Patents
Literature
4572 results about "BIOS" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
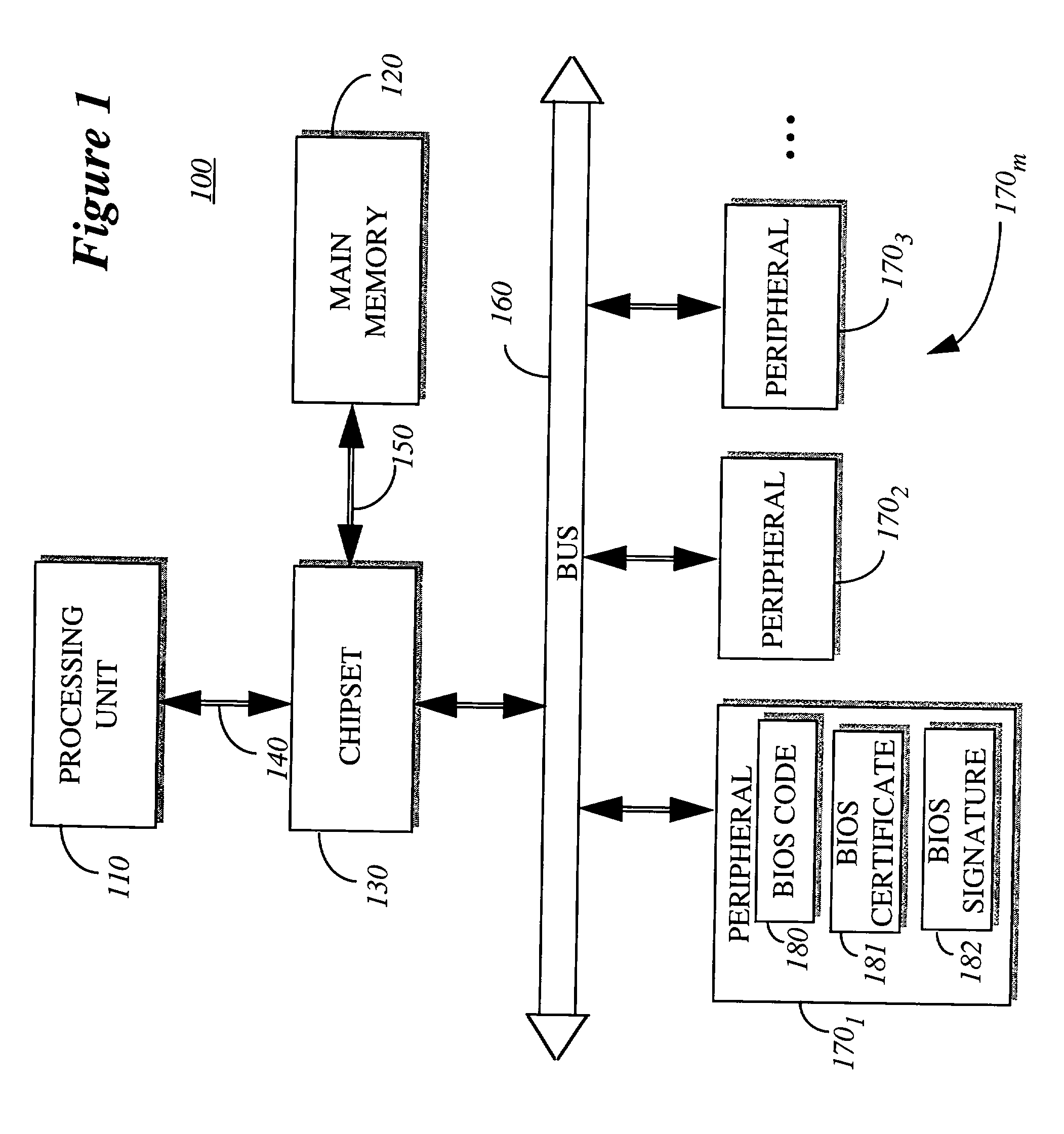
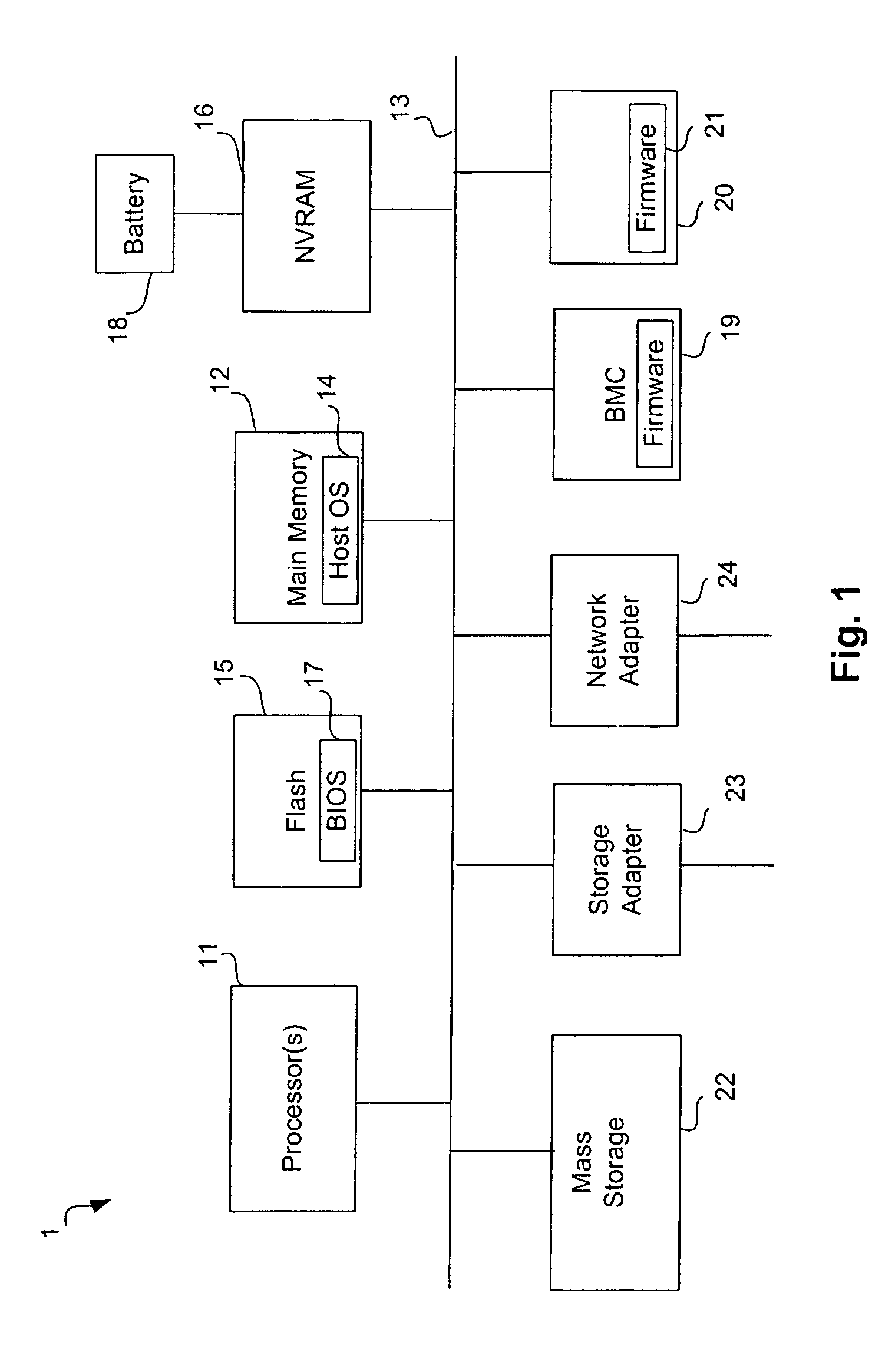
BIOS (/ˈbaɪɒs/ BY-oss; an acronym for Basic Input/Output System and also known as the System BIOS, ROM BIOS or PC BIOS) is firmware used to perform hardware initialization during the booting process (power-on startup), and to provide runtime services for operating systems and programs. The BIOS firmware comes pre-installed on a personal computer's system board, and it is the first software to run when powered on. The name originates from the Basic Input/Output System used in the CP/M operating system in 1975. The BIOS originally proprietary to the IBM PC has been reverse engineered by companies looking to create compatible systems. The interface of that original system serves as a de facto standard.
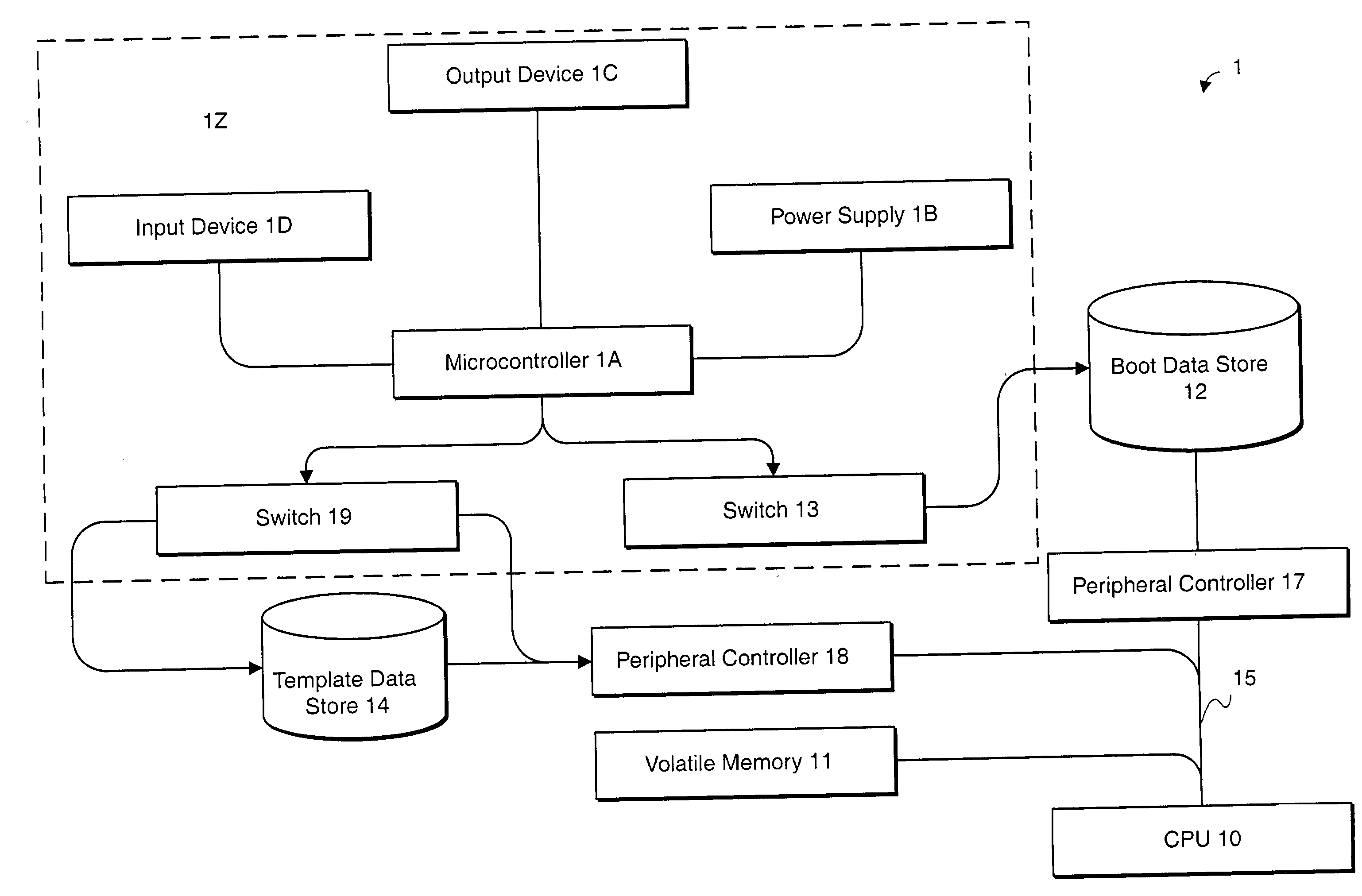
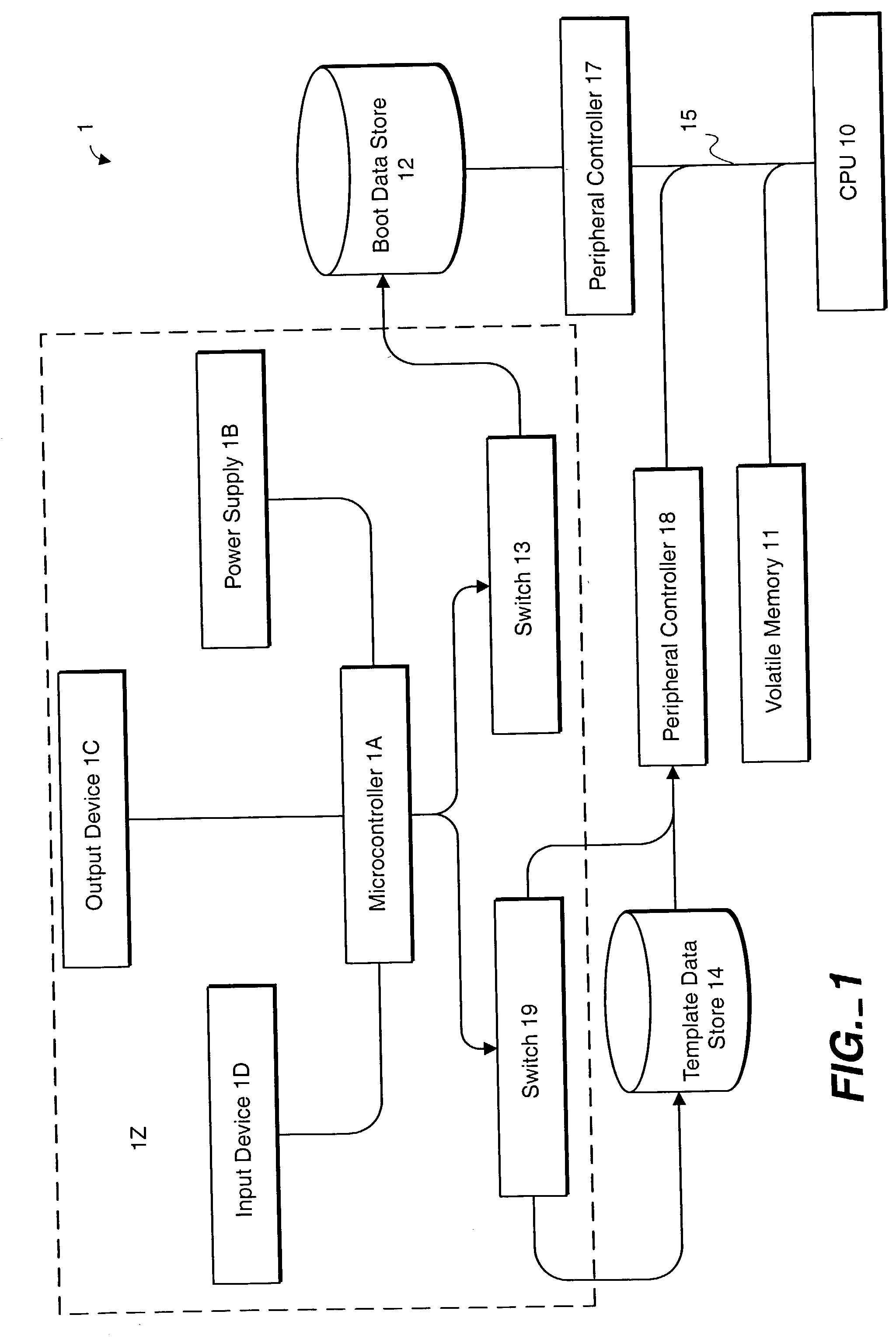
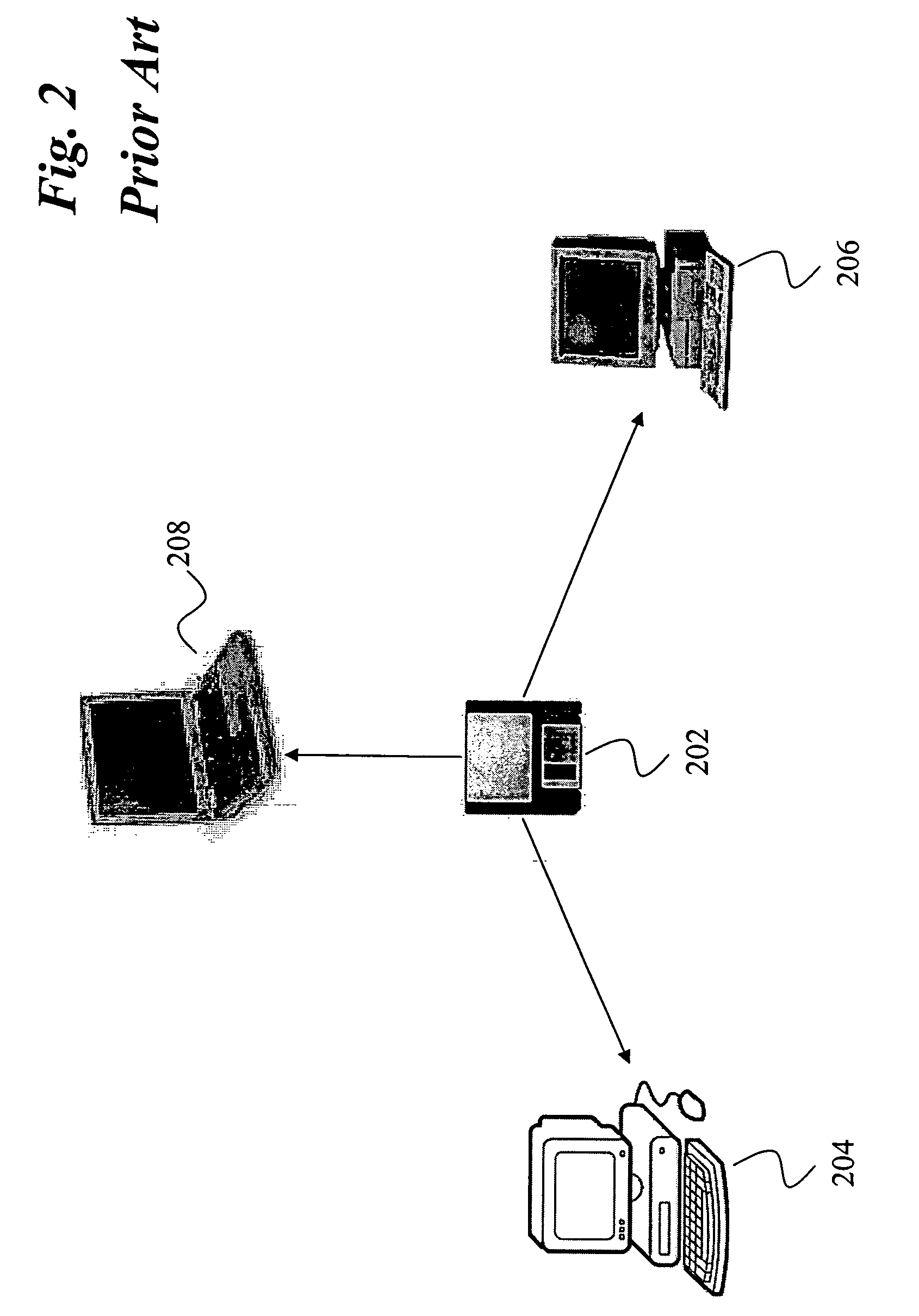
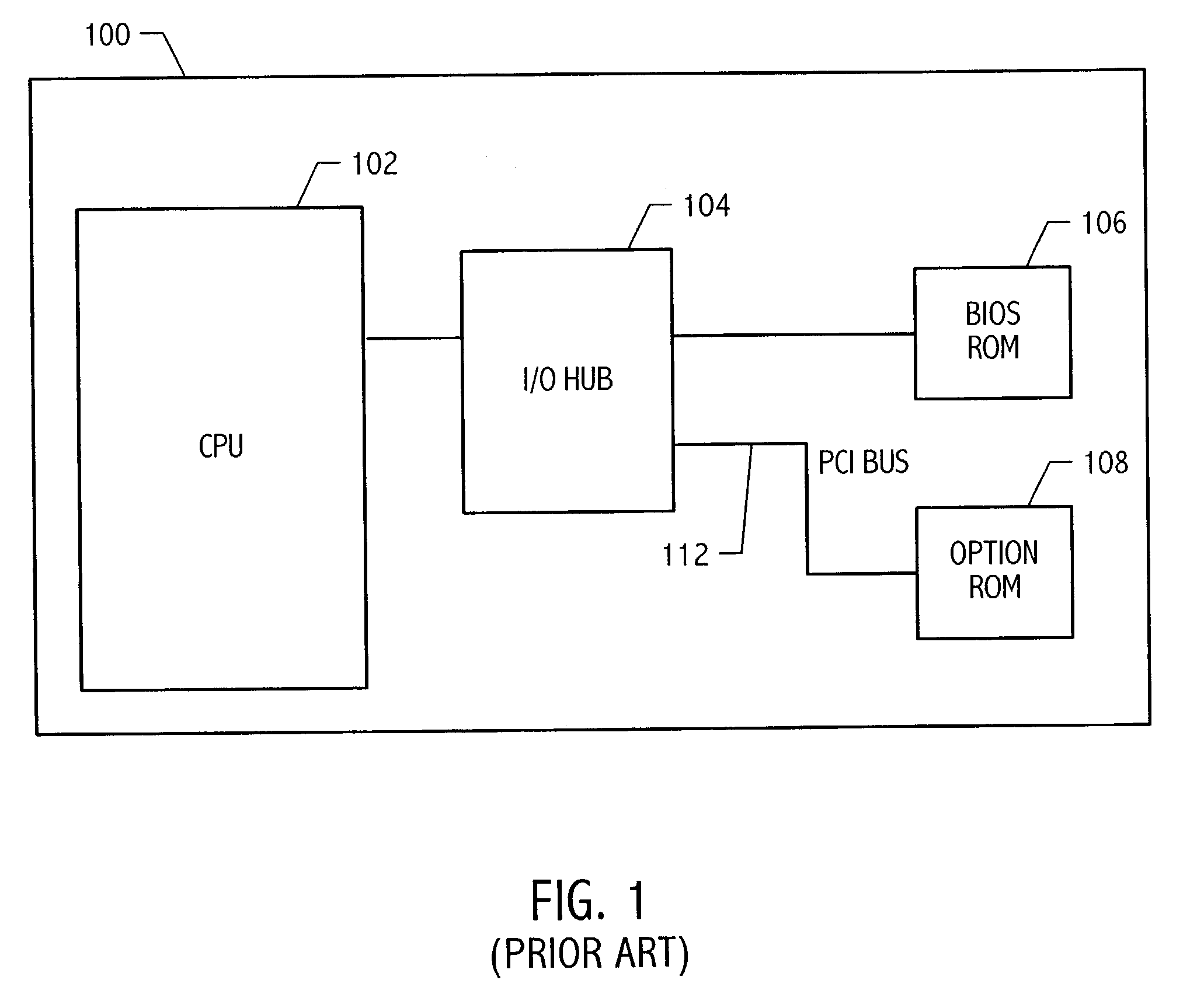
Computer with switchable components
InactiveUS20020188887A1Redundant operation error correctionRedundant hardware error correctionComputerized systemBIOS
A method or system for supporting a computer systems self repair, including the computer executed steps for booting from a first boot device, and booting from a second boot device in response to a signal indicating a need for repair. While booted from the second boot device the computer system is capable of repairing software on the first boot device. The signal may effect a logical or physical switch. Repairing software may be performed in part by copying BIOS, template, backup or archive software from a device other than the first boot device. Repairing software may be performed automatically without direction by a user or according to preset preferences.
Owner:SELF REPAIRING COMP
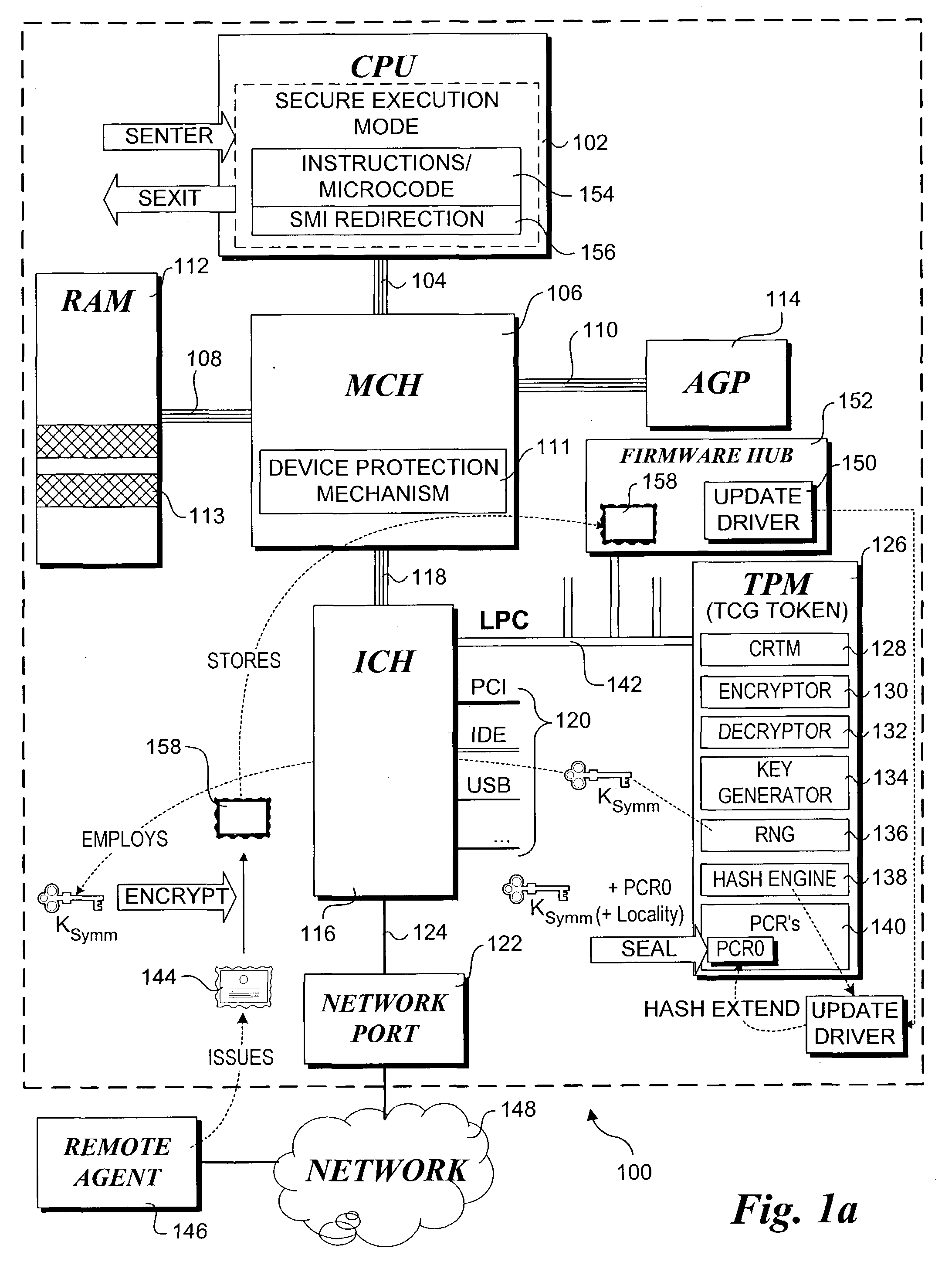
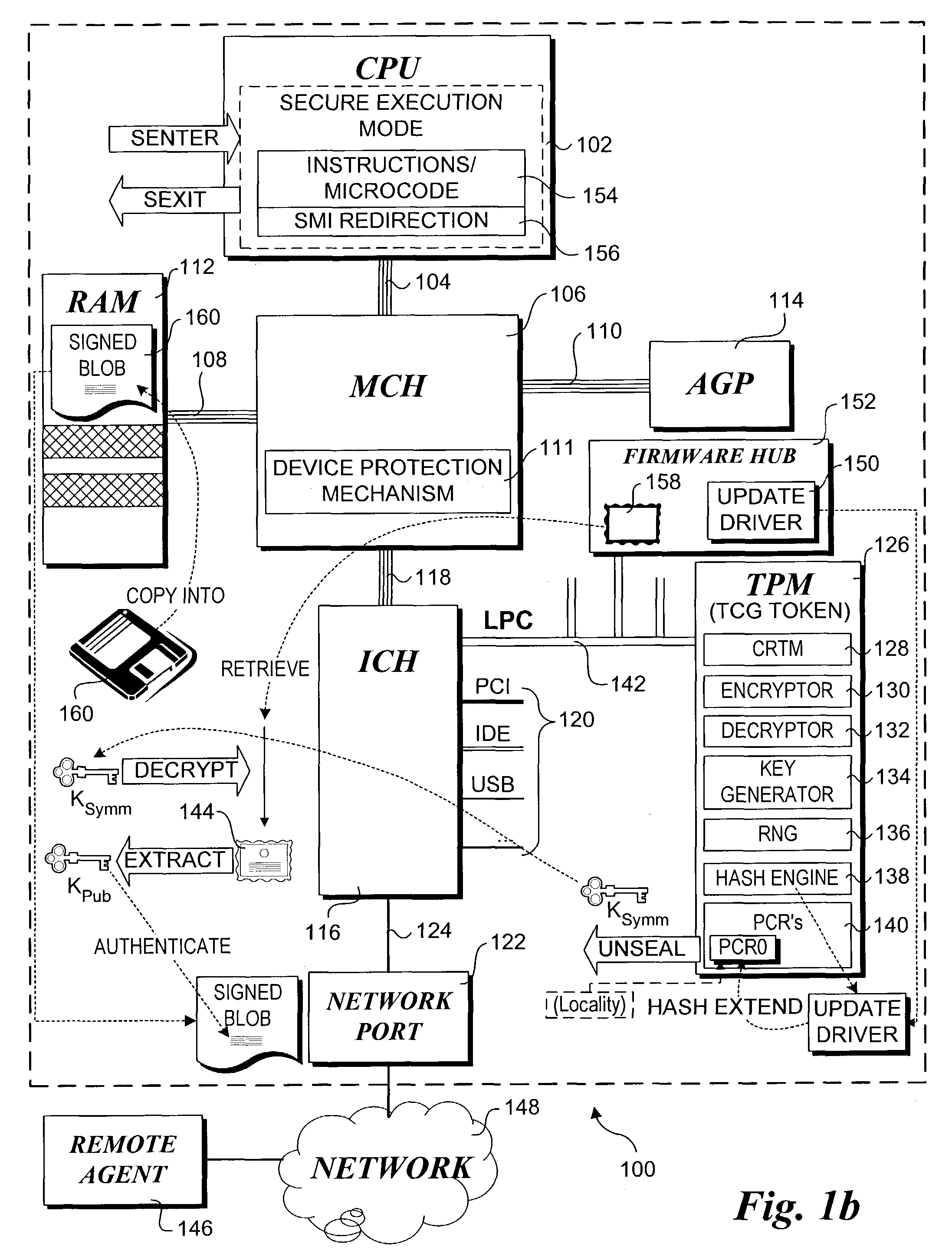
Method for performing a trusted firmware/bios update
InactiveUS20050021968A1User identity/authority verificationComputer security arrangementsTrusted Platform ModuleBIOS
A method for providing a secure firmware update. A first authentication credential is securely stored on a platform in an encrypted form using a key generated by a secure token, such as a trusted platform module (TPM). Typically, the authentication credential will identify a manufacture and the operation will be performed during manufacture of the platform. A configuration of the platform is “imprinted” such that an identical configuration is required to access the key used to decrypt the first authentication credential by sealing the key against the platform configuration. During a subsequent firmware update process, a firmware update image containing a second authentication credential is received at the platform. If the platform configuration is the same as when the key was sealed, the key can be unsealed and used for decrypting the first authentication credential. A public key in the first authentication credential can then be used to authenticate the firmware update image via the second authentication credential.
Owner:INTEL CORP
Computer network intrusion detection
InactiveUS20120297489A1Easily and efficiently identifyingRapid responseMemory loss protectionError detection/correctionBIOSVirus
A method and system of identifying an attacker device attempting an intrusion into a network. At least one managed device of the network detects an incoming TCP / IP connection by the attacker device to the network. It is determined that the incoming TCP / IP connection is a Net BIOS connection that has created an invalid logon by the attacker device, linking the invalid logon with the NetBIOS TCP / IP connection, retrieving event log information from a security event log of the network, and determining (i) that a userid of the invalid logon is a local userid defined on a local device, (ii) that the userid of the invalid logon is a userid in a list of userids used by viruses, or (iii) that the userid of the invalid logon is neither the local userid nor is in the list of userids. The retrieved event log information is stored in a central violation database.
Owner:KYNDRYL INC
Secure game download
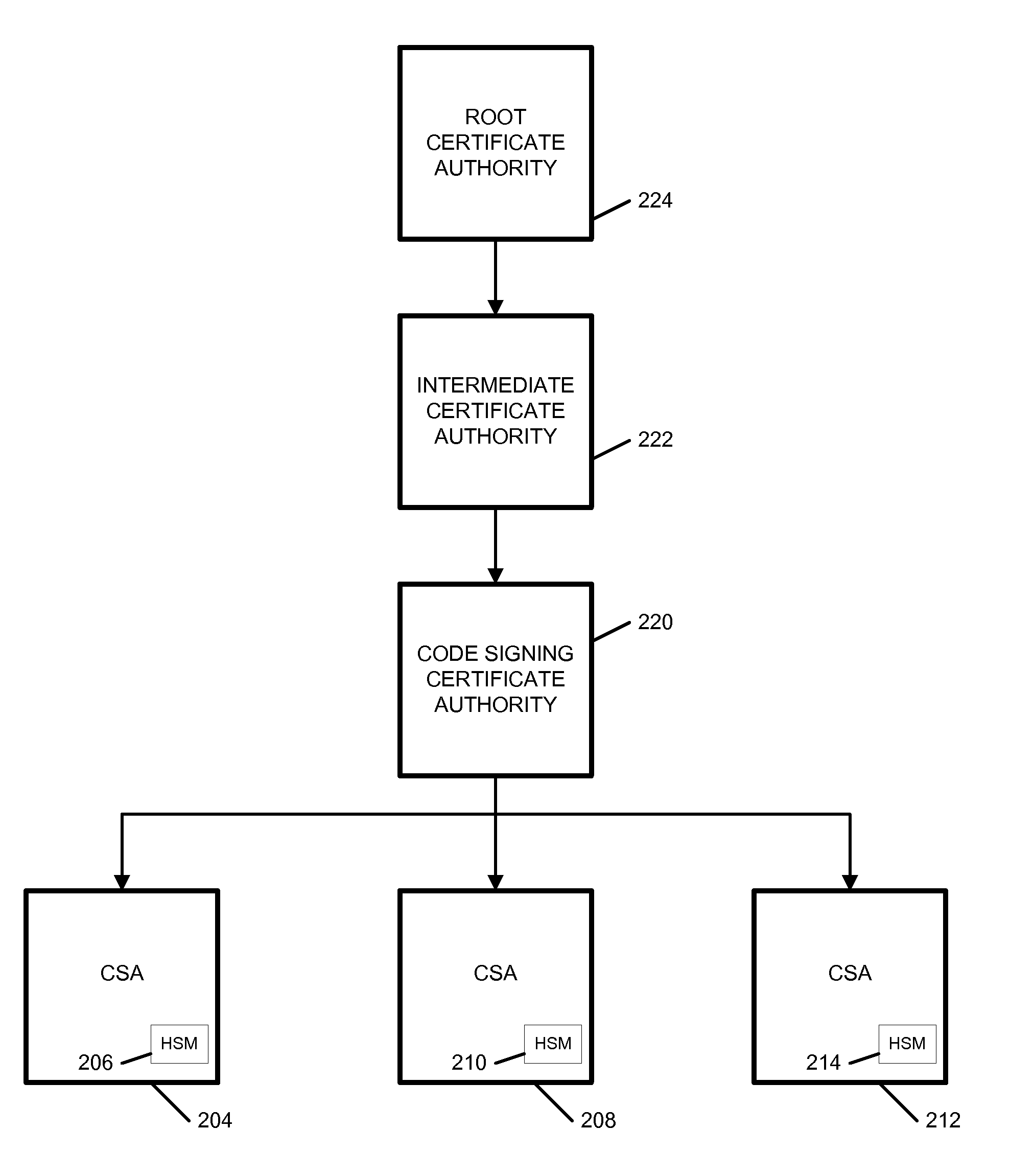
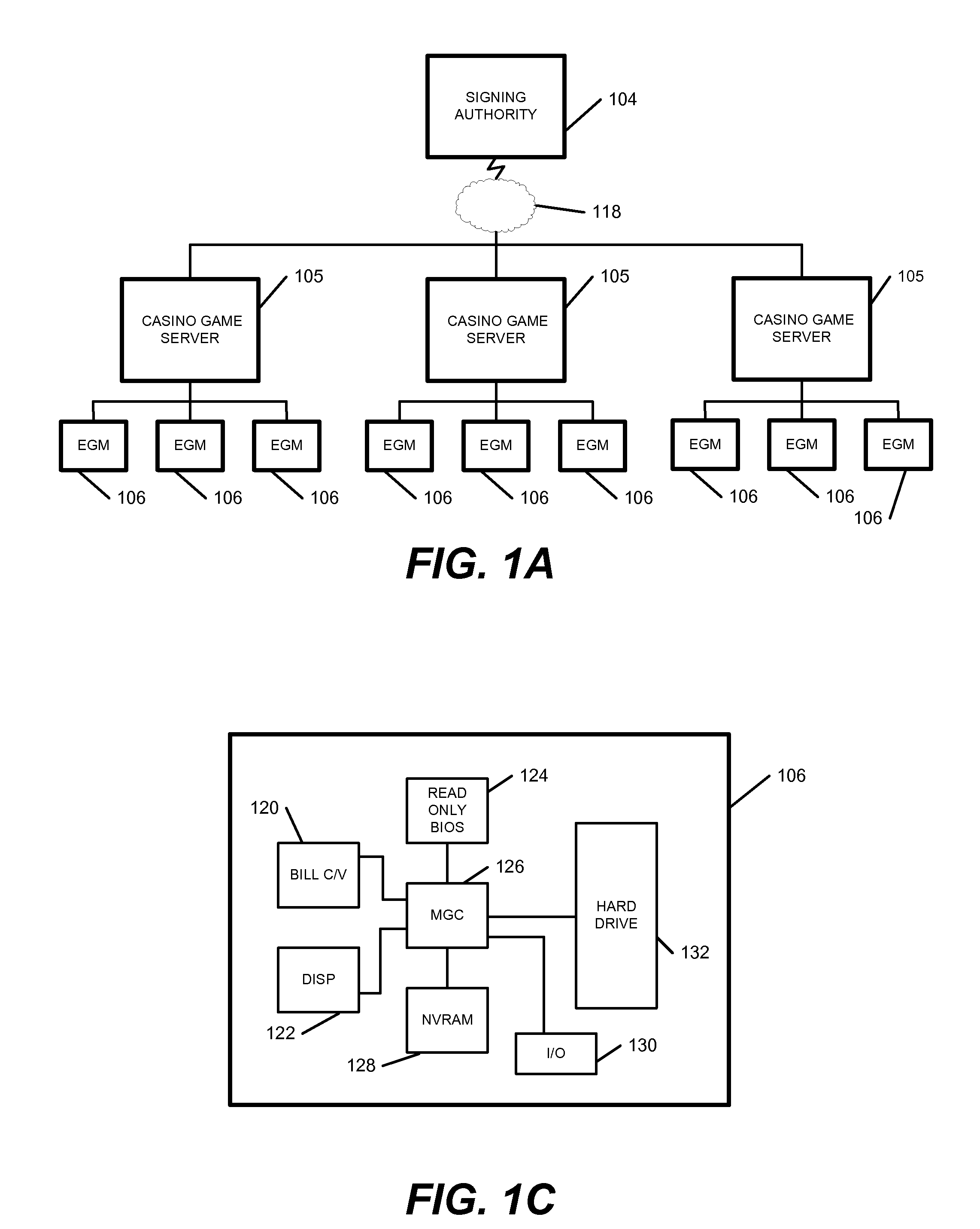
ActiveUS20060100010A1Apparatus for meter-controlled dispensingPlatform integrity maintainanceOperational systemCode signing
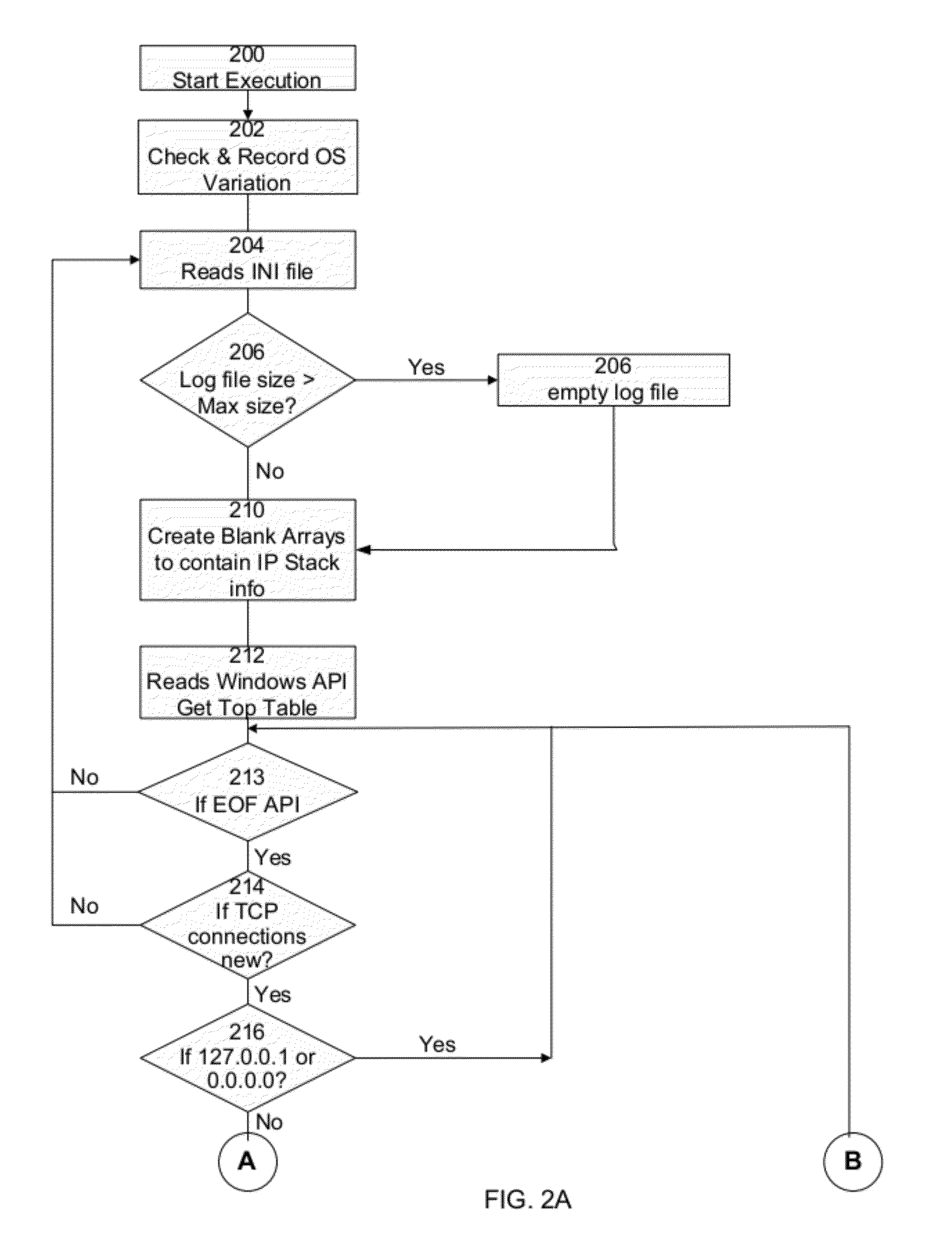
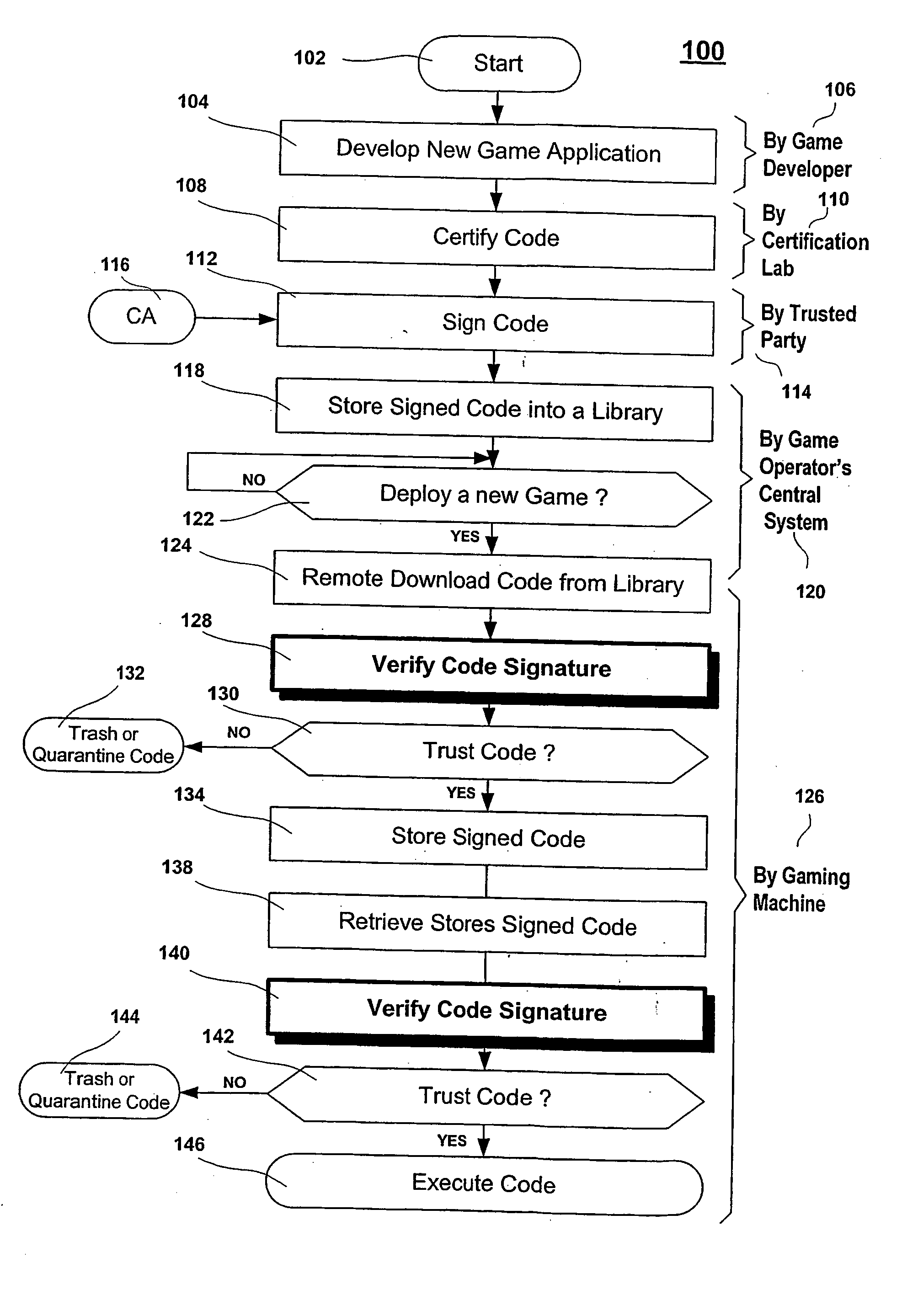
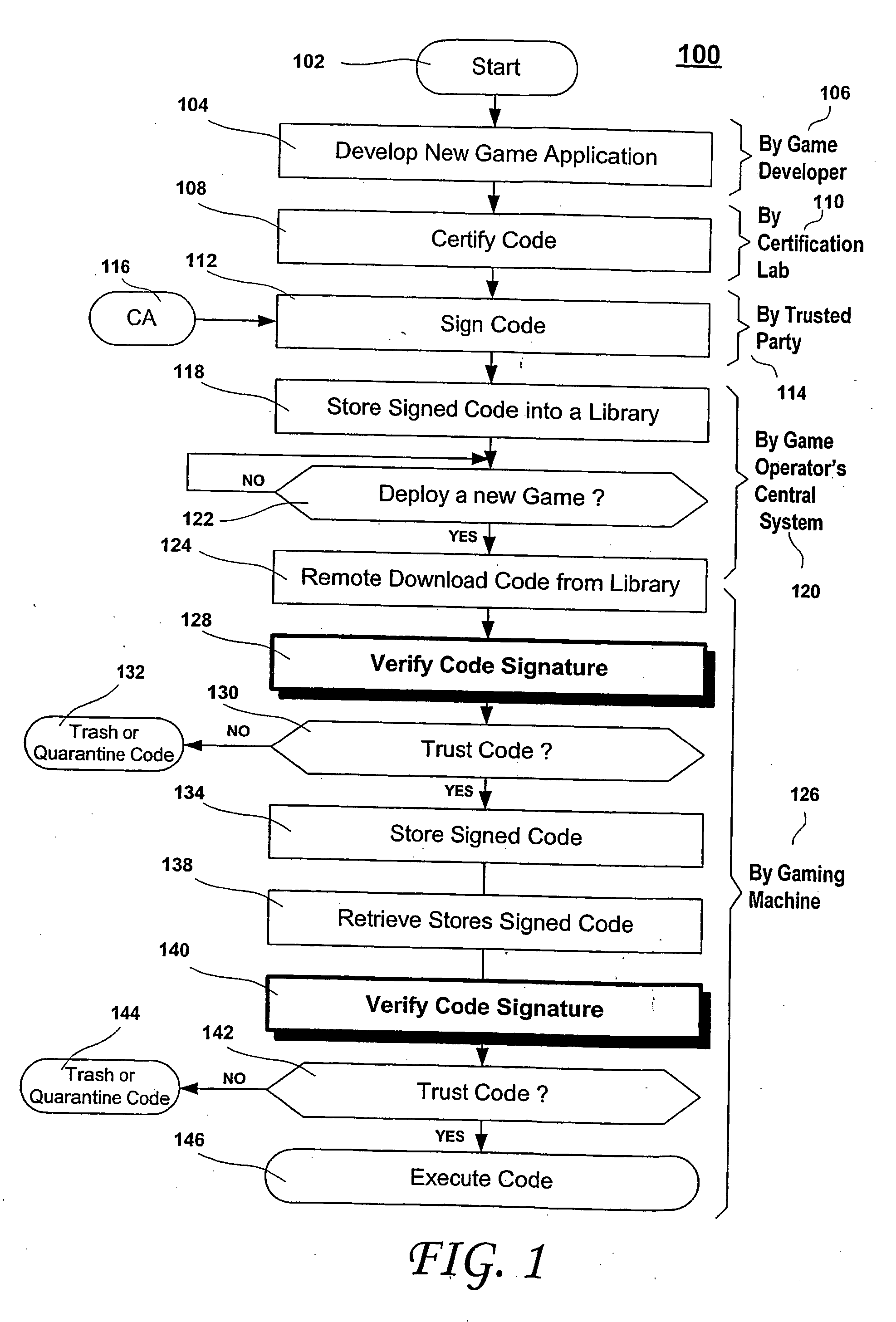
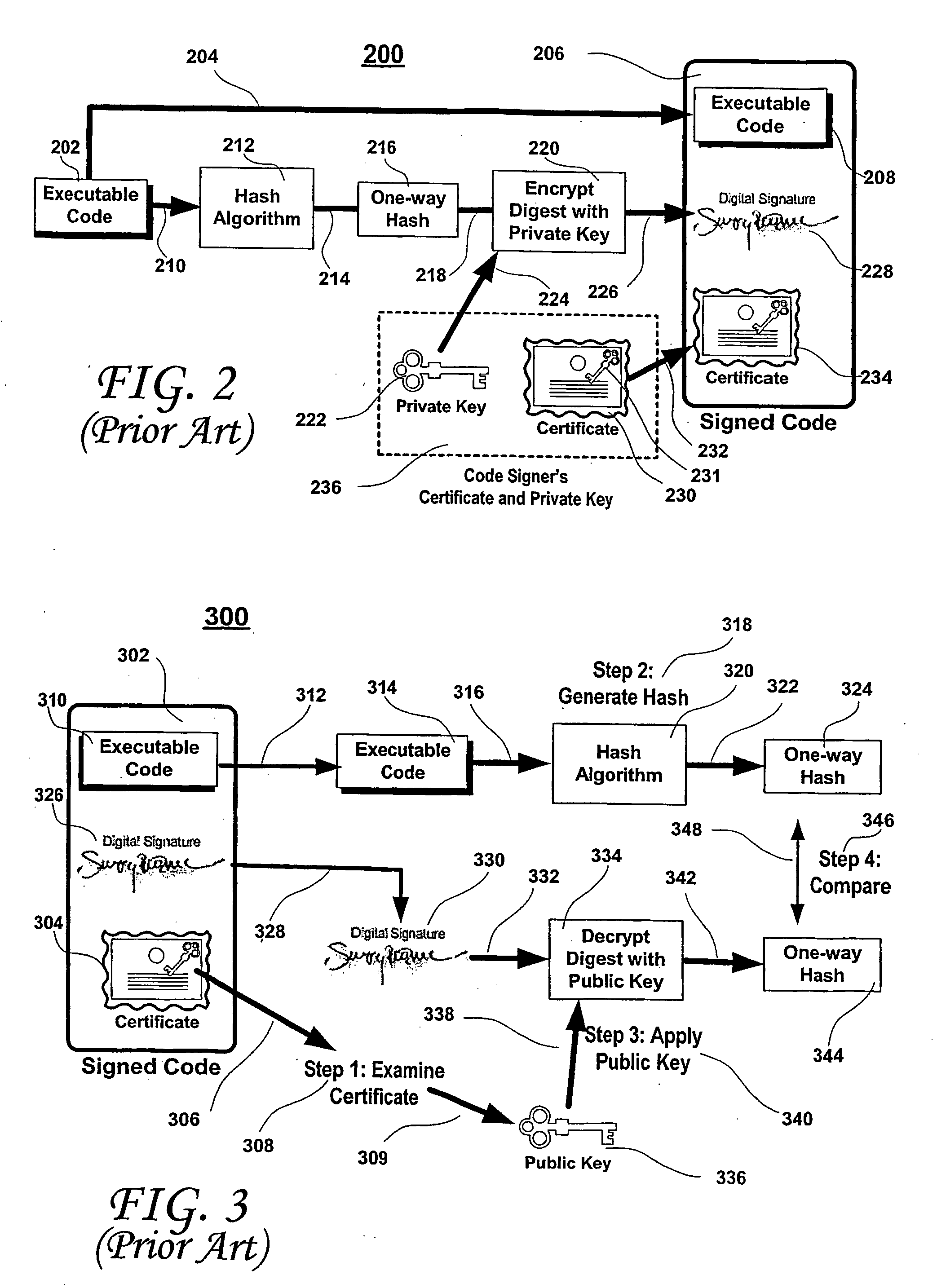
A method for gaming terminals, gaming kiosks and lottery terminals to ensure that the code-signing verification process of downloaded game software can be trusted. Drivers independently developed from the operating system supplier are embedded within the operating system kernel to verify that the micro-coded hardware components, the BIOS (808), the operating system components and the downloaded game software can be trusted.
Owner:IGT
Computer System and Method for Performing Integrity Detection on the Same
InactiveUS20090300415A1Ensure consistencyEnsures strictnessFault responseDigital data processing detailsOperational systemComputerized system
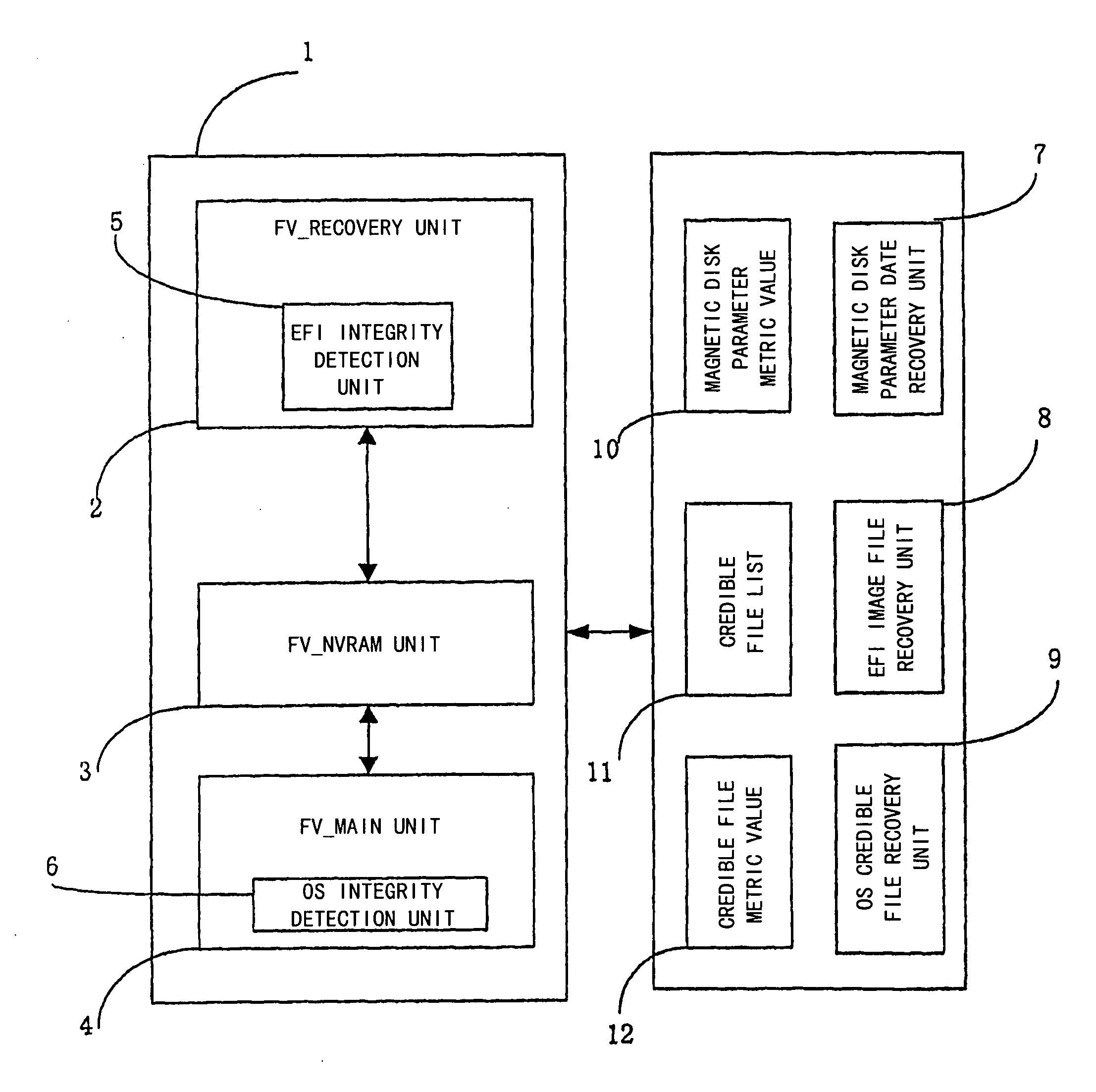
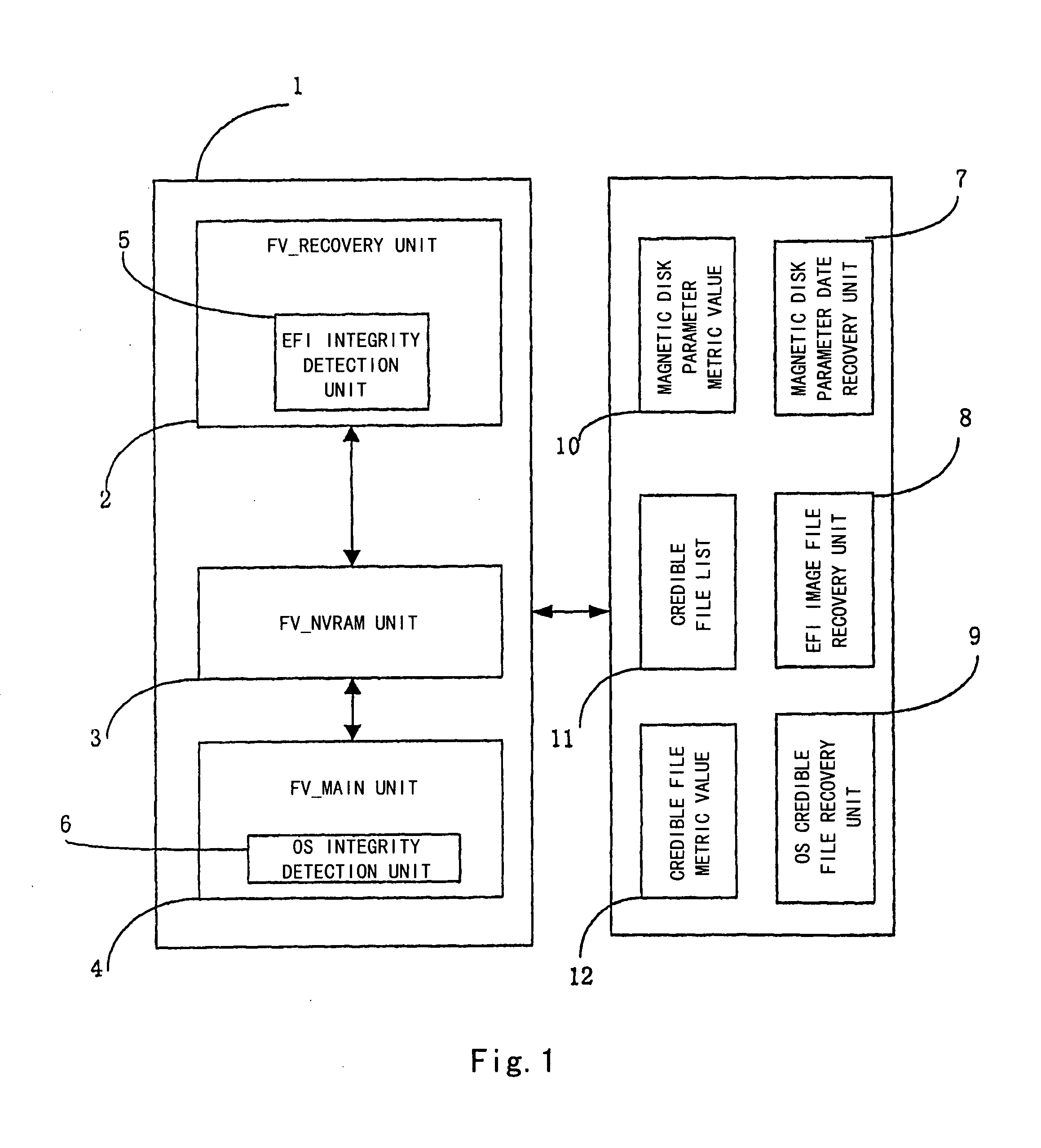
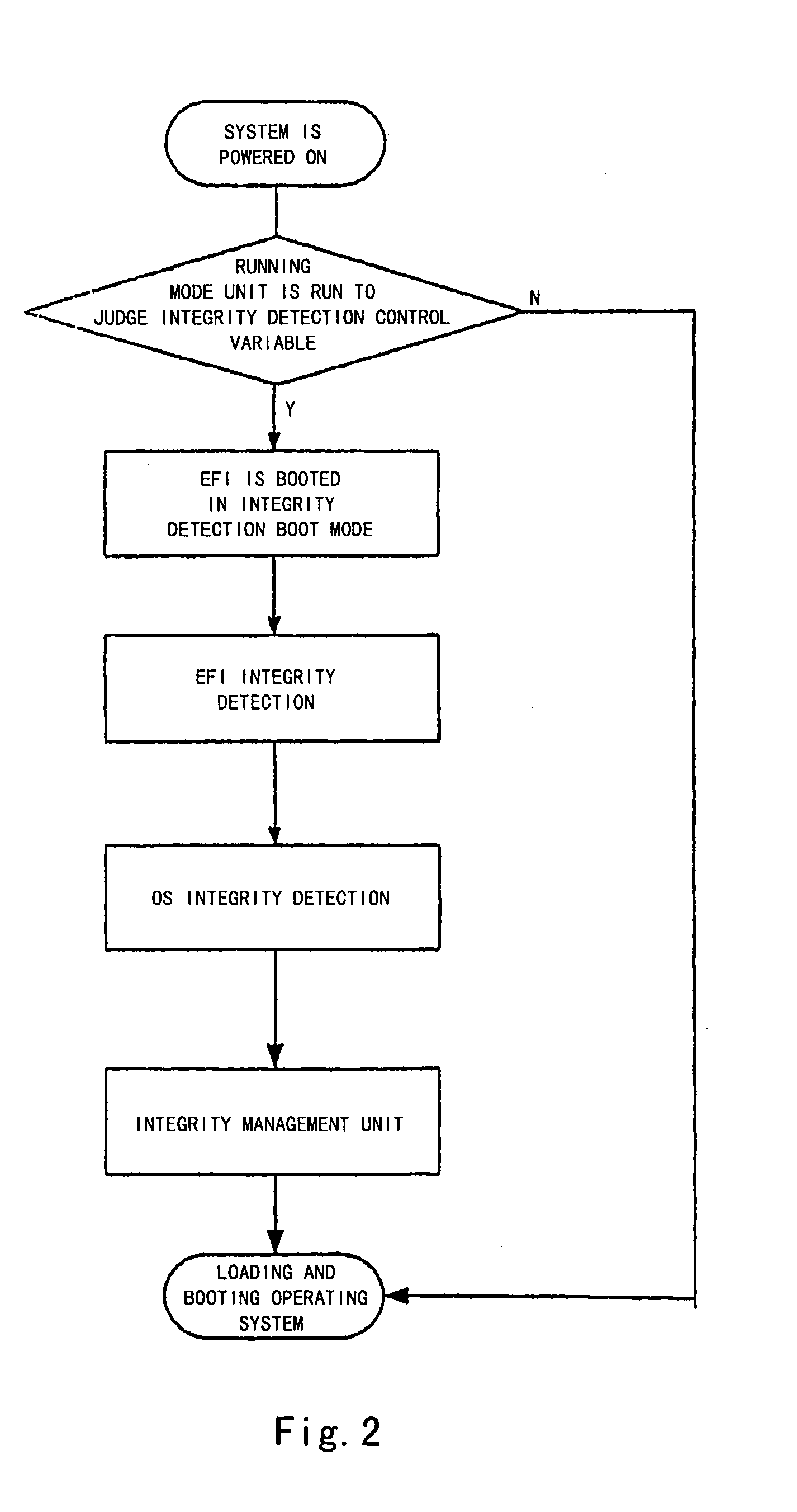
The present invention proposes a computer system and a method capable of performing integrity detection, comprising: a running mode unit which comprises an integrity detection boot variable to determine whether or not to initiate an integrity detection boot mode by judging said running mode unit; an EFI integrity detection unit (5), which is used for performing an integrity detection on EFI image codes in the integrity detection boot mode, and comprises an integrity metric value for being compared with an EFI integrity calculated value generated after the EFI integrity detection unit performs the integrity detection on the EFI image codes, to determine the integrity of the EFI image codes; an operating system integrity detection unit (6); and an integrity management unit. The present invention is based on the EFI BIOS to perform the integrity detection on the operating system during the pre-boot stage, having better reliability and security.
Owner:LENOVO (BEIJING) CO LTD
Method for BIOS authentication prior to BIOS execution
InactiveUS6401208B2User identity/authority verificationUnauthorized memory use protectionPower-on resetBIOS
Owner:INTEL CORP
Write clock and data window tuning based on rank select
A configuration register used to adjust a clock or request signal with respect to the other. Specifically, a look-up table is provided in the memory controller. The look-up table is filled at bootup such that it contains test information from a master look-up table in the system BIOS, for instance. The look-up table in the memory controller stores current test data correlative to optimal sampling times for the current configuration. Adjustable delay elements or adjustable load elements may be used to change the relative sampling time of the request signal correlative to the values stored in the memory controller look-up table.
Owner:MICRON TECH INC
System for assembling computers to provide a favorable import classification
ActiveUS7420815B2Easy to installLower levelPrinted circuit assemblingCasings/cabinets/drawers detailsBIOSElectrical and Electronics engineering
Owner:GATEWAY
Computer system having security features for authenticating different components
InactiveUS6625729B1Digital computer detailsUnauthorized memory use protectionCMOSComputerized system
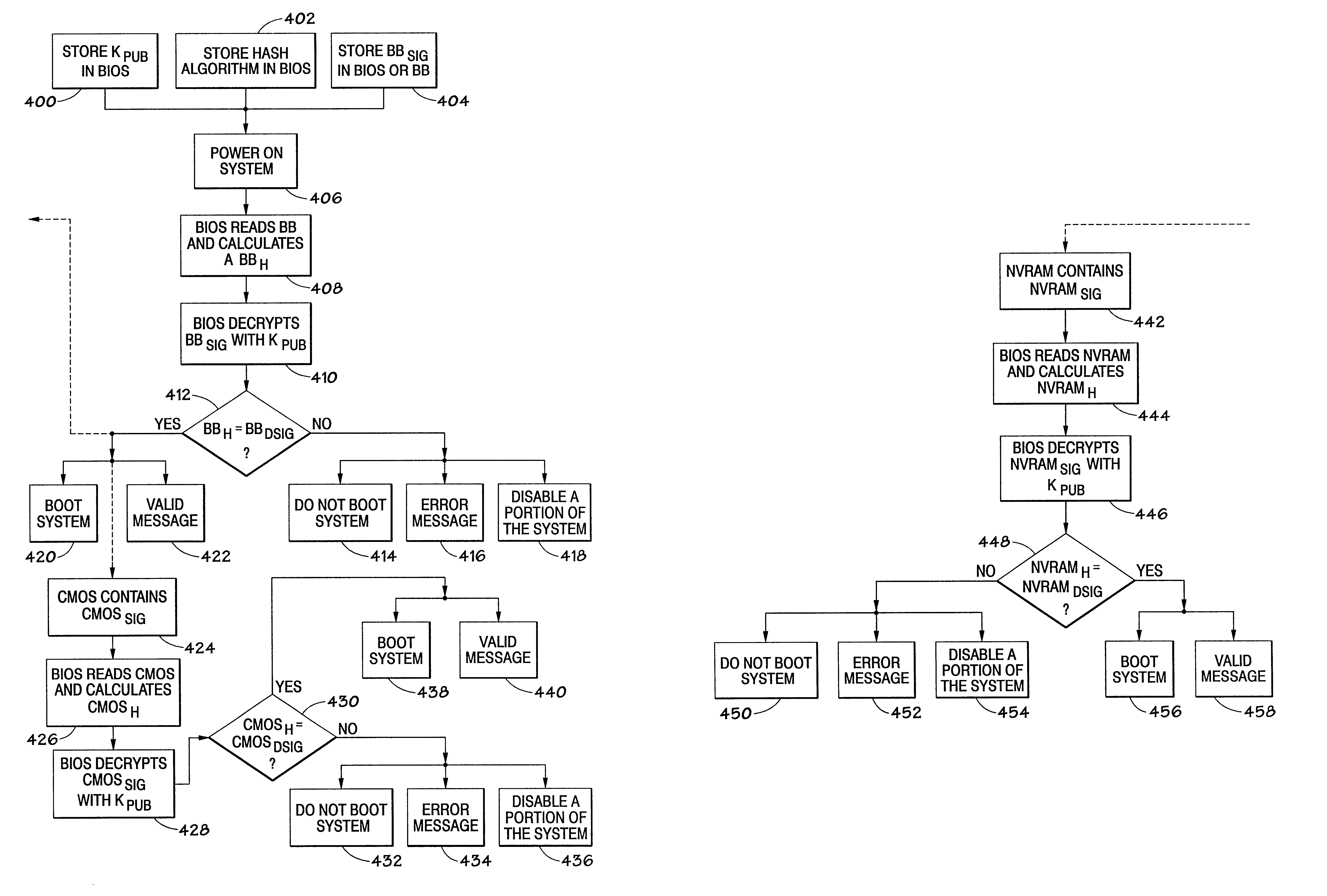
A method and apparatus for protecting a computer system. Specifically, a method and system for validating portions of memory at each power-on cycle is described. A Boot Block is used to validate the BIOS, CMOS and NVRAM of a system. The BIOS may also be used to validate the Boot Block, CMOS and NVRAM.
Owner:CONVERSANT INTPROP MANAGEMENT INC
Method for securing a computing device with a trusted platform module-tpm
InactiveUS20120151223A1Unauthorized memory use protectionHardware monitoringExternal storageHash-based message authentication code
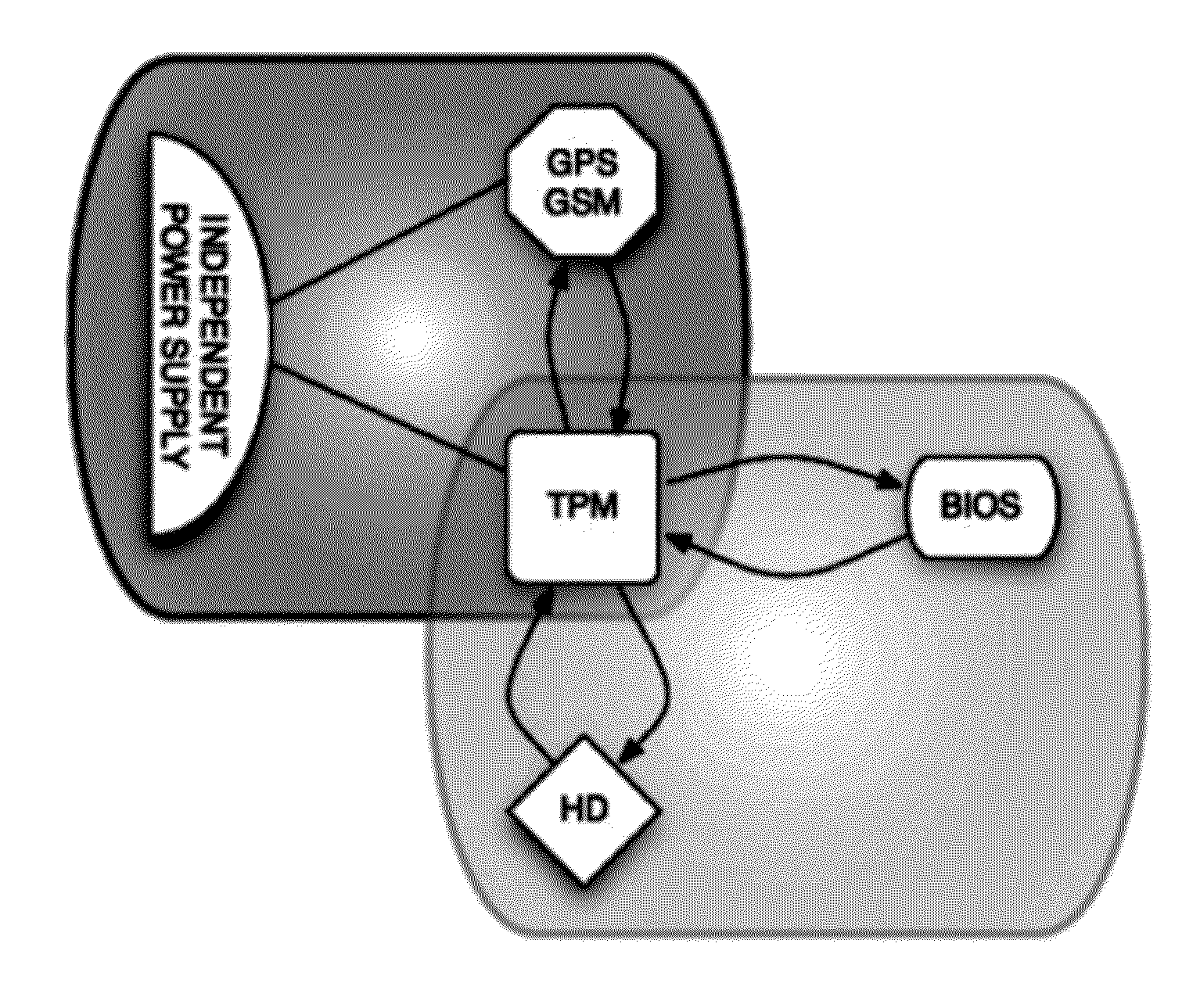
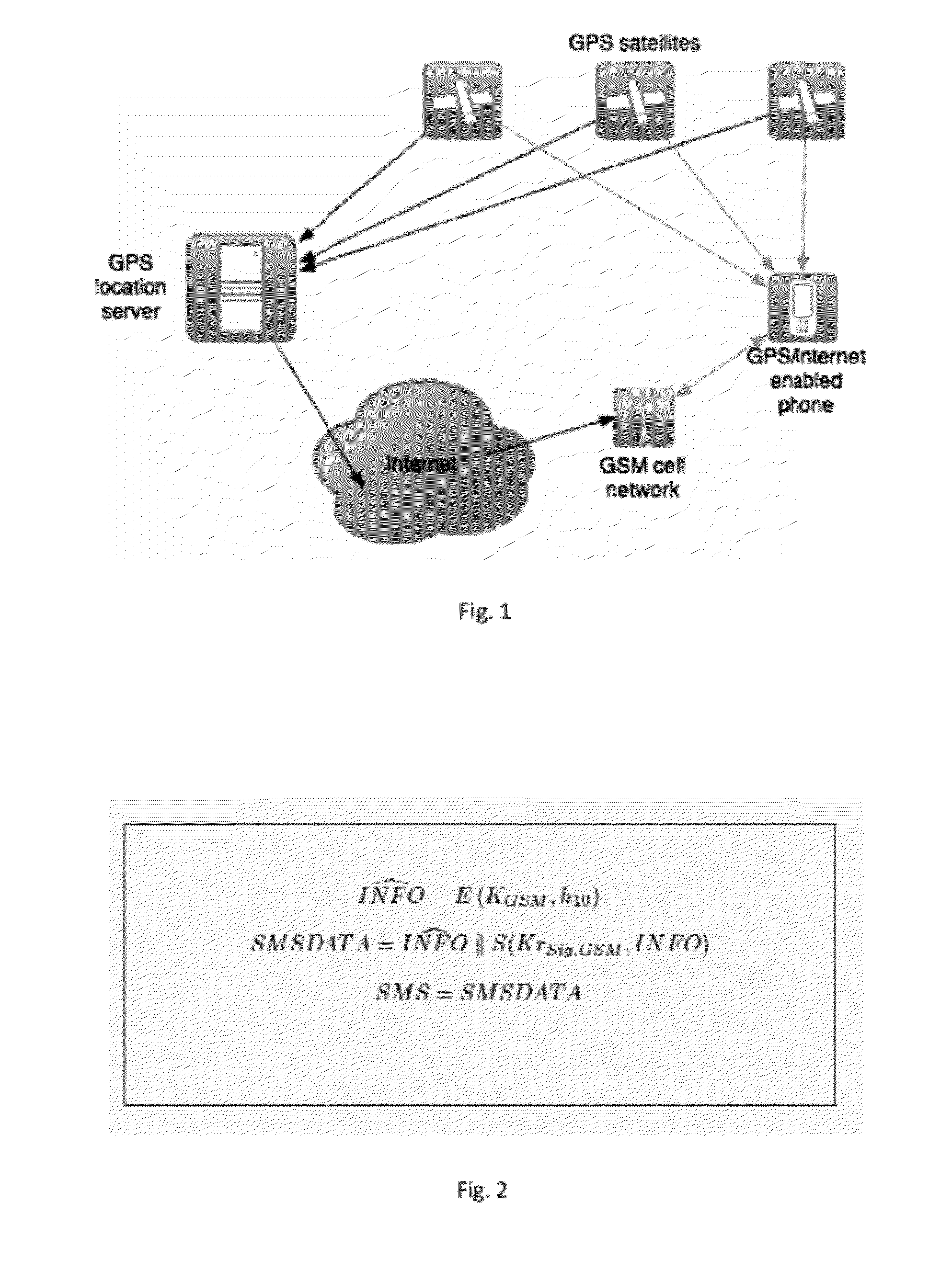
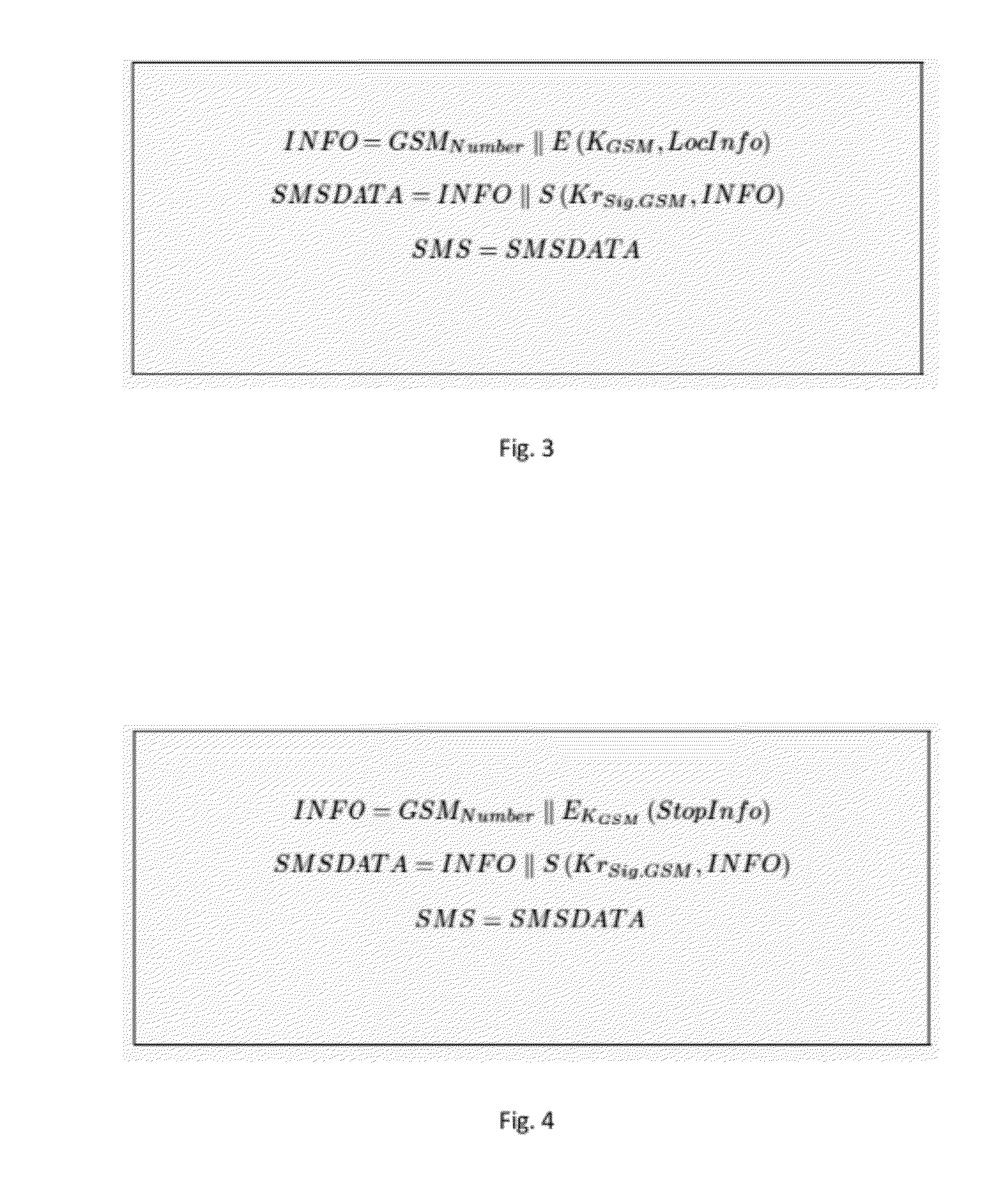
Methods, systems and computer program products for securing a computing device with data storage, power-on firmware—BIOS, geolocation and mobile data module—GPS / GSM, and a Trusted Platform Module—TPM, including establishing a shared-secret between the BIOS and the TPM, requesting the TPM to generate suitable encryption keys, namely for encrypting the data storage, supplying the user of the computing device suitable keys for external storage, calculating a hash-based message authentication codes over the BIOS, MBR, unique ID of the TPM, unique ID of the GPS / GSM module and unique ID of the BIOS; using user provided password and / or token device; using mobile data messages to secure the device if misplaced.
Owner:UNIV DE LISBOA
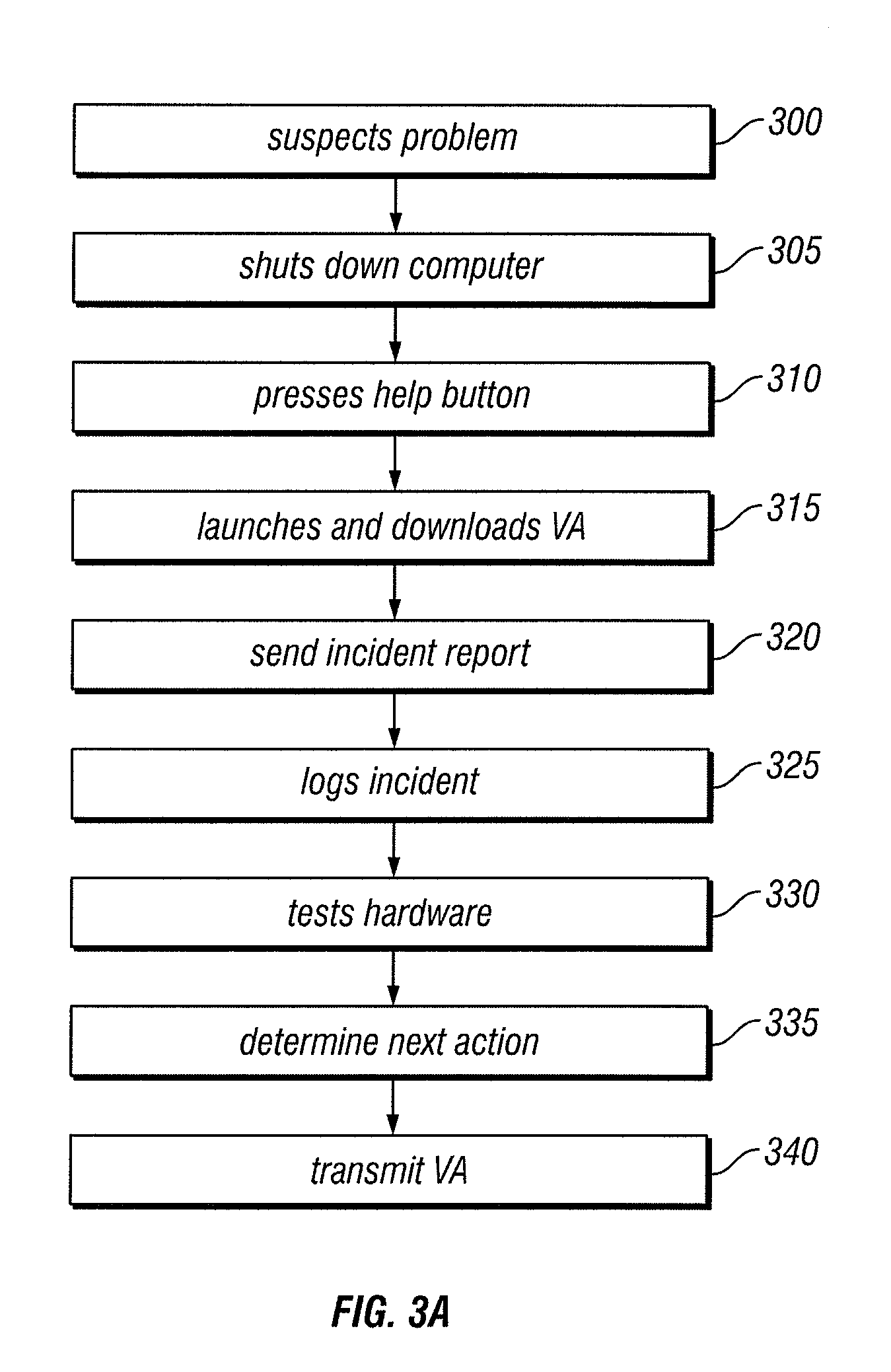
Diagnostic Virtual Appliance
InactiveUS20090037496A1Memory loss protectionDetecting faulty hardware by remote testMass storageBIOS
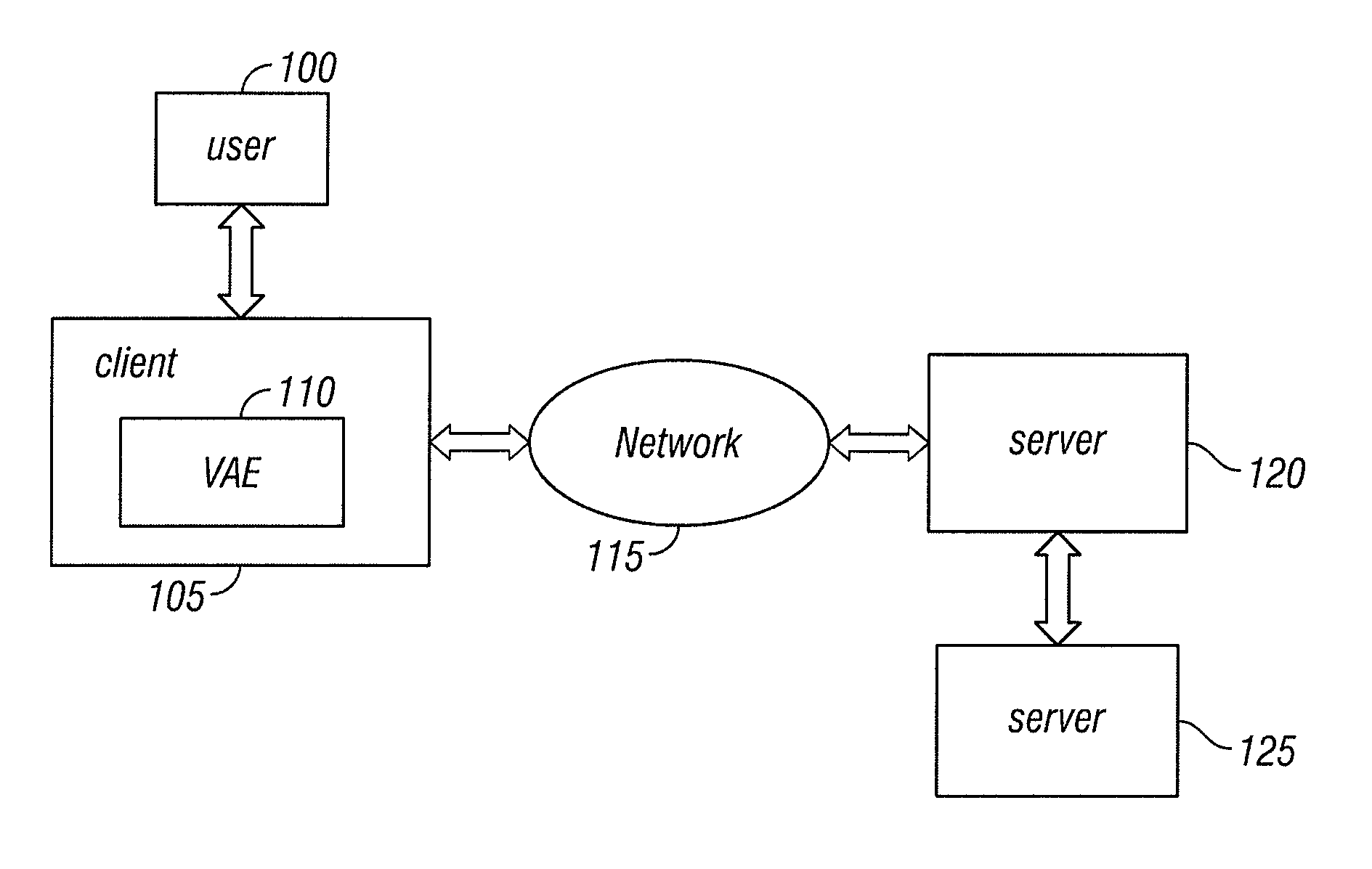
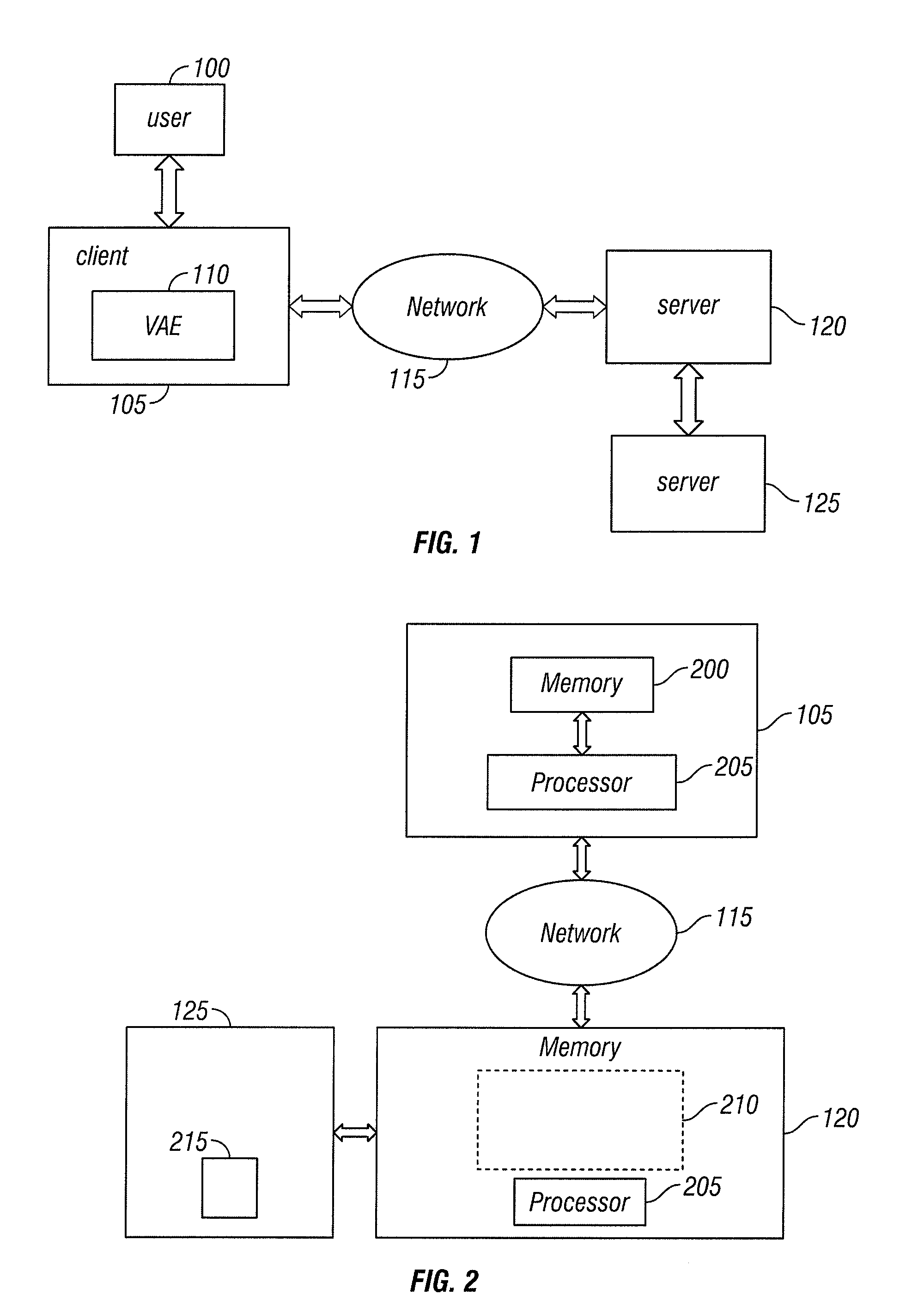
A virtual appliance environment (VAE) consists of components residing on a computer BIOS ROM and also on a mass storage device. The VAE includes a virtual appliance (VA) for diagnosing malfunctioning hardware or software. The VA for diagnosing malfunctions tests the hardware and / or software resident in the computer and transmits the results of the test to a server, which diagnoses the problem and transmits instructions to the VAE for saving the data, determining whether the computer is under warranty, and providing shipping information to a user. The VAE can also download a VA for scanning viruses. The VAE transmits the results of the virus scan to the server, which determines the type of virus infecting the computer and transmits instructions to the virtual appliance for downloading the appropriate VA for removing the virus. The VAE can save the data to another source, remove the virus, and restore the data or simply remove the virus.
Owner:SPLASHTOP INC
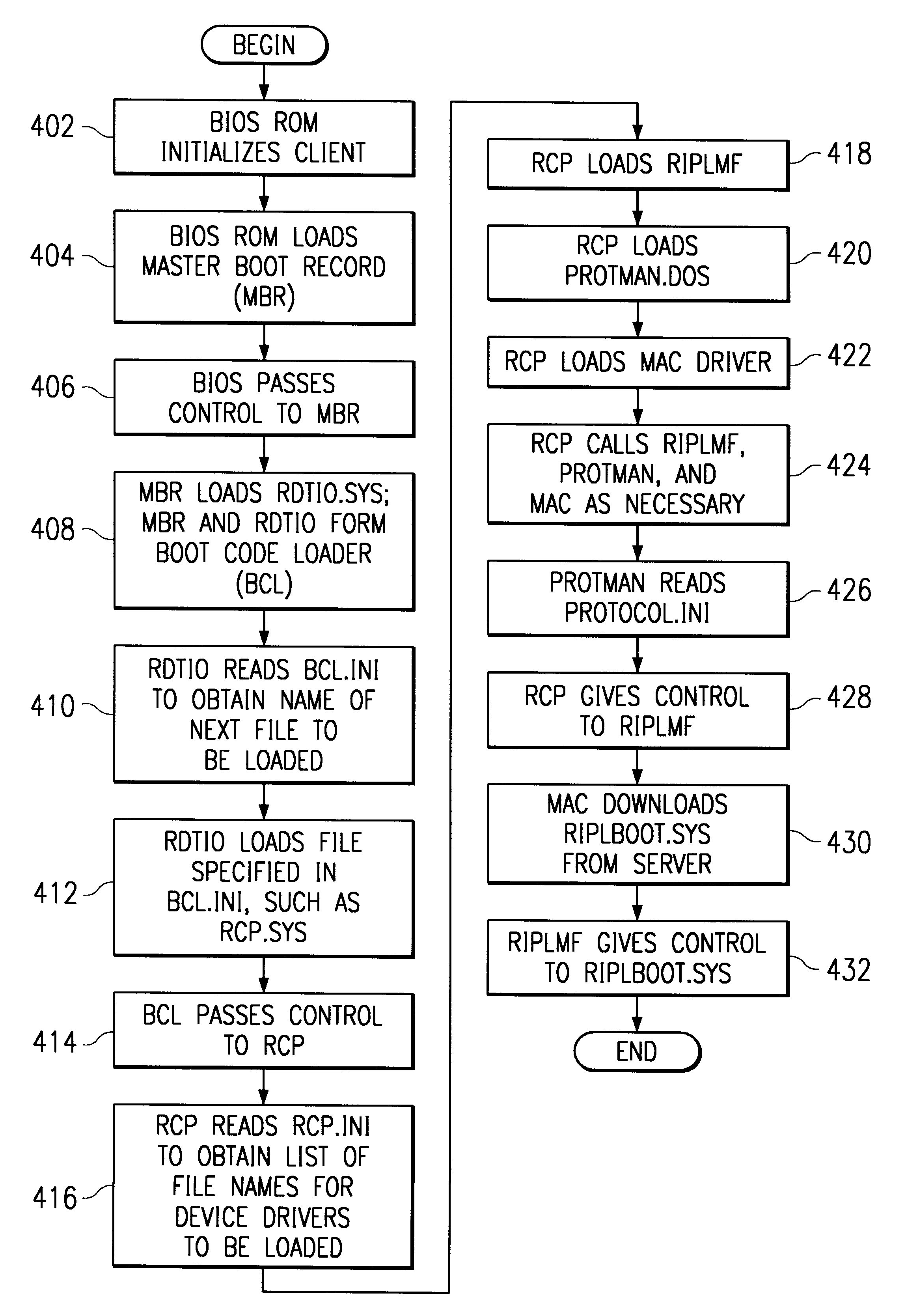
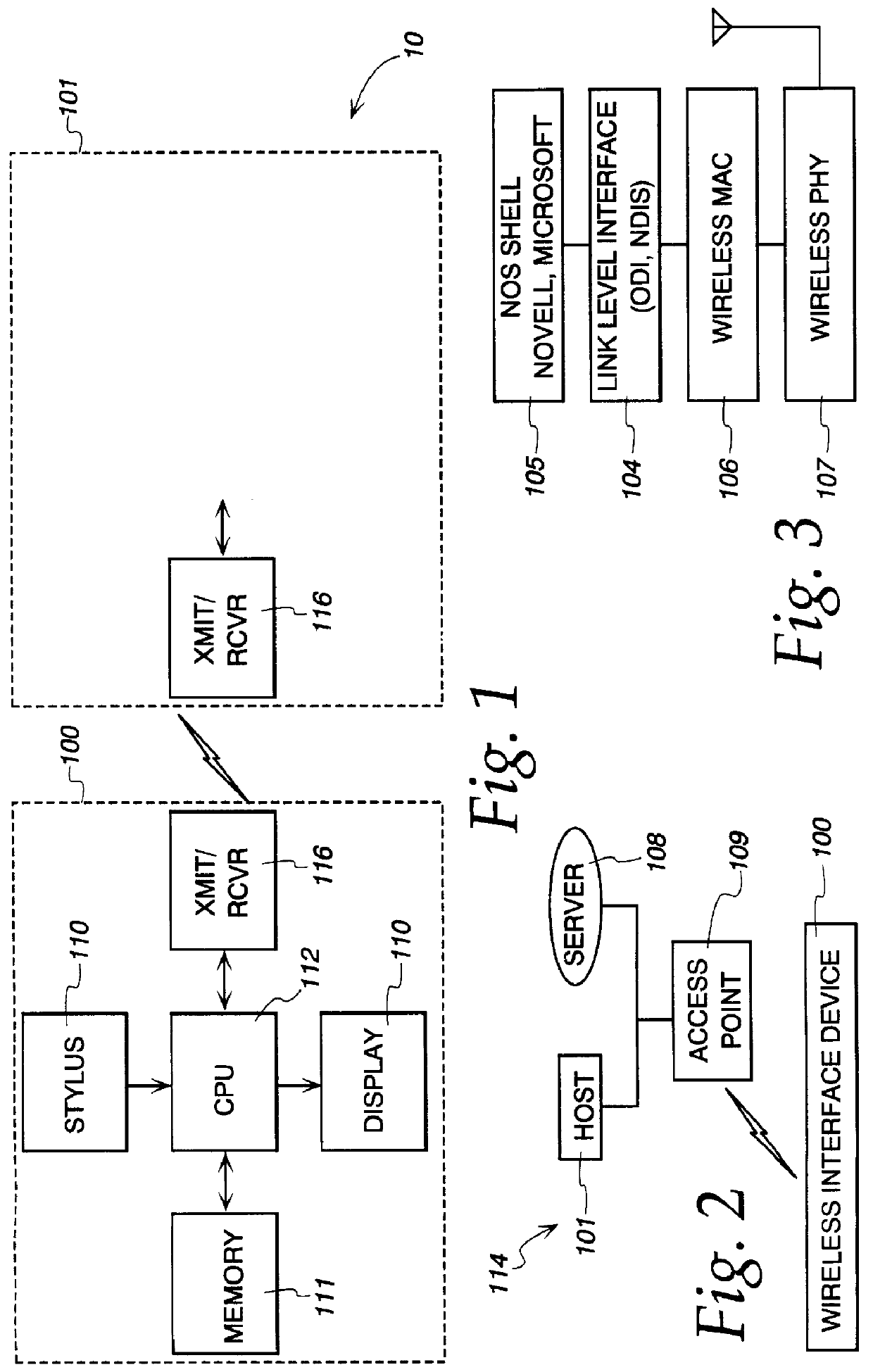
Method and apparatus for remotely booting a client computer from a network by emulating remote boot chips
A method and apparatus for booting a client computer connected to a network without a boot ROM and without an operating system is provided. Instructions from a BIOS ROM are executed to load a boot code loader from a nonvolatile, read / write memory, such as a diskette or hard disk. The boot code loader executes to load a control program from the diskette, and the control program executes to load a set of programs and / or device drivers from the diskette without loading an operating system. The set of programs and / or device drivers communicate with a network server to retrieve a boot program from the network server, and the boot program executes to complete the boot process of the client, such as downloading an operating system from the server.
Owner:MICROSOFT TECH LICENSING LLC
Licensed application installer
InactiveUS6948168B1Data processing applicationsSoftware engineeringComputer terminalApplication software
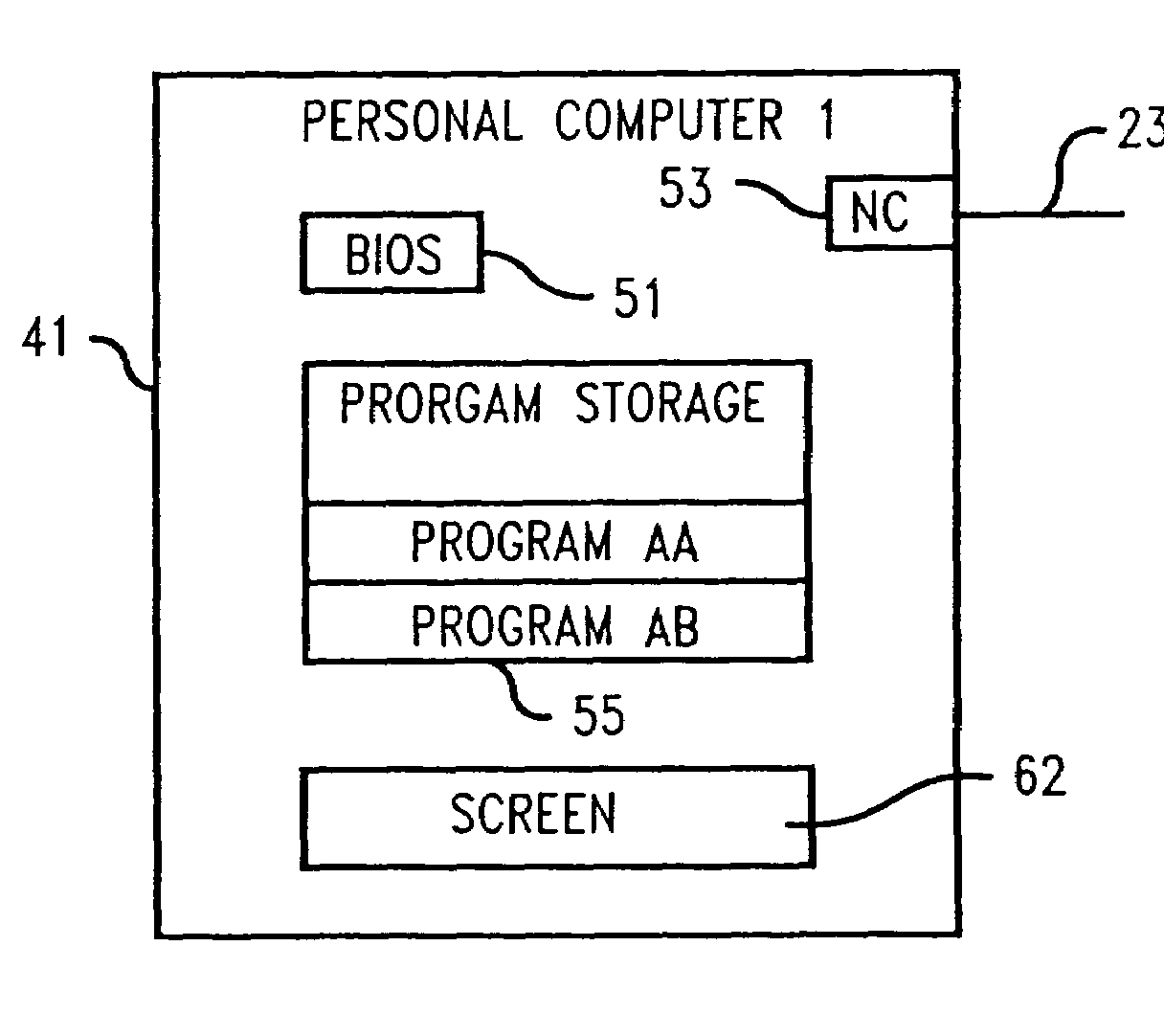
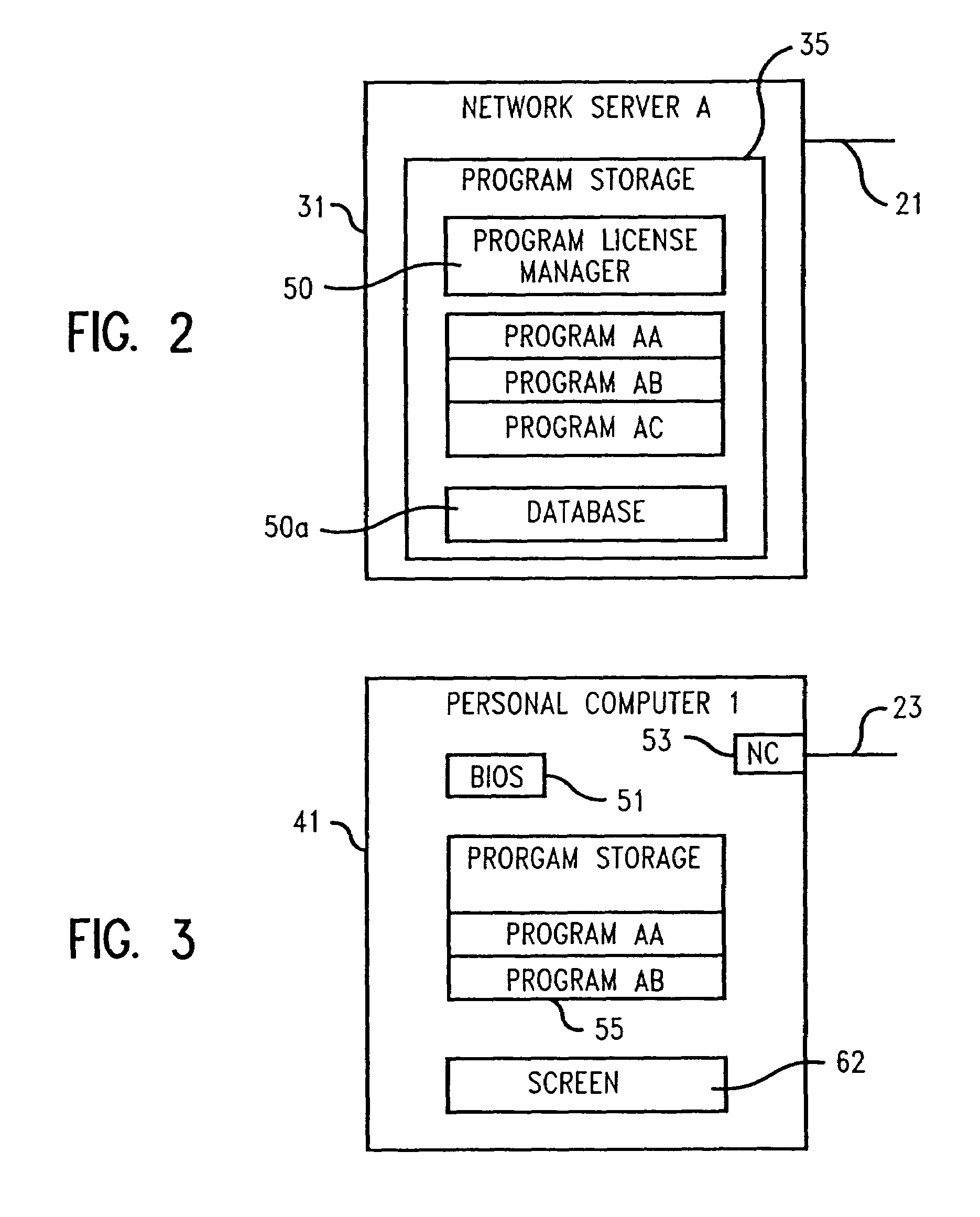
A method and system of installing licensed software on an end user's computer comprising having a program storage device and a unique computer identifier distinguishing the end user computer from other computers, e.g., a BIOS serial number or a network adapter address. The network computer contains a plurality of different software for license to end users and a database listing computer identifiers licensed to run the software. The end user computer sends to the network computer a command to run a program identifying to the end user computer the software listed as licensed by the computer identifier of the end user computer. The network computer contacts the end user computer and determine its end user computer identifier, verifies listing of the end user computer identifier in the network computer database, and identifies to the end user computer all of the software on the network computer program storage device listed as licensed by the computer identifier of the end user computer using an executable program on the network computer. The end user computer sends to the network computer a selection of the software to be downloaded. The network computer downloads the selected software and installs it on the end user computer program storage device.
Owner:ACTIVISION PUBLISHING
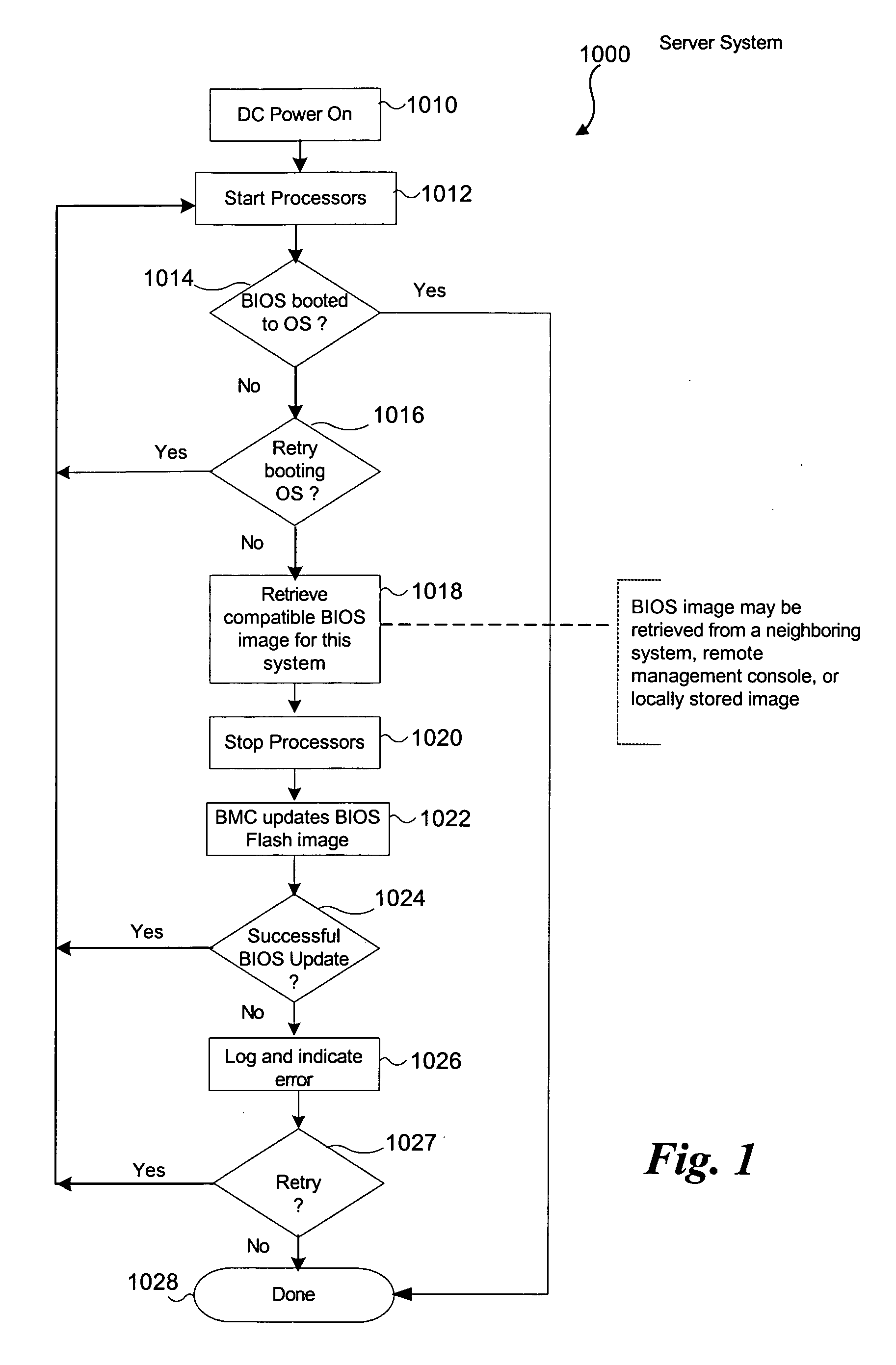
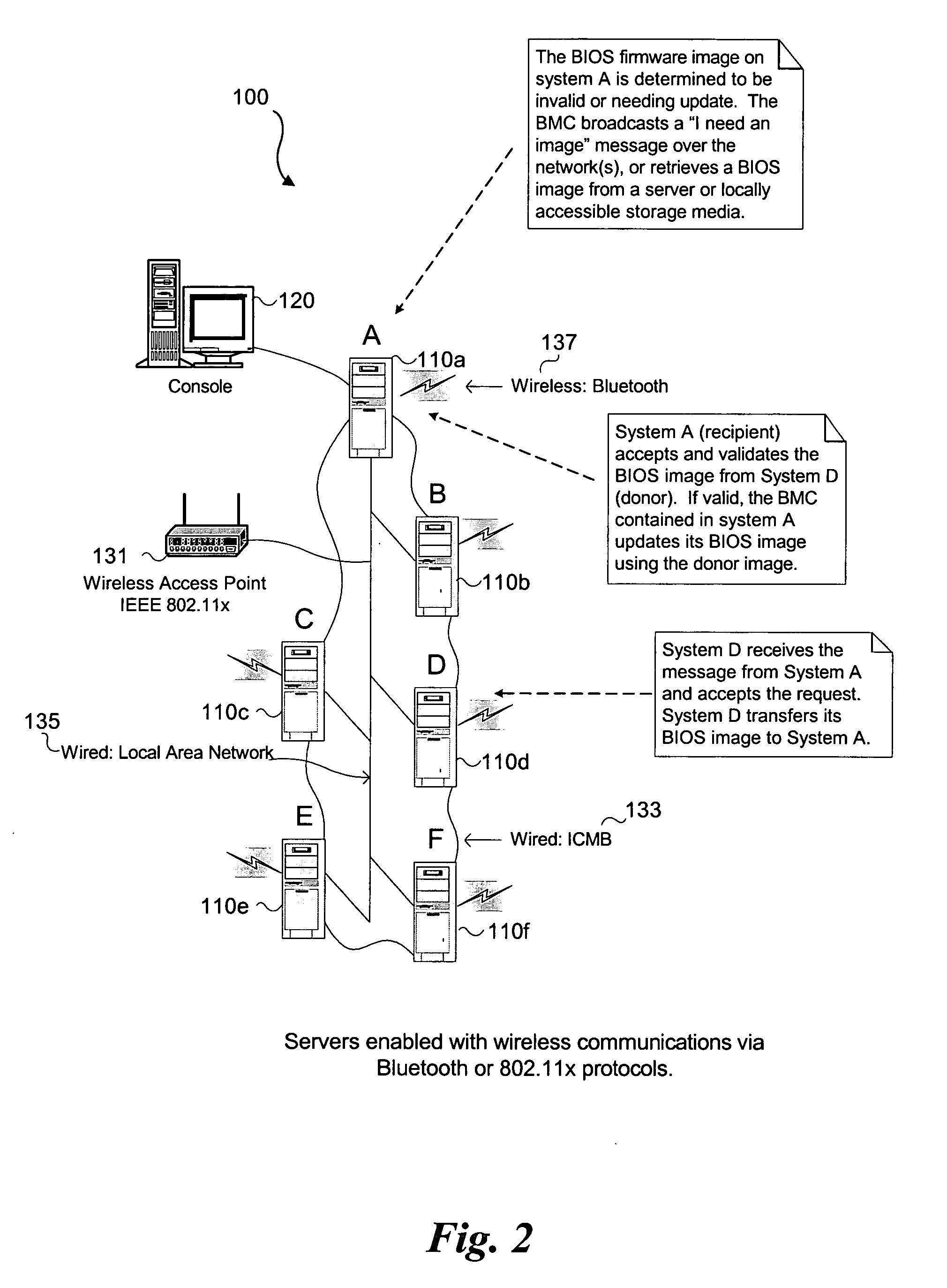
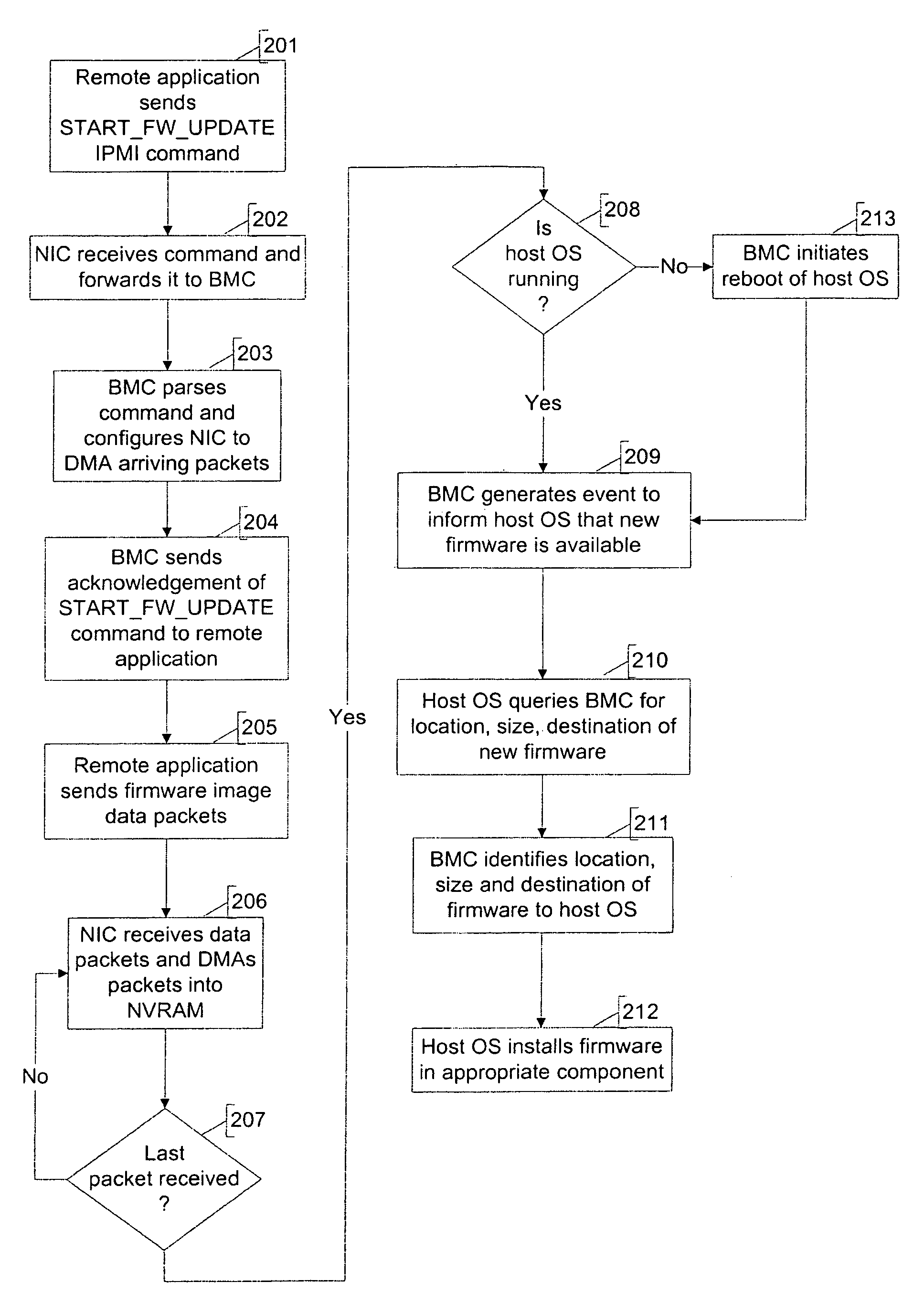
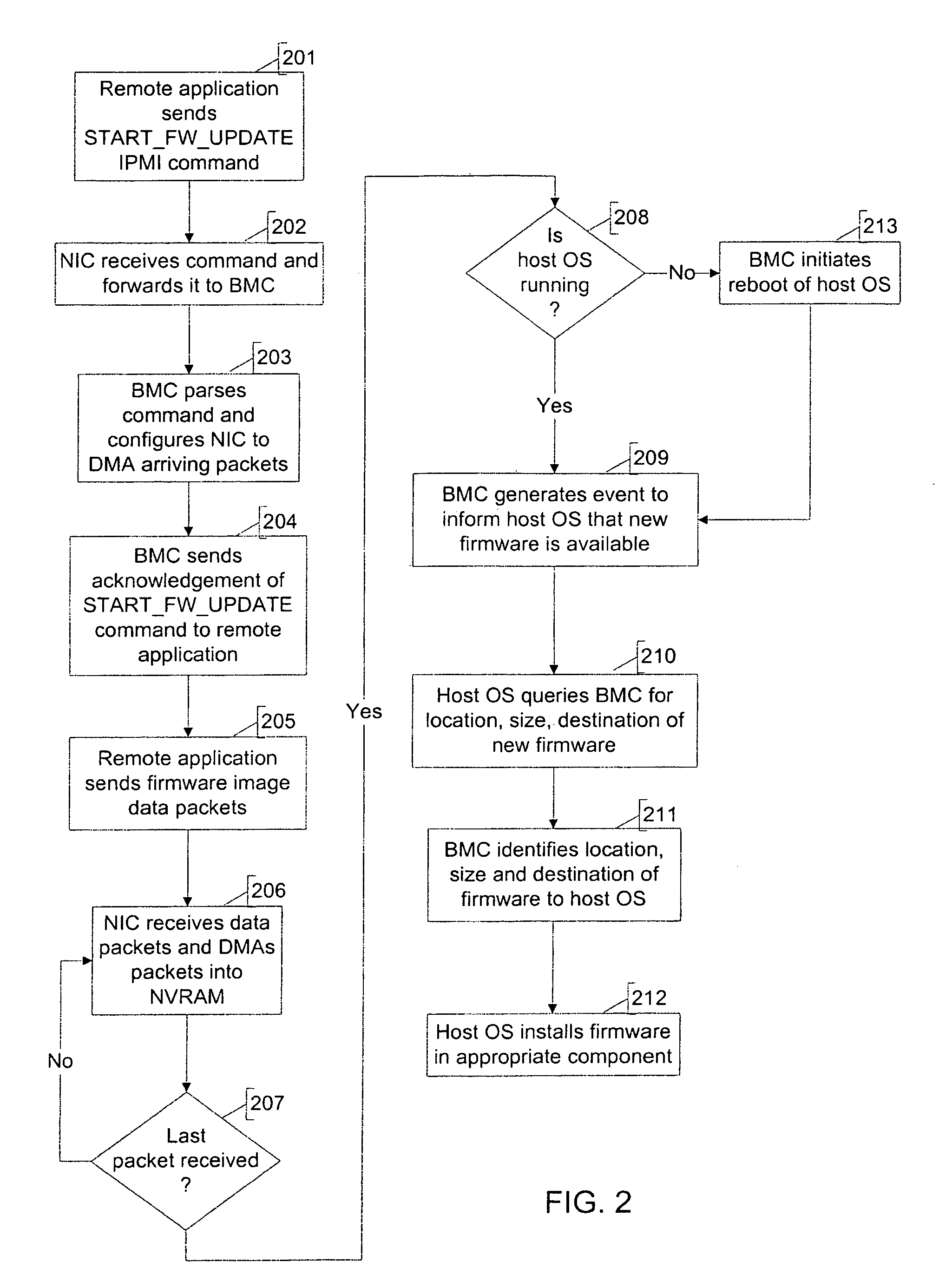
Automatic firmware update proxy
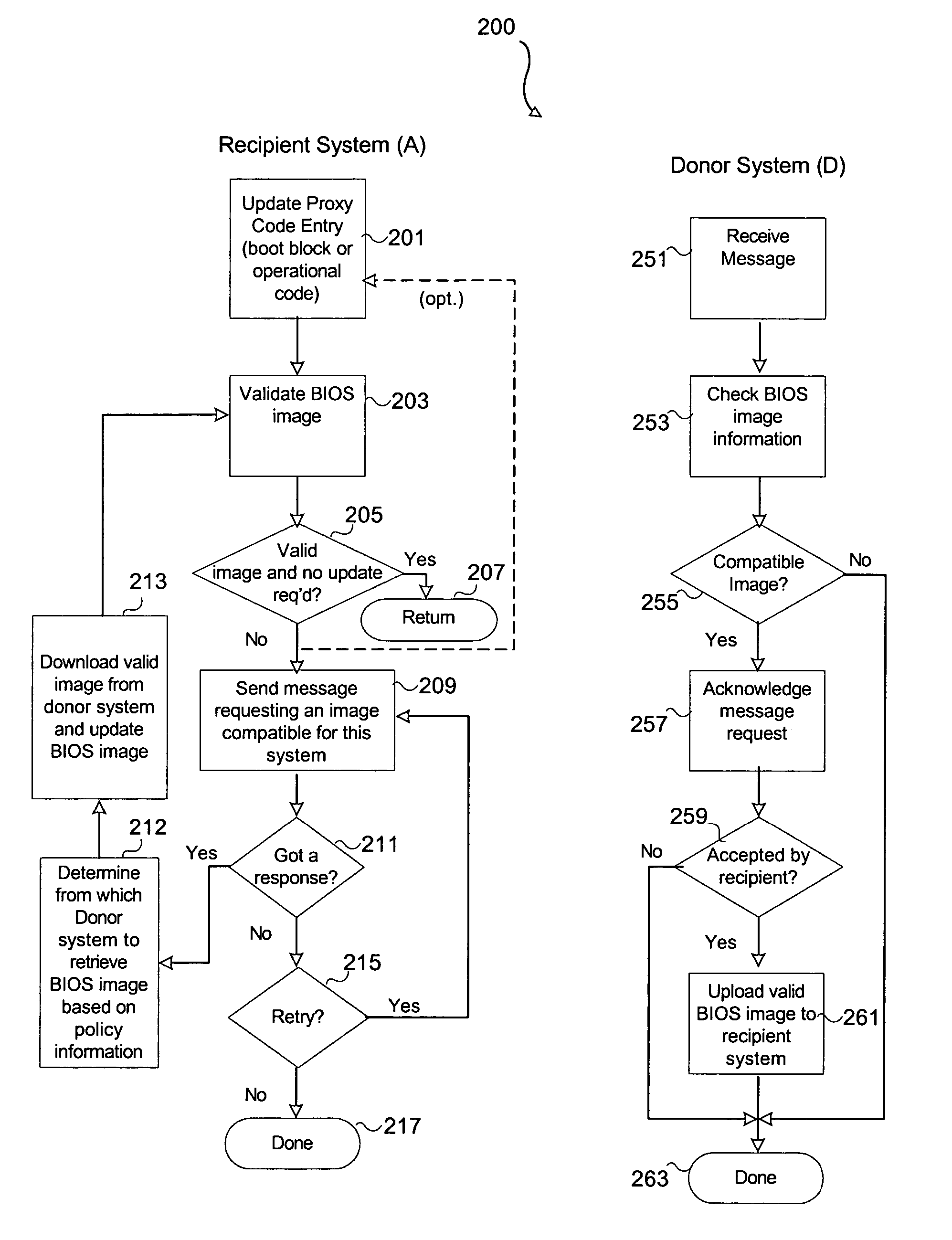
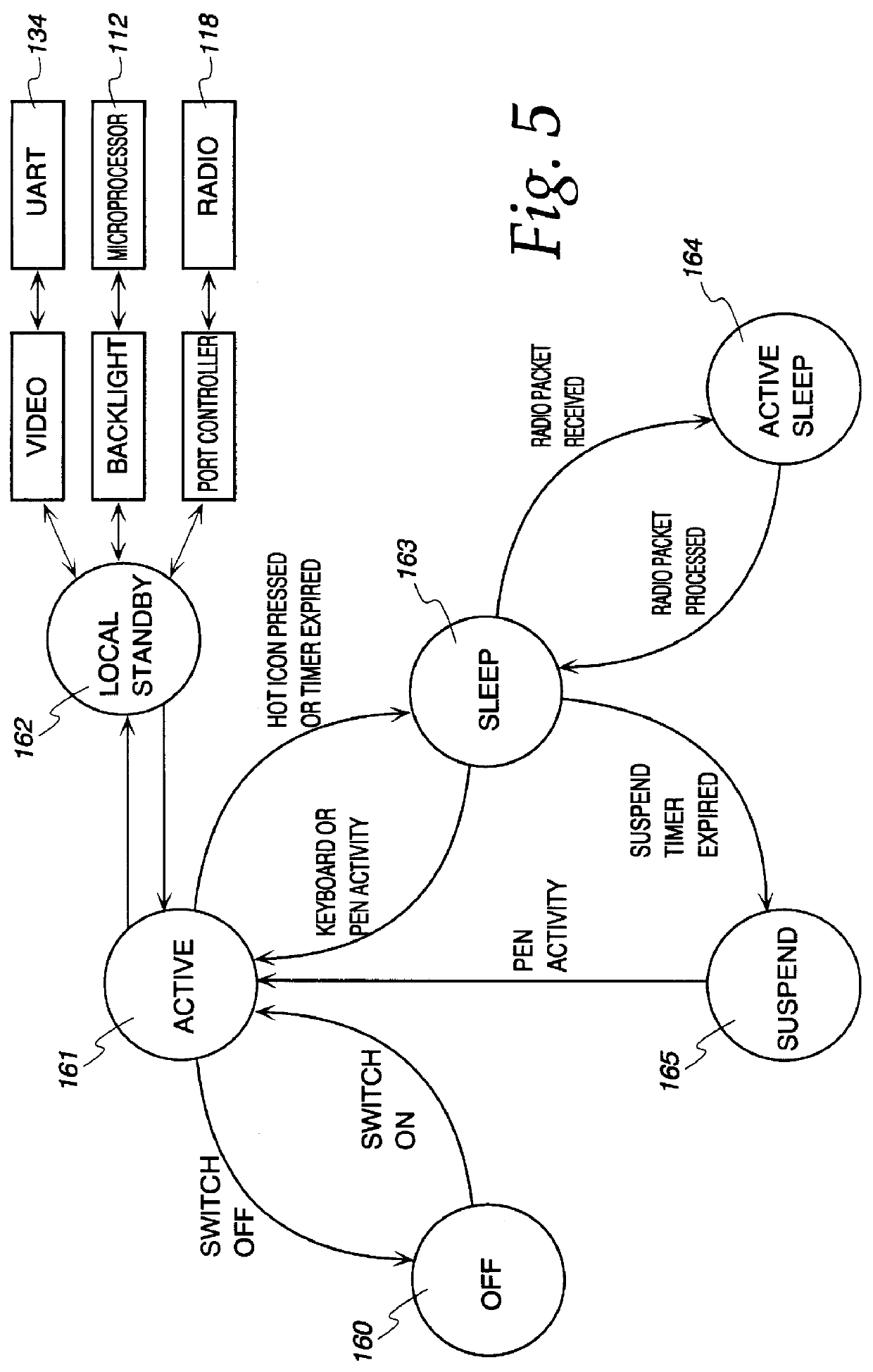
An embodiment of the present invention is a system and method relating to automatic firmware image update by proxy for BIOS or other embedded firmware image. When a server equipped with a baseboard management controller (BMC) and detects that its BIOS code image is corrupted or out of date, it may broadcast a request for an image update over an out-of-band network. One or more donor systems on the network may respond to the request and send the requestor a new image. The recipient system uses management policies to determine from which donor system to accept an update. In another embodiment, the BMC retrieves a new BIOS image from a predetermined location and updates the BIOS image accordingly.
Owner:INTEL CORP
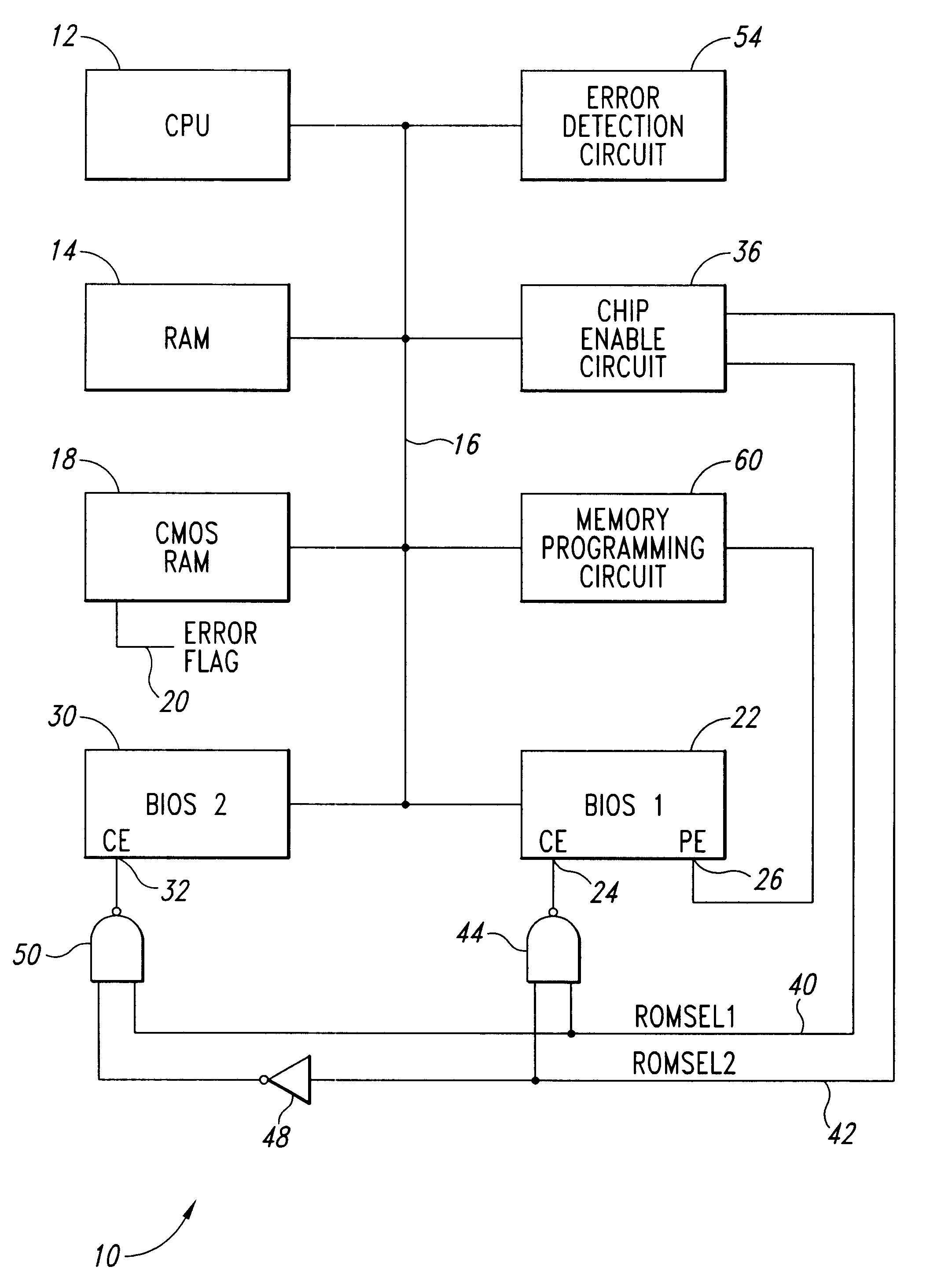
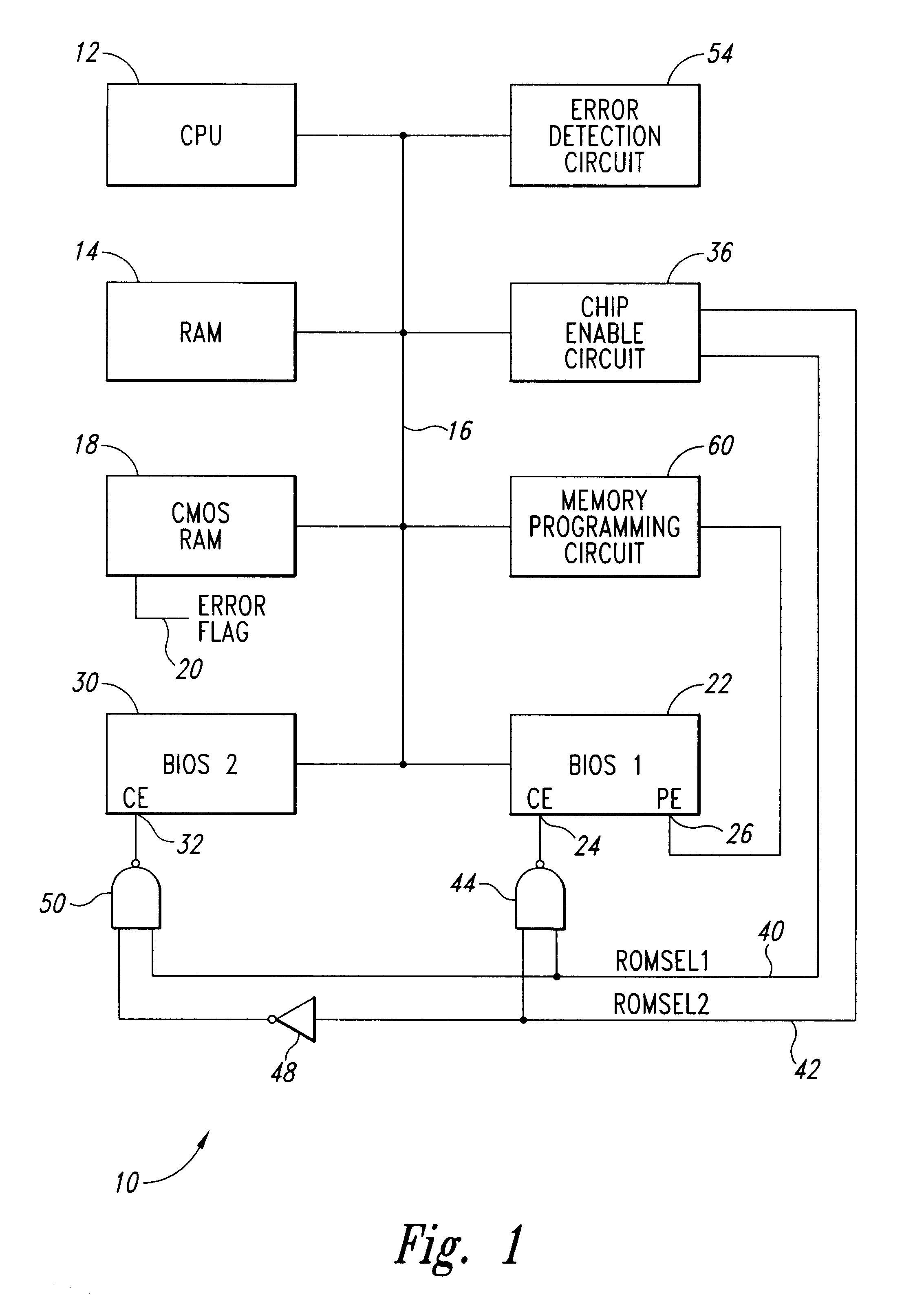
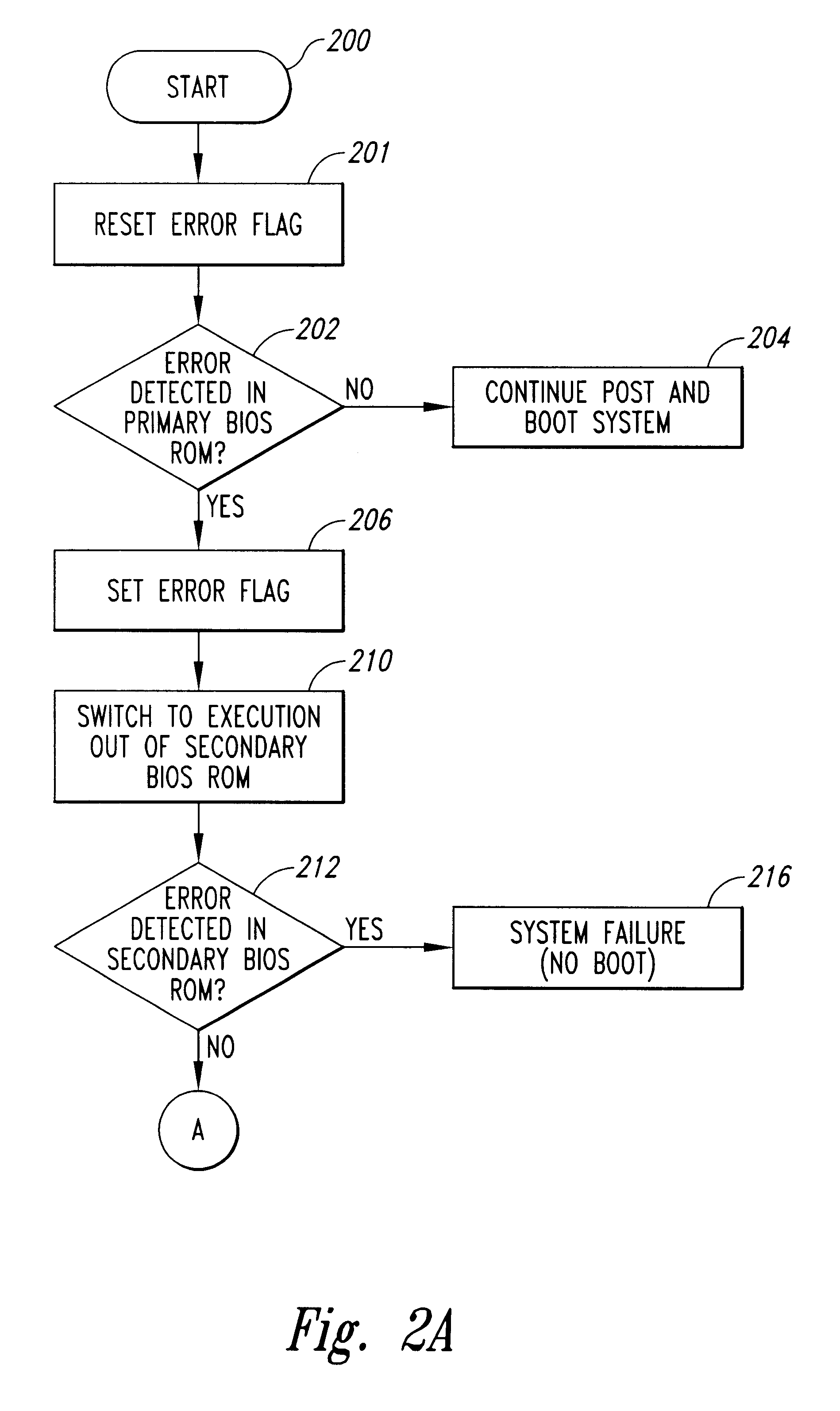
System for a primary BIOS ROM recovery in a dual BIOS ROM computer system
InactiveUS6185696B1Reliability increasing modificationsDetecting faulty hardware by power-on testRandom access memoryComputerized system
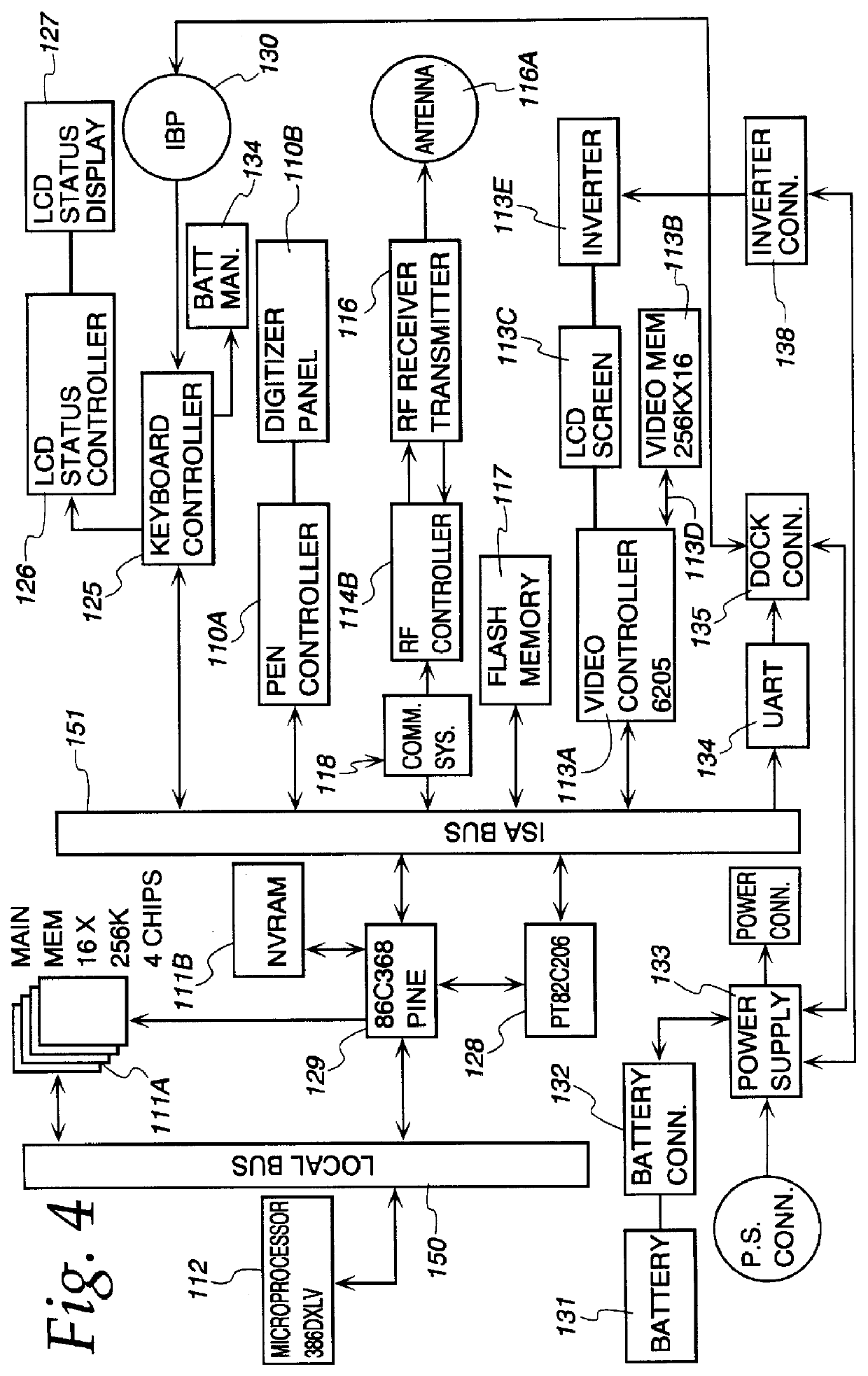
A computer system includes a dual basic input-output system (BIOS) read-only memory (ROM) system to initialize the computer. When the computer is first powered on or reset, the primary BIOS ROM is initially enabled. The computer analyzes the contents of the primary BIOS memory to detect data errors. If a data error is detected, a chip enable circuit disables the primary BIOS ROM and enables a secondary BIOS ROM containing essentially the same initialization instructions as the primary BIOS ROM. If no errors are detected in the secondary BIOS ROM, the initialization of the computer proceeds using the secondary BIOS ROM. As part of the initialization procedure, the contents of the secondary BIOS ROM are copied to a random access memory. The primary BIOS ROM can then be reprogrammed with the contents of the secondary BIOS ROM using the copy in random access memory, or from the secondary BIOS ROM itself.
Owner:MEI CALIFORNIA +1
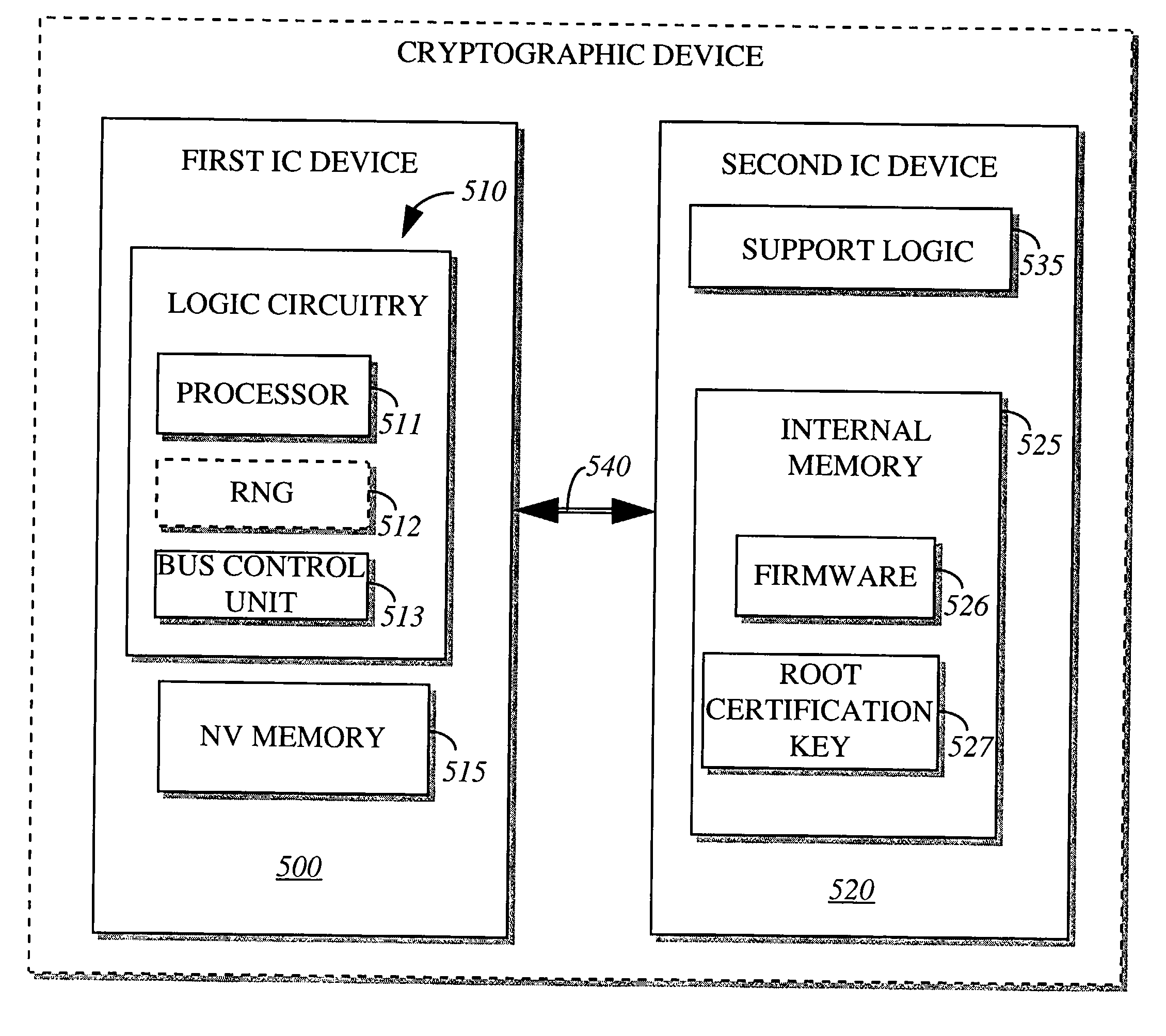
Method for BIOS authentication prior to BIOS execution
A cryptographic device is implemented in communication with a host processor to prevent the host processor from performing a standard boot-up procedure until a basic input output system (BIOS) code is authenticated. This is accomplished by a cryptographic device which is addressed by the host processor during execution of a first instruction following a power-up reset. The cryptographic device includes a first integrated circuit (IC) device and a second IC device. The first IC device includes a memory to contain firmware and a root certification key. The second IC device includes logic circuitry to execute a software code to authenticate the BIOS code before permitting execution of the BIOS code by the host processor.
Owner:INTEL CORP
System and method for securely utilizing basic input and output system (BIOS) services
InactiveUS6148387AResource allocationDigital data processing detailsVirtual memorySoftware engineering
In accordance with one aspect of the current invention, the system comprises a memory for storing instruction sequences by which the processor-based system is processed, where the memory includes a physical memory and a virtual memory. The system also comprises a processor for executing the stored instruction sequences. The stored instruction sequences include process acts to cause the processor to: map a plurality of predetermined instruction sequences from the physical memory to the virtual memory, determine an offset to one of the plurality of predetermined instruction sequences in the virtual memory, receive an instruction to execute the one of the plurality of predetermined instruction sequences, transfer control to the one of the plurality of predetermined instruction sequences, and process the one of the plurality of predetermined instruction sequences from the virtual memory. In accordance with another aspect of the present invention, the system includes an access driver to generate a service request to utilize BIOS services such that the service request contains a service request signature created using a private key in a cryptographic key pair. The system also includes an interface to verify the service request signature using a public key in the cryptographic key pair to ensure integrity of the service request.
Owner:KINGLITE HLDG INC
Multiple operating system and disparate user mass storage resource separation for a computer system
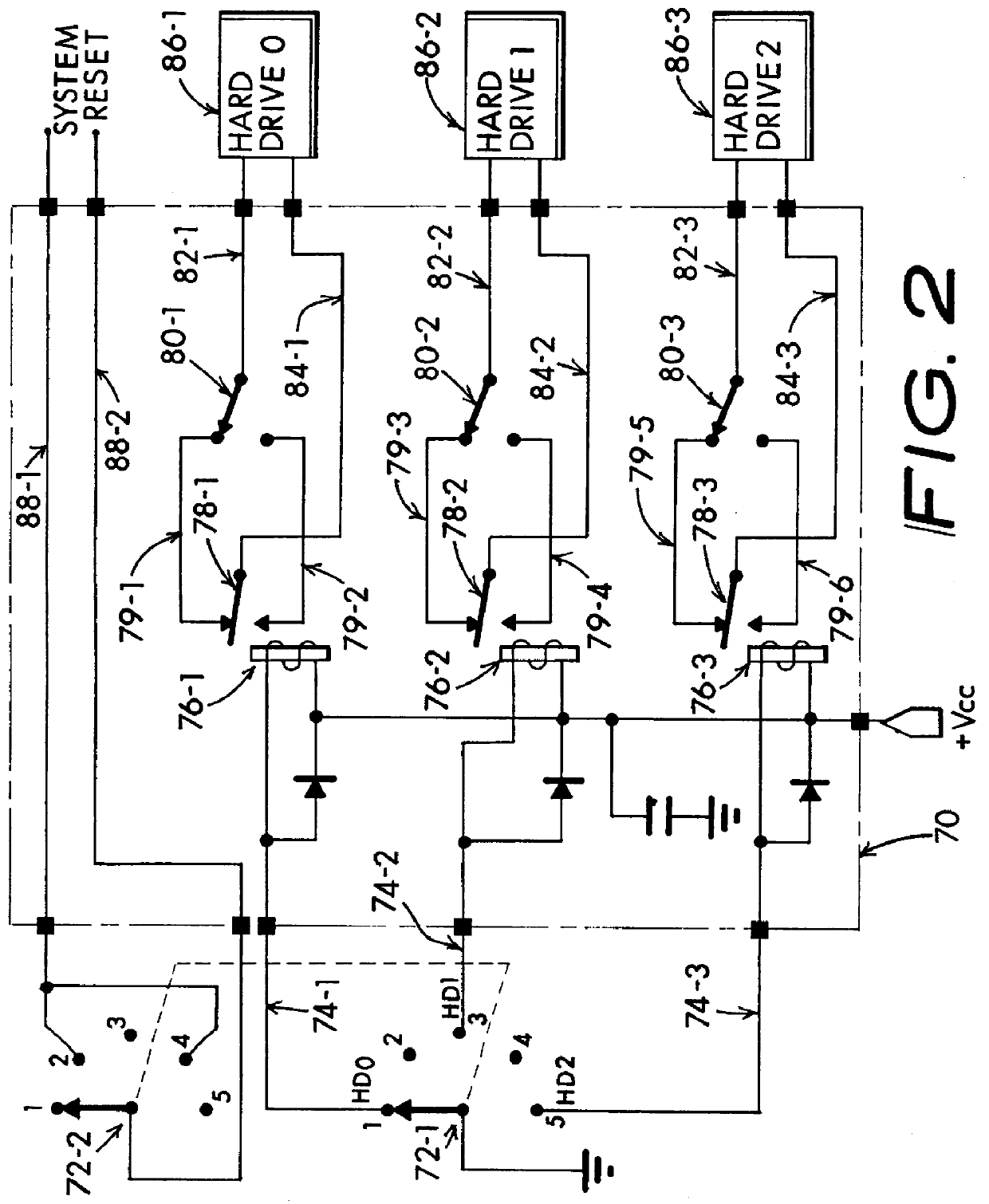
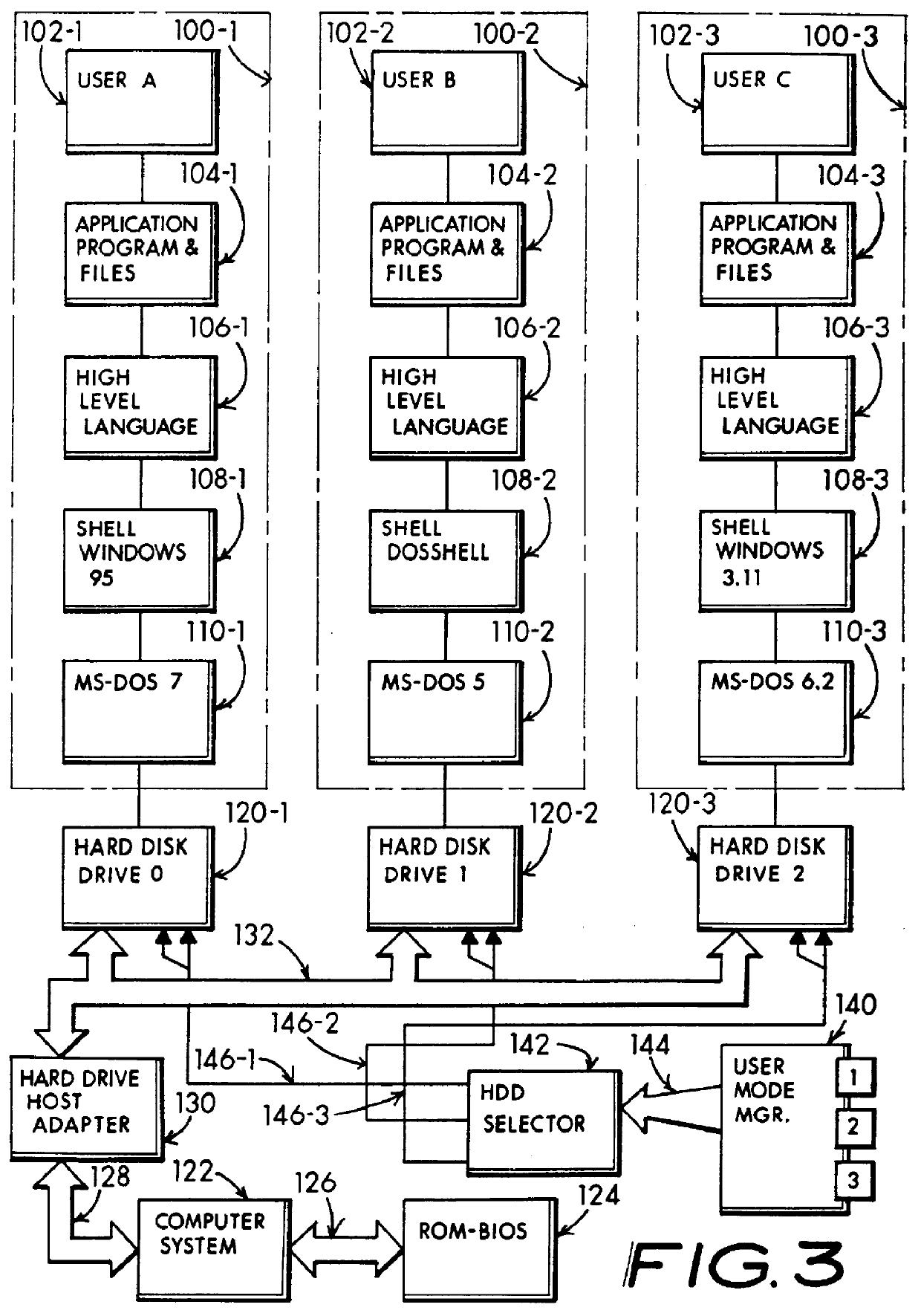
InactiveUS6067618AIsolate userAvoid possibilityDigital data processing detailsDigital computer detailsMass storageHard disc drive
A computer system including several nonconcurrently active hard disk drives ordinarily loaded with unique software bundles. Each active hard drive introduces an especial operating system setup and applications installation which is unconditionally denied access by activities obtained under another hard disk drive's software instructions. An absolute isolation between two or more user's application programs and data files is achieved while sharing a common set of computer system hardware and peripherals. Each category of nonconcurrent user operates independently without a threat of corruption from activities of another prior or subsequent user utilizing the same computer system for another disparate activity. In an IDE / ATA interface environment, a typical arrangement includes a setting of ROM-BIOS to only recognize a MASTER drive with a subsequent user determined swapping of MASTER and SLAVE modes between at least two hard drives utilizing a manual switch-over to obtain operation under operating system and programs uniquely installed on each of the intently selected MASTER drives, while denying access to the alternant SLAVE drive. In an SCSI interface environment, several drives set with the same SCSI-ID number are selected between by manually controlling a completion of the SCSI bus SEL line to the active intended drive and interrupting the SEL line to designated inactive drives. Virus corruption of one primary drive is fire-walled against inadvertent transfer into an alternate primary drive thereby assuring system operating integrity for one user category in spite of virus contamination, command errors, or careless or malicious hacking introduced by another user category.
Owner:HANGER SOLUTIONS LLC
Method and apparatus for operating a host computer from a portable apparatus
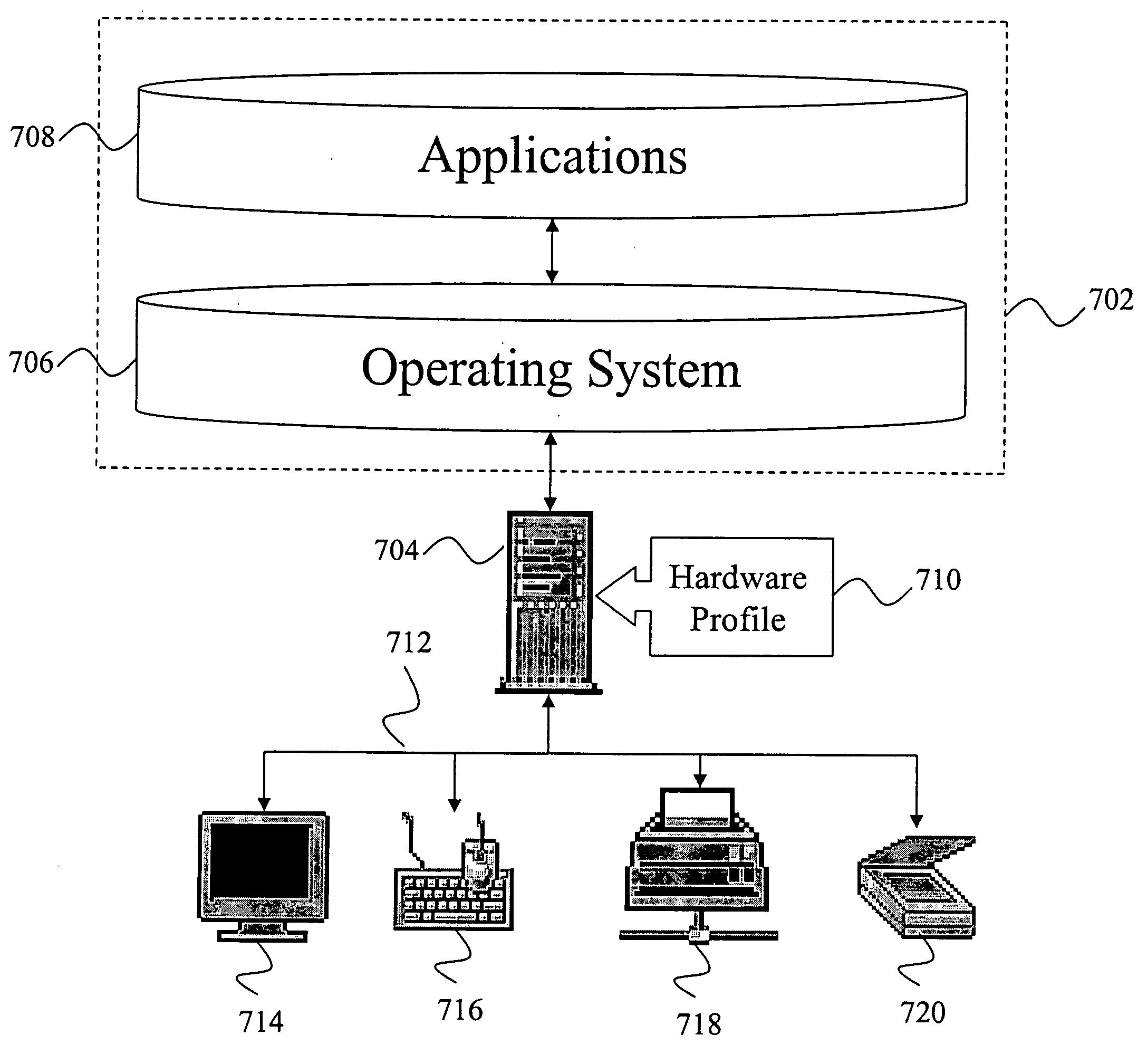
The present invention provides methods and apparatus that utilize a portable apparatus to operate a host computer. The portable apparatus including an operating system and a list of software applications is installed in a removable data storage medium. The basic input / output system (BIOS) of the host computer will directly or indirectly identify the portable apparatus as its boot drive. The host computer will further load the operating system in the portable apparatus into its random access semiconductor memory (RAM). A hardware profile is stored in the host computer, which contains information about the host computer and its peripheral devices. During the loading, the operating system will incorporate information in the hardware profile in order to fully operate the host computer and the hardware devices defined in the profile.
Owner:HUANG EVAN S
Method and system for rebooting a computer having corrupted memory using an external jumper
InactiveUS6018806AProgram loading/initiatingRedundant operation error correctionComputerized systemBIOS
A computer system includes a flash memory device for storing BIOS code. The BIOS code is stored in an unprotected area of the flash memory. A boot block, stored in a protected area of the flash memory, is used for rebooting the computer system in the event that the flash memory device becomes corrupted. During normal operation, the BIOS code is updated using a radio link. If the BIOS is corrupted while being updated, a recovery routine stored in the boot block is executed. The recovery routine permits the corrupted BIOS to be reprogrammed using a serial interface instead of the radio link.
Owner:NEC CORP
Systems and methods for facilitating activation of operating systems
ActiveUS20130031541A1Advantageously employedSoftware engineeringComputer security arrangementsOperational systemHandling system
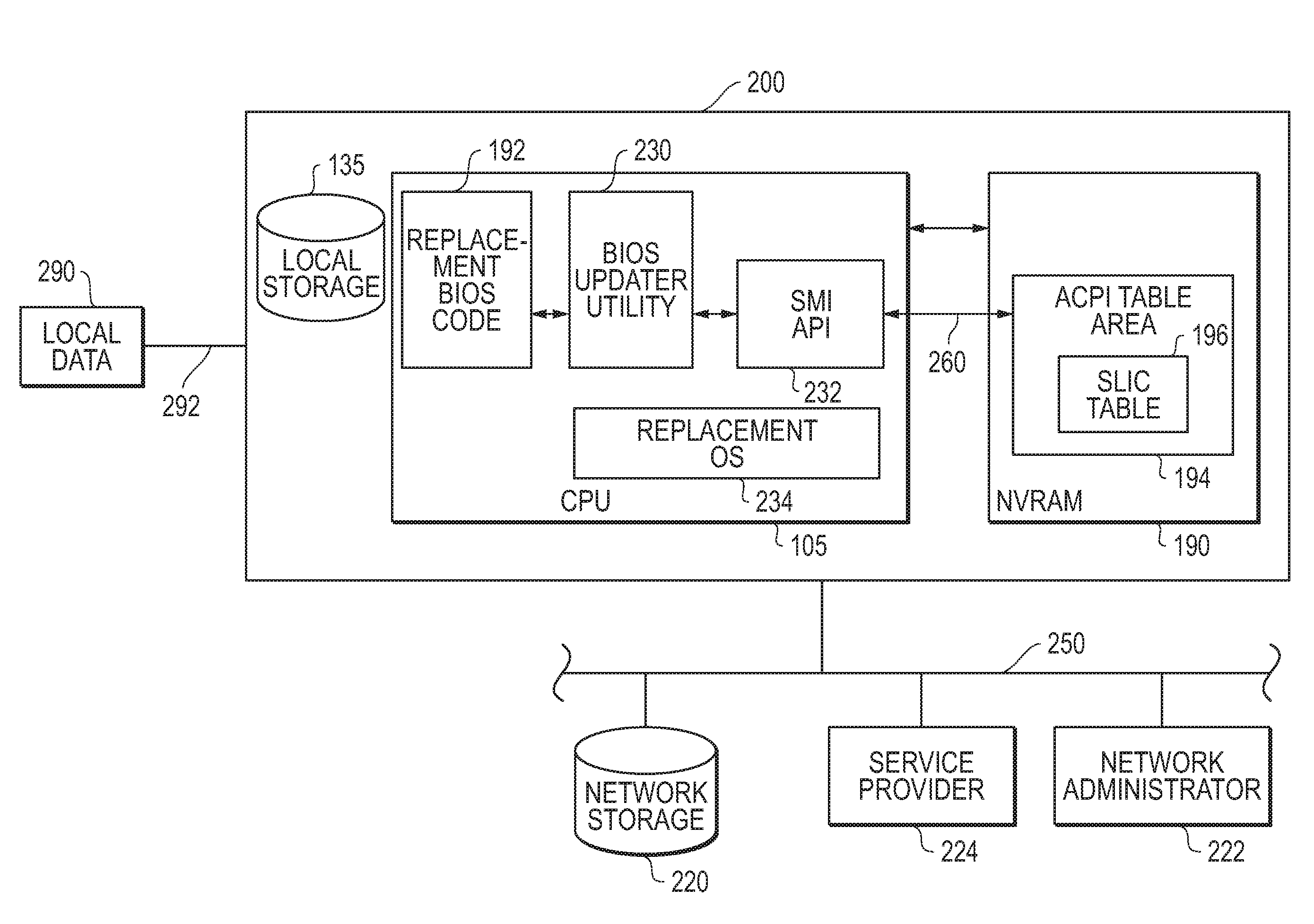
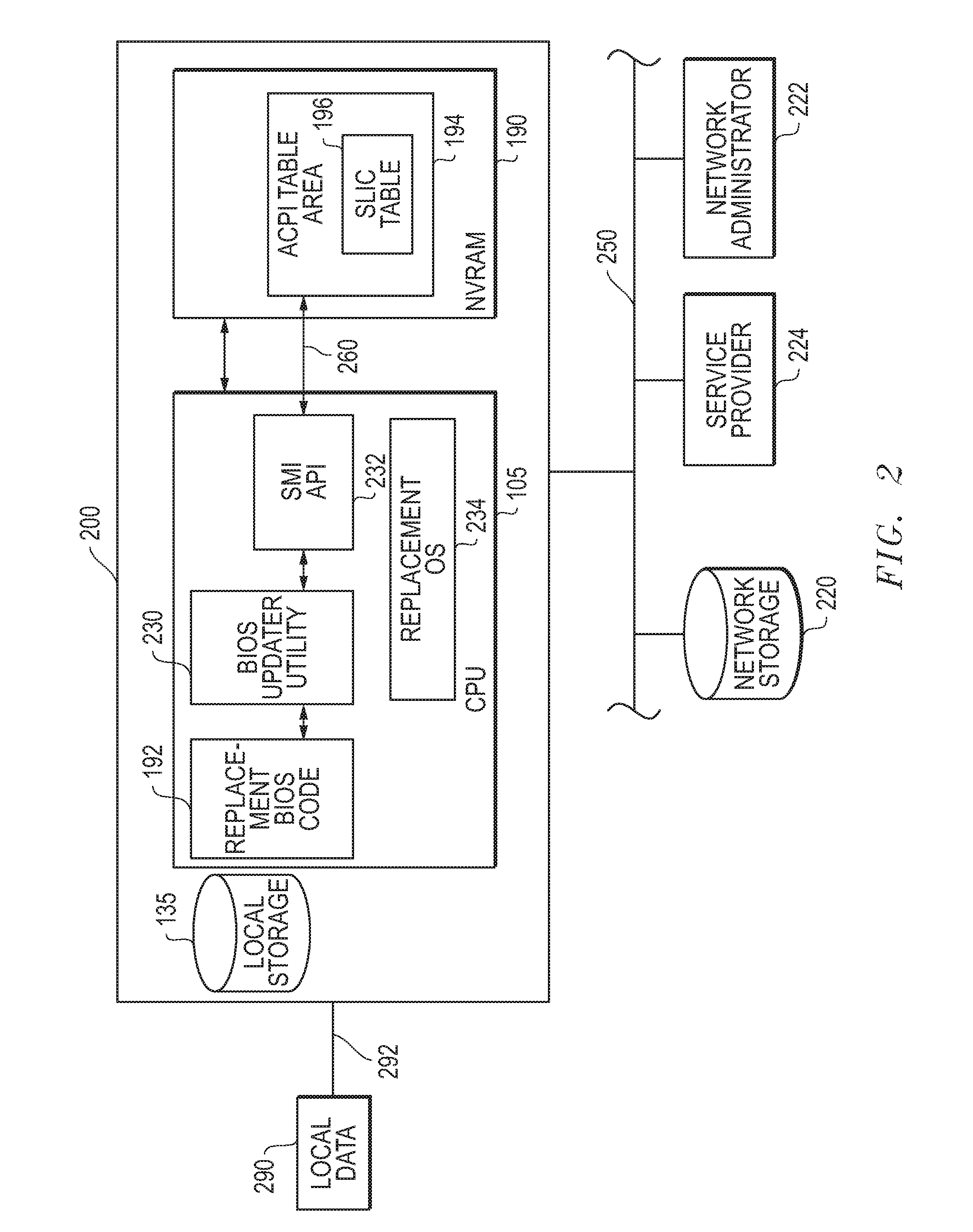
Systems and methods are disclosed that may be implemented to install and use a replacement BIOS code stored in non-volatile memory of the system BIOS to facilitate activation of a new or replacement OS on an information handling system. The replacement BIOS code may include an activation certificate of authority information to activate a different version operating system for use on an information handling system that has been previously configured with a different operating system version along with a previous BIOS code that did not include the updated OEM activation string.
Owner:DELL PROD LP
Trust chain transfer method for trusted computing platform
InactiveCN102332070ANot easy to tamper withNot easy to attackPlatform integrity maintainanceOperational systemTrusted Computing
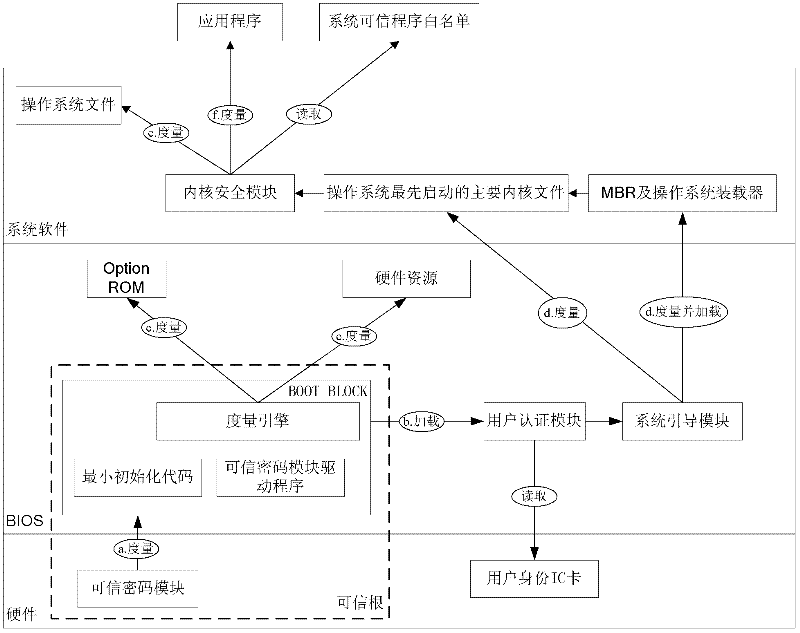
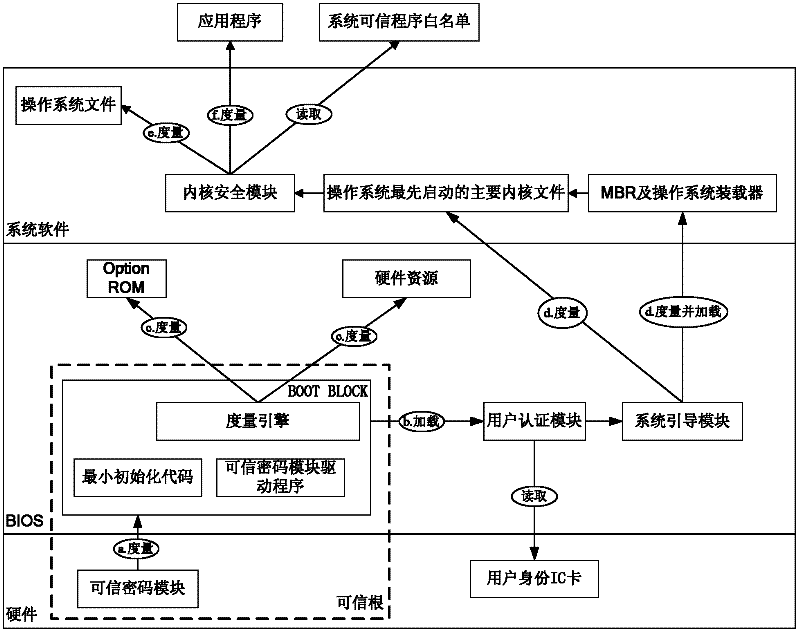
The invention discloses a trust chain transfer method for a trusted computing platform. A trusted computing module (TCM) serving as a starting point of starting a trust chain is started and actively initiated at first to verify the trustiness of a BIOS (basic input output system) chip; after the trusted BIOS chip is started, a MAIN BLOCK of the BIOS chip performs concentrated integrity verification on key files of an MBR (master boot record), an operating system loader and an operating system kernel; in the starting process of an operating system, the starting and running of an unauthorized program are prevented in a way of combining the integrity verification based on a white list and running program control; and hashing operations for the integrity verification are finished by a hardware computing engine. When a user starts any executable program, a security module in the operating system kernel checks the integrity of the program and checks whether the program is in the trusted program white list or not, and only application programs which are in the trusted program white list of the system and have integrity measures consistent with an expected value are permitted to be run. High-efficiency and fine-grained trust chain transfer is realized, the damages of viruses to system files and program files can be prevented, and the execution of the unauthorized program can be prevented.
Owner:中国人民解放军海军计算技术研究所
Egm authentication mechanism using multiple key pairs at the BIOS with pki
Executable applications on a gaming machine are verified before they can be executed, for security purposes and to comply with jurisdictional requirements. Unlike in prior systems for authenticating the executable applications, embodiments allow for new executable applications to be provided and verified over time with different private and public key pairs, even after the operating code of the gaming machine is certified by the jurisdiction and deployed in the field.
Owner:IGT
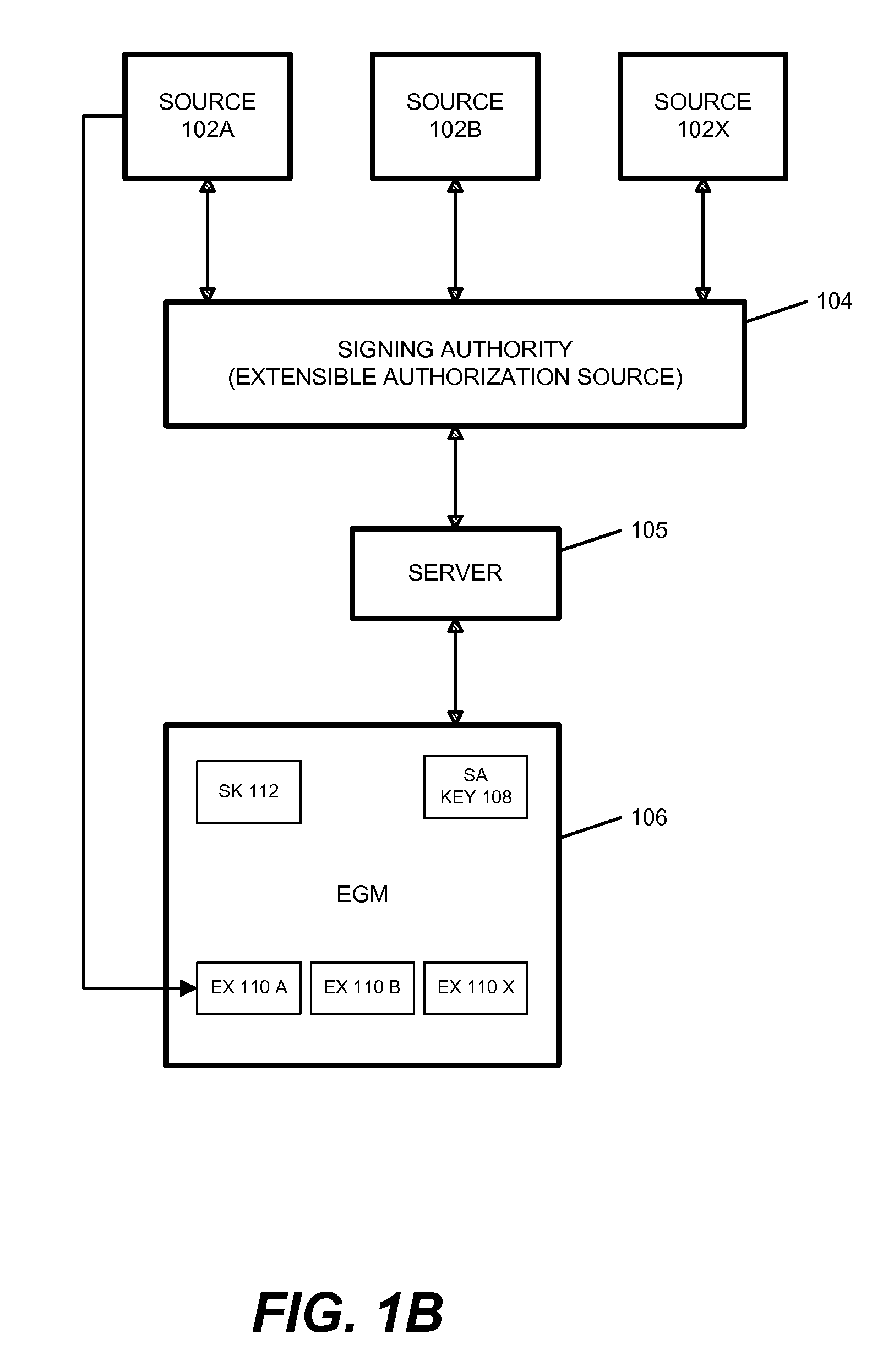
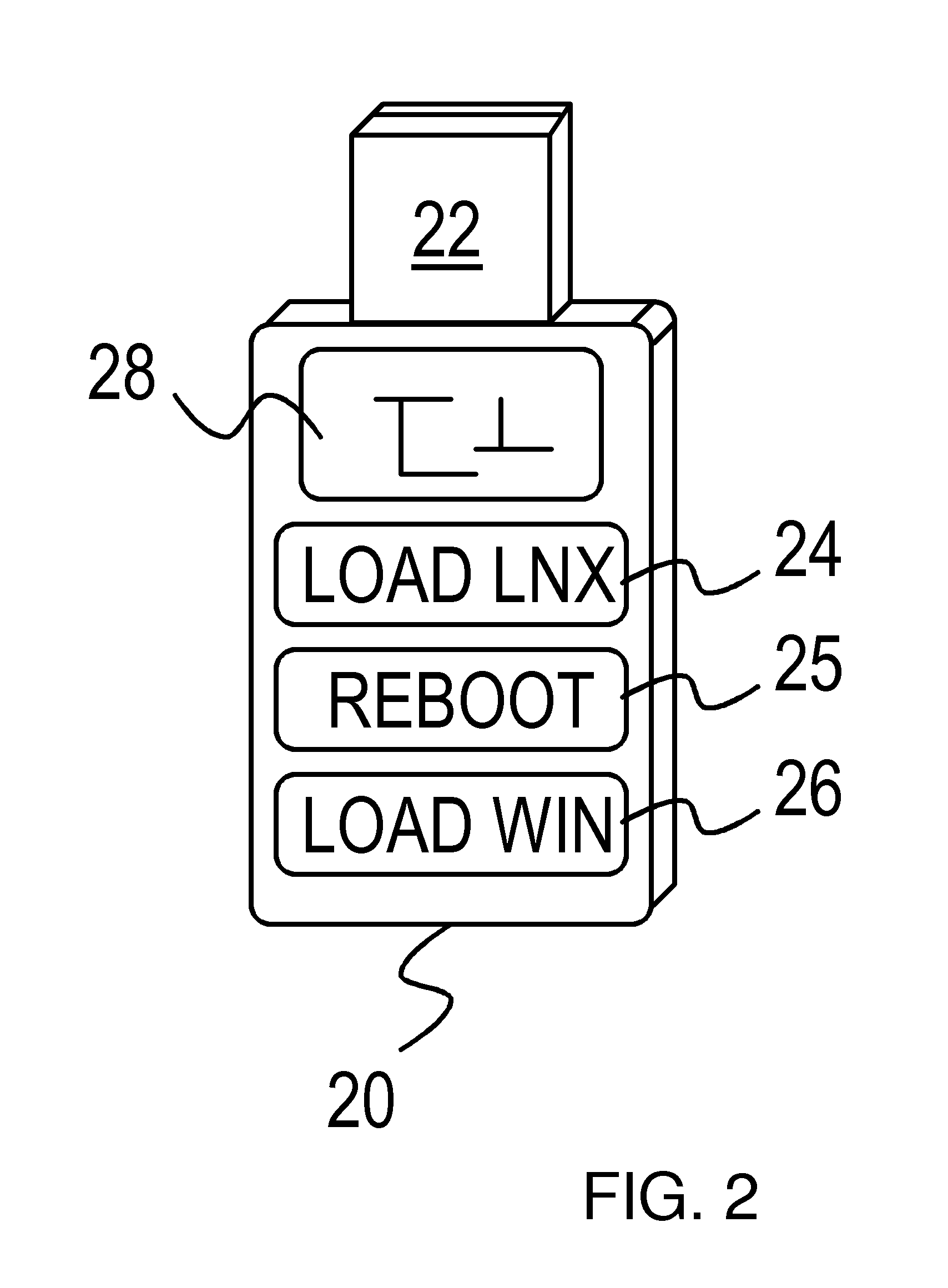
Multi-Partition USB Device that Re-Boots a PC to an Alternate Operating System for Virus Recovery
InactiveUS20080052507A1Program control using stored programsMemory loss protectionInformation controlOperational system
A multi-partition Universal Serial Bus (USB) device has a flash memory with multiple partitions of storage. Some partitions are for different operating systems and store OS images. Another partition has a control program while a user partition stores user data and user configuration information. The control program can test the multi-partition USB device and instruct the host computer BIOS to mount a partition from its flash memory as a drive of the host computer. The host computer can then be rebooted. The OS image from the flash memory is loaded into main memory during rebooting, and the host computer executes a new operating system using the new OS image. The user can press buttons on the multi-partition USB device to select which OS to load, and to begin rebooting. Virus removal programs in the alternate OS can help recover from a virus in the primary OS.
Owner:SUPER TALENT TECH CORP
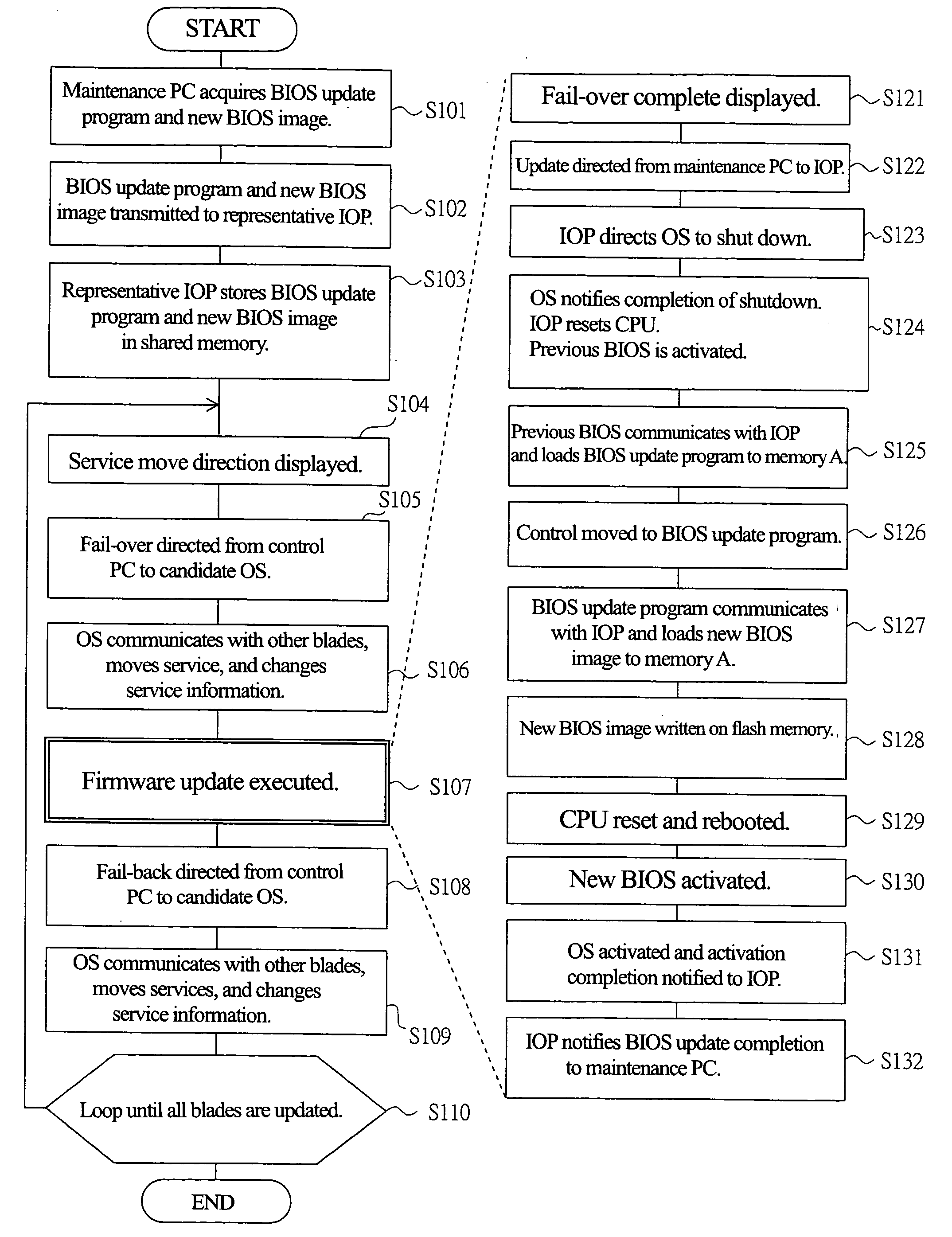
Storage system
A technique that can update the firmware with services for clients continued on a circuit board that comprises a control unit of a storage system is provided. A plurality of blade that comprise control unit have previous BIOS on flash memory. Clusters are formed including the blade which is subject to firmware update. At the time of updating the firmware, for the update candidate substrate, the processing unit including processing to move the service provided by OS of blade to be subject to firmware update processing to OS of other blade in the cluster as well as firmware update processing for updating previous BIOS of blade which no longer provides services by the use of the BIOS update program and new BIOS image.
Owner:RAKUTEN GRP INC
Use of a baseboard management controller to facilitate installation of firmware in a processing system
ActiveUS7484084B1Easy to installSoftware engineeringDigital computer detailsOperation modeEngineering
Owner:NETWORK APPLIANCE INC
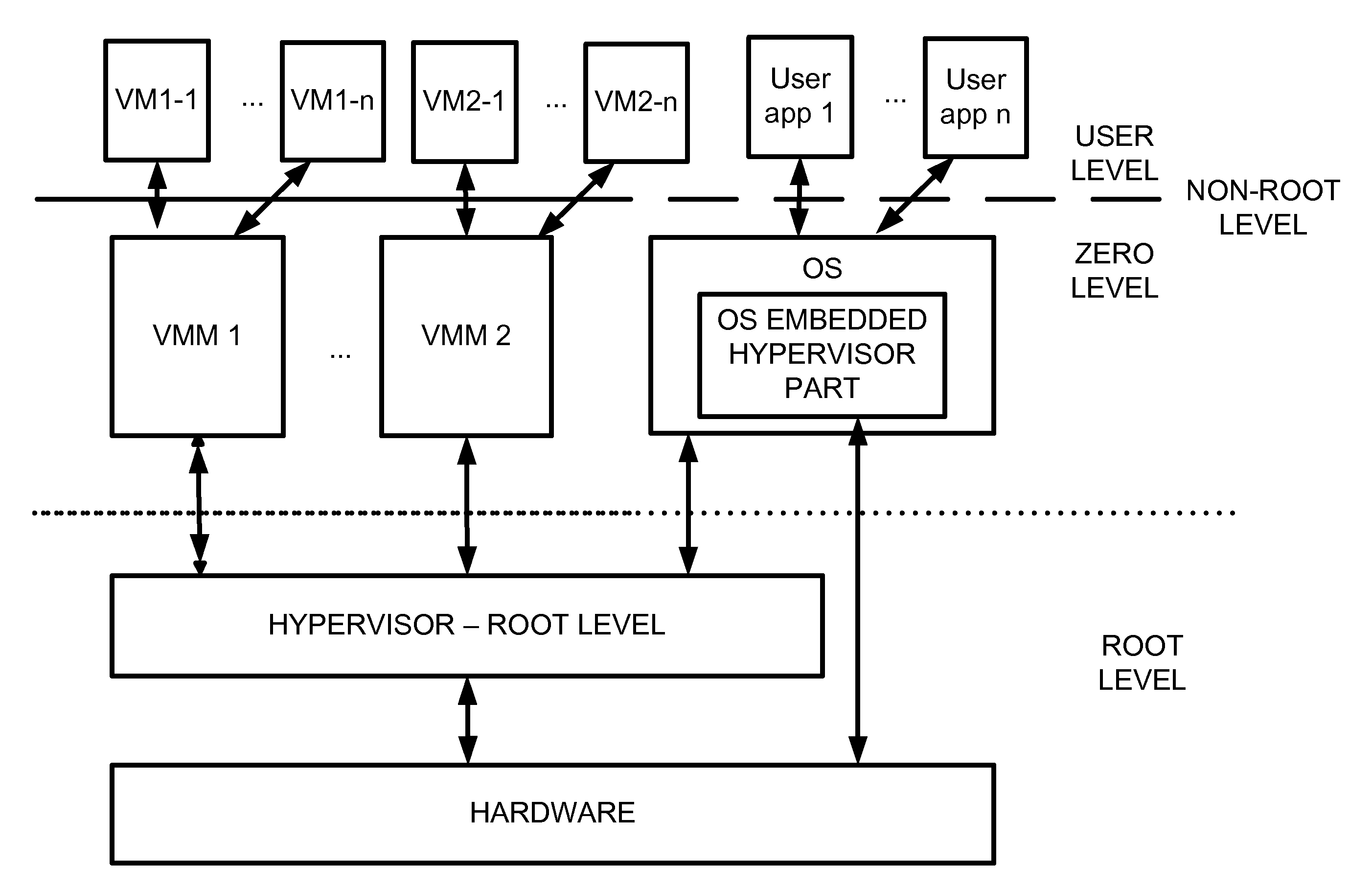
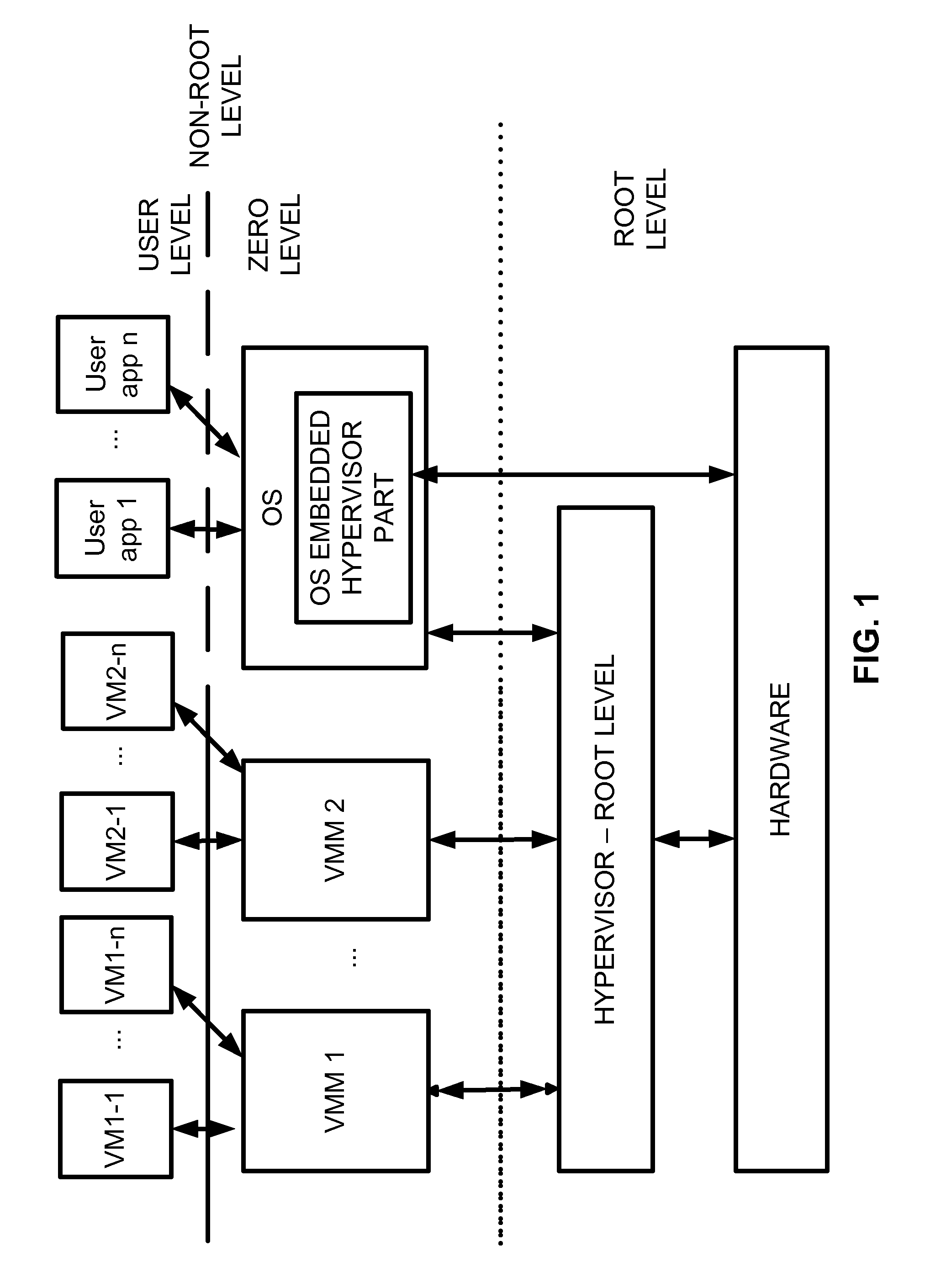
Virtualization system with hypervisor embedded in bios or using extensible firmware interface
A computer system includes a first portion of a Hypervisor is loaded into the memory as a part of an Extensible Firmware Interface upon start up and prior to loading of an operating system. The first portion is responsible for context switching, at least some interrupt handling, and memory protection fault handling. The first portion runs on a root level. An operating system is loaded into a highest privilege level. A second portion of the Hypervisor is loaded into operating system space together with the operating system, and runs on the highest privilege level, and is responsible for (a) servicing the VMM, (b) servicing the VMs, (c) enabling communication between code launched on non-root level with the second portion of the Hypervisor to perform security checks of trusted code portions and to enable root mode for the code portions if allowable. The VMM runs on the highest privilege level. A Virtual Machine is running under control of the VMM. Trusted code runs on non-root level. The first portion of the Hypervisor verifies trusted code portions during their loading or launch time, and the trusted code is executed on root level.
Owner:PARALLELS INT GMBH
Method and system for secure software provisioning
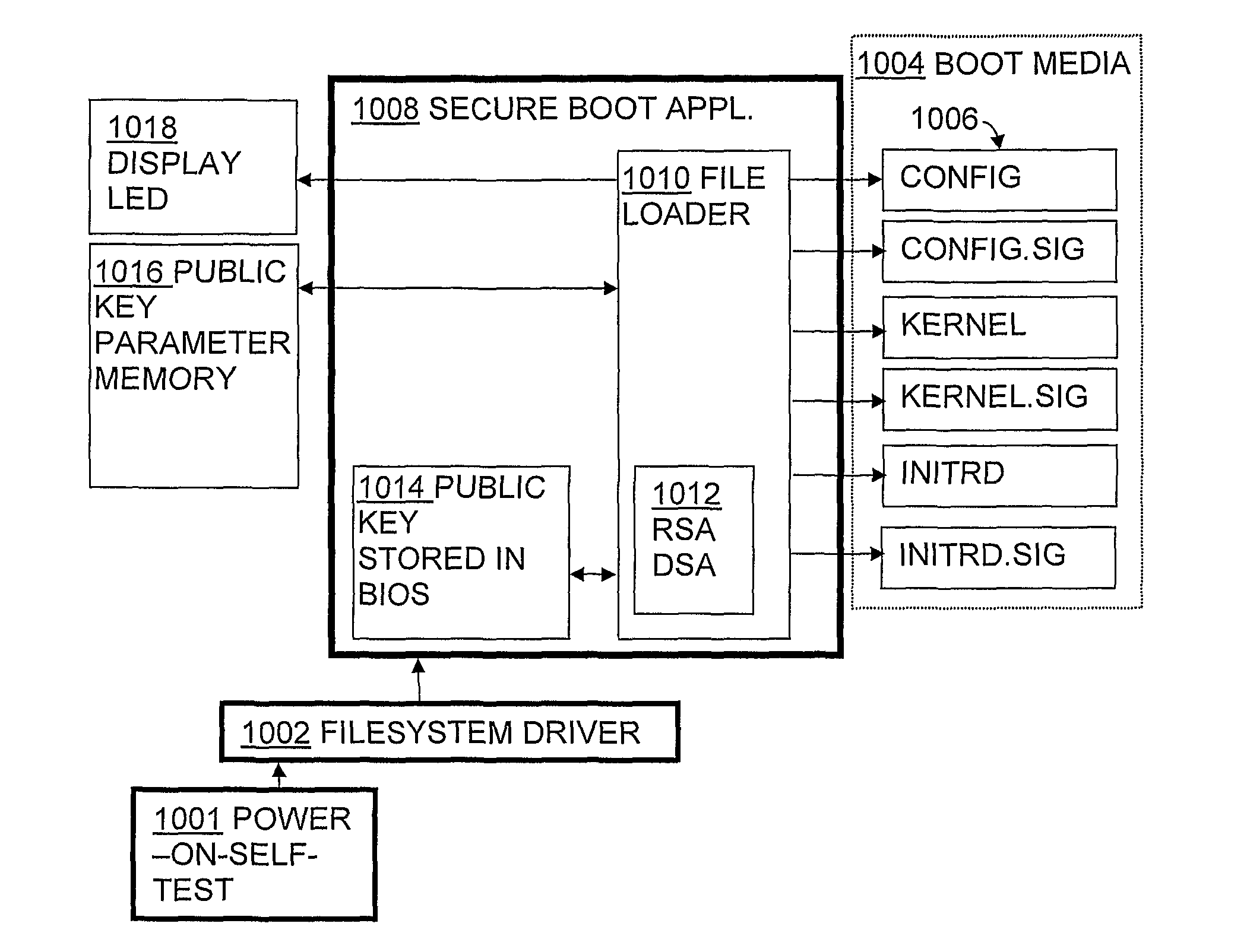
A method and system for the provisioning of software that enable large scale installation and management of software in computer units in a highly secure manner. The BIOS of the target computer unit is adapted such that upon power up the system attempts to boot from an external media. The BIOS features functions within the code for the implementing a system watchdog for assuring the system remains in a known state, a function for digital signature verification, and loads drivers for a file system. The external media includes the operating system (OS) image and other bootstrap files, each having been digitally signed with an asymmetric private key that corresponds to the public key. A programmable read-only parameter memory on the motherboard is configured to store the public keys and the (failure) state of the system independently of the primary and secondary media enabling reboot from an alternative boot path.
Owner:ONITEO
Storing system-level mass storage configuration data in non-volatile memory on each mass storage device to allow for reboot/power-on reconfiguration of all installed mass storage devices to the same configuration as last use
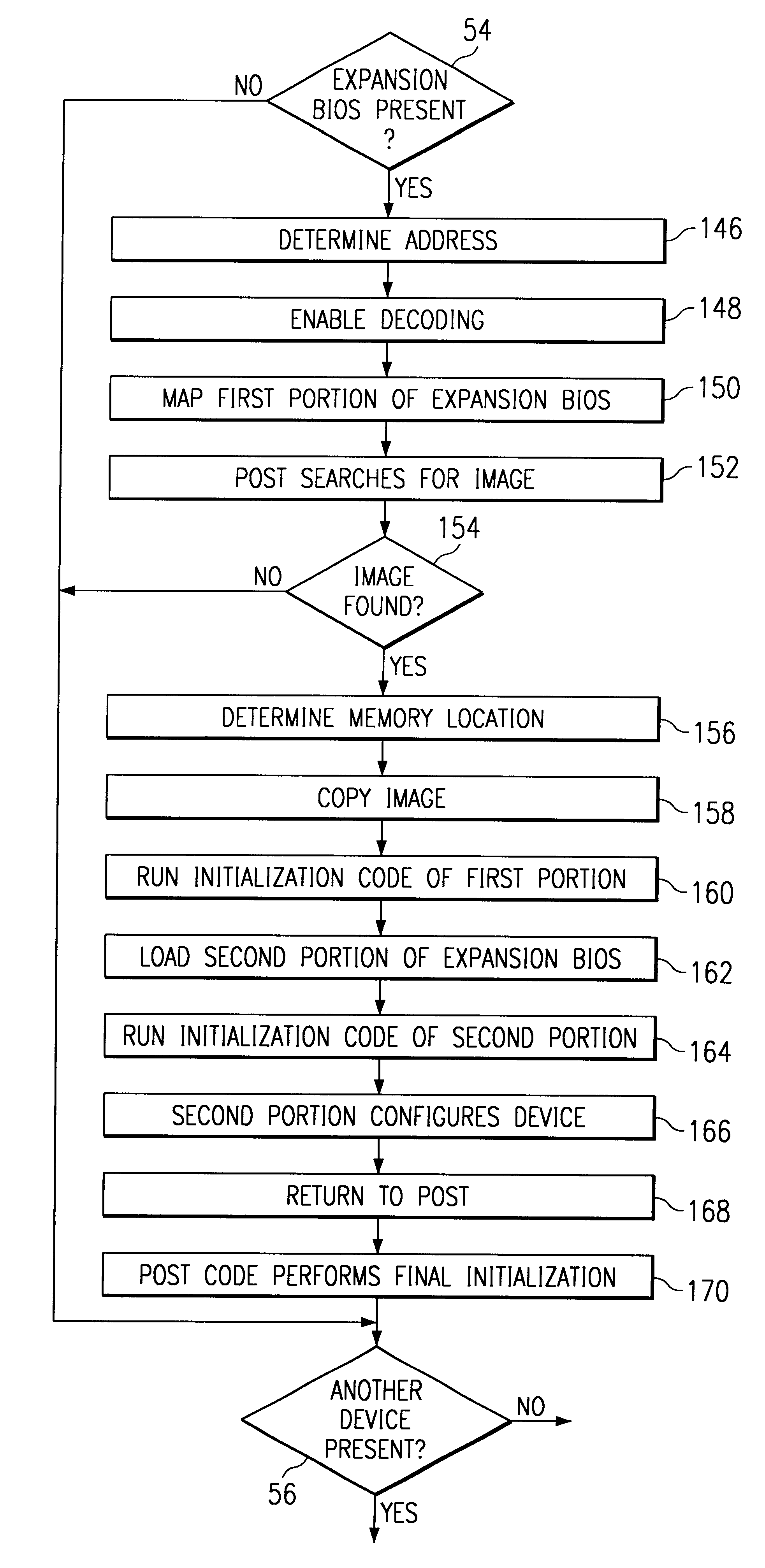
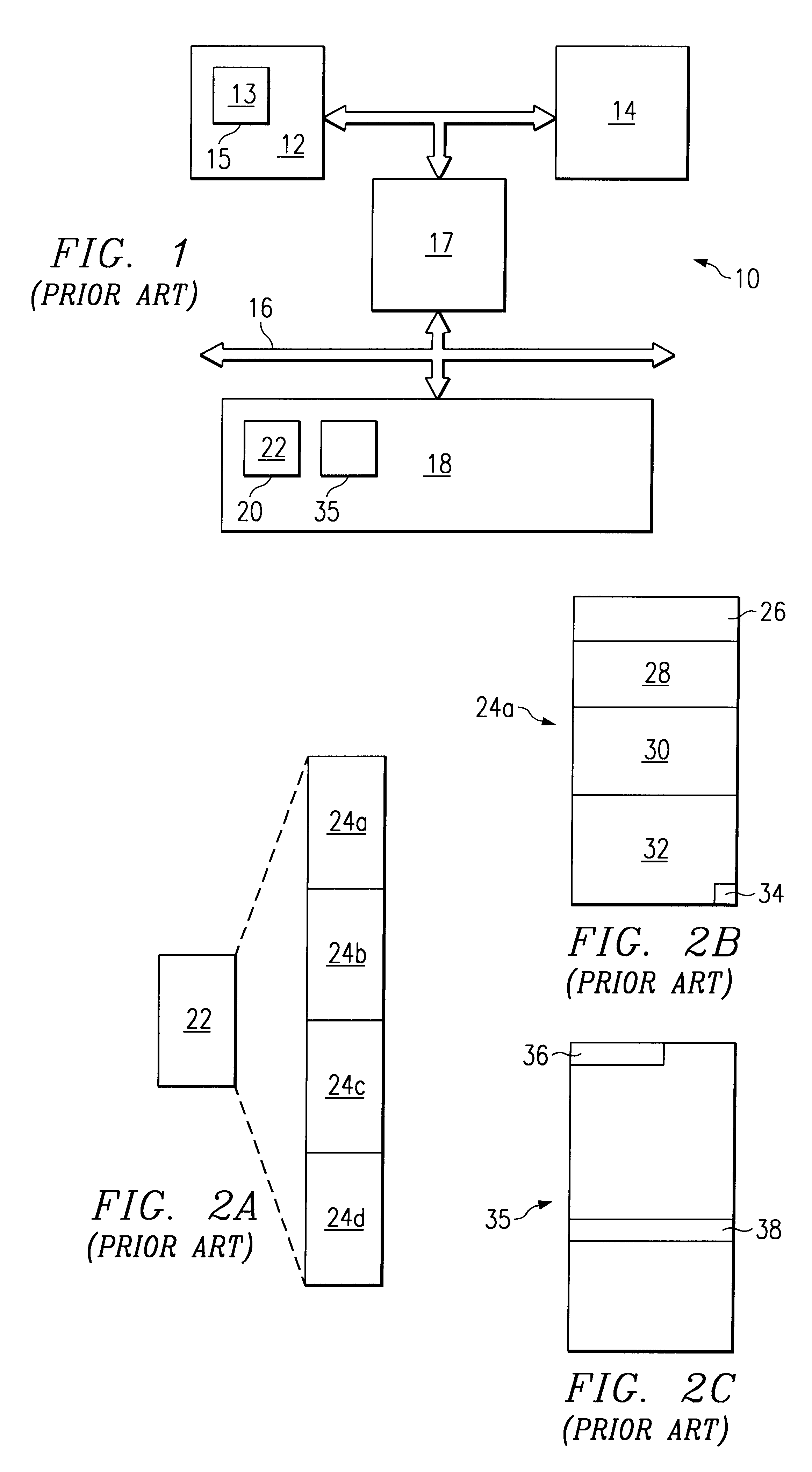
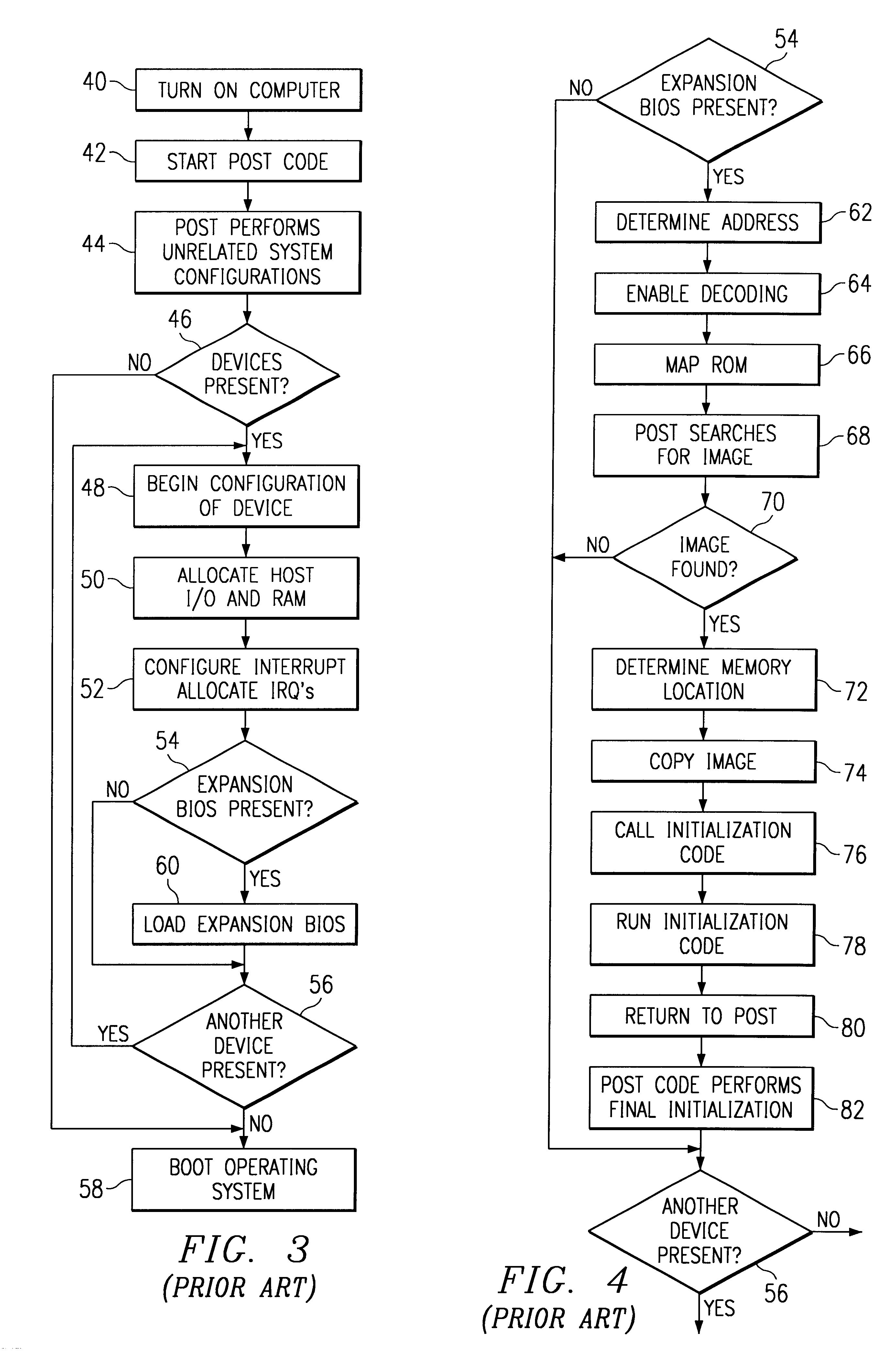
An arrangement and method are disclosed herein for operating a computer system including a host computer having system RAM. The host computer uses a BIOS to control the operation of the system. The operation of the system requires the host computer to obtain the BIOS device and store the BIOS within the system RAM. The arrangement and method of the invention allows at least a portion of the BIOS to be stored within the mass memory storage of a mass memory storage peripheral computer device rather than being stored within ROM. The BIOS may be expansion BIOS associated with a particular peripheral computer device or system BIOS associated with the host computer.
Owner:TEXAS INSTR INC
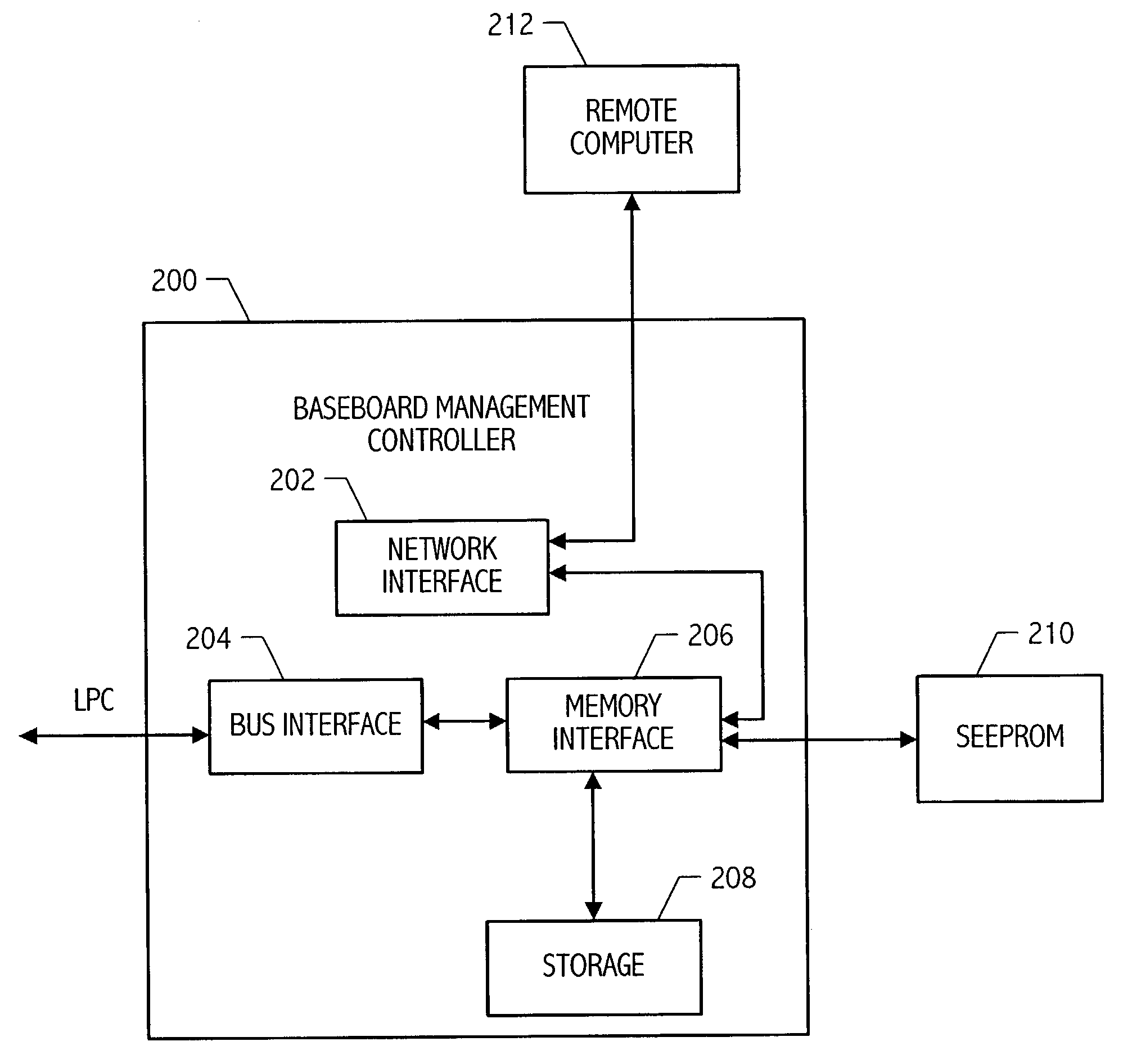
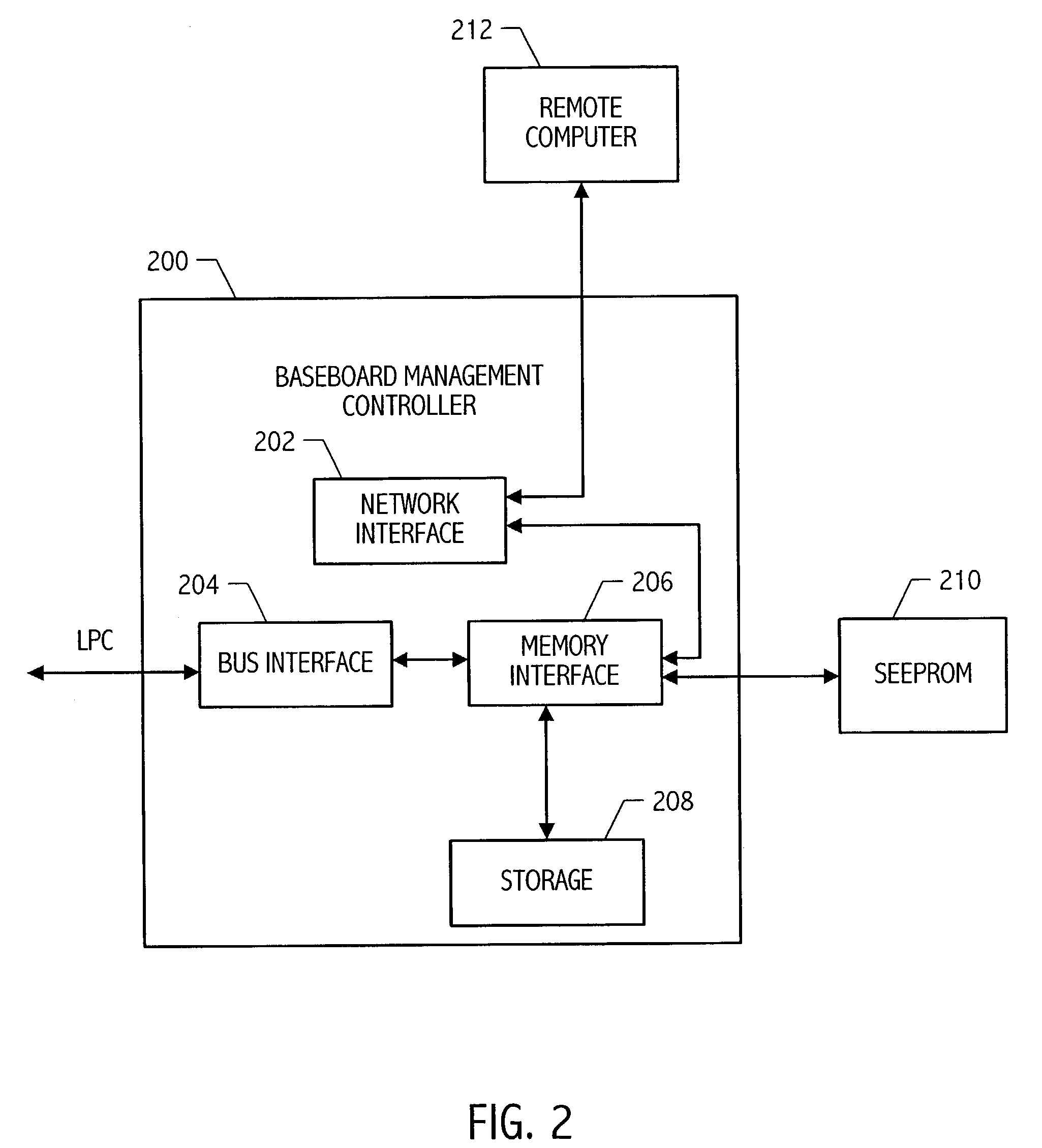
BMC-hosted boot ROM interface
A baseboard management controller (BMC) integrated circuit hosts a BIOS ROM interface. The BMC includes a bus interface responsive to an access to an address range associated with host operations, e.g., an address range associated with BIOS. The BMC includes an interface coupled to communicate with a remote computer for receiving BIOS updates and / or a BIOS patches from the remote computer. Multiple computers may each include a BMC-hosted BIOS ROM interface and may be coupled to a remote computer for communicating BIOS information between the BMCs and the remote computer.
Owner:GLOBALFOUNDRIES US INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com