Threat intelligence processing method and apparatus
A processing method and intelligence technology, applied in the field of data security, can solve the problems of inability to find malicious files in a timely and comprehensive manner, poor real-time performance and coverage, and achieve the effect of ensuring real-time and coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
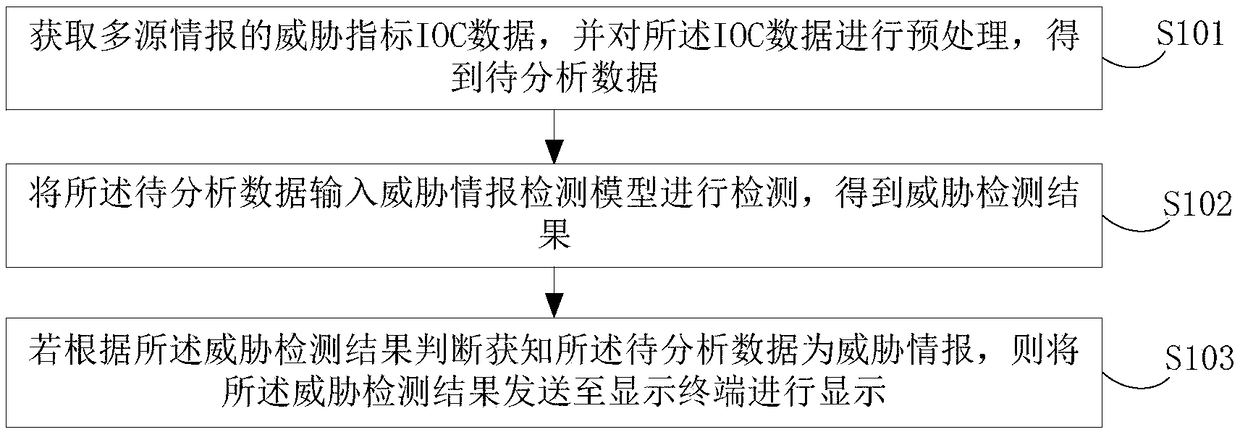
[0063] figure 1 It shows a schematic flowchart of a threat intelligence processing method provided in this embodiment, including:
[0064] S101. Obtain IOC (Indicator of Compromise, threat indicator) data of multi-source intelligence, and preprocess the IOC data to obtain data to be analyzed;
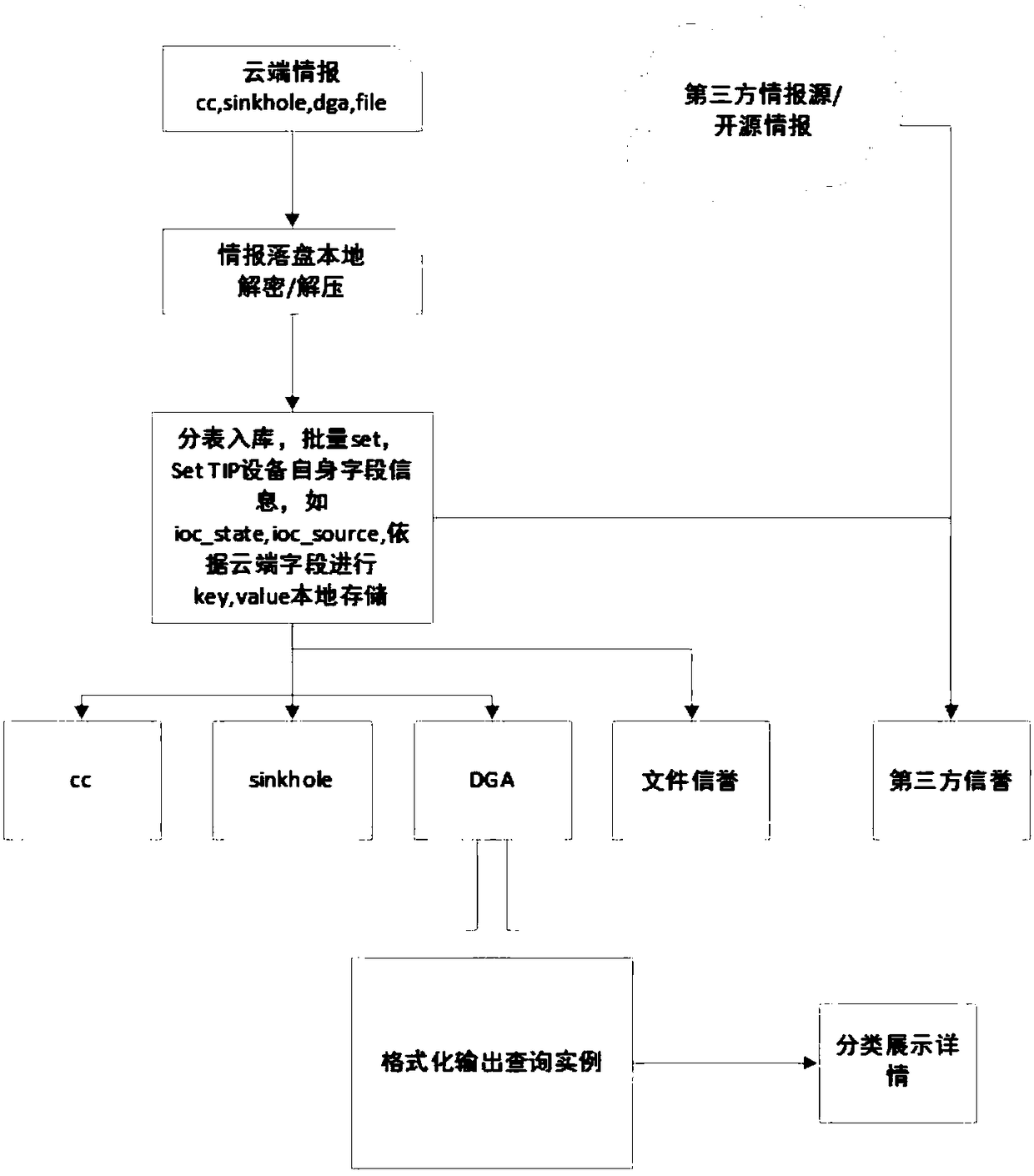
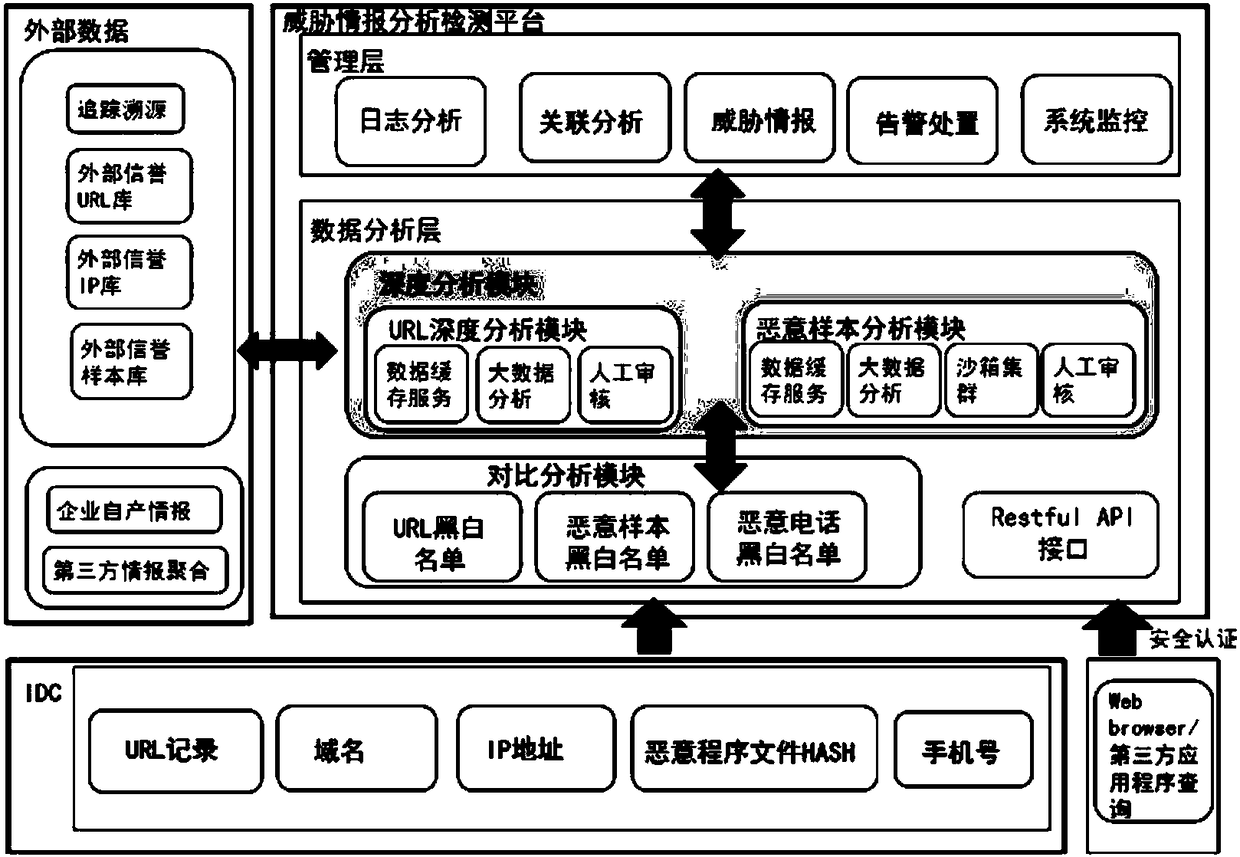
[0065] Wherein, the multi-source intelligence includes: intelligence information provided by the enterprise's self-produced intelligence, third-party intelligence aggregation part, and cloud intelligence center.
[0066] The preprocessing refers to normalizing the IOC data to facilitate subsequent data analysis.
[0067] S102. Input the data to be analyzed into a threat inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com