Method, system and device for monitoring security event
A technology of security incidents and incidents, applied in the field of network security, can solve problems such as poor versatility, and achieve the effect of improving versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to solve the problem of poor versatility of existing network information security event monitoring technologies, the present invention provides a general security event monitoring solution.
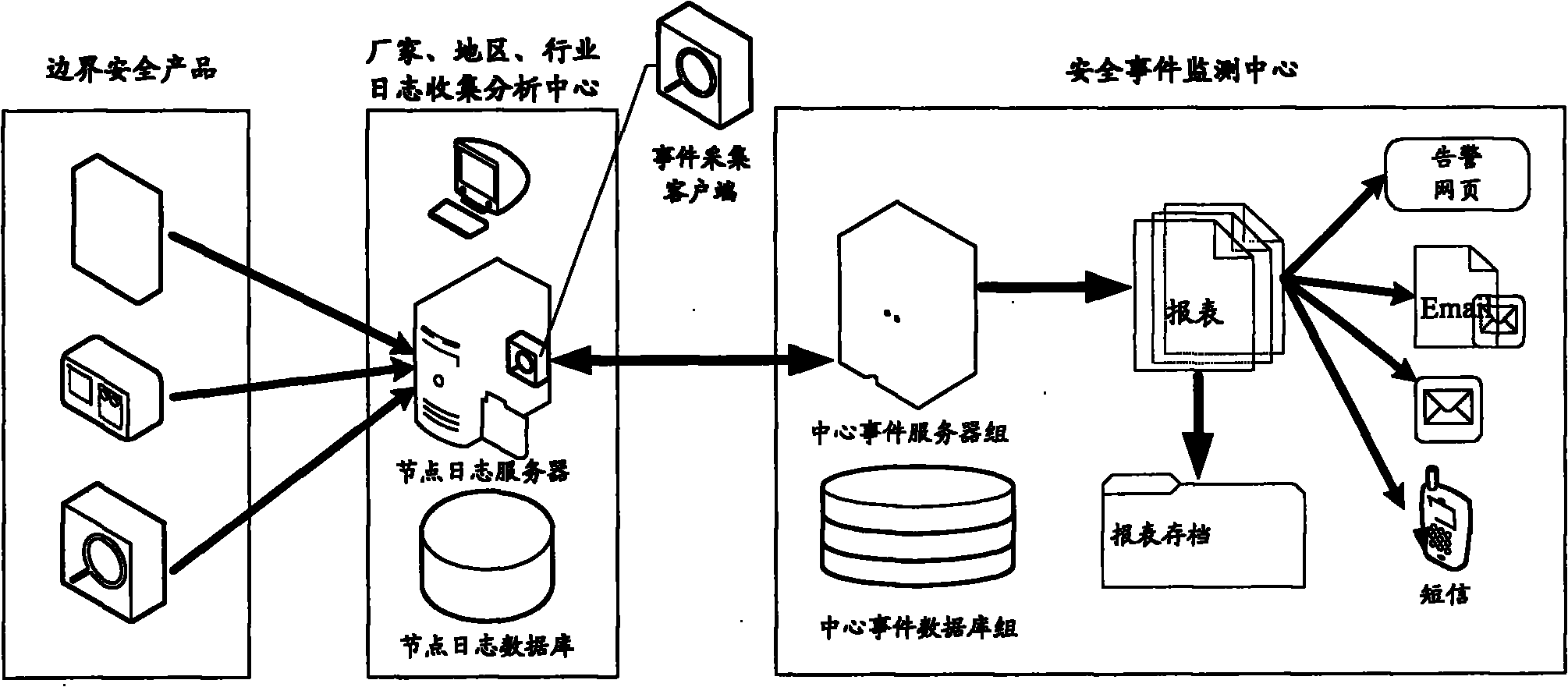
[0019] see figure 1 As shown, it is a system architecture diagram in the embodiment of the present invention, which is designed by layered processing and event collection client (agent software) plug-in.
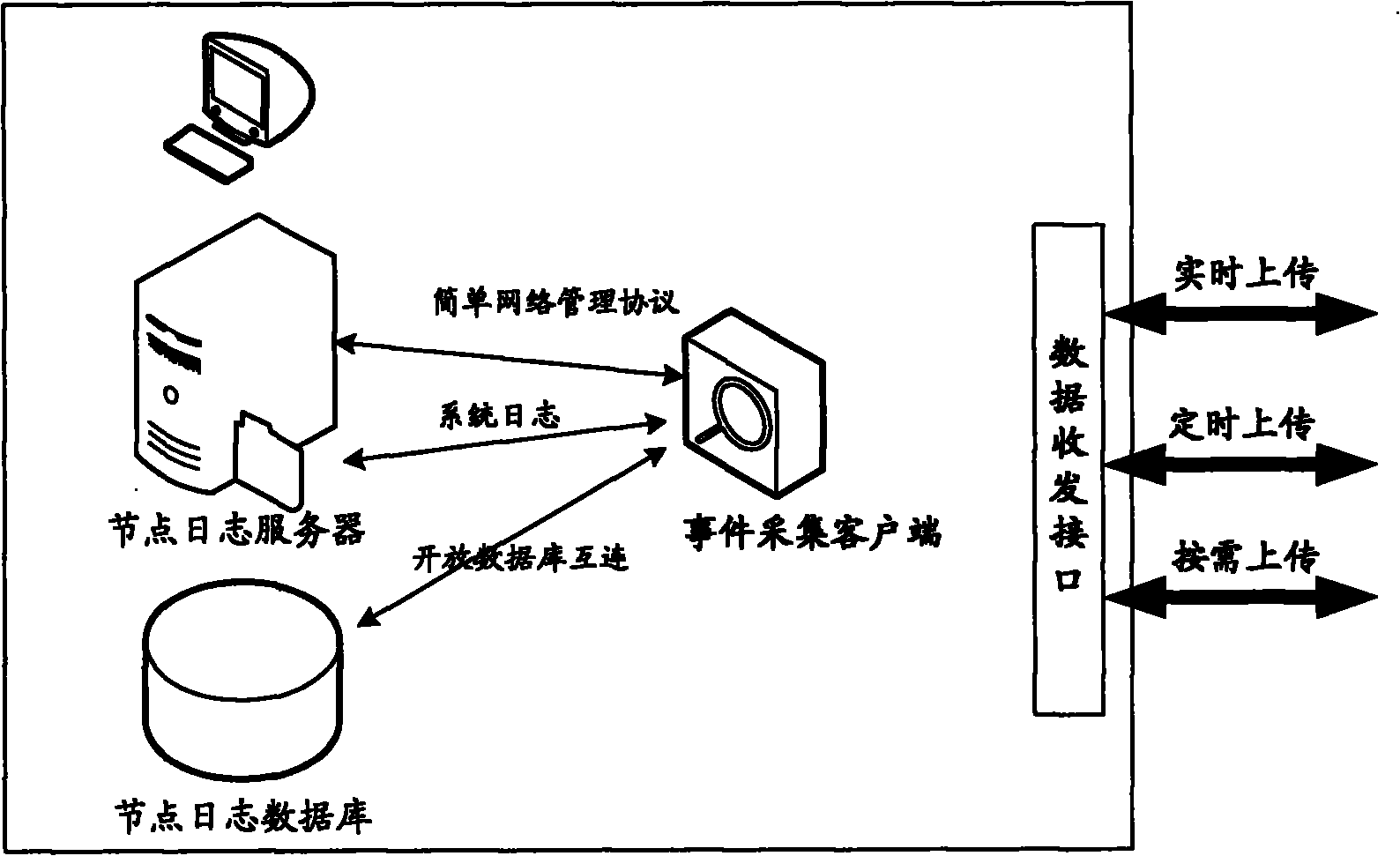
[0020] The data collection method adopts hierarchical processing. Firstly, it is divided according to manufacturers, regions, and industries. Each manufacturer collects and deploys border security product logs by itself to the manufacturer, region, and industry log collection and analysis center. Specifically, the node log server collects border security product logs. (that is, the event log of the security product under the jurisdiction of this node), and stored in the node log database.
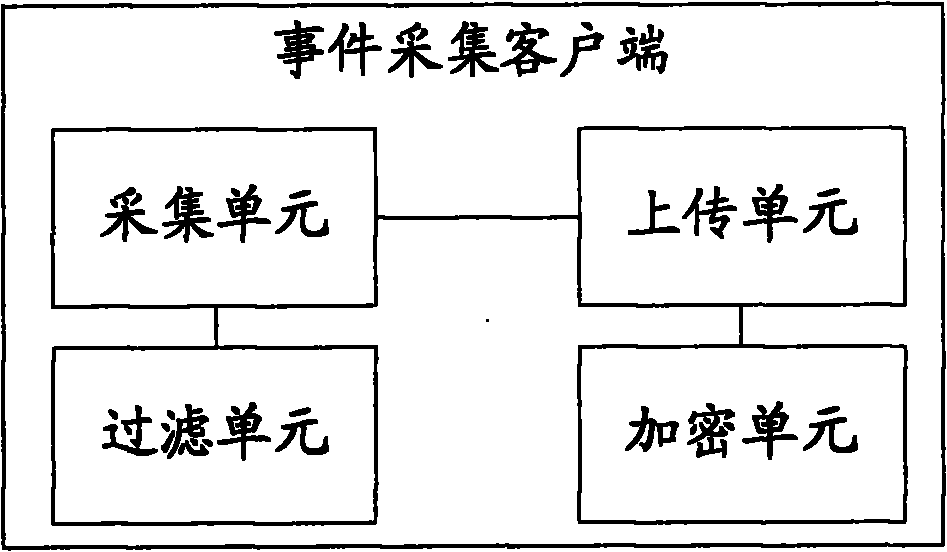
[0021] Deploy the event collection client on the node log server (can be a plug-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com