Patents
Literature
188 results about "Master boot record" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
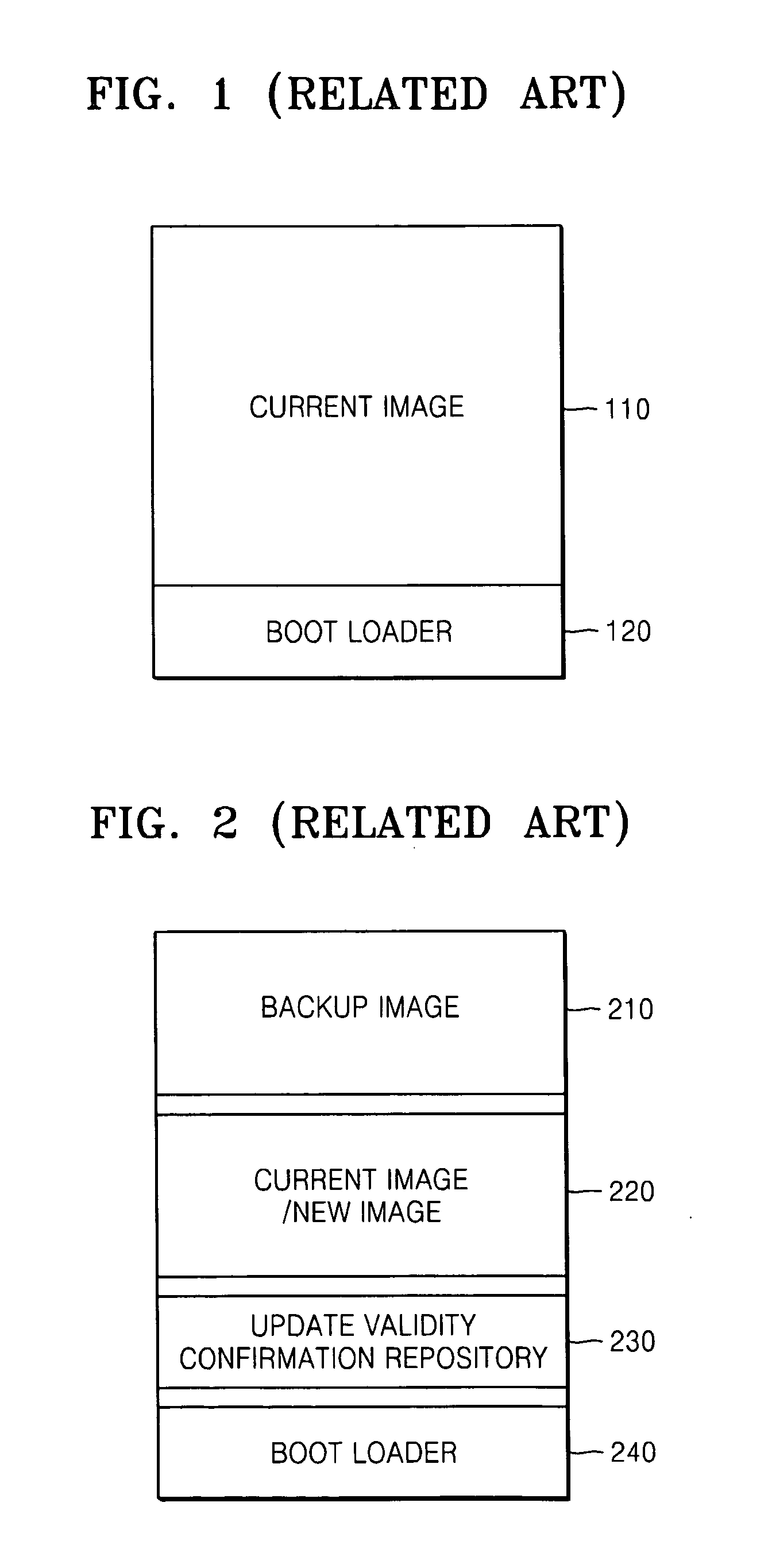
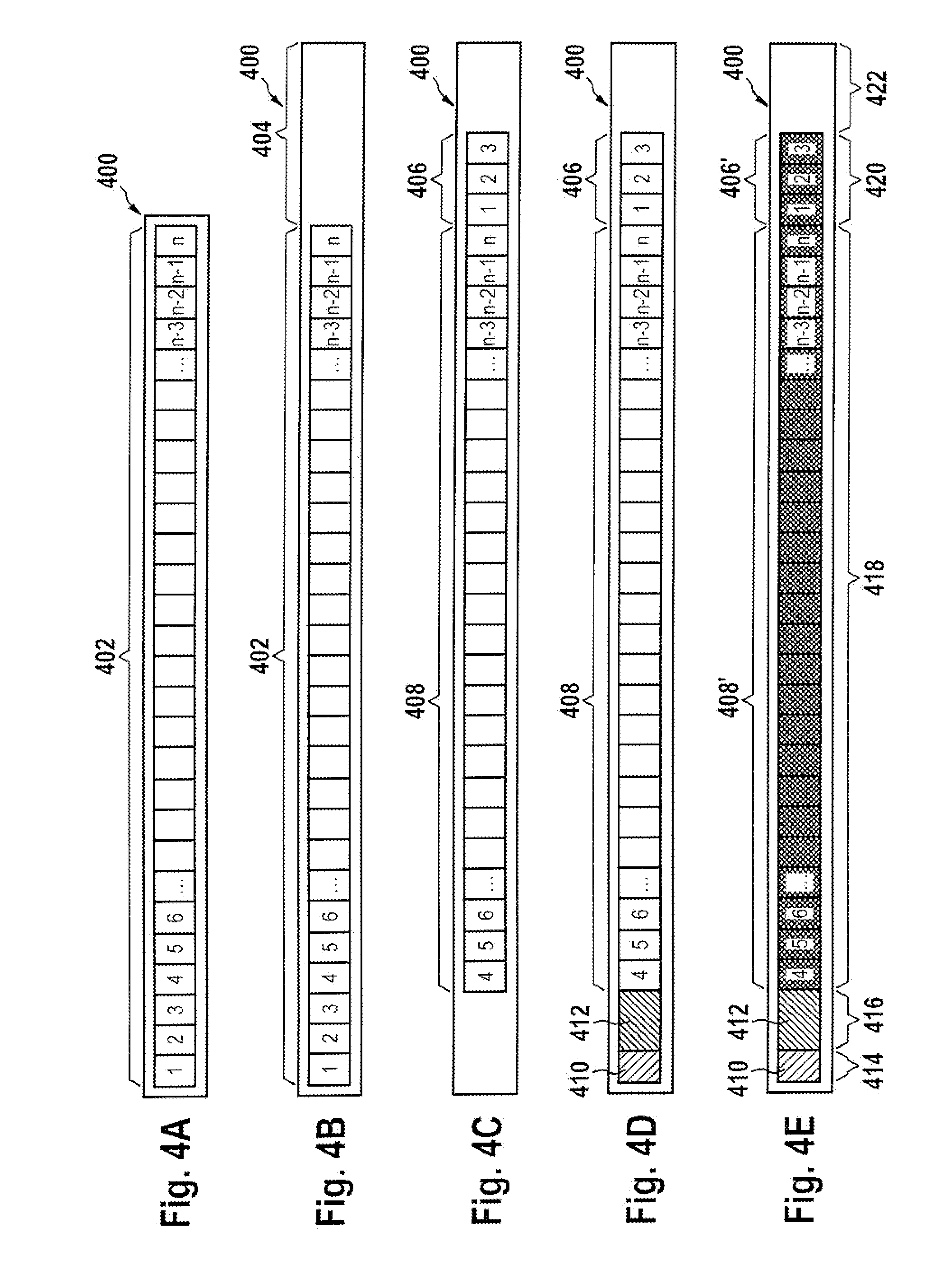
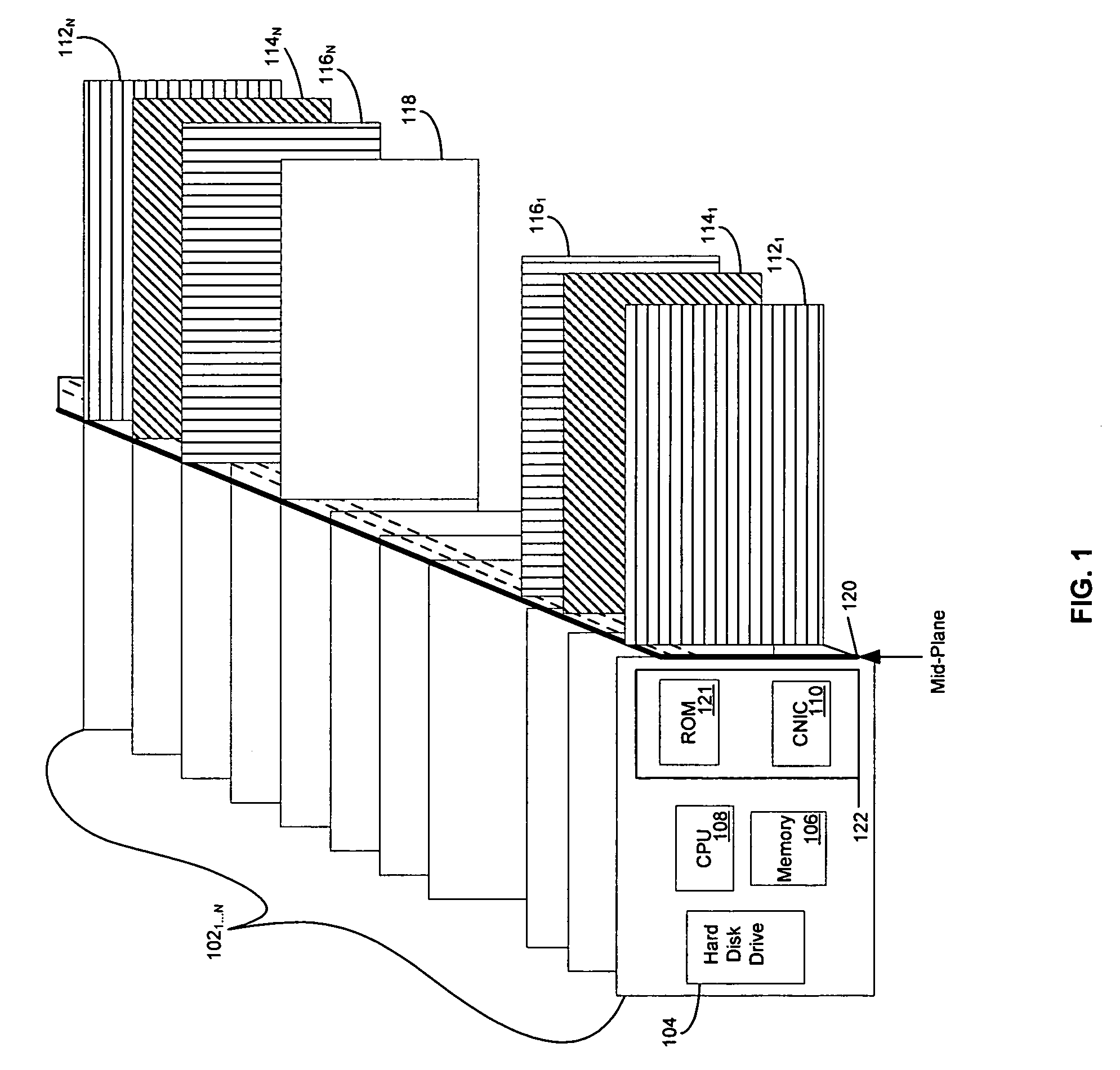
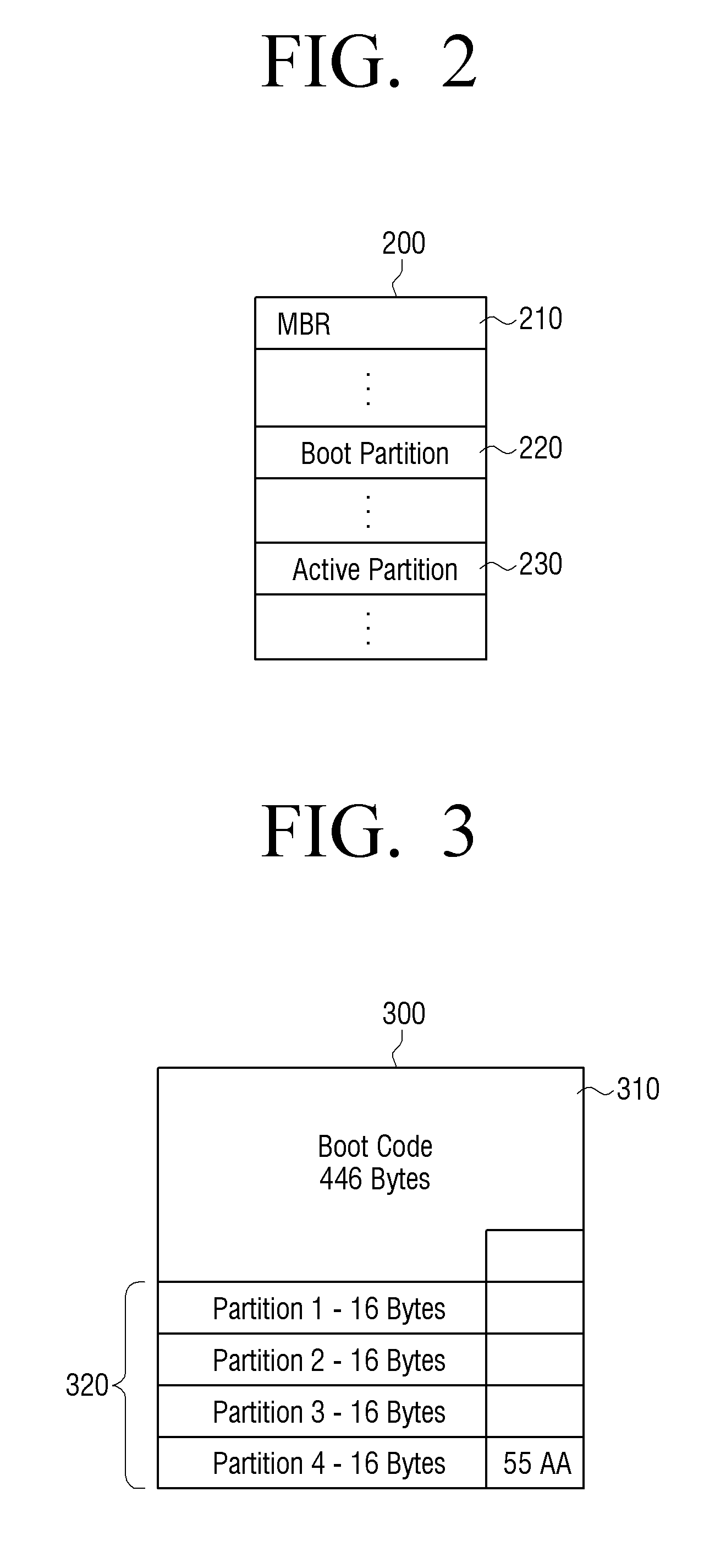
A master boot record (MBR) is a special type of boot sector at the very beginning of partitioned computer mass storage devices like fixed disks or removable drives intended for use with IBM PC-compatible systems and beyond. The concept of MBRs was publicly introduced in 1983 with PC DOS 2.0.
Method, apparatus and virtual machine for detecting malicious program
ActiveUS20140351935A1Detect presenceMemory loss protectionError detection/correctionVirtual memoryVirtual storage
Owner:BEIJING QIHOO TECH CO LTD
Detecting bootkits resident on compromised computers
ActiveUS9251343B1Unauthorized memory use protectionPlatform integrity maintainanceComputer hardwareHash table
Techniques detect bootkits resident on a computer by detecting a change or attempted change to contents of boot locations (e.g., the master boot record) of persistent storage, which may evidence a resident bootkit. Some embodiments may monitor computer operations seeking to change the content of boot locations of persistent storage, where the monitored operations may include API calls performing, for example, WRITE, READ or APPEND operations with respect to the contents of the boot locations. Other embodiments may generate a baseline hash of the contents of the boot locations at a first point of time and a hash snapshot of the boot locations at a second point of time, and compare the baseline hash and hash snapshot where any difference between the two hash values constitutes evidence of a resident bootkit.
Owner:FIREEYE SECURITY HLDG US LLC
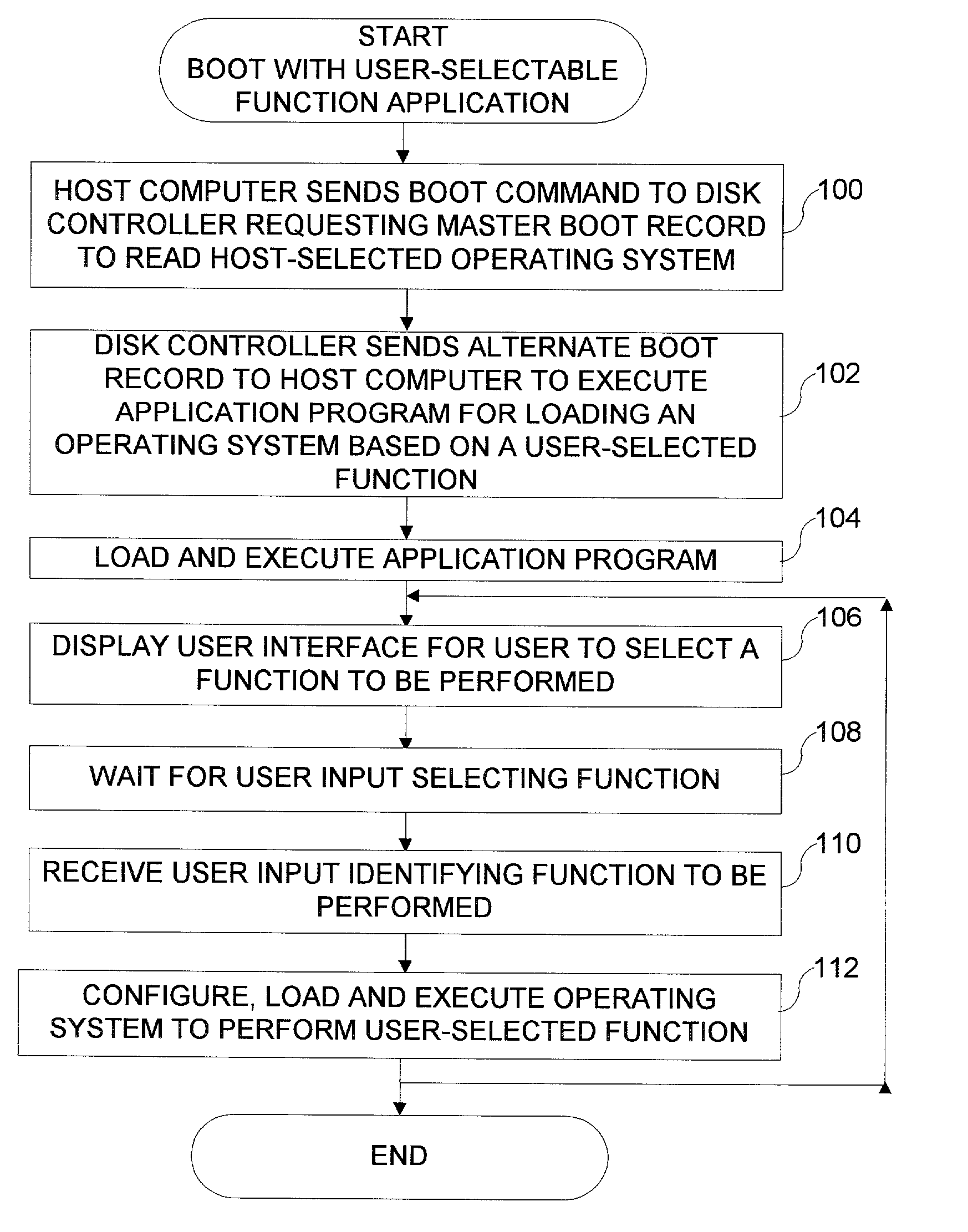
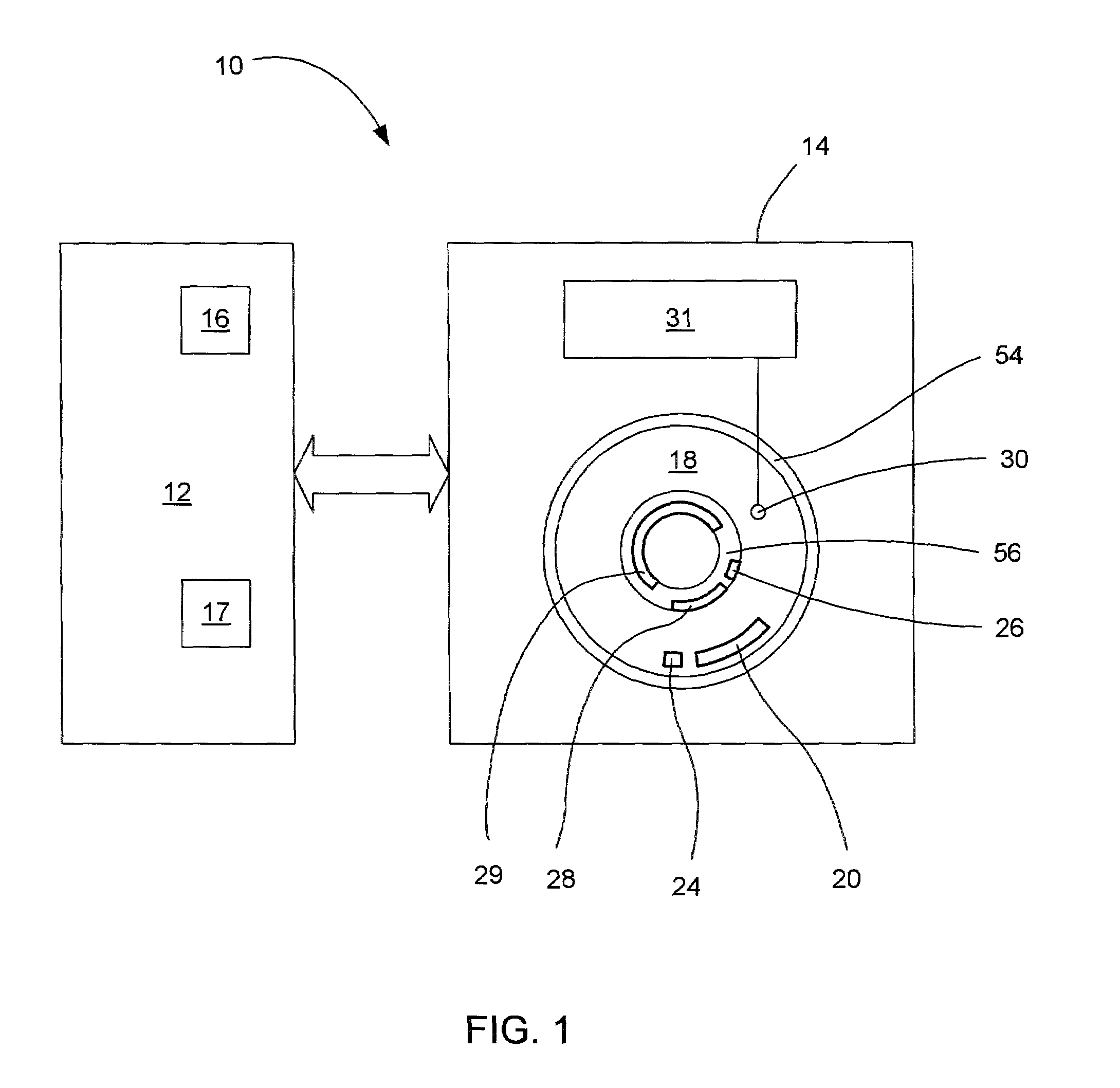
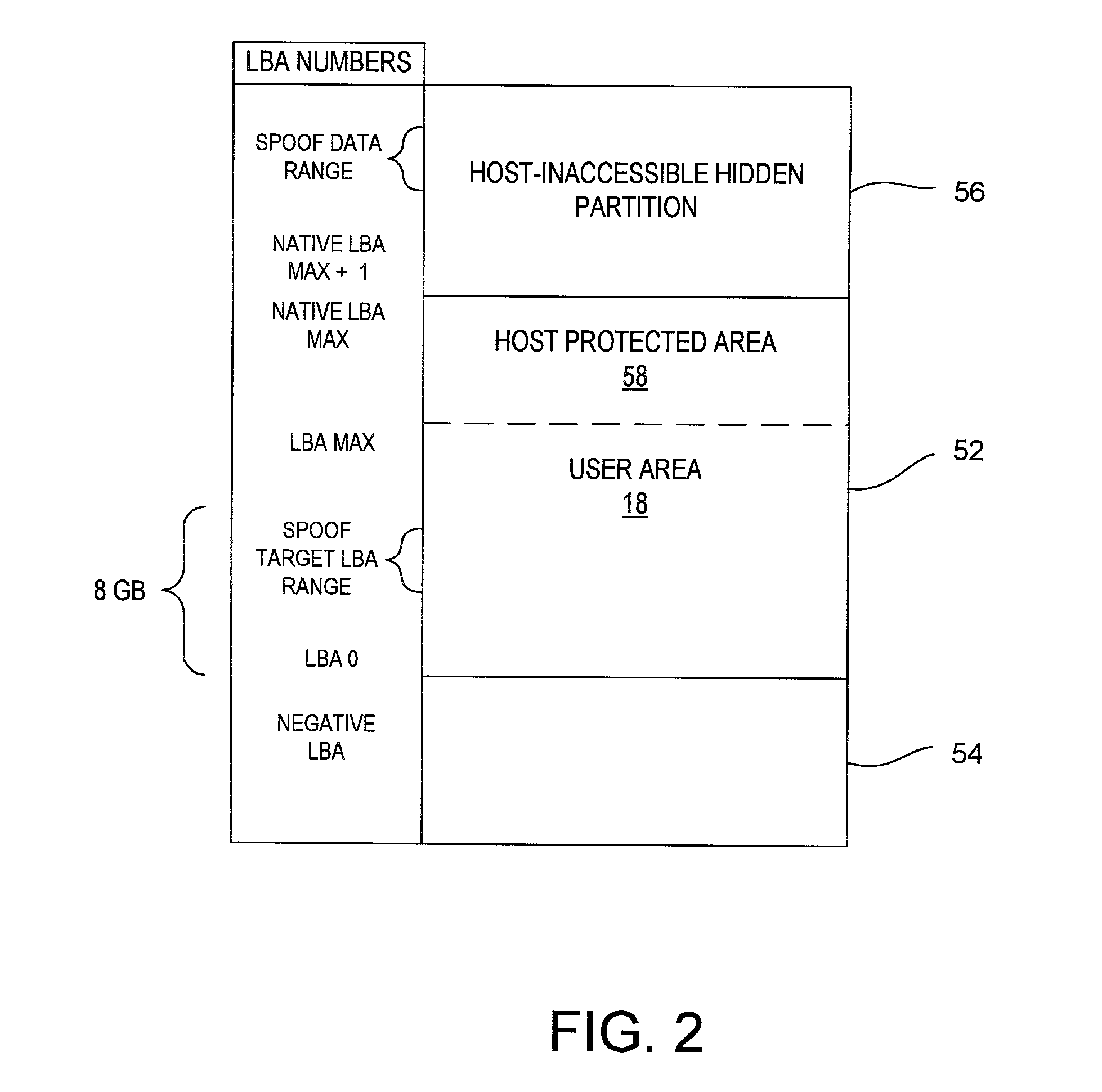
Disk drive having a protected partition configured to load an operating system for performing a user-selected function
A system for configuring, loading and executing an operating system for performing a user-selected function is disclosed. The system includes a disk drive including: a host-accessible user partition; a host-inaccessible hidden partition independent of the host-accessible user partition; and a disk controller. The user partition includes: a user partition address range; a host-selected operating system; and a host-selected master boot record. The host-inaccessible hidden partition includes: a hidden partition address range outside the user partition address range; an application program for allowing a user to select a function to perform and configuring, loading and executing an operating system to perform the selected function; and a drive-selected boot record for loading and executing the application program that allows the user to select a function and configures, loads and executes an operating system for performing the function.
Owner:WESTERN DIGITAL TECH INC
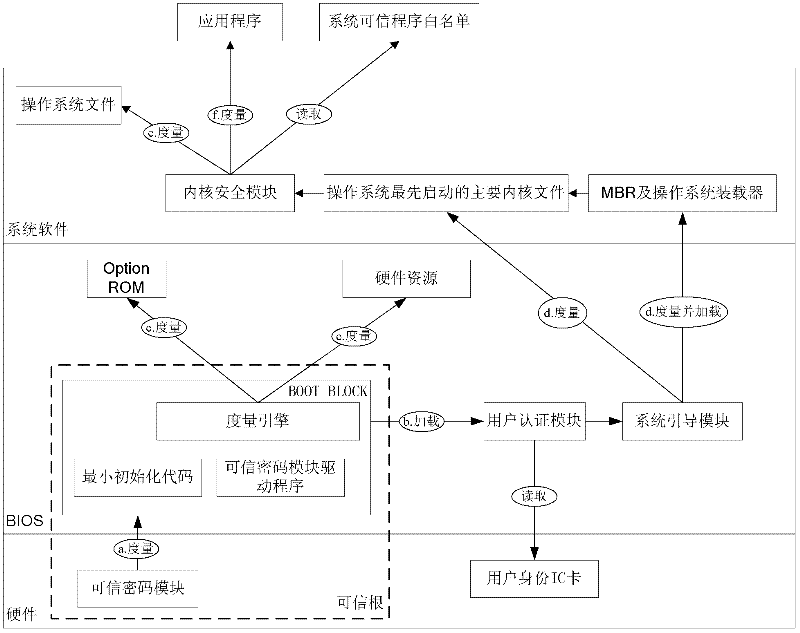
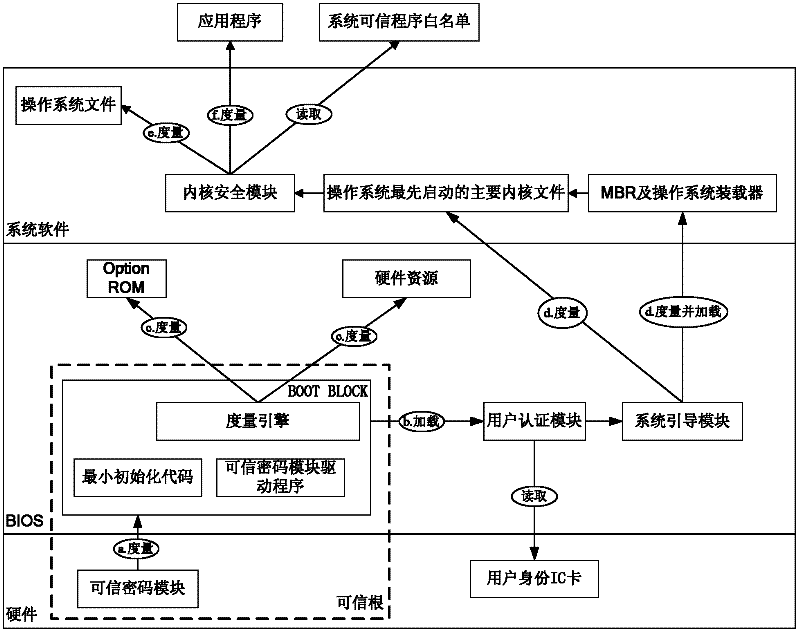
Trust chain transfer method for trusted computing platform
InactiveCN102332070ANot easy to tamper withNot easy to attackPlatform integrity maintainanceOperational systemTrusted Computing
The invention discloses a trust chain transfer method for a trusted computing platform. A trusted computing module (TCM) serving as a starting point of starting a trust chain is started and actively initiated at first to verify the trustiness of a BIOS (basic input output system) chip; after the trusted BIOS chip is started, a MAIN BLOCK of the BIOS chip performs concentrated integrity verification on key files of an MBR (master boot record), an operating system loader and an operating system kernel; in the starting process of an operating system, the starting and running of an unauthorized program are prevented in a way of combining the integrity verification based on a white list and running program control; and hashing operations for the integrity verification are finished by a hardware computing engine. When a user starts any executable program, a security module in the operating system kernel checks the integrity of the program and checks whether the program is in the trusted program white list or not, and only application programs which are in the trusted program white list of the system and have integrity measures consistent with an expected value are permitted to be run. High-efficiency and fine-grained trust chain transfer is realized, the damages of viruses to system files and program files can be prevented, and the execution of the unauthorized program can be prevented.
Owner:中国人民解放军海军计算技术研究所
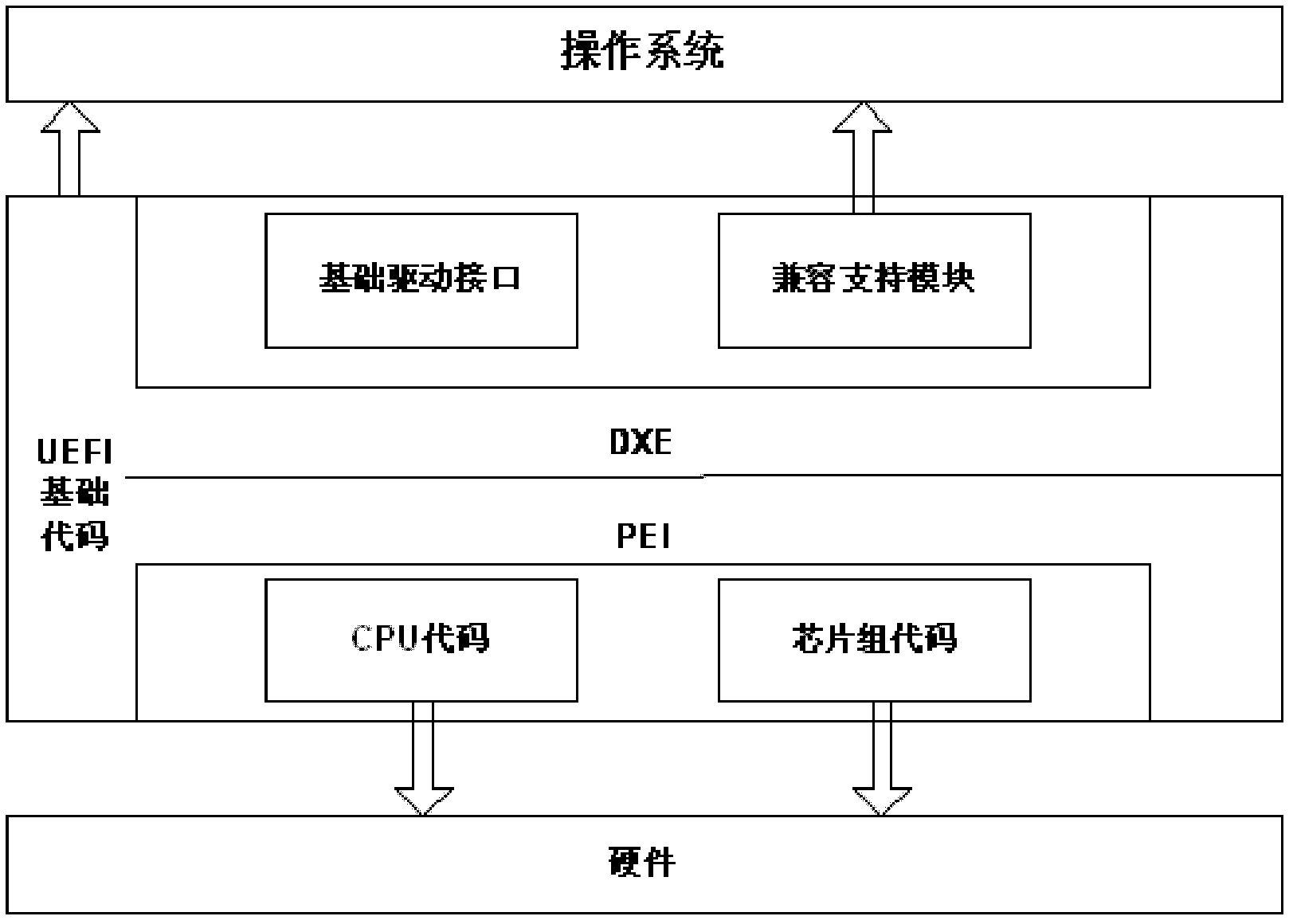
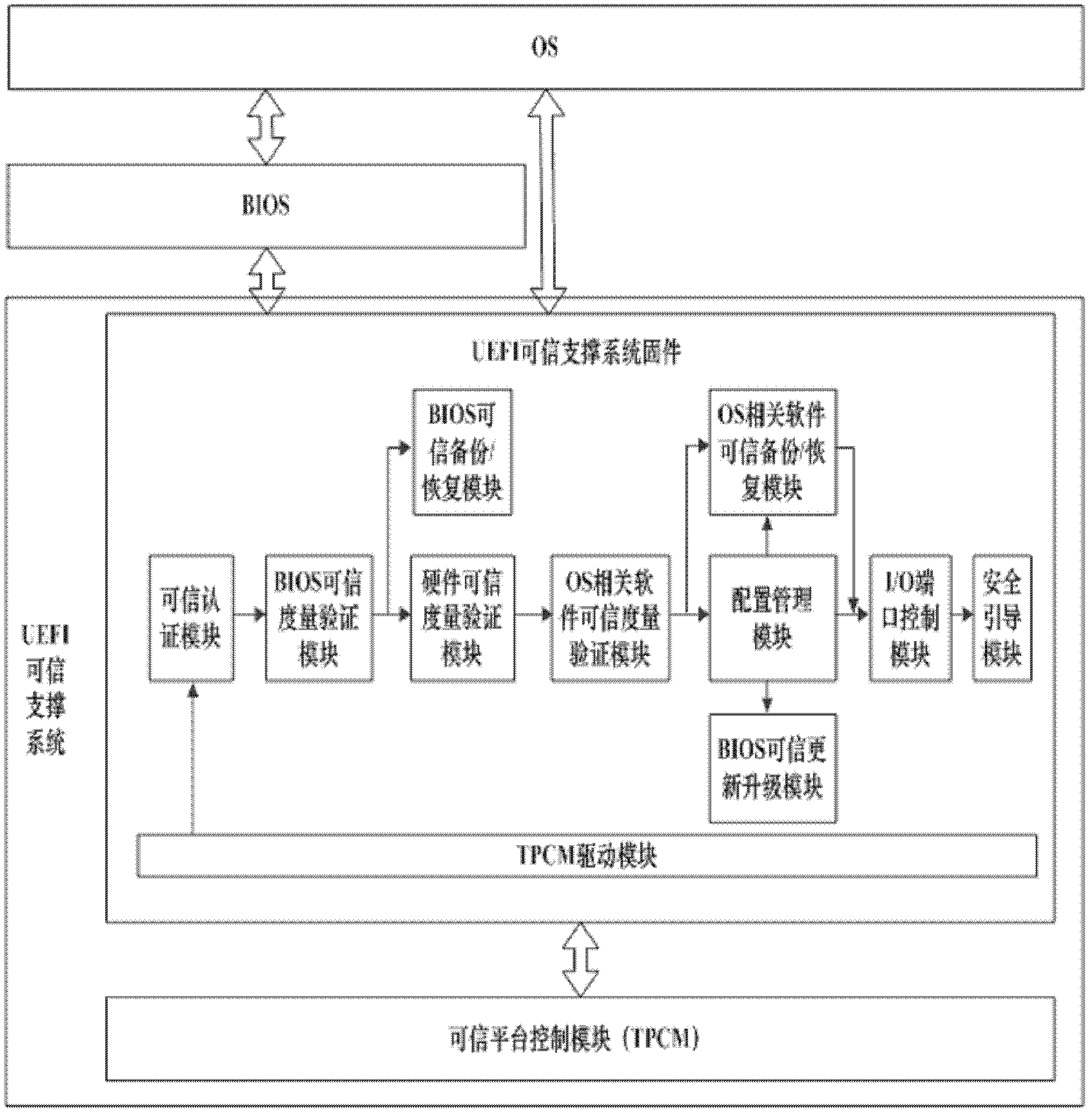
A UEFI trusted support system and control method thereof
InactiveCN102279914AReduce data volumeSimplify complexityPlatform integrity maintainanceSoftwareBackup
The invention discloses a unified extensible firmware interface (UEFI) trusted supporting system and a method for controlling the same. The UEFI trusted supporting system comprises UEFI trusted supporting system firmware and a trusted platform control module (TPCM), wherein the UEFI trusted supporting system firmware is stored on a nonvolatile memory and connected with the TPCM by a system bus; and the TPCM is connected with a trusted computation platform by the system bus. The method for controlling the UEFI trusted supporting system comprises the following steps of: firstly, loading a driver for the TPCM; secondly, sequentially authenticating the identity of users, performing measurement validation on a basis input / output system (BIOS), the characteristic data of hardware and a master boot record (MBR) / operating system (OS) Loader / OS Kernel, controlling different hardware peripheral interfaces according to an I / O strategy of the users, and performing safety guide setting on the system by a safety guide module; and finally, controlling by the BIOS or the OS. By the system and the method, trusted computation, the configuration management of the TPCM, the backup / recovery of the BIOS / MBR / OS Loader / OS Kernel and the physical protection of key data are realized on a firmware layer. The invention can be simultaneously applied to a Linux system which opens source codes and a Windows system which does not open the source codes, so that a fault does not occur in a trust chain between BIOS firmware and OS software, and the safety of a computer and the friendliness of human-computer interaction are improved.
Owner:中国人民解放军海军计算技术研究所 +1
Recovery method for master boot record of hard disk drive
InactiveUS20060041738A1Avoid backupAvoid damageError detection/correctionDigital computer detailsRecovery methodHard disc drive
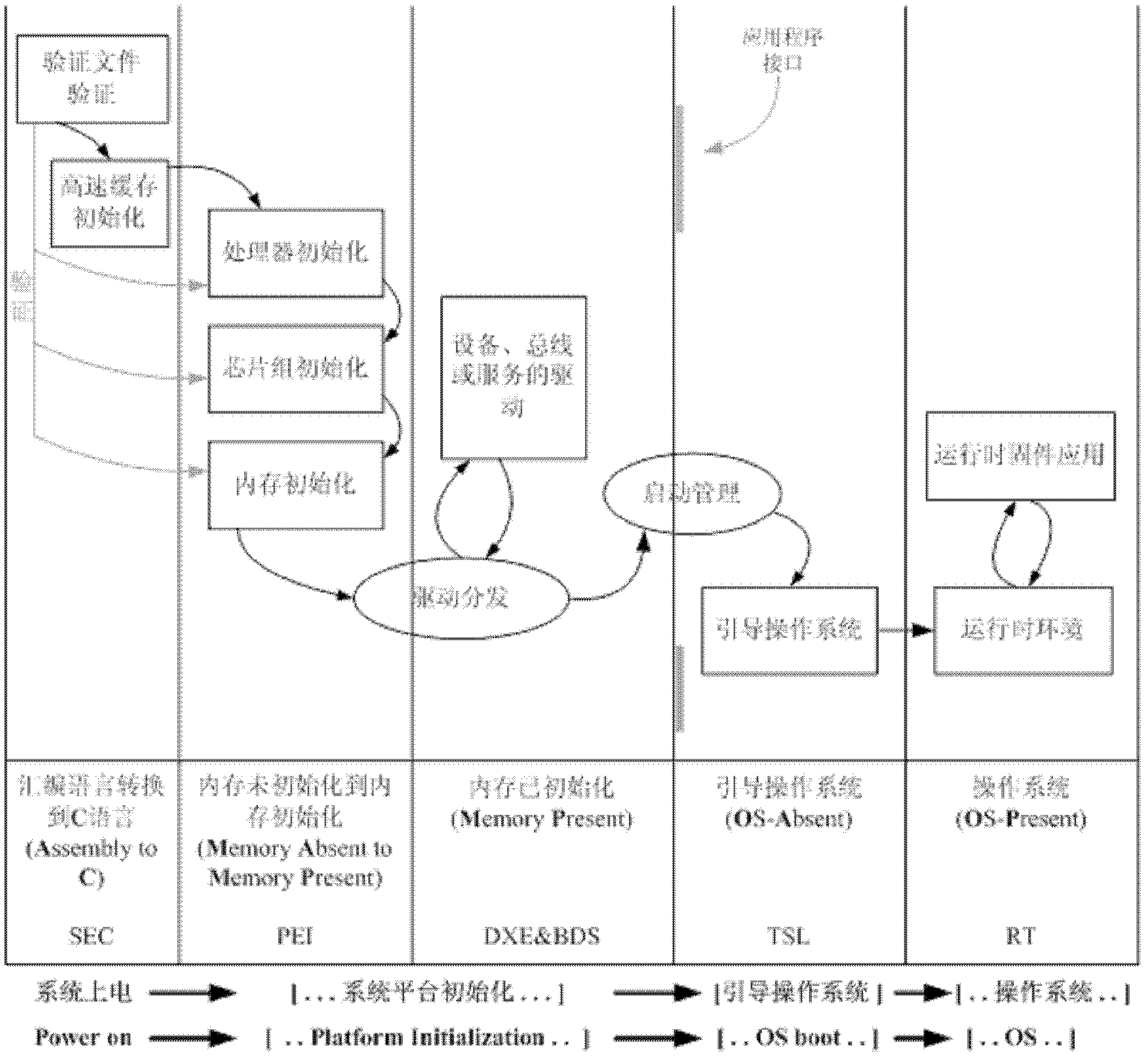
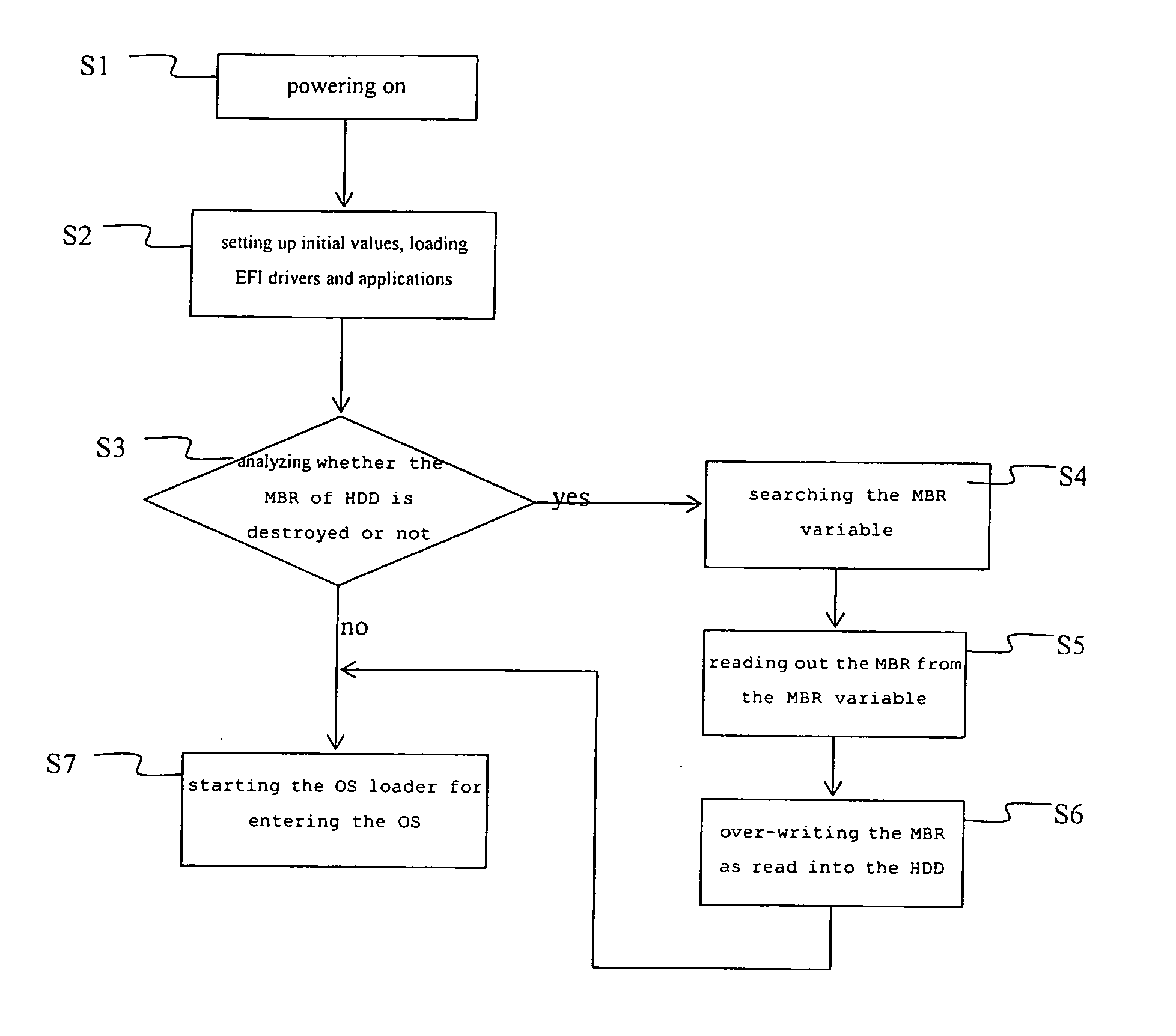
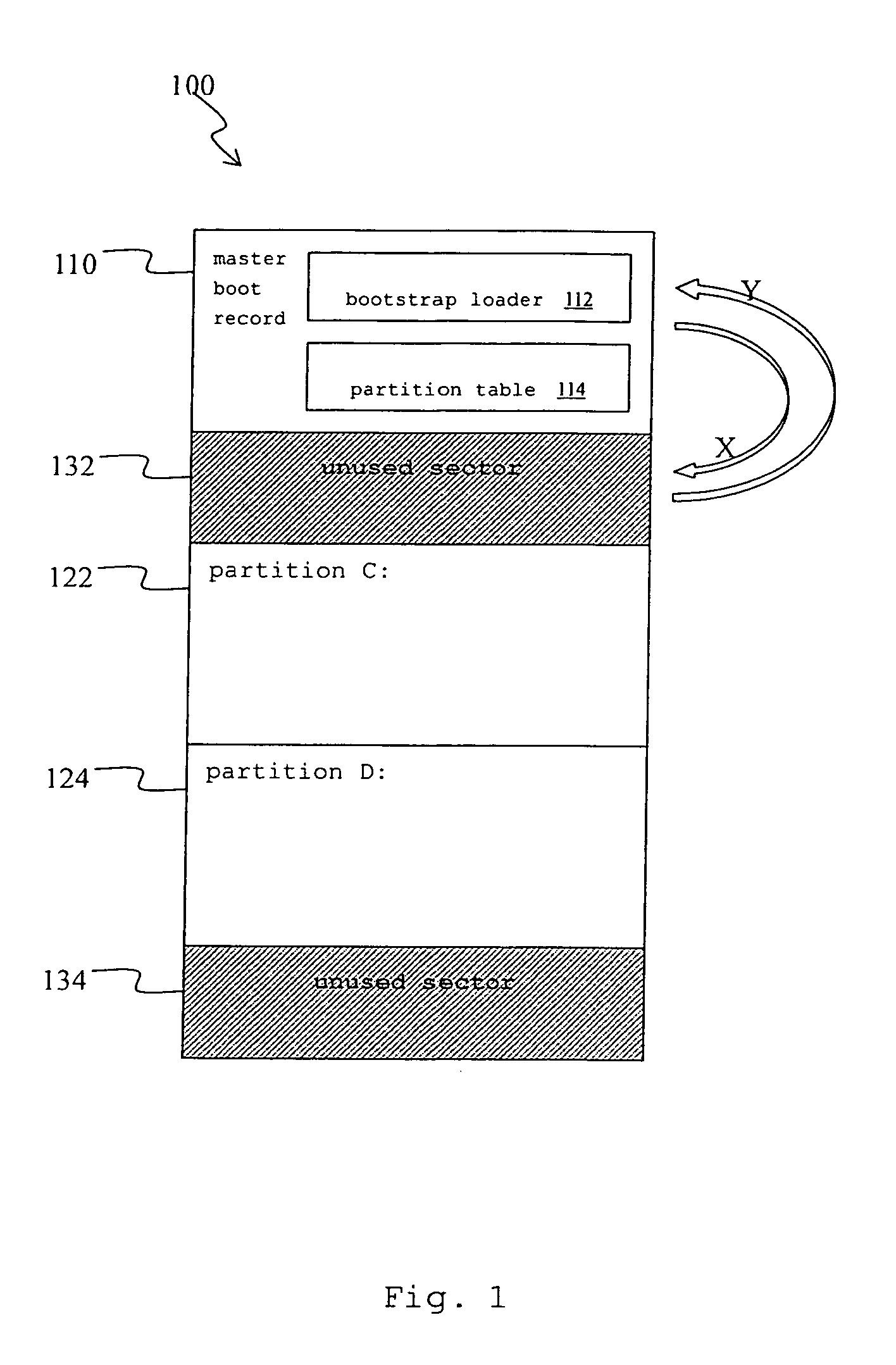
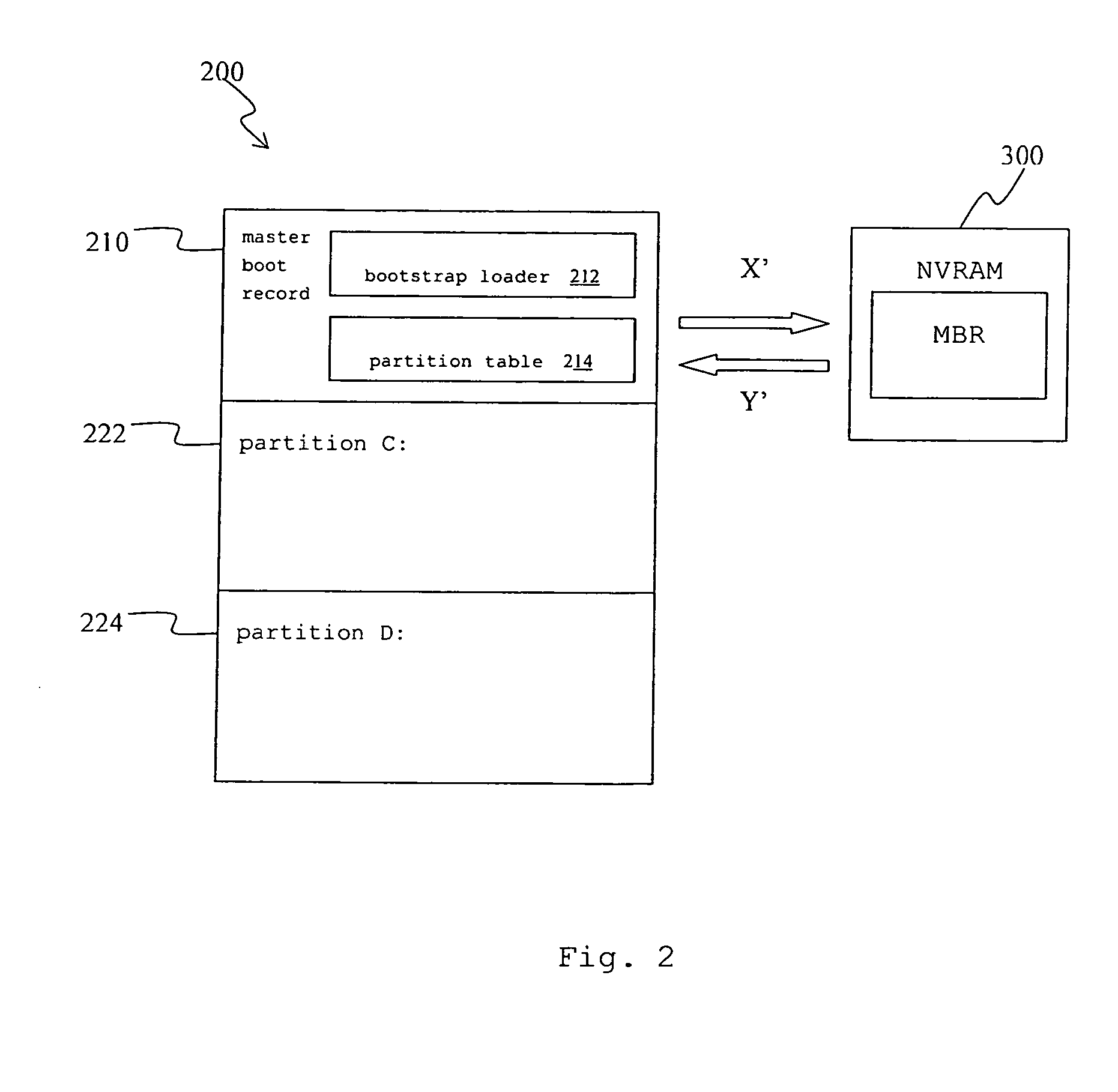
A recovery method for a master boot record of a hard disk drive is adapted to a computer system incorporating extensible firmware interface (EFI). When modification occurs in the master boot record, the extensible firmware interface stores the master boot record in an NVRAM (Non-volatile Random Access Memory) as a backup. The backup is read out for recovery of the hard disk driver if the master boot record is destroyed. The NVRAM is write-protected during runtime and the backup data stored therein is therefore free from destruction.
Owner:INSYDE SOFTWARE CORP
System and method for authenticating a gaming device
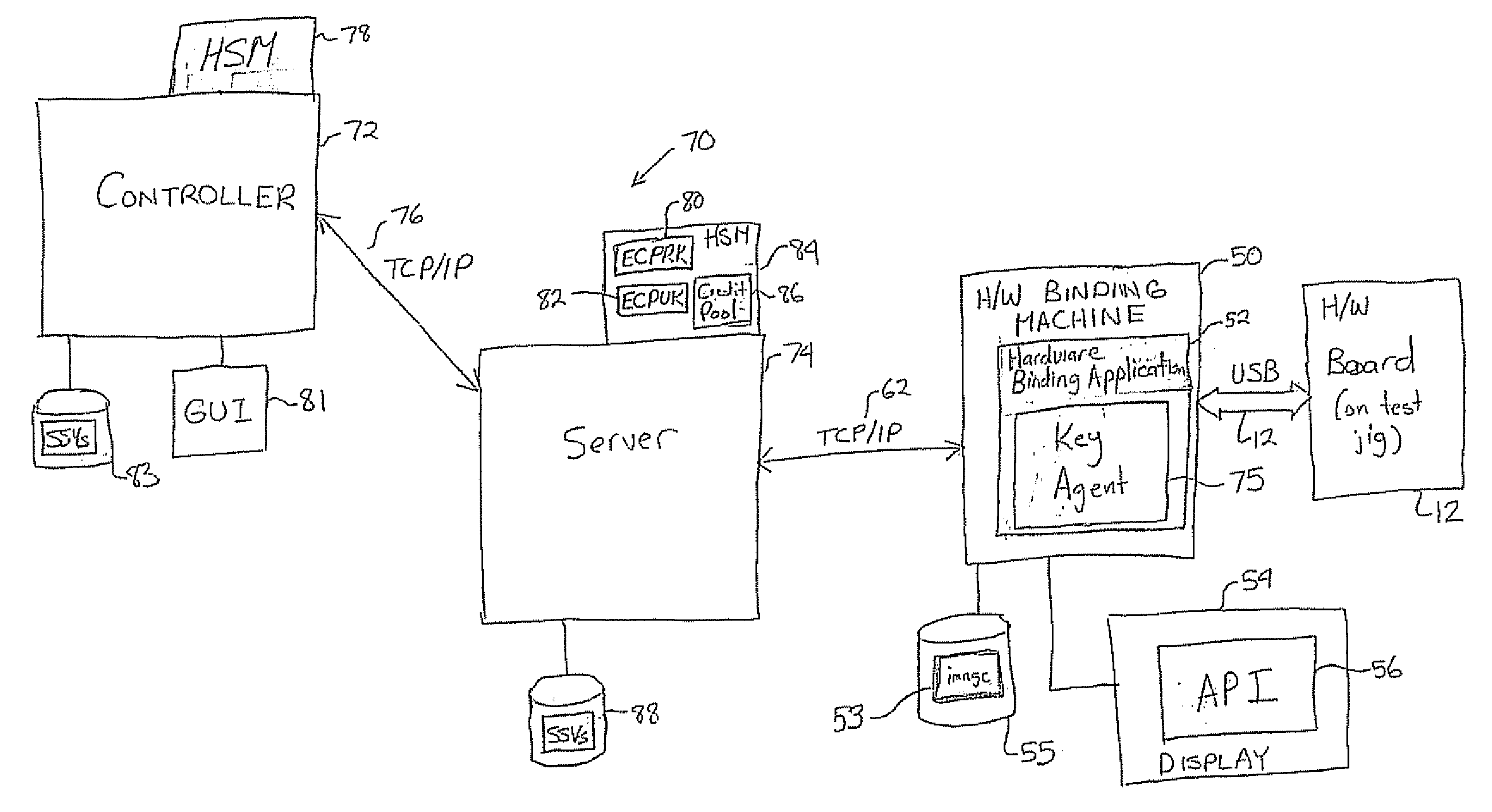
ActiveUS20080028235A1Multiple keys/algorithms usageDigital data processing detailsPersonalizationBIOS
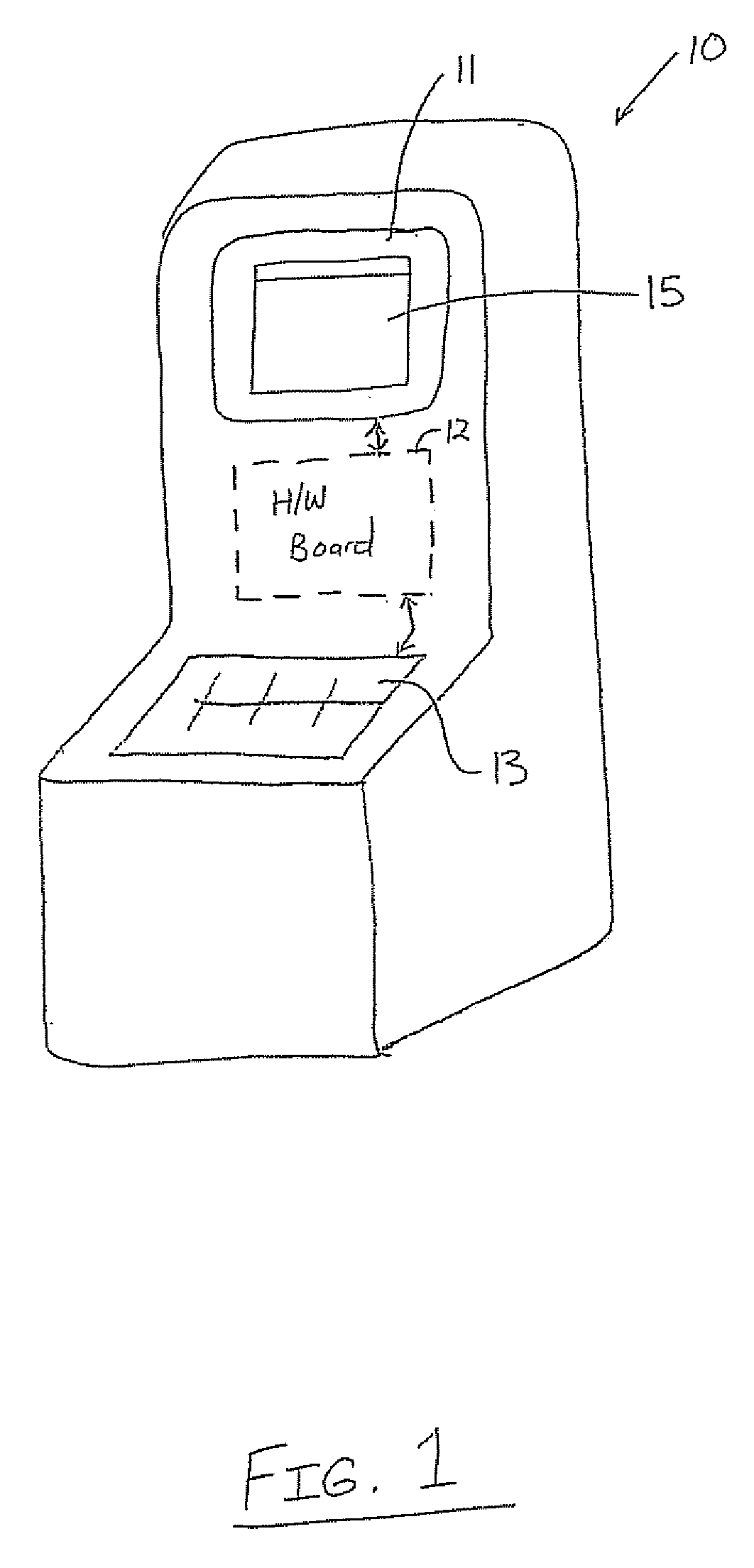
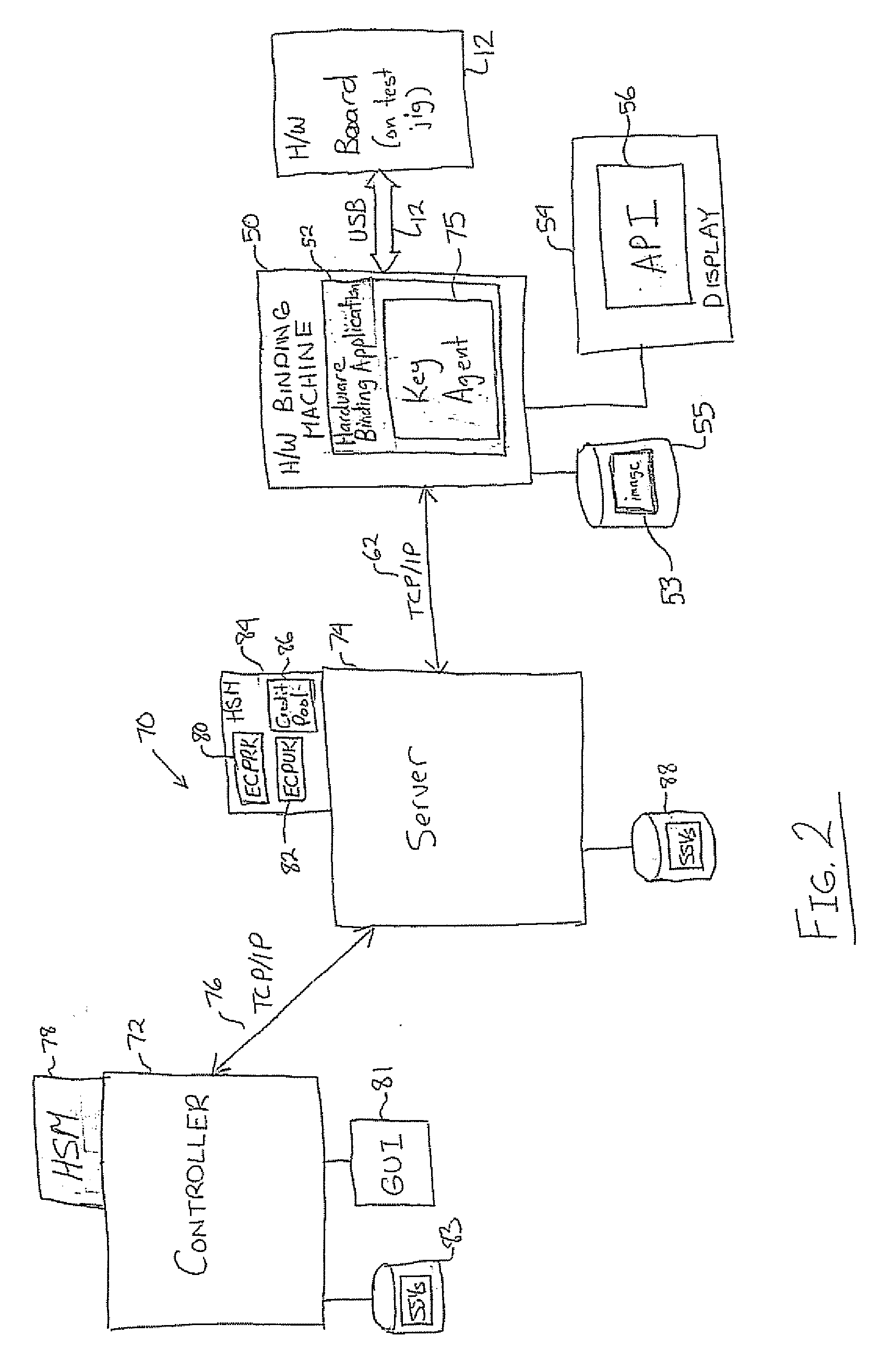
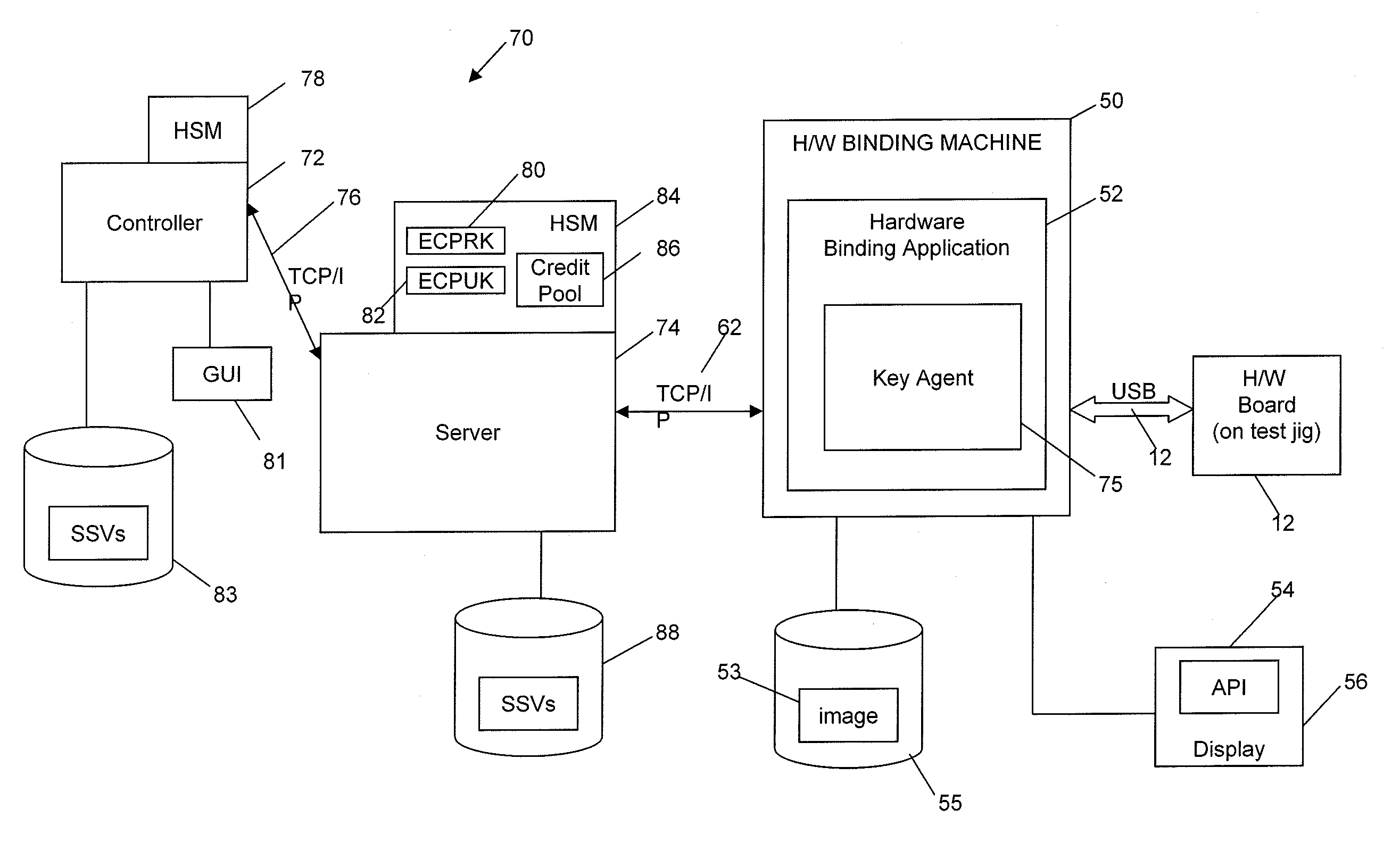
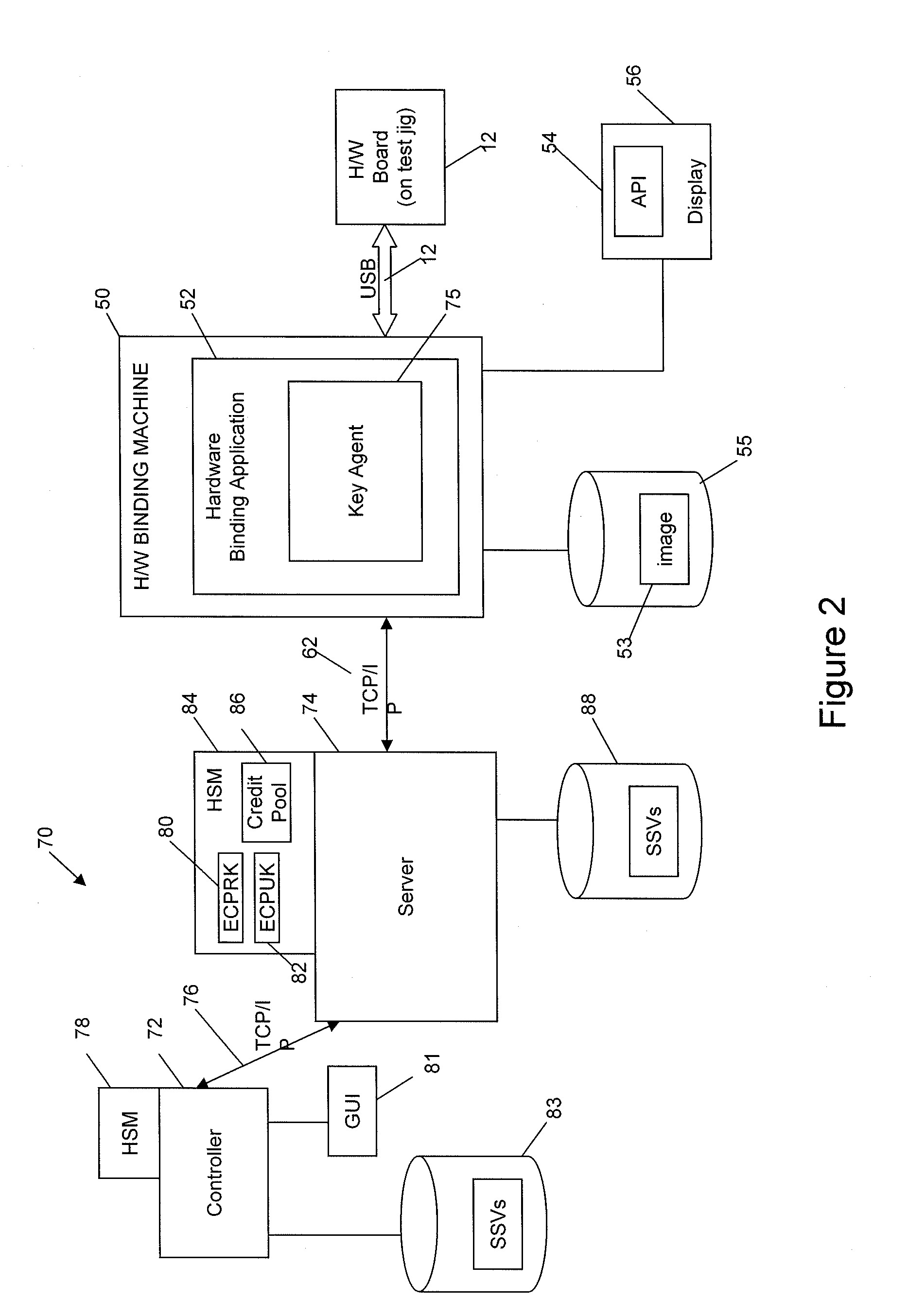
A method and system are provided for authenticating and securing an embedded device using a secure boot procedure and a full non-volatile memory encryption process that implements Elliptic Curve Pinstov-Vanstone Signature (ECPV) scheme with message recovery on a personalized BIOS and master boot record. The signature includes code that is recovered in order to unlock a key that is in turn used to decrypt the non-volatile memory. The use of ECPVS provides an implicit verification that the hardware is bound to the BIOS since the encrypted memory is useless unless properly decrypted with the proper key.
Owner:MALIKIE INNOVATIONS LTD
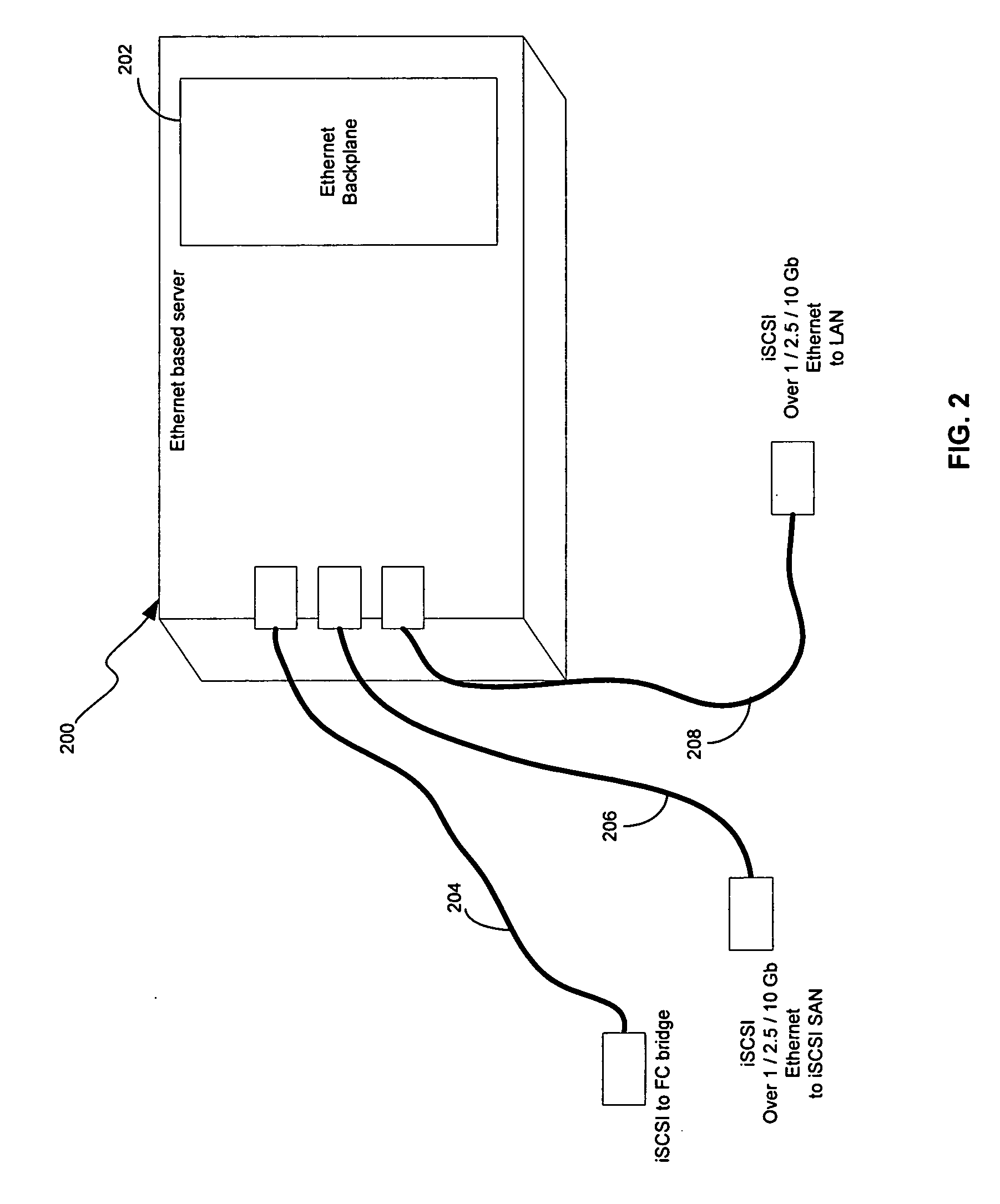
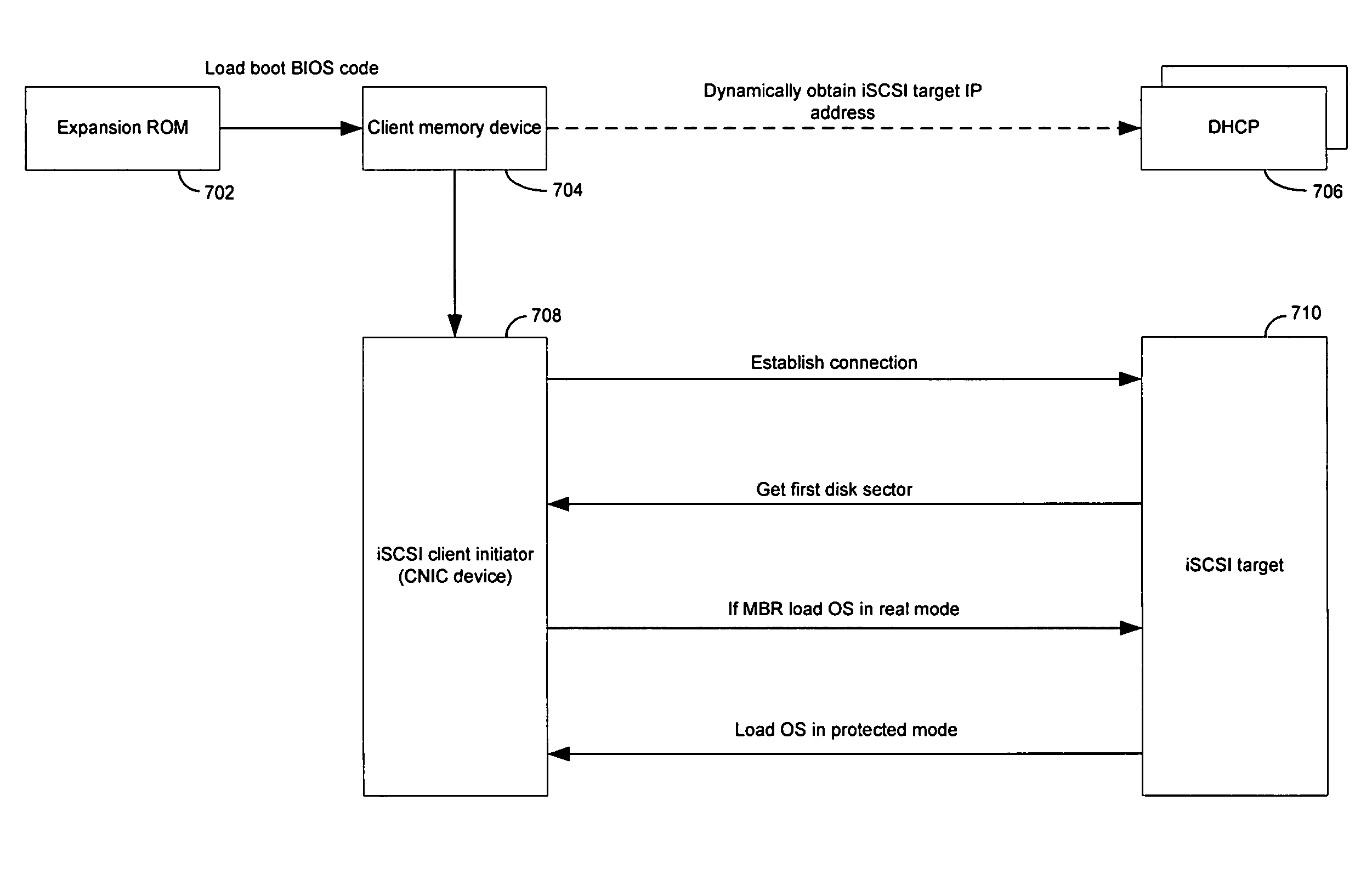
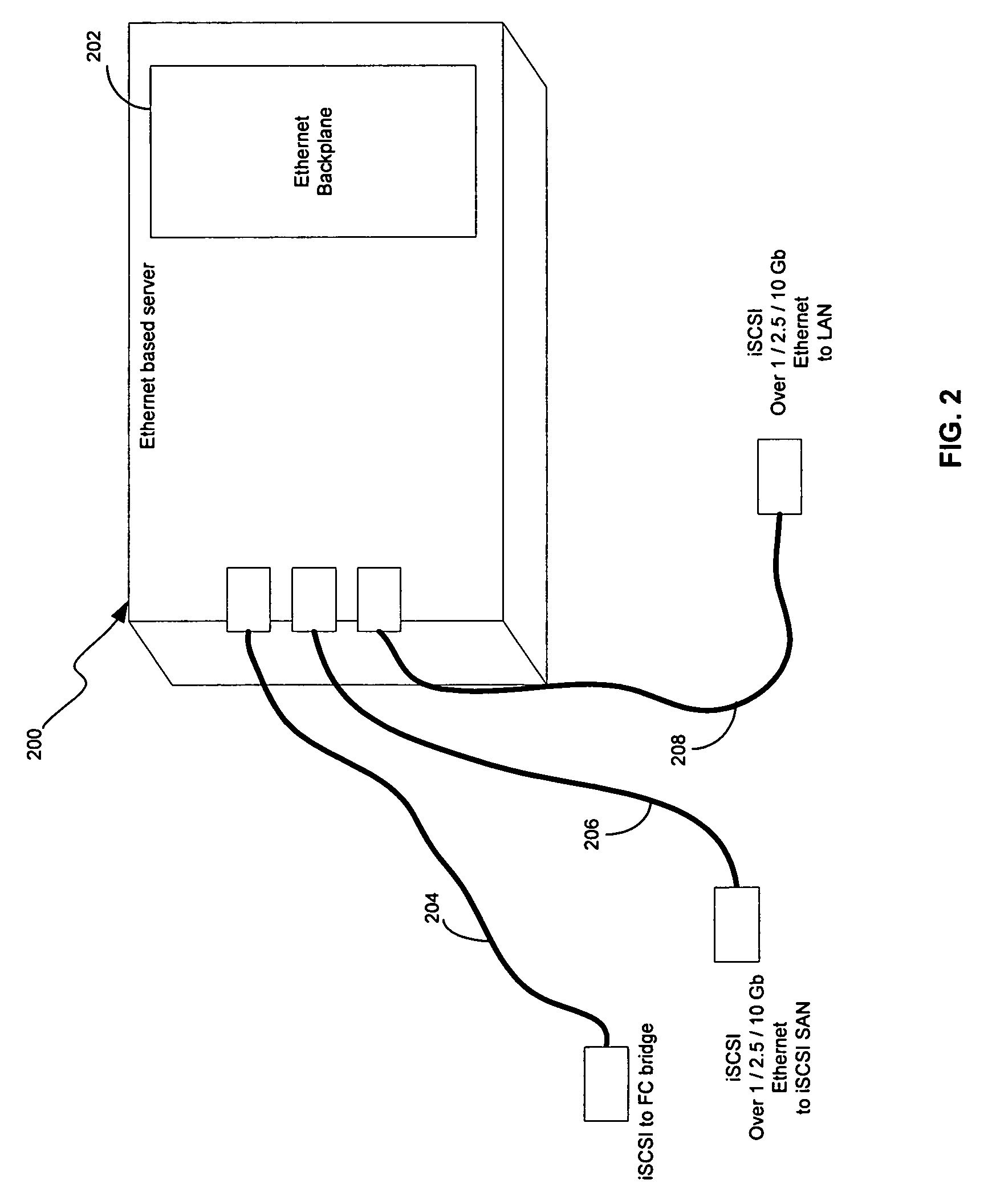
Method and system for iSCSl boot
Certain aspects of a method for iSCSI boot may include loading boot BIOS code from a host bus adapter or a network interface controller (NIC) by an iSCSI client device. A connection may be established to an iSCSI target by the iSCSI client device after loading the boot BIOS code. The boot BIOS code may be chained to at least one interrupt handler over iSCSI protocol. An operating system may be remotely booted from the iSCSI target by the iSCSI client device based on chaining the interrupt handler. An Internet protocol (IP) address and / or location of the iSCSI target may be received. At least one iSCSI connection may be initiated to the iSCSI target based on chaining at least one interrupt handler. The iSCSI target may be booted in real mode if at least one master boot record is located in the memory.
Owner:AVAGO TECH INT SALES PTE LTD
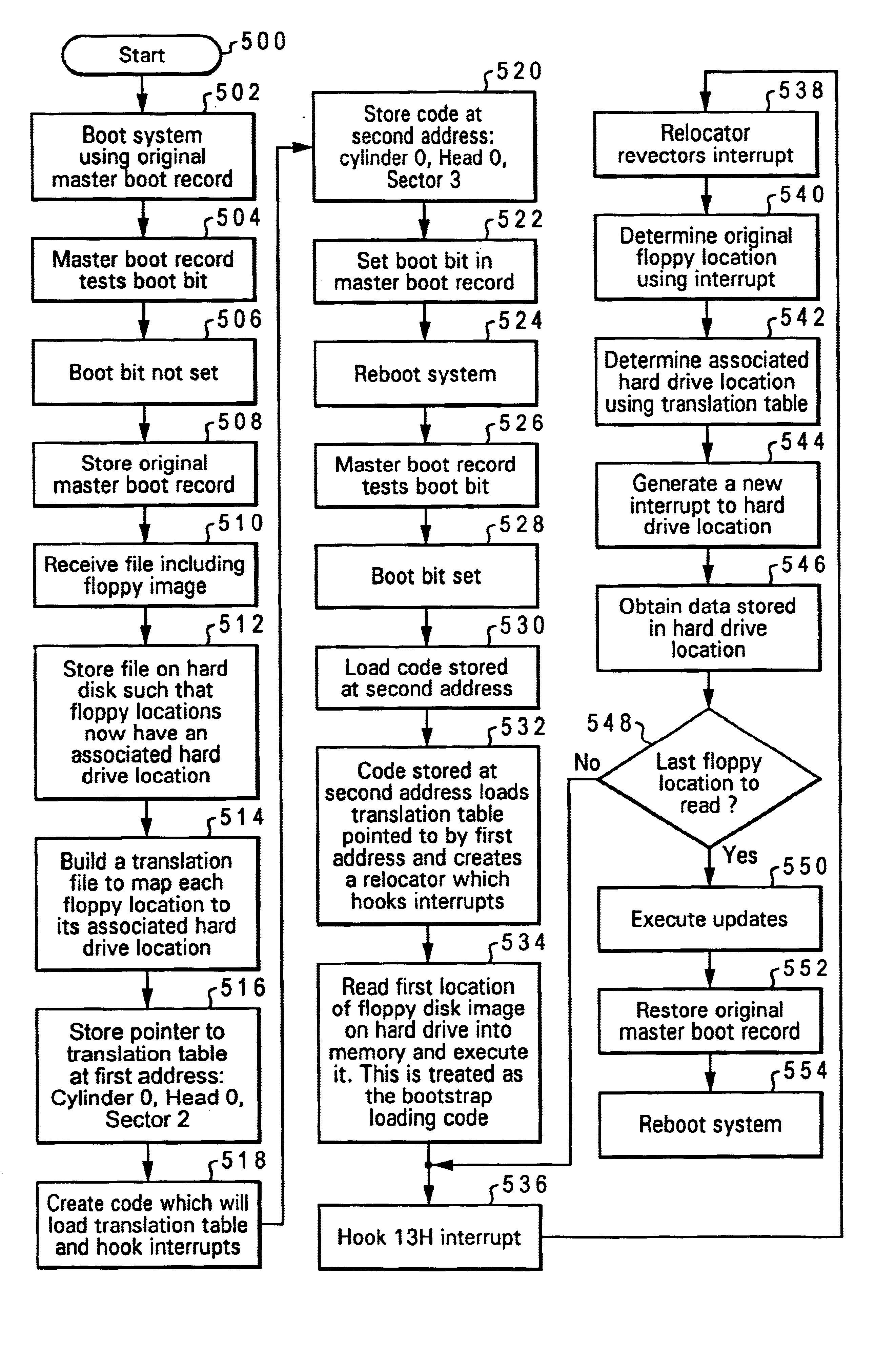
Virtual floppy diskette image within a primary partition in a hard disk drive and method for booting system with virtual diskette
A data processing system and method are described for booting a computer system from a virtual floppy diskette. A native operating system is executed by the computer system which utilizes a native file system. A boot able floppy diskette image is stored on the hard drive. The image includes a second operating system which utilizes a second file system. A master boot record stored on the hard drive is modified to include a boot bit. The boot bit is set in response to a storage of the image. The computer system is then booted from the image in response to the boot bit being set. The native operating system and the native file system are unchanged during the booting of the computer system from the image.
Owner:LENOVO PC INT
Method and system for using a trusted disk drive and alternate master boot record for integrity services during the boot of a computing platform
InactiveUS20090172378A1Digital computer detailsComputer security arrangementsHard disc driveEngineering
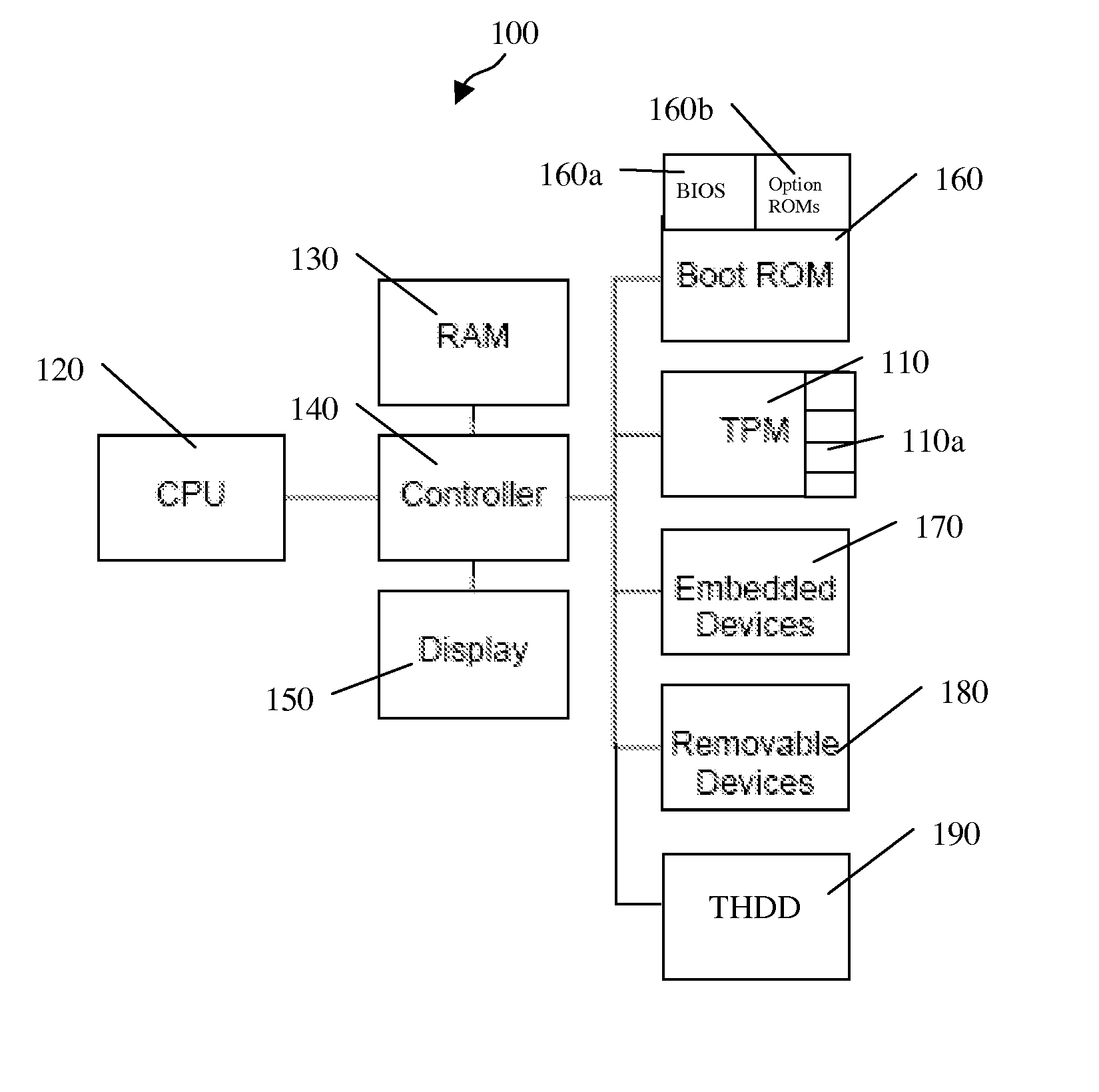
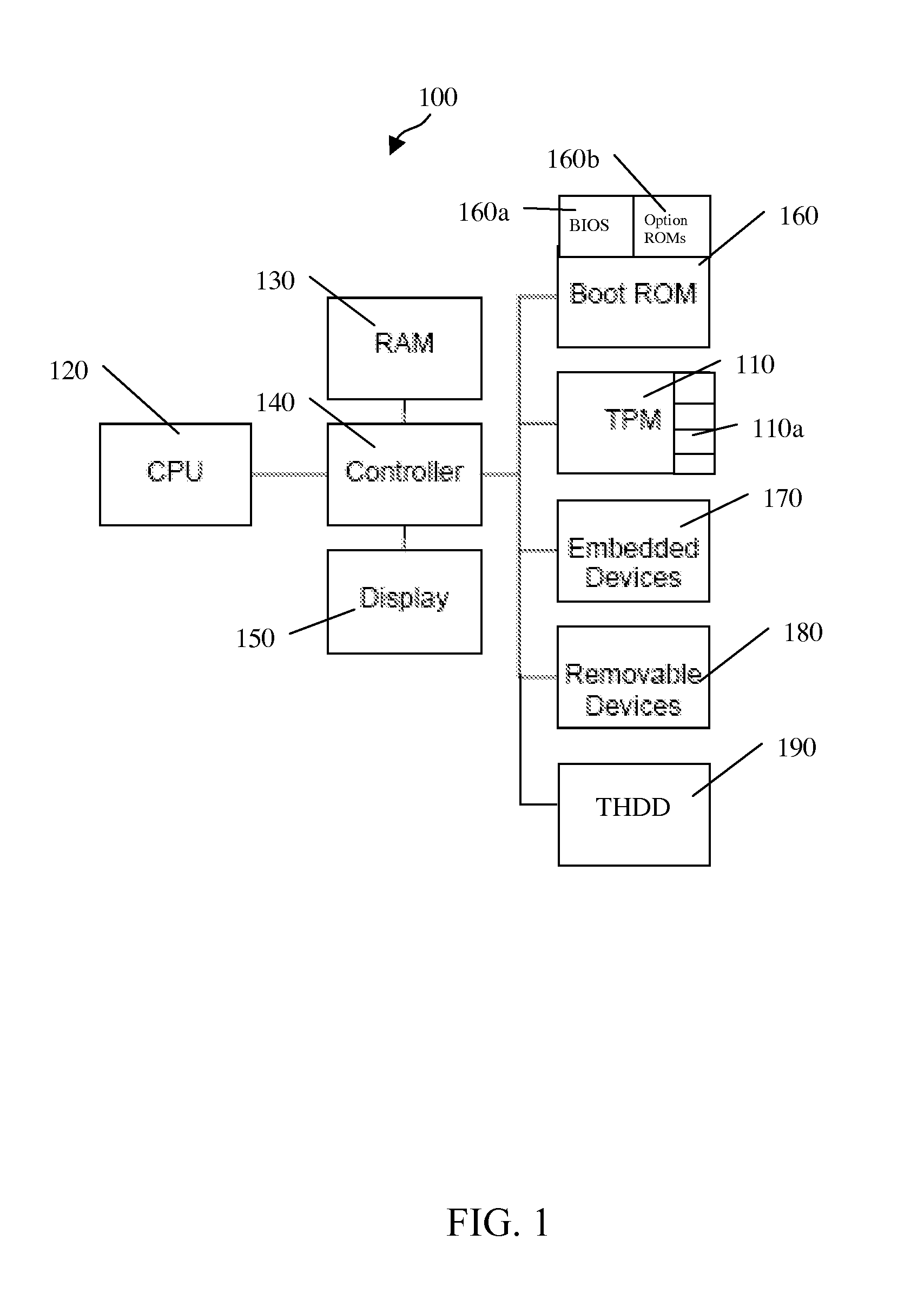
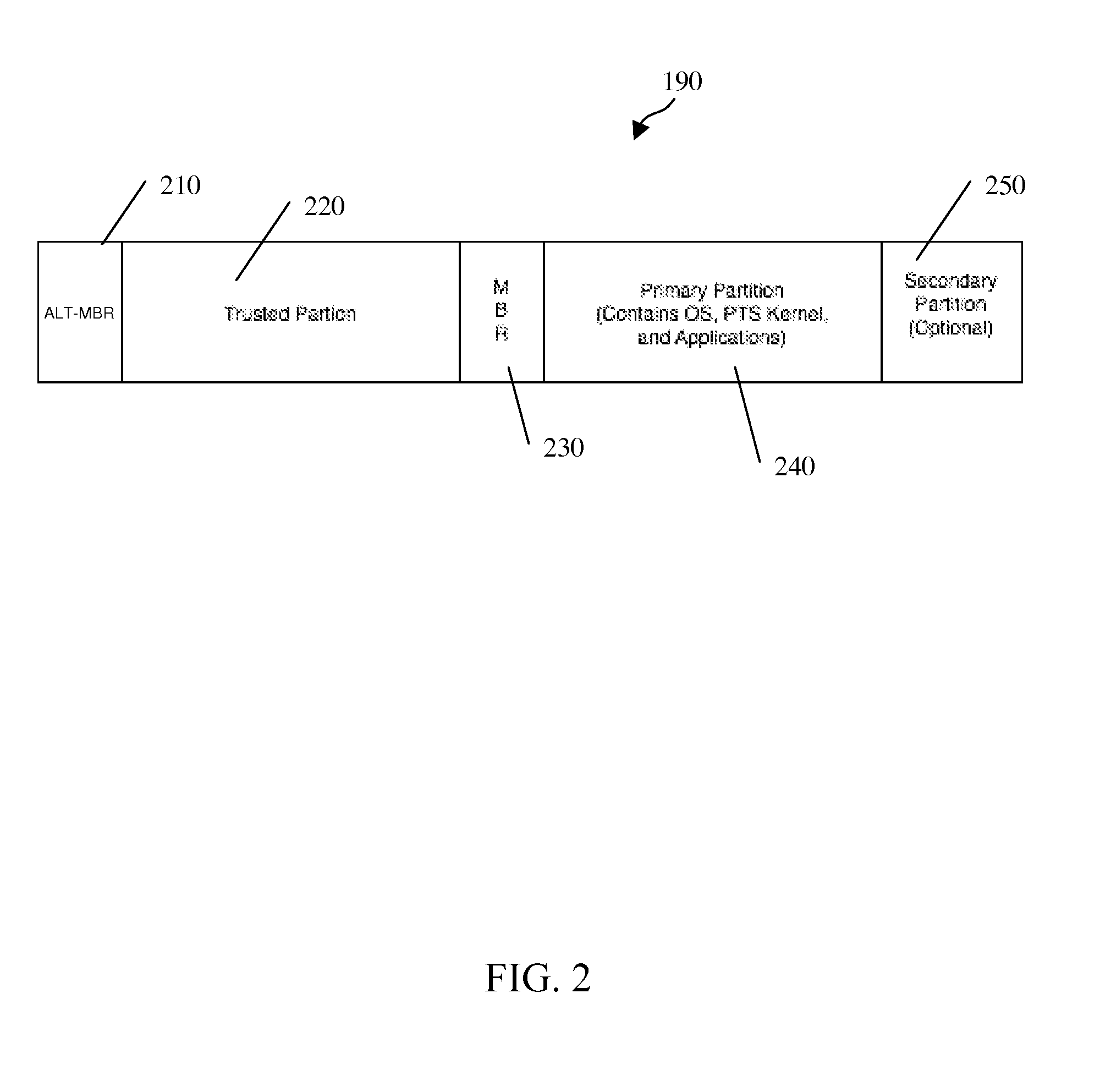
A trusted hard disk drive (“THDD”) contains cryptographic primitives and support functions in a trusted partition (“TP”). In particular, a master boot record (“MBR”) of the THDD is replaced with an alternative MBR and the normal MBR is stored elsewhere on the THDD. The program(s) loaded from the alternative MBR performs measurements of the TP. The TP, in turn, performs all necessary measurements of the MBR, a personal computer platform's OS, and the OS-present applications, including a platform trust service (“PTS”) kernel. The program(s) also performs functions to clear the PC platform's state such that any events that occurred prior to its execution do not alter the functionality of the OS-present applications. This may include clearing the PC's microprocessor, system memory and cache, for example. DRTM types of system resets may also be performed after the PC's OS has booted to force system clears without requiring OS or VMM infrastructure.
Owner:WAVE SYST
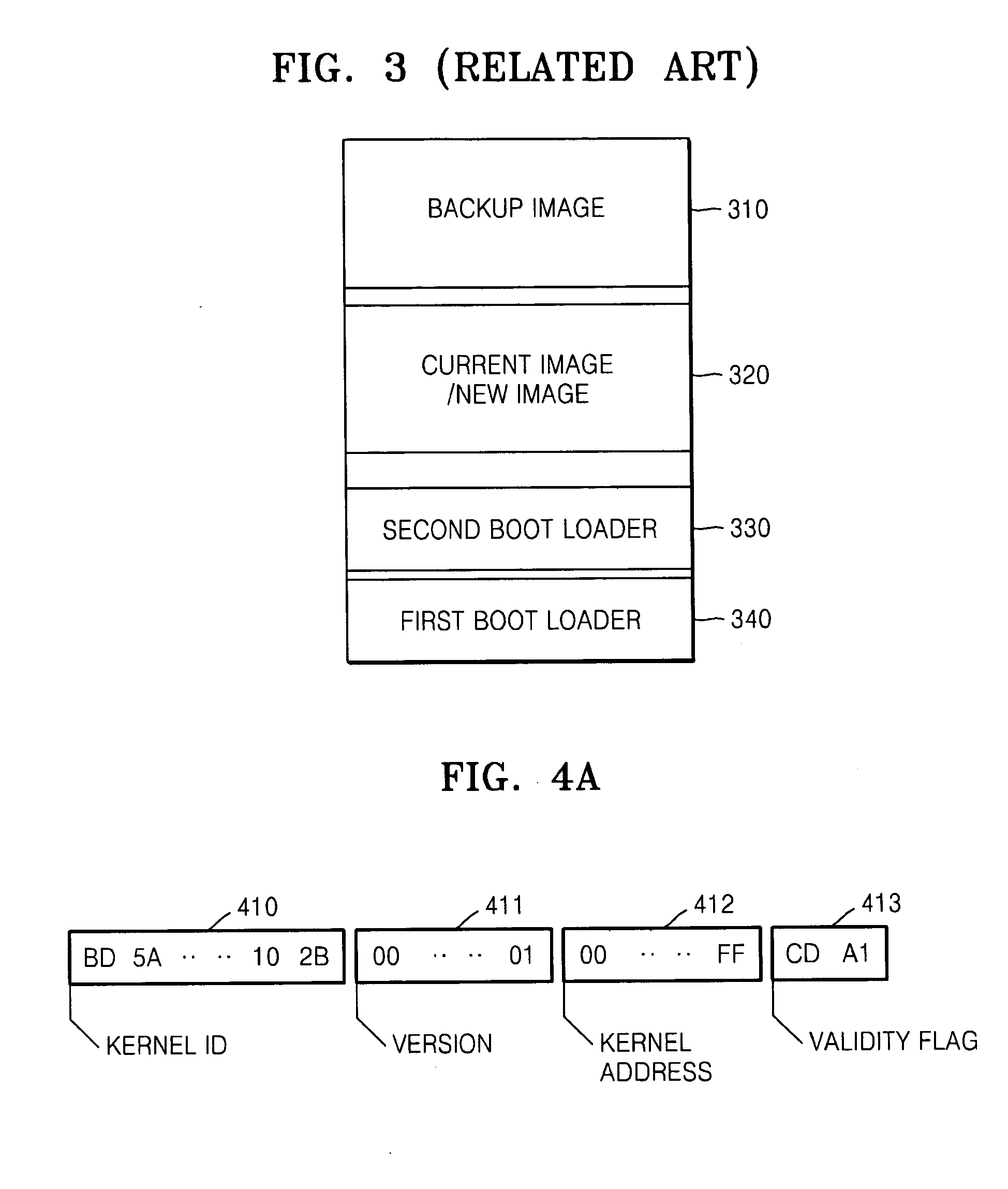
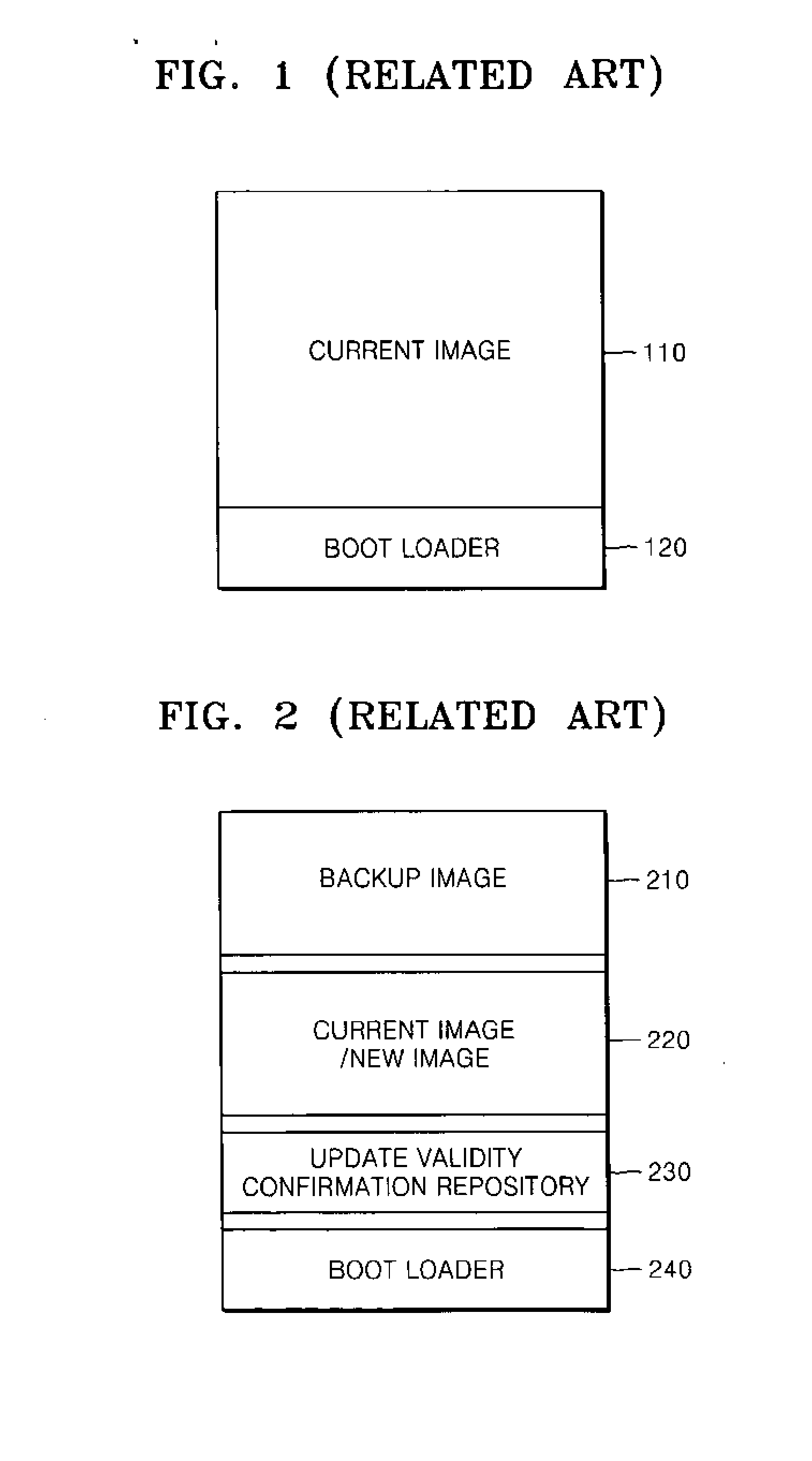
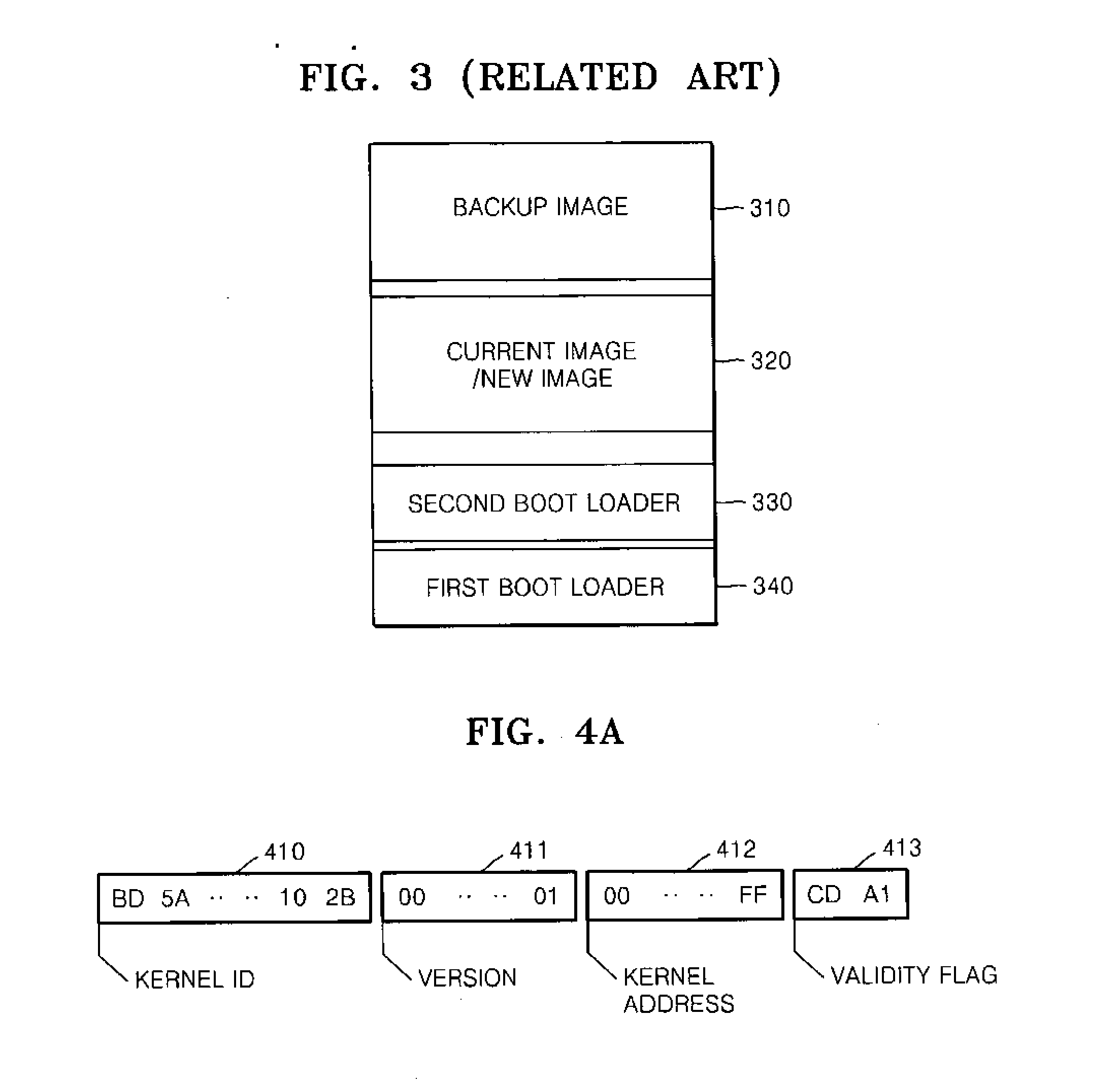
Method and system for booting and automatically updating software, and recovering from update error, and computer readable recording medium storing method
Provided are a booting method of updating software components installed in a system and recovering from an error that occurs in an update, a method and system for automatically updating the software and recovering from the error, and a computer readable recording medium storing the method. The master boot record and the backup boot record are used to stably update a kernel and effectively recover from an update error. The component configuration database is used to update a plurality of software components including a kernel in a transaction, and perfectly recover from an update error.
Owner:SAMSUNG ELECTRONICS CO LTD
MBR (Master Boot Record)-based GPS (Global Position System) track map matching method
InactiveCN102435197AImprove operational efficiencyHigh running precisionInstruments for road network navigationFault toleranceTopology information
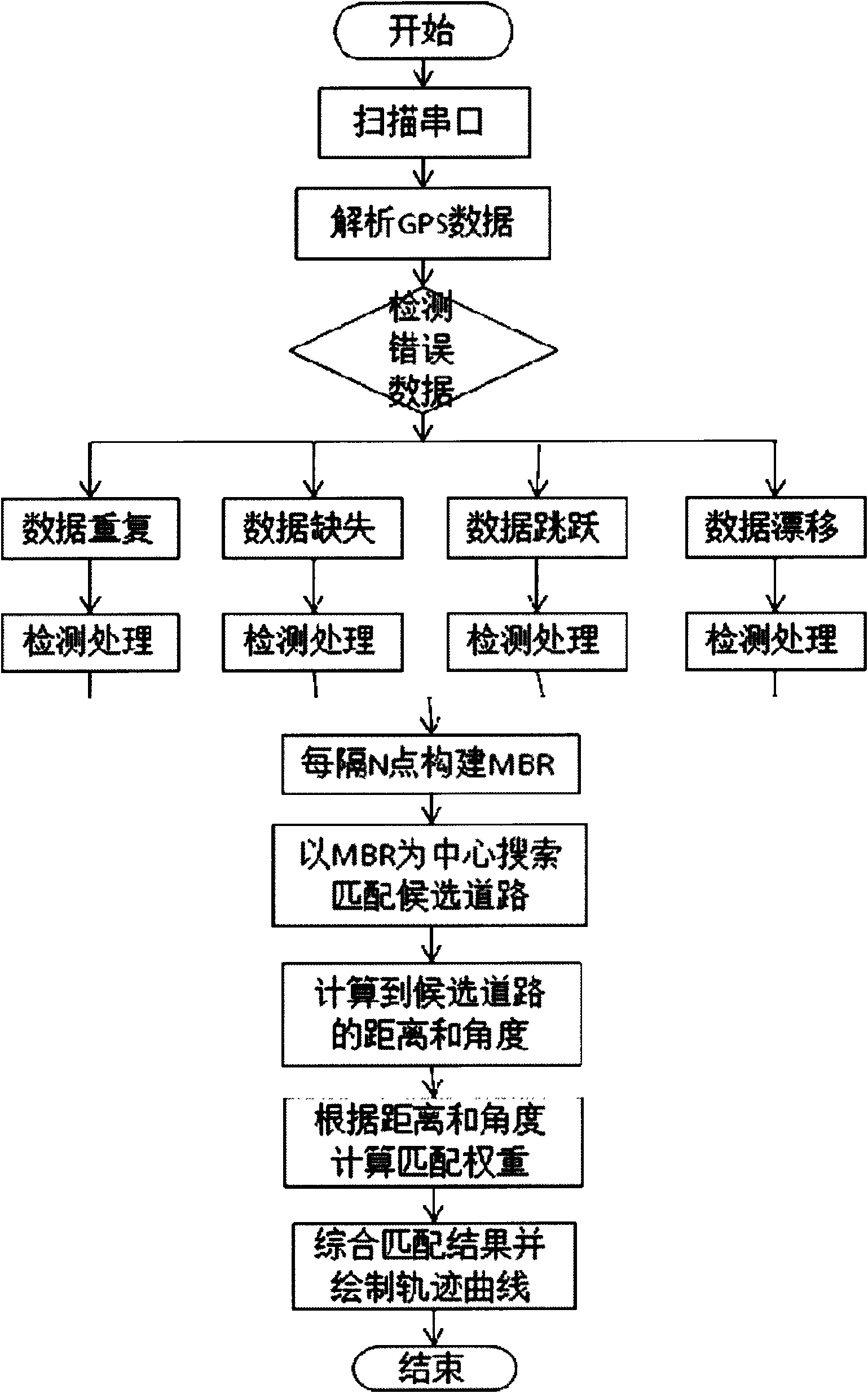
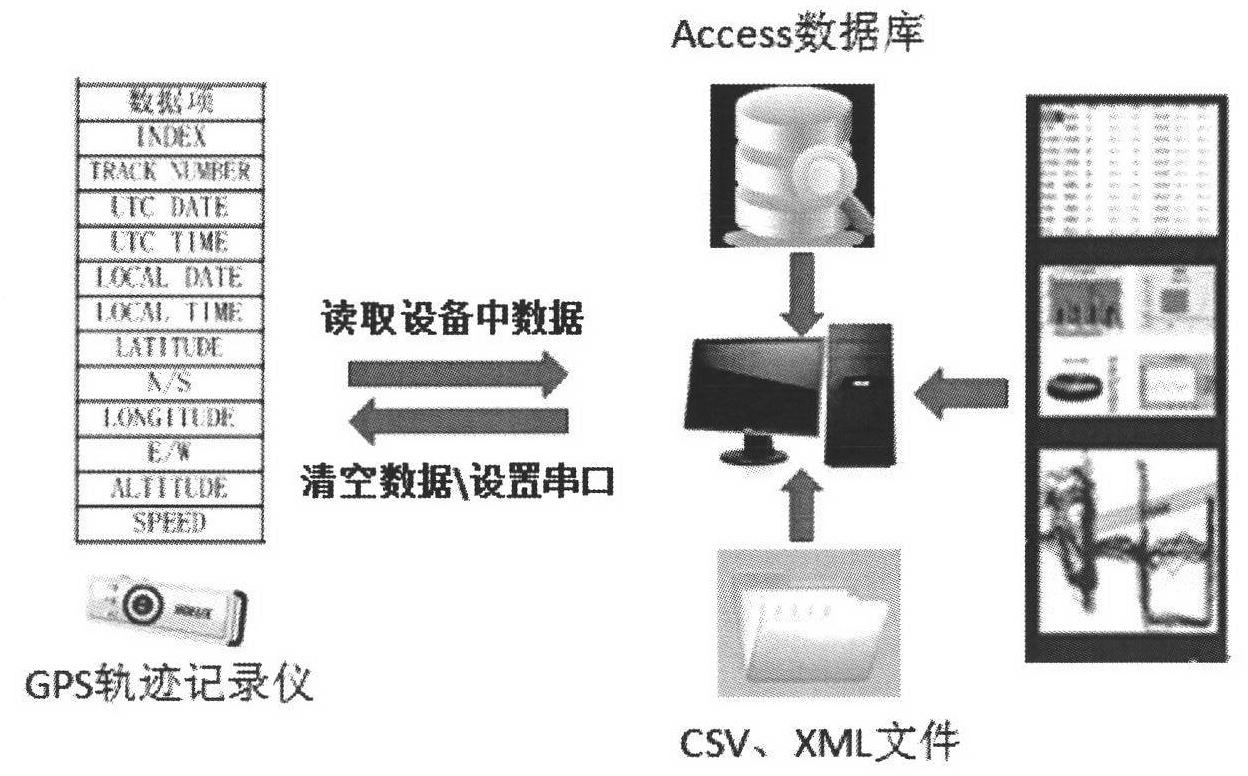
The invention discloses an MBR (Master Boot Record)-based GPS (Global Position System) track map matching method. Portable GPS equipment is connected with a computer host. The MBR-based GPS track map matching method has the following advantages and active effects: 1, historical information and road network topology information are introduced, and a matching path is judged by using the distance and angle, thus, the matching precision is improved, and errors are reduced; 2, the MBR-based GPS track map matching method is simple and effective, capable of processing larger data volume and good in real-time property, the complexity of matching calculation is lowered, and the time efficiency is increased; 3, the fault tolerance property is better, and incorrect data input is allowed; and 4, error point filtering is realized, and the positioning accuracy is further improved.
Owner:HUNAN UNIV OF SCI & TECH
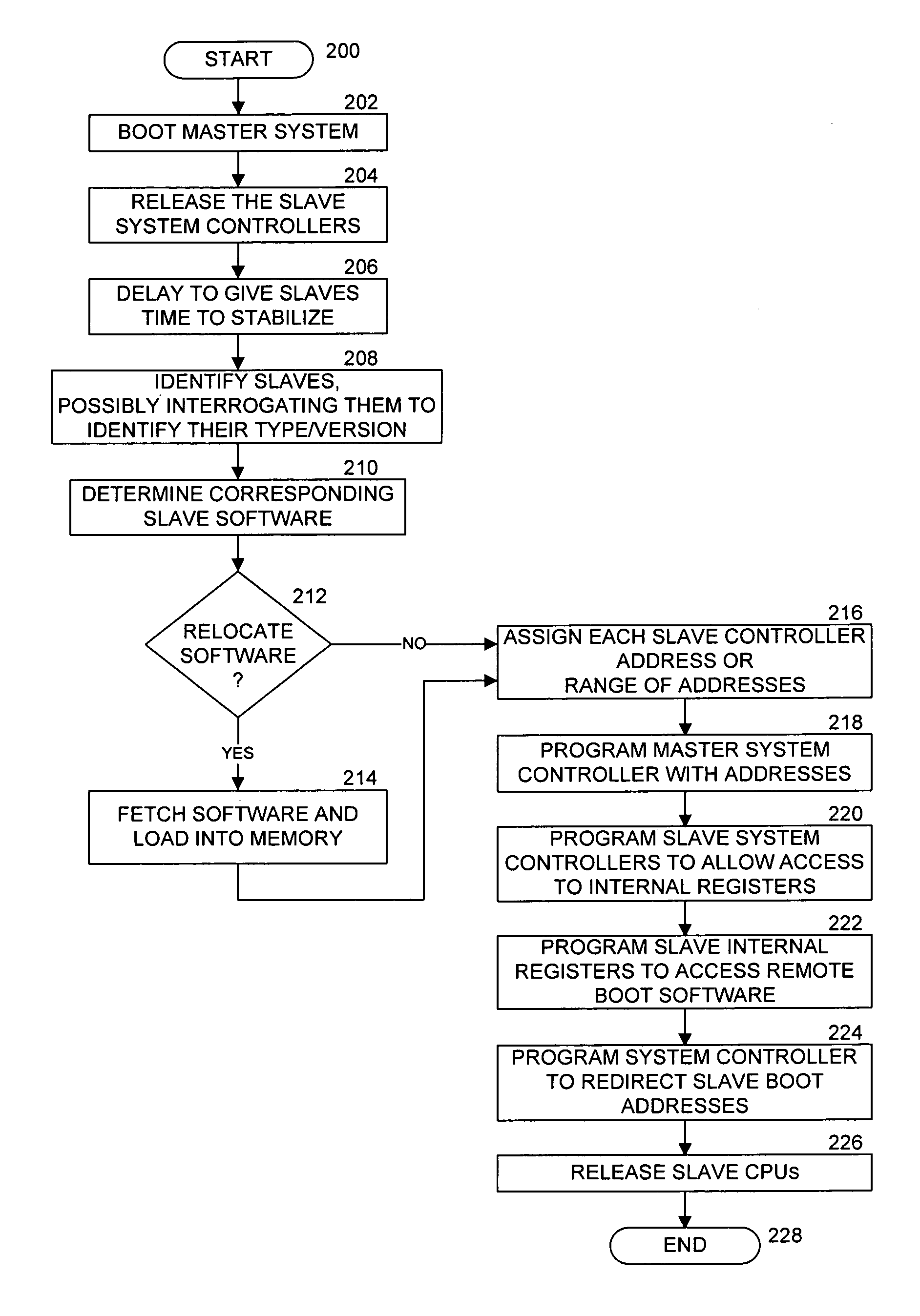
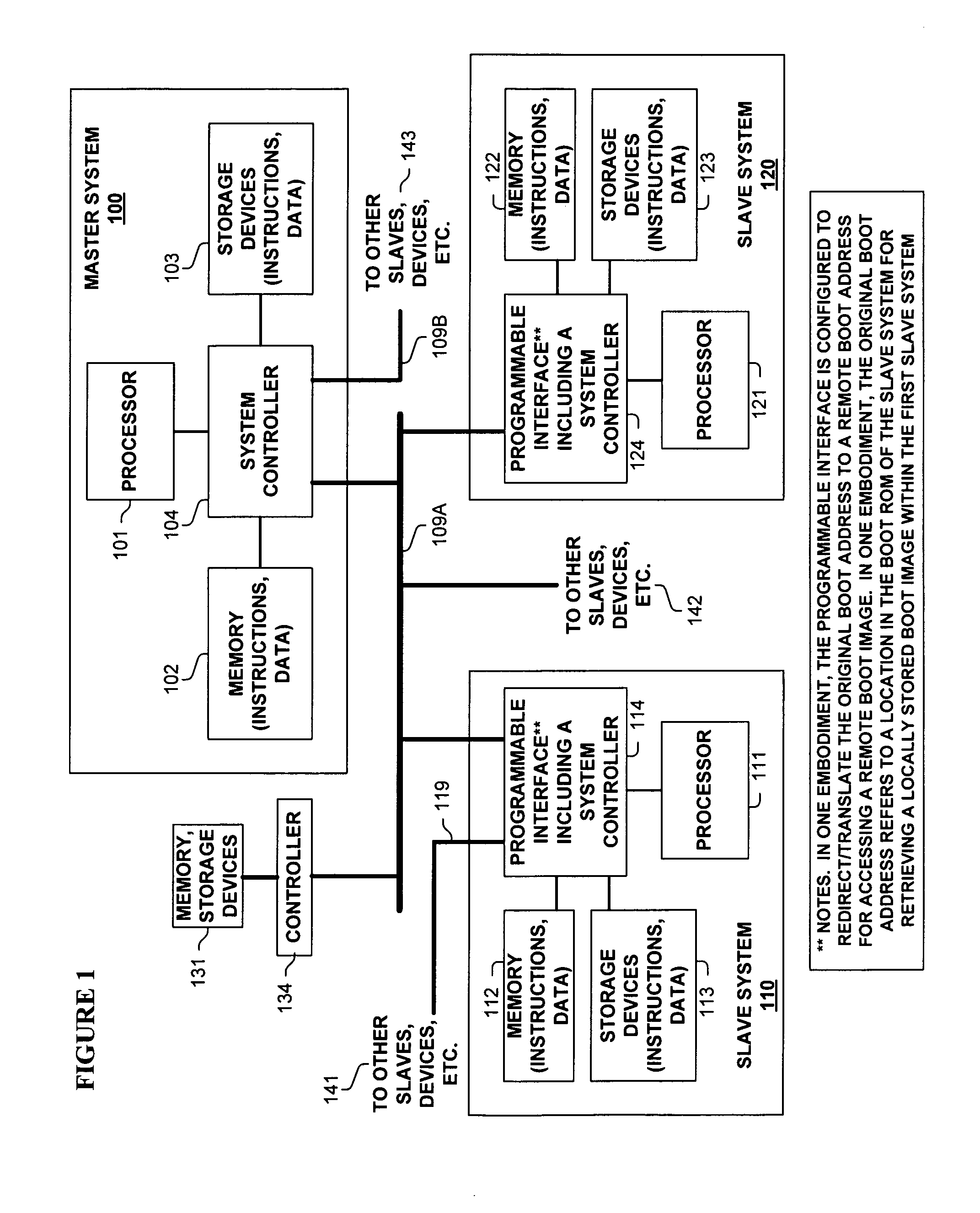
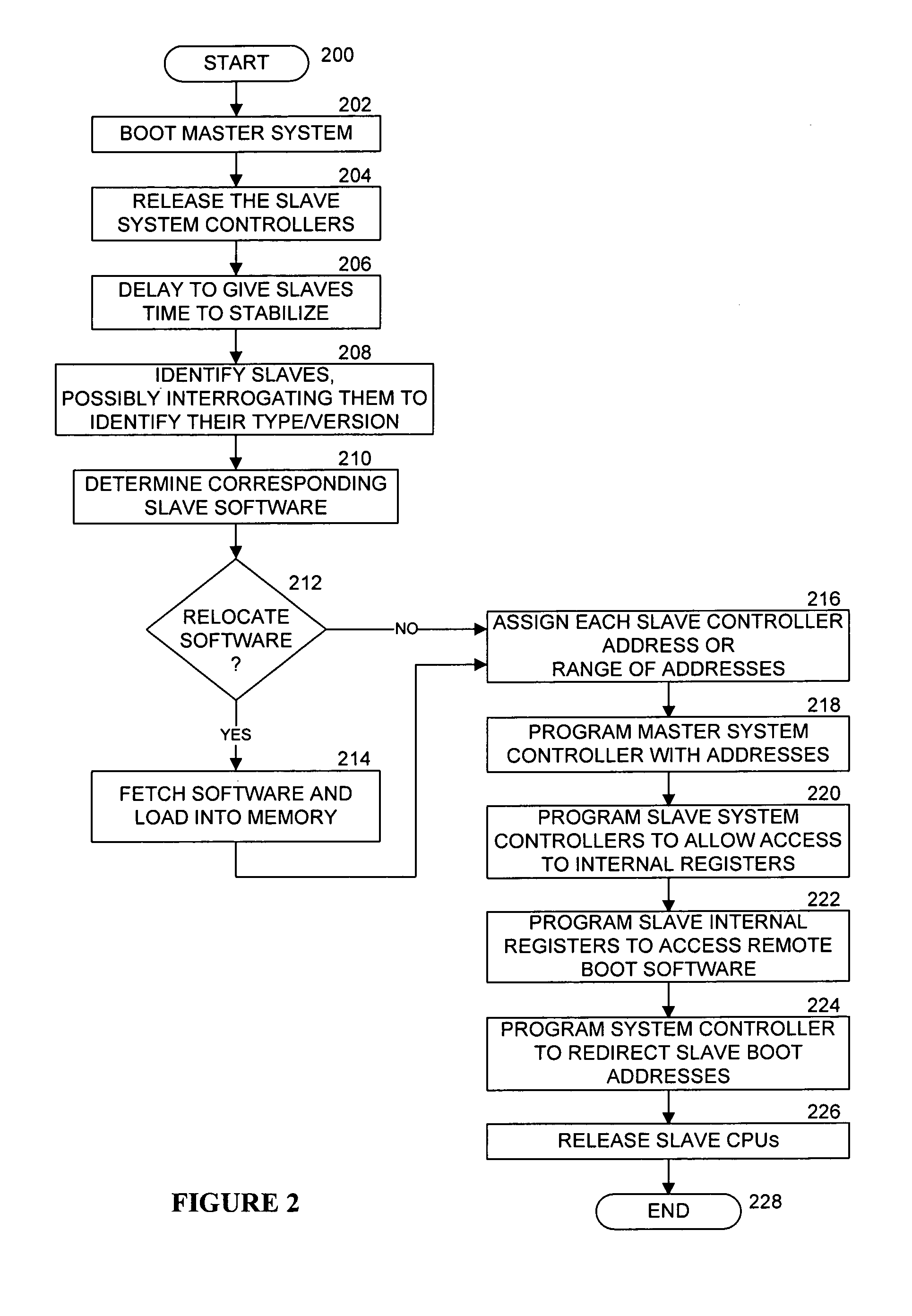
Method and apparatus for redirecting the boot operations of one or more systems
The boot operations of one or more systems may be redirected. For example, a master boot processor may configure a slave boot processor to boot over a communication bus existing between the processors, which typically eliminates the need for boot software in slave systems. This can be accomplished such as by the master system updating a programmable interface of the slave system to identify an image from which to boot, such as from a remote boot image stored external to the slave system.
Owner:CISCO TECH INC
Computer system starting method and computer terminal
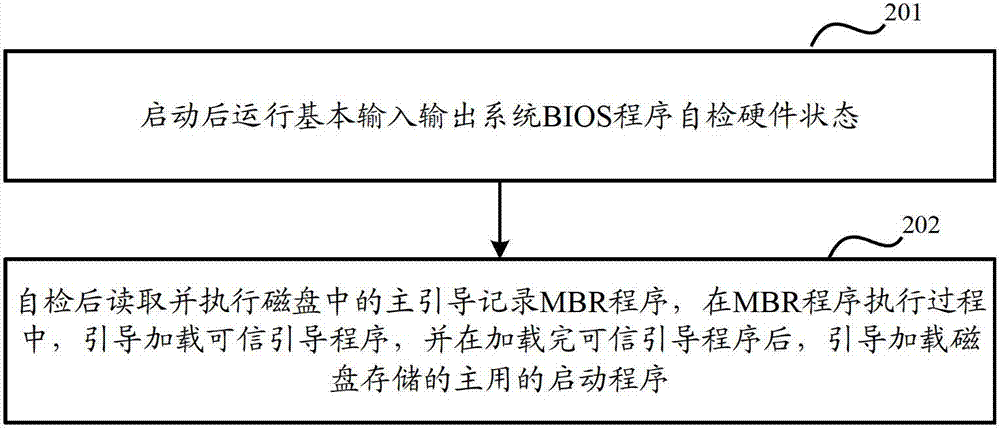
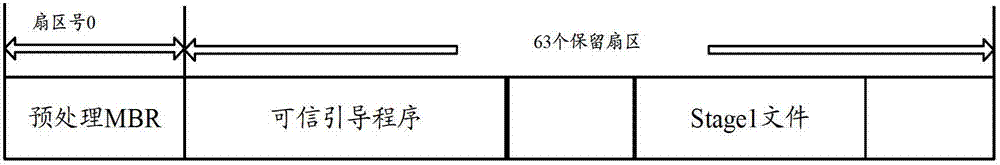
InactiveCN102830990ARealize authenticity verificationGuaranteed safe and reliableProgram loading/initiatingComputerized systemComputer terminal
The invention discloses a computer system starting method and a computer terminal. The computer system starting method comprises the following steps of: operating a program self-detection hardware state of a BIOS (Basic Input-Output System) after starting; reading and executing a MBR (Master Boot Record) program in a disk after self-detection; in an MBR program executing program, guiding and loading a trusted guide program; guiding and loading a main starting program stored in the disk after loading the trusted guiding program; in a process of loading the trusted guiding program, reading the main starting program stored in the disk so as to carry out credibility verification; when the credibility verification is not passed, reading the corresponding standby starting program in the disk to replace the main starting program which is not verified; and in a process of loading the main starting program stored in the disk, completing the starting program. According to the computer system starting method and the computer terminal provided by the invention, the starting process is safe and trusted.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method and system for booting and automatically updating software, and recovering from update error, and computer readable recording medium storing method
Provided are a booting method of updating software components installed in a system and recovering from an error that occurs in an update, a method and system for automatically updating the software and recovering from the error, and a computer readable recording medium storing the method. The master boot record and the backup boot record are used to stably update a kernel and effectively recover from an update error. The component configuration database is used to update a plurality of software components including a kernel in a transaction, and perfectly recover from an update error.
Owner:SAMSUNG ELECTRONICS CO LTD
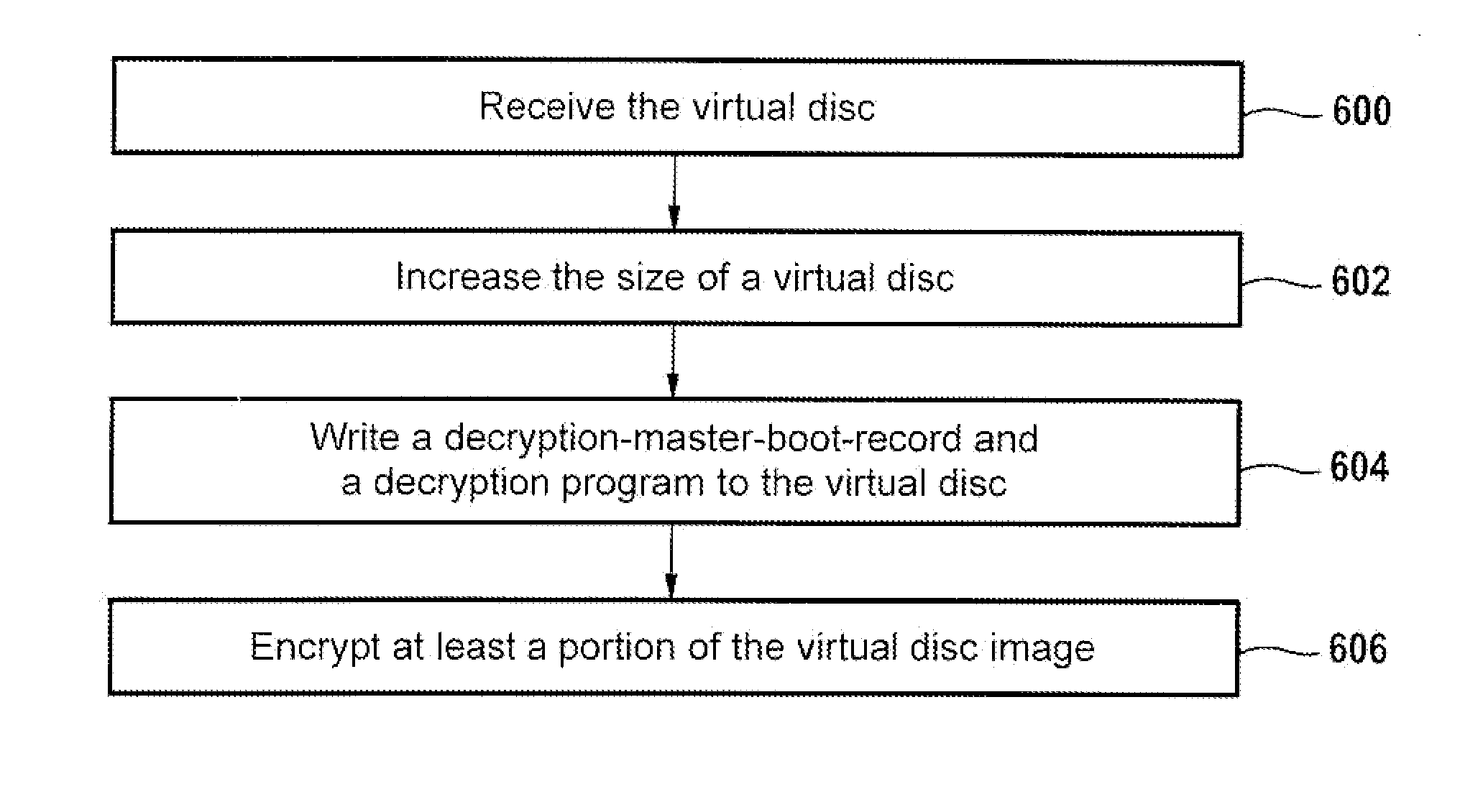
Encrypting and decrypting a virtual disc
InactiveUS20140380035A1Memory architecture accessing/allocationImage enhancementComputer hardwareMaster boot record
A computer-readable storage medium containing machine executable instructions that when executed by a processor cause the processor to encrypt a virtual disc; wherein the virtual disc comprises a virtual disc image; and wherein execution of the machine executable instructions cause the processor to: receive the virtual disc; increase the size of the virtual disc; write a decryption-master-boot-record and a decryption program to the virtual disc; encrypt at least a portion of the virtual disc image, wherein the decryption program comprises decryption-machine-executable-instructions for decrypting the at least partially encrypted virtual disc image in accordance with a cryptographic key.
Owner:IBM CORP
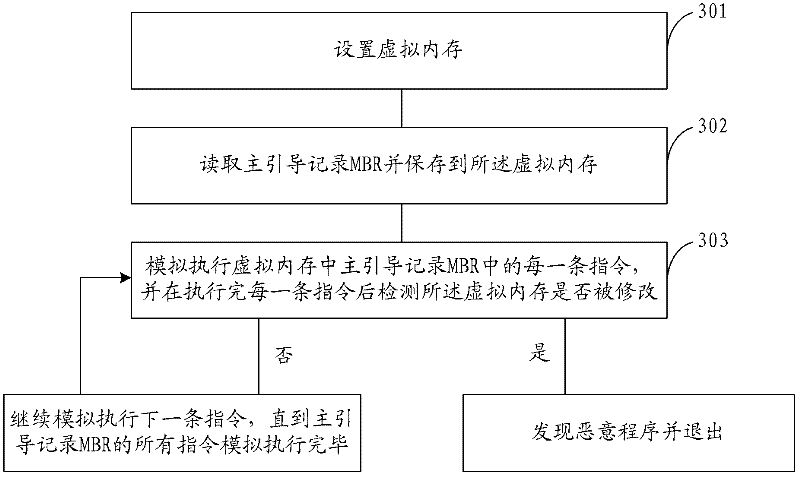
Method, device and virtual machine for detecting rogue program
ActiveCN102339371AFlexible usePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual memoryParallel computing
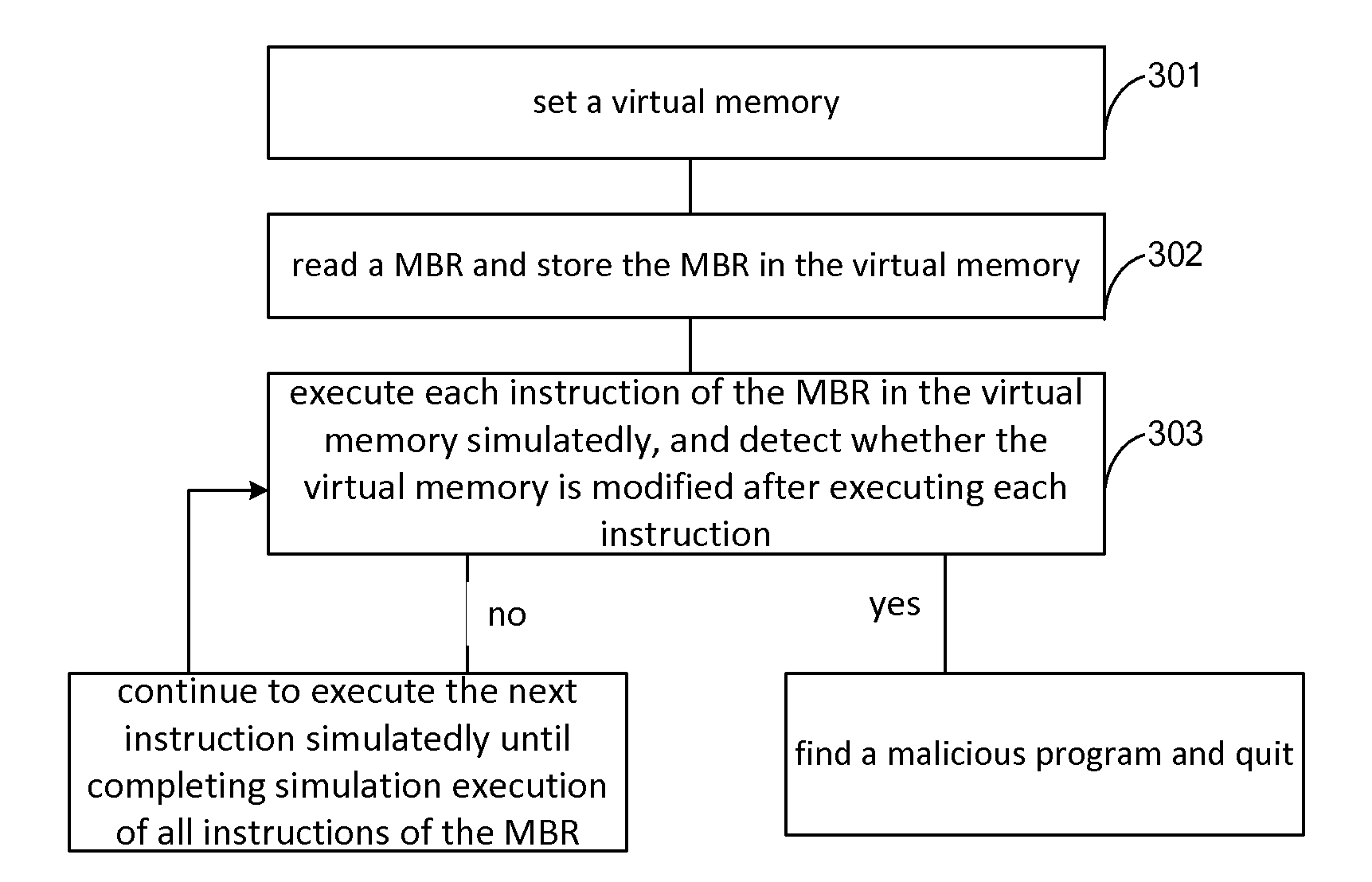
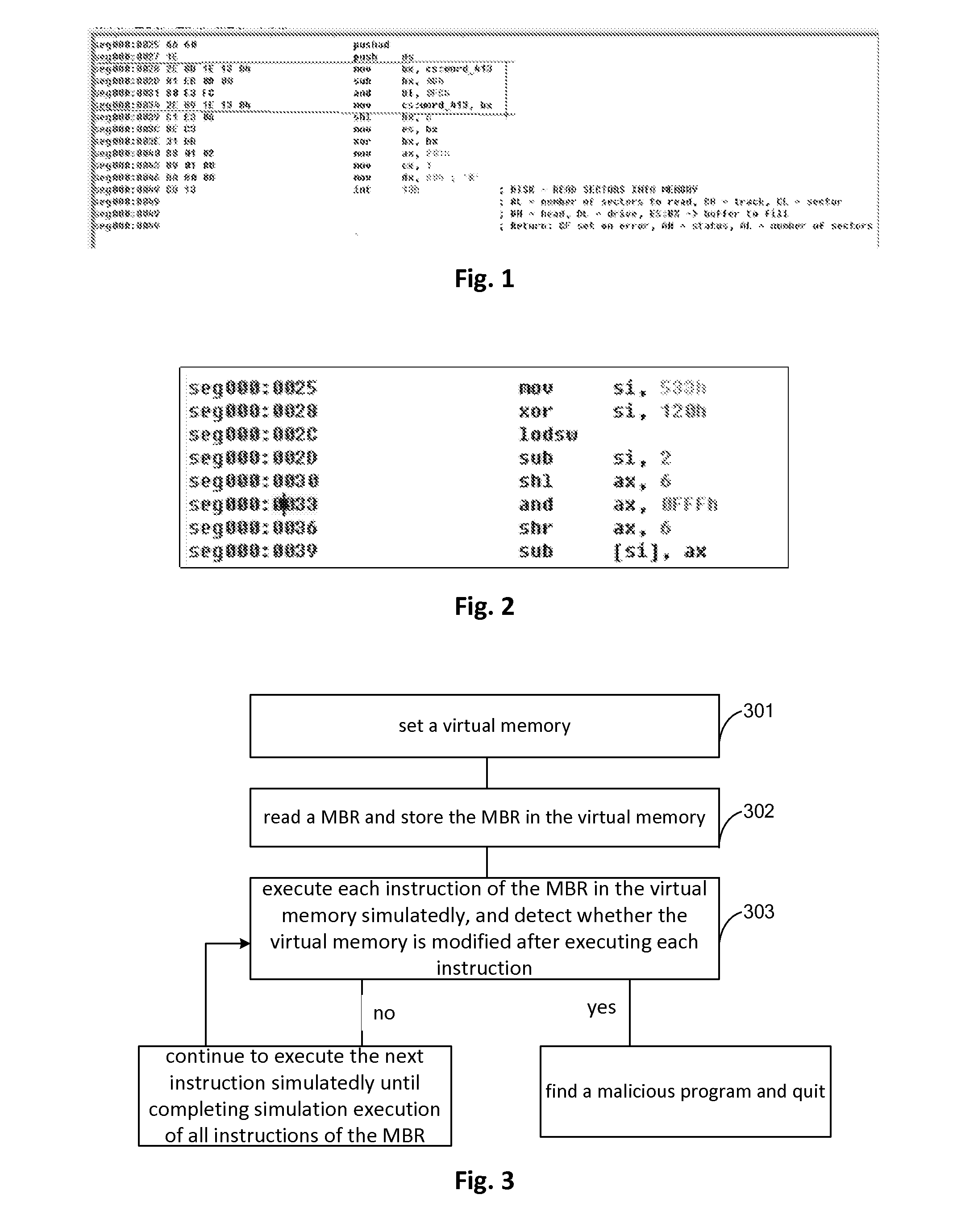
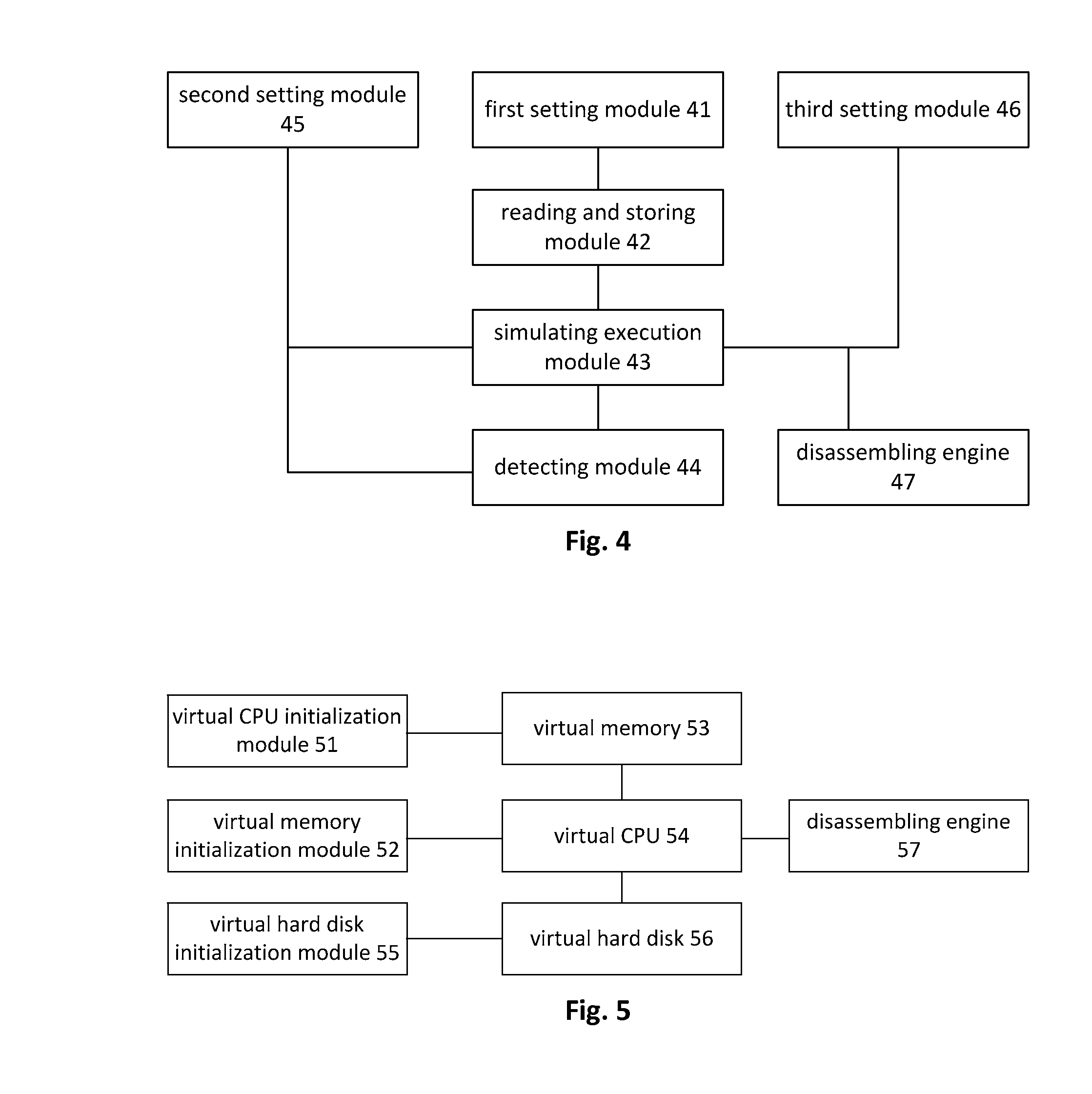
The invention provides a method, a device and a virtual machine for detecting a rogue program for solving the problem of the prior art that a transformative rogue program cannot be detected. The method comprises the following steps: setting a virtual memory; reading an MBR (Master Boot Record) and storing the MBR into the virtual memory; simulating to execute each instruction in the MBR in the virtual memory, and detecting if the virtual memory is modified after executing each instruction; and if being modified, confirming the rogue program, otherwise, continuing to simulate to execute the next instruction till finishing the simulated execution of all the instructions in the MBR. According to the method, any condition code converter technique can be ignored, and so long as an action occurs in a practical running, the action can be detected.
Owner:BEIJING HONGXIANG TECH SERVICE CO LTD
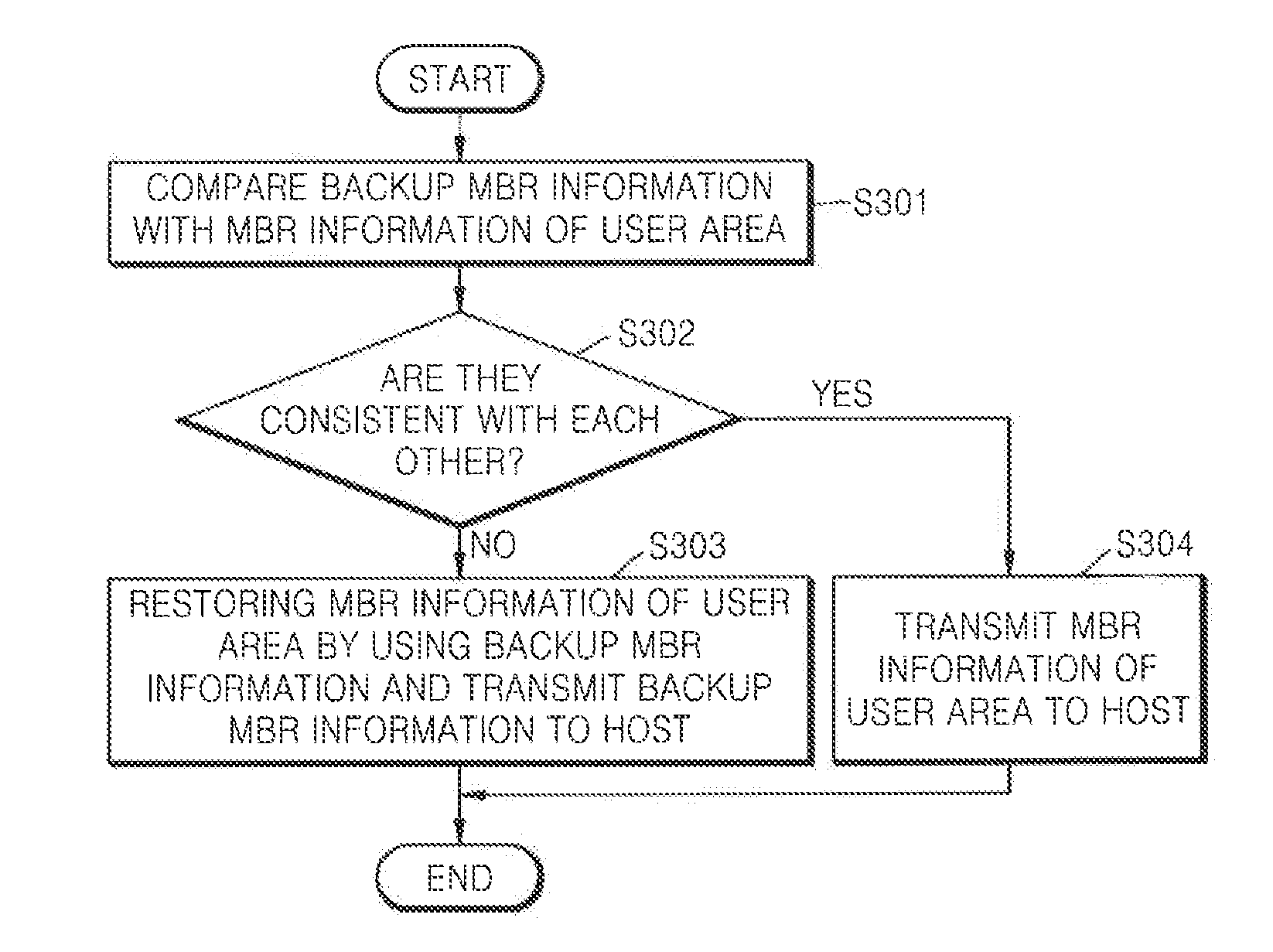
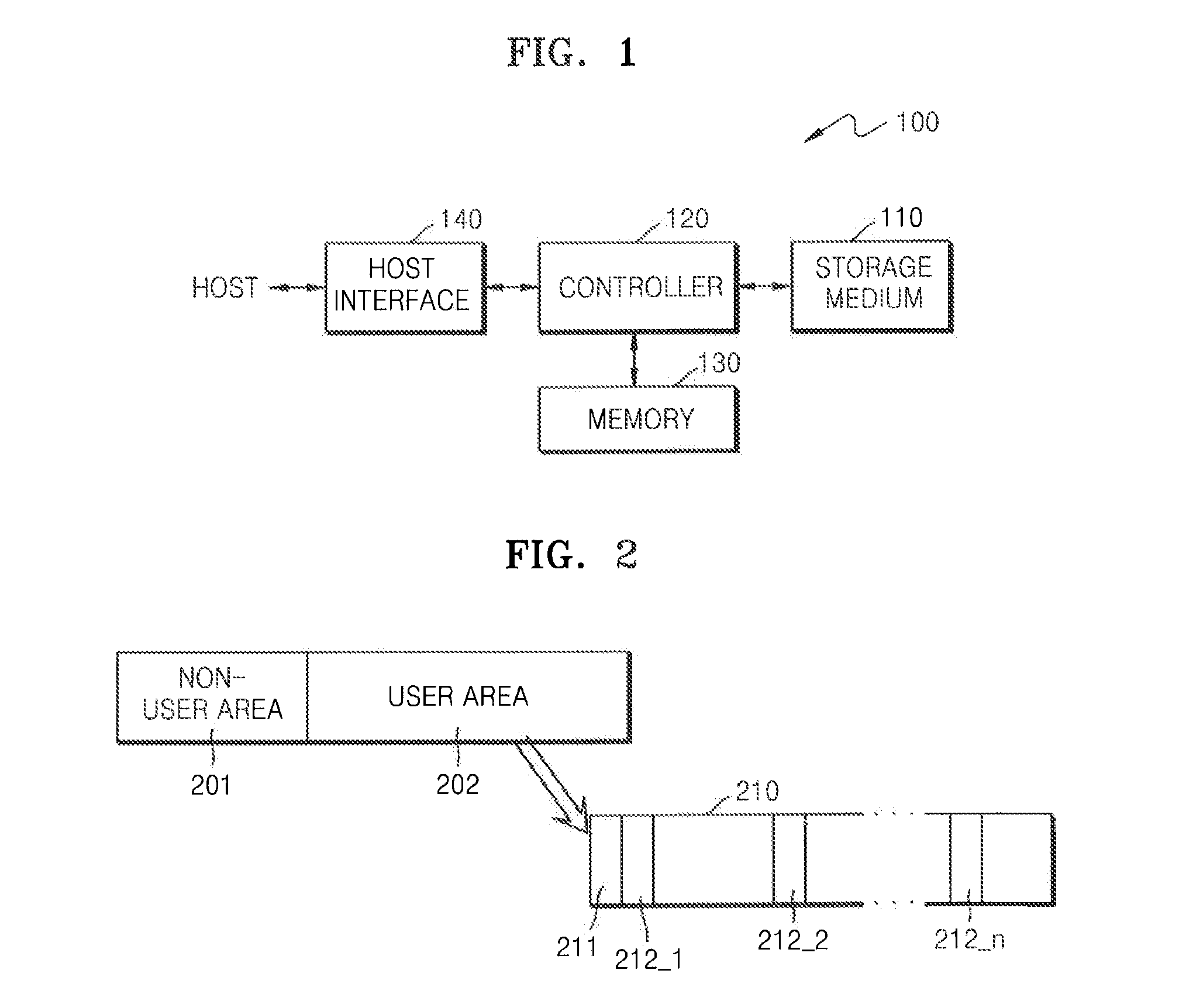
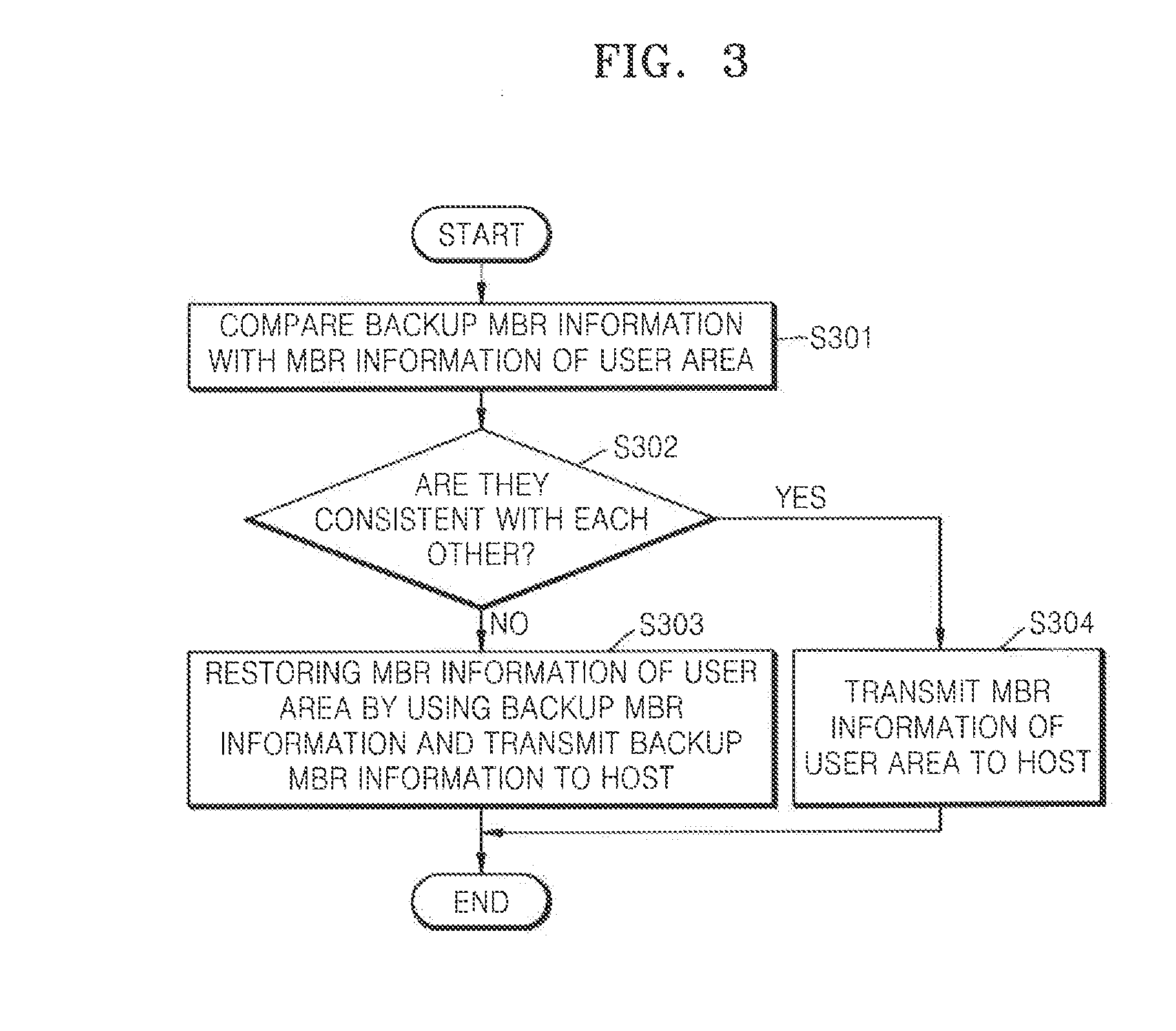
Method of restoring master boot record of storage medium, storage medium driving device, and storage medium
A storage medium driving device including a storage medium having a user area and a non-user area, and to record master boot record information that is backed up in the non-user area, and a controller to compare the backup master boot record information with master boot record information read from the user area, and to restore master boot record information recorded in the user area according to the comparison results.
Owner:SEAGATE TECH INT
MID (Mobile Internet Device) multiple operating system parallelizing method
InactiveCN101957769AExtend User ObjectExpand the scope of applicationProgram loading/initiatingExternal storageOperational system
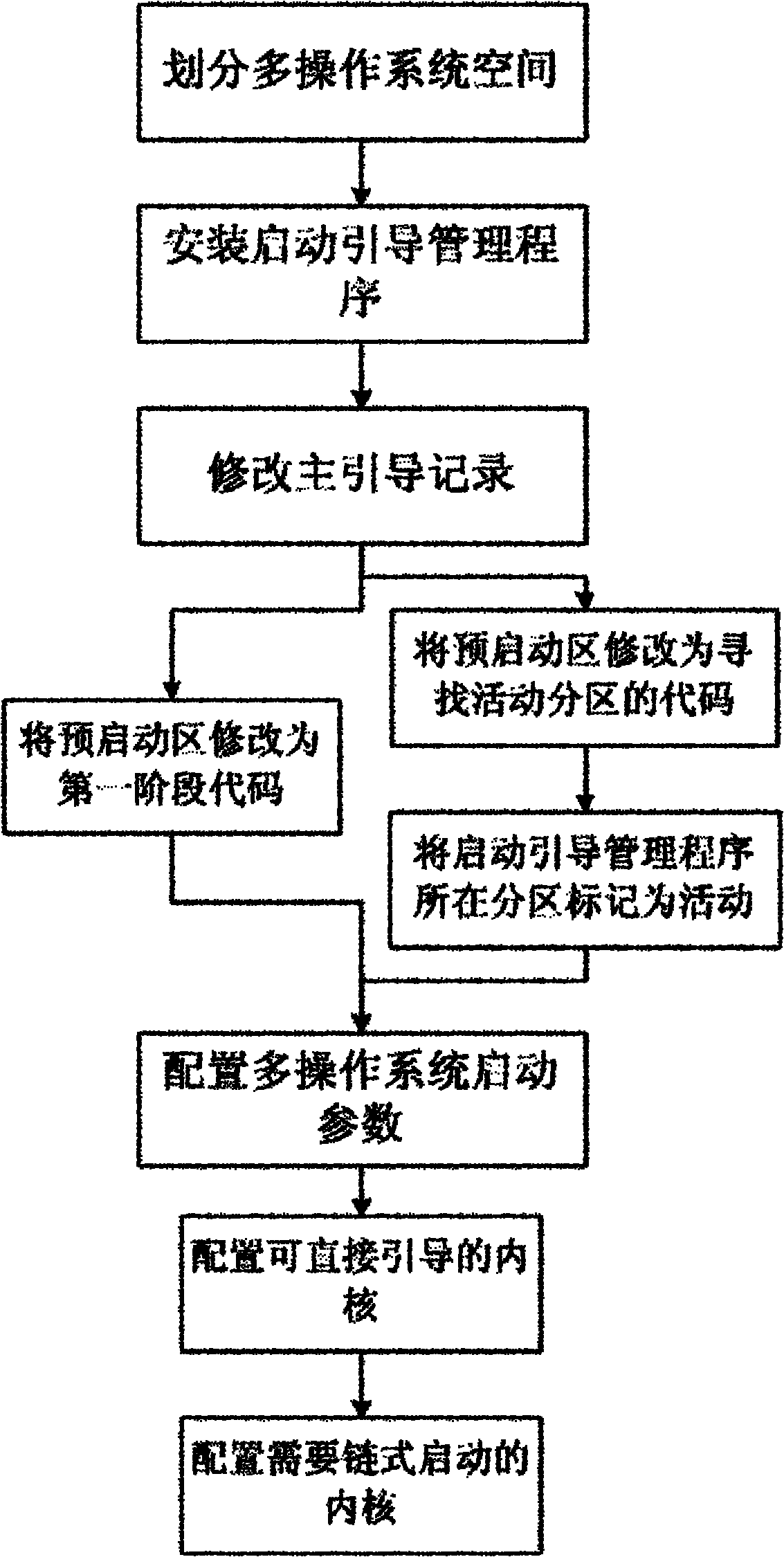
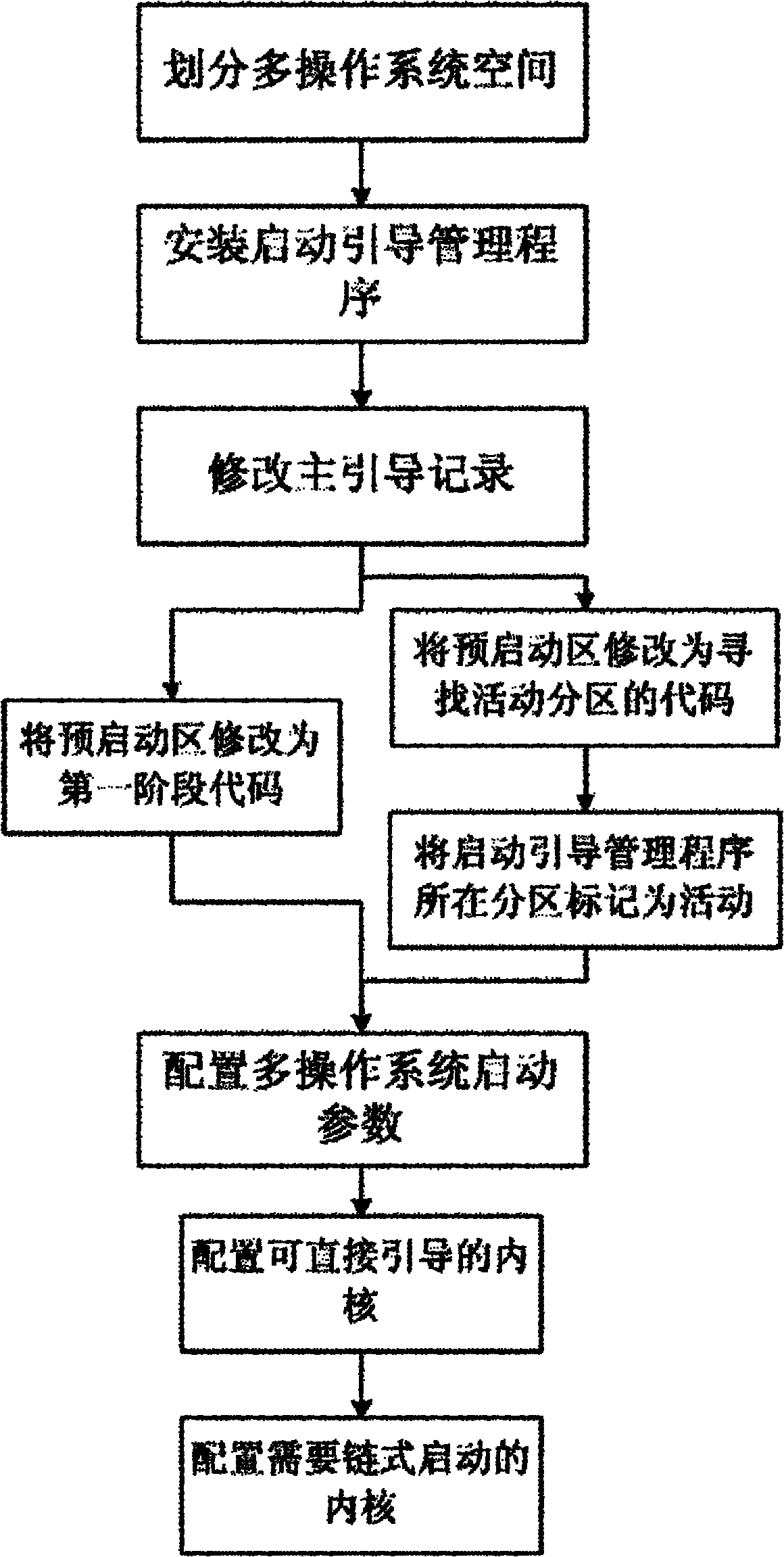
The invention discloses an MID (Mobile Internet Device) multiple operating system parallelizing method. The mater boot record of an external memory such as SSD (Solid State Disk) hardware on the MID is modified, an operation system start-up boot management program is added, the external memory is reasonably partitioned for be used by multiple operating systems, and thus, the penalization and the coexistence of two even more operating systems are achieved. The method effectively widens the user objects and the application range of the MID, a user can experience multiple operating systems without purchasing additional hardware, and the multiple operating systems can be conveniently switched through the start-up boot management program.
Owner:ZHEJIANG UNIV
Method and system for providing an event driven image for a boot record
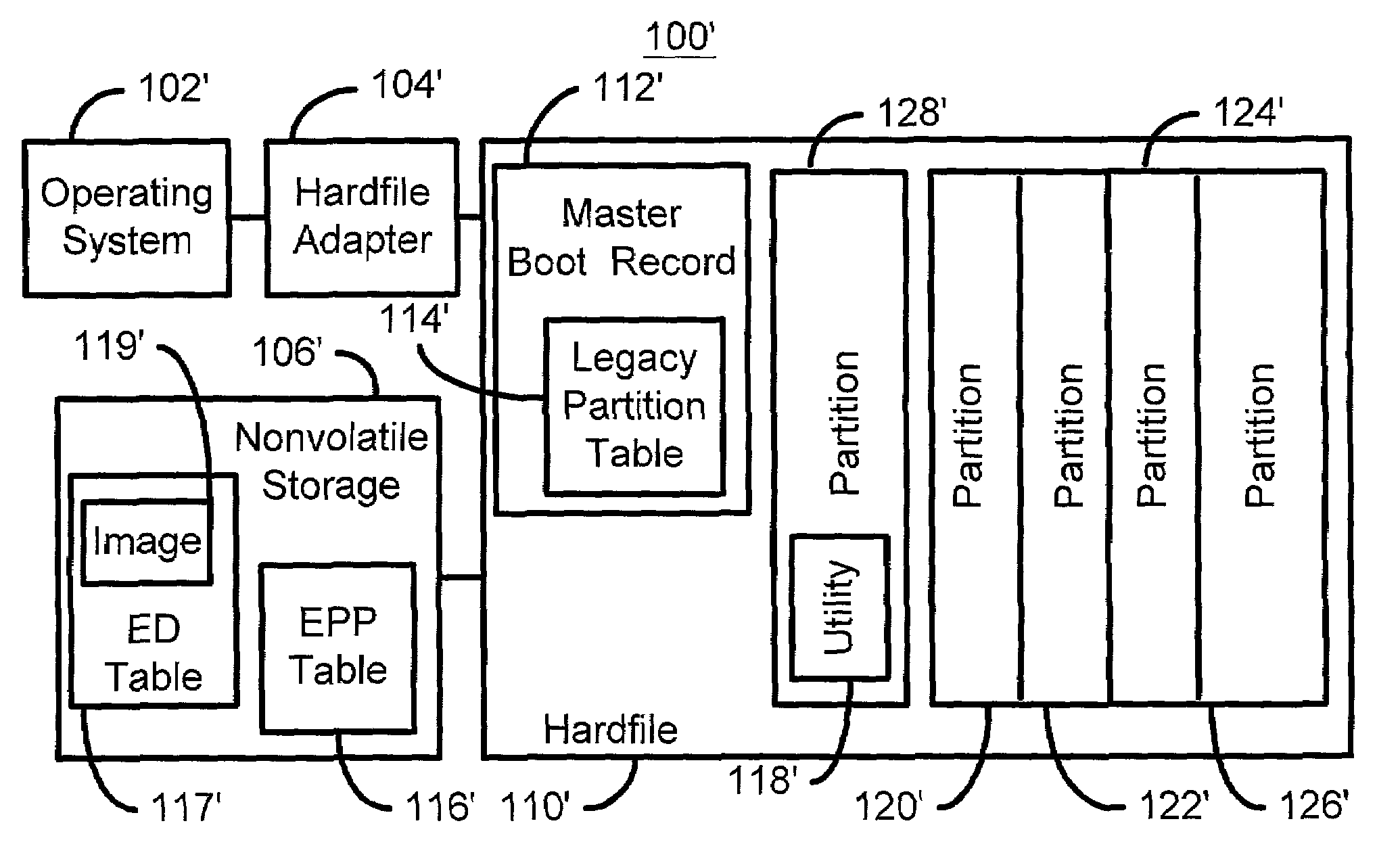
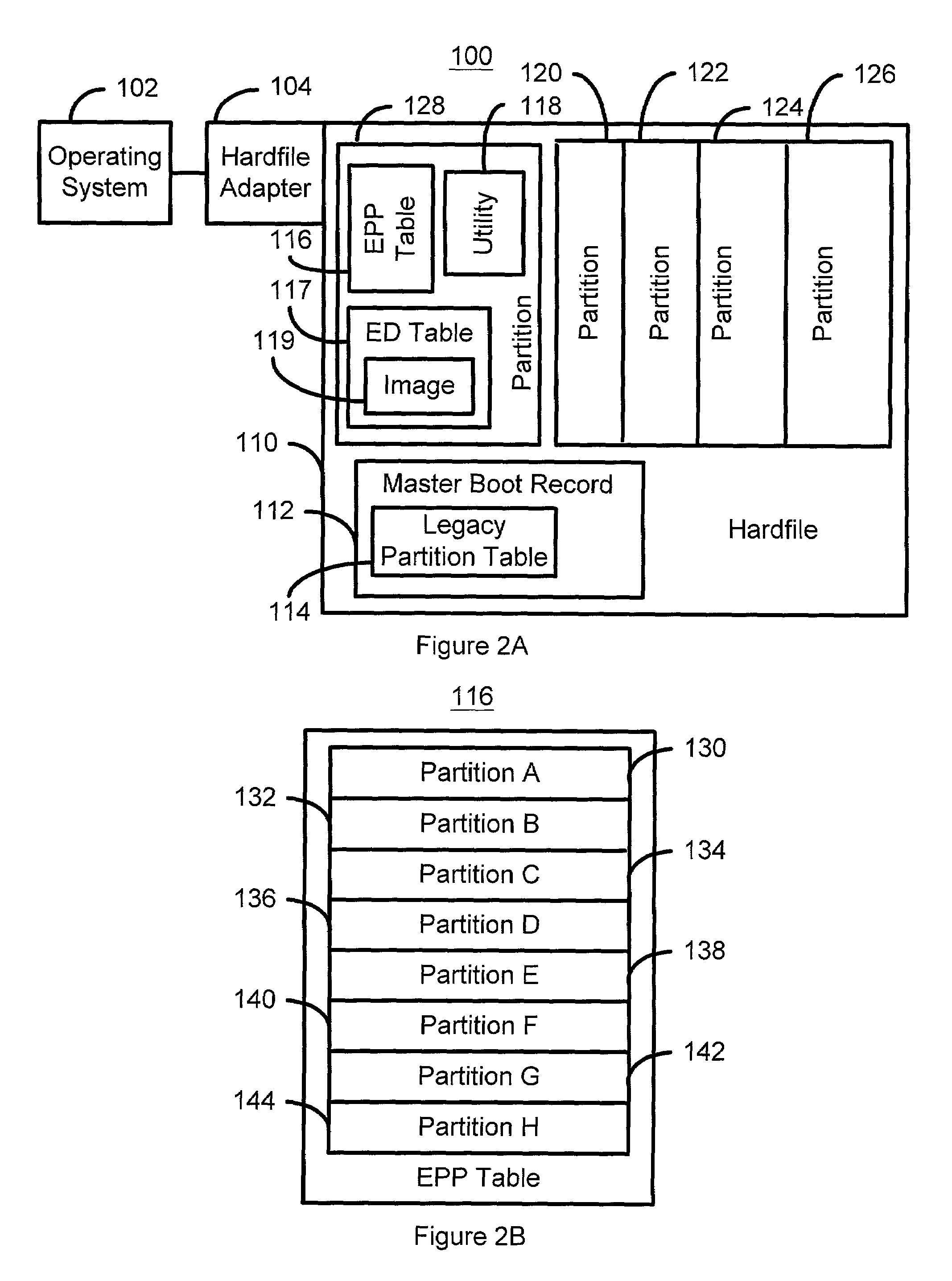
A method and system for providing an event driven hardfile image in a computer system is disclosed. The computer system includes a hardfile, a hardfile adapter, a master boot record and an operating system. The method and system include providing an extended physical partition table describing a plurality of partitions on the hardfile and defining at least one image using a utility. Each image corresponds to at least a portion of the plurality of partitions and to a corresponding event. An image is to be mapped to the master boot record in response to an occurrence of the corresponding event. The method and system also include providing an event driven table including each of the at least one image.
Owner:TWITTER INC
System and Method for Authenticating a Gaming Device
ActiveUS20120131322A1Digital data processing detailsAnalogue secracy/subscription systemsBIOSEncryption
A method and system are provided for authenticating and securing an embedded device using a secure boot procedure and a full non-volatile memory encryption process that implements Elliptic Curve Pinstov-Vanstone Signature (ECPV) scheme with message recovery on a personalized BIOS and master boot record. The signature includes code that is recovered in order to unlock a key that is in turn used to decrypt the non-volatile memory. The use of ECPVS provides an implicit verification that the hardware is bound to the BIOS since the encrypted memory is useless unless properly decrypted with the proper key.
Owner:MALIKIE INNOVATIONS LTD
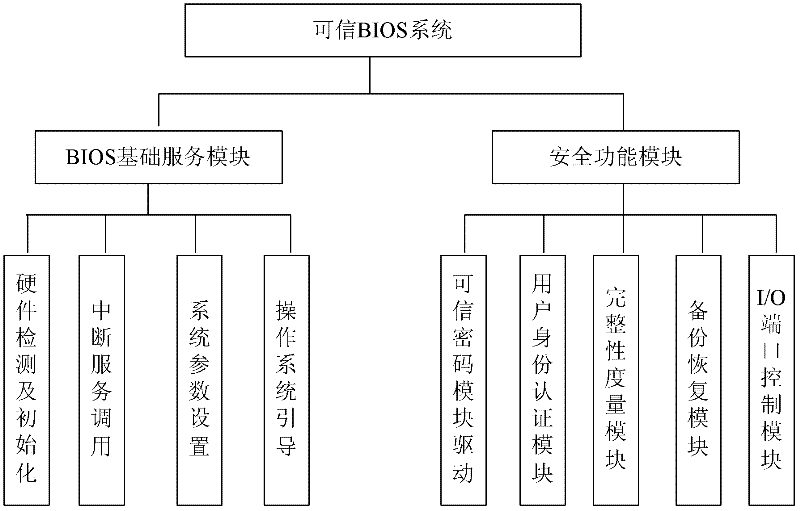
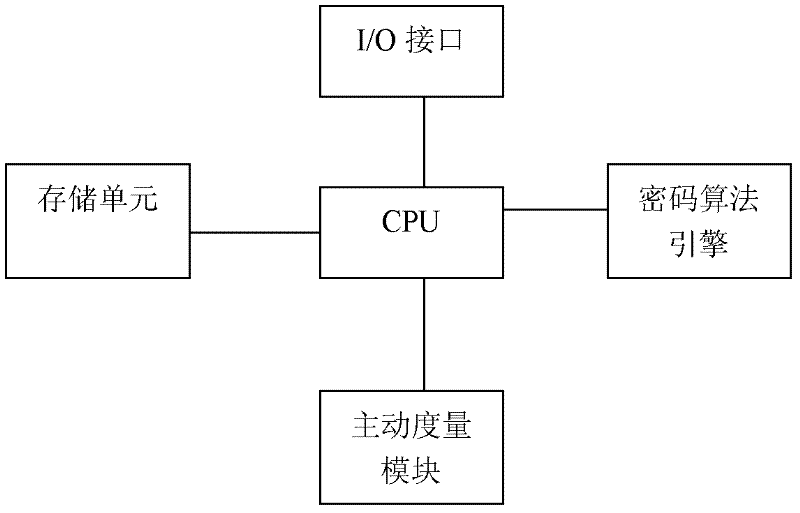
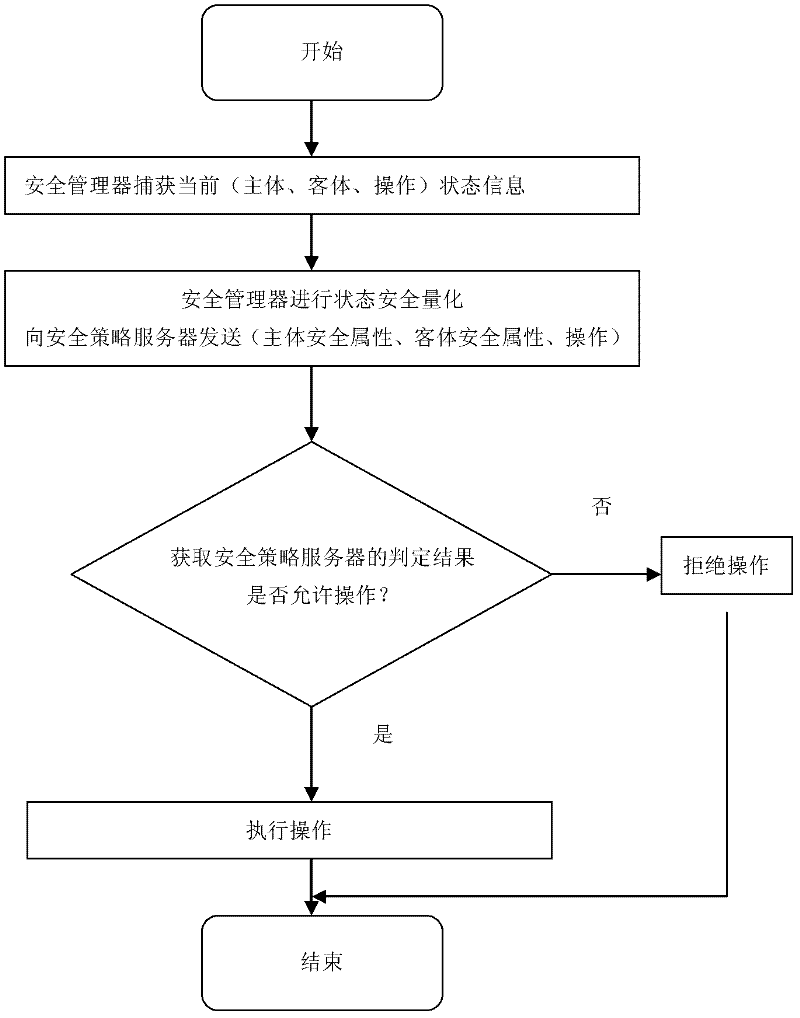
A Trusted Software Base for Proactive Security Services
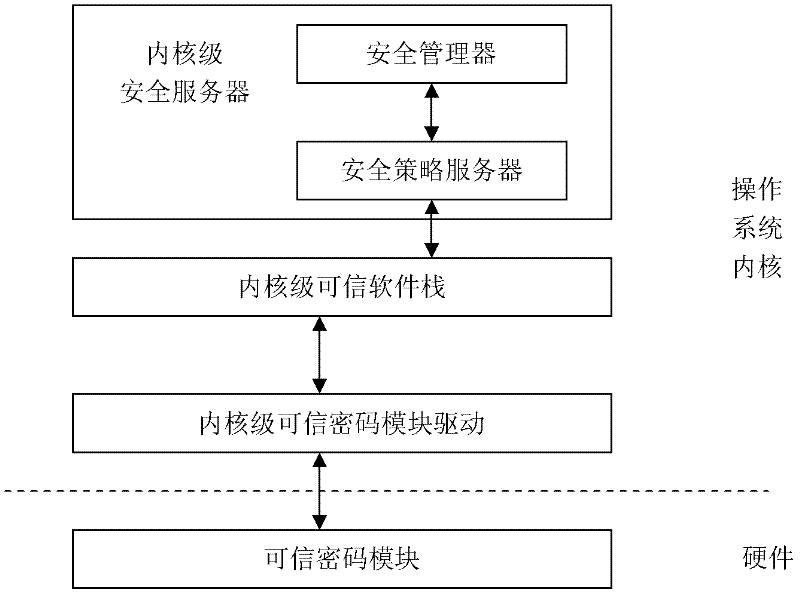
InactiveCN102270287APrevent unauthorized operationsPrevent unauthorized modificationPlatform integrity maintainanceActive safetyBIOS
The invention discloses a trusted software base providing an active security service, comprising a trusted password module and an operating system kernel. The operating system kernel is provided with a kernel-level trusted password module driver, a kernel-level trusted software stack and a kernel-level security service module; a security manager and a security strategy server are arranged in the kernel-level security service module; the trusted password module provides a hardware engine for encryption operation and hash operation, and verifies integrity of a trusted BIOS (Basic Input / Output System); the trusted BIOS is used for verifies the integrity of PC hardware devices and an MBR (Master Boot Record); the MBR is used for guiding an OS (Operating system) Loader, and verifies the integrity of the OS Loader; and the kernel-level security service module captures security related information at a key security control point in a kernel layer of the operating system, and performs access control and least privilege control. The trusted software base effectively prevents unauthorized operations and rogue programs from performing unauthorized modification on application codes and configurations, and prevents secret disclosure of application resources, thereby guaranteeing the privacy and the integrity of an application environment.
Owner:中国人民解放军海军计算技术研究所
Semiconductor memory card access apparatus, a computer-readable recording medium, an initialization method, and a semiconductor memory card
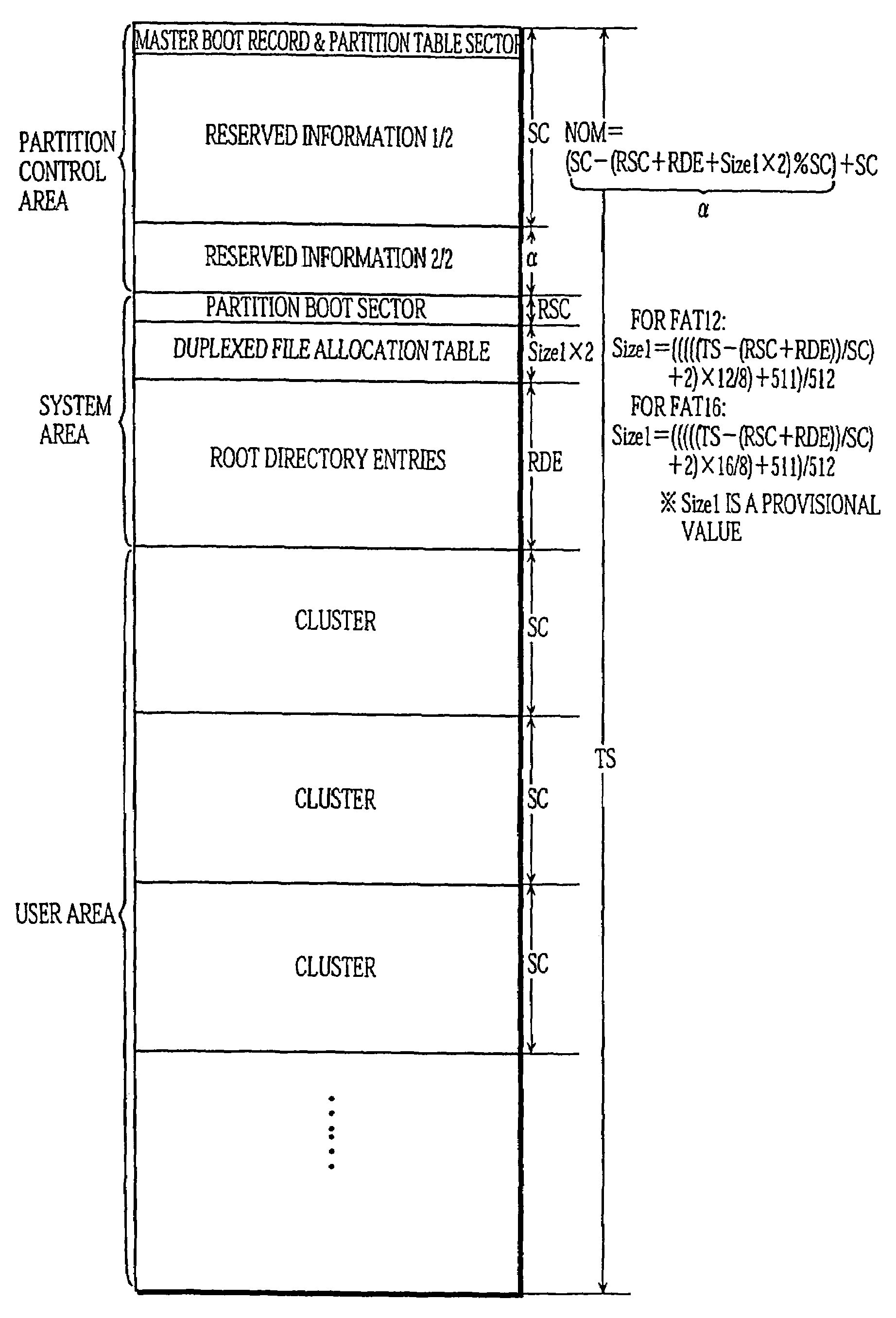
InactiveUS7143261B2Reduce processing timeExtend your lifeMemory architecture accessing/allocationInput/output to record carriersBoot sectorSemiconductor
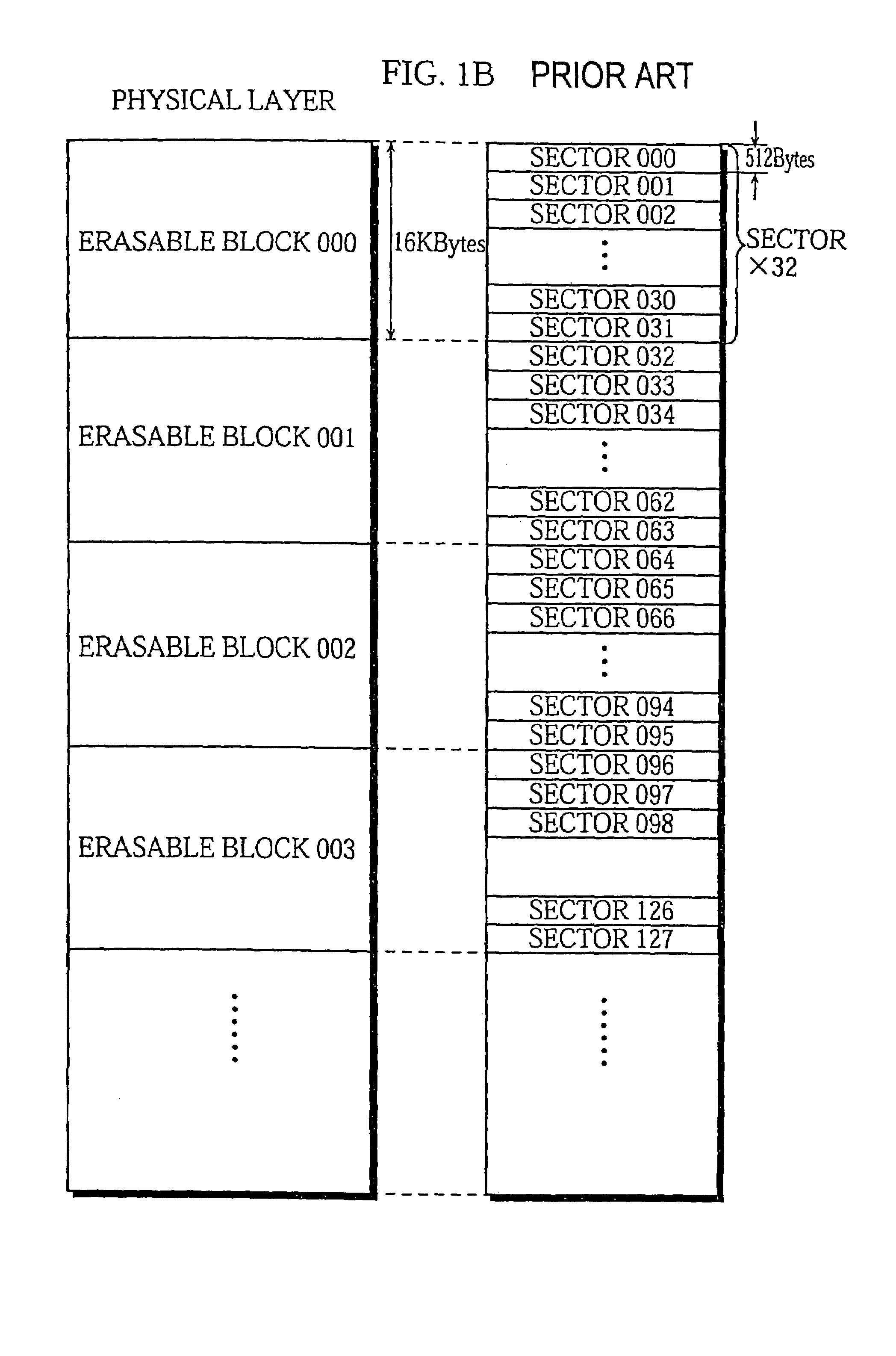
A predetermined number of erasable blocks positioned at a start of a volume area in a semiconductor memory card are provided so as to include volume management information. A user area following the volume management information includes a plurality of clusters. A data length NOM of an area from a master boot record & partition table sector to a partition boot sector is determined so that the plurality of clusters in the user area are not arranged so as to straddle erasable block boundaries. Since cluster boundaries and erasable block boundaries in the user area are aligned, there is no need to perform wasteful processing in which two erasable blocks are erased to rewrite one cluster.
Owner:PANASONIC CORP
Storage device and system starting method thereof
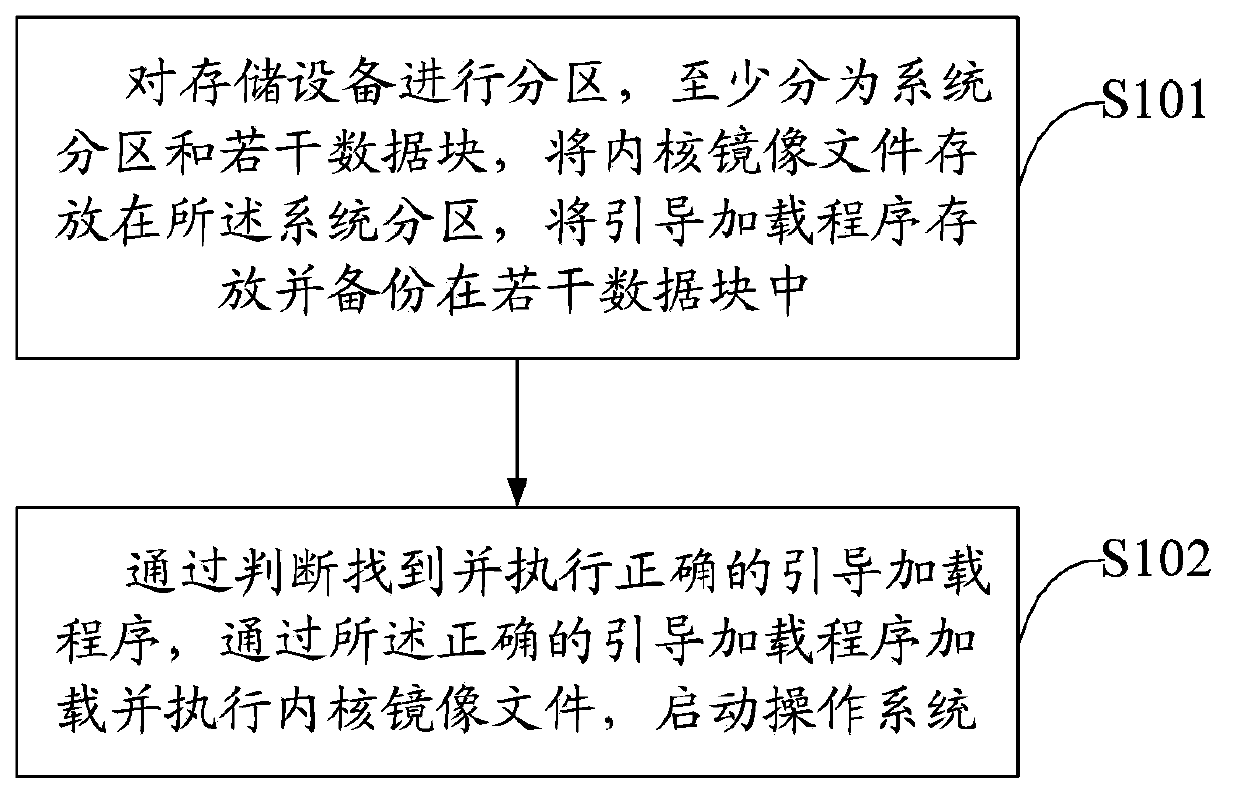
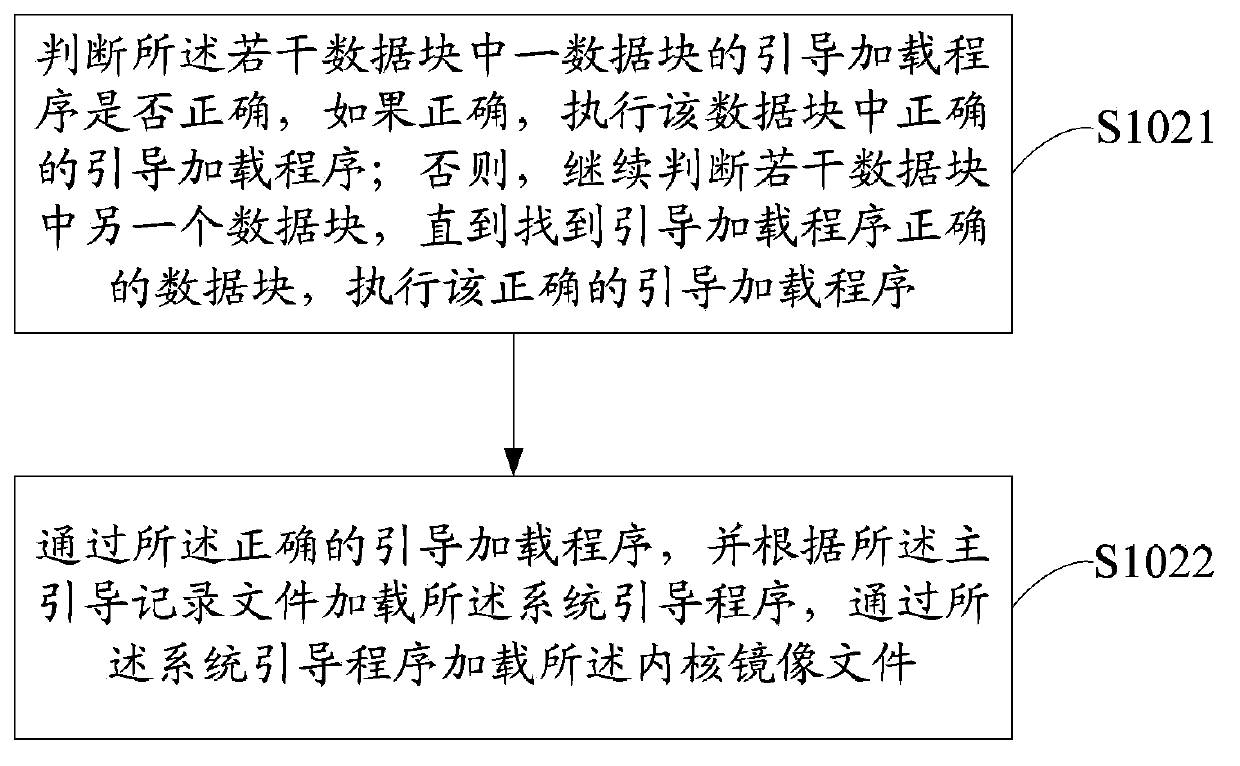
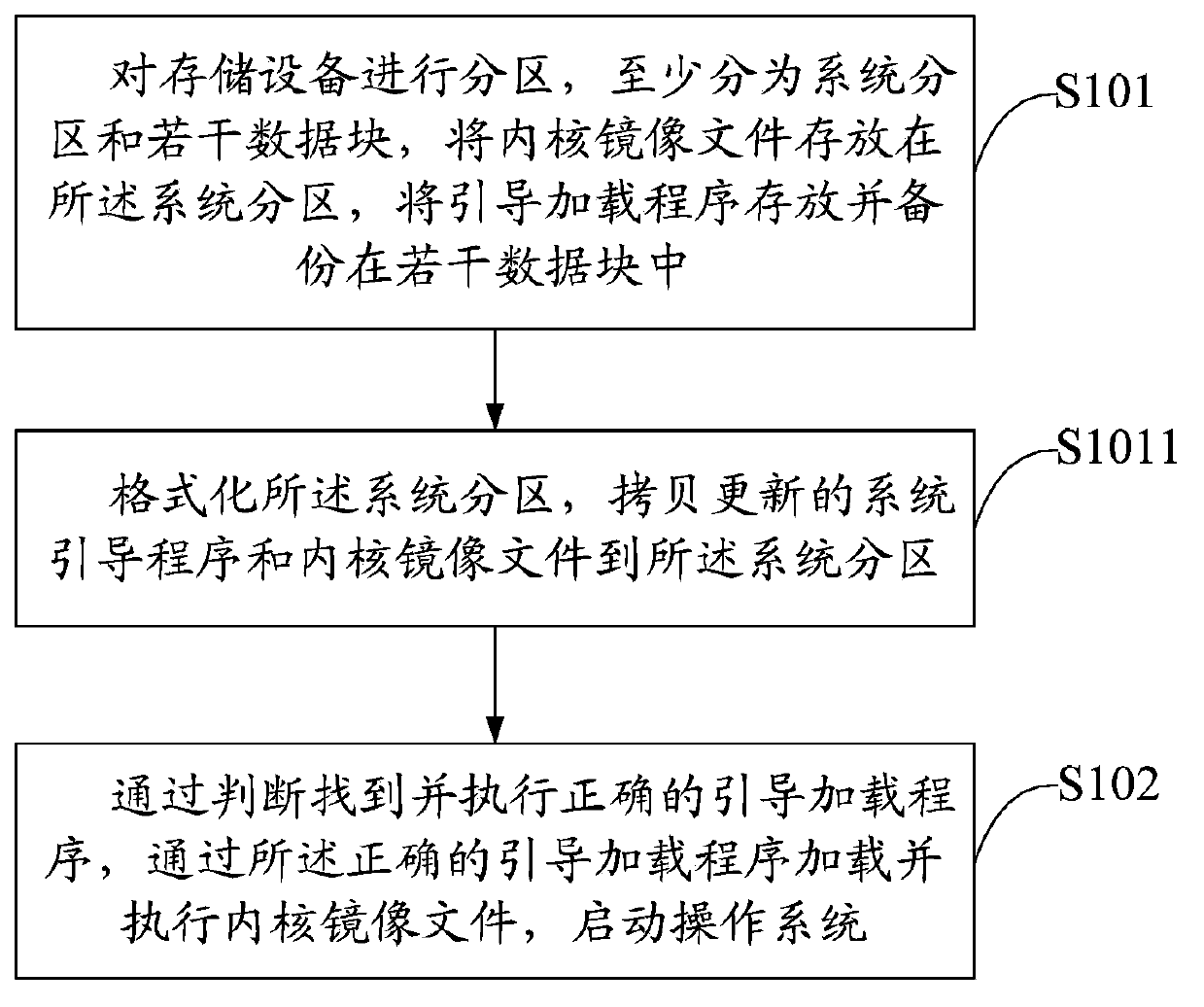
ActiveCN103970557AImprove reliabilityGuaranteed correctnessProgram loading/initiatingComputer hardwareOperational system
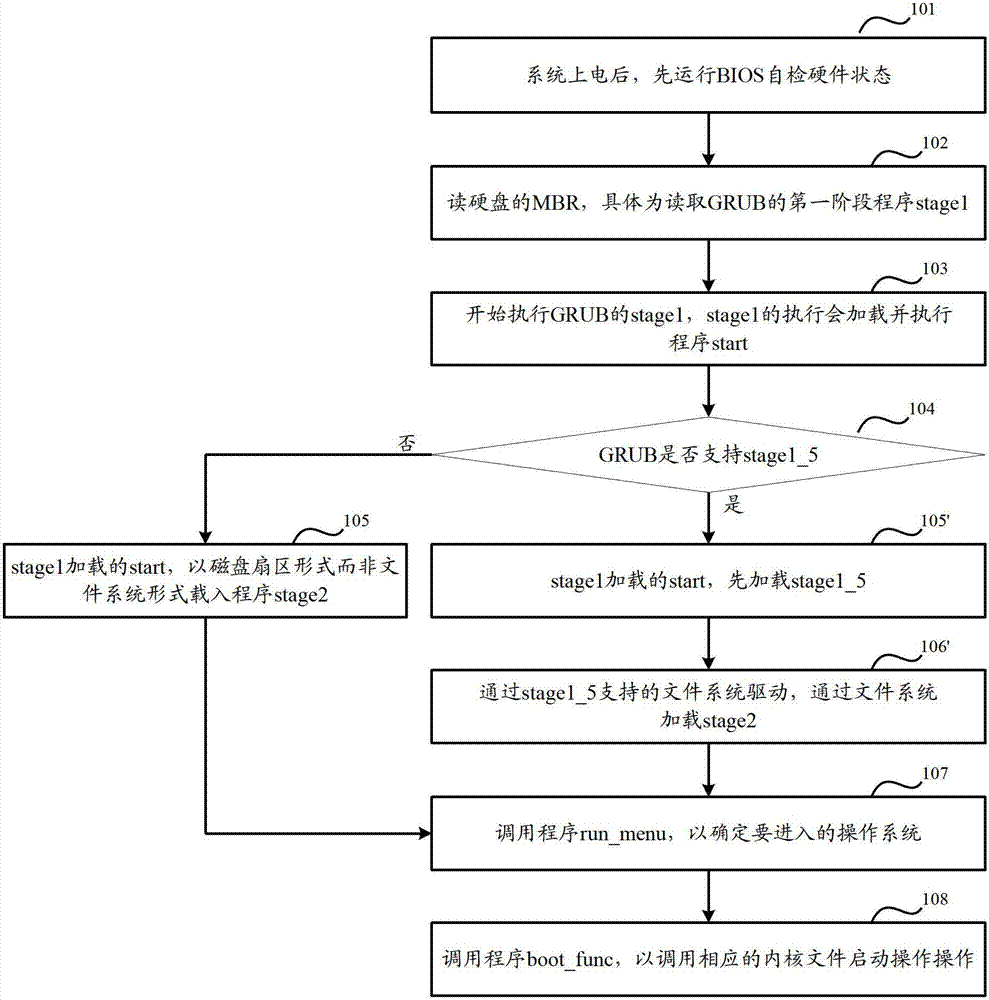
The invention discloses a storage device and a system starting method thereof. The system starting method includes partitioning the storage device into system partitions and a plurality of data blocks, storing a kernel image file into the system partitions, and storing boot loaders and backing up the data blocks; finding and executing the accurate boot loaders by judging, and loading and executing the kernel image file by the accurate boot loaders, and starting the operating system. The storage device is partitioned into the system partitions, a master boot recording area and the data blocks, the boot loaders are stored and backed up in the data block, accuracy of the boot loaders is guaranteed, success rate of the kernel image file in the loading system partition of the boot loaders is increased, and reliability in system starting of the storage device is improved.
Owner:SANECHIPS TECH CO LTD
File or folder search method and device
InactiveCN102289451AAvoid occupyingQuick responseFile access structuresSpecial data processing applicationsComputer resourcesInternal memory
A method for finding files or folders, including the following steps: acquiring a hard disk partition format; acquiring the recording addresses of all the file or folder attributes in the hard disk according to the hard disk partition format, and reading all the file or folder attributes into an internal memory according to the recording addresses of the file or folder attributes; and traversing and finding all or part of the files or folders in all the file or folder attributes read into the internal memory.Also provided is a device for finding files or folders for realizing the method above.The method and device for finding files or folders in the present invention can find files or folders rapidly, and reduce occupied computer resources.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
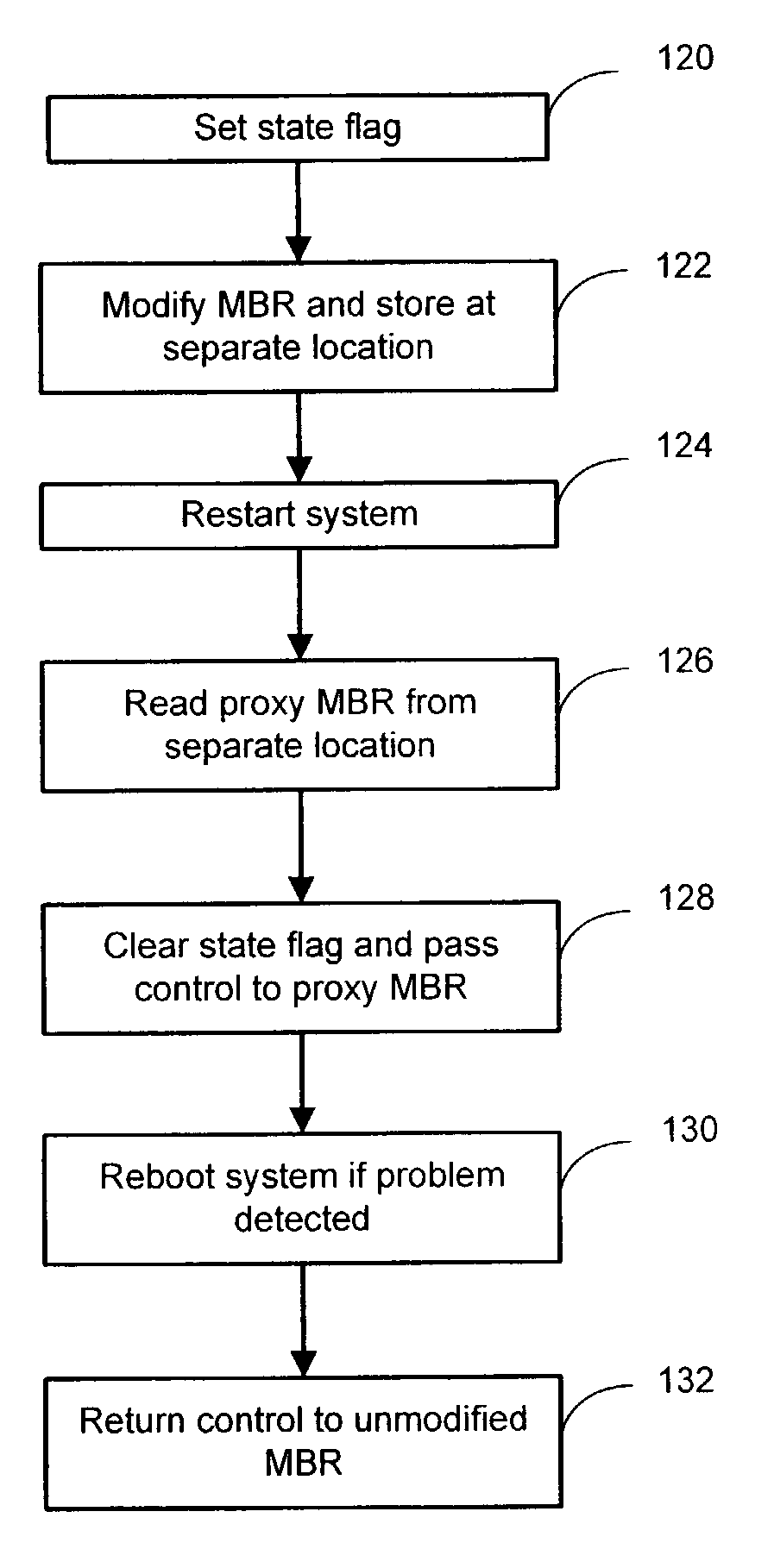
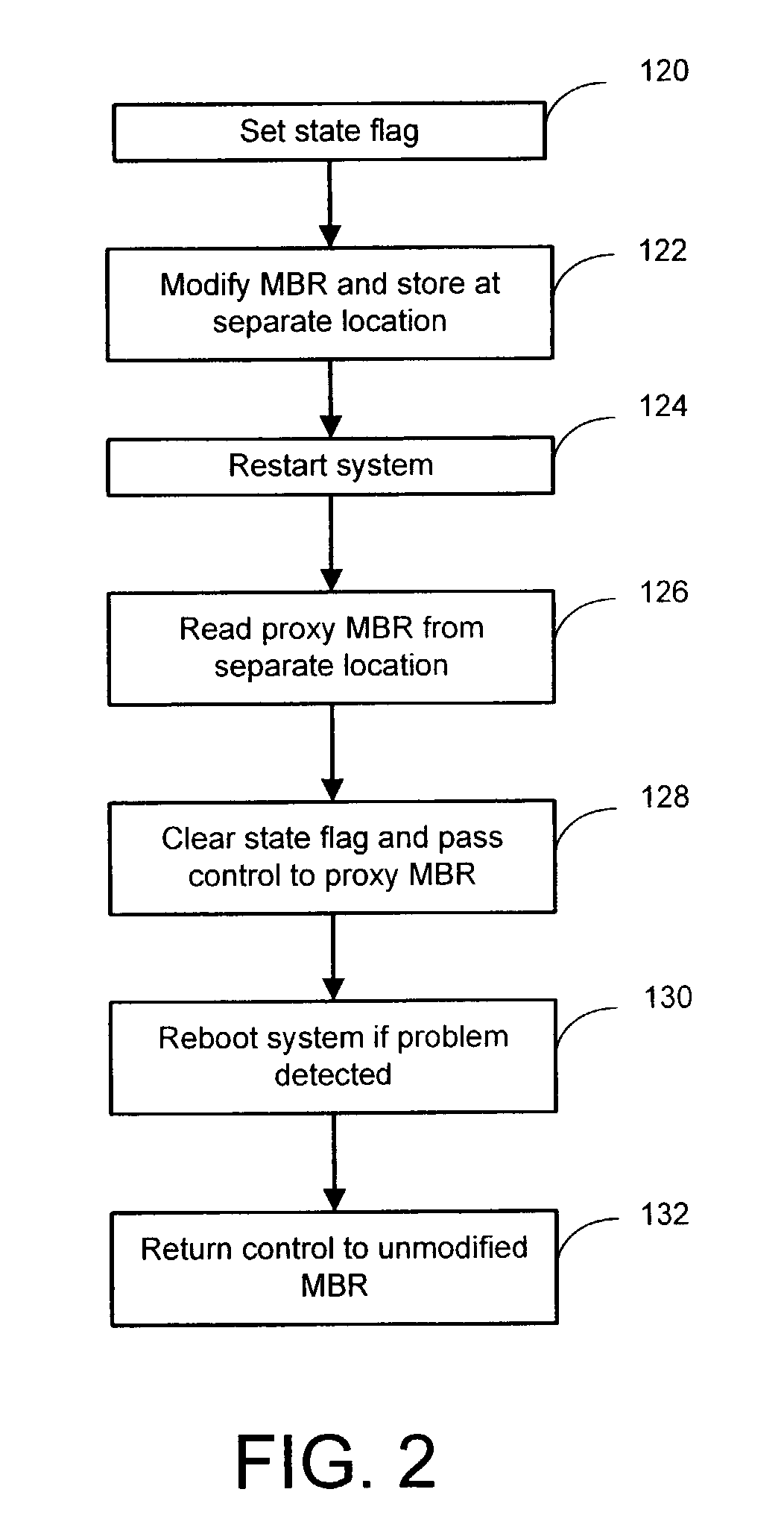
Method and system for detection and correction of entrance into an improper MBR state in a computer system
ActiveUS7194659B2Improve efficiencyImprove reliabilityError detection/correctionTransmissionComputerized systemParallel computing
Aspects for detection and correction of entrance into an improper master boot record (MBR) state in a computer system are described. The aspects include providing a proxy MBR at a predetermined location on a storage device of a computer system to provide a proxy MBR. The proxy MBR is then utilized during a restart operation. An original MBR maintained at an original location on the storage device is then utilized during a reboot operation when the utilization of the proxy MBR is unsuccessful.
Owner:TREND MICRO INC
Device, computer and method for protecting and restoring computer configuration information
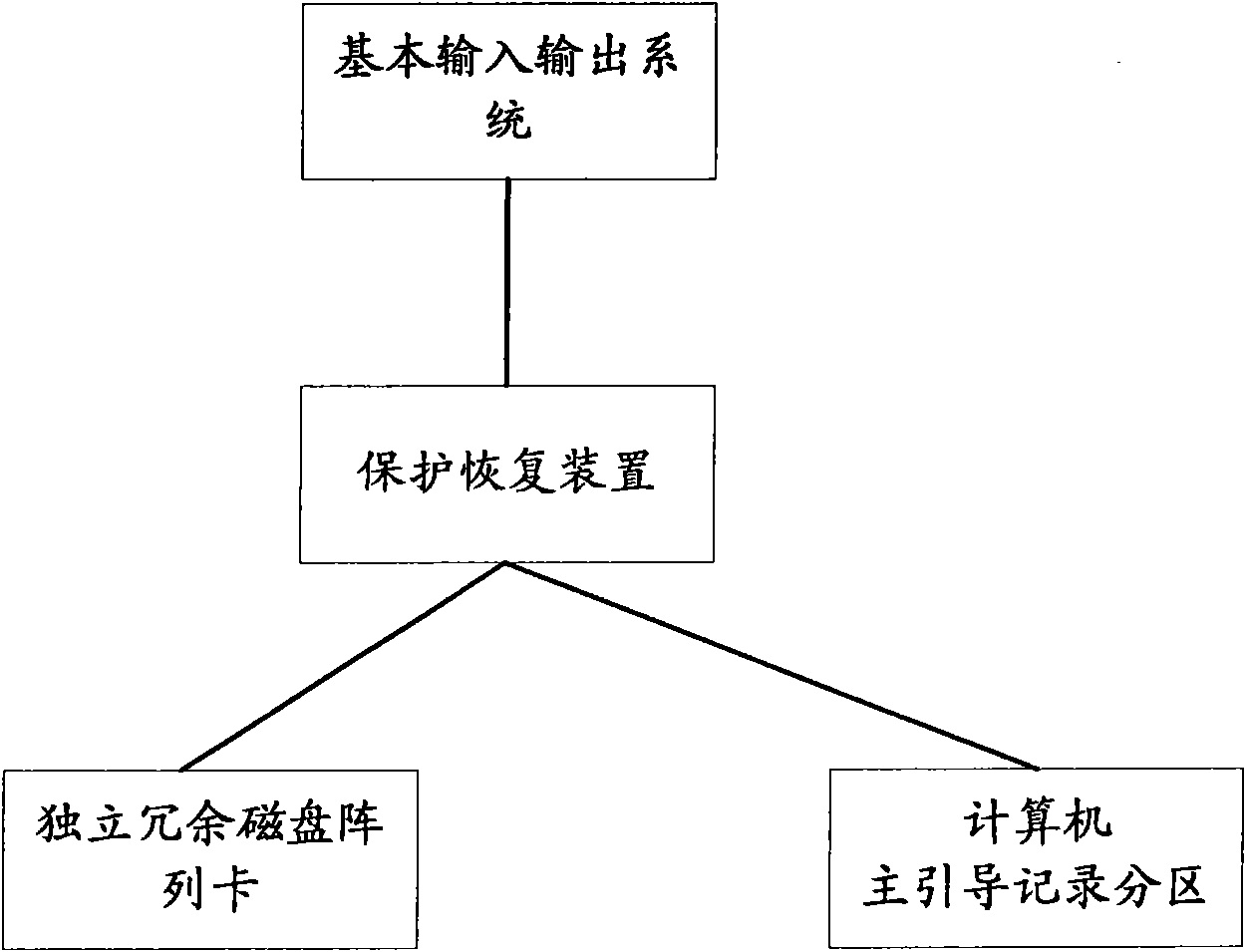
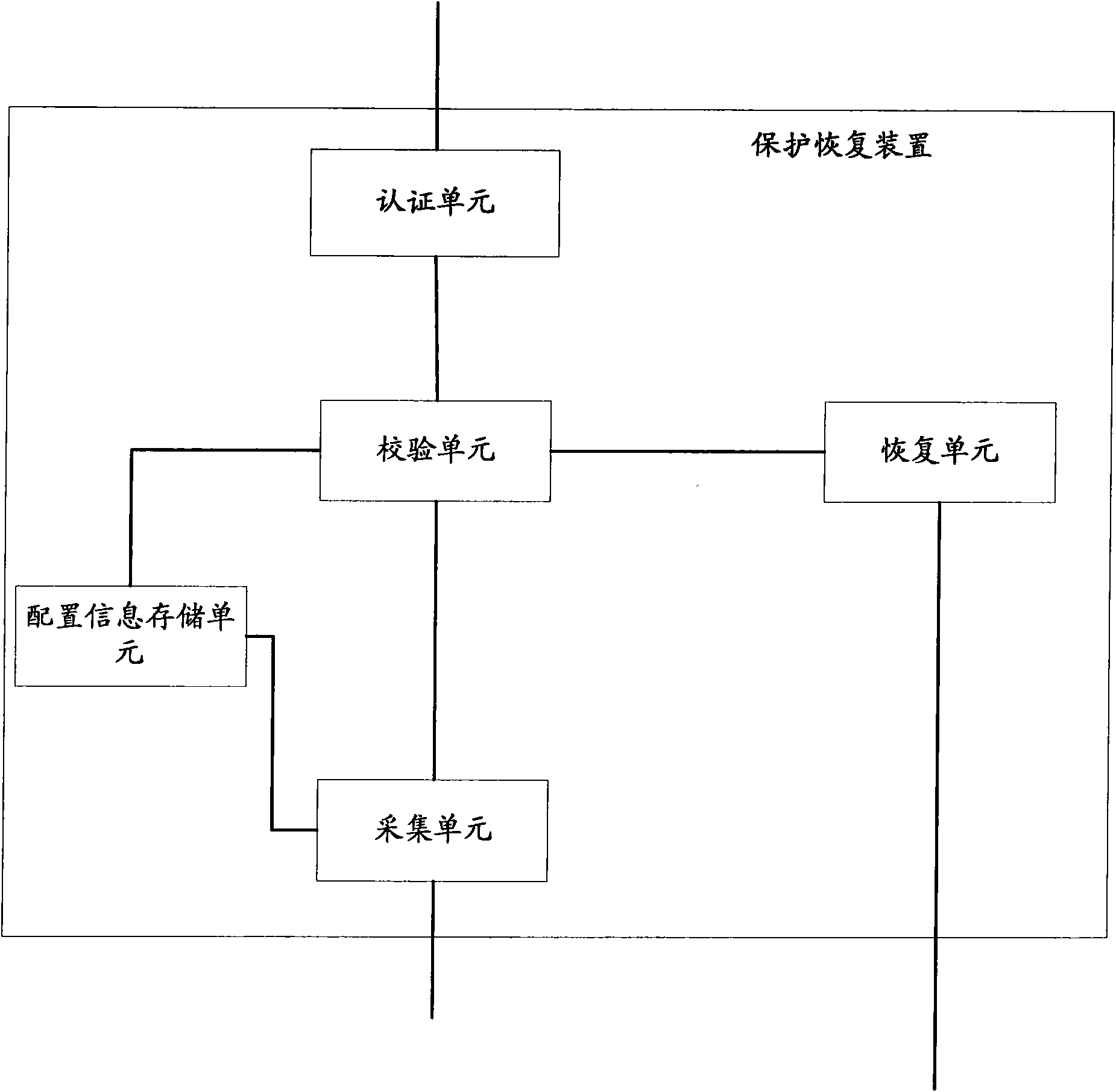
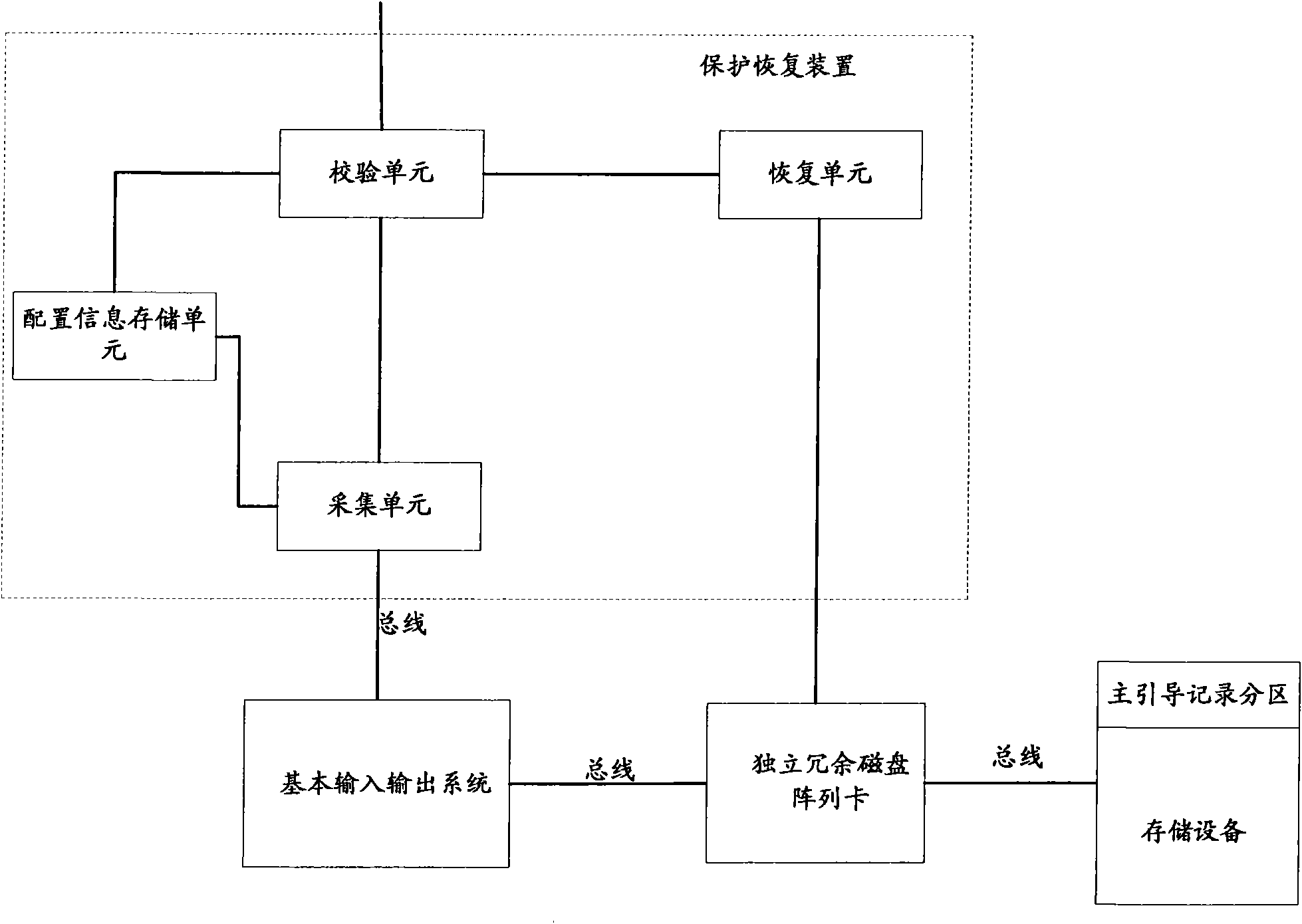
ActiveCN101593083AWill not affect normal operationGuaranteed to be correctInput/output to record carriersProgram loading/initiatingRAIDOperational system
The invention provides a device, a computer and a method for protecting and restoring an operating system; wherein, the device is applied to a computer which is provided with a memory equipment and independent redundant disk array card, and at least comprises a configuration information memory unit, a calibrating unit and a restoring unit; the configuration information memory unit is used for storing the initial independent redundant disk array configuration information and the initial master boot record partitioning configuration information, the calibrating unit is used for comparing the initial independent redundant disk array configuration information with the current independent redundant disk array configuration information, and the initial master boot record partitioning configuration information with the current master boot record partitioning configuration information, and for generating a restoring command if the comparison result is inconsistent, and the restoring unit is used for restoring the current independent redundant disk array configuration information and the current master boot record partitioning configuration information. With the adoption of the technology provided by the above preferential embodiment of the invention, under the circumstance that HPA of the memory system configuration is damaged, RAID card configuration information and hard disk MBR partitioning configuration information can be still guaranteed simultaneously, thus ensuring the next normal starting of the operating system.
Owner:LENOVO (BEIJING) CO LTD
Method and system for iSCSI boot in which an iSCSI client loads boot code from a host bus adapter and/or network interface card
Owner:AVAGO TECH INT SALES PTE LTD
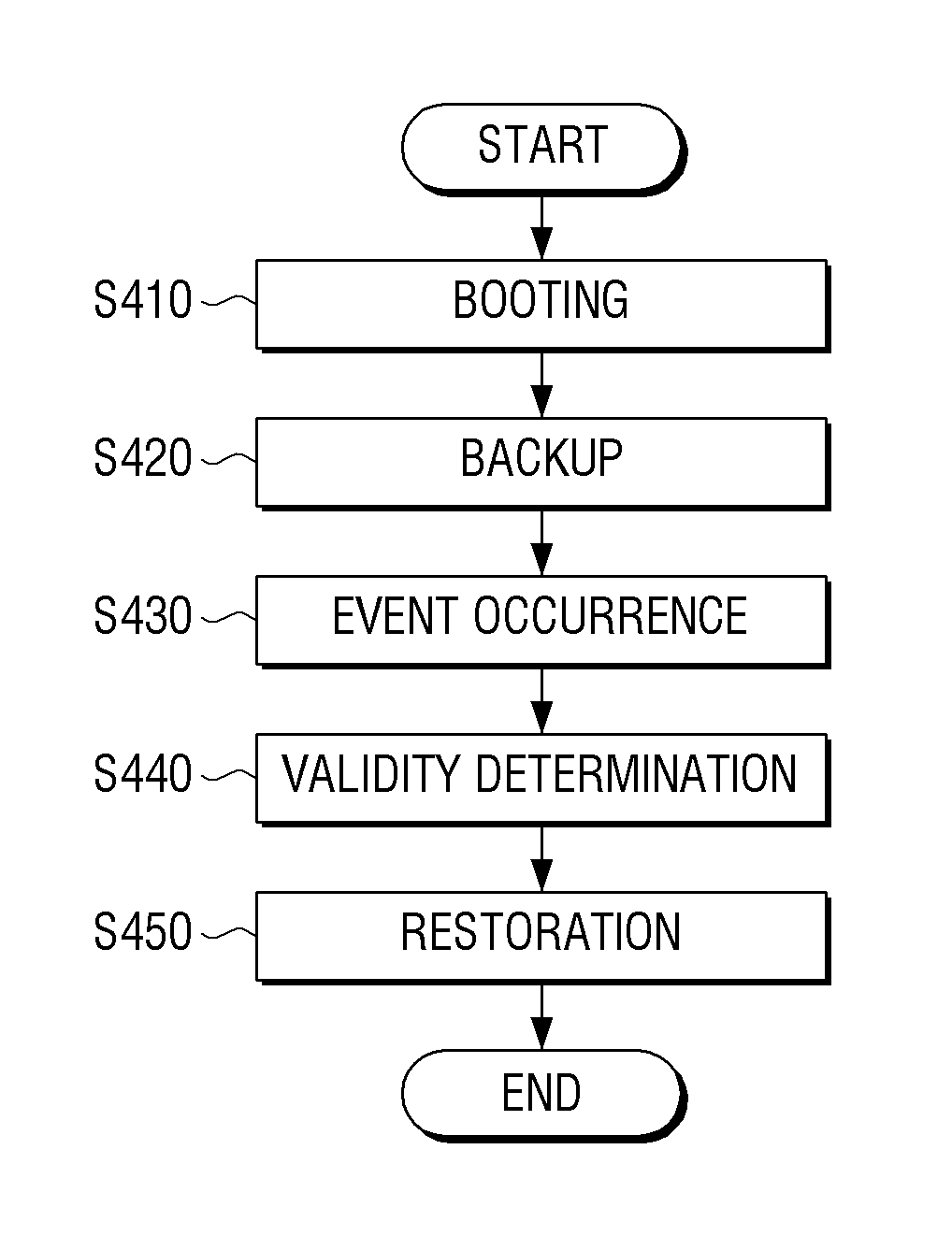
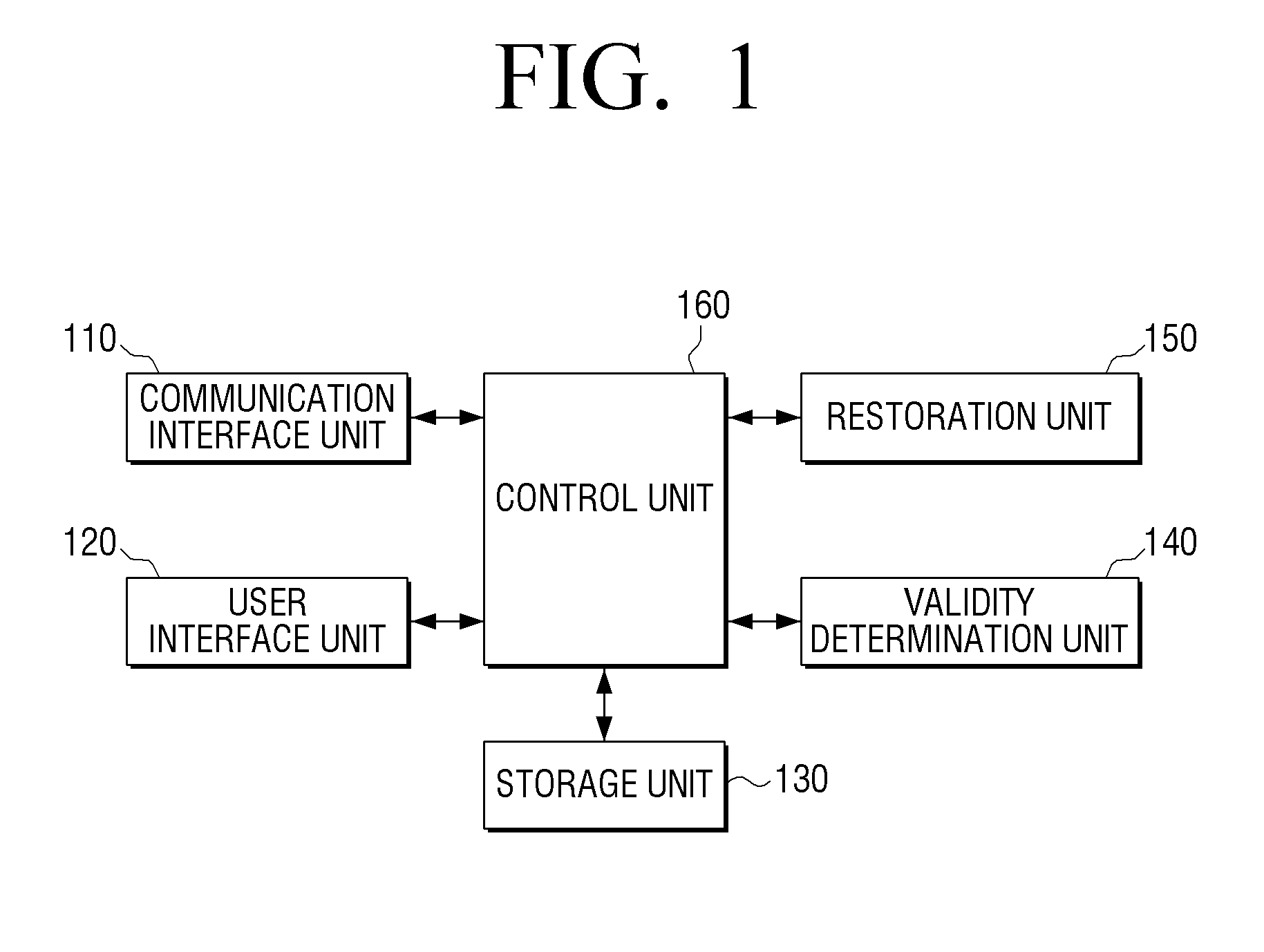
Electronic device to restore mbr, method thereof, and computer-readable medium
ActiveUS20130232325A1Digital computer detailsRedundant data error correctionOperational systemEngineering
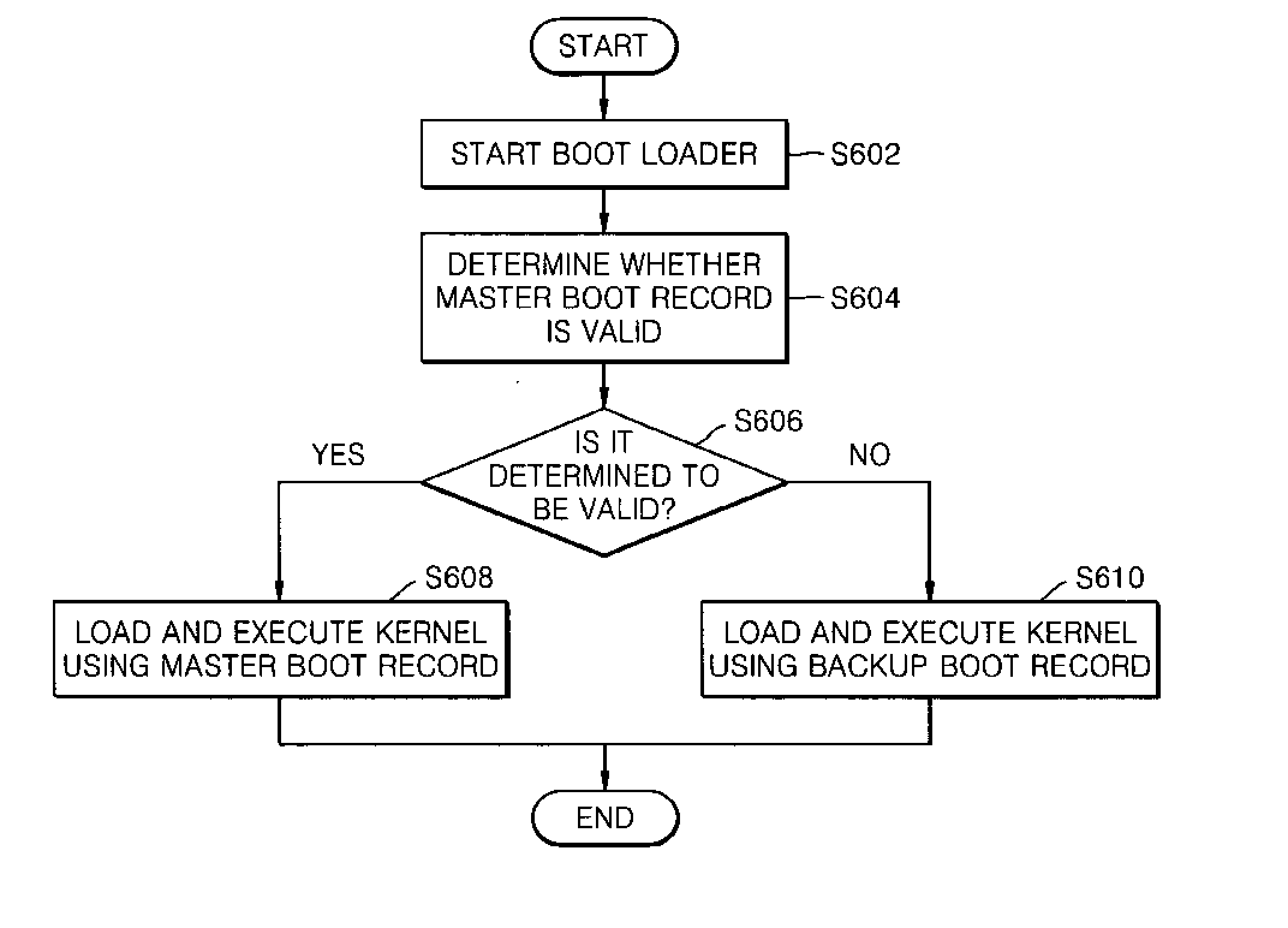
An electronic device includes a storage unit to store a master boot record (MBR) and an operating system, a control unit to boot the electronic device using the stored MBR and operating system, to generate and store backup data of the MBR in the storage unit when the electronic device is booted, a validity determination unit to determine validity of the MBR when a predetermined event has occurred, and a restoration unit to restore the MBR using the backup data stored in the storage unit if the MBR is not valid.
Owner:SAMSUNG ELECTRONICS CO LTD
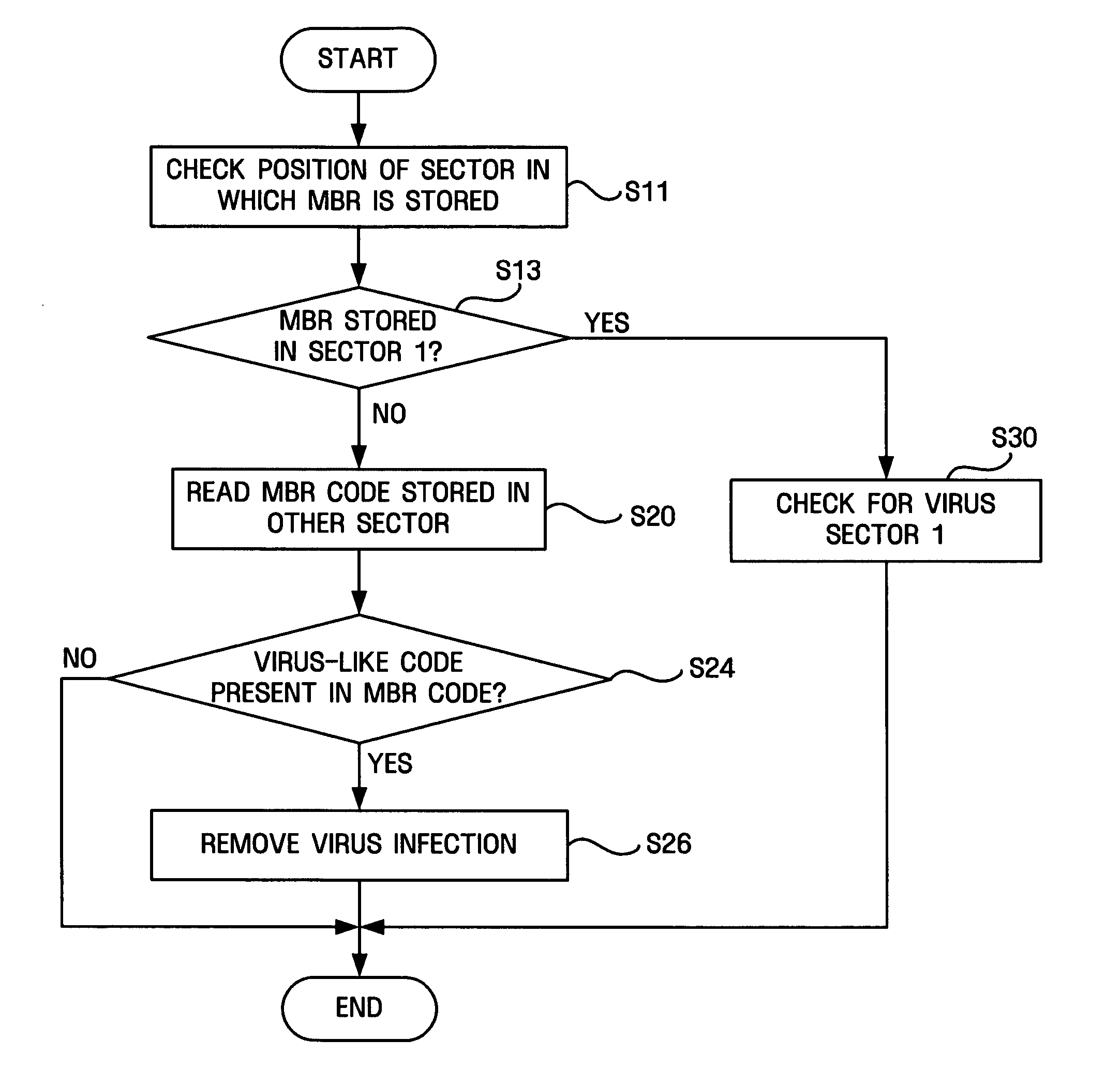
Apparatus and method for restoring master boot record infected with virus
An apparatus for and a method of restoring a master boot record infected with a virus. The apparatus comprises a first storage unit storing a master boot record (MBR), and a virus check unit searching the storage position of the MBR within the first storage unit, to determine whether the MBR is infected with the virus and, if the MBR is infected, to restore the MBR.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com