Patents
Literature
40results about How to "Guaranteed safe and reliable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Food safety risk traceability analysis system and method based on block chain
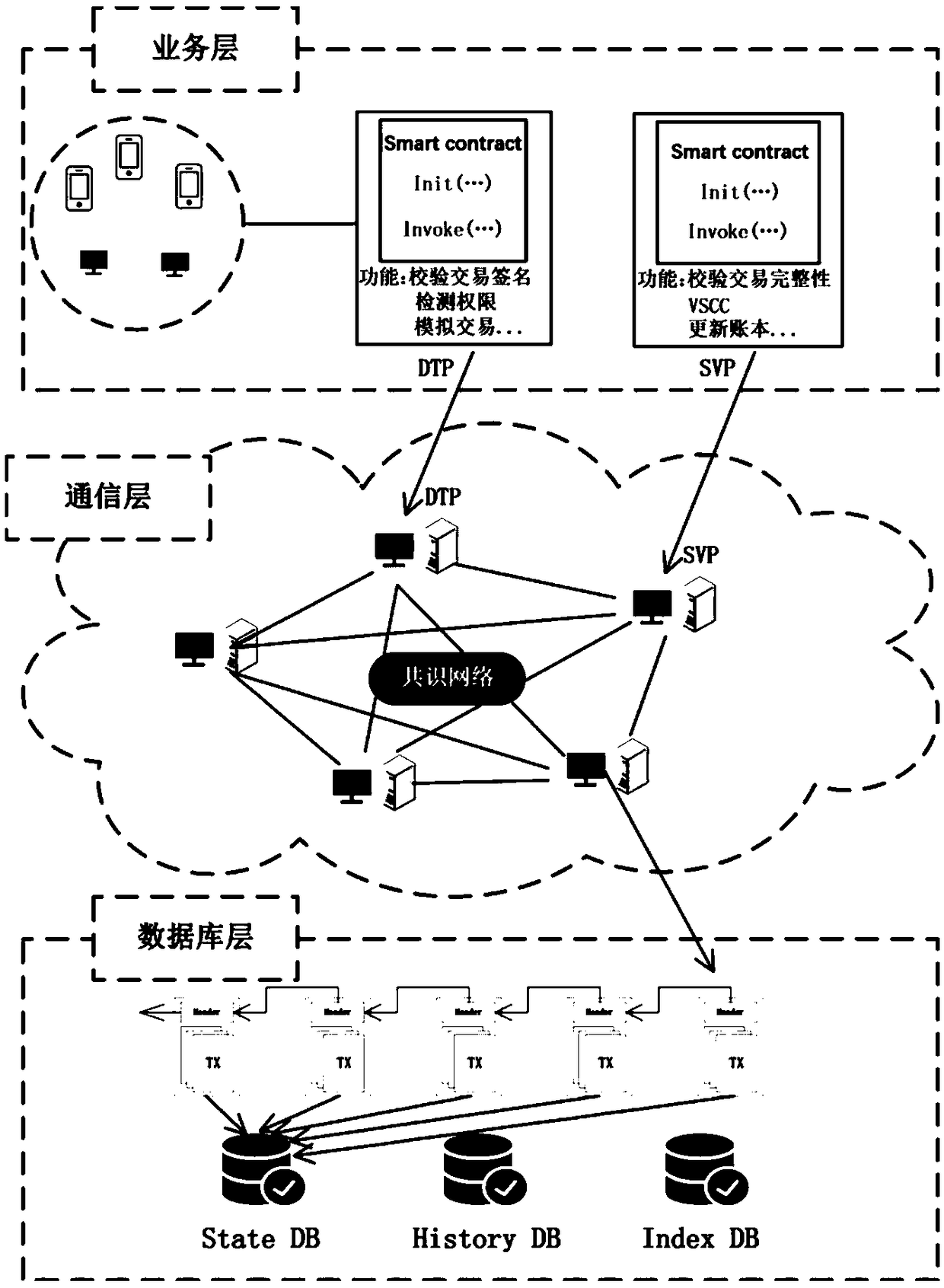
The invention relates to a food safety risk traceability analysis method and a system based on a block chain. The block chain technology is applied to a database layer and a communication layer of thesystem, and the visualization technology is applied to a service layer of the system. Data upload requires the initiator's digital signature to ensure that the data is not tampered with and that thedata is stored in the block chain. Data access is controlled by permissions to access data in the chunk chain by executing smart contracts. Use Force-Directed Graph and flow maps show the food risk traceability process. When tracing the source of food safety risk, the user can trace the source of food safety risk through Force-Directed Graph Drills up to trace the source, then down to track the flow of food, Force-Directed Graph drill-through operations are shown in conjunction with a flow map in which arrows indicate the flow direction of risky foods, where different shades of color representdifferent degrees of risk flow. The invention not only solves the problems of unsafe storage of the traditional food traceability data and the vulnerability of the central database, but also providesa friendly visual interaction interface for users.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
Two-factor authentication method based on portable TPM (PTPM) and certificateless public key signature for cloud
InactiveCN107733657AImprove computing efficiencyMake sure it's trueKey distribution for secure communicationPublic key for secure communicationPasswordTerminal equipment
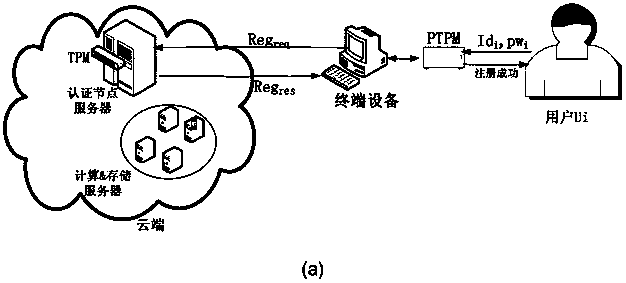
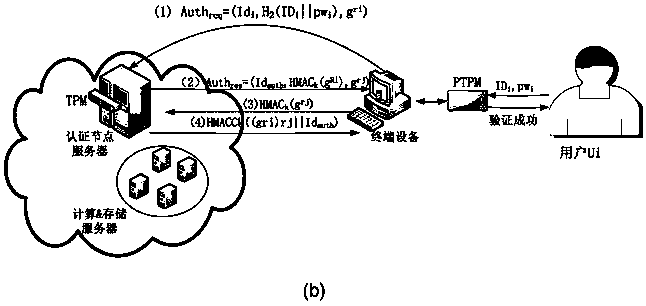
The invention discloses a scheme for implementing two-way identity authentication between a user and cloud by applying a portable TPM (PTPM) and certificateless public key cryptography to a cloud environment, aiming at solving the security problems and deficiencies existing in identity authentication between the user and the cloud in a current cloud environment in a cloud computing mode. Comparedwith existing schemes, a new scheme has the following advantages: on the basis of realizing the uniqueness of user and cloud identities through the establishment of an identity management mechanism, firstly, the PTPM is adopted to ensure the security and credibility of a terminal platform and ensure the authenticity and correctness of authentication results between the cloud and the user, and moreover, the user is supported to use any terminal equipment to complete an identity authentication process with the cloud; secondly, the new scheme implements a 'password + key' two-factor authentication process based on a certificateless public key signature algorithm; and finally, the proposed scheme can significantly improve the computing efficiency of identity authentication between the user andthe cloud while ensuring the security of EUF-CMA.
Owner:SHENYANG NORMAL UNIV
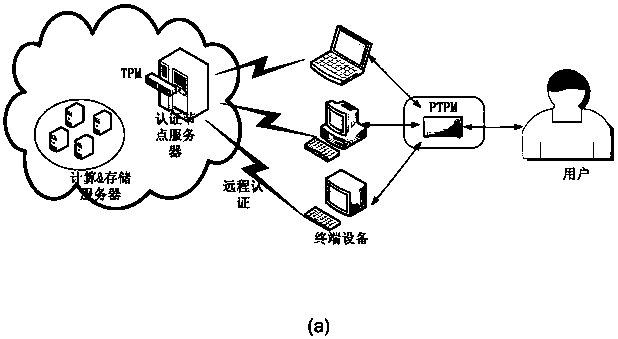
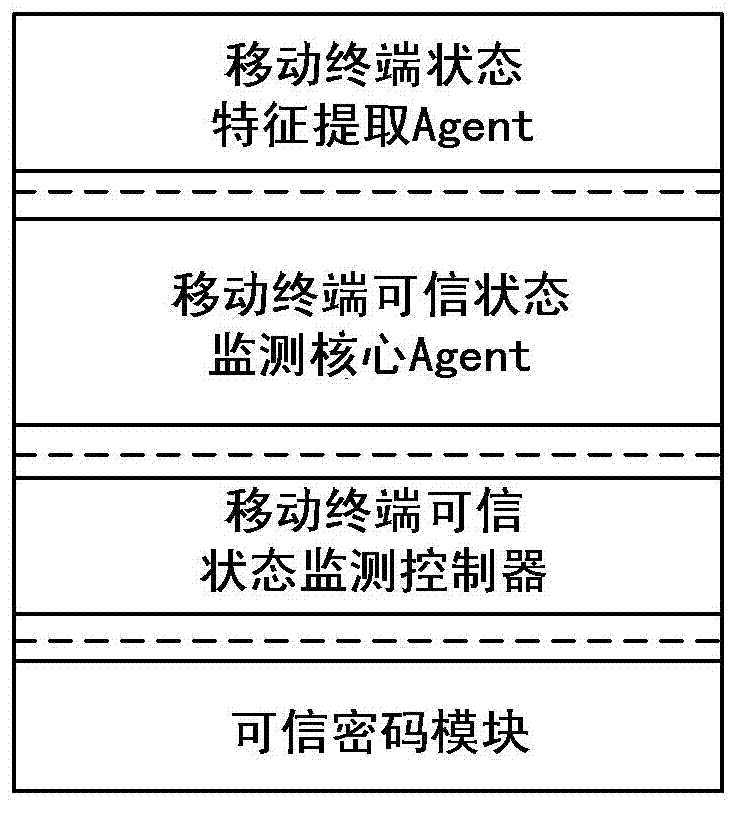
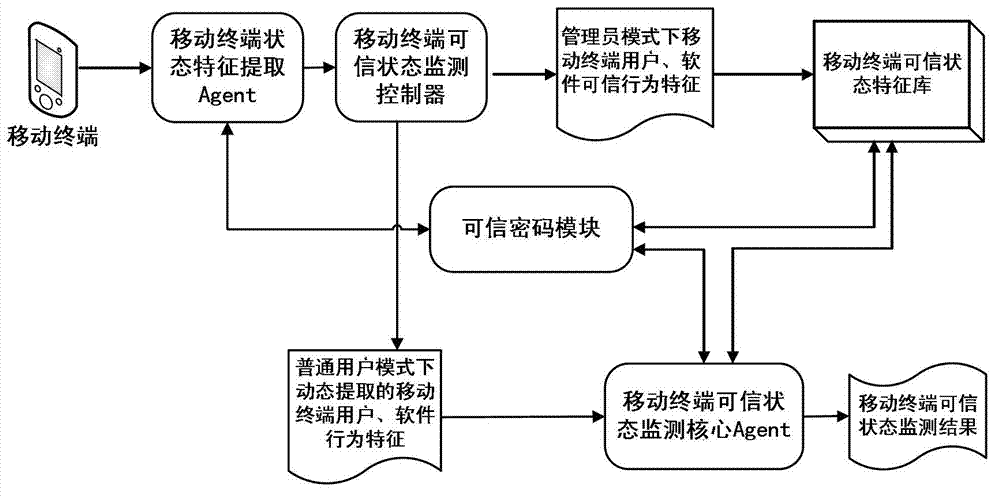
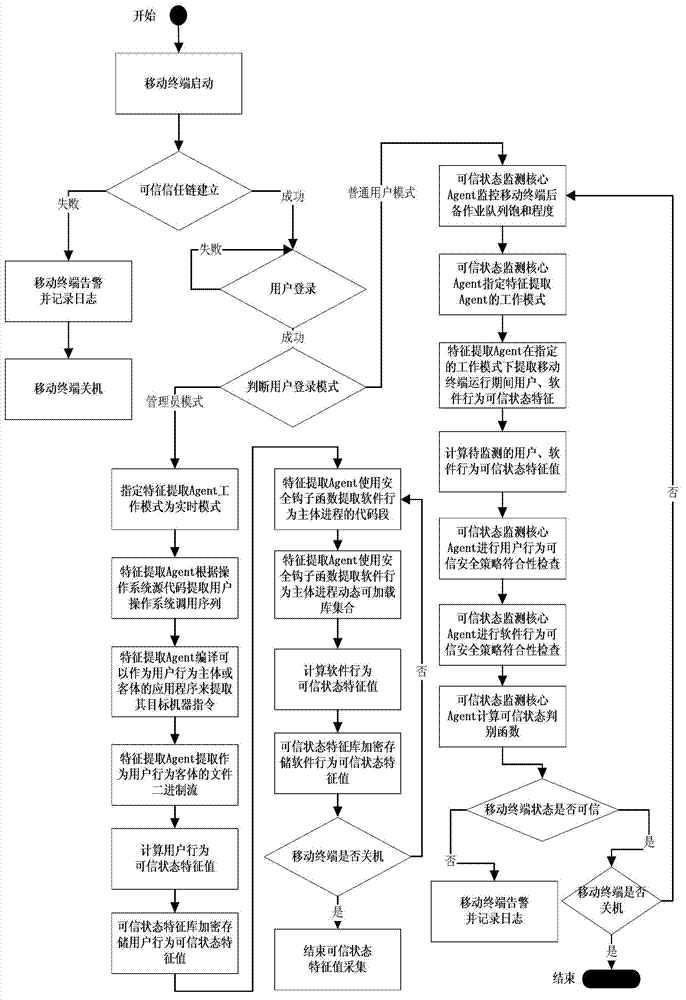
Credible Agent based MT (Mobile Terminal) credible state monitoring method
ActiveCN102760213AGuaranteed efficiency and accuracyGuaranteed safe and reliableComputer security arrangementsCondition monitoringReal-time computing
Owner:CHINA ELECTRIC POWER RES INST +3
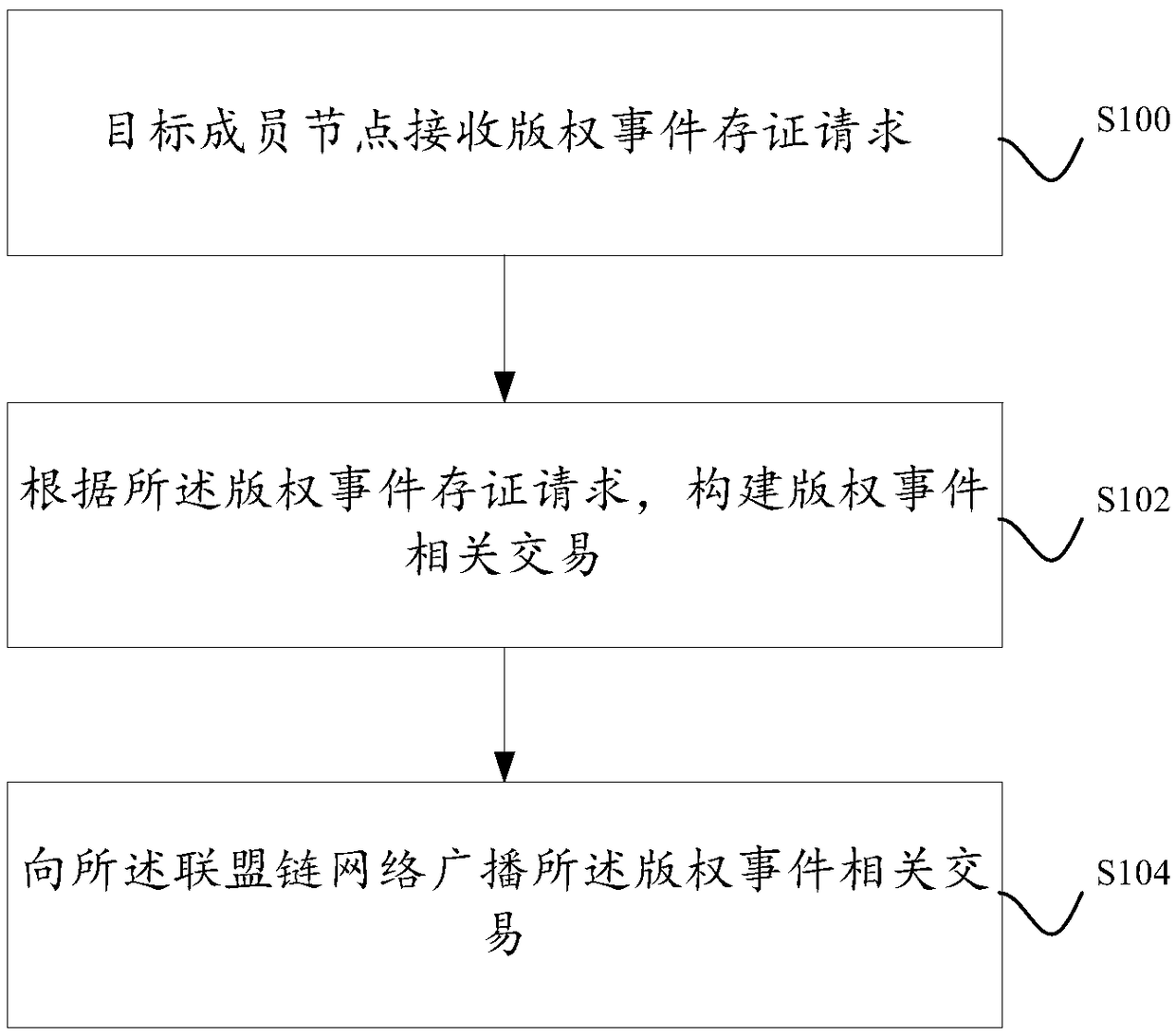
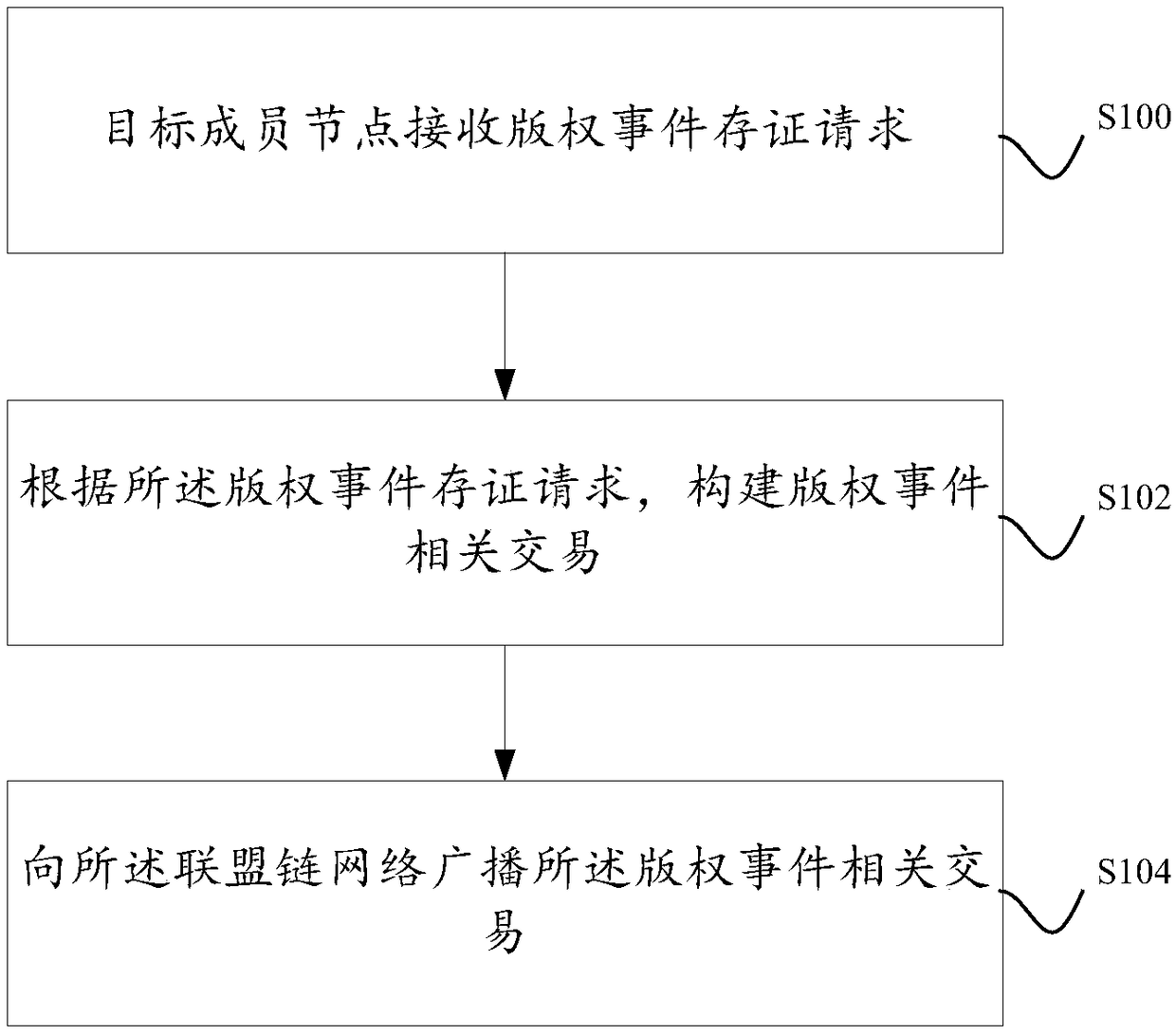
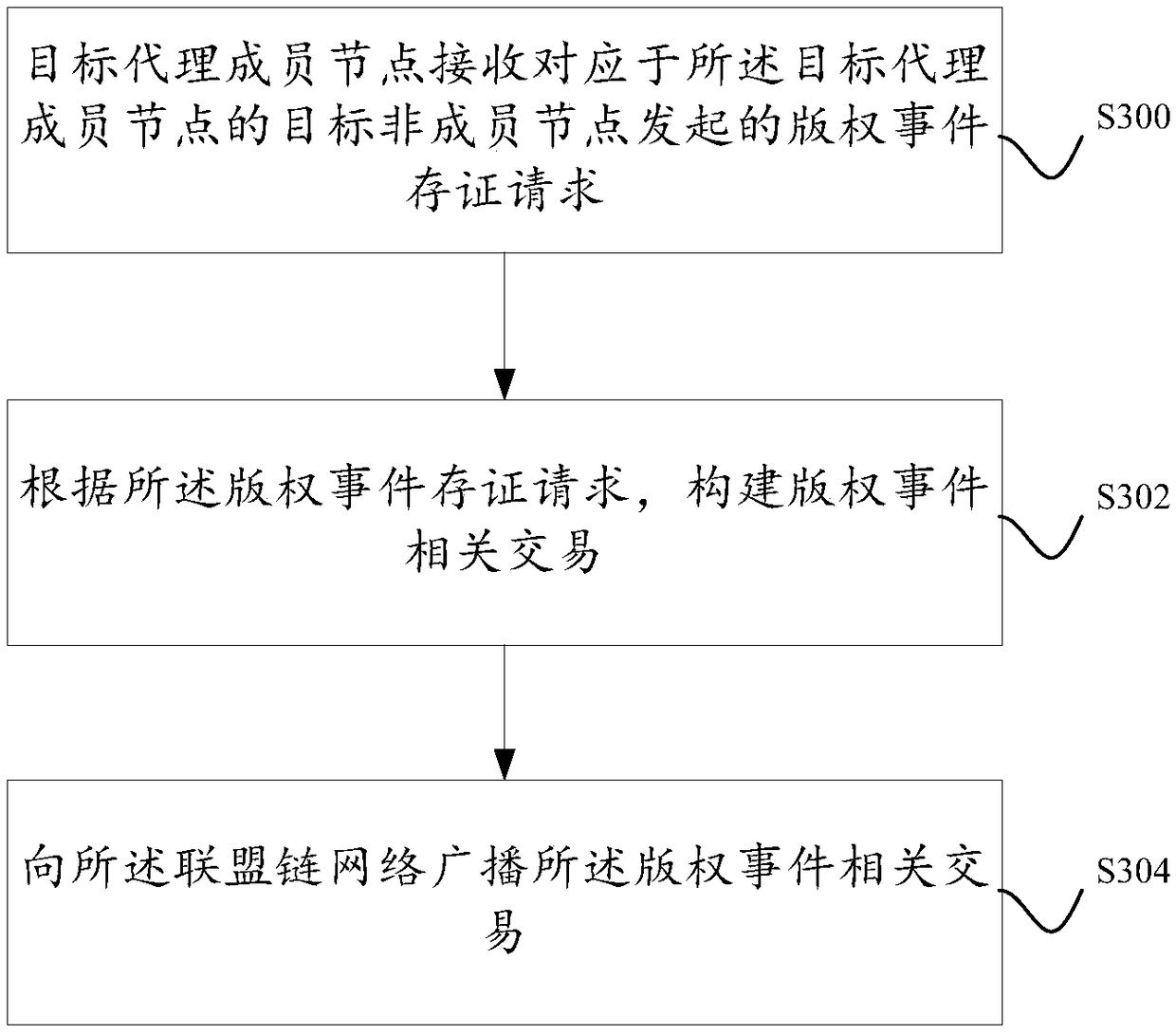
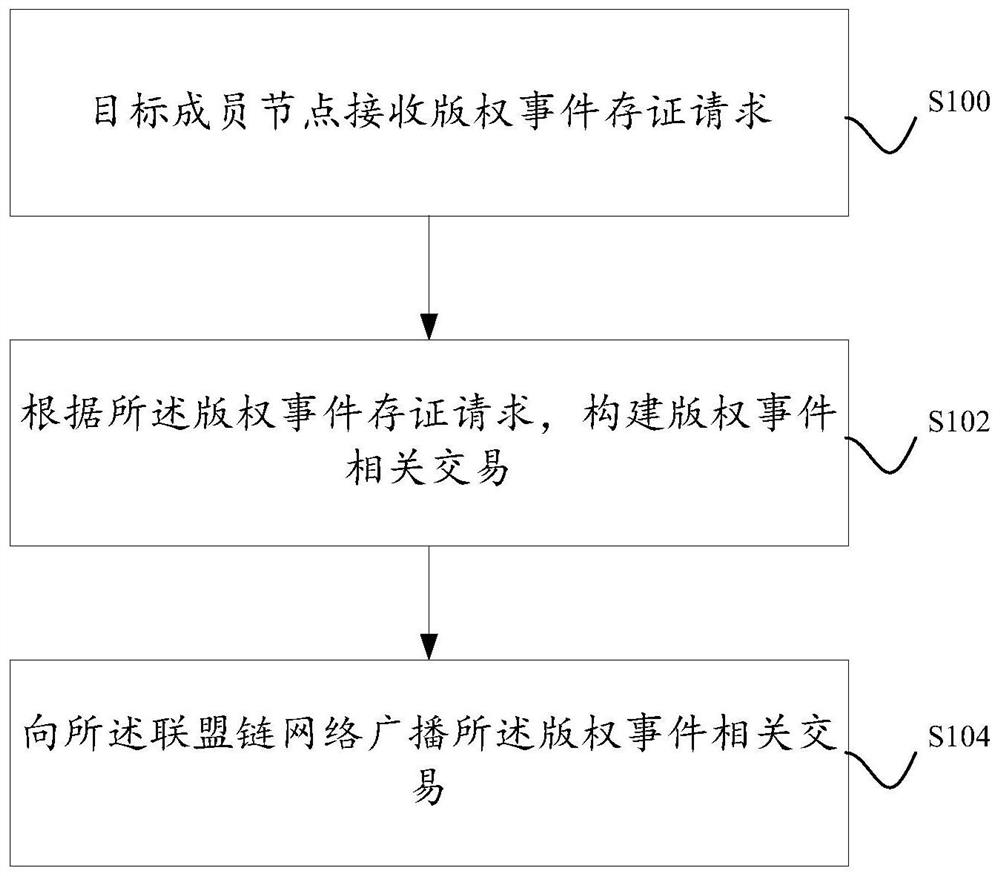
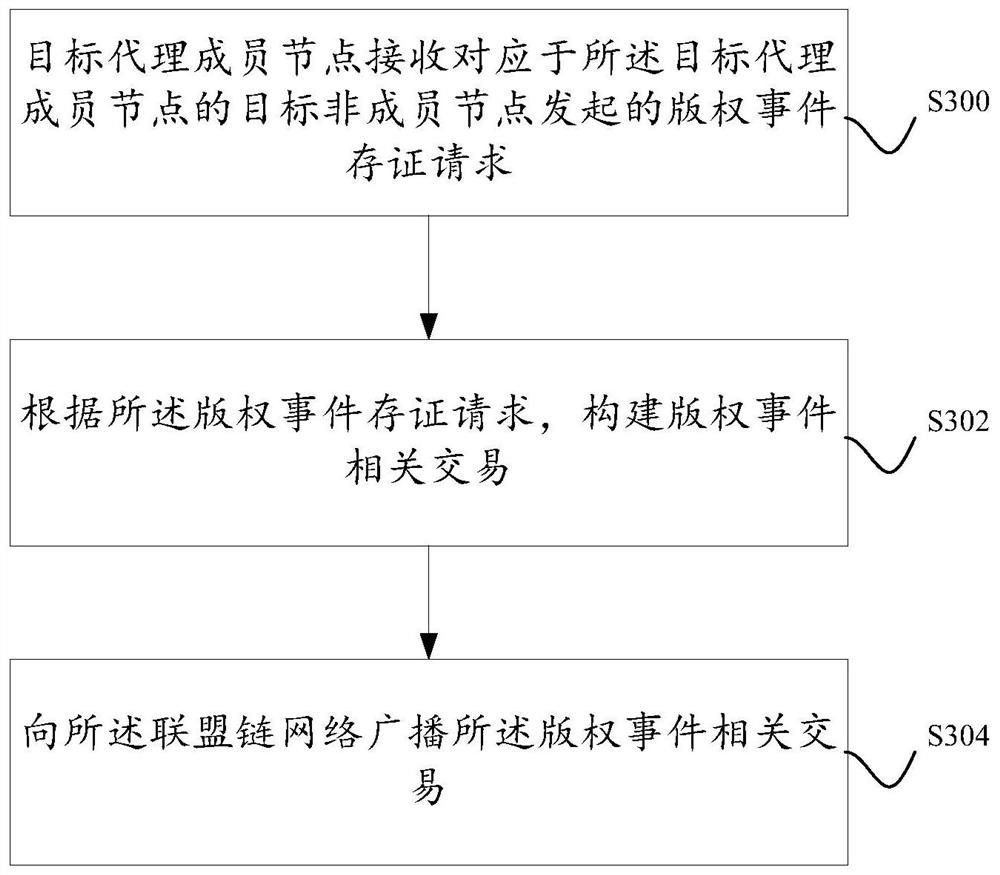
A method and system for storing copyright event authentication based on block chain
ActiveCN109274667AGuaranteed safe and reliableExamples cannot be limitedFinanceDatabase distribution/replicationChain networkAuthentication
The invention discloses a method and a system for storing copyright event based on a block chain. The devices of some works service providers that operate works-related services can be used as membernodes to form a federation chain network, and each works service provider broadcasts copyright events generated based on its own works-related services to the federation chain network, and each worksservice provider performs distributed certification based on the block chain.
Owner:ADVANCED NEW TECH CO LTD
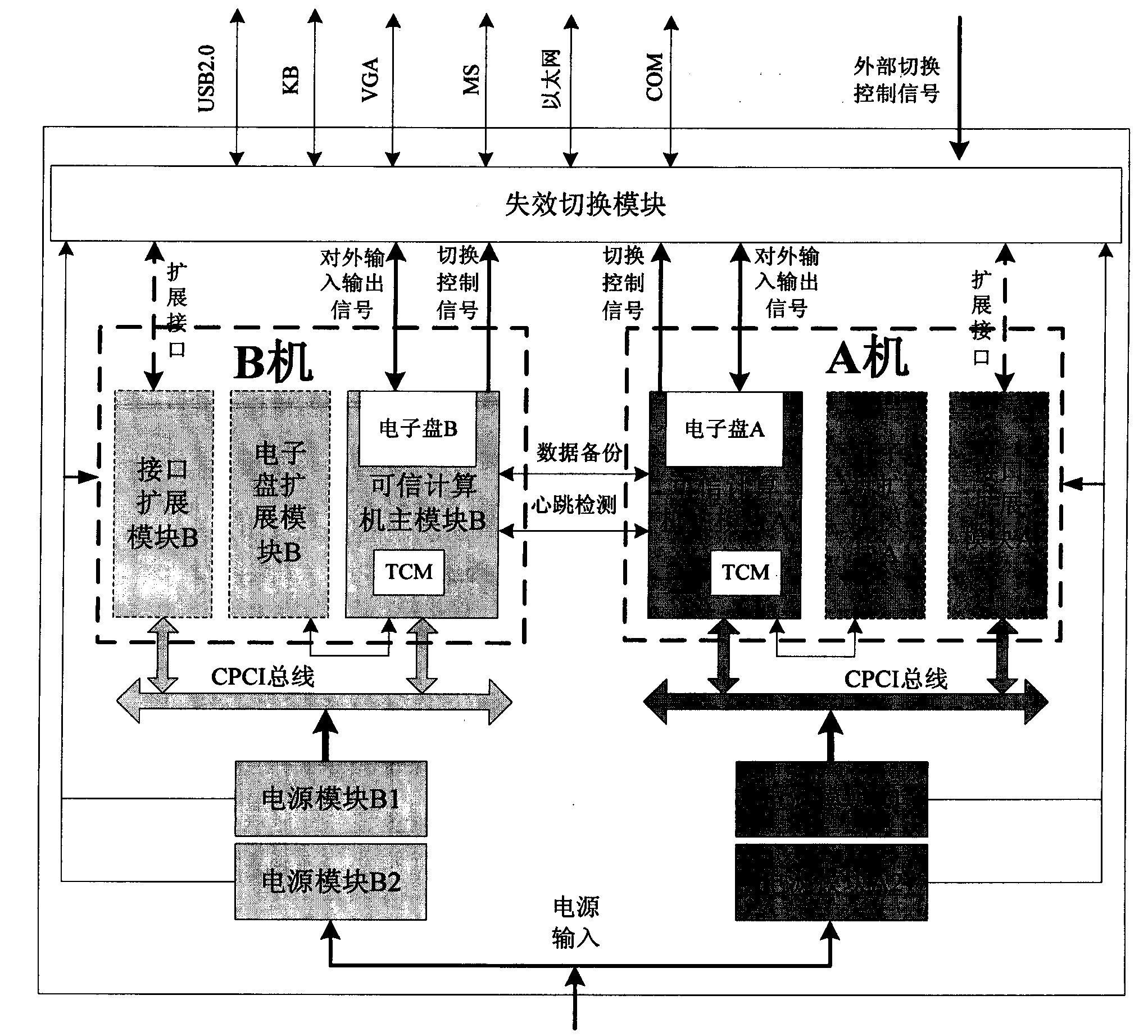
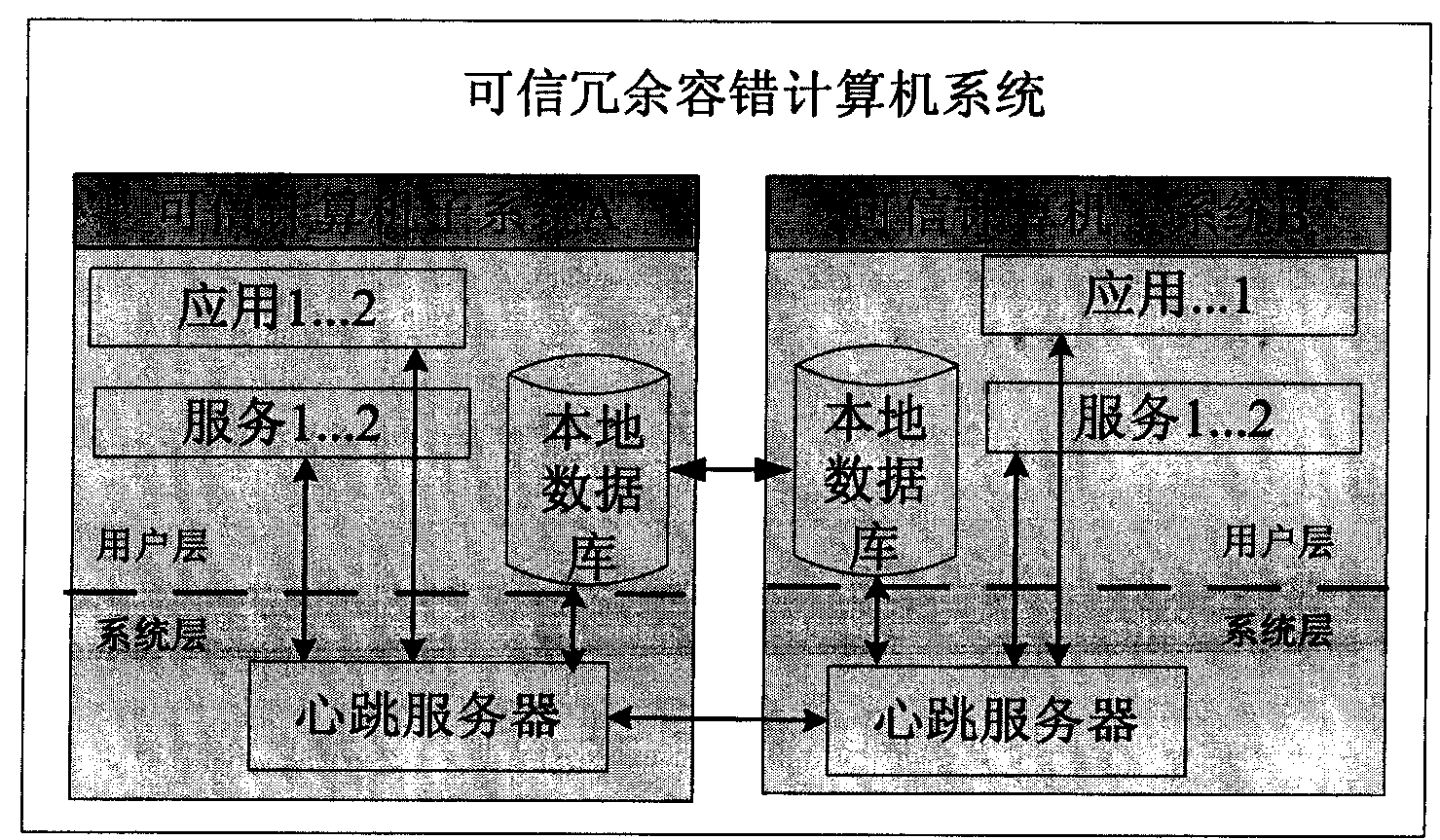
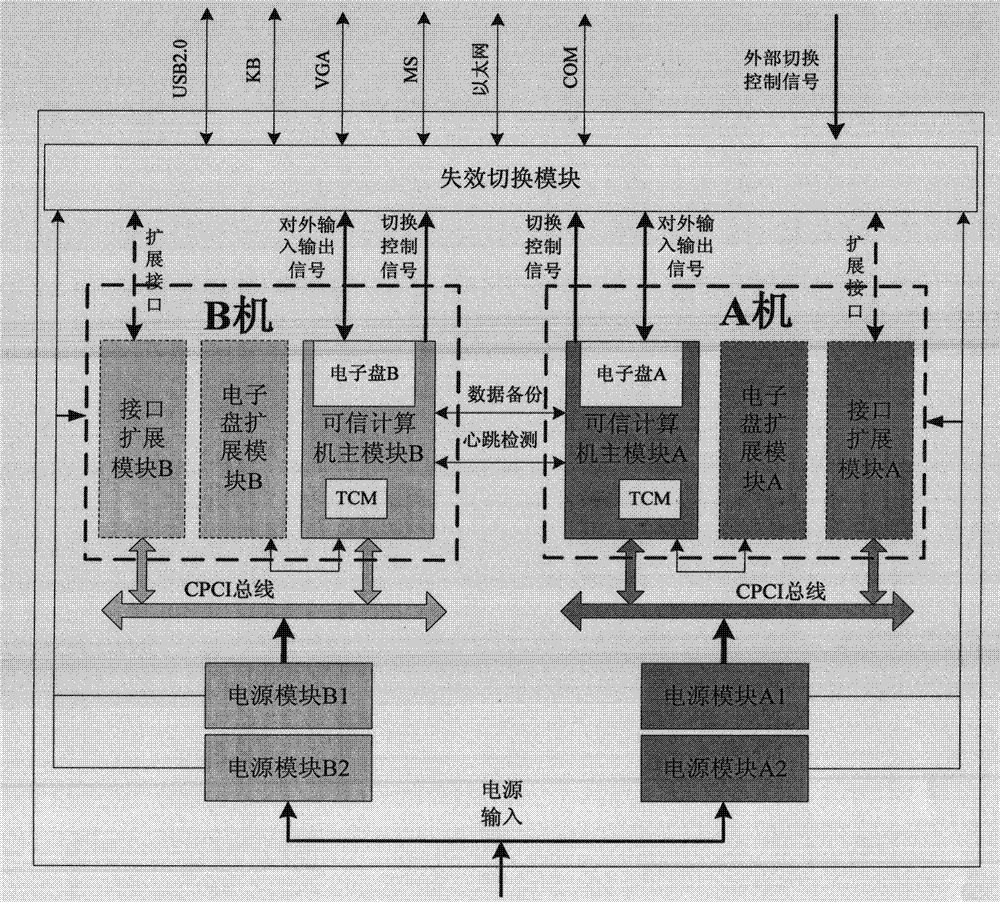
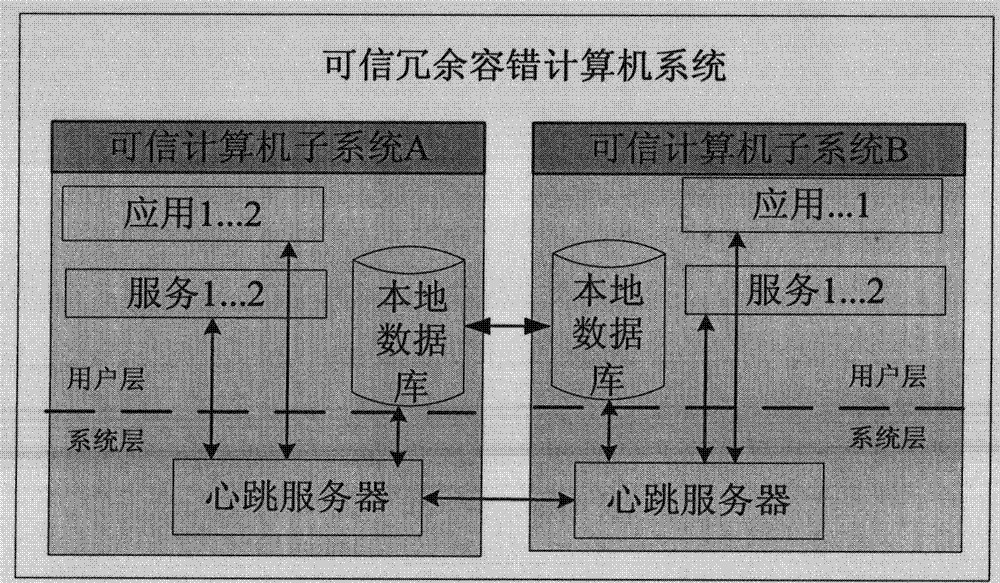
Trusted redundant fault-tolerant computer system
ActiveCN102708028AGuaranteed safe and reliableImprove mission reliabilityRedundant hardware error correctionComputerized systemTrusted Computing
The invention provides a trusted redundant fault-tolerant computer system which aims at satisfying the requirement for high safety and high reliability of systems in safety control fields. The trusted redundant fault-tolerant computer system is capable of blocking the operation of illegal programs of malicious codes, viruses and the like, protecting the system and core applications from being destroyed, protecting important information from being revealed, stolen, tampered and ruined, and shielding faults by means of a failure switching function to enable the system to work normally when faults of the system occur. The trusted redundant fault-tolerant computer system is based on a trusted cryptography module (TCM) safety chip, and a dual-computer redundant hot standby method and a compact peripheral component interconnect (CPCI) bus framework are used. Two trusted computer subsystems are configured in a computer case, each of the trusted computer subsystems is composed of a trusted computer main module (including a TCM and a flash disk), a power source module, a flash disk expansion module and an interface expansion module, and the failure switching between the two subsystems is achieved through a heartbeat server and a failure switching module.
Owner:中国人民解放军火箭军研究院突防与防御研究所
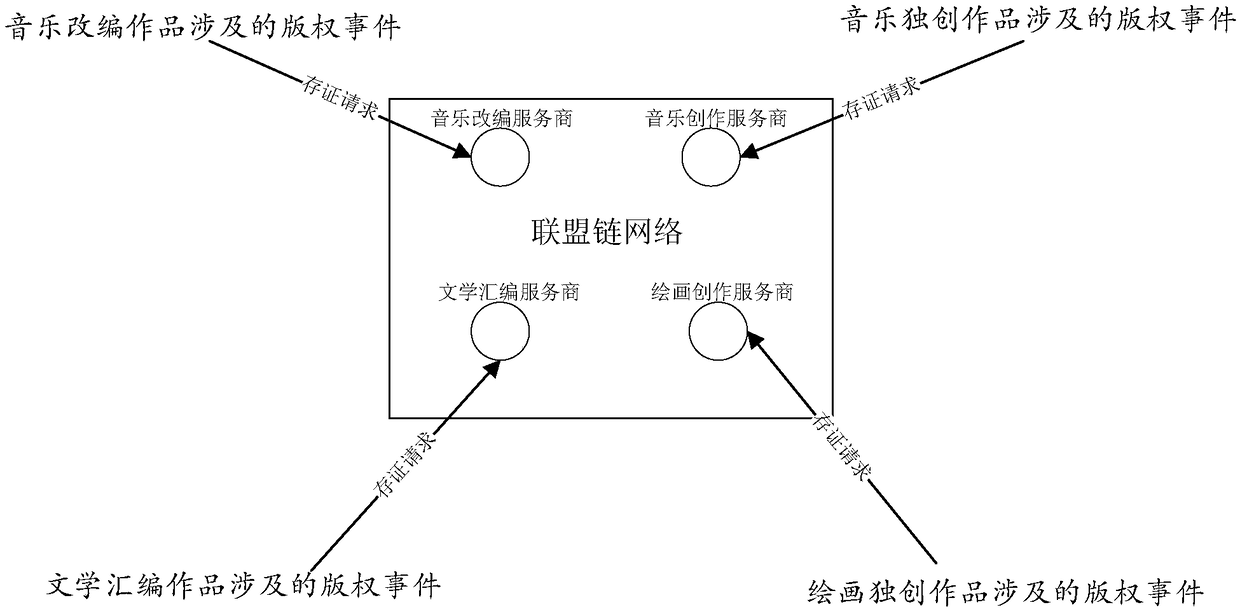
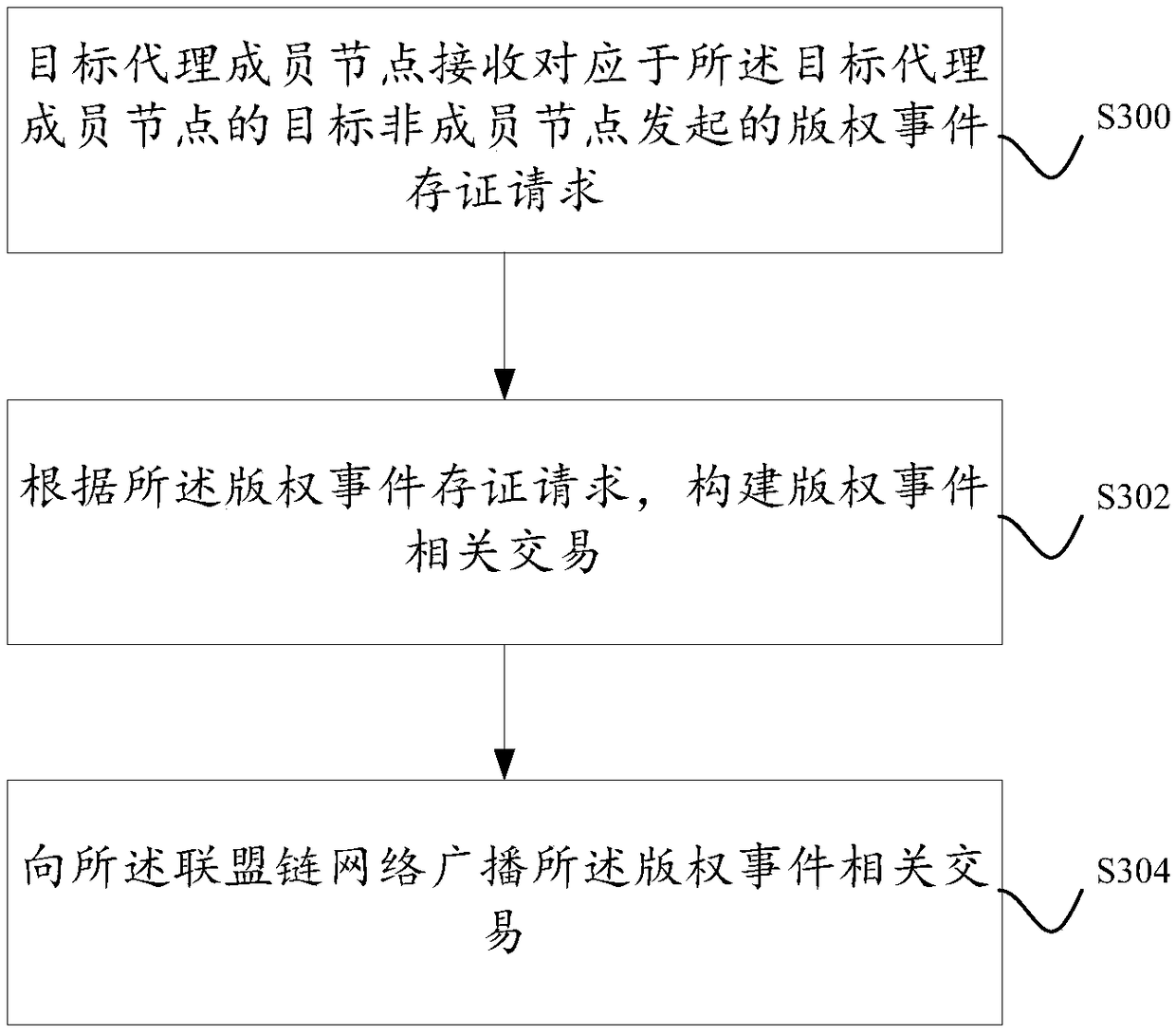
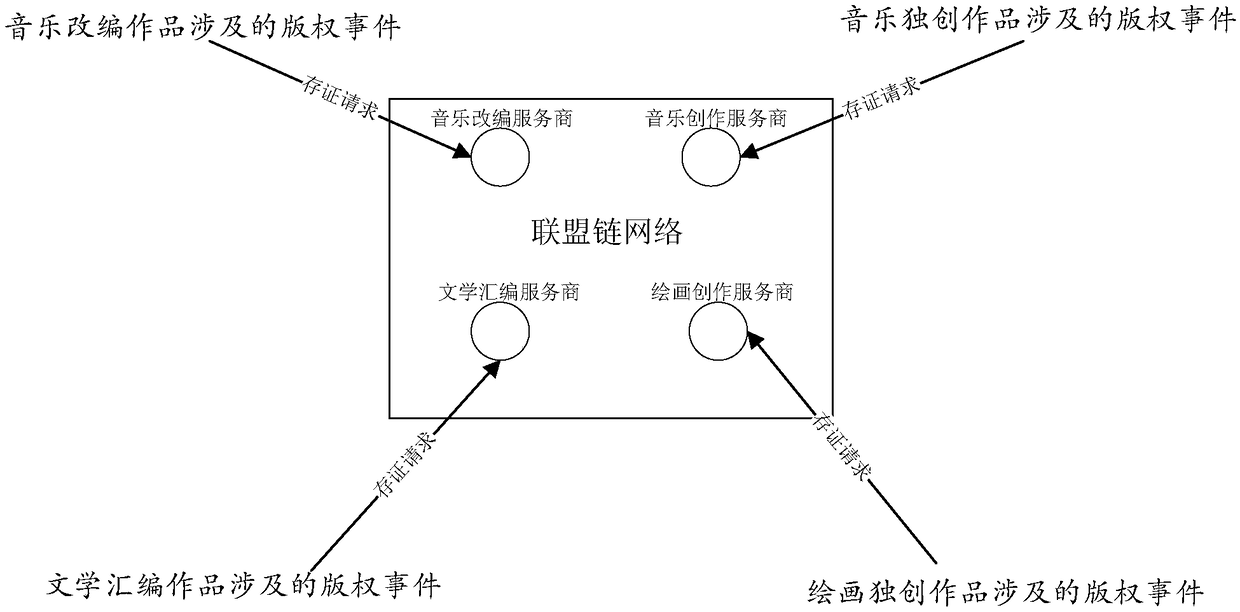
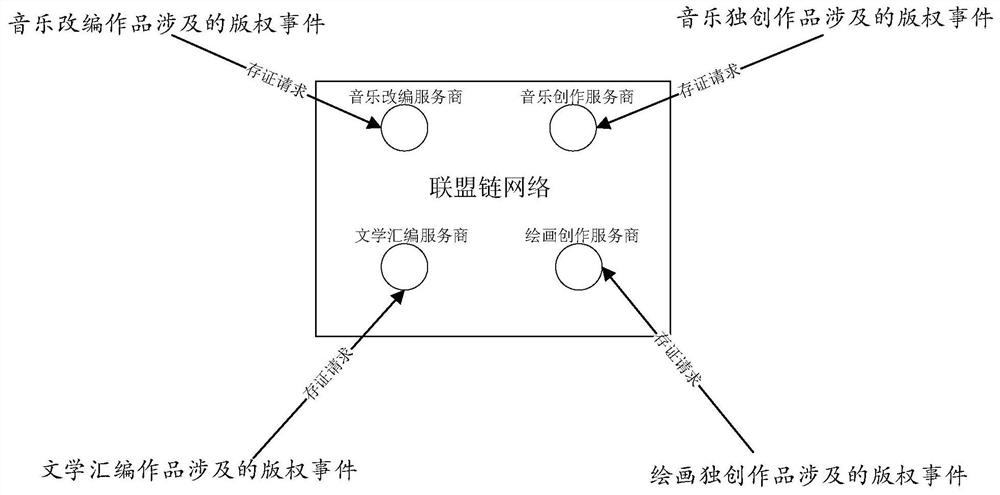
A block chain-based copyright event broker authentication method and system
ActiveCN109272385AGuaranteed safe and reliableExamples cannot be limitedOffice automationBuying/selling/leasing transactionsChain networkAuthentication
Disclosed are a block chain-based copyright event broker authentication method and system. The equipments of some works service providers that operate works-related services can be used as member nodes to form a federation chain network, and each works service provider broadcasts copyright events generated based on its own works-related services to the federation chain network, and each works service provider performs distributed certification based on the block chain. In addition, at least one proxy member node exists in each member node, and for each proxy member node, the proxy member nodehas the right to proxy non-member nodes corresponding to the proxy member node for copyright event certification.
Owner:ADVANCED NEW TECH CO LTD
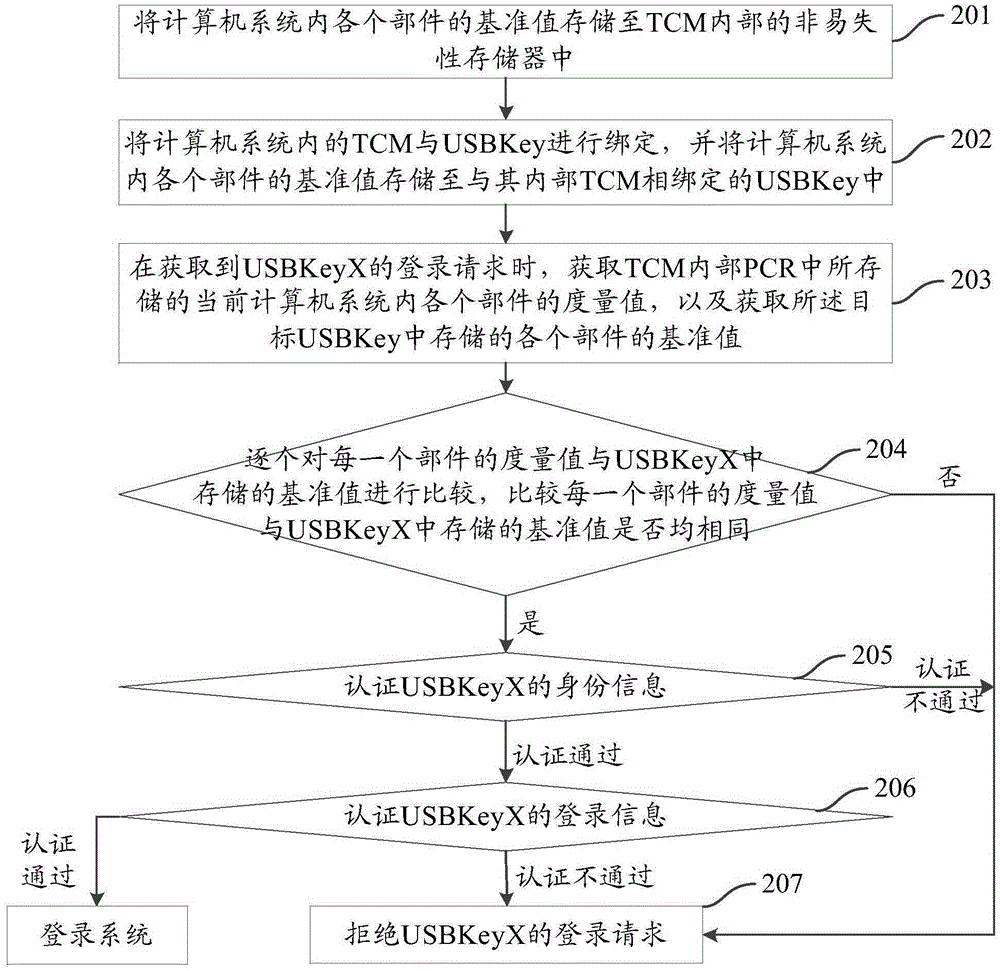
Identity authentication method and device based on trusted computing
ActiveCN105426734ARealize the second authenticationGuaranteed safe and reliableDigital data authenticationComputerized systemTrusted Computing
The invention provides an identity authentication method and device based on trusted computing. The method comprises the following steps: binding a TCM (Trusted Cryptography Module) in a computer system with a USBKey (Universal Serial Bus) in advance, and storing the reference value of each component in the computer system into the USBKey; when a login request of a target USBKey is obtained, judging whether the target USBKey is bound with the TCM in the computer system, and comparing the metric value of each component with a corresponding reference value stored in the USBKey to realize the first authentication of the target USBKey; and when the metric values of all components are the same with the reference value, authenticating the identity information of the target USBKey, and responding to the login request of the target USBKey according to an identity information authentication result to realize the secondary authentication of the target USBkey. Through the dual authentication of the target USBKey, data in the computer system can be guaranteed to be safe and trustable.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
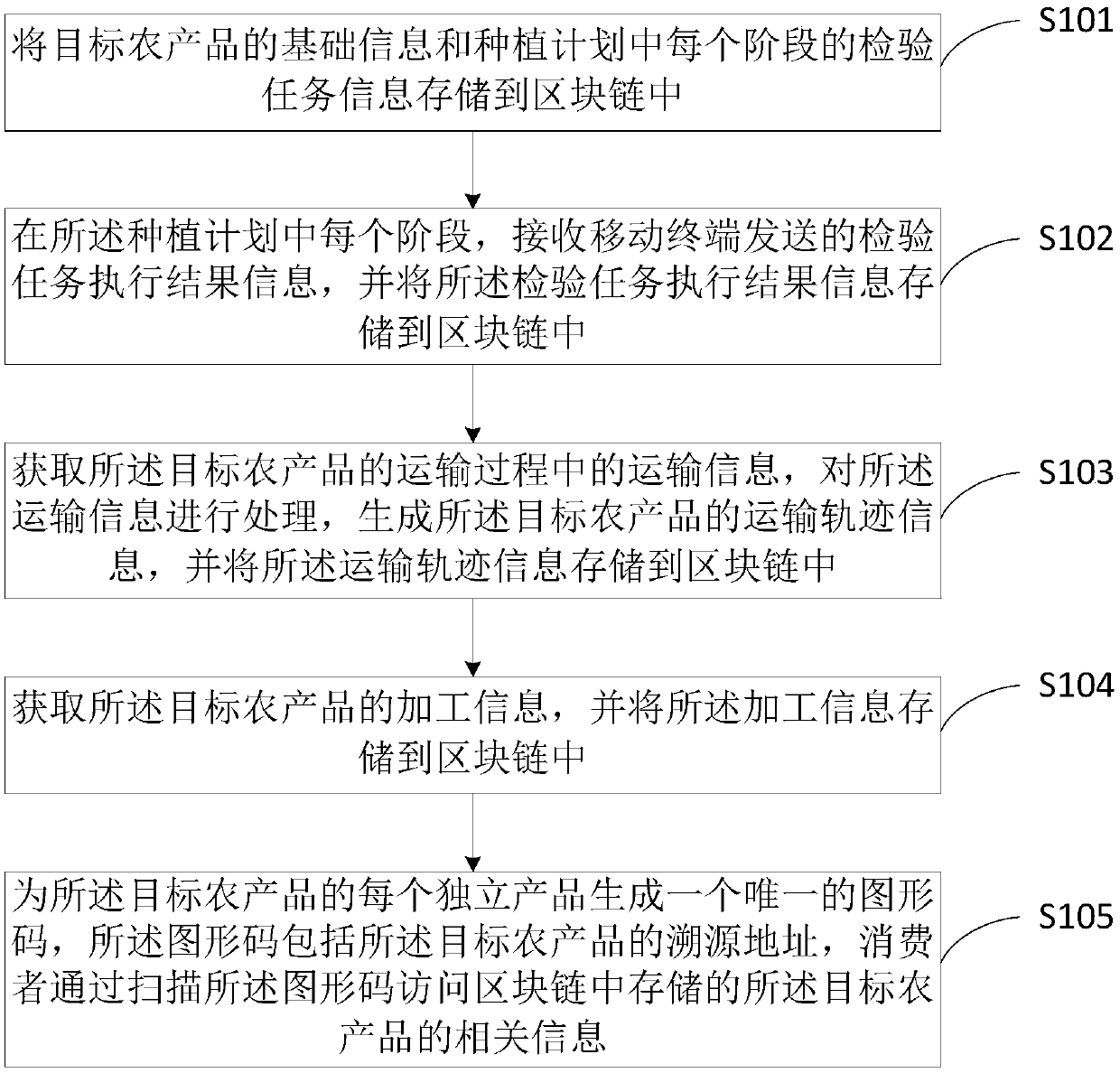
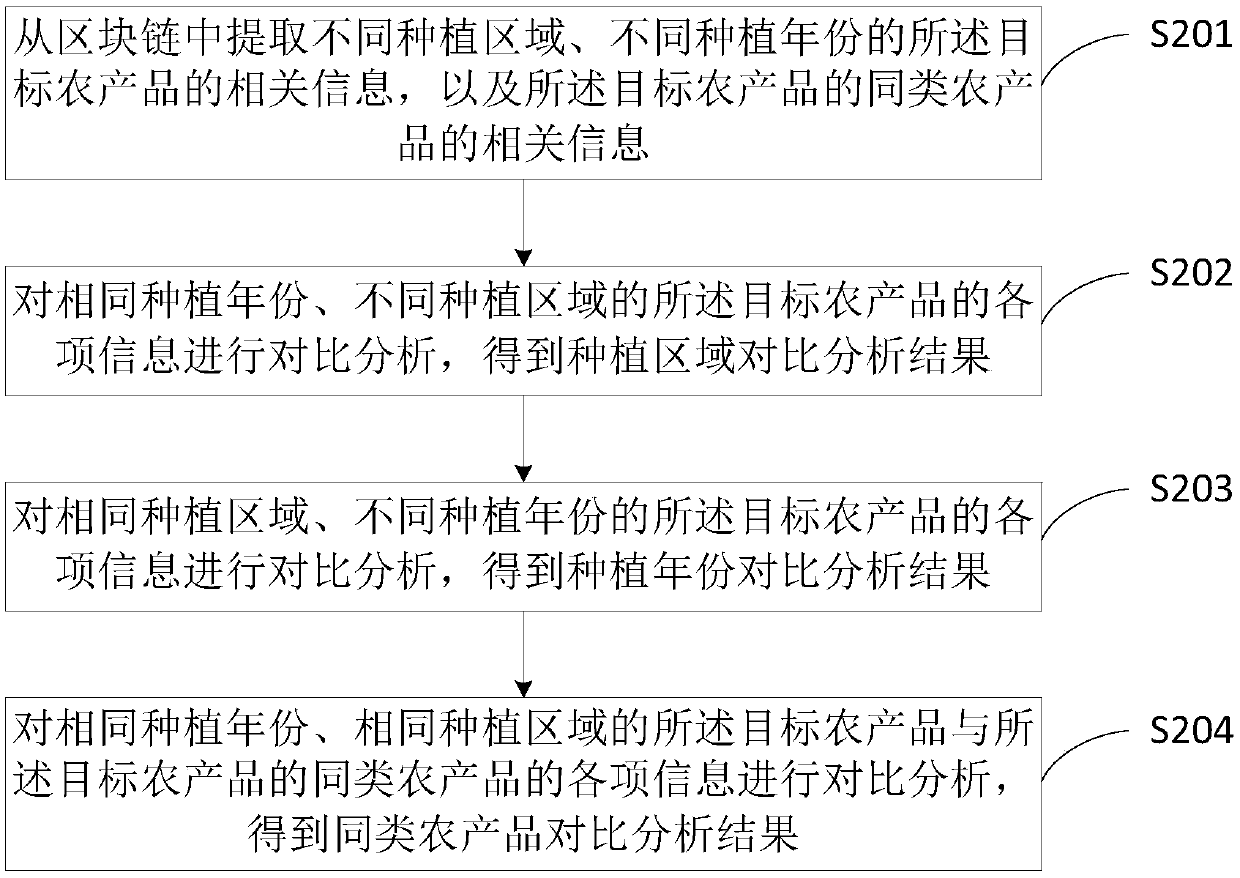
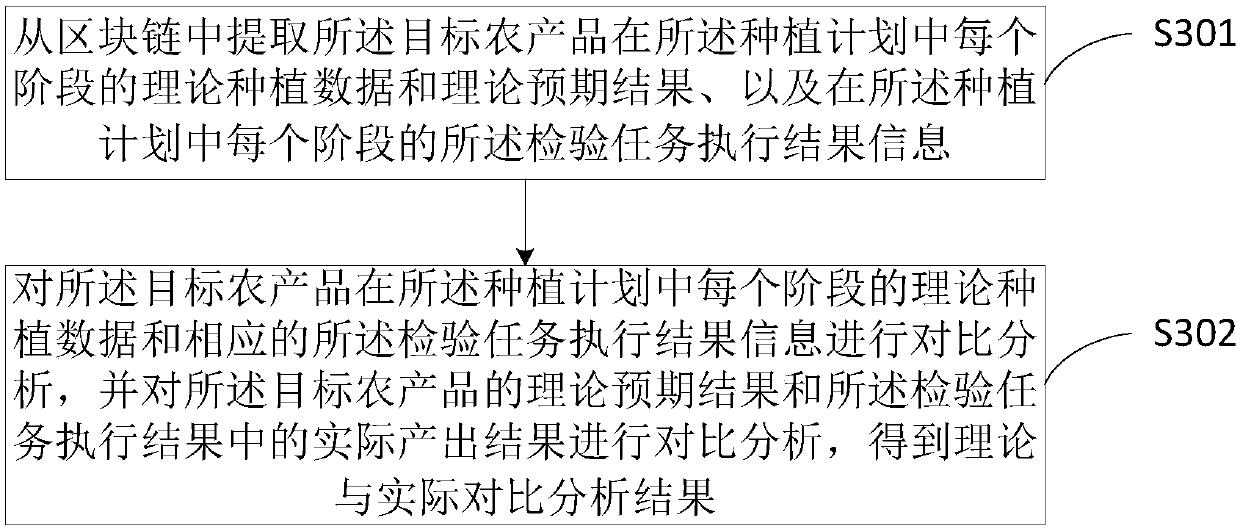
Agricultural product traceability method and system and data processing server
PendingCN109544193AGuaranteed safe and reliableScientific Data SupportDatabase distribution/replicationCo-operative working arrangementsGraphicsTamper resistance
The present application provides an agricultural product traceability method, which includes: storing basic information of a target agricultural product, inspection task information of each stage in aplanting plan, inspection task execution result information of each stage in the planting plan, transportation trajectory information of the target agricultural product, and processing information ofthe target agricultural product into a block chain; generating a unique graphic code for each independent product of the target agricultural product, wherein the graphic code includes the traceability address of the target agricultural product, and the consumer accesses the relevant information of the target agricultural product stored in the block chain by scanning the graphic code. The invention realizes that the whole process data of agricultural products from the seed stage to the final sale to the consumers is stored in the block chain. By utilizing the tamper-proof property of the blockchain, the manager and the consumers can only access the data in the block chain, but can not tamper with the data, thus ensuring the safety and reliability of the data.
Owner:黑龙江善粮味道数字农业股份有限公司
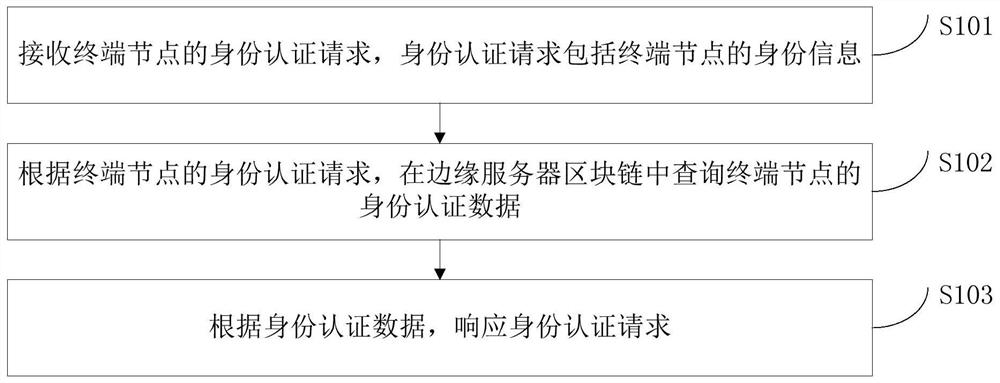
Identity authentication method and device based on block chain
PendingCN111753269AGuaranteed safe and reliableImprove usabilityDigital data authenticationEdge serverEdge computing
The invention discloses an identity authentication method and device based on a block chain. The method is applied to any edge server in an edge server block chain, and comprises the following steps:receiving an identity authentication request of a terminal node, wherein the identity authentication request comprises the identity information of the terminal node; querying identity authentication data of the terminal node in an edge server block chain according to the identity authentication request of the terminal node; and responding to the identity authentication request according to the identity authentication data. Through the implementation of the method and the device, the flexibility of terminal node identity authentication in a loose coupling environment and the availability undera distributed request are realized, so that the high-efficiency availability of an identity authentication function is ensured; and according to the embodiment of the invention, the transparency and traceability characteristics of the block chain are combined with the two-layer architecture of the edge computing, so that the terminal node is transparent to one-way information of the edge server and traceable to one-way data, and the security and credibility of an identity authentication function are ensured.
Owner:HAINAN UNIVERSITY
Virtual machine static measurement method and device based on built-in security architecture
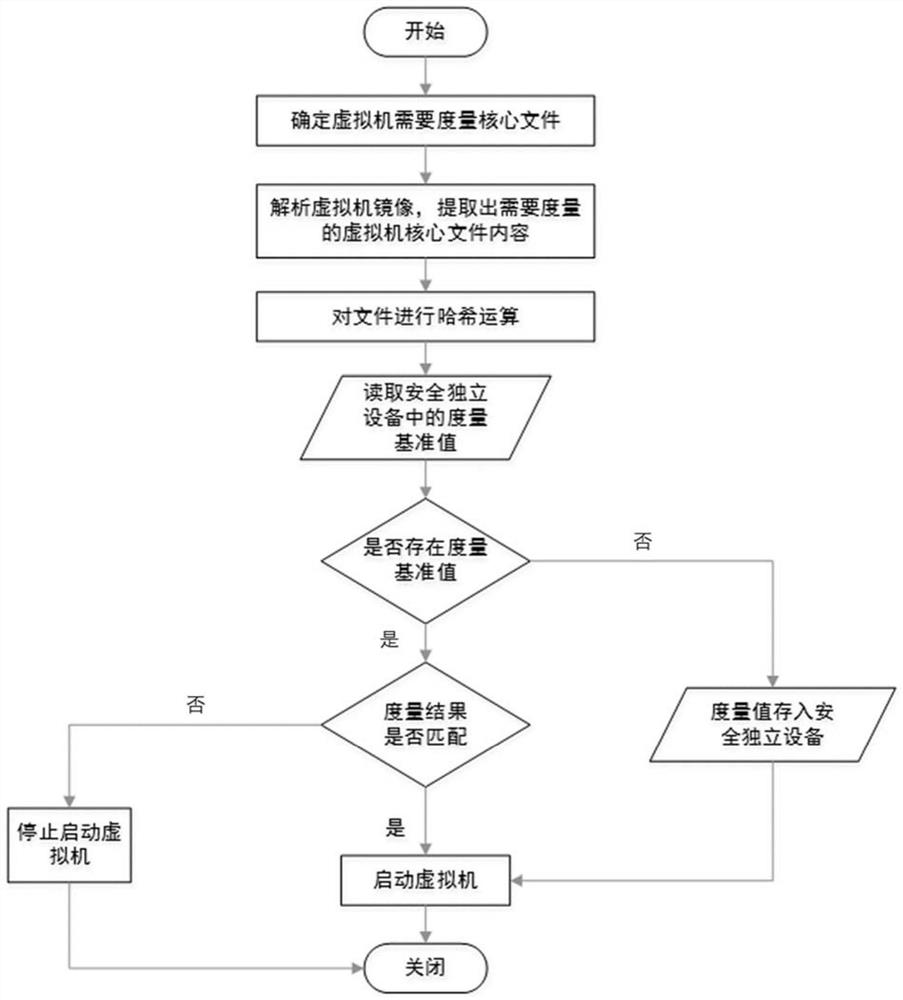
ActiveCN111638936AImprove securityEnsure safetySoftware simulation/interpretation/emulationVirtualizationSecurity measurement
The invention relates to a virtual machine static measurement method and device based on a built-in safe architecture. The method comprises the steps of in the starting process of a physical host, enabling safe independent equipment to carry out safety measurement on a host machine system and virtualization software to ensure credibility of the host machine system and the virtualization software;enabling the host machine system and the virtualization software to determine a to-be-measured virtual machine core file; analyzing the virtual machine mirror image file, extracting the content of theto-be-measured virtual machine core file, performing security measurement on the content, and generating a measurement value; if judging that the virtual machine is started for the first time, indicating that the metric value serves as a reference value to be stored in the safe independent equipment, and the virtual machine is started; and if judging that the virtual machine is not started for the first time, verifying the metric value and a reference value in the safe independent equipment, cancelling starting of the virtual machine if verification fails, and starting the virtual machine ifverification succeeds. According to the invention, the extension of the static measurement mechanism of the virtual machine to the virtual machine can be realized, and the security of the virtual machine is enhanced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Credible IOT (Internet of Things) implementation method based on TPM chip
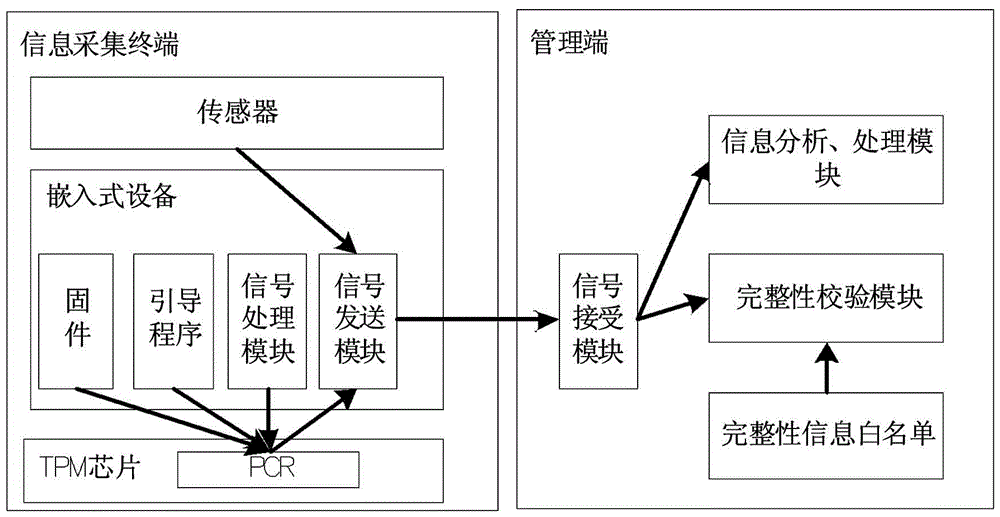
InactiveCN106125627AAdd credible attributesPracticalProgramme controlComputer controlInformation processingOperational system
The invention discloses a credible IOT (Internet of Things) implementation method based on a TPM chip, and the implementation process of the method comprises the steps: setting an information collection terminal and a management terminal, wherein the information collection terminal is information collection equipment provided with the TPM chip, and the management terminal is used for receiving the information collected by the information collection terminal and completing the information processing and analysis; collecting the integrity information of the information collection terminal through the TPM chip, enabling the integrity information to be uploaded to the management terminal, and verifying the integrity of the information collection terminal so as to judge whether the information collection terminal is credible or not. Compared with the prior art, the method employs the physical features of the TPM chip to collect the integrity information of the hardware, an operating system and an operation program of the information collection terminal, adds credible attributes to the information collection terminal, guarantees the safety and credibility of the IOT information collection terminal, is high in practicality, and is easy for popularization.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Embedded system and implementation method of secure operating system
ActiveCN103617128AAvoid destructionEnsure safetyMemory adressing/allocation/relocationComputer hardwareOperational system
The invention discloses an embedded system and an implementation method of a secure operating system. A hardware system comprises an encryption chip which supports an RSA asymmetric encryption algorithm and can provide 2048-bit private keys, and a protected nonvolatile memory. A software system carries out asymmetric encryption algorithm authentication on progresses on the basis of a Linux operating system, operations related to the private keys are accomplished in a specific memory region, namely a section with a hidden address, of the protected nonvolatile memory, only the progresses which pass authentication can run in the secure operating system at the moment, and the progresses which do not pass authentication can be killed. Due to the fact that the secure operating system has the memory protection function, the key authentication function and the like, the secure operating system is a trusted computing framework system, and has high safety. The secure operating system is mainly used in the special fields, such as the security field and confidentiality field, and can be matched with hardware systems of universal PCs, embedded tablet personal computers and the like.
Owner:湖南长城科技信息有限公司 +1
Method and system for managing and controlling mobile medium access authority in domestic operating system
InactiveCN106599690AAvoid harmGuaranteed safe and reliablePlatform integrity maintainanceOperational systemMobile device
The invention provides a method and system for managing and controlling mobile medium access authority in a domestic operating system. The method specifically comprises the following steps: managing read-write authority, an execution authority, renaming authority, deletion authority and authority change of a mobile medium; and performing transmission management and control and access management and control on the mobile medium. By adoption of the method and system provided by the invention, the mobile medium can be dynamically monitored, and a malicious code is interrupted before being executed to prevent the harms brought by the malicious code to a host and guarantee the instantaneity of management and control. The tampering of the file in the mobile medium can also be prevented to ensure the safety and feasibility of mobile devices.
Owner:HARBIN ANTIY TECH
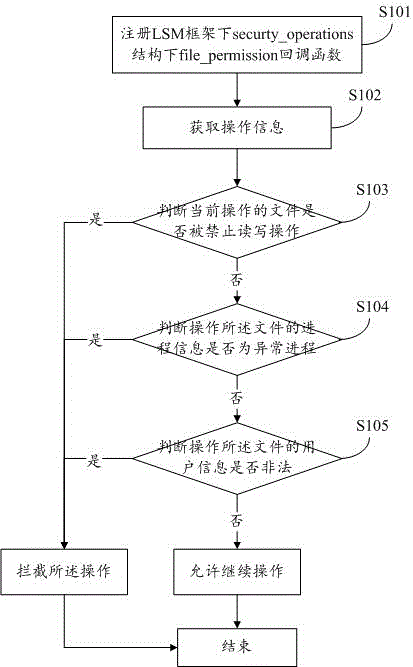
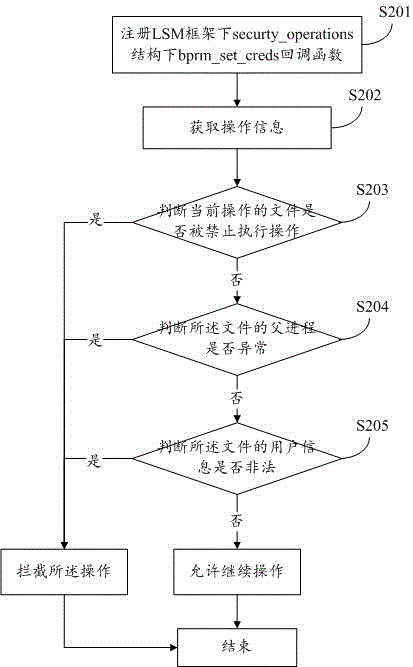
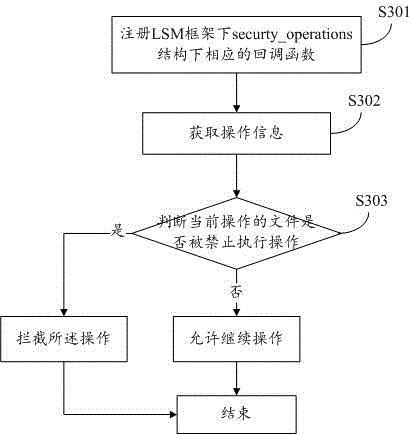
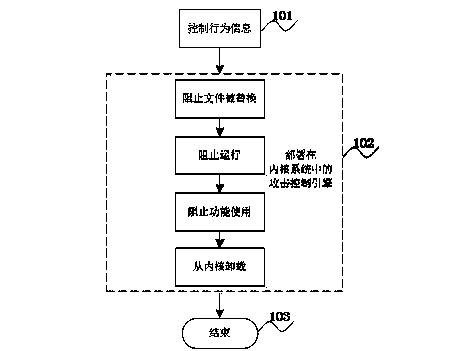
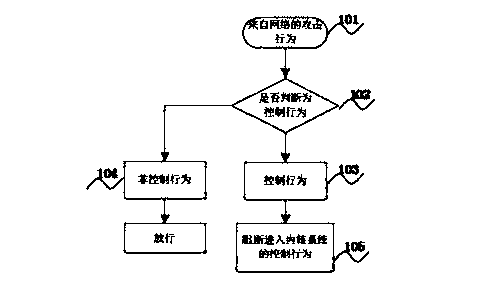
Attacking control method for protecting kernel system
InactiveCN103679015AGuaranteed safe and reliablePlatform integrity maintainanceComputer securityPilot system
The invention discloses an attacking control method for protecting a kernel system. The attacking control method includes the step 101 that an active trapping system is set up in pre-defense in a network defense system, an attacking control engine of the trapping system is arranged in the kernel system, and an attacking detection engine, an analysis engine and a control engine are set up in the kernel system of an operating system of a computer to detect and control act information, the step 102 that information from the step 101 is obtained through the attacking control engine arranged in the kernel system, and the attacking control engine can prevent files in a kernel from being maliciously attacked and replaced, prevent running of malicious acts and utilization of the functions of the malicious acts and finally uninstall the malicious acts from the kernel system, and the step 103 that the process is ended. According to the attacking control method, whether acts are control acts or not can be judged, and the malicious control acts can be timely blocked by conducting fine-grained searching and killing such as pilot system file protection check, loading system file protection check, drive module protection check and hardware supporting module protection check, and security and credibility of the kernel system are ensured.
Owner:江苏中科慧创信息安全技术有限公司
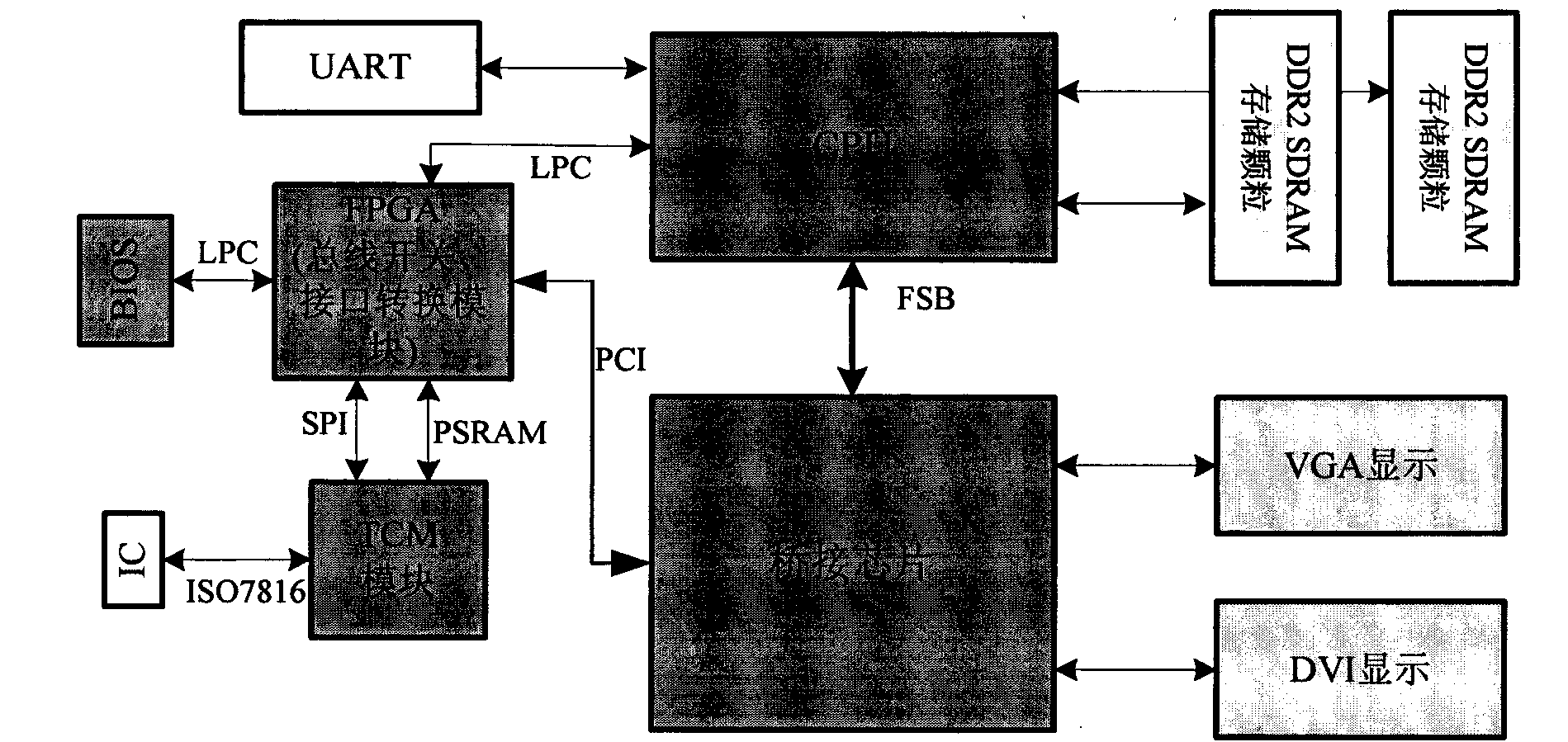
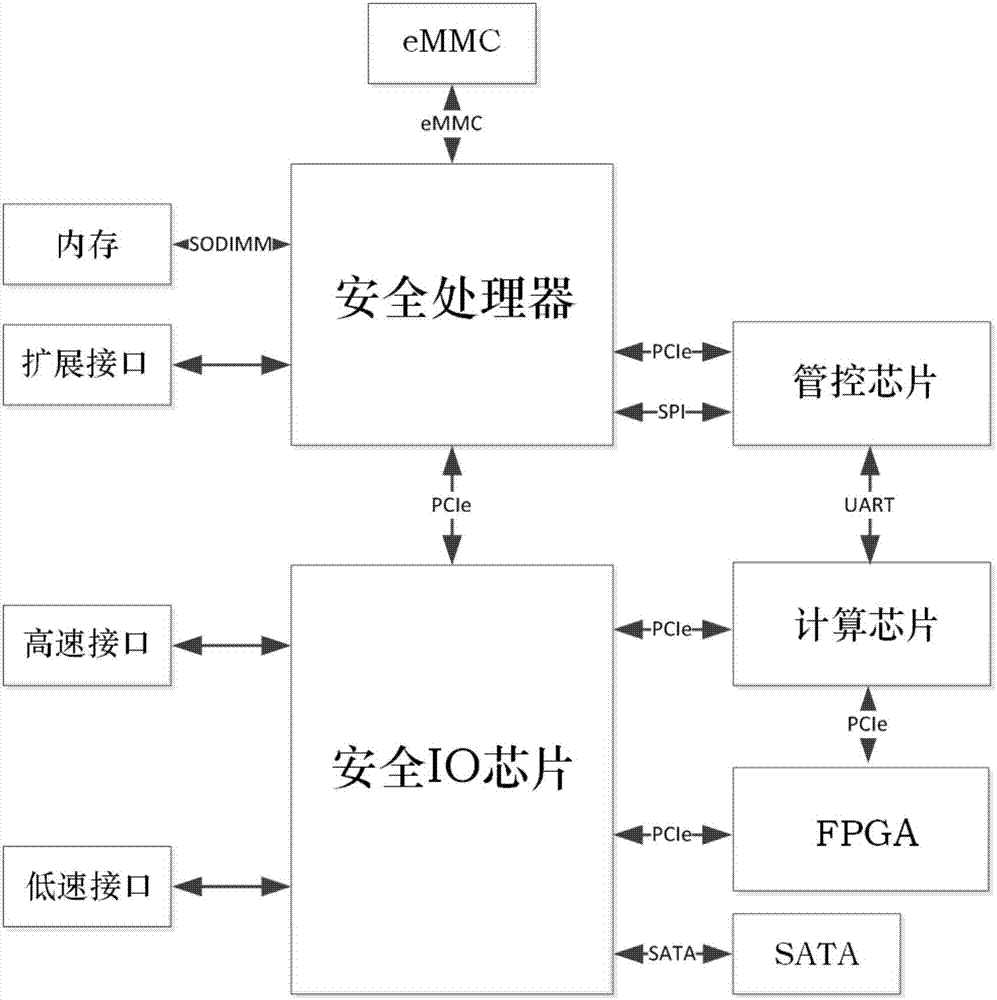
Computer mainboard framework based on domestic security processor, and operating method
InactiveCN106971110AImprove stabilityImprove securityPlatform integrity maintainanceSafe handlingFpga chip
The invention relates to a computer mainboard framework based on domestic security processor, and operating method, and belongs to the technical field of the secure and trusted design of a domestic computing platform and mainboard framework design. The framework comprises a security operator, a security IO (Input / Output) bridge sheet, a management and control chip, a computing chip and an FPGA (Field Programmable Gate Array) chip, wherein the security operator, the security IO bridge sheet, the management and control chip, the computing chip, the FPGA and other peripheral circuits realize bottom layer hardware; the security operator provides an operation control kernel and an expansion interface; the security IO bridge sheet is taken as a Switch controller to provide an IO component; the management and control chip realizes startup guidance and trusted measurement; and the computing chip and the FGPA chip realize a data decryption algorithm. The computer mainboard framework is a safe and trusted domestic autonomous computer mainboard framework.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
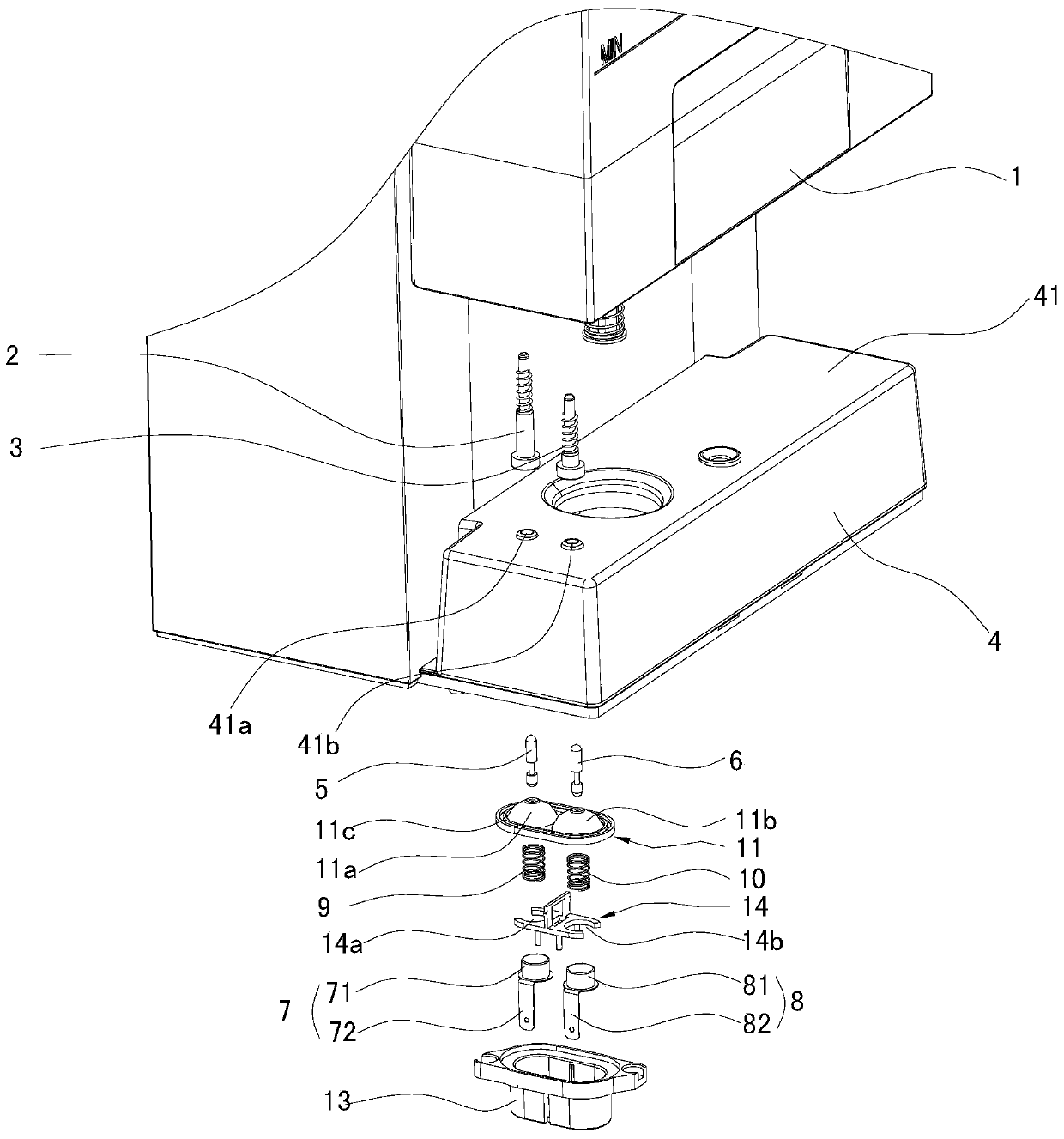
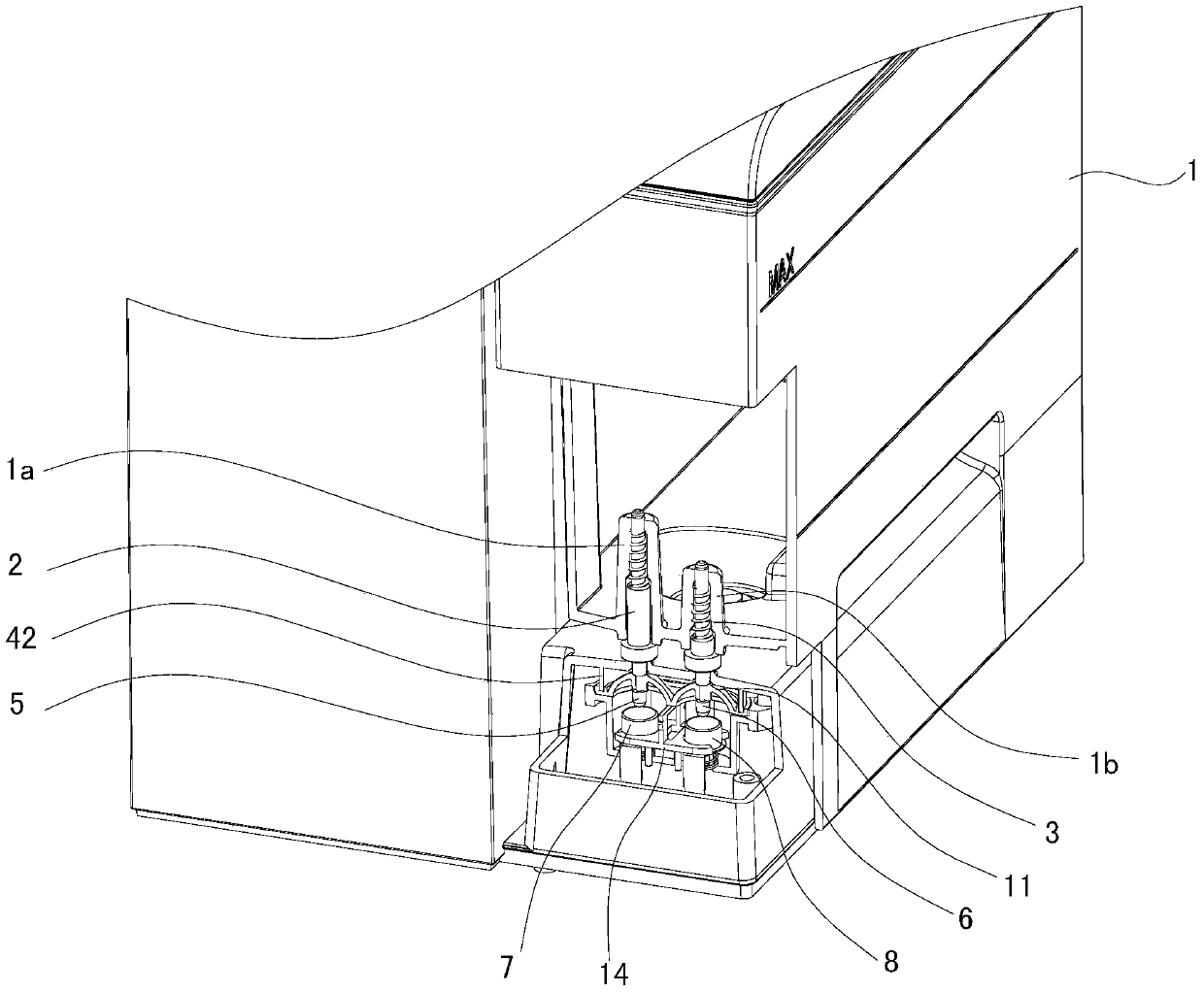
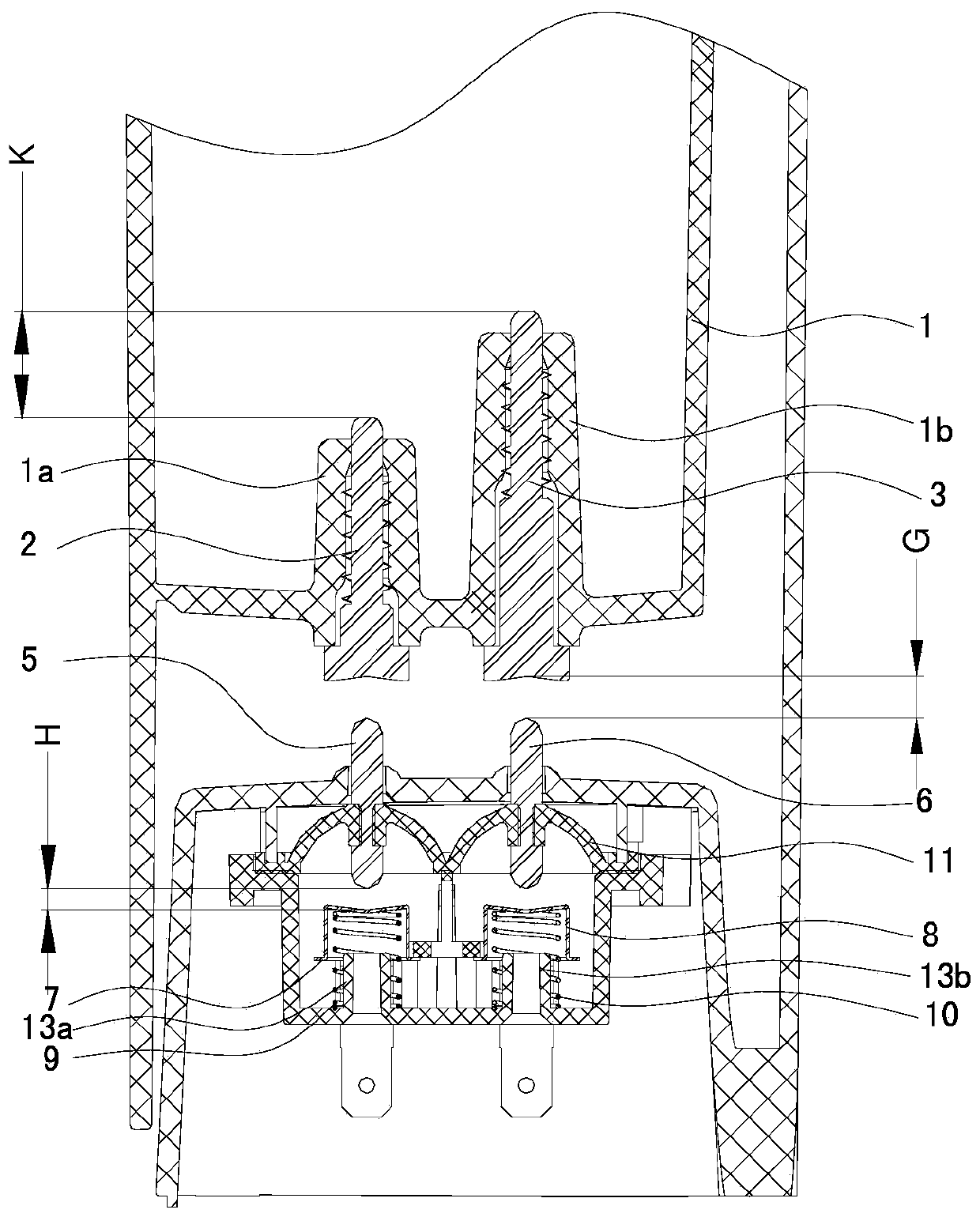
Water level detection device and Turkish coffee machine with same
InactiveCN106510470APrevention of dry burningAvoid no loadBeverage vesselsElastic componentEngineering
The invention discloses a water level detection device and a Turkish coffee machine with the same. The water level detection device comprises a base, a water tank, a first water level induction pin and a second water level induction pin, wherein the water tank is installed on the base separably; the first water level induction pin and the second water level induction pin are installed at the bottom of the water tank, the upper ends of the first water level induction pin and the second water level induction pin extend into an inner cavity of the water tank, and the lower ends of the first water level induction pin and the second water level induction pin extend out of the water tank. The water level detection device further comprises an installation box, a first conductive part, a second conductive part, a first elastic pin, a second elastic pin and a first elastic component, wherein the installation box is installed in the base; the first conductive pin and the second conductive pin are installed in the installation box; the first elastic pin and the second elastic pin are installed in the positions, corresponding to the first water level induction pin and the second water level induction pin, of the top of the base respectively and can move vertically between an off position and an on position; and the first elastic component is installed on the first elastic pin and the second elastic pin. The water level detection device is high in detection precision and can guarantee electric safety.
Owner:GUANG DONG ELEC-TECH RETOP LED DISPLAY CO LTD
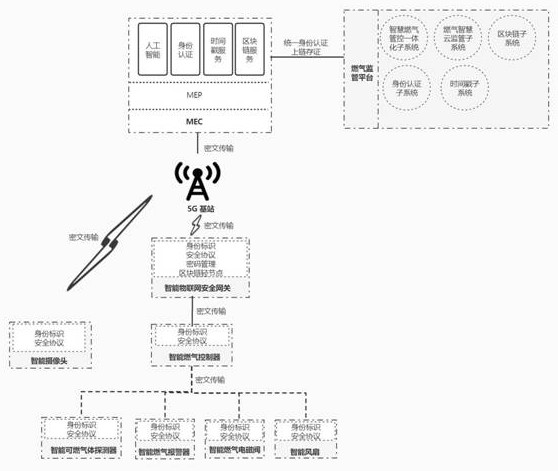
Fuel gas supervision system and supervision method
PendingCN114331759AEnsure safetyGuaranteed accuracyData processing applicationsDatabase distribution/replicationData packTimestamp
The invention is suitable for the technical field of fuel gas supervision, and provides a fuel gas supervision system, which comprises terminal equipment, an intelligent Internet of Things security gateway and a fuel gas supervision platform which are connected in sequence, the terminal equipment is used for being connected with the intelligent Internet of Things security gateway and uploading information data of the terminal equipment to the intelligent Internet of Things security gateway; the intelligent Internet of Things security gateway is used for encrypting and packaging the information data of the terminal equipment into an encrypted data packet and uploading the encrypted data packet to the gas supervision platform by using a 5G network; the fuel gas supervision platform comprises an intelligent fuel gas management and control integrated subsystem, a block chain subsystem, an identity authentication subsystem and a timestamp subsystem. According to the invention, identity authentication, a cryptographic algorithm, a block chain and edge calculation are combined with a 5G technology, so that the equipment safety problem, the data safety problem, the real-time supervision problem and the accident traceability problem in the gas supervision process are ensured, and the automation, digitization, visualization and intelligence levels of gas supervision are effectively improved.
Owner:河南中盾云安信息科技有限公司
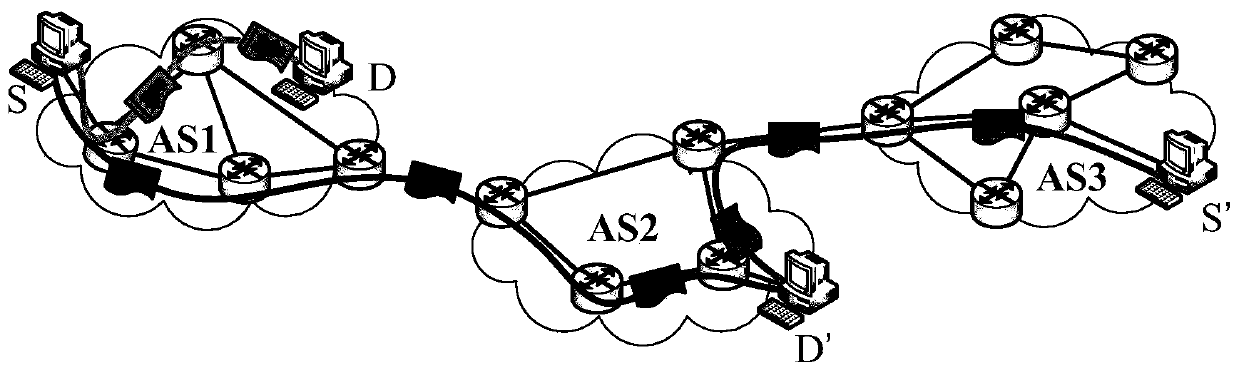
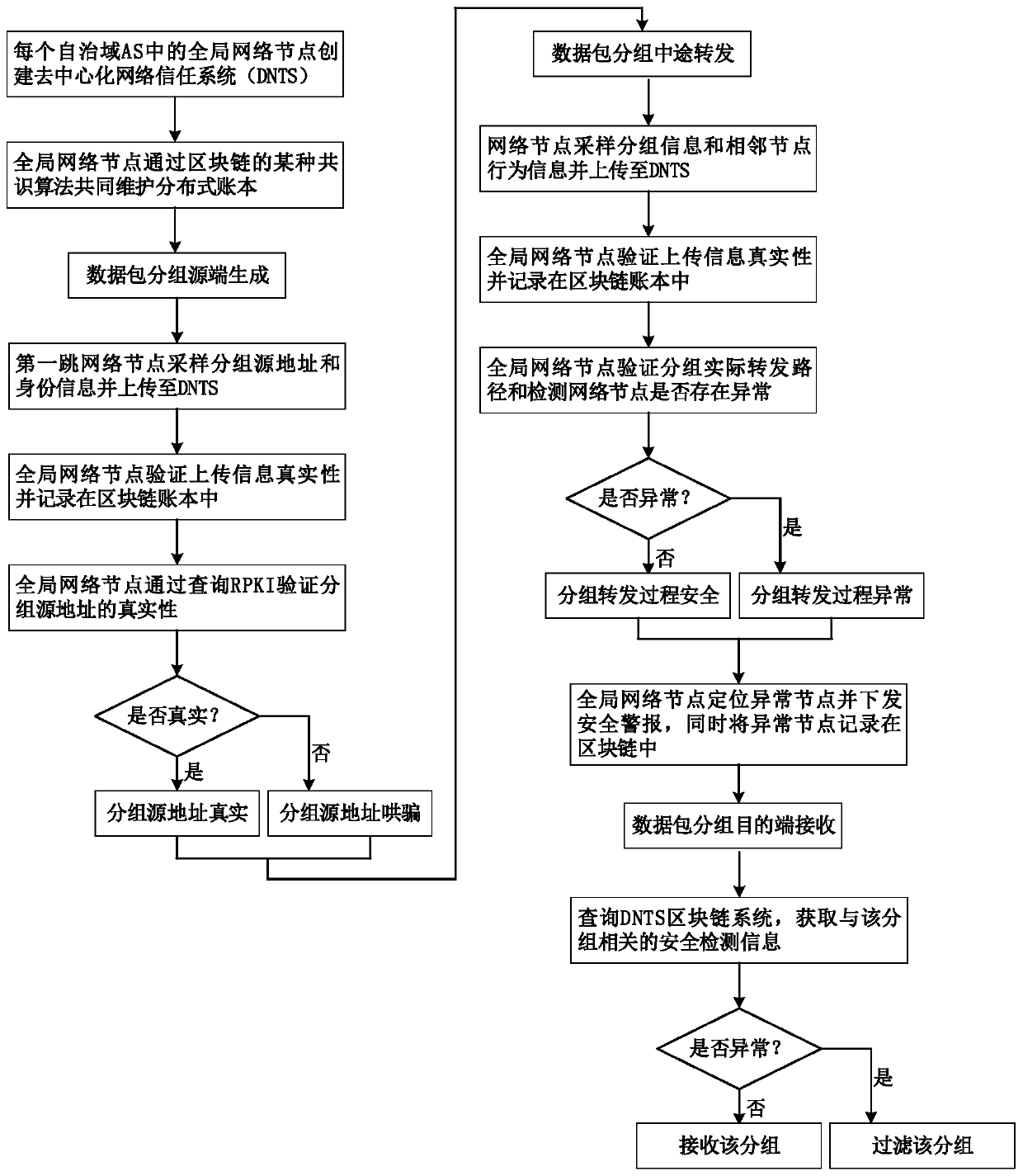
Decentralized safety guarantee method and device for packet full life cycle
ActiveCN111585984AGuaranteed safe and reliableEnsure safetyPublic key for secure communicationData packNetworked system
The invention discloses a decentralized security assurance method and device for a packet full life cycle, and the method comprises the steps: carrying out the authenticity verification of a source address and an identity of a data packet group through a distributed network node after the data packet group is generated at a communication source end; in the network forwarding process of the data packet groups, performing collaborative sampling and detection on the data packet groups through the distributed network nodes, and performing credibility verification on related routing behaviors; after the data packet group arrives at the destination end, verifying and filtering the legality of the data packet group through the destination end. According to the method, a decentralized informationmonitoring and intelligent detection technology is utilized; according to the method, the safety of the data packet groups in the whole life cycle of 'source end generation-midway forwarding-destination end receiving' is ensured, the technology has the advantages of high flexibility, strong adaptability, decentralization, robustness and the like, and the safety and credibility of the whole networksystem are ensured while the calculation overhead and the storage overhead are both considered.
Owner:TSINGHUA UNIV
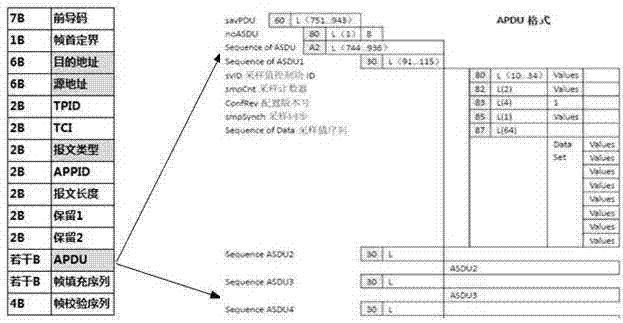
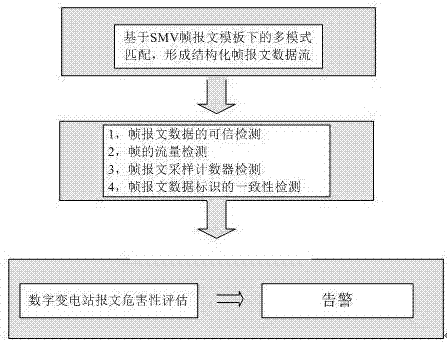
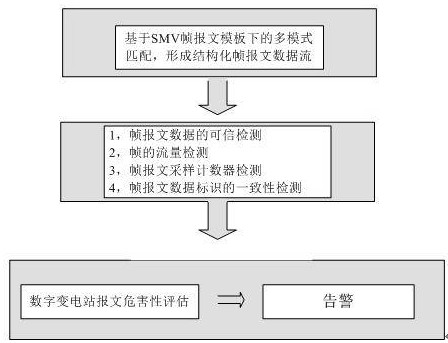
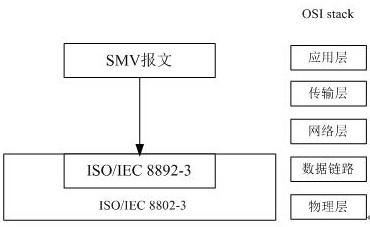
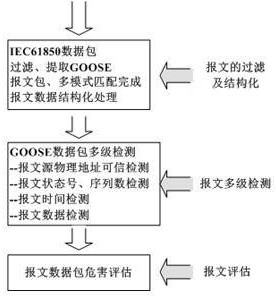
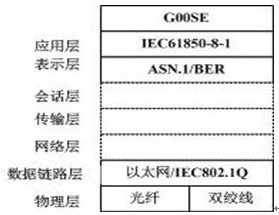
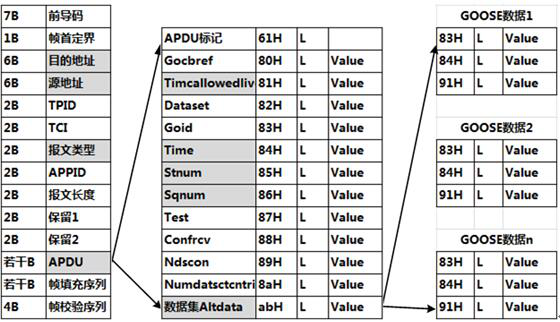
Intrusion detection method for SMV (Sampled Measured Value) message of IEC61850 digital substation
ActiveCN106936834AGuaranteed safe and reliableQuick extractionTransmissionSample MeasureDigital substation
The invention discloses an intrusion detection method for an SMV (Sampled Measured Value) message of an IEC61850 digital substation. The method mainly consists of the following three steps: rapid filtering and data structuring of the SMV message, multistage correlative detection of a data unit of an SMV frame message, and hazard assessment of the SMV message. Through adoption of the intrusion detection method, the problem that security reinforcement of the SMV message in an IEC61850 standard cannot be generally finished through encryption and digital verification methods of IEC62351 in the prior art is solved.
Owner:国网江苏省电力有限公司淮安供电分公司 +3
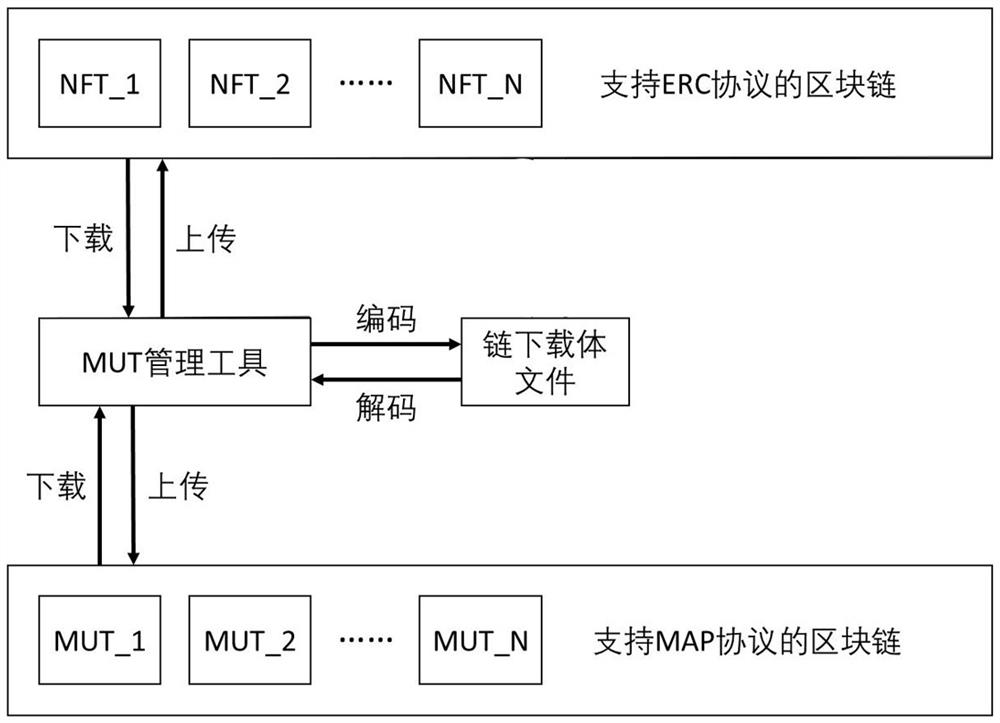
On-chain and off-chain collaborative digital asset management method and protocol for element universe application
PendingCN114707973ARealize on-chain and off-chain collaborationConsistent ownershipPayment circuitsSecuring communicationManagement toolDigital content
The invention relates to an on-chain and off-chain collaborative digital asset management method and protocol for element universe application. According to the technical scheme, the on-chain and off-chain collaborative digital asset management method for the meta universe application comprises the steps that a management tool calls a downloading interface function of a corresponding digital asset from a corresponding block chain according to a to-be-downloaded digital asset ID; after a downloading interface function of the digital assets on the block chain is called, transaction and transfer interface functions corresponding to the digital assets are set to be non-callable, and meanwhile, the block chain feeds back all digital contents corresponding to the digital assets to a management tool; the management tool packages all digital contents into an under-chain carrier file and completes private key encryption operation; and after the under-chain carrier file is packaged, the management tool obtains partial permissions of the corresponding digital assets, and the partial permissions are used for changing and calling the state of the digital assets on the block chain originally bearing the digital assets when the management tool uploads the digital assets.
Owner:中科计算技术创新研究院 +1
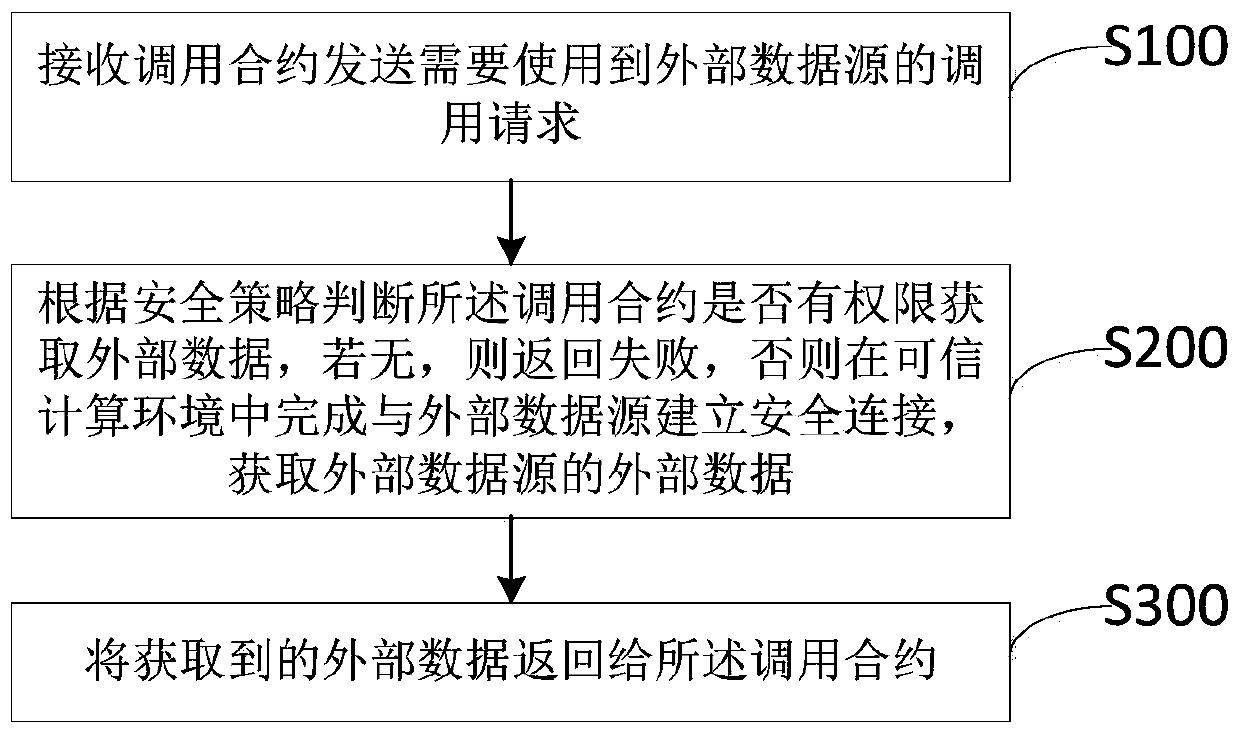
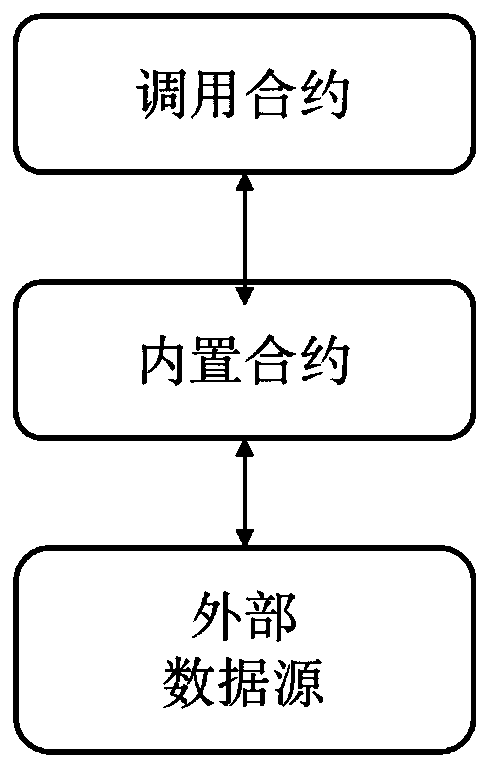
Method and device for obtaining external data from external data source in alliance block chain
InactiveCN111163093AGuaranteed safe and reliableEasy to useDigital data protectionPayment protocolsExternal dataData source
The invention discloses a method and a device for obtaining external data from an external data source in an alliance block chain. The method comprises the following steps: receiving a calling requestwhich is sent by a calling contract and needs to use the external data source; judging whether the calling contract has permission to acquire external data or not according to a security policy, if not, returning to fail, otherwise, completing the establishment of secure connection with an external data source in a trusted computing environment, and acquiring the external data of the external data source; and returning the acquired external data to the calling contract. The method and the device have the advantage that the external data can be safely, credibly and conveniently provided for the blockchain environment.
Owner:HANGZHOU QULIAN TECH CO LTD
A method of intrusion detection for iec61850 digital substation smv message
ActiveCN106936834BGuaranteed safe and reliableQuick extractionTransmissionComputer networkDigital substation
The invention discloses an intrusion detection method for an SMV (Sampled Measured Value) message of an IEC61850 digital substation. The method mainly consists of the following three steps: rapid filtering and data structuring of the SMV message, multistage correlative detection of a data unit of an SMV frame message, and hazard assessment of the SMV message. Through adoption of the intrusion detection method, the problem that security reinforcement of the SMV message in an IEC61850 standard cannot be generally finished through encryption and digital verification methods of IEC62351 in the prior art is solved.
Owner:国网江苏省电力有限公司淮安供电分公司 +3
A blockchain-based method and system for proxy deposit of copyright events
ActiveCN109272385BGuaranteed safe and reliableExamples cannot be limitedOffice automationBuying/selling/leasing transactionsEngineeringChain network
Disclosed are a blockchain-based copyright event proxy deposit method and system. The equipment of some work service providers who operate work-related businesses can be used as member nodes to form an alliance chain network. Each work service provider broadcasts copyright events based on its own work-related business to the alliance chain network. Each work service provider based on Blockchain for distributed certificate storage. In addition, there is at least one proxy member node in each member node, and for each proxy member node, the proxy member node has the authority to proxy non-member nodes corresponding to the proxy member node to deposit copyright events.
Owner:ADVANCED NEW TECH CO LTD
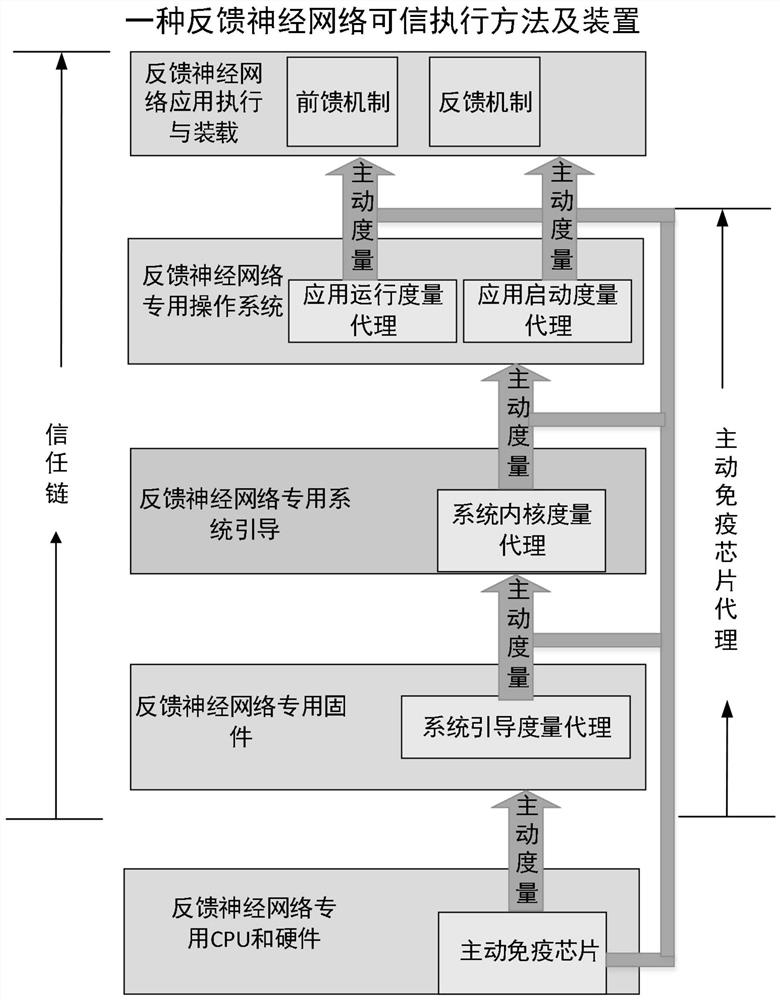
Feedback neural network trusted execution method and device
PendingCN112149800AGuaranteed safe and reliableGuaranteed uptimePlatform integrity maintainanceNeural architecturesTrusted ComputingEngineering
The invention discloses a feedback neural network trusted execution method and device, and relates to the field of deep learning and the field of information security. The system comprises a calculation component and a protection component which are parallel, and the calculation component is used for completing calculation tasks such as a feedforward mechanism module and a feedback mechanism module; the protection component is used for carrying out active measurement and active control on the calculation component through an active immune chip according to a dynamic autonomous trusted strategy; a security isolation mechanism is arranged between the computing component and the protection component, and interaction is carried out through a special access channel; the method is based on the trusted computing 3.0 technology, and the safety of the feedback neural network is improved. By performing credibility verification on each key link of feedback neural execution, the safety and credibility of feedback neural network execution are ensured.
Owner:BEIJING UNIV OF TECH
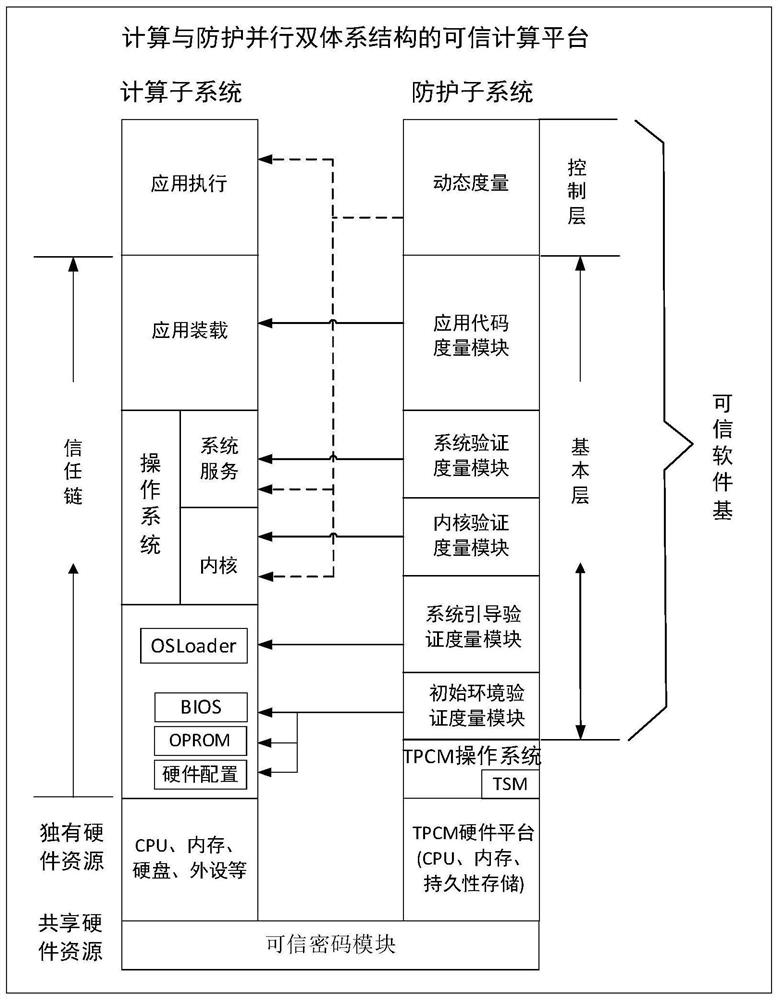
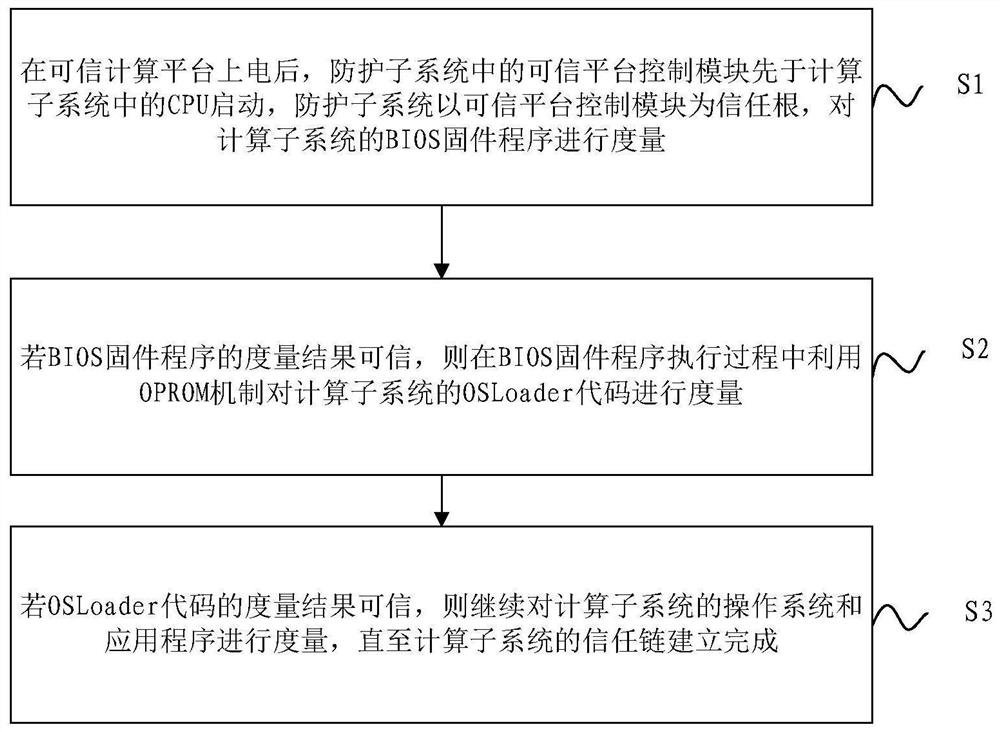
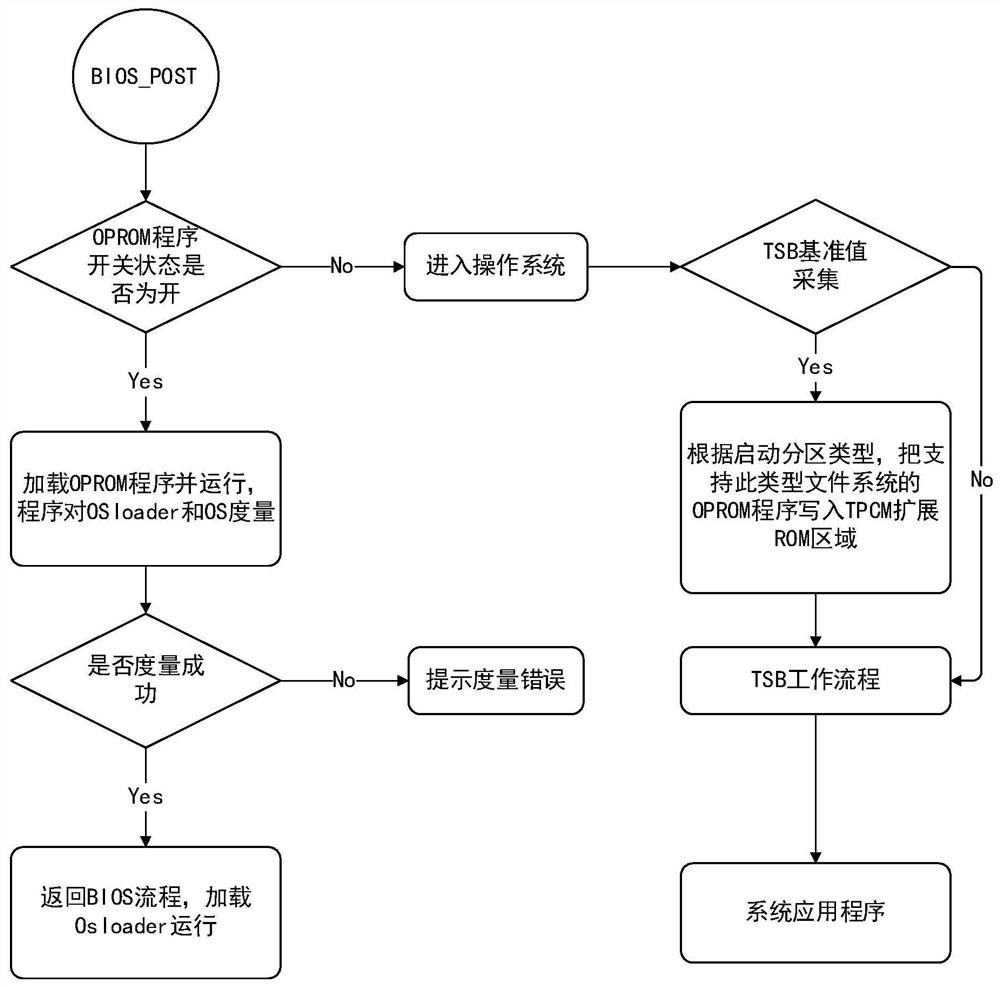
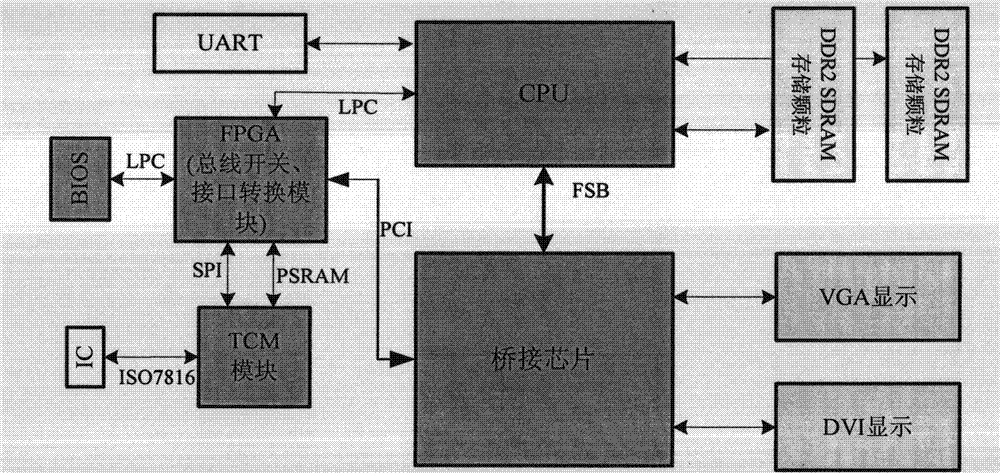
A startup measurement method and device using oprom mechanism
ActiveCN109992973BGuaranteed safe and reliableImprove securityPlatform integrity maintainanceOperational systemSoftware engineering
The invention discloses a startup measurement method and device using an OPROM mechanism. The method includes: after the trusted computing platform is powered on, the trusted platform control module in the protection subsystem is started before the CPU in the computing subsystem, and the protection subsystem The system uses the trusted platform control module as the root of trust to measure the BIOS firmware program of the computing subsystem. If the measurement result of the BIOS firmware program is credible, the OSLoader code of the computing subsystem is checked by using the OPROM mechanism during the execution of the BIOS firmware program. Perform measurement. If the measurement result of the OSLoader code is credible, continue to measure the operating system and applications of the computing subsystem until the trust chain of the computing subsystem is established. The startup measurement method provided by the present invention utilizes the OPROM mechanism to realize the startup measurement of the computer equipment without modifying the BIOS, and the startup measurement method can be adapted to all computer equipment.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
Trusted redundant fault-tolerant computer system
ActiveCN102708028BGuaranteed safe and reliableImprove mission reliabilityRedundant hardware error correctionSafety controlTrusted Computing
The invention provides a trusted redundant fault-tolerant computer system which aims at satisfying the requirement for high safety and high reliability of systems in safety control fields. The trusted redundant fault-tolerant computer system is capable of blocking the operation of illegal programs of malicious codes, viruses and the like, protecting the system and core applications from being destroyed, protecting important information from being revealed, stolen, tampered and ruined, and shielding faults by means of a failure switching function to enable the system to work normally when faults of the system occur. The trusted redundant fault-tolerant computer system is based on a trusted cryptography module (TCM) safety chip, and a dual-computer redundant hot standby method and a compact peripheral component interconnect (CPCI) bus framework are used. Two trusted computer subsystems are configured in a computer case, each of the trusted computer subsystems is composed of a trusted computer main module (including a TCM and a flash disk), a power source module, a flash disk expansion module and an interface expansion module, and the failure switching between the two subsystems is achieved through a heartbeat server and a failure switching module.
Owner:中国人民解放军火箭军研究院突防与防御研究所
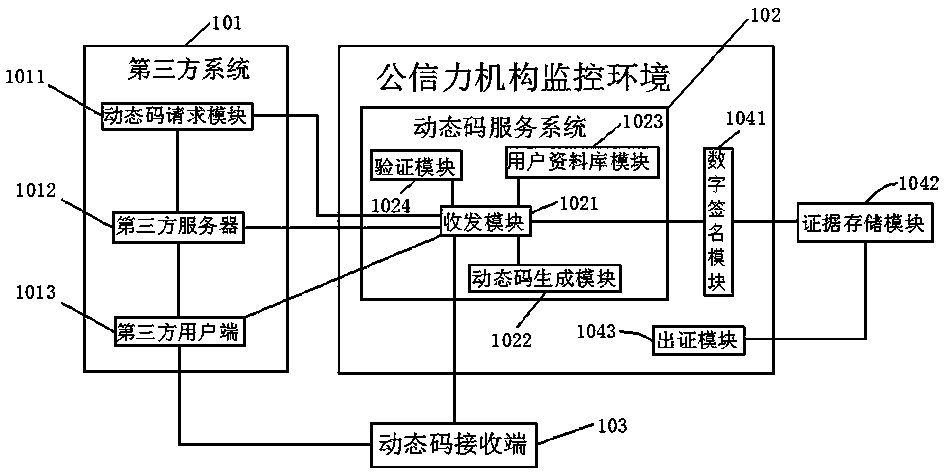
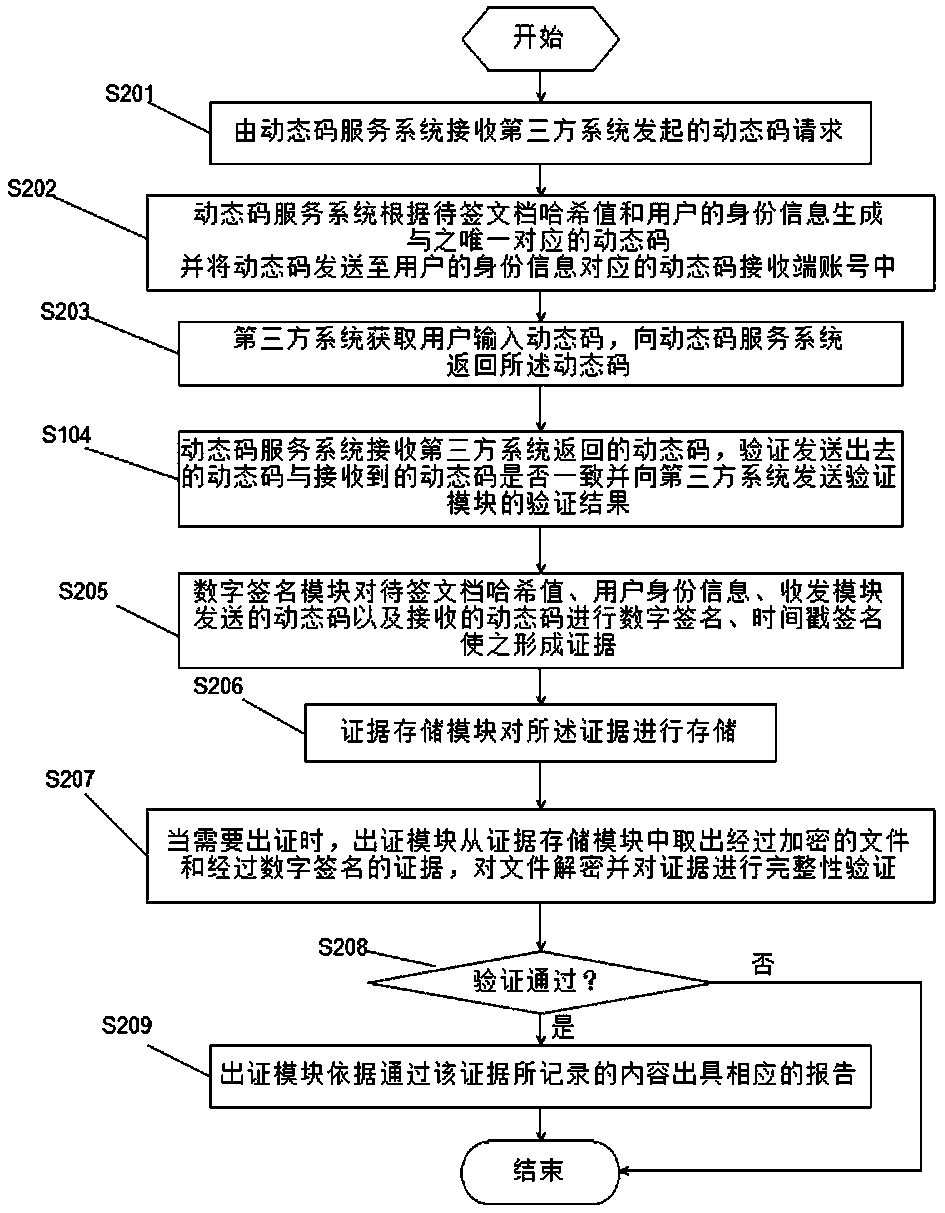
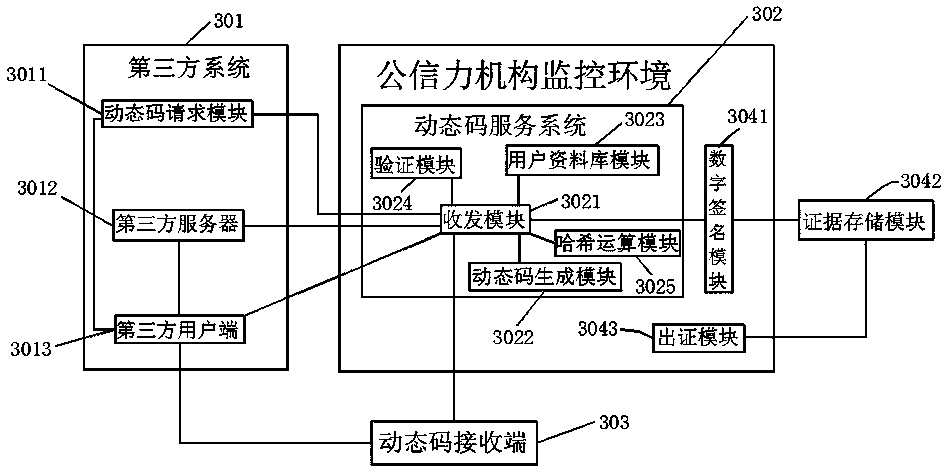
Electronic evidence processing method, system and dynamic code service system for electronic signature
ActiveCN105281913BMeet authenticityGuaranteed safe and reliableUser identity/authority verificationThird partyUser input
Owner:HANGZHOU APEMAN DATA TECH CO LTD
A method of intrusion detection for IEC61850 digital substation goose message
ActiveCN106953855BGuaranteed safe and reliableQuick extractionTransmissionDigital substationEmbedded system
The invention discloses an intrusion detection method of an IEC61850 digital substation GOOSE message. The method is mainly composed of three steps: GOOS message fast filtering and data structuring; GOOSE message multilevel association detection, and GOOSE message hazard assessment. The invention provides a realization method of intrusion detection on the IEC61850 digital substation GOOSE message, and aims at solving a problem that the safety reinforcing of the GOOSE message in the IEC61850 standard in the prior art usually cannot be accomplished through the encryption and digital verification method of the IEC62351 in an actual application.
Owner:国网江苏省电力有限公司淮安供电分公司 +3
Water level detection device and Turkish coffee machine having same
InactiveCN106510470BPrevention of dry burningAvoid no loadBeverage vesselsElastic componentEngineering
The invention discloses a water level detection device and a Turkish coffee machine with the same. The water level detection device comprises a base, a water tank, a first water level induction pin and a second water level induction pin, wherein the water tank is installed on the base separably; the first water level induction pin and the second water level induction pin are installed at the bottom of the water tank, the upper ends of the first water level induction pin and the second water level induction pin extend into an inner cavity of the water tank, and the lower ends of the first water level induction pin and the second water level induction pin extend out of the water tank. The water level detection device further comprises an installation box, a first conductive part, a second conductive part, a first elastic pin, a second elastic pin and a first elastic component, wherein the installation box is installed in the base; the first conductive pin and the second conductive pin are installed in the installation box; the first elastic pin and the second elastic pin are installed in the positions, corresponding to the first water level induction pin and the second water level induction pin, of the top of the base respectively and can move vertically between an off position and an on position; and the first elastic component is installed on the first elastic pin and the second elastic pin. The water level detection device is high in detection precision and can guarantee electric safety.
Owner:GUANG DONG ELEC-TECH RETOP LED DISPLAY CO LTD
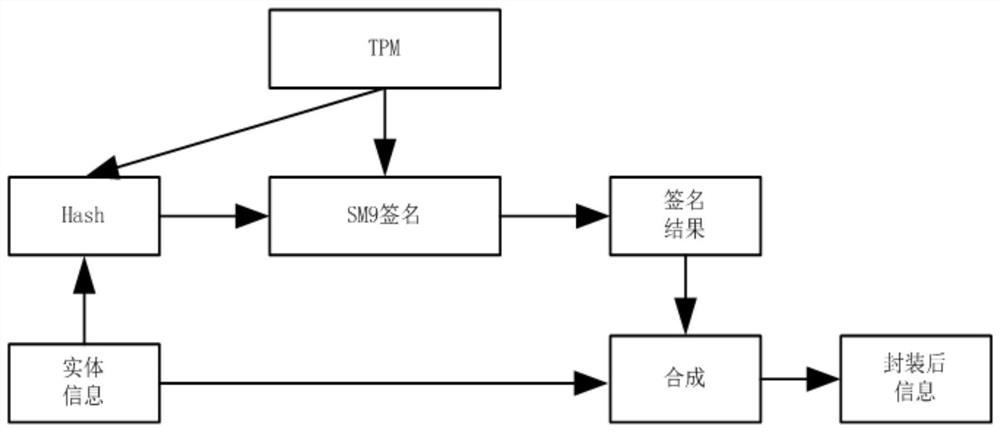
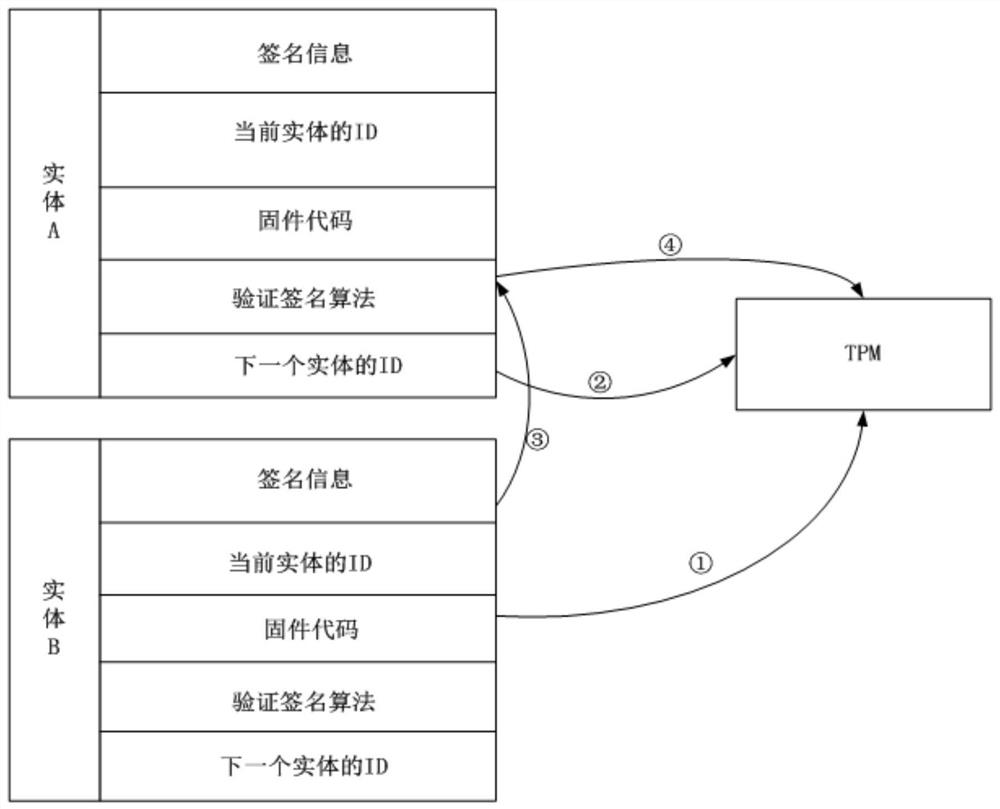
A Design Method of Trust Chain Based on SM9 Cryptographic Algorithm
ActiveCN109245899BProtection MetricsImprove integrityKey distribution for secure communicationUser identity/authority verificationAlgorithmDigital signature
The invention discloses a novel trust chain design method based on an SM9 cryptographic algorithm, and the design flow comprises initialization, the building of a secret key mapping table, the generation of signature information and the measurement verification. The beneficial effects of the invention lie in that (1), the method protects the expected measure value of an entity through employing the digital signature technology based on identity recognition, and effectively protects the integrity and reality of the information of the entity; (2), the method directly takes TPM as a trusted rootunder the condition that no CA certificate system is introduced, and the SM9 cryptographic algorithm is introduced; TPM serves as a secret key generation center, thereby achieving the flow of the digital signature and the signature verification, and guaranteeing the safe and credible of the whole process.
Owner:成都三零嘉微电子有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com