Patents
Literature
428 results about "Threat intelligence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Threat intelligence is the analysis of internal and external threats to an organization in a systematic way. The treats that threat intelligence attempts to defend against include zero-day threats, exploits and advanced persistent threats (APTs).
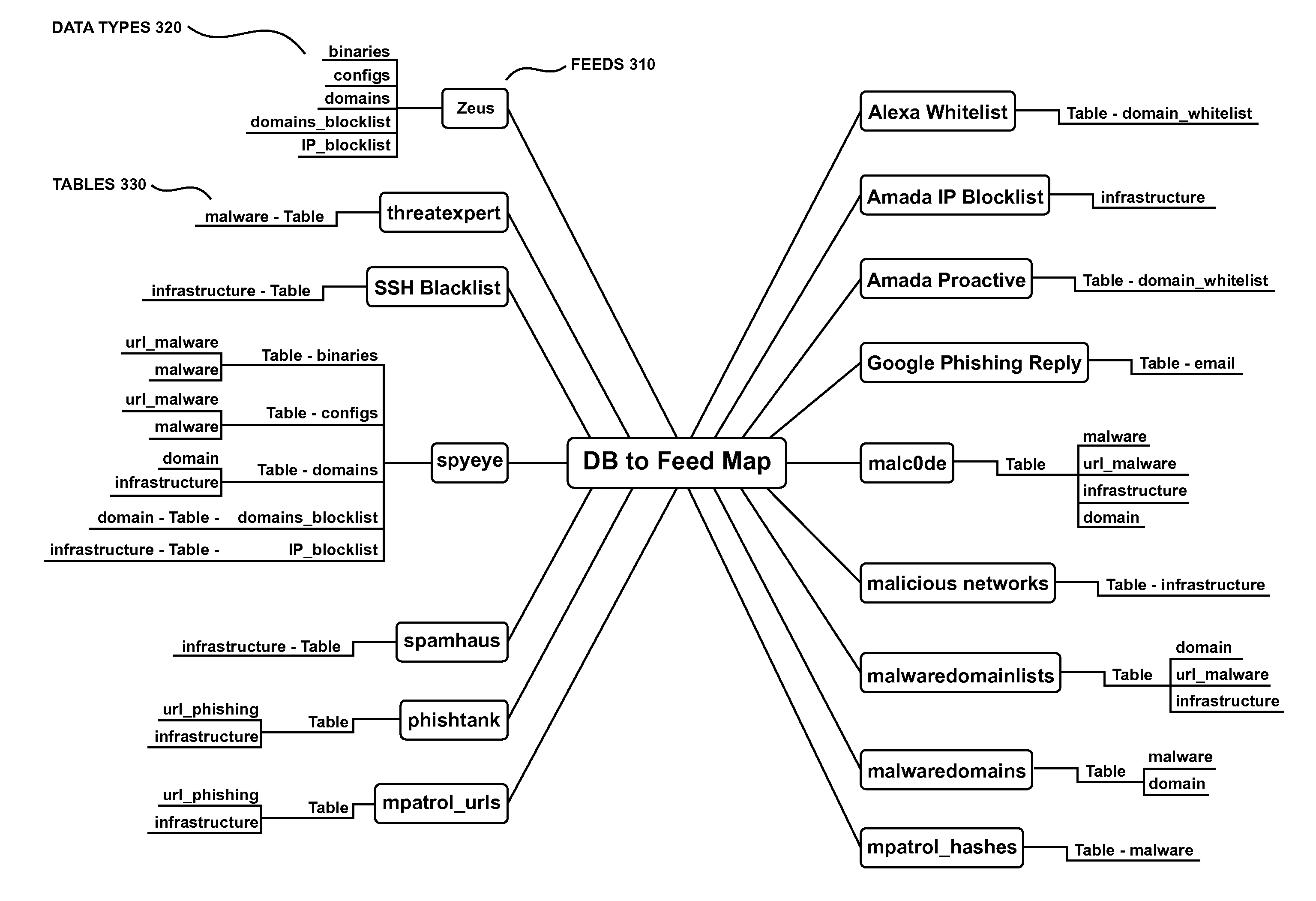
Collective Threat Intelligence Gathering System
ActiveUS20140007238A1Quality improvementImprove information qualityMemory loss protectionError detection/correctionIp addressInformation networks
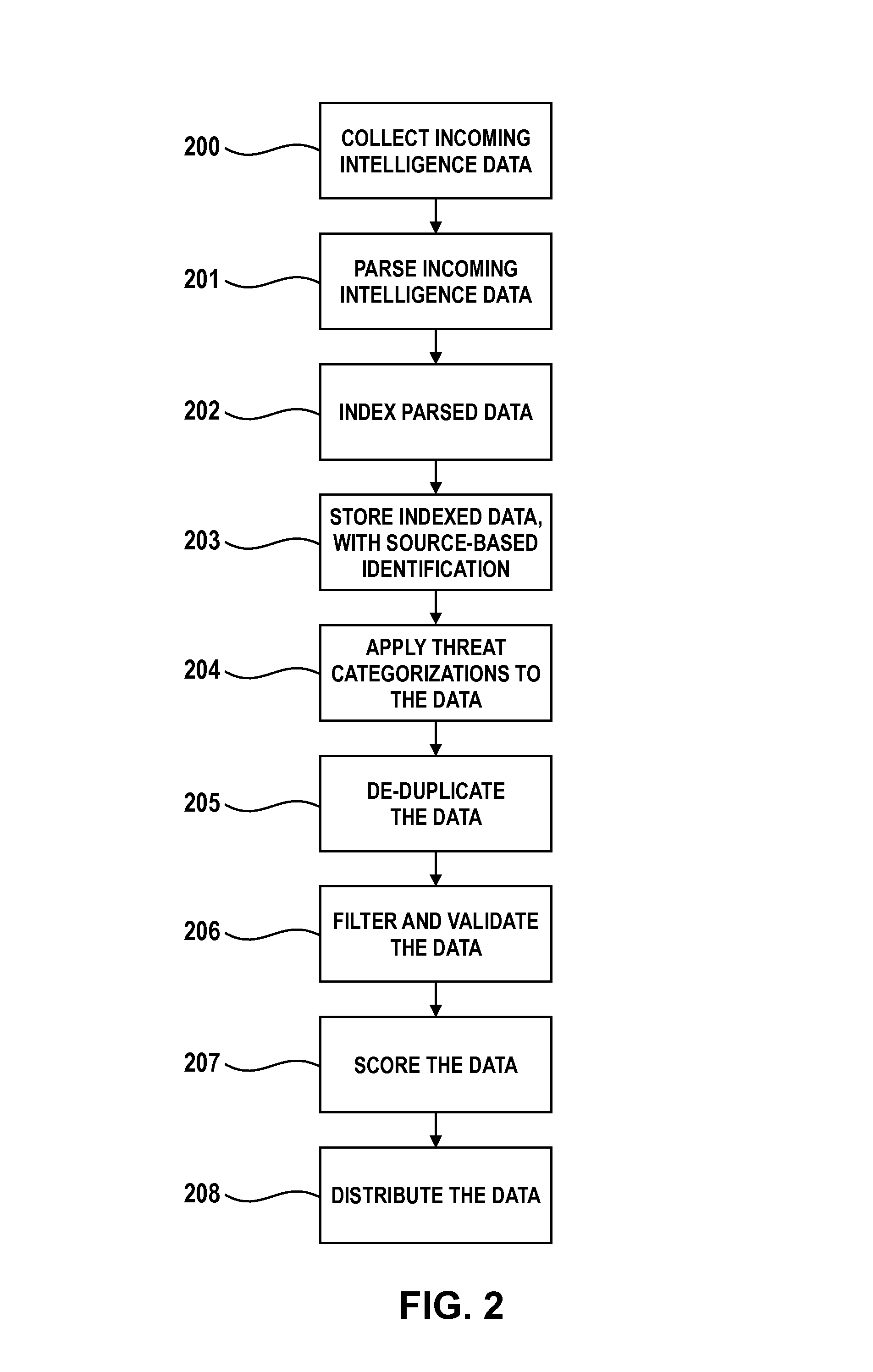
Threat intelligence is collected from a variety of different sources. The threat intelligence information is aggregated, normalized, filtered and scored to identify threats to an information network. Threats are categorized by type, maliciousness and confidence level. Threats are reported to network administrators in a plurality of threat feeds, including for example malicious domains, malicious IP addresses, malicious e-mail addresses, malicious URLs and malicious software files.
Owner:DELOITTE DEV
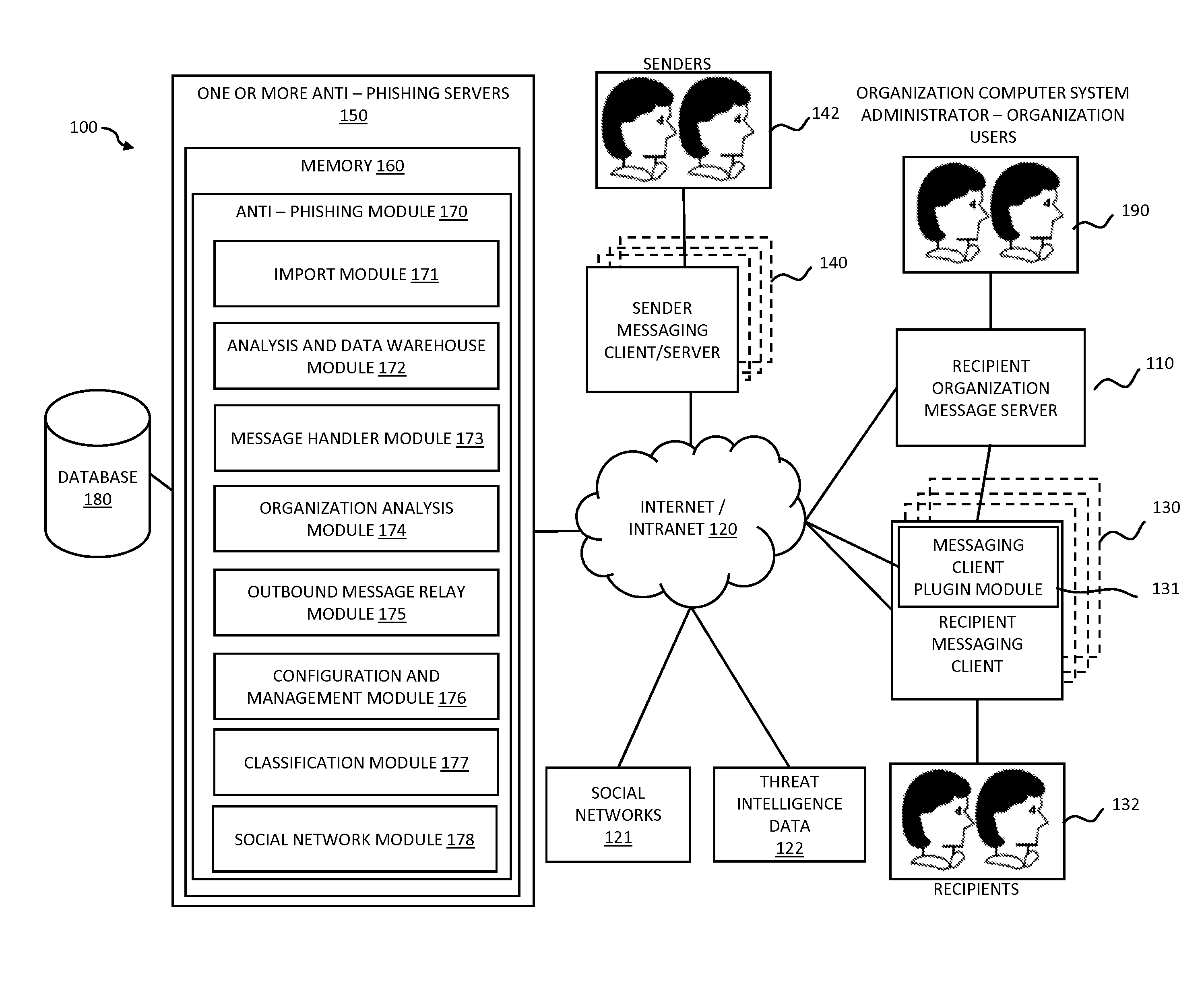
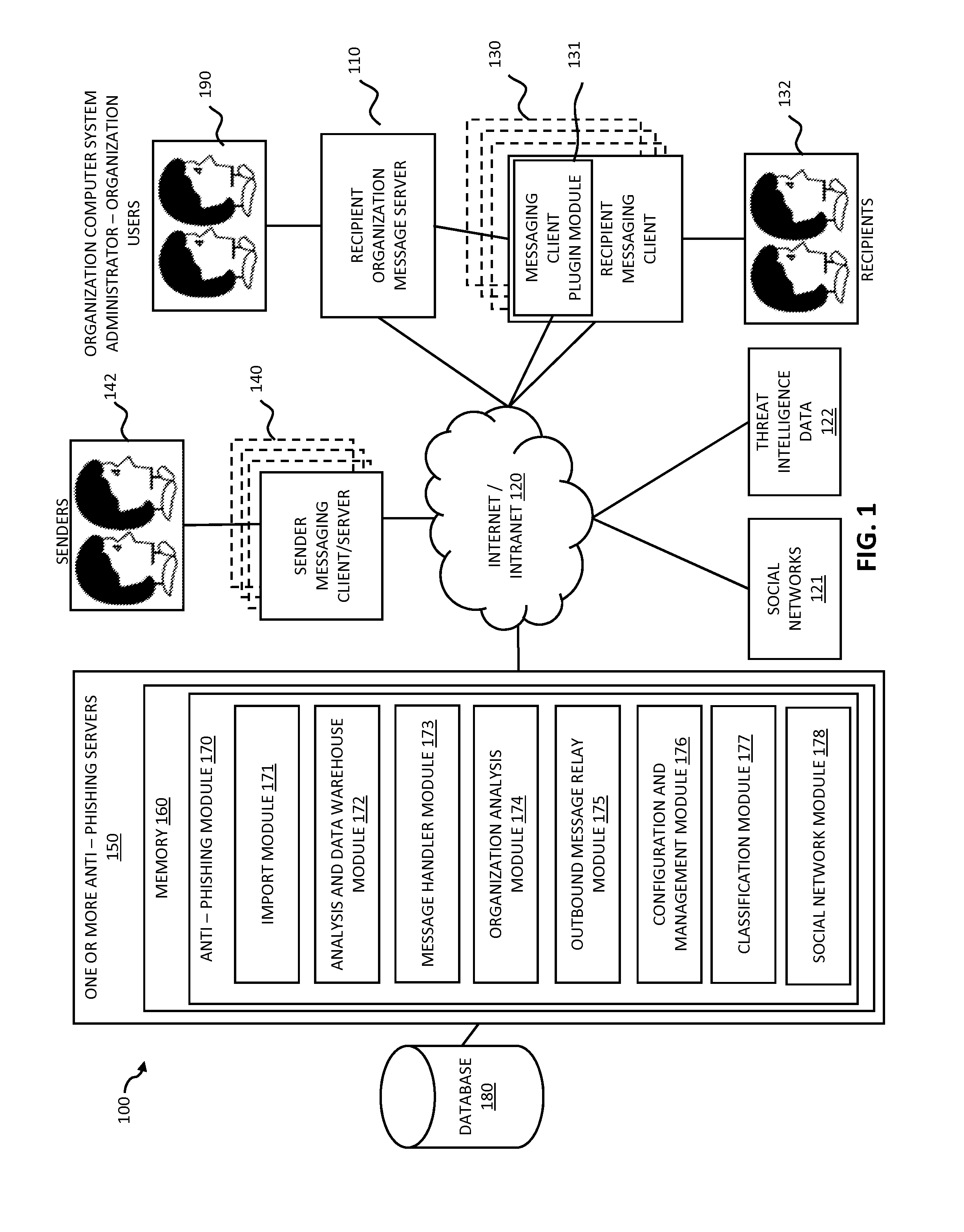
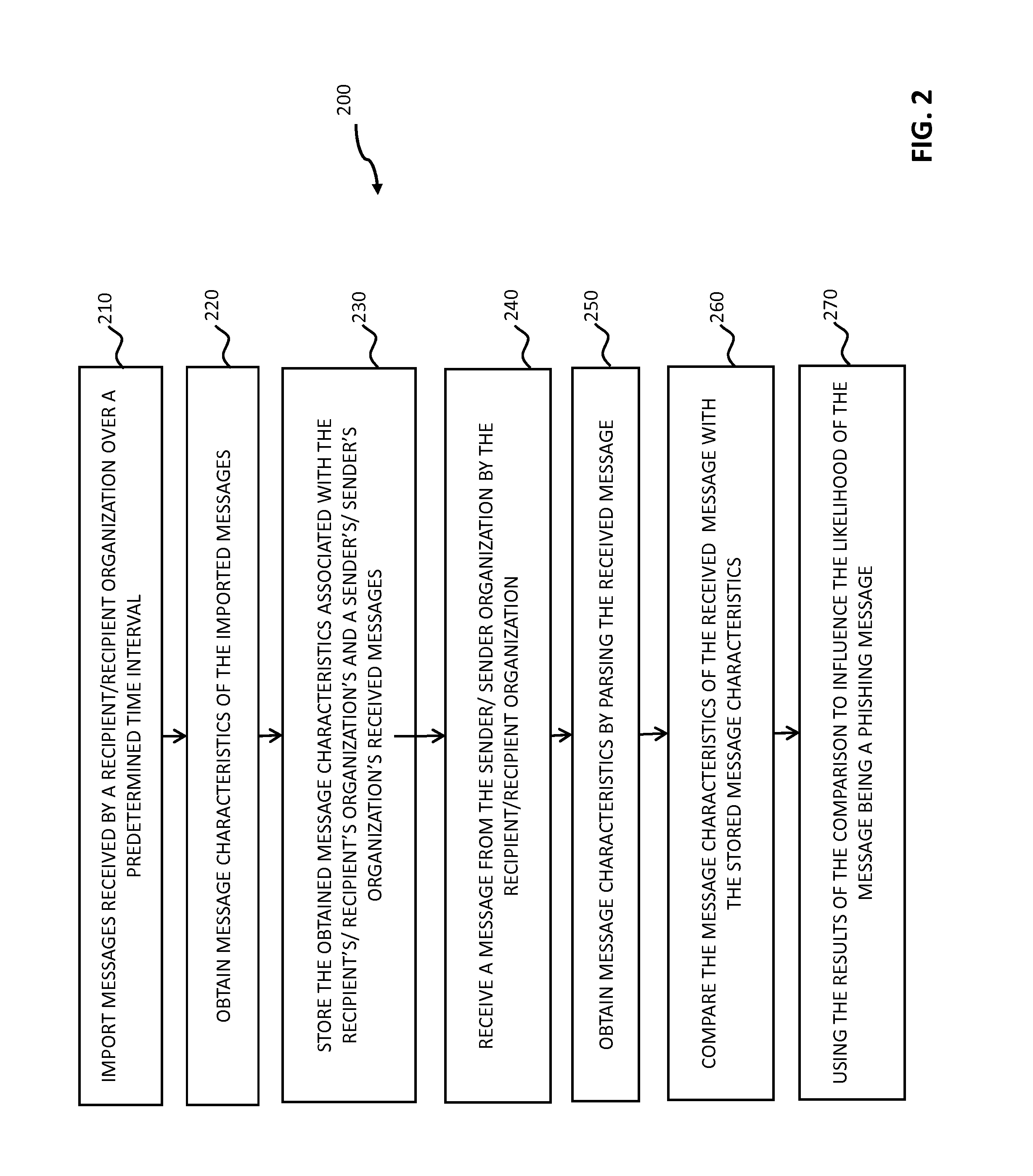
Systems and methods for electronic message analysis
ActiveUS20160014151A1Increase probabilityReduce probabilityMemory loss protectionError detection/correctionPattern matchingBackground information
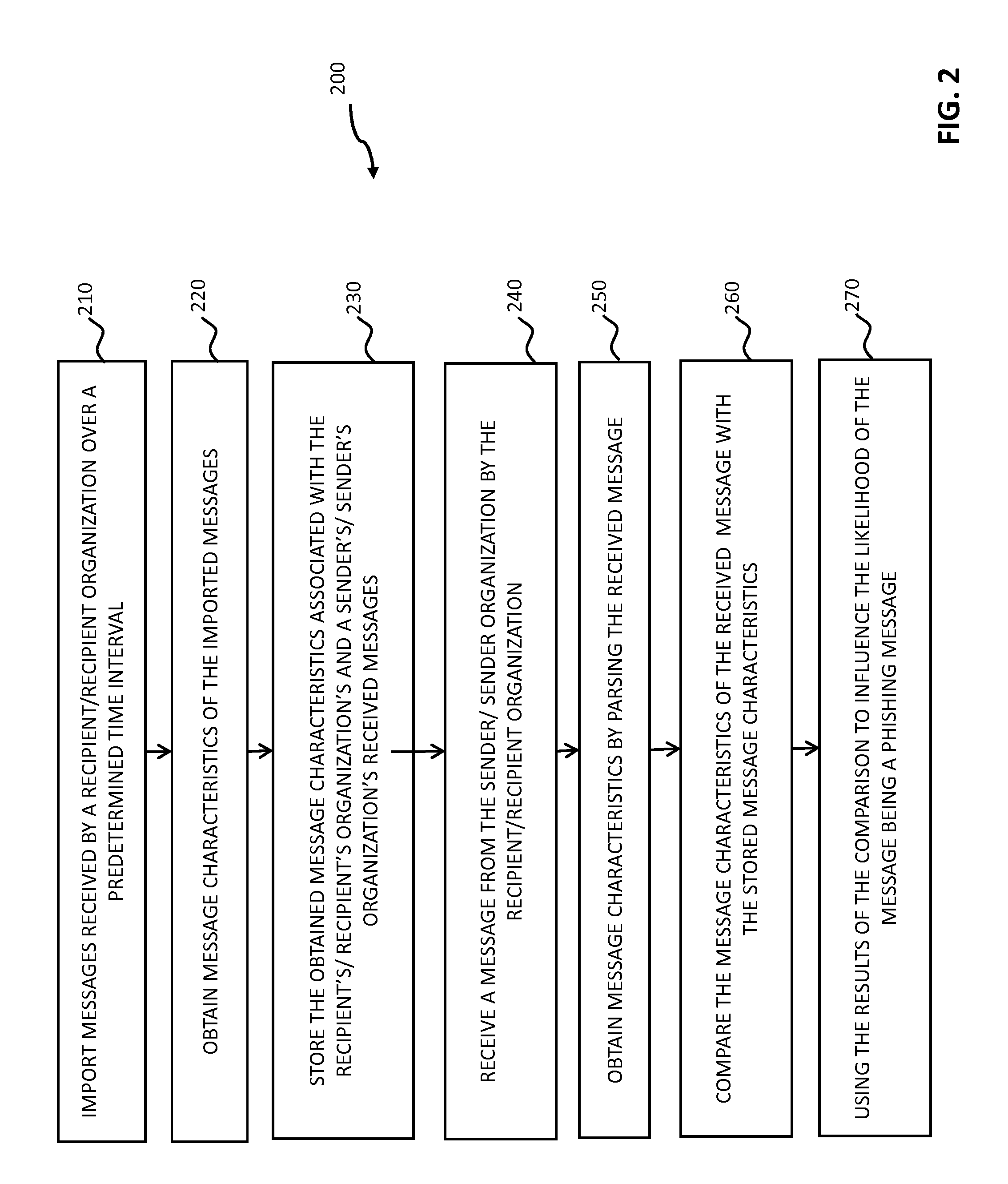
Systems and methods for analyzing electronic messages are disclosed. In some embodiments, the method comprises receiving a new received message from an indicated sender, the new received message having a first message characteristic of the indicated sender and a second message characteristic, identifying an actual sender message characteristic pattern of an actual sender using the first message characteristic, probabilistically comparing the second message characteristic to the actual sender message characteristic pattern, determining a degree of similarity of the second message characteristic to the actual sender message characteristic pattern, and influencing a probability that the indicated sender is the actual sender based upon the degree of similarity. There may be multiple message characteristics and patterns. In some embodiments, the methods may utilize pattern matching techniques, recipient background information, quality measures, threat intelligence data or URL information to help determine whether the new received message is from the actual sender.
Owner:VADE SECURE SAS
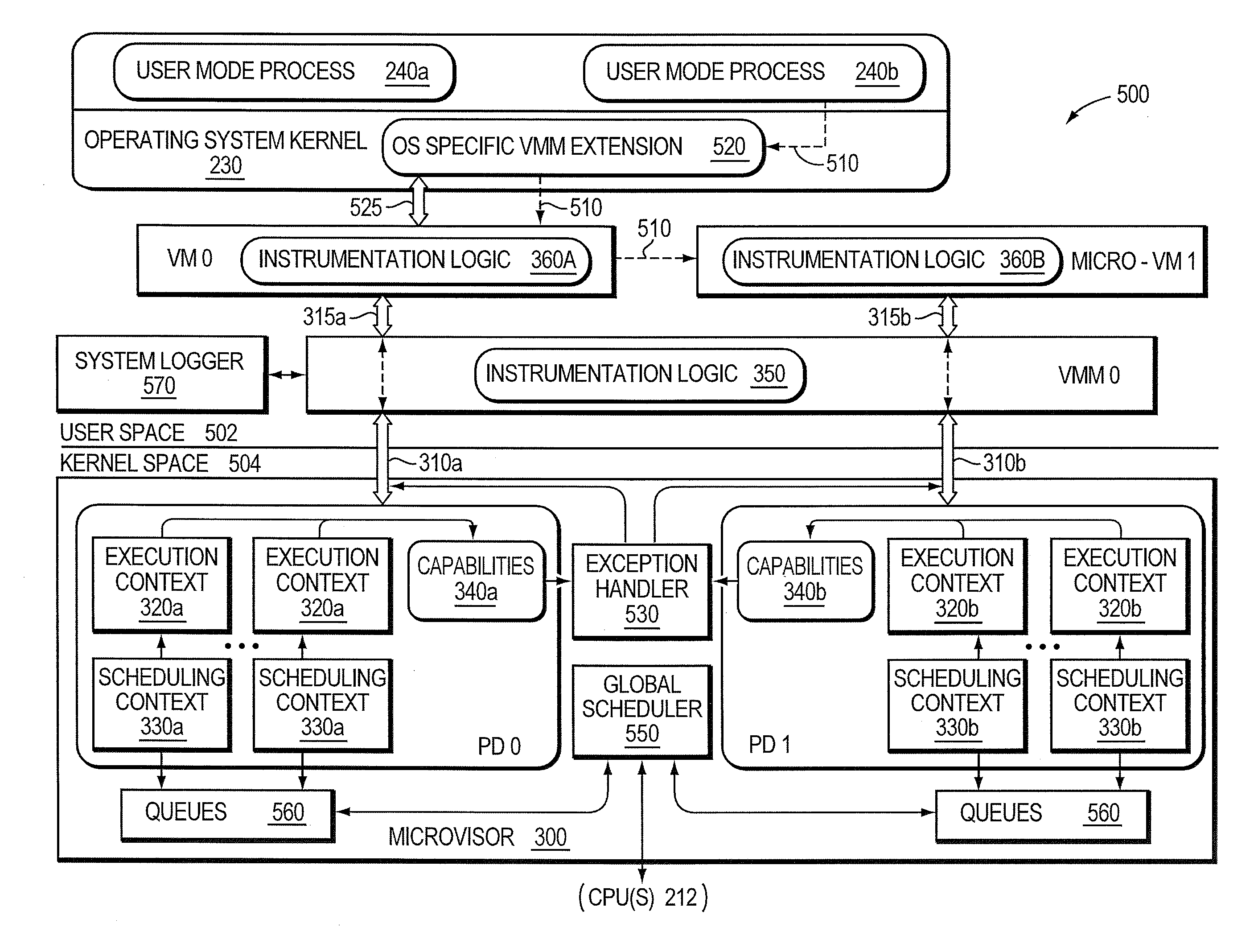
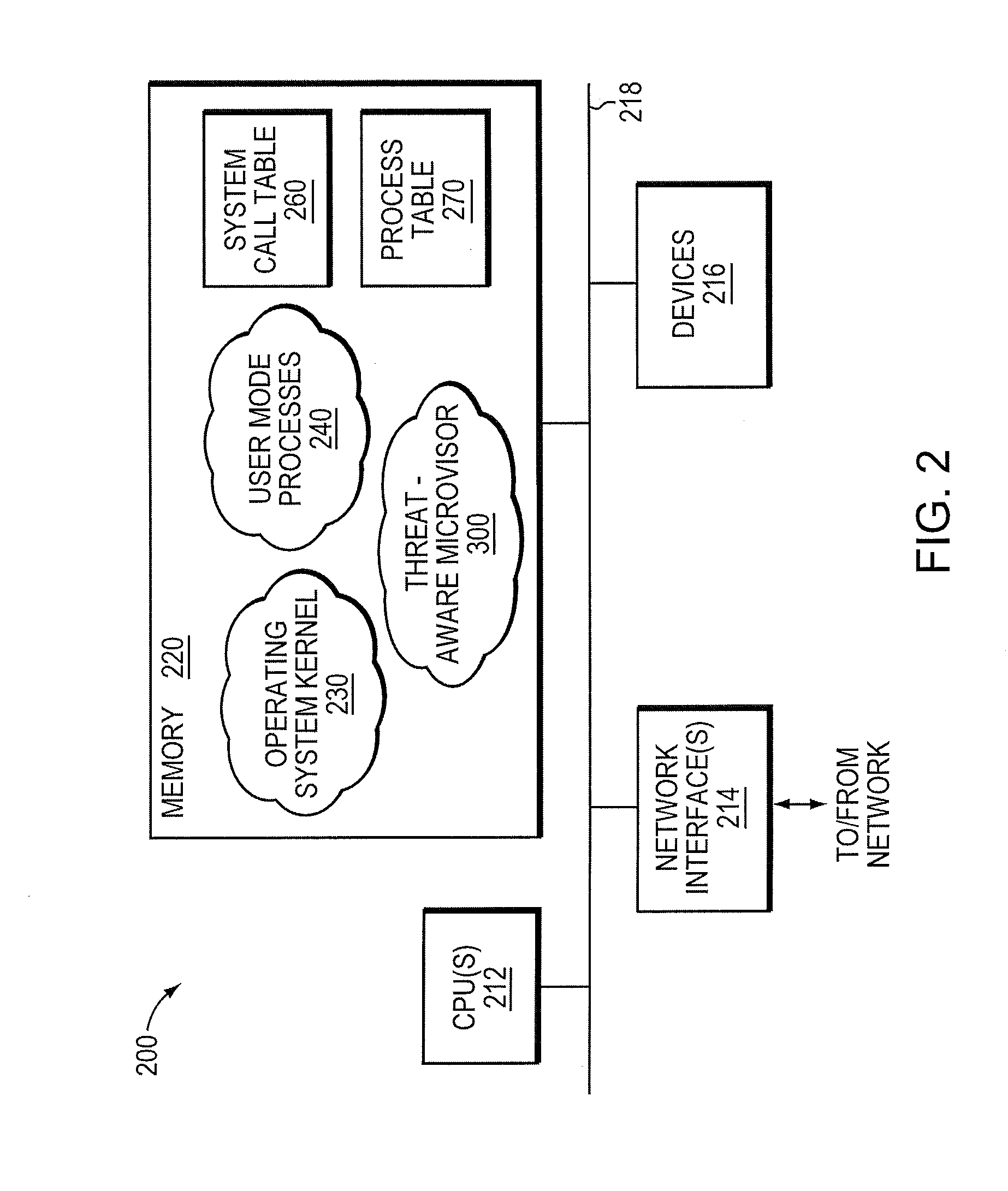
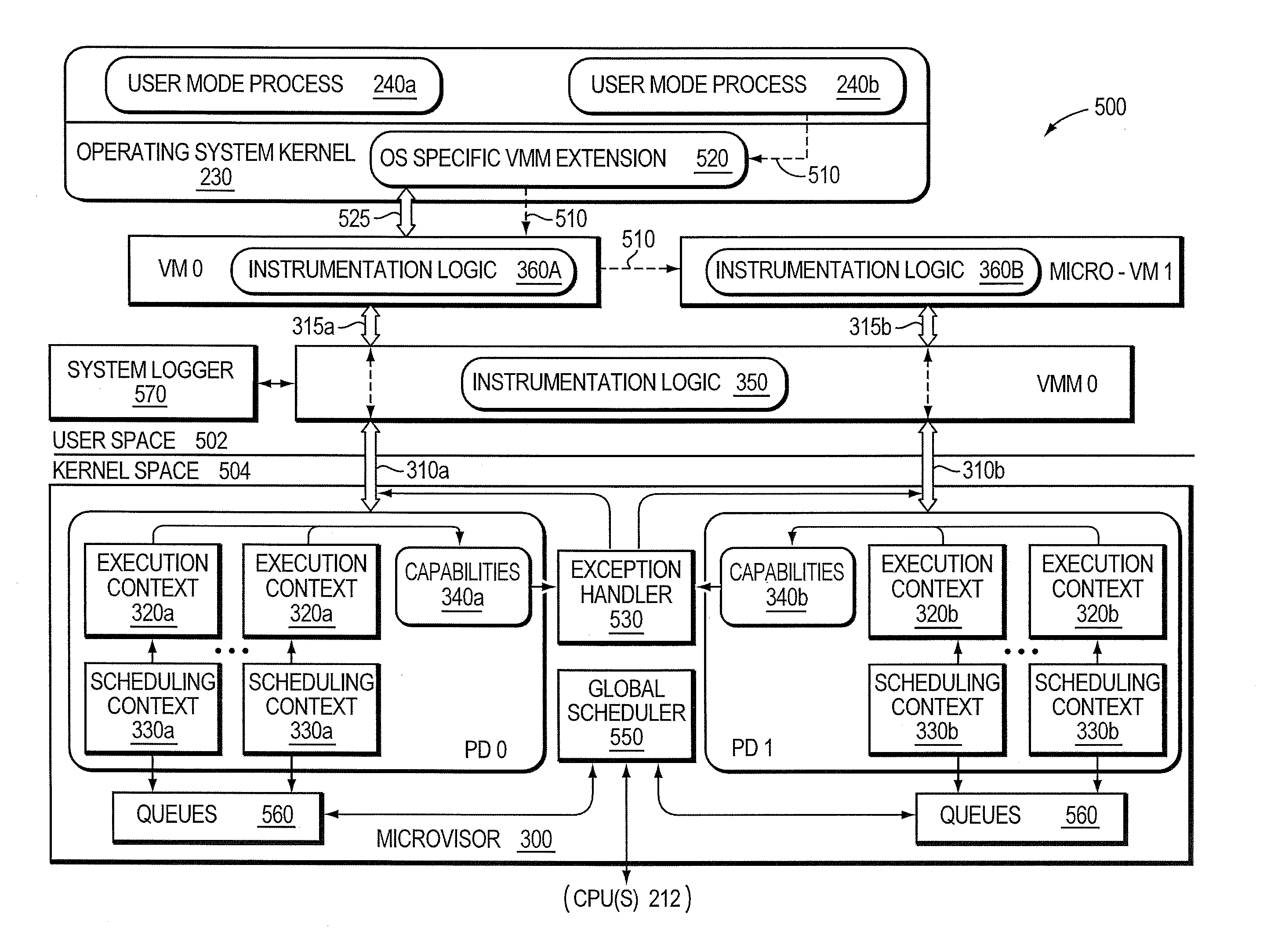
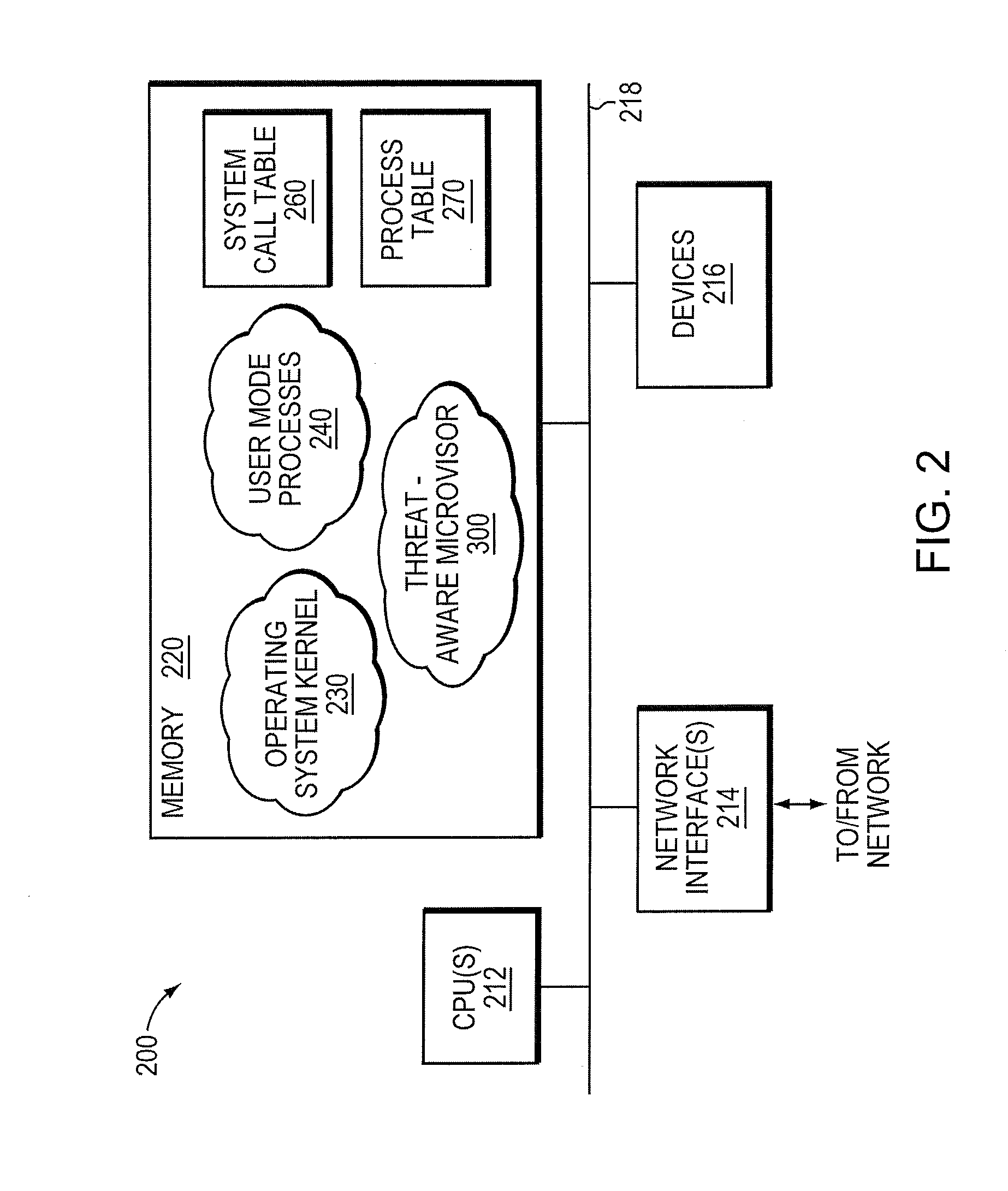
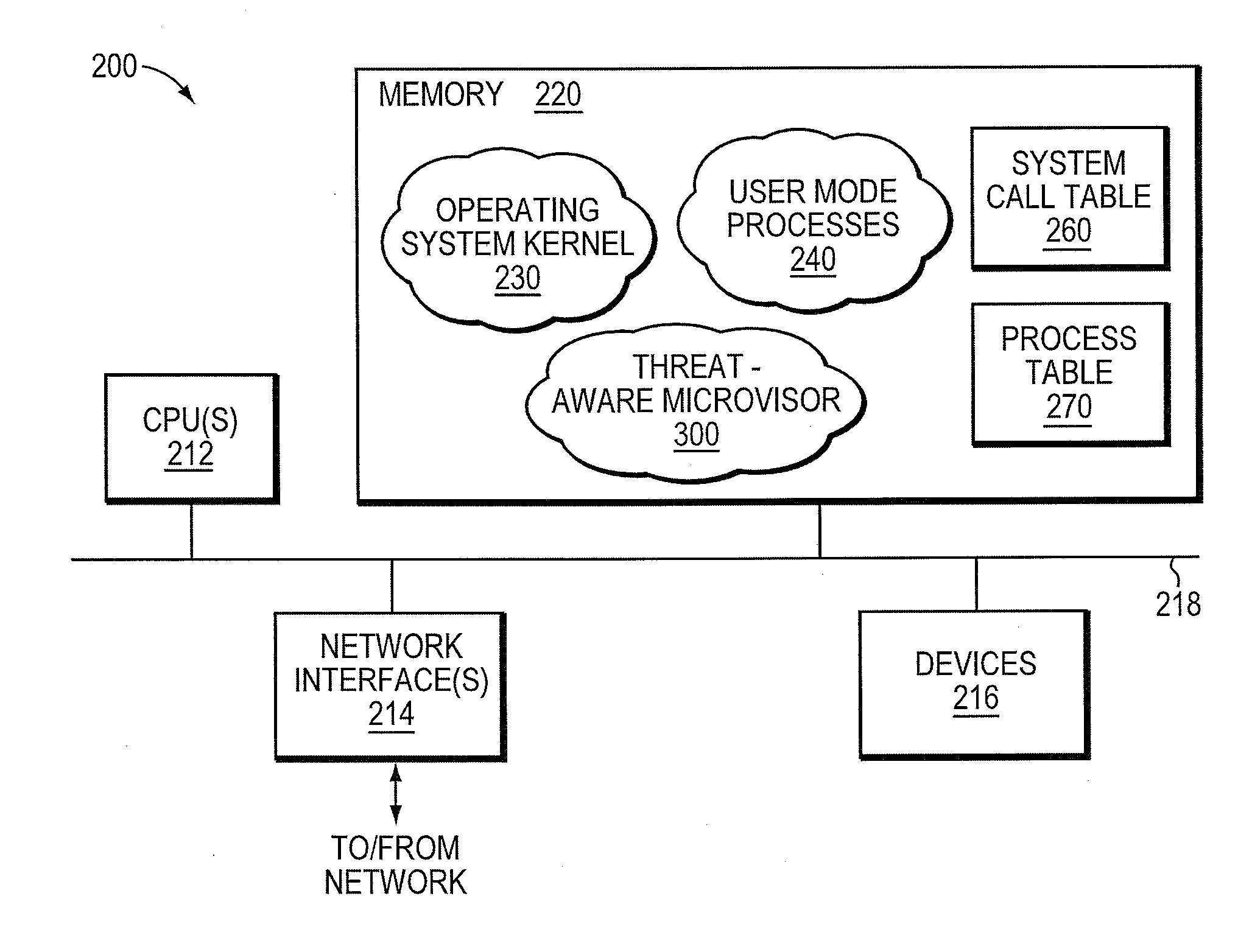
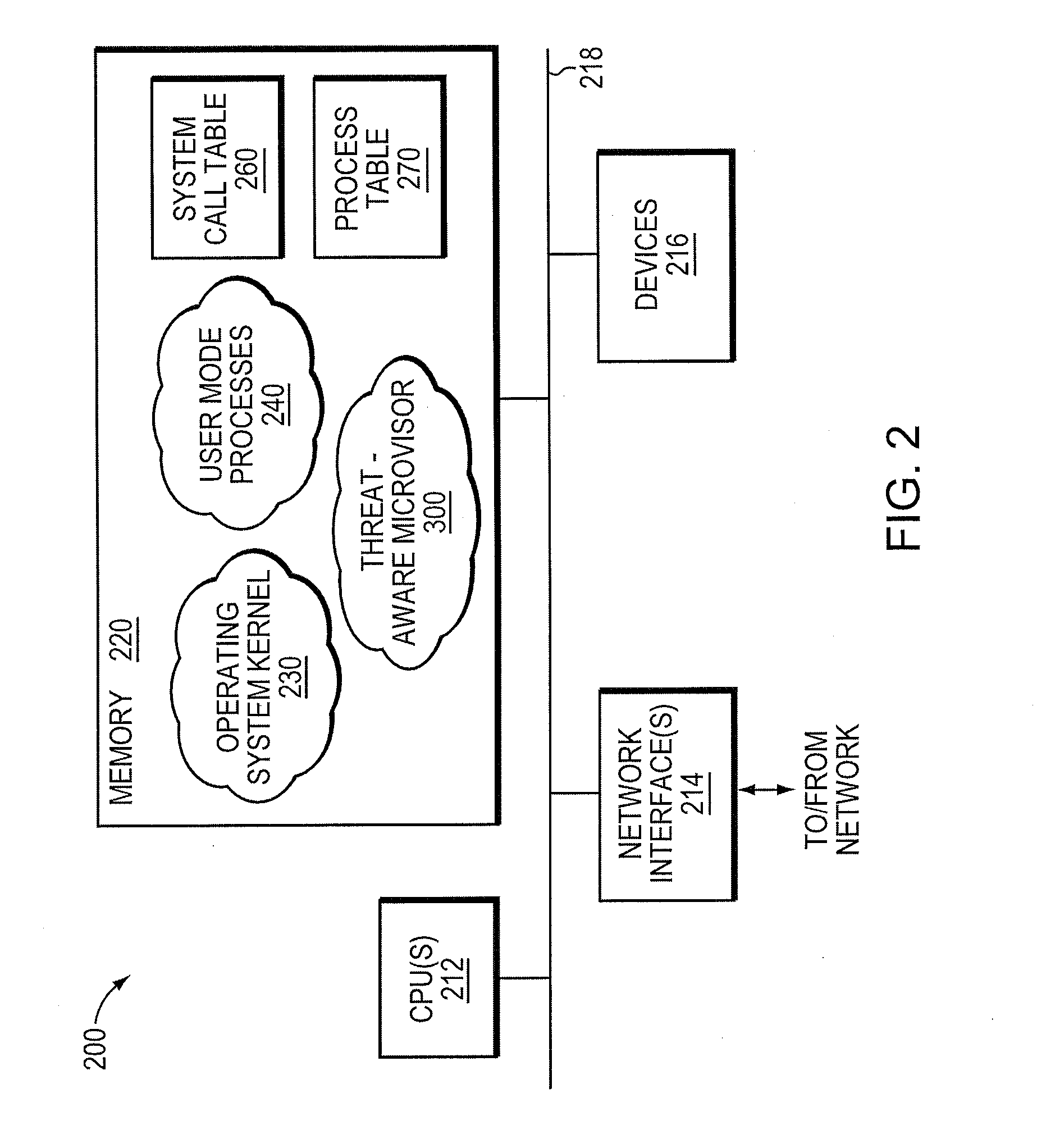
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS20150199532A1Digital data processing detailsAnalogue secracy/subscription systemsVirtualizationSecurity analysis
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS9292686B2Digital data protectionPlatform integrity maintainanceVirtualizationOperational system
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
Threat-aware microvisor
ActiveUS20150199513A1Memory loss protectionError detection/correctionOperational systemComputer module
A threat-aware microvisor is configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing on a node of a network environment. The microvisor may be embodied as a module disposed or layered beneath (underlying) an operating system kernel executing on the node to thereby control privileges (i.e., access permissions) to kernel resources, such as one or more central processing units (CPUs), network interfaces, memory, and / or devices, of the node. Illustratively, the microvisor may be configured to control access to one or more of the resources in response to a request by an operating system process to access the resource.
Owner:FIREEYE SECURITY HLDG US LLC
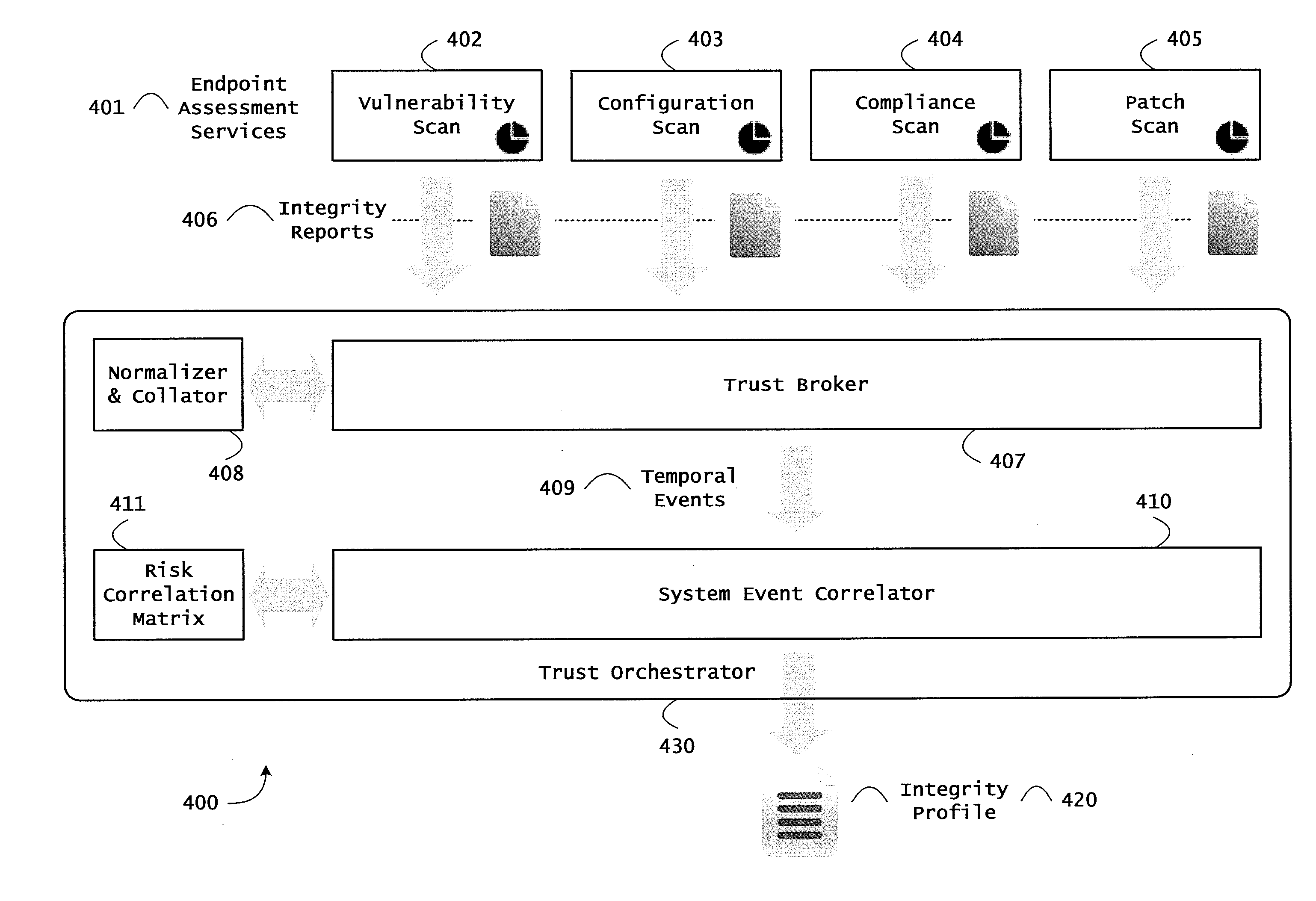
Systems and methods for network flow remediation based on risk correlation
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
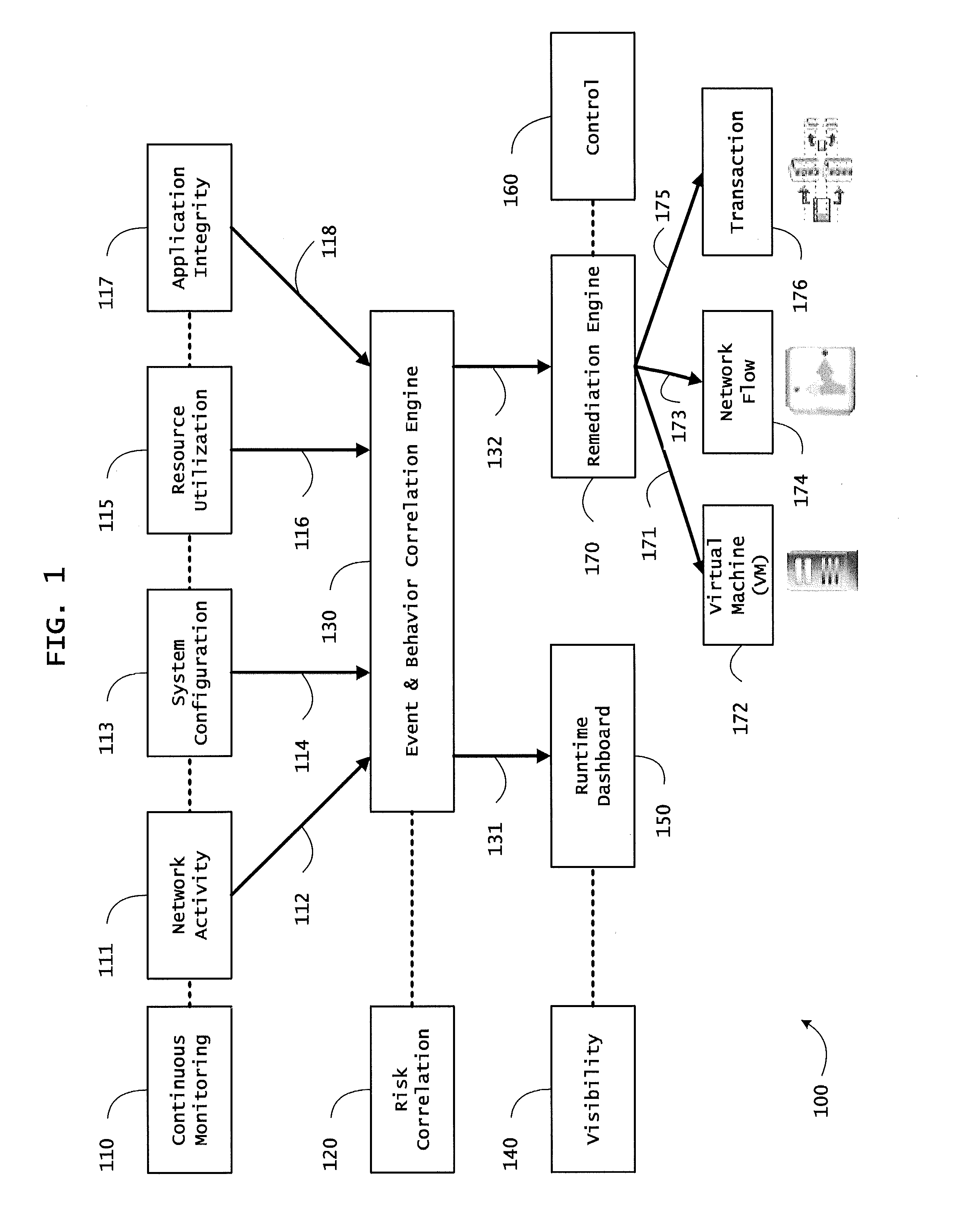
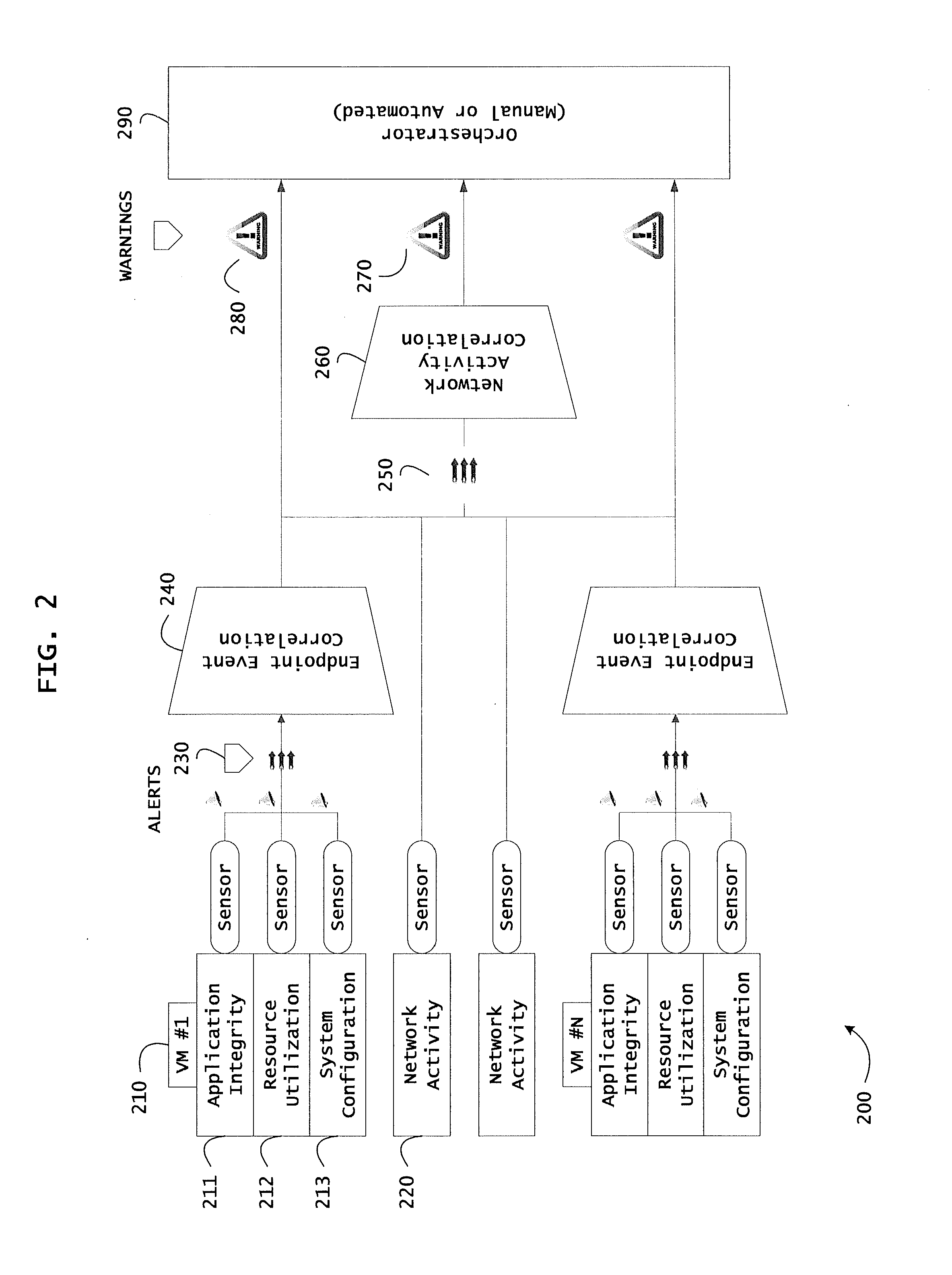
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
Collective threat intelligence gathering system
ActiveUS8813228B2Quality improvementMemory loss protectionUnauthorized memory use protectionIp addressInternet privacy
Threat intelligence is collected from a variety of different sources. The threat intelligence information is aggregated, normalized, filtered and scored to identify threats to an information network. Threats are categorized by type, maliciousness and confidence level. Threats are reported to network administrators in a plurality of threat feeds, including for example malicious domains, malicious IP addresses, malicious e-mail addresses, malicious URLs and malicious software files.
Owner:DELOITTE DEV
System and method of managing network security risks
InactiveUS20120185945A1Memory loss protectionError detection/correctionThreat intelligencePreventive action
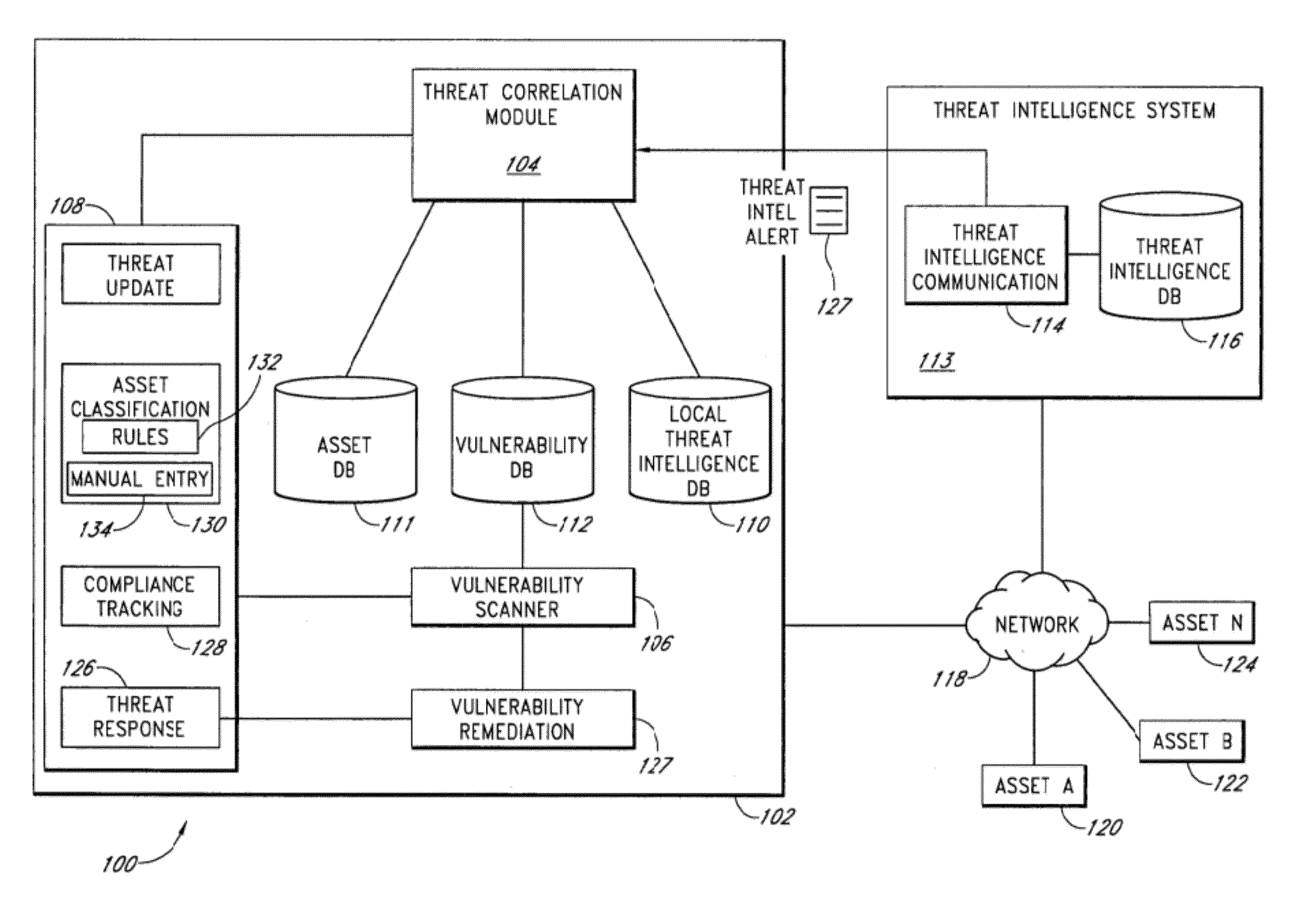
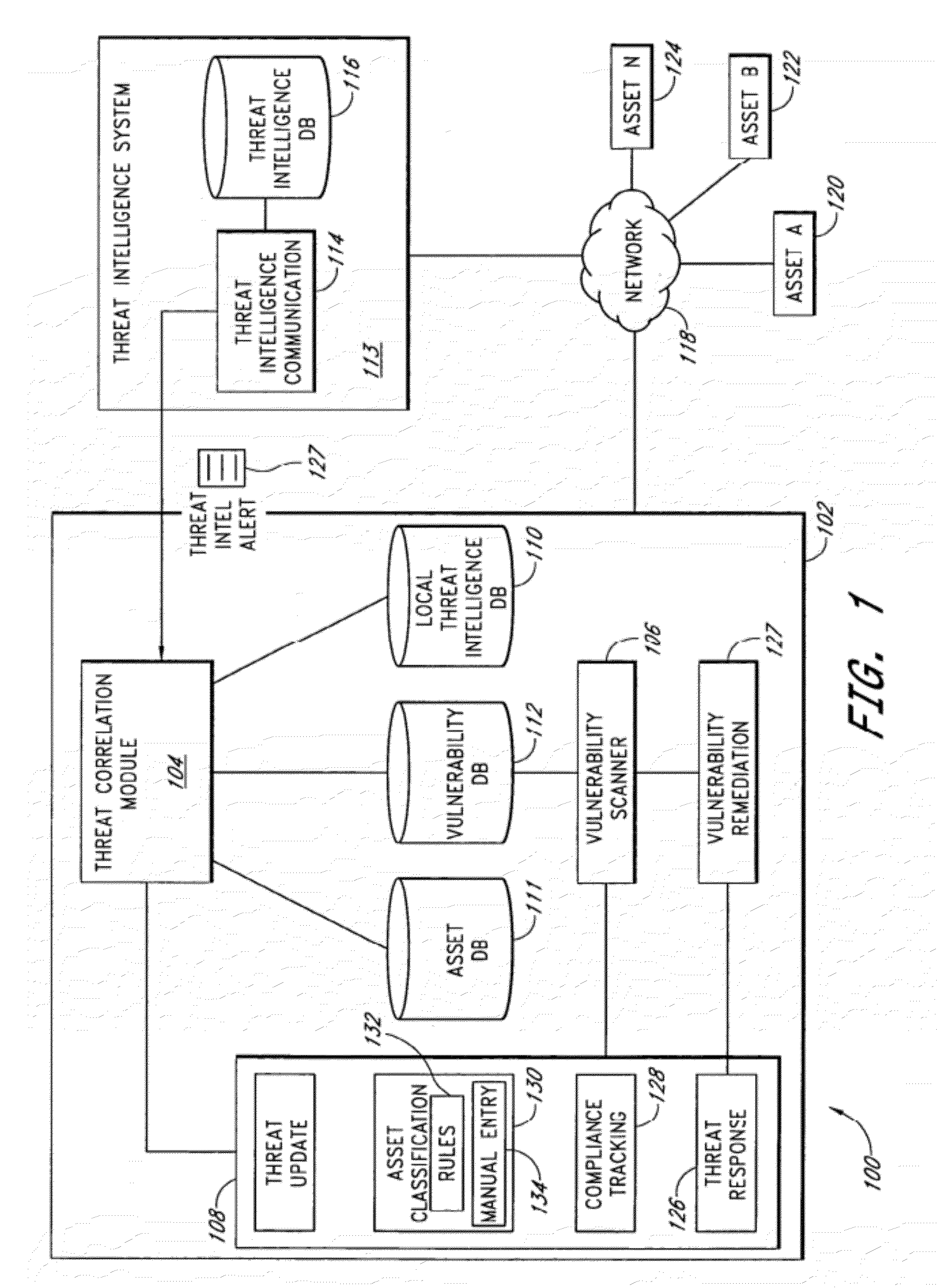
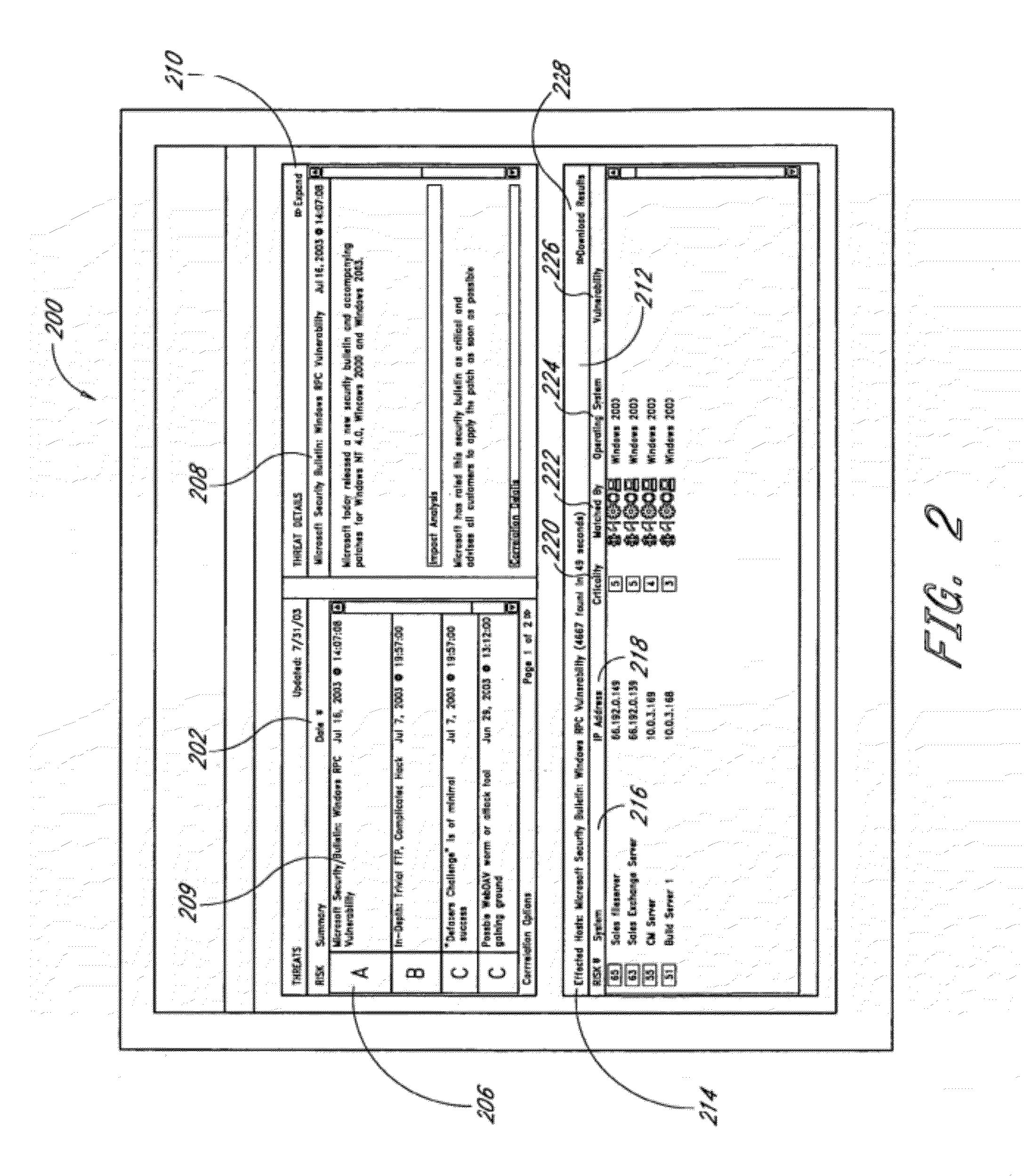
A security risk management system comprises a vulnerability database, an asset database, a local threat intelligence database and a threat correlation module. The vulnerability database comprises data about security vulnerabilities of assets on a network gathered using active or passive vulnerability assessment techniques. The asset database comprises data concerning attributes of each asset. The threat correlation module receives threat intelligence alerts that identify attributes and vulnerabilities associated with security threats that affect classes of assets. The threat correlation module compares asset attributes and vulnerabilities with threat attributes and vulnerabilities and displays a list of assets that are affected by a particular threat. The list can be sorted according to a calculated risk score, allowing an administrator to prioritize preventive action and respond first to threats that affect higher risk assets. The security risk management system provides tools for performing preventive action and for tracking the success of preventive action.
Owner:MCAFEE INC
System for Tracking Data Security Threats and Method for Same
ActiveUS20160072836A1Information obtainedMemory loss protectionError detection/correctionIp addressInternet privacy
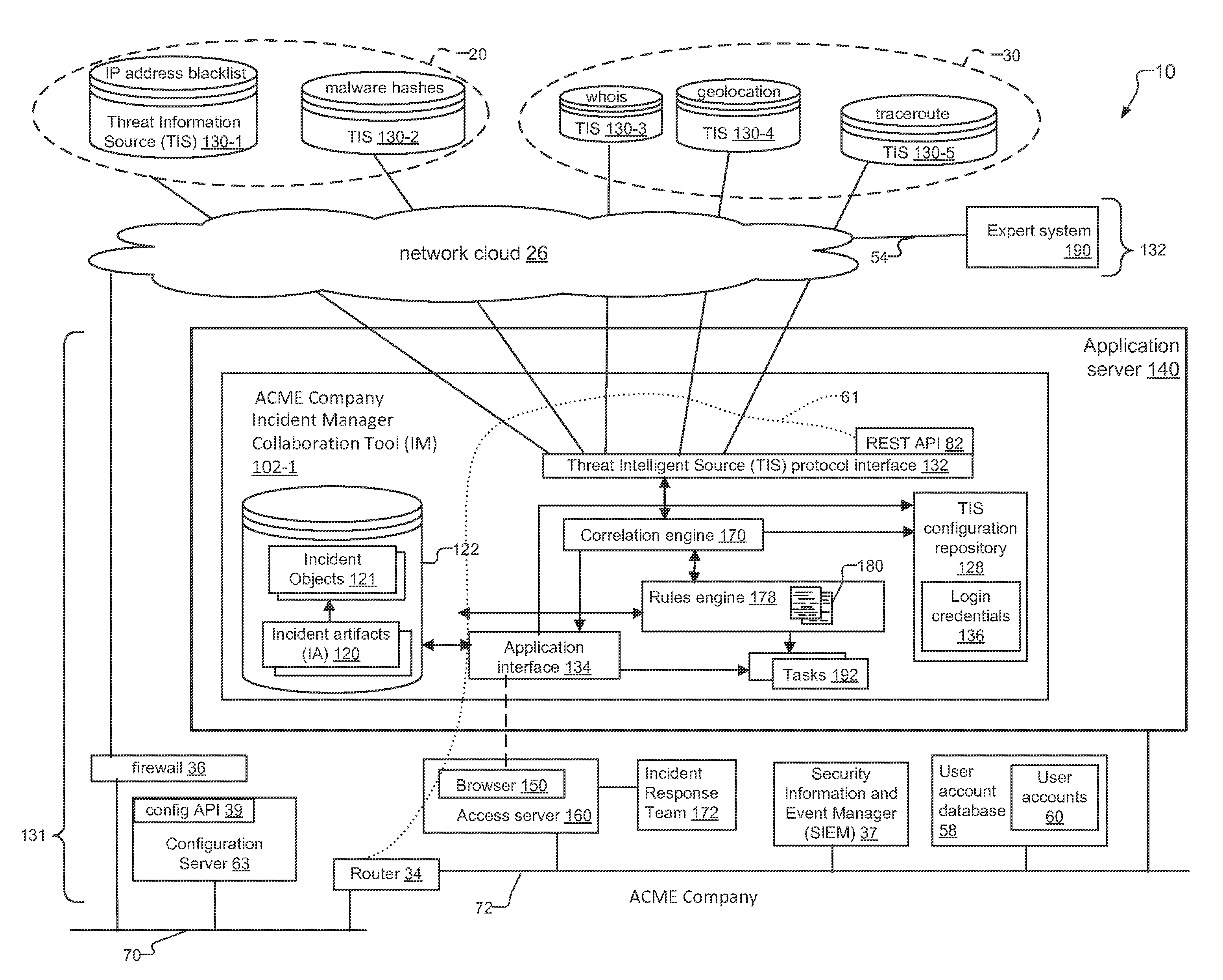
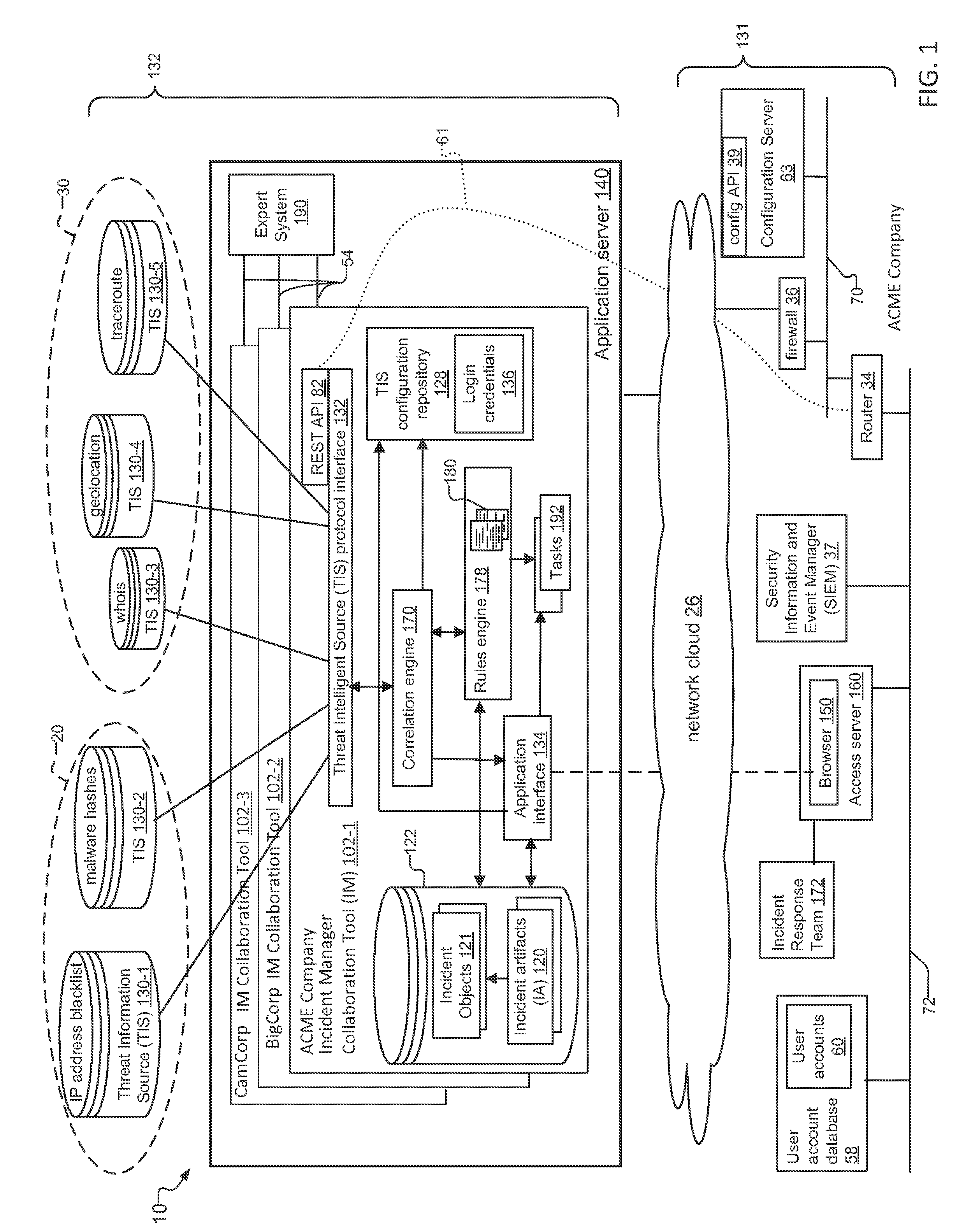
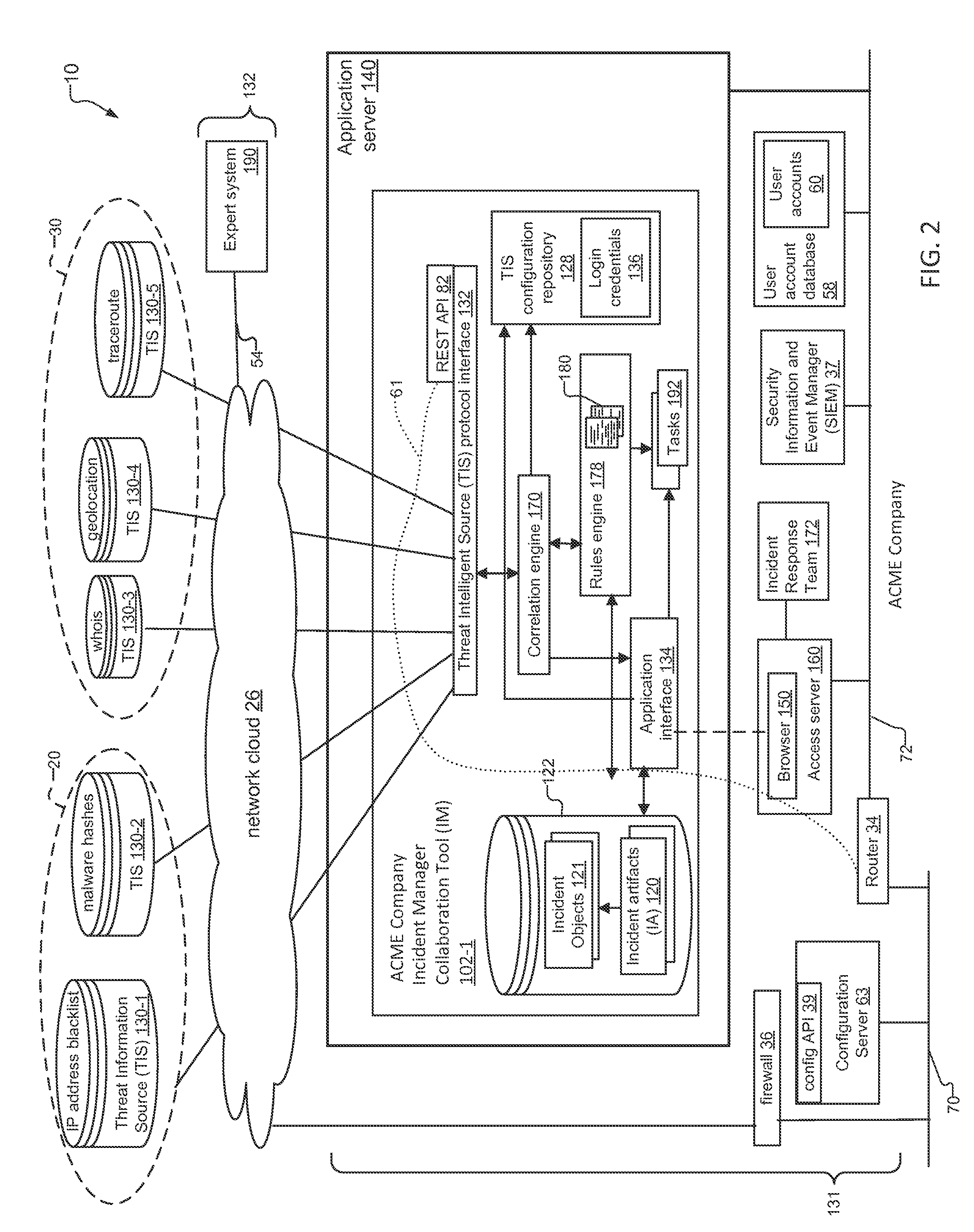
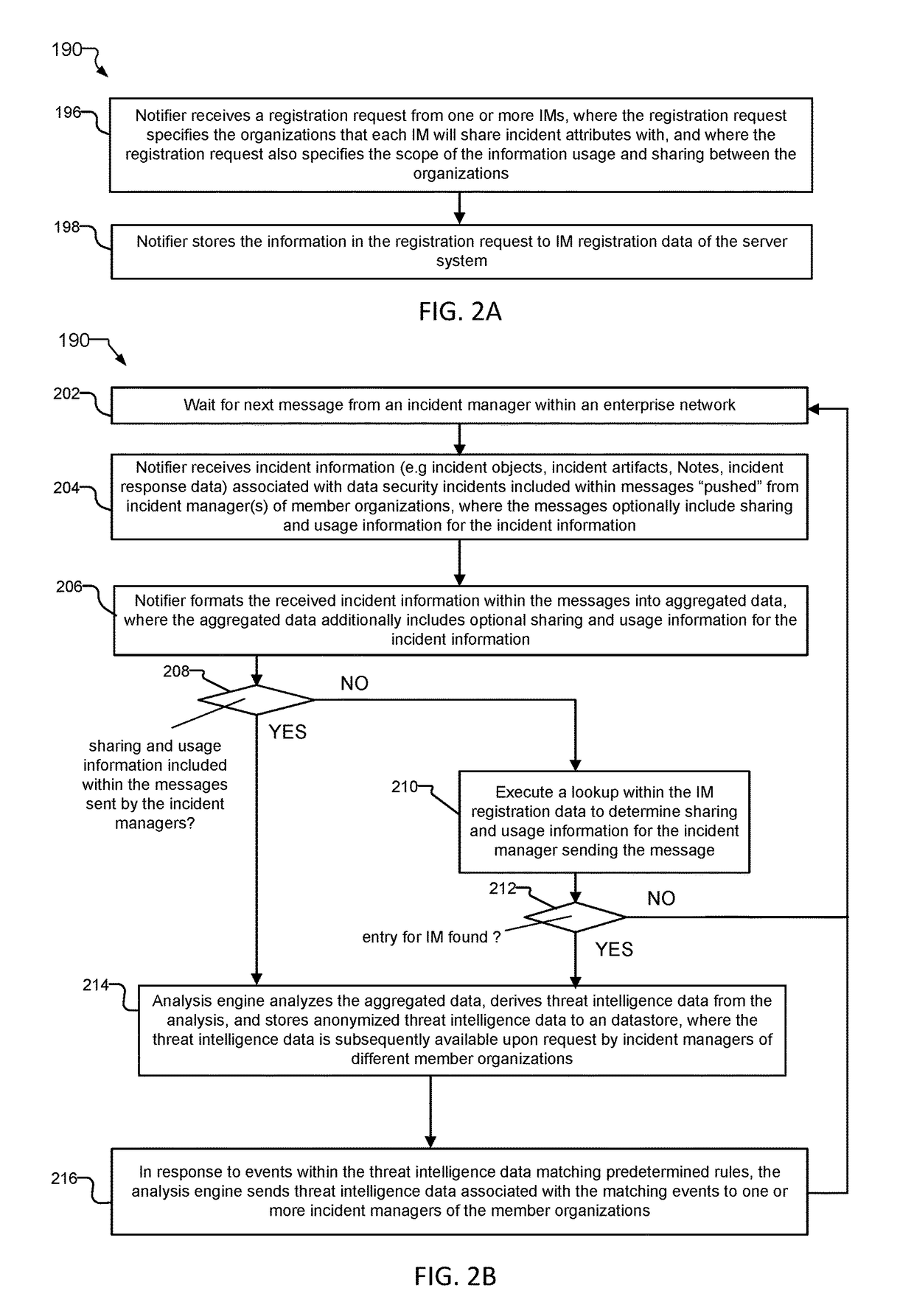
An incident response system and method for tracking data security incidents in enterprise networks is disclosed. An Incident Manager application (IM) stores incident objects and incident artifacts (IAs) created in response to the incidents, where the incident objects include the information for the incident and the IAs are associated with data resources (e.g. IP addresses and malware hashes) identified within the incident objects. In response to creation of the IAs, the IM issues queries against one or more external threat intelligence sources (TISs) to obtain information associated with the IAs and augments the IAs with the obtained information. In examples, the IM can identify known threats by comparing the contents of IAs against TIS(s) of known threats, and can identify potential trends by correlating the created incident objects and augmented IAs for an incident with incident objects and IAs stored for other incidents.
Owner:GREEN MARKET SQUARE LTD
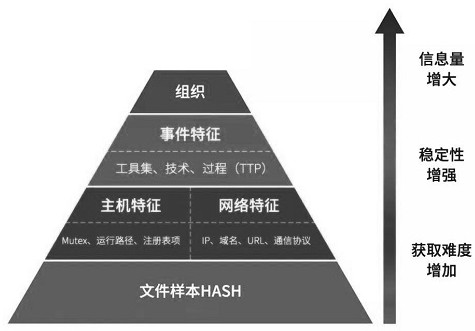
Threat intelligence analysis system for attack tracing
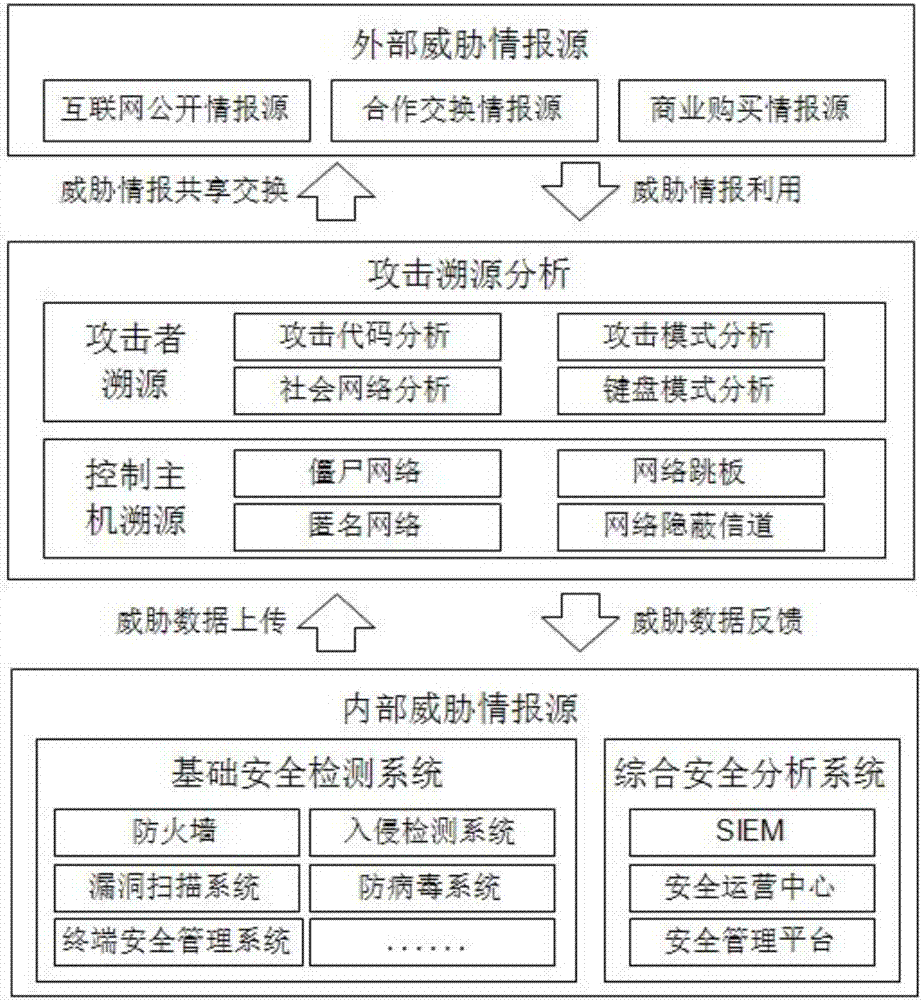
InactiveCN107046543AEasy to distinguishImprove generalizationTransmissionIntelligence analysisSecurity analysis
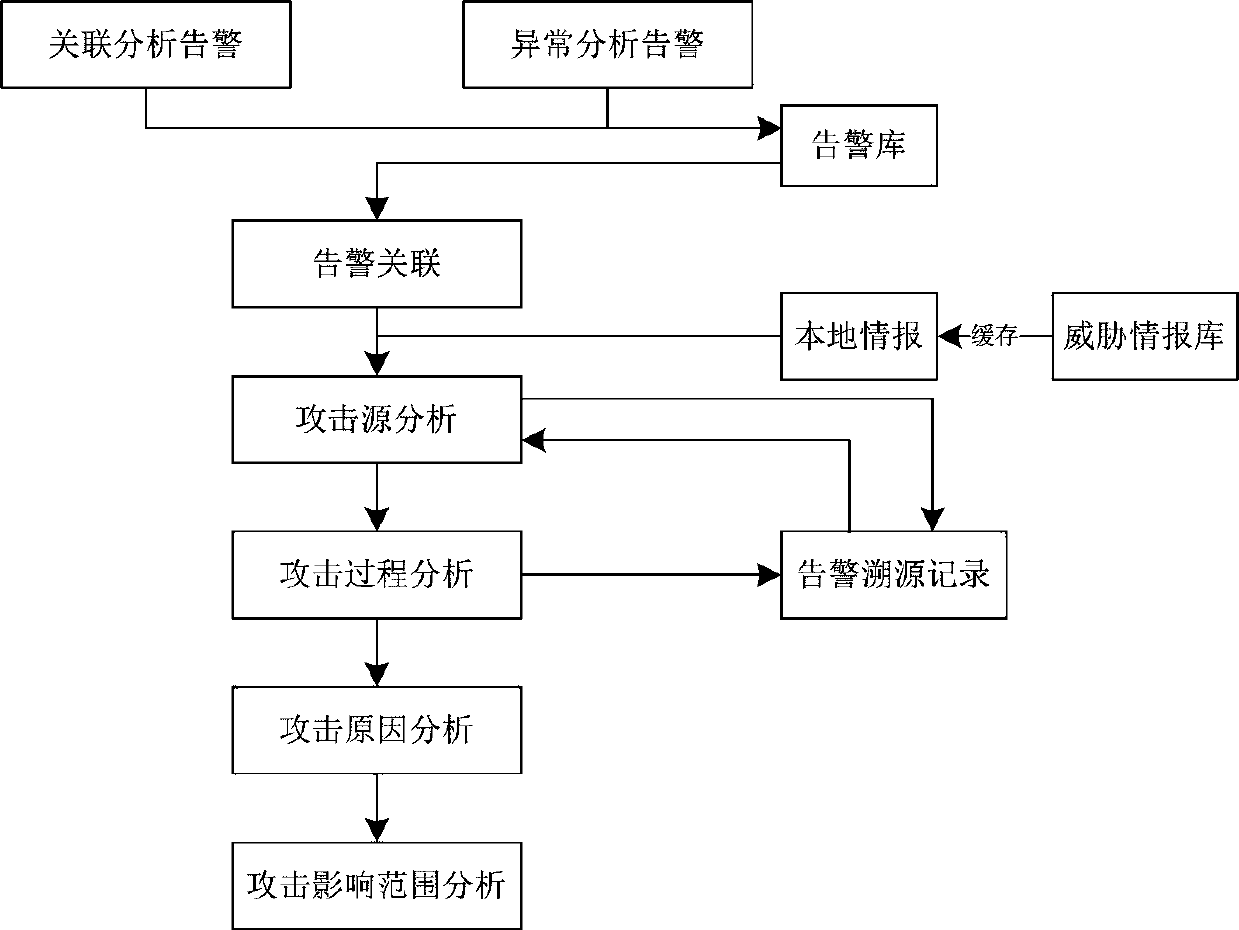
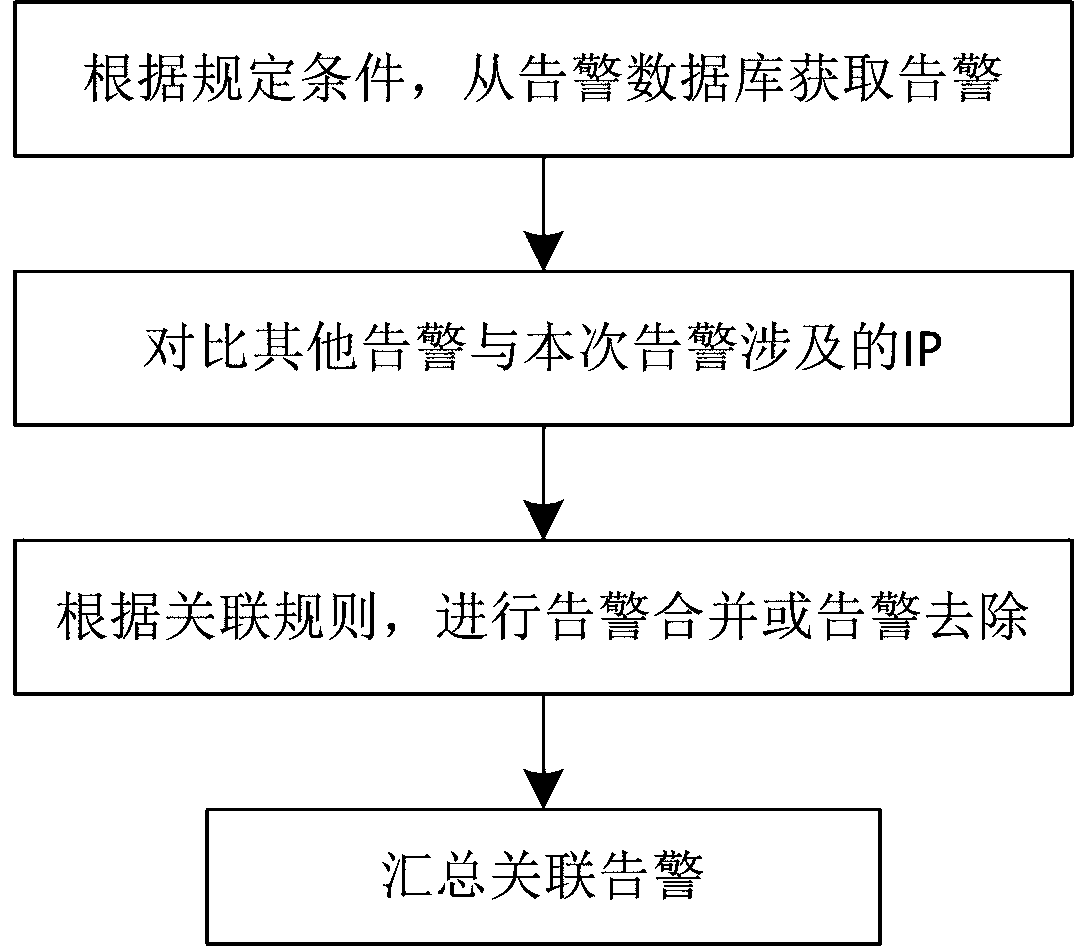
The invention discloses a threat intelligence analysis system for attack tracing. The system comprises an internal threat intelligence collection module, an external threat intelligence collection module and an attack tracing analysis module; the internal threat intelligence collection module comprises a security detection module and a security analysis module; the attack tracing analysis module comprises attacker tracing and attack host tracking; threat intelligence obtained by the internal threat intelligence collection module and the external threat intelligence collection module is uploaded to the attack tracing analysis module, the attack tracing analysis module performs attacker tracing and attack host tracking on the threat intelligence and feeds back the result to the security detection module and the security analysis module; and meanwhile, the result is performed with threat intelligence sharing and exchange with an external cooperation mechanism. The threat intelligence analysis system disclosed by the invention can not only singly and quickly accomplish threat intelligence analysis and detection, but also can provide prediction for the attacks of enterprises, the method is orientated to attack tracing, and the attack mode is analyzed from the source so as to better identify the identity of the attacker.
Owner:STATE GRID CORP OF CHINA +3
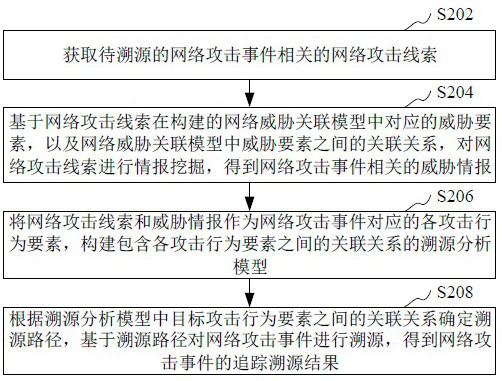
Network attack event traceability processing method and device, equipment and storage medium
The invention relates to the technical field of network security, in particular to a network attack event traceability processing method and device, equipment and a storage medium. The method comprises the steps of obtaining a network attack clue related to a to-be-traced network attack event; performing intelligence mining on the network attack clue based on the constructed network threat association model to obtain threat intelligence related to the network attack event; taking the network attack clue and the threat intelligence as attack behavior elements corresponding to the network attackevent, and constructing a traceability analysis model containing an association relationship between the attack behavior elements; and determining a traceability path according to the association relationship between the target attack behavior elements in the traceability analysis model, and performing traceability on the network attack event based on the traceability path to obtain a traceability result of the network attack event. By adopting the method, accurate tracking and tracing of the network attack event can be realized, so that the security of a computer communication network is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
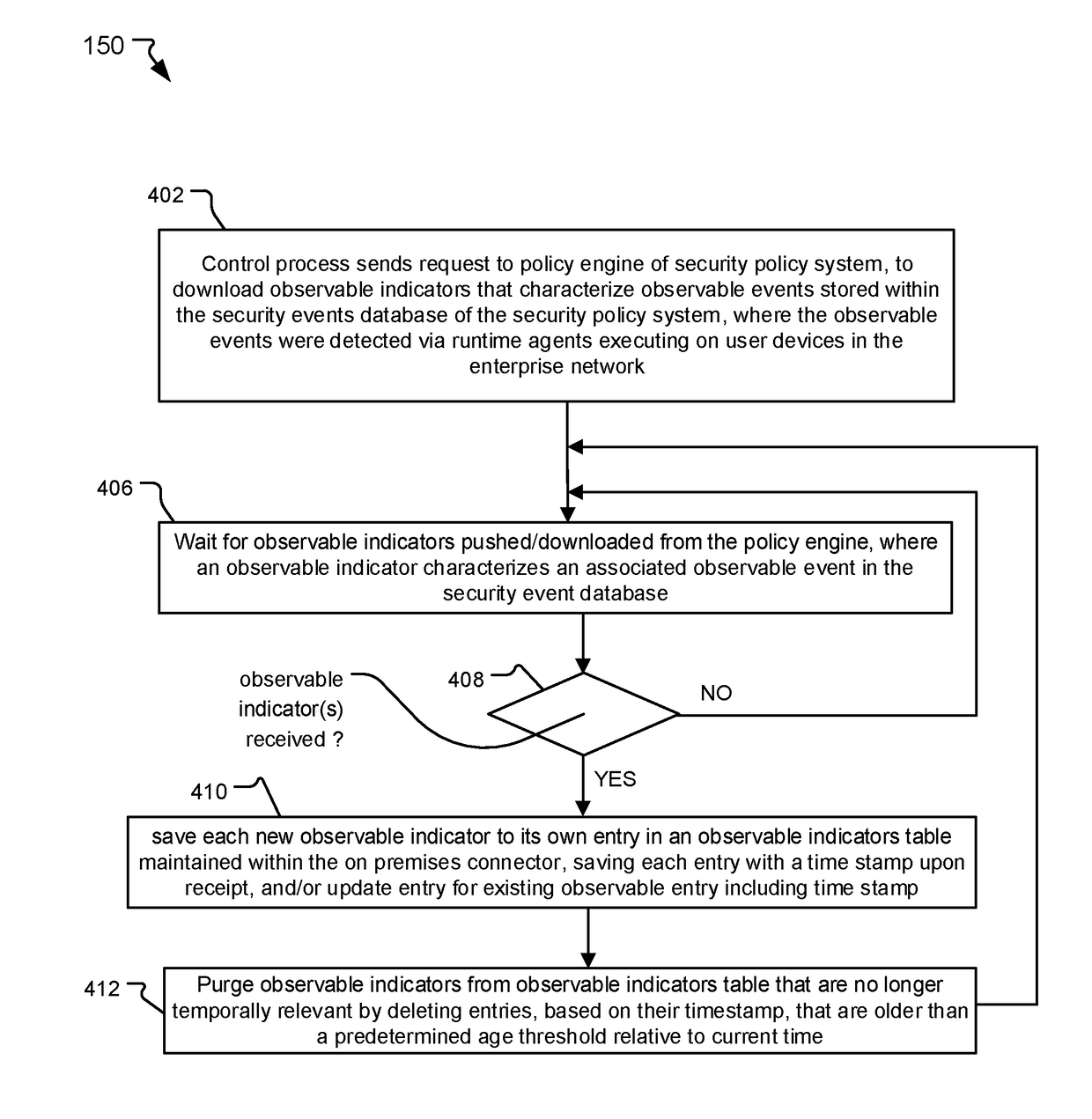
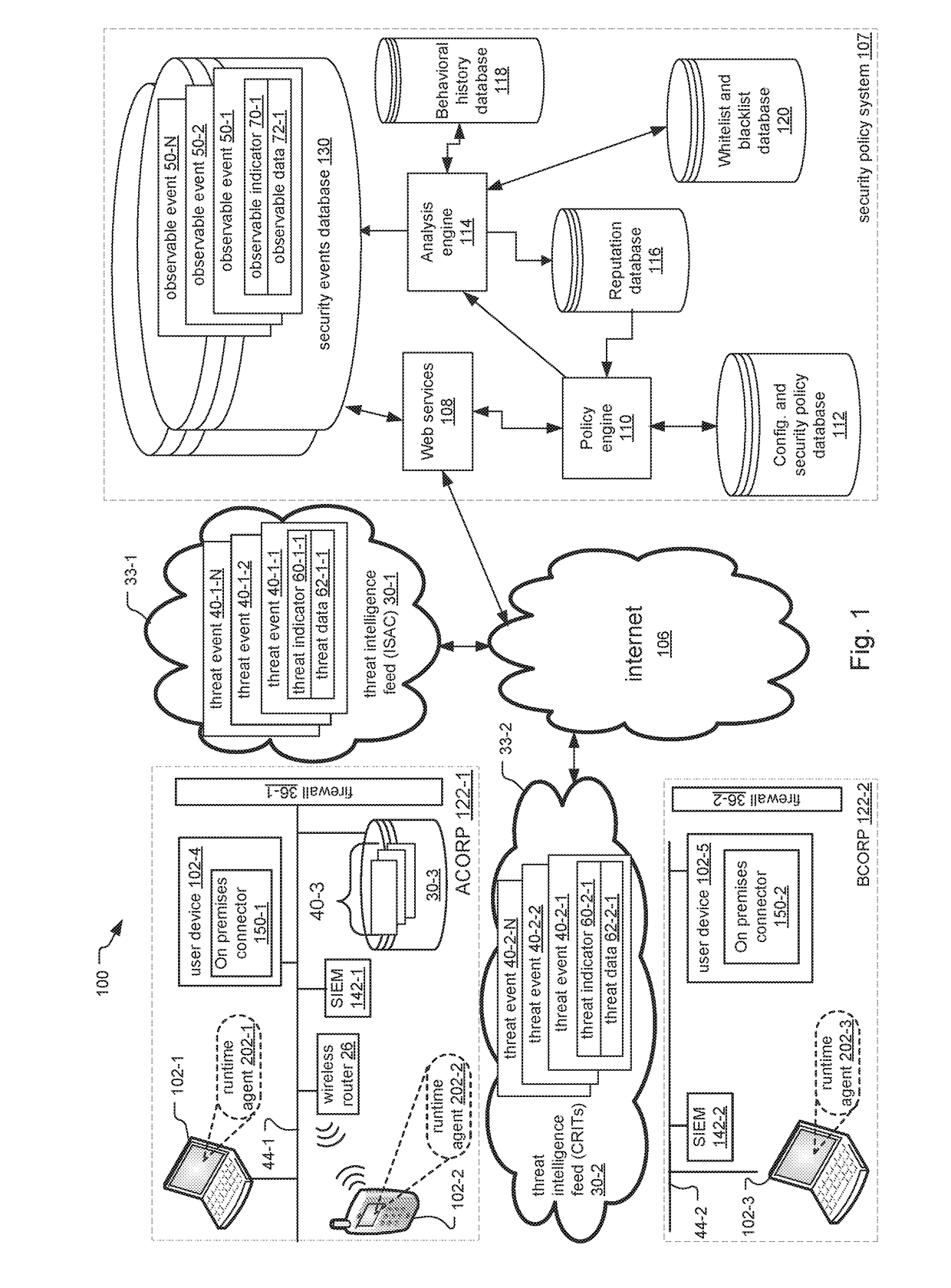
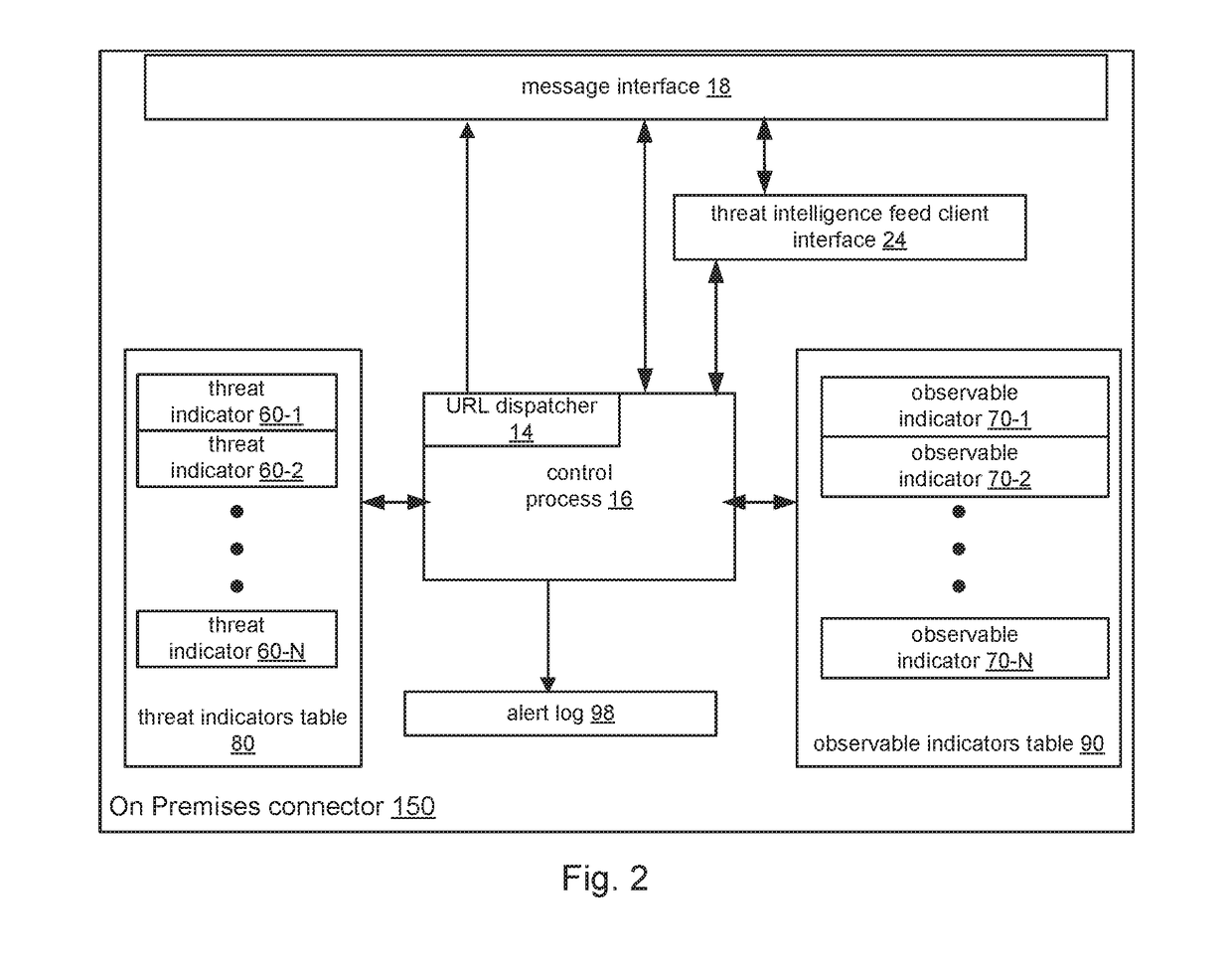
Using Private Threat Intelligence in Public Cloud
ActiveUS20170272469A1Preserving data integrityPreserving securityComputer security arrangementsTransmissionUser deviceQuery string
A distributed security system and method are disclosed that enable access to known threat events from threat intelligence feeds when the system includes public cloud components. A cloud-based security policy system stores observable events for security incidents detected by and sent from user devices within an enterprise network. The observable events include observable indicators for characterizing the observable events. The threat events within the feeds include threat indicators for characterizing the threat events. An on-premises connector within the enterprise network downloads the observable indicators from the security policy system and the threat indicators from the feeds. In response to determining that any observable indicators match any threat indicators, the on-premises connector provides access to the threat events and / or the observable events having the matching indicators. In one example, the on-premises connector generates opaque query strings for users on user devices to access the threat events / observable events having the matching indicators.
Owner:CARBON BLACK
Systems and methods for electronic message analysis
ActiveUS9501746B2Increase probabilityReduce probabilityProbabilistic networksData switching networksPattern matchingBackground information
Systems and methods for analyzing electronic messages are disclosed. In some embodiments, the method comprises receiving a new received message from an indicated sender, the new received message having a first message characteristic of the indicated sender and a second message characteristic, identifying an actual sender message characteristic pattern of an actual sender using the first message characteristic, probabilistically comparing the second message characteristic to the actual sender message characteristic pattern, determining a degree of similarity of the second message characteristic to the actual sender message characteristic pattern, and influencing a probability that the indicated sender is the actual sender based upon the degree of similarity. There may be multiple message characteristics and patterns. In some embodiments, the methods may utilize pattern matching techniques, recipient background information, quality measures, threat intelligence data or URL information to help determine whether the new received message is from the actual sender.
Owner:VADE SECURE SAS
Text data-oriented threat intelligence knowledge graph construction method
ActiveCN110717049AImprove accuracyEfficient identificationTransmissionSpecial data processing applicationsNamed-entity recognitionTheoretical computer science
The invention relates to a text data-oriented threat intelligence knowledge graph construction method. The functions of automatically extracting the key information from the text threat intelligence data and constructing the threat intelligence knowledge graph are realized. The invention provides a threat intelligence knowledge graph construction method for text data. The method comprises the following steps: defining an ontology structure in the threat intelligence field; using a threat intelligence named entity recognition model based on multiple factors and a threat intelligence entity relation extraction model based on a graph neural network to obtain threat intelligence entities and relation triples from text data, and finally storing information through a graph database to form a threat intelligence knowledge graph.
Owner:SICHUAN UNIV +1
Threat intelligence-based network threat identification method and identification system
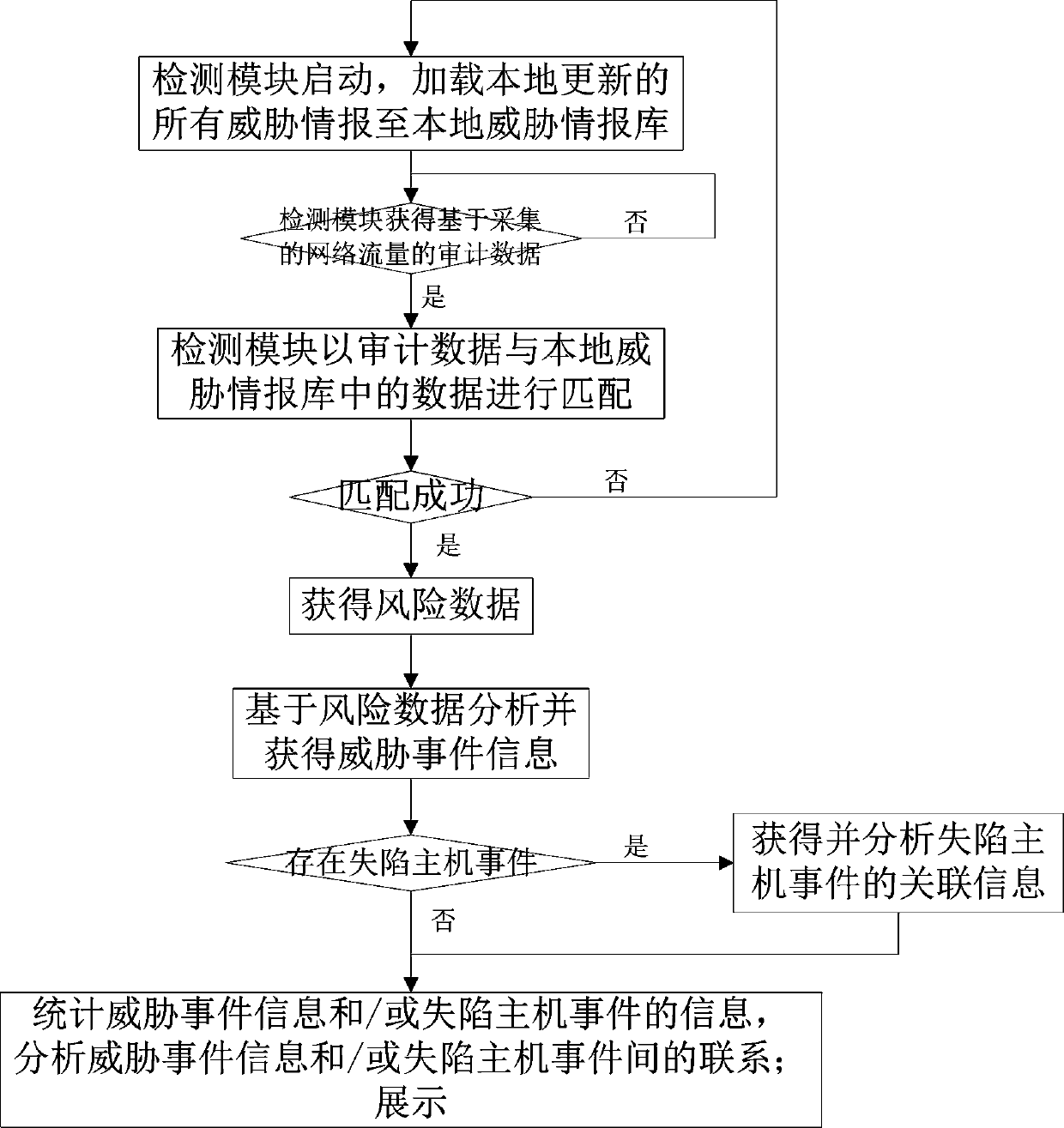
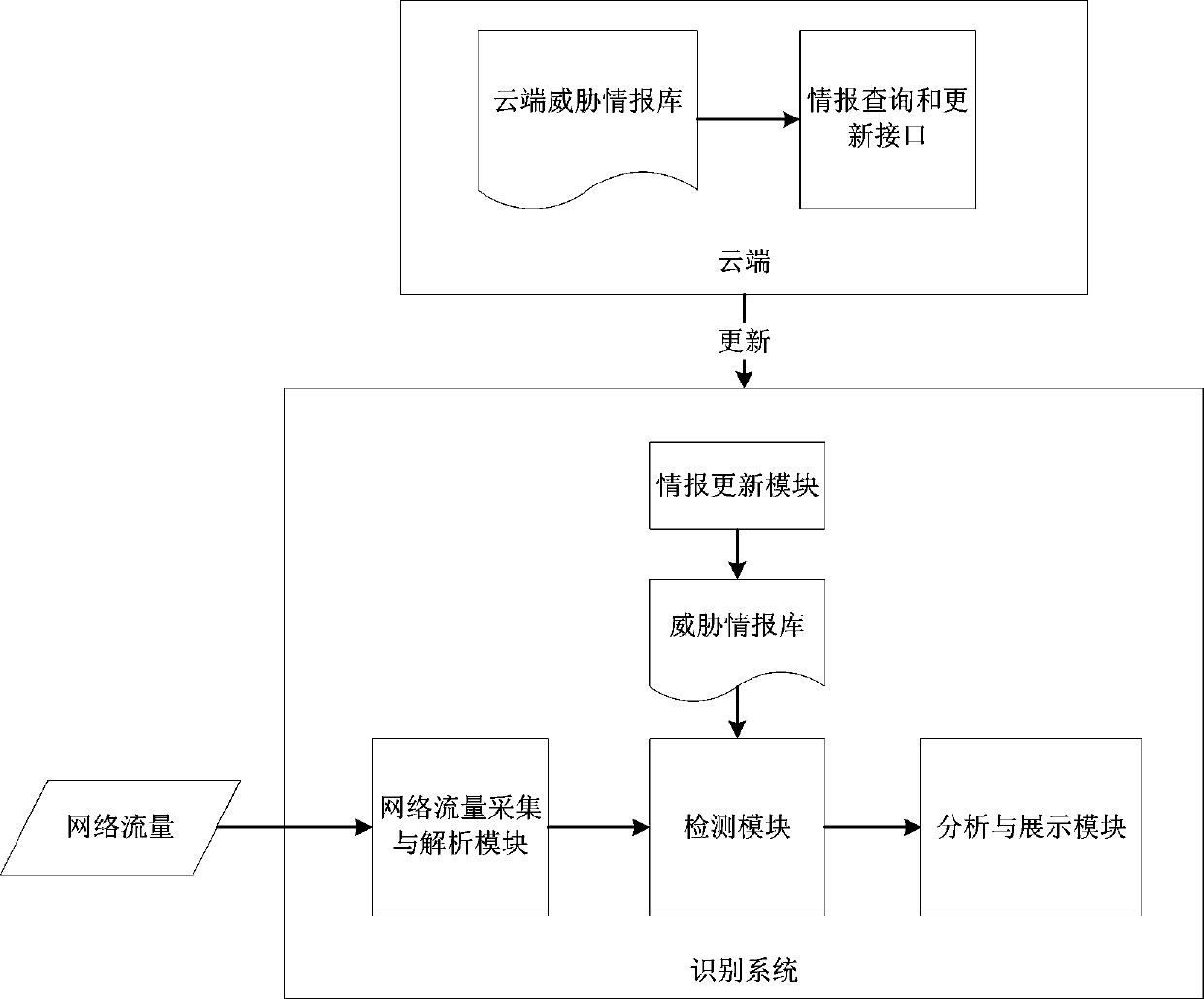
The invention relates to a threat intelligence-based network threat identification method and identification system. The method includes: after the detection module is started, loading all the threatinformation updated by the information updating module to the local; acquiring the collected and analyzed audit data, matching the audit data with data in a threat intelligence library, analyzing andacquiring threat event information based on risk data through an analysis and display module if the audit data is successfully matched with the data in the threat intelligence library, acquiring and analyzing associated information of possible lost host events, and counting, analyzing and displaying the relationship between the events. According to the invention, the threat condition of the wholenetwork is analyzed and displayed from two perspectives of threat event information and a lost host event; a collapsed host is determined, targeted attacks are accurately recognized, correlation analysis and display are carried out on the threats, the efficiency of processing network attack events is improved, the false alarm rate is low, potential threats can be found, tracing and post-processingof the threat events are greatly facilitated, attacks possibly occurring in the future are predicted, and therefore truly valuable attack events are deeply analyzed and found.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Threat intelligence oriented entity identification method and system
InactiveCN109858018AFitEasy to identifySpecial data processing applicationsCommon wordExtraction methods
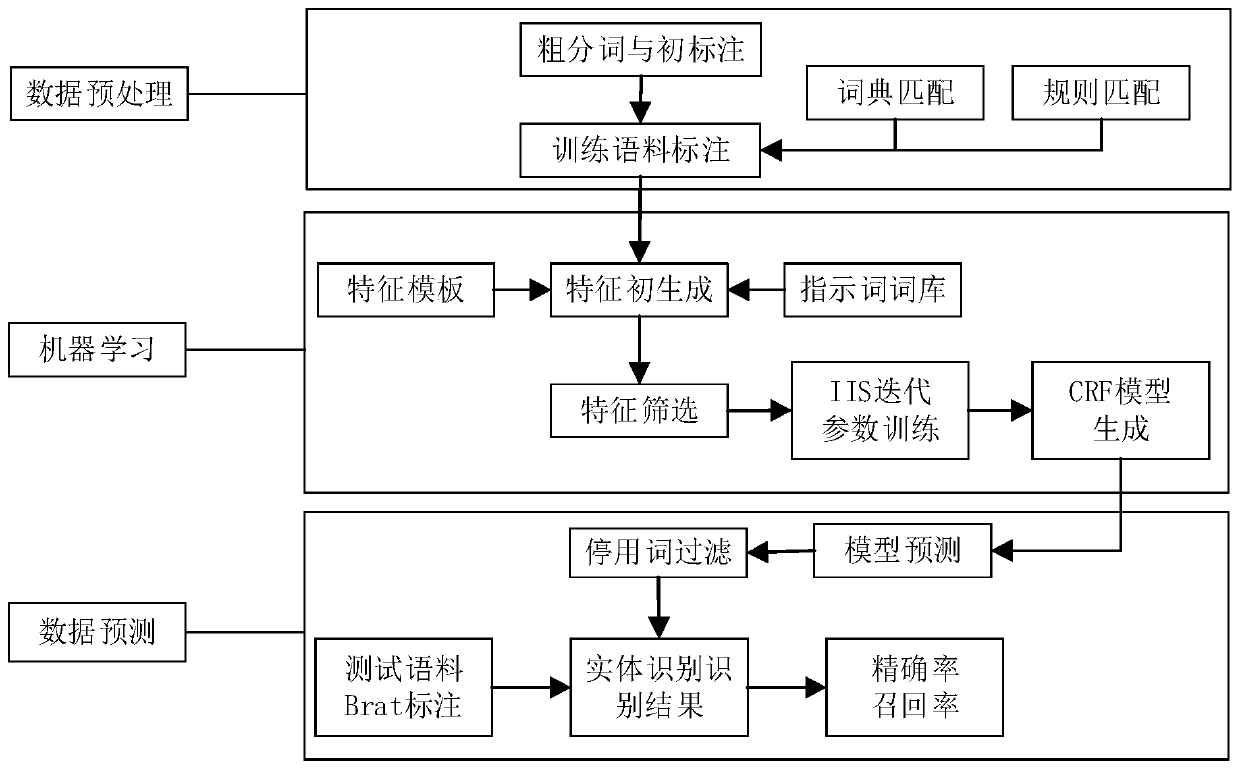
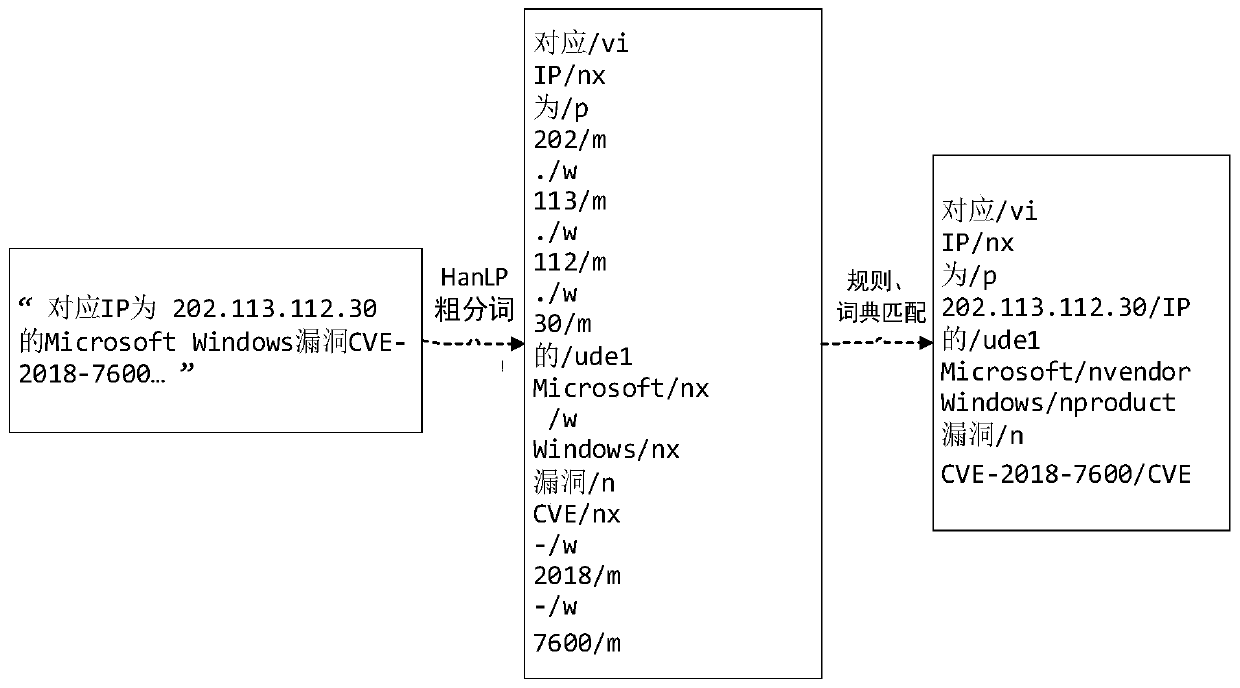
The invention relates to a threat intelligence oriented entity identification method and system. The method comprises the following steps: 1) performing coarse word segmentation on a threat information text serving as a training corpus; 2) constructing a threat information entity common word dictionary library and a rule library, and performing dictionary matching and rule matching on a coarse word segmentation result; 3) marking an entity label for each word based on a matching result to form a training set; 4) constructing a feature template, establishing an indication word bank to perfect the screening form of the feature template, generating context features for the training set by using the feature template, screening, and inputting the screened features into a machine learning modelto carry out parameter iterative training; and 5) performing coarse word segmentation, dictionary matching and rule matching on the threat information text to be identified, and performing entity identification by using the trained machine learning model. According to the threat information entity extraction method, the threat information entity extraction is completed by adopting a means of combining a rule, a dictionary and a model, so that the entity identification precision of the threat information is remarkably improved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Threat intelligence processing method and apparatus
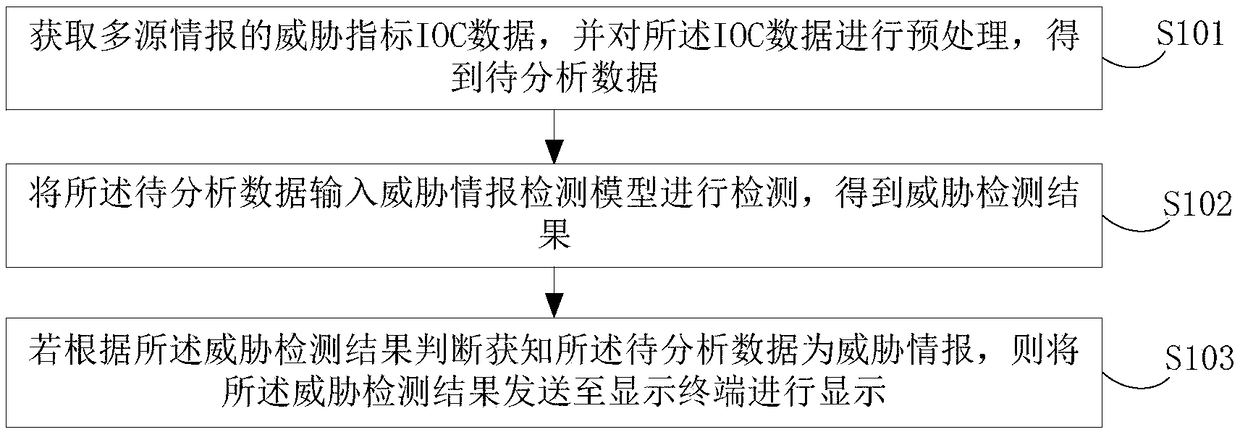
ActiveCN108460278AEasy data matchingGuaranteed real-timePlatform integrity maintainanceTransmissionAnalysis dataComputer terminal
Embodiments of the invention disclose a threat intelligence processing method and apparatus. The method comprises the steps of obtaining threat index IOC data of multisource intelligence, and preprocessing the IOC data to obtain to-be-analyzed data; inputting the to-be-analyzed data to a threat intelligence detection model for performing detection to obtain a threat detection result; and if the to-be-analyzed data is judged to be threat intelligence according to the threat detection result, sending the threat detection result to a display terminal for performing display. The apparatus comprises a data preprocessing module, a data detection module and a result display module. According to the threat intelligence processing method and apparatus, the threat index data of the multisource intelligence is obtained and is preprocessed and detected to obtain the threat detection result, and after the threat intelligence is determined, the threat detection result is sent to the display terminalfor performing display, so that the timeliness and the coverage rate of malicious IP detection and malicious file searching and killing are ensured.
Owner:BEIJING QIANXIN TECH
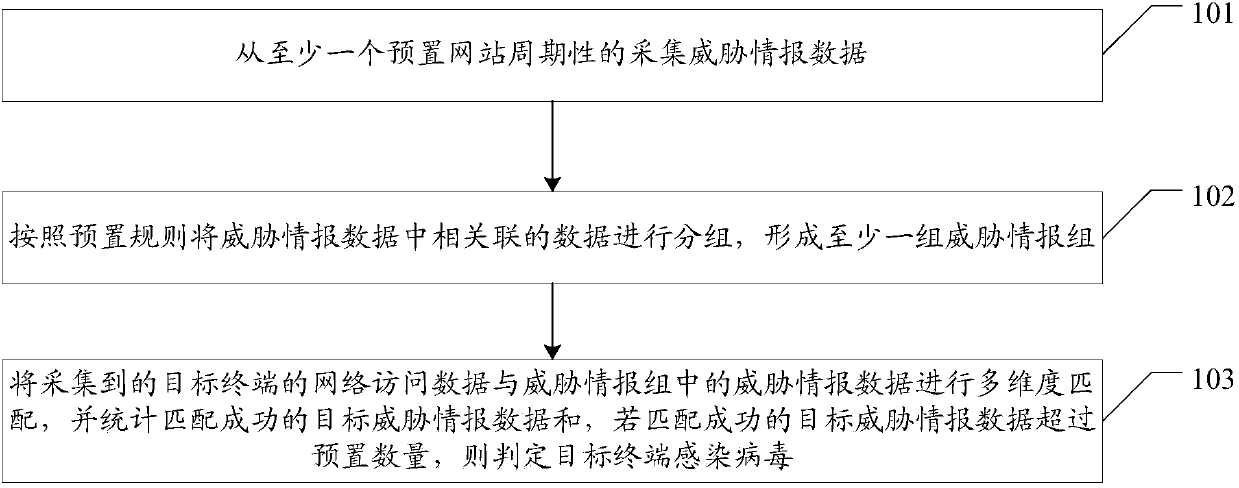
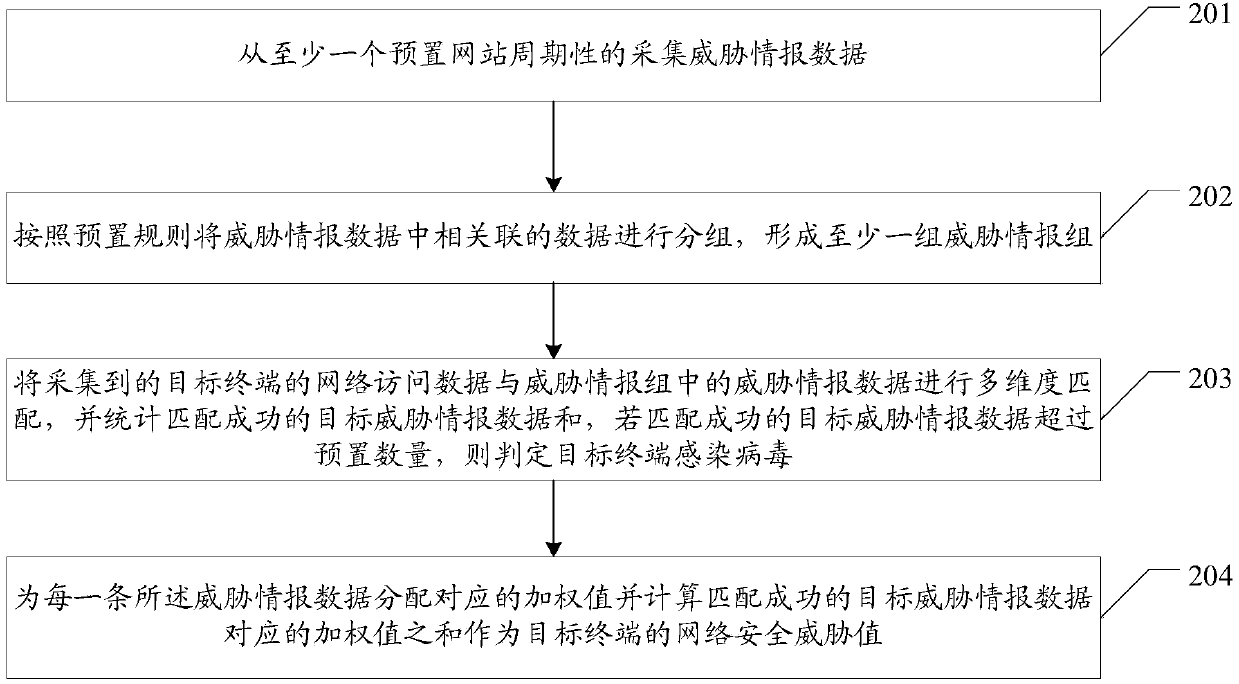
Threat intelligence-based network security detection method and system
The embodiment of the invention provides a threat intelligence-based network security detection method and system, aiming at improving the accuracy of network security detection. The method provided by the embodiment of the invention includes the following steps: periodically acquiring threat intelligence data from at least one preset website; grouping associated data in the threat intelligence data according to a preset rule to form at least one threat intelligence group, wherein the threat intelligence group includes at least one type of the threat intelligence data, and each type of the threat intelligence data includes one or more pieces of data; and performing multidimensional matching on acquired network access data of a target terminal and the threat intelligence data in the threatintelligence group, and calculating target threat intelligence data that is successfully matched, and if the number of the target threat intelligence data that is successfully matched exceeds a presetnumber, determining that the target terminal is infected with a virus.
Owner:SANGFOR TECH INC
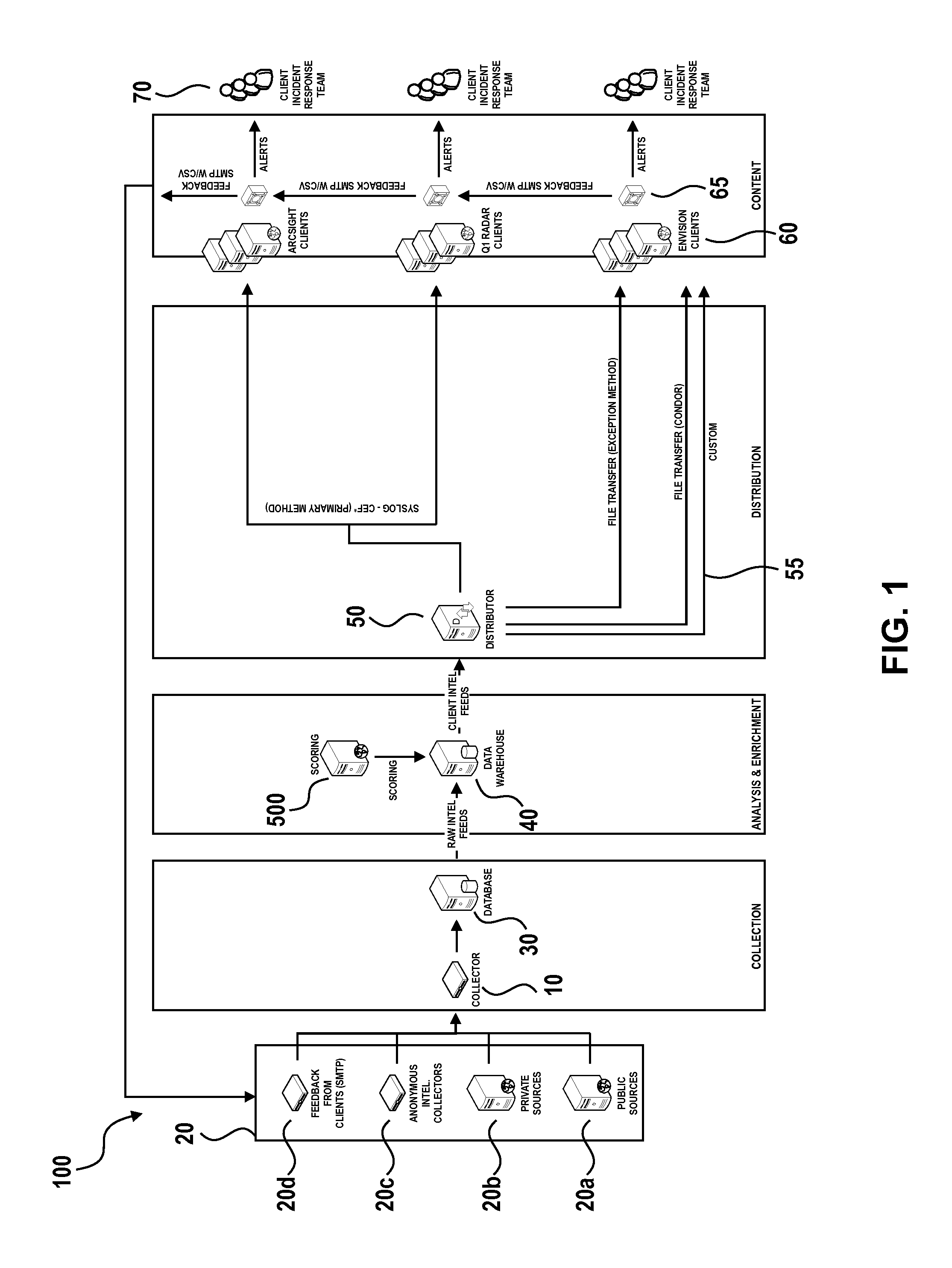
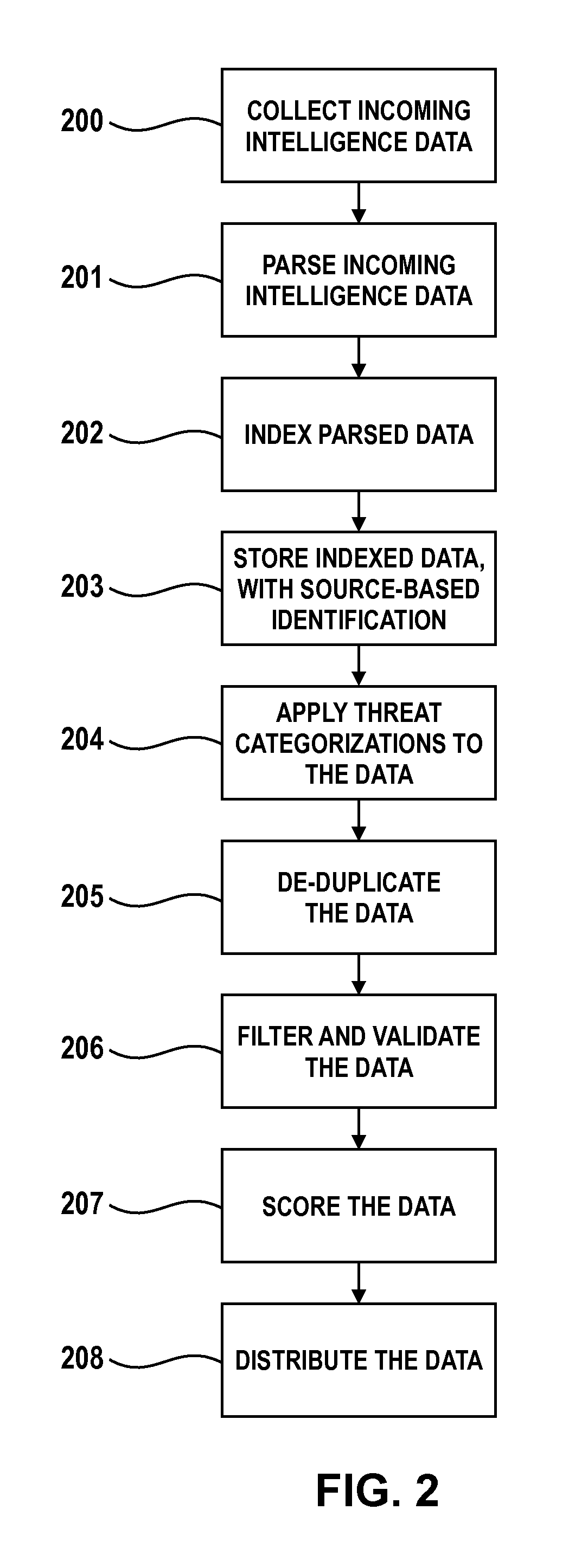
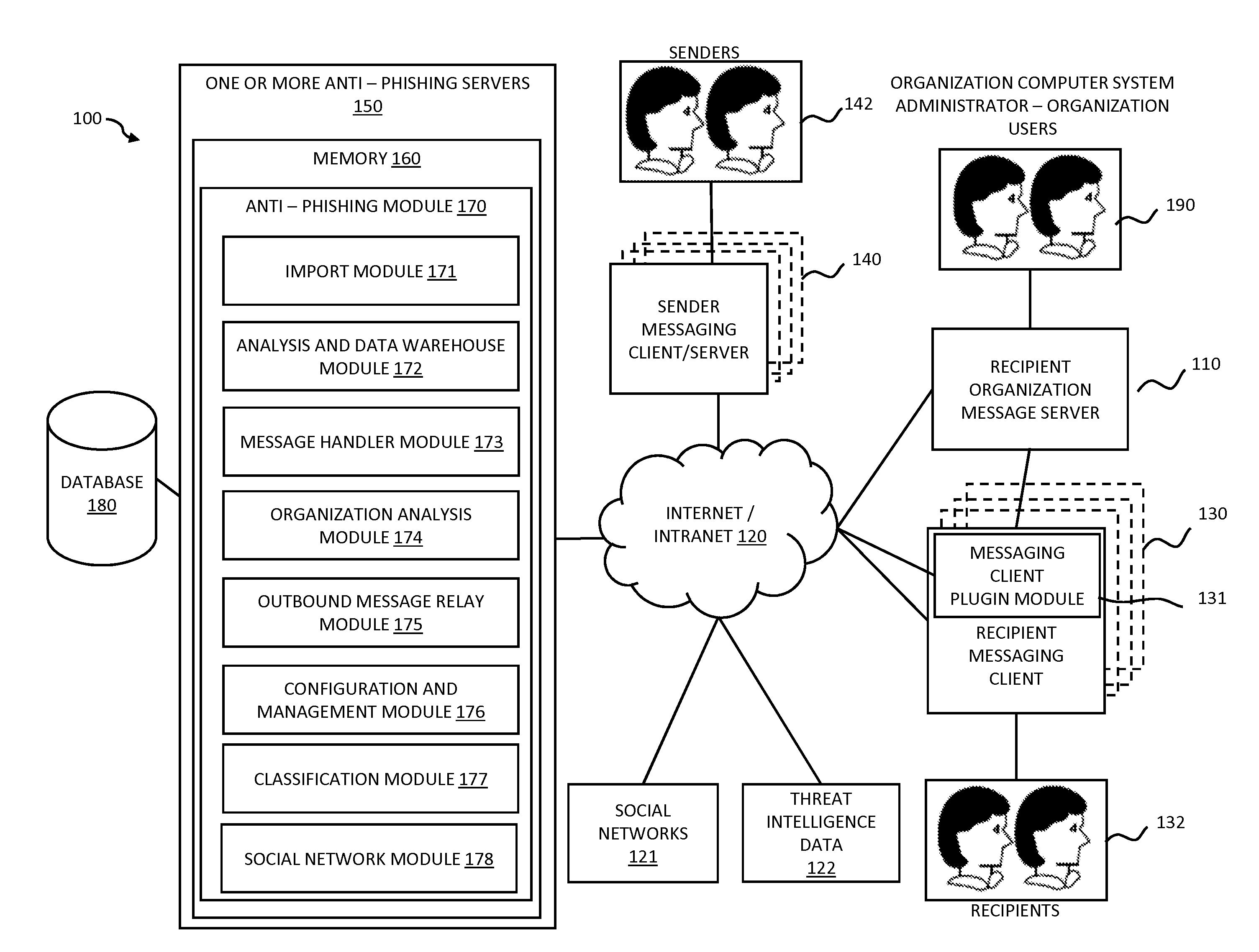
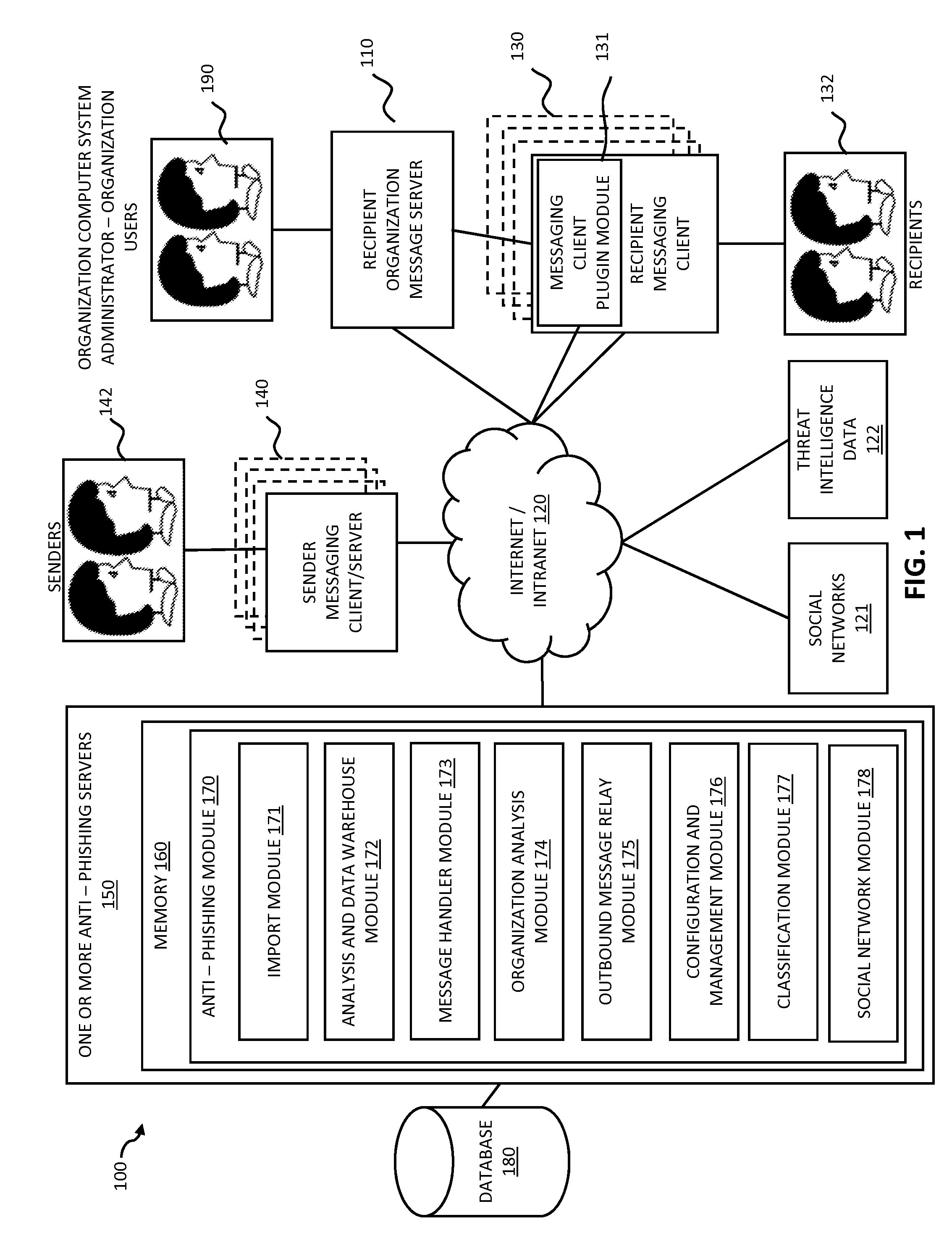
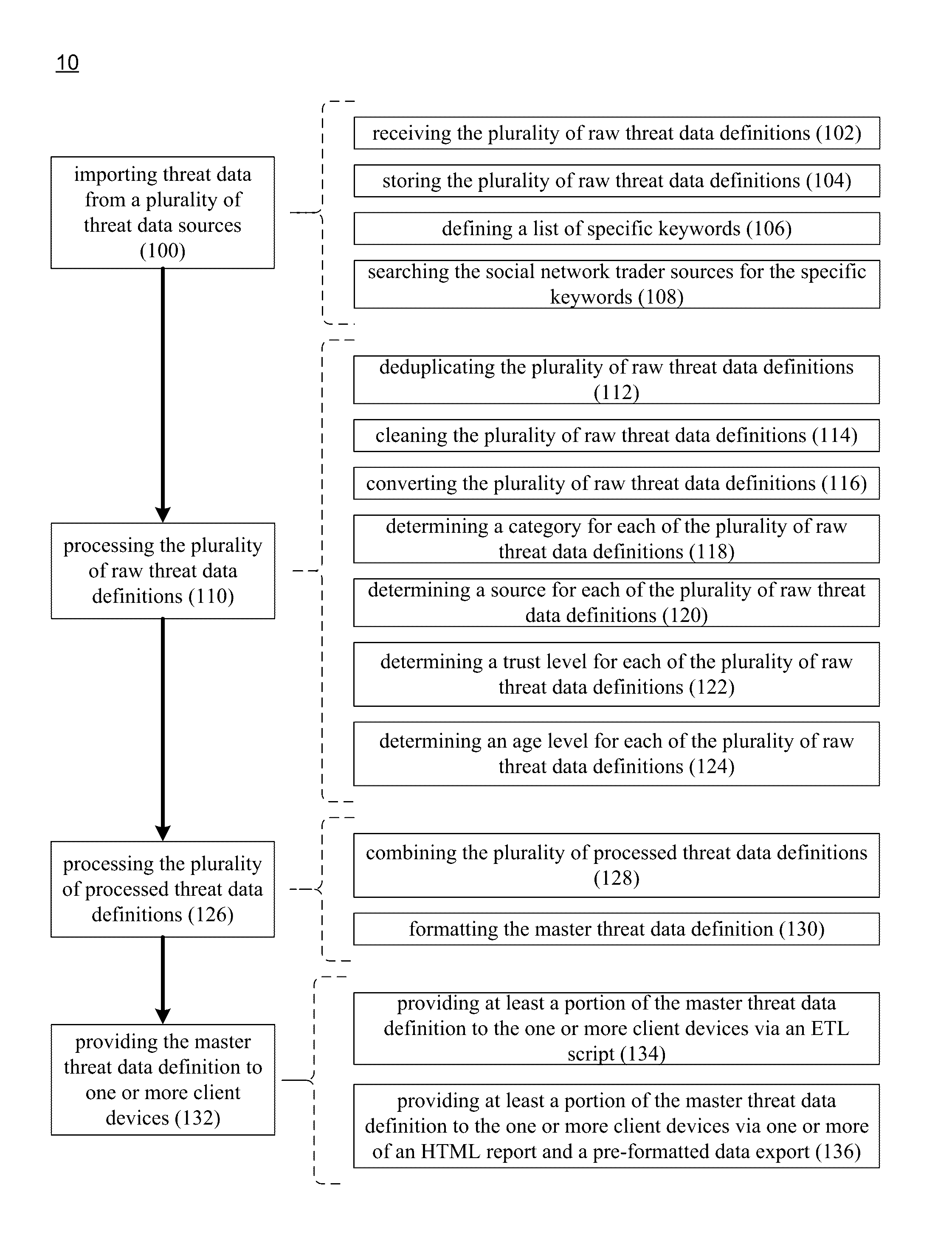
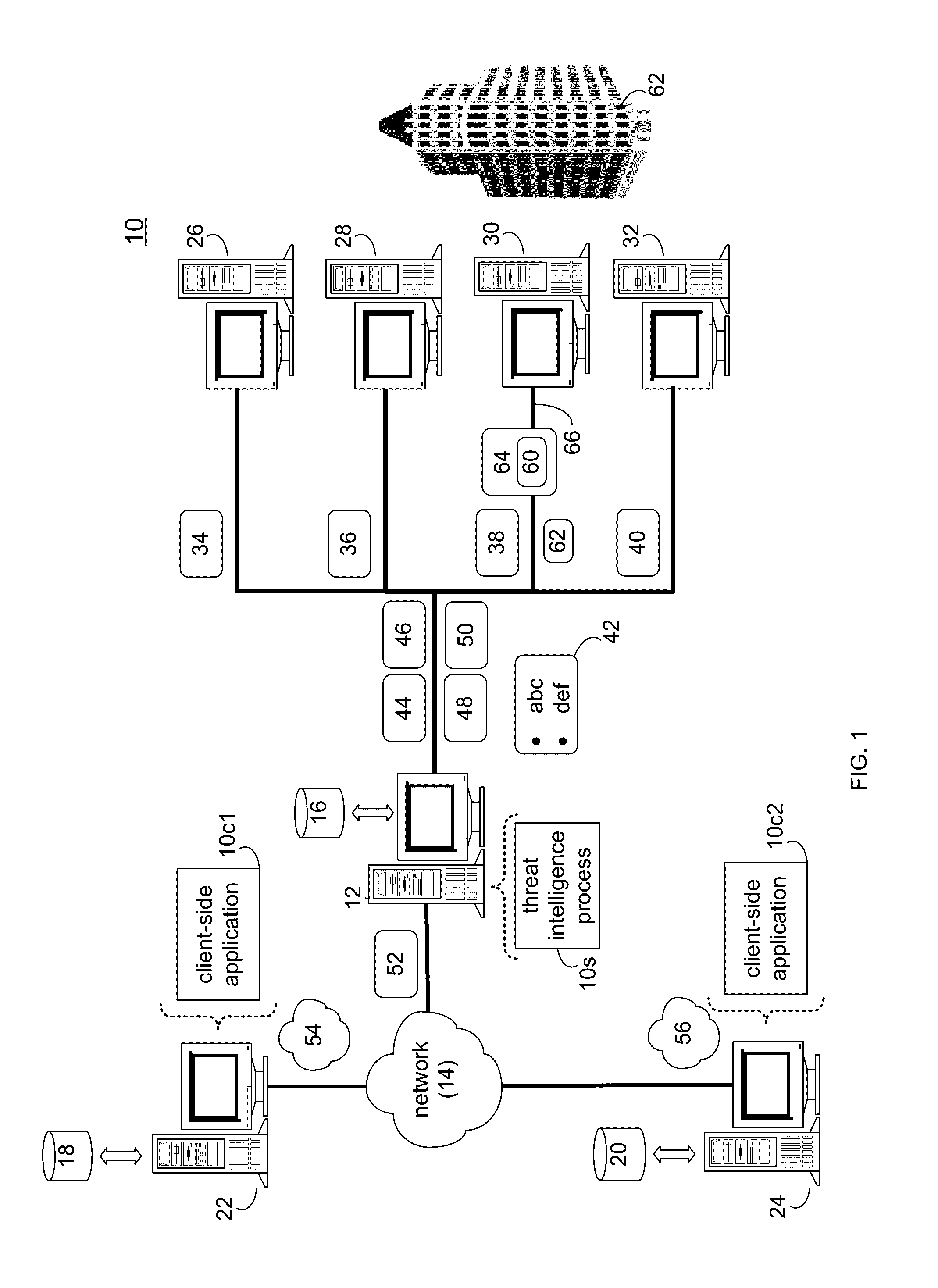
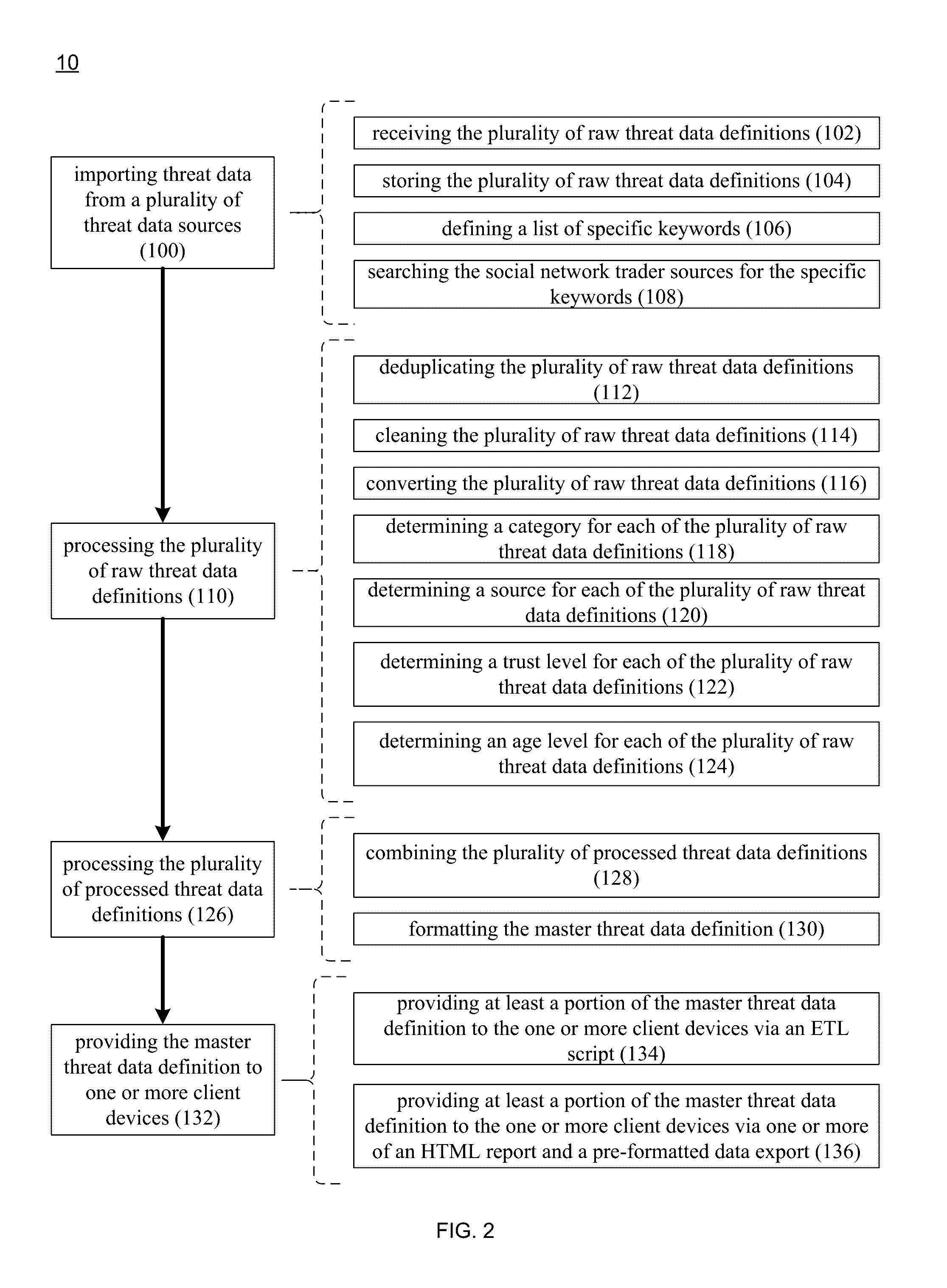
Threat intelligence system and method
A computer-implemented method, computer program product and computing system for importing threat data from a plurality of threat data sources, thus generating a plurality of raw threat data definitions. The plurality of raw threat data definitions are processed, thus generating a plurality of processed threat data definitions. The plurality of processed threat data definitions are processed to form a master threat data definition. The master threat data definition is provided to one or more client electronic devices.
Owner:RELIAQUEST HLDG LLC
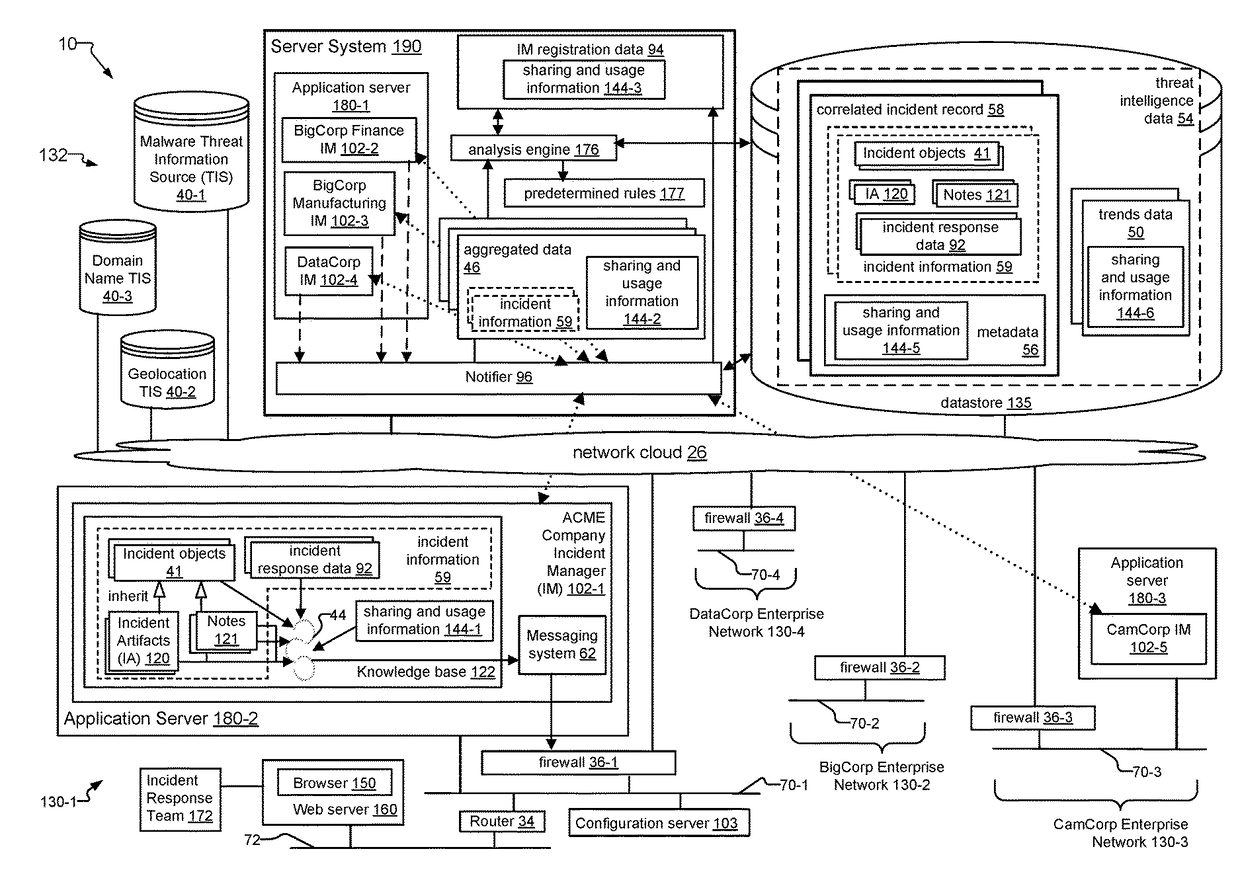
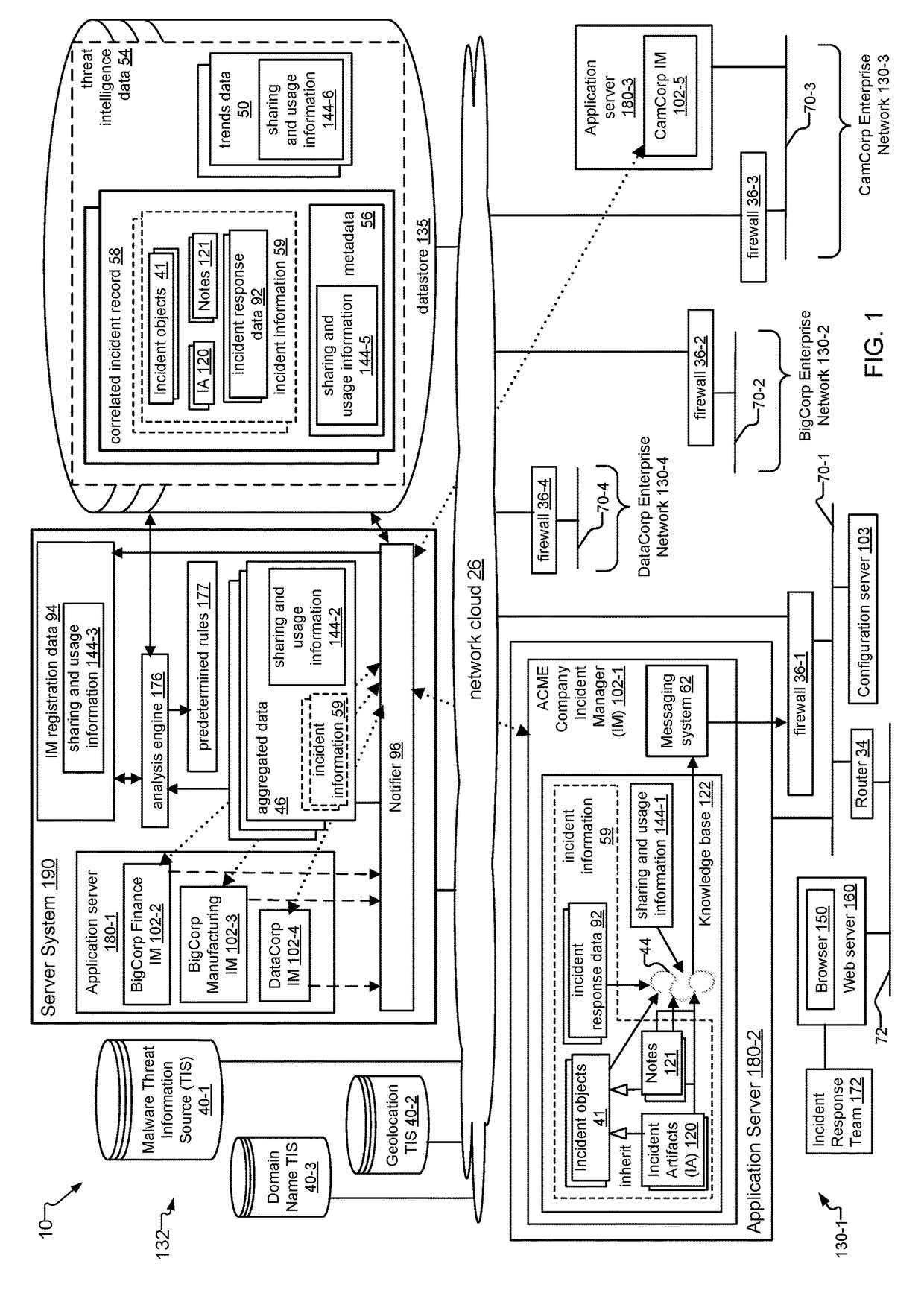
Data Security Incident Correlation and Dissemination System and Method
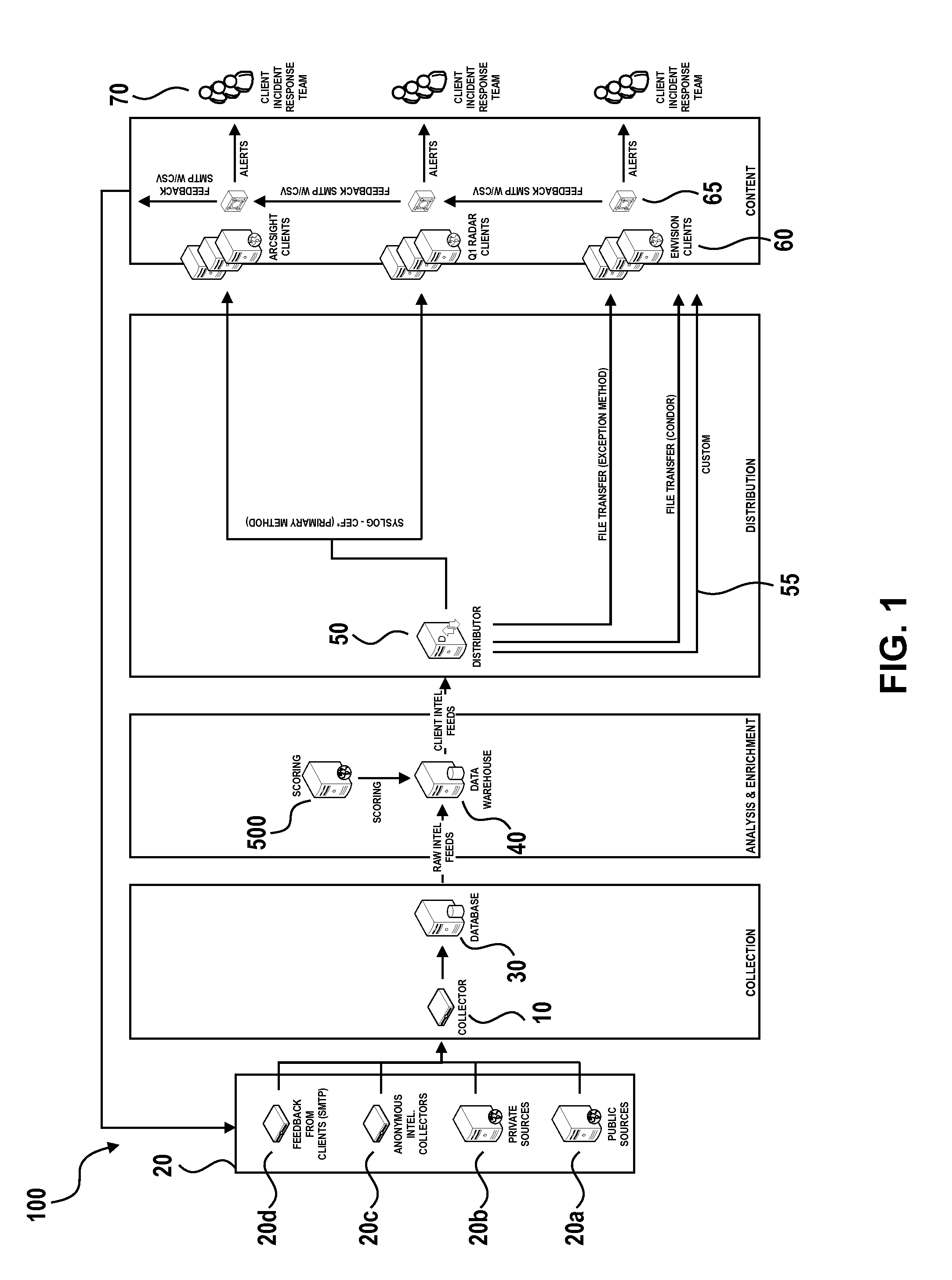
A data security incident correlation and dissemination system and method is disclosed. In an exemplary implementation of the system, a service provider of a managed security service receives incident information regarding data security incidents at different business organizations of the security service. One or more incident managers operated by different organizations send incident information, and a server system within the service provider's network creates aggregated data from the incident information received from the incident managers. The server system analyzes the aggregated data to create correlated incident records that include incident information from related data security incidents at the different organizations, and provides threat intelligence data based on the correlated incident records for the organizations. In embodiments, the server system can “push” threat intelligence data to the organizations, or the organizations can request the threat intelligence data from the server system.
Owner:GREEN MARKET SQUARE LTD
Log-based threat intelligence detection method and device
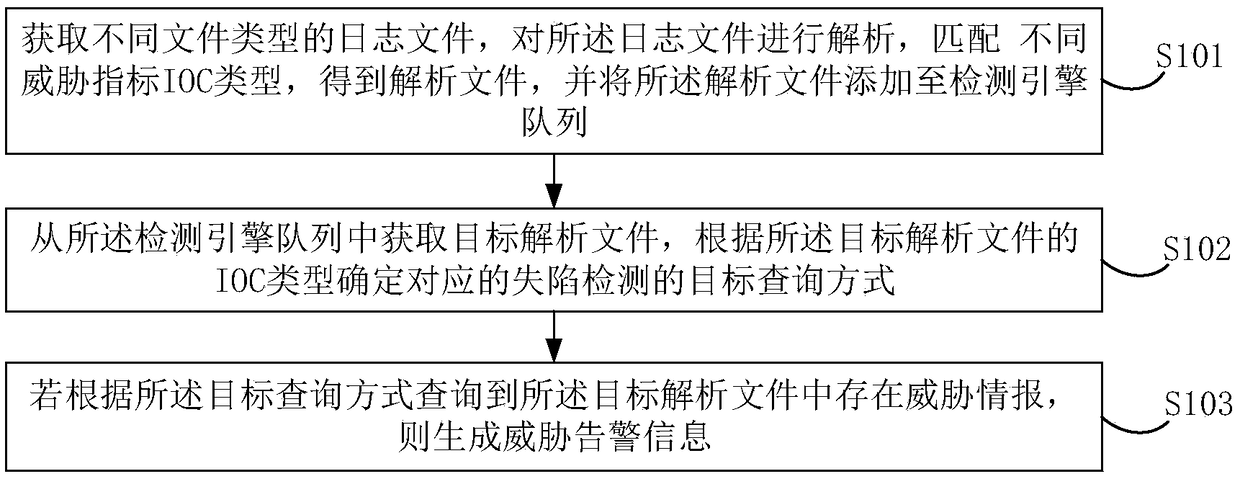
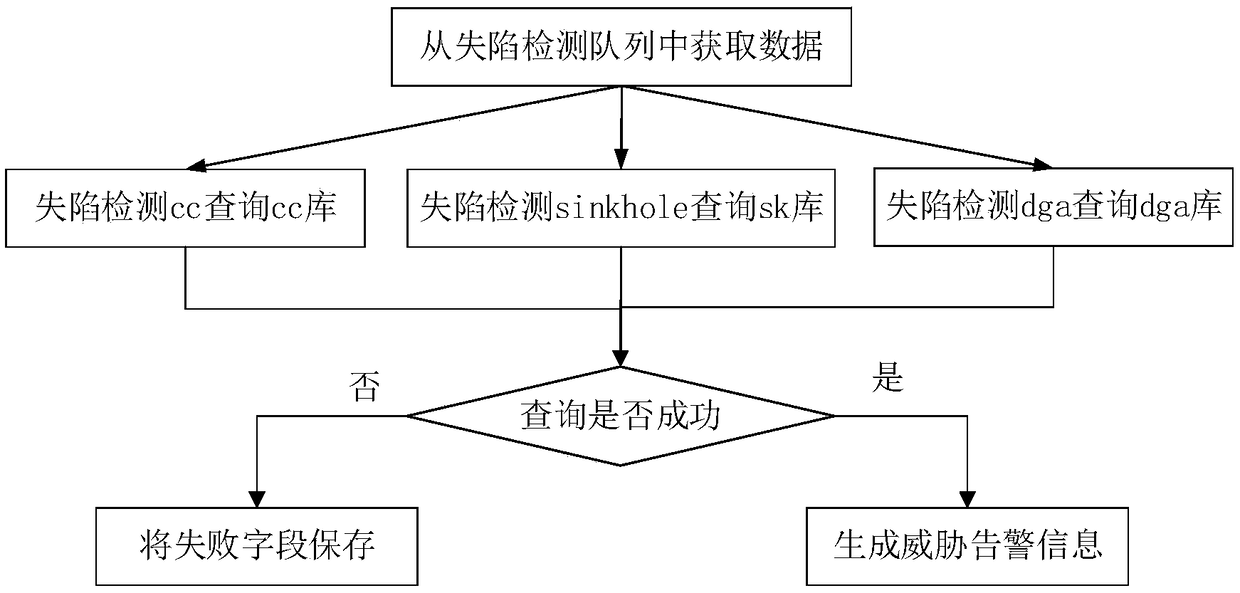
ActiveCN108763031AImprove detection efficiencyHardware monitoringPlatform integrity maintainanceTarget analysisComputer science
Embodiments of the invention disclose a log-based threat intelligence detection method and device. The method comprises the steps of obtaining log files of different file types, analyzing the log files, matching different IOC types, and adding analysis files of the different IOC types to a detection engine queue; obtaining a target analysis file from the detection engine queue, and determining a corresponding target query mode according to the IOC type of the target analysis file; and if it is queried that threat intelligence exists in the target analysis file according to the target query mode, generating threat alert information, which, for example, includes an attacked host or a malicious file. The log files of the different file types are analyzed, and the target analysis file is queried in the corresponding attack detection query mode, so that large-batch data can be processed at the same time, and the network security detection efficiency of massive data is greatly improved.
Owner:BEIJING QIANXIN TECH
Collapsed host computer detection method
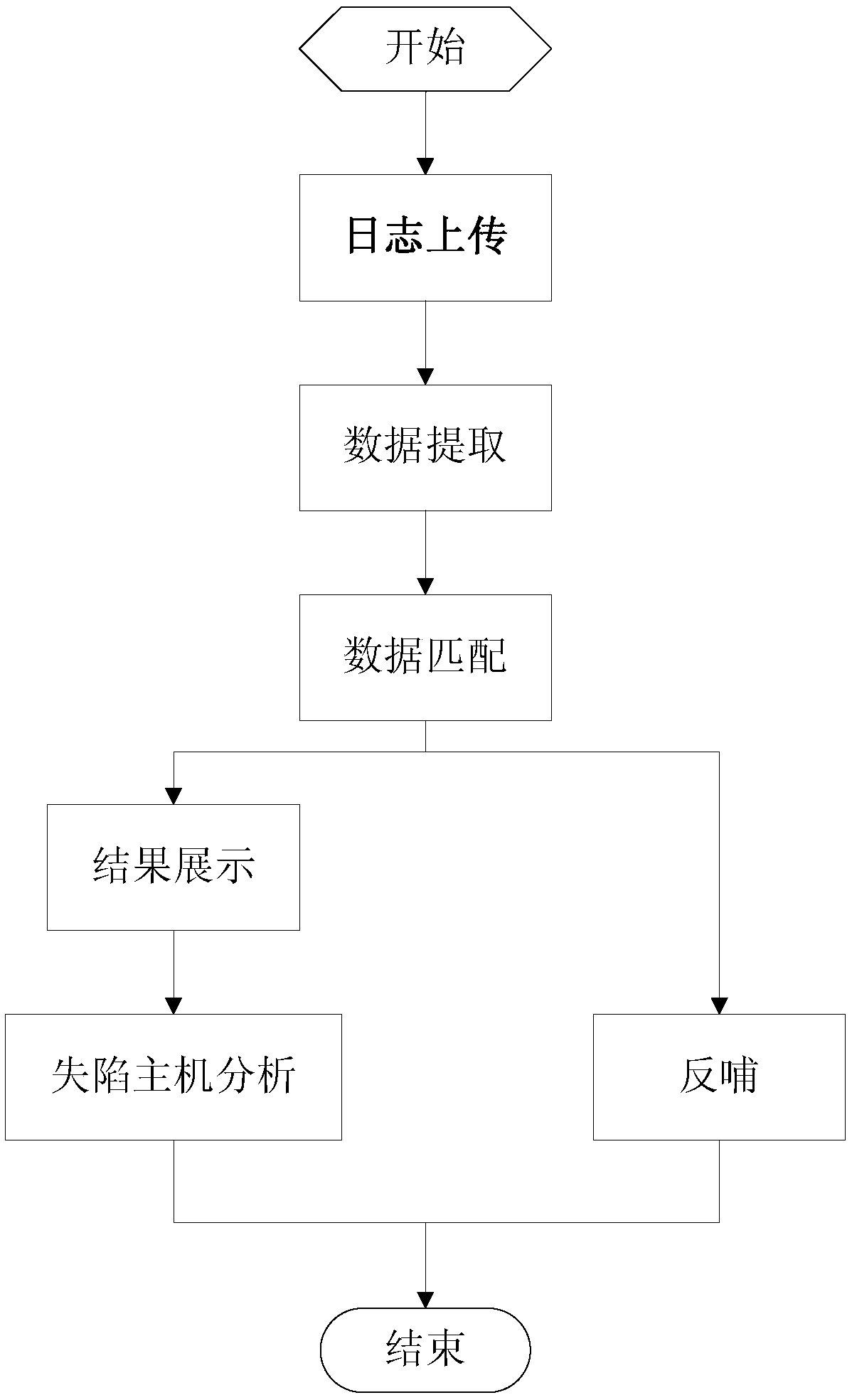
The invention discloses a collapsed host computer detection method. The method comprises: a log upload step: boundary security probe equipment uploads log data including an application access log, a URL access log, a file transmission log and a threat log generated by the traffic between security domains to a security cloud early warning platform; a data extraction step: the security cloud early warning platform aggregates log data reported by the boundary security probe equipment to a cloud big data analysis engine, the cloud big data analysis engine mines the abnormal behaviors of a user whose host deviates from a normal baseline in a network, generates abnormal behavior data, and aggregates the threat log into threat information; and a data matching steps: the security cloud early warning platform performs matching collision on the threat information and the abnormal behaviors of the user whose host deviates from the normal baseline in the network through the cloud big data analysisengine, and predicts a suspected collapsed host computer.
Owner:SHANGHAI UNIV OF ENG SCI
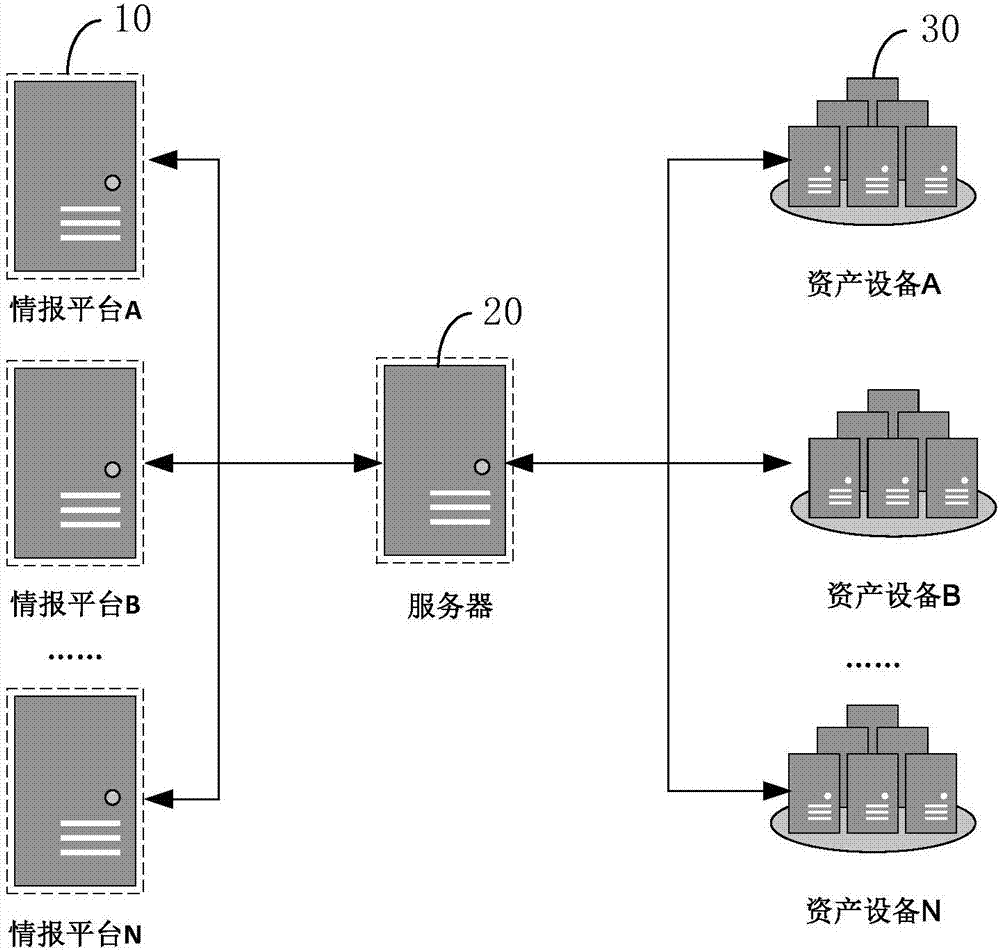
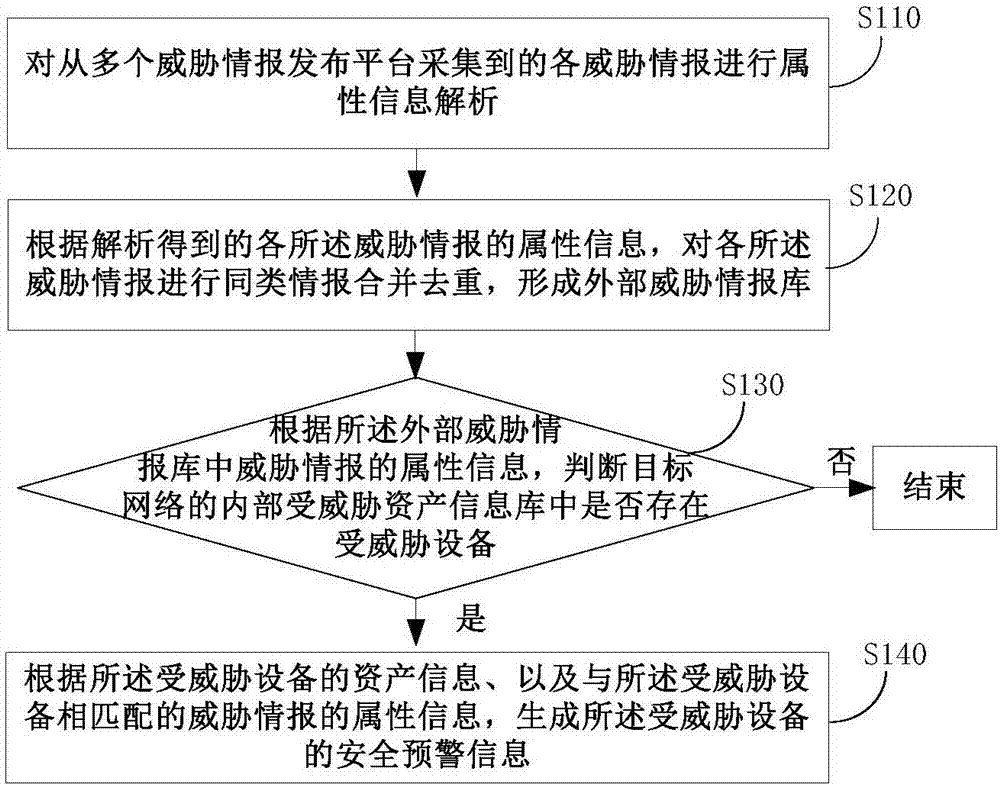
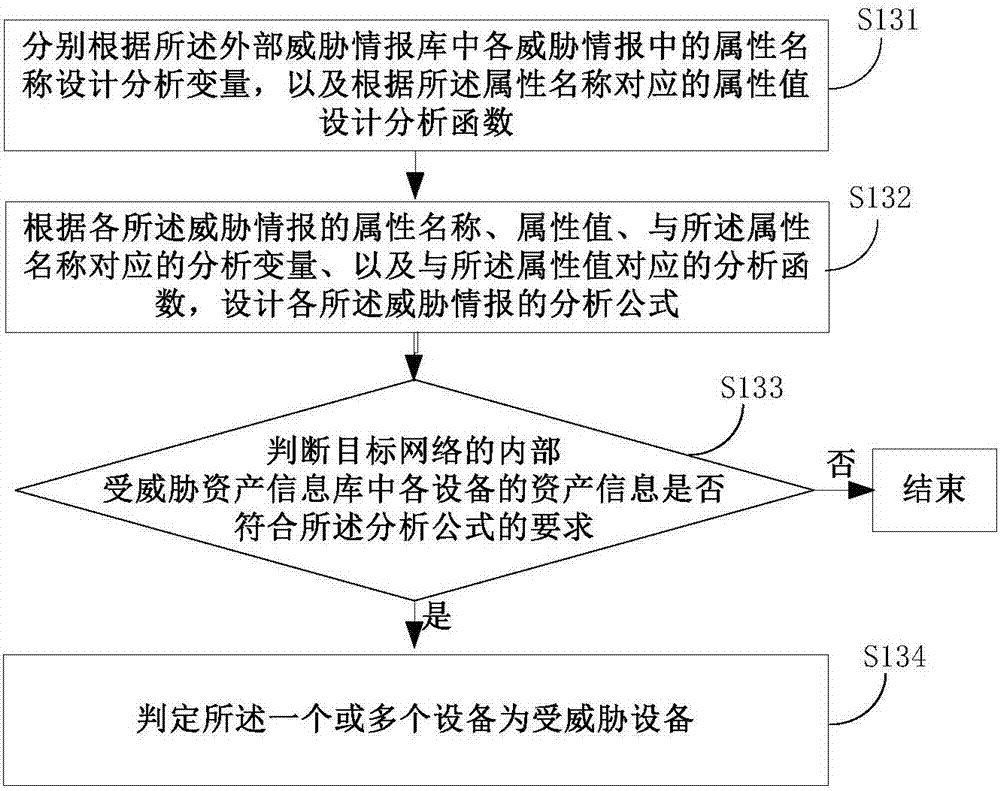
Method and device for asset safety early warning based on external threat information analysis
ActiveCN107370763AIncrease diversityImprove accuracyTransmissionInformation repositoryInformation analysis
The invention discloses a method and a device for asset safety early warning based on external threat information analysis. The method specifically comprises: through acquiring latest threat intelligence information issued by authority organizations at home and abroad, and performing similar information deduplication combination on the acquired threat intelligence information, generating final threat intelligence information in an external threat intelligence bank; then, according to attribute information of the threat information in the formed external threat intelligence bank, detecting whether a threatened device exist in an internal threatened asset information base. Since source of intelligence information in the external threat intelligence bank is wide, complementation of threat intelligence information issued by each threat intelligence issue platform can be realized, to form the external threat intelligence bank which is comprehensive and accurate in contents, and high in timeliness. At the same time, when the external threat intelligence bank is used for safe early warning on asset and equipment in a target network, a problem that intelligence information is too simple when information issued by a single threat intelligence platform is used can be prevented.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
Tracing analysis method for network attacks
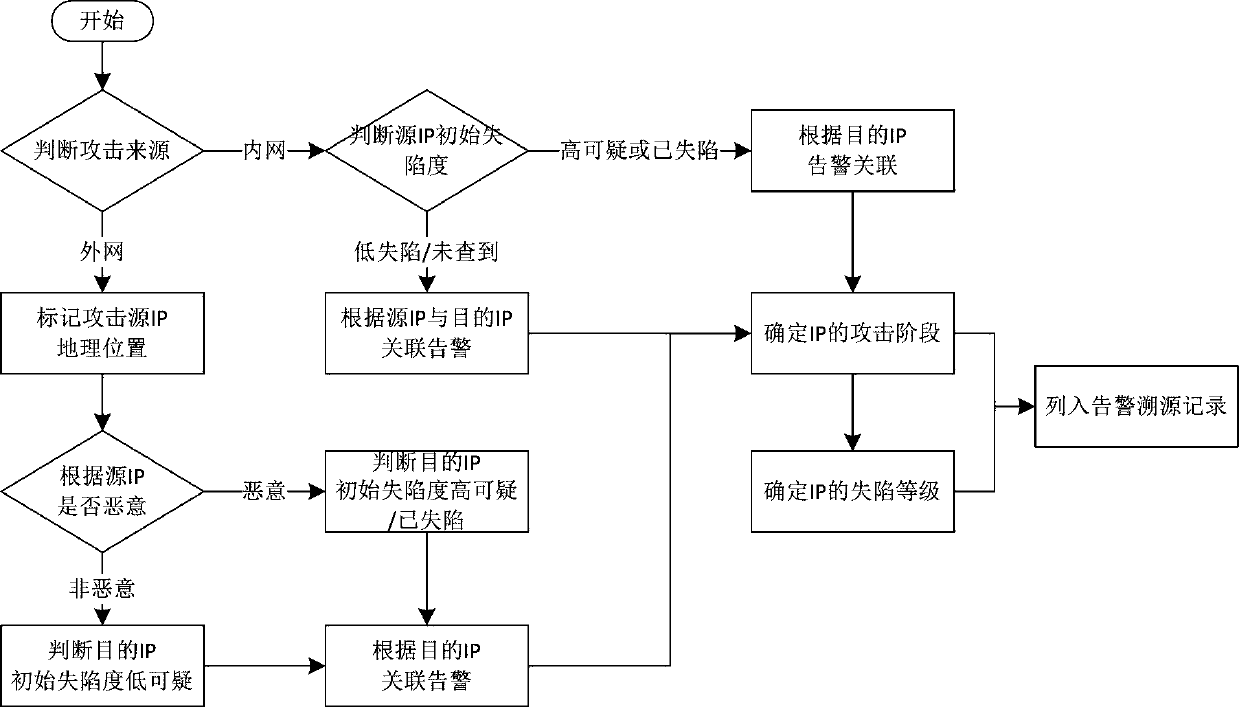
PendingCN111490970ATraceability analysis is effectiveEasy to handleData switching networksComputer networkAttack
The invention discloses a tracing analysis method for network attacks, which comprises the following steps: acquiring threat intelligence of a specified type, and caching the threat intelligence to alocal threat intelligence database; acquiring current alarm information and the local threat information, and judging the attack source of the alarm; respectively carrying out alarm association according to the attack source and / or the equipment identifier of the attack target, determining the attack stage of the equipment, and judging the equipment collapse level according to the attack stage; and obtaining asset information of the equipment, and determining the influence range of the attack according to the alarm association result. Effective traceability analysis of network attacks is achieved, various traceability results are obtained, traceability data can be updated every time traceability is conducted, and a basis is provided for network operation and maintenance personnel to handleproblems and strengthen security policies.
Owner:西安交大捷普网络科技有限公司
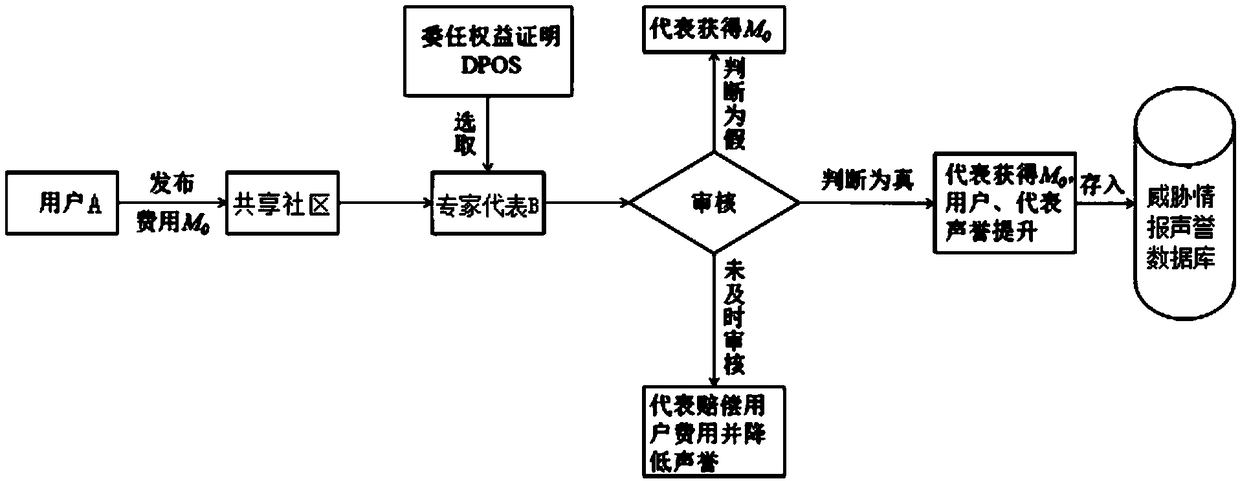
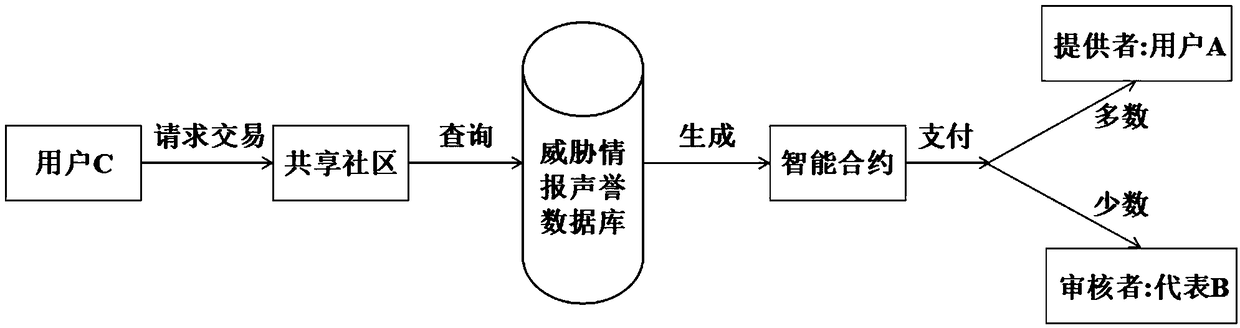
Blockchain-based threat intelligence exchange sharing system and method
InactiveCN108965247AAvoid interruptionImprove stabilityFinanceTransmissionInternet privacySecurity expert
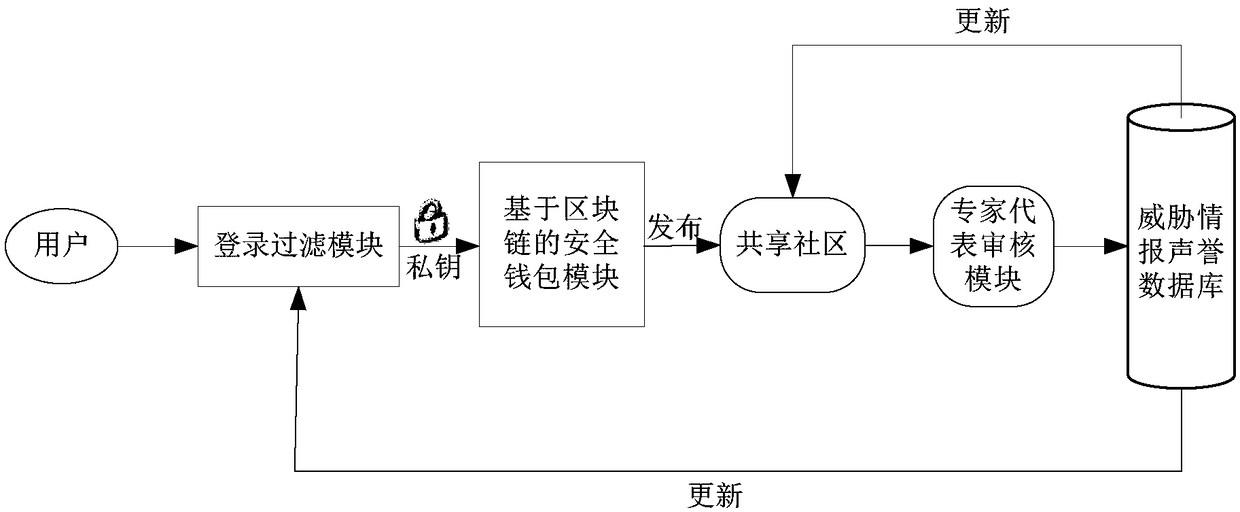
The invention relates to the field of computer network security and discloses a blockchain-based threat intelligence exchange and sharing system comprising a login filtering module, a blockchain-basedsecurity wallet module, a sharing community, an expert representative review module and a threat intelligence reputation database. Threat intelligences form an exiting security manufacturer and security expert individual are original inputs of the threat intelligence exchange and sharing system; and threat intelligences inputted by individual users subsequently are stored into the threat intelligence reputation database after examination and verification of effectiveness by expert representatives. According to the invention, threat intelligences of all sources are collected and the collectedthreat intelligences are stored and updated by the blockchain, so that the timeliness and effectiveness of threat intelligence sharing as well as the threat intelligence sharing security, confidentiality and privacy are improved.
Owner:SHANGHAI JIAO TONG UNIV
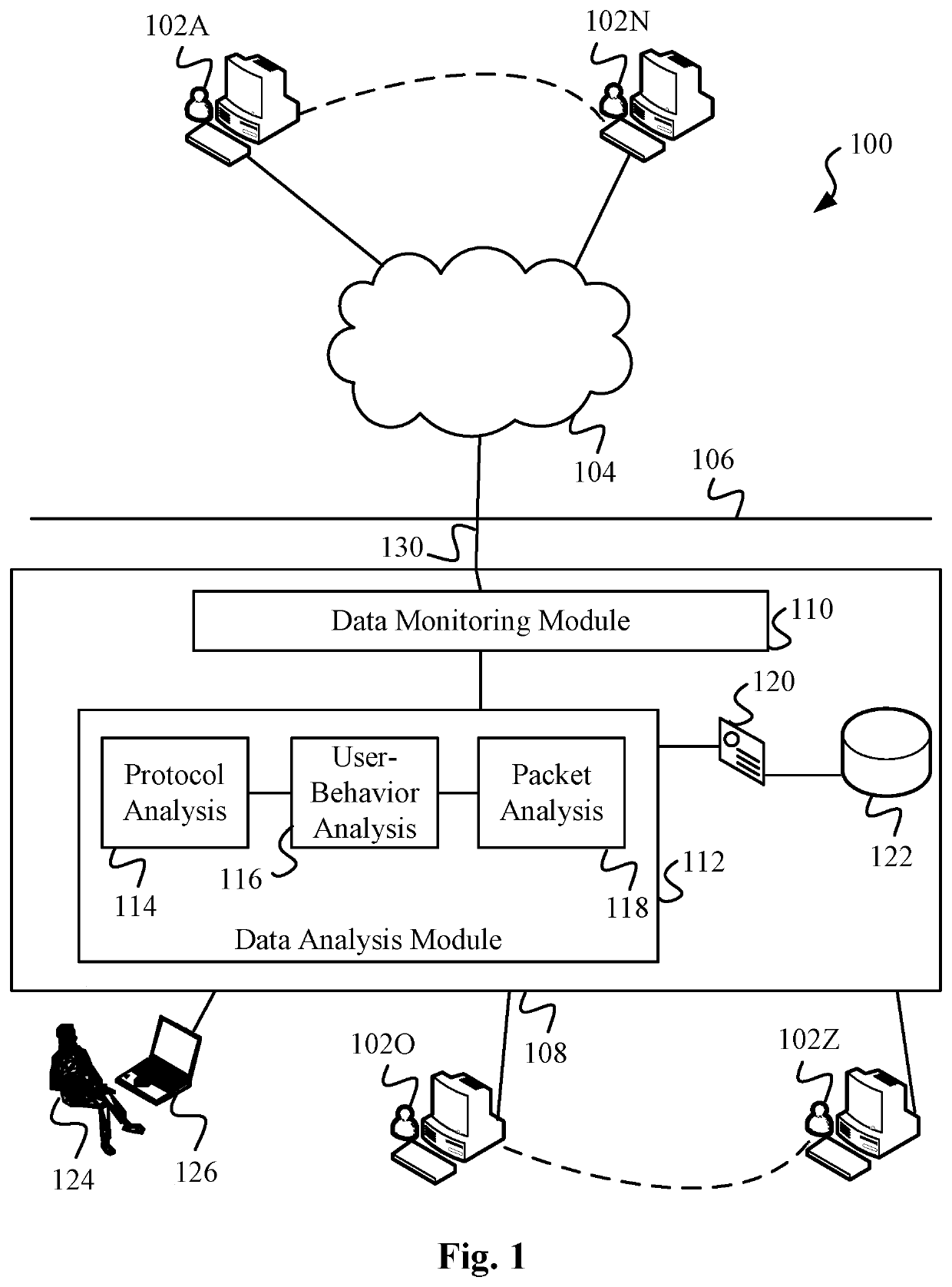
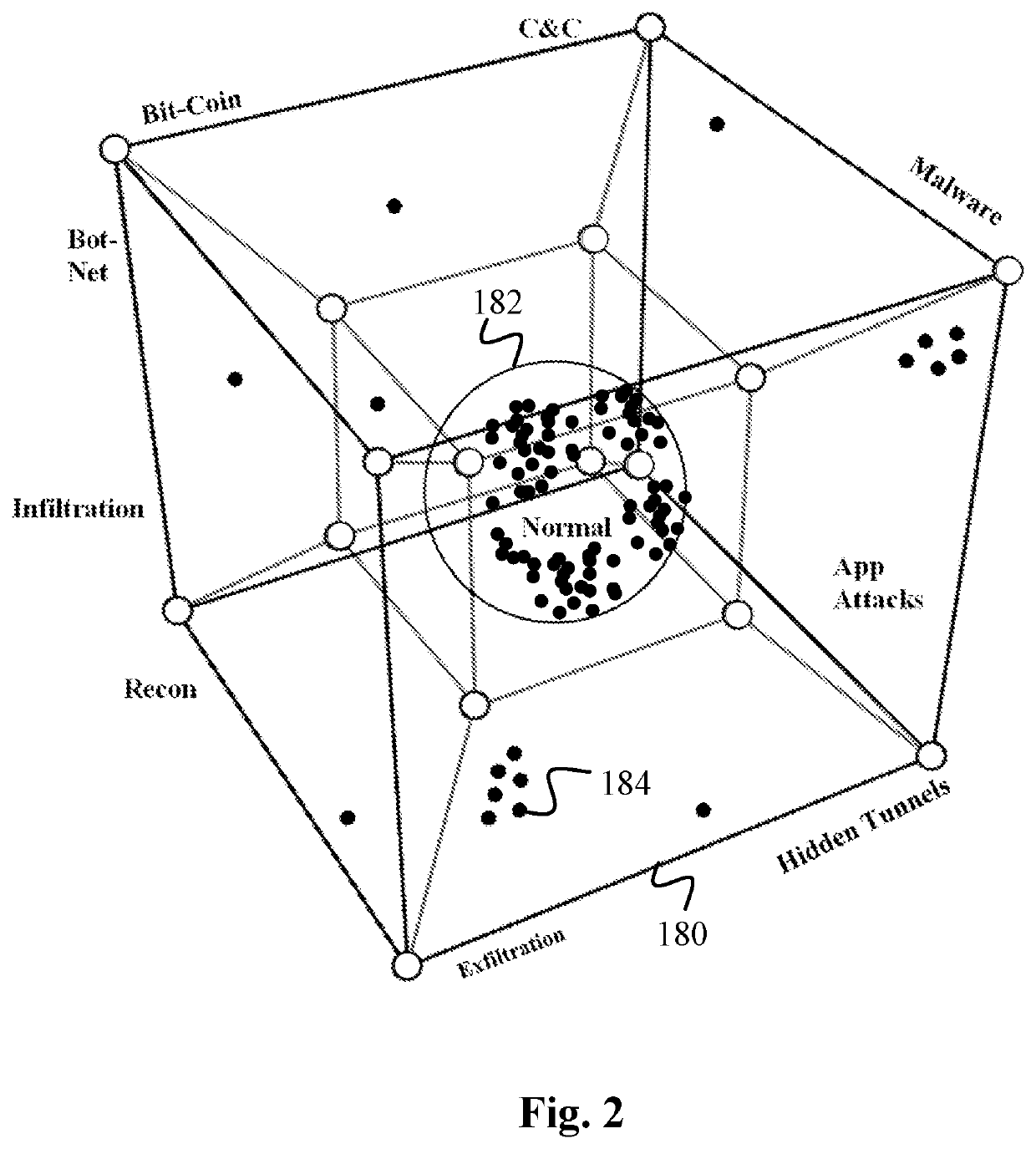
Data Surveillance for Privileged Assets based on Threat Streams
ActiveUS20200204574A1Quick fixMinimal user interactionEncryption apparatus with shift registers/memoriesCharacter and pattern recognitionStreaming dataData pack
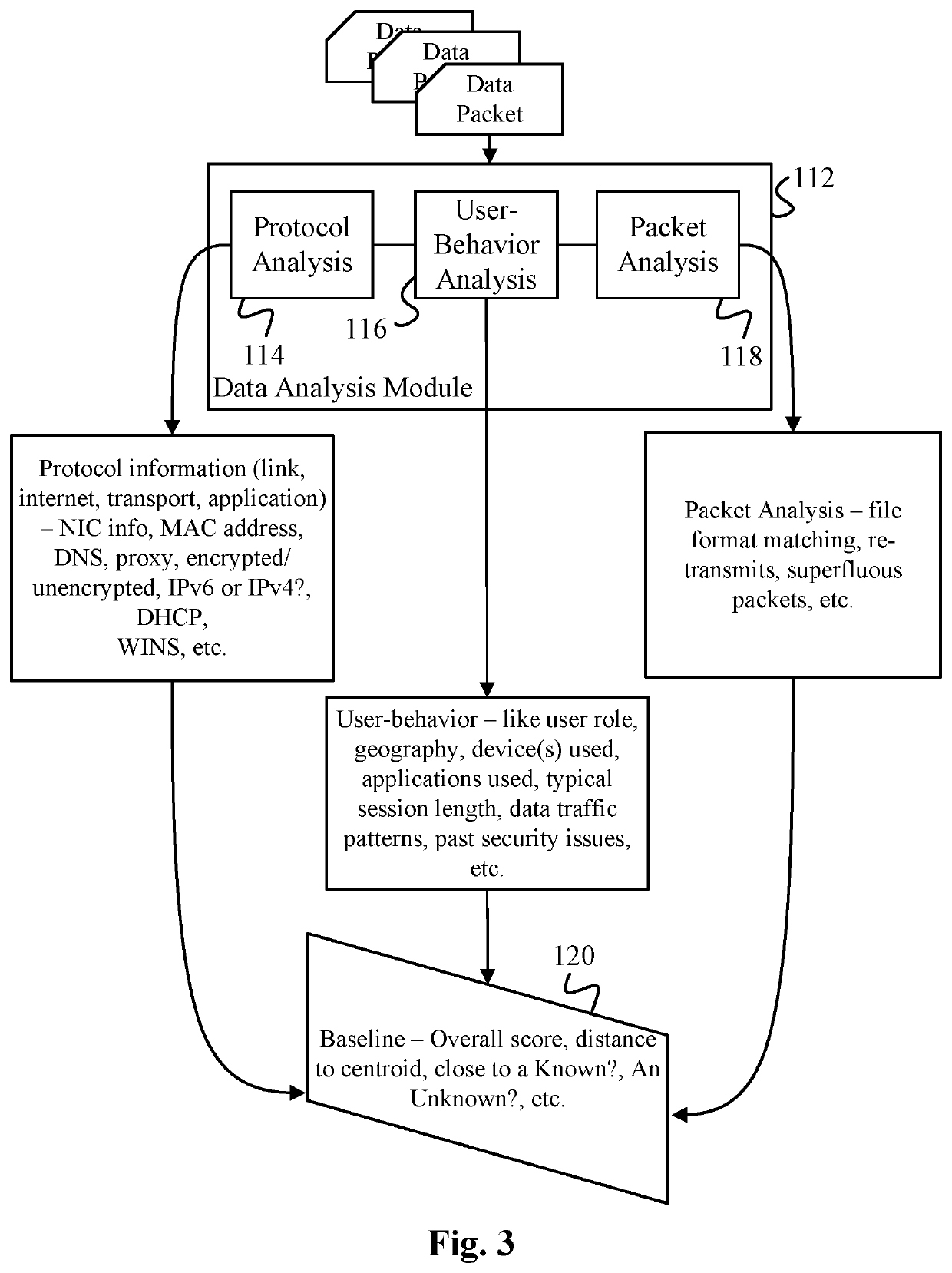
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The above data surveillance techniques are also applied for detecting intentional or unintentional exfiltration / leak of privileged data / assets between unauthorized users / groups of the organization. Such detection may be performed based on analyzing threat stream data from threat intelligence providers.
Owner:FLYING CLOUD TECH INC
System and Method for High Speed Threat Intelligence Management Using Unsupervised Machine Learning and Prioritization Algorithms
ActiveUS20170228658A1Effectively and efficiently aggregatedReduce data volumePlatform integrity maintainanceMachine learningThird partySorting algorithm
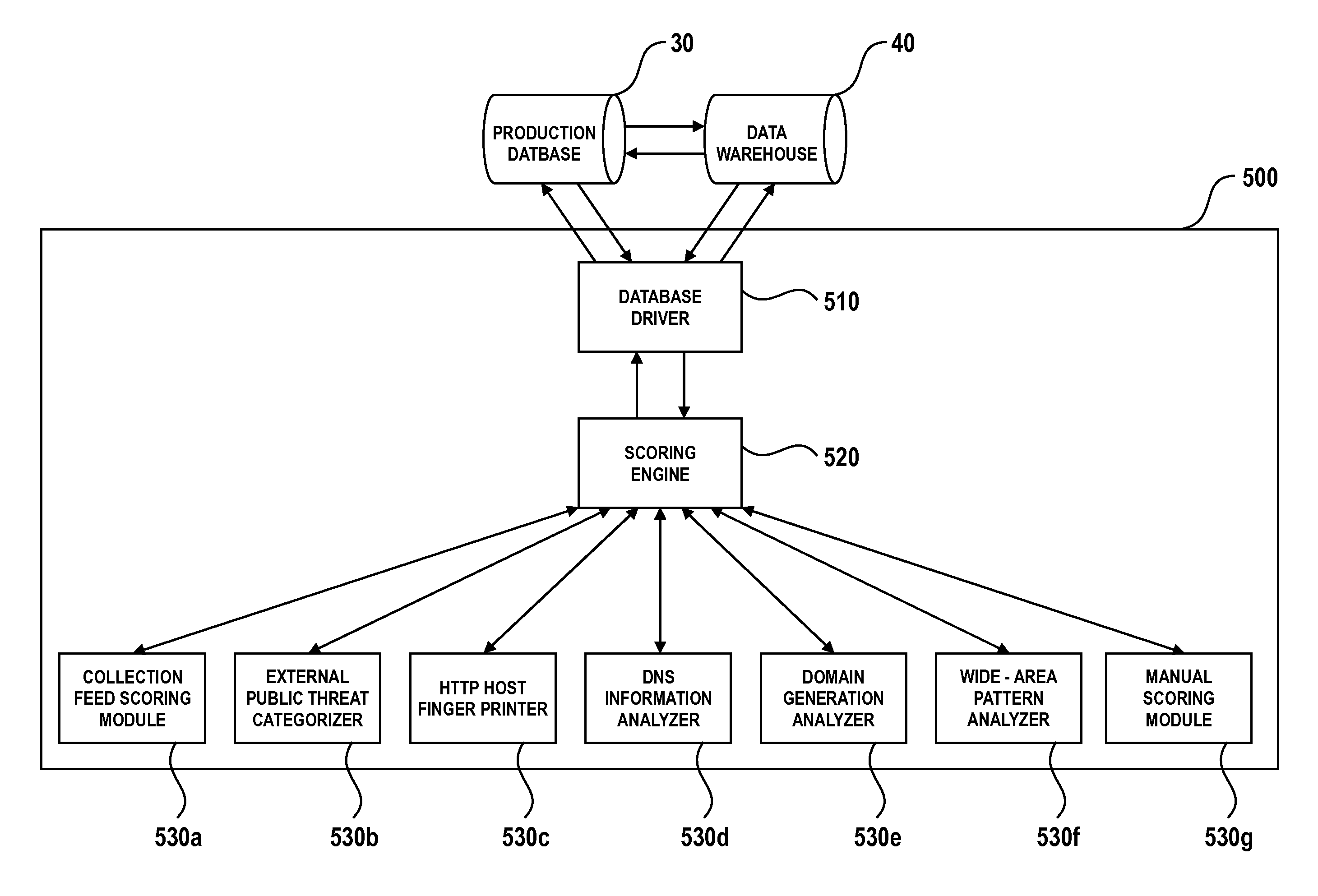
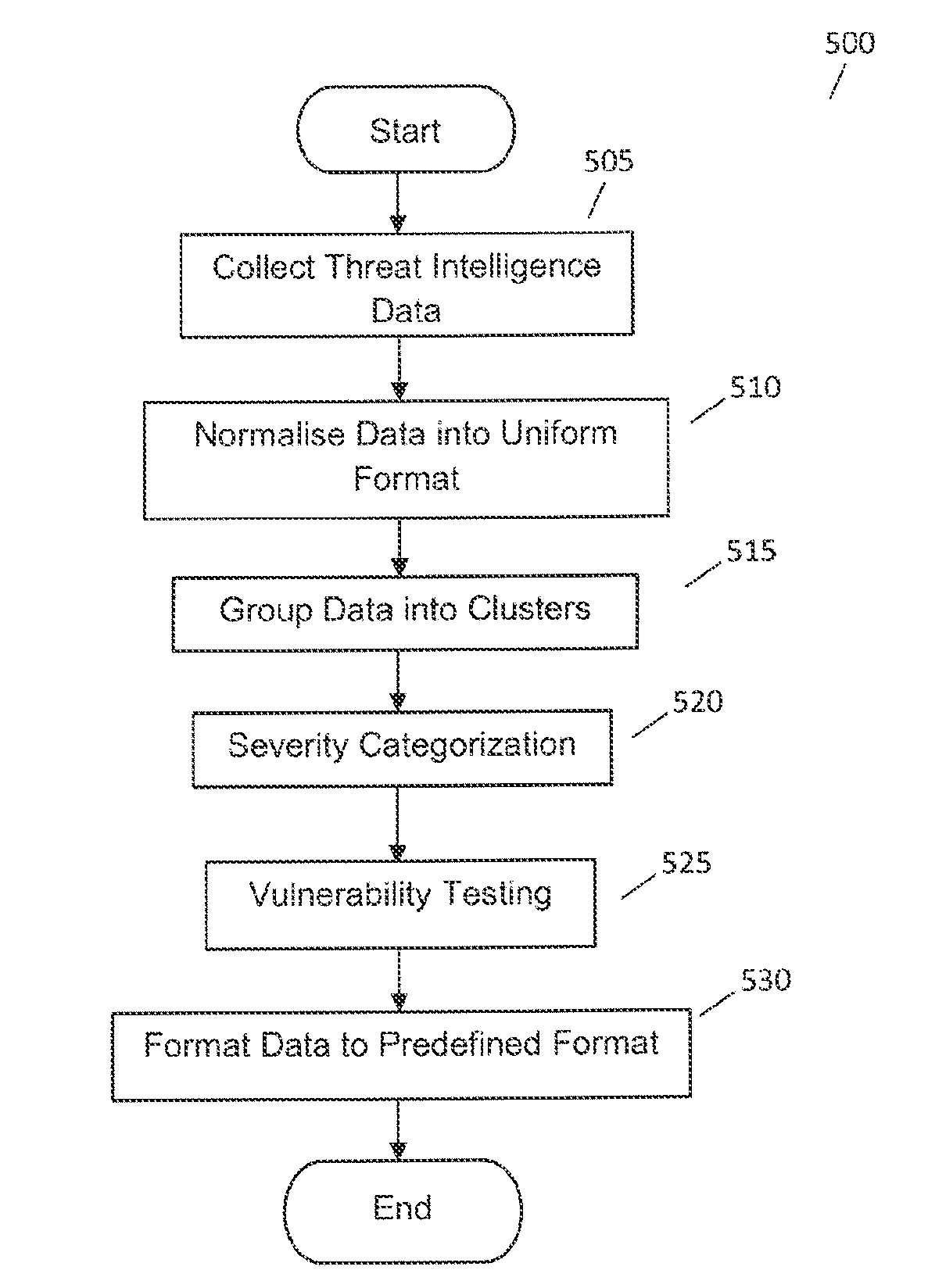
This document discloses a system and method for consolidating threat intelligence data for a computer and its related networks. Massive volumes of raw threat intelligence data are collected from a plurality of sources and are partitioned into a common format for cluster analysis whereby the clustering of the data is done using unsupervised machine learning algorithms. The resulting organized threat intelligence data subsequently undergoes a weighted asset based threat severity level correlation process. All the intermediary network vulnerabilities of a particular computer network are utilized as the critical consolidation parameters of this process. The final processed intelligence data gathered through this high speed automated process is then formatted into predefined formats prior to transmission to third parties.
Owner:CERTIS CISCO
Intelligent security event association analysis system for threat scene
PendingCN112738016APerform operations effectivelyShorten the timeCharacter and pattern recognitionData switching networksAttackInternet traffic
The invention provides an intelligent security event association analysis system for a threat scene. The intelligent security event association analysis system comprises a mass format event storage module, an analysis module and a visual display module, and the analysis module comprises an event association analysis module, a comprehensive threat analysis module, an attack chain analysis module, an attack path analysis module, a Web attack deep analysis module, a network flow metadata behavior analysis module and a network abnormal behavior analysis module. The analysis system provided by the invention can summarize and rationalize threat data to automatically screen out an attack index (IOC) as a machine-readable threat intelligence (MRTI), and uses existing log contrast matching to easily discover uncommon trends or clues and effectively perform operations on the uncommon trends or clues. By combining a team, a process and a tool together, a system platform provides an unprecedented view from which threats come for a security team, the whole event can be tracked from head to tail, and a security response can be guided and blocked through a report.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
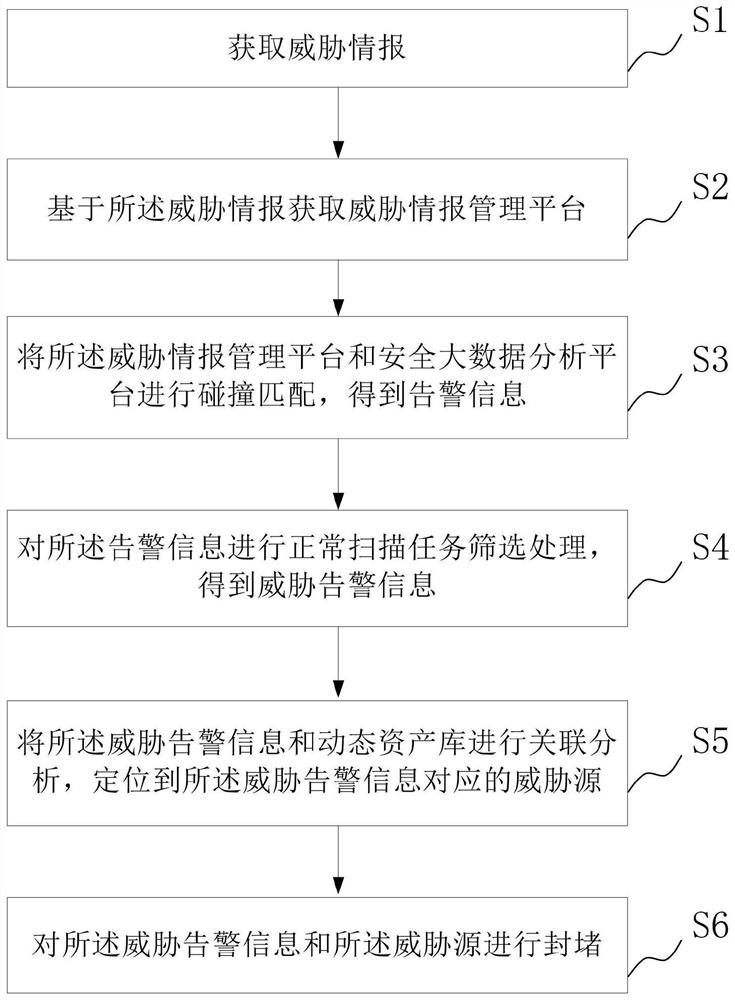
Threat intelligence defense method and system
InactiveCN111800395AEnsure safetyReduce false alarm rateTransmissionData profilingThreat intelligence
The invention provides a threat intelligence defense method and system. The method comprises the steps of acquiring threat intelligence; acquiring a threat information management platform based on thethreat information; performing collision matching on the threat intelligence management platform and the security big data analysis platform to obtain alarm information; performing normal scanning task screening processing on the alarm information to obtain threat alarm information; performing association analysis on the threat alarm information and a dynamic asset library, and positioning a threat source corresponding to the threat alarm information; and blocking the threat alarm information and the threat source. According to the invention, the network security can be effectively ensured.
Owner:云南电网有限责任公司信息中心 +1
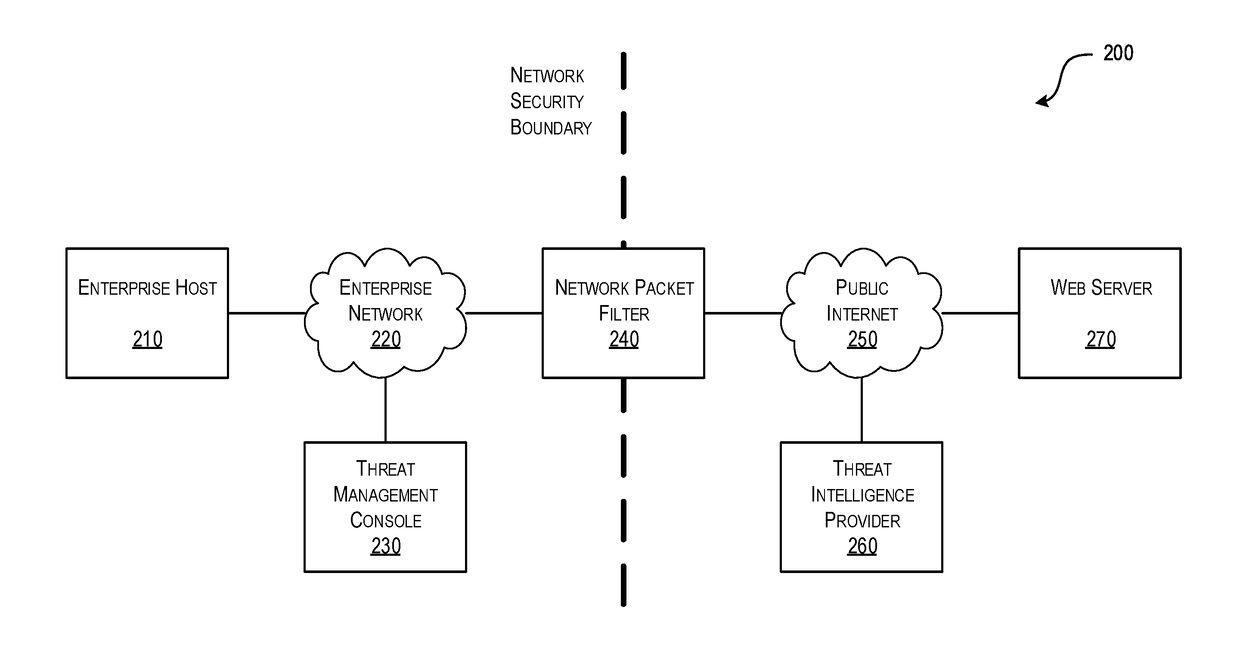
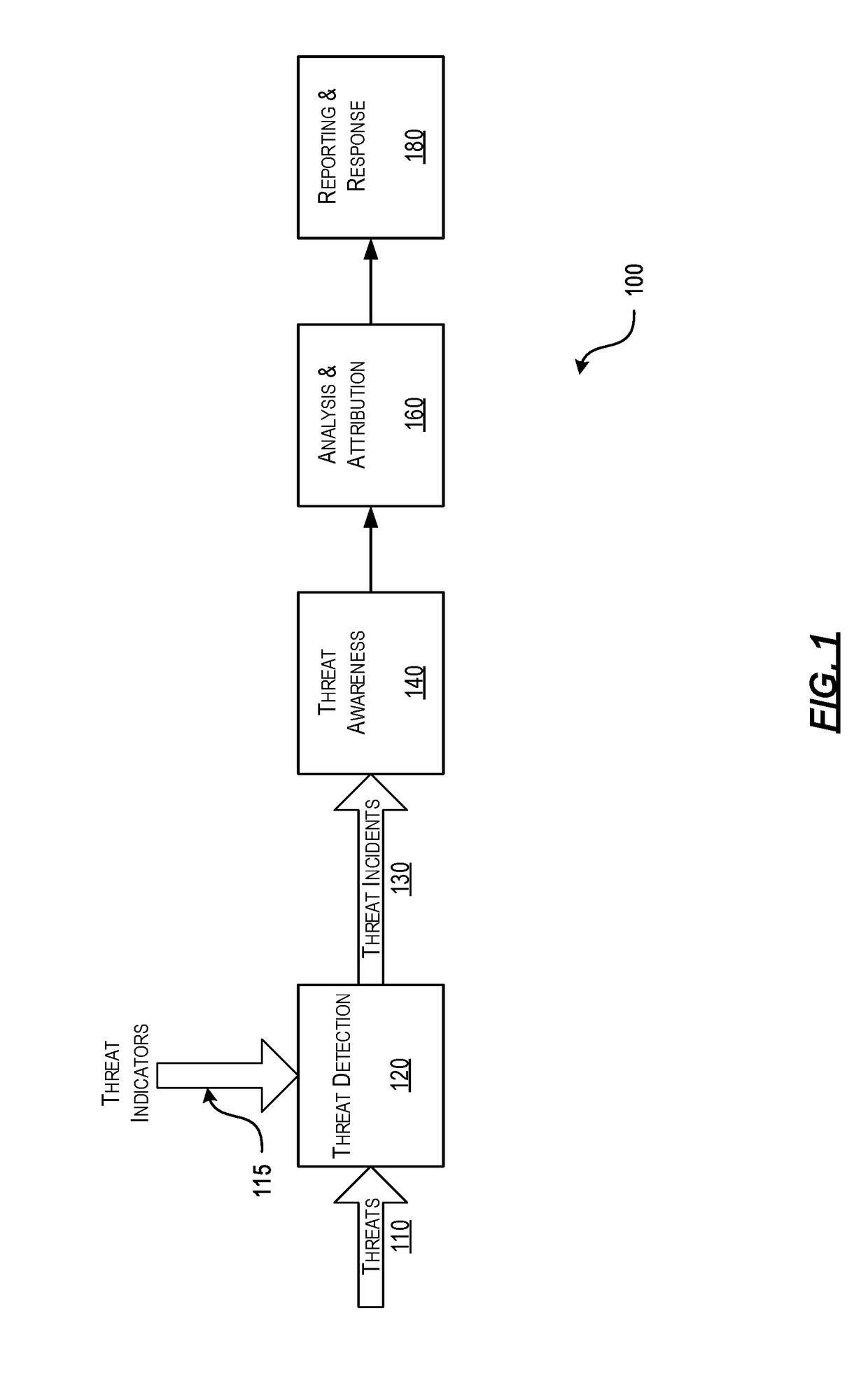
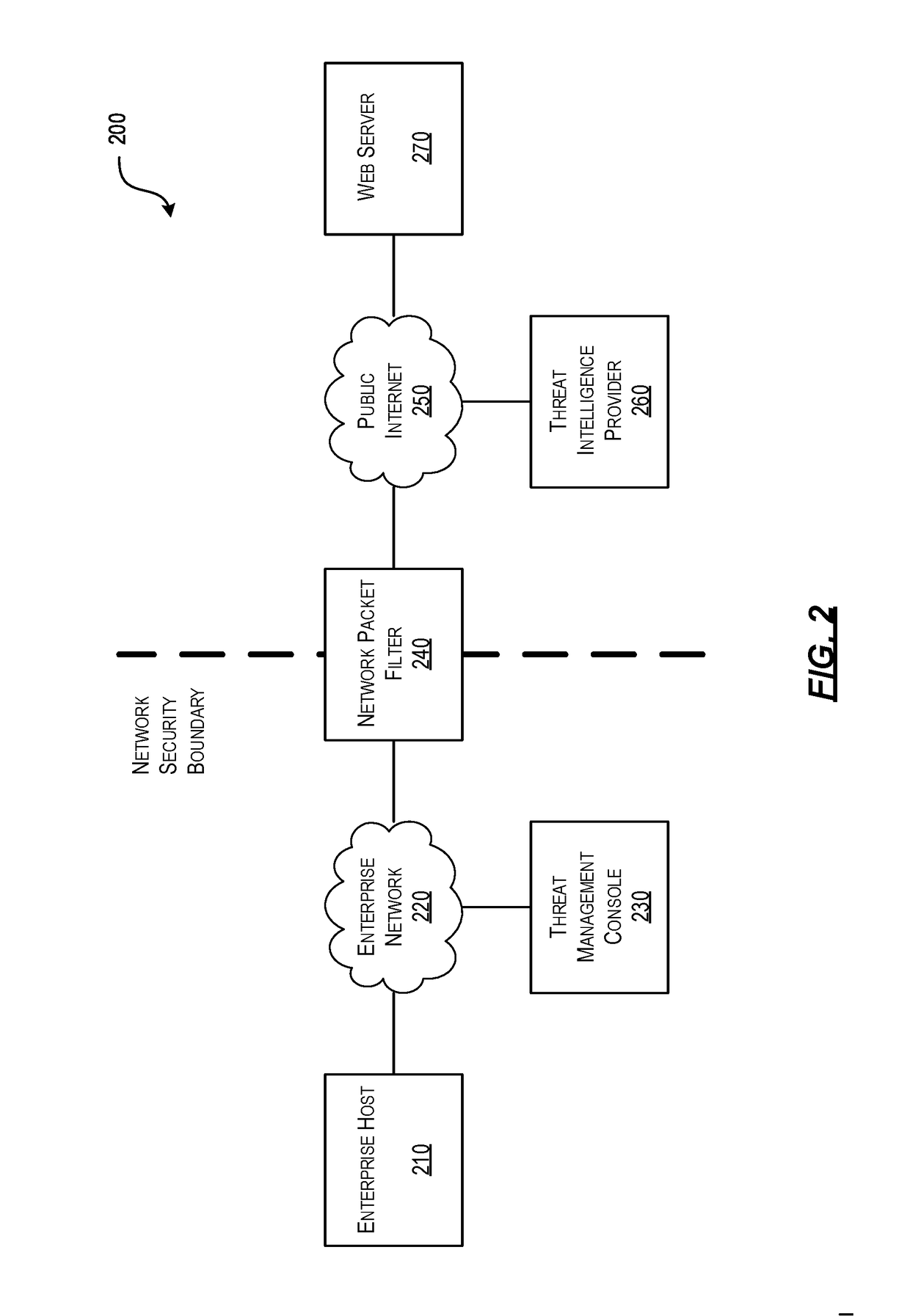
Efficient Packet Capture for Cyber Threat Analysis
Methods, systems, and computer-readable media for efficiently detecting threat incidents for cyber threat analysis are described herein. In various embodiments, a computing device, which may be located at a boundary between a protected network associated with the enterprise and an unprotected network, may combine one or more threat indicators received from one or more threat intelligence providers; may generate one or more packet capture and packet filtering rules based on the combined threat indicators; and, may capture or filter, on a packet-by-packet basis, at least one packet based on the generated rules. In other embodiments, a computing device may generate a packet capture file comprising raw packet content and corresponding threat context information, wherein the threat context information may comprise a filtering rule and an associated threat indicator that caused the packet to be captured.
Owner:CENTRIPETAL NETWORKS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com