Patents
Literature
230 results about "Cyber threat" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
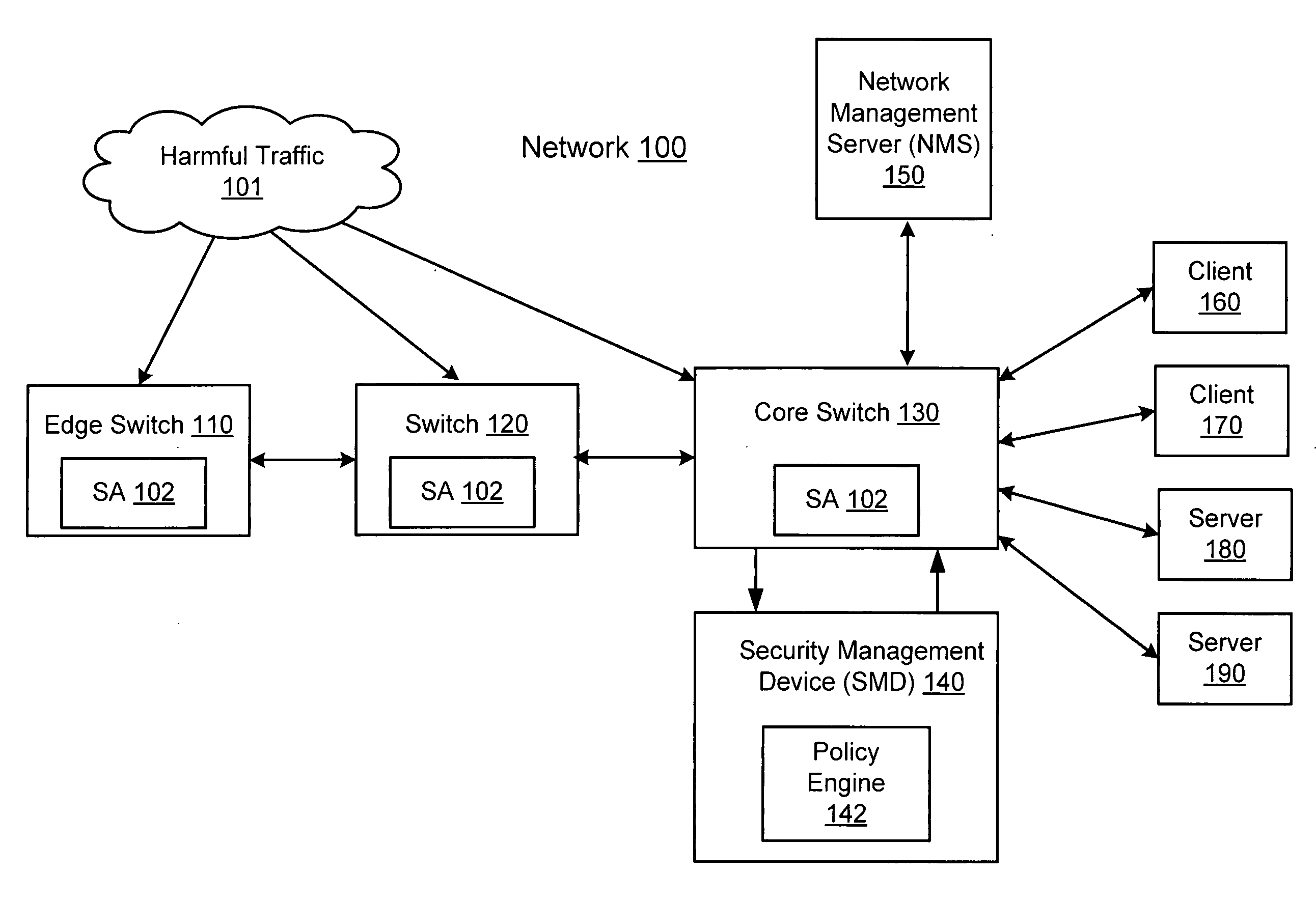
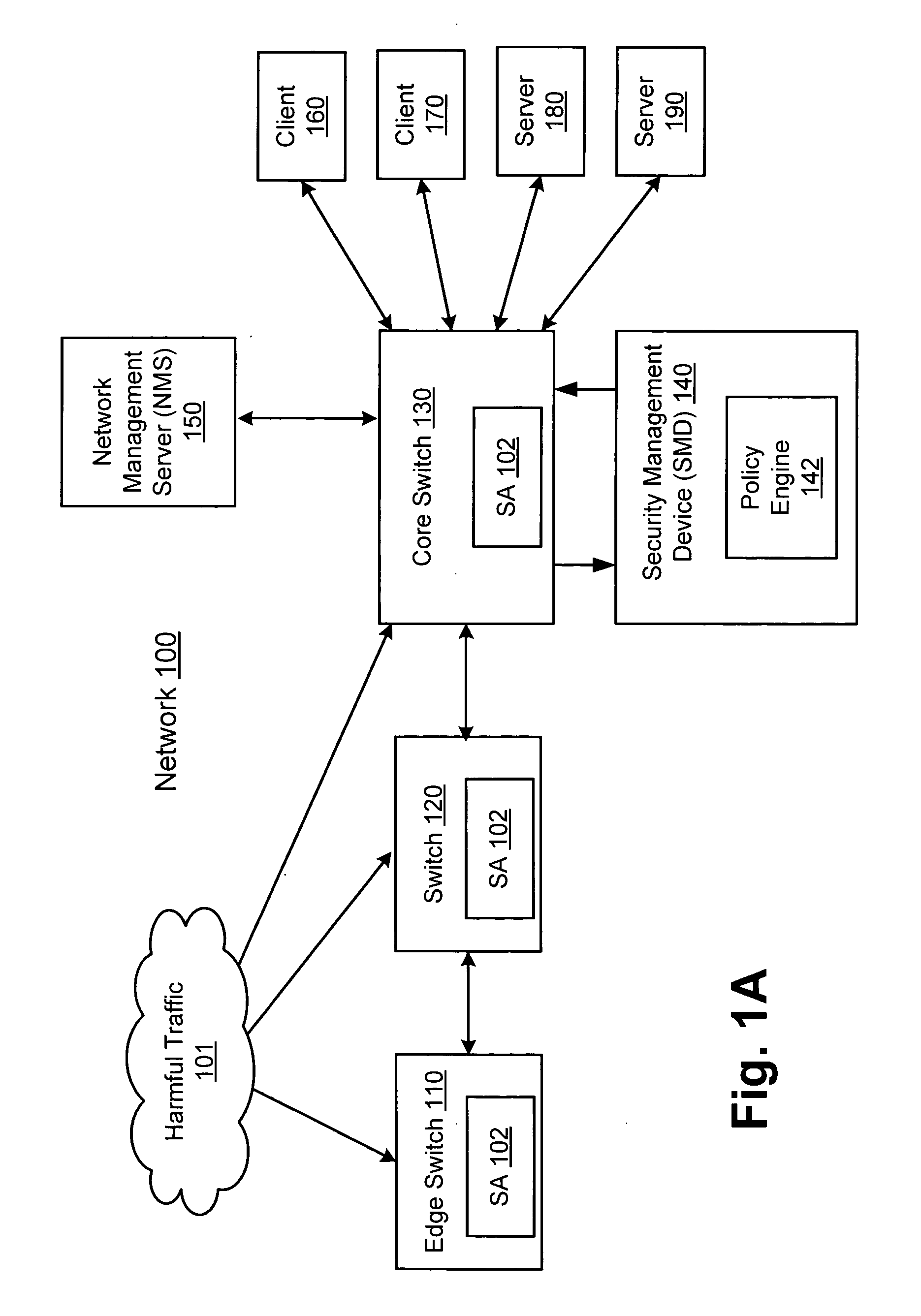
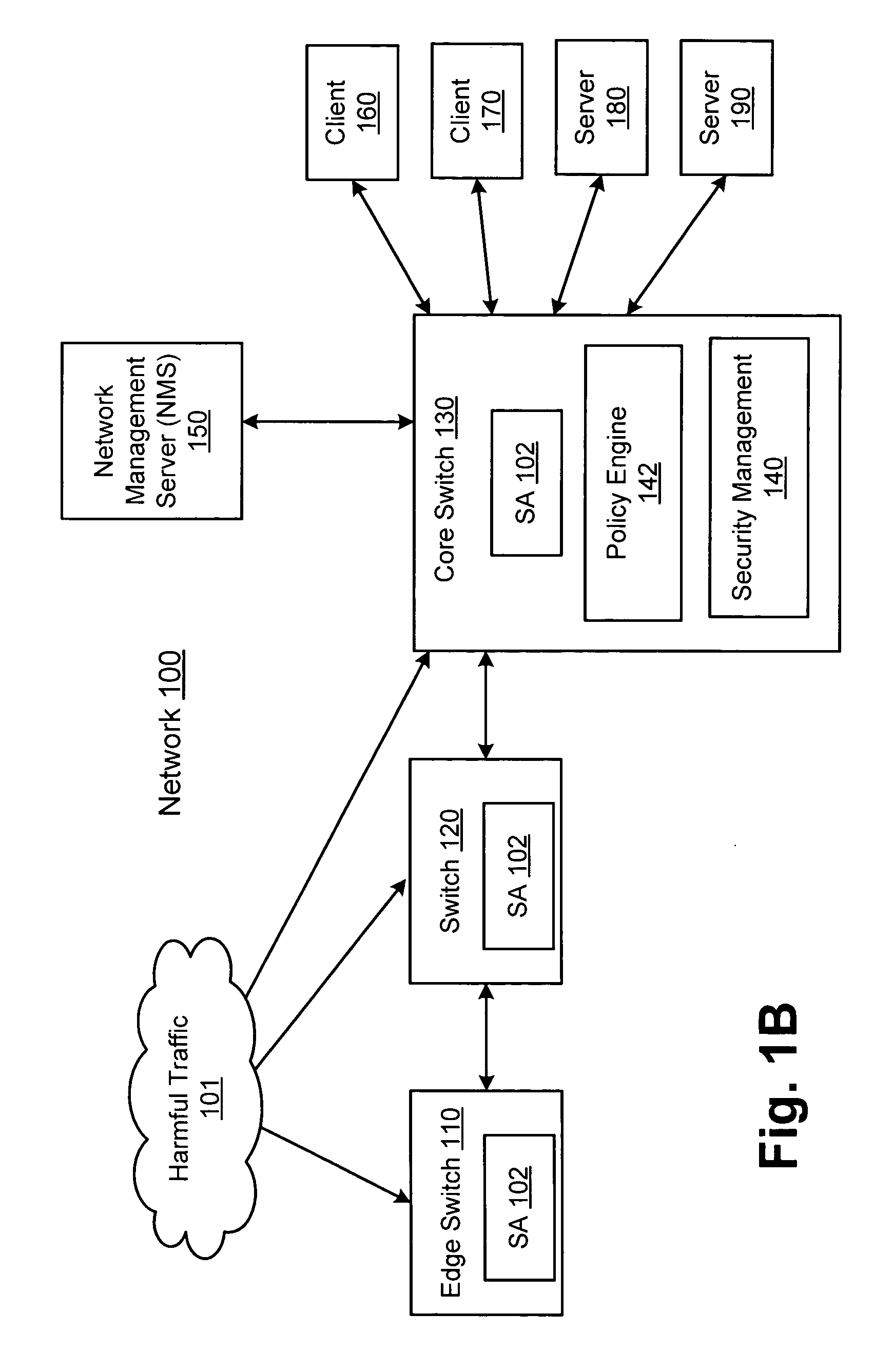
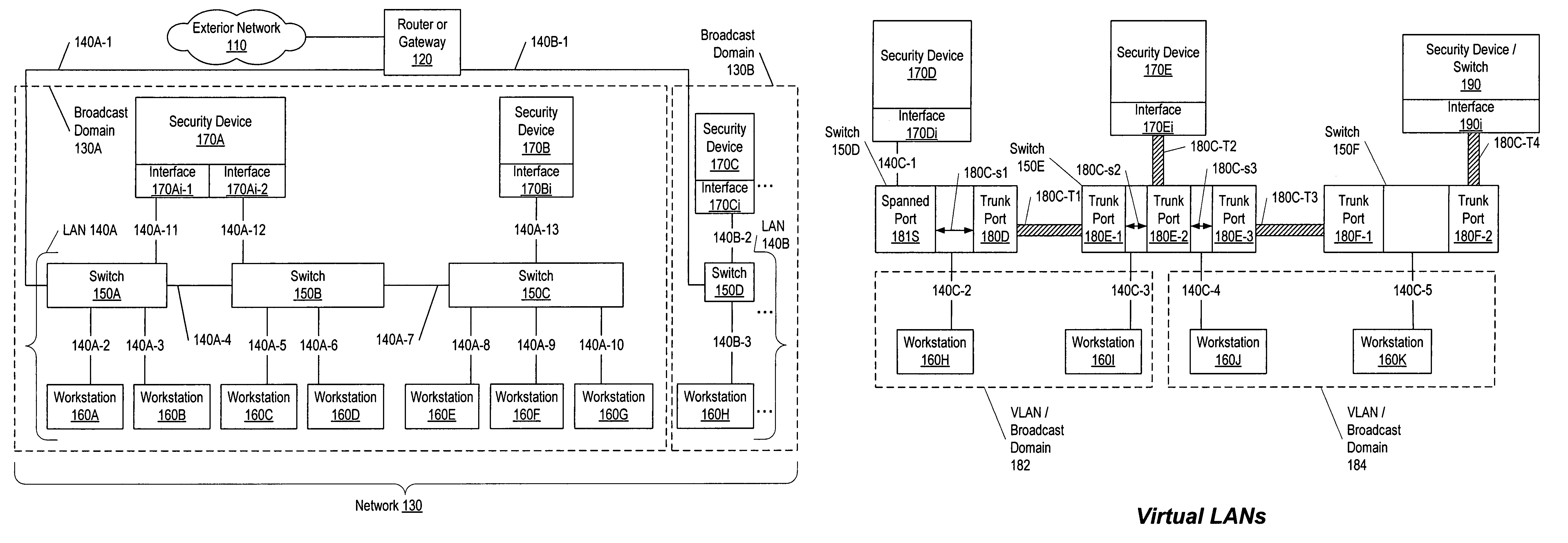
Network threat detection and mitigation
ActiveUS20070157306A1Error preventionFrequency-division multiplex detailsInternet trafficNetwork switch
A network switch automatically detects undesired network traffic and mirrors the undesired traffic to a security management device. The security management device determines the source of the undesired traffic and redirects traffic from the source to itself. The security management device also automatically sends a policy to a switch to block traffic from the source.
Owner:EXTREME NETWORKS INC
System and method for threat detection and response
InactiveUS20050018618A1Error preventionFrequency-division multiplex detailsNetwork packetDistributed computing
In accordance with varying embodiments of the invention, systems, devices and methods for analyzing a network packet received from a remote source and destined for a network resource, the network packet having associated packet data, and for identifying a plurality of network threats are disclosed.
Owner:STRATACLOUD
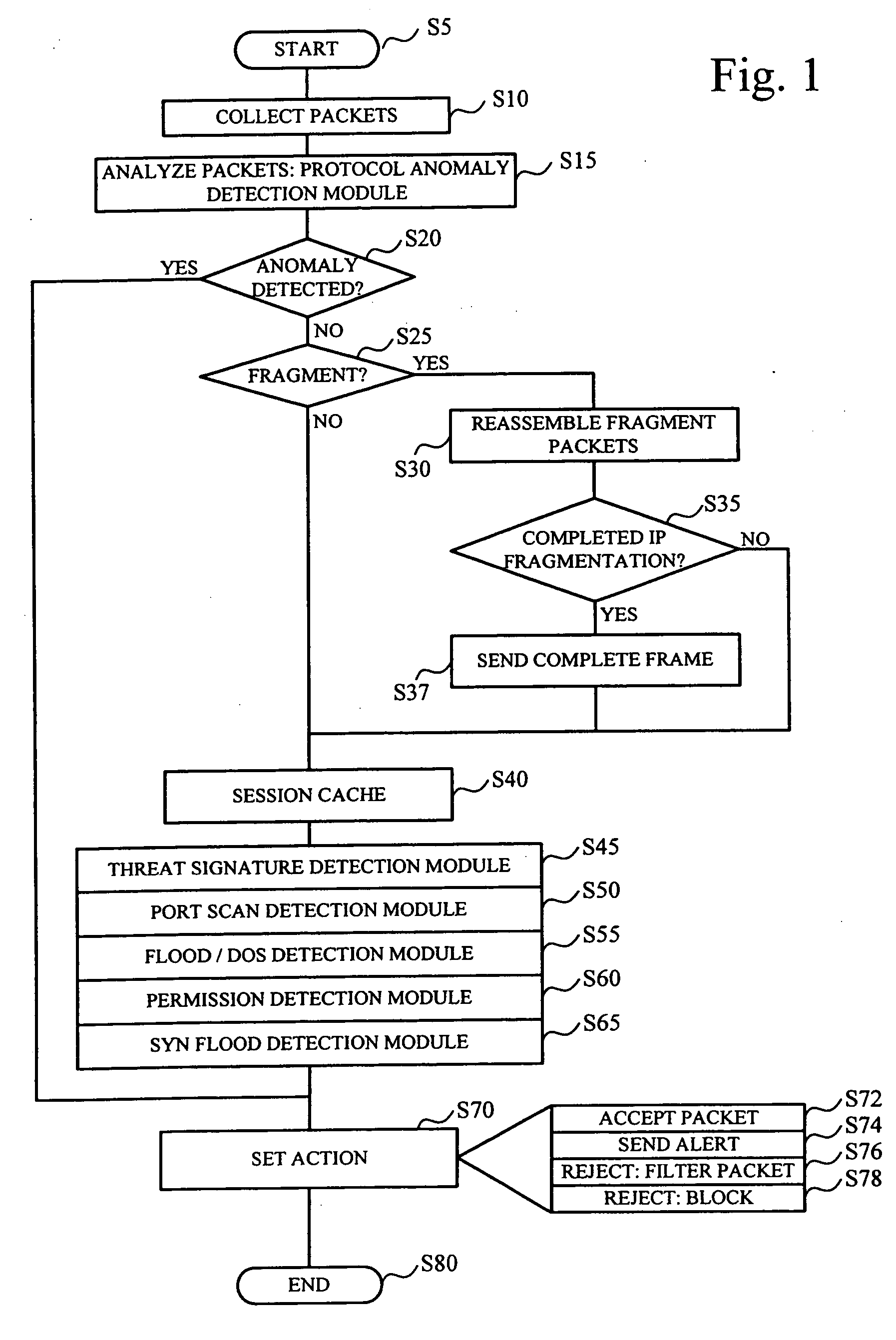
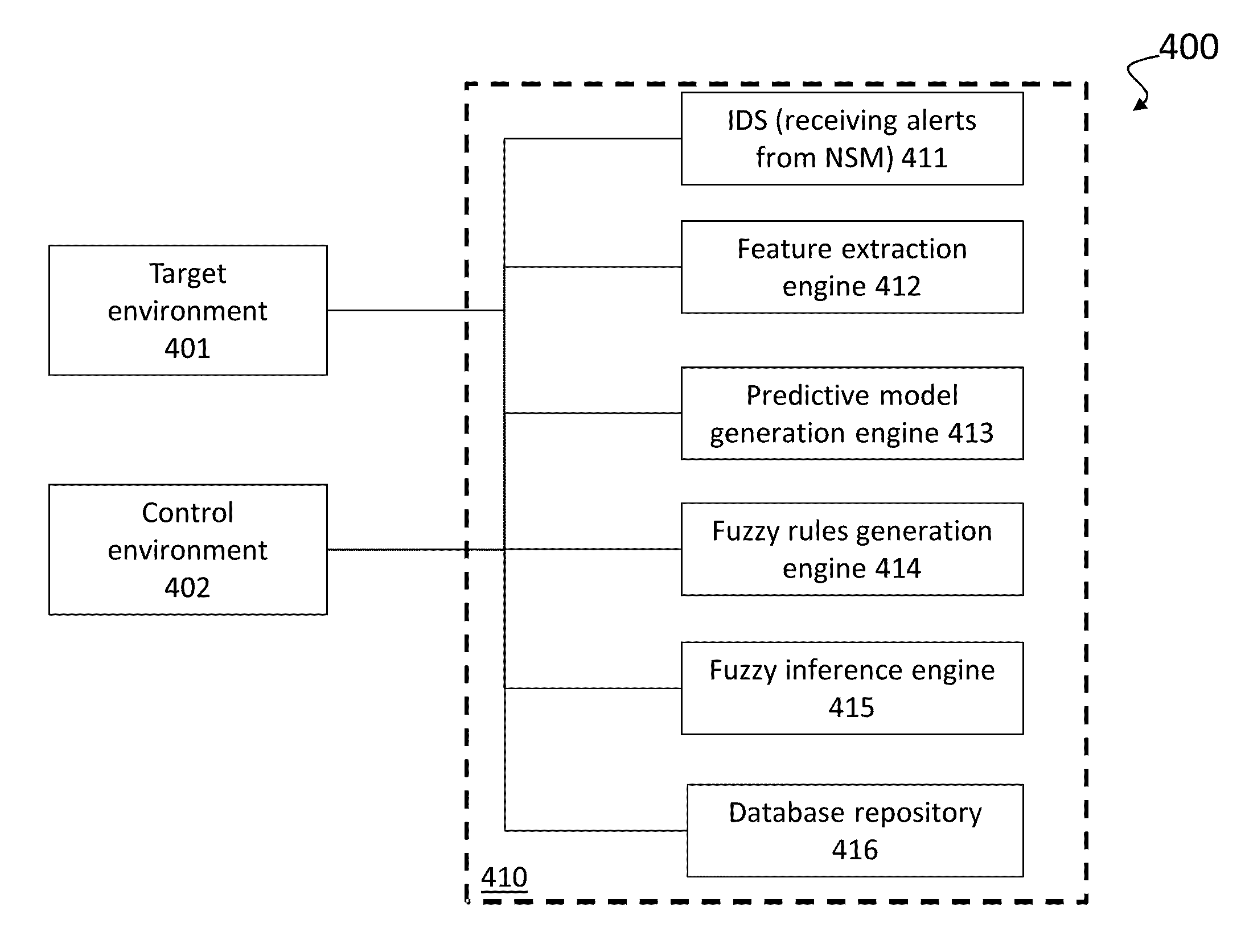
Profiling cyber threats detected in a target environment and automatically generating one or more rule bases for an expert system usable to profile cyber threats detected in a target environment
InactiveUS20150163242A1Efficiently presentedEasy to identifyMemory loss protectionError detection/correctionSecurity information and event managementSecurity information
A computer implemented method of profiling cyber threats detected in a target environment, comprising: receiving, from a Security Information and Event Manager (SIEM) monitoring the target environment, alerts triggered by a detected potential cyber threat, and, for each alert: retrieving captured packet data related to the alert; extracting data pertaining to a set of attributes from captured packet data triggering the alert; applying fuzzy logic to data pertaining to one or more of the attributes to determine values for one or more output variables indicative of a level of an aspect of risk attributable to the cyber threat.
Owner:CYBERLYTIC
System and method for a cyber intelligence hub
InactiveUS20160119365A1Advanced analyticalWeb data retrievalVisual data miningWeb crawlerCyber Space
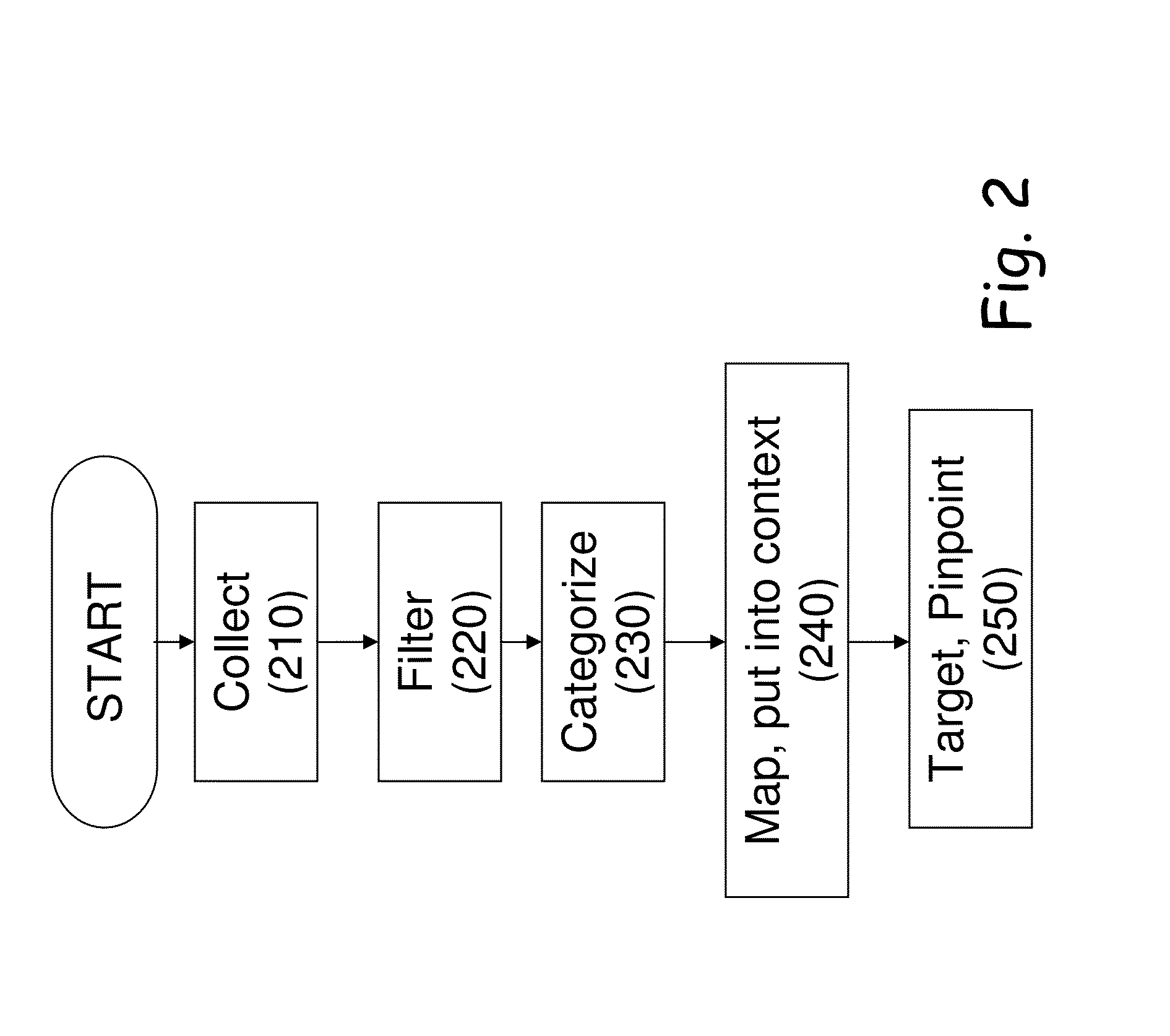
A method for defining and forming a cyber intelligence channel communicating with consumers is facing cyber threats in real time. The method includes collecting information, such that web crawlers and scrapers. The method also includes filtering the collected information, by filtering mechanisms founded on advanced algorithms. The method goes on to categorize the information into groups based on their unique characteristics, collecting capabilities and input and output constraints. The method further includes mapping the information and putting it into context and targeting and pinpointing the information, such that the data collected in the data intelligence collection unit is gathered through innovative technologies that enable automated and massive, yet targeted collection of the data that exists in the cyber space.
Owner:COMSEC CONSULTING
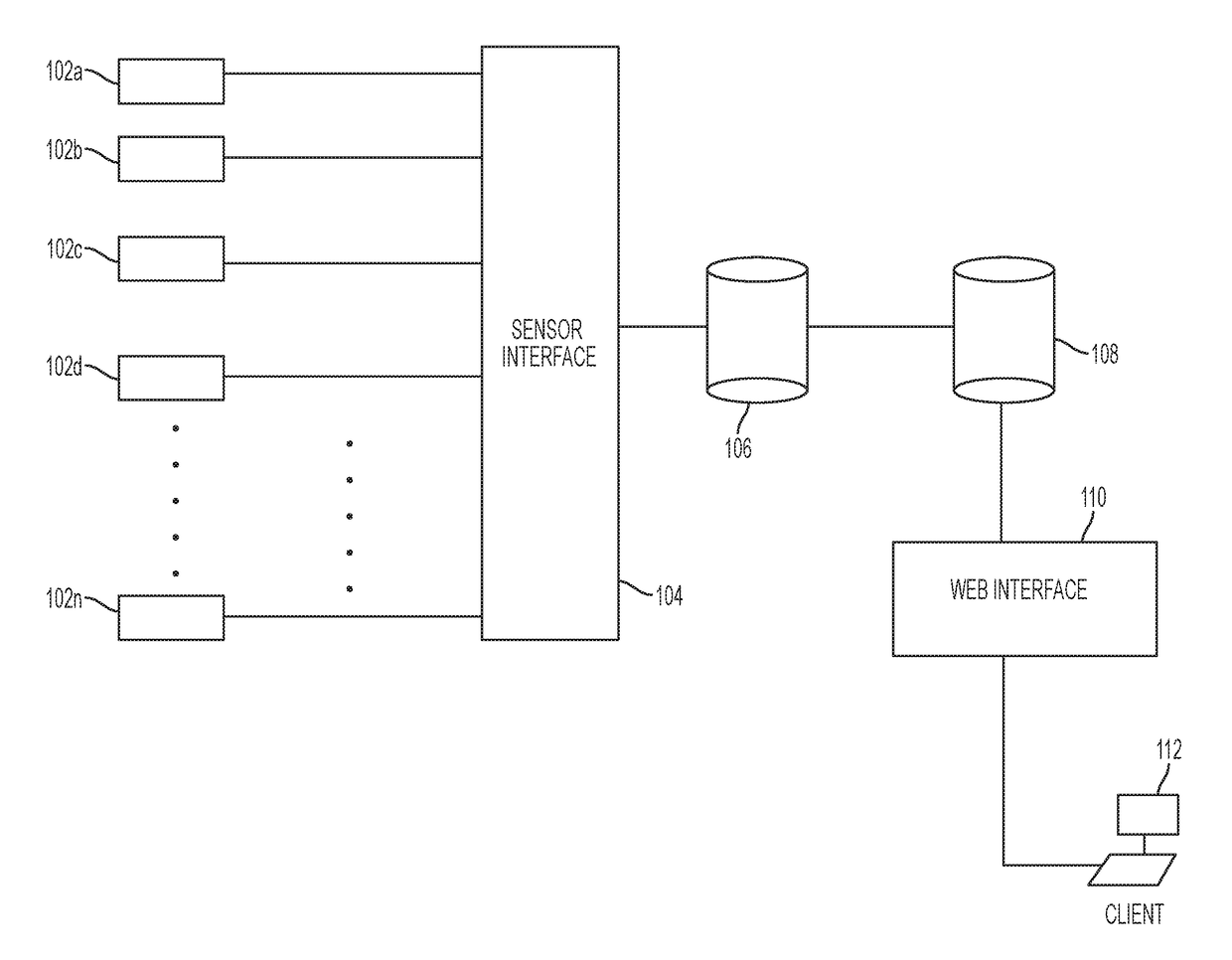
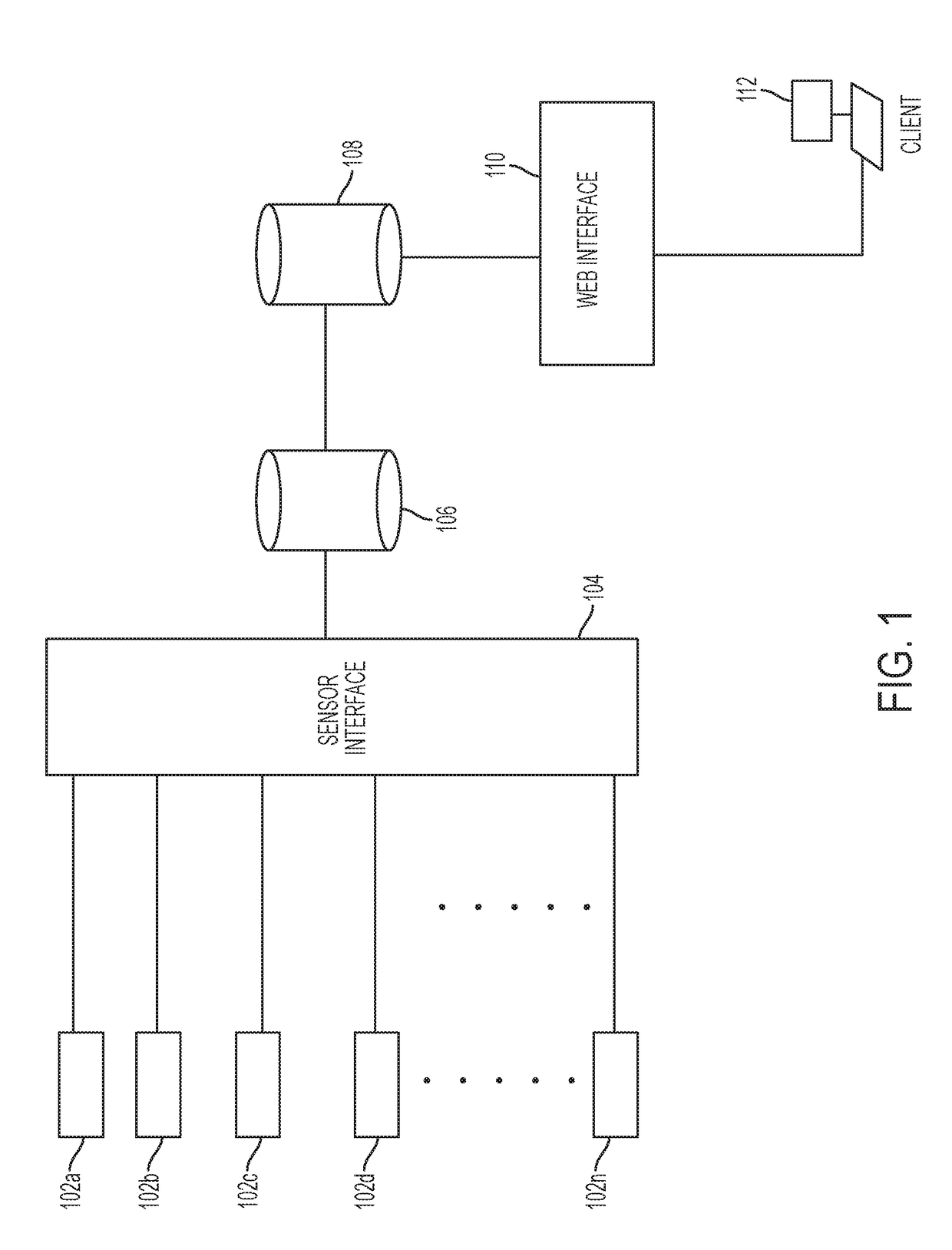
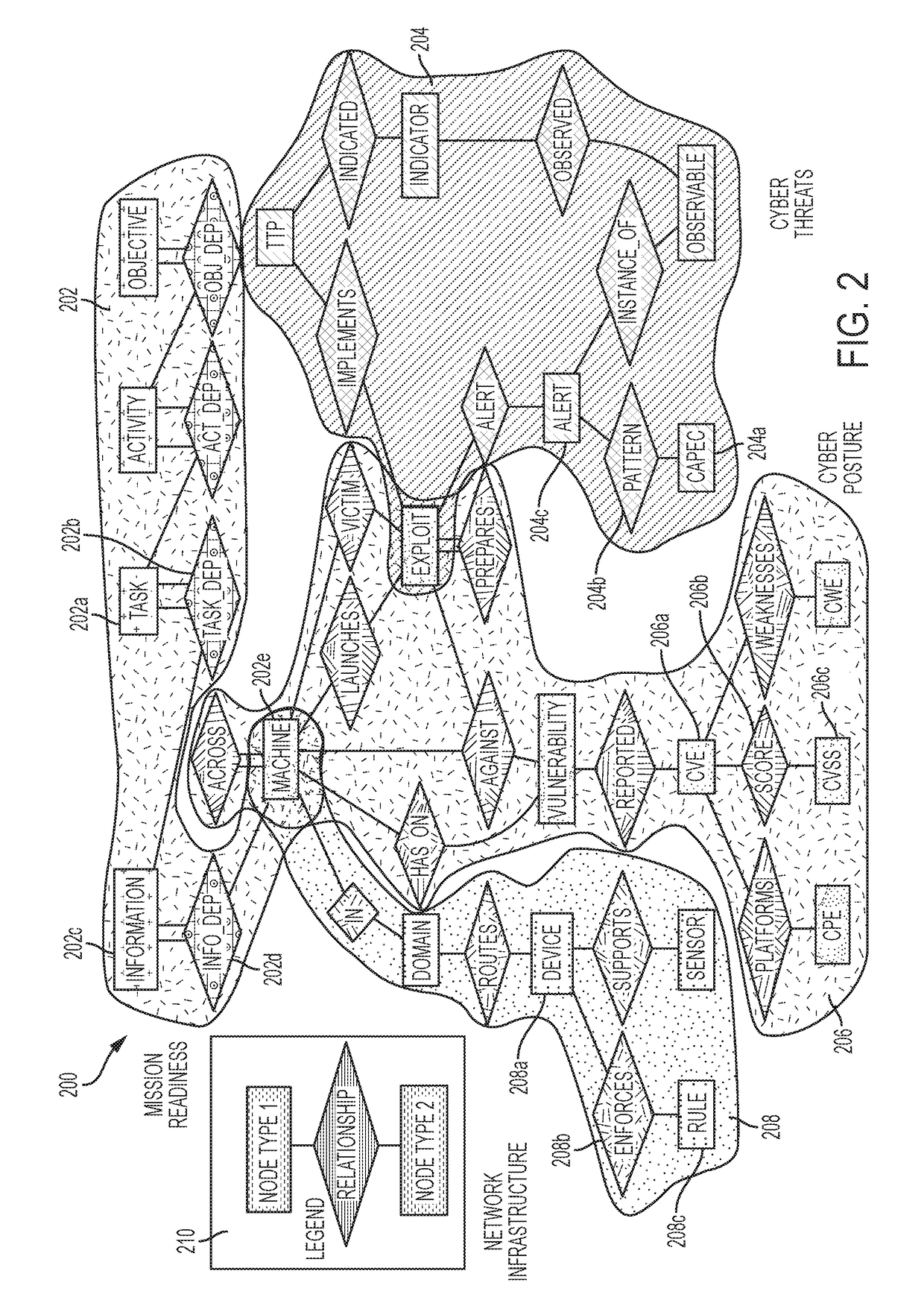
System and method for visualizing and analyzing cyber-attacks using a graph model
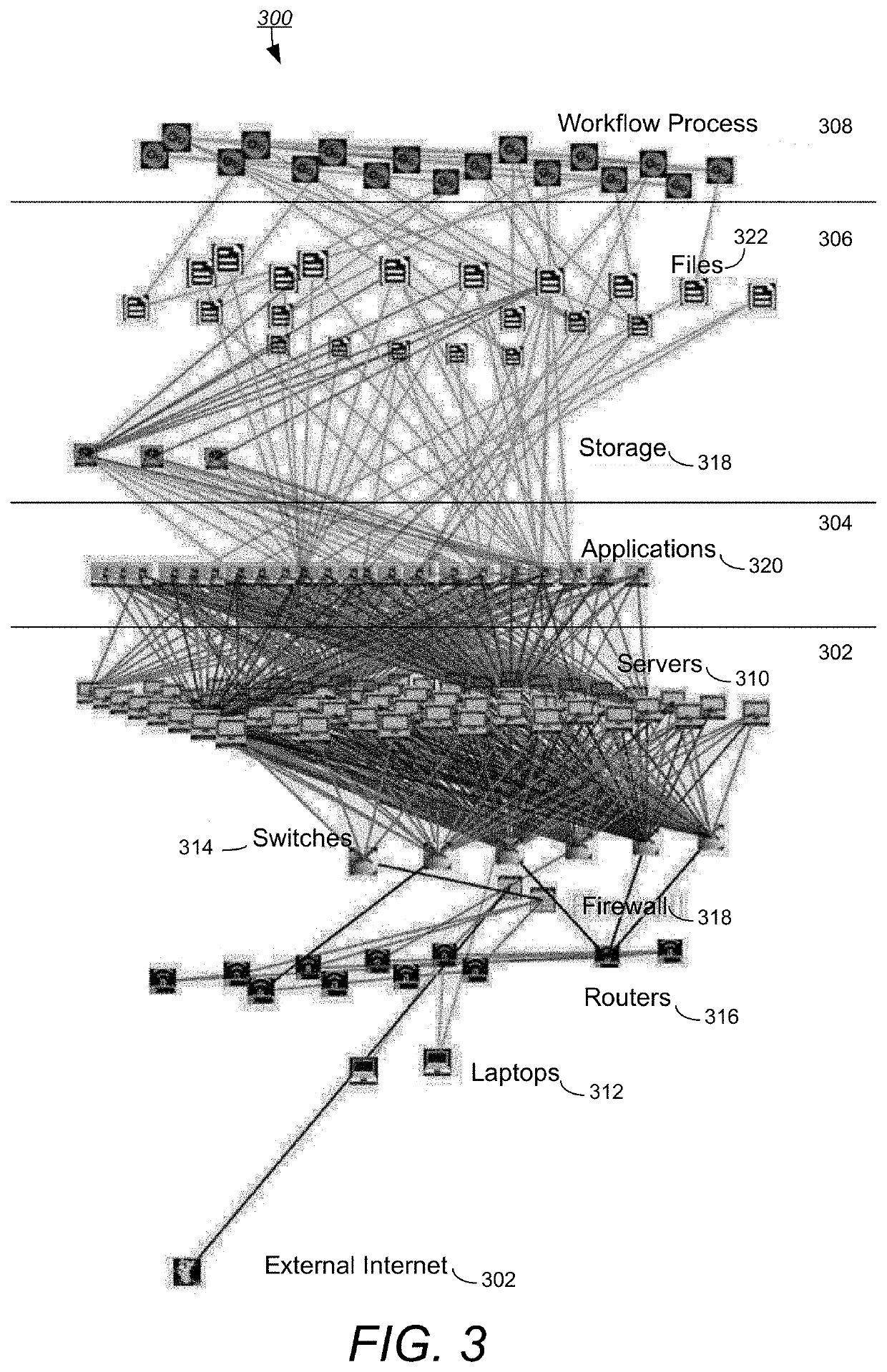
A system and method for implementing a graph database to analyze and monitor a status of an enterprise computer network is provided. In one example, a plurality of sensors can be inputted into sensor interface in which all of the data associated with the sensors in converted into a common data format. The data can be parsed into a data model that contains nodes and edges in order to generate a graph database model that can allow a network analyst to analyze the real-time status of a computer network. The graph database model can include multiple layers including an infrastructure layer, a cyber threats layer, a cyber posture layer, and a mission readiness layer. The graph database model can also be queried by a user using a domain-specific query language, so as to provide a user-friendly syntax in generating queries.
Owner:MITRE SPORTS INT LTD
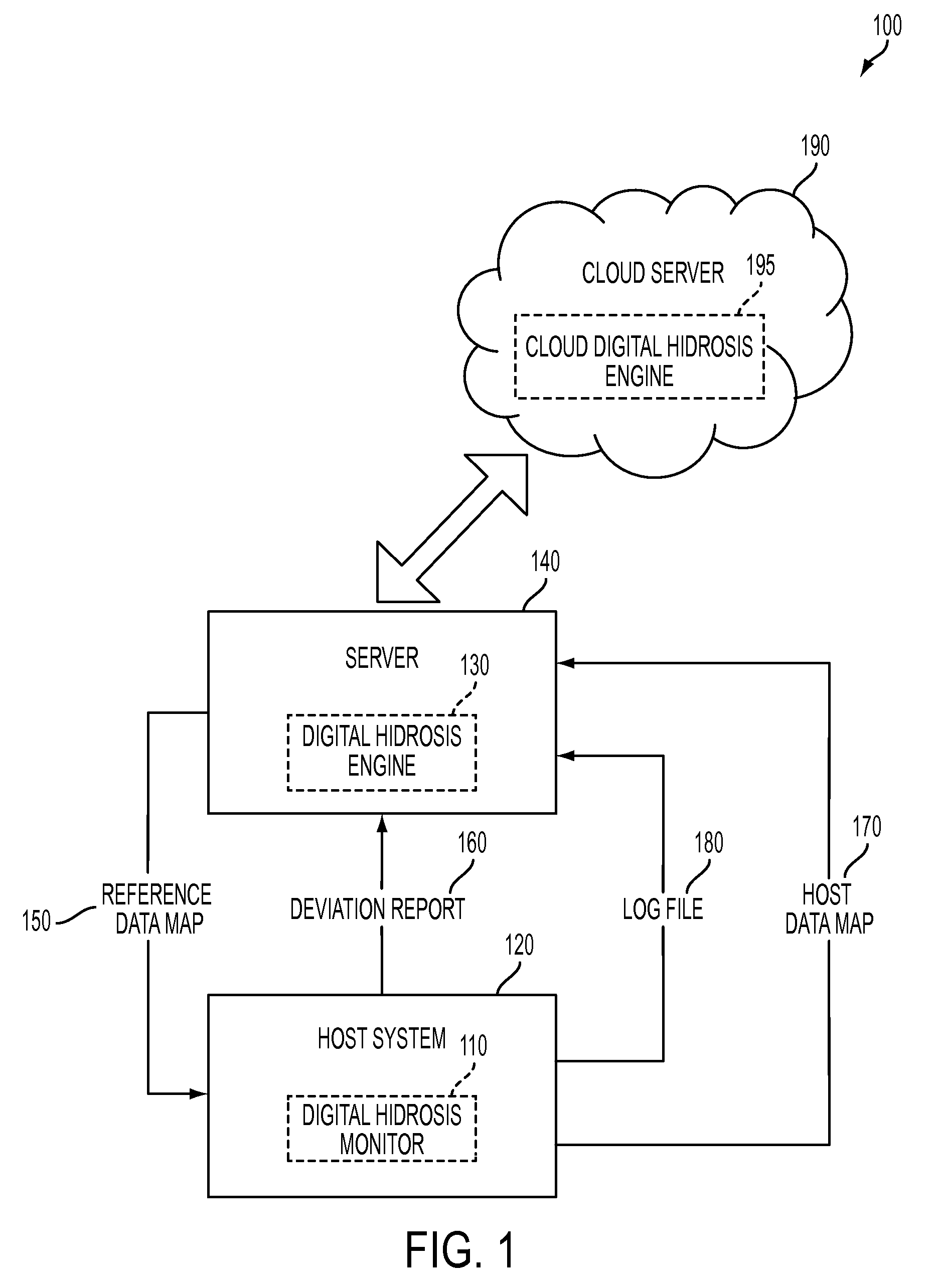
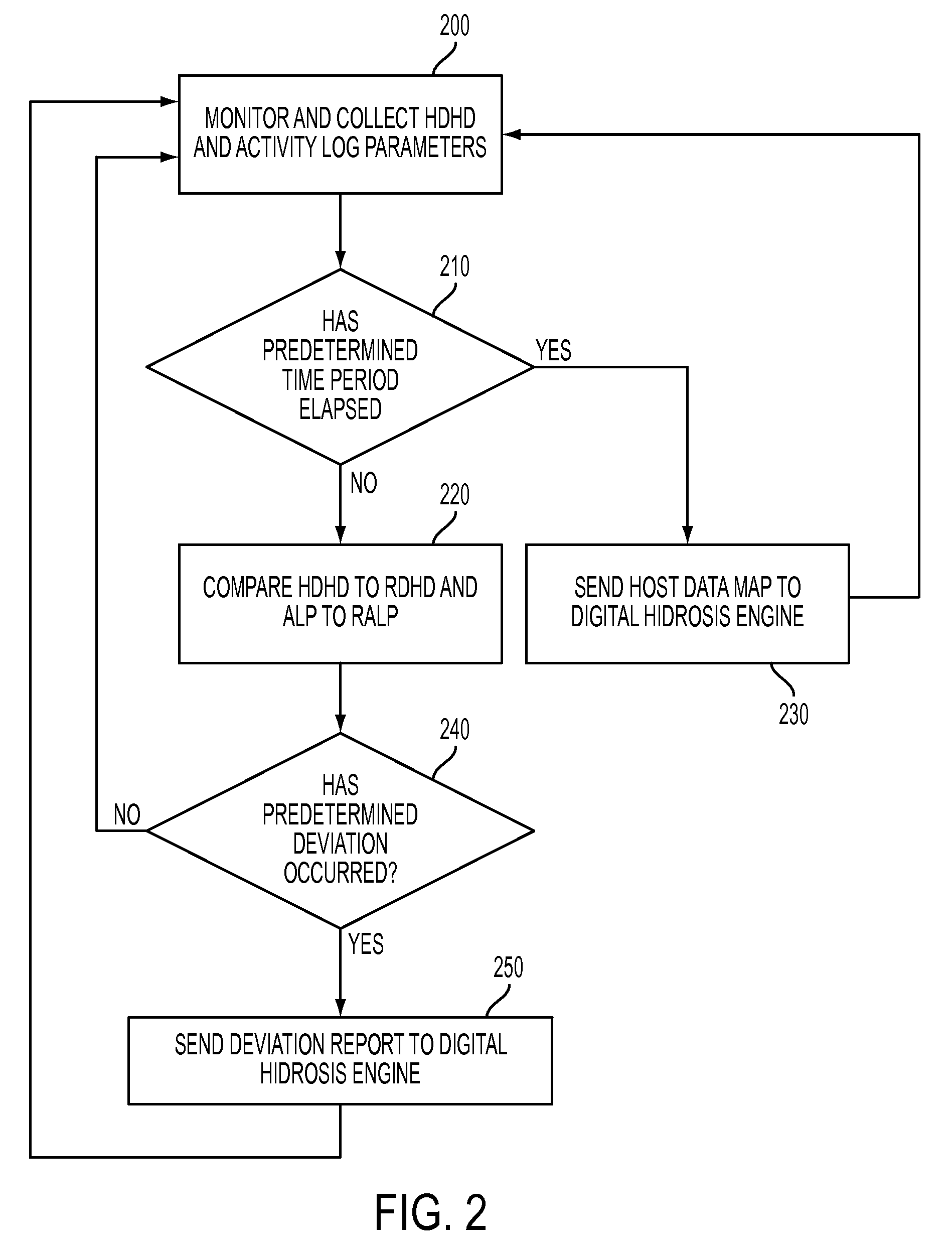
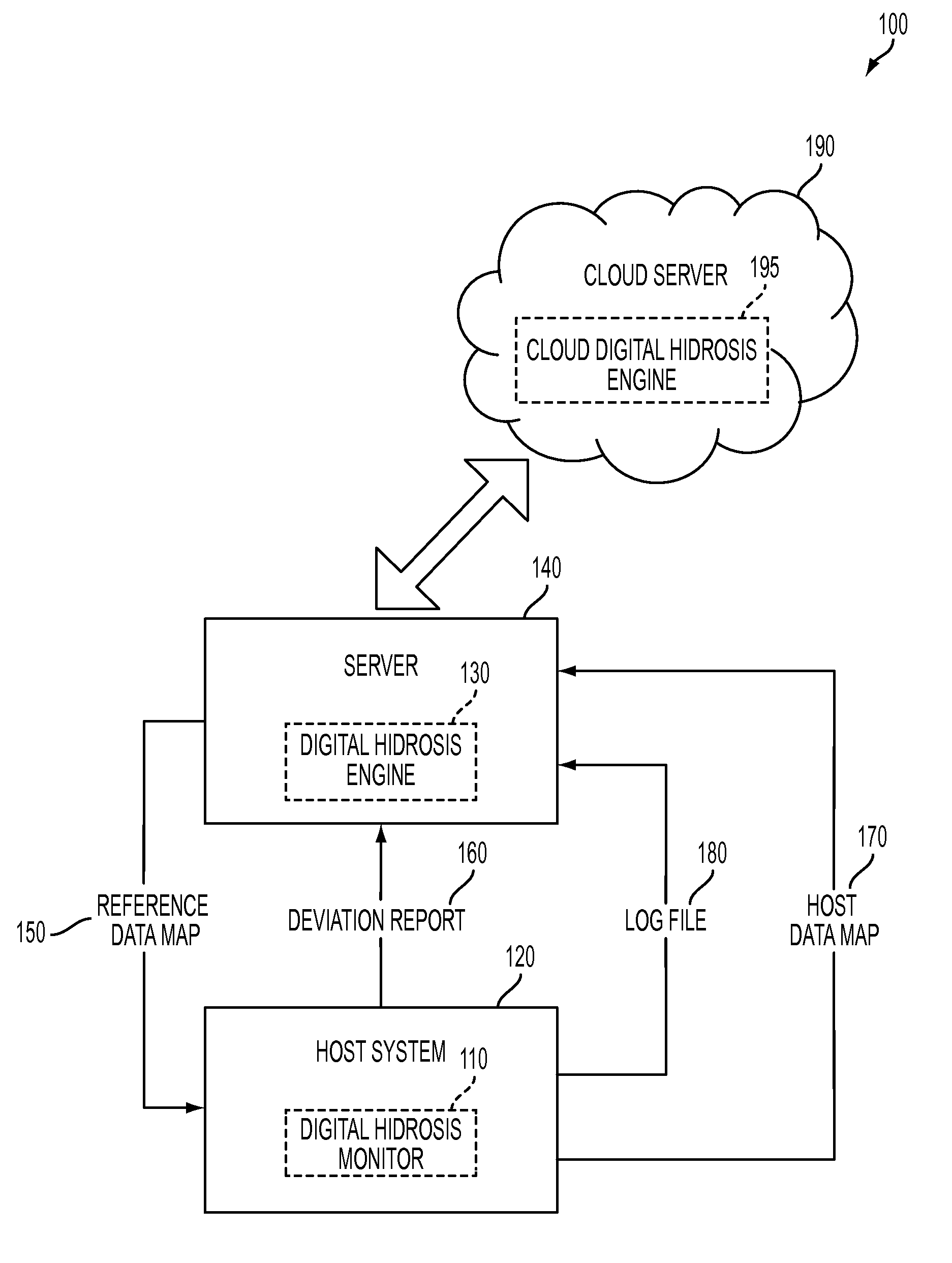
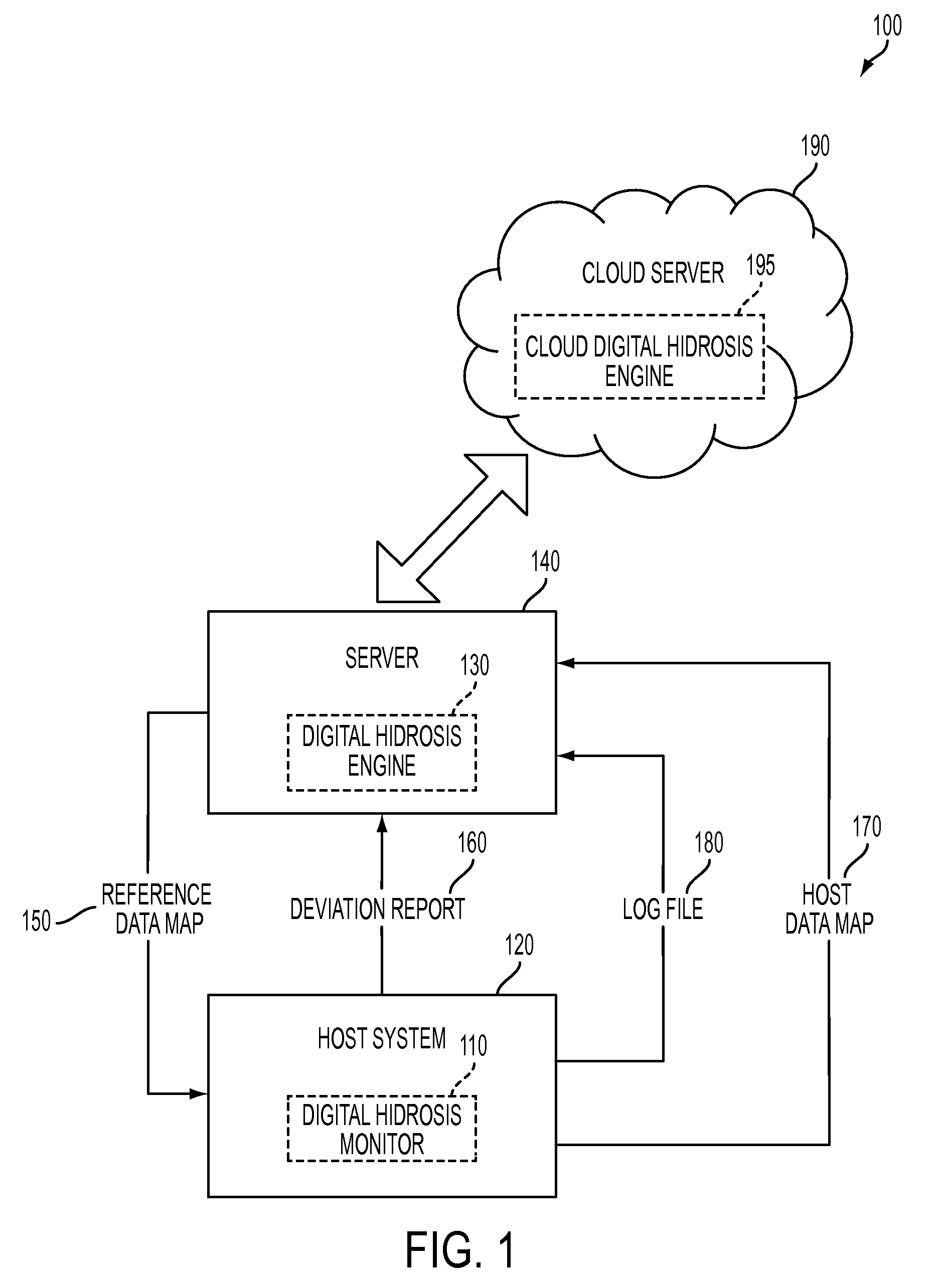
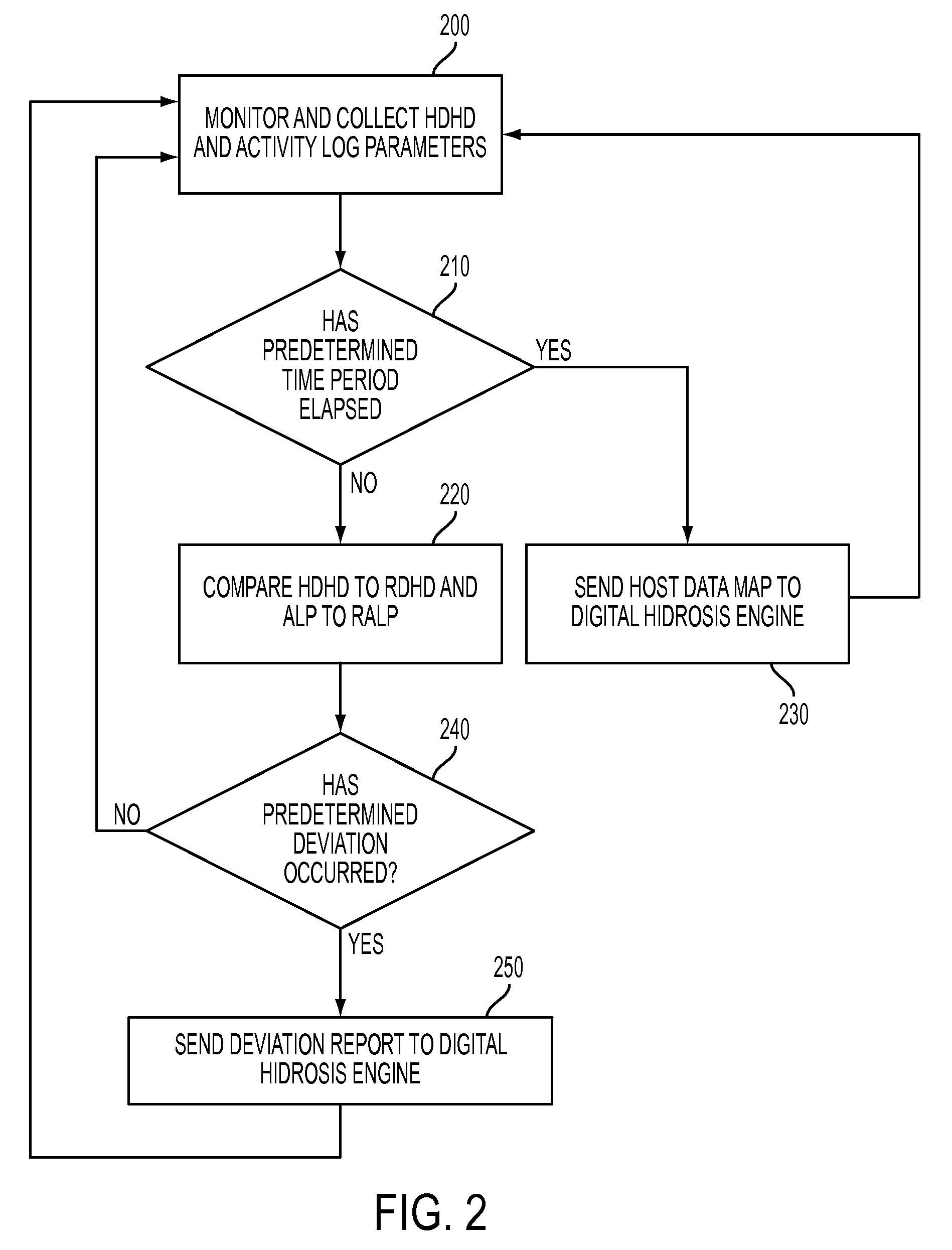
System and method for detecting potential threats by monitoring user and system behavior associated with computer and network activity
A system and method is provided to monitor user and system behavior associated with computer and network activity to determine deviations from normal behavior that represent a potential cyber threat or cyber malicious activity. The system and method uses a multi-factor behavioral and activity analysis approach to determine when a trusted insider might be exhibiting threatening behavior or when a user's computer or network credentials have been compromised and are in use by a third-party. As a result, changes in insider behavior that could be indicative of malicious intent can be detected, or an external entity masquerading as a legitimate user can be detected.
Owner:WINTERMUTE LLC
Methods and systems for cyber-physical security modeling, simulation and architecture for the smart grid
ActiveUS20130198847A1Memory loss protectionError detection/correctionInteractive softwarePhysical security
A computer-implemented method for use in evaluating at least one threat to a complex system includes identifying one or more physical components of the complex system and modeling the one or more physical components with interactive software multi-agents. The multi-agents are programmed to monitor and control at least one function of the modeled physical components. One or more threats to a target of the complex system are identified. Each threat is defined as a cyber threat or physical threat and the target is defined as a cyber component or physical component. The method includes simulating an attack on the complex system by the identified threat and assessing an impact of the attack on the complex system.
Owner:THE BOEING CO
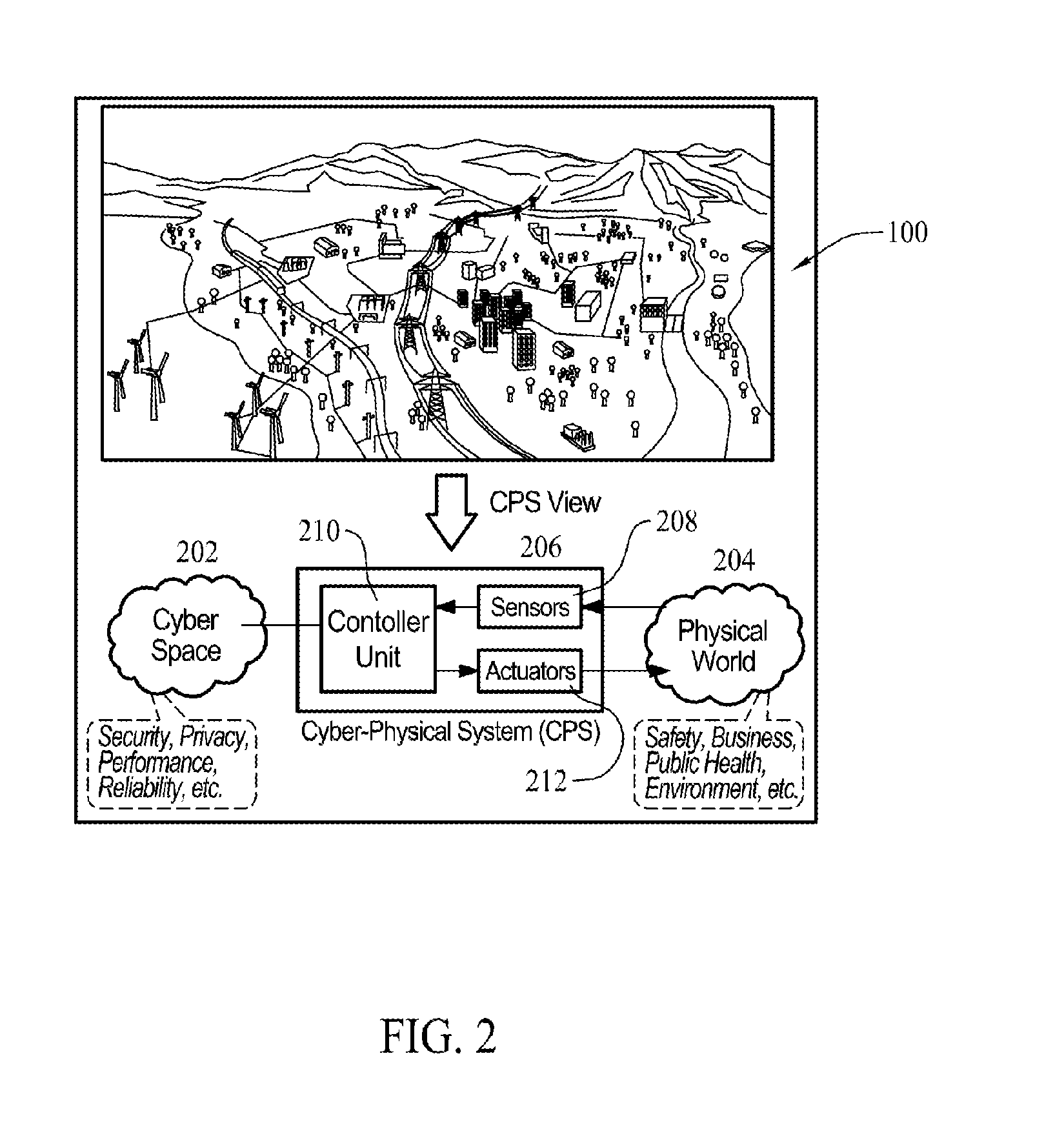
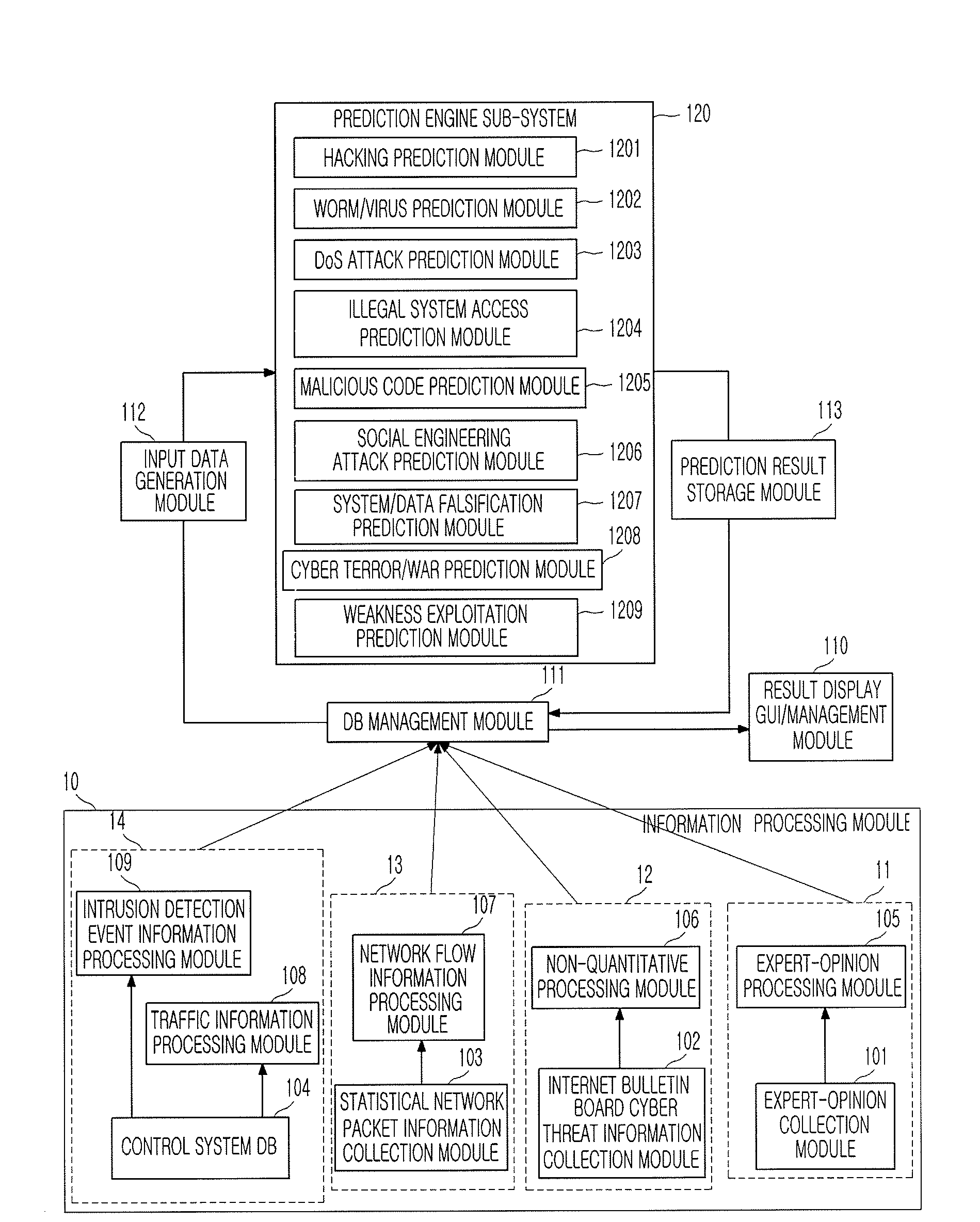
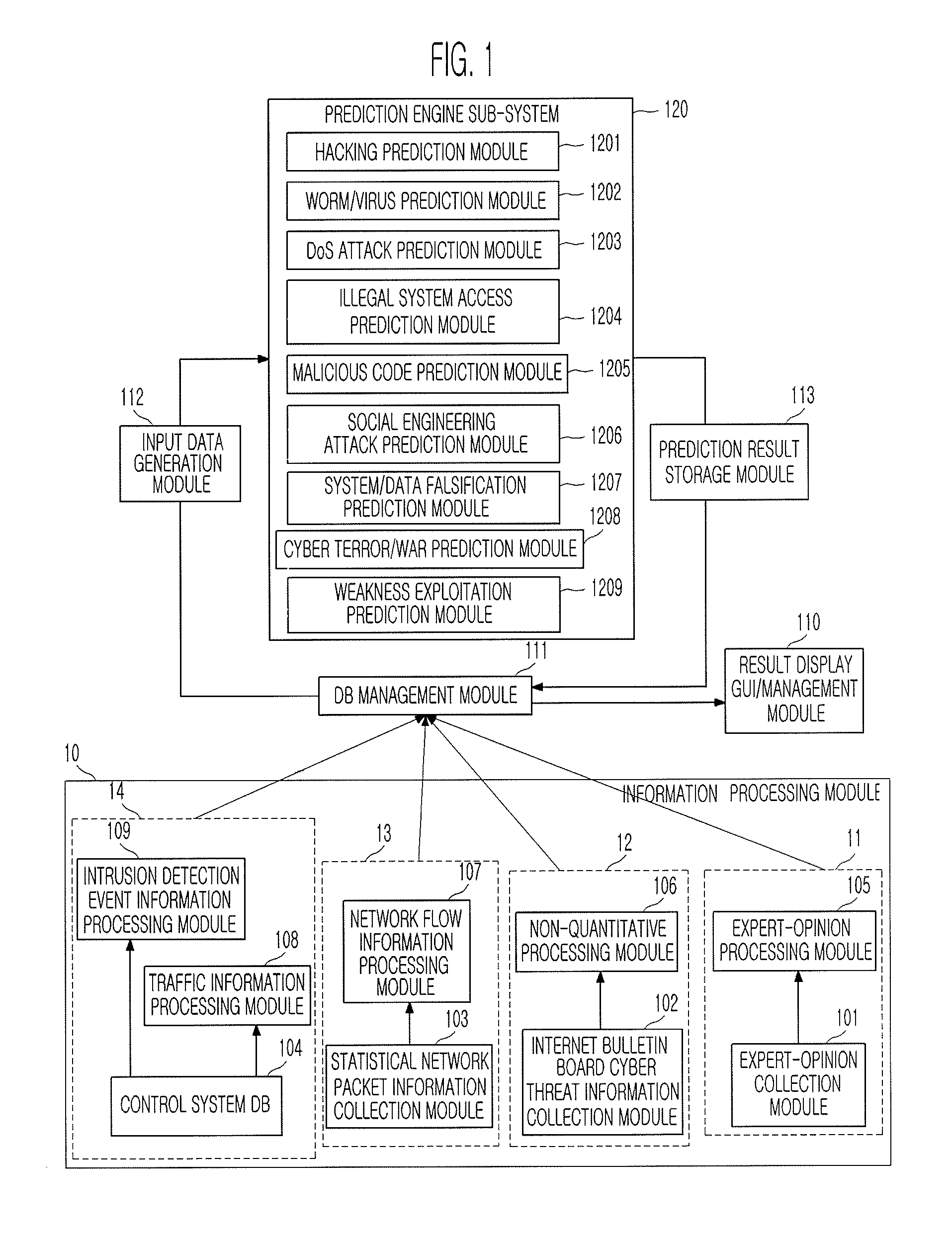
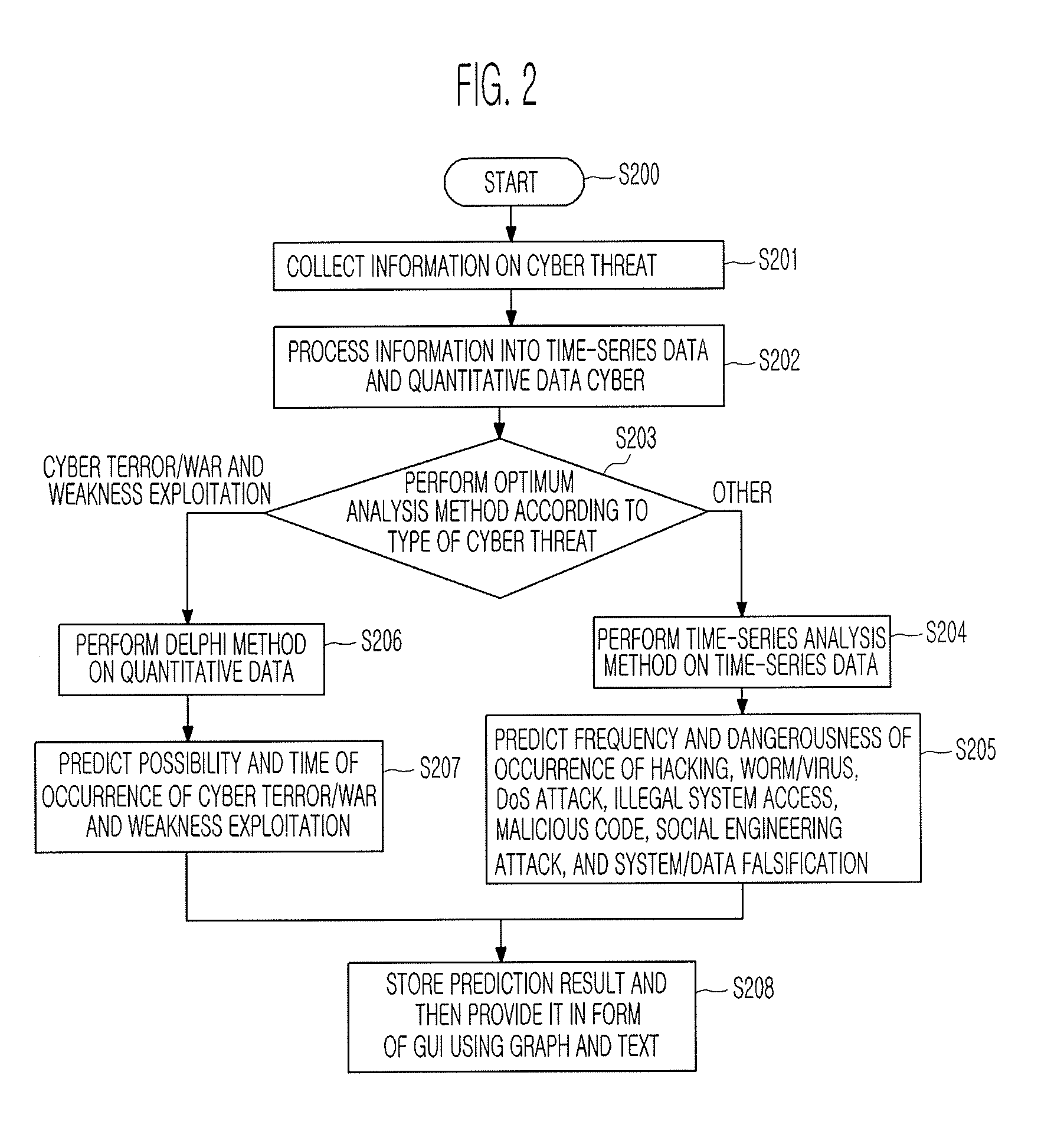
System and method for predicting cyber threat
Provided are a system and method for predicting a cyber threat. The system and method collect various variables and synthetically predict the frequency, dangerousness, possibility, and time of the occurrence of a cyber threat including hacking, a worm / virus, a Denial of Service (DoS) attack, illegal system access, a malicious code, a social engineering attack, system / data falsification, cyber terror / war, weakness exploitation, etc., using a time-series analysis method and a Delphi method, and inform a user in advance of the prediction result, thereby enabling the user to prepare against the cyber threat.
Owner:NEXWAY +1
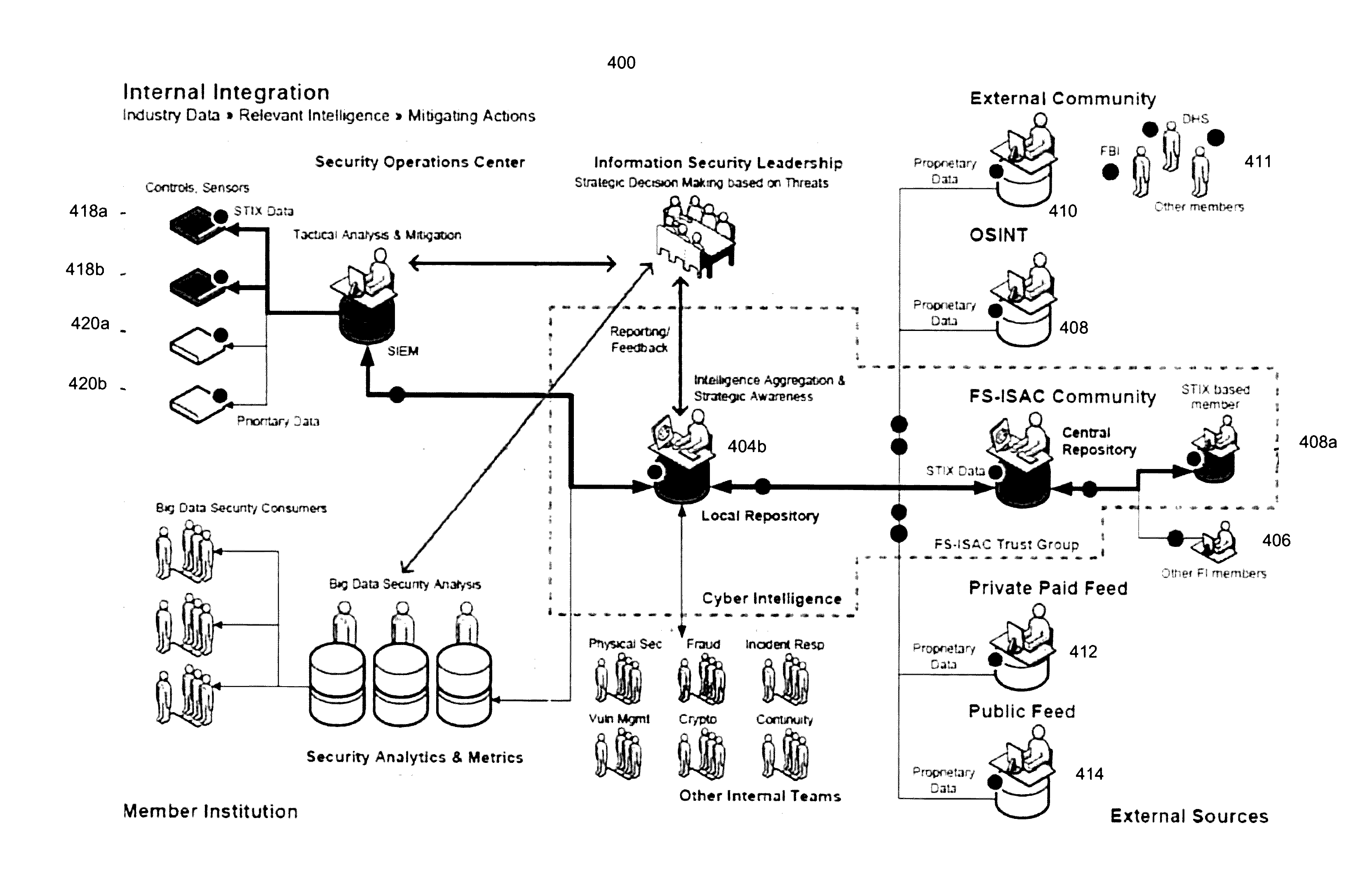
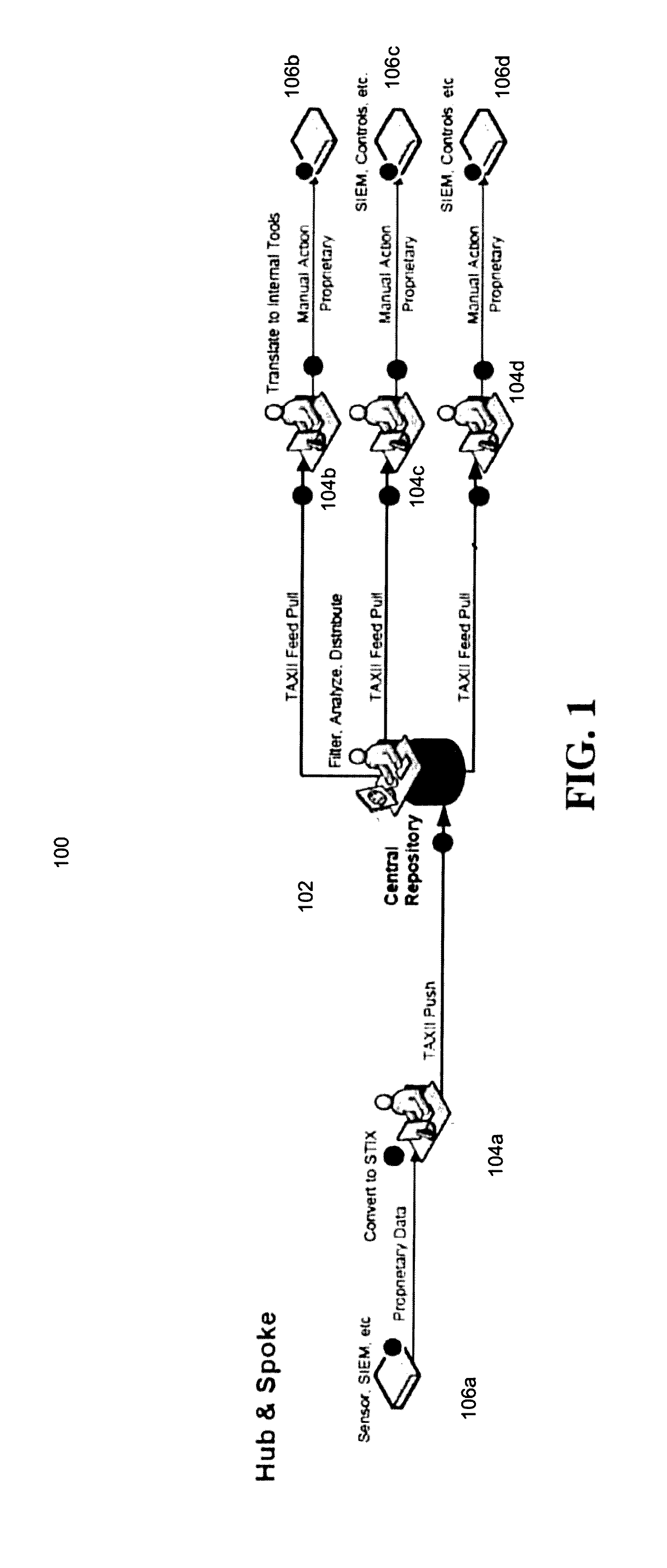
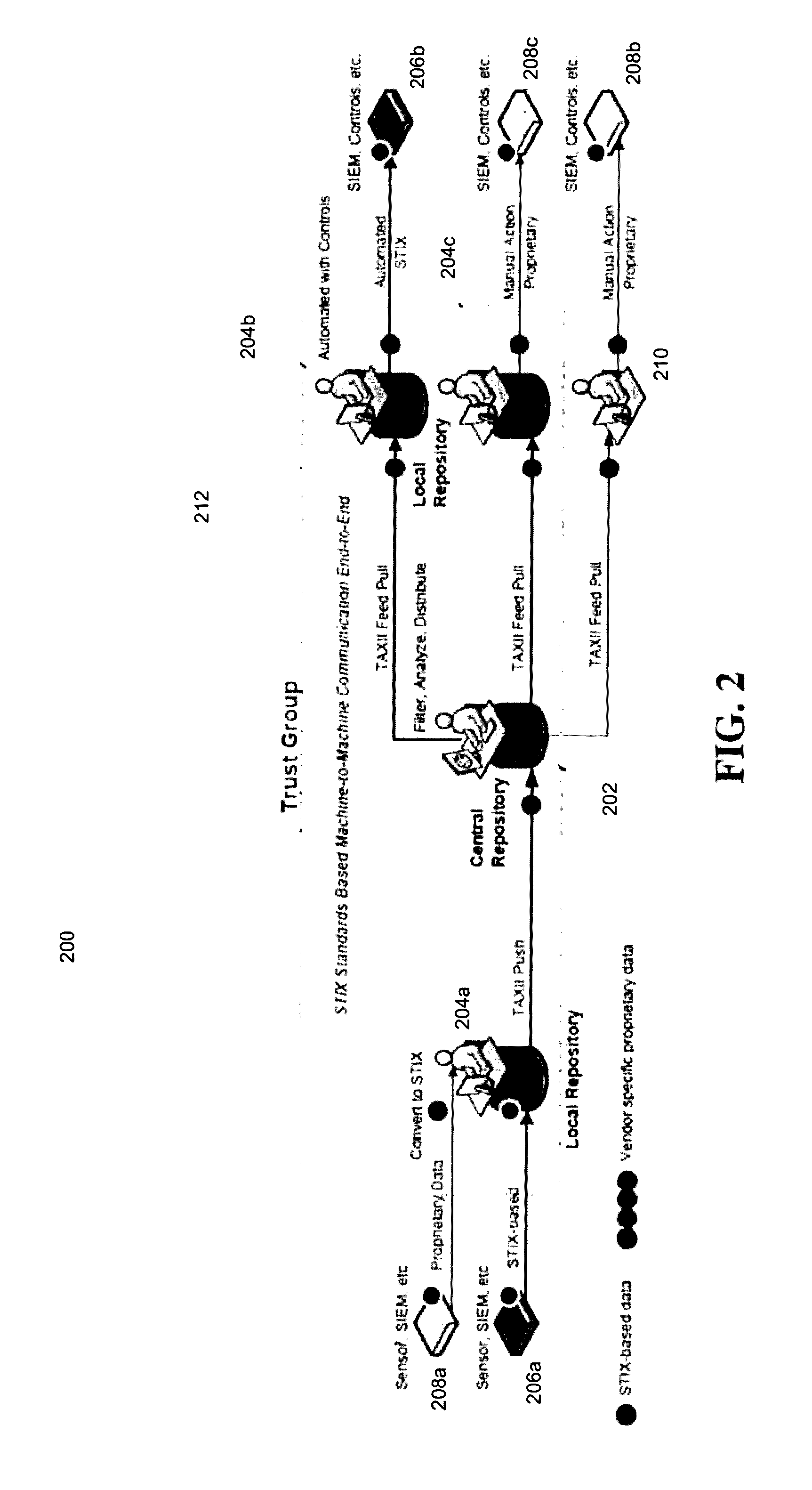
Computerized system and method for securely distributing and exchanging cyber-threat information in a standardized format
Computerized systems and methods for sharing identified cyber-threat information in a standardized and secure format. The sharing of cyber-threat information assists in preventing malicious actors from replicating successful cyber-attacks by informing potential targets of the methods employed by the malicious actors, and the defensive measures that those targets should to implement to prevent those methods from succeeding. By distributing cyber-threat information in a standardized format, the systems and methods enable participating entities to automatically analyze and implement defensive measures for cyber-threat information shared by any other participating entities. The systems and methods also permit an entity to control which threat information it shares and which other entities it shares it with in a secure manner in order to preserve that entity's security and reputation.
Owner:CELERIUM INC
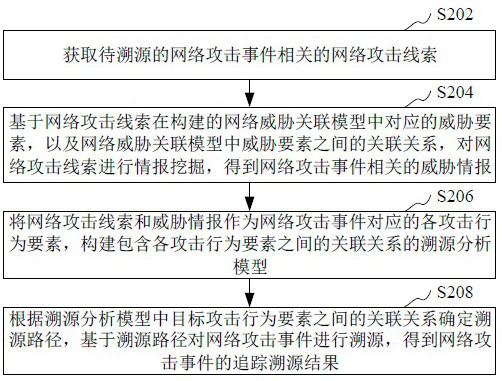
Network attack event traceability processing method and device, equipment and storage medium
The invention relates to the technical field of network security, in particular to a network attack event traceability processing method and device, equipment and a storage medium. The method comprises the steps of obtaining a network attack clue related to a to-be-traced network attack event; performing intelligence mining on the network attack clue based on the constructed network threat association model to obtain threat intelligence related to the network attack event; taking the network attack clue and the threat intelligence as attack behavior elements corresponding to the network attackevent, and constructing a traceability analysis model containing an association relationship between the attack behavior elements; and determining a traceability path according to the association relationship between the target attack behavior elements in the traceability analysis model, and performing traceability on the network attack event based on the traceability path to obtain a traceability result of the network attack event. By adopting the method, accurate tracking and tracing of the network attack event can be realized, so that the security of a computer communication network is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
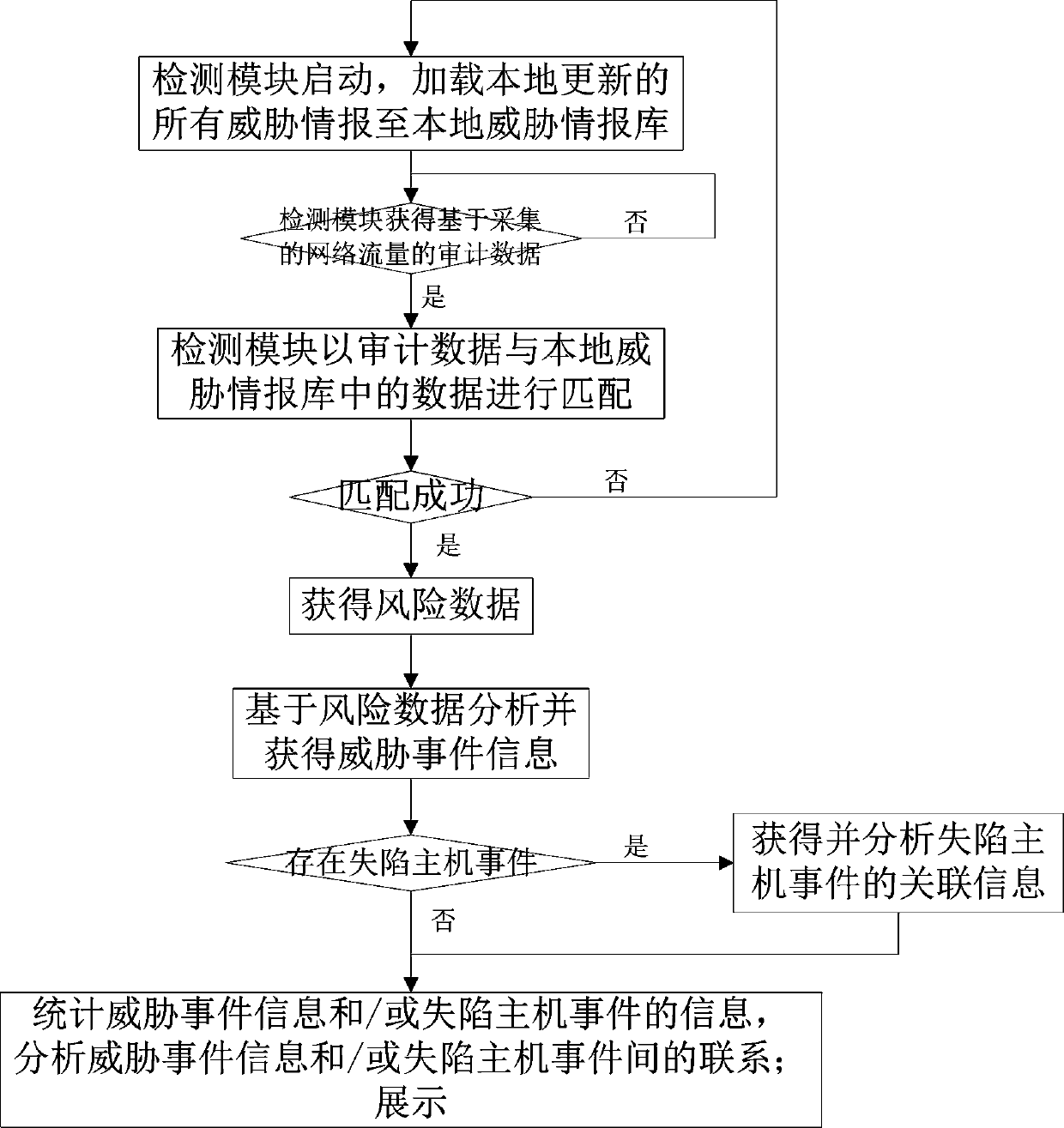
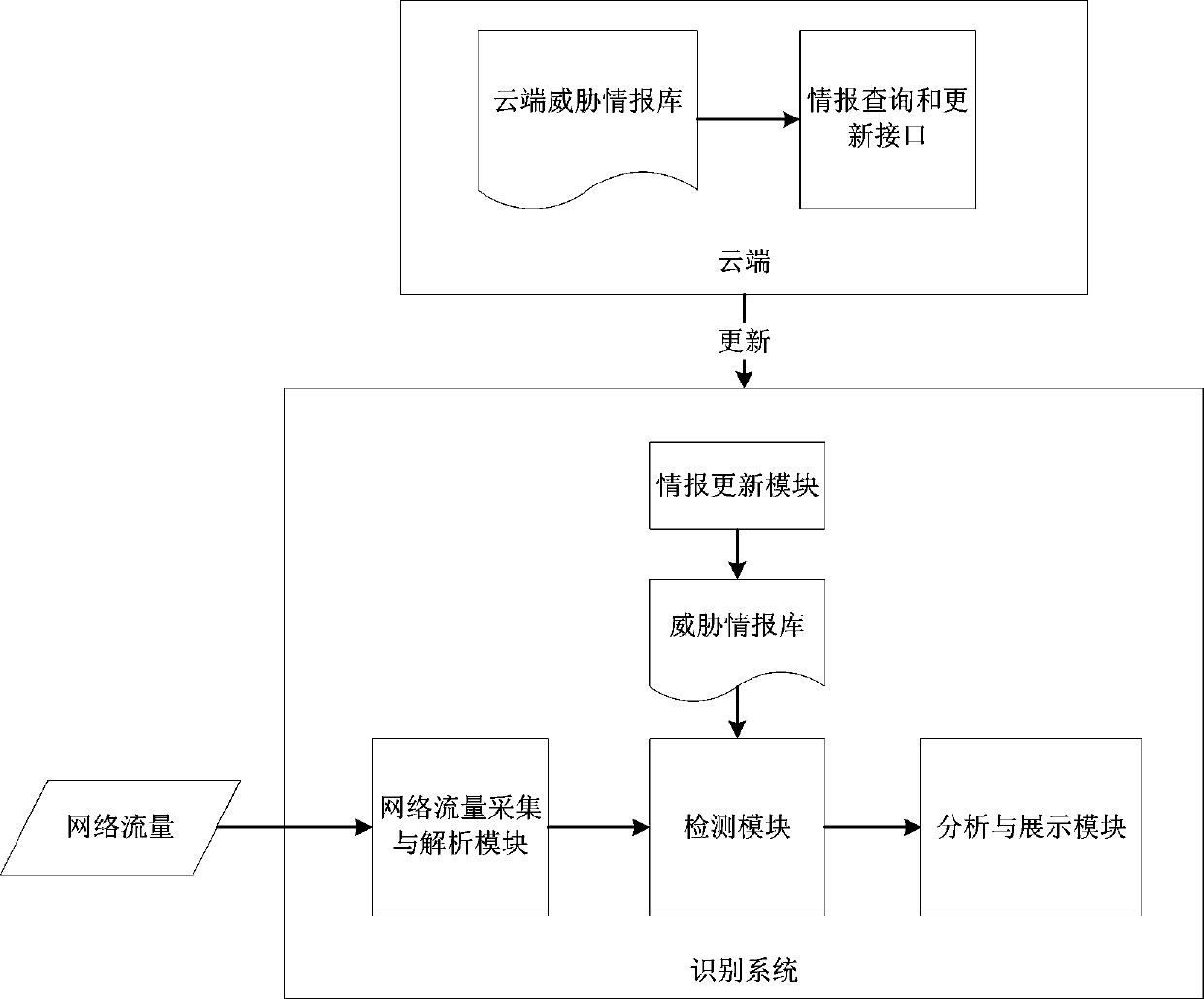
Threat intelligence-based network threat identification method and identification system
The invention relates to a threat intelligence-based network threat identification method and identification system. The method includes: after the detection module is started, loading all the threatinformation updated by the information updating module to the local; acquiring the collected and analyzed audit data, matching the audit data with data in a threat intelligence library, analyzing andacquiring threat event information based on risk data through an analysis and display module if the audit data is successfully matched with the data in the threat intelligence library, acquiring and analyzing associated information of possible lost host events, and counting, analyzing and displaying the relationship between the events. According to the invention, the threat condition of the wholenetwork is analyzed and displayed from two perspectives of threat event information and a lost host event; a collapsed host is determined, targeted attacks are accurately recognized, correlation analysis and display are carried out on the threats, the efficiency of processing network attack events is improved, the false alarm rate is low, potential threats can be found, tracing and post-processingof the threat events are greatly facilitated, attacks possibly occurring in the future are predicted, and therefore truly valuable attack events are deeply analyzed and found.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
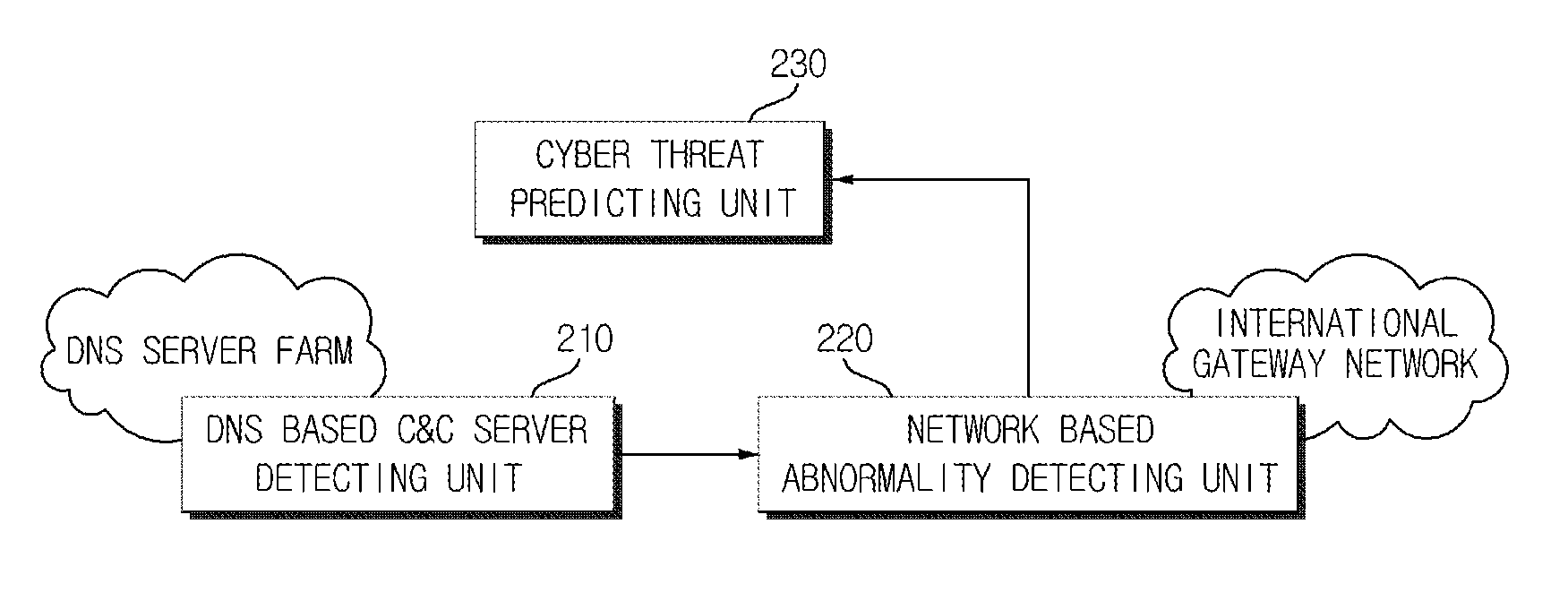
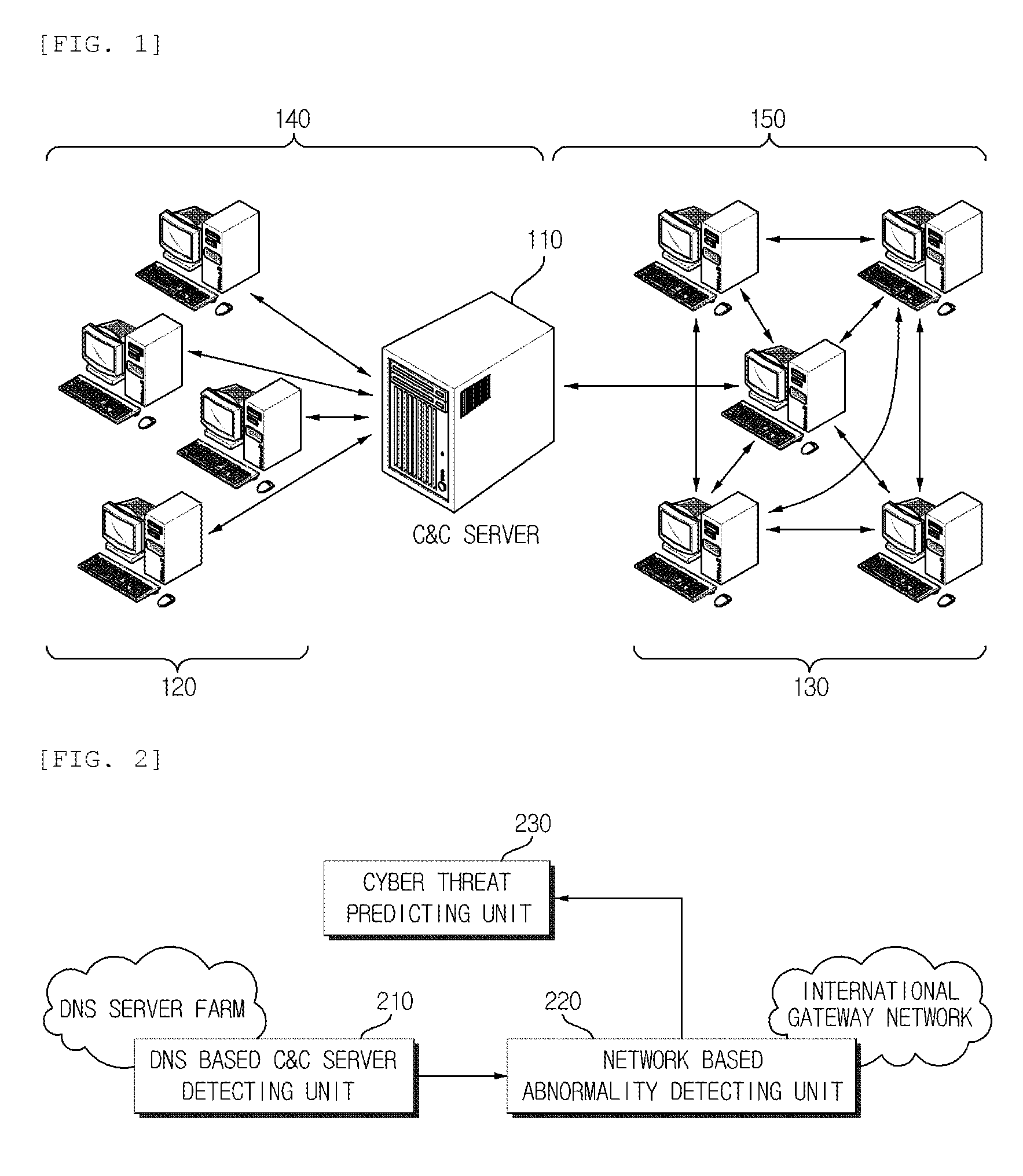
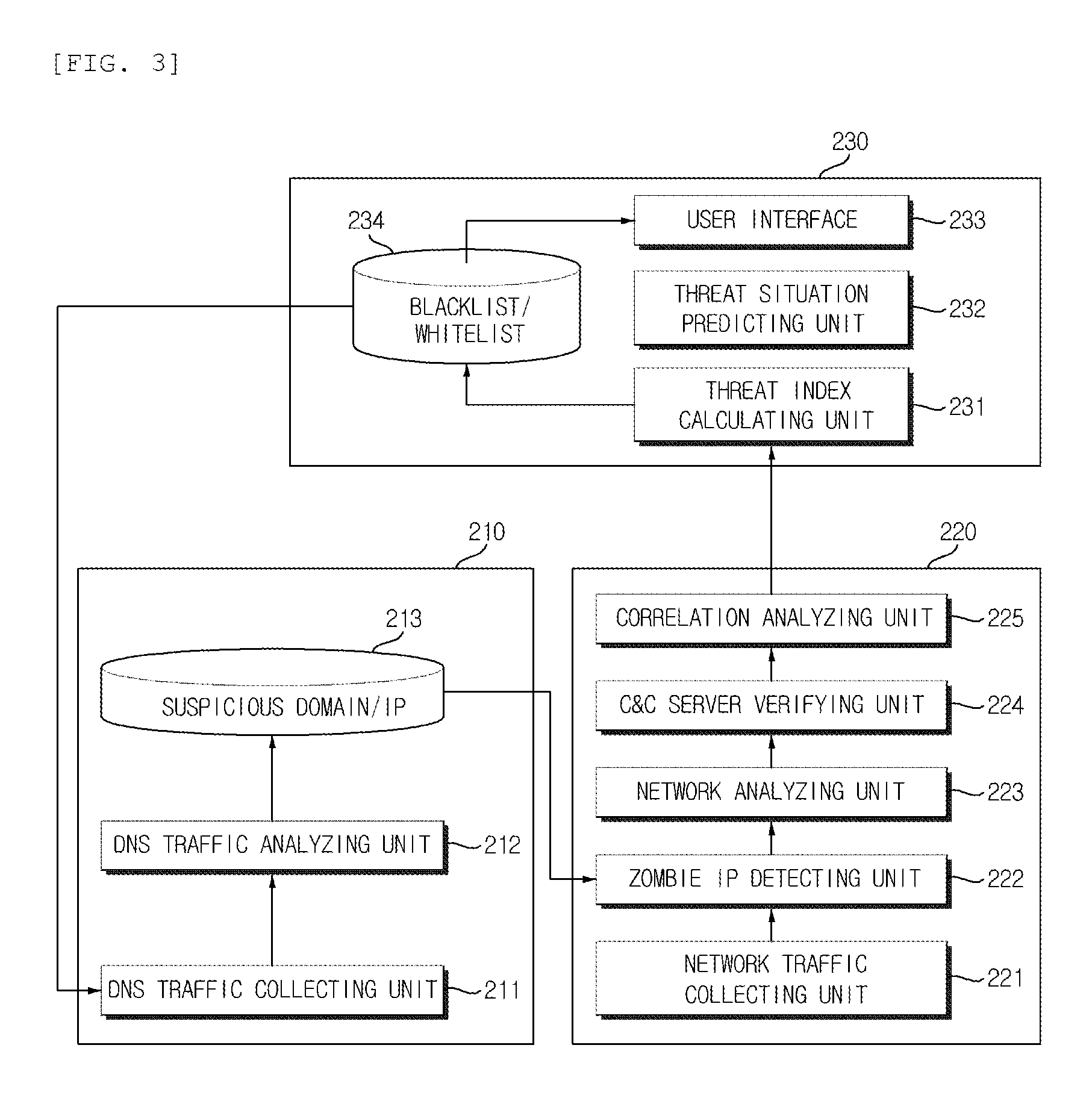
Cyber threat prior prediction apparatus and method
Disclosed are a cyber threat prior prediction apparatus, including a DNS based C&C server detecting unit configured to analyze DNS traffic to extract a domain address which is suspected as a C&C server; a network based abnormality detecting unit configured to analyze the network traffic to detect IP addresses of zombie PCs which access the C&C server and information of the zombie PCs; and a cyber threat predicting unit configured to predict a cyber threat situation based on the information of the zombie PCs.
Owner:ELECTRONICS & TELECOMM RES INST
Network security appliance
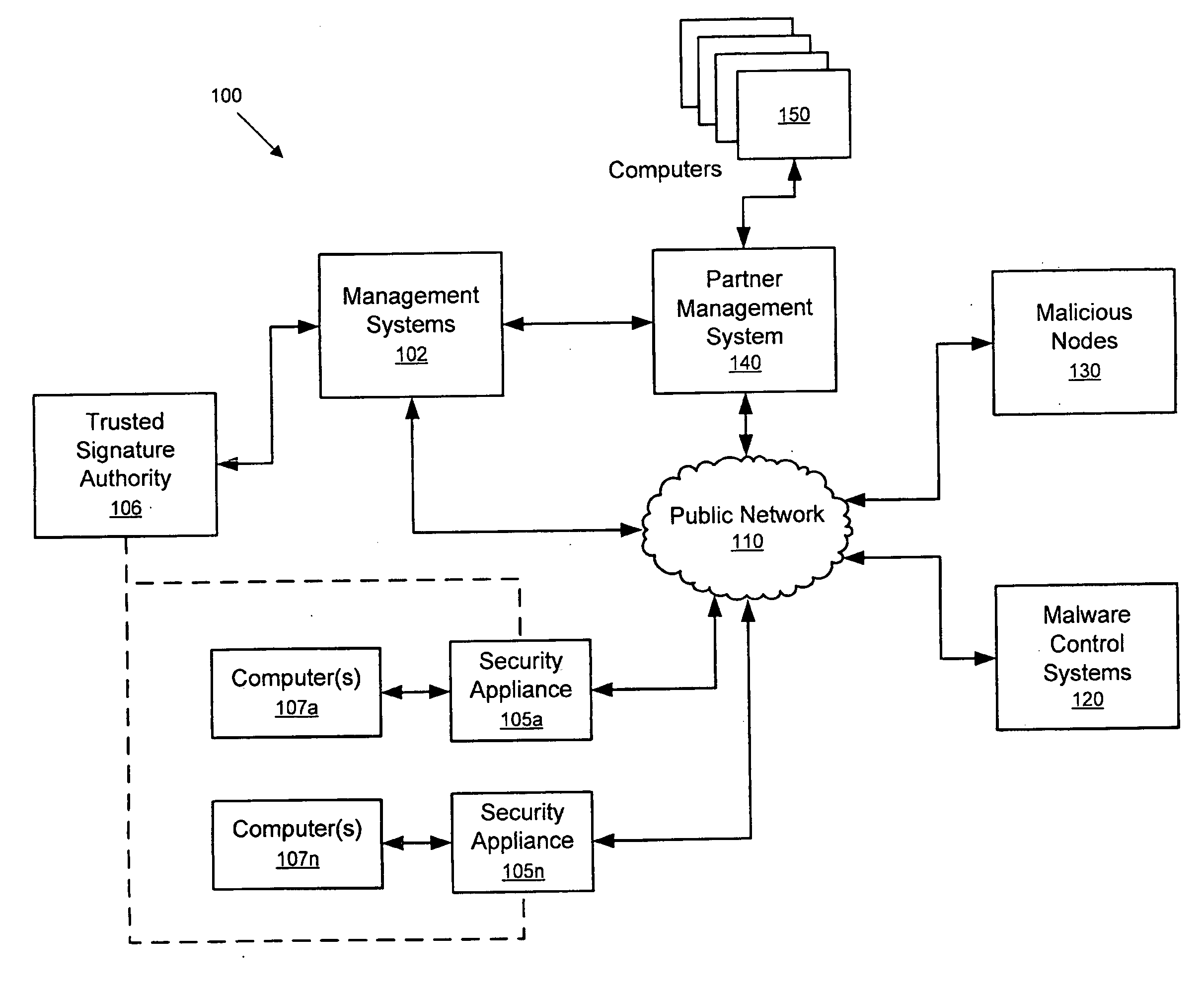
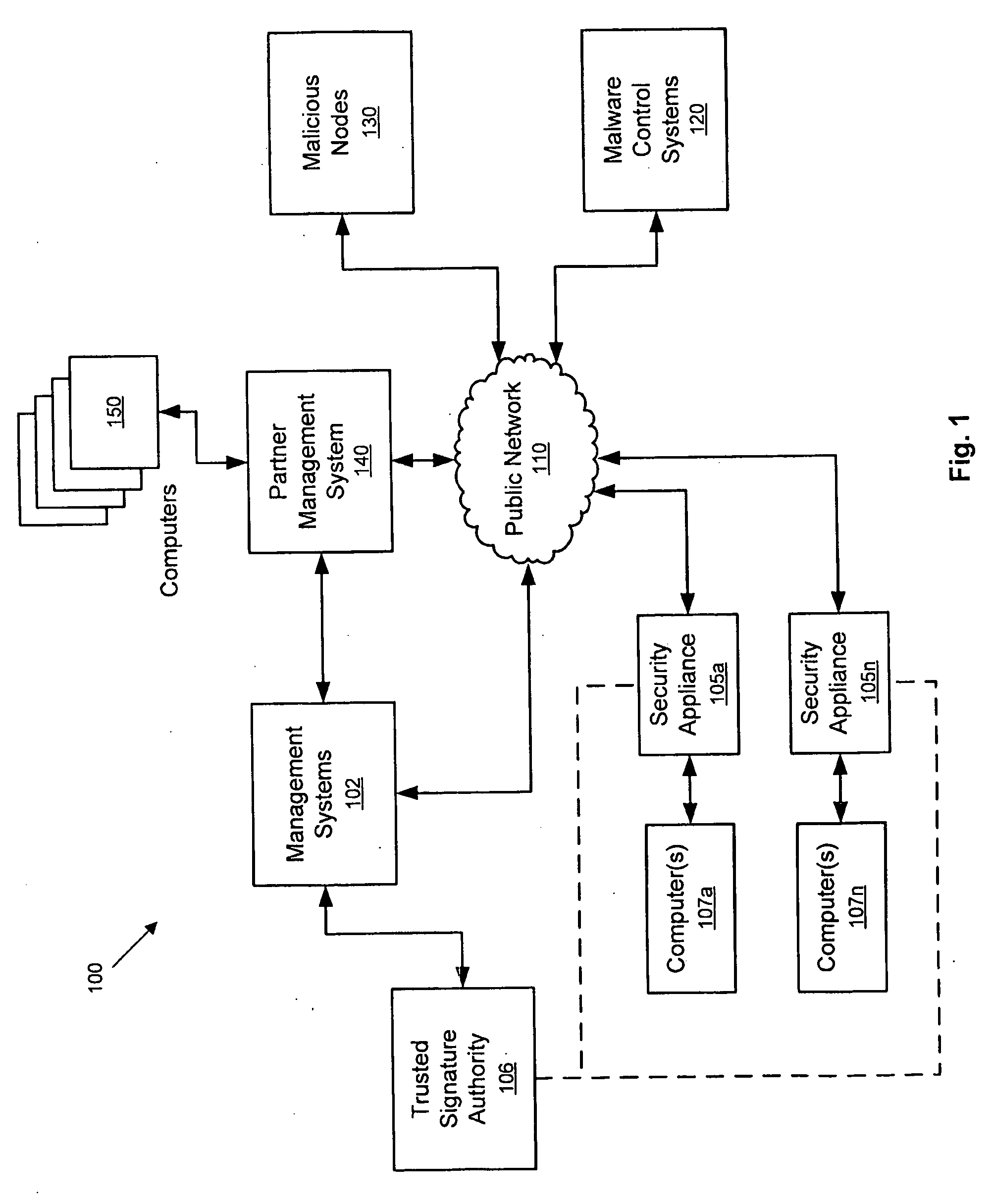
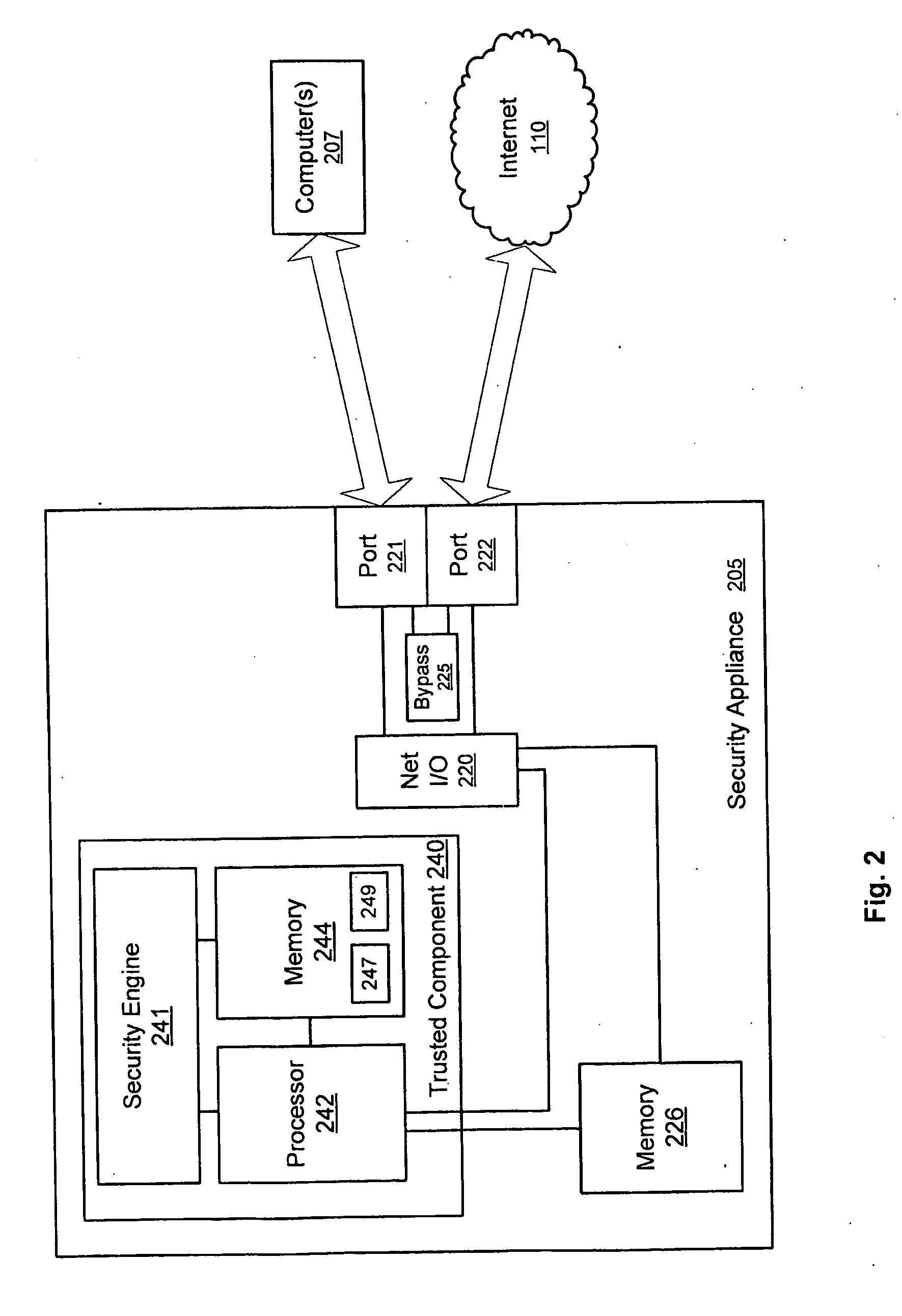
InactiveUS20100071054A1Memory loss protectionError detection/correctionComputerized systemPublic network
Systems and methods for combating and thwarting attacks by cybercriminals are provided. Network security appliances interposed between computer systems and public networks, such as the Internet, are configured to perform defensive and / or offensive actions against botnets and / or other cyber threats. According to some embodiments, network security appliances may be configured to perform coordinated defensive and / or offensive actions with other network security appliances.
Owner:VIASAT INC
Method and system for protection against network-based cyber threats
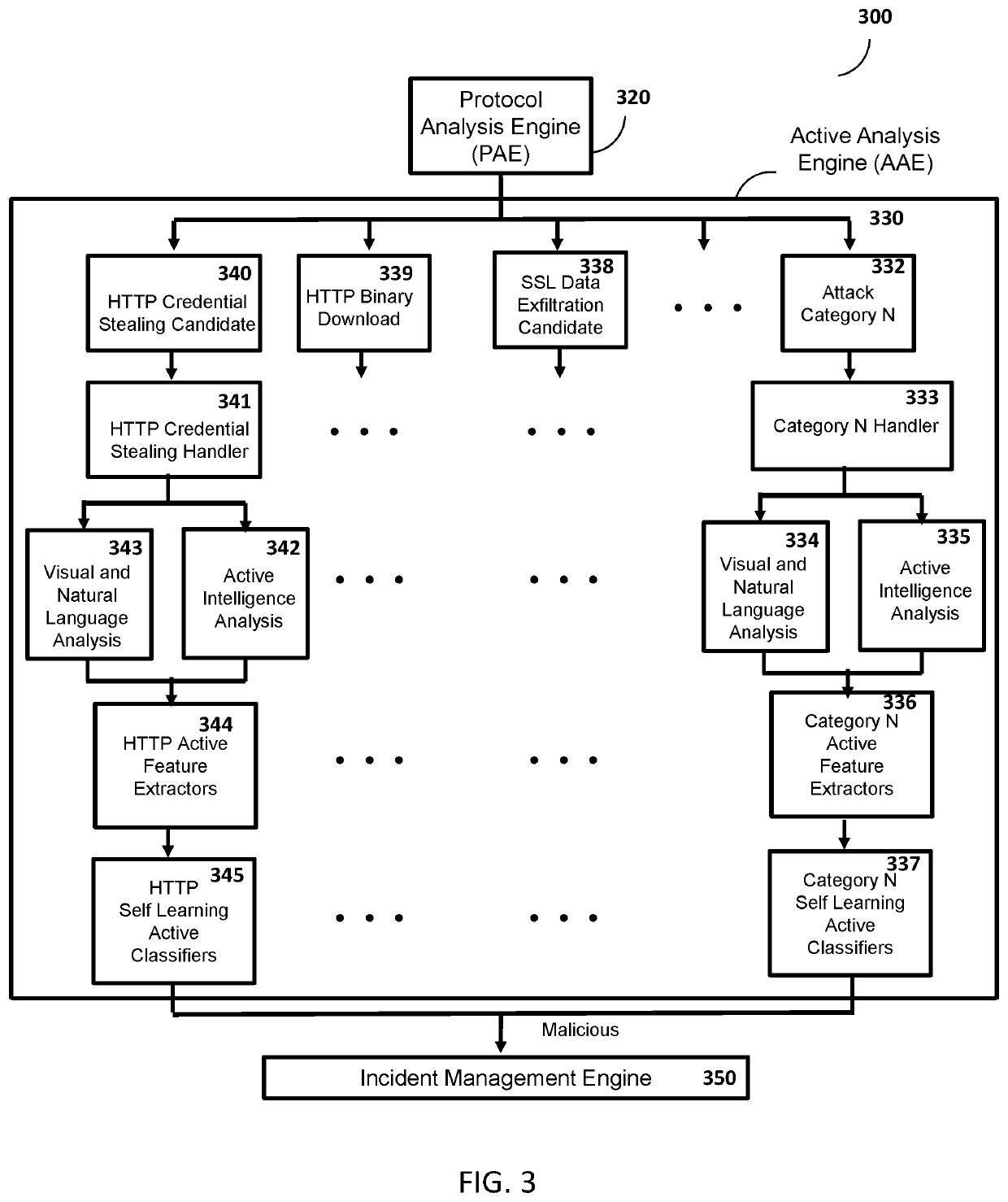
An Active Cyber Defense method and system is provided for detecting and stopping malicious cyber activity including for example Drive-By Exploits, Malicious Binaries, Data Exfiltration, Social Engineering and Credential Stealing Attacks. The system disclosed herein can be configured to detect and block multi protocol network-based cyber attacks targeting different platforms or operating systems. The system can also be configured to be scalable. The system as disclosed herein can conduct real time inspection of network traffic and can self-learn and adapt as needed to a changing cyber threat landscape.
Owner:SLASHNEXT INC
System and method for detecting potential threats by monitoring user and system behavior associated with computer and network activity
A system and method is provided to monitor user and system behavior associated with computer and network activity to determine deviations from normal behavior that represent a potential cyber threat or cyber malicious activity. The system and method uses a multi-factor behavioral and activity analysis approach to determine when a trusted insider might be exhibiting threatening behavior or when a user's computer or network credentials have been compromised and are in use by a third-party. As a result, changes in insider behavior that could be indicative of malicious intent can be detected, or an external entity masquerading as a legitimate user can be detected.
Owner:WINTERMUTE LLC
Affectedness scoring engine for cyber threat intelligence services
ActiveUS20200327223A1Digital data information retrievalPlatform integrity maintainanceManaged security serviceCyber threat intelligence
A network-accessible cyber-threat security analytics service is configured to characterize and respond to a description that includes threat indicators (e.g., IOCs), and an initial severity. Enterprises register with the service by providing identifying information, such as industry, geographies, and the like. For each threat indicator, a query is sent to each of a set of one or more security knowledge bases, and at least some of the queries are scoped by the enterprise industry / geo information specified. The knowledge bases may vary but typically include: a managed security service, a cyber threat intelligence service, and a federated search engine that searches across one or more enterprise-connected data sources. Responses to the queries are collected. A response provides an indication whether the threat indicator identified in the query has been sighted in the knowledge base and the frequency. The system then adjusts the initial severity to reflect the indications returned from querying the security knowledge bases.
Owner:IBM CORP
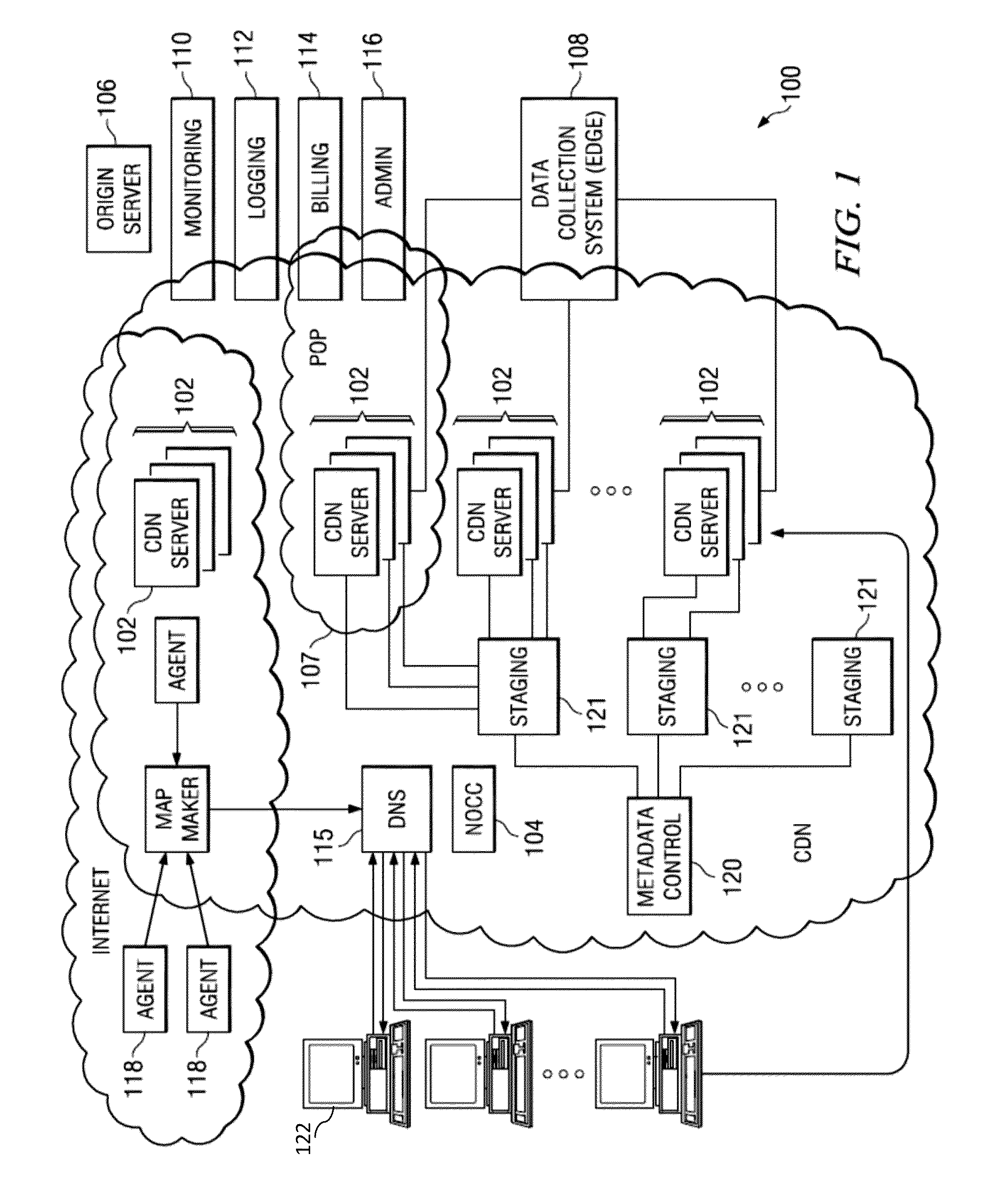
Network threat assessment system with servers performing message exchange accounting
A server has a firewall module that performs accounting of traffic seen at the server. The traffic includes message exchanges, such as HTTP requests and HTTP responses. The server tests the message exchanges to determine if they match any of several message exchange categories. The server keeps statistics on matching traffic, for example the rate of matching traffic generated by a particular requesting client. Typically, the server is a proxy server that is part of a content delivery network (CDN), and the message exchanges occur between a client requesting content, the proxy server, other servers in the CDN, and / or an origin server from which the proxy server retrieves requested content. Using the message exchange model and the statistics generated thereby, the server can flag particular traffic or clients, and take protective action (e.g., deny, alert). In an alternate embodiment, a central control system gathers statistics from multiple servers for analysis.
Owner:AKAMAI TECH INC
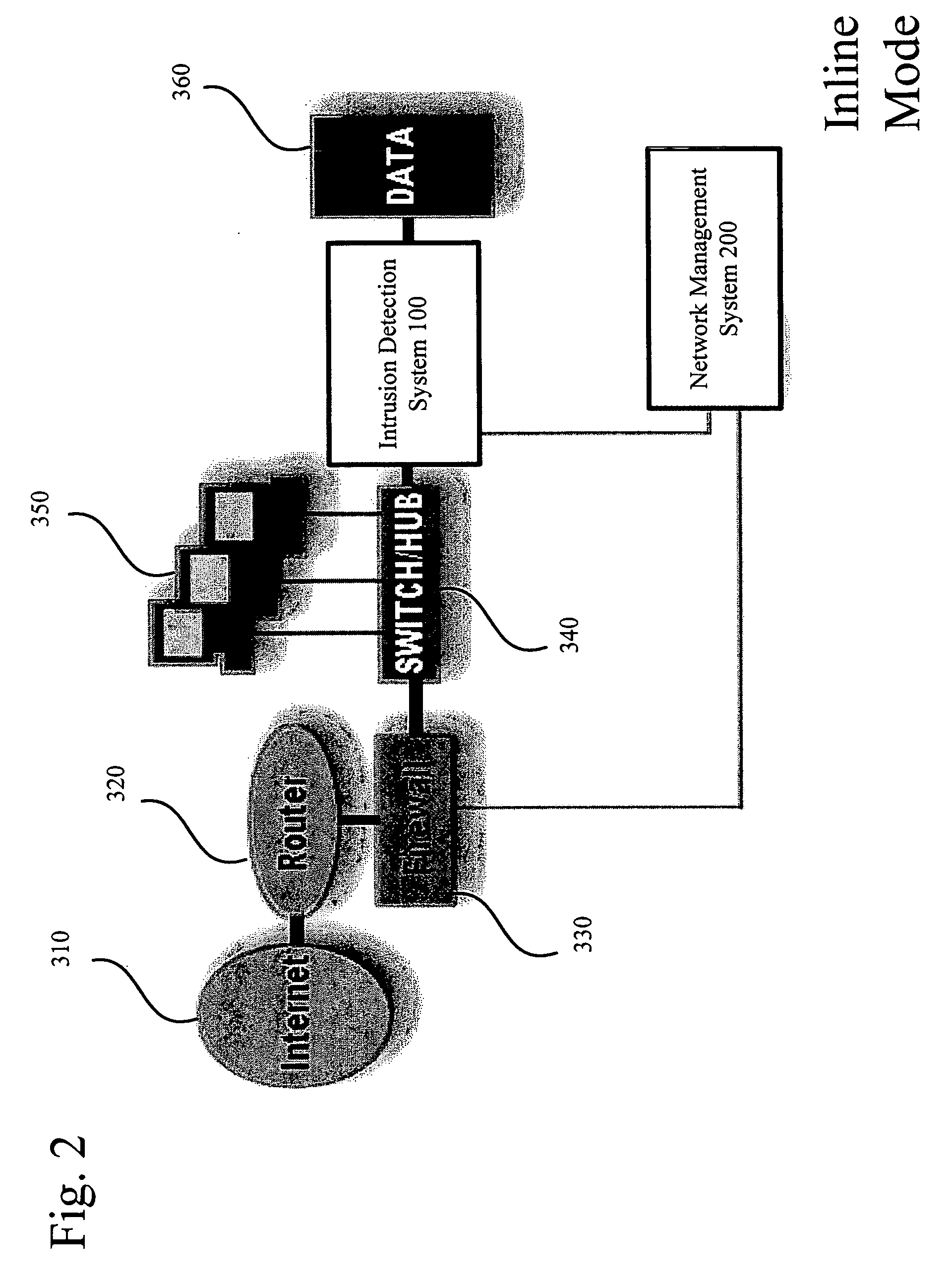
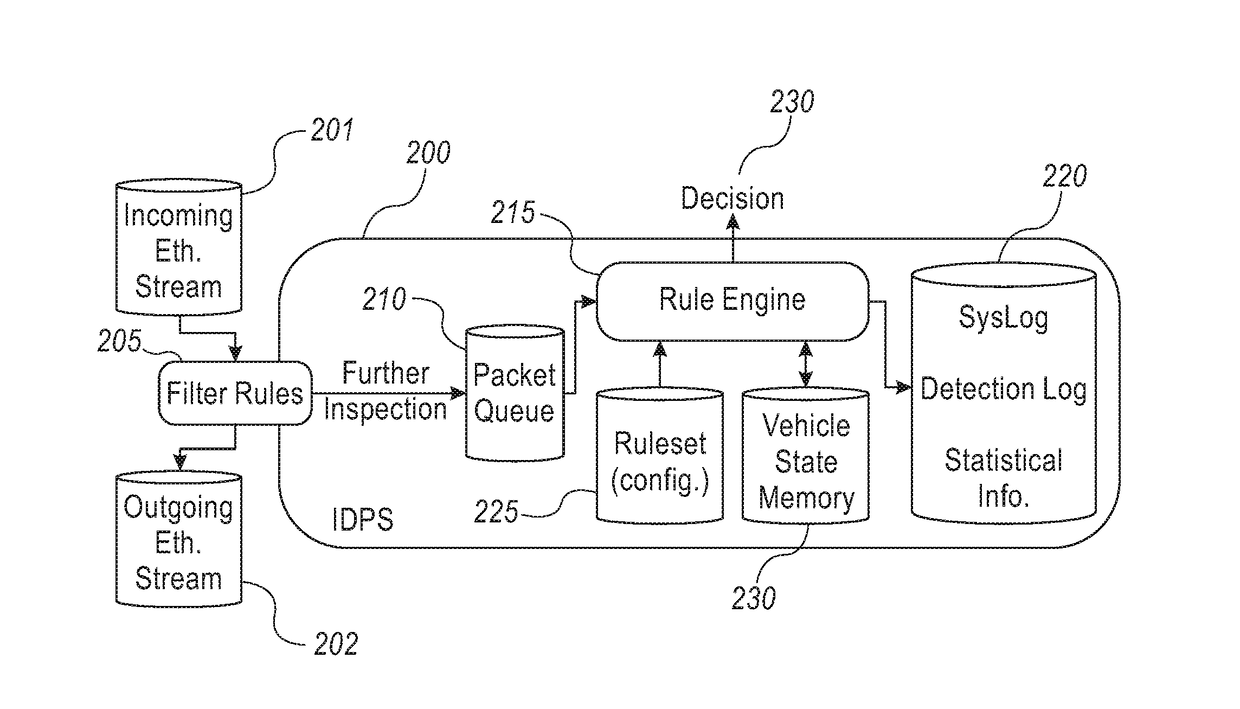
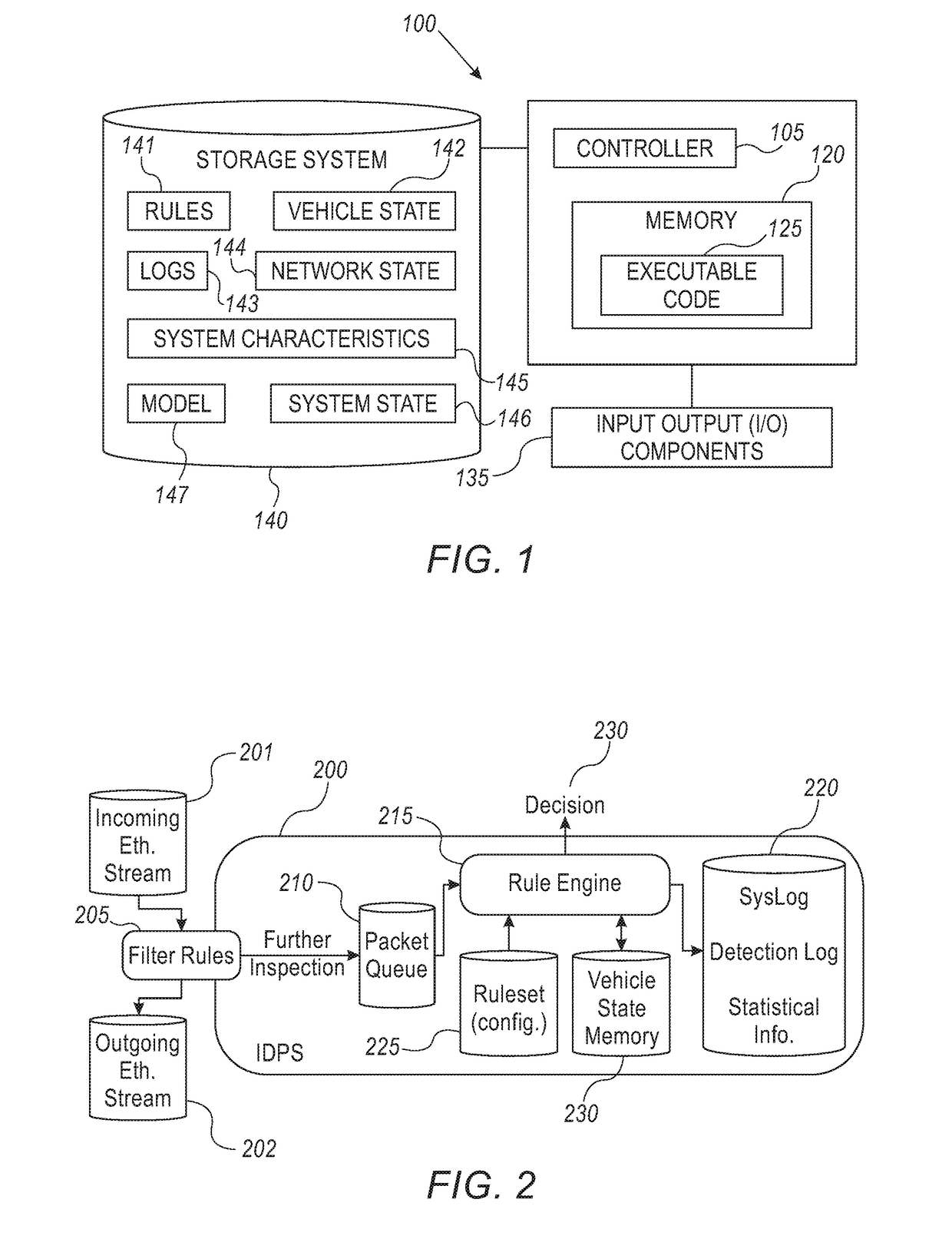
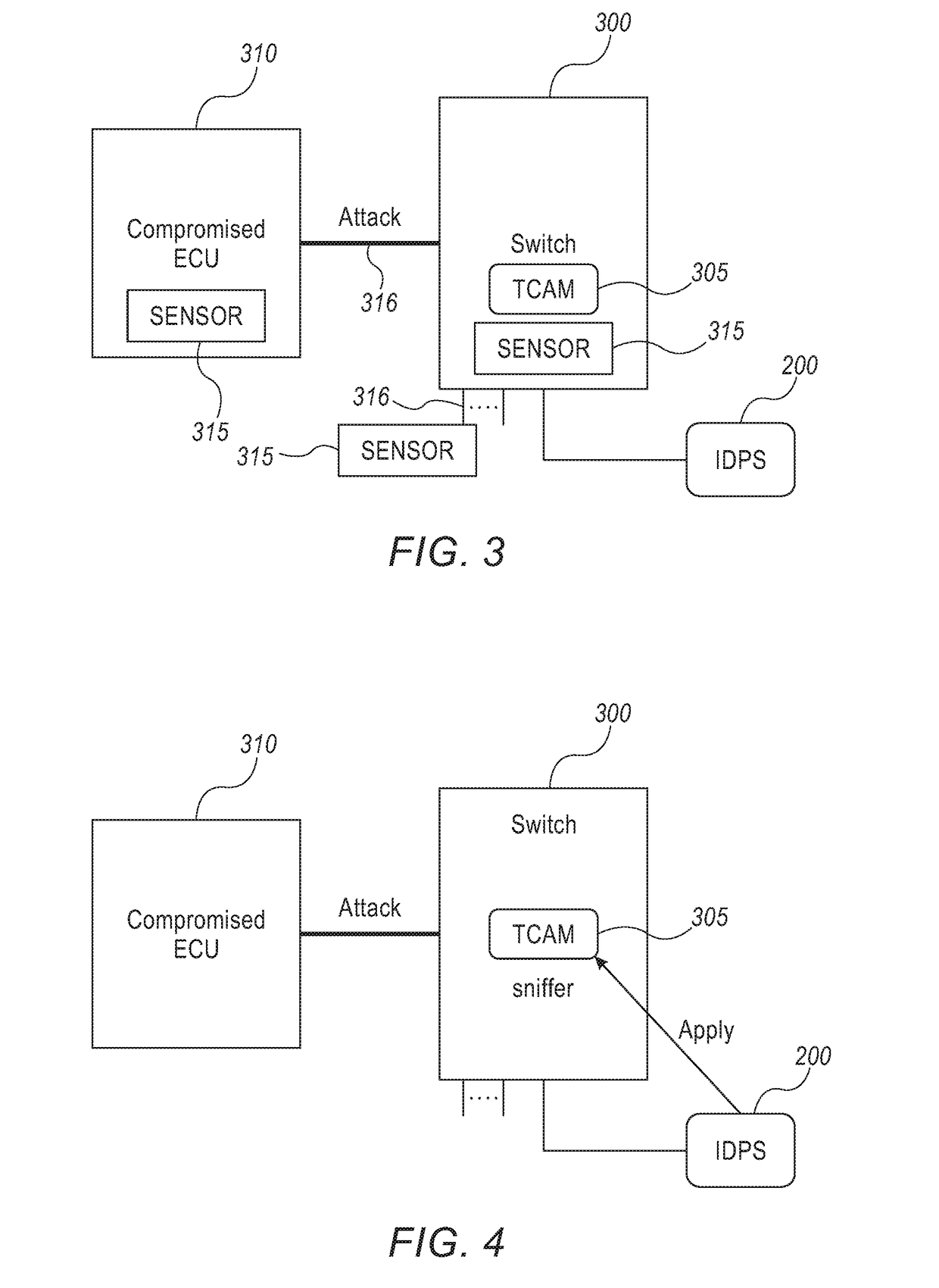
System and method for providing cyber security to an in-vehicle network
A system and method securing an in-vehicle network in a vehicle may include a switch connected to at least two segments of the in-vehicle network and an IDPS connected to the switch. The IDPS unit may be adapted to: receive network messages from the switch; determine at least some of the network messages are related to a cyber threat and configure the switch according to the cyber threat. The IDPS unit may be included in the switch.
Owner:ARGUS CYBER SECURITY LTD
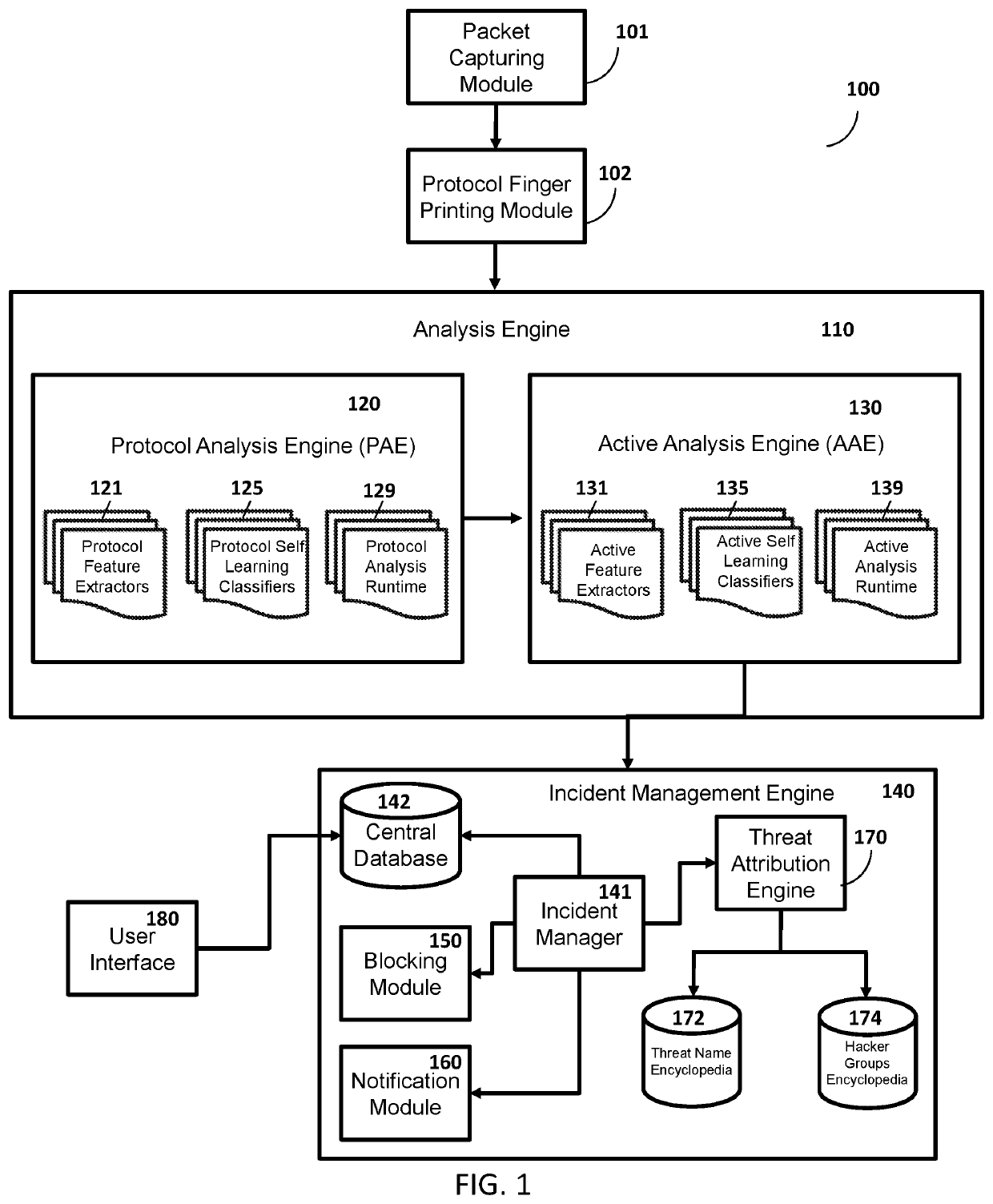
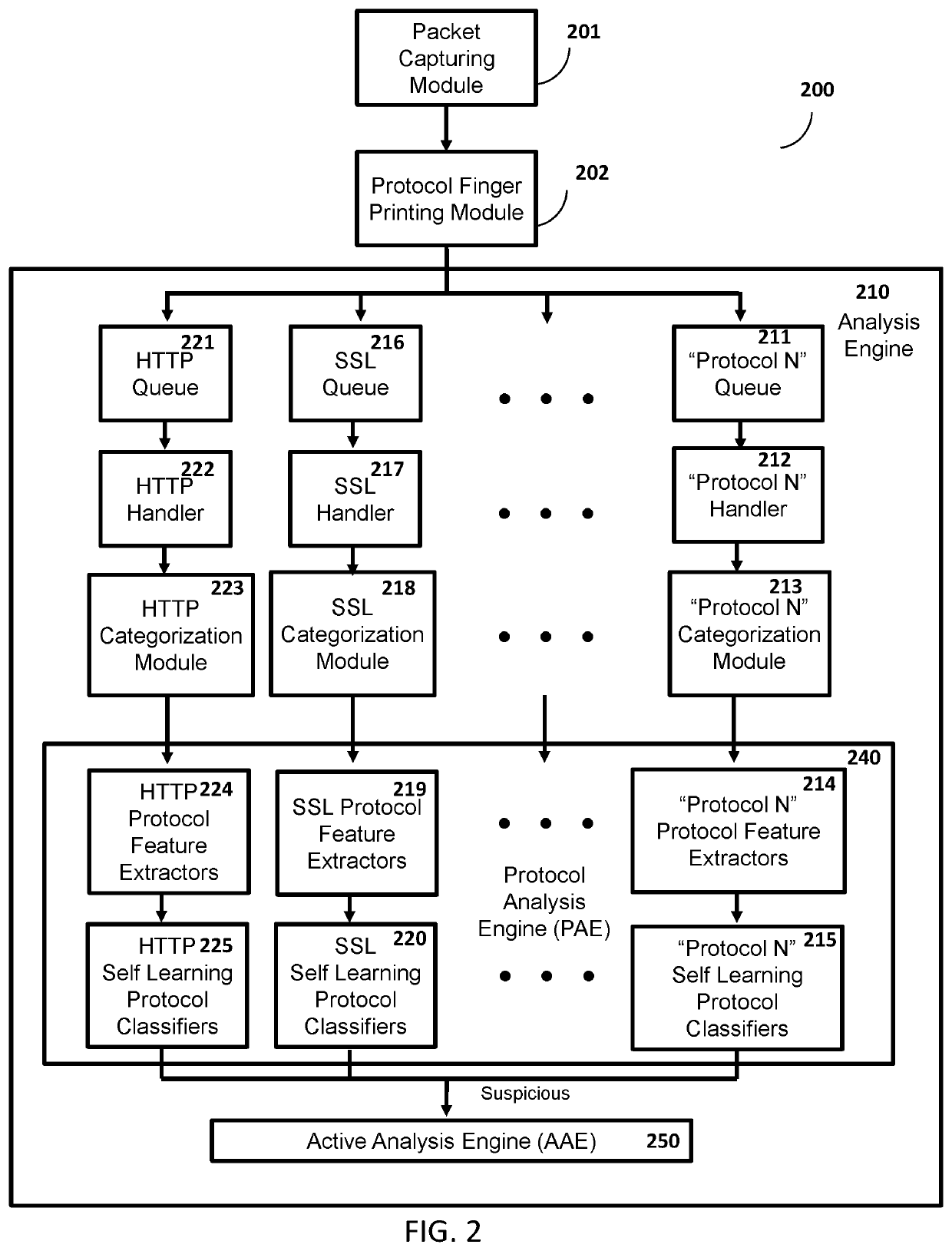
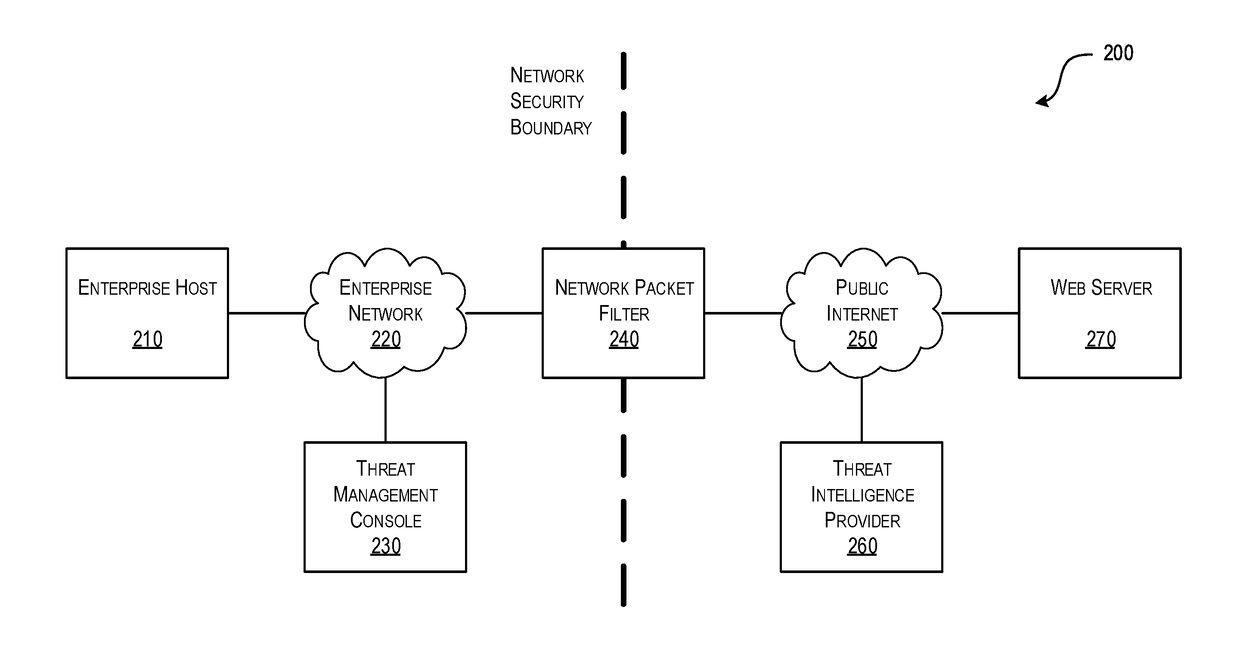
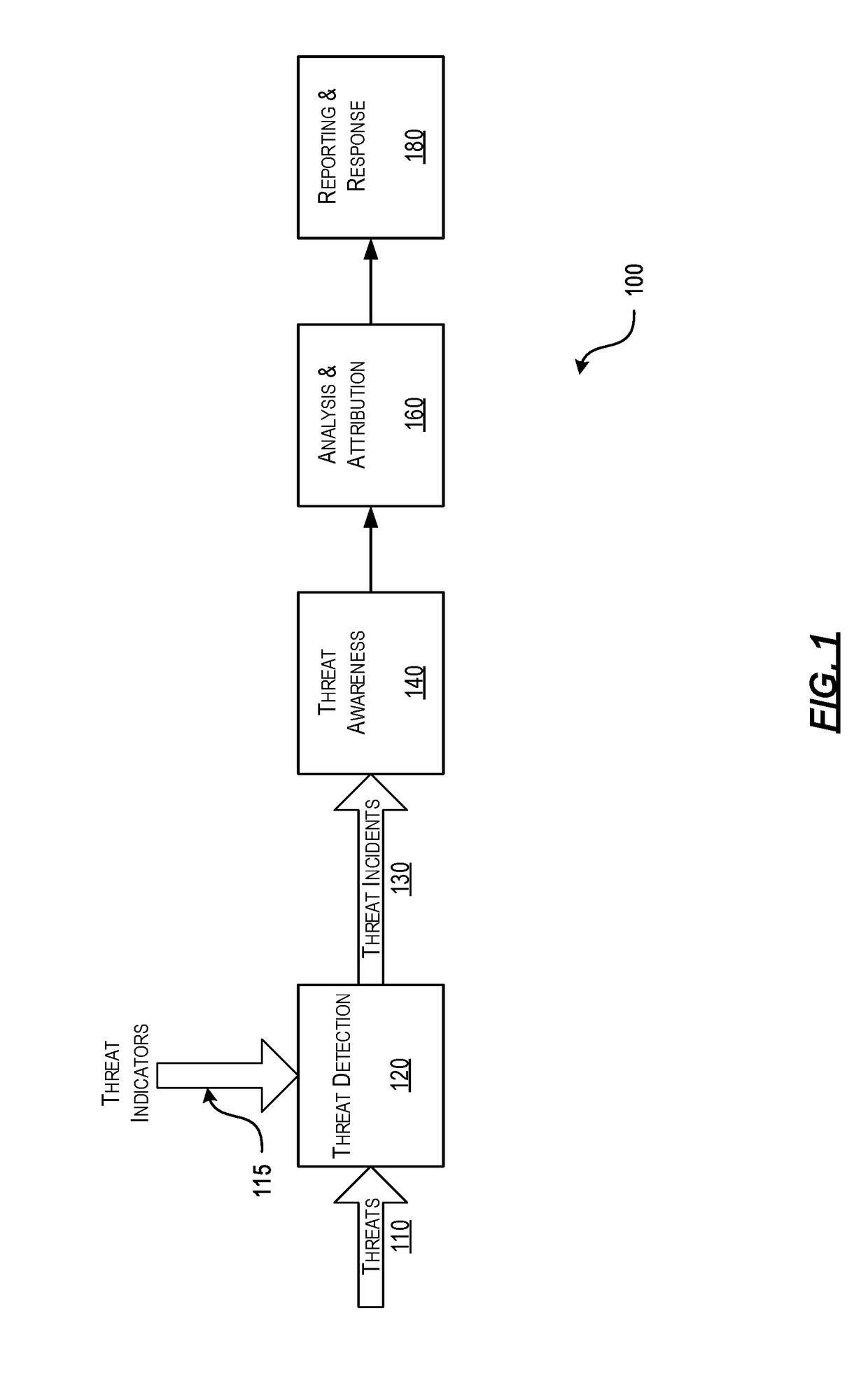
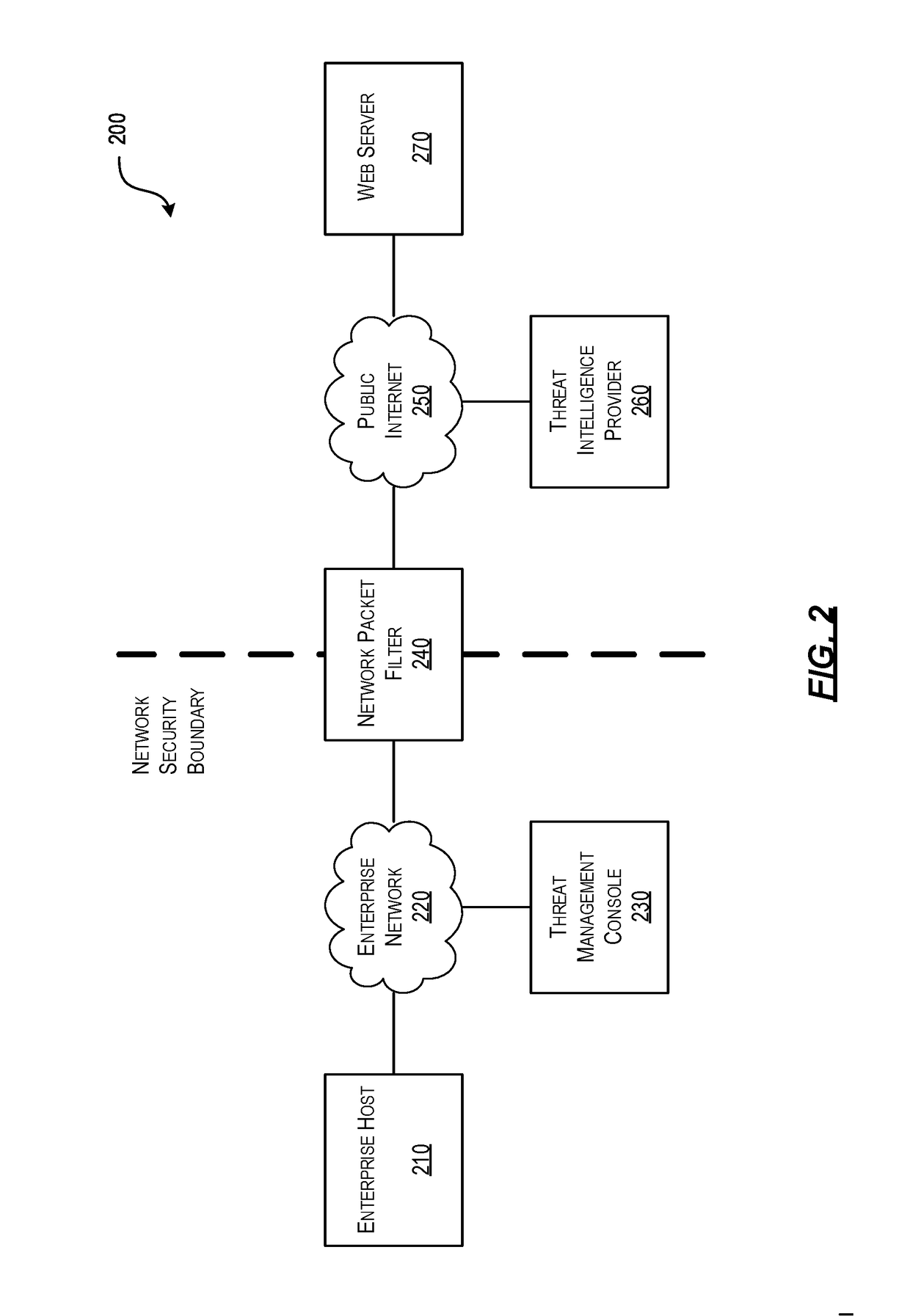
Efficient Packet Capture for Cyber Threat Analysis
Methods, systems, and computer-readable media for efficiently detecting threat incidents for cyber threat analysis are described herein. In various embodiments, a computing device, which may be located at a boundary between a protected network associated with the enterprise and an unprotected network, may combine one or more threat indicators received from one or more threat intelligence providers; may generate one or more packet capture and packet filtering rules based on the combined threat indicators; and, may capture or filter, on a packet-by-packet basis, at least one packet based on the generated rules. In other embodiments, a computing device may generate a packet capture file comprising raw packet content and corresponding threat context information, wherein the threat context information may comprise a filtering rule and an associated threat indicator that caused the packet to be captured.
Owner:CENTRIPETAL NETWORKS LLC
A computer-implemented method, a system and a computer program for identifying malicious URI data items
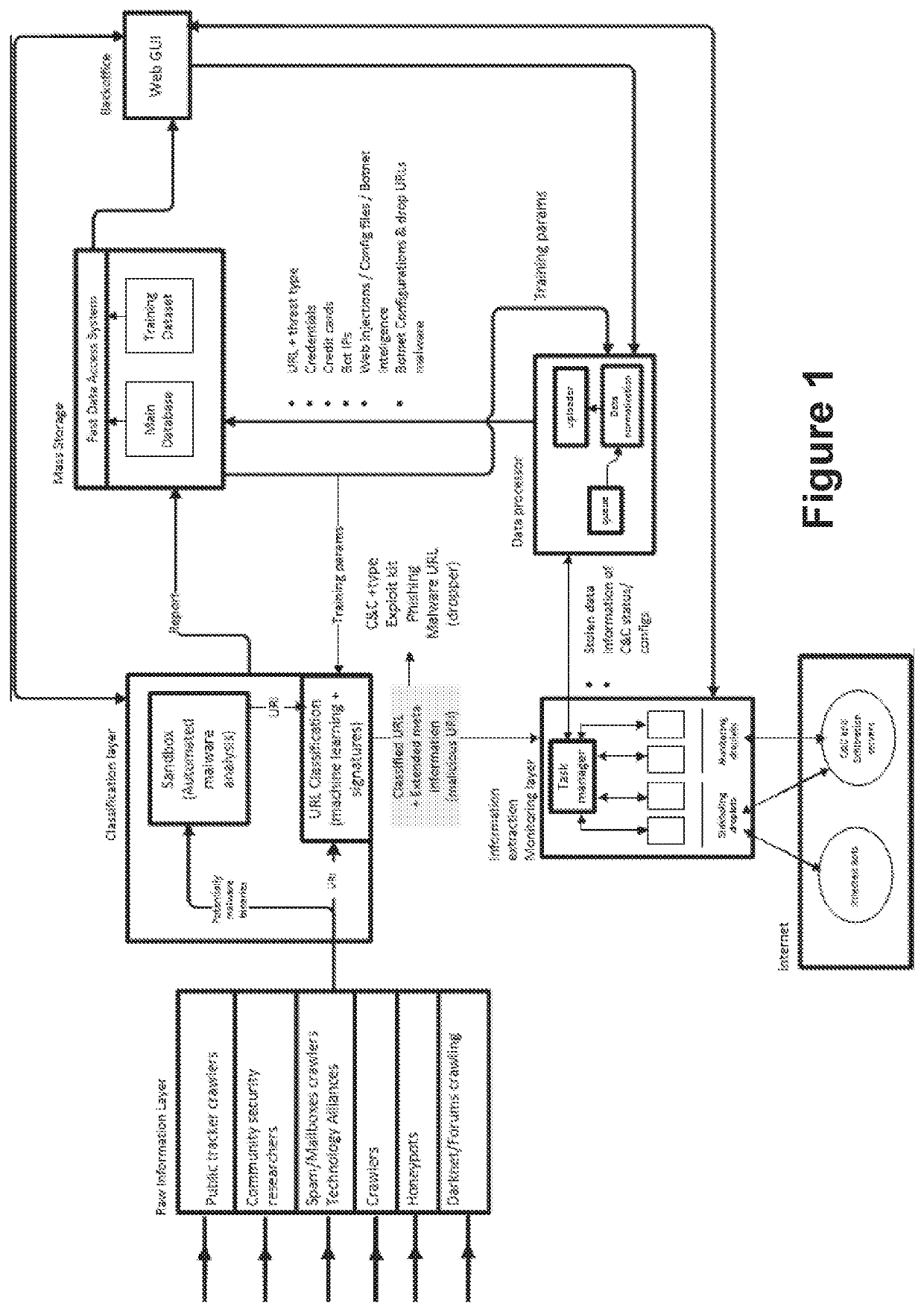
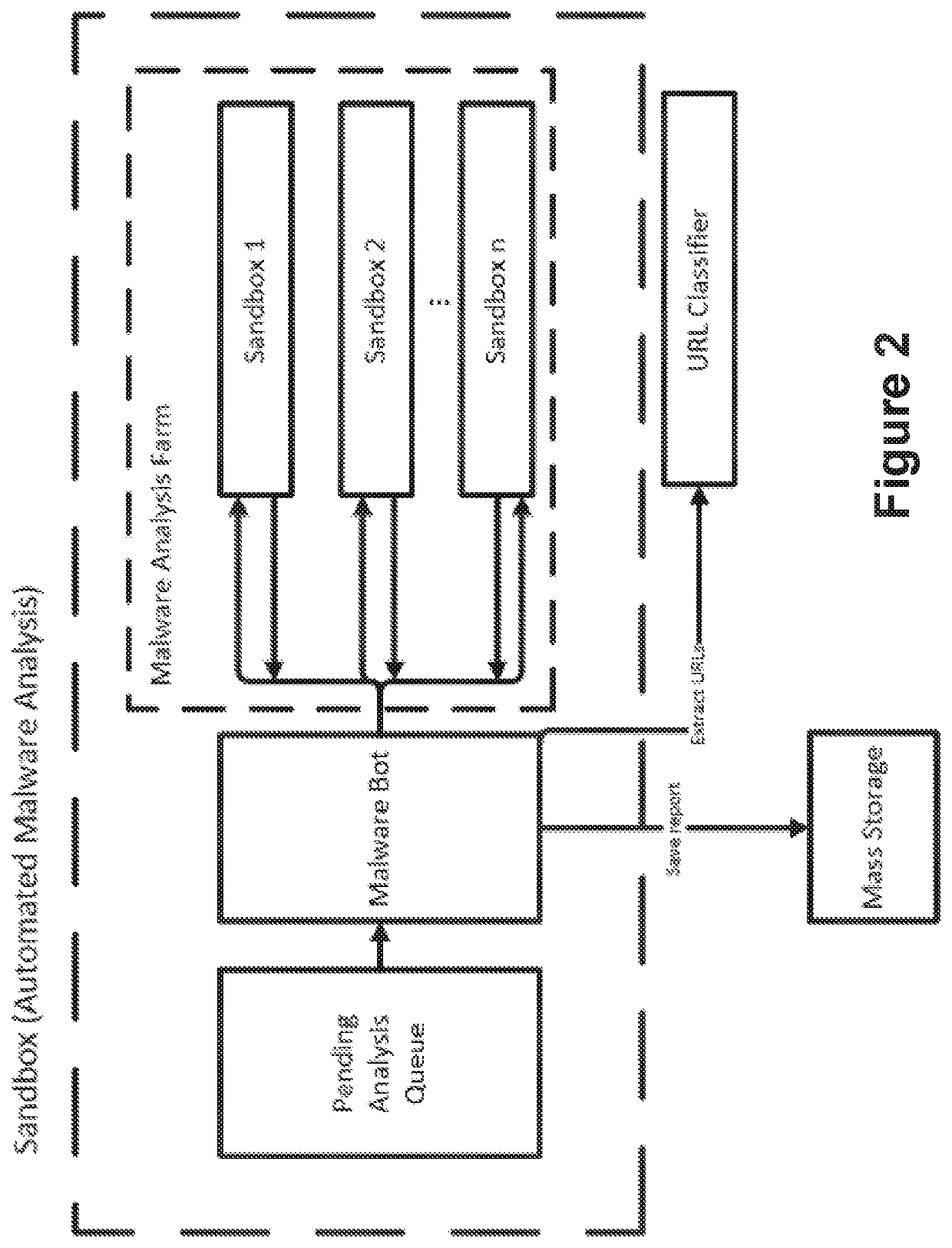
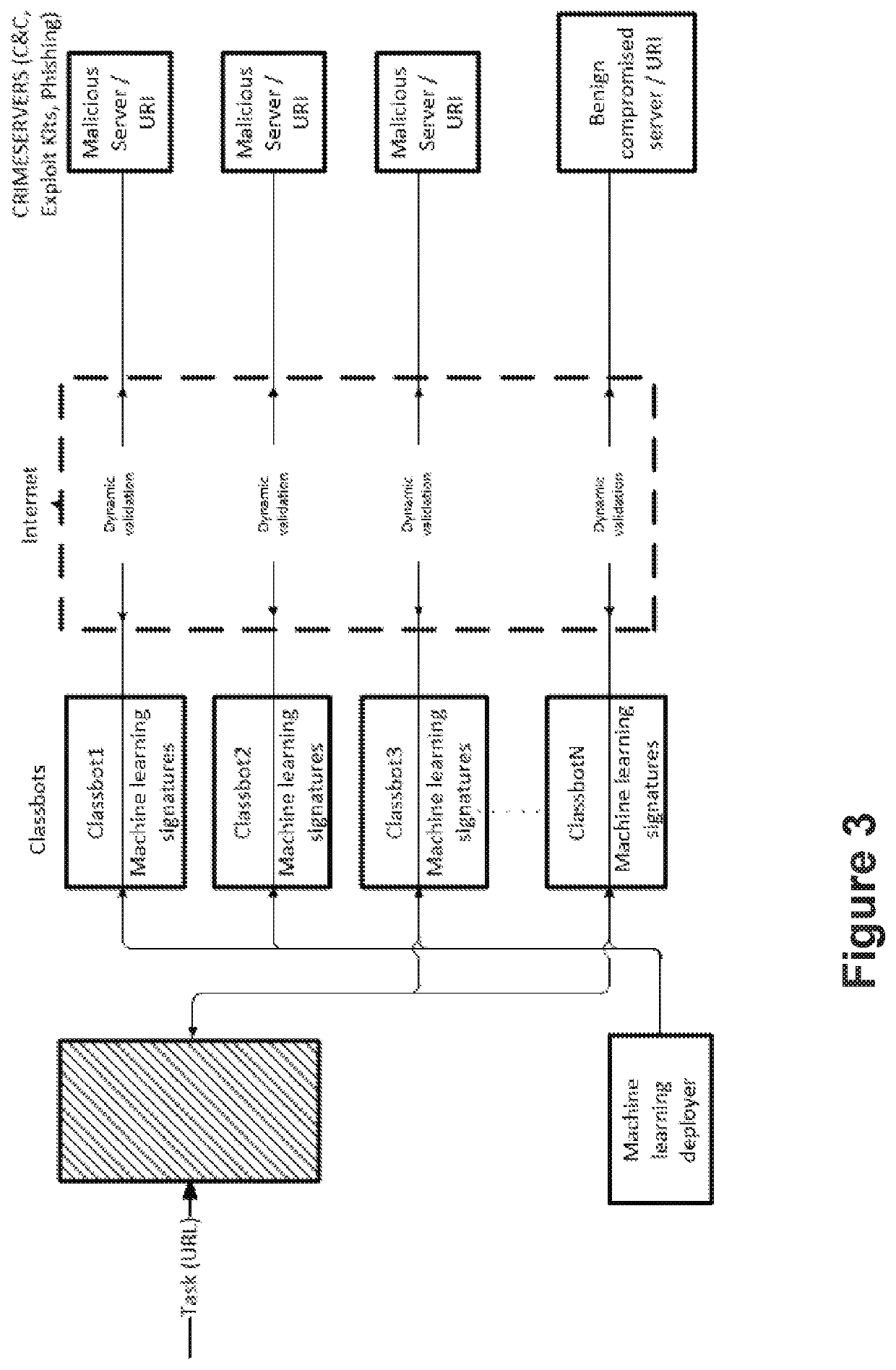
ActiveUS20200162484A1Avoid it happening againPrevent and detect data exfiltrationPlatform integrity maintainanceMachine learningMass storageEngineering
A computer-implemented method, a system and a computer program for identifying malicious URI data items are provided. The method a) gathers URI data items and b) analyses said URI data items to classify them into malicious URI data items and non-malicious URI data items. The method also c1) intercepts communications with malicious servers, identified by malicious URIs, from several computing entities, using sinkholing techniques, and uncovers and retrieves information which is being exfiltrated to said malicious or supervised servers, and c2) periodically monitors a status of the malicious servers identified by the malicious URIs, to control if they have been taken down or not, and simulates an infected bot to get updates of the commands sent from said malicious servers. The method also d) processes the uncovered information with learning algorithms, e) delivers to a mass storage device normalized and interpreted data; and f) provides warnings about potential cyber threats.
Owner:LEAP IN VALUE SL
Zero hop algorithm for network threat identification and mitigation
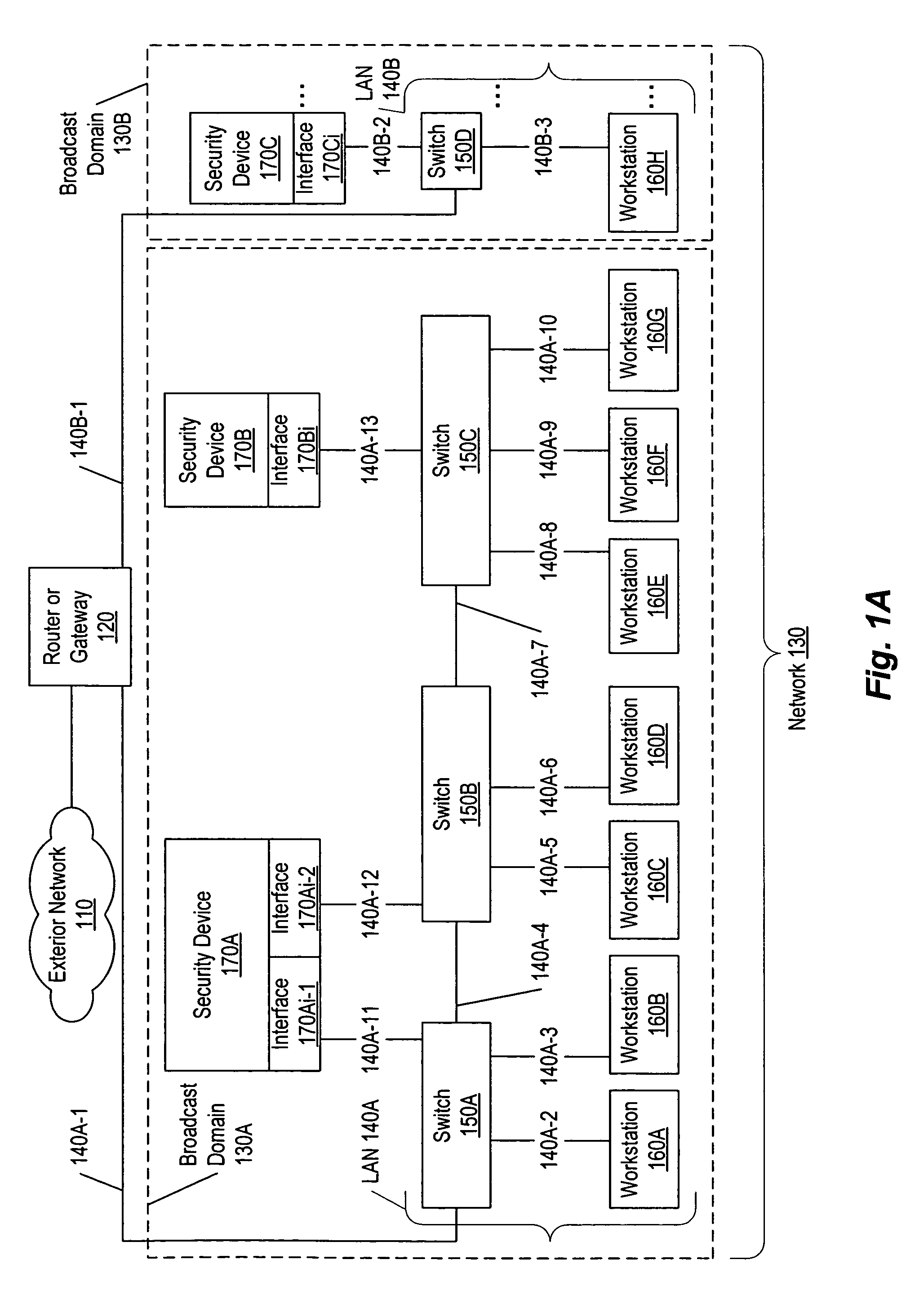
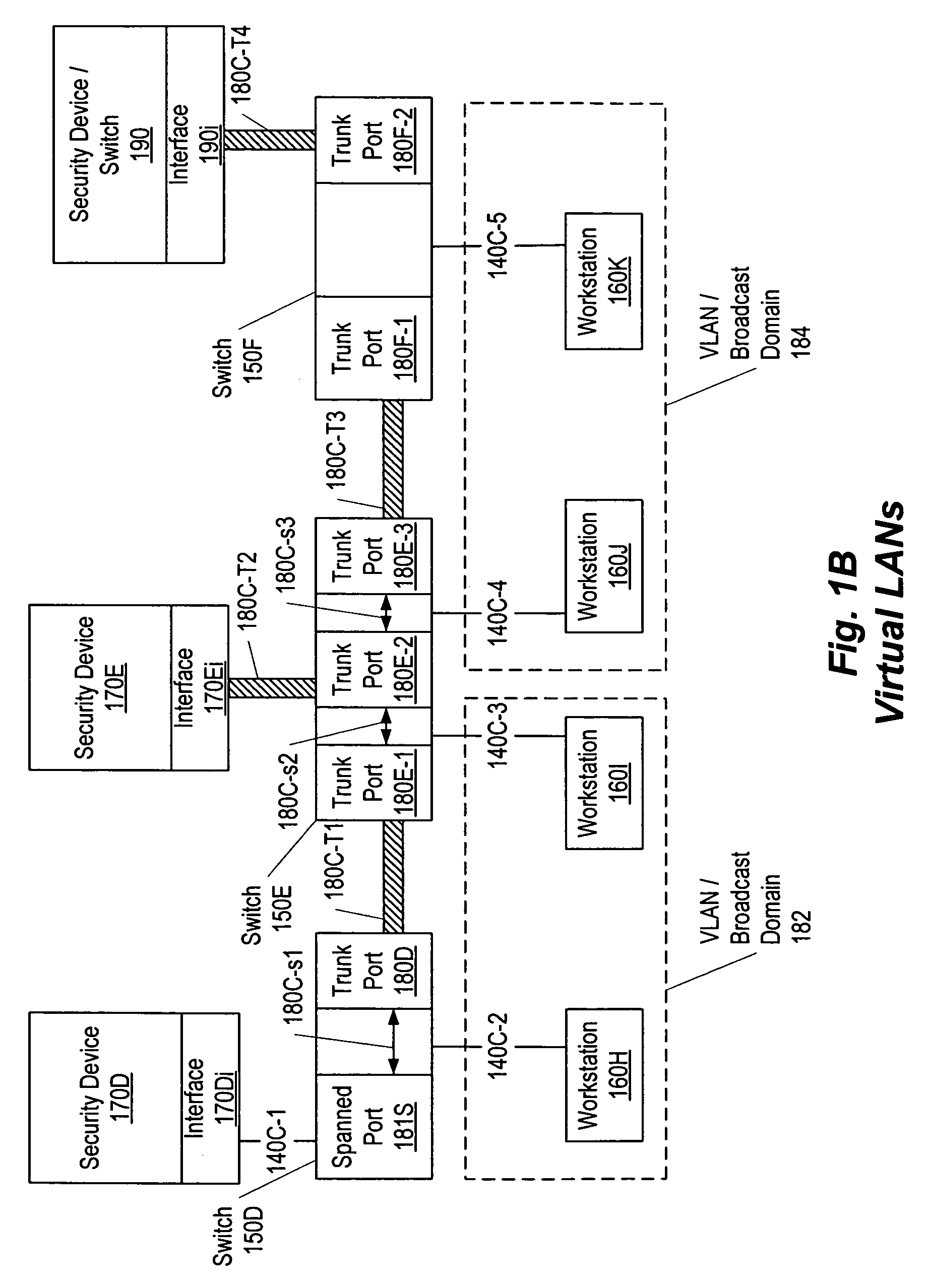
ActiveUS7596808B1Minimize overheadAvoid spreadingMemory loss protectionError detection/correctionBroadcast domainComputer science
A method, system, apparatus, and computer-readable medium to enable a set of security device interfaces within a broadcast domain to identify and mitigate attacks. For each address of a device communicating within the broadcast domain, a responsible interface is determined by a zero hop ownership determination algorithm. The algorithm operates by counting a respective number of replies observed by each of multiple interfaces. Each reply is made in response to a respective request for one address. A responsible interface is assigned to the one address using the respective number of replies observed by each respective interface. The algorithm approximates the security device interface physically closest to the address in question without querying the switches themselves and without requiring the security device interface to be in-line on the network.
Owner:SYSXNET
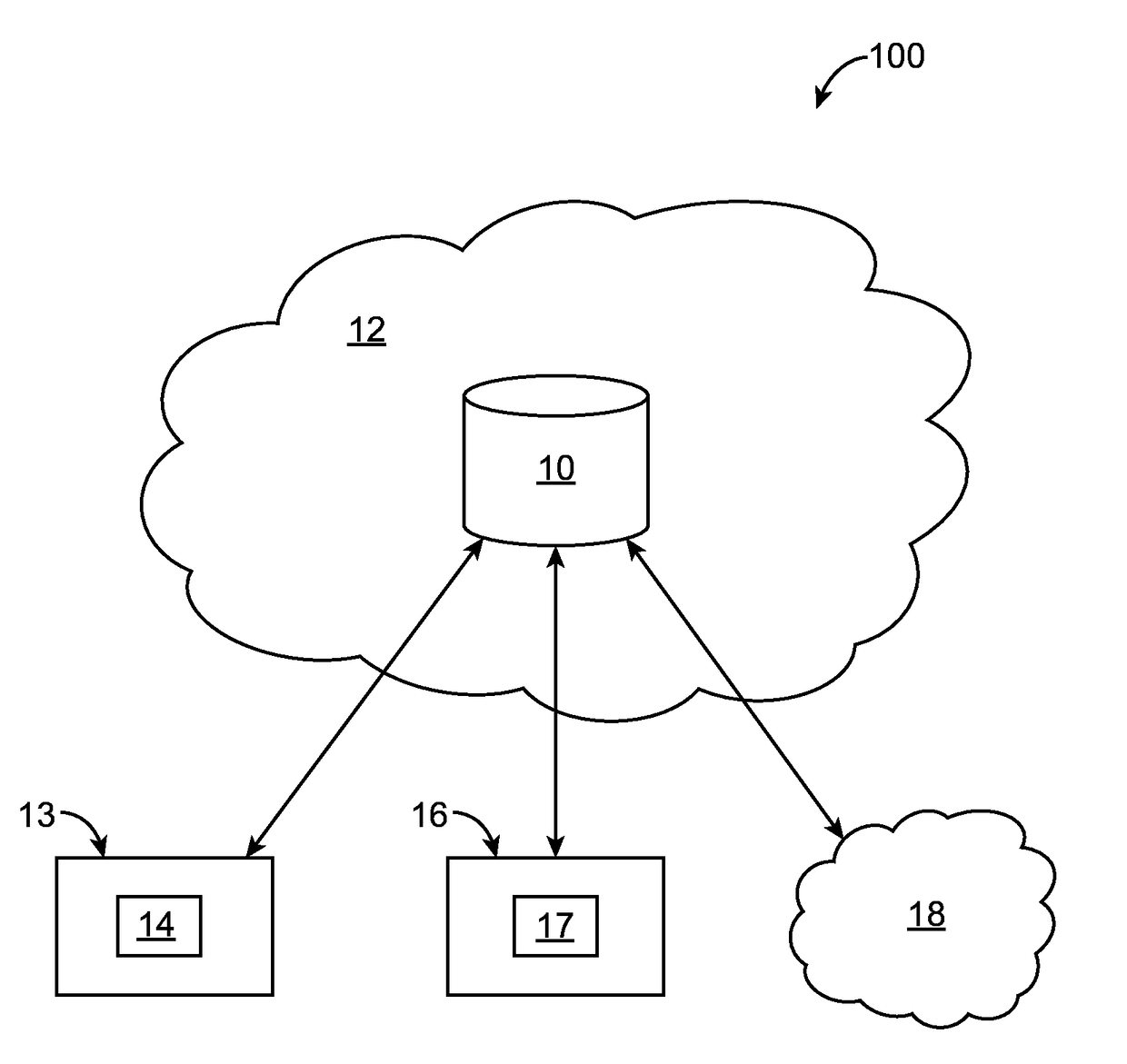
Systems and methods for detecting and preventing cyber-threats
A system (100) for detecting and preventing cyber-threats is disclosed. The system (100) can include an online-analytical-processing (OLAP) resource (102) coupled to a data mining engine (104), a reporting resource (106) and a processor (108). The processor (108) can run instructions stored within an extract-transform-load (ETL) module (112). The ETL module (112) can enable the processor (108) to extract one or more data tuples various data sources (110). The ETL module (112) can enable the processor to transform the extracted tuple(s).
Owner:ZENOPZ LLC
Method and system for data breach and malware detection
Detecting cyber threat and malware, particularly zero-day malware is a major challenge for the security community. Signature-based methods of cyber threat and malware detection are unable to detect zero-day malware. In order to detect zero-day malware and cyber threat which may have more severe impacts, a system called Compromised Detection System (CDS) and a method thereof is disclosed. The CDS uses a sophisticated approach and method based on Machine Learning to detect anomalies on the network behaviour. By such approach, CDS is able to detect unknown cyber threat and malware (aka zero day)since they will present a deviation from the normal behaviour in the network.
Owner:EFFICIENT PROTECTIONS INC
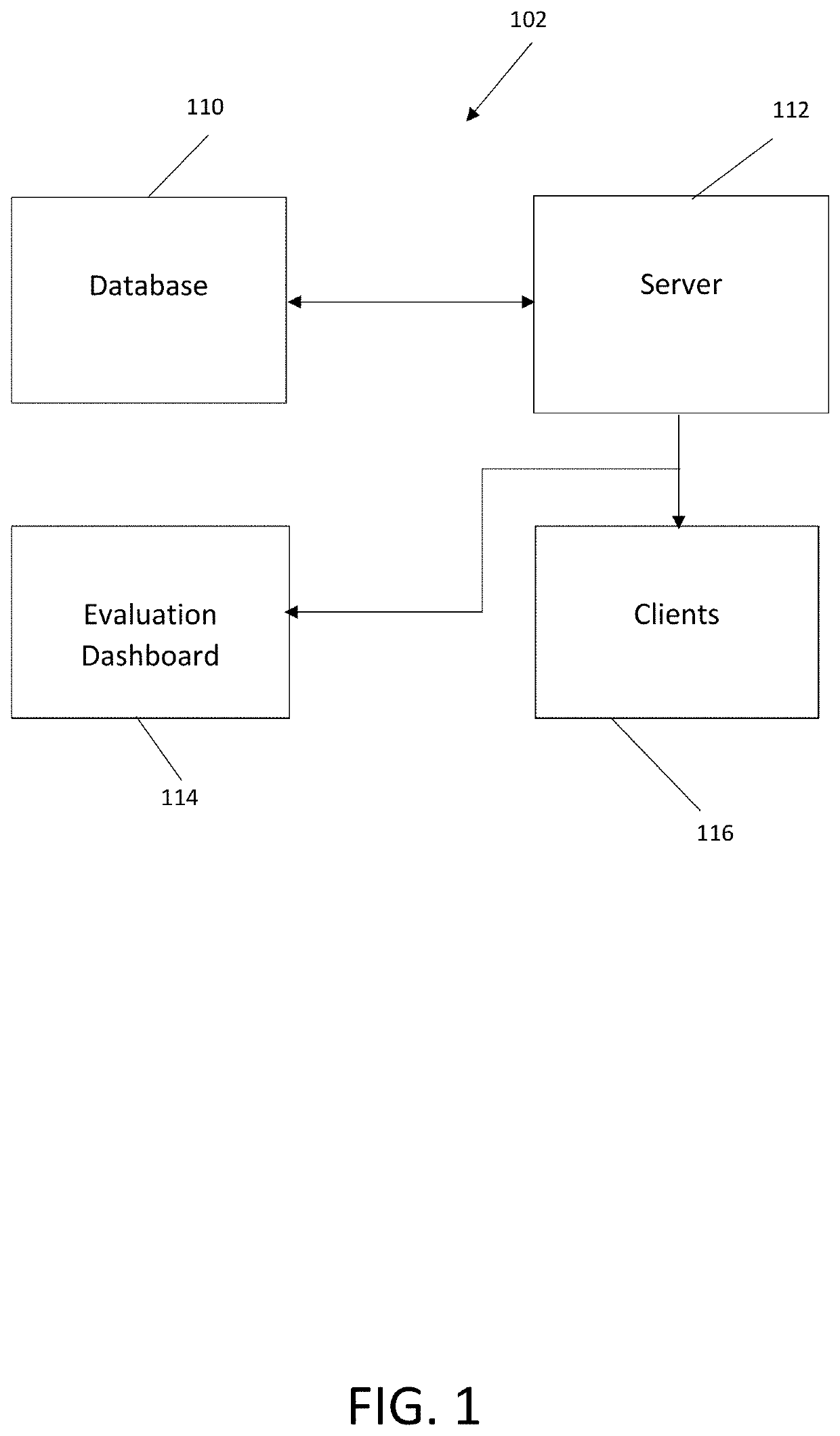
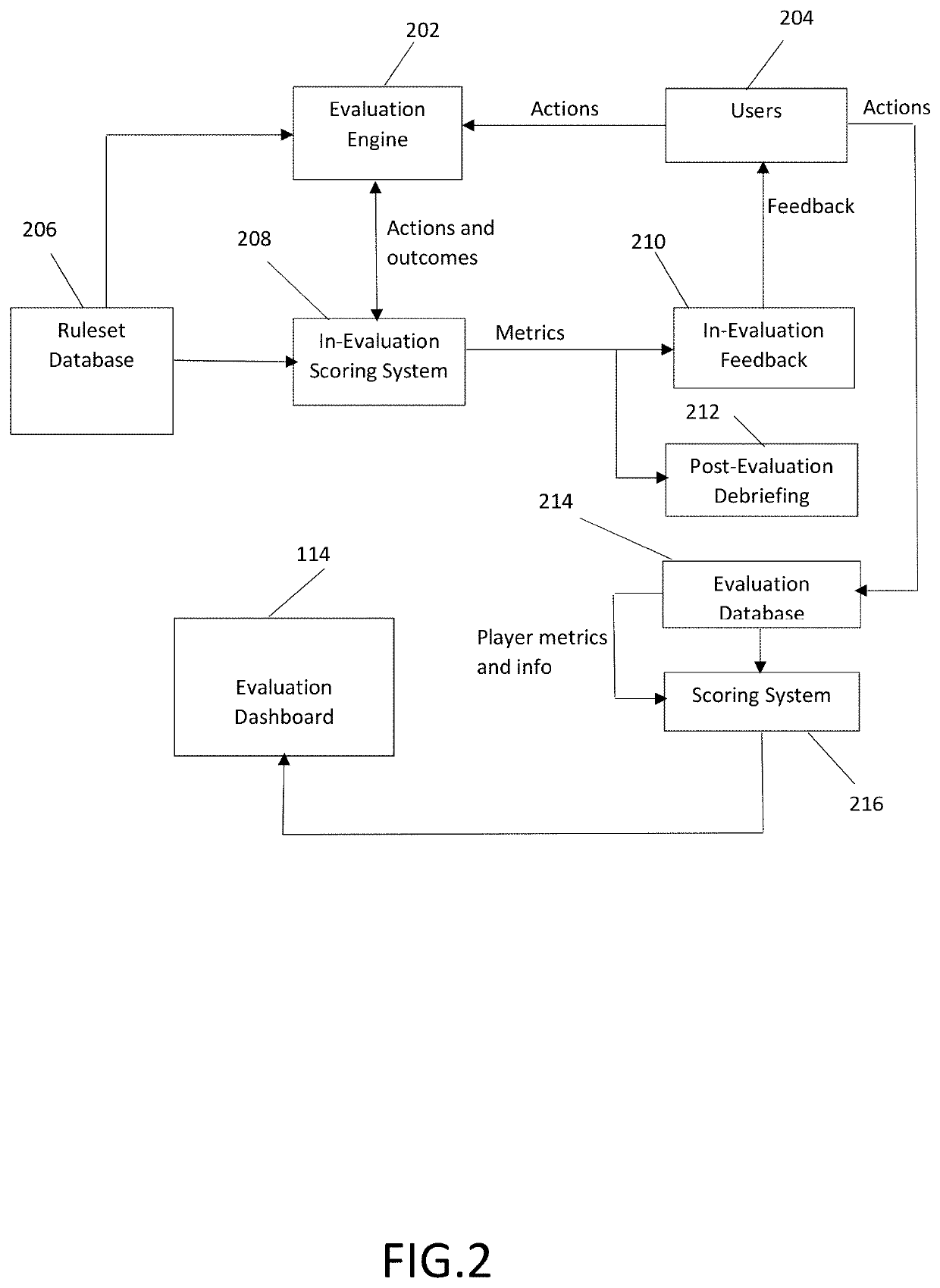
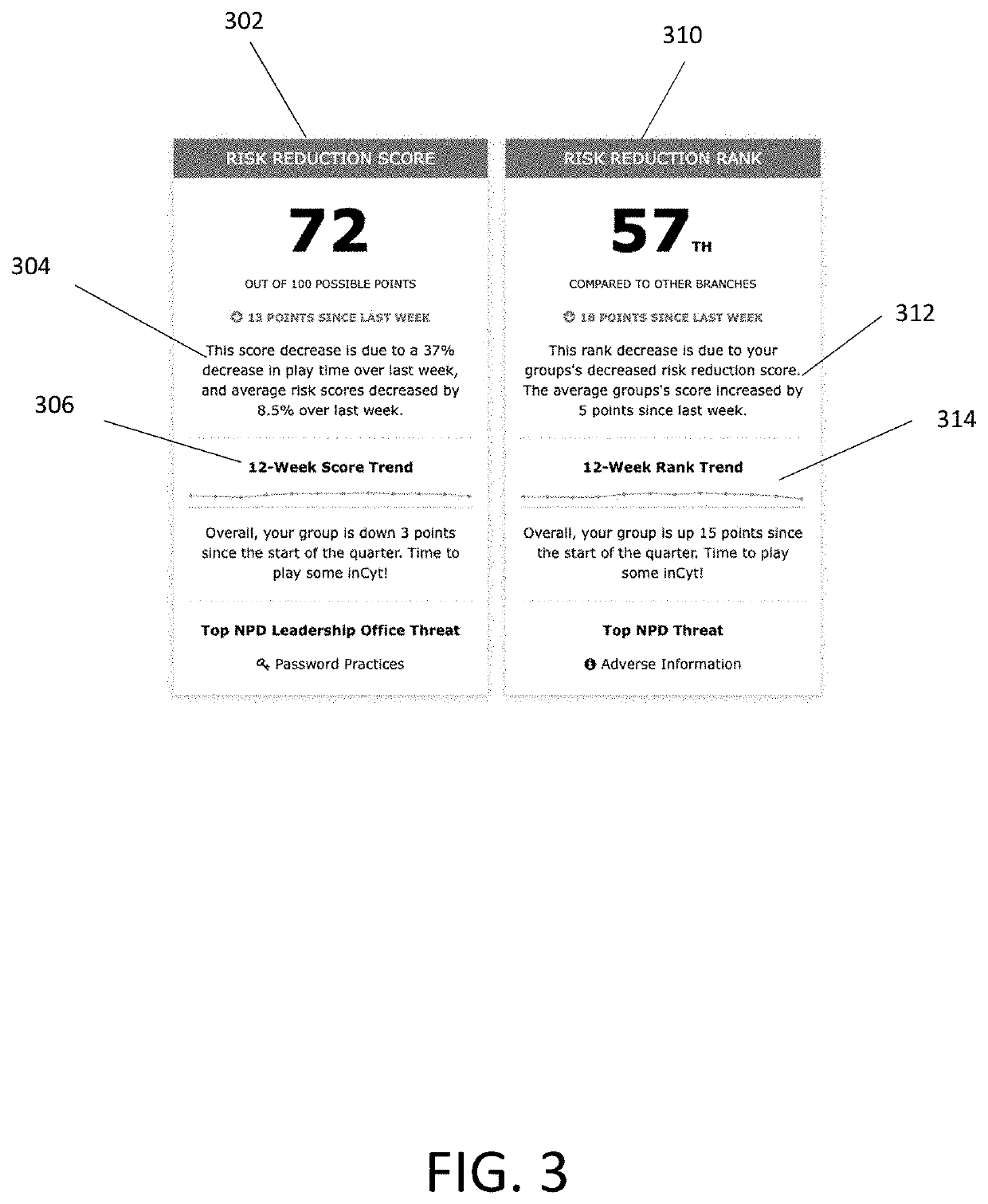
Method and system for evaluating individual and group cyber threat awareness
A system has an evaluation server that includes at least one database storing a plurality of cybersecurity awareness evaluations, the database connected to the server, a plurality of clients connected to the server and configured to run at least one of the cybersecurity awareness evaluations for play by users on user devices, the users performing actions in the evaluation including offensive actions and defensive actions, and an evaluation dashboard including an interface configured to display scoring results of the cybersecurity awareness evaluations as determined by the server, the scoring results including a plurality of offensive component scores for at least one of the users, a plurality of defensive component scores for at least one of the users, at least one composite offensive score for at least one of the users and at least one composite defensive score for at least one of the users, the composite offensive score being determined based on a plurality of the component offensive scores and the composite defensive score being determined based on a plurality of the component defensive scores.
Owner:CIRCADENCE
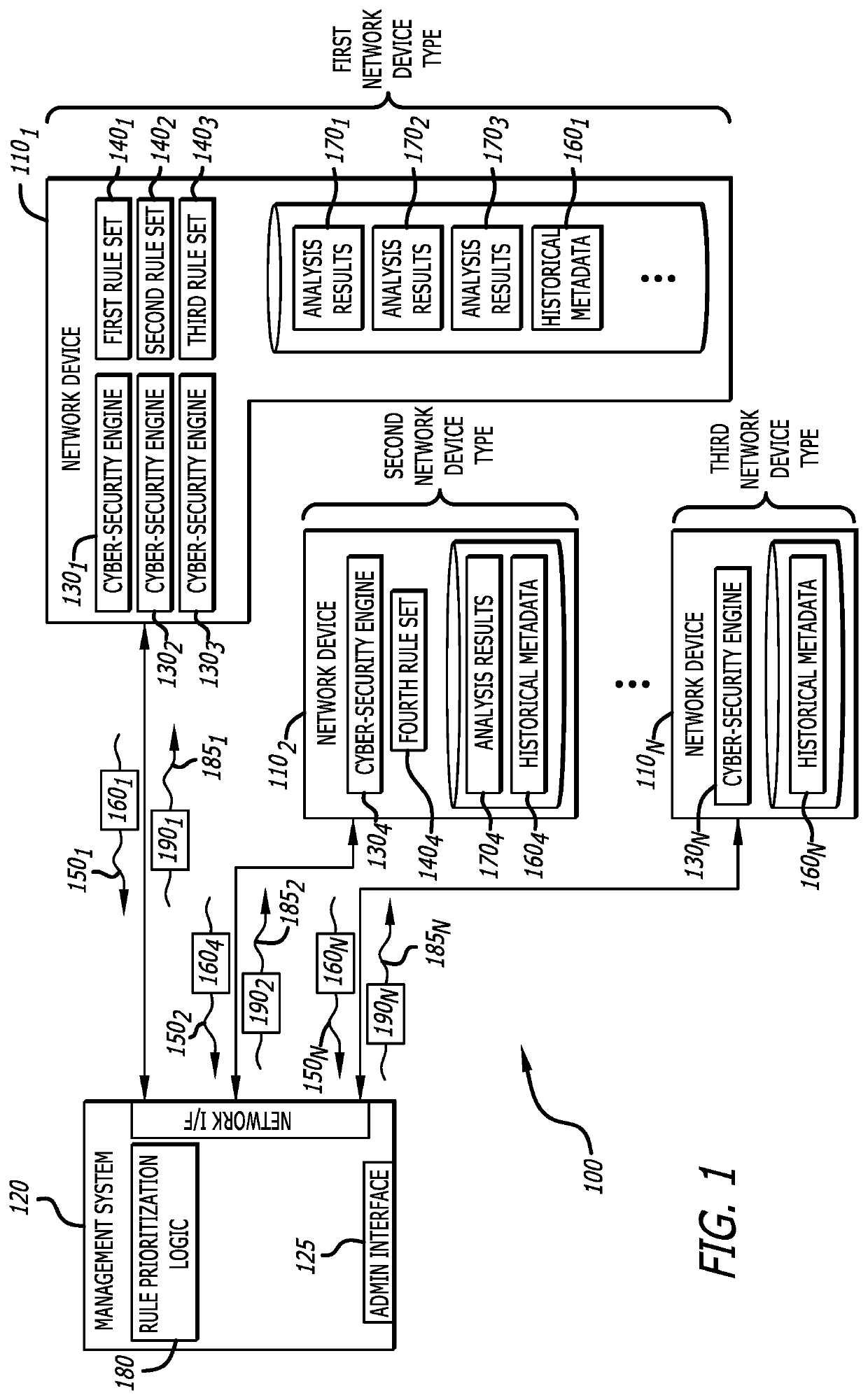
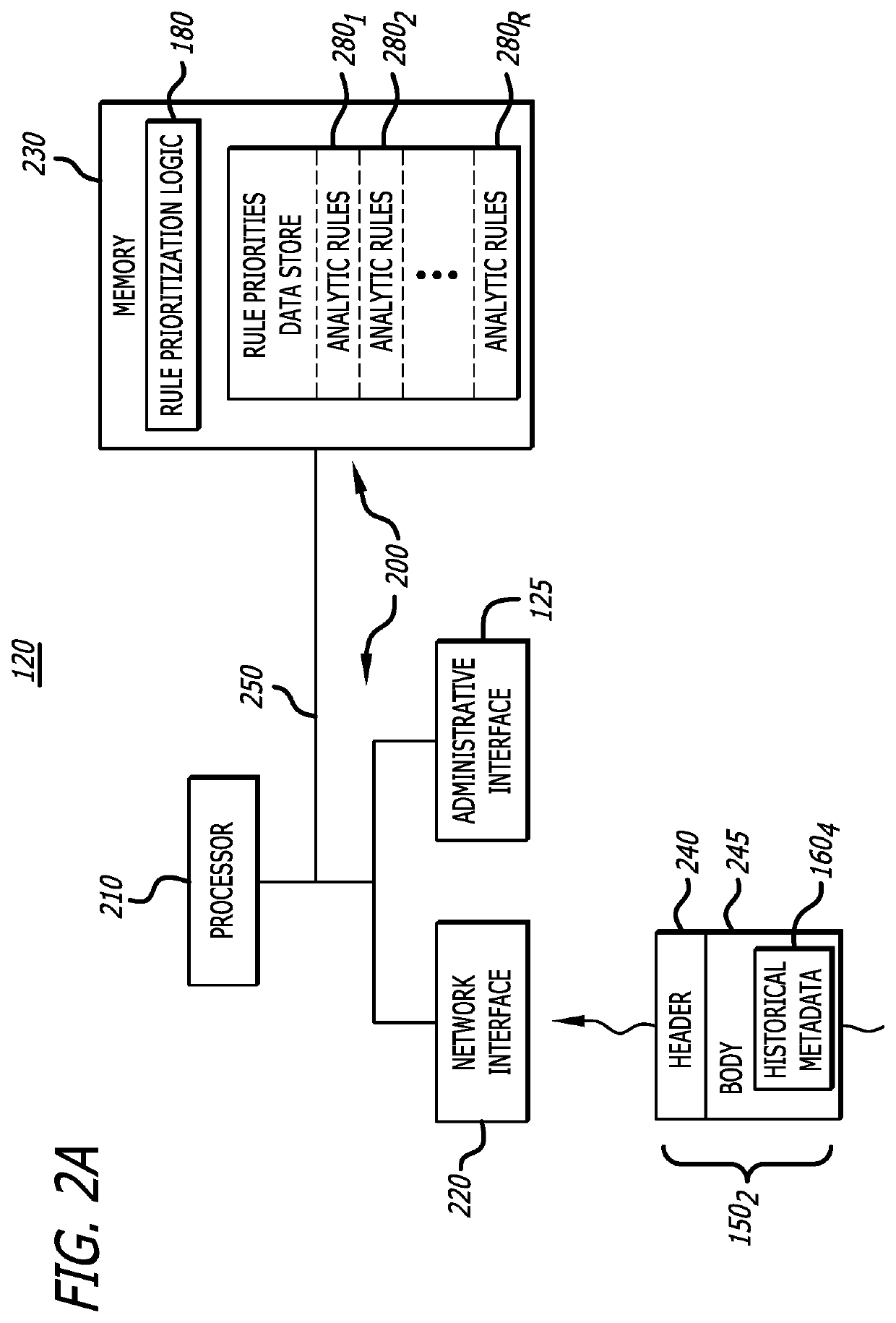
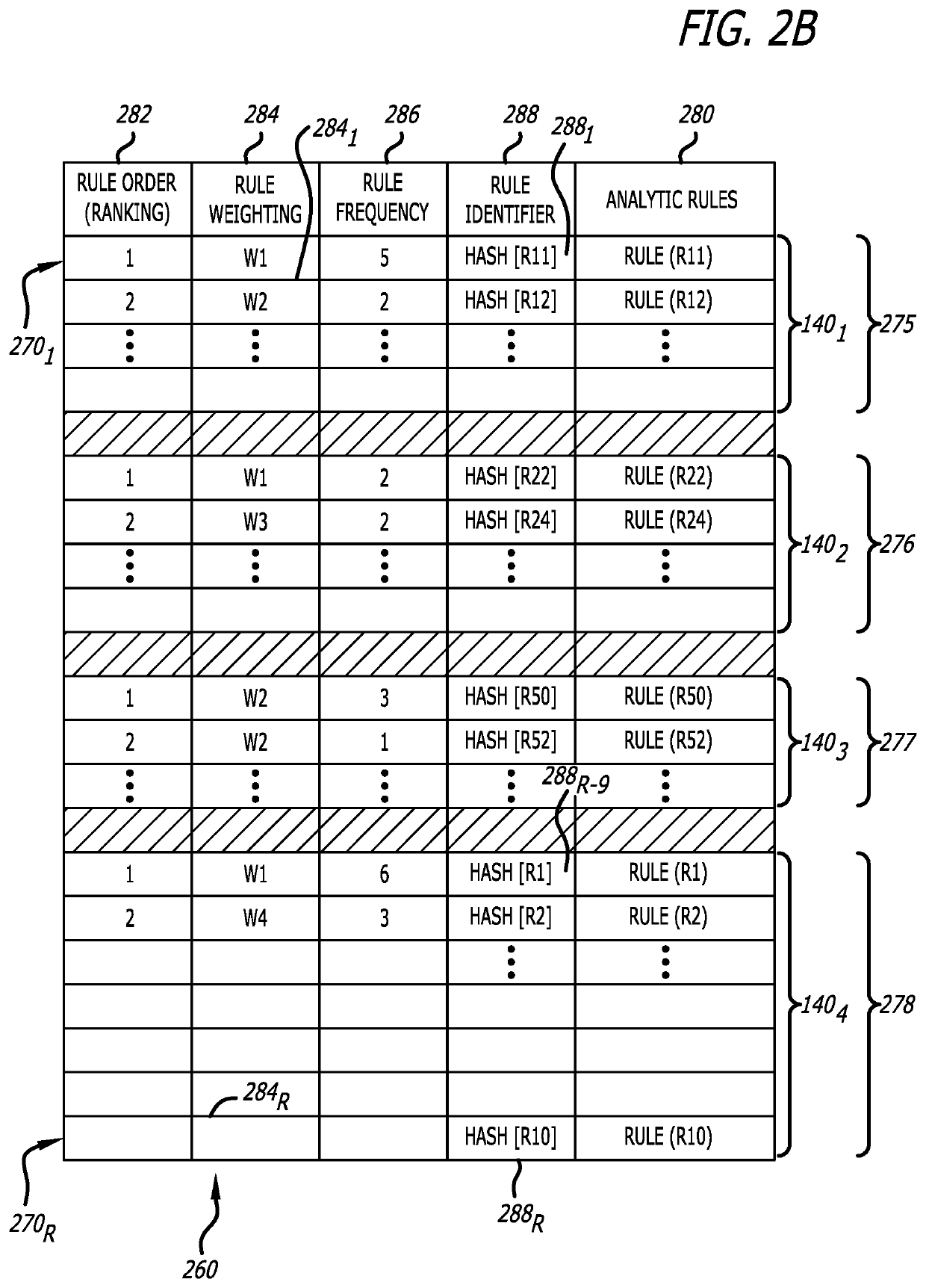
System and method for automatically prioritizing rules for cyber-threat detection and mitigation
A system and computerized method for generating an improved cyber-security rule ordering for cyber-security threat detection or post-processing activities conducted by a rules-based cyber-security engine deployed within a network device is described. Herein, historical metadata associated with analytics conducted on incoming data by a rule-based cyber-security engine and in accordance with a plurality of rules is described. These rules are arranged in a first ordered rule sequence. The historical metadata is analyzed to determine one or more salient rules from the plurality of rules. The plurality of rules are reprioritized by at least rearranging an order to a second ordered rule sequence with the one or more salient rules being positioned toward a start of the second ordered rule sequence. Thereafter, the rule-based cyber-security engine operates in accordance with the reprioritized rule set that is arranged in the second ordered rule sequence to achieve improved performance.
Owner:FIREEYE SECURITY HLDG US LLC
Model based methodology for translating high-level cyber threat descriptions into system-specific actionable defense tactics
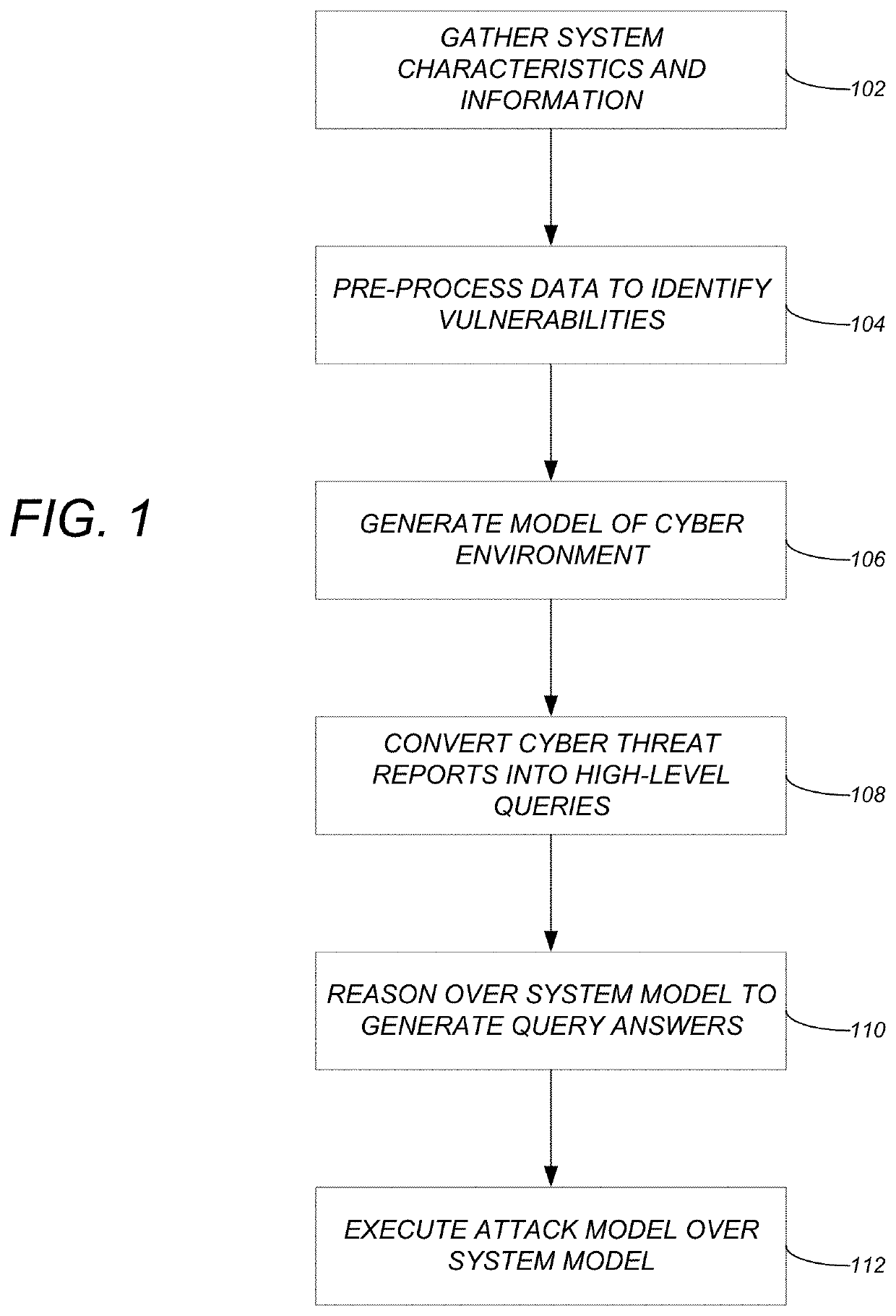
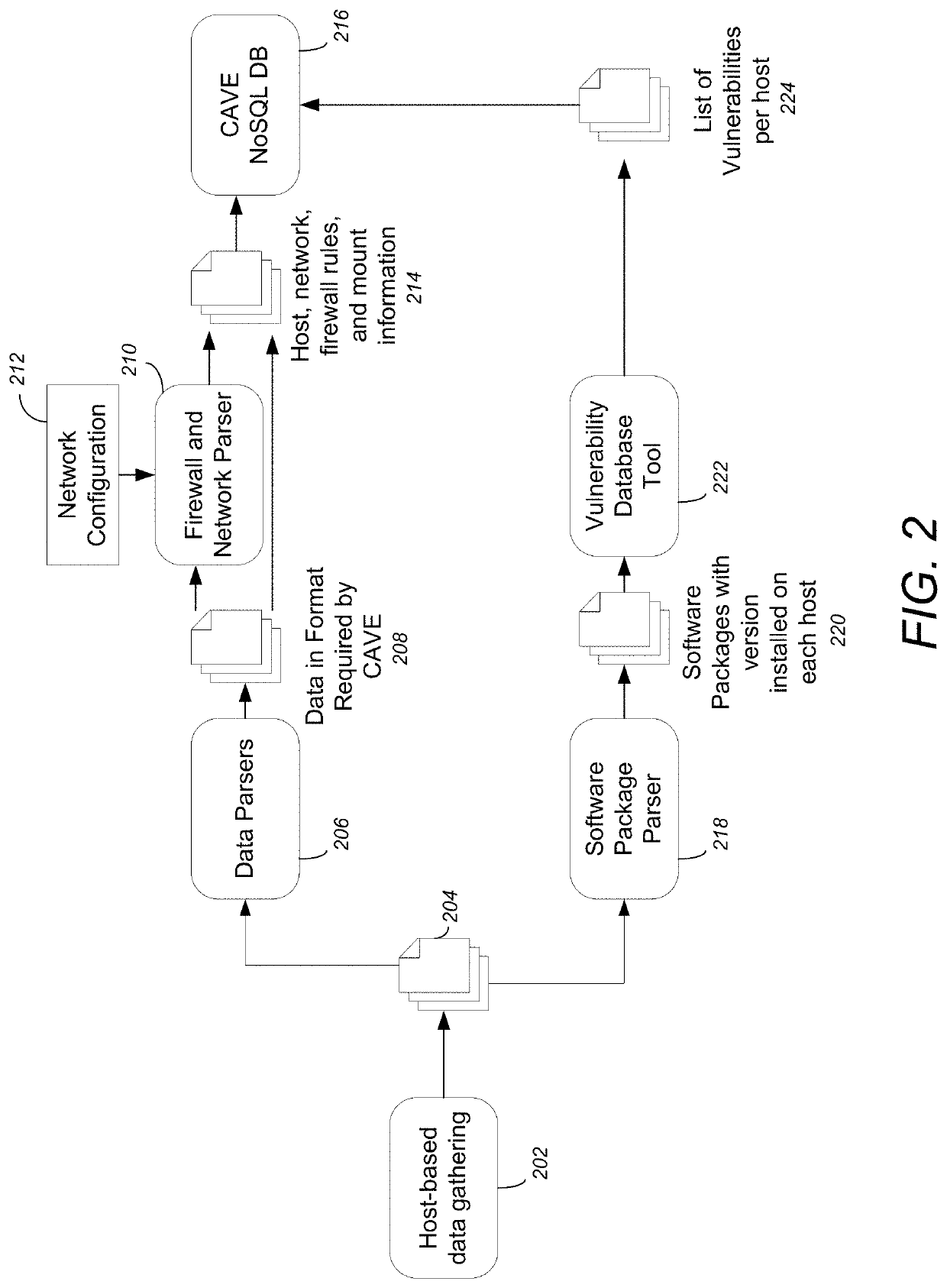
ActiveUS20200067962A1Digital data information retrievalComputer security arrangementsCyber-attackAttack model
A method, apparatus, and system provide the ability to act on cyber risks and reduce cyber attacks. System characteristics and system information for a cyber system are gathered. The system characteristics and system information are pre-processed to identify vulnerabilities that are relevant to the cyber system. A system model of a cyber environment is generated for the cyber system. One or more features are converted from cyber threat reports to one or more semantically relevant queries over the system model. The system model is reasoned over to generate one or more answers relevant to the one or more semantically relevant queries. Attack models are executed over the system model to generate actionable intelligence and reduce cyber attacks.
Owner:CALIFORNIA INST OF TECH
Network threat collaborative defense system and method based on information sharing
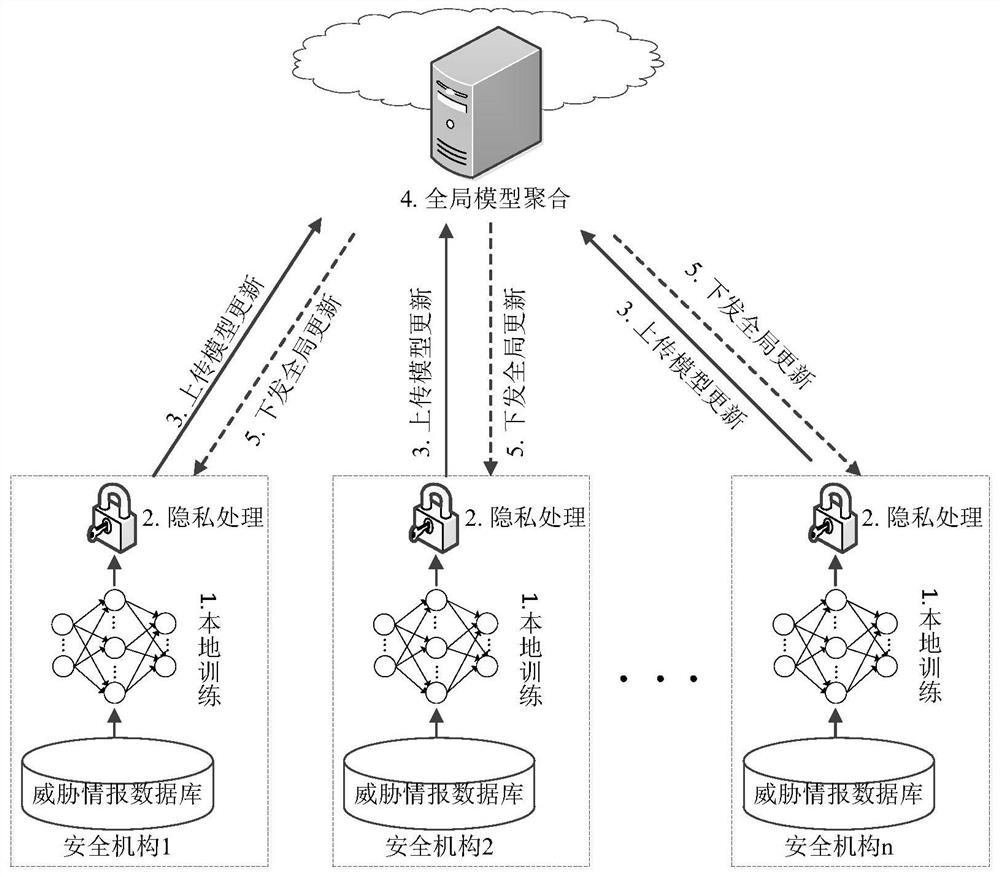
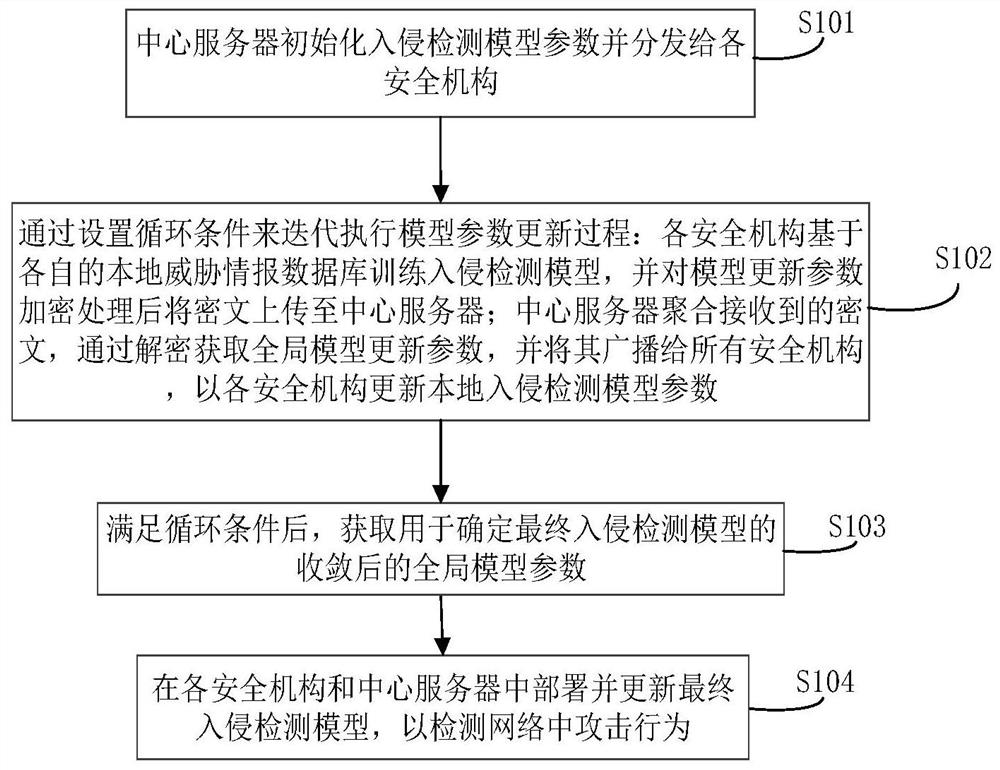
ActiveCN112217626AImprove training efficiencyEfficient sharingKey distribution for secure communicationCommunication with homomorphic encryptionCiphertextAttack
The invention belongs to the technical field of network security, and particularly relates to a network threat cooperative defense system and method based on information sharing. The method comprisesthe steps: deploying a central server and a plurality of safety mechanisms which train an intrusion detection model based on respective local threat information databases; after the model updating parameters are encrypted, uploading the ciphertext to a central server; and employing the central server for aggregating the received ciphertext to obtain global model updating parameters through decryption and broadcasting the global model updating parameters to all security mechanisms so as to update the local intrusion detection model of each security mechanism. Based on the federated learning framework, multiple security mechanisms can be helped to jointly establish a system defense model, the method can be suitable for multiple machine learning models, multiple collusion attack scenes can beresisted, the applicability is high, and the anti-attack performance of the network is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
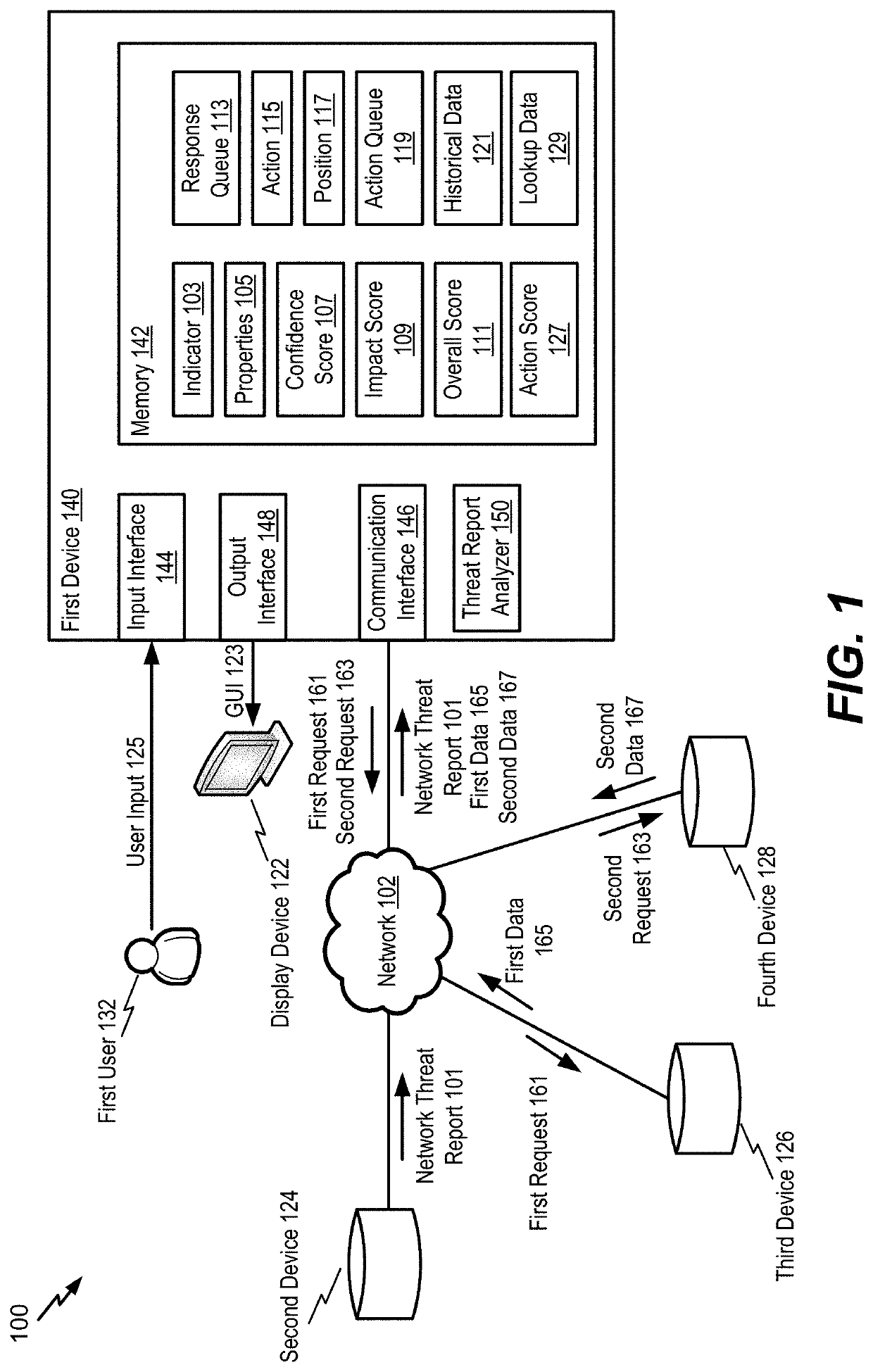
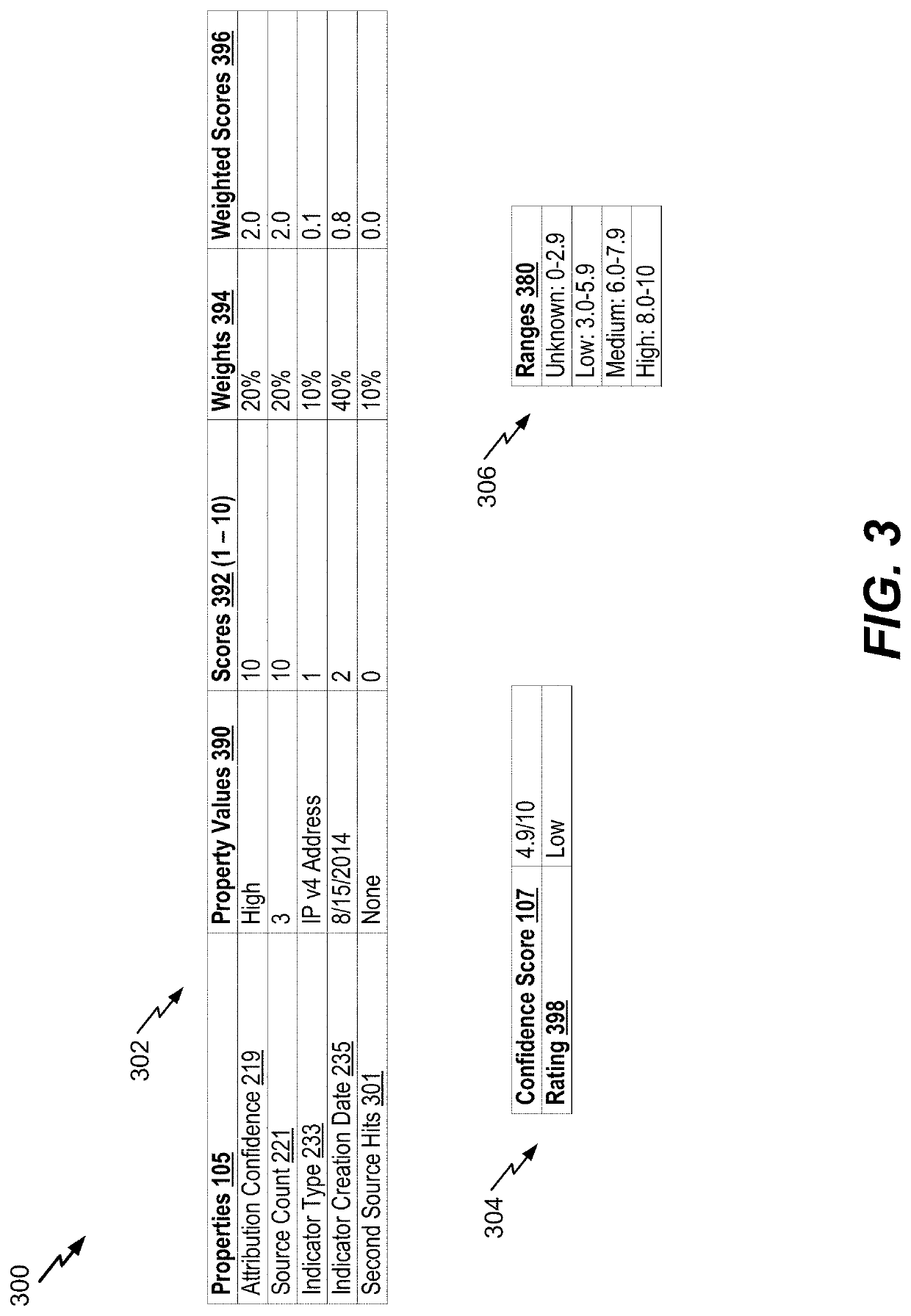
Network threat indicator extraction and response
A device includes a communication interface and a processor. The communication interface is configured to receive a network threat report. The processor is configured to extract an indicator from the network threat report. The indicator is reported to be associated with a network threat. The processor is also configured to determine, based on the indicator, a confidence score indicating a likelihood that the indicator is associated with malicious activity. The processor is further configured to determine, based on the indicator, an impact score indicating a potential severity of the malicious activity. The processor is further configured to identify, based on the indicator, the confidence score, and the impact score, an action to be performed. The action includes blocking network traffic corresponding to the indicator or monitoring network traffic corresponding to the indicator. The processor is also configured to initiate performance of the action.
Owner:THE BOEING CO
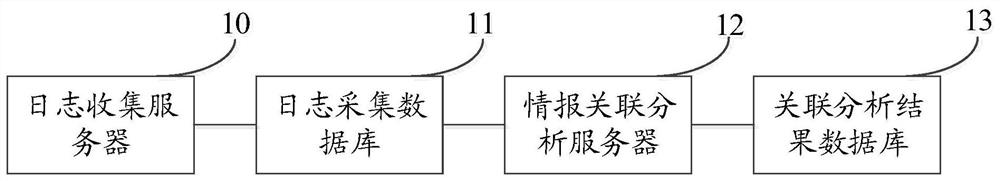
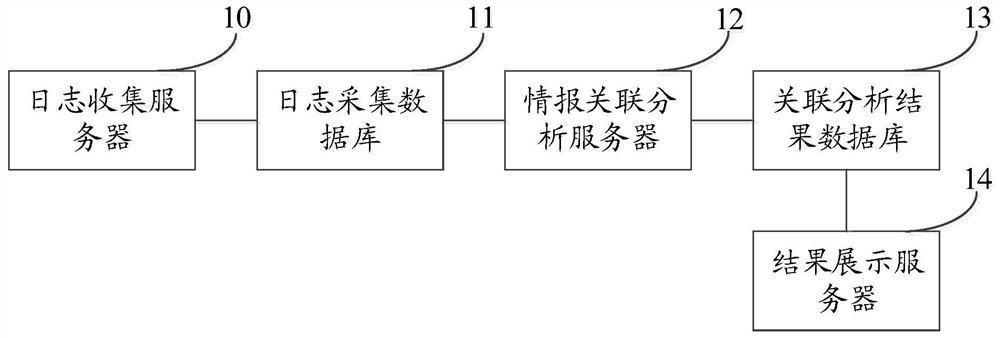
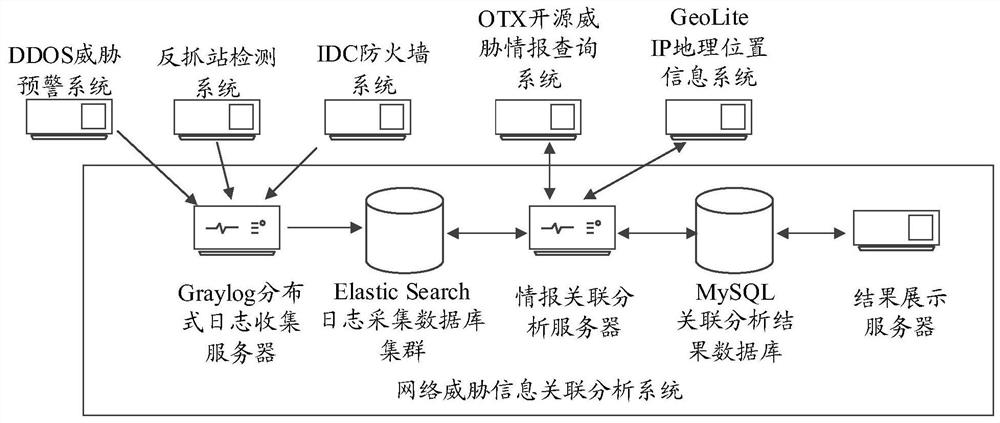
Network threat information association system and method
The embodiment of the invention provides a network threat information association analysis system and method. The system comprises a log collection server, a log collection database, an intelligence association analysis server and an association analysis result database, the log collection server collects threat information logs from the threat information monitoring systems in a preset data collection mode and records the threat information logs in a log collection database according to a preset data format; the threat information log comprises an IP address; and the information associationanalysis server acquires the threat description information of each IP address from the open source threat information query system, merges the threat description information with the threat information log containing the same IP address in the log acquisition database, obtains an association analysis result corresponding to each IP address, and stores the association analysis result in the association analysis result database. Through the embodiment of the invention, rapid association analysis of various kinds of network threat information is realized, the threat information is effectively aggregated, and powerful threat analysis is rapidly formed.
Owner:新浪技术(中国)有限公司
Profiling cyber threats detected in a target environment and automatically generating one or more rule bases for an expert system usable to profile cyber threats detected in a target environment
InactiveUS9503472B2Efficiently presentedEasy to identifyError detection/correctionFuzzy logic based systemsSecurity information and event managementSecurity information
A computer implemented method of profiling cyber threats detected in a target environment, comprising: receiving, from a Security Information and Event Manager (SIEM) monitoring the target environment, alerts triggered by a detected potential cyber threat, and, for each alert: retrieving captured packet data related to the alert; extracting data pertaining to a set of attributes from captured packet data triggering the alert; applying fuzzy logic to data pertaining to one or more of the attributes to determine values for one or more output variables indicative of a level of an aspect of risk attributable to the cyber threat.
Owner:CYBERLYTIC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com