Network security systems and methods
A file and host technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as false access blocking errors, timeouts, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
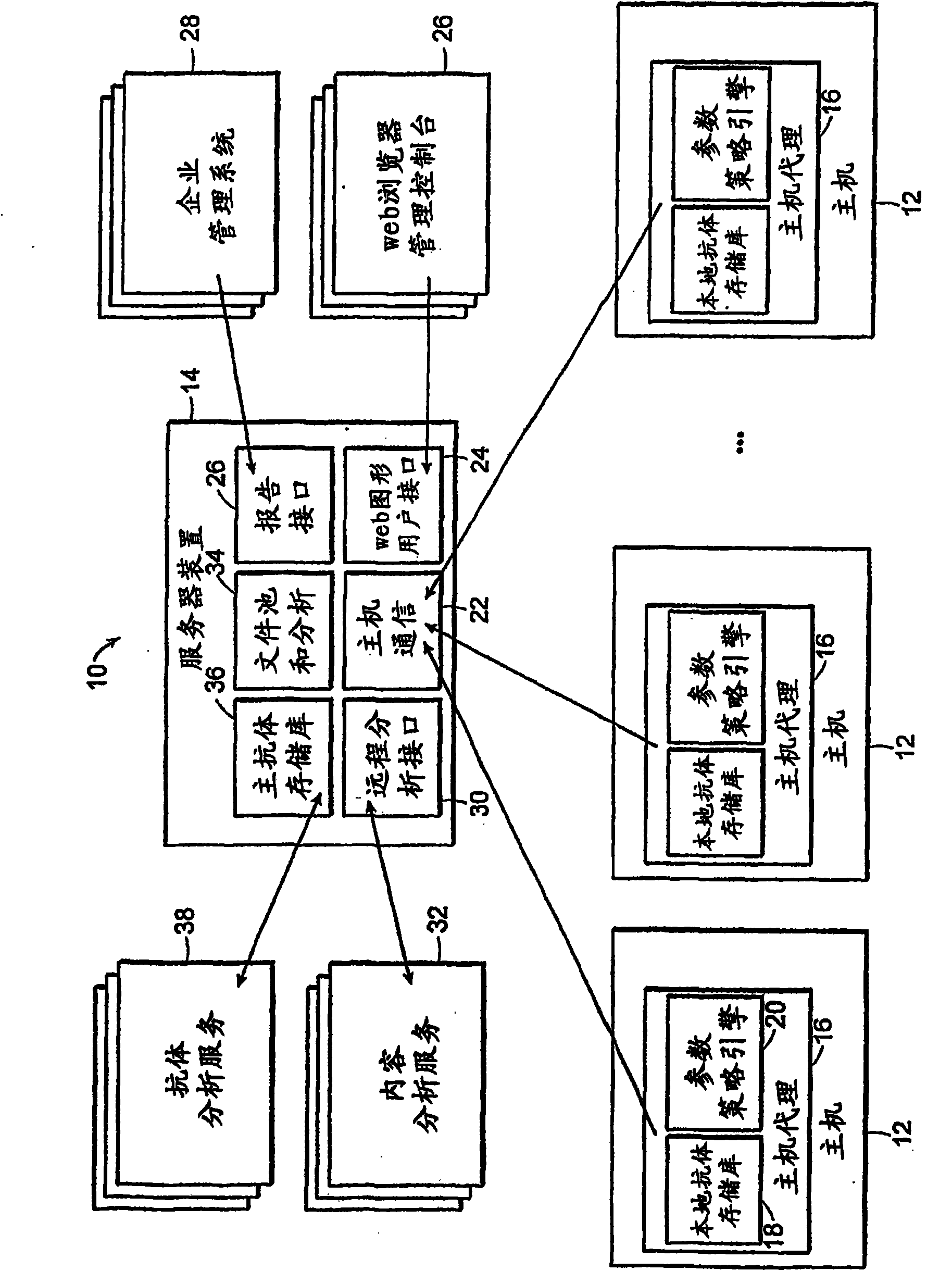
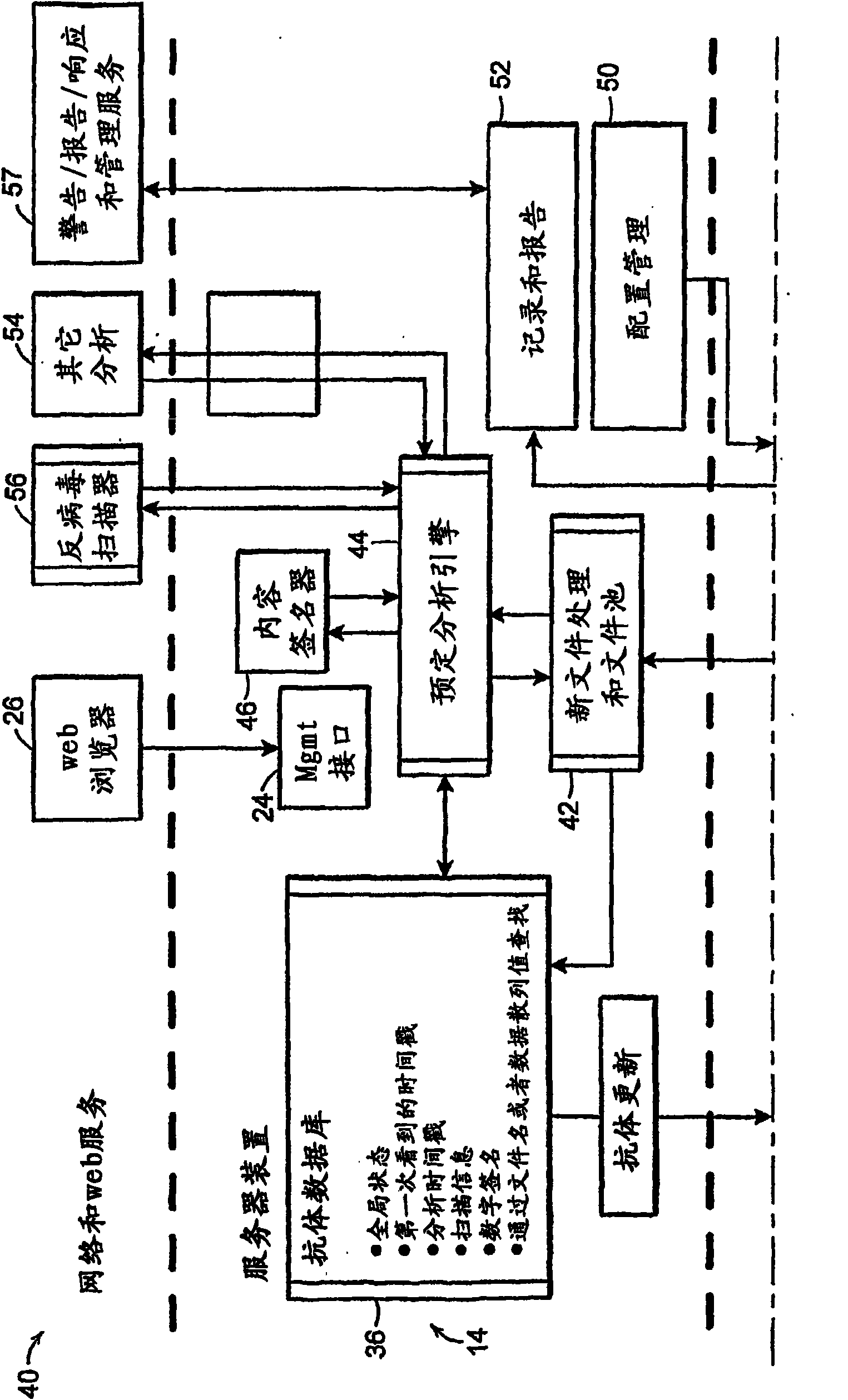
[0030] see figure 1 , also known as the Digital Antibody System (DAS)10, allows administrators to monitor, understand, and control files installed on large computer networks and protects against known and unknown viruses, worms, spyware, hackers, and social Engineering attacks and unapproved software (such as file-sharing software not intended for business use). The system includes one or more servers, one of which is shown here as server 14 (device). This server provides centralized policy management, event monitoring, agent coordination, and content analysis (such as spyware and virus scanning). A single server can support multiple hosts 12, for example hundreds or thousands of hosts. The server also maintains a database of metadata associated with the analysis, such as scan history and approval status with respect to files and programs. This metadata is known as the "antibody" of each file and program.
[0031] Each protected host 12 has a host agent 16, preferably impl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com