Patents
Literature
182 results about "Network defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
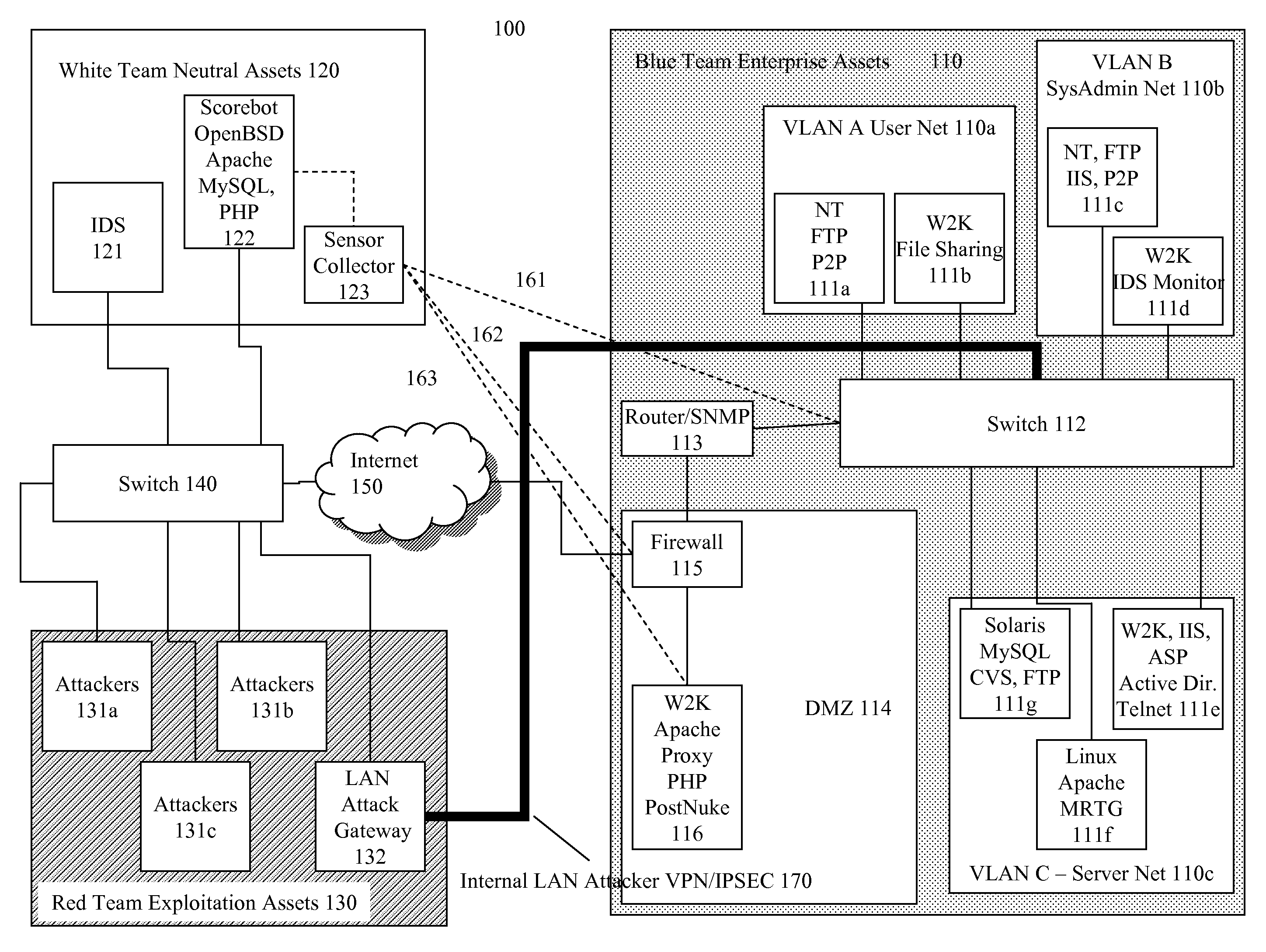
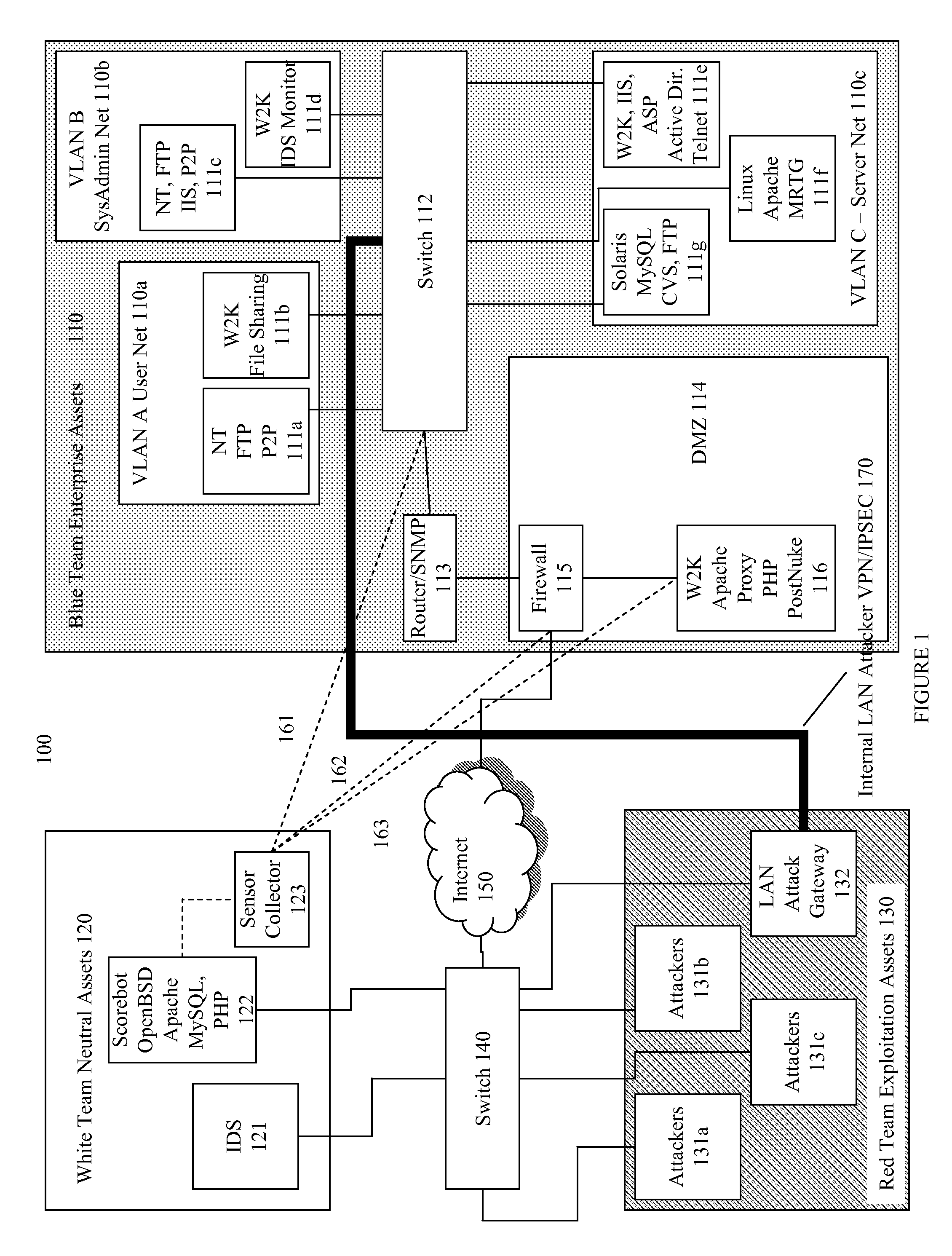
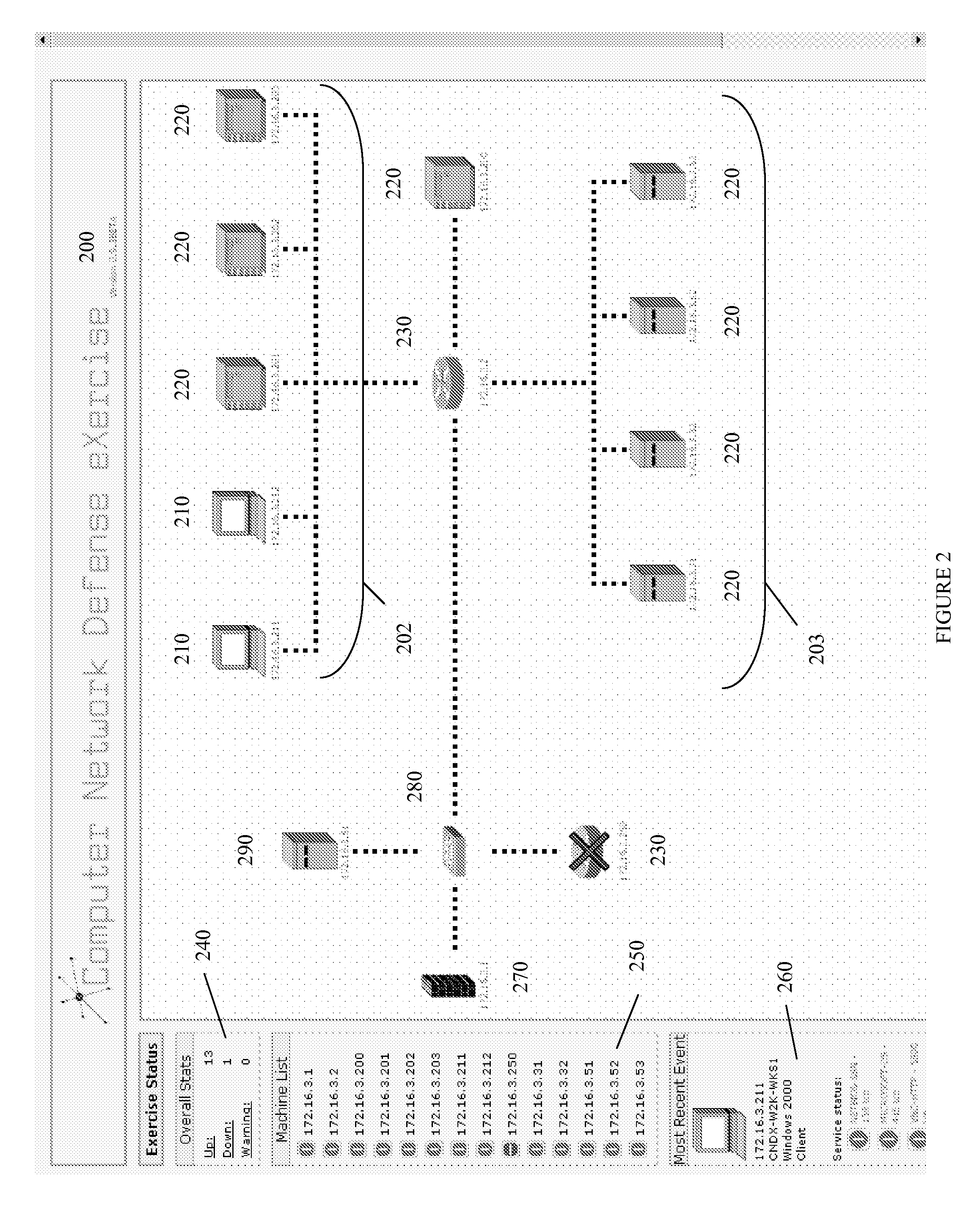
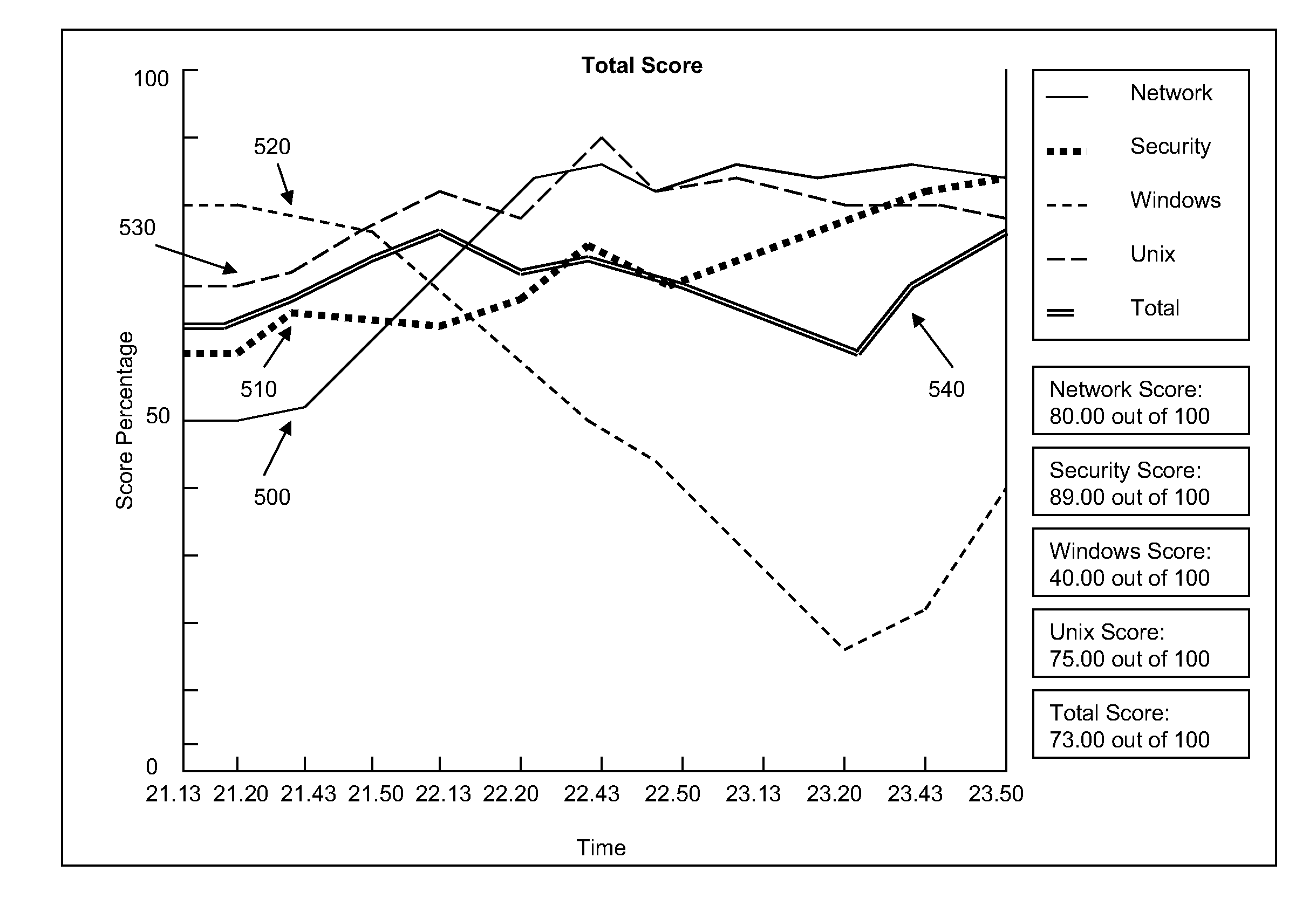
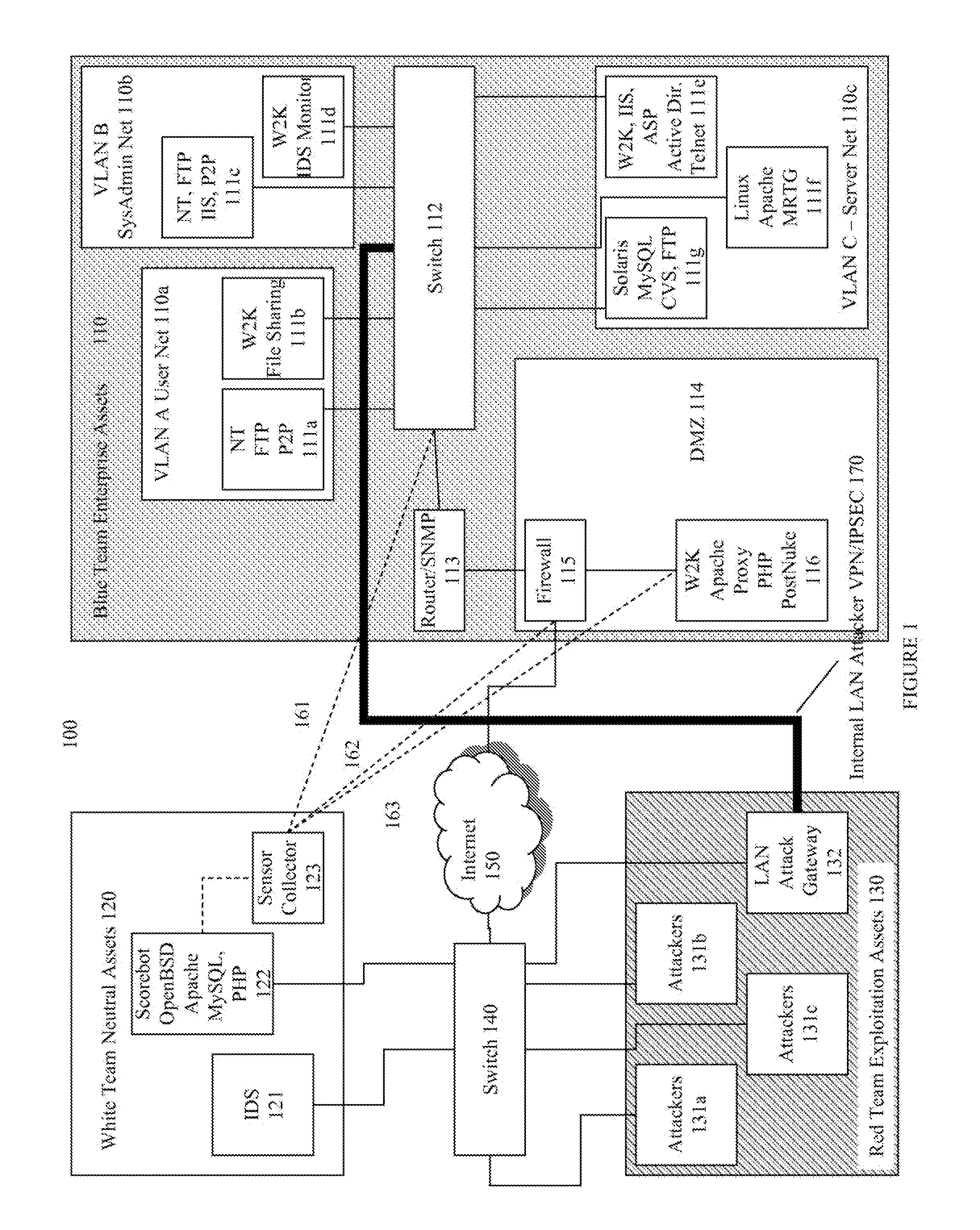
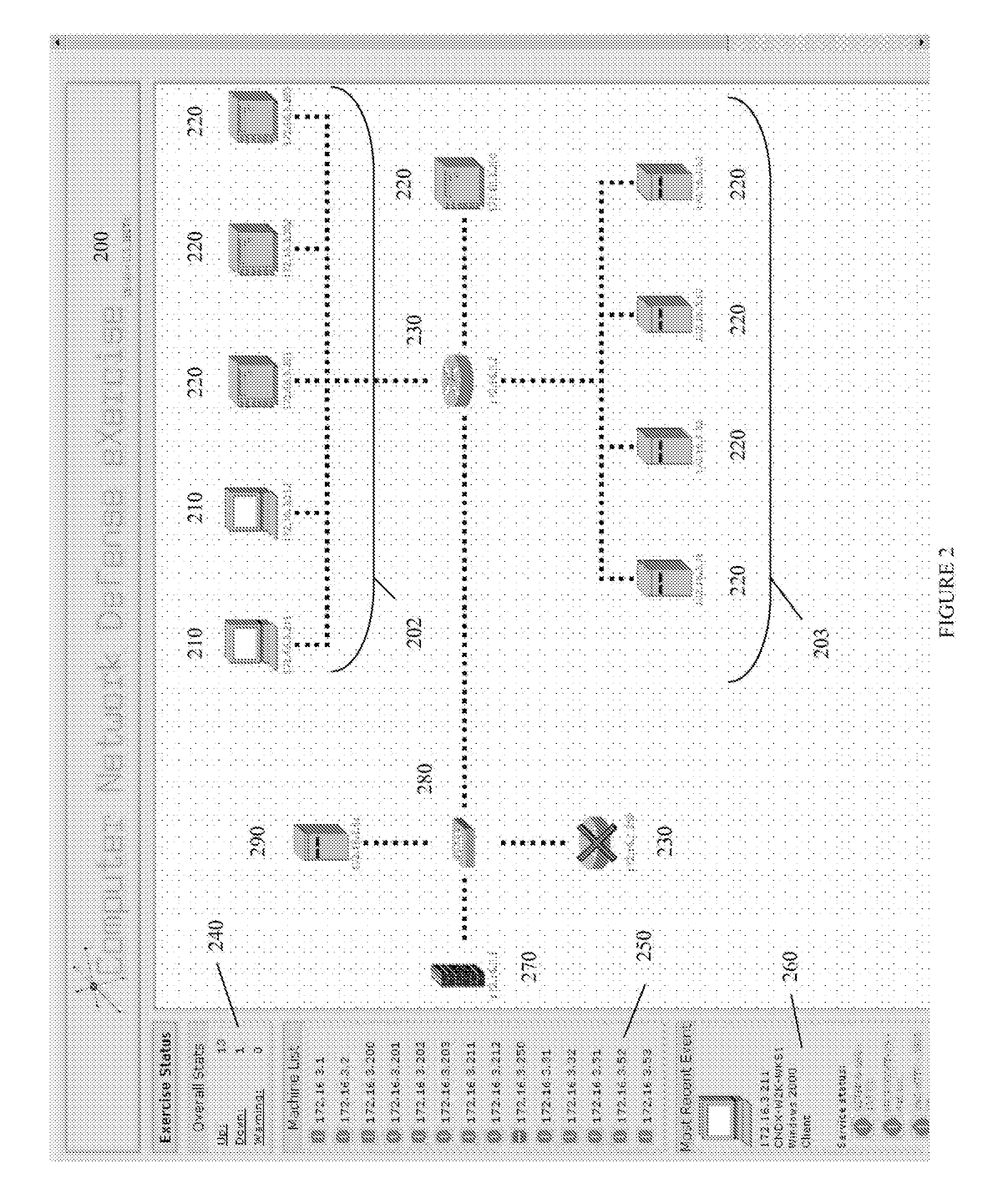
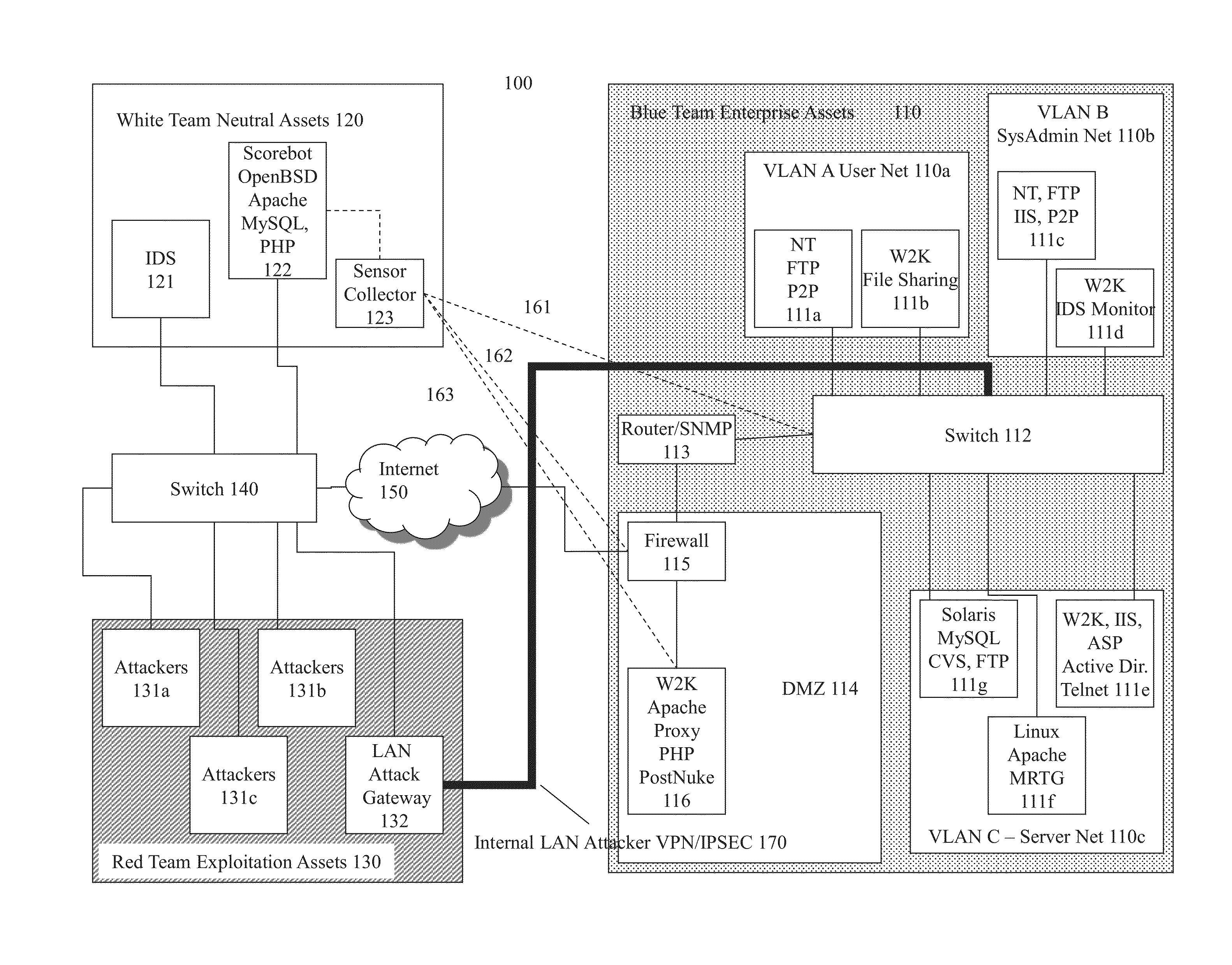
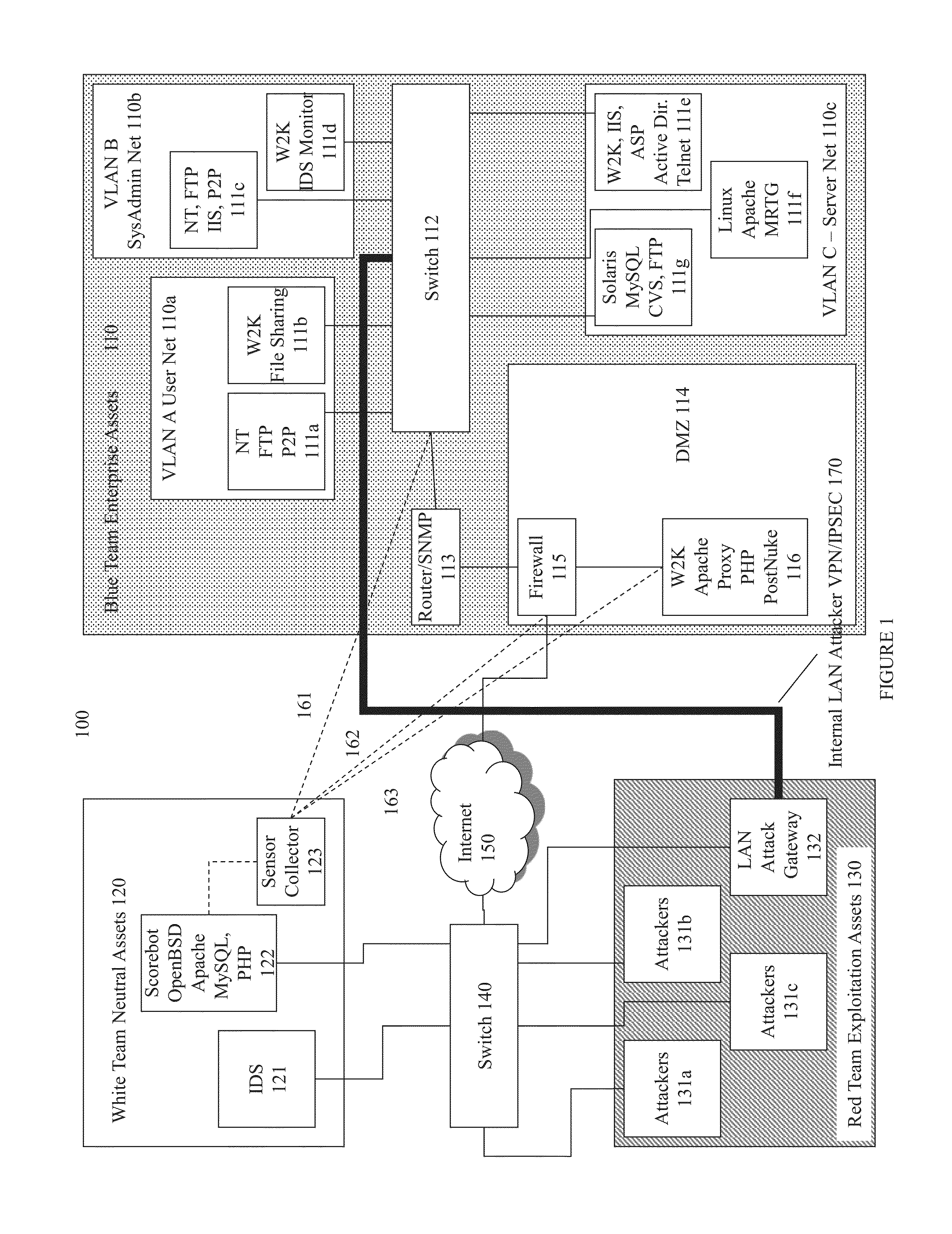
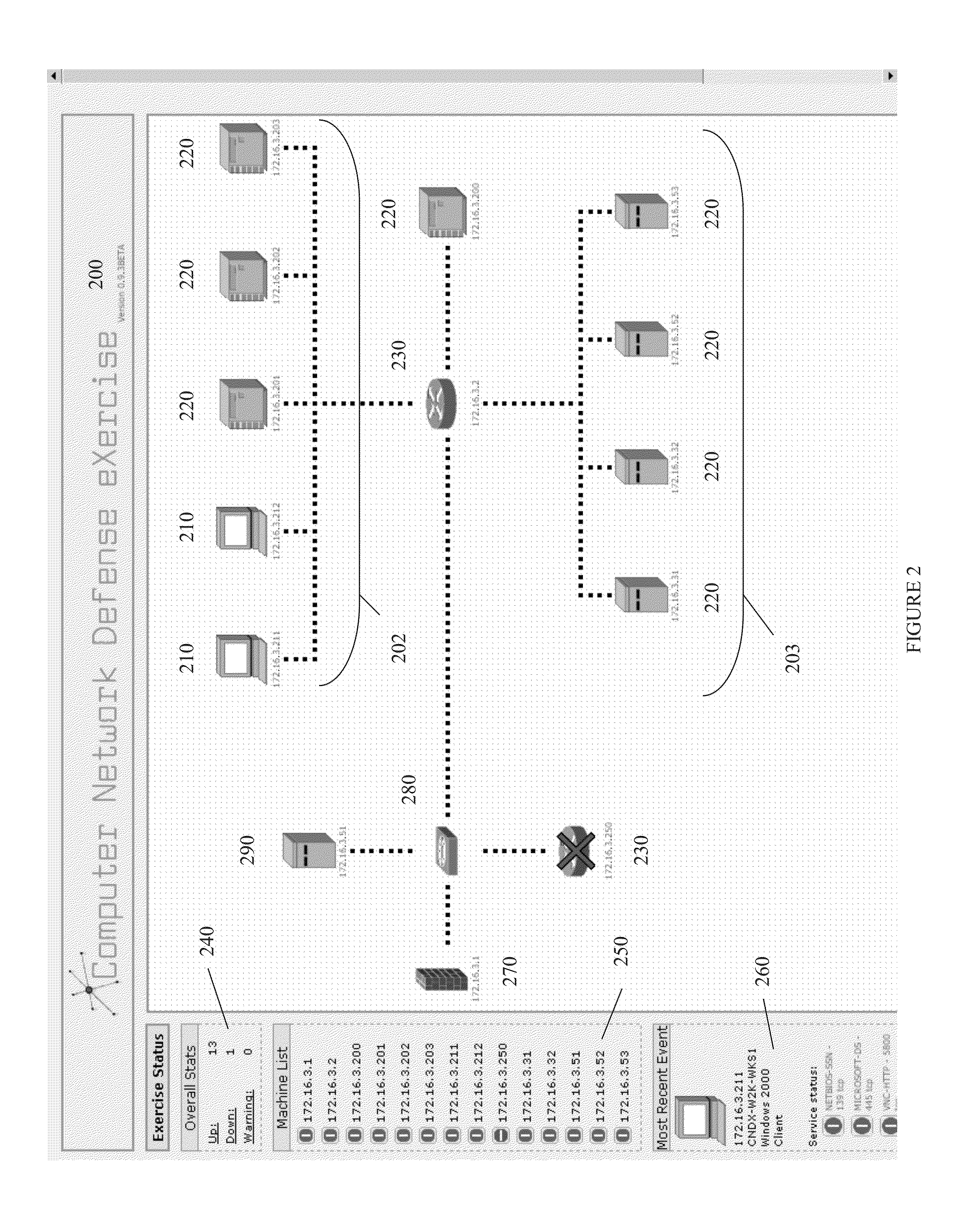
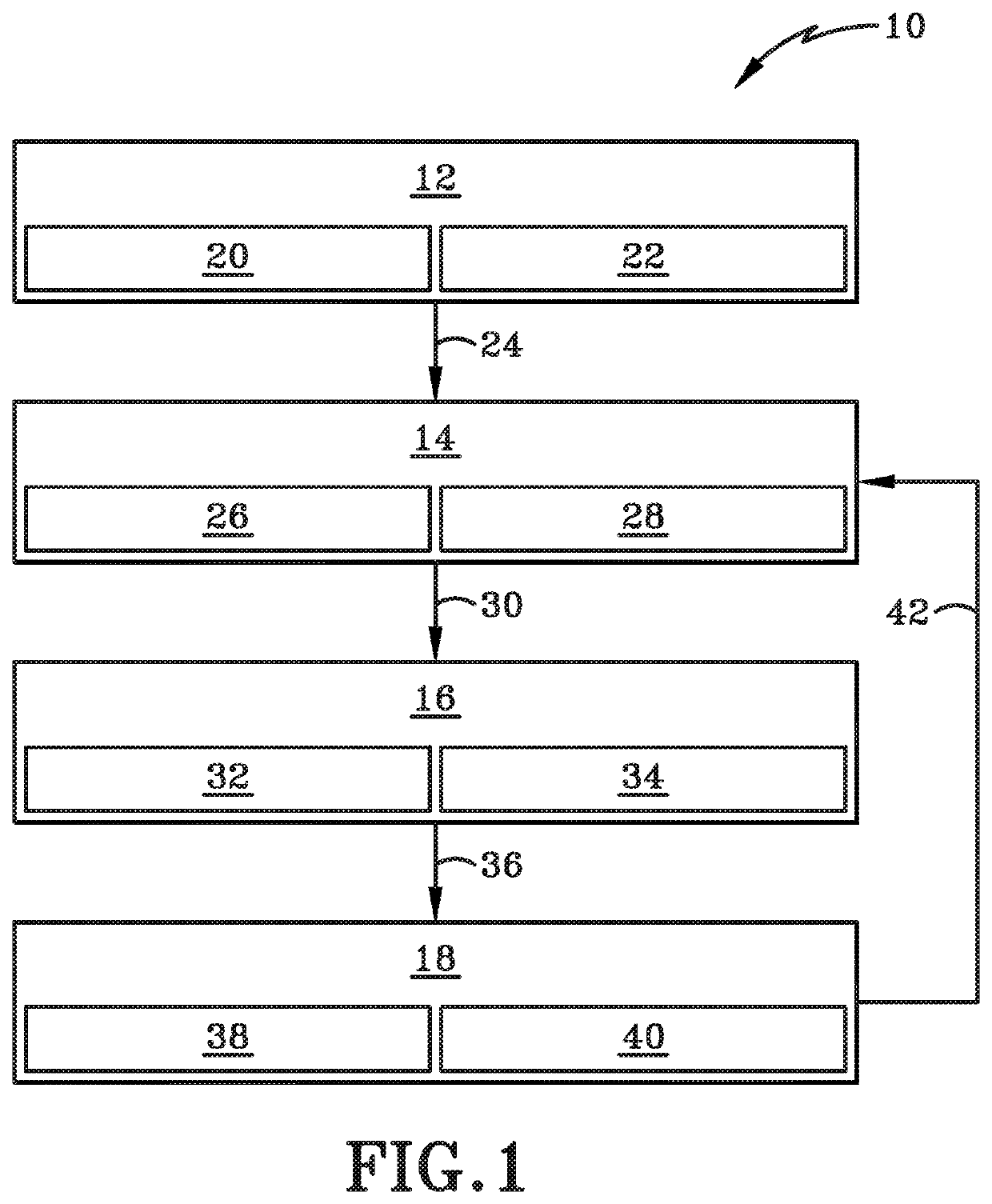
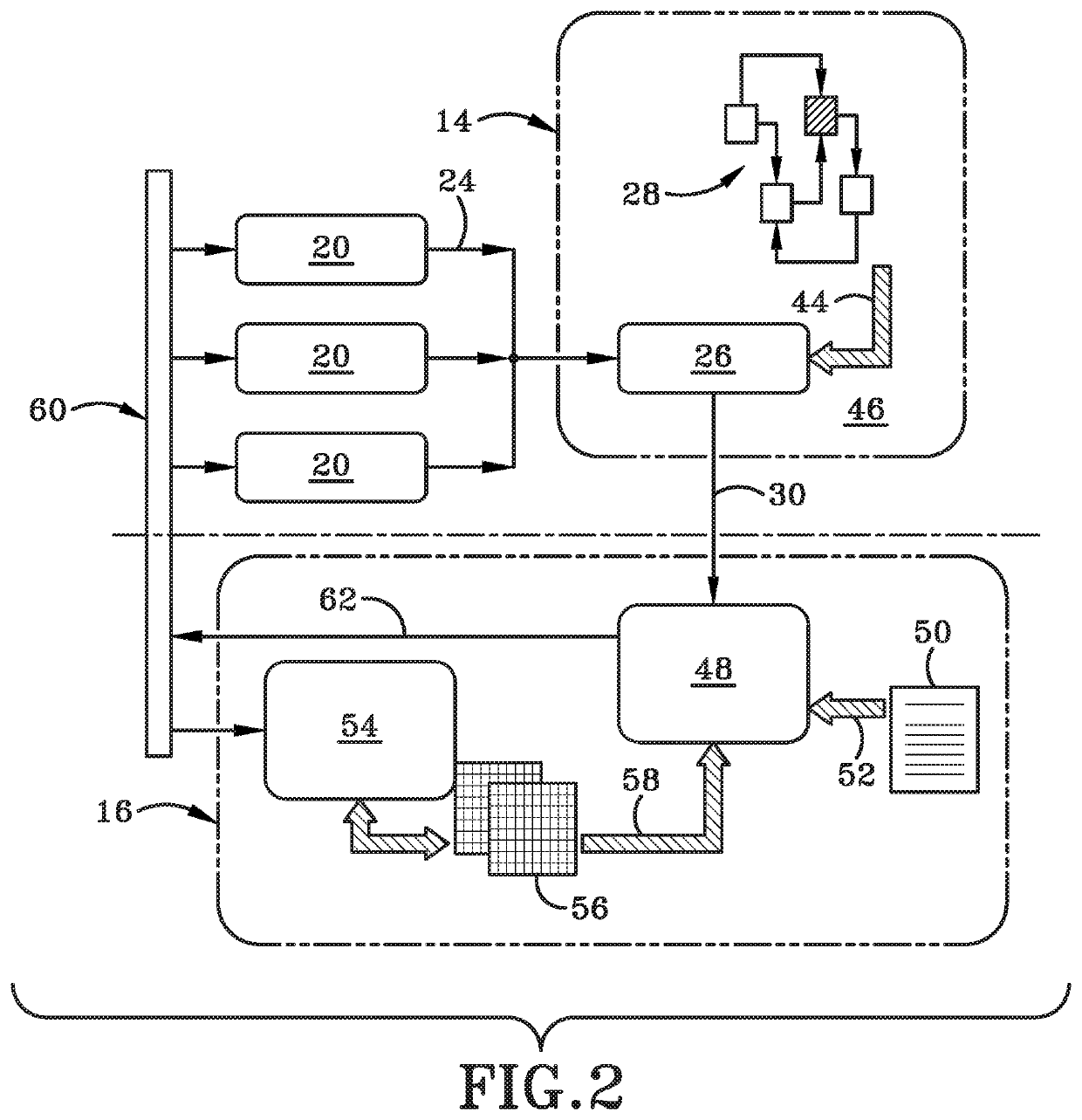
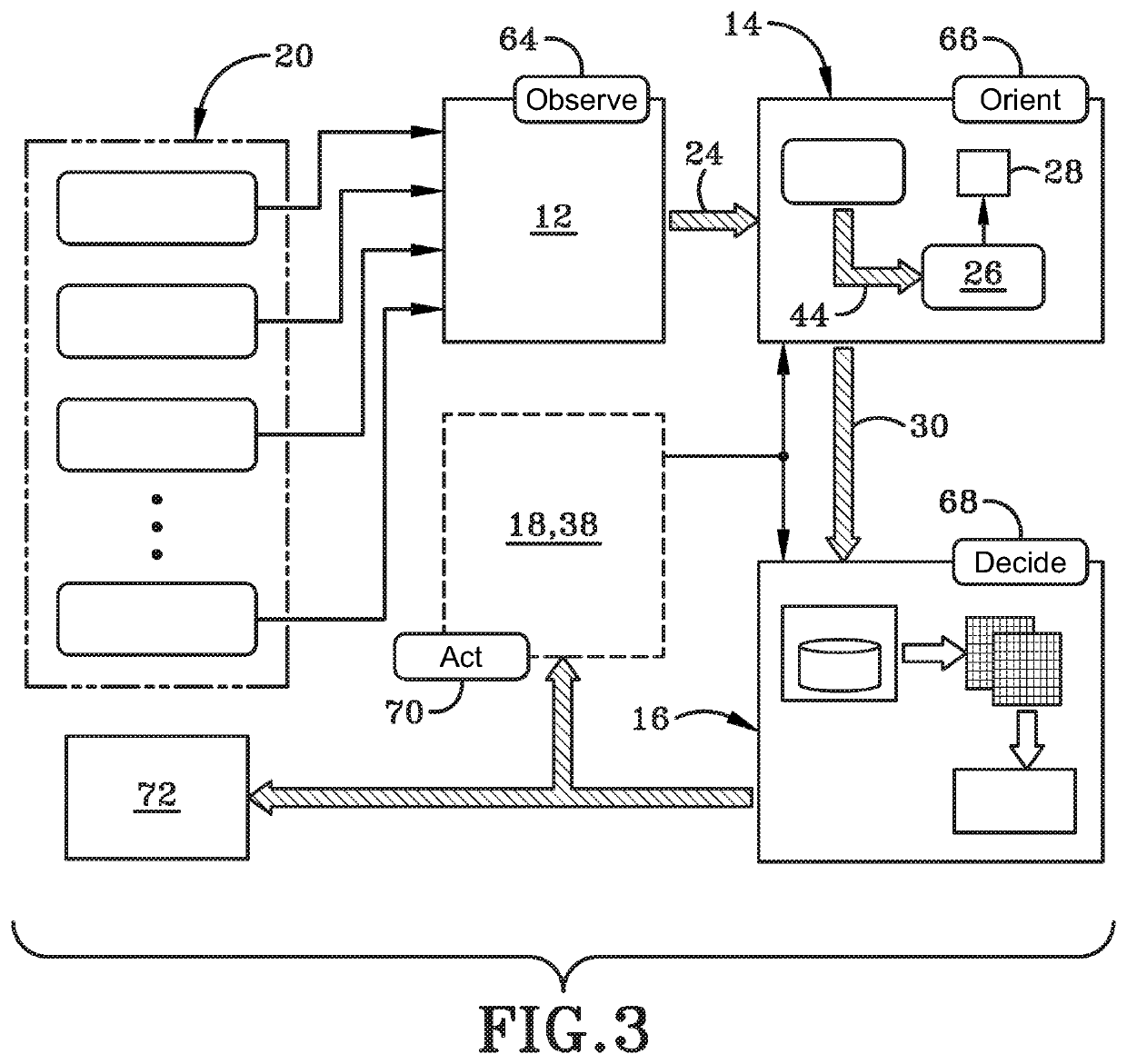
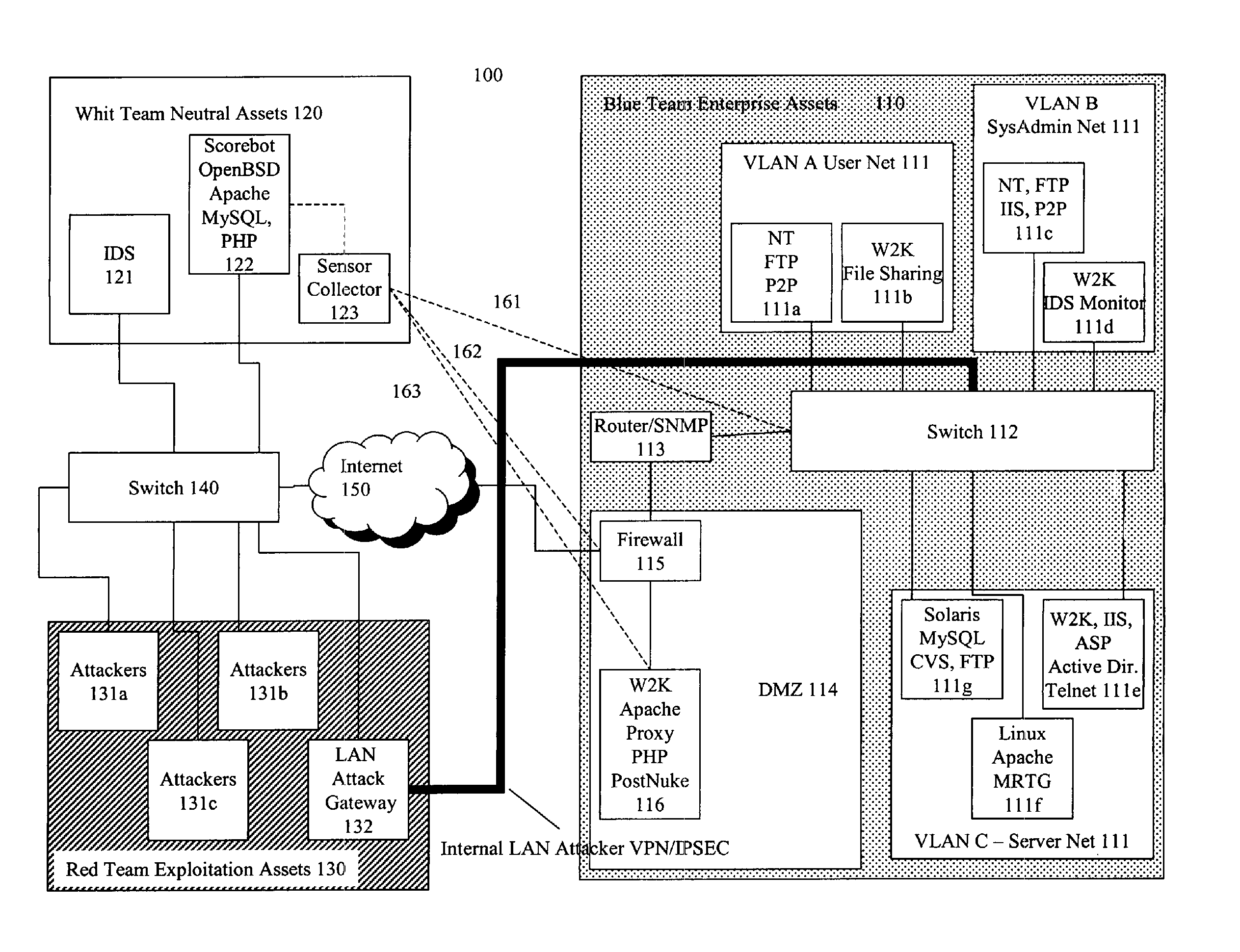
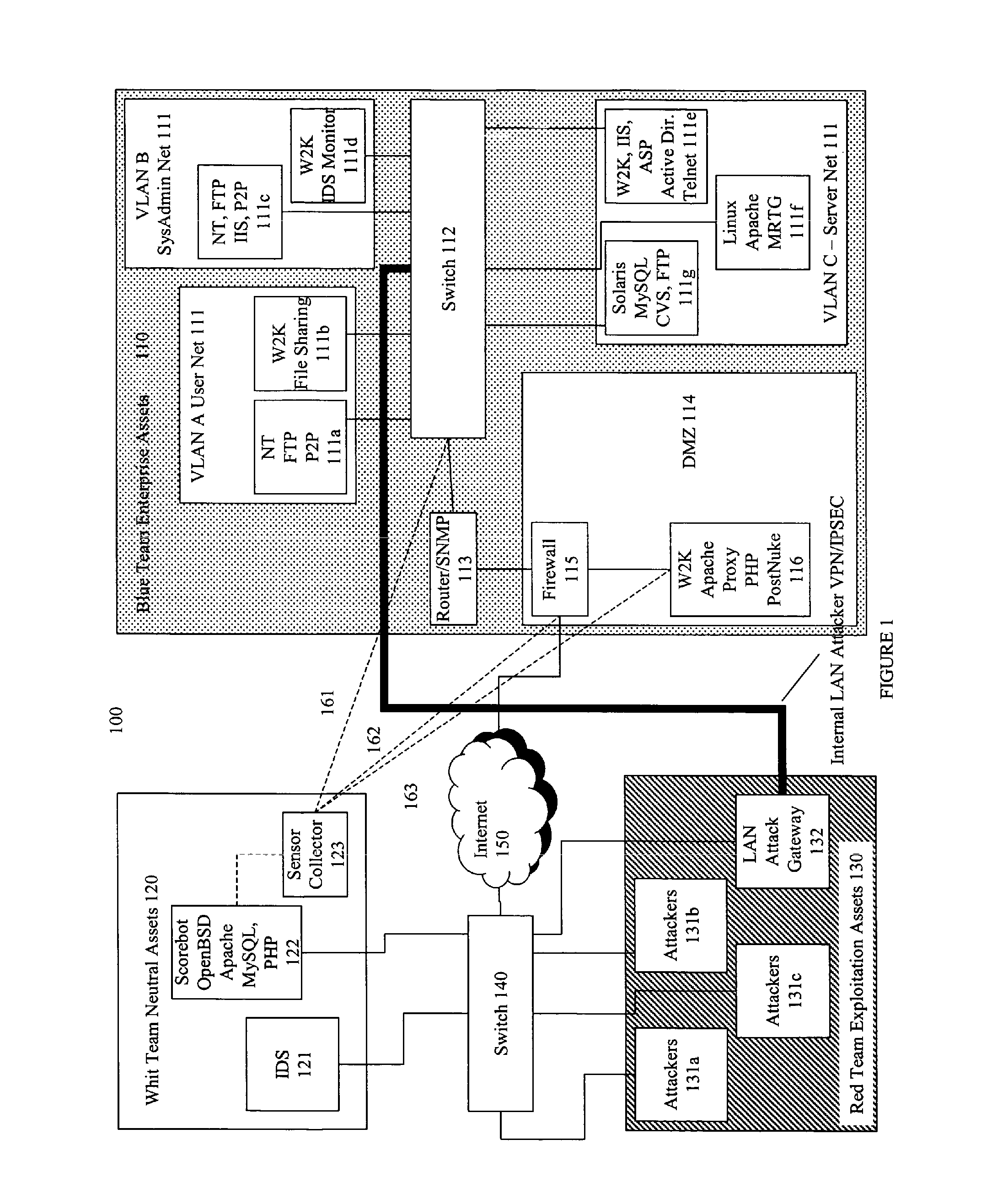
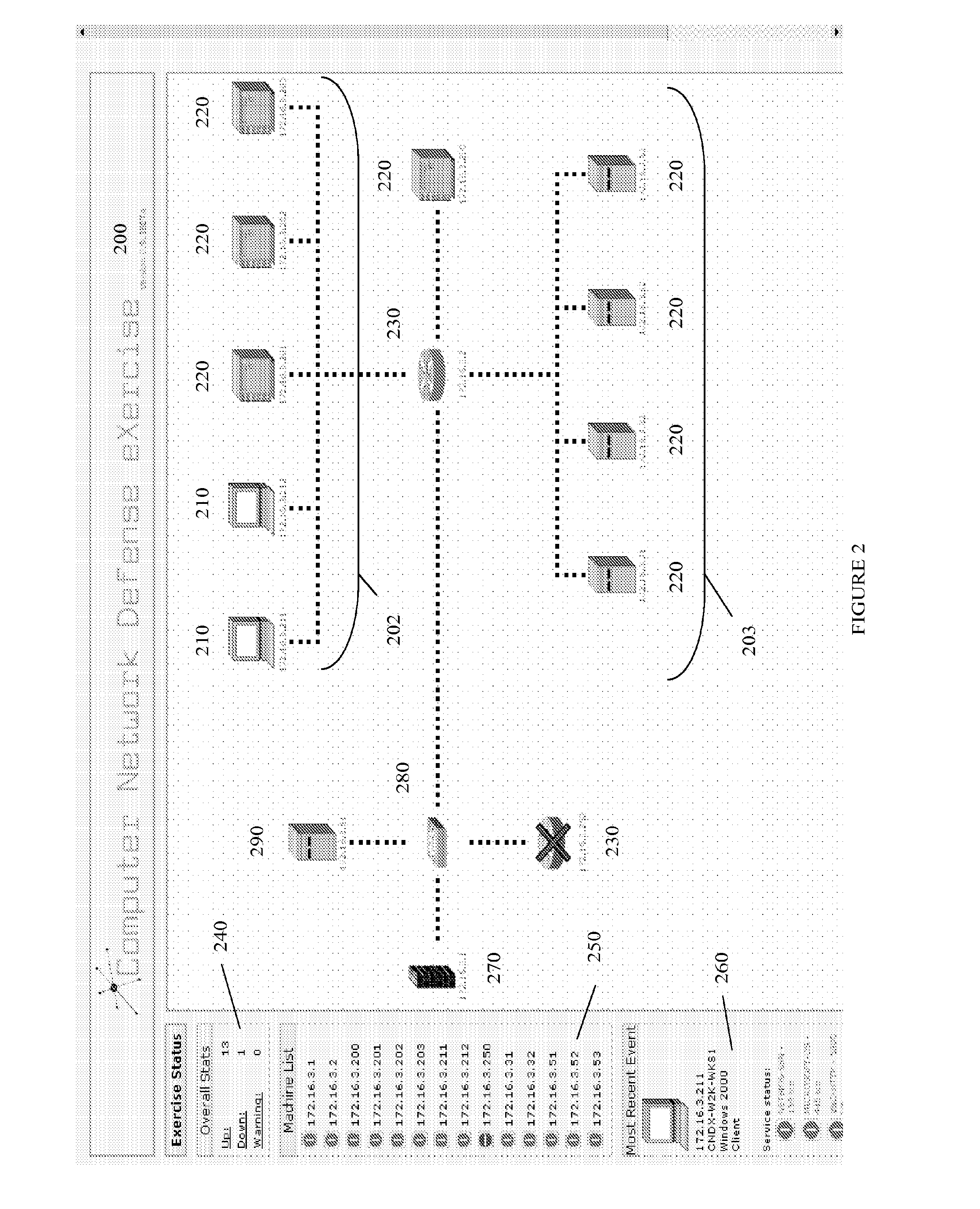
Systems and methods for implementing and scoring computer network defense exercises
ActiveUS8250654B1Easy to trainMemory loss protectionUnauthorized memory use protectionOperating systemClient system
A process for facilitating a client system defense training exercise implemented over a client-server architecture includes designated modules and hardware for protocol version identification message; registration; profiling; health reporting; vulnerability status messaging; storage; access and scoring. More particularly, the server identifies a rule-based vulnerability profile to the client and scores client responses in accordance with established scoring rules for various defensive and offensive asset training scenarios.
Owner:LEIDOS
Systems and Methods For Implementing and Scoring Computer Network Defense Exercises
A process for facilitating a client system defense training exercise implemented over a client-server architecture includes designated modules and hardware for protocol version identification message; registration; profiling; health reporting; vulnerability status messaging; storage; access and scoring. More particularly, the server identifies a rule-based vulnerability profile to the client and scores client responses in accordance with established scoring rules for various defensive and offensive asset training scenarios.
Owner:LEIDOS
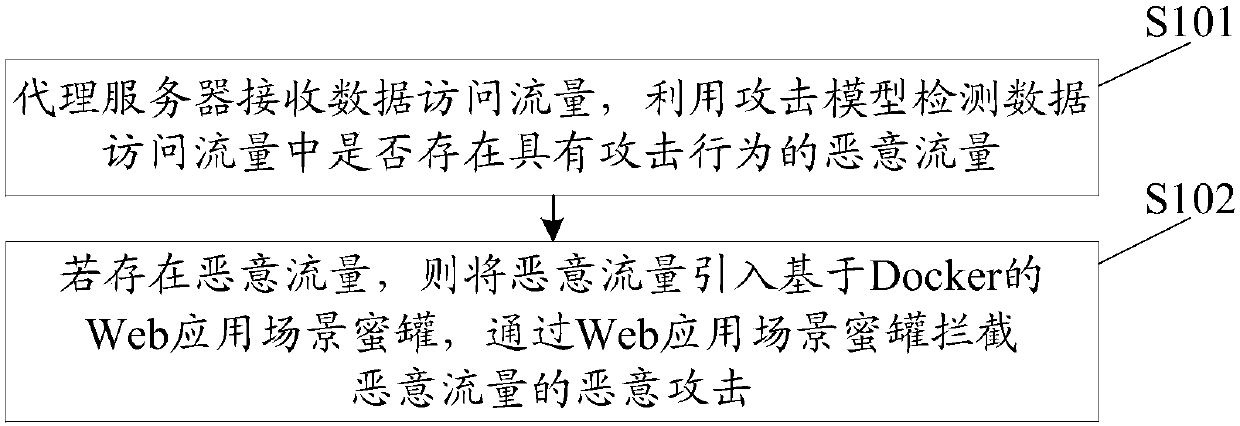
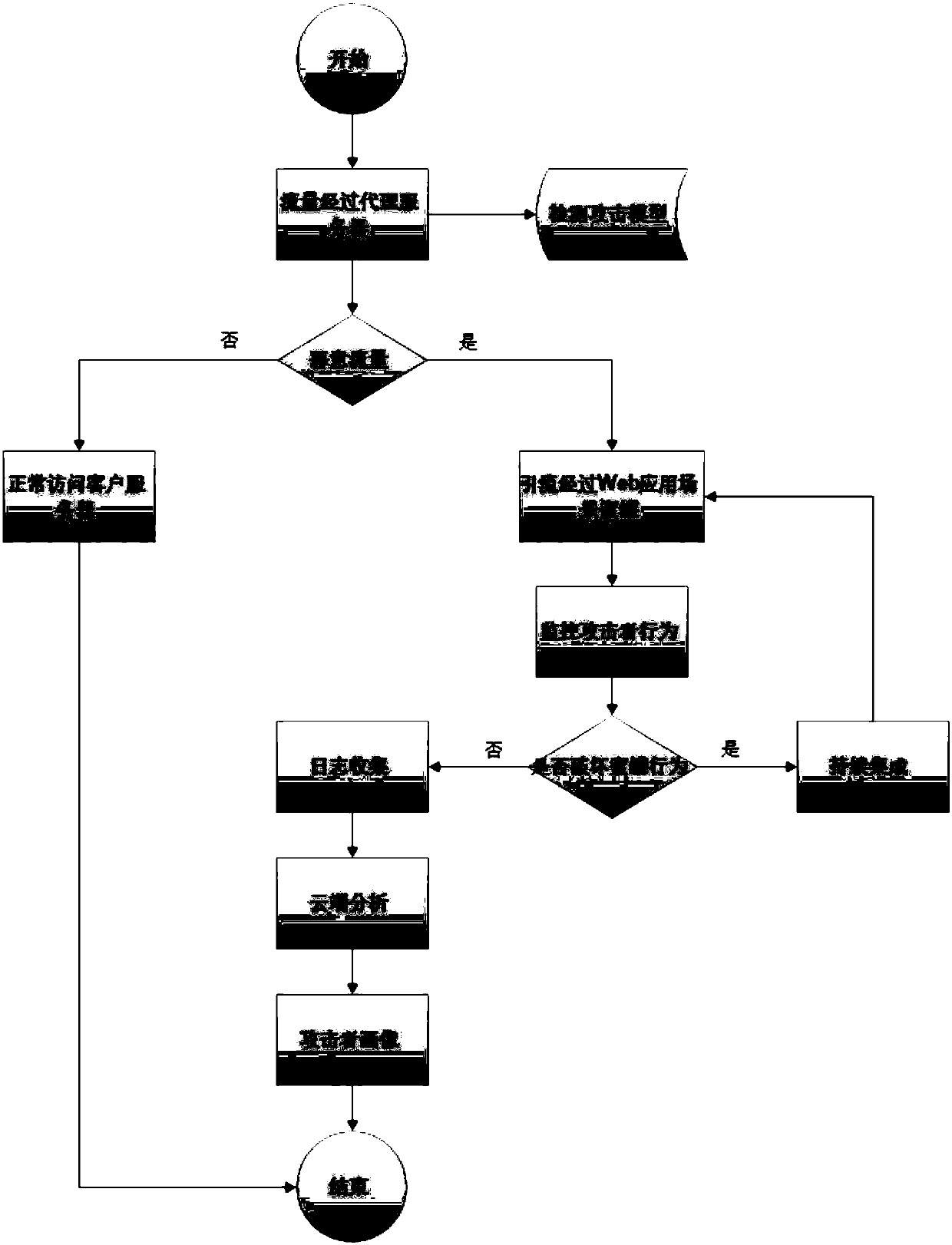
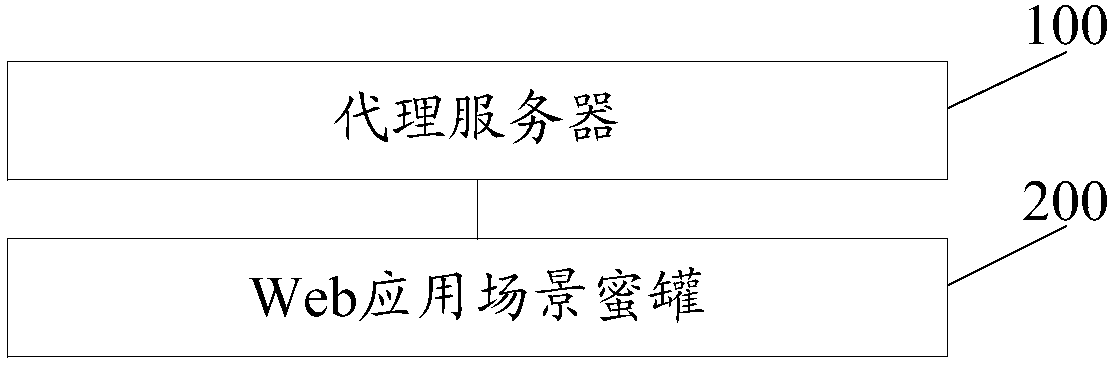
Network defense method and system based on honey pot technology
InactiveCN107707576AGuaranteed stabilityReduce attackTransmissionWeb applicationContinuous integration
The invention discloses a network defense method based on a honey pot technology. Malicious flor is introduced into a Web application scene honey pot based on Docker via a proxy server, malicious attack of malicious flow is intercepted through the Web application scene honey pot; thus, in the scheme, through deployment of the Web application scene honey pot based on Docker, network attack can be defensed actively, attack to a real goal by an attacker is delayed, the precious attack tracing time is provided for a defender. The Web application scene honey pot based on Docker also can effectivelyovercome the defect of inadaptability to real scenes of a customer, storage space is effectively reduced through a virtual Docker technology, the network is isolated, interference of honey pots is guaranteed, and the stability of the honey pot is guaranteed through continuous integration. The invention also discloses a network defense system based on the honey pot technology. The system also canhave the technical effects.
Owner:SANGFOR TECH INC
Systems and methods for implementing and scoring computer network defense exercises
Processes for the implementation and scoring of computer and network system defense exercises include base and modified scoring in accordance with various parameters and across multiple types of participants including attackers, defenders, forensic analysts, judges and referees. Effects-based scoring includes scoring for ascertaining status of an external client system by a participant in an independent client system.
Owner:LEIDOS
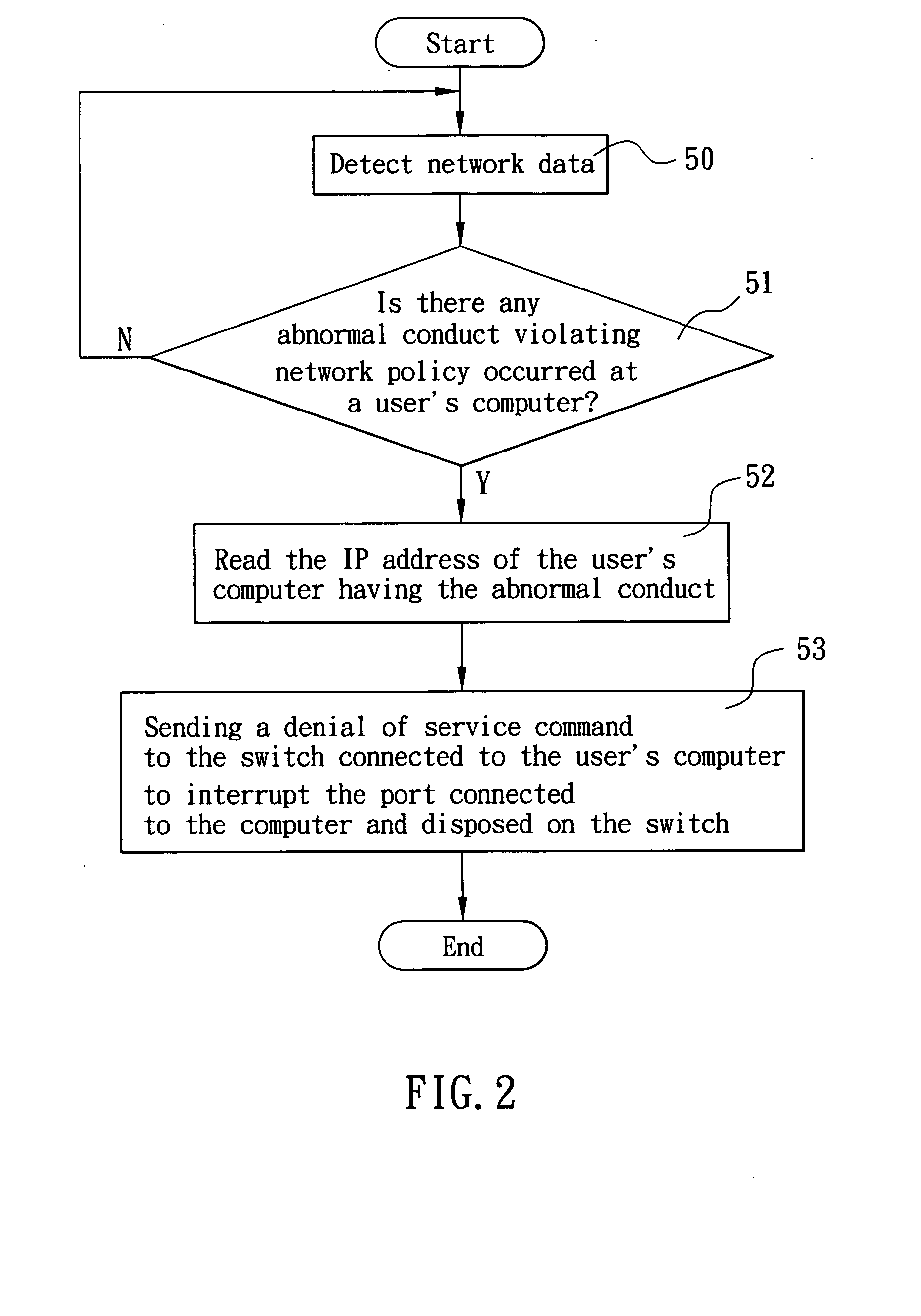
Network information security zone joint defense system
InactiveUS20060282893A1Effective preventionNetwork degradationMemory loss protectionError detection/correctionNetwork connectionNetwork switch
A network information security zone joint defense system is provided, which monitors a network connection status through a network defense appliance. Once the network defense appliance detects a user computer in a network system triggering the conditions of a network zone joint defense, the network defense appliance immediately and automatically connects to a specified network switch, such that the network switch interrupts the network access service provided for the user computer, so as to effectively prevent virus or hacker from continuing spreading virus to the same or other subnet of the network, and further prevent the virus from starting a DDoS attack or paralyzing the network server, and thus greatly reducing the damages and losses to the network system.
Owner:D-LINK
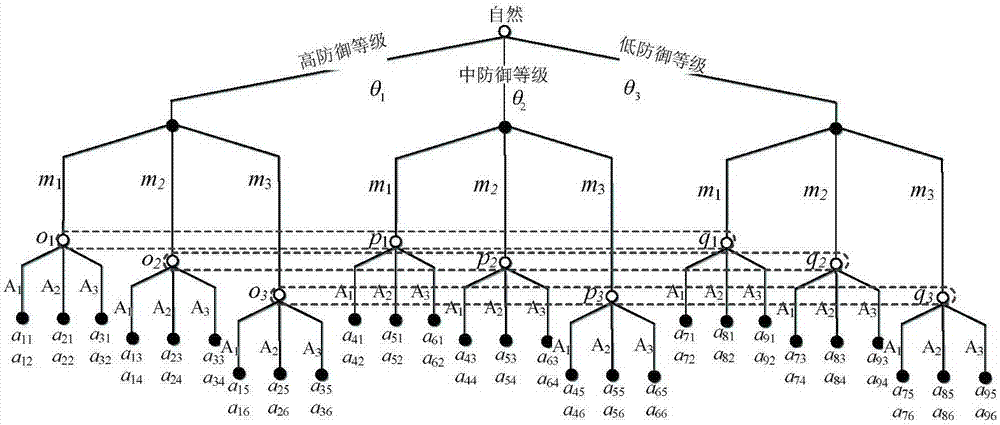
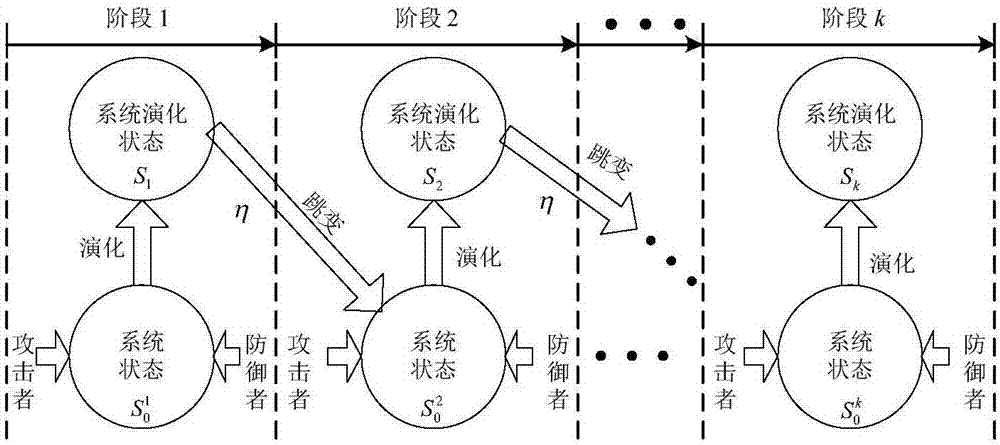
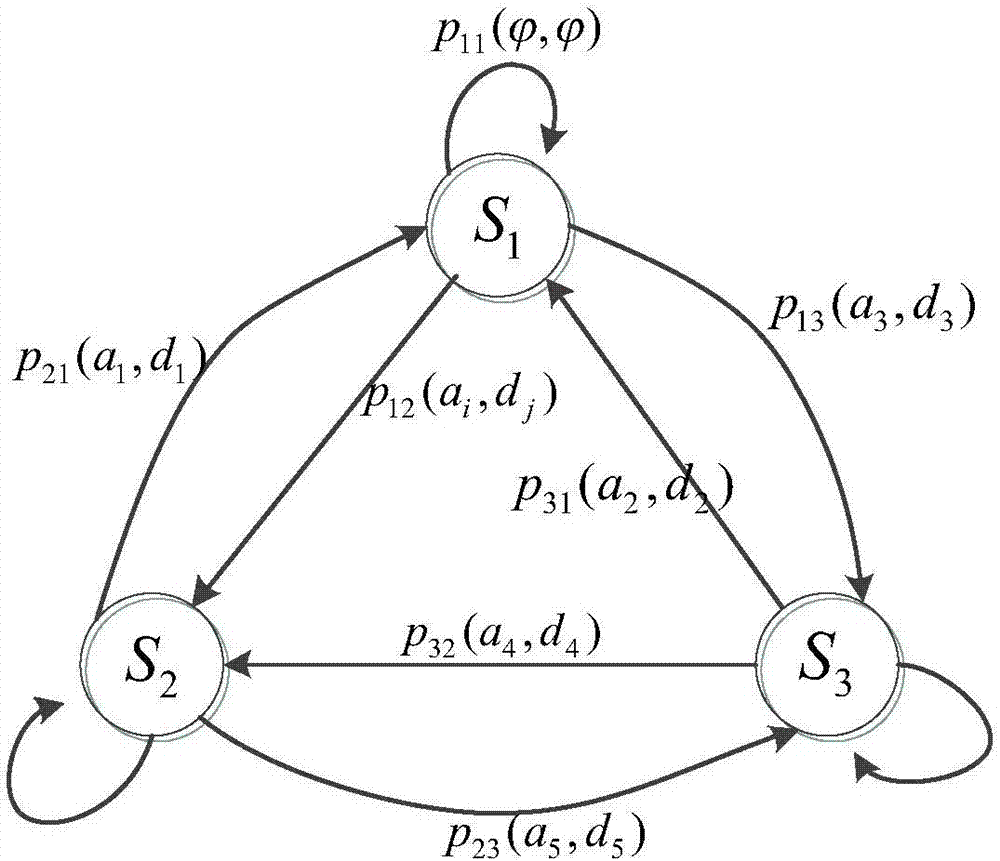
Network defense strategy selection method and apparatus based on Markov evolutionary game
The invention relates to a network defense strategy selection method and apparatus based on Markov evolutionary game. The method comprises the following steps: constructing a multi-stage Markov attack and defense evolutionary game model according to dynamic attack and defense game in a network attack and defense process, wherein the model contains a plurality of sub game stages; solving and outputting optimal defense strategies of the stages of the attack and defense game by using an optimal defense strategy selection algorithm for the multi-stage Markov attack and defense evolutionary game model. According to the network defense strategy selection method and apparatus provided by the invention, a dynamic evolution process of network attack and defense in view of the multi-stage Markov attack and defense evolutionary game model, the state skip of the evolutionary stages is described as a random process from the angle of attack and defense confrontation, and the multi-stage Markov evolutionary game is constructed on the basis of the Markov process; the total discount gain of the game is used as a target function, a discount factor eta is imported to perform discount processing on the game gains of different stages, a network security analysis method and a defense technology system are researched and searched, and thus the network defense strategy selection method and apparatus have important practical significance.
Owner:THE PLA INFORMATION ENG UNIV
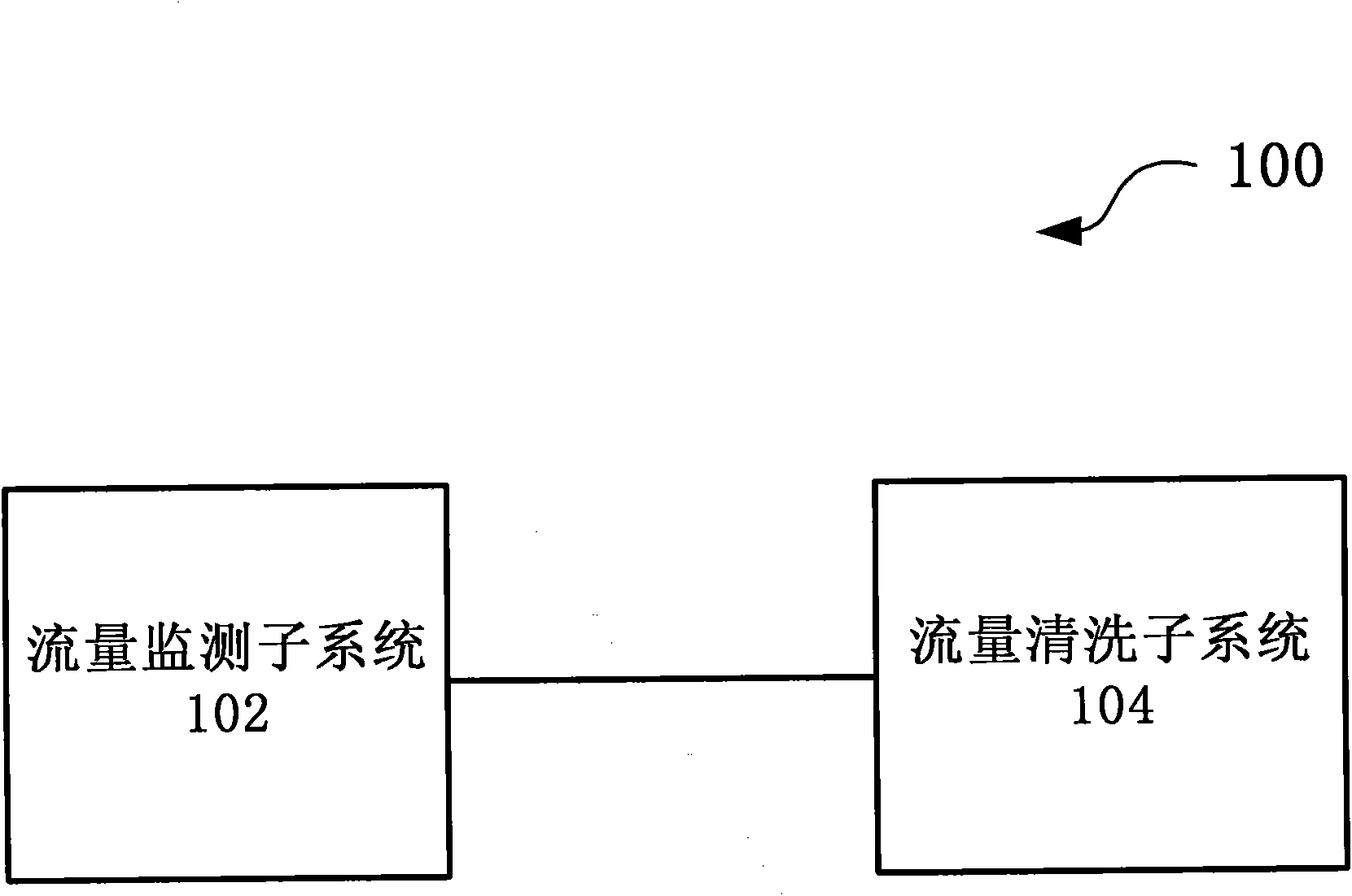
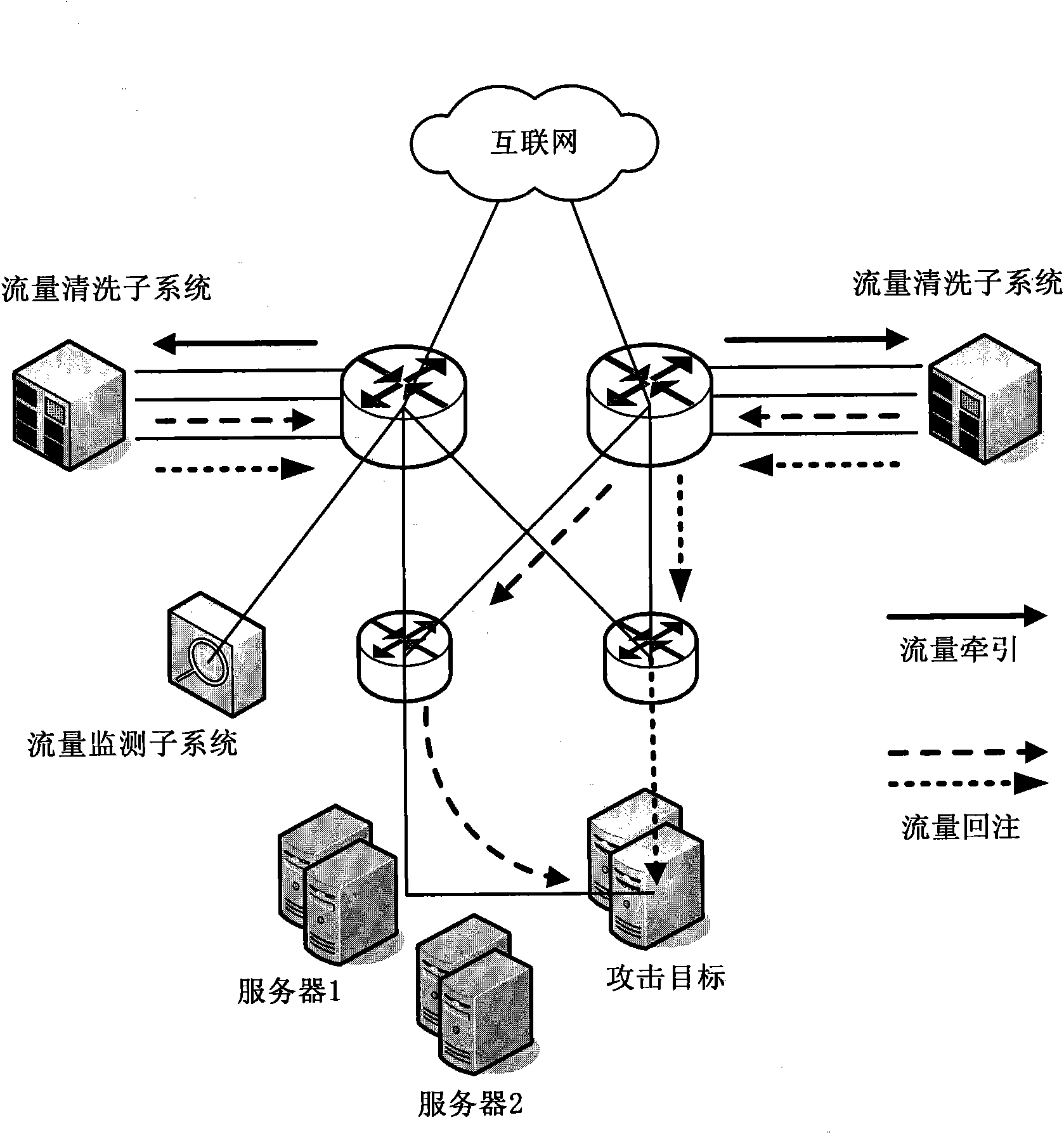
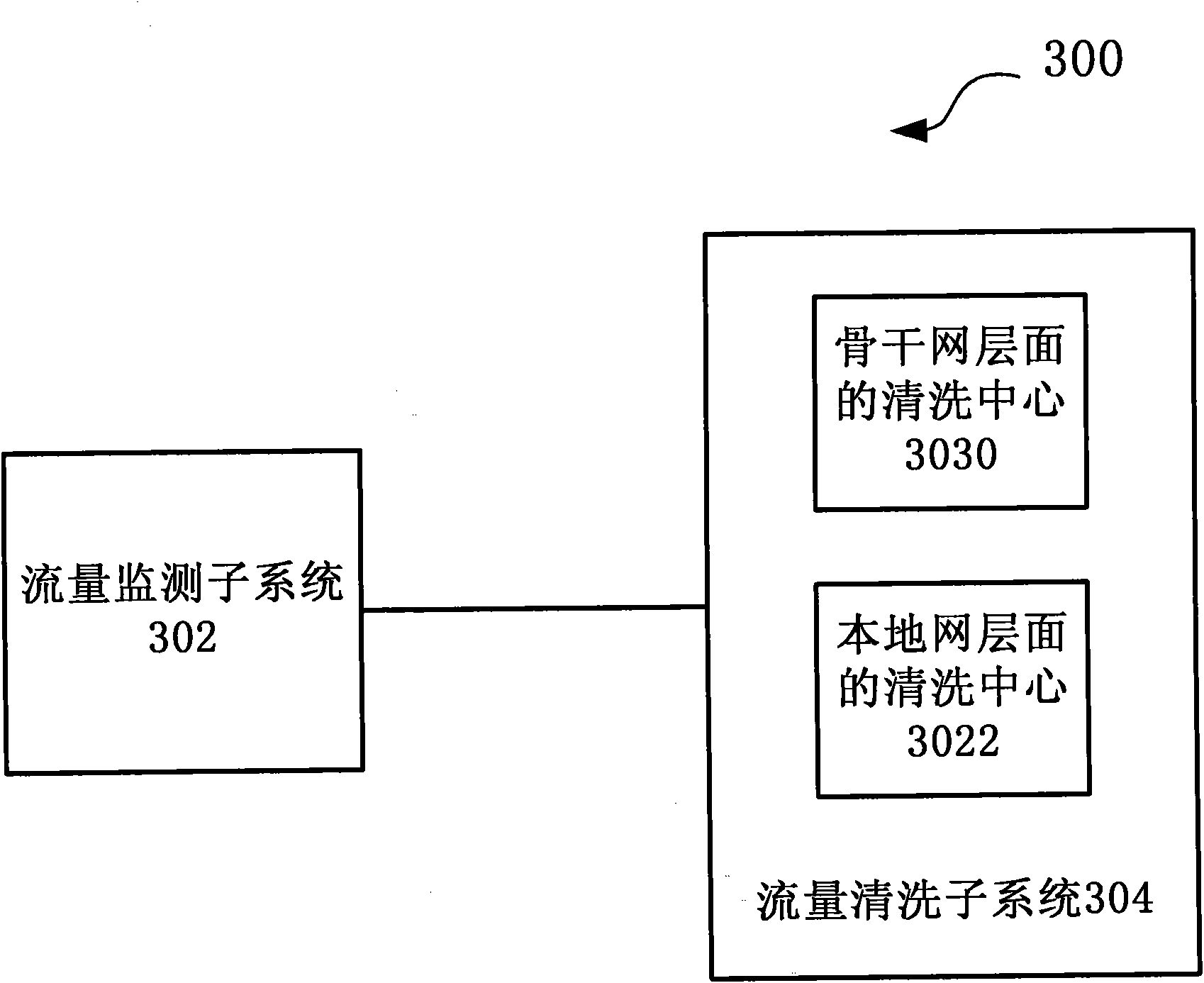
Large-scale DDoS (Distributed Denial of Service) attack defense system and method based on two-level linkage mechanism
The invention discloses large-scale DDoS (Distributed Denial of Service) attack defense system and method based on a two-level linkage mechanism. The method comprises the following steps of: monitoring the flow of a total network by a flow monitoring subsystem in real time, and searching and confirming a DDoS attack behavior; sending an alarm message for triggering a cleaning operation to a flow cleaning subsystem, and guiding the abnormal flow of the DDoS attach behavior to the flow cleaning subsystem; receiving the abnormal flow guided by the flow monitoring subsystem by the flow cleaning subsystem, cleaning the abnormal flow according to the cleaning operation triggered by the alarm message, (wherein the flow cleaning subsystem adopts the two-level architecture of a backbone network plus a local network defense system, and the two levels of cleaning system work cooperatively and clean synchronously), and injecting the cleaned cleaning flow back to a target customer network. The large-scale DDoS attack defense system and method based on the two-level linkage mechanism solve the problems of cleaning capacity, cleaning precision, and the like existing in the traditional DDoS defense technology; and on the basis of reducing the deployment cost of service scale, the large-scale DDoS attach defense capability of the total network is greatly improved, and the cleaning precision ofthe attack flow is increased.
Owner:CHINA TELECOM CORP LTD
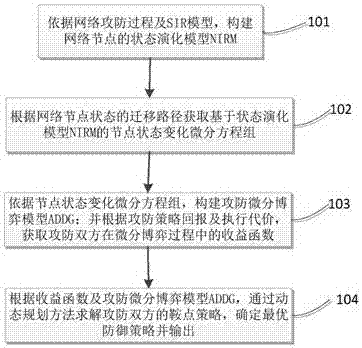
Attack and defense differential game-based network security defense decision determination method and device
The present invention relates to an attack and defense differential game-based network security defense decision determination method and a device. The method comprises the steps of constructing a state evolution model NIRM for network nodes according to an SIR model during the network attack and defense process; according to a network node state migration path, acquiring a node state change differential equation set based on the state evolution model NIRM; according to the node state change differential equation set, constructing an attack and defense differential game model ADDG; according to an attack and defense return strategy and a corresponding execution cost, executing a revenue function of the attack party and the defense party during the differential game process; according to the revenue function and the attack and defense differential game model ADDG, solving out a saddle point strategy for the attack party and the defense party through the dynamic planning method, determining an optimal defense strategy and outputting the optimal defense strategy. According to the technical scheme of the invention, the problem that actual requirements cannot be met through the traditional dynamic game analysis method can be solved. Compared with the existing network security defense strategy, the attack and defense process in the continuous and real-time engagement condition is analyzed. The timeliness, the pertinence and the guiding significance of network defense decision results are better.
Owner:THE PLA INFORMATION ENG UNIV
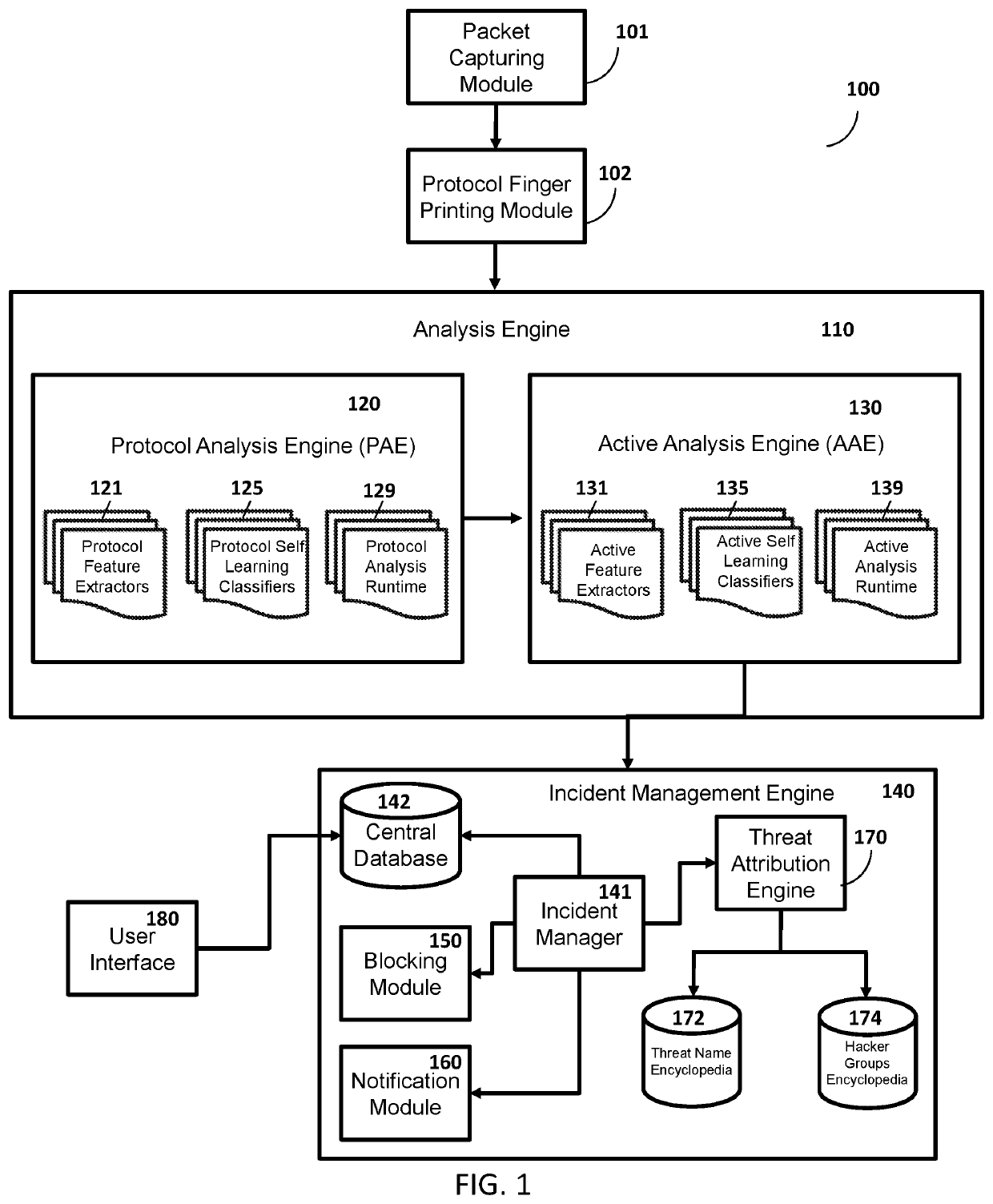
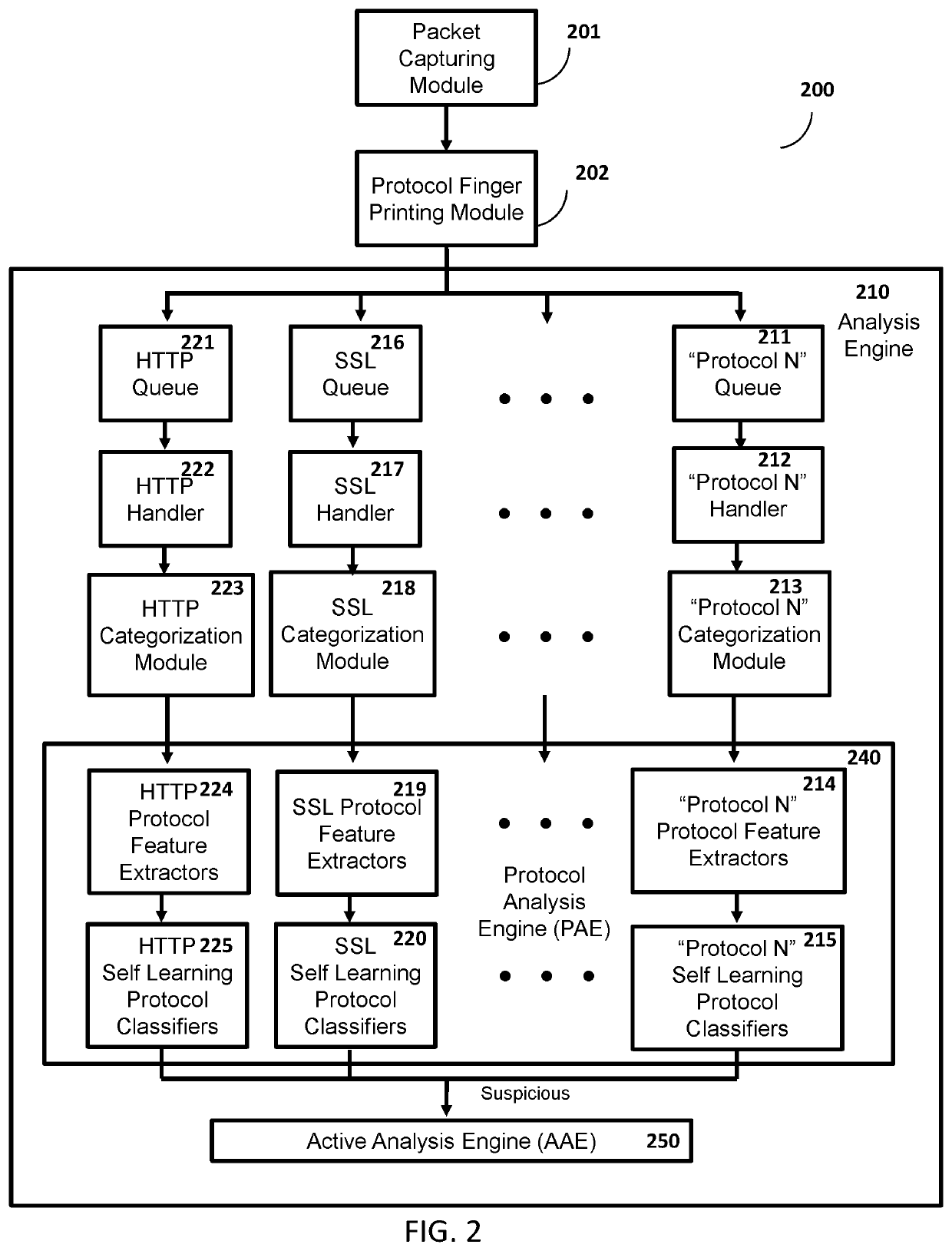
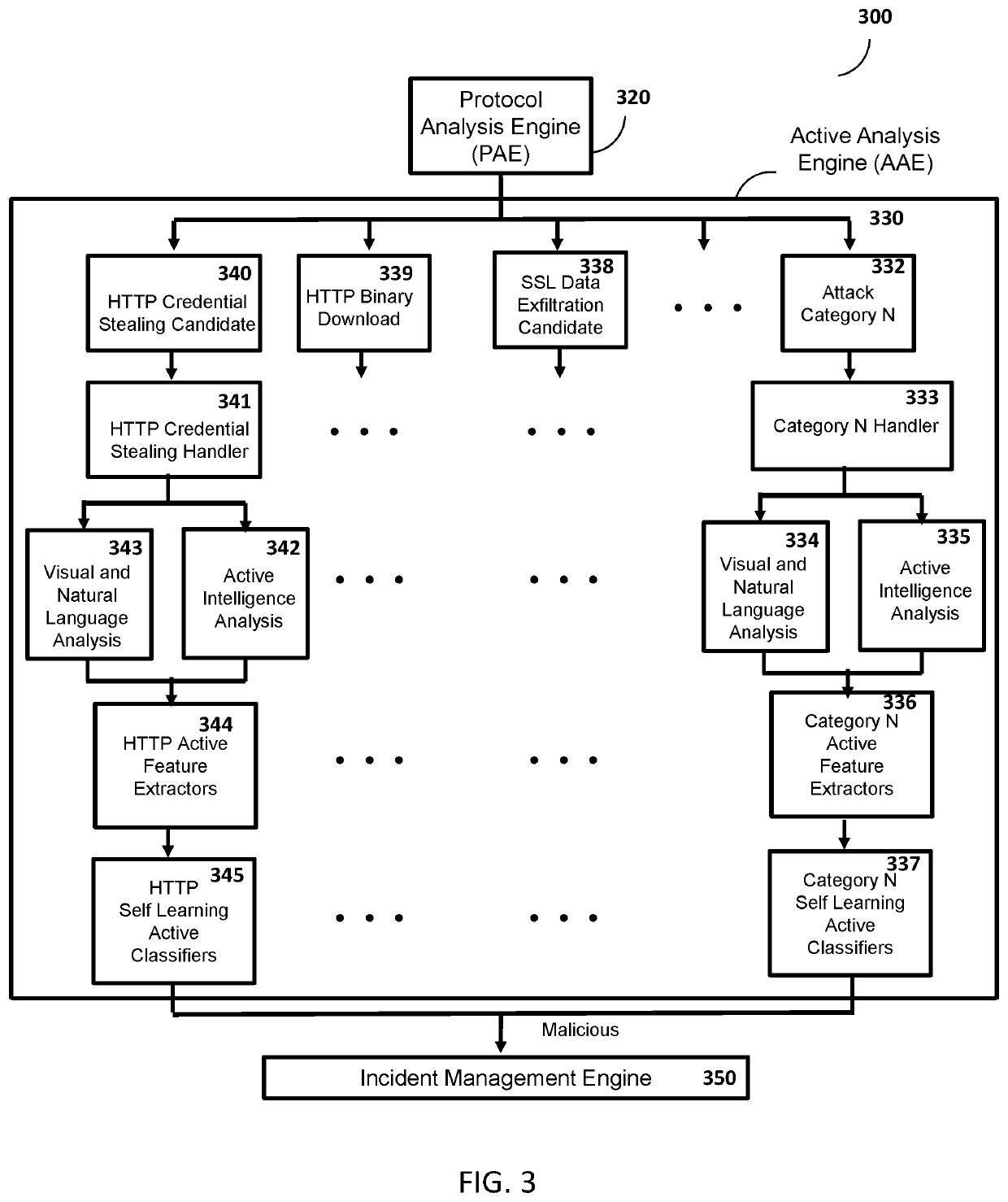
Method and system for protection against network-based cyber threats
An Active Cyber Defense method and system is provided for detecting and stopping malicious cyber activity including for example Drive-By Exploits, Malicious Binaries, Data Exfiltration, Social Engineering and Credential Stealing Attacks. The system disclosed herein can be configured to detect and block multi protocol network-based cyber attacks targeting different platforms or operating systems. The system can also be configured to be scalable. The system as disclosed herein can conduct real time inspection of network traffic and can self-learn and adapt as needed to a changing cyber threat landscape.
Owner:SLASHNEXT INC
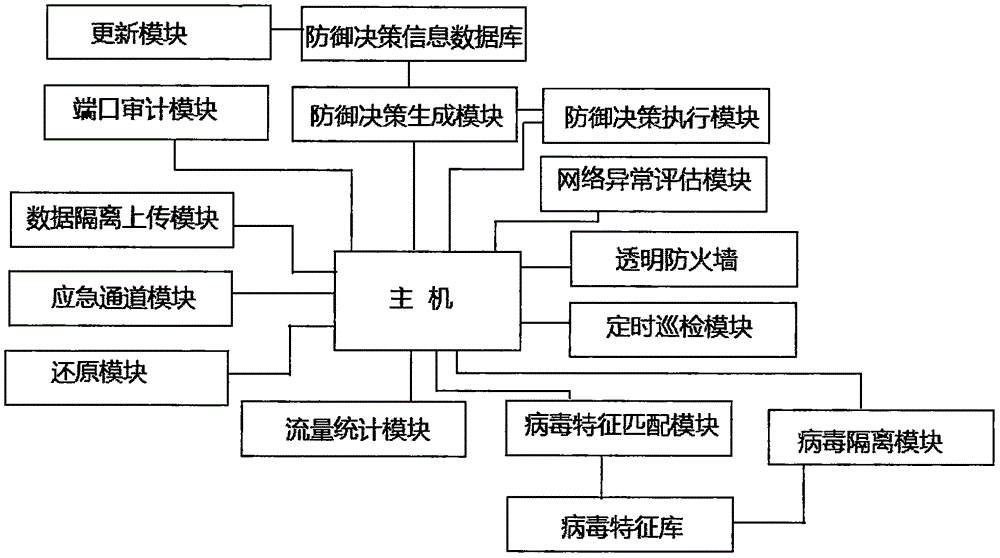
Computer network defense decision system
InactiveCN105847291AWell maintainedImprove immunityMessaging/mailboxes/announcementsPlatform integrity maintainanceDecision schemeDecision system
The invention discloses a computer network defense decision-making system, which includes a transparent firewall, a regular inspection module, a virus isolation module, a virus feature matching module, a port audit module, a traffic statistics module, a network abnormality evaluation module, a defense decision generation module, and a defense decision-making module. Execution module, emergency channel module, restore module, data isolation upload module. The present invention realizes the real-time monitoring and auditing of the network flow, maintains the good state of the network; improves the immunity of the network through the analysis and memory of the unknown intrusion behavior; and can effectively control the harm range after the intrusion, ensuring the smooth flow of the network and the service It is provided normally, and at the same time, it can automatically generate and execute different defense decision-making schemes according to different network attacks, which improves the self-repair and restoration capabilities of the system, maintains the stable operation of the network, and has data protection capabilities. The occurrence of the previous situation leading to the loss of information.
Owner:INNER MONGOLIA UNIV OF TECH
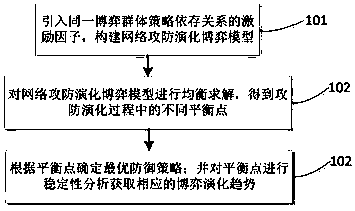
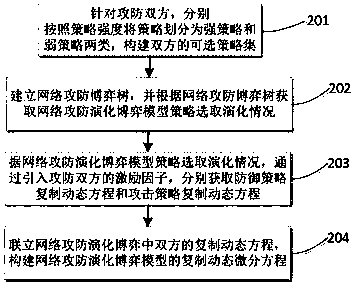
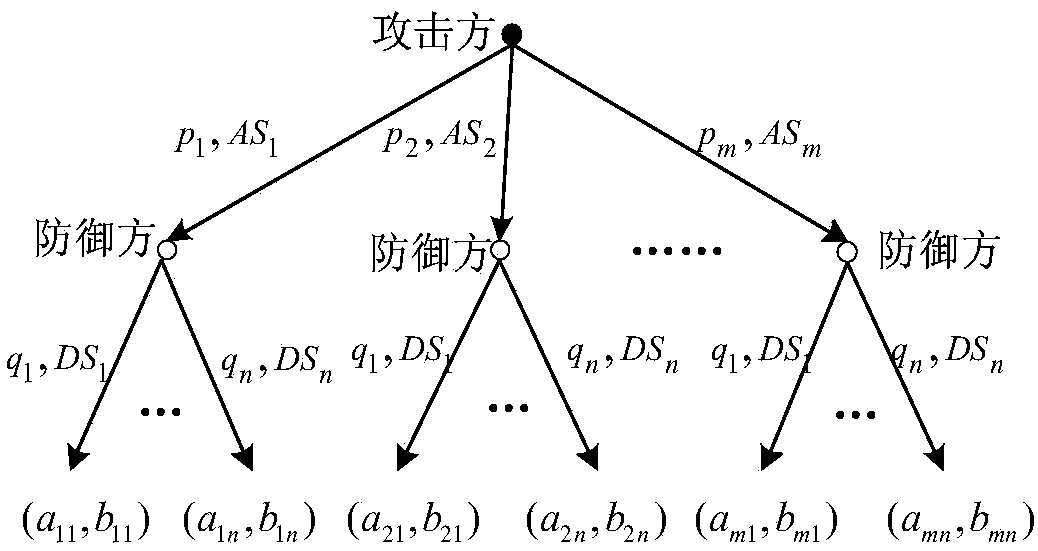
Attack and defense evolutionary game analysis based network defense action decision method
The invention belongs to the technical field of network safety, and particularly to an attack and defense evolutionary game analysis based network defense action decision method. The attack and defense evolutionary game analysis based network defense action decision method comprises the steps of introducing an excitation factor of a same game group strategy dependence relationship to build a network attack and defense evolutionary game model; performing balanced solution on the network attack and defense evolutionary game model to obtain different balance points in an attack and defense evolution process; and determining an optimal defense strategy based on the balance points; and performing stability analysis on the balance points to obtain a correspond game evolutionary trend. Accordingto the method, the excitation factor is introduced, the dynamic evolution process is copied to describe the network attack and defense process, and the network attack and defense evolutionary game model based on an improved evolutionary game theory is built; evolutionary balanced solution is carried out for the circumstances that the attacker and the defender have multiple selectable strategies, the obtained balance points are subjected to the stability analysis, the network attack and defense game model and the application scope are extended, the practicability and accuracy of the model are improved, and important guiding significance is provided for the network safety technology.
Owner:THE PLA INFORMATION ENG UNIV
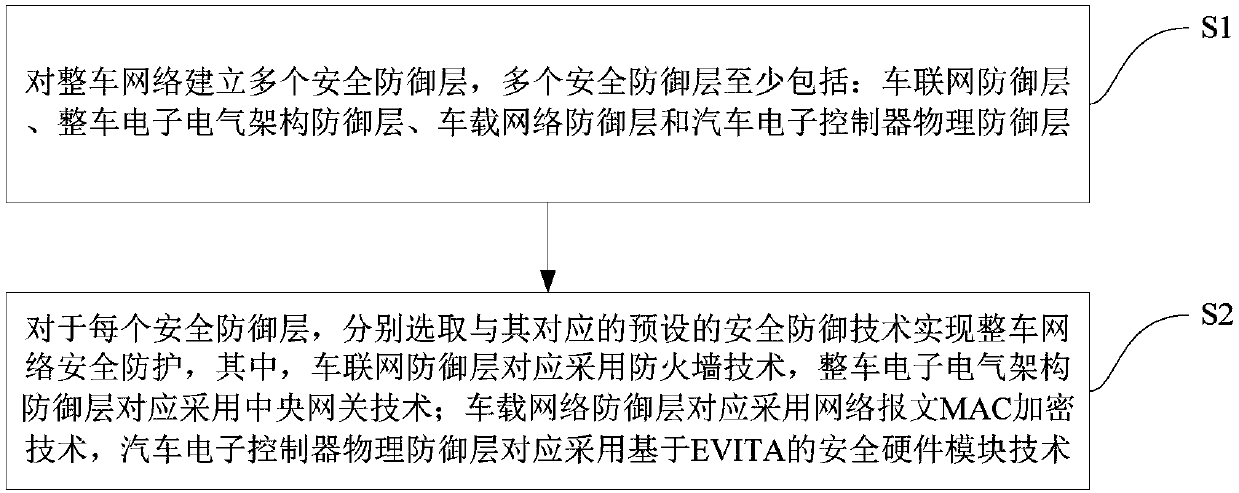
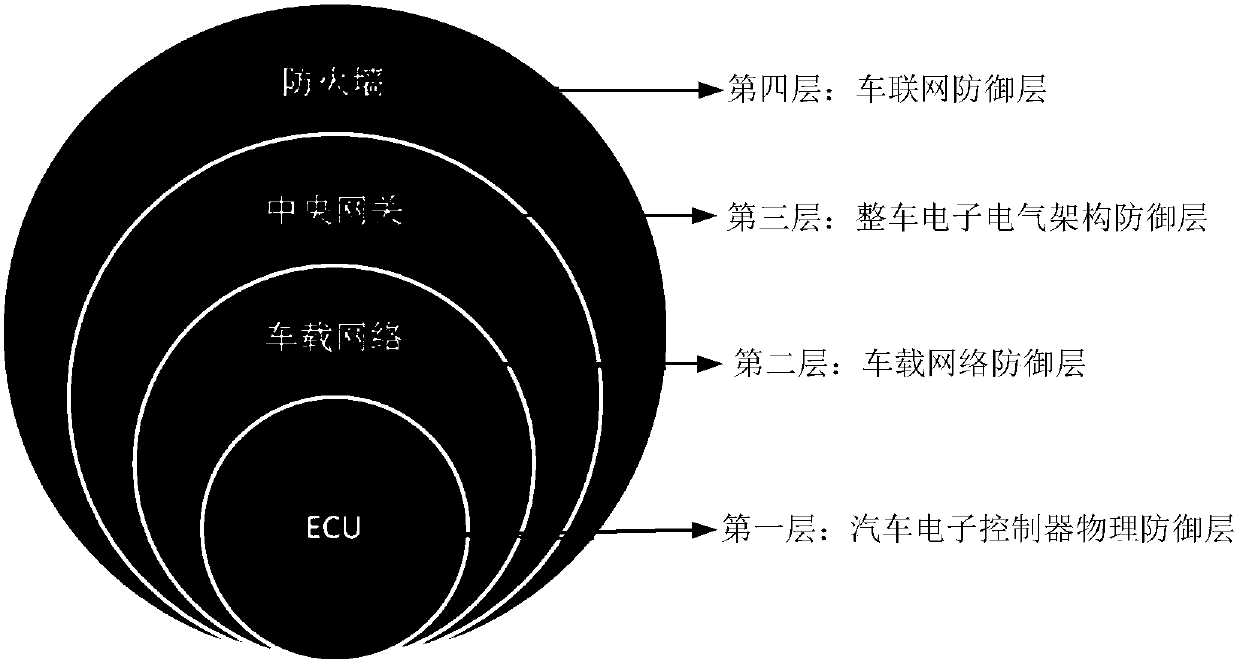
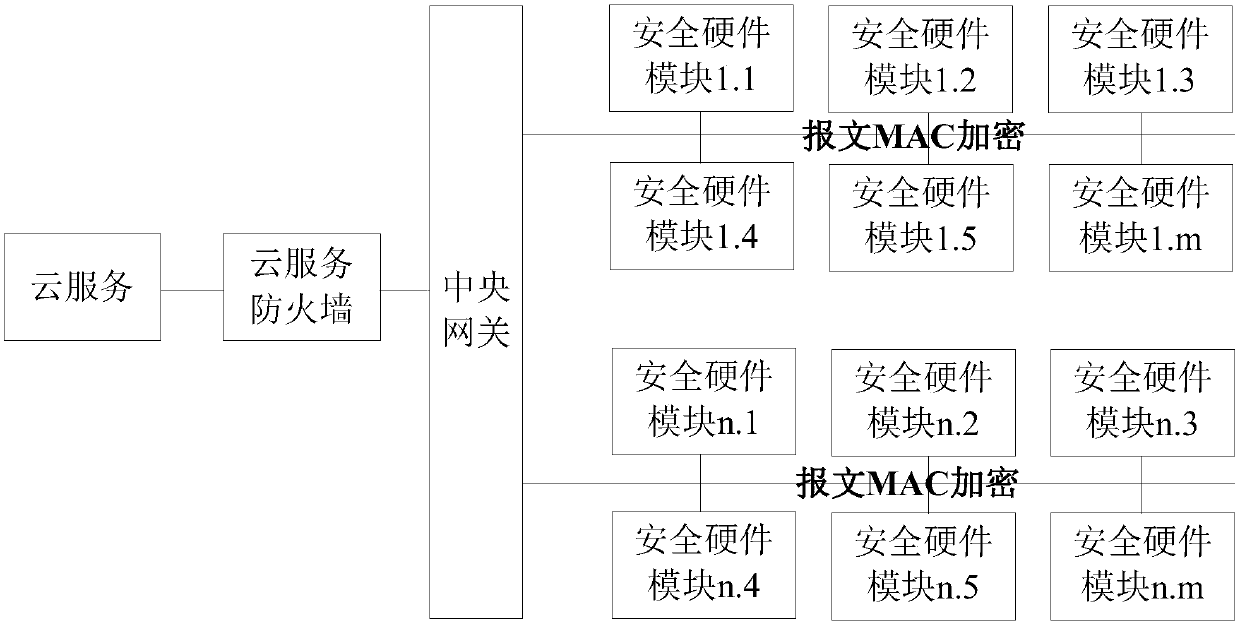
A vehicle network safety protection method based on Internet of Vehicles and a vehicle network architecture
InactiveCN109729056AImprove securityDefend against cyber attacksTransmissionElectronic controllerNetwork architecture
The invention provides a vehicle network safety protection method based on Internet of Vehicles and a vehicle network architecture. The method comprises the following steps: establishing a plurality of security defense layers for a whole vehicle network, wherein the plurality of security defense layers at least comprise an Internet of Vehicles defense layer, a whole vehicle electronic and electrical architecture defense layer, a vehicle-mounted network defense layer and an automobile electronic controller physical defense layer; For each security defense layer, selecting a preset security defense technology corresponding to the security defense layer to realize network security protection of the whole vehicle, wherein a firewall technology is correspondingly adopted by the Internet of Vehicles defense layer, and a central gateway technology is correspondingly adopted by the whole vehicle electronic and electrical architecture defense layer; Wherein the vehicle-mounted network defense layer correspondingly adopts a network message MAC encryption technology, and the automobile electronic controller physical defense layer correspondingly adopts an EVITA-based security hardware moduletechnology. The network attack can be effectively resisted, and the network security of the whole vehicle is improved.
Owner:CH AUTO TECH CORP CO LTD
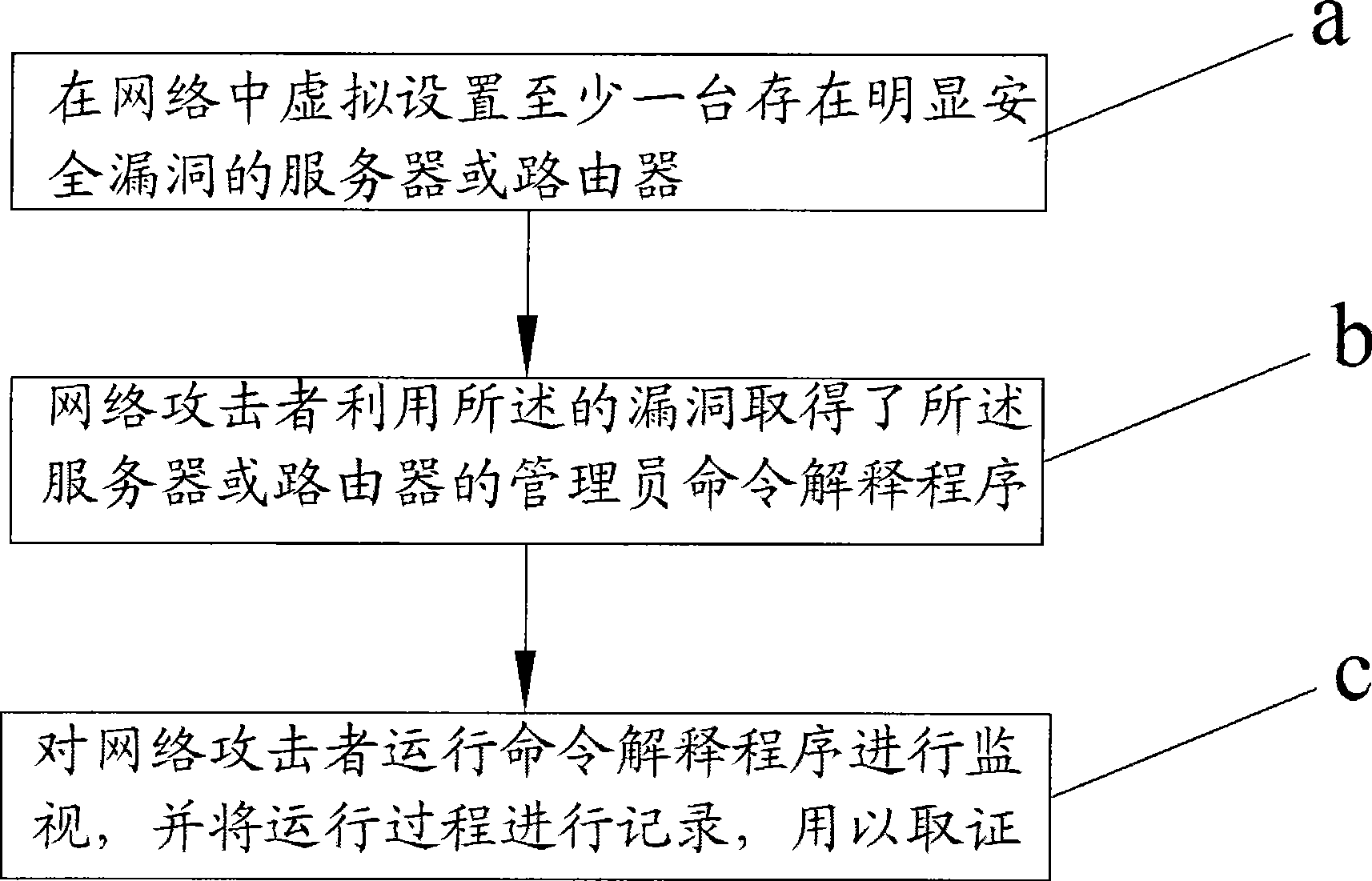
Active network defense method and system
The invention relates to an active network defense method and a system. The method for realization comprises the steps as follows: in step a, at least a server or a router with obvious security vulnerabilities is set in a network in a virtual manner; in step b, a network attacker obtains an administrator command interpreter of the server or the router by utilizing the vulnerabilities; and in step c, the command interpreter runs on the network attacker for monitoring, and the running process is recorded for obtaining evidence.
Owner:AEROSPACE INFORMATION
Network defense system and method thereof
ActiveUS20200045069A1Short response timeInhibiting consequenceMathematical modelsEnsemble learningNetwork activitySimulation
A network defense system can include a sensor alert ingestion framework adapted to monitor network activity and alert detected or suspected anomalies. A network analyzer may be coupled to the sensor alert ingestion framework to analyze the anomalies. A course of action (CoA) simulator may be coupled to the network analyzer adapted to generate a list of decision including courses of action to address the anomalies. There may be a training and feedback unit coupled to the CoA simulator to train the system to improve responses in addressing future anomalies.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
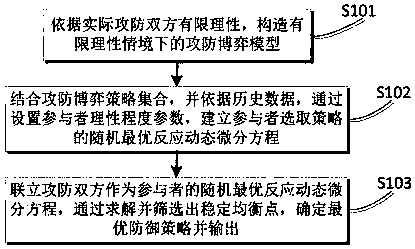
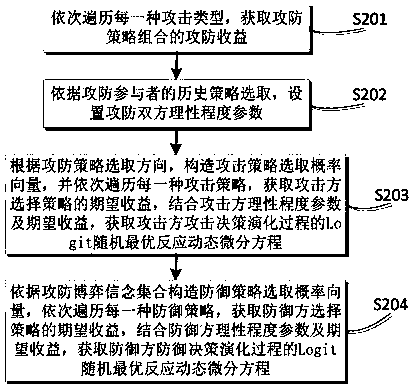
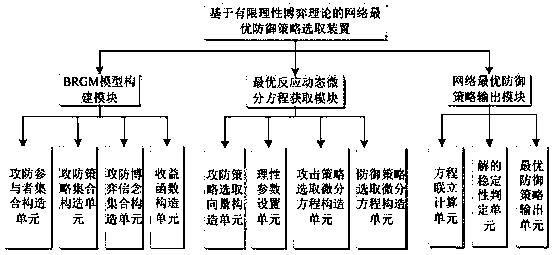
Network optimal defense strategy selection method and device based on bounded rational game theory
ActiveCN108833402AObjectively reflect randomnessObjectively reflect diversityTransmissionTheoretical computer scienceArtificial intelligence
The invention belongs to the technical field of network security and particularly relates to a network optimal defense strategy selection method and device based on a bounded rational game theory. Themethod comprises the following steps: constructing an offensive and defensive game model in a bounded rational situation according to the bounded rationality of the actual offensive and defensive sides; a random optimal reaction dynamic differential equation of a participant selection strategy is established by setting a participant rationality degree parameter in combination with an offensive and defensive game strategy set and according to historical data; the two simultaneous offensive and defensive parties are treated as the random optimal reaction dynamic differential equation of the participant; and an optimal defense strategy is determined and output by solving and screening a stable equilibrium point. Compared with the method of only giving an equilibrium solution and not analyzing the Nash equilibrium formation process, the network optimal defense strategy selection method and device based on bounded rational game theory in the present invention analyze the dynamic evolutionprocess of the bounded rational evolution game equilibrium, and the utility and the guiding significance are stronger when being applied to network defense decision; the dynamic analysis efficiency ofstrategy selection can be improved; and the network security performance is further improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
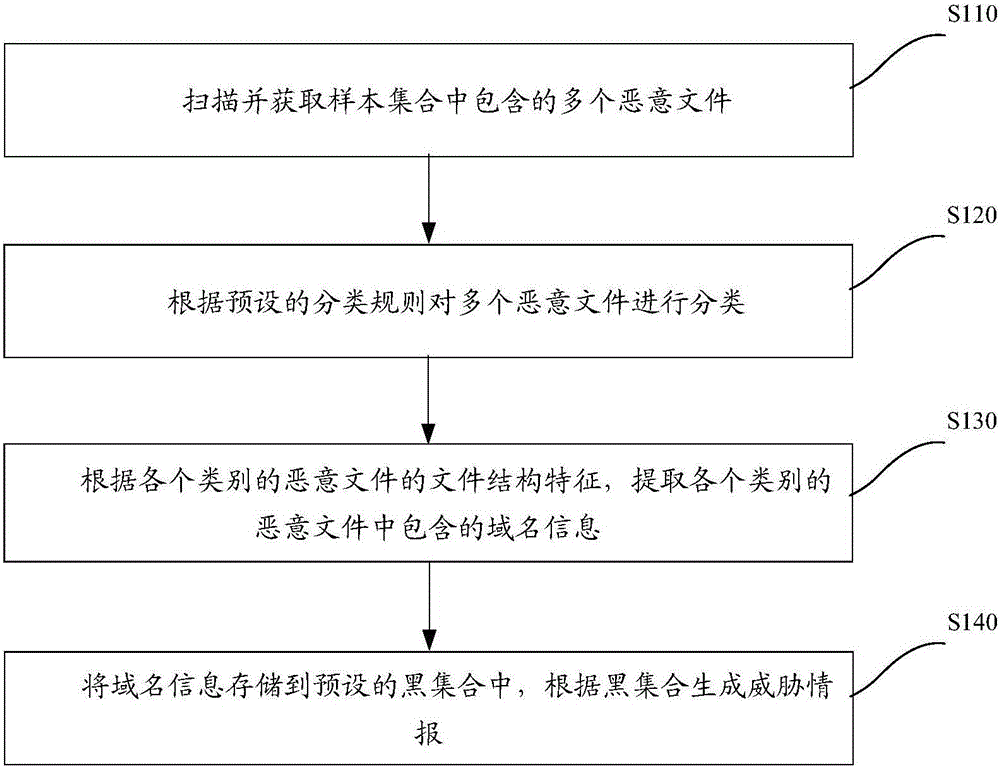
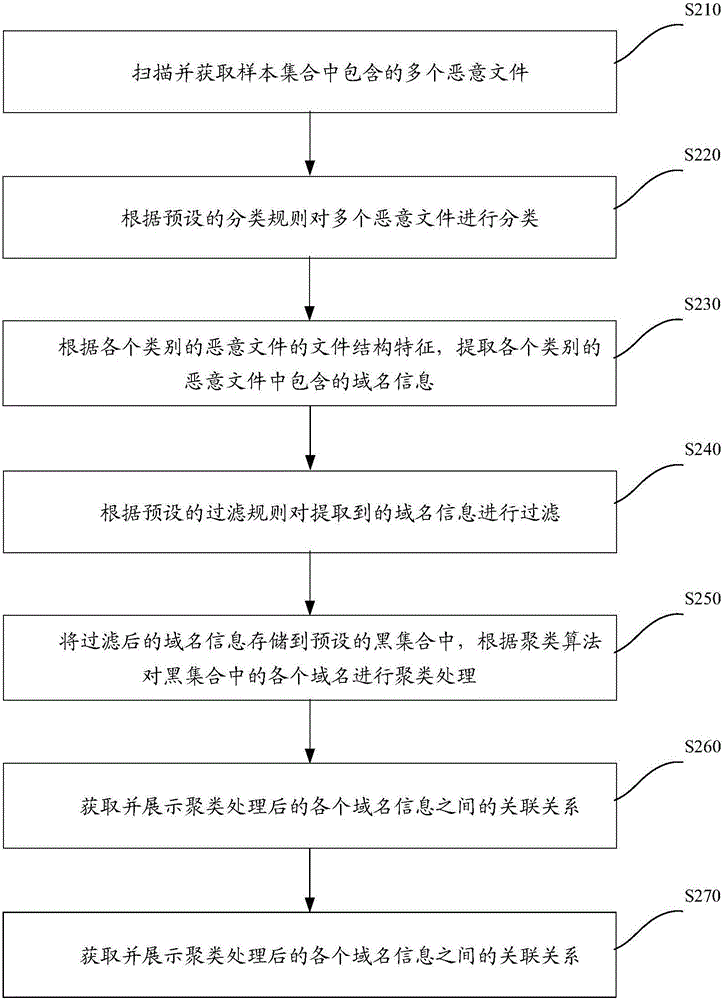
Method and device for generating threat intelligence
ActiveCN106055981AHigh incomeImprove securityPlatform integrity maintainanceDomain nameClassification rule
The invention discloses a method and device for generating threat intelligence. The method comprises the steps of scanning and obtaining multiple malicious files included in a sample set; classifying the multiple malicious files according to a preset classification rule; extracting domain name information included in various categories of malicious files according to file structure characteristics of the various categories of malicious files; and storing the domain name information into a preset black set and generating the threat intelligence according to the black set. Thus, by the method and device for generating the threat intelligence disclosed by the invention, the technical problem that the latest malicious file cannot be timey found out by a traditional network defense method due to relatively poor instantaneity can at least be solved.
Owner:360 TECH GRP CO LTD
Computer network defensive strategy conversion-oriented semantic similarity detection system
InactiveCN101950340AAchieving Semantic Consistency IdentificationSmall amount of calculationPlatform integrity maintainanceCyber-attackSyntax error
The invention discloses a computer network defensive strategy conversion-oriented semantic similarity detection system, which comprises a defensive strategy configuration module, a strategy statement processing module, a node-link configuration module, a lexical and syntax analyzing module, a measure statement processing module, a structural similarity calculating module, a key concept pair matching module, a concept similarity calculating module, a CND strategy and measure body module and a similarity accumulation calculating module. A traditional symbol description-based strategy conversion system can only detect lexical and syntax errors before and after conversion, and hardly detects semantic inconsistency before and after strategy conversion comprehensively and automatically. By employing the semantic similarity processing method, the semantic similarity detection system automatically and effectively measures semantic difference before and after the computer network defensive strategy conversion, provides a basis for accurately deploying network defensive measures for semantics, is mainly applied to a computer network defensive system, deploys defensive measures according to a certain condition based on large-scale network attack, and rapidly and effectively fulfills the aim of large-scale defensive measure deployment.
Owner:BEIHANG UNIV
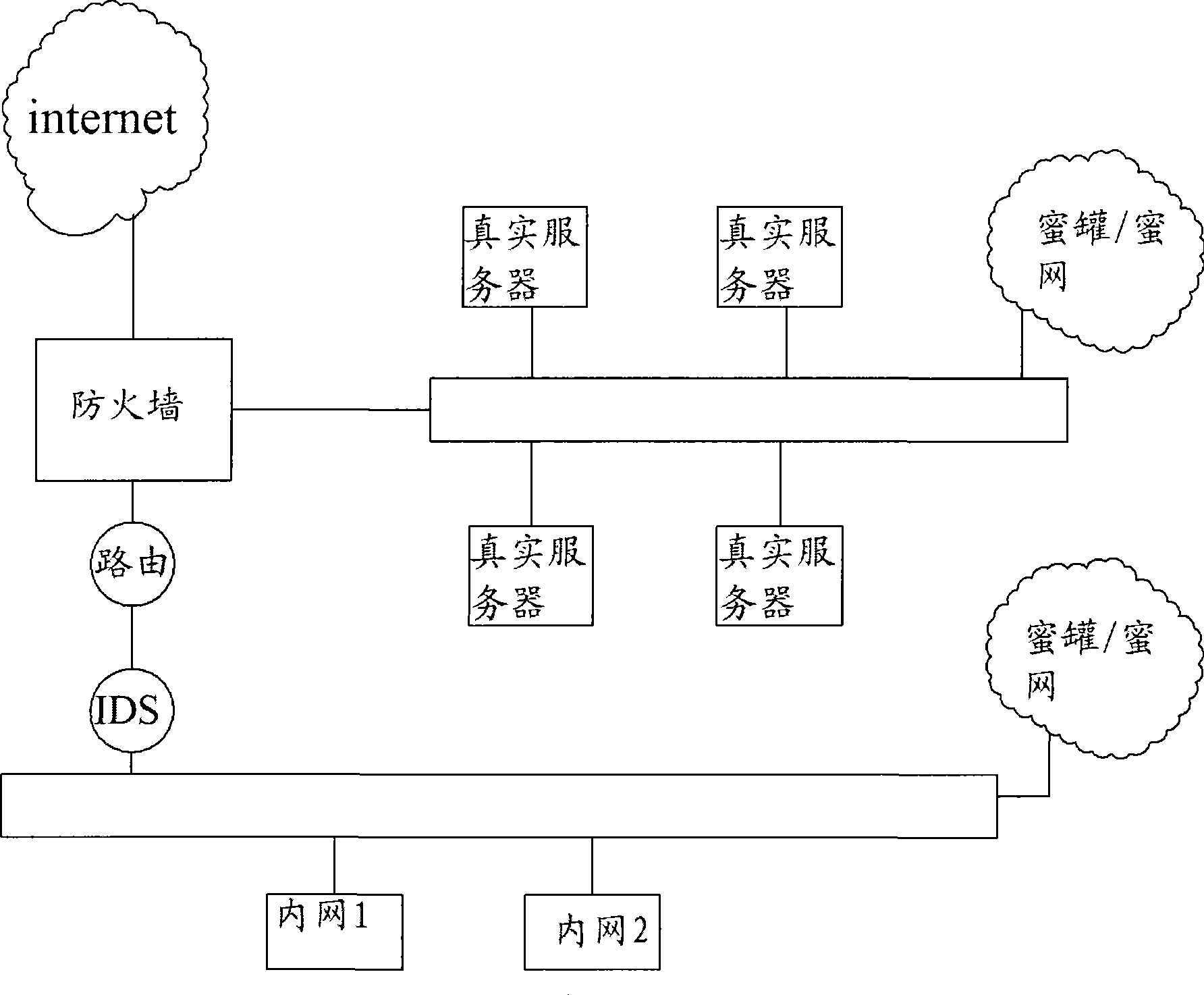
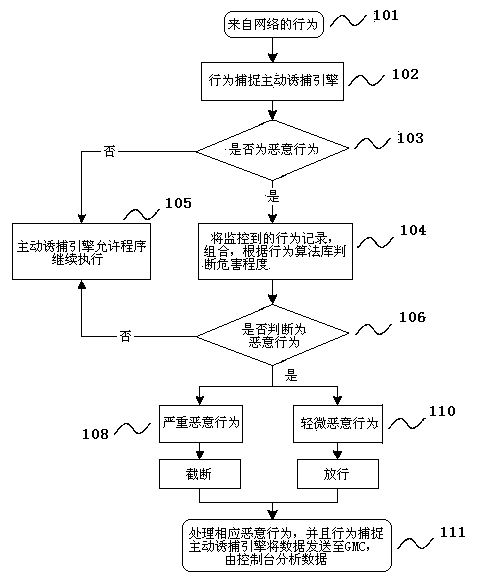
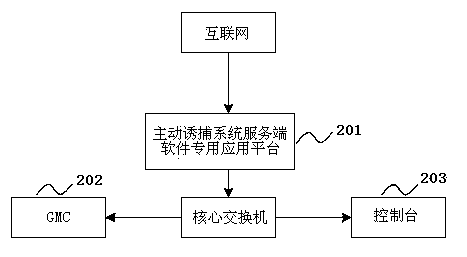
Active trapping method based on behavior capturing
InactiveCN103581104APrevent intrusionAvoid attackPlatform integrity maintainanceTransmissionFeature extractionTrapping
The invention brings forward an active trapping method based on behavior capturing. A trapping system is established in a formulated network area. The active trapping method comprises the following three links: (1) an active trapping system is established in an advance defense of a network defense system, and an active trapping engine technology is adopted; an active trapping engine, target cheating, attack capturing, attack control, attack analysis and characteristic extracting are established in multiple systems included by a computer; (2) a dynamic depth target cheating attack behavior is utilized to trap a real attack objective of an attacker; (3) and the active trapping system makes the attacker be sure of the attack target according to the aforementioned judgment results so that the real attack objective of the attacker is trapped. According to the active trapping method based on behavior capturing, known and unknown attack behaviors can be captured, the security state of the whole network is mastered and the network security level is enhanced.
Owner:江苏中科慧创信息安全技术有限公司
Method and system for network protection against cyber attacks
A method, system, and device for protecting networking computers or devices from cyber attacks, including periodically changing cyber coordinates of a communications network or system; communicating the changed cyber coordinates to corresponding or reciprocal networks and / or devices so they can maintain communications; detecting a cyber attack or receiving notification from the corresponding or reciprocal networks and / or devices of a cyber attack; and changing the cyber coordinates of the network or system upon such detection or notification and communicating the changed cyber coordinates to the corresponding or reciprocal networks and / or devices.
Owner:INVICTA NETWORKS INC
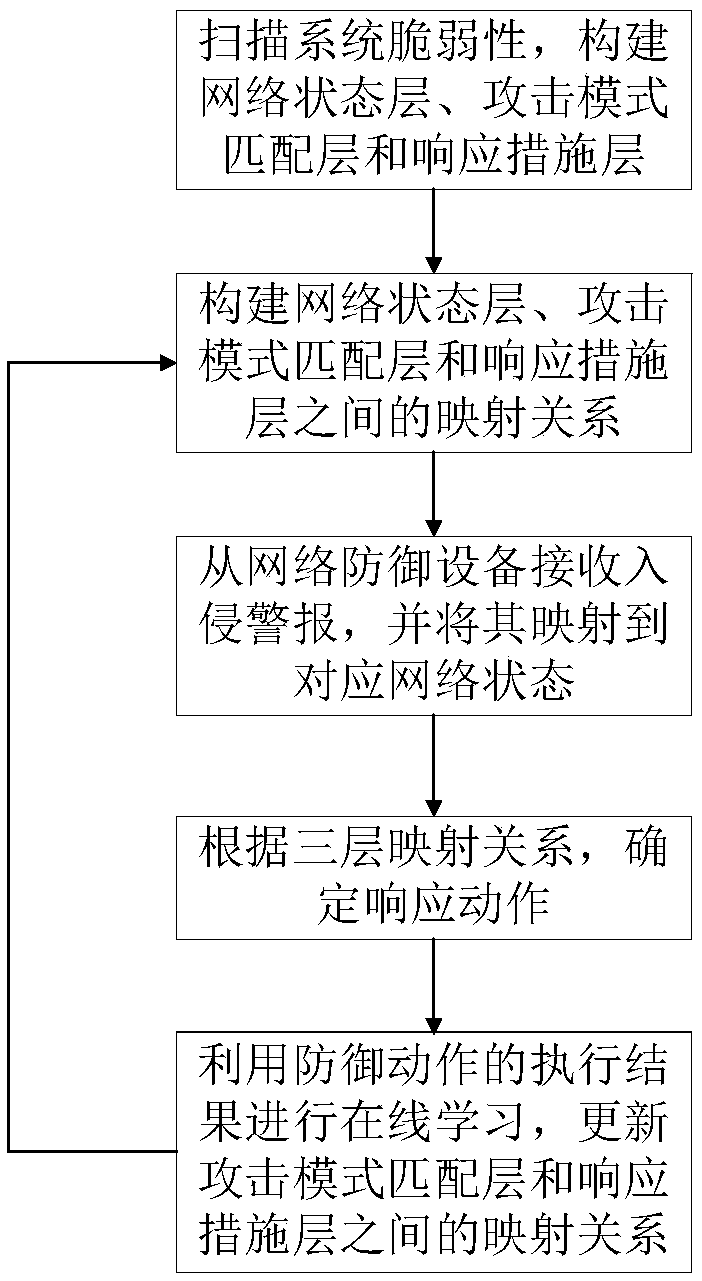
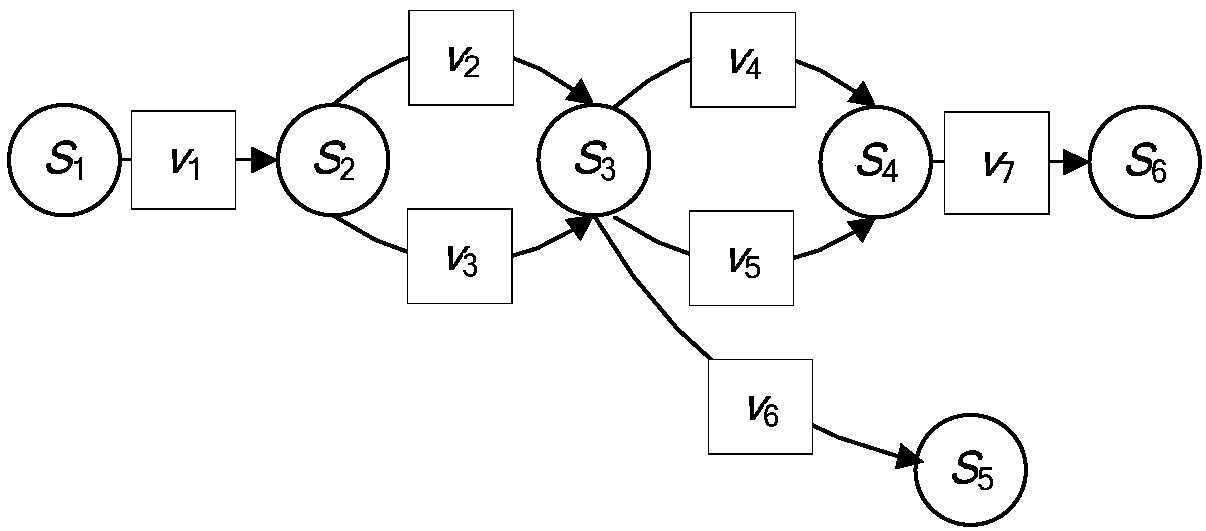
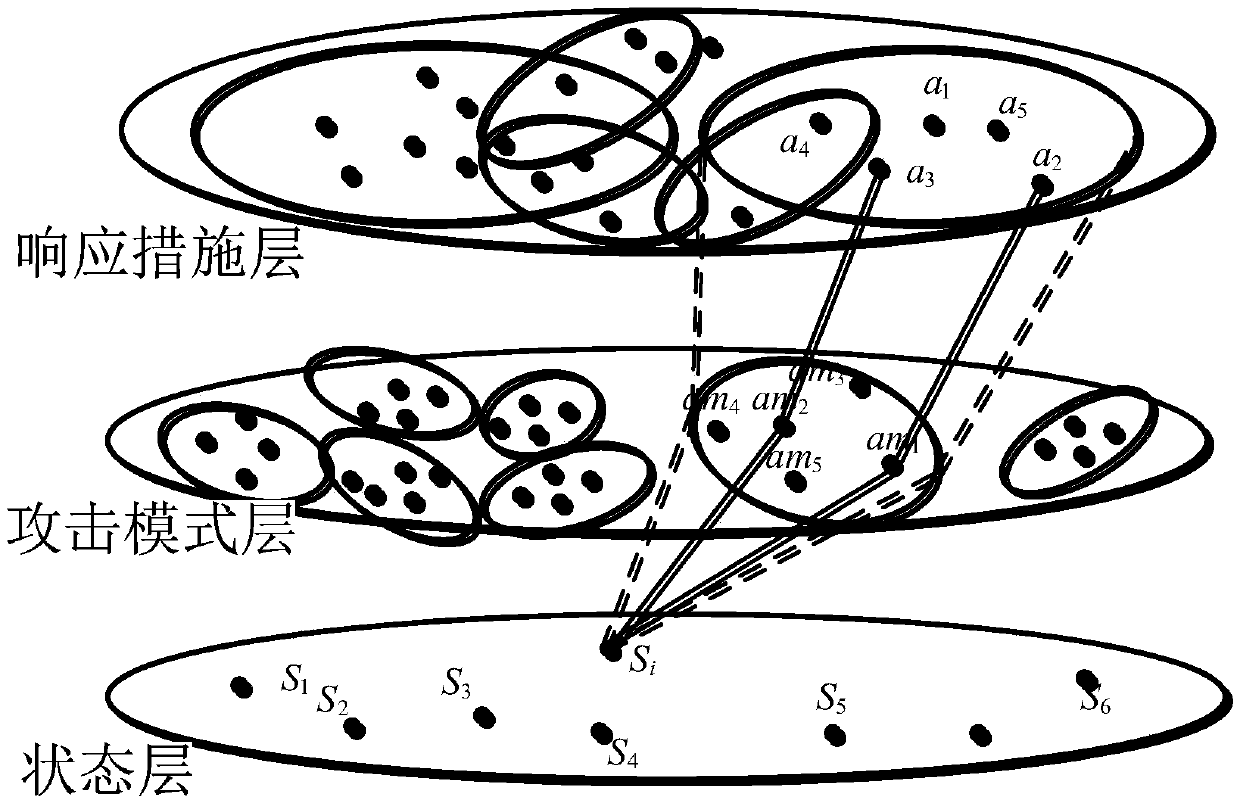
Automatic intrusion response decision making method based on Q-learning
InactiveCN108809979AImprove accuracyImprove real-time performanceComputing modelsTransmissionDecision takingInformation security
The invention belongs to the technical field of information security, and particularly relates to an automatic intrusion response decision making method based on Q-learning. The method comprises the following steps: scanning system vulnerability, constructing an attack graph, and establishing a network state layer, an attack pattern matching layer and a response measure layer according to the attack graph; establishing a mapping relationship among the network state layer, the attack pattern matching layer and the response measure layer; receiving an intrusion alarm from a network defense device, and mapping the intrusion alarm to a corresponding network state; selecting a defense action according to the mapping relationship, and notifying the system of the result; performing online learning by using the execution result of the defense action, and updating the mapping relationship between the attack pattern matching layer and the response measure layer; and returning to the step of mapping the intrusion alarm to the corresponding network state, and performing automatic response decision marking and online learning, until a defender terminates the defense. By adoption of the automatic intrusion response decision making method based on Q-learning provided by the invention, evaluation of multiple response purposes of the strategy can be achieved, the demand of multiple response purposes can be met, the instantaneity and accuracy of the intrusion detection are improved, the network resource consumption is reduced, and the overall performance of the system is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
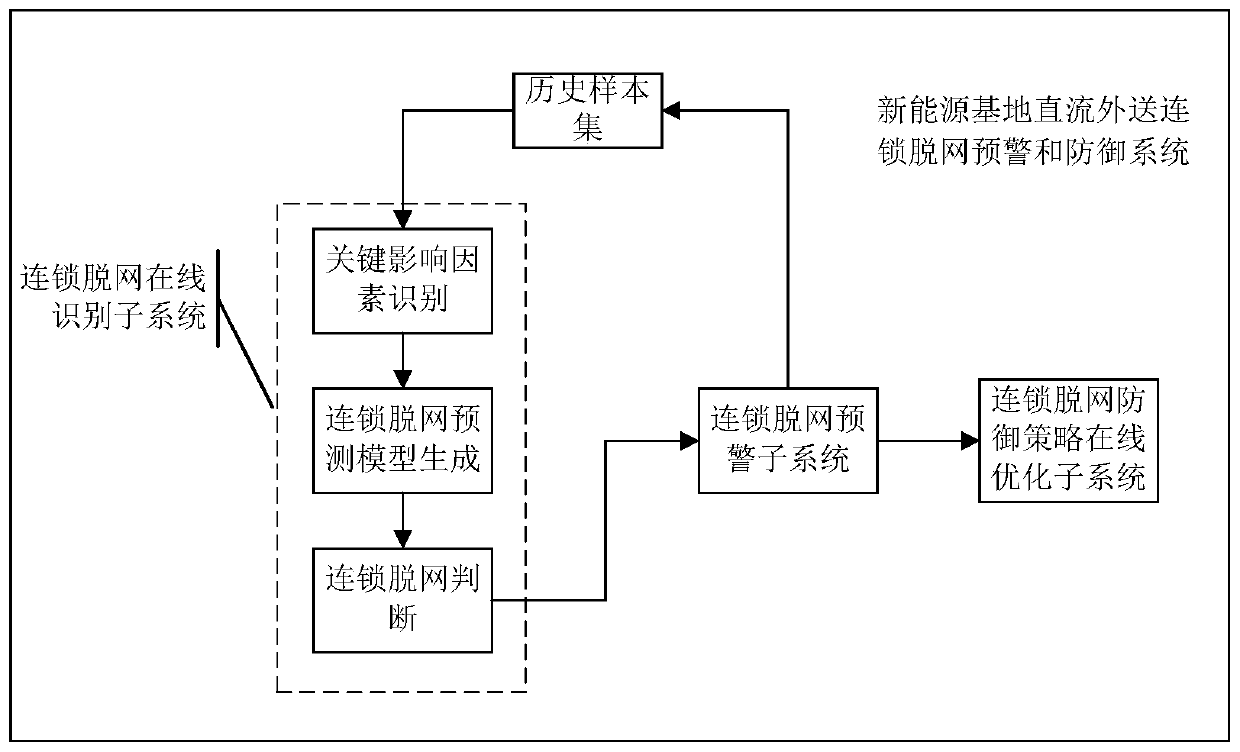
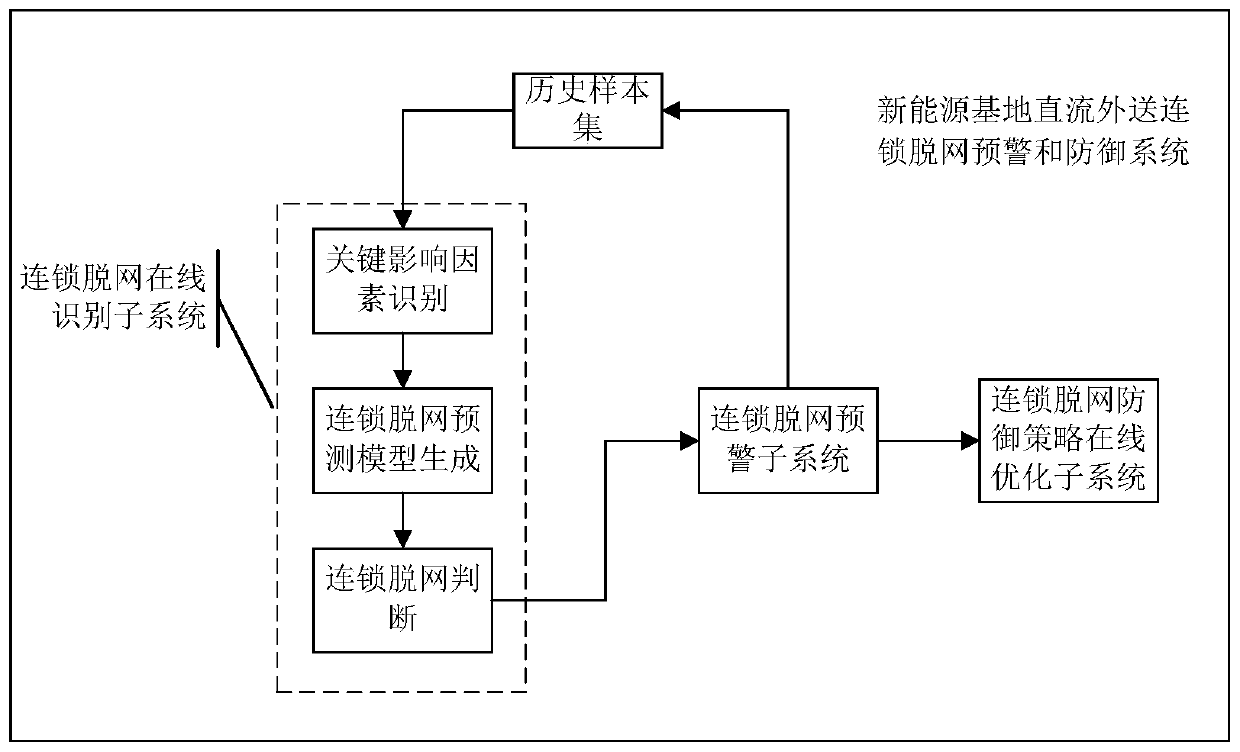
New energy base direct-current outgoing chain off-network early warning and defense system and method
ActiveCN109713668AImprove operational reliabilityReduce operational risk requirementsAc network circuit arrangementsCascading failureNew energy
The invention discloses a new energy base direct-current outgoing chain off-network early warning and defense system. The system comprises a chain off-network online identification subsystem, a chainoff-network early warning subsystem and a chain off-network defense strategy online optimization subsystem. A machine learning method is adopted to obtain key influence factors influencing chain off-network and predict whether new energy chain off-network occurs or not after anticipated faults. A cascading failure is judged according to the off-network condition of the transient stability simulation fan after failure. The new energy cascading off-network risk assessment is carried out. The prevention control and emergency regulation plan strategy online optimization calculation are carried outon the anticipated failure where cascading off-network may happen. The requirements for improving the operation reliability and reducing the operation risk of direct current delivery of a new energybase are met.
Owner:NARI TECH CO LTD +4
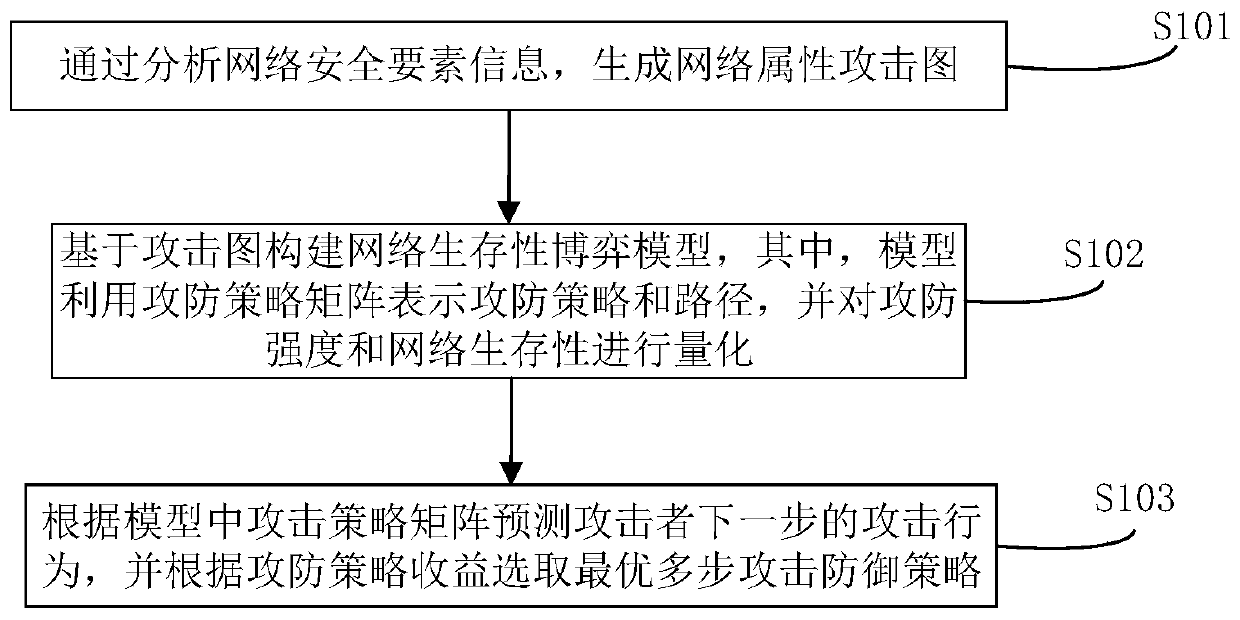
Multi-step attack dynamic defense decision selection method and system for network attack and defense
ActiveCN110602047AImprove defenseImprove security governance capabilitiesData switching networksAttack graphAttack strategy
The invention belongs to the technical field of network security, and particularly relates to a multi-step attack dynamic defense decision selection method and system for network attack and defense, and the method comprises the steps: generating a network attribute attack graph through the analysis of network security element information; constructing a network survivability game model based on the attack graph, representing an attack and defense strategy and a path by the model by utilizing an attack and defense strategy matrix, and quantifying attack and defense intensity and network survivability; predicting the next attack behavior of an attacker according to the attack strategy matrix in the model, and selecting the optimal multi-step attack defense strategy according to the attack defense strategy cost. The attack and defense strategy is implemented around the network survivability, the situation pre-judgment and defense strategy can be adjusted according to the dynamically changing attack and defense situation of the network, an easily understood and reasonable defense decision is provided for network security management personnel, the network defense capability is improved,the application prospect is good, and the method has important guiding significance and value for the network security technology.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Computer Network Defense
ActiveUS20130019312A1Memory loss protectionError detection/correctionOperational systemApplication software
Training defense of a computer network. The system includes an enterprise asset subsystem to be defended. The enterprise asset subsystem runs operating system, support services, and application programs. The system also includes a neutral subsystem that is in communication with the enterprise asset subsystem and is used to set up and run at least one exercise scenario, and score performance of enterprise asset defenders in defending the system against exploits. Exploits are launched by an exploitation subsystem communication with the enterprise asset subsystem.
Owner:LEIDOS
Malicious file detection method, system and device and readable storage medium
InactiveCN111737696ASolve problems that cannot be defended immediatelyReduce the false negative rate of detectionPlatform integrity maintainanceOperating systemThreat intelligence
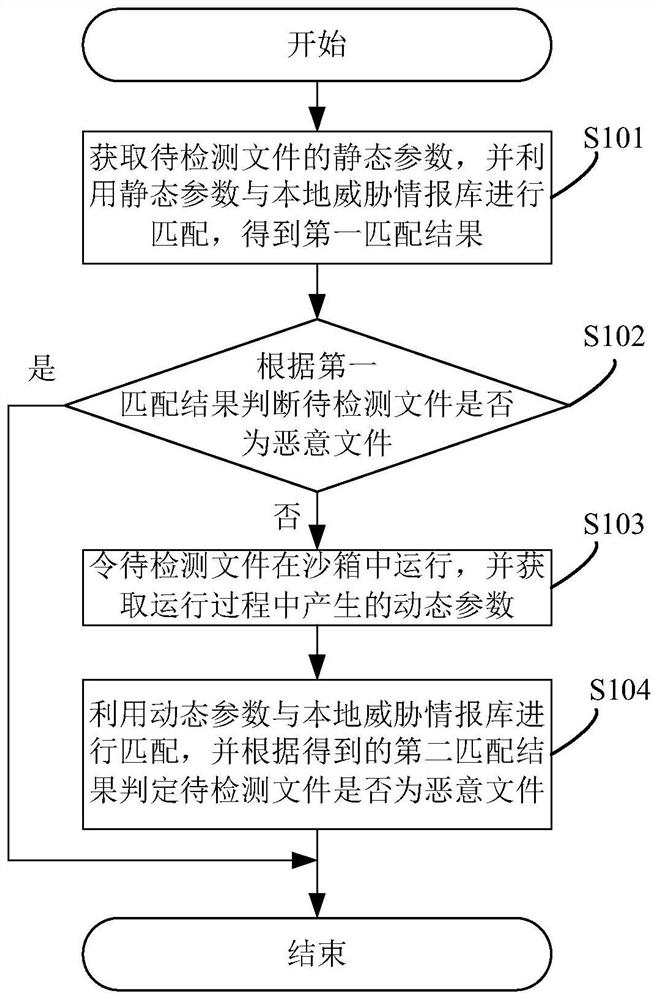
The invention discloses a malicious file detection method. The method comprises the steps: matching static parameters with a local threat information library; judging whether the to-be-detected file is a malicious file or not; if not, making the to-be-detected file to run in the sandbox, and obtaining dynamic parameters generated in the running process; and matching the dynamic parameters with alocal threat information library, and judging whether the to-be-detected file is a malicious file or not according to an obtained second matching result. According to the method, the to-be-detected file runs in the sandbox; as long as the to-be-detected file generates suspicious dynamic parameters in the running process, the to-be-detected file is marked as a malicious file, the problem that in the prior art, an unknown and newly-occurring malicious file cannot be defended immediately is solved, the missing report rate of malicious file detection is reduced, and the timeliness of network defense is improved. The invention furthermore provides a malicious file detection system and device, and a readable storage medium, which have the above beneficial effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Collaborative defense method for network protection and system
ActiveCN109587174AGood for in-depth analysisGet the effect of defenseTransmissionCentralized managementProtection system
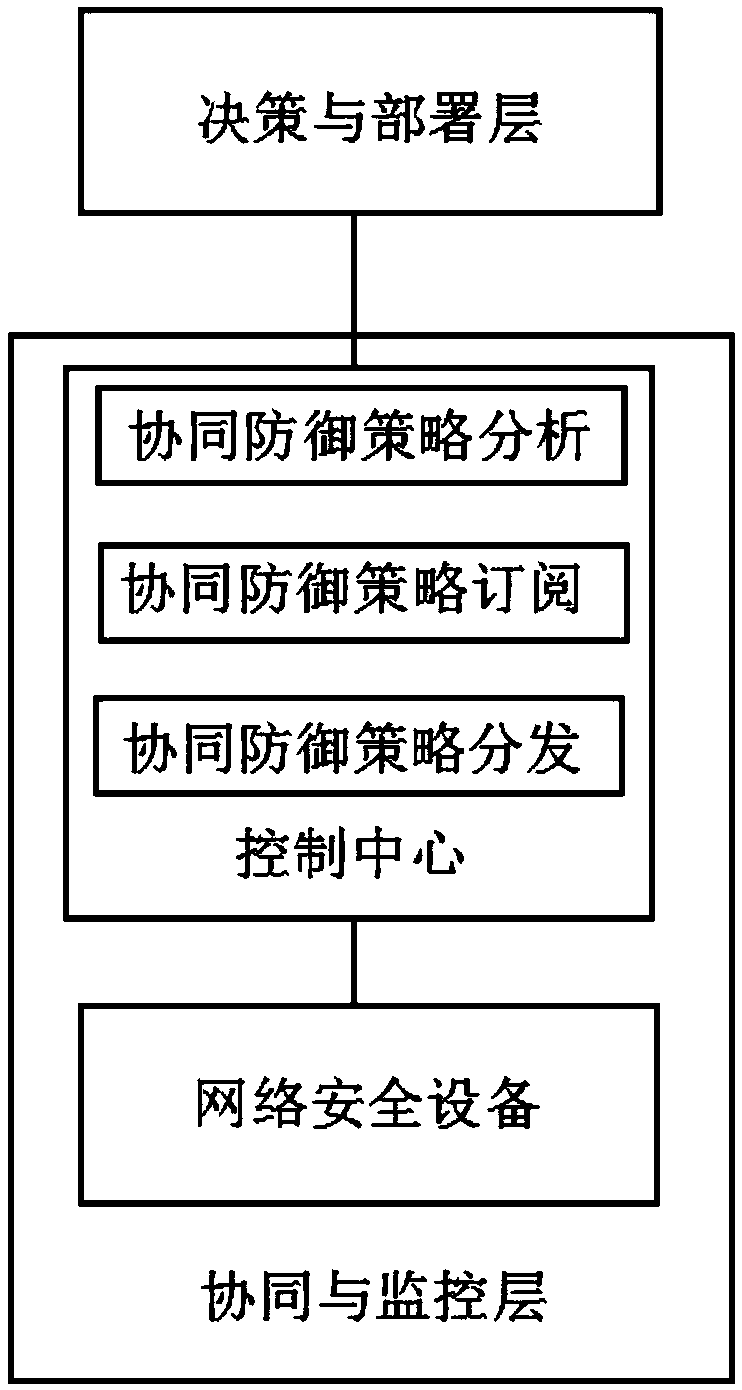
The invention discloses a collaborative defense method for network protection and system. The system comprises a decision-making and deployment layer and a collaboration and monitoring layer, whereinthe decision-making and deployment layer uses an acquired network security early warning event, a defense intension is formulated according to the defense purpose of the network security and the current situation of the network security, a network defense strategy is later generated by a decision-making engine, and a defense task is deployed according to the defense strategy; the collaboration andmonitoring layer comprises a control center and network security devices, thereby realizing collaborative task deployment between network security devices and real-time monitoring on the network defense condition; the control center is in communication connection with the decision-making and deployment layer and the network security devices for data flow control and logical control; and the control center comprises a collaborative defense strategy analysis module, a collaborative defense strategy subscription module and a collaborative defense strategy distribution module. A collaborative defense solution with security perception, collaborative protection and centralized management as the core can be given, and an active, integrated and comprehensive dynamic security protection system isrealized.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
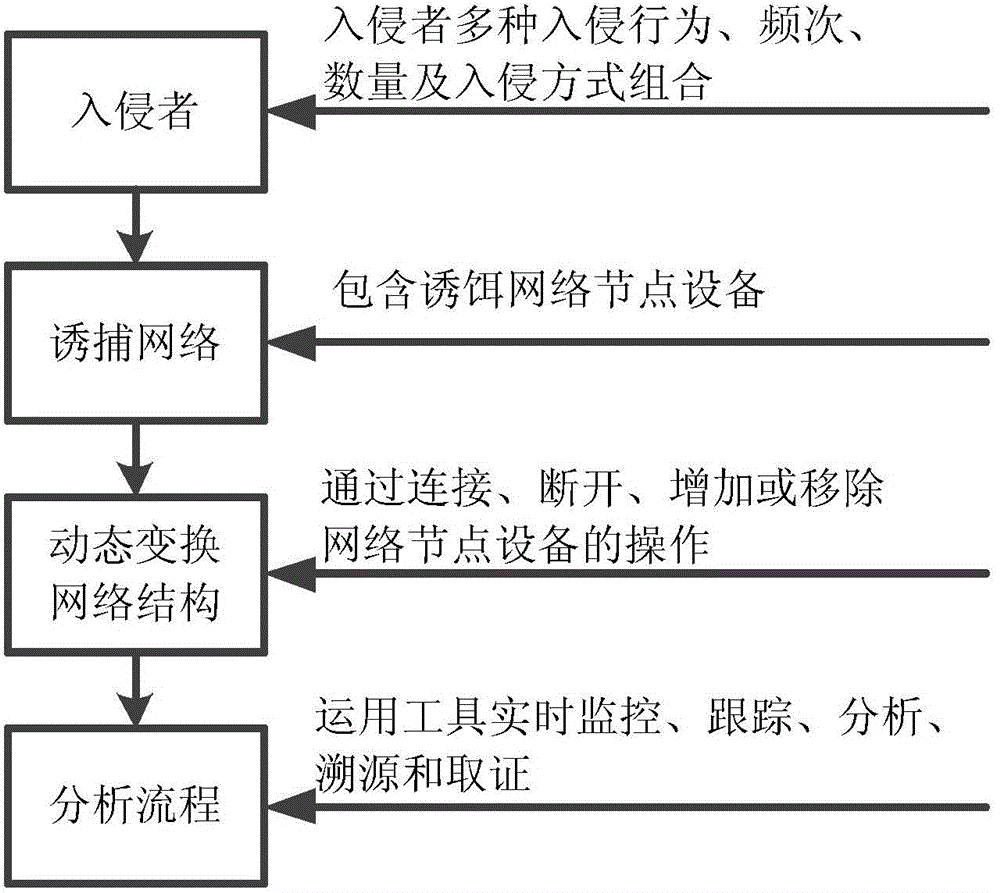
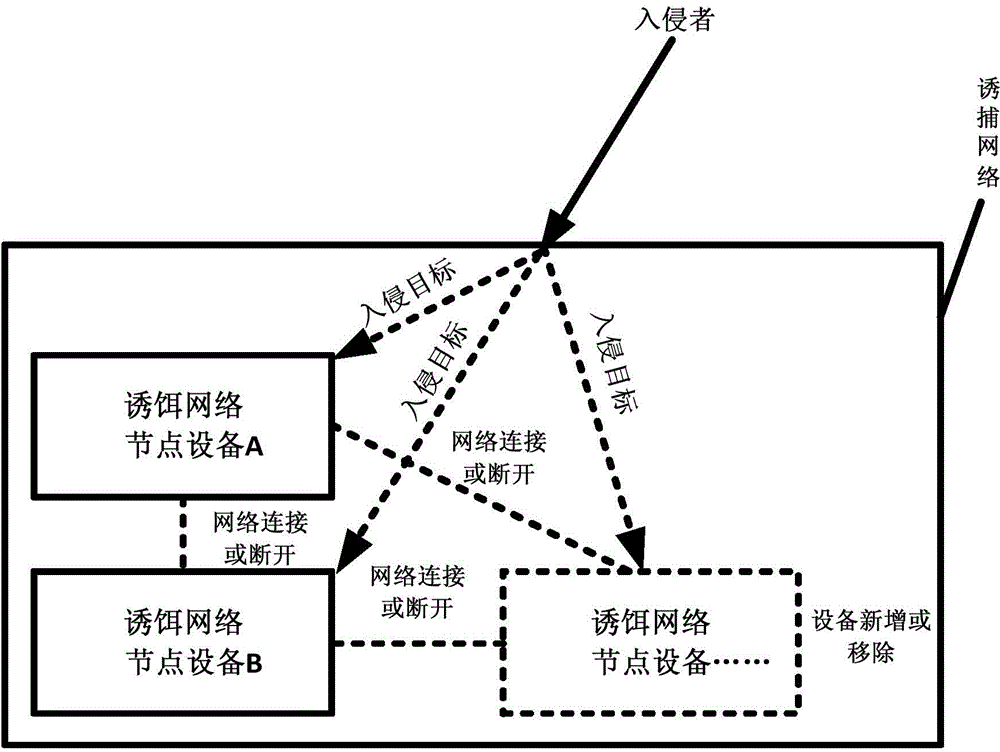
Extension defense method based on network intrusion
InactiveCN104144164AEffective real-time monitoringDelay Invasion TimePlatform integrity maintainanceData switching networksDecoyNetwork security policy
The invention belongs to the technical field of network security and discloses an extension defense method based on network intrusion. According to actual situations of intrusion behaviors of intruders, intentions and purposes of the intruders are analyzed and judged by building a trap network, related trap network node devices constituting the trap network are disconnected or connected or added or removed in real time, therefore, targets to which the intruders pay attention are changed, the intrusion priorities are changed, bait resource deployment and configuration are changed, objects intruding and percolating into the network are controlled, and delaying, monitoring, tracking, analyzing, source tracing and evidence obtaining are conducted on intrusion processes of the intruders. According to the method, an existing network can be built or deployed completely, the active defense capability of the network can be further enhanced, and the method is a novel, deep and multi-dimensional network defense strategy.
Owner:WUHAN ANWEN SCI & TECH DEV
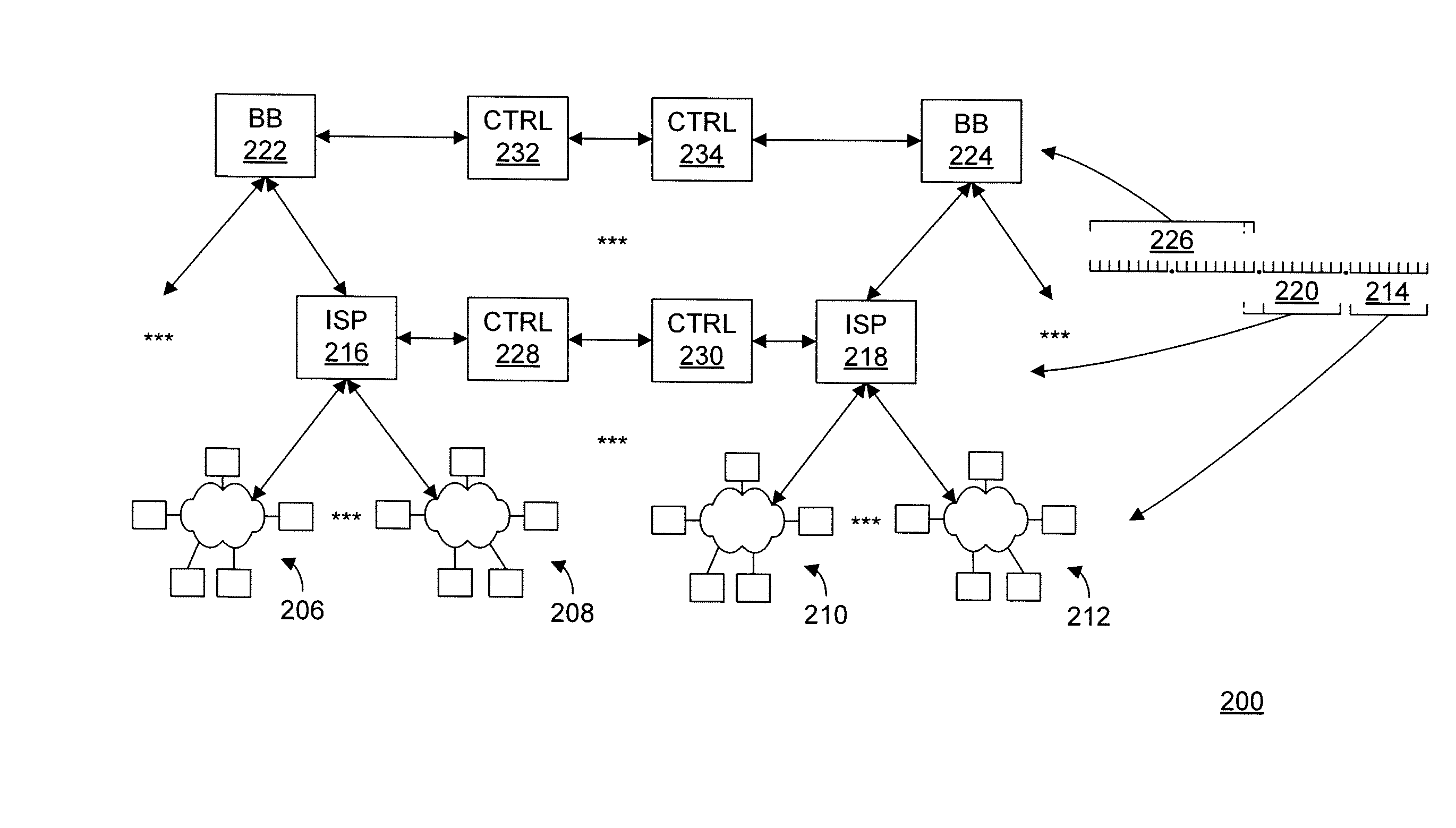
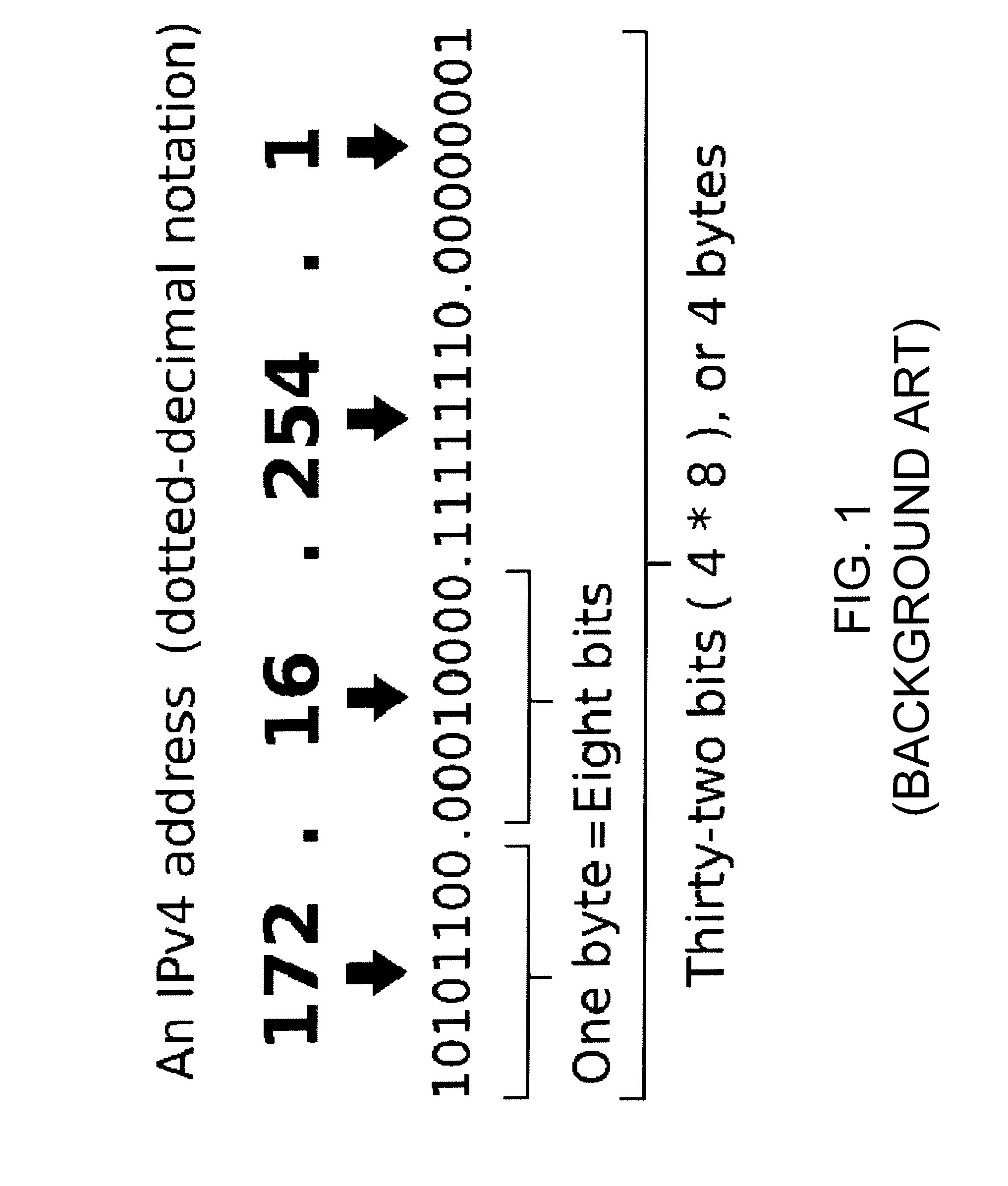
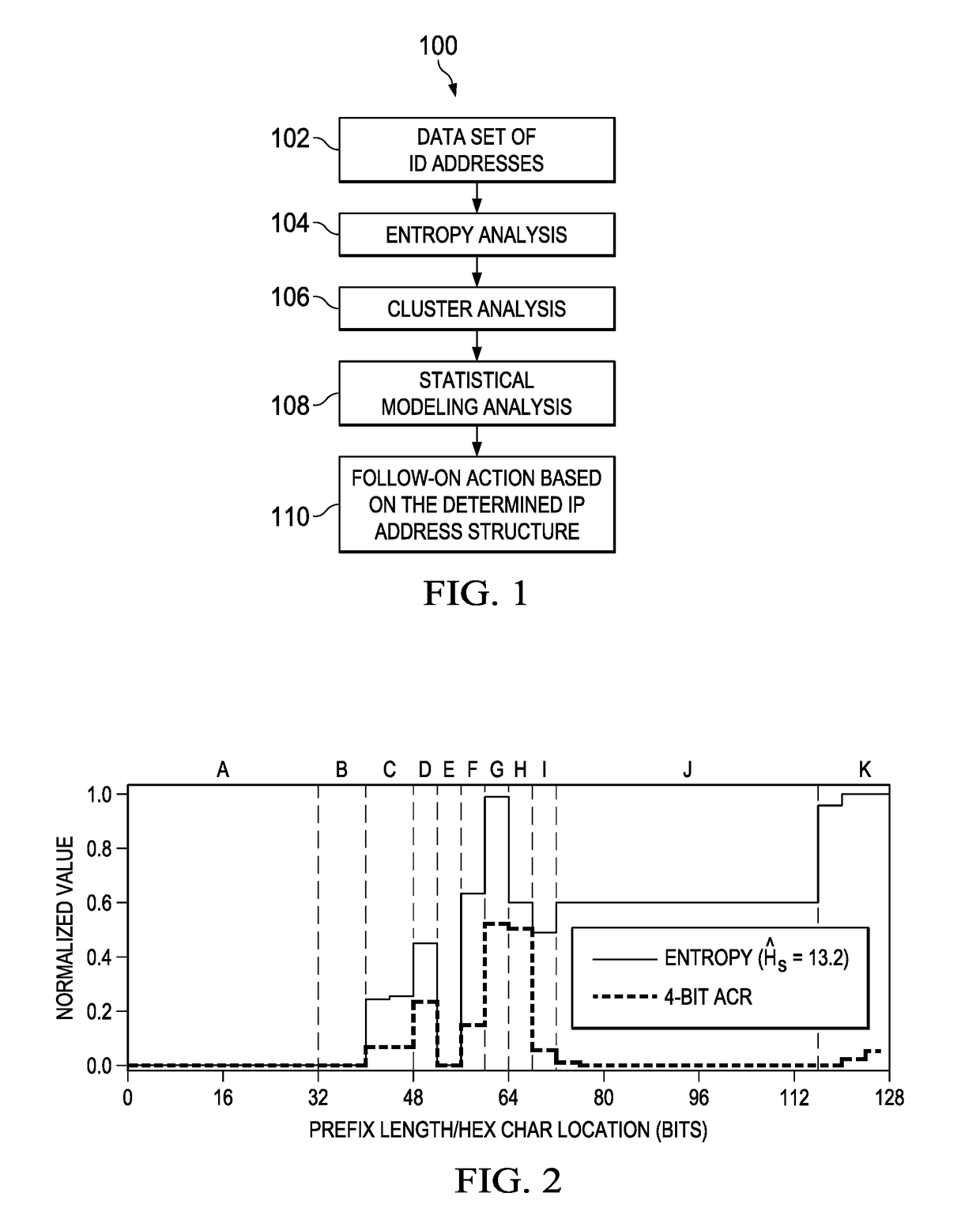
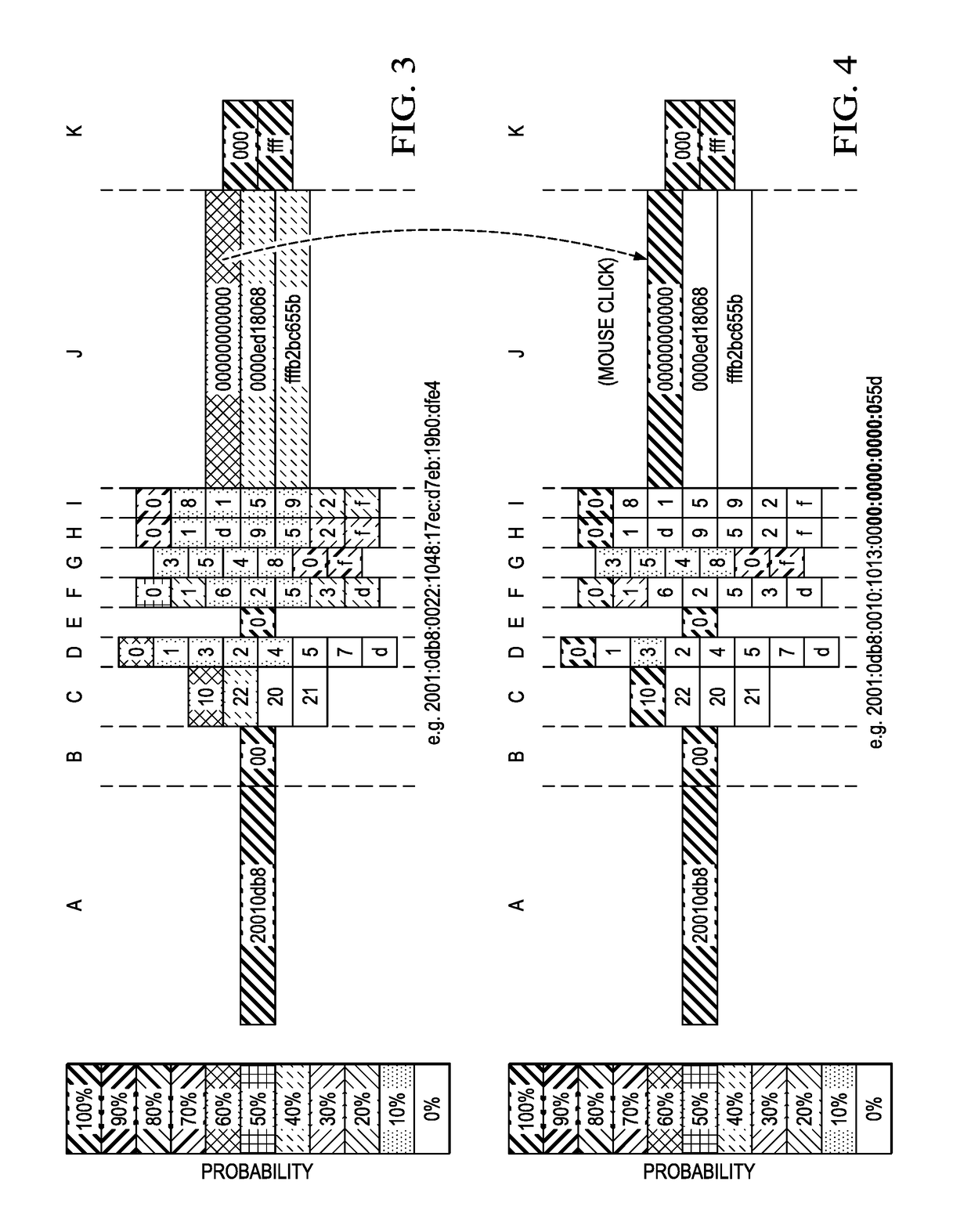
Internet address structure analysis, and applications thereof
An analysis system automates IP address structure discovery by deep analysis of sample IPv6 addresses using a set of computational methods, namely, information-theoretic analysis, machine learning, and statistical modeling. The system receives a sample set of IP addresses, computes entropies, discovers and mines address segments, builds a network model of address segment inter-dependencies, and provides a graphical display with various plots and tools to enable a network analyst to navigate and explore the exposed IPv6 address structure. The structural information is then applied as input to applications that include: (a) identifying homogeneous groups of client addresses, e.g., to assist in mapping clients to content in a CDN; (b) supporting network situational awareness efforts, e.g., in cyber defense; (c) selecting candidate targets for active measurements, e.g., traceroutes campaigns, vulnerability assessments, or reachability surveys; and (d) remotely assessing a network's addressing plan and address assignment policy.
Owner:AKAMAI TECH INC
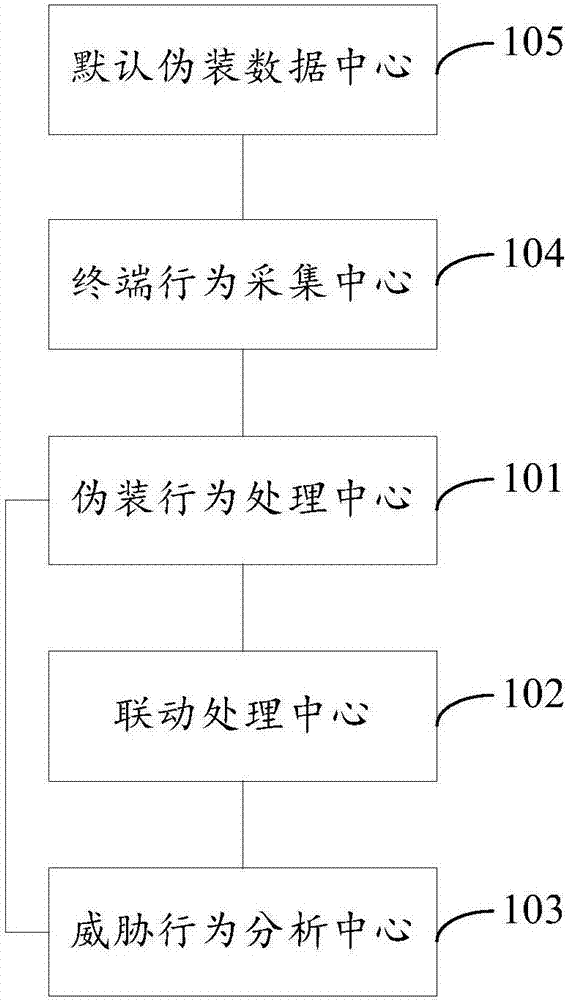
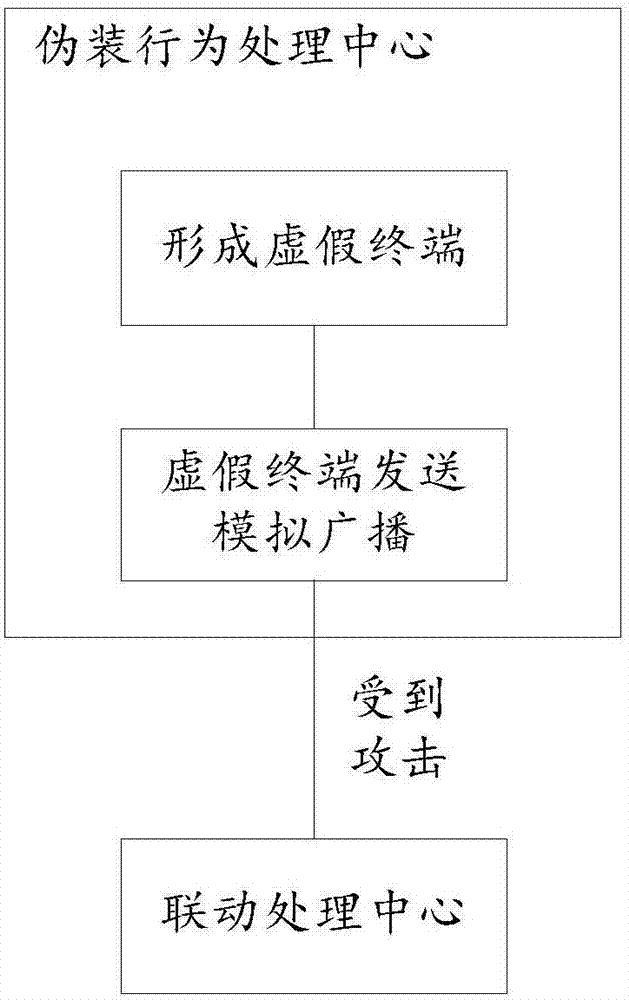
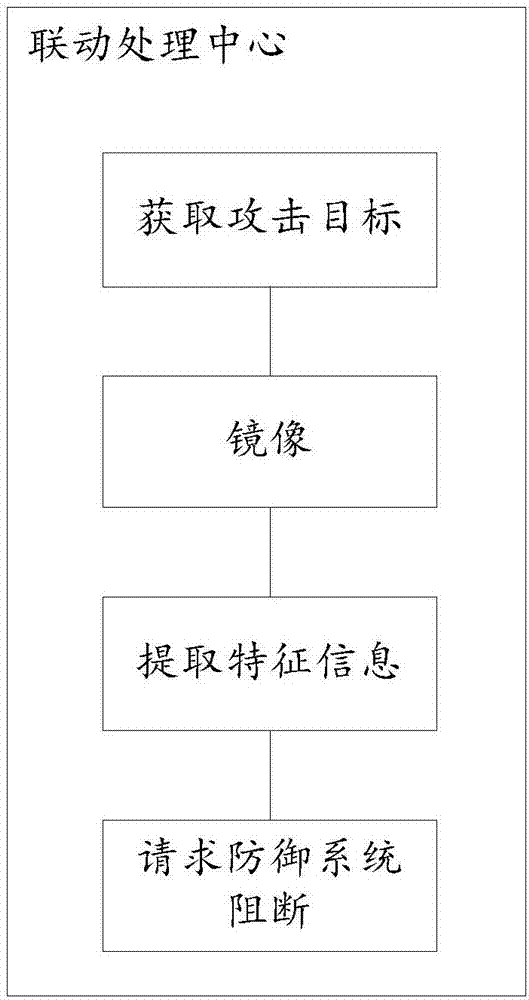
Network anti-attack device, system and method, readable medium and storage controller
The invention discloses a network anti-attack device, system and method, a readable medium and a storage controller. The network anti-attack device comprises a camouflage behavior processing center, a linkage processing center and a threatening behavior analysis center, wherein the camouflage behavior processing center is used for camouflaging a preset number of false terminals and making the false terminals to transmit analog broadcasts to a network; the linkage processing center is used for intercepting the attack and extracting attack behavior characteristics of the attack when the analog broadcasts are attacked and transmitting the attack behavior characteristics to a defensive system in the network to interrupt the attack through the defensive system; and the threatening behavior analysis center is used for receiving interrupt information transmitted by the defensive system after successfully interrupting the attack, extracting interrupt information characteristics of the interrupt information, packaging the attack behavior characteristics and the interrupt information characteristics to form a characteristic group and transmitting the characteristic group to a database to form a characteristic library. The problem that a passive defense mode falls behind virus transmission is effectively solved, an overall network defense linkage system is formed, and the security of a real terminal is improved.
Owner:BEIJING VRV SOFTWARE CO LTD
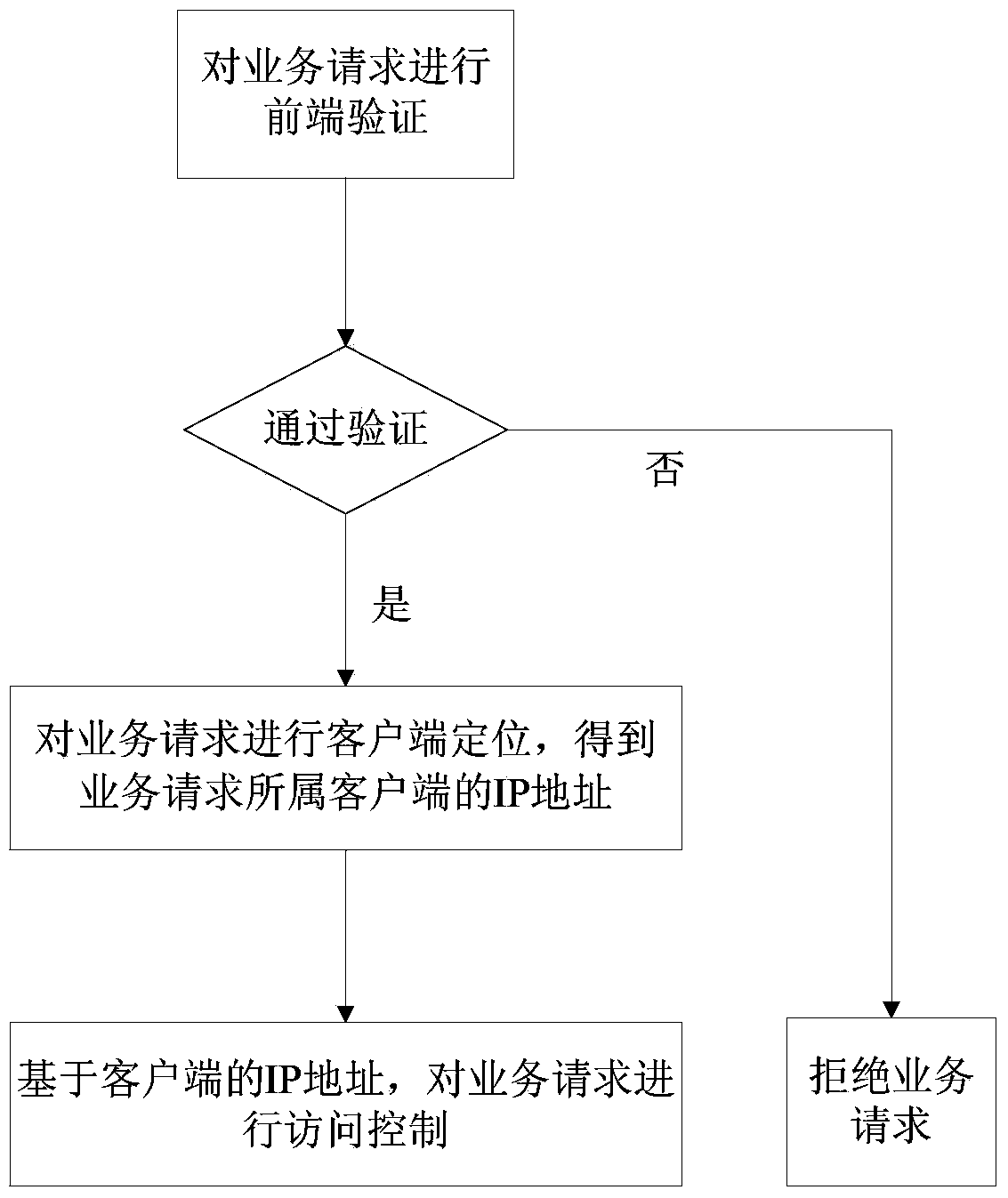
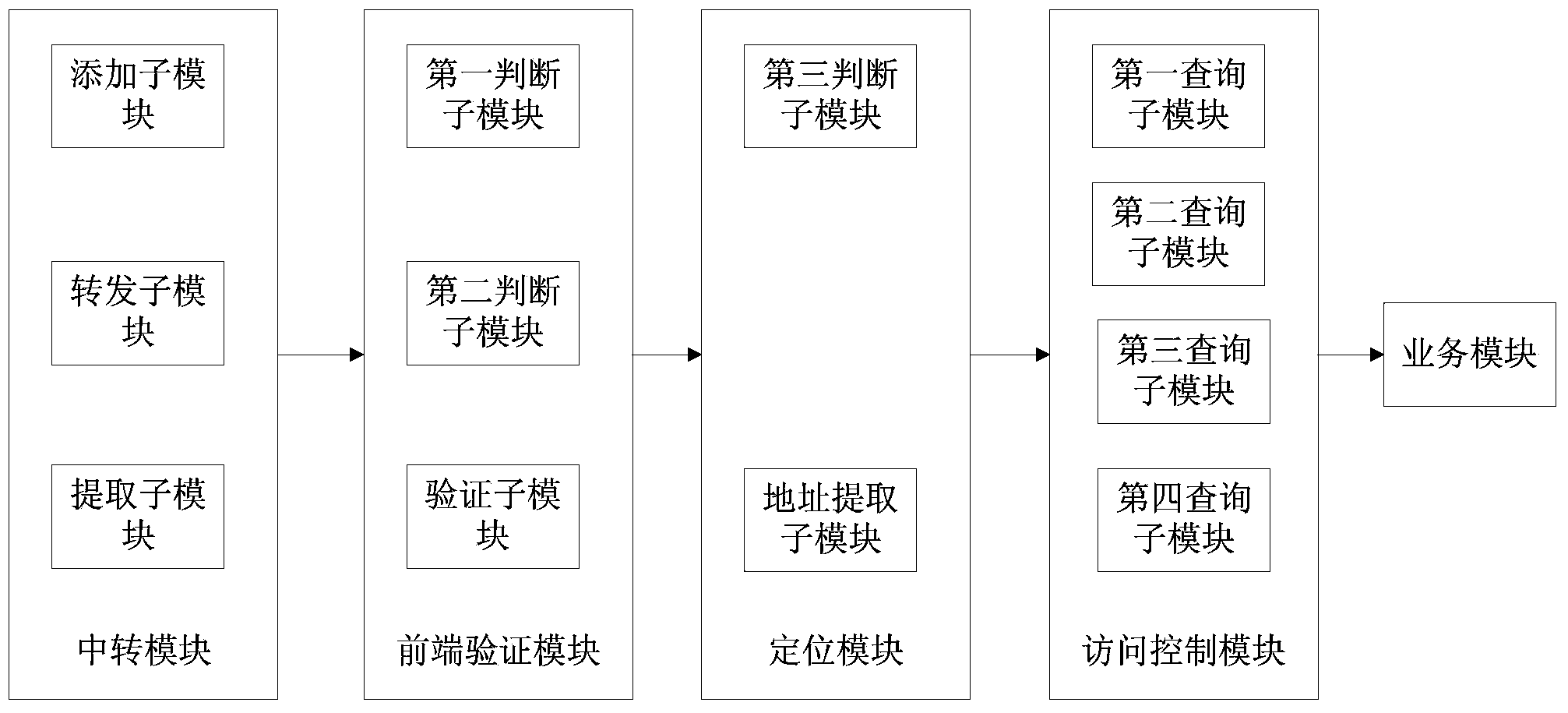
Network defense method and device
The invention provides a network defense method and device. The network defense method includes the steps of (1) conducting front end verification on a service request, executing the step (2) after verification is successfully carried out, or rejecting the service request; (2) conducting client terminal location on the service request to obtain an IP address of a client terminal to which the service request belongs; (3) based on the IP address of the client terminal, conducting access control over the service request. By means of the method and device, a client terminal locating module, an access control module and a front end verification module are combined, step-by-step pointed control strategies are accordingly achieved, and a defense system for various network applications is comprehensively achieved.
Owner:TRAVELSKY
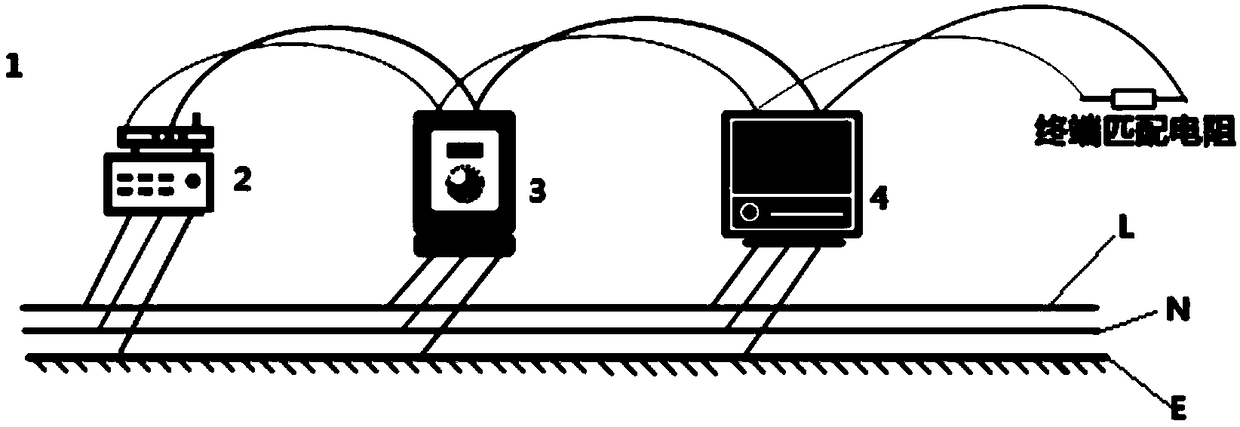
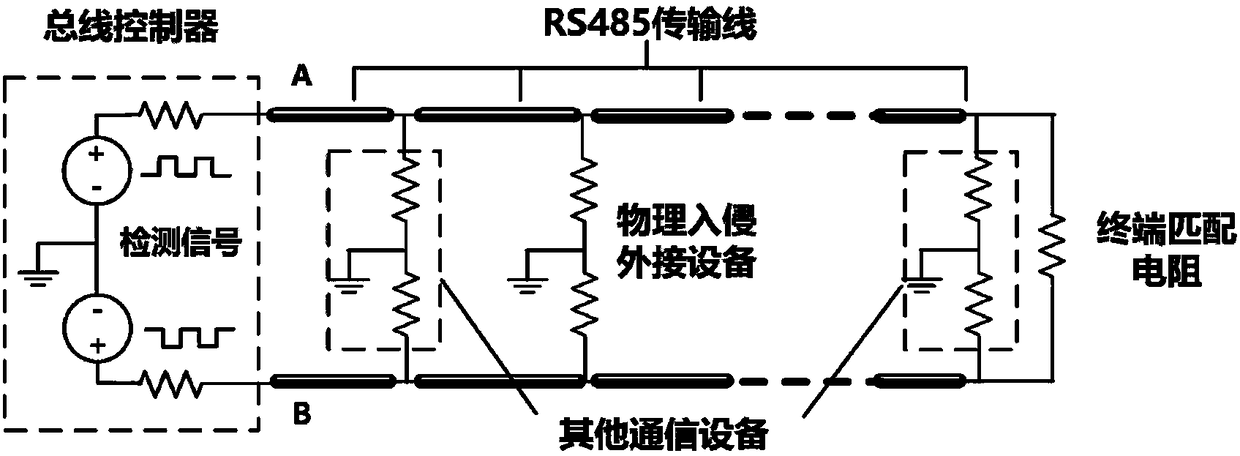
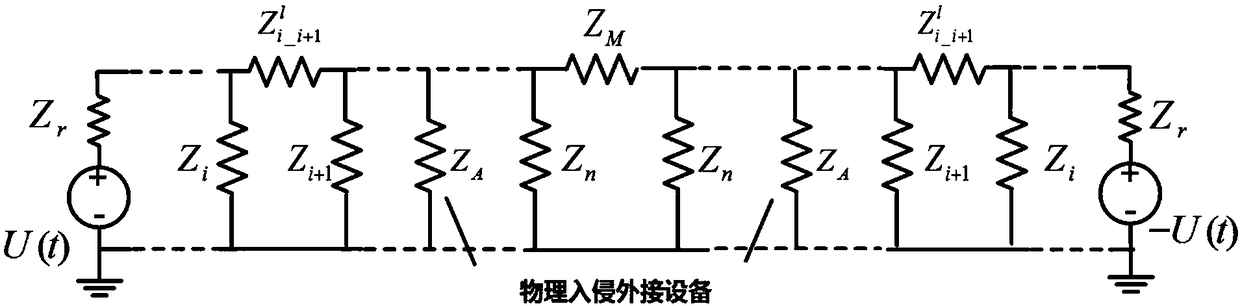
Industrial control system physical intrusion attack detection method based on serial communication bus signal analysis
ActiveCN108520187ASolve security technical issuesEffective judgmentInternal/peripheral component protectionBus networksSecure stateNoise reduction
The invention discloses an industrial control system physical intrusion attack detection method based on serial communication bus signal analysis, which comprises the following steps: detection signalis actively sent to the communication bus through a bus controller, After sampling and analyzing the signal of the communication bus, the monitoring device compares the signal with the standard signal stored in the device database, and uses the noise reduction technology and the weak signal detection technology to detect the intrusion signal in the difference signal, according to the detection results of intrusion signals caused by physical intrusion devices, any external malicious device in the system can be quickly and effectively determined and the security state that whether the system issubject to physical intrusion attack is determined. The technical problem that, in the prior art, the network security of the industrial control serial communication bus attracted by physical intrusion cannot be effectively detected by the network defense method is solved.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com