Patents
Literature
468 results about "Hacker" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or to evaluate system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground".
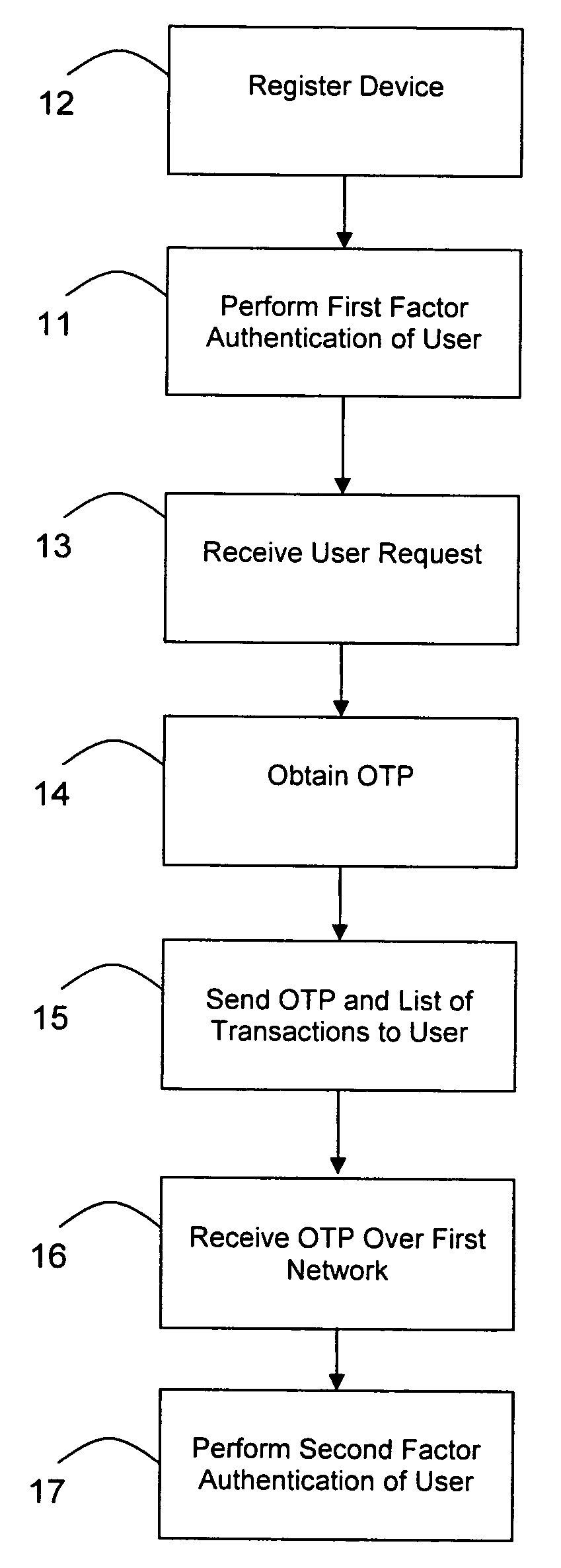
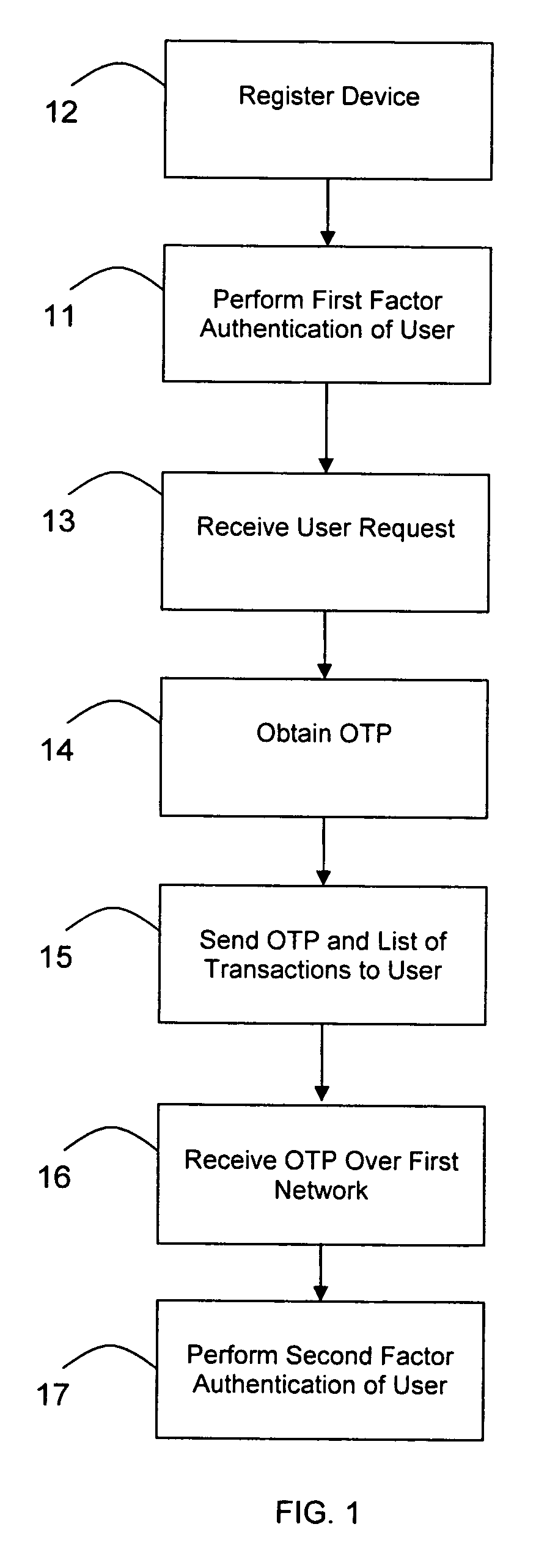
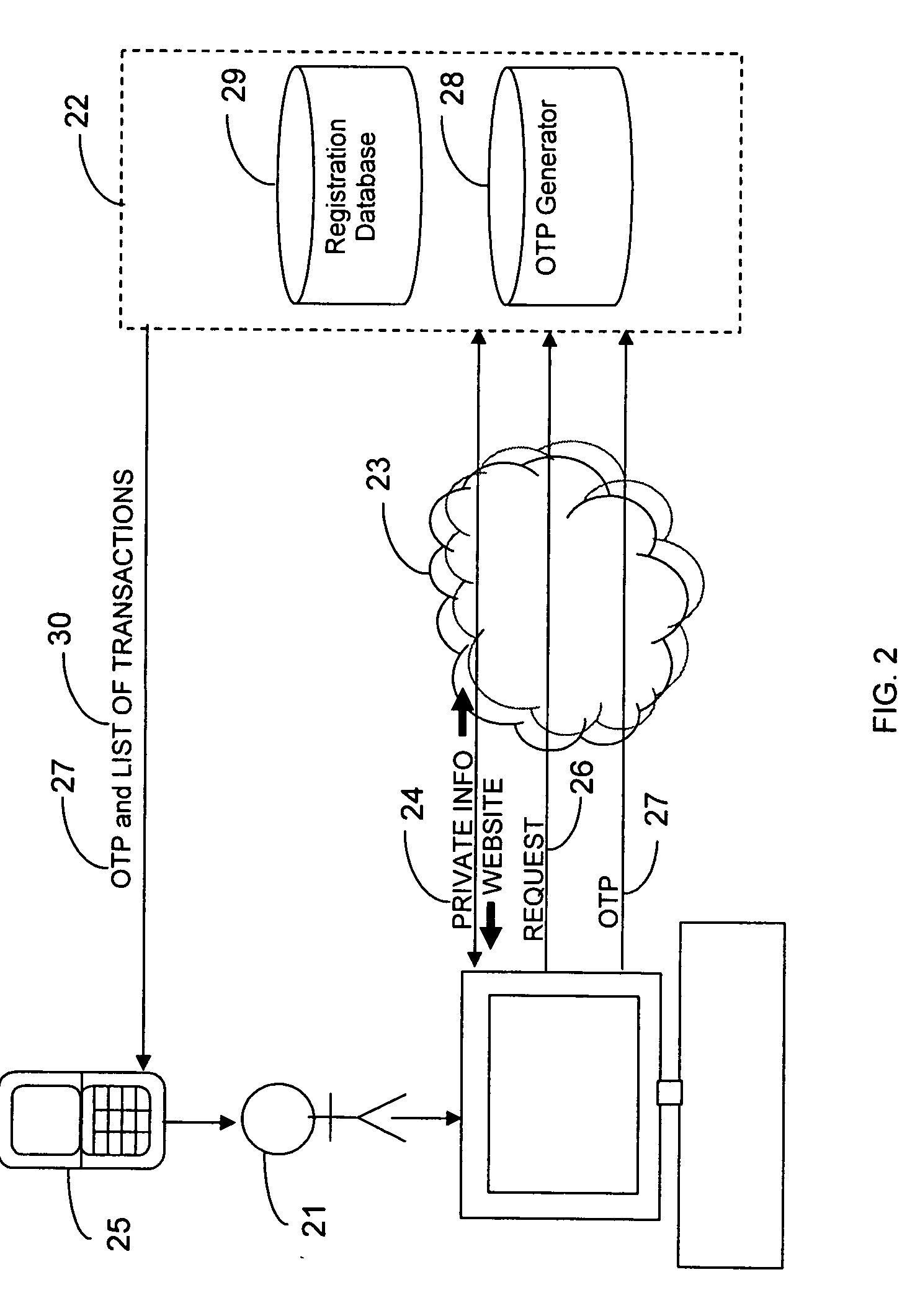
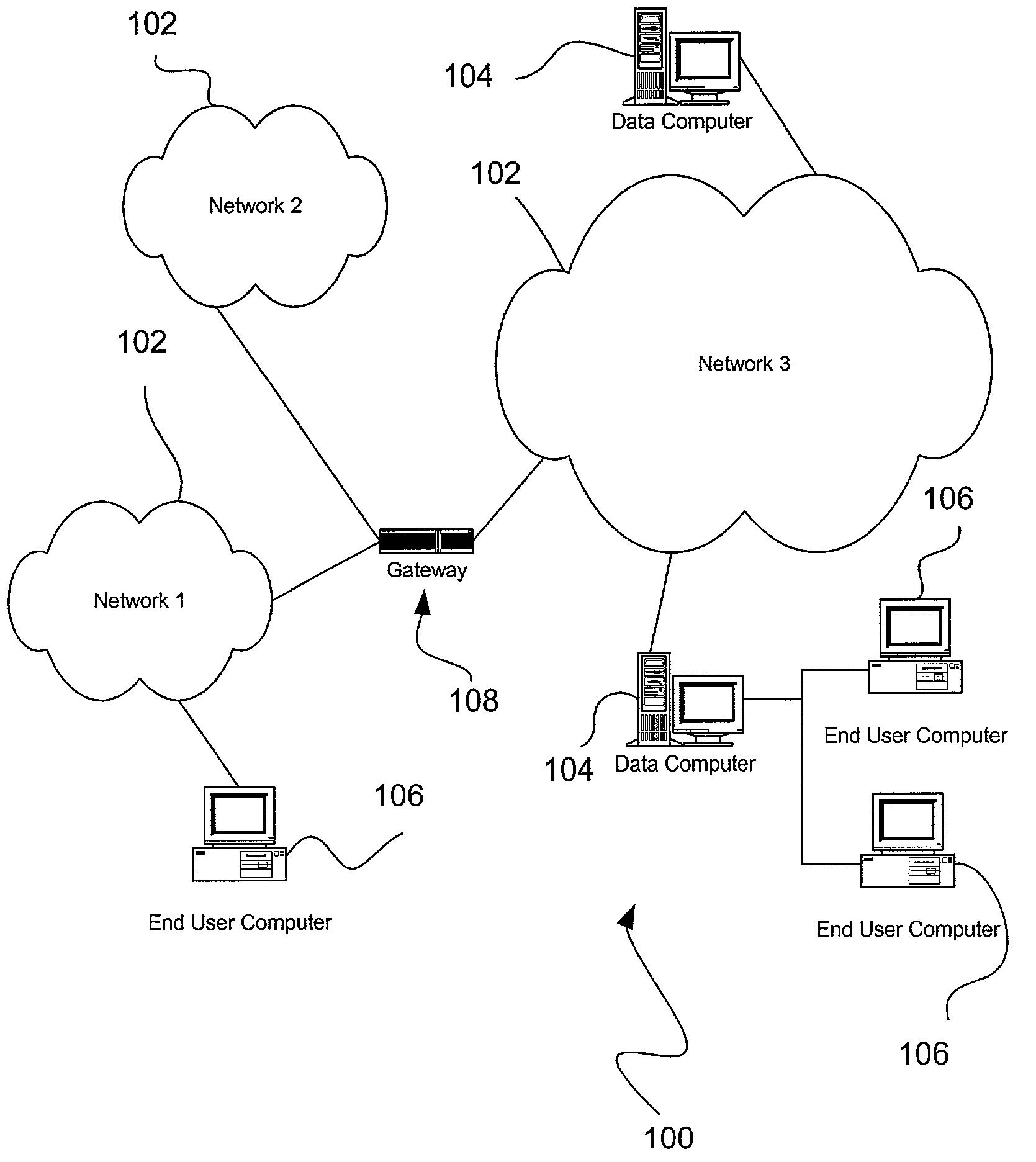
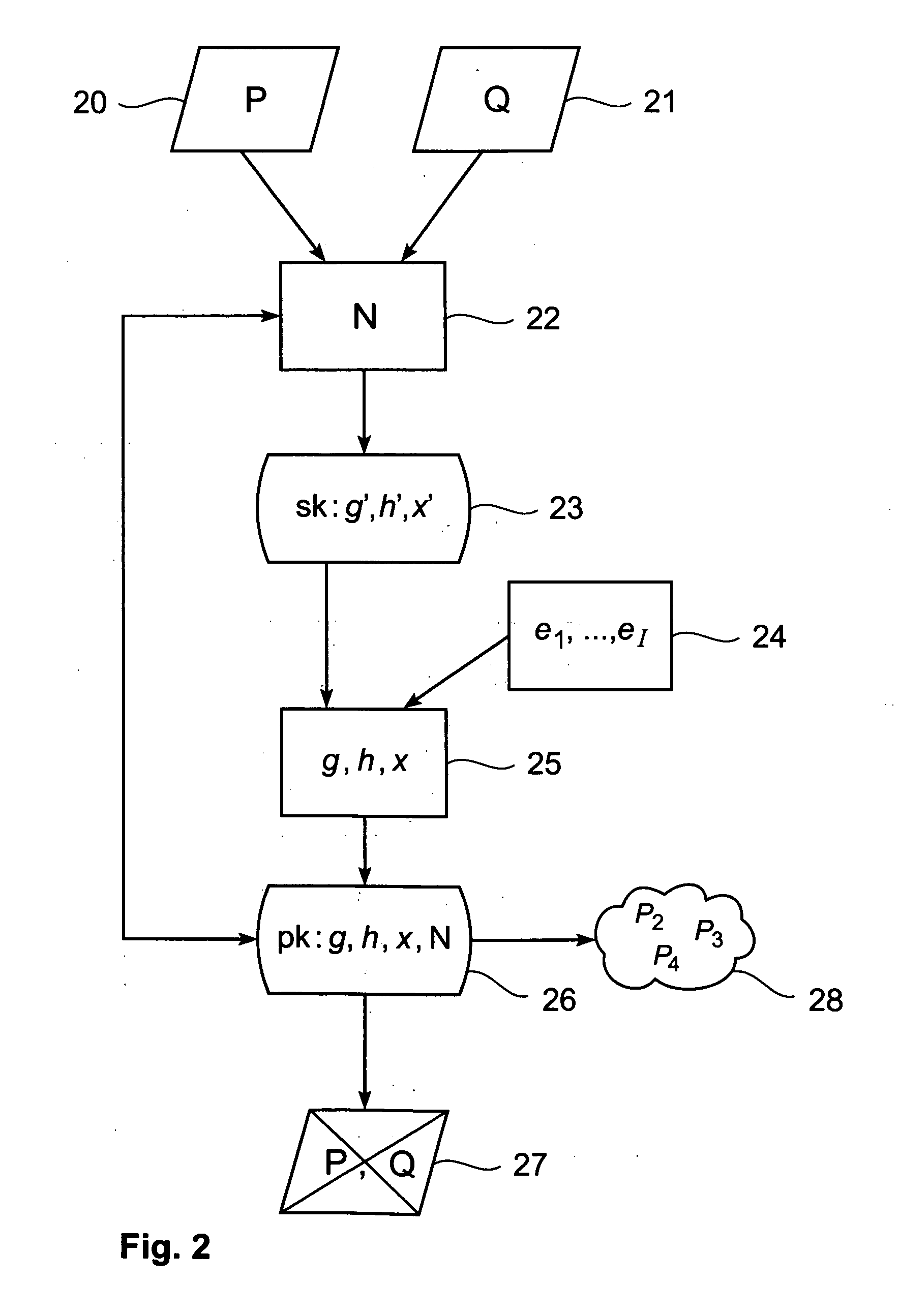
Transaction authentication over independent network
InactiveUS20090106138A1Accelerating transactionFinanceProtocol authorisationOne-time passwordCommunication device
A method of authenticating an online transaction over a first network uses 2-factor authentication of the user to defeat hacker attacks. A communication device is registered for use with the method. The communication device is configured to receive messages over a second network independent of the first network. The user is authenticated over the first network using a first factor, such as a username and password, and then initiates the transaction. A request to execute the transaction is received and a one-time password is obtained to be used as a second factor of authentication. The one-time password and details describing the transaction are sent to the communication device over the second network. The one-time password is received from the user over the first network to complete the second factor of authentication.
Owner:CLAREITY VENTURES INC
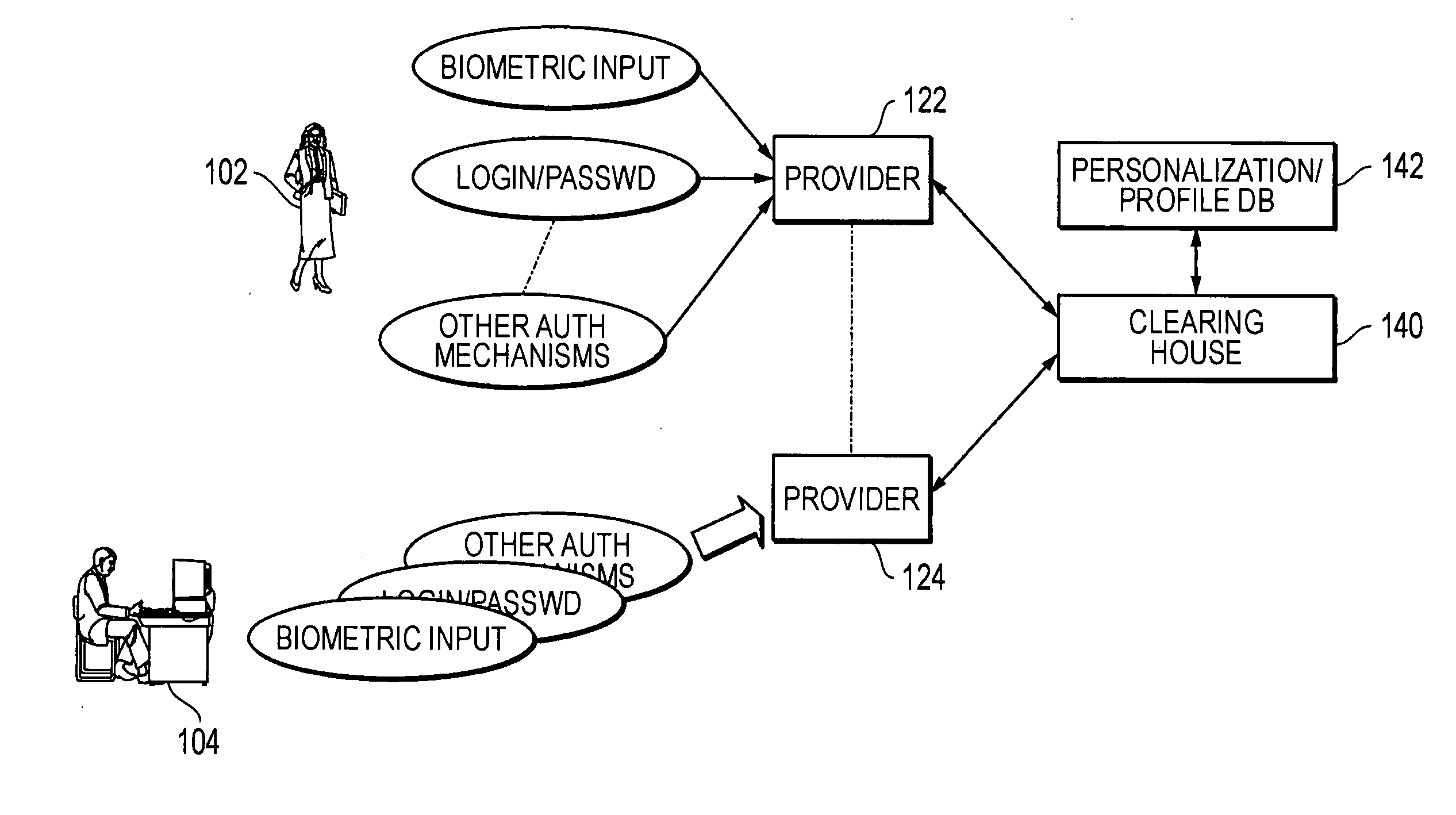
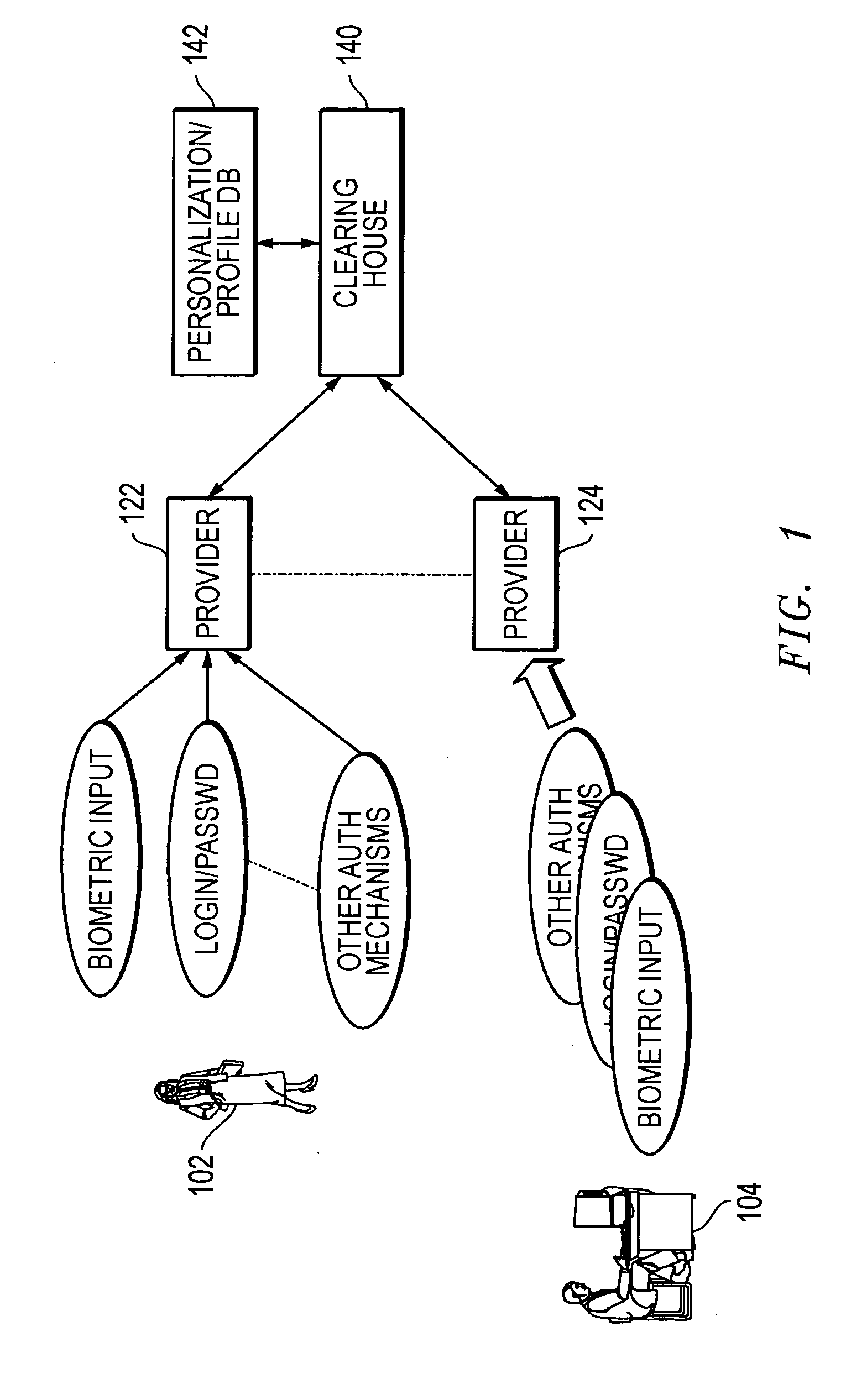
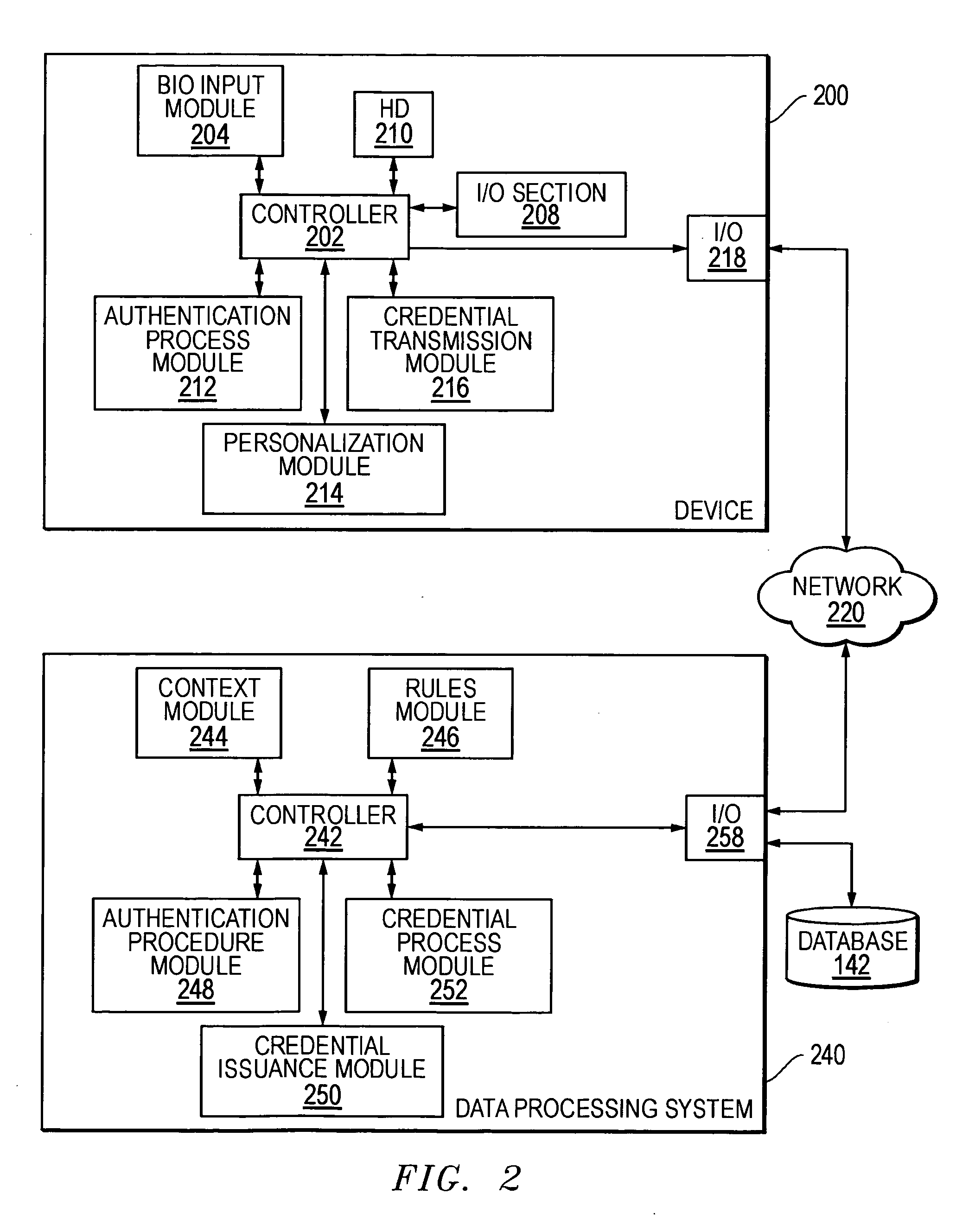
Methods and systems for using data processing systems in order to authenticate parties
InactiveUS20070079136A1Digital data processing detailsUser identity/authority verificationData processing systemBiometric data
Methods and systems perform authentication based at least in part of the context of the transaction. In one embodiment, the context can be determined and trigger different rules with regard to access to the information or ability to immediately execute the transaction. In another embodiment, a method can include registering a device as a trusted device. The device can include a biometric input module. Biometric data can be used to authenticate a user, and the user may be requested to resubmit biometric data during the same session. In a further embodiment, a hacker may obtain unauthorized access to a victim's account information. The hacker may not be authenticated because he would not have access to a currently valid credential.
Owner:SBC KNOWLEDGE VENTURES LP
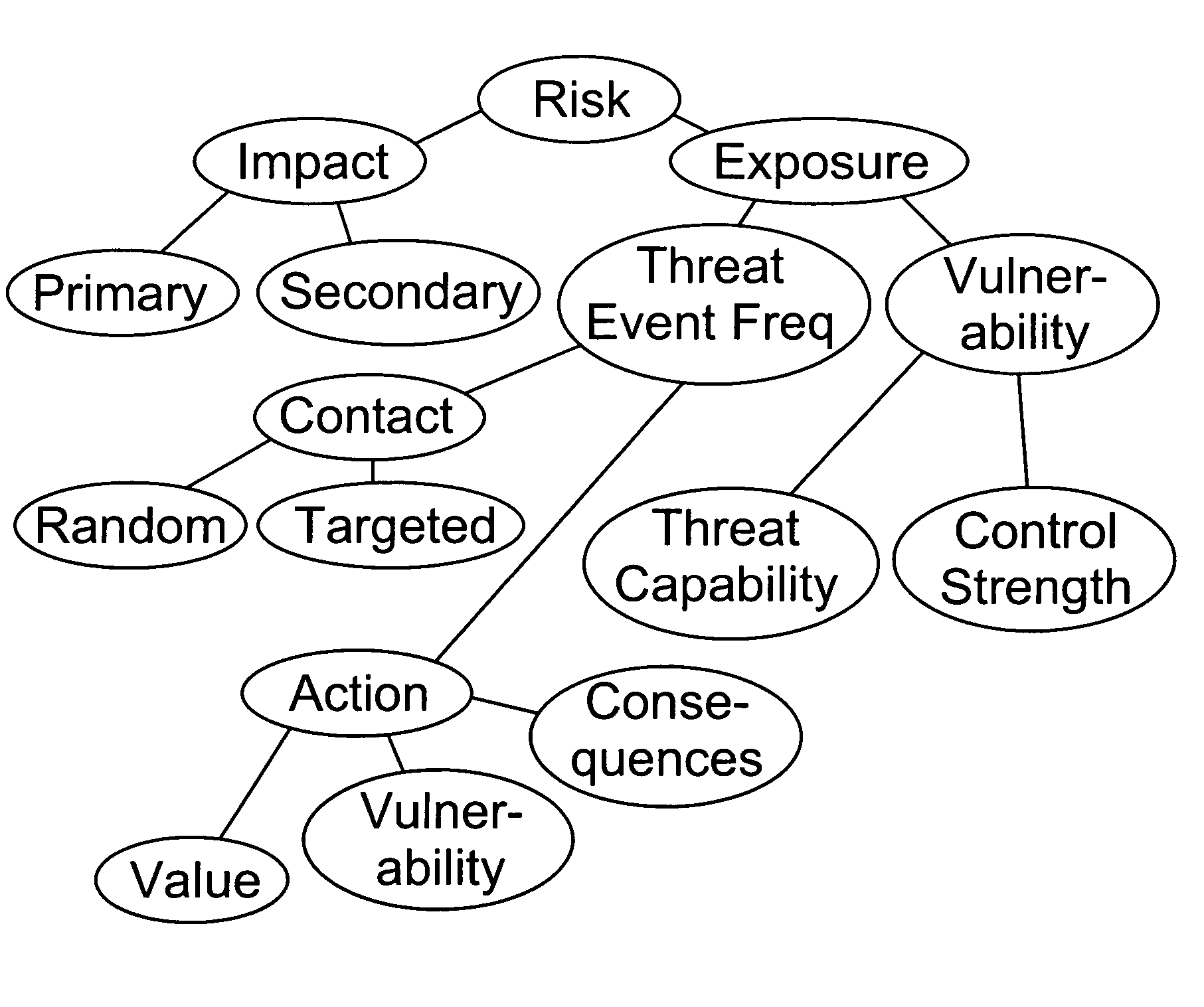
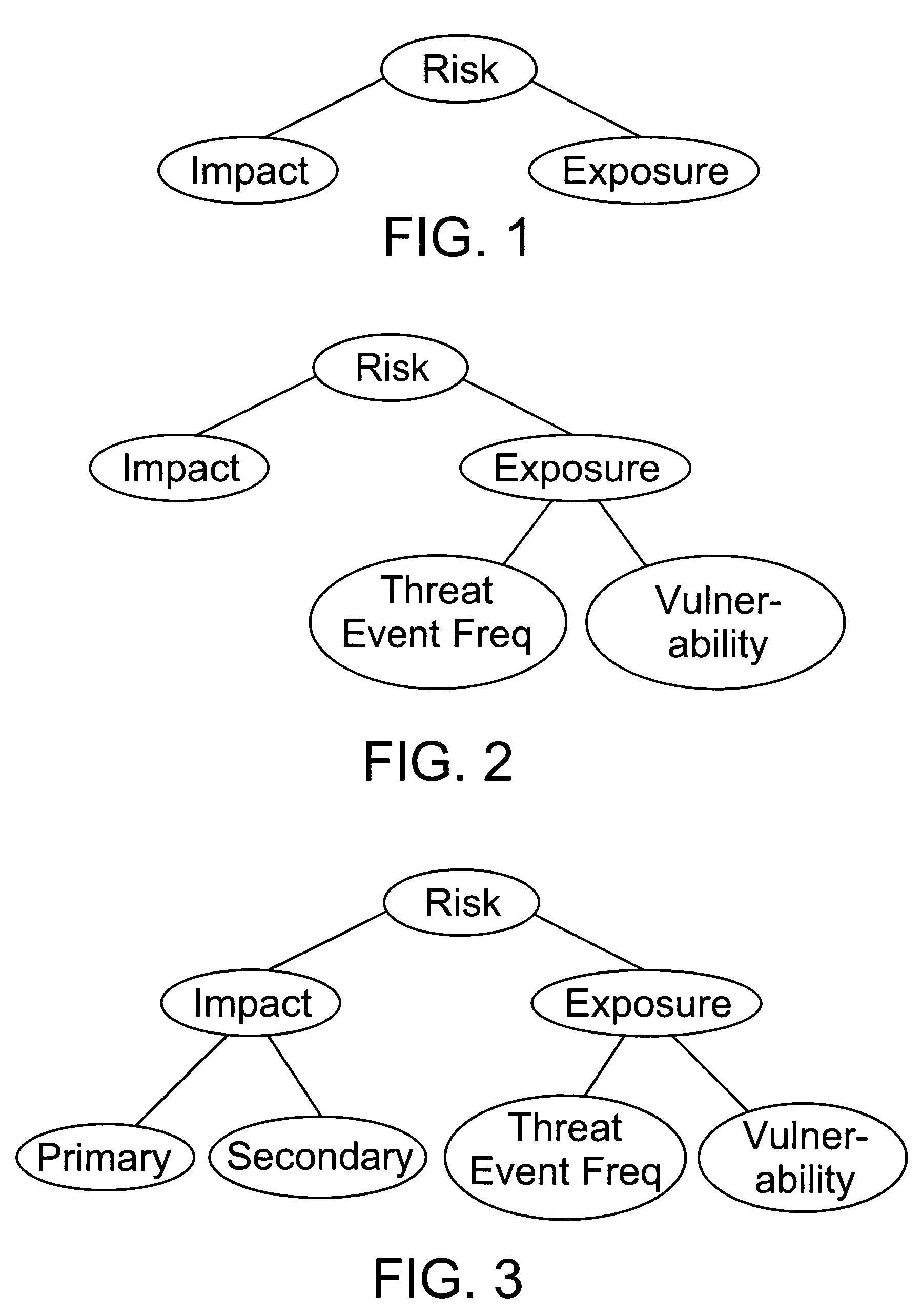
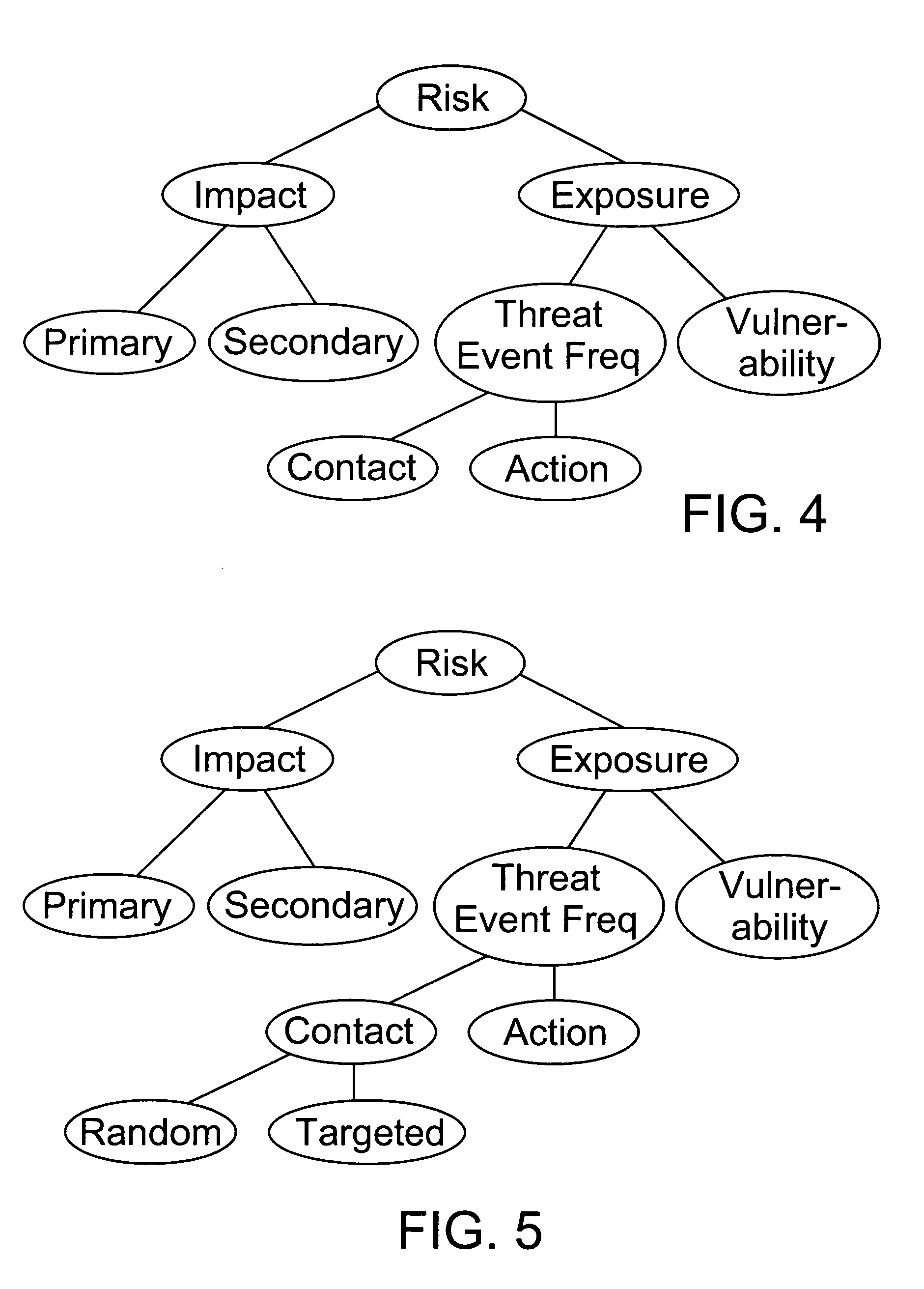
Factor analysis of information risk
InactiveUS20050066195A1Risk management decisions can become more effective and efficientGood return on investmentDigital data processing detailsComputer security arrangementsSalient objectsObject definition
The invention is a method of measuring and representing security risk. The method comprises selecting at least one object within an environment and quantifying the strength of controls of at least one object within that environment. This is done by quantifying authentication controls, quantifying authorization controls, and then quantifying structural integrity. In the preferred method, the next step is setting global variables for the environment, for example, whether the environment is subject to regulatory laws, and then selecting at least one threat community, for example, professional hackers, and then calculating information risk. This calculation is accomplished by performing a statistical analysis using the strengths of controls of said at least one object, the characteristics of at least one threat community, and the global variables of the environment, to compute a value representing information risk. The method identifies the salient objects within a risk environment, defines their characteristics and how they interact with one another, utilizing a means of measuring the characteristics, and a statistically sound mathematical calculation to emulate these interactions and then derives probabilities. The method then represents the security risk, such as the risk to information security, such as by an integer, a distribution or some other means.
Owner:JONES JACK A
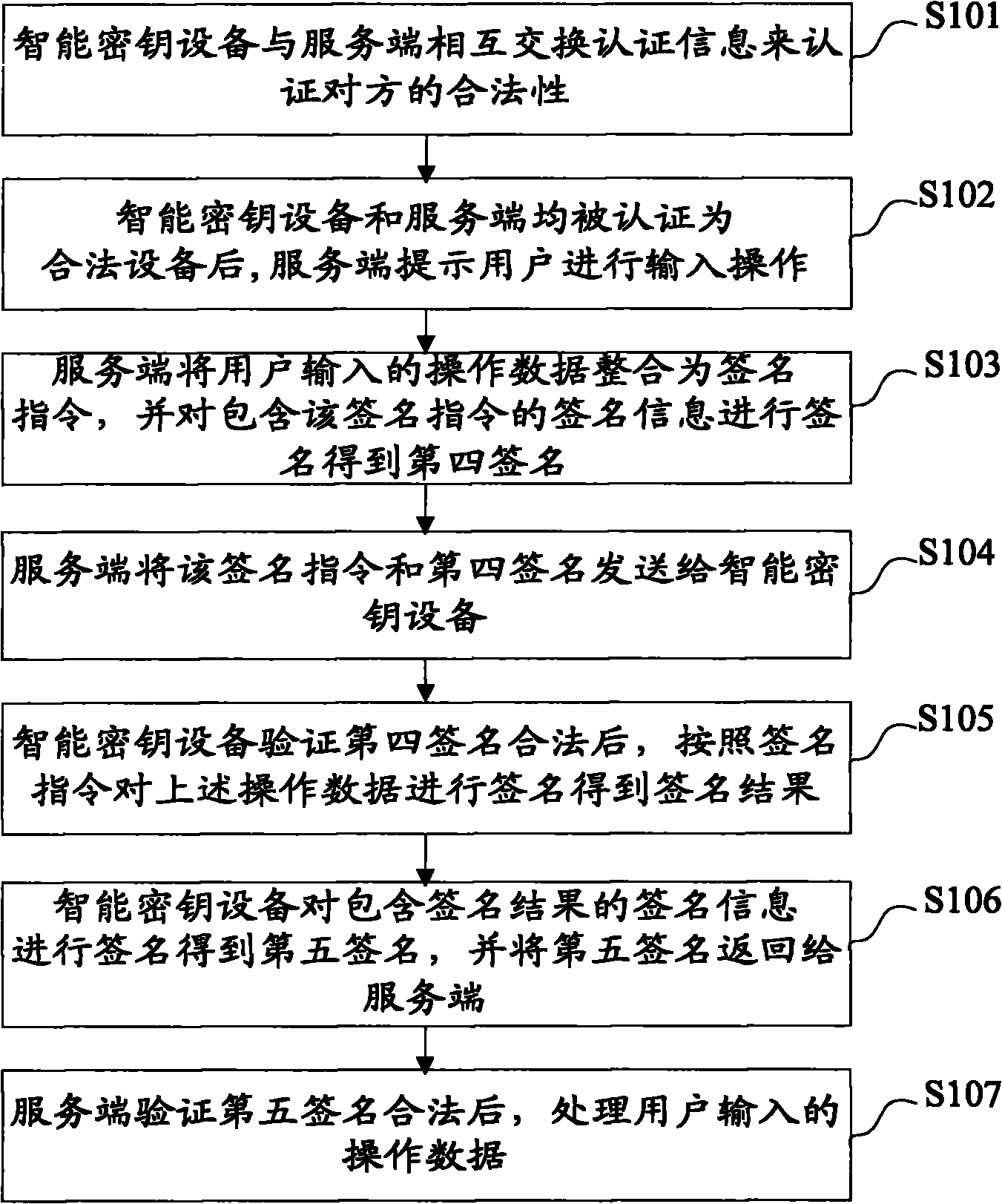
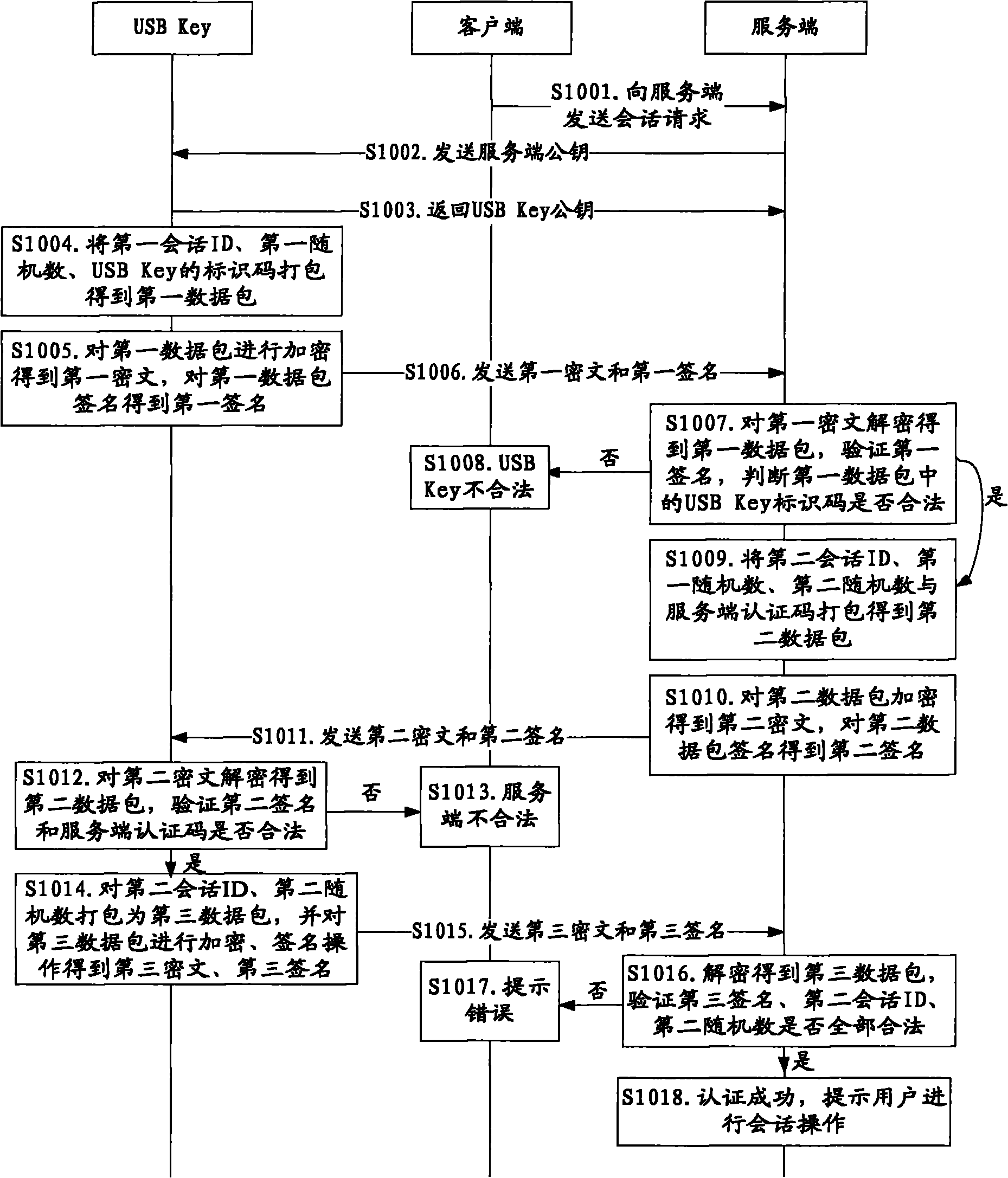
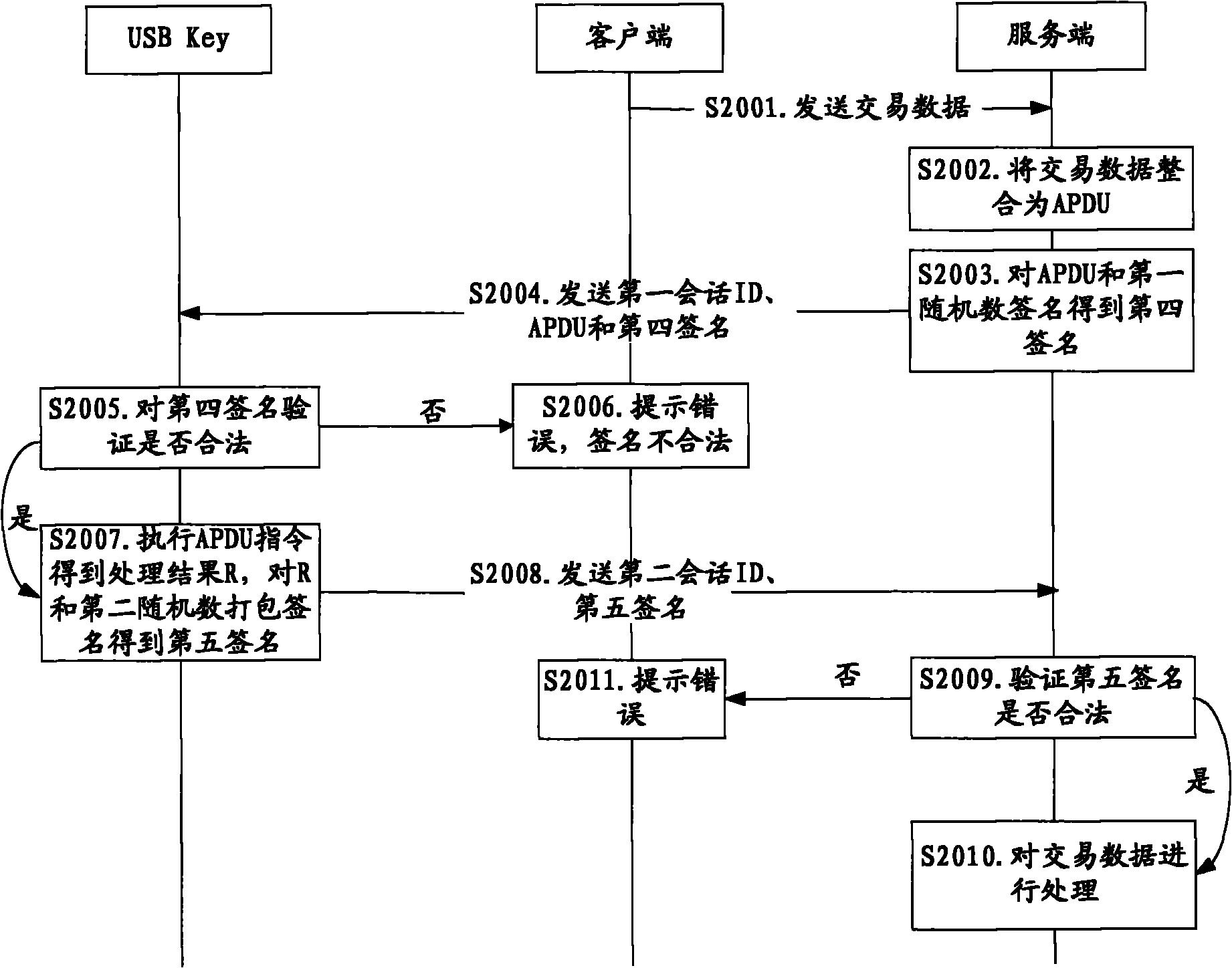
Method and system for online security trading
ActiveCN101789934ASolve the replay attack problemPrevent replay attacksKey distribution for secure communicationFinanceProtection systemOnline security
The invention discloses a method and a system for online security trading, wherein the method for the online security trading comprises the following steps that: intelligent key equipment and a server verify the validities of each other by mutually exchanging authentication information; after both sides are verified be valid by each other, the server integrates the operational data of the user into a signature command, and transfers the signature command and signature information to the intelligent key equipment by a client; after the intelligent key equipment verifies the validity of the signature information, the intelligent key equipment executes the signature command and returns the signature result to the server; and the server processes the operational data of the user according to the signature result. By the mutual authentication of the server and the intelligent key equipment and operations such as verification on the data in a session, the system can effectively judge whether the received data are valid and further prevent the replay attach of the hackers and protect the security operation of the system.
Owner:FEITIAN TECHNOLOGIES
System, method and computer program product for monitoring hacker activities
InactiveUS7093292B1Inhibitory activityMemory loss protectionError detection/correctionNetwork communicationWeb transport
A system, method and computer program product are provided for monitoring intrusion activity utilizing a plurality of firewalls. Initially, network communications are established with a plurality of computers with firewalls over a network. Such firewalls are adapted for collecting information relating to intrusion activity. Once the network communications are established, the information is collected from the firewalls of the computers utilizing the network. Further, a response is transmitted to the firewalls of the computers utilizing the network. The firewalls are adapted for preventing the intrusion activity utilizing the response.
Owner:MCAFEE LLC
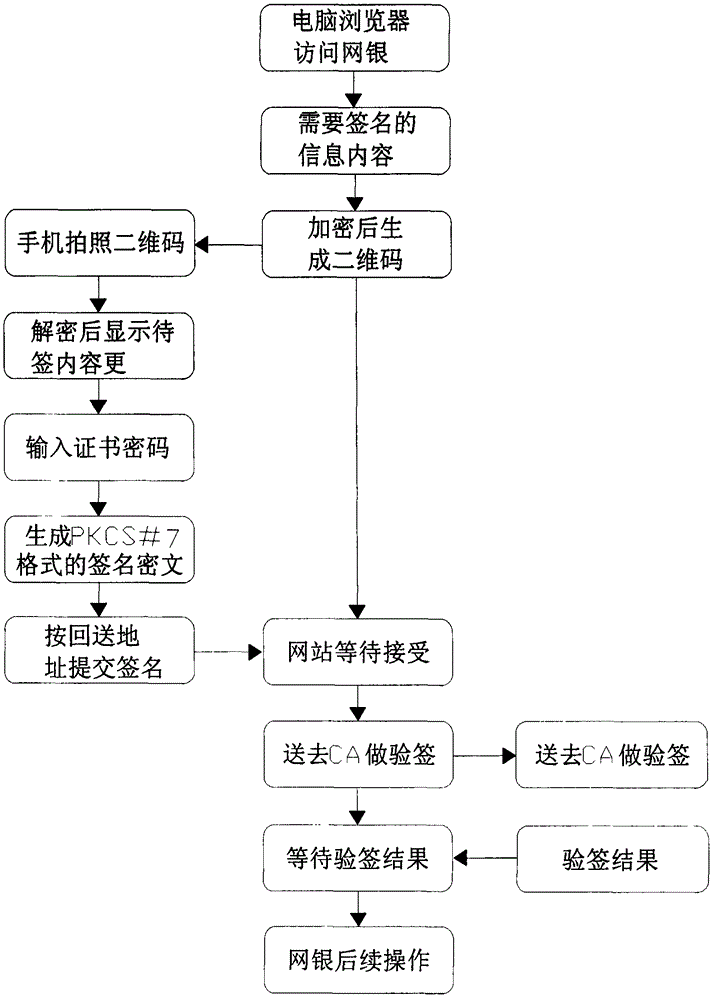
Mobile terminal digital certificate electronic signature method
ActiveCN105323062AIngenious ideaReasonable ideaUser identity/authority verificationIssuing bankInternet privacy
The invention relates to a mobile terminal digital certificate electronic signature method. According to the method, based on the characteristics of public keys and private keys and on the premise of not violating the rules prescribed by the electronic signature law, for example, a private key should be generated in a user terminal and should not leave the user terminal, a private key should not be transmitted via the network, and the like, a private key is discarded and locally and discretely stored after encryption, and the cloud uses strategies such as storing the public key and certificate to ensure that the private key is not locally cracked. In the transport layer, strategies such as double key and one-time pad are adopted to ensure that important information is not intercepted and decoded in network transmission. The identity of a certificate applicant is verified through the interface of an issuing bank, the user identity verification result of the bank counter is inherited, and therefore, remote online certificate issuing is realized in the system. The method not only can ensure that all the links of certificate applying, certificate issuing, certificate storing and certificate using are safe, but also can prevent hackers and Trojans from stealing certificate files, prevent network package-capture parsing, prevent password intercepting through screen capture and prevent an algorithm from being known through software decompiling.
Owner:BANKEYS TECH
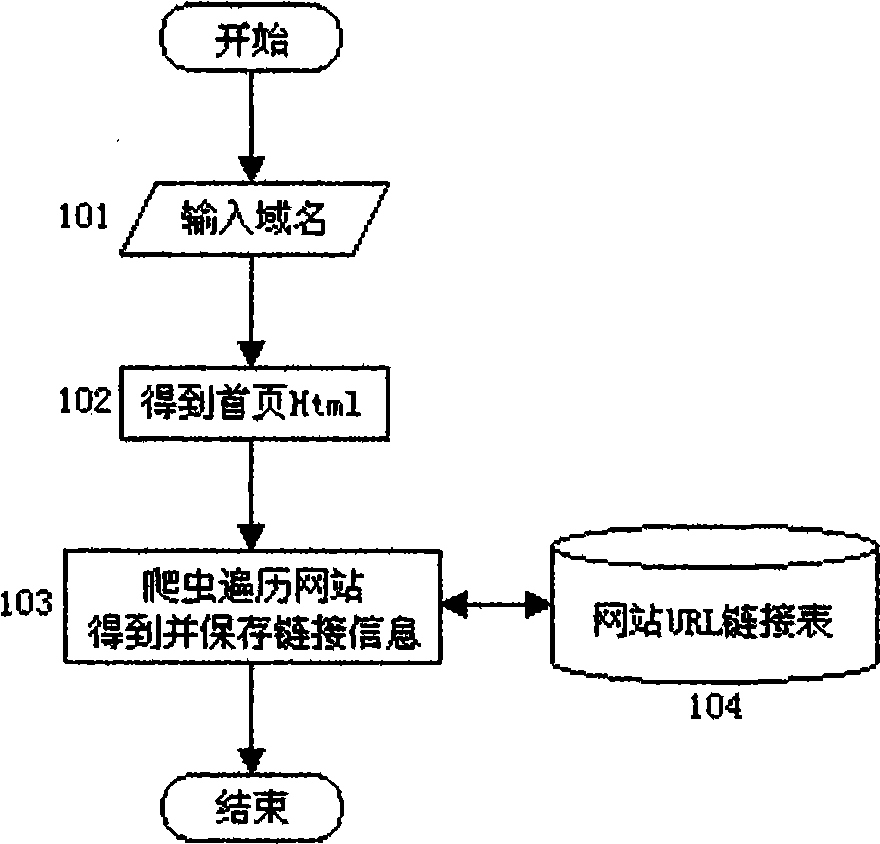
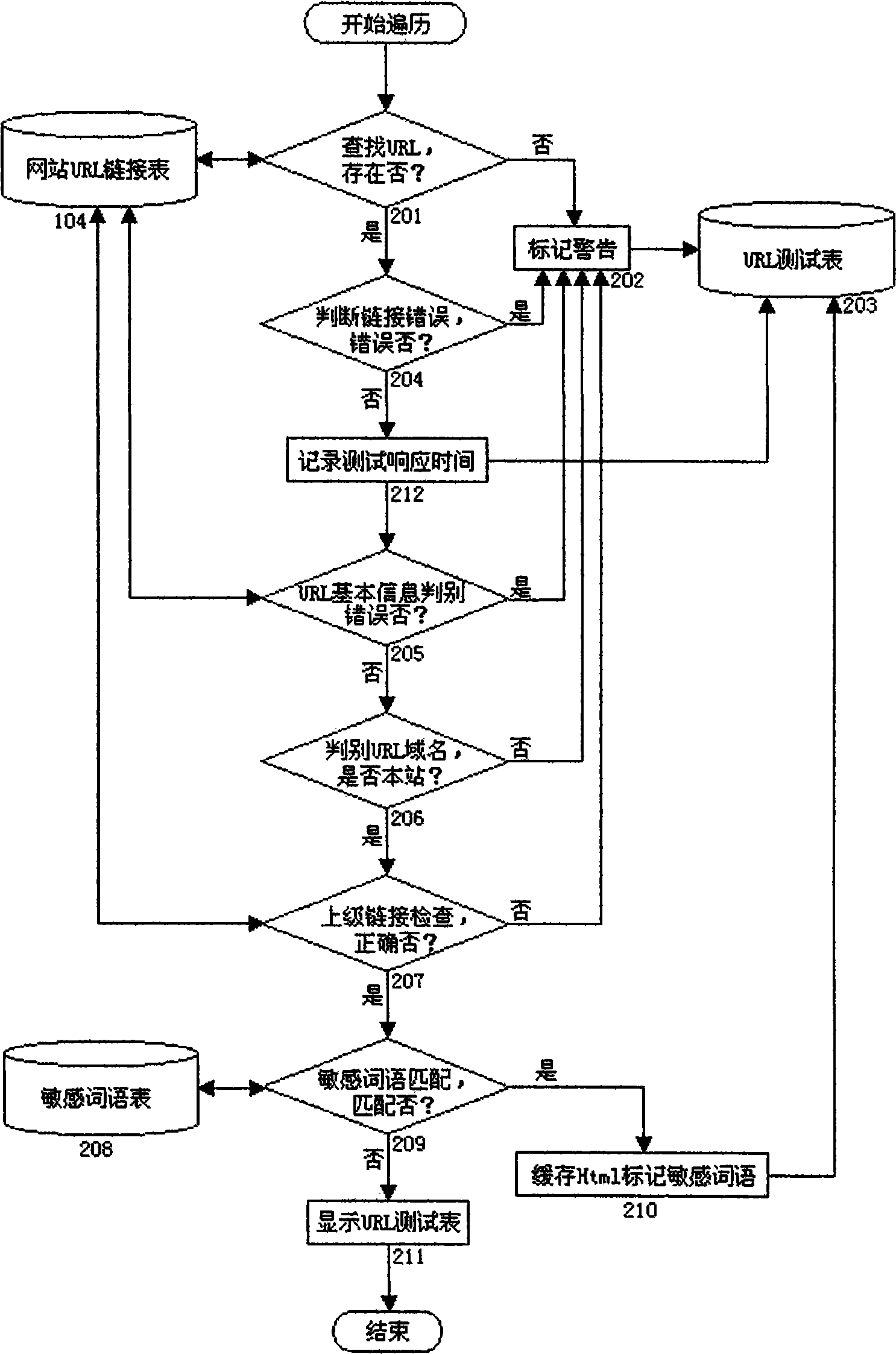
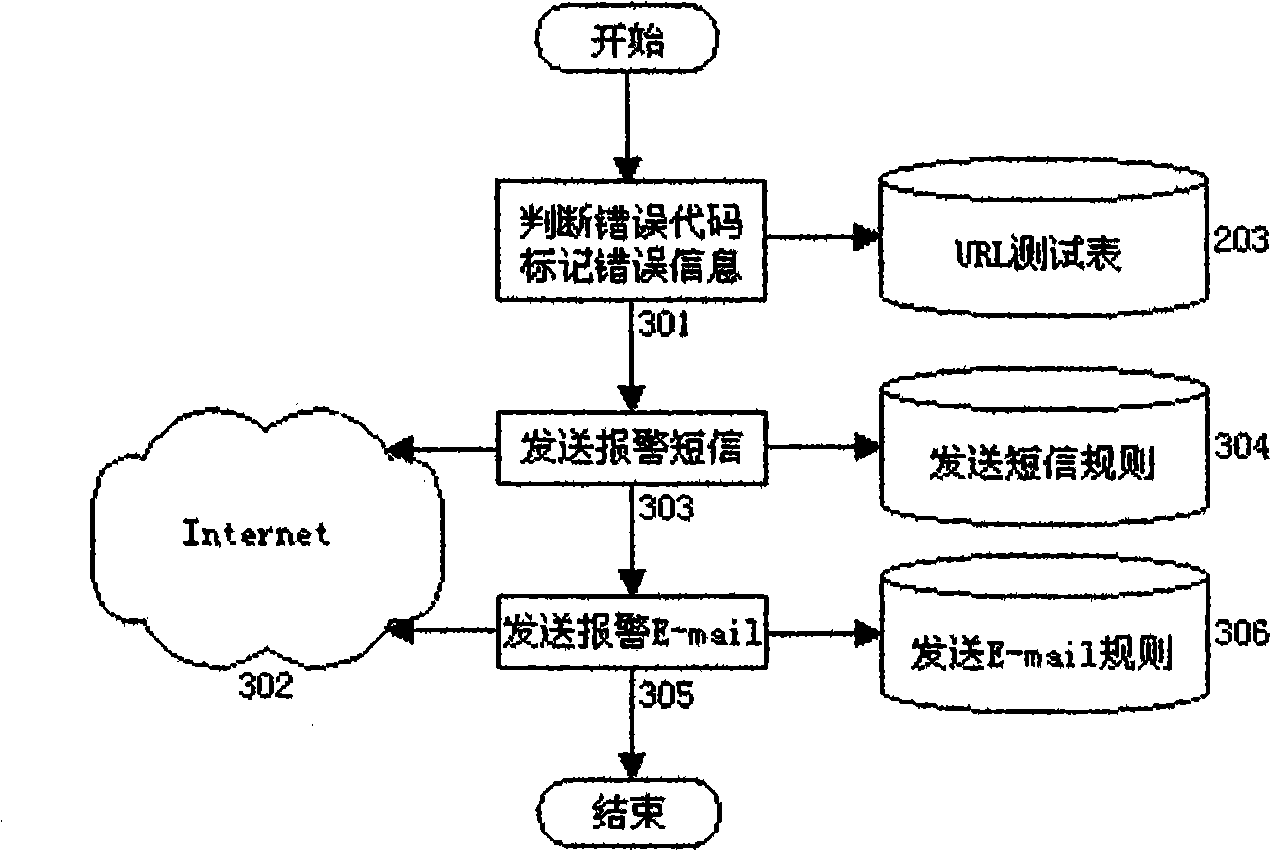
Website safety protection and test diagnosis system structure method based on crawler technology
InactiveCN101510195AEffective automated website document management methodAlarm in timePlatform integrity maintainanceSpecial data processing applicationsWeb siteSystem configuration
A website system configuration method which is based on crawler technology and used for file management, safety defense and testing diagnosis can automatically establish management files for files and URL link of website and adopts the management files as the basic foundation to judge whether the webpage is attacked by hackers and whether the link relationship is falsified so as to find the error link of the website. The method can automatically and fully test the URL response time contained in the website so as to find illegal link and 'sensitive words' in the webpage; and the method can be adopted as the tool for the website test, diagnosis, evaluation and safety defense.
Owner:刘峰 +1
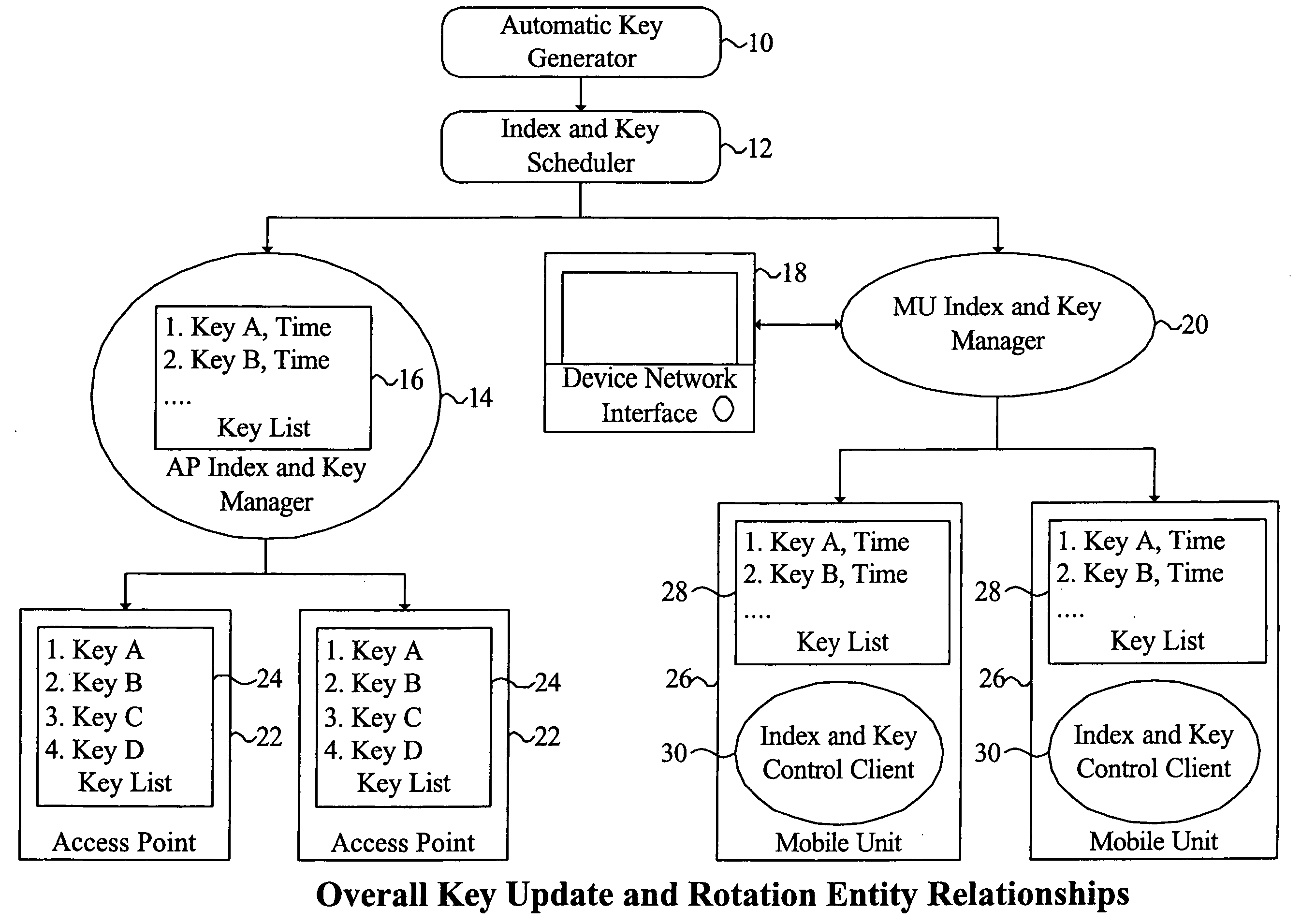
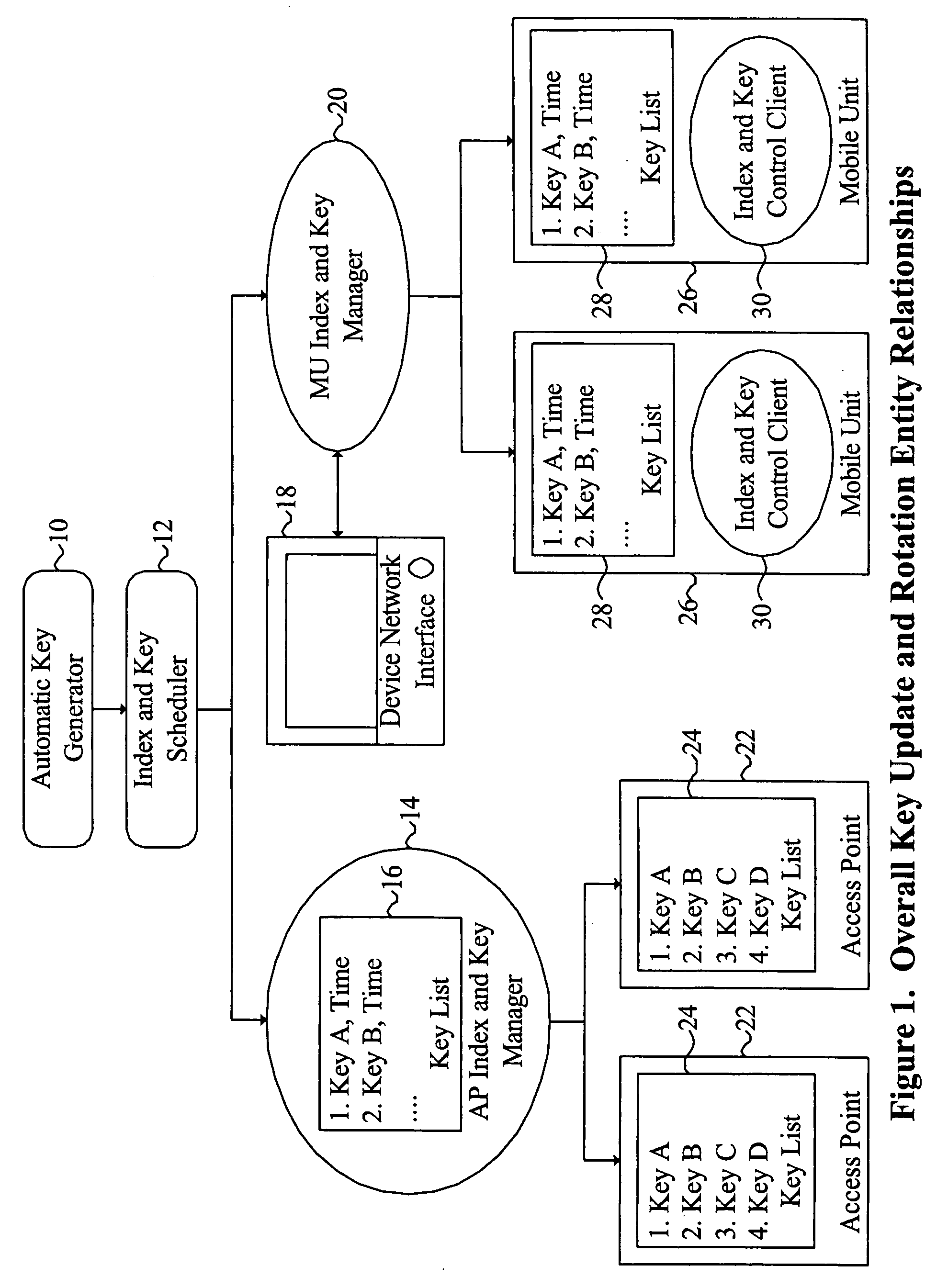
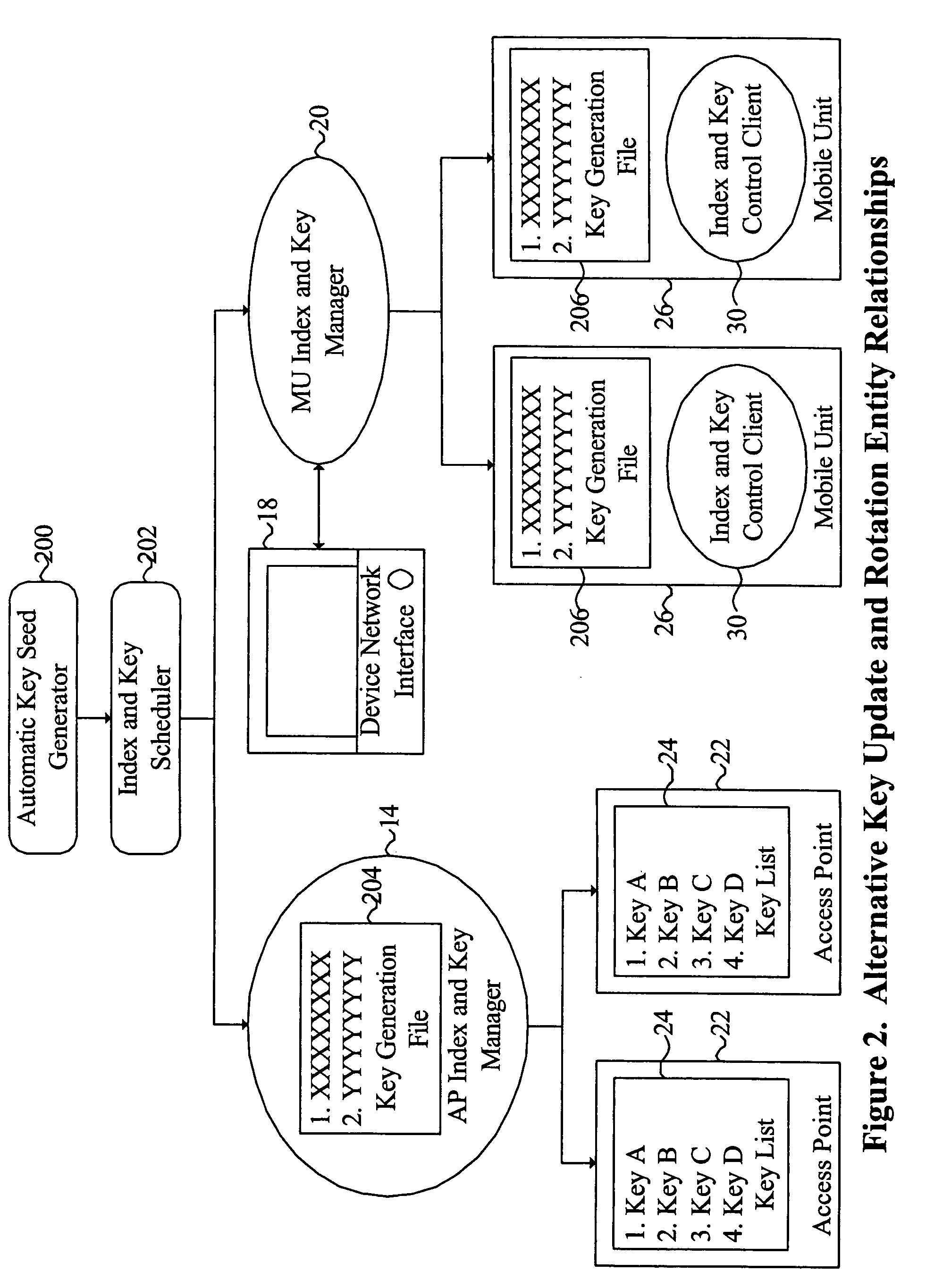
System and method for providing WLAN security through synchronized update and rotation of WEP keys
InactiveUS20060078124A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesSecure communicationInternet traffic
Owner:IVANTI INC
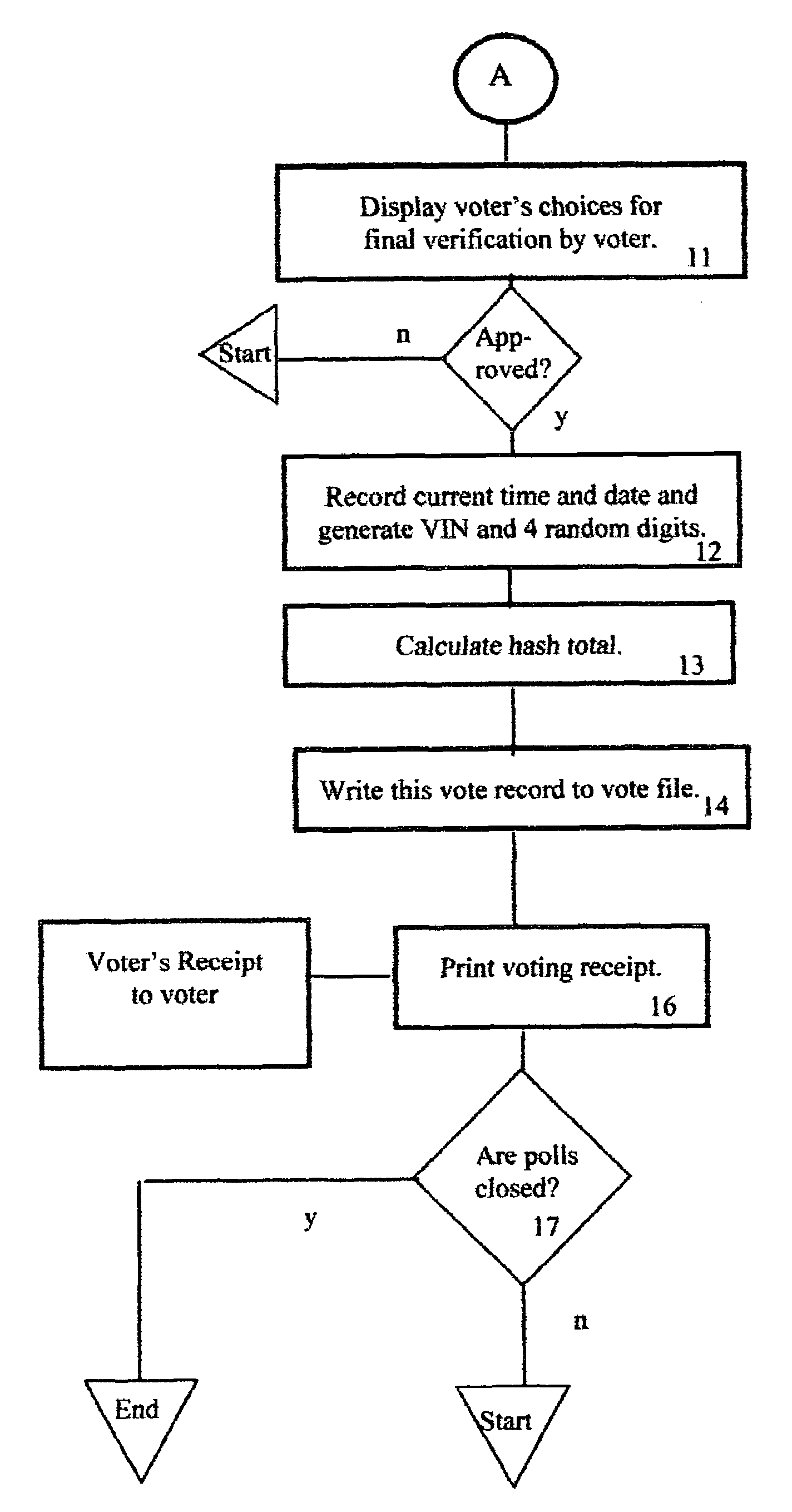
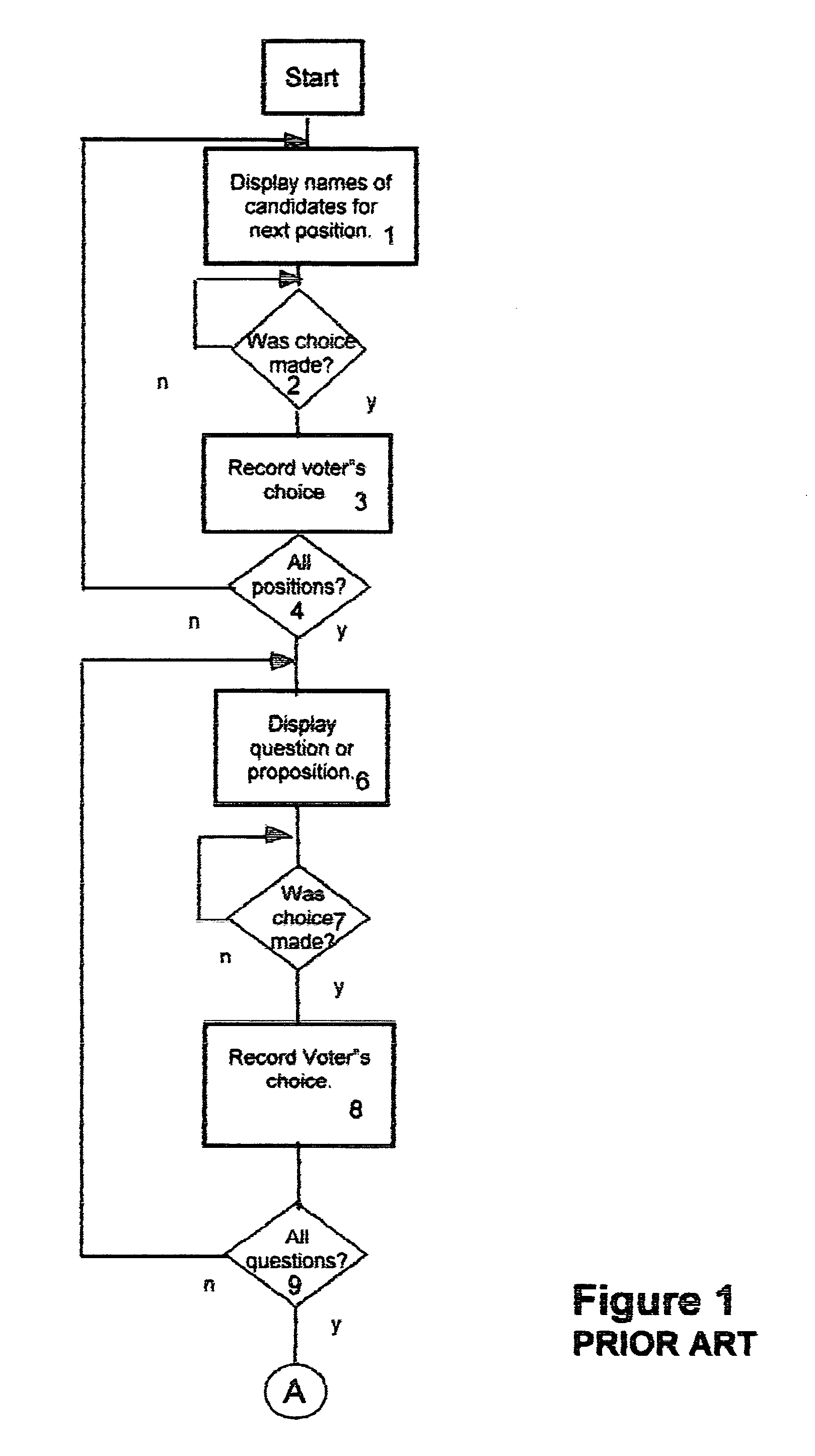
Method of accurately verifying election results without the need for a recount
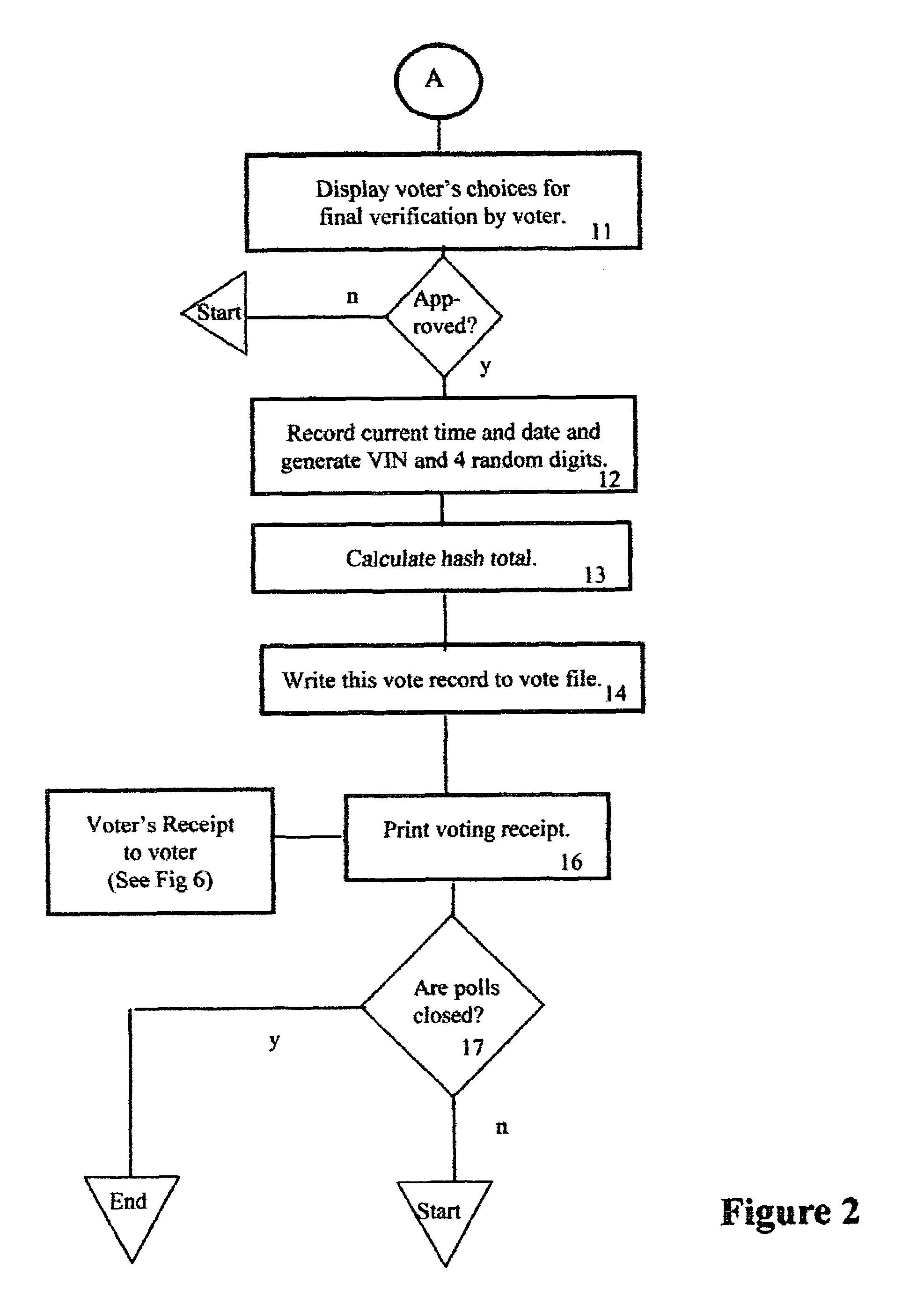
InactiveUS6971574B1Eliminate needSure easyVoting apparatusData processing applicationsComputer hardwareEncoding algorithm
Hash numbers are assigned to each individual ballot choice made by a particular voter and a hash total, establishing the voter's set of ballot choices, is recorded and a printed receipt is issued to the voter, bearing the voter's identification number, to assure him that his vote was correctly recorded along with his hash total. If the voter presents his receipt, to deny that he voted as shown on the receipt, an unfavorable comparison of the previously recorded hash total, with the hash total on the receipt, proves that the receipt was forged, and each such tampering attempt and voter ID is recorded. Recounts are unnecessary, unless the number of such recorded attempts at tampering exceed a predetermined number. A hacker attempt to change a recorded vote will fail because the hash totals of the altered ballot won't match the correct hash total because the hash encoding algorithm is secret.
Owner:HERSKOWITZ IRVING L
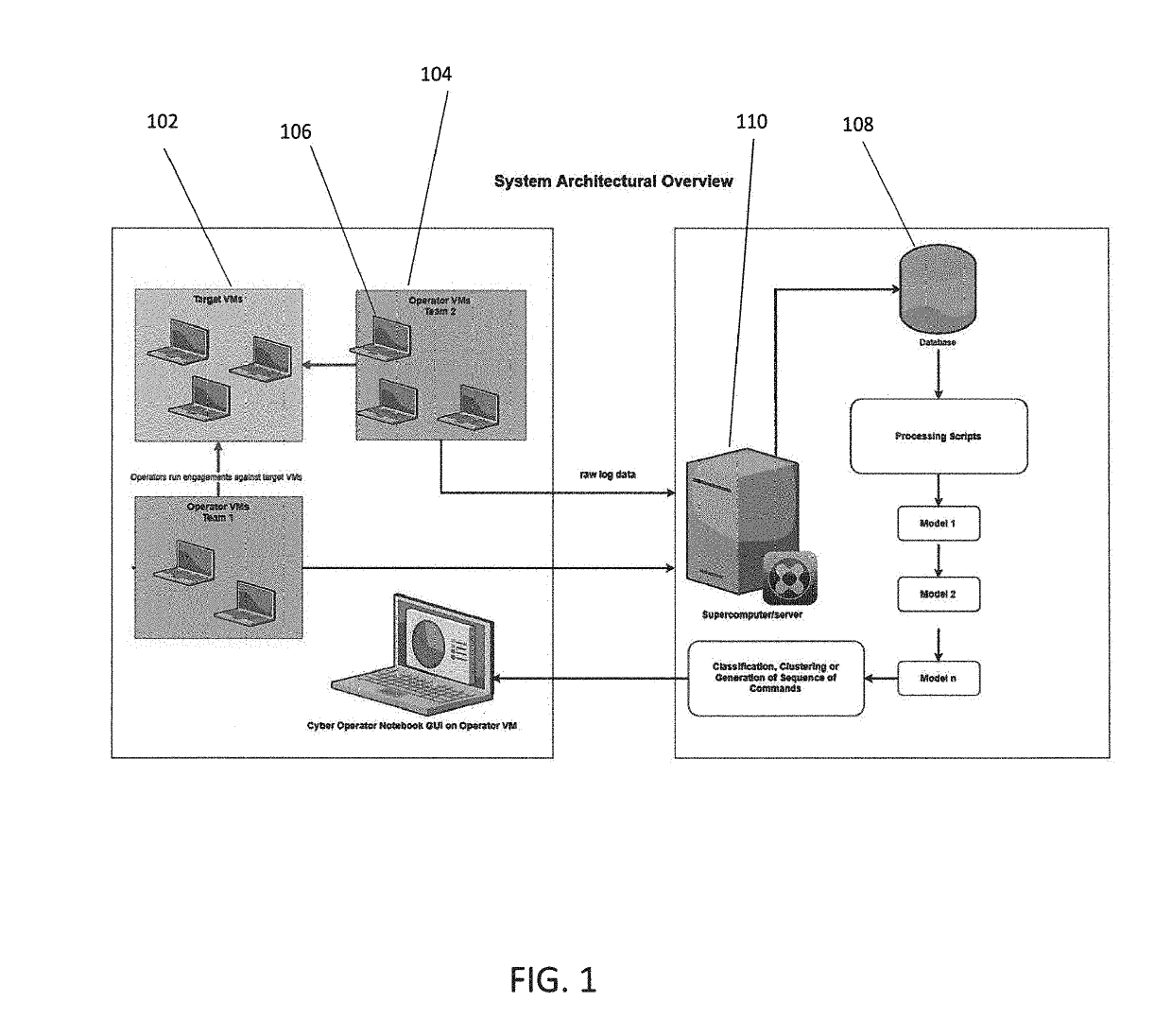
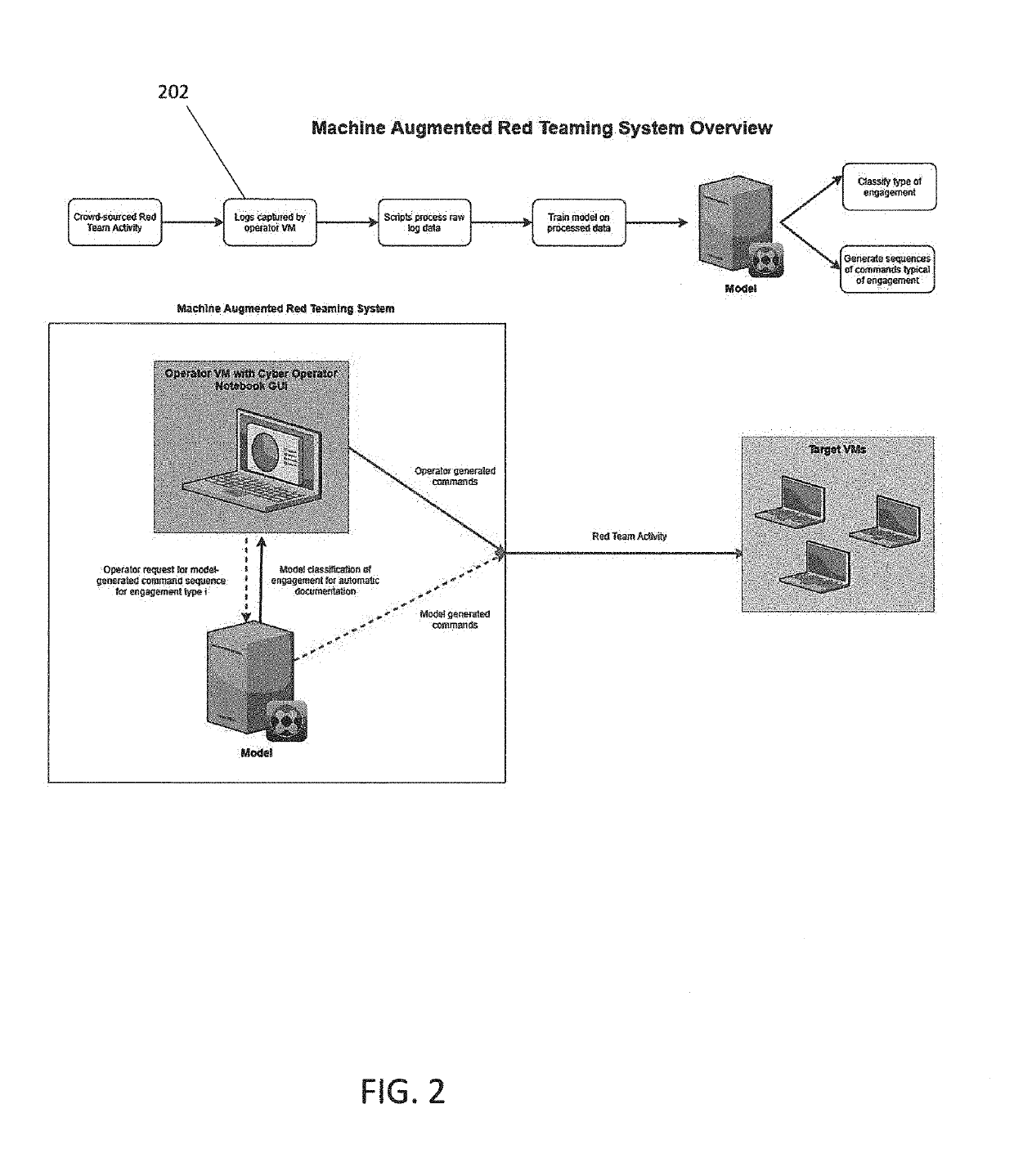
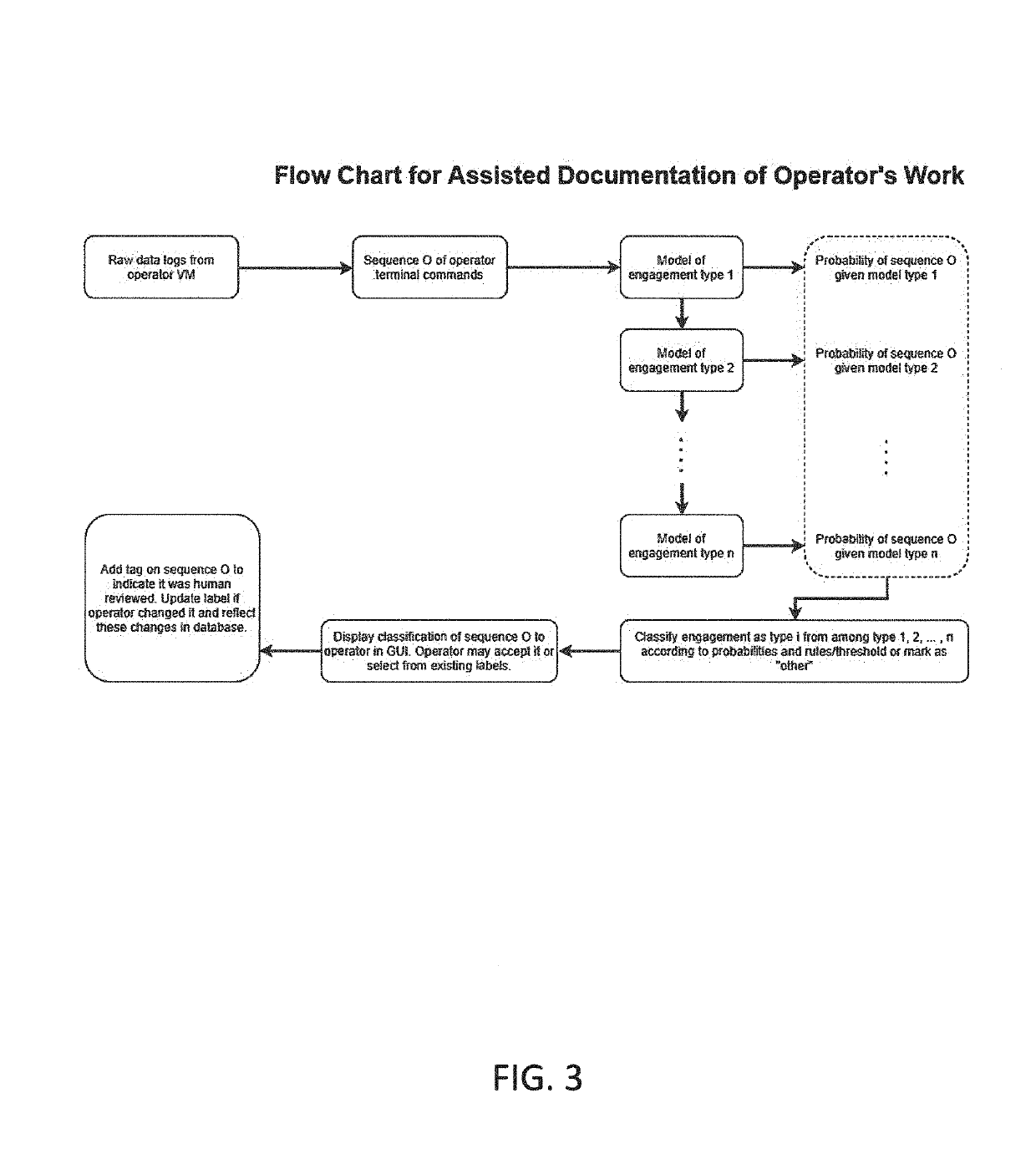
Method and system for penetration testing classification based on captured log data
Aspects of the invention comprise methods and systems for collecting penetration tester data, i.e. data from one or more simulated hacker attacks on an organization's digital infrastructure in order to test the organization's defenses, and utilizing the data to train machine learning models which aid in documenting tester training session work by automatically logging, classifying or clustering engagements or parts of engagements and suggesting commands or hints for an tester to run during certain types of engagement training exercises, based on what the system has learned from previous tester activities, or alternatively classifying the tools used by the tester into a testing tool type category.
Owner:CIRCADENCE
Network security systems and methods
A security system provides a defense from known and unknown viruses, worms, spyware, hackers, and unwanted or unknown software. The system can implement centralized policies that allow an administrator to approve, block, quarantine, or log file activities. The system maintains file meta-information in the hosts and in the server. A host detects file operations which can cause changes to file content or file name, and updates the host and / or server meta-information as a result. Changes in server meta-information are made available to hosts.
Owner:CARBON BLACK
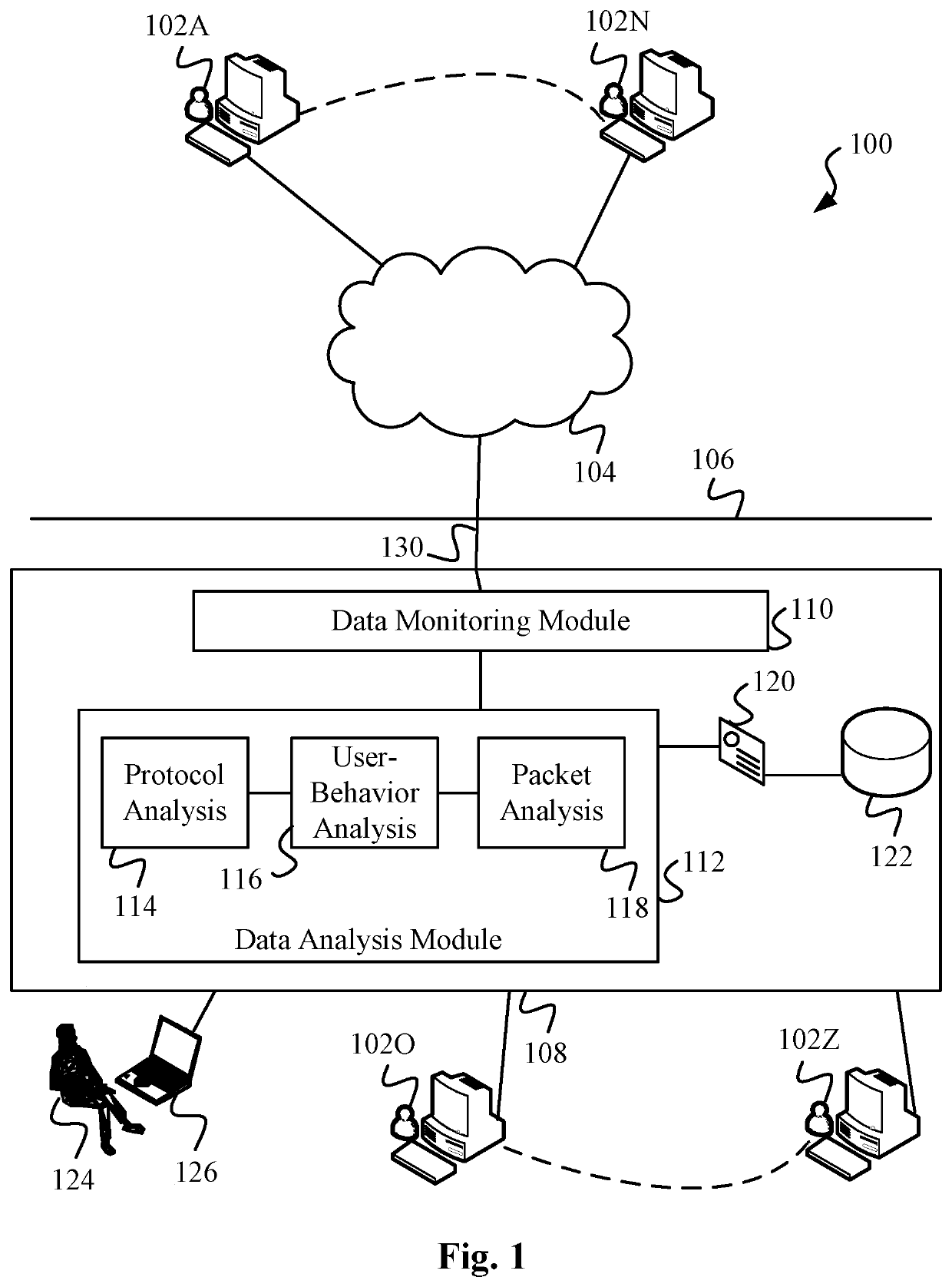
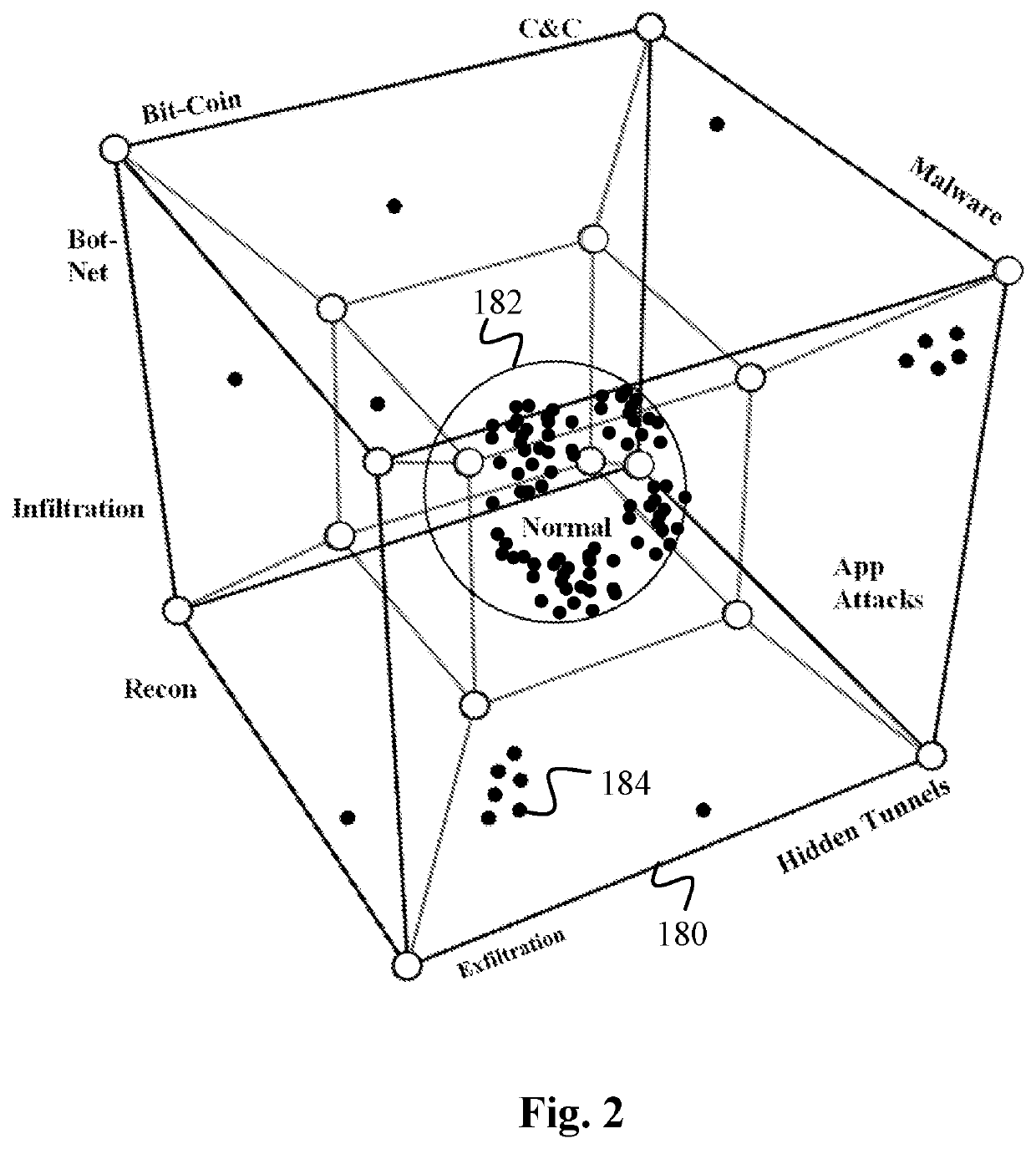
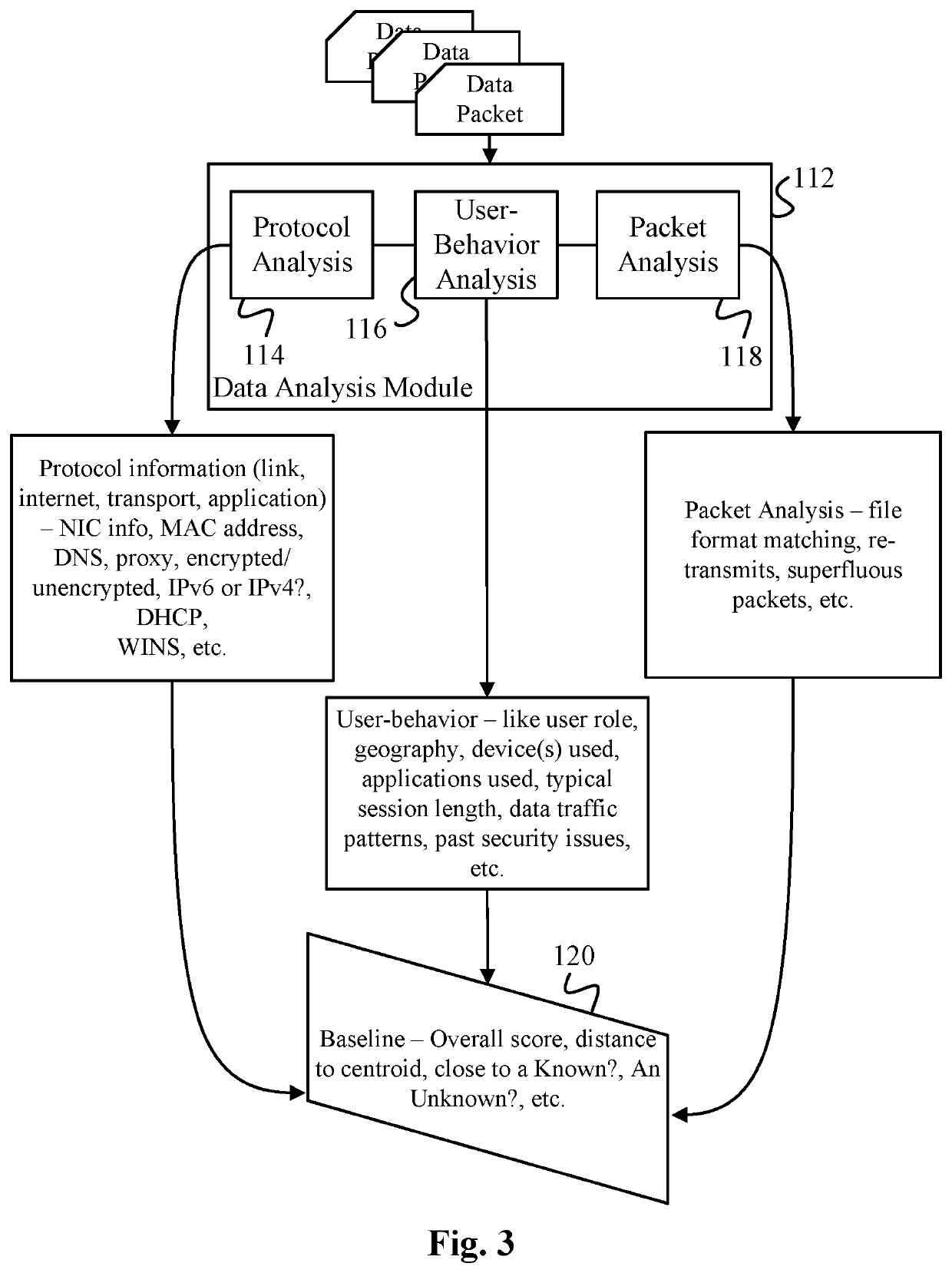
Data Surveillance for Privileged Assets based on Threat Streams
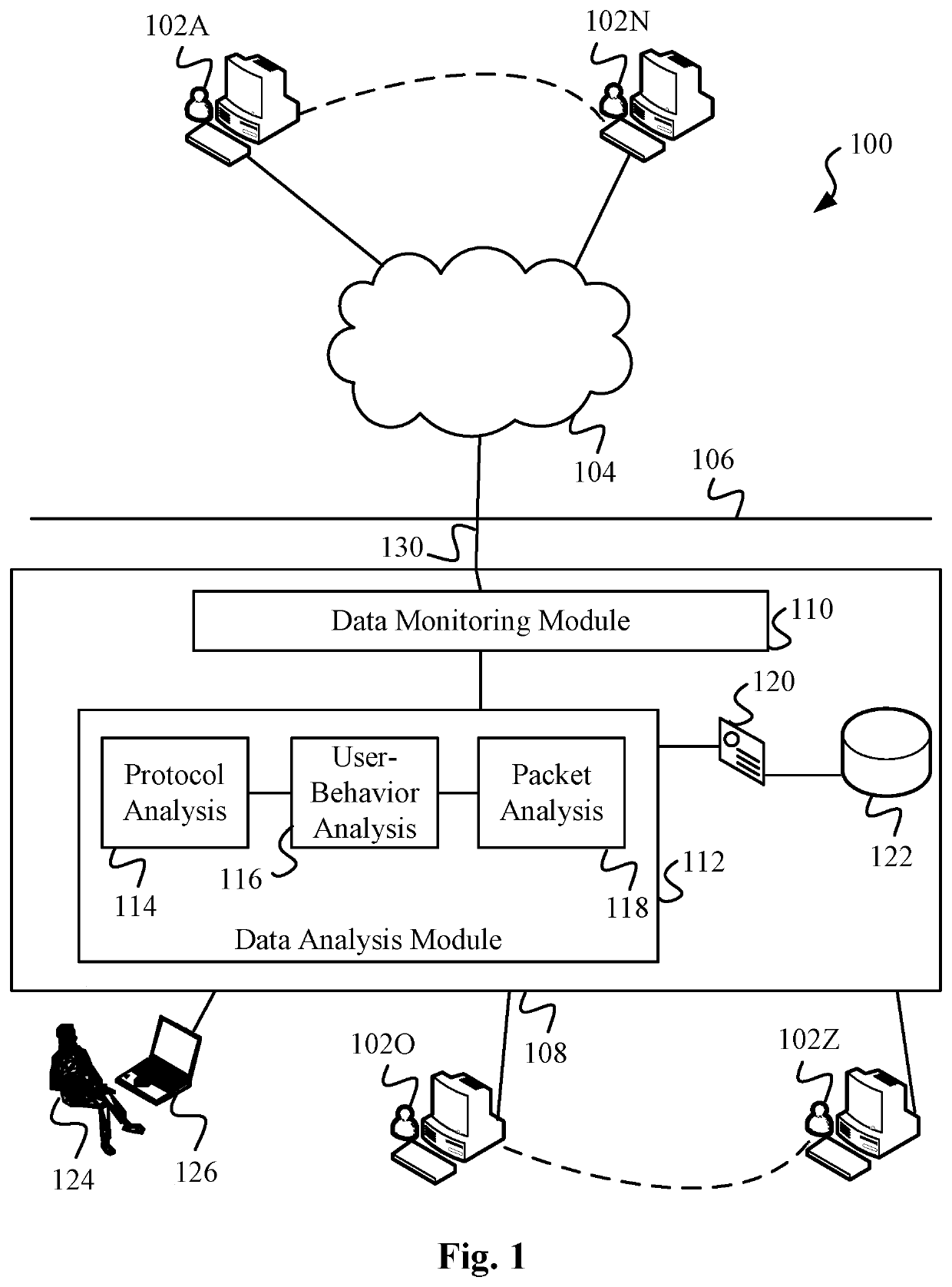
ActiveUS20200204574A1Quick fixMinimal user interactionEncryption apparatus with shift registers/memoriesCharacter and pattern recognitionStreaming dataData pack
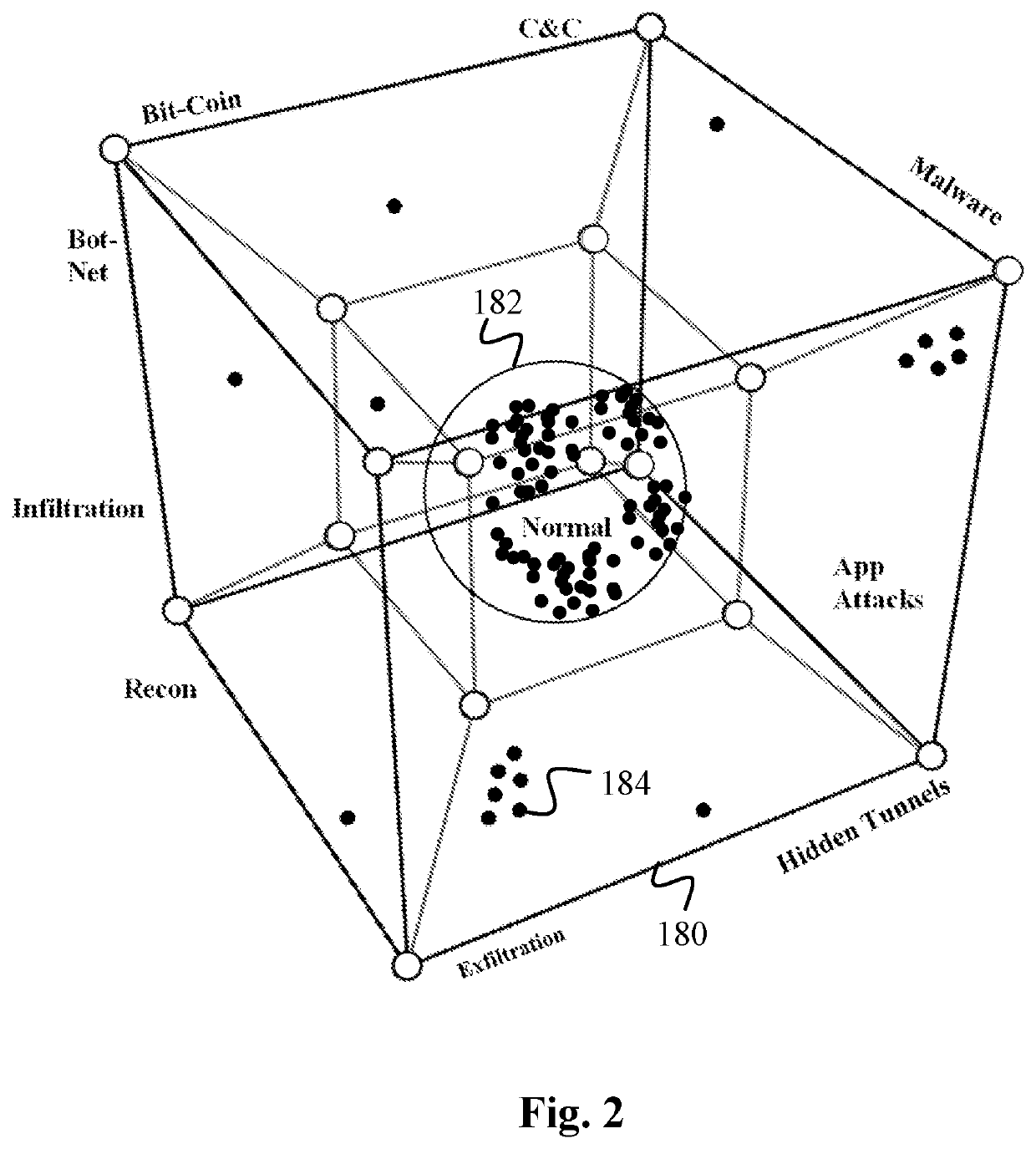
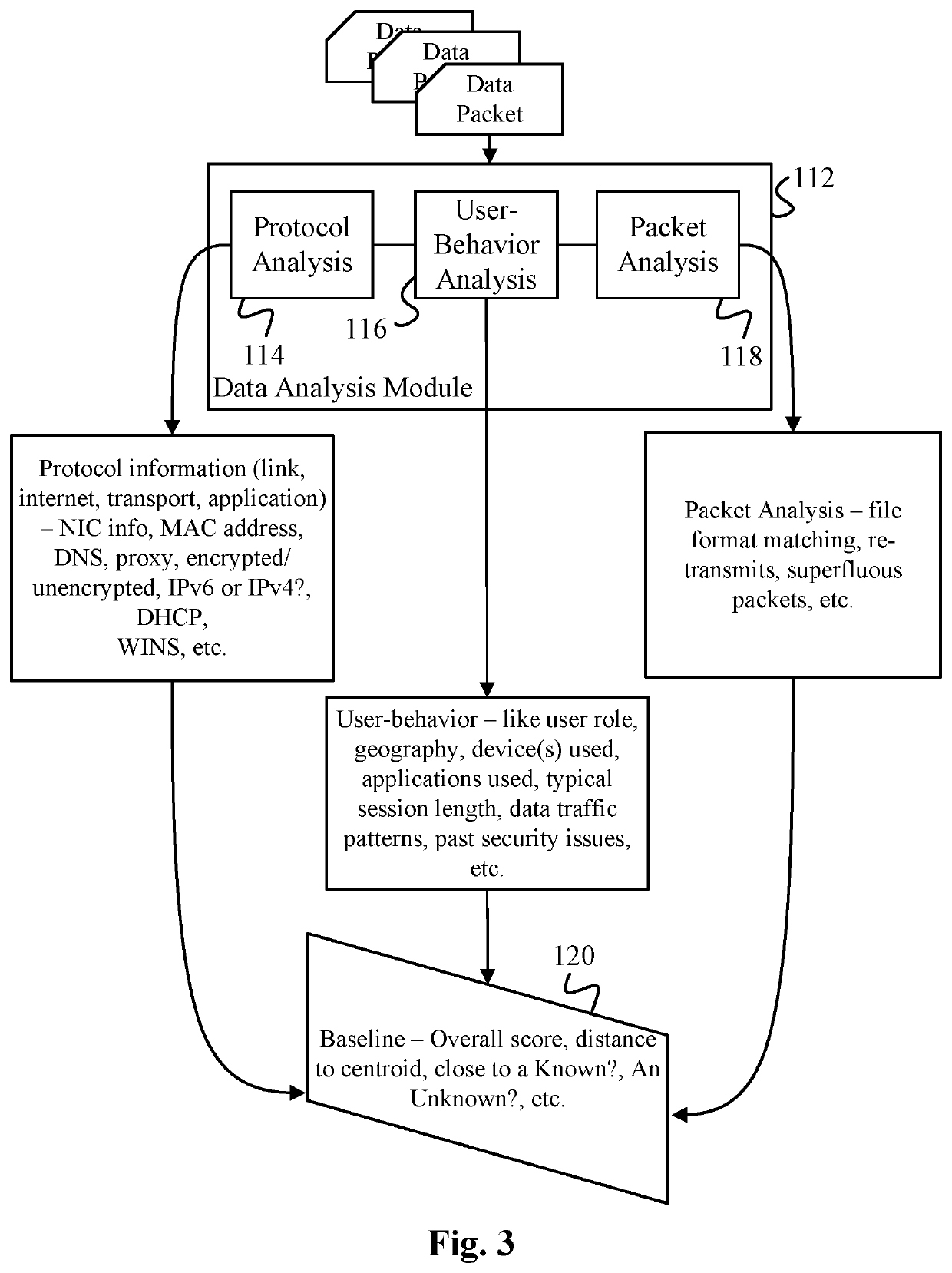
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The above data surveillance techniques are also applied for detecting intentional or unintentional exfiltration / leak of privileged data / assets between unauthorized users / groups of the organization. Such detection may be performed based on analyzing threat stream data from threat intelligence providers.
Owner:FLYING CLOUD TECH INC
A Method of Ensuring the Security of Client Software
InactiveCN102299930AEnsure communication securityNormal use will not be harmfulUser identity/authority verificationCommunications securityClient-side
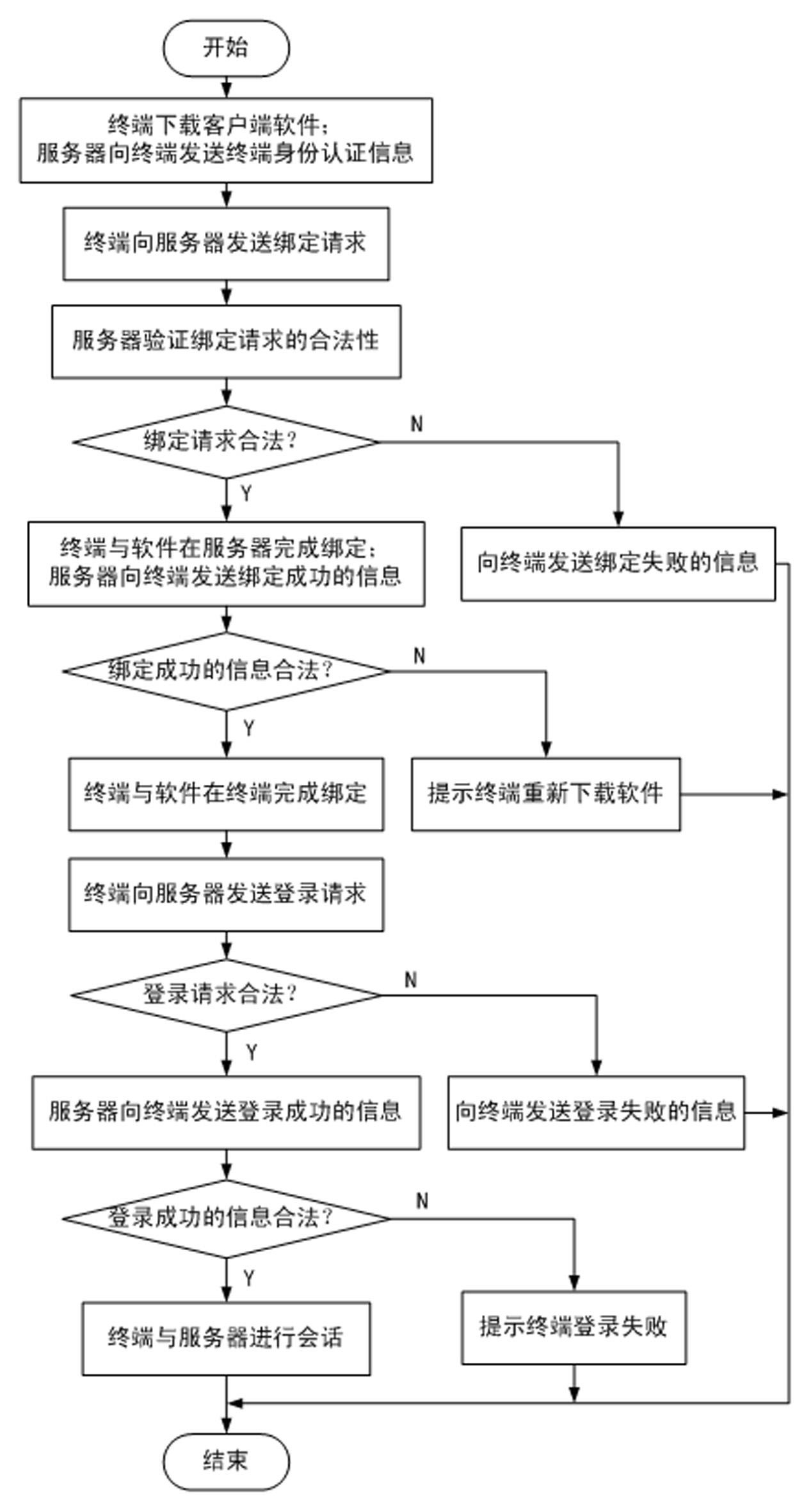
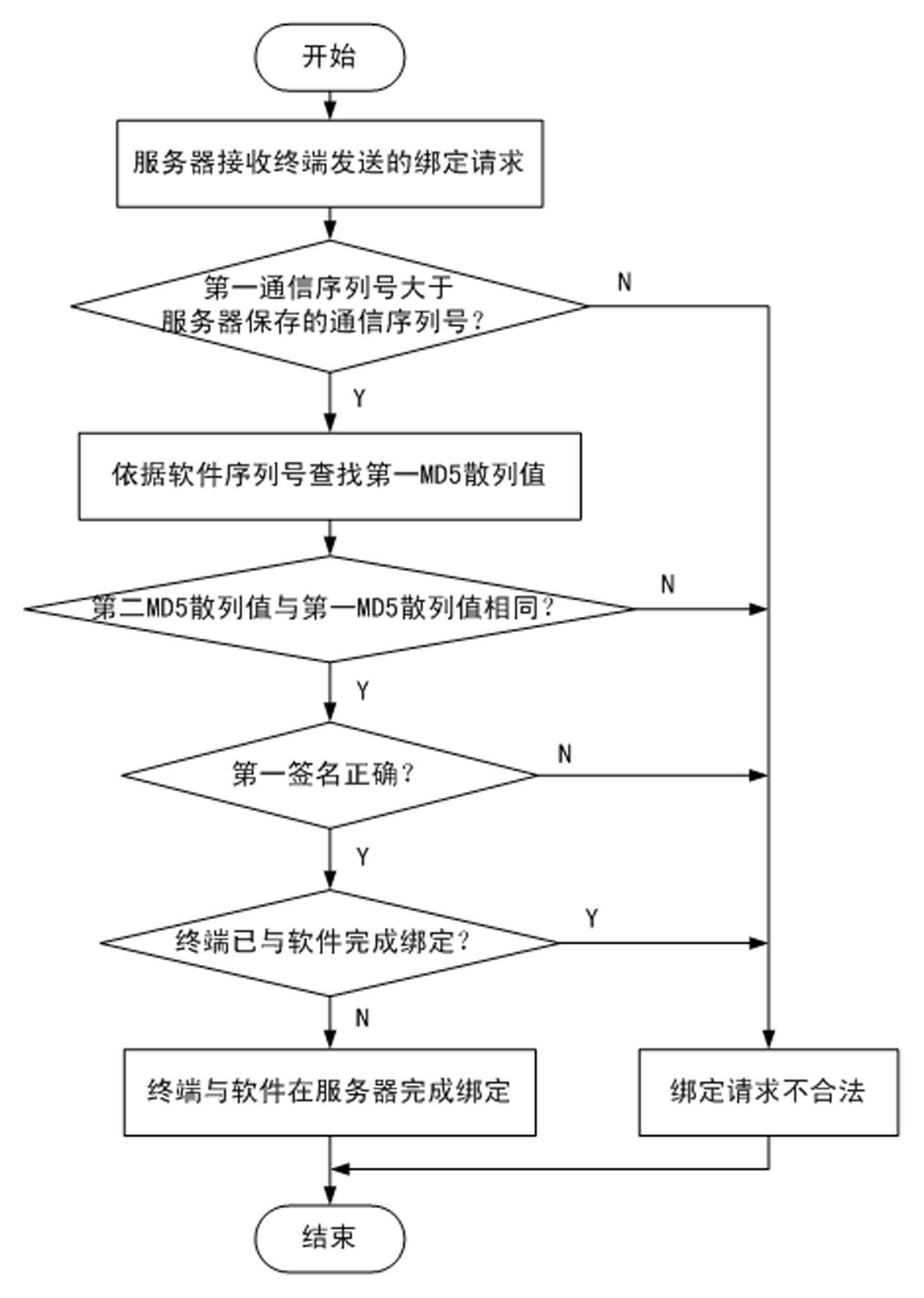
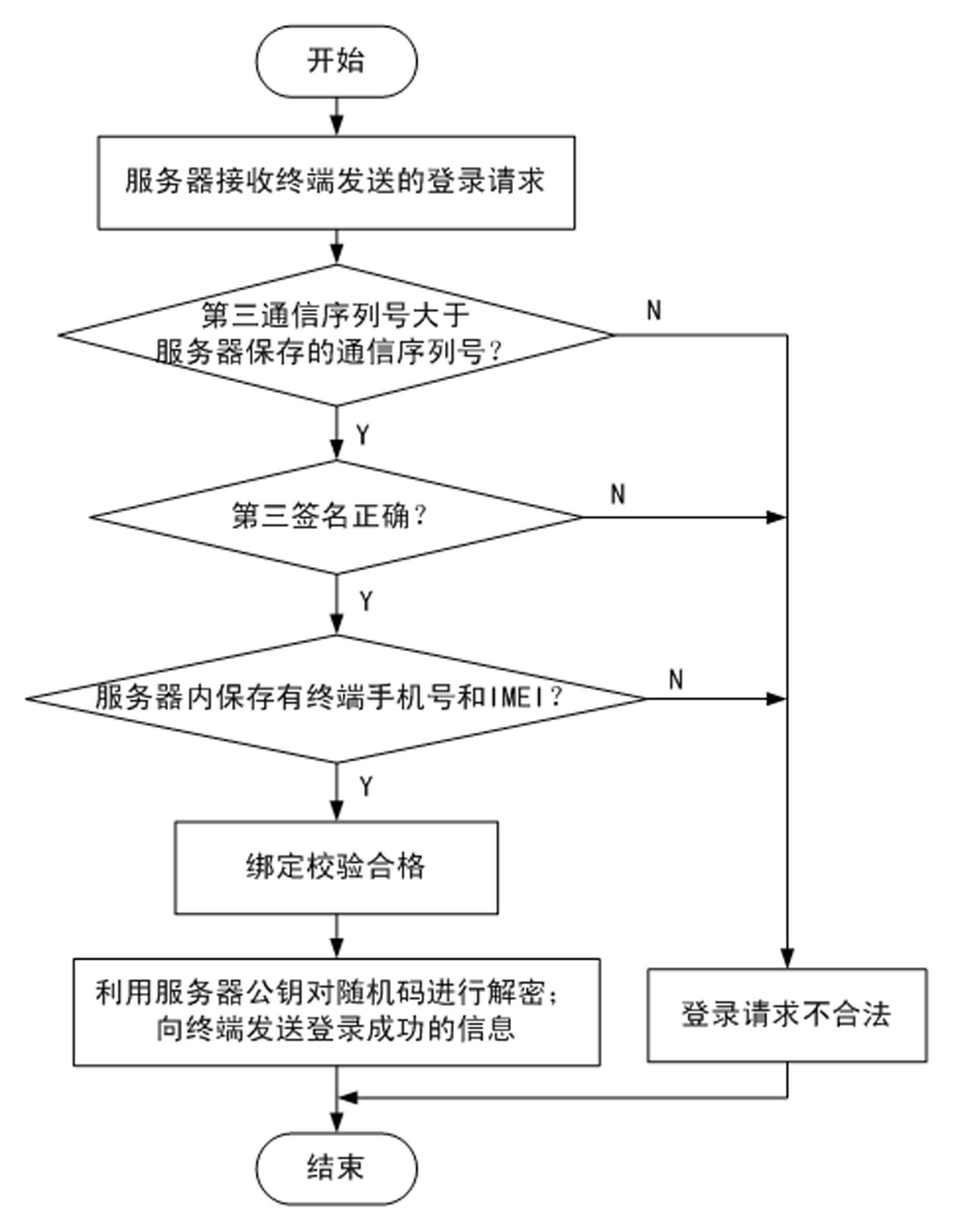
The invention discloses a method for ensuring the security of client software. The method comprises the following steps of: 1, downloading the software by using a terminal, and adding terminal identity authentication information into a software packet by using a server; 2, transmitting a binding request to the server by using the terminal; 3, verifying the legality of the binding request, and if the binding request is legal, transmitting a binding success information to the terminal; 4, verifying the legality of the binding success information; 5, transmitting a login request to the server by using the terminal; 6, verifying the legality of the login request, and if the login request is legal, transmitting a login success information to the terminal; and 7, verifying the legality of the login success information, and if the login success information is legal, keeping a session. By the method, the software can be better prevented from being falsified; the security of communication between the terminal and the server can be ensured; replay attacks can be effectively prevented; the software can be detected whether to be falsified or not; and even though a hacker downloads the software and attacks the server by falsifying the software, only the terminal cannot be used normally and the normal use of other users may not be influenced.
Owner:北京无限新锐网络科技有限公司
Unidirectional protocol isolation method and device in network
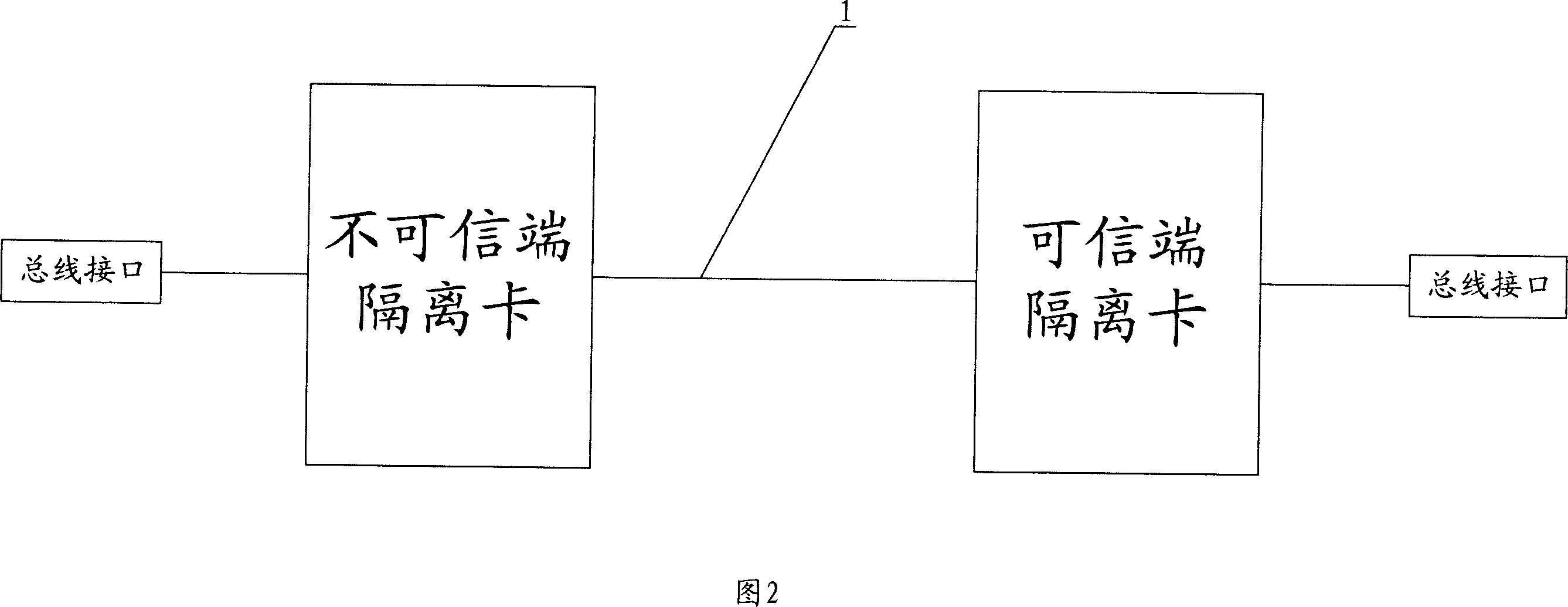
The utility model discloses a unidirectional protocol isolation method in network and the special device. The utility model truly realizes unidirectional protocol isolation between the internal and the external network, ensures the safety of the internal network, eliminates the direct dialogue between hackers and the internal network, and has the functions of virus prevention, visit control and safe auditing; the data can only be transmitted unidirectionally from the network with a lower safety grade to the network with a higher safety grade; contrarily, when the data packet is transmitted from a credible terminal to an incredible terminal, hardware circuit support is not available and the data circulation is impossible, thus data in internal network with higher grade leaking out to the network with lower grade is impossible, the security of the system is improved further.
Owner:BEIJING CITY UNIVERSITY
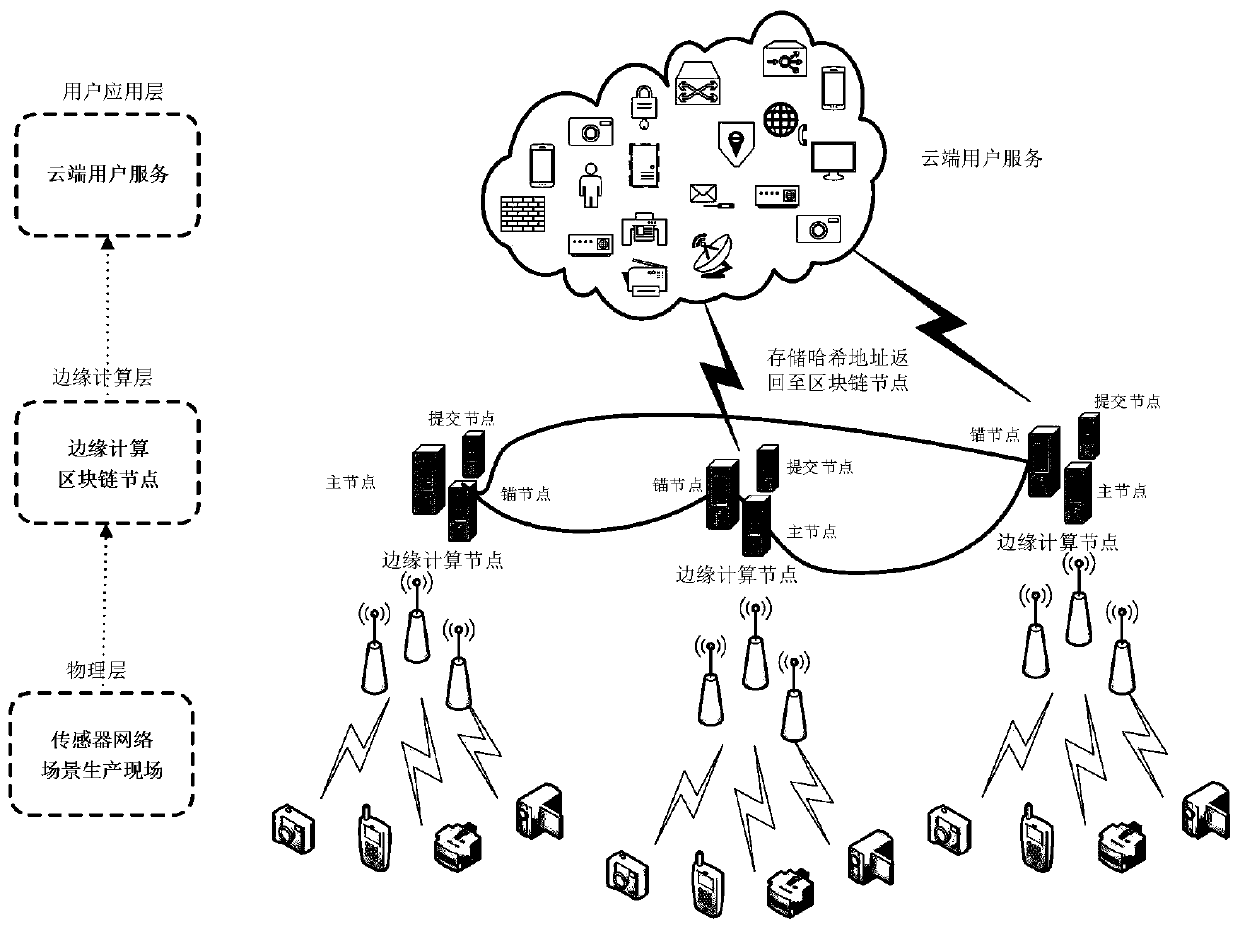
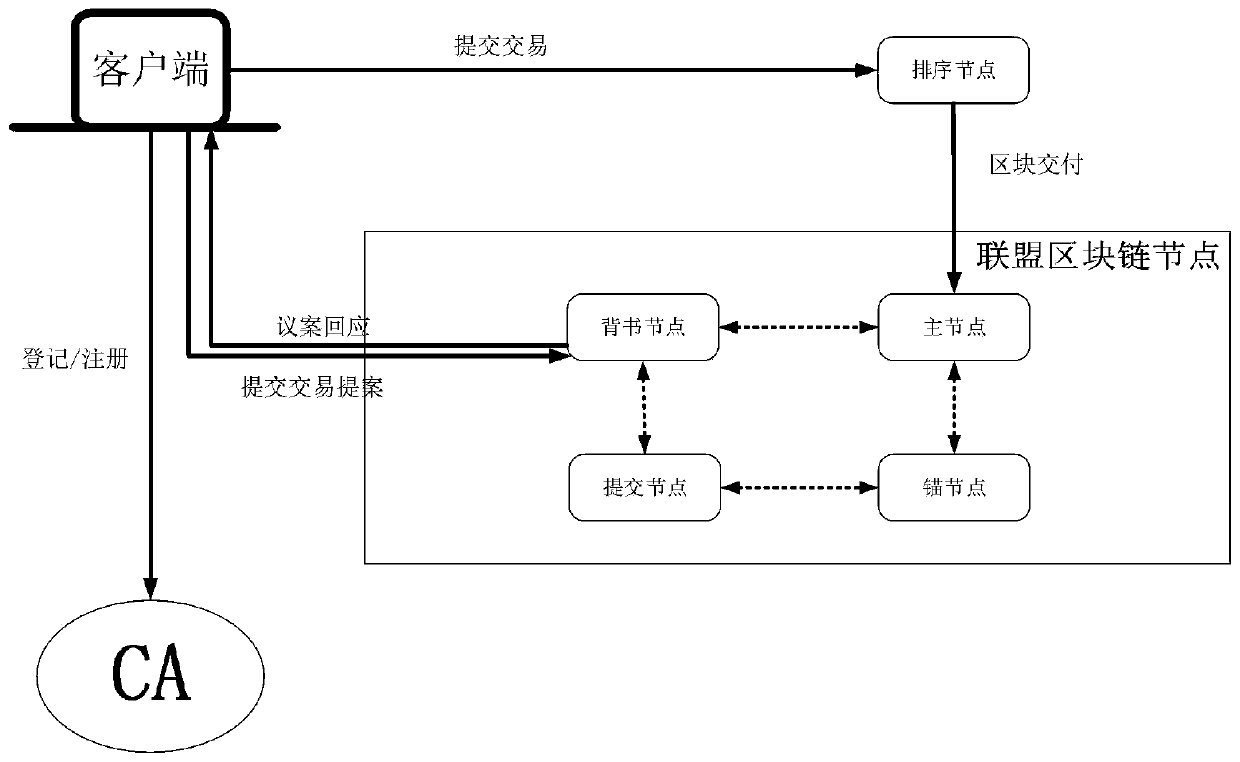
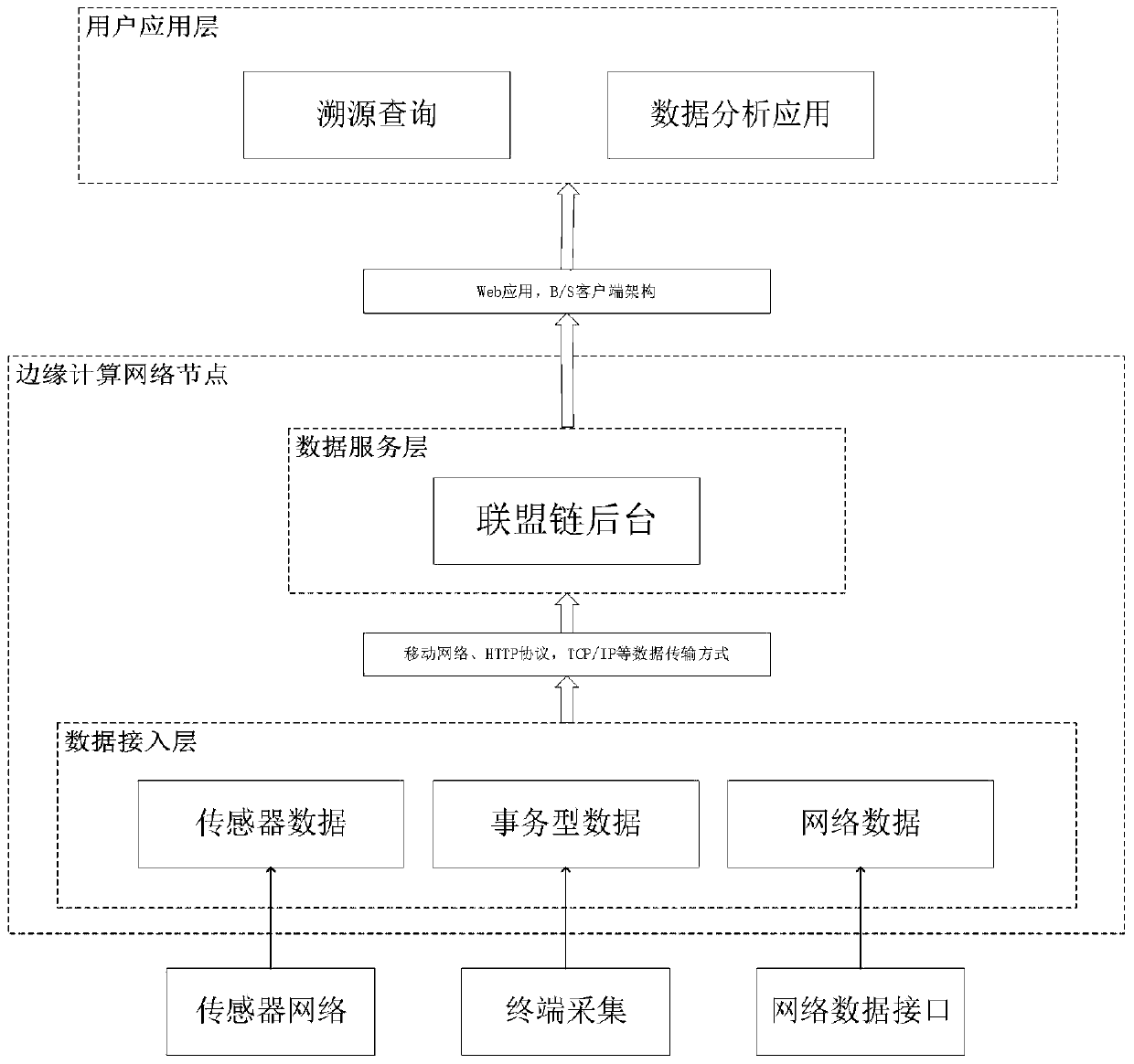
Edge computing data security and privacy protection method based on Fabric
InactiveCN110233868AResolve trust issuesImprove securityUser identity/authority verificationInformation sharingEdge computing
The invention discloses an edge computing data security and privacy protection method based on Fabric, and the method prevents the data from being damaged by artificial malicious deletion and hacker attack due to the non-tamper characteristic of a block chain. Due to the fact that a user can apply for inquiring and obtaining data at any node for building the Fabric, the data safety can be guaranteed under the condition that equipment is accidentally damaged. And the Fabric node built on the edge computing device shares the information to the alliance chain network through broadcasting. In thisway, the information is safely shared to other edge computing nodes which build the Fabric. Due to the fact that all operation on the block chain network can verify the identity of the user, it is guaranteed that only the user authorized with the query authority can obtain data from Fabric, personnel or operators who do not have qualification cannot inquire the data, and privacy data protection is completed. And finally, the protection of the Fabric on the security and privacy of the edge computing data is realized.
Owner:BEIJING UNIV OF TECH
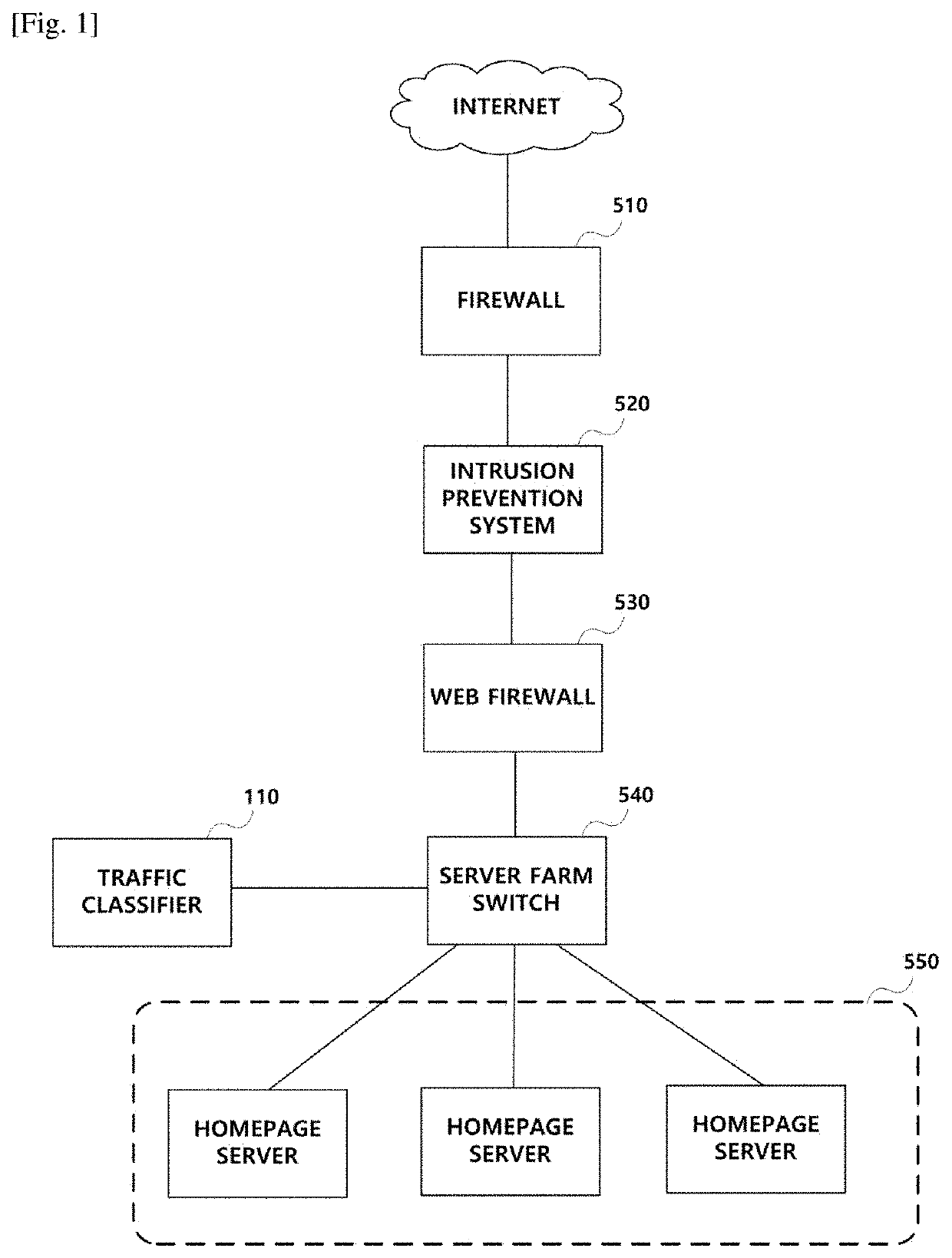
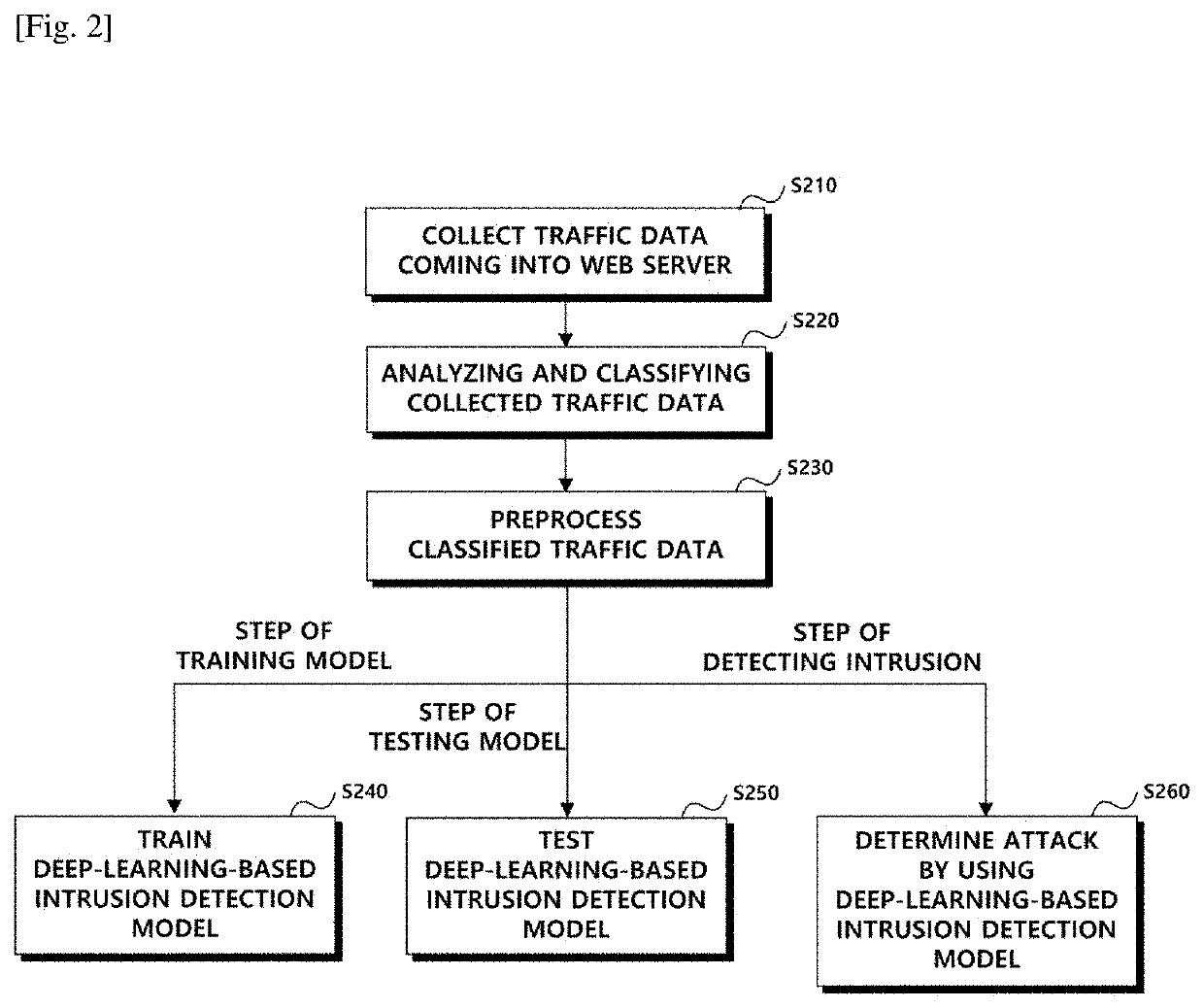
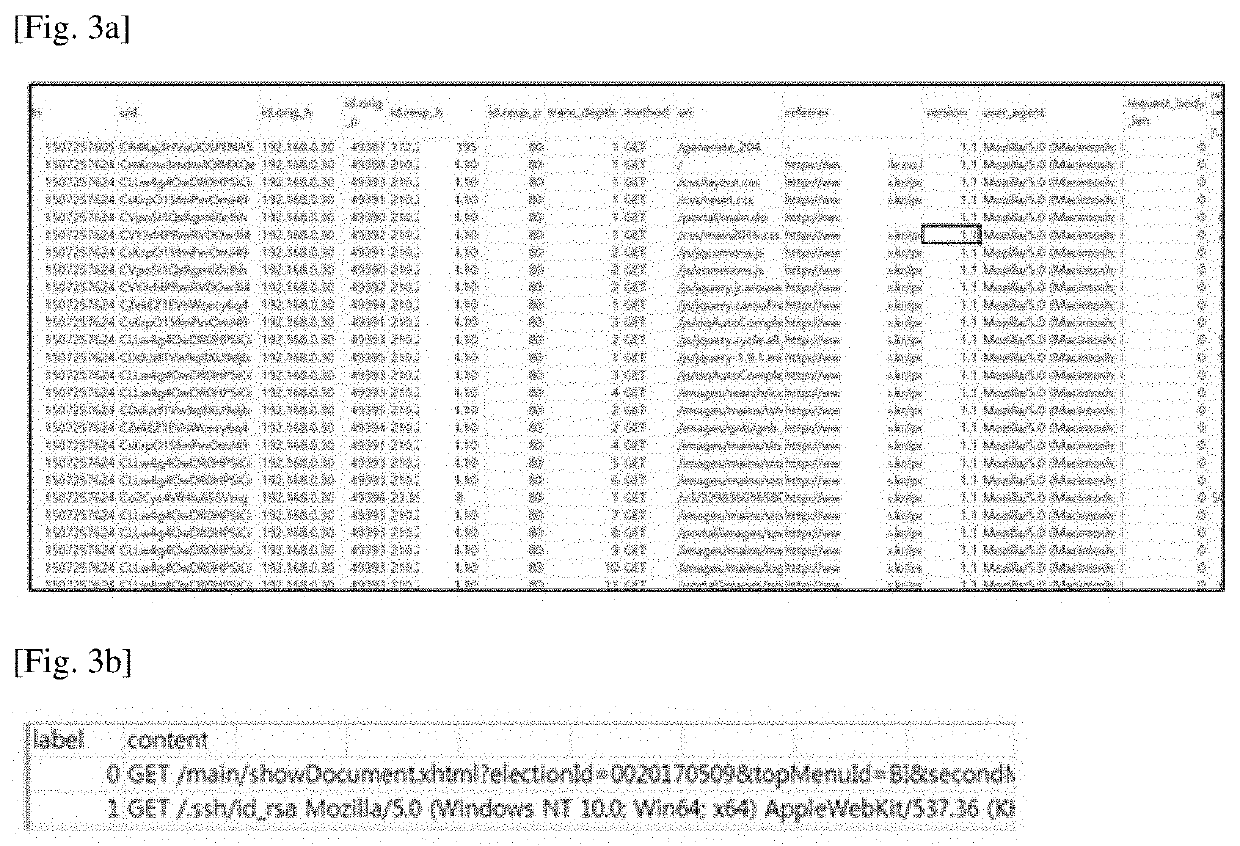
Deep-learning-based intrusion detection method, system and computer program for web applications
ActiveUS10778705B1Efficient detectionHardware monitoringCharacter and pattern recognitionTransmission protocolWeb service
The present invention relates to a deep-learning-based intrusion detection method, a system and a computer program for web applications, and more particularly, to a method, a system and a computer program for detecting whether the traffic is a hacker attack, based on an output from a deep neural network (DNN) model after setting network traffic flowing into a server farm as an input of the model. The present invention provides an effective intrusion detection system by utilizing deep neural networks in the form of complicated messages of the Web service protocol (hypertext transfer protocol (HTTP)), which is most general and representative for a company, among various application-layered services. In particular, the present invention provides a web application threat detection method, a system and a computer program implementing the same that are configured to determine security threats bypassing and intruding the detection scheme of the signature-based security system.
Owner:HOSEO UNIV ACADEMIC COOP FOUND
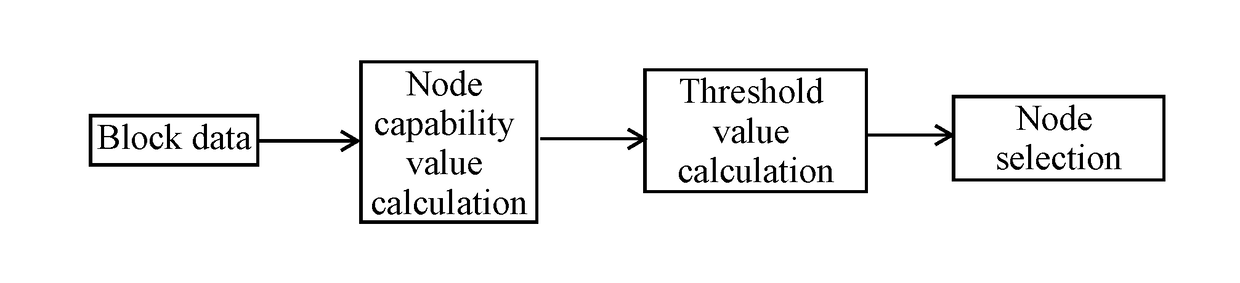
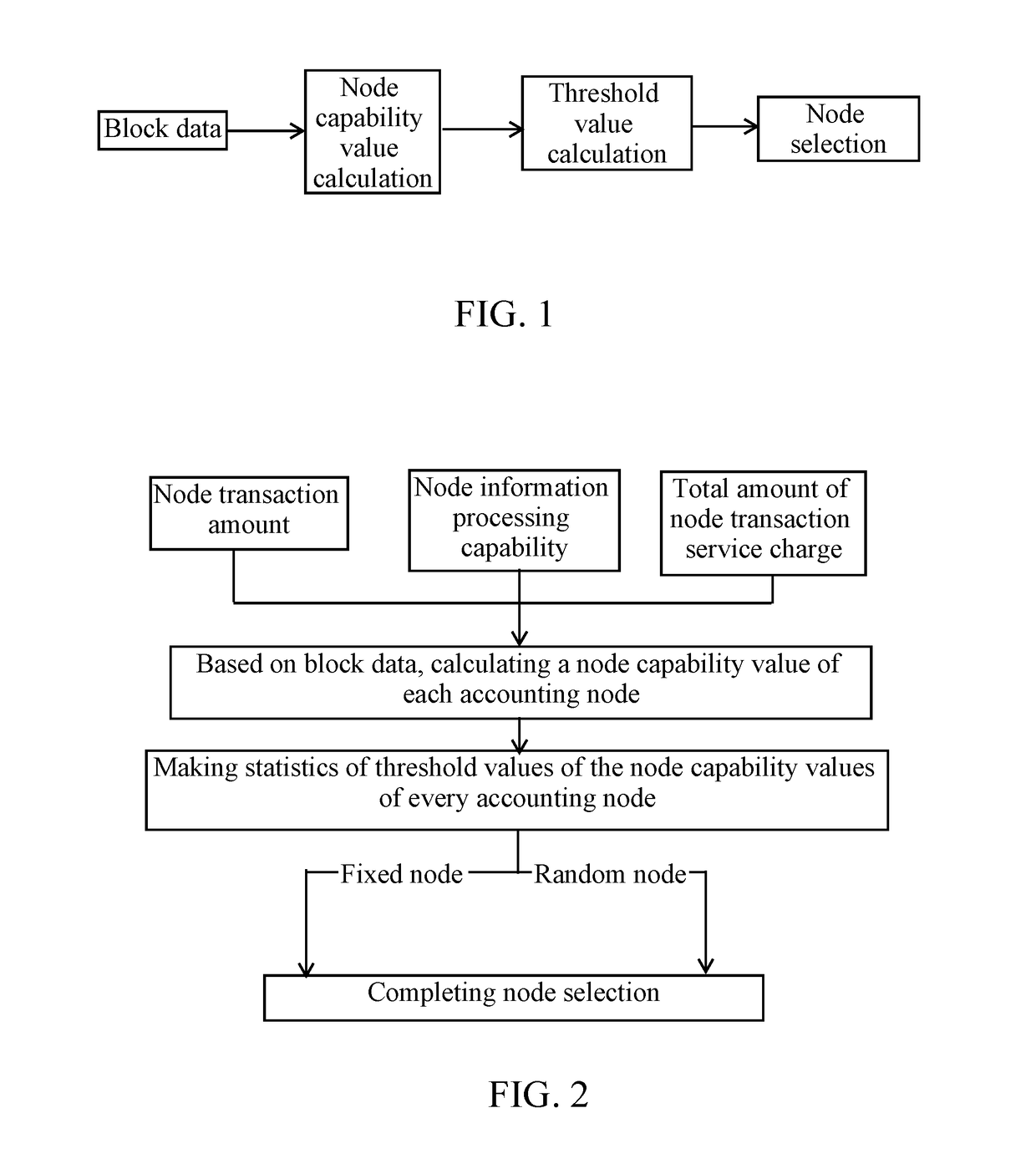
Method for intelligently selecting accounting node of blockchain
InactiveUS20180300694A1Improve securityGreat transaction amountCryptography processingDigital data protectionRandom assignmentData mining
A method for intelligently selecting an accounting node of a blockchain, relating to fields of blockchain, virtual currency and artificial intelligence, is provided, including steps of: (1), based on block data, calculating a node capability value of each accounting node; (2), making statistics of threshold values of the node capability values of every node; and (3), according to the threshold values, determining a current accounting node, and thereafter randomly selecting other nodes, so as to complete node selection. According to the present invention, based on block data and miner data of various dimensions, an intelligent distribution mechanism of accounting rights or mining rights is adopted; and meanwhile, a random distribution of accounting rights or mining rights is also adopted for avoiding hacker attacks. Therefore, on a premise of guaranteeing fairness, decentration and safety of the blockchain, problems of energy waste and low accounting efficiency due to mining conflict are solved.
Owner:BEIJING EASY AI TECHNOLOGY CO LTD
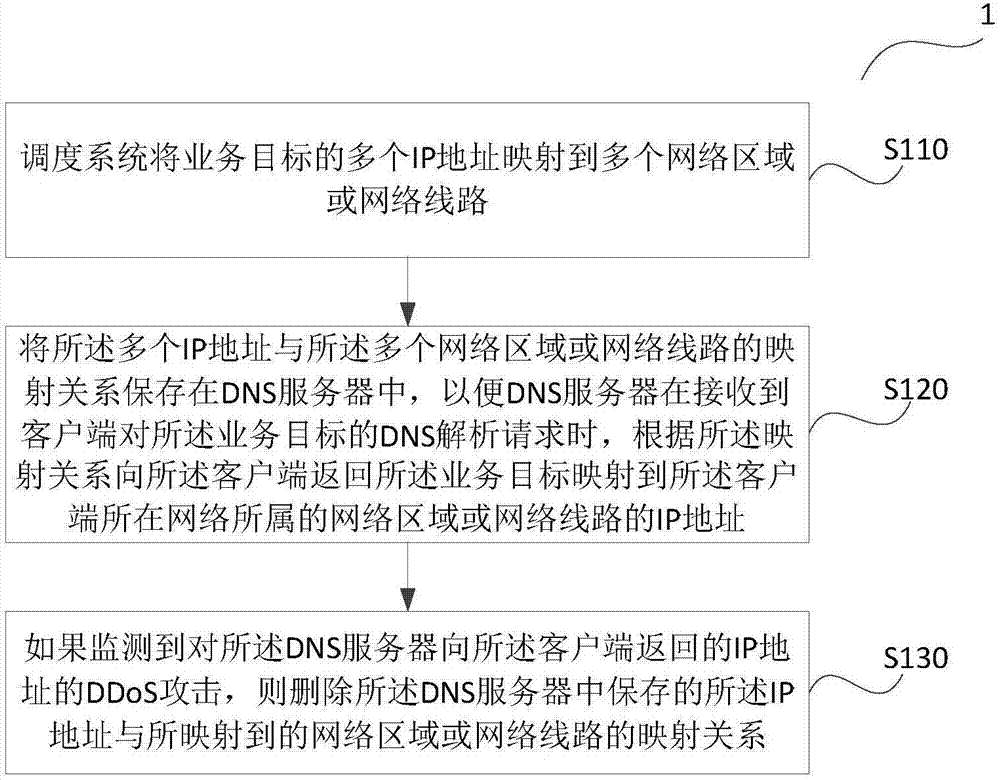
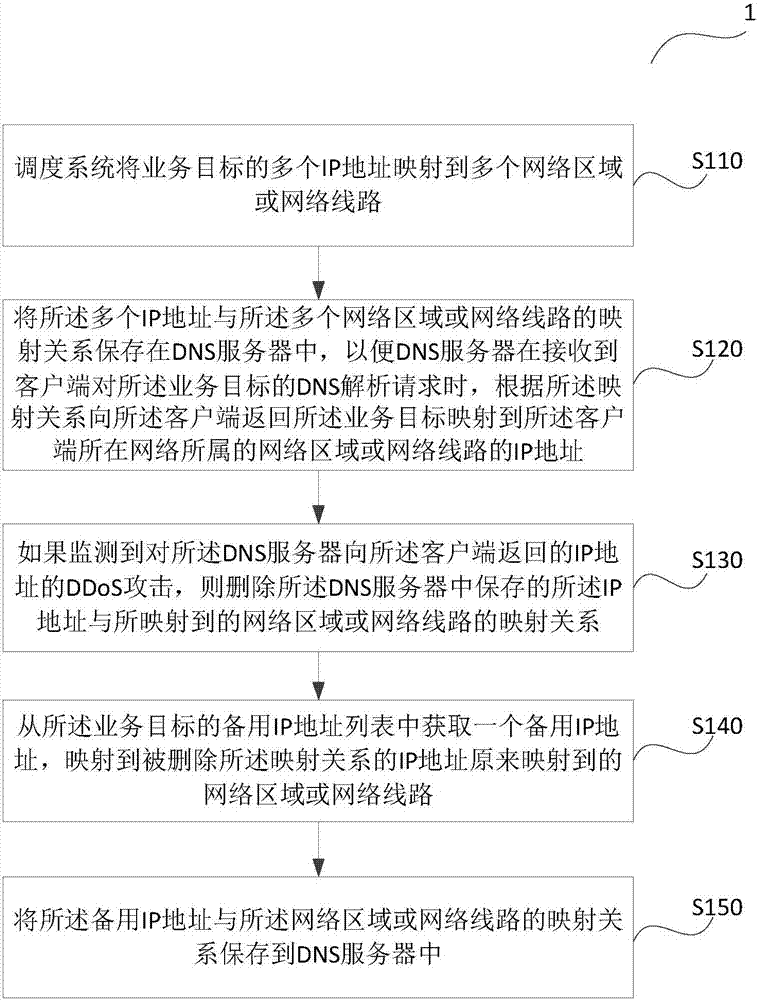
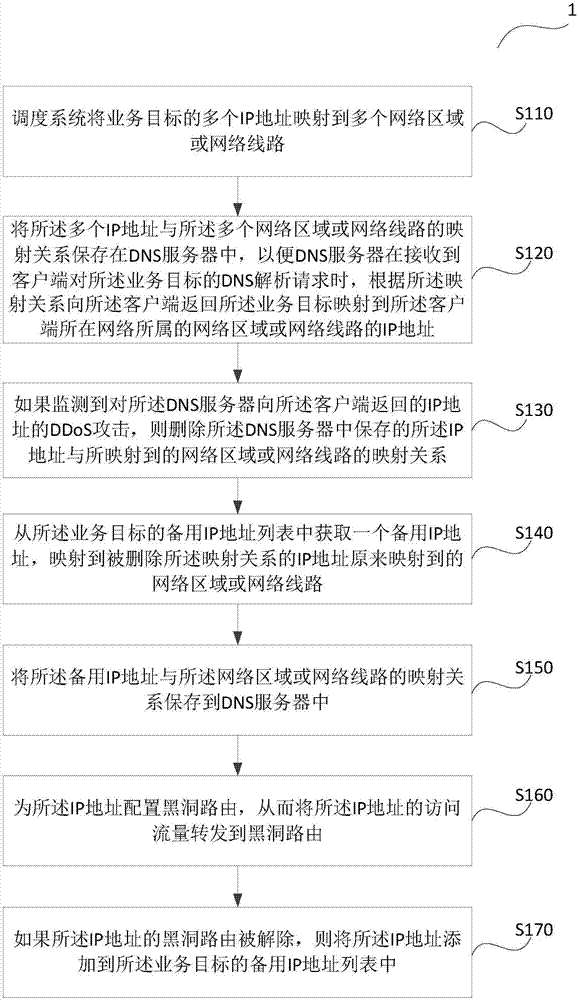
DDoS attack defense method and device
The invention provides a DDoS attack defense method and device. The method comprises the steps that a scheduling system maps multiple IP addresses of the business objective to multiple network areas or network lines, and the mapping relation of the multiple IP addresses and the multiple network areas or the network lines is saved in a DNS server so that the DNS server is enabled to return the IP address which is mapped to the network area or the network line to which the network of the client side belongs of the business objective to the client side according to the mapping relation when the DNS server receives the DNS analysis request of the client side for the business objective; if DDoS attack to the IP address returned to the client side by the DNS server is monitored, blackhole routing is configured for the IP address; and the mapping relation of the IP address and the mapped network area or the network line saved in the DNS server is deleted. According to the technical scheme, the DDoS attack initiating difficulty of the hacker can be increased and switching of the IP addresses can be realized.
Owner:ALIBABA GRP HLDG LTD
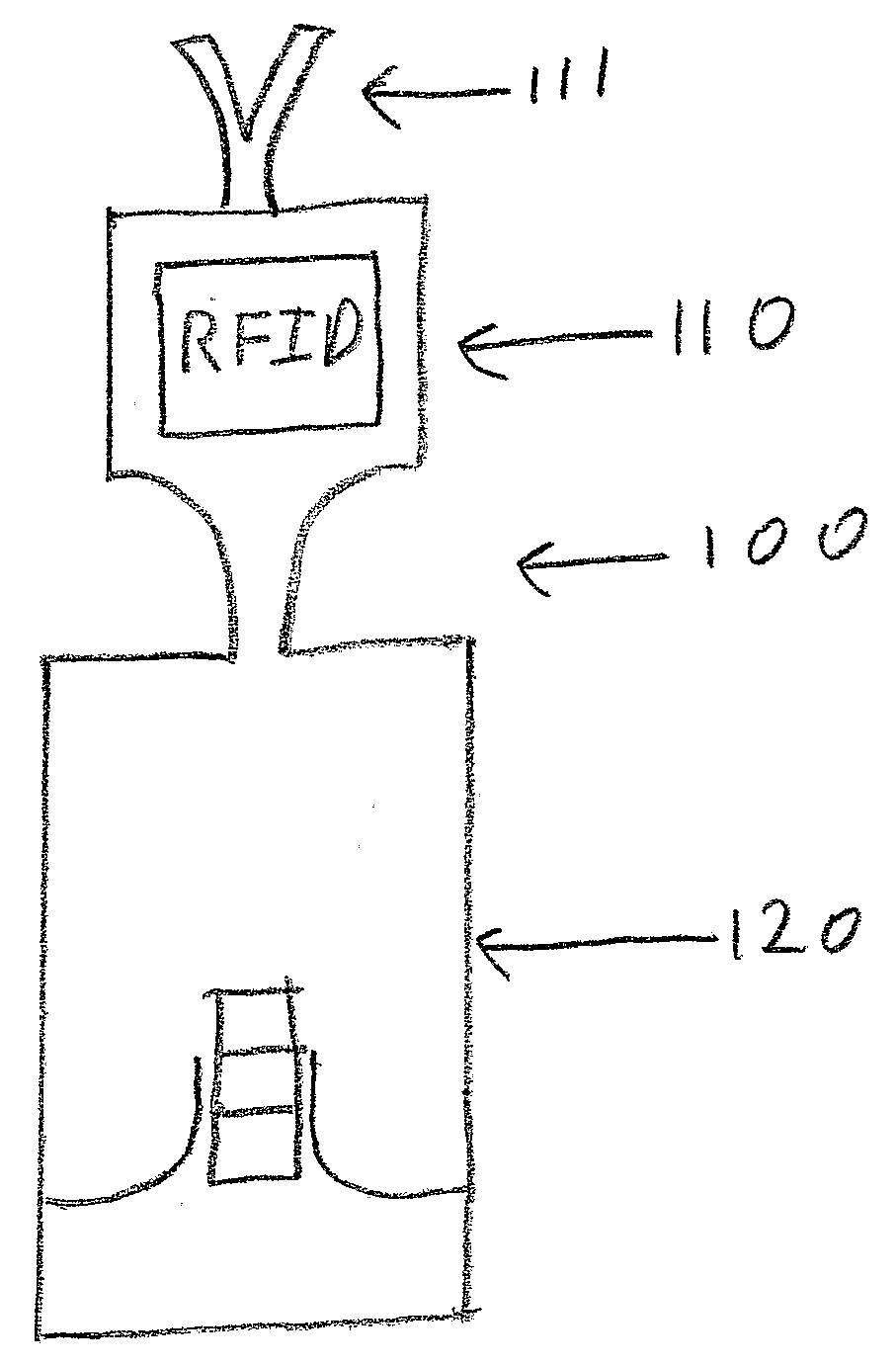
Enhanced Security Protocol For Radio Frepuency Systems
ActiveUS20080297354A1Programme controlElectric signal transmission systemsCryptographic protocolProtection system
This invention relates to security protocols for RFID systems. Systems and methods are presented to protect the system from hackers attempting to compromise the RFID system. Also, methods and systems for improving RFID security are disclosed. The systems utilize mechanisms to determine the authenticity of the RFID tags used in such systems. The systems and methods also reduce unauthorized access to the RFID system. A system and method to make tags more difficult to compromise or counterfeit is also described.
Owner:MASSACHUSETTS INST OF TECH
Systems and methods for predicting which software vulnerabilities will be exploited by malicious hackers to prioritize for patching
PendingUS20200356675A1Memory loss protectionCharacter and pattern recognitionSoftware engineeringHacker
Various embodiments for predicting which software vulnerabilities will be exploited by malicious hackers and hence prioritized by patching are disclosed.
Owner:ARIZONA STATE UNIVERSITY
Digipass for web-functional description
ActiveUS8261087B2Improve securityCost effectiveDigital data processing detailsUser identity/authority verificationInternet communicationUser needs
The DigiPass for the Web provides security for internet communication greater than that achieved by the use of a static password without requiring the user to install any software or to possess or use dedicated hardware of any kind. The user merely access an appropriate website which downloads an applet to the user's browser. This is a conventional function which is handled by the browser and does not require any expertise on the part of the user. The browser relies on a password known only to the user for authenticating the user to the browser / applet. The browser / applet interacts with the server to create an authentication key which is then stored on the user's computer. The user can invoke the authentication key dependent on the user's presentation to the browser / applet of the password. Since the password is not used outside the user-browser / applet interaction it is not subject to attacks by hackers. The authentication key is also protected from attacks by encryption although the user need not memorize any information other than the password.
Owner:ONESPAN NORTH AMERICA INC
Hacker behavior discovery and analysis based on linkage of intrusion detection and vulnerability scanning
InactiveCN105227582AReduce false positivesAvoid subsequent attacksTransmissionVulnerability scanningLinkage concept
The invention discloses a method for hacker behavior discovery and analysis based on linkage of intrusion detection and vulnerability scanning. Through linkage of an intrusion detection technology and a vulnerability scanning technology, an attack is accurately positioned or a suspicious hacker behavior is discovered, so that the hacker intrusion behavior is timely intervened to avoid loss before the hacker intrusion behavior is successful, and furthermore, an attack source is analyzed and discovered through an attack source tracking technology, and the subsequent attack behavior of the attack source is prevented by utilizing the technologies, such as blacklist.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
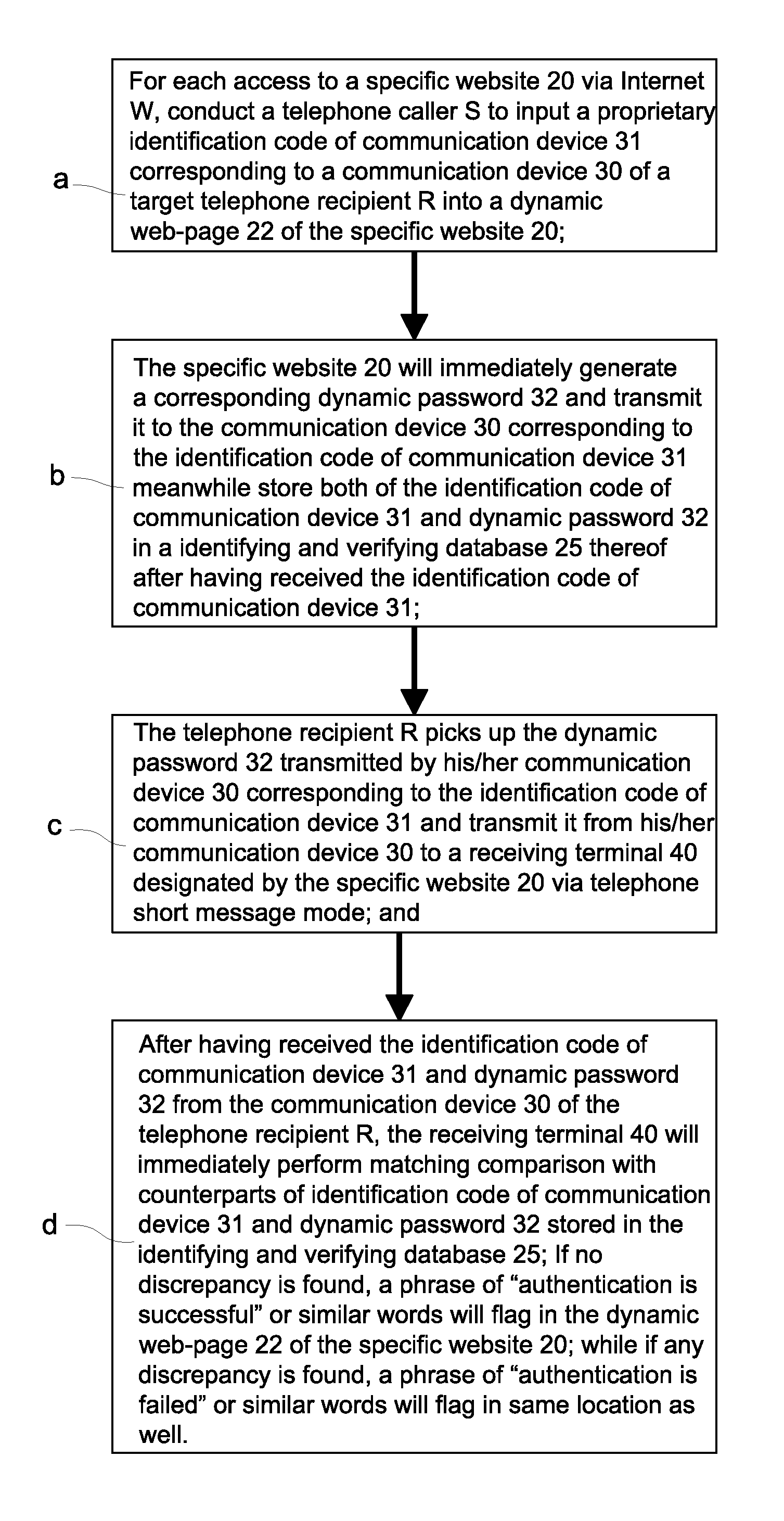
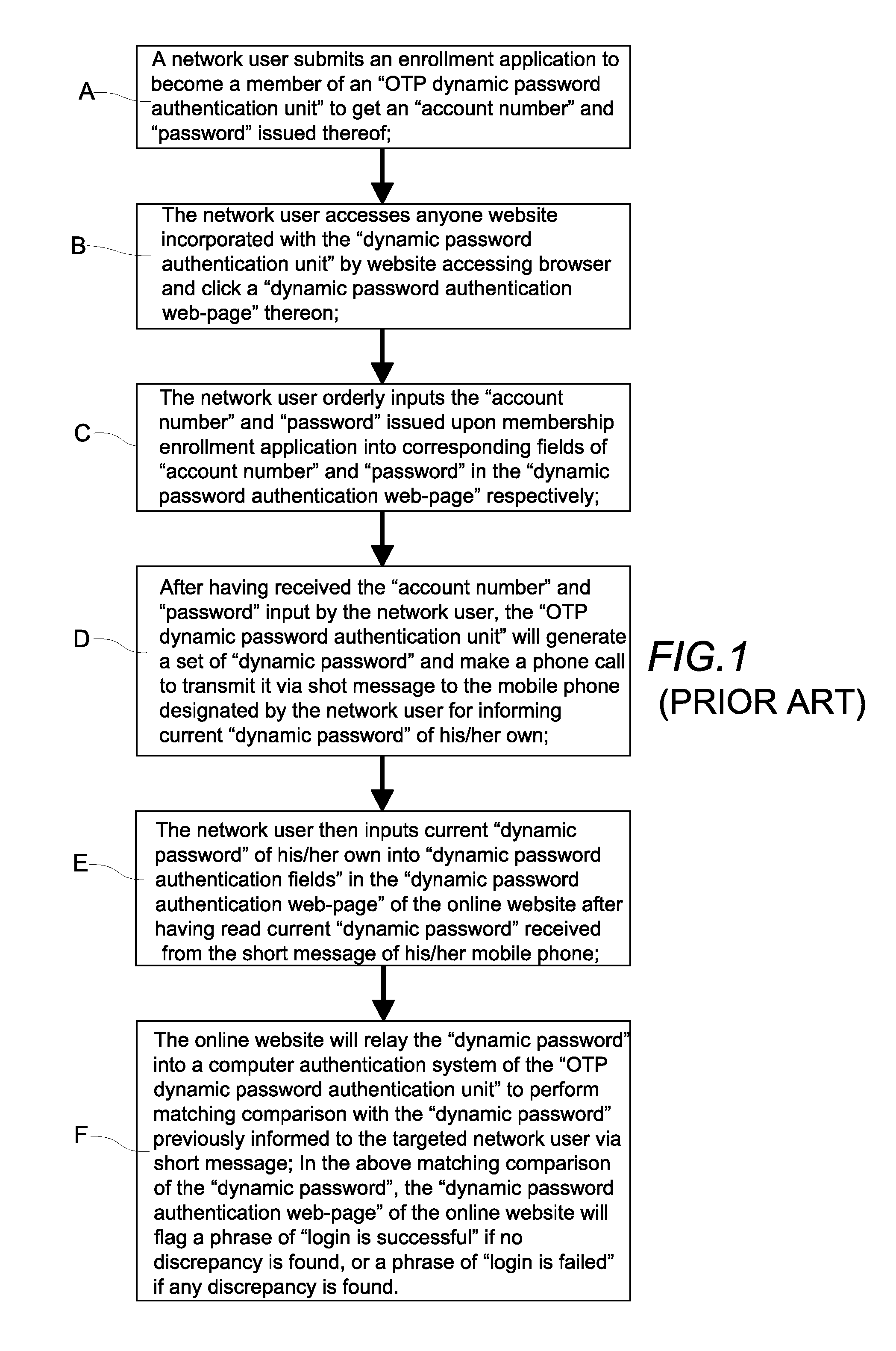
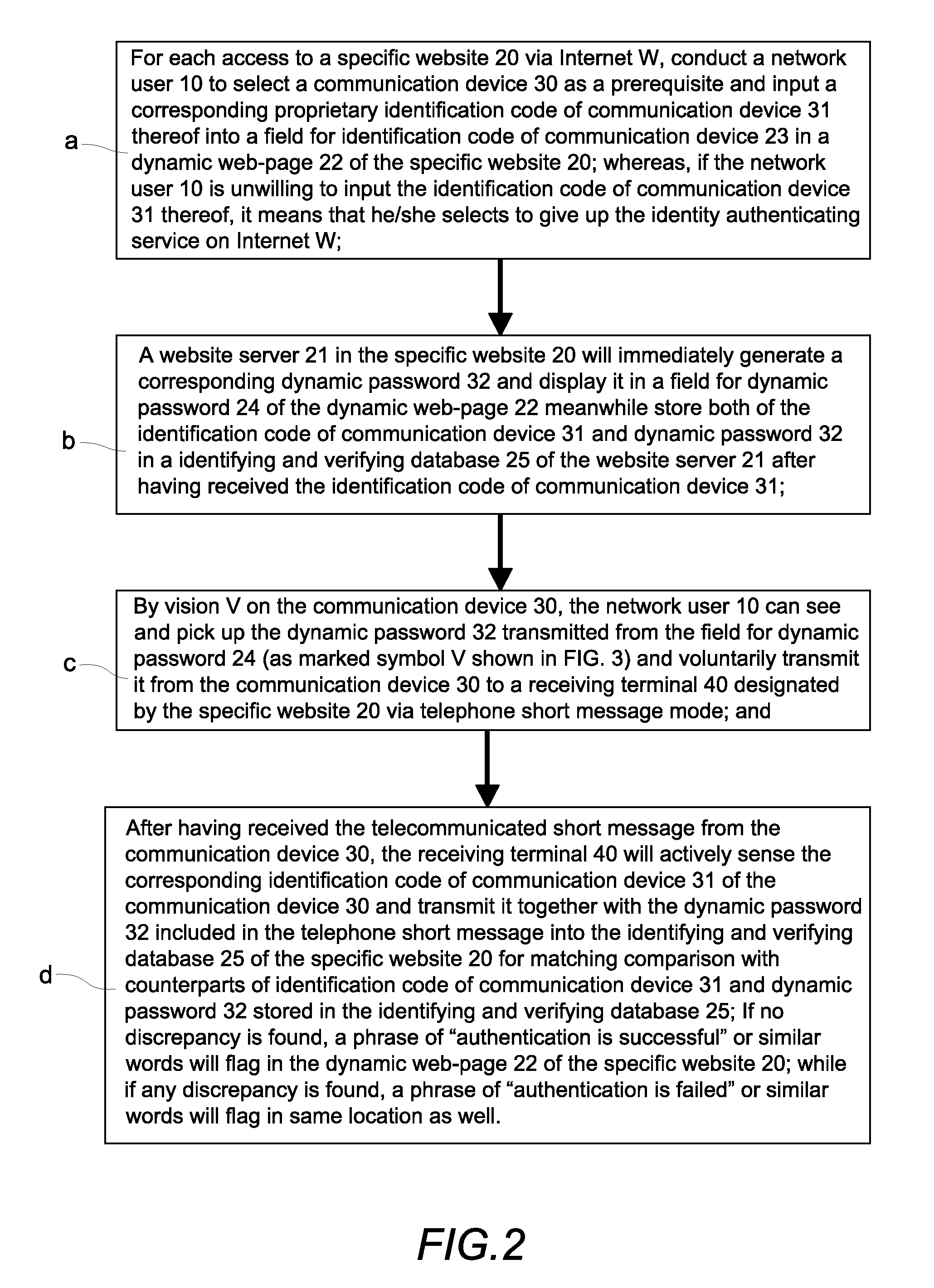
Method of identity authentication and fraudulent phone call verification that utilizes an identification code of a communication device and a dynamic password
ActiveUS8549594B2Improve security levelEasy to useUnauthorised/fraudulent call preventionDigital data processing detailsPasswordInternet users
A method of identity authentication and fraudulent phone call verification uses an identification code of a communication device and a dynamic password. The “dynamic password” is directly sent to an Internet user via a dynamic web-page of a specific website instead of by means of a traditional telephone short message. Thus, the “dynamic password” cannot be copied from the spyware infected communication device of the Internet user. Furthermore, even if the “dynamic password” is intercepted or otherwise discovered by a hacker or intruder, authentication is still secure because the dynamic password must be sent back to the specific website via a short message or the like from the same communication device having the corresponding identification code that was initially input by the Internet user in order to generate the dynamic password.
Owner:LIN CHUNG YU
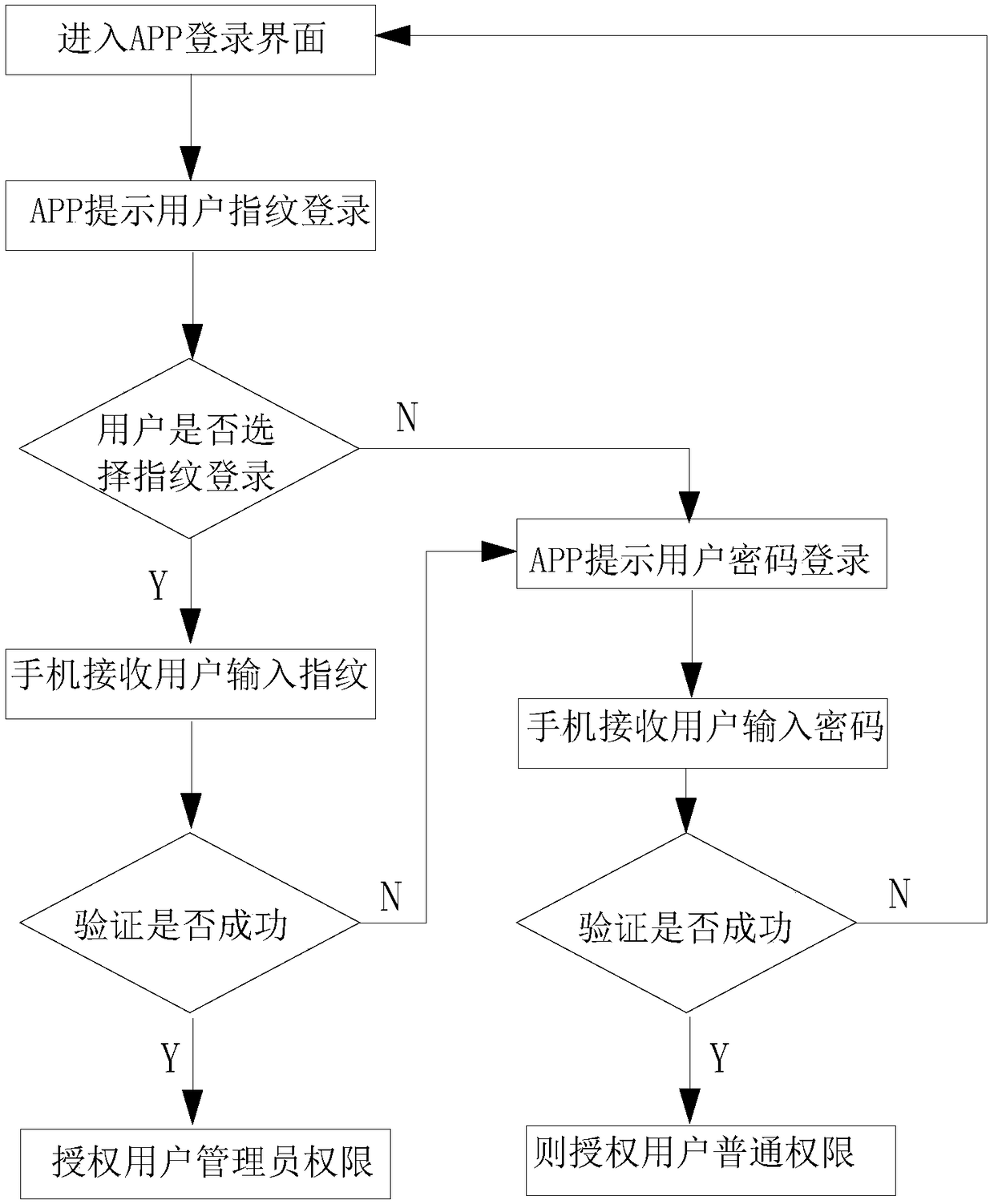
Washing machine control method and washing system
ActiveCN109402941AImprove securitySecurity control functionOther washing machinesControl devices for washing apparatusMachine controlPassword
The invention discloses a washing machine control method and a washing system. A washing machine can be controlled through an intelligent terminal, when the intelligent terminal controls the washing machine, identity authentication is needed and comprises the two modes of human body characteristic authentication and password authentication, when the washing machine detects that human body characteristic authentication of a user is successful, the user is authorized with rights of administrators, when the washing machine detects that password authentication of a user is successful, the user isauthorized with generic rights, and the rights of administrators have more control functions compared with the generic rights. According to the method, the safety of the washing machine is greatly improved, hacker attack manipulation is prevented, the users are authorized with different control rights according to different authentication modes, safer and more comprehensive control functions can be provided for the users conveniently, and use of the users is facilitated.
Owner:QINGDAO HAIER WASHING MASCH CO LTD +1
Fine-grained forward-secure signature scheme
InactiveUS20060233364A1Key distribution for secure communicationMultiple keys/algorithms usagePresent methodGranularity
The presented methods form the basis of a forward-secure signature scheme that is provably secure. Moreover, the presented methods form also the basis of a fine-grained forward-secure signature scheme that is secure and efficient. The scheme allows to react immediately on hacker break-ins such that signatures from the past still remain valid without re-issuing them and future signature values based on an exposed key can be identified accordingly. In general, each prepared signature carries an ascending index such that once an index is used, no lower index can be used to sign. Then, whenever an adversary breaks in, an honest signer can just announce the current index, e.g., by signing some special message with respect to the current index, as part of the revocation message for the current time period. It is then understood that all signatures made in prior time periods as well as all signatures make in the revoked period up to the announced index are valid, i.e., non-reputable.
Owner:IBM CORP
Data Surveillance for Privileged Assets on a Computer Network
ActiveUS20200106797A1Minimal user interactionQuick fixMachine learningTransmissionData packNetwork on
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The above data surveillance techniques are also applied for detecting intentional or unintentional exfiltration / leak of privileged data / assets between unauthorized users / groups of the organization.
Owner:FLYING CLOUD TECH INC
GOOSE message authentication method based on transformer substation
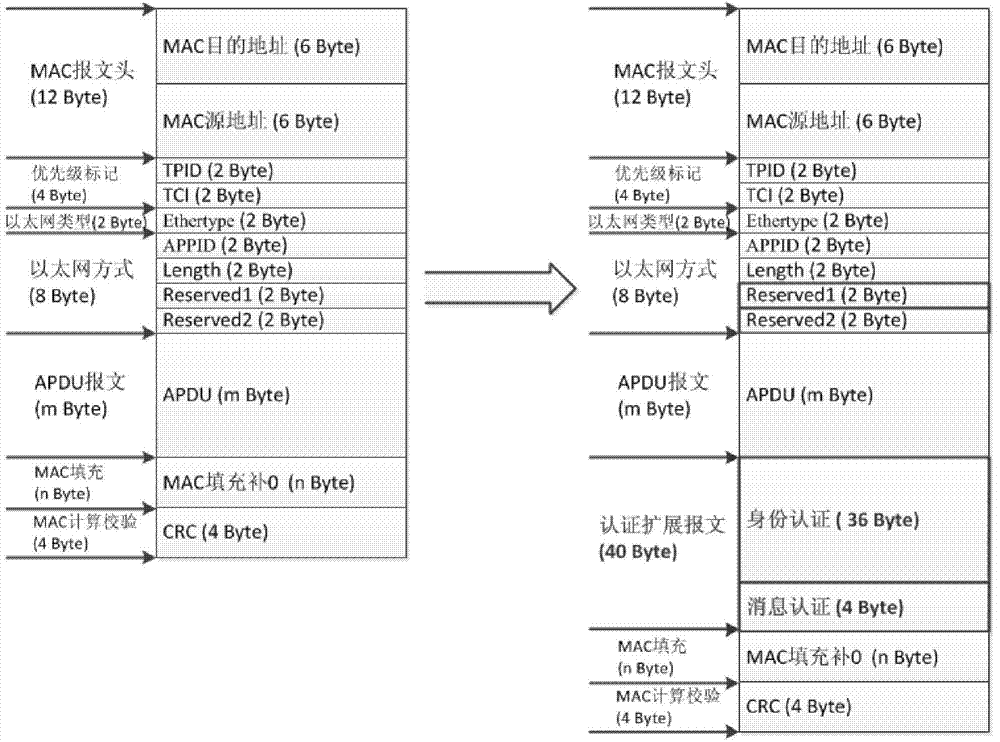
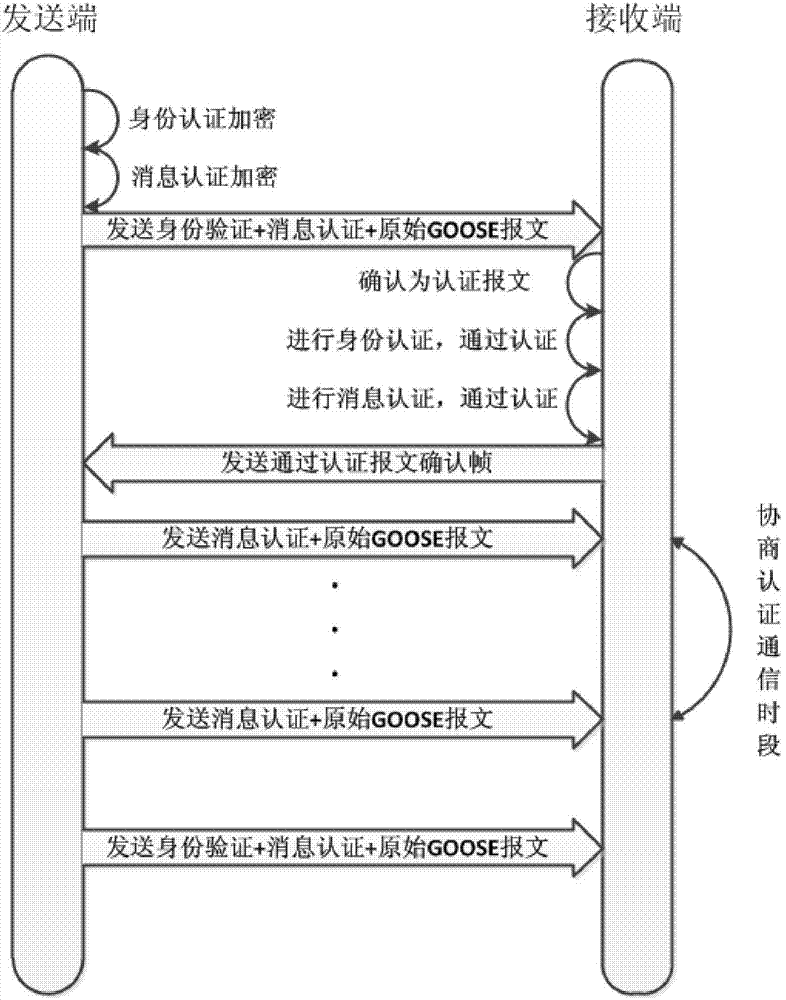
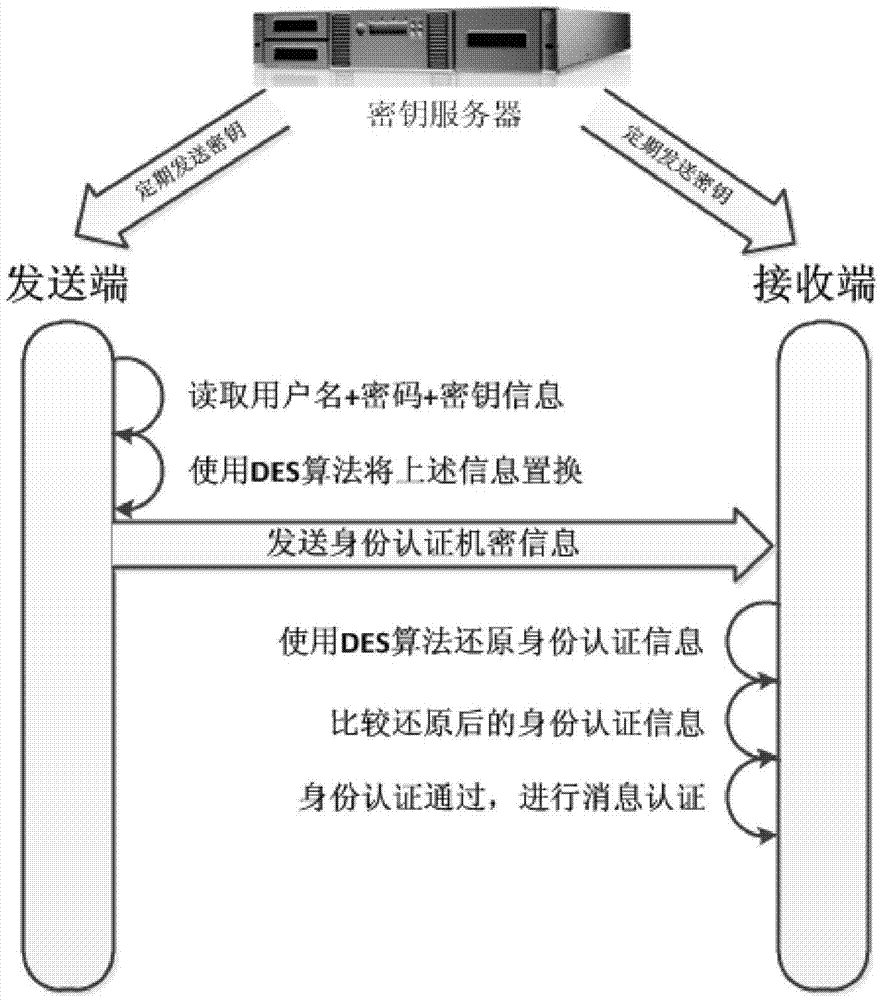
InactiveCN104506500AAvoid threatsEnsure real-time requirementsUser identity/authority verificationGooseNon-repudiation
The invention aims to provide a GOOSE message authentication method based on transformer substation communication. The method comprises the following steps: introducing identity authentication, message authentication and key management; adding the identity authentication, the message authentication and key information into a reserved field and an extension field in a GOOSE message for sending together with the original message to realize authentication of GOOSE message sending and receiving, wherein the field transform meets the TLV (Threshold Limit Value) transformational grammar of an ASN.1 basic coding rule, the original message and an authentication message can be compatible in an automatic communication system of the transformer substation, and an IEC 62351 standard is reached. By adopting the authentication method, hackers are prevented from taking the attack measures of illegal authentication, tampering, replay, repudiation and the like, so that the secrecy, integrity, availability and non-repudiation in a GOOSE message communication process based on the transformer substation are ensured.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID +1
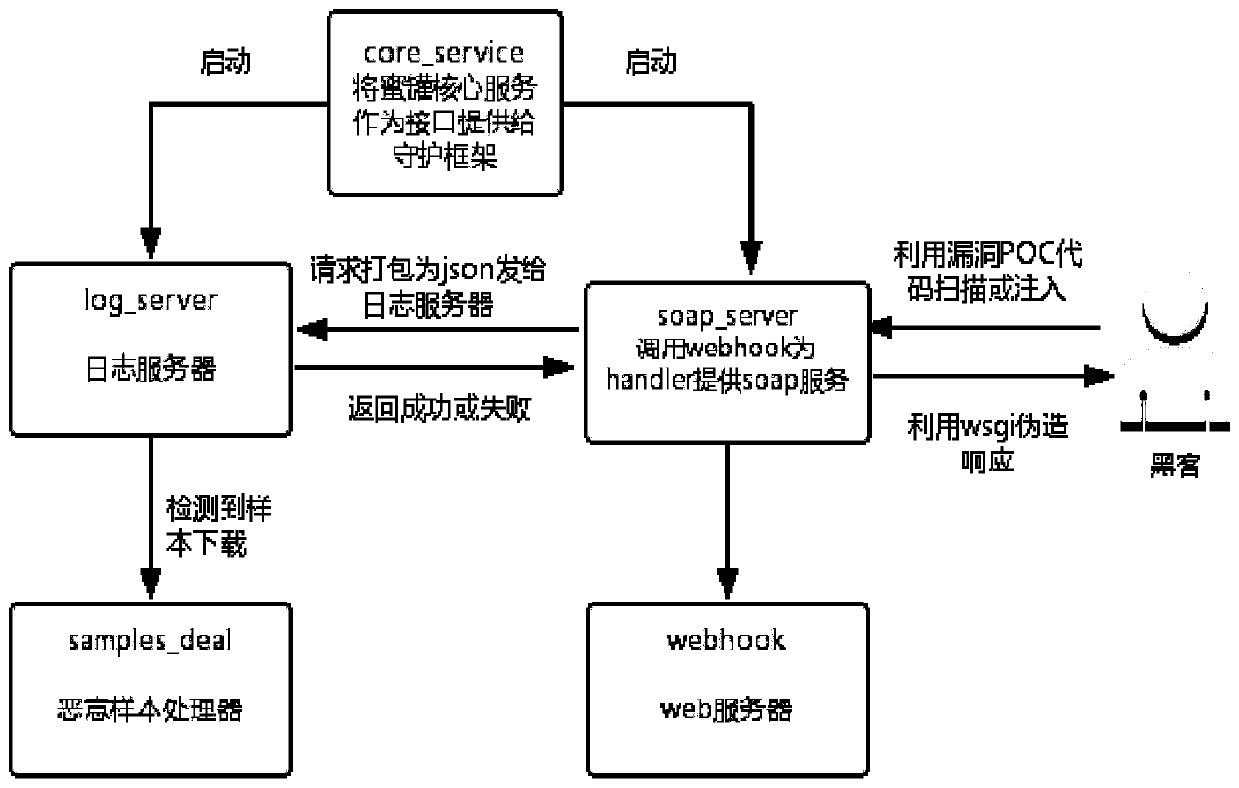
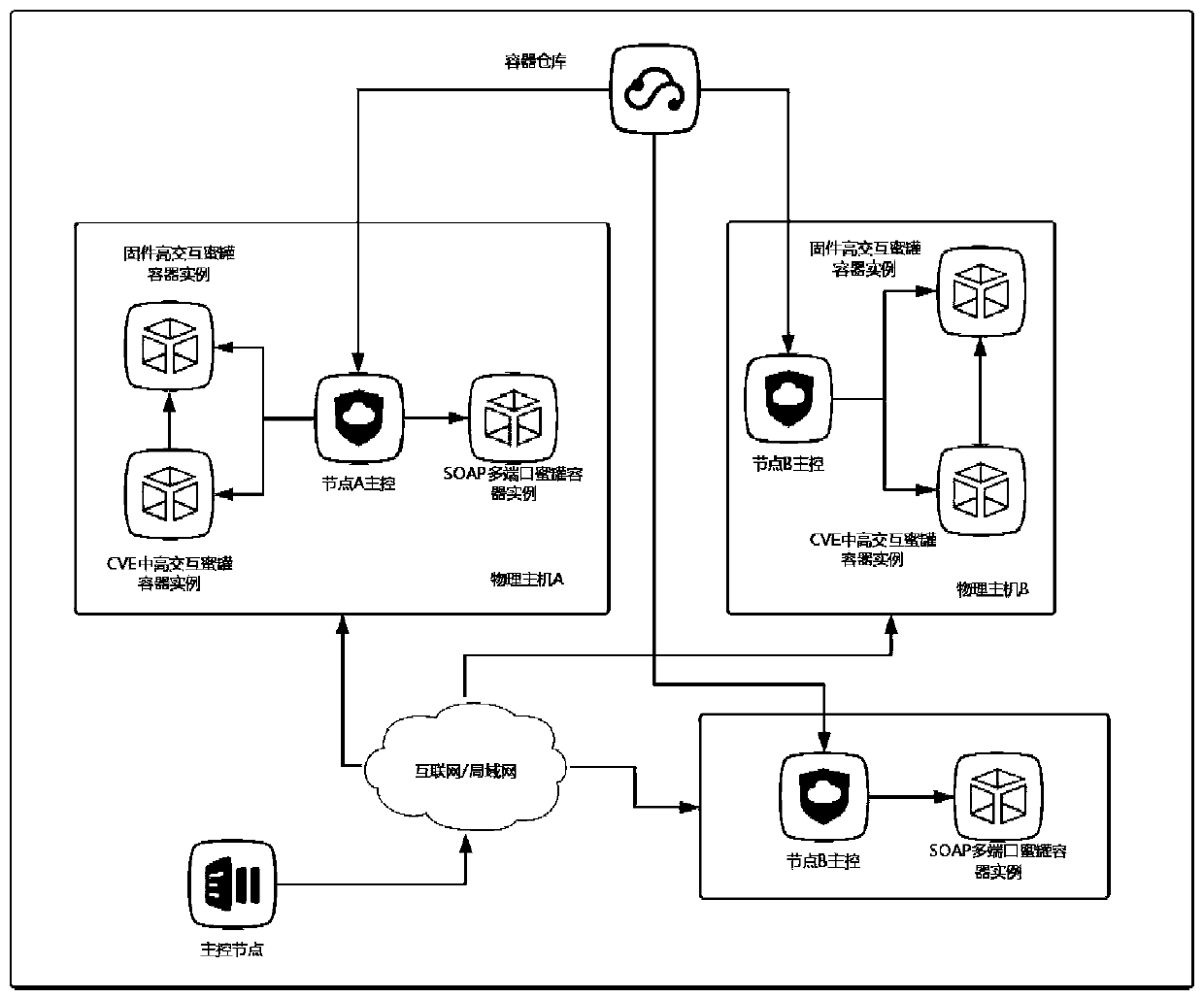
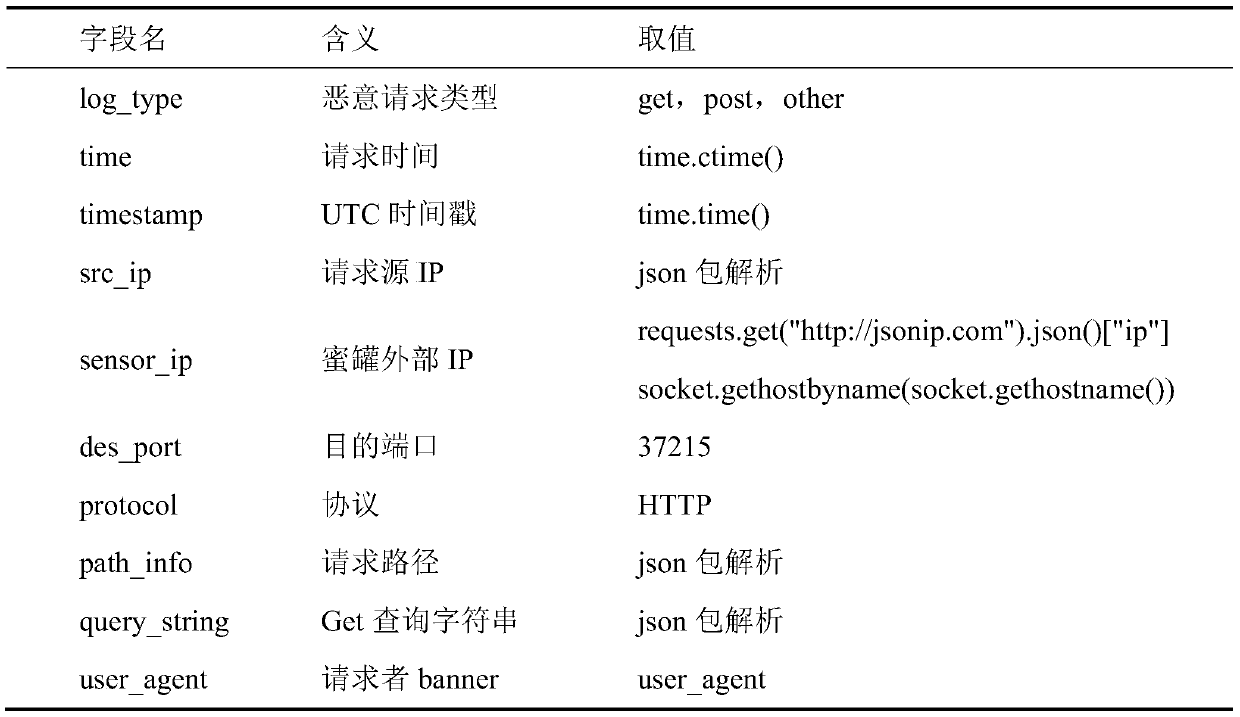
Internet of Things honeynet system based on SOAP service simulation
The invention discloses an Internet of Things honeynet system based on SOAP service simulation, and belongs to the technical field of Internet of Things security. The objective of the invention is tomonitor and collect the security state of the Internet of Things, capture the malicious request of a hacker for the Internet of Things, and collect malicious samples. According to the method, a middle-high interaction honeypot is designed according to a router SOAP service vulnerability CVE-2017-17215;; in order to prevent the situation that a hacker performs injecting service details which are not completed by the simulation serviceand the simulation service honeypot cannot respond and cannot capture subsequent malicious codes and samples, the function of supplementing the simulation servicehoneypot with the honeypot for providing the real SOAP service is realized by using equipment firmware with vulnerabilities; in order to capture more types of SOAP attacks, the SOAP port exposed mostin 2018 is analyzed, and a corresponding multi-port honeypot is manufactured. The honeypots are deployed to a plurality of nodes, a control center is designed at the same time to distribute commands and transmit files, and Docker technology packaging is assisted to achieve rapid deployment. Hackers cannot control the Internet of Things equipment through SOAP service vulnerabilities, so that the security of the Internet of Things is improved.
Owner:HARBIN INST OF TECH
Method for determining inquiry answer type bidirectional identification and business, and encipher device applying the method
InactiveCN101471770AGet rid of vulnerabilityGet rid of spying passiveCommerceSecuring communicationSecure communicationThe Internet
The invention relates to a secure communication device and a method, in particular to a device and a method for sending and receiving a code by adopting a special manner. In the question answering mutual identity and transaction confirmation method and the device adopting the method, the confirmation method comprises identity verification and transaction content confirmation, and has the characteristic of mutual authentication. An encryption device is separated from the outside completely, and has no electronic connecting interface, so that the hacker attack can be avoided, and the device can also be used in the environment of no personal computer. In the device and the method, not only does a server identify a client in a unilateralism manner, but the client also discriminates the validity of the server through checking the validity of a quenstion and answers the quenstion after confirming the validity of the quenstion only, thereby effectively resisting fishing trap. By adopting the method and the encryption device, identity verification and electronic transaction can be performed safely in unsafe environments such as an Internet bar, etc.
Owner:毛华
Method for controlling data in active defense system of Honeynet
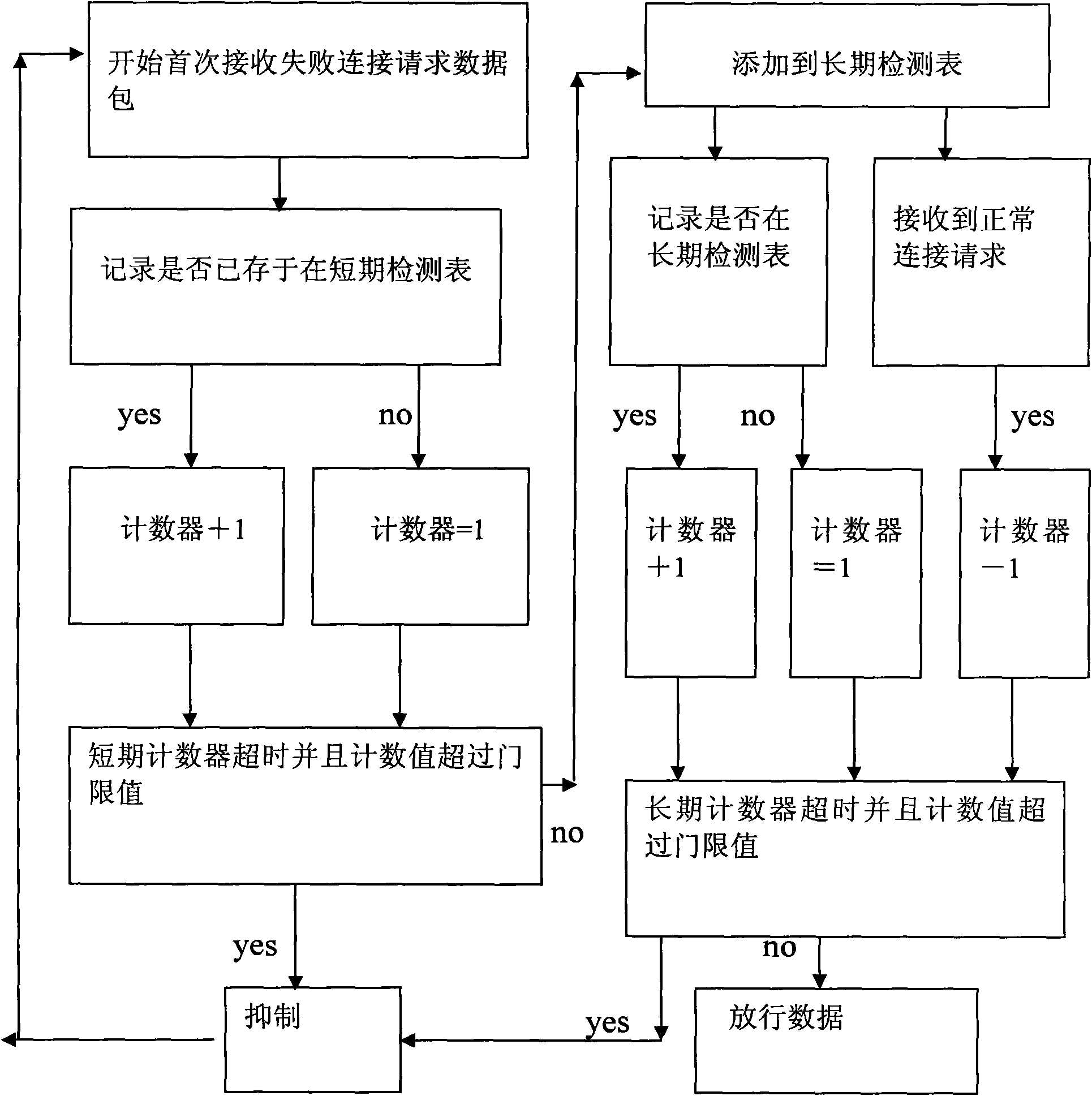
The invention relates to a method for controlling data in the active defense system of Honeynet by keeping the counting statistics for failed connections, wherein, every IP source address is provided with a counting statistic on the record thereof kept by a short-term counter: if the counting value of the short-term counter exceeds the threshold, that the worm abnormal behavior is detected is determined and the data packets sent from the IP source address are controlled, but if not, the multi-round detection mechanism is triggered and the record of the IP source address is kept in a long-term detection list; and if the timeout happens to a long-term counter, and the counting value thereof exceeds the threshold, that the worm abnormal behavior is detected is determined and the data packets are controlled, and if not, that the data packets are normal and can be released is determined. The method has the advantages that unknown or stealth aggressive behaviors which intentionally slow down the rate of the aggressive behaviors to bypass the control of firewalls, as well as low-rate aggressive behaviors can be identified, particularly, the novel aggressive behavior pattern invented by hackers can be analyzed and identified.
Owner:WUXI ZHIGAOZHI TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com