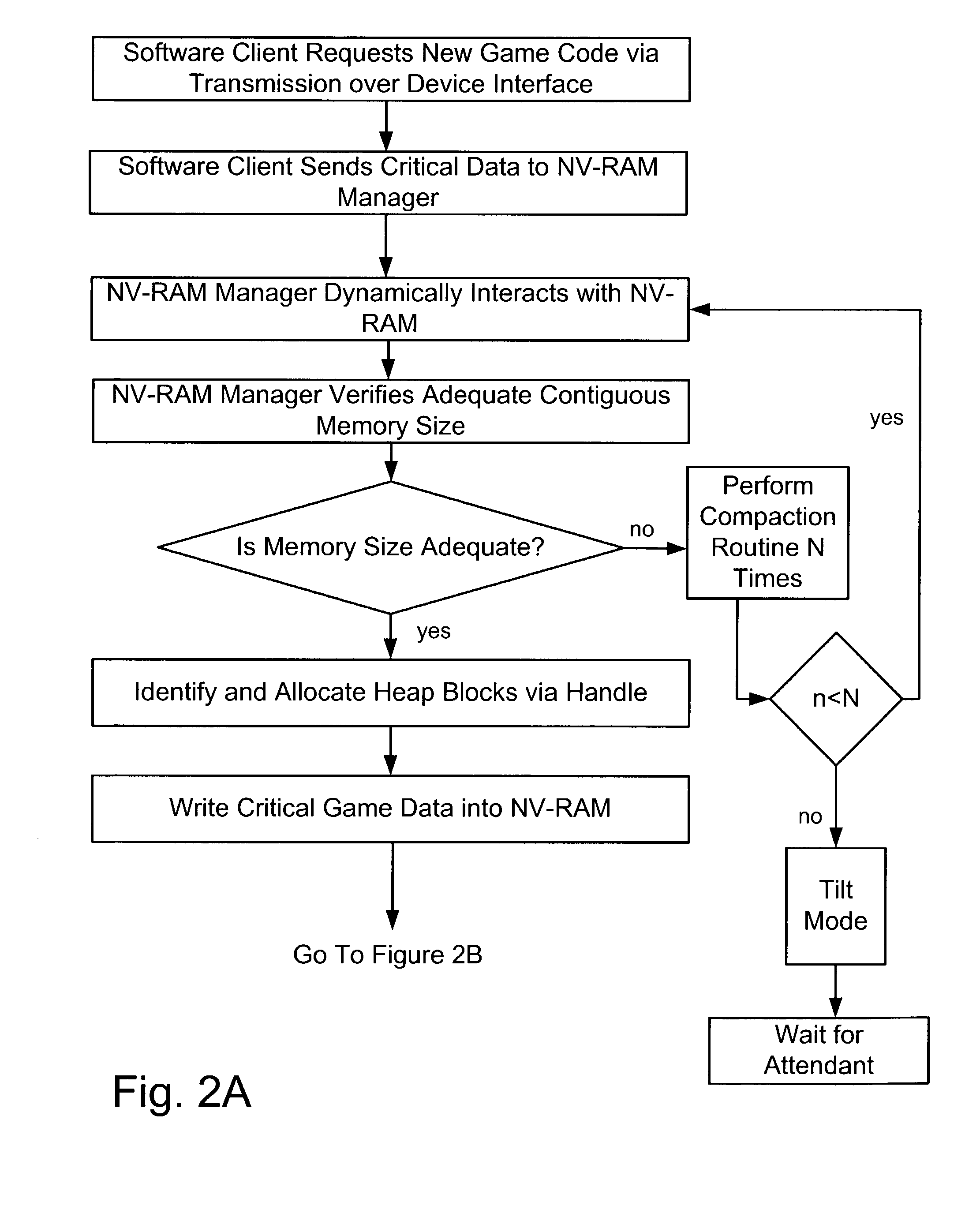
Dynamic NV-RAM
InactiveUS7111141B2Maximize useMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingDynamic storage
A method and apparatus of dynamically storing critical data of a gaming machine by allocating and deallocating memory space in a gaming machine is disclosed. One or more embodiments describe downloading or removing a new game to a gaming machine such that all existing critical data in NV-RAM memory is left intact. In one embodiment, the invention discloses a method and apparatus for dynamically allocating and deallocating memory space to accommodate either permanent or temporary storage in an NV-RAM. A method and apparatus is provided to monitor available memory space and dynamically resize the memory in NV-RAM. In one embodiment, a method is disclosed for performing an integrity check of the NV-RAM and determining whether a critical data error has occurred. In one or more embodiments, methods of compacting and shifting contents of an NV-RAM are described to consolidate available memory space or to prevent unauthorized access of NV-RAM memory.
Owner:IGT
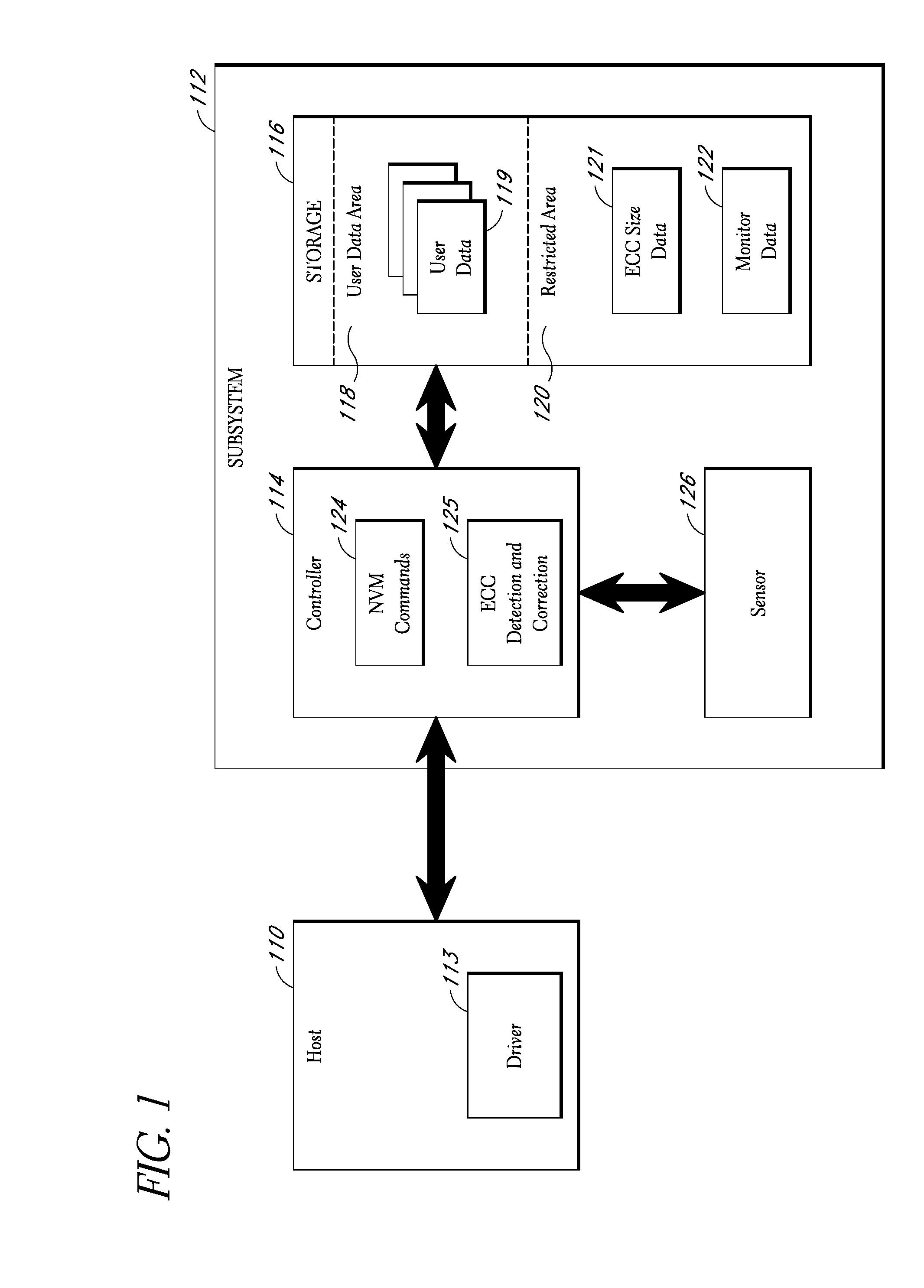
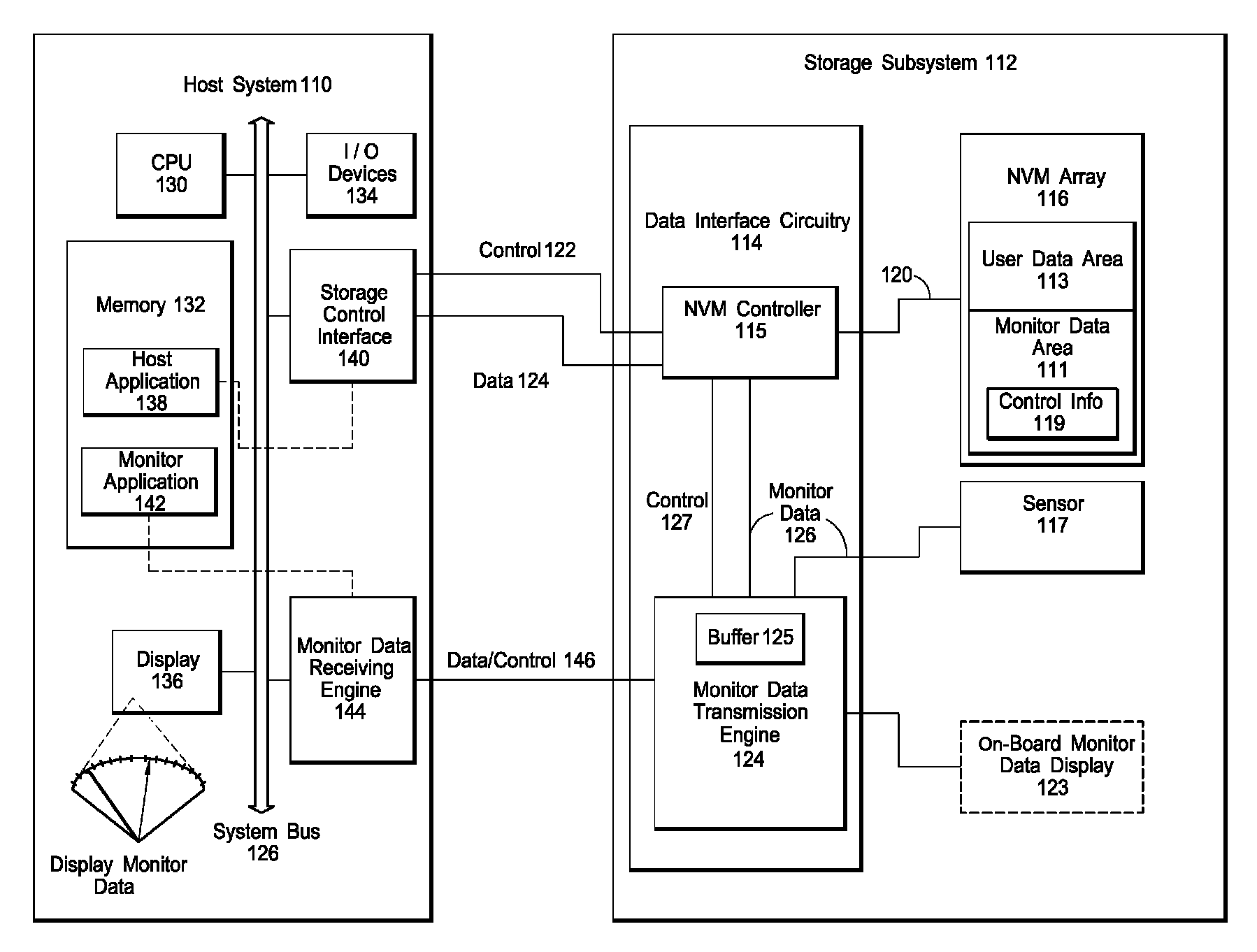
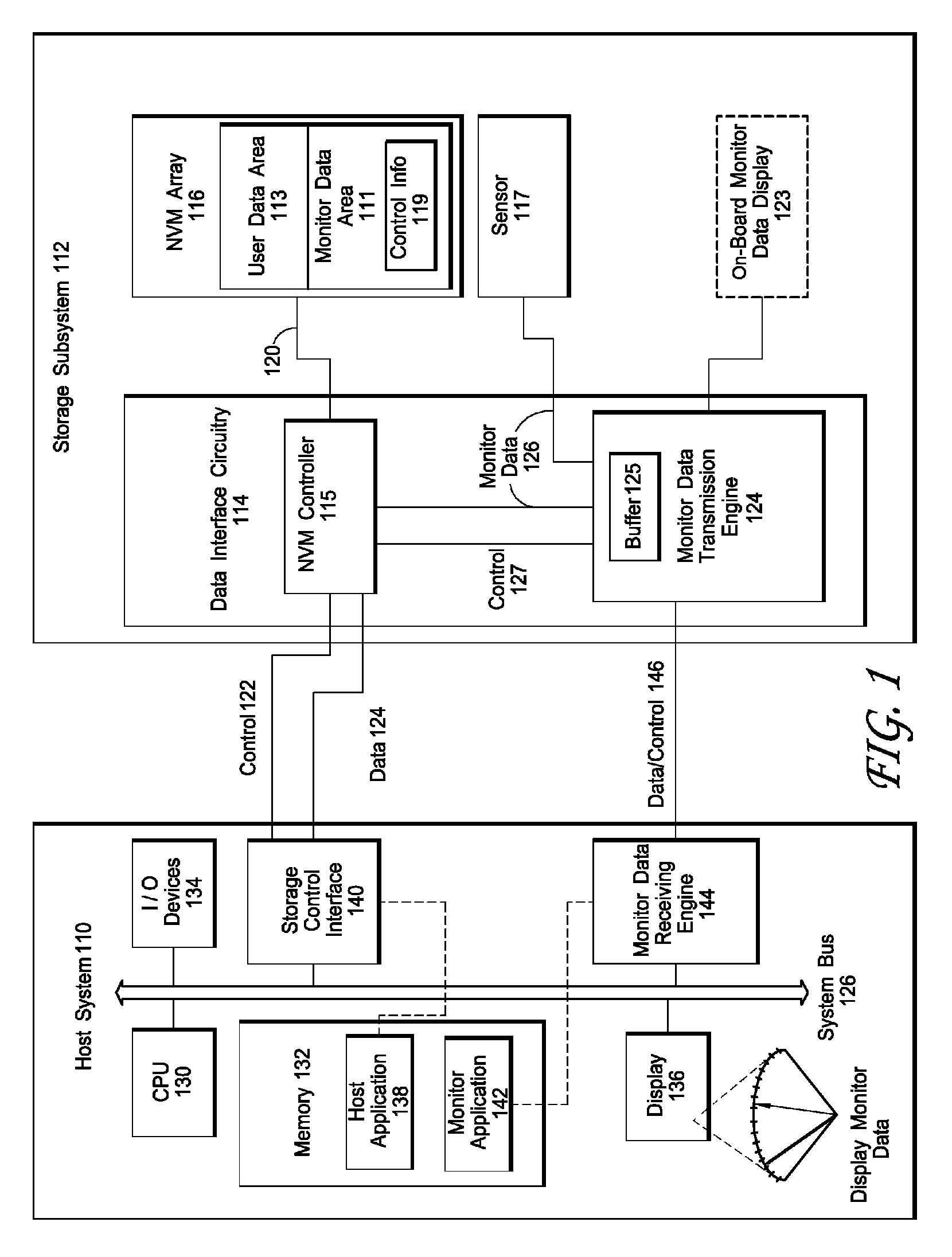
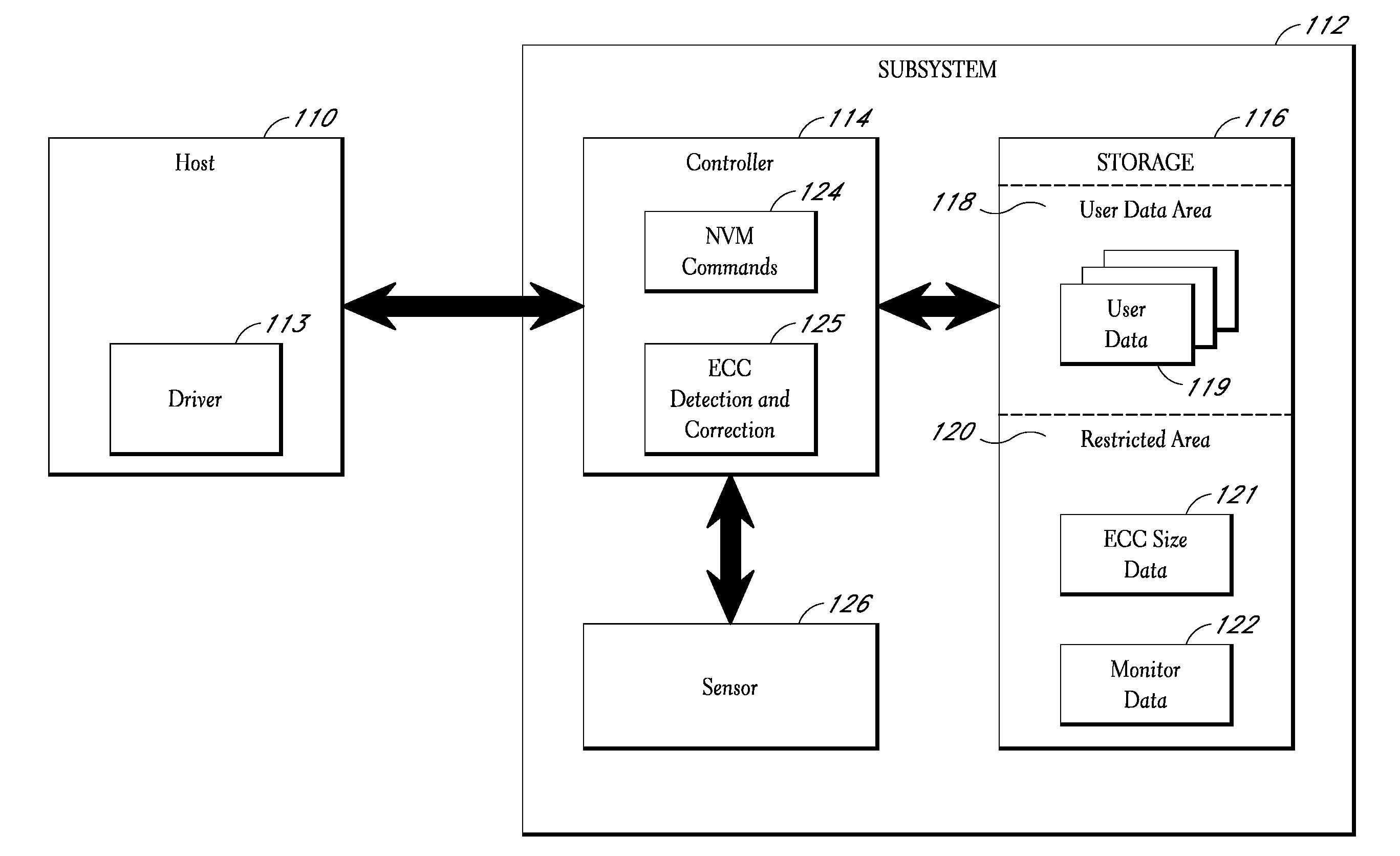
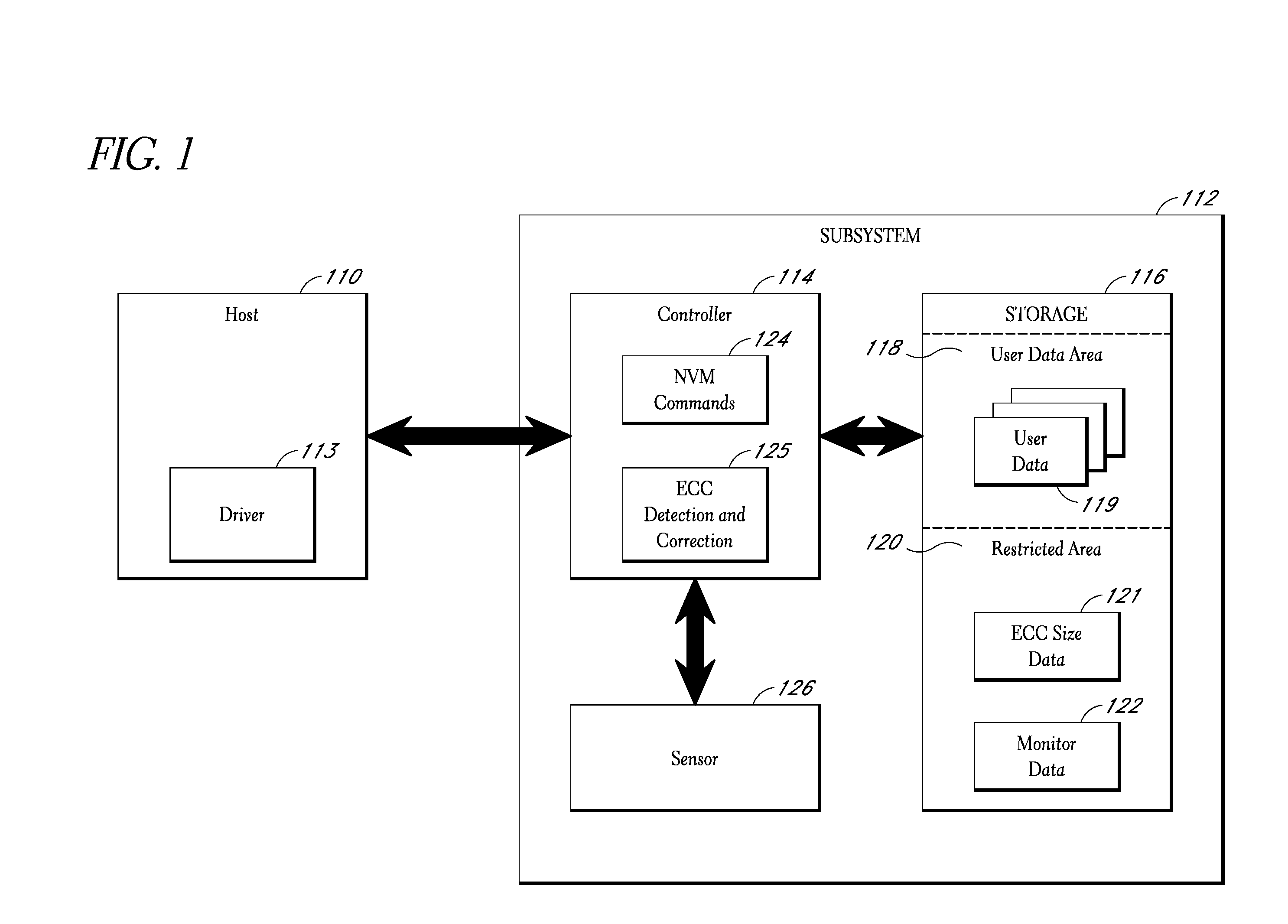
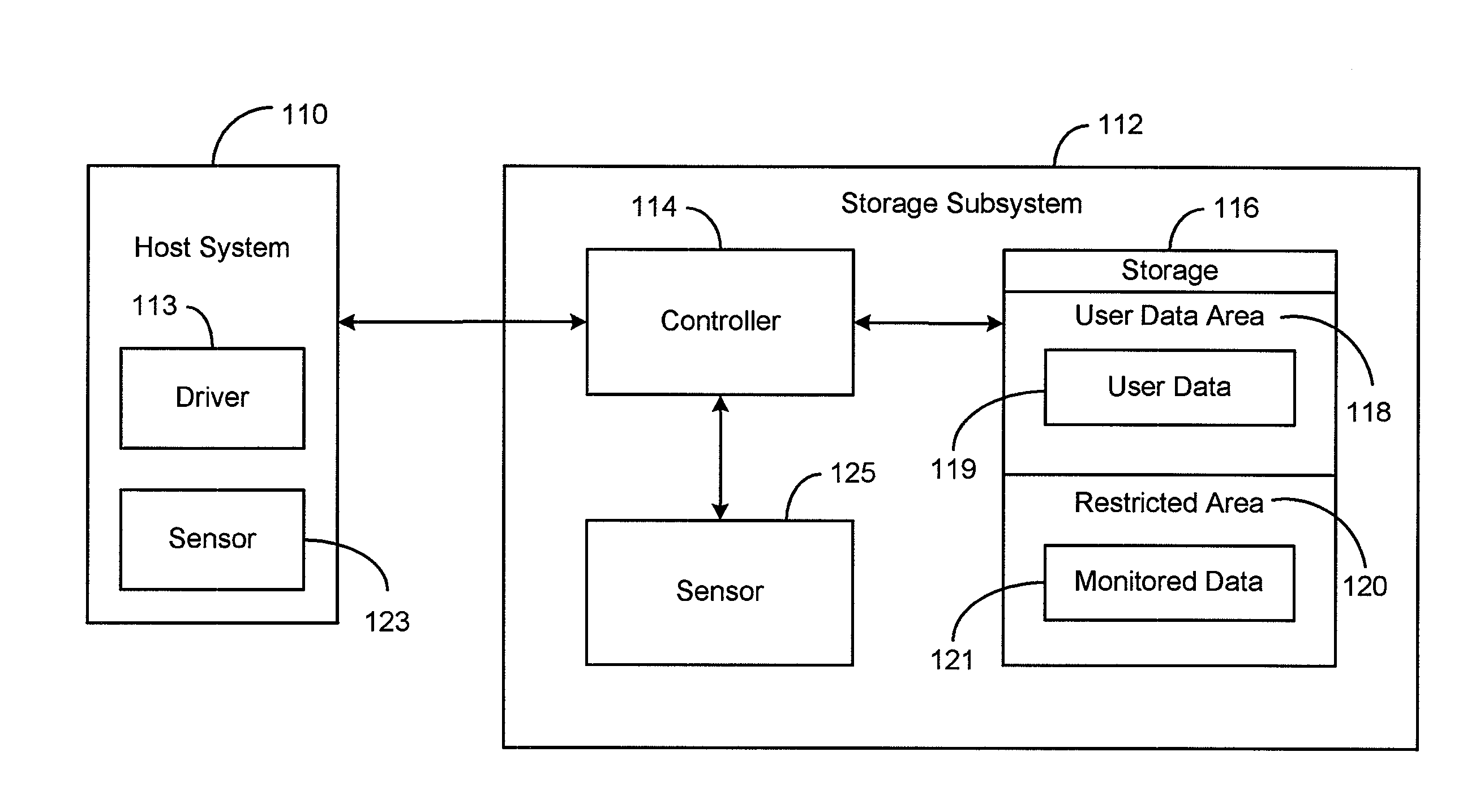
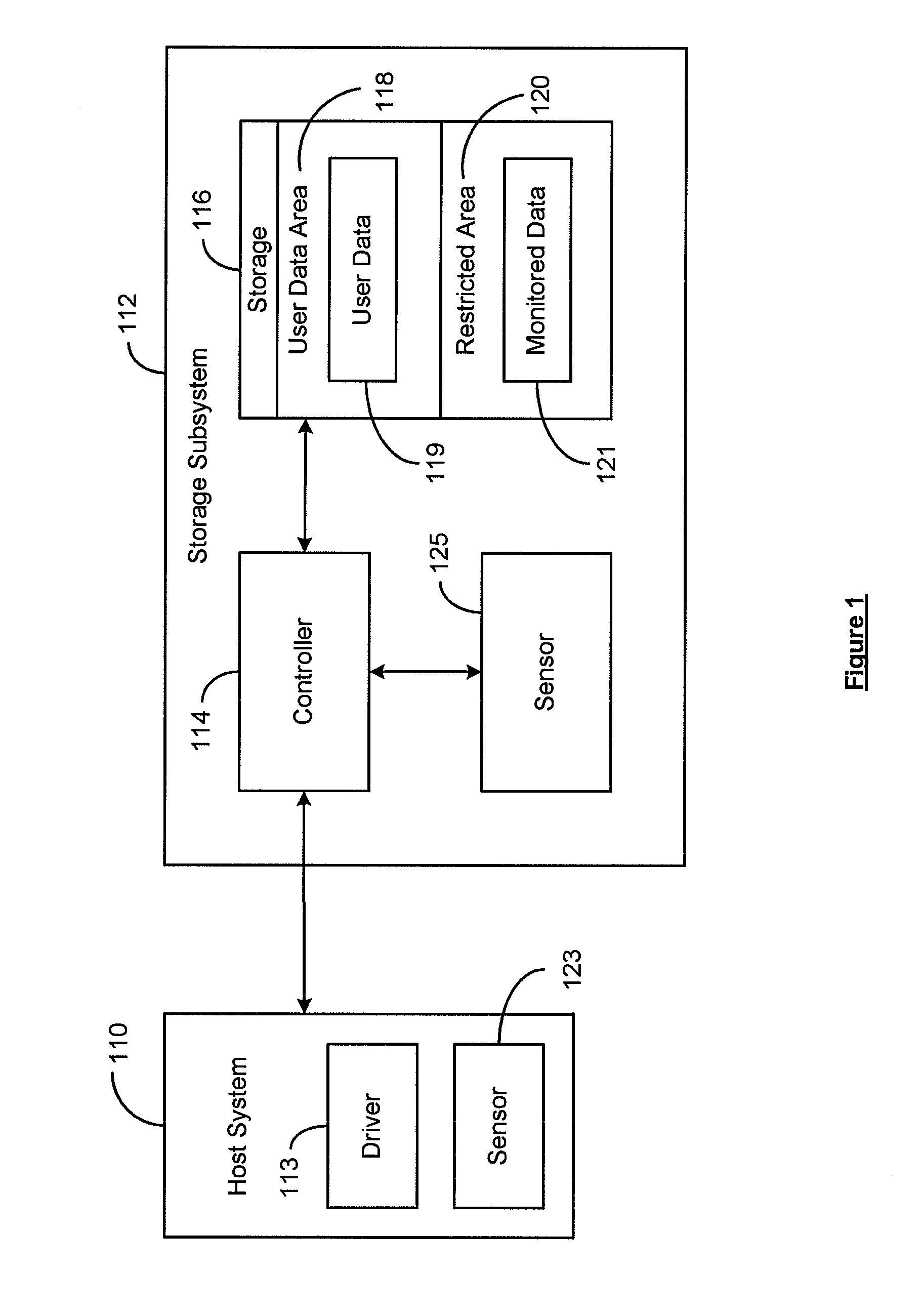
Interface for enabling a host computer to retrieve device monitor data from a solid state storage subsystem
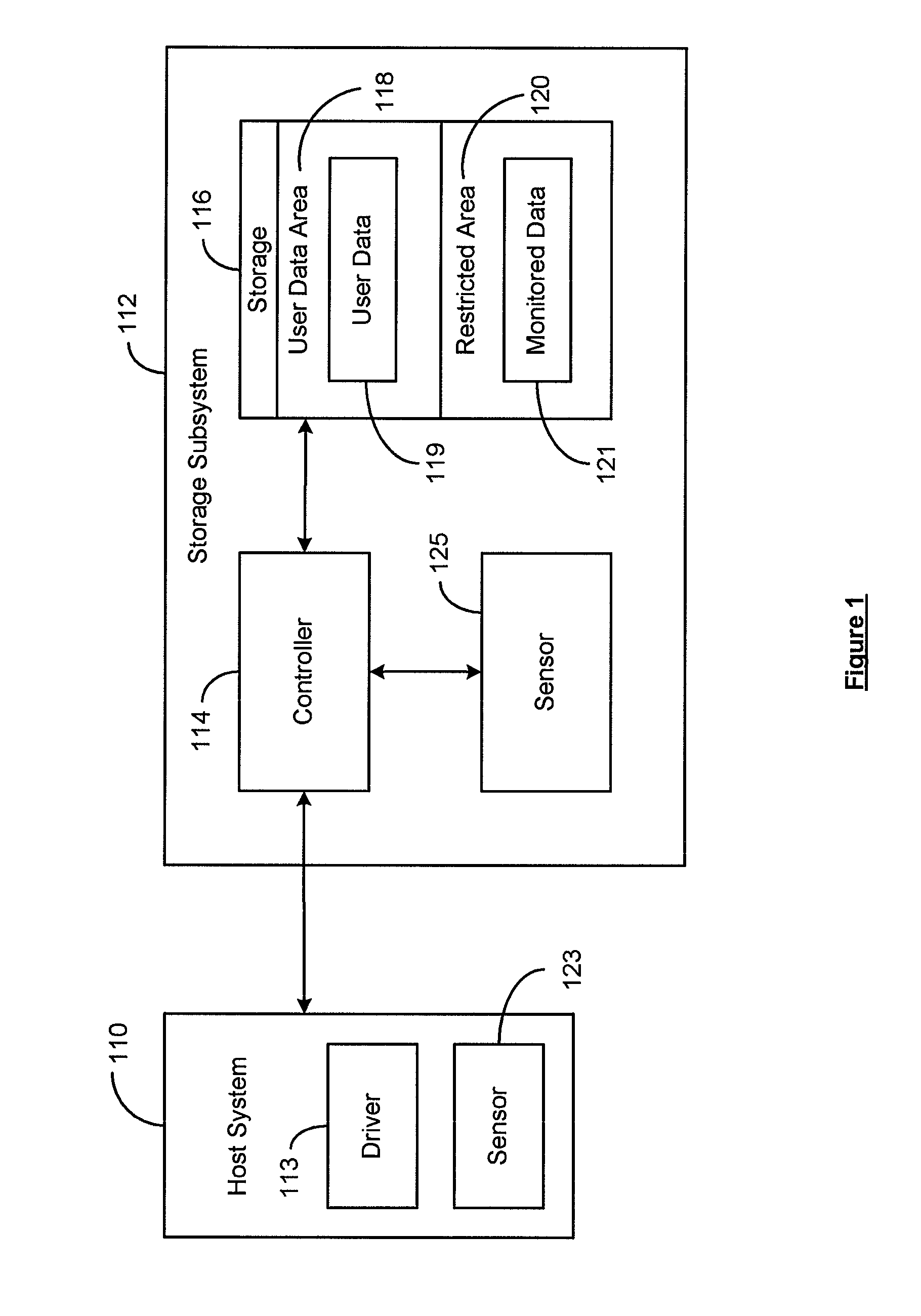
ActiveUS7962792B2Reduce eliminateReduce the possibilityReliability/availability analysisInput/output processes for data processingSolid-state storageDevice Monitor
A non-volatile storage subsystem maintains, and makes available to a host system, monitor data reflective of a likelihood of a data error occurring. The monitor data may, for example, include usage statistics and / or sensor data. The storage subsystem transfers the monitor data to the host system over a signal interface that is separate from the signal interface used for standard storage operations. This interface may be implemented using otherwise unused pins / signal lines of a standard connector, such as a CompactFlash or SATA connector. Special hardware may be provided in the storage subsystem and host system for transferring the monitor data over these signal lines, so that the transfers occur with little or no need for host-software intervention. The disclosed design reduces or eliminates the need for host software that uses non-standard or “vendor-specific” commands to retrieve the monitor data.
Owner:WESTERN DIGITAL TECH INC
Method of reducing disturbs in non-volatile memory
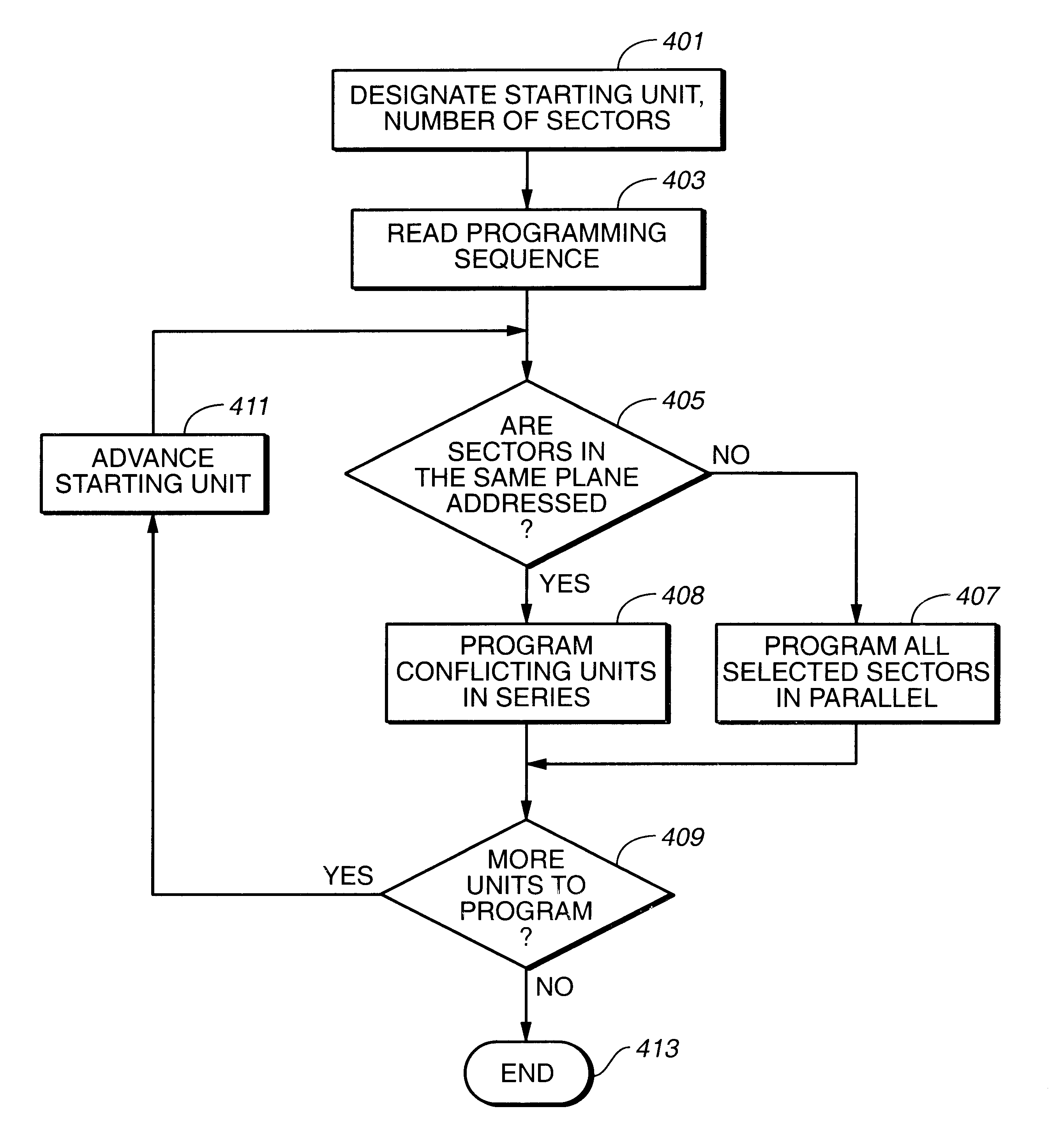
In a non-volatile memory, the displacement current generated in non-selected word lines that results when the voltage levels on an array's bit lines are changed can result in disturbs. Techniques for reducing these currents are presented. In a first aspect, the number of cells being simultaneously programmed on a word line is reduced. In a non-volatile memory where an array of memory cells is composed of a number of units, and the units are combined into planes that share common word lines, the simultaneous programming of units within the same plane is avoided. Multiple units may be programmed in parallel, but these are arranged to be in separate planes. This is done by selecting the number of units to be programmed in parallel and their order such that all the units programmed together are from distinct planes, by comparing the units to be programmed to see if any are from the same plane, or a combination of these. In a second, complementary aspect, the rate at which the voltage levels on the bit lines are changed is adjustable. By monitoring the frequency of disturbs, or based upon the device's application, the rate at which the bit line drivers change the bit line voltage is adjusted. This can be implemented by setting the rate externally, or by the controller based upon device performance and the amount of data error being generated.
Owner:SANDISK TECH LLC
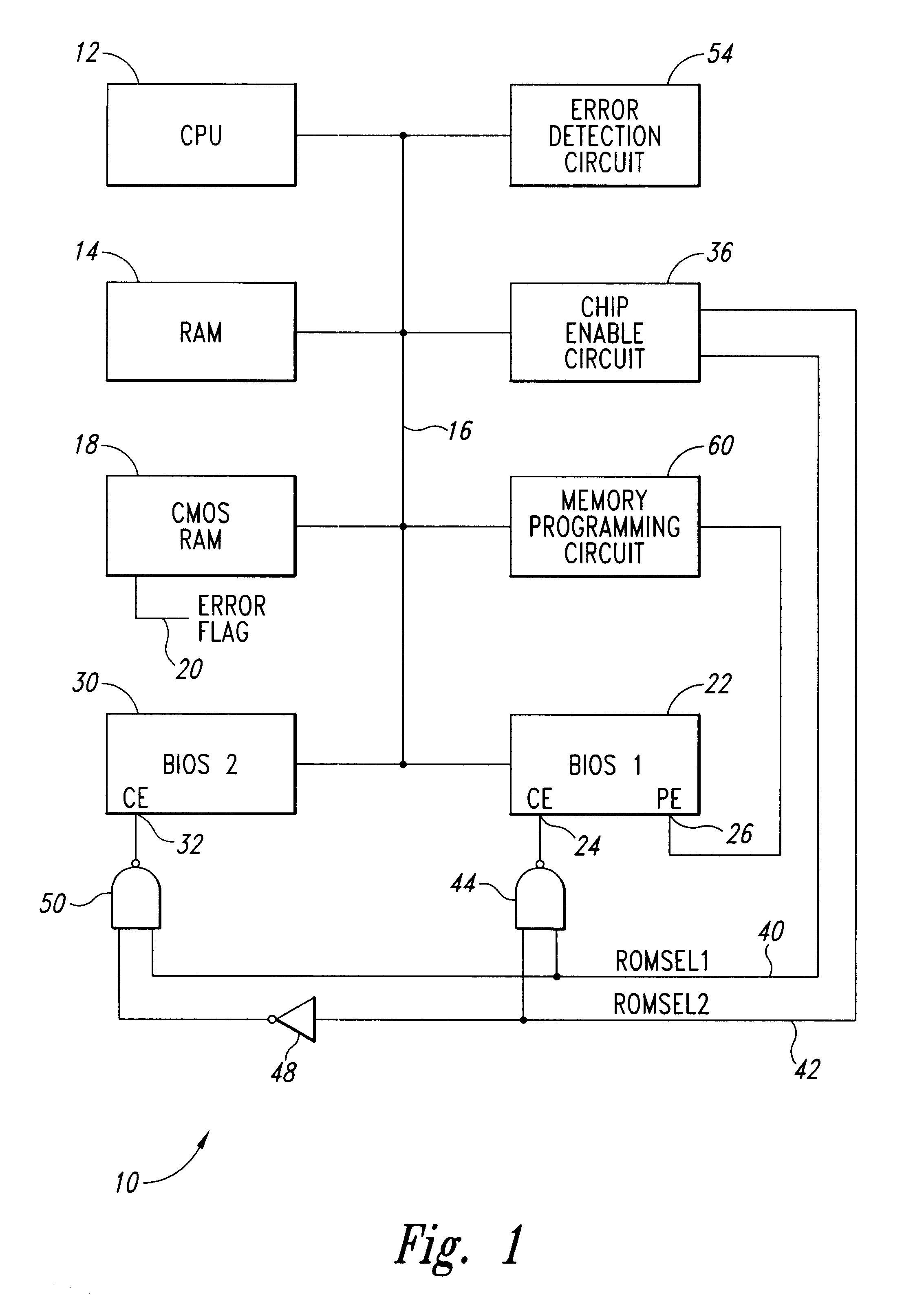
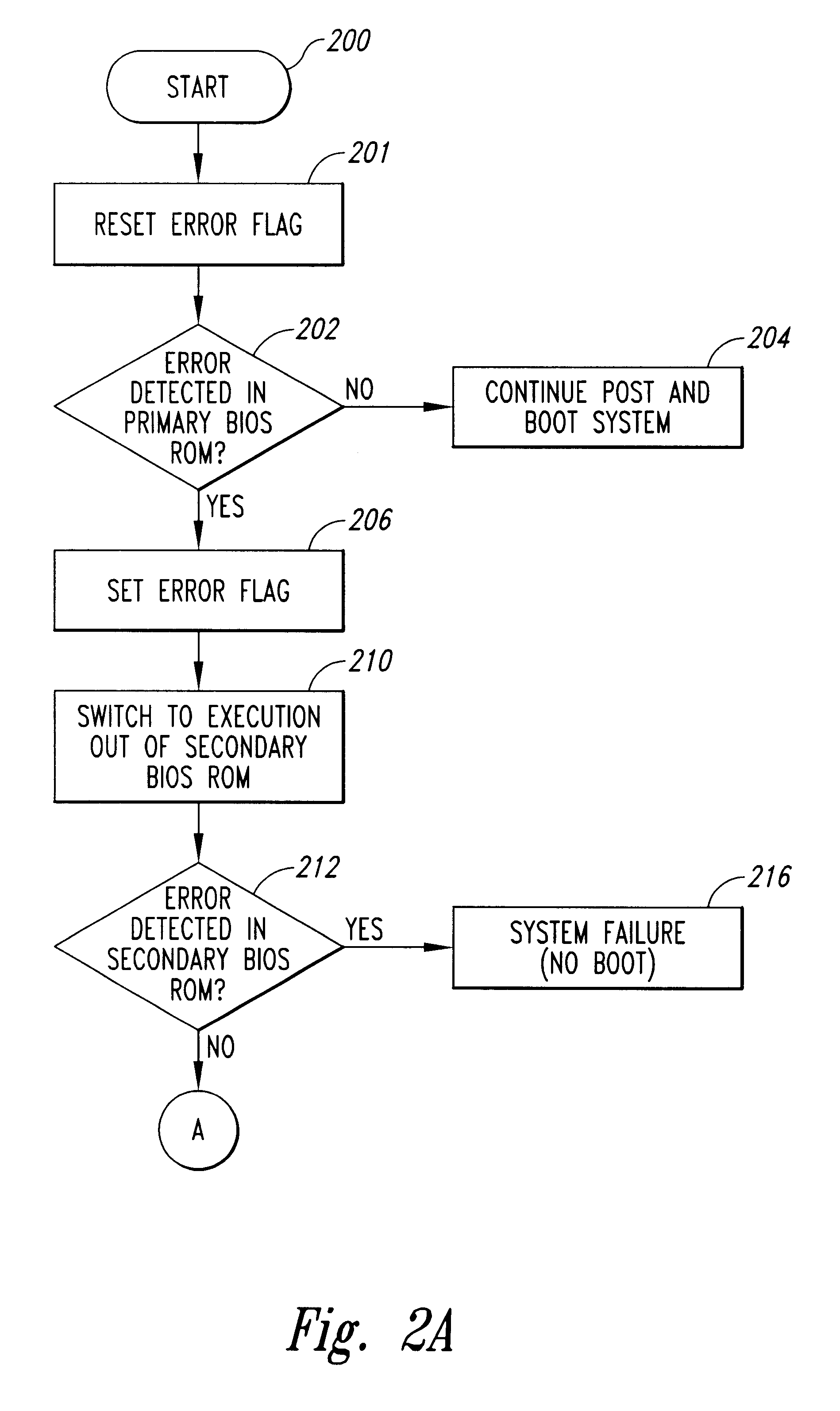
System for a primary BIOS ROM recovery in a dual BIOS ROM computer system
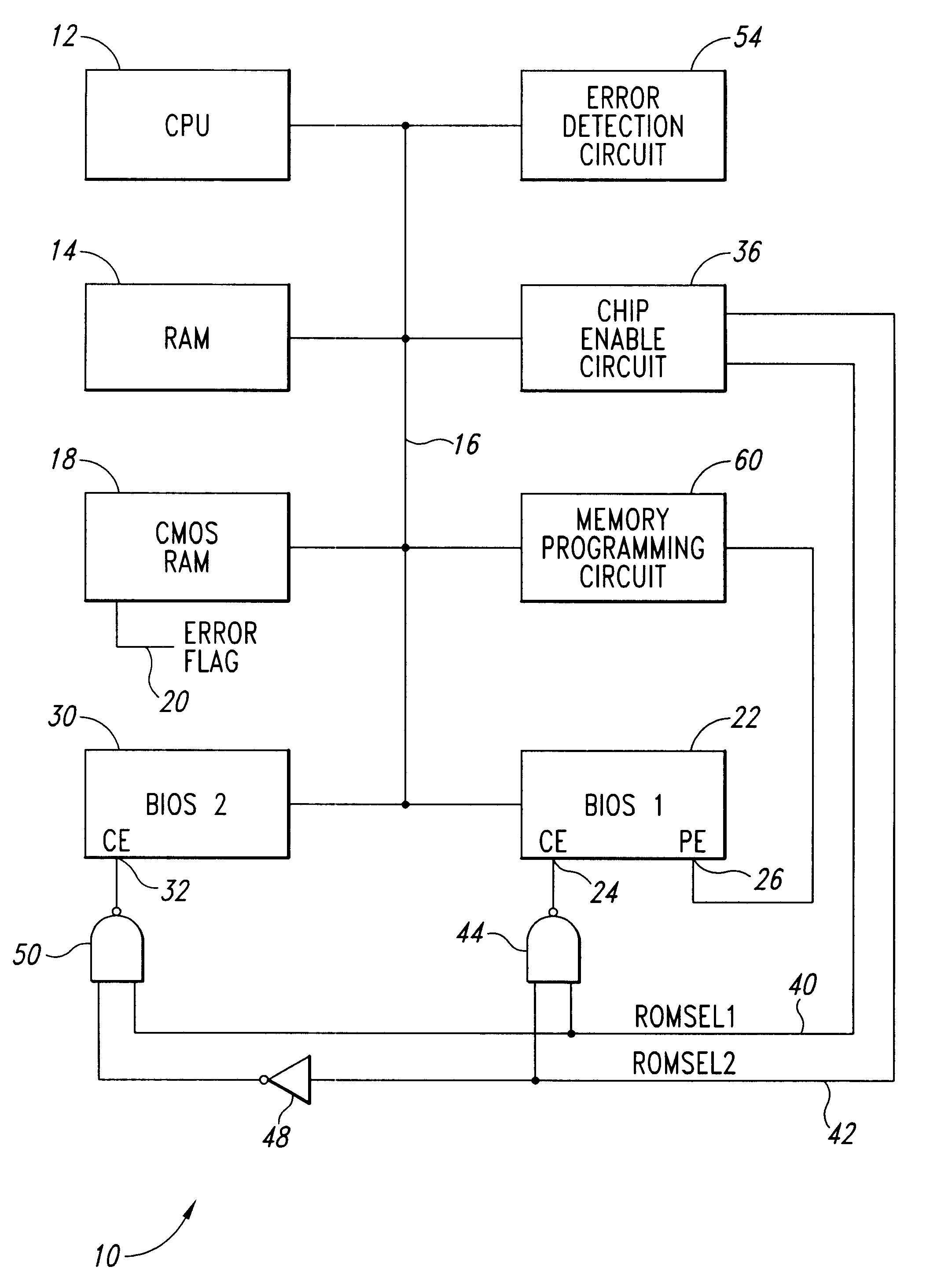
InactiveUS6185696B1Reliability increasing modificationsDetecting faulty hardware by power-on testRandom access memoryComputerized system
A computer system includes a dual basic input-output system (BIOS) read-only memory (ROM) system to initialize the computer. When the computer is first powered on or reset, the primary BIOS ROM is initially enabled. The computer analyzes the contents of the primary BIOS memory to detect data errors. If a data error is detected, a chip enable circuit disables the primary BIOS ROM and enables a secondary BIOS ROM containing essentially the same initialization instructions as the primary BIOS ROM. If no errors are detected in the secondary BIOS ROM, the initialization of the computer proceeds using the secondary BIOS ROM. As part of the initialization procedure, the contents of the secondary BIOS ROM are copied to a random access memory. The primary BIOS ROM can then be reprogrammed with the contents of the secondary BIOS ROM using the copy in random access memory, or from the secondary BIOS ROM itself.
Owner:MEI CALIFORNIA +1
Method of reducing disturbs in non-volatile memory
Owner:SANDISK TECH LLC
States encoding in multi-bit flash cells for optimizing error rate
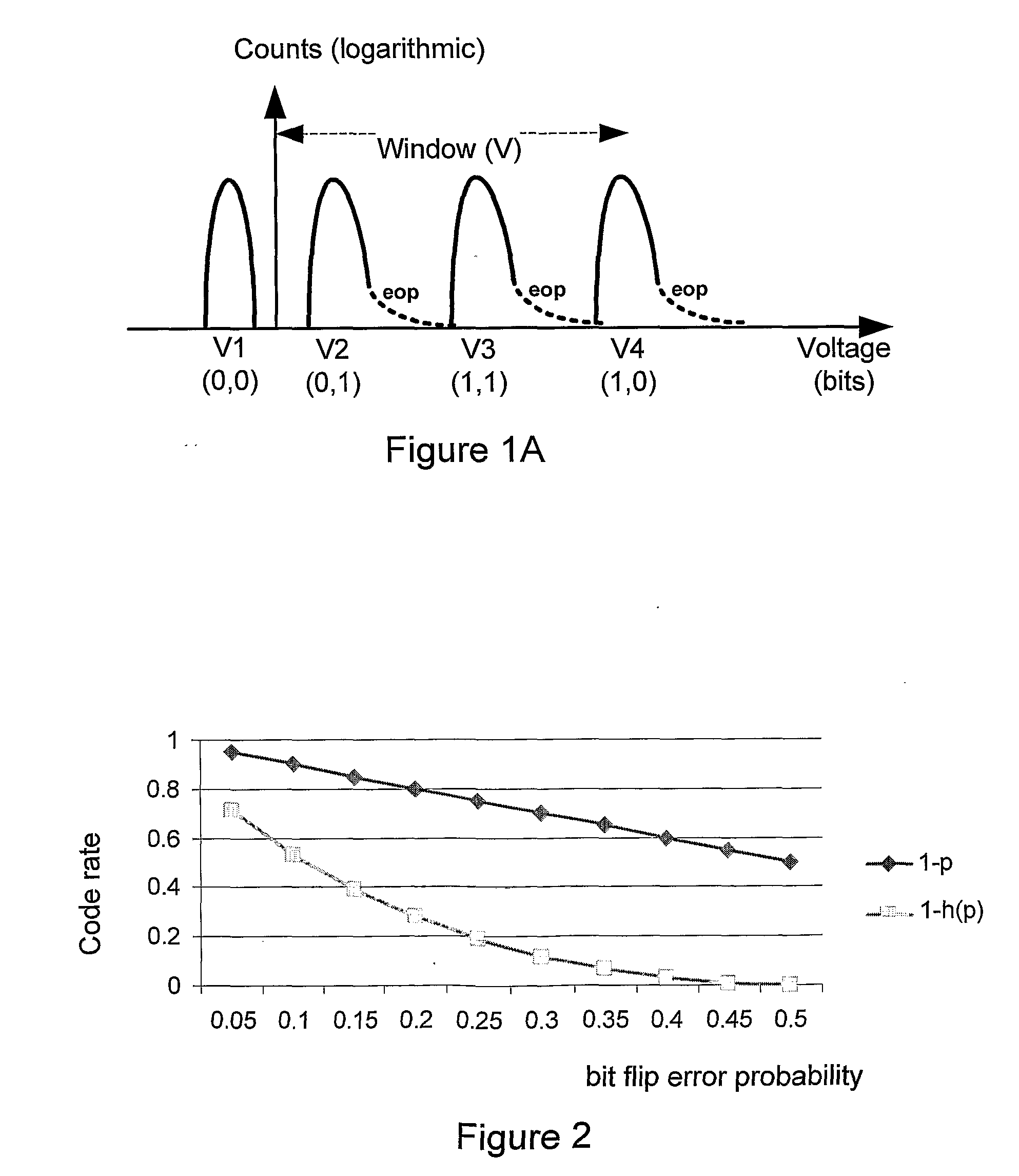
ActiveUS20080104312A1Equally distributedMemory adressing/allocation/relocationRead-only memoriesData errorCell state
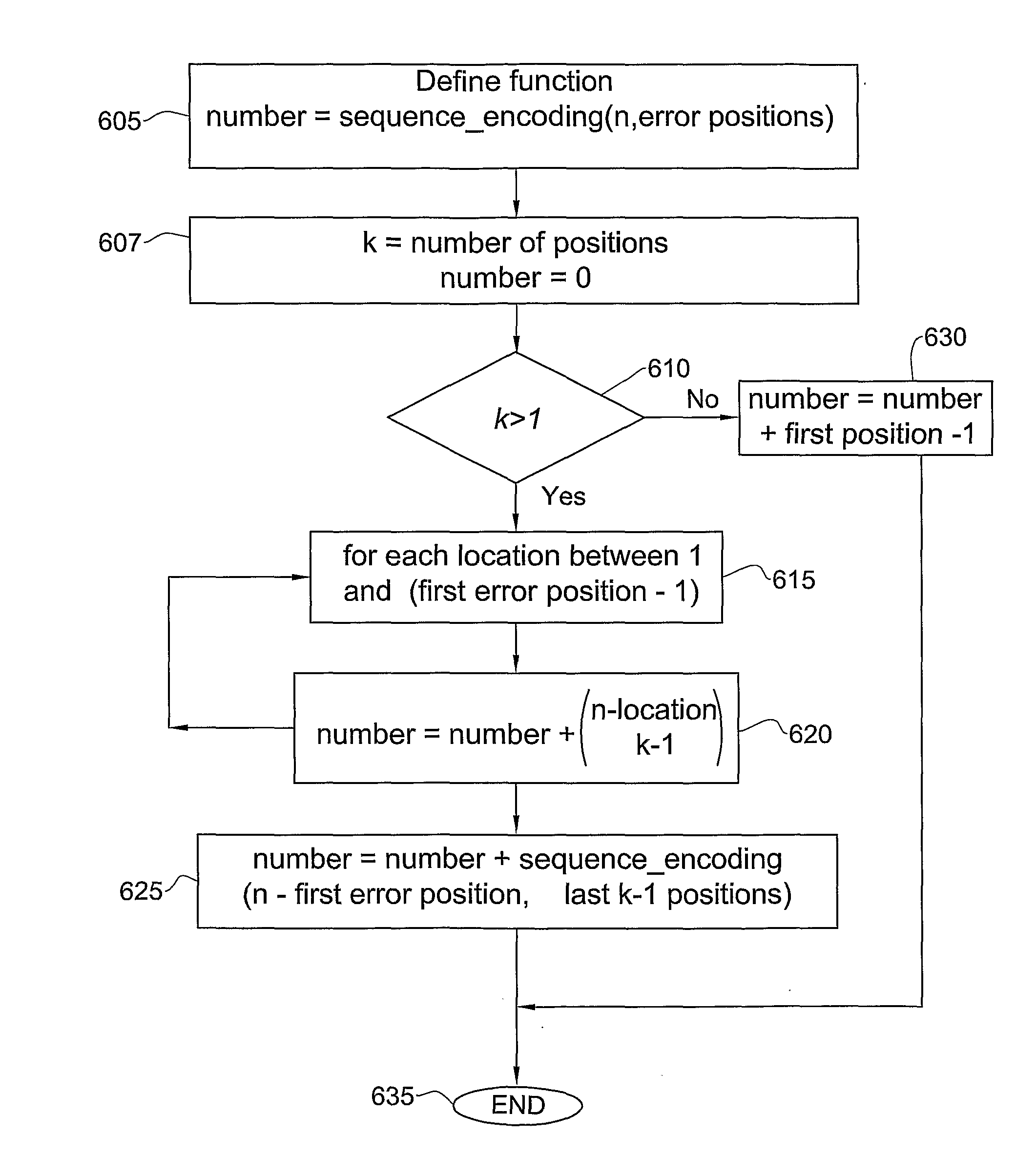
Memory cells are programmed and read, at least M=3 data bits per cell, according to a valid nonserial physical bit ordering with reference to a logical bit ordering. The logical bit ordering is chosen to give a more even distribution of error probabilities of the bits, relative to the probability distributions of the data error and the cell state transition error, than would be provided by the physical bit ordering alone. Preferably, both bit orderings have 2M−1 transitions. Preferably, the logical bit ordering is evenly distributed. The translation between the bit orderings is done by software or hardware.
Owner:WESTERN DIGITAL ISRAEL LTD
Non-Volatile Memory And Method With Post-Write Read And Adaptive Re-Write To Manage Errors
ActiveUS20110099418A1Small marginReduce memory costMemory adressing/allocation/relocationRead-only memoriesHigh densityQuality assurance
Data errors in non-volatile memory inevitably increase with usage and with higher density of bits stored per cell. For acceptable quality assurance, conventional error correction codes (“ECC”) have to correct a maximum number of error bits up to the far tail end of a statistical population. The present memory is configured to have a first portion operating with less error but of lower density storage, and a second portion operating with a higher density but less robust storage. If excessive error bits (at the far tail-end) occur after writing a group of data to the second portion, the data is adaptively rewritten to the first portion which will produce less error bits. Preferably, the data is initially written to a cache also in the first portion to provide source data for any rewrites. Thus, a more efficient ECC not requiring to correcting for the far tail end can be used.
Owner:SANDISK TECH LLC
Encoding Free View Point Data in Movie Data Container
ActiveUS20180205963A1Digital video signal modificationSelective content distributionParallaxSound sources
Multiple Holocam Orbs observe a real-life environment and generate an artificial reality representation of the real-life environment. Depth image data is cleansed of error due to LED shadow by identifying the edge of a foreground object in an (near infrared light) intensity image, identifying an edge in a depth image, and taking the difference between the start of both edges. Depth data error due to parallax is identified noting when associated text data in a given pixel row that is progressing in a given row direction (left-to-right or right-to-left) reverses order. Sound sources are identified by comparing results of a blind audio source localization algorithm, with the spatial 3D model provided by the Holocam Orb. Sound sources that corresponding to identifying 3D objects are associated together. Additionally, types of data supported by a standard movie data container, such as an MPEG container, is expanding to incorporate free viewpoint data (FVD) model data. This is done by inserting FVD data of different individual 3D objects at different sample rates into a single video stream. Each 3D object is separately identified by a separately assigned ID.
Owner:SEIKO EPSON CORP +1
Storage subsystem capable of adjusting ecc settings based on monitored conditions
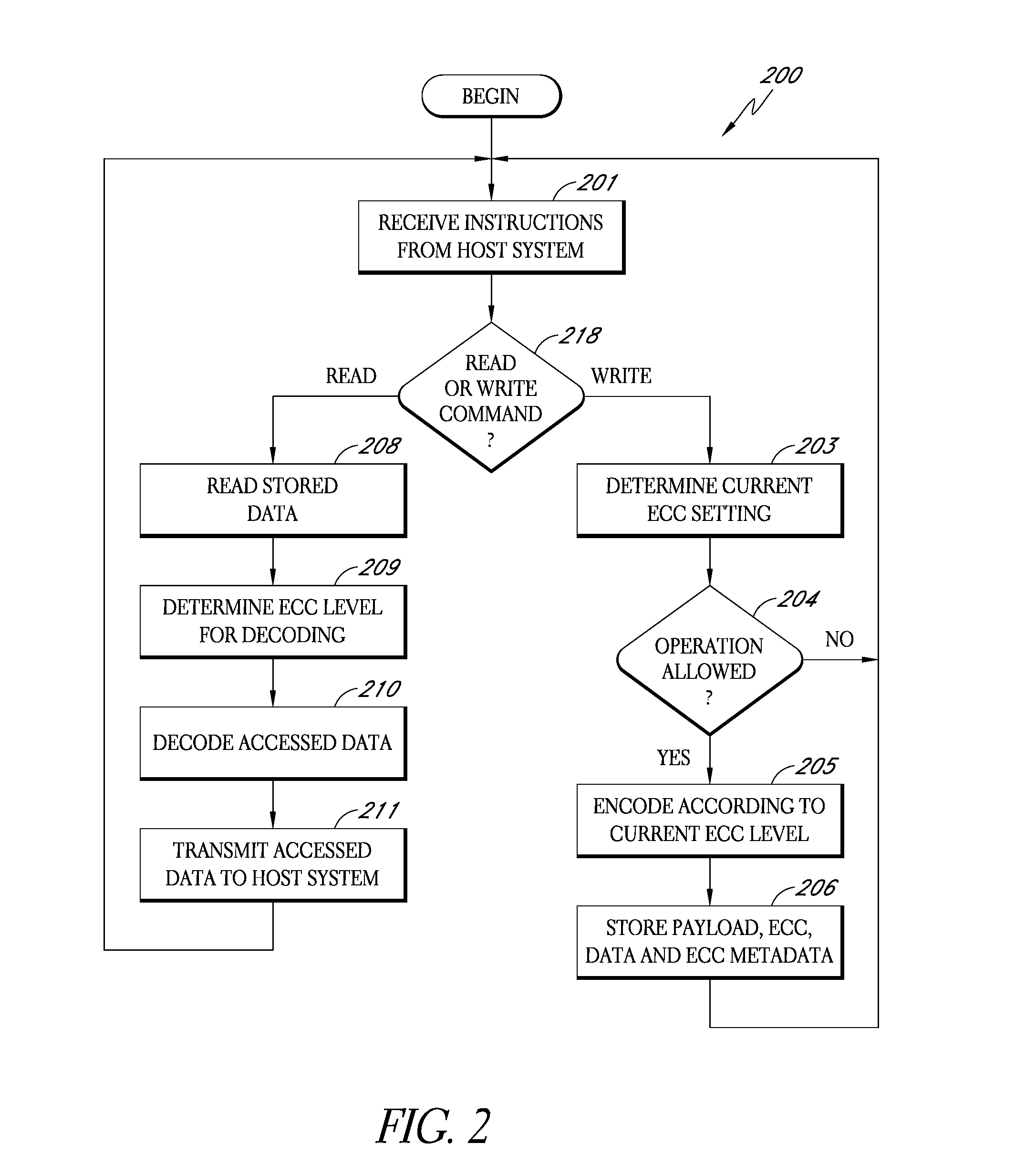
ActiveUS20090070651A1Improve the level ofIncreased ECCCode conversionCoding detailsMultiple criteriaData error
A storage subsystem monitors one or more conditions related to the probability of a data error occurring. Based on the monitored condition or conditions, the storage subsystem adjusts an error correction setting, and thus the quantity of ECC data used to protect data received from a host system. To enable blocks of data to be properly checked when read from memory, the storage subsystem stores ECC metadata indicating the particular error correction setting used to store particular blocks of data. The storage subsystem may be in the form of a solid-state non-volatile memory card or drive that attaches to the host system.
Owner:WESTERN DIGITAL TECH INC
Systems and methods for handling immediate data errors in flash memory
ActiveUS20100122113A1High densityGood effectError preventionTransmission systemsComputer architectureData error
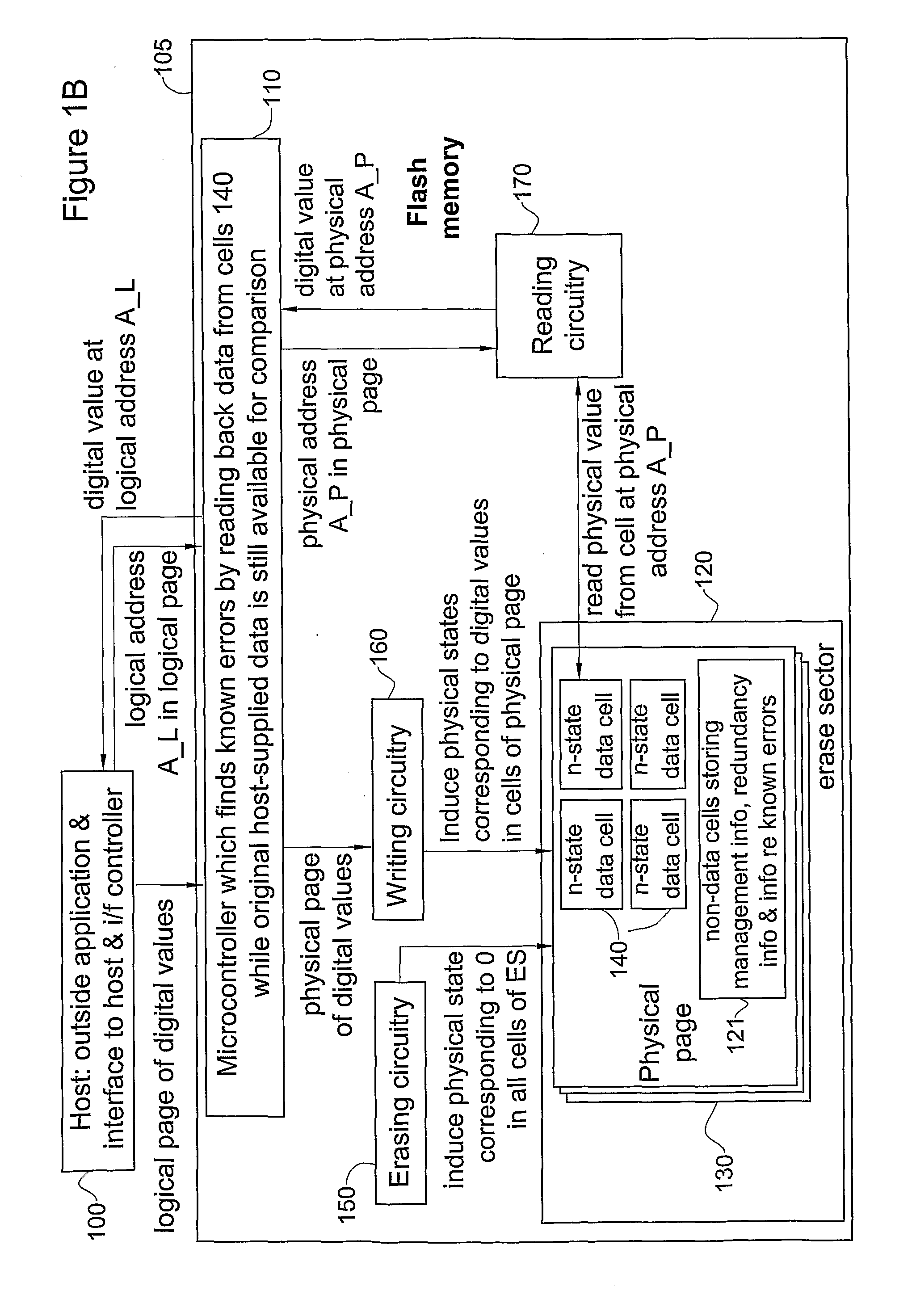
A flash memory system comprising temporary memory, writing apparatus for writing first logical data from the temporary memory into flash memory cells having at least two levels, thereby to generate a physical representation of the first logical data including known errors, reading apparatus for reading the physical representation from the cells, thereby to generate, and store in the temporary memory, second logical data which if read immediately is identical to the first logical data other than the known errors; and controlling apparatus controlling the writing apparatus and the reading apparatus and including known error ID apparatus operative to identify the known errors by comparing the first logical data to second logical data read immediately after the physical representation is generated, to store information characterizing the known errors and to use the information, when the second logical data is next read, to correct the known errors.
Owner:AVAGO TECH INT SALES PTE LTD
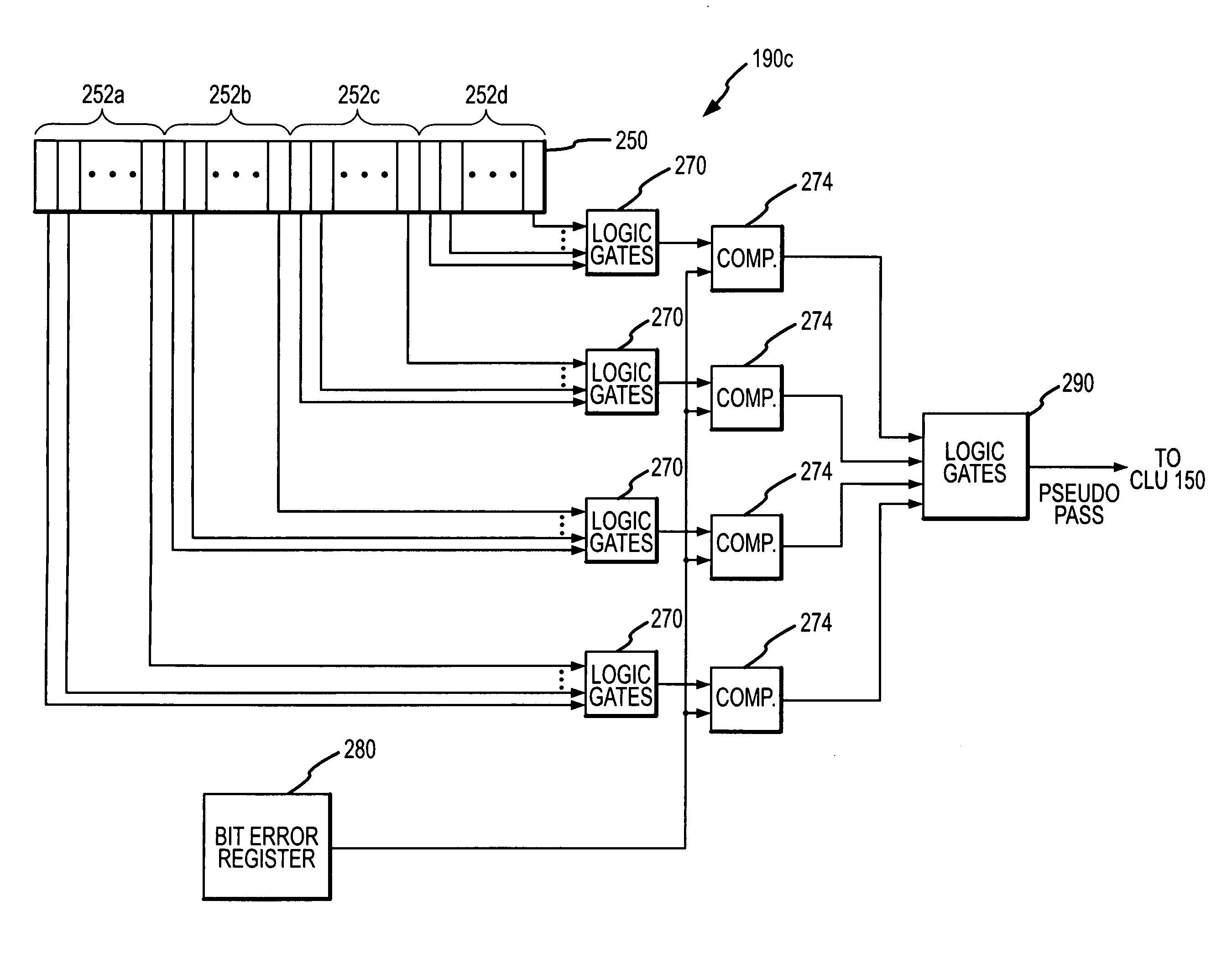
Method and system for minimizing number of programming pulses used to program rows of non-volatile memory cells
A flash memory device programs cells in each row in a manner that minimizes the number of programming pulses that must be applied to the cells during programming. The flash memory device includes a pseudo pass circuit that determines the number of data errors in each of a plurality of subsets of data that has been programmed in the row. The size of each subset corresponds to the number of read data bits coupled from the memory device, which are simultaneously applied to error checking and correcting circuitry. During iterative programming of a row of cells, the pseudo pass circuit indicates a pseudo pass condition to terminate further programming of the row if none of the subsets of data have a number of data errors that exceeds the number of data errors that can be corrected by the error checking and correcting circuitry.
Owner:MICRON TECH INC
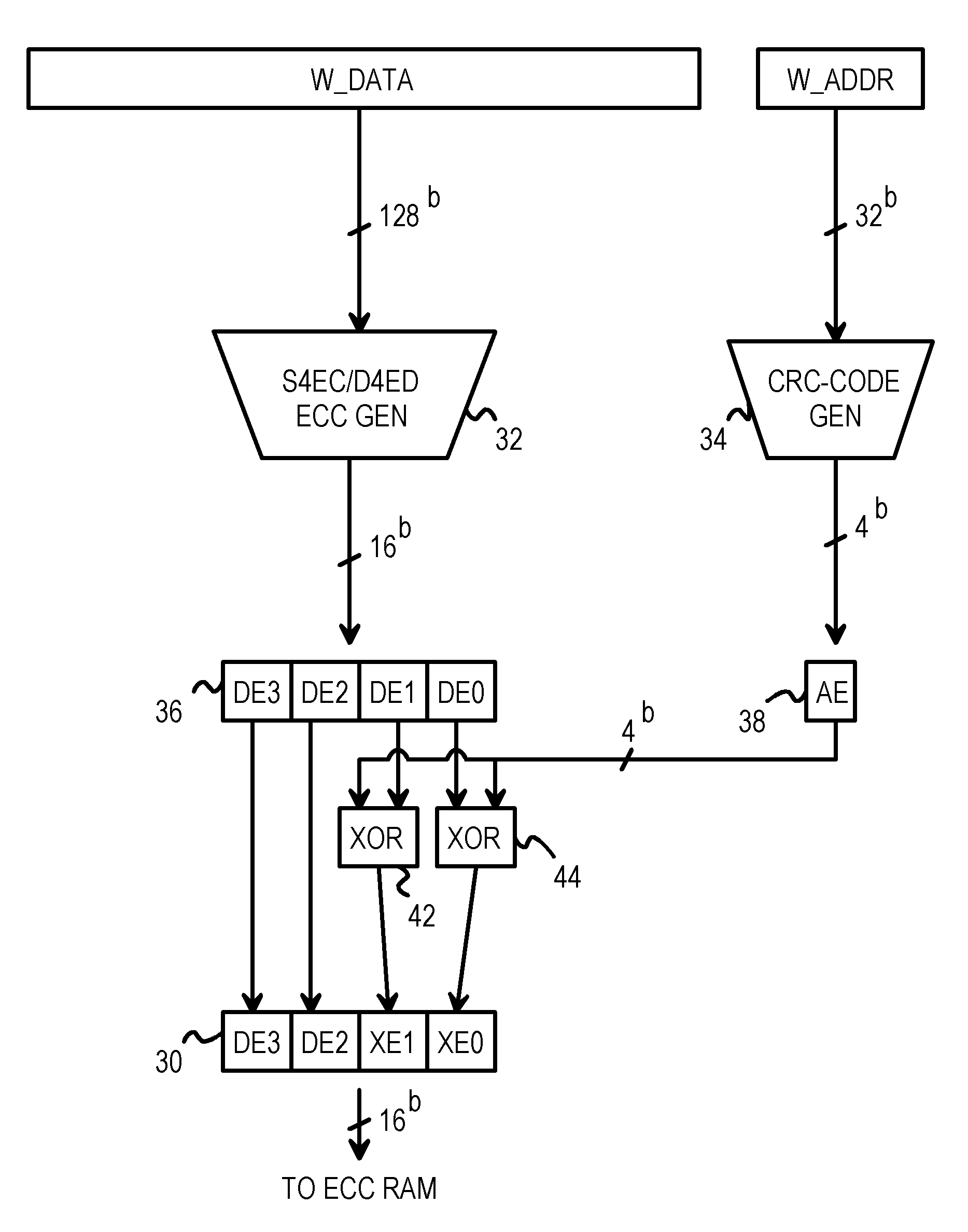
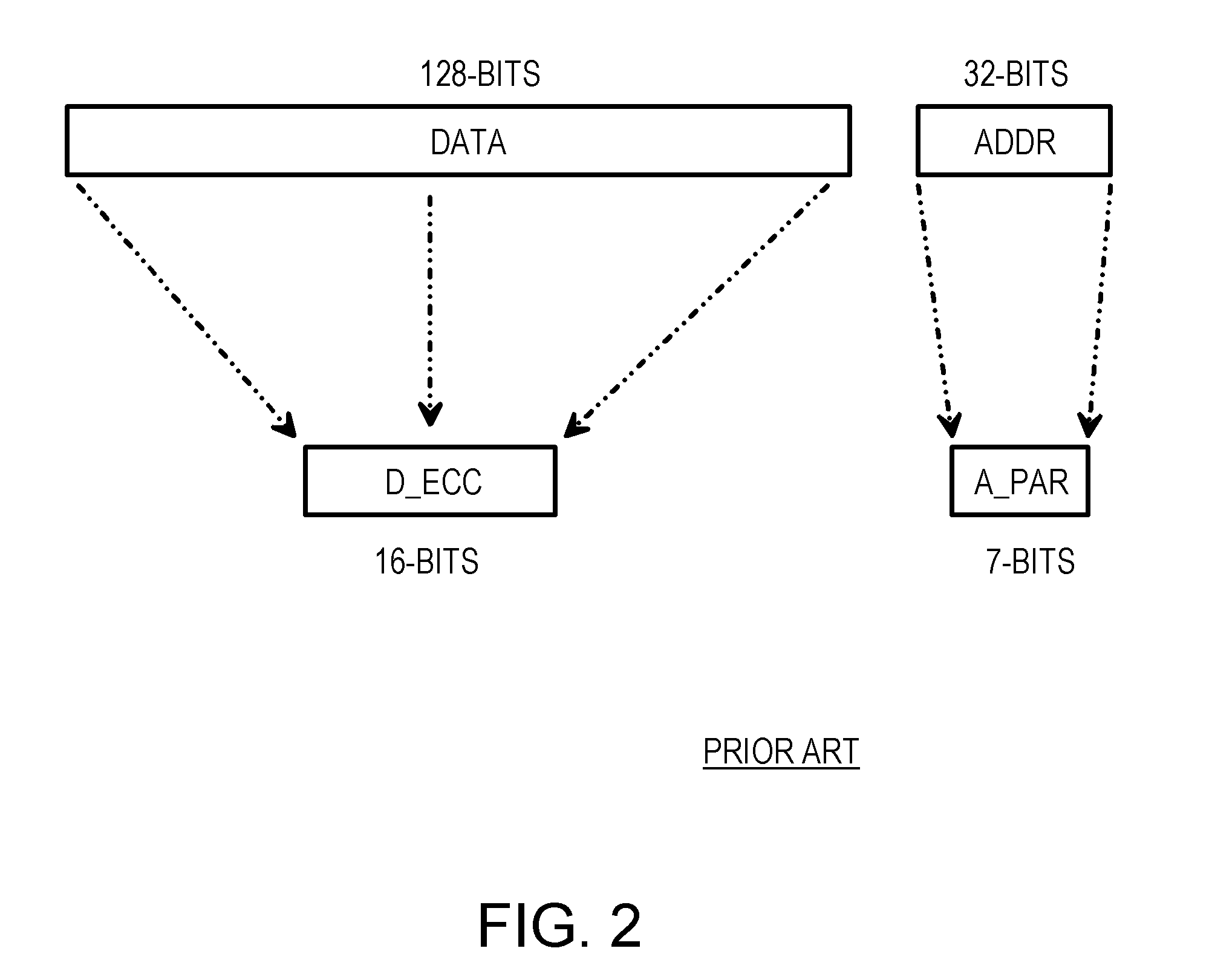
Address error detection by merging a polynomial-based CRC code of address bits with two nibbles of data or data ECC bits
A memory system provides data error detection and correction and address error detection. A Single-byte Error-Correcting / Double-byte Error-Detecting (SbEC / DbED) code with the byte being a 4-bit nibble is used to detect up to 8-bit errors and correct data errors of 4 bits or less. Rather than generating address parity, which is poor at detecting even numbers of errors, a cyclical-redundancy-check (CRC) code generates address check bits. A 32-bit address is compressed to just 4 address check bits using the CRC code. The 4 address check bits are merged (XOR'ed) with two 4-bit nibbles of the data SbEC / DbED code to generate a merged ECC codeword that is stored in memory. An address error causes a 2-nibble mis-match due to the redundant merging of the 4 address check bits with 2 nibbles of data correction code. The CRC code is ideal for detecting even numbers of errors common with multiplexed-address DRAMs.
Owner:AZUL SYSTEMS
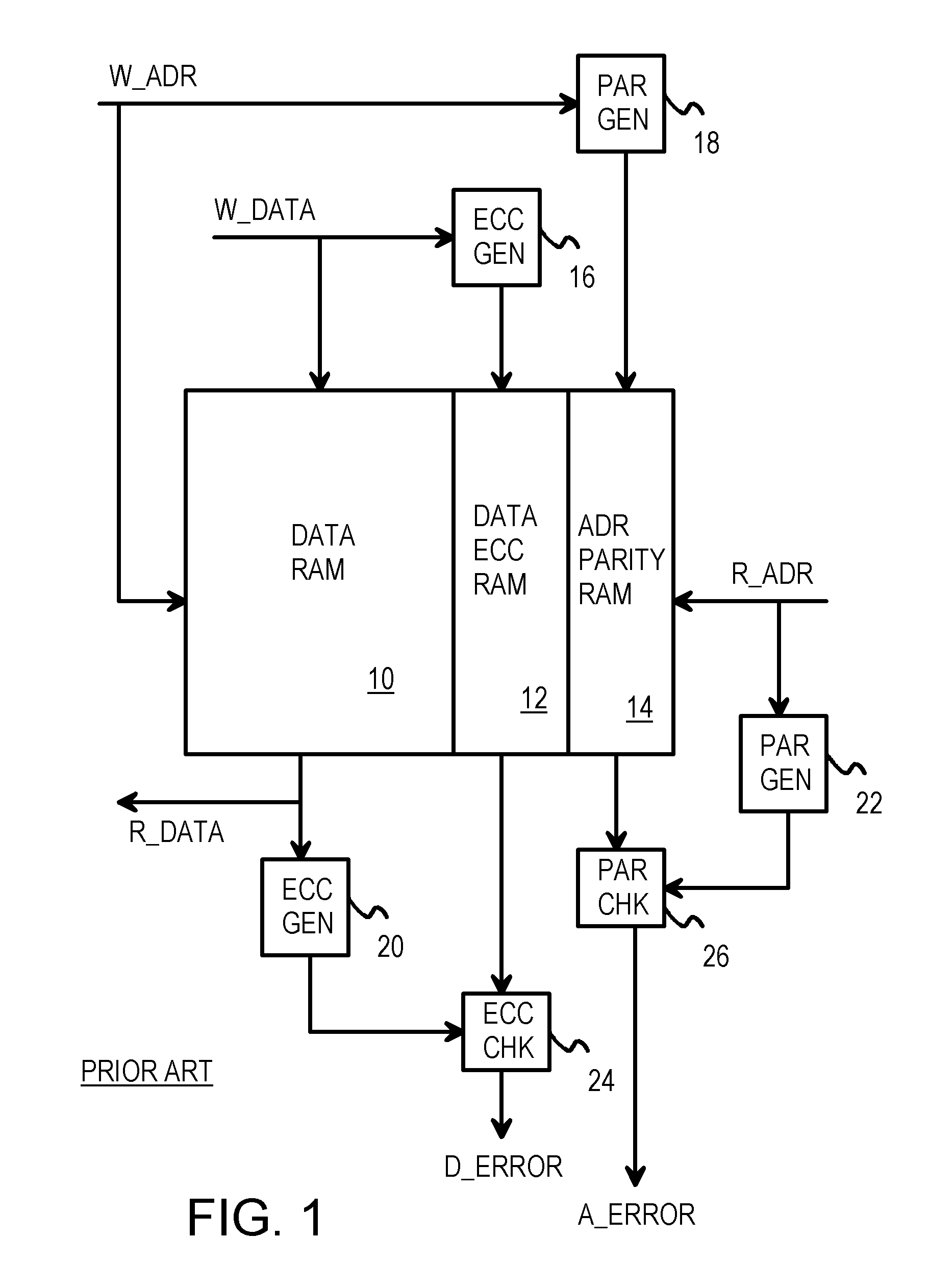
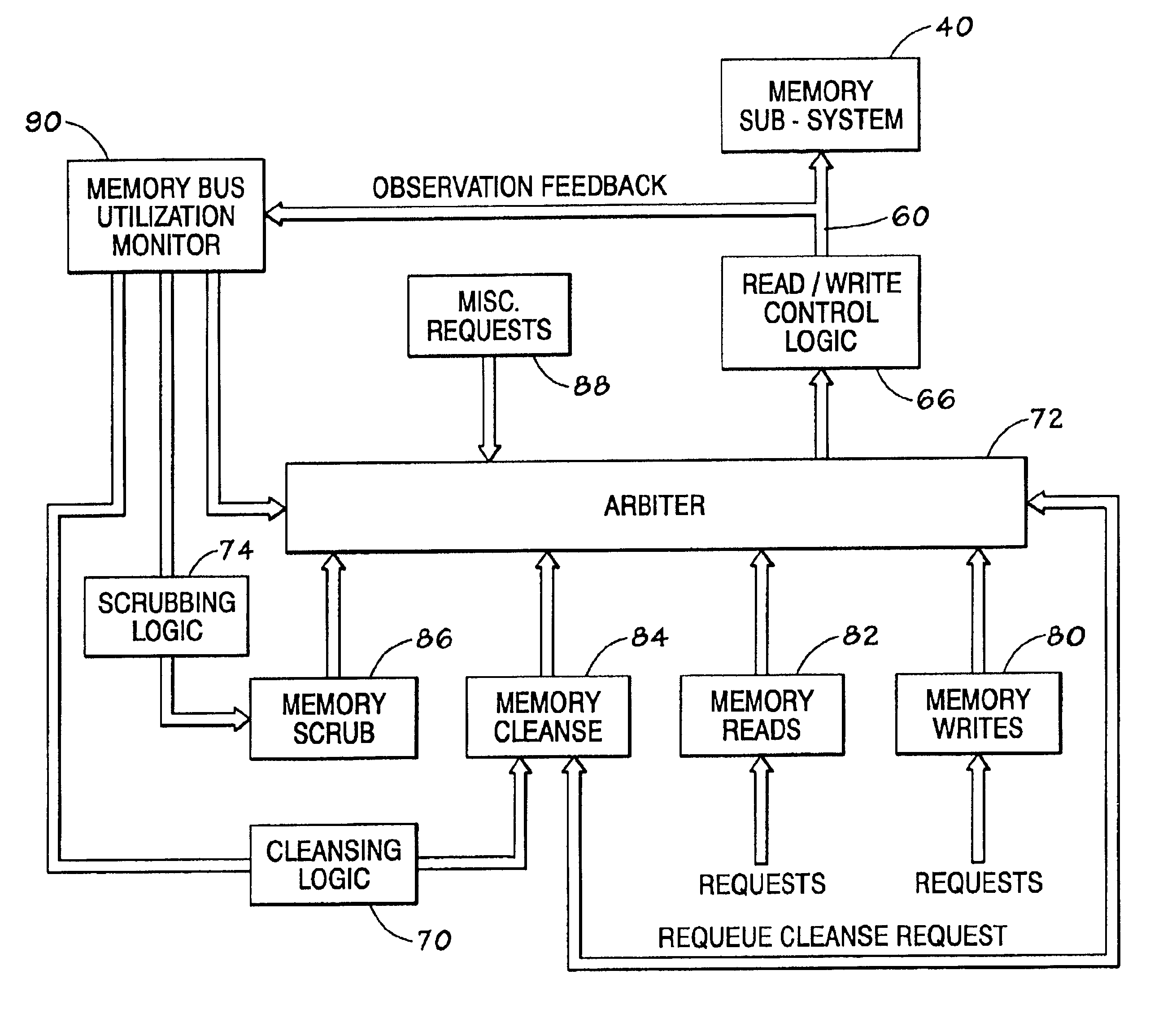
Memory sub-system error cleansing
Owner:HEWLETT PACKARD DEV CO LP
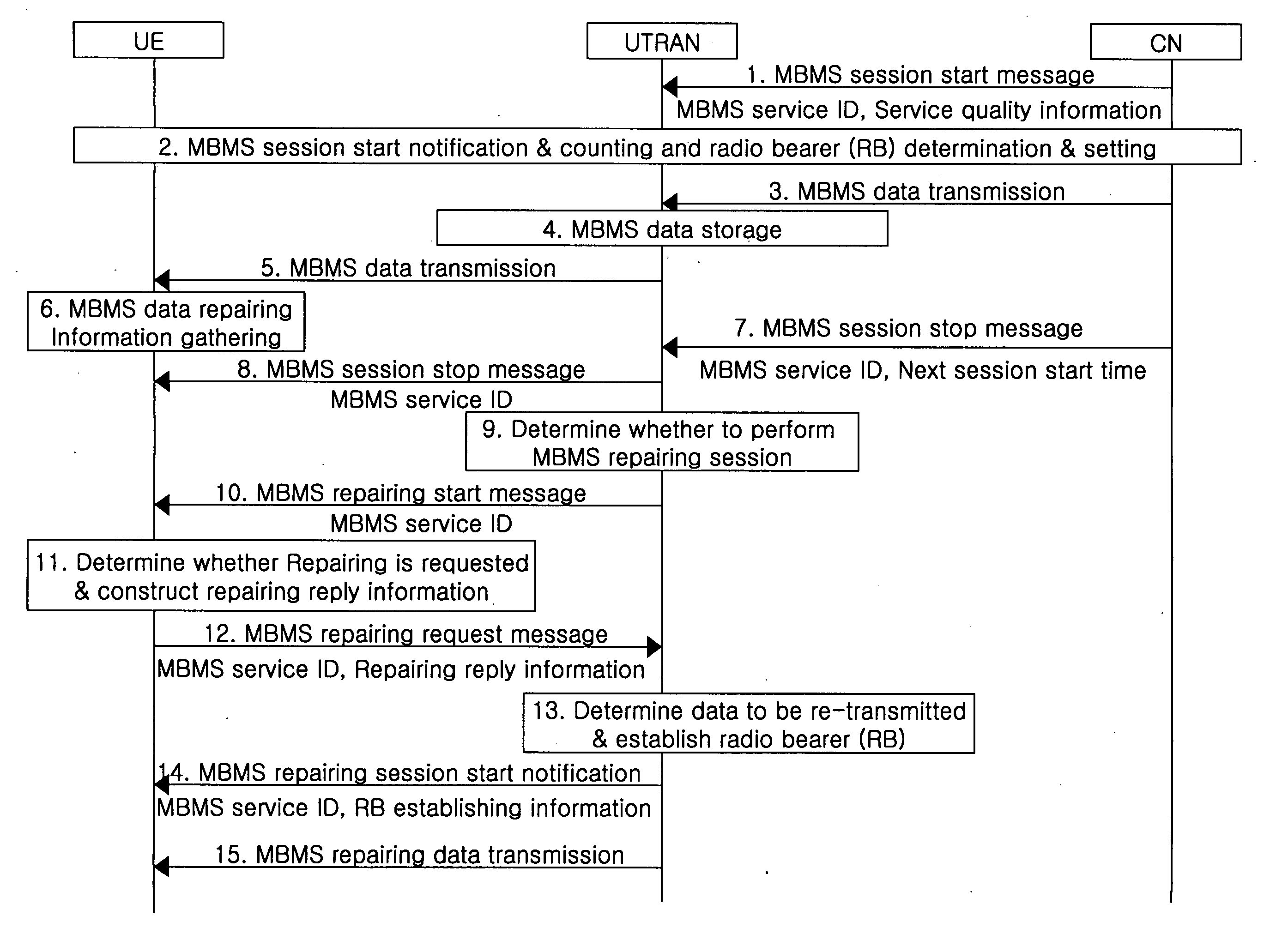
Repairing errors in data of MBMS service
ActiveUS20050185620A1Overcome problemsGuaranteed service qualityError prevention/detection by using return channelTransmission systemsQuality of serviceTerminal system
In order to guarantee service quality for a terminal for a particular point-to-multipoint service, a broadcast or multicast radio terminal system is characterized in that after the corresponding session is complete, information regarding the data that the terminal did not properly receive is informed to the UTRAN, and then the corresponding data is received upon re-transmission from the UTRAN.
Owner:LG ELECTRONICS INC
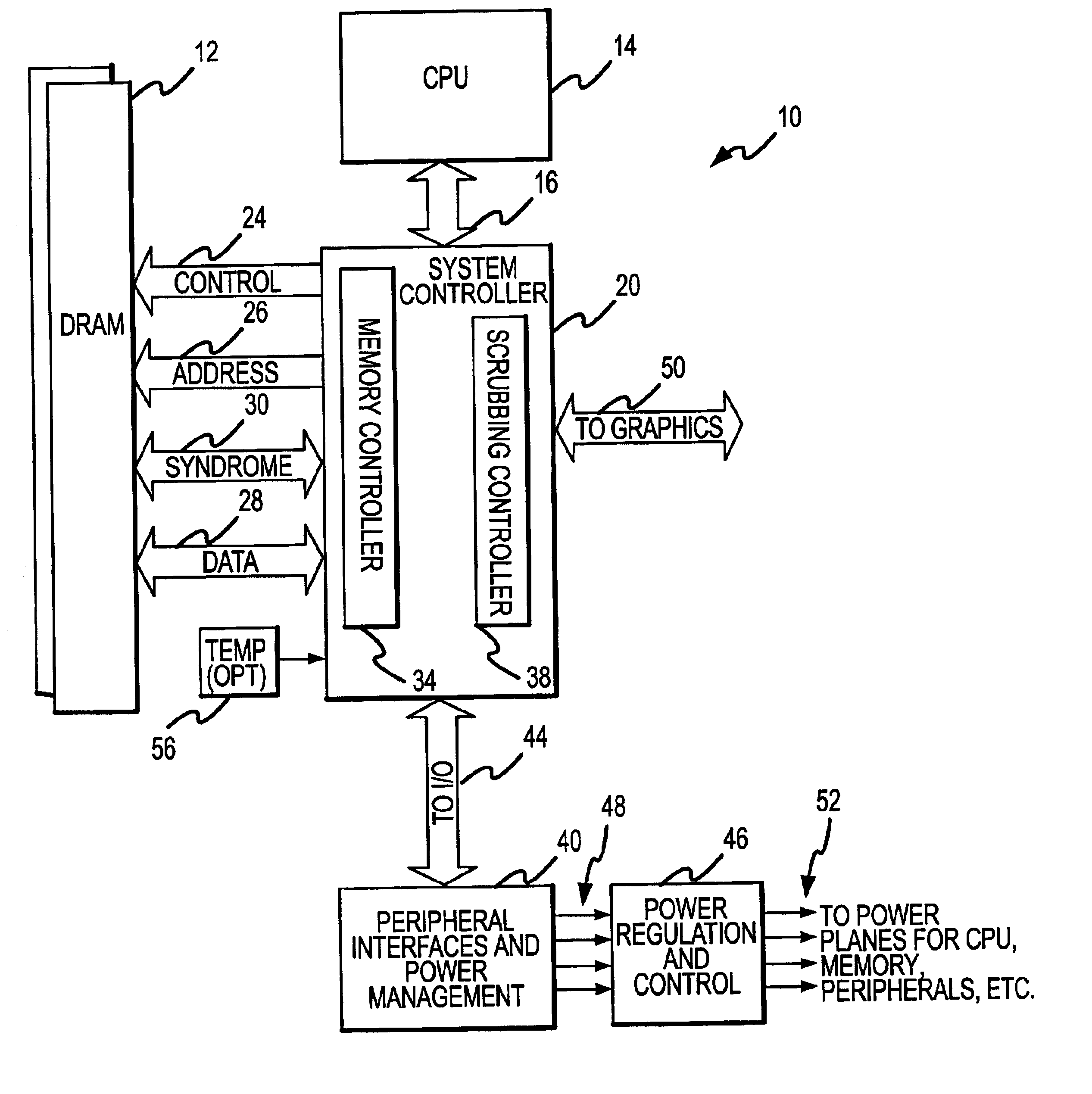
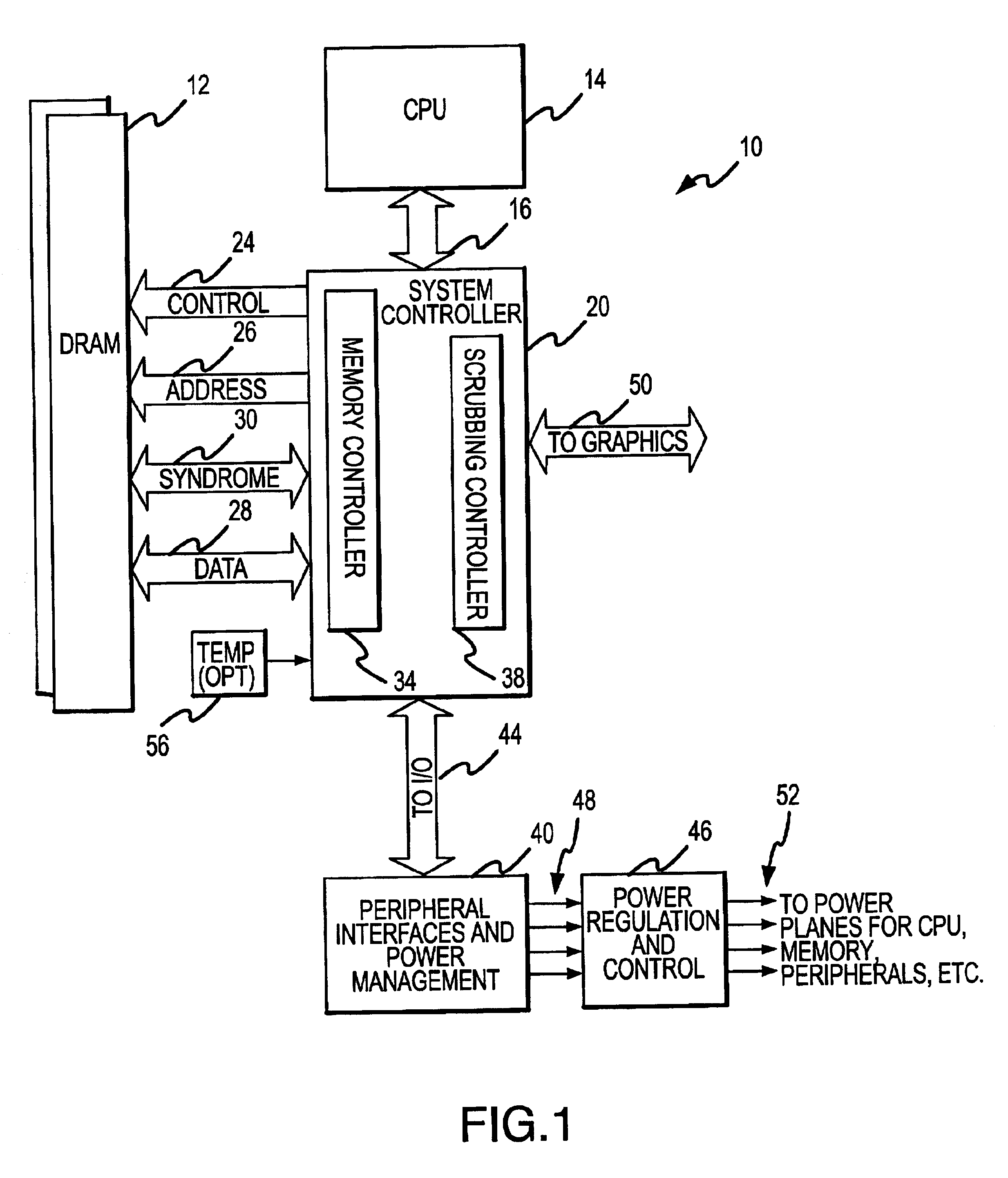
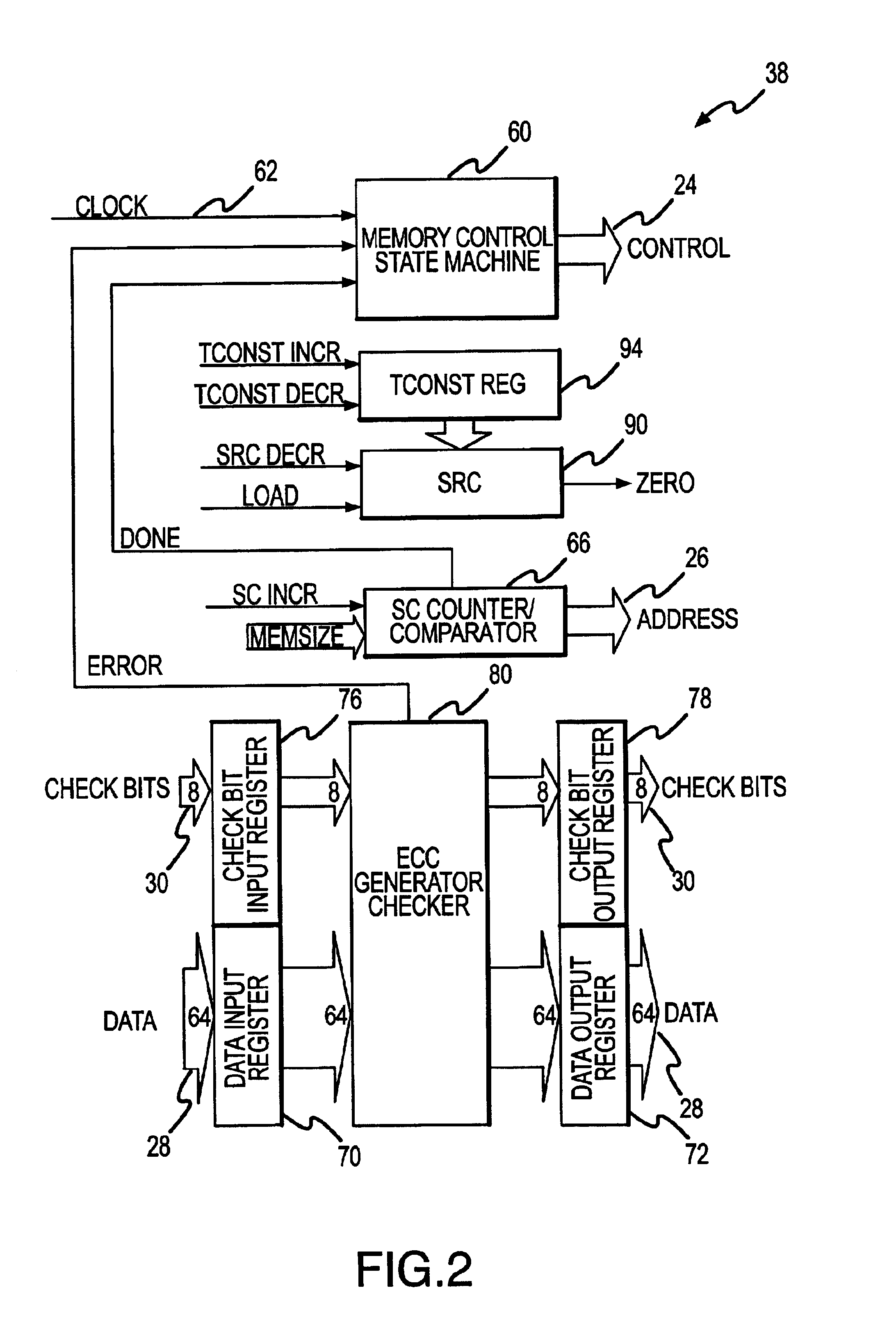
Method and system for dynamically operating memory in a power-saving error correcting mode
A scrubbing controller used with a DRAM stores data in an error correcting code format. The system then uses a memory control state machine and associated timer to periodically cause the DRAM to read the error correcting codes. An ECC generator / checker in the scrubbing controller then detects any errors in the read error correcting codes, and generates corrected error correcting codes that are written to the DRAM. This scrubbing procedure, by reading error correcting codes from the DRAM, inherently refreshes memory cells in the DRAM. The error correcting codes are read at rate that may allow data errors to be generated, but these errors are corrected in the memory scrubbing procedure. However, the low rate at which the error correcting codes are read results in a substantial power saving compared to refreshing the memory cells at a higher rate needed to ensure that no data errors are generated.
Owner:MICRON TECH INC
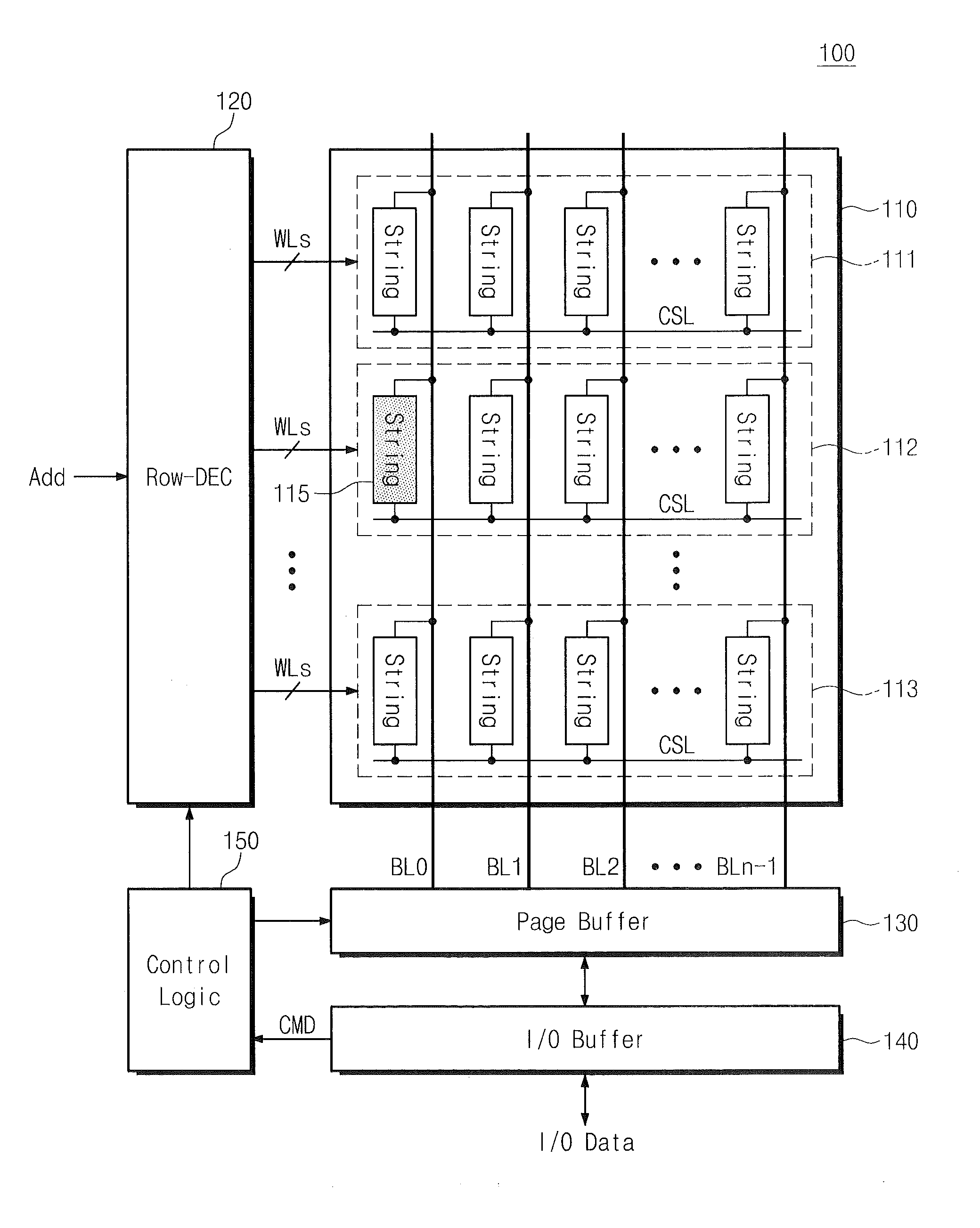
Methods of Performing Error Detection/Correction in Nonvolatile Memory Devices
ActiveUS20110209031A1Facilitate error detectionFacilitate correction operationRead-only memoriesCode conversionHigh probabilityData error
Methods of operating nonvolatile memory devices include testing a plurality of strings of nonvolatile memory cells in the memory device to identify at least one weak string therein having a higher probability of yielding erroneous read data error relative to other ones of the plurality of strings. An identity of the at least one weak string may be stored as weak column information. This weak column information may be used to facilitate error detection and correction operations. In particular, an error correction operation may be performed on a first plurality of bits of data read from the plurality of strings using an algorithm that modifies a weighting of the reliability of one or more data bits in the first plurality of bits of data based on the weak column information. More specifically, an algorithm may be used that interprets a bit of data read from the at least one weak string as having a relatively reduced reliability relative to other ones of the first plurality of data bits.
Owner:SAMSUNG ELECTRONICS CO LTD
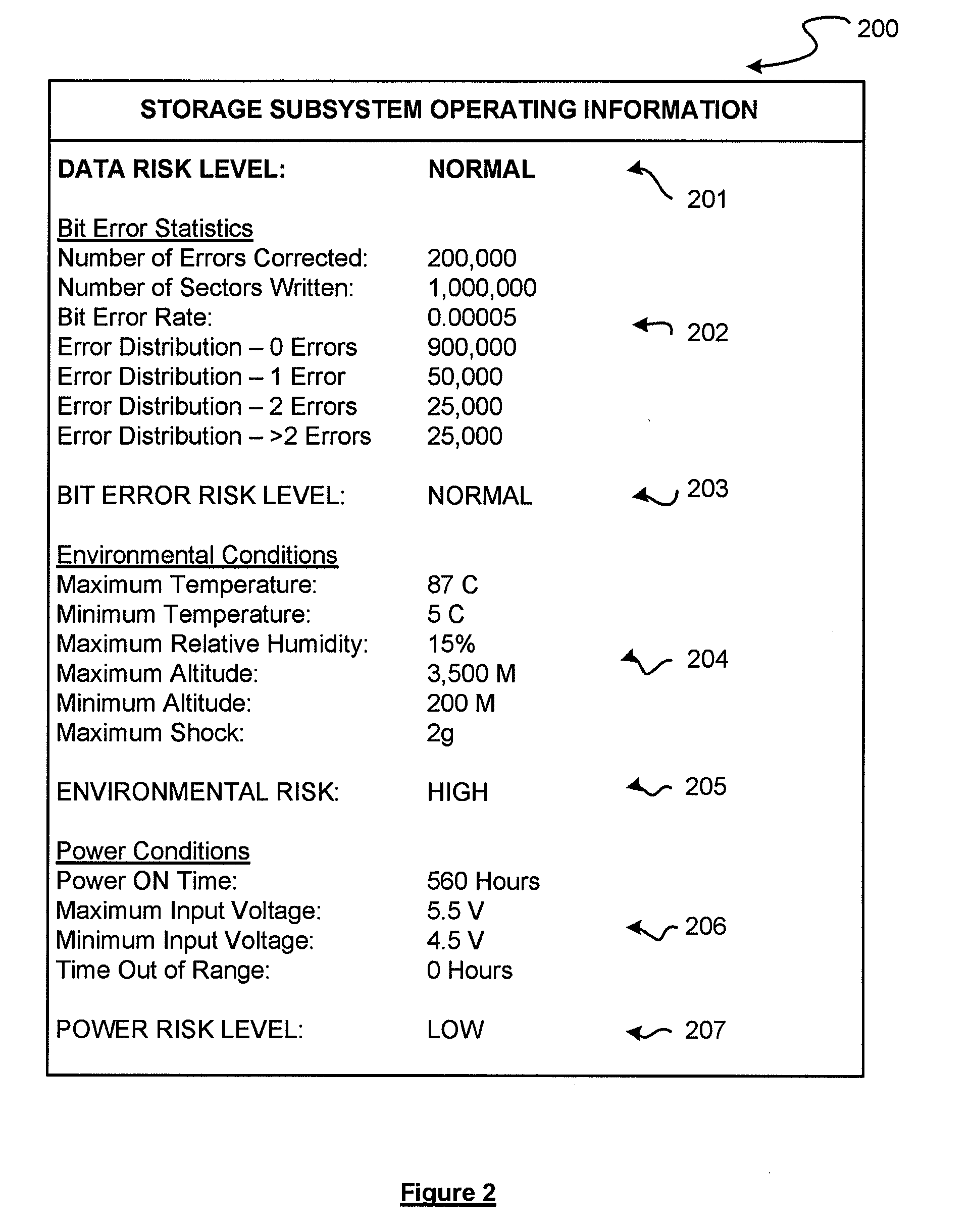
Solid state storage subsystem that maintains and provides access to data reflective of a failure risk
ActiveUS20090204852A1Hardware monitoringReliability/availability analysisSolid-state storageOperation mode
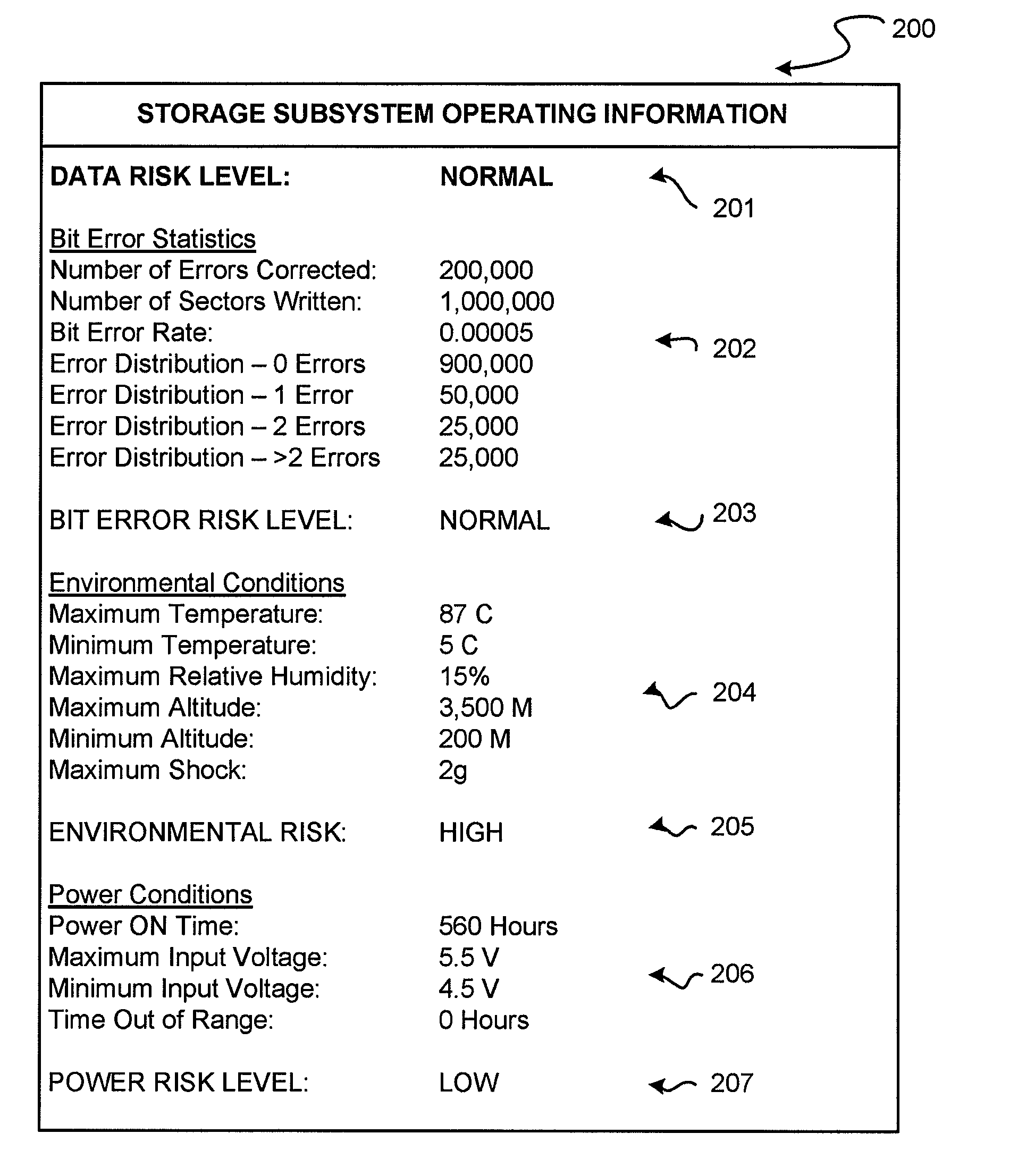
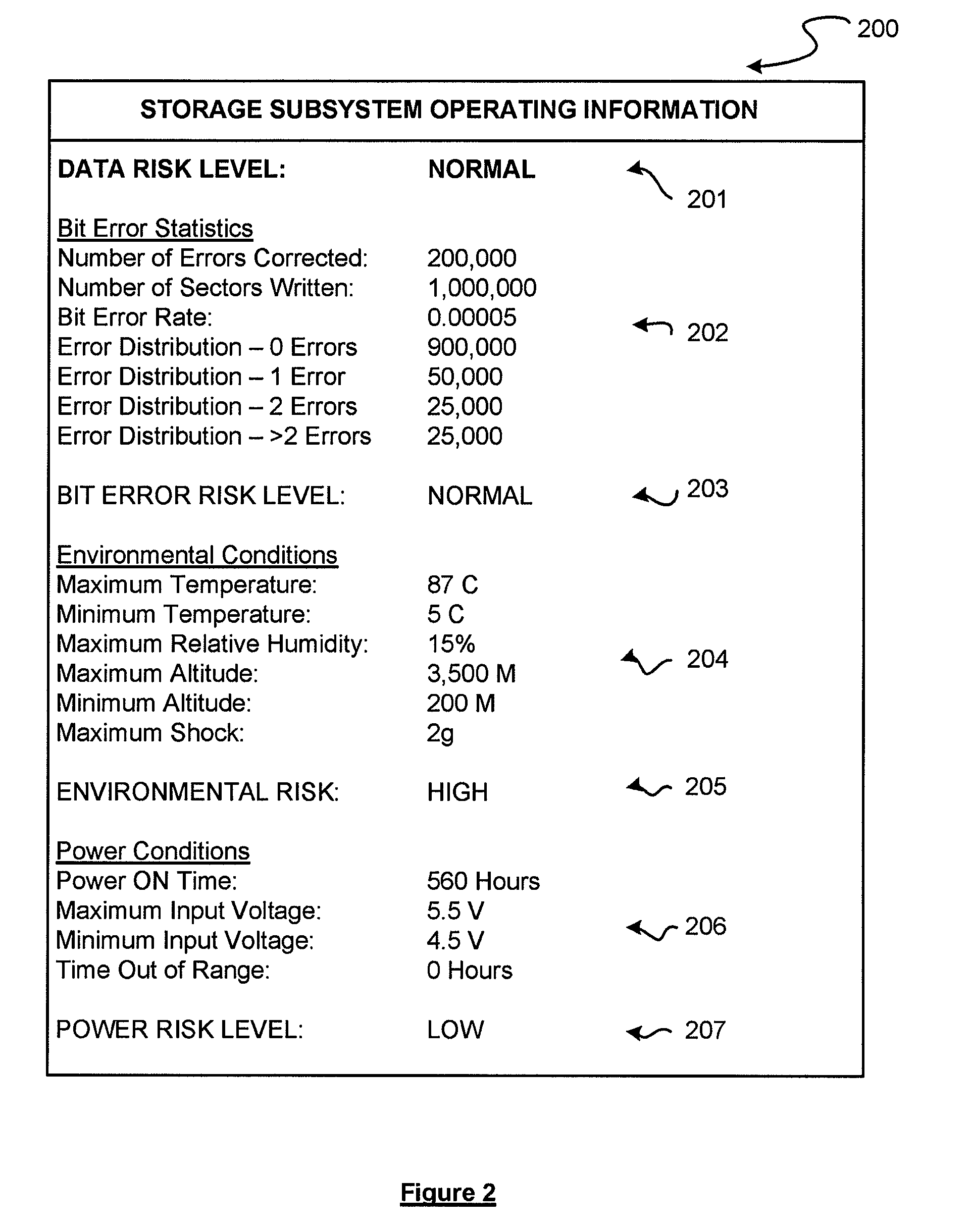
A storage subsystem is disclosed that maintains (a) statistics regarding errors detected via an ECC (error correction code) module of the storage subsystem; and / or (b) historical data regarding operating conditions experienced by the storage subsystem, such as temperature, altitude, humidity, shock, and / or input voltage level. The storage subsystem, and / or a host system to which the storage subsystem attaches, may analyze the stored data to assess a risk of a failure event such as an uncorrectable data error. The results of this analysis may be displayed via a user interface of the host system, and / or may be used to automatically take a precautionary action such as transmitting an alert message or changing a mode of operation of the storage subsystem.
Owner:WESTERN DIGITAL TECH INC
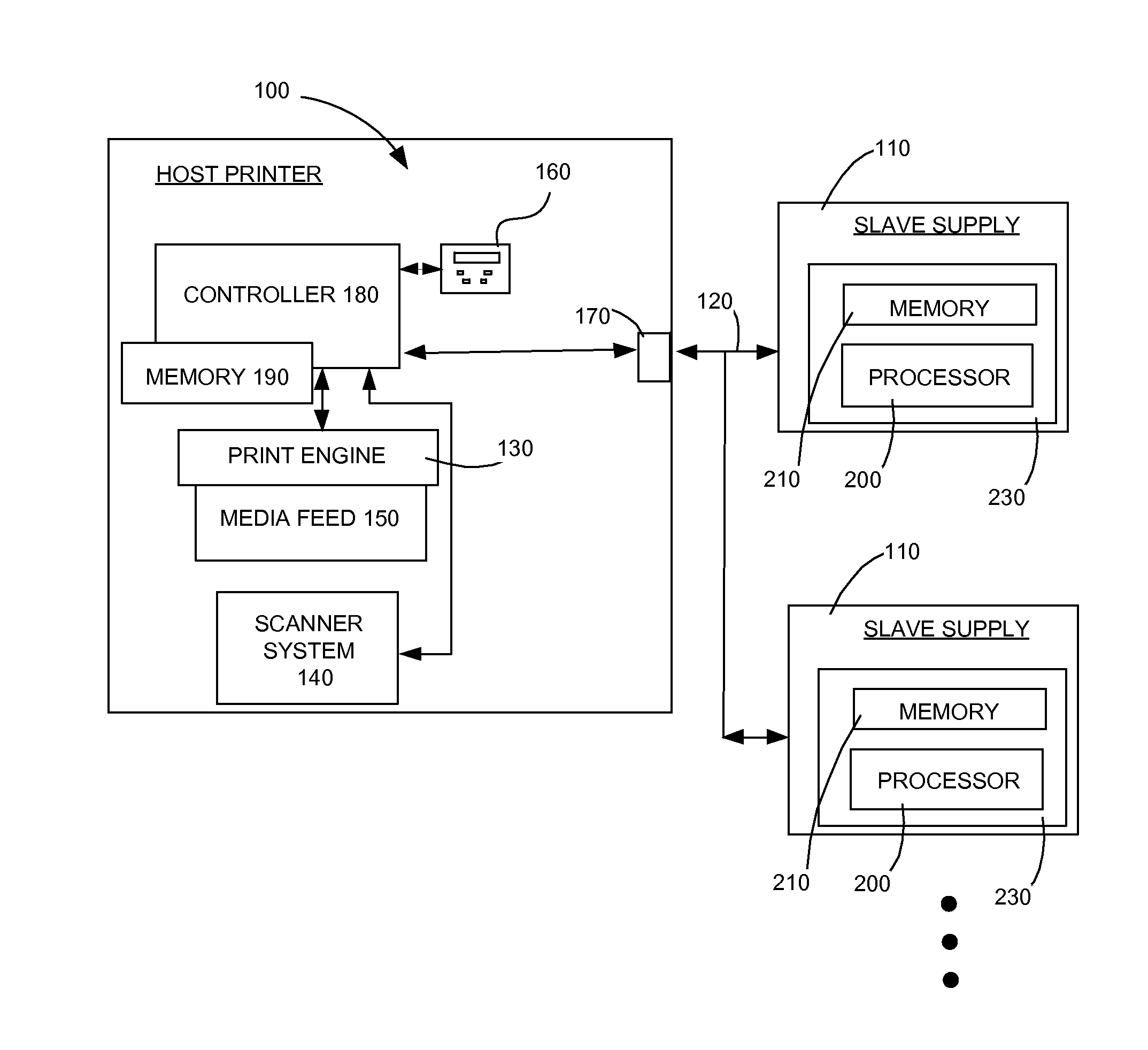
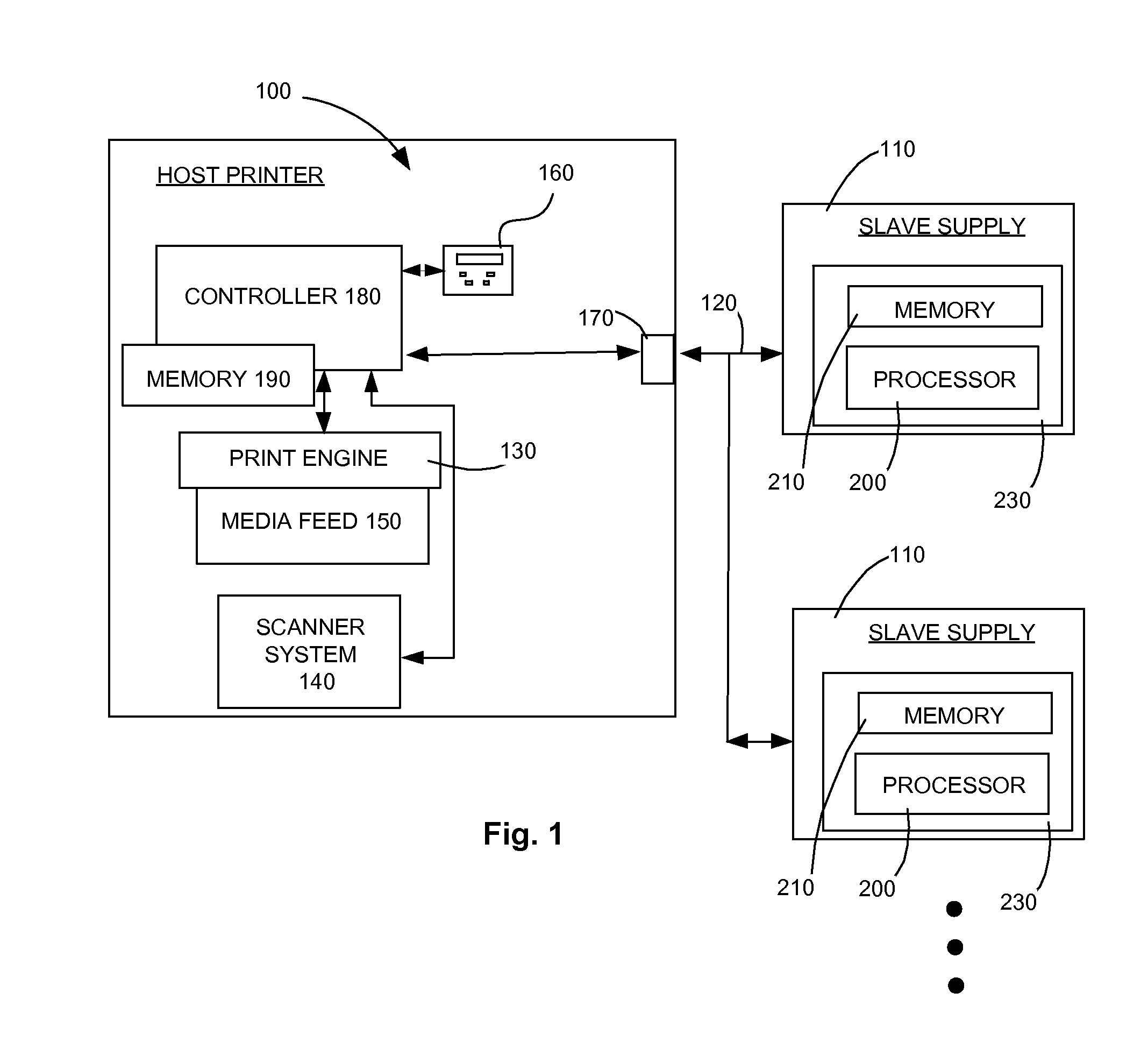
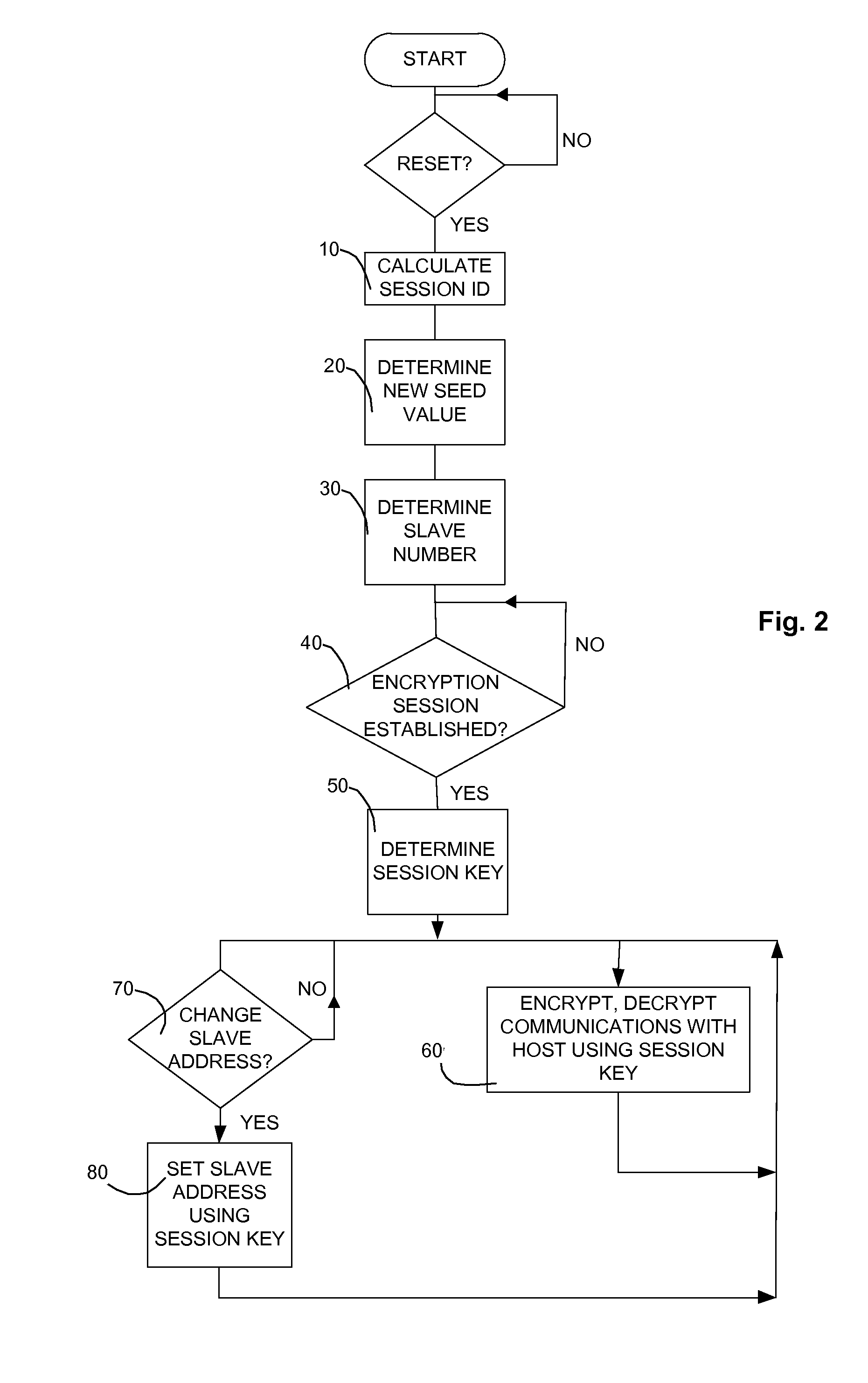
System and Method for Secured Host-slave Communication
ActiveUS20130067016A1Overcomes shortcomingNeed can be quite largeMemory architecture accessing/allocationMultiple digital computer combinationsPower cycleData error
A new system and method for communicating between a host device and one or more slave devices are presented. The system provides data error checking and correcting, data encryption, and robust slave address sequencing using a portion of a session key. The data encryption uses a second portion of the session key, which changes for each power cycle.
Owner:LEXMARK INT INC
Adjusting sampling phase in a baud-rate CDR using timing skew
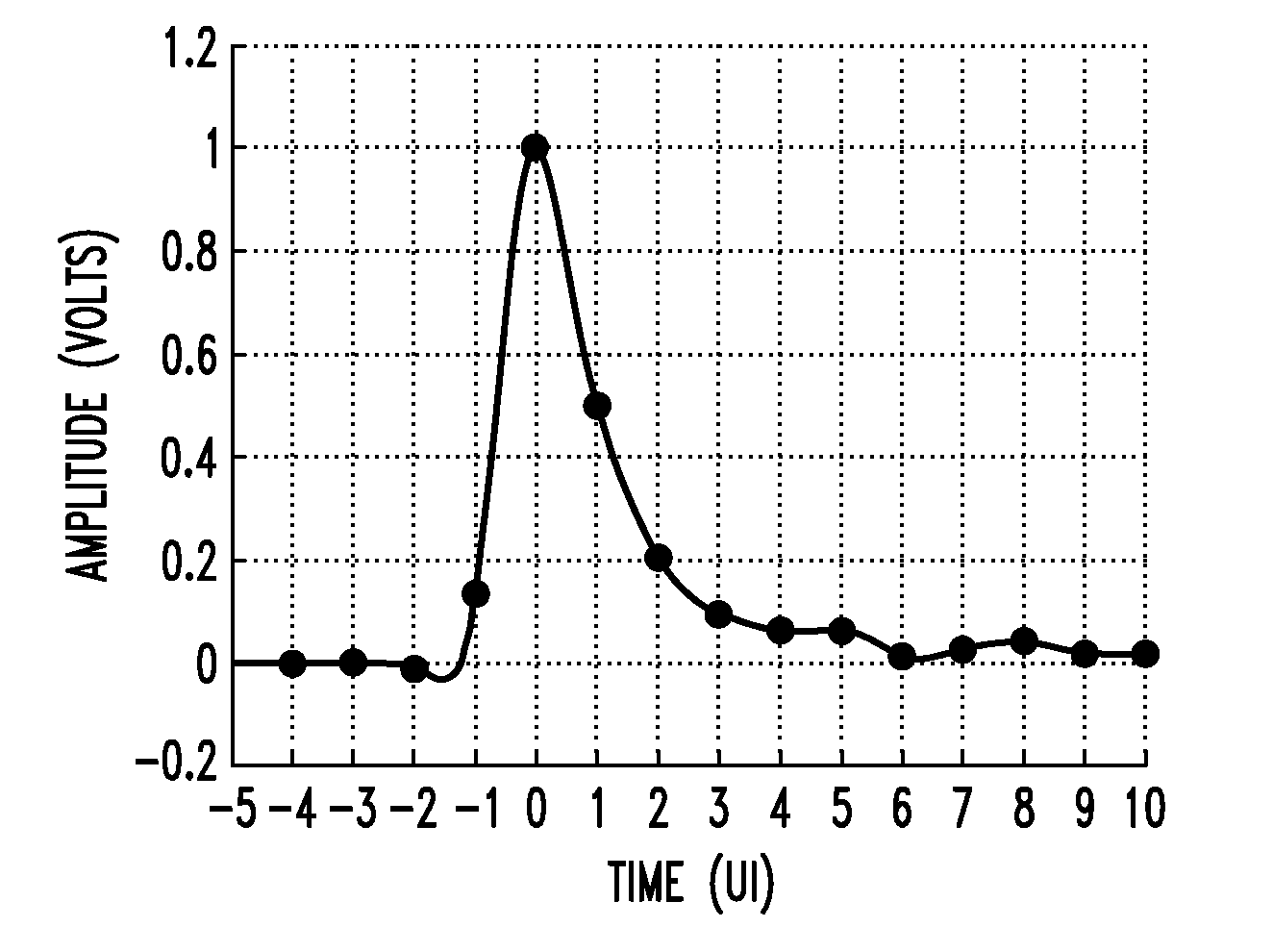
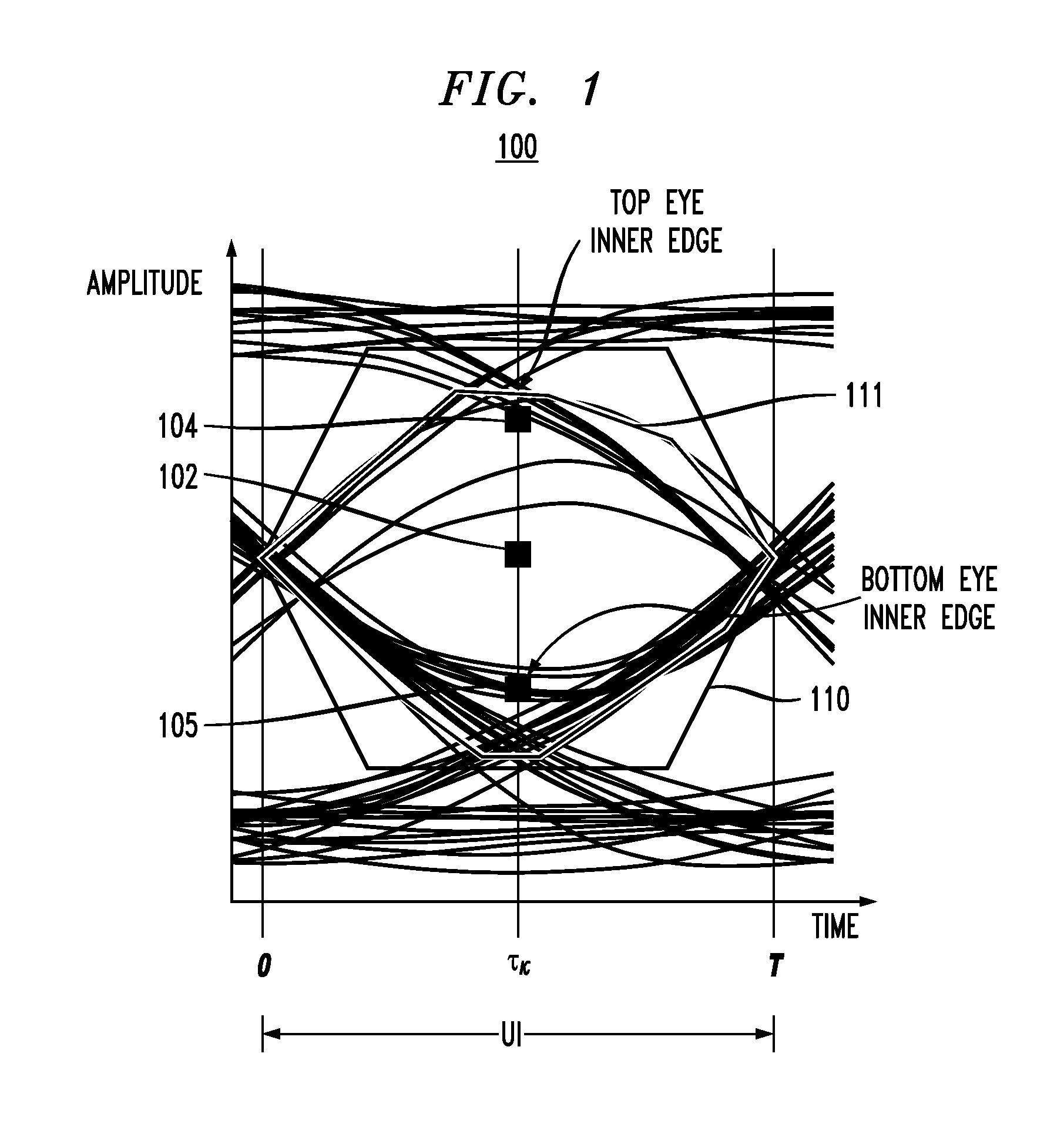
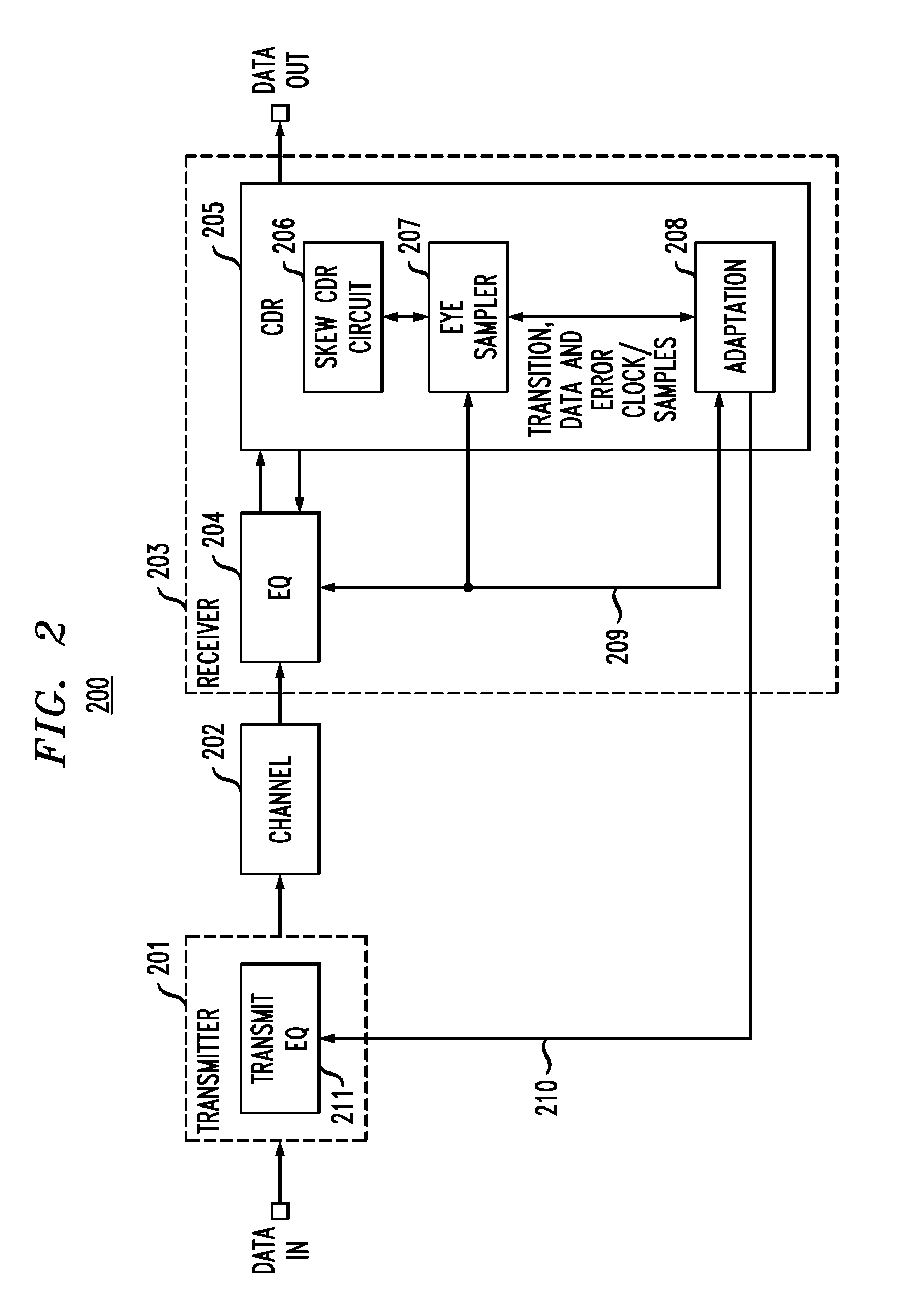
In described embodiments, a transceiver includes a baud-rate clock and data recovery (CDR) module with an eye sampler, and an adaptation module for adaptively setting parameters of various circuit elements, such as timing, equalizer and gain elements. Data sampling clock phase of the CDR module is set for sampling at, for example, near the center of a data eye detected by the eye sampler, and the phase of data error sampling latch(es) is skewed by the CDR module with respect to the phase of the data sampling latch. Since the error signal driving the timing adaptation contains the information of the pulse response that the CDR module encounters, the phase of timing error sampling latch(es) of the CDR module is skewed based on maintaining a relative equivalence of input pulse response residual pre-cursor and residual post-cursor with respect to the timing error sampling clock phase.
Owner:AVAGO TECH INT SALES PTE LTD
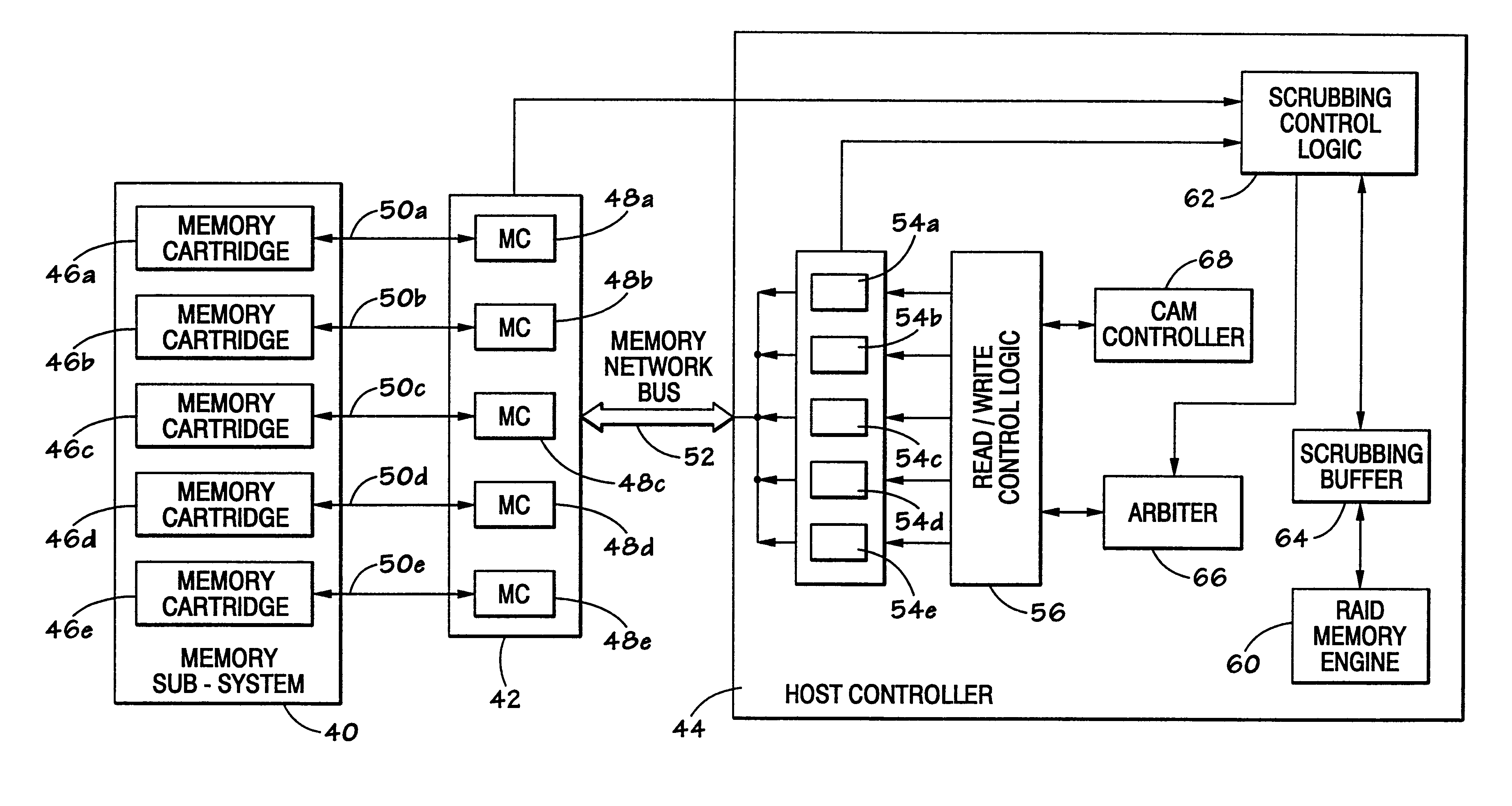
Real-time hardware memory scrubbing
A system and technique for correcting data errors in a memory device. More specifically, data errors in a memory device are corrected by scrubbing the corrupted memory device. Generally, a host controller delivers a READ command to a memory controller. The memory controller receives the request and retrieves the data from a memory sub-system. The data is delivered to the host controller. If an error is detected, a scrub command is induced through the memory controller to rewrite the corrected data through the memory sub-system. Once a scrub command is induced, an arbiter schedules the scrub in the queue. Because a significant amount of time can occur before initial read in the scrub write back to the memory, an additional controller may be used to compare all subsequent READ and WRITE commands to those scrubs scheduled in the queue. If a memory location is rewritten with new data prior to scheduled scrub corresponding to the same address location, the controller will cancel the scrub to that particular memory location.
Owner:SK HYNIX INC
Methods and apparatus for overlapping MIMO antenna physical sectors
InactiveUS8009646B2Reduce distractionsImprove performanceTransmitters monitoringSite diversityMimo antennaEngineering
Methods and apparatus for positioning antennas of a first wireless cell to form MIMO physical sectors and MIMO virtual sectors. Selecting a MIMO virtual sector for communication responsive to throughput, data throughput, signal-to-noise ratio, signal error rate, data error rate, retransmission requests, interference, rejection of multipath signals, transmission rate, and signal strength.
Owner:ROTANI
Methods and apparatus for correcting data and error detection codes on the fly
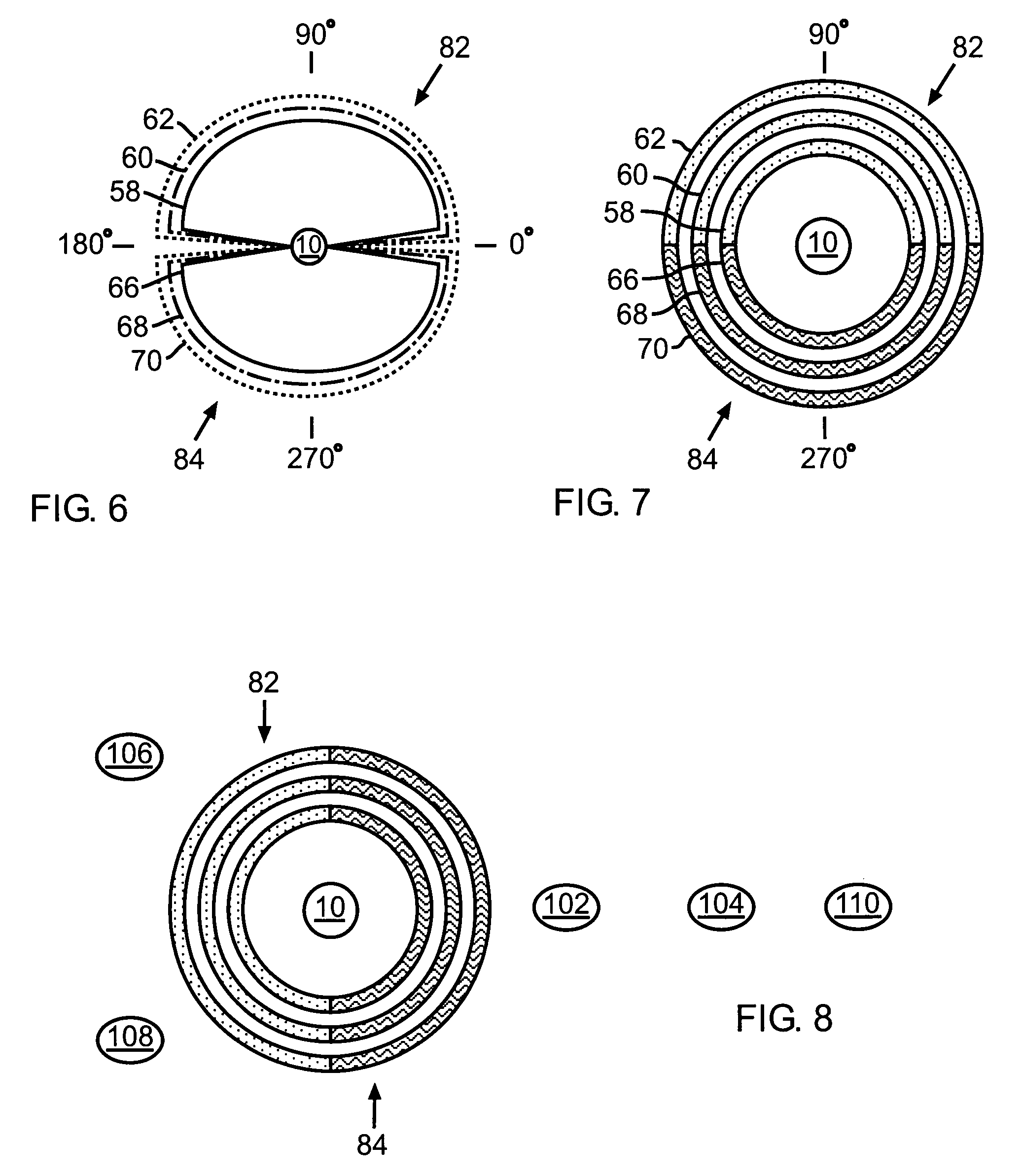
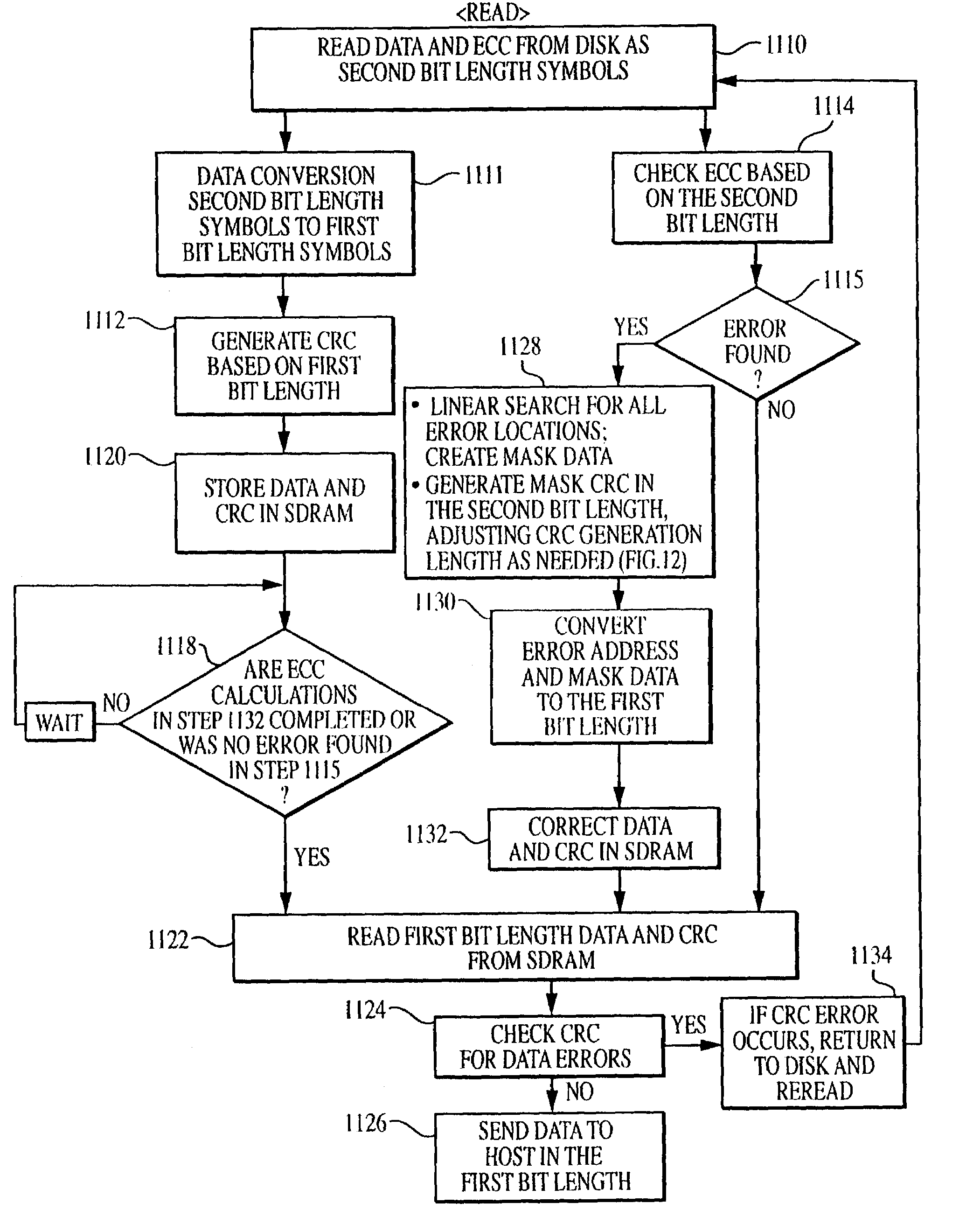
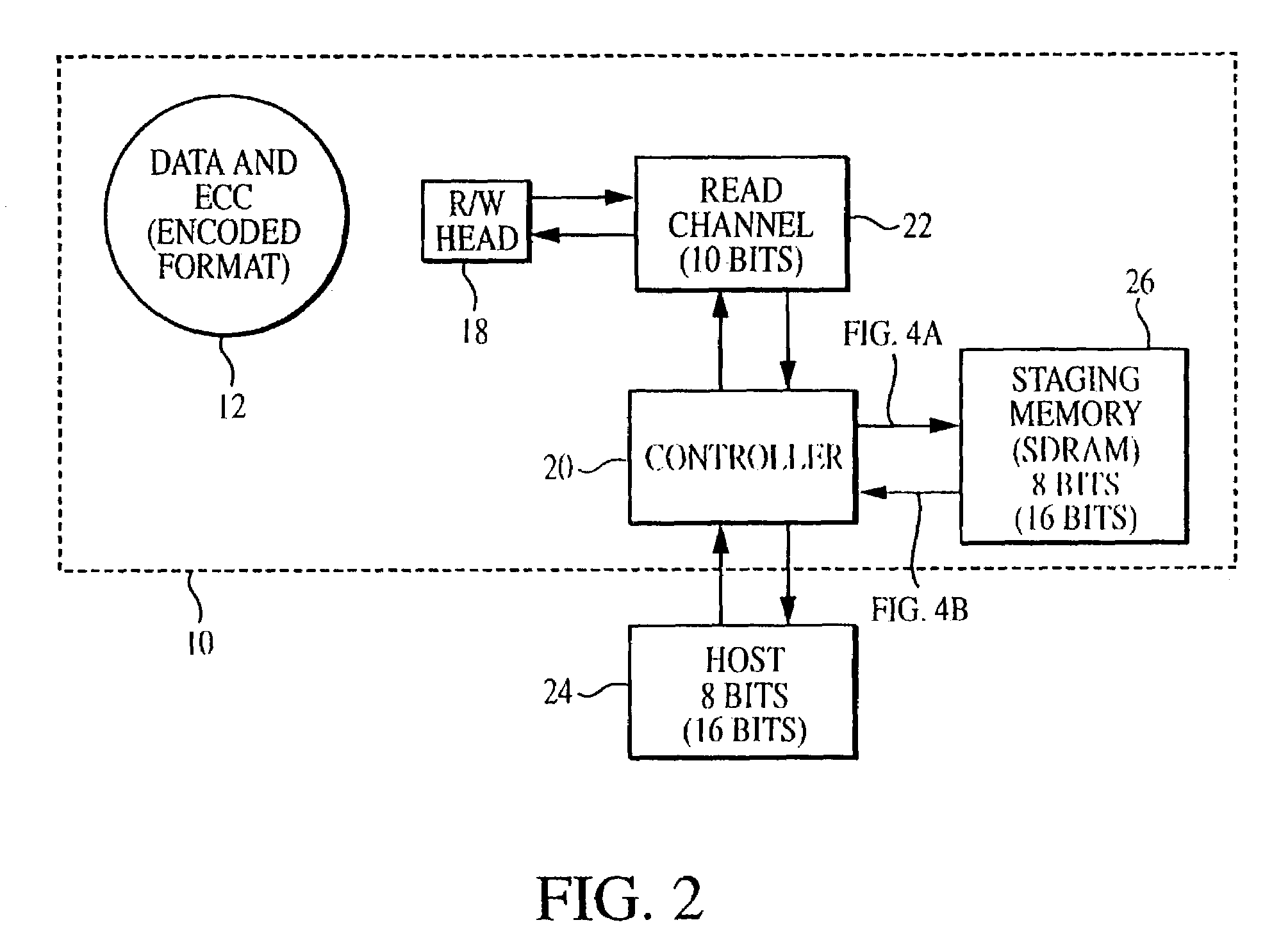
When data is read from a disk and stored in volatile memory, check bits are generated and stored in the memory using an algorithm such as cyclical redundancy check (CRC). The CRC algorithm operates on the basis of the bit length in which the data is organized, such as 8 bits. If the data has errors, an error correction code (ECC) algorithm is used to correct the data errors, but the ECC algorithm operates on the basis of symbols having a different bit length, such as 10 bits. To avoid having to re-read the data from the volatile memory to adjust the CRC value, the CRC algorithm is executed on selected mask data developed by the ECC algorithm, the CRC algorithm being executed on the basis of the second bit length to generate a CRC mask. The CRC mask corrects the stored CRC value.
Owner:TOSHIBA STORAGE DEVICE CORP
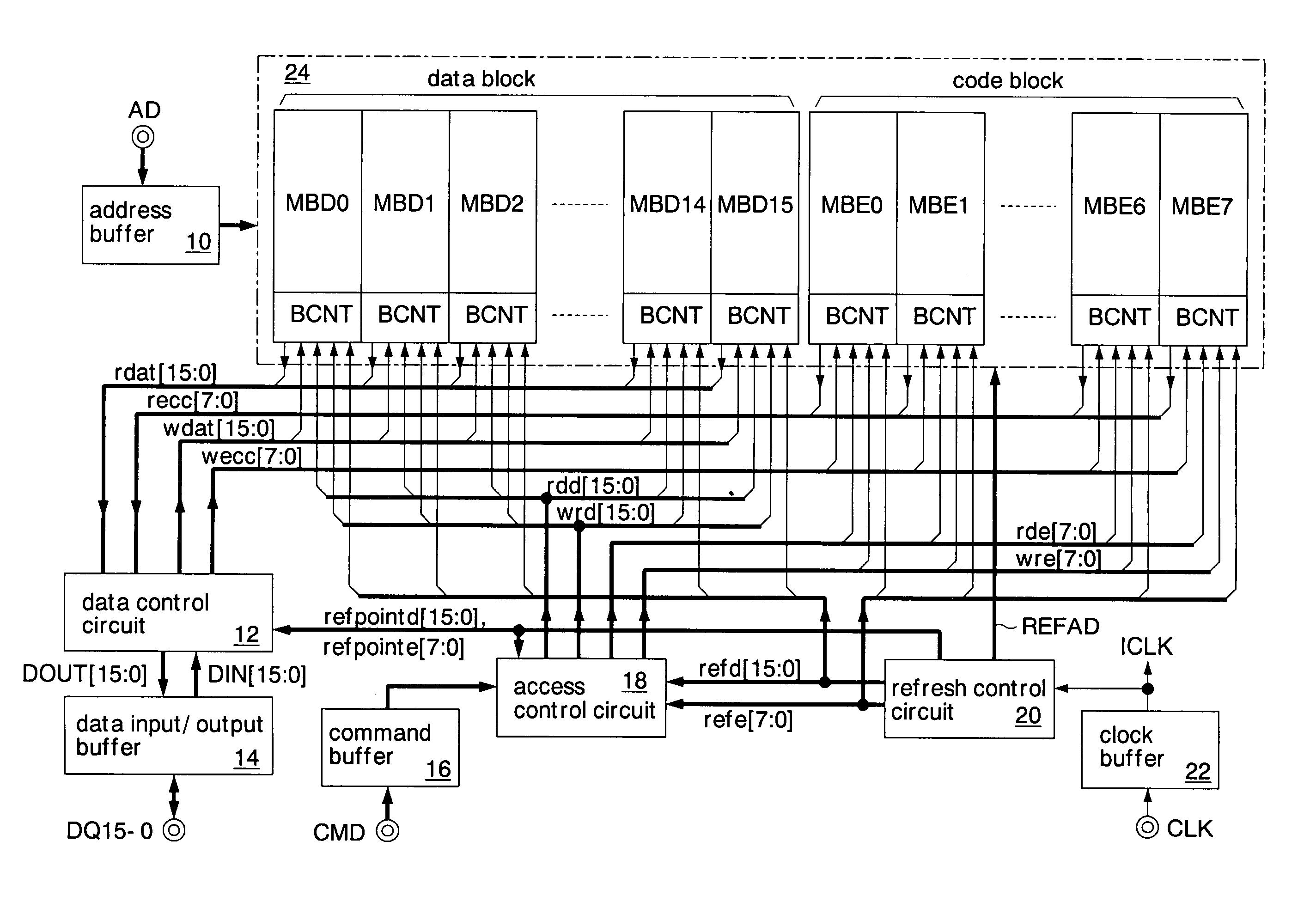
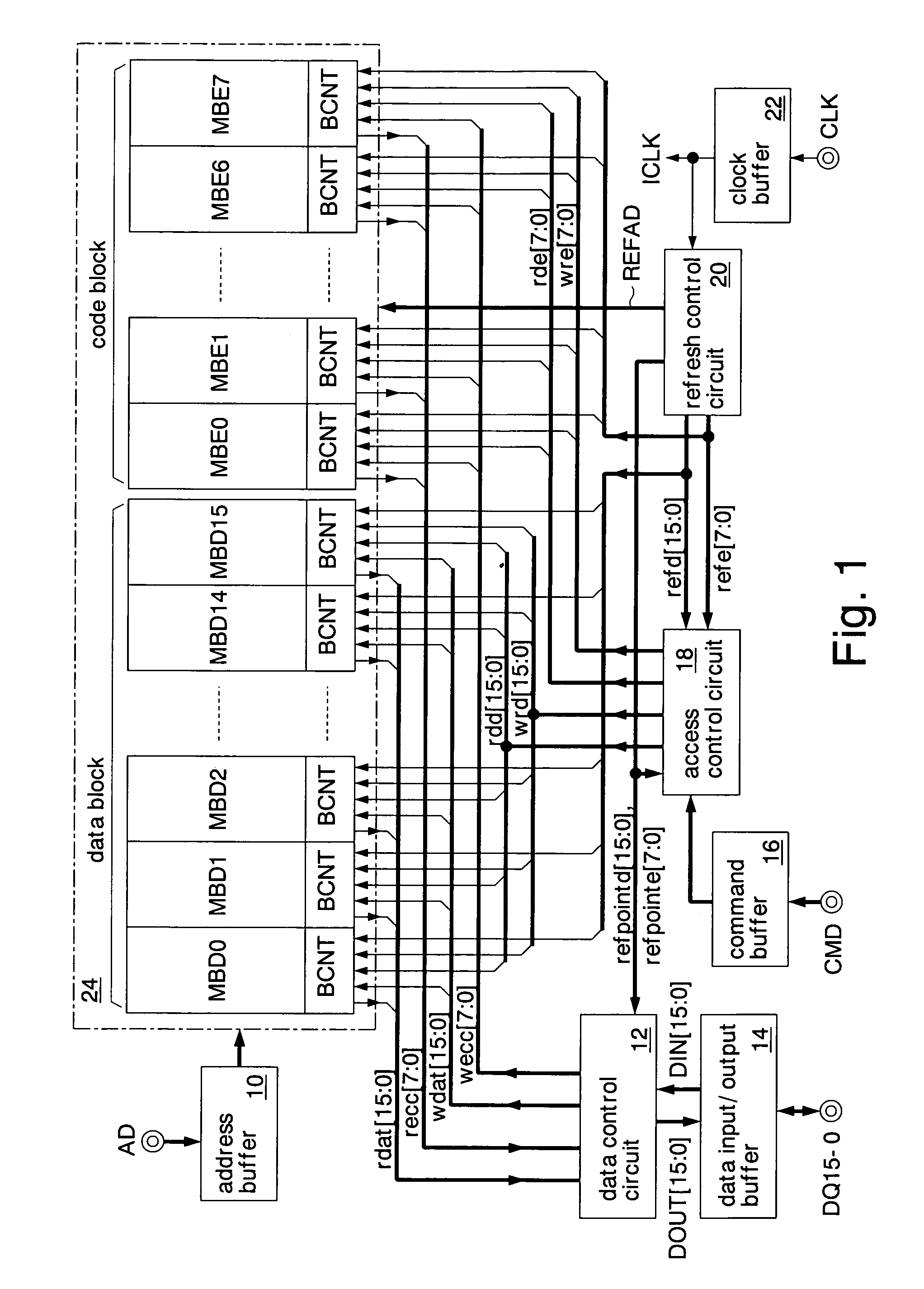
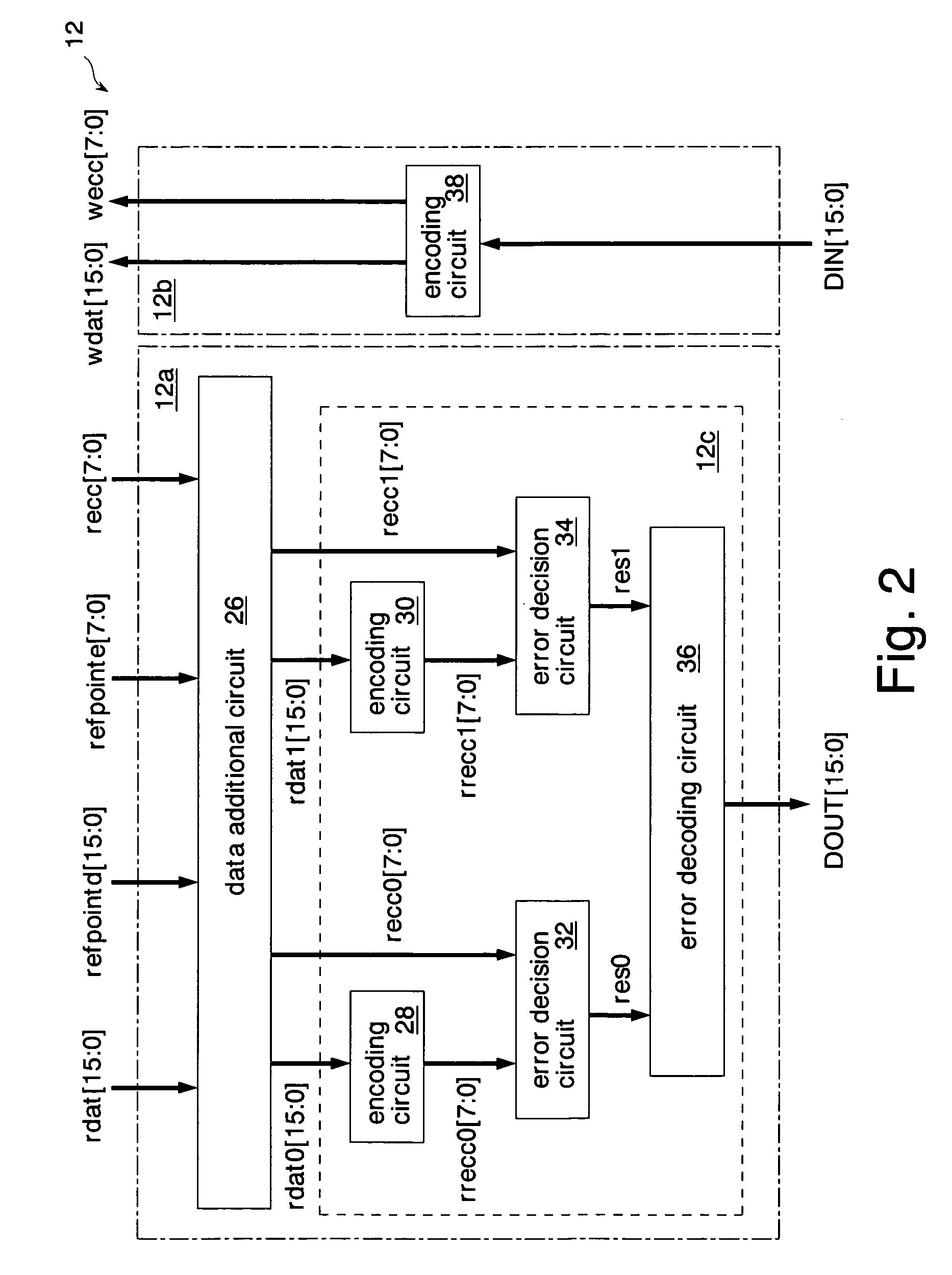
Semiconductor memory and method for operating the same
A data additional circuit adds plural types of expectation data to be read from a refresh block to data read from other blocks, respectively, to generate plural read data strings. An error correction circuit detects errors for each read data string, and sets the most reliable result of the error detection results to be true. The error correction circuit decodes data to be read from the refresh block based on a true error detection result. Moreover, the error correction circuit corrects the error of the read data string corresponding to the true error detection result. Consequently, without extending the read cycle time, a refresh operation can be hid, and errors can be corrected simultaneously. By correcting a data error read from a bad memory cell of data retention characteristics, a refresh request interval can be extended, and power consumption during a standby period can be reduced.
Owner:SOCIONEXT INC
Memory sub-system error cleansing
A system and technique for detecting data errors in a memory device. More specifically, data errors in a memory device are detected by initiating an internal READ command or cleansing operation from a set of logic which is internal to the memory system in which the memory devices reside. Rather than relying on a READ command to be issued from an external device, via a host controller, the cleansing logic initiates a cleansing routine in response to an event such as an operator instruction or a periodic schedule. By implementing the cleansing operation, the system does not rely on external READ commands to verify data integrity. Further, a monitoring device is coupled between the cleansing logic and a memory scheduler. The monitoring device provides a feed back mechanism from which to vary the frequency of certain memory requests such as the cleansing and scrubbing operations. The cleansing routine may rely on typical ECC error logging mechanisms and may be used in a RAID memory architecture. Further, the cleansing routine may be used in conjunction with other error logging and correction logic, as well as scrubbing logic.
Owner:HEWLETT PACKARD DEV CO LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com