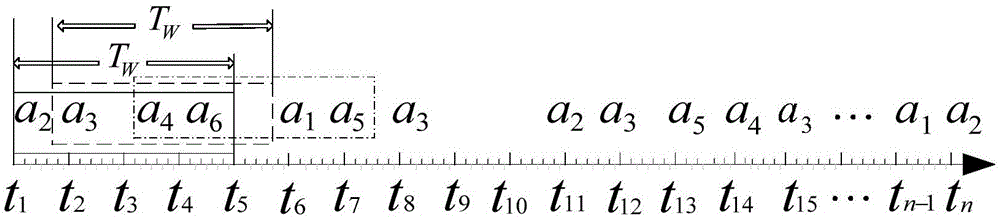Patents
Literature
783 results about "Event monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, event monitoring is the process of collecting, analyzing, and signaling event occurrences to subscribers such as operating system processes, active database rules as well as human operators. These event occurrences may stem from arbitrary sources in both software or hardware such as operating systems, database management systems, application software and processors. Event monitoring may use a time series database.
Event monitoring and management
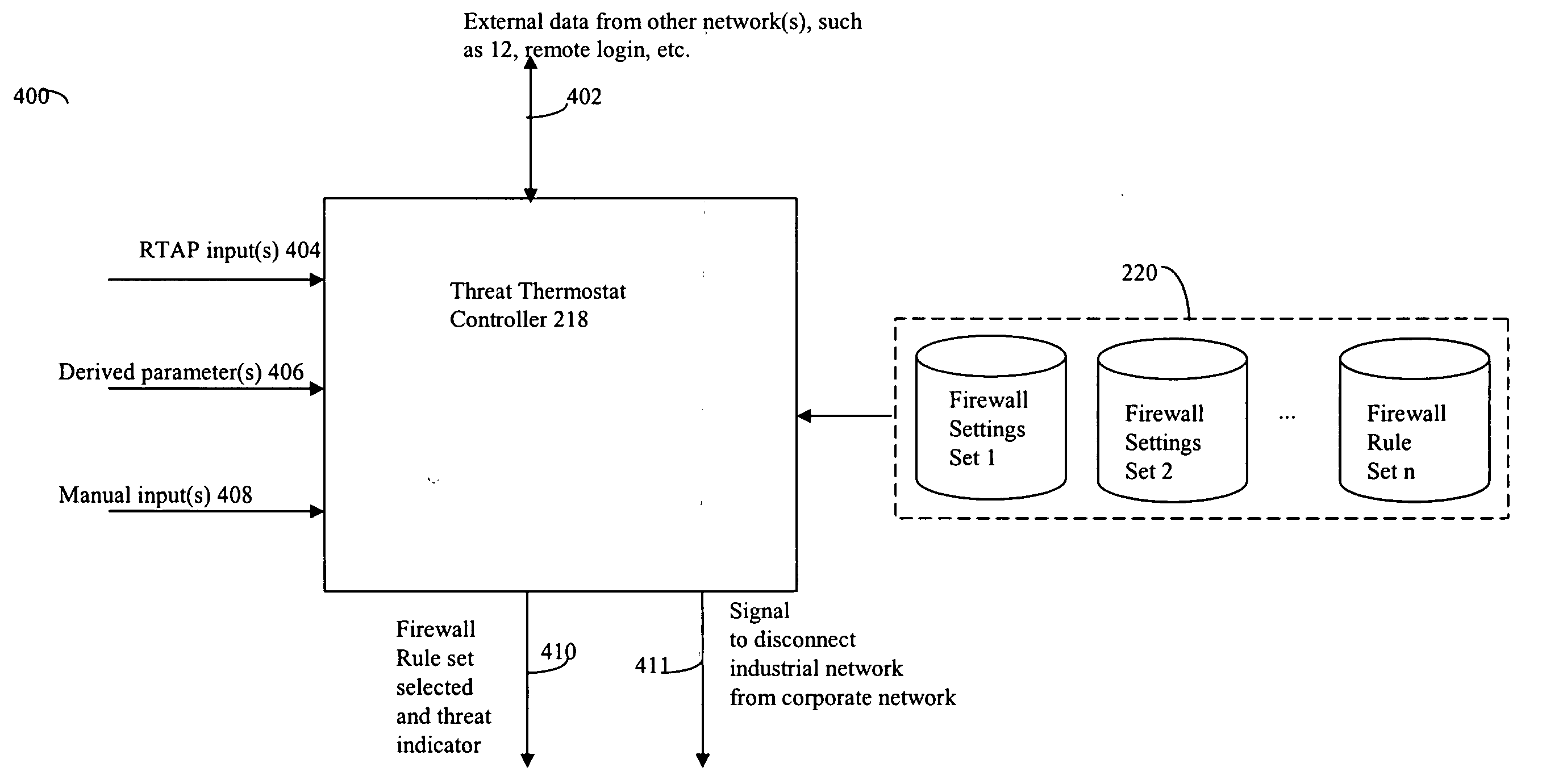
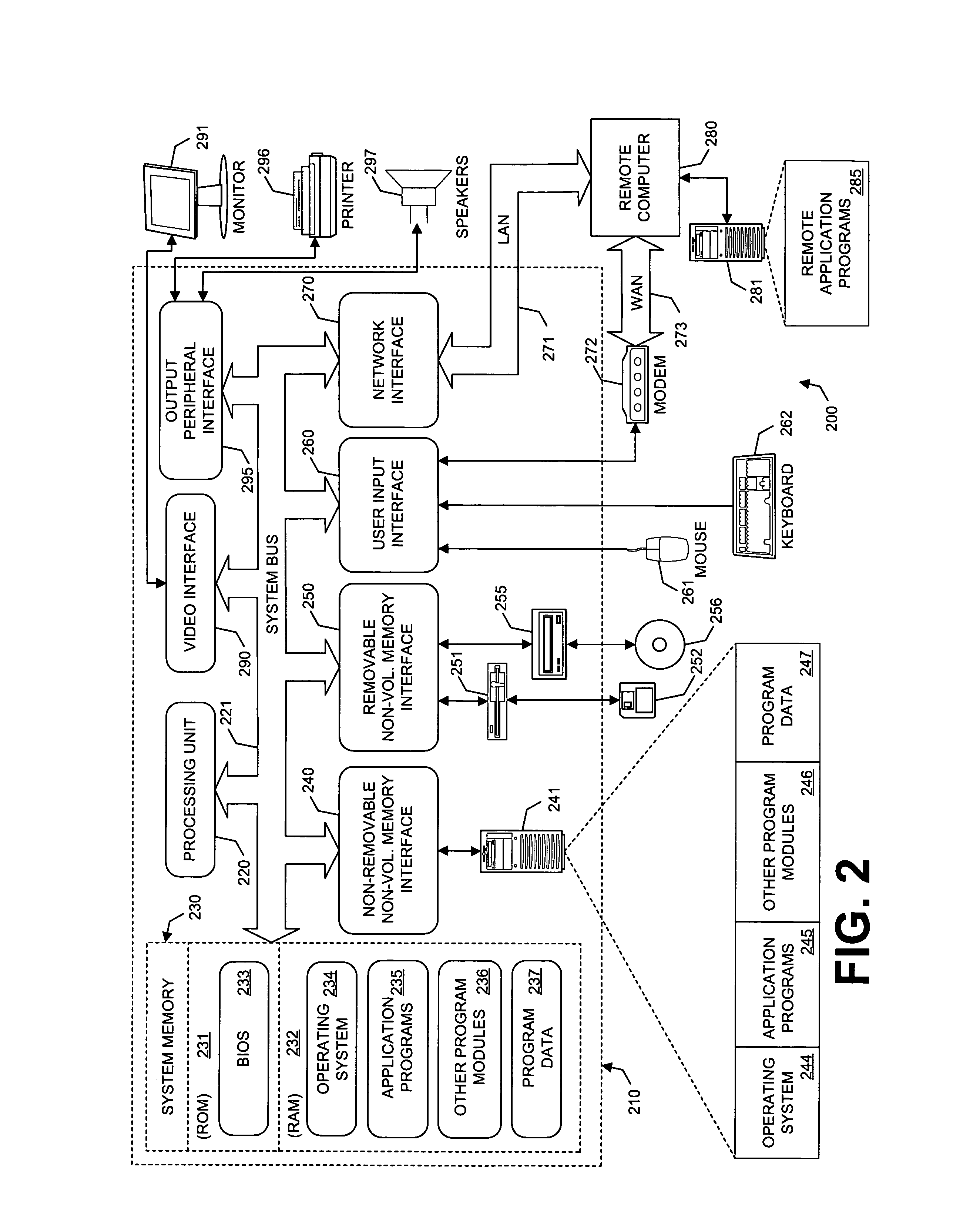
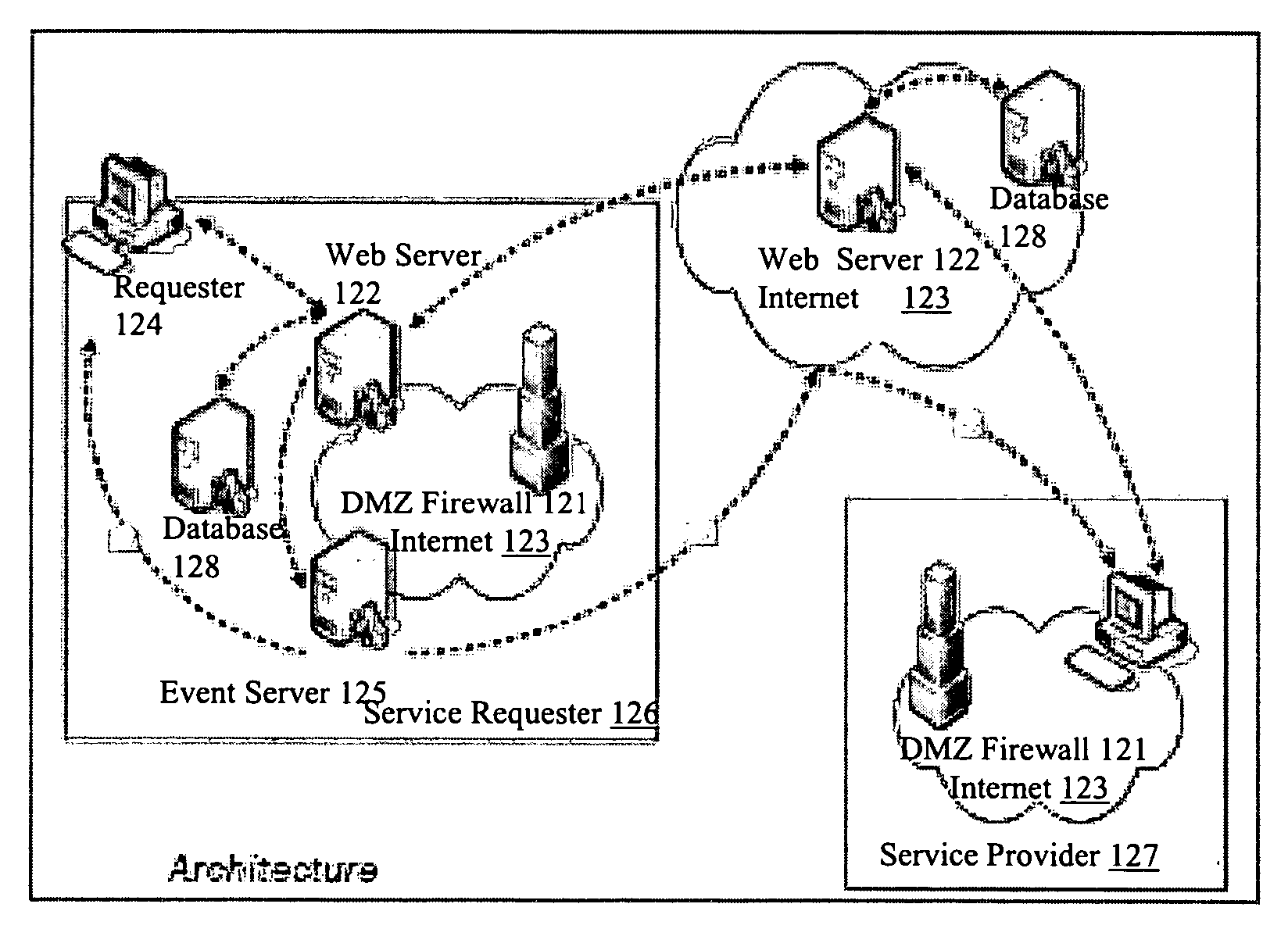
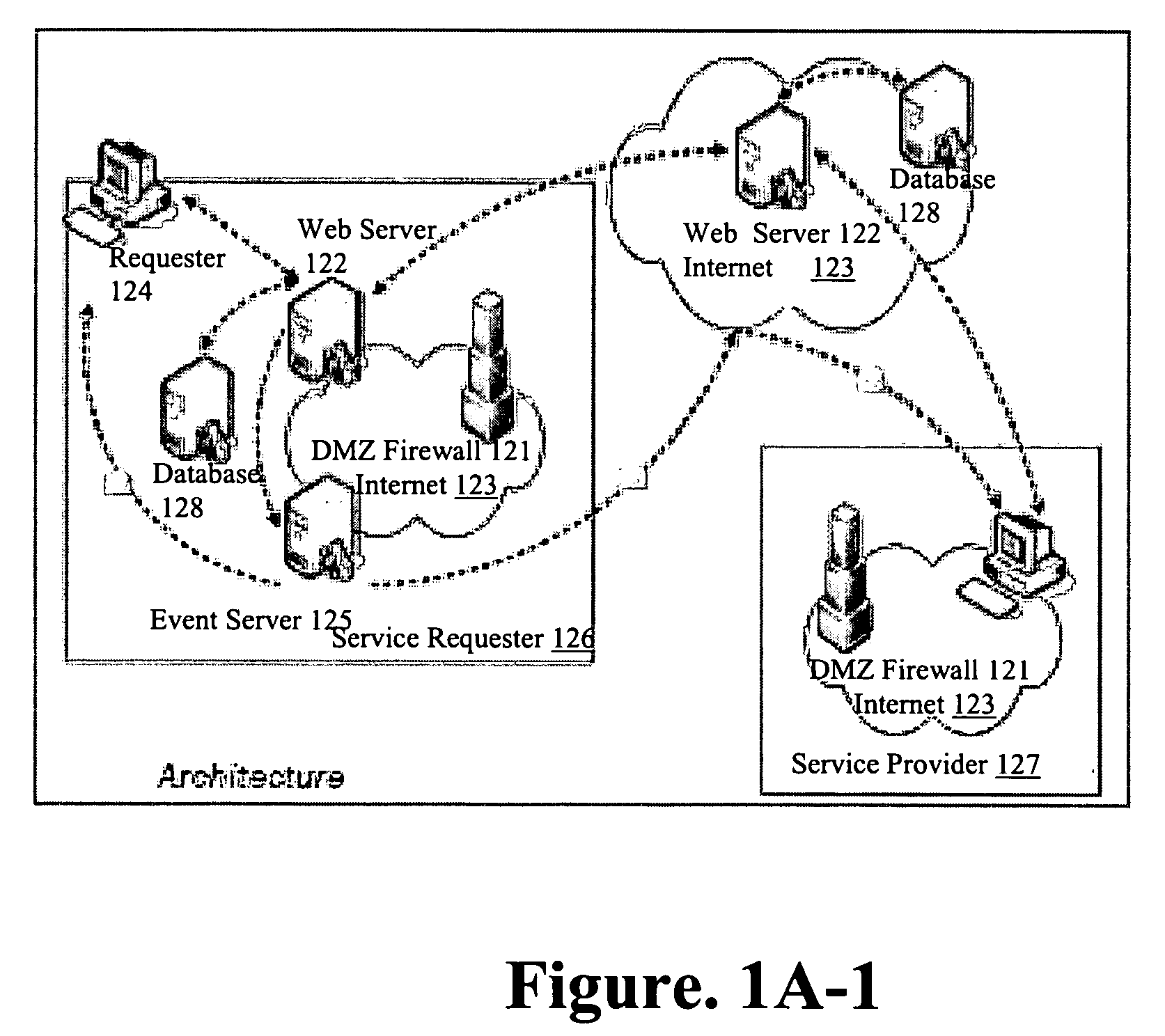
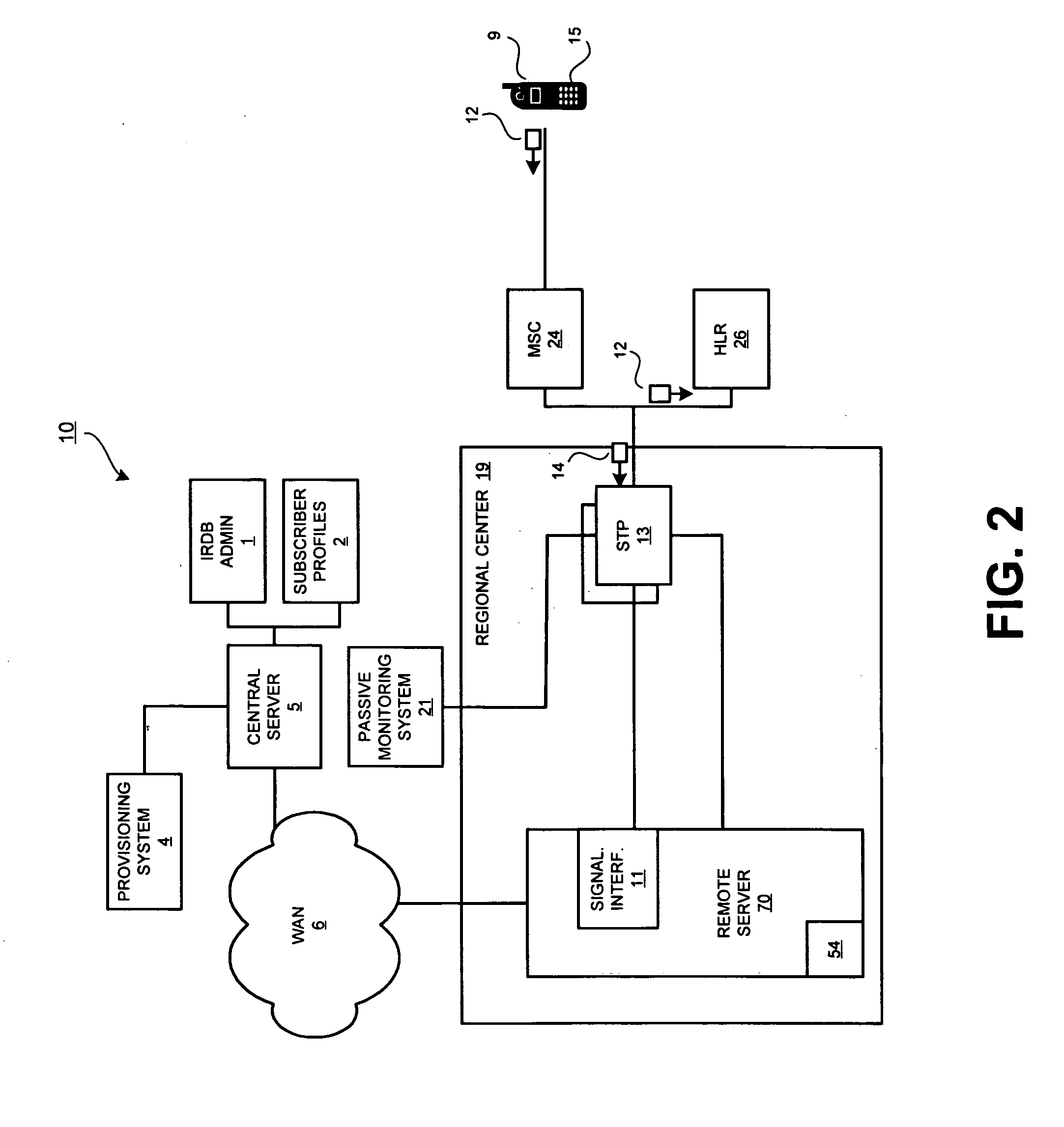
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
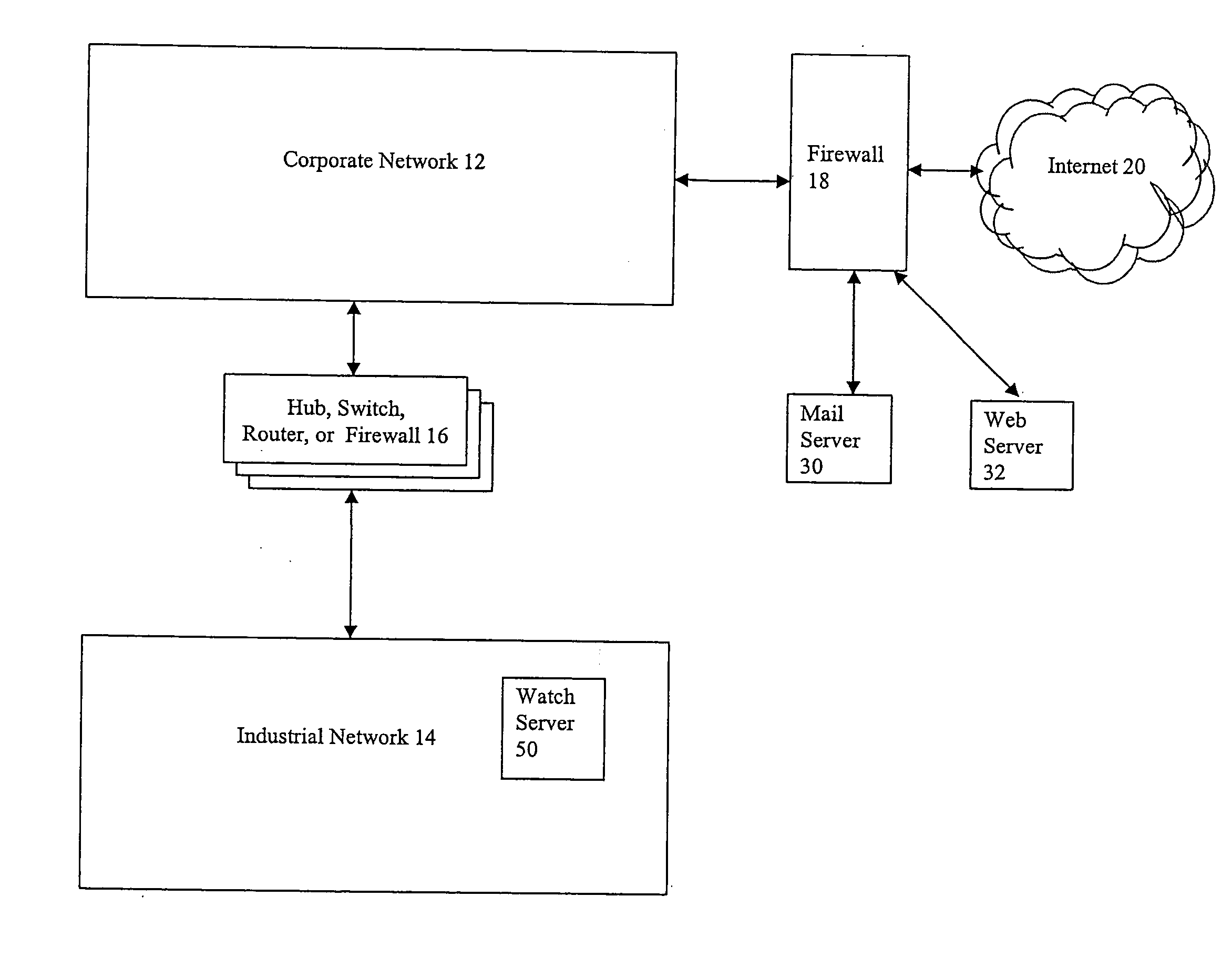
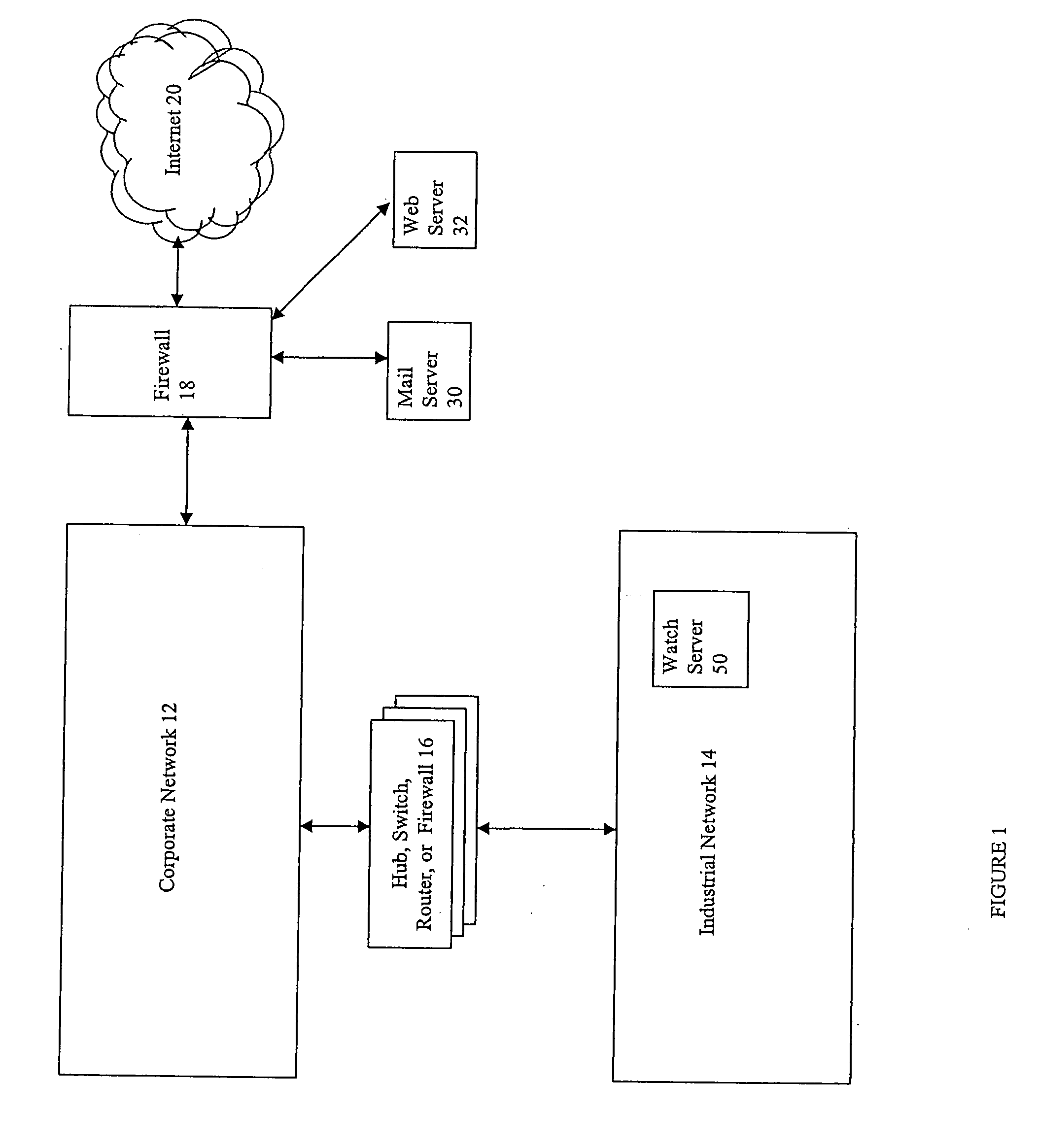
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
Neurological event monitoring and therapy systems and related methods
Systems and methods for detecting, monitoring, and / or treating neurological events based on, for example, electrical signals generated from the patient's body are disclosed. Various embodiments of the invention include a system for predicting occurrence of a neurological event in a patient's body. The system may include an implant configured to be placed in the body and detect signals indicative of an activity that precedes the neurological event, and a processing unit configured to process the detected signals so as to predict the neurological event prior to the occurrence.
Owner:CYBERKINETICS
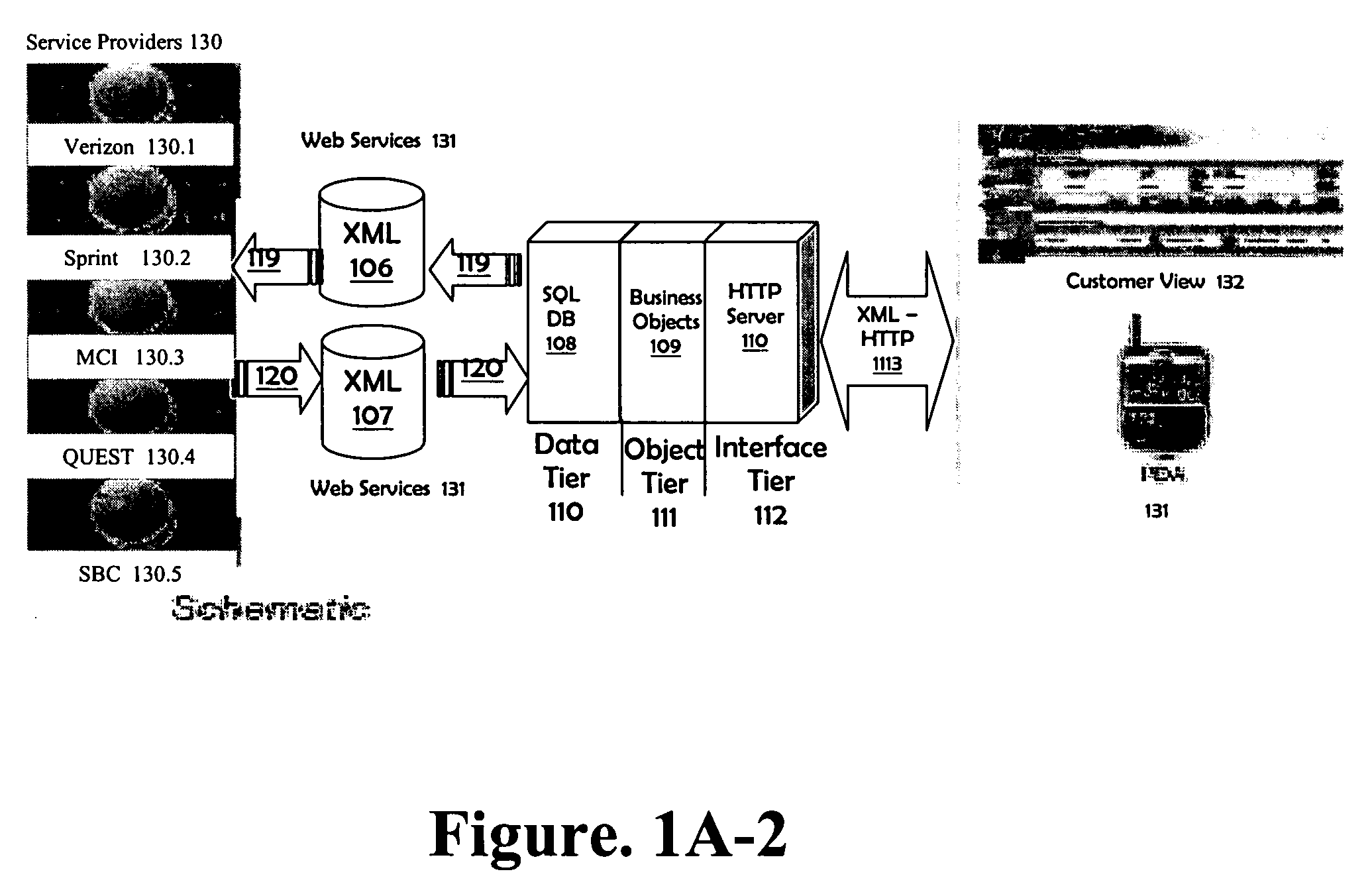
On-line service/application monitoring and reporting system
ActiveUS7379999B1Improve service qualityImprove stabilityError detection/correctionMultiple digital computer combinationsRelevant informationData file
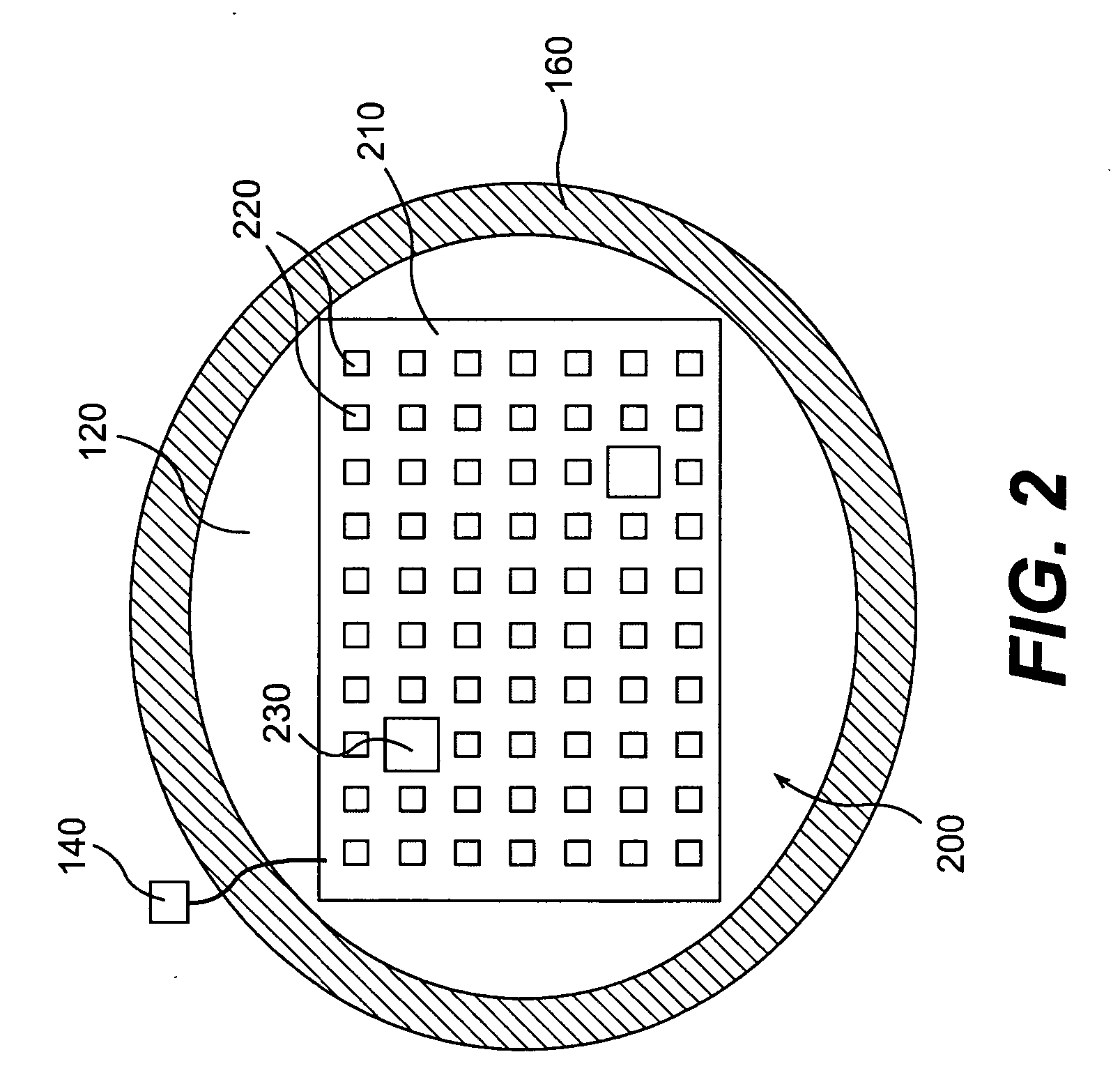
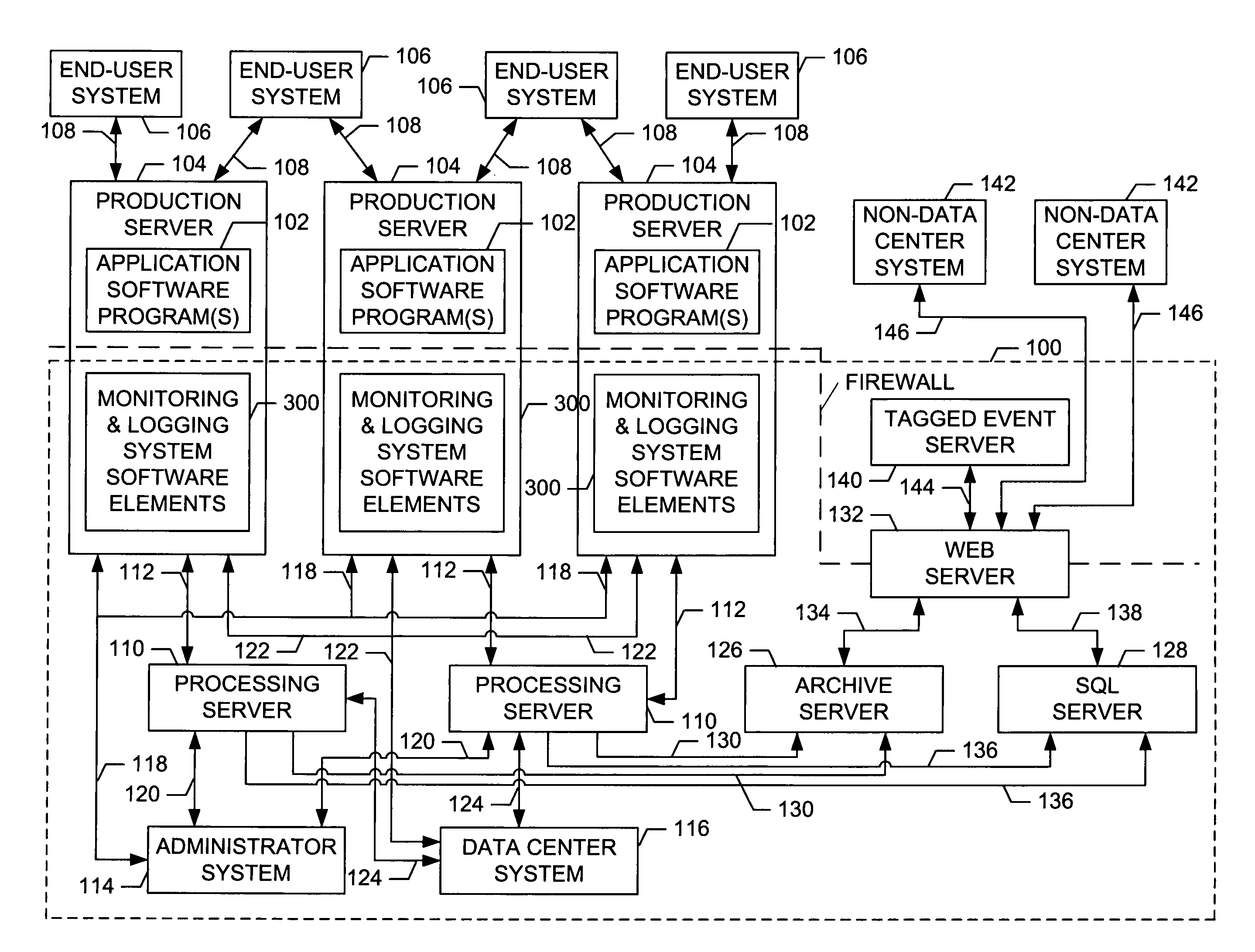
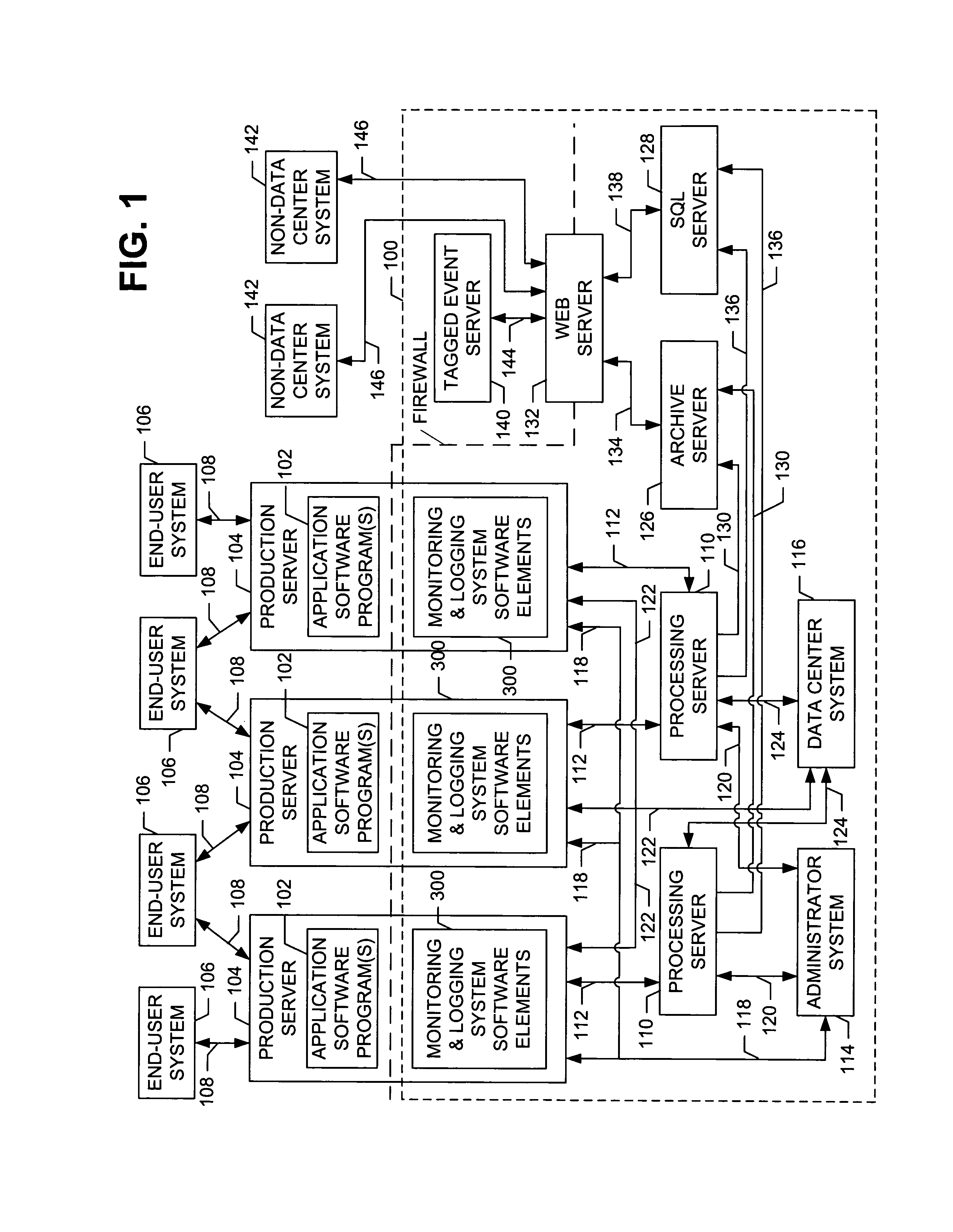
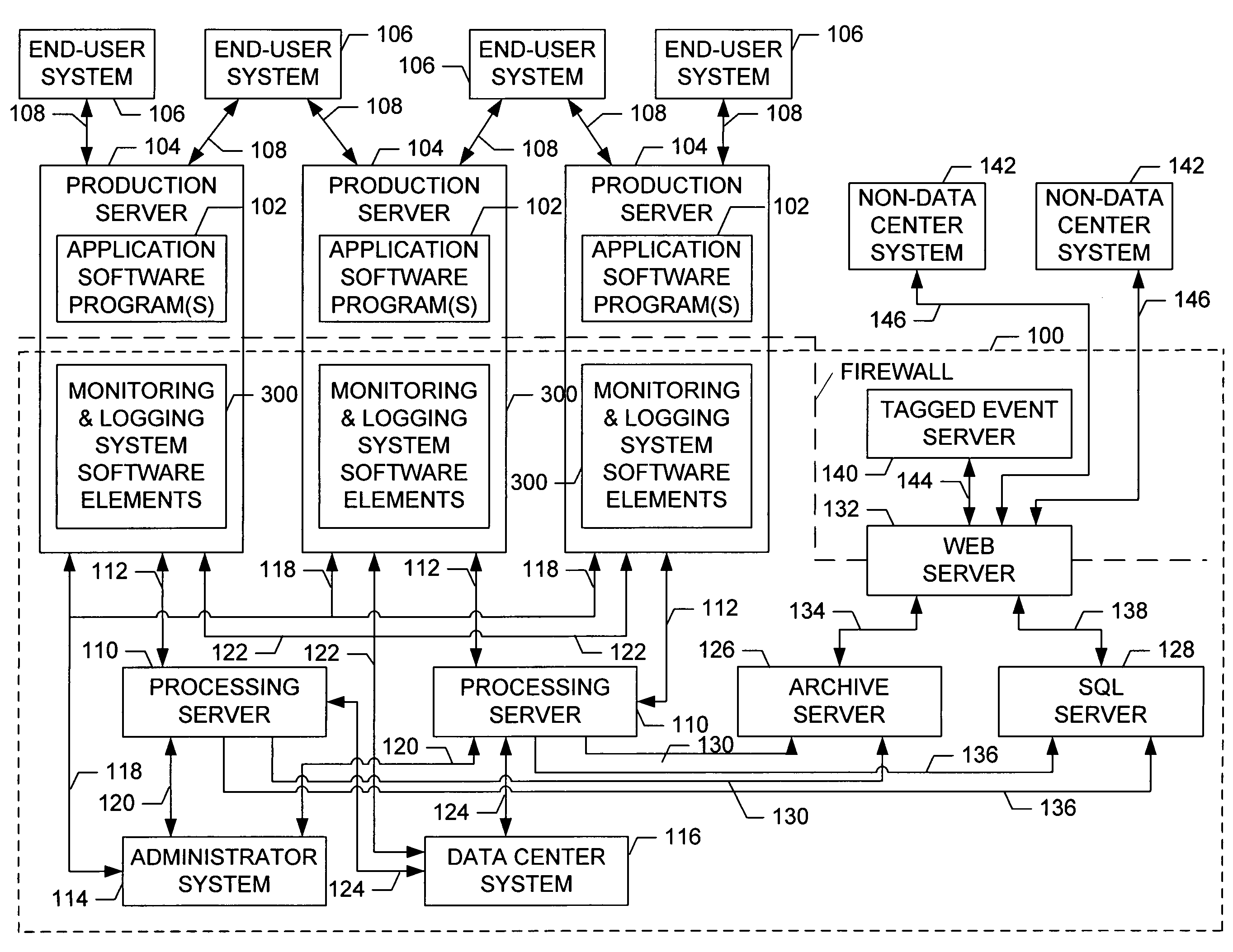
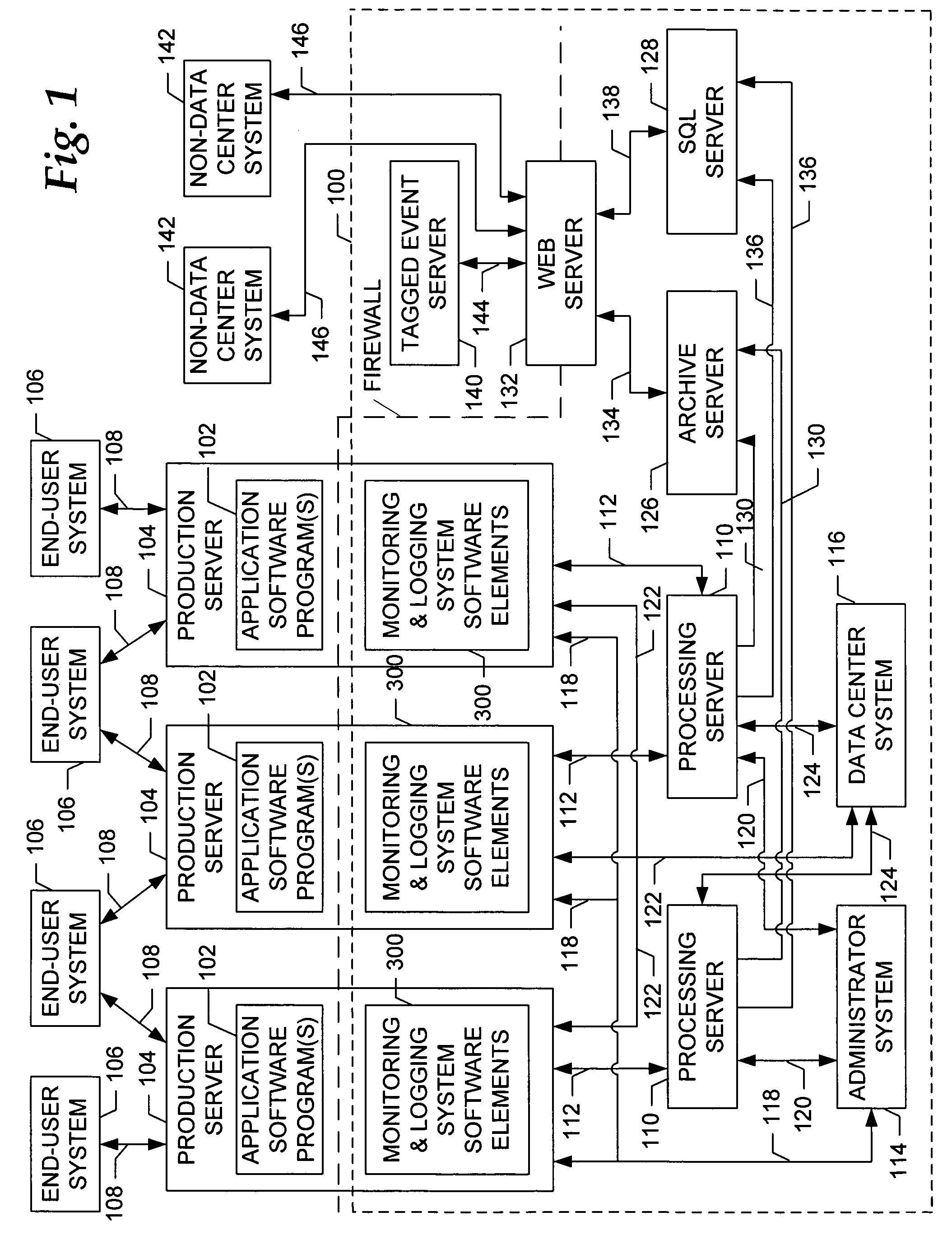
An event monitoring and logging system, including apparatuses and methods, for instrumenting an on-line application program, or service, for generating and communicating events upon the occurrence of certain conditions during the execution thereof, for monitoring generated events in real and near-real time in accordance with configurable rules, for generating and communicating selected alerts to appropriate personnel upon the exceeding of configurable thresholds, for logging generated events and related information in data files and databases for subsequent analysis, and for producing reports related to such instrumentation and generated events.
Owner:MICROSOFT TECH LICENSING LLC
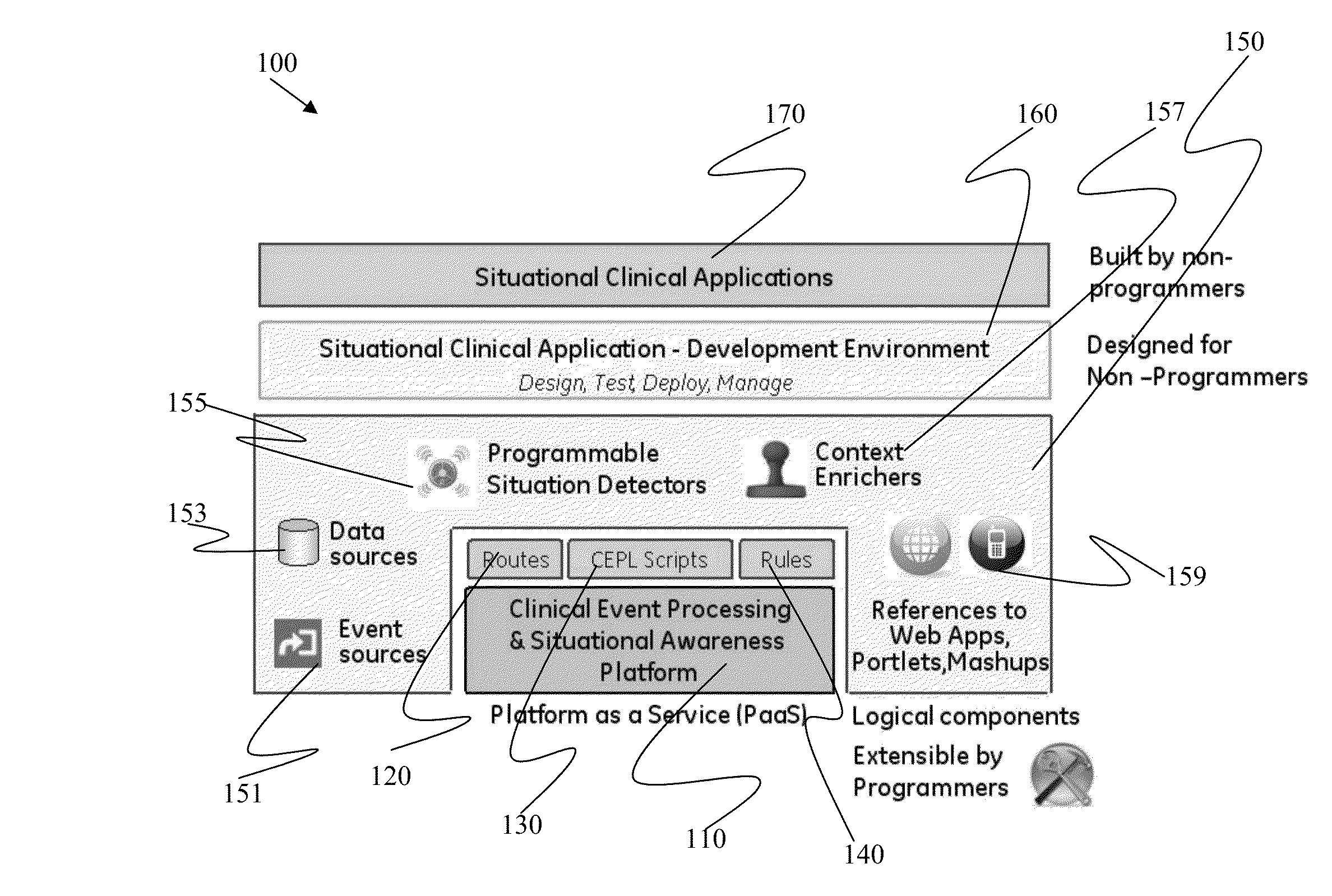
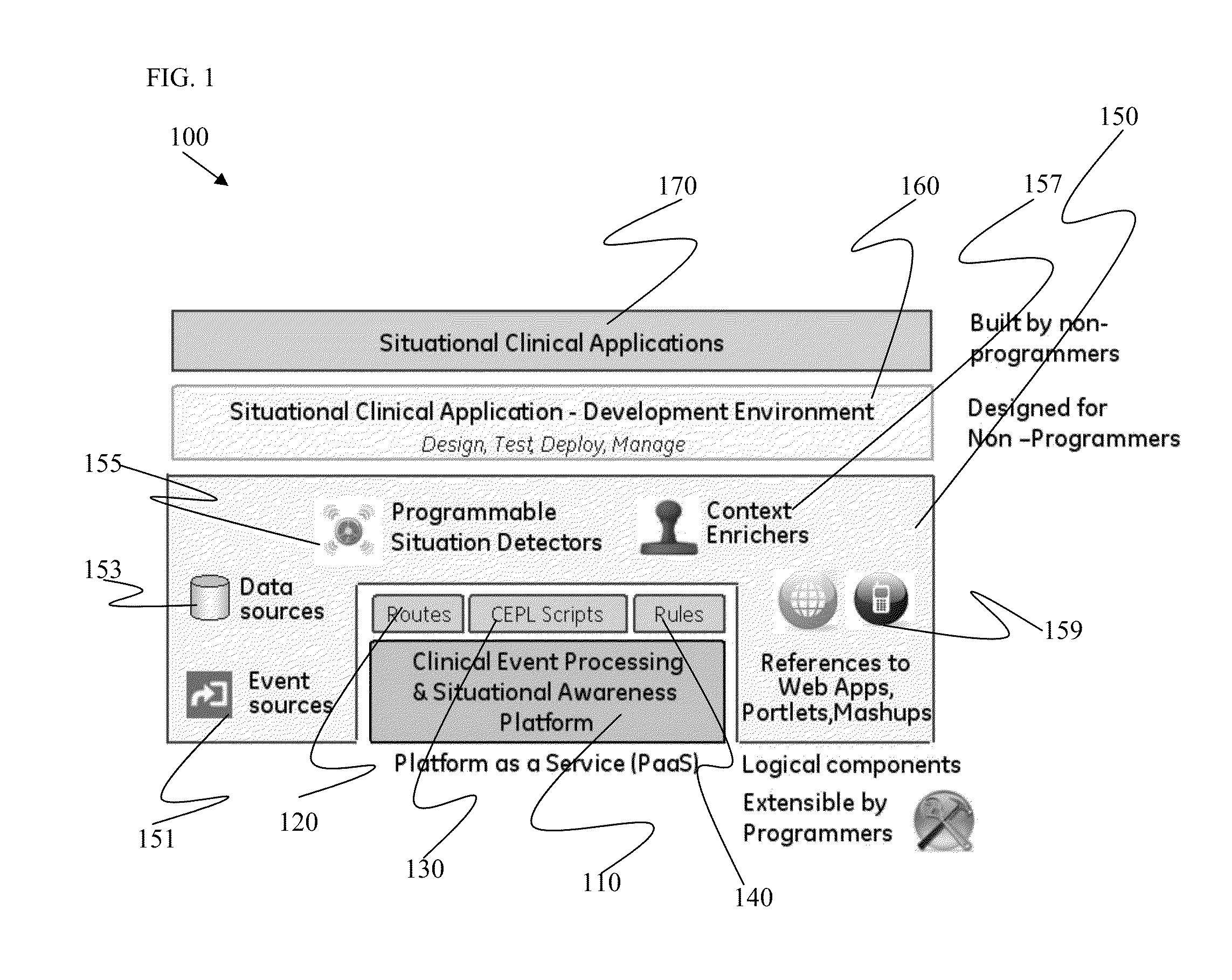
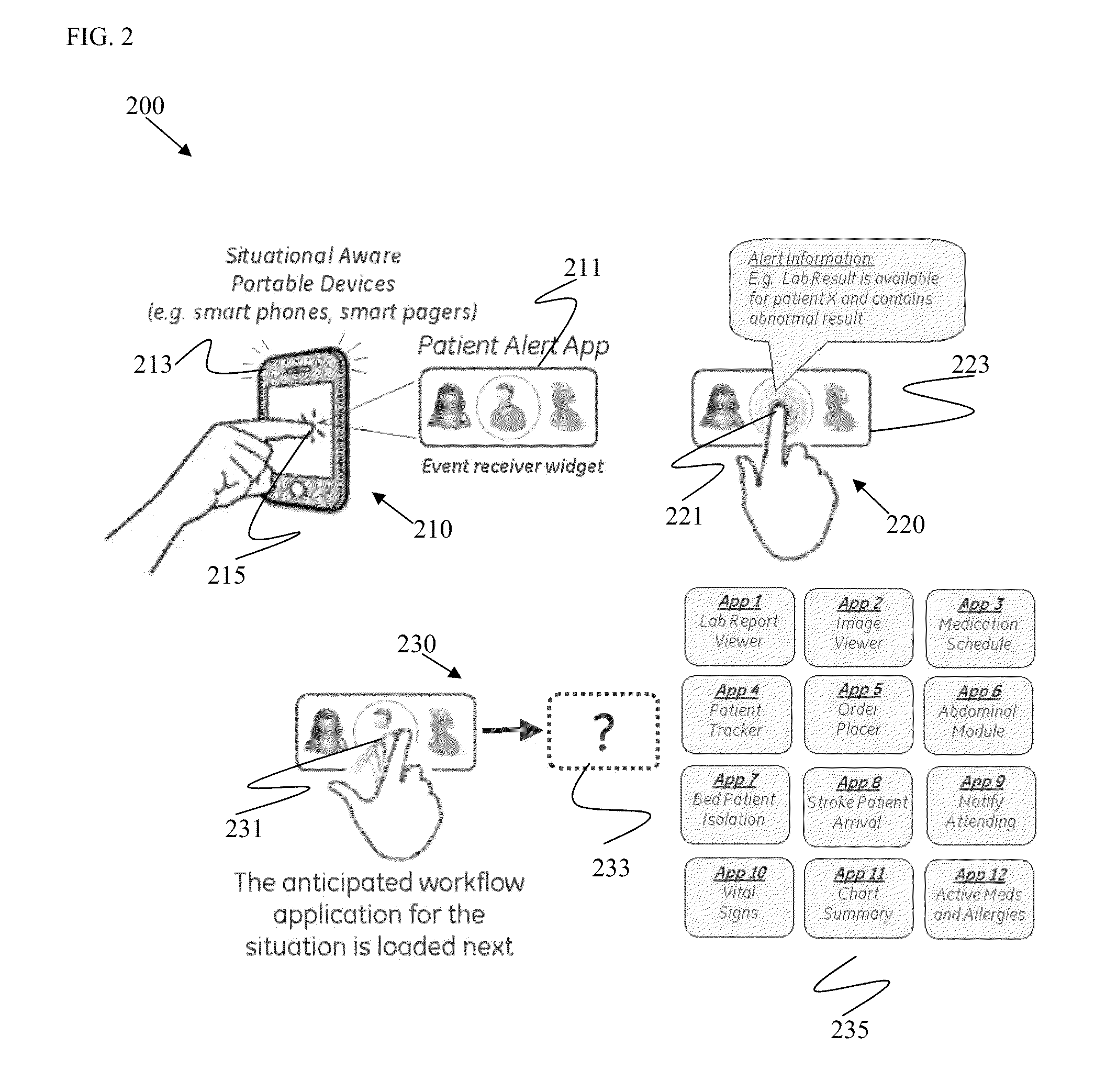
Systems and methods for situational application development and deployment with patient event monitoring
ActiveUS9052809B2Facilitate a clinician's workflowFacilitate a situational aware clinical workflowVisual/graphical programmingHealthcare resources and facilitiesClinical scenarioData source
Systems and methods for clinical event processing with situational awareness to dynamically facilitate a clinician's workflow are provided. An example clinical event processing and situational awareness system includes a clinical event processor including a clinical event processing engine and a routing engine to receive information regarding a clinical event from an event source and to process the information regarding the clinical event to determine a clinical situation based on the clinical event. The system also includes an event handler to enrich the processed information regarding the clinical event by adding a clinical context to the processed information from a data source. The system further includes a dispatcher to notify a user and launch an anticipated application for the user to facilitate a situational aware clinical workflow based on the enriched, processed information regarding the clinical event.
Owner:GENERAL ELECTRIC CO
Unified event monitoring system
InactiveUS20060178898A1Eliminates the duplicative, time-consuming, paper and fax-intensive processesOffice automationCommerceExtensibilityNetwork management
The present invention provides a system that integrates requests and responses thereto for Operation and Business Support Systems (OSS / BSS) that comprise many discrete and non-inclusive systems with disparate interfaces. The integration of these systems poses a complex problem. Moreover, costs of licenses, maintenance fees, and training for day-to-day use are prohibitively expensive. The present invention is an open and inclusive system that interfaces easily with existing OSS / BSS systems to provide visibility into all network elements and events. It is an advanced, multi-vendor management system designed to increase efficiency and productivity and reduce network administration costs by providing an integrated system for monitoring, troubleshooting, and managing the network. The present invention has as an objective to unite different systems under one common platform. The present invention collects and manipulates information centrally, within a single system, enabling critical data to be shared seamlessly between applications. This provides for Data Consolidation, Data Extendibility, and Reduced Cost. In addition, this solution is robust, as it is expandable and considerate of new systems and technologies as they emerge.
Owner:INTRACOMM
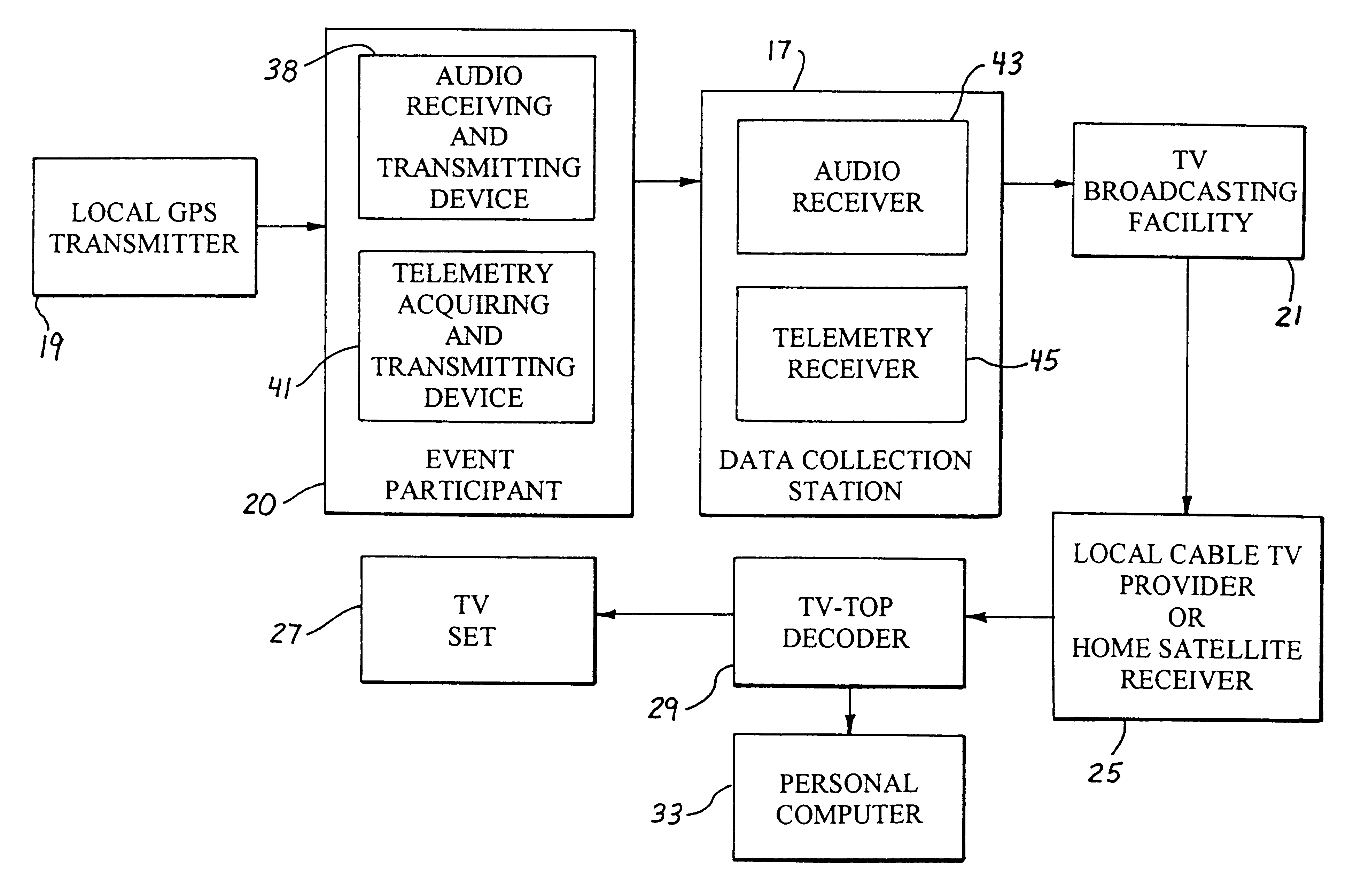
Interactive sporting-event monitoring system
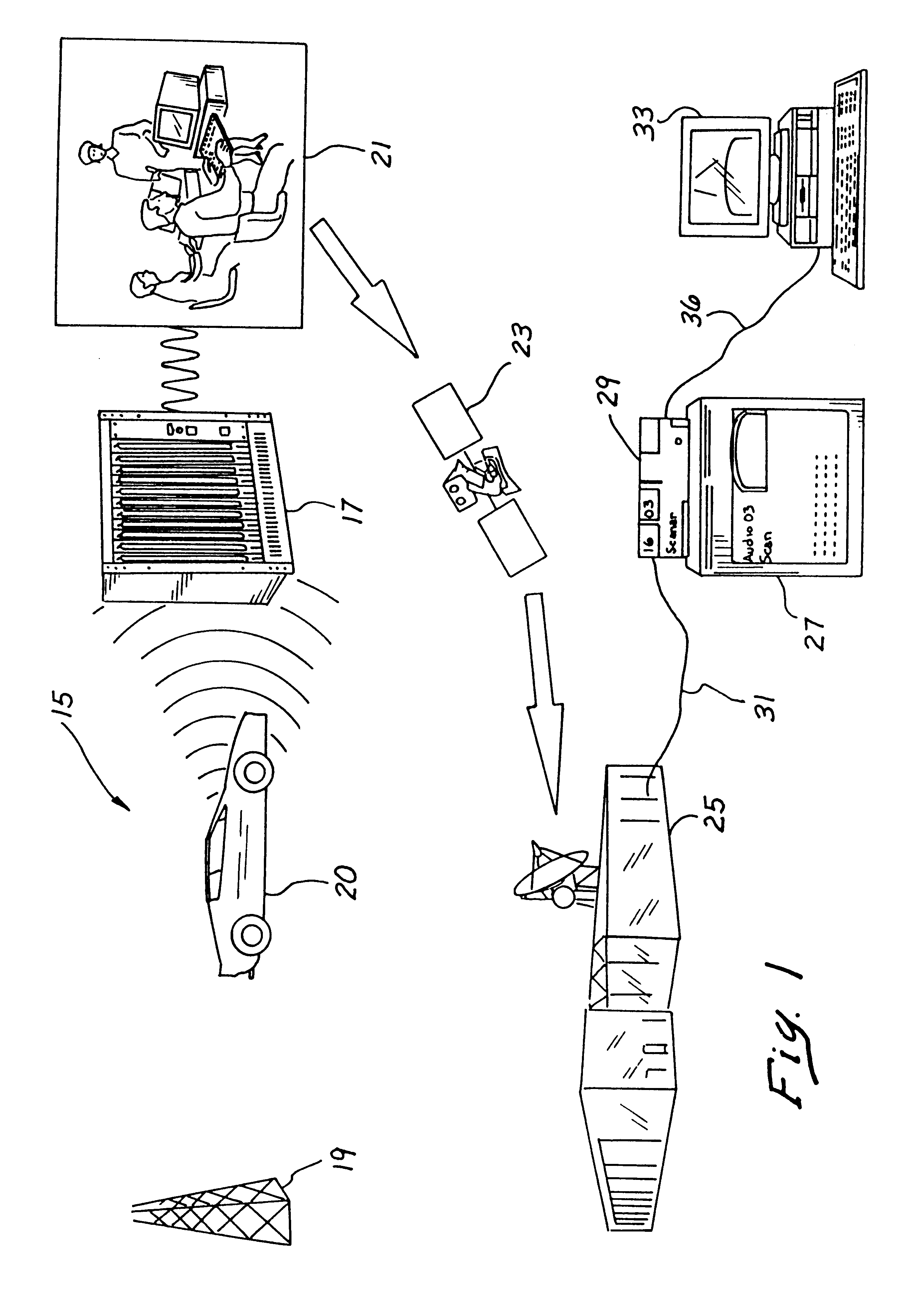
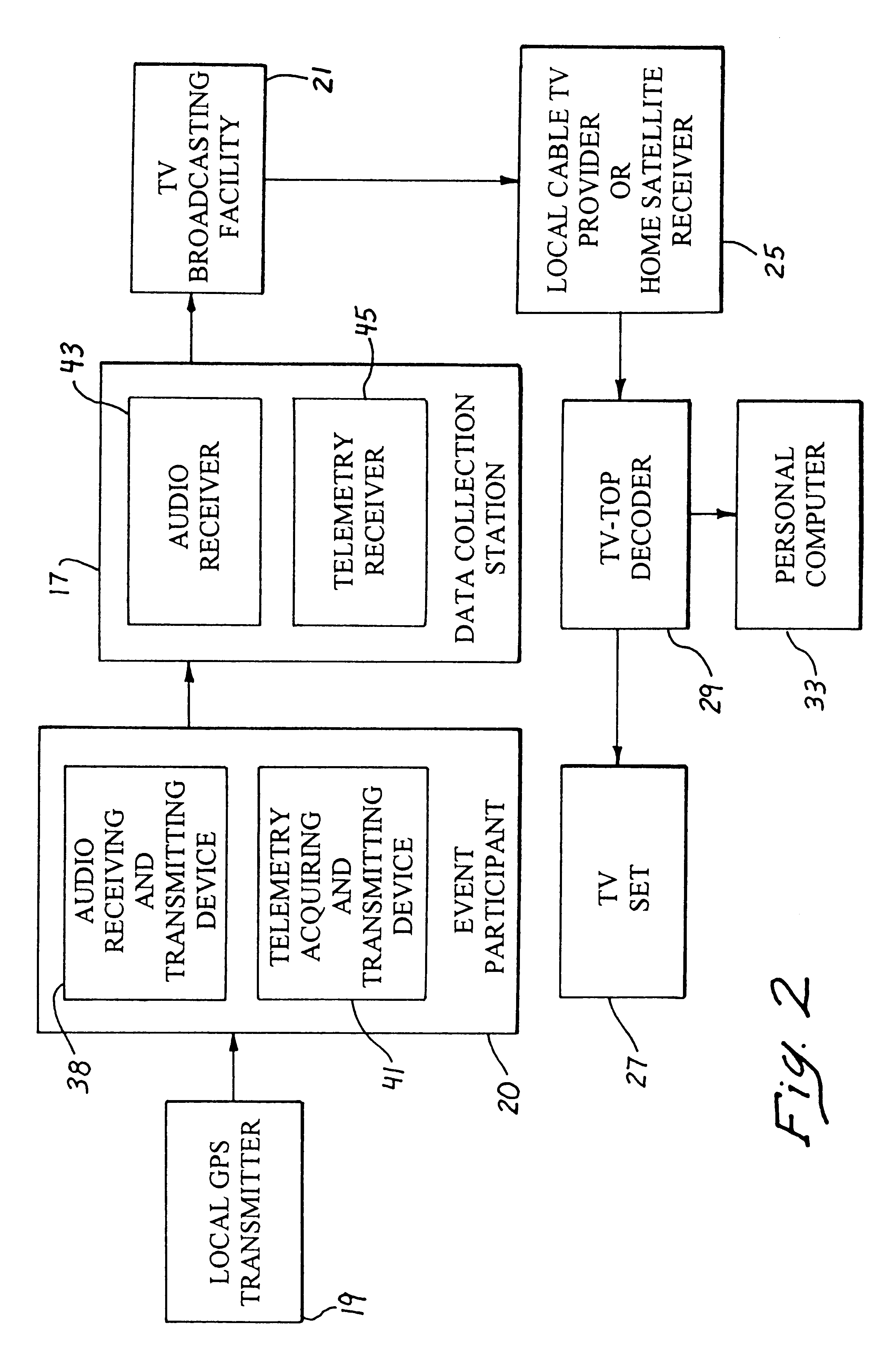
InactiveUS6195090B1Television system detailsElectric signal transmission systemsUser inputMonitoring system
An interactive sporting event monitoring system includes a determiner for determining whether video blanking interval data is present in a selected television channel, and a decoder for decoding video blanking interval data from the selected television channel. The video blanking interval data from the selected television channel comprises a number of channels of sporting-event audio information, and the decoder associates each of the plurality of channels of sporting-event audio information with a corresponding channel identifier. Each channel identifier distinguishes a corresponding channel of sporting-event audio information from other channels of sporting-event audio information. The interactive sporting event monitoring system further includes a user input for accepting a user-specified channel identifier from a user, and a monitor for placing the channel of sporting-event audio information that the user desires to monitor in a format to facilitate monitoring thereof by a user. The video blanking interval data may further include telemetry data.
Owner:RIGGINS III A STEPHEN
On-line service/application monitoring and reporting system
InactiveUS7457872B2Quality improvementImprove stabilityError detection/correctionMultiple digital computer combinationsRelevant informationData file
An event monitoring and logging system, including apparatuses and methods, for instrumenting an on-line application program, or service, for generating and communicating events upon the occurrence of certain conditions during the execution thereof, for monitoring generated events in real and near-real time in accordance with configurable rules, for generating and communicating selected alerts to appropriate personnel upon the exceeding of configurable thresholds, for logging generated events and related information in data files and databases for subsequent analysis, and for producing reports related to such instrumentation and generated events.
Owner:MICROSOFT TECH LICENSING LLC
Multisensory robot used for family intelligent monitoring service
InactiveCN101786272AKeep your family safeAll-round monitoringManipulatorSmart surveillanceLoudspeaker
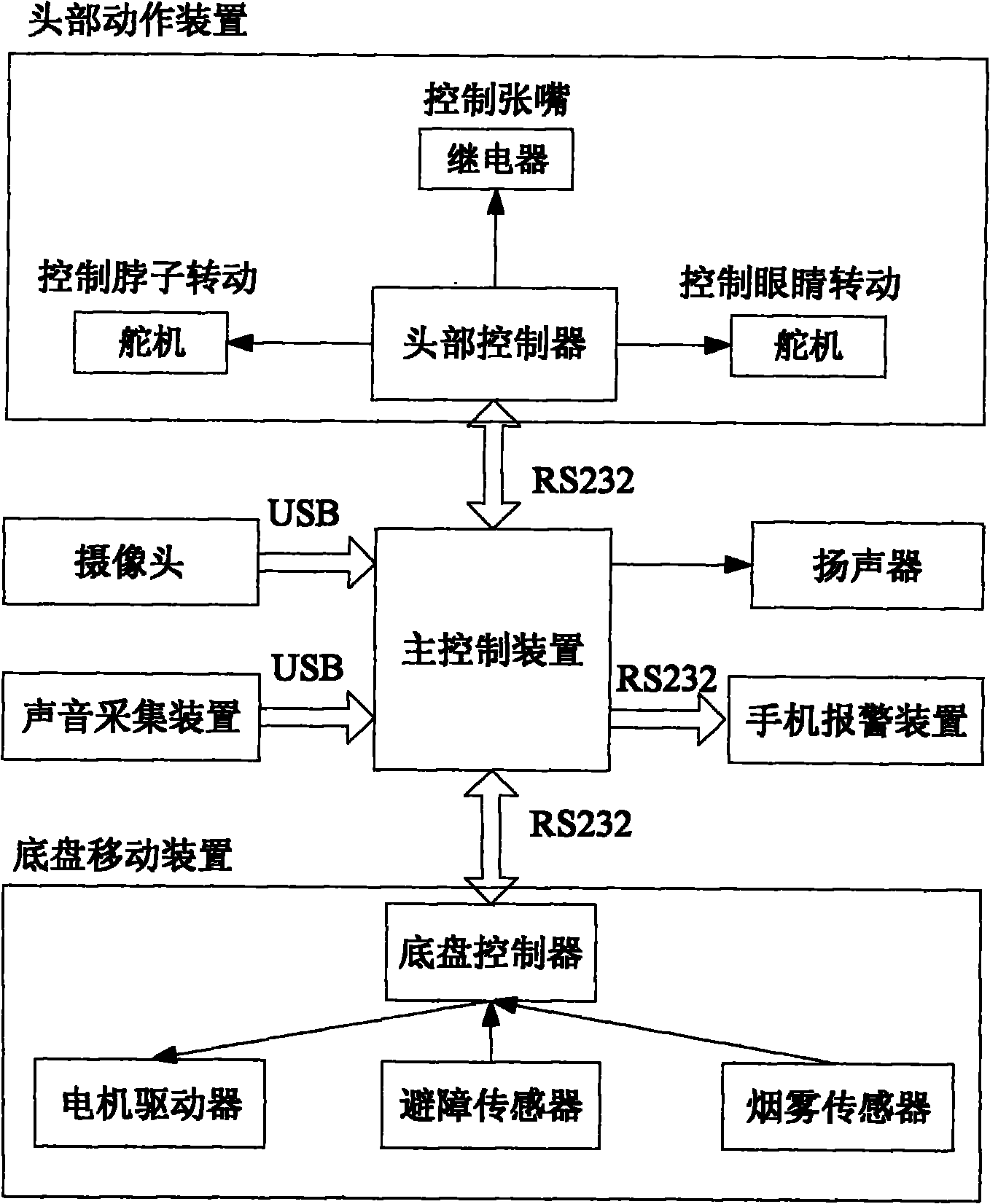
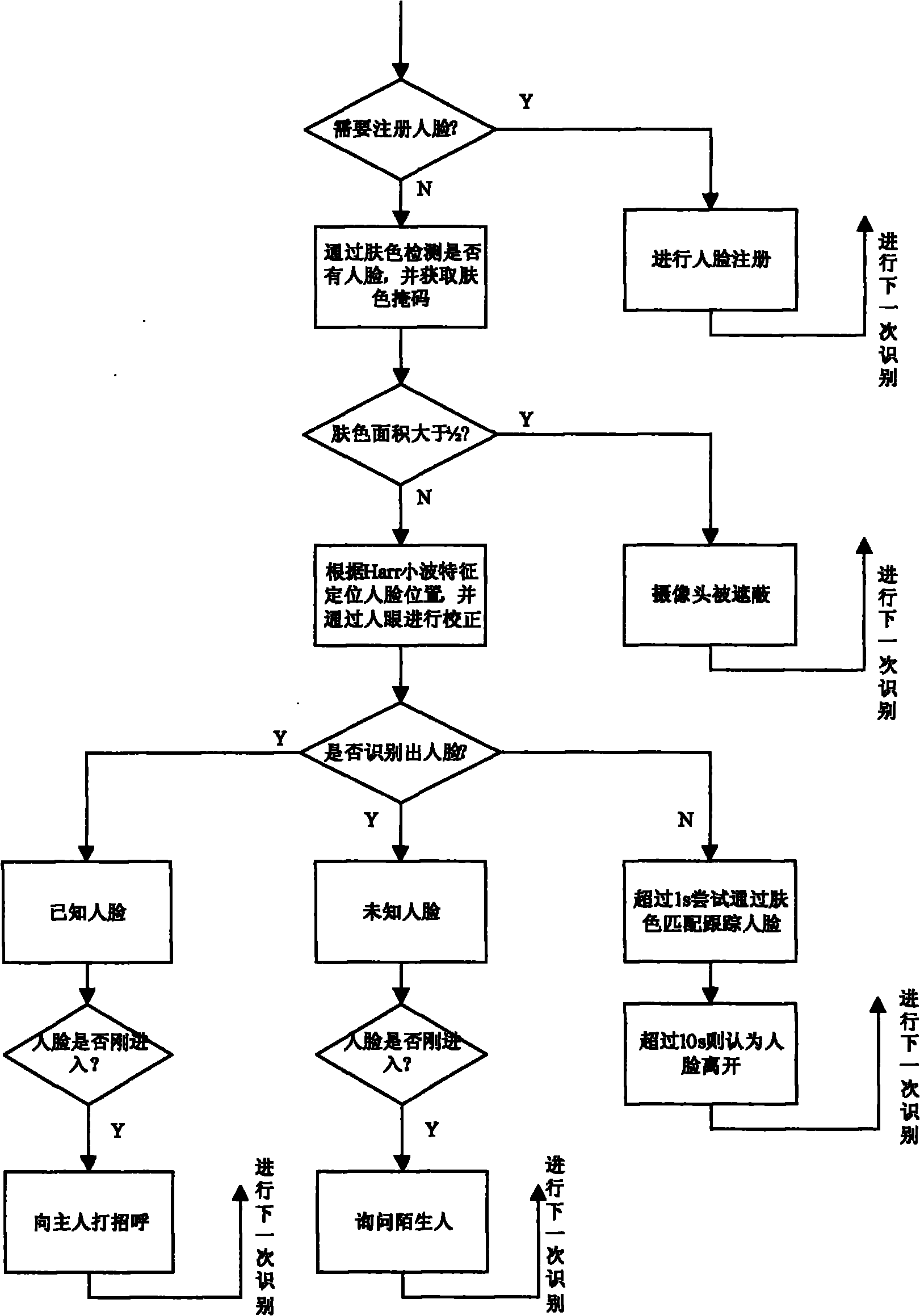
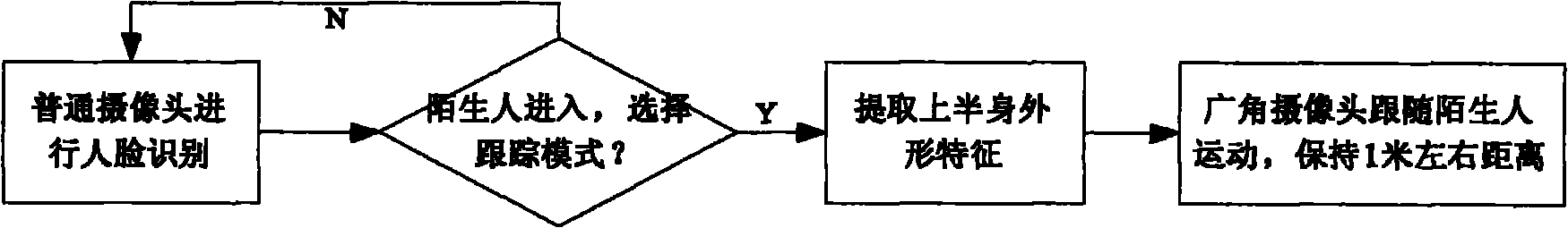
The invention discloses a multisensory robot used for family intelligent monitoring service. The robot comprises a main control device, wherein the main control device is externally connected with a camera, a sound collector, a cellphone alarm device and a loudspeaker; the main control device is also externally connected with a chassis moving device and a head gesture device; the chassis moving device consists of a chassis controller, a motor driver, an obstacle avoiding sensor and a smoke sensor; the chassis moving device is provided with a lithium battery and wheels required by a mobile platform; the main control device sends a control command to the chassis controller by a serial port to control the corresponding action of a motor and process an obstacle avoiding signal; the head gesture device consists of three steering engines and one relay; and the main control device sends a control command to a head controller by a serial port to control the head and the eyeballs of the robot to rotate and control the mouth of the robot to open and close. The multisensory robot is used for the family intelligent monitoring field, can be used for multisensory fusion and can realize the multifunction family monitoring such as face identification and anomalous event monitoring.
Owner:SHENZHEN INST OF ADVANCED TECH
Event monitoring and management
InactiveUS20070294369A1Multiple digital computer combinationsPlatform integrity maintainanceNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
Method for coordinating resources for events and system employing same
A method for coordinating resources for events, the method comprises identifying participants for an event; collecting information concerning the identified participants, the information at least comprising availability schedules; and providing an event monitoring interface to at least one participant device, the event monitoring interface presenting a representation of identified participants and at least one resource associated with the event.
Owner:SMART TECH INC (CA)
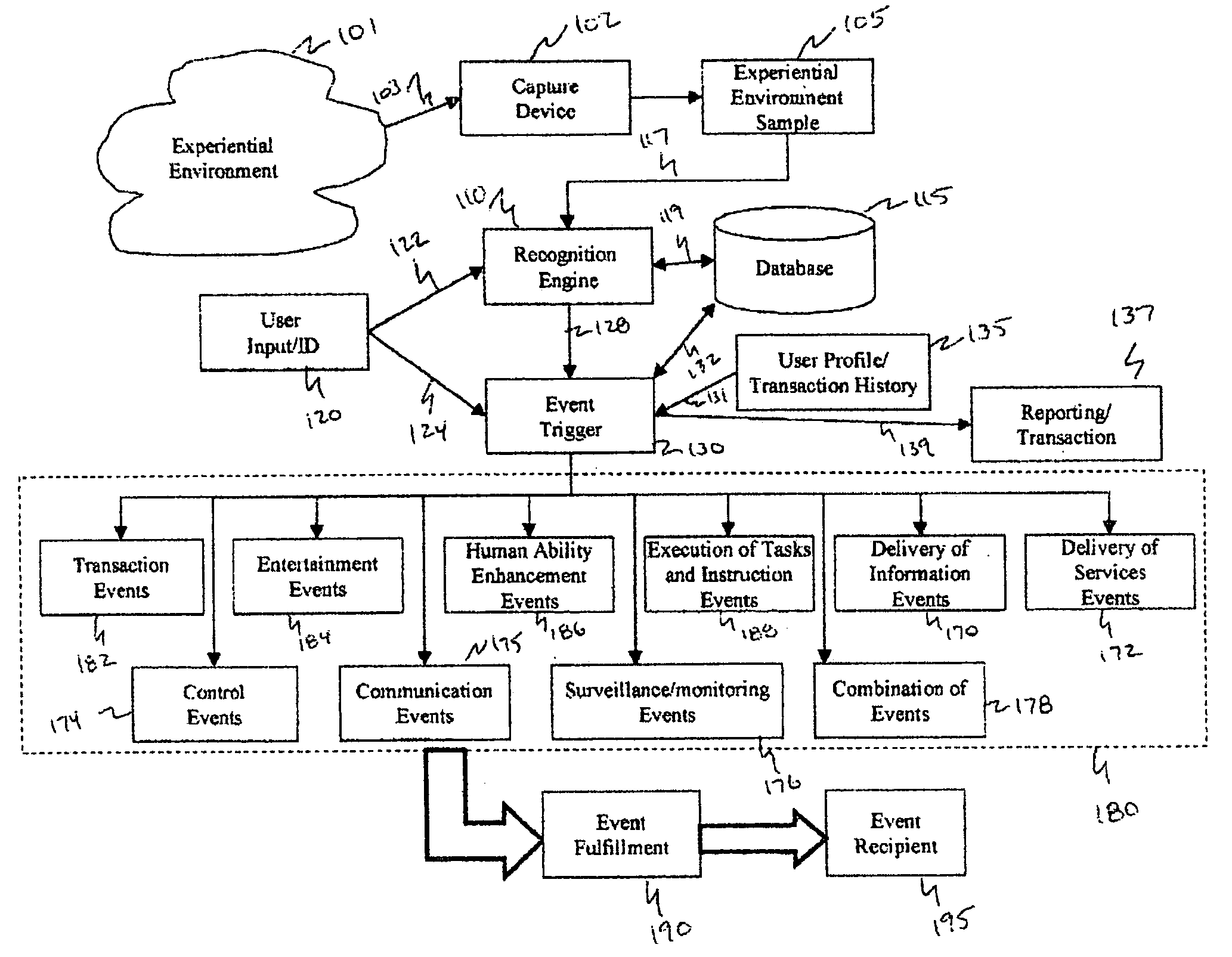
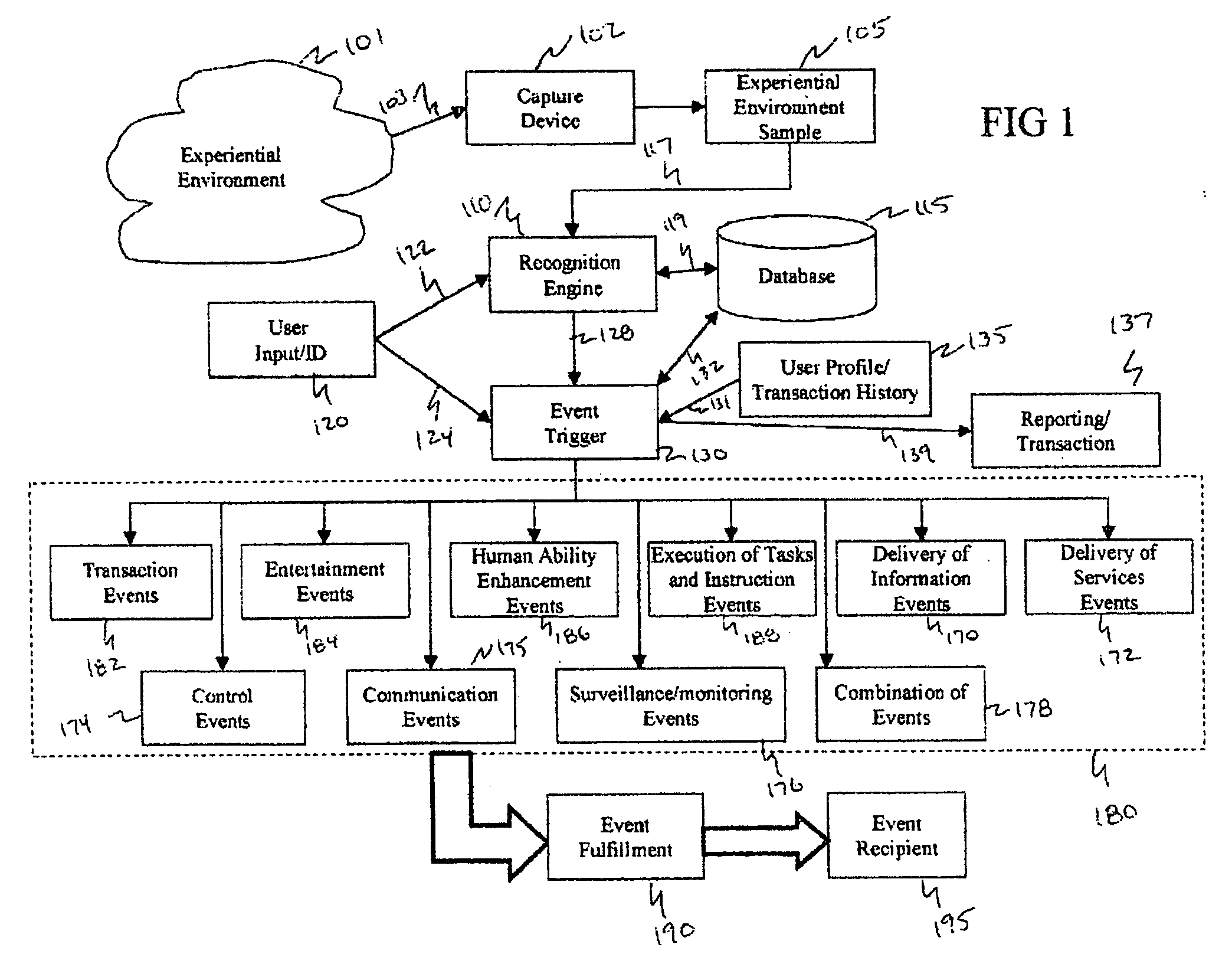
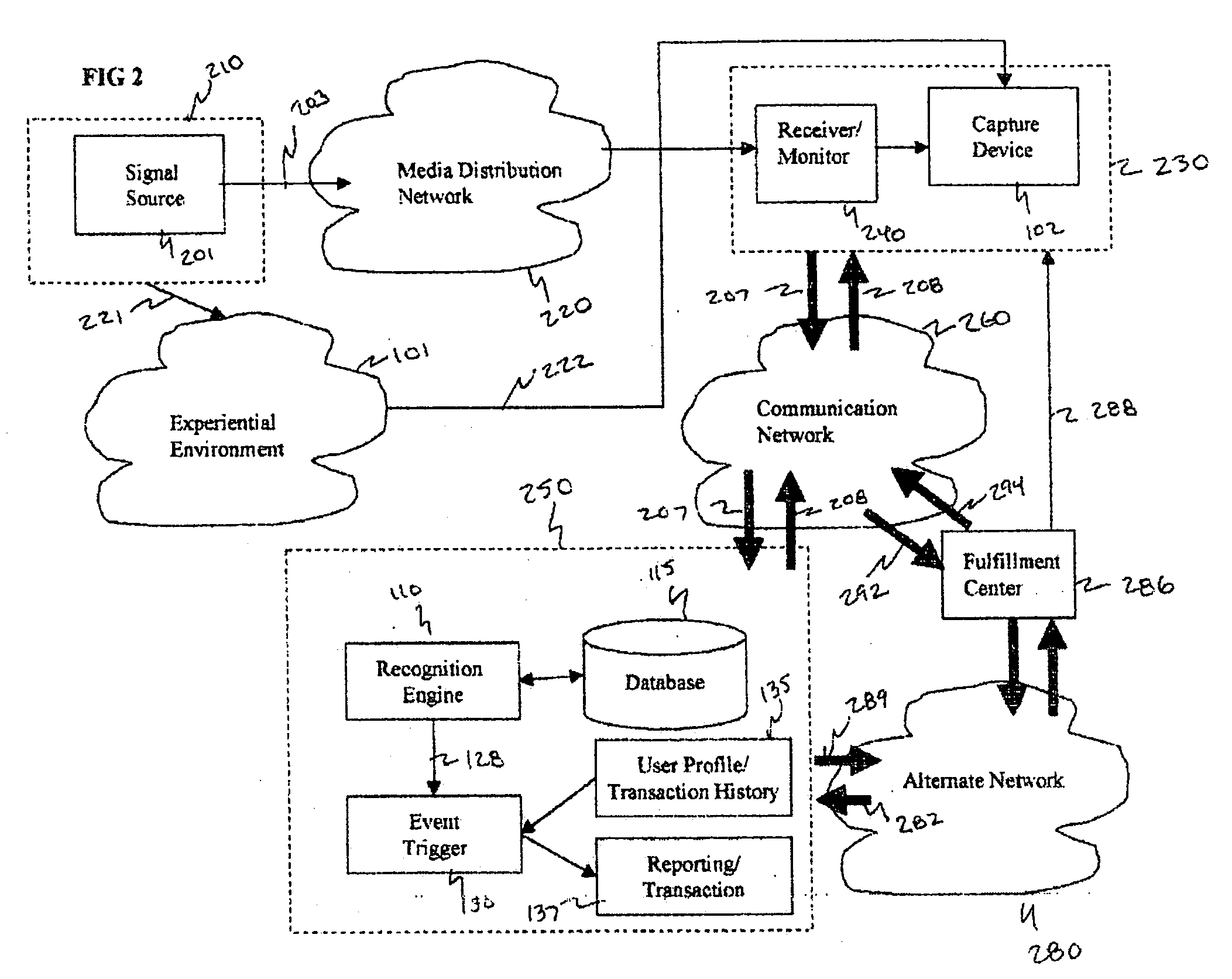
Method and system for interacting with a user in an experiential environment
InactiveUS20050267817A1Improve abilitiesFunction increaseElectrophonic musical instrumentsDiscounts/incentivesControl orientedHuman–computer interaction
A method and system for provides a user with an ability to capture a sample of an experiential environment and deliver that sample to an interactive service to trigger one or more predetermined events. In exemplary embodiments of the invention such triggered events include the delivery of information and services to the user, the execution of tasks and instructions by the service on the user's behalf, communication events, surveillance events and other control-oriented events that are responsive to the user's wishes. In other exemplary embodiments of the invention, the triggered events include transaction-oriented events, entertainment events, and events associated with enhancements to human ability or function.
Owner:SHAZAM INVESTMENTS +1
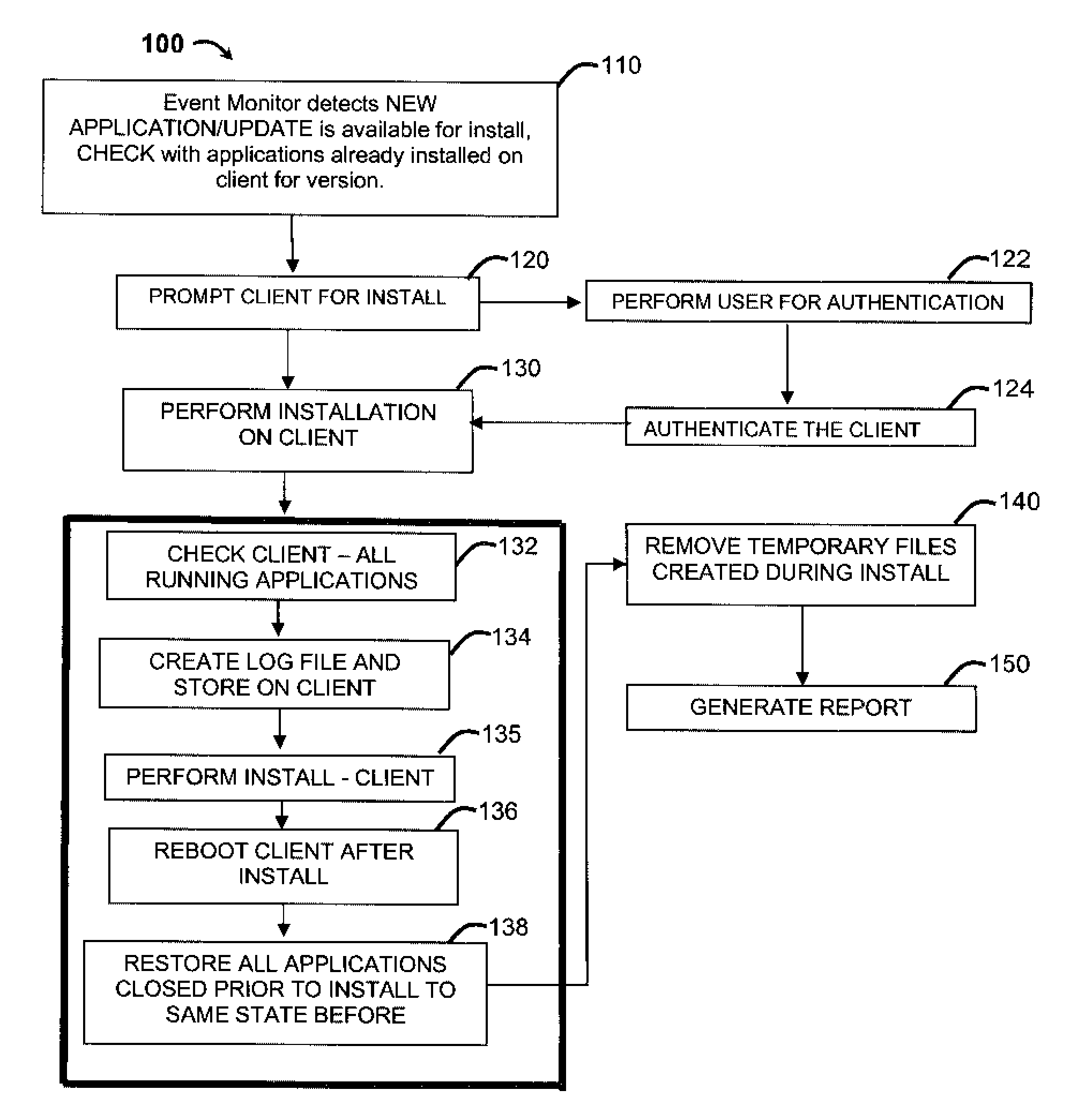
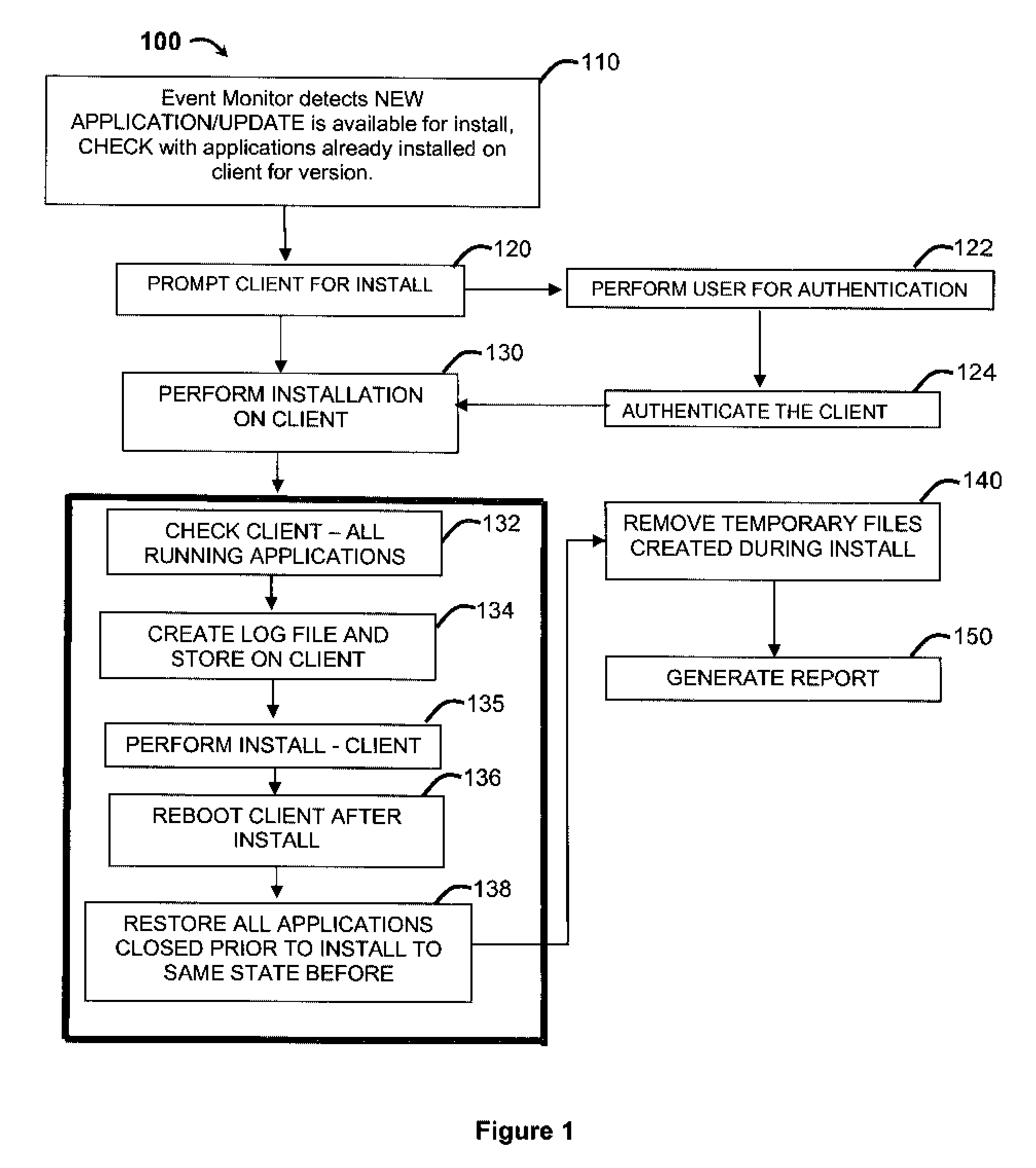
Automatic software installation and cleanup
ActiveUS20080320466A1More user friendly and efficientProgram loading/initiatingMemory systemsOperational systemApplication software
An application installation and removal system and method comprising: an operating system for controlling and maintaining resources on a computer; and an event monitor configured detect availability of an new software to be installed on the client; receive a list of new software on the client; perform installation of the software on the client wherein performing installation comprises creating a record of all user defined applications on the client immediately prior to performing the installation in a log file; installing the new software on the client; rebooting the client after the installation of the new software on the client; resorting all the user defined applications recorded in the log file to the same state as the user defined applications were prior to the installation of the new software.
Owner:GOOGLE LLC
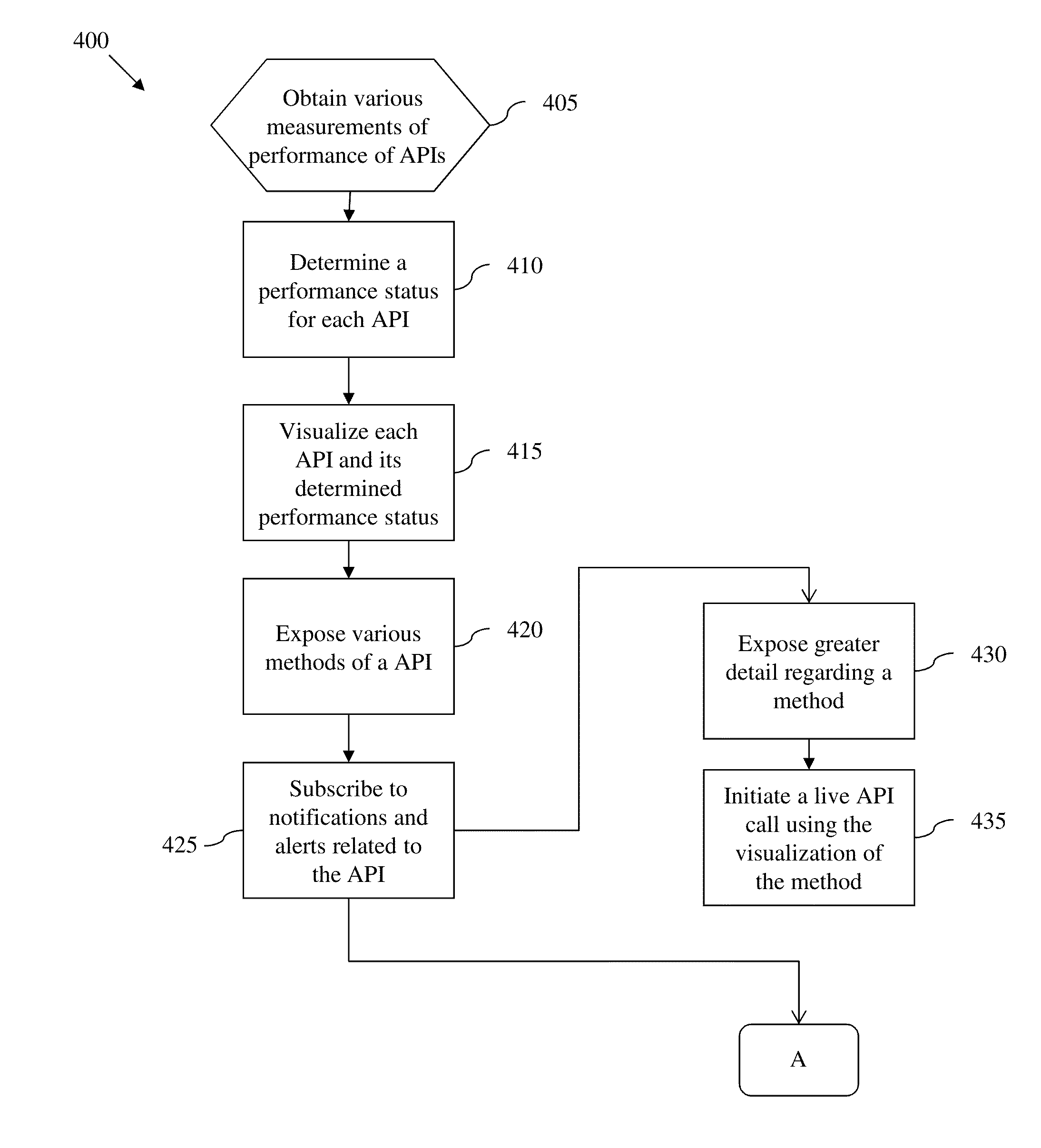
Application programming interface monitoring tool notification and escalation method and system
InactiveUS20160103750A1PerformanceInterprogram communicationHardware monitoringApplication programming interfaceComputerized system
Methods and systems for reporting performance data for application programming interfaces (APIs) are provided. A method includes receiving a subscription request from a subscriber for a particular API of a plurality of APIs, and monitoring performance of the particular API for a predetermined event that includes a change in at least one of performance status for the particular API and one or more various measurements of performance of the particular API. The method further includes comparing the predetermined event to a table or database of information that includes notification and alert rules for the particular API that specify notification policies for various predetermined events, and when the predetermined event matches at least one of the notification and alert rules, sending, by the computer system, a notification or alert to the subscriber based on the notification policy for the at least one of the notification and alert rules.
Owner:ADP
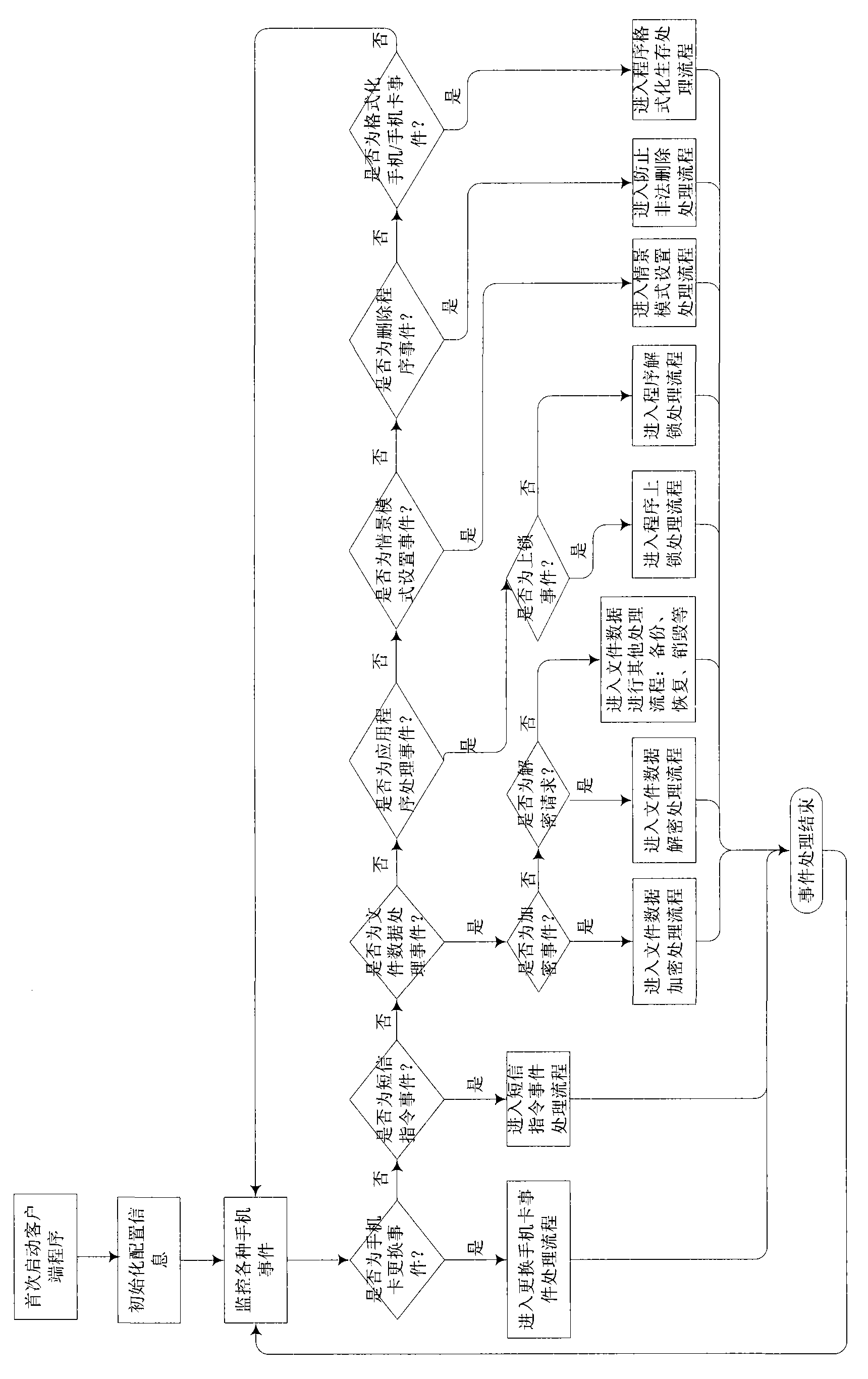
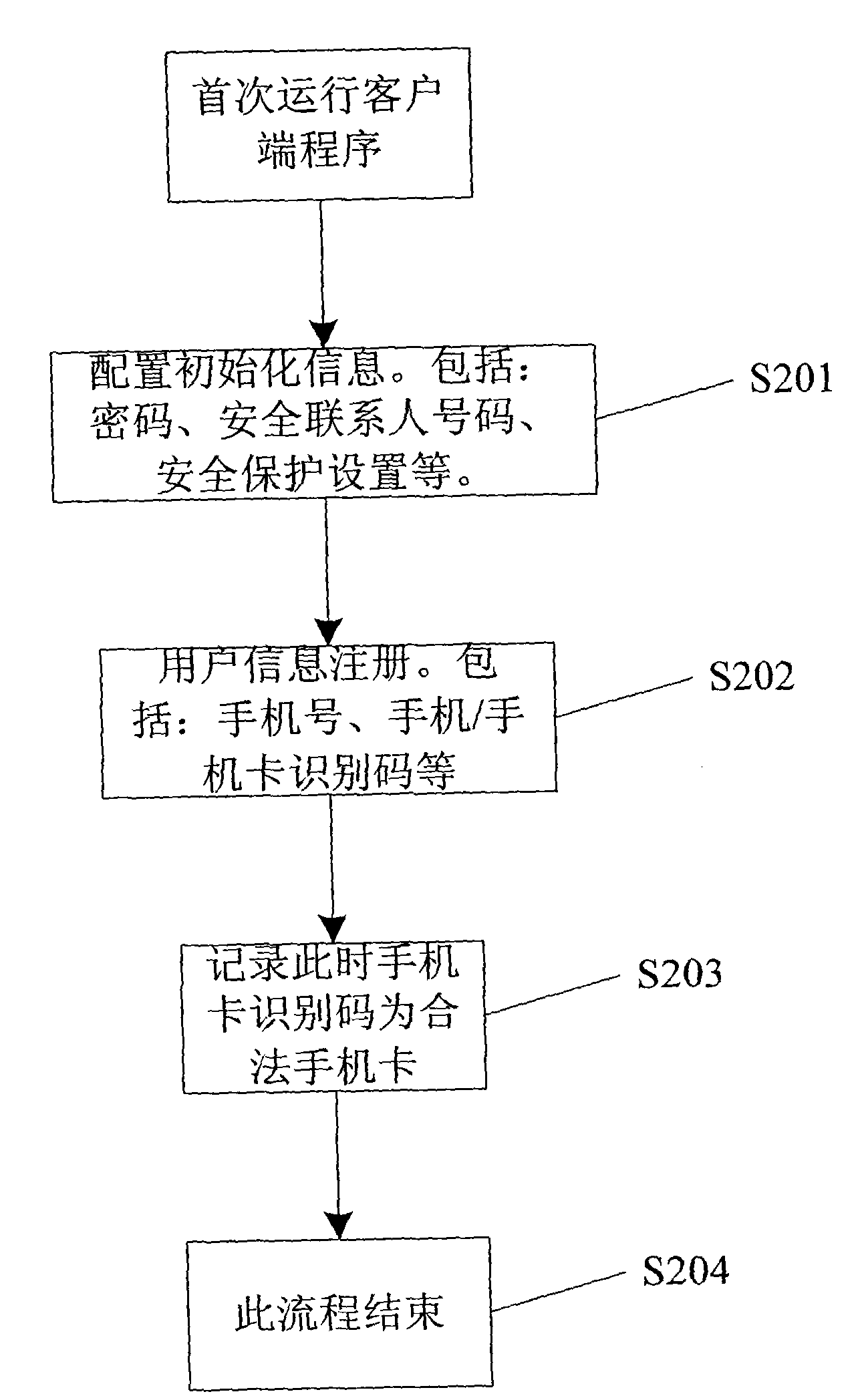
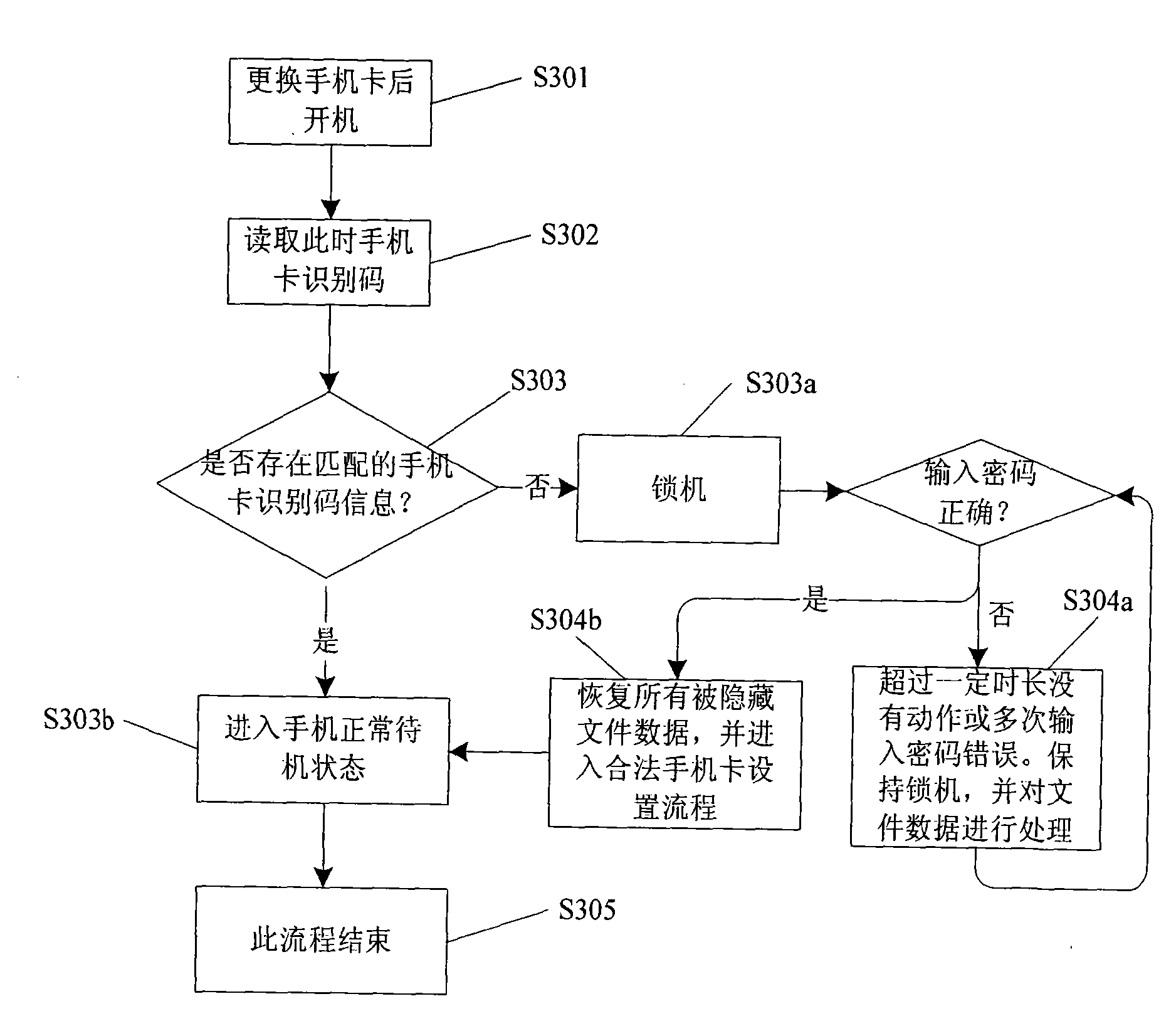
Method and system for protecting individual privacy in mobile phone
InactiveCN101616495AUser identity/authority verificationComputer security arrangementsEvent typeComputer module
The invention relates to a method and a system for protecting individual privacy in a mobile phone. The method comprises the following steps that: after a mobile phone is started up, a client back end starts and operates; events are monitored; related operation are executed according to the types of events; and after the processing of the event is finished, the client back end operates; and events are monitored continuously. The types of the monitored events comprise a mobile phone change event, a short message command event, a file data processing event, an application program processing event, a profile setting event, a program deletion event and a mobile phone / mobile phone card formatting event. The system comprises a client module and a server, wherein the client module comprises an event monitoring module, an event processing module, a communication module and a mobile phone data update and back-up and recovery module; and the server comprises a communication module, a personal information management module and a back-up / recovery module. The method and the system of the invention can realize the maximum safety protection of mobile phone privacy.
Owner:网秦无限(北京)科技有限公司
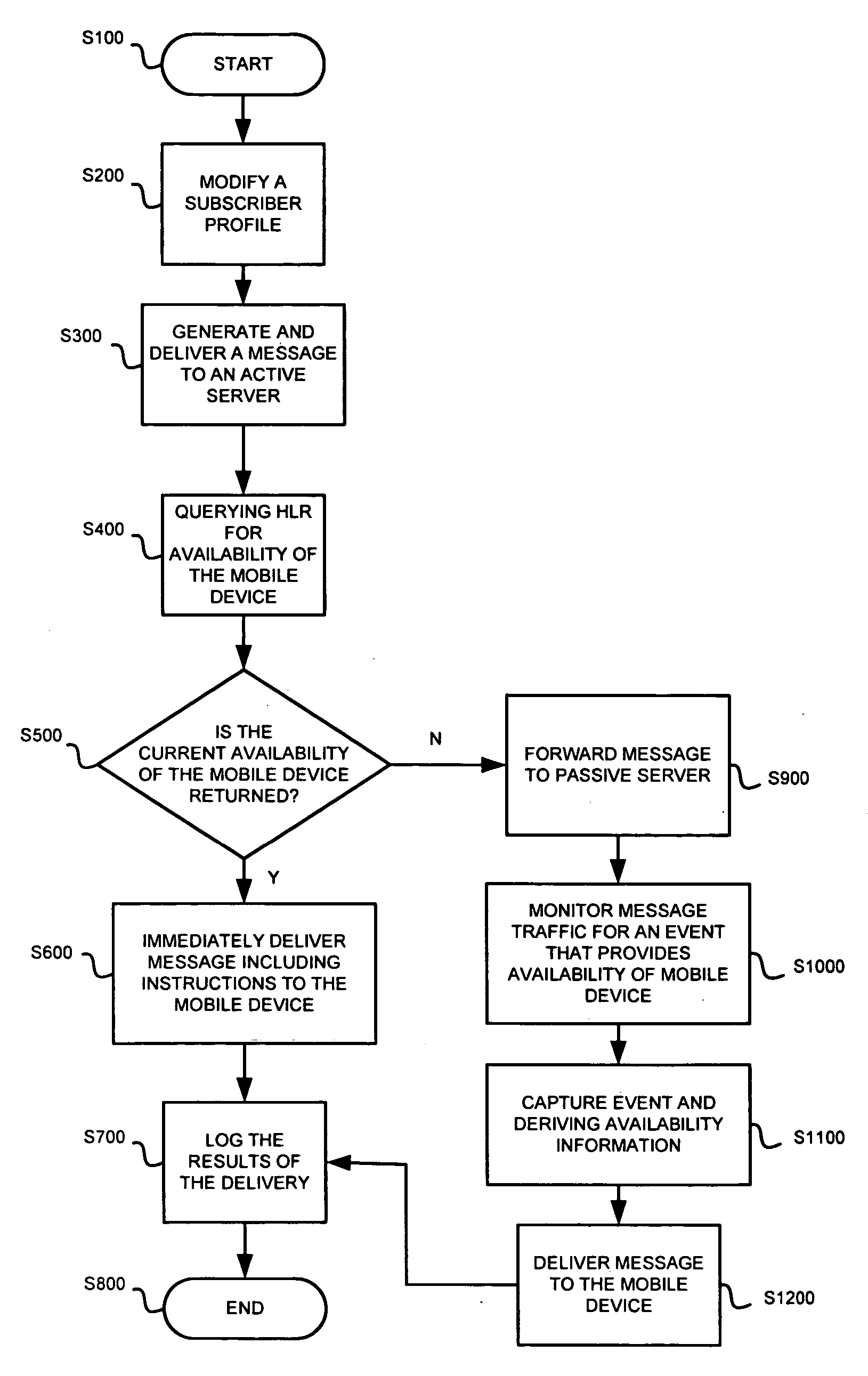
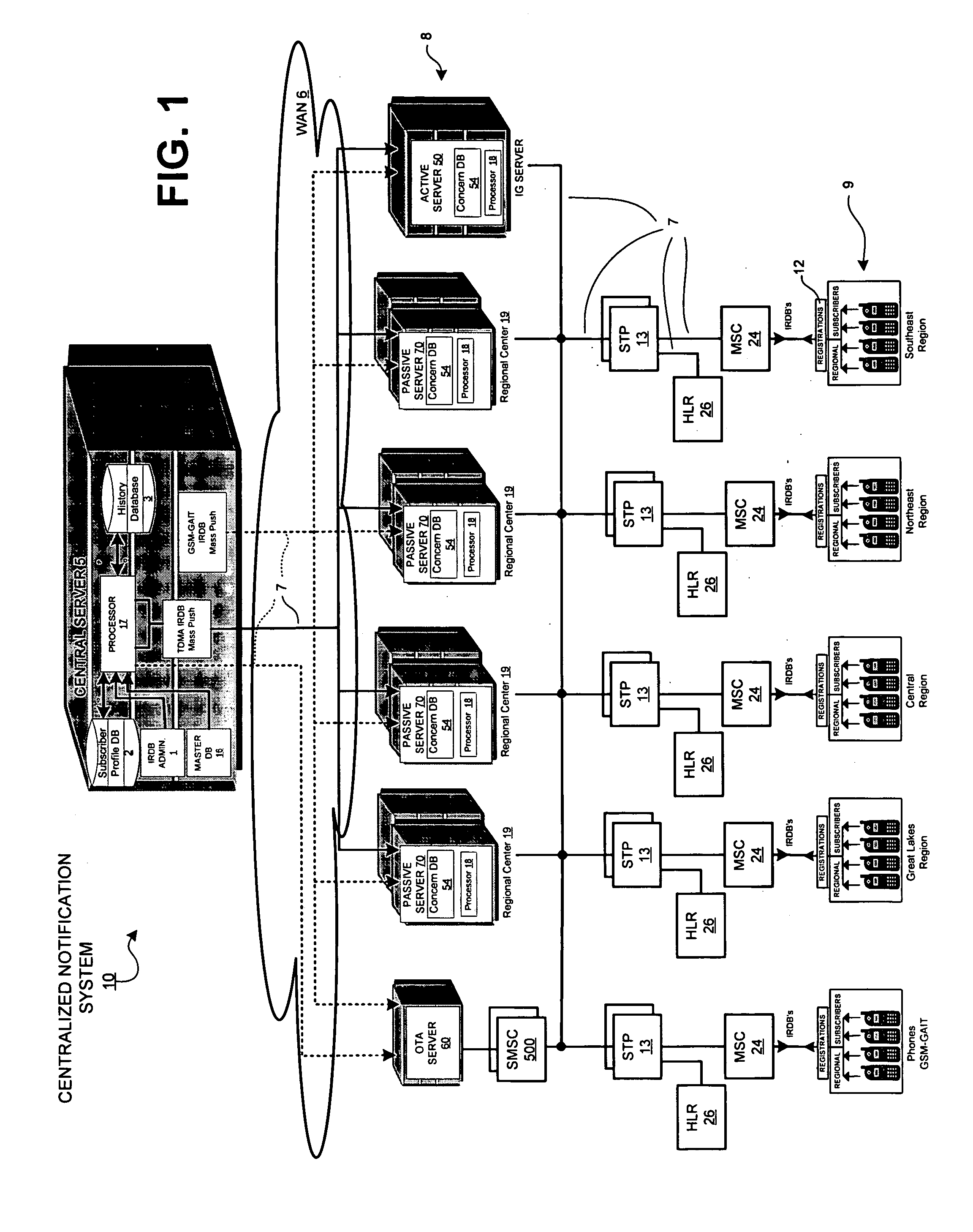
Systems and methods for management and delivery of messages in a centralized notification system
InactiveUS20060161626A1Reduces eliminates loadMultiple digital computer combinationsMessaging/mailboxes/announcementsTraffic capacityMessage routing
Systems and methods for providing centralized notification for over the air programming. The centralized notification system includes a central server that generates a message to be delivered to a mobile device. The centralized notification system includes an active server in communication with the central server that receives the message from the central server. The active server communicates with a network element that communicates with the mobile device. The active server queries the network element to determine availability of the mobile device. If the availability of the mobile device is returned from the network device, the message is directly routed to the mobile device, otherwise, the message is routed to a passive server. The passive server monitors message traffic for an event that provides availability information about the mobile device and automatically delivers the message to the mobile device in response thereto.
Owner:CINGULAR WIRELESS II LLC
LED street lamp control system based on electric power carrier communication technology
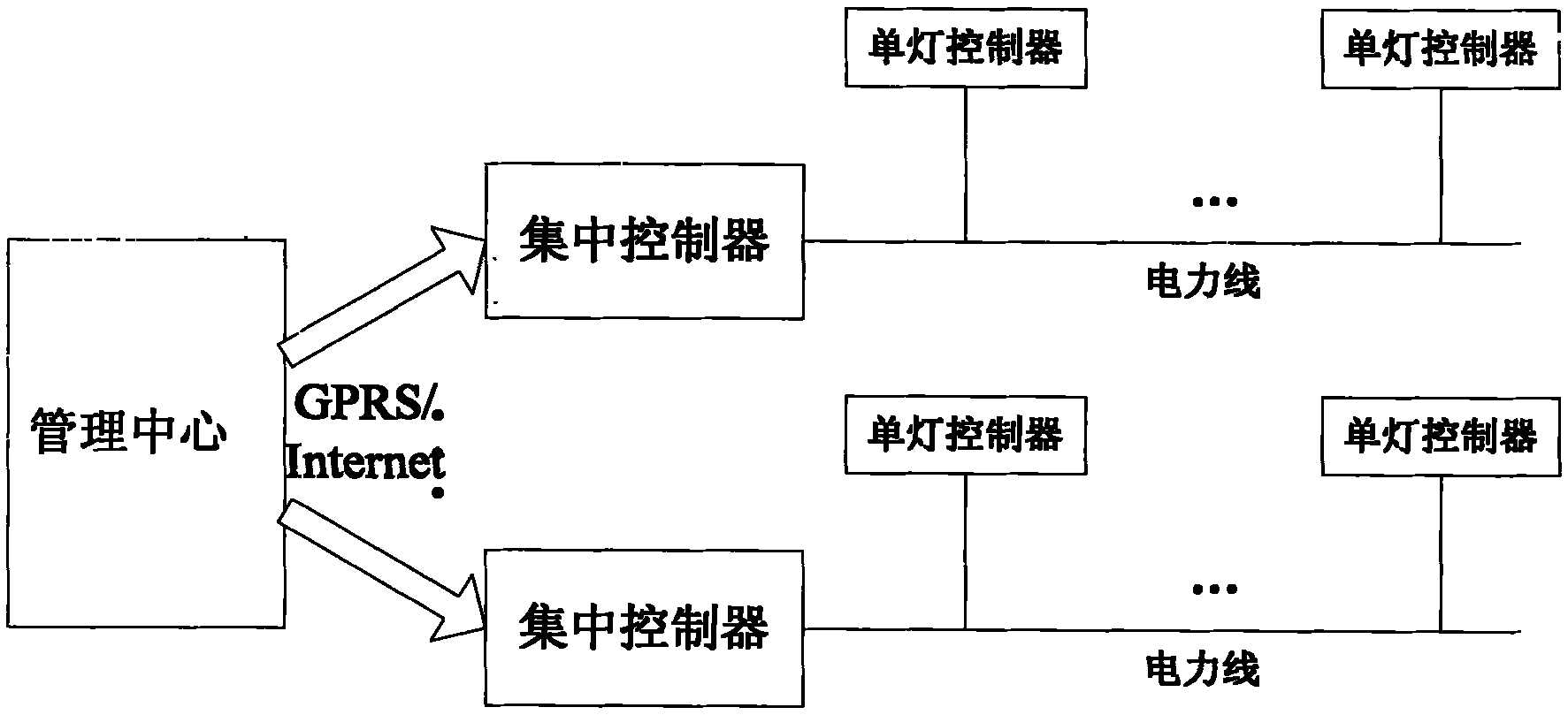
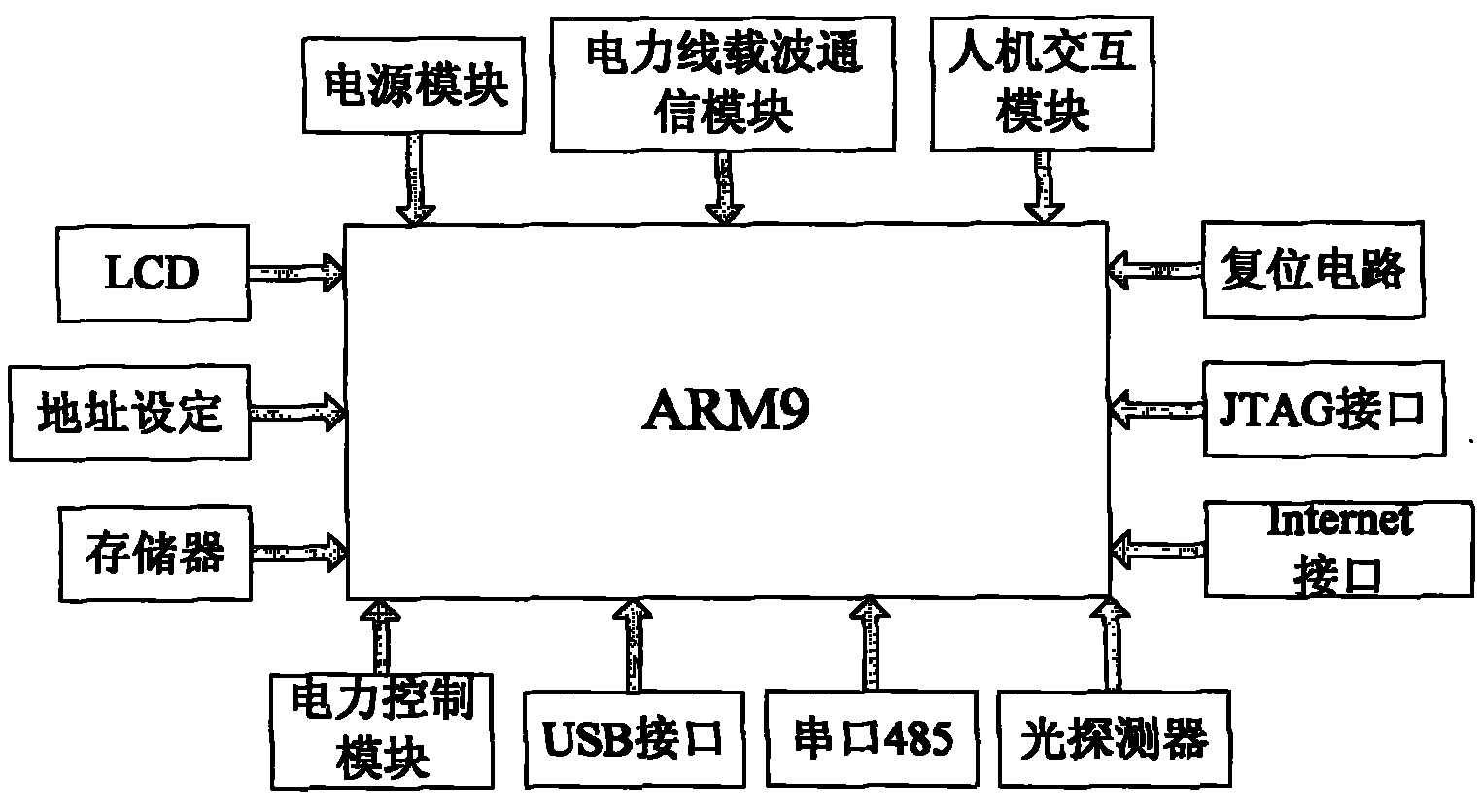
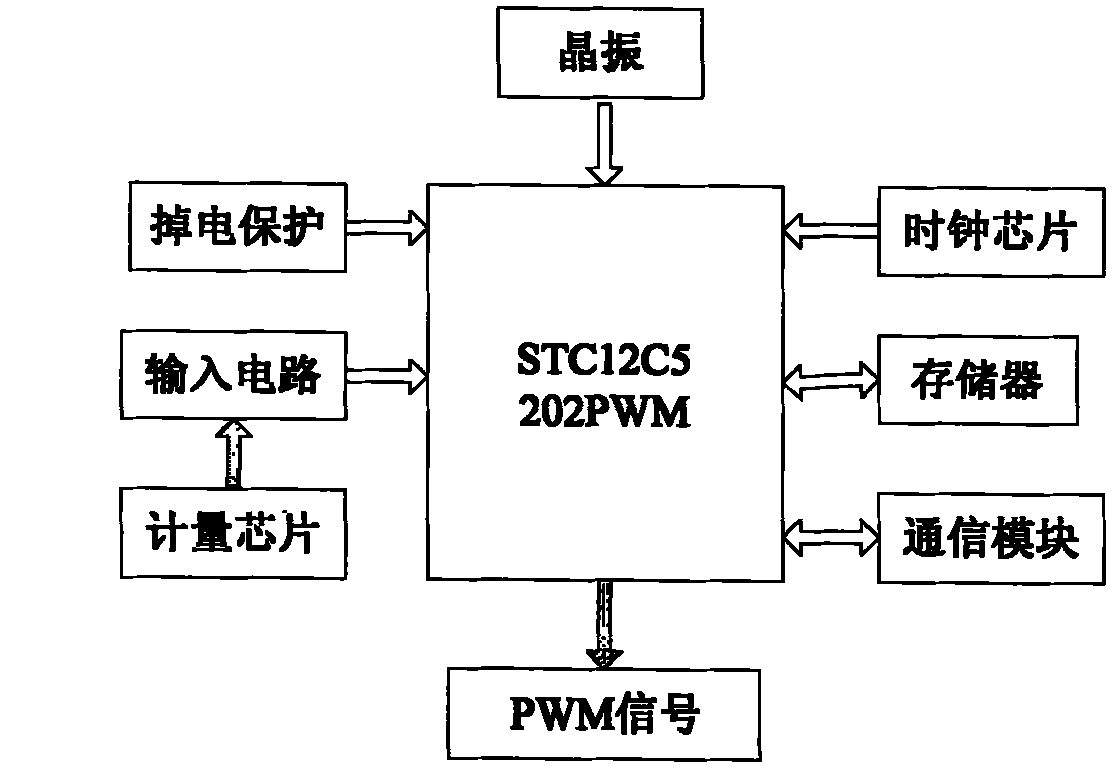
InactiveCN101969713AImprove management efficiencyWith online surveyPower distribution line transmissionElectric light circuit arrangementMicrocontrollerSystems management
The invention discloses an LED street lamp control system based on an electric power carrier communication technology, which is in a three-layer network structure comprising a single lamp controller, a centralized controller and a management center, wherein the single lamp controller takes a singlechip as a core to be in charge of controlling a street lamp and collecting street lamp working parameters; the centralized controller adopts embedded system design, operates a power line carrier technology and carries out group or single control on street lamps in areas according to preset illumination strategy and assistant illumination intensity control strategy; the management center is mainly composed of a personal computer PC and street lamp system management software to display lamp street state (luminance, voltage, current and power) information; and a GPRS wireless transmission technology or Internet network is used for realizing the remote management of the street lamp switch and luminance regulation. Thus, by using the system, operations such as scheduling events, data record reading, event monitoring, warning response and the like can be realized, and historical data can be inquired.
Owner:TIANJIN POLYTECHNIC UNIV
Cellular telephone based surveillance system
InactiveUS20050255826A1Devices with sensorClosed circuit television systemsCurrent sensorComputer science
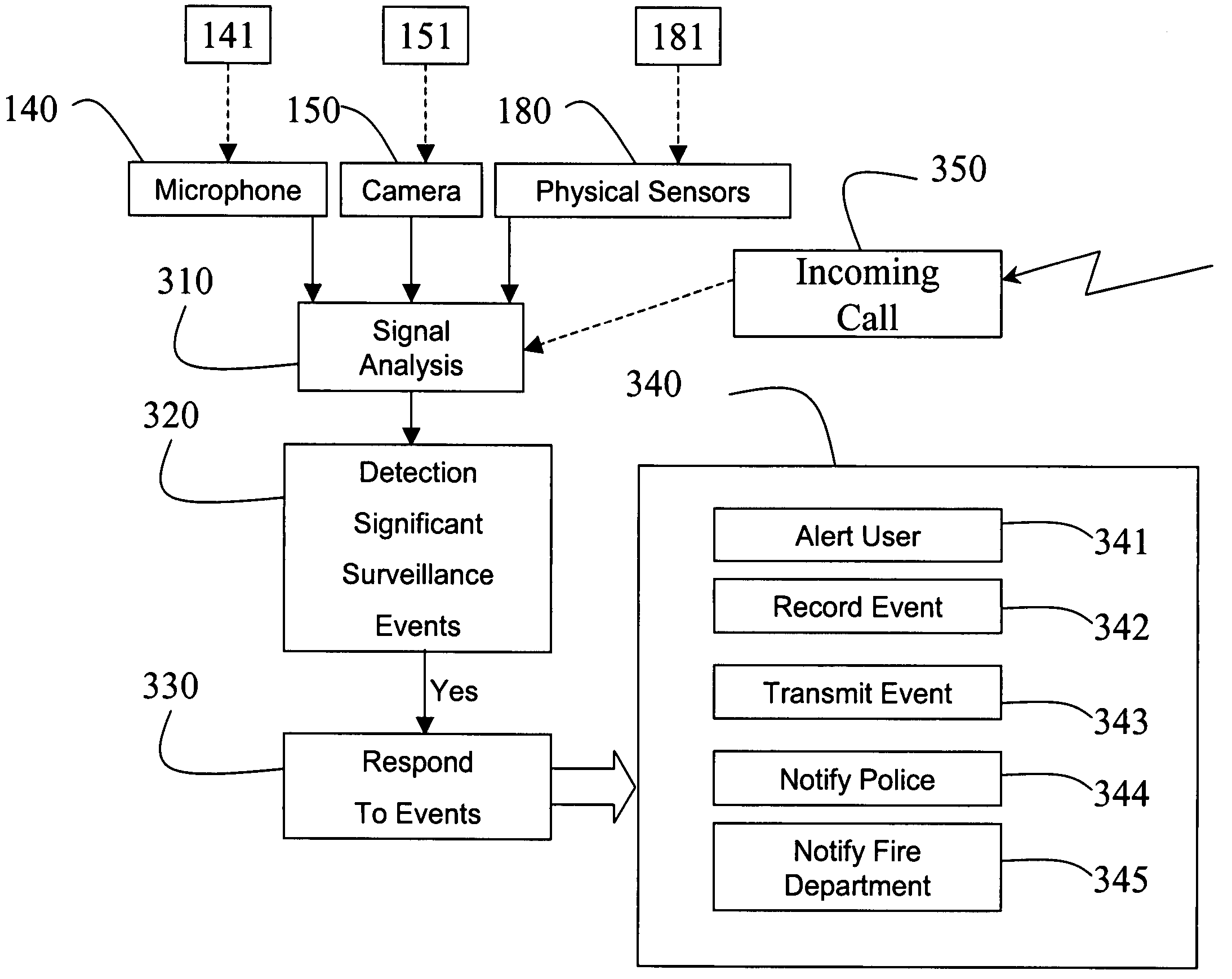
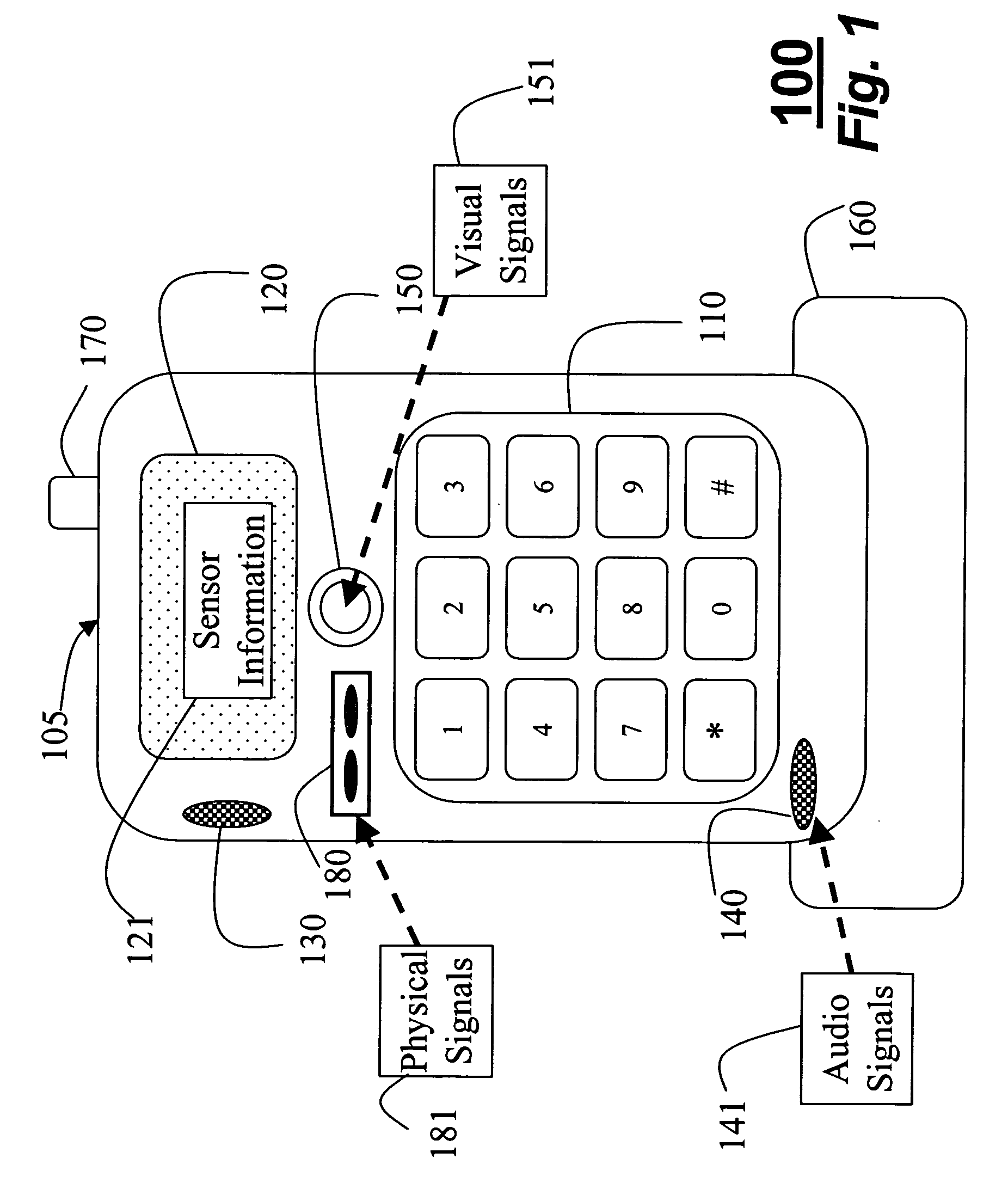
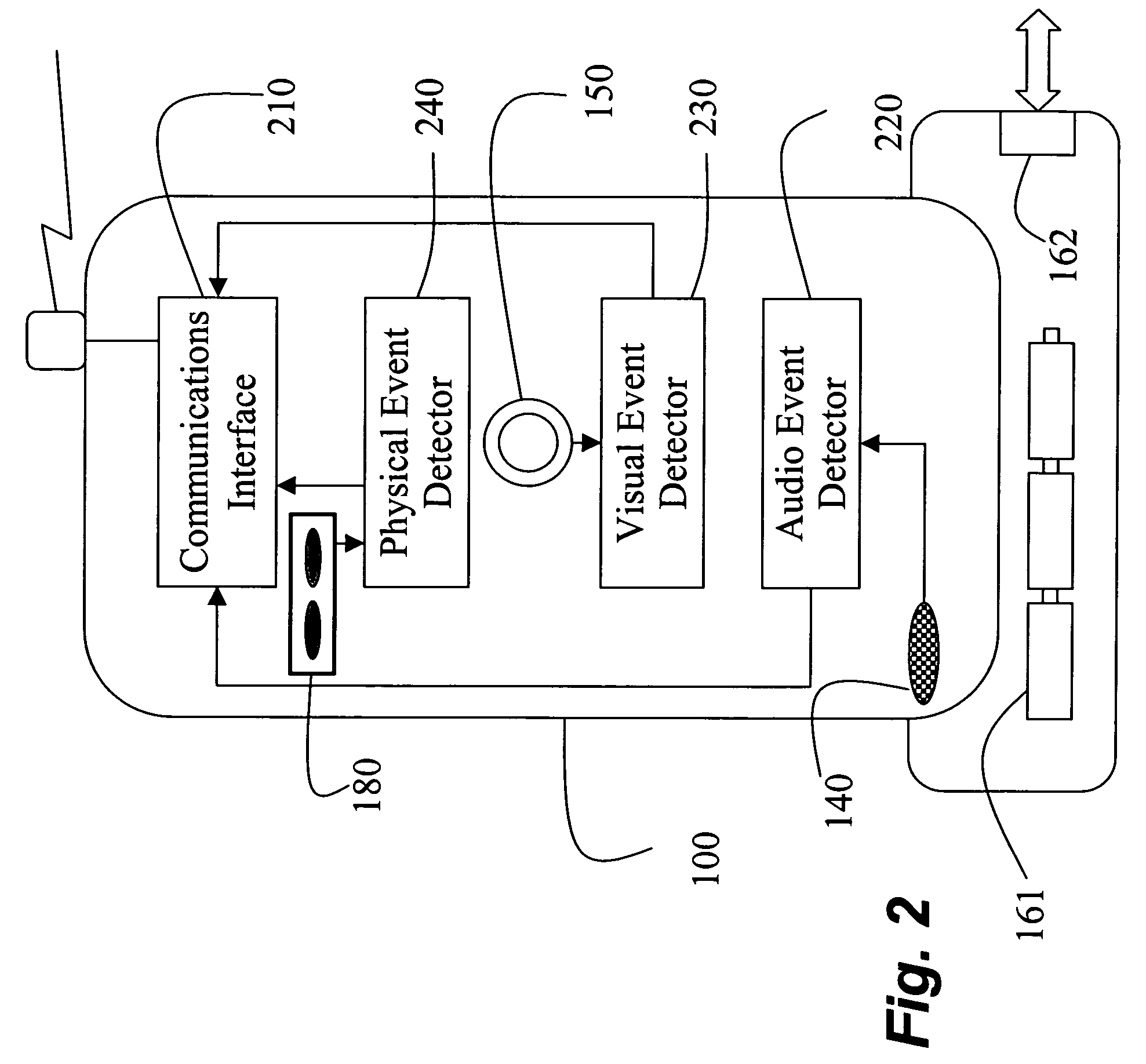
The invention provides sensors and event monitoring to a cellular telephone to perform surveillance. Using audio and visual sensing capabilities, an environment can be monitored to detect significant surveillance events and to trigger surveillance alerts in response to the events, or to report current sensor information in response to an in-coming call.
Owner:MITSUBISHI ELECTRIC RES LAB INC
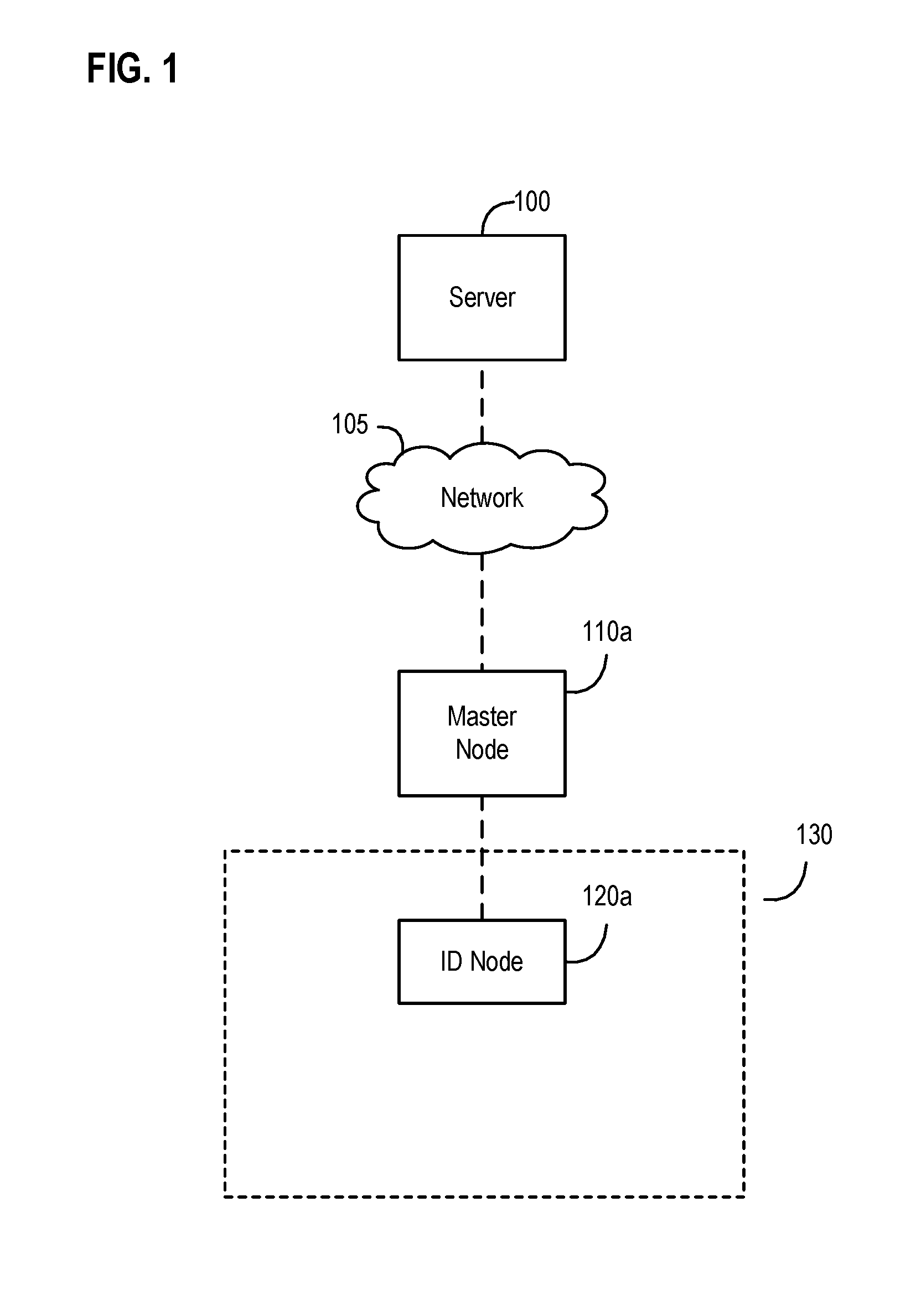
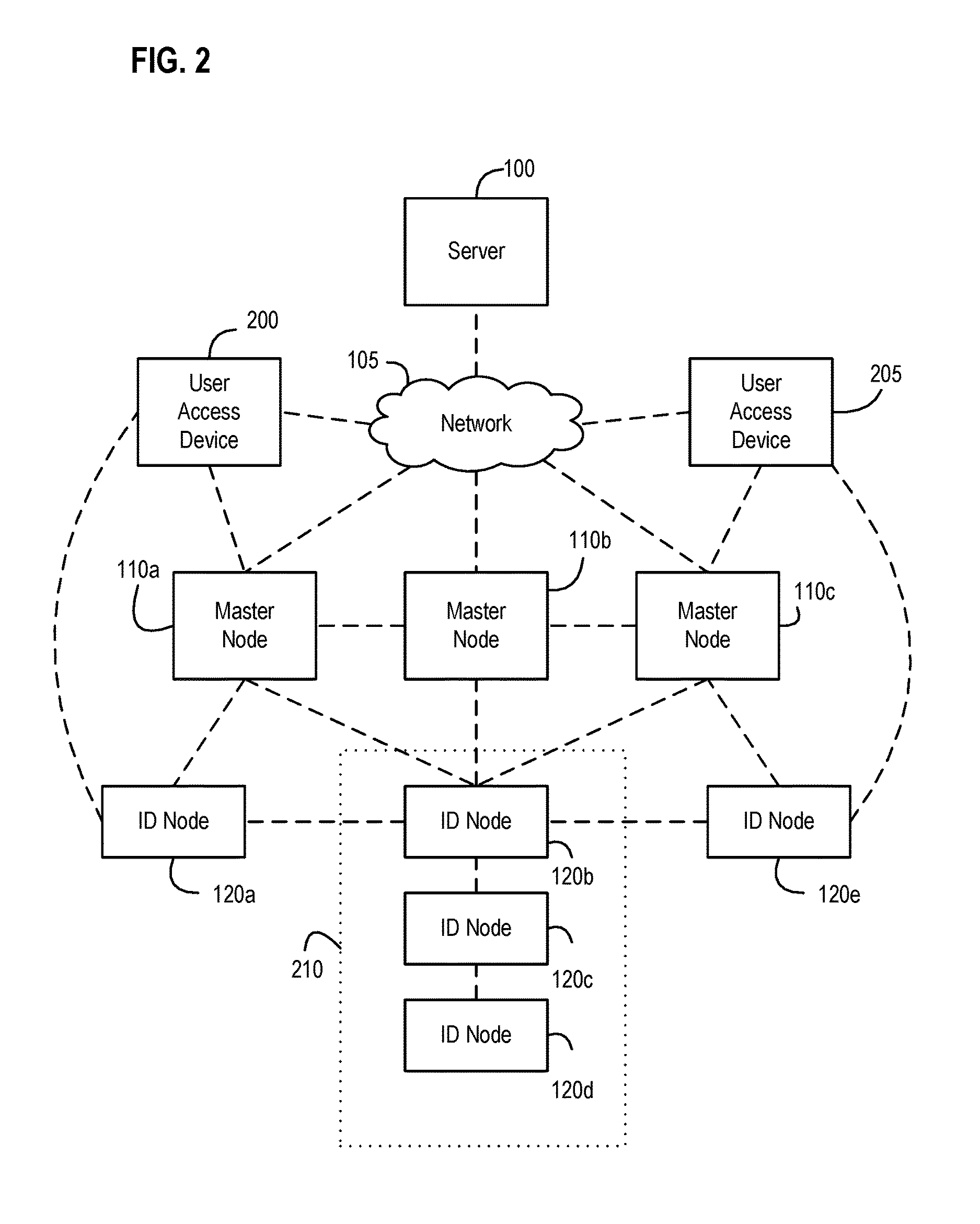
Systems, apparatus, and methods of event monitoring for an event candidate within a wireless node network based upon sighting events, sporadic events, and benchmark checkpoint events
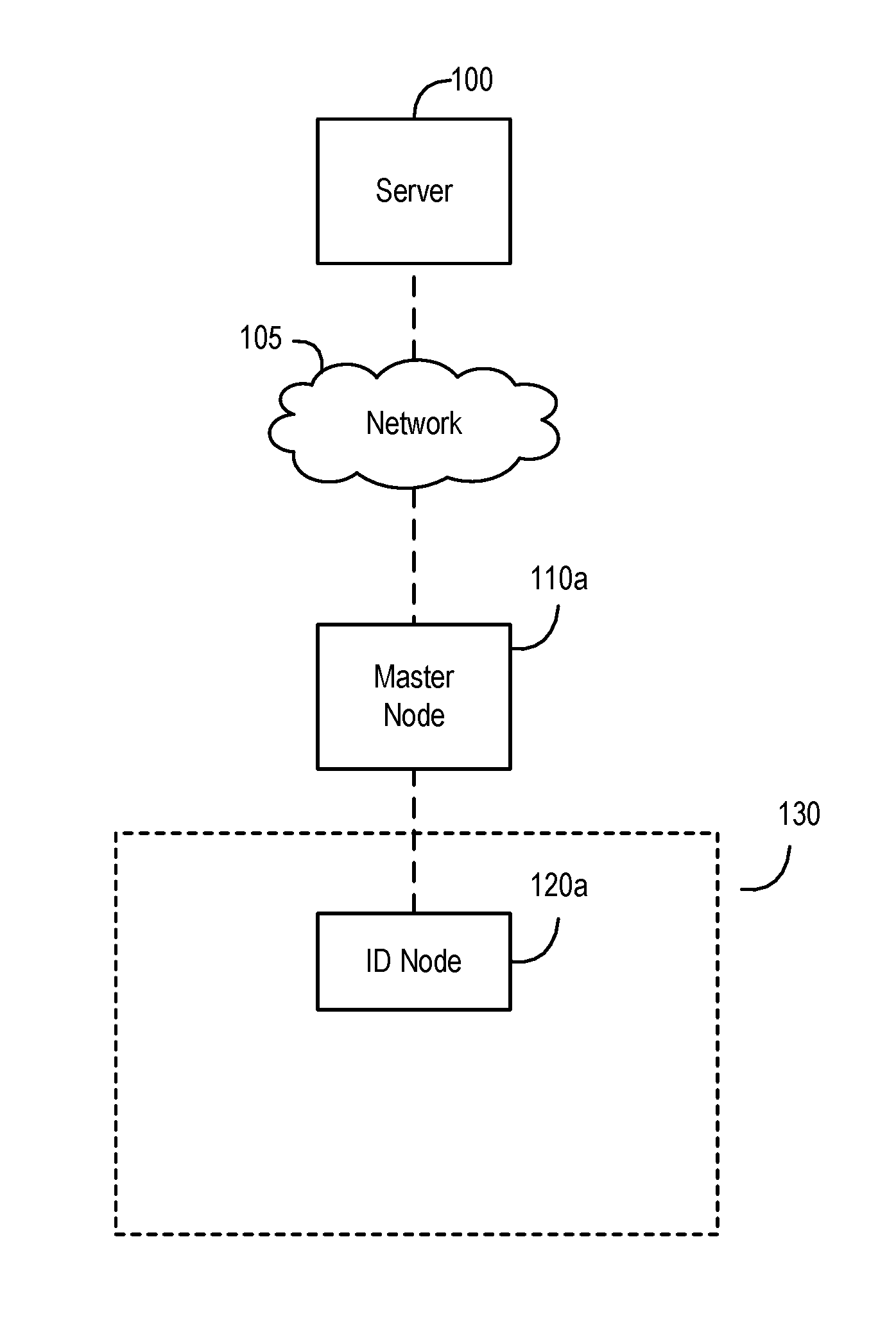
ActiveUS20170012829A1Enhanced network operationEasy to operateAssess restrictionNetwork topologiesNODALWireless mesh network
Enhanced monitoring for an event candidate, as performed by a master node in a wireless node network with a server and at least one ID node, generally has the master node detecting a first signal broadcast by the ID node; identifying the event candidate as a first sighting event when detecting the first signal; generating and reporting event data representing the first sighting event (e.g., an ID node identifier, timing, and signal strength information); identifying the event candidate as a sporadic event related to the ID node when (1) there is no identified first benchmark checkpoint event related to the ID node and (2) there is no detected subsequent signal broadcast by the ID node within a gap time period from when the latest signal from the ID node was detected; generating and reporting event data representing the sporadic event (e.g., timing and signal strength information) if the master node identifies the sporadic event; determining a signal strength average value for certain subsequent successive ID node signals including the first signal as long as an elapsed time between each of the subsequent successive signals is less than the gap time; identifying the event candidate as a first benchmark checkpoint event representing the state of the ID node based upon the signal strength average value; and generating and reporting event data representing the benchmark checkpoint event (e.g., timing and signal strength information).
Owner:FEDEX SERVICES
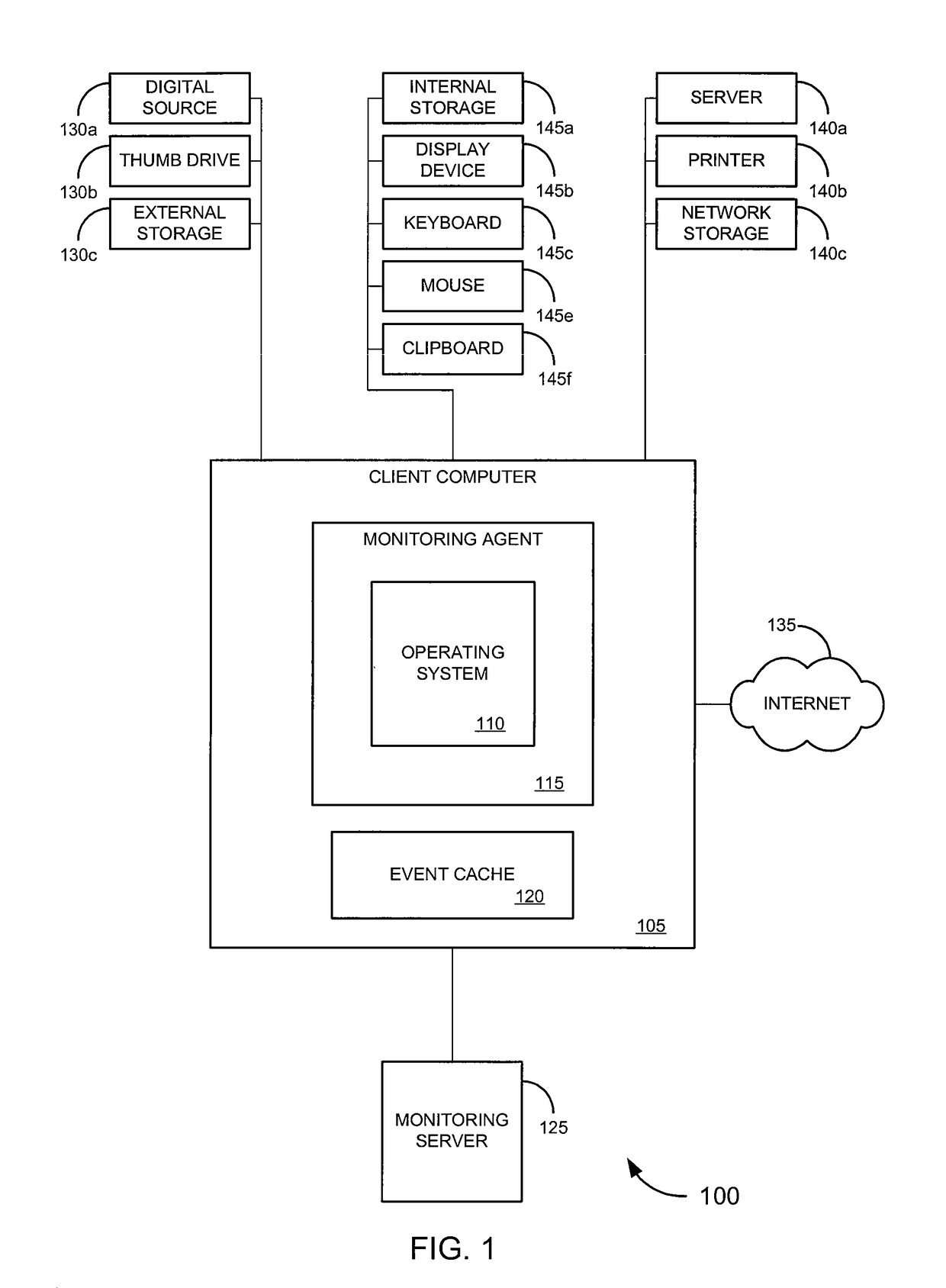
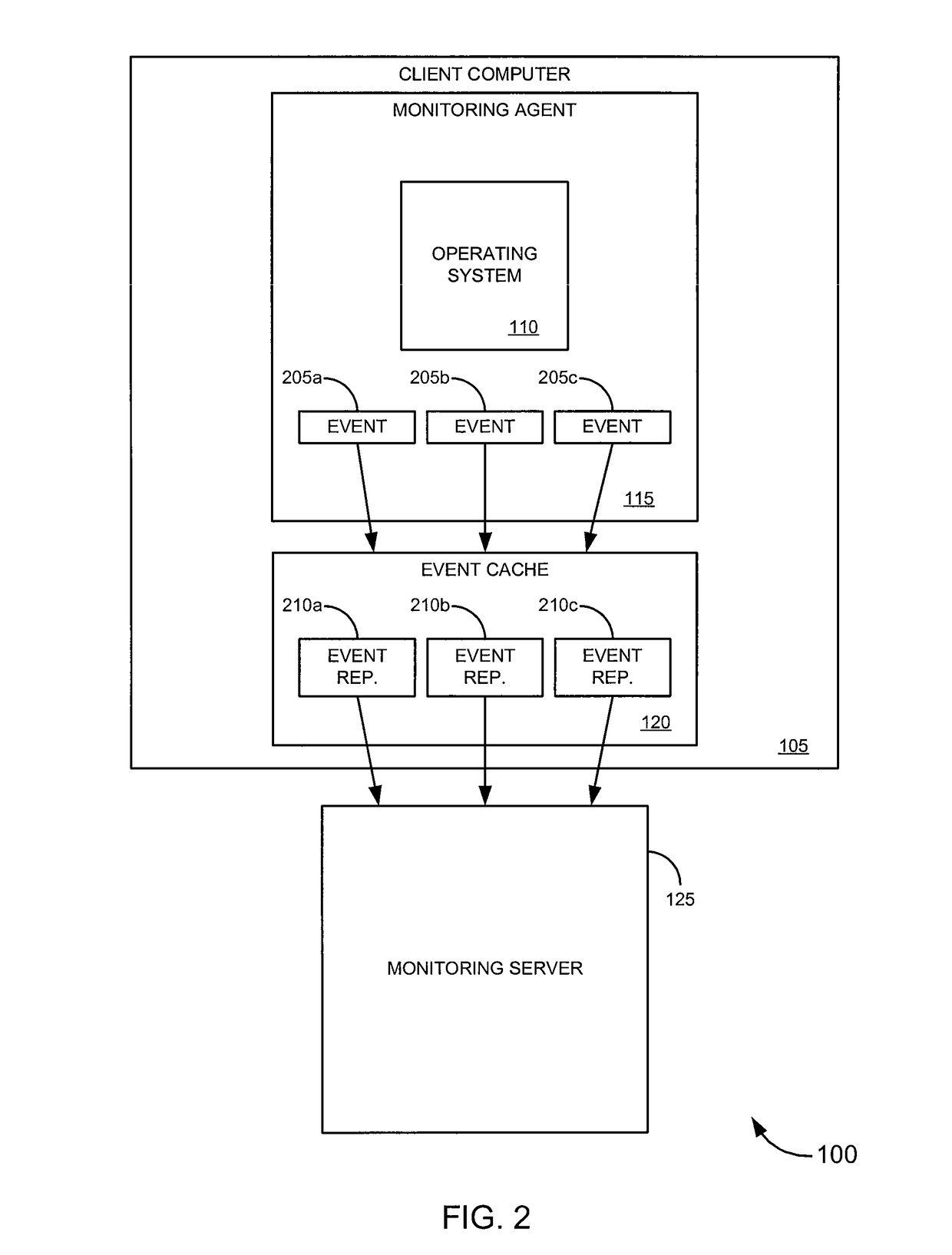
Event monitoring and collection
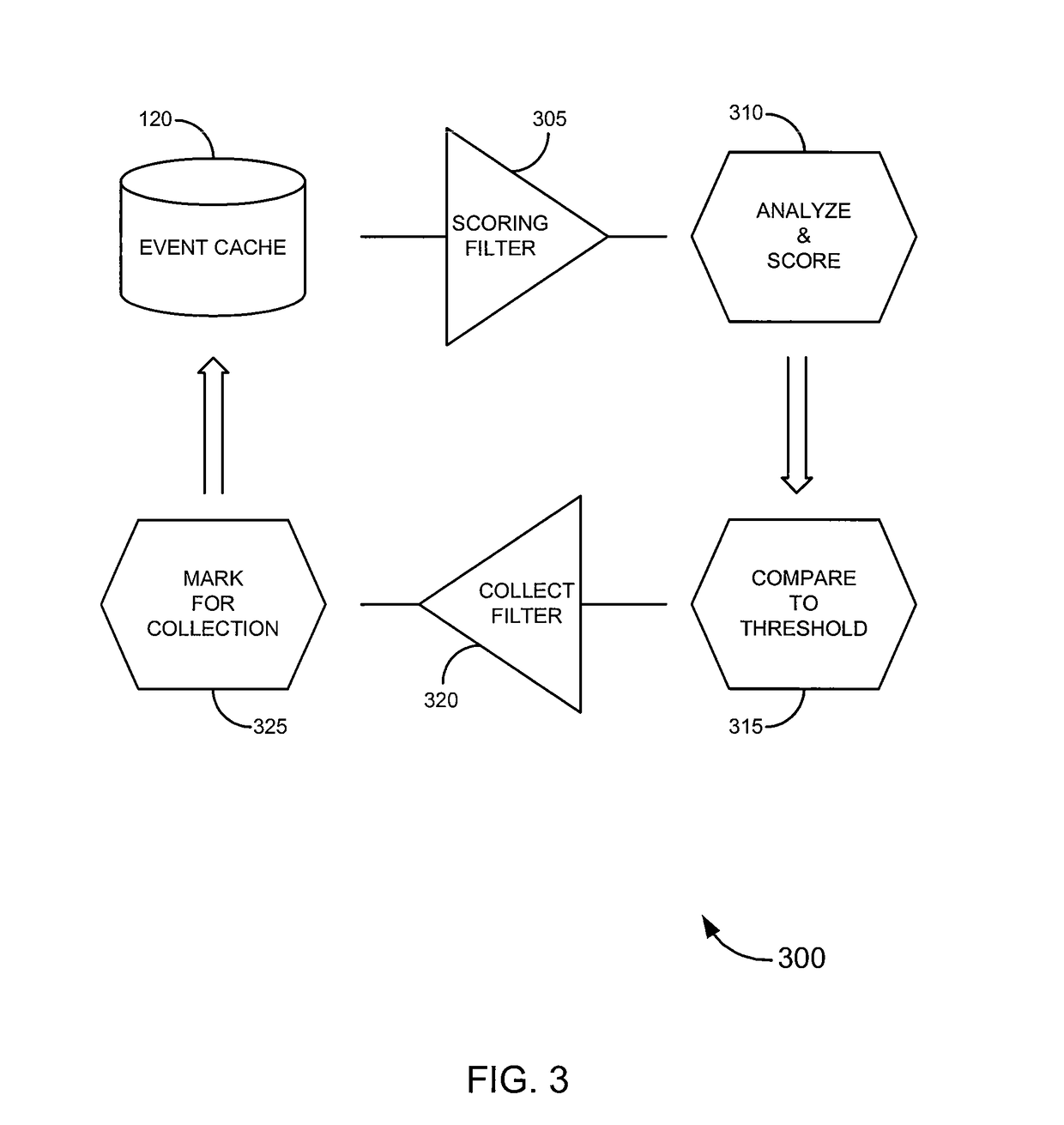
ActiveUS8122122B1PowerfulAvoid detectionDigital computer detailsComputer security arrangementsApplication softwareEvent monitoring
Embodiments of the invention provide systems, software and methods for monitoring events on a computer. In a set of embodiments, a monitoring application monitors events on a monitored computer. Each of the monitored events may be analyzed, and based on the analysis, some or all of the monitored events may be collected. A variety of rules may be used in analyzing events. In some cases, collected events can be queued, for example, by storing a representation of each collected event in an event cache. When connectivity with a monitoring computer is available, a connection with the monitoring computer may be established, and / or the queued events may be transmitted to the monitoring computer. In a particular set of embodiments, the monitoring application is designed to avoid detection by a user of the monitored computer.
Owner:SILICON VALLEY BANK
Method to configure offline player behavior within a persistent world game
ActiveUS20070298886A1Artificial lifeApparatus for meter-controlled dispensingWeb browserVirtual world
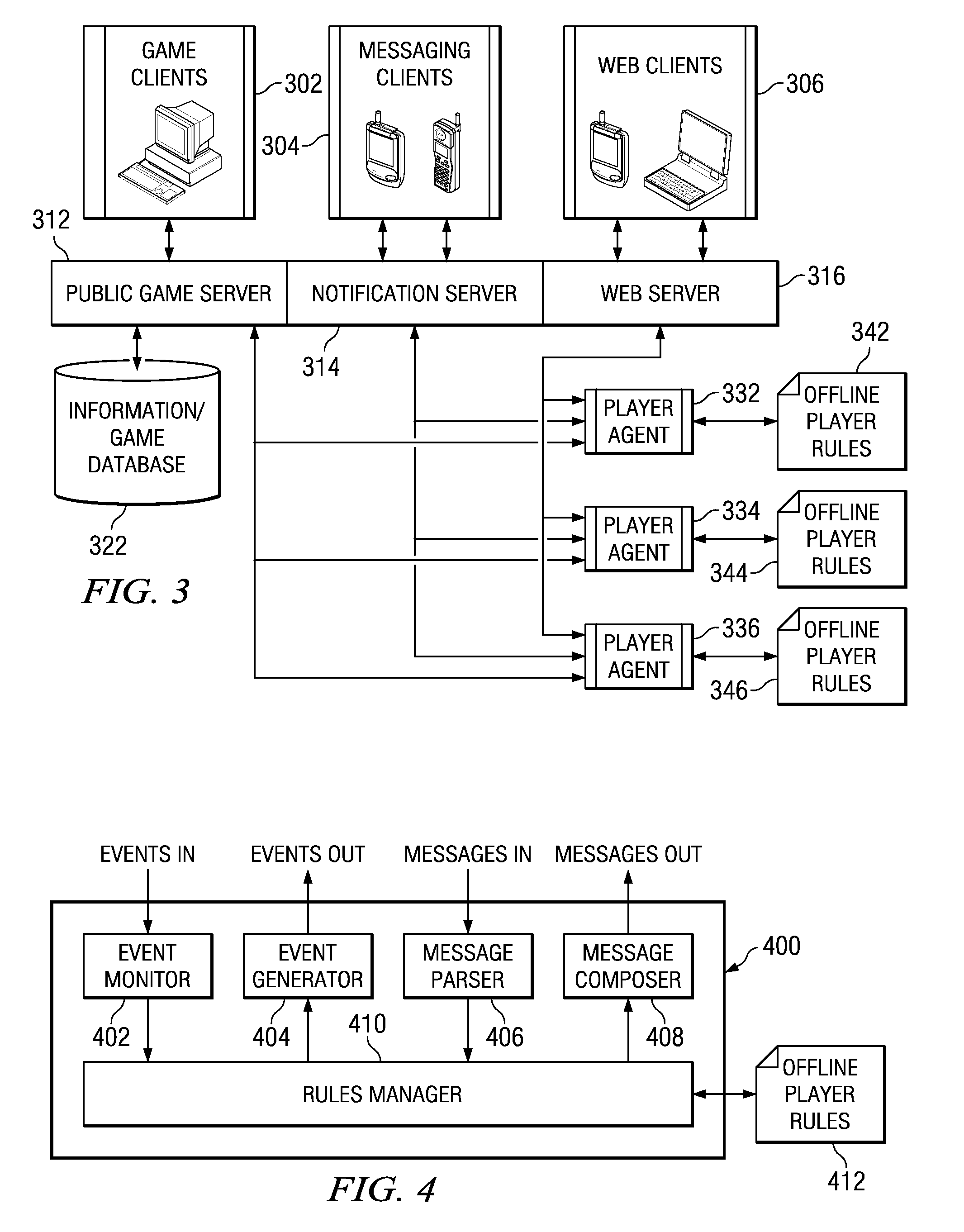
A mechanism is provided for configuring offline player behavior within a persistent world game. A player agent for an offline player includes an event monitor that monitors for events that occur in a persistent virtual world maintained by a game server. When a game event occurs that triggers an offline player rule, the player agent may generate game events on behalf of the offline player. The player agent may also receive messages from an offline player. The messages may include commands for adding, removing, or editing offline player rules. A message may also include a command to view a list of rules or fire a one-time execution of a rule upon receipt. Therefore, a player may contribute to the persistent virtual world even when offline by sending commands using a messaging client or Web browser.
Owner:WARGAMING NET
System and method for event monitoring and detection
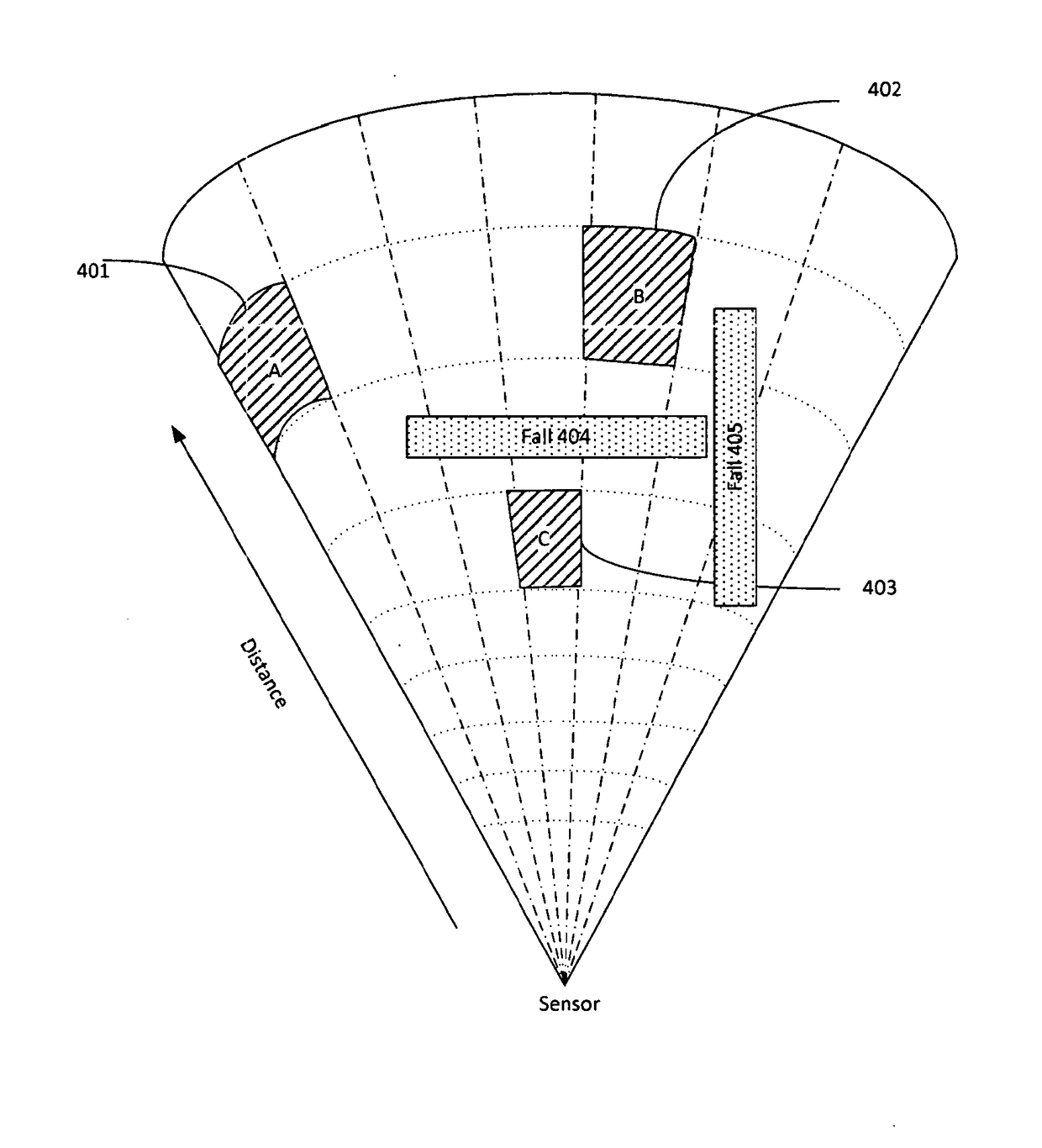
InactiveUS20170344832A1Loss of performanceImage enhancementImage analysisAlarm messageComputer terminal
A system for event detection and reporting has primary sensors for producing raw data from observing the proximate area, one or more processors for the primary sensors, for processing the raw data to produce output, a centralized controller to which each of the processors is connected, for receiving the output, a security network for communicating between the sensors, the controller, and one or more remote terminals, the security network having an alarm, and a plurality of auxiliary sensors for providing secondary sensor information to the one or more processors wherein the controller provides an alarm to the remote terminals through the security network if an event has occurred. A method of event detection has the steps of receiving a control command, alarm message and sensor information, determining if an event has occurred, and sending alarm messages and filtered sensor information to remote terminals if an event has occurred.
Owner:INNOVATIVE ALERT SYST INC
Distributive dynamic load management system and distributive dynamic load management method
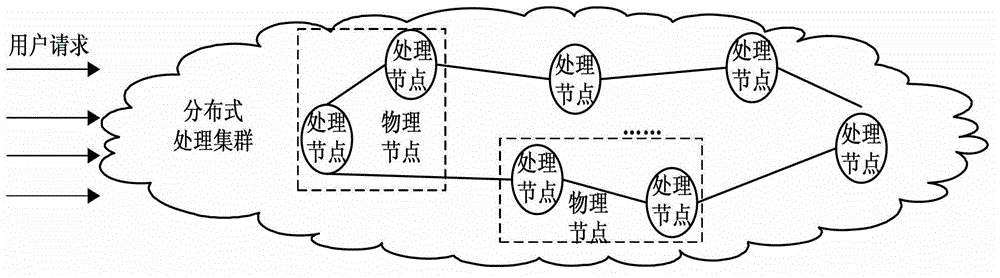
InactiveCN103188345AImprove load balancing effectAddressing Load Transfer Volatility IssuesData switching networksCluster systemsManagement system
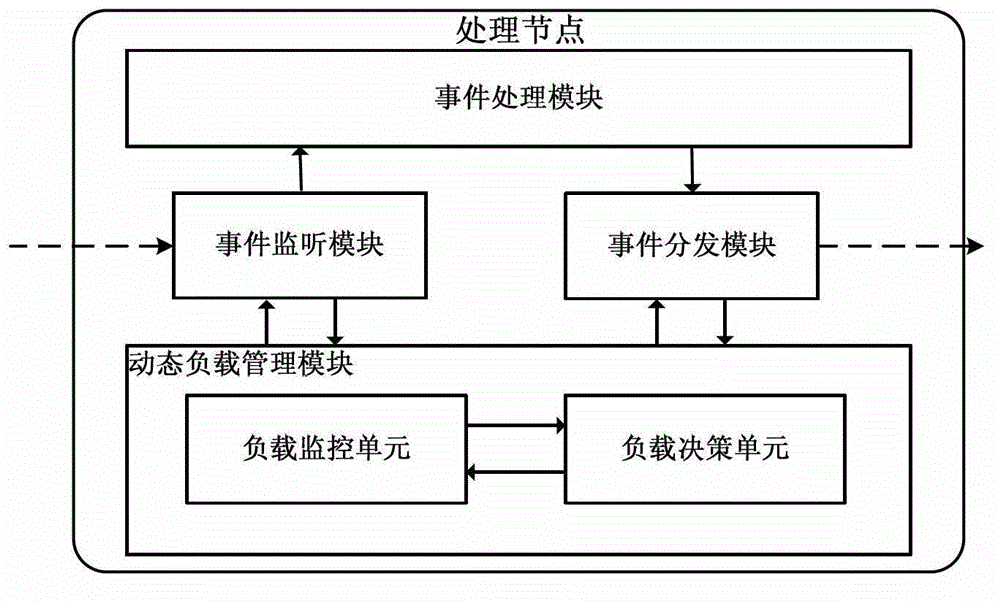
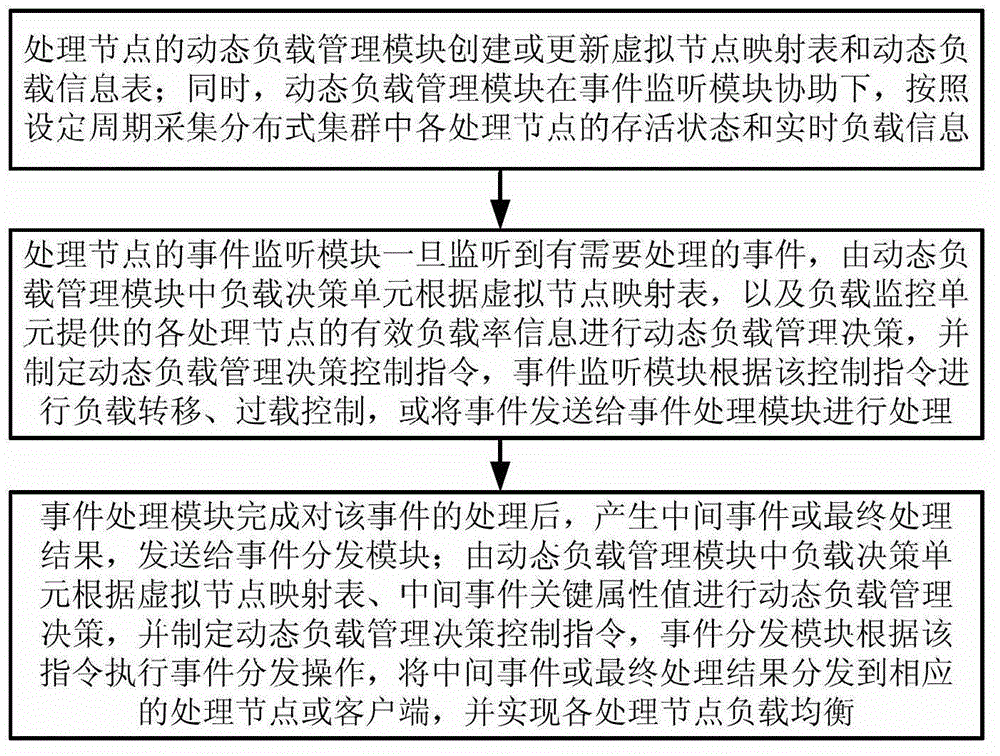
The invention discloses a distributive dynamic load management system and distributive dynamic load management method. The system consists of distributive processing clusters with dynamic load management function and P2P (Peer to Peer) complete equal frameworks. The processing clusters are not provided with central nodes controlled intensively but are provided with a plurality of processing nodes. Each processing node can independently provide distributive arbitral dynamic load management capacity and the nodes are completely same in right and dynamic load management function but same or different in event processing capacity. Each processing node is a control core of the dynamic load management system, and is provided with four modules, namely an event processing module, an event monitoring module, an event issuing module and a dynamic load management module. According to the system and the method, distributive dynamic load management can be realized under a distributive network environment, so that system load transfer fluctuation caused by change of data processing request hot spots and system load balance during node dynamic change can be effectively solved. The robustness of the system can be effectively ensured when the processing nodes of the distributive cluster system are overloaded under the P2P environment.
Owner:BEIJING UNIV OF POSTS & TELECOMM
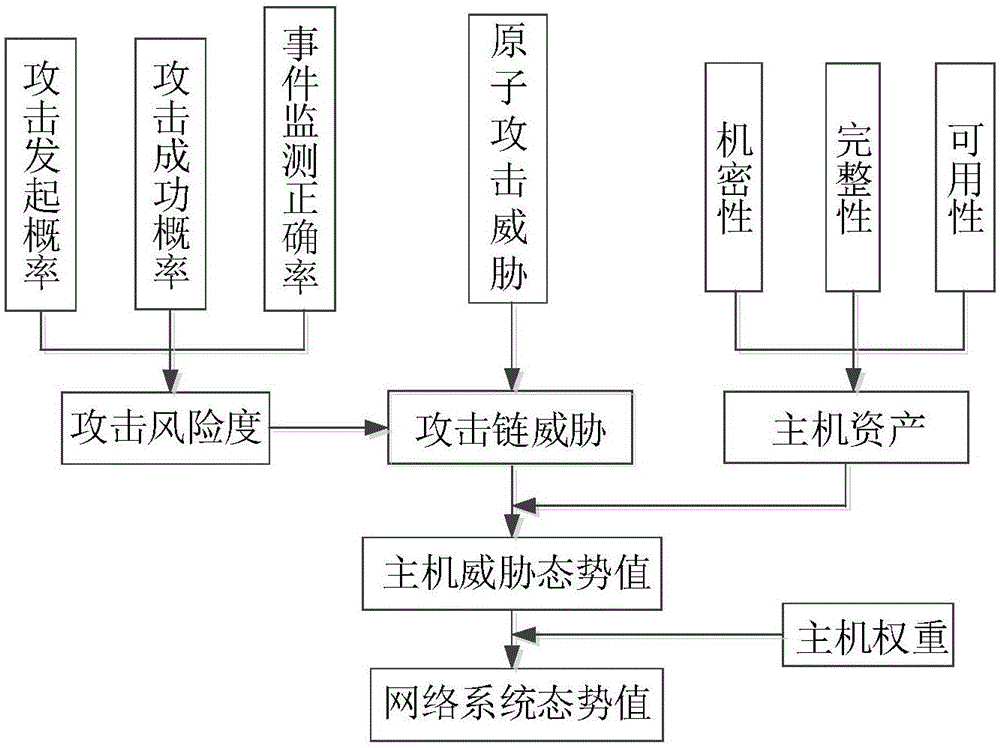
Bayesian network-based multi-step attack security situation assessment method
ActiveCN106341414AReal-time assessmentEffective assessmentPlatform integrity maintainanceTransmissionAttack graphCorrelation analysis
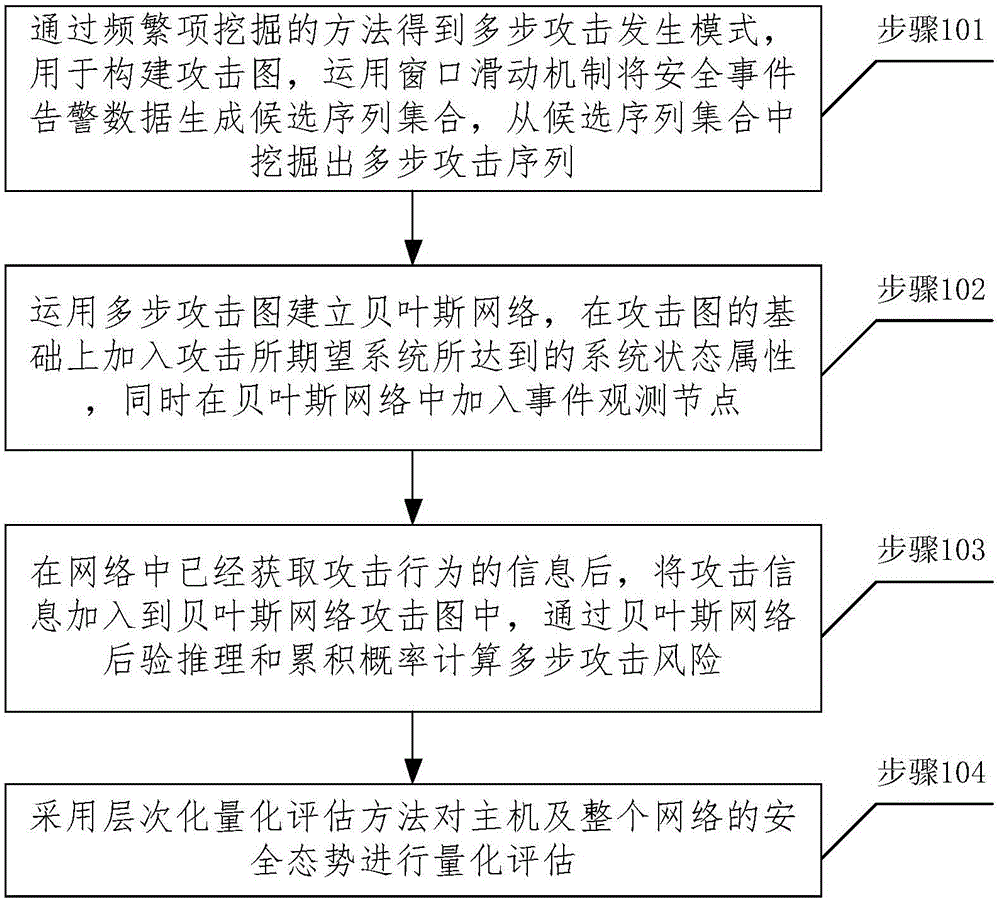
The invention relates to a network security situation assessment method, in particular, a Bayesian network-based multi-step attack security situation assessment method. The method includes the following steps that: multi-step attack generating patterns are mined through association analysis, so that an attack graph can be constructed; a Bayesian network is established according to the multi-step attack graph, attack wills, probability of success of attacks and the accuracy of event monitoring are defined as the probability attributes of the Bayesian network; based on the event monitoring, a multi-step attack risk is calculated according to the posterior reasoning and cumulative probability of the Bayesian network; and the security situations of a host and the whole network are quantitatively assessed according to a hierarchical quantitative assessment method. With the method of the invention adopted, the problem of lack of correlation analysis in a network security situation assessment process can be solved. According to the method of the invention, monitoring events are taken into risk assessment, and a network security situation assessment model is accurately established, and therefore, the effectiveness and real-time performance of the method of the invention can be enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Event-based process configuration
ActiveUS20080196006A1Simple configurationEasy to modifyFinanceLogisticsGraphicsProcess configuration
A system and method for configuring an event-based process are disclosed. A configuration module receives input describing an event-based process or modifications to an event-based process. For example, the configuration module receives as input a graphical depiction of one or more states and state transitions that comprise at least a portion of the event-based process. Using the received input description, the configuration module generates executable data, such as data formatted as an event processing language, corresponding to the input. The executable data is then communicated to an event engine which executes the executable data to implement the event-based process or modifications to an event-based process corresponding to the received input. One or more aspects of the execution of the event-based process may also be visualized, and graphically modified, though an event monitoring module.
Owner:SOFTWARE AG
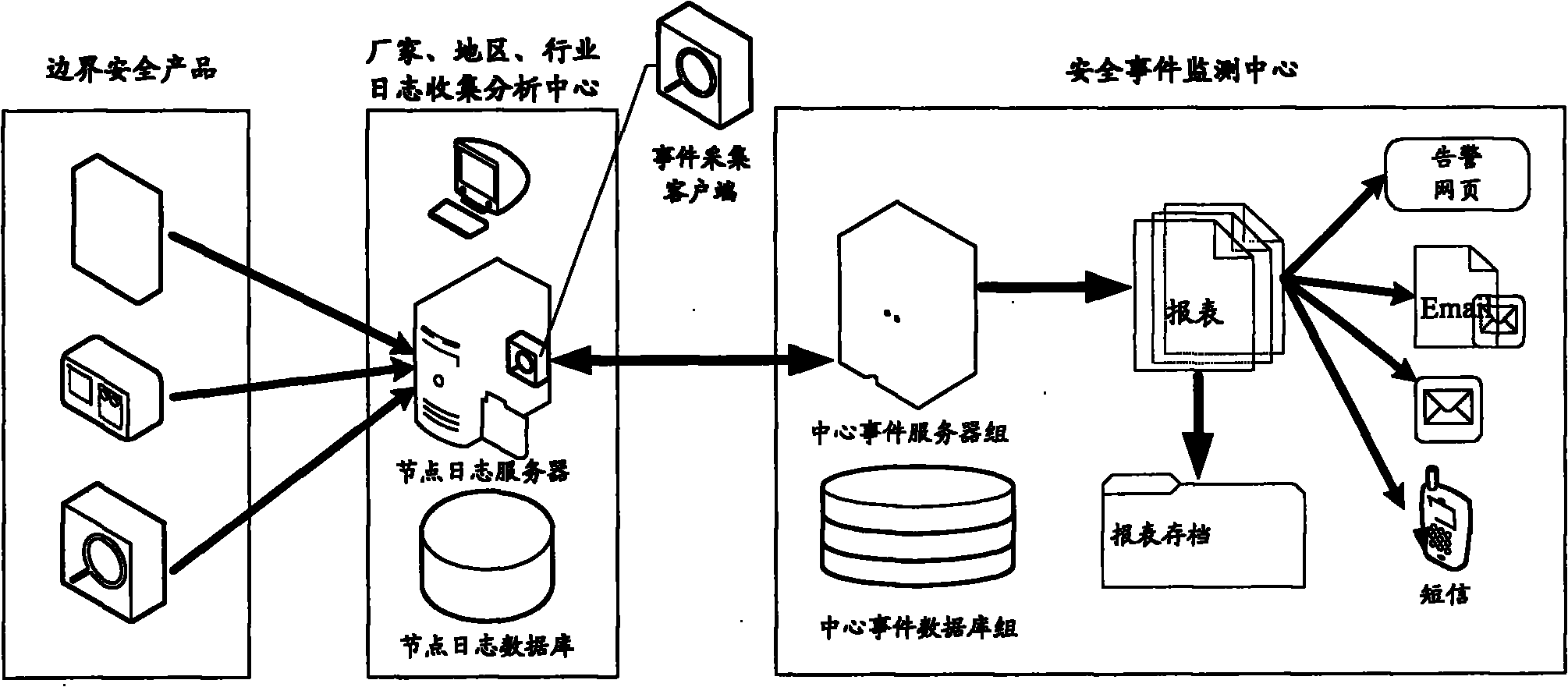
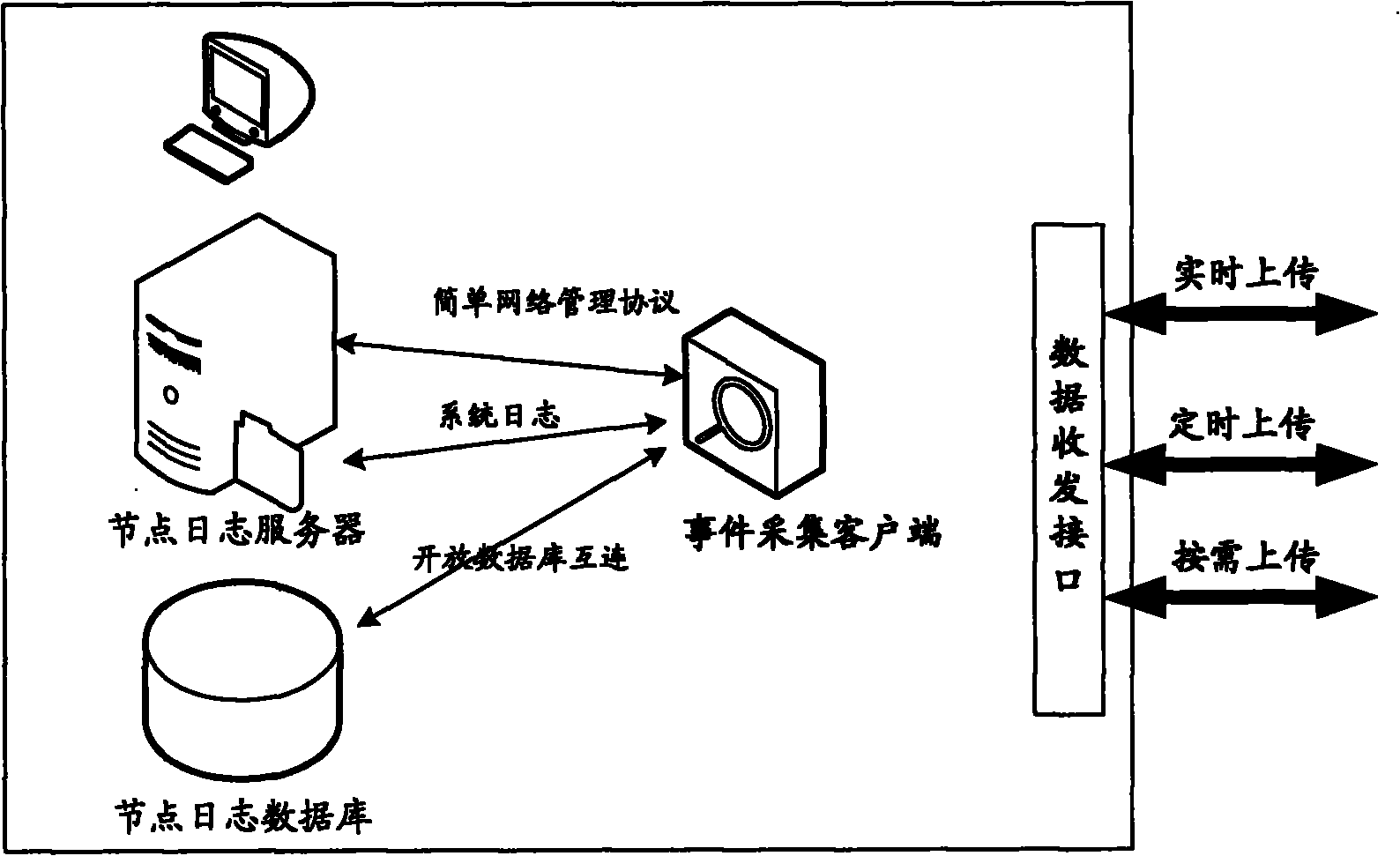
Method, system and device for monitoring security event
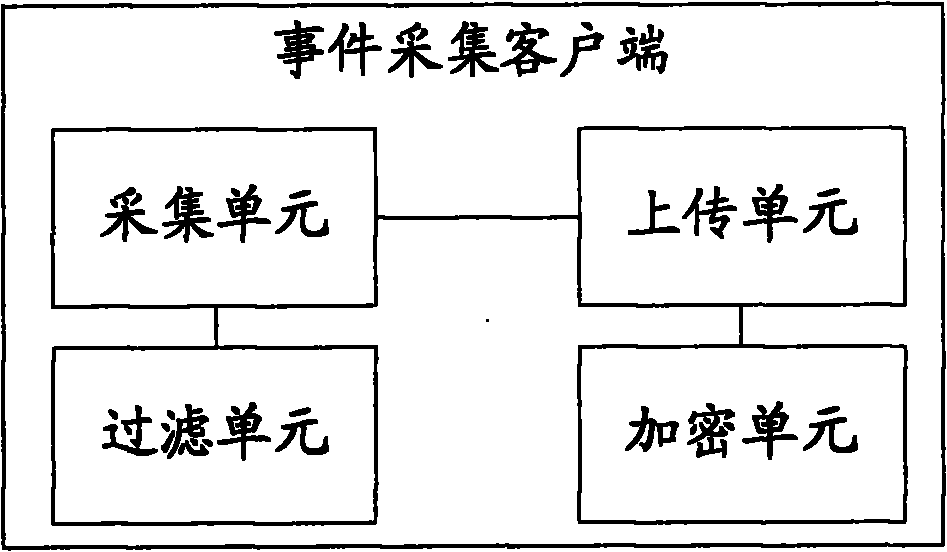
The invention discloses a method, a system and a device for monitoring a security event, which relate to the field of network security and are used for solving the problem that the generality of the conventional network information security event monitoring technique is poor. The method comprises the steps that: an event-acquiring client acquires an event log of a node in real time; the event-acquiring client uploads the acquired event log data to a security event monitoring center; and the security event monitoring center acquires the uploaded event log data and arranges the data to have a uniform format. The system comprises a node log server, the event-acquiring client and the security event-monitoring center, wherein the event-acquiring client is arranged on the node log server; the security event-monitoring center is communicated with the event-acquiring client; and the event-acquiring client comprises an acquiring unit and an uploading unit.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
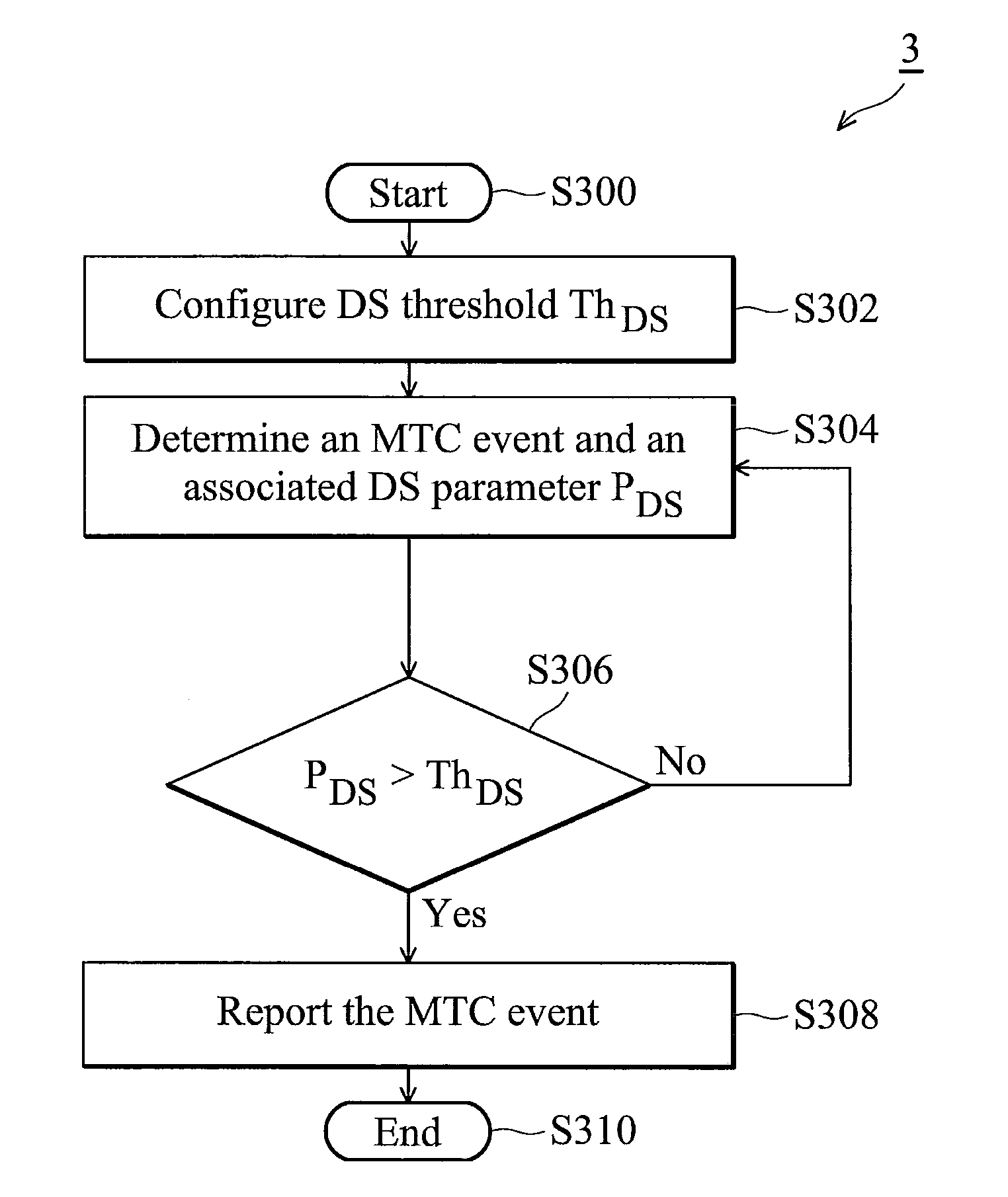
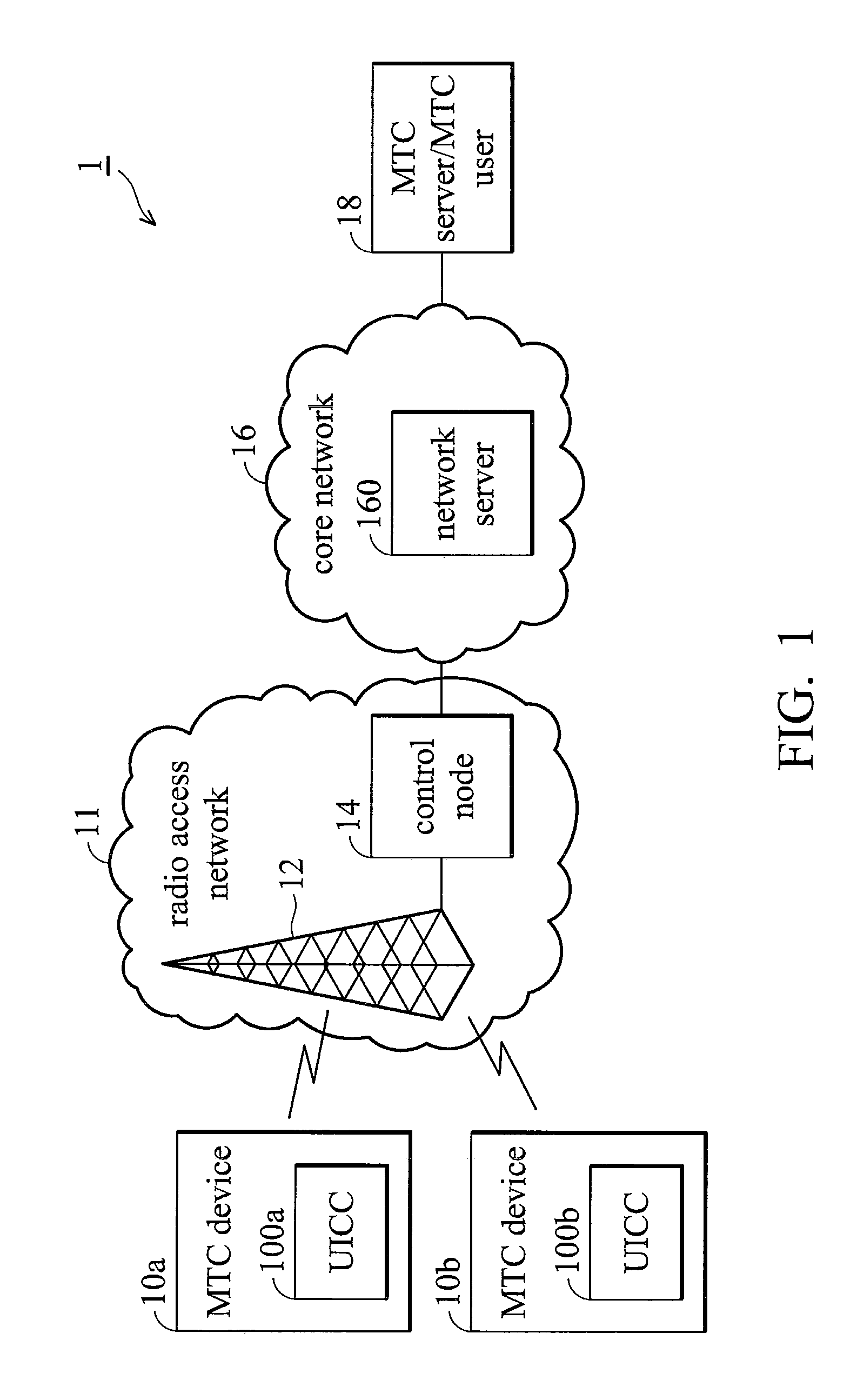
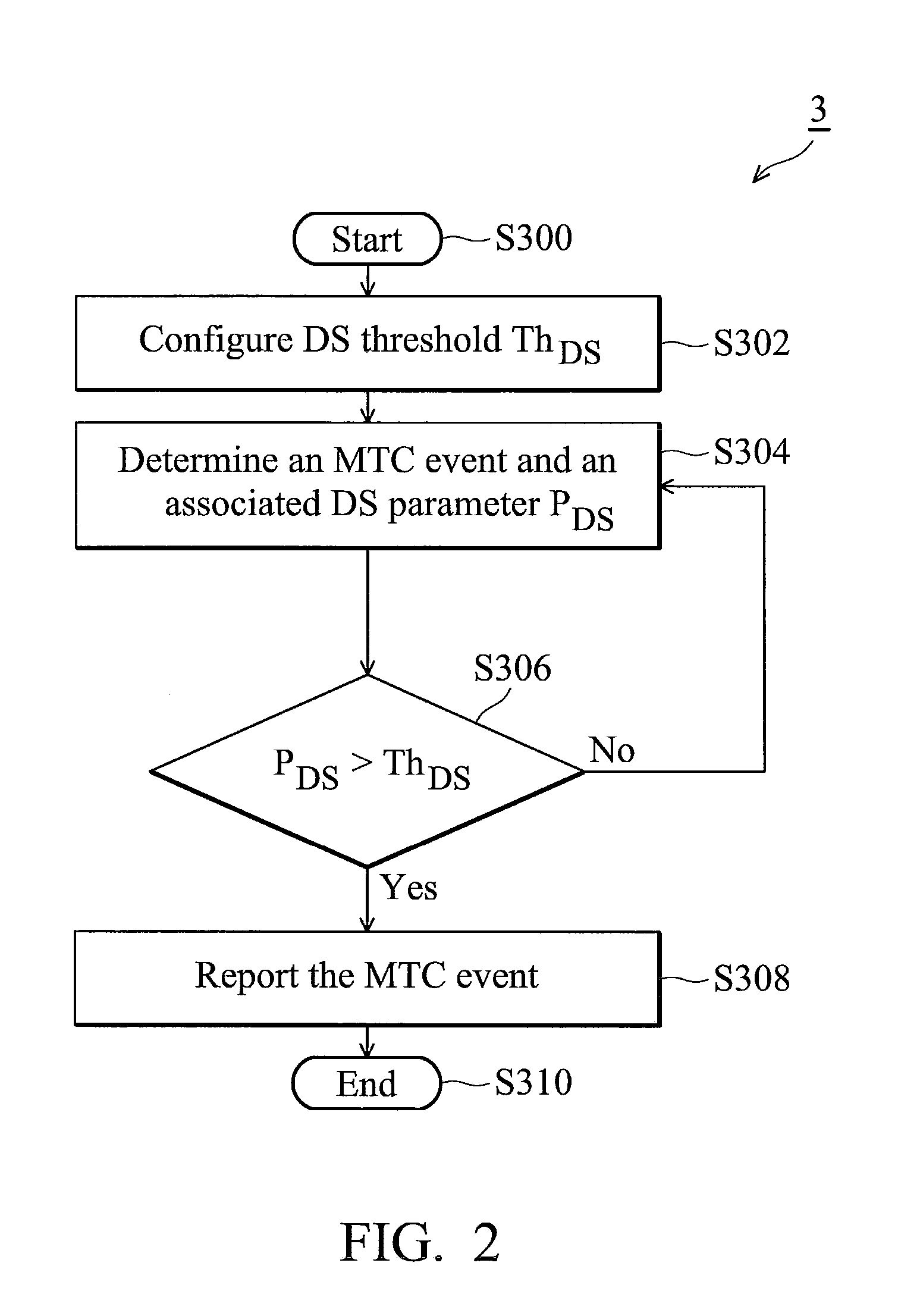
Methods for monitoring and reporting mtc events
MTC event monitoring methods and the network servers thereof. The MTC event monitoring method comprises configuring, by the network server, a detection sensitivity threshold, determining, by the network server, an MTC event at an MTC device and an associated detection sensitivity parameter, and reporting, by the network server, the MTC event to an MTC server only when the associated detection sensitivity parameter equals to or exceeds the detection sensitivity threshold.
Owner:HTC CORP
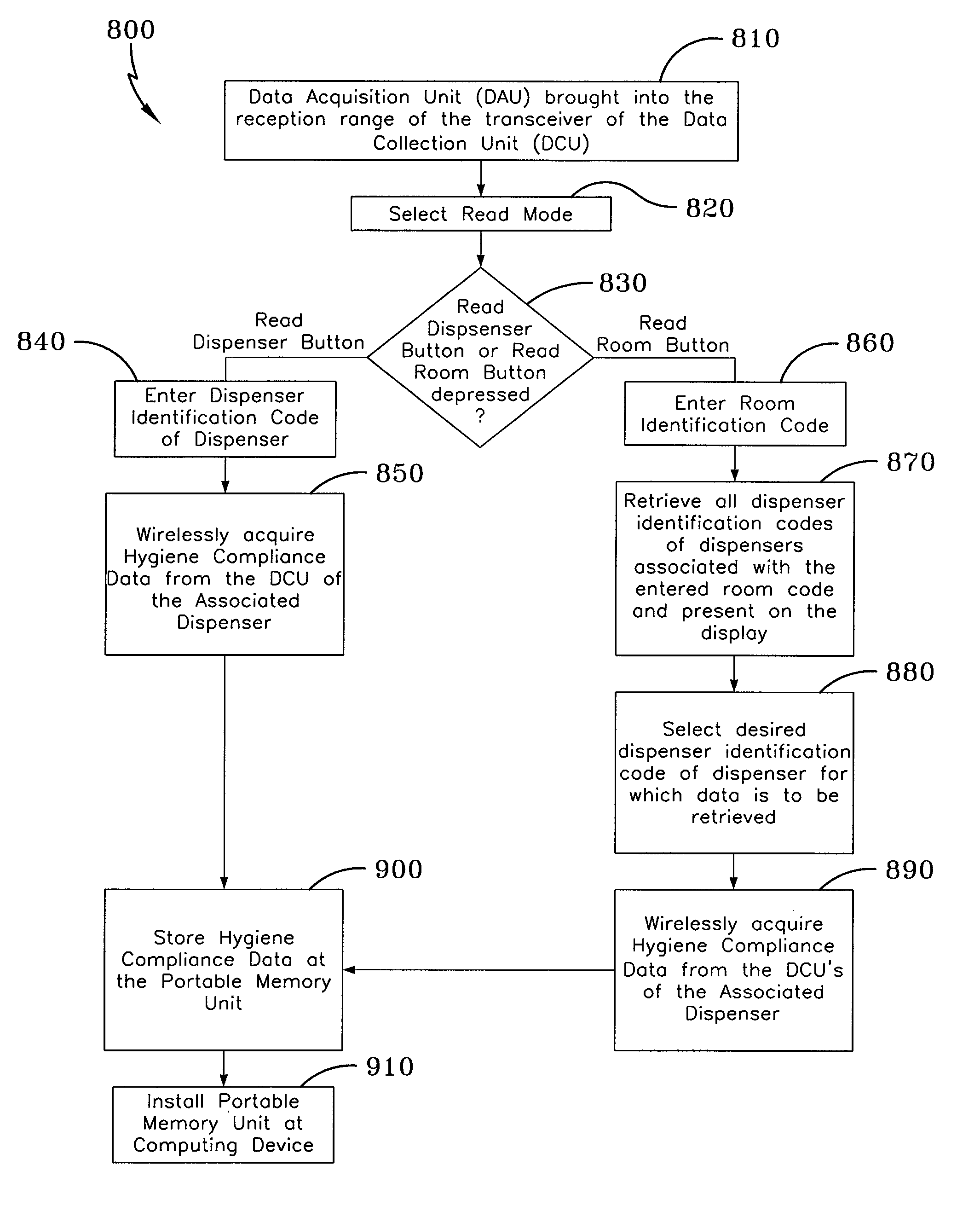
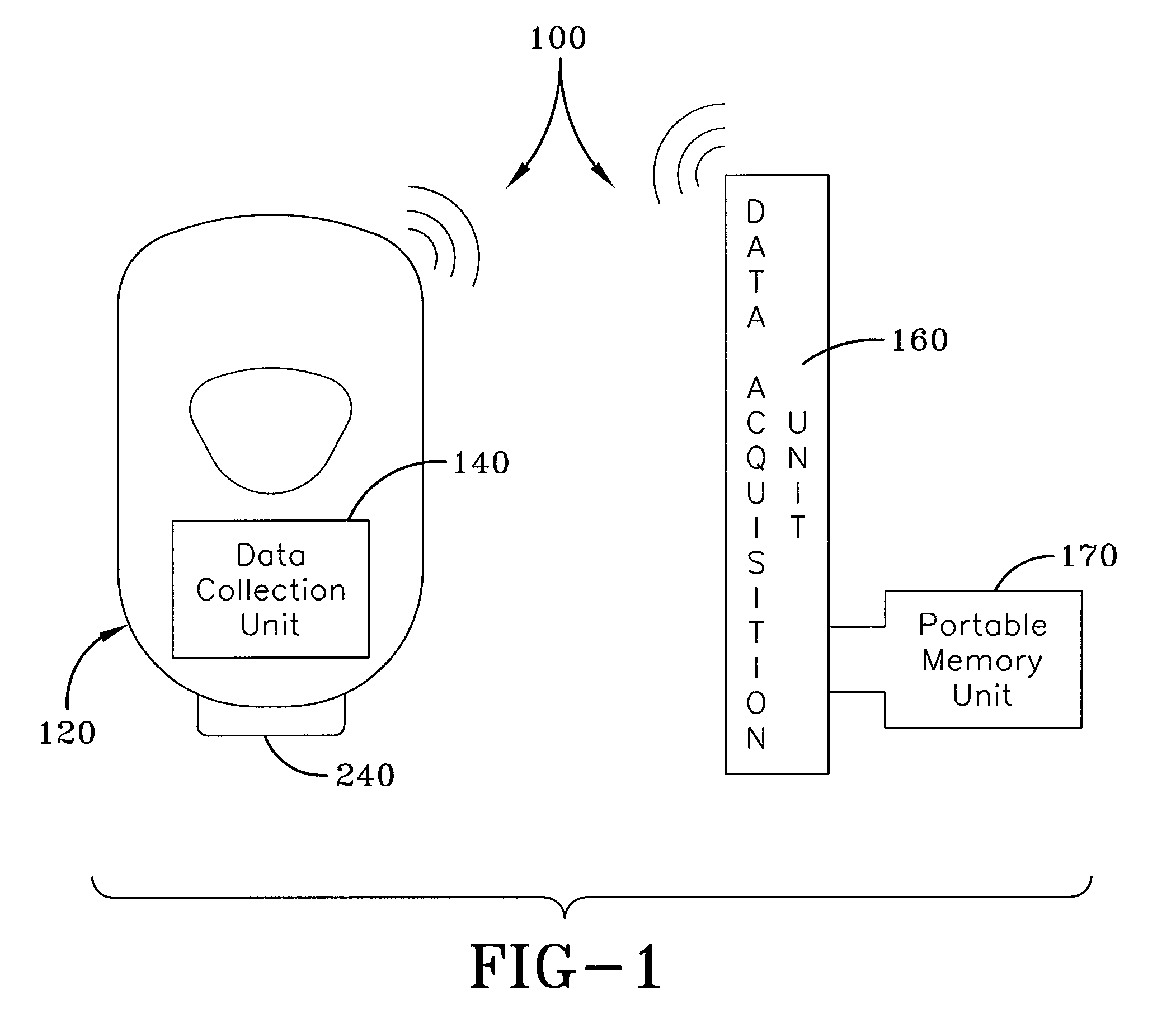
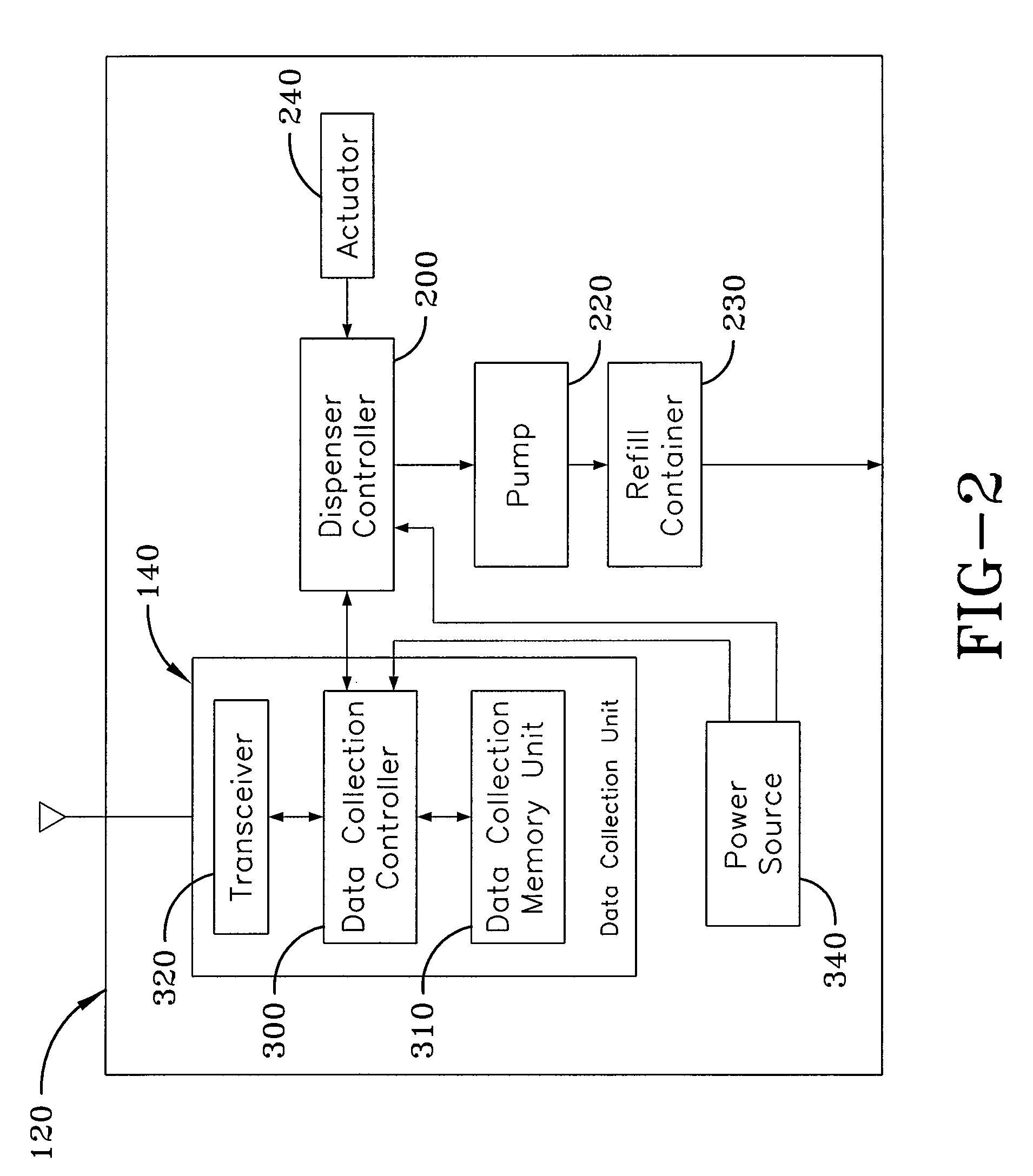
Hygiene compliance monitoring system
ActiveUS8350706B2Data processing applicationsLiquid transferring devicesTime informationCompliance Monitoring
A hygiene compliance monitoring system provides a dispenser that is associated with a data collection unit that collects dispensing events, such as the dispensement of material from the dispenser, which occurs during time segments of a predetermined duration. The hygiene event monitoring system also includes a portable data acquisition unit that is in wireless communication with the data collection unit of the dispenser. As such, when the data acquisition unit is brought within the range of reception of the data collection unit, the hygiene compliance data and time segment information are transmitted to the data acquisition unit and stored at a portable memory unit, which is removable. As such, the hygiene compliance data stored on the portable memory unit can be readily transferred to any desired computing device for analysis and report generation.
Owner:GOJO IND INC
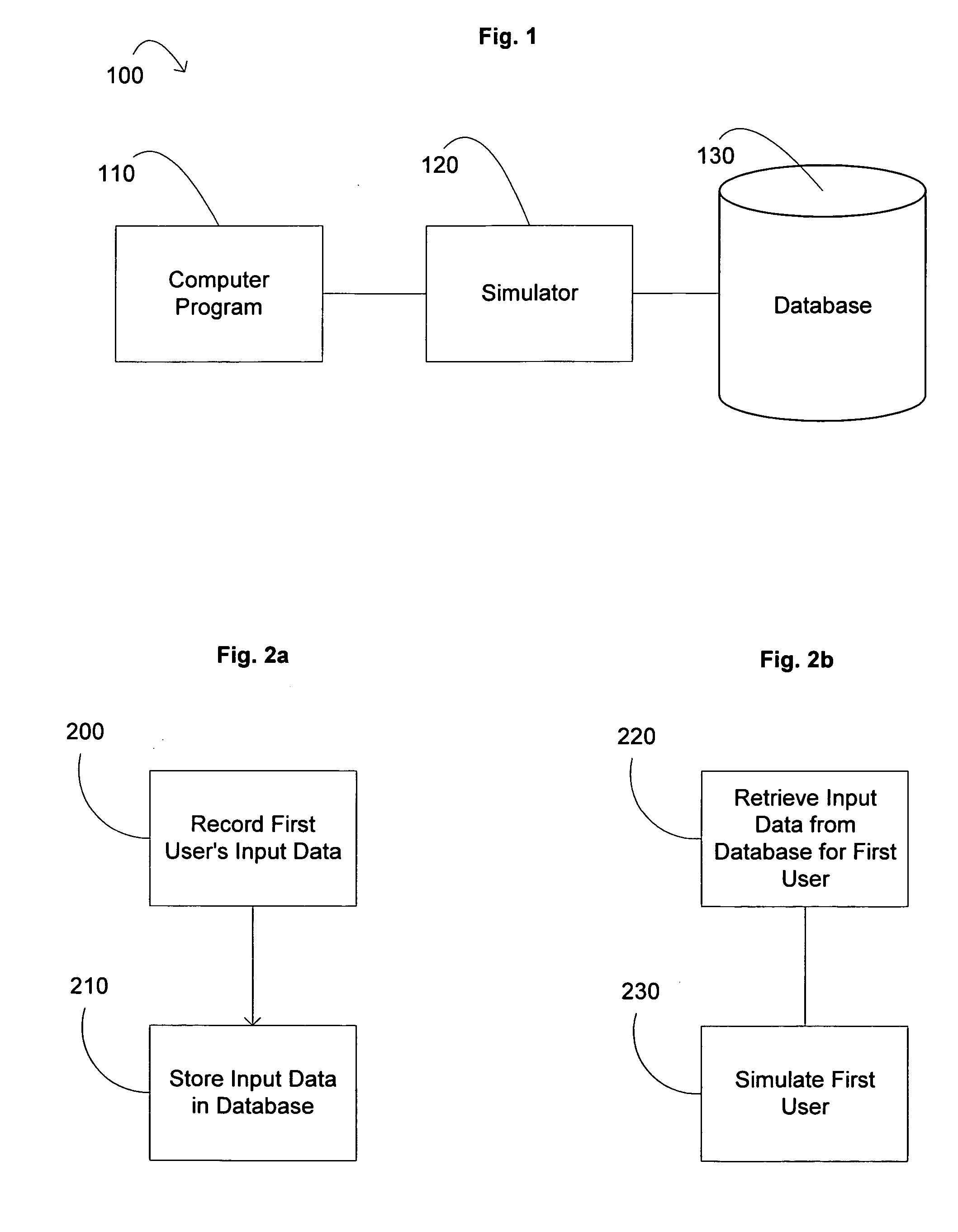
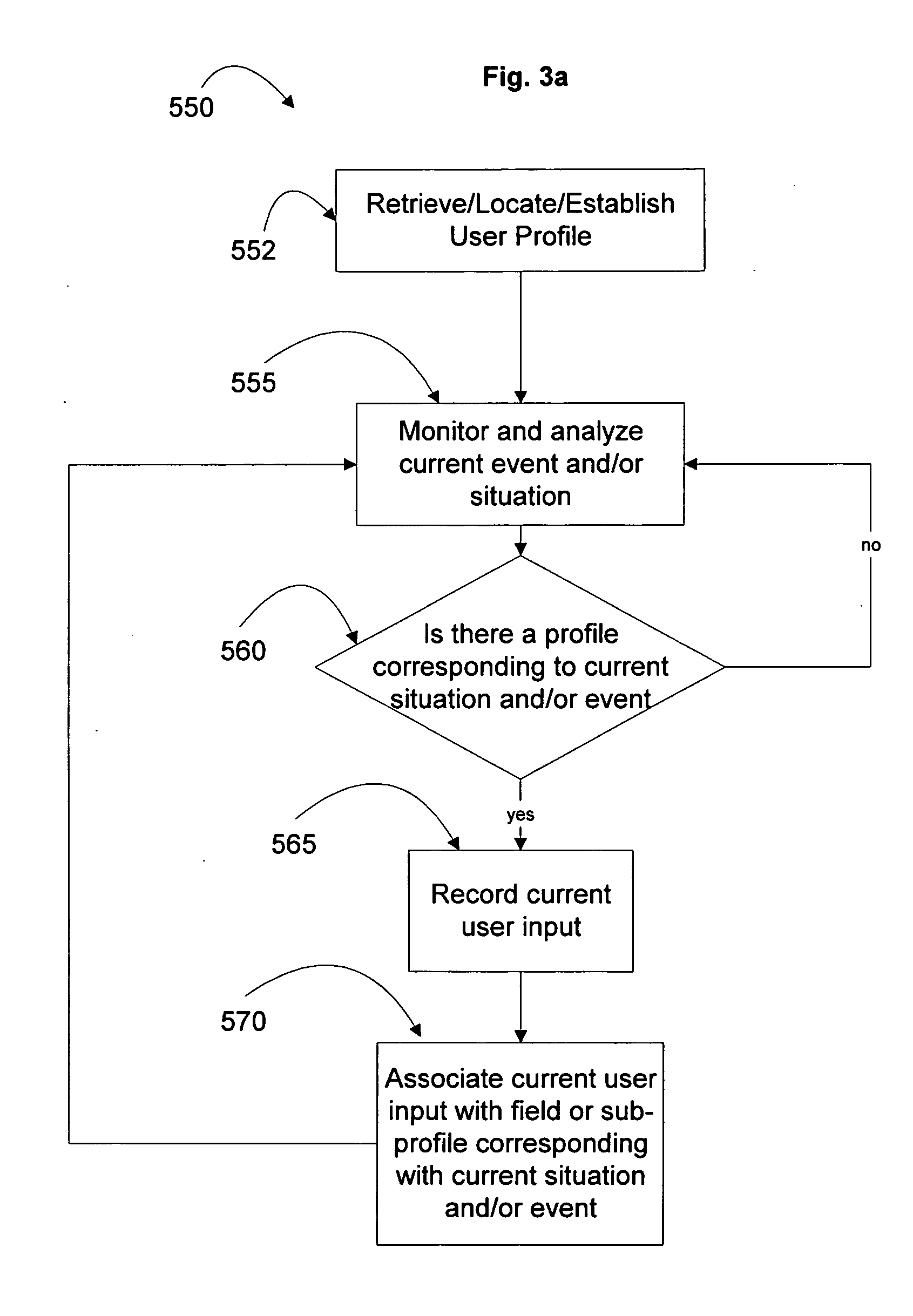
Systems and methods for simulating a particular user in an interactive computer system
The field of the invention relates to interactive computer systems and more particularly to systems and methods for simulating a particular user's behavior in an interactive computer system. In one embodiment, a computer program product includes a simulator configured to simulate a user interacting with a computer program. The simulator includes a learning mode of operation and a simulation mode of operation. During the learning mode, the simulator is configured to monitor the user's interaction with the computer program for one or more events and analyze one or more current circumstances during the occurrence of the one or more events. The simulator is further configured to record one or more user inputs in response to the occurrence of the one or more events, store the one or more user inputs in one or more data fields, and associate the one or more data fields with the one or more events and the one or more current circumstances. During the simulation mode of operation, the simulator is configured to monitor the computer program for the one or more particular events, retrieve the one or more data fields associated with the one or more particular events, analyze one or more current circumstances upon the occurrence of the one or more particular events, and invoke one or more simulated inputs based on the value of the one or more data fields in response to the occurrence of the one or more events and the one or more current circumstances.
Owner:TAKE TWO INTERACTIVE SOFTWARE
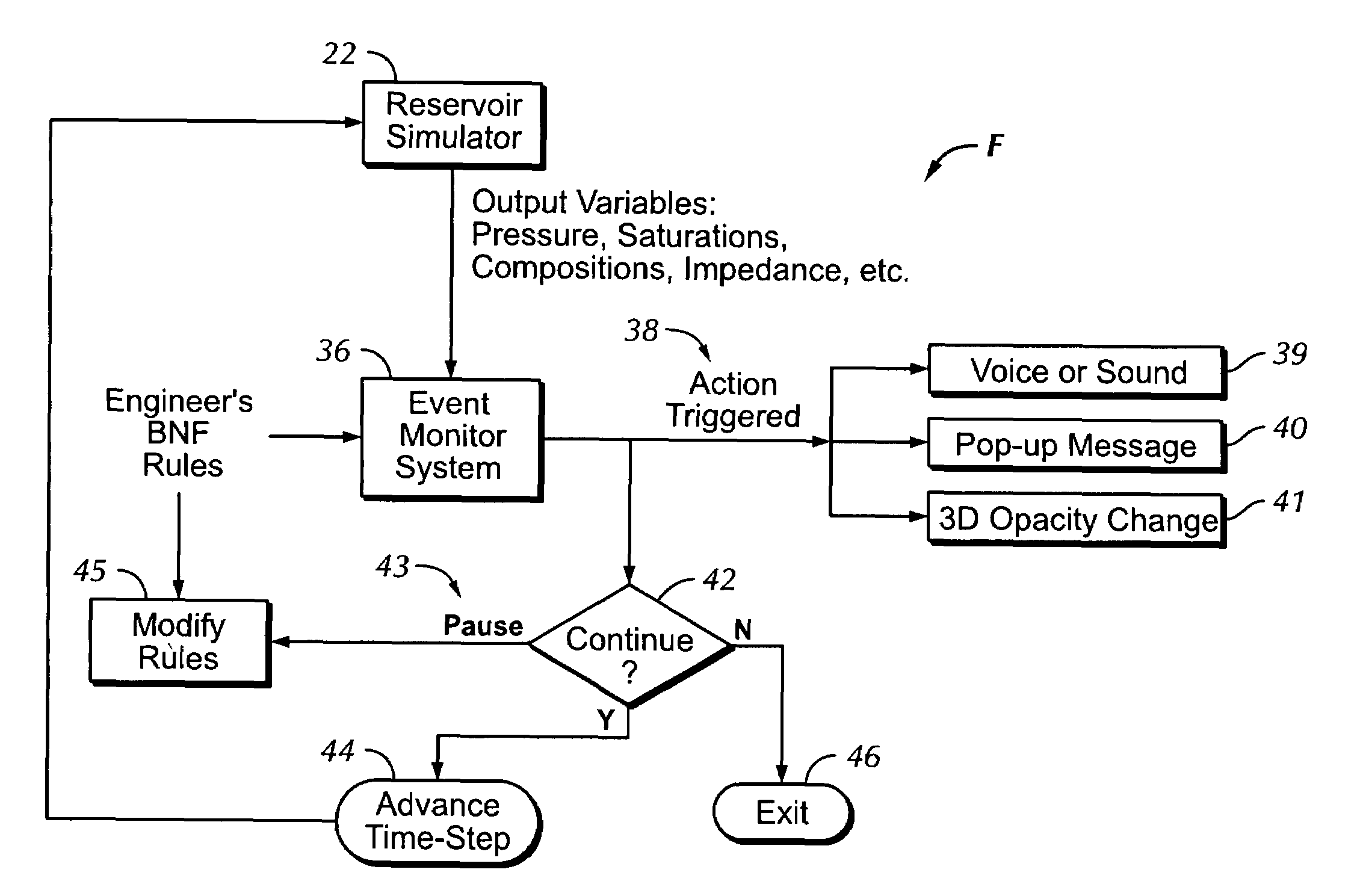
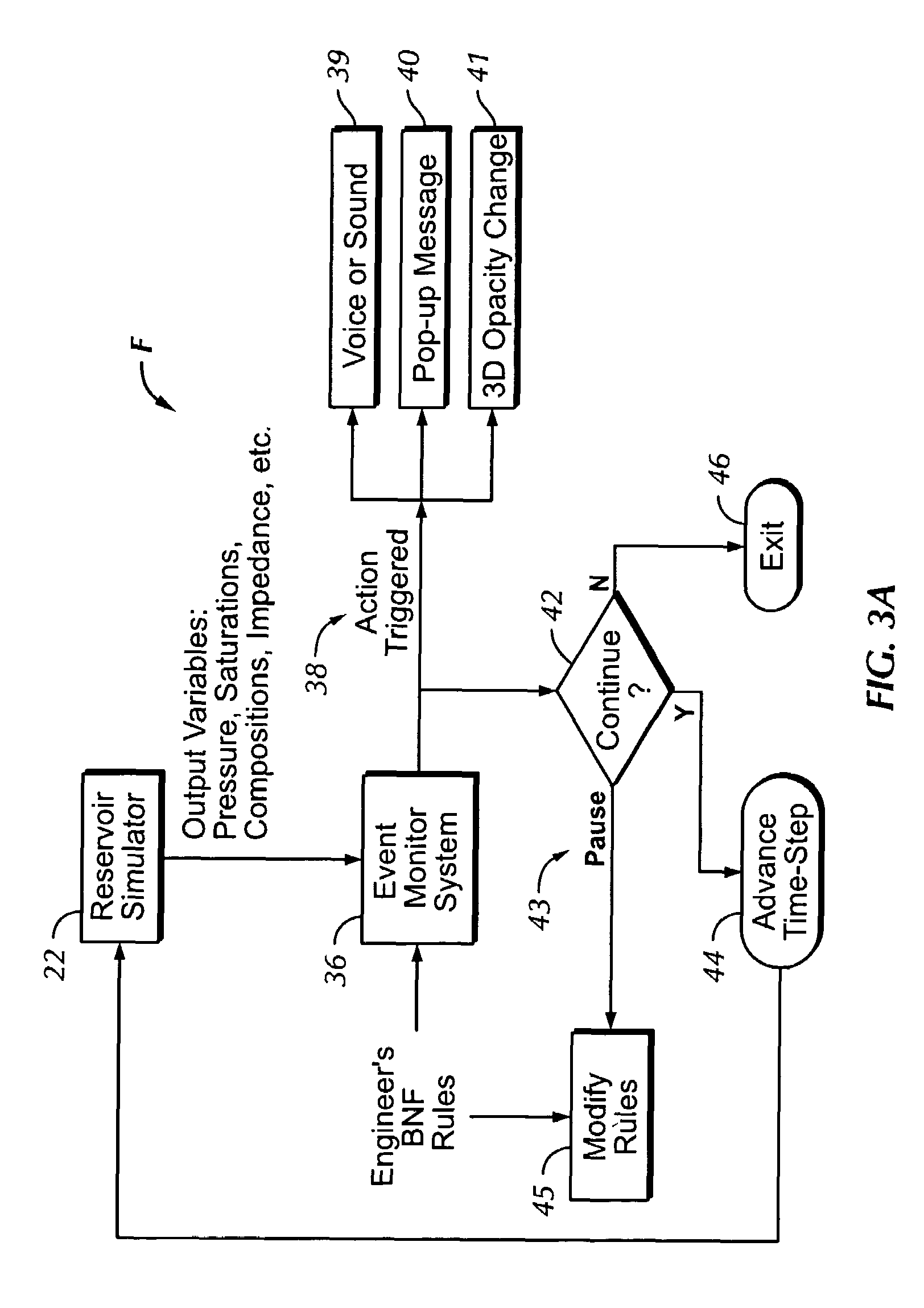
Automated event monitoring system for online reservoir simulation
ActiveUS7660711B2Electric/magnetic detection for well-loggingProgram loading/initiatingBatch processingMulti dimensional data
Owner:SAUDI ARABIAN OIL CO
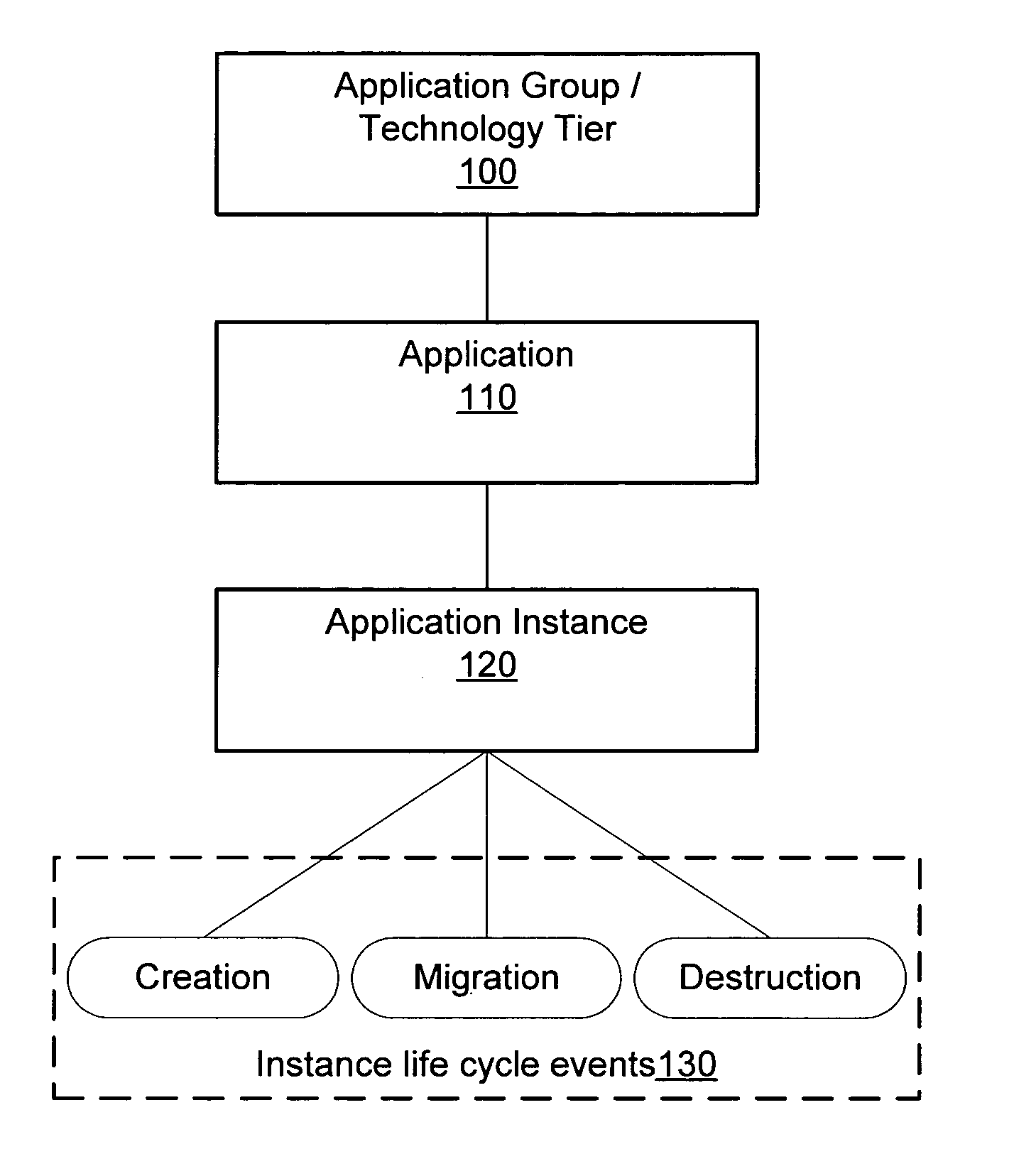
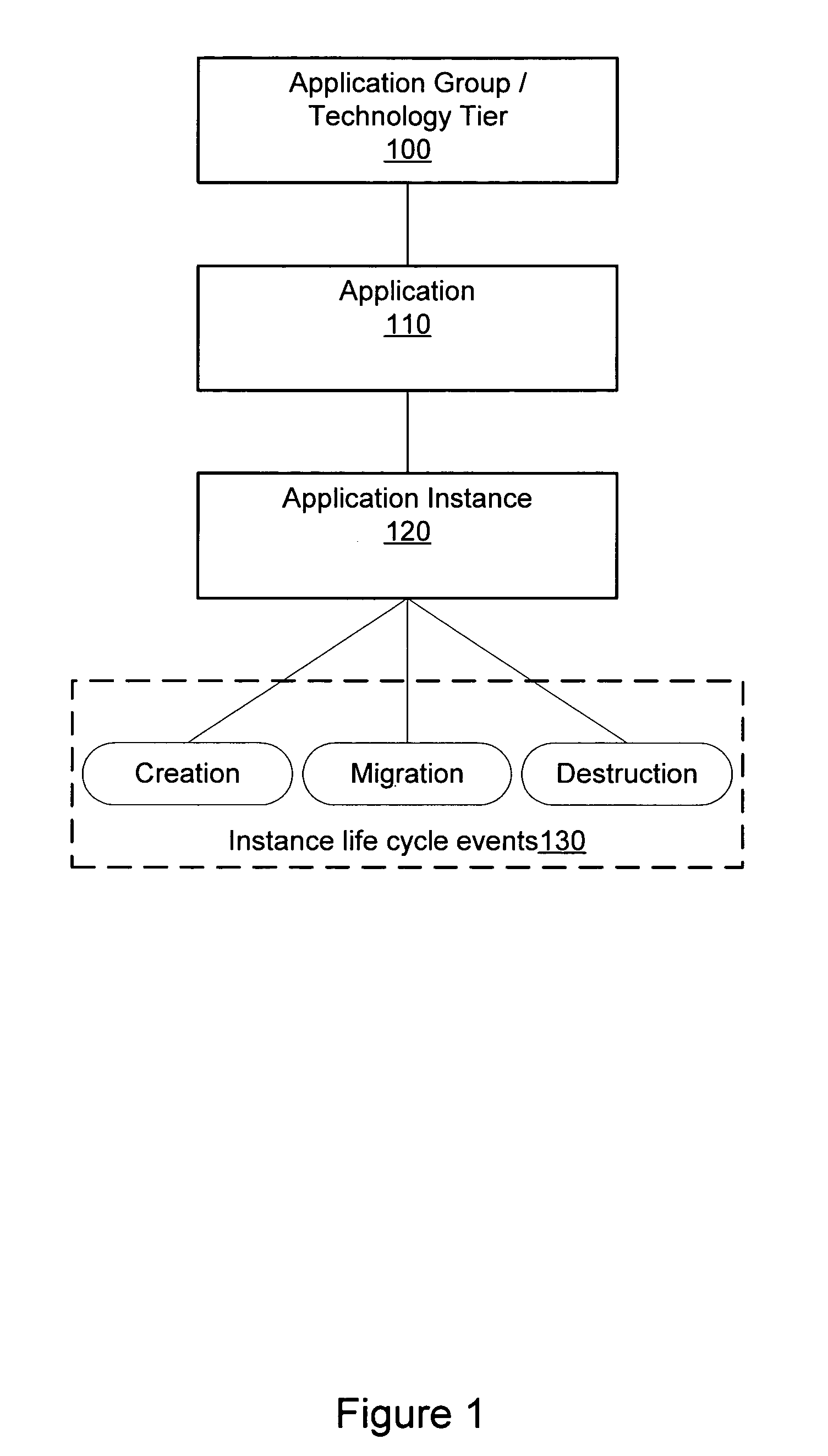
Correlation of application instance life cycle events in performance monitoring
ActiveUS7457722B1Amplifier modifications to reduce noise influenceDigital computer detailsMonitoring systemMultiple applications
A system and method for performance monitoring including instance life cycle event monitoring is disclosed. A performance monitoring system may correlate performance data to application instance life cycle events. Changes in performance at an instance level, application level or tier level may be related to application instance life cycle events such as creation, migration and destruction. In one embodiment, a performance monitoring method may include collecting performance data for one or more application instances, detecting one or more instance life cycle events associated with the one or more application instances, correlating the performance data to the one or more instance life cycle events, and storing the correlated performance data.
Owner:AVAGO TECH INT SALES PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com